Application of a Recursive Filter to a Three-Dimensional Variational Ocean Data Assimilation Sys
国际自动化与计算杂志.英文版.

国际自动化与计算杂志.英文版.1.Improved Exponential Stability Criteria for Uncertain Neutral System with Nonlinear Parameter PerturbationsFang Qiu,Ban-Tong Cui2.Robust Active Suspension Design Subject to Vehicle Inertial Parameter VariationsHai-Ping Du,Nong Zhang3.Delay-dependent Non-fragile H∞ Filtering for Uncertain Fuzzy Systems Based on Switching Fuzzy Model and Piecewise Lyapunov FunctionZhi-Le Xia,Jun-Min Li,Jiang-Rong Li4.Observer-based Adaptive Iterative Learning Control for Nonlinear Systems with Time-varying DelaysWei-Sheng Chen,Rui-Hong Li,Jing Li5.H∞ Output Feedback Control for Stochastic Systems with Mode-dependent Time-varying Delays and Markovian Jump ParametersXu-Dong Zhao,Qing-Shuang Zeng6.Delay and Its Time-derivative Dependent Robust Stability of Uncertain Neutral Systems with Saturating ActuatorsFatima El Haoussi,El Houssaine Tissir7.Parallel Fuzzy P+Fuzzy I+Fuzzy D Controller:Design and Performance EvaluationVineet Kumar,A.P.Mittal8.Observers for Descriptor Systems with Slope-restricted NonlinearitiesLin-Na Zhou,Chun-Yu Yang,Qing-Ling Zhang9.Parameterized Solution to a Class of Sylvester MatrixEquationsYu-Peng Qiao,Hong-Sheng Qi,Dai-Zhan Cheng10.Indirect Adaptive Fuzzy and Impulsive Control of Nonlinear SystemsHai-Bo Jiang11.Robust Fuzzy Tracking Control for Nonlinear Networked Control Systems with Integral Quadratic ConstraintsZhi-Sheng Chen,Yong He,Min Wu12.A Power-and Coverage-aware Clustering Scheme for Wireless Sensor NetworksLiang Xue,Xin-Ping Guan,Zhi-Xin Liu,Qing-Chao Zheng13.Guaranteed Cost Active Fault-tolerant Control of Networked Control System with Packet Dropout and Transmission DelayXiao-Yuan Luo,Mei-Jie Shang,Cai-Lian Chen,Xin-Ping Guanparison of Two Novel MRAS Based Strategies for Identifying Parameters in Permanent Magnet Synchronous MotorsKan Liu,Qiao Zhang,Zi-Qiang Zhu,Jing Zhang,An-Wen Shen,Paul Stewart15.Modeling and Analysis of Scheduling for Distributed Real-time Embedded SystemsHai-Tao Zhang,Gui-Fang Wu16.Passive Steganalysis Based on Higher Order Image Statistics of Curvelet TransformS.Geetha,Siva S.Sivatha Sindhu,N.Kamaraj17.Movement Invariants-based Algorithm for Medical Image Tilt CorrectionMei-Sen Pan,Jing-Tian Tang,Xiao-Li Yang18.Target Tracking and Obstacle Avoidance for Multi-agent SystemsJing Yan,Xin-Ping Guan,Fu-Xiao Tan19.Automatic Generation of Optimally Rigid Formations Using Decentralized MethodsRui Ren,Yu-Yan Zhang,Xiao-Yuan Luo,Shao-Bao Li20.Semi-blind Adaptive Beamforming for High-throughput Quadrature Amplitude Modulation SystemsSheng Chen,Wang Yao,Lajos Hanzo21.Throughput Analysis of IEEE 802.11 Multirate WLANs with Collision Aware Rate Adaptation AlgorithmDhanasekaran Senthilkumar,A. Krishnan22.Innovative Product Design Based on Customer Requirement Weight Calculation ModelChen-Guang Guo,Yong-Xian Liu,Shou-Ming Hou,Wei Wang23.A Service Composition Approach Based on Sequence Mining for Migrating E-learning Legacy System to SOAZhuo Zhang,Dong-Dai Zhou,Hong-Ji Yang,Shao-Chun Zhong24.Modeling of Agile Intelligent Manufacturing-oriented Production Scheduling SystemZhong-Qi Sheng,Chang-Ping Tang,Ci-Xing Lv25.Estimation of Reliability and Cost Relationship for Architecture-based SoftwareHui Guan,Wei-Ru Chen,Ning Huang,Hong-Ji Yang1.A Computer-aided Design System for Framed-mould in Autoclave ProcessingTian-Guo Jin,Feng-Yang Bi2.Wear State Recognition of Drills Based on K-means Cluster and Radial Basis Function Neural NetworkXu Yang3.The Knee Joint Design and Control of Above-knee Intelligent Bionic Leg Based on Magneto-rheological DamperHua-Long Xie,Ze-Zhong Liang,Fei Li,Li-Xin Guo4.Modeling of Pneumatic Muscle with Shape Memory Alloy and Braided SleeveBin-Rui Wang,Ying-Lian Jin,Dong Wei5.Extended Object Model for Product Configuration DesignZhi-Wei Xu,Ze-Zhong Liang,Zhong-Qi Sheng6.Analysis of Sheet Metal Extrusion Process Using Finite Element MethodXin-Cun Zhuang,Hua Xiang,Zhen Zhao7.Implementation of Enterprises' Interoperation Based on OntologyXiao-Feng Di,Yu-Shun Fan8.Path Planning Approach in Unknown EnvironmentTing-Kai Wang,Quan Dang,Pei-Yuan Pan9.Sliding Mode Variable Structure Control for Visual Servoing SystemFei Li,Hua-Long Xie10.Correlation of Direct Piezoelectric Effect on EAPap under Ambient FactorsLi-Jie Zhao,Chang-Ping Tang,Peng Gong11.XML-based Data Processing in Network Supported Collaborative DesignQi Wang,Zhong-Wei Ren,Zhong-Feng Guo12.Production Management Modelling Based on MASLi He,Zheng-Hao Wang,Ke-Long Zhang13.Experimental Tests of Autonomous Ground Vehicles with PreviewCunjia Liu,Wen-Hua Chen,John Andrews14.Modelling and Remote Control of an ExcavatorYang Liu,Mohammad Shahidul Hasan,Hong-Nian Yu15.TOPSIS with Belief Structure for Group Belief Multiple Criteria Decision MakingJiang Jiang,Ying-Wu Chen,Da-Wei Tang,Yu-Wang Chen16.Video Analysis Based on Volumetric Event DetectionJing Wang,Zhi-Jie Xu17.Improving Decision Tree Performance by Exception HandlingAppavu Alias Balamurugan Subramanian,S.Pramala,B.Rajalakshmi,Ramasamy Rajaram18.Robustness Analysis of Discrete-time Indirect Model Reference Adaptive Control with Normalized Adaptive LawsQing-Zheng Gao,Xue-Jun Xie19.A Novel Lifecycle Model for Web-based Application Development in Small and Medium EnterprisesWei Huang,Ru Li,Carsten Maple,Hong-Ji Yang,David Foskett,Vince Cleaver20.Design of a Two-dimensional Recursive Filter Using the Bees AlgorithmD. T. Pham,Ebubekir Ko(c)21.Designing Genetic Regulatory Networks Using Fuzzy Petri Nets ApproachRaed I. Hamed,Syed I. Ahson,Rafat Parveen1.State of the Art and Emerging Trends in Operations and Maintenance of Offshore Oil and Gas Production Facilities: Some Experiences and ObservationsJayantha P.Liyanage2.Statistical Safety Analysis of Maintenance Management Process of Excavator UnitsLjubisa Papic,Milorad Pantelic,Joseph Aronov,Ajit Kumar Verma3.Improving Energy and Power Efficiency Using NComputing and Approaches for Predicting Reliability of Complex Computing SystemsHoang Pham,Hoang Pham Jr.4.Running Temperature and Mechanical Stability of Grease as Maintenance Parameters of Railway BearingsJan Lundberg,Aditya Parida,Peter S(o)derholm5.Subsea Maintenance Service Delivery: Mapping Factors Influencing Scheduled Service DurationEfosa Emmanuel Uyiomendo,Tore Markeset6.A Systemic Approach to Integrated E-maintenance of Large Engineering PlantsAjit Kumar Verma,A.Srividya,P.G.Ramesh7.Authentication and Access Control in RFID Based Logistics-customs Clearance Service PlatformHui-Fang Deng,Wen Deng,Han Li,Hong-Ji Yang8.Evolutionary Trajectory Planning for an Industrial RobotR.Saravanan,S.Ramabalan,C.Balamurugan,A.Subash9.Improved Exponential Stability Criteria for Recurrent Neural Networks with Time-varying Discrete and Distributed DelaysYuan-Yuan Wu,Tao Li,Yu-Qiang Wu10.An Improved Approach to Delay-dependent Robust Stabilization for Uncertain Singular Time-delay SystemsXin Sun,Qing-Ling Zhang,Chun-Yu Yang,Zhan Su,Yong-Yun Shao11.Robust Stability of Nonlinear Plants with a Non-symmetric Prandtl-Ishlinskii Hysteresis ModelChang-An Jiang,Ming-Cong Deng,Akira Inoue12.Stability Analysis of Discrete-time Systems with Additive Time-varying DelaysXian-Ming Tang,Jin-Shou Yu13.Delay-dependent Stability Analysis for Markovian Jump Systems with Interval Time-varying-delaysXu-Dong Zhao,Qing-Shuang Zeng14.H∞ Synchronization of Chaotic Systems via Delayed Feedback ControlLi Sheng,Hui-Zhong Yang15.Adaptive Fuzzy Observer Backstepping Control for a Class of Uncertain Nonlinear Systems with Unknown Time-delayShao-Cheng Tong,Ning Sheng16.Simulation-based Optimal Design of α-β-γ-δ FilterChun-Mu Wu,Paul P.Lin,Zhen-Yu Han,Shu-Rong Li17.Independent Cycle Time Assignment for Min-max SystemsWen-De Chen,Yue-Gang Tao,Hong-Nian Yu1.An Assessment Tool for Land Reuse with Artificial Intelligence MethodDieter D. Genske,Dongbin Huang,Ariane Ruff2.Interpolation of Images Using Discrete Wavelet Transform to Simulate Image Resizing as in Human VisionRohini S. Asamwar,Kishor M. Bhurchandi,Abhay S. Gandhi3.Watermarking of Digital Images in Frequency DomainSami E. I. Baba,Lala Z. Krikor,Thawar Arif,Zyad Shaaban4.An Effective Image Retrieval Mechanism Using Family-based Spatial Consistency Filtration with Object RegionJing Sun,Ying-Jie Xing5.Robust Object Tracking under Appearance Change ConditionsQi-Cong Wang,Yuan-Hao Gong,Chen-Hui Yang,Cui-Hua Li6.A Visual Attention Model for Robot Object TrackingJin-Kui Chu,Rong-Hua Li,Qing-Ying Li,Hong-Qing Wang7.SVM-based Identification and Un-calibrated Visual Servoing for Micro-manipulationXin-Han Huang,Xiang-Jin Zeng,Min Wang8.Action Control of Soccer Robots Based on Simulated Human IntelligenceTie-Jun Li,Gui-Qiang Chen,Gui-Fang Shao9.Emotional Gait Generation for a Humanoid RobotLun Xie,Zhi-Liang Wang,Wei Wang,Guo-Chen Yu10.Cultural Algorithm for Minimization of Binary Decision Diagram and Its Application in Crosstalk Fault DetectionZhong-Liang Pan,Ling Chen,Guang-Zhao Zhang11.A Novel Fuzzy Direct Torque Control System for Three-level Inverter-fed Induction MachineShu-Xi Liu,Ming-Yu Wang,Yu-Guang Chen,Shan Li12.Statistic Learning-based Defect Detection for Twill FabricsLi-Wei Han,De Xu13.Nonsaturation Throughput Enhancement of IEEE 802.11b Distributed Coordination Function for Heterogeneous Traffic under Noisy EnvironmentDhanasekaran Senthilkumar,A. Krishnan14.Structure and Dynamics of Artificial Regulatory Networks Evolved by Segmental Duplication and Divergence ModelXiang-Hong Lin,Tian-Wen Zhang15.Random Fuzzy Chance-constrained Programming Based on Adaptive Chaos Quantum Honey Bee Algorithm and Robustness AnalysisHan Xue,Xun Li,Hong-Xu Ma16.A Bit-level Text Compression Scheme Based on the ACW AlgorithmHussein A1-Bahadili,Shakir M. Hussain17.A Note on an Economic Lot-sizing Problem with Perishable Inventory and Economies of Scale Costs:Approximation Solutions and Worst Case AnalysisQing-Guo Bai,Yu-Zhong Zhang,Guang-Long Dong1.Virtual Reality: A State-of-the-Art SurveyNing-Ning Zhou,Yu-Long Deng2.Real-time Virtual Environment Signal Extraction and DenoisingUsing Programmable Graphics HardwareYang Su,Zhi-Jie Xu,Xiang-Qian Jiang3.Effective Virtual Reality Based Building Navigation Using Dynamic Loading and Path OptimizationQing-Jin Peng,Xiu-Mei Kang,Ting-Ting Zhao4.The Skin Deformation of a 3D Virtual HumanXiao-Jing Zhou,Zheng-Xu Zhao5.Technology for Simulating Crowd Evacuation BehaviorsWen-Hu Qin,Guo-Hui Su,Xiao-Na Li6.Research on Modelling Digital Paper-cut PreservationXiao-Fen Wang,Ying-Rui Liu,Wen-Sheng Zhang7.On Problems of Multicomponent System Maintenance ModellingTomasz Nowakowski,Sylwia Werbinka8.Soft Sensing Modelling Based on Optimal Selection of Secondary Variables and Its ApplicationQi Li,Cheng Shao9.Adaptive Fuzzy Dynamic Surface Control for Uncertain Nonlinear SystemsXiao-Yuan Luo,Zhi-Hao Zhu,Xin-Ping Guan10.Output Feedback for Stochastic Nonlinear Systems with Unmeasurable Inverse DynamicsXin Yu,Na Duan11.Kalman Filtering with Partial Markovian Packet LossesBao-Feng Wang,Ge Guo12.A Modified Projection Method for Linear FeasibilityProblemsYi-Ju Wang,Hong-Yu Zhang13.A Neuro-genetic Based Short-term Forecasting Framework for Network Intrusion Prediction SystemSiva S. Sivatha Sindhu,S. Geetha,M. Marikannan,A. Kannan14.New Delay-dependent Global Asymptotic Stability Condition for Hopfield Neural Networks with Time-varying DelaysGuang-Deng Zong,Jia Liu hHTTp://15.Crosscumulants Based Approaches for the Structure Identification of Volterra ModelsHouda Mathlouthi,Kamel Abederrahim,Faouzi Msahli,Gerard Favier1.Coalition Formation in Weighted Simple-majority Games under Proportional Payoff Allocation RulesZhi-Gang Cao,Xiao-Guang Yang2.Stability Analysis for Recurrent Neural Networks with Time-varying DelayYuan-Yuan Wu,Yu-Qiang Wu3.A New Type of Solution Method for the Generalized Linear Complementarity Problem over a Polyhedral ConeHong-Chun Sun,Yan-Liang Dong4.An Improved Control Algorithm for High-order Nonlinear Systems with Unmodelled DynamicsNa Duan,Fu-Nian Hu,Xin Yu5.Controller Design of High Order Nonholonomic System with Nonlinear DriftsXiu-Yun Zheng,Yu-Qiang Wu6.Directional Filter for SAR Images Based on NonsubsampledContourlet Transform and Immune Clonal SelectionXiao-Hui Yang,Li-Cheng Jiao,Deng-Feng Li7.Text Extraction and Enhancement of Binary Images Using Cellular AutomataG. Sahoo,Tapas Kumar,B.L. Rains,C.M. Bhatia8.GH2 Control for Uncertain Discrete-time-delay Fuzzy Systems Based on a Switching Fuzzy Model and Piecewise Lyapunov FunctionZhi-Le Xia,Jun-Min Li9.A New Energy Optimal Control Scheme for a Separately Excited DC Motor Based Incremental Motion DriveMilan A.Sheta,Vivek Agarwal,Paluri S.V.Nataraj10.Nonlinear Backstepping Ship Course ControllerAnna Witkowska,Roman Smierzchalski11.A New Method of Embedded Fourth Order with Four Stages to Study Raster CNN SimulationR. Ponalagusamy,S. Senthilkumar12.A Minimum-energy Path-preserving Topology Control Algorithm for Wireless Sensor NetworksJin-Zhao Lin,Xian Zhou,Yun Li13.Synchronization and Exponential Estimates of Complex Networks with Mixed Time-varying Coupling DelaysYang Dai,YunZe Cai,Xiao-Ming Xu14.Step-coordination Algorithm of Traffic Control Based on Multi-agent SystemHai-Tao Zhang,Fang Yu,Wen Li15.A Research of the Employment Problem on Common Job-seekersand GraduatesBai-Da Qu。
数字信号处理英文版课后答案 (4)
4.24 From the figure, the filter has a finite impulse response. It may be described as a sum of impulse function as: h[n] = 0.5[n] + 0.4[n–1] + 0.3[n–2] + 0.2[n–2] The difference equation has the parallel form: y[n] = 0.5x[n] + 0.4x[n–1] + 0.3x[n–2] + 0.2x[n–3] 4.25 n h[n] The impulse response is finite, with samples as listed in the table. 0 1.000 1 0.300 2 0.090 3 0.027 4 0.000 5 0.000 6 0.000
x[n]
+
delay –0.14 delay –0.38
y[n]
4.23 n h[n]
The first ten samples of the impulse response are: 0 1.0 1 –1.2 2 –0.8 3 0.4 4 0.0 5 0.0 6 0.0 7 0.0 8 0.0 9 0.0
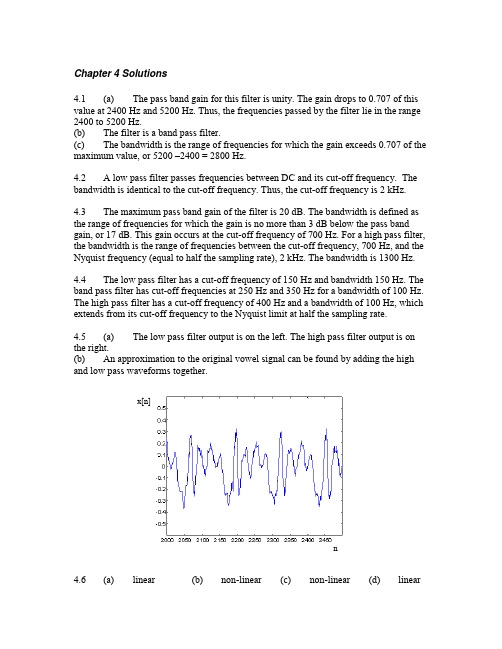
Chapter 4 Solutions 4.1 (a) The pass band gain for this filter is unity. The gain drops to 0.707 of this value at 2400 Hz and 5200 Hz. Thus, the frequencies passed by the filter lie in the range 2400 to 5200 Hz. (b) The filter is a band pass filter. (c) The bandwidth is the range of frequencies for which the gain exceeds 0.707 of the maximum value, or 5200 –2400 = 2800 Hz. 4.2 A low pass filter passes frequencies between DC and its cut-off frequency. The bandwidth is identical to the cut-off frequency. Thus, the cut-off frequency is 2 kHz. 4.3 The maximum pass band gain of the filter is 20 dB. The bandwidth is defined as the range of frequencies for which the gain is no more than 3 dB below the pass band gain, or 17 dB. This gain occurs at the cut-off frequency of 700 Hz. For a high pass filter, the bandwidth is the range of frequencies between the cut-off frequency, 700 Hz, and the Nyquist frequency (equal to half the sampling rate), 2 kHz. The bandwidth is 1300 Hz. 4.4 The low pass filter has a cut-off frequency of 150 Hz and bandwidth 150 Hz. The band pass filter has cut-off frequencies at 250 Hz and 350 Hz for a bandwidth of 100 Hz. The high pass filter has a cut-off frequency of 400 Hz and a bandwidth of 100 Hz, which extends from its cut-off frequency to the Nyquist limit at half the sampling rate. 4.5 (a) The low pass filter output is on the left. The high pass filter output is on the right. (b) An approximation to the original vowel signal can be found by adding the high and low pass waveforms together.
外文文献翻译译稿和原文

外文文献翻译译稿1卡尔曼滤波的一个典型实例是从一组有限的,包含噪声的,通过对物体位置的观察序列(可能有偏差)预测出物体的位置的坐标及速度。
在很多工程应用(如雷达、计算机视觉)中都可以找到它的身影。
同时,卡尔曼滤波也是控制理论以及控制系统工程中的一个重要课题。
例如,对于雷达来说,人们感兴趣的是其能够跟踪目标。
但目标的位置、速度、加速度的测量值往往在任何时候都有噪声。
卡尔曼滤波利用目标的动态信息,设法去掉噪声的影响,得到一个关于目标位置的好的估计。
这个估计可以是对当前目标位置的估计(滤波),也可以是对于将来位置的估计(预测),也可以是对过去位置的估计(插值或平滑)。
命名[编辑]这种滤波方法以它的发明者鲁道夫.E.卡尔曼(Rudolph E. Kalman)命名,但是根据文献可知实际上Peter Swerling在更早之前就提出了一种类似的算法。
斯坦利。
施密特(Stanley Schmidt)首次实现了卡尔曼滤波器。
卡尔曼在NASA埃姆斯研究中心访问时,发现他的方法对于解决阿波罗计划的轨道预测很有用,后来阿波罗飞船的导航电脑便使用了这种滤波器。
关于这种滤波器的论文由Swerling(1958)、Kalman (1960)与Kalman and Bucy(1961)发表。
目前,卡尔曼滤波已经有很多不同的实现。
卡尔曼最初提出的形式现在一般称为简单卡尔曼滤波器。
除此以外,还有施密特扩展滤波器、信息滤波器以及很多Bierman, Thornton开发的平方根滤波器的变种。
也许最常见的卡尔曼滤波器是锁相环,它在收音机、计算机和几乎任何视频或通讯设备中广泛存在。
以下的讨论需要线性代数以及概率论的一般知识。
卡尔曼滤波建立在线性代数和隐马尔可夫模型(hidden Markov model)上。
其基本动态系统可以用一个马尔可夫链表示,该马尔可夫链建立在一个被高斯噪声(即正态分布的噪声)干扰的线性算子上的。
系统的状态可以用一个元素为实数的向量表示。
液体火箭发动机冲击响应谱分析计算方法

为 x ( t) . 一般情况下 , 冲击加速度的测量比较容易 实现 , 因此当基础受到加速度作用时 , 质量块 m 的 运动方程可表示为
mx + cx + kx = ku ( t) + cu ( t)
.. . ..
( 1)
. 因此了解发动机工作状态下的
冲击特性 ,制定相应的抗冲击策略 , 直接关系到全 箭的结构可靠性 . 冲击响应谱在结构分析方面的用 途主要用来衡量冲击作用的效果 ,估计冲击对结构 的损伤势 [ 3 ] . 根据冲击响应谱 , 可以计算在特定冲 击作用下发动机结构零件的强度和发动机自身的 安全性 . 某新型大推力液体火箭发动机在地面试验 过程中 ,测得了全程段的时域数据 , 因测试软件功 能所限 ,不能进行冲击响应谱分析 . 基于此 ,文中从 冲击响应谱概念着手 , 基于 Matlab 软件包开发了 冲击响应谱分析软件 , 力图快速 、 方便的对液体火 箭发动机地面试验数据进行冲击响应谱分析 ,为地 面试验数据的深入分析提供辅助手段 .
3 发动机地面试验冲击响应谱计算
在对某型液体火箭发动机多次地面试验时域 数据进行分析时 ,发现燃气发生器点火时所测的冲 击响应均较大 . 考虑到发动机自身的安全性 , 以及 该启动冲击对全箭结构的影响 ,有必要对发生器启 动冲击进行冲击响应谱分析 . 因发动机地面试验数据采集软件功能所限 ,不 能进行冲击响应谱分析 ,因此地面试验结束后对所 采集的时域数据利用文中开发的 Vibsr s 冲击响应 谱分析软件进行计算 ,所得计算结果导出为 t xt 文 文中件供深入分析地面试验数据时参考 . 考虑到篇 幅所限 ,只给出燃气发生器上一个三向加速度传感 器所测的发生器启动时的冲击响应谱分析结果 . 图 3~5 分别为轴向 、 径向 、 切向加速度传感器所测的 冲击响应及利用 Vibsr s 计算得到的最大冲击响应 谱 . 计算过程中时间范围根据冲击响应的时域图形 给定 ,频率范围选择为 0. 1 ~ 10 k Hz , 其他选项采
TraceFilter用户指南

TraceFilter2 手册925-10000-002 Rev. A2004年3月26日SnapTrack公司所有传播和使用限制: 本文件包含SnapTrack产品的重要信息,未经高通公司旗下SnapTrack公司事先同意,任何非高通公司或SnapTrack公司员工或代理不得传播或使用.本文件包含或发布的所有数据和信息均为绝密,属SnapTrack公司所有,并明确保留所有权利.接收本资料,接受方同意对本文件包含的所有资料和信息严格保密,并保证未经SnapTrack公司事先书面许可,文件不会被全部或部分复制或使用,其内容不会以任何方式泄露.QUALCOMM是高通公司的注册商标和注册服务标识.SnapTrack是SnapTrack,公司的注册商标.cdma2000®是电信行业组织(TIA USA) 的注册商标.其他产品和品牌名称可能是其各自所有者的商标或注册商标.本技术出口受美国政府管制.禁止任何违法美国法律转移此技术的行为.SnapTrack, Inc.A QUALCOMM Company675 Campbell Technology ParkwaySuite 200Campbell, CA 95008U.S.A.Copyright © 2004 SnapTrack, Inc. 版权所有内容1 引言 (3)1.1 目的 (3)1.2 范围和受众 (3)1.3 结构 (3)1.4 惯例 (3)1.5 修订历史 (3)1.6 参考文件 (3)1.7 技术支持 (3)1.8 缩写 (3)2 操作和使用 (3)2.1 操作概述 (3)2.1.1 二进制跟踪文件 (3)2.1.2 跟踪过滤 (3)2.2 使用 TraceFilter2 (3)2.2.1 运行 TraceFilter2 (3)2.2.1.1 在Windows平台上运行TraceFilter2 (3)2.2.1.2 在UNIX平台上运行TraceFilter2 (3)2.2.2 命令选项 (3)2.2.3 输出文件 (3)2.2.4 使用通配符 (3)3 位置文件 (3)3.1 概述 (3)3.2 数据字段 (3)3.3 数据分隔符 (3)3.4 数据过滤 (3)3.5 良率信息 (3)3.5.1 良率统计修改有效性标准 (3)3.5.1.1 修改有效性和用户定义的掩码 (3)3.5.2 离群点信息 (3)3.6 数据字段描述 (3)3.7 使用 Microsoft Excel (3)3.8 样本使用 (3)3.8.1 按手机能力过滤 (3)4 测量文件 (3)5 文本跟踪文件 (3)5.1 概述 (3)5.2 数据字段 (3)5.3 数据过滤 (3)5.4 跟踪标题 (3)5.4.1 HP NSS (3)5.5 禁止文本跟踪文件 (3)6 修改总结文件 (3)6.1 概述 (3)6.2 数据字段 (3)7 WARN 数据文件 (3)7.1 概述 (3)7.2 数据字段 (3)8 基站历书文件 (3)8.1 概述 (3)8.2 数据过滤 (3)9 过滤的Bin 文件 (3)9.1 概述 (3)9.2 样本使用 (3)10会话记录数据文件 (3)10.1 概述 (3)10.2 数据字段 (3)10.3 样本输出 (3)10.3.1 IS-801 (3)10.3.2 GSM (3)11 实时统计文件 (3)11.1 概述 (3)11.2 数据字段 (3)11.3 样本输出 (3)A 位置文件规范 (3)A.1 字段描述 (3)A.2 样本输出 (3)A.2.1 CDMA (3)A.2.2 GSM (3)B 测量文件规范 (3)C 修改总结文件规范 (3)C.1 字段描述 (3)C.2 样本输出 (3)C.2.1 CDMA (3)C.2.2 GSM (3)D WARN 数据文件规范 (3)D.1 字段描述 (3)D.2 样本输出 (3)图Figure 2–1 TraceFilter2 操作概述 (3)Figure 9–1 过滤的 BIN文件处理 (3)表表 1-1 修订历史 (3)表 1-2 参考文件 (3)表 1-3 缩写定义 (3)表 2-1 TraceFilter2选项 (3)表 2-2 TraceFilter2 命令选项的关键字 (3)表 2-3 TraceFilter2 输出文件 (3)表 3-1 修改有效性和用户定义的掩码 (3)表 7-1 WARN Processor 统计配置参数 (3)表 7-2 WARN 数据文件设计 (3)表 10-1 会话记录数据文件 (.ses) 布局 (3)表 10-2 会话记录数据文件细节 (3)表 11-1 实时统计文件 (.rts) 数据 (3)表 A-1 位置文件数据字段 (3)表 A-2 "导航结果" 值 (3)表 A-3 ―时间源‖值 (3)表 A-4 *.csv 和 *.fix文件中―解算源‖的原始值和最终值 (3)表 A-5 *.csv 和 *.fix文件中手机能力的―空中接口‖值 (3)表 A-6 *.csv 和 *.fix文件中手机能力的―测量采集能力‖值 (3)表 A-7 *.csv 和 *.fix文件中手机能力的―位置计算能力‖值 (3)表 C-1 修改总结文件数据字段 (3)表 C-2 GPS测量扇区数据字段 (3)表 C-3 高度辅助测量扇区数据字段 (3)表 C-4 位置辅助测量扇区数据字段 (3)表 C-5 导频相位测量扇区数据字段 (3)表 C-6 RTD 测量扇区数据字段 (3)表 D-1 WARN 记录总结信息 (3)表 D-2 WARN 数据文件流量统计 (3)表 D-3 WARN 数据文件 GPS 参考站统计 (3)表 D-4 WARN 数据文件 GPS 卫星统计 (3)1 引言SnapTrack位置确定模块(PDM)为移动用户提供了位置确定服务。
毫米波雷达目标跟踪方法

毫米波雷达目标跟踪方法英文回答:Millimeter-wave radar is a technology used for detecting and tracking targets using radio waves with wavelengths in the millimeter range. It has gained significant attention in recent years due to its ability to provide high-resolution imaging and accurate target tracking in various applications such as autonomous vehicles, surveillance systems, and industrial automation.There are several methods for target tracking in millimeter-wave radar systems. One commonly used method is the Kalman filter. The Kalman filter is a recursive algorithm that estimates the state of a system based on noisy measurements over time. It is widely used in radar tracking due to its ability to handle noisy measurements and provide accurate and smooth estimates of the target's position and velocity.Another method used for target tracking in millimeter-wave radar is the particle filter. The particle filter is a non-linear filtering technique that uses a set of particles to represent the posterior probability distribution of the target's state. It is particularly useful in scenarios where the target's motion is non-linear or exhibits non-Gaussian uncertainties. The particle filter provides a flexible and robust solution for target tracking in millimeter-wave radar systems.In addition to the above methods, there are also advanced techniques such as multiple hypothesis tracking (MHT) and joint probabilistic data association (JPDA) that can be used for target tracking in millimeter-wave radar systems. These techniques consider multiple possible hypotheses and association probabilities to improve the accuracy and reliability of target tracking.Overall, target tracking in millimeter-wave radar systems can be achieved using various methods such as the Kalman filter, particle filter, MHT, and JPDA. Each method has its advantages and limitations, and the choice ofmethod depends on the specific requirements of the application.中文回答:毫米波雷达目标跟踪方法是利用毫米波范围内的无线电波进行目标检测和跟踪的技术。
scoped session is already present -回复

scoped session is already present -回复Scoped Session: An In-Depth ExplanationIntroduction:In today's digital age, ensuring secure and reliable access to web applications has become crucial. One of the commonly used techniques to achieve this is by implementing a scoped session. In this article, we will explore what a scoped session is, its significance, and how it functions to enhance security and user experience. So, let's dive right in!What is a Scoped Session?A scoped session refers to a temporary and limited-duration session created for a user when they access a web application. It acts as a virtual container that holds data related to the user's session state, preferences, and other necessary information. Each user is assigned a unique session ID, which allows the server to identify and track the user's activity throughout their session.Why are Scoped Sessions Important?Scoped sessions play a vital role in ensuring the security and reliability of web applications. By creating a separate session for each user, the risk of unauthorized access and information leakage is significantly reduced. Scoped sessions restrict the scope of session data, preventing it from being accessed or manipulated by other users. These sessions also enhance the user experience by maintaining session state and preferences across multiple pages, allowing the user to seamlessly interact with the application.How Does a Scoped Session Work?1. Session Initialization:When a user accesses a web application, the server creates a unique session ID for that user. This session ID is either generated randomly or using an algorithm that ensures uniqueness. The session ID is then stored on the server and sent back to the user's browser as a cookie or parameter in the URL.2. Request Processing:As the user interacts with the web application, subsequent requests are sent to the server along with their session ID. Thisallows the server to retrieve the specific session associated with that user and process the request accordingly. The data stored within the session, such as authentication credentials or user preferences, can be accessed and utilized.3. Session Expiration:To prevent sessions from persisting indefinitely, scoped sessions are designed with an expiration mechanism. A session can have a fixed expiration time, such as after 30 minutes of inactivity, or it can be renewed with each user interaction. When a session expires, its data is typically deleted from the server, ensuring that sensitive information is not retained longer than necessary.4. Session Termination:Users can actively terminate their sessions by logging out or closing the browser. In such cases, the session ID is invalidated, and all associated session data is immediately removed from the server. This step is crucial in protecting user accounts from unauthorized access, especially when using shared or public computers.Best Practices for Implementing Scoped Sessions:1. Secure Session Management:Implement mechanisms to prevent session hijacking and unauthorized access. Use secure cookies that are not susceptible to tampering and employ encryption techniques to protect session data during transit.2. Validate User Input:Implement robust input validation to prevent injection attacks that may exploit session handling mechanisms. Ensure that session IDs cannot be manipulated through input fields.3. Secure Session Storage:Store session data securely on the server. Use encryption and access control techniques to protect the confidentiality and integrity of the stored data.4. Regular Session Expiration:Configure appropriate session timeout values to ensure sessions expire after an appropriate period of user inactivity. This helps reduce the risk of unauthorized access and ensures sensitive session data is not retained indefinitely.Conclusion:In summary, a scoped session is a crucial component of ensuring secure and uninterrupted access to web applications. By assigning a unique session ID to each user and limiting the data accessible within a session, scoped sessions enhance security and provide a seamless user experience. Developing and implementing scoped session mechanisms following best practices helps protect both users and applications from potential security threats.。
kalman filter 的英文术语

kalman filter 的英文术语Kalman Filter(卡尔曼滤波器)是一种高效且递归的滤波器,用于估计线性动态系统的状态。
该算法由匈牙利数学家Rudolf Kalman于20世纪60年代提出,并已广泛应用于航空航天、无人驾驶、金融预测、机器人技术、传感器融合、计算机视觉等众多领域。
Key Terms and Concepts of Kalman Filter:State Estimation: The process of determining the most likely state of a system based on a set of observations. In Kalman Filter, this is achieved by combining the system's predicted state with the actual measurements.System Model: A mathematical representation of the system's behavior. It typically consists of a state equation and an observation equation. The state equation describes how the state evolves over time, while the observation equation defines how the state is related to the measurements.State Variables: The internal variables that describe the system's state at any given time. These variables are estimated using the Kalman Filter.Process Noise: Uncertainty in the system model that cannot be explained by the measurements. It represents the noise or uncertainty in the system's dynamics.Measurement Noise: Uncertainty in the measurements caused by various factors such as sensor errors, environmental disturbances, etc.Covariance Matrix: A matrix that quantifies the uncertainty associated with the estimated state variables. It is used to track the uncertainty and adjust the filter's estimates accordingly.Prediction Step: The process of estimating the system's state at the next time step based on the current state and the system model. This step involves applying the state equation to predict the next state and updating the covariance matrix.Update Step: The process of correcting the predicted state based on the actual measurements. This step involves calculating the Kalman gain, which determines how much to trust the measurements relative to the predictions, and then updating the state estimate and covariance matrix accordingly.The Kalman Filter algorithm iterates between these prediction and update steps, continuously improving the state estimation as new measurements become available. Its recursive nature allows it to process data in real-time, making it an ideal choice for many real-world applications.。
微软认证考试70-562复习题

83 questions by Lorc醤Number: 70-562Passing Score: 700Time Limit: 120 minFile Version: 2010-09-18Exam MCTS 70-562: Microsoft .NET Framework 3.5 - ApplicationDevelopementOriginal File by Nitish:/microsoft/Microsoft.TestKing.70-562.v2010-09-21.by.Nitish.100q.vce.file.htmlCorrections, layout and explanations by LorcánUpdated: 20110316Exam AQUESTION 1You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You create a custom control named OrderForm.You write the following code segment:public delegate void CheckOrderFormEventHandler(EventArgs e);private static readonly object CheckOrderFormKey = new object();public event CheckOrderFormEventHandler CheckOrderForm{add { Events.AddHandler(CheckOrderFormKey, value); }remove { Events.RemoveHandler(CheckOrderFormKey, value); }}You need to provide a method that enables the OrderForm control to raise the CheckOrderForm event.Which code segment should you use?A. protected virtual void OnCheckOrderForm(EventArgs e) {CheckOrderFormEventHandler checkOrderForm =(CheckOrderFormEventHandler)Events[typeof(CheckOrderFormEventHandler)];if (checkOrderForm != null)checkOrderForm(e);}B. protected virtual void OnCheckOrderForm(EventArgs e) {CheckOrderFormEventHandler checkOrderForm =Events[CheckOrderFormKey] asCheckOrderFormEventHandler;if (checkOrderForm != null)checkOrderForm(e);}C. CheckOrderFormEventHandler checkOrderForm = newCheckOrderFormEventHandler(checkOrderFormCallBack);protected virtual void OnCheckOrderForm(EventArgs e) {if (checkOrderForm != null)checkOrderForm(e);}D. CheckOrderFormEventHandler checkOrderForm = newCheckOrderFormEventHandler(checkOrderFormCallBack);protected virtual void OnCheckOrderForm(EventArgs e) {if (checkOrderForm != null)RaiseBubbleEvent(checkOrderForm, e);}Answer: BSection: (none)Explanation/Reference:static readonly object ourKey = new object();public event EventHandler MyEvent{add { Events.AddHandler(ourKey, value); }remove { Events.RemoveHandler(ourKey, value); }}protected void OnMyEvent(EventArgs e){EventHandler aH = Events[ourKey] as EventHandler;if (aH != null)aH(this, e);}QUESTION 2You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You derive a new validation control from the BaseValidator class.The validation logic for the control is implemented in the Validate method in the following manner: protected static bool Validate(string value){// ...}You need to override the method that validates the value of the related control.Which override method should you use?A. protected override bool EvaluateIsValid() {string value =GetControlValidationValue(this.Attributes["AssociatedControl"]);bool isValid = Validate(value);return isValid;}B. protected override bool ControlPropertiesValid() {string value =GetControlValidationValue(this.ValidationGroup);bool isValid = Validate(value);return isValid;}C. protected override bool EvaluateIsValid() {string value =GetControlValidationValue(this.ControlToValidate);bool isValid = Validate(value);return isValid;}D. protected override bool ControlPropertiesValid() {string value =GetControlValidationValue(this.Attributes["ControlToValidate"]);bool isValid = Validate(value);this.PropertiesValid = isValid;return true;}Answer: CSection: (none)Explanation/Reference:When overridden in a derived class, the BaseValidator.EvaluateIsValid method contains the code to determine whether the value in the input control is valid. The methods returns true if thevalue in the input control is valid; otherwise, false.The BaseValidator.GetControlValidationValue method gets the value associated with the specified input control. It takes the name of the input control to get the value from as a string parameter and returns the value associated with the specified input control.The BaseValidator.ControlToValidate property gets/sets the input control to validate. Its type is String.QUESTION 3You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You create a Web page that contains the following two XML fragments:01 <script runat="server">02 ►03 </script>04 <asp:ListView ID="ListView1" runat="server"05 DataSourceID="SqlDataSource1"06 ►07 >08 <ItemTemplate>09 <td>10 <asp:Label ID="LineTotalLabel" runat="server"11 Text='<%# Eval("LineTotal") %>' />12 </td>13 </ItemTemplate>The SqlDataSource1 object retrieves the data from a Microsoft SQL Server 2005 database table. The database table has a column named LineTotal.You need to ensure that when the size of the LineTotal column value is greater than seven characters, the column is displayed in red color.What should you do?A. Insert the following code segment at line 06:OnItemDataBound="FmtClr"Insert the following code segment at line 02:protected void FmtClr (object sender,ListViewItemEventArgs e) {Label LineTotal =(Label)e.Item.FindControl("LineTotalLabel");if (LineTotal.Text.Length > 7){ LineTotal.ForeColor = Color.Red; }else{ LineTotal.ForeColor = Color.Black; }}B. Insert the following code segment at line 06:OnItemDataBound="FmtClr"Insert the following code segment at line 02:protected void FmtClr (object sender,ListViewItemEventArgs e) {Label LineTotal =(Label)e.Item.FindControl("LineTotal");if (LineTotal.Text.Length > 7){ LineTotal.ForeColor = Color.Red; }else{ LineTotal.ForeColor = Color.Black; }}C. Insert the following code segment at line 06:OnDataBinding="FmtClr"Insert the following code segment at line 02:protected void FmtClr(object sender, EventArgs e) {Label LineTotal = new Label();LineTotal.ID = "LineTotal";if (LineTotal.Text.Length > 7){ LineTotal.ForeColor = Color.Red; }else{ LineTotal.ForeColor = Color.Black; }}D. Insert the following code segment at line 06:OnDataBound="FmtClr"Insert the following code segment at line 02:protected void FmtClr(object sender, EventArgs e) {Label LineTotal = new Label();LineTotal.ID = "LineTotalLabel";if (LineTotal.Text.Length > 7){ LineTotal.ForeColor = Color.Red; }else{ LineTotal.ForeColor = Color.Black; }}Answer: ASection: (none)Explanation/Reference:<asp:ListView OnItemDataBound="EventHandler" />The ItemDataBound event occurs when a data item is bound to data in a ListView control.The DataBinding event occurs when the server control binds to a data source.The DataBound event ocurs after the server control binds to a data source.The ListViewItemEventArgs.Item property gets the item that is being created or bound to data. The FindControl method searches the current naming container for the specified server control. B: The argument in e.Item.FindControl("LineTotal") is not correct since the Label control ID is "LineTotalLabel"QUESTION 4You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You define the following class:public class Product {public decimal Price { get; set; }}Your application contains a Web form with a Label control named lblPrice.You use a StringReader variable named xmlStream to access the following XML fragment:<Product><Price>35</Price></Product>You need to display the price of the product from the XML fragment in the lblPrice Label control. Which code segment should you use?A. DataTable dt = new DataTable();dt.ExtendedProperties.Add("Type", "Product");dt.ReadXml(xmlStream);lblPrice.Text = dt.Rows[0]["Price"].ToString();B. XmlReader xr = XmlReader.Create(xmlStream);Product boughtProduct =xr.ReadContentAs(typeof(Product), null) as Product;lblPrice.Text = boughtProduct.Price.ToString();C. XmlSerializer xs = new XmlSerializer(typeof(Product));Product boughtProduct = xs.Deserialize(xmlStream) asProduct;lblPrice.Text = boughtProduct.Price.ToString();D. XmlDocument xDoc = new XmlDocument();xDoc.Load(xmlStream);Product boughtProduct = xDoc.OfType<Product>().First();lblPrice.Text = boughtProduct.Price.ToString();Answer: CSection: (none)Explanation/Reference:QUESTION 5You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You create a Web form and add the following code fragment:<asp:Repeater ID="rptData" runat="server" DataSourceID="SqlDataSource1" ItemDataBound="rptData_ItemDataBound"><ItemTemplate><asp:Label ID="lblQuantity" runat="server"Text='<%# Eval("QuantityOnHand") %>' /></ItemTemplate></asp:Repeater>The SqlDataSource1 DataSource control retrieves the Quantity column values from a table named Products.You write the following code segment to create the rptData_ItemDataBound event handler:01 protected void rptData_ItemDataBound(object sender,02 RepeaterItemEventArgs e)03 {04 ►05 if(lbl != null)06 if(int.Parse(lbl.Text) < 10)07 lbl.ForeColor = Color.Red;08 }You need to retrieve a reference to the lblQuantity Label control into a variable named lbl.Which code segment should you insert at line 04?A. Label lbl = Page.FindControl("lblQuantity") as Label;B. Label lbl = e.Item.FindControl("lblQuantity") as Label;C. Label lbl = rptData.FindControl("lblQuantity") as Label;D. Label lbl = e.Item.Parent.FindControl("lblQuantity") asLabel;Answer: BSection: (none)Explanation/Reference:The RepeaterItemEventArgs.Item property gets the RepeaterItem associated with the event. The FindControl method searches the current naming container for the specified server control. QUESTION 6You create a Microsoft application by using the Microsoft .NET Framework version 3.5. Your application has a user control named UserCtrl.ascx. You write the following code fragmentto create a Web page named Default.aspx:<%@ Page Language="C#" AutoEventWireup="true" CodeFile="Default.aspx.cs" Inherits="_Default" %><html>...<body><form id="form1" runat="server"><div><asp:Label ID="lblHeader" runat="server"></asp:Label><asp:Label ID="lbFooter" runat="server"></asp:Label></div></form></body></html>You need to dynamically add the UserCtrl.ascx control between the lblHeader and lblFooter Label controls.What should you do?A. Write the following code segment in the Init event of the Default.aspxWeb page:Control ctrl = LoadControl("UserCtrl.ascx");this.Controls.AddAt(1, ctrl);B. Write the following code segment in the Init event of the Default.aspxWeb page.Control ctrl = LoadControl("UserCtrl.ascx");lblHeader.Controls.Add(ctrl);C. Add a Literal control named Ltrl between the lblHeader and lblFooterlabel controls.Write the following code segment in the Init event of the Default.aspxWeb page:Control ctrl = LoadControl("UserCtrl.ascx");D. Add a PlaceHolder control named PlHldr between the lblHeader andlblFooter label controls.Write the following code segment in the Init event of the Default.aspxWeb page:Control ctrl = LoadControl("UserCtrl.ascx");PlHldr.Controls.Add(ctrl);Answer: DSection: (none)Explanation/Reference:Anwser A would be ok if the second line was the following:this.form1.Controls.AddAt(2, ctrl);QUESTION 7You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You create two user controls named UserCtrlA.ascx and UserCtrlB.asc x. The user controls postback to the server.You create a new Web page that has the following ASPX code:<asp:CheckBox ID="Chk" runat="server"oncheckedchanged="Chk_CheckedChanged"AutoPostBack="true" /><asp:PlaceHolder ID="PlHolder" runat="server"></asp:PlaceHolder>To dynamically create the user controls, you write the following code segment for the Web page: public void LoadControls(){if (ViewState["CtrlA"] != null){Control c;if ((bool)ViewState["CtrlA"] == true){c = LoadControl("UserCtrlA.ascx");} else {c = LoadControl("UserCtrlB.ascx");}c.ID = "Ctrl";PlHolder.Controls.Add(c);}}protected void Chk_CheckedChanged(object sender, EventArgs e){ViewState["CtrlA"] = Chk.Checked;PlHolder.Controls.Clear();LoadControls();}You need to ensure that the user control that is displayed meets the following requirements:It is recreated during postbackIt retains its state.Which method should you add to the Web page?A. protected override object SaveViewState() {LoadControls();return base.SaveViewState();}B. protected override void Render(HtmlTextWriter writer) {LoadControls();base.Render(writer);}C. protected override void OnLoadComplete(EventArgs e) {base.OnLoadComplete(e);LoadControls();}D. protected override void LoadViewState(object savedState){base.LoadViewState(savedState);LoadControls();}Answer: DSection: (none)Explanation/Reference:The Control.LoadViewState method restores view-state information from a previous page request that was saved by the SaveViewState methodQUESTION 8You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You create the following controls:a composite custom control named MyControl.a templated custom control named OrderFormData.You write the following code segment to override the method named CreateChildControls() in the MyControl class:01 protected override void CreateChildControls()02 {03 Controls.Clear();04 OrderFormData oFData = new05 OrderFormData("OrderForm");06 ►07 }You need to add the OrderFormData control to the MyControl control.Which code segment should you insert at line 06?A. Template.InstantiateIn(this);Controls.Add(oFData);B. Template.InstantiateIn(oFData);Controls.Add(oFData);C. oFData.TemplateControl = (TemplateControl)Template;Controls.Add(oFData);D. this.TemplateControl = (TemplateControl)Template;this.Controls.Add(oFData);Answer: BSection: (none)Explanation/Reference:The ITemplate.InstantiateIn method, when implemented by a class, defines the Control object that child controls and templates belong to. These child controls are in turn defined within an inline template.According to Eilon Lipton's blog, here's the correct way to instantiate a template:public ITemplate MyTemplate { ... }public override void OnPreRender(EventArgs e) {if (MyTemplate != null) {Control templateContainer = new Control();MyTemplate.InstantiateIn(templateContainer);Controls.Add(templateContainer);}}QUESTION 9You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You create a composite custom control named MyControl.You need to add an instance of the OrderFormData control to the MyControl control.Which code segment should you use?A. protected override void CreateChildControls() {Controls.Clear();OrderFormData oFData = new OrderFormData("OrderForm");Controls.Add(oFData);}B. protected override void RenderContents(HtmlTextWriterwriter) {OrderFormData oFData = new OrderFormData("OrderForm");oFData.RenderControl(writer);}C. protected override void EnsureChildControls() {Controls.Clear();OrderFormData oFData = new OrderFormData("OrderForm");oFData.EnsureChildControls();if (!ChildControlsCreated)CreateChildControls();}D. protected override ControlCollectionCreateControlCollection() {ControlCollection controls = newControlCollection(this);OrderFormData oFData = new OrderFormData("OrderForm");controls.Add(oFData);return controls;}Answer: ASection: (none)Explanation/Reference:The Control.CreateChildControls method is called by the page framework to notify server controls that use composition-based implementation to create any child controls they contain in preparation for posting back or rendering.Note: When you develop a composite or templated server control, you must override this method. Controls that override the CreateChildControls method should implement the INamingContainer interface to avoid naming conflicts.QUESTION 10You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You add a TextBox control named TextBox1.You write the following code segment for validation:protected void CustomValidator1_ServerValidate(object source, ServerValidateEventArgs args) {DateTime dt = String.IsNullOrEmpty(args.Value) ? DateTime.Now : Convert.ToDateTime(args.Value);args.IsValid = (DateTime.Now - dt).Days < 10;}You need to validate the value of TextBox1.Which code fragment should you add to the Web page?A. <asp:CustomValidator ID="CustomValidator1"runat="server"ControlToValidate="TextBox1"ValidateEmptyText="True"onservervalidate="CustomValidator1_ServerValidate"></asp:CustomValidator><asp:CompareValidator ID="CompareValidator1"runat="server"Type="Date" EnableClientScript="true"ControlToValidate="TextBox1"Operator="DataTypeCheck"></asp:CompareValidator>B. <asp:CustomValidator ID="CustomValidator1"runat="server"ControlToValidate="TextBox1"ValidateEmptyText="True"onservervalidate="CustomValidator1_ServerValidate"></asp:CustomValidator><asp:RequiredFieldValidatorID="RequiredFieldValidator1"runat="server" ControlToValidate="TextBox1"InitialValue="<%= DateTime.Now; %>" ></asp:RequiredFieldValidator>C. <asp:CustomValidator ID="CustomValidator1"runat="server"ControlToValidate="TextBox1"ValidateEmptyText="True"onservervalidate="CustomValidator1_ServerValidate"></asp:CustomValidator><asp:CompareValidator ID="CompareValidator1"runat="server"Type="Date" EnableClientScript="true"ControlToValidate="TextBox1"ValueToCompare="<%= DateTime.Now; %>"></asp:CompareValidator>D. <asp:CustomValidator ID="CustomValidator1"runat="server"ControlToValidate="TextBox1"ValidateEmptyText="True"onservervalidate="CustomValidator1_ServerValidate"></asp:CustomValidator><asp:RequiredFieldValidatorID="RequiredFieldValidator1" runat="server"ControlToValidate="TextBox1"EnableClientScript="false"InitialValue="<%= DateTime.Now; %>"></asp:RequiredFieldValidator>Answer: ASection: (none)Explanation/Reference:The CompareValidator can also be used to verify that the data entered into a given control is of a certain data type, such as a date or a number. To do so, you set the Type property to a valid data type. will then validate that the user’s input can be cast into a valid instance of the given type. If all you intend is a data type check, you can also set the Operator property to DataTypeCheck.If you set the Operator property to DataTypeCheck, the CompareValidator control ignores both the ControlToCompare and ValueToCompare properties and simply indicates whether the value entered into the input control can be converted to the data type specified by the Type property. QUESTION 11You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You add an XmlDataSource control named XmlDataSource1 to the Web page.XmlDataSource1 is bound to an XML document with the following structure:<?xml version="1.0" encoding="utf-8" ?><clients><client ID="1" Name="John Evans" /><client ID="2" Name="Mike Miller"/>...</clients>You also write the following code segment in the code-behind file of the Web page:protected void BulletedList1_Click (object sender, BulletedListEventArgs e) {// ...}You need to add a BulletedList control named BulletedList1 to the Web page that is bound to XmlDataSource1.Which code fragment should you use?A. <asp:BulletedList ID="BulletedList1" runat="server"DisplayMode="LinkButton" DataSource="XmlDataSource1"DataTextField="Name" DataValueField="ID"onclick="BulletedList1_Click"></asp:BulletedList>B. <asp:BulletedList ID="BulletedList1" runat="server"DisplayMode="HyperLink"DataSourceID="XmlDataSource1"DataTextField="Name" DataMember="ID"onclick="BulletedList1_Click"></asp:BulletedList>C. <asp:BulletedList ID="BulletedList1" runat="server"DisplayMode="LinkButton"DataSourceID="XmlDataSource1"DataTextField="Name" DataValueField="ID"onclick="BulletedList1_Click"></asp:BulletedList>D. <asp:BulletedList ID="BulletedList1" runat="server"DisplayMode="HyperLink"DataSourceID="XmlDataSource1"DataTextField="ID" DataValueField="Name"onclick="BulletedList1_Click"></asp:BulletedList>Answer: CSection: (none)Explanation/Reference:DataSource ID, NOT DataSourceYou set the DataTextField to the name of the column that contains the data you wish to display to the user. You set the DataValueField to the column that contains the value(s) you wish to return to the server for a selected item.Set the DisplayMode to LinkButton to display list content as links. Use the BulletedList.Click event to post back to the server when a link button is clicked.Don't set DisplayMode to Hyperlink. When clicked, a hyperlink navigates to a URL and therefore doesn't respond to the BulletedList.Click event!QUESTION 12You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You write the following code fragment:<asp:ListBox SelectionMode="Multiple" ID="ListBox1" runat="server"></asp:ListBox><asp:ListBox ID="ListBox2" runat="server"> </asp:ListBox><asp:Button ID="Button1" runat="server" Text="Button"onclick="Button1_Click" />You need to ensure that when you click the Button1 control, a selected list of items move from the ListBox1 control to the ListBox2 control.Which code segment should you use?A. foreach (ListItem li in ListBox1.Items) {if (li.Selected) {ListBox2.Items.Add(li);ListBox1.Items.Remove(li);}}B. foreach (ListItem li in ListBox1.Items) {if (li.Selected) {li.Selected = false;ListBox2.Items.Add(li);ListBox1.Items.Remove(li);}}C. foreach (ListItem li in ListBox1.Items) {if (li.Selected) {li.Selected = false;ListBox2.Items.Add(li);}}foreach (ListItem li in ListBox2.Items) {if (ListBox1.Items.Contains(li))ListBox1.Items.Remove(li);}D. foreach (ListItem li in ListBox1.Items) {if (li.Selected)ListBox1.Items.Remove(li);}foreach (ListItem li in ListBox1.Items) {if (ListBox2.Items.Contains(li))ListBox1.Items.Remove(li);}Answer: CSection: (none)Explanation/Reference:Note: The initial answers were different. Answers C et D were split in 2 sub-answers and you had to choose C and D. I changed the answers in order to match the real exam.QUESTION 13You create a Microsoft application by using the Microsoft .NET Framework version 3.5. You write the following code fragment:<asp:DropDownList AutoPostBack="true" ID="DropDownList1" runat="server" onselectedindexchanged= "DropDownList1_SelectedIndexChanged"><asp:ListItem>1</asp:ListItem><asp:ListItem>2</asp:ListItem><asp:ListItem>3</asp:ListItem></asp:DropDownList>You also add a MultiView control named MultiView1 to the Web page. MultiView1 has three child View controls.You need to ensure that you can select the View controls by using the DropDownList1 DropDownList control.Which code segment should you use?A. int idx = DropDownList1.SelectedIndex;MultiView1.ActiveViewIndex = idx;B. int idx = DropDownList1.SelectedIndex;MultiView1.Views[idx].Visible = true;C. int idx = int.Parse(DropDownList1.SelectedValue);MultiView1.ActiveViewIndex = idx;D. int idx = int.Parse(DropDownList1.SelectedValue);MultiView1.Views[idx].Visible = true;Answer: ASection: (none)Explanation/Reference:ActiveViewIndex property is a zero base index. When set to -1, no View controls are displayed. QUESTION 14You create a Microsoft application by using the Microsoft .NET Framework version 3.5. To add a Calendar server control to a Web page, you write the following code fragment:<asp:Calendar SelectionMode="DayWeek" ID="Calendar1" runat="server"></asp:Calendar>You need to disable the non-week days in the Calendar control.What should you do?A. Add the following code segment to the Calendar1 DayRender eventhandler:if (e.Day.IsWeekend) {Day.IsSelectable = false;}B. Add the following code segment to the Calendar1 DayRender eventhandler:if (e.Day.IsWeekend) {if (Calendar1.SelectedDates.Contains(e.Day.Date))Calendar1.SelectedDates.Remove(e.Day.Date);}C. Add the following code segment to the Calendar1 SelectionChangedevent handler:List<DateTime> list = new List<DateTime>();foreach (DateTime st in (sender asCalendar).SelectedDates) {if (st.DayOfWeek == DayOfWeek.Saturday || st.DayOfWeek== DayOfWeek.Sunday) {list.Add(st);}}foreach (DateTime dt in list) {(sender as Calendar).SelectedDates.Remove(dt);}D. Add the following code segment to the Calendar1 DataBinding eventhandler:。
卡尔曼滤波算法英文格式

卡尔曼滤波算法英文格式The Kalman filter is a mathematical algorithm that represents a recursive solution to the least squares problem. It's a powerful tool for estimating the state of a system from noisy observations.This algorithm is widely used in various fields,including navigation systems, aerospace, and economics, where it helps in predicting the future state of a system based on the current state and measurements.The Kalman filter works by combining a prediction step and a measurement update step. The prediction step estimates the next state of the system, while the update step refines this prediction using new measurements.One of the key strengths of the Kalman filter is its ability to handle uncertainty in both the system's dynamics and the measurements. It does this by using a statistical approach that incorporates the uncertainty in the form of covariance matrices.Despite its complexity, the Kalman filter is relatively easy to implement and can be adapted to a wide range of applications. Its versatility and accuracy make it a popular choice for real-time state estimation.In conclusion, the Kalman filter is an essentialalgorithm for anyone working with dynamic systems. Its ability to provide accurate state estimates in the presence of noise has made it a cornerstone of modern control theory and data analysis.。
卡尔曼滤波的英文形式

卡尔曼滤波的英文形式Kalman Filter.The Kalman filter is a mathematical algorithm that estimates the state of a dynamic system from a series of measurements. It is named after Rudolf Kalman, who developed it in the 1960s. The Kalman filter is used in a wide variety of applications, including tracking, navigation, and control.How the Kalman Filter Works.The Kalman filter is a recursive algorithm that consists of two steps:1. Prediction: In the prediction step, the filter estimates the state of the system at the current time step based on the state at the previous time step and the system dynamics.2. Update: In the update step, the filter updates the estimate of the state based on the new measurement.The Kalman filter is a powerful tool for estimating the state of a dynamic system. However, it is important to note that the filter is only as good as the model of the system that is used. If the model is not accurate, then the filter will not be able to provide accurate estimates.Applications of the Kalman Filter.The Kalman filter is used in a wide variety of applications, including:Tracking: The Kalman filter can be used to track the position and velocity of a moving object. This is usefulfor applications such as tracking satellites, aircraft, and missiles.Navigation: The Kalman filter can be used to navigate a vehicle by combining measurements from a variety of sensors, such as GPS, accelerometers, and gyroscopes.Control: The Kalman filter can be used to control a system by estimating the state of the system and then using that estimate to calculate the appropriate control inputs. This is useful for applications such as controlling robots and self-driving cars.Advantages of the Kalman Filter.The Kalman filter has several advantages over other estimation methods, including:Optimality: The Kalman filter is the optimal estimator for a linear system with Gaussian noise. This means that the filter will provide the most accurate estimates possible given the available measurements.Recursion: The Kalman filter is a recursive algorithm, which means that it can be implemented in real time. Thisis important for applications where it is necessary to estimate the state of a system in a timely manner.Robustness: The Kalman filter is robust to noise and outliers. This means that the filter can still provide accurate estimates even when the measurements are noisy or contain outliers.Disadvantages of the Kalman Filter.The Kalman filter also has some disadvantages, including:Computational complexity: The Kalman filter can be computationally complex, especially for large systems. This can be a problem for applications where real-time estimation is required.Sensitivity to model errors: The Kalman filter is sensitive to errors in the model of the system. This means that the filter can provide inaccurate estimates if the model is not accurate.Initialization: The Kalman filter requires an initial estimate of the state of the system. This estimate can bedifficult to obtain, especially for complex systems.Conclusion.The Kalman filter is a powerful tool for estimating the state of a dynamic system. The filter is optimal for linear systems with Gaussian noise and is recursive, robust, and computationally efficient. However, the filter is also sensitive to model errors and requires an initial estimate of the state of the system.。
adaptive_filters_theory_and_applications_2nd

adaptive_filters_theory_and_applications_2ndBrochureMore information from /doc/e9d77d4fdd3383c4ba4cd292.html /reports/2379637/Adaptive Filters. Theory and Applications. 2nd EditionDescription:This second edition of Adaptive Filters: Theory and Applications has been updated throughout to reflect the latest developments in this field; notably an increased coverage given to the practical applications of thetheory to illustrate the much broader range of adaptive filters applications developed in recent years. Thebook offers an easy to understand approach to the theory and application of adaptive filters by clearlyillustrating how the theory explained in earlier chapters of the book is modified for the various applications discussed in detail in later chapters. This integrated approach makes the book a valuable resource forgraduate students; and the inclusion of more advanced applications including antenna arrays and wireless communications makes it a suitable technical reference for engineers, practitioners and researchers.Key features:- Offers a thorough treatment of the theory of adaptive signal processing; incorporating new material ontransform domain, frequency domain, subband adaptive filters, acoustic echo cancellation and active noisecontrol.- Provides an in–depth study of applications which now includes extensive coverage of OFDM, MIMO andsmart antennas.- Contains exercises and computer simulation problems at the end of each chapter.- Includes a new companion website hosting MATLAB? simulation programs which complement thetheoretical analyses, enabling the reader to gain an in–depth understanding of the behaviours andproperties of the various adaptive algorithms.Contents:Preface xviiAcknowledgments xxi1 Introduction 11.1 Linear Filters 11.2 Adaptive Filters 21.3 Adaptive Filter Structures 31.4 Adaptation Approaches 71.5 Real and Complex Forms of Adaptive Filters 91.6 Applications 92 Discrete–Time Signals and Systems 282.1 Sequences and z–Transform 282.2 Parseval s Relation 322.3 System Function 332.4 Stochastic Processes 35Problems 443 Wiener Filters 483.1 Mean–Squared Error Criterion 483.2 Wiener Filter Transversal, Real–Valued Case 503.3 Principle of Orthogonality 553.4 Normalized Performance Function 573.5 Extension to Complex–Valued Case 583.6 Unconstrained Wiener Filters 613.7 Summary and Discussion 79Problems 804 Eigenanalysis and Performance Surface 904.1 Eigenvalues and Eigenvectors 904.2 Properties of Eigenvalues and Eigenvectors 914.3 Performance Surface 104Problems 1125 Search Methods 1195.1 Method of Steepest Descent 1205.2 Learning Curve 1265.3 Effect of Eigenvalue Spread 1305.4 Newton s Method 1315.5 An Alternative Interpretation of Newton s Algorithm 133 Problems 1356 LMS Algorithm 1396.1 Derivation of LMS Algorithm 1396.2 Average Tap–Weight Behavior of the LMS Algorithm 141 6.3 MSE Behavior of the LMS Algorithm 144 6.4 Computer Simulations 1566.5 Simplified LMS Algorithms 1676.6 Normalized LMS Algorithm 1706.7 Affine Projection LMS Algorithm 1736.8 Variable Step–Size LMS Algorithm 1776.9 LMS Algorithm for Complex–Valued Signals 1796.10 Beamforming (Revisited) 182Problems 190Appendix 6A: Derivation of Eq. (6.39) 2057 Transform Domain Adaptive Filters 2077.1 Overview of Transform Domain Adaptive Filters 2087.2 Band–Partitioning Property of Orthogonal Transforms 2107.3 Orthogonalization Property of Orthogonal Transforms 2117.4 Transform Domain LMS Algorithm 2137.5 Ideal LMS–Newton Algorithm and Its Relationship with TDLMS 2157.6 Selection of the Transform T 2167.7 Transforms 2297.8 Sliding Transforms 2307.9 Summary and Discussion 242Problems 2438 Block Implementation of Adaptive Filters 2518.1 Block LMS Algorithm 2528.2 Mathematical Background 2558.3 The FBLMS Algorithm 2608.4 The Partitioned FBLMS Algorithm 2678.5 Computer Simulations 276Problems 279Appendix 8A: Derivation of a Misadjustment Equation for the BLMS Algorithm 285 Appendix 8B: Derivation of Misadjustment Equations for the FBLMS Algorithms 288 9 Subband Adaptive Filters 2949.1 DFT Filter Banks 2959.2 Complementary Filter Banks 2999.3 Subband Adaptive Filter Structures 3039.4 Selection of Analysis and Synthesis Filters 3049.5 Computational Complexity 3079.6 Decimation Factor and Aliasing 3089.7 Low–Delay Analysis and Synthesis Filter Banks 3109.8 A Design Procedure for Subband Adaptive Filters 3139.9 An Example 316Problems 31910 IIR Adaptive Filters 32210.1 Output Error Method 32310.2 Equation Error Method 32710.3 Case Study I: IIR Adaptive Line Enhancement 33210.4 Case Study II: Equalizer Design for Magnetic Recording Channels 343 10.5 Concluding Remarks 349 Problems 35211 Lattice Filters 35511.1 Forward Linear Prediction 35511.2 Backward Linear Prediction 35711.3 Relationship Between Forward and Backward Predictors 35911.4 Prediction–Error Filters 35911.5 Properties of Prediction Errors 36011.6 Derivation of Lattice Structure 36211.7 Lattice as an Orthogonalization Transform 36711.8 Lattice Joint Process Estimator 36911.9 System Functions 37011.10 Conversions 37011.11 All–Pole Lattice Structure 37611.12 Pole–Zero Lattice Structure 37611.13 Adaptive Lattice Filter 37811.14 Autoregressive Modeling of Random Processes 38311.15 Adaptive Algorithms Based on Autoregressive Modeling 385 Problems 400Appendix 11A: Evaluation of E[ua(n)xT(n)K(n)x(n)uTa (n)] 407Appendix 11B: Evaluation of the parameter 40812 Method of Least–Squares 41012.1 Formulation of Least–Squares Estimation for a Linear Combiner 411 12.2 Principle of Orthogonality 41212.3 Projection Operator 41512.4 Standard Recursive Least–Squares Algorithm 41612.5 Convergence Behavior of the RLS Algorithm 421Problems 43013 Fast RLS Algorithms 43313.1 Least–Squares Forward Prediction 43413.2 Least–Squares Backward Prediction 43513.3 Least–Squares Lattice 43713.4 RLSL Algorithm 44013.5 FTRLS Algorithm 453Problems 46014 Tracking 46314.1 Formulation of the Tracking Problem 46314.2 Generalized Formulation of LMS Algorithm 46414.3 MSE Analysis of the Generalized LMS Algorithm 46514.4 Optimum Step–Size Parameters 46914.5 Comparisons of Conventional Algorithms 47114.6 Comparisons Based on Optimum Step–Size Parameters 475 14.7 VSLMS: An Algorithm with Optimum Tracking Behavior 477 14.8 RLS Algorithm with Variable Forgetting Factor 48514.9 Summary 486Problems 48815 Echo Cancellation 49215.1 The Problem Statement 49215.2 Structures and Adaptive Algorithms 49515.3 Double–Talk Detection 51215.4 Howling Suppression 52115.5 Stereophonic Acoustic Echo Cancellation 524Appendix 15A: Multitaper method 542Appendix 15B: Derivation of the Two–Channel Levinson Durbin Algorithm 54916 Active Noise Control 55116.1 Broadband Feedforward Single–Channel ANC 55316.2 Narrowband Feedforward Single–Channel ANC 55916.3 Feedback Single–Channel ANC 57316.4 Multichannel ANC Systems 577Appendix 16A: Derivation of Eq. (16.46) 582Appendix 16B: Derivation of Eq. (16.53) 58317 Synchronization and Equalization in Data Transmission Systems 584 17.1 Continuous Time Channel Model 585 17.2 Discrete Time Channel Model and Equalizer Structures 58917.3 Timing Recovery 59317.4 Equalizers Design and Performance Analysis 60617.5 Adaptation Algorithms 61717.6 Cyclic Equalization 61817.7 Joint Timing Recovery, Carrier Recovery, and Channel Equalization 628 17.8 Maximum Likelihood Detection 629 17.9 Soft Equalization 63117.10 Single–Input Multiple–Output Equalization 64317.11 Frequency Domain Equalization 64517.12 Blind Equalization 649Problems 65418 Sensor Array Processing 65918.1 Narrowband Sensor Arrays 66018.2 Broadband Sensor Arrays 67818.3 Robust Beamforming 683Problems 69219 Code Division Multiple Access Systems 69519.1 CDMA Signal Model 69519.2 Linear Detectors 69919.3 Adaptation Methods 707Problems 70920 OFDM and MIMO Communications 71120.1 OFDM Communication Systems 71120.2 MIMO Communication Systems 73020.3 MIMO OFDM 743Problems 743References 746Index 761Ordering:Order Online - /doc/e9d77d4fdd3383c4ba4cd292.html /reports/2379637/ Order by Fax - using the form belowOrder by Post - print the order form below and send toResearch and Markets,Guinness Centre,Taylors Lane,Dublin 8,Ireland.Fax Order FormTo place an order via fax simply print this form, fill in the information below and fax the completed form to 646-607-1907 (from USA) or +353-1-481-1716 (from Rest of World). If you have any questions please visit/doc/e9d77d4fdd3383c4ba4cd292.html /contact/Order Information Please verify that the product information is correct.Product Format Please select the product format and quantity you require:* Shipping/Handling is only charged once per order.Contact InformationPlease enter all the information below in BLOCK CAPITALSProduct Name:Adaptive Filters. Theory and Applications. 2nd Edition Web Address:/doc/e9d77d4fdd3383c4ba4cd292.html /reports/2379637/Office Code:SCLIZ46G QuantityHard Copy (HardBack):USD 128 + USD 28 Shipping/HandlingTitle:MrMrsDrMissMsProf First Name:Last Name:Email Address: *Job Title:Organisation:Address:City:Postal / Zip Code:Country:Phone Number:Fax Number:* Please refrain from using free email accounts when ordering (e.g. Yahoo, Hotmail, AOL)Payment InformationPlease indicate the payment method you would like to use by selecting the appropriate box.Please fax this form to:(646) 607-1907 or (646) 964-6609 - From USA+353-1-481-1716 or +353-1-653-1571 - From Rest of World Pay by credit card:You will receive an email with a link to a secure webpage to enter yourcredit card details.Pay by check:Please post the check, accompanied by this form, to:Research and Markets,Guinness Center,Taylors Lane,Dublin 8,Ireland.Pay by wire transfer:Please transfer funds to:Account number833 130 83Sort code98-53-30Swift codeULSBIE2D IBAN numberIE78ULSB98533083313083Bank Address Ulster Bank,27-35 Main Street,Blackrock,Co. Dublin,Ireland.If you have a Marketing Code please enter it below:Marketing Code:Please note that by ordering from Research and Markets you are agreeing to our Terms and Conditions at/doc/e9d77d4fdd3383c4ba4cd292.html /info/terms.asp。
电气安全名词术语GB

标准名称:电气安全名词术语GB 4776-84标准编号:GB 4776-84标准正文:国家标准1984-11-30发布1988-07-01实施1基本概念1.1保安性fail-safe为防止产品本身的危险故障而设计的性能。
1.2正常状态nromal condition所有用于防止危险的设施均无损坏的状态。
1.3电气事故electric accident由电流、电磁场、雷电、静电和某些电路故障等直接或间接造成建筑设施、电气设备毁坏、人、动物伤亡,以及引起火灾和爆炸等后果的事件。
1.4触电电击electric shock电流通过人体或动物体而引起的病理、生理效应。
1.5电磁场伤害injury due to electromagnetic field人体在电磁场作用下吸收能量受到的伤害。
1.6破坏性放电介质击穿disruptive discharge dielectric breakdown固体、液体、气体介质及其组合介质在高电压作用下,介质强度丧失的现象。
破坏性放电时,电极间的电压迅速下降到零或接近于零。
1.7短路short circuit通过比较小的电阻或阻抗,偶然地或有意地对一个电路中在正常情况下处于不同电压下的两点或几点之间进行的连接。
1.8绝缘故障insulation fault绝缘电阻的不正常下降。
1.9接地故障earth fault由于导体与地连接或对地绝缘电阻变得小于规定值而引起的故障。
1.10过电流overcurrent超过额定电流的电流。
1.11过电压overvoltage超过额定电压的电压。
1.12过负载overload超过额定负载的负载。
1.13导电部分conductive part能导电,但不一定承载工作电流的部分。
1.14带电部分live part正常使用时被通电的导体或导电部分,它包括中性导体,但按惯例,不包括保护中性导体(PEN导体)。
注:此术语不一定意味着触电危险。
1.15外露导电部分exposed conductive part电气设备能被触及的导电部分。
HEVC

Bi-linear interpolation filter for chroma samples (1/8-sample) Advanced motion vector prediction Context adaptive binary arithmetic entropy coding Internal bit-depth increase (4 bits) X Low complexity entropy coding phase 2 X Transform precision extension (4 bits) Deblocking filter Adaptive loop filter X
• 从上图中可以看到一种 新的不对称运动分割预 测(Asymmetric Motion Partition,AMP),这也是 HEVC与H.264在分块预 测技术中最为不同之处。 所谓AMP即将编码单元 分割成两个大小不一致 的预测块其中一个PU单 元的宽/长为CU单元的 3/4,这种预测考虑了大 尺寸可能的纹理分布可 以有效提高大尺寸块的 预测效率
1、Picture Partitioning
1.1. Treeblock(TB) Partitioning • Pictures are divided into slices and slices are divided into a sequence of treeblocks. • A treeblock is an NxN block of luma samples together with the two corresponding blocks of chroma samples for a picture that has three sample arrays. • The treeblock concept is broadly analogous to that of the macroblock in previous standards such as H.264/AVC [6].
IBM Cognos Transformer V11.0 用户指南说明书

adaptive_filters_theory_and_applications_2nd

BrochureMore information from /reports/2379637/Adaptive Filters. Theory and Applications. 2nd EditionDescription:This second edition of Adaptive Filters: Theory and Applications has been updated throughout to reflect the latest developments in this field; notably an increased coverage given to the practical applications of thetheory to illustrate the much broader range of adaptive filters applications developed in recent years. Thebook offers an easy to understand approach to the theory and application of adaptive filters by clearlyillustrating how the theory explained in earlier chapters of the book is modified for the various applicationsdiscussed in detail in later chapters. This integrated approach makes the book a valuable resource forgraduate students; and the inclusion of more advanced applications including antenna arrays and wirelesscommunications makes it a suitable technical reference for engineers, practitioners and researchers.Key features:- Offers a thorough treatment of the theory of adaptive signal processing; incorporating new material ontransform domain, frequency domain, subband adaptive filters, acoustic echo cancellation and active noisecontrol.- Provides an in–depth study of applications which now includes extensive coverage of OFDM, MIMO andsmart antennas.- Contains exercises and computer simulation problems at the end of each chapter.- Includes a new companion website hosting MATLAB® simulation programs which complement thetheoretical analyses, enabling the reader to gain an in–depth understanding of the behaviours andproperties of the various adaptive algorithms.Contents:Preface xviiAcknowledgments xxi1 Introduction 11.1 Linear Filters 11.2 Adaptive Filters 21.3 Adaptive Filter Structures 31.4 Adaptation Approaches 71.5 Real and Complex Forms of Adaptive Filters 91.6 Applications 92 Discrete–Time Signals and Systems 282.1 Sequences and z–Transform 282.2 Parseval s Relation 322.3 System Function 332.4 Stochastic Processes 35Problems 443 Wiener Filters 483.1 Mean–Squared Error Criterion 483.2 Wiener Filter Transversal, Real–Valued Case 503.3 Principle of Orthogonality 553.4 Normalized Performance Function 573.5 Extension to Complex–Valued Case 583.6 Unconstrained Wiener Filters 613.7 Summary and Discussion 79Problems 804 Eigenanalysis and Performance Surface 904.1 Eigenvalues and Eigenvectors 904.2 Properties of Eigenvalues and Eigenvectors 914.3 Performance Surface 104Problems 1125 Search Methods 1195.1 Method of Steepest Descent 1205.2 Learning Curve 1265.3 Effect of Eigenvalue Spread 1305.4 Newton s Method 1315.5 An Alternative Interpretation of Newton s Algorithm 133 Problems 1356 LMS Algorithm 1396.1 Derivation of LMS Algorithm 1396.2 Average Tap–Weight Behavior of the LMS Algorithm 141 6.3 MSE Behavior of the LMS Algorithm 1446.4 Computer Simulations 1566.5 Simplified LMS Algorithms 1676.6 Normalized LMS Algorithm 1706.7 Affine Projection LMS Algorithm 1736.8 Variable Step–Size LMS Algorithm 1776.9 LMS Algorithm for Complex–Valued Signals 1796.10 Beamforming (Revisited) 1826.11 Linearly Constrained LMS Algorithm 186Problems 190Appendix 6A: Derivation of Eq. (6.39) 2057 Transform Domain Adaptive Filters 2077.1 Overview of Transform Domain Adaptive Filters 2087.2 Band–Partitioning Property of Orthogonal Transforms 2107.3 Orthogonalization Property of Orthogonal Transforms 2117.4 Transform Domain LMS Algorithm 2137.5 Ideal LMS–Newton Algorithm and Its Relationship with TDLMS 2157.6 Selection of the Transform T 2167.7 Transforms 2297.8 Sliding Transforms 2307.9 Summary and Discussion 242Problems 2438 Block Implementation of Adaptive Filters 2518.1 Block LMS Algorithm 2528.2 Mathematical Background 2558.3 The FBLMS Algorithm 2608.4 The Partitioned FBLMS Algorithm 2678.5 Computer Simulations 276Problems 279Appendix 8A: Derivation of a Misadjustment Equation for the BLMS Algorithm 285 Appendix 8B: Derivation of Misadjustment Equations for the FBLMS Algorithms 288 9 Subband Adaptive Filters 2949.1 DFT Filter Banks 2959.2 Complementary Filter Banks 2999.3 Subband Adaptive Filter Structures 3039.4 Selection of Analysis and Synthesis Filters 3049.5 Computational Complexity 3079.6 Decimation Factor and Aliasing 3089.7 Low–Delay Analysis and Synthesis Filter Banks 3109.8 A Design Procedure for Subband Adaptive Filters 3139.9 An Example 3169.10 Comparison with FBLMS Algorithm 318Problems 31910 IIR Adaptive Filters 32210.1 Output Error Method 32310.2 Equation Error Method 32710.3 Case Study I: IIR Adaptive Line Enhancement 33210.4 Case Study II: Equalizer Design for Magnetic Recording Channels 343 10.5 Concluding Remarks 349Problems 35211 Lattice Filters 35511.1 Forward Linear Prediction 35511.2 Backward Linear Prediction 35711.3 Relationship Between Forward and Backward Predictors 35911.4 Prediction–Error Filters 35911.5 Properties of Prediction Errors 36011.6 Derivation of Lattice Structure 36211.7 Lattice as an Orthogonalization Transform 36711.8 Lattice Joint Process Estimator 36911.9 System Functions 37011.10 Conversions 37011.11 All–Pole Lattice Structure 37611.12 Pole–Zero Lattice Structure 37611.13 Adaptive Lattice Filter 37811.14 Autoregressive Modeling of Random Processes 38311.15 Adaptive Algorithms Based on Autoregressive Modeling 385 Problems 400Appendix 11A: Evaluation of E[ua(n)xT(n)K(n)x(n)uTa (n)] 407Appendix 11B: Evaluation of the parameter 40812 Method of Least–Squares 41012.1 Formulation of Least–Squares Estimation for a Linear Combiner 411 12.2 Principle of Orthogonality 41212.3 Projection Operator 41512.4 Standard Recursive Least–Squares Algorithm 41612.5 Convergence Behavior of the RLS Algorithm 421Problems 43013 Fast RLS Algorithms 43313.1 Least–Squares Forward Prediction 43413.2 Least–Squares Backward Prediction 43513.3 Least–Squares Lattice 43713.4 RLSL Algorithm 44013.5 FTRLS Algorithm 453Problems 46014 Tracking 46314.1 Formulation of the Tracking Problem 46314.2 Generalized Formulation of LMS Algorithm 46414.3 MSE Analysis of the Generalized LMS Algorithm 46514.4 Optimum Step–Size Parameters 46914.5 Comparisons of Conventional Algorithms 47114.6 Comparisons Based on Optimum Step–Size Parameters 475 14.7 VSLMS: An Algorithm with Optimum Tracking Behavior 477 14.8 RLS Algorithm with Variable Forgetting Factor 48514.9 Summary 486Problems 48815 Echo Cancellation 49215.1 The Problem Statement 49215.2 Structures and Adaptive Algorithms 49515.3 Double–Talk Detection 51215.4 Howling Suppression 52115.5 Stereophonic Acoustic Echo Cancellation 524Appendix 15A: Multitaper method 542Appendix 15B: Derivation of the Two–Channel Levinson Durbin Algorithm 54916 Active Noise Control 55116.1 Broadband Feedforward Single–Channel ANC 55316.2 Narrowband Feedforward Single–Channel ANC 55916.3 Feedback Single–Channel ANC 57316.4 Multichannel ANC Systems 577Appendix 16A: Derivation of Eq. (16.46) 582Appendix 16B: Derivation of Eq. (16.53) 58317 Synchronization and Equalization in Data Transmission Systems 584 17.1 Continuous Time Channel Model 58517.2 Discrete Time Channel Model and Equalizer Structures 58917.3 Timing Recovery 59317.4 Equalizers Design and Performance Analysis 60617.5 Adaptation Algorithms 61717.6 Cyclic Equalization 61817.7 Joint Timing Recovery, Carrier Recovery, and Channel Equalization 628 17.8 Maximum Likelihood Detection 62917.9 Soft Equalization 63117.10 Single–Input Multiple–Output Equalization 64317.11 Frequency Domain Equalization 64517.12 Blind Equalization 649Problems 65418 Sensor Array Processing 65918.1 Narrowband Sensor Arrays 66018.2 Broadband Sensor Arrays 67818.3 Robust Beamforming 683Problems 69219 Code Division Multiple Access Systems 69519.1 CDMA Signal Model 69519.2 Linear Detectors 69919.3 Adaptation Methods 707Problems 70920 OFDM and MIMO Communications 71120.1 OFDM Communication Systems 71120.2 MIMO Communication Systems 73020.3 MIMO OFDM 743Problems 743References 746Index 761Ordering:Order Online - /reports/2379637/ Order by Fax - using the form belowOrder by Post - print the order form below and send toResearch and Markets,Guinness Centre,Taylors Lane,Dublin 8,Ireland.Fax Order FormTo place an order via fax simply print this form, fill in the information below and fax the completed form to 646-607-1907 (from USA) or +353-1-481-1716 (from Rest of World). If you have any questions please visit/contact/Order Information Please verify that the product information is correct.Product Format Please select the product format and quantity you require:* Shipping/Handling is only charged once per order.Contact InformationPlease enter all the information below in BLOCK CAPITALSProduct Name:Adaptive Filters. Theory and Applications. 2nd Edition Web Address:/reports/2379637/Office Code:SCLIZ46G QuantityHard Copy (HardBack):USD 128 + USD 28 Shipping/HandlingTitle:MrMrsDrMissMsProf First Name:Last Name:Email Address: *Job Title:Organisation:Address:City:Postal / Zip Code:Country:Phone Number:Fax Number:* Please refrain from using free email accounts when ordering (e.g. Yahoo, Hotmail, AOL)Payment InformationPlease indicate the payment method you would like to use by selecting the appropriate box.Please fax this form to:(646) 607-1907 or (646) 964-6609 - From USA+353-1-481-1716 or +353-1-653-1571 - From Rest of World Pay by credit card:You will receive an email with a link to a secure webpage to enter yourcredit card details.Pay by check:Please post the check, accompanied by this form, to:Research and Markets,Guinness Center,Taylors Lane,Dublin 8,Ireland.Pay by wire transfer:Please transfer funds to:Account number833 130 83Sort code98-53-30Swift codeULSBIE2D IBAN numberIE78ULSB98533083313083Bank Address Ulster Bank,27-35 Main Street,Blackrock,Co. Dublin,Ireland.If you have a Marketing Code please enter it below:Marketing Code:Please note that by ordering from Research and Markets you are agreeing to our Terms and Conditions at /info/terms.asp。
Recursive filter system for a video signal

专利名称:Recursive filter system for a video signal发明人:Arthur Mitchell,Anthony Richard Huggett申请号:US11809658申请日:20070601公开号:US20080002903A1公开日:20080103专利内容由知识产权出版社提供专利附图:摘要:A recursive filter system for a video image includes a memory to store a first image of stored picture elements S(x,y). Weighted values W(x,y) of luminance andchrominance of a stored picture element S(x,y) are obtained by summing weighted values B(x,y).S(x,y) of luminance and chrominance of the picture element and neighbouringpicture elements. A first proportional parameter A(x,y) is generated for the stored picture element based on a modular sum of differences between luminance and chrominance of the stored picture element and of surrounding picture elements. The first proportional parameter A(x,y) is used to generate a weighted picture element M(x,y) from a proportion of the stored picture element S(x,y) and a complementary proportion of the weighted value W(x,y). Picture elements C(x,y) of a next image and a second proportional parameter K are input and a filtered image generated by combining a proportion K of each input picture element of the next image with a complementary proportion 1−K of the weighted stored picture element M(x,y) of the first stored image using the second proportional parameter K. The filtered image is stored for processing a next succeeding image. In embodiments of the invention the second proportional parameter K may be varied pixel to pixel dependent on noise, motion and detail in a region of a picture element being processed.申请人:Arthur Mitchell,Anthony Richard Huggett地址:Winchester GB,Eastleigh GB国籍:GB,GB更多信息请下载全文后查看。
iir滤波算法c语言

iir滤波算法c语言The IIR (Infinite Impulse Response) filter is a digital filter commonly used in signal processing applications. It is a recursive filter that utilizes feedback to achieve its filtering characteristics. In this response, we will explore the IIR filter algorithm in the C programming language, discussing its working principle, implementation, advantages, disadvantages, and applications.The IIR filter algorithm operates by recursively applying a set of coefficients to the input signal and its previous output samples. This recursive nature allows the filter to have an infinite impulse response, meaning it can have a long-lasting effect on the output signal. Thefilter's response is determined by its transfer function, which is defined by the coefficients used in the algorithm.Implementing the IIR filter algorithm in C requires a basic understanding of digital signal processing concepts and programming skills. The algorithm involves maintaininga buffer to store the previous output samples, updating the buffer with each new input sample, and performing the filtering operation using the defined coefficients. The output of the filter is calculated by summing the products of the input and coefficient values.One advantage of the IIR filter algorithm is its efficiency in terms of computational resources. Compared to the FIR (Finite Impulse Response) filter, the IIR filter requires fewer operations, making it suitable for real-time applications with limited processing power. Additionally, IIR filters can achieve sharper frequency response characteristics, allowing for more precise filtering of specific frequency ranges.However, the IIR filter algorithm also has certain disadvantages. One major drawback is its susceptibility to instability. Due to the recursive nature of the filter, it can exhibit unstable behavior if the coefficient values are not carefully chosen. This instability can lead to unpredictable and undesirable output signals. Therefore, careful design and analysis of the filter coefficients arecrucial to ensure stability.The IIR filter algorithm finds applications in various domains, including audio processing, image filtering, telecommunications, and biomedical signal analysis. In audio processing, IIR filters are commonly used for tasks such as equalization, noise reduction, and echo cancellation. In image filtering, these filters can be employed for tasks like edge detection and image enhancement. In telecommunications, IIR filters are used for channel equalization and interference suppression. In biomedical signal analysis, these filters are utilized for tasks like ECG (Electrocardiogram) denoising and EEG (Electroencephalogram) analysis.In conclusion, the IIR filter algorithm in the C programming language is a powerful tool for digital signal processing applications. Its recursive nature allows for efficient processing and sharper frequency response characteristics. However, careful consideration must be given to stability issues when designing and implementing IIR filters. With its wide range of applications, the IIRfilter algorithm continues to play a significant role in various fields, contributing to advancements in signal processing and analysis.。
卡尔曼滤波英文版

卡尔曼滤波英文版The Kalman Filter: A Powerful Tool for Optimal Estimation and PredictionThe Kalman filter is a mathematical algorithm that provides an efficient computational means to estimate the state of a dynamic system from a series of measurements. Developed by Rudolf E. Kalman in 1960, this powerful tool has found widespread applications in various fields, including aerospace engineering, robotics, navigation, and signal processing. The Kalman filter is particularly useful in situations where the system being observed is subject to random disturbances or the measurements contain noise.At the heart of the Kalman filter is the concept of state estimation. In a dynamic system, the state represents the essential information needed to describe the system's behavior at a particular point in time. This state may include variables such as position, velocity, acceleration, or any other relevant parameters. The Kalman filter uses a recursive algorithm to estimate the system's state based on a series of noisy measurements, providing an optimal estimate thatminimizes the mean square error.The Kalman filter operates in two distinct phases: the prediction phase and the update phase. In the prediction phase, the algorithm uses the system's dynamics and the previous state estimate to predict the current state. This prediction is then combined with the current measurement in the update phase, where the Kalman filter calculates a weighted average of the predicted state and the measured state. The weighting factor, known as the Kalman gain, is determined based on the relative uncertainties of the prediction and the measurement.One of the key advantages of the Kalman filter is its ability to handle uncertainty and noise in the system and measurements. By continuously updating the state estimate based on the available measurements, the Kalman filter can effectively filter out the noise and provide a smooth, accurate estimate of the system's state. This makes the Kalman filter particularly useful in applications where the measurements are unreliable or subject to various sources of noise, such as sensor errors, environmental disturbances, or measurement delays.Another important aspect of the Kalman filter is its recursive nature. Instead of storing and processing all past measurements, the Kalman filter only requires the current measurement and the previous stateestimate to compute the current state estimate. This makes the algorithm computationally efficient and well-suited for real-time applications, where the system's state needs to be estimated and updated continuously.The versatility of the Kalman filter has led to its widespread adoption in a variety of applications. In the field of aerospace engineering, the Kalman filter is extensively used for aircraft and spacecraft navigation, guidance, and control. By combining measurements from multiple sensors, such as GPS, inertial measurement units, and radar, the Kalman filter can provide a robust and accurate estimate of the vehicle's position, orientation, and velocity.In the field of robotics, the Kalman filter is used to track the position and orientation of mobile robots, enabling them to navigate through complex environments and perform tasks with high precision. In signal processing, the Kalman filter is employed to remove noise and distortion from various types of signals, such as audio, video, and communication signals, improving the quality and clarity of the output.Beyond these traditional applications, the Kalman filter has also found use in emerging areas like autonomous vehicles, where it plays a crucial role in fusing data from multiple sensors (e.g., cameras, lidar, radar) to provide a comprehensive understanding of the vehicle'ssurroundings and enable accurate localization, mapping, and decision-making.The widespread adoption of the Kalman filter is a testament to its mathematical elegance and practical effectiveness. The algorithm's ability to provide optimal state estimates in the presence of uncertainty and noise has made it an indispensable tool in a wide range of fields, from aerospace to robotics and beyond.As technology continues to advance, the Kalman filter is likely to remain a fundamental component in many complex systems, enabling more accurate, reliable, and efficient solutions to a myriad of real-world problems. Its ongoing evolution and integration with emerging technologies, such as deep learning and sensor fusion, are likely to unlock even greater capabilities and applications in the years to come.。
