quantum2008-2
应用USTER QUANTUM2型清纱器控制质量的体会

关键词 : 电子清纱器; 参数设置 ; 在线检测; 质量指标 ; 纱疵 一 中 图分类 号 :S0.2 4 文献标 志码 : 文 章编 号 : 0— 1(08 0- 5 - T 131 B 1 1 4 520 }6 01 4 0 7 0 0
E p re cso ai o tol g x ein e fQu lyC nr ln t i b T yUS ER QUANT UM2 Y r e rr a n Cla e
i l id f nl edtc n s m. S E U N U a e c o i c ae nt n ol c a yr eet bt na n s —n e t gs t U T RQ A T M2ym l t nc l r o ol cud l r andf s u lk oo i ei ye e r e r y e c
0 前 言
我公 司主要 生 产 纯 棉精 梳 细 号 紧密 纱 , 产 生 过程 中全部 采用 了 U T R检 测 设备 , SE 主要 试 验仪 器 有 :S E I P C R M 型 大 容 量 测 试 仪 、 U T RHV E T U S
U T RA I S E FS型纤维 测试 仪 、 S E E T R U T R T S E 4型
和F L通 道均 有 Hl~H 66个 辅 助 点 用 于 清纱 设 定 的微调 , 根 据 需要 调节 清 纱 曲 线 。并 且 可 以 可 根 据纱疵 分级 图中管纱 纱疵 的分 布情 况和散 点 图
维普资讯
第3 6卷
第 6期
棉
纺
织
技
术
20 0 8年 6月
Co t n Te te Te h oo y t x i c n lg o l
ProLight PJ2N -FFPE-A 0.5W PC Amber Power LED 技术数据

No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320, 2015/03ProLight PJ2N-FFPE-A0.5W PC Amber Power LED Technical Datasheet Version: 1.0Features‧Good color uniformity ‧Lead free reflow soldering ‧RoHS compliant‧Instant light (less than 100ns)‧No UVIntroduction‧PJ2N qualifies as the JEDEC Level 1 MSL sensitivity level and suitable for SMD process, Pb_free reflow soldering capability, and full compliance with EU Reduction of Hazardous Substances (RoHS) legislation.Main Applications‧Backlighting ‧Signaling‧Exterior Automotive Lighting ‧Automotive Interior LightingEmitter Mechanical DimensionsNotes:1. The anode side of the device is denoted by the chamfer on the part body.2. Drawing not to scale.3. All dimensions are in millimeters.4. Unless otherwise indicated, tolerances are ±0.10mm.5. Please do not solder the emitter by manual hand soldering, otherwise it will damage the emitter.6. Please do not use a force of over 0.3kgf impact or pressure on the lens of the LED, otherwiseit will cause a catastrophic failure.*The appearance and specifications of the product may be modified for improvement without notice.2 No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320,No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320,Optical Characteristics at 150mA, T J = 25° CTotal included Viewing Angle Angle Radiation Color Dominant Wavelength λD (degrees)(degrees)Pattern Min.Typ.Max.θ0.90V2 θ1/2LambertianPC Amber587.8 nm589 nm590.4 nm160120●ProLight maintains a tolerance of ±1nm for dominant wavelength measurements.3Flux Characteristics at 150mA, T J = 25°CElectrical Characteristics at 150mA , T J = 25°CRadiation Pattern Color Part Number Emitter Luminous Flux ΦV (lm)Minimum TypicalLambertianPC AmberPJ2N-FFPE-A3036●ProLight maintains a tolerance of ±7% on flux and power measurements.●Please do not drive at rated current more than 1 second without proper heat sink.Forward Voltage V F (V)Thermal Resistance Color Min.Typ.Max.Junction to Slug (°C/ W)PC Amber2.83.23.625●ProLight maintains a tolerance of ±0.1V for Voltage measurements.No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320, Absolute Maximum RatingsParameterPC AmberDC Forward Current (mA)180Peak Pulsed Forward Current (mA)250 (less than 1/10 duty cycle@1KHz)ESD Sensitivity±4000V (Class III)(HBM per MIL-STD-883E Method 3015.7)LED Junction Temperature 120°C Operating Board Temperature -40°C -105°Cat Maximum DC Forward Current Storage Temperature -40°C -120°C Soldering Temperature JEDEC 020c 260°CAllowable Reflow Cycles 3Reverse VoltageNot designed to be driven in reverse bias4Photometric Luminous Flux Bin StructureColorBin CodeMinimumMaximumAvailable Photometric Flux (lm)Photometric Flux (lm)Color BinsPC AmberQ13035AllQ23540【1】R14045【1】●ProLight maintains a tolerance of ±7% on flux and power measurements.●The flux bin of the product may be modified for improvement without notice. ●【1】The rest of color bins are not 100% ready for order currently. Please ask for quote and order possibility.Dominant Wavelength Bin StructureColor Bin Code Minimum Dominant Maximum Dominant Wavelength (nm)Wavelength (nm)PC Amber2587.8 590.4Note: Although several bins are outlined, product availability in a particular bin varies by production run and by product performance. Not all bins are available in all colors.Forward Voltage Bin StructureColor Bin Code Minimum Voltage (V)Maximum Voltage (V)PC Amber A 2.8 3.0B 3.0 3.2D 3.2 3.4E 3.4 3.6●ProLight maintains a tolerance of ±0.1V for Voltage measurements.5No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320,No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320, Color Bin PC Amber Binning Structure Graphical Representation6Color BinsPC Amber Bin Structure Bin Codex y 20.5620 0.4370 0.5500 0.4240 0.5610 0.4160 0.57300.4260●Tolerance on each color bin (x , y) is ±0.0050.360.380.400.420.440.460.480.500.52 0.54 0.56 0.58 0.60 0.62yxPlanckian(BBL)2PC AmberSpectrum Locuswd = 587.8 nmwd = 590.4 nmNo. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320, Color Spectrum, T J = 25°C1. PC Amber70.00.20.40.60.81.0350400450500550600650700750800850R e l a t i v e S p e c t r a l P o w e r D i s t r i b u t i o nWavelength (nm)Light Output CharacteristicsRelative Light Output vs. Junction Temperature at 150mA020406080100120140160020406080100120R e l a t i v e L i g h t O u t p u t (%)Junction Temperature, T J (℃)PC AmberNo. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320, 03060901201501802100255075100125150F o r w a r d C u r r e n t (m A )Ambient Temperature (℃)0204060801001201401600.511.522.533.54A v e r a g e F o r w a r d C u r r e n t (m A )Forward Voltage (V)0.00.20.40.60.81.01.250100150200R e l a t i v e L u m i n o u s F l u xForward Current (mA)R θJ-A = 90°C/W R θJ-A = 75°C/W R θJ-A = 45°C/WR θJ-A = 60°C/W Forward Current Characteristics, T J = 25°CFig 1. Forward Current vs. ForwardVoltage for PC Amber.Fig 2. Relative Luminous Flux vs.Forward Current for PC Amber at T J =25 maintained.8Ambient Temperature vs. Maximum Forward Current1. PC Amber (T JMAX = 120°C)No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320, Typical Representative Spatial Radiation PatternLambertian Radiation Pattern90102030405060708090100-100-80-60-40-2020406080100R e l a t i v e I n t e n s i t y (%)Angular Displacement (Degrees)Soak RequirementsLevel Floor Life Standard Accelerated Environment Time Conditions Time (hours)Conditions Time (hours)Conditions1Unlimited≤30°C /168 +5/-085°C /NA NA 85% RH85% RH●The standard soak time includes a default value of 24 hours for semiconductor manufature'sexposure time (MET) between bake and bag and includes the maximum time allowed out ofthe bag at the distributor's facility.●Table below presents the moisture sensitivity level definitions per IPC/JEDEC's J-STD-020C.Soak Requirements Level Floor Life Standard Accelerated Environment Time Conditions Time (hours)Conditions Time (hours)Conditions1Unlimited≤30°C /168 +5/-085°C /NA NA 85% RH85% RH2 1 year≤30°C /168 +5/-085°C /NA NA 60% RH60% RH2a 4 weeks≤30°C /696 +5/-030°C /120 +1/-060°C / 60% RH60% RH60% RH3168 hours≤30°C /192 +5/-030°C /40 +1/-060°C / 60% RH60% RH60% RH472 hours≤30°C /96 +2/-030°C /20 +0.5/-060°C / 60% RH60% RH60% RH548 hours≤30°C /72 +2/-030°C /15 +0.5/-060°C / 60% RH60% RH60% RH5a24 hours≤30°C /48 +2/-030°C /10 +0.5/-060°C / 60% RH60% RH60% RH6Time on Label≤30°C / Time on Label30°C /NA NA (TOL)60% RH(TOL)60% RHMoisture Sensitivity Level -JEDEC Level 1No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320,10No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320, Stress TestStress Conditions Stress Duration Failure CriteriaRoom Temperature 25°C, I F = max DC (Note 1)1000 hours Note 2Operating Life (RTOL)Wet High Temperature 85°C/60%RH, I F = max DC (Note 1)1000 hours Note 2Operating Life (WHTOL)Wet High Temperature 85°C/85%RH, non-operating1000 hours Note 2Storage Life (WHTSL)High Temperature 110°C, non-operating 1000 hours Note 2Storage Life (HTSL)Low Temperature -40°C, non-operating 1000 hours Note 2Storage Life (LTSL)Non-operating-40°C to 120°C, 30 min. dwell,200 cyclesNote 2Temperature Cycle (TMCL)<5 min. transferMechanical Shock 1500 G, 0.5 msec. pulse, Note 35 shocks each 6 axis Natural Drop On concrete from 1.2 m, 3X Note 3Variable Vibration10-2000-10 Hz, log or linear sweep rate,Note 3Frequency20 G about 1 min., 1.5 mm, 3X/axisSolder Heat Resistance260°C ±5°C, 10 sec.Note 3(SHR)SolderabilitySteam age for 16 hrs., then solder dipSolder coverageat 260°C for 5 sec.on leadNotes:1. Depending on the maximum derating curve.2. Criteria for judging failureItemTest Condition Criteria for Judgement Min.Max.Forward Voltage (V F )I F = max DC --Initial Level x 1.1Luminous Flux or I F = max DCInitial Level x 0.7--Radiometric Power (ΦV )* The test is performed after the LED is cooled down to the room temperature.3. A failure is an LED that is open or shorted.11Qualification Reliability TestingNo. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320, TYPE A.12Recommended Solder Pad DesignStandard Emitter ●All dimensions are in millimeters.TYPE B.No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320, 13Reflow Soldering ConditionProfile FeatureSn-Pb Eutectic Assembly Pb-Free Assembly Average Ramp-Up Rate 3°C / second max.3°C / second max.(T Smax to T P )Preheat–Temperature Min (T Smin )100°C 150°C –Temperature Max (T Smax )150°C 200°C –Time (t Smin to t Smax )60-120 seconds 60-180 seconds Time maintained above:–Temperature (T L )183°C 217°C –Time (t L )60-150 seconds60-150 secondsPeak/Classification Temperature (T P )240°C 260°C Time Within 5°C of Actual Peak 10-30 seconds 20-40 seconds Temperature (t P )Ramp-Down Rate6°C/second max.6°C/second max.Time 25°C to Peak Temperature6 minutes max.8 minutes max.●We recommend using the M705-S101-S4 solder paste from SMIC (Senju Metal Industry Co., Ltd.) for lead-free soldering.●Do not use solder pastes with post reflow flux residue>47%. (58Bi-42Sn eutectic alloy, etc) This kind of solder pastes may cause a reliability problem to LED.●All temperatures refer to topside of the package, measured on the package body surface.●Repairing should not be done after the LEDs have been soldered. When repairing is unavoidable, a double-head soldering iron should be used. It should be confirmed beforehand whether the characteristics of the LEDs will or will not be damaged by repairing.●Reflow soldering should not be done more than three times.●When soldering, do not put stress on the LEDs during heating.●After soldering, do not warp the circuit board.t 25°C to Peakt S PreheatTimeT e m p e r a t u r eCritical Zone T L to T PRamp-upRamp-downT SmaxT Smint Pt LT PT L25IPC-020cNotes:1. Drawing not to scale.2. All dimensions are in millimeters.3. Unless otherwise indicated, tolerances are ±0.10mm.14 No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320,Notes:1. Empty component pockets sealed with top cover tape.2. 3000 pieces per reel.3. Drawing not to scale.4. All dimensions are in millimeters.15 No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320,Precaution for Use●StoragePlease do not open the moisture barrier bag (MBB) more than one week. This may cause theleads of LED discoloration. We recommend storing ProLight’s LEDs in a dry box after openingthe MBB. The recommended storage conditions are temperature 5 to 30°C and humidity lessthan 40% RH. It is also recommended to return the LEDs to the MBB and to reseal the MBB.●The slug is is not electrically neutral. Therefore, we recommend to isolate the heat sink.●We recommend using the M705-S101-S4 solder paste from SMIC (Senju Metal IndustryCo., Ltd.) for lead-free soldering.●Do not use solder pastes with post reflow flux residue>47%. (58Bi-42Sn eutectic alloy, etc) Thiskind of solder pastes may cause a reliability problem to LED.●Any mechanical force or any excess vibration shall not be accepted to apply during coolingprocess to normal temperature after soldering.●Please avoid rapid cooling after soldering.●Components should not be mounted on warped direction of PCB.●Repairing should not be done after the LEDs have been soldered. When repairing is unavoidable,a heat plate should be used. It should be confirmed beforehand whether the characteristics ofthe LEDs will or will not be damaged by repairing.●This device should not be used in any type of fluid such as water, oil, organic solvent and etc.When cleaning is required, isopropyl alcohol should be used.●When the LEDs are illuminating, operating current should be decide after considering thepackage maximum temperature.●The appearance, specifications and flux bin of the product may be modified for improvementwithout notice. Please refer to the below website for the latest datasheets./Handling of Silicone LEDsNotes for handling of silicone LEDs●Please do not use a force of over 0.3kgf impact or pressure on the silicone ,otherwise it will cause a catastrophic failure.●The LEDs should only be picked up by making contact with the sides of the LED body.●Avoid touching the silicone especially by sharp tools such as Tweezers.●Avoid leaving fingerprints on the silicone.●Please store the LEDs away from dusty areas or seal the product against dust.●When populating boards in SMT production, there are basically no restrictionsregarding the form of the pick and place nozzle, except that mechanical pressureon the silicone lens must be prevented.●Please do not mold over the silicone lens with another resin. (epoxy, urethane, etc)16 No. 89, Xiyuan Rd., Zhongli City, Taoyuan County 320,。
EP2C8Q208C8中文资料(Altera)中文数据手册「EasyDatasheet - 矽搜」

Cyclone II器件手册,第1卷ii内容章修订日期............................................... ............................喜关于本手册............................................... .............................十三如何触点Altera ..........................................................................................................................十三印刷约定....................................................................................................................十三第一节Cyclone II器件系列数据表修订记录.................................................................................................................................... 1-1第1章简介简介............................................................................................................................................低成本嵌入式处理解决方案............................................ ......................................低成本DSP解决方案.................................................................................................................特征...................................................................................................................................................参考文献.........................................................................................................................文档修订历史记录.................................................................................................................1–1 1–1 1–1 1–2 1–9 1–9第2章Cyclone II架构功能说明.......................................................................................................................... 2-1逻辑元件....................................................................................................................................... 2-2LE操作模式........................................................................................................................ 2-4逻辑阵列模块................................................................................................................................ 2-7LAB互连............................................................................................................................ 2-8LAB控制信号......................................................................................................................... 2-8MultiTrack互联..................................................................................................................... 2-10行互连.......................................................................................................................... 2-10列互连.................................................................................................................... 2-12设备路由............................................................................................................................... 2-15全局时钟网络和锁相环.......................................... ..................................... 2-16专用时钟管脚..................................................................................................................... 2-20双用时钟引脚.............................................................................................................. 2-20全局时钟网络................................................................................................................... 2-21全局时钟网络分布.............................................. .............................................. 2-23锁相环.................................................................................................................................................. 2-25嵌入式存储器............................................................................................................................. 2-27内存模式............................................................................................................................... 2-30时钟模式.................................................................................................................................... 2-31M4K路由接口.................................................................................................................. 2-31iii内容嵌入式乘法器........................................................................................................................乘法器模式............................................................................................................................嵌入式乘法器路由接口.............................................. .......................................I / O结构及特点....................................................................................................................外部存储器接口.......................................................................................................可编程驱动强度.....................................................................................................漏极开路输出........................................................................................................................摆率控制...........................................................................................................................总线防护持..........................................................................................................................................可编程上拉电阻............................................. .................................................. ...高级I / O标准支持............................................ .................................................. ..高速差分接口............................................. .................................................系列片上端接.........................................................................................................I / O组........................................................................................................................................多电压I / O接口.................................................................................................................2–32 2–35 2–36 2–37 2–44 2–49 2–50 2–51 2–51 2–51 2–52 2–53 2–55 2–57 2–60第3章配置与测试IEEE标准. 1149.1(JTAG)边界扫描支持........................................... ..................................构造.........................................................................................................................................操作模式...................................................................................................................................配置计划......................................................................................................................... Cyclone II自动单粒子翻转检测........................................... ...........................定制电路....................................................................................................................软件界面.............................................................................................................................文档修订历史记录.................................................................................................................3–1 3–5 3–5 3–6 3–7 3–7 3–7 3–8第4章热插拔和上电复位简介............................................................................................................................................旋风II热插拔规格............................................ ................................................设备可以在电源时会驱动.......................................... ...........................................I / O引脚防护持三态电期间...................................... ......................................在Cyclone II器件热插拔功能实现......................................... ..............上电复位电路...................................................................................................................."唤醒"时间Cyclone II器件........................................ ...............................................结论..............................................................................................................................................文档修订历史记录.................................................................................................................4–1 4–1 4–2 4–2 4–3 4–5 4–5 4–7 4–7第5章直流特性和时序规范运行条件........................................................................................................................... 5-1单端I / O标准.......................................................................................................... 5-5差分I / O标准.............................................................................................................. 5-7DC特性不同针类型............................................ ......................................... 5-11片上端接规格............................................. .............................................. 5-12能量消耗........................................................................................................................... 5-13时序规格.......................................................................................................................... 5-14预,决赛时序规范............................................. ................................ 5-14演出.................................................................................................................................... 5-15 ivCyclone II器件手册,第1卷内容内部时序...............................................................................................................................Cyclone II时钟时序参数............................................. ..............................................时钟网络偏移加法器.......................................................................................................IOE可编程延迟.............................................................................................................不同I默认容性负载/ O标准......................................... .................I / O延迟.......................................................................................................................................最大输入和输出时钟频率............................................ ........................................高速I / O时序规格........................................... ............................................外部存储器接口规范.............................................. ....................................JTAG时序规范..........................................................................................................PLL时序规范............................................................................................................占空比失真.........................................................................................................................DCD测量技术............................................... .................................................. ..参考文献.......................................................................................................................文档修订历史记录...............................................................................................................5–18 5–23 5–29 5–30 5–31 5–33 5–46 5–55 5–63 5–64 5–66 5–67 5–68 5–74 5–74第6章参考和订购信息软体..................................................................................................................................................器件引脚输出.....................................................................................................................................订购信息...........................................................................................................................文档修订历史记录.................................................................................................................6–1 6–1 6–1 6–2第二节.时钟管理修订记录.................................................................................................................................... 6-1第7章锁相环在Cyclone II器件简介............................................................................................................................................ 7-1Cyclone II PLL硬件概述............................................. .................................................. ... 7-2PLL参考时钟产生.............................................. .................................................. ... 7-6时钟反馈模式....................................................................................................................... 7-10正常模式.................................................................................................................................. 7-10零延迟缓冲器模式................................................................................................................ 7-11无补偿模式............................................................................................................... 7-12源同步模式........................................................................................................... 7-13硬件特性.............................................................................................................................. 7-14时钟倍频和科.............................................. .................................................. .. 7-14可编程占空比........................................................................................................... 7-15移相实施.............................................. .................................................. .... 7-16控制信号................................................................................................................................ 7-17手动时钟切换............................................................................................................. 7-20时钟................................................................................................................................................ 7-21全局时钟网络................................................................................................................... 7-21时钟控制模块....................................................................................................................... 7-24全局时钟网络时钟源产生............................................ .......................... 7-26全局时钟网络掉电............................................. .............................................. 7-28vCyclone II器件手册,第1卷。
原子物理学第2章原子的量子态全解

的温度升高时,单色辐射能量密度
最大值向短波方向移动.
0 1 2 3 4 λ(µm) 绝对黑体辐射能量密度按波长分布(实验)曲线
第二章 原子的量子态:玻尔模型
Manufacture: Zhu Qiao Zhong
4
物体辐射总能量按波长分布决定于温度.
800K
1000K
1200K
固体在温度升高时颜色的变化
矛盾二:经典的光强和时间决定光电流大小;而光电效应中只有 在光的频率大于红限时才会发生光电效应.
矛盾三:经典的驰豫时间(or:响应时间)较长 (若光强很小,电 子需较长时间吸收足够能量才能逸出),而光电效应不超过10-9s.
实验表明:光强为1μW/m2的光照射到钠靶上即有光电流产生, 这相当于500W的光源照在6.3km处的钠靶.
第二章 原子的量子态:玻尔模型
Manufacture: Zhu Qiao Zhong
10
“在目前业已基本建成的科学大厦中,物理学家似乎只要 做一些零碎的修补工作就行了;然而在物理学晴朗天空的 远处,还飘着两朵令人不安的愁云.”
——《19世纪笼罩在热和光的动力论上的阴影》 1900年4月27日于不列颠皇家科学院
1)光电流与入射光强度的关系
光电子
单色光
I
e
Is
A
V
遏止电压
光强较强 光强较弱
第二章 原子的量子态:玻尔模型
Ua o
U
Manufacture: Zhu Qiao Zhong
15
第二章 原子的量子态:玻尔模型
Manufacture: Zhu Qiao Zhong
16
2)光电子初动能与入射光频率呈线性关系,而与入射光强度
USTER [ОR]QUANTUM2控制异纤
![USTER [ОR]QUANTUM2控制异纤](https://img.taocdn.com/s3/m/4934e920cfc789eb172dc83a.png)
梳 理机 的新 型 传 动 系统
进 行链 接 , 通过触 摸 屏人 机 界面 操 作简 单 。它 可 以 让 使 用 者从 传 动 系统 中不 断地 获 得 工 艺 中 所 有 重 要运 动 的反 馈 信 息 。优 点 是 工 艺
告, 用户应该多关注这些装置。
目前 , 英 国和澳 大 利亚 正 在 在 使用 的 T s同 步 传 动 系 统 共 有 l 2 个 , 且还有 一 些 已经被 预 定 。地 而
测量纤维密度的短片段和长片段
的变 化 , 以及控 制速 度 以生产 出 重
能, 也被 应用在 试验 中。
从图 1 中的散点图上看到 , 总 的 F 异纤切次为每十万米4. 个。 F 1 2
在这种情况下 , 将植物纤维过滤功
国 际纺织导 报 2 0 0 7年第 1 1期
图 3 U T R Q A T M 2F S E U N U F异纤清纱器
3 5
纤维加 工线上棉箱中原料的喂入
量。
专家 可 以组 装 、 测 , 监 如有 必 要 还
能 通过快 速 、 安全 的因 特 网在 任 何
一
微 型喂入 T : s 以连续的纤 维重 量监测 为基础 , 通过 自动 调节
一
传动 系统开发 的合 作伙伴是 工业 控 制产品 的一个 主 要 供应 商 , 这种传动系统已首次用于纺织中。 T s同步传动 系统具有 很多优点 , 表 现 为通过使 用更 高效 、 灵 活的 更
传 动系统 , 除了启 动 和停 机 时 的 消 电流尖 峰 和 扭 矩 波动 的 问题 。 T s
系统同样是以 P C为基础的, L 而且 已经升级为 T 系列的一部分。 s 微 型 称 重 T : 一 种 先 进 s是
Quantum Computing for Computer Scientists

More informationQuantum Computing for Computer ScientistsThe multidisciplinaryfield of quantum computing strives to exploit someof the uncanny aspects of quantum mechanics to expand our computa-tional horizons.Quantum Computing for Computer Scientists takes read-ers on a tour of this fascinating area of cutting-edge research.Writtenin an accessible yet rigorous fashion,this book employs ideas and tech-niques familiar to every student of computer science.The reader is notexpected to have any advanced mathematics or physics background.Af-ter presenting the necessary prerequisites,the material is organized tolook at different aspects of quantum computing from the specific stand-point of computer science.There are chapters on computer architecture,algorithms,programming languages,theoretical computer science,cryp-tography,information theory,and hardware.The text has step-by-stepexamples,more than two hundred exercises with solutions,and program-ming drills that bring the ideas of quantum computing alive for today’scomputer science students and researchers.Noson S.Yanofsky,PhD,is an Associate Professor in the Departmentof Computer and Information Science at Brooklyn College,City Univer-sity of New York and at the PhD Program in Computer Science at TheGraduate Center of CUNY.Mirco A.Mannucci,PhD,is the founder and CEO of HoloMathics,LLC,a research and development company with a focus on innovative mathe-matical modeling.He also serves as Adjunct Professor of Computer Sci-ence at George Mason University and the University of Maryland.QUANTUM COMPUTING FORCOMPUTER SCIENTISTSNoson S.YanofskyBrooklyn College,City University of New YorkandMirco A.MannucciHoloMathics,LLCMore informationMore informationcambridge university pressCambridge,New York,Melbourne,Madrid,Cape Town,Singapore,S˜ao Paulo,DelhiCambridge University Press32Avenue of the Americas,New York,NY10013-2473,USAInformation on this title:/9780521879965C Noson S.Yanofsky and Mirco A.Mannucci2008This publication is in copyright.Subject to statutory exceptionand to the provisions of relevant collective licensing agreements,no reproduction of any part may take place withoutthe written permission of Cambridge University Press.First published2008Printed in the United States of AmericaA catalog record for this publication is available from the British Library.Library of Congress Cataloging in Publication dataYanofsky,Noson S.,1967–Quantum computing for computer scientists/Noson S.Yanofsky andMirco A.Mannucci.p.cm.Includes bibliographical references and index.ISBN978-0-521-87996-5(hardback)1.Quantum computers.I.Mannucci,Mirco A.,1960–II.Title.QA76.889.Y352008004.1–dc222008020507ISBN978-0-521-879965hardbackCambridge University Press has no responsibility forthe persistence or accuracy of URLs for external orthird-party Internet Web sites referred to in this publicationand does not guarantee that any content on suchWeb sites is,or will remain,accurate or appropriate.More informationDedicated toMoishe and Sharon Yanofskyandto the memory ofLuigi and Antonietta MannucciWisdom is one thing:to know the tho u ght by which all things are directed thro u gh allthings.˜Heraclitu s of Ephe s u s(535–475B C E)a s quoted in Dio g ene s Laertiu s’sLives and Opinions of Eminent PhilosophersBook IX,1. More informationMore informationContentsPreface xi1Complex Numbers71.1Basic Definitions81.2The Algebra of Complex Numbers101.3The Geometry of Complex Numbers152Complex Vector Spaces292.1C n as the Primary Example302.2Definitions,Properties,and Examples342.3Basis and Dimension452.4Inner Products and Hilbert Spaces532.5Eigenvalues and Eigenvectors602.6Hermitian and Unitary Matrices622.7Tensor Product of Vector Spaces663The Leap from Classical to Quantum743.1Classical Deterministic Systems743.2Probabilistic Systems793.3Quantum Systems883.4Assembling Systems974Basic Quantum Theory1034.1Quantum States1034.2Observables1154.3Measuring1264.4Dynamics1294.5Assembling Quantum Systems1325Architecture1385.1Bits and Qubits138viiMore informationviii Contents5.2Classical Gates1445.3Reversible Gates1515.4Quantum Gates1586Algorithms1706.1Deutsch’s Algorithm1716.2The Deutsch–Jozsa Algorithm1796.3Simon’s Periodicity Algorithm1876.4Grover’s Search Algorithm1956.5Shor’s Factoring Algorithm2047Programming Languages2207.1Programming in a Quantum World2207.2Quantum Assembly Programming2217.3Toward Higher-Level Quantum Programming2307.4Quantum Computation Before Quantum Computers2378Theoretical Computer Science2398.1Deterministic and Nondeterministic Computations2398.2Probabilistic Computations2468.3Quantum Computations2519Cryptography2629.1Classical Cryptography2629.2Quantum Key Exchange I:The BB84Protocol2689.3Quantum Key Exchange II:The B92Protocol2739.4Quantum Key Exchange III:The EPR Protocol2759.5Quantum Teleportation27710Information Theory28410.1Classical Information and Shannon Entropy28410.2Quantum Information and von Neumann Entropy28810.3Classical and Quantum Data Compression29510.4Error-Correcting Codes30211Hardware30511.1Quantum Hardware:Goals and Challenges30611.2Implementing a Quantum Computer I:Ion Traps31111.3Implementing a Quantum Computer II:Linear Optics31311.4Implementing a Quantum Computer III:NMRand Superconductors31511.5Future of Quantum Ware316Appendix A Historical Bibliography of Quantum Computing319 by Jill CirasellaA.1Reading Scientific Articles319A.2Models of Computation320More informationContents ixA.3Quantum Gates321A.4Quantum Algorithms and Implementations321A.5Quantum Cryptography323A.6Quantum Information323A.7More Milestones?324Appendix B Answers to Selected Exercises325Appendix C Quantum Computing Experiments with MATLAB351C.1Playing with Matlab351C.2Complex Numbers and Matrices351C.3Quantum Computations354Appendix D Keeping Abreast of Quantum News:QuantumComputing on the Web and in the Literature357by Jill CirasellaD.1Keeping Abreast of Popular News357D.2Keeping Abreast of Scientific Literature358D.3The Best Way to Stay Abreast?359Appendix E Selected Topics for Student Presentations360E.1Complex Numbers361E.2Complex Vector Spaces362E.3The Leap from Classical to Quantum363E.4Basic Quantum Theory364E.5Architecture365E.6Algorithms366E.7Programming Languages368E.8Theoretical Computer Science369E.9Cryptography370E.10Information Theory370E.11Hardware371Bibliography373Index381More informationPrefaceQuantum computing is a fascinating newfield at the intersection of computer sci-ence,mathematics,and physics,which strives to harness some of the uncanny as-pects of quantum mechanics to broaden our computational horizons.This bookpresents some of the most exciting and interesting topics in quantum computing.Along the way,there will be some amazing facts about the universe in which we liveand about the very notions of information and computation.The text you hold in your hands has a distinctflavor from most of the other cur-rently available books on quantum computing.First and foremost,we do not assumethat our reader has much of a mathematics or physics background.This book shouldbe readable by anyone who is in or beyond their second year in a computer scienceprogram.We have written this book specifically with computer scientists in mind,and tailored it accordingly:we assume a bare minimum of mathematical sophistica-tion,afirst course in discrete structures,and a healthy level of curiosity.Because thistext was written specifically for computer people,in addition to the many exercisesthroughout the text,we added many programming drills.These are a hands-on,funway of learning the material presented and getting a real feel for the subject.The calculus-phobic reader will be happy to learn that derivatives and integrals are virtually absent from our text.Quite simply,we avoid differentiation,integra-tion,and all higher mathematics by carefully selecting only those topics that arecritical to a basic introduction to quantum computing.Because we are focusing onthe fundamentals of quantum computing,we can restrict ourselves to thefinite-dimensional mathematics that is required.This turns out to be not much more thanmanipulating vectors and matrices with complex entries.Surprisingly enough,thelion’s share of quantum computing can be done without the intricacies of advancedmathematics.Nevertheless,we hasten to stress that this is a technical textbook.We are not writing a popular science book,nor do we substitute hand waving for rigor or math-ematical precision.Most other texts in thefield present a primer on quantum mechanics in all its glory.Many assume some knowledge of classical mechanics.We do not make theseassumptions.We only discuss what is needed for a basic understanding of quantumxiMore informationxii Prefacecomputing as afield of research in its own right,although we cite sources for learningmore about advanced topics.There are some who consider quantum computing to be solely within the do-main of physics.Others think of the subject as purely mathematical.We stress thecomputer science aspect of quantum computing.It is not our intention for this book to be the definitive treatment of quantum computing.There are a few topics that we do not even touch,and there are severalothers that we approach briefly,not exhaustively.As of this writing,the bible ofquantum computing is Nielsen and Chuang’s magnificent Quantum Computing andQuantum Information(2000).Their book contains almost everything known aboutquantum computing at the time of its publication.We would like to think of ourbook as a usefulfirst step that can prepare the reader for that text.FEATURESThis book is almost entirely self-contained.We do not demand that the reader comearmed with a large toolbox of skills.Even the subject of complex numbers,which istaught in high school,is given a fairly comprehensive review.The book contains many solved problems and easy-to-understand descriptions.We do not merely present the theory;rather,we explain it and go through severalexamples.The book also contains many exercises,which we strongly recommendthe serious reader should attempt to solve.There is no substitute for rolling up one’ssleeves and doing some work!We have also incorporated plenty of programming drills throughout our text.These are hands-on exercises that can be carried out on your laptop to gain a betterunderstanding of the concepts presented here(they are also a great way of hav-ing fun).We hasten to point out that we are entirely language-agnostic.The stu-dent should write the programs in the language that feels most comfortable.Weare also paradigm-agnostic.If declarative programming is your favorite method,gofor it.If object-oriented programming is your game,use that.The programmingdrills build on one another.Functions created in one programming drill will be usedand modified in later drills.Furthermore,in Appendix C,we show how to makelittle quantum computing emulators with MATLAB or how to use a ready-madeone.(Our choice of MATLAB was dictated by the fact that it makes very easy-to-build,quick-and-dirty prototypes,thanks to its vast amount of built-in mathematicaltools.)This text appears to be thefirst to handle quantum programming languages in a significant way.Until now,there have been only research papers and a few surveyson the topic.Chapter7describes the basics of this expandingfield:perhaps some ofour readers will be inspired to contribute to quantum programming!This book also contains several appendices that are important for further study:Appendix A takes readers on a tour of major papers in quantum computing.This bibliographical essay was written by Jill Cirasella,Computational SciencesSpecialist at the Brooklyn College Library.In addition to having a master’s de-gree in library and information science,Jill has a master’s degree in logic,forwhich she wrote a thesis on classical and quantum graph algorithms.This dualbackground uniquely qualifies her to suggest and describe further readings.More informationPreface xiii Appendix B contains the answers to some of the exercises in the text.Othersolutions will also be found on the book’s Web page.We strongly urge studentsto do the exercises on their own and then check their answers against ours.Appendix C uses MATLAB,the popular mathematical environment and an es-tablished industry standard,to show how to carry out most of the mathematicaloperations described in this book.MATLAB has scores of routines for manip-ulating complex matrices:we briefly review the most useful ones and show howthe reader can quickly perform a few quantum computing experiments with al-most no effort,using the freely available MATLAB quantum emulator Quack.Appendix D,also by Jill Cirasella,describes how to use online resources to keepup with developments in quantum computing.Quantum computing is a fast-movingfield,and this appendix offers guidelines and tips forfinding relevantarticles and announcements.Appendix E is a list of possible topics for student presentations.We give briefdescriptions of different topics that a student might present before a class of hispeers.We also provide some hints about where to start looking for materials topresent.ORGANIZATIONThe book begins with two chapters of mathematical preliminaries.Chapter1con-tains the basics of complex numbers,and Chapter2deals with complex vectorspaces.Although much of Chapter1is currently taught in high school,we feel thata review is in order.Much of Chapter2will be known by students who have had acourse in linear algebra.We deliberately did not relegate these chapters to an ap-pendix at the end of the book because the mathematics is necessary to understandwhat is really going on.A reader who knows the material can safely skip thefirsttwo chapters.She might want to skim over these chapters and then return to themas a reference,using the index and the table of contents tofind specific topics.Chapter3is a gentle introduction to some of the ideas that will be encountered throughout the rest of the ing simple models and simple matrix multipli-cation,we demonstrate some of the fundamental concepts of quantum mechanics,which are then formally developed in Chapter4.From there,Chapter5presentssome of the basic architecture of quantum computing.Here one willfind the notionsof a qubit(a quantum generalization of a bit)and the quantum analog of logic gates.Once Chapter5is understood,readers can safely proceed to their choice of Chapters6through11.Each chapter takes its title from a typical course offered in acomputer science department.The chapters look at that subfield of quantum com-puting from the perspective of the given course.These chapters are almost totallyindependent of one another.We urge the readers to study the particular chapterthat corresponds to their favorite course.Learn topics that you likefirst.From thereproceed to other chapters.Figure0.1summarizes the dependencies of the chapters.One of the hardest topics tackled in this text is that of considering two quan-tum systems and combining them,or“entangled”quantum systems.This is donemathematically in Section2.7.It is further motivated in Section3.4and formallypresented in Section4.5.The reader might want to look at these sections together.xivPrefaceFigure 0.1.Chapter dependencies.There are many ways this book can be used as a text for a course.We urge instructors to find their own way.May we humbly suggest the following three plans of action:(1)A class that provides some depth might involve the following:Go through Chapters 1,2,3,4,and 5.Armed with that background,study the entirety of Chapter 6(“Algorithms”)in depth.One can spend at least a third of a semester on that chapter.After wrestling a bit with quantum algorithms,the student will get a good feel for the entire enterprise.(2)If breadth is preferred,pick and choose one or two sections from each of the advanced chapters.Such a course might look like this:(1),2,3,4.1,4.4,5,6.1,7.1,9.1,10.1,10.2,and 11.This will permit the student to see the broad outline of quantum computing and then pursue his or her own path.(3)For a more advanced class (a class in which linear algebra and some mathe-matical sophistication is assumed),we recommend that students be told to read Chapters 1,2,and 3on their own.A nice course can then commence with Chapter 4and plow through most of the remainder of the book.If this is being used as a text in a classroom setting,we strongly recommend that the students make presentations.There are selected topics mentioned in Appendix E.There is no substitute for student participation!Although we have tried to include many topics in this text,inevitably some oth-ers had to be left out.Here are a few that we omitted because of space considera-tions:many of the more complicated proofs in Chapter 8,results about oracle computation,the details of the (quantum)Fourier transforms,and the latest hardware implementations.We give references for further study on these,as well as other subjects,throughout the text.More informationMore informationPreface xvANCILLARIESWe are going to maintain a Web page for the text at/∼noson/qctext.html/The Web page will containperiodic updates to the book,links to interesting books and articles on quantum computing,some answers to certain exercises not solved in Appendix B,anderrata.The reader is encouraged to send any and all corrections tonoson@Help us make this textbook better!ACKNOLWEDGMENTSBoth of us had the great privilege of writing our doctoral theses under the gentleguidance of the recently deceased Alex Heller.Professor Heller wrote the follow-ing1about his teacher Samuel“Sammy”Eilenberg and Sammy’s mathematics:As I perceived it,then,Sammy considered that the highest value in mathematicswas to be found,not in specious depth nor in the overcoming of overwhelmingdifficulty,but rather in providing the definitive clarity that would illuminate itsunderlying order.This never-ending struggle to bring out the underlying order of mathematical structures was always Professor Heller’s everlasting goal,and he did his best to passit on to his students.We have gained greatly from his clarity of vision and his viewof mathematics,but we also saw,embodied in a man,the classical and sober ideal ofcontemplative life at its very best.We both remain eternally grateful to him.While at the City University of New York,we also had the privilege of inter-acting with one of the world’s foremost logicians,Professor Rohit Parikh,a manwhose seminal contributions to thefield are only matched by his enduring com-mitment to promote younger researchers’work.Besides opening fascinating vis-tas to us,Professor Parikh encouraged us more than once to follow new directionsof thought.His continued professional and personal guidance are greatly appre-ciated.We both received our Ph.D.’s from the Department of Mathematics in The Graduate Center of the City University of New York.We thank them for providingus with a warm and friendly environment in which to study and learn real mathemat-ics.Thefirst author also thanks the entire Brooklyn College family and,in partic-ular,the Computer and Information Science Department for being supportive andvery helpful in this endeavor.1See page1349of Bass et al.(1998).More informationxvi PrefaceSeveral faculty members of Brooklyn College and The Graduate Center were kind enough to read and comment on parts of this book:Michael Anshel,DavidArnow,Jill Cirasella,Dayton Clark,Eva Cogan,Jim Cox,Scott Dexter,EdgarFeldman,Fred Gardiner,Murray Gross,Chaya Gurwitz,Keith Harrow,JunHu,Yedidyah Langsam,Peter Lesser,Philipp Rothmaler,Chris Steinsvold,AlexSverdlov,Aaron Tenenbaum,Micha Tomkiewicz,Al Vasquez,Gerald Weiss,andPaula Whitlock.Their comments have made this a better text.Thank you all!We were fortunate to have had many students of Brooklyn College and The Graduate Center read and comment on earlier drafts:Shira Abraham,RachelAdler,Ali Assarpour,Aleksander Barkan,Sayeef Bazli,Cheuk Man Chan,WeiChen,Evgenia Dandurova,Phillip Dreizen,C.S.Fahie,Miriam Gutherc,RaveHarpaz,David Herzog,Alex Hoffnung,Matthew P.Johnson,Joel Kammet,SerdarKara,Karen Kletter,Janusz Kusyk,Tiziana Ligorio,Matt Meyer,James Ng,SeverinNgnosse,Eric Pacuit,Jason Schanker,Roman Shenderovsky,Aleksandr Shnayder-man,Rose B.Sigler,Shai Silver,Justin Stallard,Justin Tojeira,John Ma Sang Tsang,Sadia Zahoor,Mark Zelcer,and Xiaowen Zhang.We are indebted to them.Many other people looked over parts or all of the text:Scott Aaronson,Ste-fano Bettelli,Adam Brandenburger,Juan B.Climent,Anita Colvard,Leon Ehren-preis,Michael Greenebaum,Miriam Klein,Eli Kravits,Raphael Magarik,JohnMaiorana,Domenico Napoletani,Vaughan Pratt,Suri Raber,Peter Selinger,EvanSiegel,Thomas Tradler,and Jennifer Whitehead.Their criticism and helpful ideasare deeply appreciated.Thanks to Peter Rohde for creating and making available to everyone his MAT-LAB q-emulator Quack and also for letting us use it in our appendix.We had a gooddeal of fun playing with it,and we hope our readers will too.Besides writing two wonderful appendices,our friendly neighborhood librar-ian,Jill Cirasella,was always just an e-mail away with helpful advice and support.Thanks,Jill!A very special thanks goes to our editor at Cambridge University Press,HeatherBergman,for believing in our project right from the start,for guiding us through thisbook,and for providing endless support in all matters.This book would not existwithout her.Thanks,Heather!We had the good fortune to have a truly stellar editor check much of the text many times.Karen Kletter is a great friend and did a magnificent job.We also ap-preciate that she refrained from killing us every time we handed her altered draftsthat she had previously edited.But,of course,all errors are our own!This book could not have been written without the help of my daughter,Hadas-sah.She added meaning,purpose,and joy.N.S.Y.My dear wife,Rose,and our two wondrous and tireless cats,Ursula and Buster, contributed in no small measure to melting my stress away during the long andpainful hours of writing and editing:to them my gratitude and love.(Ursula is ascientist cat and will read this book.Buster will just shred it with his powerful claws.)M.A.M.。
K.2系列产品用户手册说明书
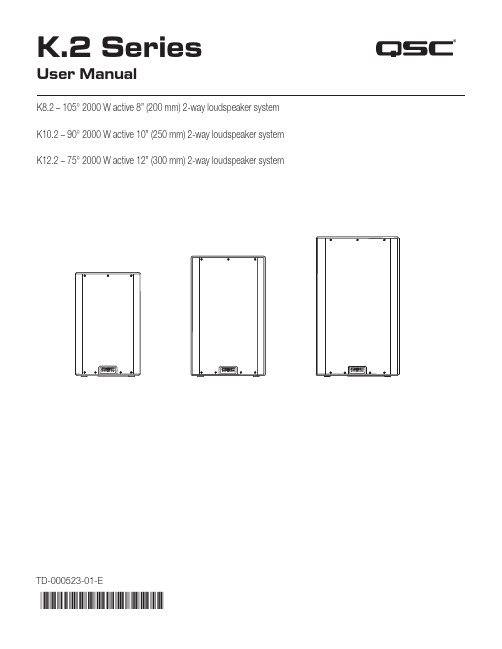
K.2 Series®User ManualK8.2 – 105° 2000 W active 8” (200 mm) 2-way loudspeaker systemK10.2 – 90° 2000 W active 10” (250 mm) 2-way loudspeaker systemK12.2 – 75° 2000 W active 12” (300 mm) 2-way loudspeaker systemTD-000523-01-E*TD-000523-01*EXPLANATION OF SYMBOLSThe term “WARNING!” indicates instructions regarding personal safety. If the instructions are not followed the result may be bodily injury or death.The term “CAUTION!” indicates instructions regarding possible damage to physical equipment. If these instructions are not followed, it may result in damage to the equipment that may not be covered under the warranty.The term “IMPORTANT!” indicates instructions or information that are vital to the successful completion of the procedure. The term “NOTE” is used to indicate additional useful information.NOTE: The intent of the lightning flash with arrowhead symbol in a triangle is to alert the user to the presence of un-insulated “dangerous” voltage within the product’s enclosure that may be of sufficient magnitude toconstitute a risk of electric shock to humans.NOTE: The intent of the exclamation point within an equilateral triangle is to alert the user to the presence of important safety, and operating and maintenance instructions in this manual.IMPORTANT SAFETY INSTRUCTIONSWARNING!: TO PREVENT FIRE OR ELECTRIC SHOCK, DO NOT EXPOSE THIS EQUIPMENT TO RAIN OR MOISTURE. DO NOT USE THIS APPARATUS NEAR WATER.1. Read these instructions.2. Keep these instructions.3. Heed all warnings.4. Follow all instructions.5. Do not use this apparatus near water.6. Clean only with a dry cloth.7. Do not block any ventilation opening. Install in accordance with the manufacturer’s instructions.8. Do not install near any heat sources such as radiators, heat registers, stoves, or other apparatus (including amplifiers)that produce heat.9. Do not defeat the safety purpose of the polarized or grounding-type plug. A polarized plug has two blades with onewider than the other. A grounding type plug has two blades and a third grounding prong. The wide blade or the third prong are provided for your safety. If the provided plug does not fit into your outlet, consult an electrician for replacement of the obsolete outlet.10. Protect the power cord from being walked on or pinched particularly at plugs, convenience receptacles, and the pointwhere they exit from the apparatus.11. Only use attachments/accessories specified by the manufacturer.12. Unplug this apparatus during lightning storms or when unused for long periods of time.13. Refer all servicing to qualified service personnel. Servicing is required when the apparatus has been damaged in anyway, such as power-supply cord or plug is damaged, liquid has been spilled or objects have fallen into the apparatus, the apparatus has been exposed to rain or moisture, does not operate normally, or has been dropped.14. The appliance coupler, or the AC Mains plug, is the AC mains disconnect device and shall remain readily operableafter installation.15. Adhere to all applicable, local codes.16. To prevent electrical shock, the power cord shall be connected to a mains socket outlet with a protective earthing connection.17. Consult a licensed, professional engineer when any doubt or questions arise regarding a physical equipment installation.18. Do not use any aerosol spray, cleaner, disinfectant or fumigant on, near or into the apparatus. Clean only with a dry cloth.19. Do not unplug the unit by pulling on the cord, use the plug.20. Do not submerge the apparatus in water or liquids.21. Keep ventilation opening free of dust or other matter.WarrantyFor a copy of the QSC Limited Warranty, visit the QSC website at Maintenance and RepairWARNING!: Advanced technology, e.g., the use of modern materials and powerful electronics, requires speciallyadapted maintenance and repair methods. To avoid a danger of subsequent damage to the apparatus, injuries to personsand/or the creation of additional safety hazards, all maintenance or repair work on the apparatus should be performed only by a QSC authorized service station or an authorized QSC International Distributor. QSC is not responsible for any injury,harm or related damages arising from any failure of the customer, owner or user of the apparatus to facilitate those repairs. Life Cycle: 10 years, Storage Temperature range: -20C to +70C, Relative Humidity range: 5 - 85% RHFCC StatementNOTE: This equipment has been tested and found to comply with the limits for a Class B digital device,pursuant to Part 15 of the FCC Rules.These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with the instructions, may cause harmful interference to radio communications. However, there is no guarantee that interference will not occur in a particular installation. If this equipment does cause harmful interference to radio or television reception, which can be determined by turning the equipment off and on, the user is encouraged to try to correct the interference by one or more of the following measures:• Reorient or relocate the receiving antenna.• Increase the separation between the equipment and receiver.• Connect the equipment into an outlet on a circuit different from that to which the receiver is connected.• Consult the dealer or an experienced radio/TV technician for help.RoHS StatementsThese products are in compliance with European Directive 2011/65/EU – Restriction of Hazardous Substances (RoHS). These products are in compliance with “China RoHS” directives per GB/T26572. The following table is provided for product use in China and its territories:These products 这些产品部件名称(Part Name)有害物质(Hazardous Substances)铅(Pb)汞(Hg)镉(Cd)六价铬(Cr(vi))多溴联苯(PBB)多溴二苯醚(PBDE)电路板组件(PCB Assemblies)X O O O O O机壳装配件(Chassis Assemblies)X O O O O O本表格依据 SJ/T 11364 的规定编制。
量子信息和量子纠缠理论

Multipartite Schmidt-correlated State
Fully separable
PPT
Fully separable (maximally entangled)
~ 1 (N)
M.J. Zhao, S.M. Fei and Z.X. Wang, Phys. Lett. A 372(2008)2552
S. Albeverio, S.M. Fei, Phys. Lett. A 276(2000)8 S. Albeverio, S.M. Fei and W.L. Yang, Comm. Theor. Phys. 38 (2002) 301
S. Albeverio, S.M. Fei and W.L. Yang, Phys. Rev. A 66 (2002) 012301 M. Horodecki, P. Horodecki and R. Horodecki, Phys. Rev. A 60, 1888 (1999)
Separable! Separable!
Separability of mixed states: no general criteria a) Peres (PPT) criterion:
Peres PRL 77, 1413 (1996)
2x2, 2x3:
PPT
Separable
Horodeckis, Phys. Lett. A 223,1 (1996)
Caltech (Kimble et al)
/~qoptics/teleport.html
Nature 390(1997) 575
Science 282(1998) 706
Wigner functions before &after
硬盘行业收购史(2000~2011)

曾经的硬盘老大,迈拓最终被希捷收购
不过,正如我们前面所说,IT市场的“1+1<2”的道理,希捷与迈拓产品重叠性太高了,收购迈拓后的希捷不可能拿下迈 拓原来的全部市场占有率,到2007-2008年,希捷的份额就开始出来下滑了,到2010年更是被西部数据超越,收购,诅 咒?
在迈拓被收购之后,几年之内硬盘市场一直相安无事,希捷虽然从2007-2008年开始份额 有所下滑,但依然是老大位置,接着是西部数据、日立、东芝与富士通,直到2009年 ... ...
西部数据收购日立硬盘、希捷收购三星硬盘,就是单纯为了巩固自己的地位吗?显然不仅 如此。笔者认为他们收购三星和日立是醉翁之意不在酒。
希捷收购三星硬盘,是为固态硬盘做准备:
三星的产品将采用希捷硬盘 希捷收购三星硬盘的协议中,有两项希捷是直接受益的:三星向希捷提供NAND闪存 芯片,用于企业及固态硬盘、混合硬盘和其他产品;希捷向三星提供硬盘,用于台式PC、 笔记本和消费电子产品。第二点很明确表明,三星的笔记本与其他消费电子产品会采用希 捷硬盘,对稳定希捷+原来三星硬盘的市场占有率起着重要作用。
2009年3月以后,传统硬盘厂商只剩下五家了,经过2010年,西部数据终于实现了多年的 夙愿,超越希捷成为硬盘老大,三星硬盘表现不佳。 2011 年,硬盘业界再次惊现两大收 购——西部数据收购日立硬盘、希捷收购三星硬盘。自此形成了硬盘的“三国鼎立”时代, 如果只是台式机市场,那么就是希捷与西部数据的“楚汉争霸”了。 2011年之后, “三国鼎立”/ “楚汉争霸”:
移动强强联合,桌面没影响: 东芝收购富士通硬盘
2010年,西部数据终于实现了十多年的夙愿,硬盘出货量超过希捷,成为全球第一的硬盘 厂商。到2011年,大家都在想西部数据如何保持自己的领先地位时,3月份传出了震惊业 界的消息:西部数据耗资43亿美元收购日立硬盘。收购了IBM硬盘的日立,最终的命运又 是被收购,还是“又”?
ReOS 2008pV2 Release Notes

ReOS 2008pV2 版本发布说明上海艾泰科技有限公司目录目录 (I)第1章导读 (2)1.1特别说明 (2)1.2内容介绍 (2)1.3升级说明 (2)第2章REOS 2008PV2新增的功能特性 (4)2.1身份绑定功能 (4)2.2策略路由 (4)2.3上网行为管理 (4)第3章REOS 2008PV2变化的功能特性 (5)3.1页面变化 (5)3.1.1基本配置—>线路配置 (5)3.1.2基本配置—>DDNS配置 (5)3.1.3高级配置—>IP/MAC (5)3.1.4安全配置—>基本选项 (5)3.1.5安全配置—>策略库 (5)3.1.6用户管理—>组管理 (6)3.1.7用户管理—>个性化管理 (6)3.1.8用户管理—>时段策略 (6)3.2命令行变化 (6)第4章REOS 2008PV2中解决的BUG (7)4.1修复R E OS2008版本的BUG (7)4.2修复R E OS2008P版本的BUG (7)第1章导读1.1特别说明目前,共有24个型号的产品支持ReOS 2008pV2版本,产品型号列举如下:HiPER 3320NB、HiPER 3310NB、HiPER 4510NB、HiPER 4520NB、HiPER 4520VF 、HiPER 4540NB、HiPER 810、HiPER 840、HiPER 2511NB 、HiPER 2610、HiPER 2620、HiPER 3311NB、HiPER 3321NB、HiPER 4240NB、HiPER 4210G、HiPER 4240G、HiPER 2511VF、HiPER 4521、HiPER 4840、UTT 3640、HiPER 811、HiPER 841、HiPER 2512NB、UTT2512。
提示:各个型号产品只能使用与其产品型号一致的软件,不同产品型号的软件不能混用。
Micro800 非隔离型 RTD 功能性插件 模块 产品目录号 2080-RTD2 说明书

接线图Micro800™ 非隔离型 RTD 功能性插件模块产品目录号2080-RTD2/idc/groups/literature/documents/wd/208 0-wd005_-mu-p.pdfFR Cette publication est disponible en français sous forme électronique (fichier PDF).Pour la télécharger, rendez-vous sur la page Internet indiquée ci-dessus.IT Questa pubblicazione è disponibile in Italiano in formato PDF. Per scaricarla collegarsi al sito Web indicato sopra.DE Diese Publikation ist als PDF auf Deutsch verfügbar. Gehen Sie auf die oben genannte Web-Adresse, um nach der Publikation zu suchen und sie herunterzuladen.ES Esta publicación está disponible en español como PDF. Diríjase a la dirección web indicada arriba para buscar y descarga esta publicación.PT Esta publicação está disponível em portugués como PDF. Vá ao endereço web que aparece acima para encontrar e fazer download da publicação.ZHZC2 Micro800™ 非隔离型 RTD 功能性插件模块出版物 2080-WD005A-ZH-P - 2010年9 月环境和机柜防止静电放电本设备适用于在污染等级 2 工业环境、过电压 II 类应用中使用 (如 IEC 60664-1 所定义),在海拔高达 2000 米 (6562 英尺) 时不降额。
Quantum Scalar i500磁带库解决方案建议书

Quantum Scalar i500磁带库解决方案建议书美国昆腾国际公司—目录—第一部分技术建议书 (3)第一章、综述 (4)1.1节备份系统总体目标 (4)1.2节磁带库方案设计原则 (4)第二章、需求分析 (6)2.1节针对磁带库的需求分析 (6)2.2节备份构架需求分析 (6)第三章、总体方案建议 (7)3.1节磁带库方案设计 (8)3.2节驱动器和槽位的考虑 (9)第四章、设备安装、测试和实施计划 (10)第五章、产品配置 (12)第六章、QUANTUM在大陆地区的售后服务机构和技术支持力量说明 (13)6.1节技术支持与服务体系 (13)6.2节技术支持与服务原则 (15)6.3节设备报修服务规程 (16)第七章、培训计划 (19)7.1 国内培训 (19)7.2 国外培训 (21)附录一 QUANTUM公司简介 (23)附录二、SCALAR I500产品介绍 (29)第一部分技术建议书第一章、综述承蒙xxx对本公司的信任和厚爱,提供我们参与其备份系统建设的机会,我们不胜感激及深表荣幸。
本方案是针对xxx系统(存储设备部分)的磁带库部分的,由美国昆腾国际公司(QUANTUM)提供。
我们将本着诚挚、科学的态度,充分考虑贵方的需求,利用我们国际领先的科技和丰富的设计、项目经验,提供最佳的专业服务,以及高性价比的系统设计方案,为贵方的计算机系统提供一套优质的数据存储备份方案。
1.1节备份系统总体目标本期工程系统采用多层体系结构。
硬件设备应包括数据库服务器、应用服务器、接口机、网络设备以及存储设备等。
系统方案详见系统结构图。
建设目标本工程系统处理能力应满足到2008年底的业务需求。
1.2节磁带库方案设计原则QUANTUM公司认为在本系统数据备份方案的具体设计中,对磁带库的选择必须遵循以下原则:技术先进性和实用性在充分满足数据备份和恢复需求的同时,应该体现技术方案的先进性。
选择目前数据备份领域成熟的先进技术和最佳实践,把先进的数据存储技术与现有的成熟技术和标准结合起来,提出合理的解决方案,并通过优化方案节省建设资金。
Quantum工作组产品线介绍

将iLayer技术运用在入门级产品 LTO-4 HH和FH(半高和全高)
– SAS和 FC接口
10
© 2009 Quantum Corporation. Company Confidential. Forward-looking information is based upon multiple assumptions and uncertainties, does not necessarily represent the company’s outlook and is for planning purposes only.
监控
诊断向导
修复向导
传统磁带库服务方式
由于缺少集成的智能,导致花费过多地管理和维护时间
众多SNMP信息发 送到外部工作站
对出现的问题分别管理 • 监视主要部件,不同的服务日志 分别存储 • 为某些故障生成SNMP信息 • 没有事件、数据的相关性信息 需要专家对问题进行分析,耗费时间 • 必须提取许多单独的日志进行人工分 析 • 需要技术支持人员对非相关性数据分 析后确定故障原因 • 大量无用报警数据被发送到远程进行 分析 • 需要高级技术专家对SNMP、SAC代 码和TapeAlerts进行分析 如果需要更多数据 • 需要多次电话支持 • 需要多次现场服务 • 解决一个问题需要多次 尝试
• 备份策略的影响 • 数据增长量的影响
可靠性不够,维护复杂
• 排错复杂 • 设备不够“聪明”
出库操作复杂
物理带库 工作组产品概览
Scalar i40
– 3U,可支持2个驱动器 – 起始容量:25数据槽,5个I/E槽(导入导 出槽) – 通过COD(按需扩容)扩展到40数据槽
Scalar i80
乌斯特成功销售150万套Quantum 2

其中 显 示 了 自 动络 筒机 全 新
,
捐物 和 献血
“
。
产 用于 卫 生 用 品 和 工 业 应 用 的 超
设计 理 念 的 定 A u to c o n
A u to
、
Au
to
c o n e r
5
进
一
步奠
欧 瑞康 中 国 区 总 裁 王 军 先 生
说 : 面 对 四 川 的 自然 灾害 我 们 视
但 是 除土 耳 其
,
m
2 FF
的功 能甚 至
( 1 筇 亿欧 元 )
巴 斯 夫 携 中石 化 增 资 南 京 基 地
9
能够检 测 能 见 度 非 常 低 的 单 根 异 纤 ;在保 持 质 量 的情 况 下 提 高 生产
力 可 以对有机和 无 机 的异 纤 进 行
,
市场 同 比 增 长
1%
14 %
外 意大利对
,
亿美元
中 国 的 出 口 基 本与 上 年 持 平 ( 微 降
) 而 对 印度 的 出 口 则 大 幅 下 降
,
中国石 化 ( S in o p e c ) 及 巴斯 夫
区 分 ;c
AY
—
—
透 过 智 能 化 方 式优
,
( B a s f ) 宣布 向中 国政 府 提 交 南京
一
了
26%
本国市场 的复苏 销售 增 长 了
8%
。
u a n
tu m
其进 行调 试
,
。
还 能 用 电容 式 传 感 器 检 测 白 色 和
此外 毛 纺 紧 密 纺 技 术
Co m p A CT 3
QuantumATK R-2020.09 产品说明说明书

QuantumATK R-2020.09QuantumATK is a leading industry-proven platform for atomic-scale modeling ofmaterials, nanostructures, and nanoelectronic devices. It includes quantum mechanical methods suchas density functional theory (DFT) with either LCAO or plane-wave basis sets and semi-empirical models, simulation engine for atomic-scale simulations using classical potentials, module for nanoscale device and transport simulations using non-equilibrium Green’s function (NEGF) methodology. QuantumATK combines the power of a Python scripting engine with the ease-of-use provided by an intuitive graphical user interface, NanoLab. All simulation engines share a common infrastructure for analysis, ion dynamics and parallel performance techniques.Downloading and Installing QuantumATK R-2020.09DownloadIf you are a customer entitled to maintenance services, you can access QuantumATK Q-2019.12 and downloadinstallation notes directly from SolvNetPlus:https://.LicenseTo run QuantumATK R-2020.09, customer must use the Synopsys Common Licensing (SCL) software, version 2018.06-SP1 or later. License key files and the latest version of SCL can be downloaded from your account on SolvNetPlus.If you are not a current customer and you wish to try out QuantumATK, please apply for a free 30-day evaluationlicense on the Synopsys EVAL portal:https:///New Features in QuantumATK R-2020.09DFT & Analysis Objects Updates●Hybrid-functional method (HSE) for LCAO, which enables accurate DFT simulations of large-scale systems withmodest computational resources. Up to 100x faster than plane-wave HSE for smaller systems, and tested on as many as 2,000 atoms.●3D-corrected k·p method to speed-up band structure and DOS calculations with plane-wave HSE from days/hours toless than a minute.●Shell DFT+1/2 method for more accurate semiconductor band gaps.●Nuclear magnetic resonance (NMR) simulations of molecules and solids, including advanced analysis of calculatedNMR shielding tensors and chemical shifts in GUI.Dynamics Updates●Improved methods to quickly obtain geometry estimates of a structure using classical force fields.●Newly added universal force field (UFF) covering the entire periodic table and thus allowing a wide range of materialsto be simulated.●Device geometry optimization improvements, resulting in better optimized device configurations.●Nudged elastic band simulation improvements, including added possibility to use more flexible constraints. Polymer Simulation●Crosslinking reaction tool for building thermoset polymers, which form cross-linked or 3D network structures, such asepoxy/amine systems, as well as rubber-like network structures.●Added support for united atoms and coarse-grained polymers to significantly accelerate simulations.●New option to create your own monomers, add monomers in existing forward and now reverse orientations, in additionto using a convenient plug-in for assigning monomer tags to define monomer linking reactions.●New user-friendly polymer analysis tools, which can be employed to plot end-to-end distances, free volume, polymersegments, molecular order parameters, and radius of gyration.Performance Improvements●2x faster ab initio molecular dynamics simulations.●Enhanced parallel performance of dynamical matrix and Hamiltonian derivatives.●Significant speed-ups and reduced memory consumption of parallel DFT-PlaneWave simulations●30-60% speed-up for the SCF loop for DFT-LCAO and semi-empirical simulations.●Improved serial and parallel performance of zero-bias NEGF calculations of symmetric and asymmetric devicegeometries.●6x speed-up and 50% reduced memory usage of projected local density of states (PLDOS) simulations.NanoLab GUI Updates●State-of-the-art new molecular builder, enabling bond lengths and angles editing, as well as a new bonds plug-in forfinding, adding, or deleting static bonds in various configurations.●Improved tool for generating good starting interface geometries, which is particularly useful when scanning acrossmultiple interfaces.●Other builder improvements, including enhanced GUI and added scripting builder functions to create devices, andimproved Packmol builder for creating amorphous configurations.●Enhanced 2D plotting framework to further tailor your plots, and an exposed plot framework API to build your owncustom plots using scripts.●User-friendly framework for setting up, submitting, and analyzing large number of simulations for more efficient high-throughput material screening.Sentaurus Materials Workbench Updates●Surface process module for setting up and running flexible simulation protocols of deposition, etching and sputtering.●Plug-in for conveniently adsorbing molecules on a surface.●New and improved features for defect simulations, including a new band gap correction method for defect trap levels,which gives more accurate results and can speed-up calculations by 75x, and the possibility to use multiple charge states in transition path list calculations.●Easy setup and analysis of a large set of different grain boundaries, as well as user-friendly script generation for linkingsimulation outputs to TCAD Raphael FX for interconnect simulations.Copyright and Proprietary Information Notice© 2020 Synopsys, Inc. This Synopsys software and all associated documentation are proprietary to Synopsys, Inc. and may only be used pursuant to the terms and conditions of a written license agreement with Synopsys, Inc. All other use, reproduction, modification, or distribution of the Synopsys software or the associated documentation is strictly prohibited.Destination Control StatementAll technical data contained in this publication is subject to the export control laws of the United States of America.Disclosure to nationals of other countries contrary to United States law is prohibited. It is the reader’s responsibility to determine the applicable regulations and to comply with them.DisclaimerSYNOPSYS, INC., AND ITS LICENSORS MAKE NO WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, WITH REGARD TO THIS MATERIAL, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE.TrademarksSynopsys and certain Synopsys product names are trademarks of Synopsys, as set forth at https://www.synopsys.com/company/legal/trademarks-brands.html. All other product or company names may be trademarks of their respective owners.Free and Open-Source Licensing NoticesIf applicable, Free and Open-Source Software (FOSS) licensing notices are available in the product installation.Third-Party LinksAny links to third-party websites included in this document are for your convenience only. Synopsys does not endorse and is not responsible for such websites and their practices, including privacy practices, availability, and content. www.。
第三届中国青年女科学家奖候选人

[1]Image segmentation by clustering of spatial patterns, Pattern Recognition Letters, 2007,他引频次:23引证文献:1.X Yang, et al., Image segmentation with a fuzzy clustering algorithm based on Ant-Tree,Signal Processing, 2008 – Elsevier2.J Fan, et al., Single point iterative weighted fuzzy C-means clustering algorithm forremote sensing image segmentation, Pattern Recognition- 20093.Cariou, et al., Unsupervised texture segmentation/classification using 2-Dautoregressive modeling and the stochastic expectation-maximization algorithmC,Pattern Recognition Letters, 20084.M Kühne, et al., A novel fuzzy clustering algorithm using observation weighting andcontext information for reverberant blind speech separation, Signal Processing, 20095.Y Xia, et al., Segmentation of brain structures using PET-CT images,20086.W Chen, et al., A 2-phase 2-D thresholding algorithm, Digital Signal Processing, 20107.Chaoshun Li, et al.,A Fuzzy Cluster Algorithm Based on Mutative Scale ChaosOptimization, Proceedings of the 5th international symposium on Neural Networks:Advances in Neural Networks, Part II,20088.Kun Qin, et al., Image Segmentation Based on Cloud Concept Analysis,20109.Long Chen, et al.,Multiple kernel fuzzy C-means based image segmentation,201010.Reddy, B.V.R., et al.,A Random Set View of Texture Segmentation,201011.Lefèvre, S., A New Approach for Unsupervised Classification in Image Segmentation,201012.Kai-jian, XIA, et al., An Image Segmentation Based on Clustering of Spatial Patternsand Watershed Algorithm, 201013.Rajeswari, M., et al., Spatial Multiple Criteria Fuzzy Clustering for Image Segmentation,201014.CH Wu, et al., A greedy strategy for images segmentation by support vector machines,201015.Wei, B.C, et al., Multi-objective nature-inspired clustering techniques for imagesegmentation, 201016.Ruta, A, Video-based Traffic Sign Detection, Tracking and Recognition, 200917.Camilus, K.S., et al., A Robust Graph Theoretic Approach for Image Segmentation,201018.WP Zhu, et al., Image segmentation by improved clustering of spatial patterns, JisuanjiYingyong Yanjiu, 200919.S Lefèvre, Une nouvelle approche pour la classification non superviséeen segmentationd’image, et gestion des connaissances: EGC'200920.Callejo, R, et al., Segmentación automática de texturas en imágenes agrícolas,201021.Marcos, I, Estrategias de clasificación de texturas en imágenes forestales hemisféricas,201022.Seo ST, et al., Co-occurrence Matrix-Based Image Segmentation IEICETRANSACTIONS ON INFORMATION AND SYSTEMS. NOV 2010, E93D(11):3128-313123.Pedrycz W, et al., Fuzzy clustering with semantically distinct families of variables:Descriptive and predictive aspects.PA TTERN RECOGNITION LETTERS. OCT 1 2010, 31(13): 1952-1958[2]Robust Shape-Based Head Tracking, Advanced Concepts for Intelligent Vision Systems,2007, 他引频次:10引证文献:1. A Bottino, et al., A fast and robust method for the identification of face landmarks inprofile images, WSEAS Transactions on Computers, 2008 - 2. D Jiang, et al., Speech driven realistic mouth animation based on multi-modal unitselection, Journal on Multimodal User Interfaces,2004.63.Chen, D, et al., Audio-Visual Emotion Recognition Based on a DBN Model withConstrained Asynchrony,20104. A Bottino, et al., Robust identification of face landmarks in profile images, 2008Proceedings of the 12th WSEAS international conference on Computers, 20085.Hou, Y, et al., Smooth Adaptive Fitting of 3D Face Model for the Estimation of Rigidand Non-rigid Facial Motion in Video Sequences, 20106.Gonzalez, I, et al., Automatic Recognition of Lower Facial Action Units, 20107.Jiang, X, et al., Perception-Based Lighting Adjustment of Image Sequences, 20108.Jiang, D, et al., Realistic mouth animation based on an articulatory DBN model withconstrained asynchrony, 20109.Y Hou, et al., 3D Face Alignment via Cascade 2D Shape Alignment and ConstrainedStructure from Motion, Advanced Concepts for Intelligent Vision Systems,200910.刘培桢,等,I RAVYSE, Hichem, S, 基于发音特征DBN 模型的嘴部动画合成,2010[3]An Efficient Physically-Based Model for Chinese Brush, Frontiers in Algorithmics, 2007,他引频次:5引证文献:1.TD Chen, Chinese Calligraphy Brush Stroke Interactive Model with Ink Diffusion Style,20102.TD Chen, Hairy Brush and Rice Paper Interactive Model with Chinese Ink PaintingStyle, 20103.Y Hou, et al., Model for Evaluating the Safety Innovation Effects in Coal Mines basedon' Security Force Engineering, 20094.MZ Zhu,et al., Virtual brush model based on statistical analysis and its application,20095.朱墨子,等, 基于统计分析的虚拟毛笔模型及其应用, 计算机工程, 2009[4]Segmentation of images using wavelet packet based feature set and Clustering Algorithm,International Journal of Information Technology, 2005, 他引频次:4引证文献:1.Lv, H, et al., Medical image segmentation based on wavelet packet and improved FCM,20082.Afifi, A, et al., Particle Swarm Optimization Based Medical Image SegmentationTechnique, 20103.吕回,等,基于小波包和改进的FCM 的医学图像分割,计算机工程与应用,20084.AFIFI. A, et al., Shape and Texture Priors for Liver Segmentation in AbdominalComputed Tomography Scans Using the Particle Swarm Optimization, 2010[5] A New Method of SAR Image Segmentation Based on Neural Network, Proceedings of the5th International Conference on Computational Intelligence and Multimedia Applications, 2003, 他引频次:3引证文献:1.徐海祥,等,基于改进的一对一支持向量机方法的多目标图像分割,微电子学与计算机,20052.徐海祥,等,彭复员,基于支持向量机方法的多目标图像分割,计算机工程与应用,20053.BU Shankar, Novel Classification and Segmentation Techniques with Application toRemotely Sensed Images, Transaction on Rough Sets VII, 2007[6] A modified particle swarm optimization algorithm for support vector machine training, TheSixth World Congress on Intelligent Control and Automation, 2006, 他引频次:3引证文献:1.Matthias Becker, et al., Traffic Analysis and Classification with Bio-Inspired andClassical Algorithms in Sensor Networks, SPECTS 2008 Committees2.Matthias Becker, et al., Sebastian Bohlmann, Helena Szczerbicka, On ClassificationApproaches for Misbehavior Detection in Wireless Sensor Networks, Journal ofComputers, Vol 4, No 5 (2009), 357-365, May 20093.Q WU, et al., Particle Swarm Optimization for Semi-supervised Support VectorMachine, 2010[7] A Novel Immune Quantum-Inspired Genetic Algorithm, Advances in Natural Computation,2005,他引频次:3引证文献:1.X You, et al. Immune Quantum Evolutionary Algorithm Based on Chaotic SearchingTechnique for Global Optimization, 20082.G Zhang, Quantum-inspired evolutionary algorithms: a survey and empirical study,20103.Xiaoming You , et al., Real-coded Quantum Evolutionary Algorithm based on ImmuneTheory for Multi-modal Optimization Problems, 2008 International Conference onComputer Science and Software Engineering[8]New method for image target recognition, Second International Conference on Image andGraphics, 2002, 他引频次:2引证文献:1.陈亮,等,基于SVM 的遥感影像目标检测中的样本选取,计算机工程与应用,20062.梅建新,等, 基于支持向量机的特定目标检测方法,武汉大学学报: 信息科学版,2004[9] A New Method for Detecting Bridges Automatically, JOURNAL OF NORTHWESTERNPolytechnical University, 2003,他引频次:2引证文献:1.Y Fu, et al., Recognition of Bridge over Water in High-Resolution Remote SensingImages, 2009 WRI World Congress on Computer Science and InformationEngineering,20092.L Zhang, et al., Adaptive river segmentation in SAR images, 2009[10]The research of the match of corresponding points in multi-view and the realization byevolutionary programming, 2004 7th International Conference on Signal Processing2004, 他引频次:1引证文献:1.Guangpeng Zhang, et al., A 3D FACIAL FEATURE POINT LOCALIZATIONMETHOD BASED ON STATISTICALSHAPE MODEL, Proc. of Internat. Conf. onAcoustics, Speech and Signal Processing ICASSP, pp. 15–20.[11]A fuzzy integral method of applying support vector machine for multi-class problem,LECTURE NOTES IN COMPUTER SCIENCE, 2006,他引频次:1引证文献:1.Hu YC, Fusing fuzzy association rule-based classifiers using Sugeno integral withordered weighted averaging operators, INTERNATIONAL JOURNAL OFUNCERTAINTY FUZZINESS AND KNOWLEDGE-BASED SYSTEMS, DEC 2007,15(6): 717-735[12]Robust object tracking based on uncertainty factorization subspace constraints optical flow,International Conference on Computational Intelligence and Security, LECTURE NOTES IN ARTIFICIAL INTELLIGENCE, 2005, 他引频次:1引证文献:1.Hou Y, et al., Robust shape-based head tracking, Advanced Concepts for IntelligentVision Systems, Proceedings, AUG 28-31, 2007, 4678: 340-351[13]On Good-Quality Edge Detection of SAR Image, Journal of Northwestern PolytechnicalUniversity, 2003, 他引频次:1引证文献:1.LI Wei-bin, et al., New operator for edge detection in SAR image, ComputerEngineering and Design 2007-17[14]An Adaptive Immune Genetic Algorithm for Edge Detection, Advanced IntelligentComputing Theories and Applications. With Aspects of Artificial Intelligence,2007,他引频次:1引证文献:1.Judy,et al., A multi-objective evolutionary algorithm for protein structure predictionwith immune operators, Computer Methods in Biomechanics and BiomedicalEngineering, V olume 12, Number 4, August 2009 , pp. 407-413(7)[15]视频监视中运动目标的检测与跟踪算法, 系统工程与电子技术, 2002, 他引频次:111引证文献:1.付晓薇,一种基于动态图像的多目标识别计数方法,武汉科技大学,20032.汪颖进,目标跟踪过程中的遮挡问题研究,华中科技大学,20043.杨俊,变电站遥视图像的识别研究,华北电力大学(河北),20044.高腾,静止背景下运动目标跟踪方法的研究,西北大学,20055.崔宇巍,运动目标检测与跟踪中有关问题的研究,西北大学,20056.胡嘉凯,智能视频监控系统中运动目标跟踪有关问题研究及其DSP实现,合肥工业大学,20067.刘天国,红外防火监视监控系统的设计与实现,吉林大学,20068.刘昕,实时视频中选定物体追踪算法的研究,吉林大学,20069.程江华,基于DSP的视频分析系统设计与实现,国防科学技术大学,200510.廖雪超,基于粒子滤波和背景建模的多目标跟踪技术的研究和实现,武汉科技大学,200611.张之稳,嵌入式视频跟踪算法的研究,山东大学,200612.乔月,基于三层动态交互体系的多目标监控系统,哈尔滨工业大学,200613.周香珍,基于DSP的目标跟踪系统的实现,南京理工大学,200614.刘青青,智能式数字视频监控系统的研究与实现,厦门大学,200415.辛瑞红,运动目标的检测与跟踪研究,北京交通大学,200716.单海涛,复杂环境下运动人体分割算法的研究,大连海事大学,200617.武爱民,视频检测与跟踪技术在行人计数中的应用研究,合肥工业大学,200718.魏瑞斌,基于多特征的运动目标跟踪,西北大学,200719.吴雪刚,一种有效的基于粒子滤波器的多目标跟踪技术,西南大学,200720.胡志刚,基于移动通信网络的视频监控系统设计与实现,国防科学技术大学,200621.于晨,基于模板匹配技术的运动物体检测的研究,重庆大学,200722.吴园,运动车辆的检测与跟踪,南京航空航天大学,200723.周敬兵,复杂背景下的目标检测与跟踪技术研究,南京理工大学,200724.罗勤,基于序列图像处理的桥墩防撞预警系统的研究,华中科技大学,200625.肖海燕,动态目标检测与跟踪技术的研究,大连理工大学,200726.汪泉,基于运动目标检测与跟踪的视频测速技术的研究与应用,南昌大学,200727.司长哲,基于DSP的火箭自动跟踪与识别系统,重庆大学,200728.高原,海背景下弱小运动目标的检测和跟踪研究,北京交通大学,200729.庄志国,视频监控系统中有遮挡运动目标的提取和重构,厦门大学,200730.杨洋,智能场景监控系统的研究及其在室内监控中的应用,吉林大学,200831.张恒娟,基于分块高斯背景的运动目标检测与跟踪技术研究,天津师范大学,200832.马杰,视频人脸检测与识别方法研究,湖南大学,200833.陈家树,像素差的平方和增强核粒子滤波的非刚体目标跟踪,西南大学,200834.黄苜,支持向量回归机粒子滤波器非刚体目标跟踪,西南大学,200835.陈方晖,基于DSP的图像识别技术研究,国防科学技术大学,200736.王柱,复杂背景下动态目标的检测与跟踪,昆明理工大学,200737.马樱,基于视频流的步态识别,昆明理工大学,200838.梁昌斌,视频监控系统中运动目标检测和跟踪技术的研究与实现,合肥工业大学,200839.王虎,运动目标检测和跟踪的研究及应用,中国海洋大学,200840.李凤凯,多运动目标的检测与跟踪算法研究,天津大学,200741.刘月明,视频目标运动轨迹提取算法的分析与仿真,哈尔滨工业大学,200742.王久明,基于高速处理器的CMOS数字图像采集系统的硬件设计,哈尔滨工业大学,200743.伍翔,视频图像中运动目标检测与跟踪方法研究与实现,哈尔滨工业大学,200744.戴若愚,基于帧间运动能量差的跟踪算法研究与实现,华中科技大学,200745.闫丽媛,单移动目标跟踪装置的研究,沈阳工业大学,200946.杨翠萍,基于图像处理的视频监控系统的研究与实现,东华大学,200947.江雪剑,东华大学,基于PTZ摄像机的跟踪算法研究,200948.贾鸿儒,遮挡情况下基于特征相关匹配的目标跟踪方法研究,东北师范大学,200949.李明君,基于计算机视觉的运动目标的检测与跟踪的研究,青岛大学,200950.杨隽姝,车辆检测与实时跟踪算法研究,华东师范大学,200951.韩亚伟,视频交通流背景提取与运动目标跟踪检测技术研究,长安大学,200952.山茂泉,运动目标检测和跟踪算法研究,大庆石油学院,200853.罗莹,网络实时音视频处理中运动检测技术的研究与实现,上海交通大学,200854.刘钢,基于小波变换的航空图像处理及动载体多目标跟踪方法研究,中国科学院研究生院(长春光学精密机械与物理研究所),200455.潘锋,仿人眼颈视觉系统的理论与应用研究,浙江大学,200556.岳润峰,等,基于小波分解与运动补偿的弹迹检测方法,兵工自动化,200757.王蓉晖,等,基于小波变换的分层块匹配多目标跟踪方法,吉林大学学报(信息科学版),200458.刘春华,等,运动中的多目标电视跟踪方法,弹箭与制导学报,200459.胡志刚,等,基于无线通信网络的视频监控研究,电脑知识与技术(学术交流),200760.程成,等,眼动交互的实时线性算法构造和实现,电子学报,200961.宋世军,等,运动人体图像分割算法研究,中国工程机械学报,200762.刘钢,等,运动背景下多目标跟踪的小波方法,光电工程,200563.门立彦,等,种视频序列中运动目标的跟踪方法,装备制造技术,200964.杨伟,等,基于mean-shift的多目标粒子滤波跟踪算法设计,光电技术应用,200965.杨伟, 等,基于Mean-shift的多目标跟踪算法的设计[J]. 红外,2009,(3).66.朱冬,等,一种改进的自适应运动目标检测算法,信息通信,200667.杨伟,等,基于mean-shift的多目标粒子滤波跟踪算法设计,红外技术,200968.蒋文斌,等,一种基于位移概率矩阵的目标跟踪方法,华中科技大学学报(自然科学版),200669.孙剑,等,基于mean-shift的快速跟踪算法设计与实现,计算机工程,200670.徐璟,DSP视频监控中运动目标检测方法研究,计算机仿真,200871.余静,等,自动目标识别与跟踪技术研究综述,计算机应用研究,200572.宋世军,等,复杂背景下运动目标的智能检测方法,计算机应用与软件,200873.唐俐,等,运动目标检测的三帧差分和背景消减研究,科技信息,200874.袁基炜,等,一种基于灰色预测模型GM(1,1)的运动车辆跟踪方法,控制与决策,200675.李衡宇,等,杨晓敏基于计算机视觉的公交车人流量统计系统,四川大学学报(自然科学版),200776.唐宏震,等,基于多分辨率分级分块处理的边缘检测方法,陕西师范大学学报(自然科学版),200777.关向荣,等,视频监视中背景的提取与更新算法,微电子学与计算机,200578.杨建国,等,基于自适应轮廓匹配的视频运动车辆检测和跟踪,西安交通大学学报,200579.王先培,等,变电站遥视智能化系统中除噪问题的研究,襄樊学院学报,200980.鹿雪娇,基于视频图像的运动物体识别与跟踪技术研究,大庆石油学院,200981.焦安霞,视频序列中动目标检测与跟踪算法的研究,哈尔滨工程大学,200882.王笑雨,运动目标检测与跟踪系统设计,哈尔滨工程大学,200883.张敏,视频监控中运动目标检测与清晰化方法的研究,江苏大学,201084.马小博,基于FPGA的视频监控跟踪系统研究,大连海事大学,201085.邓俊云,基于DAM6416P处理平台对弱小目标的检测与跟踪,南京航空航天大学,200986.余晓蓉,运动目标检测与跟踪技术研究,西安电子科技大学,201087.赵红丽,基于多光谱图像融合的视频运动目标检测[,西安电子科技大学,201088.宋岩,交通信息采集系统中运动车辆的检测与识别技术研究,黑龙江大学,200989.汪冲,运动目标检测与跟踪在鱼眼图像中的应用,哈尔滨工程大学,200990.吕斌,交通监控系统中目标跟踪与行为识别研究,中南大学,201091.刘玟,基于驾驶员眼睛状态的疲劳驾驶检测算法,华南理工大学,201092.陆珺,交通道口运动目标检测与跟踪方法的研究,江苏大,200793.陈奕奕,运动目标检测分割算法研究,武汉科技大学,201094.王二力,红外监控系统中关键技术研究,西安电子科技大学,200695.陈爱斌,基于视觉的运动目标跟踪方法研究,中南大学,201096.邹策千,等,序列图像运动目标的检测与提取,内蒙古农业大学学报(自然科学版),201097.关向荣,等,视频监视中背景的提取与更新算法,微电子学与计算机,200598.孙剑,等,基于mean-shift 的快速跟踪算法设计与实现,计算机工程,200699.何健刚,AdHoc 网络在WindowsXP 环境下的应用实例,计算机应用与软件,2008100.庄志国,视频监控系统中有遮挡运动目标的提取和重构,硕士学位论文,厦门大学,2007101.陈方晖,基于DSP 的图像识别技术研究,硕士学位论文,国防科技大学,2007 102.付晓薇,一种基于动态图像的多目标识别计数方法,硕士学位论文,武汉科技大学,2003103.李衡宇,等,基于计算机视觉的公交车人流量统计系统,四川大学学报: 自然科学版, 2007104.徐璟,DSP 视频监控中运动目标检测方法研究,计算机仿真, 2008105.肖海燕,动态目标检测与跟踪技术的研究,硕士学位论文,大连理工大学,2007 106.黄扬帆,等,改进PDA-AI方法的运动目标跟踪性能分析[J]. 重庆大学学报,2010 107.赵陈, 等,基于混合模型的运动目标检测算法[J].电子测试,2011108.曹晖. 运动多目标检测与跟踪算法研究[D]. 哈尔滨工程大学,2010109.何娜. 视频监控中运动物体自动跟踪技术的研究[D]. 南华大学,2010110.杨勇. 基于粒子滤波目标跟踪方法研究[D]. 中南林业科技大学,2009111.李姗姗. 智能视频跟踪系统中的运动目标检测与跟踪技术研究[D]. 华中科技大学: ,2009[16]角点检测技术综述, 计算机应用研究, 2006, 他引频次:94引证文献:1.李宝昭,基于匹配的图像识别算法的应用研究,硕士学位论文,广东工业大学,20072.陆兵,视频中的文本提取及其应用,硕士学位论文,河海大学,20073.庄志国,视频监控系统中有遮挡运动目标的提取和重构,硕士学位论文,厦门大学,20074.韩啸,基于遗传算法的摄像机内参数标定研究,硕士学位论文,吉林大学,20085.吴亚鹏,基于双目视觉的运动目标跟踪与三维测量,硕士学位论文,西北大学6.邓再强,基于特征点匹配的电子稳像算法研究,硕士学位论文,电子科技大学,20087.赵万金,图像自动拼接技术研究与应用,硕士学位论文,苏州大学,20088.汪心昕,基于内容的广告垃圾图像检测关键技术研究,硕士学位论文,北京邮电大学,20089.代建辉,智能交通系统车辆流量检测技术的研究,硕士学位论文,天津大学,200710.赵文闯,基于视觉的多机器人实验系统室内实时定位研究,硕士学位论文,哈尔滨工业大学,200711.兰信旭,视觉坐标测量的仿真环境设计,硕士学位论文,青岛大学,200812.刘晶晶,基于双目立体视觉的三维定位技术研究,硕士学位论文,华中科技大学,200713.刘永强,基于视觉测量的汽车车轮定位技术的研究,硕士学位论文,大连理工大学,200814.王娟,图像拼接技术研究,硕士学位论文,陕西师范大学,200815.王树峰,基于立体视觉方法的图像三维模型重建研究,硕士学位论文,南京航空航天大学200816.张晶,基于比值算法的图像拼接技术的实现,硕士学位论文,吉林大学,200917.陈光,亚像素级角点提取算法,硕士学位论文,吉林大学,200918.徐江玲,基于非平行双目视觉的三维重建,硕士学位论文,大连理工大学,200919.蒋虎,航片拼接及其与矢量地图的可视化集成技术,硕士学位论文,电子科技大学,200920.李建敏,基于轮廓片段的图像识别技术研究,硕士学位论文,厦门大学,200921.徐秀眉,基于SVG的校园导航系统开发研究,硕士学位论文,长安大学,200922.魏娟,双目视觉在自动倒车系统中的应用研究,硕士学位论文,哈尔滨工程大学,200923.张明志,基于微特征的指纹识别算法研究,硕士学位论文,厦门大学,200824.李海峰,基于要素的图像统计模型研究,硕士学位论文,北京交通大学,200925.李绍君,基于Snake模型的肿瘤显微图像分割技术研究,硕士学位论文,华东交通大学,200826.钱苏斌,曲面重建[D].硕士学位论文,江南大学,200927.倪奎,人脸器官拼接融合及其在人脸动画中的应用,硕士学位论文,中国科学技术大学,200928.阮国威,高速电脑绣花机视频运动检测分析系统,硕士学位论文,北京工商大学,200929.刘军学,移动机器人视觉检测和跟踪研究,硕士学位论文,哈尔滨工业大学,2008.30.陈二龙,PCB视觉检测系统中相机标定算法与位姿测定技术,硕士学位论文,哈尔滨工业大学,200831.徐涛,基于多个广角相机的图像拼接技术,硕士学位论文,浙江大学,201032.邹虹,基于计算机视觉的动作识别对人机界面消隐的研究,硕士学位论文,哈尔滨工业大学,200933.裴聪,基于计算机视觉中双目立体匹配技术研究,江苏大学,201034.肖建军,车辆遮挡检测的研究与应用,北方工业大学,201035.杨文鲜,基于形状的图像匹配复合模型研究,华北电力大学(北京),201036.李畅,基于曲率乘积的直接曲率尺度空间角点检测算法,硕士学位论文,南京航空航天大学,200937.钱镜洁,基于视频的车型识别技术研究,硕士学位论文,南京航空航天大学,200938.孟犇,图像局部特征技术在图像检索系统中的应用,上海交通大学,201039.赵勇,基于覆盖分类的视觉跟踪算法研究,安徽大学,201040.王靖韬,三维重建的摄像机标定技术和多尺度空间下角点检测技术的研究,内蒙古农业大学,201041.李蕊艳,基于机器视觉的芯片识别及定位软件的研究开发,硕士学位论文,西安理工大学,200942.曾东方,单晶生长过程直径检测与化料过程模式分类方法研究,硕士学位论文,西安理工大学,200943.兰昆艳,基于特征检测的车辆跟踪技术的研究,硕士学位论文,北京邮电大学,201044.彭旭,机场监控视频相关事件检测,硕士学位论文,北京邮电大学,201045.时洪光,基于双目视觉的运动目标定位研究,硕士学位论文,青岛大学,201046.戴剑锋,摄像头径向畸变自动校正系统,硕士学位论文,华南理工大学,201047.王奇,基于脸部器官关系的嘴巴检测算法研究,硕士学位论文,湖南大学,201048.吴祺,基于视觉技术的陈展交互设计与实现,硕士学位论文,浙江大学,浙江大学,201049.唐新星,具有立体视觉的工程机器人自主作业控制技术研究,博士学位论文,吉林大学,200750.王立中,基于机器视觉的奶牛体型评定中的关键技术研究,内蒙古农业大学,200951.孙文昌,等,基于熵和独特性的角点提取算法,计算机应用,200952.张裕,等,基于Harris算法的黑白棋盘格角点检测,计算机应用与软件,201053.欧剑,等,基于头部跟踪的虚拟画展系统,计算机应用,201054.兰海滨,等,基于角点检测的彩色图像拼接技术,计算机工程与设计,200955.张登银,等,边缘检测算法改进及其在QoE测定中的应用,计算机技术与发展,200956.王科俊,等,基于共面圆的双目立体视觉分步标定法,应用科技,201057.时洪光,等,双目视觉中的角点检测算法研究,现代电子技术,201058.万敏,基于角点的汉字特征提取与识别算法,宜宾学院学报,201059.李健,抗几何攻击的数字图像水印技术的研究,南京理工大学,200960.张金玲,面向空间舱内机器人遥操作的增强现实仿真场景构建技术研究,北京邮电大学,200961.谭立东,道路交通事故现场快速勘查图像信息处理技术研究,吉林大学,200962.王军南,等,基于视觉的机械臂末端执行器坐标获取,2007系统仿真技术及其应用学术会议论文集,200763.李勃,等,路况PTZ摄像机自动标定方法,中国通信学会通信软件技术委员会2009年学术会议论文集,200964.陈宇波,等,在人脸图像中确定嘴巴位置的方法,电子科技大学学报,200765.陶骏,等,特定视频采集系统中的身份识别的实现,电脑知识与技术,200966.宋洁,等,基于金字塔和模糊聚类的路面图像拼接方法,河北工业大学学报,200867.韩斌,等,改进的亚像素级快速角点检测算法,江苏科技大学学报(自然科学版),200968.张铁楠,等,针对棋盘格角点快速检测的一种新方法,计算机工程与应用,200869.赵万金,等,一种自适应的Harris角点检测算法,计算机工程,200870.王娟,师军,吴宪祥,图像拼接技术综述,计算机应用研究,200871.王立中,等,基于图像分块的多尺度Harris特征点检测算法,内蒙古大学学报(自然科学版),200972.冯宇平,等,一种用于图像序列拼接的角点检测算法,计算机科学,200973.任雁,角点检测方法研究,机械工程与自动化,200974.华瑞娟,等,一种多椭圆曲线拟合的新算法,长春理工大学学报(自然科学版),201075.顾国庆,等,基于曲率多尺度的高精度角点检测,光学技术,201076.盛遵冰,等,点对核值匹配的角点检测,计算机工程与应用,201077.马品奎,基于图像分析的超塑性自由胀形实验测量与力学解析,吉林大学,201078.倪奎,人脸器官拼接融合及其在人脸动画中的应用, 硕士学位论文,中国科学技术大学,200979.禹蒲阳,分类算法的一种改进,计算机应用与软件, 201080.吴祺, 基于视觉技术的陈展交互设计与实现, 硕士学位论文,浙江大学,201081.肖啸,等,基于数字有机体的访问控制链表(ACL) 的设计与实现,电脑知识与技术: 学术交流,200982.徐涛,基于多个广角相机的图像拼接技术, 硕士学位论文,浙江大学,201083.兰昆艳,等,基于图像金字塔光流的角点跟踪法的车辆监测系统,中国智能交通,200984.蔡胜利, 等,基于Harris角点检测的图像旋转测量[J]. 计算机测量与控制,2011,(1).85.全星慧, 等. 一种基于角点匹配的图像拼接算法研究[J]. 科学技术与工程,2011,(4).86.谭振宇, 等. 一种基于支持向量机的角点检测算法[J]. 电子测试,2011,(1).87.孙秋成. 基于机器视觉的轴径测量[D]. 吉林大学,2010.88.张炜. 基于点特征的图像拼接技术研究[D]. 河南科技大学: 2010.89.张金金. 基于SIFT的遥感影像自动配准的研究与实现[D]. 河南理工大学: 2009.90.肖若秀. 图像匹配方法研究与应用[D]. 昆明理工大学:2008.91.王静. 基于SIFT和角点检测的自动图像配准方法研究[D]. 华中科技大学: 2010.92.唐红梅. 基于辐射与空间信息的遥感图像检索[D]. 山东科技大学:2010.93.卓磊. 视频序列电子稳像技术研究[D]. 天津大学:2010.94.戴磊. 基于视觉反馈的移动机器人控制[D]. 上海交通大学:2011[17]可恢复的脆弱数字图像水印, 计算机学报, 2004, 他引频次:26引证文献:1.郭越,基于小波变换的鲁棒性与脆弱性数字水印算法的研究与实现,上海海事大学,20042.郭彦琦,数字图书馆工程中数字产品的版权保护和访问权限控制的研究和实现,上海海事大学,20043.刘为超,基于小波的数字图像认证水印研究,西安电子科技大学,20054.赵敏,医学图象数字水印系统研究与实践,苏州大学,20055.孙建梅,基于内容的图像认证技术研究,西北大学,20056.桑晓青,基于离散小波变换的数字图像篡改验证技术的研究,浙江工商大学,20067.杨艳萍,基于数字水印的图像认证技术研究,西北大学,20068.朱兴力,鲁棒图像数字水印算法及其协议研究,西南交通大学,20069.余淼,用于JPEG图像认证的数字水印算法研究,西南交通大学,200710.吴志伟,基于CRC的脆弱型文本数字水印研究与应用,中南大学,200711.廖昌兴,压缩域图像水印与隐写算法研究,西南交通大学,200812.潘季芳,差错控制数据库水印算法研究,湖南大学,200913.张宪海,数字水印技术在版权保护与内容认证中的应用研究,哈尔滨工程大学,200614.叶登攀,图像认证及视频数字水印的若干算法研究,南京理工大学,2005。
列举量子安全通信与密码学的文献

量子安全通信与密码学的文献是指关于量子安全通信和密码学领域的研究成果和理论框架。
这些文献涵盖了量子通信与密码学的基本原理、技术方法、理论模型及其在实际应用中的实验验证和工程实现等方面的内容。
本文将列举一些代表性的量子安全通信与密码学的文献,以期为相关研究人员提供参考和借鉴。
1. 《Quantum cryptography: Public key distribution and coin tossing》作者:Charles H. Bennett, Gilles Brassard出版年份:1984内容简介:这篇论文是量子密码学领域的开创性工作,首次提出了量子密钥分发和量子硬币抛掷的概念,为后续量子密码学研究奠定了理论基础。
2. 《Quantum key distribution with realistic states: A practical security analysis》作者:Christian Weedbrook, Stefano Pirandola, et al.出版年份:2012内容简介:该文献详细分析了实际量子密钥分发中存在的各种技术限制和攻击手段,并提出了相应的安全分析方法和实用性解决方案,为量子安全通信技术的应用提供了重要参考。
3. 《Quantum cryptography: Uncert本人nty in the service ofprivacy》作者:Artur Ekert出版年份:1991内容简介:本文提出了著名的Ekert协议,首次将量子纠缠状态应用于量子密钥分发过程中,对现代量子密码学理论和技术产生了深远影响。
4. 《Quantum cryptography with imperfect apparatus》作者:Vadim Makarov出版年份:2006内容简介:该文献探讨了现实量子通信系统中的实验不完美性对量子安全通信协议和技术的影响,为实际量子通信系统的安全性评估和改进提供了重要思路和方法。
A double-slit quantum eraser

where |ψ1 (r) and |ψ2 (r) represent the possibility for the particles to take path 1 or 2, respectively. The probability distribution for one particle detection at a point r is given by | r|Ψ |2 ; the cross terms ψ1 (r)|r r|ψ2 (r) and ψ2 (r)|r r|ψ1 (r) are responsible for interference. The introduction of an apparatus M capable of marking the path taken by a particle without disturbing |ψ1 (r) or |ψ2 (r) can be represented by the expansion of the Hilbert space of the system in the following way: 1 |Ψ = √ (|ψ1 (r) |M1 + |ψ2 (r) |M2 ), 2 (2)
arXiv:quant-ph/0106078v1 13 Jun 2001
I. INTRODUCTION
Wave-particle duality, a manifestation of the complementarity principle, proposes many questions about the behavior of particles in interferometers. It has long been known that which-path information and visibility of interference fringes are complementary quantities: any distinguishability between the paths of an interferometer destroys the quality (visibility) of the interference fringes. The incompatibility between which-path information and interference effects has been quantified through inequalities by various authors [1–6]. Originally, it was thought that the uncertainty principle was the mechanism responsible for the absence of interference fringes due to a which-path measurement. The first and perhaps most famous example of this idea is the Einstein-Bohr dialogue at the Fifth Solvay conference in Brussels concerning Einstein’s recoiling double-slit gedanken experiment, in which the momentum transfer from incident particles to the double-slit is measured to determine the particles’ trajectories [7,8]. However, Bohr showed that the uncertainty in the knowledge of the double-slit’s initial position was of the same order of magnitude as the space between the interference minima and maxima: interference fringes were “washed out” due to the uncertainty principle [7]. More recently, Scully and Dr¨ uhl have shown that, in certain cases, we can attribute this loss of interference not to the uncertainty principle but to quantum entanglement between the interfering particles and the measuring apparatus [9]. For example, disregarding internal degrees of freedom, we can represent the state of particles exiting an interferometer by 1 |Ψ = √ (|ψ1 (r) + |ψ2 (r) ), 2 (1)
荧光标记的纳米颗粒进入小鼠体内的活体成像实验

荧光标记的纳米颗粒进入小鼠体内的活体成像实验引言荧光标记的纳米颗粒在生物医学领域中具有广泛应用。
通过将荧光染料或荧光蛋白标记到纳米颗粒表面,可以实现对生物体内组织和细胞的高分辨率成像。
本文将介绍一种利用活体成像技术观察荧光标记的纳米颗粒进入小鼠体内的实验方法。
实验设计实验目的本实验旨在通过活体成像技术观察荧光标记的纳米颗粒在小鼠体内的分布和动态变化,以了解其在生物体内的行为。
实验步骤1.制备荧光标记的纳米颗粒:选择合适尺寸和表面性质的纳米颗粒,并将荧光染料或荧光蛋白与其结合,完成荧光标记。
2.小鼠模型制备:选择合适品系和年龄相近、健康状况良好的小鼠作为实验对象。
3.注射纳米颗粒:将荧光标记的纳米颗粒溶液注射到小鼠体内,选择合适的途径(如静脉注射、腹腔注射等)。
4.活体成像:使用荧光显微镜或活体成像系统对小鼠进行实时观察和记录,以获取纳米颗粒在小鼠体内的分布和动态变化信息。
5.数据分析:对活体成像数据进行处理和分析,包括图像处理、信号定量测量等。
实验工具与材料•荧光标记的纳米颗粒:选择合适尺寸和表面性质的纳米颗粒,并选择合适的荧光染料或荧光蛋白进行标记。
•小鼠模型:选择合适品系和年龄相近、健康状况良好的小鼠。
•注射器与针头:用于将纳米颗粒溶液注射到小鼠体内。
•荧光显微镜或活体成像系统:用于观察和记录小鼠体内纳米颗粒的分布和动态变化。
•数据处理软件:用于对活体成像数据进行处理和分析。
实验步骤详解1. 制备荧光标记的纳米颗粒在实验之前,需要选择合适尺寸和表面性质的纳米颗粒,并将荧光染料或荧光蛋白与其结合,完成荧光标记。
这一步骤可以通过化学合成、生物合成等方法完成。
2. 小鼠模型制备选择合适品系和年龄相近、健康状况良好的小鼠作为实验对象。
在实验之前,需要对小鼠进行适当的驯化和适应环境。
3. 注射纳米颗粒将荧光标记的纳米颗粒溶液注射到小鼠体内。
注射途径可以根据实验需要选择,常用的有静脉注射、腹腔注射等。
注射时需要注意剂量控制和注射速度。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
2
电子的轨道半径:
r1 , 4r1 , 9r1 ,
能量量子化:
1 2 e En mvn 2 4 o rn
2
o h n v nh rn n 2 2 mrn me
2 2
1 me 4 En n 2 8 o2 h 2
不守恒。 但原子质量较大,能量交换可忽略, ∴光子 电子系统仍可认为能量是守恒的。
3、为什么可见光观察不到康普顿效应?
可见光光子能量不够大,原子内的电子不 能视为自由,所以可见光不能产生康普顿效应。
四、康普顿散射实验的意义
支持了“光量子”概念,进一步证实了
= h
首次实验证实了爱因斯坦提出的“光量子 具有动量”的假设 p = /c = h /c = h / 证实了在微观领域的单个碰撞事件中, 动量和能量守恒定律仍然是成立的。 康普顿获得1927年诺贝尔物理学奖。
h L mvr n n 2
半径量子化:
vn e m 2 rn 4o rn
2
2
e rn 2 4o mvn
2
mvn rn nh 玻尔量子化条件: vn mrn 2 mrn 2 2 2 oh n r1 (n 1,2,3,) rn n 2 me
理论值与实验值符合较好
4
例:试求氢原子处于基态时电子的动能、势能、总 能量、角动量、动量、速度及绕转频率 e2 E1 13.6ev 80r1
1 2 e2 Ek mv 13.6ev 2 80r1
E p E1 Ek 27.2ev
34
L1 mv1r1 1.054 10
1)n=1,2,3…, 只能取整数,所以能量是量子化的,是不连续的。
2)量子化的能量称为能级。n=1,最低能级,称为基态。n>2的能级 称为激发态能级。
me 氢原子的基态能量: 1 2 2 13.6 eV E 8 o h 氢原子能级: E , E 4 , E 9 , 1 1 1
4
E0 0.60 Mev hc E 0 h 0 0
0 0 20
hc 0 E0
100 hc 1 散射光子的能量 E E0 1.20
反冲电子的能量
0 0.20 1.200
1 Ee E0 E E0 E0 0.1002 MeV 0.10 MeV 1.20
原子的塌缩:高能电子运动辐射高频波,能量下 降,原子半径趋于零。
矛 盾
原子光谱的连续:实验支持原子发光的不连续。
三、玻尔氢原子理论 基本假设
1.定态假设:原子只能处在一系列具有不连续能量的稳定 状态,简称定态,相应于定态,核外电子在一系列不连 续的稳定圆轨道上运动,但它们并不辐射电磁波。 2.频率公式:当原子从一个 Em En 能量为Em的定态跃迁到另 一个能量为En的定态时, mn h 会发射或吸收一个频率为 mn的光子。 3.角动量量子化:电子在稳 定的轨道上运动时,其轨 道角动量L=mvr必须等于 h/2的整数倍。
吴有训(1897—1977)
江西高安人,中国近代物理学 奠基人,物理学家、教育家。 1920年毕业于南京高等师范学 校。1921年赴美入芝加哥大学, 师从康普顿,1926年获博士学 位,同年秋回国,先后在江西 大学和中央大学任教,1928年 秋起任清华大学教授,物理系 主任、理学院院长。1945年10 月任中央大学校长。1950年任 中国科学院副院长。
h 0 e0 mve0 c m m0 / 1 v 2 / c 2
v v2 1 1 2 v c c c
违反相对论!
上述过程不能同时满足能量、动量守恒。
因此: 自由电子不能吸收光子,只能散射光子。
2、为什么在光电效应中不考虑动量守恒?
在光电效应中,入射的是可见光和紫外线, 光子能量低,电子与整个原子的联系不能忽略, 原子也要参与动量交换, 光子 电子系统动量
三 康普顿效应
(Compton effect)
192223年康普顿研究了X射线在石墨上的散射 1、实验规律
X 射线管 晶体 散射波长,0
光阑Leabharlann 00探 测 器
石墨体 (散射物质)
X 射线谱仪
~
j 实验
波长偏移量
射 线 源
散射体
散射角
j 0o
c (1 cos j ) 2c sin
2
j
2
c = 0.0241Å = 2.4110-3nm(实验值) c 称为电子的康普顿波长
只有当入射波长0与c可比拟时,康普顿
效应才显著,因此要用X射线才能观察到。
2、康普顿效应的理论解释 经典电磁理论难解释为什么有≠0的散射, 康普顿用光子理论做了成功的解释: X射线光子与“静止”的“自由电子”弹性 碰撞 ( 波长1Å的X射线 ,其光子能量 104 eV,
. ... ........ . . . . . ... . ....... . .. . . . ... .... . . ... . . .... .. . ... . .. ... .. . . . . . . . .. .. .. ..... . . .
散射出现了≠0的现象,
称为康普顿散射。 散射曲线的三个特点:
h 6.63 1034 c m = 2 .4310-3nm m0c 9.1 10 31 3 108 等于实验值
为什么康普顿散射中还有原波长0 呢? 这是因为光子还可与石墨中被原子核束缚
得很紧的电子发生碰撞。 内层电子束缚能103~104eV,不能视为自由,
而应视为与原子是一个整体。 所以这相当于
散射角 j 1200
曲线表明: 1、与散射物质无关,仅与散射角有关。
2、轻元素 I I 0,重元素 I I 0 。
吴有训工作的意义: 证实了康普顿效应的普遍性
证实了两种散射线的产生机制:
- 外层电子(自由电子)散射 0 -内层电子(整个原子)散射
在康普顿的一本著作 “ X Rays in theory and experiment ” (1935)中,有19处引用了 吴有训的工作。 书中两图并列作为康普顿效应 的证据。
光子和整个原子碰撞。 ∵ m原子 m光子
∴ 在弹性碰撞中,入射光子几乎不损失能量,
即 散射光子波长不变,散射线中还有与原波 长相同的射线。
三、讨论几个问题
1、为什么康普顿效应中的电子不能像光电效应 那样吸收光子,而是散射光子? 假设自由电子能吸收光子,则有
h 0 m0c 2 mc 2
20世纪50年代的吴有训
对证实康普顿效应作出了重要贡献
例题:波长为 o =0.02nm的X射线与自由电子发生碰撞 ,若从与入射角成90°角的方向观察散射线。
求:(1)散射线的波长;(2)反冲电子的动能;
h (1 cos j ) 解: mo c 34 6.63 10 (1 cos 90) 0.0024nm 31 8 9.110 3 10
J s
mv1r1 v1 2.16 106 m / s mr1 mr1
v1 f 6.6 1015 转 / s 2r1
L1 24 1 p mv1 1.99 10 kg m s r1
2.氢光谱的一般表达式 里德伯常数:
~
RH 10973731m
1
1 1 RH 2 2 T (m) T (n) m n
R 光谱项: T (n) 2 n
(n > m)
谱线的波数可以表示为两光谱项之差。
3.氢光谱的线系
赖曼系:
(紫外光)
帕邢系:
1 1 RH 2 2 1 n
能量守恒 动量守恒
mv h 0 m0 c 2 h mc 2 h 0 h
c e0 e mv
c 反冲电子质量 m m0 / 1 v 2 / c 2 c c h (1 cos j ) (1 cos j ) 解得: 0 c 0 m0 c
1、除原波长0外,出现了 移向长波方面的新的散射波 长 .
j 45o
j 90o
2、新波长 随散射角j 的 增大而增大。
3、当散射角增大时,原波 长的谱线强度降低,而新波 长的谱线强度升高。
j 135o
0.709 0.749 波长 (A)
o
实验表明: 新散射波长 >入射波长0, 波长的偏移 = 0 只与散射角j 有关, 和散射物质无关。 实验规律是:
~
二 原子的稳定性
物理学 物质 结构、相互作用、运动规律 分子或原子 电子、原子核
Rutherford model of atom
粒子散射实验 经 典 理 论
电子运动方程
v e me 2 r 4 0 r
e2
2
2
1 e2 2 me v 电子能量 E E p Ek 4 0 r 2 8 0 r
外层电子束缚能~ eV, 室温下 kT~10-2eV) 碰撞过程中能量与动量守恒
h
h 0
mv 散射X射线频率 波长 自由电子(静止)
j m0
e
碰撞光子把部分能量
传给电子 光子的能量
自由电子(静止)
h 0 p0 e0 e j c m0
h p e c
氢原子能级和能级跃迁图:
6 5 -0.85eV 4 -1.51eV
En
n
1 E n 2 E1 n
