ENHANCING INTRUSION DETECTION IN WIRELESS NETWORKS USING
InHand ER605 5G 边缘路由器 用户手册说明书

IInHand ER6055G 边缘路由器用户手册资料版本:V1.0—2023.09首先非常感谢您选择本公司产品!在使用前,请您仔细阅读本用户手册。
非本公司书面许可,任何单位和个人不得擅自摘抄、复制本书内容的部分或全部,并不得以任何形式传播。
由于不断更新,本公司不能承诺本资料与实际产品一致,同时也不承担由于实际技术参数与本资料不符所导致的任何争议,任何改动恕不提前通知。
本公司保留最终更改权和解释权。
版权所有©2023北京映翰通网络技术股份有限公司及其许可者版权所有,保留一切权利。
本手册图形界面约定1简介 (1)2硬件部分 (2)指示灯说明 (2)通过Reset按钮恢复出厂 (3)3默认配置 (4)4路由器快速联网 (5)环境准备 (5)设备联网 (6)有线接入网络 (6)蜂窝接入网络 (8)Wi-Fi(STA)接入网络 (10)5仪表盘 (11)设备信息 (11)接口状态 (11)流量统计 (12)Wi-Fi连接数 (12)客户端流量Top5 (13)6状态 (14)链路监控 (14)蜂窝信号 (14)客户端 (15)VPN (15)事件 (15)上行链路表 (18)上行链路设置 (18)8本地网络 (20)9Wi-Fi (21)10VPN (22)IPSec VPN (22)L2TP VPN (24)客户端 (24)服务器 (25)VXLAN VPN (25)11安全 (27)防火墙 (27)入站规则/出站规则 (27)端口转发 (28)MAC地址过滤 (29)策略路由 (29)12服务 (31)接口管理 (31)DHCP Server (31)DNS Server (32)固定地址列表 (32)静态路由 (32)Dynamic DNS (33)adm管理 (35)云管理 (35)远程访问控制 (36)时钟 (37)设备选项 (37)配置管理 (38)设备告警 (38)工具 (39)Ping (39)Traceroute (40)抓包 (40)日志服务器 (41)其他设置 (41)Web登陆管理 (41)设备自动重启 (42)SIP ALG (42)Edge Router605是北京映翰通面向商业联网领域推出的新一代5G边缘路由器产品,该产品为各行业提供高速安全的网络接入。
基于RF-SVM的物联网入侵检测模型

基于RF-SVM的物联网入侵检测模型摘要:近年来物联网被广泛使用于社会各个领域,大量的敏感信息由物联网设备存储、处理和发送。
同时,物联网设备受到算力资源、存储资源、电力资源等限制,难以运行复杂的网络安全系统。
使得物联网设备成为了脆弱且高价值的网络攻击目标。
本文提出一种基于随机森林和支持向量机的入侵检测模型。
通过实验分析,该模型有着较高的准确率和较低的训练及检测时间。
关键词:物联网;入侵检测;随机森林;支持向量机中图分类号:TP393.08 文献标识码:A1.引言近年来,物联网安全问题更加突出,许多研究人员使用机器学习算法进行入侵检测,获得了较好的结果。
刘等人[1]提出了使用抑制模糊聚类和PCA算法的IDS。
与贝叶斯算法和神经网络算法相比,这种方法结合了机器学习和数据挖掘技术,并证明了更高的检测效率。
张等人[2]使用K-Means聚类算法对数据集划分为不同的簇,再由SVM标记异常集群进行详细分类。
Hussain 等人[3]所提出的一种两阶段混合分类方法,在第一阶段,采用 SVM 进行异常检测,第二阶段采用人工神经网络进行误用检测。
可以看出,物联网中用于入侵检测的机器学习正在迅速增长。
本文旨在通过研究用于物联网入侵检测的机器学习模型来进一步推动这项研究。
1.2.入侵检测模型本文提出的入侵检测模型共分为3个阶段,分别为数据预处理、基于随机森林的特征提取和基于线性SVM的入侵检测。
1.a.b.数据预处理2.由于支持向量机(Support Vector Machines,SVM)的输入应为连续型,而NSL-KDD数据集中个别特征为离散型,因此需要对离散型特征进行编码处理。
为了消除指标之间的量纲影响,在数据预处理阶段对数据使用最大最小归一化进行标准化处理。
1.a.b.基于随机森林的特征提取2.特征选择网络通过随机森林(Random Forest,RF)算法选择对结果重要的最优特征组合。
不仅消除无关特征对结果的干扰,而且节省模型训练时长和计算成本。
WC27500

ANSI/NEMA WC 27500 --`,,```,,,,````-`-`,,`,,`,`,,`---S TANDARD FORA EROSPACE ANDI NDUSTRIAL E LECTRICALC ABLE--`,,```,,,,````-`-`,,`,,`,`,,`---Approved as an American National StandardANSI Approval Date: January 4, 2002NEMA Standards Publication WC 27500-2005Standard for Aerospace and Industrial Electrical CablePublished by:National Electrical Manufacturers Association1300 North 17th Street, Suite 1752Rosslyn, Virginia 22209© Copyright 2005 by the National Electrical Manufacturers Association. All rights including translation into other languages, reserved under the Universal Copyright Convention, the Berne Convention for the Protection of Literary and Artistic Works, and the International and Pan American Copyright Conventions.NOTICE AND DISCLAIMERThe information in this publication was considered technically sound by the consensus of persons engaged in the development and approval of the document at the time it was developed.Consensus does not necessarily mean that there is unanimous agreement among every person participating in the development of this document.The National Electrical Manufacturers Association (NEMA) standards and guideline publications, of which the document contained herein is one, are developed through a voluntary consensus standards development process. This process brings together volunteers and/or seeks out the views of persons who have an interest in the topic covered by this publication. While NEMA administers the process and establishes rules to promote fairness in the development of consensus, it does not write the document and it does not independently test, evaluate, or verify the accuracy or completeness of any information or the soundness of any judgments contained in its standards and guideline publications.NEMA disclaims liability for any personal injury, property, or other damages of any nature whatsoever, whether special, indirect, consequential, or compensatory, directly or indirectly resulting from the publication, use of, application, or reliance on this document. NEMA disclaims --`,,```,,,,````-`-`,,`,,`,`,,`---and makes no guaranty or warranty, express or implied, as to the accuracy or completeness of any information published herein, and disclaims and makes no warranty that the information in this document will fulfill any of your particular purposes or needs. NEMA does not undertake to guarantee the performance of any individual manufacturer or seller’s products or services by virtue of this standard or guide.In publishing and making this document available, NEMA is not undertaking to render professional or other services for or on behalf of any person or entity, nor is NEMA undertaking to perform any duty owed by any person or entity to someone else. Anyone using this document should rely on his or her own independent judgment or, as appropriate, seek the advice of a competent professional in determining the exercise of reasonable care in any given circumstances.Information and other standards on the topic covered by this publication may be available from other sources, which the user may wish to consult for additional views or information not covered by this publication.NEMA has no power, nor does it undertake to police or enforce compliance with the contents of this document. NEMA does not certify, test, or inspect products, designs, or installations for safety or health purposes. Any certification or other statement of compliance with any health or safety–related information in this document shall not be attributable to NEMA and is solely the responsibility of the certifier or maker of the statement.WC 27500-2005Page iCONTENTSPageForeword (iv)Scope (v)Section 1 REFERENCED STANDARDS (1)1.1Order of Precedence (3)Section 2 CLASSIFICATION (4)2.1General (4)2.2Cable Designation (4)2.2.1Identification Method of Cable Wire (With Shield Coverage) (5)2.2.2Conductor Size (5)2.2.3Basic Wire Specification (5)2.2.4Number of Wires per Cable (7)2.2.5Shield Style and Material (7)2.2.6Jacket Material, Color, and Temperature Rating (8)Section 3 REQUIREMENTS (11)3.1Construction (11)3.2Basic Wire (11)3.3Finished Cable (11)3.4Identification of Cable Wire (11)3.4.1Preferred Identification Method (11)3.4.2Optional Identification Method A (12)3.4.3Optional Identification Method B (14)3.4.4Optional Identification Method C (14)3.4.5Optional Identification Method D (16)3.4.6Optional Identification Method E (16)3.4.7Optional Identification Method F (16)3.5Cable Lay-Up (16)3.6Fillers and Binder Tapes (16)3.7Shield (16)3.7.1Round Shield (16)3.7.2Flat Shield (18)3.7.3Braid Angle (19)3.7.4Shield Coverage (19)3.7.5Shield Splices (19)3.8 Jacket (20)3.8.1Jacket Requirements (20)3.8.2Jacket Material (20)3.8.2.10 Taped Polyimide/Fluorinated Ethylene Propylene (21)3.9Functional Characteristics (24)3.9.1Dielectric Withstand (24)3.9.2Jacket Flaws (Shielded and Jacketed Cables Only) (24)3.9.3Conductor Continuity (24)3.9.4Cold Bend (Jacketed and Shielded-and-Jacketed Cables Only) (24)3.9.5Thermal Shock* (24)3.9.6Blocking (25)3.9.7Flammability (25)3.9.8Lamination Sealing (25)3.9.9Crosslinked Verification * (25)3.9.10Shield Solderability* (25)3.9.11Temperature Rating (25)3.10Identification of Product (25)WC 27500-2005Page ii3.10.1Wire Product Identification (26)3.10.2Cable Product Identification (26)3.10.3Identification Marker Tape (27)3.11Cable Diameter (27)3.12Cable Weight (27)3.13Continuous Lengths (27)3.14Workmanship (27)Section 4 VERIFICATION (28)4.1Classification of Inspection (28)4.2Conditions of Inspection (28)4.2.1Quality Conformance Inspection (28)4.2.2Process Control Tests (29)4.2.3Disposition of Rejections (30)4.2.4Certified Test Reports (30)4.3Methods of Inspection (30)4.3.1Inspection of Product (31)4.3.2Shield Strands (31)4.3.3Dielectric Withstand (31)4.3.4Jacket Flaws (32)4.3.5Braid Angle and Shield Coverage (32)4.3.6Cold Bend (32)4.3.7Voltage Withstand, Jacket (32)4.3.8Conductor Continuity (33)4.3.9Thermal Shock (33)4.3.10Crosslinked Verification (33)4.3.11Bend Test (33)4.3.12Jacket Wall Thickness (33)4.3.13Jacket Tensile Strength and Elongation (34)4.3.14Lamination Sealing (Tape-Wrapped Jacket, Materials 11, 12, 22, 24, 61, 62,72,74) (34)4.3.15Jacket Blocking (34)4.3.16Concentricity (35)4.3.17PTFE Tape Wrapped Jacket Delamination (35)4.3.18Shield Solderability (35)4.3.19Flammability (35)4.4Cable Diameter (35)4.5Cable Weight (36)4.5.1Measured (36)4.5.2Calculated (36)4.6Continuous Lengths (37)Section 5 PACKAGING (38)5.1General (38)Section 6 NOTES (39)6.1Appendices (39)6.2Ordering Data (39)6.2.1Acquisition Requirements (39)Appendix A CABLE DESIGN GUIDELINES (40)A.1Introduction (40)A.2Elements of Primary Wire Selection (40)A.2.1Conductor Size (40)A.2.2Conductor Type (40)A.2.3Insulation Type (40)A.3Elements of Shield Selection (40)WC 27500-2005Page iiiA.3.1Material (40)A.3.2Flat vs. Round Strands (41)A.3.3Shield Coverage (41)A.4Elements of Jacket Selection (41)A.5Cable Identification and Color Codes (41)A.6Consultation (41)Appendix B SUPERSESSIONS AND REPLACEMENTS (42)B.1Superseded Symbols (42)B.2Manned Aerospace Replacements (43)--`,,```,,,,````-`-`,,`,,`,`,,`---WC 27500-2005Page ivForewordThis standard was developed by the High Performance Wire and Cable Section of NEMA as a non-governmental standard replacement for MIL-DTL-27500 electrical cable which is widely used in aerospace and other industries.It contains:Reference standards (Section 1)Identification methods (Section 2) and requirements (Section 3.10)Construction details (Sections 2, 3)Material requirements (Section 2)ConductorsPrimary wireShieldsJacketsElectrical requirements (Section 3.8)Physical requirements (Section 3.8)Other requirements (Sections 3.11-14)Color/size/weight/lengths/markingsTest methods for above requirements (Section 4)Inspection/QC/process control procedures (Section 4)Packaging (Section 5)Notes/cross-reference/other data (Section 6)Ordering dataThe requirements contained herein are consensus requirements that have been developed over the past three decades by knowledgeable engineers in the aerospace industry.The standards or guidelines presented in a NEMA standards publication are considered technically sound at the time they are approved for publication. They are not substitutes for a product seller's or user's own judgment with respect to the particular product referenced in the standard or guideline, and NEMA does not undertake to guarantee the performance of any individual manufacturer's products by virtue of this standard or guide. Thus, NEMA expressly disclaims any responsibility for damages arising from the use, application, or reliance by others on the information contained in these standards or guidelines.Members of NEMA High Performance Wire and Cable Section that participated in the development of the current revision of this standard were:AmerCable—Houston, TXBerk-Tek a Nexans Company—Elm City, NCCable USA, Inc.—Naples, FLFisk Alloy Conductors, Inc.—Hawthorne, NJGeneral Cable—Willimantic, CTHarbour Industries, Inc.—Shelburne, VTJudd Wire, Inc.—Turners Falls, MAPhelps Dodge High Performance Conductors—Inman, SCQuirk Wire Company, Inc.—West Brookfield, MARadix Wire Company—Cleveland, OH 44132Rockbestos-Surprenant Cable Corporation—East Granby, CTThe Monroe Cable Company, Inc.—Middletown, NYTyco Electronics—Sunnyvale, CAWC 27500-2005Page vScopeThis standard contains requirements for finished cables. The component wires are covered by other referenced standards. These cables are intended for signal and low-voltage power applications with defined environment or temperature conditions found in commercial aircraft, military aircraft, and high performance vehicles.WC 27500-2005Page vi< This page is intentionally left blank. >WC 27500-2005Page 1Section 1REFERENCED STANDARDSAmerican National Standards Institute (ANSI)11 West 42nd StreetNew York, NY 10036American Society for Quality Control (ASQC)611 East Wisconsin AvenueMilwaukee, WI 53202ANSI/ASQC Z 1.4 Sampling Procedures and Tables for Inspection by Attributes --`,,```,,,,````-`-`,,`,,`,`,,`---American Society for Testing and Materials (ASTM)100 Barr Harbor DriveWest Conshohocken, PA 19428ASTM A 313/A313M-03 Standard Specification for Stainless Steel Spring Wire3-01 Soft or Annealed Copper WireASTMBASTM B 33-04 Standard Specification for Tinned Soft or Annealed Copper Wire forElectrical PurposesASTM B 272-02 Copper Flat Copper Products with Finished (Rolled or Drawn) Edges(Flat Wire and Strip)-99 Silver-Coated Soft or Annealed Copper Wire298BASTM355-95 Nickel-Coated Soft or Annealed Copper WireBASTMASTM B 624-99 High-strength, High-conductivity Copper Alloy Wire for ElectronicApplication, Standard, Specification forD3032-04 Hookup Wire Insulation, Standard Methods of TestingASTMASTM D 4066-01 Polyamide Injection and Extrusion Materials (PA)Nylon Injection andExtrusion Materials (PA)National Electrical Manufacturers Association (NEMA)1300 North 17th StreetRosslyn, VA 22209WC 52-2005 High-Temperature and Electronic Insulated Wire – Impulse DielectricTestingWC 56-1986 (R2000 R2005) 3.0kHz Insulation Continuity Proof Testing of Hook Up WireWC 65-1995 (R2003) A Reasoned Approach to Solving Solderability Problems with Tin-Coatedand Nickel-Coated Stranded Conductors in High Performance Wire andCable ApplicationsWC 67-2005 Standard for Uninsulated Conductors Used in Electrical and ElectronicApplicationsWC 72-1999 (R2004) Continuity of Coating Testing for Electrical ConductorsWC 27500-2005 Page 2© Copyright 2005 by the National Electrical Manufacturers Association.Superintendent of Documents U.S. Government Printing OfficeWashington, DC 20402H4-1 Federal Supply Code For Manufacturers, United States and Canada, Name to CodeH4-2 Federal Supply Code For Manufacturers, United States and Canada. Code to NameDepartment of DefenseStandardization Document Order Desk700 Robbins Avenue, Bldg. 4D Philadelphia, PA 19111-5094MIL-W-5086 Wire, Electrical, Polyvinyl Chloride Insulated, Copper or Copper Alloy MIL-W-8777 Wire, Electrical, Silicone-Insulated, Copper, 600 Volt, 200° C MIL-C-12000 Cable, Cord, and Wire, Electric; Packaging of MIL-DTL-25038 Wire, Electrical, High Temperature and Fire Resistant, GeneralSpecification forMIL-W-81044 Wire, Electric, Crosslinked Polyalkene, Crosslinked AlkaneimidePolymer, or Polyarylene Insulated Copper or Copper AlloyMIL-DTL-81381 Wire, Electric, Polyimide-insulated, Copper or Copper Alloy MIL-STD-104 Limits for Electrical Insulation Color MIL-STD-202 Test Methods Standard for Electronic and Electrical Component Parts MIL-STD-681 Identification Coding and Application of Hookup and Lead Wire MIL-STD-686 Cable and Cord, Electrical; Identification Marking and Color Coding of MIL-STD-2223 Test Methods for Insulated Electric WireMS25471 Wire, Electrical-Silicone, Copper, 600 Volt, 200 Deg. C, Polyester Jacket MS27110 Wire, Electrical-Silicone, Copper, 600 Volt, 200 Deg. C, FEP Jacket(ASG)National Institute for Standards and Technology (NIST)Publications Office Building 101Gaithersburg, MD 20879NBS HDBK 100 International Annealed Copper Standard (IACS)Society of Automotive Engineers (SAE)400 Commonwealth Drive Warrendale, PA 15096-0001AS50881A Wiring, Aerospace Vehicle AS22759 Wire, Electric, Fluoropolymer-insulated, Copper Or Copper AlloyNOTE–Non-Government standards and other publications are normally available from the organizations that prepare or distribute the documents. These documents also may be available in or through libraries or other informational services.--`,,```,,,,````-`-`,,`,,`,`,,`---WC 27500-2005Page 31.1 ORDER OF PRECEDENCEIn the event of a conflict between this specification and the references cited herein (except for associated detail specifications, specification sheets, or MS standards), the text of this specification shall take precedence. Nothing in this specification, however, shall supersede applicable laws or regulations unlessa specific exemption has been obtained.--`,,```,,,,````-`-`,,`,,`,`,,`---© Copyright 2005 by the National Electrical Manufacturers Association.WC 27500-2005Page 4Section 2CLASSIFICATION2.1 GENERALThe cable shall be one of the following types and shall be furnished in the basic wire size, type, numberof wires, and shield and jacket styles, as specified. (See 6.2 and 2.2.)Unjacketed - 2 to 15 wires, spirally cabled, without an overall outer jacket.Jacketed - 2 to 15 wires, spirally cabled, with an overall outer jacket.Shielded - A single wire, or 2 to 15 wires, spirally cabled, with one or two overall shields.Shielded and Jacketed - A single wire, or 2 to 15, wires spirally cabled with one or two shields andone or two jackets.2.2 CABLEDESIGNATIONCable shall be identified by a combination of digits and letters in accordance with the following: (See3.10.2.)M27500 - 22 SD 3 T 23 | | | | | | |Identification number Identificationmethod ofcable wireand shieldcoverage(See 2.2.1.)Conductorsize(See 2.2.2.)Basic wirespecification(See 2.2.3.)Number ofwires incable(See 2.2.4.)Shield styleand material(See 2.2.5.)Jacketmaterial(See 2.2.6.)Example: M27500-22SD3T23 = 22 AWG, MIL-W-22759/34, 3 conductor, tin shielded 85 %, white XLETFE jacket. --`,,```,,,,````-`-`,,`,,`,`,,`---WC 27500-2005Page 52.2.1 Identification Method of Cable Wire (With Shield Coverage)When an unshielded cable, or a cable with a minimum shield coverage of 85%, is required, specify: “-” for the preferred identification method, Table 3-1.“F” for the preferred identification method, Table 3-2.“A” for optional identification method A, Table 3-1.“G” for optional identification method A, Table 3-2.“B” for optional identification method B, Table 3-3.“K” for optional identification method C, Table 3-3.“L” for optional identification method D.“P” for optional identification method E.“S” for optional identification method F.“U” for color codes specified by the procuring activity.When a minimum shield coverage of 90% is required, specify:“C” for the preferred identification method, Table 3-1.“H” for the preferred identification method, Table 3-2.“D” for optional identification method A, Table 3-1.“J” for optional identification method A, Table 3-2.“E” for optional identification method B, Table 3-3.“M” for optional identification method C,Table 3-3.“N” for optional identification method D.“R” for optional identification method E.“T” for optional identification method F.“V” for color codes specified by the procuring activity.Table 2-1IDENTIFICATION METHODS CROSS-REFERENCEBasic wire coloring Identificationsequence85% shield coverageor unshielded 90% shield coverageStripes Colors per Table 3-1 - CStripes Colors per Table 3-2 F HSolids Colors per Table 3-1 A DSolids Colors per Table 3-2 G J By AWG, Table 3-3 Band Marks B EBy AWG, Table 3-3 Printed Numbers K M White PrintedNumbers L N White Band Marks and Stripes P RWhite ColorBands S T 2.2.2 Conductor SizeThe basic wire size shall be identified. All wires used in the cable shall be of the same size.2.2.3 Basic Wire SpecificationA letter symbol shall be used to designate the basic wire specification in accordance with Table 2-2.WC 27500-2005Page 7 2.2.4 Number of Wires per CableThe number of wires per cable shall be as designated and shall be 1 to 15 for shielded or shielded and jacketed cables, and 2 to 15 for unshielded unjacketed or unshielded jacketed cables. Cables with 10 to 15 conductors shall be limited to 12 AWG and smaller.2.2.5 Shield Style and MaterialThe shield style and material of the overall shields shall be designated by a single letter or symbol in accordance with Table 2-3.Table 2-3SHIELD MATERIALSymbolSingle Shield StyleSymbolDoubleShield Style Shield MaterialMaximumTemperatureLimit for ShieldMaterial(Information Only)U T S N F C M P G H* J E I ---VWYZRKLAB#DXQNo shieldTin-coated copper, roundSilver-coated copper, roundNickel-coated copper, roundStainless Steel, roundNickel-coated copper 27%, roundSilver-coated high strength copperalloy, roundNickel-coated high strength copperalloy, roundSilver-coated copper, flatSilver-coated high strength copperalloy, flatNickel-coated copper, flatTin-coated copper, flatNickel-coated high strength copperalloy, flat Nickel-chromium alloy, flat---150°C (302°F)200°C (392°F)260°C (500°F)400°C (752°F)400°C (752°F)200°C (392°F)260°C (500°F)200°C (392°F)200°C (392°F)260°C (500°F)150°C (302°F)260°C (500°F)400°C (752°F)--`,,```,,,,````-`-`,,`,,`,`,,`---WC 27500-2005Page 82.2.6 Jacket Material, Color, and Temperature RatingThe single jacket symbol shall be used for cables with an outer jacket only. The double jacket symbol shall be used in conjunction with a double shield symbol to describe constructions with a jacket in between two shields with another jacket over the outer shield. The single jacket symbol shall be used in conjunction with the double shield symbol to describe constructions with two overlaid shields with a single outer jacket. Unless otherwise specified (see 6.2.1, g ), jacket colors shall be as specified under the --`,,```,,,,````-`-`,,`,,`,`,,`---jacket materials in accordance with Table 2-4.WC 27500-2005Page 9 Table 2-4JACKET MATERIAL AND COLORSingle Jacket Symbol DoubleJacketSymbol Jacket MaterialMaximumTemperatureRatingFor Jacket Material(Information Only)0001020304050607083 09 103 114 124141516 175 18500511522535455565758359603614624646566675685No JacketExtruded white polyvinyl chloride (PVC)Extruded clear polyamideWhite polyamide braid impregnated with clear polyamide finisher overa polyester tapePolyester braid impregnated with high temperature finishers overpolyester tapeExtruded clear fluorinated ethylene propylene (FEP)Extruded or taped and heat sealed white polytetrafluoroethylene(PTFE)White polytetrafluoroethylene (PTFE) treated glass braid impregnatedand coated with polytetrafluoroethylene finisher over presinteredpolytetrafluoroethylene tapeCross linked white extruded polyvinylidene fluoride (PVDF)Extruded white fluorinated ethylene propylene (FEP)Extruded clear polyvinylidene fluoride (PVDF)Tape of natural polyimide combined with clear fluorinated ethylenepropylene (FEP) wrapped and heat sealed with (FEP) outer surfaceTape of natural polyimide combined with fluorinated ethylenepropylene (FEP) wrapped and heat sealed with polyimide outer surfaceExtruded white ethylene-tetrafluoroethylene copolymer (ETFE)Extruded clear ethylene-tetrafluoroethylene copolymer (ETFE)Braid of aromatic polyamide with high temperature finisher overpresintered polytetrafluoroethylene (PTFE) tapeWhite extruded ethylene chlorotrifluoro-ethylene (ECTFE)Clear extruded ethylene chlorotrifluoro-ethylene (ECTFE)---90°C (194°F)105°C (221°F)105°C (221°F)150°C (302°F)200°C (392°F)260°C (500°F)260°C (500°F)150°C (302°F)200°C (392°F)125°C (257°F)200°C (392°F)200°C (392°F)150°C (302°F)150°C (302°F)200°C (392°F)150°C (302°F)150°C (302°F)1Polyvinyl chloride materials shall not be used for aerospace applications.2Jacket material 02 is not to be used for cables having a diameter of 0.251 inch or greater.3Jacket materials 08, 58, 10, and 60 are not to be used for cables having a diameter of 0.401 inch or greater.4Not for Naval Air Systems Command Usage.5Inactive for new design.WC 27500-2005Page 10Table 2-4JACKET MATERIAL AND COLOR (continued)Single Jacket Symbol DoubleJacketSymbol Jacket MaterialTemperatureRating For JacketMaterial(Information Only)2021222324 7071727374Extruded white perfluoroalkoxy (PFA)Extruded clear perfluoroalkoxy (PFA)Tape of polyimide combined with clear fluorinated ethylene propylene(FEP) wrapped and heat sealed with opaque polyimide outer surfaceWhite, crosslinked, extruded, modified, ethylene-tetrafluoroethylenecopolymer (XLETFE)Tape layer of white polytetrafluoroethylene (PTFE) wrapped over atape layer of natural polyimide combined with FEP heated and fused260°C (500°F)260°C (500°F)200°C (392°F)200°C (392°F)260°C (500°F)--`,,```,,,,````-`-`,,`,,`,`,,`---WC 27500-2005Page 11Section 3REQUIREMENTS3.1 CONSTRUCTIONConstruction shall comply with the designation given in 2.2. This standard covers a wide variety of possible primary wires, shields, and jacket combinations. Appendix A provides design parameters that should be considered in determining which combination is appropriate for a specific application. It is strongly recommended that consultation between users and cable manufacturers be made in order to assure the most suitable cable.3.2 BASIC WIREWire used in the construction of the cable shall be qualified to the basic wire specification (Table 2-2) before cabling. The producer of the finished cable shall be a qualified source under the applicable basic wire specification, or shall ensure that qualified wire from a qualified source was used in the construction of the cable and be required to furnish on request a test report from the manufacturer of the basic wire, plus a letter certifying that the component wire meets all the individual component wire specification requirements from the builder of the cable. Color added to the insulation (such as a helical stripe or circumferential band) for the purpose of wire number identification shall not degrade the insulation as evidenced by failure to meet the requirements herein. Unless otherwise specified (see 6.2.1), the manufacturer of cable is responsible for assuring that the basic wire meets the wire specification requirements prior to being fabricated into cable.3.3 FINISHED CABLEIn addition to meeting the basic wire requirements per 3.2, the cable supplier responsible for further processing and/or the assembly of the finished cable shall assure that all functional characteristics contained within this specification are tested. Basic wire test data alone shall not be used as acceptance criteria for finished cable.3.4 IDENTIFICATION OF CABLE WIREThe basic wire insulation for single or multi-conductor cables shall provide a method of determining the wire number. Unless otherwise specified (see 6.2.1), the preferred identification method (see 3.4.1) shall be used. Stripes, tracers, and background insulation colors on the basic wires shall meet the requirements of MIL-STD-104 Class I, unless otherwise indicated or allowed by the basic wire specification.3.4.1 Preferred Identification MethodThe insulation of wire used in the cable shall be white (or basic color or natural color) with one or two colored spiral stripes in accordance with Table 3-1 or Table 3-2 as applicable. The color stripe(s) shall be in accordance with MIL-STD-681. For wire diameters larger than .300 in., a longitudinal stripe is acceptable in lieu of a spiral stripe. When braid is employed in the basic wire the stripe(s) shall be incorporated in the textile braid. When the braid is used, colored fibers shall be used for two parallel and adjacent carriers of the braid. The color identification fibers shall be woven in the opposite direction of any identification marker.WC 27500-2005 Page 123.4.2 Optional Identification Method AThe insulation shall be a solid color in accordance with Table 3-1 or Table 3-2 as applicable. Solid coloring shall be done by the manufacturer of the wire, and the coloring shall meet the requirements of the basic wire specification.--`,,```,,,,````-`-`,,`,,`,`,,`---WC 27500-2005Page 14Table 3-2CIRCUIT IDENTIFICATION COLORS FOR BASIC WIRES1Numberof Wiresin Cable Identification Colors for Respective Wires in Cable(See 3.4.1 or 3.4.2.)1 2 3 4 5 6 7 8 9101112131415 Basic (white)Red, blueRed, blue, yellowRed, blue, yellow, greenRed, blue, yellow, green, basicRed, blue, yellow, green, basic, blackRed, blue, yellow, green, basic, black, brownRed, blue, yellow, green, basic, black, brown, orangeRed, blue, yellow, green, basic, black, brown, orange, violetRed, blue, yellow, green, basic, black, brown, orange, violet, grayRed, blue, yellow, green, basic, black, brown, orange, violet, gray, red/ white2Red, blue, yellow, green, basic, black, brown, orange, violet, gray, red/ white, blue/white2Red, blue, yellow, green, basic, black, brown, orange, violet, gray, red/ white, blue/white, yellow/white2 Red, blue, yellow, green, basic, black, brown, orange, violet, gray, red/ white, blue/white, yellow/white, green/white2Red, blue, yellow, green, basic, black, brown, orange, violet, gray, red/ white, blue/white, yellow/white, green/white, black/white21 This color code was originally intended for basic wires in accordance with MIL-W-5086 and associated replacement wire andcable.2Color designation indicates a solid color with stripe (red/white - solid red insulation with a white stripe).3.4.3 Optional Identification Method BThe insulation on each wire in the cable shall be the same solid color. The color shall denote wire size in accordance with Table 3-3. In order to identify each wire in the cable, color bands shall be applied in accordance with Table 3-4. Color of the bands shall be contrasting to the base color of the insulation. The narrow bands shall be 0.030 in. to 0.120 in. wide. The wide bands shall be twice the width of the narrow bands and spaced 0.030 in. to 0.120 in. apart in a group. Group separation shall be 0.38 to 1.50 in. The distance between the beginning of one group and the end of the next group shall be 3.0 in. maximum.3.4.4 Optional Identification Method CThe insulation on each wire in the cable shall be the same solid color. The color shall denote wire size in accordance with Table 3-3. In order to identify each wire in the cable, the use of numbers printed on the insulation of the primary wire shall be used. The color of the numbers shall be a contrasting color to the base color of the insulation. The distance between the printed numbers shall be 3.0 in. maximum. --`,,```,,,,````-`-`,,`,,`,`,,`---。
IntrusionDetectionandIntrusionPrevention

Common NIDS Pitfalls
• Deployed where it does not have access to all network traffic
• Output and/or alerts are ignored • Inadequate incident response planning • Administrators become overwhelmed by an
uses • Correlation, Analysis, Alerting, Reporting • IDS and IPS adds to defense in depth
More Information
For additional references on IDS/IPS, see:
/ /rr/papers/30/1028.pdf /texts.php?op=display&id=117 /
un-tuned system • Limitations of IDS/IPS are not well
understood (updates, zero-day attacks, IDS blinding and evasion techniques)
Types of Protection
Network Resets
administrators – Data is useful in forensic investigations – Issues include false positives and negatives, large
amounts of data, requires full-time monitoring, signature updates, encrypted traffic
lbp3500维修手册

Indicates an item requiring care to avoid combustion (fire).
Indicates an item prohibiting disassembly to avoid electric shocks or problems.
1.3 Product Specifications ................................................................................................................................1- 1 1.3.1 Specifications .......................................................................................................................................................... 1- 1
1.4 Name of Parts.............................................................................................................................................1- 3 1.4.1 External View........................................................................................................................................................... 1- 3 1.4.2 Cross Section .......................................................................................................................................................... 1- 4
曙光天阔A840r-G用户手册V1.1

硬件及数据损坏负责; 8、 当服务器出现故障时,如果您不能确定故障的原因,请及时与曙光技术支持部门联系以
获得帮助; 9、 如主板 CMOS 电池失效,请使用与本机配备的电池相同型号的电池进行更换,替换下的
的稳定运行,并将可以延长服务器的使用寿命; 2、 请使用带接地保护的三芯电源线与插座,并使用220V 交流电,不正确的电源设置可能
会导致漏电、烧毁、爆炸甚至人身伤害; 3、 请不要在服务器正在运行时插拔背板连线或是移动服务器,否则将可能造成服务器当机
或是部件损坏; 4、 请尽量避免频繁重启或开关机,以延长服务器的使用寿命; 5、 请用户及时备份重要数据,曙光信息产业有限公司不为任何情况导致的数据丢失负责; 6、 请使用正版操作系统及软件,并进行正确配置。曙光信息产业有限公司对由于操作系统
声明及注意事项
感谢您选用曙光服务器!
曙光服务器将给您带来强大的应用支持和全新的性能体验。为了您能够更安全、方便的 使用曙光服务器,在使用之前,请详细阅读本节所提示的信息。
曙光服务器在设计和制造过程中均遵循了严格的标准,以保证您所使用的服务器拥有卓 越的品质和完美的“SUMA”特性。但是服务器属于精密电子设备,在使用过程中仍然可能因 为各种原因而导致异常,所以请务必明确以下事项: 1、 请将服务器放置在阴凉、干燥、通风、洁净、无强磁场的环境中使用,这有助于服务器
电池请妥善回收处理。 曙光信息产业有限公司保留对以上条款的解释权。
再次感谢您选用曙光服务器!
-3-
曙光天阔 A840r-G 服务器用户手册 V1.1
目录
第一章 系统简介 ........................
安全光栅GuardShield 450L-E说明书

The Allen-Bradley® GuardShield™ 450L-E Safety Light Curtains fromRockwell Automation are based on a unique patented transceiver technology which allows each stick to be used as a transmitter or as a receiver. The full functionality of a transceiver is provided by plug-ins inserted at the bottom of the sticks. By using only one stick type with the optimal plug-ins selected based on the requirements of the application, the GuardShield 450L portfolio is a simple, cost effective solution that offers enhanced flexibility while maintaining the highest level of safety.The enhanced Integrated Laser Alignment System (ILAS) of the GuardShield 450L-E reduces installation time by providing multiple visible laser points that optimize setup with a simple touch of the ILAS symbol on the front window of the stick. Plus, the compact design and full length protective field make it easy to integrate a GuardShield 450L-E system in hand and finger protection applications from 150 mm (5.9 in.) up to 1950 mm (76.7 in.) in increments of 150 mm (0.5 ft).The enhanced GuardShield 450L-E light curtain system is also ideal for special applications requiring advanced functions such as muting and blanking,easily set up through DIP switches located on the dedicated plug-in modules. For muting, the common set ups like 4-sensor or 2-sensor with L- and T-configuration and override function can be selected. Blanking, reducedresolution, floating blanking and teach-in fixed blanking features are available. Configure up to eight protection zones via CCW software. A cascading plug-in can also be installed for series connection of additional GuardShield 450L Safety Light Curtain systems for multi-sided machine guarding (up to four sides). All these special functions combined with the inherent flexibility of the GuardShield 450L transceiver design help to simplify your engineering logistics and minimize the stock required to address your full range of applications.For configuration, monitoring and troubleshooting, our free Connected Components Workbench software is available at our website. A separate optical interface tool is required if using Connected Components Workbench software for diagnostic information.Features and Benefits• Extended features and functionality compared to the 450L-B such as cascading, built-in muting,blanking and multiple applications configuration• Embedded functions configured quickly and easily via DIP switches or software, significantly reducing engineering effort. These include:– M uting, blanking, start mode, external device monitoring (EDM), scanning range• Leverages patented transceiver technology – each stick can be used as a transmitter or receiver via innovative plug-in modules• Enhanced Integrated Laser Alignment System (ILAS) for quick installation and reliable operation• Active protective field provides sensing over the entire length of a transceiver• Compact design 30 mm x 30 mm (1.18 in. x 1.18 in.)• Wide range of protection heights 150…1950 mm (5.9…76.7 in.) in increments of 150 mm (0.5 ft)• Resolutions:– F inger resolution (14 mm): 0.5 to 9 m (1.64…29.53 ft)– H and resolution (30 mm): 0.9 to 16.2 m (2.95…53.15 ft)• Supports cascading of multiple systems in series• Flexible mounting options allow for quick and easy installation• Configure, monitor and troubleshoot via Connected Components Workbench (CCW) software.Pre-configure multiple configurations. • IP65 enclosure rating• TÜV certified Type 4 IEC 61496-1/-2, Ple, SILcl3 per EN ISO 13849-1,IEC 62061Allen-Bradley GuardShield 450L-E Safety Light CurtainEnhanced Flexibility and Advanced Features in a Cost-Effective Safety SolutionRequired Accessories 1Replace the x with 2 (6.6 ft), 5 (16.4 ft), 10 (32.8 ft), 15 (49.2 ft), 20 (65.6 ft), or 30 (98.4 ft) for available lengths in metersOptional Accessories*Requires 450L fw version 4.00x and CCW R12 at minimum.1xxxx = 0150…1950 mm (0.5…6.4 ft) in increments of 150 mm (0.5 ft)Innovative plug-in modulesestablish transceiver as an emitter orreceiver and provide other advanced functions.Integrated Laser Alignment System accelerates setup for optimal performance at the touch of a button.General Ordering InformationLight Curtain System: Order two identical transceivers/catalog numbers. Plug-in Modules: Order one transmitter and one receiver plug-in with the desired functionality for one system – or – Order two universal plug-ins for one system. Each universal plug-in can be used as a transmitter or a receiver. To cascade systems or for muting options use thecascading plug-in.1xxxx = 0150 … 1950 mm (0.5 … 6.4 ft) in increments of 150 mm (0.5 ft).For example: “450L-E4HL 0900YD” indicates an order for 900 mm hand detection light curtain transceiver.2Optional side mounting bracket kit is available below.1 The 8-pin transmitter plug-in option allows two 8-pin cordsets to be used in one system.2Order two universal plug-ins for one system. Each universal plug-in can be used as a transmitter or a receiver.Publication 450L-PP002B-EN-P – May 2020 | Supersedes Publication 450L-PP002A-EN-P – January 2018Copyright © 2020 Rockwell Automation, Inc. All Rights Reserved. Printed in USA.Allen-Bradley, Connected Components Workbench, Expanding human potential and GuardShield are trademarks of Rockwell Automation, Inc.Trademarks not belonging to Rockwell Automation are property of their respective companies.Connect with us.。
intrusion detection method -回复

intrusion detection method -回复主题:入侵检测方法引言:随着网络的迅速发展和普及,网络安全问题变得越发突出。
入侵检测方法是保护计算机系统和网络免受未经授权访问的重要手段。
本文将详细介绍入侵检测的概念、分类和常用的入侵检测方法,并逐步回答相关问题。
第一部分:入侵检测概述1. 什么是入侵检测?入侵检测是一种用于发现和响应网络和计算机系统中潜在入侵行为的技术。
2. 入侵检测的重要性是什么?入侵检测是预防和提前发现黑客攻击、病毒传播和系统漏洞等安全问题的关键工具,有助于保护数据的机密性、完整性和可用性。
3. 入侵检测与防火墙的区别是什么?入侵检测侧重于检测和报告潜在入侵行为,而防火墙则通过过滤和阻断网络流量来预防入侵。
第二部分:入侵检测分类1. 入侵检测分为哪两类?入侵检测分为基于签名和基于行为的检测方法。
2. 什么是基于签名的入侵检测?基于签名的入侵检测使用已知攻击行为的特征(签名)来检测和识别入侵,常用于检测已知攻击和病毒。
3. 什么是基于行为的入侵检测?基于行为的入侵检测通过分析系统和网络的实际行为,检测和识别潜在的入侵,常用于检测未知攻击和零日漏洞。
第三部分:常用的入侵检测方法1. 基于签名的入侵检测方法有哪些?常见的基于签名的入侵检测方法包括:Snort、Suricata和OpenVAS 等。
2. 基于行为的入侵检测方法有哪些?常见的基于行为的入侵检测方法包括:异常检测和统计分析、机器学习和人工神经网络等。
3. 什么是异常检测和统计分析?异常检测和统计分析是通过分析系统和网络的正常行为,检测和识别与之不符的异常行为的方法,常用于检测未知攻击和新型威胁。
4. 什么是机器学习?机器学习是一种通过构建算法模型,使计算机能够从数据中学习和识别模式、进行预测和决策的方法,在入侵检测中可以用于建立模型并判断网络行为是否属于入侵。
5. 什么是人工神经网络?人工神经网络是一种模拟人脑神经元结构和功能的计算模型,可以用于学习和分类网络行为,常用于检测恶意代码和网络攻击。
Synopsys OptoDesigner 2020.09安装指南说明书

3. Troubleshooting scanning issues........................................................25
Accidental full scan proliferation by folder paths which include build or commit ID............................ 25 Solution......................................................................................................................................25
Contents
Contents
Preface....................................................................................................5
1. Scanning best practices......................................................................... 8
Indradrive 系列 故障代码

Error MessagesF9001 Error internal function call.F9002 Error internal RTOS function callF9003 WatchdogF9004 Hardware trapF8000 Fatal hardware errorF8010 Autom. commutation: Max. motion range when moving back F8011 Commutation offset could not be determinedF8012 Autom. commutation: Max. motion rangeF8013 Automatic commutation: Current too lowF8014 Automatic commutation: OvercurrentF8015 Automatic commutation: TimeoutF8016 Automatic commutation: Iteration without resultF8017 Automatic commutation: Incorrect commutation adjustment F8018 Device overtemperature shutdownF8022 Enc. 1: Enc. signals incorr. (can be cleared in ph. 2) F8023 Error mechanical link of encoder or motor connectionF8025 Overvoltage in power sectionF8027 Safe torque off while drive enabledF8028 Overcurrent in power sectionF8030 Safe stop 1 while drive enabledF8042 Encoder 2 error: Signal amplitude incorrectF8057 Device overload shutdownF8060 Overcurrent in power sectionF8064 Interruption of motor phaseF8067 Synchronization PWM-Timer wrongF8069 +/-15Volt DC errorF8070 +24Volt DC errorF8076 Error in error angle loopF8078 Speed loop error.F8079 Velocity limit value exceededF8091 Power section defectiveF8100 Error when initializing the parameter handlingF8102 Error when initializing power sectionF8118 Invalid power section/firmware combinationF8120 Invalid control section/firmware combinationF8122 Control section defectiveF8129 Incorrect optional module firmwareF8130 Firmware of option 2 of safety technology defectiveF8133 Error when checking interrupting circuitsF8134 SBS: Fatal errorF8135 SMD: Velocity exceededF8140 Fatal CCD error.F8201 Safety command for basic initialization incorrectF8203 Safety technology configuration parameter invalidF8813 Connection error mains chokeF8830 Power section errorF8838 Overcurrent external braking resistorF7010 Safely-limited increment exceededF7011 Safely-monitored position, exceeded in pos. DirectionF7012 Safely-monitored position, exceeded in neg. DirectionF7013 Safely-limited speed exceededF7020 Safe maximum speed exceededF7021 Safely-limited position exceededF7030 Position window Safe stop 2 exceededF7031 Incorrect direction of motionF7040 Validation error parameterized - effective thresholdF7041 Actual position value validation errorF7042 Validation error of safe operation modeF7043 Error of output stage interlockF7050 Time for stopping process exceeded8.3.15 F7051 Safely-monitored deceleration exceeded (159)8.4 Travel Range Errors (F6xxx) (161)8.4.1 Behavior in the Case of Travel Range Errors (161)8.4.2 F6010 PLC Runtime Error (162)8.4.3 F6024 Maximum braking time exceeded (163)8.4.4 F6028 Position limit value exceeded (overflow) (164)8.4.5 F6029 Positive position limit exceeded (164)8.4.6 F6030 Negative position limit exceeded (165)8.4.7 F6034 Emergency-Stop (166)8.4.8 F6042 Both travel range limit switches activated (167)8.4.9 F6043 Positive travel range limit switch activated (167)8.4.10 F6044 Negative travel range limit switch activated (168)8.4.11 F6140 CCD slave error (emergency halt) (169)8.5 Interface Errors (F4xxx) (169)8.5.1 Behavior in the Case of Interface Errors (169)8.5.2 F4001 Sync telegram failure (170)8.5.3 F4002 RTD telegram failure (171)8.5.4 F4003 Invalid communication phase shutdown (172)8.5.5 F4004 Error during phase progression (172)8.5.6 F4005 Error during phase regression (173)8.5.7 F4006 Phase switching without ready signal (173)8.5.8 F4009 Bus failure (173)8.5.9 F4012 Incorrect I/O length (175)8.5.10 F4016 PLC double real-time channel failure (176)8.5.11 F4017 S-III: Incorrect sequence during phase switch (176)8.5.12 F4034 Emergency-Stop (177)8.5.13 F4140 CCD communication error (178)8.6 Non-Fatal Safety Technology Errors (F3xxx) (178)8.6.1 Behavior in the Case of Non-Fatal Safety Technology Errors (178)8.6.2 F3111 Refer. missing when selecting safety related end pos (179)8.6.3 F3112 Safe reference missing (179)8.6.4 F3115 Brake check time interval exceeded (181)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand ControlsI Bosch Rexroth AG VII/XXIITable of ContentsPage8.6.5 F3116 Nominal load torque of holding system exceeded (182)8.6.6 F3117 Actual position values validation error (182)8.6.7 F3122 SBS: System error (183)8.6.8 F3123 SBS: Brake check missing (184)8.6.9 F3130 Error when checking input signals (185)8.6.10 F3131 Error when checking acknowledgment signal (185)8.6.11 F3132 Error when checking diagnostic output signal (186)8.6.12 F3133 Error when checking interrupting circuits (187)8.6.13 F3134 Dynamization time interval incorrect (188)8.6.14 F3135 Dynamization pulse width incorrect (189)8.6.15 F3140 Safety parameters validation error (192)8.6.16 F3141 Selection validation error (192)8.6.17 F3142 Activation time of enabling control exceeded (193)8.6.18 F3143 Safety command for clearing errors incorrect (194)8.6.19 F3144 Incorrect safety configuration (195)8.6.20 F3145 Error when unlocking the safety door (196)8.6.21 F3146 System error channel 2 (197)8.6.22 F3147 System error channel 1 (198)8.6.23 F3150 Safety command for system start incorrect (199)8.6.24 F3151 Safety command for system halt incorrect (200)8.6.25 F3152 Incorrect backup of safety technology data (201)8.6.26 F3160 Communication error of safe communication (202)8.7 Non-Fatal Errors (F2xxx) (202)8.7.1 Behavior in the Case of Non-Fatal Errors (202)8.7.2 F2002 Encoder assignment not allowed for synchronization (203)8.7.3 F2003 Motion step skipped (203)8.7.4 F2004 Error in MotionProfile (204)8.7.5 F2005 Cam table invalid (205)8.7.6 F2006 MMC was removed (206)8.7.7 F2007 Switching to non-initialized operation mode (206)8.7.8 F2008 RL The motor type has changed (207)8.7.9 F2009 PL Load parameter default values (208)8.7.10 F2010 Error when initializing digital I/O (-> S-0-0423) (209)8.7.11 F2011 PLC - Error no. 1 (210)8.7.12 F2012 PLC - Error no. 2 (210)8.7.13 F2013 PLC - Error no. 3 (211)8.7.14 F2014 PLC - Error no. 4 (211)8.7.15 F2018 Device overtemperature shutdown (211)8.7.16 F2019 Motor overtemperature shutdown (212)8.7.17 F2021 Motor temperature monitor defective (213)8.7.18 F2022 Device temperature monitor defective (214)8.7.19 F2025 Drive not ready for control (214)8.7.20 F2026 Undervoltage in power section (215)8.7.21 F2027 Excessive oscillation in DC bus (216)8.7.22 F2028 Excessive deviation (216)8.7.23 F2031 Encoder 1 error: Signal amplitude incorrect (217)VIII/XXII Bosch Rexroth AG | Electric Drivesand ControlsRexroth IndraDrive | Troubleshooting GuideTable of ContentsPage8.7.24 F2032 Validation error during commutation fine adjustment (217)8.7.25 F2033 External power supply X10 error (218)8.7.26 F2036 Excessive position feedback difference (219)8.7.27 F2037 Excessive position command difference (220)8.7.28 F2039 Maximum acceleration exceeded (220)8.7.29 F2040 Device overtemperature 2 shutdown (221)8.7.30 F2042 Encoder 2: Encoder signals incorrect (222)8.7.31 F2043 Measuring encoder: Encoder signals incorrect (222)8.7.32 F2044 External power supply X15 error (223)8.7.33 F2048 Low battery voltage (224)8.7.34 F2050 Overflow of target position preset memory (225)8.7.35 F2051 No sequential block in target position preset memory (225)8.7.36 F2053 Incr. encoder emulator: Pulse frequency too high (226)8.7.37 F2054 Incr. encoder emulator: Hardware error (226)8.7.38 F2055 External power supply dig. I/O error (227)8.7.39 F2057 Target position out of travel range (227)8.7.40 F2058 Internal overflow by positioning input (228)8.7.41 F2059 Incorrect command value direction when positioning (229)8.7.42 F2063 Internal overflow master axis generator (230)8.7.43 F2064 Incorrect cmd value direction master axis generator (230)8.7.44 F2067 Synchronization to master communication incorrect (231)8.7.45 F2068 Brake error (231)8.7.46 F2069 Error when releasing the motor holding brake (232)8.7.47 F2074 Actual pos. value 1 outside absolute encoder window (232)8.7.48 F2075 Actual pos. value 2 outside absolute encoder window (233)8.7.49 F2076 Actual pos. value 3 outside absolute encoder window (234)8.7.50 F2077 Current measurement trim wrong (235)8.7.51 F2086 Error supply module (236)8.7.52 F2087 Module group communication error (236)8.7.53 F2100 Incorrect access to command value memory (237)8.7.54 F2101 It was impossible to address MMC (237)8.7.55 F2102 It was impossible to address I2C memory (238)8.7.56 F2103 It was impossible to address EnDat memory (238)8.7.57 F2104 Commutation offset invalid (239)8.7.58 F2105 It was impossible to address Hiperface memory (239)8.7.59 F2110 Error in non-cyclical data communic. of power section (240)8.7.60 F2120 MMC: Defective or missing, replace (240)8.7.61 F2121 MMC: Incorrect data or file, create correctly (241)8.7.62 F2122 MMC: Incorrect IBF file, correct it (241)8.7.63 F2123 Retain data backup impossible (242)8.7.64 F2124 MMC: Saving too slowly, replace (243)8.7.65 F2130 Error comfort control panel (243)8.7.66 F2140 CCD slave error (243)8.7.67 F2150 MLD motion function block error (244)8.7.68 F2174 Loss of motor encoder reference (244)8.7.69 F2175 Loss of optional encoder reference (245)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand Controls| Bosch Rexroth AG IX/XXIITable of ContentsPage8.7.70 F2176 Loss of measuring encoder reference (246)8.7.71 F2177 Modulo limitation error of motor encoder (246)8.7.72 F2178 Modulo limitation error of optional encoder (247)8.7.73 F2179 Modulo limitation error of measuring encoder (247)8.7.74 F2190 Incorrect Ethernet configuration (248)8.7.75 F2260 Command current limit shutoff (249)8.7.76 F2270 Analog input 1 or 2, wire break (249)8.7.77 F2802 PLL is not synchronized (250)8.7.78 F2814 Undervoltage in mains (250)8.7.79 F2815 Overvoltage in mains (251)8.7.80 F2816 Softstart fault power supply unit (251)8.7.81 F2817 Overvoltage in power section (251)8.7.82 F2818 Phase failure (252)8.7.83 F2819 Mains failure (253)8.7.84 F2820 Braking resistor overload (253)8.7.85 F2821 Error in control of braking resistor (254)8.7.86 F2825 Switch-on threshold braking resistor too low (255)8.7.87 F2833 Ground fault in motor line (255)8.7.88 F2834 Contactor control error (256)8.7.89 F2835 Mains contactor wiring error (256)8.7.90 F2836 DC bus balancing monitor error (257)8.7.91 F2837 Contactor monitoring error (257)8.7.92 F2840 Error supply shutdown (257)8.7.93 F2860 Overcurrent in mains-side power section (258)8.7.94 F2890 Invalid device code (259)8.7.95 F2891 Incorrect interrupt timing (259)8.7.96 F2892 Hardware variant not supported (259)8.8 SERCOS Error Codes / Error Messages of Serial Communication (259)9 Warnings (Exxxx) (263)9.1 Fatal Warnings (E8xxx) (263)9.1.1 Behavior in the Case of Fatal Warnings (263)9.1.2 E8025 Overvoltage in power section (263)9.1.3 E8026 Undervoltage in power section (264)9.1.4 E8027 Safe torque off while drive enabled (265)9.1.5 E8028 Overcurrent in power section (265)9.1.6 E8029 Positive position limit exceeded (266)9.1.7 E8030 Negative position limit exceeded (267)9.1.8 E8034 Emergency-Stop (268)9.1.9 E8040 Torque/force actual value limit active (268)9.1.10 E8041 Current limit active (269)9.1.11 E8042 Both travel range limit switches activated (269)9.1.12 E8043 Positive travel range limit switch activated (270)9.1.13 E8044 Negative travel range limit switch activated (271)9.1.14 E8055 Motor overload, current limit active (271)9.1.15 E8057 Device overload, current limit active (272)X/XXII Bosch Rexroth AG | Electric Drivesand ControlsRexroth IndraDrive | Troubleshooting GuideTable of ContentsPage9.1.16 E8058 Drive system not ready for operation (273)9.1.17 E8260 Torque/force command value limit active (273)9.1.18 E8802 PLL is not synchronized (274)9.1.19 E8814 Undervoltage in mains (275)9.1.20 E8815 Overvoltage in mains (275)9.1.21 E8818 Phase failure (276)9.1.22 E8819 Mains failure (276)9.2 Warnings of Category E4xxx (277)9.2.1 E4001 Double MST failure shutdown (277)9.2.2 E4002 Double MDT failure shutdown (278)9.2.3 E4005 No command value input via master communication (279)9.2.4 E4007 SERCOS III: Consumer connection failed (280)9.2.5 E4008 Invalid addressing command value data container A (280)9.2.6 E4009 Invalid addressing actual value data container A (281)9.2.7 E4010 Slave not scanned or address 0 (281)9.2.8 E4012 Maximum number of CCD slaves exceeded (282)9.2.9 E4013 Incorrect CCD addressing (282)9.2.10 E4014 Incorrect phase switch of CCD slaves (283)9.3 Possible Warnings When Operating Safety Technology (E3xxx) (283)9.3.1 Behavior in Case a Safety Technology Warning Occurs (283)9.3.2 E3100 Error when checking input signals (284)9.3.3 E3101 Error when checking acknowledgment signal (284)9.3.4 E3102 Actual position values validation error (285)9.3.5 E3103 Dynamization failed (285)9.3.6 E3104 Safety parameters validation error (286)9.3.7 E3105 Validation error of safe operation mode (286)9.3.8 E3106 System error safety technology (287)9.3.9 E3107 Safe reference missing (287)9.3.10 E3108 Safely-monitored deceleration exceeded (288)9.3.11 E3110 Time interval of forced dynamization exceeded (289)9.3.12 E3115 Prewarning, end of brake check time interval (289)9.3.13 E3116 Nominal load torque of holding system reached (290)9.4 Non-Fatal Warnings (E2xxx) (290)9.4.1 Behavior in Case a Non-Fatal Warning Occurs (290)9.4.2 E2010 Position control with encoder 2 not possible (291)9.4.3 E2011 PLC - Warning no. 1 (291)9.4.4 E2012 PLC - Warning no. 2 (291)9.4.5 E2013 PLC - Warning no. 3 (292)9.4.6 E2014 PLC - Warning no. 4 (292)9.4.7 E2021 Motor temperature outside of measuring range (292)9.4.8 E2026 Undervoltage in power section (293)9.4.9 E2040 Device overtemperature 2 prewarning (294)9.4.10 E2047 Interpolation velocity = 0 (294)9.4.11 E2048 Interpolation acceleration = 0 (295)9.4.12 E2049 Positioning velocity >= limit value (296)9.4.13 E2050 Device overtemp. Prewarning (297)Troubleshooting Guide | Rexroth IndraDrive Electric Drivesand Controls| Bosch Rexroth AG XI/XXIITable of ContentsPage9.4.14 E2051 Motor overtemp. prewarning (298)9.4.15 E2053 Target position out of travel range (298)9.4.16 E2054 Not homed (300)9.4.17 E2055 Feedrate override S-0-0108 = 0 (300)9.4.18 E2056 Torque limit = 0 (301)9.4.19 E2058 Selected positioning block has not been programmed (302)9.4.20 E2059 Velocity command value limit active (302)9.4.21 E2061 Device overload prewarning (303)9.4.22 E2063 Velocity command value > limit value (304)9.4.23 E2064 Target position out of num. range (304)9.4.24 E2069 Holding brake torque too low (305)9.4.25 E2070 Acceleration limit active (306)9.4.26 E2074 Encoder 1: Encoder signals disturbed (306)9.4.27 E2075 Encoder 2: Encoder signals disturbed (307)9.4.28 E2076 Measuring encoder: Encoder signals disturbed (308)9.4.29 E2077 Absolute encoder monitoring, motor encoder (encoder alarm) (308)9.4.30 E2078 Absolute encoder monitoring, opt. encoder (encoder alarm) (309)9.4.31 E2079 Absolute enc. monitoring, measuring encoder (encoder alarm) (309)9.4.32 E2086 Prewarning supply module overload (310)9.4.33 E2092 Internal synchronization defective (310)9.4.34 E2100 Positioning velocity of master axis generator too high (311)9.4.35 E2101 Acceleration of master axis generator is zero (312)9.4.36 E2140 CCD error at node (312)9.4.37 E2270 Analog input 1 or 2, wire break (312)9.4.38 E2802 HW control of braking resistor (313)9.4.39 E2810 Drive system not ready for operation (314)9.4.40 E2814 Undervoltage in mains (314)9.4.41 E2816 Undervoltage in power section (314)9.4.42 E2818 Phase failure (315)9.4.43 E2819 Mains failure (315)9.4.44 E2820 Braking resistor overload prewarning (316)9.4.45 E2829 Not ready for power on (316)。
华为OSN3500 AU_AIS告警
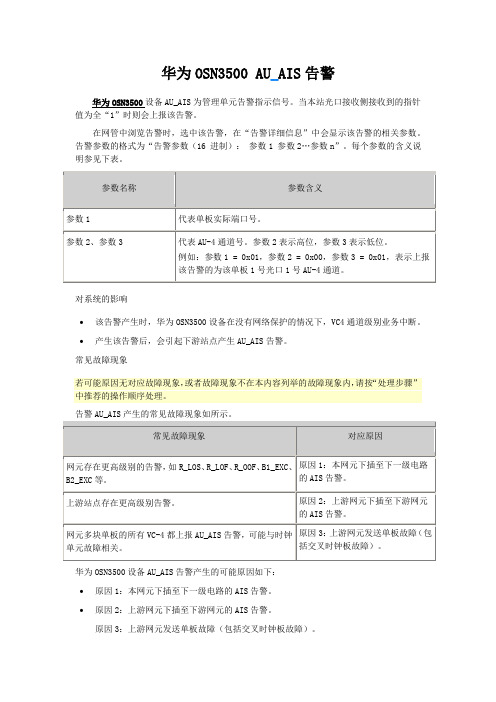
华为OSN3500 AU_AIS告警华为OSN3500设备AU_AIS为管理单元告警指示信号。
当本站光口接收侧接收到的指针值为全“1”时则会上报该告警。
在网管中浏览告警时,选中该告警,在“告警详细信息”中会显示该告警的相关参数。
告警参数的格式为“告警参数(16 进制):参数1 参数2…参数n”。
每个参数的含义说明参见下表。
对系统的影响∙该告警产生时,华为OSN3500设备在没有网络保护的情况下,VC4通道级别业务中断。
∙产生该告警后,会引起下游站点产生AU_AIS告警。
常见故障现象若可能原因无对应故障现象,或者故障现象不在本内容列举的故障现象内,请按“处理步骤”中推荐的操作顺序处理。
告警AU_AIS产生的常见故障现象如所示。
华为OSN3500设备AU_AIS告警产生的可能原因如下:∙原因1:本网元下插至下一级电路的AIS告警。
∙原因2:上游网元下插至下游网元的AIS告警。
原因3:上游网元发送单板故障(包括交叉时钟板故障)。
原因4:本网元接收单板故障。
处理步骤a. 原因1:本网元下插至下一级电路的AIS 告警。
在网管上查询本网元是否存在更高级别的告警。
2. 原因2:上游网元下插至下游网元的AIS 告警。
3. 沿VC4业务配置信号流在上游网元查询是否存在高级别告警。
4. 使用环回法沿VC4业务信号流定位最初产生AU_AIS 告警的网元。
a. 查询环回后对端是否存在AU_AIS 告警。
b.沿VC4业务信号流,内环回上游网元的东向线路板对应的VC4通道,查询环回后该上游网元是否存在AU_AIS告警。
c.硬件内环回对端发送单板的光口。
查询环回后对端是否存在AU_AIS告警。
5.定位最初产生AU_AIS告警的网元的故障单板。
a.设置网元西向线路板外环回,查询环回后该网元是否存在AU_AIS告警。
6.原因3:上游网元发送单板故障(包括交叉时钟板故障)。
a.更换最初产生AU_AIS告警的网元对应的发送单板。
查询告警是否消除。
3GPP TS 36.331 V13.2.0 (2016-06)

3GPP TS 36.331 V13.2.0 (2016-06)Technical Specification3rd Generation Partnership Project;Technical Specification Group Radio Access Network;Evolved Universal Terrestrial Radio Access (E-UTRA);Radio Resource Control (RRC);Protocol specification(Release 13)The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented.This Specification is provided for future development work within 3GPP only. The Organizational Partners accept no liability for any use of this Specification. Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organizational Partners' Publications Offices.KeywordsUMTS, radio3GPPPostal address3GPP support office address650 Route des Lucioles - Sophia AntipolisValbonne - FRANCETel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16InternetCopyright NotificationNo part may be reproduced except as authorized by written permission.The copyright and the foregoing restriction extend to reproduction in all media.© 2016, 3GPP Organizational Partners (ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC).All rights reserved.UMTS™ is a Trade Mark of ETSI registered for the benefit of its members3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational PartnersLTE™ is a Trade Mark of ETSI currently being registered for the benefit of its Members and of the 3GPP Organizational Partners GSM® and the GSM logo are registered and owned by the GSM AssociationBluetooth® is a Trade Mark of the Bluetooth SIG registered for the benefit of its membersContentsForeword (18)1Scope (19)2References (19)3Definitions, symbols and abbreviations (22)3.1Definitions (22)3.2Abbreviations (24)4General (27)4.1Introduction (27)4.2Architecture (28)4.2.1UE states and state transitions including inter RAT (28)4.2.2Signalling radio bearers (29)4.3Services (30)4.3.1Services provided to upper layers (30)4.3.2Services expected from lower layers (30)4.4Functions (30)5Procedures (32)5.1General (32)5.1.1Introduction (32)5.1.2General requirements (32)5.2System information (33)5.2.1Introduction (33)5.2.1.1General (33)5.2.1.2Scheduling (34)5.2.1.2a Scheduling for NB-IoT (34)5.2.1.3System information validity and notification of changes (35)5.2.1.4Indication of ETWS notification (36)5.2.1.5Indication of CMAS notification (37)5.2.1.6Notification of EAB parameters change (37)5.2.1.7Access Barring parameters change in NB-IoT (37)5.2.2System information acquisition (38)5.2.2.1General (38)5.2.2.2Initiation (38)5.2.2.3System information required by the UE (38)5.2.2.4System information acquisition by the UE (39)5.2.2.5Essential system information missing (42)5.2.2.6Actions upon reception of the MasterInformationBlock message (42)5.2.2.7Actions upon reception of the SystemInformationBlockType1 message (42)5.2.2.8Actions upon reception of SystemInformation messages (44)5.2.2.9Actions upon reception of SystemInformationBlockType2 (44)5.2.2.10Actions upon reception of SystemInformationBlockType3 (45)5.2.2.11Actions upon reception of SystemInformationBlockType4 (45)5.2.2.12Actions upon reception of SystemInformationBlockType5 (45)5.2.2.13Actions upon reception of SystemInformationBlockType6 (45)5.2.2.14Actions upon reception of SystemInformationBlockType7 (45)5.2.2.15Actions upon reception of SystemInformationBlockType8 (45)5.2.2.16Actions upon reception of SystemInformationBlockType9 (46)5.2.2.17Actions upon reception of SystemInformationBlockType10 (46)5.2.2.18Actions upon reception of SystemInformationBlockType11 (46)5.2.2.19Actions upon reception of SystemInformationBlockType12 (47)5.2.2.20Actions upon reception of SystemInformationBlockType13 (48)5.2.2.21Actions upon reception of SystemInformationBlockType14 (48)5.2.2.22Actions upon reception of SystemInformationBlockType15 (48)5.2.2.23Actions upon reception of SystemInformationBlockType16 (48)5.2.2.24Actions upon reception of SystemInformationBlockType17 (48)5.2.2.25Actions upon reception of SystemInformationBlockType18 (48)5.2.2.26Actions upon reception of SystemInformationBlockType19 (49)5.2.3Acquisition of an SI message (49)5.2.3a Acquisition of an SI message by BL UE or UE in CE or a NB-IoT UE (50)5.3Connection control (50)5.3.1Introduction (50)5.3.1.1RRC connection control (50)5.3.1.2Security (52)5.3.1.2a RN security (53)5.3.1.3Connected mode mobility (53)5.3.1.4Connection control in NB-IoT (54)5.3.2Paging (55)5.3.2.1General (55)5.3.2.2Initiation (55)5.3.2.3Reception of the Paging message by the UE (55)5.3.3RRC connection establishment (56)5.3.3.1General (56)5.3.3.1a Conditions for establishing RRC Connection for sidelink communication/ discovery (58)5.3.3.2Initiation (59)5.3.3.3Actions related to transmission of RRCConnectionRequest message (63)5.3.3.3a Actions related to transmission of RRCConnectionResumeRequest message (64)5.3.3.4Reception of the RRCConnectionSetup by the UE (64)5.3.3.4a Reception of the RRCConnectionResume by the UE (66)5.3.3.5Cell re-selection while T300, T302, T303, T305, T306, or T308 is running (68)5.3.3.6T300 expiry (68)5.3.3.7T302, T303, T305, T306, or T308 expiry or stop (69)5.3.3.8Reception of the RRCConnectionReject by the UE (70)5.3.3.9Abortion of RRC connection establishment (71)5.3.3.10Handling of SSAC related parameters (71)5.3.3.11Access barring check (72)5.3.3.12EAB check (73)5.3.3.13Access barring check for ACDC (73)5.3.3.14Access Barring check for NB-IoT (74)5.3.4Initial security activation (75)5.3.4.1General (75)5.3.4.2Initiation (76)5.3.4.3Reception of the SecurityModeCommand by the UE (76)5.3.5RRC connection reconfiguration (77)5.3.5.1General (77)5.3.5.2Initiation (77)5.3.5.3Reception of an RRCConnectionReconfiguration not including the mobilityControlInfo by theUE (77)5.3.5.4Reception of an RRCConnectionReconfiguration including the mobilityControlInfo by the UE(handover) (79)5.3.5.5Reconfiguration failure (83)5.3.5.6T304 expiry (handover failure) (83)5.3.5.7Void (84)5.3.5.7a T307 expiry (SCG change failure) (84)5.3.5.8Radio Configuration involving full configuration option (84)5.3.6Counter check (86)5.3.6.1General (86)5.3.6.2Initiation (86)5.3.6.3Reception of the CounterCheck message by the UE (86)5.3.7RRC connection re-establishment (87)5.3.7.1General (87)5.3.7.2Initiation (87)5.3.7.3Actions following cell selection while T311 is running (88)5.3.7.4Actions related to transmission of RRCConnectionReestablishmentRequest message (89)5.3.7.5Reception of the RRCConnectionReestablishment by the UE (89)5.3.7.6T311 expiry (91)5.3.7.7T301 expiry or selected cell no longer suitable (91)5.3.7.8Reception of RRCConnectionReestablishmentReject by the UE (91)5.3.8RRC connection release (92)5.3.8.1General (92)5.3.8.2Initiation (92)5.3.8.3Reception of the RRCConnectionRelease by the UE (92)5.3.8.4T320 expiry (93)5.3.9RRC connection release requested by upper layers (93)5.3.9.1General (93)5.3.9.2Initiation (93)5.3.10Radio resource configuration (93)5.3.10.0General (93)5.3.10.1SRB addition/ modification (94)5.3.10.2DRB release (95)5.3.10.3DRB addition/ modification (95)5.3.10.3a1DC specific DRB addition or reconfiguration (96)5.3.10.3a2LWA specific DRB addition or reconfiguration (98)5.3.10.3a3LWIP specific DRB addition or reconfiguration (98)5.3.10.3a SCell release (99)5.3.10.3b SCell addition/ modification (99)5.3.10.3c PSCell addition or modification (99)5.3.10.4MAC main reconfiguration (99)5.3.10.5Semi-persistent scheduling reconfiguration (100)5.3.10.6Physical channel reconfiguration (100)5.3.10.7Radio Link Failure Timers and Constants reconfiguration (101)5.3.10.8Time domain measurement resource restriction for serving cell (101)5.3.10.9Other configuration (102)5.3.10.10SCG reconfiguration (103)5.3.10.11SCG dedicated resource configuration (104)5.3.10.12Reconfiguration SCG or split DRB by drb-ToAddModList (105)5.3.10.13Neighbour cell information reconfiguration (105)5.3.10.14Void (105)5.3.10.15Sidelink dedicated configuration (105)5.3.10.16T370 expiry (106)5.3.11Radio link failure related actions (107)5.3.11.1Detection of physical layer problems in RRC_CONNECTED (107)5.3.11.2Recovery of physical layer problems (107)5.3.11.3Detection of radio link failure (107)5.3.12UE actions upon leaving RRC_CONNECTED (109)5.3.13UE actions upon PUCCH/ SRS release request (110)5.3.14Proximity indication (110)5.3.14.1General (110)5.3.14.2Initiation (111)5.3.14.3Actions related to transmission of ProximityIndication message (111)5.3.15Void (111)5.4Inter-RAT mobility (111)5.4.1Introduction (111)5.4.2Handover to E-UTRA (112)5.4.2.1General (112)5.4.2.2Initiation (112)5.4.2.3Reception of the RRCConnectionReconfiguration by the UE (112)5.4.2.4Reconfiguration failure (114)5.4.2.5T304 expiry (handover to E-UTRA failure) (114)5.4.3Mobility from E-UTRA (114)5.4.3.1General (114)5.4.3.2Initiation (115)5.4.3.3Reception of the MobilityFromEUTRACommand by the UE (115)5.4.3.4Successful completion of the mobility from E-UTRA (116)5.4.3.5Mobility from E-UTRA failure (117)5.4.4Handover from E-UTRA preparation request (CDMA2000) (117)5.4.4.1General (117)5.4.4.2Initiation (118)5.4.4.3Reception of the HandoverFromEUTRAPreparationRequest by the UE (118)5.4.5UL handover preparation transfer (CDMA2000) (118)5.4.5.1General (118)5.4.5.2Initiation (118)5.4.5.3Actions related to transmission of the ULHandoverPreparationTransfer message (119)5.4.5.4Failure to deliver the ULHandoverPreparationTransfer message (119)5.4.6Inter-RAT cell change order to E-UTRAN (119)5.4.6.1General (119)5.4.6.2Initiation (119)5.4.6.3UE fails to complete an inter-RAT cell change order (119)5.5Measurements (120)5.5.1Introduction (120)5.5.2Measurement configuration (121)5.5.2.1General (121)5.5.2.2Measurement identity removal (122)5.5.2.2a Measurement identity autonomous removal (122)5.5.2.3Measurement identity addition/ modification (123)5.5.2.4Measurement object removal (124)5.5.2.5Measurement object addition/ modification (124)5.5.2.6Reporting configuration removal (126)5.5.2.7Reporting configuration addition/ modification (127)5.5.2.8Quantity configuration (127)5.5.2.9Measurement gap configuration (127)5.5.2.10Discovery signals measurement timing configuration (128)5.5.2.11RSSI measurement timing configuration (128)5.5.3Performing measurements (128)5.5.3.1General (128)5.5.3.2Layer 3 filtering (131)5.5.4Measurement report triggering (131)5.5.4.1General (131)5.5.4.2Event A1 (Serving becomes better than threshold) (135)5.5.4.3Event A2 (Serving becomes worse than threshold) (136)5.5.4.4Event A3 (Neighbour becomes offset better than PCell/ PSCell) (136)5.5.4.5Event A4 (Neighbour becomes better than threshold) (137)5.5.4.6Event A5 (PCell/ PSCell becomes worse than threshold1 and neighbour becomes better thanthreshold2) (138)5.5.4.6a Event A6 (Neighbour becomes offset better than SCell) (139)5.5.4.7Event B1 (Inter RAT neighbour becomes better than threshold) (139)5.5.4.8Event B2 (PCell becomes worse than threshold1 and inter RAT neighbour becomes better thanthreshold2) (140)5.5.4.9Event C1 (CSI-RS resource becomes better than threshold) (141)5.5.4.10Event C2 (CSI-RS resource becomes offset better than reference CSI-RS resource) (141)5.5.4.11Event W1 (WLAN becomes better than a threshold) (142)5.5.4.12Event W2 (All WLAN inside WLAN mobility set becomes worse than threshold1 and a WLANoutside WLAN mobility set becomes better than threshold2) (142)5.5.4.13Event W3 (All WLAN inside WLAN mobility set becomes worse than a threshold) (143)5.5.5Measurement reporting (144)5.5.6Measurement related actions (148)5.5.6.1Actions upon handover and re-establishment (148)5.5.6.2Speed dependant scaling of measurement related parameters (149)5.5.7Inter-frequency RSTD measurement indication (149)5.5.7.1General (149)5.5.7.2Initiation (150)5.5.7.3Actions related to transmission of InterFreqRSTDMeasurementIndication message (150)5.6Other (150)5.6.0General (150)5.6.1DL information transfer (151)5.6.1.1General (151)5.6.1.2Initiation (151)5.6.1.3Reception of the DLInformationTransfer by the UE (151)5.6.2UL information transfer (151)5.6.2.1General (151)5.6.2.2Initiation (151)5.6.2.3Actions related to transmission of ULInformationTransfer message (152)5.6.2.4Failure to deliver ULInformationTransfer message (152)5.6.3UE capability transfer (152)5.6.3.1General (152)5.6.3.2Initiation (153)5.6.3.3Reception of the UECapabilityEnquiry by the UE (153)5.6.4CSFB to 1x Parameter transfer (157)5.6.4.1General (157)5.6.4.2Initiation (157)5.6.4.3Actions related to transmission of CSFBParametersRequestCDMA2000 message (157)5.6.4.4Reception of the CSFBParametersResponseCDMA2000 message (157)5.6.5UE Information (158)5.6.5.1General (158)5.6.5.2Initiation (158)5.6.5.3Reception of the UEInformationRequest message (158)5.6.6 Logged Measurement Configuration (159)5.6.6.1General (159)5.6.6.2Initiation (160)5.6.6.3Reception of the LoggedMeasurementConfiguration by the UE (160)5.6.6.4T330 expiry (160)5.6.7 Release of Logged Measurement Configuration (160)5.6.7.1General (160)5.6.7.2Initiation (160)5.6.8 Measurements logging (161)5.6.8.1General (161)5.6.8.2Initiation (161)5.6.9In-device coexistence indication (163)5.6.9.1General (163)5.6.9.2Initiation (164)5.6.9.3Actions related to transmission of InDeviceCoexIndication message (164)5.6.10UE Assistance Information (165)5.6.10.1General (165)5.6.10.2Initiation (166)5.6.10.3Actions related to transmission of UEAssistanceInformation message (166)5.6.11 Mobility history information (166)5.6.11.1General (166)5.6.11.2Initiation (166)5.6.12RAN-assisted WLAN interworking (167)5.6.12.1General (167)5.6.12.2Dedicated WLAN offload configuration (167)5.6.12.3WLAN offload RAN evaluation (167)5.6.12.4T350 expiry or stop (167)5.6.12.5Cell selection/ re-selection while T350 is running (168)5.6.13SCG failure information (168)5.6.13.1General (168)5.6.13.2Initiation (168)5.6.13.3Actions related to transmission of SCGFailureInformation message (168)5.6.14LTE-WLAN Aggregation (169)5.6.14.1Introduction (169)5.6.14.2Reception of LWA configuration (169)5.6.14.3Release of LWA configuration (170)5.6.15WLAN connection management (170)5.6.15.1Introduction (170)5.6.15.2WLAN connection status reporting (170)5.6.15.2.1General (170)5.6.15.2.2Initiation (171)5.6.15.2.3Actions related to transmission of WLANConnectionStatusReport message (171)5.6.15.3T351 Expiry (WLAN connection attempt timeout) (171)5.6.15.4WLAN status monitoring (171)5.6.16RAN controlled LTE-WLAN interworking (172)5.6.16.1General (172)5.6.16.2WLAN traffic steering command (172)5.6.17LTE-WLAN aggregation with IPsec tunnel (173)5.6.17.1General (173)5.7Generic error handling (174)5.7.1General (174)5.7.2ASN.1 violation or encoding error (174)5.7.3Field set to a not comprehended value (174)5.7.4Mandatory field missing (174)5.7.5Not comprehended field (176)5.8MBMS (176)5.8.1Introduction (176)5.8.1.1General (176)5.8.1.2Scheduling (176)5.8.1.3MCCH information validity and notification of changes (176)5.8.2MCCH information acquisition (178)5.8.2.1General (178)5.8.2.2Initiation (178)5.8.2.3MCCH information acquisition by the UE (178)5.8.2.4Actions upon reception of the MBSFNAreaConfiguration message (178)5.8.2.5Actions upon reception of the MBMSCountingRequest message (179)5.8.3MBMS PTM radio bearer configuration (179)5.8.3.1General (179)5.8.3.2Initiation (179)5.8.3.3MRB establishment (179)5.8.3.4MRB release (179)5.8.4MBMS Counting Procedure (179)5.8.4.1General (179)5.8.4.2Initiation (180)5.8.4.3Reception of the MBMSCountingRequest message by the UE (180)5.8.5MBMS interest indication (181)5.8.5.1General (181)5.8.5.2Initiation (181)5.8.5.3Determine MBMS frequencies of interest (182)5.8.5.4Actions related to transmission of MBMSInterestIndication message (183)5.8a SC-PTM (183)5.8a.1Introduction (183)5.8a.1.1General (183)5.8a.1.2SC-MCCH scheduling (183)5.8a.1.3SC-MCCH information validity and notification of changes (183)5.8a.1.4Procedures (184)5.8a.2SC-MCCH information acquisition (184)5.8a.2.1General (184)5.8a.2.2Initiation (184)5.8a.2.3SC-MCCH information acquisition by the UE (184)5.8a.2.4Actions upon reception of the SCPTMConfiguration message (185)5.8a.3SC-PTM radio bearer configuration (185)5.8a.3.1General (185)5.8a.3.2Initiation (185)5.8a.3.3SC-MRB establishment (185)5.8a.3.4SC-MRB release (185)5.9RN procedures (186)5.9.1RN reconfiguration (186)5.9.1.1General (186)5.9.1.2Initiation (186)5.9.1.3Reception of the RNReconfiguration by the RN (186)5.10Sidelink (186)5.10.1Introduction (186)5.10.1a Conditions for sidelink communication operation (187)5.10.2Sidelink UE information (188)5.10.2.1General (188)5.10.2.2Initiation (189)5.10.2.3Actions related to transmission of SidelinkUEInformation message (193)5.10.3Sidelink communication monitoring (195)5.10.6Sidelink discovery announcement (198)5.10.6a Sidelink discovery announcement pool selection (201)5.10.6b Sidelink discovery announcement reference carrier selection (201)5.10.7Sidelink synchronisation information transmission (202)5.10.7.1General (202)5.10.7.2Initiation (203)5.10.7.3Transmission of SLSS (204)5.10.7.4Transmission of MasterInformationBlock-SL message (205)5.10.7.5Void (206)5.10.8Sidelink synchronisation reference (206)5.10.8.1General (206)5.10.8.2Selection and reselection of synchronisation reference UE (SyncRef UE) (206)5.10.9Sidelink common control information (207)5.10.9.1General (207)5.10.9.2Actions related to reception of MasterInformationBlock-SL message (207)5.10.10Sidelink relay UE operation (207)5.10.10.1General (207)5.10.10.2AS-conditions for relay related sidelink communication transmission by sidelink relay UE (207)5.10.10.3AS-conditions for relay PS related sidelink discovery transmission by sidelink relay UE (208)5.10.10.4Sidelink relay UE threshold conditions (208)5.10.11Sidelink remote UE operation (208)5.10.11.1General (208)5.10.11.2AS-conditions for relay related sidelink communication transmission by sidelink remote UE (208)5.10.11.3AS-conditions for relay PS related sidelink discovery transmission by sidelink remote UE (209)5.10.11.4Selection and reselection of sidelink relay UE (209)5.10.11.5Sidelink remote UE threshold conditions (210)6Protocol data units, formats and parameters (tabular & ASN.1) (210)6.1General (210)6.2RRC messages (212)6.2.1General message structure (212)–EUTRA-RRC-Definitions (212)–BCCH-BCH-Message (212)–BCCH-DL-SCH-Message (212)–BCCH-DL-SCH-Message-BR (213)–MCCH-Message (213)–PCCH-Message (213)–DL-CCCH-Message (214)–DL-DCCH-Message (214)–UL-CCCH-Message (214)–UL-DCCH-Message (215)–SC-MCCH-Message (215)6.2.2Message definitions (216)–CounterCheck (216)–CounterCheckResponse (217)–CSFBParametersRequestCDMA2000 (217)–CSFBParametersResponseCDMA2000 (218)–DLInformationTransfer (218)–HandoverFromEUTRAPreparationRequest (CDMA2000) (219)–InDeviceCoexIndication (220)–InterFreqRSTDMeasurementIndication (222)–LoggedMeasurementConfiguration (223)–MasterInformationBlock (225)–MBMSCountingRequest (226)–MBMSCountingResponse (226)–MBMSInterestIndication (227)–MBSFNAreaConfiguration (228)–MeasurementReport (228)–MobilityFromEUTRACommand (229)–Paging (232)–ProximityIndication (233)–RNReconfiguration (234)–RNReconfigurationComplete (234)–RRCConnectionReconfiguration (235)–RRCConnectionReconfigurationComplete (240)–RRCConnectionReestablishment (241)–RRCConnectionReestablishmentComplete (241)–RRCConnectionReestablishmentReject (242)–RRCConnectionReestablishmentRequest (243)–RRCConnectionReject (243)–RRCConnectionRelease (244)–RRCConnectionResume (248)–RRCConnectionResumeComplete (249)–RRCConnectionResumeRequest (250)–RRCConnectionRequest (250)–RRCConnectionSetup (251)–RRCConnectionSetupComplete (252)–SCGFailureInformation (253)–SCPTMConfiguration (254)–SecurityModeCommand (255)–SecurityModeComplete (255)–SecurityModeFailure (256)–SidelinkUEInformation (256)–SystemInformation (258)–SystemInformationBlockType1 (259)–UEAssistanceInformation (264)–UECapabilityEnquiry (265)–UECapabilityInformation (266)–UEInformationRequest (267)–UEInformationResponse (267)–ULHandoverPreparationTransfer (CDMA2000) (273)–ULInformationTransfer (274)–WLANConnectionStatusReport (274)6.3RRC information elements (275)6.3.1System information blocks (275)–SystemInformationBlockType2 (275)–SystemInformationBlockType3 (279)–SystemInformationBlockType4 (282)–SystemInformationBlockType5 (283)–SystemInformationBlockType6 (287)–SystemInformationBlockType7 (289)–SystemInformationBlockType8 (290)–SystemInformationBlockType9 (295)–SystemInformationBlockType10 (295)–SystemInformationBlockType11 (296)–SystemInformationBlockType12 (297)–SystemInformationBlockType13 (297)–SystemInformationBlockType14 (298)–SystemInformationBlockType15 (298)–SystemInformationBlockType16 (299)–SystemInformationBlockType17 (300)–SystemInformationBlockType18 (301)–SystemInformationBlockType19 (301)–SystemInformationBlockType20 (304)6.3.2Radio resource control information elements (304)–AntennaInfo (304)–AntennaInfoUL (306)–CQI-ReportConfig (307)–CQI-ReportPeriodicProcExtId (314)–CrossCarrierSchedulingConfig (314)–CSI-IM-Config (315)–CSI-IM-ConfigId (315)–CSI-RS-Config (317)–CSI-RS-ConfigEMIMO (318)–CSI-RS-ConfigNZP (319)–CSI-RS-ConfigNZPId (320)–CSI-RS-ConfigZP (321)–CSI-RS-ConfigZPId (321)–DMRS-Config (321)–DRB-Identity (322)–EPDCCH-Config (322)–EIMTA-MainConfig (324)–LogicalChannelConfig (325)–LWA-Configuration (326)–LWIP-Configuration (326)–RCLWI-Configuration (327)–MAC-MainConfig (327)–P-C-AndCBSR (332)–PDCCH-ConfigSCell (333)–PDCP-Config (334)–PDSCH-Config (337)–PDSCH-RE-MappingQCL-ConfigId (339)–PHICH-Config (339)–PhysicalConfigDedicated (339)–P-Max (344)–PRACH-Config (344)–PresenceAntennaPort1 (346)–PUCCH-Config (347)–PUSCH-Config (351)–RACH-ConfigCommon (355)–RACH-ConfigDedicated (357)–RadioResourceConfigCommon (358)–RadioResourceConfigDedicated (362)–RLC-Config (367)–RLF-TimersAndConstants (369)–RN-SubframeConfig (370)–SchedulingRequestConfig (371)–SoundingRS-UL-Config (372)–SPS-Config (375)–TDD-Config (376)–TimeAlignmentTimer (377)–TPC-PDCCH-Config (377)–TunnelConfigLWIP (378)–UplinkPowerControl (379)–WLAN-Id-List (382)–WLAN-MobilityConfig (382)6.3.3Security control information elements (382)–NextHopChainingCount (382)–SecurityAlgorithmConfig (383)–ShortMAC-I (383)6.3.4Mobility control information elements (383)–AdditionalSpectrumEmission (383)–ARFCN-ValueCDMA2000 (383)–ARFCN-ValueEUTRA (384)–ARFCN-ValueGERAN (384)–ARFCN-ValueUTRA (384)–BandclassCDMA2000 (384)–BandIndicatorGERAN (385)–CarrierFreqCDMA2000 (385)–CarrierFreqGERAN (385)–CellIndexList (387)–CellReselectionPriority (387)–CellSelectionInfoCE (387)–CellReselectionSubPriority (388)–CSFB-RegistrationParam1XRTT (388)–CellGlobalIdEUTRA (389)–CellGlobalIdUTRA (389)–CellGlobalIdGERAN (390)–CellGlobalIdCDMA2000 (390)–CellSelectionInfoNFreq (391)–CSG-Identity (391)–FreqBandIndicator (391)–MobilityControlInfo (391)–MobilityParametersCDMA2000 (1xRTT) (393)–MobilityStateParameters (394)–MultiBandInfoList (394)–NS-PmaxList (394)–PhysCellId (395)–PhysCellIdRange (395)–PhysCellIdRangeUTRA-FDDList (395)–PhysCellIdCDMA2000 (396)–PhysCellIdGERAN (396)–PhysCellIdUTRA-FDD (396)–PhysCellIdUTRA-TDD (396)–PLMN-Identity (397)–PLMN-IdentityList3 (397)–PreRegistrationInfoHRPD (397)–Q-QualMin (398)–Q-RxLevMin (398)–Q-OffsetRange (398)–Q-OffsetRangeInterRAT (399)–ReselectionThreshold (399)–ReselectionThresholdQ (399)–SCellIndex (399)–ServCellIndex (400)–SpeedStateScaleFactors (400)–SystemInfoListGERAN (400)–SystemTimeInfoCDMA2000 (401)–TrackingAreaCode (401)–T-Reselection (402)–T-ReselectionEUTRA-CE (402)6.3.5Measurement information elements (402)–AllowedMeasBandwidth (402)–CSI-RSRP-Range (402)–Hysteresis (402)–LocationInfo (403)–MBSFN-RSRQ-Range (403)–MeasConfig (404)–MeasDS-Config (405)–MeasGapConfig (406)–MeasId (407)–MeasIdToAddModList (407)–MeasObjectCDMA2000 (408)–MeasObjectEUTRA (408)–MeasObjectGERAN (412)–MeasObjectId (412)–MeasObjectToAddModList (412)–MeasObjectUTRA (413)–ReportConfigEUTRA (422)–ReportConfigId (425)–ReportConfigInterRAT (425)–ReportConfigToAddModList (428)–ReportInterval (429)–RSRP-Range (429)–RSRQ-Range (430)–RSRQ-Type (430)–RS-SINR-Range (430)–RSSI-Range-r13 (431)–TimeToTrigger (431)–UL-DelayConfig (431)–WLAN-CarrierInfo (431)–WLAN-RSSI-Range (432)–WLAN-Status (432)6.3.6Other information elements (433)–AbsoluteTimeInfo (433)–AreaConfiguration (433)–C-RNTI (433)–DedicatedInfoCDMA2000 (434)–DedicatedInfoNAS (434)–FilterCoefficient (434)–LoggingDuration (434)–LoggingInterval (435)–MeasSubframePattern (435)–MMEC (435)–NeighCellConfig (435)–OtherConfig (436)–RAND-CDMA2000 (1xRTT) (437)–RAT-Type (437)–ResumeIdentity (437)–RRC-TransactionIdentifier (438)–S-TMSI (438)–TraceReference (438)–UE-CapabilityRAT-ContainerList (438)–UE-EUTRA-Capability (439)–UE-RadioPagingInfo (469)–UE-TimersAndConstants (469)–VisitedCellInfoList (470)–WLAN-OffloadConfig (470)6.3.7MBMS information elements (472)–MBMS-NotificationConfig (472)–MBMS-ServiceList (473)–MBSFN-AreaId (473)–MBSFN-AreaInfoList (473)–MBSFN-SubframeConfig (474)–PMCH-InfoList (475)6.3.7a SC-PTM information elements (476)–SC-MTCH-InfoList (476)–SCPTM-NeighbourCellList (478)6.3.8Sidelink information elements (478)–SL-CommConfig (478)–SL-CommResourcePool (479)–SL-CP-Len (480)–SL-DiscConfig (481)–SL-DiscResourcePool (483)–SL-DiscTxPowerInfo (485)–SL-GapConfig (485)。
无线传感器网络中一种基于接收功率异常的入侵检测算法

第36卷 第3期2009年3月计算机科学Comp uter Science Vol.36No.3Mar.2009到稿日期:2008204217 本文受国家985工程项目(基于网格的高性能计算与复杂系统仿真平台建设)资助。
王 骐(1970-),讲师,博士研究生,主要研究方向为无线传感器网络安全、嵌入式系统应用等,E 2mail :wangqi_wh @ ;王 殊(1956-),教授,博士生导师,主要研究方向为无线传感器网络、智能信号检测、传输、处理及应用等;孟中楼(1976-),博士研究生,主要研究方向为人工智能与生物仿生。
无线传感器网络中一种基于接收功率异常的入侵检测算法王 骐1,2 王 殊1 孟中楼1(华中科技大学电子与信息工程系 武汉430074)1 (湖北第二师范学院物理与电子工程系 武汉430074)2摘 要 虽然静态传感器节点计算能力和通信能力较差,但是它们具有自己独特的特征,可以获取比较稳定的临域节点信息。
利用这个特征可以检测网络异常情况以及临域节点的通信行为,为传感器网络提供安全保障。
为了使传感器节点能够检测出入侵者,需要先建立一种简单的基于临域节点的动态统计模型,然后用一种低复杂度的检测算法监测已接收到的数据包的接收功率。
首先介绍了一种基于无线传感器网络安全的入侵检测算法,然后介绍了一种基于该算法的节点协作检测技术,节点协作指的是对攻击的联合确认,以及邻居节点共同反抗入侵者的协作行为。
关键词 无线传感器网络,接收功率异常,入侵检测算法仿真,节点协作检测技术中图法分类号 TP301.6 文献标识码 A Intrusion Detection Algorithm B ased on R eception Pow er Anom aly in Wireless Sensor N et w orksWAN G Qi 1,2 WAN G Shu 1 M EN G Zhong 2lou 1(Depart ment of Electronics and Information Engineering ,Huazhong University of Science and Technology ,Wuhan 430074,China )1(Depart ment of Electronics and Physics Engineering ,Hubei University of Education ,Wuhan 430074,China )2Abstract Although static sensor nodes have low computation and communication capabilities ,but they have specific properties ,and can acquire stable neighborhood information ,which can be used for detection of anomalies in networking and behaviors of the neighbor nodes ,to provide security for wireless sensor network.To make a sensor node capable of detecting an intruder ,a simple dynamic statistical model of the neighboring nodes is needed to build ,with a low 2com 2plexity detection algorithm to monitor received packet power levels.A detection algorithm based on security scheme for wireless sensor networks was introduced ,and then a novel node cooperative detection technology based on this detection algorithm ,which refers to affirm and stand against intrusion together ,was proposed.K eyw ords Wireless sensor networks ,Reception power anomaly ,Intrusion detection ,Algorithm simulation ,Node coope 2rative detection technology 1 引言无线传感器网络是一种特殊的Ad Hoc 移动网络,是一个分布式的感知探测系统,一般部署在无人值守的环境中。
通信感知一体化混合波束赋形技术

doi:10.3969/j.issn.1003-3114.2023.04.013引用格式:朱承浩.通信感知一体化混合波束赋形技术[J].无线电通信技术,2023,49(4):689-695.[ZHU Chenghao.Hybrid Beamforming for Integrated Sensing and Communication [J].Radio Communications Technology,2023,49(4):689-695.]通信感知一体化混合波束赋形技术朱承浩(东南大学吴健雄学院,江苏南京210096)摘㊀要:为解决无线通信与感知的性能日益强大而带来的频谱资源紧缺的问题,通信感知一体化(Integrated Sens-ing and Communication,ISAC)技术逐渐开始受到重视㊂在目前最有发展潜力的毫米波(millimeter Wave,mmWave)多输入输出(Multiple Input Multiple Output,MIMO)混合波束赋形系统基础上,提出了一种通信感知一体化的波束赋形算法㊂使用均方误差(Mean Square Error,MSE)衡量该系统的通信和雷达的性能,通过引入权重因子将通信与雷达的性能指标综合考虑,得到通感一体化波束赋形系统的最优解㊂针对求解过程中的非凸优化问题,提出了基于坐标迭代的交替优化算法对问题进行求解㊂针对不同权重因子,对通信的频谱效率和雷达的波束方向图进行了仿真,仿真结果验证了所提方案可以实现通信感知一体化系统下通信与感知性能的折中㊂关键词:通感一体化;毫米波;多输入输出;混合波束赋形;坐标迭代优化法中图分类号:TN929.5㊀㊀㊀文献标志码:A㊀㊀㊀开放科学(资源服务)标识码(OSID):文章编号:1003-3114(2023)04-0689-07Hybrid Beamforming for Integrated Sensing and CommunicationZHU Chenghao(Chien-Shiung Wu College,Southeast University,Nanjing 210096,China)Abstract :In order to solve the shortage of spectrum resources caused by the increasingly powerful performance of wireless commu-nication and sensing,the technology of Integrated Sensing and Communication (ISAC)has gradually begun to receive attention.On thebasis of hybrid beamforming system for the millimeter Wave (mmWave)Multiple Input Multiple Output (MIMO)technology which hasthe most development potential at present,a beamforming algorithm of ISAC in this system is proposed.The Mean Square Error (MSE)is used to measure the performance of communication and radar in this system,and the weight factor is introduced to comprehensively consider the performance of communication and radar,to achieve the optimal solution of the beamforming system for integrated sensingand communication.To overcome the non-convex optimization problem in the process of solving,an alternative optimization algorithm based on coordinate iterative method is proposed.The spectrum efficiency of communication and the beam pattern of radar with differentweight factors are simulated.Through the simulation results,it is verified that the scheme can achieve the compromise between commu-nication and sensing performance in the integrated sensing and communication system.Keywords :ISAC;mmWave;MIMO;hybrid beamforming;coordinate iterative optimization收稿日期:2023-03-250 引言车联网㊁人机交互等应用场景对无线通信和雷达感知均提出了很高的要求[1]㊂随着无线通信技术和雷达感知技术的不断发展,通信与雷达感知这两个原本较为独立的领域展现出越来越多的联系和共同性㊂未来移动通信关键技术之一通信感知一体化(Integrated Sensing and Communication,ISAC)技术,即将无线通信和雷达感知在同一系统中进行联合设计与优化,从而提升资源利用率,降低硬件成本,实现高性能通信和高精度感知[2]㊂通信感知一体化在实现通信传输的同时,还能通过分析无线点的反射㊁散射等特性,对目标信息进行定位和识别[3]㊂通信与感知的融合可以让二者实现技术共享,在满足高性能通信的同时满足复杂多样的感知需求[4]㊂该技术具有超越传统移动通信网络连接的潜力,可以开辟民用无人机㊁智慧交通等全新业务,因此受到了学界的广泛关注[5]㊂波束赋形技术是通信感知一体化的关键技术之一㊂文献[6]提出了通信感知一体化的波束赋形方案,在通信目标信噪比的约束下以目标估计误差为优化目标㊂文献[7]在相同的约束条件下使发射矩阵接近理想的雷达方向图来提高雷达感知的性能㊂为了解决射频资源紧缺的问题,5G将毫米波(millimeter Wave,mmWave)频段写入标准,用于提升传输速率㊂毫米波通信一般使用大规模多输入多输出(Multiple Input Multiple Output,MIMO)技术来增大信号强度[8]㊂随着天线阵列规模的增加,传统的全数字结构成本已经难以承担,因此毫米波通信使用将数字与模拟波束赋形结合起来的混合波束赋形技术㊂基于毫米波频段的通感一体化波束赋形技术也得到了广泛的关注㊂文献[9]提出了通信感知一体化系统的混合波束赋形方案,在满足雷达方向图的条件下,使混合波束赋形矩阵接近理想通信矩阵㊂该方案具有较低的复杂度,且雷达性能较高㊂但是在此方案下通信性能受到抑制,无法实现通信和感知性能的权衡㊂文献[10]采用正交匹配追踪算法得到最优波束赋形矩阵,该算法迭代速度较快,然而在大数据量情况下复杂度较高,且迭代过程中会产生累积误差并影响最终结果㊂现有的研究大多将优化算法的目标设计为使混合波束赋形矩阵逼近全数字波束赋形矩阵,并且通常会在约束通信或感知一者的前提下优化另一者的性能㊂这样做的缺点在于性能上会有所损失,最终求出的结果也不会是最优的㊂因此,针对毫米波MIMO下通感一体化的性能要求,本文提出了基于最小均方误差(Mean Square Error,MSE)准则设计的混合波束赋形算法㊂通过在均方误差指标中引入因子使得优化算法与信道噪声能量相关联,使设计更加准确,同时简化了求解过程㊂通过引入辅助酉矩阵使理想雷达发射矩阵与一体化下的雷达发射矩阵维度相同,可以直接进行均方误差的计算㊂优化的目标函数含有多个待优化变量,难以直接求解,因此本文提出了交替迭代优化算法㊂在假设其他优化目标为最优解的情况下单独优化一个目标,通过不断交替循环实现系统的最优解㊂在求解模拟波束赋形矩阵时,相移器阵列受恒模约束的影响,该问题是非凸优化问题㊂针对该问题,本文提出了坐标迭代优化法来求出该优化问题的最优解㊂仿真结果表明该算法较好地兼顾了通信与感知的性能,实现了二者的融合㊂1㊀毫米波通信感知一体化系统理论基础1.1㊀毫米波大规模MIMO技术5G及今后技术的发展离不开通信速率的不断提高㊂由奈奎斯特第一准则可知,通信速率与信号的带宽成正比㊂4G技术所使用的频段较低,缺乏足够的频带资源继续拓展带宽㊂因此,为了继续提高通信速率,需要利用更高频段的毫米波段㊂相比于中低频段,毫米波段拥有数十倍以上的广阔频段,可以解决带宽资源的紧张问题[11],在毫米波段下的通信与感知性能也能得到极大的提高[12]㊂然而,毫米波也有着不容忽视的缺点,根据弗里斯传输公式[13],接收功率与波长成正比,毫米波更短的波长意味着更大的传输损耗㊂为了弥补这种损耗,在应用中多采用大规模MIMO技术对其进行补偿㊂以一维均匀排布的天线阵列为例,其天线间隔应大于半波长㊂毫米波的波长极短,因此天线间隔在毫米波段下极小,可以实现大规模MIMO传输㊂1.2㊀混合波束赋形系统在传统的全数字波束赋形系统下,每根天线都必须配备一条可以任意改变信号幅度和相位的射频链路㊂然而在大规模MIMO系统中,天线的数量激增,已无法负担为每根天线加装射频链路的巨大成本[14]㊂因此,有研究者提出了使用混合波束赋形技术㊂从图1可以看出,混合波束赋形系统的特点在于使用数个相移器构成模拟波束赋形矩阵[15],减少了数字波束赋形矩阵中射频链路的数量,在很大程度上降低了建设成本㊂其中,传输信号维度为N s,使用了N RF条射频链路,发送天线数量为N t,满足关系N sɤN RF≪N t㊂图1㊀毫米波MIMO系统混合波束赋形方案Fig.1㊀Hybrid beamforming scheme formmWave MIMO system1.3㊀通信感知一体化波束赋形技术在通信感知一体化系统中,同一种波形被同时运用于通信传输和雷达感知,这二者的功能都能通过MIMO混合波束赋形系统实现㊂因此,在求解相应的波束赋形矩阵时,可以做到同时优化通信和感知的性能,这实现了通信与感知性能的兼顾与折中,与一体化的思想一致㊂2㊀基于最小MSE准则的一体化波束赋形设计2.1㊀通信模型在混合波束赋形系统中,用户接收到的信号yɪC N sˑ1可以表示为:y=W H HF RF F BB s+W H n,(1)式中:sɪC N sˑ1为发送的数据信号向量,满足关系E(ss H)=I N s,F BBɪC N RFˑN s为数字波束赋形矩阵, F RFɪC N tˑN RF为模拟波束赋形矩阵,该矩阵仅提供相位变化,因此所有元素的模为1㊂HɪC N rˑN t为信道矩阵,N r为接收端的天线数量,WɪC N rˑN s为接收端的全数字波束赋形矩阵,nɪC N rˑ1为信道噪声矢量,服从均值为0㊁方差为σ2的复高斯分布㊂对于均匀线阵,其阵列响应矢量为:a(θ)=1㊀N[1,e j kd sin(θ),e j2kd sin(θ), ,e j(N-1)kd sin(θ)]T,(2)式中:k=2πλ,d为阵元间隔,通常取d=λ/2,N为天线数,θ为到达角或离开角㊂在毫米波频段下,信道矩阵为Saleh-Valenzuela 模型[16],可以表示为:H=㊀NtN rLðL l=1αl a r(θr,l)a H t(θt,l),(3)式中:L为多径数,αl为第l条传输路径的信道增益,服从标准复高斯分布,θr,l为第l条传输路径的到达角,θt,l为第l条传输路径的离开角㊂2.2㊀感知模型MIMO的雷达发射波束方向图为[17]:P(θ)=a H t(θ)R s a t(θ),(4)式中:R sɪC N tˑN t为发射信号的协方差矩阵,可以表示为:Rs=E(F RF F BB ss H F H BB F H RF)=F RF F BB E(ss H)F H BB F H RF=F RF F BB F H BB F H RF㊂(5)假设雷达感知的目标数量为K,相对于基站的离开角为{θt,1,θt,2, ,θt,K}㊂由式(3)可知,信道矩阵表示为L个不同离开角和到达角的散射路径的求和㊂信道的前K个散射路径即为雷达感知K个目标的路径㊂因此信道前K个路径的离开角应为雷达感知的离开角,即为{θt,1,θt,2, ,θt,K},剩下的L-K个离开角和L个到达角均服从[-π/2,π/2]的均匀分布㊂2.3㊀通信感知一体化的最小MSE模型在一体化系统的设计过程中,衡量通信系统性能的主要标准为误比特率(Bit Error Ratio,BER)等㊂在传统波束赋形设计中,通常通过降低MSE来达到降低误比特率的目的㊂本文将这一指标运用到一体化混合波束赋形的应用范围内,目的也是通过降低通信和雷达感知的均方误差来优化通信和感知的各项性能㊂通信性能的MSE定义为接收信号与原始信号的均方误差:MSE c=E( β-1y-s 2F)=E( β-1(W H HF RF F BB s+W H n)-s 2F)= tr(β-2W H HF RF F BB F H BB F H RF H H W-β-1W H HF RF F BB-β-1F H BB F H RF H H W+σ2β-2W H W+I Ns)(6)式中:引入的β因子可以将之后在功率约束下的优化求解问题大大简化,变成以β为优化目标的子问题㊂由雷达感知的波束图公式可知,雷达的波束设计等价于设计雷达的协方差矩阵㊂理想的全数字雷达发射矩阵F radɪC N tˑK为:F rad =[a t (θt ,1),a t (θt ,2), ,a t (θt ,K )]㊂(7)然而,混合波束赋形系统中的雷达发射矩阵为F RF F BB ɪCN t ˑN s,与理想的发射矩阵维度不一致,因此二者不能直接进行MSE 的计算㊂为使二者维度一致,可以引入一个辅助酉矩阵F u ɪC K ˑN s,其满足关系F u F H u =I K ,这样,理想雷达的发射矩阵可以表示为F r =F rad F u ɪCN t ˑN s㊂可以看到,引入辅助酉矩阵后,理想雷达的发射矩阵与混合波束赋形中的发射矩阵维度一致,并且原来理想雷达的方向没有改变,维持了原始的性能㊂辅助酉矩阵可以通过以下的优化问题解出:min F uF c -F rad F u 2Fs.t.㊀F u F Hu=I K{,(8)式中:F c 为理想的通信全数字波束赋形矩阵㊂对信道矩阵进行奇异值分解:H =U V H ㊂(9)取V 的前N s 列即为通信全数字波束赋形矩阵F c ㊂该优化问题表明构造辅助酉矩阵应尽可能减小全数字波束赋形下通信与雷达感知的差异,提高一体化的性能㊂该问题类似于正交普鲁克问题,可以求得F u的闭式解为[18]:F u =U 1CV H 1,(10)式中:U 1和V 1来自于F H rad F c 的奇异值分解F Hrad F c=U 11V H 1,C =[I K ,O K ˑ(N s -K )]㊂由此,雷达感知的MSE 可以定义为:MSE r = F RF F BB -F r 2F =tr(F RF F BB F H BB F H RF -F RF F BB F H r -F r F H BB F H RF +F r F Hr )㊂(11)在一体化的混合波束赋形设计中,需要同时以通信和雷达的性能作为优化对象,因此优化问题的目标函数应同时包含二者的均方误差㊂通感一体化下的混合波束赋形优化问题可以表示为:min W ,F RF ,F BB ,βρMSE c +(1-ρ)MSE r s.t.㊀(F RF )ij =1,∀i ,j F RF F BB 2FɤP ìîíïïïï,(12)式中:ρɪ[0,1]为一权重因子,代表通信性能在优化中所占的比重㊂该优化问题需要考虑模拟波束赋形矩阵的恒模约束和混合波束赋形矩阵的功率约束㊂3㊀基于交替迭代优化算法求解波束赋形设计3.1㊀基于坐标迭代的交替优化上文中通感一体化下的混合波束赋形优化问题涉及到4个待优化变量,难以直接求解㊂因此,可以每次在固定其他变量的条件下交替优化一个变量,通过多轮这样的迭代优化使目标函数最终落入目标区间内㊂①关于W 的子问题可以表示为:min W MSE c ㊂(13)将目标函数MSE c 对W 求偏导并使结果等于零可以得到W 的闭式解为:W =(HF RF F BB F H BB F H RF H H +σ2β-2I N r)-1ˑβ-1HF RF F BB ㊂(14)②关于β的子问题,由于存在发射功率的限制,只有在发射功率达到最大时β才能达到最优值㊂令F bb =β-1F BB 以简化表达,可以得到在发射功率最大时的β值为:β=P -12(tr(F RF F bb F HbbF H RF))-12㊂(15)从求解过程可以看出,若按照未引入β因子的传统MSE 标准来优化,则需要引入拉格朗日乘子将功率约束条件利用起来再进行复杂的求解,但在引入β因子后,就可以将功率约束分解为β的子问题求得闭式解,这无疑大大简化了算法流程㊂③关于F BB 的子问题可以表示为:min F BBρMSE c +(1-ρ)MSE r ㊂(16)将目标函数对F BB 求偏导并使结果等于零可以得到F BB 的闭式解为:F BB =(ρβ-2F H RF H H WW H HF RF +(1-ρ)F HRF F RF )-1ˑ(ρβ-1F H RF H H W +(1-ρ)F HRF F r )㊂(17)④关于F RF 的子问题可以表示为:min FRFρMSE c +(1-ρ)MSE rs.t.㊀(F RF )ij =1,∀i ,j{㊂(18)约束条件(F RF )ij =1,∀i ,j 使得上述优化问题是非凸的,这使得问题的理论求解十分困难㊂本文针对该问题提出坐标迭代优化法对其进行求解㊂F RF 的优化问题可以表示为:J (F RF )=ρMSE c +(1-ρ)MSE r =ρtr(β-2W H HF RF F BB F H BB F H RF H H W -β-1W HHF RF F BB -β-1F H BB F H RF H H W +σ2β-2W H W +I N s)+(1-ρ)tr(F RF F BB F H BB F H RF -F RF F BB F H r -F r F H BB F HRF +F r F H r )=ρtr(A l )+(1-ρ)tr(B l )+ρtr(β-2W H HV RF V BB V H BB V H RF H H W -2β-1W H HV RF V BB )+(1-ρ)tr(V RF V BB V H BB V H RF -2V RF V BB F H r ),(19)式中:A l =β-2W H HF -l RF F -l BB (F -l BB )H (F -l RF )H H H W -β-1W H HF -l RF F -l BB-β-1(F -l BB )H (F -l RF )H H H W +σ2β-2W H W +I Ns,(20)B l =F -l RF F -l BB (F -l BB )H (F -l RF )H -F -l RF F -l BB F Hr -F r (F -l BB )H (F -l RF )H +F r F H r,(21)式中:F -l RF 为矩阵F RF 移除第l 列后的子矩阵,F -l BB 为矩阵F BB 移除第l 行后的子矩阵,V RF 为矩阵F RF第l 列的矢量,V BB 为矩阵F BB 第l 行的矢量㊂固定矩阵F RF 其他列不变,将第l 列的矢量V RF单独作为变量优化,原优化问题可以转化为:min F RFρtr(β-2W H HV RF V BB V H BB V H RF H H W -2β-1W HHV RF V BB )+(1-ρ)tr(V RF V BB V HBBV H RF-2V RF V BB F H r)s.t.㊀(V RF )n =1,∀n ㊂(22)该优化问题同样可以用类似方法处理,每次固定V RF ,其他元素不变,将第n 个元素V RF (n )作为变量求最优解㊂令H w =W H H ,F v =V BB F H r ,由于模拟波束赋形矩阵仅有相移的功能,可令V RF (n )=e j θn ,则目标函数中与V RF (n )有关的项为:J (θn )=ρðN sm =1[β-2H w (m ,n )V BB (m )2ej2θn-2β-1H w (m ,n )ˑV BB (m )e j θn]+(1-ρ)ðN s m =1V BB (m )2e j2θn-2(1-ρ)F v (n )e j θn ㊂(23)令:X n =ðN sm =1H w (m ,n )V BB (m )2,(24)Y n =ðN s m =1H w (m ,n )V BB (m )㊂(25)求J (θn )关于θn 的偏导,使其等于零,可以求得V RF (n )的最优解为:V RF (n )=ej θn=ρβ-1Y n +(1-ρ)F v (n )ρβ-2X n +(1-ρ) V BB 2F㊂(26)对F RF 中的每个元素依次使用上述算法,即可求得当前条件下F RF 的最优解㊂基于坐标迭代的交替优化算法的详细步骤如算法1所示㊂算法1㊀交替优化算法输入:输入:H ,N s ,N RF ,N t ,N r ,P ,σ2,ρ,I max ,S min输出:F BB ,F RF ,W ,β1.㊀在约束条件(F RF )ij =1,∀i ,j 下随机初始化矩阵F RF2.根据式(9)得到通信全数字波束赋形矩阵F c ,初始化F BB =F -1RF F c3.初始化β=P -1/2(tr(F RF F BB F H BB F H RF ))-1/24.for i =1,2, ,I max do5.㊀㊀根据式(15)更新β6.㊀㊀根据式(14)更新W7.㊀㊀根据式(26)用坐标迭代优化法更新F RF 8.㊀㊀根据式(17)更新F BB9.㊀㊀根据式(6)和式(11)计算MSE c 和MSE r10.㊀㊀if ρMSE c +(1-ρ)MSE r <S min then11.㊀㊀㊀结束循环12.㊀㊀end if13.end for3.2㊀仿真分析本节通过仿真结果来分析使用基于坐标迭代的交替优化算法求解的一体化混合波束赋形系统的性能㊂仿真中,发射天线数N t =64,接收天线数N r =8,N RF =N s =4,将每条射频链路使用的发射功率归一化为1,则总系统的归一化发射功率P =4,毫米波信道多径数L =10[19],雷达检测目标K =3,离开角分别为[-45ʎ,0ʎ,45ʎ],信道中其余离开角和到达角均服从[-π/2,π/2]的均匀分布㊂图2为不同权重因子ρ下频谱效率随信噪比变化的曲线㊂可以看出,随着通信性能权重ρ的增大,混合波束赋形的频谱效率也在增大,且越来越接近全数字波束赋形下的频谱效率㊂当ρ=1时,混合波束赋形系统只考虑通信的性能,此时的频谱效率与全数字状态非常接近㊂因此可以看出,权重因子ρ的大小在优化过程中会影响一体化系统的通信性能㊂图2㊀不同权重下频谱效率随信噪比的变化曲线Fig.2㊀Curve of spectral efficiency versus signal-to-noise ratio with different weights图3为不同权重下雷达波束图与理想全数字雷达波束图的比较㊂由于ρ值越小代表雷达性能在优化中占比越大,可以看到,随着ρ值的不断下降,一体化系统下的雷达波束图与全数字下的波束图越来越接近㊂在ρ=0.7时,雷达波束存在较大的旁瓣,这会较大地干扰正确的检测目标;ρ=0.5时,旁瓣干扰仍然存在,但此时主瓣强度明显高于旁瓣,可以进行有效的检测;ρ=0.3时,旁瓣强度被显著抑制,这时的旁瓣干扰很小,主瓣方向的波束容易分辨,雷达感知的精度较高,能够准确地识别目标方位㊂由上述分析可知,本文提出的基于坐标迭代的交替优化算法在保障通信性能的同时可以实现较高的雷达感知精度,且可以通过改变权重ρ值灵活地调整通信与感知性能的占比,实现二者的权衡,达到通感一体化的效果㊂图3㊀不同权重时的雷达波束方向图Fig.3㊀Radar beam patterns with different weight factors4 结论本文使用了毫米波信道下的混合波束赋形技术实现通信感知一体化㊂通过引入因子β导出基于最小均方误差准则的通信性能优化问题,并引入辅助酉矩阵,让理想雷达发射矩阵与混合波束赋形矩阵保持维度相同,得到了基于雷达感知性能的优化问题㊂接着利用权重因子ρ结合两方面性能提出了通感一体化下的混合波束赋形优化问题㊂针对非凸优化问题提出了基于坐标迭代的交替优化算法,完成了对波束赋形优化问题的求解㊂仿真结果表明,该算法能够很好地实现通信与感知性能的折中,即在不同权重下通信与感知的性能都能有所保证,实现了通信感知一体化的效果㊂参考文献[1]㊀LIU F,CUI Y,MASOUROS C,et al.Integrated Sensingand Communications:Towards Dual-functional WirelessNetworks for 6G and Beyond[J].IEEE Journal on Select-ed Areas in Communications,2022,40(6):1728-1767.[2]㊀吴晓文,焦侦丰,刘冰,等.面向6G 的卫星通感一体化[J].移动通信,2022,46(10):2-11.[3]㊀LIU Y J,LIAO G S,XU J W,et al.Adaptive OFDM Inte-grated Radar and Communications Waveform Design Based on Information Theory [J].IEEE communications letters,2017,21(10):2174-2177.[4]㊀高飞,王文剑,刘建国,等.通感一体化融合的研究及其挑战[J].移动通信,2022,46(5):45-51.[5]㊀李萍,郭晓江.通感一体化关键技术与应用[J].中兴通讯技术,2023,29(2):72-78.[6]㊀LIU F,MASOUROS C.Joint Beamforming Design for Ex-tended Target Estimation and Multiuser Communication [C]ʊ2020IEEE Radar Conference (RadarConf20).Florence:IEEE,2020:1-6.[7]㊀LIU X,HUANG T,SHLEZINGER N,et al.Joint TransmitBeamforming for Multiuser MIMO Communications and MIMO Radar[J].IEEE Transactions on Signal Process-ing,2020,68:3929-3944.[8]㊀VOOK F W,THOMAS T A,VISOTSKY E.Massive MIMOfor mmWave Systems [C]ʊ201448th Asilomar Confer-ence on Signals,Systems and Computers.Pacific Grove:IEEE,2014:820-824.[9]㊀LIU F,MASOUROS C,PETROPULU A P,et al.Joint Ra-dar and Communication Design:Applications,State-of-the-art,and the Road Ahead[J].IEEE Transactions on Com-munications,2020,68(6):3834-3862. [10]EL AYACH O,RAJAGOPAL S,ABU-SURRA S,et al.Spatially Sparse Precoding in Millimeter Wave MIMO Sys-tems[J].IEEE Transactions on Wireless Communica-tions,2014,13(3):1499-1513.[11]RAPPAPORT T S,SHU S,MAYZUS R,et limeterWave Mobile Communications for5G Cellular:It WillWork[J].IEEE Access,2013,1(1):335-349. [12]RAI P K,IDSØE H,YAKKATI R R,et al.Localizationand Activity Classification of Unmanned Aerial VehicleUsing mmWave FMCW Radars[J].IEEE Sensors Jour-nal,2021,21(14):16043-16053.[13]罗涛,王昊.车辆无线通信网络及其应用[J].中兴通讯技术,2011,17(3):1-7.[14]邓瑾.大规模MIMO系统中的波束空间信道估计以及混合波束成形研究[D].成都:电子科技大学,2022. [15]YU X,SHEN J C,ZHANG J,et al.Alternating Minimiza-tion Algorithms for Hybrid Precoding in Millimeter WaveMIMO Systems[J].IEEE Journal of Selected Topics inSignal Processing,2016,10(3):485-500.[16]AKDENIZ M R,LIU Y,SAMIMI M K,et limeterWave Channel Modeling and Cellular Capacity Evaluation[J].IEEE Journal on Selected Areas in Communications,2014,32(6):1164-1179.[17]CHENG Z,LIAO B,HE Z,et al.Joint Design of theTransmit and Receive Beamforming in MIMO Radar Sys-tems[J].IEEE Transactions on Vehicular Technology,2019,68(8):7919-7930.[18]VIKLANDS T.Algorithms for the Weighted OrthogonalProcrustes Problem and Other Least Squares Problems[D].Sweden:UmeåUniversitet,2006.[19]LIU F,MASOUROS C.Hybrid Beamforming with Sub-arrayed MIMO Radar:Enabling Joint Sensing and Commu-nication at mmWave Band[C]ʊICASSP2019-2019IEEE International Conference on Acoustics,Speech andSignal Processing(ICASSP).Brighton:IEEE,2019:7770-7774.作者简介:㊀㊀朱承浩㊀东南大学本科在读㊂主要研究方向:通信感知一体化㊂。
Cisco Intrusion Detection System Network Modules连接

CautionAmericas Headquarters:Cisco Systems, Inc., 170 West Tasman Drive, San Jose, CA 95134-1706USAConnecting Cisco Intrusion Detection System Network Modules to the Network Cisco IDS Network Module LEDs2Connecting Cisco Intrusion Detection System Network Modules to the Network NoteCautionConnecting Cisco Intrusion Detection System Network Modules to the NetworkOnline Insertion and Removal with a Cisco IDS Network ModuleCautionCautionConnecting Cisco Intrusion Detection System Network Modules to the Network3Connecting Cisco Intrusion Detection System Network Modules to the Network Online Insertion and Removal with a Cisco IDS Network Module4Connecting Cisco Intrusion Detection System Network Modules to the NetworkTo perform online removal of a Cisco IDS network module and insertion of a replacement, follow these steps with the router in privileged EXEC mode:Step1Perform a graceful halt of the Cisco IDS network module by using the following command: Router# service-module IDS-Sensor slot/0shutdownTrying 10.10.10.1, 2129 ... OpenWait for the following status message (it may take a minute or two):%SERVICEMODULE-5-SHUTDOWN2:Service module IDS-Sensor1/0 shutdown completeStep2Unplug the network interface cable from the Cisco IDS network module.Step3Loosen the two captive screws holding the Cisco IDS network module in the chassis slot.Step4Slide the Cisco IDS network module out of the slot.Step5Align the replacement Cisco IDS network module with the guides in the chassis slot, and slide it gently into the slot.Note If the router is not fully configured with network modules, make sure that blank panels fill the unoccupied chassis slots to provide proper airflow.Step6Push the module into place until you feel its edge connector mate securely with the connector on the backplane.Step7Reconnect the network interface cable previously removed in Step2.Step8Tighten the two captive screws on the faceplate.Step9Reset the Cisco IDS network module using the reset command.Router# service-module IDS-Sensor slot/0 resetUse reset only to recover from shutdown or failed stateWarning: May lose date on the hard disc!Do you want to reset?[confirm]Step10Press Enter to confirm the request. The Cisco IDS network module resets itself.Step11Check that the network module LEDs are on and that the power and enable LEDs on the front panel also are on. This inspection ensures that connections are secure and that the new unit is operational.Connecting Cisco Intrusion Detection System Network Modules to the NetworkRelated Documents 5Connecting Cisco Intrusion Detection System Network Modules to the Network Related DocumentsFor additional information, see the following documents and resources.Obtaining Documentation, Obtaining Support, and Security GuidelinesFor information on obtaining documentation, obtaining support, providing documentation feedback,security guidelines, and also recommended aliases and general Cisco documents, see the monthlyWhat’s New in Cisco Product Documentation , which also lists all new and revised Cisco technicaldocumentation, at:/en/US/docs/general/whatsnew/whatsnew.htmlCCDE, CCENT, Cisco Eos, Cisco Lumin, Cisco StadiumVision, the Cisco logo, DCE, and Welcome to the Human Network are trademarks;Changing the Way We Work, Live, Play, and Learn is a service mark; and Access Registrar, Aironet, AsyncOS, Bringing the Meeting To You,Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, CCVP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press,Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Collaboration Without Limitation, EtherFast, EtherSwitch, EventCenter, Fast Step, Follow Me Browsing, FormShare, GigaDrive, HomeLink, Internet Quotient, IOS, iPhone, iQ Expertise, the iQ logo, iQ NetReadiness Scorecard, iQuick Study, IronPort, the IronPort logo, LightStream, Linksys, MediaTone, MeetingPlace, MGX, Networkers, NetworkingAcademy, Network Registrar, PCNow, PIX, PowerPanels, ProConnect, ScriptShare, SenderBase, SMARTnet, Spectrum Expert, StackWise, TheFastest Way to Increase Your Internet Quotient, TransPath, WebEx, and the WebEx logo are registered trademarks of Cisco Systems, Inc. and/or itsaffiliates in the United States and certain other countries.All other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not implya partnership relationship between Cisco and any other company. (0804R)Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, andfigures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional andcoincidental.© 2008 Cisco Systems, Inc. All rights reserved.Related TopicDocument Title Cisco IDS software documentation Cisco Intrusion Detection System (IDS) Hardware and Software DocumentationGuide/univercd/cc/td/doc/product/iaabu/csids/csids10/15593_01.htmRegulatory compliance and safety informationCisco Network Modules and Interface Cards Regulatory Compliance and SafetyInformation/en/US/docs/routers/access/interfaces/rcsi/IOHrcsi.html Cisco IOS software website and reference documentation Cisco IOS Software/web/psa/products/index.html?c=268438303Connecting Cisco Intrusion Detection System Network Modules to the Network Obtaining Documentation, Obtaining Support, and Security GuidelinesConnecting Cisco Intrusion Detection System Network Modules to the Network6。
AMPS-24 & AMPS-24E

A fire alarm system will not operate without any electrical power. If AC power fails, the system will operate from standby batteries only for a specified time and only if the batteries have been properly maintained and replaced regularly.
Particles of combustion or “smoke” from a developing fire may not reach the sensing chambers of smoke detectors because:
• Barriers such as closed or partially closed doors, walls, or chimneys may inhibit particle or smoke flow.
Addressable Power Supplyocument 51907
02/09/2006 Rev:
P/N 51907:C
ECN 06-075
Fire Alarm System Limitations
While a fire alarm system may lower insurance rates, it is not a substitute for fire insurance!
新格林奈特GPON设备验证试验大纲V
附件1:版本序列附件2:试验项目要素表附件3:试验项目测试列表一. 接口测试1. OLT侧PON光接口参数指标测试(需要突发式光功率计测试,测试条件不足未测试)2. ONU侧PON-R口参数指标测试(需要突发式光功率计测试,测试条件不足未测试)二. GPON功能测试1. OLT/ONU功能测试2. HGU型ONU设备基本功能测试三. 系统性能和环境试验四. 网管测试3.OLT 配置管理通过网管应能对OLT进行硬件设备、接口和功能的配置,OLT能正确执行:如图连接1)在网管系统上增加/删除/查看/修改OLT 板卡状态;2)激活/去激活PON 口和上联口,对PON 口相关参数如速率等进行配置,验证是否正常工作;3)配置业务映射规则和参数、业务带宽各项参数以及L2/L3 功能和协议参数等,验证配置后设备是否正常工作。
4.OLT 安全管理测试网管系统对于管理员/操作系统访问的安全措施。
测试步骤:1) OLT 和ONU 连接正常,网管计算机以管理员身份登录网管系统;2) 新创建一个用户,并为其指定角色,规定访问权限,然后退出网管系统;3) 以步骤2)新创建的用户登录管理系统,执行其访问权限内的操作;4) 执行其访问权限外的操作;5) 退出网管系统;6) 使用未经授权的用户名进行登录尝试;7) 以管理员登录,将资源分配到不同的管理区域,创建一个新用户,为其指定管理区域;8) 以步骤7)创建的用户登录管理系统,查看所能管理的资源并对其进行操作,退出网管系统;9) 以管理员登录,查询系统记录。
预期结果:步骤3)中,能执行相应操作。
步骤4)中,无法执行相应操作。
步骤6)中,无法正常登录,提示密码错误。
步骤8)中,能对管理区域内的资源进行操作。
步骤9)中,应查询到以上步骤相应的操作记录,包括用户名、登录时间、操作类型。
五. 异常测试六. 测试用仪表。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
ENHANCING INTRUSION DETECTION IN WIRELESS NETWORKS USING RADIO FREQUENCY FINGERPRINTING(EXTENDED ABSTRACT)Jeyanthi HallSchool of Computer ScienceCarleton University1125Colonel By DriveOttawa,Ontario,Canada email:jeyanthihall@ Michel Barbeau and Evangelos Kranakis School of Computer ScienceCarleton University1125Colonel By DriveOttawa,Ontario,Canada email:barbeau,kranakis@scs.carleton.caABSTRACTMedia access control(MAC)address spoofing can result in the unauthorized use of network resources.This paper demonstrates a novel approach,which incorporates radio frequencyfingerprinting(RFF)into a wireless intrusion de-tection system(IDS),for detecting this attack.RFF is a technique that is used to uniquely identify a transceiver based on the transient portion of the signal it generates. Moreover,the success rate of a wireless IDS is also im-proved by correlating several observations in time,using a Bayesianfilter.Simulation results,with an average suc-cess rate of(94-100%),support the feasibility of employ-ing RFF and Bayesianfiltering techniques to successfully address the aforementioned problem.KEY WORDSIntrusion Detection,Media Access Control,Radio Fre-quency Fingerprinting,Wireless Networks,Network Secu-rity,Bayesian Filter.1IntroductionUnlike wired IDSs,wireless IDSs for802.11[1]networks must also defend against attacks including rogue access points,media access control(MAC)address spoofing and password-guessing for802.1x[2](authentication standard [3]used by the802.11i security infrastructure[4]),accord-ing to Potter[5].While commercial IDS products such as AirDefense, Netstumbler and Airtraf are currently available,they tend to focus primarily on the detection of rogue access points, as indicated by Potter in[5].Although AirDefense does ad-dress the issue of MAC address spoofing,it can only make a distinction between transceivers from different manufac-turers.In terms of solutions that are open source,Kismet and Snort-wireless are used to counter war driving(driv-ing in a vehicle and searching for the presence of wireless networks)and to detect rogue access points in ad hoc net-works respectively.Finally,the use of an agent framework for detecting rogue access points and unauthorized clients (nodes)is explored by Chirumamilla and Ramamurthy in[6].The main disadvantage with this approach is the use ofa list of MAC addresses,which can be spoofed,for identi-fying authorized access points and nodes.Figure1.Signal from a802.11b TransceiverThe problem that is addressed in this paper is the mal-leability of the identifier used for access control.In the case of MAC address spoofing,the address itself(used as an identifier)is acquired over the air by an intruder and subse-quently used to gain unauthorized access to the network.What is required is a form of identification that is non-malleable(cannot be spoofed easily).Pioneered by the military to track the movement of enemy troops and sub-sequently implemented by some cellular carriers(e.g.Bell Nynex)to combat cloning fraud[7],radio frequencyfinger-printing(RFF)has been used to uniquely identify a given transceiver,based on its transceiverprint.A transceiver-print consists of features,which have been extracted from the turn-on transient portion of a signal[8].Figure1illus-trates the location of the transient from the SMC802.11b transceiver(ID:798).The key benefit of this technique is that a transient reflects the unique hardware characteristics of a transceiver and thus cannot be easily forged,unless the entire circuitry of a transceiver can be accurately replicated (e.g.theft of an authorized device).In this paper,a novel approach is presented whereby a profile of a transceiver(created using RFF)is used for anomaly-based intrusion detection.By associating a MAC address with the corresponding transceiver profile,the ca-pabilities of a wireless IDS is further enhanced.It is generally known that current IDSs render a de-cision,as to whether an observed behavior/event is normal or anomalous,based on a single observation.By delay-ing this decision until multiple observations have been an-alyzed,the level of uncertainty is reduced,resulting in a higher success rate.Thus,the Bayesianfilter,presented by Russell and Norvig in[9],has been used to achieve this goal.The remaining sections of the paper are organized as follows.The details of using RFF for anomaly-based de-tection is presented in Section2,followed by the results of the simulation in Section3.Section4briefly summarizes other related work in the area of RFF.Finally,the conclu-sions drawn are reported in Section5.2Novel Approach:RFF for Anomaly-based DetectionThis section describes the framework and the key activities that are undertaken to fulfill two primary objectives:the creation of a profile for each transceiver and the specifica-tion of the classification system.2.1Intrusion Detection FrameworkThe intrusion detection framework is illustrated in Figure2. The overall objective is to classify an observed transceiver-print as normal(belongs to the transceiver of a device with a given MAC address)or anomalous(belongs to another transceiver).Figure2.Anomaly-based Intrusion DetectionTheflow of information begins with the conversion of an analog signal to a digital signal using an analog to digital converter(will not be covered in detail).Once in a digital form,the transient portion of the signal is extracted by the transient extractor.Upon isolating the transient,the amplitude,phase and frequency components of the tran-sient are subsequently extracted by the feature extractor.In turn,these components are used for the extraction of spe-cific features that define a transceiverprint.The classifier is then used to determine the probability of a match between a transceiverprint and each of the transceiver profiles in the IDS.Finally,the Bayesianfilter is applied to render afi-nal decision regarding the status(normal/anomalous)of a transceiverprint.A transceiver profile is created by extracting the transceiverprints from a set of digital signals and storing the corresponding centroid and the covariance matrix(dis-cussed in section2.4)in a profile.This exercise is under-taken prior to the detection process.Due to factors,such as transceiver aging,there is a need to periodically update the profiles.One possible strategy would be to continuously re-calculate the centroid and the covariance matrix(after suc-cessful transceiver identification)using one or more recent transceiverprints and pre-established thresholds(e.g.clas-sification error rate).2.2Transient ExtractorAs the unique characteristics of transceivers are manifested in the transient portion of a signal,the key objective is to extract the transient using the phase characteristics of the signal,as proposed by Hall,Barbeau and Kranakis[8].In brief,the successful detection of the start of the transient is based on the fact that the variance of the phase remains constant until the start of the transient.The end of the tran-sient is identified in an experimental manner.2.3Feature ExtractorOnce the transient has been isolated,the next requirement is to extract the three primary components from the tran-sient.The amplitude and phase[10]components are ob-tained using Eq.1and Eq.2respectively.a(t)= i2(t)+q2(t)(1)θ(t)=tan−1 q(t)i(t) (2)The preferred approach for obtaining the frequency component of a non-stationary signal(e.g.transient)is the application of the Discrete Wavelet Transform(DWT) [11].Due to its lower computational complexity,as stated by Choe et al.[12]and Hippenstiel and Payal[13],the Daubechiesfilter is used to obtain the DWT coefficients.While other research teams have focused primarily on the use of a single component(e.g.amplitude or fre-quency)for feature extraction,we have opted to make use of all three components,namely amplitude,phase and fre-quency.This strategy increases the number of components from which a set of features(feature vector)are derived, thus enhancing the characterization of the transceivers.Figure3displays a signal from the SMC transceiver 798as well as the frequency component(DWT coeffi-cients)of the transient(between vertical lines in thefirst plot).Figure3.Frequency component of Transceiver798Once these components have been extracted,a feature vector,defined by the feature selection/profile definition process(discussed in Section2.6),is created to represent a transceiverprint.Please note that the term transceiver-print and feature vector will be used interchangeably in the following sections.2.4ClassifierWith regards to classification,the guiding factor is the need to determine the probability of a match between a given transceiverprint and each of the transceiver profiles.Although the Probabilistic Neural Network(PNN) [14]has been used by many research teams including Shaw and Kinsner[15]and Hunter[16],the issue of scalability (memory requirement per profile(MPP))prohibits its use in real time systems.In contrast,the MPP of a statistical classifier is very modest and is defined by Eq.3MP P(m,n)=mn+m(n2)(3) where n is the number of features,m is the size in bytes,and mn and mn2represent the memory requirement for the centroid and covariance matrix respectively.Setting n to ten and m to four,results in a MPP of440bytes in comparison to61,440bytes(2048bytes per training pattern multiplied by30patterns)required for PNN.A statistical classifier uses a set of variables,in this case a set of features,to represent a vector that is to be classified.The probability of a match is calculated using a Kalmanfilter from Bar-Shalom[17]that has been modi-fied:P(¯u)=exp −12(¯u−µ)T V−1(¯u−µ) (4)where¯u represents the feature vector to be classified,µcor-responds to the centroid(vector with elements representing the average of each of the features)and V is the covariance matrix,which characterizes the dispersion or variability of each feature with respect to one another.Eq.4returns a probability based on the relationship between an observed feature vector and the profile of a transceiver.2.5Bayesian FilterIn a wireless environment,characterized by noise and in-terference,there is a potential for increased variability be-tween signals from a given transceiver.The Bayesianfilter probabilistically estimates the state of a system from noisy observations.We will use Figure4to illustrate the appli-cation of the Bayesianfilter to10transceiverprints from transceiver SMC798.In RFF,the state is defined as a transceiver(from the transceiver space:x-axis)to which a transceiverprint from SMC798could potentially belong to.At each point in time t,a probability distribution,called belief,over the state(x t) space,represents the uncertainty and is denoted as Bel(x t). Initially,the Bel(x0)or probability is uniformly distributed at t=0.This is demonstrated by the similar height of the vertical bars(y-axis)along the x-axis for transceiverprint number one.Actual classification of the10transceiver-prints begins with transceiverprint number two on the z-axis.Therefore,at t=1,the probability distribution asso-ciated with thefirst transceiverprint(z=2)is obtained from the classifier.Thefilter sequentially estimates such beliefs using Eq.5for(t=1,2,...,10).At each iteration,the belief at time t represents the current probability that has been influenced by the probability of the previous observa-tion(transceiverprint)o t at t−1.Bel(x t)=p(x t|o t)Bel(x t−1)(5) Based on the normalized distribution at t=10,it is clearly evident that there is a high probability of a match, between the transceiverprints and transceiver SMC798.Figure4.Bayesian Probability:Transceiver7982.6Feature Selection/Profile DefinitionIn order to define a profile(for each transceiver),one must first define the composition of a transceiverprint.The keyobjective is to select a set of features that have low intra-transceiver variability (within a transceiver)and high inter-transceiver variability (between transceivers).In order to determine the two classes of variability,the use of euclidian distance (ED)and clustering techniques of Multivariate Analysis (MV A)are employed [18].The fea-tures (variables),to be analyzed using MV A,are extracted from the three components of the signal.Thus,the initial set of ten features (transceiverprint)is comprised of the following:Standard deviation of normalized amplitude,Stan-dard deviation of normalized phase,Standard deviation of normalized frequency,Variance of change in amplitude,Standard deviation of normalized in-phase data,Standard deviation of normalized quadrature data,Standard devia-tion of normalized amplitude (mean centered),Power per section,Standard deviation of phase (normalized using mean)and the Average change in DWT coefficients.In order to refrain from a detailed treatment of each feature,a brief overview of the first four features is pro-vided next:Standard deviation of normalized amplitude is defined asσAn =(A n −M an )2(6)where A n represents the normalized instantaneous ampli-tude (Eq.1)and is denoted as AiMa.While A i represents the amplitude at time instant t (i =1,2,...,N ),M a =max {A i }and it is the maximum of the instantaneous am-plitudes.Finally,the mean of the normalized amplitudesM an is defined as 1N n i =1A n .The Standard deviation of normalized phase and the Standard deviation of normalized frequency are similarly defined by substituting A i with the phase and frequency data (DWT coefficients)respectively.Variance of change in amplitude is defined asV =(D A i )−(1n N −1i =1(D A i ) 2(7)where D A i is the difference in the amplitude A i −A i +1and N is the size of the transient.The extraction of the 10features from each transient results in a set of feature vectors referred to as a cluster.In order to assess the intertransceiver variability of two or more transceivers (clusters),a centroid (composed of the average value of each of the features in the vectors)is cre-ated for each cluster.The centroids as well as the variability between the SMC transceivers are illustrated in Figure 5.Intratransceiver variability,on the other hand,is de-picted in Figure 6.The individual data curves represent the ED of each of the 31transceiverprints from the correspond-ing centroids.The transceiverprints have been sorted based on the ED in order to determine the range of the dispersion.Once the composition of a transceiverprint has been established,through an iterative process of profiling andFigure 5.Intertransceiver Variability for SMC TransceiversFigure 6.Intratransceiver Variability for SMC Transceiversclassification,a subset of these transceiverprints is used to create the profile (centroid and the covariance matrix).3SimulationThe purpose of the simulation was to primarily assess the composition of the transceiverprint based on the classifica-tion success rate (metric).In order to fulfill this objective,the following steps were carried out using a set of signals from each transceiver:For each transceiver being profiled,the predefined features were extracted from the transients.A subset (approximately 31)of the transceiverprints was selected (based on the ED)and subsequently used to create a cen-troid and covariance matrix.The remaining transceiver-prints (approximately 60)were used for testing purposes.The actual simulation was carried out by:selecting a transceiver to be tested (from a list);obtaining a set of 10consecutive transceiverprints (for that transceiver)from a given starting point (changed between each iteration)in the test data set;classifying each of the 10transceiverprints and thus obtaining the corresponding probability distribu-tions;and finally determining the transceiver with the high-est probability using the Bayesian filter.3.1Details of SimulationIn order to ensure statistical significance,100signals from each of the14802.11b transceivers(3COM-2,DLink-2,SMC-4,Spectrum-2,Breezenet-3,Lucent-1)were cap-tured for the purpose of RFF.All subsequent processing and simulations were carried out using Matlab software and associated tools.As far as the simulation platform is con-cerned,a notebook(HP Pavilion N5445),with256Mbs of memory and running XP and Matlab software,was used.3.2Simulation Results-RFF and BayesianFilterAfter running the simulation for50iterations,the follow-ing classification success rates(no.of correct classification /number of iterations)(Table1)were obtained.Based on the simulation results,there are some ob-servations that are noteworthy.First,the high success rates for most of the transceivers,especially those from the same manufacturer,attest to the quality of the characterization of the transceivers.Spectrum%Dlink%SMC% 700100552100991100759885539879810075896794100 3Com%Breezenet%Lucent%64410086410020010086310052100100100Table1.Classification Success RateSecond,an improvement in the success rates achieved by the classifer(e.g.from92%to100%and from95%to 100%for transceivers SMC794and3Com863)provides evidence to support the use of the Bayesianfilter.Finally,as expected,the success rates for transceivers SMC758,Spectrum759and Dlink553reflect the lower intertransceiver variability between transceivers from the same manufacturer.As current classifiers for RFF are typically based on some variant of neural networks e.g.PNN and Artificial Neural Network(ANN)used by Zuidweg and Zuidweg[19],and Self Organizing Maps by Kayacik et al.[20],a direct comparison of the simulation results is rather diffi-cult.Nevertheless,the type of research carried out by Choe [12]is similar to some degree.However,the number of profiled transceivers was limited to three(2-Motorola HT-220,1-Motorola MX-330)in comparison to the14 802.11b transceivers used in this project.Despite the in-creased complexity,the average success rate of(94-100%),achieved using RFF and Bayesianfilter,is consistent with their results of(94%).4Related WorkThis section provides a brief overview of the various re-search initiatives that have been undertaken to address the requirements of the RFF process.Radio Transmitter FingerprintsIn the paper by Ellis and Serinken[21],the authors examine the amplitude and phase components of signals and arrive at the conclusion that all transceivers do possess some con-sistent features.Detection of TransientsThe detection of transients,based on the variance of the amplitude,is proposed by Shaw and Kinsner[15]and Ure-ten and Serinken[22].Feature SelectionAs far as the selection of features is concerned,the use of the Probabilistic Neural Network(PNN)by Specht[23]is explored by Hunter in[16].Classification of TransceiverprintIn terms of classification,different approaches have been proposed.In the paper by Somervuo and Kohonen[24], the authors make use of the Self-Organizing Map and a Learning Vector Quantization(LVQ)algorithm to support variable-length feature sequences used for classification. While the use DWT coefficients is explored by Hippen-stiel and Payal in[13],Toonstra and Kinsner[25]exploit the properties of genetic algorithms for classification pur-poses.5ConclusionBased on the simulation results(average classification suc-cess rate of94-100%),the use of RFF and Bayesianfilter for anomaly-based intrusion detection is technically feasi-ble.More specifically,the characterization of transceivers using multiple features has proven to be effective(high classification rate).In addition,the use of a statistical clas-sifier that is memory conscious(440bytes per transceiver profile)could achieve sufficient performance for support-ing real-time applications.Furthermore,delaying thefinal decision until a sufficient number of transceiverprints have been classified,increases the confidence level and classifi-cation success rate.Nevertheless,there are some issues,which warrant further attention.First and foremost,the success rates should be improved by optimizing the composition of the transceiverprints and validating them using additional transceivers from the same manufacturer.Second,it would prove beneficial to repeat the profiling exercise periodically in order to determine the impact of various factors,e.g. transceiver aging,on the classification success rate.Finally, as far as scalability is concerned,the comparison of a singletransceiverprint to multiple transceiver profiles should only be carried out during the profiling phase.During the execu-tion phase of the IDS,the classifier and the Bayesianfilter will be applied to the target profile only,along with appro-priate thresholds(e.g.level of correlation).This will permit us to determine,whether or not,an observed transceiver-print belongs to the target transceiver,which is associated with a given MAC address.6AcknowledgmentsThe authors graciously acknowledge thefinancial sup-port received from the following organizations:Natural Sciences and Engineering Research Council of Canada (NSERC)and Mathematics of Information Technology and Complex Systems(MITACS).In addition,the authors also acknowledge the support received from Lucent,SMC, Spectrum,D-Link,BreezeNet and3COM. References[1]Working Group for Wireless Local Area Networks.IEEE Standard for Wireless LAN MAC and PHY Specifications./wireless, 1997.[2]Frank Robinson.802.11i and WPA Up -work Computing,pages79–82,2004.[3]Working Group for Wireless Local Area Net-works.Port Based Network Access Control./wireless,August2003. [4]Working Group for Wireless Local Area Net-works.MAC Security Enhancements./wireless,June2004.[5]Bruce Potter.Wireless Intrusion Detection.WirelessSecurity,pages4–5,2004.[6]Mohan K.Chirumamilla and Byrav Ramamurthy.Agent based intrusion detection and response system for wireless LANs.In Communications,pages492–496.IEEE,May2003.[7]Michael J.Riezenman.Cellular security:better,butfoes still lurk.IEEE Spectrum,pages39–42,June 2000.[8]Jeyanthi Hall,Michel Barbeau,and EvangelosKranakis.Detection of transient in radio frequency fingerprinting using signal phase.In Wireless and Optical Communications,pages13–18.ACTA Press, July2003.[9]S.J.Russell and P.Norvig.Artificial Intelligence:AModern Approach.Prentice Hall,2002.[10]John G.Proakis and Dimitris G.Manolakis.DigitalSignal Processing.Prentice Hall PTR,1996.[11]Stephane Mallat.A Wavelet Tour of Signal Process-ing.Academic Press,1999.[12]H.Choe,C.E.Poole,A.M.Yu,and H.H.Szu.Novelidentification of intercepted signals from unknown ra-dio transmitters.SPIE,2491:504–516,1995. [13]Ralph D.Hippenstiel and Yalcin Payal.Wavelet basedtransmitter identification.In International Sympo-sium on Signal Processing and its Applications,Gold Coast Australia,August1996.[14]Laurene Fausett.Fundamentals of Neural NetworksArchitectures,Algorithms and Applications.Prentice Hall,1994.[15]D.Shaw and W.Kinsner.Multifractal modelling ofradio transmitter transients for classification.In Com-munications Power and Computing,pages306–312, Winnipeg Manitoba,May1997.IEEE.[16]Andrew Hunter.Feature selection using probabilis-tic neural networks.Neural Computing and Applica-tions,9:124–132,2000.[17]X.-R.Li Y.Bar-Shalom and T.Kirubarajan.Estima-tion with Applications to Tracking and Navigation.John Wiley,2001.[18]Jr.Joseph F.Hair,Rolph E.Anderson,and WilliamC.Black Ronald L.Tatham.Multivariate Data Anal-ysis.Prentice Hall,1998.[19]Johan Zuidweg and Han Zuidweg.Next GenerationIntelligent Networks.Artech House,2002.[20]H.Gunes Kayacik,A.Nur Zincir-Heywood,and Mal-colm I.Heywood.On the Capability of an SOM based Intrusion Detection System.In Neural Net-works,pages1808–1813.IEEE,July2003.[21]K.J.Ellis and N.Serinken.Characteristics of radiotransmitterfingerprints.Radio Science,36:585–597, 2001.[22]Oktay Ureten and Nur Serinken.Detection of ra-dio transmitter turn-on transients.Electronic Letters, 35:1996–1997,1999.[23]D.F.Specht.Probabilistic neural networks for clas-sification mapping or associative memory.In IEEE International Conference on Neural Networks,pages 525–532.IEEE,1988.[24]Panu Somervuo and Teuvo Kohonen.Self-OrganizingMaps and Learning Vector Quantization for Feature Sequences.Neural Processing Letters,10:151–159, 1999.[25]J.Toonstra and W.Kinsner.Transient analysis andgenetic algorithms for classification.In WESCAN.IEEE,1995.。
