Cisco PVLAN 详解
CISCO 思科 PVLAN 配置

Securing Networks with Private VLANs and VLAN Access Control ListsDocument ID: 10601IntroductionBefore You BeginConventionsPrerequisitesComponents UsedBackground InformationImportance of Enforcing a Proper Trust ModelPrivate VLANsVLAN Access Control ListsKnown Limitations of VACLs and PVLANsExample Case StudiesPass−Through DMZExternal DMZVPN Concentrator in Parallel to FirewallRelated InformationIntroductionOne of the key factors to building a successful network security design is to identify and enforce a proper trust model. The proper trust model defines who needs to talk to whom and what kind of traffic needs to be exchanged; all other traffic should be denied. Once the proper trust model has been identified, then the security designer should decide how to enforce the model. As more critical resources are globally available and new forms of network attacks evolve, the network security infrastructure tends to become more sophisticated, and more products are available. Firewalls, routers, LAN switches, intrusion detection systems, AAA servers, and VPNs are some of the technologies and products that can help enforce the model. Of course, each one of these products and technologies plays a particular role within the overall security implementation, and it is essential for the designer to understand how these elements can be deployed. Before You BeginConventionsFor more information on document conventions, see the Cisco Technical Tips Conventions. PrerequisitesThis document describes PVLAN configurations on switches running CatOS only. For side−by−side configuration examples of PVLANs on switches running Cisco IOS and CatOS, refer to the document Configuring Isolated Private VLANs on Catalyst Switches.Not all switches and software versions support PVLANs. Refer to Private VLAN Catalyst Switch Support Matrix to determine whether your platform and software version supports PVLANs.Components UsedThis document is not restricted to specific software and hardware versions.Background InformationIdentifying and enforcing a proper trust model seems to be a very basic task, but after several years of supporting security implementations, our experience indicates that security incidents are often related to poor security designs. Usually these poor designs are a direct consequence of not enforcing a proper trust model, sometimes because what is just necessary is not understood, other times just because the technologies involved are not fully understood or are misused.This document explains in detail how two features available in our Catalyst switches, Private VLANs (PVLANs) and VLAN Access Control Lists (VACLs), can help ensure an adequate trust model in both enterprise as well as service provider environments.Importance of Enforcing a Proper Trust ModelAn immediate consequence of not enforcing an adequate trust model is that the overall security implementation becomes less immune to malicious activities. Demilitarized Zones (DMZs) are commonly implemented without enforcing the right policies, thus facilitating the activity of a potential intruder. This section analyzes how DMZs are often implemented and the consequences of a poor design. We will later explain how to mitigate, or in the best case avoid, these consequences.Usually, DMZ servers are only supposed to process incoming requests from the Internet, and eventually initiate connections to some back−end servers located at an inside or other DMZ segment, such as a database server. At the same time, DMZ servers are not supposed to talk to each other or initiate any connections to the outside world. This clearly defines the necessary traffic flows in a simple trust model; however, we often see this kind of model not adequately enforced.Designers usually tend to implement DMZs using a common segment for all servers without any control over the traffic between them. For example, all servers are located in a common VLAN. Since nothing is controlling the traffic within the same VLAN, if one of the servers is compromised, then the same server can be exploited to source an attack to any of the servers and hosts in the same segment. This clearly facilitates the activity of a potential intruder conducting a port redirection or Application Layer attack.Typically, firewalls and packet filters are only used to control incoming connections, but nothing is usually done to restrict connections originated from the DMZ. Some time ago there was a well−known vulnerability in a cgi−bin script that allowed an intruder to begin an X−term session by just sending an HTTP stream; this is traffic that should be allowed by the firewall. If the intruder was lucky enough, he or she could use another treat to get a root prompt, typically some kind of buffer overflow attack. Most of the times these kinds of problems can be avoided by enforcing a proper trust model. First, servers are not supposed to talk to each other, and second no connections should be originated from these servers to the outside world.The same comments apply to many other scenarios, going from any regular un−trusted segment up to server farms at application service providers.PVLANs and VACLs on Catalyst switches can help ensure a proper trust model. PVLANs will help by restricting the traffic between hosts in a common segment, while VACLs will contribute by providing further control over any traffic flow originated or destined to a particular segment. These features are discussed in the following sections.Private VLANsPVLANs are available on the Catalyst 6000 running CatOS 5.4 or later, on the Catalyst 4000, 2980G,2980G−A, 2948G, and 4912G running CatOS 6.2 or later.From our perspective, PVLANs are a tool that allows segregating traffic at Layer 2 (L2) turning a broadcast segment into a non−broadcast multi−access−like segment. Traffic that comes to a switch from a promiscuous port (that is, a port that is capable of forwarding both primary and secondary VLANs) is able to go out on all the ports that belong to the same primary VLAN. Traffic that comes to a switch from a port mapped to a secondary VLAN (it can be either an isolated, a community, or a two−way community VLAN) can be forwarded to a promiscuous port or a port belonging to the same community VLAN. Multiple ports mapped to the same isolated VLAN cannot exchange any traffic.The following image shows the concept.Figure 1: Private VLANsThe primary VLAN is represented in blue; the secondary VLANs are represented in red and yellow. Host−1 is connected to a port of the switch that belongs to the secondary VLAN red. Host−2 is connected to a port of the switch that belongs to the secondary VLAN yellow.When a host is transmitting, the traffic is carried in the secondary VLAN. For example, when Host−2 transmits, its traffic goes on VLAN yellow. When those hosts are receiving, the traffic comes from the VLAN blue, which is the primary VLAN.The ports where routers and firewalls are connected are promiscuous ports because those ports can forward traffic coming from every secondary VLAN defined in the mapping as well as the primary VLAN. The ports connected to each hosts can only forward the traffic coming from the primary VLAN and the secondary VLAN configured on that port.The drawing represents the private VLANs as different pipes that connect routers and hosts: the pipe that bundles all the others is the primary VLAN (blue), and the traffic on VLAN blue flows from the routers to the hosts. The pipes internal to the primary VLAN are the secondary VLANs, and the traffic traveling on those pipes is from the hosts towards the router.As the image is showing, a primary VLAN can bundle one or more secondary VLANs.Earlier in this document we said PVLANs help enforce the proper trust model by simply ensuring the segregation of hosts within a common segment. Now that we know more about Private VLANs, let us see how this can be implemented in our initial DMZ scenario. Servers are not supposed to talk to each other, but they still need to talk to the firewall or router to which they are connected. In this case, servers should be connected to isolated ports while routers and firewalls should be attached to promiscuous ports. By doing this, if one of the servers is compromised, the intruder won't be able to use the same server to source an attack to another server within the same segment. The switch will drop any packet at wire speed, without any performance penalty.Another important note is that this kind of control can only be implemented at the L2 device because all servers belong to the same subnet. There is nothing a firewall or router can do since servers will try to communicate directly. Another option is to dedicate a firewall port per server, but this is likely too expensive, difficult to implement, and does not scale.In a later section, we describe in detail some other typical scenarios in which you can use this feature. VLAN Access Control ListsVACLs are available on the Catalyst 6000 series running CatOS 5.3 or later.VACLs can be configured on a Catalyst 6500 at L2 without the need for a router (you only need a Policy Feature Card (PFC) ). They are enforced at wire speed so there is no performance penalty in configuring VACLs on a Catalyst 6500. Since the lookup of VACLs is performed in hardware, regardless of the size of the access list, the forwarding rate remains unchanged.VACLs can be mapped separately to primary or secondary VLANs. Having a VACL configured on a secondary VLAN allows filtering the traffic originated by hosts without touching the traffic generated by routers or firewalls.By combining VACLs and Private VLANs it is possible to filter traffic based on the direction of the traffic itself. For example, if two routers are connected to the same segment as some hosts (servers for example), VACLs can be configured on secondary VLANs so that only the traffic generated by the hosts is filtered while the traffic exchanged between the routers is untouched.VACLs can be easily deployed to enforce the proper trust model. Let's analyze our DMZ case. Servers at the DMZ are supposed to serve incoming connections only, and they are not expected to initiate connections to the outside world. A VACL can be applied to their secondary VLAN in order to control the traffic leaving these servers. It is crucial to note that when using VACLs, the traffic is dropped in hardware so there is no impact on the CPU of the router nor of the switch. Even in the case that one of the servers is involved in a Distributed Denial of Service (DDoS) attack as a source, the switch will drop all illegitimate traffic at wire speed, without any performance penalty. Similar filters can be applied in the router or firewall where servers are connected to, but this usually has severe performance implications.Known Limitations of VACLs and PVLANsWhen configuring filtering with VACLs, you should be careful with regard to the fragment handling on the PFC, and that the configuration is tuned according to the specification of the hardware.Given the hardware design of the PFC of the Supervisor 1 of the Catalyst 6500, it is better to explicitly denythe icmp fragments. The reason is that Internet Control Message Protocol (ICMP) fragments and echo−reply are considered the same by the hardware, and by default the hardware is programmed to explicitly permit fragments. So if you want to stop echo−reply packets from leaving the servers, you explicitly have to configure this with the line deny icmp any any fragment. The configurations in this document take this into account.There is a well−known security limitation to PVLANs, which is the possibility that a router forwards traffic back out of the same subnet from which it came. A router can route traffic across isolated ports defeating the purpose of PVLANs. This limitation is due to the fact that PVLANs are a tool that provides isolation at L2, not at Layer 3 (L3).There is a fix to this problem, which is achieved by means of VACLs configured on the primary VLANs. The case study provides the VACLs that need to be configured on the primary VLAN to drops the traffic originated by the same subnet and routed back to the same subnet.On some line cards, the configuration of PVLAN mappings / maps / trunking ports is subject to some restrictions where multiple PVLAN mappings have to belong to different port Application−Specific Integrated Circuits (ASICs) in order to get configured. Those restrictions are removed on the new port ASIC Coil3. Please refer to the latest Catalyst switch documentation on software configuration for these details.Example Case StudiesThe following section describes three case studies, which we believe are representative of most implementations and give the details related to the security deployment of PVLANs and VACLs.These scenarios are:•Pass−Through DMZ•External DMZ•VPN Concentrator in Parallel to FirewallPass−Through DMZThis is one of the most commonly deployed scenarios. In this example, the DMZ is implemented as a transit area between two firewall routers as illustrated in the image below.Figure 2: Pass−Through DMZIn this example, DMZ servers are supposed to be accessed by external as well as internal users, but they don't need to communicate with each other. In some cases, DMZ servers need to open some kind of connection to an internal host. At the same time, internal clients are supposed to access the Internet without restrictions. A good example will be the one with Web servers at the DMZ, which need to communicate with a database server located in the inside network, and having inside clients accessing the Internet.The external firewall is configured to allow incoming connections to the servers located at the DMZ, but usually no filter or restrictions are applied to the outgoing traffic, particularly the traffic originated in the DMZ. As we discussed earlier in this document, this can potentially facilitate the activity of an attacker for two reasons: the first one, as soon as one of the DMZ hosts is compromised, all other DMZ hosts are exposed; the second one, an attacker can easily exploit an outgoing connection.Since DMZ servers don't need to talk to each other, the recommendation is to make sure they are isolated atL2. The servers ports will be defined as PVLANs isolated ports, while the ports connecting to the two firewalls will be defined as promiscuous. Defining a primary VLAN for the firewalls, and a secondary VLAN for the DMZ servers will achieve this.VACLs will be used to control the traffic originated in the DMZ. This will prevent an attacker from being able to open an illegitimate outgoing connection. It is important to keep in mind DMZ servers will not only need to reply with the traffic corresponding to client sessions, but they will also need some additional services, such as Domain Name System (DNS) and maximum transmission unit (MTU) path discovery. So, the ACL should allow all services needed by the DMZ servers.Testing Pass−Through DMZIn our test−bed we have implemented a DMZ segment with two routers configured as bed servers,server_dmz1 and server_dmz2. These servers are supposed to be accessed by outside as well as inside clients, and all HTTP connections are authenticated by using an internal RADIUS server (CiscoSecure ACS for UNIX). Both internal and external routers are configured as packet filter firewalls. The following picture illustrates the test−bed, including the addressing scheme used.Figure 3: Pass−Through DMZ Test−BedThe following list collects the fundamental configuration steps of PVLANs. The Catalyst 6500 is used as the L2 switch in the DMZ.•Server_dmz_1 is connected to port 3/9•Server_dmz_2 is connected to port 3/10•The internal router is connected to port 3/34•The external router is connected to port 3/35We chose the following VLANs:•41 is the primary VLAN•42 is the isolated VLANPrivate VLAN ConfigurationThe following configuration sets the PVLANs on the ports involved.ecomm−6500−2 (enable) set vlan 41 pvlan primaryVTP advertisements transmitting temporarily stopped,and will resume after the command finishes.Vlan 41 configuration successfulecomm−6500−2 (enable) sh pvlanPrimary Secondary Secondary−Type Ports−−−−−−− −−−−−−−−− −−−−−−−−−−−−−−−− −−−−−−−−−−−−41 − −ecomm−6500−2 (enable) set vlan 42 pvlan isolatedVTP advertisements transmitting temporarily stopped,and will resume after the command finishes.Vlan 42 configuration successfulecomm−6500−2 (enable) set pvlan 41 42 3/9−10Successfully set the following ports to Private Vlan 41,42:3/9−10ecomm−6500−2 (enable) set pvlan mapping 41 42 3/35Successfully set mapping between 41 and 42 on 3/35ecomm−6500−2 (enable) set pvlan mapping 41 42 3/34Successfully set mapping between 41 and 42 on 3/34Port Name Status Vlan Duplex Speed Type−−−−− −−−−−−−−−−−−−−−−−− −−−−−−−−−− −−−−−−−−−− −−−−−− −−−−− −−−−−−−−−−−−3/9 server_dmz1 connected 41,42 a−half a−10 10/100BaseTX3/10 server_dmz2 connected 41,42 a−half a−10 10/100BaseTX3/34 to_6500_1 connected 41 auto auto 10/100BaseTX3/35 external_router_dm connected 41 a−half a−10 10/100BaseTXVACL Configuration on the Primary VLANThis section is crucial to improve security on the DMZ. As described in the Known Limitations of VACLs and PVLANs section, even if servers belong to two different secondary VLANs or to the same isolated VLAN, there is still a way an attacker can use to make them communicate to each other. If the servers try to communicate directly, they will not be able to do it at L2 because of the PVLANs. If the servers are compromised and then configured by an intruder in such a way that the traffic for the same subnet is sent to the router, this one will route the traffic back on the same subnet, thus defeating the purpose of the PVLANs.Therefore, a VACL needs to be configured on the primary VLAN (the VLAN that carries the traffic from the routers) with the following policies:Allow the traffic whose source IP is the IP of the router••Deny the traffic with both source and destination IPs being the DMZ subnet•Allow all the rest of the trafficecomm−6500−2 (enable) sh sec acl info protect_pvlanset security acl ip protect_pvlan−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−1. permit ip host 172.16.65.193 any2. permit ip host 172.16.65.201 any3. deny ip 172.16.65.192 0.0.0.15 172.16.65.192 0.0.0.154. permit ip any anyecomm−6500−2 (enable) sh sec aclACL Type VLANS−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−− −−−− −−−−−protect_pvlan IP 41This ACL will not affect the traffic generated by the servers; it will only prevent the routers from routing the traffic coming from the servers back to the same VLAN. The first two statements allow the routers to send messages such as icmp redirect or icmp unreachable to the servers.VACL Configuration on the Secondary VLANThe following configuration logs are used to show how we setup a VACL to filter the traffic generated by the servers. By configuring this VACL we want to achieve the following:•Allow ping from servers (allow echo)•Prevent echo replies from leaving the servers•Allow HTTP connections originated from outside•Allow RADIUS authentication (UDP port 1645) and accounting (UDP port 1646) traffic•Allow DNS traffic (UDP port 53)We want to prevent all the rest of the traffic.As far as fragmentation is concerned, we assume the following on the server segment:•The servers will not generate fragmented traffic•The servers might receive fragmented trafficGiven the hardware design of the PFC of the Supervisor 1 of the Catalyst 6500, it is better to explicitly denythe icmp fragments The reason is that ICMP fragments and echo−reply are considered the same by thehardware, and by default the hardware is programmed to explicitly permit fragments. So if you want to stopecho−reply packets from leaving the servers you explicitly have to configure this with the line deny icmp anyany fragment.ecomm−6500−2 (enable) Set sec acl ip dmz_servers_out deny icmp any any fragmentecomm−6500−2 (enable) Set sec acl ip dmz_servers_out permit icmp host 172.16.65.199 any ech ecomm−6500−2 (enable) Set sec acl ip dmz_servers_out permit icmp host 172.16.65.202 any ech ecomm−6500−2 (enable) Set sec acl ip dmz_servers_out permit tcp host 172.16.65.199 eq 80 an ecomm−6500−2 (enable) Set sec acl ip dmz_servers_out permit tcp host 172.16.65.202 eq 80 an ecomm−6500−2 (enable) Set sec acl ip dmz_servers_out permit udp host 172.16.65.199eq 1645 host 172.16.171.9 eq 1645ecomm−6500−2 (enable) Set sec acl ip dmz_servers_out permit udp host 172.16.65.202eq 1645 host 172.16.171.9 eq 1645ecomm−6500−2 (enable) Set sec acl ip dmz_servers_out permit udp host 172.16.65.199eq 1646 host 172.16.171.9 eq 1646ecomm−6500−2 (enable) Set sec acl ip dmz_servers_out permit udp host 172.16.65.202eq 1646 host 172.16.171.9 eq 1646ecomm−6500−2 (enable) Set sec acl ip dmz_servers_out permit udp host 172.16.65.199 any eq 5 ecomm−6500−2 (enable) Set sec acl ip dmz_servers_out permit udp host 172.16.65.202 any eq 5 ecomm−6500−2 (enable) Commit sec acl allecomm−6500−2 (enable) Set sec acl map dmz_servers_out 42ecomm−6500−2 (enable) sh sec aclACL Type VLANS−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−− −−−− −−−−−protect_pvlan IP 41dmz_servers_out IP 42ecomm−6500−2 (enable) sh sec acl info dmz_servers_outset security acl ip dmz_servers_out−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−1. deny icmp any any fragment2. permit icmp host 172.16.65.199 any echo3. permit icmp host 172.16.65.202 any echo4. permit tcp host 172.16.65.199 eq 80 any established5. permit tcp host 172.16.65.202 eq 80 any established6. permit udp host 172.16.65.199 eq 1645 host 172.16.171.9 eq 16457. permit udp host 172.16.65.202 eq 1645 host 172.16.171.9 eq 16458. permit udp host 172.16.65.199 eq 1646 host 172.16.171.9 eq 16469. permit udp host 172.16.65.202 eq 1646 host 172.16.171.9 eq 164610. permit udp host 172.16.65.199 any eq 5311. permit udp host 172.16.65.202 any eq 53Testing the ConfigurationThe following output was captured when PVLANs where configured but no VACL were yet applied. This testis showing that from the external router the user is able to ping the internal router as well as the servers.external_router#ping 172.16.65.193Type escape sequence to abort.Sending 5, 100−byte ICMP Echos to 172.16.65.193, timeout is 2 seconds:!!!!external_router#ping 172.16.65.202Type escape sequence to abort.Sending 5, 100−byte ICMP Echos to 172.16.65.202, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round−trip min/avg/max = 1/2/4 msexternal_router#ping 172.16.65.199Type escape sequence to abort.Sending 5, 100−byte ICMP Echos to 172.16.65.199, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round−trip min/avg/max = 1/1/4 msThe following example shows that we are able to ping from the servers to the external network, the default gateway, but not the servers belonging to the same secondary VLAN.server_dmz1#ping 203.5.6.10Type escape sequence to abort.Sending 5, 100−byte ICMP Echos to 203.5.6.10, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round−trip min/avg/max = 1/2/4 msType escape sequence to abort.Sending 5, 100−byte ICMP Echos to 172.16.65.193, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round−trip min/avg/max = 4/4/4 msserver_dmz1#ping 172.16.65.202Type escape sequence to abort.Sending 5, 100−byte ICMP Echos to 172.16.65.202, timeout is 2 seconds:.....Success rate is 0 percent (0/5)After mapping the VACLs, the ping from the external router is not going to succeed any more:external_router#ping 172.16.65.199Type escape sequence to abort.Sending 5, 100−byte ICMP Echos to 172.16.65.199, timeout is 2 seconds:.....Success rate is 0 percent (0/5)The following example shows the server receiving HTTP GET requests from the internal network: server_dmz1#debug ip http urlHTTP URL debugging is onserver_dmz1#debug ip hhtp tranHTTP transactions debugging is onserver_dmz1#debug ip http authHTTP Authentication debugging is onserver_dmz1#*Mar 7 09:24:03.092 PST: HTTP: parsed uri '/'*Mar 7 09:24:03.092 PST: HTTP: client version 1.0*Mar 7 09:24:03.092 PST: HTTP: parsed extension Connection*Mar 7 09:24:03.092 PST: HTTP: parsed line Keep−Alive*Mar 7 09:24:03.092 PST: HTTP: parsed extension User−Agent*Mar 7 09:24:03.092 PST: HTTP: parsed line Mozilla/4.7 [en] (X11; I; SunOS 5.5.1 sun4u) *Mar 7 09:24:03.092 PST: HTTP: parsed extension Host*Mar 7 09:24:03.092 PST: HTTP: parsed line 172.16.65.199*Mar 7 09:24:03.092 PST: HTTP: parsed extension Accept*Mar 7 09:24:03.092 PST: HTTP: parsed line image/gif, image/x−xbitmap, image/jpeg, image/ *Mar 7 09:24:03.092 PST: HTTP: parsed extension Accept−Encoding*Mar 7 09:24:03.092 PST: HTTP: parsed line gzip*Mar 7 09:24:03.096 PST: HTTP: parsed extension Accept−Language*Mar 7 09:24:03.096 PST: HTTP: parsed line en*Mar 7 09:24:03.096 PST: HTTP: parsed extension Accept−Charset*Mar 7 09:24:03.096 PST: HTTP: parsed line iso−8859−1,*,utf−8*Mar 7 09:24:03.096 PST: HTTP: Authentication for url '/' '/' level 15 privless '/'*Mar 7 09:24:03.096 PST: HTTP: authentication required, no authentication information was *Mar 7 09:24:03.096 PST: HTTP: authorization rejected*Mar 7 09:24:22.528 PST: HTTP: parsed uri '/'*Mar 7 09:24:22.532 PST: HTTP: client version 1.0*Mar 7 09:24:22.532 PST: HTTP: parsed extension Connection*Mar 7 09:24:22.532 PST: HTTP: parsed line Keep−Alive*Mar 7 09:24:22.532 PST: HTTP: parsed extension User−Agent*Mar 7 09:24:22.532 PST: HTTP: parsed line Mozilla/4.7 [en] (X11; I; SunOS 5.5.1 sun4u) *Mar 7 09:24:22.532 PST: HTTP: parsed extension Host*Mar 7 09:24:22.532 PST: HTTP: parsed line 172.16.65.199*Mar 7 09:24:22.532 PST: HTTP: parsed extension Accept*Mar 7 09:24:22.532 PST: HTTP: parsed line image/gif, image/x−xbitmap, image/jpeg, image/ *Mar 7 09:24:22.532 PST: HTTP: parsed extension Accept−Encoding*Mar 7 09:24:22.532 PST: HTTP: parsed line gzip*Mar 7 09:24:22.532 PST: HTTP: parsed extension Accept−Language*Mar 7 09:24:22.532 PST: HTTP: parsed line en*Mar 7 09:24:22.532 PST: HTTP: parsed extension Accept−Charset*Mar 7 09:24:22.532 PST: HTTP: parsed line iso−8859−1,*,utf−8*Mar 7 09:24:22.532 PST: HTTP: parsed extension Authorization*Mar 7 09:24:22.532 PST: HTTP: parsed authorization type Basic*Mar 7 09:24:22.532 PST: HTTP: Authentication for url '/' '/' level 15 privless '/'*Mar 7 09:24:22.532 PST: HTTP: Authentication username = 'martin' priv−level = 15 auth−typ *Mar 7 09:24:22.904 PST: HTTP: received GET ''External DMZThe external DMZ scenario is probably the most accepted and widely deployed implementation. An externalDMZ is implemented by using one or more interfaces of a firewall, as shown the figure below.Figure 4: External DMZUsually the requirements for DMZs tend to be the same regardless of the design implementation. As in theprevious case, DMZ servers are supposed to be accessible from external clients as well as from the internal network. DMZ servers will eventually need access to some internal resources, and they are not supposed totalk to each other. At the same time, no traffic should be initiated from the DMZ to the Internet; these DMZservers should only reply with traffic corresponding to incoming connections.。
pvlan与vlan的区别及详解

pvlan与vlan的区别虚拟局域网(VLAN)是驻地网必须具备的特性之一。
目前普遍应用的802.1q,主要是针对企业应用设置的,起到网段隔离和多址联播的作用。
如果用在驻地网上,便可能破坏多址联播特性,引起网络运行效率的降低。
例如10个用户同时点播一个视频节目,视频服务器要响应10次请求,在网络骨干层要传输10次,造成大量的带宽消耗。
如果用户数目多到一定程度,整个网络便有可能瘫痪。
思科的PVLAN技术有效解决了这一问题,在一组端口发出请求时,骨干层只传输一次,再分到每个端口,因此大大提高了网络的运行效率。
IDC环境是一个典型的多客户的服务器群结构,每个托管客户从一个公共的数据中心中的一系列服务器上提供Web服务。
这样,属于不同客户的服务器之间的安全就显得至关重要。
一个保证托管客户之间安全的通用方法就是给每个客户分配一个VLAN和相关的IP子网。
通过使用VLAN,每个客户被从第2层隔离开,可以防止任何恶意的行为和Ethernet的信息探听。
然而,这种分配每个客户单一VLAN和IP子网的模型造成了巨大的扩展方面的局限。
这些局限主要有以下几方面:• VLAN的限制:LAN交换机固有的VLAN数目的限制• 复杂的STP:对于每个VLAN,一个相关的Spanning-tree的拓扑都需要管理• IP地址的紧缺:IP子网的划分势必造成一些地址的浪费• 路由的限制:如果使用HSRP,每个子网都需相应的缺省网关的配置在一个IDC中,流量的流向几乎都是在服务器与客户之间,而服务器间的横向的通信几乎没有。
Cisco在IP地址管理方案中引入了一种新的VLAN机制,服务器同在一个子网中,但服务器只能与自己的缺省网关通信。
这一新的VLAN特性就是专用VLAN (private VLAN,pVLAN)。
这种特性是Cisco公司的专有技术,但特别适用于IDC。
专用VLAN是第2层的机制,在同一个2层域中有两类不同安全级别的访问端口。
PVLAN详解

Jul14Private VLANs Revisited62 CommentsTweetDue to the non-decreasing interest to the post about Private VLANs, I decided to make another one, more detailed – including a diagram and verification techniques.IntroductionTo begin with, recall that VLAN is essentially a broadcast domain. Private VLANs (PVANs) allow splitting the domain into multiple isolated broadcast “subdomains”, introducing sub-VLANs inside a VLAN. As we know, Ethernet VLANs can not communicate directly with each other – they require a L3 device to forward packets between separate broadcast domains. The same restriction applies to PVLANS – since the subdomains are isolated at Level 2, they need to communicate using an upper level (L3/packet forwarding) device – such as router.In reality, different VLANs normally map to different IP subnets. When we split a VLAN using PVLANs, hosts in different PVLANs still belong to the same IP subnet, yet now they need to use a router (L3 device) to talk to each other (for example, by using Local Proxy ARP). In turn, the router may either permit or forbid communications between sub-VLANs using access-lists. Commonly, these configurations arise in “shared” environments, say ISP co-location, where it’s beneficial to put multiple customers into the same IP subnet, yet provide a good level of isolation between them.Private VLANs TerminologyThe following is the reference diagram that we are going to use to illustrate Private VLAN concepts and functionality.For our sample configuration, we take VLAN 1000 and divide it into three PVLANs – sub-VLAN 1012 (R1 and R2), sub-VLAN 1034 (R3 and R4) and sub-VLAN 1055 (router R5 only). Router R6 will be used as layer 3 device, to resolve the layer 3 communication issue. We name VLAN 1000 as “Primary” and c lassify the ports, assigned to this VLAN, based on their types:∙Promiscuous (“P”) port: Usually connects to a router. This port type is allowed to send and receive L2 frames from any other port on the VLAN.∙Isolated (“I”) port: This type of port is only allowed to communicate with “P”-ports – i.e., they are “stub” port. You commonly see these ports connecting to hosts.∙Community (“C”) port: Community ports are allowed to talk to their buddies, sharing the same community (group) and to “P”-ports.In order to implement sub-VLAN behavior, we need to define how packets are forwarded between different types of ports. We group the VLANs in “Primary” and “Secondary”.∙Primary VLAN (VLAN 1000 in our example). This VLAN is used to forward frames downstream from “P”-ports to all other port types (“I” and “C” ports) in the system.Essentially, Primary VLAN embraces all ports in the domain, but only transports framesfrom the router to hosts (from “P” to “I” and “C”).∙Secondary Isolated VLAN: forwards frames from “I” ports to “P” ports. Since Isolated ports do not exchange frames with each other, we can use just ONE isolated VLAN toconnect all I-Port to the P-port.∙Secondary Community VLANs: Transport frames between community ports (C-ports) within to the same group (community) and forward frames upstream to the P-ports of the primary VLAN.How Private VLANs WorkHere are the key aspects of Private VLAN functioning:∙The Primary VLAN delivers frames downstream from the router (promisc port) to all mapped hosts.∙The Isolated VLAN transports frames from the stub hosts upstream to the router∙The Community VLANs allow bi-directional frame exchange withing a single group, in addition to forwarding frames upstream towards “P”-ports.∙Ethernet MAC address learning and forwarding procedure remain the same, as well as broadcast/multicast flooding procedure within boundaries of primary/secondary VLANs.Private VLANs could be trunked. The secondary VLAN numbers are used to tag frames, just as with regular VLANs, and the primary VLAN traffic is trunked as well. However, you need to configure Private VLAN specific settings (bindings, mappings) on every participating swtich, as it’s not possible to use VTPv2 to dissiminate that information . This due to the fact that VTPv2 has no TLVs to carry private VLANs information. VTPv3 was designed to overcome this limitation among others.Configuring Private VLANsWe have primary VLAN 1000, Isolated VLAN 1005 (R5) Community VLAN 1012 (R1, R2) and Community VLAN 1034 (R3, R4).Step 1:First, disable VTP, i.e. enable VTP transparent mode. After disabling VTP, create Primary and Secondary VLANs and bind them into PVLAN domain:SW1:vtp mode transparent!! Creating primary VLAN, which is shared among secondary’s!vlan 1000private-vlan primary!! Community VLAN for R1 and R2: allows a “subVLAN” within a Primary VLAN!vlan 1012private-vlan community!! Community VLAN for R3 and R4!vlan 1034private-vlan community!! Isolated VLAN: Connects all stub hosts to router.! Remember - only one isolated vlan per primary VLAN.! In our case, isolates R5 only.!vlan 1055private-vlan isolated!! Associating the primary with secondary’s!vlan 1000private-vlan association 1012,1034,1055This step is needed is to group PVLANs into a shared domain and establish a formal association (for syntax checking and VLAN type verifications). Repeat the same operations on SW2, since VTP has been disabled.Step 2:Configure host ports and bind them to the respective isolated PVLANs. Note that a host port belongs to different VLANs at the same time: downstream primary and upstream secondary. Also, enable trunking between switches, to allow private VLANs traffic to pass between switches.SW1:!! Community port (links R1 to R2 a nd “P”-ports)!interface FastEthernet0/1description == R1switchport private-vlan host-association 1000 1012switchport mode private-vlan hostspanning-tree portfast!! Community port (links R3 to R4 and “P”-ports)!interface FastEthernet0/3description == R3switchport private-vlan host-association 1000 1034switchport mode private-vlan hostspanning-tree portfast!! Isolated port (uses isolated VLAN to talk to “P”-ports) !interface FastEthernet0/5description == R5switchport private-vlan host-association 1000 1055switchport mode private-vlan hostspanning-tree portfast!! Trunk port!interface FastEthernet 0/13switchport trunk encapsulation dot1qswitchport mode trunkSW2:interface FastEthernet0/2description == R2switchport private-vlan host-association 1000 1012switchport mode private-vlan hostspanning-tree portfast!interface FastEthernet0/4description == R4switchport private-vlan host-association 1000 1034switchport mode private-vlan hostspanning-tree portfast!! Trunk port!interface FastEthernet 0/13switchport trunk encapsulation dot1qswitchport mode trunkNext, Verify the configuration on SW1:Rack1SW1#show vlan id 1012VLAN Name Status Ports---- -------------------------------- --------- ------------------------------- 1012 VLAN1012 active Fa0/13VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------ 1012 enet 101012 1500 - - - - - 0 0Remote SPAN VLAN----------------DisabledPrimary Secondary Type Ports------- --------- ----------------- ------------------------------------------ 1000 1012 community Fa0/1Rack1SW1#show vlan id 1034VLAN Name Status Ports---- -------------------------------- --------- ------------------------------- 1034 VLAN1034 active Fa0/13VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------ 1034 enet 101034 1500 - - - - - 0 0Remote SPAN VLAN----------------DisabledPrimary Secondary Type Ports------- --------- ----------------- ------------------------------------------ 1000 1034 community Fa0/3Rack1SW1#show vlan id 1055VLAN Name Status Ports---- -------------------------------- --------- ------------------------------- 1055 VLAN1055 active Fa0/13VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------ 1055 enet 101055 1500 - - - - - 0 0Remote SPAN VLAN----------------DisabledPrimary Secondary Type Ports------- --------- ----------------- ------------------------------------------ 1000 1055 isolated Fa0/5Rack1SW1#show interfaces fastEthernet 0/13 trunkPort Mode Encapsulation Status Native vlanFa0/13 desirable 802.1q trunking 1Port Vlans allowed on trunkFa0/13 1-4094Port Vlans allowed and active in management domainFa0/13 1,1000,1012,1034,1055Port Vlans in spanning tree forwarding state and not prunedFa0/13 1,1000,1012,1034,1055Verify on SW2:Rack1SW2#show vlan id 1000VLAN Name Status Ports---- -------------------------------- --------- ------------------------------- 1000 VLAN1000 active Fa0/13VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------ 1000 enet 101000 1500 - - - - - 0 0Remote SPAN VLAN----------------DisabledPrimary Secondary Type Ports------- --------- ----------------- ------------------------------------------1000 1012 community Fa0/2, Fa0/61000 1034 community Fa0/4, Fa0/61000 1055 isolated Fa0/6Rack1SW2#show vlan id 1012VLAN Name Status Ports---- -------------------------------- --------- ------------------------------- 1012 VLAN1012 active Fa0/13VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------ 1012 enet 101012 1500 - - - - - 0 0Remote SPAN VLAN----------------DisabledPrimary Secondary Type Ports------- --------- ----------------- ------------------------------------------ 1000 1012 community Fa0/2, Fa0/6Rack1SW2#show vlan id 1034VLAN Name Status Ports---- -------------------------------- --------- ------------------------------- 1034 VLAN1034 active Fa0/13VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------ 1034 enet 101034 1500 - - - - - 0 0Remote SPAN VLAN----------------DisabledPrimary Secondary Type Ports------- --------- ----------------- ------------------------------------------ 1000 1034 community Fa0/4, Fa0/6Rack1SW2#show vlan id 1055VLAN Name Status Ports---- -------------------------------- --------- -------------------------------1055 VLAN1055 active Fa0/13VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------1055 enet 101055 1500 - - - - - 0 0Remote SPAN VLAN----------------DisabledPrimary Secondary Type Ports------- --------- ----------------- ------------------------------------------1000 1055 isolated Fa0/6Rack1SW2#show interface fastEthernet 0/13 trunkPort Mode Encapsulation Status Native vlanFa0/13 desirable 802.1q trunking 1Port Vlans allowed on trunkFa0/13 1-4094Port Vlans allowed and active in management domainFa0/13 1,1000,1012,1034,1055Port Vlans in spanning tree forwarding state and not prunedFa0/13 1,1000,1012,1034,1055Step 3:Create a promiscuous port and configure downstream mappings. Here we add secondary VLANs for which traffic is received by this particular “P”-port. Primary VLAN is used to send traffic downstream to all “C” and “I” ports per their associations.SW2:!! Promiscuous port, mapped to all secondary VLANs!interface FastEthernet0/6description == R6switchport private-vlan mapping 1000 1012,1034,1055switchport mode private-vlan promiscuousspanning-tree portfastVerify the promiscuous port configuration:Rack1SW2#show int fa 0/6 switch | beg privateAdministrative Mode: private-vlan promiscuousOperational Mode: private-vlan promiscuousAdministrative Trunking Encapsulation: negotiateOperational Trunking Encapsulation: nativeNegotiation of Trunking: OffAccess Mode VLAN: 1 (default)Trunking Native Mode VLAN: 1 (default)Administrative Native VLAN tagging: enabledVoice VLAN: noneAdministrative private-vlan host-association: noneAdministrative private-vlan mapping: 1000 (VLAN1000) 1012 (VLAN1012) 1034 (VLAN1034) 1055 (VLAN1055)Administrative private-vlan trunk native VLAN: noneAdministrative private-vlan trunk Native VLAN tagging: enabledAdministrative private-vlan trunk encapsulation: dot1qAdministrative private-vlan trunk normal VLANs: noneAdministrative private-vlan trunk private VLANs: noneOperational private-vlan:1000 (VLAN1000) 1012 (VLAN1012) 1034 (VLAN1034) 1055 (VLAN1055)If you need to configure an SVI on a switch to communicate with private VLAN members, you should add an interface corresponding to Primary VLAN only. Obviously that’s because all secondary VLANs are “subordinates” of primary. After an SVI has been created, you have to map the required secondary VLANs to the SVI (just like with a promiscuous port) in order to make communications possible. You may exclude some mappings from SVI interface, and limit it to communicating only with certain secondary VLANs.SW1:!! SW1 SVI is mapped to all secondary VLANs!interface Vlan 1000ip address 10.0.0.7 255.255.255.0private-vlan mapping 1012,1034,1055SW2:!! SW2 SVI is mapped to 1012/1034 only, so it’s cant communicate with R5!interface Vlan1000ip address 10.0.0.8 255.255.255.0private-vlan mapping 1012,1034Now to verify the configuration, configure R1-R6 in terfaces in subnet “10.0.0.0/24” and ping broadcast addresses.Rack1R1#ping 10.0.0.255 repeat 1Type escape sequence to abort.Sending 1, 100-byte ICMP Echos to 10.0.0.255, timeout is 2 seconds:Reply to request 0 from 10.0.0.7, 4 msReply to request 0 from 10.0.0.2, 4 msReply to request 0 from 10.0.0.6, 4 msReply to request 0 from 10.0.0.8, 4 msRack1R3#ping 10.0.0.255 repeat 1Type escape sequence to abort.Sending 1, 100-byte ICMP Echos to 10.0.0.255, timeout is 2 seconds:Reply to request 0 from 10.0.0.7, 4 msReply to request 0 from 10.0.0.4, 4 msReply to request 0 from 10.0.0.6, 4 msReply to request 0 from 10.0.0.8, 4 msRack1R5#ping 10.0.0.255 repeat 1Type escape sequence to abort.Sending 1, 100-byte ICMP Echos to 10.0.0.255, timeout is 2 seconds:Reply to request 0 from 10.0.0.7, 1 msReply to request 0 from 10.0.0.6, 1 msRack1R6#ping 10.0.0.255 repeat 1Type escape sequence to abort.Sending 1, 100-byte ICMP Echos to 10.0.0.255, timeout is 2 seconds:Reply to request 0 from 10.0.0.1, 4 msReply to request 0 from 10.0.0.7, 4 msReply to request 0 from 10.0.0.2, 4 msReply to request 0 from 10.0.0.5, 4 msReply to request 0 from 10.0.0.3, 4 msReply to request 0 from 10.0.0.4, 4 msReply to request 0 from 10.0.0.8, 4 msLastly, there is another feature, called protected port or “Private VLAN edge”. The feature is pretty basic and is available even on low-end Cisco switches. It allows isolating ports in the same VLAN. Specifically, all ports in a VLAN, marked as protected are prohibited from sending frames to each other (but still allowed to send frames to other (non-protected) ports within the same VLAN). Usually,ports configured as protected are also configured not to receive unknown unicast (frame with destination MAC address not in switch’s MAC table) and multicast frames flooding for added security .Example:interface range FastEthernet 0/1 - 2switchport mode accessswitchport protectedswitchport block unicastswitchport block multicast。
图文详解cisco vpn
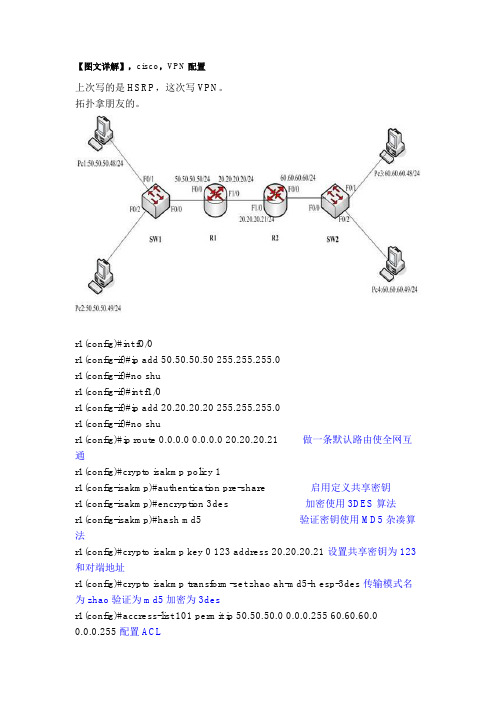
【图文详解】,cisco,VPN配置上次写的是HSRP,这次写VPN。
拓扑拿朋友的。
r1(config)#int f0/0r1(config-if)#ip add 50.50.50.50 255.255.255.0r1(config-if)#no shur1(config-if)#int f1/0r1(config-if)#ip add 20.20.20.20 255.255.255.0r1(config-if)#no shur1(config)#ip route 0.0.0.0 0.0.0.0 20.20.20.21 做一条默认路由使全网互通r1(config)#crypto isakmp policy 1r1(config-isakmp)#authentication pre-share 启用定义共享密钥r1(config-isakmp)#encryption 3des 加密使用3DES算法r1(config-isakmp)#hash md5 验证密钥使用MD5杂凑算法r1(config)#crypto isakmp key 0 123 address 20.20.20.21 设置共享密钥为123和对端地址r1(config)#crypto isakmp transform-set zhao ah-md5-h esp-3des 传输模式名为zhao验证为md5加密为3desr1(config)#accress-list 101 permit ip 50.50.50.0 0.0.0.255 60.60.60.00.0.0.255配置ACLr1(config)#crypto map jin 1 ipsec-isakmp 创建crypto map名字为jinr1(config-crypto-map)#set peer 20.20.20.21 指定链路对端IP地址r1(config-crypto-map)#set transfrom-set zhao 指定传输模式zhaor1(config-crypto-map)#match address 101 指定应用访控列表r1(config)#int f0/0r1(config)#crypto map jin 应用到接口r2(config)#int f0/0r2(config-if)#ip add 60.60.60.60 255.255.255.0r2(config-if)#no shur2(config-if)#int f1/0r2(config-if)#ip add 20.20.20.21 255.255.255.0r2(config-if)#no shur2(config)#ip route 0.0.0.0 0.0.0.0 20.20.20.20 做一条默认路由使全网互通r2(config)#crypto isakmp policy 1r2(config-isakmp)#authentication pre-share 启用定义共享密钥r2(config-isakmp)#encryption 3des 加密使用3DES算法r2(config-isakmp)#hash md5 验证密钥使用MD5杂凑算法r2(config)#crypto isakmp key 0 123 address 20.20.20.20 设置共享密钥为123和对端地址r2(config)#crypto isakmp transform-set zhao ah-md5-h esp-3des 传输模式名为zhao验证为md5加密为3desr2(config)#accress-list 101 permit ip 60.60.60.0 0.0.0.255 50.50.50.00.0.0.255 配置ACLr2(config)#crypto map jin 1 ipsec-isakmp 创建crypto map名字为jinr2(config-crypto-map)#set peer 20.20.20.21 指定链路对端IP地址r2(config-crypto-map)#set transfrom-set zhao 指定传输模式zhaor2(config-crypto-map)#match address 101 指定应用访控列表r2(config)#int f0/0r2(config)#crypto map jinvpcs1:ip 50.50.50.48 50.50.50.50 24vpcs2:ip 50.50.50.49 50.50.50.50 24vpcs3:ip 60.60.60.48 60.60.60.60 24vpcs4:ip 60.60.60.49 60.60.60.60 24之后ping测试。
cisco交换机VLAN技术

所属VLAN
VLAN 5
VLAN 10
……
主机A
1.1.1.5
主机B
1.1.2.5
主机C
1.1.1.8
主机D
1.1.2.8
ICND 2.0—0-12
基于协议的VLAN
CISCO交换机配置 以太网交换机
VLAN表
协议类型 IPX协议 IP协议 ……
所属VLAN
VLAN 5
VLAN 10
……
主机A
主机B
交换规则
CISCO交换机配置
主机和交换机之间传送的是untagged报文 交换机之间用干道链路(Trunk)连接 交换机用Tag来标识报文所属的VLAN 干道链路上传输的是Tagged Frame 不同VLAN之间在二层不能相互通讯
ICND 2.0—0-22
跨越多个交换机的VLAN配置
ICND 2.0—0-7
解决方法二:VLAN
VLAN的引入,为解决广播报文的泛滥提供了新的方法
CISCO交换机配置
一个VLAN,一个广播域
VLAN2
L2
VLAN3
L2
VLAN4
广播 报文
L2
L2
L2
财务部
人事部
销售部
ICND 2.0—0-8
VLAN的划分
CISCO交换机配置
基于交换机端口 基于MAC地址 基于协议 基于IP子网
思考:需要VLAN之间通信怎么办?
ICND 2.0—0-17
跨越交换机的VLAN报文转发
CISCO交换机配置
C
D
A
B
ICND 2.0—0-18
VLAN端口
Access端口,只能传送标准以太网帧的端口。
Cisco PVLAN 详解 不错 完整详细

Cisco PVLAN 详解PVLAN即私有VLAN(Private VLAN),PVLAN采用两层VLAN隔离技术,只有上层VLAN全局可见,下层VLAN相互隔离。
每个pVLAN包含2种VLAN :主VLAN(primary VLAN)和辅助VLAN(Secondary VLAN)。
辅助VLAN(Secondary VLAN)包含两种类型:隔离VLAN(isolated VLAN)和团体VLAN(community VLAN)。
pVLAN中的两种接口类型:处在pVLAN中的交换机物理端口,有两种接口类型。
①混杂端口(Promiscuous Port)②主机端口(Host Port)Catalyst3560, 45、65系列支持配置pVLAN的实例:SwitchA(config)#vlan 100SwitchA(config-vlan)#private-vlanprimary!设置主VLAN 100SwitchA(config)#vlan 200SwitchA(config-vlan)#private-vlan community!设置团体VLAN 200SwitchA(config)#vlan 300SwitchA(config-vlan)#private-vlan isolated!设置隔离VLAN 300SwitchA(config)#vlan 100SwitchA(config-vlan)#private-vlan association 200,300!将辅助VLAN关联到主VLANSwitchA(config)#interface vlan 100SwitchA(config-if)#private-vlan mapping add200,300!将辅助VLAN映射到主VLAN接口,允许pVLAN入口流量的三层交换SwitchA(config)# interface fastethernet 0/2SwitchA(config-if)#switchport mode private-vlan hostSwitchA(config-if)#switchport private-vlan host-association 100 200!2号口划入团体VLAN 200SwitchA(config)# interface fastethernet 0/3SwitchA(config-if)#switchport mode private-vlan hostSwitchA(config-if)#switchport private-vlan host-association 100 300!3号口划入隔离VLAN 300SwitchA(config)# interface fastethernet 0/1SwitchA(config-if)#switchport mode private-vlan promiscuousSwitchA(config-if)#switchport private-vlan mapping 100 add200-300!1号口杂合模式关于端口隔离Switch(config)# interface gigabitethernet1/0/2Switch(config-if)# switchport protectedPVLAN通常用于企业内部网,用来防止连接到某些接口或接口组的网络设备之间的相互通信,但却允许与默认网关进行通信。
VMWARE Cisco PVLAN 配置

Cisco PVLAN的配置∙2010/05/09∙网络技术∙1,890 views∙没有评论PVLAN即私有VLAN(Private VLAN),PVLAN采用两层VLAN隔离技术,只有上层VLAN全局可见,下层VLAN相互隔离。
每个pVLAN 包含2种VLAN :主VLAN(primary VLAN)和辅助VLAN(Secondary VLAN)。
辅助VLAN(Secondary VLAN)包含两种类型:隔离VLAN(isolated VLAN)和团体VLAN(community VLAN)。
pVLAN中的两种接口类型:处在pVLAN中的交换机物理端口,有两种接口类型。
①混杂端口(Promiscuous Port)②主机端口(Host Port)Catalyst3560, 45, 65系列支持配置pVLAN的实例:SwitchA(config)#vlan 100SwitchA(config-vlan)#private-vlanprimary!设置主VLAN 100SwitchA(config)#vlan 200SwitchA(config-vlan)#private-vlan community!设置团体VLAN 200SwitchA(config)#vlan 300SwitchA(config-vlan)#private-vlan isolated!设置隔离VLAN 300SwitchA(config)#vlan 100SwitchA(config-vlan)#private-vlan association 200,300!将辅助VLAN关联到主VLANSwitchA(config)#interface vlan 100SwitchA(config-if)#private-vlan mapping add200,300!将辅助VLAN映射到主VLAN接口,允许pVLAN入口流量的三层交换SwitchA(config)# interface fastethernet 0/2SwitchA(config-if)#switchport mode private-vlan hostSwitchA(config-if)#switchport private-vlan host-association 100 200!2号口划入团体VLAN 200SwitchA(config)# interface fastethernet 0/3SwitchA(config-if)#switchport mode private-vlan hostSwitchA(config-if)#switchport private-vlan host-association 100 300!3号口划入隔离VLAN 300SwitchA(config)# interface fastethernet 0/1SwitchA(config-if)#switchport mode private-vlan promiscuousSwitchA(config-if)#switchport private-vlan mapping 100 add200-300!1号口杂合模式CatOS的配置set vlan 100 pvlan-type primaryset vlan 200 pvlan-type communityset vlan 300 pvlan-type isolatedset pvlan 100 200 5/1set pvlan 100 300 5/2set pvlan mapping 100,200 15/1set pvlan mapping 100,300 15/1 //指定混杂模式的接口参考资料:/n6630/blog/item/c6e6974cb3d362fdd62afc64.html /133058/56824/coghost/blog/item/4f4dfb22e3bdd5a24723e83e.html /view/1065646.htm关于端口隔离Switch(config)# interface gigabitethernet1/0/2Switch(config-if)# switchport protectedCatalyst 29 35系列支持网关及共享口不敲protected 即可通信。
PVLAN---思科的私有vlan

PVLAN注意事项:PVLAN 只能在VTP transparent模式配置PVLAN 在一个primary vlan下可以有多个secondary vlansecondary vlan 下:可以有island port 、community port 、promiscuous port。
island port 仅可以和promiscuous port 相互通信。
community port 可以和communi ty port 、promiscuous port 相互通信。
Unicast Reverse Path Forwarding (uRPF) does not work well with PVLAN host ports, so uRPF must not beused in combination with PVLAN.(uRPF 端口不可以用在PVLAN host port上,不能与PVLAN结合使用)。
可通信的端口主VLAN端口公共VLAN端口孤立VLAN端口与主VLAN通信是是是与同一从VLAN通信N/A 是否与其他从VLAN通信N/A 否否配制命令:第一步:定义主vlanswitch(config)# vlan (vlan-id)switch(config-vlan)# private-vlan primaryswitch(config-vlan)# exit第二步:设置辅助vlan,将主/辅助vlan 帮定在一起switch(config)# vlan (primary-vlan-id)switch(config-vlan)# private-vlan association {add|remove}(aue-vlan)第三步:switch(config)# interface vlan (primary-vlan-id)switch(config-if)# privst-vlan mapping (辅助vlan-id)第四步:Switch config-vlan # private-vlan [primary | isolated | community] 定义vl an类型Config-if# switchport mode private-vlan {host | promiscuous}配置从vlan的接口模式host表示团体模式或隔离模式promiscuous是混杂模式Config-if# switchport private-vlan host-association primary_vlan_id second ary_vlan_id把团体端口和隔离端口划分到私有vlan中例如:Vlan 202Private-vlan primaryPrivate-vlan association 440Vtp mode transpoarent 必须设置成透明模式Vlan 440Private-vlan isolatedint fast 5/2switchport mode private-vlan promiscuous 设置混杂模式switchport private-vlan mapping 202 440 把这个端口放到主vlan中,可以和从vlan 440的端口通信int fast 5/1switchport mode private-vlan host 定义为host端口,此端口可是隔离或团体模式,具体视它加入的vlan模式而定switchport private-vlan host –association 202 440 定义它属于的主vlan 202中的隔离vlan440int vlan 202private-vlan mapping add 440 定义三层的虚拟端口vlan202 为私有vlan 440对外的通信端口第五步:校验命令show interfaces private_vlan mapping 查看私有vlan的配置信息show vlan private-vlan type 显示私有vlan的配置信息。
CISCO ME3400的VLAN及PVLAN配置过程

CISCO ME3400的VLAN及PVLAN配置过程前言本文档主要知识为两部分:第一部分:VLAN配置:实现ME3400 1-12口(129.x.x.x)及13-24(139.x.x.x)口的分别IP连通。
第二部分:PVLAN配置:实现1-12口(129.x.x.x)及13-24(139.x.x.x)口之间的IP连通。
第一节背景知识介绍ME3400交换机介绍:ME3400交换机有24个FE接口,2个GE接口,根据网络规划,我们将前12个FE口划分为VLAN 129,用于RMPB、RBCX、OMCR的接入,后12个FE口划分为VLAN 139,用于RMNIC和OMCB的接入。
PVLAN介绍:(1)在Private VLAN的概念中,交换机端口有三种类型:Isolated port,Communityport, Promiscuous port;它们分别对应不同的VLAN类型:Isolated port属于Isolated PVLAN,Community port属于Community PVLAN,而代表一个Private VLAN 整体的是Primary VLAN,前面两类VLAN需要和它绑定在一起,同时它还包括Promiscuous port。
(2)在Isolated PVLAN中,Isolated port只能和Promiscuous port通信,彼此不能交换流量即使是在同一个Isolated PVLAN中。
在Community PVLAN中,Community port不仅可以和Promiscuous port通信,而且在同一个Community PVLAN彼此也可以交换流量。
Promiscuous port 与路由器或第3层交换机接口相连,它收到的流量可以发往Isolated port和Community port。
(3)接口的类型可以分为三种:UNI--用来连接主机,例如PC,iphone;ENI--类似UNI,能配置一些协议例如CDP、STP、LLDP、LACP; NNI--用来连接其他交换机或者路由器。
PVLAN技术及其在企业中的应用分析

PVLAN技术及其在企业中的应用分析阐述了VLAN技术及其局限性,分析了PVLAN技术的特点和产生背景及其应用场合,结合实例介绍了PVLAN在DCS-3926s交换机下的配置,总结了PVLAN技术应用于企业网络管理的优势。
标签:虚拟局域网(VLAN)专用虚拟局域网(PVLAN)网络管理数据安全在交换式以太网诞生之初,主机之间通过透明网桥在2层直接完成交换,过程简单且速度很快,但会引起广播风暴的问题。
为限制广播风暴,可以通过路由器对网络进行分段,这在一定程度上改善了网络性能,然而随着网络规模的日益扩大,单纯地依靠增加路由器数量来优化网络的做法显得成本太高。
VLAN的出现改善了这一局面,通过使用VLAN,主机之间从第2层隔被离开,通常的做法是给每个VLAN配置一个IP子网,VLAN间的通信可以通过3层交换机或路由器来完成,现在绝大多数的园区网都是这么规划和配置的。
在网络安全问题越来越突出的形式下,主机或服务器经常需要在链路层完全隔离(对于链路层通信的独立性要求越来越高),此时,VLAN和IP子网——对应的网络模型表现出了在可扩展方面的局限性,比如:VLAN数目的限制、IP地址的紧缺、路由的限制等。
PVLAN(Private VLAN,即私有VLAN,也叫专有VLAN)可以很好地解决上述问题,它可以使交换机的端口属于不同VLAN,但使用同一网段的地址,从本质上来说,PVLAN是一种允许在一个IP子网下划分多个VLAN的技术,它隔断了主机在2层上的通信,却允许所有的主机与同一个网关进行3层上的通信。
一、PVLAN技术为满足多种类型的通信需求,PVLAN中使用了主VLAN、从VLAN、混杂端口、公共端口、孤立端口等概念,下面我们简单介绍一下这些概念。
一个PVLAN可包含一个主VLAN(Primary VLAN)和多个从VLAN (Secondary VLAN)。
处于主VLAN中的交换机端口叫做混杂端口(Promiscuous port);从VLAN有两种类型:公共VLAN和孤立VLAN,处于公共VLAN中的交换机端口叫做公共端口(Community port),处于孤立VLAN中的交换机端口叫做孤立端口(Isolated port);从VLAN必须和主VLAN建立关联关系后才能正常工作,PVLAN实际上是指建立了关联关系后的一个主VLAN和多个从VLAN 的组合体,通常情况下,一个PVLAN可以包含多个公共VLAN,但只能包含一个孤立VLAN,各种类型的端口之间的互访关系可以用表1来说明:二、PVLAN在DCS-3926s交换机下的实现下面以神州数码的DCS-3926s交换机为例,介绍PVLAN的具体配置方法和配置过程。
SVLAN,CVLAN,PVLAN区别

在传统VLAN技术上发展出几种不一样的扩展技术---PVLAN (Private VLAN)、SuperVLAN、SVLAN(Stack VLAN)Primary vlan, Isolated PVLAN,Community PVLAN是属于PVLAN(Private VLAN)的观念楼主谈的SVLAN,CVLAN,PVLAN是属于SVLAN(Stack VLAN)的观念应该要从Q-in-Q工作原理来看:QinQ采用的是层次化VLAN技术区分用户和运营商的VLAN:C-VLAN和P-VLAN(S-VLAN),数据在私网中传输时带一个私网的tag,定义为C -VLAN Tag (Customer VLAN tag=用户VLAN),数据进入到服务商的骨干网后,在打上一层公网的VLAN tag,定义为P-VLAN Tag(Service Provider VLAN tag=S-VLAN=SPVLAN=服务商VLAN)。
到目的私网后再把P-VLAN Tag剥除,为用户提供了一种较为简单的二层VPN隧道。
SVLAN=Stack VLAN(就是所谓的QinQ)CVLAN=Customer VLAN =用户VLANPVLAN =SVLAN=Service Provider VLAN =SPVLAN=服务商VLANVLAN:一个VLAN就是一个广播域,用一个标签来表示.(802.1q 标准定义,在以太网ethernetII/802.3的SA后加面增加4字节用来给这个以太网帧打标签和优先级值)PVLAN:private vlan,VLAN的一种应用,是完全从实际应用角度而言的,用以实现一个VLAN 内的用户之间有些能通信,有些不能通信,但这个VLAN里的所有用户都能通过同一个端口出去或者访问服务器这样一个实际需求包含primary VLAN,isolated VLAN和communicate VLAN,其中isloate VLAN和communicate VLAN绑定在primary VLAN上,isolated PVLAN内的用户之间互相隔离,但可以和primary vlan内的Promiscuous port通信, communicate PVLAN 内的用户之间可以互相通信,也能与primary vlan内的Promiscuous port通信.SVLAN和CVLAN: Service provider VLAN和customer VLAN,由802.1ad定义, QinQ,在一个VLAN里再增一层标签,成为双标签的VLAN,外层的就是SVLAN,内层的就是CVLAN你提出的最后一个问题:"这三者SVLAN、PVLAN、CVLAN之间是否可以配合使用"当一个交换机启用double tagging mode也即802.1q tunneling的时候,用户数据包自身携带VID的就是CVLAN,进入交换机后,会被再打上一层标签SVLAN,成为一个双标签的数据,如果用户是ungtagged的数据包,交换机可以打上两层标签,内层打上端口的PVID成为CVLAN,外层打上SPVLAN.还可以是直接接把PVID作为SPVLAN,成为单标签数据.交换机处理时可以根据内层标签也可以根据外层标签,交换机不同可以有不同的实现方式.SVLAN和CVLAN是孪生兄弟,相对的概念,就是配合使用的,PVLAN是802.1q的应用方式,而VLAN和SLV AN能共存在,所以这三者完全可以配合使用。
vlan

Vlan1.定义sVlan(virtual lan)虚拟局域网(802.1Q工业标准、dot.1q都能表示vlan)二层协议Cisco交换机中存在4096个vlan(0~4095):其中0和4095是隐藏看不到的,1为本地vlan也称谓缺省vlan(native vlan),vlan 1不可删除。
在不做任何配置的时候所有接口都默认在vlan 1中。
其中1~1001和1006~4094属于以太网类型,1002、1003、1004、1005预留给fddi 和令牌环形网络类型。
2.原理源和目的是否在同一个vlan内(是否有相同的vlan ID),若相同则转发,若不同则丢弃。
在数据帧进入到交换机后转发时会给打上tag标记(标记里面包含vlan-id)。
相同vlan能相互通信,不同vlan不能相互通信(仅限于二层交换机,三层能通过某些手段实现通信)tag占32位。
3.ISL(inter-switch link)交换机间链路(此标记由于与其他品牌不兼容基本已经过时)目前vlan各类流量封装802,1Q标记并放如同一个物理链路中。
是cisco私有的链路聚集封装方式,在帧前封装isl报头(26字节)修改数据帧的FCS多加一个ISLFCS多加4个字节。
4.Vlan IDVlan字段其长度是12比特Vlan ID为0表示其为优先级帧Vlan ID为4095为保留5.vlan的作用I.隔离广播Ii.提高网络安全性Iii.灵活构建虚拟工作组(虚拟局域网)6.vlan的分类I基于端口基于交换机的端口,实施起来容易Ii基于mac 基于主机的mac划分,线路边锋仍能使用不用做更改。
Iii基于子网vlsm,节省端口Iv基于协议ip/ipx/pim,只能运行一个协议。
V自定义vlan划分自己定义的划分方式。
7.链路类型I.接入(access):将接口设定为永久的非链路聚集(放在终端设备接入)access默认为交换机上所有接口的模式。
CISCO路由器VPN讲解jvl

Host A
Host B
Router A
Router B
什么是端到端的VPN?
IKE阶段1
Host A
Host B
Router A
Router B
10.0.1.3
10.0.2.3
IKE 阶段 1
协商建立IKE安全通道所使用的参数
协商建立IKE安全通道所使用的参数
IKE阶段1
协商建立IKE安全通道所使用的参数,包括:加密算法Hash算法DH算法身份认证方法存活时间
隧道机制
IP VPN可以理解为:通过隧道技术在公众IP/MPLS网络上仿真一条点到点的专线 。隧道是利用一种协议来传输另外一种协议的技术,共涉及三种协议,包括:乘客协议、隧道协议和承载协议。
被封装的原始IP包
新增加的IP头
IPSec头
乘客协议
隧道协议
承载协议
原始IP包
经过IPSec封装后
隧道带来的好处
土豆两块钱一斤
fefe23fgrNMop7
对称密钥交换
对称加密和hash都要求通信双方具有相同的密钥
问题:怎样在双方之间安全地传递密钥?
密钥
哈哈,要是敢直接传递密钥,我就只好偷看了
密钥
DH算法的基本原理
Router A
Router B
生成一个整数 p
生成一个整数 q
把 p发送到对端
p
把 q发送到对端
数字签名认证
+ ID Information
加密
Hash_I
解密
Hash_I
私钥
公钥
本地
远端
Hash
=
+ 身份信息
斐讯交换机PVLAN技术

斐讯交换机PVLAN技术上海斐讯数据通信技术有限公司2008年11月25日目 录1.前 言 (3)2.介 绍 (4)3.背景知识 (5)3.1.什么是PVLAN (5)3.2.IVL和SVL (5)4.实 验 (7)4.1.简单的PVLAN实验 (7)4.1.1.实验目的 (7)4.1.2.实验拓扑 (7)4.1.3.实验设备 (7)4.1.4.预期效果 (8)4.1.5.配置及显示信息 (8)4.1.6.数据流程 (11)4.1.7.“广播问题”及解决 (13)4.1.8.实验小结 (19)4.2.引申的一个实验 (20)4.2.1.实验目的 (20)4.2.2.实验拓扑 (20)4.2.3.实验设备 (20)4.2.4.预期效果 (21)4.2.5.配置及显示信息 (21)4.2.6.数据流程 (26)4.2.7.实验小结 (27)1.前言本文档适合阅读者:已经对交换机原理及vlan知识有比较深刻的了解。
简述:通过阅读本文档,理解PVLAN、SVL、IVL,斐讯交换机相关配置; 理解vlan shared-learning及switchport shared-learning2.介绍在一些情况下,我们需要在二层(Layer 2)阻止网络终端设备之间的通信,而不需要通过设置不同的网段,开启三层功能来实现这个要求。
这样的设置可以减少IP 地址的浪费。
Private VLAN(PVLAN)能够实现在同一 IP网段的网络终端设备在二层的网络隔离,你能够在交换机上设置一些端口,只能够访问特定的端口,如:默认网关、服务器等。
3.背景知识3.1.什么是PVLANPVLAN 是由Cisco定义的,配置PVLAN可以在相同的IP网段或广播域,在二层实现端口间的隔离及通信。
你可以指派端口类型,来实现控制此端口与其他端口的通信。
根据Cisco定义,PVLAN中有三种类型的端口∶promiscuous(混杂)、isolated(隔离)和community(团体):Promiscuous端口可以访问VLAN内的所有其他端口,此端口经常用于连接外联路由器、本地领导、网络管理设备、服务器、管理工作站等。
Cisco IPSec VPN 配置详解【范本模板】
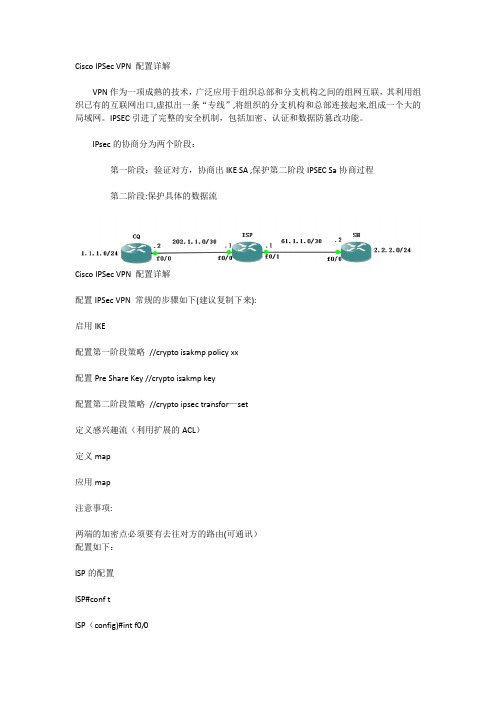
Cisco IPSec VPN 配置详解VPN作为一项成熟的技术,广泛应用于组织总部和分支机构之间的组网互联,其利用组织已有的互联网出口,虚拟出一条“专线”,将组织的分支机构和总部连接起来,组成一个大的局域网。
IPSEC引进了完整的安全机制,包括加密、认证和数据防篡改功能。
IPsec的协商分为两个阶段:第一阶段:验证对方,协商出IKE SA ,保护第二阶段IPSEC Sa协商过程第二阶段:保护具体的数据流Cisco IPSec VPN 配置详解配置IPSec VPN 常规的步骤如下(建议复制下来):启用IKE配置第一阶段策略//crypto isakmp policy xx配置Pre Share Key //crypto isakmp key配置第二阶段策略//crypto ipsec transfor—set定义感兴趣流(利用扩展的ACL)定义map应用map注意事项:两端的加密点必须要有去往对方的路由(可通讯)配置如下:ISP的配置ISP#conf tISP(config)#int f0/0ISP(config—if)#ip add 202.1。
1。
1 255.255.255.252ISP(config-if)#no shISP(config—if)#int f0/1ISP(config—if)#ip add 61.1。
1.1 255.255。
255.252ISP(config-if)#no shCQ(左边路由器)的配置:CQ#conf tCQ(config)#int f0/0CQ(config-if)#ip add 202.1。
1.2 255。
255.255.252CQ(config-if)#no shCQ(config-if)#int lo 0CQ(config-if)#ip add 1.1.1。
1 255。
255.255。
0CQ(config-if)#no shCQ(config-if)#exitCQ(config)#ip route 0。
PVLAN原理及配置

PVLAN原理Catalyst3560, 45, 65系列支持 PVLANpvlan的解释对于pvlan看了许多之后有些摸不到头脑,在网上看了此篇文章后有些明了。
转过来供大家参考pVLAN基本概念:1.规则VLAN域一个常规的VLAN实际上就可以看作是一个规则的VLAN域。
比如VLAN100,我们可以将它看作是一个“域”,这个“域”的编号,或者说名字是“VLAN100”。
2.子域、Primary VLAN、Secondary VLANpVLAN就是把一个规则的VLAN域划分为一个或多个子域。
当把一个规则的VLAN域划分子域后,原来的“规则VLAN域”现在就叫做“Primary Vlan”,这个“Primary VLAN”编号,或者说名字就是原来“规则VLAN域”的名字。
划分出来的子域我们把它叫做“Secondary VLAN”,这个VLAN是有两种属性。
3.“Secondary VLAN”的属性、“Isolated VLAN”、“Community VLAN”“Secondary VLAN”有两种属性:一种是“isolated”,我们把它叫做“Isolated VLAN”;另一种是“c ommunity”,我们把它叫做“Community VLAN”。
一个“Secondary VLAN”必须、且只能被赋予其中某一种属性。
这两种属性的“Secondary VLAN”都有一些规则,下面我们会讲到。
4.pVLAN中的两种接口类型处在pVLAN中的交换机物理端口,有两种接口类型:①混杂端口(Promiscuous Port)②主机端口(Host Port)其中“混杂端口”是隶属于“Primary VLAN”的;“主机端口”是隶属于“Secondary VLAN”的。
前面我们说过,因为“Secondary VLAN”是具有两种属性的,那么可想而知,处于“Secondary VLAN”当中的“主机端口”依“Secondary VLAN”属性的不同而不同,也就是说“主机端口”会继承“Secondary VLAN”的属性。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Cisco PVLAN 详解
PVLAN即私有VLAN(Private VLAN),PVLAN采用两层VLAN隔离技术,只有上层VLAN全局可见,下层VLAN相互隔离。
每个pVLAN包含2种VLAN :主VLAN(primary VLAN)和辅助VLAN(Secondary VLAN)。
辅助VLAN(Secondary VLAN)包含两种类型:隔离VLAN(isolated VLAN)和团体VLAN(community VLAN)。
pVLAN中的两种接口类型:处在pVLAN中的交换机物理端口,有两种接口类型。
①混杂端口(Promiscuous Port)
②主机端口(Host Port)
Catalyst3560, 45, 65系列支持
配置pVLAN的实例:
SwitchA(config)#vlan 100
SwitchA(config-vlan)#private-vlan
primary
!设置主VLAN 100
SwitchA(config)#vlan 200
SwitchA(config-vlan)#private-vlan community
!设置团体VLAN
200
SwitchA(config)#vlan 300
SwitchA(config-vlan)#private-vlan isolated
!设置隔离VLAN
300
SwitchA(config)#vlan 100
SwitchA(config-vlan)#private-vlan association 200,300 !将辅助VLAN关联到主
VLAN
SwitchA(config)#interface vlan 100
SwitchA(config-if)#private-vlan mapping add
200,300
!将辅助VLAN映射到主VLAN接口,允许pVLAN入口流量的三层交
换
SwitchA(config)# interface fastethernet 0/2
SwitchA(config-if)#switchport mode private-vlan host
SwitchA(config-if)#switchport private-vlan
host-association 100 200
!2号口划入团体VLAN 200
SwitchA(config)# interface fastethernet 0/3
SwitchA(config-if)#switchport mode private-vlan host
SwitchA(config-if)#switchport private-vlan host-association 100 300
!3号口划入隔离VLAN 300
SwitchA(config)# interface fastethernet 0/1
SwitchA(config-if)#switchport mode private-vlan promiscuous
SwitchA(config-if)#switchport private-vlan mapping 100 add 200-300
!1号口杂合模式
关于端口隔离
Switch(config)# interface gigabitethernet1/0/2
Switch(config-if)# switchport protected
PVLAN通常用于企业内部网,用来防止连接到某些接口或接口组的网络设备之间的相互通信,但却允许与默认网关进行通信。
尽管各设备处于不同的pVLAN 中,它们可以使用相同的IP子网。
pVLAN 的3种port: isolated,community ,promiscuous。
pVLAN 的3种子VLAN.
p VLAN通常用于企业内部网,用来防止连接到某些接口或接口组的网络设备之间的相互通信,但却允许与默认网关进行通信。
尽管各设备处于不同的pVLAN中,它们可以使用相同的IP子网。
pVLAN 的3种port:
isolated,community ,promiscuous。
pVLAN 的3种子VLAN :
primary VLAN , isolated VLAN(second vlan), community VLAN(second vlan)。
pVLAN通信范围:
primary VLAN:可以和所有他所关联的isolated VLAN,community VLAN通信. community VLAN:可以同那些处于相同community VLAN内的community port通信,也可以与pVLAN中的promiscuous端口通信。
(每个pVLAN可以有多个community VLAN)
isolated VLAN:不可以和处于相同isolated VLAN内的其它isolated port通信,只可以与promisuous端口通信。
(每个pVLAN中只能有一个isolated VLAN)
pVLAN限制:
pVLAN要求使用VTPv1或VTPv2。
pVLAN必须工作于Transparent模式。
禁止将第 3层VLAN接口配置为辅助VLAN。
EtherChannel或SPAN目标端口不支持pVLAN。
配置命令:
//建立primary VLAN
vlan 10 private-vlan primary
//建立isolated VLAN
vlan 11 private-vlan isolated
//建立community VLAN
vlan 12 private-vlan community
//关联primary VLAN与Second VLANs
vlan 10 private-vlan association 11,12
//配置promiscuous
interface G0/0
switchport
switchport mode private-vlan promiscuous
switchport private-vlan mapping 10 11,12
注:这里promiscuous port可以属于多个secondary VLAN,但只可以属于一个primary VLAN,就好像普通的access port只能属于一个vlan是一样的。
//配置isolated port
interface G0/1
switchport
switchport mode private-vlan host
switchport private-vlan host-association 10 11
//配置community port
interface G0/2
switchport
switchport mode private-vlan host
switchport private-vlan host-association 10 12
注意:
1>在private vlan里 switchport access vlan xxx 这一句已经不起作用了。
起作用的是 switchport private-vlan host-association 10 11这一句,这一句把端口放入primary vlan 10和secondary vlan 11。
2>在配置vlan的3层地址的时候,只可以配置在primary VLAN上,从这里也可以看出,primary VLAN在某些地方是和普通vlan一样工作的,secondary VLAN 则更特殊一些。
pVLAN使用方案:。
