华为交换机 s5700 SSH 配置
华为交换机配置SSH

3. 配置步骤(SSH认证方式为口令认证)[Quidway] rsa local-key-pair create& 说明:如果此前已完成生成本地密钥对的配置,可以略过此项操作。
[Quidway] user-interface vty 0 4[Quidway-ui-vty0-4] authentication-mode scheme[Quidway-ui-vty0-4] protocol inbound ssh[Quidway] local-user client001[Quidway-luser-client001] password simple huawei[Quidway-luser-client001] service-type ssh[Quidway] ssh user client001 authentication-type passwordSSH的认证超时时间、重试次数以及服务器密钥更新时间可以采取系统默认值,这些配置完成以后,您就可以在其它与以太网交换机连接的终端上,运行支持SSH1.5的客户端软件,以用户名client001,密码huawei,访问以太网交换机了。
本文来自: IXPUB技术社区() 详细出处参考:/viewthread.php?tid=699243&page=1[root@main ~]#在交换机的system-view视图下生成本地密钥,位数为1024[H3C]rsa local-key-pair createThe local-key-pair will be created.The range of public key size is (512 ~ 2048).NOTES: If the key modulus is greater than 512,It will take a few minutes.Input the bits in the modulus[default = 1024]:Generating keys.........++++++........................++++++..Done![H3C]OK,现在就可以SSH到交换机了.附H3C交换机SSH的基本配置.local-user rootpassword simple 66070511service-type ssh telnetlevel 3ssh user root authentication-type allssh user root service-type stelnet#user-interface aux 0user-interface vty 0 4authentication-mode schemeuser privilege level 3protocol inbound ssh#H3C工程师配置& 说明:如果此前已完成生成本地密钥的配置,可以略过此步操作。
华为S5700配置远程登录

设置VTY用户界面AAA验证方式:system-viewuser-interfacevty 0 4Authentication-mode aaaquitaaalocal-user user-name password cipher passwordlocal-user user-name service-type ssh配置VTY用户密码验证方式system-viewuser-interfacevty numberauthentication-mode passwordset authenticationpassword【cipher password】配置VTY用户优先级system-viewuser-interface vty interface-numberuser privilege lever level配置VTY用户通过STelnet方式登录1、配置VTY 用户界面的用户级别和验证方式system-viewuser-interfacevty 0 4Authentication-mode aaaquitaaalocal-user user-name password cipher passwordlocal-user user-name service-type ssh2、配置VTY 用户界面支持SSH 协议system-viewuser-interfacevty 0 4authentication-modeaaaprotocol inboundssh3、配置ssh用户并指定服务方式system-viewssh user user-name #创建ssh用户rsa local-key-pair create或dsa local-key-pair create #产生RSA或DSA密钥对ssh user user-name authentication-type{password|rsa|password-rsa|all |dsa | password-dsa }#配置SSH 用户的认证方式ssh user username service-type { stelnet | all } #配置Stelnet用户服务方式为说telnet或all4、使能Stelnet服务器功能system-viewstelnet server enable。
华为S5700交换机操作手册

华为S5700交换机操作手册MEth 0/0/1 属于管理口system-view[Quidway]interface MEth 0/0/1[Quidway]ip adddress 192.168.5.2 255.255.255.0 #设置管理ip配置连接密码打开web操作sysaaalocal-user huawei password cipher adminlocal-user huawei level15local-user huawei ftp-directory flash;local-user hawed service-type telnet terminal httpCONSOLE:通过密码:[Quidway]user-interface con 0[Quidway-ui-console0]authentication-mode password[Quidway-ui-console0]set authentication password simple h3c[Quidway-ui-console0]user privilege level 3------------->可以不配置,默认级别是3通过用户名和密码:[Quidway]local-user quidway[Quidway-luser-quidway]password simple h3c[Quidway-luser-quidway]service-type terminal level 3[Quidway]user-interface con 0[Quidway-ui-console0]authentication-mode schemeTELNET:通过密码:[Quidway]user-interface vty 0 4[Quidway-ui-vty0-4]authentication-mode password [Quidway-ui-vty0-4]set authentication password simple h3c [Quidway-ui-vty0-4]user privilege level 3通过用户名和密码:[Quidway]user-interface vty 0 4[Quidway-ui-vty0-4]authentication-mode password [Quidway-ui-vty0-4]set authentication password simple h3c [Quidway]local-user quidway[Quidway-luser-quidway]password simple h3c [Quidway-luser-quidway]service-type telnet level 3默认是VRP1.74和1.44是没有缺省用户名和密码的。
华为S5700 SSH远程管理配置实例
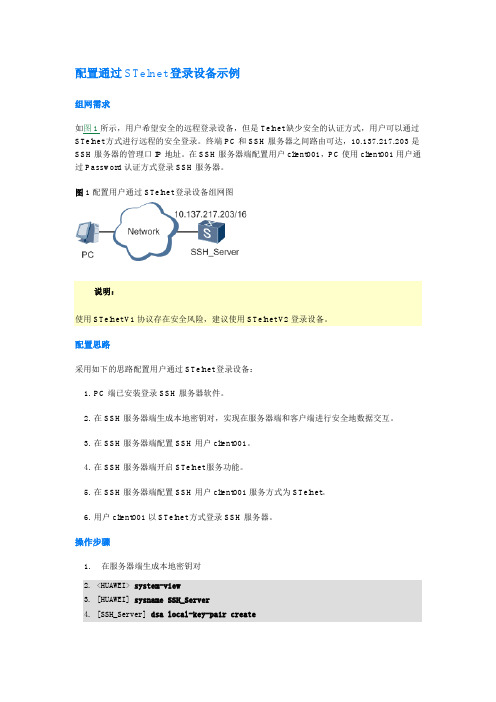
配置通过STelnet登录设备示例组网需求如图1所示,用户希望安全的远程登录设备,但是Telnet缺少安全的认证方式,用户可以通过STelnet方式进行远程的安全登录。
终端PC和SSH服务器之间路由可达,10.137.217.203是SSH服务器的管理口IP地址。
在SSH服务器端配置用户client001,PC使用client001用户通过Password认证方式登录SSH服务器。
图1 配置用户通过STelnet登录设备组网图说明:使用STelnet V1协议存在安全风险,建议使用STelnet V2登录设备。
配置思路采用如下的思路配置用户通过STelnet登录设备:1.PC端已安装登录SSH服务器软件。
2.在SSH服务器端生成本地密钥对,实现在服务器端和客户端进行安全地数据交互。
3.在SSH服务器端配置SSH用户client001。
4.在SSH服务器端开启STelnet服务功能。
5.在SSH服务器端配置SSH用户client001服务方式为STelnet。
6.用户client001以STelnet方式登录SSH服务器。
操作步骤1.在服务器端生成本地密钥对2.<HUAWEI> system-view3.[HUAWEI] sysname SSH_Server4.[SSH_Server] dsa local-key-pair create: The key name will be:HUAWEI_Host_DSA.: The key modulus can be any one of the following : 512, 1024,2048.: If the key modulus is greater than 512, it may take a fewminutes.8.Please input the modulus[default=2048]:: Generatingkeys...Info: Succeeded in creating the DSA host keys.10.在服务器端创建SSH用户# 配置VTY用户界面。
华为交换机配置SSH登陆方法

华为交换机配置SSH登陆方法一、配置设备基本信息首先,我们需要对华为交换机进行一些基本的配置,包括设置设备名称、域名和管理口IP地址等信息。
可通过以下命令进行配置:sysname 设备名称domain domain-name 域名interface 接口名称ip address ip-address { mask , mask-length }其中,设备名称为自定义的名称,域名为网络中的域名,IP地址为管理口的IP地址。
配置完成后,可以通过display current-configuration命令来查看当前的配置信息。
二、生成SSH密钥对生成SSH密钥对是配置SSH登录的重要步骤。
华为交换机支持RSA、DSA和ECDSA等多种加密算法。
以下是生成RSA密钥对的命令示例:sysname 设备名称user-interface vty 0 4ssh authentication-type rsa生成密钥对的具体步骤如下:1.创建RSA密钥对:rsa local-key-pair create创建密钥对时,系统会要求设置密钥长度,可以根据实际需求选择合适的长度。
2.显示密钥对信息:display rsa local-key-pair该命令可以查看当前设备的RSA密钥对信息。
3.导出密钥对到文件:rsa export local-key-pair file file-name通过该命令可以将生成的密钥对保存到文件中,方便备份和导入到其他设备中。
三、配置SSH登录在华为交换机上配置SSH登录,需要设置SSH服务参数、用户权限和登录方式等。
以下是配置SSH登录的命令示例:sysname 设备名称ssh server enablessh authentication-type default allssh user 用户名 authentication-type aaassh user 用户名 service-type stelnet其中,第一条命令用于启用SSH服务,第二条命令设置默认认证方式为全部认证(包括密码和密钥认证),第三条命令设置用户的认证方式为AAA认证,第四条命令设置用户的服务类型为STelnet。
S5700交换机初始化和配置

华为S5700交换机初始化和配置TELNET远程登录方法:1,交换机开启Telnet服务<Huawei>system-view #进入系统视图[Huawei]telnet server ? #查看有enable还是disable选项,选择对应的开启方式。
[Huawei]telnet server enable #enable选项开启Telnet服务(普通系列一般为这个)[Huawei]undo telnet server disable #disable选项开启Telnet服务(CE高端系列一般为这个)2,配置VTY用户界面的最大个数(同时可以登录的最大数)[Huawei]user-interface maximum-vty 15 #默认是5,这个可以不设置3,配置VTY用户界面的终端属性[Huawei]user-interface vty 0 14 #上面是15所有这里是0 14 如果选择默认这里是0 4 [Huawei-ui-vty0-14]protocol inbound telnet #配置vty支持telnet协议4,配置VTY用户界面的用户验证方式[Huawei-ui-vty0-14]authentication-mode aaa #配置用户终端的身份验证模式为aaa认证为aaa认证[Huawei-ui-vty0-14]quit #退出vty配置界面5,配置登录验证方式[Huawei]aaa #进入aaa配置模式[Huawei-aaa]local-user admin1234 password ? #查看可以选择的密码选择[Huawei-aaa]local-user admin1234 password simple Huawei1234 #密码选项simple 账号admin1234 密码Huawei1234 (普通系列一般为这个)[Huawei-aaa]local-user admin1234 password irreversible-cipher Huawei12#$ #密码选项irreversible-cipher 账号admin1234 密码Huawei12#$ (CE高端系列一般为这个)[Huawei-aaa]local-user admin1234 service-type telnet #配置接入服务类型,如果还需要SSH 登录请加上[Huawei-aaa]local-user admin1234 privilege level 3 #配置账号的级别,默认3级是超级管理员的权限[Huawei-aaa]quit #退出<Huawei>telnet 127.0.0.1 #测试telnet配置是否OK<Huawei>save #保存配置===================================================================华为S5700交换机初始化和配置SSH和TELNET远程登录方法:AAA是指:authentication(认证)、authorization(授权)、accounting(计费)的简称,是网络安全的一种管理机制;Authentication是本地认证/授权,authorization和accounting是由远处radius(远程拨号认证系统)服务或hwtacacs(华为终端访问控制系统)服务器完成认证/授权;AAA是基于用户进行认证、授权、计费的,而NAC方案是基于接入设备接口进行认证的,在实际应用中,可以使用AAA的一种或两种服务。
华为交换机S5700设置远程sshtelnet登录

华为交换机S5700设置远程sshtelnet登录AAA是指:authentication(认证)、authorization(授权)、accounting(计费)的简称,是⽹络安全的⼀种管理机制;Authentication是本地认证/授权,authorization和accounting是由远处radius(远程拨号认证系统)服务或hwtacacs(华为终端访问控制系统)服务器完成认证/授权;AAA是基于⽤户进⾏认证、授权、计费的,⽽NAC⽅案是基于接⼊设备接⼝进⾏认证的,在实际应⽤中,可以使⽤AAA的⼀种或两种服务如果是⼀台刚初始化过的华为交换机,需要输⼊两次相同的密码作为登录交换机的登录密码交换机上有console 端⼝ MEth管理端⼝ usb端⼝通过串⼝线配置S5700 的管理IP地址,串⼝线接在交换机的console⼝,ip设置完成后⽹线接在ETH⼝:<Quidway> system-view[Quidway] interface MEth 0/0/1[Quidway] interface MEth 0/0/1[Quidway-MEth0/0/1]ip address x.x.x.x 255.255.255.0 ///设置MEth管理端⼝的ip地址[Quidway-MEth0/0/1]quit[Quidway]ip route-static 0.0.0.0 0.0.0.0 x.x.x.x(gateway)[Quidway-MEth0/0/1]display ip interface MEth 0/0/1 ///查看MEth管理端⼝的配置信息[Quidway]添加⽤户,设置ssh telent远程登录<Quidway> system-view ///进⼊系统配置模式[Quidway]aaa ///进⼊AAA模式[Quidway-aaa]local-user chy password cipher qaz123456 ///设置本地⽤户名和密码 cipher加密[Quidway-aaa]local-user chy service-type ssh telnet ///设置⽤户设置登录ssh telnet服务[Quidway-aaa]display ssh server status ///查看ssh服务是否⽣效[Quidway-aaa]display telnet server status ///查看telnet服务是否⽣效[Quidway-aaa]local-user chy privilege level 15 ///设置⽤户级别[Quidway-aaa]q ///退出AAA模式设置vty 0 4远程登陆的虚拟端⼝VTY是路由器的远程登陆的虚拟端⼝,0 4表⽰可以同时打开5个会话,line vty 0 4是进⼊VTY端⼝,对VTY端⼝进⾏配置,⽐如说配置密码,或者ACL.[Quidway]user-interface vty 0 4 ///进⼊vty 0 4远程虚拟端⼝[Quidway-ui-vty0-4]authentication-mode aaa ///为虚拟⽤户终端配置AAA⾝份验证模式[Quidway-ui-vty0-4]user privilege level 15 ///为虚拟⽤户终端配置⽤户级别[Quidway-ui-vty0-4]protocol inbound all ///为虚拟⽤户终端配置使⽤的协议,all即都⽀持[Quidway-ui-vty0-4]protocol inbound telnet ///为虚拟⽤户终端配置telnet协议,即可以使⽤telnet远程登录[Quidway-ui-vty0-4]protocol inbound ssh ///为虚拟⽤户终端配置ssh协议,即⽤户可以使⽤ssh远程登录[Quidway]ssh user chy authentication-type password ///为chy⽤户设置ssh认证为password,此命令对设置单⼀⽤户设置来说⽐较实⽤[Quidway]ssh authentication-type default password ///设置ssh默认的认证⽅式为密码认证,对设置多个⽤户来说很实⽤[Quidway]ssh user chy service-type stelnet ///为chy⽤户设置ssh认证服务类型为stelnet[Quidway]display ssh user-information chy ///查看ssh服务chy⽤户的配置信息[Quidway]q ///退出系统设置视图<Quidway>save ///保存设置配置登陆IP地址<Quidway> system-view //进⼊系统配置模式[Quidway]interface Vlanif 1 //进⼊三层 vlanif 接⼝[Quidway-Vlanif1]ip address 192.168.0.1 255.255.255.0 //配置管理 IP 地址创建web登录管理账号[Quidway]http server enable ///系统视图下开启http服务[Quidway]http secure-server enable ///系统视图下开启http安全服务即https[Quidway]aaa //系统视图下进⼊aaa模式[Quidway-aaa]local-user admin privilege level 15 ///配置 http 登录名权限[Quidway-aaa]local-user admin service-type http /// 开启 http 登录服务[Quidway-aaa]quit /// 退出aaa模式创建vlan<Quidway>system-view ///进⼊系统配置模式[Quidway]vlan 10 ///创建vlan 10[Quidway-vlan10]quit ///退出系统配置模式[Quidway]interface Vlanif 10 ///进⼊配置vlan 10的模式[Quidway-Vlanif10]ip address 192.168.0.1 255.255.255.0 ///为vlan 10配置IP地址和掩码[Quidway-vlan10]quit ///退出系统配置模式[Quidway-GigabitEthernet0/0/2] ///进⼊端⼝2[Quidway-GigabitEthernet0/0/2]port link-type access ///端⼝类型设置为access[Quidway-GigabitEthernet0/0/2]port default vlan 10 ///将port加⼊到我们创建好的vlan 10[Quidway-GigabitEthernet0/0/2]display vlan ///查看配置的vlan信息[Quidway]q ///退出系统设置视图批量创建vlan<Quidway>system-view ///进⼊系统配置模式[Quidway]vlan batch 2 to 19 ///批量创建vlan 2-19 ,系统都会有⼀个默认的vlan 1 [Quidway]display vlan ///查看vlan信息[Quidway]q ///退出系统设置视图批量删除vlan<Quidway>system-view ///进⼊系统配置模式[Quidway]undo vlan batch 2 to 19 ///批量删除vlan 2-19 ,系统都会有⼀个默认的vlan 1[Quidway]display vlan ///查看vlan信息[Quidway]q ///退出系统设置视图批量把端⼝加⼊到vlan 10<Quidway>system-view ///进⼊系统配置模式[Quidway]interface range GigabitEthernet 0/0/1 to GigabitEthernet 0/0/6///将1⼝到6⼝添加到port-group,此处系统默认的给1⼝到6⼝添加到1个组⾥了。
配置华为交换机ssh方式登录

配置华为交换机ssh方式登录LAB2:配置SSH登陆(Passworkd认证)1.配置VTY界面的认证方式和协议[HW_FW]user-interface vty 0 4[HW_FW-ui-vty0-4]authentication-mode aaa[HW_FW-ui-vty0-4]protocol inbound ssh2.创建SSH用户,认证方式为password[HW_FW]ssh user sshuser[HW_FW]ssh user sshuser authentication-type password 3.配置Client的密码为C1sco123,服务方式为ssh[HW_FW]aaa[HW_FW-aaa]local-user sshuser password cipher C1sco123 [HW_FW-aaa]local-user sshuser service-type ssh4.生成密钥对[HW_FW]rsa local-key-pair create20:30:02 2014/06/02The key name will be: HW_FW_HostThe range of public key size is (512 ~ 2048).NOTES: If the key modulus is greater than 512,It will take a few minutes.Input the bits in the modulus[default = 768]:2048 Generating keys..........++++++...++++++ ..........................................++++++++ ..............++++++++5.启用STelent/SFTP服务[HW_FW]stelnet server enable[HW_FW]sftp server enable6.启用STelnet和SFTP[HW_FW]ssh user sshuser service-type stelnet[HW_FW]ssh user sshuser service-type sftp注:如果用户采用SFTP服务登录时,需要执行ssh user sftp-directory命令,配置SSH用户的SFTP服务授权目录。
s5700 ssh用法

s5700 ssh用法SSH(Secure Shell)是一种加密的网络传输协议,用于在不安全的网络环境中实现安全的远程登录和数据传输。
华为S5700系列交换机支持SSH功能,可以帮助您安全地管理网络设备。
要在S5700交换机上使用SSH,请按照以下步骤操作:1. 配置加密密钥:交换机上配置SSH时,首先需要生成一对加密密钥,用于加密和解密数据。
使用以下命令配置加密密钥:```crypto key generate rsa```2. 配置SSH:使用以下命令启用SSH服务,并设置端口号、加密算法等参数:```interface vlan 1ip address 192.168.1.1 255.255.255.0crypto map SSL-MAP-1map ip address 192.168.1.1 255.255.255.0map layer 3 address 192.168.1.1 255.255.255.0```3. 配置登录认证:使用以下命令配置SSH登录认证,指定用户名和密码:```user-interface vlan 1authentication ip-address your-username your-password ```4. 保存配置:使用以下命令保存配置:```save```完成以上步骤后,您可以通过SSH客户端(如PuTTY)连接到S5700交换机。
在使用SSH连接时,请确保使用正确的IP地址、端口号、用户名和密码。
需要注意的是,为了保证安全,建议使用加密的SSH传输数据,避免使用明文传输。
同时,定期更改密码也是提高安全性的重要措施。
华为S5700汇聚层交换机参数

Quidway S5700系列全千兆企业网交换机产品概述:Q uidway S5700系列全千兆企业网交换机(以下简称S5700),是华为公司为满足大带宽接入和以太网多业务汇聚而推出的新一代绿色节能的全千兆高性能以太网交换机。
它基于新一代高性能硬件和华为公司统一的VRP?( Versatile RoutingPlatform)平台,具备大容量、高密度千兆端口,可提供万兆上行,充分满足客户对高密度千兆和万兆上行设备的需求,同时针对企业网用户的园区网接入、汇聚、IDC千兆接入以及千兆到桌面等多种应用场景,融合了可靠、安全、绿色环保等先进技术,采用简单便利的安装维护手段,帮助客户减轻网络规划、建设和维护的压力,助力企业搭建面向未来的IT网络。
S5700系列以太网交换机为盒式设备,机箱高度为1U,提供标准型(SI)和增强型(EI)两种产品版本。
标准型支持二层和基本的三层功能,增强型支持复杂的路由协议和更为丰富的业务特性。
产品规格:强大的多业务支持能力S5700支持IGMP v1/v2/v3 Snooping/Filter/FastLeave/Proxy等协议。
S5700支持线速的跨VLAN组播复制功能,支持捆绑端口的组播负载分担,支持可控组播,可以充分满足IPTV 和其他组播业务的需求。
S5700支持MCE 功能,实现了不同VPN用户在同一台设备的隔离,有效解决用户数据安全问题,同时降低用户投资成本。
完备的高可靠保护机制S5700不仅支持传统的STP/RSTP/MSTP生成树协议,还支持SmartLink和RRPP等增强型以太网技术,可以实现毫秒级链路保护倒换,保证高可靠性的网络质量。
此外,针对Smartlink 和 RRPP均提供多实例功能,可实现链路负载分担,进一步提高了链路带宽利用率。
S5700支持以太Trunk(E-Trunk)功能。
在使用ETrunk之后,CE设备可以通过E-Trunk双归接入到两台PE设备上。
华为S5700-HI系列高速 ги格勒网关开关系列说明书

BrochureProduct OverviewBased on next-generation, high-performance hardware and Huawei Versatile Routing Platform (VRP), the S5700-HI provides excellent NetStream function, flexible Ethernet networking, comprehensive VPN tunneling technologies, diversified security mechanisms, mature IPv6 features, and are easy to manage and maintain. All these features make the S5700-HI the best choice as an access switch on large and medium-sized campus networks or data centers and aggregation switch on smallcampus networks.S5700-HI mentioned in this document refers to the whole S5700-HI series including S5710-HI, and descriptions about S5710-HI are unique features of S5710-HI.Models and AppearancesModels and AppearanceDescriptionS5700-28C-HI● 24x10/100/1000Base-T ports●Subcards supported: 4x1000Base-X SFP subcard, 2x10GE SFP+ subcard, and 4x10GE SFP+ subcard● Double swappable AC/DC power supplies ●Forwarding performance: 96 Mpps ●Switching capacity: 256GbpsS5700-28C-HI-24S● 24x100/1000Base-X ports●Subcards supported: 4x1000Base-X SFP subcard, 2x10GE SFP+ subcard, and 4x10GE SFP+ subcard● Double swappable AC/DC power supplies ● Forwarding performance: 96 Mpps ● Switching capacity: 256GbpsS5710-108C-PWR-HI (front)● 48x10/100/1000BASE-T ports and 8 x 10GE SFP+ ports●Three slots on the front panel: support 16x1000Base-X SFP subcard and 16x10/100/1000Base-T subcard●One slot at the real panel: supports 4x40GE QSFP+ subcard and 4x10GE SFP+ subcardS5710-108C-PWR-HI (back) ●Double swappable AC power supplies ●Forwarding performance: 504 Mpps ●Switching capacity: 1024GbpsFeatures and HighlightsVarious Combinations of Ports●The S5710-HI has four subcard slots that can accommodate various extended subcards to provide high-density10GE/40GE uplink ports. With its eight fixed 10GE SFP+ ports, the S5710-HI can have different subcards installed to provide flexible combination of ports, including 48xGE+8x10GE, 96xGE+8x10GE, 96xGE+12x10GE, and 96xGE+8x10GE+4x40GE. In addition, the S5710-HI provides both optical and electrical ports for flexible access and supports PoE+. The flexible port combinations meet different bandwidth upgrading requirements and protect customers' investment.Comprehensive VPN Technologies●The S5700-HI allows users in different VPNs to connect to the same switch and isolates users through multi-instance routing. The S5700-HI supports Multi-Protocol Label Switching (MPLS) QoS, MPLS Traffic Engineering (TE), Virtual Leased Line (VLL), Virtual Private LAN Service (VPLS), and Layer 3 Virtual Private Network (L3VPN). They can provide high-quality private line access services for enterprises and are cost-effective case-shaped MPLS switches.Flexible Ethernet Networking●In addition to traditional Spanning Tree Protocol (STP), Rapid Spanning Tree Protocol (RSTP), and Multiple Spanning Tree Protocol (MSTP), the S5700-HI supports Huawei-developed Smart Ethernet Protection (SEP) technology and the latest Ethernet Ring Protection Switching (ERPS) standard. SEP is a ring protection protocol specific to the Ethernet link layer, and applies to various ring network topologies, such as open ring topology, closed ring topology, and cascading ring topology. This protocol is reliable, easy to maintain, and implements fast protection switching within 50 ms. ERPS is defined in ITU-T G.8032. It implements millisecond-level protection switching based on traditional Ethernet MAC and bridging functions.●The S5700-HI supports Smart Link and Virtual Router Redundancy Protocol (VRRP), which implement backup of uplinks. One S5700-HI switch can connect to multiple aggregation switches through multiple links, significantly improving reliability of access devices. In addition, the S5700-HI provides multiple connection fault detection mechanisms, including Ethernet OAM (IEEE 802.3ah/802.1ag /ITU Y.1731) and Bidirectional Forwarding Detection (BFD). The S5700-HI (except S5710-HI) provides hardware-based 3.3 ms Ethernet OAM detection cycle and 10 ms BFD detection cycle.Diversified Security Control●With enhanced network admission control (NAC) functions, the S5700-HI supports 802.1x authentication, MAC address authentication, Portal authentication, and hybrid authentication, and can dynamically delivery user policies such as VLANs, QoS policies, and access control lists (ACL).●The S5700-HI provides a series of mechanisms to defend against DoS attacks and user-targeted attacks. DoS attacks are targeted at switches and include SYN flood, Land, Smurf, and ICMP flood attacks. User-targeted attacks include bogus DHCP server attacks, IP/MAC address spoofing, DHCP request flood, and change of the DHCP CHADDR value. You can specify DHCP snooping trusted and untrusted ports to ensure that users connect only to the authorized DHCP server.●The S5700-HI supports strict ARP learning. This feature prevents ARP spoofing attackers from exhausting ARP entries so that users can connect to the Internet normally.Easy-Operation●The S5700 supports Easy-Operation, a solution that provides auto configuration, plug-and-play, USB-based deployment, and batch remote upgrade. The Easy-Operation solution facilitates device deployment, upgrade, service provisioning, and other management and maintenance operations, and also greatly reduces costs of operation and maintenance.●The S5700 can be managed and maintained using Simple Network Management Protocol (SNMP) V1, V2, and V3, Command Line Interface (CLI), web-based network management system, or Secure Shell (SSH) V2.0. Additionally, it supportsremote network monitoring (RMON), multiple log hosts, port traffic statistics collection, and network quality analysis that help in network consolidation and reconstruction.●The S5700-HI can use the GARP VLAN Registration Protocol (GVRP) to implement dynamic distribution, registration, and propagation of VLAN attributes. GVRP reduces manual configuration workload and ensures correct configuration. Besides, the S5700-HI supports the MUX VLAN function, which involves a principal VLAN and multiple subordinate VLANs. Subordinate VLANs are classified into group VLANs and separate VLANs. Ports in the principal VLAN can communicate with ports in subordinate VLANs. Ports in a subordinate group VLAN can communicate with each other, whereas ports in a subordinate separate VLAN can communicate only with ports in the principal VLAN.●EasyDeploy: The Commander collects information about the topology of the client connecting to the Commander and saves client startup information based on the topology. The client can be replaced without configuration. Configuration and scripts can be delivered to the client in batches. In addition, the configuration delivery result can be queried.●The Commander can collect and display power consumption on the entire network.Mature IPv6 Technologies●The S5700-HI uses the mature, stable Versatile Routing Platform (VRP) and supports IPv4/IPv6 dual stacks, IPv6 routing protocols (RIPng, OSPFv3, BGP4+, and IS-IS for IPv6), and IPv6 over IPv4 tunnels including manual, 6-to-4, and Intra-Site Automatic Tunnel Addressing Protocol (ISATAP) tunnels. With these IPv6 features, the S5700-HI can be deployed on a pure IPv4 network, a pure IPv6 network, or a shared IPv4/IPv6 network, helping realize IPv4-to-IPv6 transition.Excellent Network Traffic Analysis●The S5700-HI provides the NetStream function and can function as a NetStream data exporter. It periodically collects data traffic statistics, encapsulates the statistics in standard V5, V8, or V9 packets, and sends the packets to the NetStream data collector according to NetStream configuration. The collected statistics are then processed to dynamically generate reports, analyze traffic attributes, and generate alarms on abnormal traffic. The NetStream function helps you optimize network structure and adjust resource deployment in a timely manner.●The S5700-HI supports the sFlow function. It uses a method defined in the sFlow standard to sample traffic passing through it and sends sampled traffic to the collector in real time. The collected traffic statistics are used to generate statistical reports, helping enterprises maintain their networks.Product SpecificationsFixed ports 24 10/100/1000Base-T 24 100/1000Base-X 48 10/100/1000BASE-T, 810GE SFP+Extended slots 1 extended slot:●Optional subcard 1: 2 10GESFP+ interface card●Optional subcard 2: 4 10GESFP+ interface card●Optional subcard 3: 41000BASE-X interface card 1 extended slot:●Optional subcard 1: 2 10GESFP+ interface card●Optional subcard 2: 4 10GESFP+ interface card●Optional subcard 3: 41000BASE-X interface card3 front extended slots:●Optional subcard 1: 1610/100/1000BASE-Tinterface card●Optional subcard 2: 161000BASE-X interfacecard1 rear extended slot:●Optional subcard 1: 410GE SFP+ interfacecard (no GE autoadaption)●Optional subcard 2: 440GE QSFP+ interfacecardMAC address table IEEE 802.1d compliance32K MAC address entries IEEE 802.1d compliance32K MAC address entriesIEEE 802.1d compliance456K MAC address entriesMAC address learning andMAC address learning and aging Static, dynamic, and blackhole MAC address entriesPacket filtering based on source MAC addresses MAC address learning and agingStatic, dynamic, and blackholeMAC address entriesPacket filtering based on sourceMAC addressesagingStatic, dynamic, andblackhole MAC addressentriesPacket filtering based onsource MAC addressesVLAN 4K VLANsGuest VLAN and voice VLANGVRPMUX VLANVLAN assignment based on MAC addresses, protocols, IP subnets, policies, and ports1:1 and N:1 VLAN MappingReliability RRPP ring topology and RRPP multi-instanceSmart Link tree topology and Smart Link multi-instance, providing the millisecond-level protectionswitchoverSEPERPS(G.8032)BFD for OSPF, BFD for IS-IS, BFD for VRRP, and BFD for PIMSTP(IEEE 802.1d), RSTP(IEEE 802.1w), and MSTP(IEEE 802.1s)BPDU protection, root protection, and loop protectionMPLS features MPLS L3VPNMPLS L2VPN(VPWS/VPLS)MPLS-TEMPLS QoSIP routing Static routing, RIPv1/v2, OSPF, IS-IS, BGP, and ECMPIPv6 features Neighbor Discovery (ND)Path MTU (PMTU)IPv6 ping, IPv6 tracert6to4 tunnel, ISATAP tunnel, and manually configured tunnelACLs based on the source IPv6 address, destination IPv6 address, Layer 4 ports, or protocol typeIPv6 Static routing, RIPng, OSPFv3, IS-ISv6, BGP4+, ECMPMulticast IGMP v1/v2/v3 snooping and IGMP fast leaveMLD v1/v2 snoopingMulticast forwarding in a VLAN and multicast replication between VLANsMulticast load balancing among member ports of a trunkControllable multicastPort-based multicast traffic statisticsIGMPv1/v2/v3, MLDv1/v2, PIM-SM, PIM-DM, PIM-SSM, MSDPQoS/ACL Rate limiting on packets sent and received by an interfacePacket redirectionPort-based traffic policing and two-rate three-color CAREight queues on each portWRR, DRR, PQ, WRR+PQ, and DRR+PQ queue scheduling algorithmsWREDRe-marking of the 802.1p priority and DSCP priorityPacket filtering at Layer 2 to Layer 4, filtering out invalid frames based on the source MAC address,destination MAC address, source IP address, destination IP address, TCP/UDP port number,protocol type, and VLAN IDRate limiting in each queue and traffic shaping on portsSecurity User privilege management and password protectionDoS attack defense, ARP attack defense, and ICMP attack defenseBinding of the IP address, MAC address, interface, and VLANPort isolation, port security, and sticky MACBlackhole MAC address entriesLimit on the number of learned MAC addresses802.1x authentication and limit on the number of users on an interfaceAAA authentication, RADIUS authentication, HWTACACS authentication, and NACSSH v2.0Hypertext Transfer Protocol Secure (HTTPS)CPU defenseBlacklist and whitelistOAM Hardware OAM:●EFM OAM●CFM OAM●Y.1731 performance test(hardware-level delay andjitter detection) Hardware OAM:●EFM OAM●CFM OAM●Y.1731 performance test(hardware-level delay and jitterdetection)Software OAM:●EFM OAM●CFM OAM●Y.1731 performancetestManagement and maintenance iStackMAC Forced Forwarding (MFF)Virtual cable testSNMP v1/v2c/v3RMONWeb-based NMSSystem logs and alarms of different levels 802.3az EEEsFlowNetStreamDying gaspOperating environment ●Operating temperature: 0°Cto 50°C●Relative humidity: 5% to 95%(non-condensing)●Operating temperature: 0°C to50°C●Relative humidity: 5% to 95%(non-condensing)●Operating temperature:0°C to 50°C●Relative humidity: 5%to 95% (non-condensing)Input voltage AC:●Rated voltage range: 100 V to240 V AC, 50/60 Hz●Maximum voltage range: 90 Vto 264 V AC, 50/60 Hz AC:●Rated voltage range: 100 V to240 V AC, 50/60 Hz●Maximum voltage range: 90 Vto 264 V AC, 50/60 HzAC:●Rated voltage range:100 V to 240 V AC,50/60 Hz●Maximum voltagerange: 90 V to 264 VDC:●Rated voltage range: –48 V to–60 V, DC●Maximum voltage range: –36V to –72 V, DC DC:●Rated voltage range: –48 V to–60 V, DC●Maximum voltage range: –36V to –72 V, DCAC, 50/60 HzDC:●Rated voltage range: –48 V to –60 V, DC●Maximum voltagerange: –36 V to –72 V,DCPower consumption <76 W <80 W < 1680 W (Device: 240W,PoE: 1440W)Networking and ApplicationsOn Medium-sized Enterprise NetworksThe S5710-HI can function as a core switch on a medium-sized enterprise network. With four extended slots, the S5710-HI can have various subcards installed to provide more interfaces and bandwidth for fast increasing services.On Large-sized Enterprise NetworksThe S5700-HI can function as an access device on a large-sized enterprise network or an aggregation device on a small-sized or medium-sized campus network. It supports link aggregation and dual-homing to improve network reliability.In Data CentersThe S5700-HI can be used in a data center. It connects to gigabit servers and aggregates traffic from the servers to uplink devices through trunk links. If multiple servers are available, an S5700 stack can be used to facilitate network maintenance and improve network reliability.Ordering InformationThe following table lists ordering information of the S5700-HI series switches.Part Number Description02353631 S5700-28C-HI-24S (24xGig SFP, with 1 interface slot)02353630S5700-28C-HI (24xEthernet 10/100/1000 ports, with 1 interface slot)02354043 S5710-108C-PWR-HI (48xEthernet 10/100/1000 ports, 8x10 Gig SFP+, PoE+, with 4 interface slots) 03021JYN 2x10 Gig SFP+ Interface Card (used in S5700-HI series)03021JYM 4x10 Gig SFP+ Interface Card (used in S5700-HI series)03021JYP 4xGig SFP Interface Card (used in S5700-HI series)03021PED 16xGig SFP Interface Card (used in S5710-HI series)03021NXB 16xEthernet 10/100/1000 ports Interface Card (used in S5710-HI series)03021NKW 4x40 Gig QSFP+ Interface Card (used in S5710-HI series)03021PHQ 4x10 Gig SFP+ Interface Card (used in S5710-HI series)02310GBM 170W DC Power Module (used in S5700-HI series)02130966 170W AC Power Module (used in S5700-HI series)02130971 350W AC Power Module (used in S5710-HI series)02130984 1150W AC PoE Power ModuleMore InformationFor more information about Huawei Campus Switches, visit or contact us in the following ways:●Global service hotline: /en/service-hotline●Logging in to the Huawei Enterprise technical support website: /enterprise/●Sending an email to the customer service mailbox: ********************Copyright © Huawei Technologies Co., Ltd. 2018. All rights reserved.No part of this document may be reproduced or transmitted in any form or by any means without prior writtenconsent of Huawei Technologies Co., Ltd.Trademarks and Permissionsand other Huawei trademarks are trademarks of Huawei Technologies Co., Ltd.All other trademarks and trade names mentioned in this document are the property of their respective holders.NoticeThe purchased products, services and features are stipulated by the contract made between Huawei and thecustomer. All or part of the products, services and features described in this document may not be within thepurchase scope or the usage scope. Unless otherwise specified in the contract, all statements, information, and recommendations in this document are provided "AS IS" without warranties, guarantees or representations of any kind, either express or implied.The information in this document is subject to change without notice. Every effort has been made in the preparation of this document to ensure accuracy of the contents, but all statements, information, and recommendations in this document do not constitute a warranty of any kind, express or implied. Huawei Technologies Co., Ltd. Address:Huawei Industrial Base Bantian, Longgang Shenzhen 518129 People's Republic of ChinaWebsite:。
华为交换机S5720常用配置

4、Eth-Trunk 相关配置
• # 创建Eth-Trunk 1。 • <Quidway> system-view • [Quidway] sysname Switch • [Switch] interface eth-trunk 1 • [Switch-Eth-Trunk1] quit • #向Eth-Trunk中加入成员接口,将GE0/0/3加入
vlan 100 to 200 • [Switch-Eth-Trunk1] quit
5、 交换机接口开启关闭配置
• [Switch] interface gigabitethernet 0/0/3 • [Switch-GigabitEtherneห้องสมุดไป่ตู้0/0/3] shutdown • [Switch-GigabitEthernet0/0/3] undo
钥 • public-key-code end //退出公钥编辑视图,
这是在hex-data输入合法后,将生成密钥 • ssh user xxx assign rsa-key yyy //为SSH用户分
配公钥yyy
1、交换机接登录配置
• 如果创建的认证方式为password或password-rsa的SSH用户 • 则需要在AAA视图下创建同名的local-user用户 • 1、aaa • 2、local-user xxx password cipher ******* • 3、local-user xxx service-type ssh (不要设置成all,否则ssh进
•
//配置用户xxx的认证方式
1、交换机接登录配置
• 下面开始按认证方式的不同进行不同的配置操 作
• 配置认证方式为password • ssh user xxx authentication-type password • //该命令适用于本地认证或HWTACACS认证
s5700常用配置

华为S5700交换机初始化和配置SSH和TELNET远程登录方法基础设置:配置登陆IP地址<Quidway> system-view //进入系统配置模式[Quidway]interface Vlanif 1 //进入三层vlanif 接口[Quidway-Vlanif1]ip address192.168.0.1 255.255.255.0 //配置管理 IP 地址创建web登录管理账号[Quidway]http server enable ///系统视图下开启http服务[Quidway]http secure-server enable ///系统视图下开启http安全服务即https[Quidway]aaa //系统视图下进入aaa模式[Quidway-aaa]local-user admin privilege level 15 ///配置 http 登录名权限[Quidway-aaa]local-user admin service-type http /// 开启 http 登录服务[Quidway-aaa]quit /// 退出aaa 模式如果telnet能登录,但console反而不能登录的话,则需在aaa里把要登录的账户赋予权限[Quidway-aaa]local-user admin service-type terminal ssh telnet ftp创建vlan<Quidway>system-view ///进入系统配置模式[Quidway]vlan 10 ///创建vlan 10[Quidway-vlan10]quit ///退出系统配置模式[Quidway]interface Vlanif 10 ///进入配置vlan 10的模式[Quidway-Vlanif10]ip address 192.168.0.1 255.255.255.0 ///为vlan 10配置IP地址和掩码[Quidway-vlan10]quit ///退出系统配置模式[Quidway-GigabitEthernet0/0/2] ///进入端口2[Quidway-GigabitEthernet0/0/2]port link-type access///端口类型设置为access[Quidway-GigabitEthernet0/0/2]port default vlan 10 ///将port加入到我们创建好的vlan 10[Quidway-GigabitEthernet0/0/2]display vlan ///查看配置的vlan信息[Quidway]q ///退出系统设置视图批量创建vlan<Quidway>system-view ///进入系统配置模式[Quidway]vlan batch 2 to 19 ///批量创建vlan 2-19 ,系统都会有一个默认的vlan 1[Quidway]display vlan ///查看vlan信息[Quidway]q ///退出系统设置视图批量删除vlan<Quidway>system-view ///进入系统配置模式[Quidway]undo vlan batch 2 to 19 ///批量删除vlan 2-19 ,系统都会有一个默认的vlan 1[Quidway]display vlan ///查看vlan信息[Quidway]q ///退出系统设置视图批量把端口加入到vlan 10<Quidway>system-view ///进入系统配置模式[Quidway]interface range GigabitEthernet 0/0/1 to GigabitEthernet 0/0/6///将1口到6口添加到port-group,此处系统默认的给1口到6口添加到1个组里了。
华为交换机配置SSH登陆方法

华为交换机配置SSH登陆方法网络应用2008-04-06 12:15:43 阅读1093 评论3 字号:大中小订阅2.1 VRP1.74-01052.1.1 牛刀小试# 创建SSH用户,并配置相应的权限local-user huawei service-type administrator ssh password simple 3comlocal-user adm service-type operator ssh password simple adm# 设置系统所支持的远程登录协议SSH及最大连接数5[0-5可选,并可选择附加acl规则] protocol inbound ssh 5# 产生本地RSA密钥对rsa local-key-pair create# 配置SSH用户的验证方式为本地密码ssh user adm authentication-type passwordssh user huawei authentication-type password2.1.2 一夫当关# 创建SSH用户,并配置相应的权限local-user huawei service-type administrator ssh password simple 3comlocal-user adm service-type operator ssh password simple adm# 设置系统所支持的远程登录协议SSH及最大连接数5[0-5可选,并可选择附加acl规则] protocol inbound ssh 5# 产生本地RSA密钥对,但是disp current-configuration此命令是不显示的。
rsa local-key-pair create# 进入公共密钥视图,配置客户端产生的公钥,p1是名字,可以任意指定,密钥产生见下章# 配置的顺序一定不能颠倒,密钥的内容此处仅是举例,看过第三章请再配置rsa peer-public-key p1public-key-code beginhex 308186hex 028180hex 91ADC5A6 7C855676 2958E6E9 960559D6 3F606C86 5BE1C74C EA313F81hex BAC7437D 297A422C 8A0D9C9E AAC8276D E0DC21B9 DCA937C2 846AFFDFhex 987AEFE1 6204CC63 0C881FC1 7848297C 82B0B443 5EEDA260 27A7B744 hex 3280B68E 84194DCD 78D89B9E 35EF76C2 B382A538 80DBBA80 60219F04 hex E5034168 60EEC72A 53598B6F FB3A5365hex 0201hex 25public-key-code end# 配置SSH用户的验证方式为RSA方式,all同时包含了RSA和password方式ssh user adm authentication-type rsassh user huawei authentication-type all2.1.3 不要忘记# 本地管理员权限用户[使用console口登录],这个不需密码local-user 3com service-type administrator# 本地管理员权限用户[使用console口登录],这个需要密码local-user a service-type administrator password simple a# 既然配置成功了SSH,那就关掉telnet吧[允许telnet用户数为0]protocol inbound telnet 0#AAA需要打开aaa-enable2.1.4 选配的参数# 设置服务器密钥的更新时间,路由器缺省不对服务器密钥进行更新。
S5700交换机初始化和配置

华为S5700交换机初始化和配置TELNET远程登录方法:1,交换机开启Telnet服务<Huawei>system-view #进入系统视图[Huawei]telnet server #查看有enable还是disable选项,选择对应的开启方式。
[Huawei]telnet server enable #enable选项开启Telnet服务(普通系列一般为这个)[Huawei]undo telnet server disable #disable选项开启Telnet服务(CE高端系列一般为这个)2,配置VTY用户界面的最大个数(同时可以登录的最大数)[Huawei]user-interface maximum-vty 15 #默认是5,这个可以不设置3,配置VTY用户界面的终端属性[Huawei]user-interface vty 0 14 #上面是15所有这里是0 14 如果选择默认这里是0 4[Huawei-ui-vty0-14]protocol inbound telnet #配置vty支持telnet协议4,配置VTY用户界面的用户验证方式[Huawei-ui-vty0-14]authentication-mode aaa #配置用户终端的身份验证模式为aaa认证为aaa认证[Huawei-ui-vty0-14]quit #退出vty配置界面5,配置登录验证方式[Huawei]aaa #进入aaa配置模式[Huawei-aaa]local-user admin1234 password #查看可以选择的密码选择[Huawei-aaa]local-user admin1234 password simple Huawei1234 #密码选项simple 账号admin1234 密码Huawei1234 (普通系列一般为这个)[Huawei-aaa]local-user admin1234 password irreversible-cipher Huawei12#$ #密码选项irreversible-cipher 账号admin1234 密码Huawei12#$ (CE高端系列一般为这个)[Huawei-aaa]local-user admin1234 service-type telnet #配置接入服务类型,如果还需要SSH登录请加上[Huawei-aaa]local-user admin1234 privilege level 3 #配置账号的级别,默认3级是超级管理员的权限[Huawei-aaa]quit #退出<Huawei>telnet #测试telnet配置是否OK<Huawei>save #保存配置===================================================================华为S5700交换机初始化和配置SSH和TELNET远程登录方法:AAA是指:authentication(认证)、authorization(授权)、accounting(计费)的简称,是网络安全的一种管理机制;Authentication是本地认证/授权,authorization和accounting是由远处radius(远程拨号认证系统)服务或hwtacacs(华为终端访问控制系统)服务器完成认证/授权;AAA是基于用户进行认证、授权、计费的,而NAC方案是基于接入设备接口进行认证的,在实际应用中,可以使用AAA的一种或两种服务。
华为_S5700_基础配置命令

华为 S5700 基础配置命令以下配置中,红色字体是需要自定义的.#清除设备配置<Quidway>reset saved-configurationWarning: The action will delete the saved configuration in the device.The configuration will be erased to reconfigure. Continue? [Y/N]:Y<Quidway>rebootWarning: All the configuration will be saved to the configuration file for the next startup:flash:/vrpcfg.zip, Continue?[Y/N]:NSystem will reboot! Continue?[Y/N]:Y# 设置设备的名称为GSH-FZ-Front<Quidway> system-view[Quidway] sysname Quidway# 设置查看设备的时区,时间<Quidway> clock timezone BJ add 8<Quidway> clock datetime 18:20:30 2012-02-08<Quidway> display clock#telnet 远程登录<Quidway> system-view[Quidway] aaa//////[Quidway-aaa] local-user ccssoft password cipher p@ssw0rd privilege level 15 [Quidway-aaa] local-user ccssoft password simple ccssoft[Quidway-aaa] local-user ccssoft service-type telnet[Quidway-aaa] local-user ccssoft privilege level 15 //特权等级设置[Quidway-aaa] quit[Quidway]user-interface vty 0 4 //设置5个虚拟终端,也就是说最多有5个终端同时连接[Quidway - vty0-4]authentication-mode aaa //验证方式设置[Quidway -ui-vty0-4]quit#ssh 远程登录步骤 1 在服务器端生成本地密钥对<Quidway> system-view[Quidway] sysname SSH Server[SSH Server] rsa local-key-pair createThe key name will be: Quidway_HostThe range of public key size is (512 ~ 2048).NOTES: If the key modulus is greater than 512,It will take a few minutes.Input the bits in the modulus[default = 512]: 768Generating keys..........++++++++++++..........++++++++++++ ...................................++++++++......++++++++步骤 2 在服务器端配置VTY 用户界面[SSH Server] user-interface vty 0 4[SSH Server-ui-vty0-4] authentication-mode aaa[SSH Server-ui-vty0-4] protocol inbound ssh[SSH Server-ui-vty0-4] quit说明若配置登录协议为SSH,则S5700 设备将自动禁止Telnet 功能。
华为交换机配置SSH登陆方法

华为交换机配置SSH登陆方法网络应用2008-04-06 12:15:43 阅读1093 评论3 字号:大中小订阅2.1 VRP1.74-01052.1.1 牛刀小试# 创建SSH用户,并配置相应的权限local-user huawei service-type administrator ssh password simple 3comlocal-user adm service-type operator ssh password simple adm# 设置系统所支持的远程登录协议SSH及最大连接数5[0-5可选,并可选择附加acl规则] protocol inbound ssh 5# 产生本地RSA密钥对rsa local-key-pair create# 配置SSH用户的验证方式为本地密码ssh user adm authentication-type passwordssh user huawei authentication-type password2.1.2 一夫当关# 创建SSH用户,并配置相应的权限local-user huawei service-type administrator ssh password simple 3comlocal-user adm service-type operator ssh password simple adm# 设置系统所支持的远程登录协议SSH及最大连接数5[0-5可选,并可选择附加acl规则] protocol inbound ssh 5# 产生本地RSA密钥对,但是disp current-configuration此命令是不显示的。
rsa local-key-pair create# 进入公共密钥视图,配置客户端产生的公钥,p1是名字,可以任意指定,密钥产生见下章# 配置的顺序一定不能颠倒,密钥的内容此处仅是举例,看过第三章请再配置rsa peer-public-key p1public-key-code beginhex 308186hex 028180hex 91ADC5A6 7C855676 2958E6E9 960559D6 3F606C86 5BE1C74C EA313F81hex BAC7437D 297A422C 8A0D9C9E AAC8276D E0DC21B9 DCA937C2 846AFFDFhex 987AEFE1 6204CC63 0C881FC1 7848297C 82B0B443 5EEDA260 27A7B744 hex 3280B68E 84194DCD 78D89B9E 35EF76C2 B382A538 80DBBA80 60219F04 hex E5034168 60EEC72A 53598B6F FB3A5365hex 0201hex 25public-key-code end# 配置SSH用户的验证方式为RSA方式,all同时包含了RSA和password方式ssh user adm authentication-type rsassh user huawei authentication-type all2.1.3 不要忘记# 本地管理员权限用户[使用console口登录],这个不需密码local-user 3com service-type administrator# 本地管理员权限用户[使用console口登录],这个需要密码local-user a service-type administrator password simple a# 既然配置成功了SSH,那就关掉telnet吧[允许telnet用户数为0]protocol inbound telnet 0#AAA需要打开aaa-enable2.1.4 选配的参数# 设置服务器密钥的更新时间,路由器缺省不对服务器密钥进行更新。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
华为交换机s5700 SSH 配置需求:PC机客户端通过SSH能够远程登录交换机进行远程管理。
步骤一,生成本地密钥对:
[test]rsa local-key-pair create
The key name will be: Auotnavi-callcenter-01_Host
The range of public key size is (512 ~ 2048).
NOTES: If the key modulus is greater than 512,
It will take a few minutes.
Input the bits in the modulus[default = 512]:1024
Generating keys...
.++++++
............++++++
...............++++++++
.++++++++
步骤二,配置VTY用户界面:
[Auotnavi-callcenter-01]user
[Auotnavi-callcenter-01]user-interface vty 0 4
[Auotnavi-callcenter-01-ui-vty0-4]authentication-mode aaa
[Auotnavi-callcenter-01-ui-vty0-4]protocol inbound ssh
步骤三,创建SSH用户及密码
#aaa
#local-user root password simple 123456
#local-user root privilege level 3
#local-user root service-type ssh
步骤四: 配置ssh用户的认证方式和服务方式
[Quidway] ssh user 用户名authentication-type password
或[Quidway] ssh authentication-type default password #如果用户过多可直接设置默认的认证方式
[Quidway] ssh user username service-type {sftp | stelnet | all } #这步骤没有配置,可能出现server refused to start a shell/command.
步骤五:使能ssh服务
[Quidway] stelnet server enable。
