CCNA、CCNP、CCIE模拟试题
思科认证CCNA认证试题与答案中文版

答案:D 注释:这个题目不是太严谨,应该加上子网掩码. A:224. 0. 0. 5 是多播地址 B: 127. 0.0. 0 保留作为测试使用 C:网络地址 26、 设置主接口由 up 转 down 后延迟 30 秒切换到备份接口,主 接口 由 down 转 up 后 60 秒钟切换回主接口的配置为()
忍一句,息一怒,饶一着,退一步。——《增广贤文》
人之为学,不日进则日退,独学无友,则孤陋而难成;久处一方,则习染而不自觉。——《顾炎武》
答案:D 注释:255. 255. 255. 255 是全网广播,DHCP 客户端发送全网广播来 查 找 DHCP 服务器. 24、 下而有关 NAT 叙述正确的是() (A) NAT 是英文“地址转换”的缩写,又称地址翻译 (B) XAT 用来实现私有地址与公用网络地址之间的转换 (C) 当内部网络的主机访问外部网络的时候,一定不需要 NAT (D) 地址转换的提出为解决 IP 地址紧张的问题提供了一个有效途 径 答案:ABD 25、 以下属于正确的主机的 IP 地址的是()
(A) arp-a (B) traceroute (C) routeprint (D) displayiprouting-table
答案:D 23、 D0. 0. 0 (B) 10. 0. 0. 1 (0127. 0. 0. 1 (D)255. 255. 255. 255
192. 168. 1. 1
答案:D 注释:PC 的'默认网关要指向路由器的以太网口的 IP 地址. 28、 ISDNB 信道速率是()
(A) 16kbps (B) 64kbps
2015年思科模拟题:CCNA、CCNP、CCIE模拟试题

2015年思科模拟题:CCNA、CCNP、CCIE模拟试题ccna1.which of the following types of packets will be allowed entry when a serial interface's inbound access list has been configured to prohibit entry for tcp and udp ports 21, 23 and 25? (select three options.)a. smtpb. stpc. ftpd. telnete. httpf. pop32.one of the trainees assigned to you want to know which services use tcp. what can you tell him? (select three options.)a. dhcpb. smtpc. snmpd. ftpe. httpf. tftp3.which of the following network masks would you use to reduce any wastage of ip addresses in point-to- point wan links on a network that supports vlsm?a. /38b. /30c. /27d. /23e. /184.how would you configure a router to avoid situations such as split horizon issues hampering routing updates on a frame relay network?a. configure a separate sub-interface for each pvc with a unique dlci and subnet assigned to the subinterface.b. configure each frame relay circuit as a point-to-point line to support multicast and broadcast traffic.c. configure one sub-interface to disperse into multiple pvc connections to multiple remote router interfaces.d. configure as many as possible sub-interfaces on the same subnet.5.with regard to isdn, which of the following are true? (choose all that apply.)a. legacy ddr can use port information to defineinteresting traffic.b. legacy ddr can configure multiple dialer configurations on the same interface.c. legacy ddr can use acls to define interesting traffic.d. hdlc or ppp can be used to encapsulate isdn d channel information.e. the bri interfaces on isdn routers with dialer profiles configured cannot belong to multiple dialer pools.f. dialer profiles cannot use acls to define interesting traffic.ccnp- bsci6.which of the following is a characteristic of link-state protocols?a. a network topology change generates an update that is broadcast to every router onthe network.b. the periodic routing update interval is slightly different in each router on a subnet.c. each router creates a routing table that only includes its directly connected neighbors.d. link-state protocols send routing updates only when there is a change in the networktopology.7.what is the term associated with synchronizing the routing tables after a topology change occurs?a. floodingb. broadcastingc. convergenced. summarization8.which of the following must be determined first by the router in order to route the data?a. the distance metric of the datab. the source address of the datac. which routing protocol is used by the datad. whether the protocol suite of the data is active9.you are a technician at abc. abc has the subnet/mask of 172.29.100.0/26 set aside for small remote locations. each location will have 5 ip devices connected to the network. which vlsm mask will provide the minimum number of hosts you require?a. /27b. /28c. /29d. /30e. /3110.you are a trainee technician at abc. your instructor shows you the following route summarization entry: 192.168.134.0/22 your instructor wants to know how many class c addresses are contained in this summarization. what would your reply be?a. 1b. 2c. 4d. 8e. 16- bcmsn11.which command enables an etherchannel bundle on a catalyst 2900xl switch?a. port groupb. set port channel onc. port etherchannel enabled. set etherchannel port enable12.which two statements about dynamic vlans are true? (choose two)a. each switch port is assigned to a specific vlan.b. dynamic vlans require a vlan membership policy server.c. devices are in the same vlan regardless of which port they attach to.d. dynamic vlan assignment are made through the command interface.13.which statement is correct about 802.1q trunking? (select all that apply)a. both switches must be in the same vtp domain.b. the encapsulation type of both ends of the trunk does not have to match.c. the native vlan on both ends of the trunk must be vlan 1.d. 802.1q trunking can only be configured on a layer 2 port.e. in 802.1q trunking, all vlan packets are tagged on the trunk link, except the native vlan.14.you need to take advantage of fastethernet ports. which two actions avoid configuration problems that cause the port to be automatically disabled? (choose two)a. allow some ports in a channel to be disabled.b. configure the ports in a channel as dynamic vlan ports.c. configure all ports in a channel to operate at the same speed and duplex mode.d. assign all ports in a channel to the same vlan orconfigure them as trunk ports.15.what is the cause of jitter?a. variable queue delaysb. packet dropsc. transmitting too many small packetsd. compression- bcran16.regarding dhcp, dhcp relay and dhcp server are mutually exclusive.a. none of the choices.b. truec. false only for certain ios versiond. falsee. false only for ios version below v1017.a lapd address field can be 1 or 2 bytes long.a. trueb. falsec. true only in the usd. true only in asiae. true only in europe18.which of the following are valid functions of the lock dte modem attribute (choose all that apply)?a. disable uart.b. enable uart.c. locks the data speed between the computer motherboard and the rs232 port.d. locks the data speed between the modem and the dte device.19.which of the following are not the valid types of atm addresses (choose all that apply)?a. dccb. gctc. bspd. icde. nsapf. aed20.which of the following are not the valid types of x.25 plp packet fields (choose all that apply)?a. user datab. lcic. gfid. ptie. none of the choices.- cit21.you are a technician at . your newly appointed abc trainee wants to know what the similarities between topology diagrams and network configuration tables are.what would your reply be? (choose all that apply.)a. both share few components.b. both share many of the same components.c. both define physical memory components.d. both are used for troubleshooting.e. both use lines and symbols to represent network components.22.you are a technician at . your newly appointed abc trainee wants to know what the default action for the output of debug and system error messages is. what would your reply be?a. output goes to the remote console if logging is off.b. output is sent to the console terminal.c. error logging automatically invokes debug output to the designated tftp server.d. output configuration requires a tftp server to write filese. output is written to a syslog server.23.you are the network administrator at . abc hasa switched network. you want to control the designation of the spanning-tree root bridge in the abc network. what should you do?a. by enabling uplink-fast on the ports of the desired switch.b. by lowering the bridge priority on the desired switch.c. by setting a lower mac address on the designated switch.d. by raising the bridge id on one switch.24.you are a technician at abc. you receive a report from several abc users who complain that they get slow responses when sending and receiving email, especially when browsing the internet. you investigate the complaint by checking the output of a ping command issued from her computer and find that it indicates intermitted success and failures messages, when attempting to contact the email server. a tracert to the corporate internet gateway router shows high latency and occasional time out messages.what would be the most effective troubleshooting approach if you are to determine the cause of the slow response time?a. bottom-up approachb. random access approachc. divide and conquer approachd. top-down approache. top-down rule-out approach25.you are a technician at . your newly appointed abc trainee wants to know what features make ospf more suitable than rp in large network installations. what would your reply be? (choose all that apply.)a. diffusing update algorithmb. no hop count limitationc. higher routing update overheadd. faster convergencee. lower routing update overheadccie26.you are the network administrator at abc. you are troubleshooting a network problem. you want to trace the route to a unix workstation that you want to reach through the internet. however, traceroute does not work.currently, there is an inbound access-list applied to the serial interface on router 1. an entry in the access-list states "access-list 101 permit tcp any any". what access-list entry may you need to be added to the access-list in order to get traceroute to work?a. access-list 101 permit udp any anyb. access-list 101 permit icmp any any time-exceeded access-list 101 permit icmp any any port-unreachablec. access-list 101 permit icmp any any time-exceeded access-list 101 permit icmp any any net-unreachabled. access-list 101 permit icmp any any echo access-list 101 permit icmp any any net-unreachablee. access-list 101 permit udp any any access-list 101 permit icmp any any protocol-unreachable27.what does the bgp backdoor command do?a. it changes the distance of an ibgp route to 20.b. it changes the distance of an ebgp route to 200.c. it changes the distance of an igp route to 20.d. it does not effect any changes in distance of the route.e. it changes the distance of an igrp route to 200.28.which of the following dns resource records is not valid?a. nsb. ptrc. mxd. fqdne. a29.which of the following features is provided by rip v2that were previously not possible with rip v1? (choose all that apply.)a. classless routing and split-horizon.b. poison reverse and updating to multicast addresses.c. poison reverse and classless routing.d. classless routing and updating to multicast addresses.e. route tag and classless routing.30.which of the following statements is valid when taking custom queuing into account?a. custom queuing has the ability to restrict a particular type of traffic to a given bandwidth not matter what is load is like on that link.b. custom queuing looks at groups of packets from the similar source-destination pairs.c. custom queuing will not proceed to a next queue unless the current queue is empty.d. custom queuing can prevent one type of traffic from dominating a busy link.。
CCNA考试题

C C N A考试题(总9页) -CAL-FENGHAI.-(YICAI)-Company One1-CAL-本页仅作为文档封面,使用请直接删除第一部分:选择题1:提供可靠数据传输、流控的是OSI的第几层()A、表示层B、网络层C、传输层D、会话层E、链路层2:子网掩码产生在那一层()A、表示层B、网络层C、传输层D、会话层3:当路由器接收的IP报文的目的地址不是本路由器的接口IP地址,并且在路由表中未找到匹配的路由项,采取的策略是()A、丢掉该分组B、将该分组分片C、转发该分组D、以上答案均不对4:当一台主机从一个网络移到另一个网络时,以下说法正确的是()A、必须改变它的IP地址和MAC地址B、必须改变它的IP地址,但不需改动MAC地址C、必须改变它的MAC地址,但不需改动IP地址D、MAC地址、IP地址都不需改动5:ISO提出OSI的关键是()A、系统互联B、提高网络速度C、为计算机制定标准D、经济利益6:OSI参考模型按顺序有哪些层()A、应用层、传输层、网络层、物理层B、应用层、表示层、会话层、网络层、传输层、数据链路层、物理层C、应用层、表示层、会话层、传输层、网络层、数据链路层、物理层D、应用层、会话层、传输层、物理层7:LAN的拓扑形式一般以()为主。
A、总线型B、环型C、令牌环D、载波侦听与冲突检测CSMA/CD8:网段地址154.27.0.0的网络,若不做子网划分,能支持()台主机A、254B、1024C、65,534D、16,777,2069:路由器网络层的基本功能是()。
A、配置IP地址B、寻找路由和转发报文C、将MAC地址解释成IP地址10:选出基于TCP协议的应用程序()。
A、PINGB、TFTPC、TELNETD、OSPF11:某公司申请到一个C类IP地址,但要连接6个的子公司,最大的一个子公司有26台计算机,每个子公司在一个网段中,则子网掩码应设为()。
A、255.255.255.0B、255.255.255.128C、255.255.255.192D、255.255.255.22412:B类地址的缺省掩码是()。
iscoccnp模拟试题与答案

C i s c o C C N P842-813e x a m Question:1uses layer 3 switches in the Core of their network. Which method of Layer 3 switching uses a forwarding information base (FIB)A. Topology-based switchingB. Demand-based switchingC. Route cachingD. Flow-based switchingE. None of the other alternatives applyAnswer: AQuestion:2You need to design the VLAN scheme for the network. Which two statements are true about best practices in VLAN design (Select two)A. Routing should occur at the access layer if voice VLANs are utilized. Otherwise, routingshould occur at the distribution layer.B. Routing should always be performed at the distribution layer.C. VLANs should be localized to a switch.D. VLANs should be localized to a single switch unless voice VLANs are being utilized.E. Routing should not be performed between VLANs located on separate switches. Answer: B, CQuestion:3If you needed to transport traffic coming from multiple VLANs (connected between switches),and your CTO was insistent on using an open standard, which protocol would you useA.B. spanning-treeC.D. ISLE. VTPF.Answer: CQuestion:4Under what circumstances should an administrator prefer local VLANs overend-to-endVLANsA. Eighty percent of traffic on the network is destined for Internet sites.B. There are common sets of traffic filtering requirements for workgroups located in multiplebuildings.C. Eighty percent of a workgroup’s traffic is to the workgroup’s own local server.D. Users are grouped into VLANs independent of physical location.E. None of the other alternatives applyAnswer: AQuestion:5What are some virtues of implementing end-to-end VLANs (Choose two)A. End-to-end VLANs are easy to manage.B. Users are grouped into VLANs independent of a physical location.C. Each VLAN has a common set of security and resource requirements for all members.D. Resources are restricted to a single location.Answer: B, CQuestion:6Which of the following statements is true about the 80/20 rule (Select all that apply)A. 20 percent of the traffic on a network segment should be localB. no more than 20 percent of the network traffic should be able to move across a backbone.C. no more than 80 percent of the network traffic should be able to move across a backbone.D. 80 percent of the traffic on a network segment should be localAnswer: B, DQuestion:7The LAN is becoming saturated with broadcasts and multicast traffic. What could you do to help a network with many multicasts and broadcastsA. Creating smaller broadcast domains by implementing VLANs.B. Separate nodes into different hubs.C. Creating larger broadcast domains by implementing VLANs.D. Separate nodes into different switches.E. All of the above.Answer: AQuestion:8The LAN switches are being configured to support the use of Dynamic VLANs. Which of the following are true of dynamic VLAN membership (Select all that apply) A. VLAN membership of a user always remains the same even when he/she is moved toanother location.B. VLAN membership of a user always changes when he/she is moved to another location.C. Membership can be static or dynamic.D. Membership can be static only.E. None of the other alternatives apply.Answer: A, CQuestion:9The LAN switches are being configured to support the use of Dynamic VLANs. What should be considered when implementing a dynamic VLAN solution (Select two)A. Each switch port is assigned to a specific VLAN.B. Dynamic VLANs require a VLAN Membership Policy Server.C. Devices are in the same VLAN regardless of which port they attach to.D. Dynamic VLAN assignments are made through the command line interface. Answer: B, CQuestion:10In the three-layer hierarchical network design model; what’s associated with the access layer(Select two)A. optimized transport structureB. high port densityC. boundary definitionD. data encryptionE. local VLANsF. route summariesAnswer: B, EQuestion:11You are assigning VLANs to the ports of switch PG1. What VLAN number value is anassigned to the default VLANA. VLAN 1003B. VLAN 1C. VLAN OND. VLAN AE. VLAN 0Answer: BQuestion:12The VLANs in switch PG1 are being modified. Which of the following are updated in PG1every time a VLAN is modified (Select all that apply)A. Configuration revision numberB. Configuration revision flag fieldC. Configuration revision reset switchD. Configuration revision databaseE. None of the other alternatives apply.Answer: A, DQuestion:13What is a characteristic of assigning a static VLAN membershipA. VMPS server lookup is requiredB. Easy to configureC. Easy of adds, moves, and changesD. Based on MAC address of the connected deviceAnswer: BQuestion:14Static VLANs are being used on the network. What is true about static VLANsA. Devices use DHCP to request their VLAN.B. Attached devices are unaware of any VLANs.C. Devices are assigned to VLANs based on their MAC addresses.D. Devices are in the same VLAN regardless of which port they attach to. Answer: BQuestion:15Two switches are connected via a trunk using VTP. Which VTP information does a Catalyst switch advertise on its trunk ports when using VTP (Select two)A. STP root statusB. VTP modeC. Negotiation statusD. Management domainE. Configuration revision numberAnswer: D, EQuestion:16You need to investigate a VTP problem between two switches. The lack of which two prevents VTP information from propagating between switches (Select two)A. A root VTP serverB. A trunk portC. VTP priorityD. VLAN 1E. None of the other alternatives applyAnswer: B, DQuestion:17PG1 and PG2 are switches that communicate via VTP. What is the default VTP advertisement intervals in Catalyst switches that are in server or client modeA. 30 secondsB. 5 minutesC. 1 minuteD. 10 secondsE. 5 secondsF. None of the other alternatives applyAnswer: BQuestion:18You want to configure switch PG1 to propagate VLAN information across the network using VTP. What must be configured on a Cisco switch in order to advertise VLANinformationA. VTP modeB. VTP passwordC. VTP revision numberD. VTP pruningE. VTP domain nameF. None of the other alternatives applyAnswer: EQuestion:19The switches have all been upgraded to use VTP version 2. What are two benefits provided in VTP Version 2 that are not available in VTP Version 1 (Select two)A. VTP version 2 supports Token Ring VLANsB. VTP version 2 allows VLAN consistency checksC. VTP version 2 allows active redundant links when used with spanning treeD. VTP version 2 reduces the amount of configuration necessaryE. VTP version 2 saves VLAN configuration memoryAnswer: A, BQuestion:20The network administrator needs to enable VTP pruning within thenetwork. What action should a network administrator take to enable VTP pruning on an entiremanagement domainA. Enable VTP pruning on any switch in the management domainB. Enable VTP pruning on any client switch in the domainC. Enable VTP pruning on a VTP server in the management domainD. Enable VTP pruning on every switch in the domainE. None of the other alternatives applyAnswer: CQuestion:21VTP is configured on switch PG1. Which of the following features were added in VTP version2 that were not previously supported in VTP version 1 (Select two)A. Supports Token Ring VLANs.B. Allows VLAN consistency checks.C. Saves VLAN configuration memory.D. Reduces the amount of configuration necessary.E. Allows active redundant links when used with spanning tree.Answer: A, BQuestion:22The switches are configured to use VTP. What’s true about the VLAN trunking protocol (VTP) (Select two)A. VTP messages will not be forwarded over nontrunk links.B. VTP domain names need to be identical. However, case doesn’t matter.C. A VTP enabled device which receives multiple advertisements will ignore advertisementswith higher configuration revision numbers.D. A device in “transparent” V TP mode will not forward VTP messages.E. VTP pruning allows switches to prune VLANs that do not have any active ports associatedwith them.Answer: A, DQuestion:23Switch PG1 and PG2 both belong to the VTP domain. What’s true about the switch operation in VTP domains (Select all that apply)A. A switch can only reside in one management domainB. A switch is listening to VTP advertisements from their own domain onlyC. A switch is listening to VTP advertisements from multi domainsD. A switch can reside in one or more domainsE. VTP is no longer supported on Catalyst switchesAnswer: A, BQuestion:24VTP devices in a network track the VTP revision number. What is a VTP configurationrevision numberA. A number for identifying changes to the network switch.B. A number for identifying changes to the network router.C. A number for identifying changes to the network topology.D. None of the other alternatives apply.Answer: CQuestion:25Switch PG1 is configured to use the VLAN Trunking Protocol (VTP). What does PG1 advertise in its VTP domainA. The VLAN ID of all known VLANs, the management domain name, and the total number oftrunk links on the switch.B. The VLAN ID of all known VLANs, a 1-bit canonical format (CF1 Indicator), and the switchconfiguration revision number.C. The management domain name, the switch configuration revision number, the knownVLANs, and their specific parameters.D. A 2-byte TPID with a fixed value of 0x8100 for the management domain number, theswitch configuration revision number, the known VLANs, and their specific parameters.E. None of the other alternatives apply.Answer: CQuestion:26VTP switches use advertisements to exchange information with each other. Which of thefollowing advertisement types are associated with VTP (Select all that apply)A. Domain advertisementsB. Advertisement requests from clientsC. Subset advertisementsD. Summary advertisementsAnswer: B, C, DQuestion:27Switch PG1 is part of the VTP domain. What’s true of VTP Pruning within this domain (Select all that apply)A. It does not prune traffic from VLANs that are pruning-ineligibleB. VLAN 1 is always pruning-eligibleC. it will prune traffic from VLANs that are pruning-ineligibleD. VLAN 2 is always pruning-ineligibleE. None of the other alternatives apply.Answer: AQuestion:28What action should you execute if you wanted to enable VTP pruning on your entire management domainA. Enable VTP pruning on any client switch in the management domain.B. Enable VTP pruning on any switch in the management domain.C. Enable VTP pruning on every switch in the management domain.D. Enable VTP pruning on a VTP server in the management domain.E. Disable VTP pruning on a VTP server in the management domain.Answer: DQuestion:29Switch PG1 is configured with VTP. Which two VTP modes will make PG1 capable of creatingand deleting VLANs on itself (Select two)A. ClientB. ServerC. TransparentD. Pass-throughE. No-negotiateAnswer: B, CQuestion:30When the Catalyst switch PG1 is enabled to use VTP, which information does it advertise onits trunk ports (Select two)A. VTP modeB. STP root statusC. Negotiation statusD. Management domainE. Configuration revision numberAnswer: D, EQuestion:31Two switches are connected via a trunk link. In this network, the original frame is encapsulated and an additional header is added before the frame is carried over a trunk link.At the receiving end, the header is removed and the frame is forwarded to the assigned VLAN.This describes which technologyA. DISLB. ISLC. DTPD. IEEEE. MPLSF. None of the other alternatives applyAnswer: BQuestion:32The core switches use trunks to connect to each other. How doestrunking keep track of multiple VLANsA. It tags the data frame with VLAN information and recalculates the CRC valueB. It encapsulates the data frame with a new header and frame check sequenceC. It modifies the port index of a data frame to indicate the VLAND. It adds a new header containing the VLAN ID to the data frameE. None of the other alternatives applyAnswer: AQuestion:33The core switches are configured to use trunks. Which three statementsare correct with regard to the IEEE standard (Select three)A. The IEEE frame format adds a 4 byte field to a Ethernet frameB. The packet is encapsulated with a 26 byte header and a 4 byte FCSC. The protocol uses point-to-multipoint connectivityD. The protocol uses point-to-point connectivityE. The IEEE frame uses multicast destination of 0x01-00-0c-00-00F. The IEEE frame retains the original MAC destination addressAnswer: A, D, FQuestion:34Switch PG1 has been configured with DTP using the desirable option. Which statementdescribes Dynamic Trunking Protocol (DTP) desirable modeA. The interface actively attempts to convert the link to a trunk link.B. The interface is put into permanent trunking mode but prevented from generating DTPframes.C. The interface is put into permanent trunking mode and negotiates to convert the link into atrunk link.D. The interface is put into a passive mode, waiting to convert the link to a trunk link.E. None of the other alternatives applyAnswer: AQuestion:35You need to configure a new switch for trunking. Which switch command enables a trunking protocol that appends a four byte CRC to the packetA. Switch(config-if)#switchport trunk encapsulation dot1qB. Switch(config-if)#switchport trunk encapsulation itefC. Switch(config-if)#switchport trunk encapsulation fddiD. Switch(config-if)#switchport trunk encapsulation islE. None of the other alternatives applyAnswer: DQuestion:36While using a packet analyzer, you notice four additional bytes being added to the packets inthe network. Which protocol inserts a four byte tag into the Ethernet frame and recalculates CRC valueA. DTPB. VTPC.D. ISLE. None of the other alternatives applyAnswer: CQuestion:37You need to configure a new switch to support DTP. Which DTP switchport mode parameter sets the switch port to actively send and respond to DTP negotiation framesA. AccessB. No negotiateC. TrunkD. Dynamic desirableE. Dynamic autoF. None of the other alternatives applyAnswer: DQuestion:38A new switch was just configured using the “switchport trunk native vlan 7”command. What does this interface command accomplishA. Causes the interface to apply ISL framing for traffic on VLAN 7B. Configures the trunking interface to forward traffic from VLAN 7C. Configures the interface to be a trunking port and causes traffic on VLAN 7 to be taggedD. Configures the trunking interface to send traffic from VLAN 7 untaggedE. None of the other alternatives applyAnswer: DQuestion:39You need to connect two core switches via an ISL trunk. Which statement is true regarding the configuration of ISL trunksA. A Catalyst switch cannot have ISL and IEEE trunks enabled.B. All Catalyst switches support ISL trunking.C. A Catalyst switch will report giants if one side is configured for ISL while the other side isnot.D. ISL trunking requires that native VLANs match.E. None of the other alternatives applyAnswer: CQuestion:40Which of the following technologies would an Internet Service Provider use to supportoverlapping customer VLAN ID’s over transparent LAN servicesA. tunnelingB. ATMC. SDHD. IP Over Optical NetworkingE. ISLAnswer: AQuestion:41If you were to configure an ISL Ethernet trunk between two Cisco switches, named PG1 andPG2, what would you have to include at the end of the link for the trunk to operate correctly(Select two)A. An identical VTP mode.B. An identical speed/duplex.C. An identical trunk negotiation parameter.D. An identical trunk encapsulation parameter.Question:42Refer to the exhibit. On the basis of the information provided in the exhibit, which two sets of procedures are best practicesfor Layer 2 and 3 failover alignment (Choose two.)A .Configure the D-SW1 switch as the active HSRP router and the STP root for all VLANs.Configure the D-SW2 switch as the standby HSRP router and backup STP root for all VLANs.B. Configure the D-SW1 switch as the standby HSRP router and the STP root for VLANs 11 and 110.Configure the D-SW2 switch as the standby HSRP router and the STP root for VLANs 12 and 120.C. Configure the D-SW1 switch as the active HSRP router and the STP root for VLANs 11 and 110.Configure the D-SW2 switch as the active HSRP router and the STP root for VLANs 12 and 120.D. Configure the D-SW2 switch as the active HSRP router and the STP root for all VLANs.Configure the D-SW1 switch as the standby HSRP router and backup STP root for all VLANs.E. Configure the D-SW1 switch as the active HSRP router and the backup STP root for VLANs 11 and 110.Configure the D-SW2 switch as the active HSRP router and the backup STP root for VLANs 12 and 120.F. Configure the D-SW1 switch as the standby HSRP router and the backup STP root for VLANs12 a nd 120.Configure the D-SW2 switch as the standby HSRP router and the backup STP root for VLANs 11 and 110.Answer: CFExplanation:Basically, each of the routers that provides redundancy for a given gateway address is assigned to a common HSRP group. One router is elected as the primary, or active, HSRP router, another is elected as the standby HSRP router, and all the others remain in the listen HSRP state. The routers exchange HSRP hello messages at regular intervals, so they can remain aware of each。
ccnp的试题全中文

CCNP级别网络工程师面试题1、解决路由环问题的方法有(ABD) A.水平分割 B.路由保持法 C.路由器重启D.定义路由权的最大值2、下面哪一项正确描述了路由协议(C) A.允许数据包在主机间传送的一种协议 B.定义数据包中域的格式和用法的一种方式C.通过执行一个算法来完成路由选择的一种协议D.指定MAC地址和IP地址捆绑的方式和时间的一种协议3、以下哪些内容是路由信息中所不包含的(A) A.源地址 B.下一跳 C.目标网络D.路由权值4、以下说法那些是正确的(BD)A.路由优先级与路由权值的计算是一致的B.路由权的计算可能基于路径某单一特性计算,也可能基于路径多种属性C.如果几个动态路由协议都找到了到达同一目标网络的最佳路由,这几条路由都会被加入路由表中D.动态路由协议是按照路由的路由权值来判断路由的好坏,并且每一种路由协议的判断方法都是不一样的5、IGP的作用范围是(C) A.区域内 B.局域网内 C.自治系统内 D.自然子网范围内6、距离矢量协议包括(AB) A.RIP B.BGP C.IS-IS D.OSPF7、关于矢量距离算法以下那些说法是错误的(A) A.矢量距离算法不会产生路由环路问题 B.矢量距离算法是靠传递路由信息来实现的C.路由信息的矢量表示法是(目标网络,metric)D.使用矢量距离算法的协议只从自己的邻居获得信息求职胜经/简历亮出你的精彩简历写作技巧,...面试前准备才是...8、如果一个内部网络对外的出口只有一个,那么最好配置(A) A.缺省路由 B.主机路由 C.动态路由9、BGP是在(D)之间传播路由的协议 A.主机 B.子网C.区域(area)D.自治系统(AS)10、在路由器中,如果去往同一目的地有多条路由,则决定最佳路由的因素有(AC) A.路由的优先级 B.路由的发布者 C.路由的metirc值 D.路由的生存时间11、在RIP协议中,计算metric值的参数是(D) A.MTU B.时延 C.带宽D.路由跳数12、路由协议存在路由自环问题(A) A.RIP B.BGP C.OSPF D.IS-IS13、下列关于链路状态算法的说法正确的是:(bc) A.链路状态是对路由的描述B.链路状态是对网络拓扑结构的描述C.链路状态算法本身不会产生自环路由D.OSPF 和RIP都使用链路状态算法14、在OSPF同一区域(区域A)内,下列说法正确的是(d) A.每台路由器生成的LSA都是相同的B.每台路由器根据该最短路径树计算出的路由都是相同的C.每台路由器根据该LSDB计算出的最短路径树都是相同的 D.每台路由器的区域A的LSDB(链路状态数据库)都是相同的15、在一个运行OSPF的自治系统之内:(ad) A.骨干区域自身也必须是连通的 B.非骨干区域自身也必须是连通的C.必须存在一个骨干区域(区域号为0)D.非骨干区域与骨干区域必须直接相连或逻辑上相连16、下列关于OSPF协议的说法正确的是:(abd) A.OSPF支持基于接口的报文验证B.OSPF支持到同一目的地址的多条等值路由C.OSPF是一个基于链路状态算法的边界网关路由协议D.OSPF发现的路由可以根据不同的类型而有不同的优先级17、禁止RIP协议的路由聚合功能的命令是(c) A.undo rip B.auto-summanyC.undo auto-summanyD.undo network10.0.0.018、下列静态路由配置正确的是(d) A.ip route129.1.0.016serial0 B.ip route10.0.0.216129.1.0.0 C.ip rout e129.1.0.01610.0.0.2D.ip route129.1.0.0255.255.0.010.0.0.219、以下不属于动态路由协议的是(d) A.RIP B.ICMP C.IS-ISD.OSPf20、三种路由协议RIP、OSPF、BGP和静态路由各自得到了一条到达目标网络,在华为路由器默认情况下,最终选选定(b)路由作为最优路由 A.RIP B.OSPF C.BGPD.静态路由21、IGP包括如下哪些协议(acd) A.RIP B.BGP C.IS-IS D.OSPF22、路由环问题会引起(abd) A.慢收敛 B.广播风暴 C.路由器重起D.路由不一致23、以下哪些路由表项要由网络管理员手动配置(a) A.静态路由B.直接路由C.动态路由D.以上说法都不正确24、在运行Windows98的计算机中配置网关,类似于在路由器中配置(a) A.直接路由 B.默认路由 C.动态路由 D.间接路由25、关于RIP协议,下列说法正确的有:(ac) A.RIP协议是一种IGP B.RIP协议是一种EGPC.RIP协议是一种距离矢量路由协议D.RIP协议是一种链路状态路由协议欢迎您的下载,资料仅供参考!致力为企业和个人提供合同协议,策划案计划书,学习资料等等打造全网一站式需求。
网络工程师CCNA证书考试题库

网络工程师CCNA证书考试题库网络工程师是当今社会上一种备受青睐的职业,具备CCNA证书是成为一名合格网络工程师的基本要求之一。
CCNA(Cisco Certified Network Associate)是思科公司提供的一种权威的网络证书,考试内容涵盖了网络基础知识、路由器和交换机配置、网络安全等方面的内容。
下面将为大家整理一份网络工程师CCNA证书考试题库,供大家参考和复习。
一、网络基础知识1. OSI参考模型中,哪一层负责确定数据如何在网络中传输?A. 应用层B. 传输层C. 网络层D. 数据链路层2. IP地址的子网掩码用来做什么?A. 区分网络地址和主机地址B. 确定网络的物理拓扑C. 控制网络访问权限D. 提高网络安全性3. TCP协议是一种什么类型的协议?A. 面向连接型B. 面向无连接型C. 面向消息型D. 面向数据流型4. 下面哪种传输介质是最适合用于在大楼内部连接不同楼层的网络设备?A. 双绞线B. 同轴电缆C. 光纤D. 无线电波二、路由器和交换机配置1. 在路由器上配置静态路由需要设置哪些参数?A. 出接口B. 下一跳地址C. 网关地址D. 子网掩码2. 交换机的VLAN技术主要用来实现什么功能?A. 提高网络传输速度B. 划分不同的广播域C. 增加网络安全性D. 实现无线网络连接3. 在路由器上配置NAT技术的目的是什么?A. 增加网络带宽B. 实现内网主机与外网通信C. 提高网络可靠性D. 实现跨平台数据传输4. 交换机端口默认是属于哪个VLAN?A. VLAN1B. VLAN10C. VLAN100D. VLAN1000三、网络安全1. 以下哪种加密算法用于保护传输过程中的数据机密性?A. DESB. MD5C. RSAD. SHA2. 防火墙的作用是什么?A. 限制网络带宽的使用B. 监控网络流量C. 阻止非法入侵D. 加快网络数据传输速度3. 在网络安全方面,ACL(访问控制列表)主要用来控制什么?A. 网络拓扑B. 主机访问权限C. 广播域D. 数据传输速度4. DDos攻击是指什么?A. 拒绝服务攻击B. 数据泄露攻击C. 蠕虫攻击D. 恶意代码攻击通过以上网络工程师CCNA证书考试题库的复习,相信大家可以更加全面地了解CCNA考试的内容要求,提升自己的备考水平。
CCIE模拟考试题_思科认证考试.doc

CCIE模拟考试题_思科认证考试1.What statement is FALSE with respect to the operation of Unidirectional Link Detection?A. It negotiates the Unidirectional Link Detection link state during physical signaling.B. It performs tasks that autonegotiation cannot perform.C. It works by exchanging protocol packets between the neighboring devices.D. Both devices on the link must support Unidirectional Link Detection and have it enabled on respective ports.2.What is true concerning Traffic contract, Traffic shaping, and Traffic policing in ATM networks?A. They are parameters of PNNI set during PNNI configuration.B. They are forms of QoS features used in ATM networks.C. They are types of SVCs.D. They are types of PVCs.E. They are only used between ATM switches to control traffic flows.3.Which are the primary reasons to use traffic shaping? (Select two)A. To control the maximum rate of traffic transmitted or received on an interface.B. To control access to available bandwidth.C. To define Layer 3 aggregate or granular incoming or outgoing bandwidth rate limits.D. To control the average queue size by indicating to the end hosts when they should temporarily slow down transmission of packets.E. To ensure that traffic conforms to the policies established for it.4.In a bridged network running IEEE 802.1d spanning tree, what parameter will a bridge take form the root bridge?A. MaxageB. Forwarding delayC. Hello timeD. All of the above5.What statement is FALSE concerning the use of SPAN on the Catalyst 6500?A. It is possible to configure SPAN to have a Gigabit port, such as source port, and a 10/100 port as the destination port.B. If the source port is configured as a trunk port, the traffic on the destination port will be tagged as well, regardless of the configuration on the destination port.C. When a SPAN session is active the destination port does not participate in Spanning Tree.D. With SPAN an entire VLAN can be configured to be the source.E. In one SPAN session it is possible to monitor multiple ports that do not belong to the same VLAN.。
ccna考试试题库

ccna考试试题库CCNA(Cisco Certified Network Associate)考试是思科认证网络专家的初级认证,主要测试考生在网络基础、路由、交换、无线和安全等方面的知识。
以下是一些模拟CCNA考试的试题和答案:1. 什么是子网掩码,它有什么作用?答案:子网掩码是一种IP地址的附加信息,用于指定IP地址中网络部分和主机部分的界限。
它的作用是允许路由器区分IP地址中的网络地址和主机地址,从而实现不同网络之间的路由。
2. 描述静态路由和动态路由的区别。
答案:- 静态路由:由网络管理员手动配置的路由信息,不随网络结构的变化而自动调整。
- 动态路由:由路由器根据网络拓扑的变化自动生成和更新的路由信息。
3. 什么是VLAN,它有什么好处?答案: VLAN(虚拟局域网)是一种在交换机上划分不同网络的技术,即使物理上连接在同一交换机上,也可以属于不同的VLAN。
VLAN的好处包括提高安全性、减少广播域、提高网络管理的灵活性等。
4. 简述TCP和UDP的区别。
答案:- TCP(传输控制协议):提供可靠的、面向连接的传输服务,有流量控制和拥塞控制机制。
- UDP(用户数据报协议):提供不可靠的、无连接的传输服务,适用于对实时性要求高的应用。
5. 什么是DHCP,它的作用是什么?答案: DHCP(动态主机配置协议)是一种网络管理协议,用于自动分配IP地址和其他网络配置信息给网络中的设备。
它的作用是简化网络配置,避免IP地址冲突。
6. 什么是NAT,它在网络中扮演什么角色?答案: NAT(网络地址转换)是一种技术,允许多个设备共享一个公共IP地址与互联网通信。
它在网络中扮演的角色是节省IP地址资源,隐藏内部网络结构。
7. 什么是STP(生成树协议)?答案: STP(生成树协议)是一种网络协议,用于在局域网中防止网络环路的产生。
通过创建一个无环的逻辑拓扑,STP确保网络的稳定性和可靠性。
8. 描述OSPF(开放最短路径优先)协议的工作原理。
CCNA CCNP CCIE模拟试题

CCNA、CCNP、CCIE模拟试题1.Which of the following types of packets will be allowed entry when a serial interface's inbound access list has beenconfigured to prohibit entry for TCP and UDP ports 21, 23 and 25? (Select three options.)A. SMTPB. STPC. FTPD. TelnetE. HTTPF. POP32.One of the trainees assigned to you want to know which services use TCP. What can you tell him? (Select three options.)A. DHCPB. SMTPC. SNMPD. FTPE. HTTPF. TFTP3.Which of the following network masks would you use to reduce any wastage of IP addresses in point-to- point WAN links on a network that supports VLSM?A. /38B. /30C. /27D. /23E. /184.How would you configure a router to avoid situations such as split horizon issues hampering routing updates on a FrameRelay network?A. Configure a separate sub-interface for each PVC with a unique DLCI and subnet assigned to the subinterface.B. Configure each Frame Relay circuit as a point-to-point line to support multicast and broadcast traffic.C. Configure one sub-interface to disperse into multiple PVC connections to multiple remote router interfaces.D. Configure as many as possible sub-interfaces on the same subnet.5.With regard to ISDN, which of the following are true? (Choose all that apply.)A. Legacy DDR can use port information to define interesting traffic.B. Legacy DDR can configure multiple dialer configurations on the same interface.C. Legacy DDR can use ACLs to define interesting traffic.D. HDLC or PPP can be used to encapsulate ISDN D channel information.E. The BRI interfaces on ISDN routers with dialer profiles configured cannot belongto multiple dialer pools.F. Dialer profiles cannot use ACLs to define interesting traffic.6.Which of the following is a characteristic of link-state protocols?A. A network topology change generates an update that is broadcast to every router on the network.B. The periodic routing update interval is slightly different in each router on a subnet.C. Each router creates a routing table that only includes its directly connected neighbors.D. Link-state protocols send routing updates only when there is a change in the network topology.7.What is the term associated with synchronizing the routing tables after a topology change occurs?A. floodingB. broadcastingC. convergenceD. summarization8.Which of the following must be determined first by the router in order to route the data?A. the distance metric of the dataB. the source address of the dataC. which routing protocol is used by the dataD. whether the protocol suite of the data is active9.You are a technician at ABC. ABC has the subnet/mask of 172.29.100.0/26 set aside for small remote locations. Each location will have 5 IP devices connected tothe network.Which VLSM mask will provide the minimum number of hosts you require?A. /27B. /28C. /29D. /30E. /3110.You are a trainee technician at ABC. Your instructor shows you the following route summarization entry:192.168.134.0/22 Your instructor wants to know how many class C addresses are contained in this summarization.What would your reply be?A. 1B. 2C. 4D. 8E. 1611.Which command enables an EtherChannel bundle on a Catalyst 2900XL switch?A. Port groupB. Set port channel onC. Port etherchannel enableD. Set etherchannel port enable12.Which two statements about dynamic VLANs are true? (Choose two)A. Each switch port is assigned to a specific VLAN.B. Dynamic VLANs require a VLAN Membership Policy Server.C. Devices are in the same VLAN regardless of which port they attach to.D. Dynamic VLAN assignment are made through the command interface.13.Which statement is correct about 802.1Q trunking? (Select all that apply)A. Both switches must be in the same VTP domain.B. The encapsulation type of both ends of the trunk does not have to match.C. The native VLAN on both ends of the trunk must be VLAN 1.D. 802.1Q trunking can only be configured on a Layer 2 port.E. In 802.1Q trunking, all VLAN packets are tagged on the trunk link, except the native VLAN.14.You need to take advantage of FastEthernet ports. Which two actions avoid configuration problems that cause the port to be automatically disabled? (Choose two)A. Allow some ports in a channel to be disabled.B. Configure the ports in a channel as dynamic VLAN ports.C. Configure all ports in a channel to operate at the same speed and duplex mode.D. Assign all ports in a channel to the same VLAN or configure them as trunk ports.15.What is the cause of jitter?A. Variable queue delaysB. Packet dropsC. Transmitting too many small packetsD. Compression16.Regarding DHCP, DHCP relay and DHCP server are mutually exclusive.A. None of the choices.B. TrueC. False only for certain IOS versionD. FalseE. False only for IOS version below V1017.A LAPD Address field can be 1 or 2 bytes long.A. TrueB. FalseC. True only in the USD. True only in AsiaE. True only in Europe18.Which of the following are valid functions of the lock DTE modem attribute (Choose all that apply)?A. Disable UART.B. Enable UART.C. Locks the data speed between the computer motherboard and the RS232 port.D. Locks the data speed between the modem and the DTE device.19.Which of the following are not the valid types of ATM addresses (Choose all that apply)?A. DCCB. GCTC. BSPD. ICDE. NSAPF. AED20.Which of the following are NOT the valid types of X.25 PLP packetfields(Choose all that apply)?A. User DataB. LCIC. GFID. PTIE. None of the choices.21.You are a technician at . Your newly appointed ABC trainee wants to know what the similarities between Topology Diagrams and Network Configuration Tables are.What would your reply be? (Choose all that apply.)A. Both share few components.B. Both share many of the same components.C. Both define physical memory components.D. Both are used for troubleshooting.E. Both use lines and symbols to represent network components.22.You are a technician at . Your newly appointed ABC trainee wants to know what the default action for the output of debug and system error messages is.What would your reply be?A. Output goes to the remote console if logging is off.B. Output is sent to the console terminal.C. Error logging automatically invokes debug output to the designated TFTP server.D. Output configuration requires a TFTP server to write filesE. Output is written to a Syslog server.23.You are the network administrator at . ABC has a switched network.You want to control the designation of the spanning-tree root bridge in the ABC network. What should you do?A. By enabling uplink-fast on the ports of the desired switch.B. By lowering the bridge priority on the desired switch.C. By setting a lower MAC address on the designated switch.D. By raising the bridge ID on one switch.24.You are a technician at ABC. You receive a report from several ABC users who complain that they get slow responses when sending and receiving email, especially when browsing the Internet. You investigate the complaint by checking the output of a ping command issued from her computer and find that it indicates intermitted success and failures messages, when attempting to contact the email server. A tracert to the corporate Internet gateway router shows high latency and occasional time out messages.What would be the most effective troubleshooting approach if you are to determine the cause of the slow response time?A. Bottom-up approachB. Random access approachC. Divide and conquer approachD. Top-down approachE. Top-down rule-out approach25.You are a technician at . Your newly appointed ABC trainee wants to know what features make OSPF more suitable than RP in large network installations.What would your reply be? (Choose all that apply.)A. Diffusing Update AlgorithmB. No hop count limitationC. Higher routing update overheadD. Faster convergenceE. Lower routing update overhead26.You are the network administrator at ABC. You are troubleshooting a network problem. You want to trace the route to a Unix workstation that you want to reach through the Internet. However, Traceroute does not work.Currently, there is an inbound access-list applied to the serial interface on Router 1. An entry in the access-list states "access-list 101 permit tcp any any". What access-list entry may you need to be added to the access-list in order to get traceroute to work?A. access-list 101 permit udp any anyB. access-list 101 permit icmp any any time-exceeded access-list 101 permit icmp any any port-unreachableC. access-list 101 permit icmp any any time-exceeded access-list 101 permit icmp any any net-unreachableD. access-list 101 permit icmp any any echo access-list 101 permit icmp any any net-unreachableE. access-list 101 permit udp any any access-list 101 permit icmp any any protocol-unreachable27.What does the BGP backdoor command do?A. It changes the distance of an iBGP route to 20.B. It changes the distance of an eBGP route to 200.C. It changes the distance of an IGP route to 20.D. It does not effect any changes in distance of the route.E. It changes the distance of an IGRP route to 200.28.Which of the following DNS resource records is not valid?A. NSB. PTRC. MXD. FQDNE. A29.Which of the following features is provided by RIP v2 that were previously not possible with RIP v1? (Choose all that apply.)A. Classless routing and split-horizon.B. Poison reverse and updating to multicast addresses.C. Poison reverse and classless routing.D. Classless routing and updating to multicast addresses.E. Route tag and classless routing.30.Which of the following statements is valid when taking Custom Queuing into account?A. Custom queuing has the ability to restrict a particular type of traffic to agiven bandwidth not matter what is load is like on that link.B. Custom queuing looks at groups of packets from the similar source-destination pairs.C. Custom queuing will not proceed to a next queue unless the current queue is empty.D. Custom queuing can prevent one type of traffic from dominating a busy link.。
思科认证考试(CCNA)考试模拟题集锦(1-71题)及答案培训资料

思科认证考试(C C N A)考试模拟题集锦(1-71题)及答案思科认证考试(CCNA)考试模拟题集锦(1-71题)及答案19及答案1. [OxNx] During a TFTP transfer using Cisco Routers what is the numeric value, in decimal, of the destination port field of the User Datagram Protocol (UDP) header? a) 96b) 47c) a random number above 1024d) 69e) none of the above2. [CxNx] What is the standard encapsulation method used by Cisco routers for the Internet Protocol (IP) on it’s Ethernet interfaces?a) SNAPb) ARPAc) NOVELL-ETHERd) DARPAe) Ethernet_802.33. [CxNx] What will be the correct command on a Cisco router to set the IP address of an interface assuming you are at the "router(config-if)#" prompt?a) ip address 1.1.1.1 255.255.255.0b) ip address 1.1.1.1c) ip 1.1.1.1d) ip 1.1.1.1 255.255.255.0e) none of the above4. [CxNx] Which commands will display the IP addresses of all interfaces on a Cisco Router? (Choose all that apply)a) show ip routeb) show ip addressc) show ip interfaced) show interfacee) display ip addresses5. [CxNx] Which of the following commands will display the contents of the ARP cache of your Cisco router?a) show ip arp cacheb) show ip routec) show ip arpd) show arpe) there is no way to display the ARP cache6. [CxNx] Reverse Address Resolution Protocol (RARP) is the process:a) Where an IP host resolves it’s IP address by broadcasting it’s MAC address to the network and a BOOTP server assigns it an IP address.b) Where an IP host resolves it’s MAC address by broadcasting to the local network it’s IP address.c) Where an IP host tries to resolve the MAC address of a destination by sending a network broadcast. The destination responds to the broadcast with it’s MAC address.d) Where an IP host resolves a destination IP address by sending a broadcast on the local network and the destination host responds with it’s IP address.7. [OxNx] Which of the following applications requires the connection-oriented layer four protocol, TCP? (Choose all that apply)a) Telnetb) FTPc) TFTPd) SNMPe) none of the above8. [RxNx] Which of the following are link state Routing Protocols.(Choose all that apply.)a) IPb) OSPFc) RIPd) EIGRPe) IS-IS9. [CxNx] Of the following commands, identify the correct one for clearing the IP arp table in memory of the router.a) clear ip arp-cacheb) clear ip arp-tablec) clear arp-cached) clear arp-tablee) clear arp-ram10. [CxNx] Which of the following explains the correct definition of administrative distance as it pertains to Cisco’s IOS?a) The process by which routers select an administrator for an autonomous system.b) The process where a router will select the best path to a destination network.c) The process where a router will distance itself from other routers due to it’s lack of administrative experience.d) The process where a router will prioritize routing protocols so that in the event two routing protocols have conflicting next hop addresses, the routing protocol with the lowest administrative distance will take priority.e) The process where a router will prioritize routing protocols so that in the event two routing protocols have conflicting next hop addresses, the routing protocol with the highest administrative distance will take priority.11. [ExNx] Collisions occur whena) multiple packets are placed on a serial linkb) multiple stations listen for traffic and transmit at the same timec) when multiple tokens are on a ring simultaneouslyd) beaconing process takes place12. [RINx] How many subnets are possible with a Class C address and a subnet mask of255.255.255.252?a) 32b) 30c) 60d) 62e) 413. [RxNx] What commands will list all protocols that are currently being routed? (Choosea) show ip protocolb) show protocolc) show rund) show starte) All of the above14. [xxNx] Which of the following are true of access lists?a) Access list should have at least one permit statement.b) The last configured line should always be a permit statement.c) Every access-list will implicitly deny all traffic.d) Access-lists are processed top down.e) All of the above.15. [xxNx] If the access-group command is configured on an interface and there is noaccess-list created which of the following is most correct?a) An error message will appear.b) The command will be executed and deny all traffic out.c) The command will be executed and permit all traffic out.d) The command will be executed and permit all traffic in and out.e) The command will be executed and deny all traffic in and out.16. [xxNx] What is the result of the command?" access-list 101 permit tcp any 172.16.0.0 0.0.255.255 established"a) telnet sessions will be permitted regardless of the source addressb) telnet sessions will be denied regardless of the source addressc) telnet sessions will be denied if initiated from any address other than 172.16.0.0networkd) telnet sessions will be permitted to the 172.16.0.0 network onlye) telnet sessions will be denied to the 172.16.0.0 network only17. [xxNx] Which is generally true of the location of access-lists? (Choose all that apply.)a) Standard lists will most likely be placed close to the destination.b) Standard lists will most likely be placed close to the source.c) Extended lists will most likely be placed close to the destination.d) Extended lists will most likely be placed close to the source.e) It does not matter.18. [RxNx] Which of the following is most correct?a) IP is to TCP. as IPX is to SPX.b) RTMP is to Appletalk as IP RIP is to IP.c) NLSP is to IPX as OSPF is to IP.d) a is true.e) b is true.f) a & b are true.g) c is true.h) b & c are true.i) a, b and c are true.19. [ExNx] If Host A sends a packet to Host B over ethernet and Host B is not active:a) The packet will time out.b) The packet will be removed by Host A.c) The NVRAM of Host B will remove the packet.e) The packet will be removed by the token monitor.Coding Key and InformationThe first character represents the category of question.A - ATMB - BridgingC - Cisco specificE - EthernetF - Frame relayH - HDLCI - FDDIN - ISDNO - OSI modelP - PPPR - RoutingS - SwitchingT - Token ringX - X.25x - Not applicableThe second character represents protocol.A - AppletalkB - Banyan VinesD - DecnetI - IPL - Dial on DemandN - NLSPO - OSPFX - IPXx - Not ApplicableThe third character represents the certification that the question will help you prepare for.N - CCNA Exam #640-407P - CCNPAdvanced Cisco Router Configuration (ACRC) Exam 640-403Cisco LAN Switch Configuration (CLSC) Exam #640-404Cisco Monitoring and Troubleshooting Dial-up Services Exam #640-405Cisco Internetworking Troubleshooting ( CIT) Exam #640-406D - CCDA & CCDPCisco Design Specialist Exam #9E0-004Cisco Internetwork Design#640-025We will reserve the fourth character for future use.As an example, when you come across a question coded "BXDx", it signifies a question that will help you gain the CCDA or CCDP certification.CCNA试题1-19答案1. [OxNx] During a TFTP transfer using Cisco Routers what is the numeric value, in decimal,a) 96b) 47c) a random number above 1024d) 69e) none of the aboveAnswerd) 69Here is a sampling of other port numbers and the application they are associated with. The first 8 of these protocols are automatically forwarded through the router by using thehelper-address commandTrivial File Transfer (TFTP) (port 69)Domain Name System (port 53)IEN-116 Name Server (port 42)Time service (port 37)NetBIOS Name Server (port 137)NetBIOS Datagram Server (port 138)Boot Protocol (BootP) client and server datagrams (port 67)TACACS service (port 49)Simple Mail Transfer Protocol (25)File Transfer Protocol (21)Simple Network Management Protocol (161)2. [CxNx] What is the standard encapsulation method used by Cisco routers for the Internet Protocol (IP) on it’s Ethernet inte rfaces?a) SNAPb) ARPAc) NOVELL-ETHERd) DARPAe) Ethernet_802.3Answerb) ARPASNAP is the default encapsulation for a token ring interface NOVELL-ETHER is the default encapsulation for a ipx interface.3. [CxNx] What will be the correct command on a Cisco router to set the IP address of an interface assuming you are at the "router(config-if)#" prompt?a) ip address 1.1.1.1 255.255.255.0b) ip address 1.1.1.1c) ip 1.1.1.1d) ip 1.1.1.1 255.255.255.0e) none of the aboveAnswera) ip address 1.1.1.1 255.255.255.0If you are not in the configuration mode, the ip address can be set by using the setup mode. Configuring interface Ethernet0/0:Is this interface in use? [yes]:IP address for this interface [10.10.10.1]: 10.10.10.1Number of bits in subnet field [16]: 16Class A network is 10.0.0.0, 16 subnet bits; mask is /24Take note when using the setup mode the mask is configured using the number of subnet bits.4. [CxNx] Which commands will display the IP addresses of all interfaces on a Cisco Router? (Choose all that apply)a) show ip routeb) show ip addressc) show ip interfaced) show interfacee) display ip addressesAnswerc) show ip interfaced) show interfaceExamples of each of these commands are shown below:Router_A#sh int e0/0Ethernet0/0 is up, line protocol is upHardware is AmdP2, address is0010.7b15.bd41(bia 0010.7b15.bd41)Internet address is 10.10.10.1/24MTU 1500 bytes, BW 10000 Kbit,DLY 1000 usec,rely 255/255, load 1/255Encapsulation ARPA, loopback not set,keepalive set (10 sec)ARP type: ARPA, ARP Timeout 04:00:00Last input never, output 00:00:06,output hang neverLast clearing of "show interface"counters neverQueueing strategy: fifoOutput queue 0/40, 0 drops;input queue 0/75,0 drops5 minute input rate 0 bits/sec,0 packets/sec5 minute output rate 0 bits/sec,0 packets/sec0 packets input, 0 bytes,0 no bufferReceived 0 broadcasts, 0 runts,0 giants,0 throttles, 0 input errors, 0 CRC,0 frame, 0 overrun, 0 ignored,0 input packets with dribblecondition detected127 packets output, 11802 bytes,0 underruns0 output errors, 0 collisions,2 interface resets0 babbles, 0 late collision,0 deferred0 lost carrier, 0 no carrier0 output buffer failures, 0 outputbuffers swapped outRouter_A#sh ip int e0/0Ethernet0/0 is up, line protocol is upInternet address is 10.10.10.1/24Broadcast address is 255.255.255.255Address determined bynon-volatile memoryMTU is 1500 bytesHelper address is not setDirected broadcast forwarding is enabledOutgoing access list is not setInbound access list is not setProxy ARP is enabledSecurity level is defaultSplit horizon is enabledICMP redirects are always sentICMP unreachables are always sentICMP mask replies are never sentIP fast switching is enabledIP fast switching on the sameinterface is disabledIP multicast fast switching is enabledRouter Discovery is disabledIP output packet accounting is disabledIP access violation accounting isdisabledTCP/IP header compression is disabledProbe proxy name replies are disabledGateway Discovery is disabledPolicy routing is disabledNetwork address translation is disabled5. [CxNx] Which of the following commands will display the contents of the ARP cache of your Cisco router?a) show ip arp cacheb) show ip routed) show arpe) there is no way to display the ARP cacheAnswerc) show ip arpExample:Router_A#sh ip arpProtocol Address Age(min) Hardware Address Type InterfaceInternet 1.1.1.2 - 0010.7b15.bd50 ARPA FastEthernet1/0Internet 10.10.10.1 - 0010.7b15.bd41 ARPA Ethernet0/06. [CxNx] Reverse Address Resolution Protocol (RARP) is the process:a) Where an IP host resolves it’s IP address by broadcasting it’s MAC address to the network and a BOOTP server assigns it an IP address.b) Where an IP host resolves it’s MAC address by broadcasting to the local network it’s IP address.c) Where an IP host tries to resolve the MAC address of a destination by sending a network broadcast. The destination responds to the broadcast with it’s MAC address.d) Where an IP host resolves a destination IP address by sending a broadcast on the local network and the destination host responds with it’s IP address.e)There is no such process.Answera) Where an IP host resolves it’s IP address by broadcasting it’s MAC address to the network and a BOOTP server assigns it an IP address.Choice C describes Address Resolution Protocol (ARP). A host never has to resolve it’s o wn MAC address. The MAC address is burned into the Network Interface card. When the host is booted the MAC address will be loaded into memory.7. [OxNx] Which of the following applications requires the connection-oriented layer four protocol, TCP? (Choose all that apply)a) Telnetb) FTPc) TFTPd) SNMPe) none of the aboveAnswera) Telnetb) FTPTFTP and SNMP use layer 4 UDP.8. [RxNx] Which of the following are link state Routing Protocols.(Choose all that apply.)a) IPb) OSPFc) RIPd) EIGRPe) IS-ISb) OSPFe) IS-ISA link state routing protocol advertises, to it’s neighbors, the state of the link whenthe state of the link changes.A distance vector routing protocol advertises its routing table periodically.9. [CxNx] Of the following commands, identify the correct one for clearing the IP arp table in memory of the router.a) clear ip arp-cacheb) clear ip arp-tablec) clear arp-cached) clear arp-tablee) clear arp-ramAnswerc) clear arp-cacheIf you have changed an ip address or a NIC card on a host you might use this command toreset the cache.10. [CxNx] Which of the following explains the correct definition of administrativedistance as it pertains to Cisco’s IOS?a) The process by which routers select an administrator for an autonomous system.b) The process where a router will select the best path to a destination network.c) The process where a router will distance itself from other routers due to it’s lack of administrative experience.d) The process where a router will prioritize routing protocols so that in the event two routing protocols have conflicting next hop addresses, the routing protocol with the lowest administrative distance will take priority.e) The process where a router will prioritize routing protocols so that in the event two routing protocols have conflicting next hop addresses, the routing protocol with thehighest administrative distance will take priority.Answerd) The process where a router will prioritize routing protocols so that in the event two routing protocols have conflicting next hop addresses, the routing protocol with the lowest administrative distance will take priority.Cisco uses administrative distances (AD) to measure the reliability of the routing protocol. The lower the (AD) the more reliable the protocol.Router_C#sh ip routeCodes: C - connected, S - static,I - IGRP, R - RIP,M - mobile, B - BGPD - EIGRP, EX - EIGRP external, O - OSPF,IA - OSPF inter areaN1 - OSPF NSSA external type 1, N2 - OSPFNSSA external type 2E1 - OSPF external type 1,E2 - OSPF external type 2,i - IS-IS, L1 - IS-IS level-1,L2 - IS-IS level-2, * -candidate defaultU - per-user static route, o - ODRGateway of last resort is not set172.16.0.0/24 is subnetted, 2 subnetsC 172.16.1.0 is directly connected,Serial1C 172.16.2.0 is directly connected,Serial0I 10.0.0.0/8 [100/8576] via 172.16.1.1,00:00:09, Serial1[100/8576] via 172.16.2.1, 00:00:19,Serial0The 100 in bold is the administrativedistance for IGRP.A partial list of administrative distances is included below:Protocol ADEIGRP 90IGRP 100OSPF 110RIP 120BGP 180If a router hears a IP RIP and a IGRP update for the same network the router will discard the rip information. IP RIP uses h op count as it’s metric, while IGRP uses a composite metric including bandwidth and load, speed is the primary consideration.11. [ExNx] Collisions occur whena) multiple packets are placed on a serial linkb) multiple stations listen for traffic and transmit at the same timec) when multiple tokens are on a ring simultaneouslyd) beaconing process takes placeAnswerb) multiple stations listen for traffic and transmit at the same timeCollisions is a term that is used in an ethernet environment. Ethernet can be described as a listen then transmit scenario. First a station will listen for traffic if no traffic is sensed then a transmission will take place. If two stations transmit at the same time collisions will occur. The first station to detect the collision sends out a jamming signal to alert all stations a collision has occurred. At this point these stations set up a random interval timer when the timer expires re-transmission will occur.Token ring is a token passing process a station can transmit only when he has the token. There never can be multiple tokens on the ring. Early token release allows up to two data frames to be transmitted on a token ring LAN at the same time. Collisions do not occur on a token ring.Because of the point to point nature of serial links collisions do not occur.Beaconing is a term used in a token passing environment.12. [RINx] How many subnets are possible with a Class C address and a subnet mask of 255.255.255.252?a) 32b) 30c) 60d) 62e) 4Answerd) 62The above mask is using 6 bits to describe subnets. The formula used to determine the number of subnets (not including the all 0’s or all 1’s subnet) is 2n - 2 were n is the number of subnet bits. This is the number to use when configuring a ip address with the setup dialog.13. [RxNx] What commands will list all protocols that are currently being routed? (Choose all that apply.)a) show ip protocolb) show protocolc) show rund) show starte) All of the aboveAnswerb) show protocolc) show runShow ip protocol will show just the ip routing protocols that are currently configured. Show start may or may not show the current routed protocols.Below is the output of show protocolRouter_B#show protocolGlobal values:Internet Protocol routing is enabledAppletalk routing is enabledBRI0 is administratively down, line protocol is downBRI0:1 is administratively down, line protocol is downBRI0:2 is administratively down, line protocol is downSerial0 is administratively down, line protocol is downSerial1 is administratively down, line protocol is downSerial2 is administratively down, line protocol is downSerial3 is administratively down, line protocol is downTokenRing0 is administratively down, line protocol is down14. [xxNx] Which of the following are true of access lists?a) Access list should have at least one permit statement.b) The last configured line should always be a permit statement.c) Every access-list will implicitly deny all traffic.d) Access-lists are processed top down.e) All of the above.Answere) All of the above.Every access list has an implicit deny all at the end. What would the need be to create a access list with just deny statements. Access-list are processed from the top downtherefore the order of each statement could be critical, for instance suppose you createdan access list and the first line was a permit any and the next line was a deny. Sinceit’s top down processing a packet would be permitted to pass on the first line and the second line would never be executed. An extended list will give you a "match count" thatwill help in determining what the most efficient order should be.15. [xxNx] If the access-group command is configured on an interface and there is noaccess-list created which of the following is most correct?a) An error message will appear.b) The command will be executed and deny all traffic out.c) The command will be executed and permit all traffic out.d) The command will be executed and permit all traffic in and out.e) The command will be executed and deny all traffic in and out.Answerd) The command will be executed and permit all traffic in and out.There are two steps to use an access list .1. Create the list2. Place the access list on a interfaceThe analogy I use in class is:Suppose you reside in a gated community. The community is not protected until you hire the guard and then place him at the gate. If you hire the guard and never place him at the gateall traffic will be permitted.When there is no access list on an interface it is implicit permit anyWhen an access list is placed on a interface it is implicit deny any16. [xxNx] What is the result of the command?" access-list 101 permit tcp any 172.16.0.0 0.0.255.255 established"a) telnet sessions will be permitted regardless of the source addressb) telnet sessions will be denied regardless of the source addressc) telnet sessions will be denied if initiated from any address other than 172.16.0.0networkd) telnet sessions will be permitted to the 172.16.0.0 network onlye) telnet sessions will be denied to the 172.16.0.0 network onlyAnswerc) telnet sessions will be denied if initiated from any address other than 172.16.0.0networkThe secret to this question is the key word "established." Established means that thepacket will be permitted unless it is the first part of the three way handshake. Recallthat when we initiate a TCP connection we have no ACK. How can we acknowledge a sequence number from the other side when we have not established a session with him?17. [xxNx] Which is generally true of the location of access-lists? (Choose all that apply.)a) Standard lists will most likely be placed close to the destination.b) Standard lists will most likely be placed close to the source.c) Extended lists will most likely be placed close to the destination.d) Extended lists will most likely be placed close to the source.e) It does not matter.Answera) Standard lists will most likely be placed close to the destination.d) Extended lists will most likely be placed close to the source.A standard list will only check the source address. It makes no difference where the packet is going. If you place a standard list close to the source you could very well be denying that traffic to go to other destinations. An extended list can be placed close to the source because we can permit or deny traffic based upon the source and destination address. This insures that only traffic we wish to have denied is denied.18. [RxNx] Which of the following is most correct?a) IP is to TCP. as IPX is to SPX.b) RTMP is to Appletalk as IP RIP is to IP.c) NLSP is to IPX as OSPF is to IP.d) a is true.e) b is true.f) a & b are true.g) c is true.h) b & c are true.i) a, b and c are true.Answeri) a, b and c are true.19. [ExNx] If Host A sends a packet to Host B over ethernet and Host B is not active:a) The packet will time out.b) The packet will be removed by Host A.c) The NVRAM of Host B will remove the packet.d) The packet will "die" when it reaches the terminator.e) The packet will be removed by the token monitor.Answerd) The packet will "die" when it reaches the terminator.20—39及答案20. [TxNx] If Host A sends a packet to Host B over token ring, and Host B is not active: a) The packet will time out.b) The packet will be removed by Host A.c) The NVRAM of Host B will remove the packet.d) The packet will "die" when it reaches the terminator.e) The packet will be removed by the token monitor.21. [TxNx] If Host A sends a packet to Host B over token ring: Host A dies after transmitting, and Host B is not active:a) The packet will time out.b) The packet will be removed by Host A.c) The NVRAM of Host B will remove the packet.d) The packet will "die" when it reaches the terminator.e) The packet will be removed by the Active monitor.22. [FxNx] BECN and FECN are:a) Used to provide keepalives in a Frame Relay environmentb) Used to provide error checking in a Frame Relay environmentc) Used to provide congestion information in a Frame Relay environmentd) Used to provide flow control parameters in a Frame Relay environmente) BECN and FECN are not used in a Frame Relay environment.23. [RxNx] Which of the following are benefits of a Link-State routing protocol? (Chooseall that apply.)a) Allows the use of a more robust addressing scheme.b) Allows for a larger scalable networkc) Reduces convergence timed) Allows "supernetting"e) All of the above.24. [OxNx] Which of the following are reasons for the OSI model?a) Standardizes interfacesb) Allows modular engineeringc) Facilitates learning and teachingd) All of the above.25. [RxNx] Which of the following is NOT a ROUTING protocol:a) OSPFb) RIPc) IPXd) EIGRPe) NLSP26. [RxNx] Which statement is NOT true about link state protocols:a) Link state advertisements are sent to all routers in an area.b) Each router executes the SPF algorithm.c) Link state routers keep a topological database of the network.d) Link state routers include the originating router s routing table.e) Link state routers know of possible alternate paths to a particular network.27. [RxNx] Which of the following would NOT appear in a routing table?a) Next hop addressb) Interface Port referencesc) MAC addressd) Network addresse) Metrics28. [OxNx] Which statement is true of the Datalink OSI layer ?a) 802.3 is the MAC sub layer.b) No such thingc) MAC sublayer provides the connection to the network layer.d) MAC sublayer uses SAPS to access the network layer.e) SAP sublayer uses the MAC layer to access the LAN medium.29. [RINx] Given the IP address of 193.243.12.43 and a subnet mask of 255.255.255.128, what is the subnet address?a) 194.243.12.32b) 193.243.0.0c) 194.243.12.43d) 193.243.12.128e) None of the above.30. [CxNx] Cisco uses a naming convention to identify frame types. Which four of the following mappings are correct?Cisco_name = Common_namea) cisco_II = Ethernet_IIb) arpa = Ethernet_IIc) sap = Ethernet_802.3d) sap = Ethernet_802.2 LLCe) Novell Ether = Ethernet_802.2 LLCf) cisco_802 = Ethernet_802.2 LLCg) snap = Token Ring Snaph) snap = Ethernet_SNAP31. [RxNx] In order to communicate throughout an internetwork, which of the following are required. Choose Two.a) The use of a routable protocol such as NetBEUI or LATb) A hierarchical naming scheme server such as DNSc) A host file at each communicating deviced) A two part network addressing scheme such as Network/Hoste) The use of a routable protocol such as IP or IPXf) The use of a routable protocol such as TCP or IPX32. [CxNx] What is the default route on an IP network? Choose one.a) This is the route that will be chosen first by IP for delivery of a datagram.b) The address of the nearest downstream neighbor in a Token ring network.c) At the router, it is the route used to direct frames for which the next hop has not been explicitly listed in the routing table.d) Any static route listing in a routing table.e) When all conditions are equal, the best route for delivery of IP datagrams.33. [CxNx] A caret symbol (^) inserted into a failed command indicates which of the following. Choose one.a) Numeric data is required for this command.b) The point in a command where you can simply press return to complete the syntax string.c) The point in a command where you have entered an incorrect command, keyword or argument.d) The point in a command where you must enter a required value.e) This is a normal indicator for any failed command.34. [RXNx] The metric used by IPX RIP is:a) hopsb) ticksc) costd) ticks and hopse) None of the above.35. [xINx] Which one of the following masks has the nickname of the "serial mask"?a) 255.255.255.192b) 255.255.255.224c) 255.255.255.240d) 255.255.255.248e) 255.255.255.252。
CCNP测试题(修改版)
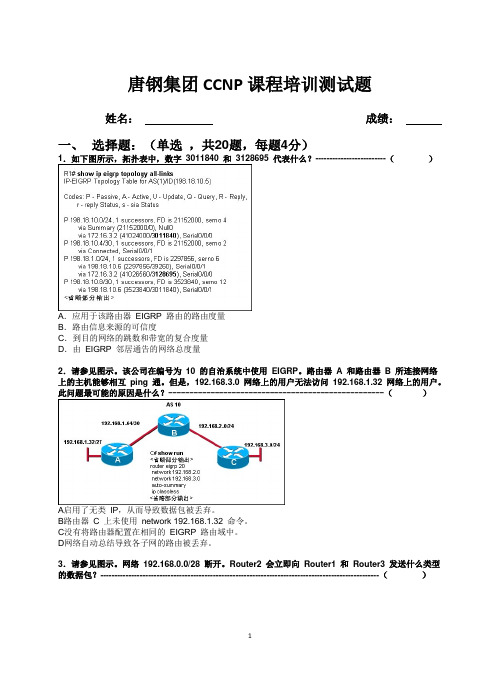
唐钢集团CCNP课程培训测试题姓名:成绩:一、选择题:(单选,共20题,每题4分)1.如下图所示,拓扑表中,数字3011840 和3128695 代表什么?-------------------------()A.应用于该路由器EIGRP 路由的路由度量B.路由信息来源的可信度C.到目的网络的跳数和带宽的复合度量D.由EIGRP 邻居通告的网络总度量2.请参见图示。
该公司在编号为10 的自治系统中使用EIGRP。
路由器A 和路由器B 所连接网络上的主机能够相互ping 通。
但是,192.168.3.0 网络上的用户无法访问192.168.1.32 网络上的用户。
此问题最可能的原因是什么?---------------------------------------------------()A启用了无类IP,从而导致数据包被丢弃。
B路由器C 上未使用network 192.168.1.32 命令。
C没有将路由器配置在相同的EIGRP 路由域中。
D网络自动总结导致各子网的路由被丢弃。
3.请参见图示。
网络192.168.0.0/28 断开。
Router2 会立即向Router1 和Router3 发送什么类型的数据包?---------------------------------------------------------------------------------------------------()A查询网络192.168.0.0/28 的查询数据包B到224.0.0.9 的确认数据包C发送到255.255.255.255 的更新数据包D包含R2 新路由表的数据包发送到192.168.1.1 和192.168.2.1 的单播更新数据包4.请参见图示。
所有接口都已配置为如图所示的带宽。
假设所有路由器都是使用默认的EIGRP 配置作为路由协议,那么从172.16.1.0/16 网络发往192.168.200.0/24 网络的数据包会采用哪一条路径?--------------------------------------------------------------------------------------------------------------------()A. A-B-EB. A-C-EC. A-D-ED.数据包会在A、B、E 和A、C、E 路径之间实施负载均衡。
ccna考试题及答案

ccna考试题及答案1. 以下哪项是网络层的功能?A. 路由选择B. 错误检测C. 流量控制D. 封装数据包答案:A2. 在OSI模型中,哪一层负责在网络中传输数据?A. 应用层B. 传输层C. 会话层D. 网络层答案:D3. 以下哪个协议是用于在IP网络中发现网络设备的?A. ARPB. RARPC. ICMPD. OSPF答案:A4. 在TCP/IP模型中,哪一层与OSI模型的传输层相对应?A. 应用层B. 互联网层C. 网络接口层D. 传输层答案:D5. 以下哪个地址是一个有效的IPv4地址?A. 192.168.1.256B. 192.168.1.1C. 10.0.0.0D. 172.16.300.1答案:B6. 在配置路由器时,以下哪个命令用于进入全局配置模式?A. enableB. configure terminalC. privileged execD. user exec答案:B7. 以下哪个命令用于在Cisco设备上显示当前配置?A. show running-configB. show startup-configC. show configD. show current-config答案:A8. 在Cisco设备上,以下哪个命令用于保存当前的配置到启动配置文件?A. copy running-config startup-configB. copy startup-config running-configC. save running-configD. save startup-config答案:A9. 以下哪个命令用于在Cisco设备上查看所有接口的状态?A. show interfacesB. show ip interface briefC. show interface statusD. show running-config interface答案:B10. 在Cisco设备上,以下哪个命令用于关闭接口?A. shutdownB. no shutdownC. disableD. no enable答案:A11. 以下哪个命令用于在Cisco设备上启用接口?A. shutdownB. no shutdownC. disableD. no enable答案:B12. 在配置静态路由时,以下哪个命令用于指定下一跳地址?B. ip static-routeC. route ipD. static-route ip答案:A13. 以下哪个命令用于在Cisco设备上清除ARP表?A. clear arp-cacheB. clear arpC. clear arp tableD. clear ip arp答案:D14. 在配置动态路由协议时,以下哪个命令用于在接口上启用RIP?A. ip rip enableB. ip rip receiveD. network rip答案:C15. 以下哪个命令用于在Cisco设备上查看RIP路由表?A. show ip ripB. show ip route ripC. show ripD. show ip protocols答案:B16. 在配置EIGRP时,以下哪个命令用于指定自动汇总?A. metric weightsB. auto-summaryC. network auto-summaryD. no auto-summary答案:B17. 以下哪个命令用于在Cisco设备上查看EIGRP邻居?A. show ip eigrp neighborsB. show eigrp neighborsC. show ip eigrpD. show eigrp interfaces答案:A18. 在配置OSPF时,以下哪个命令用于指定路由器ID?A. router-idB. router ospfC. networkD. area答案:A19. 以下哪个命令用于在Cisco设备上查看OSPF路由表?A. show ip ospfB. show ip ospf databaseC. show ospfD. show ip route ospf答案:D20. 在配置VLAN时,以下哪个命令用于创建一个新的VLAN?A. vlan databaseB. configure terminalC. vlan [vlan-id]D. new-vlan答案:C21. 以下哪个命令用于将接口分配给VLAN?A. switchport mode accessB. switchport mode trunkC. switchport access vlan [vlan-id]D. switchport trunk vlan [vlan-id]答案:C22. 在配置交换机时,以下哪个命令用于将接口设置为Trunk 模式?A. switchport mode accessB. switchport mode trunkC. switchport access vlan [vlan-id]D. switchport trunk vlan [vlan-id]答案:B23. 以下哪个命令用于在Cisco设备上查看VLAN配置?A. show vlanB. show vlan briefC. show vlan detailD. show vlan all答案:B24. 在配置VTP时,以下哪个命令用于将交换机设置为VTP服务器模式?A. vtp mode serverB. vtp mode clientC. vtp mode transparentD. vtp mode off答案:A25. 以下哪个命令用于在Cisco设备上查看VTP状态?A. show vtp statusB. show vtp statisticsC. show vtp passwordD. show vtp configuration答案:A26. 在配置STP时,以下哪个命令用于设置根桥?A. spanning-tree root primaryB. spanning-tree root secondaryC. spanning-tree root primary [priority]D. spanning-tree root secondary [priority]答案:C27. 以下哪个命令用于在Cisco设备上查看STP状态?A. show spanning-treeB. show spanning-tree detailC. show spanning-tree summaryD. show spanning-tree interface答案:A28. 在配置VLAN Trunking Protocol (VTP) 时,以下哪个命令用于设置VTP域名?A. vtp domain [domain-name]B. vtp password [password]C. vtp mode [mode]D. vtp version [version]答案:A29. 以下哪个命令用于在Cisco设备上查看当前的VTP版本?A. show vtp statusB. show vtp statisticsC. show vtp passwordD. show vtp configuration答案:A30. 在配置端口安全时,以下哪个命令用于限制接口上可以学习到的最大MAC地址数量?A. switchport port-security maximum [mac-count]B. port-security maximum [mac-count]C. switchport port-security violation restrictD. port-security violation shutdown答案:A这些题目和答案仅供学习和参考之用,实际的CCNA考试内容和形式可能会有所不同。
ccna测试题及答案

ccna测试题及答案CCNA测试题及答案一、选择题1. 在Cisco设备上,以下哪个命令用于查看当前的路由表?A. show ip routeB. show running-configC. show interface statusD. show version答案:A2. 以下哪个协议用于在网络中自动发现其他设备?A. ARPB. CDPC. ICMPD. TCP答案:B3. 以下哪个命令用于配置Cisco设备上的接口?A. configure terminalB. interfaceC. ip addressD. hostname答案:A二、填空题4. 在Cisco设备上,使用命令_________可以查看接口的配置信息。
答案:show interface5. 静态路由配置中,_________命令用于指定下一跳地址。
答案:ip route6. 动态路由协议可以自动适应网络变化,其中_________是最常见的一种。
答案:RIP(路由信息协议)三、简答题7. 请简述VLAN(虚拟局域网)的作用。
答案:VLAN是一种将局域网内不同物理位置的设备划分为同一逻辑网络的技术,主要用于隔离广播域,提高网络的安全性和效率。
8. 描述交换机和路由器在网络中的基本功能。
答案:交换机主要用于局域网内部,通过MAC地址表来转发数据帧,实现数据包在局域网内的快速交换。
路由器则工作在网络层,使用IP地址来转发数据包,连接不同的网络,并进行路径选择。
四、计算题9. 假设一个子网掩码为255.255.255.192,计算这个子网的可用IP地址范围。
答案:可用IP地址范围为192.168.1.0到192.168.1.62(包含两端)。
五、实验题10. 请根据以下配置文件,列出Router1的接口配置信息。
```Router1show running-configinterface FastEthernet0/0ip address 192.168.1.1 255.255.255.0duplex autospeed auto!interface FastEthernet0/1no ip addressshutdown!interface Serial0/0/0ip address 10.0.0.1 255.255.255.252clock rate 64000!router ospf 1network 192.168.1.0 0.0.0.255 area 0network 10.0.0.0 0.0.0.3 area 0!```答案:- FastEthernet0/0: IP地址为192.168.1.1,子网掩码为255.255.255.0,双工模式和速度均为自动。
ccie考试题及答案

ccie考试题及答案1. 以下哪项技术用于在IP网络中进行流量工程?A. OSPFB. BGPC. MPLSD. EIGRP答案:C. MPLS2. 在Cisco设备上,如何配置以太网接口的全双工模式?A. speed 100fullB. duplex fullC. speed 100halfD. duplex half答案:B. duplex full3. 在Cisco交换机上,如何查看当前的VLAN配置?A. show vlanB. show interfacesC. show running-configD. show ip interface brief答案:A. show vlan4. 以下哪种协议用于在IP网络中进行动态路由选择?A. ARPB. ICMPC. RIPD. OSPF答案:D. OSPF5. 在Cisco设备上,如何关闭接口上的CDP(Cisco Discovery Protocol)?A. no cdp runB. no cdp enableC. cdp disableD. cdp no enable答案:A. no cdp run6. 以下哪种类型的ACL(访问控制列表)可以基于源IP地址来过滤流量?A. 标准ACLB. 扩展ACLC. 命名ACLD. 动态ACL答案:A. 标准ACL7. 在Cisco设备上,如何配置静态路由?A. ip route 0.0.0.0 0.0.0.0 <next-hop-ip>B. ip route <network> <subnet-mask> <next-hop-ip>C. ip route <interface> <next-hop-ip>D. ip route <network> <subnet-mask> <interface>答案:B. ip route <network> <subnet-mask> <next-hop-ip>8. 以下哪种技术用于在不同网络之间传输IPX流量?A. GREB. OSPFC. EIGRPD. RIP答案:A. GRE9. 在Cisco设备上,如何查看当前的路由表?A. show ip routeB. show running-configC. show interfacesD. show ip interface brief答案:A. show ip route10. 以下哪种协议用于在网络设备之间发现和学习邻居信息?A. CDPB. OSPFC. EIGRPD. RIP答案:A. CDP。
CCNACCNP网络工程师面试题

网络工程师岗位基础面试题适用于CCNA/CCNP基础1: 交换机是如何转发数据包的交换机通过学习数据帧中的源MAC地址生成交换机的MAC 地址表,交换机查看数据帧的目标MAC地址,根据MAC地址表转发数据,如果交换机在表中没有找到匹配项,则向除接受到这个数据帧的端口以外的所有端口广播这个数据帧;2 简述STP的作用及工作原理.作用1 能够在逻辑上阻断环路,生成树形结构的拓扑;2 能够不断的检测网络的变化,当主要的线路出现故障断开的时候,STP还能通过计算激活阻起到断的端口,起到链路的备份作用;工作原理: STP将一个环形网络生成无环拓朴的步骤:选择根网桥Root Bridge 选择根端口Root Ports选择指定端口Designated Ports生成树机理每个STP实例中有一个根网桥每个非根网桥上都有一个根端口每个网段有一个指定端口非指定端口被阻塞 STP是交换网络的重点,考察是否理解.3:简述传统的多层交换与基于CEF的多层交换的区别简单的说:传统的多层交换:一次路由,多次交换基于CEF的多层交换:无须路由,一直交换.4、DHCP的作用是什么,如何让一个vlan中的DHCP服务器为整个企业网络分配IP地址作用:动态主机配置协议,为客户端动态分配IP地址.配置DHCP中继,也就是帮助地址.因为DHCP是基于广播的,vlan 或路由器隔离了广播5:有一台交换机上的所有用户都获取不了IP地址,但手工配置后这台交换机上的同一vlan 间的用户之间能够相互ping通,但ping不通外网,请说出排障思路.1:如果其它交换机上的终端设备能够获取IP地址,看帮助地址是否配置正确; 2:此交换机与上连交换机间是否封装为Trunk.3:单臂路由实现vlan间路由的话看子接口是否配置正确,三层交换机实现vlan间路由的话看是否给vlan配置ip地址及配置是否正确.4:再看此交换机跟上连交换机之间的级连线是否有问题; 排障思路.6:什么是静态路由什么是动态路由各自的特点是什么静态路由是由管理员在路由器中手动配置的固定路由,路由明确地指定了包到达目的地必须经过的路径,除非网络管理员干预,否则静态路由不会发生变化;静态路由不能对网络的改变作出反应,所以一般说静态路由用于网络规模不大、拓扑结构相对固定的网络;静态路由特点1、它允许对路由的行为进行精确的控制;2、减少了网络流量;3、是单向的;4、配置简单;动态路由是网络中的路由器之间相互通信,传递路由信息,利用收到的路由信息更新路由表的过程;是基于某种路由协议来实现的;常见的路由协议类型有:距离矢量路由协议如RIP 和链路状态路由协议如OSPF;路由协议定义了路由器在与其它路由器通信时的一些规则;动态路由协议一般都有路由算法;其路由选择算法的必要步骤 1、向其它路由器传递路由信息; 2、接收其它路由器的路由信息;3、根据收到的路由信息计算出到每个目的网络的最优路径,并由此生成路由选择表;4、根据网络拓扑的变化及时的做出反应,调整路由生成新的路由选择表,同时把拓扑变化以路由信息的形式向其它路由器宣告;动态路由适用于网络规模大、拓扑复杂的网络; 动态路由特点:1、无需管理员手工维护,减轻了管理员的工作负担;2、占用了网络带宽;3、在路由器上运行路由协议,使路由器可以自动根据网络拓朴结构的变化调整路由条目;能否根据具体的环境选择合适的路由协议7:简述有类与无类路由选择协议的区别有类路由协议:路由更新信息中不含有子网信息的协议,如RIPV1,IGRP无类路由协议:路由更新信息中含有子网信息的协议,如OSPF,RIPV2,IS-IS,EIGRP 是否理解有类与无类8:简述RIP的防环机制1.定义最大跳数 Maximum Hop Count 15跳2.水平分割 Split Horizon 默认所有接口开启,除了Frame-Relay的物理接口,可用ship interface 查看开启还是关闭3.毒化路由 Poizoned Route4.毒性反转 Poison Reverse RIP基于UDP,UDP和IP都不可靠,不知道对方收到毒化路由没有;类似于对毒化路由的Ack机制5.保持计时器 hold-down Timer 防止路由表频繁翻动6.闪式更新 Flash Update7.触发更新 Triggered Update 需手工启动,且两边都要开 Router config-if ip rip triggered当启用触发更新后,RIP不再遵循30s的周期性更新时间,这也是与闪式更新的区别所在; RIP的4个计时器:更新计时器update: 30 s无效计时器invalid: 180 s 180s没收到更新,则置为possible down状态保持计时器holddown: 180s 真正起作用的只有60s刷新计时器flush: 240s 240s没收到更新,则删除这条路由如果路由变成possible down后,这条路由跳数将变成16跳,标记为不可达;这时holddown 计时器开始计时;在holddown时间内即使收到更优的路由,不加入路由表;这样做是为了防止路由频繁翻动; 什么时候启用holddown计时器:“当收到一条路由更新的跳数大于路由表中已记录的该条路由的跳数”9:简述电路交换和分组交换的区别及应用场合.电路交换连接1根据需要进行连接2每一次通信会话期间都要建立、保持,然后拆除在电信运营商网络中建立起来的专用物理电路分组交换连接1将传输的数据分组2多个网络设备共享实际的物理线路3使用虚电路/虚通道Virtual Channel传输若要传送的数据量很大,且其传送时间远大于呼叫时间,则采用电路交换较为合适;当端到端的通路有很多段的链路组成时,采用分组交换传送数据较为合适;10:简述PPP协议的优点.支持同步或异步串行链路的传输支持多种网络层协议支持错误检测支持网络层的地址协商支持用户认证允许进行数据压缩11: pap和chap认证的区别PAP口令验证协议 Password Authentication Protocol是一种简单的明文验证方式;NAS 网络接入服务器,NetworkAccessServer要求用户提供用户名和口令,PAP以明文方式返回用户信息;很明显,这种验证方式的安全性较差,第三方可以很容易的获取被传送的用户名和口令,并利用这些信息与NAS建立连接获取NAS提供的所有资源;所以,一旦用户密码被第三方窃取,PAP无法提供避免受到第三方攻击的保障措施;CHAP挑战-握手验证协议 Challenge-Handshake AuthenticationProtocol是一种加密的验证方式,能够避免建立连接时传送用户的真实密码;NAS向远程用户发送一个挑战口令challenge,其中包括会话ID和一个任意生成的挑战字串arbitrary challengestring;远程客户必须使用MD5单向哈希算法one-wayhashing algorithm返回用户名和加密的挑战口令,会话ID以及用户口令,其中用户名以非哈希方式发送;CHAP对PAP进行了改进,不再直接通过链路发送明文口令,而是使用挑战口令以哈希算法对口令进行加密;因为服务器端存有客户的明文口令,所以服务器可以重复客户端进行的操作,并将结果与用户返回的口令进行对照;CHAP为每一次验证任意生成一个挑战字串来防止受到再现攻击replayattack;在整个连接过程中,CHAP将不定时的向客户端重复发送挑战口令,从而避免第3方冒充远程客户remote clientimpersonation进行攻击;12:ADSL是如何实现数据与语音同传的物理层:频分复用技术.高频传输数据,低频传输语音具体讲解的话可以说明:调制,滤波,解调的过程.13:OSPF中那几种网络类型需要选择DR,BDR广播型网络和非广播多路访问NBMA网络需要选.14:OSPF中完全末梢区域的特点及适用场合特点:不能学习其他区域的路由不能学习外部路由完全末梢区域不仅使用缺省路由到达OSPF自主系统外部的目的地址,而且使用这个缺省路由到达这个区域外部的所有目的地址.一个完全末梢区域的ABR不仅阻塞AS外部LSA,而且阻塞所有汇总LSA.适用场合:只有一出口的网络.15:OSPF中为什么要划分多区域1、减小路由表大小2、限制lsa的扩散3、加快收敛4、增强稳定性16:NSSA区域的特点是什么1.可以学习本区域连接的外部路由;2.不学习其他区域转发进来的外部路由17:你都知道网络的那些冗余技术,请说明.交换机的冗余性:spanning-tree、ethernet-channel 路由的冗余性:HSRP,VRRP,GLBP. 有必要的话可以详细介绍18:HSRP的转换时间是多长时间10s19:标准访问控制列表和扩展访问控制列表的区别.标准访问控制列表:基于源进行过滤扩展访问控制列表: 基于源和目的地址、传输层协议和应用端口号进行过滤20:NAT的原理及优缺点.原理:转换内部地址,转换外部地址,PAT,解决地址重叠问题.优点:节省IP地址,能够处理地址重复的情况,增加了灵活性,消除了地址重新编号,隐藏了内部IP地址.缺点:增加了延迟,丢失了端到端的IP的跟踪过程,不能够支持一些特定的应用如:SNMP,需要更多的内存来存储一个NAT表,需要更多的CPU来处理NAT的过程.21: 对称性加密算法和非对称型加密算法的不同对称性加密算法的双方共同维护一组相同的密钥,并使用该密钥加密双方的数据,加密速度快,但密钥的维护需要双方的协商,容易被人窃取;非对称型加密算法使用公钥和私钥,双方维护对方的公钥一对,并且各自维护自己的私钥,在加密过程中,通常使用对端公钥进行加密,对端接受后使用其私钥进行解密,加密性良好,而且不易被窃取,但加密速度慢.22: 安全关联的作用SA分为两步骤:1.IKE SA,用于双方的对等体认证,认证对方为合法的对端;2.IPSec SA,用于双方认证后,协商对数据保护的方式.23: ESP和AH的区别ESP除了可以对数据进行认证外,还可以对数据进行加密;AH不能对数据进行加密,但对数据认证的支持更好 .24: snmp的两种工作方式是什么,有什么特点首先,SNMP是基于UDP的,有两种工作方式,一种是轮询,一种是中断. 轮询:网管工作站随机开端口轮询被管设备的UDP的161端口. 中断:被管设备将trap报文主动发给网管工作站的UDP的162端口. 特点:轮询一定能够查到被管设备是否出现了故障,但实时性不好. 中断实时性好触发更新,但不一定能够将trap报文报告给网管工作站.网络工程师应掌握的50个路由器知识要点1、什么时候使用多路由协议当两种不同的路由协议要交换路由信息时,就要用到多路由协议;当然,路由再分配也可以交换路由信息;下列情况不必使用多路由协议:从老版本的内部网关协议 Interior Gateway Protocol,I G P升级到新版本的I G P; 你想使用另一种路由协议但又必须保留原来的协议;你想终止内部路由,以免受到其他没有严格过滤监管功能的路由器的干扰; 你在一个由多个厂家的路由器构成的环境下;2、什么是距离向量路由协议距离向量路由协议是为小型网络环境设计的;在大型网络环境下,这类协议在学习路由及保持路由将产生较大的流量,占用过多的带宽;如果在9 0秒内没有收到相邻站点发送的路由选择表更新,它才认为相邻站点不可达;每隔30秒,距离向量路由协议就要向相邻站点发送整个路由选择表,使相邻站点的路由选择表得到更新;这样,它就能从别的站点直接相连的或其他方式连接的收集一个网络的列表,以便进行路由选择;距离向量路由协议使用跳数作为度量值,来计算到达目的地要经过的路由器数;例如,R I P使用B e l l m a n - F o r d算法确定最短路径,即只要经过最小的跳数就可到达目的地的线路;最大允许的跳数通常定为1 5;那些必须经过1 5个以上的路由器的终端被认为是不可到达的; 距离向量路由协议有如下几种: IP RIP、IPX RIP、A p p l e Talk RT M P和I G R P;3、什么是链接状态路由协议链接状态路由协议更适合大型网络,但由于它的复杂性,使得路由器需要更多的C P U资源;它能够在更短的时间内发现已经断了的链路或新连接的路由器,使得协议的会聚时间比距离向量路由协议更短;通常,在1 0秒钟之内没有收到邻站的H E L LO报文,它就认为邻站已不可达;一个链接状态路由器向它的邻站发送更新报文,通知它所知道的所有链路;它确定最优路径的度量值是一个数值代价,这个代价的值一般由链路的带宽决定;具有最小代价的链路被认为是最优的;在最短路径优先算法中,最大可能代价的值几乎可以是无限的;如果网络没有发生任何变化,路由器只要周期性地将没有更新的路由选择表进行刷新就可以了周期的长短可以从3 0分钟到2个小时;链接状态路由协议有如下几种: IP OSPF、IPX NLSP和I S - I S; 一个路由器可以既使用距离向量路由协议,又使用链接状态路由协议吗可以;每一个接口都可以配置为使用不同的路由协议;但是它们必须能够通过再分配路由来交换路由信息;4、什么是访问表访问表是管理者加入的一系列控制数据包在路由器中输入、输出的规则;它不是由路由器自己产生的; 访问表能够允许或禁止数据包进入或输出到目的地;访问表的表项是顺序执行的,即数据包到来时,首先看它是否是受第一条表项约束的,若不是,再顺序向下执行;如果它与第一条表项匹配,无论是被允许还是被禁止,都不必再执行下面表项的检查了; 每一个接口的每一种协议只能有一个访问表;5、支持哪些类型的访问表一个访问表可以由它的编号来确定;具体的协议及其对应的访问表编号如下: ◎I P标准访问表编号:1~9 9 ◎I P扩展访问表编号:1 0 0~1 9 9 ◎I P X标准访问表编号:8 0 0~8 9 9 ◎I P X扩展访问表编号:1 0 0 0~1 0 9 9 ◎AppleTa l k访问表编号:6 0 0~6 9 9提示在Cisco IOS Release11.2或以上版本中,可以用有名访问表确定编号在1~199的访问表;6、如何创建IP标准访问表一个I P标准访问表的创建可以由如下命令来完成: Access-list access list number {permit | deny} source source-mask 在这条命令中:◎access list number:确定这个入口属于哪个访问表;它是从1到9 9的数字; ◎permit | deny:表明这个入口是允许还是阻塞从特定地址来的信息流量; ◎source:确定源I P地址;◎s o u r c e - m a s k:确定地址中的哪些比特是用来进行匹配的;如果某个比特是"1",表明地址中该位比特不用管,如果是"0"的话,表明地址中该位比特将被用来进行匹配;可以使用通配符; 以下是一个路由器配置文件中的访问表例子: Router show access-lists Standard IP access list 1deny 204.59.144.0, wildcard bits 0.0.0.255 ermit any7、什么时候使用路由再分配路由再分配通常在那些负责从一个自治系统学习路由,然后向另一个自治系统广播的路由器上进行配置;如果你在使用I G R P或E I G R P,路由再分配通常是自动执行的;8、什么是管理距离管理距离是指一种路由协议的路由可信度;每一种路由协议按可靠性从高到低,依次分配一个信任等级,这个信任等级就叫管理距离;对于两种不同的路由协议到一个目的地的路由信息,路由器首先根据管理距离决定相信哪一个协议;9、如何配置再分配在进行路由再分配之前,你必须首先:1 决定在哪儿添加新的协议;2 确定自治系统边界路由器ASBR;3)决定哪个协议在核心,哪个在边界;4)决定进行路由再分配的方向;可以使用以下命令再分配路由更新这个例子是针对OSPF的:routerconfig-routerredistribute protocol process-id metric metric- value metric-type type - value subnets 在这个命令中:◎protocol:指明路由器要进行路由再分配的源路由协议;主要的值有: bgp、eqp、igrp、isis、ospf、static ip 、connected和rip; ◎process-id:指明OSPF的进程ID;◎metric:是一个可选的参数,用来指明再分配的路由的度量值;缺省的度量值是0;10、为什么确定毗邻路由器很重要在一个小型网络中确定毗邻路由器并不是一个主要问题;因为当一个路由器发生故障时,别的路由器能够在一个可接受的时间内收敛;但在大型网络中,发现一个故障路由器的时延可能很大;知道毗邻路由器可以加速收敛,因为路由器能够更快地知道故障路由器,因为hello 报文的间隔比路由器交换信息的间隔时间短;使用距离向量路由协议的路由器在毗邻路由器没有发送路由更新信息时,才能发现毗邻路由器已不可达,这个时间一般为10~90秒;而使用链接状态路由协议的路由器没有收到hello报文就可发现毗邻路由器不可达,这个间隔时间一般为10秒钟;11、距离向量路由协议和链接状态路由协议如何发现毗邻路由器使用距离向量路由协议的路由器要创建一个路由表其中包括与它直接相连的网络,同时它会将这个路由表发送到与它直接相连的路由器;毗邻路由器将收到的路由表合并入它自己的路由表,同时它也要将自己的路由表发送到它的毗邻路由器;使用链接状态路由协议的路由器要创建一个链接状态表,包括整个网络目的站的列表;在更新报文中,每个路由器发送它的整个列表;当毗邻路由器收到这个更新报文,它就拷贝其中的内容,同时将信息发向它的邻站;在转发路由表内容时没有必要进行重新计算;注意使用IGRP和EIGRP的路由器广播hello报文来发现邻站,同时像OSPF一样交换路由更新信息;EIGRP为每一种网络层协议保存一张邻站表,它包括邻站的地址、在队列中等待发送的报文的数量、从邻站接收或向邻站发送报文需要的平均时间,以及在确定链接断开之前没有从邻站收到任何报文的时间;12、什么是自治系统一个自治系统就是处于一个管理机构控制之下的路由器和网络群组;它可以是一个路由器直接连接到一个LAN上,同时也连到Internet上;它可以是一个由企业骨干网互连的多个局域网;在一个自治系统中的所有路由器必须相互连接,运行相同的路由协议,同时分配同一个自治系统编号;自治系统之间的链接使用外部路由协议,例如B G P;13、什么是BGPBGPBorder GatewayProtocol是一种在自治系统之间动态交换路由信息的路由协议;一个自治系统的经典定义是在一个管理机构控制之下的一组路由器,它使用IGP和普通度量值向其他自治系统转发报文; 在BGP中使用自治系统这个术语是为了强调这样一个事实:一个自治系统的管理对于其他自治系统而言是提供一个统一的内部选路计划,它为那些通过它可以到达的网络提供了一个一致的描述;14、BGP支持的会话种类BGP相邻路由器之间的会话是建立在TCP协议之上的;TCP协议提供一种可靠的传输机制,支持两种类型的会话:o 外部BGPEBGP:是在属于两个不同的自治系统的路由器之间的会话;这些路由器是毗邻的,共享相同的介质和子网;o 内部BGPIBGP:是在一个自治系统内部的路由器之间的会话;它被用来在自治系统内部协调和同步寻找路由的进程;BGP路由器可以在自治系统的任何位置,甚至中间可以相隔数个路由器;注意"初始的数据流的内容是整个BGP路由表;但以后路由表发生变化时,路由器只传送变化的部分;BGP不需要周期性地更新整个路由表;因此,在连接已建立的期间,一个BGP发送者必须保存有当前所有同级路由器共有的整个BGP路由表;BGP路由器周期性地发送Keep Alive消息来确认连接是激活的;当发生错误或特殊情况时,路由器就发送Notification消息;当一条连接发生错误时,会产生一个 notification消息并断开连接;"-来自RFC11654、BGP操作;15、BGP允许路由再分配吗允许;因为BGP主要用来在自治系统之间进行路由选择,所以它必须支持RIP、OSPF和 IGRP 的路由选择表的综合,以便将它们的路由表转入一个自治系统;BGP是一个外部路由协议,因此它的操作与一个内部路由协议不同;在BGP中,只有当一条路由已经存在于IP路由表中时,才能用NETWORK命令在BGP路由表中创建一条路由;16、如何显示在数据库中的所有BGP路由要显示数据库中的所有BGP路由,只需在EXEC命令行下输入: how ipbgp paths 这个命令的输出可能是:Address Hash RefcountMetricPath 0 x 2 9 7 A9 C 0 2 0 i17、什么是水平分割水平分割是一种避免路由环的出现和加快路由汇聚的技术;由于路由器可能收到它自己发送的路由信息,而这种信息是无用的,水平分割技术不反向通告任何从终端收到的路由更新信息,而只通告那些不会由于计数到无穷而清除的路由;18、路由环是如何产生的由于网络的路由汇聚时间的存在,路由表中新的路由或更改的路由不能够很快在全网中稳定,使得有不一致的路由存在,于是会产生路由环;19、什么是度量值度量值代表距离;它们用来在寻找路由时确定最优路由;每一种路由算法在产生路由表时,会为每一条通过网络的路径产生一个数值度量值,最小的值表示最优路径;度量值的计算可以只考虑路径的一个特性,但更复杂的度量值是综合了路径的多个特性产生的;一些常用的度量值有: ◎跳步数:报文要通过的路由器输出端口的个数; ◎Ticks:数据链路的延时大约1/18每秒;◎代价:可以是一个任意的值,是根据带宽,费用或其他网络管理者定义的计算方法得到的; ◎带宽:数据链路的容量;◎时延:报文从源端传到目的地的时间长短; ◎负载:网络资源或链路已被使用的部分的大小; ◎可靠性:网络链路的错误比特的比率;◎最大传输单元MTU:在一条路径上所有链接可接受的最大消息长度单位为字节; IGRP使用什么类型的路由度量值这个度量值由什么组成 IGRP使用多个路由度量值;它包括如下部分: ◎带宽:源到目的之间最小的带宽值; ◎时延:路径中积累的接口延时;◎可靠性:源到目的之间最差的可能可靠性,基于链路保持的状态; ◎负载:源到目的之间的链路在最坏情况下的负载,用比特每秒表示; ◎MTU:路径中最小的M T U值;20、度量值可以修改或调整吗加一个正的偏移量;这个命令的完整结构如下:可以使用OFFSET-LIST ROUTER子命令为访问表中的网络输入和输出度量值添加一个正的偏移量;offset-list {in|out} offset access-list no offset-list {in|out} offset access-list 如果参数LIST的值是0,那么OFFSET参数将添加到所有的度量值;如果OFFSET的值是0,那么就没有任何作用;对于IGRP来说,偏移量的值只加到时延上;这个子命令也适用于RIP 和hello路由协议; 使用带适当参数的NO OFFSET- LIST命令可以清除这个偏移量;在以下的例子中,一个使用IGRP的路由器在所有输出度量值的时延上加上偏移量10: offset-list out 10下面是一个将相同的偏移量添加到访问表121上的例子: offset-list out 10 12121、每个路由器在寻找路由时需要知道哪五部分信息所有的路由器需要如下信息为报文寻找路由◎目的地址:报文发送的目的主机;◎邻站的确定:指明谁直接连接到路由器的接口上; ◎路由的发现:发现邻站知道哪些网络;◎选择路由:通过从邻站学习到的信息,提供最优的与度量值有关到达目的地的路径; ◎保持路由信息:路由器保存一张路由表,它存储所知道的所有路由信息;22、Cisco路由器支持的路由协议与其他厂家设备的协议兼容吗除了IGRP和EIGRP,Cisco路由器支持的所有路由协议都与其他厂家实现的相同协议兼容;IGRP和EIGRP是Cisco的专利产品;23、RIP路由表的表项的信息说明了什么。
CCNA认证试题(中文+答案)

CCNA认证试题一(附答案和解析)中文版(一)1、目前,我国应用最为广泛的LAN标准是基于()的以太网标准.(A) IEEE 802。
1(B) IEEE 802。
2(C) IEEE 802.3(D)IEEE 802.5答案:C参考知识点:现有标准:IEEE 802.1 局域网协议高层IEEE 802.2 逻辑链路控制IEEE 802。
3 以太网IEEE 802.4 令牌总线IEEE 802。
5 令牌环IEEE 802.8 FDDIIEEE 802。
11 无线局域网记住IEEE802.1-——-—--IEEE802。
5的定义以太网是一种计算机局域网组网技术.IEEE制定的IEEE 802。
3标准给出了以太网的技术标准.它规定了包括物理层的连线、电信号和介质访问层协议的内容。
以太网是当前应用最普遍的局域网技术.它很大程度上取代了其他局域网标准,如令牌环、FDDI和ARCNET。
以太网的标准拓扑结构为总线型拓扑,但目前的快速以太网(100BASE—T、1000BASE-T标准)为了最大程度的减少冲突,最大程度的提高网络速度和使用效率,使用交换机(Switch)来进行网络连接和组织,这样,以太网的拓扑结构就成了星型,但在逻辑上,以太网仍然使用总线型拓扑的C***A/CD介质访问控制方法.电气电子工程师协会或IEEE(Institute of Electrical and Electronics Engineers)是一个国际性的电子技术与信息科学工程师的协会.建会于1963年1月1日。
总部在美国纽约市。
在150多个国家中它拥有300多个地方分会。
目前会员数是36万.专业上它有35个专业学会和两个联合会。
IEEE发表多种杂志,学报,书籍和每年组织300多次专业会议。
IEEE定义的标准在工业界有极大的影响.下面列出:IEEE802.3以太网标准802。
3--——---—— 10Base以太网标准802.3u-—------ 100Base-T(快速以太网)802.3z—-—————— 1000Base-X(光纤吉比特以太网)802.3ab———-——-— 1000Base—T(双绞线吉比特以太网)2、对于这样一个地址,192。
CCNA综合测试

CCNA培训综合考试姓名: 分数:一、选择题(30*1)1.传输层的PDU是( ),网络层的PDU是( )A. 分段B. 数据包C. 数据帧D. 比特流2.数据封装的顺序是什么( )A. 数据-数据包-数据帧-比特流-分段B. 数据-比特流-数据包-数据帧-分段C. 数据-分段-数据帧-比特流-数据包D. 数据-分段-数据包-数据帧-比特流3.常见的端口号SMTP( ) POP3( )A.20B.21C.23D.25E. 1104.IPv4地址是(),MAC地址是( )A. 192.168.1.1/24B. ::1C. 0053.4500.00005. 什么样的寄存器的值是不加载startup-config( )A. 0x2102B. 0x2142C.0x2100D. 0x21016.Cisco路由器保存配置的命令是( )A. copy run startB. copy tftp flashC. copy run startD. write 7.Cisco路由器中特权模式( ),全局模式( )用下列什么符号A. >B. #C. (config)#D. (config-if)8.Cisco的CDP协议不能实现的功能有A. 设备标识B. 地址列表C. 工作平台D.看到设备的VLAN信息9.A,B,C类地址私有地址的范围是A类( ),B类( )A. 127.0.0.1B. 172.16.0.0-172.31.255.255.C. 192.168.0.0-192.168.255.255D. 10.0.0.0-10.255.255.25510.192.168.1.0/25 的网络地址( )主机地址数量( )A. 192.168.1.128B. 192.168.1.255C. 254D. 12611.主机的IP地址可以通过静态配置和( )方式得到?A. HSRPB. DHCPC. OSPFD. VTP12.switch是( )层设备,router是( )层设备A,物理层,B.数据链路层,C.网络层 D.数据链路层13. 双绞线的最大传输距离是( )MA.100B.200C.50D.100014.交换机一般工作在( )双工模式,Hub只能工作在( )双工模式 A,全双工 B.半双工 C. 单工15.交换机的工作原理是基于( )的学习,基于( )的转发A.源MACB. 源IPC.,目标MACD.目标IP16.请选出各种路由协议在Cisco路由器中的管理距离EIGRP( ),OSPF( ) A. 120 B. 90 .C. 110 D.15017.公有的的vlan中继(trunk)协议有是( )A. 802.1qB. ISL .C. VTPD.sopf18.Cisco交换机通过( )协议同步VLAN信息A. 802.1qB. ISL .C. VTPD.sopf19.下面那种模式不是VTP的模式的是( )A透明模式 B服务器模式 C客户模式 D,主动模式20.距离矢量的代表协议是( )和链路状态的代表协议是( )A. RIPB.BGPC. SOPFD. 静态路由协议21.运行STP的端口从阻塞到转发要经过( ) 秒A. 10B. 20 .C. 30D.5022.不是内部网关路由协议是 ( )A.RIPB.OSPFC.EIGRPD.BGP23.WAN在OSI七层模型中的哪两层,A. 网络层和数据链路层B. 物理层和数据链路层C.传输层和网络层D.应用层和物理层24.标准ACL的特点是( )和扩展ACL的特点是( )A. 标准的只能对源IP地址检测,B.扩展的能对源/目IP,源/目端口,协议检测C标准的能对源/目IP,源/目端口,协议检测D. 扩展的只能对源IP地址检测,25.那种NAT能实现只有( )一对多A.动态NATB.静态NATC.PAT26.下列NAT能实现双向访问? ( )A.动态NATB.静态NATC.PAT27.下列( )条件不是触发NAT的条件?A. inside方向进B. outside方向出C.匹配ACLD. 目标地址可以ping通 28.常见的无线通信标准不包括? ( )A.802.11aB.802.11bC.802.11gD.802.1Q29.802.11b/Gz中互不干扰的信道不包括( )?A.1B.6C.11D.1230.802.11G它们的最大传输速率是( )A.54mbpsB.11mbpsC.100mbpsD.10mbps二、判断题(10*2)用Y/N表示1. TCP是可靠连接,UDP不是可靠连接。
ccnp测试题及答案

ccnp测试题及答案1. 在CCNP认证中,关于VLAN的以下哪个说法是正确的?A. VLAN是将交换机端口划分为多个广播域B. VLAN是将路由器端口划分为多个广播域C. VLAN是将无线接入点划分为多个广播域D. VLAN是将服务器划分为多个广播域答案:A2. 在Cisco网络设备中,哪个命令用于创建一个新的VLAN?A. `switchport mode access`B. `switchport mode trunk`C. `vlan database`D. `configure terminal`答案:C3. 以下哪个协议用于在不同VLAN之间路由?A. EIGRPB. OSPFC. RIPD. VTP答案:A4. 在Cisco设备上,如何将接口配置为Trunk模式?A. `switchport mode access`B. `switchport mode trunk`C. `interface vlan 1`D. `interface fastethernet 0/1`答案:B5. 以下哪个命令用于在Cisco设备上查看VLAN信息?A. `show vlan`B. `show interfaces`C. `show ip interface brief`D. `show running-config`答案:A6. 在CCNP考试中,关于EIGRP协议的以下哪个说法是错误的?A. EIGRP是一个距离矢量路由协议B. EIGRP使用DUAL算法计算最短路径C. EIGRP支持VLSM和CIDRD. EIGRP仅在Cisco设备上可用答案:D7. 在Cisco设备上,如何配置EIGRP的自动汇总?A. `router eigrp 100`B. `no auto-summary`C. `ip summary-address eigrp 100 0.0.0.0 0.0.0.0`D. `metric weights 0 1 1 1 0 0 0 1`答案:C8. 以下哪个命令用于在Cisco设备上查看EIGRP邻居?A. `show ip eigrp neighbors`B. `show ip ospf neighbors`C. `show ip rip neighbors`D. `show ip eigrp interface`答案:A9. 在CCNP考试中,关于OSPF协议的以下哪个说法是正确的?A. OSPF仅在Cisco设备上可用B. OSPF使用RIP算法计算最短路径C. OSPF支持VLSM和CIDRD. OSPF使用广播来发现邻居答案:C10. 在Cisco设备上,如何配置OSPF的Hello和Dead间隔?A. `ip ospf hello-interval 10`B. `ip ospf dead-interval 40`C. `timers 10 40`D. `ospf hello-interval 10 dead-interval 40`答案:C结束语:以上是CCNP测试题及答案,希望对您的学习和准备有所帮助。
