Session A-T3-3 ADVANCED COURSE IN PROGRAMMABLE CONTROLS FOR ENGINEERING TECHNOLOGY
UG题库

一、单项选择题(共188小题)1、试题编号:200520401000810,状态:可用,答案:RetEncryption(B)。
UG软件默认的角色为()。
A. Advanced roleB. Essentials (recommended ) roleC. Essentials with full menus2、试题编号:200520401000910,状态:可用,答案:RetEncryption(C)。
新建工具条的命令为()。
A. Format-customize-toolbar-newB. Insert-customize-toolbar-newC. Tools-customize-toolbar-newD.Edit-customize-toolbar-new3、试题编号:200520401001010,状态:可用,答案:RetEncryption(D)。
默认情况下,资源管理器在窗口左侧,将其设置在窗口右侧执行如下()操作。
A. Edit-User Interface-Layout-(Display Resource Bar) On RightB. Insert-User Interface-Layout-(Display Resource Bar) On RightC. Preferences-Palettes-Layout-(Display Resource Bar) On RightD. Preferences-User Interface-Layout-(Display Resource Bar) On Right4、试题编号:200520401001110,状态:可用,答案:RetEncryption(D)。
UG6.0中默认的"Datum Coordinate System"在位于第()层。
A.1B.11C.21D.615、试题编号:200520401001210,状态:可用,答案:RetEncryption(B)。
siemens s7-plcsim advanced v5.0 update 1 readme说明书

SIMATICIndustrial softwareReadme SIMATIC S7-PLCSIM Advanced V5.0 Update 1 ReadmeGeneral informationThis Readme file contains information about SIMATIC S7-PLCSIM Advanced V5.0 Update 1.This information should be considered more recent than the product documentation and replaces corresponding information in the product documentation and installation instructions.Updates provided by S7-PLCSIM V5.0 Update 1S7-PLCSIM Advanced V5.0 Update 1 provides updates to select internal components.Corrections to the S7-PLCSIM Advanced V5.0 Function Manual Addition to section 4.1.2 Restrictions due to antivirus programsSymantec Endpoint Protection 14.3In addition to the Symantec Endpoint Protection 14.3 virus scanner mentioned in the S7-PLCSIM Advanced manual, note the following restriction.If you use Npcap with Symantec Endpoint Protection, select one of the following options:•Uninstall Symantec Endpoint Protection.•Use Symantec Endpoint Protection with Npcap V1.60 or earlier.Trend Micro Office ScanNote that the supported version of Trend Micro Office Scan is V14.0 and not Trend Micro Office Scan V12.0. Addition to Section 6.5 Simulating a redundant S7-1500R/H systemNoteSystem IP address for switched communicationIf you have activated a system IP address for switched communication, you can only communicate locally via TCP/IP using this system IP address. External communication is not possible.© Siemens AG 2023. All rights reservedA5E38332429-AM, V5.0 Upd1, 01/2023 1Readme SIMATIC S7-PLCSIM Advanced V5.0 Update 1 2 A5E38332429-AM, V5.0 Upd1, 01/2023 Addition to Section 7.3.1 Synchronize simulation partner cycle-controlled SingleStep operating modesNote the addition of footnote 4 for the following table:Table 1 Cycle-controlled operating modes (SingleStep)1 TimeSinceSameSyncPoint_ns / TimeSinceAnySyncPoint_ns being set to 0 in the first SyncPointReached callback event in the new operating mode. Siemens recommends that the SingleStep operating mode not be changed during operation.2 In addition, the minimum scan cycle time of OB 1 is overwritten in this operating mode. When you define a minimum cycle time of 200 ms, the minimum distance between two cycle control points is 200 virtual milliseconds. The default setting is 100 ms.3 Send clock of the I/O system (PROFIBUS or PROFINET) that is to be used for the cycle-controlled synchronization of the virtual controller. You set the send clock of the respective I/O system in the STEP 7 properties, for example, in the properties of the PROFINET interface of the CPU (Advanced options > Real time settings > I/O communication > Send clock).4 During the execution of these operating modes, the input parameter of the first callback event returns the value 0 for TimeSinceSameSyncPoint_ns / TimeSinceAnySyncPoint_ns. Subsequent callback events for TimeSinceSameSyncPoint_ns / TimeSinceAnySyncPoint_ns then return values other than 0. Addition to Section 8.6.1 Interfaces - Information and settingsUnregisterInstance()In addition to the information in Section 8.6.1, paragraph "UnregisterInstance()" of the S7-PLCSIM Advanced Function Manual, note the following information:Do not log off any S7-PLCSIM Advanced instance while the instance is being started via the Control Panel or API code. Wait until the PowerOn action for this instance is complete before logging off the instance.Readme SIMATIC S7-PLCSIM Advanced V5.0 Update 1 A5E38332429-AM, V5.0 Upd1, 01/2023 Siemens AG Digital Industries Postfach 48 48 90026 NÜRNBERG GERMANY。
特斯拉 Model S 用户手册说明书

ELECTRIC FORD EXPLORER> F uturistic, aerodynamic body is less than 4.5 metres long for exploring in compact European cities and beyond > A ero-optimised alloy wheels from19- to 21-inches> C arefully curated colours includenew Arctic Blue and Blue My Mind> S culpted, sporty, heated frontseats with integrated headrestsand massage for the driver> A vailable ambient lighting candisplay 10 colours> S tandard comfort includeskeyless entry, heated steeringwheel, dual-zone climate controland hands-free tailgate foraccessing 450-litre bootspace> 12 ultrasonic sensors – 5 cameras– 3 radars – for advanced driverassistance technologies includingAssisted Lane Change and ClearExit Assist4T he innovative new Explorer crossover leads the way for a new wave of bold, iconic electric vehicles that are steeped in Ford’s American roots and designed for Europe DESIGNKey design details includedistinctive front shieldgraphic, floating roof effect,signature lights, and glass-embedded rear window pillargraphicsSOUNDBARSophisticated soundbar speakerMEGACONSOLE17-litre MegaConsole can hold a15-inch laptop or multiple 1.5-litredrinks bottlesDC FAST CHARGINGDC fast charging enables 10-80 per centcharging in 25 minutes1, with access tomore than 450,000 charging stationsacross EuropeINTERIORCalm, minimalist, digitally-inspiredinterior features a wrap-aroundcockpit effectSYNC MOVESYNC Move connected infotainmentintroduces a 15-inch moveablescreen concealing the secureMy Private Locker2Wirelessly integrate Android Autoand Apple CarPlay3. A wirelesssmartphone charger is standard1 C harge time based on manufacturer computer engineering simulations. The charging rate decreases as battery reaches full capacity. Your results may vary based on peak charging times and battery state of charge. Officially homologated driving range will be published closer to on-sale date.2 D on’t drive while distracted or while using handheld devices. Use voice-operated systems when possible. Some features may be locked out while the vehicle is in gear. Not all features are compatible with all phones.3 R equires phone with active data service and compatible software. SYNC Move does not control 3rd party products while in use. 3rd parties are solely responsible for their respective functionality. Qi wireless charging may not be compatible with all mobile phones.4 D river-assist features are supplemental and do not replace the driver’s attention, judgement and need to control the vehicle. It does not replace safe driving. See owner’s Manual for details and limitations.。
QuantStudio 3和QuantStudio 5实时PCR系统使用说明书

QuantStudio 3 and QuantStudio 5 Real-Time PCR SystemsConnect to your data anytime, anywhereThe modern laboratory is undergoing a technological revolution. Today’s scientific breakthroughs emerge in a context of unparalleled connectivity. Lab instruments not only are more compact, automated, powerful, and accessible, but also can store and can connect to platformsthat can share vast amounts of data, facilitating scientific advances through global collaboration.As your trusted partner at the leading edge of this era of innovation, we’ve developed the Applied Biosystems™QuantStudio™ 3 and 5 Real-Time PCR Systems. These high-performance benchtop instruments allow you to remotely monitor your runs, as well as easily access and securely share results with colleagues anywhere, anytime when connected to Thermo Fisher Cloud. With your data always within reach and shareable, the answers shaping the future of science are never far away.Connect with your future234•Q uickly share data setsand protocols online•S end large files securelyaround campus or aroundthe world•I ntegrate and analyzemultiple data sets anddata types into oneproject•A ccess experiment runsfrom any location, anytime,with remote monitoring•W i-Fi–enabled connectivity•U tilize portable devices to quicklyanalyze data when you need to* With Internet access and ThermoFisher ConnectInteractivityCollaboration* Accessibility*• Interactive touch screen•R un and edit directly from touch screen•E asy and intuitive interfaceThese instruments provide our latest advancements in touch-screen usability, allowing you to stay connectedto your data easily. They’re designed for both new and experienced users who need simple and affordable real-time PCR systems without compromising performance or quality.Access, analyze, and share data anytime, anywhere—Remotely monitor your runs, analyze sophisticated data sets in minutes, store data in a secure space, and share results online with colleagues across institutions and around the world, with Web browser–based software. Monitor your runs in real time from mobile devices through the Instrument Connect mobile app.Obtain results you can trust—Detect differences in target quantity as small as 1.5-fold in singleplex reactions, and obtain 10 logs of linear dynamic range.Establish standard operating procedures and compliance with ease—Locked protocol templates,in-run quality control (QC) feedback, and QC traceabilityof consumables offer greater control of experimental data. Real-time data mark-up language (RDML) export is available for compatibility with MIQE guidelines.Helps save valuable time—3 or 6 independent temperature zones for flexibility to run multiple experiments simultaneously. Fast thermal cycling is also available, enabling results in less than 30 minutes.Get started quickly—Instrument is factory-calibratedfor optical and thermal accuracy, quick installation, and immediate use.Skip the learning curve—With preoptimized protocol templates, training is minimized for new users, allowing you to focus on your research.Maximize benchtop space—Compact instrument can be configured as a stand-alone unit or with a computer to fit most laboratory needs.Get a premium instrument at an affordable price—Innovation doesn’t have to come at a premium price.Get the state-of-the-art Applied Biosystems functionality and industrial design that you’ve come to know, with the QuantStudio family of instruments.Discover the QuantStudio 3 and 5 Real-Time PCR SystemsThe QuantStudio 3 and 5 Real-Time PCR Systems are the latest additions to our family of QuantStudio systems.56• Interactive touch-screen interface and simplified Applied Biosystems TM QuantStudio ™ Design and Analysis Software make it easy to get started and stay organized• Easily identifiable icons guide you through the workflow to set up runs and analyze experiments• Graphical interface allows easy editing of experimental conditions (Figure 1A)• Interactive touch screen allows you to manipulate view to a particular graph or data point (Figure 1B)• Option to pause a real-time PCR run on demand• Preoptimized protocol templates allow quick selection of default protocols for standard applications • L ocked workflow feature allows for experimental consistency in tightly controlled environments InteractivitySimple, intuitive software—at your fingertipsFigure 1. Graphical interface allows (A ) easy editing of thermal cycling conditions and viewing of plate layout, as well as (B) viewing of amplification plotsand drilling down to a subset of sample wells.BA7Web-based or online:• Web browser–based system configuration with PC or Mac ™ computers• Streamlined software for improved usability and analysis response time• E nables secure access of your data when and where you want it• No software to install, no additional fees, and no versions to update• Monitor and check instrument status• Real-time run monitoring with Instrument Connect mobile appDesktop:• Simple co-located computer system configuration • Streamlined software for improved usability and analysis response timeFor more information about the Thermo Fisher Connect platform and data security, go to /connectTwo ways to access QuantStudio Design and Analysis SoftwareAccess with Web browser–based software Co-locate with computer8Applied Biosystems ™ Analysis Modules are innovative cloud-based data analysis applications that bring together multiple data sets in one convenient place, and render them in stunning data visualizations for enhanced analysis and insights.CollaborationFast and powerful secondary analysis software to extract and share resultsAnywhere, anytime accessAccess your data with a compatible browser on any device. Eachregistered user has a PIN-protected account on Thermo Fisher Connect.Fast and powerful analysisAnalysis speeds up to 10 times faster than our desktop software version, to help analyze more data and gain insights more quickly than before using Thermo Fisher Connect.Easy to useOne-click quality checks and comparisons between different visualizations, for simple and convenient data analysis.Integrated analysis solution Integrate your experiments into a single project—analyze various groups of data, such as time course experiments or cell line comparisons, and pick ideal settings to easily compare data.Superior securityPowered by Amazon Web Services ™, the Thermo Fisher Connect platform helps protect your data in a highly secure environment using 256-bit encryption and physical security measures.MIQE guideline supportThe instrument software allows users to save predefined analysis settings for auto-exporting run data into their format of choice, including RDML (real-time data mark-up language, compliant withMIQE guidelines) export format.9Figure 3. Relative quantification module for gene expression analysis. With this module, you can customize groupings of data within projects for a thorough comparison of data. The module also includes integrated correlation,volcano, and cluster plot analysis, with the ability to drill down to amplification plots.Figure 2. Absolute quantification module for gene expression analysis. The module enables analysis of genes of interest with the use of a standard curve. Additional flexibility is achieved by importing standard curves from other experiments.Figure 4. Genotyping analysis module. This module expands on existing Applied Biosystems ™ TaqMan ® Genotyper ™ software with improved visuals and integrated traces of allelic discrimination plots. The module allows for thorough quality control of SNP assays to accurately reflect true signals vs. background noise.Absolute quantificationRelative quantificationGenotypingThe Applied Biosystems Analysis Modules include:10Utilizing proven Applied Biosystems ™ OptiFlex ™ technology and VeriFlex ™ Blocks, QuantStudio 3 and 5 systems offerimproved data accuracy and sensitivity for a broad range of genomic applications, such as analyses of gene expression, microRNAs and noncoding RNAs, SNP genotyping, copy number variation, mutation detection, drug metabolism enzymes, and protein expression.Generate high-quality data for a variety of applicationsPerformance you can trustFigure 5. The QuantStudio 3 and 5 systems provide sensitive detection and high-confidence target discrimination down to 1.5-folddifferences. (A ) Amplification plots for 1.5-fold dilutions of a KAZ plasmid amplified with Applied Biosystems ™ PE2 TaqMan ® Assay under Fast run conditions using TaqMan ® Fast Advanced Master Mix. Quantities assayed, and C t (SD): 1,000 copies, 27.9 (0.063); 1,500 copies, 27.4 (0.059); 3,000 copies, 26.4 (0.060); 4,500 copies, 25.8 (0.047); 6,667 copies, 25.2 (0.049); 10,000 copies, 24.5 (0.041). NTC = no-template control. (B ) Standard curve generated from the C t values.BAFigure 6. Real-time PCR reproducibility. This plot shows results from amplification of KAZ target plasmid DNA in 10-fold dilutions using the 96-well block. The data show highly reproducible results over 10 logs of inputtemplate amount, illustrating the broad linear dynamic range of the system.Precise quantification with 1.5-fold discriminationExcellent reproducibility and 10-log dynamic range11The QuantStudio 3 and 5 systems support probe-based assays as well as intercalating dyes. TaqMan ® probe-based assays, developed with powerful algorithms and optimized master mixes, enable outstanding specificity and sensitivity. Applied Biosystems ™ SYBR ™ Green chemistry is an economical alternative for target identification or initial screening assays. The QuantStudio 3 system has 4 filters calibrated for FAM ™/SYBR Green, VIC ™/JOE ™, NED ™/TAMRA ™, and ROX ™ dyes. The QuantStudio 5 System offers 96- w ell and 384-well format options, allowing for a broader range of detection chemistries and assay multiplexing. The 96-well format has 6 excitation filters (450–680 nm) and 6 emission filters (500–730 nm), and the 384-well format has 5 excitation filters (450–650 nm) and 5 emission filters (500–700 nm).Generate high-quality data for a variety of applicationsAssay flexibility to support your applicationGenotyping analysisFigure 9. Allelic discrimination plot with traces using real-time PCR data. Cluster plot of 44 gDNA samples and 4 no-template controls (NTCs) genotyped using Applied Biosystems ™ T aqMan ® SNP Genotyping Assay C_29086771_20, with both PCR and allelic discrimination performed on the QuantStudio 5 Real-Time PCR System. The novel use of real-time PCR data to plot SNP cluster progress aids in calling ambiguous samples and reduces run times by displaying the optimal number of cycles necessary for maximum cluster separation.Figure 8. Multiplex reaction with 4 targets plus passive reference.Whole-plate amplification plots of 96 replicates of cDNA made from universal human RNA (UHR) amplified under Fast run conditions using AppliedBiosystems ™ TaqMan ® Multiplex Master Mix with Mustang Purple ™ passive reference dye. Targets and labels: FZD1 labeled with FAM dye, APOE labeled with VIC dye, CD44 labeled with ABY ™ dye, GAPDH labeled with JUN ™ dye.Melt curve analysisMultiplex gene expressionFigure 7. Melt curve analysis using the online version of the software. In this experiment, 96 replicates of human genomic DNA were amplified using Applied Biosystems ™ SYBR ™ Select Master Mix with primers for RNase P followed by a dissociation step. The reactions were run under Fast run conditions, showing C t uniformity with a mean of 25.7 (SD 0.077), and thermal uniformity as measured by the derivative peak with a melting temperature (T m ) of 84.17°C (SD 0.07°C).For more information about TaqMan Assays and formats, go to/taqmanTechnical specificationsQuantStudio 3QuantStudio 59696 or 3840.1 mL block: 10–30 μL 0.2 mL block: 10–100 μL 96-well 0.1 mL block: 10–30 μL 96-well 0.2 mL block: 10–100 μL 384-well: 5–20 μL27 cm x 50 cm x 40 cm27 cm x 50 cm x 40 cmBright white LED Bright white LED4 coupled filters96-well: 6 decoupled filters384-well: 5 coupled filters450–600 nm/500–640 nm96-well: 450–680 nm/500–730 nm384-well: 450–650 nm/500–700 nm Multiplexing Up to 4 targets96-well: up to 6 targets384-well: up to 5 targetsOptional OptionalPeltier Peltier3 VeriFlex zones96-well: 6 VeriFlex zones384-well: NA0.2 mL block: 6.5°C/sec 0.1 mL block: 9.0°C/sec 0.2 mL block: 6.5°C/sec 0.1 mL block: 9.0°C384-well block: 6.0°C/sec3.66°C/sec 3.66°C/sec0.4°C0.4°C0.25°C0.25°CRun time<30-minute runs96-well block: <30-minute runs384-well block: <35-minute runsFAM/SYBR Green, VIC/JOE/HEX/TET, ABY/NED/TAMRA/Cy®3, JUN, ROX/ Texas Red™FAM/SYBR Green, VIC/JOE/HEX/TET, ABY/NED/TAMRA/Cy3, JUN, ROX/ Texas Red, Mustang Purple, Cy®5/LIZ™, Cy®5.5Fast/standard Fast/standardNo Yes, with no additional fees 1 copy 1 copySensitivity Detect differences as small as 1.5-fold in target quantities in singleplexreactions Detect differences as small as 1.5-fold in target quantities in singleplex reactions1213Service and support to help meet your changing needsSmartStart orientationEvery QuantStudio 3 and QuantStudio 5 system includes a SmartStart orientation to get you up and running quickly in your lab. The orientation includes basic qPCR familiarization and setup with both Thermo Fisher Connect and online Instrument Management. QuantStudio 5 system owners receive a personalized qPCR application training.Online instrument management Sign in to your account to access the award-winning* free online Instrument Management** tool that enables faster responses to requests for service or service quotes, plus fast connection to key instrument and service information.Comprehensive instrument warrantyOur factory-trained and certified field service engineers (FSEs) are focused on delivering the highest-quality workmanship. During the warranty period, all qualifying repairs, including engineer time and travel, are covered.Flexible service plansChoose from a variety of serviceoptions that balance your budget,productivity, uptime, and regulatoryrequirements. Plans start with themost basic repair models and scale topremium offerings including advancedsupport and compliance services.On-site service plans are optimal forlabs that have time-sensitive workand need to get their instrumentback online quickly. These plansinclude guaranteed response timesin most regions, scheduled plannedmaintenance, and automatic softwareupdates. The AB Repair Center plan isa cost-effective choice for customerswho can allow their instrument to besent away for repair—this plan providesa loaner instrument so that customerscan maintain productivity while theirinstrument is being repaired.Professional servicesOur services are designed to helpyou balance business and regulatoryrequirements—from risk assessment,hardware/software qualification, fullsystem validation, and LIMS interfacingservices to data storage and backupsolutions. We partner with you to helpmitigate regulatory risks, get yourprocesses up and running, and helpensure data integrity across your lab.Training coursesOur application and instrument trainingprograms are led by scientists whoaim to enhance your workday throughexperimental design best practices,workflow training, and instrumenttroubleshooting. Hands-on classes areavailable at our Thermo Fisher Scientifictraining centers or in your lab.Technical supportIf you have questions aboutproduct selection or use, assay orexperimental design, data analysis, ortroubleshooting, contact our team oftechnical support scientists or accessour online product and applicationsupport tools.Financing optionsIf you’re looking for acceleratedreturn on investment, technologyprotection, or cash flow management,our innovative financing options canhelp meet your company’s budgetaryneeds and bottom-line goals. Contactyour local sales representative formore details.For a full schedule of courses, including self-paced online classes, go to /training * 2012 Oracle Fusion Middleware Innovation Award.** Online Instrument Management tool not available in all regions.14Service plans at a glanceTarget 2 business days*Guaranteed 2business days*Guaranteednext businessday*✓✓✓✓✓✓✓✓✓✓✓10% discountoptional add-on in selectedregions✓✓✓✓✓✓✓✓✓✓✓✓✓✓✓✓✓✓Response times vary by region.15Ordering informationHow to reach usTo find your order support or technical support team, go to /contactusFor product FAQs, protocols, training courses, and webinars, go to /technicalresources For more info, go to/quantstudio3-5For Research Use Only. Not for use in diagnostic procedures. © 2017 Thermo Fisher Scientific Inc. All rights reserved. All trademarksare the property of Thermo Fisher Scientific and its subsidiaries unless otherwise specified. TaqMan is a registered trademark of RocheMolecular Systems, Inc., used under permission and license. Cy is a registered trademark of GE Healthcare. Mac is a trademark of Apple Inc.Amazon Web Services is a trademark of Amazon Technologies, Inc. Oracle is a trademark of Oracle International Corporation.COL03261 0117。
DMC 3000 快速使用指南说明书

Radiation. Safety.DMC 3000 Quick User’s GuideHealth PhysicsDivisionWelcome to your DMC 3000!In approaching the opportunity to create a more refined Personal Electronic Dosimeter, we wanted to address first and foremost the needs and desiresof our users. We are the leading manufacturer of systems and equipment to protect people and goods from nuclear risks, and designed our next generation dosimeter accordingly.DMC 3000. Radiation Safety. Perfected.A. DMC 3000 with standardclip attached.ABCD EIn this box:B. Torx Screwdriver for batterycover/clip removal.C. Single spare AAA alkaline battery.D. Optional front-facing clip.E. Optional belt clip.Mirion Technologies Health Physics DivisionYour DMC 3000: At a GlanceA t A G l a n c eA B C D EFGH JA. ‘+’ button. Press in pause mode to cycle through available parameters.B. Ultra bright red LED.C. ‘-’ button. Press in pause mode to cycle through available measurements.D. Speaker.E. Location of detector.F. 8-Character backlit LCD display.G. Trio of LEDs for alarm and dose increment notification.H. Wide, durable clip, replaceable with optional belt clip.I. Battery compartment for 1 AAA battery.J. Attachment rail for optional front-facing clip.IC A-3-Turning on your DMC 30001. From pause mode, press and hold the ‘+’ button for 3 seconds.Turning off your DMC 30001. Press and hold the ‘+’ buttonfor 3 seconds.2. The display will change to ‘Enter.’3. Rapidly release the ‘+’ button, and press the ‘-’ button.4. After a beep and LED flash the unit will be in runmode.2. The display will change to ‘Exit.’3. Rapidly release the ‘+’ button, and press the ‘-’ button.4. After a beep and LED flash the unit will be in pausemode.:PAUSE :ENTER :EN b ER:EXI b :EXIT :PAUSEMirion Technologies Health Physics DivisionS e t t i n g U pSetting Alarms for your DMC 30001. From pause mode, press and hold the ‘-’ for 3 seconds.2. The display will change to ‘Set Thr.’3. Rapidly release the ‘-’ button, and press the ‘+’ button.4. The DMC 3000 will enter programming mode.5. Press the ‘-’ button until you reach the parameter to be changed.*6. Press ‘+’ to start modifying the selected parameter. (display blinks)7. Press or hold** ‘+’ or ‘-’ to raise or lower the threshold value, respectively.8. Wait for 5 seconds for the DMC to return to step 4.9. Wait 10 seconds more for the DMC to return to pause mode.**Press to change the value up or down in single increments, hold to rapidly change the value up or down.:PAUSE 33S:E b . b HR S:ET. T HR d :RESE t:PAUSE*Rate Alarm setting used for this example.ALARMALARMALARMALARM-5-Key Features of your DMC 3000A B C•Multiple alarm indications including: - Vibrating alarm.- 85 dB (A) audible alarm.- Forward facing, ultra bright LED. - Trio of alarm LEDs on front face.A. Red (Flash) LED for standard alarms and alarm warnings.B. Green (Flash) LED for gamma and x-ray dose increment at preset intervals.C. Blue (Flash) LED for secondary channel (HP 0.07 or Neutron increments at preset intervals.)• Set points easily programmable via pushbuttons for Dose Alarm, Dose Warning, Rate Alarm, Rate Warning, and Time Limit Alarm.• Wide viewing angle LCD backlit display.• Extensive historical data stored in non-volatile memory.• Units configurable in either mSv, μSv, or mrem.•Factory Upgradeable Firmware.Mirion Technologies Health Physics Division S p e c i fi cCharacteristics of your DMC 3000• Energy response (X-ray and gamma) from15 keV to 7 Mev.• Energy response better than ± 20%.(typically ± 10%) from 16 keV to 7 Mev.• Display units: mSv, μSv, mrem.• Dose measurement display range: between1 μSv and 10 Sv. (0.1 mrem to 1,000 rem.)• Rate measurement display range: between10 μSv/hr and 10 Sv/h. (1 mrem/h to 1,000rem/h.)• Optional extended rate display between1 μSv/h and 10 Sv/h.(0.1 mrem/h to 1,000 rem/h.)• 9 months of battery life under typical use (in run mode 8 hours a day, 5 daysa week, with nominal alarms).• 2,500 hours typical battery life incontinuous run mode (< 0.2% of thetime in alarm.)• Waterproof: 1 meter up to one hour.• Shock and drop resistant.Caring for your DMC 3000 When the battery starts to approach the end of its life, the DMC 3000 will display an alert mes-sage, and in run mode is coupled with periodicflashes of the LED and chirps of the speaker. The battery can be changed by removing the two Torx screws on the back cover and replac-ing it with a single (1.5V) AAA alkaline battery.: b A b-09In run mode, once the battery gets low, the DMC willalso display remaining hours of battery life.-7-Radiation. Safety.Health Physics DivisionAmericasMirion Technologies (MGPI), Inc.5000 Highlands Pkwy Suite 150Smyrna GA, 30082T: +1 770 432 2744AsiaMirion Technologies Shanghai Branch Room 801, 78 Jianchang San Lu, Zhabei District, Shanghai 200436, ChinaT: +86 21 6180 6920EuropeMirion Technologies (MGPI) S.A.Lieu-dit Calès, route d’Eyguières,13113 Lamanon, FranceT : +33 490 595 959154858EN-B。
ZEISS Humphrey Field Analyzer 3 (HFA3) 软件版本1.5 升级指

How do I upgrade an HFA3 instrumentto software version 1.5?ZEISS Quick Help: Humphrey® Field Analyzer 3 (HFA3)This document reviews the steps to connect HFA Review Software for use with an HFA3 instrument.Software media packageTo connect your HFA3 Software, you will use HFA Software Media Package, which contains two USB driveswith everything you need to complete your software installation. The USB drives will be labeled SW [Software] and UD [User Document].• HFA3 Instrument Upgrade Software is labeled “SW”• HFA3 Instrument User Manual is labeled “UD”NOTE: Proceed with version 1.5 update only if your current version device databasehas been backed up. Follow these steps.1. Go to Login screen.2. Log in as Administrator3. Select the Settings icon located in the Toolbar at the top of the screen.4. Navigate to the Maintenance screen to observe the Database backup interval set up for your device.Note: If no networking or backup location has been set up on your device, contact your IT Administrator to ensure the “Smart” backup is performed before proceeding with the software upgrade.5. I nsert the white USB drive with the SW label containing the software update into one of the USB connections located on the front of the HFA3 device.6. Navigate to Settings > Maintenance screen and select Perform update. A confirmation screen will appear.7. Select Yes to start Update Wizard.8. A popup screen will appear with the update. Highlight the update and select Run .9. T he “InstallShield Wizard for Humphrey Field Analyzer 3” screen will appear. Click Next to continue.Note: If the error message “Error copying NK bin” appears during installation, select OK and follow the instructions on the screen. Once the InstallShield Wizard has finished aborting installation, reboot the device and repeat the installation. This is an infrequent communication error that may occur at any point in the installation process. Follow the on-screen instructions through the rest of the software upgrade process.Note: If the following message appears, select Runin the popup and proceed.• T here may be brief sequences when the screen goes black for several seconds. Wait for the next on-screen prompt.• D o not touch the screen or type on the keyboard during the installation process except as directed by theon-screen prompts.• T here may be screens that show a progress bar. Occasionally, the progress bar will stop for several seconds,but the installation is still in progress.• T here will be several prompts for going to the next step or confirming a step. Respond to these promptsby using the touchscreen or the cursor driven by the keyboard or external mouse.• Select Finish from the InstallShield Wizard Complete screen.• T he background screen will turn black. A message will appear letting you know the instrument is goingto shut down and to start it again after shutdown. Click Close and wait for the instrument to shut down.Once shut down, remove the USB drive from the HFA3.0297S E R .10829 C Z -I /2019T h e c o n t e n t s o f t h i s r e f e r e n c e g u i d e m a y d i f f e r f r o m t h e c u r r e n t s t a t u s o f a p p r o v a l o f t h e p r o d u c t i n y o u r c o u n t r y . P l e a s e c o n t a c t y o u r r e g i o n a l r e p r e s e n t a t i v e f o r m o r e i n f o r m a t i o n . S u b j e c t t o c h a n g e i n d e s i g n a n d s c o p e o f d e l i v e r y a n d a s a r e s u l t o f o n g o i n g t e c h n i c a l d e v e l o p m e n t . H u m p h r e y a n d H F A a r e e i t h e r t r a d e m a r k s o r r e g i s t e r e d t r a d e m a r k s o f C a r l Z e i s s M e d i t e c , I n c . i n t h e U n i t e d S t a t e s a n d /o r o t h e r c o u n t r i e s . © 2019 C a r l Z e i s s M e d i t e c , I n c . A l l c o p y r i g h t s r e s e r v e d .• T urn the instrument ON by pressing the Power Button. The instrument will boot up and the screen may be black for several minutes. Wait until the InstallShield Wizard screen appears again. Allow the installer to complete the software update.• The InstallShield Wizard Complete screen will appear again. Click Finish to exit the Wizard.• You may now safely run the updated Humphrey Field Analyzer 3 Software.Refer to the HFA3 User Manual Instructions for Use for safe and effective operation of the instrument.Carl Zeiss Meditec AG Goeschwitzer Strasse 51–5207745 Jena GermanyCarl Zeiss Meditec, Inc.5160 Hacienda Drive Dublin, CA 94568USA。
CourseForge_SDS

CourseForge_SDSCourseForgeChris Schlechty, Kenneth Kuan, Scott Clifford, Guanyu Chu, Kansu Dincer, Sarah Tachibana, Andy Hou System Design Specification and Planning Document Draft 1.09April 25, 2007CSE 403 - CSRocks Inc.1. IntroductionCourseForge relies on a LAMP architecture. User and course information is stored ina MySQL database, which is accessed via AJAX XMLHttpRequest calls to PHPfunctions which make queries and convert the result to XML. The XML data isparsed and put on screen via Javascript/DOM modification. The database itself is populated using both data given to us by UW, as well as data collected using a Java screen scraper to parse professor ratings information.The modular breakdown of CourseForge follows: prior to interacting with thescheduling system, users must login. The Login module manages authentication, new user registration, and password recovery. The rest of the interface is representedthrough a Student module, which contains a VisualSchedule and a Search module.The VisualSchedule module manages individual Tabs, while the Search modulehandles queries and addition of courses to the schedule.2. Implementation view3. Design view - UML class diagram4. Process view – UML sequence diagrams5. Database Schema6. Design Alternatives and/or AssumptionsWe considered a few alternative representations and implementations of CourseForge before settling on the current version with our customer. These included: ? Information Gathering: We weren’t originally sure whether UW would provide us the course information necessary to implement our system, so weput thought into a screen scraper module that would periodically parse theonline course catalog. This would of course be more inconvenient, but for thetime being UW has given us a copy of a quarter’s worth of course information.We assume that, should CourseForge see widespread use, UW will continueto give us access to the necessary informationSchedule Representation: Given the limited screen estate available to us, we tried to think of other ways to represent the visual schedule. One was have a separate graph for each day. Times would be aligned horizontally, and eachrow would consist of a class, with a horizontal bar representing that class’duration. However, this view doesn’t allow for a holistic week view, andstudents are presumably already used to the day-per-column view used in thecurrent Visual Schedule, which we decided to stick with.General assumptions for this architecture include:We assume that Javascript, AJAX, and PHP will all support our object-oriented design. Javascript in particular is a more procedural language, andmay require extra effort to fit into the rest of the framework.We assume that Google Web Toolkit will provide us with coherent modules to piece together. GWT makes creating AJAX applications much easier, but depending on the resulting modules, it may be difficult to test and/or modifyin the future.1. Team StructureCourseforge will be divided into three main teams for the work up to the beta release: test team, AJAX team, and serverside/database team. There is member crossover between teams, and the serverside/database team will all be assimilated into the other teams once their work is complete.The test team is responsible for unit testing, user testing, and system testing,though everyone is expected to run prelim tests on their own code. This team is composed of: Kansu, Scott, Kenneth, and Andy. The AJAX team is responsible for java coding, HTML, CSS, and other UI-related features. It is composed of: Scott, Kansu, Andy, and Kenneth. Finally, the database team is responsible for the PHP coding and the setup/maintenance of the database. It is composed of: Chris and Guanyu. Chris is primarily database; Guanyu is primarily PHP.2. Project Schedule3. Risk Assessment1. Test Plan1.Unit test strategyo Unit tests will exercise the modules.o We will establish an artificial environment in which the module can live and then invoke the routines of the module. We will consider a test passedonly if the module satisfies its predetermined behavior.o Unit tests will be run every time a developer wishes to add/update the module to the repository.2.System test strategyo This type of testing will be used to test the functionality of the subsystems and the overall system.o The tests will highly depend on the use cases prepared for development.o System tests will be run once after every build./doc/4842452f0066f5335a81219f.html ability test strategyo With the usability tests, we aim to test the ease and efficieny with which our product can be used.o We will use both the prototypes and the actual product tested by real people from within the target audience.o Prototype testing will be (and to some extent has been) employed during the early design stages. Product testing will be accomplished once for theuser interface and once more with nearly full product functionality (beta?).4.The client-server nature of the product and the variety of tools used bring up anadditional challenge for the testing team. The scarcity of the tools available to test dynamic content such as JavaScript (AJAX in particular) on the client end is another obstacle. High source code coverage will be our goal.5.We will use bugzilla for bug tracking purposes. The developer / tester whoemploys the unit testing will post a bug report to notify the rest of the team about the bug.2. Documentation PlanThere are two types of documentation we would like to provide which correspond to strictly internal use and internal/external use.The internal documentation, which only developers will view, will consist of bug tracking, source control, and code comments. We will track bugs using Bugzilla, and we will use Subversion for source control.The code comments will be produced as modules and components are coded. The idea behind this is to write comments while the code written is fresh in the developers mind. This way, the developer may give better explanations of their code. Also, if another team member would like to edit or understand a component, having the comments their immediately allows for easier understanding and the team members do not necessarily have to explain their code verbally if something is not clear (provided the comments are adequate).The conventions that we will use for commenting is as follows:1.Header/Overview Description of Componentsa.Title of the component.b.Brief overview of the component.2.Function Explanationsa.Short explanation of functionality.b.List of parameters if applicable.c.Return value if applicable.3.Inline comments/doc/4842452f0066f5335a81219f.html ed at the developers discretion for clarity.The internal/external documentation will serve as a reference for both developers and users of the system. This will allow for a centralized source of documentation so that two forms of documentation (one for developers and one for users) will not need to be updated when changes are made.These documents will be written in the form of help guides for the CourseForge sys tem. The goal is to make them much like the “Help” guides you would find in any standard program these days. The documents would be accessible via a “Help” link on the system UI.The help guides will be formatted as follows:Finally, we will write an installation guide which will describe the process of installing our project on a personal server.。
VigorACS 2 Quick Start Guide

V i g o r A C S2U n i f i e d M a n a g e m e n t S y s t e mManual Version: 1.0Software Version: V2.3.1Date: August 17, 2018Table of Contents1. Platform for Windows 7 or 10 (5)1.1 Installation for Java (5)1.2 Installation for MariaDB (9)1.3 Installation for VigorACS 2 (14)1.4 StartMySQL/MariaDB Databse (23)1.5 Start VigorACS (23)2. Platform for Linux (25)2.1 Installation for MariaDB, Java and VigorACS (25)2.2 Start MySQL/MariaDB Databse (31)2.3 Start VigorACS (31)2.4 Edit VigorACS IP (31)3. Registering VigorACS 2 (32)3.1 Registration for VigorACS via Windows Platform (32)4. Configuration on CPE Device (37)4.1 Set ACS URL on CPE (37)4.2 Invoke Remote Management for CPE (39)4.3 Enable WAN Connection on CPE (40)5. Troubleshooting (42)1.P l a t f o r m f o r W i n d o w s7o r10Please follow the procedure listed below to install VigorACS 2 completely. The installation for different platforms might be different.T o start up the VigorACS, the normal procedure is listed as follows:(I)Installation for Java(II)Installation for MariaDB(III)Installation for VigorACS 2(IV)Start MySQL/MariaDB Database.(V)Edit VigorACS IP.(VI)Start VigorACS.Info VigorACS 2 can be operated only by a host with 64-bit operation system.1.1I n s t a l l a t i o n f o r J a v a1.Install Java by clicking “java-1.8.0-openjdk-1.8.1.151-1.b12…” to execute the installation.2.The first page will be shown as follows. Click Next to get into next page.3.Then, check “I accept the terms…” and click the Next button.4.In this page, optional features will be listed for you to specify the destination folder forJAVA driver installation. Choose the one you need and click Next.5.In the following page, just click Install.6.Wait for a while to install the required features.7.When the following page appears, the installation is completed. Click Finish to exit theinstalling program.1.2I n s t a l l a t i o n f o r M a r i a D B1.Install MariaDB by clicking “mariadb-10.2.10-winx64” (based on your PC condition) it toexecute the installation.2.When the welcome screen appears, please click Next for next step.3.On this dialog box, check the box of “I accept the terms….” and click Next.4.Select the way for the features to be installed. Then click Next.5.If you want to configure password for MariaDB server, please check Modify password… andtype the password. It depends on your request. Otherwise, simply click Next.6.Modify the default instance properties if required. Then click Next.7.On this dialog box, click Next.8.On this dialog box, click Install.9.The installation program starts to install required files for MariaDB to your computer. Waitfor several seconds.10.After finishing the configuration, please click Finish to exit the wizard.1.3I n s t a l l a t i o n f o r V i g o r A C S2It is time to install VigorACS main program. Follow the steps below.1.Click Setup to run VigorACS 2 setup wizard.2.When the following dialog appears, choose Local Database / Remote Database and clickNext.3.Select the directory that MariaDB being installed (done in 1.2) and click Next4.In this dialog box, choose Rebuild Database (for rebuilding the VigorACS database) orUpgrade Database (for upgrading the database). For the first time using, please choose Rebuild Database. Then click Next.5.Click Next. If you have configured MySQL/MariaDB previously and specified password for it,you have to type the password in this page and then click Next.6.Set the maximum memory and minimum memory. Click Next.7.Setup ACS HTTP and HTTPS port, we'll suggest using others port instead of default 80 and443 port to prevent conflict.Info The port number defined here will be used for opening VigorACS later.8.Determine the home path and click Next. The default directory used by this program isC:\Users. You can modify it if you want and please make sure the length of directory is not over 100 characters, otherwise you might encounter problem of VigorACS in installation.9.Determine the destination folder and click Next. The default directory used by thisprogram is C:\Program Files\VigorACS. You can modify it if you want and please make sure the length of directory is not over 100 characters, otherwise you might encounter problem of VigorACS in installation.10.Determine the start menu folder and click Next. The default directory used by thisprogram is VigorACS. You can modify it if you want and please make sure the length of directory is not over 100 characters, otherwise you might encounter problem of VigorACS in installation.11.In this dialog, check the box of “Create a desktop shortcut” for your necessity. Click Next.12.Now, the program is ready to install necessary features and files to your computer. Pleaseclick Install to start.13.Please wait for a while to complete the installation.14.While installing, the following screen will appear to show that MariaDB has been activated.Please wait for next dialog appearing.15.Now the program has completed the installation of VigorACS 2. Click Finish to exit it.1.4S t a r t M y S Q L/M a r i a D B D a t a b s eAfter installing VigorACS, install program will register MySQL/MariaDB to Windows Service.MySQL /MariaDB will startup automatically after installing VigorACS or rebooting system.Normally, you don't need to worry about this step on Windows. But if you find any problems on VigorACS, you should check mysql/mariadb first. Please go to Windows Service check theMySQL/MariaDB Service starts or not.1.5S t a r t V i g o r A C S1.Login VigorACS. Use a web browser and type “localhost:portnumber”. Note that the portnumber must be the one defined for HTTP and HTTPS port while installing VigorACS. Forexample, if HTTPS is defined as 8011, then the URL will be “localhost:8011”.2.The login page of VigorACS will be shown as the following. Please type “root” as user nameand “admin123” as password and type the authentication code. Then click Login.3.For the first time to access into the web user interface, a warning message appears first.Please click the Change password button to change the default password for networksecurity. If not, click Cancel to access into the web user interface of VigorACS and changethe password later.4.After clicking Login, main screen of VigorACS 2 will be shown as below.2.P l a t f o r m f o r L i n u xT o start up the VigorACS under Linux, please execute"/usr/local/vigoracs/VigorACS/bin/vigoracs.sh" instruction. A list of menu items will be shown as follows.1.Start mysql/mariadb2.Shutdown mysql/mariadb3.Start VigorACS4.Shutdown VigorACS5.Edit bind IP of VigorACS Server (please key in IP or server name)6.Set the Max. and Min. memory value of running java (it will be valid after restartingVigorACS)7.View the Max. and Min. memory value of running java8.exit2.1I n s t a l l a t i o n f o r M a r i a D B,J a v a a n d V i g o r A C SFollow the steps listed below to install VigorACS under Linux:1.Login Linux with root or the root privilege.2.Download the ACS installation tar.bz2 package and extract it via below command:#bzip2 -cd VigorACS_Unix_Like_xxxxxx_xxxxx.tar.bz2 | tar xvf -or#tar -jxv -f VigorACS_Unix_Like_xxxxxx_xxxxx.tar.bz23.Decompress the setup packagesbzip2 -cd VigorACS_Unix_Like_xxxxxx_xxxxx.tar.bz2 |tar xvf –4.Change the permissions mode of install.sh and uninstall.sh.chmod 755 install.shchmod 755 uninstall.sh5.Execute ./install.sh installation file.Please make sure you have /usr/bin/sh first. If you don't have /usr/bin/sh, please enter the command:#ln -s /bin/sh /usr/bin/sh6.The system will ask to create vigoracs, enter “y” to proceed.7.Next, the system will ask you to install xfonts-base and fontconfig, just enter “y” toproceed.8.Next, please select the item number which you want to execute. Note that VigorACSsupports Linux OS. The program will detect the system you have in your computer.(1) Install mysql/mariadb(2) Change root password and security configuration of mysql/mariadb(3) Install or Upgrade java(4) Install VigorACS(5) Upgrade VigorACS(6) Redirect the database path of VigorACS to remote host (7) Exitinput select num:InfoIf your computer has installed MariaDB and java previously, ignore theinstallation of them. Otherwise, install all the required items (MariaDB, Java and VigorACS) for your system. Item number 5 is used to upgrade VigorACS, so it is not necessary for you to execute for the first time of installation.9. Input 1 to install MariaDB first. Notice that it will setup blank as default password. You canchange the password by using the following command.#/usr/local/mysql/bin/mysqladmin--defaults-file=/usr/local/mysql/f -u root password 'newpassword'InfoThe password configured by the command above will be effective onlywhen there is no password set for database root before.Follow the instructions on the screen to finish the MariaDB installation.ter, input 2 to change root password and security configuration of mysql/mariadb.Info The password set in this step is used for VigorACS 2 to login database.11.Input 3 to install Java.Follow the instructions on the screen to finish the Java installation.12.Input 4 to install VigorACS. It is suggested to use ACS customized MariaDB database. Whenasked to enter MariaDB password, press “Enter” if you haven’t changed the password via the command. Then, confirm that TR-069 database has been installed successfully.Wait and follow the instructions on the screen to finish the installation.13. Now, input 6 to redirect the database path of VigorACS to remote host. For remotedatabase, please execute such step on remote host.14. Input 7 to finish and exit the installation.Info 1 Step 13 is required for establishing remote database only . You can ignore it while building local database.Info 2T o prevent port conflicts, we'll suggest that using other ports for HTTP and HTTPS instead of default 80 and 443.2.2S t a r t M y S Q L/M a r i a D B D a t a b s eAfter installing VigorACS, mysql/mariadb daemon has started. You can to see it using "ps-ef|grep mysql" instruction. Use the menu item 1 / 2 to start / shutdown mysql/mariadb.2.3S t a r t V i g o r A C SAfter installing VigorACS, access “/usr/local/vigoracs/VigorACS/bin”, execute “./vigoracs.sh”.Select item 3 to start VigorACS.If you ever reboot the machine after installing VigorACS, just select item 1 to startmysql/mariadb first. Then, select item 3 to start VigorACS.2.4E d i t V i g o r A C S I PWhen starting the VigorACS at first time on Linux, startup program will ask you input Server IP or input Enter key by using the IP address of the host. Once you input the IP address, VigorACS will keep it on startway.txt. Next time, if you want to change it, you can select item 5 to editstartway.txt using vi editor.3. R e g i s t e r i n g V i g o r A C S 2For the first time to activate VigorACS 2, the system will ask you to register VigorACS 2 onto DrayT ek MyVigor server . Refer to the following sections to register VigorACS 2 on differentplatforms.Info 1 While installing VigorACS, install program will register MySQL/MariaDB toWindows Service. MySQL/MariaDB will startup automatically after installingVigorACS or rebooting system. Normally , you don't need to worry about this step on Windows. But if you find any problems on VigorACS, you should checkmysql/mariadb first. Please go to Windows Service check the MySQL/MariaDB Service starts or not.Info 2After installing VigorACS, the software will startup automatically . Normally ,you don't need to worry about this step on Windows. But, if you find any problem on VigorACS, you could shut down VigorACS and start VigorACS again. 3.1 R e g i s t r a t i o n f o r V i g o r A C S v i a W i n d o w s P l a t f o r mBelow shows the steps to register VigorACS 2:1. Login VigorACS. Use a web browser and type “localhost:portnumber”. Note that the portnumber must be the one defined for HTTP and HTTPS port while installing VigorACS. For example, if HTTPS is defined as 8011, then the URL will be “localhost:8011”.2. The login page of VigorACS will be shown as the following. Please type “root” as user nameand “admin123” as password and type the authentication code. Then click Login.Info“root” and “admin123” are default settings.3. A License Error dialog appears as follows. Simply click Active.4. A login page for MyVigor web site will be popped up automatically . Type your account (username) and password in this page. Then, click Login.InfoIf you do not have any account, simply click Create an account now to create a new one for using the service provided by MyVigor web site.5.MyVigor will verify and authenticate if the user account you typed is allowed to access intothe web site. If yes, the following screen will appear.6.Type a nickname for VigorACS and click Add.7.After clicking Add, you can see the following screen. Click OK.8.You will get a device information page as shown below. If you are the new user of VigorACS,you can get a free charge of 30-day service of VigorACS. Simply click the Trial button.9.From the following screen, check the box of “I have read and accept the above….” andclick Next.10.In the page below, click Register.11.When the VigorACS License Information page appears, the service is ready for you to use.Click Login to ACS to use VigorACS service.12.The login page will appear as follows. Type the default settings of User Name (root) andPassword (admin123) and type the authentication code. Then, click Login.13.Now, the main screen of VigorACS will be shown as follows.4.C o n f i g u r a t i o n o n C P E D e v i c e4.1S e t A C S U R L o n C P ET o manage CPEs through VigorACS, you have to set ACS URL on CPE first and set username and password for VigorACS.1.Connect one CPE (e.g., Vigor2862 series).2.Open a web browser (for example, IE, Mozilla Firefox or Netscape) on your computer andtype http://192.168.1.1.3.Please type username and password on the window. If you don’t know the correctusername and password, please consult your dealer to get them. In this section, we takethe figures displayed on Windows as examples.4.Go to System Maintenance -> TR-069.•Please set URL as the following and type username and password for ACS server,for the connected CPE with authentication:http://{IP address of VigorACS}:80/ACSServer/services/ACSServlet•Please set URL as the following, for the connected CPE without authentication: http://{IP address of VigorACS}:80/ACSServer/services/UnAuthACSServlet•Please set URL as the following, for the connected CPE with authentication and the data transmission between CPE and VigorACS 2 with encryption (SSL).https://{IP address of VigorACS}:443/ACSServer/services/ACSServlet•Please set URL as the following, for the connected CPE without authentication but the data transmission between CPE and VigorACS 2 with encryption (SSL)https://{IP address of VigorACS}:443/ACSServer/services/UnAuthACSServlet5.Fill Username and Password for VigorACS 2 Server for authentication. Please enter as thefollowing:Username: acsPassword: password6.For the username and password of CPE client, it is not necessary for you to type them.7.Click Enable for Periodic Inform Settings.4.2I n v o k e R e m o t e M a n a g e m e n t f o r C P EYou have to make sure that the CPE device you want to connect supports VigorACS 2 features.Please consult your dealer if you have no idea in it.1.Suppose WAN IP of CPE device has been setup successfully. And you can access into Internetwithout difficulty.2.Login the device (e.g., Vigor2862) by web.3.Go to System Maintenance>>Management.4.Check Allow management from the Internet to set management access control.4.3E n a b l e W A N C o n n e c t i o n o n C P EYou have to make sure the CPE device you want to connect has been configured properly and can access into Internet.1.Login the device (e.g., Vigor2862) by web.2.Open WAN>>Internet Access.3.Choose Static or Dynamic IP as Access Mode and click Details Page for WAN2.4.The following web page appears. Click Enable and Specify an IP address. Enter correctWAN IP address, subnet mask and gateway IP address for your CPE. Then click OK.VigorACS 2 Quick Start Guide41InfoReboot the CPE device and re-log into VigorACS 2. CPE which has registered to VigorACS 2 will be captured and displayed on the home page of VigorACS 2.VigorACS 2 Quick Start Guide42 5. T r o u b l e s h o o t i n gWhen you try to invoke VigorACS 2 and get the following error message, please locate the file of “server .log ” from C:/Program Files/VigorACS/server/default/log and send the file to yourdealer for further assistance.For Linux system, please locate the file of “server .log ” from/usr/local/vigoracs/VigorACS/server/default/log/ and send the file to your dealer for further assistance.。
AquaMaster 4 软件 FEW410 430 和 FET410 430 软件版本 3KXF2

—A B B M E A SU R EM ENT & A N A LY TI C S | R ELE A S E NOTE | R N/FE W410/FE W430/FE T410/FE T430/001-EN R E V BAquaMaster4 softwareFEW410/430 and FET410/4301 Software change detailsNew features:• Diagnosis for detecting default sensor setting due to NV memory issues.Bug fixes:• Totalizer reset option enabled with “Advance Access Level” for Non - Metrology approved devices.• Excessive power consumption in sensor.• Sensor firmware update.2 RecommendationsThis upgrade is advised for:• Devices with the above-mentioned issues • Devices that have software/firmware part code as mentioned in the release note.3 Product supportEmail: **********************.com—AquaMaster 4software FEW410/430 and FET410/430Software version:3KXF208402U0113/03.04.00 Release date: 15th June 2023Measurement made easyR N /F E W 410/F E W 430/F E T 410/F E T 430/001-E N R e v . B 06.2023—We reserve the right to make technical changes or modify the contents of this document without prior notice. With regard to purchase orders, the agreed particulars shall prevail. ABB does not accept any responsibility whatsoever for potential errors or possible lack of information in this document.We reserve all rights in this document and in the subject matter and illustrations contained therein. Any reproduction,disclosure to third parties or utilization of its contents – in whole or in parts – isforbidden without prior written consent of ABB. ©ABB 2023—ABB LimitedMeasurement & Analytics Oldends Lane,Stonehouse, GL10 3TA United KingdomTel: +44 (0) 1453 826661 Fax: +44 (0) 1453 829671email: **********************.com/measurement。
Fujitsu PRIMERGY Linux安装后操作指南(适用于x86版本3.0)说明书

2005-11-01 Notes on Using Red Hat Enterprise Linux AS (v.3 for x86) PrefaceAbout This ManualThis manual provides notes on PRIMERGY operation with Linux installed. Be sure to read this manual before using Linux.Intended ReadersThis manual is intended for persons who operate PRIMERGY.Organization of This ManualThis manual consists of the following chapters:Chapter 1 Notes on OperationThis chapter provides notes on operation after installation. Be sure to read this chapterbefore operating PRIMERGY with Linux installed.Chapter 2 Addition of Peripheral Devices and Option CardsThis chapter explains the procedures for adding peripheral devices and cards afterinstallation and provides notes on adding these options. Read this chapter as required.Chapter 3 OthersThis chapter explains other functions and provides other notes such as notes on limits.Operation VerificationThe operations of the products described in this manual have been confirmed by Fujitsu. Please note, however, that these operations are subject to change without prior notice.Support & ServiceA support service(SupportDesk Product basic service), available for a fee, provides customers usingLinux with an enhanced sense of security and confidence. Customers concluding a support and service agreement are entitled to receive support in such areas as assistance with queries regarding this manual and questions and problems that may come up during the installation and operation of this product.Please consider taking advantage of this service option by concluding a support and service agreement with us.CopyrightAll rights Reserved, Copyright (C) FUJITSU LIMITED 20051. Notes on Operation1.1 Assignment of Device NamesLinux assigns device names to a variety of devices, such as the hard disk drive, in the order that it recognizes them during its startup sequence. If the system is restarted after a device such as a hard disk drive or controller fails, the assigned device names may be changed because the system cannot recognize a device that has failed.Example: When hard disk drives are connected to SCSI ID 1, 2, and 3, device names /dev/sda, /dev/sdb, and /dev/sdc are assigned respectively to the disk drives. If /dev/sdb failsunder this condition, the device previously assigned /dev/sdc/ is moved up by one andrecognized as /dev/sdb after the system is restarted.If an assigned device is unexpectedly changed, it may prevent the system from starting or,in the worst case, may damage your data. If a device fault is detected, therefore, Fujitsurecommends starting the system in rescue mode and checking for hardware faults beforerestarting the system (*1). Repair the hardware fault, restore the system by means suchas the backup tape, and then restart the system.*1 For details on starting the system in rescue mode, see Section 1.4, "Starting theSystem in Rescue Mode."After starting the system, use the fdisk command to check whether the relevant hard diskdrive can be recognized, and take necessary steps such as checking for hardware errormessages in /var/log/messages.1.2 Installation of Red Hat Enterprise Linux AS (v.3 for x86) PackagesRed Hat Enterprise Linux provides installation types so that the optimum system can be constructed according to the use purpose. For this reason, packages required for your purposes might not be installed. If a required package has not been installed, log in as the root and install it by executing the following procedure:Install the necessary packages by using the installation CDs (1/4 to 4/4) that have beencreated according to the Installation Procedure included in the driver kit.# mount -r /dev/cdrom /mnt/cdrom# cd /mnt/cdrom/RedHat/RPMS# rpm -ivh <package_file>Example: To install package "make"# rpm -ivh make-3.79.1-17.i386.rpm# cd /# umount /mnt/cdrom# eject* Remove the CD.1.3 Installing and Setting Up Global Array Manager (GAM)Use Global Array Manager (GAM) as a RAID management tool in a system with a mounted onboard SCSI-RAID and SCSI-RAID card (PG-142E3).For details on installing GAM-Client (Windows), see "Outline of Installation Procedure for Global Array Manager-Client", which is an attachment.The GAM-Server (Linux) installation procedure is explained below.[Notes]1)The screen display may become unstable during GAM installation or GAM service startup.This is not an operational problem.2)Specify the port numbers shown below for GAM service.Take care when configuring firewall settings.Port numbers: 157,158(1)To install GAM-Server (Linux), insert the driver CD into the CD-ROM drive, and entercommands as follows:# mount -r /dev/cdrom /mnt/cdrom# cd /mnt/cdrom/UTY/GAM/Linux# rpm -ivh gam-server-6.02-21.i386.rpm# rpm -ivh gam-agent-6.02-21.i386.rpm- Enter the following only if onboard SCSI for RX200 S2# rpm -ivh 1030SNMPAgent-2.4-3.i386.rpm# sh ./insgam* Confirm that “GAM is installed successfully.” is displayed.# cd /# umount /mnt/cdrom# eject* Remove the CD.(2)For user accounts in Linux, create "gamroot" as a user account with GAM administratorauthority and then create user accounts (e.g., "gamuser") with user authority.(If a user account with user authority has already been created, another account need not be created.) # adduser gamroot# passwd gamrootChanging password for user gamrootNew-password <--- Enter a password.Retype new password <--- Re-enter the same password for confirmation.passwd: all authentication tokens updated successfully* Create a user account with user authority in the same way as explained above.(3)Edit three lines as shown below in the /etc/sysconfig/gam file.Events can be posted to GAM-Client after this editing is completed.# vi /etc/sysconfig/gam[Before editing]START_GAMEVENT=nGAMEVENT_OPTIONS=""[After editing]START_GAMEVENT=y <--- Change "n" to "y".GAMEVENT_OPTIONS="-h ip-address" <--- Specify the IP address of the managementWindows system on which GAM-Client isinstalled.[Before editing]START_GAMEVLOG=n[After editing]START_GAMEVLOG=y <--- Change "n" to "y".(4)Restart the system.# shutdown -r now* The following message may be displayed after the system starts. It does not indicate an operational problem.[Message]gamagent: gamagent: Connection refusedgamagent connect failure1.4 Starting the System in Rescue ModeUsing only one of the installation CDs that have been created according to the Installation Procedure included in the driver kit, you can start the system in rescue mode. This may enable system recovery in the event of a problem that prevents the system from starting normally.This section explains only how to start the system as one that has minimum functionality.Start the system in rescue mode as follows:(1)Start the system from installation CD 1/4 that was created according to the InstallationProcedure included in the driver kit. Enter the appropriate response in the following window,and press the [Enter] key.(2)In the Choose a Language window, select "English" and select "OK."(3)In the Keyboard Type window, select "jp106" and select "OK."If an accessory keyboard such as of a flat display (PG-R1DP3) is used, select "us" here.(4)In the following window, select "Yes."(5)In the following window, select "Add Device."(6)In the Driver List window, select the drivers for the devices installed in the system, and select"OK." The following drivers must be selected:[onboard SCSI type for TX200 S2][onboard SCSI type or onboard SCSI-RAID type for RX200 S2]Two drivers must be selected. Select drivers as follows:1.Select the driver shown below, and select "OK.""LSI Logic Fusion MPT Base Driver (mptbase)"2.The Device Selection window is displayed. Select "AddDevice."3. A list of drivers is displayed. Select the driver shown below, and select "OK.""LSI Logic Fusion MPT SCSI Driver (mptscsih)"[SCSI-RAID card(PG-140D1/PG-142E3) for TX200 S2][onboard SCSI-RAID type for RX300 S2]Select the driver shown below, and select "OK.""LSI MegaRAID controller (megaraid2)"(7)Make sure that the selected driver is displayed in the following window, and select "Done."(8)The Setup Networking window is displayed. Select "No" because network settings need not beconfigured at this time.(9)Select "Continue" in the Rescue window.(10)If the root partition (/) in the existing Linux system has been mounted successfully under/mnt/sysimage, this is reported in the Rescue window. Select "OK."(11)When the prompt is displayed, enter the chroot command to change the root path to the harddisk drive.sh-2.05b# chroot /mnt/sysimage(12)This completes startup in rescue mode. To exit rescue mode, enter the exit command twice.sh-2.05b# exit <--- Exit from the chroot environment.sh-2.05b# exit <--- Exit from the rescue mode.1.5 Power-off at ShutdownPower is not automatically turned off at shutdown.When [Power down] is displayed on the console screen, press the power switch to turn off the power.Note that the power is automatically turned off when the system is shut down in an environment in which ServerView is installed.2. Addition of Peripheral Devices and Option Cards2.1 Adding a SCSI DiskThe number of LUNs is set to 1 by default. To add a SCSI disk, shared disk, or tape library, log in as the root and define the number of LUNs as shown below. Multiple LUN referencing is enabled after the system is started next.(1)Add the following lines to /etc/modules.conf:options scsi_mod max_scsi_luns=N <--- Add* N is the number of LUNs. Define the appropriate number.(2)Enter the mkinitrd command to create initrd.To create initrd, enter the mkinitrd command appropriate for the type of kernel used.* Enter the following command to check the type of kernel used:# uname -r[2.4.21-32.0.1.EL (kernel for single CPU)]# cp /boot/initrd-2.4.21-32.0.1.EL.img /boot/initrd-2.4.21-32.0.1.EL.img.bak# mkinitrd -f /boot/initrd-2.4.21-32.0.1.EL.img 2.4.21-32.0.1.EL[2.4.21-32.0.1.EL smp (kernel for multi-CPU)]#cp /boot/initrd-2.4.21-32.0.1.ELsmp.img /boot/initrd-2.4.21-32.0.1.ELsmp.img.bak# mkinitrd -f /boot/initrd-2.4.21-32.0.1.EL smp.img 2.4.21-32.0.1.EL smp(3)Restart the system.Enter the following command to restart the system.# shutdown -r now2.2 Adding Option CardsIf any of the option cards supported by the models listed in the following table is added after system installation, kudzu is automatically started at system startup. This section explains the operations that enable the system to automatically recognize the added card at each subsequent system startup.The table lists models and the option cards supported by them.TX200 S2 RX200 S2 RX300 S2PG-128 V -- -- SCSI cardPG-130L -- V V PG-140D1V V -- SCSI-RAID cardPG-142E3V V -- PG-1852 V V -- PG-1853 V -- -- PG-1853L -- V -- PG-1862 V V -- PG-1882 V -- -- PG-1882L -- V V PG-1892 V -- -- LAN cardPG-1892L -- V V PG-FC106V V V onboard Fibre-Channel cardPG-FC107V V VSCSI cardPG-128 -- -- V SCSI-RAID cardPG-142E3-- -- V PG-1852 -- -- V PG-1853 -- -- V PG-1862 -- -- V PG-1882 -- -- V LAN cardPG-1892 -- -- V PG-FC106-- -- V Raiser Card Fibre-Channel cardPG-FC107-- -- VV: Supported --: Not supported- TX200 S2 or RX300 S2If any of the option cards supported by the models listed in the above table is added after system installation, kudzu is automatically started at system startup. To add a fibre channel card, follow the steps below. Except for a fibre channel card, select "configure."To add a LAN card, configure network settings according to the instructions displayed in the window. Login as a root user at system startup, and perform the operations explained in Section 2.3, "Executing mkinitrd."This section explains the operations that enable the system to automatically recognize the added card at each subsequent system startup.[A fibre channel card is added](1)If a fibre channel card is added after system installation,kudzu is automatically started at system startup.Always select "ignore ."(2)Add the following line to /etc/modules.conf.If SCSI or SCSI-RAID device is installed in the system,number the end of "scsi_hostadapter", as "2, 3, ...".options scsi_mod max_scsi_luns=128 Add- RX200 S2If any of the option cards supported by the models listed in the above table is added after systeminstallation, kudzu is automatically started at system startup.To add a fibre channel card or LAN card, follow the steps below.Except for a fibre channel card and LAN card, select "configure." Login as a root user at system startup, and perform the operations explained in Section 2.3, "Executing mkinitrd."This section explains the operations that enable the system to automatically recognize the added card at each subsequent system startup.[A LAN card(PG-1852, PG-1862, PG-1882L or PG-1892L) is added](1)If any of the LAN cards supported by the models listed in the above table is addedafter system installation, kudzu is automatically started at system startup.Always select " ignore."(2)Add the following lines to /etc/modules.conf.[ PG-1852, PG-1853L,PG-1892L, or PG-1882L]alias eth0 e1000alias eth1 e1000alias eth2 e1000 <--- Add[ PG-1862]alias eth0 e1000alias eth1 e1000alias eth2 e1000 <--- Addalias eth3 e1000 <--- Add(3)Set up the network.[ PG-1852, ,PG-1853L ,PG-1892L, or PG-1882L]# netconfig -d eth0# netconfig -d eth1# netconfig -d eth2[ PG-1862]# netconfig -d eth0# netconfig -d eth1# netconfig -d eth2# netconfig -d eth3[A fibre channel card is added](1)If a fibre channel card is added after system installation,kudzu is automatically started atsystem startup.Always select "ignore ."(2)Add the following line to /etc/modules.conf.If SCSI or SCSI-RAID device is installed in the system,number the end of "scsi_hostadapter",as "2, 3, ...".options scsi_mod max_scsi_luns=128 Add2.3 Executing mkinitrd(1) Create initrd by executing the mkinitrd command.Create initrd by executing the mkinitrd command according to the kernel used.* Enter the following command to check the kernel used:# uname -rCommand execution examples are shown below.[2.4.21-32.0.1.EL (kernel for a single CPU)]# cp /boot/initrd-2.4.21-32.0.1.EL.img /boot/initrd-2.4.21-32.0.1.EL.img.bak# mkinitrd -f /boot/initrd-2.4.21-32.0.1.EL.img 2.4.21-32.0.1.EL[2.4.21-32.0.1.EL smp (kernel for multi-CPUs)]# cp /boot/initrd-2.4.21-32.0.1.EL smp.img /boot/initrd-2.4.21-32.0.1.ELsmp.img.bak# mkinitrd -f /boot/initrd-2.4.21-32.0.1.EL smp.img 2.4.21-32.0.1.EL smp(2) Restart the system.Restart the system as follows:# shutdown -r now3. Others3.1 Sound FunctionNo sound function is supported.3.2 PCI Hot Plug FunctionThe PCI hot plug function is not supported.3.3 Usable KernelsThe kernels that can be used vary depending on the hardware conditions.See the table below for the kernels that can be used.Note that middleware specifications might limit the kernel to be selected. In this case, select the kernel in accordance with the middleware specifications.Hardware conditionsKernel to be selectedMemory Number of logical CPUs (*1)for single CPU1CPU Kernel Up to 4 GB2 or more CPUs Kernel for multi-CPUMore than 4 GB and up to 8 GB No conditions Kernel for multi-CPU(*1) Even when only one CPU is installed, the number of logical CPUs is 2if Hyper Threading = Enabled.3.4 Distribution LimitationsOperation is not guaranteed if one of the following CPU, memory, and file system limitations is exceeded:Maximum number of logical CPUs: 16Maximum memory size: 8 GBFile system: Less than 1 TB3.5 Installation ProcedureFor information on the procedure for installing Red Hat Enterprise Linux ES (v.3 for x86), see the Installation Procedure included in the "Installation Kit" downloaded from Download Search.Attachment Outline of Global Array Manager Client Installation* Perform this operation only when an onboard SCSI-RAID or a SCSI-RAID card (PG-140D1 or PG-142E3) are mounted.* GAM-Client runs on Windows2000 and Windows2003. Prepare a management Windows system.1. Insert the driver CD into the CD-ROM drive in the management Windows system.2. Execute setup.exe in RHEL3¥UTY¥GAM¥Windows on the driver CD.3. When the "Welcome" window is displayed, click "Next."4. The "Software License Agreement" window is displayed. Read the statements and click "Yes" if youaccept the terms of this agreement.5. The "Select Components" window (Figure 1) is displayed. Confirm that the check box before "GlobalArray Manager Client" is selected. Clear the "Global Array Manager Server" and "SAN Array Manager Client" check boxes, and click "Next."Figure 1* "SAN Array Manager Client" is not supported. Do not install it.6.The "Choose Destination Location" window is displayed.Click "Browse," specify the location that you want as the installation destination, and click "Next."* If GAM-Client is already installed, a message confirmingwhether to overwrite is displayed. Click "OK" to continue.7. A dialog box for specifying the GAM-Client installation destination is displayed. Click "Next." and thesetup program starts copying files.8. The "Setup Complete" window is displayed.Click "Finish" to exit the GAM-Client installation wizard.-- END --。
西门子PLM软件NX数字模拟产品功能说明书
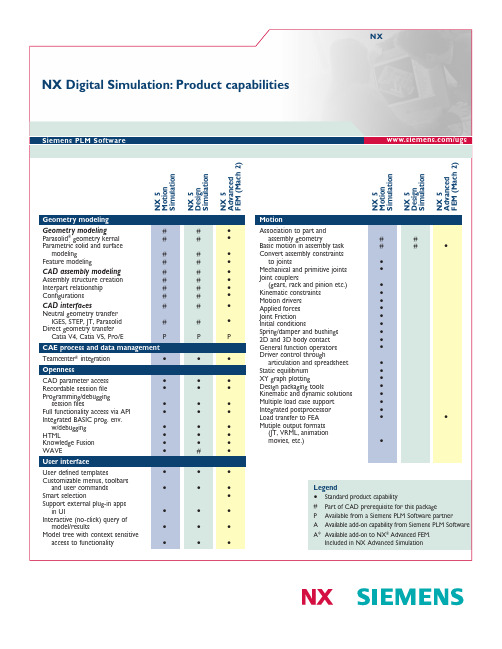
Legend•Standard product capability#Part of CAD prerequisite for this packageP Available from a Siemens PLM Software partnerA Available add-on capability from Siemens PLM Software A*Available add-on to NX ®Advanced FEM.Included in NX Advanced SimulationNX Digital Simulation:Product capabilitiesNX/ugsSiemens PLM Software MotionAssociation to part and assembly geometry##Basic motion in assembly task ##•Convert assembly constraints to joints•Mechanical and primitive joints •Joint couplers(gears,rack and pinion etc.)•Kinematic constraints •Motion drivers •Applied forces •Joint Friction •Initial conditions•Spring/damper and bushings •2D and 3D body contact •General function operators •Driver control througharticulation and spreadsheet •Static equilibrium •XY graph plotting •Design packaging tools•Kinematic and dynamic solutions •Multiple load case support •Integrated postprocessor •Load transfer to FEA ••Mutiple output formats (JT,VRML,animation movies,etc.)•N X 5D e s i g n S i m u l a t i o nN X 5A d v a n c e d F E M (M a c h 2)N X 5M o t i o n S i m u l a t i o nN X 5M o t i o n S i m u l a t i o nN X 5D e s i g n S i m u l a t i o nN X 5A d v a n c e d F E M (M a c h 2)Geometry modelingGeometry modeling##•Parasolid ®geometry kernal ##•Parametric solid and surface modeling##•Feature modeling##•CAD assembly modeling##•Assembly structure creation ##•Interpart relationship ##•Configurations##•CAD interfaces##•Neutral geometry transfer IGES,STEP,JT,Parasolid ##•Direct geometry transfer Catia V4,Catia V5,Pro/EPPPCAE process and data management Teamcenter ®integration •••OpennessCAD parameter access •••Recordable session file •••Programming/debugging session files•••Full functionality access via API •••Integrated BASIC prog.env.w/debugging •••HTML•••Knowledge Fusion •••WAVE •#•User interfaceUser defined templates•••Customizable menus,toolbars and user commands •••Smart selection•Support external plug-in apps in UI•••Interactive (no-click)query of model/results•••Model tree with context sensitive access to functionality•••N X 5D e s i g n S i m u l a t i o nN X 5A d v a n c e d F E M (M a c h 2)N X 5D e s i g n S i m u l a t i o nN X 5A d v a n c e d F E M (M a c h 2)FE model building Geometry defeature tools –topologydiagnosis,geometry repair,CAD featuresuppression,stitch surface,remove hole/fillet,partition••Non-manifold topology generation for volumes•CAE topology•CAE geometry –creation and deletion,mid-surfacing (constant and variable thicknesses)•Automatic topology abstraction –abstraction control,auto stitch geometry,auto merge small regions,auto pinch••Manual topology modification tools•Meshing••0D,1D,and 2D elements •2D mapped meshing •3D elements••Automatic meshing asst.–geometric abstraction and mesh generation in one tool/step ••Batch meshing •Transition meshing•Manual meshing tools –sweeping,revolve,surface coating,interactive controls,etc.•Automatic meshing controls –local element sizing,curvature control•General modeling tools••Axi-symmetric meshing•Mesh display and control –display filters••Material property creation and management –isotropic,anisotropic,orthotropic,linear,nonlinear,thermal,etc.••Mass property calculations •Load summation•Physical property creation and management ••Mesh quality checks –coincident nodes,free edge checks,element shape checks,etc.••FE grouping –by association to geometry,bc’s,material,etc.)•FE collectors and sets •FE append•FEM on assembly••FE model on CAD assembly••Beam modeling•Model update from CAD••FEM model update based on geometry change ••FEM model update based on assembly change••FE model buildingBoundary conditions••Application methods ••On geometry••Local coordinate system ••On FE entities •Friction definition •Time variation•Constraints –statics,dynamics,thermal,symmetric,contact,etc.••Structural loads••Structural thermal –flux,radiation,generation••Advanced thermal –convection,temperature –linear and nonlinear,simple radiation,thermal coupling,adv.radiation•Flow –bc’s,flow surface/blockage/screen definition,fluid domain definition •Axi-symmetric boundary conditions •Automatic contact detection and setup ••Automated load transfer •Laminate composites ASolution setupStructural linearStatic and buckling analysis••Structural linear dynamicsNormal modes••Direct frequency response •Direct transient response •Modal frequency response •Modal transient response•Structural nonlinearStatic,transient,geometric,elastic/plastic material ••Implicit solver •Explicit solver•Structural contact and connection modelingSurface-to-surface contact ••Node-to-node contact •Rigid elements•Constraint elements •Glue connection••ThermalSteady-state•Diurnal solar heatingA Rigid-body transient motion A Transient A Conduction A Convection A RadiationAN X 5D e s i g n S i m u l a t i o nN X 5A d v a n c e d F E M (M a c h 2)N X 5D e s i g n S i m u l a t i o nN X 5A d v a n c e d F E M (M a c h 2)Solution setup Fluid dynamicsSteady-state/transient flow A Incompressible flow A Compressible flow A Laminar/turbulent flow A Internal/external flow A Motion-induced flowA Multiple rotational frames of reference A Forced and natural convectionA Conjugate and radiation heat transferACoupled physicsThermal-structural •A Fluid-thermalA FE data export••Abaqus (inp)A Ansys A Nastran•A*FE data import••Abaqus (fil,inp)A Ansys (rst)A Nastran (op2,dat)•A*NX I-deas ®(unv,afu,bun)•FE results visualizationContour displays (continuous or iso-lines)••Vector displays ••Isosurface displays ••Cutting planes••Advanced lighting control ••Animations••Complex dynamic response results •Multiple viewports••Probing of results on nodes••Postprocessing data table w/sort/criteria ••Results listings••Transparency display ••Local coordinate system ••XY graphing•Synchronized contour and XY plotting displays •Annotated graphs•Output (JT,VMRL,postscript,tif,etc.)••Meta solutionDurability••FE parameter optimization••Dynamic forced response simulation A Laminate composites analysisAN X N a s t r a nN X M u l t i -p h y s i c sN X N a s t r a nN X M u l t i -p h y s i c sSolutions Structural linearStatic •Modal •Buckling•Structural nonlinearStatic •Transient •Geometric•Elastic/plastic material •Hyperelastic material •Gasket material •Nonlinear buckling •Implicit solver •Explicit solver•Structural contact and connection modelingSurface-to-surface contact •Node-to-node contact •Spot welds •Rigid elements•Constraint elements •Glue connection•Structural linear dynamicsModal transient •Modal frequency •Direct transient •Direct frequency •Shock spectrum •Random vibration •Rotor dynamics•ThermalSteady-state,transient••Temperature-dependent properties ••Nonlinear thermal contact•Thermal couplings (welded,bolted,bonded)•Disjoint meshes support in assembly modeling•Surface-to-surface radiative heat transfer ••Hemicube-based view factor calculation •Radiation in participating media •Radiation enclosures•Environmental radiative heating •Orbital modeling and analysis •Specular,transmissive surfaces ••Convection••Forced and natural convection correlations •Hydraulic fluid networks •Joule heating •Phase change•Heater and thermostat modeling ••Material charring and ablation •Transient rigid body motion •Peltier cooler modeling•Heat sink models and modeler•PCB modeler/xchange (ECAD/MCAD)ASolutionsFluid dynamicsSteady-state/transient flow •Incompressible flow •Compressible flow •Laminar/turbulent flow•Forced and natural convection•Conjugate and radiation heat transfer •Porous media modeling •Nonlinear fluid properties •Humidity and condensation•Automatic fluid domain and boundary layer meshing•Flow induced by rigid body motion •Automated connection of disjoint fluid meshes •Fan models•Embedded 2D/3D flow blockages •General scalars and particle tracking •Non-Newtonian fluids•Multiple rotating frames-of-reference•Coupled physicsAcoustics•Acoustics-structural •Subsonic aeroelastic •Supersonic aeroelastic •Fluid-thermal•Thermal-structural ••Fluid-structural•Interface to multi-body dynamics (ADAMS and RecurDyn)•SolversIterative ••Sparse direct•Shared memory processing •Distributed memory processing •(1)•Optimization ••Cyclic symmetry ••Axi-symmetric••FE-based finite volume solver•Advanced capabilitySuperelement/substructuring ••Solution customization (DMAP)•Solution customization (user subroutine)•(1)Available in Enterprise versions only.Note:The NX Nastran and NX Multi-Physics solver suites are comprised of multiple products.Please check the individual product fact sheets to determine the simulation capabilities contained in each core bundle or add-on module.ContactSiemens PLM SoftwareAmericas8004985351Europe+44(0)1276702000Asia-Pacific852********/plm©2007.Siemens Product Lifecycle Management Software Inc.All rights reserved.Siemens and the Siemens logo are registered trademarks of Siemens AG. Teamcenter,NX,Solid Edge,Tecnomatix,Parasolid,Femap,I-deas,JT,UGS Velocity Series,Geolus and the Signs of Innovation trade dress are trademarks or registered trademarks of Siemens Product Lifecycle Management Software Inc.or its subsidiaries in the United States and in other countries.All other logos,trademarks,registered trademarks or service marks used herein are the property of their respective holders.9/07。
Pearson BTEC Level 3 Nationals 计算机基础辅助文件说明书

*P51808RA0120*Turn over Instructions• Use black ink or ball-point pen.• Fill in the boxes at the top of this page with your name,centre number and learner registration number.• Answer all questions.• Answer the questions in the spaces provided– there may be more space than you need.Information• The total mark for this paper is 90.• The marks for each question are shown in brackets– use this as a guide as to how much time to spend on each question.Advice• Read each question carefully before you start to answer it.• Try to answer every question.• Check your answers if you have time at the end.P51808RA©2018 Pearson Education Ltd.1/1/1/1/1/1*P51808RA0220*2Answer ALL questions. Write your answers in the spaces provided. Please refer to the Information Booklet in order to answer Question 1.1Arnold has a number of bouncy castles that customers can hire for special events such as birthday parties. He wants to create a website to advertise these bouncycastles and to take payments from customers.Section 1 of the Information Booklet provides details about the website andits requirements.Some of the website requirements can be seen in Figure 1a.(a) Identify two inputs the website must accept from the user.(2)Input1 .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... Input2 .................................................................................................................................................................................................................................................................................... ....................................................................................................................................................................................................................................................................................(b) Identify two processes the website code should perform.(2)Process1 .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... Process2 .................................................................................................................................................................................................................................................................................... ....................................................................................................................................................................................................................................................................................*P51808RA0320*Turn over3*P51808RA0420*4(e) Arnold is going to use the orders page to receive payment details.State the protocol Arnold should use and explain why this is needed.(4)Protocol .................................................................................................................................................................................................................................................................................... Explanation .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... ....................................................................................................................................................................................................................................................................................*P51808RA0520*Turn over5 (f) Figure 1b contains the text and formatting requirements for the ‘Bouncy Castle Designs’ page. Figure 1c shows the HTML code for the page. Identify two lines of the code that do not meet the formatting requirements and describe how the code can be corrected.(6) ONE Line number .................................................................................................................................................................................................................................................................................... Correction ................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................ TWO Line number .................................................................................................................................................................................................................................................................................... Correction ................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................(Total for Question 1 = 20 marks)*P51808RA0620*6Please refer to the Information Booklet in order to answer Question 2.2Martha is a science student. She uses a program to record the temperature at 12:00pm every day over 4 weeks. The temperature is stored in degrees (Celsius) as awhole number. She uses a procedural language for this program.(a) Martha uses an array to store the temperatures. The array is shown here.1012121191111161717131416131215161315151419201817151315 Identify the output from the array if these print statements are used:(2)print(item[1][1]) .................................................................................................................................................................................................................................................................................... print(item[2][4]) ....................................................................................................................................................................................................................................................................................(b) Martha will use functions in her program.Describetwo features that may be specified when writing a function.(4)Feature1 .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... Feature2 .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... ....................................................................................................................................................................................................................................................................................*P51808RA0720*Turn over7 (c) Martha would like to know how many days in the month had a temperature of 13 degrees. Explain why Martha would use a count occurrences algorithm and not a linear search.(4)................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................ (d) Martha needs to find the average temperature each week. The average is calculated by adding all temperatures recorded in a week and then dividing this value by 7. Explain why Martha would use truncation.(3)........................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................*P51808RA0820*8Martha has written an algorithm using pseudocode for her program. This can be seenin Figure 2 in Section 2 of the information booklet.(e) Describe what the algorithm in Figure 2 does.(4).................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... ....................................................................................................................................................................................................................................................................................(f) Describe one way that the algorithm in Figure 2 could be improved.(3) .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... .................................................................................................................................................................................................................................................................................... ....................................................................................................................................................................................................................................................................................(Total for Question 2 = 20 marks)*P51808RA0920*Turn over9 Please refer to the Information Booklet in order to answer Question 3.3 Edward owns a car maintenance business. He employs several mechanics. Edward wants a program to manage the arrangements when a car is booked in for repair. The program must also choose which mechanic to repair the car. Section 3 of the Information Booklet provides details about the requirements of this program. (a) Edward wants to make sure his staff enter the car registration plate in the correct format. Develop an algorithm using pseudocode that meets the requirements shown in Figure 3a and Figure 3b .(8)........................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................*P51808RA01020*10 ................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................。
GeneralAssemblyresolution62127:大会62127号决议

United Nations A/RES/62/127General Assembly Distr.: General24 January 2008Sixty-second sessionAgenda item 62 (b)07-47139Resolution adopted by the General Assembly[on the report of the Third Committee (A/62/432)]62/127. Implementation of the World Progra mme of Action concerning Disabled Persons: realizing the MillenniumDevelopment Goals for persons with disabilities The General Assembly,Recalling its previous resolutions concerning persons with disabilities, particularly resolution 60/131 of 16 December 2005, in which it recognized the important role of the World Programme of Action concerning Disabled Persons1 in the achievement of the Millennium Development Goals,Recalling also its resolutions on the Standard Rules on the Equalization of Opportunities for Persons with Disabilities,2Welcoming the adoption of the Convention on the Rights of Persons with Disabilities and the Optional Protocol thereto3 on 13 December 2006,Recalling the 2005 World Summit, held from 14 to 16 September 2005, at which Heads of State and Government, inter alia, expressed their resolve to ensure the timely and full realization of develop ment goals and objectives, including the Millennium Development Goals,4 and recognizing the importance of incorporating the perspective of persons with disabilities in the implementation of the outcomes of major United Nations conferences and summits, with a view to achieving the internationally agreed development goals, including those contained in the United Nations Millennium Declaration,5Aware that there are at least 650 million persons with disabilities worldwide and that the majority of them live in conditions of poverty, and in this regard recognizing the critical need to address the negative impact of poverty on persons with disabilities,_______________1 A/37/351/Add.1 and Corr.1, annex, sect. VIII, recommendation I (IV).2 Resolution 48/96, annex.3 Resolution 61/106, annexes I and II.4 See resolution 60/1, para. 17.5 See resolution 55/2.A/RES/62/1272Convinced that addressing the profound social, cultural and economic disadvantage experienced by many persons with disabilities and that promoting the progress ive removal of barriers to their full and effective participation in all aspects of development will further the equalization of opportunities and contribute to the realization of a “society for all” in the twenty-first century,Reaffirming the need to include the rights of persons with disabilities in the development efforts at the national, regional and international levels to achieve the Millennium Development Goals, and in this regard stress ing the need to improve the complementarity and synergy in the implementation of the three main United Nations mechanis ms, namely, the Convention on the Rights of Persons with Disabilities, the World Programme of A ction concerning Disabled Persons and the Standard Rules on the Equalization of Opportunities for Persons with Dis abilities, each of which constitutes an important building-block in the steps to achieve time-bound and quantifiable commitments set forth in the outcomes of major United Nations conferences and su mmits in the economic, social and related fields, Recognizing the importance of the principles and policy guidelines contained in the World Programme of A ction, the Convention and the Standard Rules in influencing the promotion, formulation and evaluation of the policies, plans, programmes and actions at the national, regional and international levels to further equalize opportunities for persons with disabilities,Convinced that the forthcoming periodic reviews of global progress as well as obstacles encountered in implementing the outcome of the Millennium Summit require the inclusion of an evaluation of the measures taken to achieve the Millennium Development Goals as they impact on persons with disabilities,1. Takes note of the report of the Secretary-General;62. Welcomes the work of the Special Rapporteur on disability of the Commiss ion for Social Development;3. Calls upon States that have not yet done so to consider signing and ratifying the Convention on the Rights of Persons with Disabilities and the Optional Protocol thereto3 as a matter of priority;4. Expresses concern about the pers istent gap between policy and practice regarding mainstreaming the perspective of persons with disabilities, inclu ding their rights and well-being, in the work of the United Nations in realizing the Millennium Development Goals;5. Encourages States to involve persons with disabilities on an equal bas is with other persons in the formulation of strategies and plans, in particular those pertaining to them;6. Encourages States, in cooperation with, inter alia, intergovernmental organizations, non-governmental organizations as well as regional and international financial institutions, and the private sector, as appropriate, to be guided by the objectives of the World Programme of A ction concerning Dis abled Persons1 as well as those of the Convention on the Rights of Persons with Disabilities and the Standard Rules on the Equa lization of Opportunities for Persons with Dis abilities2 in their work and to examine and ensure that development strategies, policies and programmes aimed at implementing internationally agreed development goa ls, _______________6 A/62/157.A/RES/62/127 including the Millennium Development Goals, are inclus ive of issues concerningpersons with disabilities and promote the equalization of opportunities for all by:(a) Ensuring access ibility, also through reasonable accommodation to enablepersons with disabilities to live independently and participate fully in all aspects oflife and to participate as agents and beneficiaries of development;(b) Providing appropriate and access ible social services and safety nets forpersons with disabilities to ensure improved well-being for all;(c) Ensuring an adequate standard of living and social protection for personswith disabilities, including through access to poverty and hunger eradication programmes, inclus ive quality education, in particular free and comp ulsory primaryeducation and secondary education, as well as the same range, quality and standardof free or affordable health care as provided to other persons, and the promotion offull employment and decent work for all;(d) Promoting and strengthening national capacities for participatory,democratic and accountable processes and mechanis ms that further the equalizationof opportunities for the full and effective participation of persons with disabilities incivil and political, economic, social and cu ltural life;7. Encourages States to collect and analyse appropriate information,including statistical and research data that are disaggregated by age and sex, on thesituation of persons with disabilities, bearing in mind appropriate protection ofpersonal data, for purposes of policy planning, analysis and evaluation that includethe perspective of persons with disabilities, and in this regard invites States to availthems elves of the technical services of the Statistics Divis ion of the Department ofEconomic and Social A ffairs of the Secretariat;8. Urges relevant entities of the United Nations system, including agencies,funds and programmes, and invites international and regional development financeinstitutions to take concrete measures to incorpora te the perspective of persons with disabilities, including accessibility requirements, in development cooperation and development finance activities;9. Reaffirms the role of the United Nations V oluntary Fund on Disability,and encourages States, intergovernmental organizations, concerned non-governmental organizations and the private sector to continue to support the Fund with a view to strengthening its capacity to support catalytic and innovative activities to implementfully the development goals and objectives of the World Programme of A ction, theStandard Rules and the Convention, including the work of the Special Rapporteur,and to facilitate international cooperation, including building national capacities,with emphas is on priorities for action identified in the present resolution;10. Encourages all relevant parties to bear in mind the situation of personswith dis abilities in the United Nations system-wide coherence discuss ions, withoutprejudice to the outcome of those discuss ions;11. Calls upon States to include in country reports, in connection with theforthcoming periodic reviews of progress in achieving the Millennium DevelopmentGoals, a review and evaluation of the impact of development efforts on the rights,well-being and livelihood of persons with disabilities;12. Reaffirms its commitment to respect and promote, without discrimination,the rights of indigenous persons with disabilities, and urges States to take effectivemeasures to continue to improve their economic and social conditions;3A/RES/62/127413. Requests the Secretary-General to give higher priority to concerns and issues of persons with disabilities and their inclusion within the work programme of the United Nations system and within existing resources, and to strengthen the role of the United Nations and its development programmes and agencies in mainstreaming disability issues, taking into account the perspective of persons with disabilities within the work of the United Nations system by:(a) Promoting the inclus ion of the perspect ive of persons with disabilities in the policies, programmes and projects of the Secretariat and the other United Nations bodies and agencies on a broader scale and with higher priority, on the basis of a holistic approach in the work done in the fields of social development, human rights and non-discrimination, and in this regard ensuring that the 2010 World Programme on Population and Housing Censuses is inclus ive of the perspective of persons with disabilities;(b) Further strengthening action in all countries and providing assistance to developing countries, in particular to least developed countries, with special attention to persons with disabilities in vulnerable circumstances;(c) Assisting Member States in formulating comprehens ive and coherent policies and action plans, as well as projects, including pilot projects, that promote, inter alia, international cooperation and technical assistance, particularly to enhance the capacities of government agencies, as well as civil society, including organizations of persons with disabilities, to implement programmes on dis ability;14. Decides that the fifth review and appraisal of the World Programme of Action, to be conducted by the General Assembly in 2008, shall direct special attention to the issues raised in the present resolution;15. Also decides to rename the International Day of Disabled Persons, observed every year on 3 December, the International Day of Persons with Disabilities;16. Requests the Secretary-General:(a) To submit an analytical and policy-oriented report on the fifth review and appraisal of the World Programme of Action to the General Assembly at its s ixty-third session as a contribution to the forthcoming periodic reviews of the progress as well as obstacles encountered in implementing the goals of the Millennium Summit, particularly the Millennium Development Goals;(b) To present, as an anne x to the report requested in subparagraph (a) above, proposed updates of the World Programme of Action, in accordance with paragraph 201 of the World Programme, bearing in mind the current s ituation of persons with disabilities around the world, as well as the developments in the global policy framework regarding persons with dis abilities, including the Convention on the Rights of Persons with Disabilities.76th plenary meeting18 December 2007。
Sleepware G3 Alice NightOne 快速上手指南说明书

Sleepware G3 Training Module Alice NightOne Quick Start GuidePreparing the Device1.Remove battery cover from the back of the Alice NightOne device.2.Place the Oximetry Module connector into the connection on the Alice NightOne device (bottom leftcorner).3.Secure the cable in place with the screw provided.4.Insert 2 new AA batteries with (+) ends matching (+) symbol on the bottom of the battery chamber(batteries not included). (Battery Life: 10-12 hours of recording)5.Next, add the device to Sleepware G3 by connecting one end of the USB cable to the Alice NightOnedevice, and the other end to the computer running Sleepware G3. Sleepware G3 will automaticallydetect the device and add it to the toolbar. It will remain there until removed manually. Or, you can add it manually by selecting Devices on the Sleepware G3 toolbar. Then, Add Device>Alice NightOne>OK.Adding the Device to Sleepware G3Create ConfigurationsUse the Build Channel Configurations tool to create your configurations/list of channels to be recorded. (The Alice NightOne device does not have to be connected to the computer to create your configurations/list of channels. Your selections will be stored on your computer.) The configuration files are located by default: (Windows 7) C:\ProgramData\PhilipsRespironics\SleepwareG3\Configuration\AliceNightOneCreating your ConfigurationsYou can create configurations for basic diagnostic testing as well as for therapeutic testing. Alice NightOne can connect wirelessly to any Philips Respironics (CPAP, BiPAP, autoPAP, AutoSV and AVAPS) device having Bluetooth® capability, including available Philips Respironics devices with the Bluetooth Accessory Module installed or internal Bluetooth functionality.Loading Information onto the Device for a Study1.Remove the battery cover on the back of the Alice NightOne device.2.Connect one end of the USB cable to the Alice NightOne device.3.Connect the other end of the USB cable to the computer with Sleepware G3 installed.4.Sleepware G3 will automatically detect the connection and, after a short while, go from No Signal toIDLE. The Good Study Indicator (GSI) will illuminate, as shown in the image on the right below, letting you know communication with the device has been successfully established.Loading Configuration and Patient Information onto the Device5.Click on the dropdown arrow on the Alice NightOne toolbar, and select Configure Device.6.Add Information under the tabs: Main, Patient Stats, Auto Start, and Good Study Indicator.*Note: Patient Information cannot be edited post-acquisition unless the database is connected.o Tab 1: “Main”▪Enter the patient’s name, birth date, gender, and Patient ID.▪Select the desired configuration.▪View the device storage status (internal memory).o Tab 2: “Patient Stats” - Enter the patient’s height and w eight (BMI is auto-calculated).o Tab 3: “Auto Start” - (Since Alice NightOne has Auto-On feature, only under unusual circumstances is there a need for Program Start.)o Tab 4: “Good Study Indicator (GSI)”▪Enable GSI.▪Indicate Good Study Target Duration.▪Select Channels to be evaluated for GSI.7.Click the Send button. The information will be sent to Alice NightOne. If a diagnostic configuration isused, the device is ready for testing!PAP Configuration8.If a PAP configuration is being utilized, keep Alice NightOne connected to the computer in the IDLEstatus.9.In Sleepware G3, access the dropdown menu for Alice NightOne in the device display area. SelectConnect to Therapy Device.10.Select the type of wireless connection: Bluetooth via Bluetooth Accessory Module or Bluetooth builtinto CPAP. If you choose Bluetooth via Bluetooth Accessory Module, enter the last 4 digits of theaccessory module serial number in the space provided. If you choose Bluetooth built into CPAP, enter the last 4 digits of the therapy device serial number.11.Select OK.12.When both devices are powered on, they can be synched. Follow the Bluetooth Accessory Modulepairing instructions to initiate this synchronization. For Alice NightOne, all that is necessary is to poweron the device. The wireless connection icon on the Alice NightOne device will be solid green when it is successfully paired to the therapy deviceRetrieving Data from Alice NightOne after a Study1.Remove the battery cover on the back of the Alice NightOne device.2.Connect one end of the USB cable to the Alice NightOne device.3.Connect the other end of the USB cable to the computer with Sleepware G3 installed. (Studies arestored on the internal memory of Alice NightOne. The device has a 4 GB memory with average study sizes of 50 MB).4.Sleepware G3 will detect the Alice NightOne for download, and show a message stating, “Enteringdownload mode.” If this does not happen automatically, select File>Import>Alice NightOne data. The Alice NightOne Download Utility will open showing the studies contained in the device memory.5.Place a check mark in the box in the “I mport” column for the patient whose study you would like toimport.6.Select Import. You will get an import status message and a message stating the download wassuccessful.7.If importing one patient only, this study will open in Sleepware G3. If importing multiple studies, thepatients will appear on the Start Page of Sleepware G3. Double click on the patient name to open the recorded study and begin scoring.Consult the Sleepware G3 Online Help and Alice NightOne manuals for additional information.1122255 R00JDW 04/09/2015。
Avaya Aura Session Manager Overview and Specification

Avaya Aura® Session Manager Overview and SpecificationRelease 6.3Issue 2May 2013© 2013 Avaya Inc.All Rights Reserved.NoticeWhile reasonable efforts have been made to ensure that the information in this document is complete and accurate at the time of printing, Avaya assumes no liability for any errors. Avaya reserves the right to make changes and corrections to the information in this document without the obligation to notify any person or organization of such changes.Documentation disclaimer“Documentation” means information published by Avaya in varying mediums which may include product information, operating instructions and performance specifications that Avaya generally makes available to users of its products. Documentation does not include marketing materials. Avaya shall not be responsible for any modifications, additions, or deletions to the original published version of documentation unless such modifications, additions, or deletions were performed by Avaya. End User agrees to indemnify and hold harmless Avaya, Avaya's agents, servants and employees against all claims, lawsuits, demands and judgments arising out of, or in connection with, subsequent modifications, additions or deletions to this documentation, to the extent made by End User.Link disclaimerAvaya is not responsible for the contents or reliability of any linked websites referenced within this site or documentation provided by Avaya. Avaya is not responsible for the accuracy of any information, statement or content provided on these sites and does not necessarily endorse the products, services, or information described or offered within them. Avaya does not guarantee that these links will work all the time and has no control over the availability of the linked pages. WarrantyAvaya provides a limited warranty on its hardware and Software (“Product(s)”). Refer to your sales agreement to establish the terms of the limited warranty. In addition, Avaya’s standard warranty language, as well as information regarding support for this Product while under warranty is available to Avaya customers and other parties through the Avaya Support website: . Please note that if you acquired the Product(s) from an authorized Avaya reseller outside of the United States and Canada, the warranty is provided to you by said Avaya reseller and not by Avaya. “Software” means computer programs in object code, provided by Avaya or an Avaya Channel Partner, whether as stand-alone products or pre-installed on hardware products, and any upgrades, updates, bug fixes, or modified versions. LicensesTHE SOFTWARE LICENSE TERMS AVAILABLE ON THE AVAYA WEBSITE, /LICENSEINFO ARE APPLICABLE TO ANYONE WHO DOWNLOADS, USES AND/OR INSTALLS AVAYA SOFTWARE, PURCHASED FROM AVAYA INC., ANY AVAYA AFFILIATE, OR AN AUTHORIZED AVAYA RESELLER (AS APPLICABLE) UNDER A COMMERCIAL AGREEMENT WITH AVAYA OR AN AUTHORIZED AVAYA RESELLER. UNLESS OTHERWISE AGREED TO BY AVAYA IN WRITING, AVAYA DOES NOT EXTEND THIS LICENSE IF THE SOFTWARE WAS OBTAINED FROM ANYONE OTHER THAN AVAYA, AN AVAYA AFFILIATE OR AN AVAYA AUTHORIZED RESELLER; AVAYA RESERVES THE RIGHT TO TAKE LEGAL ACTION AGAINST YOU AND ANYONE ELSE USING OR SELLING THE SOFTWARE WITHOUT A LICENSE. BY INSTALLING, DOWNLOADING OR USING THE SOFTWARE, OR AUTHORIZING OTHERS TO DO SO, YOU, ON BEHALF OF YOURSELF AND THE ENTITY FOR WHOM YOU ARE INSTALLING, DOWNLOADING OR USING THE SOFTWARE (HEREINAFTER REFERRED TO INTERCHANGEABLY AS “YOU” AND “END USER”), AGREE TO THESE TERMS AND CONDITIONS AND CREATE A BINDING CONTRACT BETWEEN YOU AND AVAYA INC. OR THE APPLICABLE AVAYA AFFILIATE (“AVAYA”).Avaya grants you a license within the scope of the license types described below, with the exception of Heritage Nortel Software, for which the scope of the license is detailed below. Where the order documentation does not expressly identify a license type, the applicable license will be a Designated System License. The applicable number of licenses and units of capacity for which the license is granted will be one (1), unless a different number of licenses or units of capacity is specified in the documentation or other materials available to you.“Designated Processor” means a single stand-alone computing device.“Server” means a Designated Processor that hosts a software application to be accessed by multiple users.Concurrent User LicenseConcurrent User License (CU). End User may install and use the Software on multiple Designated Processors or one or more Servers, so long as only the licensed number of Units are accessing and using the Software at any given time. A “Unit” means the unit on which Avaya, at its sole discretion, bases the pricing of its licenses and can be, without limitation, an agent, port or user, an e-mail or voice mail account in the name of a person or corporate function (e.g., webmaster or helpdesk), or a directory entry in the administrative database utilized by the Software that permits one user to interface with the Software. Units may be linked to a specific, identified Server.CopyrightExcept where expressly stated otherwise, no use should be made of materials on this site, the Documentation, Software, or hardware provided by Avaya. All content on this site, the documentation and the Product provided by Avaya including the selection, arrangement and design of the content is owned either by Avaya or its licensors and is protected by copyright and other intellectual property laws including the sui generis rights relating to the protection of databases. You may not modify, copy, reproduce, republish, upload, post, transmit or distribute in any way any content, in whole or in part, including any code and software unless expressly authorized by Avaya. Unauthorized reproduction, transmission, dissemination, storage, and or use without the express written consent of Avaya can be a criminal, as well as a civil offense under the applicable law.Third Party Components“Third Party Components” mean certain software programs or portions thereof included in the Software that may contain software (including open source software) distributed under third party agreements (“Third Party Components”), which contain terms regarding the rights to use certain portions of the Software (“Third Party Terms”). Information regarding distributed Linux OS source code (for those Products that have distributed Linux OS source code) and identifying the copyright holders of the Third Party Components and the Third Party Terms that apply is available in the Documentation or on Avaya’s website at: http:// /Copyright. You agree to the Third Party Terms for any such Third Party Components.Preventing Toll Fraud“Toll Fraud” is the unauthorized use of your telecommunications system by an unauthorized party (for example, a person who is not a corporate employee, agent, subcontractor, or is not working on your company's behalf). Be aware that there can be a risk of Toll Fraud associated with your system and that, if Toll Fraud occurs, it can result in substantial additional charges for your telecommunications services. Avaya Toll Fraud interventionIf you suspect that you are being victimized by Toll Fraud and you need technical assistance or support, call Technical Service Center Toll Fraud Intervention Hotline at +1-800-643-2353 for the United States and Canada. For additional support telephone numbers, see the Avaya Support website: . Suspected security vulnerabilities with Avaya products should be reported to Avaya by sending mail to: securityalerts@.2 Avaya Aura® Session Manager Overview and Specification 6.3May 2013TrademarksAvaya® and Avaya Aura® are registered trademarks of Avaya Inc. in the United States of America and/or other jurisdictions.All non-Avaya trademarks are the property of their respective owners. Linux® is the registered trademark of Linus Torvalds in the U.S. and other countries.Downloading DocumentationFor the most current versions of Documentation, see the Avaya Support website: .Contact Avaya SupportSee the Avaya Support website: for product notices and articles, or to report a problem with your Avaya product. For a list of support telephone numbers and contact addresses, go to the Avaya Support website: , scroll to the bottom of the page, and select Contact Avaya Support.4 Avaya Aura® Session Manager Overview and Specification 6.3May 2013ContentsChapter 1: Introduction (7)Purpose (7)Intended audience (7)Document changes since last issue (7)Related resources (7)Documentation (7)Training (9)Avaya Mentor videos (9)Support (9)Warranty (10)Chapter 2: Session Manager overview (11)Feature description (11)Policy-based routing (12)Centralized applications (12)SIP Proxy and Registrar functionality (12)Normalization of disparate networks (12)Application Sequencing (13)Personal Profile Manager (13)Centralized SIP trunking (13)New in this release (14)Chapter 3: Interoperability (15)Product compatibility (15)Supported Avaya endpoints (15)Deployment options (17)Operating System compatibility (18)Third-Party PBX Integration (18)Chapter 4: Performance specifications (19)Capacity and scalability specification (19)Dial plan specification (22)Tail end hop off (22)Call Admission Control specification (23)Redundancy and high availability (23)Survivable Core (25)Survivable Remote (25)Chapter 5: Security (27)Security specification (27)Port utilization (27)Chapter 6: Licensing requirements (29)Glossary (31)Index (33)Chapter 1: IntroductionPurposeThis document describes tested product characteristics and capabilities, including productoverview and feature descriptions, interoperability, performance specifications, security, andlicensing requirements.Intended audienceThis document is intended for people who want to gain a high-level understanding of theproduct features, functions, capacities, and limitations.Document changes since last issueThe following changes have been made to this document since the last issue:•Updated the topic New in this release in the chapter Session Manager overview.•Updated the topic Supported Avaya servers in the chapter Interoperability.•Updated the topic Capacity and scalability specification in the chapter Performancespecifications.Related resourcesDocumentationSee the following related documents.Introduction8 Avaya Aura® Session Manager Overview and Specification 6.3May 2013SupportTrainingThe following courses are available on https://. To search for thecourse, in the Search field, enter the course code and click Go .Avaya Mentor videosAvaya Mentor is an Avaya-run channel on YouTube that includes technical content on how toinstall, configure, and troubleshoot Avaya products.Go to /AvayaMentor and perform one of the following actions:•Enter a key word or key words in the Search Channel to search for a specific productor topic.•Scroll down Playlists, and click the name of a topic to see the available list of videosposted on the site.SupportVisit the Avaya Support website at for the most up-to-datedocumentation, product notices, and knowledge articles. You can also search for releaseIntroductionnotes, downloads, and resolutions to issues. Use the online service request system to createa service request. Chat with live agents to get answers to questions, or request an agent toconnect you to a support team if an issue requires additional expertise.WarrantyAvaya provides a 90-day limited warranty on Session Manager. See the sales agreement orother applicable documentation for more information about the terms of the limited warranty.In addition, see the standard warranty and details about Session Manager support during thewarranty period on the Avaya Support website at https:// under Help &Policies> Policies & Legal > Maintenance and Warranty Information. See also Help &Policies > Policies & Legal > License Terms.10 Avaya Aura® Session Manager Overview and Specification 6.3May 2013Chapter 2: Session Manager overviewSession Manager is a SIP routing and integration tool that is a core component of the Avaya Aura®Enterprise Edition solution. Session Manager integrates all SIP devices across the entire enterprise network within a company and leverages the existing PBX infrastructure. Session Manager provides the following advantages:•Business agility driven through holistic enterprise architectures for connecting users, applications, and multivendor solutions.•New cost savings from SIP connectivity and reduced public switched telephone network (PSTN) usage through centralized, enterprise-wide routing.•Lower total cost of ownership with a centralized, easy-to-use management interface and the efficient deployment of enterprise-wide central applications.•Unprecedented enterprise-wide scalability with support for truly global deployments.•Strong reliability, security, and redundancy support.Feature descriptionSession Manager integrates and simplifies the existing communication infrastructure,combining existing PBXs and other communications systems, regardless of the vendor, into acohesive, centrally managed, SIP-based communications network.Specifically, Session Manager:•Normalizes disparate networks— integrates with third-party equipment and endpoints.•Provides centralized routing of calls using an enterprise wide numbering plan.•Offers centralized management through System Manager, including configuration of userprofiles and efficient deployment of enterprise-wide centralized applications.•Communicates with Session Border Controller and provides protection at the edge of theenterprise network.•Interconnects Communication Manager and Avaya Communication Server 1000 andprovides multiple feature support for SIP and non-SIP endpoints.•Enables third-party E911 emergency call service for enterprise users.•Centralizes Presence Services, providing scale and reduced network complexity with avariety of endpoints and communication servers.•Supports truly converged voice and video bandwidth management.Session Manager overview•Provides application sequencing capability, thus enabling incremental applicationdeployments without PBX upgrades.•Provides outstanding geographic redundancy.Policy-based routingCustomers can define their call routing policy with Session Manager. Using these policies, theycan control when calls are made, how the call load is balanced, and how calls are routed duringnetwork failures.•Least-cost routing, also called time-of-day routing, chooses the lowest cost route from alist of service providers on a time-of-day or time-of-week basis. This results in cost savingsfor the enterprise.•Alternate routing routes calls around network failures on a global basis and uses globalPSTN fallback when the internal network is unavailable.•Load balancing distributes calls to a SIP entity to multiple IP addresses. You canadminister Session Manager to select from multiple IP addresses for a given entity andselect these hosts based on administered priorities and weights.•Call admission control reroutes calls when the WAN link to a branch fills up.Centralized applicationsSession Manager provides connectivity for centralized Avaya applications such as AvayaAura® Messaging, Avaya Voice Portal, and Avaya Meeting Exchange™. Each PBX, gateway,or location connects to the centralized application through Session Manager rather thanindividually. Session Manager also connects to SIP-enabled adjuncts, making themanagement and deployment of adjuncts much simpler than methods where each PBXconnects to its own adjunct.SIP Proxy and Registrar functionalitySession Manager functions as the SIP Proxy and Registrar server of the enterprise network.Normalization of disparate networksSession Manager normalizes and adapts disparate SIP protocols to meet the strict SIPstandards of the network. With normalization of disparate networks, third-party PBXs work witheach other and with Avaya equipment enabling customers to realize true vendorinteroperability.Feature description For example, Cisco and other PBXs can connect with Session Manager and operate with eachother and with Avaya equipment. Session Manager converts the headers in SIP messagesthat display calling and called-party information in the format required by each switch in acall.Application SequencingWith Application Sequencing you can define and manage a set of applications for callsequencing based on the communication profile of the user. Each application in a sequenceprocesses all requests and can deny, modify, or forward initial SIP requests. The following aresome examples of sequenced applications:•Billing Service•Voice Monitor•Communication Manager Feature Server•Call Blocker•Personal assistant•Meeting CoordinatorSession Manager also supports third-party PBX endpoint application sequencing. Typicalapplications include blocking calls based on user preferences, directing calls to users whenthey move across the Avaya Aura® enterprise, and augmenting caller identification informationfor incoming and outgoing calls. You can enable Application Sequencing without upgrading ormodifying the code on existing third-party PBX equipment. See Administering Avaya Aura®Session Manager for details.Personal Profile ManagerPersonal Profile Manager (PPM) maintains and manages the personal information of the enduser in the system. SIP endpoints communicate with PPM to retrieve configuration information,such as dial plans, buttons, and contact lists, to add or update contacts, and to save device-specific data. With PPM, endpoints can attach to the network to download profile data andstore data back in the network for easy access across multiple user devices.Centralized SIP trunkingCentralized SIP trunking routes all network traffic, including branch site traffic, through theenterprise core site. In this approach, Session Manager provides redundant connections to aSIP service provider using the Gateway or SBC. Centralized SIP trunking enables enterprisesto save on operational costs.Session Manager overviewHowever, the setup should have more than one hub-site to avoid the risk of a single point offailure.New in this releaseSIP Call Loop Elimination:Session Manager provides administration features to track and terminate SIP call loopinginstances in the network.Multi Device Access:With the Multi Device Access feature, a SIP user can register multiple SIP endpoints with thesame extension. Session Manager forks any incoming calls of the user simultaneously to theregistered SIP devices. When the call is answered at one of the devices, Session Managercancels the call request to the other devices.Dial Plan Transparency:During a network outage, Dial Plan Transparency (DPT) preserves the dial plan and reroutesall calls that are generated after the detection of the outage to the PSTN.SIP sessions count:Session Manager Element Manager collects, monitors, and logs the number of concurrent SIPsessions in the system. The system raises an alarm when the number of concurrent SIP INVITEsessions exceeds the number of authorized Session licenses.Session Manager SNMP MIB:Session Manager enables administrators to download a zip archive file containing SessionManager supported SNMP MIBs, alarm traps, and informs.For details about these features, see Administering Avaya Aura® Session Manager.Chapter 3: InteroperabilityProduct compatibilityFor the latest and most accurate compatibility information, see https:///CompatibilityMatrix/Index.aspx.Supported Avaya endpointsSession Manager 6.3 supports the following Avaya endpoints:Endpoints Notes9600 Series IP Deskphones with Deskphone SIP 2.6.6,6.0, 6.1, or 6.2. Specifically:•9620, 9620C, 9620L, 9630, 9630G, 9640, 9640G, 9650,9650C with Deskphone SIP 2.6.6•9601, 9608, 9611, 9621, 9641 with Deskphone SIP6.2.296x1 Series SIP endpoints (9608SIP, 9611SIP, 9621SIP,9641SIP, 9611SIPCC, 9608SIPCC, 9621SIPCC,9641SIPCC) – fw 6.2.2Call Center Agent endpoints (9621 and 9641 with customfaceplates) - 6.2, and one-X Agent (6.2.2)ADVD Administered as a 9640SIPphone, with 1.1.2Flare Communicator Windows 1.0Flare Experience Windows 1.0 and 1.1Flare Communicator iPad 1.0Flare Experience iPad 1.0 and 1.1VDI Communicator 1.0Supported as an endpointcontrolled by one-XCommunicator 6.1.7 as a SIP client in shared control modeone-X Communicator 6.1 for WindowsFor CS1000 7.5 and Session Manager. Supports all three audio modes.One-X communicator does not support Session Manager prior to Session Manager 6.0.one-X Communicator for MacOS 1.0.4 SIP only and does not supportCES. Supports all three audiomodes.One-X communicator does notsupport Session Manager priorto Session Manager 6.0.One-X Mobile iOS SIP Client – 6.2 (or later)This version does not supportthe Multi Device Access (MDA)feature.11xx and 12xx SIP endpoints.Treated as 3rd party endpoints.PPM cannot download data tothese endpoints.Radvision SIP endpoints: XT1000, XT1000 Piccolo, XT1200, XT4000, XT5000Treated as 3rd party endpoints. PPM cannot download data to these endpoints.1603SW-I SIP endpoint, such as BlazeAvaya 10x0 video endpoints (such as Lifesize, aliased as96x0SIP) as follows:•1010/20: AV_PP1_4_7_3_5.cmg•1030/40/50: AV_RM1_4_7_3_5.cmg46xx endpoints1.UniSTIM is a non-SIP endpoint that is supported as part of the overall AvayaAura® solution. UniSTIM endpoints do not register with Session Manager butregister to a CS1000.2.Older SIP endpoints will not support all features in release 6.3, but can stillregister to Session Manager (for example, 46xx).InteroperabilityDeployment optionsDeployment optionsSession Manager can be deployed under the following environments in an enterprise.Avaya supported hardware for large enterprisesA large enterprise can have upto 10 Session Manager instances supporting 1,00,00 users.HardwareThe supported servers for Session Manager 6.3 are:•S8800, S8510 (upgrades only), HP DL360G7, and Dell R610 for Session Manager as aappliance.•S8800, S8510, HP DL360G7, Dell R610 servers and S8300D for Survivable Remote.For a list of components and specifications for these servers, see Implementing AvayaAura® Session Manager.VMware virtualized environmentExisting customers who have a VMware IT infrastructure can deploy Session Manager as avirtual application on VMware.Session Manager on VMware is capable of supporting the following user capacities:1.Capacity footprint 1 - 3,500 users under normal conditions and 4,000 users underfailure conditions.2.Capacity footprint 2 - 7,000 users under normal conditions and 8,000 users underfailure conditions.3.Capacity footprint 3 - 10,000 users under normal conditions and 12,000 users underfailure conditions.HardwareThe customer provides the servers and the VMware infrastructure including the VMwarelicenses. For details on Session Manager in a VMware® vSphere ™ 5.1 virtualizationenvironment, see the Session Manager using VMware® in the Virtualized EnvironmentDeployment Guide available on the support site.System Platform for midsize enterpriseAvaya Aura® solution, that includes Session Manager as an application, is installed as aSystem Platform template on a single server. Midsize Enterprise supports enterprises with 250- 2400 users, 1 to 5 locations.HardwareThe HP ProLiant DL360 G7 is the only supported server for Midsize Enterprise 6.2.2. Fordetails on Mid-size Enterprise Session Manager, see the Avaya Aura® Solution for MidsizeEnterprise documentation, available on the support site.InteroperabilityOperating System compatibilitySession Manager 6.3 and Branch Session Manager 6.3 support Red Hat Enterprise Linux(RHEL) 6.2. The underlying SIP container is IBM WAS 8.0.x server.The Branch Session Manager 6.3 and Midsize Enterprise Solution 6.3 templates include RHEL6.2 as the underlying operating system for the Branch Session Manager and the SessionManager components running on an Avaya Aura® Midsize Enterprise Solution.Third-Party PBX IntegrationSession Manager works with Cisco UCM, Siemens Highpath, Alcatel Lucent OmniPBX, andAastra systems with direct SIP connections. You can program each of these third-party PBXsso that Session Manager can perform inter-PBX routing.Chapter 4: Performance specificationsCapacity and scalability specificationEntities Numbers(supportedlimits)NotesCore Avaya Aura®Session Manager (SM)instances10Dial Patterns * Locations/ Pattern * Routing Policies 300,000Assuming 20 telephone numbers for eachSIP Entity. The number can be interpreted asonly 300,000 individual phone numbers canbe routed, but these are patterns. If thenumbers can be grouped for a givendestination, fewer entries are required.SIP Domains1,000SIP Entities25,000SIP Entity Links75,000 1.Assuming 3 links for each SIP entitysuch as UDP, TCP, and TLS links.2.Assuming that each SIP Entity is linkedto two Session Managers (forredundancy) with only one transportprotocol used. In this case, there wouldneed to be 50,000 links.In both cases, the inter-Session Managerentity links need to be counted towards thelimit.SIP Entity Links / SM10,000Adaptations25,000Assuming one Adaptation for each SIPEntity. At the most, there can be oneAdaptation for each SIP Entity and some SIPEntity may not require any Adaptation. Adaptation Entries250,000Includes both ingress and egress entries. Regular Expressions100Performance specificationsUsers/SM on VMWare•3,500 (undernormalcondition)•4,000 (underfailurecondition)•7,000 (undernormalcondition)•8,000 (underfailurecondition)•10,000(undernormalcondition)•12,000(under failurecondition)Different capacity footprints as supported in the Session Manager 6.3.2 release.SM Communication Profiles (Users)100,000The number will be less if users havePresence.SM Communication Profiles/SM 12,000Same as Simultaneous Subscribed Stations/SM.Maximum no. of Primary Users/SM 10,00012,000 (under failure condition)Branch SM instances250Per Branch SM performance•Users/survivable embedded•User/survivable •700•2,000BHCC / SM400,000 Session creations/second/SM100Session creations /second/ BSM10Session creations/ second /survivable embedded SM 3Capacity and scalability specificationPerformance specifications100,000Assumes 125 sessions per second.Simultaneoussessions/SMFor details about the listed entities, see Administering Avaya Aura® Session Manager Release6.3.Dial plan specificationWith Session Manager, call routing is controlled by two interdependent schemes:•A global enterprise-wide numbering plan used for centralized routing that is administeredon a centralized management console.•One or more local, geographically significant dial plans administer on Avaya AuraCommunication Manager, or other vendor PBX. Local dial plans specify the actual digitsdialed within the constraints of the numbering plan.Session manager adjusts routing information (digits and domains) to accommodate thenumbering plan or dial plans as required.The numbering plan describes the overall numbering scheme that the enterprise uses forcentralized routing. Session Manager uses two different numbering plans for analysis androuting:•E.164 Public Numbering Plan•Enterprise Canonical (Private Numbering Plan)Tail end hop offSession Manager can route outgoing calls to local trunks at each location so that all usersacross the network enterprise can save toll charges for calls that go off the network. Thisconfiguration is called tail end hop off (TEHO).For example, a call from Tokyo to Los Angeles can be routed through a company intranet andthen sent to the PSTN from the Los Angeles PBX, which is similar to a local call from LosAngeles. And calls bound for Tokyo are routed through the Tokyo PBX.The following figure illustrates how TEHO works:。
PI System Explorer User's Guide

Navigating the PI System Explorer ........................................................................9
Identifying Major Components .................................................................................10 Menu Bar / Toolbar ..................................................................................................12 Browser....................................................................................................................28 Viewer ......................................................................................................................30 Palette......................................................................................................................31 Working with Databases ..........................................................................................32
seabios a disk read error occurred -回复

seabios a disk read error occurred -回复Seabios: A Disk Read Error OccurredIntroduction:In the world of computer systems, errors can occur at any time, potentially disrupting our work and causing frustration. One such error that users may encounter is the "A Disk Read Error Occurred" message while using the Seasbios software. In this article, we will explore the causes of this error and provide step-by-step instructions to resolve it.I. Understanding Seabios:Seabios is an open-source firmware for x86-based systems, often used as a replacement for a computer's native BIOS. It provides compatibility with various operating systems, enabling users to run alternative software on their machines. Seabios interacts with the hardware components of a system to boot an operating system. However, due to various reasons, errors can occur, leading to the "A Disk Read Error Occurred" message.II. Causes of the Error:1. Misconfigured Boot Order:One common cause of the "A Disk Read Error Occurred" message is a misconfigured boot order. This occurs when the system tries to boot from a non-bootable disk or device. To resolve this issue, we need to verify and correct the boot order settings in Seabios.2. Corrupted Boot Sector:Another possible cause is a corrupted boot sector on the bootable disk. This can happen due to a sudden power loss, improper shutdown, or malware infection. In such cases, the disk becomes unreadable, resulting in the error message. Fixing the corrupted boot sector is essential to resolve the error.III. Resolving the Error:To resolve the "A Disk Read Error Occurred" message, follow the steps below:Step 1: Enter Seabios Configuration:Start your computer and press the designated key (commonly F2, Del, or Esc) to access the boot menu or BIOS settings. Navigate to the "Boot" or "Startup" tab and locate the Seabios settings.Step 2: Verify Boot Order:In the Seabios settings, ensure that the boot order is correctly configured. The primary boot device should be the disk where the operating system is installed. Adjust the boot order if necessary, saving changes before exiting the configuration menu.Step 3: Check Connections and Cables:If the boot order is correctly configured, turn off the computer and check the connections and cables of the disk. Ensure that they are securely connected and not damaged. Faulty connections or cables can cause disk read errors.Step 4: Repair the Boot Sector:If the connections and cables are not the issue, the next step is to repair the corrupted boot sector. Insert the installation media for your operating system (e.g., a USB drive or DVD) and restart the computer. Press the appropriate key (usually F12 or Esc) to access the boot menu and boot from the installation media.Step 5: Access Recovery/Repair Options:On the installation media, select the option to repair or recover the operating system. This will launch the recovery/repair tool provided by your operating system. Follow the on-screen instructions to access the command prompt or repair options.Step 6: Repair the Boot Sector:Once you have access to the command prompt or repair options, execute the appropriate commands to repair the boot sector. The specific commands may vary depending on the operating system. For Windows, running the "bootrec /fixboot" and "bootrec /fixmbr" commands should resolve the issue.Step 7: Restart the System:After successfully repairing the boot sector, restart the computer and check if the "A Disk Read Error Occurred" message has been resolved. If the error persists, further investigation may be required, such as scanning the disk for errors or seeking professional assistance.Conclusion:Encountering the "A Disk Read Error Occurred" message while using Seabios can be frustrating but can generally be resolved by verifying the boot order and repairing the boot sector. Following the step-by-step instructions provided in this article should help resolve the issue and allow you to resume using your computer smoothly. Remember, if the error persists, it is crucial to seek professional assistance to avoid further damage to your system.。
Cisco VPN AnyConnect Secure Mobility Client 3.0(HR

Cisco VPN Any Connect Secure Mobility Client 3.0 [HRA] Connection GuideOnce the Cisco AnyConnect Secure Mobility Client [HRA] is installed on your machine you should be able to see the following icon on the task barCisco Any Connect Client IconClick on the icon for Cisco AnyConnect and it will pop-up the window as shown below.It has the Network Access Manager (currently connected to a wired connection) and the VPN sectionNetwork access manager automatically detects network on end user’s mac hine based on the availability (wired, wireless, etc.)In order to get connected to the HRA VPN using the Wifi follow the below instructions:If this is the first time connecting to this WiFi network select the WiFi from the Network section in Any Connect.Enter information for the connection including SSID, Security Privacy setting and KeyAfter computer is associated with the WiFi network you will see IP address and status changes to “connected” in Network Access Manager. Now click on connect.During the connection phase, VeriSign Personal Trust Agent will prompt for the password, which is nothing but your certificate password [formerly HGRA password] Enter password and click ConnectVPN tunnel will be established and user can connect to network resources they have permission to reach.NOTE–Authentication method remains same for the HRAAfter successful connection with the Cisco Any Connect client you should see the Cisco VPN icon as shown below –Cisco Any Connect Client Connected IconIf this is the first time connecting to a Wi-Fi network and the network SSID is Non-Broadcast which cannot be detected automatically, click on the Advanced link in Any Connect Client.On the Advanced popup window, Click Networks tab, to view the Network Access Manager Configuration tabTo add your Non-BroadCast network, click the Add button on the Configuration Tab.1. Select Media will be on Wireless as default2. Enter the Descriptive name for your network[i.e.Home] that will appear in the AnyConnect Client Network Pulldown3. Enter the SSID defined when your networkwas established4. From the pull down list, select the securityencryption settings designated for thisnetwork by the net work’s administrator5. Enter the Key set for your encryption set forthis network by the network’s administrator6. Click OK buttonClick the Red X to close the Network Access Manager Configuration tabAfter computer is associated with the WiFi network you will see IP address and status changes to “connected” in Network Access Manager. Now click on connect.During the connection phase, VeriSign Personal Trust Agent will prompt for the password, which is nothing but your certificate password [formerly HGRA password] Enter password and click ConnectVPN tunnel will be established and user can connect to network resources they have permission to reach.NOTE–Authentication method remains same for the HRAAfter successful connection with the Cisco Any Connect client you should see the Cisco VPN icon as shown below –Cisco Any Connect Client Connected Icon。
FortiGate Session Life Support Protocol(FGSP)用户指南说

FortiGate Session Life Support Protocol (FGSP) Author: Jason GraunNetwork Security ArchitectContentsIntroduction (2)FGSP Deployment scenario (2)Deployment considerations (4)Requirements (4)Configuration Procedure (5)Understanding Session Synchronization Details (8)Firewalling of Asymmetric Traffic (10)UTM flow-based inspection and Asymmetric Traffic (11)FGSP vs FGCP Active-Active (12)IntroductionThis document assumes knowledge of FortiGate Clustering Protocol (FGCP).FortiGate Session Life Support Protocol (FGSP) was introduced in FortiOS 5.0. However in previous versions of FortiOS this feature was known as “standalone session sync” and only supported TCP sessions, did not support asymmetric traffic and had other deployment limitations. FGSP was designed to overcome these limitations. It supports asymmetric traffic, TCP, UDP, ICMP sessions as well as NAT sessions. FGSP also supports configuration synchronization between FortiGates. The use of traffic load-balancers to share load across two FortiGates is possible with FGSP. FGSP is well suited for networks using equal cost load balancing of links between routers. Also called equal-cost multi-path (ECMP) routing or multipath routing.FGSP Deployment scenarioECMP routing is very common in large networks using OSPF. Typically when ECMP is in use routers will route packets based on a source/destination IP pair. Figure 1 below shows an example network with ECMP. Assume 192.168.1.50 and 192.168.1.100 are both sending traffic to 172.16.1.50 and 172.16.1.100 respectively, it is very likely that the traffic will each take a different path in the network. 172.16.1.50/192.168.1.50 might take the left path in the network and 172.16.1.100/192.168.1.100 would take the right path in the network.Figure 1When using FGSP both FortiGates are in an active state and will process packets, which is the desired function when using ECMP routing in a network. FGSP’s many advantage in this scenario is that the interfaces do not have to be Layer-2 adjacent to each other as they do in FGCP. Each interface can have its own IP address in a different subnet as shown in Figure 1. This allows the FortiGate to be a stateful firewall and even with traffic taking diverse paths in the network.In figure 1, a failure of any device along the data path will result in no loss of data because the opposite FortiGate will take over handling all existing traffic. Sessions will have already been synced prior to failure as a result of implementing FGSP.Deployment considerationsThe following are important aspects that should be understood when discussing deployments of FGSP.•FortiGates running FGSP act as independent devices when compared to FGCP. Interface IP addresses must be unique to each interface, there are no shared IP addresses, and there is no clustering.•FortiGate configurations are not automatically synchronized. It must first be enabled.•The same ForitGate models should be used for both peers to avoid uneven performance.•The names of the interfaces, including VLAN interfaces, aggregate interfaces, etc… must be the same on both peers.•It is possible to synchronize sessions from only specific VDOMs.•Session synchronizations filters can be enabled to only synchronize specific traffic.•You cannot run FGSP and FGCP at the same time on the same FortiGates.•VRPP is supported in FGSP.•Performance limitations should be considered in case of a failover scenario. One device must be able to handle the load of both.RequirementsA FortiGate running FortiOS 5.0 or later is required. It is recommended to use the latest available GA patch. This configuration example uses two FortiGate 140D’s running FortiOS 5.0 patch 6 (build 0271).Configuration ProcedureFigure 2CLI CommandsFGSP parameters are configured fromStep 1 – Begin with Two FactoryIf needed issue the following commanexecute factoryresetAnswer YES to the prompt and the Fed from the CLI only. There are some similarities to FG tory Default FortiGatesommand to return the FortiGates to factory default.the FortiGates will reboot with a default configuration.to FGCP configurations.ation.Step 2 – Configure Session Synchronization PeersFGT-A in figure 2 above has an IP address of 10.10.10.2 configured on port3.FGT-B in figure 2 above has an IP address of 10.10.10.1 configured on port3.FGT-A:config system session-syncedit 1set peerip 10.10.10.1set peervd "root"set syncvd "vdom_1"FGT-B:config system session-syncedit 1set peerip 10.10.10.2set peervd "root"set syncvd "vdom_1"The syncvd tells the FortiGate to synchronize sessions that exist in the “vdom_1” VDOM. Sessions in the “root” VDOM will not be synchronized. To synchronize more than one VDOM, add additional statements for each VDOM that requires session synchronization. The peerip and peervd settings will be the same, only the syncvd setting will change.The peervd of root tells the FortiGate that sessions will be synchronized using the root VDOM as the transport mechanism. The peerip IP address must be in the same VDOM as the peervd setting. In figure 2 the port3 is in the “root” VDOM.When VDOMs are not enabled the peervd setting defaults to “root” and is only visible using “show full-configuration”.If VDOMs are not enabled the peervd setting defaults to root.FGT-A:config system session-syncedit 1set peerip 10.10.10.1set syncvd "root"FGT-B:config system session-syncedit 1set peerip 10.10.10.2set syncvd "rootStep 3 – Enable Configuration SynchronizationConfiguration Synchronization in FGSP synchronizes firewall policies, UTM policies, etc… It does not synchronize, by design, interface IP addresses and BGP peer information as these settings must be unique.To enable configuration synchronization, on both FortiGates issue the following commandsconfig system haset standalone-config-sync enableReboot both FortiGates after enabling the command.Standalone configuration synchronization uses a very similar process as FGCP. There is a master/backup relationship between the two FortiGates similar to FGCP but only of configuration synchronization not session information. In fact you will see a familiar message on the FortiGate’s console after the reboot. These are the same messages seen in FGCP configurations.slave's configuration is not in sync with master's, sequence:0slave's configuration is not in sync with master's, sequence:1slave's configuration is not in sync with master's, sequence:2slave's configuration is not in sync with master's, sequence:3slave's configuration is not in sync with master's, sequence:4slave starts to sync with masterWith configuration synchronization is enabled, configuration changes to one FortiGate will synchronize to the other. Keep in mind both firewalls are active when using FGSP.Step 4 – Add Session SynchronizationNow the two FortiGates are setup to synchronize configuration and sessions between themselves we must tell the FortiGates what type of sessions should be synchronized. FGSP synchronizes IPv4 and IPv6 TCP, UDP, ICMP, expectation (asymmetric sessions), and NAT sessions. All of the configuration is done in HA system settings. Session-pickup must first be enabled.Synchronizes NAT sessions.config system haset session-pickup enableset session-pickup-nat enableSynchronizes UDP and ICMP sessions.config system haset session-pickup enableset session-pickup-connectionless enableSynchronizes exception sessions also called asymmetric sessionsconfig system haset session-pickup enableset session-pickup-expectation enableStep 5 – Session Synchronization Filter (optional)There maybe scenarios when you only want to synchronize sessions of certain types of traffic. For example only sessions for specific IP addresses can by synchronized. In the configuration below only traffic sourced from 192.168.1.50 to 172.16.1.50 would be synchronized.Specific IP addressesconfig system session-syncedit 1config filterset dstaddr 172.16.1.50 255.255.255.255set srcaddr 192.168.1.50 255.255.255.255At this point the FortiGates have a basic FGSP configuration that will synchronize sessions and configuration between the two firewalls.Understanding Session Synchronization DetailsSession synchronization statisticsBelow is the output from diagnose sys session sync.Here we can see what types of sessions will be synchronized, how many sessions have been synchronized to the peer FortiGate, how many sessions have been synchronized to this FortiGate and the filter configuration if one is created.FGT-A # diagnose sys session syncsync_ctx: sync_started=1, sync_tcp=1, sync_others=1,sync_expectation=1, sync_redir=0, sync_nat=1.sync: create=12:0, update=0, delete=0:0, query=14recv: create=14:0, update=0, delete=0:0, query=12ses pkts: send=0, alloc_fail=0, recv=0, recv_err=0 sz_err=0nCfg_sess_sync_num=5, mtu=16000sync_filter:1: vd=0, szone=0, dzone=0, saddr=0.0.0.0:0.0.0.0, daddr=0.0.0.0:0.0.0.0, sport=0-65535, dport=0:65535The sync_started=1let’s us know that synchronization is working. If this is set to zero then something is not correct with session synchronization. The other sync values show that TCP, connectionless, asymmetric and NAT sessions will all be synchronized.The two fields sync: create=12:0 and recv: create=14:0show that this FortiGate has synchronized 12 sessions to its peer and has received 14 sessions from its peer.The sync_filter shows the configured filter. In this case no filter is created so all sessions will be synchronized. The vd=0 indicates that sessions in the root VDOM will be synchronized.New Session FlagBelow is the output from diagnose sys session list.Under “state” we can see a new flag called “synced”. The flag indicates that this FortiGate created the session and has synchronized the session to its peer. In other words for this session FGT-A, in Figure 1, is the firewall that built this session and inspection will happen on it. If we looked at the peer FortiGate, FGT-B, we would see the same session however the “synced” flag would be missing. The new flag is important in troubleshooting since it lets us see which FortiGate is handling a particular session. When FortiGates are deployed in networks that use ECMP/multi-path routing such as in Figure 1, sessions will be built by both FortiGates and the “synced” flag is the key piece in understanding which FortiGate is handling a particular session.FGT-A from Figure 1.session info: proto=6 proto_state=05 duration=469 expire=0 timeout=3600 flags=00000000 sockflag=00000000 sockport=21 av_idx=0 use=4origin-shaper=reply-shaper=per_ip_shaper=ha_id=0 policy_dir=0 tunnel=/state=log may_dirty ndr syncedstatistic(bytes/packets/allow_err): org=544/9/1 reply=621/7/0 tuples=2orgin->sink: org pre->post, reply pre->post dev=46->45/45->46gwy=10.2.2.1/10.1.1.1hook=pre dir=org act=noop 192.168.1.50:45327->172.16.1.100:21(0.0.0.0:0) hook=post dir=reply act=noop 172.16.1.100:21->192.168.1.50:45327(0.0.0.0:0) pos/(before,after) 0/(0,0), 0/(0,0)misc=0 policy_id=1 id_policy_id=0 auth_info=0 chk_client_info=0 vd=0serial=00002deb tos=ff/ff ips_view=1 app_list=2000 app=16427dd_type=0 dd_mode=0per_ip_bandwidth meter: addr=192.168.1.50, bps=633Session Synchronization Traffic LinkSession synchronization can take up a fair amount of bandwidth so you should use a dedicated link not data bearing interfaces. The session synchronization traffic is UDP based and there is no option for a backup link. As a result it is very important that the link between the FortiGates always be maintained. The link should be direct and not connect through other intermediate network switches.NAT session synchronizationFGSP can synchronize NAT sessions however when taking failover into consideration extra attention to the NAT configuration is required. When using NAT in a firewall policy the default option of “Use Destination Interface Address” is not ideal. Looking at Figure 2 we can see that port1 on FGT-A and FGT-B are connected to the same layer-2 network. In a firewall policy if the default NAT option of “Use Destination Interface Address” is selected then all traffic is tied to the IP address of port1 on FGT-A. If a failure occurs on FGT-A all traffic will essentially beblack-holed since the IP address on port1 is now gone. To overcome this an Overloaded IP Pool should be used. Overload is the default type and is visible via “show full-configuration”.config firewall ippooledit "FGSP-ippool"set startip 172.31.1.1set endip 172.31.1.254Firewalling of Asymmetric TrafficFGSP is designed to enforce firewall policy on asymmetric traffic, including cases where the TCP 3-way handshake is split between two FortiGates. Looking at Figure 3, FGT-A receives the TCP-SYN, FGT-B receives the TCP-SYN-ACK and FGT-A receives the TCP-ACK. Under normal conditions a firewall will drop this connection since the 3-way handshake was not seen by the same firewall. However two FortiGates with FGSP configured will be able to properly pass traffic since the firewall sessions are synchronized. If traffic will be highly asymmetric, as described above, the following command must be enabled on both FortiGates.config system haset session-pickup enableset session-pickup-expectation enableThis asymmetric function can also work with UDP and ICMP traffic. The following command needs to enabled on both FortiGates.config system haset session-pickup enableset session-pickup-connectionless enableSynchronizing asymmetric traffic can be very useful in situations where multiple Internet connections from different ISPs are spread across two FortiGates. Since it is typically not possible to guarantee Internet bound traffic leaving via an ISP will return using the exact same ISP, FGSP provides critical firewall functions in this situation.FGSP also has applications in virtualized computing environments where virtualized hosts move between data centers. The firewall session synchronization features of FGSP allow for more flexibility than in traditional firewalling functions.Figure 3UTM Flow-based Inspection and Asymmetric TrafficUTM inspection (flow or proxy based) for a session is not expected to work properly if the traffic in the session is balanced across more than one FortiGate in either direction. Flow-based UTM should be used in FGSP deployments.For an environment where traffic is symmetric, UTM can be used with the following limitations:1)No session synchronization for the sessions inspected using proxy-based UTM. Sessions will drop andneed to be reestablished upon data path failover.2)Sessions with flow-based UTM will failover however inspection after the failover may not work.A single FortiGate must see both the request and reply traffic for UTM inspection to function correctly. For environments where asymmetric traffic is expected, UTM should not be used.FGSP vs FGCP Active-ActiveFGSP and FGCP are both methods for enabling high availability with FortiGate firewalls however there are differences which are important to understand. FortiGate Clustering Protocol (FGCP) is deployed using two FortiGates in either an active-passive or active-active configuration. FGCP Active-Active differs from FGSP in that FortiGates using FGCP appear as a single logical firewall to all other networking devices. Using FGCP the FortiGates share the same layer-2 and layer-3 configurations. FGCP requires that the FortiGates are layer-2 adjacent since they share a virtual MAC address in order to create a single logical firewall. These requirements when using FGCP do not work in asymmetric traffic scenarios or in situations where the FortiGates must have unique IP addresses (Figure 1) for proper function within a network. FGSP is always active-active and must be deployed using unique IP addresses on each interface.Copyright© 2010 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, and FortiGuard®, are registered trademarks of Fortinet, Inc., and otherFortinet names herein may also be trademarks of Fortinet. All other product or company names may be trademarks of their respective owners.Performance metrics contained herein were attained in internal lab tests under ideal conditions. Network variables, different networkenvironments and other conditions may affect performance results, and Fortinet disclaims all warranties, whether express or implied, except tothe extent Fortinet enters a binding contract with a purchaser that expressly warrants that the identified product will perform according to theperformance metrics herein. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’sinternal lab tests. Fortinet disclaims in full any guarantees. Fortinet reserves the right to change, modify, transfer, or otherwise revise thispublication without notice, and the most current version of the publication shall be applicable. Certain Fortinet products are licensed under U.S.Patent No. 5,623,600.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Session A-T3-3 ADVANCED COURSE IN PROGRAMMABLE CONTROLS FOR ENGINEERINGTECHNOLOGYWm. Ted EvansUniversity of Toledo, Toledo, Ohio; Email:wevans@1. INTRODUCTIONProgrammable Logic Controllers (PLCs) have been found in industry since the early 1970’s and the application of PLCs has long been considered a required course for majors in Electrical Engineering Technology. A first course in PLCs is found in most 2 year programs, usually in the sophomore year. Content of a first course includes learning the PLCs instructions, some programming structures and the hardware one or more types of PLC. A second course, preferably taught in the senior year of a four-year technology program, should be structured to maximize the student’s employability. The content of this course is the topic of this paper.The content of the course should include applications of PLCs to both analog and digital processes. The analog portion should include an introduction to the PID algorithm from both from a theoretical and a practical point of view. Digital programs should include a number of more difficult programming applications.Software should be introduced that familiarizes the student with an array of software types needed in the manufacturing environment. Software for Human-Machine-Interface (HMI) development should be included. Also, software to successfully implement a network should be introduced. A list of potential projects including hardware will be discussed. Hardware types will be discussed including recommendations of equipment to purchase.2. COURSE DISTINCTIVESAfter a first course, the emphasis of the material should change dramatically. Emphasis in the first course was to acquire the tools necessary to build a PLC program for control of real time applications. The second course will deal with the aspects of building a system. The second course is intended to build an attitude that very difficult systems problems can be broken down into more manageable parts, each of which can be solved. A basic programming skill level is assumed for success in the second course. What is significantly more difficult than PLC programming is integration of all the components including programming into a complete system. Smart devices such as the Allen-Bradley PanelView operator interface or servo drive are devices used to interface to the PLC instead of push buttons, pilot lights and switches. ThePID instruction and several other more complicated programming instructions are some of the more difficult instructions to master. Listed below are several of the exercises used in this course.3. COMMUNICATIONA WITH PROCESSORSA procedure for attaching to SLC processors using DF-1 and DH-485 is used to demonstrate the multi-faceted approach that most PLC vendors use to attach a computer to the PLC. Methods used are intended to attach and set up the PLC for use as networked device. Also discussed are data highway types, approaches to communicate peer-to- peer and other communication topics in PLC communications.4. HUMAN-MACHINE-INTERFACEThe goal is to create an active interface between the PLC or group of PLCs and the operator. These are called Human-Machine-Interfaces or HMIs. Operators have been required to monitor and interpret much more information in the machine they operate than in the past. As a result, interfaces have become more complex. The operator may be called on to rapidly decide whether the machine is operating correctly or not. Alarms, machine modes, historical data, and real-time decision-making information are necessary to control many machines today.HMIs are divided roughly into two main groups. First is the dedicated HMI, a push-button, numeric data entry replacement device with little capability of storing data-base information for the machine. Typically these HMIs are stand-alone. Second is the HMI that is part of the data-base package used to store and retrieve process information from the machine. These HMIs usually run on a network of computers.Typical of the first group are products such as PanelView and PanelMate. Typical of the second group are products such as Fix Dynamics, Allen-Bradley RSView32 or WonderWare. For simpler applications, the PanelView will be selected. While it is not as sophisticated as the second, the process of building screens is similar. Also, the process of networking the processor to the HMI is similar.5. MSG BLOCKThe Message (MSG) instruction is also studied. A lab was devised that allows the student to send and receive messages between two or more PLCs. Block Transfer instructions are also used in some PLCs to communicate between various devices. Up to 64 words may be transmitted at a time using the Block Transfer Read (BTR) or Block Transfer Write (BTW) instruction. The remote device, however, is a device communicated to through remote I/O and using Allen-Bradley’s I/O files: M0 and M1 as opposed to the MSG instructions.6. PID BLOCKIn its simplest form, the PID block is used as a single block with no input contacts and surrounded by only two Scaling Blocks (Scaling with Parameters – SCP) in the mid-level rack mount SLC 5/03 processor from Allen-Bradley. The SCP blocks are configured to retrieve a numerical value from the analog input channel, linearly scale the input and move the resultant value to the PID block.HMI displays are used to allow the operator to run the process from the display. To run the PID successfully, several parameters should be displayed either to set the process in motion or to adjust the process once it is in motion.A ramp block is a function block that is added in front of a PID block to change the setpoint (SP) over a period of time instead of immediately. It is constructed in the PLC diagram to increment from the old SP to the new SP in increments of 1. More sophisticated ramp blocks allow the ramp rate to be set by an operator or engineer.When the PID block is switched from manual to auto, the function responds to the SP presently available to the block. If the process is sensitive to sudden changes in PID output, the program should include logic to give the output a signal matching the present flow when the block is in manual. This is commonly referred to as bumpless transfer.Processes are described using flow diagrams. Symbols for diagrams are defined by the organization - Instrumentation, Systems, and Automation Society (ISA). Letter codes are written in circles representing various devices that control a process.7. ASCII BLOCKSOnly the ASCII WRITE (AWT) and ASCII READ (ARD) will be used to demonstrate communication between serial devices. The AWT or AWA instruction is appropriate for the Write instruction. Since no appended characters need be appended to the string, the AWT instruction may be preferred. The ASCII blocks demonstrate communication between PLCs and devices such as bar code readers or weigh scales.8. FAULT RECOVERY INSTRUCTIONSChapter 12 of the SLC 500 and MicroLogix 1000 Instruction Set Reference Manual is dedicated to understanding interrupts in the PLC. Four major types of routines are introduced. They are the User Fault, Selectable Timed Interrupt, Discrete Input Interrupt and I/O Interrupt.The User Fault Routine is used to protect the processor from shutting down when a fault occurs. The other three routines interrupt the processor scan and run a program to accomplish a particular high priority task.When a recoverable or non-recoverable user fault occurs, the processor goes to Status Table location S:29 and reads a number corresponding to a program file handling the fault. If the fault is a recoverable fault, the program in the file can correct the problem and clear the fault bit, allowing the processor to fully recover from the fault. Of course, if the problem occurs again, the fault will occur again.9. STEPPER AND SERVO CONTROLOne SLC 5/03 was used to control an automatic storage and retrieval system of pallets. This is commonly referred to as an ASRS. Two different motion control cards were used to control the horizontal and vertical motion of the positioning belts used to move the pallet-extracting device. Although an engineer would not select two different types of control cards to install in such an installation, the two cards selected were a stepper control card and a servo control card. Specifically, the stepper control card was the SLC Stepper Controller Card (1746-HSTP) and the servo card was the SLC Servo Controller Card (1746-HSRV).When starting the program development of the stepper motor, the first object should be to control the drive manually. If possible, the drive should be controlled with a simple test program to give the engineer simple control of the axis. In this case, no program is necessary. Entry of the configuration and command words is seen as all that is necessary to control the drive manually. To configure the SLC Servo Module, data is written to the M0 file, not the Output Data File as was the case with the stepper controller card. Use a copy file to transfer data to the M0 file.10. DEVICE-NET NETWORKDeviceNet is a relatively easy I/O network to install and configure. It will be discussed in part by using a manual from Allen-Bradley, the DeviceNet Starter Kit Installation Manual. DeviceNet is an extension of CanBus. DeviceNet is an easy-to-implement network that uses CanBus as well as additional software drivers to implement industrial networks. The DeviceNet Starter Kit is a good point to introduce the capabilities of an industrial network to students.11. CONTROLOGIXThe ControlLogix platform is suited for the high-end application while the CompactLogix platform is more suited for the lower-end application. Costs are also comparatively lower for the CompactLogix platform.Each of these processor types uses RSLogix 5000 software and can be programmed in a similar manner. Assigning of tags and building of programs is similar through the product line. Creation of tags is one of the first differences found to be a major change from the SLC programming experience. As discussed in the Logix5000 Quick Start Manual, tags are no longer automatically assigned but given names only as the programmer (you) assign them. Tag databases are just that, a data base. With the creation of a new tag, the entire function of that tag is defined. The name is the name used above the contact. The type is a bit, integer, or other type used in the definition of how the data is actually stored.12. SAFETYAllen-Bradley, Jokab and Banner Engineering are only some of a long list of safety equipment manufacturers. Use of information from their catalogs gives an insight into proper design of a circuit as it pertains to safety in an industrial setting13. OTHER PLCsPLCs have moved in many different directions over the last few years. One direction is toward a standardization of languages of the various PLCs so projects can more easily be moved between different hardware platforms. This standardization has become the IEC 1131 specification.14. NETWORKS AND PROTOCOLSIt is not enough to know that everything uses Ethernet and thus be able to ‘get by’ when implementing a modern control network using Ethernet. Knowledge of multitasking is needed as well as a background pertaining to proper configuration of each device on the network on the plant floor. The same Ethernet cable is now be able to transmit office or business data as well as process monitor and control data and embedded device data.15. AUTOCADD ELECTRICALGenerating of electrical schematic drawings can be a very manual task. Either AutoCAD or other graphic package is most often selected and the drawings are generated using a symbol library purchased from a source or created by the user.16. SUMMARYToday, PLC programming involves engineering hours and the money necessary to generate the engineering hours for the job. Companies do not have an infinite supply of either money or hours to appropriate to any project. Programming intelligently is a high priority in today’s engineering environment.Some of the projects listed in the paper are very difficult when studied thoroughly. Two or three weeks of intense work should be allowed to master various aspects of these projects. It is very humbling for some students to even be required to re-learn the basics of logging on to the PLC in order to be able to program on-line.The goal of the second course in PLCs is to aid the student in the interview process to find a good job. In order to do this, the student must be informed and interested in the potential job. If the job includes PLC programming, courses such as the one outlined in this paper should aid in that task.REFERENCESSample of Existing Texts on Programmable Logic ControllersDavid A. Geller, (2005). Programmable Controllers Using the Allen-Bradley SLC-50 Family, Pearson, 2nd Ed.John R. Hackworth, Fred D. Hackworth, (2004). Programmable Logic Controllers – Programming Methods and Application, PearsonHugh Jack, (2003). Automating Manufacturing Systems with PLC’s, unpublishedThomas Kissel, (1986). Understanding and Using Programmable Controllers, PrenHallS. Brian Morriss. (2000). Programmable Logic Controllers, PrenHallJon Stenerson , (2004). Programming PLCs Using Rockwell Automation Controllers, Pearson Jon Stenerson, (2004). Fundamentals of Programmable Logic Controllers, Sensors, and Communications, 3rd Ed., PrenHallFred Swainston, (1992). A Systems Approach to Programmable Controllers, DelmarJohn Webb, Ronald A. Reis, (1999). Programmable Logic Controllers, Principles and Applications, 2nd Ed, PrenHallSystems Manuals used for the Lab Experiences:PanelBuilder 32 Software, Getting Results, Allen-BradleySLC Modular Processors, User Manual, Allen-BradleyDeviceNet Starter Kit Installation Manual, Alley-BradleySLC 500 Instruction Set Reference Manual, Allen-BradleyLogix5000 Quick Start Manual, Allen-Bradley。
