The Optimistic Update Theorem for Path Delay Testing in Sequential Circuits
Optimal and efficient path planning for partially known environments

Optimal and Efficient Path Planning for Partially-Known EnvironmentsAnthony StentzThe Robotics Institute; Carnegie Mellon University; Pittsburgh, PA 15213AbstractThe task of planning trajectories for a mobile robot has received considerable attention in the research literature. Most of the work assumes the robot has a complete and accurate model of its environment before it begins to move; less attention has been paid to the problem of partially known environments. This situation occurs for an exploratory robot or one that must move to a goal location without the benefit of a floorplan or terrain map. Existing approaches plan an initial path based on known information and then modify the plan locally or replan the entire path as the robot discovers obstacles with its sensors, sacrificing optimality or computational efficiency respectively. This paper introduces a new algorithm, D*, capable of planning paths in unknown, partially known, and changing environments in an efficient, optimal, and complete manner.1.0IntroductionThe research literature has addressed extensively the motion planning problem for one or more robots moving through a field of obstacles to a goal. Most of this work assumes that the environment is completely known before the robot begins its traverse (see Latombe [4] for a good survey). The optimal algorithms in this literature search a state space (e.g., visibility graph, grid cells) using the dis-tance transform [2] or heuristics [8] to find the lowest cost path from the robot’s start state to the goal state. Cost can be defined to be distance travelled, energy expended, time exposed to danger, etc.Unfortunately, the robot may have partial or no information about the environment before it begins its traverse but is equipped with a sensor that is capable of measuring the environment as it moves. One approach to path planning in this scenario is to generate a “global”path using the known information and then attempt to “locally” circumvent obstacles on the route detected by the sensors [1]. If the route is completely obstructed, a new global path is planned. Lumelsky [7] initially assumes the environment to be devoid of obstacles and moves the robot directly toward the goal. If an obstacle obstructs the path, the robot moves around the perimeter until the point on the obstacle nearest the goal is found. The robot then proceeds to move directly toward the goal again. Pirzadeh [9] adopts a strategy whereby the robot wanders about the environment until it discovers the goal. The robot repeatedly moves to the adjacent location with lowest cost and increments the cost of a location each time it visits it to penalize later traverses of the same space. Korf [3] uses initial map information to estimate the cost to the goal for each state and efficiently updates it with backtracking costs as the robot moves through the environment.While these approaches are complete, they are also suboptimal in the sense that they do not generate the lowest cost path given the sensor information as it is acquired and assuming all known, a priori information is correct. It is possible to generate optimal behavior by computing an optimal path from the known map information, moving the robot along the path until either it reaches the goal or its sensors detect a discrepancy between the map and the environment, updating the map, and then replanning a new optimal path from the robot’s current location to the goal. Although this brute-force, replanning approach is optimal, it can be grossly inefficient, particularly in expansive environments where the goal is far away and little map information exists. Zelinsky [15] increases efficiency by using a quad-tree [13] to represent free and obstacle space, thus reducing the number of states to search in the planning space. For natural terrain, however, the map can encode robot traversability at each location ranging over a continuum, thus rendering quad-trees inappropriate or suboptimal.This paper presents a new algorithm for generating optimal paths for a robot operating with a sensor and a map of the environment. The map can be complete, empty, or contain partial information about the environment. ForIn Proceedings IEEE International Conference on Robotics and Automation, May 1994.regions of the environment that are unknown, the map may contain approximate information, stochastic models for occupancy, or even a heuristic estimates. The algorithm is functionally equivalent to the brute-force,optimal replanner, but it is far more efficient.The algorithm is formulated in terms of an optimal find-path problem within a directed graph, where the arcs are labelled with cost values that can range over a continuum. The robot’s sensor is able to measure arc costs in the vicinity of the robot, and the known and estimated arc values comprise the map. Thus, the algorithm can be used for any planning representation, including visibility graphs [5] and grid cell structures. The paper describes the algorithm, illustrates its operation, presents informal proofs of its soundness, optimality, and completeness, and then concludes with an empirical comparison of the algorithm to the optimal replanner.2.0The D* AlgorithmThe name of the algorithm, D*, was chosen because it resembles A* [8], except that it is dynamic in the sense that arc cost parameters can change during the problem-solving process. Provided that robot motion is properly coupled to the algorithm, D* generates optimal trajecto-ries. This section begins with the definitions and notation used in the algorithm, presents the D* algorithm, and closes with an illustration of its operation.2.1DefinitionsThe objective of a path planner is to move the robot from some location in the world to a goal location, such that it avoids all obstacles and minimizes a positive cost metric (e.g., length of the traverse). The problem space can be formulated as a set of states denoting robot loca-tions connected by directional arcs , each of which has an associated cost. The robot starts at a particular state and moves across arcs (incurring the cost of traversal) to other states until it reaches the goal state, denoted by . Every state except has a backpointer to a next state denoted by . D* uses backpointers to represent paths to the goal. The cost of traversing an arc from state to state is a positive number given by the arc cost function . If does not have an arc to , then is undefined. Two states and are neighbors in the space if or is defined.Like A*, D* maintains an list of states. The list is used to propagate information about changes to the arc cost function and to calculate path costs to states in the space. Every state has an associated tag ,such that if has never been on the list, if is currently on the list, andG X G Y b X ()Y =Y X c X Y ,()Y X c X Y ,()X Y c X Y ,()c Y X ,()OPEN OPEN X t X ()t X ()NEW =X OPEN t X ()OPEN =XOPEN if is no longer on the list. For each state , D* maintains an estimate of the sum of the arc costs from to given by the path cost function . Given the proper conditions, this estimate is equivalent to the optimal (minimal) cost from state to , given by the implicit function . For each state on the list (i.e.,), the key function,, is defined to be equal to the minimum of before modification and all values assumed by since was placed on the list. The key function classifies a state on the list into one of two types:a state if , and a state if . D* uses states on the listto propagate information about path cost increases (e.g.,due to an increased arc cost) and states to propagate information about path cost reductions (e.g.,due to a reduced arc cost or new path to the goal). The propagation takes place through the repeated removal of states from the list. Each time a state is removed from the list, it is expanded to pass cost changes to its neighbors. These neighbors are in turn placed on the list to continue the process.States on the list are sorted by their key function value. The parameter is defined to be for all such that . The parameter represents an important threshold in D*: path costs less than or equal to are optimal, and those greater than may not be optimal. The parameter is defined to be equal to prior to most recent removal of a state from the list. If no states have been removed,is undefined.An ordering of states denoted by is defined to be a sequence if for all such that and for all such that . Thus, a sequence defines a path of backpointers from to . A sequence is defined to be monotonic if( a n d) o r ( and ) for all such that . D* constructs and maintains a monotonic sequence , representing decreasing current or lower-bounded path costs, for each state that is or was on the list. Given a sequence of states , state is an ancestor of state if and a descendant of if .For all two-state functions involving the goal state, the following shorthand notation is used:.Likewise, for sequences the notation is used.The notation is used to refer to a function independent of its domain.t X ()CLOSED =X OPEN X X G h G X ,()X G o G X ,()X OPEN t X ()OPEN =k G X ,()h G X ,()h G X ,()X OPEN X OPEN RAISE k G X ,()h G X ,()<LOWER k G X ,()h G X ,()=RAISE OPEN LOWER OPEN OPEN OPEN k min min k X ()()X t X ()OPEN =k min k min k min k old k min OPEN k old X 1X N {,}b X i 1+()X i =i 1i ≤N <X i X j ≠i j (,)1i ≤j <N ≤X N X 1X 1X N {,}t X i ()CLOSED =h G X i ,()h G X i 1+,()<t X i ()OPEN =k G X i ,()h G X i 1+,()<i 1i ≤N <G X {,}X OPEN X 1X N {,}X i X j 1i j N ≤<≤X j 1j i N ≤<≤f X ()f G X ,()≡X {}G X {,}≡f °()2.2Algorithm DescriptionThe D* algorithm consists primarily of two functions: and .is used to compute optimal path costs to the goal, and is used to change the arc cost function and enter affected states on the list. Initially, is set to for all states,is set to zero, and is placed on the list. The first function,, is repeatedly called until the robot’s state,, is removed from the list (i.e.,) or a value of -1 is returned, at which point either the sequence has been computed or does not exist respectively. The robot then proceeds to follow the backpointers in the sequence until it eitherreaches the goal or discovers an error in the arc cost func-tion (e.g., due to a detected obstacle). The second function,, is immediately called to cor-rect and place affected states on the list. Let be the robot’s state at which it discovers an error in .By calling until it returns ,the cost changes are propagated to state such that . At this point, a possibly new sequence has been constructed, and the robot continues to follow the backpointers in the sequence toward the goal.T h e a l g o r i t h m s f o r a n d are presented below. The embedded routines are , which returns the state on the list with minimum value ( if the list is empty);, which returns for the list (-1 if the list is empty);, which deletes state from the list and sets ; and , w h i c h c o m p u t e s i f , if , and i f , s e t s and , and places or re-positions state on the list sorted by .In function at lines L1 through L3,the state with the lowest value is removed from the list. If is a state (i.e.,), its path cost is optimal since is equal to the old . At lines L8 through L13, each neighbor of is examined to see if its path cost can be lowered. Additionally,neighbor states that are receive an initial path cost value, and cost changes are propagated to each neighbor that has a backpointer to , regardless of whether the new cost is greater than or less than the old. Since these states are descendants of , any change to the path cost of affects their path costs as well. The backpointer of is redirected (if needed) so that the monotonic sequence is constructed. All neighbors that receive a new pathPROCESS STATE –MODIFY COST –PROCESS STATE –MODIFY COST –c °()OPEN t °()NEW h G ()G OPEN PROCESS STATE –X OPEN t X ()CLOSED =X {}X {}c °()MODIFY COST –c °()OPEN Y c °()PROCESS STATE –k min h Y ()≥Y h Y ()o Y ()=Y {}PROCESS STATE –MODIFY COST –MIN STATE –OPEN k °()NULL GET KMIN –k min OPEN DELETE X ()X OPEN t X ()CLOSED =INSERT X h new ,()k X ()h new =t X ()NEW =k X ()min k X ()h new ,()=t X ()OPEN =k X ()min h X ()h new ,()=t X ()CLOSED =h X ()h new =t X ()OPEN =X OPEN k °()PROCESS STATE –X k °()OPEN X LOWER k X ()h X ()=h X ()k min Y X NEW Y X X X Y Y {}cost are placed on the list, so that they will propagate the cost changes to their neighbors.If is a state, its path cost may not be optimal.Before propagates cost changes to its neighbors, its optimal neighbors are examined at lines L4 through L7 to see if can be reduced. At lines L15 through L18, cost changes are propagated to states and immediate descendants in the same way as for states. If is able to lower the path cost of a state that is not an immediate descendant (lines L20 and L21), is placed back on the list for future expansion. It is shown in the next section that this action is required to avoid creating a closed loop in the backpointers. If the path cost of is able to be reduced by a suboptimal neighbor (lines L23 through L25), the neighbor is placed back on the list. Thus, the update is “postponed” until the neighbor has an optimal path cost.Function: PROCESS-STATE ()L1L2if then return L3;L4if then L5for each neighbor of :L6if and then L7;L8if then L9for each neighbor of :L10if or L11( and ) or L12( and ) then L13;L14else L15for each neighbor of :L16if or L17( and ) then L18;L19else L20if and then L21L22else L23if and and L24 and then L25L26return OPEN X RAISE X h X ()NEW LOWER X X OPEN X OPEN X MIN STATE ()–=X NULL =1–k old GET KMIN –()=DELETE X ()k old h X ()<Y X h Y ()k old ≤h X ()h Y ()c Y X ,()+>b X ()Y =h X ()h Y ()c Y X ,()+=k old h X ()=Y X t Y ()NEW =b Y ()X =h Y ()h X ()c X Y ,()+≠b Y ()X ≠h Y ()h X ()c X Y ,()+>b Y ()X =INSERT Y h X ()c X Y ,()+,()Y X t Y ()NEW =b Y ()X =h Y ()h X ()c X Y ,()+≠b Y ()X =INSERT Y h X ()c X Y ,()+,()b Y ()X ≠h Y ()h X ()c X Y ,()+>INSERT X h X (),()b Y ()X ≠h X ()h Y ()c Y X ,()+>t Y ()CLOSED =h Y ()k old >INSERT Y h Y (),()GET KMIN ()–In function , the arc cost function is updated with the changed value. Since the path cost for state will change, is placed on the list. When is expanded via , it computes a new and places on the list.Additional state expansions propagate the cost to the descendants of .Function: MODIFY-COST (X, Y, cval)L1L2if then L3return 2.3Illustration of OperationThe role of and states is central to the operation of the algorithm. The states (i.e.,) propagate cost increases, and the states (i.e.,) propagate cost reductions. When the cost of traversing an arc is increased, an affected neighbor state is placed on the list, and the cost increase is propagated via states through all state sequences containing the arc. As the states come in contact with neighboring states of lower cost, these states are placed on the list, and they sub-sequently decrease the cost of previously raised states wherever possible. If the cost of traversing an arc isdecreased, the reduction is propagated via states through all state sequences containing the arc, as well as neighboring states whose cost can also be lowered.Figure 1: Backpointers Based on Initial PropagationFigure 1 through Figure 3 illustrate the operation of the algorithm for a “potential well” path planning problem.MODIFY COST –Y X OPEN X PROCESS STATE –h Y ()h X ()c X Y ,()+=Y OPEN Y c X Y ,()cval=t X ()CLOSED =INSERT X h X (),()GET KMIN ()–RAISE LOWER RAISE k X ()h X ()<LOWER k X ()h X ()=OPEN RAISE RAISE LOWER OPEN LOWER GThe planning space consists of a 50 x 50 grid of cells .Each cell represents a state and is connected to its eight neighbors via bidirectional arcs. The arc cost values are small for the cells and prohibitively large for the cells.1 The robot is point-sized and is equipped with a contact sensor. Figure 1 shows the results of an optimal path calculation from the goal to all states in the planning space. The two grey obstacles are stored in the map, but the black obstacle is not. The arrows depict the backpointer function; thus, an optimal path to the goal for any state can be obtained by tracing the arrows from the state to the goal. Note that the arrows deflect around the grey, known obstacles but pass through the black,unknown obstacle.Figure 2: LOWER States Sweep into WellThe robot starts at the center of the left wall and follows the backpointers toward the goal. When it reaches the unknown obstacle, it detects a discrepancy between the map and world, updates the map, colors the cell light grey, and enters the obstacle cell on the list.Backpointers are redirected to pull the robot up along the unknown obstacle and then back down. Figure 2illustrates the information propagation after the robot has discovered the well is sealed. The robot’s path is shown in black and the states on the list in grey.states move out of the well transmitting path cost increases. These states activate states around the1. The arc cost value of OBSTACLE must be chosen to be greater than the longest possible sequence of EMPTY cells so that a simple threshold can be used on the path cost to determine if the optimal path to the goal must pass through an obstacle.EMPTY OBSTACLE GLOWER statesRAISE statesLOWER statesOPEN OPEN RAISE LOWER“lip” of the well which sweep around the upper and lower obstacles and redirect the backpointers out of the well.Figure 3: Final Backpointer ConfigurationThis process is complete when the states reach the robot’s cell, at which point the robot moves around the lower obstacle to the goal (Figure 3). Note that after the traverse, the backpointers are only partially updated.Backpointers within the well point outward, but those in the left half of the planning space still point into the well.All states have a path to the goal, but optimal paths are computed to a limited number of states. This effect illustrates the efficiency of D*. The backpointer updates needed to guarantee an optimal path for the robot are limited to the vicinity of the obstacle.Figure 4 illustrates path planning in fractally generated terrain. The environment is 450 x 450 cells. Grey regions are fives times more difficult to traverse than white regions, and the black regions are untraversible. The black curve shows the robot’s path from the lower left corner to the upper right given a complete, a priori map of the environment. This path is referred to as omniscient optimal . Figure 5 shows path planning in the same terrain with an optimistic map (all white). The robot is equipped with a circular field of view with a 20-cell radius. The map is updated with sensor information as the robot moves and the discrepancies are entered on the list for processing by D*. Due to the lack of a priori map information, the robot drives below the large obstruction in the center and wanders into a deadend before backtracking around the last obstacle to the goal. The resultant path is roughly twice the cost of omniscientGLOWER OPEN optimal. This path is optimal, however, given the information the robot had when it acquired it.Figure 4: Path Planning with a Complete MapFigure 5: Path Planning with an Optimistic MapFigure 6 illustrates the same problem using coarse map information, created by averaging the arc costs in each square region. This map information is accurate enough to steer the robot to the correct side of the central obstruction, and the resultant path is only 6% greater incost than omniscient optimal.Figure 6: Path Planning with a Coarse-Resolution Map3.0Soundness, Optimality, andCompletenessAfter all states have been initialized to and has been entered onto the list, the function is repeatedly invoked to construct state sequences. The function is invoked to make changes to and to seed these changes on the list. D* exhibits the following properties:Property 1: If , then the sequence is constructed and is monotonic.Property 2: When the value returned by e q u a l s o r e x c e e d s , t h e n .Property 3: If a path from to exists, and the search space contains a finite number of states, will be c o n s t r u c t e d a f t e r a fi n i t e n u m b e r o f c a l l s t o . I f a p a t h d o e s n o t e x i s t , will return -1 with .Property 1 is a soundness property: once a state has been visited, a finite sequence of backpointers to the goal has been constructed. Property 2 is an optimality property.It defines the conditions under which the chain of backpointers to the goal is optimal. Property 3 is a completeness property: if a path from to exists, it will be constructed. If no path exists, it will be reported ina finite amount of time. All three properties holdX t X ()NEW =G OPEN PROCESS STATE –MODIFY COST –c °()OPEN t X ()NEW ≠X {}k min PROCESS STATE –h X ()h X ()o X ()=X G X {}PROCESS STATE –PROCESS STATE –t X ()NEW =X G regardless of the pattern of access for functions and .For brevity, the proofs for the above three properties are informal. See Stentz [14] for the detailed, formal p r o o f s. C o n s i d e r P r o p e r t y 1 fi r s t. W h e n e v e r visits a state, it assigns to point to an existing state sequence and sets to preserve monotonicity. Monotonic sequences are subsequently manipulated by modifying the functions ,,, and . When a state is placed on the list (i.e.,), is set to preserve monotonicity for states with backpointers to .Likewise, when a state is removed from the list, the values of its neighbors are increased if needed to preserve monotonicity. The backpointer of a state ,, can only be reassigned to if and if the sequence contains no states. Since contains no states, the value of every state in the sequence must be less than . Thus, cannot be an ancestor of , and a closed loop in the backpointers cannot be created.Therefore, once a state has been visited, the sequence has been constructed. Subsequent modifications ensure that a sequence still exists.Consider Property 2. Each time a state is inserted on or removed from the list, D* modifies values so that for each pair of states such that is and is . Thus, when is chosen for expansion (i.e.,), the neighbors of cannot reduce below , nor can the neighbors, since their values must be greater than . States placed on the list during the expansion of must have values greater than ; thus, increases or remains the same with each invocation of . If states with values less than or equal to are optimal, then states with values between (inclusively) and are optimal, since no states on the list can reduce their path costs. Thus, states with values less than or equal to are optimal. By induction,constructs optimal sequences to all reachable states. If the a r c c o s t i s m o d i fi e d , t h e f u n c t i o n places on the list, after which is less than or equal to . Since no state with can be affected by the modified arc cost, the property still holds.Consider Property 3. Each time a state is expanded via , it places its neighbors on the list. Thus, if the sequence exists, it will be constructed unless a state in the sequence,, is never selected for expansion. But once a state has been placedMODIFY COST –PROCESS STATE –PROCESS STATE –NEW b °()h °()t °()h °()k °()b °()X OPEN t X ()OPEN =k X ()h X ()X X h °()X b X ()Y h Y ()h X ()<Y {}RAISE Y {}RAISE h °()h Y ()X Y X X {}X {}OPEN h °()k X ()h Y ()c Y X ,()+≤X Y ,()X OPEN Y CLOSED X k min k X ()=CLOSED X h X ()k min OPEN h °()k min OPEN X k °()k X ()k min PROCESS STATE –h °()k old h °()k old k min OPEN h °()k min PROCESS STATE –c X Y ,()MODIFY COST –X OPEN k min h X ()Y h Y ()h X ()≤PROCESS STATE –NEW OPEN X {}Yon the list, its value cannot be increased.Thus, due to the monotonicity of , the state will eventually be selected for expansion.4.0Experimental ResultsD* was compared to the optimal replanner to verify its optimality and to determine its performance improve-ment. The optimal replanner initially plans a single path from the goal to the start state. The robot proceeds to fol-low the path until its sensor detects an error in the map.The robot updates the map, plans a new path from the goal to its current location, and repeats until the goal isreached. An optimistic heuristic function is used to focus the search, such that equals the “straight-line”cost of the path from to the robot’s location assuming all cells in the path are . The replanner repeatedly expands states on the list with the minimum value. Since is a lower bound on the actual cost from to the robot for all , the replanner is optimal [8].The two algorithms were compared on planning problems of varying size. Each environment was square,consisting of a start state in the center of the left wall and a goal state in center of the right wall. Each environment consisted of a mix of map obstacles (i.e., available to robot before traverse) and unknown obstacles measurable b y t h e r o b o t ’s s e n s o r. T h e s e n s o r u s e d w a s omnidirectional with a 10-cell radial field of view. Figure 7 shows an environment model with 100,000 states. The map obstacles are shown in grey and the unknown obstacles in black.Table 1 shows the results of the comparison for environments of size 1000 through 1,000,000 cells. The runtimes in CPU time for a Sun Microsystems SPARC-10processor are listed along with the speed-up factor of D*over the optimal replanner. For both algorithms, the reported runtime is the total CPU time for all replanning needed to move the robot from the start state to the goal state, after the initial path has been planned. For each environment size, the two algorithms were compared on five randomly-generated environments, and the runtimes were averaged. The speed-up factors for each environment size were computed by averaging the speed-up factors for the five trials.The runtime for each algorithm is highly dependent on the complexity of the environment, including the number,size, and placement of the obstacles, and the ratio of map to unknown obstacles. The results indicate that as the environment increases in size, the performance of D*over the optimal replanner increases rapidly. The intuitionOPEN k °()k min Y gˆX ()gˆX ()X EMPTY OPEN gˆX ()h X ()+g ˆX ()X X for this result is that D* replans locally when it detects an unknown obstacle, but the optimal replanner generates a new global trajectory. As the environment increases in size, the local trajectories remain constant in complexity,but the global trajectories increase in complexity.Figure 7: Typical Environment for Algorithm ComparisonTable 1: Comparison of D* to Optimal Replanner5.0Conclusions5.1SummaryThis paper presents D*, a provably optimal and effi-cient path planning algorithm for sensor-equipped robots.The algorithm can handle the full spectrum of a priori map information, ranging from complete and accurate map information to the absence of map information. D* is a very general algorithm and can be applied to problems in artificial intelligence other than robot motion planning. In its most general form, D* can handle any path cost opti-mization problem where the cost parameters change dur-ing the search for the solution. D* is most efficient when these changes are detected near the current starting point in the search space, which is the case with a robot equipped with an on-board sensor.Algorithm 1,00010,000100,0001,000,000Replanner 427 msec 14.45 sec 10.86 min 50.82 min D*261 msec 1.69 sec 10.93 sec 16.83 sec Speed-Up1.6710.1456.30229.30See Stentz [14] for an extensive description of related applications for D*, including planning with robot shape,field of view considerations, dead-reckoning error,changing environments, occupancy maps, potential fields,natural terrain, multiple goals, and multiple robots.5.2Future WorkFor unknown or partially-known terrains, recentresearch has addressed the exploration and map building problems [6][9][10][11][15] in addition to the path finding problem. Using a strategy of raising costs for previously visited states, D* can be extended to support exploration tasks.Quad trees have limited use in environments with cost values ranging over a continuum, unless the environment includes large regions with constant traversability costs.Future work will incorporate the quad tree representation for these environments as well as those with binary cost values (e.g., and ) in order to reduce memory requirements [15].Work is underway to integrate D* with an off-road obstacle avoidance system [12] on an outdoor mobile robot. To date, the combined system has demonstrated the ability to find the goal after driving several hundred meters in a cluttered environment with no initial map.AcknowledgmentsThis research was sponsored by ARPA, under contracts “Perception for Outdoor Navigation” (contract number DACA76-89-C-0014, monitored by the US Army TEC)and “Unmanned Ground Vehicle System” (contract num-ber DAAE07-90-C-R059, monitored by TACOM).The author thanks Alonzo Kelly and Paul Keller for graphics software and ideas for generating fractal terrain.References[1] Goto, Y ., Stentz, A., “Mobile Robot Navigation: The CMU System,” IEEE Expert, V ol. 2, No. 4, Winter, 1987.[2] Jarvis, R. A., “Collision-Free Trajectory Planning Using the Distance Transforms,” Mechanical Engineering Trans. of the Institution of Engineers, Australia, V ol. ME10, No. 3, Septem-ber, 1985.[3] Korf, R. E., “Real-Time Heuristic Search: First Results,”Proc. Sixth National Conference on Artificial Intelligence, July,1987.[4] Latombe, J.-C., “Robot Motion Planning”, Kluwer Aca-demic Publishers, 1991.[5] Lozano-Perez, T., “Spatial Planning: A Configuration Space Approach”, IEEE Transactions on Computers, V ol. C-32, No. 2,February, 1983.OBSTACLE EMPTY [6] Lumelsky, V . J., Mukhopadhyay, S., Sun, K., “Dynamic Path Planning in Sensor-Based Terrain Acquisition”, IEEE Transac-tions on Robotics and Automation, V ol. 6, No. 4, August, 1990.[7] Lumelsky, V . J., Stepanov, A. A., “Dynamic Path Planning for a Mobile Automaton with Limited Information on the Envi-ronment”, IEEE Transactions on Automatic Control, V ol. AC-31, No. 11, November, 1986.[8] Nilsson, N. J., “Principles of Artificial Intelligence”, Tioga Publishing Company, 1980.[9] Pirzadeh, A., Snyder, W., “A Unified Solution to Coverage and Search in Explored and Unexplored Terrains Using Indirect Control”, Proc. of the IEEE International Conference on Robot-ics and Automation, May, 1990.[10] Rao, N. S. V ., “An Algorithmic Framework for Navigation in Unknown Terrains”, IEEE Computer, June, 1989.[11] Rao, N.S.V ., Stoltzfus, N., Iyengar, S. S., “A ‘Retraction’Method for Learned Navigation in Unknown Terrains for a Cir-cular Robot,” IEEE Transactions on Robotics and Automation,V ol. 7, No. 5, October, 1991.[12] Rosenblatt, J. K., Langer, D., Hebert, M., “An Integrated System for Autonomous Off-Road Navigation,” Proc. of the IEEE International Conference on Robotics and Automation,May, 1994.[13] Samet, H., “An Overview of Quadtrees, Octrees andRelated Hierarchical Data Structures,” in NATO ASI Series, V ol.F40, Theoretical Foundations of Computer Graphics, Berlin:Springer-Verlag, 1988.[14] Stentz, A., “Optimal and Efficient Path Planning for Unknown and Dynamic Environments,” Carnegie MellonRobotics Institute Technical Report CMU-RI-TR-93-20, August,1993.[15] Zelinsky, A., “A Mobile Robot Exploration Algorithm”,IEEE Transactions on Robotics and Automation, V ol. 8, No. 6,December, 1992.。
《人工智能-一种现代方法》第四版习题答案

2.1 Define in your own words the following terms: agent, agent function, agent program, rationality, reflex agent, model-based agent, goal-based agent, utility-based agent, learning agent. The following are just some of the many possible definitions that can be written:
1.11 “surely computers cannot be intelligent-they can do only what their programmers tell them.” Is the latter statement true, and does it imply the former? This depends on your definition of “intelligent” and “tell.” In one sense computers only do what the programmers command them to do, but in another sense what the programmers consciously tells the computer to do often has very little to do with what the computer actually does. Anyone who has written a program with an ornery bug knows this, as does anyone who has written a successful machine learning program. So in one sense Samuel “told” the computer “learn to play checkers better than I do, and then play that way,” but in another sense he told the computer “follow this learning algorithm” and it learned to play. So we’re left in the situation where you may or may not consider learning to play checkers to be s sign of intelligence (or you may think that learning to play in the right way requires intelligence, but not in this way), and you may think the intelligence resides in the programmer or in the computer
3.2 IS Extension...................................... 8

Automatic Instruction Set Design Through Efficient Instruction Encoding for Application-Specific ProcessorsJong-eun Lee jelee@poppy.snu.ac.krKiyoung Choikchoi@azalea.snu.ac.krNikil D.Duttdutt@Architectures and Compilers for Embedded Systems(ACES)Center for Embedded Computer Systems,University of California,Irvine,CA92697Technical Report#02-23Center for Embedded Computer SystemsUniversity of California,Irvine,CA92697,USAMay2002—Updated April2003AbstractApplication-specific instructions can significantly improve the performance,energy-efficiency,and code size of configurable processors.While generating new instructions from application-specific operation patterns has been a common way to improve the instruction set(IS)of a configurable pro-cessor,automating the design of IS’s for given applications poses new challenges.This IS synthesis typically requires these questions to be answered:how to create as well as utilize new instructions in a systematic manner,and how to choose the best set of application-specific instructions taking into account the conflicting effects of adding new instructions?To address these problems,we present a novel IS synthesis framework that optimizes the performance for the given data path architecture through an efficient instruction encoding.We build a library of new instructions with various encoding alternatives and select the best set while satisfying the instruction bitwidth con-straint.We formulate the problem using integer linear programming and also present an effective heuristic algorithm.Experimental results using our technique generate instruction sets that show improvements of up to about40%over the native instruction set for several realistic benchmark applications running on typical embedded RISC processors.Contents1Introduction4 2Motivation6 3Related Work73.1Automatic IS Synthesis (7)3.2IS Extension (8)4Instruction Set Synthesis Framework94.1Instruction Sets (9)4.2Features (10)4.2.1Structure-Centric IS Synthesis (10)4.2.2Optimized Instruction Encoding (11)4.3Generation of Optimal C-Instructions (12)4.3.1Creating C-Instructions (12)4.3.2Selecting C-Instructions (13)4.4Utilization of C-Instructions in Code Generation (13)5Creating C-Instructions145.1Rescheduling the Operations (14)5.2Generalizing with Operand Classes (15)6Selecting C-Instructions166.1Instruction Set Selection (16)6.2ILP Problem Formulation (18)6.3Heuristic Algorithm (19)7Experiments207.1Experimental Setup (20)7.2Comparison of ILP and Heuristic Algorithm (21)7.3Comparison of Basic,Synthesized and Native IS’s for SH-3 (22)7.4Comparison of Basic,Synthesized and Native IS’s for MIPS (23)8Conclusion24 9Acknowledgements25 A Proof of NP-hardness28List of Figures1Customizing the instruction set of an application-specific instruction set processor (ASIP) (5)2Instruction sets (9)3Application-specific instruction set synthesis framework (10)4Flexible instruction format and the instruction code space (11)5Synthesisflow to generate optimal C-instructions (12)6Cycle reduction by rescheduling the operations of a basic instruction sequence.RR,EX,MEM,and WB are the four pipe stages,and the horizontal lines repre-sent the cycles or the control steps;the diagrams illustrate the execution of theinstructions as they go through the pipeline,performing their operations at differ-ent pipe stages in different cycles.The right-hand side diagram shows that the datadependency,represented by arrows,is still satisfied in the C-instruction CXX (14)7Creating C-instructions from a basic instruction sequence (16)8Heuristic algorithm for C-instruction selection (29)9Subroutine update-benefit (30)10Performance of the native and the synthesized IS’s,normalized to that of the basic IS(SH-3) (30)11Performance of the native and the synthesized IS’s,normalized to that of the basic IS(MIPS) (31)List of Tables1C-instructions and associated information (17)2Comparison of ILP and heuristic algorithm(SH-3) (22)3Comparison of synthesized IS’s with the basic&native IS’s(SH-3) (22)4Comparison of synthesized IS’s with the basic&native IS’s(MIPS) (24)AbstractApplication-specific instructions can significantly improve the performance,energy-efficiency, and code size of configurable processors.While generating new instructions from application-specific operation patterns has been a common way to improve the instruction set(IS)of a con-figurable processor,automating the design of IS’s for given applications poses new challenges. This IS synthesis typically requires these questions to be answered:how to create as well as utilize new instructions in a systematic manner,and how to choose the best set of application-specific in-structions taking into account the conflicting effects of adding new instructions?To address these problems,we present a novel IS synthesis framework that optimizes the performance for the given data path architecture through an efficient instruction encoding.We build a library of new instruc-tions with various encoding alternatives and select the best set while satisfying the instruction bitwidth constraint.We formulate the problem using integer linear programming and also present an effective heuristic algorithm.Experimental results using our technique generate instruction sets that show improvements of up to about40%over the native instruction set for several realistic benchmark applications running on typical embedded RISC processors.1IntroductionConfigurable processors are application-specific synthesizable processors where the instruction set(IS)and/or microarchitectural parameters such as registerfile size,functional unit bitwidth, etc.can be easily changed for different applications at the time of the processor design.Eas-ier integration and manufacturing,and architectural and implementationalflexibility make them better suited for embedded processors in system-on-a-chip(SOC)designs than off-the-shelf pro-cessors[1].With the commercial offerings of such configurable processors[2,3]and the recent development in the retargetable compiler technology[4–6]as well as the increased interest in the platform-based SOCs employing configurable processors,the problem of IS customization for application-specific IS processors(ASIPs)is drawing more and more attention from both industry and academia[7–12].Customizing the IS of an ASIP requires several phases of time-consuming processes(Fig.1). First,the application program can be compiled and simulated for the initial IS of the processor, generating some profiling results.By analyzing the results,one can identify potentially useful “new”instructions,which can be included in the new IS while there may be some other instruc-tions removed from the old IS.This new IS can then be used to retarget the toolchain(compiler, assembler,simulator,etc.),generating a new set of analysis results.These results can lead to an-other set of new instructions and the process of customizing the IS continues until the desired goal (performance,code size,etc.)is reached.Thus,even with a retargetable toolchain available,de-signing an IS optimized for a given application involves complex optimization tasks.Furthermore, when it comes to the automatic design of such IS’s,which is called IS synthesis,there are even greater challenges.For instance,how can we generate“new”instructions in a systematic manner, that might help achieve the optimization goal,and also how can we utilize them in later compila-tion stages?Further,considering the conflicting effects of adding application-specific instructionsCompiler 1 /build IS ver. 2IS ver. 1Application ProgramsPerform. (IS2)Assembly /Perform. (IS1)Assembly /Simulator 1Simulator 2Compiler 2 /build Figure 1.Customizing the instruction set of an application-specific instruction set processor (ASIP).(potentially increasing the performance;however,at the cost of the increased resources such as the chip area,the cycle time,and the instruction bitwidth),how can we find the best set of such new instructions for the given application as well as the given resources?To address these prob-lems,we need an IS synthesis framework which can,preferably,be used for modern configurable processors.Since the early 1990’s,there have been different approaches to application-specific IS synthe-sis [13–18].However,they are often targeted for their own architectural styles (quite different from pipelined RISC architectures),and therefore difficult to apply in the context of RISC-based configurable processors.Also,none of them are designed as a methodology to improve an existing processor,which has become increasingly important in SOC platform-based designs.In this paper,we present an IS synthesis framework that is targeted for modern RISC-based configurable proces-sors,also with advanced features such as multi-cycle instruction support and complex instruction encoding.Our framework takes a structure-centric approach—it tries to improve the processor only by changing the IS for a given data path architecture.In this way we can eliminate the need for costly re-engineering of the entire processor design as well as easily accommodate the need for IS specialization arising in SOC designs.With a fixed data path architecture,customization can be made in such areas as the instruction encoding,the number of (application-specific)instructions,and their definitions,etc.Since such instruction encoding and application-specific instructions can significantly affect the code size,performance,and energy-efficiency,the IS design should be well crafted for any embedded processor that needs to be optimized under limited resources.Although the proposed IS synthesis framework can generally support different optimization goals,in this paper we focus on performance improvement through IS synthesis.To achieve maxi-mal performance improvement,our technique first builds a library of candidate application-specific instructions with various encoding alternatives satisfying the architectural constraints,and then se-lects the best set satisfying the instruction encoding constraint coming from the instruction bitwidth limitation.We formulate the problem using an integer linear programming (ILP)framework.Butsince solving an ILP problem takes a prohibitively long time even for a moderately sized prob-lem,we also present an effective heuristic algorithm.Experimental results show that our proposed technique can synthesize IS’s that generate up to about40%performance improvement over the processor’s native1IS for different application domains.The contributions of our work are three-fold.First,it is aimed at modern RISC pipelined archi-tectures with multi-cycle instruction support—representative of current configurable processors—while most existing methodologies[15,16,18]apply to only VLIW-like processors.Second,it tries to improve a given processor hardware through IS specialization,which makes our technique suitable for an emerging class of configurable processors that build on existing,popular ISA fami-lies.Third,our technique takes instruction encoding into account so that the obtained IS can be as compact and efficient as those manually designed by experts.The rest of this paper is organized as follows.In Section2we introduce application-specific instruction set synthesis using motivating examples and in Section3we summarize related work. In Section4we present the IS synthesis framework and outline the synthesisflow.The two major steps in theflow are discussed in more detail in Section5and Section6.In Section7we demon-strate the efficacy of our techniques through experiments on typical embedded RISC processors running realistic applications,and conclude the paper in Section8.2MotivationWe illustrate the potential for significant performance improvements using application-specific instructions on a typical embedded RISC processor(the Hitachi SH-3[19])and a realistic appli-cation(the H.263decoder algorithm).Initial profiling of the H.263decoder application shows that about50%of the actual execution time is spent in a simple function that does not contain any function calls and which consists of only two nested loops,either one of which,depending on a conditional,is actually executed.One of these inner-most loops,when processed by an SH-3 targeted GCC compiler,generates13native instructions that executes in14cycles(not includ-ing branch stall).By devising a custom instruction that takes6cycles,the loop is reduced to4 instructions that execute in9cycles.Alternatively,the entire loop can be encoded into a single custom instruction that executes in7cycles.In this example,it is obvious that greater performance enhancement and code size reduction can be obtained by introducing custom instructions than by relying on traditional compiler optimizations or assembly coding.However,those two custom instructions require4and5register arguments respectively:since one SH-3register argument requires4bits,each of these seemingly attractive custom instructions cannotfit into a16bit instruction.On the other hand,if wefix the positions of register arguments for these custom instructions,we do not need to specify arguments and only the opcodes(operation codes)need to be specified(similar to a function call withfixed register arguments).Furthermore, such instructions are easily handled by compilers in a manner similar to function calls.Although such custom instructions can be used very effectively and do not cause an argument encoding problem,they are only suitable for the hot spots of the application,where the introduction of custom instructions can be justified by their heavy dynamic usage counts.1By“native”we mean the existing IS for a processor family.Another way to improve performance through IS specialization is to combine frequently occur-ring operation patterns into complex instructions,where a complex instruction is an instruction with more than one micro-operation.Such a methodology is particularly useful since it automates the task offinding promising patterns over the entire application program.Even though there have been similar works for VLIW-like architectures[16,18],to our knowledge no prior work has ad-dressed pipelined RISC architectures.VLIW-like architectures have ample hardware resources supporting multiple parallel operations.Therefore performance improvements can easily be ob-tained by defining and using a complex instruction with multiple parallel operations rather than using a sequence of simple instructions.But a typical RISC architecture has little or no instruction level parallelism and thus cannot benefit from parallel operations combined into one complex in-struction.However,even in RISC architectures with no explicit instruction level parallelism,we can exploit the parallelism in between the pipeline stages:auto inc/decrement load/store are typical examples.Many other possibilities that combine multiple operations from different pipeline stages are also feasible,and can contribute to performance improvements over the processor’s native IS. Due to the instruction bitwidth constraint,however,instruction sets may not have the full power to express all the possible combinations of the operations in the hardware.Furthermore,each processor family has its own IS quirks.For instance the SH-3has a two-operand IS with an implicit destination:a typical SH-3ADD instruction assumes the destination is the same as one of the source operands.This instruction encoding restriction adversely affects the performance, which further motivates the need for an application-specific instruction encoding method.One practical consideration is that it is very difficult to add any new complex instructions into an existing IS,due to the limited size of the IS code space.One possibility is to use“undefined”instruction opcodes,which,however,often provide too small a code space for complex instruc-tions.Another way to solve this problem is to define a basic IS using only a part of the instruction code plex instructions can then be created in an application-specific manner and added into the remaining code space.To gain performance benefit in this manner,the generated com-plex instructions should be optimized in terms of their encoding so that more of those instructions can be located within the limited instruction code space.These observations motivate our code space-economical instruction set synthesis technique.3Related WorkWe summarize the related work in two categories:instruction set synthesis and ISA(Instruction Set Architecture)enhancement.The former deals with the automatic generation of instruction sets for specific applications and shares a similar context with this paper.The latter includes manual customization of existing ISAs for specific applications and sometimes exploits similar opportunities.The synthesis of application-specific IS’s have been approached in different ways:application-centric and structure-centric,depending on which part of the ISA is decidedfirst.In application-centric approaches[16–18],the IS isfirst optimized from the application’s behavior using thetechniques similar to[20].The hardware is later designed to implement the instruction set,man-ually or automatically.Among the approaches in this direction,PEAS-I[17]is most similar to our approach in that both approaches assume a basic IS and target pipelined RISC architectures. However,PEAS-I has afixed set of instructions from which a subset is selected;thus instruction encoding is never an issue,unlike in our approach.Other approaches,however,tend to presume their own architectural styles(e.g.,‘transport triggered architecture’in[18])and thus cannot be applied to modern pipelined RISC processors.More importantly they do not give any hints on how to improve an existing processor architecture,which can be very helpful particularly in the context of configurable processor-based SOC design.Structure-centric approaches[13–15]have a structural model of the architecture either implicitly assumed or as an explicit input and try tofind the best instruction set matching the application.This approach has the advantage that it can leverage existing processor designs.However,previous work in this direction has not fully addressed the issue of instruction encoding:opcode and operand fields all havefixed widths.As a result,the instruction bitwidth cannot be fully utilized as in custom processors,leading to limited performance improvement for the same bitwidth or increased instruction bitwidth and code size.Our approach is significantly different,since multiplefield widths are allowed for the same operand type,with different benefits and cost profiles,so that the optimal set of complex instructions,depending on the application,can be selected satisfying the instruction bitwidth constraint.The application-specific ISA customization has received much attention recently as commercial configurable processors become available.For instance,Zhao et al.[7]demonstrated24times performance improvement in a case study with a commercial configurable processor core.They expanded the data path width through configuration and added several custom instructions such as bit operations,compound instructions,and parallel processing on the widened data path.Our approach is significantly different,since it automates the design of application-specific instructions, aims to improve the processor by changing only the IS(minimizing the change in the data path), and generates the instructions that can easily be supported by compilers without re-coding the program.The bitwidth optimization technique in this paper has similarity with other bitwidth reduction techniques.Typically in synthesizing application-specific hardware from behavioral description, the smallest bitwidth can be chosen for data path components to achieve smaller area and lesser energy consumption[21,22].Even instruction set processors sometimes have reduced-bitwidth instruction set architecture(rISA),of which the main benefit is smaller code size.Examples of the rISA instruction set include Thumb[23]of the ARM7TDMI processor and MIPS16[24]of the MIPS processor.Recently,Halambi et al.[25,26]have proposed compilation and design space exploration techniques to take advantage of the rISA more effectively.Further extending the rISA scheme,Kwon et al.[27]proposed a new ISA called PARE(Partitioned Registers Extension), which is an enhanced version of the Thumb ing the concept of the partitioned registerfile, they could further reduce the bitwidth of register operandfields and increase that of immediate or opcodefield,thereby reducing the entire code size.In this paper we deal with the problem ofSynthesized ISNative IS C−InstructionsBasic ISFigure2.Instruction sets.synthesizing instruction sets that are optimized in the bitwidth of each operand and opcodefield, and also competitive(in terms of the performance)to the native IS by supporting application-specific complex operation patterns with the synthesized instructions.4Instruction Set Synthesis FrameworkWe now present our IS synthesis framework that improves the processor architecture through IS specialization.We introduce various IS’s,present the salient features of our framework,and outline the IS synthesisflow.To be able to generate application-specific instructions automatically,we need to define“in-structions”and how a“new”instruction can be defined.Some of the previous ASIP synthesis approaches[17]have assumed a set of potential“special”instructions,out of which an application-specific set of special instructions can be defined for each application.In those approaches,a new instruction can be chosen only from the predefined pool of instructions;therefore,the generation of new,application-specific instructions is limited by,not only dependent on,the predefined set of special instructions.In our IS synthesis framework,instead of explicitly defining the set of possi-ble new instructions,we define a basic IS once for each ing the resource usage and timing information of basic instructions,combinations of basic instructions can be generated with possibly less number of execution cycles or control steps than their basic instructions versions. Instructions built in this way are called C-instructions,2which are the result of our IS synthesis flow.Fig.2illustrates the relationship between the three IS’s relevant to our IS synthesis approach. The native IS is the existing IS of the processor,which is presumably optimized for general appli-cations and may include its own complicated instructions as well as simple ones.From the native IS,the basic IS is defined,which serves three purposes.First,a basic instruction is defined to have only one micro-operation,to facilitate the construction of C-instructions.Second,the basic IS, together with the resource usage and timing information of each basic instruction,represent the processor data path in a ready-to-use form for the IS synthesis.This information includes the num-ber of each resource type(functional units,ports,buses)that may be used at each pipeline stage. Third,the basic IS is defined to have the simplest instruction format,so that the saved code space may be used for new instructions generated for each application.The union of the basic IS and the C-instructions generated for each application is called the synthesized IS for the application.2C-instruction means compound-operation instruction,that is,an instruction with more than one micro-operation.resource usage info Basic IS w/ hardwareApplication code in Basic IS assembly Execution profilingBasic IS C−Instructions D−InstructionsData path structureFigure 3.Application-specific instruction set synthesis framework.In addition to the C-instructions,users may want to have custom instructions that are designed by hand,often with the designers’intuition.In our IS synthesis framework,these instructions are called D-instructions ,which may be difficult to discover with an automatic method unlike with C-instructions.These needs arise especially when the application-specific instruction is very complex as in FFT (Fast Fourier Transform)operations,or special functional units can be afforded.Although these instructions are very effective in boosting the application performance,they pose very difficult problems for automation,in both the instruction design phase and the code generation phase of compilers.Our IS synthesis methodology deals only with the automated generation and application of C-instructions for application-specific IS processors.In our IS synthesis scheme,an application-specific IS consists of the basic instructions,C-instructions,and D-instructions as illustrated in Fig.3.While the basic instructions are provided by the user as a part of the architecture description,the C-instructions are synthesized using the information from both the data path architecture and the application program.The D-instructions,which may be generated manually by an expert,take effect on the code space allocated for the C-instructions.In this subsection,we highlight the two main features of our proposed IS synthesis framework.4.2.1Structure-Centric IS SynthesisCurrently,a typical approach to the application-specific IS synthesis is first identify the most promising operation patterns from the application and later implement the application-specific instructions using additional hardware such as special functional units.However,in that approach it is difficult to find an optimal IS (e.g.,of maximal performance for the given power,area budget)due to the difficulty of foreknowing the hardware implementation characteristics during the synthe-sis step.As a result,an iterative optimization strategy is unavoidable,which may involve hardware synthesis for the IS design.Also,since the data path is heavily changed for the new IS,the huge cost of re-engineering the entire processor design is another disadvantage of this approach.2w1w22w2Code spacew1imm2imm1R3R2R1opcode immediate R2R1opcode Figure 4.Flexible instruction format and the instruction code space.Our IS synthesis framework takes a structure-centric approach.In the structure-centric IS syn-thesis,an optimal IS can be more directly found within the limited hardware change allowed,as the data path structure is given and frozen from the beginning of the IS synthesis process.The IS synthesis system tries to find a better IS exercising the data path more efficiently for the given application.Hence,our IS synthesis framework explicitly takes inputs of the data path architecture as well as of the application program.Another benefit of this approach is that it readily enables IS specialization—improving the processor architecture through only the IS modification—which has become important in the platform-based SOCs employing configurable processors.4.2.2Optimized Instruction EncodingPrevious work on IS synthesis has taken a very simplistic view on the instruction format;typically,all synthesized instructions have the same format,with the number of (maximum)operands and their bitwidths determined before the IS synthesis.However,custom-designed IS’s of embedded processors have varying formats for different instructions in order to maximize the utilization of the limited instruction bitwidth,and even encoded operands are often used.For example,an immediate field may take 8bits in the ADDI instruction while it may take only 4bits in the ADD +LOAD type instructions.Register fields may also have a reduced width to allow more operands to be encoded,at the cost of accessing only a subset of the registers in that instruction.For example,the SH-3microprocessor has complex load instructions,which have the (implicit)R0register as their destination so that the destination register need not be specified at all.Our IS synthesis framework addresses this problem of diverse instruction formats through the instruction code space and the operand class .First,to allow different instruction formats in a single IS,our framework does not constrain the opcode/operand field widths;rather,the operand fields may have different bitwidths (determined by the synthesis process itself)and only the opcode field width is later set to use the remaining bits of the instruction bitwidth.Thus,the only condition to be satisfied in this scheme is that the sum of the code space (defined as 2ˆthe number of bits needed for operands )of every instruction should not exceed the allowed total code space (defined as 2ˆthe instruction bitwidth )(see Fig.4).Obviously,this condition guarantees that every in-struction will be given an opcode,possibly with a different field width.Second,to support the operand encoding as well as the multiple choices for operand field widths,our technique employs the concept of operand class,which encapsulates the field width,the set of compatible operand instances,and an (optional)encoding scheme.The operand classes provide a convenient means to generalize the operands encountered in the assembly code of the application into various versions。
图着色问题的新遗传算法

收稿日期:2007206226基金项目:国家自然科学基金资助(60374063)作者简介:韩丽霞(19802),女,西安电子科技大学博士研究生,E 2mail :lxhan2006@.图着色问题的新遗传算法韩丽霞1,王宇平2(1.西安电子科技大学理学院,陕西西安 710071;2.西安电子科技大学计算机学院,陕西西安 710071)摘要:针对遗传算法求解图着色问题需多次产生初始种群的问题,提出了一种改进算法.该算法采用比较机制,淘汰不可行的基因,然后使用动态的适应度函数,使得有效个体以较大的概率存活到下一代种群中,从而达到无需多次产生初始种群的目的.与传统框架下的算法相比,新算法求得最优解的时间至少缩短了51%,且具有从一个局部最优解快速跳到下一个局部最优解,最终收敛到全局最优解的优点.关键词:图着色问题;遗传算法;局部搜索;全局收敛中图分类号:TB11 文献标识码:A 文章编号:100122400(2008)022*******Novel genetic algorithm for the graph coloring problemH A N L i 2x i a 1,W A N G Yu 2pi ng2(1.School of Science ,Xidian Univ.,Xi ′an 710071,China ;2.School of Computer Science and Technology ,Xidian Univ.,Xi ′an 710071,China )Abstract : Generic genetic algorithms need generate initial population iteratively for solving the coloringproblem.Based on this problem ,an improved algorithm is presented.The novel algorithm adopts acomparative mechanism to eliminate the unfeasible genes ,and gives the valid individual a greaterprobability to survive to the next generation by using the dynamic fitness function.Thus ,the proposedalgorithm avoids the repetitious production of the initial pared with the algorithms underthe traditional architecture ,the proposed algorithm can shorten the time of finding the optimal solution atleast by up to 51percent.Moreover ,the novel algorithm has the advantages of jumping f rom a localoptimal solution to next one quickly and converging to the global optimal solution in the end.K ey Words : graph coloring problem ;genetic algorithm ;local search ;global convergence 图着色问题是图论中一个经典的组合优化问题,无论在理论上还是工程应用中均具有良好的应用背景,如发射台的频率分配问题.由于工作频率相同的发射台之间产生相互干扰的电势,为了消除干扰,给不同的发射台分配不同的互不干扰的工作频率就是一个经典的图着色问题.由于图着色问题是遗传算法(N P )2难问题,不存在多项式时间的精确算法,因此,对图着色问题的研究主要集中在启发式算法上.近几年来,遗传算法[1~4]成为研究的热点,且在求解图着色问题上,取得了不俗的效果.Eiben [1]利用遗传算法对32着色图进行了系统的研究;Fleurent 和Ferland [2]将禁忌搜索法与遗传算法相结合,提出了求解图着色问题的混合遗传算法;Morgenstern [3]提出了分布式、基于种群的多策略算法.一般遗传算法在求解图着色问题时,要多次产生初始种群,不仅耗费了时间,而且损失了有效的种群信息.针对这一点弊端,笔者提出了图着色问题的新遗传算法.新的杂交算子和动态的适应度函数相结合,避免了多次产生初始种群,损失有效的种群信息的弊端,且有利于减少算法的运行时间,不失是遗传算法求解图着色问题的一个好的框架.将新旧框架在同样环境下,对同样的着色问题进行仿真,仿真结果表明了新框架的优越性.2008年4月第35卷 第2期 西安电子科技大学学报(自然科学版)J OU R NAL O F XI D IAN U N IV E R S I T Y Apr.2008Vol.35 No.21 图着色问题给定图G=(V,E),其中V=n,E=m,图着色问题就是要用最少的颜色对图G的顶点进行着色,要求相邻的两个顶点着不同的颜色.实际上,对图G=(V,E)的顶点着色就是要把图G的顶点集V分割成若干个不相交的子集,而且每个子集中的任意两点都不相邻(这样的集合称为独立集).图G的一个正常k2点着色,就是把图G的顶点集V分成k个独立集的一个分类{V1,V2,…,V k}.令C(k)={1,2,…,k}表示k种颜色,则图G的k2点着色定义如下:定义1 图G的k2点着色是从图G的顶点集V到C(k)的一个映射σ,当且仅当u,v∈V且(u,v)∈E 时,σ(u)≠σ(v).图G的所有k2点着色σ构成的集合,记为S k(G),若S k(G)≠0,则称图G是k2点可着色的.定义2 使图G为k2点着色的最小颜色数k称为图G的色数,记为χ(G).2 遗传算法211 遗传算法求解图着色问题的旧框架 以往的遗传算法在求解图着色问题时,对给定的k0种颜色(令k=k0),产生初始种群,在遗传算子的作用下,求解k2着色;若找到k2着色方案,令k=k-1,重新产生初始种群,求解k2着色,直到找到问题的χ(G)2着色方案为止.显然,多次产生初始种群,损失了种群中已有的分割信息,浪费了计算时间.笔者针对这一特点,提出了新遗传算法,该算法既可以保留种群中的分割信息,又有利于减少算法的运行时间,得到问题的k2着色方案后,可以快速找到(k-1)2着色方案.212 遗传算法考虑到图着色问题的特点,采用整数表示法编码个体.即每个着色方案x,对应于一个长度为n的染色体x1x2…x n,其中x i表示图G顶点v i所着的颜色.21211 适应度函数对个体x=(x1x2…x n),构造罚函数为p(x)=∑ni=1,j=i+1q(v i,v j),其中,q(v i,v j)=1,(v i,v j)∈E,x i=x j0,否则,即p(x)为染色体x违反着色约束的边的数目.定义适应度函数为f(x)=p(x)+m・k(x)-δ-1,其中k(x)是染色体x=(x1x2…x n)中所用的颜色数,δ为已求得的k2点可着色方案中所用的颜色最小值.不同于以往的遗传算法求解图着色问题的适应度函数,该适应度函数会随着算法的进化,动态的发生变化.每当找到所用颜色更少的k2可着色方案,目标函数都会发生变化.21212 杂交算子设x=(x1x2…x n)和y=(y1y2…y n)是参加杂交的两个父代个体,依次对基因x i(i=1,…,n)和y i (i=1,…,n),分如下两种情况进行杂交.情况1 当基因xi<δ和y i<δ时,若存在顶点j∈[1,2,…,n],使得(v i,v j)∈E且x i=x j(着相同的颜色)令xi=y i;情况2 否则,令xi=min{x i,y i}.显然,情况1的杂交方式可以减少遗传算法的盲目搜索,而情况2的杂交方式,使得个体所用的着色颜色数逐渐减少,将着色问题的搜索空间缩小.在该杂交算子的作用下,有效的顶点分割信息得到保留,又会产生一些新的个体.杂交算子可以减少杂交后代所用的颜色k(k≥δ),而适应度函数又可以保证所用颜色为(δ-1)种的染色体以较大的概率存活到下一代种群中,因而,杂交算子和动态的适应度函数协同作用,可以013 西安电子科技大学学报(自然科学版) 第35卷达到多次产生种群同样的作用,而又不损失有效的基因信息,这就为遗传算法求解图着色问题提供了不用多次产生初始种群的一种新框架.21213 局部搜索为了提高算法的收敛速度,提出了新的局部搜索算子.对杂交产生的每个后代个体x=(x1x2…x n),进行如下局部搜索,伪码过程如下:For i=1:n do Randomly generate an integer c∈C(δ) x′=(x1…x i-1cx i+1…x n) If f(x)>f(x′),x=x′End do.该局部搜索算子可以有效、快速的搜索图着色问题的空间,每次对个体x的一个基因xi进行扰动,若得到更好的个体,则替换x;否则,进行下一次扰动,最终得到的新个体x,作为局部搜索算子的后代.21214 变异算子对染色体x=(x1x2…x n)的每个基因x i(i=1,2,…,n)依次以等概率在颜色类C(k)={1,2,…,k}中随机选择新的颜色x′i(x′i∈C(k},得到的新的变异个体记为x′=(x′1x′2…x′n).显然,该变异算子有利于保持种群的多样性,可以有效的帮助算法跳出局部最优解,而且,该变异算子具有简单、易执行的特点.213 新遗传算法(NG A)1)(初始化)给定种群规模N,杂交概率、变异概率分别为p c,p m,随机产生N个个体作为初始种群,记为P(0),令进化代数t=0;2)(杂交):以杂交概率p c在P(t)中选择参加杂交的个体.对每对个体x与y,用杂交算子产生后代x′与y′,这些后代的集合记为O1;3)(局部搜索)对O1中每个个体x,进行局部搜索,得到新的后代的集合记为O2;4)(变异):以变异概率p m在O2中选择参加变异的个体,用变异算子产生变异后代.这些后代的集合记为O3;5)(选择):在P(t)∪O1∪O2∪O3中选择最好的N个个体作为下一代种群P(t+1),令t=t+1;6)若终止条件成立,则停;否则,转2).3 收敛性分析定义3 称个体y是从x通过杂交和变异可达的,如果P{M・C(x)=y}>0,其中M・C(x)表示由个体x通过杂交和变异产生的个体,P{・}表示随机事件{・}的概率.引理1 若一个遗传算法满足如下两个条件[5]:a)对可行域S中任意两个个体x和y,通过杂交和变异是可达的;b)种群序列P(0),P(1),…,P(t),…是单调的.则遗传算法以概率1收敛到问题的全局最优解.定理1(全局收敛性) N GA以概率1收敛到全局最优解.证明 1)事实上,x被选上参加杂交的概率为pc>0.设c是由x通过杂交产生的任一后代,而z是从c由局部搜索产生的新后代,z被选上参加变异的概率为pm>0,则经杂交和变异由x产生y的概率满足Prob{M・C(x)=y}≥p c・p m Prob{M(z)=y}.设z=(z1z2…z n),z=(y1y2…y n),由变异算子知,从x i产生y i的概率为1/δ,Prob{M(z)=y}=1δ・1δ…・1δ=1δn >0 ,113第2期 韩丽霞等:图着色问题的新遗传算法Prob {M ・C (x )=y}≥p c ・p m ・Prob {M (z )=y}=p c ・p mδn >0 ,故y 是由x 通过杂交和变异可达的.2)事实上,由算法的选择策略知,P (0),P (1),…,P (t ),…是单调的.综合1)和2)知,N GA 以概率1收敛到全局最优解.4 仿真实验为了测试算法的有效性,对4个标准图着色算例进行了求解:M YCIE13,M YCIE14,M YCIE15和M YCIE16(http :///COLOR/instances.ht ml ).为了验证笔者所提算法N GA 的有效性,保证对比的公平性,将N GA 和旧框架下算法(O GA )在同样的环境下,对各问题均运行了10次,对比结果见表1.表1记录了两算法的运行结果(O GA 2代表算法在旧框架下的算法运行结果,N GA 2表示笔者所提算法的结果).表1 两种算法的运行结果算例O GA N GA 最好解/%代数时间/s 最好解/%代数时间/s M YCIE134/1005140120784/100215011016M YCIE145/10014182157195/100616110014M YCIE156/100311218117906/1001217812500MYCIE167/10060.0188194007/7022159217000 注:最好解表示算法在运行过程中得到的所用颜色数最小的着色方案所用的颜色数;代数t 和时间分别表示算法求得最优解的运行中所用代数和时间的平均值.从表1中可以明显的看出,文中算法N GA 对4个问题均求得了最优解,10次运行中,文中算法对3个问题在有限代内均找到问题的最优解.相较于O GA 算法,N GA 以更大的概率、较少的代数、更短的时间求得问题的最优解.而O GA 算法需要花费N GA 算法约两倍的时间,但求得问题的最优解的百分比不如N GA ,足见遗传算法中,保留有效的基因信息(顶点分割信息),无论对算法的有效性还是算法的时间复杂度都具有重要的意义.图1和图2分别比较了算法O GA 和N GA 在求解M YCIE15和M YCIE16问题时的过程.图1 O GA 和N GA 求解M YCIE15的过程从图1和图2可以看出,N GA 算法中,种群中的有效基因信息的保留,有利于快速逼近下一个局部最优解.如图1(a )所示,算法N GA 找到132着色方案后,算法搜索到122着色、112着色,…,72着色,只需要一代搜索,就可以找到颜色数更小的着色方案;而O GA 算法每找到一个局部最优解后需要几代搜索才能找到下一个局部最优解.从图2(a )中可以看出,N GA 对M YCIE16的搜索,相较于O GA 中(图2(b )),搜索曲线也平缓了许多,213 西安电子科技大学学报(自然科学版) 第35卷图2 O GA 和N GA 求解M YCIE16的过程而O GA 重复产生初始种群,导致了违反约束的边的数目达到了60之多.由此可见,每得到颜色数更小的着色方案,重新产生初始种群,造成了巨大的时间浪费,损失了有效的遗传信息,新算法的提出有效提高了遗传算法求解图着色问题的潜力.5 结束语提出了求解图着色问题的新的遗传算法,设计了比较杂交算子和动态的适应度函数.实际上,新的算法为遗传算法求解图着色问题提供了一种新的框架,即无需多次产生初始种群.相较于遗传算法求解着色问题以往的框架,该框架既保留了有效的遗传信息,又减少了算法的时间,是一种有潜力的算法.参考文献:[1]Eiben A E ,Vender Hauw J K ,Van Hemert J I.Graph Coloring with Adaptive Evolutionary Algorithms [J ].Journal ofHeuristics ,1996,4(1):16224.[2]Fleurent C ,Ferland J A.G enetic and Hybrid Algorithms for Graph Coloring [J ].Annals of Operations Research ,1995,63(3):4372463.[3]Morgenstern C.Distributed Coloration Neighborhood Search [J ].Discrete Mathematic and Theoretical Computer Science ,1996,26(5):3352358.[4]杨淑媛,刘芳,焦李成.一种基于量子染色体的遗传算法[J ].西安电子大学学报,2004,31(1):76281.Yang Shuyuan ,Liu Fang ,Jiao Licheng.A Novel G enetic Algorithm Based on the Quantum Chromosome[J ].Journal of Xidian University ,2004,31(1):76281.[5]Back T.Evolutionary Algorithms in Theory and Practice [M ].New Y ork :Oxford University Press ,1996:21228.(编辑:齐淑娟) 313第2期 韩丽霞等:图着色问题的新遗传算法。
A Continuous-Time Version of the Principal-Agent Problem

A Continuous-Time Version of the Principal-AgentProblem.Yuliy SannikovOctober25,2007AbstractThis paper describes a new continuous-time principal-agent model,in which the output is a diffusion process with drift determined by the agent’s unobserved effort.The risk-averse agent receives consumption continuously.The optimal contract,basedon the agent’s continuation value as a state variable,is computed by a new methodusing a differential equation.During employment the output path stochasticallydrives the agent’s continuation value until it reaches a point that triggers retirement,quitting,replacement or promotion.The paper explores how the dynamics of theagent’s wages and effort,as well as the optimal mix of short-term and long-termincentives,depend on the contractual environment.1Keywords:Principal-agent model,continuous time,optimal contract,career path,retirement,promotionJEL Numbers:C63,D82,E21I am most thankful to Michael Harrison for his guidance and encouragement to develop a rigorous continuous time model from my early idea and for helping me get valuable feedback,and to Andy Skrzypacz for a detailed review of the paper and for many helpful suggestions.I am also grateful to Darrell Duffie, Yossi Feinberg,Xavier Gabaix,Bengt Holmstrom,Chad Jones,Gustavo Manso,Paul Milgrom,John Roberts,Thomas Sargent,Florian Scheuer,Sergio Turner,Cheng Wang,Ivan Werning and Robert Wilson for valuable feedback,and to Susan Athey for comments on an earlier version.1Introduction.The understanding of dynamic incentives is central in economics.How do companies moti-vate their workers through piecerates,bonuses,and promotions?How is income inequality connected with productivity,investment and economic growth?How dofinancial contracts and capital structure give incentives to the managers of a corporation?The methods and results of this paper provide important insights to many such questions.This paper introduces a continuous-time principal-agent model that focuses on the dynamic properties of optimal incentive provision.We identify factors that make the agent’s wages increase or decrease over time.We examine the degree to which current and future outcomes motivate the agent.We provide conditions under which the agent eventually reaches retirement in the optimal contract.We also investigate how the costs of creating incentives and the dynamic properties of the optimal contract depend on the contractual environment:the agent’s outside options,the difficulty of replacing the agent, and the opportunities for promotion.Our new dynamic insights are possible due to the technical advantages of continuous-time methods over the traditional discrete-time ones.Continuous time leads to a much simpler computational procedure tofind the optimal contract by solving an ordinary differ-ential equation.This equation highlights the factors that determine optimal consumption and effort.The dynamics of the agent’s career path are naturally described by the drift and volatility of the agent’s payoffs.The geometry of solutions to the differential equation allows for easy comparisons to see how the agent’s wages,effort and incentives depend on the contractual environment.Finally,continuous time highlights many essential features of the optimal contract,including the agent’s eventual retirement.In our benchmark model a risk-averse agent is tied to a risk-neutral principal forever after employment starts.The agent influences output by his continuous unobservable effort input.The principal sees only the output:a Brownian motion with a drift that depends on the agent’s effort.The agent dislikes effort and enjoys consumption.We assume that the agent’s utility function has the income effect,that is,as the agent’s income increases it becomes costlier to compensate him for effort.Also,we assume that the agent’s utility of consumption is bounded from below.At time0the principal can commit to any history-dependent contract.Such a contract specifies the agent’s consumption at every moment of time contingent on the entire past output path.The agent demands an initial reservation utility from the entire contract inorder to begin,and the principal offers a contract only if he can derive a positive profit from it.After we solve our benchmark model,we examine how the optimal contract changes if the agent may quit,be replaced or promoted.As in related discrete-time models,the optimal contract can be described in terms of the agent’s continuation value as a single state variable,which completely determines the agent’s effort and consumption.After any history of output the agent’s continuation value is the total future expected utility.The agent’s value depends on his future wages and effort.While in discrete time the optimal contract is described by cumbersome functions that map current continuation values and output realizations into future continuation values and consumption,continuous time offers more natural descriptors of employment dynamics: the drift and volatility of the agent’s continuation value.The volatility of the agent’s continuation value is related to effort.The agent has incentives to put higher effort when his value depends more strongly on output.Thus, higher effort requires a higher volatility of the agent’s value.The agent’s optimal effort varies with his continuation value.To determine optimal effort,the principal maximizes expected output minus the costs of compensating the agent for effort and the risk required by incentives.If the agent is very patient,so that incentive provision is costless,the optimal effort decreases with the agent’s continuation value due to the income effect.Apart from this extreme case,the agent’s effort is typically nonmonotonic because of the costs of exposing the agent to risk.The drift of the agent’s value is related to the allocation of payments over time.The agent’s value has an upward drift when his wages are backloaded,i.e.his current consump-tion is small relative to his expected future payoff.A downward drift of the agent’s value corresponds to frontloaded payments.The agent’s intertemporal consumption is distorted to facilitate the provision of incentives.The drift of the agent’s value always points in the direction where it is cheaper to provide the agent with incentives.Unsurprisingly,when the agent gets patient,so that incentive provision is costless,his continuation value does not have any drift.Over short time intervals,our optimal contract resembles that of Holmstrom and Mil-grom(1987)(hereafter HM),who study a simple continuous-time model in which the agent gets paid at the end of afinite time interval.HM show that optimal contracts are linear in aggregate output when the agent has exponential utility with a monetary cost of effort.2 2Many other continuous-time papers have extended the linearity results of HM.Schattler and Sung (1993)develop a more general mathematical framework for such results,and Sung(1995)allows the agentThese preferences have no income effect.According to Holmstrom and Milgrom(1991), the model of HM is“especially well suited for representing compensation paid over short period.”Therefore,it is not surprising that the optimal contract in our model is also approximately linear in incremental output over short time periods.In the long-run,the optimal contract involves complex nonlinear patterns of the agent’s wages and effort.In our benchmark setting,where the contract binds the agent to the principal forever,the agent eventually reaches retirement.After retirement,which occurs when the agent’s continuation value reaches a low endpoint or a high endpoint,the agent receives a constant stream of consumption and stops putting effort.The agent eventually reaches retirement in the optimal contract for two reasons.First, as shown in Spear and Wang(2005),the agent must retire when his continuation payoffbecomes very low or very high.3For the low retirement point,the assumption that the agent’s consumption utility is bounded from below implies that payments to the agent must stop when his value reaches the lower bound.For the high continuation values,retirement becomes optimal due to the income effect.When the agent’s consumption is high,it costs too much to compensate him for positive effort.Second,retirement depends on the relative time preferences of the agent and the principal.If the agent had a higher discount rate than the principal,then with time the principal’s benefit from output outweighs the cost of the agent’s effort.Under these conditions,it is sensible to avoid permanent retirement by allowing the agent to suspend effort temporarily.However,when the agent is equally patient as the principal,our result implies that the agent eventually reaches permanent retirement in the optimal contract.4Of course,retirement and other dynamic properties of the optimal contract depend on the contractual environment.The agent cannot be forced to stop consuming at the low retirement point if he has acceptable outside opportunities.Then,the agent quits instead of retiring at the low endpoint.If the agent is replaceable,the principal hires a new agent when the old agent reaches retirement.The high retirement point may also be replaced with promotion,an event that allows the agent to gain greater human capital,and manage larger and more important projects with higher expected output.5to control volatility as well.Hellwig and Schmidt(2002)look at the conditions for a discrete-time principal-agent model to converge to the HM solution.See also Bolton and Harris(2001),Ou-yang(2003)and Detemple,Govindaraj and Loewenstein(2001)for further generalization and analysis of the HM setting.3See also Wang(2006)for an extension of Spear and Wang(2005)to equilibrium in labor markets.4See DeMarzo and Sannikov(2006),Farhi and Werning(2006a)and Sleet and Yeltekin(2006)for examples where the agent is less patient than the principal.5I thank the editor Juuso Valimaki for encouraging me to investigate this possibility.The contractual envirnoment matters for the dynamics of the agent’s wages.We already mentioned that the drift of the agent’s continuation value always points in the direction where it is cheaper to create incentives.Since better outside options make it more difficult to motivate and retain the agent,it is not surprising that wages become more backloaded with better outside options.Lower payments up front cause the agent’s continuation value to drift up,away from the point where he is forced to quit.When the employer can offer better promotion opportunities,the agent’s wages also become backloaded in the optimal contract.The agent is willing to work for lower wages up front when he is motivated by future promotions.Thesefindings highlight the factors that may affect the agent’s wage structure in internal labor markets.Is the agent motivated more by wages in the short run,or those in the long run in an optimal contract?Contracts in practice use both short-term incentives,as piecework and bonuses,and long-term ones,as promotions and permanent wage increases.In our model, the ratio of the volatilities of the agent’s consumption and his continuation value measures the mix of short-term and long-term incentives.Wefind that the optimal contract uses stronger short-term incentives when the agent has better outside options,which interfere with the agent’s incentives in the long run.In contrast,when the principal has greater flexibility to replace or promote the agent,the optimal contract uses stronger long-term incentives and keeps the agent’s wages more constant in the short run.Wefind that the agent puts higher effort and the principal gets greater profit when the optimal contract relies on stronger long-term incentives.It is difficult to study these dynamic properties of the optimal contract using discrete-time models.Without theflexibility of the differential equation that describes the dynamics of the optimal contract in continous time,traditional discrete-time models produce a more limited set of results.Spear and Srivastava(1987)show how to analyze dynamic principal-agent problems in discrete time using recursive methods,with the agent’s continuation value as a state variable.6Assuming that the agent’s consumption is nonnegative and that his utility is separable in consumption and effort,they show that the inverse of the agent’s marginal utility of consumption is a martingale.An earlier paper of Rogerson (1985)demonstrates this result on a two-period model.7However,this restriction is not6Abreu,Pearce and Stacchetti(1986)and(1990)study the recursive structure of general repeated games.7This condition,called the inverse Euler equation,has received a lot of attention in recent macroeco-nomics literature.For example,see Golosov,Kocherlakota and Tsyvinski(2003)and Farhi and Werning (2006b).very informative about the optimal path of the agent’s wages,since a great diversity of consumption profiles in different contractual environments we study satisfy this restriction.In its early stage,this paper was inspired by Phelan and Townsend(1991)who develop a method for computing optimal long-term contracts in discrete time.There are strong sim-ilarities between our continuous-time solutions and their discrete-time example,implying that ultimately the two approaches are different ways of looking at the same thing.Their computational method relies on linear programming and multiple iterations to converge to the principal’s value function.While their method is quiteflexible and applicable to a wide range of settings,it is far more computationally intensive than our method of solving a differential equation.Also,as we discussed earlier,our characterization allows for analytic comparisons to study how the optimal contract depends on the contractual environment.Because general discrete-time models are difficult to deal with,one may be tempted to restrict attention to the special tractable case when the agent is patient.As the agent’s discount rate converges to0,efficiency becomes attainable,as shown in Radner(1985)and Fudenberg,Holmstrom and Milgrom(1990).8However,wefind that optimal contracts when the agent is patient do not deliver many important dynamic insights:the agent’s continuation value becomes driftless,and the agent’s effort,determined without taking the cost of incentives into account,is decreasing in the agent’s value.Concurrently with this paper,Williams(2003)also develops a continuous-time principal-agent model.The aim of that paper is to present a general characterization of the optimal contract using a partial differential equation and forward and backward stochastic differ-ential equations.The resulting contract is written recursively using several state variables, but due to greater generality,the optimal contract is not explored in as much detail.More recently,a number of other papers started using continuous-time methodology. DeMarzo and Sannikov(2006)study the optimal contract in a cash-flow diversion model using the methods from this paper.Biais et al.(2006)show that the contract of DeMarzo and Sannikov(2006)arises in the limit of discrete-time models as the agent’s actions become more frequent.Cvitanic,Wan and Zhang(2006)study optimal contracts when the agent gets paid once,and Westerfield(2006)develops an approach that uses the agent’s wealth, as opposed to his continuation value,as a state variable.The paper is organized as follows.Section2presents the benchmark setting and for-mulates the principal’s problem.Section3presents an optimal contract and discusses its properties:the agent’s effort and consumption,the drift and volatility of his continuation 8Also,Fudenberg,Levine and Maskin(1994)prove a Folk Theorem for general repeated games.value and retirement points.The formal derivation of the optimal contract is deferred to the Appendix.Section4explores how the agent’s outside options and the possibilities for replacement and promotion affect the dynamics of the agent’s wages,effort and incentives. Section5studies optimal contracts for small discount rates.Section6concludes the paper.2The Benchmark Setting.Consider the following dynamic principal-agent model in continuous time.A standard Brownian motion Z={Z t,F t;0≤t<∞}on(Ω,F,Q)drives the output process.The total output X t produced up to time t evolves according todX t=A t dt+σdZ t,where A t is the agent’s choice of effort level andσis a constant.The agent’s effort is a stochastic process A={A t∈A,0≤t<∞}progressively measurable with respect to F t, where the set of feasible effort levels A is compact with the smallest element0.The agent experiences cost of effort h(A t),measured in the same units as the utility of consumption, where h:A→ is continuous,increasing and convex.We normalize h(0)=0and assume that there isγ0>0such that h(a)≥γ0a for all a∈A.The output process X is publicly observable by both the principal and the agent.The principal does not observe the agent’s effort A,and uses the observations of X to give the agent incentives to make costly effort.Before the agent starts working for the principal,the principal offers him a contract that specifies a nonnegativeflow of consumption C t(X s;0≤s≤t)∈[0,∞)based on the principal’s observation of output.The principal can commit to any such contract.We assume that the agent’s utility is bounded from below and normalize u(0)=0.Also,we assume that u:[0,∞)→[0,∞)is an increasing,concave and C2function that satisfies u (c)→0as c→∞.For simplicity,assume that both the principal and the agent discount theflow of profit and utility at a common rate r.If the agent chooses effort level A t,0≤t<∞,his average expected utility is given byE r ∞0e−rt(u(C t)−h(A t))dt ,and the principal gets average profitE r ∞0e−rt dX t−r ∞0e−rt C t dt =E r ∞0e−rt(A t−C t)dt .Factor r in front of the integrals normalizes total payoffs to the same scale asflow payoffs.We say that an effort process{A t,0≤t<∞}is incentive compatible with respect to {C t,0≤t<∞}if it maximizes the agent’s total expected utility.2.1The Formulation of The Principal’s Problem.The principal’s problem is to offer a contract to the agent:a stream of consumption {C t,0≤t<∞}contingent on the realized output and an incentive-compatible advice of effort{A t,0≤t<∞}that maximizes the principal’s profitE r ∞0e−rt(A t−C t)dt (1) subject to delivering to the agent a required initial value of at leastˆWE r ∞0e−rt(u(C t)−h(A t))dt ≥ˆW.(2) We assume that the principal can choose not to employ the agent,so we are only interested in contracts that generate nonnegative profit for the principal.3The Optimal Contract.In this section,we heuristically derive an optimal contract and discuss its basic properties. In Appendix A we formally show that an optimal contract takes the form presented in this section.Only for this section,assume that an optimal contract can be written in terms of the agent’s continuation value W t as a single state variable.The continuation value W t is the total utility that the principal expects the agent to derive from the future after a given moment of time t.In the optimal contract,W t will play the role of the unique state descriptor that determines how much the agent gets paid,what effort level he is supposed to choose,and how W t itself changes with the realization of output.The principal must design a contract that specifies functions c(W),theflow of the agent’s consumption,a(W), the recommended effort level,and the law of motion of W t driven by the output path X t. Three objectives must be met.First,the agent must have sufficient incentives to choose therecommended effort levels.Second,payments,recommended effort and the law of motion must be consistent,so that the state descriptor W t represents the agent’s true continuation stly,the contract must maximize the principal’s profit.Before we describe the dynamic nature of the contract,note that the principal has the option to retire the agent with any value W∈[0,u(∞)),where u(∞)=lim c→∞u(c).To retire the agent with value u(c),the principal offers him constant consumption c and allows him to choose zero effort.Denote the principal’s profit from retiring the agent byF0(u(c))=−c.Note that the principal cannot deliver any value less than0,because the agent can guarantee himself nonnegative utility by always taking effort0.In fact,the only way to deliver value 0is through retirement.Indeed,if the future payments to the agent are not always0,the agent can guarantee himself a strictly positive value by putting effort0.We call F0the principal’s retirement profit.Given the agent’s consumption c(W)and recommended effort a(W),the evolution of the agent’s continuation value W t can be written as,(3) dW t=r(W t−u(c(W t))+h(a(W t)))dt+rY(W t)(dX t−a(W t)dt)σdZ twhere rY(W)is the sensitivity of the agent’s continuation value to output.When the agent takes the recommended effort level,dX t−a(W t)dt has mean0,and so r(W t−u(c(W t))+ h(a(W t)))is the drift of the agent’s continuation value.To account for the value that the principal owes to the agent,W t grows at the interest rate r and falls due to theflow of repayments r(u(c(W t))−h(a(W t))).We will see later that in the optimal contract,W t responds to output in the employment interval(0,W gp)and stops when it reaches0or W gp,leading to retirement.After the agent is retired,he stops putting effort and receives constant consumption utility ru(c(W t))=rW t.The sensitivity rY(W t)of the agent’s value to output affects the agent’s incentives.If the agent deviates to a different effort level,his actual effort affects only the drift of X t. The agent has incentives to choose effort that maximizes the expected change of W t minus the cost of effortrY(W t)a−rh(a).Since it is costly to expose the agent to risk,in the optimal contract Y(W t)is set at theminimal level that induces effort level a(W t).We denote this level byγ(a)=min{y∈[0,∞):a∈arg max a ∈A ya −h(a )}.(4)Functionγ(a)is increasing in a.For the binary action case A={0,a},γ(a)=h(a)/a. When A is an interval and h is a differentiable function,γ(a)=h (a)for a>0.We come to the crucial part where we describe the optimal choice of payments c(W) and effort recommendations a(W).Consider the highest profit F(W)that the principal can derive when he delivers to the agent value W.Function F(W)together with the optimal choices of a(W)and c(W)satisfy the HJB equationrF(W)=maxa>0,c r(a−c)+F (W)r(W−u(c)+h(a))+F (W)2r2γ(a)2σ2.(5)The principal is maximizing the expected currentflow of profit r(a−c)plus the expected change of future profit due to the drift and volatility of the agent’s continuation value.Equation(5)can be rewritten in the following form suitable for computationF (W)=mina>0,c F(W)−a+c−F (W)(W−u(c)+h(a))rγ(a)2σ2/2.(6)To compute the optimal contract,the principal must solve this differential equation by settingF(0)=0(7) and choosing the largest slope F (0)≥F 0(0)such that the solution F satisfiesF(W gp)=F0(W gp)and F (W gp)=F 0(W gp)(8) at some point W gp≥0,where F (W gp)=F 0(W gp)is called the smooth-pasting condition.9 Let functions c:(0,W gp)→[0,∞)and a:(0,W gp)→A be the minimizers in equation (6).A typical form of the value function F(0)together with a(W),c(W)and the drift of the agent’s continuation value are shown in Figure1.Theorem1,which is proved formally in Appendix A,characterizes optimal contracts.Theorem 1.The unique concave function F≥F0that satisfies(6),(7)and(8)9If r is sufficiently large,then the solution of(6)with boundary conditions F(0)=0and F (0)=F(0) satisfies F(W)>F0(W)for all W>0.In this case W gp=0and contracts with positive profit do not exist.-0.2-0.4-0.6-0.8√c,h(a)=0.5a2+0.4a,r=0.1andσ=1.Point W∗is Figure1:Function F for u(c)=the maximum of F.characterizes any optimal contract with positive profit to the principal.For the agent’s starting value of W0>W gp,F(W0)<0is an upper bound on the principal’s profit.If W0∈[0,W gp],then the optimal contract attains profit F(W0).Such a contract is based on the agent’s continuation value as a state variable,which starts at W0and evolves according todW t=r(W t−u(C t)+h(A t))dt+rγ(A t)(dX t−A t dt)(9) under payments C t=c(W t)and effort A t=a(W t),until the retirement timeτ.Retirement occurs when W t hits0or W gp for thefirst time.After retirement the agent gets constant consumption of−F0(Wτ)and puts effort0.The intuition why the agent’s continuation value W t completely summarizes the past history in the optimal contract is the same as in discrete time.The agent’s incentives are unchanged if we replace the continuation contract that follows a given history with adifferent contract that has the same continuation value W t.10Therefore,to maximize the principal’s profit after any history,the continuation contract must be optimal given W t. It follows that the agent’s continuation value W t completely determines the continuation contract.Let us discuss optimal effort and consumption using equation(5).The optimal effortmaximizesra+rh(a)F (W)+r2σ2γ(a)2F (W)2,(10)where ra is the expectedflow of output,−rh(a)F (W)is the cost of compensating the agent for his effort,and−r2σ2γ(a)2F (W)is the cost of exposing the agent to income uncertainty to provide incentives.These two costs typically work in opposite directions, creating a complex effort profile(see Figure1).While F (W)decreases in W because F is concave,F (W)increase over some ranges of W.11However,as r→0,the cost of exposing the agent to risk goes away and the effort profile becomes decreasing in W,except possibly near endpoints0and W gp(see Section5).The optimal choice of consumption maximizes−c−F (W)u(c).(11)Thus,the agent’s consumption is0when F (W)≥−1/u (0),in the probationary interval [0,W∗∗],and it is increasing in W according to F (W)=−1/u (c)above W∗∗.Intuitively, 1/u (c)and−F (W)are the marginal costs of giving the agent value through current con-sumption and through his continuation payoff,respectively.Those marginal costs must be equal under the optimal contract,except in the probationary interval.There,consumption zero is optimal because it maximizes the drift of W t away from the inefficient low retirement point.Why is it optimal for the principal to retire the agent if his continuation payoffbecomes sufficiently large?This happens due to the income effect:when theflow of payments to the agent is large enough,it costs the principal too much to compensate the agent for his effort,so it is optimal to allow effort0.When the agent gets richer,the monetary cost of 10This logic would fail if the agent had hidden savings.With hidden savings,the agent’s past incentives to save depend not only on his current promised value,but also on how his value would change with savings level.Therefore,the problem with hidden savings has a different recursive structure,as discussed in the conclusions.11F (W)increases at least on the interval[0,W∗],where c=0and sign F (W)=sign(rW−u(c)+ h(a))>0(see Theorem2).When W is smaller,the principal faces a greater risk of triggering retirement by providing stronger incentives.delivering utility to the agent rises indefinitely(since u (c)→0as c→∞)while the utility cost of output stays bounded above0since h(a)≥γ0a for all a.High retirement occurs even before the cost of compensating the agent for effort exceeds the expected output from effort,since the principal must compensate the agent not only for effort,but also for risk (see(10)).While it is necessary to retire the agent when W t hits0and it is optimal to do so if W t reaches W gp,there are contracts that prevent W t from reaching0or W gp by allowing the agent to suspend effort temporarily.Those contracts are suboptimal:in the optimal contract the agent puts positive effort until he is retired forever.12 The drift of W t is connected with the allocation of the agent’s wages over time.Section 5shows that the drift of W t becomes zero when the agent becomes patient,to minimize intertemporal distortions of the agent’s consumption.In general,the drift of W t is nonzero in the optimal contract.Theorem2shows that the drift of W t always points in the direction where it is cheaper to provide incentives.Theorem2.Until retirement,the drift of the agent’s continuation value points in the direction in which F (W)is increasing.Proof.From(5)and the Envelope Theorem,we haver(W−u(c)+h(a))F (W)+r2σ2γ(a)2F (W)2=0(12)Since F (W)is always negative,W−u(c)+h(a)has the same sign as F (W).QEDBy Ito’s lemma,(12)is the drift of−1/u (C t)=F (W t)on[W∗∗,W gp].Thus,in our model the inverse of the agent’s marginal utility is a martingale when the agent’s consump-tion is positive.The analogous result in discrete time wasfirst discovered by Rogerson (1985).In the next subsection we discuss the paths of the agent’s continuation value and income, and the connections between the agent’s incentives,productivity and income distribution in the example in Figure1.Before that,we make three remarks about possible extensions of our model.Remark1:Retirement.If the agent’s utility was unbounded from below(e.g.expo-nential utility),our differential equation would still characterize the optimal contract,but the agent may never reach retirement at the low endpoint.To take care of this possibility, 12This conclusion depends on the assumption that the agent’s discount rate is the same as that of the principal.If the agent’s discount rate was higher,the optimal contract may allow the agent to suspend effort temporarily.。
梯度下降法更新参数

梯度下降法更新参数英文回答:Gradient descent is an optimization algorithm commonly used in machine learning and deep learning to update the parameters of a model. It is an iterative method that aims to find the minimum of a cost function by adjusting the parameters in the direction of steepest descent.The basic idea behind gradient descent is to compute the gradient of the cost function with respect to each parameter and update the parameters in the opposite direction of the gradient. This process is repeated until the algorithm converges to a minimum or until a predefined number of iterations is reached.The update rule for gradient descent can be expressed as follows:θ = θ α ∇J(θ)。
where θ represents the parameters of the model, α is the learning rate, J(θ) is the cost function, and ∇J(θ) is the gradient of the cost function with respect to θ.The learning rate α determines the step size of each parameter update. A larger learning rate can lead to faster convergence, but it may also cause the algorithm to overshoot the minimum. On the other hand, a smaller learning rate may result in slower convergence, but it can help the algorithm to find a more precise minimum.To illustrate how gradient descent works, let's consider a simple example of linear regression. In linear regression, we aim to find the best-fit line that minimizes the sum of squared differences between the predicted and actual values.Suppose we have a dataset with two features (x1 and x2) and a target variable (y). We initialize the parameters (θ0 and θ1) randomly and compute the cost function J(θ) using the current parameters. Then, we compute thegradients ∇J(θ) with respect to each parameter and update the parameters using the update rule.For each iteration, we calculate the gradients and update the parameters until the algorithm converges or reaches the maximum number of iterations. The algorithm continues to adjust the parameters in the direction of steepest descent, gradually reducing the cost function and improving the model's performance.中文回答:梯度下降法是一种常用的优化算法,用于更新模型的参数。
Paths, Trees, and Flowers
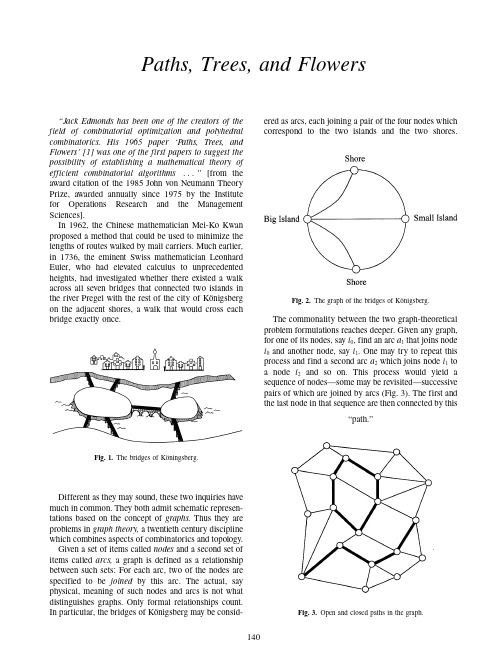
Paths,Trees,and Flowers“Jack Edmonds has been one of the creators of the field of combinatorial optimization and polyhedral combinatorics.His1965paper‘P aths,Trees,and Flowers’[1]was one of the first papers to suggest the possibility of establishing a mathematical theory of efficient combinatorial algorithms...”[from the award citation of the1985John von Neumann Theory Prize,awarded annually since1975by the Institute for Operations Research and the Management Sciences].In1962,the Chinese mathematician Mei-Ko Kwan proposed a method that could be used to minimize the lengths of routes walked by mail carriers.Much earlier, in1736,the eminent Swiss mathematician Leonhard Euler,who had elevated calculus to unprecedented heights,had investigated whether there existed a walk across all seven bridges that connected two islands in the river Pregel with the rest of the city of Ko¨nigsberg on the adjacent shores,a walk that would cross each bridge exactly once.Different as they may sound,these two inquiries have much in common.They both admit schematic represen-tations based on the concept of graphs.Thus they are problems in graph theory,a twentieth century discipline which combines aspects of combinatorics and topology. Given a set of items called nodes and a second set of items called arcs,a graph is defined as a relationship between such sets:For each arc,two of the nodes are specified to be joined by this arc.The actual,say physical,meaning of such nodes and arcs is not what distinguishes graphs.Only formal relationships count. In particular,the bridges of Ko¨nigsberg may be consid-ered as arcs,each joining a pair of the four nodes whichcorrespond to the two islands and the two shores. The commonality between the two graph-theoretical problem formulations reaches deeper.Given any graph, for one of its nodes,say i0,find an arc a1that joins node i0and another node,say i1.One may try to repeat this process and find a second arc a2which joins node i1to a node i2and so on.This process would yield a sequence of nodes—some may be revisited—successive pairs of which are joined by arcs(Fig.3).The first andthe last node in that sequence are then connected by this“path.”Fig.2.The graph of the bridges of Ko¨nigsberg.Fig.1.The bridges of Ko¨ningsberg.Fig.3.Open and closed paths in the graph.(Think of a route along street segments joining inter-sections.)If each pair of nodes in a graph can be con-nected by a path,then the whole graph is considered connected.A path in a graph is called closed if it returns to its starting point(Fig.3).Mei-Ko Kwan’s“Chinese Postman Problem,”as it is now generally called(since first suggested by Alan Goldman,then of NBS),is to determine,in a given connected graph,a shortest closed path which traverses every arc at least once—delivers mail on every assigned street block.Euler also considers closed paths meeting all arcs,but aims at characterizing all graphs which accommodate an Euler tour,a closed path that crosses each arc exactly once.As Euler found,they are precisely those connected graphs in which each node attaches to an even number of arcs,or in other words,every node is of even degree.By this result,there can be no Euler tour over the bridges of Ko¨nigsberg.Euler’s examination typifies the classical combinatorial query:Do certain constructs exist and if so,how many?The following question also illustrates the flavor of classical combinatorics:how many isomers are there of the hydrocarbon C n H2n+2?Each such isomer(Fig.4)is characterized by the joining patterns of the carbon atoms as nodes and bonds as arcs.The corresponding arrangements,therefore,represent graphs.These graphs have a very special property:For any two of their nodes there exists a unique connecting path without repeat arcs.Such a graph is called a“tree.”Every isomer defines a tree of carbon atoms whose nodes are of degree four or less.Conversely,every such tree uniquely characterizes an isomer.In graph-theoret-ical terms,the question is:How many trees with n nodes are there with node degrees not exceeding four?(For n=40,the number is62,481,801,147,341,as deter-mined by ingenious use of“generating functions.”) Here is one more topic in the same vein.A match-maker has a list of k single men and l single women.Her experience of many years enables her to discern which pairs are compatible.She considers a number of com-patible matches that might be arranged simultaneously. How can she be sure that she arrived at the largest possible number of such matches?A theorem by one of the founders of graph theory, the Hungarian mathematician De´nes Ko¨nig in1931, suggests an answer to that question.He considered theFig.4.The carbon graphs of the isomers of C6H14.Fig.5.A matching in a graph;two of the augmenting paths arehighlighted by........graph whose nodes are the matchmaker’s clients and whose arcs join the compatible pairs,leading to the graph-theoretical concept of matching.A matching in a graph is any subset of its arcs such that no two arcs in the matching meet at a common node(Fig.5). Similar concepts are that of a packing or independent set,namely,a subset of the nodes no two of which are connected by an arc,and of a cover,namely,a subset of the nodes that meets every arc.The matchmaker’s graph has the special property that each of its nodes is of one of two kinds,male or female, and every arc connects nodes of different gender.For such a bipartite graph,Ko¨nig’s theorem states that the number of arcs in a maximum matching equals the number of nodes in a minimum cover.However,this deep result ignores the problem of actually finding a minimum cover in order to prove the optimality of a matching.Given a particular matching in any graph,an exposed node is one that is not met by any arc of the matching.An alternating path,that is,a path whose every other arc is part of the matching,is called augmenting if it connects two exposed nodes.Indeed,switching arcs in and out of the matching along an augmenting path results in a new matching with one more arc in it.It is a1957theorem by the French mathematician Claude Berge that a larger matching exists not merely if,but also only if,the current matching admits an augmenting path.The classical graph theorist would look at this elegant characterization of maximum matchings and ask:what more needs to be said?That outlook had been changing during and after W orld W ar II.The extensive planning needs,military and civilian,encountered during the war and post-war years now required finding actual solutions to many graph-theoretical and combinatorial problems,but with a new slant:Instead of asking questions about existence or numbers of solutions,there was now a call for “optimal”solutions,crucial in such areas as logistics, traffic and transportation planning,scheduling of jobs, machines,or airline crews,facility location,microchip design,just to name a few.George B.Dantzig’s celebrated“Simplex Algorithm”for linear program-ming was a key achievement of this era.The Chinese Postman is a case in point.He does not care about how many tours of his street blocks there are to choose from nor whether there are indeed Euler tours. He cares about delivering his mail while walking the shortest possible distance.(Admittedly,mail carriers, Chinese and otherwise,don’t really think in terms of the Chinese Postman Problem.But how about garbage collection in a big city?)And then there were computers,and the expectation that those electronic wizards would handle applied combinatorial optimizations even if faced with the large numbers of variables which typically rendered manual computations impractical.Enter Jack Edmonds.Edmonds did his undergradu-ate work at the George W ashington University.He recounts—as one of the pioneers featured in the volume History of Mathematical Programming:A Collection of P ersonal Reminiscences[20]Ϫhis varied interests and activities of that period.Thus he designed toys and games with expectations of monetary rewards, which unfortunately did not materialize.A stint as a copy boy at the W ashington Post found him at the night desk during President Eisenhower’s heart attack in1955.Mathematics,however,survived as his over-riding interest.Fascinated by the study of polytopes by the Canadian Mathematician H.S.M.Coxeter, Edmonds’master thesis at the University of Maryland (1959)addressed the problem of embedding graphs into surfaces[6].Fig.6.Jack Edmonds.In1959he joined NBS,became a founding member of Alan Goldman’s newly created Operations Research Section in1961,and was steered towards precisely the endeavor of developing optimization algorithms for problems in graph theory and combinatorics.In particular,he was drawn to two fundamental problems: the“Maximum Packing Problem”and the“Minimum Cover Problem”of determining largest packings and smallest covers,respectively,in a given graph[2]. Edmonds quickly recognized the major challenge of that task,a challenge that he called“the curse of exponentiality.”While plainly“finite,”many of the known graph-theoretical algorithms required exponen-tial effort,or their authors had not detailed their proce-dures in a way that avoided such exponentiality. Consider the“Maximum Matching Problem”of finding the largest matching in a given graph.Recall that a matching can be enlarged whenever there is an augmenting path,that is,an alternating path connecting two exposed nodes.As a consequence,there exists an “algorithm”which in a finite number of steps—every-thing is finite here—determines whether a matching is maximum or shows how to improve it.“All”that’s needed is to examine,at each step,the alternating paths originating at exposed nodes.It’s just that there are so darn many of them!In a general framework,computational problems have a natural size,for instance,the number of nodes or arcs in a graph.For algorithms,computational effort can then be defined as the number of basic computational steps,such as individual additions or multiplications, and depends on problem size.If computational effort increases as fast or faster than exponentially with problem size,then it is said to require exponential effort. P olynomial time,by contrast,—Edmonds used the term good—prevails if computational effort is bounded by a power d of problem size n.The notation O(n d)is used to indicate that level of complexity.Regardless of technological progress,computers are helpless when faced with exponential effort.T o wit, the“Traveling Salesman Problem.”Here a connected graph is given along with a particular length for each arc.What is wanted is a closed path of least total length that visits every node.The sequence of visits essentially defines such a round trip.Consider,for instance,the 48state capitals of the contiguous United States and W ashington,DC,as nodes of a graph with an arc between any two of them.From a base in W ashington, all those capitals are to be visited while minimizing the total distance traveled.Thus there are48!(factorial) round trips in the running.A future supercomputer, spending1nanosecond per trip,would require more than3ϫ1044years to examine all possible trips.Stressing the integral role of complexity,Edmonds became the leading proponent of a new direction:to develop good algorithms for problems in graph theory and combinatorics(or to identify problems for which such algorithms can be proven not to exist).This has spawned a new area of research that has grown and flourished for four decades and is still going strong.It is not by accident that a graph-theoretical optimization problem,namely,the Traveling Salesman Problem,is now frequently used as a complexity standard,calling a problem NP-complete if it requires computational effort equivalent to that of the Traveling Salesman Problem. In1961,while attending a summer workshop at the RAND corporation in Santa Monica,California, Jack Edmonds discovered a good algorithm for the Maximum Matching Problem,whose complexity he conservatively pegged at O(n4).That algorithm is described in the paper P aths,Trees, and Flowers[1].In its title,the words“paths”and “trees”refer to the standard graph-theoretical concepts. The algorithms augmenting paths are found by a“tree search”combined with a sophisticated process of shrinking certain subgraphs called blossoms into single nodes of a reduced graph.Hence the term“flowers”in the title.Why was it a breakthrough?The answer is that all good graph-theoretical algorithms known at the time addressed“unimodular”problems such as the“Shortest Path”and“Network Flow”problems,the rigorous proof for the latter having been given by Edmonds with collab-oration by Richard M.Karp[13].These are problems that could be formulated as integrality-preserving linear programs,which by themselves did not create good algorithms but indicated the potential for such. Edmonds’matching algorithm was the very first instance of a good algorithm for a problem outside that mold.In addition,P aths,Trees,and Flowers contributed a major theoretical result:a generalization of Ko¨nig’s theorem that holds for matchings in all kinds of graphs, not just bipartite ones.Edmonds also conjectured in this paper that both the Maximum Packing Problem and the Minimum Cover Problem were intrinsically harder than the Maximum Matching Problem.Indeed,both of the former problems were subsequently shown to be NP-complete.In one of his seminal papers[3-10]published in the Journal of Research of the National Bureau of Standards,Edmonds[7]extended his algorithm to find matchings that optimize the sum of given arc weights, and,perhaps more importantly,he laid the foundationfor a polyhedral interpretation of matching theory which was pursued,for instance,in the doctoral thesis by William R.Pulleyblank[15]advised by Edmonds. Subsequently,Edmonds found other good algorithms, for instance,in his path-breaking research on combina-torial abstractions of matrices,called matroids[4,12, 14-17,19].And,last but not least,he and Ellis L. Johnson used the matching paradigm to arrive at a first good algorithm for the Chinese Postman Problem[18]. In1969,Edmonds accepted a professorship of mathematics at the University of W aterloo,where a list of distinguished doctoral students is testament to his special gift of guiding and motivating young mathemati-cians.He remains to this day an active and highly influential researcher in the field of graph theory and combinatorics.Why is it important to identify even a few graph-theoretical and combinatorial problems with good solution algorithms,when there is such a great variety of real-life optimization tasks,most of them defined in a less clear-cut fashion?The utility of good algorithms for idealized problems and their theory is that they sug-gest generalizations,variations,promising avenues of attack,treatable approximations,iterative applications, and also flag problem formulations best to avoid.In all these roles,Edmonds’matching algorithm has been an indispensable and inspirational part of the toolkit for combinatorial optimization and its multiple applications to modern technology.Prepared by Christoph Witzgall with help by Ronald Boisvert,Geraldine Cheok,Saul Gass,Alan Goldman, and James Lawrence.Bibliography[1]Jack Edmonds,Paths,Trees,and Flowers,Canad.J.Math.17,449-467(1965).[2]Jack Edmonds,Covers and Packings in a Family of Sets,Bull.Amer.Math.Soc.68,494-499(1962).[3]Jack Edmonds,Existence of k-Edge Connected Ordinary Graphswith Prescribed Degrees,J.Res.Natl.Bur.Stand.68B,73-74 (1964).[4]Jack Edmonds,Minimum Partition of a Matroid into Indepen-dent Subsets,J.Res.Natl.Bur.Stand.69B,67-72(1965).[5]Jack Edmonds,Lehman’s Switching Game and a Theorem ofTutte and Nash-Williams,J.Res.Natl.Bur.Stand.69B,73-77 (1965).[6]Jack Edmonds,On the Surface Duality of Linear Graphs,J.Res.Natl.Bur.Stand.69B,121-123(1965).[7]Jack Edmonds,Maximum Matching and a Polyhedron with0,1-V ertices,J.Res.Natl.Bur.Stand.69B,125-130(1965). [8]Jack Edmonds and D.R.Fulkerson,Transversals and MatroidPartition,J.Res.Natl.Bur.Stand.69B,147-153(1965). [9]Jack Edmonds,Optimum Branchings,J.Res.Natl.Bur.Stand.71B,233-240(1967).[10]Jack Edmonds,Systems of Distinct Representatives and LinearAlgebra,J.Res.Natl.Bur.Stand.71B,241-245(1967). [11]Jack Edmonds,Matroid Partition,in Mathematics of the Deci-sion Sciences,P art I,(Proceedings of the Fifth Summer Seminar on the Mathematics of the Decision Sciences,Stanford Univer-sity,Stanford,CA,1967),American Mathematical Society, Providence,RI(1968)pp.335-345.[12]Jack Edmonds,Submodular Functions,Matroids,and CertainPolyhedra,in Combinatorial Structures and their Applications (Proceedings of the Calgary International Conference on Combi-natorial Structures and their Applications,University of Calgary, Calgary,Alberta,Canada,1969),Gordon and Breach,New Y ork (1970)pp.69-81.[13]Jack Edmonds and Richard M.Karp,Theoretical Improvementsin Algorithmic Efficiency for Network Flow Problems,in Combinatorial Structures and their Applications(Proceedings of the Calgary International Conference on Combinatorial Structures and their Applications,University of Calgary, Calgary,Alberta,Canada,1969),Gordon and Breach,New Y ork (1970)pp.93-96.[14]Jack Edmonds,Matroids and the Greedy Algorithm,Math.Programming1,127-136(1971).[15]W.Pulleyblank and Jack Edmonds,Facets of1-MatchingPolyhedra,in Hypergraph Seminar(Proceedings of the First W orking Seminar on Hypergraphs,Ohio State Univ.,Columbus, Ohio,1972)Lecture Notes in Mathematics V ol.411,Springer-V erlag,Berlin(1974)pp.214-242.[16]Jack Edmonds,Edge-Disjoint Branchings,in CombinatorialAlgorithms(Courant Computer Science Symposium9,Naval Postgraduate School,Monterey,CA,1972),Algorithmics Press, New Y ork(1973)pp.91-96.[17]Peyton Y oung and Jack Edmonds,Matroid Designs,J.Res.Natl.Bur.Stand.77B,15-44(1973).[18]Jack Edmonds and Ellis L.Johnson,Matching,Euler T ours,andthe Chinese Postman,Math.Programming5,88-124(1973).[19]Jack Edmonds,Matroid Intersection,in Discrete Optimization I(Proceedings of the Advanced Research Institute on Discrete Optimization and Systems Applications,Alberta,Canada,1977);Ann.Discrete Math.4,39-49(1979).[20]Jan Karel Lenstra,Alexander H.G.Rinnooy Kan,AlexanderSchrijver,History of Mathematical Programming,A Collection of P ersonal Reminiscences,North-Holland,Amsterdam(1991).。
目标障碍解决方案英语

目标障碍解决方案英语《Overcoming Obstacles to Achieve Your Goals》Setting goals is an important part of life, whether they are personal or professional. However, obstacles can often stand in the way of achieving these goals. These obstacles can come in many forms, such as lack of motivation, fear of failure, or simply not knowing how to start. Fortunately, there are strategies to overcome these obstacles and achieve your goals.First and foremost, it is important to clearly define your goals. When you have a clear idea of what you want to achieve, it becomes easier to develop a plan to overcome any obstacles that may arise. Setting specific, measurable, attainable, relevant, and time-bound (SMART) goals can help you stay focused and motivated.Another common obstacle is the fear of failure. Many people are afraid to take risks and try new things because they are scared of failing. However, it is important to remember that failure is a natural part of the learning process. Instead of letting fear hold you back, use it as motivation to push yourself out of your comfort zone and grow as a person.Lack of motivation is another obstacle that can prevent you from reaching your goals. To overcome this, it is important to surround yourself with positive influences and create a supportive environment. This can include seeking out mentors, joining groups or communities of like-minded individuals, and setting up a reward system for reaching milestones.Lastly, not knowing where to start can be a major obstacle when working towards your goals. To solve this, break down your goals into smaller, manageable tasks. This makes the overall goal seem less daunting and allows you to focus on one step at a time.In conclusion, obstacles are a natural part of the goal-setting process. However, by clearly defining your goals, overcoming the fear of failure, staying motivated, and breaking down tasks, you can successfully overcome these obstacles and achieve your goals. Remember that setbacks are a part of the journey, and with determination and perseverance, you can overcome any obstacles in your path.。
改进粒子群优化算法英文

改进粒子群优化算法(英文)Particle Swarm Optimization (PSO) is a metaheuristic optimization algorithm that simulates the collective behavior of birds in a flock, leveraging continuous self-adaptation and information sharing to search for optimal solutions. While PSO has been widely applied in various optimization problems, it still has certain limitations that need improvement to enhance its performance.Here are several directions to improve the Particle Swarm Optimization algorithm:1. Enhancing Particle Movement Strategy: Traditional PSO relies on random velocity and position update strategies, which may lead to convergence to local optima. By introducing nonlinear and adaptive movement strategies such as exponential inertia weight and adaptive acceleration coefficients, the global search capability of particles can be enhanced, improving the convergence speed and accuracy of the algorithm.2. Introducing Multi-Objective Optimization: PSO was originally designed for solving single-objective optimization problems, yet many real-world problems involve conflicting objectives. By improving the Multi-Objective Particle Swarm Optimization algorithm, incorporating the computation of multi-objective fitness functions and updating strategies specifically tailored for multi-objective optimization, the algorithm can identify a set of best feasible solutions, forming a Pareto front.3. Considering Constraint Handling: When dealing with constrained optimization problems, the traditional PSO algorithm may generate solutions that do not satisfy the constraints. By introducing constraint handling approaches such as penalty function methods or improved constraint saturation functions, the offending solutions can be penalized and pushed towards feasible regions, thereby increasing the feasibility of the search process.4. Adapting Parameter Adjustment: The parameter settings in Particle Swarm Optimizationalgorithm significantly impact its performance. Traditional PSO often utilizes statically set parameters, which may not adapt to the problem characteristics and variations. By introducing adaptive parameter mechanisms, such as adaptive inertia weight and dynamically adjusted acceleration coefficients, the parameters can be adaptively tuned based on the progress of the search, enhancing the robustness and global search capability of the algorithm.5. Global Convergence Analysis: The global convergence of the Particle Swarm Optimization algorithm is a crucial factor in ensuring its performance. Conducting detailed theoretical analysis of the algorithm's global convergence and designing corresponding convergence proofs or convergence rate analysis methods can improve the interpretability and controllability of the algorithm.In practical applications, improving the Particle Swarm Optimization algorithm can be tailored to specific problem characteristics and requirements. By optimizing the algorithm's design and parameter adjustments, the global search capability, convergence speed, and stability can be improved, making it applicable to more complex optimization problems.。
乐观对人生的英语作文

Optimism is a vital perspective that can significantly influence ones life.It is the ability to see the positive side of things,to expect the best outcome in every situation,and to maintain a hopeful outlook even in the face of adversity.Here are some ways in which optimism can shape and enhance our lives:1.Health Benefits:Optimistic individuals tend to have better physical health.Studies have shown that optimism can reduce the risk of heart disease,lower blood pressure,and even improve immune function.2.Mental Wellbeing:A positive outlook can protect against depression and anxiety. Optimists are more likely to cope with stress effectively and bounce back from negative experiences.3.Relationships:Optimism fosters stronger relationships.People who are optimistic are generally more likable and approachable,which can lead to deeper connections with others.4.Career Success:In the professional world,an optimistic attitude can lead to greater success.Employers often prefer employees who are positive and can motivate their teams, even in challenging situations.5.Problem Solving:Optimists are more likely to approach problems with a solutionoriented mindset.They are less likely to be paralyzed by setbacks and more likely to seek creative ways to overcome obstacles.6.Longevity:Some research suggests that optimistic people may live longer.The stressreducing effects of optimism could contribute to a longer,healthier life.7.Happiness:Perhaps the most obvious benefit of optimism is increased happiness. People who expect good things to happen are more likely to experience joy and contentment.8.Resilience:Optimism builds resilience.It helps individuals to endure hardships and to view challenges as opportunities for growth rather than insurmountable barriers.9.Goal Achievement:Setting and achieving goals is often easier for optimists.They are more likely to persist in the face of failure and to view each attempt as a step closer to their objectives.10.Influence on Others:An optimistic person can inspire and uplift those around them.This positive influence can create a ripple effect,improving the mood and outlook of a whole community or group.In conclusion,optimism is not just a personality trait but a powerful tool that can transform ones life.It encourages a proactive approach to living,fosters a supportive social network,and contributes to a more fulfilling and successful existence.Embracing optimism means choosing to see the glass as half full,even when it seems to be half empty.。
一种LOM的工艺规划与优化的CAD-CAM系统

A CAD/CAM system for process planning and optimization in LOM(Laminated Object Manufacturing)ANTHONY PANG1,AJAY JONEJA1,*,DAVID M2and MATTHEW YUEN21Department of IEEM,and2Department of Mechanical Engineering,Hong Kong University of Science and Technology,Clear Water Bay,Kowloon,Hong KongE-mail:joneja@ust.hkReceived November1998and accepted June2000Rapid Prototyping(RP)technologies have emerged as a powerful set of manufacturing technologies in recent years.While these technologies invariably provide tremendous time savings over traditional methods for the manufacture of design prototypes,most are still quite ine cient.This paper proposes two ideas:(i),that these processes can be signi®cantly optimized by using better process planning;and(ii),that several of these technologies use similar core planning technologies for optimization.The®rst hypothesis is veri®ed in this paper by presenting an improved process planning system for one RP technology,Laminated Object Manufacturing(LOM).The second observation led us to develop an open architecture planning system for a host of RP technologies.A testbed software system using these ideas has been developed and is presented in this paper.While the method-ologies developed can work with the current industry standard STL format for storing object CAD data,the software is planned purely to work using exact solid models and direct slicing methods.1.Introduction and problem descriptionRapid Prototyping(RP)is the collective name of a set of di erent technologies used to manufacture parts by constructively building them by layers.The name is due mainly to their current use:predominantly for prototype fabrications,though research has progressed into build-ing functional parts(or even molding tools)using some of these processes such as Selective Laser Sintering(SLS) using metal or ceramic powders.The most popular of these include Stereolithography,Fused Deposition Modeling(FDM),Laminated Object Manufacturing (LOM),3D printing,and SLS(Jacobs,1992;Yan and Gu,1996).A common element among most of these is that each builds the part as a combination of many thin layers,called slices.Each layer is built by processing ma-terial through2D vector movements of the tool(except in the case of3D printing).The tool is usually a laser beam that can cut material(in the case of LOM),change the physical properties of photo-polymers(in the case of Ste-reolithography),or cause fusion of polymer coatings(e.g., in SLS).While the tool for FDM is a deposition head,it also executes2D vector motions to complete each layer. The attraction of RP is its ability to automatically convert solid models of complex,even multiple,linked parts,into physical prototypes,within a comparatively short time.The technology is still new,however,and therefore much of the research e ort is still concentrated on its hardware and materials aspects.An excellent col-lection of information on this area is maintained elec-tronically by Bohn(2000).In the recent literature,the concentration on the software issues related to RP has been in the areas of part representation formats(Bohn, 1997),and in the generation of slice geometry from the solid model(Dolenc,1994;Jamieson and Hacker,1995; Kulkarni and Dutta,1996).Some other research on the computer-aided processing side was necessitated by the initial choice of part information storage format,still used in all the industrial systems.The format,called the STL-format,stores a triangulated surface model of the solid(s)that are to be manufactured.The triangulation was useful since it allowed for fast and simple computa-tion of slice geometry for the model(by reducing all in-tersection computations into a single class of e cient and robust plane±plane intersections).Yet the triangulation and computational inaccuracies often led to topological irregularities in the constructed slices,sometimes leading to drastic errors in the path planning.Several researchers have worked on problems arising due to the format (Bohn,1993,1995;Makela and Dolenc,1993).Recently, there have been other e orts towards the integration of successful CAD technologies into RP systems(Rajago-palan et al.,1995;Campbell,1996;Ng and Tan,1997).*Corresponding author0740-817XÓ2001``IIE''IIE Transactions(2001)33,345±355One geometrical issue that researchers have raised is that of the importance of build direction(that is,the orien-tation of the part model)to the surface®nish.This is related mainly to the staircase texture resulting from the layer-wise building process.The problem is discussed in Jacobs(1992)which is also probably the best introduc-tion to many of these technologies.An interesting feature of these technologies is that their commercialization has been nearly concurrent with their technological growth.Perhaps as a result,most hardware for RP comes bundled with a proprietary software sys-tem,which often has a closed architecture.This makes it di cult to modify the built in planning methods.We feel that several of these planners are non-optimal,however, and that signi®cant build-time savings can be achieved by additional optimization of the processes.We are not aware of any signi®cant e ort being currently directed into the optimization of tool paths for RP processes. Further,these closed architecture planners make it di -cult for researchers to experiment with di erent buildstrategies in their e orts to improve the surface®nish, part strength,etc.This paper addresses some of these issues,and demonstrates the successful implementation of an integrated CAD/CAM process planner for RP.The focus of this paper is on the LOM,which was®rst developed commercially by Helisys Inc,who are currently the leading supplier of LOM machines in the world.In a later section,we demonstrate how several of the optimi-zation methods developed can apply equally well to most vector-based RP processes.Recent research on LOM has been reported by Klosterman et al.(1997),who have applied it to the production of functional composite laminates,such as composite tools and molds.Several material systems have been examined,including mono-lithic ceramic(SiC),ceramic matrix composites(SiC/ SiC),and polymer matrix composites(glass/epoxy)Re-alistic tools and molds are being created from these ma-terials using the LOM process with little modi®cation. Figure1shows the basics of the LOM process.The object is built of layers of epoxy-coated paper provided through the feeder roll.The pro®le of the part in each slice is cut by the laser,whose power and speed are set to burn through a single layer.Upon completion of the layer,the platform with the partially built part is lowered, and the roll advanced to cut the subsequent layer.At each stage,a heated roller glues the current layer to the par-tially built part.At the end of the build operation,the part is completely embedded within a rectangular block of epoxy-glued paper.In order to facilitate the removal of the surrounding waste material,it is normal practice to additionally cut a grid of cuts exterior to the part on each slice,as shown in Fig.1.In the current state of the art,there are at least two reasons for ine ciency in the process planning for LOM. The®rst arises due to the need to waste rather a large amount of time in cutting the waste removal grids at each layer.While not much statistical information regarding the wasted e ort is available,for the few parts we have processed in our labs,approximately40%of the total cutting time was used in processing the waste removal grids.One reason for this waste of cutting energy and time is that current software allows only a uniform sized, rectangular grid to be generated for waste removal. The second cause of wasted time is due to the sequence of the generation of the cuts.Typically,LOM processors will®rst cut all the part edges of the slice,followed by all the grid lines.This leads to potential ine ciency:while the total cutting time(the time when the laser is on)is constant for each layer,the time it takes to``jump'' between subsequent edges(for each successive edge that is not connected)depends purely on the sequence of the cuts.A simpli®ed example of this is shown in Fig.2 (a and b).The®gure shows each edge(in this case,each edge is a straight line)to be traversed by the laser,with number tags.Assuming the left,bottom corner of the box to be the home position of the laser,a naive algorithm would draw the three loops in order:traveling along the arcs in the following order(in Fig.2a):1-2-3-4-5-6-7-8-9-10-11-12-13-14-15.The total non-machining distanceis Fig.1.LOM process(based on the Helisysstructure).Fig.2.(a)Naõve path plan;and(b)alternative path plan.346Pang et al.proportional to the length of curves5,10and15.A di erent solution yielding the same outcome could be achieved as shown in Fig.2b,by moving along:1-2-3-4-5-6-2-7-8-9-10-11-12-13-9-14.In this case,the total non-machining time is proportional to2´(length of curves 2,9),and obviously less than the naive case.In the following section,strategies for possible improvement are described.2.A new methodology for process and path planningThe problem of waste removal in LOM is stated as fol-lows:Given a solid part embedded in a rectangular block, generate cuts such that the entire block can be disassembled into the part and a set of other pieces.Several points make this a di cult problem:(i)the partusually has a complex geometry described by analytical surfaces;(ii)the cuts need not be planar;(iii)even for given planar cuts and polyhedral objects,disassembly analysis is known to be a di cult problem(Dutta and Woo,1995);(iv)in general,even if a minimum area of cuts can be generated to remove all the waste,the total length of the laser motion required may not be minimal (this is since a vertical cut requires several more layers of paper than an inclined one of the same area);(v)even for the minimum total length for waste removal cuts over all layers,it is not clear whether the total cutting time is minimal(since the optimization of laser motion must be performed separately for each layer);and®nally(vi) technological factors dictate a preference of near-vertical cuts over near-horizontal ones.With this in view,we proposed a scheme that appears to yield tremendous decreases in processing times.The implemented methods are described below.Note that it is much simpler to remove a convex solid from its surrounding block.The algorithms to generate removal cuts for a convex polyhedron resemble those for generating parting planes for molding tools.Further, convex hull algorithms are computationally e cient and robust for the large data sizes required for complex in-dustrial parts.The strategy therefore is to®rst generate cuts to allow removal of the convex hull of the part,and in the region within the convex hull,generate the tradi-tional,rectangular grids to remove the small amount of remaining waste.We show an example to demonstrate the method,and allow a comparison with the traditional grid solution. Next,we discuss the algorithms.Figure3shows a simple part,with the wireframe rectangular box depicting the ®nal built-up LOM object.Figure4(a and b)shows two of the slices,at di erent heights,for this object.The traditional hatch grids required for waste removal are equally spaced along the two orthogonal axes,and it is easily seen that these slices require more time/energy in cutting the grids than the part outline itself.The®rst step in our methodology is to compute the convex hull for the part.This is done,as mentioned be-fore,for ease of implementation of the hull removal cutting planes.Figure5shows the object,with its convex hull in a wireframe.However most parts that are manu-factured using RP are not polyhedral.Our methodology therefore uses an approximate convex cover of the part, which is computed from the following set of3D points:(i)For each linear edge of the part:collect bothvertices.(ii)For each circular arc:approximate the arc by N linear segments,and use vertices of these seg-ments.We currently use eight segments(that is,approximate a full circular arc by a regular oc-tagon).The octagon is inscribed if the arc belongsto a hole(concave adjacent face)and circum-scribed otherwise.(iii)For sculptured surfaces(described by the solid modeler in our system using NURBS),we use thede®ning control points.Most common analyticalsurface description methods,including NURBS,B-splines and Bezier patches possess the convexhull property(Peigl and Tiller,1995),hence theconvex hull of their control points will cover thepart.Fig.3.Simple object with surrounding waste inLOM.Fig.4.The part sliced into:(a)slice A;and(b)slice B,with waste removal grids.CAD/CAM system for process planning and optimization in LOM347Our problem is therefore now subdivided into two sub-problems:(i)waste removal from around a convex polyhedron;and (ii)removal of the waste material be-tween the faces of the convex cover and the part.2.1.Removing the convex object from the surroundingrectangular box Before determination of the cutting planes for the convex object,we must determine the orientation of the object;that is,we must decide upon the orientation of the object (and therefore of its convex cover)with respect to the machine coordinate frame.The vertical orientation of parts in RP is of special signi®cance:if we build an object along its longest axis (the diameter of the point set),it will typically require the most number of layers,and therefore a longer build time.However,as recognized by several researchers (Jacobs,1992;Lan et al .,1996),this orienta-tion determines the surface ®nish,as well as on the part build strength.Since we solely focus here on the path planning aspects,we assume that the vertical orientation of the part is given (using methods similar to Lan et al .(1996)).Therefore we only need to determine the hori-zontal orientation.This selection does not have any e ect on the build quality,or time.The criterion we use is to minimize the amount of paper wasted.This simple con-sideration leads us to the objective of ®nding the mini-mum width of the part's shadow when viewed orthographically from any horizontal direction.We then align the part on the machine such that the vertical ori-entation is maintained as speci®ed above,and the hori-zontal orientation is aligned such that the direction of the LOM paper roll advance is orthogonal to it.The idea is demonstrated in Fig.6.In the case where the part is too long to ®t on the paper (since the roll has a ®xed width),we rotate the part until it ®ts inside the roll,with su cient allowance.2.1.1.Determination of the cutting planesOnce the orientation of the object (and its convex cover)is ®xed,the cutting planes to remove the convex cover from the rectangular enclosure can be determined.This operation can be visualized as being similar to removing a molded part from the enclosing dies.Likewise,the algo-rithm to generate the parting planes is similar to those used for determination of the parting planes for die cast parts (an excellent reference on the determination of the ¯attest parting line is Majhi et al .(1996)).This is done by ®rst determining an appropriate parting line along the pro®le of the convex hull,followed by the determination of the parting planes.In general,the parting line is not planar.One di erence from molding,however,is that in LOM,we would prefer to have near vertical parting planes.This is since near-horizontal parting planes result in widely spread cut lines between neighboringlayersFig.5.Convex cover of thepart.Fig.6.Orienting the part to minimize paper consumption.348Pang et al.forming each parting plane.For instance,a horizontal plane would require cuts on subsequent layers to be in-®nitely far apart.Close to horizontal planes therefore require some peeling e ort that could damage the part during the waste removal process.We select a parting line that is¯attest when viewed from a horizontal direction. Further,since we have oriented the part such that its minimum width is along the direction of paper advance (X-axis in Fig.6above),we select the parting line that is ¯attest with respect to the Y-axis.The reason for choos-ing a¯at parting line is that it will result in near vertical cutting planes,which are most conducive for the removal process,while giving a relatively low cutting time(since they result in a lower total area of cutting planes).The algorithm is described below.Algorithm1:Forming a¯attest(w.r.t.a direction,y) parting line of a convex polyhedron,PStep0.Preparatory step:(a)Project each vertex V i of polygon to point P i on aplane perpendicular to y(b)Construct convex hull of P i,with vertices VC j(c)Find vertices PC j on polyhedron correspondingto each of VC jA simple case is shown in Fig.7above,with a convex polyhedron whose vertices,v1,v9are projected on the plane to its left as shown.The convex hull of the pro-jected points on the plane is the loop vc1,vc2,vc3,vc4, vc5,vc6,vc1which yields the parting polygon formed by vertices v1,v2,v3,v4,v5,v6and v1.Note that the parting line can travel on the surface of P,either along edges of P,or on the interior of faces of P. Figure7is an example where it lies entirely along the edges.The latter case occurs when a vector parallel to y lies entirely on a face of P.At this stage,we have an ordered set of structures,PC j,where each PC j is either a single vertex,or pair of vertices.The possible cases are discussed below.A typical case of the®rst type will be shown in Fig.9,where there are one or more of a sequence of two-vertex PC j's between a pair of single vertex PC j's.Since P is convex,there can be a maximum of two points on P corresponding to a given vertex of VC j.In the case below,the problem of forming the¯attest line between PCs and PCw is equivalent to®nding the shortest path inside the polygon{PCs,PCt1,PCu1, PCv1,PCw,PCv2,PCu2,PCt2,PCs}.This can be done by®rst¯attening the corresponding facets onto a plane, and®nding the shortest path for the corresponding pla-nar polygon.A simple(though not optimal)algorithm that we use is shown below.Step1.For each vertex pair on(the¯attened)polygon, construct a graph G such that:If vertex PC i is visible from PC j,PC i,PC j areconnected with arc of weight=distance(PC i,PC j).e Dijkstra's shortest path algorithm(Aho et al.,1974)for®nding shortest path betweenPCs and PCw in G.The algorithm is easy to implement and runs quite fast for our particular problem,due to the relatively small sized polygons we need to handle.The only exception to this case is in the event that the entire set of PC j's has two vertices.This can occur when each facet forming the loop contributing to the convex hull of the projection is parallel to the y-direction(a simple example is when viewing an orthogonally placed cube from an axial direction).In this case,we do not have a start vertex for our search in Step2.In this case,we denote each vertex from the pair in PC i as PCi1and PCi2, with PCi1having the higher y-coordinate value,and PCi2 having the lower y-coordinate value(see Fig.8).Then we can use the observation of Majhi et al.(1996)that the point with the maximum y-coordinate value from among PCi2's will lie on the shortest path.The algorithm then runs basically as above,with this vertex being the start as well as the endvertex.Fig.7.Forming the partingpolygon.Fig.8.First case for some y-parallel facets in P.CAD/CAM system for process planning and optimization in LOM349Algorithm2:Extending the parting lines to form the cutting planesWe begin with the parting line(generated by the algo-rithm above),and use it to form the optimal parting planes using the following simple algorithm.For the en-closing box of the part,if we view it along the y-direction, we call the four faces of the box parallel to the y-direction as Right,Top,Left,and Bottom faces(or,R,T,L,B respectively for brevity).The parting line is a3D polygon formed by line segments joining vertices V i.Step0.For each vertex V i,®nd the closest wall from{L, R,T,B};(break ties arbitrarily)Denote the closest vertex as P i.Step1.For each vertex V i,going counterclockwise looking along y-directionIf closest-wall(V i)is same as closest-wall(V i+1) Form plane(V i,V i+1,P i+1,P i);Else If closest-wall(V i)is adjacent to closest-wall(V i+1){W=next-clockwise-wall(closest-wall(V i+1));P i+1¢=projection of P i on W;Form plane(V i,P i,P i+1¢,V i+1);Form plane(V i+1,P i¢,P i+1);}Else If closest-wall(V i)is opposite to closest-wall(V i+1){W=next counterclockwise wall toclosest-wall(V i);P i¢=projection of P i on W;P i+1¢=projection of P i+1on W;Form plane(V i,P i,P i¢);Form plane(V i,P i¢,P i+1¢,V i+1);Form Plane(V i+1,P i+1¢,P i);}Note:while three points are su cient to de®ne a plane, we sometimes write all the four points that form the vertices of the parting plane in the above,merely for ease of visualization.Figure9below shows the three cases, and the corresponding planes.Finally,Fig.10shows the cutting planes generated for our earlier example of Fig.5.2.2.Waste removal between convex cover and partThe next step is to determine the cutting planes for the portion between the convex cover and the part itself.In our current implementation,we remove this excess ma-terial by using the traditional,naõve rectangular grid pattern.While this is still potentially wasteful,we have now restricted this wasted e ort to merely within the convex cover of the object.Research is underway to discover improve this portion of the planning±but it is clear that the resolution of this problem is as complex as solving the entire problem(generating cutting planes for the original part directly).Figure11shows one of the slices of the part,with the four sets of cuts:the part edges, the convex hull edges,the convex cover removal cuts,and the internal grids.The process of slicing the object is relatively simple±it constitutes®nding the intersection of a series of hori-zontal planes with the part,its convex cover,and the cutting planes.The®nal step is to use standard algo-rithms to generate the internal grid lines on slices where the convex cover and the part cross sections are not identical.We also note that in our system,we use an openly published direct slicing®le format.Several such formats exist openly(for example,the CLI format(Anon, 2000a)).The format we use is a simpler,but more com-pact one(Anon,2000b).Therefore,no conversion to STL formats is used.Our use of direct slices may not have much implication technically,but computationally,we believe it results in tremendous savings,since the data set is many orders of magnitude smaller.This saving iseven Fig.9.The cutting planesformation.Fig.10.Generation of the cutting planes for the convex cover.350Pang et al.more evident in the next stage,when we embark upon the optimization of the path plans for the laser for each slice.2.3.Path planning for slicesOnce the slice data has been generated,we need to plan for the machining motion.Typically,this is achieved via a laser which is focussed and adjusted to cut precisely one layer,while moving at a prescribed velocity.Each edge in the slice is cut by the laser exactly once.If the laser needs to move between two edges that are not connected,it is turned o .In traditional practice,the sequence in which the laser moves is unplanned.All existing systems merely take the edge geometry data in the sequence that the embedded solid modeler presents it in,and processes them as such.After completion of the slice geometry,all X -parallel grids are machined,in a zig-zag path,followed by all the Y -parallel grids.There is not much indication that the sequence of machining in¯uences any of the build prop-erties;it only a ects the total processing time for the slice.This was shown earlier in Fig.2(a and b).Therefore,it seems to make sense to optimize the motion of the laser.It is obvious that for a given slice,the total time that the laser spends machining is always constant (since it travels across each edge exactly once,at the prescribed velocity).However,in a typical layer,the laser also needs to make many jumps (motions when it is o ).The objective,therefore,is to minimize the total jump time for each layer.The formulation is given below:There are three non-machining move types:from the home position of the laser to the start of the ®rst curve;the moves between the end of one curve and the start of the next one;and ®nally,the move from the end of the last curve to the home position (the ®rst and last motions may be ignored if the machine can use the same time to advance the paper roll).The speci®cation of the tool planbasically depends on two decisions at each step:which is the next arc to be machined,and what is the `sense'of drawing the i th arc (that is,whether we machine from v i 1to v i 2,or from v i 2to v i 1).In Fig.12above,if the sequence of machining is curve-i followed by curve-j ,then the jump distance depends on the sense of machining the two curves.For example,if the machining is from v i 1to v i 2and v j 2to v j 1,the tool jumps for the distance between v i 2to v j 2,and so on.We use two sets of variables to depict these two decisions:X i1if start vertex of arc i is v i 1,0if start vertex of arc i is v i 2.&Y ij 1if the i th arc drawn is arc j ,0otherwise.nClearly,all X i 's and Y ij 's can either be zero or one.The objective function aims to minimize the total non-machining time,which is directly proportional to the total distance traveled between subsequent arcs traversed:minimize:n j 1Y 1j X j a 0j 1ÀX j a 1j n j 1Y nj X j a 1j 1ÀX j a 0jn À1i 1 n j 1Y ijn t 1Y i 1Y t Z jt23Z jt X j X t a jt X j 1ÀX t b jt 1ÀX j X t c jt1ÀX j 1ÀX t d jtwhere n is the total number of curves to be machined,a ij =distance(v i 2,v j 1);b ij =distance(v i 2,v j 2);c ij =distance(v i 1,v j 1);d ij =distance(v i 1,v j 2);a 0j =distance(home,vj 1);a 1j =distance(home,vj 2).and distance (a ,b )computes the Euclidean distancebetween points a and b.Fig.11.The internal grid lines to remove part from its convexcover.Fig.12.The path optimization problem.CAD/CAM system for process planning and optimization in LOM 351The®rst term in the objective function denotes the jump distance from the home position to the start of the®rst edge;the second term,the jump distance from the end of the last curve back to the home position;the third term is the sum of the jump times for all curves from the ®rst to the last.This is a non-linear problem(being quadratic in X i,X j,Y ij,and Y i+1,t)and is intractable for any problem of useful size.However,several heuristics may be applied to arrive at some improvements from the naõve path.We use a Genetic Algorithm(GA)to attempt this optimization(for an introduction to GA's,(Murty, 1995)).The formulation of the GA is described below. There are two sets of decisions which completely de-termine any feasible solution:(i)the sequence in which the curves need to be drawn;and(ii)the end point of each curve that is the start vertex.To capture these two as-pects,a two-chromosome organism is constructed,with an X-and a Y-chromosome.Each chromosome has the same number of genes±the number of curves that the tool needs to machine,gNgenes.The input to the problem is a set of gNgenes arcs,each with two(possibly coinci-dent)vertices,v1and v2.The X-chromosome for any organism is a permutation of[1..nGenes].The i th gene of the X-chromosome=K implies that the i th curve to be machined by the tool is curve K.The Y-chromosome is an array of[0,1]values.If the i th gene of a Y-chromosome is equal to zero,then the i th curve will be machined from v1..to..v2.If the gene is equal to one,then that curve will be machined from v2..to..v1.The reproduction of organisms needs a little care:since the X-chromosome is a permutation,we cannot use a direct crossover method to generate the progeny.We use therefore permutation-based crossover,PMX,as sug-gested in Murty(1995).The Y-chromosome genes are independent of each other,so for this chromosome,we just use a two point crossover,with randomly generated crossover points.We have performed some preliminary testing with the GA,and a simple example is presented here,with the results.The GA was implemented using C++,and exe-cuted on a colony of100organisms,with a cloning ratio of0.15(the best15%of solutions are cloned in the subsequent generation,and no migration(that is,no new random solutions are introduced in each generation).The following®gures show a simple test slice(generated by the traditional method),and the results of the GA.The edges are numbered in Fig.13for reference.By the naõve strategy,the machining sequence can be depicted by the following two chromosomes:X-chromosome: 1234567891011121314151617181920212223 2425262728293031323334353637383940414243 44454647484950515253545556575859.Y-chromosome: 000000000000000000000001110001100 00110000000000000000000000. Using this strategy,we get,for our example,the total non-cutting travel distance is equal to111.827cm. Finally,Table1summarizes the results of running the same data through the GA:The®nal sequence:X-chromosome: 1234567891011124814151617181320212223 2455262731293047323334583637383940414243 44454652195150492853542556573559.and Y-chromosome: 000000000000000000000000000000000 00000001000000000100000000.The approximate computing time for100iterations was 33.89seconds,running on a pentium166MHz PC.We note that signi®cant improvements on the computing are still possible,since:(i)our code is not optimized for speed;and(ii)we spent signi®cant time,in each iteration, to record the outcomes into®les,for reference.In Fig.13.Slice level path planning.Table1.Path optimization using the GAIterations Distance(cm)0111.82710109.0385098.685210095.805750092.0146352Pang et al.。
不确定过程中增长性定理的一个证明

不确定过程中增长性定理的一个证明刘乐;贾耿华【摘要】不确定变量用来描述非确定性现象,不确定过程就是一列随时间或空间变化的不确定变量.本文对不确定过程的增长性态进行研究,并给出相关证明.【期刊名称】《洛阳师范学院学报》【年(卷),期】2017(036)011【总页数】3页(P19-21)【关键词】不确定变量;不确定过程;增长性态【作者】刘乐;贾耿华【作者单位】洛阳师范学院数学科学学院,河南洛阳471934;洛阳理工学院数理部,河南洛阳471023【正文语种】中文【中图分类】O231刘宝碇教授[1]于2007创立了不确定理论,用以研究人类的主观不确定性.作为处理主观判断或专家数据等不精确信息的新工具,不确定性理论已引起了越来越多学者的关注,已经成功应用于不确定规划[2]、不确定金融[3-4]、不确定微分方程[3-4]等等领域中.定理1.1[1] 令(Γ,L)是可测集, L是Γ的σ-代数,称Λ∈L为一个事件,用M(Λ)来表示相信一个事件Λ会发生的信度. 如果M满足以下几条公理:公理1.(正规性)M(Γ)=1;公理2.(自对偶性)对任意事件Λ,有公理3.(次可数可加性)对可数事件列{Λi},有则称M为不确定测度,并且称(Γ, L,M)为一个不确定空间.定义1.1[1] 不确定变量是从不确定空间(Γ, L, M)到实数集R的一个可测函数,也就是说,对任意R中的Borel集B,集合{ξ∈B}={γ∈Γ|ξ(γ)∈B}是一个事件.不确定积分是指不确定过程关于典范过程的积分.2009年,刘宝碇教授 [8] 给出了一种重要的不确定过程典范过程的定义.定义1.2[8] 假设不确定过程Ct满足如下三个条件:(1)C0=0,几乎所有的轨道Lipschitz连续;(2)Ct具有独立稳态增量;(3)对于时间t,增量Cs+t-Cs 是一个具有期望为0和方差为t2的正态不确定变量,其不确定分布是则称不确定过程为典范过程.定义1.3[8] 假设Xt是一个不确定过程, Ct为一个典范过程,在[a,b]中任意插入若干个分点(这里插入k-1个)a=t1<t2<…<tk+1=b来划分[a,b],设作和式当Δ→0时,如果和式几乎处处收敛并且有限,我们就称此极限值为不确定过程Xt 关于Ct的不确定积分,记为).定理1.2[1] (Markov Inequality)设ξ为一个不确定变量,任给t>0和p>0,我们有M{|ξ|≥t}≤.定理设为一个关于不确定典范过程的不确定积分,则存在另一个不确定典范过程使得σ(s)dC(s)=(σ2(s)dC(s)), a.s.对于所有的t>0.证明 (1)由于为变上限积分函数,因此,令并研究的某些性质:(a) 由不确定积分定义,易见是一个具有稳态性、独立增量的过程. 从而是一个不确定典范过程.(2)令则对任意t,我们有σ(s)dC(s)=σ(s)dC(s), a.s.事实上,由的定义,对所有的n,存在un,使得σ2(s)ds<σ2(s)ds+对所有的ε>0,令于是M{Αn}≤=<·.又等价于1另外,由和的定义,容易得出).(3)由(1),(2)即可推得事实上,由的定义得再由t(τ)的定义得从而有=σ(s)dC(s)=σ(s)dC(s)a.s.本文对不确定过程的增长性态进行了研究,给出了证明过程,为以后的不确定微分系统性能分析奠定基础.【相关文献】[1] Liu B. Uncertainty Theory[M]. 2nd ed. Berlin: Springer-Verlag, 2007.[2] Zhu Y. Uncertain optimal control with application to a portfolio selection model[J]. Cyber-netics and Systems, 2010,41(7):535-547.[3] Liu B. Uncertainty Theory: A branch of mathematics for modeling human uncertainty[M]. Springer-Verlag, Berlin, 2010.[4] Peng J, Gao Y. A new option pricing model for stocks in uncertainty markets[J]. International Journal of Operations Research, 2011,8(2):18-26.[5] Chen X., Liu B. Existence and uniqueness theorem for uncertain differential equations[J]. Fuzzy Optimization and Decision Making, 2010,9(1):69-81.[6] Tao N, Zhu Y. Attractivity and stability analysis of uncertain di_erential systems[J]. InternationalJournal of Bifurcation and Chaos, 2015,25(2):1550022-1.[7] Tao N, Zhu Y. Stability and attractivity in optimistic value for dynamical systems with uncertainty[J]. International Journal of General Systems, 2016,45(4):418-433.[8] Liu B. Some research problems in uncertainty theory[J]. Journal of Uncertain Systems, 2009, 3(1):3-10.。
乐观的循环的英语作文

Optimism is a powerful force that can significantly impact ones life.It is a positive outlook on life,which allows individuals to see the brighter side of things,even in the face of adversity.The cycle of optimism is a continuous process that feeds on itself, creating a selfsustaining loop of positivity.This essay will explore the various aspects of the optimistic cycle and how it can be harnessed to improve ones overall wellbeing.Firstly,the foundation of the optimistic cycle lies in the individuals mindset.A person who is optimistic by nature tends to approach life with a positive attitude.They believe in their ability to overcome challenges and are more likely to take on new opportunities. This positive mindset is the starting point of the cycle,as it sets the tone for how one perceives and reacts to lifes events.Secondly,the optimistic mindset leads to proactive behavior.When faced with difficulties,an optimistic person is more likely to take action and seek solutions rather than dwelling on the problem.This proactive approach not only helps in resolving the issue at hand but also reinforces the individuals belief in their ability to handle challenges. This,in turn,strengthens their optimistic outlook,creating a positive feedback loop.Moreover,the optimistic cycle is further fueled by the support and encouragement from others.When people around us recognize and appreciate our positive attitude,they are more likely to offer their support and encouragement.This external validation can significantly boost ones selfesteem and confidence,further reinforcing the optimistic mindset.In addition,the optimistic cycle also benefits from the individuals ability to learn from experiences.Optimistic individuals are more likely to view setbacks as learning opportunities rather than failures.This growth mindset allows them to gain valuable insights from their experiences,which can be applied to future challenges.As a result, they become better equipped to handle similar situations,further enhancing their optimistic outlook.Furthermore,the optimistic cycle is characterized by a strong sense of resilience. Optimistic individuals are better able to bounce back from setbacks and maintain their positive outlook even in the face of adversity.This resilience not only helps them to overcome challenges but also serves as a source of inspiration for others,creating a ripple effect of positivity.Lastly,the optimistic cycle culminates in the individuals overall wellbeing.The continuous reinforcement of a positive mindset,proactive behavior,support from others, learning from experiences,and resilience all contribute to a happier,healthier,and morefulfilling life.This sense of wellbeing further strengthens the optimistic outlook, completing the cycle and ensuring its ongoing sustainability.In conclusion,the cycle of optimism is a selfsustaining process that begins with a positive mindset and is reinforced through proactive behavior,external validation,learning from experiences,resilience,and overall wellbeing.By understanding and harnessing the power of this cycle,individuals can significantly improve their quality of life and contribute to a more positive and optimistic world.。
乐观拥抱挑战的英语作文

Embracing challenges with optimism is a vital attitude that can significantly impact ones personal and professional growth.Challenges are an inevitable part of life,and how we approach them can define our success and happiness.Here is an essay that explores the importance of maintaining an optimistic mindset when facing challenges.Title:Embracing Challenges with OptimismLife is a series of challenges,each presenting an opportunity for growth and learning.It is not the absence of challenges that defines a successful life,but rather how we choose to face them.Optimism,as a powerful tool,can transform the way we approach these obstacles,turning potential setbacks into stepping stones towards success.Understanding the Role of OptimismOptimism is the belief that good things will happen,even in the face of adversity.It is a positive outlook that encourages us to see the silver lining in every cloud.When we embrace challenges with optimism,we are more likely to:1.Maintain a Positive Attitude:A positive attitude helps in reducing stress and anxiety, which are common responses to challenges.It allows us to stay calm and focused on finding solutions.2.Increase Resilience:Optimistic individuals are more resilient.They are better equipped to bounce back from failures and learn from their experiences.3.Enhance Creativity:Optimism fosters an environment where creativity can thrive.It encourages us to think outside the box and explore innovative solutions to problems.4.Improve ProblemSolving Skills:With an optimistic mindset,we are more likely to approach problems with a problemsolving attitude rather than a problemavoiding one.5.Boost Motivation:Optimism can be a powerful motivator.It pushes us to keep going, even when the odds seem stacked against us.Strategies for Embracing Challenges Optimistically1.Change Your Perspective:Shift your focus from whats going wrong to what you can learn from the situation.This change in perspective can help you see challenges as opportunities for growth.2.Set Realistic Goals:While its important to aim high,setting unrealistic goals can lead to disappointment.Break down your challenges into smaller,achievable goals.3.Practice Gratitude:Cultivate an attitude of gratitude.Recognize and appreciate the good things in your life,even when faced with difficulties.4.Surround Yourself with Positivity:The people you spend time with can influence your outlook.Surround yourself with optimistic individuals who inspire and support you.5.Learn from the Past,Plan for the Future:Reflect on past challenges and how you overcame e these experiences to inform your approach to future obstacles.6.Stay Flexible:Be willing to adapt your plans when necessary.Flexibility is key to navigating through unexpected challenges.7.Take Care of Your Health:Physical health significantly impacts mental wellbeing. Exercise,eat well,and get enough sleep to keep your body and mind in optimal condition.ConclusionIn conclusion,embracing challenges with optimism is not just about seeing the bright side of things its about actively choosing to approach lifes difficulties with a mindset that seeks growth and learning.By adopting an optimistic outlook,we can transform the way we face challenges,turning them into catalysts for personal development and success. Remember,its not about avoiding challenges but about facing them headon with a positive and resilient spirit.。
Neural-optimal control algorithm for real-time regulation of in-line

Neural-optimal control algorithm for real-time regulation of in-linestorage in combined sewer systemsSuseno Darsono,John badie *Department of Civil and Environmental Engineering,Colorado State University,Fort Collins,CO 80523-1372,USAReceived 29October 2005;received in revised form 15September 2006;accepted 16September 2006Available online 9November 2006AbstractAttempts at implementing real-time control systems as a cost-effective means of minimizing the pollution impacts of untreated combined sewer overflows have largely been unsustained due to the complexity of the real-time control problem.Optimal real-time regulation of flows and in-line storage in combined sewer systems is challenging due to the need for complex optimization models integrated with urban stormwater runoff prediction and fully dynamic routing of sewer flows within 5e 15min computational time increments.A neural-optimal control algorithm is presented that fully incorporates the complexities of dynamic,unsteady hydraulic modeling of combined sewer system flows and optimal coordinated,system-wide regulation of in-line storage.The neural-optimal control module is based on a recurrent Jordan neural network archi-tecture that is trained using optimal policies produced by a dynamic optimal control module.The neural-optimal control algorithm is demon-strated in a simulated real-time control experiment for the King County combined sewer system,Seattle,Washington,USA.The algorithm exhibits an effective adaptive learning capability that results in near-optimal performance of the control system while satisfying the time con-straints of real-time implementation.Ó2006Elsevier Ltd.All rights reserved.Keywords:Artificial intelligence;Combined sewers;Hydraulic sewer models;Neural networks;Optimal control;Real-time control;Urban stormwater management1.IntroductionA combined sewer system (CSS)is a type of urban drainage network constructed for collecting and transporting both urban wastewater and stormwater flows;i.e.,combined wet and dry weather flows.These systems create serious pollution problems in adjacent water bodies when high storm flow loadings result in discharges exceeding interceptor sewer and treatment plant bined sewers are no longer constructed,but are still found in many large cities worldwide.The high cost and disruption to residences and businesses of converting to separated systems,or adding sufficient off-line detentionstorage capacity,have motivated the search for cost-effective methods for controlling combined sewer overflows (CSOs).In addition,stormwater alone often carries high pollution loads,and in the U.S.,federal and state standards are requiring assurance that storm runoff does not pollute adjacent rivers and streams (U.S.EPA,1999).In some cases,sewer separation can actually increase pollution to adjacent receiving waters since stormwater combined with sanitary flows may have previously been treated,whereas stormwater is often directly discharged into receiving waters in separated systems (AMSA,1994).Real-time regulation of in-line storage in combined sewer systems through control of gates,pumps,and weirs is an approach to reducing untreated overflows that has been suc-cessfully demonstrated in several cities including Milwaukee,USA (Loucks et al.,2004),Quebec,Canada (Pleau et al.,2005),Tielt,Belgium (Vanrolleghem et al.,2005),Saverne,*Corresponding author.Tel.:þ19704916898;fax:þ19704917727.E-mail addresses:sdarsono@ (S.Darsono),labadie@ (badie).1364-8152/$-see front matter Ó2006Elsevier Ltd.All rights reserved.doi:10.1016/j.envsoft.2006.09.005Environmental Modelling &Software 22(2007)1349e1361/locate/envsoftFrance(Vazquez et al.,2003),and Ense-Bremen,Germany (Weyand,2002).Unfortunately,these examples of successful ongoing implementations are rare due to past difficulties in the robustness and reliability of required computer control equipment,sensor and communication devices,as well as inadequate software and modeling capabilities.Schutze et al. (2002)claim,however,that current advances in hardware and software technologies have overcome many of these past obstacles,and at reasonable cost,thereby providing a renewed impetus for implementation of real-time control of CSSs.The maximum utilization of spatially distributed in-line storage in a combined sewer system is an inexpensive method (relative to capital construction)of reducing the polluting effects of untreated spills to receiving waters(Labadie, 1993).The goal is to provide optimal regulation of control structures in the sewer network such that CSOs are minimized or even eliminated.The hypothesis is that aggregate in-line storage capacity in a combined sewer network is often sizable, and if properly managed over time and space,can help reduce pollution from untreated CSOs to adjacent water bodies.Even if elimination of CSOs is not possible under ideal control strat-egies,incorporation of real-time control into plans for constructing additional detention storage and other facilities may reduce sizing requirements of these facilities,and there-fore costs,by making optimum use of available in-line and detention storage.Real-time control(RTC)is most effective if integrated over the entire sewer network,resulting in a large-scale,spatially distributed optimal control problem.According to Pleau et al.(2005),most current RTC implementations are limited to local reactive or supervisory control.Aside from the large-scale nature of integrated,system-wide or global optimal control,the optimization is highly nonlinear,requiring integra-tion with models for accurately simulating stormwater runoff and sewer hydraulics,including fully dynamic unsteadyflow modeling in the sewer network.The optimization is also dynamic,with further computational stress arising from the need to repeatedly solve the optimal control problem within 5e15min time intervals as rainfall forecasts and measured levels andflows are updated in real-time.With computational time and complexity the primary limi-tation in employing the accurate models necessary for effec-tive real-time control,application of dynamic or recurrent artificial neural networks(ANN)may provide the analysis speed,generalization ability and high fault tolerance needed for effective implementation.Presented herein is an explora-tion of the potential usefulness of dynamic artificial neural networks for real-time control of combined sewer systems.A highly accurate,but computationally time consuming,opti-mal control model is utilized to provide the training data set for a recurrent ANN under a wide range of sewer inflow con-ditions.Performance of the ANN is compared with the optimal control module using validation data sets not included in the ANN training.The combined sewer system of the King County Wastewater Treatment Division,Washington,USA is chosen as a case study to demonstrate the viability of the neu-ral-optimal control model.2.Optimal control module2.1.FormulationAccording to Vanrolleghem et al.(2005),there are three basic approaches to real-time control of CSSs:volume-based RTC,pollution-based RTC and emission-based RTC. Although Rauch and Harremoe¨s(1999)show that minimiza-tion of pollution impacts is not necessarily achieved with vol-ume-based RTC,Duchesne et al.(2004)explain that the computational complexity of receiving water quality models, and the dearth of available data necessary for calibration of such models in urban areas,makes volume-based RTC the most practical approach.Therefore,reducing the occurrence and magnitude of CSOs,and thereby reducing pollution im-pacts on receiving waters,is the primary goal of the real-time control system.The primary objectives are to minimize untreated overflows while maximizing through-flows to the wastewater treatment plant for a storm event occurring over T time intervals:minimizeu;xX Tt¼1X2mþni¼mþnþ1c it u2itþX mi¼1w i s2i;Tþ1ð1Þsubject to:s tþ1¼s tþð0:5ðBðkÞtu tþBðkÞtÀ1u tÀ1Þþr tÞconvð2Þ0s tþ1s maxÀqðkÞ;hðkÞÁð3Þ0u t u maxÀqðkÞ;hðkÞÁð4Þwhere u t¼ðu1t;.;u mt;u mþ1;t;.;u mþn;t;u mþnþ1;t;.;u2mþnÞT is the vector of node discharge rates(m3/s)at the end of time interval t throughout the sewer network(initial release rates u0are assumed to be given),with m representing the number of control structures such as regulators,pump stations,weirs, orifices,etc.,in the system.It is assumed that the portion of the state vectorðs1t;.;s mtÞrepresents temporary storage accumu-lated behind these structures located in the interceptor and lat-eral or trunk sewers(m3).It is assumed that check structures are not directly located within the interceptor sewer,but rather regulators control discharges from each lateral into the inter-ceptor,as well as bypassed overflows to the receiving waters if the interceptor sewer is surcharged at that location.The interceptor sewer is divided into n sections correspond-ing to the location of each regulator controlling discharges from a lateral sewer.The portion of the state vector ðs mþ1;t;.;s mþn;tÞrepresents zero storage nodes within the in-terceptor sewer that are specified for the convenience offlow routing calculations.The portion of the control vector ðu1t;.;u mtÞrepresents controlled discharges from each regu-lator or pump station into the interceptor sewer or downstream trunk sewer;the portionðu mþ1;t;.;u mþn;tÞareflows at each section of the interceptor sewer;and the portion ðu mþnþ1;t;.;u2mþn;tÞrepresents untreated overflows from the1350S.Darsono,badie/Environmental Modelling&Software22(2007)1349e1361system at regulator stations and other control structures.A typical configuration for a regulator station is shown in Fig.1.The routing matrices B ðk Þt in Eq.(2)are current estimates at iteration k of routing coefficients calculated from a fully dy-namic sewer hydraulics model,as described subsequently in more detail.The vectors q ðk Þ;h ðk Þrepresent sewer discharges and heads,respectively,over each sewer section i and discrete time interval t as also simulated by the hydraulic model.Max-imum capacities on temporarystorage s max q ðk Þ;h ðk ÞÞÀand node discharge u max q ðk Þ;h ðk ÞÞÀare shown to be dynamic func-tions of q ðk Þ;h ðk Þsince these bounds are dependent on hydrau-lic flows and heads throughout the sewer network.These iteratively adjusted restrictions on temporary in-line storage and discharges prevent upstream surcharge conditions from occurring in the lateral or trunk sewers.Duchesne et al.(2001)claim that some surcharging should be allowed for maximum utilization of in-line storage in a combined sewer network,but this also can increase the danger of upstream flooding if inaccurate predictions of sewer inflows occur.The objective function of Eq.(1)minimizes total weighted overflows (squared)from the CSS,where the weighting coef-ficients c it can vary both spatially and temporally.That is,receiving water impacts may be more sensitive to overflows at certain locations than others.Tidal and other temporal influ-ences may also necessitate changes in the weighting coeffi-cients over time.Notice that spills are squared in the objective function,which has a number of benefits.First,min-imizing the squared spills has a smoothing effect on the solu-tion,and tends to produce more stable discharges,avoiding oscillations and surges in the sewer system.In addition,adja-cent water bodies can better absorb the polluting effects of spills if they are smoothed over time,rather than a first-flush shock of untreated spills that can intensify damage to aquatic habitat and species.The final term in the objective function P m i ¼1w i s 2i ;T þ1min-imizes residual storage in the system at the end of the opera-tional time horizon,which indirectly maximizes through-flow to the wastewater treatment plant.Weighting factors w i serve to tradeoff this objective with the primary objective of mini-mizing untreated spills.If forecasts indicate that a storm eventmay be immediately followed by another,it may be necessary to increase this weighting factor to provide sufficient capacity for the on-coming event.The constraints in Eq.(2)essentially maintain mass balance in each sewer reach,where r t is spatially distributed storm-water inflows to the CSS predicted from an urban stormwater runoff model,such as the RUNOFF module of the U.S.EPA SWMM model (Huber and Dickinson,1988).These predic-tions are assumed to be updated in real-time as the storm event progresses and new rainfall forecasts are generated.Since the discharges u t are instantaneous flow rates,they are averaged over the time interval and multiplied by a conversion factor conv to convert them to storage units per time interval.2.2.Iterative calculation of hydraulic sewer flowsThe ðm þn ÞÂð2m þn Þrouting matrices B ðk Þt in Eq.(2)account for attenuation and lagging of upstream releases to downstream nodes and system spills.The superscript (k )isan iteration index indicating that elements of B ðk Þt are updated through successive solution of a fully dynamic unsteady flow model that solves the complete Saint Venant equations throughout the sewer network.Although it is possible to di-rectly incorporate numerical approximations of the linearized Saint Venant equations as constraints in the above formulation,as proposed by Unver and Mays (1990),this results in an unwieldy,large-scale quadratic programming problem when applied to an entire sewer network over a dynamic time hori-zon.Linearizing the Saint Venant equations also removes important nonlinear terms and prevents accurate simulation of complex hydraulic conditions in the sewers,such as transi-tions between supercritical and subcritical flow regimes.A method originally proposed by Labadie (1993)suggests an iterative approach involving successive solution of the op-timal control model and the hydraulic sewer routing model (Fig.2).The optimal control model OPTCON is first executed with current approximations of the routing coefficients (i.e.,elements of matrix B ðk Þt ),as well as initial estimates of bounds on temporary storage and discharge (i.e.,Eqs.(3)and (4)).Op-timal node discharge control solutions u Ãt are then converted into gate or pump settings,and the sewer network is again sim-ulated using the complete Saint Venant equations.Based on these results,the routing coefficients used in the optimal con-trol model are updated as:f b ij g ðk þ1Þt¼ðu ðk þ1Þjt Þ=ðu ðk þ1Þit Þ,as shown in Fig.3,where u ðk þ1Þit represent flows simulated using the dynamic hydraulic routing model under the current opti-mal gate or pump settings.Routing matrix elements f b ij g ðk Þt for any iteration k are positive if node i receives outflow from node j ,or 0if the two nodes are unconnected.For spillsand downstream releases from node i ,f b ij g ðk Þt¼1.Along with routing coefficients,limits on sewer reach storage s max ðq ðk þ1Þ;h ðk þ1ÞÞand discharge limits u max ðq ðk þ1Þ;h ðk þ1ÞÞare updated from the hydraulic sewer simulation model in the next iteration to assure hydraulic feasibility of solutions from the optimal control model.Although the control problem defined by Eqs.(1)e (4)re-flects a simplified problem of volume and discharge control inu m +n +i ,tFig.1.Typical regulator station with both regulator gate and outfall gate.1351S.Darsono,badie /Environmental Modelling &Software 22(2007)1349e 1361a combined sewer network,interactive simulation using the complete Saint Venant equations allows bounds on flows through gates and regulators in the control model and maximum sewer levels to be adjusted based on levels calculated by thehydraulic simulation model that guarantee sufficient head for downstream releases.Convergence occurs when successive cal-culations of routing coefficients coincide to a desired error tol-erance.In effect,inclusion of the routing coefficients in Eq.(2)is a means of indirectly incorporating the complete Saint Venant equations into the optimal control algorithm.2.3.Solution of Saint Venant equationsThe fully dynamic unsteady flow module UNSTDY is applied to one-dimensional hydraulic routing in a combined sewer network,including flows through junctions and control structures (Chen and Chai,1991).The basic Saint Venant equations of conservation of mass and momentum are solved in UNSTDY using a fully implicit numerical scheme:v A v t þv q v x¼q [ð5Þv ðr q Þv t þv ðr qV Þv x þr gA v hv xþr gA ÀS 0ÀS f Á¼0ð6Þwhere for each sewer section,A is flow cross-sectional area;q is discharge;h is depth of flow;V is mean velocity;q [is lateral flow per unit length of the sewer section;x is longitudinal dis-tance;t is time;S 0is bed slope;S f friction slope;r is fluid mass density;and g is gravitational acceleration.Application of the fully implicit finite difference numerical scheme used in UNSTDY has the advantage of producing sta-ble solutions that do not require time step restrictions from the Courant conditions.The model includes routines for calculat-ing transitions between subcritical and supercritical flow condi-tions,with supercritical flows solved using the kinematic wave equations.The Preissmann slot technique allows evaluation of unsteady flow in a storm sewer network under submerged con-ditions,where a hypothetical slot at the top of the pipe can at-tain higher pressurized flow wave celerity,thereby allowing the same set of unsteady flow equations to be applied to surcharge flow conditions.The width of the slot in UNSTDY is assumed to be 0.1%of the maximum width of a conduit under surcharg-ing conditions.In UNSTDY ,the upstream boundary conditions are based on stormwater inflow predictions from the RUNOFF module of the U.S.EPA SWMM model (Huber and Dickinson,1988).Downstream boundary conditions can be defined as dis-charge hydrographs,stage hydrographs,stage-discharge rating curves,or storage basins.The hydraulic routing module can handle a branched sewer network using a dendritic system of junctions with up to three inflow branches and one outflow pipe.The hydraulic equations for sewer flow through a confluence junction are the continuity and energy equations (Chen and Chai,1991).Since real-time operation of urban drainage networks requires in-line or off-line storage for detaining storm flood hydrographs from up-stream areas,control devices are required to regulate storage of stormwater flow.UNSTDY allows inclusion of weirs,sluice gates,radial gates,siphons,in-line and side orifices,wet-wellFig.2.Flow chart of successive,iterative solution of optimal control modelOPTCON and hydraulic sewer model UNSTDY .1352S.Darsono,badie /Environmental Modelling &Software 22(2007)1349e 1361and dynamic head pump stations,and storage facilities in the sewer network routing.2.4.Optimization algorithmSeveral optimization algorithms have been proposed for real-time,online solution of the problem embodied in Eqs.(1)e (4),or similar formulations.These include the general-ized reduced gradient algorithm (GRG)(Duchesne et al.,2004),projected Lagrangian method (MINOS)(Pleau et al.,2005),regulator theory (LDQ control)(Marinaki et al.,1999),and genetic algorithms (Butler and Schu ¨tze,2005).Since all of these algorithms are assumed to be implemented in an online,real-time environment,the sewer hydraulics mod-eling is unduly simplified to accommodate the use of these algorithms.The optimization problem of Eqs.(1)e (4),includ-ing iterative evaluation of dynamic,unsteady sewer hydraulics using UNSTDY ,is efficiently solved using discrete time opti-mal control theory based on Pontryagin’s maximum principle (Pontryagin et al.,1962),with use of penalty functions for indirectly accommodating the state-space constraints (Eq.(3)).Details on the OPTCON algorithm can be found in Albuquerque and Labadie (1997),where the same algorithm was also applied to optimal regulation of an irrigation canal under fully dynamic,unsteady flow conditions.3.Neural network module3.1.Jordan recurrent ANN architectureThe OPTCON optimal control module for minimizing CSOs is easily solved off-line for sewer networks,but integra-tion with the RUNOFF model for watershed inflow predictions and successive execution of the sewer hydraulics model UNSTDY may exceed the clock time limitations required for real-time implementation,particularly for large-scale com-bined sewer networks.Neural networks are important methods of artificial intelligence related to computational intelligenceand learning.Several studies have shown that artificial neural networks (ANN)are an effective tool for controlling complex,nonlinear systems (Parisini and Zoppoli,1994).Adaptive control of combined sewer systems in real-time requires a re-current ANN to model dynamic operational trajectories.The Jordan architecture (Fig.4)selected for the ANN struc-ture adapts well with time-varying systems,since the main purpose of the dynamic neural control module is to compute optimal real-time gate controls based on current and previous rainfall data and previous gate control decisions:v h j ðt Þ¼X I i ¼1w h j ;i þK y i ðt ÞþX K k ¼1w h jk x k ðt À1Þþq hjð7Þz j ðt Þ¼h jv hj ðt Þ ;j ¼1;.;J ð8Þv o k ðt Þ¼X J j ¼1w o kj z j ðt Þþq okð9Þx k ðt Þ¼o k Àv o kðt ÞÁ;k ¼1;.;K ð10Þwhere I is the total number of external inputs applied to neu-rons in the input layer;K is the total number of internal inputs originating from neurons of the output layer and applied to K neurons in the input layer in the next time step;J is the total number of neurons in the hidden layer;w h ji is the synaptic weight of connection of neuron i in the input layer to neuron j in the hidden layer;w o kj is the synaptic weight of connection of neuron j in the hidden layer to neuron k in the output layer;y i ðt Þis the external input signal entering neuron i in the input layer at time t ;x k ðt Þis the output from neuron k in the output layer,serving as internal input to the input layer in the next time step;q h j is the threshold or bias unit applied to neuron j in the hidden layer;q o k is the threshold or bias unit applied to neuron k in the output layer;v h j ðt Þis the net internal activity level of neuron j in the hidden layer;v o k ðt Þis the net internal activity level of neuron k in the output layer;z j ðt Þis theoutputFig.3.Calculation of routing coefficients used in optimal control model from flows simulated by numerical hydraulic model.1353S.Darsono,badie /Environmental Modelling &Software 22(2007)1349e 1361from neuron j in the hidden layer produced from operation of activation function h jðv h jðtÞÞon net internal activity v h jðtÞfor neuron j;and o kðv o kðtÞÞis the activation function operating on net internal activity v o kðtÞfor neuron k in the output layer.The logistic function is the commonly used activation func-tion for multilayer perceptrons that guarantees output in the range0y jðtÞ1(Haykin,1994):z jðtÞ¼h jv hjðtÞ¼11þeÀv jðtÞð11Þx kðtÞ¼o k Àv okðtÞÁ¼11þeÀv o kðtÞð12ÞInternal inputs to the recurrent ANN are current,lag-1,and lag-2spatially distributed rainfall data,recognizing the likely correlation of successive rainfall inputs over time and space. To facilitate smooth,dynamic operation of gates in the system, gate-opening controls from the previous time period serve as internal inputs to the ANN.Since current period gate openings are the output of the ANN,the number of output neurons is the same as the number of gate controls in the system.3.2.Training and testing of recurrent ANNTraining of the dynamic neural control module is a super-vised learning process for determining the optimal connection weights w h ji,w o kj and bias weights q h j,q o k from the input/output training data set.The input data are rain gauge measurements for various historical storm events and the output data set are the optimal gate controls calculated off-line by the optimal control module.Training of the Jordan recurrent network follows the standard generalized delta rule(Freeman,1994)in-volving feed-forward and error back-propagation calculations. The process begins with standard normal transformation of the input e output training set data,since the activation function in the neural network can only produce outputs in the range be-tween0and1.Re-transformation of neuron output values from neurons in the output layer results in actual gate control settings.Initial weights are determined using random number generation,and a gradient-type optimization procedure adjusts the connection weights until the sum-of-squares error deviation between ANN outputs and training set outputs is minimized (Haykin,1994).Fig.4.Schematic of Jordan architecture recurrent artificial neural network. 1354S.Darsono,badie/Environmental Modelling&Software22(2007)1349e1361Optimal values of the learning parameter and momentum constant are based on experimental procedures to minimize error and maximize convergence efficiency of the training algorithm.However,training of recurrent neural networks may suffer from slow convergence to local minima and must be conducted with great care(Hassoum,1995).The learning process is embedded in an experimental procedure to evaluate the minimum square error(MSE)for determining the opti-mum number of neurons in the hidden layer.Testing the dynamic neural control module is a process of evaluating model parameters from the learning or training step and is equivalent to a validation of the model.Since testing is an evaluation of the performance of the previously estimated model parameters,the input and output data sets for estimating parameters(for training)should be different from the input and output data set for validating the parameters(for testing).4.Case study:West Point combined sewer system, Seattle,Washington,USA4.1.Description of case studyThe West Point Treatment Plant collection system of the King County Wastewater Treatment Division,Seattle,Wash-ington,USA is used for demonstrating the capabilities of the neural-optimal control algorithm.The portion of the service area of the West Point Treatment Plant that is included in this modeling study covers over26,000ha,which includes 160km of gravity sewers with diameters up to3.66m,11 pumping stations and17regulator stations(Fig.5).Although the average capacity of the West Point Treatment Plant is 5.83m3/s,the plant has been recently expanded to handle wet weather peakflow rates up to19.3m3/s.Fig.5shows the extent of the West Point combined sewer system as mod-eled in this study,but it should be noted that this configuration does not reflect recent expansions,upgrades and improve-ments to the King County wastewater system designed to sub-stantially reduce the volume and frequency of combined sewer overflows(King County,2004).Although not up-to-date,this configuration was deemed acceptable for demonstrating the viability of the neural-optimal control algorithm.Metro Seattle,which merged with King County as a single agency in1994,originally developed the CATAD Computer Augmented Treatment and Disposal system in the early 1970s,one of thefirst attempts to implement a supervisory control and data acquisition(SCADA)system for real-time regulation of in-line storage in a combined sewer system. With the main control center located at the West Point Treat-ment Plant,CATAD is designed to monitor and control pump and regulator stations,including telemetry of real-time data on water levels,gate positions,tide levels,and pump speed data (King County,2004).Recent attempts have been made to upgrade CATAD to monitor rainfall andflow conditions in the major trunk sewers and interceptors for model prediction of sewer inflows and optimal control of selected regulator sta-tion gates in real-time.Unfortunately,problems at the Interbay Pump Station and computer hardware have prevented use of the predictive control components in CATAD.4.2.RUNOFF model calibration and validationLabadie(1993)describes calibration of the RUNOFF model for predicting stormwater inflows from the Seattle area urban catchments into the combined sewer system.Model calibration was conducted by staff of the King County Depart-ment of Natural Resources,Wastewater Treatment Division (formerly Metro Seattle).The West Point service area was por-tioned into400drainage subbasins.Subbasin characteristics including average slope,overlandflow lengths,roughness coefficients,percent imperviousness,and infiltration parame-ters were evaluated in the calibration,with further validation studies comparing simulated inlet hydrographs with measured flows for storm events not included in the calibration.Ten-minute rainfall data for the stormwater modeling were collected at17sites within the Seattle City limits,along with measurements at the National Weather Service station at SeaTac Airport and Sand Point in North Seattle.Flow data for model calibration were measured at more than60 points throughout the West Point service area using transport-ableflow meters.4.3.UNSTDY hydraulic model developmentStormwater hydrographs generated from the RUNOFF model are routed into22inlet locations serving as upstream boundary conditions and lateral inflows to the combined sewer network(Fig.5).The sewer network modeled in UNSTDY is confined to only those portions with1.22m diameter pipe sizes and higher,with smaller pipe sections modeled using kinematic wave approximations.For the numerical modeling, the sewer network was divided into260sections,with distance between sections ranging from18.3m to91.4m based on desired numerical accuracy,changes in slope or existence of a weir or other control structure.Pipe and gate sizes,slopes, roughness coefficients and junction data were provided to the hydraulic model,along with rating tables for downstream boundary conditions based on the normalflow approximation. The UNSTDY hydraulic module routes inlet stormwater hydrographs through the sewer network,with dry weather flows provided as initialflow conditions.To facilitate linkage of the hydraulic model with the optimal control module,UN-STDY allows specification of optimal regulator station releases calculated from OPTCON as interior boundary conditions,and then calculating the gate openings required to produce those flows.4.4.Optimal control moduleFor this demonstration,Fig.5depicts the regulator sta-tions assumed available for simulated real-time control, with the remaining uncontrollable regulator stations modeled in UNSTDY asfixed weirs.Although the optimal control module is confined to optimization of the regulator stations1355S.Darsono,badie/Environmental Modelling&Software22(2007)1349e1361。
Abstract On the DóòòD×ó Analysis of Interacting Pushdown ùòD×ó Systems

On the Analysis of Interacting Pushdown SystemsVineet KahlonNEC Labs America, Princeton,NJ08540,USA.Aarti GuptaNEC Labs America, Princeton,NJ08540,USA.AbstractPushdown Systems(PDSs)has become an important paradigm for program analysis.Indeed,recent work has shown a deep con-nection between inter-procedural dataflow analysis for sequential programs and the model checking problem for PDSs.A natural extension of this framework to the concurrent domain hinges on the,somewhat less studied,problem of model checking Interact-ing Pushdown Systems.In this paper,we therefore focus on the model checking of Interacting Pushdown Systems synchronizing via the standard primitives-locks,rendezvous and broadcasts,for rich classes of temporal properties-both linear and branching time. We formulate new algorithms for model checking interacting PDSs for important fragments of LTL and the Mu-Calculus.Additionally, we also delineate precisely the decidability boundary for each of the standard synchronization primitives thereby settling the prob-lem.1.IntroductionIn recent years,Pushdown Systems(PDSs)has emerged as a pow-erful,unifying framework for efficiently encoding inter-procedural dataflow analysis.Given a sequential program,abstract interpreta-tion isfirst used to get afinite representation of the control part of the program while recursion is modeled using a stack.Push-down systems then provide a natural framework to model such abstractly interpreted structures.A PDS has afinite control part corresponding to the valuation of the variables of the program and a stack which provides a means to model recursion.Dataflow analysis then exploits the fact that the model checking problem for PDSs is decidable for very expressive classes of properties-both linear and branching time(cf.[1,17]).Not only has this powerful framework been useful in encoding the many different dataflow analyses but has,in many cases,led to strictly more expressive dataflow frameworks than those provided by classical inter-procedural dataflow analysis.Many variants of the basic PDS model like Weighted Pushdown System[16],Extended Weighted Pushdown System[11],etc.,have been proposed and applied to various application domains thus highlighting(i)the deep connec-tion between dataflow analysis and the model checking problem for PDSs,and(ii)the usefulness of PDSs as a natural model for program analysis.However,most of this work has focused only on the analysis of sequential programs.Analogous to the sequential case,inter-procedural dataflow analysis for concurrent multi-threaded pro-grams can be formulated as a model checking problem for inter-acting PDSs.But,there has only been limited work on the model checking of interacting PDSs.Early work focused on the model checking of PDSs interacting via pairwise rendezvous.While for a single PDS the model checking problem is efficiently decidable for very expressive logics,it was shown in[15]that even simple prop-erties like reachability become undecidable for systems with only two threads but where the threads synchronize using CCS-style pairwise rendezvous.In[10],an even stronger result was given. It was shown that the model checking problem for even pairwise reachability,and hence multi-indexed LTL formulae,is undecid-able,in general,even for systems with just two PDSs synchronizing via locks.However,the more important contribution of[10]was that the problem of deciding simple pairwise reachability for the practi-cally important paradigm of PDSs interacting via nested locks was shown to be efficiently decidable.In[9],the decidability result for PDSs synchronizing via nested locks was further extended to single-index LTL properties.These results demonstrate that there are important fragment of temporal logics and useful models of interacting PDSs for which efficient decidability results can be ob-tained.It is important that such fragments be identified for each of the standard synchronization primitives.Indeed,formulating effi-cient algorithms for model checking interacting Pushdown Systems lies at the core of scalable dataflow analysis for concurrent pro-grams.Furthermore,of fundamental importance also is the need to delineate precisely the decidability/undecidability boundary of the model checking problem for PDSs interacting via the standard syn-chronization primitives.Indeed,there is currently little work on un-derstanding exactly where the decidability/undecidability boundary of the model checking problem for interacting PDSs lies.An insight into the causes of undecidability often plays a key role in devising effective techniques to surmounting the undecidability barrier in practice.In this paper,we study the problem of model checking PDSs interacting via the standard communication primitives-locks,pair-wise and asynchronous rendezvous,and broadcasts.Locks are primitives commonly used to enforce mutual exclusion.Asyn-chronous Rendezvous and Broadcasts model,respectively,theand constructs of Java, while Pairwise Rendezvous are inspired by the CCS process alge-bra.Moreover,we also consider the practically important paradigm of PDSs communicating via nested locks.Most real-world con-current programs use locks in a nested fashion,viz.,each thread can only release the lock that it acquired last and that has not yet been released.Indeed,practical programming guidelines used by software developers often require that locks be used in a nestedfashion.In fact,in Java and C#locking is syntactically guaranteed to be nested.As part of previous work[9],it has been shown that the model checking problem is efficiently decidable for single-index LTL properties for Dual-PDS systems interacting via nested locks.How-ever,a number of interesting properties about concurrent programs, like data races,can only be expressed as double-indexed properties. In this paper,we therefore consider double-indexed LTL properties. Furthermore,most of the work on the model checking of concur-rent programs has focused on safety and linear-time properties with little work addressing the more complex branching-time properties. Hence from the branching-time spectrum,we consider Alternation-free Mu-Calculus properties.It turns out that unlike single-index LTL properties,the decid-ability scenario for double-indexed LTL properties is more inter-esting.While the model checking problem for single-index LTL properties is robustly decidable,it is not decidable,in general,for double-index LTL but only for certain fragments.Undecidability of a sub-logic of double-indexed LTL hinges on whether it is ex-pressive enough to encode the disjointness of the context-free lan-guages accepted by the PDSs in the given Multi-PDS system as a model checking problem which,in turn,depends on the tempo-ral operators allowed by the logic.This provides a natural way to characterize fragments of double-indexed LTL for which the model checking problem is decidable.We use,where,to denote the fragment comprised of for-mulae of the form,where is double-indexed LTL formula in positive normal form(where only atomic propositions are negated) built using the operators and the Boolean connec-tives and.Here“next-time’,“sometimes”,,“until”,“always”,and“infinitely-often”denote the standard tempo-ral operators and is the“existential path quantifier”.Obviously, is the full-blown double-indexed LTL.In this paper,we not only formulate efficient procedures for fragments of double-indexed LTL for which the model checking for Dual-PDS system is decidable but also delineate precisely the decidability/undecidability boundary for each of the standard syn-chronization primitives thereby settling the problem.Specifically, we show the following.The model checking problems for and,viz.,for-mulae in PNF allowing(i)only the“until”temporal opera-tor,or(ii)only the“always”and the“eventual”temporal operators are,in general,undecidable even for Dual-PDS sys-tems wherein the PDSs do not interact at all with each other.The fact that the undecidability results hold even for systems with non-interacting PDSs may seem surprising atfirst.How-ever,we note that allowing doubly-indexed properties(wherein atomic propositions are interpreted over pairs of control states of the PDSs comprising the given Dual-PDS system)allows us to explore precisely that portion of the state space of the given Dual-PDS system where the PDSs are coupled tightly enough to accept the intersection of the context-free languages accepted by them,thereby yielding undecidability.This is the key reason why the model checking problem for single-indexed LTL properties is robustly decidable for PDSs interacting via nested locks,while for doubly indexed properties it is decid-able only for very restricted fragments that do not allow this strong coupling.The above results imply that in order to get decidability for Dual-PDS systems,interacting or not,we have to restrict ourselves to either the sub-logic or the sub-logic.For these sub-logics,the decidability of the model checking problem depends on the synchronization prim-itive used by the PDSs.For PDSs interacting via pairwise rendezvous we get the sur-prising result that model checking problem is decidable for the sub-logic.In fact,we show that the decidability result extends to PDS interacting via locks,asynchronous rendezvous and broadcasts.For the other fragment,viz.,,it is already known that the model checking problem is undecid-able for both the sub-logics and(and hence for )for PDSs interacting using either non-nested locks[10]or pairwise rendezvous[15].The undecidability result forbroadcasts and asynchronous rendezvous,both of which are more expressive than pairwise rendezvous,then follows.This settles the model checking problem for all the standard syn-chronization primitives.Finally,for the practically important paradigm of PDSs interact-ing via nested locks,we show that the model checking problem is efficiently decidable for both the sub-logics and .The procedure for single-index LTL properties for PDSs syn-chronizing via nested locks,given in[9],involves reducing the model checking problem to the computation of-closures of regular sets of configurations of the given Dual-PDS system.For single-index properties,this was accomplished via a Dual Pumping Lemma,which,unfortunately,does not hold for the double-indexed case.In fact,the undecidability of the model checking problem for doubly indexed formulae shows that such a reduction cannot exist in general.Thus model checking double-indexed LTL properties requires a different approach.To get a model checking procedure for,given an au-tomaton accepting the set of configurations satisfying a formula of,wefirst formulate efficient procedures for comput-ing an automaton accepting the set of all configurations that satisfy,where is a temporal operator that can be used in a formula of.Recursively applying these procedures starting from the atomic propositions and proceeding ‘outwards’in the given formula then gives us the desired model checking algorithm.A natural question that arises is that if model check-ing is decidable then why not full-blown double-indexed LTL model checking.Indeed,using the automata theoretic approach, one can reduce the LTL model checking problem to deciding whether the formula,holds at the initial state of the product of given Dual-PDS system and the B¨u chi Automaton,,for the given LTL property.Here green characterizes thefinal states of.The key point is that given two global configurations and of a Dual-PDS system comprised of PDSs and with nested locks,the simple reach-ability problem,viz.,whether is reachable from is decidable (via the Decomposition Result of section4).However,in order to check whether has an accepting computation,we have to de-cide whether a configuration is reachable from under the B¨u chi constraints imposed by taking the product with.For instance, using a double-indexed formula of the form(“always”),we can set that constraint to be the following:every visible action of is followed immediately by same visible action of,and conversely,every visible action of is preceded by the same vis-ible action of.Now let be the initial configuration and a configuration in which both and are in theirfinal control states.Then checking for the reachability of from under the B¨u chi constraint,tantamounts to checking for the disjointness of the context free languages accepted by and-an undecidable problem.Note that for non-interacting PDSs,the above mentionedmatching condition can still be enforced but only when modelchecking for double-indexed properties,not just single-index prop-erties.On the other hand,when using rendezvous or broadcastprimitives both of which already allow the PDSs to be strong cou-pled together,even single index properties result in undecidability.Broadly speaking,we get undecidability if either the model or theproperty is expressive enough to couple the PDSs strongly.In casestrongly coupling is not possible,it turns out that the Decomposi-tion Result is a powerful tool that allows us to reduce the modelchecking problem for a Multi-PDS system to its individual PDSsrendering the problem not just decidable but efficiently so.Guided by the above observations,for model checkingwe reduce the problem to a set of simple reachability problems.Towards that end,given a formula of,we consider theequivalent problem of model checking for.Then the pos-itive normal form of is a formula built using the temporal opera-tors and,where is the“universal path quantifier”.Since is a‘simple reachability’property the problem is decidable, even though constructing an automaton accepting from theautomaton is more complicated due to the branching nature ofthe property.For the branching-time spectrum,we consider the model check-ing problem for Alternation-free Mu-Calculus formulae.For lackof space,we focus only on single-index properties.For such proper-ties,wefirst show that the model checking problem for PDSs com-municating via nested locks is efficiently decidable.Given a Multi-PDS system comprised of the PDSs,...,,and a formula,where is an alternation-fee Mu Calculus formula in-terpreted over the control states of,we start by constructing theproduct of and,the Alternating Automaton for.Eachsuch product is represented as an Alternating Pushdown System(APDS)[1]which incorporates the branching structure of the origi-nal PDS.For model checking the Multi-PDS program for,we need to compute the-closure of regular sets of global con-figurations of the system comprised of all the APDSs.The main complexity here lies in the fact that we have to reasonabout lock interaction along all paths of tree-like models of APDSseach having potentially infinitely many states.This complexity is overcome by our contribution showing howto decompose the computation of the-closure of a regular setof configurations of a Dual-PDS system synchronizing vianested locks to that of its constituent PDSs.This decompositionallows us to avoid the state explosion problem.To achieve the de-composition,we leverage the new concept of Lock-Constrained Al-ternating Multi-Automata Pairs(LAMAPs)which is used to captureregular sets of configurations of a given Multi-PDS system withnested locks.An LAMAP accepting a regular set of configura-tions of a Dual-PDS system comprised of PDSs and isa pair,where is an Alternating Multi-Automata (AMA)(see[1])accepting the regular set of local configurations of APDS corresponding to thread occurring in the global con-figurations of in.The lock interaction among threads is encoded in the acceptancecriterion for an LAMAP whichfilters out those pairs of local con-figurations of and which are not simultaneously reachabledue to lock interaction.Indeed,for a pair of tree-like modelsand for and in the individual APDS and,respec-tively,to act as a witness for in the Dual-PDS system ,they need to be reconcilable with respect to each other.Rec-oncilability means that for each path in there must exist a path in such that the local computations of and corre-sponding to and,respectively,can be executed in an interleaved fashion in,and vice versa.For two individual paths and reconcilability can be decided by tracking patterns of lock acqui-sition along and.To check reconcilability of the trees and,however,we need to track lock acquisition patterns along allpaths of in APDS.A key difficulty here is that since thedepth of the tree could be unbounded,the number of local pathsof in could be unbounded forcing us to potentially track an unbounded number of acquisition lock acquisition patterns.How-ever,the crucial observation is that since the number of locks inthe Dual-PDS system isfixed,so is the number of all possibleacquisition patterns.An important consequence is that instead ofstoring the lock acquisition patterns for each path of tree,weneed only store the different patterns encountered along all pathsof the tree.This ensures that the set of patterns that need be trackedisfinite and bounded which can therefore be carried out as part ofthe control state of PDS.Decomposition is then achieved byshowing that given an LAMAP,if is an AMA accepting the-closure of the configurations of the individualthread accepted by,then,the LAMAP ac-cepts the-closure of the regular set of configurations of theDual-PDS system accepted by.Thus,broadly speaking,thedecomposition results from maintaining the local configurations ofthe constituent PDSs separately as AMAs and computing the-closures on these AMAs individually for each PDS for which exist-ing efficient techniques can be leveraged.This yields decidabilityfor PDSs interacting via nested locks.For PDSs communicating viarendezvous and broadcasts,we show the decidability does not holdfor the full-blown single-indexed Alternation-free Mu-Calculus butonly for certain fragments.The rest of the paper is organized as follows.We begin by intro-ducing the system model in section2.The new decision procedures for model checking double-indexed and prop-erties for PDSs synchronizing via nested locks are formulated in section5and6,respectively.The procedures for for PDSs interacting via rendezvous and broadcasts are given in section7.In section8,we give the undecidability results for and. The model checking procedure for single-index Alternation free Mu-Calculus are given in section9and we conclude with some comments in section10.2.System ModelIn this paper,we consider multi-threaded programs wherein threads synchronize using the standard primitives-locks,pairwise ren-dezvous,asynchronous rendezvous and broadcasts.Each thread is modeled as a Pushdown System(PDS)[1].A PDS has afinite control part corresponding to the valuation of the variables of the thread it represents and a stack which models recursion.Formally, a PDS is afive-tuple,where is afinite set of control locations,Act is afinite set of actions,is afinite stack alphabet,and is afinite set of transition rules.If then we write.A configuration of is a pair,where denotes the control location and the stack content. We call the initial configuration of.The set of all configura-tions of is denoted by.For each action,we define a relation as follows:if,thenfor every.Let be a multi-PDS system comprised of the PDSs,...,, where.In addition to,we assume that each has special actions symbols labeling transitions imple-menting synchronization primitives.These synchronizing action symbols are shared commonly across all PDSs.In this paper,we consider the following standard primitives:Locks:Locks are used to enforce mutual exclusion.Transitions acquiring and releasing lock are labeled with and ,respectively.Rendezvous(Wait-Notify):We consider two notions of ren-dezvous:CCS-style Pairwise Rendezvous and the more expres-sive Asynchronous Rendezvous motivated by the and primitives of Java.Pairwise send and receive ren-dezvous are labeled with and,respectively.Ifand are pairwise send and receive transitions ofand,respectively,then for the rendezvous to be enabled both and have to simultaneously be in local control states and.In that case both the send and receive transitions are fired synchronously in one execution step.If is in butis not in then cannot execute the send transition,and vice versa.Asynchronous Rendezvous send and receive transitions, on the other hand,are labeled with and,respectively.The difference between pairwise rendezvous and asynchronous rendezvous,is that while in the former case the send transition is blocking,in the latter it is non-blocking.Thus a transition of the form can be executed irrespective of whether a matching receiver of the form is currently enabled or not,but the receive cannot.Broadcasts(Notify-All):Broadcast send and receive rendezvous, motivated by the and primitives of Java, are labeled with and,respectively.If is a broadcast send transition and,...,are the matching broadcast receives,then the receive transitions block pending the enabling of the send transition.The send transi-tions,on the other hand,is non-blocking and can always be executed and its execution is carried out synchronously with all the currently enabled receive transitions labeled with.A concurrent program with PDSs and locksis formally defined as a tuple of the form=,where for each,is a pushdown system(thread),and for each,is the possible set of values that lock can be assigned.A global configuration of is a tuple where are,respectively,the configurations of PDSsand the values of the locks.If no thread holds lock in configuration,then,else is the thread currently holding it.The initial global configuration of is, where is the initial configuration of PDS.Thus all locks are free to start with.We extend the relation to global global configurations of in the usual way.The reachability relation is the reflexive and transitive clo-sure of the successor relation defined above.A sequence of global configurations of is a computation if is the initial global configuration of and for each,, where either for some,,or for some,or or pairwise rendezvous send or receive ,or asynchronous rendezvous send or receive,or broadcast send or receive.Given a thread and a reachable global configurationof,we use Lock-Set to denote the set of locks held by in,viz.,the set.Also,given a thread and a reachable global configurationof,the projection of onto,denoted by,is defined to be the configuration of the concurrent program comprised solely of the thread,where if and, otherwise(locks not held by are freed).Relative Expressive Power of Synchronization Primitives.In proving the decidability results,we will exploit the following ex-pressiveness relations:Pairwise Rendezvous Asynchronous Ren-dezvous Broadcasts,where stand for the relation can be simu-lated by(see[7]for details).LocksFigure1.Nested Lock Access.Additionally,we also consider the practi-cally important case of PDSs with nested access to locks.Indeed, in practice,a large fraction of concurrent programs can either be modeled as threads communicating solely using locks or can be reduced to such systems by applying standard abstract interpreta-tion techniques or by exploiting separation of data from control. Moreover,standard programming practice guidelines typically rec-ommend that programs use locks in a nested fashion.In fact,in languages like Java and C#locks are guaranteed to be nested.We say that a concurrent program accesses locks in a nested fashion iff along each computation of the program a thread can only release the last lock that it acquired along that computation and that has not yet been released.As an example infigure1,the thread comprised of procedures and accesses locks and in a nested fashion whereas the thread comprised of proceduresreleases lock before lock even though lock was the last one to be acquired.3.Model Checking Linear Time PropertiesWe start by formulating efficient procedures for fragments of multi-indexed Linear Temporal Logic for which the model checking problem for Dual-PDS systems is decidable.Furthermore,we delineate precisely the decidability/undecidability boundary for the problem for each of the standard synchronization primitives thereby completely settling it.Correctness Properties.The problem of model checking Dual-PDS systems for the full-blown single-index LTL was shown to be efficiently decidable in[9].However,a lot of interesting properties like the presence of data races can only be expressed as double-indexed linear-time properties.In this paper,we therefore consider double-indexed Linear Temporal Logic(LTL)formulae.Conven-tionally,for a given LTL formula if and only if is satisfied along all paths starting at the initial state ing path quantifiers,we may write this as.Equivalently,we can model check for the dual property.Fur-thermore,we can assume that is in positive normal form(PNF), viz.,the negations are pushed inwards as far as possible using De-Morgan’s Laws:,, ,.For Dual-PDS systems,it turns out that the model checking problem is not decidable for the full-blown double-indexed LTL but only for certain fragments.Decidability hinges on the set of temporal operators that are allowed in the given property which, in turn,provides a natural way to characterize such fragments.We use,where,to denote the fragment of double-indexed LTL comprised of formulae in positive normal form(where only atomic propositions are negated)built using the operators and the Boolean connectives(a)(b)Figure3.Forward vs.Backward Acquisition HistoryThe key point is that the simultaneous reachability of two control locations of and depends not merely on the locksets held at these locations but also on patterns of lock acquisition along the computation paths of leading to these control locations.These patterns are captured using the notions of backward and forward acquisition histories.Indeed,if executesfirst it acquires and does not release it along any path leading to.This prevents from acquiring which it requires in order to transit from to.Similarly if executesfirst,it acquires thereby preventing from transiting from to which requires it to acquire and release lock.This creates an unresolvable cyclic dependency.These dependencies can be formally captured using the notions of backward and forward acquisition histories.Definition(Forward Acquisition History)For a lock held byat a control location,the forward acquisition history of along a local computation of leading from to,denoted by,is the set of locks that have been acquired(and possibly released)by since the last acquisition of by in traversing forward along from to.Observe that along any local computations and of and leading to control locations and,respectively,and.Also, along any local computations and of and leading to control locations and,respectively,and.The reason does not hold but does is because of the existence of the cyclic dependency that andwhereas no such dependency exists for the second case.Definition(Backward Acquisition History).For a lock held by at a control location,the backward acquisition history of along a local computation of leading from to, denoted by,is the set of locks that were released (and possibly acquired)by since the last release of by in traversing backwards along from to.The concepts of backward and forward acquisition histories are used to decide whether given two global configurations and of,whether is reachable from.The notion of forward acquisition history is used in the case where no locks are held in and that of backward acquisition history in the case where no locks are held in.This is illustrated infigure3where we want to decide whether is backward reachable from.First,we assume that all locks are free in(case(i)infigure3).In that case,we track the of each lock.In our example,lock,initially held at,isfirst released at.Then all locks released before thefirst release of belongs to the of.Thus,belongs to the of but does not.On other hand,if in all locks are free(case(ii)in figure4),then we track the of each lock.If a lock held at is last acquired at then all locks acquired since the last acquisition of belong to the of.Thus in our example,belongs to the forward acquisition history of but does not.。
未来我们会更好英语作文

未来我们会更好英语作文Title: "Towards a Brighter Future: An Optimistic Outlook on Progress"In the course of human history, there have been countless challenges and obstacles that humanity has faced. From wars and conflicts to pandemics and natural disasters, our journey has been marked by trials and tribulations. However, amidst the chaos and uncertainty, there has always been one constant: our resilience and ability to adapt and overcome.As we stand on the threshold of the future, it is natural to wonder what lies ahead. Will we continue to grapple with the same issues that have plagued us for centuries, or are we on the brink of a new era of progress and prosperity? While the answer to this question remains uncertain, there are reasons to be optimistic about the future.One of the key factors driving optimism about thefuture is the rapid pace of technological advancement. In recent decades, we have witnessed unprecedented breakthroughs in fields such as artificial intelligence, biotechnology, and renewable energy. These advancementshave the potential to revolutionize our world, making life easier, healthier, and more sustainable for all.Take, for example, the field of artificial intelligence. In the past, AI was seen as little more than a sciencefiction fantasy. However, recent advancements in machine learning and neural networks have made AI a reality, with applications ranging from virtual assistants to autonomous vehicles. In the years to come, AI has the potential to revolutionize industries ranging from healthcare to transportation, improving efficiency and enhancing our quality of life.Similarly, biotechnology holds tremendous promise for the future. Recent breakthroughs in gene editing technologies such as CRISPR have opened up newpossibilities for treating and curing diseases, potentiallyeliminating conditions that have plagued humanity for centuries. In addition to healthcare, biotechnology also has the potential to revolutionize agriculture, enabling us to feed a growing global population while minimizing the environmental impact of farming.Another reason for optimism about the future is the growing global awareness of the need for sustainability and environmental conservation. In recent years, there has been a groundswell of support for initiatives aimed at combating climate change, protecting endangered species, and preserving natural habitats. From the Paris Agreement to the rise of the electric vehicle market, there are signs that the world is waking up to the urgent need to address environmental issues before it's too late.Furthermore, the increasing interconnectedness of the world through technology and globalization has thepotential to foster greater cooperation and understanding among nations. While conflicts and tensions still exist, the internet and social media have made it easier than ever for people from different cultures and backgrounds toconnect and communicate with one another. As barriers to communication continue to fall, there is hope that we can overcome the prejudices and misunderstandings that have divided us in the past.Of course, it would be naive to ignore the challenges and obstacles that still lie ahead. Climate change, geopolitical tensions, and socioeconomic inequality arejust a few of the issues that we will need to confront inthe years to come. However, by harnessing the power of technology, fostering greater global cooperation, and remaining committed to the principles of sustainability and social justice, there is reason to believe that we can overcome these challenges and build a better future for all.In conclusion, while the future may be uncertain, there are reasons to be optimistic about what lies ahead. Fromthe rapid pace of technological advancement to the growing global awareness of the need for sustainability and environmental conservation, there are signs that we are on the brink of a new era of progress and prosperity. By working together and remaining committed to building abrighter future, we can overcome the challenges that lie ahead and create a world that is more peaceful, prosperous, and sustainable for generations to come.。
有关现值汉密尔顿函数的注解

Part 3. The Essentials of Dynamic OptimisationIn macroeconomics the majority of problems involve optimisation over time. Typically a representative agent chooses optimal magnitudes of choice variables from an initial time until infinitely far into the future. There are a number of methods to solve these problems. In discrete time the problem can often be solved using a Lagrangean function. However in other cases it becomes necessary to use the more sophisticated techniques of Optimal Control Theory or Dynamic Programming . This handout provides an introduction to optimal control theory.Special Aspects of Optimisation over Time∙ Stock - Flow variable relationship.All dynamic problems have a stock-flow structure. Mathematically the flow variables are referred to as control variables and the stock variables as state variables. Not surprisingly the control variables are used to affect (or steer) the state variables. For example in any one period the amount of investment and the amount of money growth are flow variables that affect the stock of output and the level of prices which are state variables.∙ The objective function is additively seperable. This assumption makes the problem analytically tractable. In essence it allows us to separate the d ynamic problem into a sequence of separate (in the objective function) one period optimisation problems. Don't be confused, the optimisation problems are not separate because of the stock-flow relationships, but the elements of the objective function are. To be more precise the objective function is expressed as a sum of functions (i.e. integral or sigma form) each of which depends only on the variables in that period. For example utility in a given period is independent of utility in the previous period.1. Lagrangean TechniqueWe can apply the Lagrangean technique in the usual way.Notationt y = State variable(s) =t μControl variable(s)The control and state variables are related according to some dynamic equation,()t y f y y t t t t ,,1μ=-+ (1)Choosing t μ allows us to alter the change in t y . If the above is a production function we choose =t μ investment to alter t t y y -+1 the change in output over the period. Why does time enter on its own? This would represent the trend growth rate of output.We might also have constraints that apply in each single period such as,()0,,≤t y G t t μ(2)The objective function in discrete time is of the form,()∑=Tt ttt y F 0,,μ(3)The first order conditions with respect to t y are,1. Optimal Control TheorySuppose that our objective is maximise the discounted utility from the use of an exhaustible resource over a given time interval. In order to optimise we would have to choose the optimal rate of extraction. That is we would solve the following problem,()()dt e E S U Max t TEρ-⎰0subject to,()t E dtdS-= )0(S S =()free T S =Where ()t S denotes the stock of a raw material and ()t E the rate of extraction. By choosing the optimal rate of extraction we can choose the optimal stock of oil at each period of time and so maximise utility. The rate of extraction is called the control variable and the stock of the raw material the state variable. By finding the optimal path for the control variable we can find the optimal path for the state variable. This is how optimal control theory works.The relationship between the stock and the extraction rate is defined by a differential equation (otherwise it would not be a dynamic problem). This differential equation is called the equation of motion . The last two are conditions are boundary conditions. The first tells us the current stock, the last tells us we are free to choose the stock at the end of the period. If utility is always increased by using the raw material this must be zero. Notice that the time period is fixed. This is called a fixed terminal time problem.The Maximum PrincipleIn general our prototype problem is to solve,()dt u y t F V Max Tu⎰=0,,()u y t f ty,,=∂∂ ()00y y =To find the first order conditions that define the extreme values we apply a set of condition known as the maximum principle.Step 1. Form the Hamiltonian function defined as,()()()()u y t f t u y t F u y t H ,,,,,,,λλ+=Step 2. Find,),,,(λu y t H Max uOr if as is usual you are looking for an interior solution, apply the weaker condition,0),,,(=∂∂uu y t H λAlong with,()∙=∂∂y u y t H λλ,,,()∙=∂∂λλy u y t H ,,,()0=T λStep 3. Analyse these conditions.Heuristic Proof of the Maximum PrincipleIn this section we can derive the maximum principle , a set of first order conditions that characterise extreme values of the problem under consideration.The basic problem is defined by,()dt u y t F V Max Tu⎰=0,,()u y t f ty,,=∂∂()00y y =To derive the maximum principle we use attempt to solve the problem using the 'Calculus of Variations'. Essentially the approach is as follows. The dynamic problem is to find the optimal time path for ()t y , although that we can use ()t u to steer ()t y . It ought to be obvious that,()()0=∂∂t u t VWill not do. This simply finds the best choice in any one period without regard to any future periods. Think of the trade off between consumption and saving. We need to choose the paths of the control (state) variable that gives us the highest value of the integral subject to the constraints. So we need to optimise in every time period, given the linkages across periods and the constraints. The Calculus of Variations is a way to transform this into a static optimisation problem.To do this let ()*t u denote the optimal path of the control variable and consider each possible path as variations about the optimal path.()()()t P t u t u ε+=*(3)In this case ε is a small number (the maths sense) and ()t P is a perturbing curve. It simply means all paths can be written as variations about the optimal path. Since we can write the control path this way we can also (must) write the path of the state variable and boundary points in the same way.()()()t q t y t y ε+=*(4)T T T ∆+=*ε(5)T T T y y y ∆+=*ε(6)The trick is that all of the possible choice variables that define the integral path are now functions of .ε As ε varies we can vary the whole path including the endpoints so this trick essentially allows us to solve the dynamic problem as a function of ε as a static problem. That is to find the optimum (extreme value) path we choose the value of ε that satisfies,0=∂∂εV(7) given (3) to (6).Since every variable has been written as a function of ε, (7) is the only necessary condition for an optimum that we need. When this condition is applied it yields the various conditions that are referred to as the maximum principle .In order to show this we first rewrite the problem in a way that allows us to include the Hamiltonian function,()()()dt y u y t f t u y t F V Max Tu ⎪⎪⎭⎫ ⎝⎛-+=∙⎰,,,, 0λWe can do this because the term inside the brackets is always zero provided the equation of motion is satisfied. Alternatively as,()()dt y t u y t H V Max Tu∙-=⎰λ0,,(1)Integrating (by parts)1the second term in the integral we obtain,()()()()()T T u y T y dt t y t u y t H V Max λλλ-+⎭⎬⎫⎩⎨⎧+=⎰∙000,,(2)Now we apply the necessary condition (7) given (3) to (6).Recall that to differentiate an Integral by a Parameter we use Leibniz's rule, (page 9). After simplification this yields,()()()()[]()0,,,0=∆-∆+⎭⎬⎫⎩⎨⎧∂∂+⎥⎦⎤⎢⎣⎡+∂∂=∂∂=∙⎰T T t T y T T u y t H dt t p u H t q y H V λλλεε (3)The 3 components of this integral provide the conditions defining the optimum. In particular,()()()⎰=⎭⎬⎫⎩⎨⎧∂∂+⎥⎦⎤⎢⎣⎡+∂∂∙ελT dt t p u Ht q y H 00requires that,∙-=∂∂λyHand 0=∂∂u HWhich is a key part of the maximum principle.The Transversality Condition1Just letdt y y dt y T TT⎰⎰∙∙-=0λλλTo derive the transversality condition we have to analyse the two terms,()[]()0,,,=∆-∆=T Tt y T T u y t H λλFor out prototype problem (fixed terminal time) we must have .0=∆T Therefore the transversality condition is simply that,()0=T λThe first two conditions always apply for 'interior' solutions but the transversality condition has to be defined by the problem at hand. For more on this see Chiang pages 181-184.The Current Value HamiltonianIt is very common in economics to encounter problems in which the objective function includes the following function t e ρ-. It is usually easier to solve these problems using the current value Hamiltonian. For example an optimal consumption problem may have an objective function looking something like,()()dt et C U tρ-∞⎰0Where ρ represents the rate of time discount. In general the Hamiltonian for such problems will be of the form,()()()()u y t f t e u y t F u y t H t ,,,,,,,λλρ+=-The current value Hamiltonian is defined by,()()()u y t f t m u y t F H CV ,,,,+=(1)Where ()()t e t t m ρλ-=. The advantage of the current value Hamiltonian is that the system defined by the first order equations is usually easier to solve. In addition to (1) an alternative is to write,()()()t t CV e u y t f t m e u y t F H ρρ--+=,,,,(2)The Maximum ConditionsWith regard to (2) the first two conditions are unchanged. That is,μμ∂∂=∂∂CVH H and λλ∂∂=∂∂CV H H (3)The third condition is also essentially the same since,∙=∂∂=∂∂λyH y H CVHowever it is usual to write this in terms of ∙m . Since,t t me e m ρρρλ--∙∙-=We can write the third condition as,m yH m CVρ+∂∂-=∙(4)The endpoint can similarly be stated in terms of m since t e m ρλ= the conditio n ()0=T λmeans that,()()0==T e T T m ρλOr,()0=-T e T m ρ(5)Ramsey model of optimal savingIn the macroeconomics class you have the following problem,Choose consumption to maximise,()()dt t c u e B U t t ⎰∞=-=0βWhere ()g θηρβ---=1 subject to the following constraint,()()()()()()t k g t c t k f t k +--=∙ηIn this example ()t c u =, ()t k y =. The Hamiltonian is,()()()()()()()[]g n t c t k f t t C u Be H t +--+=-λβThe basic conditions give us,()()()()0=-'=∂∂-t t c u Be t c Ht λβ (1)()()()()()[]()t g n t k f t t k H λλ =+-'-=∂∂ (2)Plus,()()()()()()t k g t c t k f t k+--=∙η(3)Now we must solve these. Differentiate the right-hand side of (1) with respect to time.This gives you ()t λwhich can then be eliminated from (2). The combined condition can then be rewritten as,()()()()()()[]g t r t c u t c u t cθρ--'''-=This is the Euler equation. If you assume the instantaneous utility function is CRRA as in class and you calculate the derivatives you should get the same expression.。
强化学习PPT

Inputs
RL System
Outputs (“actions”)
Reinforcement Learning – Learn from interaction
learn from its own experience, and the objective is to get as much reward as possible. The learner is not told which actions to take, but instead must discover which actions yield the most reward by trying them.
V
(s)
Vk 1(s)
(s,a)
Pa ss
Rsas
Vk
(s)
a
s
Vk
1(s)
max a
s
Pa ss
Rsas
Vk
(s)
Policy Iteration Value Iteration
动态规划方法
V (st ) E rt1 V (st 1s)t
rt 1 st 1
T
TT
T
TT
描述一个环境(问题)
Accessible vs. inaccessible Deterministic vs. non-deterministic Episodic vs. non-episodic Static vs. dynamic Discrete vs. continuous
The most complex general class of environments are inaccessible, nondeterministic, non-episodic, dynamic, and continuous.
如何赶上技术进步英语作文

如何赶上技术进步英语作文Catching Up with Technological Advances.In today's rapidly evolving world, technological progress is shaping our lives in profound and unprecedented ways. It's not just about the latest gadgets or software updates; it's about how these advancements are altering the way we work, learn, communicate, and even think. Keeping up with this relentless pace can be challenging, but it's not impossible. Here are some key strategies to help you stay relevant and ahead of the technological curve.1. Embrace a Lifelong Learning Mindset.The foundation of staying ahead of technology is a continuous quest for knowledge. This means being open to new ideas, concepts, and skills. Embrace the mindset that learning is a lifelong journey, not just something you doin school. Engage in regular professional development courses, read industry-related books and articles, andparticipate in online forums and communities where experts share their insights.2. Stay Connected and Engaged.Staying connected to the technological pulse requires more than just following trends. It's about understanding the underlying principles and potential applications of new technologies. Subscribe to technology news sources, follow industry leaders on social media, and attend conferences and workshops to stay abreast of the latest developments.3. Invest in Yourself.Investing in your own skill development is crucial. Whether it's through formal education, online courses, or self-directed learning, make sure you're constantly upgrading your toolbox. Prioritize skills that are in high demand or have the potential to transform your field. For example, data analytics, artificial intelligence, and cybersecurity are areas that are rapidly growing and offer excellent career opportunities.4. Practice Technical Fluency.Being technically fluent doesn't mean you have to be an expert in every technology. It means being able to understand, evaluate, and apply technology effectively. This requires a basic understanding of technologyprinciples and the ability to navigate different tools and platforms. Embrace the opportunity to learn new software, programming languages, or hardware devices that can enhance your work or personal life.5. Adapt to Change.The pace of technological change is accelerating, and it's important to cultivate a mindset of adaptability. Be prepared to pivot when necessary, embrace new workflows, and experiment with different approaches. Don't be afraid to fail; often, failure is the stepping stone to success.6. Collaborate and Network.Technology is often a team sport, and collaboration can be a powerful tool. Connect with other professionals, share ideas, and work together to solve problems. Join professional organizations, participate in meet-ups and conferences, and build a network of peers who can provide support, feedback, and new perspectives.7. Leverage Technology to Enhance Your Productivity.One of the best ways to stay ahead of the technological curve is to use technology itself to enhance your productivity. Utilize tools like project management software, automation platforms, and artificial intelligence assistants to streamline your workflow and focus on more strategic tasks.8. Maintain a Balanced Lifestyle.While staying up-to-date with technology is important, it's crucial not to牺牲 your personal life. Make time for hobbies, relaxation, and social activities to maintain a healthy work-life balance. This will help you avoid burnoutand stay refreshed, creative, and engaged.In conclusion, keeping up with technological progress requires a commitment to continuous learning, adaptability, and collaboration. By investing in yourself, staying connected, and leveraging technology to enhance your productivity, you can stay ahead of the curve and take advantage of the opportunities presented by the rapidly evolving technological landscape.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
JOURNAL OF ELECTRONIC TESTING: Theory and Applications, 4, 285-290 (1993) ©1993 Kluwer Academic Publishers, Boston. Manufactured in The Netherlands. The Optimistic Update Theorem for Path Delay Testing in Sequential Circuits SOUMITRA BOSE, PRATHIMA AGRAWAL, AND VISHWANI D. AGRAWALAT&T Bell Laboratories, Murray Hill, NJ 07974Received February 5, 1993. Revised April 5, 1993.Editor: K. SalujaAbstract. For sequential circuit path delay testing, we propose a new update rule for state variables whereby flip-flops are updated with their correct values provided they are destinations of at least one robustly activated path delay fault. Existing algorithms in the literature, for robust fault simulation and test generation, assign unknown values to off-path latches that have non-steady signals at their inputs in the previous vector. Such procedures are pessimistic and predict low fault coverages. They also have an adverse effect on the execution time of fault simulation especially if the circuit has a large number of active paths. The proposed update rule avoids these problems and yet guarantees robustness.Keywords: Fault simulation, path delay faults, test generation, timing analysis.1. IntroductionA robust delay test for a path in a combinational circuit consists of propagating a transition along the path and ensuring that the off-path sensitizing signals do not cause the path destination to change state before the transition has traversed the entire path. The validity of such a test is guaranteed irrespective of other delays in the circuit, and this condition is referred to as combinational robustness. In sequential circuits, several latches may be path destinations for many faults activated simultaneously by the same vector. Consider the fault effect propagation in the subsequent vector of one particular fault, referred to as the primary fault. For subsequent robust detection of the primary fault, it is necessary that none of the other simultaneously activated secondary faults mask the primary fault effect propagation. This criterion is often referred to as sequential robustness.Consider a primary path delay fault that gets activated by some vector of an input sequence. We will refer to that vector as the activation vector for the primary fault. For the fault effect to propagate from the destination latch in the next vector, some other latch might be required to have a specified value. However, that latch may be the destination of another secondary path fault also activated by the activation vector. One might desire that the propagation of the effect of the primary fault is independent of the presence of the secondary fault. In such situations, existing algorithms assign unknown values to latches having non-steady signals at their inputs [1], [2]. There are adverse consequences if such a pessimistic update rule is used. Other than predicting low fault coverages, a separate analysis of the fault effect propagation may be necessary for every active fault. In fault simulation, if the number of active faults is large, the entire simulation will be slow. In this article, we present an alternative update rule that can alleviate these problems.2. BackgroundTo represent the signal state in two consecutive vectors, we use a 7-valued algebra consisting of the 6-valued system of Smith [3] and an additonal logic value, X, representing unknown. Smith's logic is suitable to reason about combinational circuits with fully specified inputs. The additonal value, X, is necessary for sequential circuits and combinational circuits with unspecified inputs.Smith's algebra consists of 6 values: p0, p1, s0, s1, -0, -1 and can be thought of as consisting of tuples (pds, fv), where pds is path detectability status and fv is the final value. These logic values describe the timing behavior of the circuit during the interval,286 Bose, Agrawal, and Agrawaldenoted by <V n, V n+1>, between any two consecutivevectors V n and V n+1. During any such interval, a signal may undergo hazards (static or dynamic), but will always settle down to a definite final value (for combinational circuits with fully specified inputs) and this value, which may be 0 or 1, represents the second component of the tuple.For a signal g, pds(g) = s for the interval < V n, V n+l > if the signal remains stable during the entire interval. It is set to p if there exists at least one path along which a transition propagates and the signal g is guaranteed not to change until the transition along that path has reached g. More than one active path terminating at g may exist, in which case, all transitions along these paths must reach g before g can change. The time of transition will then depend upon the slowest of these paths. Note that a pds value of p does not necessarily mean that a complete path from input to output exists in the combinational circuit. However, it does guarantee that at least one partial path from an input to that signal exists. The pds component is set to - if neither s nor p is true. Thus a logic value of -1 represents either a static-1 hazard or a non-robustly propagating rising transition (as at the output of an OR gate with multiple rising transitions at inputs).The unknown value, X, represents those signals whose final values are not known. For such signals, the pds components are not relevant and, semantically, X means the final value can be either 0 or 1. The evaluation tables for this 7-valued logic, as shown in Figure 1, are a direct extension of the 6-valued logic of Smith [3].As an example, we consider the sequential circuit shown in Figure 2. It has two latches, LI and L2, one input I, six gates Gl, ..., G6, and one primary output G6. The circuit is simulated for the following 4-vector input sequence <V1, V2, V3, V4> = 1000. The latches are assumed to have a reset state and are initialized to 0. The first vector, I = 1, is applied for sufficiently long interval so that all signals stabilize to their steady states. The subsequent three vectors are then applied at the rated clock interval. We will focus our attention on transitions propagating along the following paths:F1: I, G1, G2F2: L1,G3, G4F3: L1, G3, G2F4: L2, G5, G6F5: L1,G6AND s0 P0 -0 s1 pl -1Xs0 s0 sO s0 s0 s0 s0 s0P0 s0 -0 -0 p0 -0 -0 -0-0 s0 -0 -0 -0 -0 -0 -0s1 s0 p0 -0 s1 pl -1 Xp1 s0 -0 -0 pl pl pl X-1 s0 -0 -0 -1 pl -1 XX s0 -0 -0 X X X XOR s0 p o-0 s1 p1 -1Xs0 s0 p o-0 s1 p1 -1Xp0 p0 p0 p0 s1 -1-1X-0 -0 p0 -0 s1 -1-1Xs1 s1 s1 s1 s1 s1 s1 s1p1 p1 -1 -1 s1 -1-1-1-1 -1 -1 -1 s1 -1-1-1X X X X s1 -1-1XFig. 1. Evaluation tables for 7-valued logic.Figures 2(a) and 2(b) show the state of signals during two vector intervals: <V1, V2> and <V2, V3>. The latches are marked with fault identifiers corresponding to those paths along which transitions propagate robustly. These faults correspond to paths along which all signals have their pds component set to p. For instance, Figure 2(a) shows latch L1 marked with F1to indicate that this latch will clock in a faulty value if path I, G1 and G2 is slow. Figure 2(b) has L1 marked with F1and F3 while latch L2 is marked with two faults: F l and F2. The reason for marking latch L1 with two faults is as follows: if the rising transition at the input of L1 (Figure 2(a)) fails to arrive on time, the falling transition at the input of L1 in the following vector will also fail to arrive. Therefore, the fault F l is propagated to latch L1 in the following vector. However, if L1 does clock in the correct value, but the path L1, G3 and G2 is slow, then also L1 will latch an incorrect value. Thus, both F l and F3 are in the fault list at L1.Consider simulation of the vector pair <V3, V4>. Propagation of the fault effect of F3 from latch L1The Optimistic Update Theorem for Path Delay Testing in Sequential Circuits 287(a) Simulation of vector pair <V1, V2>(b) Simulation of vector pair <V2, V3>Fig. 2. Signal values in first 3 vectors.depends on the logic state in L2which in turn, depends on faults F1and F2. Existing algorithms [1], [2] assign an unknown value, X, to latches like L2while considering the propagation of fault effects from latches like L1. This is shown in Figure 3(a). Assigning an X to L2 for the fault F3 drives the primary output to X. Hence F3 is not detected. Now consider the fault effect of F2from latch L2. Latch L1 is assigned a value X, which drives the primary output G6to X. This is shown in Figure 3(b). Hence, fault F2is also undetected. Now consider fault F l, which causes incorrect values in both latches. It is easy to show that only F1 is declared detectable by the given input sequence. In reality, it can be easily verified that the presence of any combination of these five faults will cause the circuit to fail. This example demonstrates that updating latches with unknown values causes a low (pessimistic) fault coverage prediction.3. Optimistic Update of LatchesConsider an update rule in which all latches with non-steady signals at their inputs are updated with their fault-free circuit values, provided they are destinations of at least one robustly activated path. This condition can be verified easily (in constant time) by ensuring that the pds component for the latch input signal was p in the previous vector. Latches with static hazards and dynamic hazards due to non-robust propagation are updated with an unknown value (X). This rule can be stated as follows:Optimistic Update Rule: For any latch whose input is not steady at either 0 or 1, assume fault free value in the subsequent vector, provided the latch is the path destination of at least one robustly activated fault.We will apply the optimistic update rule to the example of Section 2. Figure 4 shows the signal values for the vector pair <V3, V4>. Note that using optimistic values for both latches, all five path delay faults are found detectable. The fault effects for F1and F2 at latch L2 are propagated robustly along the path G5and G6. In addition, the path consisting of L2, G5and G6(fault F4) is also sensitized. Fault effect of F3 is propagated through G6to the output. Hence all five faults are detected.The Optimistic Update Theorem for Path Delay Testing in Sequential Circuits 289update rule in all prior vectors. The signal value at the path destination at the end of the activation vector may be incorrect due to two possible reasons. Either the activated path is slow or the state of the circuit is incorrect, thus preventing the off-path signals to sensitize the fault. The latter situation occurs only if the optimistic update rule has been applied to a latch in a previous vector, and the state of the latch is indeed incorrect due to a delayed transition. In either case, it is possible to show that at the end of the activation vector, the path destination has a faulty value. Since we assume fault free values (optimistic update) only if a latch is a destination of at least one robustly activated path, the incorrectness of the circuit state (in the presence of faults that were robustly activated) is also independent of other delays in the circuit. Subsequent to activation, the fault may eventually be detected at a primary output. Similar to the concept of fault activation in combinational circuits [3], such a failure in a sequential circuit is not diagnosable. However, the condition for fault detectability can be stated as follows:Optimistic Update Theorem: Any fault found detectable by using optimistic update of latch variables, if present in the circuit, is guaranteed to cause failure and cannot be masked by other path delay faults in the circuit.We first prove some auxiliary properties about signal values specified by the optimistic update rule. We will then use these properties to prove correctness of the optimistic update theorem. We assume that all signal values at nodes in the circuit have been obtained from the 7-valued algebra of Figure 1. Since the optimistic update rule has been applied for all latches throughout the entire intput sequence, the signal values may be different from the values hi the actual physical circuit which may have one or more path delay faults. The auxiliary properties deal with the relationship between the signal values in the actual (faulty) circuit and those evaluated by the 7-valued algebra and the optimistic update rule. Lemma 1: A node in a sequential circuit with a stable value (s1 or s0), as specified by applying the 7-valued algebra and the optimistic update rule, attains this value (in the actual physical circuit) irrespective of the presence or absence of any delay fault.Proof. Examination of the truth table reveals that for a gate to have a stable output, either at least one input must have a stable controlling value or all inputs have steady non-controlling values. Hence, for a stable gateoutput to have a logic value in the real circuit that isdifferent from the value in the fault-free circuit, it isnecessary that at least one stable input is affected bythe fault. We use induction arguments first on thelevels of the circuit and then on the successivevectors. Since the inputs to the combinationalnetwork (primary inputs and latch outputs) remainunchanged at their stable values irrespective of slowpaths, it follows by induction on the levels of thecircuit that no gate of the network with a stable valueis affected by delay faults. Since this is true in the firsttwo time frames, it follows by induction onsuccessive vectors that the lemma is true universally.• Lemma 2: Any signal in the circuit that has a finalvalue of 0 (1), as specified by applying the 7-valuedalgebra and the optimistic update rule, may have afinal value of 1 (0) in the actual physical circuit onlyif some robustly activated path fault caused anerroneous latch state in a previous vector.Proof. Intuitively, this lemma says that if the actualcircuit (with one or more faults) is slowed downarbitrarily in vector N, the logic value to which anynode stabilizes can be complementary to the finalvalue predicted by the optimistic update rule only ifsome robustly activated fault caused an incorrect latchstate in a previous vector. Note that the comparisonhere is between the signal in the actual circuit and thevalue obtained by the 7-valued algebra and theoptimistic update rule. This lemma applies only tothose signals that do not evaluate to X, i.e., signalsthat attain a 0 or 1 final value.We will first prove that the above is true in thetime frame immediately after the first fault (or faults)was activated robustly. Then by induction onsuccessive time frames, it will follow that this is trueuniversally. The proof for the first time frame usesinduction on the levels of the circuit.Consider primary and pseudo-primary inputs (latchoutputs). Primary inputs cannot have different finalvalues in the actual physical circuit. The only possiblelogic values for pseudo-primary inputs are s1 and p1(s0 and p0) if the final stabilization value is 1 (0). Thelemma does not apply to signals with logic value Xand -1 and -0 are never assigned to inputs of thecombinational network. From Lemma 4, any signalwith value s1 or s0, attains that value in the actualcircuit irrespective of the absence or presence of anydelay fault. By definition of the update rule, pseudo-primary inputs with the value p1 (p0) attain the values0 (s1) in290 Bose, Agrawal, and Agrawalthe actual circuit if robustly activated faults cause incorrect latch states. Thus, the lemma is true for pseudo-primary inputs and trivially true for the primary inputs to the combinational network.Now, we consider gates at level two. If the output of a gate, as evaluated by the algebra and the update rule, has a dominant value, i.e., the value is caused when at least one input has the dominant logic value, the signal may have the complementary non-dominant output value in the actual circuit only if there exists at least one input in the actual circuit with the opposite final value. Since this is not possible for primary and pseudo-primary inputs unless there is an activated fault causing an incorrect latch state, the lemma holds for all gates at level two. Such an argument can be easily extended to a gate with a non-dominant output final value. For inverters which are single input gates, the lemma is true trivally. •Consider path fault f and its activation vector N. We assume that latches have been updated optimistically in all prior vectors. For a circuit with fault f, robustness is guaranteed in the following sense: for a circuit with fault f, the path destination is guaranteed to latch an incorrect value irrespective of whether the state of the circuit is different from that evaluated by using the optimistic update rule. The destination flip-flop may latch an incorrect value either due to f or due to some other path being slow in vector N (combinational robustness) or due to the failure of off-path signals in sensitizing the fault. The last condition arises due to delayed robustly propagating transitions in previous vectors (sequential robustness). In either case, failures are not diagnosable. Moreover, the faults found detectable by this update procedure, if present in the circuit, are guaranteed to cause failure independent of other circuit delays.Proof of the Optimistic Update Theorem. The proof considers all possible primitive gate types and transitions (rising and falling) from the on-path input to the output of a gate lying on the path under consideration. We outline the proof for an AND gate, G, lying on the path corresponding to the fault f. The arguments for an OR gate are similar.Consider a falling transition at the on-path input of the AND gate G. Since the path fault f was robustly activated, the off-path input, as evaluated by the 7-valued algebra and the optimistic update rule, has to be s1. Considering the possibility of this off-path signal in the actual circuit to have a value different from s1 in the presense of other delay faults, we find that it is impossible as shown in Lemma 1.We next consider a rising transition on the on-path input of gate G. The off-path input can have a value p1, s1or -1. If the value is s1, then this node is invariant with respect to circuit delays, as shown in Lemma 1. If the value is p1or -1, from Lemma 2, we can assert that if a robustly activated fault caused a delayed transition at a latch input in the actual circuit, the off-path signal may have a final value 0, i.e., logic value s0, p0or -0. Even when the final value of this off-path input is indeed 0, the destination flip-flop of path f is guaranteed to latch in an incorrect value. •5. ConclusionThe state variable update rule proposed in this article guarantees robustness in the presence of arbitrary delays in the circuit. It has applications to delay fault test generation and fault simulation of sequential circuits. The optimistic update rule can be used in both fault activation and fault effect propagation phases. A fault simulation algorithm using this update rule is described in a recent article [4]. As shown there, its impact on fault simulation is two fold: prediction of a higher and a more realistic fault coverage and reduction in the effort required for fault effect propagation. References1. T.J. Chakraborty, V.D. Agrawal, and M.L. Bushnell, "Path delayfault simulation algorithms for sequential circuits," Proc. Asian Test Symp. pp. 52-56, November 1992.2. I. Pomeranz, L.N. Reddy, and S.M. Reddy, "SPADES: a simulatorfor path delay faults in sequential circuits," Proc. European Design Automation Conference, pp 428-435, September 1992.3. G.L. Smith, "Model for delay faults based upon paths," Proc.Inter. Test Conf, pp 342-349, September 1985.4. S. Bose, P. Agrawal, and V.D. Agrawal, "A path delay faultsimulator for sequential circuits," Proc. Sixth Inter. Conf. on VLSI Design, pp 269-274, January 1993.5. K. Fuchs, F. Fink, and E.S. Schulz "DYNAMITE: an efficientautomatic test pattern generation system for path delay faults,"IEEE Trans. on Computer-Aided Design, vol. 10, pp 1323-1335, October 1991.。
