A Survey of Graph Algorithms in Extensions to the Streaming Model of Computation 1
petrel-属性建模

Nugget: Degree of dissimilarity at zero • Vertical
distance.
Basic Statistics
Example of Experimental Variogram calculation Semi-variance for 1 Lag distance Semi-variance for 2 lag distance
- Determine Layer thickness - Determine directions/degree of Anisotropy - Determine correlation/connectedness of facies data
Used as Quality Control to compare data before and after modeling process
Variogram Map
Good for visualizing anisotropy and its direction.
Sample Variogram
Good for finding Major and minor Range horizont
Variogram Map – Theory
EXERCISE A WELL with a string of porosity values in depth steps of 1m: 3, 5, 7, 6, 4, 1, 1, 4. Calculate the variogram values for lags 1, 2, 3, and 4 m respectively. Plot the variogram. Is there a pattern?
图形数字推理题英语作文

图形数字推理题英语作文In the realm of logical and analytical thinking, pattern recognition plays a pivotal role. This essay delves into the fascinating world of visual and numerical reasoning, where the ability to discern patterns is not just a skill but anart form. It is through these patterns that we can solve complex problems and make sense of the world around us.Visual Reasoning:Visual reasoning tests often present a series of shapes or figures that follow a certain pattern. The challenge is to identify the rule governing the sequence and predict the next shape in the series. This type of reasoning is not only crucial for solving puzzles but also for developing a keen eye for detail and a strategic approach to problem-solving.For instance, consider a sequence of shapes where each subsequent figure is a combination of the two preceding shapes. To solve this, one must recognize the pattern of combination and apply it to determine the next figure in the sequence.Numerical Reasoning:Numerical reasoning, on the other hand, involves identifying patterns within a series of numbers. These patterns can be based on simple arithmetic operations, such as addition or multiplication, or they can be more complex, involving factors, prime numbers, or even geometric progressions.A common numerical pattern might involve a sequence where each number is the result of adding a constant value to the previous number. To excel at numerical reasoning, one must be adept at performing quick calculations and recognizing the mathematical principles at play.The Importance of Pattern Recognition:The ability to recognize patterns is not only a valuableskill in academic and professional settings but also in everyday life. It helps us make informed decisions, from understanding trends in data to predicting outcomes in various scenarios.Moreover, pattern recognition is a fundamental aspect of learning and innovation. It is through the recognition of patterns that we can draw connections between seemingly disparate ideas, leading to creative insights and breakthroughs.In conclusion, both visual and numerical reasoning are essential components of a well-rounded cognitive toolkit. They challenge us to think critically and analytically, pushing the boundaries of our logical capabilities. By mastering the art of pattern recognition, we can unlock a deeper understanding of the world and enhance our problem-solving skills.。
人工智能的数学基础 英文

人工智能的数学基础英文The Mathematical Foundations of Artificial Intelligence Artificial Intelligence (AI) is the field of computer science that aims to create intelligent machines that can learn and solve problems like humans. The mathematical foundations of AI are key to understanding and developing the algorithms and models that power this technology. Here wewill take a closer look at the math behind AI.1. Linear AlgebraLinear Algebra is an essential part of building algorithms that can learn from data. Most of the data in AI is represented as vectors and matrices. Linear algebra helps us to manipulate and transform these vectors and matrices in efficient ways. The concepts of vectors, matrices, and linear transformations are fundamental to understanding thestructure of the data and the models used in AI.2. CalculusCalculus is the study of how things change. It is used in AI to optimize the parameters of models to minimize the error in predictions. The gradient of a function gives us the direction of greatest increase, which is used to update the parameters in the optimization process. Calculus is particularly important in deep learning algorithms, which use neural networks with many layers of interconnected nodes to process data.3. Probability and StatisticsProbability and Statistics are essential for building probabilistic models in AI. These models are used to makepredictions based on uncertain or incomplete data.Probability theory gives us the tools to calculate the likelihood of different outcomes, while statistical inference lets us draw conclusions about a population based on a sample of data. Many machine learning algorithms such as naïve Bayes, decision trees, and random forests are based on probabilistic models.4. Graph TheoryGraph Theory is used to represent and analyze the relationships between objects in AI. Graphs are used to model the structure of data, such as social networks or the connections between web pages. Graph algorithms are used in search algorithms, clustering, and recommendation systems.ConclusionIn conclusion, these are some of the main mathematical foundations of artificial intelligence. Linear algebra, calculus, probability, statistics, and graph theory providethe tools to build algorithms that can learn from data, optimize models, make predictions, and represent and analyze the relationships between objects. As AI continues to develop and impact our daily lives, a solid understanding of these mathematical concepts is essential for anyone interested inthis field.。
consistences 单位

consistences 单位Consistences is a unit that measures the level of consistency or conformity in a given system or set of data. In various fields such as economics, mathematics, and statistics, consistences plays a significant role in determining the validity and reliability of observations or measurements. This article aims to provide a comprehensive understanding of consistences and its applications by addressing various aspects and concepts related to this unit.To begin with, consistences can be defined as a measure of how closely individual observations or measurements adhere to the central tendency or overall trend of a dataset. It quantifies the degree of agreement or conformity within a set of data, allowing researchers and analysts to assess the consistency and reliability of their findings. Consistences are particularly important in scientific research and statistical analysis, as they help ensure the accuracy and reproducibility of results.There are several types of consistences commonly used in different disciplines. One such measure is the consistency of survey responses, which assesses the extent to which participants' answers align with one another. This type of consistences is crucialin fields like social sciences and market research, where accurate and reliable data collection is essential for drawing valid conclusions. Researchers often use statistical tools such as Cronbach's alpha or intraclass correlation to evaluate the consistences of survey responses.Another type of consistences is observed in economic indicators and financial data. In this context, consistences refer to the stability and predictability of economic variables over time. For instance, the consistency of inflation rates or stock market returns assists policymakers, investors, and analysts in assessing the reliability and usefulness of these indicators for decision-making. Tools like autocorrelation analysis and time series models are employed to measure the consistences of economic and financial data.Consistences can also be examined in mathematical equations and models. In mathematics, the consistency of equations reflects the degree to which the solutions of a system of equations satisfy all the given equations simultaneously. Mathematicians often use techniques like matrix operations or substitution methods to determine the consistences of mathematical systems. Similarly, incomputer science and programming, the consistency of code or algorithms ensures that they produce the same output for the same input consistently.In addition to assessing consistences within a dataset, it is also crucial to consider the consistency between multiple datasets or sources of information. When combining data from different studies or sources, researchers need to ensure that the data are consistent and compatible. Discrepancies or inconsistencies between datasets may lead to erroneous conclusions or misleading results. Techniques such as data normalization, data cleaning, and cross-validation analysis are employed to check for consistences between different datasets.The concept of consistences is closely related to the notions of reliability, validity, and reproducibility. To establish the reliability of a measurement or observation, consistences are assessed by conducting repeat measurements or experiments under similar conditions. Validity, on the other hand, refers to the extent to which a measurement or observation measures what it claims to measure. Ensuring consistences within a dataset is crucial for establishing the validity of the findings. Finally, for research to beconsidered reproducible, the consistences of the data and methodology used must allow others to obtain similar results independently.In conclusion, consistences are an essential unit that assists in evaluating the conformity and reliability of data, observations, and measurements. Consistences can be measured in various fields, including economics, mathematics, and statistics. By assessing the degree of agreement within a dataset or between different datasets, researchers can determine the validity, reliability, and reproducibility of their findings. Understanding consistences is vital for ensuring accurate and robust analysis in scientific research and data-driven decision-making processes.。
监控技术是福是祸英语作文

监控技术是福是祸英语作文Surveillance Technology: A Double-Edged SwordThe rapid advancement of technology has brought about a myriad of changes in our daily lives, and one of the most significant developments has been the proliferation of surveillance technology. From security cameras in public spaces to the ubiquitous presence of smartphones and the internet, our every move is being monitored and recorded. This has led to a heated debate over the merits and drawbacks of this technology, with proponents arguing that it enhances safety and security, while critics contend that it infringes on personal privacy and civil liberties.On the positive side, surveillance technology has undoubtedly played a crucial role in maintaining public order and preventing crime. Security cameras installed in high-risk areas have proven to be effective deterrents, as potential criminals are aware that their actions are being monitored and can be easily identified. This has led to a decrease in the incidence of vandalism, theft, and other forms of criminal activity in these areas. Moreover, the footage captured by these cameras has often been instrumental in solving crimes, providing law enforcement with vital evidence that can lead to theapprehension and conviction of offenders.In the wake of terrorist attacks and other acts of violence, the importance of surveillance technology has become even more pronounced. Governments and law enforcement agencies have increasingly relied on advanced surveillance systems, such as facial recognition software and data mining techniques, to identify and track potential threats. This has enabled them to thwart numerous plots and prevent countless lives from being lost. The ability to monitor the movements and communications of suspected individuals has been a valuable tool in the fight against terrorism and other forms of organized crime.Furthermore, surveillance technology has also been beneficial in the realm of public health and safety. During the COVID-19 pandemic, for instance, contact tracing apps and thermal imaging cameras have been used to identify and isolate infected individuals, helping to slow the spread of the virus and protect vulnerable populations. Similarly, in the event of natural disasters or other emergencies, surveillance systems can be utilized to monitor the situation, coordinate rescue efforts, and ensure the well-being of affected communities.However, the widespread use of surveillance technology has also raised significant concerns about privacy and civil liberties. Many individuals feel that their right to privacy is being compromised, astheir every action and interaction is being recorded and potentially accessed by authorities or private entities. This has led to a growing sense of unease and a fear of being constantly under scrutiny, which can have a detrimental impact on personal freedom and the overall quality of life.Moreover, there are valid concerns about the potential for abuse and misuse of surveillance data. Authoritarian regimes and oppressive governments have been known to use surveillance technology to monitor and suppress dissent, target minority groups, and maintain a stranglehold on power. Even in democratic societies, there have been instances where surveillance data has been used for nefarious purposes, such as political espionage, discrimination, and the infringement of individual rights.Another issue that has come to the forefront is the lack of transparency and accountability surrounding the use of surveillance technology. In many cases, the public is unaware of the extent and nature of the surveillance measures being implemented, and there is a lack of clear guidelines and oversight mechanisms to ensure that these technologies are being used responsibly and ethically. This has led to a growing demand for greater transparency and the establishment of robust regulatory frameworks to protect the rights of citizens.Furthermore, the increasing reliance on artificial intelligence and algorithmic decision-making in surveillance systems has raised concerns about bias, accuracy, and the potential for discrimination. Algorithms can perpetuate and amplify existing societal biases, leading to disproportionate targeting and monitoring of certain groups, such as racial minorities and marginalized communities. This can further exacerbate existing inequalities and undermine the principles of fairness and equal treatment under the law.In conclusion, the debate over the role of surveillance technology in our society is a complex and multifaceted one. While it has undoubtedly provided valuable benefits in terms of public safety, security, and emergency response, the potential for abuse and the infringement of civil liberties cannot be ignored. As we continue to navigate this rapidly evolving technological landscape, it is crucial that we strike a delicate balance between the need for security and the preservation of individual privacy and freedom. This will require a collaborative effort between policymakers, technology experts, civil society organizations, and the general public to develop robust ethical frameworks and regulatory mechanisms that ensure the responsible and accountable use of surveillance technology. Only then can we fully harness the potential of this technology while safeguarding the fundamental rights and liberties that are the cornerstone of a free and democratic society.。
英语 算法 -回复

英语算法-回复以下是我根据题目内容所写的一篇1500-2000字的英文文章:Title: An Overview of Algorithms [English Algorithm]Introduction:In the world of computer science, algorithms play a fundamental role in solving problems efficiently. They represent a step-by-step method to process inputs and produce desired outputs. In this article, we will delve into the subject of algorithms and explore their significance in various domains.Section 1: Understanding AlgorithmsTo comprehend algorithms, we must first define what they are. An algorithm refers to a well-defined set of instructions designed to solve a specific problem or perform a particular task. Algorithms can be found in almost every aspect of our lives, from simple everyday routines, such as making a sandwich, to complex scientific computations.Section 2: The Mechanics of AlgorithmsAlgorithms follow a specific structure, known as a flowchart, whichoutlines each step required to accomplish a goal. They typically involve input, processing, and output stages. The input stage involves gathering necessary information, while the processing stage involves applying various operations or calculations to the inputs. Lastly, the output stage produces the desired result.Section 3: Types of AlgorithmsThere are several types of algorithms, each serving a different purpose. Sorting algorithms, for example, are designed to arrange elements in a specific order, such as numerical or alphabetical. Examples of sorting algorithms include Bubble Sort, Insertion Sort, and Quick Sort. Searching algorithms, on the other hand, help locate specific elements within a dataset. Some commonly used searching algorithms include Linear Search and Binary Search. Other types of algorithms include pathfinding algorithms, graph algorithms, and genetic algorithms.Section 4: Importance of AlgorithmsAlgorithms are crucial in various fields and industries. They are extensively used in computer programming, where efficient algorithms can significantly improve the performance of software applications. Algorithms are also employed in data analysis, wherethey enable researchers to identify patterns, trends, and correlations within large datasets. In addition, algorithms are utilized in artificial intelligence systems, autonomous vehicles, and medical diagnostic tools.Section 5: Algorithm Design and AnalysisDeveloping an algorithm involves careful planning and consideration. The design and analysis of algorithms aim to optimize their efficiency and accuracy. Design techniques, such as divide and conquer, dynamic programming, and greedy algorithms, help in solving complex problems. Additionally, the analysis of algorithms focuses on evaluating their time complexity and space complexity, providing insights into their efficiency.Section 6: Challenges and Ethical ConsiderationsWhile algorithms have numerous benefits, they also present challenges and ethical considerations. One significant challenge is the need for algorithms to handle large datasets, as processing massive amounts of data can be time-consuming andresource-intensive. Additionally, ethical concerns arise when algorithms are used for automated decision-making, such as in the criminal justice system or loan approvals, as biases anddiscrimination can be unintentionally embedded in the algorithms.Conclusion:Algorithms are the backbone of problem-solving in the world of computer science. They provide a systematic approach to process data and generate desired outcomes. Understanding different algorithm types, their design and analysis, and their significance in various domains is essential to harnessing the full potential of algorithms. As technology continues to advance, algorithms will continue to evolve and shape the world around us.。
算法分析与设计 第二版 英文版 (潘彦 著) 清华大学出版社 课后答案--solu9

This file contains the exercises,hints,and solutions for Chapter 9of the book ”Introduction to the Design and Analysis of Algorithms,”2nd edition,byA.Levitin.The problems that might be challenging for at least some students are marked by ;those that might be difficult for a majority of students are marked by .Exercises 9.11.Give an instance of the change-making problem for which the greedy al-gorithm does not yield an optimal solution.2.Write a pseudocode of the greedy algorithm for the change-making prob-lem,with an amount n and coin denominations d 1>d 2>...>d m as its input.What is the time efficiency class of your algorithm?3.Consider the problem of scheduling n jobs of known durations t 1,...,t n for execution by a single processor.The jobs can be executed in any order,one job at a time.You want to find a schedule that minimizes the total time spent by all the jobs in the system.(The time spent by one job in the system is the sum of the time spent by this job in waiting plus the time spent on its execution.)Design a greedy algorithm for this problem. Does the greedy algo-rithm always yield an optimal solution?4.Design a greedy algorithm for the assignment problem (see Section 3.4).Does your greedy algorithm always yield an optimal solution?5.Bridge crossing revisited Consider the generalization of the bridge cross-ing puzzle (Problem 2in Exercises 1.2)in which we have n >1people whose bridge crossing times are t 1,t 2,...,t n .All the other conditions of the problem remain the same:at most two people at the time can cross the bridge (and they move with the speed of the slower of the two)and they must carry with them the only flashlight the group has.Design a greedy algorithm for this problem and find how long it willtake to cross the bridge by using this algorithm.Does your algorithm yields a minimum crossing time for every instance of the problem?If it does–prove it,if it does not–find an instance with the smallest number of people for which this happens.6.Bachet-Fibonacci weighing problem Find an optimal set of n weights {w 1,w 2,...,w n }so that it would be possible to weigh on a balance scale any integer load in the largest possible range from 1to W ,provided a. weights can be put only on the free cup of the scale.b. weights can be put on both cups of the scale.1课后答案网 w w w .k h d a w .c o m7.a.Apply Prim’s algorithm to the following graph.Include in the priority queue all the vertices not already in the tree.b.Apply Prim’s algorithm to the following graph.Include in the priority queue only the fringe vertices (the vertices not in the current tree which are adjacent to at least one tree vertex).8.The notion of a minimum spanning tree is applicable to a connected weighted graph.Do we have to check a graph’s connectivity before ap-plying Prim’s algorithm or can the algorithm do it by itself?9.a.How can we use Prim’s algorithm to find a spanning tree of a connected graph with no weights on its edges?b.Is it a good algorithm for this problem?10. Prove that any weighted connected graph with distinct weights hasexactly one minimum spanning tree.11.Outline an efficient algorithm for changing an element’s value in a min-heap.What is the time efficiency of your algorithm?2课后答案网 w h d a w .c o mHints to Exercises 9.11.As coin denominations for your counterexample,you may use,among a multitude of other possibilities,the ones mentioned in the text:d 1=7,d 2=5,d 3=1.2.You may use integer divisions in your algorithm.3.Considering the case of two jobs might help.Of course,after forming a hypothesis,you will have to either prove the algorithm’s optimality for an arbitrary input or find a specific counterexample showing that it is not the case.4.You can apply the greedy approach either to the entire cost matrix or to each of its rows (or columns).5.Simply apply the greedy approach to the situation at hand.You may assume that t 1≤t 2≤...≤t n .6.For both versions of the problem,it is not difficult to get to a hypothesis about the solution’s form after considering the cases of n =1,2,and 3.It is proving the solutions’optimality that is at the heart of this problem.7.a.Trace the algorithm for the graph given.An example can be found in the text of the section.b.After the next fringe vertex is added to the tree,add all the unseen vertices adjacent to it to the priority queue of fringe vertices.8.Applying Prim’s algorithm to a weighted graph that is not connected should help in answering this question.9.a.Since Prim’s algorithm needs weights on a graph’s edges,some weights have to be assigned.b.Do you know other algorithms that can solve this problem?10.Strictly speaking,the wording of the question asks you to prove two things:the fact that at least one minimum spanning tree exists for any weighted connected graph and the fact that a minimum spanning tree is unique if all the weights are distinct numbers.The proof of the former stems from the obvious observation about finiteness of the number of spanning trees for a weighted connected graph.The proof of the latter can be obtained by repeating the correctness proof of Prim’s algorithm with a minor adjustment at the end.11.Consider two cases:the key’s value was decreased (this is the case needed for Prim’s algorithm)and the key’s value was increased.3课后答案网 w w w .k h d a w .c o mSolutions to Exercises 9.11.Here is one of many such instances:For the coin denominations d 1=7,d 2=5,d 3=1and the amount n =10,the greedy algorithm yields one coin of denomination 7and three coins of denomination 1.The actual optimal solution is two coins of denomination 5.2.Algorithm Change (n,D [1..m ])//Implements the greedy algorithm for the change-making problem //Input:A nonnegative integer amount n and//a decreasing array of coin denominations D//Output:Array C [1..m ]of the number of coins of each denomination //in the change or the ”no solution”messagefor i ←1to m doC [i ]← n/D [i ]n ←n mod D [i ]if n =0return Celse return ”no solution”The algorithm’s time efficiency is in Θ(m ).(We assume that integer di-visions take a constant time no matter how big dividends are.)Note also that if we stop the algorithm as soon as the remaining amount becomes 0,the time efficiency will be in O (m ).3.a.Sort the jobs in nondecreasing order of their execution times and exe-cute them in that order.b.Yes,this greedy algorithm always yields an optimal solution.Indeed,for any ordering (i.e.,permutation)of the jobs i 1,i 2,...,i n ,the total time in the system is given by the formula t i 1+(t i 1+t i 2)+...+(t i 1+t i 2+...+t i n )=nt i 1+(n −1)t i 2+...+t i n .Thus,we have a sum of numbers n,n −1,...,1multiplied by “weights”t 1,t 2,...t n assigned to the numbers in some order.To minimize such a sum,we have to assign smaller t ’s to larger numbers.In other words,the jobs should be executed in nondecreasing order of their execution times.Here is a more formal proof of this fact.We will show that if jobs are ex-ecuted in some order i 1,i 2,...,i n ,in which t i k >t i k +1for some k,then the total time in the system for such an ordering can be decreased.(Hence,no such ordering can be an optimal solution.)Let us consider the other job ordering,which is obtained by swapping the jobs k and k +1.Obvi-ously,the time in the systems will remain the same for all but these two 4课后答案网 w w w .k h d a w .c o mjobs.Therefore,the difference between the total time in the system for the new ordering and the one before the swap will be[(k −1j =1t i j +t i k +1)+(k −1j =1t i j +t i k +1+t i k )]−[(k −1j =1t i j +t i k )+(k −1j =1t i j +t i k +t i k +1)]=t i k +1−t i k <0.4.a.The all-matrix version:Repeat the following operation n times.Select the smallest element in the unmarked rows and columns of the cost matrix and then mark its row and column.The row-by-row version:Starting with the first row and ending with the last row of the cost matrix,select the smallest element in that row which is not in a previously marked column.After such an element is selected,mark its column to prevent selecting another element from the same col-umn.b.Neither of the versions always yields an optimal solution.Here isa simple counterexample:C = 122100 5.Repeat the following step n −2times:Send to the other side the pair of two fastest remaining persons and then return the flashlight with the fastest person.Finally,send the remaining two people together.Assuming that t 1≤t 2≤...≤t n ,the total crossing time will be equal to (t 2+t 1)+(t 3+t 1)+...+(t n −1+t 1)+t n =ni =2t i +(n −2)t 1=n i =1t i +(n −3)t 1.Note:For an algorithm that always yields a minimal crossing time,seeGünter Rote,“Crossing the Bridge at Night,”EATCS Bulletin,vol.78(October 2002),241—246.The solution to the instance of Problem 2in Exercises 1.2shows that the greedy algorithm doesn’t always yield the minimal crossing time for n >3.No smaller counterexample can be given as a simple exhaustive check for n =3demonstrates.(The obvious solution for n =2is the one generated by the greedy algorithm as well.)5课后答案网 w w w .kh d a w .c o m6.a.Let’s apply the greedy approach to the first few instances of the problem in question.For n =1,we have to use w 1=1to balance weight 1.For n =2,we simply add w 2=2to balance the first previously unattainable weight of 2.The weights {1,2}can balance every integral weights up to their sum 3.For n =3,in the spirit of greedy thinking,we take the next previously unattainable weight:w 3=4.The three weights {1,2,4}allow to weigh any integral load l between 1and their sum 7,with l ’s binary expansion indicating the weights needed for load l :Generalizing these observations,we should hypothesize that for any posi-tive integer n the set of consecutive powers of 2{w i =2i −1,i =1,2,...n }makes it possible to balance every integral load in the largest possible range,which is up to and including n i =12i −1=2n −1.The fact that every integral weight l in the range 1≤l ≤2n −1can be balanced with this set of weights follows immediately from the binary expansion of l,which yields the weights needed for weighing l.(Note that we can obtain the weights needed for a given load l by applying to it the greedy algorithm for the change-making problem with denominations d i =2i −1,i =1,2,...n.)In order to prove that no set of n weights can cover a larger range of consecutive integral loads,it will suffice to note that there are just 2n −1nonempty selections of n weights and,hence,no more than 2n −1sums they yield.Therefore,the largest range of consecutive integral loads they can cover cannot exceed 2n −1.[Alternatively,to prove that no set of n weights can cover a larger range of consecutive integral loads,we can prove by induction on i that if any mul-tiset of n weights {w i ,i =1,...,n }–which we can assume without loss of generality to be sorted in nondecreasing order–can balance every integral load starting with 1,then w i ≤2i −1for i =1,2,...,n.The basis checks out immediately:w 1must be 1,which is equal to 21−1.For the general case,assume that w k ≤2k −1for every 1≤k <i.The largest weight the first i −1weights can balance is i −1k =1w k ≤ i −1k =12k −1=2i −1−1.If w i were larger than 2i ,then this load could have been balanced neither with the first i −1weights (which are too light even taken together)nor with the weights w i ≤...≤w n (which are heavier than 2i even individ-ually).Hence,w i ≤2i −1,which completes the proof by induction.This immediately implies that no n weights can balance every integral load up to the upper limit larger than n i =1w i ≤ n i =12i −1=2n −1,the limit attainable with the consecutive powers of 2weights.]b.If weights can be put on both cups of the scale,then a larger range can 6课后答案网 w w w .k h d a w .be reached with n weights for n >1.(For n =1,the single weight still needs to be 1,of course.)The weights {1,3}enable weighing of every integral load up to 4;the weights {1,3,9}enable weighing of every inte-gral load up to 13,and,in general,the weights {w i =3i −1,i =1,2,...,n }enable weighing of every integral load up to and including their sum of n i =13i −1=(3n −1)/2.A load’s expansion in the ternary system indicates the weights needed.If the ternary expansion contains only 0’s and 1’s,the load requires putting the weights corresponding to the 1’s on the opposite cup of the balance.If the ternary expansion of load l,l ≤(3n −1)/2,contains one or more 2’s,we can replace each 2by (3-1)to represent it in the form l =n i =1βi 3i −1,where βi ∈{0,1,−1},n = log 3(l +1) .In fact,every positive integer can be uniquely represented in this form,obtained from its ternary expansion as described above.For example,5=123=1·31+2·30=1·31+(3−1)·30=2·31−1·30=(3−1)·31−1·30=1·32−1·31−1·30.(Note that if we start with the rightmost 2,after a simplification,the new rightmost 2,if any,will be at some position to the left of the starting one.This proves that after a finite number of such replacements,we will be able to eliminate all the 2’s.)Using the representation l = n i =1βi 3i −1,we can weigh load l by placing all the weights w i =3i −1for negative βi ’s along with the load on one cup of the scale and all the weights w i =3i −1for positive βi ’s on the opposite cup.Now we’ll prove that no set of n weights can cover a larger range of con-secutive integral loads than (3n −1)/2.Each of the n weights can be either put on the left cup of the scale,or put on the right cup,or not to be used at all.Hence,there are 3n −1possible arrangements of the weights on the scale,with each of them having its mirror image (where all the weights are switched to the opposite pan of the scale).Eliminating this symmetry,leaves us withjust (3n −1)/2arrangements,which can weight at most (3n −1)/2different integral loads.Therefore,the largest range of consecutive integral loads they can cover cannot exceed (3n −1)/2.7.a.Apply Prim’s algorithm to the following graph:7课后答案网 w w w.k h d a w .c o mthe edges ae,eb,ec,and cd.b.Apply Prim’s algorithm to the following graph:the edges ab,be,ed,dc,ef,ei,ij,cg,gh,il,gk.8.There is no need to check the graph’s connectivity because Prim’s algo-rithm can do it itself.If the algorithm reaches all the graph’s vertices (via edges of finite lengths),the graph is connected,otherwise,it is not.9.a.The simplest and most logical solution is to assign all the edge weights to 1.8课a w .c o mb.Applying a depth-first search (or breadth-first search)traversal to get a depth-first search tree (or a breadth-first search tree),is conceptually simpler and for sparse graphs represented by their adjacency lists faster.10.The number of spanning trees for any weighted connected graph is a pos-itive finite number.(At least one spanning tree exists,e.g.,the one obtained by a depth-first search traversal of the graph.And the number of spanning trees must be finite because any such tree comprises a subset of edges of the finite set of edges of the given graph.)Hence,one can always find a spanning tree with the smallest total weight among the finite number of the candidates.Let’s prove now that the minimum spanning tree is unique if all the weights are distinct.We’ll do this by contradiction,i.e.,by assuming that there exists a graph G =(V,E )with all distinct weights but with more than one minimum spanning tree.Let e 1,...,e |V |−1be the list of edges com-posing the minimum spanning tree T P obtained by Prim’s algorithm with some specific vertex as the algorithm’s starting point and let T be an-other minimum spanning tree.Let e i =(v,u )be the first edge in the list e 1,...,e |V |−1of the edges of T P which is not in T (if T P =T ,such edge must exist)and let (v,u )be an edge of T connecting v with a vertex not in the subtree T i −1formed by {e 1,...,e i −1}(if i =1,T i −1consists of vertex v only).Similarly to the proof of Prim’s algorithms correctness,let us replace (v,u )by e i =(v,u )in T .It will create another spanning tree,whose weight is smaller than the weight of T because the weight of e i =(v,u )is smaller than the weight of (v,u ).(Since e i was chosen by Prim’s algorithm,its weight is the smallest among all the weights on the edges connecting the tree vertices of the subtree T i −1and the vertices adjacent to it.And since all the weights are distinct,the weight of (v,u )must be strictly greater than the weight of e i =(v,u ).)This contradicts the assumption that T was a minimum spanning tree.11.If a key’s value in a min-heap was decreased,it may need to be pushedup (via swaps)along the chain of its ancestors until it is smaller than or equal to its parent or reaches the root.If a key’s value in a min-heap was increased,it may need to be pushed down by swaps with the smaller of its current children until it is smaller than or equal to its children or reaches a leaf.Since the height of a min-heap with n nodes is equal to log 2n (by the same reason the height of a max-heap is given by this formula–see Section 6.4),the operation’s efficiency is in O (log n ).(Note:The old value of the key in question need not be known,of paring the new value with that of the parent and,if the min-heap condition holds,with the smaller of the two children,will suffice.)9课后答案网 w w w.k h d a w .c o mExercises 9.21.Apply Kruskal’s algorithm to find a minimum spanning tree of the follow-ing graphs.a.b.2.Indicate whether the following statements are true or false:a.If e is a minimum-weight edge in a connected weighted graph,it must be among edges of at least one minimum spanning tree of the graph.b.If e is a minimum-weight edge in a connected weighted graph,it must be among edges of each minimum spanning tree of the graph.c.If edge weights of a connected weighted graph are all distinct,the graph must have exactly one minimum spanning tree.d.If edge weights of a connected weighted graph are not all distinct,the graph must have more than one minimum spanning tree.3.What changes,if any,need to be made in algorithm Kruskal to make it find a minimum spanning forest for an arbitrary graph?(A minimum spanning forest is a forest whose trees are minimum spanning trees of the graph’s connected components.)10课后答案网h d a w .c o m4.Will either Kruskal’s or Prim’s algorithm work correctly on graphs that have negative edge weights?5.Design an algorithm for finding a maximum spanning tree –a spanning tree with the largest possible edge weight–of a weighted connected graph.6.Rewrite the pseudocode of Kruskal’s algorithm in terms of the operations of the disjoint subsets’ADT.7. Prove the correctness of Kruskal’s algorithm.8.Prove that the time efficiency of find (x )is in O (log n )for the union-by-size version of quick union.9.Find at least two Web sites with animations of Kruskal’s and Prim’s al-gorithms.Discuss their merits and demerits..10.Design and conduct an experiment to empirically compare the efficienciesof Prim’s and Kruskal’s algorithms on random graphs of different sizes and densities.11. Steiner tree Four villages are located at the vertices of a unit squarein the Euclidean plane.You are asked to connect them by the shortest network of roads so that there is a path between every pair of the villages along those roads.Find such a network.11课后答案网ww w.kh d aw .c omHints to Exercises 9.21.Trace the algorithm for the given graphs the same way it is done for another input in the section.2.Two of the four assertions are true,the other two are false.3.Applying Kruskal’s algorithm to a disconnected graph should help to an-swer the question.4.The answer is the same for both algorithms.If you believe that the algorithms work correctly on graphs with negative weights,prove this assertion;it you believe this is not to be the case,give a counterexample for each algorithm.5.Is the general trick of transforming maximization problems to their mini-mization counterparts (see Section6.6)applicable here?6.Substitute the three operations of the disjoint subsets’ADT–makeset (x ),find (x ),and union (x,y )–in the appropriate places of the pseudocode given in the section.7.Follow the plan used in Section 9.1to prove the correctness of Prim’s algorithm.8.The argument is very similar to the one made in the section for the union-by-size version of quick find.9.You may want to take advantage of the list of desirable characteristics in algorithm visualizations,which is given in Section 2.7.10.n/a11.The question is not trivial because introducing extra points (called Steinerpoints )may make the total length of the network smaller than that of a minimum spanning tree of the square.Solving first the problem for three equidistant points might give you an indication how a solution to the problem in question could look like.12课后答案网ww w.kh d aw .c omSolutions to Exercises9.21.a.后课13b.⇒⇒⇒⇒⇒⇒14课c⇒⇒⇒⇒⇒课2.a.True.(Otherwise,Kruskal’s algorithm would be invalid.)b.False.As a simple counterexample,consider a complete graph withthree vertices and the same weight on its three edgesc.True(Problem10in Exercises9.1).15d.False (see,for example,the graph of Problem 1a).3.Since the number of edges in a minimum spanning forest of a graph with |V |vertices and |C |connected components is equal to |V |−|C |(this for-mula is a simple generalization of |E |=|V |−1for connected graphs),Kruskal (G )will never get to |V |−1tree edges unless the graph is con-nected.A simple remedy is to replace the loop while ecounter <|V |−1with while k <|E |to make the algorithm stop after exhausting the sorted list of its edges.4.Both algorithms work correctly for graphs with negative edge weights.One way of showing this is to add to all the weights of a graph with negative weights some large positive number.This makes all the new weights positive,and one can “translate”the algorithms’actions on the new graph to the corresponding actions on the old one.Alternatively,you can check that the proofs justifying the algorithms’correctness do not depend on the edge weights being nonnegative.5.Replace each weight w (u,v )by −w (u,v )and apply any minimum spanning tree algorithm that works on graphs with arbitrary weights (e.g.,Prim’s or Kruskal’s algorithm)to the graph with the new weights.6.Algorithm Kruskal (G )//Kruskal’s algorithm with explicit disjoint-subsets operations //Input:A weighted connected graph G = V,E//Output:E T ,the set of edges composing a minimum spanning tree of G sort E in nondecreasing order of the edge weights w (e i 1)≤...≤w (e i |E |)for each vertex v ∈V make (v )E T ←∅;ecounter ←0//initialize the set of tree edges and its size k ←0//the number of processed edges while ecounter <|V |−1k ←k +1if find (u )=find (v )//u,v are the endpoints of edge e i kE T ←E T ∪{e i k };ecounter ←ecounter +1union (u,v )return E T 7.Let us prove by induction that each of the forests F i ,i =0,...,|V |−1,of Kruskal’s algorithm is a part (i.e.,a subgraph)of some minimum span-ning tree.(This immediately implies,of course,that the last forest in the sequence,F |V |−1,is a minimum spanning tree itself.Indeed,it contains all vertices of the graph,and it is connected because it is both acyclic and has |V |−1edges.)The basis of the induction is trivial,since F 0is16课后答案网ww w.kh d aw .c ommade up of |V |single-vertex trees and therefore must be a subgraph of any spanning tree of the graph.For the inductive step,let us assume that F i −1is a subgraph of some minimum spanning tree T .We need to prove that F i ,generated from F i −1by Kruskal’s algorithm,is also a part of a minimum spanning tree.We prove this by contradiction by assuming that no minimum spanning tree of the graph can contain F i .Let e i =(v,u )be the minimum weight edge added by Kruskal’s algorithm to forest F i −1to obtain forest F i .(Note that vertices v and u must belong to different trees of F i −1–otherwise,edge (v,u )would’ve created a cycle.)By our assumption,e i cannot belong to T .Therefore,if we add e i to T ,a cycle must be formed (see the figure below).In addition to edge e i =(v,u ),this cycle must contain another edge (v ,u )connecting a vertex v in the same tree of F i −1as v to a vertex u not in that tree.(It is possible that v coincides with v or u coincides with u but not both.)If we now delete the edge (v ,u )from this cycle,we will obtain another spanning tree of the entire graph whose weight is less than or equal to the weight of T since the weight of e i is less than or equal to the weight of (v ,u ).Hence,this spanning tree is a minimum spanning tree,which contradicts the assumption that no minimum spanning tree contains F i .This com-pletes the correctness proof of Kruskal’s algorithm.8.In the union-by-size version of quick-union ,each vertex starts at depth 0of its own tree.The depth of a vertex increases by 1when the tree it is in is attached to a tree with at least as many nodes during a union operation.Since the total number of nodes in the new tree containing the node is at least twice as much as in the old one,the number of such increases cannot exceed log 2n.Therefore the height of any tree (which is the largest depth of the tree’s nodes)generated by a legitimate sequence of unions will not exceed log 2n.Hence,the efficiency of find (x )is in O (log n )because find (x )traverses the pointer chain from the x ’s node to the tree’s root.9.n/a10.n/a17课后答案.kh d aw .c om11.The minimum Steiner tree that solves the problem is shown below.(Theother solution can be obtained by rotating the figure 90◦.)A popular discussion of Steiner trees can be found in “Last Recreations:Hydras,Eggs,and Other Mathematical Mystifications”by Martin Gard-ner.In general,no polynomial time algorithm is known for finding a minimum Steiner tree;moreover,the problem is known to be NP -hard (see Section 11.3).For the state-of-the-art information,see,e.g.,The Steiner Tree Page at /steiner/.18课后答案网ww w.kc omExercises 9.31.Explain what adjustments if any need to be made in Dijkstra’s algorithm and/or in an underlying graph to solve the following problems.a.Solve the single-source shortest-paths problem for directed weighted graphs.b.Find a shortest path between two given vertices of a weighted graph or digraph.(This variation is called the single-pair shortest-path prob-lem .)c.Find the shortest paths to a given vertex from each other vertex of a weighted graph or digraph.(This variation is called the single-destination shortest-paths problem .)d.Solve the single-source shortest-path problem in a graph with nonneg-ative numbers assigned to its vertices (and the length of a path defined as the sum of the vertex numbers on the path).2.Solve the following instances of the single-source shortest-paths problem with vertex a as the source:a.b.3.Give a counterexample that shows that Dijkstra’s algorithm may not work for a weighted connected graph with negative weights.19课案w w.kh d aw .c om4.Let T be a tree constructed by Dijkstra’s algorithm in the process of solving the single-source shortest-path problem for a weighted connected graph G .a.True or false:T is a spanning tree of G ?b.True or false:T is a minimum spanning tree of G ?5.Write a pseudocode of a simpler version of Dijkstra’s algorithm that finds only the distances (i.e.,the lengths of shortest paths but not shortest paths themselves)from a given vertex to all other vertices of a graph represented by its weight matrix.6. Prove the correctness of Dijkstra’s algorithm for graphs with positive weights.7.Design a linear-time algorithm for solving the single-source shortest-paths problem for dags (directed acyclic graphs)represented by their adjacency lists.8.Design an efficient algorithm for finding the length of a longest path in a dag.(This problem is important because it determines a lower bound on the total time needed for completing a project composed of precedence-constrained tasks.)9.Shortest-path modeling Assume you have a model of a weighted con-nected graph made of balls (representing the vertices)connected by strings of appropriate lengths (representing the edges).a.Describe how you can solve the single-pair shortest-path problem with this model .b.Describe how you can solve the single-source shortest-paths problem with this model .10.Revisit Problem 6in Exercises 1.3about determining the best route fora subway passenger to take from one designated station to another in a well-developed subway system like those in Washington,DC and London,UK.Write a program for this task.20课后答案网ww w.kh d aw .c om。
正确对待算法的作文题目

正确对待算法的作文题目英文回答:When it comes to dealing with algorithms, it is important to approach them with a balanced perspective. On one hand, algorithms have greatly improved our lives by providing efficient solutions to complex problems. For example, search engines like Google use algorithms toquickly deliver relevant search results, saving us time and effort. Algorithms also play a crucial role in various industries, such as finance, healthcare, and transportation, where they help optimize processes and make informed decisions.However, it is equally important to acknowledge the potential drawbacks and ethical concerns associated with algorithms. One major concern is the issue of bias. Algorithms are created by humans and can inadvertentlyreflect the biases and prejudices of their creators. For instance, facial recognition algorithms have been found tohave higher error rates for people with darker skin tones, leading to potential discrimination. Another concern is the lack of transparency and accountability in algorithmic decision-making. When algorithms are used to make important decisions, such as in hiring or loan approvals, it iscrucial to ensure that they are fair, unbiased, and explainable.To address these concerns, it is necessary to have regulations and guidelines in place to govern the development and use of algorithms. Governments and organizations should promote transparency andaccountability by requiring algorithmic systems to be auditable and explainable. Additionally, there should be diversity and inclusivity in the teams developingalgorithms to minimize biases. Regular audits and evaluations of algorithms should be conducted to identify and rectify any biases or errors.Moreover, it is essential to educate the public about algorithms and their impact. Many people are unaware of how algorithms work and the potential consequences of their use.By promoting digital literacy and providing accessible resources, individuals can make informed decisions and actively engage in discussions about algorithmic fairness and ethics.In conclusion, algorithms have become an integral partof our lives, bringing numerous benefits and conveniences. However, we must approach them with caution and address the potential biases and ethical concerns they may pose. By implementing regulations, promoting transparency, and educating the public, we can ensure that algorithms are developed and used in a responsible and fair manner.中文回答:谈到处理算法时,我们需要以平衡的态度来对待它们。
AUGMENTEDQUAD-EDGE–3DDATASTRUCTURE…
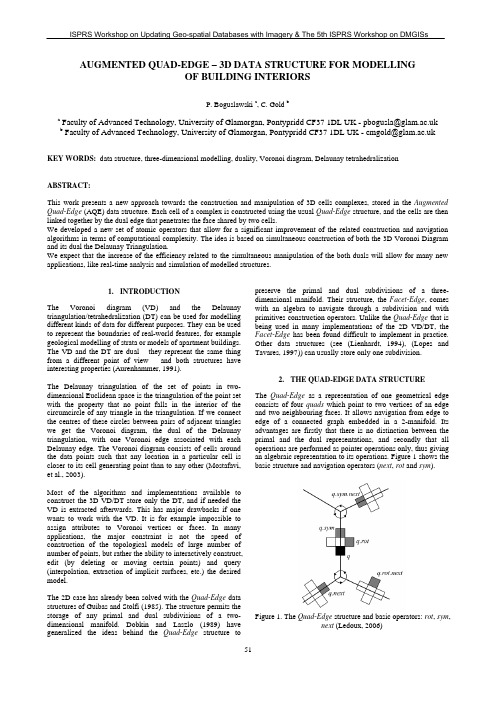
AUGMENTED QUAD-EDGE – 3D DATA STRUCTURE FOR MODELLINGOF BUILDING INTERIORSP. Boguslawski a, C. Gold ba FacultyofAdvancedTechnology,UniversityofGlamorgan,************************************.ukb FacultyofAdvancedTechnology,UniversityofGlamorgan,**********************************.uk KEY WORDS: data structure, three-dimensional modelling, duality, Voronoi diagram, Delaunay tetrahedralizationABSTRACT:This work presents a new approach towards the construction and manipulation of 3D cells complexes, stored in the Augmented Quad-Edge (AQE) data structure. Each cell of a complex is constructed using the usual Quad-Edge structure, and the cells are then linked together by the dual edge that penetrates the face shared by two cells.We developed a new set of atomic operators that allow for a significant improvement of the related construction and navigation algorithms in terms of computational complexity. The idea is based on simultaneous construction of both the 3D Voronoi Diagram and its dual the Delaunay Triangulation.We expect that the increase of the efficiency related to the simultaneous manipulation of the both duals will allow for many new applications, like real-time analysis and simulation of modelled structures.1.INTRODUCTIONThe Voronoi diagram (VD) and the Delaunay triangulation/tetrahedralization (DT) can be used for modelling different kinds of data for different purposes. They can be usedto represent the boundaries of real-world features, for example geological modelling of strata or models of apartment buildings. The VD and the DT are dual – they represent the same thing from a different point of view – and both structures have interesting properties (Aurenhammer, 1991).The Delaunay triangulation of the set of points in two-dimensional Euclidean space is the triangulation of the point set with the property that no point falls in the interior of the circumcircle of any triangle in the triangulation. If we connect the centres of these circles between pairs of adjacent triangles we get the Voronoi diagram, the dual of the Delaunay triangulation, with one Voronoi edge associated with each Delaunay edge. The Voronoi diagram consists of cells around the data points such that any location in a particular cell is closer to its cell generating point than to any other (Mostafavi,et al., 2003).Most of the algorithms and implementations available to construct the 3D VD/DT store only the DT, and if needed the VD is extracted afterwards. This has major drawbacks if one wants to work with the VD. It is for example impossible to assign attributes to Voronoi vertices or faces. In many applications, the major constraint is not the speed of construction of the topological models of large number of number of points, but rather the ability to interactively construct, edit (by deleting or moving certain points) and query (interpolation, extraction of implicit surfaces, etc.) the desired model.The 2D case has already been solved with the Quad-Edge data structures of Guibas and Stolfi (1985). The structure permits the storage of any primal and dual subdivisions of a two-dimensional manifold. Dobkin and Laszlo (1989) have generalized the ideas behind the Quad-Edge structure to preserve the primal and dual subdivisions of a three-dimensional manifold. Their structure, the Facet-Edge, comes with an algebra to navigate through a subdivision and with primitives construction operators. Unlike the Quad-Edge that is being used in many implementations of the 2D VD/DT, the Facet-Edge has been found difficult to implement in practice. Other data structures (see (Lienhardt, 1994), (Lopes and Tavares, 1997)) can usually store only one subdivision.2.THE QUAD-EDGE DATA STRUCTUREThe Quad-Edge as a representation of one geometrical edge consists of four quads which point to two vertices of an edge and two neighbouring faces. It allows navigation from edge to edge of a connected graph embedded in a 2-manifold. Its advantages are firstly that there is no distinction between the primal and the dual representations, and secondly that all operations are performed as pointer operations only, thus giving an algebraic representation to its operations. Figure 1 shows the basic structure and navigation operators (next, rot and sym).Figure 1. The Quad-Edge structure and basic operators: rot, sym,next (Ledoux, 2006)3. AUGMENTED QUAD-EDGE (AQE)The AQE (Ledoux and Gold, in press), (Gold, et al., 2005) uses the Quad-Edge to represent each cell of a 3D complex, in either space. For instance, each tetrahedron and each Voronoi cell are independently represented with the Quad-Edge , which is a boundary representation. With this simple structure, it is possible to navigate within a single cell with the Quad-Edge operators, but in order to do the same for a 3D complex two things are missing: a ways to link adjacent cells in a given space, and also a mechanism to navigate to the dual space. In this case two of the four org pointers are not used in 3D. The idea is to use the free face pointers in the Quad-Edge to link two cells sharing a face. This permits us to link cells together in either space, and also to navigate from a space to its dual. Indeed, we may move from any Quad-Edge to a Quad-Edge in the dual cell complex, and from there we may return to a different cell in the original cell complex.The AQE is high in storage but it is computationally efficient (Ledoux, 2006). Each tetrahedron contains 6 edges – each one is represented by four quads containing 3 pointers. This makes a total of 72 pointers. The total number of pointers for the dual is also 72. It makes a total of 144 pointers for each tetrahedron. However we preserve valuable properties which are crucial in real-time computations.Construction and navigation In previous work the theoretical basis of the storage and manipulation of 3D subdivisions with use of the AQE were described (Ledoux and Gold, in press) and it was shown that this model worked.The main construction operator is MakeEdge . It creates a single edge, that at the moment of creation it is not linked to any other edge. The Splice operator is used to link edges in the same subdivision. Edges in the dual subdivisions are linked one-by-one later using the through pointer.a)b)Figure 2. Flip operators (Ledoux, 2006): a) flip14 is used when a new point is inserted. Its reverse is flip41; b) flip23 is used when the structure has to be modified in order to preserve thecorrect DT. Its reverse is flip32.When a new point is inserted in the structure of the DT, four new tetrahedra are created inside the already existing one that contains the newly inserted point. Then the enclosing tetrahedron is removed. The new corresponding Voronoi points are calculated and another tetrahedron is created separately in the dual subdivision. Then all edges are linked together and, to maintain a properly built DT structure, subdivisions are modified by flip operators. Two basic flip operators are shown in Figure 2.Another requirement for the navigation is the through pointer that links together both dual subdivisions (Ledoux and Gold, in press), (Ledoux, 2006). The org pointers that are not used in 3D allow for making a connection to the dual edge. With this operator it is possible to go to the dual subdivision and back to the origin. It is the only way to connect two different cells in the same subdivision.Figure 3. The through pointer is used to connect both dualsubdivisions (Ledoux, 2006)To get the shared face of two cells, the adjacent operator is used. It is a complex operator that consists of a sequence of through and other basic operators. (Ledoux, 2006)4. ATOMIC OPERATORS The general algorithm of the point insertion to the DT/VD structure was described by Ledoux (2006). In our current work we have implemented and improved the way of building the whole structure.Algorithm 1: ComplexMakeEdge (DOrg, DDest, VOrg, VDest)// DOrg, DDest – points defined edge in DT // VOrg, VDest – points defined edge in VDe1:=MakeEdge(DOrg, DDest); e2:=MakeEdge(VOrg, VDest); e1.Rot.V:=e2;e2.InvRot.V:=e1.Sym;The most fundamental operator is ComplexMakeEdge which creates two edges using MakeEdge (Ledoux, 2006). They are dual and the one belongs to the DT and the second to the VD. The V pointer from the Quad-Edge structure is used to link them as shown in Algorithm 1. We claim that the connection between the newly created edges in both dual subdivisions has a very important property – it is permanent and not changed by any other operator.Algorithm 2: InsertNewPoint(N) – ComplexFflip14// N – new point inserted to the DT1.Find tetrahedron which contain point N2.Calculate 4 new Voronoi points3.Create new edges with using ComplexMakeEdge withpoint N and new Voronoi points4.Assign through pointers5.Disconnect origin edges of tetrahedron using Splice6.Connect edges of 4 new tetrahedra using Splice7.Add 4 new tetrahedra to a stack8.while necessary do flip23 or flip32 for tetrahedra fromthe stackFigure 4. fli p14 divides origin tetrahedron ABCD into 4 new The first operation in the point insertion to the structure is flip14 (Fig. 2a). It divides space occupied by tetrahedron ABCD into four smaller ones (Fig. 4). The inserted point N is a vertex shared by new tetrahedra. As mentioned above, this version of the algorithm is an improvement over Ledoux (2006). The significant aspect is that we don’t remove the origin tetrahedra and create 4 new. Edges from the origin tetrahedron are disconnected and used to create 4 new. Thus no edges are deleted from the DT structure. What is more, the same applies to the VD because dual edges are linked together permanently. Only new edges are added to the structure.Tetra- hedronEdges from originABCD tetrahedronused to create 4 newNewly created edgesT I CA, AD DC, CN, AN, DNT II AB, BD DA, AN, BN, DNT III BC, CD DB, BN, CN, DNT IV - BA, AC, CB, BN, AN, CNTable 5. Edges used in flip14Table 5 in conjunction with Fig. 2a) shows which edges are created and which ones are taken from the origin tetrahedron. The operation of point insertion does not demand any modification to the whole structure except for local changes of a single cell. This case is implemented in the ComplexFlip14 operator (Algorithm 2). The structure created this way keeps all new cells connected, and navigation between them, and within the whole structure, remains possible. The new complex operator is more efficient because it requires fewer operations to insert a point and modify the structure.Tetra-hedronEdges from origintetrahedra used tocreate new onesNewlycreatededgesDeletededgesT’ Ifrom TI: BEfrom TII: BD, ABAE, AD,DEAB (from TI) T’ IIfrom TI: AEfrom TII: AD, CACE, CD,DECA (from TI) T’ IIIfrom TI: CEfrom TII: CD, BCBE, BD,DEBC (from TI)Table 6. Edges used in flip23Algorithm 3: flip23(TI, TII):// TI, TII – two adjacent tetrahedra1.Calculate 3 new Voronoi points2.Copy edges and create new ones as shown in Table 63.Assign through pointers4.Disconnect edges of 2 original tetrahedra using Splice5.Connect edges of 3 new tetrahedra using Splice6.Remove spare edges (see Table 6)7.Remove 2 old Voronoi points8.Add 6 new tetrahedra to the stackTetra-hedronEdges from origintetrahedra used tocreate new onesNewlycreatededgesDeleted edges T Ifrom T’I: BEfrom T’II: CEfrom T’III:AEAB, BC,CAT IIfrom T’I: AB, BDfrom T’II: BC, CDfrom T’III: CA, AD-from T’I: AE,AD, DEfrom T’II: BE,BD, DEfrom T’III: CE,CD, DETable 7. Edges used in flip32Algorithm 4: flip32(TI, TII, TIII):// TI, TII, TIII – three tetrahedra adjacent in pairs1.Calculate 2 new Voronoi points2.Copy some edges and create new ones as shown inTable 73.Assign t hrough pointers4.Disconnect edges of 3 origin tetrahedra using Splice5.Connect edges of 2 new tetrahedra using Splice6.Remove spare edges (see Table 7)7.Remove 3 old Voronoi points8.Add 6 new tetrahedra to the stackFinally all edges are linked together to give a correctly built structure. Then correctness tests are performed. They check if the new tetrahedra have built the correct DT structure. If not, flip23 (Algorithm 3) or flip32 (Algorithm 4) are executed(Ledoux, 2006). Edges taking part in these operators are listed in Tables 6 and 7 and showed in Fig. 2b).To check the validity of our assumptions a special computer application was created. The implementation showed that our new complex operators work. The number of required operations for creation and deletion of edges and assignment of pointers has significantly decreased from the previous work of (Gold, et al., 2005).PUTER AIDED MODELLING Emergency planning and design of buildings are major issues for many people especially after 11th September 2001. To manage disasters effectively they need tools for rapid building plan compilation, editing and analysis.In many cases 2D analysis is inadequate for modelling building interiors and escape routes. 3D methods are needed. This is more obvious in disciplines such as geology (with complex adjacencies between rock types) and building construction (with security aspects). There is no appropriate data structure to describe those issues in a “3D GIS” context.Figure 8. The AQE is an appropriate structure for the modelling of building interiors. (Ledoux, 2006)The new operators can be used for advanced 3D modelling. In our opinion the AQE is a good structure for the modelling of building interiors (Fig. 8). Faces in the structure are stored twice, so every wall separating two rooms can have different properties on each side. It can help to make models not only of simple buildings but also of overpasses, tunnels and other awkward objects. It will be possible to create systems for disaster management, for example to simulate such phenomena as spreading fire inside buildings, flooding, falling walls, terrorist activity, etc.Another example is navigation in buildings, which requires the primal graph for forming rooms and the dual graph for making connections between rooms. Even though one can be reconstructed from the other, they both are needed for full real-time query and editing. These graphs need to be modifiable in real-time to take account of changing scenarios. This 3D Data Structure will assist applications in looking for escape routes from buildings.6.CONCLUSIONSOur current work involved the development and improvement of the atomic construction operations similar to the Quad-Edge. When we complete all atomic operators and prove their correctness, we will be able to use binary operations for location of quads in the stored structures. That will improve the efficiency of algorithms and allow for their use in real-time applications.In future work we will try to create a basic program for the modelling of building interiors and implement new functions such as the evaluation of optimal escape routes. We believe that such basis “edge algebra” has many practical advantages, and that it will be a base for many future applications.REFERENCESAurenhammer, F., 1991. Voronoi diagrams: A survey of a fundamental geometric data structure. ACM Computing Surveys, 23 (3), pp. 345-405.Dobkin, D. P. and Laszlo, M. J., 1989. Primitives for the manipulation of three-dimensional subdivisions. Algorithmica, 4, pp. 3-32.Gold, C. M., Ledoux, H. and Dzieszko, M., 2005. A Data Structure for the Construction and Navigation of 3D Voronoi and Delaunay Cell Complexes. WSCG’2005 Conference, Plzen, Czech Republic.Guibas, L. J. and Stolfi, J., 1985. Primitives for the manipulation of general subdivisions and the computation of Voronoi diagrams. ACM Transactions on Graphics, 4, pp. 74-123.Ledoux, H. and Gold, C. M., in press. Simultaneous storage of primal and dual three-dimensional subdivisions. Computers, Environment and Urban Systems.Ledoux, H., 2006. Modelling three-dimensional fields in geoscience with the Voronoi diagram and its dual. Ph.D. dissertation, School of Computing, University of Glamorgan, Pontypridd, Wales, UK.Lienhardt, P., 1994. N-dimensional generalized combinatioral maps and cellular quasi-manifolds. International Journal of Computational Geometry and Applications, 4 (3), pp. 275-324. Lopes, H. and Tavares, G., 1997. Structural operators for modelling 3-manifolds. Proceedings 4th ACM Symposium on Solid Modeling and Applications, Atlanta, Georgia, USA, pp. 10-18.Mostafavi, M. A., Gold, C. M. and Dakowicz, M., 2003. A Delete and insert operations in Voronoi/Delaunay methods and applications. Computers & Geosciences, 29 (4), pp. 523-530.。
基于知识图谱的水稻病虫害智能诊断系统

基于知识图谱的水稻病虫害智能诊断系统
于合龙1,2†,沈金梦1†,毕春光1,2,梁 婕3,陈慧灵4
(1 吉林农业大学 信息技术学院,吉林 长春 130118; 2 吉林农业大学 智慧农业研究院,吉林 长春 130118; 3 悉尼科技大学 工程与信息技术学院,悉尼 2007; 4 温州大学 计算机与人工智能学院,浙江 温州 325035)
收稿日期:2021–01–06 网络首发时间:2021–06–09 11:32:50 网络首发地址:https://kns.cHale Waihona Puke /kcms/detail/44.1110.S.20210609.1114.002.html 作者简介:于合龙 (1974—),男,教授,博士,E-mail: yuhelong@;沈金梦 (1995—),女,硕士研究生,E-mail:
关键词: 知识图谱;确定性因子模型;水稻病虫害;智能诊断 中图分类号: S435.11;TP182 文献标志码: A 文章编号: 1001-411X(2021)05-0105-12
Intelligent diagnostic system for rice diseases and pests based on knowledge graph
华南农业大学学报 Journal of South China Agricultural University 2021, 42(5): 105-116
DOI: 10.7671/j.issn.1001-411X.202101010
于合龙, 沈金梦, 毕春光, 等. 基于知识图谱的水稻病虫害智能诊断系统 [J]. 华南农业大学学报, 2021, 42(5): 105-116. YU Helong, SHEN Jinmeng, BI Chunguang, et al. Intelligent diagnostic system for rice diseases and pests based on knowledge graph[J]. Journal of South China Agricultural University, 2021, 42(5): 105-116.
基于图论的图像分割算法研究

基于图论的图像分割算法研究重庆大学硕士学位论文(学术学位)学生姓名:***指导教师:葛亮副教授专业:计算机软件与理论学科门类:工学重庆大学计算机学院二O一四年四月Research of Image Segmentation Algorithms based on Graph TheoryA Thesis Submitted to Chongqing Universityin Partial Fulfillment of the Requirement for theMaster’s Degree of EngineeringByJunduo YangSupervised by Associate Professor Liang GeSpecialty: Computer Software and TheoryCollege of Computer Science ofChongqing University, Chongqing, ChinaApril 2014摘要图像分割是计算机视觉中一个基本而关键的研究方向。
图像分割是将图像划分成若干个区域的过程,以便于人类理解图像内容或计算机处理图像信息。
迄今为止,大量的图像分割算法已被提出,其中基于图论的图像分割算法由于具有成熟严谨的图论理论的支撑以及良好的分割结果近年来备受关注。
本文回顾了图论的基础知识,并将图像与图的对应方式进行了描述,在此基础上,分类详细介绍基于图论的图像分割算法,并挑选每一类中有代表性的算法进行了比较和分析。
基于图论的图像分割将图像映射为带权无向的图,在图结构上,利用图论的知识将图划分成若干个子图,从而完成图像分割。
图的最小生成树、图割准则、图的最短路径等都已成功地应用于图像分割。
归一化切分(Normalized Cut,NCut)是一种基于图割准则的图像分割算法,它构建了一个全局优化的图分割准则并利用谱聚类进行求解。
NCut的分割结果体现了图像的全局特征,而且NCut倾向于对图像进行比较均衡的分割,这是它的优点。
算法导论第4版英文版

Title: Introduction to Algorithms, Fourth Edition (English Version)The fourth edition of Introduction to Algorithms, also known as "CLRS" among its legion of fans, is a comprehensive guide to the theory and practice of algorithms. This English version, targeted at a global audience, builds upon the legacy of its predecessors, firmly establishing itself as the standard reference in the field.The book's unparalleled reputation is founded on its ability to bridge the gap between theory and practice, making even the most complex algorithm accessible to a wide audience. Coverage ranges from fundamental data structures and sorting algorithms to more advanced topics like graph algorithms, dynamic programming, and computational geometry.The fourth edition boasts numerous updates and improvements over its predecessors. It includes new algorithms and techniques, along with expanded discussions on existing ones. The updated material reflects the latest research and best practices in the field, making this edition not just a sequel but a complete reboot of the text.The book's hallmark approach combines mathematical rigor with practical implementation, making it an invaluable resource for students, researchers, and professionals alike. Each chapter is meticulously crafted, introducing key concepts through carefully chosen examples and exercises. The accompanyingonline resources also provide additional challenges and solutions, further enhancing the learning experience.In conclusion, Introduction to Algorithms, Fourth Edition (English Version) is more than just a textbook; it's a roadmap to understanding the intricacies of algorithms. Its comprehensive nature and timeless quality make it a must-have for anyone serious about mastering the art and science of algorithm design.。
Nested dissection A survey and comparison of various nested dissection algorithms

Nested Dissection:A survey and comparison of variousnested dissection algorithmsManpreet S.Khaira Gary ler Thomas J.ShefflerJanuary1992CMU-CS-92-106RSchool of Computer ScienceCarnegie Mellon UniversityPittsburgh,PA15213AbstractMethods for solving sparse linear systems of equations can be categorized under two broad classes-direct and iterative.Direct methods are methods based on gaussian elimination.This report discusses one such direct method namely Nested dissection.Nested Dissection,originally proposed by Alan George,is a technique for solving sparse linear systems efficiently.This report is a survey of some of the work in the area of nested dissection and attempts to put it together using a common framework.This research was sponsored by the National Science Foundation under Contract R-9016641.The views and conclusions contained in this document are those of the authors and should not be interpreted as representing official policies,either expressed or implied,of the National Science Foundation or the ernment.Keywords:gaussian elimination,nested dissection,graph separators,fill-inContents1Introduction22An Overview of Gaussian Elimination22.1Gaussian elimination22.2The graph theoretic interpretation42.3Band matrices63Nested Dissection93.1Graph separators103.2Elimination ordering algorithms103.2.1Alan George’s Nested Dissection Method103.2.2Generalized Nested Dissection133.2.3Gilbert’s modification to Generalized Nested Disection143.3Separator trees143.4A bound on thefill for Gilbert’s algorithm153.5A bound on operation count for Gilbert’s algorithm173.6Euclidean norm andfill-in193.7Elimination ordering algorithms as tree traversals204Parallel Nested Dissection214.1The basic parallel algorithm214.2An example with lots offill-in234.3A comparison with the sequential algorithm24 5Conclusion25 6Acknowledgements251IntroductionMethods for solving sparse linear systems of equations can be categorized under two broad classes-direct and iterative.Direct methods are methods based on gaussian elimination.This report discusses one such direct method namely Nested dissection.Nested Dissection,originally proposed by Alan George,is a technique for solving sparse linear systems efficiently.There is a lot of literature on subsequent work in this area.This report is a survey of some of the work in the area of nested dissection and attempts to put it together using a common framework.This report also highlights the fact that all the nested dissection algorithms are variations of a single general algorithm,thereby answering the question that is the main goal of this survey namely-Are the various nested dissection algorithms completely distinct?Minimization algorithms for the solution of linear systems,which may be viewed equivalently as iterative methods,are beyond the scope of this report but are discussed in[Joh87].In section2we present the matrix approach to gaussian elimination and then show the equivalent graph theoretic version.Band matrices are used as an example to explain some of the basic ideas involved in gaussian elimination.Nested dissection is introduced in section3.The various nested dissection methods are also presented.The notion of separators and separator trees for graphs is explained.In section3.6the idea of Euclidean norm and its connection tofill-in is described.Finally,the various versions of nested dissection methods are shown to be different forms of tree traversal algorithms of a separator tree in section 3.7.Section4presents the parallel nested dissection algorithm and compares it with the sequential one.2An Overview of Gaussian Elimination2.1Gaussian eliminationWe are given a system of equations,where is an matrix,is a vector of variables of length,and is a constant vector of length.In order tofind by Gaussian Elimination two steps need to be performed1.Reduce to upper triangular form.(i.e.,Find such that is upper triangular)2.Solve system.If is an symmetric positive definite matrix,the solution process consists of the following two steps1.Factor by means of row operations towhere is lower triangular and is diagonal.2.Solve the systemsThe amount of time required to factor using naive methods is3and the time required to solve the systems of equations is2if is dense.On the other hand,if is sparse(i.e.,contains mostlyzero elements)then by avoiding operating on and storing zeros,we may be able to save time and storage space.However,the factorization of may create non zero entries in(and)in positions where contains zeros.The new nonzeros so created are calledfill-in.The factorization of into can de described by the following steps.Setting00we can write11111111111111111 1111111111112222112221222221222 2221Here is a positive scalar,is a vector of length,and is an symmetric positive definite matrix.Also,222.Hence,finally12...112 (1)and12 (1)It can be easily shown that112We refer to performing the kth step of factorization as eliminating variable.Un-eliminated variables and are referred to as being connected if their corresponding off-diagonal components inare nonzero.As was explained earlier,as the factorization proceeds unconnected variables can become connected(zero elements becoming nonzero i.e.,fill-in).Lemma2.1([Par61])The elimination of variable pairwise connects all variables,to which was connected at the point of its elimination.Proof:In the equations describing the factorization of,note that eliminating modifies by subtracting the rank-one matrix from it,forming.The matrix has nonzeros in positionfor all and corresponding to nonzero components in.Assuming no cancellation in the subtraction, must have nonzeros in the same positions.The above treatment was taken from[Geo73].2.2The graph theoretic interpretationIn this section we will try to develop an understanding of gaussian elimination using graph theory.Let Graph be the graph associated with matrix,such that each variable in the system of equations is associated with a vertex 1...,and that for each nonzero entry there is an edge with head and tail.Such a graph represents the nonzero structure of the matrix[Par61].If Mis symmetric,Graph will be an undirected graph.However,if is not symmetric,, Graph will have directed edges.We will ignore self loops created by the non zero elements along the principal diagonal of the matrix.The following definitions describe operations that will prove useful in later sections.Definition2.2If and are graphs,then if and. Lemma2.3Graph,where Graph Graph Lemma2.4Graph1Graph,is the transitive closure of.The above lemma follows easily by using the series expansion of1and noting that the transitive closure of is the summation of the integral powers of.The next section gives an example that explains the definitions and lemmas described in this section more clearly.Fill-in manifests itself on the graph as additional edges during the elimination process.Pivoting along a diagonal element in is equivalent to removal of a vertex from the graph.Definition2.5The deficiency of,is the set of edges defined by:This represents the set offill-in edges due to elimination of vertex v.Definition2.6The graph:is called the v-elimination graph of G.The v-elimination graph is the graph that results from the gaussian elimination of vertex v from the original graph.Definition2.7An elimination ordering is a bijection:12...and is an ordered graph.This graph may be used as an aid in selecting an elimination ordering that produces minimal fill-in.13451345145141451451411Elimination order = {2, 3,5,4,1}Elimination order = {3,5,4,2,1}Total fill-in = 1Total fill-in = 4Step #1Step #2Step #3Step #4Figure 1:Fill-in with different elimination ordersFor an ordered graph,,the elimination process1...1is the sequence of graphs that result from the elimination of the vertices in the order specified by.The totalfill-in is given by11Thefill-in that occurs with the elimination of a particular vertex is a function of where that vertex occurs in the elimination ordering.However,finding an elimination ordering that produces minimumfill-in for a given graph is a problem that has been demonstrated to be complete[[GJ79]].Hence,Reducing a graph to the null graph by successively eliminating vertices1,2, ...,is precisely analogous to performing gaussian elimination on matrix choosing as pivots the diagonal elements that correspond to1,2,...,.Definition2.8A system that may be solved with nofill-in,(i.e.,,is called a monotone transitive graph or a perfect elimination graphIt can be observed that thefill-in edges added during gaussian elimination(i.e.,on insertion into the original graph will result in a perfect elimination graph,Rose termed this the monotone transitive extension of a graph and also characterized these graphs as triangulated graphs[Ros72].A triangulated graph is one in which every cycle of length4contains a chord.Figure1shows thefill-in resulting from two different elimination orders.Hence,finding a good elimination ordering is essential in reducing the amount offill-in that occurs during gaussian elimination.2.3Band matricesOne application of gaussian elimination that has special properties is that of band matrices.An example where band matrices come up is in the solution of differential equations at discrete points.Input:.Goal:such that222210000 121000 012100 001210 000121 00001212......623...621The tridiagonal matrix in Equation1is very sparse,particularly when we take more points.Gaussianelimination could be disastrous if variables are removed in an order that results in a lot offill-in.Consider the graph of the matrix in Equation1.For the linear system in Equation1the tridiagonal matrix correspondsto the graph in Figure2.123456Figure2:Graph for a band matrixThe problem with applying gaussian elimination on sparse matrices is that,if we are not careful,we can introduce lots offill(i.e.,new nonzero entries).For example,in Figure3,represents nonzero entries,represents zero entries,and represents zero or non-zero entries in a matrix 1...5.If we pivot on11in order to obtain a zero entry at21and51,we may introduce nonzeros at entries.Thatis,in Graph we had edges21,13,and15and,after one row operation to eliminate 21,we may introduce edges23and25.Similarly,we may introduced two edges when we eliminate51.Figure3:Fill introduced by Gaussian EliminationLet11and let Graph.After pivoting on11we get a new matrix1101111Can we reduce thefill-in by reordering the rows and columns of the band matrix in Equation1?Consider:1 3 52 4 61213211521121124112612200020002In this way we are pivoting on the odd vertices and135.Then,according to the Fill-in Lemma,Graphwherebecause3and,in the original graph,2332and 2334,respectively,where represents1or more iterations.123456Figure4:Original Graph246Figure5:GraphTherefore,we can pivot on the odd elements and get afill-in graph half the size of the original graph,as shown in Figure7.12342Figure6:Original tridiagonal matrix graph242Figure7:Graph3.1Graph separatorsA separator of a graph is a relatively small set of vertices whose removal causes the graph to fall apart into a number of smaller pieces.Let be a class of graphs closed under the subgraph relation(i.e.,if2and 1is a subgraph of2then1).The class satisfies the-separator theorem if there are constants 10such that a separator set with at most vertices separates the graph into componentswith at most vertices each.Most algorithms based on separators are recursive,firstfinding a separator for the whole graph and then finding separators for the components.For these algorithms to work on a graph of class,all subgraphs of this graph must also be of class.Hence,the requirement that be closed under the subgraph relation. Example:The class of binary trees is closed under the subgraph relation(Why?Separation at any vertex separates the graph into smaller binary trees).Lemma3.1The class of binary trees satisfies a1-separator theorem for2-separator theorem for22. In more recent work,Djidjev proved that the theorem also holds for2)time and(log)space.George‘s scheme uses the fact that removal of()(21precisely)vertices from a square grid leaves four square grids, each roughly2 2.Example:Figure9shows a square grid.Removal of the middle column and middle row(separator set) separates the graph into four subgraphs as explained earlier.A 7X7 GRID GRAPH WITH THE SEPARATOR SET INDICATEDFigure9:Nested dissection of a gridThe algorithm is as follows.Assume that is one less than a power of two.For1...define1if221i.e.number of twos in the prime factorization of1Also,01and1Let21For1...define setsNow,number the unknowns(verices)in1,followed by those in2and so on,finally numbering the unknowns in(see Figure10).Graphs where is not equal to one less than a power of two may be handled by adding some number of dummy vertices.This algorithm results in(log)fill-in.S 3S 3S 2S 3NESTED DISSECTION OF A MESHS 1S 2Figure 10:Separator sets in the nested dissection of a gridWhy the method works:Consider a mesh consistingof 2squares called elements,formed by subdividingthe unit square 0101into 2small squares of side 1,and having a vertex/node at each of the 12grid points.With this mesh,we associate the symmetric positive definite system ,where 12and each is associated with a node of .Also,0iff and are associated with the nodes of the same element.In other words,if and are the vertices of the same small square or element then the corresponding matrix component i.e.,will be nonzero.However,if there is no element that has both and as vertices then is zero.As an example consider the nested dissection ordering of a ingthe algorithm described above the order in which the rows and columns get removed(note removal is not elimination-it is the removal that the ordering algorithm performs)is indicated in thefigure.The verticesfrom sets marked3subdivide the mesh into4subsets which are mutually independent in the sense that ifand are in different subsets,then0i.e.,is not connected to.In the same way vertices in the figure from the2sets subdivide each of these subsets into4subsets which are also mutually independent.As was mentioned in the algorithm,the vertices in the3sets get the highest elimination ordering numbers. The vertices from2sets get lower ones and the1vertices get the lowest ordering numbers.Thus in general the unknowns corresponding to vertices in1are numberedfirst(will get eliminated in the gaussian eliminationfirst),followed by those in2and so on.The way in which the unknowns from a particular set are ordered does not affect thefinal result.Recall thatfill-in will occur i.e.,an edge will be inserted between vertices and on removal of a vertex iff both and are connected to.So the elimination of vertices can only causefill-in within each subset of the set of mutually independent subsets mentioned earlier.This results in a very limited amount offill-in(for proof refer to[Geo73]).3.2.2Generalized Nested DissectionThis algorithm is Lipton,Rose and Tarjan’s original version of the generalized nested dissection algorithm [LRT79].Let be a class of graphs closed under the subgraph relation on which the-separator theorem where is the separator set.The removal of divides the rest of into two components and where and need not neccessarily be connected components.Let contain unnumbered vertices,contain and contain unnumbered vertices.Number the unnumbered vertices in arbitrarily from-+1to.In other words,we are assigning the vertices of the highest numbers.Delete all edges whose endpoints are both in.Apply the algorithm recursively to the subgraph induced by to number the unnumbered vertices in from=--+1to=-.Apply the algorithm recursively to the subgraph induced by to number the unnumbered vertices of from=---+1to=--.To begin,call the algorithm with all vertices unnumbered with=1,=,and=0.This will number the vertices in from1to.In this algorithm the vertices in the separator are included in the recursive call but are not renumbered.For any graph all of whose subgraphs satisfy the2)total operation count,although the coefficients of actualfill-in and operation count are very large.However,the authors believe that their worst case bounds are very pessimistic and that the algorithm would be useful for very large graphs.3.2.3Gilbert’s modification to Generalized Nested DisectionA variation to the generalized nested dissection algorithm described previously has been proposed for separators that divide the graph into more than two pieces[Gil80].This algorithm assumes that the separator splits the graph into pieces12....A separate recursive call is made for each part, 1.If there are no more than0vertices,then simply number the vertices arbitrarily in the range given.Find a separator with2)total operation count for planar graphs,finite element graphs,graphs of bounded genus and graphs of bounded degree with-separator theorems it may perform even better[Gil80].In summary,Alan George’s nested dissection algorithm solves a system of linear equations defined on an square grid.The generalized nested dissection algorithm,as its name suggests,is a generalization of this method to any system of equations defined on a planar or almost-planar graphs.Gilbert’s algorithm as explained earlier is a minor modification of the generalized nested dissection algorithm.3.3Separator treesThe nested dissection algorithms are based onfinding separators.The recursion of these algorithms suggests a natural decomposition of graphs in terms of their separators.At the highest level is a separator that divides the graph into components.These components themselves have separators,and so on.At the lowest levels are components that may not be divided any further(possibly singleton vertex sets).This decomposition can be described in terms of a structure called a separator tree.A separator tree for a graph is shown in Figure11.A separator tree for a graph,hence,is a tree whose internal nodes are separators and whose leaves are the components of the graph that may not be divided any further.Hence each node in the separator tree is a subgraph of the original graph and may contain many vertices of.In the original generalized nested dissection algorithm the separator trees are binary trees(2-ary).For Gilbert’s modified algorithm the separator trees are-ary(2)while those in Alan George’s method are4-ary.The root of a separator tree is at level0.The level of any node in the tree is the length of the path from the root to that node. Lemma3.3Let=(,,)ba an ordered graph.Then(,)is an edge of(defined earlier)if and only if there exists a path=[=12...1=]in such that111for2This lemma states that an edge()fills in if and only if there is a path from to containing onlyvertices deleted before either or.The lemma may be used to calculate bounds onfill-in due to nested dissection.Consider a node of the separator tree,and its subtrees12....There are no paths between and initially for.The elements of are given higher elimination numbers than thosein and.Hence,there can not be afill-in edge between any member of and.Thus,the separator tree shows that the only possiblefill-in that may occur is along the edges of the tree,or between the vertices of an individual node of the tree.This fact may be used to calculate bounds on the total amount offill-in using a nested dissection ordering algorithm for some classes of graphs.THE GRAPH SEPARATOR TREE OF THE GRAPHFigure11:A graph and its family of separators3.4A bound on thefill for Gilbert’s algorithmIn this section we will prove that Gilbert’s algorithm causes logfill in a planar graph.We actually prove this bound for a class of graphs that satisfies the-separator theorem with constants 1and0and is closed under subgraph and contraction.Suppose no vertex graph in has more than edges.When Gilbert’s nested dissection algorithm is applied to a graph in with0 vertices,the number offill edges with at least one endpoint in the top level separator(the root of the separator tree)is.Proof:We shall refer to the nodes of the separator tree for as nodes and to the vertices of graph as vertices. Hence a node in the separator tree can have several graph vertices in it.Let be the set of nodes of the separator tree for,and let be the set of nodes on level of the tree.Thus,and01...For any given node,let be the number of vertices in.Consider level of the separator tree.We will countfill to the root of the separator tree(say)from nodes of the tree at level.Every subtree rooted at level is connected,since in Gilbert’s algorithm every separator splits up the graph into a number of connected components.Contract each of these subtrees into a single vertex.Remove all the vertices of this graph except contracted vertices and vertices in.Throw out edges between vertices in.Let the resulting graph be.Since is obtained from by contraction and removal of vertices and edges,is in and hence has at most edges.From the discussions in section3.3,it is clear that there will befill to a vertex in from a level k node only if there is an edge in from to a contracted vertex corresponding to.Each such edge accounts for at most onefill edge from each vertex of in,orfill edges in all.Let be the size offill to from level nodes and be the degree in of the contracted vertex corresponding to node.Hence, Let be the set of level nodes with degree greater than in the contracted graph.Then,max(2)Consider the subgraph of that is induced by the vertices of and the contracted vertices of.By the2vertices.The subgraph is in so12(3) Equations(2)and(3)imply12Now222Hence the totalfill is.Thefill when eliminating is the union over every internal separator tree node of thefill edges whose higher-numbered vertex is in that node plus thefill edges within the external nodes(leaves)of the tree.A fill edge whose higher numbered endpoint is in a given internal node has its other endpoint in a descendant of that node.Thus if a given internal node is the root of a subtree containing m vertices then by the lemma just proved the number offill edges with higher numbered endpoints in that node is.If we sum this over all the internal nodes of the separator tree we get log.Thefill within an external node is edges,for a total over the whole graph of edges.Thus the bound forfill for the entire atmost02graph is log.Now a planar graph with vertices has at most36edges.Planar graphs are closed under contraction because any edge in an embedding of the graph in a plane can be shrunk without disturbing the embedding. Planar graphs are also closed under subgraph.Hence,by the above analysis thefill that occurs in a planar graph due to Gilbert’s algorithm is log.This analysis has been taken from[GT87].3.5A bound on operation count for Gilbert’s algorithmIt can be shown that in a graph,eliminating vertex takes arithmetic operations propotional to the square of the degree of([GL81]).Let be a perfect elimination graph corresponding to.contains not only the edges in,but also thefill edges produced as a result of eliminating vertices in the order obtained by the application of the nested dissection algorithm to.We will make a directed graph by orienting each edge in from the endpoint with lower ordering number to the endpoint with the higher one.Let the out-degree of be.Then the cost of eliminating is2.Hence,the operation count for the entire elimination is2.Let be the set of nodes of the separator tree of.Let be the set of nodes on level of the tree.Let24be the sum over all vertices of the square of the out-degree.Now,every subtree rooted at level is connected.Let be the graph obtained by contracting each subtree into a single vertex and deleting all edges in that are not incident on contracted vertices.Let be a vertex of in node on level of the separator tree,and let be an edge of.Now,the edges of are directed edges from the lower-numbered endpoint to the higher-numbered endpoint.Also,because lower numbered vertices are at the same or higher level than higher numbered vertices in the separator tree,either and are both in node,or there is an edge in joining and the contracted vertex corresponding to .If is the number of vertices in node and is the number of edges incident on contracted vertexin,then is at most,so25 Lemma3.5([GT87])Let be a planar bipartite graph with vertices(and hence at most24edges). There is a function from the edges of to the vertices of such that for all edges,is an endpoint of;and for all vertices,for at most two different edges.is planar and bipartite.Hence by the lemma stated above we can associate each edge of with one of its endpoints in such a way that at most two edges are associated with each vertex.Gilbert calls the edges associated with contracted vertices red vertices and those associated with vertices of on levels0through 1of the separator tree blue edges.Of the edges incident on contracted vertex,let be red and be blue.By the lemma at most two edges are associated with in.So,2and. So Equation5becomes26 The following mathematical inequality if well know:If,and are real numbers then23222So,3222333232331232max(7) The bound on thefirst two terms of Equation7is easy to calculate.We examine the bound to28Consider some node on level of the separator tree.The vertices in are vertices of.Each vertex has at most two blue edges incident on it(since is planar and bipartite and by lemma3.5).Since has only those edges of that are incident on the contracted vertices at level,the other endpoints of the blue edges mentioned earlier are contracted vertices.Now,the blue edges out of may be incident on different contracted vertices.But by examining Equation8it is clear that if all the blue edges out of are incident on the same contracted vertex then the sum will be larger.Hence,we can assume that all blue edges coming from the vertices in the same node go to the same contracted vertex.Now let be a contracted vertex.Blue edges incident on may come from many different levels.Let be the node closest to the root such that a blue edge exists for.Then,all the blue edges incident on come from nodes on the tree path from to.If the number of vertices of in the subtree rooted at is,the number of vertices of on this tree path is at most1212212 (12)So,,the number of edges incident on,is also12.Hence,209Hence,210The subtrees rooted at level are disjoint.So the inner sum is at most.Therefore the whole sum is.211 Substituting Equation11in Equation7and summing over all levels yields2312312 Now12and212,this is at most233321212332Thefirst sum is32and the second is.The third sum converges to a constant,so the entire expression is32.3.6Euclidean norm andfill-inThe Euclidean norm of a graph and its relation to thefill-in that gaussian elimination may cause is discussed in this section.Without loss of generality,assume that is an embedded triangulated planar graph.In such graphs,the separators must be cycles.Definition3.6A simple cycle is a simple cycle separator of if the vertices interior to are less than or equal to28(for1323separator)..For the sake of simplicity,we will take13Definition3.8The element graph corresponding to,where=and share a face in GExample:For a triangulated graph,=.If is a simple cycle then=.Recall that pivoting caused cliques to form.So the element graph gives an idea of the amount offill-in.Given the matrix,we will start with and triangulate it.We will rip out vertices from and replace them by a clique whose size is determined by the face created due to removal of the respective。
离散数学英文书籍

离散数学英文书籍Discrete mathematics is a vital field of study that encompasses a wide range of mathematical concepts and techniques. It is a fundamental branch of mathematics that has numerous applications in various areas, including computer science, engineering, and operations research. The study of discrete mathematics involves the analysis of discrete, or non-continuous, mathematical structures and the relationships between them.One of the key aspects of discrete mathematics is the study of sets, which are collections of distinct objects. Sets can be used to represent a wide range of mathematical concepts, from numbers and symbols to more complex entities such as functions and relations. The study of sets and their properties, including set operations such as union, intersection, and complement, is an essential component of discrete mathematics.Another important aspect of discrete mathematics is the study of logic, which involves the analysis of the validity and truthfulness of statements. This includes the study of propositional logic, predicate logic, and Boolean algebra, which are used to represent and manipulate logical statements in a formal and rigorous manner.Combinatorics, the study of the enumeration, combination, and permutation of discrete structures, is also a crucial component of discrete mathematics. This field encompasses topics such as counting techniques, graph theory, and the analysis of algorithms, which are essential for understanding and solving a wide range of practical problems.Discrete mathematics also includes the study of number theory, which deals with the properties of integers and their relationships. This includes topics such as divisibility, prime numbers, and modular arithmetic, which have applications in cryptography, computer science, and other fields.In addition to these core topics, discrete mathematics also encompasses a wide range of other areas, such as recurrence relations, generating functions, and discrete probability theory. These topics are essential for understanding and analyzing complex systems and algorithms, and have numerous applications in fields such as computer science, engineering, and economics.One of the key benefits of studying discrete mathematics is the development of critical thinking and problem-solving skills. The rigorous and logical nature of the subject requires students to analyze problems, identify relevant information, and develop creativesolutions. This skill set is highly valued in a wide range of professional and academic settings, and is essential for success in fields such as computer science, engineering, and operations research.Another important aspect of discrete mathematics is its emphasis on mathematical proofs. The study of discrete mathematics involves the development and analysis of mathematical proofs, which are essential for understanding the underlying principles and relationships that govern discrete structures. This focus on proof-based reasoning is a valuable skill that is highly sought after in many academic and professional fields.Overall, the study of discrete mathematics is a highly valuable and important field of study that has numerous applications in a wide range of disciplines. Whether you are interested in computer science, engineering, operations research, or any other field that involves the analysis of discrete structures, the study of discrete mathematics is an essential component of your educational and professional development.。
算法英语-

算法英语AlgorithmIntroductionAn algorithm is a set of step-by-step instructions that solve a problem or accomplish a particular task. Algorithms have been in use for thousands of years, but the concept of algorithm as we know it today was first introduced in the 9th century by the Persian mathematician Al-Khwarizmi. Algorithms are used in a wide range of fields, including computer programming, mathematics, physics, engineering, and finance.Why Are Algorithms Important?Algorithms are important for several reasons:1. Efficiency: Algorithms are designed to solve problems quickly and accurately.2. Reproducibility: Algorithms can be used to solve the same problem over and over again, producing the same result each time.3. Scalability: Algorithms can be used on large data sets, making them useful for big data applications.4. Reliability: Algorithms are reliable if they are tested thoroughly and written correctly, making them an important tool in safety-critical applications.Types of AlgorithmsThere are many different types of algorithms, each with its own unique characteristics. Here are a few of the most common types of algorithms:1. Sorting algorithms: These algorithms arrange data sets in a particular order, such as alphabetical or numerical.2. Searching algorithms: These algorithms are used to search for a particular item within a data set.3. Graph algorithms: These algorithms are used to analyze relationships between objects in a data set.4. Optimization algorithms: These algorithms are used to find the best solution to a problem.5. Machine learning algorithms: These algorithms are used in artificial intelligence and are designed to learn from data.Algorithm DesignDesigning an algorithm involves several steps, including:1. Understanding the problem: The first step in designing an algorithm is to understand the problem that needs to be solved.2. Breaking down the problem: After understanding the problem, it is often useful to break it down into smaller, more manageable parts.3. Identifying the inputs and outputs: It is important to identify what information the algorithm will take in, and what information it will output.4. Selecting a strategy: Once the problem has been broken down, the next step is to select a strategy for solving it, based on the available data and analytical tools.5. Testing and refining: After the algorithm has been designed, it is important to test it thoroughly to make sure it works as expected. If necessary, the algorithm can be refined and improved.Examples of AlgorithmsThere are many examples of algorithms in everyday life. Here are a few examples:1. A recipe is an algorithm for cooking a particular dish.2. A map is an algorithm for finding a particular location.3. The process of finding the shortest route between two points on a map is an algorithm.4. A computer program that calculates a mortgage payment is an algorithm.ConclusionAlgorithms are an important tool in many fields, including computer programming, mathematics, physics, engineering, and finance. They allow us to solve problems quickly and accurately, and they are crucial for many safety-critical applications. Understanding the basics of algorithm design can help us create more efficient, reliable, and scalable solutions to complex problems.。
近似算法

| A(I ) OPT(I ) | K
构造一个新实例 I ,使
sj s j , vj ( K 1)v j
15
则 I 和 I 有相同的解,且
A(I) (K 1)A(I )
OPT(I) (K 1)OPT(I )
| A(I) OPT(I) | K
令R ,选取V (G)中的最大度点v加入到R中
并删除与v关联的边,再在V (G) \ R中选最大
度点,重复直到E(G) .
这个算法的近似度是无界的(Page 396).
20
另一个直观的启发式方法:在G中任选一条边e, 将它的一个端点(设为v)加入到C中,然后删除边e 以及所有与v关联的边,再选取另一条边,重复这 个步骤,直到G不再有边 。
scheme.
12
1. 平面图着色
由四色定理,每个平面图是4可着色的。另外判断一 个图是不是2可着色是相当容易的。对于求平面图G 的色数这个问题,可采用如下算法:
(1) 若G没有边,则输出1; (2) 若G有边,判断G是否2可着色,若是则输出2,
否则输出4.
这是一个差界为1的近似算法.
13
2. 困难结果:背包问题
然而要找一个有效的近似算法也并不乐观,甚至存在 一些困难问题,似乎连“合理”的近似算法都可能不存 在,除非NP=P。
2
组合优化问题Π是一个最大(或最小)化问题。它 由三部分组成:
(1) 一个实例的集合DΠ; (2) 对每个实例 I ∈DΠ,存在I的一个候选解的有限 集合SΠ(I); (3) 对DΠ中的一个实例I的每个候选解σ∈SΠ(I), 存在一个值fΠ(σ),称为σ的解值。
这个近似算法的近似度也是无界的!
最大团算法时间复杂度

最大团算法时间复杂度Finding the maximum clique in a graph is a challenging problem in graph theory with many practical applications. One popular algorithm used to solve this problem is the Bron–Kerbosch algorithm, which is known for its effectiveness in finding the maximum clique in a graph. This algorithm has a time complexity of O(3^n/3), where nis the number of vertices in the graph. Despite its computational efficiency, the Bron–Kerbosch algorithm can still be time-consuming for large graphs with a large number of vertices.在图论中,找到图中的最大团是一个具有挑战性的问题,具有许多实际应用。
解决这个问题使用的一种流行算法是Bron-Kerbosch算法,以其在图中找到最大团的有效性而闻名。
该算法的时间复杂度为O(3^n/3),其中n是图中顶点的数量。
尽管Bron-Kerbosch算法在计算效率方面表现出色,但对于具有大量顶点的大图仍然可能耗时。
One of the reasons why finding the maximum clique in a graph is a challenging problem is because the problem is NP-hard, meaning that it is difficult to find an efficient algorithm that can solve it in polynomial time. The NP-hardness of the maximum clique problemstems from the fact that checking whether a given subset of vertices forms a clique is a combinatorial problem that requires checking all possible combinations of vertices, which is inherently time-consuming.在图中找到最大团是一个具有挑战性的问题的原因之一是因为这个问题是NP难的,这意味着很难找到一个能够在多项式时间内解决它的高效算法。
ext4 磁盘块分配算法

ext4 磁盘块分配算法英文回答:Introduction.The ext4 file system is a widely used journaling file system for Linux systems. It is known for its high performance and reliability, and it has been adopted by many popular distributions, such as Ubuntu, Red Hat Enterprise Linux, and CentOS.One of the key components of the ext4 file system isits disk block allocation algorithm. This algorithm determines how data is stored on the disk and how it is accessed by the operating system. The ext4 file system uses a combination of techniques to optimize disk space utilization and performance.Extent-Based Allocation.One of the most important techniques used by the ext4 file system is extent-based allocation. An extent is a contiguous block of disk space that is allocated to a single file. This allows the file system to avoid the overhead of managing individual blocks, which can improve performance.The ext4 file system uses a variety of algorithms to determine the size and location of extents. These algorithms take into account factors such as the size of the file, the amount of free space on the disk, and the performance characteristics of the disk.Block Groups.Another important technique used by the ext4 file system is block groups. A block group is a contiguous region of the disk that contains a fixed number of blocks. Block groups are used to improve the performance of the file system by reducing the number of seeks that are required to access data.The ext4 file system uses a variety of algorithms to determine the size and location of block groups. These algorithms take into account factors such as the size of the disk, the number of files on the disk, and the performance characteristics of the disk.Disk Block Allocation Algorithm.The ext4 file system uses a combination of extent-based allocation and block groups to allocate disk blocks to files. The algorithm works as follows:1. When a file is created, the file system allocates an extent to the file.2. If the extent is not large enough to hold the entire file, the file system allocates additional extents to the file.3. The file system allocates the extents to the file ina way that minimizes the number of seeks that are required to access the data.4. When a file is deleted, the file system deallocates the extents that were allocated to the file.The ext4 file system's disk block allocation algorithm is designed to optimize disk space utilization and performance. The algorithm uses a combination of techniques to achieve this goal, including extent-based allocation and block groups.中文回答:简介。
动物园人脸识别的英语作文

In recent years,the integration of technology into various aspects of daily life has been a topic of considerable debate.One such area where technology has made its presence felt is in the realm of zoos,specifically through the implementation of facial recognition systems.This essay aims to explore the implications of such technology in zoos,discussing both its potential benefits and the ethical considerations that arise.The use of facial recognition in zoos is not a new concept.It has been implemented in various forms,ranging from enhancing security to improving the visitor experience.For instance,some zoos have adopted this technology to streamline the entry process,allowing visitors to enter the premises with a simple scan of their face.This not only speeds up the process but also reduces the need for physical tickets,contributing to a more ecofriendly approach.Moreover,facial recognition can be used to personalize the visitor experience.By recognizing returning visitors,zoos can offer tailored recommendations for exhibits or events that the visitor might be interested in.This level of personalization can significantly enhance the overall experience,making the visit more memorable and engaging.However,the implementation of facial recognition in zoos also raises several ethical concerns.Privacy is a significant issue,as the collection and storage of biometric data can potentially be misused or lead to breaches. There is also the question of consent,as not all visitors may be comfortable with their facial features being scanned and recorded.Another ethical concern is the potential for discrimination.Facial recognition technology has been criticized for its inaccuracies,particularly when it comes to recognizing people of color.This could lead to unfair treatment or exclusion of certain individuals,which is a serious concern in any public space,including zoos.Furthermore,the use of facial recognition in zoos could be seen as an overreach of surveillance.While the technology may offer benefits in terms of security and personalization,it also raises questions about the extent to which we are willing to be monitored in public spaces.This is a broader societal issue that extends beyond zoos but is worth considering in this context.In terms of supporting data,a study conducted by the National Institute of Standards and Technology in the United States found that some facial recognition algorithms had significant accuracy issues,particularly with darkerskinned individuals.This highlights the need for further development and testing of the technology to ensure it is fair and unbiased.On the other hand,a report by the International Association of Amusement Parks and Attractions showed that the use of technology, including facial recognition,has led to an increase in visitor satisfaction in theme parks and similar attractions.This suggests that,when implemented correctly,facial recognition can contribute to a positive visitor experience.In conclusion,the use of facial recognition in zoos presents a complexissue with both potential benefits and ethical concerns.While it can enhance security,streamline entry processes,and personalize the visitor experience,it also raises questions about privacy,consent,and potential discrimination.As with any technology,it is essential to weigh these factors carefully and ensure that the implementation of facial recognition in zoos is done responsibly and ethically.。
图表英语四级作文

图表英语四级作文Title: Analysis of Graphs: Strategies for English Four-Level Composition。
Introduction。
Graph analysis is a vital skill for English learners, especially for those preparing for the Four-Level Examination. In this essay, we will delve into effective strategies for interpreting and writing about graphs in English, aiming to enhance your proficiency in this area.Understanding the Graph。
Firstly, it's crucial to thoroughly understand the graph presented. Pay close attention to the title, axes labels, units, and any additional information provided. This initial step sets the foundation for accurate interpretation and analysis.Describing Trends。
Next, describe the trends depicted in the graph.Identify any significant increases, decreases, fluctuations, or patterns. Utilize appropriate vocabulary to articulate these trends, such as "rise," "fall," "peak," "plummet," "fluctuate," etc. Remember to include specific data pointsor percentages to support your descriptions.Making Comparisons。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
weight component is added to each edge, giving us data items of the form (u, v, w(u, v )). Some lower bounds on the space required for streaming algorithms can be proven using counting techniques. For example, in [BGW03], lower bounds are provided for deterministic and randomized algorithms for O(1)-pass streaming algorithms for finding common neighborhoods of vertices. Another approach to proving lower bounds is to use results from communication complexity ([KN96]). We provide a brief description of the main ideas behind the communication complexity approach below.
2
Lower Bounds
When receiving an input graph G(V, E ) as a stream, we assume, unless otherwise stated, the graph is given as a stream of edges (u, v ) ∈ E in no particular order. If the graph is weighted, an additional 2
2
Department of Mathematics and Computer Science, Skidmore College, Saratoga Springs, NY 12866. email:来自oconnellT@1
graph is presented as a stream of edges is also an important research question. For many graph properties, it is impossible to determine whether a given graph has the property in a single pass using o(n) space where n is the number of vertices in the graph ([FKM+05b]). (One notable exception is the problem of computing the number of triangles in a graph for which a 1-pass streaming algorithm appears in [BKS02]). Because of the inherent difficulty in solving graph problems in the 1-pass streaming model, extensions to the streaming model have been proposed. The most obvious extension is to allow multiple passes over the stream with the hope that the number of passes will be quite small in relation to the size of the stream. In [HRR00], it is suggested that studying the tradeoff between the number of passes and the amount of space required by streaming algorithms is an important research topic. Beyond allowing multiple passes there are three main extensions currently discussed in the literature: 1. The Semi-Streaming model ([FKM+05a]) in which the algorithm is given Θ(n logk n) space where n is the number of vertices in the graph and k is any constant. In this case, the algorithm has enough internal memory to store the vertices but not necessarily the edges in the graph. 2. The W-Stream model ([R03]) in which the algorithm is allowed to write an intermediate stream as it reads the input stream. This intermediate stream, which can be at most a constant factor larger than the original stream, is used as the input stream for the next pass. 3. The Stream-Sort model ([R03], [ADR+04]) in which the algorithm is not only allowed to create intermediate streams but also to sort these streams in a single pass. In this chapter, we survey the algorithms that have been developed for these extended models. For a more general survey of streaming algorithms, see [M03] and [BBD+02]. While the emphasis of this chapter is on the actual algorithms developed, we begin with a discussion of lower bounds on the space required to solve graph problems in the streaming model to motivate the discussion of the other models.
1
Introduction
With our ever increasing ability to generate enormous amounts of information, comes a need to process that information more efficiently. In particular, we need to be able to process data that cannot fit into internal memory (i.e. RAM) and to do so in such a way that our access to external storage is efficient. Recently, there has been interest in a model of computation called the streaming model which has its origins in [HRR00] and also in [MP91]. In the streaming model, the data is presented sequentially in a single pass while the internal memory available is sufficient only to store a small portion of the data. The motivation for the streaming model is that sequential access to disk can be implemented very efficiently yet making multiple passes over large data sets may be prohibitively expensive or, in some cases, impossible because of the transient nature of the data. A number of papers consider computing various statistics in one pass over a stream ([AMS99], [M03]). However, determining the types of graph problems that can be solved efficiently when the
1
This is a preprint of a paper that will appear in Fundamental Problems in Computing: Essays in Honor of
Professor Daniel J. Rosenkrantz (S. S. Ravi and Sandeep K. Shukla eds.), Springer-Verlag, 2007.
