SMSREC-STAFF-RPG-ETHICS-FORM-revised-NOV-2011
CSR - Ethics (1)

Ethics and the Law
Legal standards will, and always have to be, by their nature, consensus minimal standards of impropriety, beneath which an individual merits punishment: but action above the set level is not always „right‟
Pagano’s 9 Ways to Achieve Ethical Behaviour
1. Leadership by top management 2. Realistic goal setting 3. An ethics audit 4. A code of ethics 5. An ethics committee at the board level 6. An ethics advocate within the business 7. A mechanism for whistle-blowing 8. Ethics training for managers 9. An independent board of directors
(Adapted from Crane & Matten, 2010)
A practical approach
Apply Pagano‟s six tests to consider the ethics of a business action :
1. Is it legal? 2. Does it represent the greatest good for the greatest number? 3. Does this represent a universal standard? 4. How would you feel if this appeared in the media? 5. Would you want this to happen to you? 6. Should you consider getting an independent second opinion?
Native Instruments MASCHINE MK3 用户手册说明书

The information in this document is subject to change without notice and does not represent a commitment on the part of Native Instruments GmbH. The software described by this docu-ment is subject to a License Agreement and may not be copied to other media. No part of this publication may be copied, reproduced or otherwise transmitted or recorded, for any purpose, without prior written permission by Native Instruments GmbH, hereinafter referred to as Native Instruments.“Native Instruments”, “NI” and associated logos are (registered) trademarks of Native Instru-ments GmbH.ASIO, VST, HALion and Cubase are registered trademarks of Steinberg Media Technologies GmbH.All other product and company names are trademarks™ or registered® trademarks of their re-spective holders. Use of them does not imply any affiliation with or endorsement by them.Document authored by: David Gover and Nico Sidi.Software version: 2.8 (02/2019)Hardware version: MASCHINE MK3Special thanks to the Beta Test Team, who were invaluable not just in tracking down bugs, but in making this a better product.NATIVE INSTRUMENTS GmbH Schlesische Str. 29-30D-10997 Berlin Germanywww.native-instruments.de NATIVE INSTRUMENTS North America, Inc. 6725 Sunset Boulevard5th FloorLos Angeles, CA 90028USANATIVE INSTRUMENTS K.K.YO Building 3FJingumae 6-7-15, Shibuya-ku, Tokyo 150-0001Japanwww.native-instruments.co.jp NATIVE INSTRUMENTS UK Limited 18 Phipp StreetLondon EC2A 4NUUKNATIVE INSTRUMENTS FRANCE SARL 113 Rue Saint-Maur75011 ParisFrance SHENZHEN NATIVE INSTRUMENTS COMPANY Limited 5F, Shenzhen Zimao Center111 Taizi Road, Nanshan District, Shenzhen, GuangdongChina© NATIVE INSTRUMENTS GmbH, 2019. All rights reserved.Table of Contents1Welcome to MASCHINE (25)1.1MASCHINE Documentation (26)1.2Document Conventions (27)1.3New Features in MASCHINE 2.8 (29)1.4New Features in MASCHINE 2.7.10 (31)1.5New Features in MASCHINE 2.7.8 (31)1.6New Features in MASCHINE 2.7.7 (32)1.7New Features in MASCHINE 2.7.4 (33)1.8New Features in MASCHINE 2.7.3 (36)2Quick Reference (38)2.1Using Your Controller (38)2.1.1Controller Modes and Mode Pinning (38)2.1.2Controlling the Software Views from Your Controller (40)2.2MASCHINE Project Overview (43)2.2.1Sound Content (44)2.2.2Arrangement (45)2.3MASCHINE Hardware Overview (48)2.3.1MASCHINE Hardware Overview (48)2.3.1.1Control Section (50)2.3.1.2Edit Section (53)2.3.1.3Performance Section (54)2.3.1.4Group Section (56)2.3.1.5Transport Section (56)2.3.1.6Pad Section (58)2.3.1.7Rear Panel (63)2.4MASCHINE Software Overview (65)2.4.1Header (66)2.4.2Browser (68)2.4.3Arranger (70)2.4.4Control Area (73)2.4.5Pattern Editor (74)3Basic Concepts (76)3.1Important Names and Concepts (76)3.2Adjusting the MASCHINE User Interface (79)3.2.1Adjusting the Size of the Interface (79)3.2.2Switching between Ideas View and Song View (80)3.2.3Showing/Hiding the Browser (81)3.2.4Showing/Hiding the Control Lane (81)3.3Common Operations (82)3.3.1Using the 4-Directional Push Encoder (82)3.3.2Pinning a Mode on the Controller (83)3.3.3Adjusting Volume, Swing, and Tempo (84)3.3.4Undo/Redo (87)3.3.5List Overlay for Selectors (89)3.3.6Zoom and Scroll Overlays (90)3.3.7Focusing on a Group or a Sound (91)3.3.8Switching Between the Master, Group, and Sound Level (96)3.3.9Navigating Channel Properties, Plug-ins, and Parameter Pages in the Control Area.973.3.9.1Extended Navigate Mode on Your Controller (102)3.3.10Navigating the Software Using the Controller (105)3.3.11Using Two or More Hardware Controllers (106)3.3.12Touch Auto-Write Option (108)3.4Native Kontrol Standard (110)3.5Stand-Alone and Plug-in Mode (111)3.5.1Differences between Stand-Alone and Plug-in Mode (112)3.5.2Switching Instances (113)3.5.3Controlling Various Instances with Different Controllers (114)3.6Host Integration (114)3.6.1Setting up Host Integration (115)3.6.1.1Setting up Ableton Live (macOS) (115)3.6.1.2Setting up Ableton Live (Windows) (116)3.6.1.3Setting up Apple Logic Pro X (116)3.6.2Integration with Ableton Live (117)3.6.3Integration with Apple Logic Pro X (119)3.7Preferences (120)3.7.1Preferences – General Page (121)3.7.2Preferences – Audio Page (126)3.7.3Preferences – MIDI Page (130)3.7.4Preferences – Default Page (133)3.7.5Preferences – Library Page (137)3.7.6Preferences – Plug-ins Page (145)3.7.7Preferences – Hardware Page (150)3.7.8Preferences – Colors Page (154)3.8Integrating MASCHINE into a MIDI Setup (156)3.8.1Connecting External MIDI Equipment (156)3.8.2Sync to External MIDI Clock (157)3.8.3Send MIDI Clock (158)3.9Syncing MASCHINE using Ableton Link (159)3.9.1Connecting to a Network (159)3.9.2Joining and Leaving a Link Session (159)3.10Using a Pedal with the MASCHINE Controller (160)3.11File Management on the MASCHINE Controller (161)4Browser (163)4.1Browser Basics (163)4.1.1The MASCHINE Library (163)4.1.2Browsing the Library vs. Browsing Your Hard Disks (164)4.2Searching and Loading Files from the Library (165)4.2.1Overview of the Library Pane (165)4.2.2Selecting or Loading a Product and Selecting a Bank from the Browser (170)4.2.2.1[MK3] Browsing by Product Category Using the Controller (174)4.2.2.2[MK3] Browsing by Product Vendor Using the Controller (174)4.2.3Selecting a Product Category, a Product, a Bank, and a Sub-Bank (175)4.2.3.1Selecting a Product Category, a Product, a Bank, and a Sub-Bank on theController (179)4.2.4Selecting a File Type (180)4.2.5Choosing Between Factory and User Content (181)4.2.6Selecting Type and Character Tags (182)4.2.7List and Tag Overlays in the Browser (186)4.2.8Performing a Text Search (188)4.2.9Loading a File from the Result List (188)4.3Additional Browsing Tools (193)4.3.1Loading the Selected Files Automatically (193)4.3.2Auditioning Instrument Presets (195)4.3.3Auditioning Samples (196)4.3.4Loading Groups with Patterns (197)4.3.5Loading Groups with Routing (198)4.3.6Displaying File Information (198)4.4Using Favorites in the Browser (199)4.5Editing the Files’ Tags and Properties (203)4.5.1Attribute Editor Basics (203)4.5.2The Bank Page (205)4.5.3The Types and Characters Pages (205)4.5.4The Properties Page (208)4.6Loading and Importing Files from Your File System (209)4.6.1Overview of the FILES Pane (209)4.6.2Using Favorites (211)4.6.3Using the Location Bar (212)4.6.4Navigating to Recent Locations (213)4.6.5Using the Result List (214)4.6.6Importing Files to the MASCHINE Library (217)4.7Locating Missing Samples (219)4.8Using Quick Browse (221)5Managing Sounds, Groups, and Your Project (225)5.1Overview of the Sounds, Groups, and Master (225)5.1.1The Sound, Group, and Master Channels (226)5.1.2Similarities and Differences in Handling Sounds and Groups (227)5.1.3Selecting Multiple Sounds or Groups (228)5.2Managing Sounds (233)5.2.1Loading Sounds (235)5.2.2Pre-listening to Sounds (236)5.2.3Renaming Sound Slots (237)5.2.4Changing the Sound’s Color (237)5.2.5Saving Sounds (239)5.2.6Copying and Pasting Sounds (241)5.2.7Moving Sounds (244)5.2.8Resetting Sound Slots (245)5.3Managing Groups (247)5.3.1Creating Groups (248)5.3.2Loading Groups (249)5.3.3Renaming Groups (251)5.3.4Changing the Group’s Color (251)5.3.5Saving Groups (253)5.3.6Copying and Pasting Groups (255)5.3.7Reordering Groups (258)5.3.8Deleting Groups (259)5.4Exporting MASCHINE Objects and Audio (260)5.4.1Saving a Group with its Samples (261)5.4.2Saving a Project with its Samples (262)5.4.3Exporting Audio (264)5.5Importing Third-Party File Formats (270)5.5.1Loading REX Files into Sound Slots (270)5.5.2Importing MPC Programs to Groups (271)6Playing on the Controller (275)6.1Adjusting the Pads (275)6.1.1The Pad View in the Software (275)6.1.2Choosing a Pad Input Mode (277)6.1.3Adjusting the Base Key (280)6.1.4Using Choke Groups (282)6.1.5Using Link Groups (284)6.2Adjusting the Key, Choke, and Link Parameters for Multiple Sounds (286)6.3Playing Tools (287)6.3.1Mute and Solo (288)6.3.2Choke All Notes (292)6.3.3Groove (293)6.3.4Level, Tempo, Tune, and Groove Shortcuts on Your Controller (295)6.3.5Tap Tempo (299)6.4Performance Features (300)6.4.1Overview of the Perform Features (300)6.4.2Selecting a Scale and Creating Chords (303)6.4.3Scale and Chord Parameters (303)6.4.4Creating Arpeggios and Repeated Notes (316)6.4.5Swing on Note Repeat / Arp Output (321)6.5Using Lock Snapshots (322)6.5.1Creating a Lock Snapshot (322)6.5.2Using Extended Lock (323)6.5.3Updating a Lock Snapshot (323)6.5.4Recalling a Lock Snapshot (324)6.5.5Morphing Between Lock Snapshots (324)6.5.6Deleting a Lock Snapshot (325)6.5.7Triggering Lock Snapshots via MIDI (326)6.6Using the Smart Strip (327)6.6.1Pitch Mode (328)6.6.2Modulation Mode (328)6.6.3Perform Mode (328)6.6.4Notes Mode (329)7Working with Plug-ins (330)7.1Plug-in Overview (330)7.1.1Plug-in Basics (330)7.1.2First Plug-in Slot of Sounds: Choosing the Sound’s Role (334)7.1.3Loading, Removing, and Replacing a Plug-in (335)7.1.3.1Browser Plug-in Slot Selection (341)7.1.4Adjusting the Plug-in Parameters (344)7.1.5Bypassing Plug-in Slots (344)7.1.6Using Side-Chain (346)7.1.7Moving Plug-ins (346)7.1.8Alternative: the Plug-in Strip (348)7.1.9Saving and Recalling Plug-in Presets (348)7.1.9.1Saving Plug-in Presets (349)7.1.9.2Recalling Plug-in Presets (350)7.1.9.3Removing a Default Plug-in Preset (351)7.2The Sampler Plug-in (352)7.2.1Page 1: Voice Settings / Engine (354)7.2.2Page 2: Pitch / Envelope (356)7.2.3Page 3: FX / Filter (359)7.2.4Page 4: Modulation (361)7.2.5Page 5: LFO (363)7.2.6Page 6: Velocity / Modwheel (365)7.3Using Native Instruments and External Plug-ins (367)7.3.1Opening/Closing Plug-in Windows (367)7.3.2Using the VST/AU Plug-in Parameters (370)7.3.3Setting Up Your Own Parameter Pages (371)7.3.4Using VST/AU Plug-in Presets (376)7.3.5Multiple-Output Plug-ins and Multitimbral Plug-ins (378)8Using the Audio Plug-in (380)8.1Loading a Loop into the Audio Plug-in (384)8.2Editing Audio in the Audio Plug-in (385)8.3Using Loop Mode (386)8.4Using Gate Mode (388)9Using the Drumsynths (390)9.1Drumsynths – General Handling (391)9.1.1Engines: Many Different Drums per Drumsynth (391)9.1.2Common Parameter Organization (391)9.1.3Shared Parameters (394)9.1.4Various Velocity Responses (394)9.1.5Pitch Range, Tuning, and MIDI Notes (394)9.2The Kicks (395)9.2.1Kick – Sub (397)9.2.2Kick – Tronic (399)9.2.3Kick – Dusty (402)9.2.4Kick – Grit (403)9.2.5Kick – Rasper (406)9.2.6Kick – Snappy (407)9.2.7Kick – Bold (409)9.2.8Kick – Maple (411)9.2.9Kick – Push (412)9.3The Snares (414)9.3.1Snare – Volt (416)9.3.2Snare – Bit (418)9.3.3Snare – Pow (420)9.3.4Snare – Sharp (421)9.3.5Snare – Airy (423)9.3.6Snare – Vintage (425)9.3.7Snare – Chrome (427)9.3.8Snare – Iron (429)9.3.9Snare – Clap (431)9.3.10Snare – Breaker (433)9.4The Hi-hats (435)9.4.1Hi-hat – Silver (436)9.4.2Hi-hat – Circuit (438)9.4.3Hi-hat – Memory (440)9.4.4Hi-hat – Hybrid (442)9.4.5Creating a Pattern with Closed and Open Hi-hats (444)9.5The Toms (445)9.5.1Tom – Tronic (447)9.5.2Tom – Fractal (449)9.5.3Tom – Floor (453)9.5.4Tom – High (455)9.6The Percussions (456)9.6.1Percussion – Fractal (458)9.6.2Percussion – Kettle (461)9.6.3Percussion – Shaker (463)9.7The Cymbals (467)9.7.1Cymbal – Crash (469)9.7.2Cymbal – Ride (471)10Using the Bass Synth (474)10.1Bass Synth – General Handling (475)10.1.1Parameter Organization (475)10.1.2Bass Synth Parameters (477)11Working with Patterns (479)11.1Pattern Basics (479)11.1.1Pattern Editor Overview (480)11.1.2Navigating the Event Area (486)11.1.3Following the Playback Position in the Pattern (488)11.1.4Jumping to Another Playback Position in the Pattern (489)11.1.5Group View and Keyboard View (491)11.1.6Adjusting the Arrange Grid and the Pattern Length (493)11.1.7Adjusting the Step Grid and the Nudge Grid (497)11.2Recording Patterns in Real Time (501)11.2.1Recording Your Patterns Live (501)11.2.2The Record Prepare Mode (504)11.2.3Using the Metronome (505)11.2.4Recording with Count-in (506)11.2.5Quantizing while Recording (508)11.3Recording Patterns with the Step Sequencer (508)11.3.1Step Mode Basics (508)11.3.2Editing Events in Step Mode (511)11.3.3Recording Modulation in Step Mode (513)11.4Editing Events (514)11.4.1Editing Events with the Mouse: an Overview (514)11.4.2Creating Events/Notes (517)11.4.3Selecting Events/Notes (518)11.4.4Editing Selected Events/Notes (526)11.4.5Deleting Events/Notes (532)11.4.6Cut, Copy, and Paste Events/Notes (535)11.4.7Quantizing Events/Notes (538)11.4.8Quantization While Playing (540)11.4.9Doubling a Pattern (541)11.4.10Adding Variation to Patterns (541)11.5Recording and Editing Modulation (546)11.5.1Which Parameters Are Modulatable? (547)11.5.2Recording Modulation (548)11.5.3Creating and Editing Modulation in the Control Lane (550)11.6Creating MIDI Tracks from Scratch in MASCHINE (555)11.7Managing Patterns (557)11.7.1The Pattern Manager and Pattern Mode (558)11.7.2Selecting Patterns and Pattern Banks (560)11.7.3Creating Patterns (563)11.7.4Deleting Patterns (565)11.7.5Creating and Deleting Pattern Banks (566)11.7.6Naming Patterns (568)11.7.7Changing the Pattern’s Color (570)11.7.8Duplicating, Copying, and Pasting Patterns (571)11.7.9Moving Patterns (574)11.7.10Adjusting Pattern Length in Fine Increments (575)11.8Importing/Exporting Audio and MIDI to/from Patterns (576)11.8.1Exporting Audio from Patterns (576)11.8.2Exporting MIDI from Patterns (577)11.8.3Importing MIDI to Patterns (580)12Audio Routing, Remote Control, and Macro Controls (589)12.1Audio Routing in MASCHINE (590)12.1.1Sending External Audio to Sounds (591)12.1.2Configuring the Main Output of Sounds and Groups (596)12.1.3Setting Up Auxiliary Outputs for Sounds and Groups (601)12.1.4Configuring the Master and Cue Outputs of MASCHINE (605)12.1.5Mono Audio Inputs (610)12.1.5.1Configuring External Inputs for Sounds in Mix View (611)12.2Using MIDI Control and Host Automation (614)12.2.1Triggering Sounds via MIDI Notes (615)12.2.2Triggering Scenes via MIDI (622)12.2.3Controlling Parameters via MIDI and Host Automation (623)12.2.4Selecting VST/AU Plug-in Presets via MIDI Program Change (631)12.2.5Sending MIDI from Sounds (632)12.3Creating Custom Sets of Parameters with the Macro Controls (636)12.3.1Macro Control Overview (637)12.3.2Assigning Macro Controls Using the Software (638)12.3.3Assigning Macro Controls Using the Controller (644)13Controlling Your Mix (646)13.1Mix View Basics (646)13.1.1Switching between Arrange View and Mix View (646)13.1.2Mix View Elements (647)13.2The Mixer (649)13.2.1Displaying Groups vs. Displaying Sounds (650)13.2.2Adjusting the Mixer Layout (652)13.2.3Selecting Channel Strips (653)13.2.4Managing Your Channels in the Mixer (654)13.2.5Adjusting Settings in the Channel Strips (656)13.2.6Using the Cue Bus (660)13.3The Plug-in Chain (662)13.4The Plug-in Strip (663)13.4.1The Plug-in Header (665)13.4.2Panels for Drumsynths and Internal Effects (667)13.4.3Panel for the Sampler (668)13.4.4Custom Panels for Native Instruments Plug-ins (671)13.4.5Undocking a Plug-in Panel (Native Instruments and External Plug-ins Only) (675)13.5Controlling Your Mix from the Controller (677)13.5.1Navigating Your Channels in Mix Mode (678)13.5.2Adjusting the Level and Pan in Mix Mode (679)13.5.3Mute and Solo in Mix Mode (680)13.5.4Plug-in Icons in Mix Mode (680)14Using Effects (681)14.1Applying Effects to a Sound, a Group or the Master (681)14.1.1Adding an Effect (681)14.1.2Other Operations on Effects (690)14.1.3Using the Side-Chain Input (692)14.2Applying Effects to External Audio (695)14.2.1Step 1: Configure MASCHINE Audio Inputs (695)14.2.2Step 2: Set up a Sound to Receive the External Input (698)14.2.3Step 3: Load an Effect to Process an Input (700)14.3Creating a Send Effect (701)14.3.1Step 1: Set Up a Sound or Group as Send Effect (702)14.3.2Step 2: Route Audio to the Send Effect (706)14.3.3 A Few Notes on Send Effects (708)14.4Creating Multi-Effects (709)15Effect Reference (712)15.1Dynamics (713)15.1.1Compressor (713)15.1.2Gate (717)15.1.3Transient Master (721)15.1.4Limiter (723)15.1.5Maximizer (727)15.2Filtering Effects (730)15.2.1EQ (730)15.2.2Filter (733)15.2.3Cabinet (737)15.3Modulation Effects (738)15.3.1Chorus (738)15.3.2Flanger (740)15.3.3FM (742)15.3.4Freq Shifter (743)15.3.5Phaser (745)15.4Spatial and Reverb Effects (747)15.4.1Ice (747)15.4.2Metaverb (749)15.4.3Reflex (750)15.4.4Reverb (Legacy) (752)15.4.5Reverb (754)15.4.5.1Reverb Room (754)15.4.5.2Reverb Hall (757)15.4.5.3Plate Reverb (760)15.5Delays (762)15.5.1Beat Delay (762)15.5.2Grain Delay (765)15.5.3Grain Stretch (767)15.5.4Resochord (769)15.6Distortion Effects (771)15.6.1Distortion (771)15.6.2Lofi (774)15.6.3Saturator (775)15.7Perform FX (779)15.7.1Filter (780)15.7.2Flanger (782)15.7.3Burst Echo (785)15.7.4Reso Echo (787)15.7.5Ring (790)15.7.6Stutter (792)15.7.7Tremolo (795)15.7.8Scratcher (798)16Working with the Arranger (801)16.1Arranger Basics (801)16.1.1Navigating Song View (804)16.1.2Following the Playback Position in Your Project (806)16.1.3Performing with Scenes and Sections using the Pads (807)16.2Using Ideas View (811)16.2.1Scene Overview (811)16.2.2Creating Scenes (813)16.2.3Assigning and Removing Patterns (813)16.2.4Selecting Scenes (817)16.2.5Deleting Scenes (818)16.2.6Creating and Deleting Scene Banks (820)16.2.7Clearing Scenes (820)16.2.8Duplicating Scenes (821)16.2.9Reordering Scenes (822)16.2.10Making Scenes Unique (824)16.2.11Appending Scenes to Arrangement (825)16.2.12Naming Scenes (826)16.2.13Changing the Color of a Scene (827)16.3Using Song View (828)16.3.1Section Management Overview (828)16.3.2Creating Sections (833)16.3.3Assigning a Scene to a Section (834)16.3.4Selecting Sections and Section Banks (835)16.3.5Reorganizing Sections (839)16.3.6Adjusting the Length of a Section (840)16.3.6.1Adjusting the Length of a Section Using the Software (841)16.3.6.2Adjusting the Length of a Section Using the Controller (843)16.3.7Clearing a Pattern in Song View (843)16.3.8Duplicating Sections (844)16.3.8.1Making Sections Unique (845)16.3.9Removing Sections (846)16.3.10Renaming Scenes (848)16.3.11Clearing Sections (849)16.3.12Creating and Deleting Section Banks (850)16.3.13Working with Patterns in Song view (850)16.3.13.1Creating a Pattern in Song View (850)16.3.13.2Selecting a Pattern in Song View (850)16.3.13.3Clearing a Pattern in Song View (851)16.3.13.4Renaming a Pattern in Song View (851)16.3.13.5Coloring a Pattern in Song View (851)16.3.13.6Removing a Pattern in Song View (852)16.3.13.7Duplicating a Pattern in Song View (852)16.3.14Enabling Auto Length (852)16.3.15Looping (853)16.3.15.1Setting the Loop Range in the Software (854)16.4Playing with Sections (855)16.4.1Jumping to another Playback Position in Your Project (855)16.5Triggering Sections or Scenes via MIDI (856)16.6The Arrange Grid (858)16.7Quick Grid (860)17Sampling and Sample Mapping (862)17.1Opening the Sample Editor (862)17.2Recording Audio (863)17.2.1Opening the Record Page (863)17.2.2Selecting the Source and the Recording Mode (865)17.2.3Arming, Starting, and Stopping the Recording (868)17.2.5Using the Footswitch for Recording Audio (871)17.2.6Checking Your Recordings (872)17.2.7Location and Name of Your Recorded Samples (876)17.3Editing a Sample (876)17.3.1Using the Edit Page (877)17.3.2Audio Editing Functions (882)17.4Slicing a Sample (890)17.4.1Opening the Slice Page (891)17.4.2Adjusting the Slicing Settings (893)17.4.3Live Slicing (898)17.4.3.1Live Slicing Using the Controller (898)17.4.3.2Delete All Slices (899)17.4.4Manually Adjusting Your Slices (899)17.4.5Applying the Slicing (906)17.5Mapping Samples to Zones (912)17.5.1Opening the Zone Page (912)17.5.2Zone Page Overview (913)17.5.3Selecting and Managing Zones in the Zone List (915)17.5.4Selecting and Editing Zones in the Map View (920)17.5.5Editing Zones in the Sample View (924)17.5.6Adjusting the Zone Settings (927)17.5.7Adding Samples to the Sample Map (934)18Appendix: Tips for Playing Live (937)18.1Preparations (937)18.1.1Focus on the Hardware (937)18.1.2Customize the Pads of the Hardware (937)18.1.3Check Your CPU Power Before Playing (937)18.1.4Name and Color Your Groups, Patterns, Sounds and Scenes (938)18.1.5Consider Using a Limiter on Your Master (938)18.1.6Hook Up Your Other Gear and Sync It with MIDI Clock (938)18.1.7Improvise (938)18.2Basic Techniques (938)18.2.1Use Mute and Solo (938)18.2.2Use Scene Mode and Tweak the Loop Range (939)18.2.3Create Variations of Your Drum Patterns in the Step Sequencer (939)18.2.4Use Note Repeat (939)18.2.5Set Up Your Own Multi-effect Groups and Automate Them (939)18.3Special Tricks (940)18.3.1Changing Pattern Length for Variation (940)18.3.2Using Loops to Cycle Through Samples (940)18.3.3Using Loops to Cycle Through Samples (940)18.3.4Load Long Audio Files and Play with the Start Point (940)19Troubleshooting (941)19.1Knowledge Base (941)19.2Technical Support (941)19.3Registration Support (942)19.4User Forum (942)20Glossary (943)Index (951)1Welcome to MASCHINEThank you for buying MASCHINE!MASCHINE is a groove production studio that implements the familiar working style of classi-cal groove boxes along with the advantages of a computer based system. MASCHINE is ideal for making music live, as well as in the studio. It’s the hands-on aspect of a dedicated instru-ment, the MASCHINE hardware controller, united with the advanced editing features of the MASCHINE software.Creating beats is often not very intuitive with a computer, but using the MASCHINE hardware controller to do it makes it easy and fun. You can tap in freely with the pads or use Note Re-peat to jam along. Alternatively, build your beats using the step sequencer just as in classic drum machines.Patterns can be intuitively combined and rearranged on the fly to form larger ideas. You can try out several different versions of a song without ever having to stop the music.Since you can integrate it into any sequencer that supports VST, AU, or AAX plug-ins, you can reap the benefits in almost any software setup, or use it as a stand-alone application. You can sample your own material, slice loops and rearrange them easily.However, MASCHINE is a lot more than an ordinary groovebox or sampler: it comes with an inspiring 7-gigabyte library, and a sophisticated, yet easy to use tag-based Browser to give you instant access to the sounds you are looking for.What’s more, MASCHINE provides lots of options for manipulating your sounds via internal ef-fects and other sound-shaping possibilities. You can also control external MIDI hardware and 3rd-party software with the MASCHINE hardware controller, while customizing the functions of the pads, knobs and buttons according to your needs utilizing the included Controller Editor application. We hope you enjoy this fantastic instrument as much as we do. Now let’s get go-ing!—The MASCHINE team at Native Instruments.MASCHINE Documentation1.1MASCHINE DocumentationNative Instruments provide many information sources regarding MASCHINE. The main docu-ments should be read in the following sequence:1.MASCHINE Getting Started: This document provides a practical approach to MASCHINE viaa set of tutorials covering easy and more advanced tasks in order to help you familiarizeyourself with MASCHINE.2.MASCHINE Manual (this document): The MASCHINE Manual provides you with a compre-hensive description of all MASCHINE software and hardware features.Additional documentation sources provide you with details on more specific topics:▪Controller Editor Manual: Besides using your MASCHINE hardware controller together withits dedicated MASCHINE software, you can also use it as a powerful and highly versatileMIDI controller to pilot any other MIDI-capable application or device. This is made possibleby the Controller Editor software, an application that allows you to precisely define all MIDIassignments for your MASCHINE controller. The Controller Editor was installed during theMASCHINE installation procedure. For more information on this, please refer to the Con-troller Editor Manual available as a PDF file via the Help menu of Controller Editor.▪Online Support Videos: You can find a number of support videos on The Official Native In-struments Support Channel under the following URL: https:///NIsupport-EN. We recommend that you follow along with these instructions while the respective ap-plication is running on your computer.Other Online Resources:If you are experiencing problems related to your Native Instruments product that the supplied documentation does not cover, there are several ways of getting help:▪Knowledge Base▪User Forum▪Technical Support▪Registration SupportYou will find more information on these subjects in the chapter Troubleshooting.1.2Document ConventionsThis section introduces you to the signage and text highlighting used in this manual. This man-ual uses particular formatting to point out special facts and to warn you of potential issues. The icons introducing these notes let you see what kind of information is to be expected:This document uses particular formatting to point out special facts and to warn you of poten-tial issues. The icons introducing the following notes let you see what kind of information can be expected:Furthermore, the following formatting is used:▪Text appearing in (drop-down) menus (such as Open…, Save as… etc.) in the software and paths to locations on your hard disk or other storage devices is printed in italics.▪Text appearing elsewhere (labels of buttons, controls, text next to checkboxes etc.) in the software is printed in blue. Whenever you see this formatting applied, you will find the same text appearing somewhere on the screen.▪Text appearing on the displays of the controller is printed in light grey. Whenever you see this formatting applied, you will find the same text on a controller display.▪Text appearing on labels of the hardware controller is printed in orange. Whenever you see this formatting applied, you will find the same text on the controller.▪Important names and concepts are printed in bold.▪References to keys on your computer’s keyboard you’ll find put in square brackets (e.g.,“Press [Shift] + [Enter]”).►Single instructions are introduced by this play button type arrow.→Results of actions are introduced by this smaller arrow.Naming ConventionThroughout the documentation we will refer to MASCHINE controller (or just controller) as the hardware controller and MASCHINE software as the software installed on your computer.The term “effect” will sometimes be abbreviated as “FX” when referring to elements in the MA-SCHINE software and hardware. These terms have the same meaning.Button Combinations and Shortcuts on Your ControllerMost instructions will use the “+” sign to indicate buttons (or buttons and pads) that must be pressed simultaneously, starting with the button indicated first. E.g., an instruction such as:“Press SHIFT + PLAY”means:1.Press and hold SHIFT.2.While holding SHIFT, press PLAY and release it.3.Release SHIFT.Unlabeled Buttons on the ControllerThe buttons and knobs above and below the displays on your MASCHINE controller do not have labels.。
美国商务部管制清单索引

ALPHABETICAL INDEXTO THE COMMERCE CONTROL LISTThis index is not an exhaustive list of controlled items.Description ECCN Citation Ablative liners, thrust or combustion chambers .................................................................. 9A106.a Abrin ................................................................................................................................. 1C351.d.1 Absettarov (Central European tick-borne encephalitis virus) ..................................... 1C360.a.1.a.1 Absolute reflectance measurement equipment .................................................................... 6B004.a Absorbers of electromagnetic waves ...................................................................................... 1C001 Absorbers, hair type ...............................................................................................1C001.a Note 1.a Absorbers, non-planar & planar ....................................................................... 1C001.a Note 1.b&c Absorption columns ............................................................................................................. 2B350.e Accelerators (electro-magnetic radiation) ............................................................................ 3A101.b Accelerators or coprocessors, graphics .............................................................................. 4A003.d Accelerometer axis align stations .............................................................................. 7B003, 7B101 Accelerometer test station .......................................................................................... 7B003, 7B101 Accelerometers & components therefor ................................................................ 7A101 Accelerometers & accelerometer components ........................................................................ 7A001 Acoustic beacons ........................................................................................................... 6A001.a.1.b Acoustic beam forming software ...................................................................................... 6D003.a.1 Acoustic hydrophone arrays, towed ............................................................................. 6A001.a.2.b Acoustic location & object detection systems ............................................................... 6A001.a.1.b Acoustic, marine, terrestrial equipment .................................................................................. 6A991 Acoustic mounts, noise reduction equipment for vessels .............................................. 8A002.o.3.a Acoustic-optic signal processing devices ......................................................................... 3A001.c.3 Acoustic positioning systems ......................................................................................... 6A001.a.1.d Acoustic projectors ........................................................................................................ 6A001.a.1.c Acoustic seabed survey equipment ................................................................................ 6A001.a.1.a Acoustic systems, diver deterrent ....................................................................................... 8A002.r Acoustic systems, marine ..................................................................................................... 6A001.a Acoustic transducers ...................................................................................................... 6A001.a.2.c Acoustic underwater communications systems ............................................................... 5A001.b.1 Acoustic vibration test equipment .......................................................................................... 9B006 Acoustic wave devices ......................................................................................................... 3A001.c Acoustic-wave device manufacturing equipment and systems .................................. 3B991.b Note Active compensating system rotor clearance control software ............................................ 9D004.d Active flight control system software .................................................................................. 7D003.e Active flight control system technology .............................................................................. 7E004.b Active magnetic bearing systems......................................................................................... 2A001.c Active acoustic systems .................................................................................................... 6A001.a.1 Export Administration Regulations Bureau of Industry and Security January 9, 2012Actively cooled mirrors .................................................................................................... 6A005.e.1 Adaptive control software .................................................................................................... 2D992.a Adaptive control software ................................................................................................. 2D002.b.2 ADCs (analog-to-digital converters).................................................................................... 3A101.a ADCs (analog-to-digital converters)................................................................................. 3A001.a.5 ADCs (analog-to-digital converters).................................................................................... 4A003.e Aero gas turbine engine/assemblies/component test software............................................. 9D004.b Aero gas turbine engines ......................................................................................................... 9A001 Aerodynamic isotope separation plant/element housings ................................................. 0B001.a.3 Aerodynamic separation process systems & components ................................................... 0B001.d Aerosol challenge testing chambers ..................................................................................... 2B352.g Aerosol generating units specially designed for fitting to the systems specified in 2B352.h.1 or h.2 ...................................................................................... 2B352.h.3 Aflatoxins .......................................................................................................................... 1C351.d.2 African horse sickness virus ........................................................................................... 1C352.a.17 African swine fever virus (animal pathogens) .................................................................. 1C352.a.1 Agitators (chemical manufacturing) .................................................................................... 2B350.b AHRS (Attitude Heading Reference Systems), source code .................................................. 7D002 Air traffic control software ............................................................................................... 6D003.h.1 Air independent power systems (for underwater use) ..........................................................8A002.j Air compressors and filtration systems designed for filling air cylinders ............................8A992.l Air Traffic Control software application programs ................................................................ 6D993 Airtight vaults ......................................................................................................................... 0A981 Airborne altimeters ................................................................................................................. 7A006 Airborne altimeters ................................................................................................................. 7A106 Airborne communication equipment ...................................................................................... 7A994 Airborne radar equipment ....................................................................................................... 6A998 Aircraft .................................................................................................................................... 7A994 Aircraft, civil ........................................................................................................................ 9A991.b Aircraft, demilitarized .......................................................................................................... 9A991.a Aircraft, n.e.s........................................................................................................................... 9A991 Aircraft, trainer ....................................................................................................................... 9A018 Aircraft breathing equipment and parts ............................................................................... 9A991.e Aircraft (military) pressurized breathing equipment ........................................................... 9A018.d Aircraft inertial navigation systems & equipment ............................................................... 7A103.a Aircraft inertial navigation systems & equipment .................................................................. 7A003 Aircraft parts and components ............................................................................................. 9A991.d Akabane virus ................................................................................................................ 1C360.b.1.a Alexandrite ........................................................................................................................... 6C005.b Alexandrite lasers........................................................................................................... 6A005.c.2.b Align & expose step & repeat equipment (wafer processing) ..........................................3B001.f.1 Alignment equipment for equipment controlled by 7A .......................................................... 7B001 Export Administration Regulations Bureau of Industry and Security January 9, 2012Description ECCN Citation Alkylphenylene ethers or thio-ethers, as lubricating fluids .............................................. 1C006.b.1 Alloy strips, magnetic .......................................................................................................... 1C003.c Alloyed materials production systems and components ......................................................... 1B002 Alloyed metal materials in powder or particulate form ....................................................... 1C002.b Alloyed metal materials in the form of uncomminuted flakes, ribbons, or thin rods .......... 1C002.c Alloys, aluminum ................................................................................................................. 1C202.a Alloys, aluminum ........................................................................................................... 1C002.a.2.d Alloys, magnesium ........................................................................................................ 1C002.a.2.e Alloys, metal powder or particulate form ............................................................................ 1C002.b Alloys, nickel ............................................................................................................... 1C002.a.2.a Alloys, niobium.............................................................................................................. 1C002.a.2.b Alloys, titanium.................................................................................................................... 1C202.b Alpha-emitting radionuclides, compounds, mixtures, products or devices ............................ 1C236 Altimeters, airborne ................................................................................................................ 7A006 Altimeters, radar or laser types ............................................................................................. 7A106 Alumina fibers ......................................................................................................... 1C010.c Note 1 Aluminides ........................................................................................................................ 1C002.a.1 Aluminides, nickel ......................................................................................................... 1C002.a.1.a Aluminides, titanium...................................................................................................... 1C002.a.1.b Aluminum alloys ............................................................................................................ 1C002.a.2.d Aluminum alloy/powder or particulate form ............................................................... 1C002.b.1.d Aluminum alloys as tubes/solid forms/forgings ................................................................. 1C202.a Aluminum electroplating equipment .................................................................................... 2B999.i Aluminum gallium nitride (AlGaN) “substrates”, i ngots, boules, or otherpreforms of those materials ................................................................................................. 3C005 Aluminum nitride (AlN) “substrates”, ingots, boules, or other preforms ofthose materials ..................................................................................................................... 3C005 Aluminum organo-metallic compounds ................................................................................. 3C003 Aluminum oxide powder, fine ................................................................................................ 0C201 Aluminum powder, spherical .......................................................................................... 1C111.a.1 Aluminum powder (spherical) production equipment ............................................................ 1B102 Amalgam electrolysis cells, lithium isotope separation .................................................. 1B233.b.3 Amalgam pumps, lithium and/or mercury ........................................................................ 1B233.b.2 Ammonia, aqueous ................................................................................................................. 1C980 Ammonia crackers ......................................................................................................... 0B004.b.2.d Ammonia distillation towers .......................................................................................... 0B004.b.4.b Ammonia synthesis converters & units .................................................................................. 1B227 Ammonia-hydrogen exchange plant ................................................................................. 0B004.a.2 Ammonia-hydrogen exchange equipment and components ........................................... 0B004.b.2 Ammonium bifluoride ............................................................. see ammonium hydrogen fluoride Ammonium hydrogen fluoride ......................................................................................... 1C350.d.1 Ammonium nitrate, including certain fertilizers containing ammonium nitrate .................... 1C997 Export Administration Regulations Bureau of Industry and Security January 9, 2012Description ECCN Citation Ammunition hand-loading equipment .................................................................................... 0B986 Amorphous alloy strips ........................................................................................................... 1C003 Amplifiers, microwave solid state .................................................................................... 3A001.b.4 Amplifiers, pulse .................................................................................................................. 3A999.d Analog instrumentation tape recorders ............................................................................. 3A002.a.1 Analog computers ................................................................................................................... 4A101 Analog-to-digital converters ................................................................................................ 3A101.a Analog-to-digital converters, integrated circuits .............................................................. 3A001.a.5 Analog-to-digital conversion equipment ............................................................................. 4A003.e Analyzers, network .............................................................................................................. 3A002.e Analyzers, spectrum .......................................................................................................... 3A002.c.1 Andes virus ....................................................................................................................... 1C351.a.1 Angular displacement measuring instruments ..................................................................... 2B206.c Angular measuring instruments ........................................................................................ 2B006.b.2 Angular measuring instruments .............................................................................................. 2B206 Angular-linear inspection equipment (hemishells) ................................................................. 2B206 Angular-linear inspection equipment (hemishells) .............................................................. 2B006.c Angular rate sensors ................................................................................................................ 7A002 Animal pathogens .................................................................................................................. 1C352 Annealing or recrystallizing equipment ...................................................................... 3B991.b.1.c.1 Antennae, for microwave power source ............................................................................ 0B001.i.3 Antennae, phased array ...................................................................................................... 5A001.d Antennae, phased array (for radar) ...................................................................................... 6A008.e Anti-vibration mounts (noise reduction), civil vessels .................................................. 8A002.o.3.a Antimony hydrides.................................................................................................................. 3C004 Aramid fibers & filamentary materials ................................................................................ 1C210.a Aramid fibers & filamentary materials ................................................................................ 1C010.a Arc remelt & casting furnaces ............................................................................................. 2B227.a Argon ion lasers ................................................................................................................... 6A205.a Argon ion lasers ................................................................................................................... 6A005.a Armor body ............................................................................................................................. 1A005 Armor plate drilling machines ............................................................................................. 2B018.a Armor plate planing machines ............................................................................................. 2B018.b Armor plate quenching presses ............................................................................................ 2B018.c Arms machinery, equipment, gear, parts, and accessories ..................................................... 2B018 Arms (small) chambering machines .................................................................................... 2B018.o Arms (small) deep hole drilling machines and drills therefor ............................................. 2B018.p Arms (small) rifling machines ............................................................................................. 2B018.q Arms (small) spill boring machines ......................................................................................2B018.r Aromatic polyimides ......................................................................................................... 1C008.a.3 Aromatic polyamide-imides .............................................................................................. 1C008.a.2 Aromatic polyetherimides ................................................................................................. 1C008.a.4 Export Administration Regulations Bureau of Industry and Security January 9, 2012Description ECCN Citation Array processor microcircuits .................................................................................. 3A001.a.3 Note Array processors/assemblies ................................................................................................. 4A004 Array processors/assemblies ................................................................................................... 4A003 Arrays of aerosol generating units or spray booms, specially designed forfitting to aircraft, “lighter than air vehicles,”or “UAVs”............................................ 2B352.h.2 Arsenic trichloride ............................................................................................................ 1C350.b.1 Arsenic hydrides ..................................................................................................................... 3C004 Asphalt paving mixtures ......................................................................................................... 1C980 Aspheric optical elements .................................................................................................... 6A004.e Assemblies to enhance performance by aggregation of computing elements ..................... 4A994.c Asynchronous transfer mode (ATM) equipment ......................................................... 5A991.c.10.d Asynchronous transfer mode (ATM), technology for the developmentof equipment employing ................................................................................................ 5E001.c.1 Atomic vapor laser isotope separation plant ..................................................................... 0B001.a.6 Atomic vapor laser isotope separation process equipment .................................................. 0B001.g Atomic frequency standards ................................................................................................ 3A002.g Atomic transition solid state lasers ...............................................................................6A005.a or b Attitude Heading Reference Systems (AHRS), source code software ................................... 7D002 Attitude control equipment for missiles .................................................................................. 7A116 Aujeszky’ disease virus (Porcine herpes virus) ................................................................ 1C352.a.6 Austenitic stainless steel plate, valves, piping, tanks and vessels ....................................... 2B999.n Autoclave temperature, pressure or atmosphere regulation technology ................................. 1E103 Autoclaves, ovens and systems ............................................................................................ 0B002.a Automated control systems, submersible vehicles .............................................................. 8A002.b Automatic drug injection systems ........................................................................................... 0A981 Automotive, diesel, and marine engine lubricating oil ........................................................... 1C980 Avian influenza virus ........................................................................................................ 1C352.a.2 Aviation engine lubricating oil ............................................................................................... 1C980 Avionic equipment, parts, and components ............................................................................ 7A994 Avionics EMP/EMI protection technology ............................................................................ 7E102 Bacillus anthracis .............................................................................................................. 1C351.c.1 Bacteria ................................................................................................................................ 1C351.c Bacteria ................................................................................................................................ 1C354.a Bacteria ................................................................................................................................ 1C352.b Baffles .................................................................................................................................. 0A001.h Baffles (rotor tube), gas centrifuge ................................................................................... 0B001.c.7 Balancing machines ............................................................................................................. 2B119.a Balancing machines ............................................................................................................. 7A104.a Balancing instrumentation ................................................................................................... 7A104.b Balancing machines, centrifugal multiplane ........................................................................... 2B229 Balancing mahcines, centrifugal multiplane ....................................................................... 2B999.m Ball bearings, precision hardened steel and tungsten carbide .............................................. 1C999.a Export Administration Regulations Bureau of Industry and Security January 9, 2012Description ECCN Citation Ball bearings, Radial ............................................................................................................... 2A101 Ball & solid roller bearings .................................................................................................. 2A001.a Band-pass filters, tunable .................................................................................................. 3A001.b.5 Barium metal vapor lasers ................................................................................................... 6A005.b Bartonella quintana ........................................................................................................... 1C351.b.1 Batch mixers .......................................................................................................................... 1B117 Bathymetric survey systems .......................................................................................... 6A001.a.1.b Batons, shock .......................................................................................................................... 0A985 Batons, spiked ......................................................................................................................... 0A983 Bay cable systems .......................................................................................................... 6A001.a.2.e Bay cable systems software ............................................................................................ 6D003.a.3 Bayonets ............................................................................................................................... 0A918.b Beam lead bonders, stored program controlled equipment ........................................... 3B991.b.3.b Beam steering mirrors ....................................................................................................... 6A004.a.4 Beamforming techniques ............................................................................................... 6A001.a.2.c Bearings, ball & solid roller ................................................................................................. 2A001.a Bearings, gas centrifuge .................................................................................................... 0B001.c.4 Bearings, gas centrifuge .................................................................................................... 0B001.c.5 Bearings, high precision/temperature/special ......................................................................... 2A001 Bearings, magnetic (active) ................................................................................................. 2A001.c Bearings, magnetic (suspension) ...................................................................................... 0B001.c.4 Bearings, precision hardened steel and tungsten carbide ..................................................... 1C999.a Bellow valves .................................................................................................................... 0B001.b.1 Bellow valves .................................................................................................................. 0B001.d.6 Bellows forming dies ........................................................................................................... 2B999.b Bellows manufacturing equipment ...................................................................................... 2B999.b Bellows or rings, gas centrifuge........................................................................................ 0B001.c.6 Bellows seal valves ............................................................................................................... 2A226 Bellows seal valves .............................................................................................................. 2B350.g Bellows sealed valves, n.e.s. ................................................................................................. 2A999 Bellows-forming mandrels................................................................................................... 2B228.c Bellows-forming dies ........................................................................................................... 2B228.c Benzilic acid...................................................................................................................... 1C350.b.2 Beryllium metal, alloys, compounds, or manufactures......................................................... 1C230 Beryllium metal particulate......................................................................................... 1C111.a.2.a.4 Beryllium/beryllium substrate blanks .................................................................................. 6C004.d Biological containment facilities, ACDP level 3 or 4 .......................................................... 2B352.a Biological isolators ............................................................................................................2B352.f.2 Biological manufacturing equipment & facilities ................................................................... 2B352 Biological safety cabinets ..................................................................................................2B352.f.2 Bismaleimides ................................................................................................................... 1C008.a.1 Bismuth ................................................................................................................................... 1C229 Export Administration Regulations Bureau of Industry and Security January 9, 2012。
IBM TRIRIGA 用户体验框架说明书
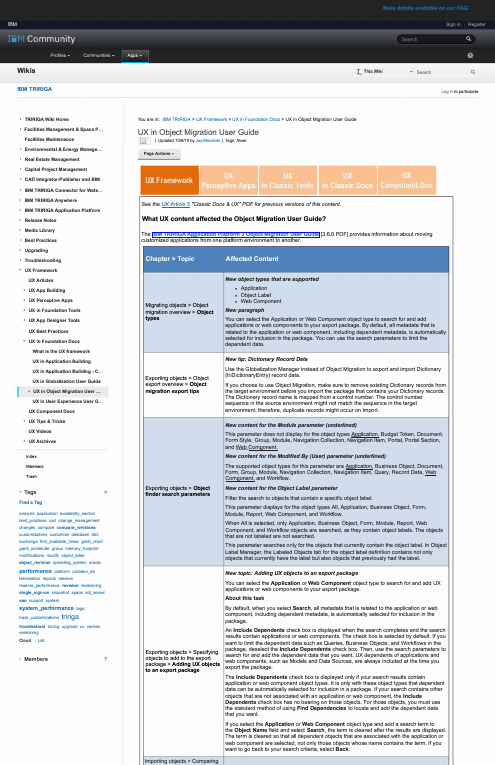
IBMTCM CommunityProfiles -Communities -WikisIBMTRIRIGA► TRIRIGA Wiki Home► Facilities Management & Space P ...Facilities Maintenance► Environmental & Energy Manage ...► Real Estate Management► Capital Project Management► CAD Integrator-Publisher and BIM► IBM TRI R IGA Connector for Wats ...► IBM TRIRIGA Anywhere► IBM TRI R IGA Application Platform► Release Notes► Media Library► Best Practices► Upgrading► Troubleshooting-UX F rameworkUXArticles► UX A pp Building• UX Perceptive Apps• UX in Foundation Tools• UX A pp Designer ToolsUX B est Practices-UX i n Foundation DocsWhat is the UX f rameworkUX i n Application BuildingUX i n Application Building -C ...UX i n Globalization User Guide• UX i n Object Migration User .. .UX i n User Experience User G .. .UX C omponent Docs► UX T ips & TricksUXVideos• UX A rchivesIndexMembersTrash... Tags Find a Tag.,analysis application availability_sectionbest_practices cad change_managementchanges compare compare_revisionscustomizations customize database db2exchange find_available_times gantt_chartgantt_scheduler group memory_footprintmodifications modify object_labelobject_revision operating_system oracleperformance platform problem_determination reports reservereserve_performance revision revisioningsingle_sign-on snapshot space sql_serversso support systemsystem_performance tags:track_ c ustomizations tri r i Q 8troubleshoot tuning upgrade ux versionversioningCloud List► Members ., -I .. This Wiki -Search Sign in Register Q. 0 Q Log in to participate You are in: IBM TRIRIGA > UX Framework > UX in Foundation Docs > UX in Object Migration User Guide UX in Object Migration User Guide §I Updated 10/8/19 by Jay.Manaloto I Tags: None Page Actions -UX F r amewo r k ux Component Doc See the UX A rticle 5 "Classic Docs & UX" PDF for previous versions of this content. What UX content affected the Object Migration User Guide? The IBM T RIRIGAAP-P-lication Platform 3 Object Migration User G uide [3.6.0 PDF] provides information about moving customized applications from one platform environment to another. Migrating objects > Object migration overview> Object types Exporting objects > Object export overview > Object migration export tips Exporting objects > Object finder search parameters Exporting objects > Specifying objects to add to the export package > Adding UX objects to an export package Importing objects > ComparingNew object types that are supported ■Application ■Object Label ■Web Component New paragraph You can select the Application or Web Component object type to search for and add applications or web components to your export package. By default, all metadata that is related to the application or web component, including dependent metadata, is automatically selected for inclusion in the package. You can use the search parameters to limit the dependent data. New tip: Dictionary Record Data Use the Globalization Manager instead of Object Migration to export and import Dictionary (triDictionaryEntry) record data. If you choose to use Object Migration, make sure to remove existing Dictionary records from the target environment before you import the package that contains your Dictionary records. The Dictionary record name is mapped from a control number. The control number sequence in the source environment might not match the sequence in the target environment; therefore, duplicate records might occur on import. New content for the Module parameter (underlined) This parameter does not display for the object types AP-P-lication, Budget Token, Document, Form Style, Group, Module, Navigation Collection, Navigation Item, Portal, Portal Section, and Web ComP-onent. New content for the Modified By (User) parameter (underlined) The supported object types for this parameter are AP-P-lication, Business Object, Document, Form, Group, Module, Navigation Collection, Navigation Item, Query, Record Data, Web ComP-onent, and Workflow. New content for the Object Label parameter Filter the search to objects that contain a specific object label. This parameter displays for the object types All, Application, Business Object, Form, Module, Report, Web Component, and Workflow. When All is selected, only Application, Business Object, Form, Module, Report, Web Component, and Workflow objects are searched, as they contain object labels. The objects that are not labeled are not searched. This parameter searches only for the objects that currently contain the object label. In Object Label Manager, the Labeled Objects tab for the object label definition contains not only objects that currently have the label but also objects that previously had the label. New topic: Adding UX objects to an export package You can select the A pplication or Web Component object type to search for and add UX applications or web components to your export package. About this task By default, when you select Search, all metadata that is related to the application or web component, including dependent metadata, is automatically selected for inclusion in the package. An Include Dependents check box is displayed when the search completes and the search results contain applications or web components. The check box is selected by default. If you want to limit the dependent data such as Queries, Business Objects, and Workflows in the package, deselect the Include Dependents check box. Then, use the search parameters to search for and add the dependent data that you want. UX dependents of applications andweb components, such as Models and Data Sources, are always included at the time you export the package.The Include Dependents check box is displayed only if your search results containapplication or web component object types. It is only with these object types that dependent data can be automatically selected for inclusion in a package. If your search contains other objects that are not associated with an application or web component, the Include Dependents check box has no bearing on those objects. For those objects, you must use the standard method of using Find Dependencies to locate and add the dependent data that you want. If you select the Application or Web Component object type and add a search term to the Object Name field and select Search, the term is cleared after the results are displayed. The term is cleared so that all dependent objects that are associated with the application or web component are selected, not only those objects whose name contains the term. If you want to go back to your search criteria, select Back.。
FortiSwitch

DATA SHEETFortiSwitch ™ Secure Access FamilyHighlights§Designed for installations from desktops to wiring closets§Ideal for SD-Branch deployments §Centralized security and accessmanagement from FortiGate interfaces with FortiLink§Optimal for converged network environments; enabling voice, data, and wireless traffic to be delivered across a single network§Supports non-FortiLink deployments through onboard GUI, API, or command line configuration§Up to 48 ports in a compact 1 RU form factor§Stackable up to 300 switches per FortiGate, depending on model§Supports Wire-speed switching and Store and Forward forwarding modeThe FortiSwitch TM Secure Access Family deliversoutstanding security, performance, and manageability. Secure, Simple, and Scalable, FortiSwitch is the right choice for threat-conscious businesses of all sizes. Tightly integrated into the Fortinet Security Fabric via FortiLink, FortiSwitch can be managed directly from the familiar FortiGate interface. This single pane of glass management provides complete visibility and control ofusers and devices on the network regardless of how they connect. This makes the FortiSwitch ideal for SD-Branch deployments with applications that range from desktop to data center aggregation, enabling businesses to converge their security and network access.Security Fabric Integration through FortiLinkFortiLink is an innovative proprietary management protocol that allows our FortiGate Next Generation Firewall toseamlessly manage any FortiSwitch. FortiLink enables the FortiSwitch to become a logical extension of the FortiGate, integrating itdirectly into the Fortinet Security Fabric. This management option reduces complexity and decreases management costs as network security and access layer functions are enabled and managed through a single console. FortiLink integration enables centralized policy management, including role-based access and control, making it easy to implement and manage. This control and manageability make FortiSwitch ideal for SD-Branch deployments.Product OfferingsFS-108E, 108E-POE, 108E-FPOE, 124E, 124E-POE, 124E-FPOE, 148E, 148E-POE, 224D-FPOE, 224E, 224E-POE, 248D,248E-POE, 248E-FPOE, 424D, 424D-POE, 424D-FPOE, 448D, 448D-POE, 448D-FPOE, 424E-FIBER, M426E-FPOE, 424E, 424E-POE, 424E-FPOE, 448E, 448E-POE, 448E-FPOE,524-D, 524D-FPOE, 548D, 548D-FPOECloud Management OptionFortiGate CloudDATA SHEET | FortiSwitch™ Secure Access FamilyFeaturesLAG support for FortiLink Connection YesActive-Active Split LAG from FortiGate to FortiSwitches for Advanced Redundancy Yes (with FS-2xx, 4xx, 5xx)FORTISWITCH2XXD, 4XXD, 5XXD SERIESFORTISWITCH2XXE, 4XXE SERIESFORTISWITCH1XXE SERIES Layer 2Jumbo Frames Yes Yes YesAuto-negotiation for Port Speed and Duplex Yes Yes YesMDI/MDIX Auto-crossover Yes Yes YesIEEE 802.1D MAC Bridging/STP Yes Yes YesIEEE 802.1w Rapid Spanning Tree Protocol (RSTP)Yes Yes YesIEEE 802.1s Multiple Spanning Tree Protocol (MSTP)Yes Yes YesSTP Root Guard Yes Yes YesSTP BPDU Guard Yes Yes YesEdge Port / Port Fast Yes Yes YesIEEE 802.1Q VLAN Tagging Yes Yes YesPrivate VLAN Yes Yes NoIEEE 802.3ad Link Aggregation with LACP Yes Yes YesUnicast/Multicast traffic balance over trunking port (dst-ip, dst-mac, src-dst-ip, src-dst-mac, src-ip, src-mac)Yes Yes YesIEEE 802.1AX Link Aggregation Yes Yes Yes Spanning Tree Instances (MSTP/CST)15/115/115/1IEEE 802.3x Flow Control and Back-pressure Yes Yes YesIEEE 802.3 10Base-T Yes Yes YesIEEE 802.3u 100Base-TX Yes Yes YesIEEE 802.3z 1000Base-SX/LX Yes Yes YesIEEE 802.3ab 1000Base-T Yes Yes YesIEEE 802.3ae 10 Gigabit Ethernet4xx and 5xx Family N/A N/ADATA SHEET | FortiSwitch™ Secure Access FamilyFeaturesTelnet / SSH Yes Yes Yes HTTP / HTTPS Yes Yes Yes SNMP v1/v2c/v3Yes Yes Yes SNTP Yes Yes Yes Standard CLI and Web GUI Interface Yes Yes YesDATA SHEET | FortiSwitch ™ Secure Access Family5FeaturesAdditional RFC and MIB SupportRFC 2571 Architecture for Describing SNMP Yes Yes Yes DHCP ClientYes Yes Yes RFC 854 Telnet Server Yes Yes Yes RFC 2865 RADIUSYes Yes Yes RFC 1643 Ethernet-like Interface MIB Yes Yes Yes RFC 1213 MIB-IIYes Yes Yes RFC 1354 IP Forwarding Table MIBYes Yes Yes RFC 2572 SNMP Message Processing and Dispatching Yes Yes Yes RFC 1573 SNMP MIB II Yes Yes Yes RFC 1157 SNMPv1/v2c Yes Yes Yes RFC 2030 SNTPYes Yes Yes RFC 6933 Entity MIB (Version 4)Yes Yes Yes RFC 3621 Power Ethernet MIBYes Yes Yes RFC 3433 Entity Sensor Management Information BaseYes Yes Yes RFC 2819 Remote Network Monitoring Management Information BaseYes Yes Yes RFC 2787 Definitions of Managed Objects for the Virtual Router Redundancy Protocol Yes Yes Yes RFC 2620 RADIUS Accounting Client MIB Yes Yes Yes RFC 2618 RADIUS Authentication Client MIB Yes Yes Yes RFC 2576 Coexistence between SNMP versions Yes Yes Yes RFC 2573 SNMP Applications Yes Yes Yes RFC 2571 SNMP Frameworks Yes Yes Yes RFC 2233 Interface MIB Yes Yes Yes RFC 1493 Bridge MIBYes Yes Yes RFC 3289 Management Information Base for the Differentiated Services Architecture Yes Yes -RFC 2934 Protocol Independent Multicast MIB for IPv4Yes Yes -RFC 2932 IPv4 Multicast Routing MIBYes Yes -RFC 2674 Definitions of Managed Objects for Bridges with Traffic Classes, Multicast Filtering and Virtual LAN ExtensionsYesYes -RFC 2362 Protocol Independent Multicast-Sparse Mode (PIM-SM)Yes Yes -RFC 2328 OSPF v2Yes Yes -RFC 1850 OSPFv2 MIB Yes Yes -RFC 1724 RIPv2 MIBYes Yes -RFC 3289 Management Information Base for the Differentiated Services Architecture YesYes-RFC 2934 Protocol Independent Multicast MIB for IPv4Yes (4XX/5XX only)Yes (4XX only)-RFC 2932 IPv4 Multicast Routing MIBYes (4XX/5XX only)Yes (4XX only)-RFC 2674 Definitions of Managed Objects for Bridges with Traffic Classes, Multicast Filtering and Virtual LAN ExtensionsYesYes -RFC 2362 Protocol Independent Multicast-Sparse Mode (PIM-SM)Yes (4XX/5XX only)Yes (4XX only)-RFC 2328 OSPF v2Yes Yes -RFC 1850 OSPFv2 MIB Yes Yes -RFC 1724 RIPv2 MIBYesYes-DATA SHEET | FortiSwitch ™ Secure Access Family6Specifications* Fortinet Warranty Policy:/doc/legal/EULA.pdfFortiSwitch 108E FortiSwitch 108E-POE FortiSwitch 108E-FPOEDATA SHEET | FortiSwitch ™ Secure Access Family7* Fortinet Warranty Policy: /doc/legal/EULA.pdfSpecificationsFortiSwitch 124E FortiSwitch 124E-POEFortiSwitch 124E-FPOEDATA SHEET | FortiSwitch™ Secure Access Family8* Fortinet Warranty Policy: /doc/legal/EULA.pdfSpecificationsFortiSwitch 148E FortiSwitch 148E-POEDATA SHEET | FortiSwitch ™ Secure Access Family9Specifications* Fortinet Warranty Policy:/doc/legal/EULA.pdfFortiSwitch 224D-FPOE FortiSwitch 224EFortiSwitch 224E-POEDATA SHEET | FortiSwitch ™ Secure Access Family10Specifications* Fortinet Warranty Policy:/doc/legal/EULA.pdfFortiSwitch 248E-POEFortiSwitch 248E-FPOEFortiSwitch 248D11* Fortinet Warranty Policy:/doc/legal/EULA.pdfFortiSwitch 424D-FPOEFortiSwitch 424DFortiSwitch 424D-POE12* Fortinet Warranty Policy:/doc/legal/EULA.pdfFortiSwitch 448D-FPOEFortiSwitch 448DFortiSwitch 448D-POEFORTISWITCH-424E-FIBER* Fortinet Warranty Policy: /doc/legal/EULA.pdfFortiSwitch 424E-Fiber FortiSwitch M426E-FPOE1314* Fortinet Warranty Policy:/doc/legal/EULA.pdfFortiSwitch 424E-FPOEFortiSwitch 424EFortiSwitch 424E-POE15FORTISWITCH 448E-FPOE48x GE RJ45 and 4x 10GE SFP+ portsNote: SFP+ ports are compatible with 1 GE SFP 1* Fortinet Warranty Policy: /doc/legal/EULA.pdfFortiSwitch 448E-FPOEFortiSwitch 448E FortiSwitch 448E-POE16*FS-524D, FS-524D-FPOE, FS-548D, FS-548D-FPOE Power Supply Units are Hot-Swappable** Fortinet Warranty Policy: /doc/legal/EULA.pdfFortiSwitch 548D-FPOE FortiSwitch 548DFortiSwitch 524D-FPOE FortiSwitch 524DProduct SKU DescriptionFortiSwitch 108E FS-108E Layer 2 FortiGate switch controller compatible switch with 8 GE RJ45 + 2 SFP ports, line AC and PSE dual powered. Fanless. FortiSwitch 108E-POE FS-108E-POE Layer 2 FortiGate switch controller compatible PoE+ switch with 8 GE RJ45 + 2 SFP ports,4 port PoE with maximum 65 W PoE limit. Fanless.FortiSwitch 108E-FPOE FS-108E-FPOE Layer 2 FortiGate switch controller compatible PoE+ switch with 8 GE RJ45 + 2 SFP ports,8 port PoE with maximum 130 W PoE limit. Fanless.FortiSwitch 124E FS-124E Layer 2 FortiGate switch controller compatible switch with 24 GE RJ45 + 4 SFP ports. Fanless.FortiSwitch 124E-POE FS-124E-POE Layer 2 FortiGate switch controller compatible PoE+ switch with 24 GE RJ45 + 4 SFP ports, 12 port PoE with maximum 185 W limit. FortiSwitch 124E-F-POE FS-124E-FPOE Layer 2 FortiGate switch controller compatible PoE+ switch with 24 GE RJ45 + 4 SFP ports, 24 port PoE with maximum 370 W limit. FortiSwitch 148E FS-148E Layer 2 FortiGate switch controller compatible switch with 48 GE RJ45 + 4 SFP ports.FortiSwitch 148E-POE FS-148E-POE Layer 2 FortiGate switch controller compatible PoE+ switch with 48 GE RJ45 + 4 SFP ports, 24 port PoE with maximum 370 W limit. FortiSwitch 224D-FPOE FS-224D-FPOE Layer 2/3 FortiGate switch controller compatible PoE+ switch with 24 GE RJ45 + 4 SFP ports,24 port PoE with maximum 370 W limit.FortiSwitch 224E FS-224E Layer 2/3 FortiGate switch controller compatible switch with 24 GE RJ45 + 4 SFP ports. Fanless.FortiSwitch 224E-POE FS-224E-POE Layer 2/3 FortiGate switch controller compatible PoE+ switch with 24 GE RJ45 + 4 SFP ports,12 port PoE with maximum 180 W limit.FortiSwitch 248D FS-248D Layer 2/3 FortiGate switch controller compatible switch with 48 GE RJ45 + 4 SFP ports.FortiSwitch 248E-POE FS-248E-POE Layer 2/3 FortiGate switch controller compatible PoE+ switch with 48 GE RJ45 + 4 SFP ports,24 port PoE with maximum 370 W limit.FortiSwitch 248E-FPOE FS-248E-FPOE Layer 2/3 FortiGate switch controller compatible PoE+ switch with 48 GE RJ45 + 4 SFP ports,48 port PoE with maximum 740 W limit.FortiSwitch 424D FS-424D Layer 2/3 FortiGate switch controller compatible switch with 24 GE RJ45 + 2x 10 GE SFP+ ports.FortiSwitch 424D-POE FS-424D-POE Layer 2/3 FortiGate switch controller compatible PoE+ switch with 24 GE RJ45 + 2x 10 GE SFP+ ports,24 port PoE with maximum 185 W limit.FortiSwitch 424D-FPOE FS-424D-FPOE Layer 2/3 FortiGate switch controller compatible PoE+ switch with 24 GE RJ45 + 2x 10 GE SFP+ ports,24 port PoE with maximum 370 W limit.FortiSwitch 448D FS-448D Layer 2/3 FortiGate switch controller compatible switch with 48 GE RJ45 + 4x 10 GE SFP+ ports.FortiSwitch 448D-POE FS-448D-POE Layer 2/3 FortiGate switch controller compatible PoE+ switch with 48 GE RJ45 + 4x 10 GE SFP+ ports,48 port PoE with maximim 370 W limit.FortiSwitch 448D-FPOE FS-448D-FPOE Layer 2/3 FortiGate switch controller compatible PoE+ switch with 48 GE RJ45 + 4x 10 GE SFP+ ports,48 port PoE with maximum 740 W limit.FortiSwitch 424E-Fiber FS-424E-Fiber Layer 2/3 FortiGate switch controller compatible switch with 24x GE SFP and 4x 10 GE SFP+ UplinksFortiSwitch M426E-FPOE FS-M426E-FPOE Layer 2/3 FortiGate switch controller compatible PoE+/UPoE switch with 16x GE RJ45, 8x 2.5 RJ45, 2x 5 GE RJ45 and4x 10 GE SFP+, 24 port PoE with maximum 420 W limit.FortiSwitch 424E FS-424E Layer 2/3 FortiGate switch controller compatible switch with 24 GE RJ45, 4x 10 GE SFP + ports.FortiSwitch 424E-POE FS-424E-POE Layer 2/3 FortiGate switch controller compatible switch with 24 GE RJ45, 4x 10 GE SFP + ports,24 port PoE with maximum 283.5 W limit.FortiSwitch 424E-FPOE FS-424E-FPOE Layer 2/3 FortiGate switch controller compatible switch with 24 GE RJ45, 4x 10 GE SFP + ports,24 port PoE with maximum 433.7 W limit.FortiSwitch 448E FS-448E Layer 2/3 FortiGate switch controller compatible switch with 48 GE RJ45, 4x 10 GE SFP + ports.FortiSwitch 448E-POE FS-448E-POE Layer 2/3 FortiGate switch controller compatible switch with 48 GE RJ45, 4x 10 GE SFP + ports, 48 port PoE with maximum 421 W limit.FortiSwitch 448E-FPOE FS-448E-FPOE Layer 2/3 FortiGate switch controller compatible switch with 48 GE RJ45, 4x 10 GE SFP + ports, 48 port PoE with maximum 772 W limit.FortiSwitch 524D FS-524D Layer 2/3 FortiGate switch controller compatible switch with 24 GE RJ45, 4x 10 GE SFP+ and 2x 40 GE QSFP+ ports. FortiSwitch 524D-FPOE FS-524D-FPOE Layer 2/3 FortiGate switch controller compatible PoE+ switch with 24 GE RJ45, 4x 10 GE SFP+, 2x 40 GE QSFP+ ports,24 port PoE with maximum 400 W limit.FortiSwitch 548D FS-548D Layer 2/3 FortiGate switch controller compatible switch with 48 GE RJ45, 4x 10 GE SFP+ and 2x 40 GE QSFP+ ports. FortiSwitch 548D-FPOE FS-548D-FPOE Layer 2/3 FortiGate switch controller compatible PoE+ switch with 48 GE RJ45, 4x 10 GE SFP+ and 2x 40 GE QSFP+ ports,48 port PoE with maximum 750 W limit.FortiSwitch Cloud Management License*FC-10-WMSC1-190-02-DD FortiSwitch Cloud Management License subscription 1 Year Contract.17AccessoriesFortiSwitch Advanced Features License FS-SW-LIC-200SW License for FS-200 Series Switches to activate Advanced Features.FS-SW-LIC-400SW License for FS-400 Series Switches to activate Advanced Features.FS-SW-LIC-500SW License for FS-500 Series Switches to activate Advanced Features.External Redundant AC Power Supply FRPS-740Redundant AC power supply for up to 2 units: FS-224D-FPOE, FS-248D-FPOE, FS-424D-FPOE, FS-448D-POE and FS-424D-POE. Redundant AC Power Supply FS-PSU-150AC power supply for FS-548D and FS-524D.FS-PSU-600AC power supply for FS-524D-FPOE.**FS-PSU-900AC power supply for FS-548D-FPOE.*** When managing a FortiSwitch with a FortiGate via FortiGate Cloud, no additional license is necessary.** Provides additional PoE capacity.For details of Transceiver modules, see the Fortinet Transceivers datasheet.Note that all PoE FortiSwitches are Alternative-A. Copyright © 2020 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, FortiCare® and FortiGuard®, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.FST-PROD-DS-SW3FS-SA-DAT-R38-202007。
Infoprint 250 導入と計画の手引き 第 7 章ホスト
SUBNETMASK
255.255.255.128
Type of service...............: TOS
*NORMAL
Maximum transmission unit.....: MTU
*LIND
Autostart.....................:
AUTOSTART
*YES
: xx.xxx.xxx.xxx
: xx.xxx.xxx.xxx
*
(
)
IEEE802.3
60 1500
: xxxx
48 Infoprint 250
31. AS/400
IP
MTU
1
1
IPDS TCP
CRTPSFCFG (V3R2)
WRKAFP2 (V3R1 & V3R6)
RMTLOCNAME RMTSYS
MODEL
0
Advanced function printing............:
AFP
*YES
AFP attachment........................:
AFPATTACH
*APPC
Online at IPL.........................:
ONLINE
FORMFEED
*CONT
Separator drawer......................:
SEPDRAWER
*FILE
Separator program.....................:
SEPPGM
*NONE
Library.............................:
Sedex_ETI_Audit_Checklist_Form_社会责任审核中英文版(for_4_pillar)_个人翻译
Section 1Forced labour强迫劳动1.1Contracts合同1.1a a. Do all workers have a contract of employment detailing their rights and obligations as well as notice and grievance procedures.所有的员工有雇佣合同详细描述其权利义务以及注意事项和申诉程序.1.1b b. Can workers voluntarily leave their employment after reasonable notice.理由合理的员工可自如离职吗?1.1c c. Is there a process in place for workers to receive their final salary payment if they do not return e.g., after Chinese New Year.是否有一个程序/处理方式保证员工能够收到他们最后的薪水如果他们不再返岗,比如春节后.1.1d d. Are there any clauses in contracts that would restrict workers leaving.合同中有没有条款限制员工离职?1.1e e. Are there any financial arrangements e.g. loans which would restrict workers leaving.有没有经济纠纷比如借款限制了员工的离职?1.1f f. Are there clauses in the contract / job description for security guards which allow them to restrict worker movements?合同条款中有关门卫的职位描述有没有限制员工的行动的?1.1g g. Are workers free to leave at the end of their shift and not unreasonably delayed by e.g. security checks.员工下班后可自由离开,不会被不合理的要求延时,比如保安检查.1.2Personnel files个人档案1.2a a. Do employers keep only copies of ID’s and Right to Work checks.雇主只有保存员工身份证复印件和工作检查的权利.1.2b b. Whether originals are returned to workers.原件是否返还给员工?1.2c c. If it is a legal requirement to retain original documents, do workers give their written consent and can they retrieve their documents at any time.如果法律要求保留原始档案, 有员工书面同意书吗, 并且员工可以随时要回他们的档案吗?1.2d d. Where there are loans to workers are they covered by a signed agreement from both parties and do they detail repayments, terms and conditions.当员工借款时会签署双方同意的协议吗, 协议中明确规定了还款条件?1.2e e. Is there a procedure in place to either re- assign any outstanding loan to a new employer or a process for early repayment, such that a loan does not prevent a worker leaving employment?是否有适当的程序或者是重新分配未偿贷款到一个新的雇主或者是提前还款, 使得不会因为贷款阻止员工离职?1.2f f. Is there a process for preventing worker debt from e.g. recruitment fees, and how is this checked.是否有阻止员工因为例如招募费产生的欠款的程序以及怎么被检查?1.3Wage deductions, any deposits or withholdings (other than mandatory e.g. tax and social insurance) to establish:工资扣减, 任何保证金或押金(非强制的如税收和社会保险)的设立1.3a a. That there is a written agreement to the deduction, signed by the worker.有员工签署的书面扣款协议吗?1.3b b. That deductions are reasonable and meet the law.这种扣除是合理的,符合法律要求的?1.3c c. That any deductions do not reduce wages to below minimum legal wage.任何扣除不会使工资低于法定最低工资?1.3d d. Whether deductions are for disciplinary reasons and whether this is legal.扣除是否因为纪律原因, 这种扣除是否合法?1.3e e. That deposits are not taken for workplace essentials such as PPE.押金不能是工作场所必需品如PPE的.1.3f f. That deposits are not a compulsory condition of gaining employment.押金不会作为就业的强制条件.1.3g g. That any agreed (by the worker) and withheld deposits / withholdings are returned to the worker as appropriate.所有经员工同意的押金或者扣缴款返还给员工吗?1.3h h. That there are no other deductions when commencing, during, or as a condition of employment.没有其他扣款在工作开始,期间或者作为雇佣的条件.1.4Where there is any prison labour (legally required in some countries), the auditor must record the details of such employment checking:如果有监狱劳工(一些国家法律要求的), 审核员必须详细记录这种雇佣检查.1.4a a. That any prisoners are working voluntarily.所有囚犯是自愿工作?1.4b b. That the work is under the control of the legal authority.这种工作是在法律控制下.1.4c c. Pay and hours meet the law.报酬和工作时间符合法律要求.以下为员工访谈内容1.5Are workers working voluntarily and can they leave their employment after reasonable notice. Do they know the procedure for giving notice?员工自愿工作,在合理的告知后可自愿离职. 员工知道告知程序吗?1.6Have any workers made deposits and if so what for and when will they be repaid.员工为何付押金和何时偿还?1.7Do workers’ pay deposits for essential work items such as PPE?员工因为工作需要付押金吗? 比如个人防护设备.1.8Whether they have possession of their original documents, e.g. passports / ID’s and if not why not.员工是否自己持有自己的原始档案, 比如护照,身份证, 如没有,为什么没有?1.9Where workers must surrender their original ID’s for legal reasons, do they know how to retrieve them.员工会因为法律要求必须交出他们的身份证吗, 他们知道如何取回来吗?1.10Do workers feel free to leave site during breaks and rest time and at the end of shift.员工可以自由离开现场在休息和下班时间?1.11Can they refuse to do overtime and if so how.员工可以拒绝加班吗? 如果可以,如何操作?1.12Are any searches performed on workers handled with respect and without restricting movement e.g. leaving at the end of shift? 会对员工进行怀有敬意的并且不可现在限制行动的搜查吗? 例如下班离开时.1.13Are dormitories secure, and do workers feel that they can leave them when they wish.宿舍安全吗? 员工想离开时可以自由离开吗?1.14If there are hours restrictions e.g. curfews, do workers feel these are reasonable.如果有时间限制, 例如宵禁, 员工们觉得这些都是合理的吗?1.15If any workers have loans have they agreed in writing to the amount and the terms and do they understand and believe them to be reasonable.如果员工有借款, 有员工书面同意的协议, 他们理解数目和条款并且认同是合理的吗?1.16Whether workers have ever noticed other workers who were forced to work at this site.是否有员工曾经注意到有其他员工被强迫劳动?Section 2Freedom of Association自由结社2.1Whether there is a site policy on freedom of association.是否有关于结社自由的政策?2.2Checks whether management recognises and negotiates with any unions present.检查是否管理部门认可并且和现有的工会等协商.2.32.3. Checks that management places no restriction on the establishment and growth of free and representative workers organisations - including unions.检查管理的地方没有限制建立和发展具有代表性的工人组织,包括工会2.4Where the right to freedom of association is restricted under law, workforce rights are recognised by organising parallel means e.g. workers committees.结社自由的权利受法律限制,劳动力权利通过组织类似的方式被认可, 例如工人委员会.2.5Where unions are legally allowed checks:工会合法的检查a. Whether there is a union on site.是否有工会b. If workers are free to join the union if they wish.工人可以自由加入工会,如果他们愿意c. That union officials are freely elected and allowed to perform their functions -with paid time off if a legal requirement.工会成员是自由选取的并且有权执行他们的工作---如果法律有要求下班后也是需要被支付的.d. If the employer takes deductions for union fees checks that, workers have given written consent that deductions are legal, recorded on wage slips and paid to the union.如果雇主需要扣除会费则检查: 工人需给予书面文件说明这是合法的, 并且记录在工资表中然后付给工会.2.6Where workers are represented by a union or workers committee checks:检查工人被工会或工人委员会代表的部分:a. Whether the worker representatives are volunteers and how they are elected.员工代表是否自愿及他们是如何被选出的?b. That workers are aware of their union or worker representatives.员工们都知道他们的工会和员工代表吗?c. That the group which represents workers is independent of management and represents workers effectively.代表工人的组织是独立管理的并且能有效代表工人.d. The meeting minutes are published with agreed actions and responsibilities.会议记录通过被认可的行动和责任而发布.e. That management shows evidence of responding to concerns and proposals raised in the meetings.管理层出示证据显示对于关心的问题和建议有在会议上被提出来.f. Whether there is a collective bargaining agreement and if so what % of the workforce is covered?是否有一个集体谈判协议, 如有, 劳动力覆盖百分比是多少?g. What feedback arrangements are made for workers who do not wish to join the union e.g. other workers groups, suggestion box, worker survey, confidential hot line.不希望加入工会的员工如何反馈意见呢? 比如工人群体, 意见箱, 员工调查,保密热线等.2.7Where workers are not represented by a union or workers committee and the law allows, checks:对于法律允许的员工不被工会和职工委员会代表的地方则检查:a. For any policies or procedures preventing workers from joining or forming a union.有没有政策和程序阻止员工加入或者形成一个联盟?b. The site’s attitude if workers wish to join or form a union.对于员工加入或者形成一个联盟工厂的态度是什么?c. How management and workers communicate in the absence of a union or worker’s committee.在没有工会和职工委员会的情况下, 管理层和工人如何沟通?d. Examines files to establish whether any disciplinary actions or sackings for workers attempting to start or join a union.检查文件以确定是否有任何处分或开除试图创建或加入一个联盟的工人?2.8Examines the personnel files of any union or worker representatives to check:检查工会成员或者工人代表的个人档案:a. Whether there are any disciplinary records from management.有没有处分记录?b. Any evidence of union or worker representatives being discriminated against.有没有证据显示工会成员或职工代表被歧视/区别对待?c. Evidence of union members being dismissed.工会成员被解雇的证据.d. Whether there is payment for time spent in a representative function.行使员工代表的时间被支付工资吗?2.9Establishes whether there have been any strikes at the site and records the dates and circumstances at least as observations.是否有罢工? 记录日期和状况以及至少观测到的情况.以下为员工访谈内容2.10Establish whether any workers are members of a trade union or aware of a trade union on site.确认任何员工是否是工会会员或者知道工会存在?2.11Whether they feel free to join a union if they choose.员工可以自由选择加入工会?2.12Whether workers are aware of their rights to organise and bargain collectively.工人们是否知道他们有权组织和集体议价.2.13Are workers aware of who their representatives are.员工知道他们的代表是谁吗?2.14If workers elect their representatives freely, either for a union or a workers committee.不管是对于工会还是员工委员会, 员工都可以自由选择他们的代表参加吗?2.15If workers are satisfied with their representatives and feel that they are effective.工人是否满意他们的代表,并且认为他们是有效的?2.16Whether any policies and procedures have been communicated to workers by e.g. briefings, worker handbook and for non-native speakers or those of limited literacy what was the form of communication.是否相应的政策和程序通过比如简报, 员工手册和给那些非本地的或者文化程度有限的人的交流了并且按照什么形式?2.17Whether collective bargaining agreements have been circulated to workers.是否集体谈判协议传递给所有员工?2.18If workers are aware of any meeting minutes and actions resulting from these.员工是否知道任何的会议纪要和这些行动产生的结果?2.19If facilities are provided for trade union activities.是否提供工会活动的场所或实施?2.20Whether they know of any discrimination against worker reps.他们是否知道任何对工人代表的歧视吗?2.21 Whether they are aware of any strikes / industrial action at the site and if so record the circumstances.他们是否知道公司有罢工或者类似的情况发生过?2.22Interview worker representatives / union representatives and check:面谈员工代表和工会代表.a. Are they free from management interference.他们没有受到管理者干扰.b. How were they elected and was it by the workforce.他们是如何被选出的, 是不是通过全体员工?c. Do they feel they are permitted to be effective.他们觉得自己是有效的吗?d. Do they have facilities for union duties including paid time off?有行使工会职责的场所/设施吗包括带薪休假?e. Whether there is instances of reps being discriminated against or unfairly dismissed.是否有员工代表受歧视和不公正解雇的实例?f. Whether they have been given any training on how to negotiate with management.是否培训过员工如何与管理层协商?g. Whether they are able to communicate grievances to management including supporting workers in disputes between co- workers with supervisors etc.他们是否能够向管理层表达不满包括支持员工当员工与上司争论时?h. Are they able to negotiate with management including collectively bargain.他们可以和管理层协商包括集体议价吗?Section 3Health and Safety健康安全3.1Checks whether there is a Health & Safety policy and procedures in place at the site, appropriate to the size and complexity, both for the workplace and any associated residential facilities.是否有一个健康安全政策, 适合于工作场所大小和状况, 并且适合工作场所以及任何相关的居住场所/设施.3.2Whether there are appropriate Health & Safety risk assessments / site inspections carried out on a regular basis, how is this recorded and what actions are taken to minimise the risks / hazards found. These should cover at least (but not be limited to):是否有一个合适的健康安全风险评估/实地检查被定期执行? 怎么记录的? 采取哪些行动降低发现的风险? 他应该包括以下几点:3.2a a. Working environment.工作环境3.2b b. Machinery chemicals and other hazards.设备,化学品和其他危险3.2c c. Workers in hazardous roles.危险岗位3.2d d. Young workers / disabled workers / women and other potentially vulnerable workers.童工, 残疾工人, 女工和其他潜在的易受伤害的工人.3.2ee. Personal protective equipment, its issue and use.个人防护设备, 发放和使用.3.2f f. Worker facilities and resources, e.g. dormitory and canteen.员工的设施和资源, 例如宿舍和餐厅.3.2g g. Fire risks.火灾风险3.2h h. Accidents and on site injuries.事故及现场受伤.3.2i i. Restricted areas, are maintained where appropriate, e.g. access to hazardous chemicals storage areas.限制区, 保持在合适的地方, 如需要权限进入危险化学品储存区域3.3Checks whether the following documents are available:检查下面的文件:3.3a a. Building licenses and construction approval from appropriate authorities.建筑许可证和建设主管部门的批准3.3b b. Valid inspection certificates as per local regulations.符合当地法规的有效检验证书.3.3c c. Machine maintenance reports.机器维修报告.3.3d d. Records of fire drills.消防演习记录.3.3e e. Appropriate approval certificates for e.g. water use and disposal, waste disposal, hazardous waste.批准证书: 如水的使用和处置, 废物处理, 危险废物.3.3f f. Any local inspection certificates by local agencies / government e.g. fire, hazardous substances, waste & water use and disposal, gas emissions.所有当地政府机构出具的检验证书如: 火灾, 有害物质, 废物和水的利用和处置, 气体排放.3.3g g. Any prosecutions from relevant authorities and what was the outcome.所有有关当局的检举,结果如何?3.3h h. Safety training records and worker training certificates if appropriate e.g. for fork lift truck driving.安全培训记录和员工培训证书, 例如叉车行驶证.3.3i i. Accident / injury / sickness register, and any necessary licenses, certifications for e.g. performing first aid function and / or related Health & Safety functions.事故/伤害/疾病登记, 和任何必要的许可证, 例如执行急救功能和/或有关健康与安全的功能.3.3j j. Risk assessment reports and action plans for reducing / eliminating the risks identified.风险评估报告和减小或消除可识别风险的行动计划.3.3k k. Hazardous waste history and tracking records (e.g. disposal certificates).危险废物的历史记录(如处理证书)3.3l l. Blood policy and procedures (linked to first aid / injuries).血的政策和程序(与急救/伤害有关的)3.3m m. Needle and blade control policies.针和刀片的控制程序.3.3n n. Electrical safety certificates and records of maintenance checks.电气安全证书和维修检查记录3.3o o. Water test for potability.饮用水测试3.3p p. Records of distribution and maintenance of PPE and whether any charge to workers.个人防护设备的分配和维修记录, 是否收费?3.3q q. Checks purchase records for all necessary protective equipment, ensures that there is a clear history of this being bought and replaced on a regular basis.检查采购记录对于所有必要的防护装备, 确保有一个清晰的购买和定期更换的历史记录.3.3r r. Site insurance for e.g. workplace, employer liability, worker accident, fire.保险对于: 如:工作场所, 雇主责任, 工伤事故, 火灾.3.3s s. Material Safety Data Sheet (MSDS) for each hazardous chemical kept on site.现场有每个危险化学品的MSDS3.3t t. Any necessary approvals / certificates for using hazardous machinery or chemicals.使用危险设备和化学品的批准证书.3.4Checks if there is a Health & Safety committee and whether workers are represented.是否有健康安全委员会及是否员工被代表a. Examines any minutes of meetings.检查会议记录b. Notes if any action taken.记录采取的任何行动3.5For any machinery on site checks documentation.对于现场所有设备检查文件a. Machinery safety certificate (if required).设备安全证书b. That maintenance records are up to date.维修记录是最新的3.6For Health & Safety training records checks that training is appropriate to the task.健康安全培训记录检查3.6a a. Use of machinery.设备使用3.6b b. Working with and disposal of chemicals.化学品处置3.6c c. First aid and safety.急救和安全3.6d d. Housekeeping.内务3.6e e. Personal protective equipment.个人防护设备3.6f f. Records of training kept in workers personnel files.保存培训记录在员工人事档案中3.7What action is taken against anyone who disregards Health & Safety rules and if this is disciplinary does this happen at all levels, workers and management.对那些不顾健康和安全规则的采取什么措施?如果这是纪律要求, 会适用于各阶层包括工人和管理层吗?3.8During the site tour, auditor makes appropriate checks on e.g. (but not limited to):现场审查3.8a a. Fire evacuation plans for workplace and accommodation.工作场所和宿舍的消防疏散计划3.8b b. Noise and dust levels and records any risk to workers.噪声和粉尘浓度记录及任何危害工人的风险.3.8c c. At least 2 exits on each floor and all exits are unblocked and unlocked.每个楼层至少有两个出口,所有出口畅通无阻.3.8d d. Firefighting equipment is sufficient, up to date and meets local regulations.消防设备是充足, 最新的, 符合当地法律要求.3.8e e. That accommodation is not attached to the production area.宿舍不靠近生产区域3.8f f. That safety precautions in accommodation and worksite are checked regularly to include, fire fighting equipment, exits, regular fire drills, health and hygiene checks, structural safety certificates.在住宿和工作场所的安全防范措施需定期检查, 包括:灭火设备, 出口, 定期的消防演习, 健康和卫生检查, 结构安全证书.3.8g g. Sufficient clean and hygienic toilets separated by gender & meet the law.足够的干净和卫生厕所(按性别区分, 符合法律要求的)3.8h h. That workers have free access to toilets.员工可以自由进入厕所.3.8i i. That machines are operated in a safe manner with e.g. correct guarding, 2 button operation, correct safety precautions, including warning signs as necessary.正确安全操作机器: 正确的指导, 两按钮操作, 正确的安全措施,包括必要的警告标志3.8j j. Electrical installation safety e.g. plugs, wiring, cut outs and other control devices.电气安装安全例如插头, 接线, 切断口和其他控制装置.3.8k k. That ventilation, light, temperature, noise level is appropriate and meets the local laws as well as sufficient for worker comfort.通风, 光线, 温度, 噪音水平是适当的符合当地的法律法规以及足够满足工人的舒适度.3.8l l. That any hazardous chemicals have MSDS, adequate storage with precautions for spillage, properly labelled, and that workers are correctly trained to use them.所有危险化学品都有MSDS, 足够的存储空间预防泄露, 合理标记, 工人被培训如何正确使用它们,3.8m m. That PPE is being correctly used, is free of charge and that workers are fully trained in correct usage and benefits.正确使用个人防护设备, 免费的, 工人被培训正确有利使用防护设备.3.8n n. That working areas have adequate space, with sufficient east of access and exit.工作区域有足够的空间,足够的入口和出口3.8o o. Those medical facilities are appropriate for the size of site and number of workers and meets legal requirements..根据法规要求, 医疗设施满足现场大小和工人人数的要求.3.8p p. That any childcare facilities are legal and meet any local laws / regulations.托儿设施是合法的, 符合当地法律要求的.3.9Check whether there is an Health & Safety committee and are there worker representatives.是否有健康安全委员会, 是否有员工代表?以下为员工访谈内容3.10What training have workers received?员工接受什么培训?3.11Do they know the trained first aiders are and are there enough of them on each shift.他们知道谁是受过培训的急救员, 并且每个班次都有足够的急救员?3.12Are they aware of the types of common accidents occurring at this site?他们知道可能发生在现场的常见事故吗?3.13Do they know what to do in case of accidents?当事故发生时他们知道做什么吗?3.14The intervals between fire drills.消防演习间隔3.15Do they feel safe and secure in the workplace and are they happy with the general condition e.g. canteen, hygiene facilities, housekeeping, accommodation etc.他们对工作环境感觉安全, 对总体条件满意吗? 比如食堂, 卫生设施, 内务, 宿舍等等3.16Do they use PPE and have they been trained in its correct use. Do they understand the risks of not using it?培训正确使用个人防护设备吗? 他们清楚不使用的危害吗?3.17What arrangements are made for them when they are sick?员工生病时如何处理?3.18How receptive are managers to any concerns raised on Health & Safety.管理者对健康和安全提出的任何问题是如何接受的?3.19What action is taken against anyone who disregards Health & Safety rules and if this is disciplinary does this happen at all levels, workers and management.对那些不顾健康和安全规则的, 采取什么措施? 如果这是纪律要求, 会适用于各阶层, 包括工人和管理层吗?3.20Do they have free access to toilets?他们自由进入厕所吗? Section 4Child Labour and Young Workers童工和未成年工4.1Whether the site has a policy on child labour and written procedures on how to ensure that children are not employed at the site.有相应的关于童工的书面资料吗?4.2Whether the policy on child labour is clear, communicated to workers and displayed.此资料明确吗以及被沟通给员工吗?4.3That there are systems in place to check the age of all workers particularly at the point of recruitment.有相应的检查员工年龄的资料吗尤其是在招募的时候?4.4That all personnel files contain copies of proof of age for each worker such as:个人资料包含年龄证明如:a. Worker ID with photo.ID.b. Birth certificate.出生证.c. Notary or medical checks / examination prior to employment.体检.d. National insurance or social insurance numbers.社保号.e. Ration cards.定量供应卡.f. Written documents / affidavits.手写文件/宣誓书.g. School leaving certificates.毕业证书.h. School diplomas.学位.i. And that such documentation is valid and genuine.这些都是有效的并真实的吗?4.5That no worker is under 15 years or the law requirement if this is higher. If age 14 is allowed in accordance with developing country exceptions (ILO convention 138) the lower age may apply. 无小于15周岁的或者法律要求的最高年龄, 是否有发展中国家的豁免条款对于14周岁是最低的?4.6That if any historical child labour is found i.e. workers hired at below minimum age that are now above legal age, the auditor checks whether the current system is sufficiently robust to prevent this happening in the future.是否有之前的童工被发现?4.7That all young workers (up to age 18 years) meet all local legal requirements which may include (but not be limited to):未成年工符合法律要求:a. Registration with local authority.当地政府注册.b. Consent of parent or guardian.父母或者监护人的同意.c. Contract and appropriate documents state limitations on type of work e.g. no hazards or night work.合同或相关文件标明其受限的工作类型, 如无危害或者夜班.d. Records of medical examinations in personnel files (annual if required by law).个人档案中的体检.4.8That the site keeps a list of young workers and their job roles.未成年工清单及工作角色.4.9Check hiring and termination records for the previous 12 months to check if any pattern of sacking young workers prior to audit.一年内雇佣及终止记录是否有未成年工的解雇在稽核前.4.10Evaluates any training / apprenticeships schemes in operation and records the terms and conditions.评估培训或者培训生计划并且记录条款Checks if these meet the law. This may include but not be limited to:是否合法:a. Signature of parent or guardian.父母或者监护人的签字.b. Registered with local authority.当地政府的注册.c. Pay and benefits according to law e.g. wage rates, hours worked, time as trainee / apprentice, social security payments and other benefits.工资和福利符合法律, 如工资率, 工时, 培训时长, 社保支付及其它福利.4.11That the site has a system in place to check age at subcontractors / any homeworkers.是否有确认外包及家庭工作者的文件吗?4.12That any vocational training is of an appropriate nature e.g. does not involve working with hazardous chemicals or heavy machinery.职业训练是合适的吗?如不涉及危险化学品或者重型机械的工作.4.13Checks whether the site has remediation policies and procedures to remove any child labour found and supporting them with educational / vocational training. This should include but not be limited to:工厂有矫正措施或程序关于去除童工并且支持他们去受教育或者职业培训:a. A statement requiring any child no longer works.要求任何童工不能再继续工作的声明.b. A method for keeping the child safe and protected whilst not being at risk and not being required to work.保持童工的安全及保护他们不处于危险之中及不被要求工作.c. Requirement for the payment of a stipend.奖学金/固定薪金的支付要求.d. The need to contact the child’s parents.联系他们的父母.e. Possible re-allocation of work to an adult family member.工作分配给一个成年人.f. Local education programmes for any child found.当地对于儿童的教育计划.4.14Checks whether any previously found child has been successfully remediated and whether they meet the conditions in 4.13.检查先前发现的儿童是否被成功的矫正并且是否他们符合4.13.4.15Where any child is found, the auditor and management must:如果发现童工a. Agree it is not acceptable to dismiss them.承认解雇他们是不可接受的.b. Take immediate action to remove the child form hazards.将他们从可能的风险移开.c. Agree with management appropriate interim arrangements for the child and a commitment for remediation.同意管理层合适的临时安排并且对于矫正的承诺.d. Agree policies and procedures for remediation as per ETI code.同意根据ETI 做矫正的政策.e. Immediately inform the customer and where this would breach confidentiality agreements to encourage the supplier to initiate a discussion with their customer.立即通知客户并鼓励供应商与客户沟通.f. Capture the identity and age of the child e.g. ID number, home address, and any personnel details.采集相应信息: ID号, 家庭住址及其它.4.16Where there are child care facilities, checks that they are staffed appropriately and safe, meeting local laws and sufficient distance between then and the work place to ensure that the children are not exposed to hazards or able to enter the workplace.是否有儿童保育设施, 是否有适合的工作人员并且安全, 且与工作场所有足够的距离使得不会有危险及不会进入工作场所.以下为员工访谈内容4.17Ask whether there are children working on the site.问是否有孩子在这人工作?4.18Check whether young workers (up to 18 yrs.) are engaged in hazardous, night or overtime work or work that would interfere with the necessary legal education.是否有未成年工在做危险的, 夜班的或者超时的工作以及工作是否妨碍了必要的合法的教育?4.19Whether any young workers interviewed are comfortable with their employment conditions.面谈的未成年工是否对于工作条件满意呢?4.20Whether young workers employment conditions meet the local and international requirements.未成年工的雇佣条件合法吗?4.21Checks whether workers are satisfied with any child care facilities.是否员工对于儿童护理机构是满意的?4.22Are workers clear on the site’s policy towards the employment of children and young workers?员工对于公司关于童工和未成年工的雇佣政策清楚吗?Section5Living Wages最低薪水5.1Whether all hourly / weekly / monthly paid workers as well as any piece rate workers are paid at least the legal minimum wage rate (usually stated for standard hours excluding overtime).是否每小时/周/月的工资大于最低标准, 计件工资也如此(排除加班)5.2Where any workers are paid below the minimum rate the auditor should record the amount and detail how wages compare with any accepted living wage as well as legal minimums.有人低于最低工资吗?5.3Where any workers are found to be earning below the minimum legal wage, the auditor should record –where possible - what % of the total workforce are affected.是否有任何岗位的工人工资低于最低标准及可能的影响范围.5.4Whether overtime wage rates are paid at the legally required rate for e.g. weekly overtime, weekly rest day overtime, public holiday and annual leave overtime. Where there is no legal requirement for premium pay check that the premium is in line with industry best practice.加班工资按规定支付吗?5.5In cases where there is a legally accepted living wage, auditors shall clearly report what the amount is and how it has been calculated e.g. market basket of goods etc.如有,记录最低工资标准及如何计算的.5.6Whether all legally required allowances and benefits are provided to workers e.g. social insurance.是否有其它法定要求的津贴福利提供如社保.5.7Whether any legally allowed deductions are correctly calculated such as social security payments, union dues etc. and promptly paid to the appropriate agency e.g. government / unions. 是否合法的扣除费用被记录, 如社保, 工会会费并且向对应的部门支付.5.8Check that wages are not withheld as a deposit. 工资不可被扣作押金等.5.9Check whether wages are reduced or deducted as a form of punishment, and if yes is this on line with national law.工资有被扣作为罚款吗? 有法律支持吗?5.10Carry out wages review in conjunction with the hours review and check the calculation for wages to ensure accuracy and that wages are in agreement with hours worked and the law. Evidence should be cross checked through worker interview. 工资工时的对应及计算正确.。
A10GbsBiCMOSAdaptiveCableEqualizer_slicer_DETAIL
A10GbsBiCMOSAdaptiveCableEqualizer_slicer_DETAIL A 10Gb/s BiCMOS Adaptive Cable EqualizerGuangyu Evelina Zhang ,Student Member,IEEE,and Michael M.Green ,Member,IEEEAbstract—A 10Gb/s adaptive equalizer IC using SiGe BiCMOS technology is described.The circuit consists of the combination of an analog equalizer and an adaptive feedback loop for minimizing the inter-symbol interference (ISI)for a variety of cable charac-teristics.The adaptive loop functions using a novel slope-detection circuit which has a characteristic that correlates closely with the amount of ISI.The chip occupies an area of 0.87mm 0.81mm and consumes a power of 350mW with 3.3V power supply.This adaptive equalizer is able to compensate for a cable loss up to 22dB at 5GHz while maintaining a low bit-error rate.Index Terms—Adaptive equalizers,broadband communication,BiCMOS,BiCMOS analog integrated circuits,equalizers,wire communication cable.I.I NTRODUCTIONAS BIT RATES increase in broadband data communica-tion systems,the nonideal effects of the channel have an increasingly important impact on the quality of the signal.In particular,the loss (caused by skin effect and dielectric loss)in copper causes signi?cant attenuation of the transmitted data at high frequencies.At bit rates of 10Gb/s and higher,even a rela-tively short section of copper can cause signi?cant distortion of the data.In order to avoid bit errors and successfully receive the data signal,equalization is required.Since often the exact char-acteristic of the channel is not known,adaptive equalization is desirable.A block diagram of a typical receiver is shown in Fig.1.The equalizer is the ?rst block in the receiver,after which the re-stored data is then applied to the CDR.As an example of a copper cable characteristic,Fig.2shows the measured trans-mission characteristic for two RU-256copper cables,one with length 4feet;the other with length 15feet.At 5GHz the 4-foot cable exhibits a loss of 5dB at 5GHz;the 15-foot cable ex-hibits a loss of 13dB,which would result in a completely closed eye.One of the goals of this circuit design was to make the circuit adaptive such that the inter-symbol interference (ISI)is minimized for a wide range of cable characteristics.In theory,the transfer function of a copper cable should be monotonically decreasing.The nonmonotonicities in Fig.2are due to re?ec-tions that come from discontinuities in the connectors and mis-matches between the cables and the measurement equipment.In general the analog equalizer presented in this paper is not well-suited for media that exhibit large amounts of re?ections.However,as will be demonstrated shortly,for the characteristicsManuscript received January 14,2005;revised July 18,2005.This work was supported by Qlogic,Jazz Semiconductor,and UC Discovery Grant Com 01-10086.The authors are with the Department of Electrical Engineering and Com-puter Science,University of California,Irvine,CA 92697-2625USA (e-mail:mgreen@/doc/b0f35cd37f1922791688e8f6.html ).Digital Object Identi?er 10.1109/JSSC.2005.857354shown in Fig.2the equalizer described here has been shown to function well.At relatively low bit rates,most adaptive equalizers have been implemented using a digital approach [1],[2].Design of a dig-ital equalizer at the receiver side involves a delay element and a decision circuit that requires a recovered clock.The extraction of the clock depends on the input data of the clock and data re-covery (CDR)circuit,which increases the system complexity and could lead to problems with CDR locking.On the other hand,an analog approach is often preferred for higher speeds for its low power consumption and simplicity.A number of papers have been reported on analog cable equalization at bit rates on the order of 100Mb/s [3]–[5].Recently,two papers re-ported cable equalizers with bit-rates up to 3.5Gb/s [6],[7].InCMOS equalizer operating at 10Gb/s was presented [8]where more design effort was needed to overcome the gain limitations of CMOS.An analog FIR approach to 10Gb/s equalization was presented in [9].A BiCMOS process was chosen for this design due to boththehighand high intrinsic gain of the bipolar transistors.In particular,it was critical that the slicer used in the adaptive feedback loop (explained in Section III)exhibited high gain in order to restore the logic levels.This paper,which is an expanded version of the paper pre-sented in [10],is organized as follows.Section II discusses the principle of operation for the equalizer and adaptive loop.Section III describes the circuit design details for eachblock.Measurement results of prototypes are presented in Section IV .Finally,conclusions are drawn in Section V .II.P RINCIPLE OF O PERATIONTo understand the equalizer’s operation,we ?rst consider the operation of a simpli?ed linear circuit,shown in Fig.3oper-ating at a bit rate normalized to 1b/s.A rudimentary cable model shown in Fig.3(a),consisting of four RC sections,is used for this illustration.As mentioned in the previous section,this medium exhibits a monotonically decreasing transfer function.Thus,we would expect the ISI to be dominated by the attenu-ation of short (i.e.,1UI)pulses.In other words,the worst ISI would come from an isolated logic “1”of duration 1UI sur-rounded by strings of logic “0.”This is illustrated in Fig.4,where the response of the Fig.3(a)cable model,withset to 0.188,is shown for three different input pulse widths:1s,2s,and 3s.Clearly the worst case ISI comes from the shortest pulse width.Thus,our approach for designing the equalizer and adaptation loop is to reduce the ISI of a singlepulse,described as follows.0018-9200/$20.00?2005IEEEFig.1.Block diagram of broadband receiver including equalizer.TABLE IO PTIMUM T RANSIENT C HARACTERISTICS OF E QUALIZER FOR T HREE D IFFERENT C ABLE MODELSFig.2.S for two copper cables.As shown in Fig.3(b),thesignal from the cable is applied to an LC bandpass ?lter centered at 0.5Hz witha of 2.The equalizeroutput consists of a weighted sum of the originalsignal from thecableand the bandpassoutput .As illus-trated in Fig.3(b),weightingparameterdetermines the proportion of each signal that is summed at the output.Inparticular,if the input signal has a DC voltageswingbe.A sketch of the response at each node to a 1-s input pulse is shown in Fig.3(c).The linear equal-izer ’s transfer function is givenby(1)At DC,the transfer functiongivesfrequency (i.e.,0.5Hz),the transferfunctiongivesThe equalizer ’s operation can be illustrated in the time domain by considering its response to a 1-s unit interval pulse.This is shown in the curve labeled “cable output ”in Fig.5.As mentioned earlier,since the cable exhibits nearly unity gain at DC and signi ?cant attenuation at the Nyquist rate of 0.5Hz,the output pulsewidth is reduced.The equalizer operates by reducing the DC voltage swing while maintaining the gain at 0.5Hz,resulting in an increased pulse width.This is illustrated in Fig.5,where the equalizer pulse response is shown for threedifferent valuesof .In thiscasegives zero ISI.Note that the stage that follows this equalizer would require suf ?cient gain in order to restore the appropriate DC logic swing.We now consider a group of three different cable characteris-tics [parameterized by different valuesofin the Fig.3(a)cable model]and for each characteristic determine the valueof such that the ISI is zero.In doing this we can observe the equalizer ’s behavior at the optimum settings and identify a suitable method for adaptation.The cable pulse responses are shown in Fig.6(a).The resulting equalizer output wave-forms are shown in Fig.6(b),where for each ofthevalues,weightingparamter was set to its optimumvalue such that the pulsewidth for each waveform is exactly 1s.Table I lists the characteristics of each waveform.Note from this table that although the voltage swings and slew rates vary widely (more than 50%over the rangeof ),these values track each other,resulting in transition times that show much less variation (less than 15%).Thus,it is feasible to use this equalizer output transi-tion time as a rough measurement of ISI to be used in the adap-tive loop,where the optimum transition time is approximately 60%of the unit interval.(This optimum transition time value depends on the of the LC tank circuit;for this example a of 2was chosen because that is approximately the same value asFig.3.Linear circuit normalized to 1b/s forillustration.Fig.4.Pulse responses of cable.that of the LC tank used in the transistor-level implementation described in the next section.)The above analysis was based on a simpli ?ed linear circuit.As will be described in the following sections,the actual cir-cuit realization,based on current-mode logic (CML)techqniues,is of course nonlinear.However,the primary concern for min-imizing the ISI is to set precisely the timing of the zero cross-ings.In the vicinity of the zero crossings,CML circuitry in fact behaves nearly linearly.As will be shown shortly,the analysis given here does indeed apply to the actual transistor-level cir-cuitry.III.C IRCUIT D ESIGNThe block diagram of the adaptive equalizer is shown in Fig.7.The feedforward path consists of three parts:1)equalizer ? lter,which functions as a high-pass ?lter whose character-istics can be adjusted and whose operation was described in the previous section;2)slicer,which restores the full logic levels after the equalizer ?lter;and 3)output driver,which is used to drive an external50load.The feedback path consists of two slope detectors and an integrator,used to compare the difference between the transition times of the equalizer ?lter output and the slicer output.Each part will be described in detail asfollows.Fig.5.Pulse response of RC ladder (for C =0:125)and linear equalizer output for three different values of .A.Feedforward PathThe equalizer ?lter schematic is shown in Fig.8.The input data is applied to a peaked ampli ?er which resonates at thewith bandwidth of 9GHz (“slow ”path).Theoutputsand are applied to the mixer.The output of the mixer is thus the weighted sumofand with the weighting determinedby.Fig.9shows the magnitude transfer function for three different valuesof,exhibiting a maximum equal-ization of 22dB (de ?ned as the ratio of the gain at 5GHz to the DC gain).To demonstrate that this equalizer behaves like the linear pro-totype presented in Section II,the following simulation is per-formed.An input pulse with 100ps pulsewidth is applied to the(a)(b)Fig.6.(a)Pulse response of three different cable characteristics.(b)Pulse response of equalizer with optimum value of chosen for each cablecharacteristic.Fig.7.Adaptive equalizer blockcable 1followed by the equalizer ?lter.Byadjusting ,the output transitiontimevaries accordingly.The output pulsewidth varies directly with the value of the control voltageas shown in Fig.10.Notethatps corresponds to zero ISI,consistent with the results given in Section II.We observe that the pulses in Fig.10(which come from the transistor-level realization of the equalizer)look quite different from the pulses in Fig.5(which come from the simple linear model of the equal-izer).The reason for this difference is that the circuit realization is nonlinear due to the saturating characteristics of the CML blocks.However,in the vicinity of the zero crossings,the CML blocks behave linearly.Thus,the pulse widths of the Fig.10waveforms are consistent with those of Fig.5.1Thecable model used in this simulation is based on a behavioral model thatapproximates the characteristic in Fig.2corresponding to a length of 15feet.The relationbetweenand can be characterized by coef ?cientwith units of ps/mV .Simulation gives a valueof approximately 1.5ps/mV;i.e.,if is increased by 1mV ,the equalizer transition time decreases by 1.5ps.B.Feedback PathAs discussed in Section II,the feedback path functions to set the transition time of the equalizer ?lter output to a ?xed value of approximately 60ps so that the ISI is minimized.To accomplish this,the equalizer ?lter output is applied to the input of a slicer.The slicer,shown in Fig.11,is implemented by two cascaded CML buffers.The ?rst buffer exhibits fast transition time and corrects the signal amplitude.The second buffer is capacitively loaded so that it produces an output with a ?xed transition time of 60ps,independent of the input transition time.Thus,eachFig.8.Equalizer ?lterschematic.Fig.9.Magnitude plot of equalizer output for three different controlvoltages.Fig.10.Relation between output pulsewidth and transition time.transition at the equalizer ?lter output (where the transition time varies)always results in a transition at the slicer output with a 60ps transition time.In order to compare the transition times of these two signals a transition time detector is required.The transition time detector plays a critical role in the equal-izer circuit performance.Traditionally,such detectors are made up of a high-pass ?lter and recti ?er [4].However,the design ofaFig.11.Slicer schematic.recti ?er that operates at 10Gb/s is dif ?cult.In this circuit a dif-ferent approach was used,where the detection is performed by a single stage.As illustrated in Fig.12(a),theinputsand are applied to the gates of a CMOS differential pair.For a slow transition of either polarity,the source-coupled node voltage is minimum when the differential input is 0.Thus,the response to any input transition is a negative pulse whose amplitude is de-termined by the differential pair design.However,a faster tran-sition will have a smaller pulse amplitude due to the capacitance that is always present at the source-coupled node.Fig.12(b)shows 100ps input pulses with two different transition times;Fig.12(c)shows the corresponding detector output waveforms.The energy contained in each negative pulse is nearly propor-tional to the input transition time.In the feedback path,two detectors —one connected to the equalizer ?lter output,the other connected to the slicerFig.12.(a)Transition detector circuit.(b)Input waveforms.(c)Outputwaveforms.Fig.13.Schematic of integrator with common-mode feedback circuit.output —give output pulses whose energy is proportional to the input transition time.The pulses from both detector outputs are then applied to the differential inputs of an integrator (shown in Fig.13,including the common-mode feedback circuit);the integratoroutput,which is fed back to the equalizer,responds to the difference in transition time between the de-tector inputs.When the adaptive loop reachessteady-state,will be set such that the equalizer output will exhibitthe same transition time as the slicer output,thus minimizing the ISI.Although this circuit should function as a transition time detector,it is also sensitive to the signal levels of the input.In particular,if there is any mismatch in the DC levels between the two detector outputs,there will be a steady-state error in the equalization.Fortunately,the nonlinearity of the equalizer itself maintains a logic level that is independent of the equalizer settings,which can be observed in Fig.10.Thus,care needs to be taken only in ensuring that the logic levels of the input and output of the transition detectors are well-matched.The transferfunctionof the Fig.13integrator is givenbyFig.14.Operation of slicer and integrator.whereand .The integratortimeis set to 75ns.To illustrate the operation of the slicer and integrator,simulation was performed by varying theequalizer transitiontimeand observing the control voltage.The simulation results are shown in Fig.14.The combination of detector and integrator can be characterized by detectorgainwith units of mV/ps,where is proportional to the transi-tion density.SimulationgivesmV/ps for this circuit。
人员分配及人力调配(ppt 33页((英文版)

Director of Human Resources
Strategy, external/internal, policy, standards, service quality, organisational Learning and cultures
HRD Manager
Site Services & Occupational Health
Employment law
9
BS3403 HRM
Development of HRM/Personnel
STAGE 3 Strategic Manager
Competitive Advantage
STAGE 2
Contracts Service Manager
Regulative accountability
BS3403 Human Resource Management
Chris Jarvis
Sept 001
BS3403 HRM
Schedule
Lectures Case study discussion Coursework 50%, Examination 50% On-line Forum/Bulletin Board Study guide and Learning Resources
STAGE 1
Admin. Service Manager
Records and administration
Problem-solving, power and innovation
10
BS3403 HRM
Clerks & Innovators
Personnel administrator Clerk of works: chores, reactive, little authority, difficult to prove success, cost not profit centre Contracts manager & Architect – deploy systems + innovate (Tyson & Fell 1986)
行政管理风险管理

Examination Objectives 检查目的
Do risk management policies identify, control and mitigate risks? 风险管理方针是否能识别、控制并化解风险 Are Board’s guidelines for retention of risk reasonable? 董事会关于保留风险的指引是否合理 Is significant or catastrophic loss covered? 重大的或灾难性损失是否得到补偿 Are record-keeping practices adequate? 记录是否充分 Is there corrective action when controls are deficient? 控制不完善时是否有整改措施
Conversely 从反面说
It’s not cost justified to insure losses which are not severe or predictable---improve controls 不严重的、可预计的损失的发生不是合理成本 —加强控制
Board of Directors Determines 董事会决定
The maximum loss the bank is able or willing to assume 银行能够或者愿意承担的最大损失 …The insurance deductible —扣除保费
Types of Insurance Coverage 保险类型
Fidelity Bond 忠实保险契约 Combination Safe Depository 综合保险箱 Directors & Officer’s Liability 董事与负责人的责任 Fiduciary Insurance Coverage 信托险 Mortgage Errors & Omissions 抵押错误 Cash Letter Insurance 现金运送险 General Liability 一般责任险 Fire Insurance 火险
PIC S VMP 验证主计划(中英文对照)

OPERATIONAL QUALIFICATION STERILE PROCESS VALIDATIONCLEANING VALIDATION (1/25)1. DOCUMENT HISTORYAdoption by PIC/S Committee 10 - 11 December 1998Entry into force of version PR 1/99-1 01 March 1999Entry into force of version PI 006-1 01 September 20012. INTRODUCTIONThe basic principles and application of qualification and validation are describedin Annex 15 to the PIC/S and EU Guide to GMP. This document comprises individual Recommendations on four topics relating to Equipment Qualification and Process Validation in pharmaceutical manufacture, as follows:Ø Validation Master PlanØ Installation and Operational QualificationØ Non-Sterile Process ValidationØ Cleaning ValidationThe four Recommendations comprising this document define general principles pertaining to each of the topics.2. 导言PIC/S和EU GMP指导原则的附录15中对确认(Qualification)和验证(Validation)的基本原则及应用进行了阐述。
三维身体扫描:共享协议以确保可比较的数据收集说明书

3D Body Scanning: Towards Shared Protocols forData CollectionAddressing the needs of the body scanning community for ensuring comparable datacollectionSimeon GillSchool of MaterialsThe University of Manchester Manchester, UK*************************.ukSteven HayesSchool of MaterialsThe University of ManchesterManchester, UK**************************.ukChristopher J. ParkerSchool of MaterialsThe University of ManchesterManchester, UK********************************.ukAbstract— Currently, there are no public, universal or easily applied protocols for capturing body scan data, which may result in discrepancies in the captured scan data; a series issue in a scientific field. This paper presents a step-by-step process that forms the basic procedure for capturing, storing, processing, and using body scan data based on that currently used at The University of Manchester. Here, the entire scan capturing protocol is explained from recruitment through to the scan process itself and final following up on the participant post-scanning. This process has allowed the Apparel Design Engineering cluster within the School of Materials to increase the repeatability, accuracy, and professionalism of their work in 3D Body Scan research, with the intention to disseminate this protocol throughout research and industry.Keywords—Anthropometrics; Body Scanning; Ergonomics; MethodologyI.I NTRODUCTIONAlthough 3D body scanning can be considered to a degree as a mature technology - being originally developed in the 70’s [1] –the process of capturing body scans is still not standardized in protocol or practice. The importance of this is highlighted by previous research [2]–[4] that notes that differences in measurement definitions influences the obtained dimensions to statistically significant amounts. Consequently, a need exists to produce, disseminate, and create adoption of a universal protocol in 3D Body Scanning to bring unity and conformity to the process of capturing body scans. Current standards [5] do not provide sufficient detail for all aspects of the process..This paper presents a step-by-step process that forms the basic procedure for capturing, storing, processing, and using body scan data based on that currently used at The University of Manchester. These scans are captured in a private cubicle with the participant minimally clothed, scans are captured using light sources and image capture devices and are only able to capture the body surface. Capture devices are similar to Kinect sensors [6] (used as a physical interactive data input device for PC and X-Box), and do not present any dangers to the participant.II.A S HARED P ROTOCOL FOR B ODY S CANNINGA.Body Scanning and Ethical ProceduresDuring the scan capture process it is not possible to viewimages of the scanned subject and upon processing the scanappears as a point cloud for analysis (see Fig. 1). Data arecaptured by scanning personnel, who have received suitabletraining in capturing body scans and each scan session is theresponsibility of a member of trained University staff.All specific ethics approval documents refer directly to theprocess document and require separate approval for deviations from the standard methods. A copy of each project’s specificethics approval documentation is kept which allows for bettermanagement of all scanning activity and for project specificrequirements to be catered for.Fig. 1.Example of scanimage as seen on screen atscan capture and duringanalysisA copy of the scanprocedure is madeavailable to allparticipants before beingscanned and is displayedin a prominent positionin the location wherebody scans are beingcaptured. Deviationsfrom the scan procedurerequire the ethicscommittee to be notified for their consideration. The processdocument forms the backbone for all future projects allowingdeviations to be noted, and are not required full approval againfor standard practices.B.Step by step procedure1)Recruitment to body scanningRecruitment of participants to be scanned is by one of thefollowing methods:International Workshop of Advanced Manufacturing and Automation (IWAMA 2016)∙Individuals invited to participate in body scanning sessions whilst the scanner is situated offsite; e.g.during outreach activities.∙Open calls using social media, posters, and word of mouth, etc. This is primarily managed through theonline booking system based on Eventbrite through theUniversity webpages(/our-research/facilities/bodyscanning/bookabodyscan/)2)Explanation of the body scanning process and details of consentEach participant has the opportunity to have the scanning process explained to them and be referred to the systematic procedure detailing the process from start to finish.The systematic guide and a copy of the consent form are provided for the participant to read before scanning. The consent form is retained, though a blank copy is available on the website for scrutiny by participants.A general body scanning information sheet, and a sheet related to specific scan projects, is provided to each participant before scanning. The general information sheet indicates the type of underwear that should be worn during the scan process and the types of scan outputs that will be provided.Scanning is only undertaken by trained personnel, whose names will be recorded on the consent form and all scanning is the responsibility of a member of university staff whose contact details is made available to participants.3)Participants complete their record in the databaseAn encrypted and password protected database available on a single PC is used to record identifying and contextual data separate from any scanned image. This is then backed up to encrypted and password protected hard disks that are kept at separate secured locations.The database can only be accessed by members of the scanning team with a password, and will store personal details of each participant; as well as manual measurements not recorded by the scanner.Completion of each participant database record generates a unique code that is used to name the scan file and retain anonymity of the scan participant whilst linking the scan file to the database entry.4)Print and sign the consent form (Participant and scanning personnel)A copy of the consent form is then printed from the database and once read is initialed and signed by the participant and the names of both scanning personnel are recorded. The signed copy of the consent form has details of the manual measurements recorded on it and after completion of the scan is stored in a secure location. A blank copy of the consent form is available for each participant online.5)Manual measurements taken prior to the scanning processTo enable full analysis of the scan data a number of manual measurements are taken:∙[D2] Height –the shoes are removed for this measurement∙[D3] Head Circumference –taken to help understand garment opening requirements∙[D4] Min Max hand – taken to help understand garment opening requirements∙[D5] Hand length –taken as a reference for garment opening requirementsMeasurements are taken manually in accordance with detailed methods that are available for the participants to view before giving consent and during the process.6)Using a private changing cubicle, change into underwear and record weightParticipants are directed to a private changing cubicle adjoining the body scanner and requested to change down to their underwear. Should the scanner be located where this is not possible then, participants are provided with a gown for privacy to wear when travelling between the changing cubicle and scanner.Participants are instructed to step onto the weighing scales in the private changing area and the scanning personnel from a remote screen record weight. Participants are asked if they would like to know their weight and have it recorded on the output.Due to the nature of the scanner, it is explained that underwear must be close fitting as detailed on the information sheet. Appropriate underwear is made available to wear over or in place of the participants own, should they not have close fitting underwear.At no point should the participant be undressed whilst in view of the scanning personnel or other participants.7)Enter the scanner booth and adopt the scan postureBefore entering the scanning booth, the scan position of the body is explained to the participant and a definition provided for their reference. The participant is then instructed to enter the scanning booth and adopt the required scan posture.Whilst the participant is in the scan booth (and before the scanner is activated) the scanning personnel inputs the unique code from the consent form to name the scan file. This retains the anonymity of the participant but allows the scan to be matched with the details in the participant record during analysis.The participant stands in the scan position and has their scan captured, remaining in the scan booth until the scan is complete and a usable image is collected; approximately one minute. Once the scan has been captured, it is checked on screen and if a rescan is necessary; communicated to the participant verbally. Once a suitable scan is captured then the participant returns to the changing area/ cubicle to get dressed.8)Leave scanner booth and get dressed in the private changing areaOn completion of the scan, the participant re-enters the changing area (directly connected to the scanning booth) and dresses in their original clothing in full privacy. On leaving thechanging area the participant is offered a copy of their scan data printed out showing a front, back, and side view and displaying their measurements.9)Following scan capture and debriefEach participant is offered a print out of their scan data on completion of the process and the opportunity to take a copy of their scan files. Participants are offered the opportunity to have their weight and height recorded on the printed sheets. Electronic copies of their scan data can be requested by personal email and will be sent where practical. Participants may also be sent summary data by email should they request this following from their scan.10)Notes on the procedureA minimum of two scanning personnel must be present at all times one of which must be an experienced and approved staff member. The participant is free to withdraw from the activity at anytime even though the consent form has been signed. If a participant withdraws from the activity during the data collection period, all data is destroyed immediately.11)Data usage and storageAny anonymized scan data taken from the scanner location is kept on encrypted computers, or within encrypted folders on storage devices. All scan data is backed up on encrypted external hard drives and kept in a secure locked location with controlled access. This is a separate hard drive to the one used to back up the participant database.Measurements taken from scans and scan images themselves may be used within publications (academic and non-academic). In instances of scan images being used, the faces on scan avatars/ point clouds/ etc. are obscured to ensure anonymity. Examples of scan outputs used in publications are provided to participants when necessary.C.Protocol for data management (storage and backing up)All body scanning activity within The University of Manchester is conducted on the understanding that all data collected contributes to the general data pool. Any embargos on data use or participant contact are detailed in the specific project ethics approval documentation of which a copy is kept with the scanning technology and a reference is made, by note and ethics approval code, in the Project Categories field within the participant database. All data collected through body scanning is stored on the PC used for data collection for both the body scans and participant records.Each is backed up in duplicate to encrypted Hard Drives or USB’s kept separately and in a secured loc ation. Where possible these drives are password protected.1)Participant RecordsCopies of the database are kept in the FileMaker Pro database format. For the purpose of each study data will be extracted from the database into excel sheets, this does not include the participants name but instead uses the scan code to allow these details to be matched to measurement data taken from the body scans. e of body scan dataAny use of body scanning data adheres to the following conditions unless consent has been granted by the participant, and this has been signed off by the ethics committee of The University of Manchester.Data is blinded (named with a code) on receipt, stored as blinded and double-blinded (named with secondary code) before use in publication.Double blinded scan data issued in publications and lists of anonymous double blinded scan measurements may be used in teaching and in the development of research.Any screen shots of the scan image captured from the scan files have identifiable data such as face profile removed before any publication.1)Prior to being scannedBefore participants are scanned they are provided with details explaining the process, those booking online go through the website to book an appointment. Here a video is provided detailing the process as well as copies of the consent form; scan information sheet and samples of the data output from the body scanner:Participants who have not booked through the website are provided with hard copies of these details and the opportunity to access the video guiding on the process prior to being body scanned.2)Post being scannedParticipants are provided with a printed copy of their body scan, including an extensive list of body measurements. All participants are offered the opportunity to take away a copy of their electronic scan data, copies in .obj format (which can be quickly produced) and can be opened using a number of existing computer programs.E.Outline of Database and rationale for data collectedParticipant’s details are recorded in a data base that also creates the unique scan ID.The eight character participant code is created as the database record is being completed. The code consists of a four digit unique identifier, a code for gender (M or F); a letter code for ethnicity and two digits for age. Having this data in the code helps with managing the scans, and later matching of specific scans with specific participants data the during analysis. A record is also kept of the person responsible for capturing each scan.The notes section in the records allows for the capture of specific project details or for other important data that may be relevant to future data analysis. This may include whether the participant is employed as a fit model or if they participate to a high level within a sport.F.Scanning personnel and trainingThe capturing of body scan data at each session will be the responsibility of an experienced member of University Staff; it will also be supported by trained scanning personnel. These scanning personnel may be other University staff, PG or UG students who will have been provided with in-house training onhow to capture scans and dealing with scan participants. Names of the scanning personnel and staff member will be recorded on the consent form and contact details for the staff member responsible for the scan capture session will be made available to participants.III.C ONCLUSIONThe protocol outlined within this paper has been developed by the Apparel Design Engineering cluster within the School of Materials, University of Manchester through a co-design methodology, utilizing design thinking to research, specify, develop, and deliver the final solution. The result has been to create a uniform and useful user experience that ensures that ethical requirements are met at all stages, experiments and measures are repeatable, and the body scanning experience can be controlled, improved, and applied equally to all those who participate in our research; an important aspect of Service Design. This has created a better research environment within our research cluster with a greater level of professionalism relating to each point highlighted within the above protocol.Further collecting data against these protocols, ensures that it can analyzed in the knowledge that participants are dressed and stood in a similar manner. Adoption of these protocols will ensure that all users of body scanning systems collect full and accurate data about their participants, especially details not captured by the scanner, but required for future data analysis.A CKNOWLEDGMENTThis protocol for 3D Body scanning was developed by the Apparel Design Engineering cluster, School of Materials, University of Manchester, with additional input from Gianpaolo Vignali, Louise Reid, and Kathryn Downey. More information is available at: http://goo.gl/6Y4Tbo.R EFERENCES[1] E. J. Lovesey, “The development of a 3-dimensional anthropometricmeasuring technique,” Appl. Ergon., vol. 5, no. 1, pp. 36–41, 1974. [2] S. Gill, C. J. Parker, S. Hayes, P. Wren, and A. Panchenko, “The TrueHeight of the Waist: Explorations of automated body scanner waist definitions of the TC2 scanner,” in 5th International Conference and Exhibition on 3D Body Scanning Technologies, 2014, pp. 55–65.[3] D.-E. Kim, K. LaBat, E. Bye, M. Sohn, and K. Ryan, “A study of scangarment accuracy and reliability,” J. Text. Inst., vol. 106, no. 8, pp. 853–861, 2015.[4] L. Mckinnon and C. L. Istook, “Body scan ning: The effects of subjectrespiration and foot positioning on the data integrity of scanned measurements,” J. Fash. Mark. Manag., vol. 6, no. 2, pp. 103–121, 2002.[5] BSI, “BS EN ISO 20685:2010: 3-D scanning methodologies forinternationally compatible anthropometric databases,” British Standards Institute, London, UK, 2010.[6] G. M. Ryan, “Visual Target Tracking,” 8,682,028, 2014.。
思科数据中心网络管理器(DCNM)系统管理配置指南说明书

C H A P T E R S e n d d o c u m e n t c o m m e n t s t o n e x u s 7k -d o c f e e d b a ck @c i s c o.c o m 13-1Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-0113Working With Threshold RulesThis chapter describes how to configure threshold rules using Cisco Data Center Network Manager(DCNM).This chapter includes the following sections:•Information About Threshold Rules, page 13-1•Configuring Threshold Rules, page 13-4Information About Threshold RulesThis section includes the following topics:•Threshold Rules Overview, page 13-1•Threshold Rule Examples, page 13-2Threshold Rules OverviewCisco DCNM provides a feature that you use to specify rising or falling threshold rules for sample variablesin collected statistical data. Depending on the rule definition, a set of actions are performed by Cisco DCNM.You define the threshold rule on the Threshold Rules page, and you apply the threshold rule to the existingchart.This section includes the following topics:•Rising Threshold, page 13-1•Falling Threshold, page 13-2•Threshold Rule Properties, page 13-2•Threshold Rule Actions, page 13-2Rising ThresholdThe rising threshold is the upper threshold for a sample variable. When the current sampled variable isgreater than or equal to the specified threshold, a set of actions is performed.Chapter13 Working With Threshold Rules Information About Threshold RulesF I N A L D R A F TFalling ThresholdThe falling threshold is the lower threshold for a sample variable. When the current sampled variable islower than or equal to the specified threshold a set of actions is performed.Note You can specify only one rising threshold and one falling threshold for a single sampled variable.Threshold Rule PropertiesThreshold rule properties are as follows:•Name—Specifies the threshold rule name.•Frequency—Specifies the number of times the sampled variable must cross a threshold before triggering any actions.•Period—Specifies the interval of time the frequency is monitored.•Repeat—Prevents the timer from resetting after triggering an action within the period.•Trend—Specifies the rising or falling threshold.Threshold Rule ActionsThreshold rule actions are as follows:•Send an email or SMS to a mail server or mail to SMS gateway.•Run a script on the server.•Send an event to the current DCNM JMS channel.Threshold Rule ExamplesNote The granularity of a period is driven by the minimal interval of the collected data. Consequently, the period must be higher than that interval.This section includes the following topics:•Trigger an Action Each Time a Threshold is Crossed, page13-2•Trigger an Action Only Once in a Period When a Threshold is Crossed, page13-3•Trigger an Action Every Fourth Period When a Threshold is Crossed, page13-4Trigger an Action Each Time a Threshold is CrossedTo trigger an action each time a threshold is crossed, set properties as follows:•Frequency—1•Repeat—YesFigure13-1 shows the trigger action when you set rule properties to the preceding values.Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01F I N A L D R A F T 13-3Cisco DCNM System Management Configuration Guide, Release 5.x OL-23625-01Chapter 13 Working With Threshold RulesInformation About Threshold RulesFigure 13-1T rigger an Action Each Time a Threshold is CrossedIf the sampled variable crosses the threshold, an action is taken the first time it crosses the threshold. As a result, an action is performed each time the threshold is crossed.Trigger an Action Only Once in a Period When a Threshold is CrossedTo trigger an action only once in a period when a threshold is crossed, set properties as follows:•Frequency—1•Period—300•Repeat—NoFigure 13-2 shows the trigger action when you set rule properties to the preceding values.Figure 13-2T rigger an Action Only Once When a Threshold is Crossed Within a PeriodIf the sampled variable crosses the threshold, an action is taken the first time it crosses the threshold. For the remaining 5 minutes, an action will not be taken. As a result, an action is performed only once during the specified period.F I N A L D R A F T Cisco DCNM System Management Configuration Guide, Release 5.x OL-23625-01Chapter 13 Working With Threshold RulesConfiguring Threshold Rules Trigger an Action Every Fourth Period When a Threshold is Crossed To trigger an action every fourth period when a threshold is crossed, set properties as follows:•Frequency—4•Period—300•Repeat—NoFigure 13-3 shows the trigger action when you set rule properties to the preceding values.Figure 13-3T rigger an Action Every Fourth Period When a Threshold is CrossedIf the sampled variable crosses the threshold, an action is taken the fourth time it crosses the threshold. For the remaining 5 minutes, an action is not taken. As a result, an action is performed only once during the specified period.Configuring Threshold RulesThis section includes the following topics:•Creating Threshold Rules, page 13-4•Deleting Threshold Rules, page 13-5•Editing Threshold Rules, page 13-6•Viewing Threshold Rules, page 13-6•Applying a Threshold Rule to a Chart, page 13-6Creating Threshold RulesYou can create threshold rules using Cisco DCNM.DETAILED STEPSStep 1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules .Chapter13 Working With Threshold RulesConfiguring Threshold RulesF I N A L D R A F TStep2From the toolbar, choose New, and then choose New Threshold Rule.The Details and Threshold Bindings tabs appear in the Details pane, with the Details tab open.Step3Create a threshold rule as follows:a.In the Name field, enter a name.b.In the Description field, enter a description of the threshold rule.After you have enter a description, the Rising Threshold check box is automatically checked and theThreshold field in the Settings area is outlined in red.Note A field outlined in red indicates that an entry is required. A field outlined in yellow indicatesthat the entry is satisfactory.c.In the Settings area, enter a value in the Threshold field.Once you have entered a value, the three options in the Action area are outlined in red.d.In the Action area, provide one of the following:–Enter email addresses (delimited with commas)–Select Sent Event to forward events to the DCNM Event Browser–Enter a script nameThe script receives all data regarding the crossed threshold. The script can be written in anyprogramming language and saved in one of the directories of the system PATH.Note Ensure that the Cisco DCNM server is configured for an SMTP server. For more informationabout configuring the Cisco DCNM server, see the Cisco DCNM Installation and LicensingGuide, Release 5.x.e.(Optional) In the corresponding Settings and Action areas, configure a Falling Threshold.f.(Optional) Click the Threshold Bindings tab to view bindings.g.Click Deploy.The rule is deployed.When you exit Cisco DCNM and Save Pending Changes is checked in the Warning dialog box, click Yesto save the rule.Deleting Threshold RulesYou can delete rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules.The rules appear in the Summary pane.Step2From the Summary pane, right-click the appropriate rule.Cisco DCNM System Management Configuration Guide, Release 5.x OL-23625-01Chapter13 Working With Threshold Rules Configuring Threshold RulesF I N A L D R A F TStep3From the drop-down list, choose Delete Threshold Rule.A warning dialog box appears and displays “Are you sure you want to delete?”Step4Click Yes.The rule is deleted.Editing Threshold RulesYou can view threshold rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules.The rules appear in the Summary pane.Step2Edit any appropriate areas.Note You cannot edit the Name field.Viewing Threshold RulesYou can view threshold rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose DCNM Server Administration > Threshold Rules.The rules appear in the Summary pane.Step2Click on a rule to view it.Applying a Threshold Rule to a ChartYou can apply threshold rules using Cisco DCNM.DETAILED STEPSStep1From the Feature Selector pane, choose the appropriate feature. For example, if you wanted to see statistics for an Ethernet port, choose Interfaces > Physical > Ethernet.The available devices appear in the Summary pane.Step2From the Summary pane, choose the appropriate device.Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01Chapter13 Working With Threshold RulesConfiguring Threshold RulesF I N A L D R A F TStep3Click the Statistics tab.Step4In the toolbar, click New Chart and then from the drop-down list choose the chart that you want to view.For example, if you wanted to see statistics for traffic, choose Traffic Statistics Chart.Step5In the chart toolbar, click Launch Threshold Setting.Cisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01Chapter13 Working With Threshold Rules Configuring Threshold RulesF I N A L D R A F TCisco DCNM System Management Configuration Guide, Release 5.xOL-23625-01。
Model Code of safe practice Part 19 contents

EI MODEL CODE OF SAFE PRACTICE PART 19:FIRE PRECAUTIONS AT PETROLEUM REFINERIESAND BULK STORAGE INSTALLATIONS3RD EDITIONNOVEMBER 2012Published byENERGY INSTITUTE, LONDONThe Energy Institute is a professional membership body incorporated by Royal Charter 2003Registered charity number 1097899The Energy Institute (EI) is the leading chartered professional membership body supporting individuals and organisations across the energy industry. With a combined membership of over 14 000 individuals and 300 companies in 100 countries, it provides an independent focal point for the energy community and a powerful voice to engage business and industry, government, academia and the public internationally.As a Royal Charter organisation, the EI offers professional recognition and sustains personal career development through the accreditation and delivery of training courses, conferences and publications and networking opportunities. It also runs a highly valued technical work programme, comprising original independent research and investigations, and the provision of EI technical publications to provide the international industry with information and guidance on key current and future issues.The EI promotes the safe, environmentally responsible and efficient supply and use of energy in all its forms and applications. In fulfilling this purpose the EI addresses the depth and breadth of energy and the energy system, from upstream and downstream hydrocarbons and other primary fuels and renewables, to power generation, transmission and distribution to sustainable development, demand side management and energy efficiency. Offering learning and networking opportunities to support career development, the EI provides a home to all those working in energy, and a scientific and technical reservoir of knowledge for industry.This publication has been produced as a result of work carried out within the Technical Team of the EI, funded by the EI’s Technical Partners. The EI’s Technical Work Programme provides industry with cost-effective, value-adding knowledge on key current and future issues affecting those operating in the energy sector, both in the UK and internationally.For further information, please visit The EI gratefully acknowledges the financial contributions towards the scientific and technical programmefrom the following companiesBG Group NexenBP Exploration Operating Co Ltd Phillips 66BP Oil UK Ltd Premier OilCentrica RWE npowerChevron Saudi AramcoConocoPhillips Ltd Shell UK Oil Products LimitedEDF Energy Shell U.K. Exploration and Production LtdENI SSEE. ON UK StatoilExxonMobil International Ltd Talisman Energy (UK) LtdInternational Power Total E&P UK plcKuwait Petroleum International Ltd Total UK LimitedMaersk Oil North Sea UK Limited ValeroMurco Petroleum Ltd World Fuel ServicesHowever, it should be noted that the above organisations have not all been directly involved in the development of this publication, nor do they necessarily endorse its content.Copyright © 2012 by the Energy Institute, London.The Energy Institute is a professional membership body incorporated by Royal Charter 2003.Registered charity number 1097899, EnglandAll rights reservedNo part of this book may be reproduced by any means, or transmitted or translated intoa machine language without the written permission of the publisher.ISBN 978 0 85293 634 4Published by the Energy InstituteThe information contained in this publication is provided for general information purposes only. Whilst the Energy Institute and the contributors have applied reasonable care in developing this publication, no representations or warranties, express or implied, are made by the Energy Institute or any of the contributors concerning the applicability, suitability, accuracy or completeness of the information contained herein and the Energy Institute and the contributors accept no responsibility whatsoever for the use of this information. Neither the Energy Institute nor any of the contributors shall be liable in any way for any liability, loss, cost or damage incurred as a result of the receipt or use of the information contained herein.Hard copies can be obtained from: Portland Customer Services, Commerce Way, Whitehall Industrial Estate, Colchester CO2 8HP, UK.t: +44 (0)1206 796 351 e: sales@Electronic access to EI and IP publications is available via our website, Documents can be purchased online as downloadable pdfs or on an annual subscription for single users and companies.For more information, contact the EI Publications Team.e: pubs@CONTENTSPage Foreword (8)Key technical changes (10)Acknowledgements (12)Key principles (13)Overview (14)1 Introduction (16)1.1 Introduction (16)1.2 Scope (16)1.3 A pplication (16)1.4 Risk-based fire and explosion hazard management (FEHM) (17)1.5 Legislative trends in FEHM assessment and provision of fire risk reduction measures 181.6 International application (19)1.7 Risk drivers (20)1.7.1 Legislation (20)1.7.2 Life safety (20)1.7.3 Environmental impacts (20)1.7.4 Asset loss (22)1.7.5 Business interruption (22)1.7.6 Reputation (22)1.7.7 Insurance (22)2 Hazards (23)2.1 Introduction (23)2.2 Fire-related properties of petroleum and its products (23)2.3 Combustion of petroleum and its products (24)2.3.1 General (24)2.3.2 Fires (25)2.3.3 Explosions/boiling liquid expanding vapour explosion (25)2.4 Smoke and gases from fire (27)2.4.1 General (27)2.5 Fire and explosion scenarios (27)2.5.1 General (27)2.5.2 Scenarios (27)2.5.3 Unignited product releases (29)2.5.4 Pool fires (29)2.5.5 Atmospheric storage tank fires (30)2.5.6 Jet fires (32)2.5.7 Boiling liquid expanding vapour explosions (32)2.5.8 Vapour cloud explosions (32)2.5.9 Flash fires (34)2.6 Consequences (34)2.6.1 General (34)2.6.2 Thermal flux - consequence assessment (34)2.6.3 Overpressures (35)2.6.4 Flammable/toxic vapour clouds (36)2.6.5 Blast effects/missiles (37)2.7 Fire and explosion modelling (37)2.7.1 General (37)2.7.2 Types of model (38)3 FEHM process (40)3.1 Introduction (40)3.2 Fire scenario analysis (40)3.2.1 Identification of major fire scenarios, hazards and hazard characteristics (41)3.2.2 Typical scenarios for various installations/areas (42)3.2.3 Design/credible scenario selection (45)3.2.4 Fire and explosion modelling (48)3.3 Risk reduction options (48)3.4 FEHM policy (51)3.5 Implementation (52)3.5.1 Practices and procedures (52)3.5.2 Fire systems integrity assurance (52)3.5.3 Inspection and testing of fire systems (52)3.5.4 Fire response pre-planning (53)3.5.5 Competency development (53)3.5.6 Monitoring (53)4 Fire prevention (54)4.1 Introduction (54)4.2 Control of flammable substances (54)4.2.1 General principles (54)4.2.2 Liquid releases (55)4.2.3 Flammable atmospheres (55)4.2.4 Isolation/depressurisation (56)4.2.5 Flammable gas/vapour dispersion (56)4.3 Atmospheric monitoring (56)4.4 Control of sources of ignition (57)4.4.1 General (57)4.4.2 Static electricity (58)4.4.3 Lightning (59)4.5 Permit-to-work systems (59)4.6 Maintenance practices (60)4.6.1 General (60)4.6.2 Hot work (61)4.6.3 Electrical equipment used for maintenance (61)4.6.4 Hand tools (61)4.6.5 Chemical cleaning (62)4.6.6 High pressure water (62)4.7 Housekeeping (62)4.8 Installation layout (63)4.8.1 General (63)4.8.2 Boundaries (64)4.8.3 Storage tank layout/secondary containment (64)4.8.4 Process plant layout (66)4.8.5 Fire-fighting access (66)4.8.6 Drainage systems and tertiary containment (67)4.8.7 Fire protection and other safety critical equipment (69)4.8.8 Pipework/flanges (69)4.9 Buildings fire precautions (69)5 Fire, liquid and flammable gas detection (71)5.1 Introduction (71)5.2 Principles of fire and flammable gas detection - Options, applications and designissues (71)5.2.1 Flammable gas detection (71)5.2.2 Toxic gas detection (76)5.2.3 Liquid leak detection (76)5.2.4 Fire detection (77)5.2.5 General design guidance (84)5.3 Control system executive actions (84)5.4 Fire/Gas alarm and warning systems (85)6 Fire protection (86)6.1 Introduction (86)6.1.1 Passive and active fire protection (86)6.2 Passive fire protection - Options, applications and design issues (87)6.2.1 General (87)6.2.2 Applications and design issues (88)6.2.3 Maintenance of PFP (89)6.3 Active fire protection (90)6.3.1 General (90)6.4 Extinguishing media (90)6.4.1 General (90)6.4.2 Water (90)6.4.3 Foam (91)6.4.4 Dry powder (dry chemical) (98)6.4.5 Gaseous agents (99)6.5 Fixed system - options, applications and design issues (101)6.5.1 General (101)6.5.2 Fire water systems (101)6.5.3 Water spray systems (102)6.5.4 Fixed monitors (103)6.5.5 Sprinkler systems (103)6.5.6 Water mist systems (103)6.5.7 Foam systems (104)6.5.8 Dry powder (dry chemical) systems (112)6.5.9 Gaseous systems (112)7 Response strategies and options (115)7.1 Introduction (115)7.2 Incident response strategies (115)7.2.1 Unignited gas release (115)7.2.2 Flammable liquid pool fire (118)7.2.3 Gas/liquid release, flash fire and jet fire (120)7.2.4 Unconfined/semi-confined vapour cloud explosions (121)7.2.5 Fireball/boiling liquid expanding vapour explosion (122)7.2.6 Controlled burn (CB) (122)7.3 Occupational fire brigades (123)7.3.1 Overview (123)7.3.2 Options for installation fire response (123)7.4 Organisation of occupational fire brigades (128)7.5 Competency standards for installation emergency responders (ERs) (128)7.6 Fire response equipment (128)7.6.1 Fire-fighting equipment (128)7.6.2 Emergency responder (ER) personal protective equipment (133)7.6.3 Inspection and maintenance (135)7.6.4 Critical equipment and resources, vulnerability and siting (135)8 Maintaining FEHM policy (137)8.1 Introduction (137)8.2 Organisation of emergency procedures (137)8.3 Incident pre-planning (137)8.4 Recognition of hazards (138)8.5 Control of incidents (138)8.6 Training of personnel (139)8.7 Pre-fire plans (140)8.8 Scenario-specific emergency response plans (ERPs) (141)8.9 Maintaining incident response (142)8.9.1 Training and emergency response plans (ERPs) (142)8.9.2 Dynamic risk assessment (143)8.9.3 Fire systems integrity assurance (143)Annexes:Annex A Relevant UK and European legislation (145)A.1 Nature of legislation (145)A.2 Seveso II Directive and COMAH Regulations (145)A.3 Complementary regulations (147)A.4 Licensing and enforcement (151)Annex B Fire-related hazards of petroleum and its products (152)B.1 Introduction (152)B.2 Boiling points (or ranges), flash points and ignition temperatures ofpetroleum and its products (152)B.3 IP classification of petroleum and its products (153)B.4 Flammable limits of petroleum and its products (154)B.5 Typical substances with potential to form a large vapour cloud in event ofan atmospheric storage tank overfill (154)Annex C Typical installations/areas - Fire and explosion hazard management (detection and protection) (156)C.1 Introduction (156)C.2 Storage tanks (156)C.3 Process areas (159)C.4 LPG storage installations (160)C.5 LNG installations (160)C.6 Marine facilities (161)C.7 Buildings (162)C.8 Road tanker loading racks/gantries (165)C.9 Rail tanker loading racks/gantries (165)Annex D Typical application rates (166)D.1 Introduction (166)D.2 Cooling using water (166)D.3 Control of burning using water (167)D.4 Extinguishment using water (168)D.5 Storage tanks (168)D.6 Water supply (171)D.7 Foam application rates (171)D.8 Pool fire foam application (172)D.9 Tank fire foam application (173)D.10 Gaseous systems (177)D.11 Incident experience (178)Annex E Emergency response team competence (182)E.1 Introduction (182)E.2 Example ER competency mapping profile (186)Annex F Classification of fires (195)F.1 Introduction (195)F.2 Class A – Fires involving solid materials (195)F.3 Class B – Fires involving liquids or liquefiable solids (195)F.4 Class C – Fires involving gases (195)F.5 Class D – Fires involving metals (195)F.6 Class E – Fires involving electrical equipment (196)F.7 Class F – Fires involving cooking oils (196)F.8 Other classification schemes (196)Annex G Example installation-specific emergency response plan (ERP) (197)G.1 Introduction (197)G.2 Explanatory notes to text aspect of installation-specific ERP (197)G.3 Effects maps (201)G.4 Radiant heat examples (201)Annex H Glossaries of terms and abbreviations (202)H.1 Introduction (202)H.2 Terms (202)H.3 Abbreviations (214)Annex I References, Bibliography and further information (217)I.1 Introduction (217)I.2 Key publishers of FEHM publications (217)I.3 Codes of practice, design standards, specifications, guidance, etc (218)I.4 Industry organisations (231)I.5 Other safety organisations (234)I.6 Standards and approvals organisations (235)FOREWORDEI Fire precautions at petroleum refineries and bulk storage installations (EI 19) provides guidance on selecting, implementing and monitoring the continuing performance of installation-specific justified risk reduction measures – from prevention through detection, protection systems to mitigation measures – to reduce the risk from design event fires at installations that process and store crude oil, petroleum, intermediates and refined products.In line with recent legislation in the UK, Europe and elsewhere in the world, EI 19 does not set out prescriptive practices for adoption. Instead, it provides good practice guidance on options that may be appropriate to implement in order to satisfy pertinent risk drivers such as legislation, safety, environmental protection, asset protection, reputation and business continuity. The publication is based upon a framework of risk-based fire and explosion hazard management (FEHM) to achieve this, although it recognises that other approaches can be used. NB: Although the term ‘explosion’ is used within this definition it should also be realised that not every substance or hazardous circumstance will give rise to potential explosion conditions or create an explosion but for the purposes of this publication the term will be used throughout for consistency.The guidance in this publication should assist process safety engineers, safety advisors, designers, emergency planners or others with responsibility for fire and explosion hazard management to meet the pertinent requirements of the European Seveso II Directive, whether installations are classified lower or upper tier.This publication is based primarily on the UK and European legislative framework, publications and good practice. However, its guidance is internationally applicable provided it is read, interpreted and applied in conjunction with relevant national and local requirements.It can be used as a basis for establishing a consistent fire and explosion hazard management policy for companies with multi-installation operations within a country or across several countries.The third edition of EI 19 was commissioned by the Energy Institute’s Process Safety Committee, contracted to Resource Protection International and directed by a Steering Group. It supersedes the second edition, published in 2007. Whilst amendments have been made throughout, major changes have been made to:−Define key principles.−Enhance guidance on consideration of environmental impacts of fire-fighting and the need for environmental risk assessment; in particular, containment system capacityand firewater management.−Provide guidance on fire response for ethanol and related polar substance handling/ storage; in particular, pertinent foam types.−Enhance guidance on fire and explosion scenarios, consequences and modelling.−Provide guidance on control measures for vent fires.−Include guidance on potential scenarios, the role of congestion, incident consequences and examples of substances with a propensity to form large flammable vapour clouds.−Clarify basis for determining whether scenarios are credible by referencing their likelihood to risk tolerability criteria.−Enhance guidance on storage tank layout, secondary and tertiary containment systems requirements.−E nhance guidance on detection systems.−Define need for a policy on passive fire protection (PFP).−Provide guidance on PFP maintenance.−Update guidance on halon substitute gaseous extinguishing media.−Provide guidance on fire water systems.−Enhance guidance on foam systems for storage tanks.−Enhance guidance on option of controlled burn (CB).−Provide guidance on rapid intervention vehicles (RIVs) and mobile incident response units (MIRUs), and typical fire equipment on board.−Provide guidance on vulnerability and siting of critical equipment and resources.−Enhance guidance on control of incidents by defining command structure.−Enhance guidance on scenario-specific ERPs.−Enhance guidance on dynamic risk assessment (DRA).−Enhance guidance on typical FEHM (detection and protection) measures at various other installation areas.−Provide guidance on typical FEHM (detection and protection) measures for road and rail tanker loading racks/gantries.−Enhance guidance on water supply requirements.−Revise minimum foam solution application rates and consider foam application to prevent boilover.−Define requirements for emergency responder (ER) competence.The 2nd edition of this publication was being finalised at the time of the Buncefield bulk storage installation major accident in December 2005 and since then there have been changes in the regulatory approach to fire precautions at such installations, encompassing fire prevention measures, incident detection techniques, fire protection, fire-fighting and response and emergency planning requirements. Some of these relate to process considerations, which are not specifically covered in detail in this 3rd edition of this publication but may be relevant for overall FEHM – wherever possible these are addressed. In addition to changes in the regulatory approach there have been new developments in hardware, understanding of potential to cause vapour cloud explosions (VCEs), changes in thinking in issues such as human and organisational factors, and new approaches to fire response. It is not within the scope of this publication to describe all of these and as such, users may wish to consult the relevant Buncefield investigation reports for more detail. However, where appropriate, and where they enhance the overall guidance in this publication, such measures are given credit. It should also be noted that whilst a great deal of focus has been placed on this particular incident in recent years, the circumstances that led up to it, and the recommended prevention and mitigation measures, this publication is also relevant to other types of fire incident types and scenarios. Consequently, some of the guidance contained herein may not always be relevant to the particular type of incident mentioned.The information contained in this publication is provided for general information purposes only. Whilst the Energy Institute and the contributors have applied reasonable care in developing this publication, no representations or warranties, express or implied, are made by the Energy Institute or any of the contributors concerning the applicability, suitability, accuracy or completeness of the information contained herein and the Energy Institute and the contributors accept no responsibility whatsoever for the use of this information. Neither the Energy Institute nor any of the contributors shall be liable in any way for any liability, loss, cost or damage incurred as a result of the receipt or use of the information contained herein. This publication may be further reviewed from time to time. It would be of considerable assistance in any future revision if users would send comments or suggestions for improvement to:The Technical Department, Energy Institute61 New Cavendish StreetLONDON, W1G 7ARe: technical@KEY TECHNICAL CHANGESThis section sets out in a generalised form, the key technical changes between the 2nd and 3rd editions of EI 19 (EI Fire precautions at petroleum refineries and bulk storage installations).The key technical changes are to:−Define key principles.−Enhance guidance on consideration of environmental impacts of fire-fighting and the need for environmental risk assessment. Section 1.7.3.−Provide guidance on the required capacity (e.g. via secondary and tertiary containment) to hold safely the anticipated or foreseeable volume of hazardous liquids, includingfirewater. Section 1.7.3.−Enhance guidance on firewater management, including the option of recirculation.Sections 1.7.3, 2.5.5, 4.8.3, 4.8.6, 6.5.2, 7.2.6, 8.7, and Annexes D.6 and D.11.−Provide guidance on fire response for ethanol and related polar substance handling/ storage; in particular, pertinent foam types. Sections 2.2 and 6.4.3.−Refer to special hazards in storage and handling of petroleum additives, such as diesel cetane improvers. Section 2.2.−Enhance guidance on fire and explosion scenarios, consequences and modelling with reference to incident experience (e.g. from large atmospheric storage tank fires(LASTFIRE) project); e.g. VCEs, bund fires, boilover. Sections 2.5.4, 2.5.5 and 2.5.8.−Provide guidance on control measures for vent fires. Section 2.5.5.1.−Include guidance on potential scenarios, their likelihood in areas with a lack of congestion, incident consequences and examples of substances with a propensity toform large flammable vapour clouds. Section 2.5.8 and annex B.5.−Clarify conditions under which flash fires might occur. Section 2.5.9.−Revise guidance on overpressure consequences. Section 2.6.3.−Enhance guidance on fire and explosion modelling. Section 2.7.1.−Clarify basis for determining whether scenarios are credible by referencing their likelihood to risk tolerability criteria. Section 3.2.3.−Consider merits of using cost benefit analysis (CBA) in design/credible scenario selection. Section 3.2.3.−Clarify general principles in controlling flammable substances. Section 4.2.1.−Provide guidance on isolation of sources of ignition. Section 4.4.1.−Clarify circumstances when it might be appropriate to use a smaller than usual separation distance between tanks and other items of plant when designing a facility.Section 4.8.1.−Enhance guidance on storage tank layout/secondary containment. Section 4.8.3.−Clarify intent of bund volume compared to storage tank operating capacity.Section 4.8.3.−Provide guidance on benefits/disbenefits of using double or full containment-type tanks in reducing the consequences of a loss of containment. Section 4.8.3.−Provide guidance on tertiary containment systems, and their capacity rating.Section 4.8.6.−Refer to need to consider facility topography and the potential path of vapour and liquid releases when locating fire protection and other safety critical equipment.Section 4.8.7.−Provide guidance on location of flanges/pipework, and the vulnerability of long bolt flanges. Section 4.8.8.−Enhance guidance on detection systems (e.g. flammable gas, toxic gas, liquid and fire detection, gas imaging and their application) to assist implementation by capturing the experience gained and equipment developments. Section 5.−Refer to safety integrity of detection control systems. Section 5.3.−Define need for a policy on PFP. Section 6.2.2.−Provide guidance on maintenance of PFP. Section 6.2.3.−Provide guidance on water quality and type for use as firewater. Section 6.4.2.−Update guidance on gaseous extinguishing media that have reduced impacts to air compared to halons. Section 6.4.5.−Provide guidance on fire water systems and winterisation. Section 6.5.2.−Enhance guidance on foam systems for storage tanks. Section 6.5.7.−Provide guidance on the need for assurance of ongoing integrity of enclosures where gaseous extinguishing systems are used. Section 6.5.9.−Provide guidance on the appropriateness of using foam to blanket vapours from LNG etc. Section 7.2.1.4.−Clarify guidance on when to evacuate areas during emergency response to potential BLEVE situations. Section 7.2.5.−Provide guidance on availability of operations/maintenance personnel to serve as auxiliary ERs when installation-wide events occur. Section 7.3.3.2.−Enhance guidance on option of CB, including its development as a design philosophy and operational strategy. Section 7.2.6.−Provide guidance on RIVs and MIRUs, and typical fire equipment on board.Section 7.6.1.−Provide guidance on vulnerability and siting of critical equipment and resources.Section 7.6.4.−Enhance guidance on control of incidents by defining command structure.Section 8.5.−Enhance guidance on scenario-specific ERPs. Section 8.7.−Enhance guidance on DRA. Section 8.9.2.−Provide listing of environmental protection regulations. Annex A.3 (viii).−Enhance guidance on typical FEHM (detection and protection) measures for storage tanks, process areas, LNG installations, marine beths and jetties, etc. Annex C.−Provide guidance on typical FEHM (detection and protection) measures for road and rail tanker loading racks/gantries. Annex C.8 and annex C.9.−Clarify applicability of insulation in providing fire protection. Annex D.2(ii).−Provide guidance on cooling atmospheric tanks impinged by flame. Annex D.5(iii). −Enhance guidance on water supply requirements. Annex D.6.−Clarify context of scenario for foam/cooling water example. Annex D.6, Box D.1−Revise minimum foam solution application rates and consider foam application to prevent boilover. Annexes D.8 and D.9.−Define requirements for ER competence. Annex E.1.−Update listing of references and bibliography (e.g. codes of practice, design standards, specifications, guidance, etc.). Annex I.ACKNOWLEDGEMENTSThe 3rd edition of EI Fire precautions at petroleum refineries and bulk storage installations (EI 19) was commissioned by the Energy Institute’s Process Safety Committee. The project was contracted to Resource Protection International, whose contributors were Paul Watkins, Dr Niall Ramsden and Mark Plastow. The project was directed by a Steering Group that comprised:David Athersmith Consultant (member, Distribution and Marketing Safety Committee)James Coull Total UK Limited (member, Process Safety Committee)Ian Herbert ABB Global ConsultancyGerry Johnson Fulcrum Consultants (member, Joint Oil and Industry Fire Forum)Evert Jonker Shell Global Solutions International DownstreamMarc McBride (Chairperson) Centrica (Chair, Process Safety Committee)Dr Mike Nicholas Environment AgencyKen Palmer Consultant (member, Distribution and Marketing Safety Committee)Mark Samuels Essex Fire & Rescue (pp Chief Fire Officers Association)Dr Mark Scanlon (Secretary) Energy Institute (Secretary, Process Safety Committee)Stuart Warburton Essar Oil UK Ltd. Stanlow RefineryKevin Westwood BP (Secretary, Joint Oil and Industry Fire Forum) The Institute wishes to record its appreciation of the work carried out by them in providing technical direction to the project.Significant comments on the draft of this publication were received during its technical reviews from:David Athersmith ConsultantJames Coull Total UK LimitedMartin Hassett WorleyParsonsJohn Henderson and others British Chemical Engineering Contractors Association (BCECA)Ian Herbert ABB Global ConsultancyDavid Hughes ValeroGerry Johnson Fulcrum ConsultantsEvert Jonker Shell Global Solutions International DownstreamMarc McBride CentricaBruce McGlashan Environment AgencyDr Mike Nicholas Environment AgencyKen Palmer ConsultantRoger Roue The Society of International Gas T anker and T erminal Operators (SIGTTO)Stuart Warburton Essar Oil UK Ltd. Stanlow RefineryKevin Westwood BPSuch comments have been considered and, where appropriate, incorporated. The Institute wishes to record its appreciation of the work carried out by them and others who participated during the technical review.Project co-ordination and technical editing was carried out by Dr Mark Scanlon (Energy Institute).。
International-Human-Resource-Management国际人力资源管理 (1

Corporations
• HRM typically refers to those activities undertaken by an organisation to utilize human resources effectively,
Boxhall and Purcell give a broader definition as ‘human resources management includes the firm’s work system and its employment practices. It embraces both individual and collective aspects of people management’
• HR planning • Staffing (recruitment, selection, placement) • Performance management • Training and development • Compensation (remuneration) and benefits • Industrial relations
International Organisational structure
Chief executive/Headquarters
Production
Marketing
Finance
Personnel
International division
International geographic structure
What changes when HRM goes international?
实验伦理英文作文

实验伦理英文作文Experiment Ethics。
Experiment ethics is an essential aspect of scientific research that aims to ensure the safety, well-being, and dignity of human and animal subjects involved in the study. It is the responsibility of researchers to conduct their experiments in an ethical and responsible manner that upholds the principles of integrity, honesty, and respect.The use of human subjects in research requires informed consent, which means that the participants are fully aware of the purpose, procedures, and potential risks of the study. Researchers must ensure that the participants are not coerced or misled into participating in the study and that their privacy and confidentiality are protected.Animal research also requires ethical considerations to minimize pain and suffering and ensure responsible care and use of animals. Researchers must follow strict guidelinesand regulations to ensure that the animals are treated humanely and that their welfare is a top priority.It is also important for researchers to consider the potential impact of their research on society and the environment. They must ensure that their experiments are not harmful to the environment or have negative consequences for society.Overall, experiment ethics is crucial for maintaining the integrity of scientific research and ensuring that the rights and welfare of human and animal subjects are protected. Researchers must follow ethical guidelines and regulations to ensure that their research is conducted in a responsible and respectful manner.。
APQC-美国生产力标杆协会-业务流程管理(BPM)-2011最新版本框架全文

流程改进的框架经验表明,基准测试推动显着改进的潜力完全在于进行开箱即用的比较并寻找通常在行业内范式中找不到的见解。
为了实现这一有益的基准测试,APQC流程分类框架sm(PCF)作为一种高级,行业中立的企业流程模型,允许组织从跨行业的角度来看待他们的业务流程。
这个跨行业框架经历了超过15年的全球数千个组织的创造性使用。
PCF为APQC的开放标准基准sm性能指标数据库奠定了基础,这是世界上同类数据中最大的,以及全球行业领导者咨询委员会的工作。
随着数据库进一步制定定义,流程和措施,PCF将继续得到加强。
PCF,相关措施和定义可免费下载/osb。
还提供个人评估的在线基准门户。
为了获得行业内基准测试所固有的价值,APQC网站上也提供了行业特定框架。
因此,组织可以选择与特定流程改进需求最相关的框架,无论是基准测试,业务流程管理/重新设计还是内容管理。
历史流程分类框架最初被设想为业务流程的分类和APQC成员组织可以通过其共同语言对其流程进行基准测试的共同语言。
最初的设计涉及APQC和80多个组织,他们对推动美国和全球基准测试的使用非常感兴趣。
自1992年成立以来,PCF已对其大部分内容进行了更新。
这些更新使框架与组织在全球开展业务的方式保持同步。
2008年,APQC和IBM共同致力于加强跨行业的PCF,并开发了许多行业特定的流程框架。
APQC感谢各个成员组织和个人成员的贡献,他们为开发此版本的PCF以及之前的每个版本贡献了时间,内容和专业知识。
这些贡献和建议对于使框架保持最新并与全世界的企业相关至关重要。
过程配置fr amework sm运作流程1.0 > > > 发展愿景和战略2.0开发和管理产品和服务> > > 3.0市场和销售产品与服务> > > 4.0提供产品和服务> > > 5.0管理客户服务管理和支持服务7.0管理信息技术8.0管理财务资源12.0管理知识,改进和变革11.0管理外部关系10.0管理环境健康与安全(EHS)9.0获取,构建和管理财产6.0开发和管理人力资本期待APQC流程分类框架是一个不断发展的模型,APQC将继续不断加强和改进。
信息管理与信息系统专业英语 伦理道德作文

信息管理与信息系统专业英语伦理道德作文全文共3篇示例,供读者参考篇1Ethics and Morality in Information Management and Information SystemsIntroductionIn the rapidly evolving field of information management and information systems, ethical and moral considerations have become increasingly important. With the rise of big data, artificial intelligence, and cybersecurity threats, professionals in this field are faced with unique ethical dilemmas that require careful navigation. This essay will explore the ethical and moral implications of information management and information systems, the importance of ethical decision-making, and strategies for ethical behavior in this field.Ethical and Moral ImplicationsEthical issues in information management and information systems can range from data privacy and security breaches to the ethical use of artificial intelligence and automation. For example, the collection and use of personal data by companiesand organizations have raised concerns about privacy and consent. The development and deployment of AI systems have also raised ethical questions about bias, transparency, and accountability. Furthermore, the growing threat of cyber attacks and data breaches has highlighted the importance of ethical behavior in information security and data protection.The Importance of Ethical Decision-MakingEthical decision-making is crucial in information management and information systems to ensure the trust and confidence of stakeholders. Ethical behavior not only protects individuals' rights and interests but also upholds the reputation and credibility of professionals in this field. By adhering to ethical principles and codes of conduct, professionals can minimize the risk of legal liabilities, reputational damage, and other negative consequences. Moreover, ethical decision-making promotes fairness, justice, and social responsibility in the use of information and technology.Strategies for Ethical BehaviorTo promote ethical behavior in information management and information systems, professionals can adopt several strategies. Firstly, they can familiarize themselves with ethical principles, codes of conduct, and industry standards in this field.By understanding the ethical implications of their work, professionals can make informed decisions and take responsible actions. Secondly, professionals can assess the ethical impact of their projects, initiatives, and decisions on individuals, organizations, and society at large. By incorporating ethical considerations into their decision-making process, professionals can mitigate potential risks and harm. Lastly, professionals can seek guidance, support, and feedback from ethical mentors, colleagues, and experts in this field. Through collaboration, reflection, and dialog, professionals can enhance their ethical awareness, competence, and integrity.ConclusionIn conclusion, ethics and morality play a crucial role in information management and information systems. By addressing ethical issues, dilemmas, and challenges in this field, professionals can foster trust, transparency, and accountability in their work. Through ethical decision-making, professionals can uphold the rights, interests, and values of individuals and organizations. By promoting ethical behavior, professionals can contribute to the ethical development and use of information and technology in society.References:- More, D. (2020). Ethical challenges for information management professionals in a digital world. Journal of Information Ethics, 29(2), 148-165.- Johnson, D. G. (2018). Ethics in an age of information and communication technology. Journal of Business Ethics, 147(4), 703-707.- Floridi, L. (2019). Five ethical principles for technological maturity in the 21st century. Information and Management, 56(2), 189-199.篇2Information management and information systems play a crucial role in today's digital age. With the constant advancements in technology and the increasing reliance on data, professionals in this field are faced with numerous ethical and moral dilemmas. It is essential for individuals in the information management and information systems field to adhere to a strict code of ethics to ensure the responsible use and handling of data.One of the key ethical issues that professionals in this field face is privacy and confidentiality. In this digital age, there is a constant threat to the privacy of individuals' data. It is importantfor professionals in the field to ensure that they handle data in a secure and confidential manner. They must also be transparent with their clients about how their data is being used and stored. Violating privacy and confidentiality can have serious consequences, including legal repercussions and damage to the organization's reputation.Another ethical issue that professionals in information management and information systems face is the accuracy and reliability of data. It is essential for professionals to ensure that the data they collect and analyze is accurate and reliable. Making decisions based on faulty or biased data can have serious implications, not only for the organization but also for society as a whole. Professionals must also be transparent about how data is collected and analyzed to ensure that there is no manipulation or misrepresentation of information.In addition to privacy and accuracy, professionals in this field must also consider the implications of their work on society. The data that is collected and analyzed can have far-reaching consequences, and professionals must consider the potential impact of their work on individuals and communities. They must ensure that their work promotes social justice and equality and does not contribute to discrimination or harm.Furthermore, professionals in information management and information systems must also consider the environmental impact of their work. The increasing reliance on technology and data centers has a significant carbon footprint, and professionals must take steps to minimize their impact on the environment. This includes using energy-efficient technology, minimizing electronic waste, and promoting sustainable practices in the field.In conclusion, ethical considerations are essential in the field of information management and information systems. Professionals must adhere to a strict code of ethics to ensure the responsible use and handling of data. By prioritizing privacy and confidentiality, accuracy and reliability, social responsibility, and environmental sustainability, professionals can ensure that their work has a positive impact on society and the world as a whole. It is essential for individuals in this field to stay informed about current ethical issues and to continuously reflect on their practices to uphold the highest standards of ethics and morality in their work.篇3Ethics and morals play a crucial role in the field of information management and information systems. Asprofessionals in this field, we are responsible for handling and managing sensitive information in a trustworthy and ethical manner. This requires us to adhere to certain ethical principles and guidelines to ensure the security and integrity of the information we deal with.One of the key ethical considerations in information management is privacy. As information managers, we are entrusted with personal and confidential information from individuals and organizations. It is our ethical responsibility to protect this information from unauthorized access or disclosure. This means implementing secure data storage and transmission systems, as well as following strict privacy policies and procedures. We must also respect the rights of individuals to control their own personal information and only use it for the purposes for which it was intended.Another important ethical consideration in information management is transparency. We must be honest and transparent in our dealings with clients and stakeholders, providing them with accurate and truthful information about how their data is being collected, stored, and used. This includes being upfront about any potential risks or limitations associatedwith the systems and technologies we use, as well as informing them of their rights and options regarding their data.Integrity is also a key ethical principle in information management. We must ensure that the information we manage is accurate, reliable, and up-to-date. This means following strict quality control measures, verifying the accuracy of data before processing it, and taking steps to correct any errors or discrepancies that may arise. We must also ensure that the information we manage is used in an ethical and responsible manner, and that it is not manipulated or misused for personal gain or unethical purposes.In addition to these ethical considerations, information management professionals must also adhere to a code of conduct that governs their behavior and responsibilities. This code of conduct outlines the ethical principles and standards that professionals in the field should follow, including honesty, integrity, respect for privacy, and transparency. Violating this code of conduct can result in disciplinary action, including loss of professional certification or even legal consequences.Overall, ethics and morals are essential components of information management and information systems. By upholding ethical standards and principles, professionals in thisfield can build trust with their clients and stakeholders, protect sensitive information from unauthorized access, and ensure the integrity and reliability of the information they manage. Ultimately, ethical behavior in information management is not just a professional obligation – it is a moral imperative that reflects our commitment to doing the right thing and upholding the values of honesty, integrity, and respect.。
创新科技署企业支援计划(ESS)短片 - 创科署说明书

Enterprise Support Scheme (ESS) videoThe “Enterprise Support Scheme” or “ESS” of Innovation and Technology Commission provides funding support to local companies to conduct in-house research and development, and encourages the private sector to invest in research and development with a view to promoting innovation and technological development and creating more technology-related job opportunities.If your company is incorporated in Hong Kong, holds a current business registration certificate, and neither a government subvented organization nor a subsidiary of any government subvented organization, you can apply for the ESS. Every approved project receives up to a maximum of HK$10 million in funding which is provided on a dollar-for-dollar matching basis. Not only does the company own the intellectual property rights from the project, after completion of the project, the Government would not recoup its contribution.Tam Chi Ming, Chief Executive Officer of Vitelic Technology (International) Ltd. said, “Most of our team have over 30 years of experience in integrated circuit (IC) production. They have accumulated skills in IC design and crafting, as well as the technology of IC equipment. It is very competitive in the semiconductor market. We have to drive our development faster than other companies in order to get a share in the market. So, we applied for the ESS. Of course, we hope to have more capital and speed up the research and development progress. At the same time, through the ESS, we can strengthen our capabilities in spinning off our business and financing in the future.”Elena Chan, Senior Project Manager of Vitelic Technology (International) Ltd. said, “The project that we received funding support is about the research and development of a plasma etching machine. The plasma etching machine is commonly used in wafer production. The assembled integrated circuit being produced is widely applied in daily-life electronic appliances, mobile phones and computers’ CPUs. Our etching machine is developed with our proprietary gas distribution plate and cooling system which enhance the etching performance. What’s more, whether the required specifications is for a 4-inch and 6-inch wafer commonly used for academic research or a 8-inch wafer for industry mass production, our etching machine is compatible with the specifications, meeting the demands of different users. Due to the high production cost of an etching machine, the payback period is longer. Success in applying for the ESS can reduce our investment risk and enables us to select and purchase more parts and equipment with better quality, increasing the project success rate. Our goal for the first phase is toprovide etching machines for the academic institutions in the Greater Bay Area and prepare for the research and development of commercial etching machines.”Tam Chi Ming, Chief Executive Officer of Vitelic Technology (International) Ltd. said, “As early as in 2016, we had started a project via the support of the ESS. In the project, we used silicon carbide, a third generation semiconducting material to produce high-voltage power devices. This product makes power products more efficient, smaller and lighter. Through this product, we hope to create better conditions for the deployment of green energy technology. From as large as high speed rails to as small as energy saving home appliances, the device could be used. This product has now obtained more than 20 patents from Europe and the U.S.A.The ESS allows us to fully own the intellectual property rights from the project which become our valuable assets and provides funding support for the filing of patents. Besides, projects supported by the ESS are of outstanding quality and the results of the projects are highly recognised in the industry. So, the ESS has helped boosting my clients’ confidence in our product. We have successfully commercialised the product and it is widely used in the electric vehicles currently available in the market, new generation power stations, solar power systems and data centres.It is not easy to carry out research and development projects in Hong Kong but with the support from the ESS, our company has successfully invented a new product. And with this new product. we have also attracted investors to co-invest in setting up a start-up with us. This start-up has now become one of the well-known semiconductor component suppliers in China. Meanwhile, our company has nurtured more local talents for the semiconductor industry. Therefore, applying for the ESS has indeed brought us more opportunities, moved us to go further and grow faster.”The “Enterprise Support Scheme” invites applications all year round. Simply follow the application guide. fill in the online form and submit the required documents. To learn more, please visit our website: https://.hk/l-eng/ess.asp.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
ANNEX A: ETHICS REVIEW FORM – STAFF & RESEARCH POSTGRADUATES
Name: _________________________________________________________________________________________ Division/Institute/Centre: ________________________________________________________________________ Project Title/Research Being Undertaken: __________________________________________________________ ________________________________________________________________________________________________ Names of Other Staff involved (if appropriate): _____________________________________________________
________________________________________________________________________________________________
If your research includes any of the above aspects, you will need to describe more fully how you plan to deal with the ethics issues raised by your research. Your proposal will be subject to a full ethics review. In such cases, the following information is required to be submitted (along with this form) to the Ethics Committee for approval:
▪ A copy of your research proposal
▪ A summary statement, highlighting the ethical aspects and how they will be addressed
Please note that it is your responsibility to follow the University’s Code of Practice on Ethical Standards and any relevant academic or professional guidelines in the conduct of your study. This includes providing appropriate information sheets and consent forms, and ensuring confidentiality in the storage and use of data. Any significant change in the question, design or conduct over the course of the research should be notified to the School’s Research Ethics Committee Secretary and may require a new application for ethics approval. Signed: ____________________________________ Date: _____________________________
FORM REVISED NOVEMBER 2011。
