Assignment 2
Assignment2

Reading Report ⅠSource of the reading material InternetTitle The Road to Success Author Andrew CarnegieSummary:In this article , the author tells us a prime condition and great secret for achieving success during our future career life . That is , concentrating our energy , thought , and capital exclusively upon the business in which we are engaged . It is well that young men should begin at the beginning and occupy the most subordinate positions . Once we have begun in one line , we should resolve to fight it out on that line , lead in it , adopt every improvement , have the best machinery , and know the most about it .Reflection or Response:During our future life , we should act as what the author told us , that is aiming for the highest , concentrating , expenditure always within revenue and being patient . If we keep the belief that ―My place is at the top‖ in mind , we will be successful someday . A s Emerson says,―no one can cheat you out of ultimate success but yourselves.‖Vocabulary explanation list:1.subordinate adj. 次要的,从属的2.threshold n. 开始,开端,极限3.janitor n. 守卫,门警,管理人4.extensive adj. 广阔的,广泛的5.exclusively adv. 排外地,专有地6.scatter v. 分散,散开,撒开7.tumble v. 翻倒,摔倒,倒塌8.speculate v. 推测,思索9.expenditure n. 支出,花费10.at the threshold of 在…的开始11.salutary adj. 有益的,有用的,有益健康的12.put all one's eggs in one basket 孤注一掷1.But if by chance the professional sweeper is absent any morning, the boy who has the genius of the future partner in him will not hesitate to try his hand at the broom.【结构解析】“by chance”的意思是“碰巧”,“who has the genius of the future partner in him”是定语从句修饰“the boy”。
Assignment 2,有车一族翻译

Assignment 225 years ago, what China’s consumer most wanted was a color TV set, besides, “buy wheels” means buy a bicycle. Today, China has made a great change. After more than 30 years’ economic reform, Chinese people becomes richer and richer. With the development of national car Industry, car price have been ratcheting down, which means ordinary people can afford a car.Zhangming, an employee in a foreign company, bought a car last year, when it comes to the reason why he bought the car, he said that buying a car is always his dream. When he was a child, he saw people driving freely for shopping and traveling in the foreign movies. He really admired this kind of life. Now, given that his income was pretty good and the car price was acceptable, he decided to buy one, which later led him to a more convenient and colorful life. He can drive to work comfortably while listening the music instead of taking the bus. Besides, he can drive the car to travel with friends to suburban areas on weekends. comparing to the days that having not yet bought this car, he had to stay at home or strolling within the downtown. The car owner like Zhangming, they have experienced both happiness and annoyance from their cars. The first is traffic jam. As the number of private cars increases, cities’ traffic problem has been increasingly severe. Therefore, Zhangming has to leave home at 7:00 a.m. everyday for work to make sure staying ahead of 8:00 a.m. working time, in spite of the close proximity to his company. Secondly, the oilprice is increasing everyday, which pushed up the running costs of the car. As for many car owners, they may be able to afford a car, but unable to run it.“If the traffic keeps worsening and gasoline price continues to rise,” he added, “I’m going to take subway to work, which only takes 20 minutes. The ticket price is quite lower than the cost of driving.”Zhang’s idea is typical for general car owners. With the development of public transportation in China becomes more and more convenient and comfortable, an increasing number of car owners would prefer public transportation. The Chinese people, like many in other foreign metropolises, would certainly undergo a circle in transportation that they begin with private cars but end up with public transportation service.。
Assignment2(1)

DS 310Assignment 2Please submit your solution to Canvas by 11:59pm,February 24th.Problem 1-Logistic Regression (10pts)Let g (z )=11+e −z be the logistic function.Please •(5pts)Show that d dz g (z )=g (z )(1−g (z ))•(5pts)Show that 1−g (z )=g (−z )•(Optional)Consider the cross entropy loss function for logistic regression simplified so there is only one training example:J (θ)=−y log h θ(x )−(1−y )log(1−h θ(x )),h θ(x )=g (θT x )=11+e −θT x (1)Show that the partial derivative with respect to θj is:∂∂θj J (θ)=(h θ(x )−y )x j (2)Problem 2-Multi-class Logistic Regression (10pts)For multi-class classification using binary logistic regression,one way is to use the One-vs-All (One-vs-Rest)as we discussed in the class.Another way is to extend the binary logistic regression to multi-class logistic regression using softmax function.Assume there are K classes,for a data sample x ∈R n ×1,the predicted probability that x belongs to class k is given as (for simplicity,we don’t add intercept)P (y =k |x ;W )=exp(w T k x ) K i =1exp(w T i x )(3)where w k ∈R n ×1is the parameters to be learned.•(3pts)Please simplify Eq.(3)for K=2.Does the simplified one have the same formatas binary logistic regression?Hint:exp(w T 2x )exp(w T 1x )=exp((w 2−w 1)T x )•(5pts)Assume that K=3,x =[1,2,2],w 1=[1,0,1],w 2=[0,1,1]and w 3=[1,1,0],please calculate P (y =1|x ;W ),P (y =2|x ;W ),and P (y =3|x ;W ).•(2pts)For the above example,i.e.,x =[1,2,2].Based on the calculation,which class should we classify x =[1,2,2]and why?•(Optional)For simplicity of notation,let’s denote y k =P (y =k |x ;W ),with P (y =k |x ;W )=exp(w T k x ) K i =1exp(w T i x )as defined in Eq.(3),please derive the partial derivative ∂y k ∂w j ,j =kProblem 3(5pts)You run gradient descent for 15iterations with α=0.3and compute J (θ)after each iteration.You find that the value of J (θ)decreases quickly then levels off.Based on this,which of the following conclusions seems most plausible?A:Rather than use the current value of α,it would be more promising to try a larger value of α(say α=1.0).B:α=0.3is an effective choice of learning rate.C:Rather than use the current value of α,it would be more promising to try a smaller value of α(say α=0.1).Problem 4(5pts)Suppose you have the following training set,and fit a logistic regression classifier h θ(x )=g (θ0+θ1x 1+θ2x 2).Which of the following are true?Check all that apply.A:J (θ)will be a convex function,so gradient descent should converge to the global minimum.B:Adding polynomial features (e.g.,instead using h θ(x )=g (θ0+θ1x 1+θ2x 2+θ3x 21+θ4x 1x 2+θ5x 22)could increase how well we can fit the training data.C:The positive and negative examples cannot be separated using a straight line.So,gradient descent will fail to converge.D:Because the positive and negative examples cannot be separated using a straight line, linear regression will perform as well as logistic regression on this data.Problem5(5pts)Suppose you train a logistic classifier hθ(x)=g(θ0+θ1x1+θ2x2).You obtainθ0=−6,θ1=1andθ2=0.Which of the followingfigures represents the decision boundary found by your classifier?(a)A(b)B(c)C(d)DProblem6Feature Scaling(10pts)For the data samples shown below,please perform normalization and standardization.x1x2y1.52.00.3-1.0 2.0-0.2-2.0-1.00.12.0-2.50.4Problem7Use Sklearn Logistic Regression(10pts)We will use the implementation of Sklearn for Logistic Regression.Please download the notebookfile“Assignment2Q5”from Canvas.You can either upload the notebookfile to Google Colab tofinish this question or run locally.Following the instructions in the notebook andfill in the key code.After that, in the browser,click on“File”,Select“Print”,and choose“Save as PDF”.Submit the pdf along with your solution to other problems to Canvas.。
assignment-2

assignment-2 Questions of module01Read the chapter01-chapter03 of textbook, answer the following questions:1.Discuss the meaning of each of the following terms:(a) dataData is the physical symbols that represent different kinds of information.(b) databaseA Shared collection of logically related data (and a description of this data), designed to meet the information needs of an organization.(c) database management systemDatabase management system is a software system that enables users to define, create, and maintain the database and that provides controlled access to this database.(d) data independenceThis is essentially the separation of underlying file structures from the programs that operate on them,also called program-data independence.(e) views.A virtual table that does not necessarily exist in the database but is generated by the DBMS from the underlying base tables whenever it’s accessed.2.What is the difference between conceptual and logical data models? Giveexamples of each.Conceptual data models: Used to describe data independently of any system;Purpose is to represent the concepts of the real world;Used in early stages of database design;Example: entity-relationship (E-R) modelLogical data models:Used in DBMSs for the organization of data at a level that abstracts from physical structuresExample:the relational data modelthe network data modelthe hierarchical data model3.Define the terms relation, schema, instance and attribute. Give examples.Relations is a table with columns and rows.Example:Courses(course,tutor,room)The schema represents the structure of the data .Example:Schema of Courses is (Course, Tutor, Room)The instance represents the actual values.Example:The instances of Courses are the contents of the tables4.What is the purpose of the three levels (i.e. physical, logical and external) fora DBMS?Separate each user’s view of the database from the way the database is physically represented.5.What is the difference between the DML and DDL parts of SQL? What partwould you use to (i) create a table to hold information about employees, (ii) add information about a new employee to the table, and (iii) find out thesalary of one of the employees?The database administrator often interacts with the database via a “Data Definition Language” or DDL.Database users interact with the database via a “Data Manipulation Language” or DML.DDL DML DML6.Describe the five components of the DBMS environment and discuss howthey relate to each other.Hardware:The computer system(s) that the DBMS and the application programs run on. This can range from a single PC, to a single mainframe(主机), to anetwork of computers.Software:The DBMS software and the application programs, together with theoperating system, including network software if the DBMS is being used over a network.Data:Used by the organization.The data acts as a bridge between the hardware and software components and the human components.Procedures:Instructions and rules(操作说明和规则)that should be applied to the design and use of the database and DBMS.People:Includes DBMS designers and implementers(实现者), database designers, database administrators ( DBAs), application programmers, and end-users.7.What is logical data independence?Logical data independence refers to the immunity of the external schema to the changes in the conceptual schema.8.what is physical data independence?Physical data independence refers to the immunity of the conceptual schema to the changes in the internal schema.。
高级写作 Assignment2 (2)

WangKang0901010303Class 3Review of “The Decline and Fall of the British University”IntroductionUniversities are probably the most common institutions in the modern society. Almost every young man gets the opportunity to be exposed to one university. However, in the past, the universities are places that not everybody has a chance to get into. The gate of the universities was open only to a few people who could read and write and wanted to learn. The universities are places that people in there can achieve and disseminate knowledge. So Dr. Mark Tarver who used to be a lecturer in a university thought that the British university is in a decline and fall in his article “The Decline and Fall of the British University”.SummaryIn the article, Dr. Mark Tarver said that the education in university had changed over these years. In his years as a lecturer, he experienced the expansion of the university system happened in the post-war Britain. The universities had to peg their incomes and reduce the funding for students. So the universities were forced to face the choice of less money and redundancies or reduce their demands. And because of this kind of expansion, the educational quality of the university had fallen. If the universities want more money, they have to keep the students as more as possible. So it is getting harder for the lecturers to fail their students, and the lecturers have to simplify their assignments. And so did the lecturers’ quality. Tarver said that today’slecturers believe that the more papers they write, the better a lecturer they will be. So the lecturers began to concentrate on working with paper after paper. Tarver believed that such a kind of life of a lecturer was a lie so he quitted and this new kind of educational system would bring the students less knowledge and more debts. Arguments and EvaluationIn his article, Dr. Mark Tarver pointed out three problems as his arguments to convince his thesis. In his opinion, the British universities were in a decline and fall. He believed that today’s educational system is getting worse and worse. However, there are some important points that Dr. Mark Tarver should have considered carefully when he makes his viewpoint. Tarver thought the expansion of the university system has bad influence for modern universities. Actually, the expansion can help to disseminate the modern knowledge to some degree. It would improve the level of education. It would be much easier for normal people to get higher education. And the educational quality is not really falling. Because there are more and more people get into the university, the lecturers’ assignments should adapt to the overall standard of students’knowledge. So the lecturers should not fail so many students. Dr. Mark Tarver pointed out some potential risks in today’s Britain universities. For example, the lecturers’ paper works may really have some disadvantages to the lecturers’ quality. Yet most of his evidence was based on his own experience as a lecturer in a computer school, which was too unbalanced to judge the whole situation of Britain universities. Actually in some other universities, the situation was not like what Tarver had said. So it was not right to believe what Dr. Mark Tarver said just because of his personalexperience.ConclusionAs a former lecturer of a university, Dr. Mark Tarver awakens people of the potential dangers of the modern educational system of the universities. He pointed out the shortage of the modern system of university education. However, his view of this current situation is somehow too rash and his understanding of it is obviously limited. So we should recognize the reality clearly and try to find out the advantage of today’s educational system.(611words)。
assignment-2(附答案)

====Word行业资料分享--可编辑版本--双击可删====Passage 1 (TAP, Translation Journal)Winners do not dedicate their lives to a concept of what they imagine they should be; rather, they are themselves and as such do not use their energy putting on a performance, maintaining pretence, and manipulating others. They are aware that there is a difference between being loving and acting loving, between being stupid and acting stupid, between being knowledgeable and acting knowledgeable. Winners do not need to hide behind a mask. Winners are not afraid to do their own thinking and to use their own knowledge. They can separate facts from opinions and don’t pretend to have all the answers. They listen to others, evaluate what they say, but come to their own conclusions. Although winners can adore and respect other people, they are not totally defined, demolished, bound, or awed by them.Winners do not play “helpless”, nor do they play the blaming game. Instead, they assume responsibility for their own lives.成功者不会穷其毕生之精力,执着于自我之臆想。
COMP9021-Assignment2

COMP9021 Assignment 2如果您需要任何关于本门课程的帮助,请联系vx codingtutor因为专业,所以信赖^_^1.1. Aims. The purpose of the assignment is to:•design and implement an interface based on the desired behaviour of an application program;•practice the use of Python syntax;•develop problem solving skills.1.2. Submission. Your program will be stored in a file named sudoku.py. After you have developed andtested your program, upload it using Ed (unless you worked directly in Ed). Assignments can be submittedmore than once; the last version is marked. Your assignment is due by August 9, 10:00am. 1.3. Assessment. The assignment is worth 13 marks. It is going to be tested against a number of input files.For each test, the automarking script will let your program run for 30 seconds.Late assignments will be penalised: the mark for a late submission will be the minimum of the awarded markand 13 minus the number of full and partial days that have elapsed from the due date.The outputs of your programs should be exactly as indicated.1.4. Reminder on plagiarism policy. You are permitted, indeed encouraged, to discuss ways to solve theassignment with other people. Such discussions must be in terms of algorithms, not code. But you mustimplement the solution on your own. Submissions are routinely scanned for similarities that occur when studentscopy and modify other people’s work, or work very closely together on a single implementation. Severe penaltiesapplyA sudoku grid consists of 9 lines and 9 columns, making up 81 cells, that are grouped in nine 3x3 boxes. In asudoku puzzle, some but not all of the cells already contain digits between 1 and 9. Here is an example of asudoku puzzle.Solving a sudoku puzzle means completing the grid so that each digit from 1 to 9 occurs once and only once inevery row, once and only one in every column, and once and only once in every box. For instance, the previouspuzzle has the following solutionSolving a sudoku puzzle is a very common assignment; it is not difficult and moderatelyinteresting as a“solution” (the completed grid) tells nothing about how the solution was reached. More interesting solvers arelogical in the sense that they (possibly partially only) solve the puzzle in steps and at every step, explain howthey made some progress; they do so by using some of the well known techniques that most people who solvesudoku puzzles apply. Two remarks are in order.•Methods that only discover digits in empty cells are fairly limited; most methods need to keep track ofthe list of possible digits that can go into a given cell, and making progress might mean reducing thatlist. To apply techniques of the second kind, it is necessary to first mark the grid.•Often, it is not possible to completely solve a puzzle using exclusively the chosen methods; at somepoint no progress can be made and then a random guess has to be made to either put a digit into agiven empty cell, or to remove a digit from the list of possible digits that can go into a given cell. Itmight subsequently be necessary to backtrack and make alternative guesses if the earlier guesses turnout to be inconsistent with a solution.For this assignment, you will have to implement two such techniques, based on the notions of forced digitsand preemptive sets described in the paper A Pencil-and-Paper Algorithm for Solving Sudoku Puzzles by J. F.Crook, Notices of the AMS, 56(4), pp. 460–468. Before anything else, you should study this paper. The forceddigits technique is applied first, followed by the preemptive set technique. When no progress can be made, theforced digits techniques could be applied again, but that might not yield anything; an alternative would be totry and fill some empty cell with one of the possible digits for that cell and apply the preemptive set techniqueapplied again, knowing that that guess might prove wrong and that other possible digits might have to be usedinstead. In this assignment, we will stop at the point where the preemptive set technique can no longer beapplied; hence we can expect that our implementation will only partially solve most puzzles. But the techniqueis very powerful and as explained in the article, subsumes many of the well known techniques. You will design and implement a program that will read a sudoku grid whose representation is stored in a filefilename.txt and create a Sudoku object, with a number of methods:a method preassess() that prints out to standard output whether the representation is correct andhas no digit that occurs twice on the same row, on the same column or in the same box; •a method bare_tex_output() that outputs some Latex code to a file, filename_bare.tex, that canbe compiled by pdflatex to produce a pictorial representation of the grid;•a method forced_tex_output() that outputs some Latex code to a file, filename_forced.tex, thatcan be compiled by pdflatex to produce a pictorial representation of the grid to which the forced digitstechnique has been applied;•a method marked_tex_output() that outputs some Latex code to a file, filename_marked.tex, thatcan be compiled by pdflatex to produce a pictorial representation of the grid to which the forced digitstechnique has been applied and that has been marked;•a method worked_tex_output() that outputs some Latex code to a file, filename_worked.tex, thatcan be compiled by pdflatex to produce a pictorial representation of the grid to which the forced digitstechnique has been applied, that has been marked, and to which the preemptive set technique has beenapplied.The input is expected to consist of 9 lines of digits, with possibly lines consisting of spaces only that will beignored and with possibly spaces anywhere on the lines with digits. If the input is incorrect, that is, does notsatisfy the conditions just spelled out, then the program should generate a SudokuError with Incorrect inputas message.Here is a possible interaction:The preassess() method prints out There is clearly no solution. in case some row, column or boxcontains twice the same digit, and There might be a solution. otherwise, that is, in case no row, columnor box contains twice the same digit.For the .tex files output by the program, pay attention to the expected format, including spaces and blanklines. Lines that start with % are comments; there are 9 such lines. The output of your program redirectedto a file will be compared with the expected output saved in a file (of a different name ofcourse) using thediff command. For your program to pass the associated test, diff should silently exit, which requires thatthe contents of both files be absolutely identical, character for character, including spaces and blank lines.The forced_tex_output() method produces a file designed to depicts the grid where all forced digits havebeen added. A forced digit is a digit that must fill an empty cell in a box because that box does not containthat digit yet and all other empty cells in that box are on a row or on a column that contains that digit. Asforced digits are being discovered and fill empty cells, more forced digits might be discovered that could notbe discovered in the first round. So the program must make sure that no forced digit can be added to the gridthat will be produced when executing that method. The provided examples illustrate.The marked_tex_output() method produces a file designed to depicts the grid where all forced digits havebeen added and all possible digits have been added to the corners of the empty cells. The possible digits for anempty cell are the the digits that do not occur on the same row, on the same column or in the same box. Theprovided examples illustrate.The worked_tex_output() method produces a file designed to depicts the grid where all forced digits have beenadded, all possible digits have been added to the corners of the empty cells, and the preemptive set techniquehas been applied until it cannot allow one to eliminate any possible digit from any cell (which might be becausethe puzzle has been solved). The provided examples illustrate.The 13 marks will be distributed as follows:•1 mark for preassess();•3 marks for bare_tex_output();•3 marks for forced_tex_output();•3 marks for marked_tex_output();•3 marks for worked_tex_output()。
assignment2

Chap24/11P, 33,44P; Chap25/8P,9PProblem 1 (Chap 24/11P) A point charge q is placed at one corner of a cube of edge a . What is the flux through each of the cube faces? [Solution]Note that when a point charge is placed at one corner of a cube, the field lines from the charge is tangential to the three faces meeting at the point charge (See the above diagram). So the flux through the these faces must be zero.To find the flux through the other faces, we can build a large cube composed of 8 identical smaller cubes and place the charge at the center of the large one (See the above diagram). According to the Gauss ’ law, 0encE q εΦ=, the flux flowing out of the large cube is 0E qεΦ=.Note that the faces of the large cube is composed of 24 faces of the smaller cube, and the fluxes through each smaller face have the same value due to the symmetry, namely24each small face q εΦ=. This is just the flux through each of the other three faces of a cube when a point charge q is placed at its corner.[Problem 2] Chap24/25P. Charge is distributed uniformly throughout the volume of an infinitely long cylinder of radius R . (a) Show that, at a distance r from the cylinder axis (for r R <),2r E ρε=where ρis the volume charge density. (b)Write an expression for E when r R > .[Solution] Due to the cylindrical symmetry of the charge distribution, we choose a circular cylinder of radius r and height h , coaxial with the charged cylinder, as the Gaussian surface (asshown in the diagram). Two end caps are included to ensure the Gaussian surface is closed. Then the electric field lines will flow throught out of the cylindrical part of the Gaussian surface uniformly and perpendicularly no matter r R < or r R > if the charge is positive.:ρhAccordingly, the electric flux through the Gaussian surface is given by(2)E E rh πΦ=where E is the field magnitude at the cylindrical surface of radius r and 2rh π is the area of this side surface.On the other hand, the net charge enclosed by the Gaussian surface is given by22(), for (), for encr h r R q R h r R ρπρπ⎧<⎪=⎨>⎪⎩Applying the Gauss ’s law 0encE q εΦ=, we have the magnitude of the electric field at a distancer from the cylinder axis as20, for 2, for 2rr R E R r R rρερε⎧<⎪⎪=⎨⎪>⎪⎩The direction of the field is radially outward.[Problem 3] Chap24/33. A planar slab of thickness d and volume charge densityρ.[Solution](1) The magnitude of the electric field inside the slab, at a distance x from the central plane of theslab.The charge distribution has a planar symmetry, so we choose a closed cylinder perpendicular to the slab as the Gaussian surface. The end caps of area A are located at a distance x from the central plane of the slab, above and below respectively.From the symmetry, we know that the electric field Eat any point on the end caps must havethe same magnitude and be perpendicular to the caps in an either outward or inward direction.( In the above diagram, the electric field lines are assumed to flow out of the end caps. ) So the flux through the end caps is determined by12cap cap EA Φ=Φ=For the cylindrical part, the electric field is parallel to the surface at any point so that there is no flux through it, namely,0cyl Φ=The total flux through the Gauss surface is given by122cly cap cap EA Φ=Φ+Φ+Φ=And the charge enclosed by this Gauss surface is2enc xA ρρ=⋅According the the Gauss ’ law 0/enc ρεΦ= , we have022/EA xA ρε=So the magnitude of the electric field at a distance x<d/2 from the central plane is given by0/E x ρε=(2) The magnitude of the electric field outside the slab, at a distance x from the central plane ofthe slab.Similarly, we choose a closed cylinder as the Gaussian surface. The distance from the end caps to the central plane now satisfies x >d /2, as shown in the above diagram. The total flux through the Gaussian surface is still122cly cap cap EA Φ=Φ+Φ+Φ=,But the enclosed charge is given by enc Ad ρρ=. Then the Gauss ’ law 0/enc ρεΦ= reduces to02/EA Ad ρε=So that the magnitude of electric field outside the slab is always0/2E d ρε=,independent of the distance x from the central plane.[Problem 4] Chap.24/44P The figure shows a spherical shell of charge with uniform volme charge density ρ. Plot E due to the shell for distances r from the center of t he shell ranging from zero to 30cm. Assume that 631.010C/m ρ-=⨯, 10cm a = and 20cm b =.[Solution ] According to the spherical symmetry of the charge distribution, we choose a concentric sphere of radius r as the Gaussian surface. The net charge enclosed by this surface is133enc23330, for ( S in the diagam)4(), for ( S34(), for ( S in the diagam)3r a r a q a r b b a r b πρπρ⎧⎪<⎪-⎪=⋅≤<⎨⎪⎪-⋅≥⎪⎩Since the electric field Eat any point on the Gaussiansurface must have the same magnitude and be perpendicular to the surface in any case, the electric flux Φ through the Gaussian surface is always given by24E r πΦ=⋅.Then the Gauss ’ law 0/enc ρεΦ=reduces to 24encq E r πε⋅=, so the magnitude of the electricfield inside the sphere at a distance r from the centre is332033200, for(), for 3(), for 3r a r a E a r b r b a r b r ρερε⎧⎪<⎪⎪-⎪=⋅≤<⎨⎪⎪-⎪⋅≥⎪⎩. Substituting 10cm a =, 20cm b = and 31C/m ρμ= we have3220, for 10cm (0.001), for 10cm 20cm , for 20cm r A r E r r Br r ⎧<⎪⎪-⎪=≤<⎨⎪⎪≥⎪⎩ with -1-137664(N C m )A ≈⋅⋅ and -12263.65(N C m )B ≈⋅⋅.From these expressions we can get the value of the field magnitude at any positions. For example,3976(N/C)E ≈ at 10cm r =, 6591(N/C)E ≈ at 20cm r =, and 2929(N/C)E ≈ at30cm r =. Also we can find30.002(1)0dE A dr r=+> and2240.006(1)0d E A dr r =-< for 10cm 20cm r ≤<. The dependence of E on the distance r is given in the following figure.0.000.050.100.150.200.250.30-100001000200030004000500060007000E =3976N/CE =6591N/CE (N /C )r (m)E =2929N/CChap 25/ 8PA nonconducting sphere of radius R . The electric field inside the sphere 30()4qr E r Rπε=. TakeV =0 at the center. V (r )=? Potential difference between the surface and the center? Which point has a higher potential if q is positive?[Solution](a) Suppose point P located inside the sphere at a distance r from the center O . Set V=0 at the center, the potential at P is given by()P OV r E ds =-⋅⎰Since Eis directed radially, we choose a pathalong the field lines from O to P as shown in the diagram. The differential displacement dsof this path is parallel to the electric field(here we have assumed q is positive) and has length dr ’, so the integral is evaluated as22''333'0'0000'()(')''4428r rr rr r qr q r qr V r E r dr dr R R Rπεπεπε=====-=-=-=-⎰⎰If the charge q is negative, it is easy to find that this result still holds.(b) On the surface, the potential is0()8q V R Rπε=-This is also the difference in potential between the point on the surface and the center.(c) If q is positive, the potential on the surface is negative, which means the potential at the center is higher. We can also get this conclusion according to the positive work done by the electric field when a positive charge is moved from O to P .Chap 25/ 9PThe same sphere as that in 8P, but take V =0 at infinity. [Solution]Since the potential is set as zero at infinity, thepotential at point P is now given byinfinity()PV r E ds =-⋅⎰According the formula of the field due to auniformly-charged sphere, the electric field Eat adistance r ’ from the center is directed radially and has magnitude2300', for ' (inside the sphere)4('), for ' (outside the sphere)4'qr r R R E r q r R r πεπε⎧<⎪⎪=⎨⎪>⎪⎩We choose a path along the field lines from infinity to point P so that the differential displacement dslocated at r ’ is antiparallel to the field and has length -dr ’(Note here '0dr < since 'r decreases from ∞ to point P). The potential at P can be calculated as2''''3''''00''223300000''22233000'()(')'(')'''44''()4'84883(3)888r Rr rr Rr rr r Rr r R r R r rr r Rq qr V r E r dr E r dr dr dr R r qqr qqr qr R R R Rq qr q R r R R Rπεπεπεπεπεπεπεπεπεπε=====∞==∞====∞==-⋅-⋅=-⋅-=+-=--=-=-⎰⎰⎰⎰The difference between the center and the surface is given by0003()(0)488q q q V r R V r RRRπεπεπε=-==-=-The value of the potential at P is different from the result in 8P since different potential reference is chosen, while the potential difference is independent of the location of the zero-potential point.V =。
Assignment 2答案

1.1选择题1. 在下列运算符中,( d )优先级最高。
(a) <= (b )*= (c )+ (d )*2. 在下列运算符中,( d )优先级最低。
(a) ! (b )&& (c )!= (d )?:3.设i=1,j=2,则表达式i+++j 的值为( c )。
(a) 1 (b )2 (c )3 (d )44.设i=1,j=2,则表达式 ++i+j 的值为( d )。
(a)1 (b )2 (c )3 (d )45.在下列表达式选项中,( c )是正确。
(a )++(a++) (b )a++b (c )a+++b (d )a++++b6.已知i=0,j=1,k=2,则逻辑表达式 ++i||--j&&++k 的值为( b )。
(a) 0 (b )1 (c )2 (d )37. 执行下列语句后,x 的值是( d ),y 的值是( c )。
int x , y ;x = y = 1; ++ x || ++ y ;(a) 不确定 (b) 0 (c) 1 (d) 28.设X 为整型变量,能正确表达数学关系1< X < 5的C++逻辑表达式是( bcd )。
(a) 1<X<5 (b) X==2||X==3||X==4(c) 1<X&&X<5 (d) !(X<=1)&&!(X>=5)9. 已知x=5,则执行语句x += x -= x*x ;后,x 的值为( c )。
(a)25 (b )40 (c )-40 (d )2010. 设a=1,b=2,c=3,d=4,则条件表达式a<b ?a :c<d ?c :d 的值为( a )。
(a) 1 (b )2 (c )3 (d )411. 逗号表达式“(x=4*5,x*5),x+25的值为( d )。
(a) 25 (b )20 (c )100 (d )451.2把下列数学表达式写成c++算术表达式1.y x +++11111 答案:1/(1+1/(1+1/(x+y)))2.48cos 21π+ 答案:sqrt(1+3.14159/2*cos(48*3.14159/180))1.3 阅读下列程序,写出执行结果1.#include <iostream.h>void main(){int a = 1, b = 2, x, y;cout << a++ + ++b << endl;cout << a % b << endl;x = !a>b; y = x-- && b;cout << x << endl;cout << y << endl;}答案:42-12.#include <iostream.h>void main(){int x,y,z,f;x = y = z = 1;f = --x || y-- && z++;cout << "x =" << x << endl;cout << "y =" << y << endl;cout << "z =" << z << endl;cout << "f =" << f << endl;}答案:x = 0y = 0z = 2f = 11.4编程题1.输入一个三位整数,将它反向输出。
Assignment 2 英语翻译

Assignment 2Class:________17电子_________Name:_____________奚落__Student No.:______1703712097_____Direction: You are allowed 30 minutes to translate the following English passage into Chinese.First ever black hole image releasedAstronomers have taken the first ever image of a black hole, which is located in a distant galaxy. It measures 40 billion km across -- three million times the size of the Earth -- and has been described by scientists as “a monster”. The black hole is 500 million trillion km away and was photographed by a network of eight telescopes across the world. Details have been published today in Astrophysical Journal Letters. Prof Heino Falcke, of Radboud University in the Netherlands, who proposed the experiment, t old BBC News that the black hole was found in a galaxy called M87. “It is one of the heaviest black holes that we think exist. It is an absolute monster, the heavyweight champion of black holes in the Universe.” The image shows an intensely bright “ring of fire”, as Prof Falcke describes it, surrounding a perfectly circular dark hole. The bright halo is caused by superheated gas falling into the hole. The light is brighter than all the billions of other stars in the galaxy combined - which is why it can be seen at such distance from Earth. The edge of the dark circle at the centre is the point at which the gas enters the black hole, which is an object that has such a large gravitational pull, not even light can escape.词汇first ever 有史以来第一个;有生以来第一个Astronomer n. 天文学家galaxy n. 星系measure + 数据长达/高达/宽达……telescope n. 望远镜propose vt. 提议;倡导heavyweight champion 重量级冠军intensely bright 极为明亮的;巨亮的intensely adv. 极其;非常(extremely)perfectly circular 呈现出完美圆形的halo n. 光圈superheated adj. 超级高温的;超级热的all sth. combined 所有……加起来gravitational pull 引力;地心引力________天文学家首次拍摄到位于遥远星系中的黑洞的图像。
(完整word版)北航研究生算法设计与分析Assignment_2

用分支定界算法求以下问题:某公司于乙城市的销售点急需一批成品,该公司成品生产基地在甲城市。
甲城市与乙城市之间共有n 座城市,互相以公路连通。
甲城市、乙城市以及其它各城市之间的公路连通情况及每段公路的长度由矩阵M1 给出。
每段公路均由地方政府收取不同额度的养路费等费用,具体数额由矩阵M2 给出。
请给出在需付养路费总额不超过1500 的情况下,该公司货车运送其产品从甲城市到乙城市的最短运送路线。
具体数据参见文件:m1.txt: 各城市之间的公路连通情况及每段公路的长度矩阵(有向图); 甲城市为城市Num.1,乙城市为城市Num.50。
m2.txt: 每段公路收取的费用矩阵(非对称)。
思想:利用Floyd算法的基本方法求解。
程序实现流程说明:1.将m1.txt和m2.txt的数据读入两个50×50的数组。
2.用Floyd算法求出所有点对之间的最短路径长度和最小费用。
3.建立一个堆栈,初始化该堆栈。
4.取出栈顶的结点,检查它的相邻的所有结点,确定下一个当前最优路径上的结点,被扩展的结点依次加入堆栈中。
在检查的过程中,如果发现超出最短路径长度或者最小费用,则进行”剪枝”,然后回溯。
5.找到一个解后,保存改解,然后重复步骤4。
6.重复步骤4、5,直到堆栈为空,当前保存的解即为最优解。
时间复杂度分析:Floyd算法的时间复杂度为3O N,N为所有城市的个数。
()该算法的时间复杂度等于DFS的时间复杂度,即O(N+E)。
其中,E为所有城市构成的有向连通图的边的总数。
但是因为采用了剪枝,会使实际运行情况的比较次数远小于E。
求解结果:算法所得结果:甲乙之间最短路线长度是:464最短路线收取的费用是:1448最短路径是:1 3 8 11 15 21 23 26 32 37 39 45 47 50C源代码(注意把m1.txt与m2.txt放到与源代码相同的目录下,下面代码可直接复制运行):#include<stdlib.h>#include<stdio.h>#include<time.h>#include<string.h>#define N 50#define MAX 52void input(int a[N][N],int b[N][N]);void Floyd(int d[N][N]);void fenzhi(int m1[N][N],int m2[N][N],int mindist[N][N],int mincost[N][N]);int visited[N],bestPath[N];void main(){clock_t start,finish;double duration;int i,j,mindist[N][N],mincost[N][N],m1[N][N],m2[N][N]; /* m1[N][N]和m2[N][N]分别代表题目所给的距离矩阵和代价矩阵*/// int visited[N],bestPath[N];FILE *fp,*fw;// system("cls");time_t ttime;time(&ttime);printf("%s",ctime(&ttime));start=clock();for(i=0;i<N;i++){visited[i]=0;bestPath[i]=0;}fp=fopen("m1.txt","r"); /* 把文件中的距离矩阵m1读入数组mindist[N][N] */if(fp==NULL){printf("can not open file\n");return;}for(i=0;i<N;i++)for(j=0;j<N;j++)fscanf(fp,"%d",&mindist[i][j]);fclose(fp); /* 距离矩阵m1读入完毕*/fp=fopen("m2.txt","r"); /* 把文件中的代价矩阵m2读入数组mincost[N][N] */if(fp==NULL){printf("can not open file\n");return;}for(i=0;i<N;i++)for(j=0;j<N;j++)fscanf(fp,"%d",&mincost[i][j]);fclose(fp); /* 代价矩阵m2读入完毕*/input(m1,mindist); /* mindist[N][N]赋值给m1[N][N],m1[N][N]代表题目中的距离矩阵*/input(m2,mincost); /* mincost[N][N]赋值给m2[N][N],m2[N][N]代表题目中的代价矩阵*/for(i=0;i<N;i++) /* 把矩阵mindist[i][i]和mincost[i][i]的对角元素分别初始化,表明城市到自身不连通,代价为0 */{mindist[i][i]=9999;mincost[i][i]=0;}Floyd(mindist); /* 用弗洛伊德算法求任意两城市之间的最短距离,结果存储在数组mindist[N][N]中*//*fw=fopen("1.txt","w");for(i=0;i<N;i++){for(j=0;j<N;j++)fprintf(fw,"%4d ",mindist[i][j]);fprintf(fw,"\n");}fclose(fw);// getchar();//*/Floyd(mincost); /* 用弗洛伊德算法求任意两城市之间的最小代价,结果存储在数组mincost[N][N]中*//*fw=fopen("2.txt","w");for(i=0;i<N;i++){for(j=0;j<N;j++)fprintf(fw,"%4d ",mincost[i][j]);fprintf(fw,"\n");}fclose(fw);// getchar();//*/fenzhi(m1,m2,mindist,mincost); /* 调用分支定界的实现函数,寻找出所有的可行路径并依次输出*/finish=clock();duration = (double)(finish - start) / CLOCKS_PER_SEC;printf( "%f seconds\n", duration );//*/}void Floyd(int d[N][N]) /* 弗洛伊德算法的实现函数*/{int v,w,u,i;for(u=0;u<N;u++){for(v=0;v<N;v++){for(w=0;w<N;w++)if(d[v][u]+d[u][w]<d[v][w]){//printf("v,w,u,d[v][u],d[u][w],d[v][w] %d %d %d %d %d %d",v+1,w+1,u+1,d[v][u],d[u][w],d[v][ w]);getchar();d[v][w]=d[v][u]+d[u][w];}}}}void input(int a[N][N],int b[N][N]) /* 把矩阵b赋值给矩阵a */{int i,j;for(i=0;i<N;i++)for(j=0;j<N;j++)a[i][j]=b[i][j];}void fenzhi(int m1[N][N],int m2[N][N],int mindist[N][N],int mincost[N][N]){int stack[MAX],depth=0,next,i,j; /* 定义栈,depth表示栈顶指针;next指向每次遍历时当前所处城市的上一个已经遍历的城市*/int bestLength,shortestDist,minimumCost,distBound=9999,costBound=9999;int cur,currentDist=0,currentCost=0; /* cur指向当前所处城市,currentDist和currentCost分别表示从甲城市到当前所处城市的最短距离和最小代价,currentDist和currentCost初值为0表示从甲城市出发开始深度优先搜索*/stack[depth]=0; /* 对栈进行初始化*/stack[depth+1]=0;visited[0]=1; /* visited[0]=1用来标识从甲城市开始出发进行遍历,甲城市已被访问*/while(depth>=0) /* 表示遍历开始和结束条件,开始时从甲城市出发,栈空,depth=0;结束时遍历完毕,所有节点均被出栈,故栈也为空,depth=0 *//* 整个while()循环体用来实现从当前的城市中寻找一个邻近的城市*/{cur=stack[depth]; /* 取栈顶节点赋值给cur,表示当前访问到第cur号城市*/ next=stack[depth+1]; /* next指向当前所处城市的上一个已经遍历的城市*/for(i=next+1;i<N;i++) /* 试探当前所处城市的每一个相邻城市*/{if((currentCost+mincost[cur][N-1]>costBound)||(currentDist+mindist[cur][N-1]>=distBound)){ /* 所试探的城市满足剪枝条件,进行剪枝*///printf("here1 %d %d %d %d %d %d %d\n",cur,currentCost,mincost[cur][49],costBound,curre ntDist,mindist[cur][49],distBound); getchar();//printf("%d %d %d %d %d %d",cur,i,m1[cur][i],currentCost,mincost[cur][49],costBound); getchar();continue;}if(m1[cur][i]==9999) continue; /* 所试探的城市不连通*/if(visited[i]==1) continue; /* 所试探的城市已被访问*/if(i<N) break; /* 所试探的城市满足访问条件,找到新的可行城市,终止for循环*/ }if(i==N) /* 判断for循环是否是由于搜索完所有城市而终止的,如果是(i==N),进行回溯*/{// printf("here");getchar();depth--;currentDist-=m1[stack[depth]][stack[depth+1]];currentCost-=m2[stack[depth]][stack[depth+1]];visited[stack[depth+1]]=0;}else /* i!=N,表示for循环的终止是由于寻找到了当前城市的一个可行的邻近城市*/{//printf("%d %d %d %d %d %d\n",cur,i,m1[stack[depth]][i],m2[stack[depth]][i],currentCost,curre ntDist);//getchar();currentDist+=m1[stack[depth]][i]; /* 把从当前所处城市到所找到的可行城市的距离加入currentDist */currentCost+=m2[stack[depth]][i]; /* 把从当前所处城市到所找到的可行城市的代价加入currentCost */depth++; /* 所找到的可行城市进栈*/stack[depth]=i; /* 更新栈顶指针,指向所找到的可行城市*/stack[depth+1]=0;visited[i]=1; /* 修改所找到的城市的访问标志*/if(i==N-1) /* i==N-1表示访问到了乙城市,完成了所有城市的一次搜索,找到一条通路*/{// printf("here\n");for(j=0;j<=depth;j++) /* 保存当前找到的通路所经过的所有节点*/ bestPath[j]=stack[j];bestLength=depth; /* 保存当前找到的通路所经过的所有节点的节点数*/shortestDist=currentDist; /* 保存当前找到的通路的距离之和*/minimumCost=currentCost; /* 保存当前找到的通路的代价之和*///costBound=currentCost;distBound=currentDist; /* 更新剪枝的路径边界,如果以后所找到的通路路径之和大于目前通路的路径之和,就剪枝*/if(minimumCost>1500) continue; /* 如果当前找到的通路的代价之和大于1500,则放弃这条通路*/printf("最短路径:%3d,路径代价:%3d,所经历的节点数目:%3d,所经历的节点如下:\n",shortestDist,minimumCost,bestLength+1); /* 输出找到的通路的结果*/bestPath[bestLength]=49;for(i=0;i<=bestLength;i++) /* 输出所找到的通路所经过的具体的节点*/ printf("%3d ",bestPath[i]+1);(完整word版)北航研究生算法设计与分析Assignment_2 printf("\n");depth--; /* 连续弹出栈顶的两个值,进行回溯,开始寻找新的可行的通路*/currentDist-=m1[stack[depth]][stack[depth+1]];currentCost-=m2[stack[depth]][stack[depth+1]];visited[stack[depth+1]]=0;depth--;currentDist-=m1[stack[depth]][stack[depth+1]];currentCost-=m2[stack[depth]][stack[depth+1]];visited[stack[depth+1]]=0;// getchar();}}}}。
assignment 2

Assignment 2 (Chapter 3/4/5)1. Translate the following sentences into English.1)我们确定搞两个开放:一个是对内开放,一个是对外开放。
2)汉字在历史上有过不可磨灭的功绩。
3)姑娘有点不好意思了,脸上泛着红潮。
4)多年来那个地区一直有严重的失业现象。
5)他挣的钱几乎难以维持生活。
6)我昨天没上学,一来是因为天气不好,二来是因为我不舒服。
7)他把事情一五一十地都给老师讲了。
8)他每天要处理许多棘手的问题9)他就知道脚踩两只船。
10)学生们急得像热锅上的蚂蚁一样。
11)人们利用科学去了解自然,改造自然。
12)老年人如夕阳,少年人如朝阳。
老年人如秋后之柳,少年人如春间之草。
13)机械能可以变成电能,电能也可以变成机械能。
2. Translate the following sentences into English!1)杨宪益长年生活学习在国外,大学毕业后,他的生活习惯和内在气质,都已与中国同胞截然不同。
2)就在这时,他为了兴办学校,广泛招聘人才,向我发出了邀请。
3. Translate the following sentences into Chinese!1)Nevertheless, they all emphasize that pollution of air and water, noise and congestion, and themechanization of the work process are very real and very serious problems.然而,他们都强调:水和空气污染,噪音和交通拥挤,机械性的工作等问题的确是很严重的问题。
2)He was one of 15 children in the family.。
waiting for reviewer assignment两次

waiting for reviewer assignment两次1. 引言1.1 概述本文旨在探讨作者在等待审稿人分派过程中的经历和心态变化,并分享应对策略。
审稿人分派是学术写作过程中的一环,它决定了论文最终是否能够进入审稿阶段。
然而,这个过程有时会导致作者焦虑和不确定性,尤其是当第一次等待审稿人分派没有成功时。
1.2 目的本文的目的是回顾作者两次等待审稿人分派的经历,并从中总结出积极的心态和应对策略。
通过分享这些经验,希望能给其他作者在面对类似情况时提供一些建议和思考方向。
1.3 结构本文将按照以下结构展开叙述。
首先,在第二章中,将详细描述作者第一次等待审稿人分派的过程以及相关心理变化;接着,在第三章中,将介绍第二次等待审稿人分派的经历总结、反思与启示;最后,在第四章中,将进行整体性的总结回顾,并提供针对于待评审心态建议与思考、写作经验分享与方法探讨。
通过这样一个完整的框架,读者能够全面了解并从中获取有用的信息和启发。
2. 第一次等待审稿人分派:第一次等待审稿人分派是在投稿后经历的一个重要环节。
在这个部分中,我将描述我经历的具体过程,并分享我在心理上的变化以及应对策略。
2.1 过程描述:在提交我的文章后,我期望能够尽快得到审稿人的分派并开始进行评审过程。
然而,这个过程却花费了相当长的时间。
起初,我通过系统收到了一封确认邮件,告知我的稿件已成功提交。
然后,按照期刊的规定流程,我的文章进入了等待审稿人分派的阶段。
等待期间,我时常登录到投稿系统查看我的状态是否有更新。
但是,在那段时间里,并没有任何与审稿人相关的消息到达。
天数一天天地过去了,我开始感到担忧和不安。
2.2 心理变化:最初的几天里,我仍然抱有希望,认为可能只是需要更多时间来指派合适的审稿人。
然而,随着时间继续推移而没有任何消息,我开始感到沮丧和焦虑。
这个漫长的等待过程让我想到自己文章可能会被拒绝或者被置于较低优先级。
我开始质疑自己的写作能力和研究内容的质量。
CETP1_Assignment2_Solution
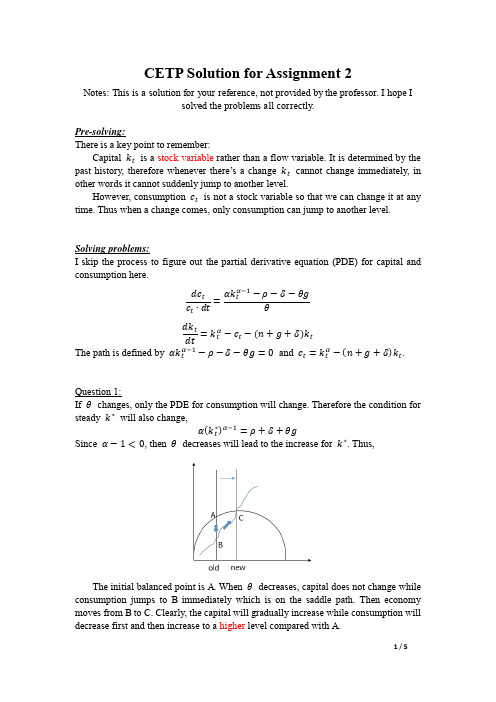
CETP Solution for Assignment 2Notes: This is a solution for your reference, not provided by the professor. I hope Isolved the problems all correctly.Pre-solving:There is a key point to remember:Capital k t is a stock variable rather than a flow variable. It is determined by the past history, t herefore whenever there’s a change k t cannot change immediately, in other words it cannot suddenly jump to another level.However, consumption c t is not a stock variable so that we can change it at any time. Thus when a change comes, only consumption can jump to another level. Solving problems:I skip the process to figure out the partial derivative equation (PDE) for capital and consumption here.dc t c t∙dt =αk tα−1−ρ−δ−θgθdk tdt=k tα−c t−(n+g+δ)k tThe path is defined by αk tα−1−ρ−δ−θg=0and c t=k tα−(n+g+δ)k t.Question 1:If θchanges, only the PDE for consumption will change. Therefore the condition for steady k∗will also change,α(k t∗)α−1=ρ+δ+θgSince α−1<0, then θdecreases will lead to the increase for k∗. Thus,The initial balanced point is A. When θdecreases, capital does not change while consumption jumps to B immediately which is on the saddle path. Then economy moves from B to C. Clearly, the capital will gradually increase while consumption will decrease first and then increase to a higher level compared with A.Also there are two more cases we can talk about. In both of extension cases the economy moves in the same way as the above one. The only difference between these three cases is the magnitude of consumption in the balanced growth state.The capital will gradually increase while consumption will decrease first and then increase to an equal level compared with A in the left figure, while to a lower level in the right figure.(It’s encouraged to consider all these cases, however we only solve the first case in the following questions. We can think that the exogenous variable such as θ,g and δonly changes a little, therefore the new balanced state also changes a little compared with the old state which excludes the case 2 and case 3.)Question 2:If g changes, both of the two PDE will change. Firstly we consider the PDE for capital,α(k t∗)α−1=ρ+δ+θgSince α−1<0, then g decreases will lead to the increase for k∗.Now let’s t alk about the curve of c t=k tα−(n+g+δ)k t.Two endpoints on X-axisLet c t=0, thenk tα−(n+g+δ)k t=0Clearly one of the solution is 0 and another is k tα−1=n+g+δ. Therefore another solution is increasing as g decreases which means the gap on X-axis will be larger. Peak point horizontally=0,At the peak point which is the maximum point, we have dc tdk tαk tα−1−(n+g+δ)=0Therefore,k t#=(n+g+δα)1α−1=(∆α)1α−1Since α−1<0, then g decreases will lead to the increase for k t#. Therefore the peak point will move to the right horizontally.Peak point verticallySubstitute k t#into the equation, we can obtain the height for peak point c t#,c t#=(k t#)α−(n+g+δ)k t#Then we can check the relation between c t#and g,dc t# dg =−k t#=−(∆α)1α−1<0Then g decreases will lead to the increase for c t#. Therefore the peak point will move to the up vertically.Now combine the above three properties for the curve, we can obtainAbove all, we have figured out the change in both PDE,There may be two possible saddle path, one of which is in blue and another is in red: ●In first case, the consumption level immediately jumps from initial point A to alower level B1and then gradually increases to a higher level at C compared withA. And capital k gradually increases to a higher level.●In second case, the consumption level immediately jumps from initial point A to ahigher level B2and then gradually increases to a much higher level at C compared with A. And capital k gradually increases to a higher level.Question 3:According to αk tα−1−ρ−δ−θg=0and c t=k tα−(n+g+δ)k t and α=0.5, solve this equation set, we can easily get:k t∗=1()2c t∗=12(θg+ρ+δ)−n+g+δ4(θg+ρ+δ)2Question 4:When government is added into the model, the PDE is as follow:dc t t =αk tα−1−ρ−δ−θgdk tdt=k tα−G t−c t−(n+g+δ)k tClearly, only the PDE for capital is changed. Consider the government spending is permanent, then we will get the following figure,The consumption level jumps from initial point A to a lower level B and this point is namely the balanced growth state under permanent situation. The jump-gap here equals to the government spending raising ∆G.However if people know this government spending raising is just temporal, they will reduce their consumption less than∆G. If they directly jump to point B, then the economy is now on the balanced growth path in the new system, and therefore this economy will not move any more before the exit of government extra spending. However, people know that they will go back to point A and it’s their optimal choice to reach some point C on the original saddle path immediately after the exit of government extra spending. Thus, only if they jump to some point B1between A and B, the new system can force the economy to move gradually in advance.Therefore, people will reduce their consumption to B1which is between A and B immediately. Then move from B1to C during which capital is changing gradually, thus this process is not a jump. The economy reaches the saddle path at C at the moment government spending returns to its initial level. Finally, the economy goes back to A following the saddle path.Suppose government raises the spending at t1and ends it at t2, and according to the class notes we know rate of returns is defined by r t=α∙k tα−1−δ, therefore r t is decreasing as k t.2014/12/28End。
Assignment 2 增词与减词

Asignment 2 增词与减词试译下列各句,注意斜体词前后需要增减的词---按括弧内要求增减不同词类1. My work, my falmily, my friends were more than encough to fill my time. (斜体名词前后增加动词)完成工作,陪伴家人,结交朋友已经完全填满了我的生活。
2. “This is grasping at straws, I know,” said the helpless man. (斜体名词前后增加形容词)“我知道,这是在抓救命稻草。
”他无助的说。
3. A seagull saw the light from my window and darted up to it. (斜体动词前后增加副词)一只海鸥看见从我窗户透出的亮光,就迅速飞奔向它。
4. He began to see things and to understand.(斜体不及物动词后增加名词)他开始了解事物并且理解深意。
5. He was wrinkled and black, with scant gray hair. (斜体形容词前后增加名词)他脸上布满皱纹,皮肤黝黑,头发稀疏且灰白。
6. Very acute problems exist among them. (斜体名词前增加表复数的词)他们之间存在着一些非常严重的问题。
7. The retreat commenced in all haste. (斜体名词前后增加名词)军队在匆忙中开始撤退。
8. They had always been able to control things. Now control was getting away from all of them.(增加表时间的词)以前,他们总是可以控制所有的事情,但是现在,控制权已经完全脱离了他们。
9. The little boy brought with him knife, scissors and what not, tinkling in his pocket. (斜体名词后增加语气词)这个小孩带的小刀啊,剪刀啊以及一些别的东西在口袋里叮叮当当的响10. 但是,我却看到了一次最雄伟、最瑰丽的日出景象。
Assignment 2

Assignment 2: Figures of Speech IDirections: Translate the following sayings or shining expressions and try to use them in your future writing, if possible. (Please write the answers in blue)1)Country road, take me home. 乡村小路,带我回家。
2) Seeing is believing.眼见为信。
3) Love me, love my dog. 爱屋及乌。
4) A stitch in time saves nine. 小洞不补,大洞吃苦。
5) First come, first served. 捷足先登/先到先得。
6) A Tale of Two Cities 《双城记》7) All roads lead to Rome. 条条大路通罗马。
8) No pains, no gains. 不劳无获。
9) Knowledge is power. 知识就是力量。
10) East or west, home is best. 金窝银窝,不如自己的狗窝。
11) Employment is enjoyment.就业是享受。
12) Penny wise, pound foolish. 小事聪明,大事糊涂(意同:抓了芝麻,丢了西瓜)13) No news is good news. 没消息就是好消息。
14) Great minds think alike.英雄所见略同。
15) A good dog deserves a good bone.有劳得奖/有功者受赏。
Direction: Please write another 5 English sayings which you know well. (Please write the saying in English in blue)16. A fox may grow gray, but never good.17. A friend is easier lost than found.18. Even Homer sometimes nods.19. Strike the iron while it is hot.20. Think twice before you do.。
磁核共振assignment-2

Assignment 2 - InstructionsThe folder attached to the email contains the "raw" data from acquisition of a 13C NMR spectrum of 'sample A'. The sample is an ca. 3:1 mixture of two diastereomers with MF C 25H 48O 9. Both diastereomers are C s symmetric and each shows 13 signals in the 13C NMR spectrum (12 signals representing a pair of enantiotopic carbons and 1 representing a single carbon) . What you need to do:• process the FID contained in the folder referred to above• in the attached form, using boxes 1-13, list the 13 signals for the major diastereomer according to the instructions below for reporting 'chemical shift'. In the assignment column, indicate with an * that signal that represents a single carbon• in the attached form, in boxes 16-28, list the 13 signals for the minor diastereomer according to the instructions below for reporting 'chemical shift'. In the assignment column, indicate with an * that signal that represents a single carbon Note:Threesignalsfortheminorisomerare'hard'tofind(************,77,and27)because they are close to signals for the major isomer (or solvent). To 'see' those signals you will need to maximize the resolution by using "zero filling"(increasing digital resolution by increasing SI) and "resolution enhancement" (processing with Gaussian broadening (GFP) with GB set between 0-1 and LB set between 0 and -1)13C NMR DATA instrument125 (500 MHz for 1H) or 150 (600 MHz for 1H). solventthe molecular formula for the solvent used, i.e, CDCl 3, CD 3COCD 3, C 6D 6, etc. chemical shift in descending order, normally rounded to 1 decimal place (2decimal places are used to differentiate between separatesignals that would otherwise have the same shift if listed toonly 1 decimal place).multiplicity s , d , t , q (determined by INEPT, DEPT, HSQC, or HMQC);leave blank if unknown. When a signal represents 2 ormore C ʼs (e.g. a Et 3Si group), this is indicated, for exampleby, t ×3 (or e.g., d&t , for two different C ʼs). (for this problemthere is insufficient data to assign)assignmentassign the signal using the appropriate numbering system;e.g., C-3, CH 3O, CH 3C-7 (the Me at C-7). If the assignmentcan only be narrowed down to 2 or 3 possibilities, soindicate by e.g., C-3 or C-4 Make assignments only whenconfident of accuracy (i.e., correlation data). Otherwiseleave blank. Do not make guesses! (for this problem thereis insufficient data to assign)sample A (3:1)13C NMR DATA 125CDCl3MHz instrument solvent Chemical Shift Mult.Assignment Chemical Shift Mult.Assignment1.2.3.4.5.6.7.8.9.10.11.12.13.14.15.16.17.18.19.20.21.22.23.24.25.26.27.28.29.。
Assignment2题库(1)chap2

Assignment 2题库True/FalseIndicate whether the statement is true or false.__T__ works of computers and the Internet that connects them to each other form the basic technological structure that underlies virtually all electronic commerce.__F__ 2. The USENET was the earliest of the networks that eventually combined to become what we now call the Internet.__T__ 3. E-mail was born in 1972 when a researcher wrote a program that could send and receive messages over the Defense Department network.__T__ 4. In 1989, the NSF permitted two commercial e-mail services, MCI Mail and CompuServe, to establish limited connections to the Internet for the sole purpose of exchanging e-mail transmissions with users of the Internet.__T__ 5. A network of computers that are located close together—for example, in the same building—is called a local area network.__F__ 6. The Internet provides a high degree of security in its basic structure.__T__ 7. Although fax, telephone, e-mail, and overnight express carriers have been the main communications tools for business for many years, extranets can replace many of them at a lower cost.__F__ 8. An intranet extends beyond the organization that created it.__F__ 9. The “virtual” part of VPN means that the connectio n seems to be a temporary, internal network connection, but the connection is actually permanent.__T__ 10. VPN software must be installed on the computers at both ends of the transmission.__F__ 11. The technologies used (public networks, private networks, or VPNs) are independent of organizational boundaries.__T__ 12. IP addresses appear as five numbers separated by periods.__F__ 13. SMTP is a common protocol used for sending and retrieving e-mail.__T__ 14. IMAP is a newer e-mail protocol that performs the same basic functions as POP, but includes additional features.__T__ 15. The POP protocol provides support for MIME.__T__ 16. At a technological level, the Web is nothing more than software that runs on computers that are connected to the Internet.__T__ 17. The set of rules for delivering Web page files over the Internet is in a protocol called the Hypertext Transfer Protocol (HTTP).__F__ 18. An HTML document is similar to a word-processing document in that it specifies how a particular text element will appear.__T__ 19. Domain names are sets of words that are assigned to specific IP addresses.__F__ 20. The Internet Corporation for Actualized Names and Nuances has the responsibility of managing domain names and coordinating them with the IP address registrars.__F__ 21. HTML is a meta language because users can create their own markup elements that extend the usefulness of XML.__T__ 22. SGML offers a system of marking up documents that is independent of any software application.__T__ 23. The term cascading is used because designers can apply many style sheets to the same Web page, one on top of the other.__T__ 24. The higher the bandwidth, the faster data files travel and the faster Web pages appear on your screen.__T__ 25. Asymmetric connections provide the same bandwidth for each direction.Multiple ChoiceIdentify the choice that best completes the statement or answers the question.__c__ 1. The combination of telephone lines and the closed switches that connect them to each other is called a ____.N c. circuitb. WAN d. pathway__d__ 2. On a packet-switched network, files and e-mail messages are broken down into small pieces, called ____.a.Messages c. circuitsb. pieces d. packets__c__ 3. When packets leave a network to travel on the Internet, they must be translated intoa standard format. ____ usually perform this translation function.a.Switches c. Routersb. Bridges d. Routing algorithms__d__ 4. Routers and the telecommunications lines connecting them are collectively referred to as ____.a.backbone routers c. an asynchronous backboneb. Internet routers d. the Internet backbone__c__ 5. A(n) ____ does not extend beyond the boundaries of a particular organization.a.Internet c. intranetb. extranet d. ARPANET__a__ 6. A(n) ____ is like a separate, covered commuter lane on a highway (the Internet) in which passengers are protected from being seen by the vehicles traveling in the other lanes.a.VPN c. extranetb. IP wrapper d. IAP__c__ 7. A(n) ____ is a connection that uses public networks and their protocols to send data in a way that protects the data as well as a private network would, but at a lower cost.a.public network c. virtual private networkb. virtual public network d. private network__c__ 8. A ____ is a collection of rules for formatting, ordering, and error checking data sent across a network.a.routing algorithm c. protocolb. backbone router d. packet__c__ 9. ____ determine how the sending device indicates that it has finished sending a message, and how the receiving device indicates that it has received the message.a.Routers c. Protocolsb. Bridges d. Adapters__a__ 10. In networking applications, an 8-bit number is often called a(n) ____.a.octet c. piconetb. netbit d. bit__a__ 11. Network engineers have devised a number of stopgap techniques to stretch the supply of IP addresses. One of the most popular techniques is ____.a.subnetting c. sub-blockingb. subletting d. piconetting__b__ 12. A computer called a ____ converts private IP addresses into normal IP address when it forwards packets from those computers to the Internet.a.routing algorithm device c. subnet translation deviceb. network address translation device d. private network device__a__ 13. The ____ numbering system uses 16 characters.a.hexadecimal c. Binaryb. decimal d. ASCII__c__ 14. IPv6 uses a ___ number for addresses.a. 32-bit c. 128-bitb. 56-bit d. 256-bit__c__ 15. The purpose of a(n) ____ is to respond to requests for Web pages from Web clients.a. URL c. Web serverb. e-mail d. top-level domain__a__ 16. ____ specifies the format of a mail message and describes how mail is to be administered on the e-mail server and transmitted on the Internet.a.SMTP c. MIMEb. TCP/IP d. POP__a__ 17. A newer e-mail protocol that performs the same basic functions as POP, but includes additional features, is known as ____.a.IMAP c. POPIb. SMTP d. IPOP__c__ 18. ____ lets users create and manipulate e-mail folders and individual e-mail messages while the messages are still on the e-mail server.a.POP c. IMAPb. SMTP d. MIME__b__ 19. ____ is a set of rules for handling binary files, such as word-processing documents, spreadsheets, photos, or sound clips, that are attached to e-mail messages.a.IMAP c. SMTPb. MIME d. POP__c__ 20. The combination of the protocol name and the domain name is called the ____.a.URT c. URLb. URO d. HTTP__d__ 21. HTML was developed by ____.a.ARPANET c. Ted Nelsonb. NSF d. Tim Berners-Lee__a__ 22. ____ was the first Web browser that became widely available for personalcomputers.a. Mosaic c. Internet Explorerb. Netscape d. CompuServe__a__ 23. ____ are sets of words that are assigned to specific IP addresses.a.Domain names c. Octetsb. URLs d. Piconets__b__ 24. The early versions of ____ let Web page designers create text-based electronic documents with headings, title bar titles, bullets, lines, and ordered lists.a.HTTP c. SGMLb. HTML d. XML__b__ 25. In HTML, hyperlinks are created using the HTML ____ tag.a.head c. titleb. anchor d. olEssay1. As an individual packet travels from one network to another, the computers through which the packet travels determine the best route for getting the packet to its destination. Describe this process.Ans: The computers that decide how to best forward each packet are called routing computers, router computers, routers, gateway computers (because they act as the gateway from a LAN or WAN to the Internet) or border routers (because they are located at the border between the organization and the Internet.) The programs on the routers that determine the best path contain rules called routing algorithms. The programs apply these algorithms to information they have stored in routing tables or configuration tables. This information includes lists of connections that lead to particular groups of other routers, rules that specify which connection to use first, and rules for handling instances of heavy packet traffic and network congestion.2. What is the difference between a public network and a private network?Ans: The open architecture philosophy developed for the evolving ARPANET, which later became the core of the Internet, included the use of a common protocol for all computers connected to the Internet and four key rules for message handling:①Independent networks should not require any internal changes to be connected to the network,②Packets that do not arrive at their destinations must be retransmitted from their source network,③Router computers act as receive-and-forward devices; they do not retain information about the packets that they handle, and④No global control exists over the network.3. Identify the four key rules for message handling.Ans: The TCP controls the disassembly of a message or a file into packets before it is transmitted over the Internet, and it controls the reassembly of those packets into their original formats when they reach their destinations. The IP specifies the addressing details for each packet, labeling each with the packet’s origination and destination addresses.4.What is the difference between TCP and IP?Ans: The TCP controls the disassembly of a message or a file into packets before it is transmitted over the Internet, and it controls the reassembly of those packets into their original formats when they reach their destinations. The IP specifies the addressing details for each packet, labeling each with the packet’s origination and destination addresses.5. What are the advantages of Bluetooth technology?Ans: One major advantage of Bluetooth technology is that it consumes very little power, which is an important consideration for many devices. Another advantage is that Bluetooth devices can discover each other and exchange information automatically. For example, a person using a laptop computer in a temporary office can print to a local Bluetooth-enabled printer without logging in to the network or installing software in either device. The printer and laptop computer electronically recognize each other as Bluetooth devices and immediately can begin exchanging information.。
Assignment 2(1)
A. B. C. D.
a trade deficit is always good. a trade deficit is always bad. a trade deficit may be good or bad. a trade surplus is always bad.
16. When the real exchange rate rises:
19. If the real exchange rate between the United States and Japan remains unchanged, and the
inflation rate in the United States is 6 percent and the inflation rate in Japan is 3 percent, the: A. dollar will appreciate by 3 percent against the yen. B. yen will appreciate by 3 percent against the dollar. C. yen will appreciate by 6 percent against the dollar. D. yen will appreciate by 9 percent against the dollar.
theory, if velocity is constant, then ______ determines real GDP and ______ determines nominal GDP. A. the productive capability of the economy; the money supply B. the money supply; the productive capability of the economy C. velocity; the money supply D. the money supply; velocity
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Problem 1 (Con’t)
At 8 A.M. today the quality technician randomly selected 16 bottles from the filling line. The mean amount of cola contained in the bottles is 31.38 ounces.
Should this lot be accepted or rejected?
பைடு நூலகம்
Cola, Inc., does not wish to underfill the bottles. On the other hand, it cannot overfill each bottle. Its records indicate that the amount of cola follows the normal probability distribution when the production is stable. The mean amount per bottle is 31.2 ounces and the population standard deviation is 0.4 ounces.
Problem 2 (Con’t)
An inspection will be conducted to check the quality of the incoming goods. A sample of 100 windows are inspected and 7 of them are broken.
Problem 2
Consider a process that a manufacturer purchases 10,000 window glasses from a supplier outside the organization.
Each window glass can be classified as conforming or nonconforming depends on whether it is broken. If less than 5% of the glasses are broken, then the incoming glasses are acceptable.
Is this an unlikely result of the normal stable process? Is it likely the process is putting too much soda in the bottles? Is the process asking for intervention/ actions of technicians?
Problem 1
The Quality Assurance Department for Cola, Inc., maintains records regarding the amount of cola in its Jumbo bottle. The actual amount of cola in each bottle is critical, but varies a small amount from one bottle to the next.
