weighted composition operator from Hardy to Zygmund type spaces
HEAVY EQUIPMENT OPERATOR

SA 9663 (07/08)MSP-98 – Attachment ESAUDI ARAMCO/CONTRACTOR MEDICAL EXAMINATION GI 7.025 – Attachment #1FOR HEAVY EQUIPMENT OPERATORSPHYSICIAN’S EXAMINATION FORM**(UPON COMPLETING FORM, PHYSICIAN SHALL SIGN IN THE BOX AT THE BOTTOMAND VERIFY SIGNATURE WITH HIS PERSONAL STAMP AND HIS FACILITY STAMP)SAUDI ARAMCO BADGE #NAMEEMPLOYEEPRINT)(PLEASECOMPANY NAME DATEPRINT)(PLEASEABNORMAL VISION NORMAL1 – The vision shall not be less than 20/40 in each eye separately,with or without the use of eyeglasses or contact lenses.2 – Color vision and visual fields should be normal.3 – Diplopia is UNACCEPTABLE.HEARING NORMAL ABNORMAL4 – Hearing shall be adequate for normal speech communicationwith or without a hearing aid.POTENTIAL SUDDEN INCAPACITY NORMAL ABNORMAL5 – Any condition likely to cause sudden incapacity isUNACCEPTABLE. This includes, but is not limited to, ahistory of seizures after the age of 5 years, vestibular disorders, heartdisease, and diabetes mellitus.MISCELLANEOUS – The following must be considered: NORMAL ABNORMAL6 – Impairment of musculo-skeletal capacities.7 – Coordination and progressive or disabling neurologicaldisease.8 – A history of psychiatric illness or emotional instability.9 - Substance abuse.10 – Medication and its side effects.FIT TO WORK? YES NOREMARKS:PHYSICIAN’S NAME (PLEASE PRINT) PHYSICIAN’S SIGNATUREFACILITY NAME (PLEASE PRINT) FACILITY LOCATION (CITY)FACILITY TELEPHONE #SA 9647 (07/08) Saudi Aramco GI 7.025 Attachment #2SAUDI ARAMCO/CONTRACTORREQUEST FOR HEAVY EQUIPMENT OPERATORCERTIFICATION TEST*MAIL TO SUPERVISOR FOR LOCATION LISTED AT BOTTOM OF PAGECheck appropriate box: SAUDI ARAMCO CONTRACTORCheck appropriate box: ONSHORE OFFSHORESAUDI ARAMCO INFORMATIONUSER Dept.: Org. Code: Telephone #:CONTRACTOR INFORMATIONCompany Name: Company Contact Name:Title:Mailing Address JobRoom or Box #: Telephone #:#:FaxCity:City Code: Saudi Aramco Contract #:Date:Contract OPERATOR INFORMATIONOperator Name: Saudi Aramco ID#: Expiration Date:Saudi Arab Government (SAG) License (if required) Expiration Date:ATTACH COPY OF THE FOLLOWING DOCUMENTS. PLACE CHECK IN BOX TO VERIFY.Saudi Aramco Sponsoring Letter (For Contractors Only)Saudi Aramco ID (if required)SAG Public Driver’s License or Heavy SAG License (if required) with Specific Equipment Stamp 9663“Physician’s Examination Form” – Completed, Signed, and StampedSATwo Recent Photographs for Each Certification ApplicationCrane Manufacturer & Model #: Crane Capacity:ATTACHMENTS EQUIPMENT EQUIPMENT BOOMFly Jib Backhoe Loader – Skid (Bobcat)Luffing Jib Boom Truck – Articulating Loader - WheelPower Pin Fly Boom Truck - Telescoping Manlift - HydraulicSuper Lift Bulldozer Manlift - ScissorSwingaway - Hydraulic Crane - Mobile Manlift - TelescopingSwingaway – Manual Crane - Pedestal Sideboom - PipelayerNo Attachments Crane - Tower Straddle CarrierForklift TelehandlerGradall Tractor-ScraperGrader TraxcavatorSPECIALIZED CRANE OPERATIONS (Written Test Only)Manbasket Operations Pick & Carry Operations Tandem Crane Lifts Requesting Superintendent (Print Name):Signature: Date:Area: Supervisor, CAITD-Driver/HEOPTU, P.O. Box 41772, Riyadh 11531 KSA Phone 01-285-2190/2188, Fax *Central01-285-2122; *Eastern Area: Supervisor, EAITD-Driver/HEOPTU, P.O. Box 89, Dhahran 31311 KSA, Phone 03-876-1857/4501, Fax 03-876-4430; *Western Area: Supervisor, WAITD-Driver/HEOPTU, P.O. Box 5250, Jeddah 21422 KSA, Phone 02-427-4214/4147, Fax 02-427-4202。
惠普彩色激光打印机 Pro M454 和惠普彩色激光多功能一体机 Pro M479 维修手册说明书
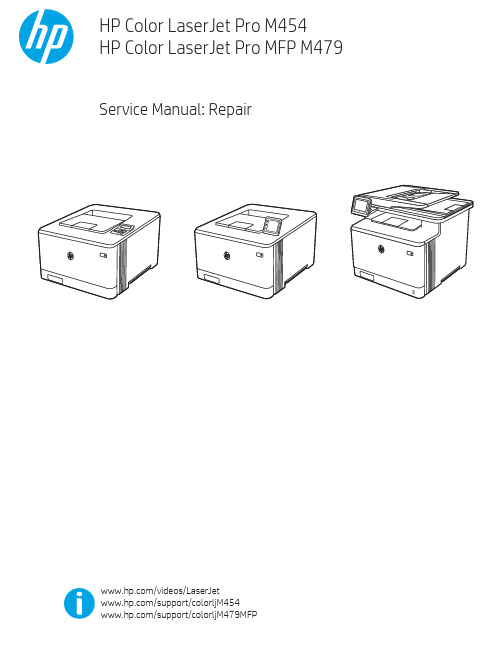
Table -1 Revision history Revision number 1
Revision date 6/2019
Revision notes HP LaserJet Pro M454 HP LaserJet Pro MFP M479 Repair manual initial release
Additional service and support for HP internal personnel HP internal personnel, go to one of the following Web-based Interactive Search Engine (WISE) sites: Americas (AMS) – https:///wise/home/ams-enWISE - English – https:///wise/home/ams-esWISE - Spanish – https:///wise/home/ams-ptWISE - Portuguese – https:///wise/home/ams-frWISE - French Asia Pacific / Japan (APJ) ○ https:///wise/home/apj-enWISE - English ○ https:///wise/home/apj-jaWISE - Japanese ○ https:///wise/home/apj-koWISE - Korean ○ https:///wise/home/apj-zh-HansWISE - Chinese (simplified)
Find information about the following topics ● Service manuals ● Service advisories ● Up-to-date control panel message (CPMD) troubleshooting ● Install and configure ● Printer specifications ● Solutions for printer issues and emerging issues ● Remove and replace part instructions and videos ● Warranty and regulatory information
海尔电子洗衣机产品说明书

Section 6: Parts DataDC50X264310131211216547Cabinet GroupKey Part Number Description Quantity * 9960-285-008Door Assy., Loading Complete-Wht (2)* 9960-285-011Door Assy., Loading Complete-SS (2)* 9960-285-007Door Assy., Loading Complete-Chrome/BLK/SS (2)1 9960-284-002Door Assy., Loading-SS(ring only) (2)1 9960-284-004Door Assy., Loading-Chrome(ring only) (2)2 9982-353-002Plate Assy., Hinge (Wht) No Pin (2)2 9982-353-001Plate Assy., Hinge (SS) No Pin (2)* 9545-012-015Screw, Hinge to Door (8)* 8640-413-002Nut, Hinge to Door (8)3 9212-002-004Glass, Door (2)4 9206-413-002Gasket, Glass Black (2)* 9548-117-000Support, Door Glass (2)5 9206-420-005Gasket, Outer Rim Black (2)6 9244-082-001Handle, Loading Door (2)* 9545-018-017Screw, Handle 1/4-20 x 3/8 (4)* 9531-033-003Stud, Door Catch (2)* 8640-413-001Nut, Hex (2)* 8640-413-003Nut, Acorn (2)* 9086-015-002Catch, Loading Door (2)* 8638-190-009Pop Rivet for mtg. catch (4)* 8641-582-006Lockwasher (4)* 8640-399-001Spring Nut (6)7 9989-521-003Panel Assy., Front- Lower (Wht) (1)7 9989-521-001Panel Assy., Front- Lower (SS) (1)8 9989-517-003Panel Assy., Front- Upper (Wht) (1)8 9989-517-001Panel Assy., Front- Upper (SS) (1)* 9277-054-001Insulation Front Panel, half moon (top) (2)* 9277-054-002Insulation Front Panel, half moon (bottom) (2)9 9545-008-014Screw, FLHDCR, 10B x 1 (14) (6)* 8641-585-001 Lockwasher* 8640-399-001Nut, Spring (12)10 9544-069-002Strap, Hinge (Wht) (2)10 9544-069-005Strap, Hinge (SS/Black) (2)* 9545-012-028Screw, Hinge to Panel (8)11 9545-052-001Screw, Door to Hinge Strap (Special Black Type) (2)12 8641-436-003Washer, Fiber (2)13 9021-041-001Acceptor, Coin (1)* 9486-149-001Retainer, Coin Acceptor (2)14 9545-053-002Screw (4)* 9801-099-001Switch, Optical (1)Cabinet Group ContinuedKey Part Number Description Quantity15 9994-032-001Escutcheon, Upper (1)16 9435-039-002Trim, Overlay-Upper Blue (1)16 9435-039-001 Trim, Overlay-Upper Black (1)17 9994-033-001Escutcheon, Lower (1)18 9435-023-001Trim, Overlay-Lower Blue (1)18 9435-031-001Trim, Overlay-Lower Black (1)* 9545-020-009Screw (20)19 9412-167-002Nameplate Stack Dryer Express Blue (1)19 9412-167-001Nameplate Stack Dryer Express Black (1)20 9866-005-001Lint Drawer Assembly Blue (2)20 9866-005-004Lint Drawer Assembly Black (2)21 9435-024-001Overlay Trim, Lint Drwr-Blue (1)21 9435-032-001Overlay Trim, Lint Drwr-Black (1)* 9532-074-003Felt Seal ( back of lint screen assembly ) (2)* 9805-033-002Lint Screen Assembly ONLY (no front) (2)* 9555-057-008Replaceable Lint Screen Only (2)22 8650-012-004Lock and Key, Lint Drawer (2)* 6292-006-010Key 6101 only (2)* 9095-043-001Cam, Lock (2)* 9545-008-001Lint Screen Strap Hold Down Screws 10Bx 1/4 (32)23 9857-198-001Controls Assy, Blue (1)23 9857-198-003Controls Assy, Black (1)* 9627-869-001Harness, Electronic Control (1)24 8650-012-003Lock and Key, Control (1)* 9095-041-001Cam, Lock (1)* 6292-006-007Key only 6324 (1)* 9627-855-003Harness, Heat Sensor (1)* 8640-276-002Wire Nut Connector Grey (4)25 9501-004-003Sensor Temp Control (2)26 9501-008-001Bracket for Heat Sensor Mounting (Under Basket) w/ sensor..2* 9545-045-005Screw, Round Head (Mounts sensor; phillips head) (2)* 9209-037-002Gromm.et, 3/16 ID (2)* 8544-006-001Leg, Leveling 1/2” (4)* 9074-320-001 Cover, Cabinet (Top) (1)* 9277-041-017 Insulation Cabinet Cover (1)* 9732-276-001Kit for Dryers without Neutral and using 208-240 volt (1)* 9732-102-013LP Kit for 50Lb Stk Dryers (1)* 9732-243-001Stack Dryer Trunion Puller (1)* 9544-041-002 Strap - Bead Tie (1)27 9942-038-005 Vault, Coin Box (1)* 9545-008-024 Screws, Mounting-Coin Vault (2)28 9897-099-002 Coin Box Assy, Large Blue (1)28 9807-099-004 Coin Box Assy, Large Black (1)191526252792531089Control Parts GroupKey Part Number Description Quantity * 9857-198-001Controls Assy, Electronic Mounted With Membrane Switch, BLU (1)* 9857-198-003Controls Assy, Electronic Mounted With Membrane Switch, BLK (1)1 9826-008-001 Trough Assembly (1)2 9032-062-002 Button-Push, Control, Blue (2)2 9032-062-001 Button-Push, Control, Black (2)3 9538-166-011Spacer-Metal, 4mm (4)4 9486-158-001 Retainer-Push Button (2)5 8640-424-002Nut-Hex, Elastic stop, #4-40 (4)6 8652-130-038Terminal-Grounding clip (1)7 9534-365-001Spring-Flat, Control (1)8 9545-008-001Screw-Hex, #10B x 1/4 (2)9 9545-044-010 Screw-Hex, #10B x 1/4 (10)9 8641-582-005Washer-External tooth, #6 (10)10 9435-038-001Overlay-Control, Coin, Black (1)10 9435-038-002Overlay-Control, Coin, Blue (1)11 9021-041-001Acceptor-Coin, Optical (1)* 9486-149-001Retainer, Coin Acceptor (1)12 9545-053-002Screw (4)* 9801-099-001 Optical Sensor, Replacement (1)Note: Jumpers required if using 1.5 Control on Older Machines (P9 Connection)* 8220-155-001 Wire Assy, Jumper, 30Lb Stack Coin (1)* 8220-155-002 Wire Assy, Jumper, 50Lb Stack Coin (1)Door Switch GroupPart NumberDescription Quantity9539-487-001Door Switches (2)Hinge Plate Cover1 9074-340-002 Cover-Hinge, Black .....................................................................22 8636-008-010 Screw-TRHDCR, 10B x 3/8, Black.. (4)12Bearing Housing GroupKey Part Number Description Quantity J1 9241-189-002 Housing, Bearing (2)J2 9036-159-003Bearing, Ball Rear..................................................................... .2 * 9538-183-001 Spacer, Bearing (2)* 9036-159-001Bearing, Ball Front .................................................................... .2 J5 9545-017-017Bolt, 1/2 x 3/4 . (8)J7 8640-417-002Nut, 1/2 (8)* 9803-201-001Bearing Housing Complete Ass’y (includes bearings,spacer) (2)J4 9545-017-018Screw 1/2 x 1 1/2 (4)Burner Housing GroupKey Part Number Description Quantity * 9803-207-001 Housing Assembly, Burner (2)1a 9452-730-001Service Burner Plate Front... (2)1 9452-729-001 Service Plate baffl e Recirculation Chamber Clean Out (2)* 9545-008-006Screws (8)2 9545-008-001Screw (16)18 9003-220-001Angle, Burner Support (2)* 9545-008-006Screw (4)17 9048-020-002Burner, Main (4)* 9545-008-006Screw 10AB x 3/8” (4)* 9454-824-001 Panel, Back Burner Housing (2)4 9545-008-001Screw 10B x1/4” (8)5 9875-002-003Electrode Assy, Ignition (2)19 9545-045-001Screw, Electrode Mtg 8B x 1/4” (4)7 9379-186-001Valve, Gas Shut Off (1)8 9857-134-001Control Assy, Gas (2)9 9381-012-001Manifold, Assy (2)* 9425-069-021Orifi ce, Burner-Natural #27 (4)* 9425-069-022Orifi ce, Burner-LP #44 (4)10 9029-175-001Bracket, Manifold (2)22 8615-104-038Pipe Plug in end of Burner Manifold (2)* 9545-008-006Screw (4)12 9576-203-002Thermostat, Hi-Limit (2)* 9538-142-001Spacer, Hi-Limit (4)* 9545-045-007 Screw 8B x 3/4” (4)13 9074-329-001Cover, Hi-Limit Stat Ignitor (2)* 9545-008-006Screw (6)* 9576-207-008Thermostat, Safety Shutoff (2)* 9545-008-006Screw (4)15 9825-062-001Cover, Safety Stat (2)* 9545-008-024Screw (6)16 9857-116-003Control, Ignition Fenwall (3 trybox) (2)* 9732-102-013Kit, LP Conversion 50Lb Stack Kit (2)* 9838-018-003Welded One Piece Gas Pipe Assembly (1)Part # 8533-085-001 9/14Burner Housing Group Photos10221092221851A141594851613Rear ViewKey Part Number Description Quantity * 9627-861-001Wire Harness Overtemperature Switch/Air Switch (2)* 9801-098-001Switch Assy, Air Flow (2)1 9539-461-009Switch, Air Flow (2)2 9029-200-001 Bracket, Switch- Air Flow (2)3 9008-007-001Actuator, Switch (2)4 9451-169-002Pin, Cotter (2)5 9545-020-001Screw 4-40 x 5/8” (4)* 8640-401-001Nut, Special Twin .#4-40 (2)* 9550-169-003Shield, Switch (2)6 9376-322-001Motor, Drive (2)7 9452-770-001Plate, Motor Mounting (1)* 9545-029-008Bolt 3/8” - 16 x 3/4” (8)* 8641-582-003Lockwash Spring 3/8 (8)8 9545-018-019Screw, Motor Plate to Back Assy. 1/4-20x 2 1/2 (8)* 8641-582-007Lockwasher 1/4 (8)9 9538-163-006Spacr (8)* 8641-581-017Flat Washer 1/4 x 7/8 (24)* 9209-086-002Rubber Grommet (8)* 9538-166-006Grommet Spacers (8)* 9545-028-013Screw, Set (4)10 9962-018-002Back Assy, Blower Hsg (2)11 9991-053-001Support Assy, Intermed. Pulley (2)12 9545-029-010Bolt, Rd Hd 3/8-16 x 1 1/4 (6)12 8640-415-004Nut Flange Wizlock 3/8” - 16 (6)12 8641-581-035Washer, Flat (6)13 9545-029-003Bolt, 3/8-16 x 1 1/2 (2)14 9861-022-001Arm Assy-Tension, Complete (2)* 9487-200-003Ring-Retaining (6)15 9908-048-003Pulley Assy, Intermediate with bronze fl ange bearing (2)* 9036-145-002Bronze Flange Bearing (4)16 9908-047-002Pulley Driven Tumbler (2)17 9040-076-009Belt, Drive Motor (2)18 9040-073-011Belt, Driven Intermediate to Tumbler (2)19 9534-151-000Spring, Tension (2)20 9099-012-005Chain, Tension (2)21 9248-022-002Hook, Tension (2)* 9451-146-001Pin, Damper Hinge (2)* 9074-334-001 Cover Duct Upper (1)22 9973-032-001 Heat Recirculation Assembly Duct (2)* 9453-169-013Motor Pulley - Driver (1)* 9545-028-013Set Screws (2) (2)* 9278-043-001Impeller23 8641-581-026Washer, Flat 1/2” for Tumbler Pulley (2)24 9545-017-009Bolt, 1/2”-13 x 1 1/4 (2)25 8641-582-016Washer, Star 1/2” for Tumbler Pulley (2)* 9545-008-001Screw 10 Bx 1/4” (6)* 9545-014-004Bolt, 5/16-18 x 5/8” (8) (8)5/16-18* 8640-400-003Nut,* 9538-184-001Spacer, Shaft (2)* 9487-234-005Ring Tolerance (2)* 9125-007-001Damper Inside Duct Exhaust (2)* 9125-007-002Damper Inside Duct Exhaust (1)* 8520-141-000Nut, Spring (4)* 9074-335-001Cover Duct Lower (1)* 9545-008-024Screw 10ABx 3/8” (72)* 9029-173-001Bracket for Wire Harness Under Burner Housing (2)Part # 8533-085-001 9/14Part # 8533-085-001 9/14Rear View Photos1264722Rear Panel & Cover GroupKey Part Number Description Quantity19208-090-001Rear Guard Side Panel 1 (2)4 9545-008-024Screws 10 AB x 3/8 (30)5 8502-649-001Label - Connection Electrical (1)8 9208-089-001Rear Guard Back Panel (2)10 8502-600-001Label Warning & Notice (1)11 8502-645-001Label - Instructions (1)12 9109-113-001Transition Assembly Outlet (1)13 9074-320-001 Top Cover Dryer Panel (1)14 9550-188-001 Top Burner Housing Heat Shield Inlet (1)15 9074-321-001 Top Panel Burner Housing Cover (1)Part # 8533-085-001 9/141851113121514Tumbler GroupKey Part Number Description Quantity 9848-131-001Tumbler Assembly Galvanized w/spider (2)G2 9568-013-001Spider Assembly (2)G3 9497-226-002Rod, Tumbler (6)G4 8640-417-005Nut, 1/2 - 13 (6)G6 8641-590-002Washer, Special (6).............................................................................AR G7 9552-013-000Shim* 9848-130-002Tumbler Assembly Stainless Steel (2)G1 9848-130-001Tumber Assembly Galvanized (2)Part # 8533-085-001 9/14Control Assembly GroupKey Part Number DescriptionQuantity* 9857-189-001 Control Assmbly Complete (all below included) .............................1* 9108-117-001 Control Box Cover ..................................................................... 1* 8220-001-478 Wire Assembly Green 7” ............................................................ 1* 8639-621-007 Screw #10-32 x 12 Green ............................................................1* 8641-582-006 Lockwasher Ext Tooth #10 ..........................................................13 9897-026-002 Terminal Block Main Power Middle ...............................................14 9897-026-001 Terminal Block ............................................................................2* 9545-045-012 Screw #8 ABx 1/2 for terminal block ............................................6 5 8711-011-001 Transformer Ignition ...................................................................2* 9545-008-024 Screws 10AB x 3/8” ...................................................................46 9982-348-001 Plate Assembly MTG Ignition Control............................................2* 9545-008-024 Screws 10B x 1/4” MTG Above Plate and Others ...........................47 9857-116-003 Ignition Control ..........................................................................2* 8640-411-003 #6-32 Nuts ................................................................................48 9631-403-009 Wire Assembly High Voltage Upper ..............................................19 9627-860-001 Wire Harness Ignition Control Upper ............................................110 9627-860-002 Wire Harness Ignition Control Lower ............................................1* 9053-067-002 Bushing Wire 7/8” .......................................................................413 9200-001-002 Fuseholder Assembly ..................................................................314 8636-018-001 Fuse 1.5 Amp .............................................................................315 5192-299-001 Relay Power ...............................................................................216 9897-035-001 Terminal Block Assembly Main Power Inlet ...................................1* 9545-008-024 Screw #8 AB x 1/2” ....................................................................2* 8220-062-036 Wire Assembly Red/Black 14” ......................................................1* 8220-062-037 Wire Assembly Red/White 14” .....................................................1* 8220-062-038 Wire Assembly White 14” ............................................................221 9627-864-004 Wire Harness Motor Extension .....................................................2* 9527-007-001 Stand Off - Wire Saddle / Arrowhead ..........................................13* 9545-031-005 Screw 6 B x 3/8” ........................................................................422 9558-029-003 Strip Terminal Marker (Behind Input Power) ..................................124 9627-863-001 Wire Harness Main Extension Access Under Burner Housing .........123 9631-403-008 Wire Ass’y - High Voltage Lower ..................................................125 9627-859-001 Wire Harness - Main Power (1)Part # 8533-085-001 9/14Control Assembly GroupPart # 8533-085-001 9/1416252223245Coin AccecptorKey Part Number Description Quantity1 9021-041-001Coin Accecptor, Optical (1)Replacement (1)2 9801-099-001Sensor-Optical,3 9545-039-002Screw, Heighth Bar, 3mm (2)* 9486-136-001 Retainer, Coin Acceptor (1)* 9545-053-002 Screw (4)Part # 8533-085-001 9/14NotesPart # 8533-085-001 9/14NotesPart # 8533-085-001 9/14Section 7: VoltageConversionPart # 8533-085-001 9/14Part # 8533-085-001 9/14Instructions - Convert a Dual Voltage Stack Dryer from 120V to 208-240V with Neutral Wire Only1. Remove incoming power from the dryer. Use a known working voltmeter to check power.2. Remove the cover of both the upper and lower control box assemblies from the dryer using a 5/16” wrench.3. Move the black/blue wire from the N position of the main power terminal block to the L2 position of the mainpower terminal block in the upper control box assembly. See Figure 6 below.4. Move the white wire of the upper motor harness to an upper inner left terminal in the middle terminal block in thelower control box assembly. See Figure 6 below.5. Move the orange wire of the upper motor harness to an upper inner left terminal in the middle terminal block inthe lower control box assembly. See Figure 6 below.6. Move the white wire of the lower motor harness to a lower inner left terminal in the middle terminal block in thelower control box assembly. See Figure 6 below.7. Move the orange wire of the lower motor harness to a lower inner left terminal in the middle terminal block in thelower control box assembly. See Figure 6 below.8. Reconnect power to the dryer and test to ensure proper operation; one line voltage to L1, one line voltage to L2,the neutral to N, and the earth ground to E.9. Reinstall the cover of both the upper and lower control box assemblies from the dryer using a 5/16” wrench.Part # 8533-085-001 9/14NotesPart # 8533-085-001 9/14Section 9: MaintenancePart # 8533-085-001 9/14MaintenanceDaily1. Clean lint screen by unlocking and sliding out in their tracks for access. Use soft brush ifnecessary. Failure to do so will slow drying and increase gas usage and temperatures through out the dryer.2. Check lint screen for tears. Replace if necessary.Monthly1. Remove lint accumulation from end bells of motor.2. Clean lint from lint screen compartment.3. Remove lint and dirt accumulation from top of the dryer and all areas above, and around theburners and burner housing. Failure to keep this portion of the dryer clean can lead to a buildup of lint creating a fi re hazard.4. Inspect Recirculation burner housing for excessive buildup.5. Place a few drops of light oil on top and bottom pivots of the clothes door hinge.6. Grease bearings and shaft of intermediate drive pulley.Quarterly1. Check belts for looseness, wear or fraying.2. Inspect gasket of door glass for excessive wear.3. Check tightness of all fasteners holding parts to support channel.4. Check tightness of tumbler shaft retaining nut. MUST MAINTAIN 150 FOOT LBS.5. Remove lint accumulation from primary air ports in burners.6. Grease pivot pins and tension arms where in contact with each other.Semiannually1. Remove and clean main burners.2. Remove all orifi ces and examine for dirt and hole obstruction.3. Remove all lint accumulation. Remove front panel, lint screen housing and remove lintaccumulation.Annually1. Check intermediate pulley bearings for wear.2. Check and remove any lint accumulation from exhaust system.NOTE: DRYER MUST NOT BE OPERATED WITHOUT LINT SCREEN IN PLACE。
[JMAA384(2)(2011)683-689]Sums of weighted composition operators on H(infinity)
![[JMAA384(2)(2011)683-689]Sums of weighted composition operators on H(infinity)](https://img.taocdn.com/s3/m/4297912baf45b307e971970f.png)
1
j
N,
N j=1
u
j
C
ϕ
j
is
compact
on
H∞
if
and
only if
(
N j=1
u j Cϕ j )(
f
)
∈
A(D)
for
every
f
∈ H∞. This is a generalization
of Theorem 2 given in [11].
We denote by B(H∞) the closed unit ball of H∞. For z, w ∈ D, the pseudo-hyperbolic distance between z and w is given
for
every
1
j,
N.
Note that if |ϕ j(zn)| → 1 as n → ∞ for some 1 j N, then it is easy to see that there exists a subsequence {zn } of {zn}n satisfying {zn } ∈ Z .
Sums of weighted composition operators on H∞
Kei Ji Izuchi a,1, Shûichi Ohno b,∗,2
a Department of Mathematics, Niigata University, Niigata 950-2181, Japan b Nippon Institute of Technology, Miyashiro, Minami-Saitama 345-8501, Japan
3GPP TS 36.331 V13.2.0 (2016-06)

3GPP TS 36.331 V13.2.0 (2016-06)Technical Specification3rd Generation Partnership Project;Technical Specification Group Radio Access Network;Evolved Universal Terrestrial Radio Access (E-UTRA);Radio Resource Control (RRC);Protocol specification(Release 13)The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organizational Partners and shall not be implemented.This Specification is provided for future development work within 3GPP only. The Organizational Partners accept no liability for any use of this Specification. Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organizational Partners' Publications Offices.KeywordsUMTS, radio3GPPPostal address3GPP support office address650 Route des Lucioles - Sophia AntipolisValbonne - FRANCETel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16InternetCopyright NotificationNo part may be reproduced except as authorized by written permission.The copyright and the foregoing restriction extend to reproduction in all media.© 2016, 3GPP Organizational Partners (ARIB, ATIS, CCSA, ETSI, TSDSI, TTA, TTC).All rights reserved.UMTS™ is a Trade Mark of ETSI registered for the benefit of its members3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational PartnersLTE™ is a Trade Mark of ETSI currently being registered for the benefit of its Members and of the 3GPP Organizational Partners GSM® and the GSM logo are registered and owned by the GSM AssociationBluetooth® is a Trade Mark of the Bluetooth SIG registered for the benefit of its membersContentsForeword (18)1Scope (19)2References (19)3Definitions, symbols and abbreviations (22)3.1Definitions (22)3.2Abbreviations (24)4General (27)4.1Introduction (27)4.2Architecture (28)4.2.1UE states and state transitions including inter RAT (28)4.2.2Signalling radio bearers (29)4.3Services (30)4.3.1Services provided to upper layers (30)4.3.2Services expected from lower layers (30)4.4Functions (30)5Procedures (32)5.1General (32)5.1.1Introduction (32)5.1.2General requirements (32)5.2System information (33)5.2.1Introduction (33)5.2.1.1General (33)5.2.1.2Scheduling (34)5.2.1.2a Scheduling for NB-IoT (34)5.2.1.3System information validity and notification of changes (35)5.2.1.4Indication of ETWS notification (36)5.2.1.5Indication of CMAS notification (37)5.2.1.6Notification of EAB parameters change (37)5.2.1.7Access Barring parameters change in NB-IoT (37)5.2.2System information acquisition (38)5.2.2.1General (38)5.2.2.2Initiation (38)5.2.2.3System information required by the UE (38)5.2.2.4System information acquisition by the UE (39)5.2.2.5Essential system information missing (42)5.2.2.6Actions upon reception of the MasterInformationBlock message (42)5.2.2.7Actions upon reception of the SystemInformationBlockType1 message (42)5.2.2.8Actions upon reception of SystemInformation messages (44)5.2.2.9Actions upon reception of SystemInformationBlockType2 (44)5.2.2.10Actions upon reception of SystemInformationBlockType3 (45)5.2.2.11Actions upon reception of SystemInformationBlockType4 (45)5.2.2.12Actions upon reception of SystemInformationBlockType5 (45)5.2.2.13Actions upon reception of SystemInformationBlockType6 (45)5.2.2.14Actions upon reception of SystemInformationBlockType7 (45)5.2.2.15Actions upon reception of SystemInformationBlockType8 (45)5.2.2.16Actions upon reception of SystemInformationBlockType9 (46)5.2.2.17Actions upon reception of SystemInformationBlockType10 (46)5.2.2.18Actions upon reception of SystemInformationBlockType11 (46)5.2.2.19Actions upon reception of SystemInformationBlockType12 (47)5.2.2.20Actions upon reception of SystemInformationBlockType13 (48)5.2.2.21Actions upon reception of SystemInformationBlockType14 (48)5.2.2.22Actions upon reception of SystemInformationBlockType15 (48)5.2.2.23Actions upon reception of SystemInformationBlockType16 (48)5.2.2.24Actions upon reception of SystemInformationBlockType17 (48)5.2.2.25Actions upon reception of SystemInformationBlockType18 (48)5.2.2.26Actions upon reception of SystemInformationBlockType19 (49)5.2.3Acquisition of an SI message (49)5.2.3a Acquisition of an SI message by BL UE or UE in CE or a NB-IoT UE (50)5.3Connection control (50)5.3.1Introduction (50)5.3.1.1RRC connection control (50)5.3.1.2Security (52)5.3.1.2a RN security (53)5.3.1.3Connected mode mobility (53)5.3.1.4Connection control in NB-IoT (54)5.3.2Paging (55)5.3.2.1General (55)5.3.2.2Initiation (55)5.3.2.3Reception of the Paging message by the UE (55)5.3.3RRC connection establishment (56)5.3.3.1General (56)5.3.3.1a Conditions for establishing RRC Connection for sidelink communication/ discovery (58)5.3.3.2Initiation (59)5.3.3.3Actions related to transmission of RRCConnectionRequest message (63)5.3.3.3a Actions related to transmission of RRCConnectionResumeRequest message (64)5.3.3.4Reception of the RRCConnectionSetup by the UE (64)5.3.3.4a Reception of the RRCConnectionResume by the UE (66)5.3.3.5Cell re-selection while T300, T302, T303, T305, T306, or T308 is running (68)5.3.3.6T300 expiry (68)5.3.3.7T302, T303, T305, T306, or T308 expiry or stop (69)5.3.3.8Reception of the RRCConnectionReject by the UE (70)5.3.3.9Abortion of RRC connection establishment (71)5.3.3.10Handling of SSAC related parameters (71)5.3.3.11Access barring check (72)5.3.3.12EAB check (73)5.3.3.13Access barring check for ACDC (73)5.3.3.14Access Barring check for NB-IoT (74)5.3.4Initial security activation (75)5.3.4.1General (75)5.3.4.2Initiation (76)5.3.4.3Reception of the SecurityModeCommand by the UE (76)5.3.5RRC connection reconfiguration (77)5.3.5.1General (77)5.3.5.2Initiation (77)5.3.5.3Reception of an RRCConnectionReconfiguration not including the mobilityControlInfo by theUE (77)5.3.5.4Reception of an RRCConnectionReconfiguration including the mobilityControlInfo by the UE(handover) (79)5.3.5.5Reconfiguration failure (83)5.3.5.6T304 expiry (handover failure) (83)5.3.5.7Void (84)5.3.5.7a T307 expiry (SCG change failure) (84)5.3.5.8Radio Configuration involving full configuration option (84)5.3.6Counter check (86)5.3.6.1General (86)5.3.6.2Initiation (86)5.3.6.3Reception of the CounterCheck message by the UE (86)5.3.7RRC connection re-establishment (87)5.3.7.1General (87)5.3.7.2Initiation (87)5.3.7.3Actions following cell selection while T311 is running (88)5.3.7.4Actions related to transmission of RRCConnectionReestablishmentRequest message (89)5.3.7.5Reception of the RRCConnectionReestablishment by the UE (89)5.3.7.6T311 expiry (91)5.3.7.7T301 expiry or selected cell no longer suitable (91)5.3.7.8Reception of RRCConnectionReestablishmentReject by the UE (91)5.3.8RRC connection release (92)5.3.8.1General (92)5.3.8.2Initiation (92)5.3.8.3Reception of the RRCConnectionRelease by the UE (92)5.3.8.4T320 expiry (93)5.3.9RRC connection release requested by upper layers (93)5.3.9.1General (93)5.3.9.2Initiation (93)5.3.10Radio resource configuration (93)5.3.10.0General (93)5.3.10.1SRB addition/ modification (94)5.3.10.2DRB release (95)5.3.10.3DRB addition/ modification (95)5.3.10.3a1DC specific DRB addition or reconfiguration (96)5.3.10.3a2LWA specific DRB addition or reconfiguration (98)5.3.10.3a3LWIP specific DRB addition or reconfiguration (98)5.3.10.3a SCell release (99)5.3.10.3b SCell addition/ modification (99)5.3.10.3c PSCell addition or modification (99)5.3.10.4MAC main reconfiguration (99)5.3.10.5Semi-persistent scheduling reconfiguration (100)5.3.10.6Physical channel reconfiguration (100)5.3.10.7Radio Link Failure Timers and Constants reconfiguration (101)5.3.10.8Time domain measurement resource restriction for serving cell (101)5.3.10.9Other configuration (102)5.3.10.10SCG reconfiguration (103)5.3.10.11SCG dedicated resource configuration (104)5.3.10.12Reconfiguration SCG or split DRB by drb-ToAddModList (105)5.3.10.13Neighbour cell information reconfiguration (105)5.3.10.14Void (105)5.3.10.15Sidelink dedicated configuration (105)5.3.10.16T370 expiry (106)5.3.11Radio link failure related actions (107)5.3.11.1Detection of physical layer problems in RRC_CONNECTED (107)5.3.11.2Recovery of physical layer problems (107)5.3.11.3Detection of radio link failure (107)5.3.12UE actions upon leaving RRC_CONNECTED (109)5.3.13UE actions upon PUCCH/ SRS release request (110)5.3.14Proximity indication (110)5.3.14.1General (110)5.3.14.2Initiation (111)5.3.14.3Actions related to transmission of ProximityIndication message (111)5.3.15Void (111)5.4Inter-RAT mobility (111)5.4.1Introduction (111)5.4.2Handover to E-UTRA (112)5.4.2.1General (112)5.4.2.2Initiation (112)5.4.2.3Reception of the RRCConnectionReconfiguration by the UE (112)5.4.2.4Reconfiguration failure (114)5.4.2.5T304 expiry (handover to E-UTRA failure) (114)5.4.3Mobility from E-UTRA (114)5.4.3.1General (114)5.4.3.2Initiation (115)5.4.3.3Reception of the MobilityFromEUTRACommand by the UE (115)5.4.3.4Successful completion of the mobility from E-UTRA (116)5.4.3.5Mobility from E-UTRA failure (117)5.4.4Handover from E-UTRA preparation request (CDMA2000) (117)5.4.4.1General (117)5.4.4.2Initiation (118)5.4.4.3Reception of the HandoverFromEUTRAPreparationRequest by the UE (118)5.4.5UL handover preparation transfer (CDMA2000) (118)5.4.5.1General (118)5.4.5.2Initiation (118)5.4.5.3Actions related to transmission of the ULHandoverPreparationTransfer message (119)5.4.5.4Failure to deliver the ULHandoverPreparationTransfer message (119)5.4.6Inter-RAT cell change order to E-UTRAN (119)5.4.6.1General (119)5.4.6.2Initiation (119)5.4.6.3UE fails to complete an inter-RAT cell change order (119)5.5Measurements (120)5.5.1Introduction (120)5.5.2Measurement configuration (121)5.5.2.1General (121)5.5.2.2Measurement identity removal (122)5.5.2.2a Measurement identity autonomous removal (122)5.5.2.3Measurement identity addition/ modification (123)5.5.2.4Measurement object removal (124)5.5.2.5Measurement object addition/ modification (124)5.5.2.6Reporting configuration removal (126)5.5.2.7Reporting configuration addition/ modification (127)5.5.2.8Quantity configuration (127)5.5.2.9Measurement gap configuration (127)5.5.2.10Discovery signals measurement timing configuration (128)5.5.2.11RSSI measurement timing configuration (128)5.5.3Performing measurements (128)5.5.3.1General (128)5.5.3.2Layer 3 filtering (131)5.5.4Measurement report triggering (131)5.5.4.1General (131)5.5.4.2Event A1 (Serving becomes better than threshold) (135)5.5.4.3Event A2 (Serving becomes worse than threshold) (136)5.5.4.4Event A3 (Neighbour becomes offset better than PCell/ PSCell) (136)5.5.4.5Event A4 (Neighbour becomes better than threshold) (137)5.5.4.6Event A5 (PCell/ PSCell becomes worse than threshold1 and neighbour becomes better thanthreshold2) (138)5.5.4.6a Event A6 (Neighbour becomes offset better than SCell) (139)5.5.4.7Event B1 (Inter RAT neighbour becomes better than threshold) (139)5.5.4.8Event B2 (PCell becomes worse than threshold1 and inter RAT neighbour becomes better thanthreshold2) (140)5.5.4.9Event C1 (CSI-RS resource becomes better than threshold) (141)5.5.4.10Event C2 (CSI-RS resource becomes offset better than reference CSI-RS resource) (141)5.5.4.11Event W1 (WLAN becomes better than a threshold) (142)5.5.4.12Event W2 (All WLAN inside WLAN mobility set becomes worse than threshold1 and a WLANoutside WLAN mobility set becomes better than threshold2) (142)5.5.4.13Event W3 (All WLAN inside WLAN mobility set becomes worse than a threshold) (143)5.5.5Measurement reporting (144)5.5.6Measurement related actions (148)5.5.6.1Actions upon handover and re-establishment (148)5.5.6.2Speed dependant scaling of measurement related parameters (149)5.5.7Inter-frequency RSTD measurement indication (149)5.5.7.1General (149)5.5.7.2Initiation (150)5.5.7.3Actions related to transmission of InterFreqRSTDMeasurementIndication message (150)5.6Other (150)5.6.0General (150)5.6.1DL information transfer (151)5.6.1.1General (151)5.6.1.2Initiation (151)5.6.1.3Reception of the DLInformationTransfer by the UE (151)5.6.2UL information transfer (151)5.6.2.1General (151)5.6.2.2Initiation (151)5.6.2.3Actions related to transmission of ULInformationTransfer message (152)5.6.2.4Failure to deliver ULInformationTransfer message (152)5.6.3UE capability transfer (152)5.6.3.1General (152)5.6.3.2Initiation (153)5.6.3.3Reception of the UECapabilityEnquiry by the UE (153)5.6.4CSFB to 1x Parameter transfer (157)5.6.4.1General (157)5.6.4.2Initiation (157)5.6.4.3Actions related to transmission of CSFBParametersRequestCDMA2000 message (157)5.6.4.4Reception of the CSFBParametersResponseCDMA2000 message (157)5.6.5UE Information (158)5.6.5.1General (158)5.6.5.2Initiation (158)5.6.5.3Reception of the UEInformationRequest message (158)5.6.6 Logged Measurement Configuration (159)5.6.6.1General (159)5.6.6.2Initiation (160)5.6.6.3Reception of the LoggedMeasurementConfiguration by the UE (160)5.6.6.4T330 expiry (160)5.6.7 Release of Logged Measurement Configuration (160)5.6.7.1General (160)5.6.7.2Initiation (160)5.6.8 Measurements logging (161)5.6.8.1General (161)5.6.8.2Initiation (161)5.6.9In-device coexistence indication (163)5.6.9.1General (163)5.6.9.2Initiation (164)5.6.9.3Actions related to transmission of InDeviceCoexIndication message (164)5.6.10UE Assistance Information (165)5.6.10.1General (165)5.6.10.2Initiation (166)5.6.10.3Actions related to transmission of UEAssistanceInformation message (166)5.6.11 Mobility history information (166)5.6.11.1General (166)5.6.11.2Initiation (166)5.6.12RAN-assisted WLAN interworking (167)5.6.12.1General (167)5.6.12.2Dedicated WLAN offload configuration (167)5.6.12.3WLAN offload RAN evaluation (167)5.6.12.4T350 expiry or stop (167)5.6.12.5Cell selection/ re-selection while T350 is running (168)5.6.13SCG failure information (168)5.6.13.1General (168)5.6.13.2Initiation (168)5.6.13.3Actions related to transmission of SCGFailureInformation message (168)5.6.14LTE-WLAN Aggregation (169)5.6.14.1Introduction (169)5.6.14.2Reception of LWA configuration (169)5.6.14.3Release of LWA configuration (170)5.6.15WLAN connection management (170)5.6.15.1Introduction (170)5.6.15.2WLAN connection status reporting (170)5.6.15.2.1General (170)5.6.15.2.2Initiation (171)5.6.15.2.3Actions related to transmission of WLANConnectionStatusReport message (171)5.6.15.3T351 Expiry (WLAN connection attempt timeout) (171)5.6.15.4WLAN status monitoring (171)5.6.16RAN controlled LTE-WLAN interworking (172)5.6.16.1General (172)5.6.16.2WLAN traffic steering command (172)5.6.17LTE-WLAN aggregation with IPsec tunnel (173)5.6.17.1General (173)5.7Generic error handling (174)5.7.1General (174)5.7.2ASN.1 violation or encoding error (174)5.7.3Field set to a not comprehended value (174)5.7.4Mandatory field missing (174)5.7.5Not comprehended field (176)5.8MBMS (176)5.8.1Introduction (176)5.8.1.1General (176)5.8.1.2Scheduling (176)5.8.1.3MCCH information validity and notification of changes (176)5.8.2MCCH information acquisition (178)5.8.2.1General (178)5.8.2.2Initiation (178)5.8.2.3MCCH information acquisition by the UE (178)5.8.2.4Actions upon reception of the MBSFNAreaConfiguration message (178)5.8.2.5Actions upon reception of the MBMSCountingRequest message (179)5.8.3MBMS PTM radio bearer configuration (179)5.8.3.1General (179)5.8.3.2Initiation (179)5.8.3.3MRB establishment (179)5.8.3.4MRB release (179)5.8.4MBMS Counting Procedure (179)5.8.4.1General (179)5.8.4.2Initiation (180)5.8.4.3Reception of the MBMSCountingRequest message by the UE (180)5.8.5MBMS interest indication (181)5.8.5.1General (181)5.8.5.2Initiation (181)5.8.5.3Determine MBMS frequencies of interest (182)5.8.5.4Actions related to transmission of MBMSInterestIndication message (183)5.8a SC-PTM (183)5.8a.1Introduction (183)5.8a.1.1General (183)5.8a.1.2SC-MCCH scheduling (183)5.8a.1.3SC-MCCH information validity and notification of changes (183)5.8a.1.4Procedures (184)5.8a.2SC-MCCH information acquisition (184)5.8a.2.1General (184)5.8a.2.2Initiation (184)5.8a.2.3SC-MCCH information acquisition by the UE (184)5.8a.2.4Actions upon reception of the SCPTMConfiguration message (185)5.8a.3SC-PTM radio bearer configuration (185)5.8a.3.1General (185)5.8a.3.2Initiation (185)5.8a.3.3SC-MRB establishment (185)5.8a.3.4SC-MRB release (185)5.9RN procedures (186)5.9.1RN reconfiguration (186)5.9.1.1General (186)5.9.1.2Initiation (186)5.9.1.3Reception of the RNReconfiguration by the RN (186)5.10Sidelink (186)5.10.1Introduction (186)5.10.1a Conditions for sidelink communication operation (187)5.10.2Sidelink UE information (188)5.10.2.1General (188)5.10.2.2Initiation (189)5.10.2.3Actions related to transmission of SidelinkUEInformation message (193)5.10.3Sidelink communication monitoring (195)5.10.6Sidelink discovery announcement (198)5.10.6a Sidelink discovery announcement pool selection (201)5.10.6b Sidelink discovery announcement reference carrier selection (201)5.10.7Sidelink synchronisation information transmission (202)5.10.7.1General (202)5.10.7.2Initiation (203)5.10.7.3Transmission of SLSS (204)5.10.7.4Transmission of MasterInformationBlock-SL message (205)5.10.7.5Void (206)5.10.8Sidelink synchronisation reference (206)5.10.8.1General (206)5.10.8.2Selection and reselection of synchronisation reference UE (SyncRef UE) (206)5.10.9Sidelink common control information (207)5.10.9.1General (207)5.10.9.2Actions related to reception of MasterInformationBlock-SL message (207)5.10.10Sidelink relay UE operation (207)5.10.10.1General (207)5.10.10.2AS-conditions for relay related sidelink communication transmission by sidelink relay UE (207)5.10.10.3AS-conditions for relay PS related sidelink discovery transmission by sidelink relay UE (208)5.10.10.4Sidelink relay UE threshold conditions (208)5.10.11Sidelink remote UE operation (208)5.10.11.1General (208)5.10.11.2AS-conditions for relay related sidelink communication transmission by sidelink remote UE (208)5.10.11.3AS-conditions for relay PS related sidelink discovery transmission by sidelink remote UE (209)5.10.11.4Selection and reselection of sidelink relay UE (209)5.10.11.5Sidelink remote UE threshold conditions (210)6Protocol data units, formats and parameters (tabular & ASN.1) (210)6.1General (210)6.2RRC messages (212)6.2.1General message structure (212)–EUTRA-RRC-Definitions (212)–BCCH-BCH-Message (212)–BCCH-DL-SCH-Message (212)–BCCH-DL-SCH-Message-BR (213)–MCCH-Message (213)–PCCH-Message (213)–DL-CCCH-Message (214)–DL-DCCH-Message (214)–UL-CCCH-Message (214)–UL-DCCH-Message (215)–SC-MCCH-Message (215)6.2.2Message definitions (216)–CounterCheck (216)–CounterCheckResponse (217)–CSFBParametersRequestCDMA2000 (217)–CSFBParametersResponseCDMA2000 (218)–DLInformationTransfer (218)–HandoverFromEUTRAPreparationRequest (CDMA2000) (219)–InDeviceCoexIndication (220)–InterFreqRSTDMeasurementIndication (222)–LoggedMeasurementConfiguration (223)–MasterInformationBlock (225)–MBMSCountingRequest (226)–MBMSCountingResponse (226)–MBMSInterestIndication (227)–MBSFNAreaConfiguration (228)–MeasurementReport (228)–MobilityFromEUTRACommand (229)–Paging (232)–ProximityIndication (233)–RNReconfiguration (234)–RNReconfigurationComplete (234)–RRCConnectionReconfiguration (235)–RRCConnectionReconfigurationComplete (240)–RRCConnectionReestablishment (241)–RRCConnectionReestablishmentComplete (241)–RRCConnectionReestablishmentReject (242)–RRCConnectionReestablishmentRequest (243)–RRCConnectionReject (243)–RRCConnectionRelease (244)–RRCConnectionResume (248)–RRCConnectionResumeComplete (249)–RRCConnectionResumeRequest (250)–RRCConnectionRequest (250)–RRCConnectionSetup (251)–RRCConnectionSetupComplete (252)–SCGFailureInformation (253)–SCPTMConfiguration (254)–SecurityModeCommand (255)–SecurityModeComplete (255)–SecurityModeFailure (256)–SidelinkUEInformation (256)–SystemInformation (258)–SystemInformationBlockType1 (259)–UEAssistanceInformation (264)–UECapabilityEnquiry (265)–UECapabilityInformation (266)–UEInformationRequest (267)–UEInformationResponse (267)–ULHandoverPreparationTransfer (CDMA2000) (273)–ULInformationTransfer (274)–WLANConnectionStatusReport (274)6.3RRC information elements (275)6.3.1System information blocks (275)–SystemInformationBlockType2 (275)–SystemInformationBlockType3 (279)–SystemInformationBlockType4 (282)–SystemInformationBlockType5 (283)–SystemInformationBlockType6 (287)–SystemInformationBlockType7 (289)–SystemInformationBlockType8 (290)–SystemInformationBlockType9 (295)–SystemInformationBlockType10 (295)–SystemInformationBlockType11 (296)–SystemInformationBlockType12 (297)–SystemInformationBlockType13 (297)–SystemInformationBlockType14 (298)–SystemInformationBlockType15 (298)–SystemInformationBlockType16 (299)–SystemInformationBlockType17 (300)–SystemInformationBlockType18 (301)–SystemInformationBlockType19 (301)–SystemInformationBlockType20 (304)6.3.2Radio resource control information elements (304)–AntennaInfo (304)–AntennaInfoUL (306)–CQI-ReportConfig (307)–CQI-ReportPeriodicProcExtId (314)–CrossCarrierSchedulingConfig (314)–CSI-IM-Config (315)–CSI-IM-ConfigId (315)–CSI-RS-Config (317)–CSI-RS-ConfigEMIMO (318)–CSI-RS-ConfigNZP (319)–CSI-RS-ConfigNZPId (320)–CSI-RS-ConfigZP (321)–CSI-RS-ConfigZPId (321)–DMRS-Config (321)–DRB-Identity (322)–EPDCCH-Config (322)–EIMTA-MainConfig (324)–LogicalChannelConfig (325)–LWA-Configuration (326)–LWIP-Configuration (326)–RCLWI-Configuration (327)–MAC-MainConfig (327)–P-C-AndCBSR (332)–PDCCH-ConfigSCell (333)–PDCP-Config (334)–PDSCH-Config (337)–PDSCH-RE-MappingQCL-ConfigId (339)–PHICH-Config (339)–PhysicalConfigDedicated (339)–P-Max (344)–PRACH-Config (344)–PresenceAntennaPort1 (346)–PUCCH-Config (347)–PUSCH-Config (351)–RACH-ConfigCommon (355)–RACH-ConfigDedicated (357)–RadioResourceConfigCommon (358)–RadioResourceConfigDedicated (362)–RLC-Config (367)–RLF-TimersAndConstants (369)–RN-SubframeConfig (370)–SchedulingRequestConfig (371)–SoundingRS-UL-Config (372)–SPS-Config (375)–TDD-Config (376)–TimeAlignmentTimer (377)–TPC-PDCCH-Config (377)–TunnelConfigLWIP (378)–UplinkPowerControl (379)–WLAN-Id-List (382)–WLAN-MobilityConfig (382)6.3.3Security control information elements (382)–NextHopChainingCount (382)–SecurityAlgorithmConfig (383)–ShortMAC-I (383)6.3.4Mobility control information elements (383)–AdditionalSpectrumEmission (383)–ARFCN-ValueCDMA2000 (383)–ARFCN-ValueEUTRA (384)–ARFCN-ValueGERAN (384)–ARFCN-ValueUTRA (384)–BandclassCDMA2000 (384)–BandIndicatorGERAN (385)–CarrierFreqCDMA2000 (385)–CarrierFreqGERAN (385)–CellIndexList (387)–CellReselectionPriority (387)–CellSelectionInfoCE (387)–CellReselectionSubPriority (388)–CSFB-RegistrationParam1XRTT (388)–CellGlobalIdEUTRA (389)–CellGlobalIdUTRA (389)–CellGlobalIdGERAN (390)–CellGlobalIdCDMA2000 (390)–CellSelectionInfoNFreq (391)–CSG-Identity (391)–FreqBandIndicator (391)–MobilityControlInfo (391)–MobilityParametersCDMA2000 (1xRTT) (393)–MobilityStateParameters (394)–MultiBandInfoList (394)–NS-PmaxList (394)–PhysCellId (395)–PhysCellIdRange (395)–PhysCellIdRangeUTRA-FDDList (395)–PhysCellIdCDMA2000 (396)–PhysCellIdGERAN (396)–PhysCellIdUTRA-FDD (396)–PhysCellIdUTRA-TDD (396)–PLMN-Identity (397)–PLMN-IdentityList3 (397)–PreRegistrationInfoHRPD (397)–Q-QualMin (398)–Q-RxLevMin (398)–Q-OffsetRange (398)–Q-OffsetRangeInterRAT (399)–ReselectionThreshold (399)–ReselectionThresholdQ (399)–SCellIndex (399)–ServCellIndex (400)–SpeedStateScaleFactors (400)–SystemInfoListGERAN (400)–SystemTimeInfoCDMA2000 (401)–TrackingAreaCode (401)–T-Reselection (402)–T-ReselectionEUTRA-CE (402)6.3.5Measurement information elements (402)–AllowedMeasBandwidth (402)–CSI-RSRP-Range (402)–Hysteresis (402)–LocationInfo (403)–MBSFN-RSRQ-Range (403)–MeasConfig (404)–MeasDS-Config (405)–MeasGapConfig (406)–MeasId (407)–MeasIdToAddModList (407)–MeasObjectCDMA2000 (408)–MeasObjectEUTRA (408)–MeasObjectGERAN (412)–MeasObjectId (412)–MeasObjectToAddModList (412)–MeasObjectUTRA (413)–ReportConfigEUTRA (422)–ReportConfigId (425)–ReportConfigInterRAT (425)–ReportConfigToAddModList (428)–ReportInterval (429)–RSRP-Range (429)–RSRQ-Range (430)–RSRQ-Type (430)–RS-SINR-Range (430)–RSSI-Range-r13 (431)–TimeToTrigger (431)–UL-DelayConfig (431)–WLAN-CarrierInfo (431)–WLAN-RSSI-Range (432)–WLAN-Status (432)6.3.6Other information elements (433)–AbsoluteTimeInfo (433)–AreaConfiguration (433)–C-RNTI (433)–DedicatedInfoCDMA2000 (434)–DedicatedInfoNAS (434)–FilterCoefficient (434)–LoggingDuration (434)–LoggingInterval (435)–MeasSubframePattern (435)–MMEC (435)–NeighCellConfig (435)–OtherConfig (436)–RAND-CDMA2000 (1xRTT) (437)–RAT-Type (437)–ResumeIdentity (437)–RRC-TransactionIdentifier (438)–S-TMSI (438)–TraceReference (438)–UE-CapabilityRAT-ContainerList (438)–UE-EUTRA-Capability (439)–UE-RadioPagingInfo (469)–UE-TimersAndConstants (469)–VisitedCellInfoList (470)–WLAN-OffloadConfig (470)6.3.7MBMS information elements (472)–MBMS-NotificationConfig (472)–MBMS-ServiceList (473)–MBSFN-AreaId (473)–MBSFN-AreaInfoList (473)–MBSFN-SubframeConfig (474)–PMCH-InfoList (475)6.3.7a SC-PTM information elements (476)–SC-MTCH-InfoList (476)–SCPTM-NeighbourCellList (478)6.3.8Sidelink information elements (478)–SL-CommConfig (478)–SL-CommResourcePool (479)–SL-CP-Len (480)–SL-DiscConfig (481)–SL-DiscResourcePool (483)–SL-DiscTxPowerInfo (485)–SL-GapConfig (485)。
Glider Flying Handbook说明书

Glider Flying Handbook2013U.S. Department of TransportationFEDERAL AVIATION ADMINISTRATIONFlight Standards Servicei iPrefaceThe Glider Flying Handbook is designed as a technical manual for applicants who are preparing for glider category rating and for currently certificated glider pilots who wish to improve their knowledge. Certificated flight instructors will find this handbook a valuable training aid, since detailed coverage of aeronautical decision-making, components and systems, aerodynamics, flight instruments, performance limitations, ground operations, flight maneuvers, traffic patterns, emergencies, soaring weather, soaring techniques, and cross-country flight is included. Topics such as radio navigation and communication, use of flight information publications, and regulations are available in other Federal Aviation Administration (FAA) publications.The discussion and explanations reflect the most commonly used practices and principles. Occasionally, the word “must” or similar language is used where the desired action is deemed critical. The use of such language is not intended to add to, interpret, or relieve a duty imposed by Title 14 of the Code of Federal Regulations (14 CFR). Persons working towards a glider rating are advised to review the references from the applicable practical test standards (FAA-G-8082-4, Sport Pilot and Flight Instructor with a Sport Pilot Rating Knowledge Test Guide, FAA-G-8082-5, Commercial Pilot Knowledge Test Guide, and FAA-G-8082-17, Recreational Pilot and Private Pilot Knowledge Test Guide). Resources for study include FAA-H-8083-25, Pilot’s Handbook of Aeronautical Knowledge, FAA-H-8083-2, Risk Management Handbook, and Advisory Circular (AC) 00-6, Aviation Weather For Pilots and Flight Operations Personnel, AC 00-45, Aviation Weather Services, as these documents contain basic material not duplicated herein. All beginning applicants should refer to FAA-H-8083-25, Pilot’s Handbook of Aeronautical Knowledge, for study and basic library reference.It is essential for persons using this handbook to become familiar with and apply the pertinent parts of 14 CFR and the Aeronautical Information Manual (AIM). The AIM is available online at . The current Flight Standards Service airman training and testing material and learning statements for all airman certificates and ratings can be obtained from .This handbook supersedes FAA-H-8083-13, Glider Flying Handbook, dated 2003. Always select the latest edition of any publication and check the website for errata pages and listing of changes to FAA educational publications developed by the FAA’s Airman Testing Standards Branch, AFS-630.This handbook is available for download, in PDF format, from .This handbook is published by the United States Department of Transportation, Federal Aviation Administration, Airman Testing Standards Branch, AFS-630, P.O. Box 25082, Oklahoma City, OK 73125.Comments regarding this publication should be sent, in email form, to the following address:********************************************John M. AllenDirector, Flight Standards Serviceiiii vAcknowledgmentsThe Glider Flying Handbook was produced by the Federal Aviation Administration (FAA) with the assistance of Safety Research Corporation of America (SRCA). The FAA wishes to acknowledge the following contributors: Sue Telford of Telford Fishing & Hunting Services for images used in Chapter 1JerryZieba () for images used in Chapter 2Tim Mara () for images used in Chapters 2 and 12Uli Kremer of Alexander Schleicher GmbH & Co for images used in Chapter 2Richard Lancaster () for images and content used in Chapter 3Dave Nadler of Nadler & Associates for images used in Chapter 6Dave McConeghey for images used in Chapter 6John Brandon (www.raa.asn.au) for images and content used in Chapter 7Patrick Panzera () for images used in Chapter 8Jeff Haby (www.theweatherprediction) for images used in Chapter 8National Soaring Museum () for content used in Chapter 9Bill Elliot () for images used in Chapter 12.Tiffany Fidler for images used in Chapter 12.Additional appreciation is extended to the Soaring Society of America, Inc. (), the Soaring Safety Foundation, and Mr. Brad Temeyer and Mr. Bill Martin from the National Oceanic and Atmospheric Administration (NOAA) for their technical support and input.vv iPreface (iii)Acknowledgments (v)Table of Contents (vii)Chapter 1Gliders and Sailplanes ........................................1-1 Introduction....................................................................1-1 Gliders—The Early Years ..............................................1-2 Glider or Sailplane? .......................................................1-3 Glider Pilot Schools ......................................................1-4 14 CFR Part 141 Pilot Schools ...................................1-5 14 CFR Part 61 Instruction ........................................1-5 Glider Certificate Eligibility Requirements ...................1-5 Common Glider Concepts ..............................................1-6 Terminology...............................................................1-6 Converting Metric Distance to Feet ...........................1-6 Chapter 2Components and Systems .................................2-1 Introduction....................................................................2-1 Glider Design .................................................................2-2 The Fuselage ..................................................................2-4 Wings and Components .............................................2-4 Lift/Drag Devices ...........................................................2-5 Empennage .....................................................................2-6 Towhook Devices .......................................................2-7 Powerplant .....................................................................2-7 Self-Launching Gliders .............................................2-7 Sustainer Engines .......................................................2-8 Landing Gear .................................................................2-8 Wheel Brakes .............................................................2-8 Chapter 3Aerodynamics of Flight .......................................3-1 Introduction....................................................................3-1 Forces of Flight..............................................................3-2 Newton’s Third Law of Motion .................................3-2 Lift ..............................................................................3-2The Effects of Drag on a Glider .....................................3-3 Parasite Drag ..............................................................3-3 Form Drag ...............................................................3-3 Skin Friction Drag ..................................................3-3 Interference Drag ....................................................3-5 Total Drag...................................................................3-6 Wing Planform ...........................................................3-6 Elliptical Wing ........................................................3-6 Rectangular Wing ...................................................3-7 Tapered Wing .........................................................3-7 Swept-Forward Wing ..............................................3-7 Washout ..................................................................3-7 Glide Ratio .................................................................3-8 Aspect Ratio ............................................................3-9 Weight ........................................................................3-9 Thrust .........................................................................3-9 Three Axes of Rotation ..................................................3-9 Stability ........................................................................3-10 Flutter .......................................................................3-11 Lateral Stability ........................................................3-12 Turning Flight ..............................................................3-13 Load Factors .................................................................3-13 Radius of Turn ..........................................................3-14 Turn Coordination ....................................................3-15 Slips ..........................................................................3-15 Forward Slip .........................................................3-16 Sideslip .................................................................3-17 Spins .........................................................................3-17 Ground Effect ...............................................................3-19 Chapter 4Flight Instruments ...............................................4-1 Introduction....................................................................4-1 Pitot-Static Instruments ..................................................4-2 Impact and Static Pressure Lines................................4-2 Airspeed Indicator ......................................................4-2 The Effects of Altitude on the AirspeedIndicator..................................................................4-3 Types of Airspeed ...................................................4-3Table of ContentsviiAirspeed Indicator Markings ......................................4-5 Other Airspeed Limitations ........................................4-6 Altimeter .....................................................................4-6 Principles of Operation ...........................................4-6 Effect of Nonstandard Pressure andTemperature............................................................4-7 Setting the Altimeter (Kollsman Window) .............4-9 Types of Altitude ......................................................4-10 Variometer................................................................4-11 Total Energy System .............................................4-14 Netto .....................................................................4-14 Electronic Flight Computers ....................................4-15 Magnetic Compass .......................................................4-16 Yaw String ................................................................4-16 Inclinometer..............................................................4-16 Gyroscopic Instruments ...............................................4-17 G-Meter ........................................................................4-17 FLARM Collision Avoidance System .........................4-18 Chapter 5Glider Performance .............................................5-1 Introduction....................................................................5-1 Factors Affecting Performance ......................................5-2 High and Low Density Altitude Conditions ...........5-2 Atmospheric Pressure .............................................5-2 Altitude ...................................................................5-3 Temperature............................................................5-3 Wind ...........................................................................5-3 Weight ........................................................................5-5 Rate of Climb .................................................................5-7 Flight Manuals and Placards ..........................................5-8 Placards ......................................................................5-8 Performance Information ...........................................5-8 Glider Polars ...............................................................5-8 Weight and Balance Information .............................5-10 Limitations ...............................................................5-10 Weight and Balance .....................................................5-12 Center of Gravity ......................................................5-12 Problems Associated With CG Forward ofForward Limit .......................................................5-12 Problems Associated With CG Aft of Aft Limit ..5-13 Sample Weight and Balance Problems ....................5-13 Ballast ..........................................................................5-14 Chapter 6Preflight and Ground Operations .......................6-1 Introduction....................................................................6-1 Assembly and Storage Techniques ................................6-2 Trailering....................................................................6-3 Tiedown and Securing ................................................6-4Water Ballast ..............................................................6-4 Ground Handling........................................................6-4 Launch Equipment Inspection ....................................6-5 Glider Preflight Inspection .........................................6-6 Prelaunch Checklist ....................................................6-7 Glider Care .....................................................................6-7 Preventive Maintenance .............................................6-8 Chapter 7Launch and Recovery Procedures and Flight Maneuvers ............................................................7-1 Introduction....................................................................7-1 Aerotow Takeoff Procedures .........................................7-2 Signals ........................................................................7-2 Prelaunch Signals ....................................................7-2 Inflight Signals ........................................................7-3 Takeoff Procedures and Techniques ..........................7-3 Normal Assisted Takeoff............................................7-4 Unassisted Takeoff.....................................................7-5 Crosswind Takeoff .....................................................7-5 Assisted ...................................................................7-5 Unassisted...............................................................7-6 Aerotow Climb-Out ....................................................7-6 Aerotow Release.........................................................7-8 Slack Line ...................................................................7-9 Boxing the Wake ......................................................7-10 Ground Launch Takeoff Procedures ............................7-11 CG Hooks .................................................................7-11 Signals ......................................................................7-11 Prelaunch Signals (Winch/Automobile) ...............7-11 Inflight Signals ......................................................7-12 Tow Speeds ..............................................................7-12 Automobile Launch ..................................................7-14 Crosswind Takeoff and Climb .................................7-14 Normal Into-the-Wind Launch .................................7-15 Climb-Out and Release Procedures ..........................7-16 Self-Launch Takeoff Procedures ..............................7-17 Preparation and Engine Start ....................................7-17 Taxiing .....................................................................7-18 Pretakeoff Check ......................................................7-18 Normal Takeoff ........................................................7-19 Crosswind Takeoff ...................................................7-19 Climb-Out and Shutdown Procedures ......................7-19 Landing .....................................................................7-21 Gliderport/Airport Traffic Patterns and Operations .....7-22 Normal Approach and Landing ................................7-22 Crosswind Landing ..................................................7-25 Slips ..........................................................................7-25 Downwind Landing ..................................................7-27 After Landing and Securing .....................................7-27viiiPerformance Maneuvers ..............................................7-27 Straight Glides ..........................................................7-27 Turns.........................................................................7-28 Roll-In ...................................................................7-29 Roll-Out ................................................................7-30 Steep Turns ...........................................................7-31 Maneuvering at Minimum Controllable Airspeed ...7-31 Stall Recognition and Recovery ...............................7-32 Secondary Stalls ....................................................7-34 Accelerated Stalls .................................................7-34 Crossed-Control Stalls ..........................................7-35 Operating Airspeeds .....................................................7-36 Minimum Sink Airspeed ..........................................7-36 Best Glide Airspeed..................................................7-37 Speed to Fly ..............................................................7-37 Chapter 8Abnormal and Emergency Procedures .............8-1 Introduction....................................................................8-1 Porpoising ......................................................................8-2 Pilot-Induced Oscillations (PIOs) ..............................8-2 PIOs During Launch ...................................................8-2 Factors Influencing PIOs ........................................8-2 Improper Elevator Trim Setting ..............................8-3 Improper Wing Flaps Setting ..................................8-3 Pilot-Induced Roll Oscillations During Launch .........8-3 Pilot-Induced Yaw Oscillations During Launch ........8-4 Gust-Induced Oscillations ..............................................8-5 Vertical Gusts During High-Speed Cruise .................8-5 Pilot-Induced Pitch Oscillations During Landing ......8-6 Glider-Induced Oscillations ...........................................8-6 Pitch Influence of the Glider Towhook Position ........8-6 Self-Launching Glider Oscillations During Powered Flight ...........................................................8-7 Nosewheel Glider Oscillations During Launchesand Landings ..............................................................8-7 Tailwheel/Tailskid Equipped Glider Oscillations During Launches and Landings ..................................8-8 Aerotow Abnormal and Emergency Procedures ............8-8 Abnormal Procedures .................................................8-8 Towing Failures........................................................8-10 Tow Failure With Runway To Land and Stop ......8-11 Tow Failure Without Runway To Land BelowReturning Altitude ................................................8-11 Tow Failure Above Return to Runway Altitude ...8-11 Tow Failure Above 800' AGL ..............................8-12 Tow Failure Above Traffic Pattern Altitude .........8-13 Slack Line .................................................................8-13 Ground Launch Abnormal and Emergency Procedures ....................................................................8-14 Abnormal Procedures ...............................................8-14 Emergency Procedures .............................................8-14 Self-Launch Takeoff Emergency Procedures ..............8-15 Emergency Procedures .............................................8-15 Spiral Dives ..................................................................8-15 Spins .............................................................................8-15 Entry Phase ...............................................................8-17 Incipient Phase .........................................................8-17 Developed Phase ......................................................8-17 Recovery Phase ........................................................8-17 Off-Field Landing Procedures .....................................8-18 Afterlanding Off Field .............................................8-20 Off-Field Landing Without Injury ........................8-20 Off-Field Landing With Injury .............................8-20 System and Equipment Malfunctions ..........................8-20 Flight Instrument Malfunctions ................................8-20 Airspeed Indicator Malfunctions ..........................8-21 Altimeter Malfunctions .........................................8-21 Variometer Malfunctions ......................................8-21 Compass Malfunctions .........................................8-21 Glider Canopy Malfunctions ....................................8-21 Broken Glider Canopy ..........................................8-22 Frosted Glider Canopy ..........................................8-22 Water Ballast Malfunctions ......................................8-22 Retractable Landing Gear Malfunctions ..................8-22 Primary Flight Control Systems ...............................8-22 Elevator Malfunctions ..........................................8-22 Aileron Malfunctions ............................................8-23 Rudder Malfunctions ............................................8-24 Secondary Flight Controls Systems .........................8-24 Elevator Trim Malfunctions .................................8-24 Spoiler/Dive Brake Malfunctions .........................8-24 Miscellaneous Flight System Malfunctions .................8-25 Towhook Malfunctions ............................................8-25 Oxygen System Malfunctions ..................................8-25 Drogue Chute Malfunctions .....................................8-25 Self-Launching Gliders ................................................8-26 Self-Launching/Sustainer Glider Engine Failure During Takeoff or Climb ..........................................8-26 Inability to Restart a Self-Launching/SustainerGlider Engine While Airborne .................................8-27 Self-Launching Glider Propeller Malfunctions ........8-27 Self-Launching Glider Electrical System Malfunctions .............................................................8-27 In-flight Fire .............................................................8-28 Emergency Equipment and Survival Gear ...................8-28 Survival Gear Checklists ..........................................8-28 Food and Water ........................................................8-28ixClothing ....................................................................8-28 Communication ........................................................8-29 Navigation Equipment ..............................................8-29 Medical Equipment ..................................................8-29 Stowage ....................................................................8-30 Parachute ..................................................................8-30 Oxygen System Malfunctions ..................................8-30 Accident Prevention .....................................................8-30 Chapter 9Soaring Weather ..................................................9-1 Introduction....................................................................9-1 The Atmosphere .............................................................9-2 Composition ...............................................................9-2 Properties ....................................................................9-2 Temperature............................................................9-2 Density ....................................................................9-2 Pressure ...................................................................9-2 Standard Atmosphere .................................................9-3 Layers of the Atmosphere ..........................................9-4 Scale of Weather Events ................................................9-4 Thermal Soaring Weather ..............................................9-6 Thermal Shape and Structure .....................................9-6 Atmospheric Stability .................................................9-7 Air Masses Conducive to Thermal Soaring ...................9-9 Cloud Streets ..............................................................9-9 Thermal Waves...........................................................9-9 Thunderstorms..........................................................9-10 Lifted Index ..........................................................9-12 K-Index .................................................................9-12 Weather for Slope Soaring .......................................9-14 Mechanism for Wave Formation ..............................9-16 Lift Due to Convergence ..........................................9-19 Obtaining Weather Information ...................................9-21 Preflight Weather Briefing........................................9-21 Weather-ReIated Information ..................................9-21 Interpreting Weather Charts, Reports, andForecasts ......................................................................9-23 Graphic Weather Charts ...........................................9-23 Winds and Temperatures Aloft Forecast ..............9-23 Composite Moisture Stability Chart .....................9-24 Chapter 10Soaring Techniques ..........................................10-1 Introduction..................................................................10-1 Thermal Soaring ...........................................................10-2 Locating Thermals ....................................................10-2 Cumulus Clouds ...................................................10-2 Other Indicators of Thermals ................................10-3 Wind .....................................................................10-4 The Big Picture .....................................................10-5Entering a Thermal ..............................................10-5 Inside a Thermal.......................................................10-6 Bank Angle ...........................................................10-6 Speed .....................................................................10-6 Centering ...............................................................10-7 Collision Avoidance ................................................10-9 Exiting a Thermal .....................................................10-9 Atypical Thermals ..................................................10-10 Ridge/Slope Soaring ..................................................10-10 Traps ......................................................................10-10 Procedures for Safe Flying .....................................10-12 Bowls and Spurs .....................................................10-13 Slope Lift ................................................................10-13 Obstructions ...........................................................10-14 Tips and Techniques ...............................................10-15 Wave Soaring .............................................................10-16 Preflight Preparation ...............................................10-17 Getting Into the Wave ............................................10-18 Flying in the Wave .................................................10-20 Soaring Convergence Zones ...................................10-23 Combined Sources of Updrafts ..............................10-24 Chapter 11Cross-Country Soaring .....................................11-1 Introduction..................................................................11-1 Flight Preparation and Planning ...................................11-2 Personal and Special Equipment ..................................11-3 Navigation ....................................................................11-5 Using the Plotter .......................................................11-5 A Sample Cross-Country Flight ...............................11-5 Navigation Using GPS .............................................11-8 Cross-Country Techniques ...........................................11-9 Soaring Faster and Farther .........................................11-11 Height Bands ..........................................................11-11 Tips and Techniques ...............................................11-12 Special Situations .......................................................11-14 Course Deviations ..................................................11-14 Lost Procedures ......................................................11-14 Cross-Country Flight in a Self-Launching Glider .....11-15 High-Performance Glider Operations and Considerations ............................................................11-16 Glider Complexity ..................................................11-16 Water Ballast ..........................................................11-17 Cross-Country Flight Using Other Lift Sources ........11-17 Chapter 12Towing ................................................................12-1 Introduction..................................................................12-1 Equipment Inspections and Operational Checks .........12-2 Tow Hook ................................................................12-2 Schweizer Tow Hook ...........................................12-2x。
单位内部认证船舶英语考试(试卷编号231)

单位内部认证船舶英语考试(试卷编号231)1.[单选题]The difference between measured and desired values is called _________.A)offsetB)errorC)deviationD)set答案:C解析:【注】deviation:偏差2.[单选题]What is international NAVTEX based on?A)TerrestrialB)NBDPC)Satellite.D)Digital答案:B解析:【注】国际NAVTEX业务是基于NBDP技术的。
3.[单选题]_____ is NOT a part of the main switchboard.A)Bus-barB)LoadC)ParallelingD)Shore答案:D解析:【注】shore connection box:岸电接线箱4.[单选题]The development of ______ led to the fully automatic ARPA systems installed on commercial ships.A)SeaTalkB)powerfulC)chartplotterD)small-scale答案:B解析:5.[单选题]The abbreviation of “PF” in the electrotechnics field equivalents to______.A)powerB)power6.[单选题]Which statement about the gyrocompass is FALSE?A)ItsB)ItC)ItD)If答案:A解析:7.[单选题]Brushless generators are designed to operate without the use of _____.A)brushesB)slipC)commutatorsD)all答案:D解析:8.[单选题]The gyrocompass error resulting from your vessel's movement in OTHER than an east-west direction is called ______.A)dampingB)ballisticC)quadrantalD)speed答案:D解析:【注】damping error:阻尼误差;quadrantal error:象限差9.[单选题]AIS stands for ______.A)AtlanticB)AutomaticC)AstronomicalD)Audio答案:B解析:10.[单选题]The marine high-voltage power system is rated higher than ______ but not higher than _______.A)440B)38011.[单选题]The DPU in the DataChief C20 alarm and monitoring system stands for ______.A)DocumentB)DistributedC)DepartmentD)Display答案:B解析:12.[单选题]The steering gear provides a movement to the rudder in response to a signal from the______.A)bridgeB)MCRC)transmissionD)engine答案:A解析:13.[单选题]The magnetic field is provided by electromagnets so arranged that adjacent poles have _____.A)oppositeB)theC)negativeD)positive答案:A解析:【注】磁场由电磁铁产生,电磁铁布置成相邻的磁极磁性相反。
On obtaining OWA operator weights a short survey

On obtaining OW A operator weights:a short surveyof recent developmentsRobert Full´e rE¨o tv¨o s Lor´a nd UniversityDepartment of Operations ResearchP´a zm´a ny P´e ter s´e t´a ny1/C,H-117Hungaryrfuller@cs.elte.huAbstract—The determination of ordered weighted averaging(OW A)operator weights is a very important issue of applyingthe OWA operator for decision making.One of thefirst ap-proaches,suggested by O’Hagan,determines a special class ofOW A operators having maximal entropy of the OWA weightsfor a given level of orness;algorithmically it is based on thesolution of a constrained optimization problem.In2001,using themethod of Lagrange multipliers,Full´e r and Majlender solved thisconstrained optimization problem analytically and determinedthe optimal weighting vector.In2003Full´e r and Majlender alsosuggested a minimum variance method to obtain the minimalvariability OW A operator weights.In this paper we give a shortsurvey of some later works that extend and develop these models.I.O BTAINING OWA OPERATOR WEIGHTSAn OWA operator of dimension n is a mapping F:R n→Rthat has an associated weighting vector W=(w1,...,w n)Tof having the propertiesw1+···+w n=1,0≤w i≤1,i=1,...,n,and such thatF(a1,...,a n)=ni=1w i b i,where b j is the j th largest element of the collection of the aggregated objects{a1,...,a n}.In[4],Yager introduced two characterizing measures asso-ciated with the weighting vector W of an OW A operator.The first one,the measure of orness of the aggregation,is definedasorness(W)=1n−1ni=1(n−i)w i.and it characterizes the degree to which the aggregation is like an or operation.It is clear that orness(W)∈[0,1]holds for any weighting vector.The second one,the measure of dispersion of the aggrega-tion,is defined asdisp(W)=−ni=1w i ln w iand it measures the degree to which W takes into account all information in the aggregation.It is clear that the actual type of aggregation performed by an OW A operator depends upon the form of the weighting vec-tor.A number of approaches have been suggested for obtaining the associated weights,i.e.,quantifier guided aggregation[4], [5],exponential smoothing[7]and learning[6].O’Hagan[1]determined OW A operator weights and sug-gested a maximum entropy method,which formulates the OW A operator weight problem as a constrained nonlinear optimization model with a predefined degree of orness as its constraint and the entropy as its objective function.This approach is based on the solution of he following mathematical programming problem:maximize−ni=1w i ln w is.t.1n−1ni=1(n−i)w i=α,0≤α≤1ni=1w i=1,0≤w i≤1,i=1,...,n.In2001,using the method of Lagrange multipliers,Full´e r and Majlender[2]solved this constrained optimization problem analytically and determined the optimal weighting vector.By their method,the associated weighting vector is easily obtained byln w j=j−1n−1ln w n+n−jn−1ln w1w j=n−1w n−j1w j−1nandw n=((n−1)α−n)w1+1(n−1)α+1−nw1thenw1[(n−1)α+1−nw1]n=((n−1)α)n−1[((n−1)α−n)w1+1] In2003Full´e r and Majlender[3]also suggested a minimum variance method to obtain the minimal variability OW A op-erator weights.A set of OW A operator weights with minimal variability could then be generated.Their approach requiresthe solution of the following mathematical programming prob-lem:minimize D 2(W )=1n ·n i =1 w i −1n2s .t .orness(w )=n i =1n −iw i =α,0≤α≤1,w 1+···+w n =1,0≤w i ≤1,i =1,...,n.II.E XTENSIONSIn 2004Liu and Chen [37]showed the equivalence of ge-ometric OWA operator and maximum entropy OWA operator weights.In 2005Wang and Parkan [35]presented a minimax dis-parity approach,which minimizes the maximum disparity between two adjacent weights under a given level of orness.Their approach was formulated as:minimizemax i =1,2,...,n −1|w i −w i +1|s .t .orness(w )=n i =1n −in −1w i =α,0≤α≤1,w 1+···+w n =1,0≤w i ≤1,i =1,...,n.In 2005Majlender [6]developed a maximal R´e nyi entropymethod for generating a parametric class of OWA operators and the maximal R´e nyi entropy OW A weights.His approach was formulated as:maximize H β(w )=11−βlog 2n i =1w βis .t .orness(w )=n i =1n −in −1w i =α,0≤α≤1,w 1+···+w n =1,0≤w i ≤1,i =1,...,n.where β∈R and H 1(w )=− ni =1w i log 2w i .In 2007Liu [18]proved that the solutions of the minimum variance OWA operator problem under given orness level and the minimax disparity problem for OW A operator are equiv-alent,both of them have the same form of maximum spread equidifferent OWA operator.He also introduced the concept of maximum spread equidifferent OW A operator and proved its equivalence to the minimum variance OW A operator.In 2007Wang et al [12]introduces two models determining as equally important OWA operator weights as possible for a given orness degree.Their models can be written asminimize J 1=n −1 i =1(w i −w i +1)2s .t .orness(w )=n i =1n −in −1w i =α,0≤α≤1,w 1+···+w n =1,0≤w i ≤1,i =1,...,n.andminimize J 2=n −1 i =1w i w i +1−w i +1w i2s .t .orness(w )=n i =1n −in −1w i =α,0≤α≤1,w 1+···+w n =1,0≤w i ≤1,i =1,...,n.In 2007Llamazares [11]proposed determining OW A opera-tor weights regarding the class of majority rule that one shouldwant to obtain when individuals do not grade their preferences between the alternatives.In 2005Cheng et al [44]evaluated airline service quality uisng OW A operators.The OW A weighting vector and the fuzzy quantifiers are strongly related.An intuitive way for shaping a monotonic quantifier,is by means of the threshold that makes a separation between the regions of what is satisfactory and what is not.Therefore,the characteristics of a threshold can be directly related to the OW A weighting vector and to its metrics:the attitudinal character and the ually these two metrics are supposed to be independent,although some limitations in their value come when they are considered jointly.In 2005Troiano and Yager [45]argued that these two metrics are strongly related by the definition of quantifier threshold,and theyshowed how they can be used jointly to verify and validate a quantifier and its threshold.In 2006Xu [42]investigated the dependent OW A operators,and developed a new argument-dependent approach to deter-mining the OW A weights,which can relieve the influence of unfair arguments on the aggregated results.In 2006Zadrozny and Kacprzyk [46]discussed the use of the Yagers OW A operators within a flexible querying interface.Their key issue is the adaptation of an OW A operator to the specifics of a users query.They considered some well-known approaches to the manipulation of the weights vector and proposed a new one that is simple and efficient.They discussed the tuning (selection of weights)of the OW A operators,and proposed an algorithm that is effective and efficient in the context of their FQUERY for Access package [9],[10].In 2006[29]Chang et al proposed a dynamic fuzzy OWA model to deal with problems of group multiple criteria deci-sion making.Their proposed model can help users to solve MCDM problems under the situation of fuzzy or incomplete information.In 2006Wang et al [27]developed the query system of practical hemodialysis database for a regional hospital in Taiwan,which can help the doctors to make more accurate decision in hemodialysis.They built the fuzzy membership function of hemodialysis indices based on experts interviews.They proposed a fuzzy OWA query method,and let the decision makers (doctors)just need to change the weights of attributes dynamical,then the proposed method can revise the weight of each attributes based on aggregation situation and the system will provide synthetic suggestions to the decision makers.AcknowledgmentsThis work has been partially supported by the BME Mobil Innovation Centre,Integrated Project No.2.2:Optimal Designof Network Resources,funded by the Hungarian National Office for Research and Technology.R EFERENCES[1]M.O’Hagan,Aggregating template or rule antecedents in real-time expertsystems with fuzzy set logic,in:Proc.22nd Annual IEEE Asilomar Conf.Signals,Systems,Computers,Pacific Grove,CA,198881-689.[2]R.Full´e r and P.Majlender,An analytic approach for obtaining maximalentropy OW A operator weights,Fuzzy Sets and Systems,124(2001)53-57 [3]R.Full´e r and P.Majlender,On obtaining minimal variablity OW Aoperator weights,Fuzzy Sets and Systems,136(2003)203-215.[4]R.R.Yager,Ordered weighted averaging aggregation operators in multi-criteria decision making,IEEE Trans.on Systems,Man and Cybernetics, 18(1988)183-190.[5]R.R.Yager,Families of OW A operators,Fuzzy Sets and Systems,59(1993)125-148.[6]R.R.Yager and D.Filev,Induced ordered weighted averaging operators,IEEE Trans.on Systems,Man and Cybernetics–Part B:Cybernetics, 29(1999)141-150.[7] D.Filev and R.R.Yager,On the issue of obtaining OW A operatorweights,Fuzzy Sets and Systems,94(1998)157-169[8]P.Majlender,OW A operators with maximal Renyi entropy,Fuzzy Setsand System,155(2005)340360.[9]Kacprzyk J.,Zadrozny:The paradigm of computing with words inintelligent database querying.In Zadeh L.A.,Kacprzyk J.,eds.:Computing with Words in Information/Intelligent Systems.Part1.Foundations.Part2.Applications.Springer-Verlag,Heidelberg and New York(1999)382398.[10]Kacprzyk J.,Zadrozny S.:Computing with words in intelligent databasequerying:standalone and internet-based rmation Sciences (134)(2001)71109[11]Llamazares,B.,Choosing OWA operator weights in thefield of SocialChoice,INFORMATION SCIENCES,177(21),pp.4745-4756.2007. [12]Wang YM,Luo Y,Liu XW,Two new models for determining OW Aoperator weights COMPUTERS&INDUSTRIAL ENGINEERING52(2): 203-209MAR2007[13]Yeh DY,Cheng CH,Yio HW,Empirical research of the principalcomponent analysis and ordered weighted averaging integrated evaluation model on software projects CYBERNETICS AND SYSTEMS38(3):289-3032007[14]Wang YM,Parkan C,A preemptive goal programming method foraggregating OWA operator weights in group decision making INFORMA-TION SCIENCES177(8):1867-1877APR152007[15]Wu J,Liang CY,Huang YQ,An argument-dependent approach todetermining OW A operator weights based on the rule of maximum entropy INTERNATIONAL JOURNAL OF INTELLIGENT SYSTEMS,22(2): 209-221FEB2007[16]Xu ZS,Chen J,An interactive method for fuzzy multiple attribute groupdecision making INFORMATION SCIENCES177(1):248-263JAN1 2007[17]Sadiq,R.,Tesfamariam,S.Probability density functions based weightsfor ordered weighted averaging(OW A)operators:An example of wa-ter quality indices EUROPEAN JOURNAL OF OPERATIONAL RE-SEARCH,182(3),pp.1350-1368.2007[18]Liu,X.,The solution equivalence of minimax disparity and minimumvariance problems for OWA operators,INTERNATIONAL JOURNAL OF APPROXIMATE REASONING,45(1),pp.68-81.2007[19]Cheng CH,Chang JR,Ho TH Dynamic fuzzy OW A model for evaluatingthe risks of software development CYBERNETICS AND SYSTEMS37(8):791-813DEC2006[20]Xu ZS A note on linguistic hybrid arithmetic averaging operatorin multiple attribute group decision making with linguistic information GROUP DECISION AND NEGOTIATION15(6):593-604NOV2006 [21]Liu XW,Lou HW Parameterized additive neat OW A operators withdifferent orness levels INTERNATIONAL JOURNAL OF INTELLIGENT SYSTEMS21(10):1045-1072OCT2006[22]Liu XW,On the properties of equidifferent OW A operator INTERNA-TIONAL JOURNAL OF APPROXIMATE REASONING43(1):90-107 SEP2006[23]Cheng CH,Chang JR,MCDM aggregation model using situationalME-OWA and ME-OWGA operators,INTERNATIONAL JOURNAL OF UNCERTAINTY FUZZINESS AND KNOWLEDGE-BASED SYSTEMS 14(4):421-443AUG2006[24]Ahn BS,On the properties of OW A operator weights functions withconstant level of orness,IEEE TRANSACTIONS ON FUZZY SYSTEMS, 14(4):511-515AUG2006[25]Xu ZH,Induced uncertain linguistic OW A operators applied to groupdecision making,INFORMATION FUSION7(2):231-238JUN2006 [26]Marchant T,Maximal orness weights with afixed variability for owa op-erators,INTERNATIONAL JOURNAL OF UNCERTAINTY FUZZINESS AND KNOWLEDGE-BASED SYSTEMS14(3):271-276JUN2006 [27]Wang JW,Chang JR,Cheng CH,Flexible fuzzy OW A querying methodfor hemodialysis database,SOFT COMPUTING10(11):1031-1042SEP 2006[28]Xinwang Liu,On the maximum entropy parameterized interval approx-imation of fuzzy numbers,FUZZY SETS AND SYSTEMS,157869-878.2006[29]J.-R.Chang,T.-H.Ho,C.-H.Cheng,A.-P.Chen,Dynamic fuzzy OW Amodel for group multiple criteria decision making,SOFT COMPUTING, 10543-554.2006[30]Liu XW,Some properties of the weighted OW A operator,IEEETRANSACTIONS ON SYSTEMS MAN AND CYBERNETICS PART B-CYBERNETICS,36(1):118-127FEB2006[31]Nasibov,E.N.,Aggregation of fuzzy information on the basis of decom-positional representation,CYBERNETICS AND SYSTEMS ANALYSIS, 41(2),pp.309-318.2005[32]Xu ZS,An overview of methods for determining OW A weights,INTER-NATIONAL JOURNAL OF INTELLIGENT SYSTEMS20(8):843-865 AUG2005[33]Lan H,Ding Y,Hong J,Decision support system for rapid prototyp-ing process selection through integration of fuzzy synthetic evaluation and an expert system INTERNATIONAL JOURNAL OF PRODUCTION RESEARCH43(1):169-194JAN12005[34]ArfiB,Fuzzy decision making in politics:A linguistic fuzzy-set ap-proach(LFSA),POLITICAL ANALYSIS13(1):23-56WIN2005 [35]Ying-Ming Wang,Celik Parkan,A minimax disparity approach forobtaining OW A operator weights,INFORMATION SCIENCES,175(2005) 20-29.2005[36]Liu XW,On the methods of decision making under uncertainty withprobability information,INTERNATIONAL JOURNAL OF INTELLI-GENT SYSTEMS,19(12):1217-1238DEC2004[37]Xinwang Liu and Lianghua Chen,On the properties of parametricgeometric OW A operator,INTERNATIONAL JOURNAL OF APPROXI-MATE REASONING,35pp.163-178.2004[38]Chiclana F,Herrera-Viedma E,Herrera F,et al.Induced orderedweighted geometric operators and their use in the aggregation of multi-plicative preference relations INT J INTELL SYST19(3):233-255MAR 2004[39]Beliakov G.,How to build aggregation operators from data INT JINTELL SYST,18(8):903-923AUG2003[40]Xu,Z.,Da,Q.Approaches to obtaining the weights of the orderedweighted aggregation operators Dongnan Daxue Xuebao(Ziran Kexue Ban)/Journal of Southeast University(Natural Science Edition),33(1), pp.94-962003[41]Zadrozny S,Kacprzyk J,On tuning OW A operators in aflexible queryinginterface,LECTURE NOTES IN COMPUTER SCIENCE4027:97-108 2006[42]Xu ZS,Dependent OW A operators,LECTURE NOTES IN ARTIFI-CIAL INTELLIGENCE3885:172-1782006[43]Troiano L,Yager RR On the relationship between the quantifier thresh-old and OW A operators LECTURE NOTES IN ARTIFICIAL INTELLI-GENCE3885:215-2262006[44]Ching-Hsue Cheng,Jing-Rong Chang,Tien-Hwa Ho,and An-Pin Chen,Evaluating the Airline Service Quality by Fuzzy OW A Operators in: Vincent Torra,Yasuo Narukawa,Sadaaki Miyamoto(Eds.):Proceedings of the Modeling Decisions for Artificial Intelligence:Second International Conference,MDAI2005,Tsukuba,Japan,July25-27,2005,LNAI3558, Springer,pp.77-88.2005[45]L.Troiano and R.R.Yager,A meaure of dispresion for OW A operators,in:Y.Liu,G.Chen and M.Ying eds.,Proceedings of the Eleventh International Fuzzy systems Association World Congress,July28-31,2005, Beijing,China,2005Tsinghua University Press and Springer,[ISBN7-302-11377-7]pp.82-87.2005[46]Liu,X.-W.,Chen,L.-H.The equivalence of maximum entropy OW A op-erator and geometric OW A operator,International Conference on Machine Learning and Cybernetics,5,pp.2673-2676.2003[47]Leon,T.,Zuccarello,P.,Ayala,G.,de Ves,E.,Domingo,J.,Applyinglogistic regression to relevance feedback in image retrieval systems, PATTERN RECOGNITION,40(10),pp.2621-2632.2007[48]Wang,Y.-M.,Luo,Y.,Hua,Z.,Aggregating preference rankings usingOWA operator weights,INFORMATION SCIENCES,177(16),pp.3356-3363.2007[49]Amin,G.R.,Notes on properties of the OW A weights determinationmodel,COMPUTERS&INDUSTRIAL ENGINEERING,52(4),pp.533-538.2007[50]Wang YM,Luo Y,Liu XW,Two new models for determining OW Aoperator weights,COMPUTERS&INDUSTRIAL ENGINEERING52(2):203-209MAR2007[51]Hong DH A note on the minimal variability OW A operator weightsINTERNATIONAL JOURNAL OF UNCERTAINTY FUZZINESS AND KNOWLEDGE-BASED SYSTEMS14(6):747-752DEC2006[52]Liu XW An orness measure for quasi-arithmetic means,IEEE TRANS-ACTIONS ON FUZZY SYSTEMS,14(6):837-848DEC2006[53]Amin GR,Emrouznejad A,An extended minimax disparity to determinethe OW A operator weights,COMPUTERS&INDUSTRIAL ENGINEER-ING50(3):312-316JUL2006[54]Smith PN,Flexible aggregation in multiple attribute decision making:Application to the Kuranda Range Road upgrade,CYBERNETICS AND SYSTEMS,37(1):1-22JAN-FEB2006[55]Liu XW,On the properties of equidifferent RIM quantifier with gener-ating function,INTERNATIONAL JOURNAL OF GENERAL SYSTEMS 34(5):579-594OCT2005Thefinal version of this paper appeared in:Pro-ceedings of the5-th IEEE International Conferenceon Computational Cybernetics(ICCC2007),October19-21,2007,Gammarth,Tunisia,[ISBN:978-1-4244-1146-7],2007pp.241-244.。
关于S^p空间上加权复合算子的有界性及嵌入映射的紧性

LIN Qingze ,LIU Junming ,W U Yutian
(1.School of Applied Mathematics,Guangdong University of Technology,Guangzhou 510520,China; 2.Sch0ol of Financial Mathematics& Statistics,Guangdong University of Finance,Guangzhou 510521,China)
:,H Cf o 称为加权复合算子.文章给出了当 1 q P o。, ∈So。时,
,
加权复合算子 , 从 空间 到 Sq上 的有界性 的充 要条件.然后通过推广 经典 的 Fejer.Riesz不等式证明 了当 1<P 。。时,Sp到 圆盘代数 A 上 的嵌入 映射是紧 的.
收稿 日期 :2017-12-18 基金项 目:国家 自然科学基金数学天 元基金项 目 (11626065) 作者简介:林庆泽 (1994一),男,广东揭 阳人,硕士研 究生,研 究方 向:复分析与 函数空间
E-m ail:gdlqz ̄e.gzhu.edu.cn.
通信作者:刘军 明 (1985一),男,江西吉安人,博士,研 究方 向:复分析与函数空间,
is called the weighted com position operator.In this paper,we give the necessary and
suf icient conditions for the boundedness of ,西 from Sv into Sq when 1 q P ∞ , ∈ o。.Then,by generalizing the classical Fejer-Riesz inequality,we prove that
DB33∕T 1136-2017 建筑地基基础设计规范

5
地基计算 ....................................................................................................................... 14 5.1 承载力计算......................................................................................................... 14 5.2 变形计算 ............................................................................................................ 17 5.3 稳定性计算......................................................................................................... 21
主要起草人: 施祖元 刘兴旺 潘秋元 陈云敏 王立忠 李冰河 (以下按姓氏拼音排列) 蔡袁强 陈青佳 陈仁朋 陈威文 陈 舟 樊良本 胡凌华 胡敏云 蒋建良 李建宏 王华俊 刘世明 楼元仓 陆伟国 倪士坎 单玉川 申屠团兵 陶 琨 叶 军 徐和财 许国平 杨 桦 杨学林 袁 静 主要审查人: 益德清 龚晓南 顾国荣 钱力航 黄茂松 朱炳寅 朱兆晴 赵竹占 姜天鹤 赵宇宏 童建国浙江大学 参编单位: (排名不分先后) 浙江工业大学 温州大学 华东勘测设计研究院有限公司 浙江大学建筑设计研究院有限公司 杭州市建筑设计研究院有限公司 浙江省建筑科学设计研究院 汉嘉设计集团股份有限公司 杭州市勘测设计研究院 宁波市建筑设计研究院有限公司 温州市建筑设计研究院 温州市勘察测绘院 中国联合工程公司 浙江省电力设计院 浙江省省直建筑设计院 浙江省水利水电勘测设计院 浙江省工程勘察院 大象建筑设计有限公司 浙江东南建筑设计有限公司 湖州市城市规划设计研究院 浙江省工业设计研究院 浙江工业大学工程设计集团有限公司 中国美术学院风景建筑设计研究院 华汇工程设计集团股份有限公司
operators with intuitionistic fuzzy information and their application to group decision making

Some induced geometric aggregation operators with intuitionistic fuzzy information and their application to group decision makingGuiwu Wei*Department of Economics and Management,Chongqing University of Arts and Sciences,Yongchuan,Chongqing,402160,PR China1.IntroductionAtanassov[1,2]introduced the concept of intuitionistic fuzzy set(IFS)characterized by a membership function and a non-membership function,which is a generalization of the concept of fuzzy set[44]whose basic component is only a membership function.The intuitionistic fuzzy set has received more and more attention since its appearance[1–39].Gau and Buehrer[6] introduced the concept of vague set.But Bustince and Burillo[7] showed that vague sets are intuitionistic fuzzy sets.Szmidt and Kacprzyk[9]proposed some solution concepts such as the intuitionistic fuzzy core and consensus winner in group decision making with intuitionistic fuzzy preference relations,and developed an approach to aggregate the individual intuitionistic fuzzy preference relations into a social fuzzy preference relation based on fuzzy majority equated with a fuzzy linguistic quantier. Atanassov et al.[3]proposed an intuitionistic fuzzy interpretation of multiple persons MADM,in which each decision maker is asked to evaluate at least a part of the alternatives in terms of their performance with respect to each predefined attribute.They also developed a method for multiple persons MADM and proposed some examples.Li[10]investigated MADM with intuitionistic fuzzy information and constructed several linear programming models to generate optimal weights for attribute.Lin[16]presented a new method for handling multiple attribute fuzzy decision making problems,where the characteristics of the alternatives are represented by intuitionistic fuzzy sets.The proposed method allows the degrees of satisfiability and non-satisfiability of each alternative with respect to a set of attribute to be represented by intuitionistic fuzzy sets,respectively.Furthermore,the proposed method allows the decision maker to assign the degree of membership and the degree of non-membership of the attribute to the fuzzy concept‘‘importance.’’Liu and Wang[17]developed an evaluation function for the decision making problem to measure the degrees to which alternatives satisfy and do not satisfy the decision maker’s requirement.Then,they proposed the intuitionistic fuzzy point operators,and defined a series of new score functions for the MADM problems based on intuitionistic fuzzy point operators and evaluation function.Based on the arithmetic aggregation operators [41–43,45–52],Xu[18]developed the intuitionistic fuzzy arithmetic averaging(IFAA)operator and the intuitionistic fuzzy weighted averaging(IFWA)operator.Furthermore,Xu[19]developed the intuitionistic fuzzy ordered weighted averaging(IFOWA)operator, and the intuitionistic fuzzy hybrid aggregation(IFHA)operator.XuApplied Soft Computing10(2010)423–431A R T I C L E I N F OArticle history:Received1August2008Received in revised form13May2009 Accepted2August2009Available online8August2009Keywords:Intuitionistic fuzzy numbersInterval-valued intuitionistic fuzzy numbersOperational lawsInduced intuitionistic fuzzy ordered weighted geometric(I-IFOWG)operator Induced interval-valued intuitionistic fuzzy ordered weighted geometric(I-IIFOWG) operator A B S T R A C TWith respect to multiple attribute group decision making(MAGDM)problems in which both the attribute weights and the expert weights take the form of real numbers,attribute values take the form of intuitionistic fuzzy numbers or interval-valued intuitionistic fuzzy numbers,some new group decision making analysis methods are developed.Firstly,some operational laws,score function and accuracy function of intuitionistic fuzzy numbers or interval-valued intuitionistic fuzzy numbers are introduced. Then two new aggregation operators:induced intuitionistic fuzzy ordered weighted geometric(I-IFOWG) operator and induced interval-valued intuitionistic fuzzy ordered weighted geometric(I-IIFOWG)operator are proposed,and some desirable properties of the I-IFOWG and I-IIFOWG operators are studied,such as commutativity,idempotency and monotonicity.An I-IFOWG and IFWG(intuitionistic fuzzy weighted geometric)operators-based approach is developed to solve the MAGDM problems in which both the attribute weights and the expert weights take the form of real numbers,attribute values take the form of intuitionistic fuzzy numbers.Further,we extend the developed models and procedures based on I-IIFOWG and IIFWG(interval-valued intuitionistic fuzzy weighted geometric)operators to solve the MAGDM problems in which both the attribute weights and the expert weights take the form of real numbers, attribute values take the form of interval-valued intuitionistic fuzzy numbers.Finally,some illustrative examples are given to verify the developed approach and to demonstrate its practicality and effectiveness.ß2009Elsevier B.V.All rights reserved.*Tel.:+862349891870;fax:+862349891870. E-mail address:weiguiwu@.Contents lists available at ScienceDirect Applied Soft Computingj o ur n a l ho m e pa g e:w w w.e l s e vi e r.c om/l o ca t e/as o c1568-4946/$–see front matterß2009Elsevier B.V.All rights reserved.doi:10.1016/j.asoc.2009.08.009[20]developed some geometric aggregation operators,such as the intuitionistic fuzzy weighted geometric(IFWG)operator,the intuitionistic fuzzy ordered weighted geometric(IFOWG)operator, and the intuitionistic fuzzy hybrid geometric(IFHG)operator and gave an application of the IFHG operator to multiple attribute group decision making with intuitionistic fuzzy information.Xu[21] defined some new intuitionistic preference relations,such as the consistent intuitionistic preference relation,incomplete intuitio-nistic preference relation and acceptable intuitionistic preference relation,and studied their properties and also developed a method for group decision making with intuitionistic preference relations and a method for group decision making with incomplete intuitionistic preference relations,respectively.Xu[22]investigated the group decision making problems in which all the information provided by the decision makers is expressed as intuitionistic fuzzy decision matrices where each of the elements is characterized by intuitionistic fuzzy number,and the information about attribute weights is partially known,which may be constructed by various forms.Li[14]extended the linear programming techniques for multidimensional analysis of preference(LINMAP)to develop a new methodology for solving MADM problems in intuitionistic fuzzy environments.Xu[23]investigated the intuitionistic fuzzy MADM with the information about attribute weights is incompletely known or completely unknown,a method based on the ideal solution was ter,Atanassov and Gargov[4,5]further introduced the interval-valued intuitionistic fuzzy set(IVIFS),which is a general-ization of the IFS.The fundamental characteristic of the IVIFS is that the values of its membership function and non-membership function are intervals rather than exact numbers.Burillo[8]defined the concepts of correlation and correlation coefficient of IVIFSs,and developed two decomposition theorems of the correlation of IVIFSs in terms of the correlation of interval-valued fuzzy sets and the entropy of the intuitionistic fuzzy sets,and the correlation of intuitionistic fuzzy sets.Hong[31]generalized the concepts of correlation and correlation coefficient of IVIFSs in a general probability space.Hung and Wu[32]proposed a method to calculate the correlation coefficient of IVIFSs by means of‘‘centroid’’. Xu[24]proposed a new approach to deriving the correlation coefficients of IVIFSs.The prominent characteristic of the approach is that it can guarantee that the correlation coefficient of any two IVIFSs equals one if and only if these two IVIFSs are the same,and can relieve the influence of the unfair arguments on thefinal results. Grzegorzewski[33]proposed some distances between intuitionistic fuzzy sets and/or interval-valued fuzzy sets based on the Hausdorff metric.Wang[34]used evidential reasoning algorithms to solve MADM in which the information on the attribute’s weights is incomplete and attribute’s values is interval intuitionistic fuzzy numbers.Xu[25]proposed the interval-valued intuitionistic fuzzy weighted averaging(IIFWA)operator.Furthermore,Xu[25] developed the interval-valued intuitionistic fuzzy ordered weighted averaging(IIFOWA)operator and the interval-valued intuitionistic fuzzy hybrid aggregation(IIFHA)operator and gave an application of the IIFHA operator to multiple attribute group decision making with interval-valued intuitionistic fuzzy information.Xu[28]developed the interval-valued intuitionistic fuzzy weighted geometric(IIFWG) operator.Furthermore,Xu[26]developed the interval-valued intuitionistic fuzzy ordered weighted geometric(IIFOWG)operator and the interval-valued intuitionistic fuzzy hybrid geometric(IIFHG) operator.In this paper,we investigate the MAGDM problems,in which both the attribute weights and the expert weights take the form of real numbers,attribute values take the form of intuitionistic fuzzy numbers or interval-valued intuitionistic fuzzy numbers.Then,we propose two new aggregation operators called induced intuitio-nistic fuzzy ordered weighted geometric(I-IFOWG)operator and induced interval-valued intuitionistic fuzzy ordered weighted geometric(I-IIFOWG)operator which are an extension of induced ordered weighted geometric(IOWG)operator proposed by Xu and Da[27]and study some desirable properties of the I-IFOWG and I-IIFOWG operators,such as commutativity,idempotency and monotonicity.An I-IFOWG and IFWG(intuitionistic fuzzy weighted geometric)operators-based approach is developed to solve the MAGDM problems in which both the attribute weights and the expert weights take the form of real numbers,attribute values take the form of intuitionistic fuzzy numbers.Further,we extend the developed models and procedures based on I-IIFOWG and IIFWG(interval-valued intuitionistic fuzzy weighted geo-metric)operators to solve the MAGDM problems in which both the attribute weights and the expert weights take the form of real numbers,attribute values take the form of interval-valued intuitionistic fuzzy numbers.In order to do so,the remainder of this paper is set out as follows.In the next section,we introduce some basic concepts related to intuitionistic fuzzy sets and a new aggregation operator called induced intuitionistic fuzzy ordered weighted geometric (I-IFOWG)operator is proposed,and some desirable properties of the I-IFOWG operators are studied,such as commutativity, idempotency and monotonicity.In Section3,An I-IFOWG and IFWG(intuitionistic fuzzy weighted geometric)operators-based approach is developed to solve the MAGDM under the intuitio-nistic fuzzy environment.In Section4a new aggregation operator called induced interval-valued intuitionistic fuzzy ordered weighted geometric(I-IIFOWG)operator is proposed,and some desirable properties of the I-IIFOWG operators are studied,such as commutativity,idempotency and monotonicity.In Section5,An I-IIFOWG and IIFWG(interval-valued intuitionistic fuzzy weighted geometric)operators-based approach is developed to solve the MAGDM under the interval-valued intuitionistic fuzzy environ-ment.In Section6,some illustrative examples are pointed out.In Section7we conclude the paper and give some remarks.2.Induced intuitionistic fuzzy ordered weighted geometric (I-IFOWG)operatorIn the following,we shall introduce some basic concepts related to intuitionistic fuzzy sets.Definition1.Let X be a universe of discourse,then a fuzzy set is defined as:A¼x;m A xðÞh i x2Xjf g(1) which is characterized by a membership function m A:X!0;1½ , where m A xðÞdenotes the degree of membership of the element x to the set A[44].Atanassov[1,2]extended the fuzzy set to the IFS,shown as follows:Definition2.An IFS A in X is given byA¼x;m A xðÞ;n A xðÞh i x2Xjf g(2) where m A:X!0;1½ and n A:X!0;1½ ,with the condition0m A xðÞþn A xðÞ1;8x2XThe numbers m A xðÞand n A xðÞrepresent,respectively,the membership degree and non-membership degree of the element x to the set A.Definition3.For each IFS A in X,ifp A xðÞ¼1ÀmAxðÞÀn A xðÞ;8x2X(3) Then p A xðÞis called the degree of indeterminacy of x to A[1,2].G.Wei/Applied Soft Computing10(2010)423–431 424Definition 4.Let ˜a¼m ;n ðÞbe an intuitionistic fuzzy number,a score function S of an intuitionistic fuzzy value can be represented as follows [39]:S ˜aðÞ¼m Àn ;S ˜aðÞ2À1;1½ :(4)Definition 5.Let ˜a¼m ;n ðÞbe an intuitionistic fuzzy number,an accuracy function H of an intuitionistic fuzzy value can be repre-sented as follows [31]:H ˜aðÞ¼m þn ;H ˜aðÞ20;1½ (5)to evaluate the degree of accuracy of the intuitionistic fuzzy value˜a¼m ;n ðÞ,where H ˜a ðÞ20;1½ .The larger the value of H ˜a ðÞ,the more the degree of accuracy of the intuitionistic fuzzy value ˜a.As presented above,the score function S and the accuracyfunction H are,respectively,defined as the difference and the sum of the membership function ˜m A x ðÞand the non-member-ship function ˜nA x ðÞ.Hong and Choi [31]showed that the relation between the score function S and the accuracy function H is similar to the relation between mean and variance in statistics.Based on the score function S and the accuracy function H ,in the following,Xu [20]give an order relation between two intuitionistic fuzzy values,which is defined as follows:Definition 6.Let ˜a1¼m 1;n 1ðÞand ˜a 2¼m 2;n 2ðÞbe two intuitio-nistic fuzzy values,s ˜a1ðÞ¼m 1Àn 1and s ˜a 2ðÞ¼m 2Àn 2be the scores of ˜aand ˜b ,respectively,and let H ˜a 1ðÞ¼m 1þn 1and H ˜a 2ðÞ¼m 2þn 2be the accuracy degrees of ˜aand ˜b ,respectively,then if S ˜aðÞ<S ˜b,then ˜a is smaller than ˜b ,denoted by ˜a <˜b ;if S ˜aðÞ¼S ˜b ,then (1)if H ˜a ðÞ¼H ˜b ,then ˜a and ˜b represent the same information,denoted by ˜a¼˜b ;(2)if H ˜a ðÞ<H ˜b,˜a is smaller than ˜b,denoted by ˜a <˜b .Definition 7.Let ˜aj ¼m j ;n jj ¼1;2;ÁÁÁ;n ðÞbe a collection of intuitionistic fuzzy values,and let IFWG:Q n !Q ,ifIFWG v ˜a 1;˜a 2;ÁÁÁ;˜a n ðÞ¼Yn j ¼1˜a j v j ¼Y n j ¼1m j v j ;1ÀY n j ¼11Àn jÀÁv j;0@1A(6)wherev ¼v 1;v 2;ÁÁÁ;v n ðÞTbethe weight vector of˜aj j ¼1;2;ÁÁÁ;n ðÞ,and v j >0,Xn j ¼1v j ¼1,then IFWG is calledthe intuitionistic fuzzy weighted geometric (IFWG)operator[20].Example 1.Assume v ¼0:3;0:4;0:2;0:1ðÞ,˜a1¼0:3;0:5ðÞ,˜a 2¼0:2;0:6ðÞ,˜a 3¼0:7;0:2ðÞ,and ˜a 4¼0:4;0:3ðÞ,then IFWG v ˜a1;˜a 2;˜a 3;˜a 4ðÞ¼0:30:3Â0:20:4Â0:70:2Â0:40:1;1Àð1À0:5Þ0:3Âð1À0:6Þ0:4Âð1À0:2Þ0:2Âð1À0:3Þ0:1Þ¼0:311;0:480ðÞDefinition 8.Let ˜aj ¼m j ;n jj ¼1;2;ÁÁÁ;n ðÞbe a collection of intuitionistic fuzzy values,an intuitionistic fuzzy ordered weighted geometric (IFOWG)operator of dimension n is a mapping IFOWG:Q n !Q ,that has an associated weight vector w ¼w 1;w 2;ÁÁÁ;w n ðÞTsuch that w j >0and X n j ¼1w j ¼1.Furthermore,IFOWG w ˜a 1;˜a 2;ÁÁÁ;˜a n ðÞ¼Yn j ¼1˜as j ðÞw j ¼Y n j ¼1m s j ðÞw j ;1ÀY n j ¼11Àn s j ðÞÀÁwj 0@1A(7)where s 1ðÞ;s 2ðÞ;ÁÁÁ;s n ðÞðÞis a permutation of 1;2;ÁÁÁ;n ðÞ,suchthat ˜a s j À1ðÞ!˜a s j ðÞfor all j ¼2;ÁÁÁ;n .[20].Example 2.Let ˜a 1¼0:5;0:3ðÞ,˜a 2¼0:4;0:5ðÞ,˜a 3¼0:8;0:1ðÞ,and ˜a 4¼0:6;0:3ðÞbe four intuitionistic fuzzy values,by (4),we calcu-late the scores of ˜aj j ¼1;2;3;4ðÞ:S ˜a1ðÞ¼0:5À0:3¼0:2;S ˜a 2ðÞ¼0:4À0:5¼À0:1S ˜a 3ðÞ¼0:8À0:1¼0:7;S ˜a 4ðÞ¼0:6À0:3¼0:3SinceS ˜a 3ðÞ>S ˜a 4ðÞ>S ˜a 1ðÞ>S ˜a 2ðÞthus˜as 1ðÞ¼0:8;0:1ðÞ;˜a s 2ðÞ¼0:6;0:3ðÞ;˜as 3ðÞ¼0:5;0:3ðÞ;˜as 4ðÞ¼0:4;0:5ðÞSuppose that w ¼0:2;0:3;0:4;0:1ðÞis the weighting vector of the IFOWG operator.Then,by (7),it follows thatIn the following,we shall develop an induced intuitionisticfuzzy ordered weighted geometric (I-IFOWG)operator which is an extension of induced ordered weighted averaging (IOWG)operator proposed by Xu and Da [27].Definition 9.An induced intuitionistic fuzzy ordered weighted geometric (I-IFOWG)operator is defined as follows:where w ¼w 1;w 2;ÁÁÁ;w n ðÞT is a weighting vector,such thatw j >0,Xn j ¼1w j ¼1,j ¼1;2;ÁÁÁ;n ,˜as j ðÞ¼m s j ðÞ;n s j ðÞ is the ˜a i value of the IFOWG pair u i ;˜ai h i having the j th largest u i u i 20;1½ ðÞ,and u i in u i ;˜ai h i is referred to as the order IFOWG w ˜a1;˜a 2;˜a 3;˜a 4ðÞ¼0:80:2Â0:60:3Â0:50:4Â0:40:1;1Àð1À0:1Þ0:2Âð1À0:3Þ0:3Âð1À0:3Þ0:4Âð1À0:5Þ0:1¼0:567;0:288ðÞI-IFOWG w u 1;˜a 1h i ;u 2;˜a 2h i ;ÁÁÁ;u n ;˜a n h i ðÞ¼Yn j ¼1˜as j ðÞw j ¼Y n j ¼1m s j ðÞw j ;1ÀY n j ¼11Àn s j ðÞÀÁwj 0@1A(8)G.Wei /Applied Soft Computing 10(2010)423–431425inducing variable and ˜ai ˜a i ¼m i ;n i ðÞðÞas the intuitionistic fuzzy values.The I-IFOWG operator has the following properties similar to those of the IOWG operator [27].Theorem 1(Commutativity ).I-IFOWG w u 1;˜a1h i ;u 2;˜a 2h i ;ÁÁÁ;u n ;˜a n h i ðÞ¼I-IFOWG w u 1;˜a 01;u 2;h À˜a02i ;ÁÁÁ;u n ;˜a 0n Þwhere u 1;˜a 01 ;u 2;˜a 02 ;ÁÁÁ;u n ;˜a 0n ÀÁis any per-mutation of u 1;˜a 1h i ;u 2;˜a 2h i ;ÁÁÁ;u n ;˜a n h i ðÞ.Proof.LetI-IFOWG w u 1;˜a 1h i ;u 2;˜a 2h i ;ÁÁÁ;u n ;˜a n h i ðÞ¼Yn j ¼1˜a s j ðÞw j I-IFOWG wu 1;˜a01;u 2;˜a 02 ;ÁÁÁ;u n ;˜a 0n ÀÁ¼Y n j ¼1˜a0s j ðÞ w jSince u 1;˜a 01 ;u 2;˜a 02 ;ÁÁÁ;u n ;˜a 0n ÀÁis any permutation ofu 1;˜a1h i ;u 2;˜a 2h i ;ÁÁÁ;u n ;˜a n h i ðÞ,we have ˜a s j ðÞ¼˜a 0s j ðÞj ¼1;2;ÁÁÁ;ðn Þ,and thenI-IFOWG w u 1;˜a 1h i ;u 2;˜a 2h i ;ÁÁÁ;u n ;˜a n h i ðÞ¼I-IFOWG w u 1;˜a 01 ;u 2;˜a 02 ;ÁÁÁ;u n ;˜a 0n ÀÁ&Theorem 2(Idempotency ).If ˜aj ˜a j ¼m j ;n j¼˜a ˜a ¼m ;n ðÞðÞfor all j ,then I-IFOWG w u 1;˜a 1h i ;ðu 2;˜a2h i ;ÁÁÁ;u n ;˜a n h iÞ¼˜a Proof.Since ˜aj ¼˜a for all j ,we have I-IFOWG w u 1;˜a1h i ;u 2;˜a 2h i ;ÁÁÁ;u n ;˜a n h i ðÞ¼Yn j ¼1˜a w j ¼Y n j ¼1m w j ;1ÀY n j ¼11Àn ðÞw j 0@1A ¼mP nj ¼1w j ;1À1Àn ðÞP nj ¼1w j ¼m ;n ðÞ¼˜a &Theorem 3(Monotonicity ).If ˜aj ˜a 0j for all j ,then I-IFOWG w u 1;˜a 1h i ;u 2;˜a 2h i ;ÁÁÁ;u n ;˜a n h i ðÞ I-IFOWG w u 1;˜a 01 ;u 2;˜a 02 ;ÁÁÁ;u n ;˜a 0n ÀÁProof.LetI -IFOWG w u 1;˜a 1h i ;u 2;˜a 2h i ;ÁÁÁ;u n ;˜a n h i ðÞ¼Yn j ¼1˜as j ðÞw j I -IFOWG wu 1;˜a01 ;u 2;˜a 02 ;ÁÁÁ;u n ;˜a 0n ÀÁ¼Y n j ¼1˜a0s j ðÞ w jSince ˜aj ˜a 0j for allj ,itfollows that˜as j ðÞ ˜a 0s j ðÞj ¼1;2;ÁÁÁ;n ðÞ,thenI-IFOWG w u 1;˜a 1h i ;u 2;˜a 2h i ;ÁÁÁ;u n ;˜a n h i ðÞ I-IFOWG w u 1;˜a 01 ;u 2;˜a 02 ;ÁÁÁ;u n ;˜a 0n ÀÁ&Example 3.Assume we have four IFOWG pairs u j ;˜a jgiven u 1;˜a1h i ¼0:4;0:5;0:3ðÞh i ;u 2;˜a 2h i ¼0:2;0:4;0:5ðÞh i u 3;˜a3h i ¼0:8;0:6;0:2ðÞh i ;u 3;˜a 3h i ¼0:3;0:4;0:3ðÞh i That we desire to aggregate using the weighting vectorw ¼0:2;0:4;0:1;0:3ðÞ.Performing the ordering the IFOWG pairs with respect to the first component,we get u s 1ðÞ;˜as 1ðÞ¼0:8;0:6;0:2ðÞh i u s 2ðÞ;˜a s 2ðÞ ¼0:4;0:5;0:3ðÞh i u s 3ðÞ;˜a s 3ðÞ ¼0:3;0:4;0:3ðÞh i u s 4ðÞ;˜a s 4ðÞ ¼0:2;0:4;0:5ðÞh i This ordering includes the ordered intuitionistic fuzzy argu-ments˜as 1ðÞ¼0:6;0:2ðÞ;˜as 2ðÞ¼0:5;0:3ðÞ;˜as 3ðÞ¼0:4;0:3ðÞ;˜as 4ðÞ¼0:4;0:5ðÞAnd from this,we get an aggregated value3.An approach to group decision making based onintuitionistic fuzzy informationLet A ¼A 1;A 2;ÁÁÁ;A m f g be a discrete set of alternatives,and G ¼G 1;G 2;ÁÁÁ;G n f g be the set of attributes,v ¼v 1;v 2;ÁÁÁ;v n ðÞis the weighting vector of the attribute G j j ¼1;2;ÁÁÁ;n ðÞ,wherev j >0,Xn j ¼1v j ¼1.Let D ¼D 1;D 2;ÁÁÁ;D t f g be the set of decisionmakers,n ¼n 1;n 2;ÁÁÁ;n n ðÞbe the weighting vector of decisionmakers,with n k >0,X t k ¼1n k ¼1.Suppose that ˜R k ¼˜r k ðÞi j m Ân¼m k ðÞi j ;n k ðÞi jm Ânis the intuitionistic fuzzy decision matrix,wherem k ðÞi jindicates the degree that the alternative A i satisfies the attribute G j given by the decision maker D k ,n k ðÞi j indicates the degree that the alternative A i does not satisfy the attribute G j given by the decision maker D k ,m k ðÞi j &0;1½ ,n k ðÞi j &0;1½ ,m k ðÞi j þn k ðÞi j 1,i ¼1;2;ÁÁÁ;m ,j ¼1;2;ÁÁÁ;n ,k ¼1;2;ÁÁÁ;t .In the following,we apply the I-IFOWG and IFWG operator to multiple attribute group decision making based on intuitionistic fuzzy information.The method involves the following steps (Procedure &):Step 1.Utilize the decision information given in matrix ˜Rk ,and the I-IFOWG operator which has associated weighting vector w ¼w 1;w 2;ÁÁÁ;w n ðÞT˜ri j ¼m i j ;n i j ¼I-IFOWG w u 1;˜r 1ðÞi j D E ;u 2;˜r 2ðÞi j D E ;ÁÁÁ;u t ;˜r t ðÞi j D E;i ¼1;2;ÁÁÁ;m ;j ¼1;2;ÁÁÁ;n(9)to aggregate all the decision matrices ˜Rk k ¼1;2;ÁÁÁ;t ðÞinto a collective decision matrix ˜R¼˜r i j ÀÁm Ân ,where u ¼u 1;u 2;ÁÁÁ;f u t g be the weighting vector of decision makers.Step 2.Utilize the decision information given in matrix ˜R,and the IFWG operator˜ri ¼m i ;n i ðÞ¼IFWG v ˜r i 1;˜r i 2;ÁÁÁ;˜r in ðÞ;i ¼1;2;ÁÁÁ;m (10)I-IFOWG w 0:4;0:5;0:3ðÞh i ;0:2;0:4;0:5ðÞh i ;ð0:8;0:6;0:2ðÞh i ;0:3;0:4;0:3ðÞh iÞ¼0:60:2Â0:50:4Â0:40:1Â0:40:3;1Àð1À0:2Þ0:2Âð1À0:3Þ0:4Âð1À0:3Þ0:1Âð1À0:5Þ0:3¼0:474;0:350ðÞG.Wei /Applied Soft Computing 10(2010)423–431426to derive the collective overall preference values ˜ri i ¼1;ð2;ÁÁÁ;m Þof the alternative A i ,where v ¼v 1;v 2;ÁÁÁ;v n ðÞT is the weighting vector of the attributes.Step 3.Calculate the scores S ˜ri ðÞi ¼1;2;ÁÁÁ;m ðÞof the collective overall intuitionistic fuzzy preference values ˜ri i ¼1;2;ÁÁÁ;m ðÞto rank all the alternatives A i i ¼1;2;ÁÁÁ;ðm Þand then to select the best one(s)(if there is no difference between two scores S ˜ri ðÞand S ˜r j ÀÁ),then we need to calculate the accuracy degrees H ˜ri ðÞand H ˜r j ÀÁof the collective overall intuitionistic fuzzy preference values ˜ri and ˜r j ,respectively,and then rank the alternatives A i and A j in accordance with the accuracy degrees H ˜ri ðÞand H ˜r j ÀÁ.Step 4.Rank all the alternatives A i i ¼1;2;ÁÁÁ;m ðÞand select thebest one(s)in accordance with S ˜ri ðÞand H ˜r i ðÞi ¼1;2;ÁÁÁ;m ðÞ:Step 5.End.In what follows,we shall extend the developed models and procedures to solve the MAGDM problems in which both the attribute weights and the expert weights take the form of real numbers,attribute values take the form of interval-valued intuitionistic fuzzy numbers.4.Induced interval-valued intuitionistic fuzzy ordered weighted geometric (I-IIFOWG)operatorAtanassov and Gargov [4,5]further introduced the interval-valued intuitionistic fuzzy set (IVIFS),which is a generalization ofthe IFS.The fundamental characteristic of the IVIFS is that thevalues of its membership function and non-membership function are intervals rather than exact numbers.Definition 10.Let X be a universe of discourse,An IVIFS ˜Aover X is an object having the form [4,5]:˜A ¼x ;˜m A x ðÞ;˜nA x ðÞh i x 2X j f g (11)where ˜m A x ðÞ&0;1½ and ˜nA x ðÞ&0;1½ are interval numbers,and 0 sup ˜m A x ðÞðÞþsup ˜nA x ðÞðÞ 1;8x 2X For convenience,let ˜m A x ðÞ¼a ;b ½ ,˜n A x ðÞ¼½c ;d ,so ˜A ¼a ;b ½ ;ðc ;d ½ ÞDefinition 11.Let ˜a¼a ;b ½ ;c ;d ½ ðÞbe an interval-valued intuitio-nistic fuzzy number,a score function S of an interval-valued intuitionistic fuzzy value can be represented as follows [25,28]:S ˜aðÞ¼a Àc þb Àd;S ˜aðÞ2À1;1½ (12)Definition 12.Let ˜a¼a ;b ½ ;c ;d ½ ðÞbe an interval-valued intuitio-nistic fuzzy number,a accuracy function H of an interval-valued intuitionistic fuzzy value can be represented as follows [25,28]:H ˜aðÞ¼a þb þc þd2;H ˜aðÞ20;1½ (13)to evaluate the degree of accuracy of the interval-valuedintuitionistic fuzzy value ˜a¼a ;b ½ ;c ;d ½ ðÞ,where H ˜a ðÞ20;1½ .The larger the value of H ˜aðÞ,the more the degree of accuracy of the interval-valued intuitionistic fuzzy value ˜a.As presented above,the score function S and the accuracyfunction H are,respectively,defined as the difference and the sum of the membership function ˜m A x ðÞand the non-membership function ˜nA x ðÞ.Xu [25]showed that the relation between the score function S and the accuracy function H is similar to the relation between mean and variance in statistics.Based on the score function S and the accuracy function H ,in the following,Xu [25,28]give an order relation between two interval-valued intuitionistic fuzzy values,which is defined as follows:Definition 13.Let ˜a1¼a 1;b 1½ ;c 1;d 1½ ðÞand ˜a 2¼a 2;b 2½ ;c 2;d 2½ ðÞbe two interval-valued intuitionistic fuzzy values,s ˜a1ðÞ¼ða 1Àc 1þb 1Àd 1Þ=2and s ˜a2ðÞ¼ða 2Àc 2þb 2Àd 2Þ=2be the scores of ˜a and ˜b,respectively,and let H ˜a 1ðÞ¼ða 1þc 1þb 1þd 1Þ=2and H ˜a 2ðÞ¼ða 2þc 2þb 2þd 2Þ=2be the accuracy degrees of ˜aand ˜b ,respectively,then if S ˜a ðÞ<S ˜b ,then ˜a is smaller than ˜b ,denotedby ˜a<˜b ;if S ˜a ðÞ¼S ˜b ,then if (1)H ˜a ðÞ¼H ˜b ,then ˜a and ˜b represent the same information,denoted by ˜a ¼˜b ;(2)if H ˜aðÞ<H ˜b,˜a is smaller than ˜b ,denoted by ˜a <˜b .Xu [28]developed the interval-valued intuitionistic fuzzyweighted geometric (IIFWG)operator.Definition 14.Let ˜aj ¼a j ;b j ÂÃ;c j ;d j ÂÃÀÁj ¼1;2;ÁÁÁ;n ðÞbe a col-lection of interval-valued intuitionistic fuzzy values,and let IIFWG:Q n !Q ,ifwhere v ¼v 1;v 2;ÁÁÁ;v n ðÞT be the weight vector of˜a j j ¼1;2;ÁÁÁ;n ðÞ,and v j >0,P nj ¼1v j ¼1,then IIFWG is called the interval-valued intuitionistic fuzzy weighted geometric (IIFWG)operator.Example 4.Assume v ¼0:2;0:3;0:1;0:4ðÞ,˜a1¼0:3;0:5½ ;0:2;½ð0:3 Þ,˜a2¼0:4;0:7½ ;0:1;0:2½ ðÞ,˜a 3¼0:1;0:2½ ;0:7;0:8½ ðÞand ˜a 4¼0:5;0:7½ ;0:1;0:3½ ðÞ,then IIFWG v ˜a1;˜a 2;˜a 3;˜a 4ðÞ¼ð½0:30:2Â0:40:3Â0:10:1Â0:50:4;0:50:2Â0:70:3Â0:20:1Â0:70:4 ;½1Àð1À0:2Þ0:2Âð1À0:1Þ0:3Âð1À0:7Þ0:1Âð1À0:1Þ0:4 ;½1Àð1À0:3Þ0:2Âð1À0:2Þ0:3Âð1À0:8Þ0:1Âð1À0:3Þ0:4¼ ½0:3594;0:5774 ;½0:2124;0:3574Furthermore,Xu [26]developed the interval-valued intuitio-nistic fuzzy ordered weighted geometric (IIFOWG)operator.Definition 15.Let ˜aj ¼a j ;b j ÂÃ;c j ;d j ÂÃÀÁj ¼1;2;ÁÁÁ;n ðÞbe a col-lection of interval-valued intuitionistic fuzzy values.An interval-valued intuitionistic fuzzy ordered weighted geometric (IIFOWG)operator of dimension n is a mapping IIFOWG:Q n !Q ,that has an associated vector w ¼w 1;w 2;ÁÁÁ;w n ðÞT such that w j >0and P nj ¼1w j ¼1.Furthermore,IIFOWG w ˜a 1;˜a 2;ÁÁÁ;˜a n ðÞ¼Yn j ¼1˜a s j ðÞw j ¼Y n j ¼1a s j ðÞw j ;Y n j ¼1b s j ðÞwj 2435;1ÀY n j ¼11Àc s j ðÞÀÁw j ;1ÀY n j ¼11Àd s j ðÞÀÁw j 24350@1A(15)IIFWG v ˜a1;˜a 2;ÁÁÁ;˜a n ðÞ¼Y n j ¼1˜a j v j ¼Y n j ¼1a j v j ;Y n j ¼1b j vj 2435;1ÀY n j ¼11Àc jÀÁv j;1ÀY n j ¼11Àd jÀÁv j24350@1A(14)G.Wei /Applied Soft Computing 10(2010)423–431427。
认知无线电中基于加权硬判决的协作频谱感知算法英文

论文集锦We ig h t e d Ha r d Co m b in a t io n fo rCo o p e r a t ive S p e c t r u m S e n s in g in Co g n it ive R a d io Ne t w o r k sLi Jia jun1,2,Tan Zhe nhui1,2,Ai Bo1,Y ang Shan11State Key Laboratory of Rail Traf c Contro l and Safety,Beijing Jiaotong Univers ity,Beijing100044,P.R.China2Research Institute of Broadband Wireles s Mobile Co mmun ications,Beijing Jiaotong Univers ity,Beijing100044, P.R.ChinaAbstr act:Weighted one bit hard combination for cooperative spectrum sensing is proposed in this paper.Two thresholds are adopted to divide the possible energy value into three weighted regions. If the energy value falls into the corresponding region,it will be judged as“1”,no information or“0”.When the pr obability of false alar m is constrained to be constant,the objective is to maximize the probability of detection.The optimization problem is simplified by separating th e weight of the mid dle region into sever al intervals.Simulation results show that the sensing perfor mance of the proposed scheme is much better than that of the traditional one bit har d combination scheme and almost the same as that of the equal gain combination(EGC)scheme. Moreover,compared with the traditional one bit hard combination,fewer average sensing bits are required to transmit to the data fusion center with the proposed method.Key wor ds:cognitive radio;cooperative spectrum sensing;har d combination;the pr obability of detection I.INTRODUCTIONCognitive radio(CR)is a promising technique to improve the spectral efficiency of the wireless netwo rks[1].As one of the mo st impor tant com ponents of CR,spectrum sensing enables the secondary users to adapt to the environment by detecting the spectrum holes without causing interference to the primary network.C oo per ativ e sp ectr um s ensin g h as been proposed as a solution to combat the multipath fading or shadowing effects[2-4].Information from the cooperative secondary users is combined in the fusion centre to make the final decision. Traditional one-bit hard decision for cooperative spectrum sensing has been investigated in[3-5], in which secondary users exchange only one-bit decisions rather than the sensing statistics.Soft combination in cooperative spectrum sensing has been proposed in[6-7],which outperforms one-bit hard decision.However,the soft combination scheme requires much more overhead,e.g.the perf ect channel state inf ormation between theprimary users and secondary users are required for the maximum ratio combination(MRC).Double-threshold energy detection has been studied in [9-11].In[9],only the secondary uses with enough information send their local1-bit decisions to the data fusion centre.As a result,the average sen sing bits decr eases at the expense of the sensing performance loss.Re-detection is needed when the energy detection value falls into the middle region[10].Therefore the sensing period will last a long time to achieve a good detection performance.In[11],only the secondar y user with the highest energy detection value makes the decision using the conventional energy detection method if all the cooperative secondary detection values fall into the middle region.Otherwise,the sensing process is the same as[9].However,it is not realistic to assume that the data fusion centre knows the highest energy detection value and the sensing performance is almost the same as that of the traditional one-bit hard combination when the probability of false alarm is larger than0.001.I n this pap er,the weig hted on e bit har d combination scheme f or cooperative spectrum sensing is proposed.Two thresholds are adopted to divide the observation energy value into three weighted regions:“1”and“0”or no information. The corresponding weights of each region and the thresholds are joined optimized to maximum the probability of detection in the fusion centre. The weight of the middle region is separated into several in tervals to simplify the optimization pr ob lem.Sim ulation r es ults sho w that ou r proposed scheme has much better performance than that of the traditional one-bit hard scheme. Meanwhile the average sensing bit of our proposed method is the same as that of[9]with the same double thr esholds.And the prop osed scheme exhibits almost the same performance as the EGC scheme.The rest of this paper is organized as follows:In Section II.the weighted one bit hard combination scheme is proposed and system perf ormance is evaluated analytically.Numerical results are presented and compared with the traditional one bit hard combination and EGC schemes in Section III.Finally,Section IV concludes the paper.II.SYSTEM MODELA.Local Spectr um Sensin gThe binary hypothesis test for spectrum sensing at the nth time instant is formulated as:1:()():()()()H r n w nH r n x n w n==+(1) where r(n)is the signal to be detected,x(n)is theprimary signal with powerσx2,and()w n is the complex additive white Gaussian noise(AWGN)with zero-mean and varianceσn2.Without loss of generality,it is assumed that all the powers of thelocal noise are the same andσn2is normalized to be1.Hand H1denote the hypotheses corresponding to the absence and presence of the primary signal respectively.The local decision statistic is given by21|()|MnS r n==∑(2) where M is the number of samples.When there is only noise present,21|()|MnS w n==∑(3) Then the prob ability of f alse alarm can be expressed as[8](,)22()()2fMP P SMλΓλΓ=>=(4) where(,)Γis the incomplete gamma function,()Γis the gamma f unction andλis the final threshold of the local detector to decide whether there is a primary user present.When there is primary signal present,211|()()|MnS x n w n===+∑(5)The probability of detection can be expressed as [12,Eq.2.1-124]论文集锦12()(2,)d M P P S Q M λγλ=>=(6)where 222/2/2x n xγσσσ==denotes th e signal to no is e r atio (SNR ),221()/2(,)(/)m x a m bQ a b x x a e ∞+=∫1()d m I ax x is the generalized Marcum ’s Q function and 1()m I denotes the modi ed Bessel function of the rst kind.In a fading channel,we have()()d d d P P f γγγγ′=∫(7)where ()f γis the probability density function(PDF)of SNR.B.Cooper ative Spectr um Sensin gSuppose there are N secondary users to perform cooperative spectrum sensing.As shown in Figure 1,two thresholds (12,λλ)are designed for one-bit hard combination of the proposed cooperative spectrum sensing,which divides the whole range of the decision statistic of the local spectrum sensing into three regions.The following weights are adopted in our proposed scheme:ω0=0,ω1,ω2=1.In the fusion centre,if the energy value falls into the corresponding region,it will be judged as "1",no information or "0".And the decision rule adopted is given by211110N N D other wiseω+= (8)where 1N is the number of local detectors the energies of which are greater than 1λand less than 2λ,2N is the number of local detectors the energies of which are greater than 2λ.Obviously,1ωshould be more than 11/N and less than 1.1λ2λ1ω12=ω00=ωFig.1the structure of the weighted cooperativespectrum sensing with two thresholdsLet 2f Q be the probability that one or mor e observation local energy values are greater than 2λand 1f Q be the probability that more th an 111/N ω=%observation local energy values ar e greater than 1λand less than 2λ.Here,x is the largest integer that is no more than x .W e have22021(0|)1(1)Nf f Q P N H P ===(9)111201012212(0|)(|)()(1)(1)Nf j N jNf f Nf j N Njf f Q P N H P Nj H NP P j P P P ======+∑∑%%(10)where f n P is the probability that the local energyvalue is greater than n λand according to (4)0(,)22()()2n fn n M P P S M λΓλ=>=ΓΓ(11)We have12(,())22n fn M MP λΓ=Γ(12)where Γ-1(,)denotes the inverse of the incompletegamma function.Then the probability of false alarm in the fusion centre can be expressed as12f f f Q Q Q =+(13)Suppose all the channels between the primaryu ser and s eco nd ary user s are ind epen dent identically distributed.The probability of detection in the fusion centre can be expressed as12212121(1)(1)()(1)N Nd d d Nj Njd d d d j N Q P P N P P P P j==++∑%(14)where dn P is the probability that the local energyvalue is greater than n λwhen there is primary present according to (6)and (7).Therefore,the objective of the sensing problem is to find the optimal ω1,λ1and λ2to maximize d Q .In CR systems,the probability of false alarmQ f is designed to be constant.So the optimization problem can be formulated as121,,121{(,,)}max d Q λλωλλω(15)Subject to12f f f Q Q Q +=(16)11/1N ω≤<≤(17)2101f f P P <<<(18)As described above,when the number of the cooperative users N is fixed,1ωcan be divided into N-1intervals,each interval optimization problem can be written as,max 12max{(,)},2,,di di i i Q Q i N λλ==L (19)Subject to12f i f i f Q Q Q +=(20)11/1/(1)ii ω<(21)1N i =%(22)2101f i f i P P <<<(23)According to (9)-(13)and (20),1i λcan be written as a function of 2i λ,i.e.12()i i f λλ=.Then thereis only one variable to maximize 12(,)d i i i Q λλ.Although it is hard to get the analytical form of 2()i f λespecially when N is very large,1i λcan be obtained by finding the root of (20)for a given 2i λ.Therefore the optimal threshold and weight are derived by searching,which can be done of ine in practice.If the thresholds are selected r andomly,the probability of detection of the proposed scheme may be even worse than the traditional one-bit hard combination.The optimal thresholds of each interval are searched as follows:1)Choose initial 2()f i Q k =,k=1.2)Calculate 2()i k λaccording to (9),(11)and (12).3)Calculate 1()i k λaccording to (10)-(13).4)Ob tain ()di Q k accord ing to (14)or thesimulation.5)Let 22(1)()f i f i Q k Q k +=+.If 2(1)f i Q k +<f Q ,k=k+1,go to step 2.Else,nd ,max di Q .After getting each local maximum ,max di Q ,i =2,…,N,the global optimum of the probability of detection ismax 2,max ,max max{,,}d d dN D Q D =L (24)Let 00{}P P H =and 11{}P P H =.The average number of the sensing bits can be calculated as:100110111111(()|)(1(()|))(()|)(1(()|))l Navg l Nll Nl NlNlP N N l H K P lP N N l H NlP N N l H P lP N N l H ======+=∑∑(25)Consequently,the normalized average numberof sensing bit is010********{|}{|}avgK K P P S H NP P S H λλλλ==<<<<(26)where 1λand 2λare the optimal thresholds of ourproposed scheme.III.SIMULA TION RESULTSI n or der to illustr ate our theoretical r esults,computer simulations are carried out.The number of cooperative secondary users and the number of samples adopted are N=4and M=100.“OR ”rule is employed for the traditional one-bit hard combination.The equal gain combination (EGC)[7]is employed for the soft combination.It is assumed that the fading coef cient of the primary signal keeps constant during the energy detection progress.Figure 2and Figure 3show the probability of missed detection vs.average SNR over Rayleigh channels for the proposed weighted one-bit hard combination,traditional one-bit hard combination and EGC schemes when the probability of false alarm Q f is equal to 0.01and 0.05respectively.论文集锦Th e o ptimal thr esho lds and weigh t 1ωare obtain ed numerically as descr ibed in Section II,which can be done offline in practice.It is shown that o ur pr opo sed scheme has m uch better performance than the traditional one-bit hard combination scheme and approaches to the EGC scheme.When Q f is constrained higher,the performance of the proposed method is closer to the EGC scheme.Table I Optimal thresholds under Rayleigh channelsSNR(dB)-15-10-50Q f =0.05λ1120.440120.911120.496120.849Q f =0.05λ2140.123138.991139.971139.123Q f =0.01λ1127.558127.675127.920127.125Q f =0.01λ2149.173148.917148.437150.327Table I lists the optimal thresholds and 1N %of ourproposed scheme over Rayleigh channels.Then the theoretical probability of false alarm Q f can be obtained from (9),(10)and (12).Fig.4presents the-15-12-9-6-3010-310-210-110Averag e SNR (dB)th e p r o b o b i l i t y o f m i s s e d d e t e c t i o n 1-Q dWeighte d 1-bitTraditiona l1-b it EGCFig.2Q m Vs.average SNR under Rayleighchannels when Q f =0.01-15-12-9-6-3010-410-310-210-110Averag e SNR (dB)th e p r o b o b i l i t y o f m i s s e d d e t e c t i o n 1-Q dWeighted 1-bitTrad itio nal 1-bit E GCFig.3Q m Vs.average SNR under Rayleighchannelswhen Q f =0.05-15-10-500.010.020.030.040.050.06S N R(dB)Q fthe or y Q f =0.05sim ula tion Q f =0.05the or y Q f =0.01sim ula tion Q f =0.01Fig.4Theoretical and simulated Q f with the optimalthresholds over Rayleigh channels-15-12-9-6-3010-410-310-210-110Ave ra ge SNR (dB)t h e p r o b o b i l i t y o f m i s s e d d e t e c t i o n 1-Q dFixed Weighte d 1-bit Q f =0.05fixe d We ighte d 1-bit Q f =0.01Optim al Weighte d 1-bit Q f =0.05Optim al Weighte d 1-bit Q f =0.01Fig.5Q m Vs.average SNR with xedand optimal thresholds-15-10-500.70.750.80.850.90.9511.051.1A vera ge SNR (dB)N o r m a l i z e d a v e r a g e s e n s i n g b i t Traditona l1-bitWeighte d 1-bit A WGN Weighte d 1-bit R ayle ighFig.6Normalized average sensing bit Vs.averageSNR when Q f =0.05-15-10-500.70.750.80.850.90.9511.051.1A vera ge SNR (dB)No r ma l i z e da v e r a g e s e n s i n gb i t Tradit ona l 1-bitWeighte d 1-bit A WGN Weighte d 1-bit Ra yleighFig.7Normalized average sensing bit Vs.averageSNR when Q f =0.01theo r etical an d sim u lated Q f with t he list parameters.It is clear that our proposed scheme described in Section 2is pr acticab le and Q f remains constant after the optimization.Figure 5plots the performance of the proposed scheme with the optimal thresholds and fixed thresholds.The xed thresholds and weight for the proposed is set to be 11/21ω≤<,1λ=127.6747,2λ=148.9174when Q f =0.01and 11/21ω≤<,1λ=120.849,2λ=139.123when Q f =0.05.It can be seen that the proposed method with the fixed thr esh olds an d weight alm ost h as the same performance with that with the optimal thresholds and weight.This indicates that the proposed method is also applicable in the case that the channel conditions between the primary user and secondary user are different.Figure 6and Figure 7show the normalized sensing bits for our proposed method and the traditional 1-bit hard combination method.The thresholds used are the optimal thresholds over Rayleigh fading channels.It can be observed that fewer average sensing bits are needed to transmit to the data fusion centre compared with traditional 1-bit hard combination method.Because there is no bit transmitted to the data fusion centre when the energy value falls into the middle region,the average sensing bits are the same as [9]with the same thresholds.IV .CONCLUSIONSW eighted one-bit hard combination for cooperativespectr um sensing has been pr opo sed in this paper.Three regions with two thresholds,which are allocated with weights,have been adopted to m aximize the probability of detection.The weight of the middle region has been separated into several intervals to simplify the optimization problem.Simulation results have demonstrated that the probability of detection of the proposed scheme improves much more than that of the conventional one-bit hard combination.It also has shown thatthe probability of detection of the proposed scheme approaches to that of the EGC scheme,while fewer average sensing bits are transmitted to the data fusion centre compared to the conventional one bit hard combination method.Acknowledg ementsThis work is supported in part by the Hi-tech research and development program of China (2009AA011805),National Natural Science Fou ndation of China (61032002),the Important National Science and Technology Speci c Projects of China (2009ZX03003-007)and the Joint State Key Program of the National Natural Science Foundation of China and the National Railway Ministry of China (60830001).References[1]HAYKIN S.Cognitive Radio:Brain-empowered WirelessCommunications,Selected Areas in Communications [J].IEEE Journal on,2005,23(2):201–220.[2]GANESAN G,LI Ye.Cooperative Spectrum Sensing inCognitive Radio Networks[C]//Proceedings of DySPAN 2005.Baltimore,Maryland USA:IEEE Press,2005:137–143.[3]GHASEMI A,SOUSA E S.Collaborative SpectrumSensing for OpportunisticAccess in Fading Environments [C]//Proceedings of DySPAN 2005.Baltimore,Maryland USA:IEEE Press,2005:131–136.[4]RENZO M Di,GRAZIOSI F,SANYUCCI F.CooperativeSpectrum Sensing in Cognitive Radio Networks over Correlated Log-Normal Shadowing [C]//Proceedings of VTC 2009-Spring.Barcelona,Spain:IEEE Press,2009:1–5.[5]MISH RA S M,SAH AI A ,BROD ERSE N R W.Cooperative Sensing among Cognitive Radios [C]//Proceedings of ICC ’06.Istanbul,Turkey:IEEE Press,2006:1658–1663.[6]YUAN Y,ANXIN L,KAY AMA H.Study on Soft DecisionBased Cooperative Sensing in Cognitive Radio Network [C]//Proceedings of VTC 2009-Fall.Anchorage,Alaska USA:IEEE Press,2009:1–5.[7]MA Jun,ZHAO Guodong,LI Ye.Soft Combination andDetection for Cooperative Spectrum Sensing in Cognitive Radio Networks [J].Wireless Communications,IEEE论文集锦Transactions on,2008,17(11):4502–4507.[8]DIGHAN F F,ALOUINI M S,and SIMON M K.Onthe Energy Detection of Unknown Signals over Fading Channels[C]//Proceedings of ICC’03,Anchorage,Alaska USA:IEEE Press,2003:3575–3579.[9]SUN Chunhua,ZHANG Wei,Letaief K B.CooperativeSpectrum Sensing for Cognitive Radios under Bandwidth Constraints[C]//Proceedings of WCNC2007.Hong Kong:IEEE Press,2007:1–5.[10]WU Jinbo,LUO Tao,YUE Guangxin.An EnergyDetection Algorithm Based on Double-Threshold in Cognitive Radio Systems[C]//Proceedings of ICISE’09, Nanjing,China:IEEE Press,2009:493–496.[11]DUAN Lili,ZHANG Lei,CHU Yujun,et al.CooperativeSpectrum Sensing with Double Threshold Detection Based on Reputation in Cognitive Radio[C]//Proceedings of WiCom’09.Beijing,China:IEEE Press,2009:1–4. [12]PRAOKIS J G.Digital Communications[M].4th ed.New Y ork,McGraw-Hill,2001.Bio grap hiesLi J iaju n,received his B.S.degree in communication engineering from Beijing Jiaotong University in2007.He is currently working toward the Ph.D degree in communication and information system in Beijing Jiaotong University.His current research interests include cognitive radio networks and cooperative networks.Email:jiajunlisun@Tan Zh enh u i,received his PhD degree in Communi-cation and Information System from Nanjing Institute of Engineering(present Southeast University)in1987.He is now working in Beijing Jiaotong University as a professor. He is member of the state863Hi-Tech Project’s Specialists Committee for three consecutive tenures,member of the evaluation group of the Commission for Academic Degree Affairs of the State Council,member of the Commission for Academic Degree Affairs of Beijing,fellow of China Association of Communications,deputy director of the Committee for Automation of China Association of Railways,member of Committee for Academic Exchanges of China Association of Railways,and member of the editorial boards of both Chinese Journal of Electronics,Journal of the China Railways Society,Transprotation System Engineering and Information,Chinese Railways,and Research on Metropolitan Rail Transportation.His research interest is mainly in communication and information systems,including digital mobile communications,spread spectrum communications, adaptive ltering algorithms,and applications of digital signal processing(DSP)in communications,etc.Email:zhhtan@ Ai Bo,received a B.S.Degree from Engineering College of Armed Police Force in1997,a Master and Dr.degree from Xidian University in2002and2004in China,respectively. From2005to2007,he worked as a Post Dr.research fellow in Dept.of E\&E,state key lab.on microwave and digital communications in Tsinghua University in China and graduated with great honors of Excellent Postdoctoral Research Fellow in T singhua University.He is now working in Beijing Jiaotong University as an associate professor.He is an editorial committee member of journal of Wireless Personal Communications,Recent Patents on Electrical Engineering, Compu ter Si mulati ons,In format ion an d El ect ro nic Engineering,an IEEE Senior member and a senior member of Electronics Institute of China(CIE).His current interests are the research and applications of OFDM techniques with emphasis on synchronization,HPA linearization techniques, radio propagation and channel modeling,GSMRailway systems.Email:boai@Y a ng Sh an,re ceive d his B.S.degre e in comm unic ation engineering from Jilin University in2005,the M.S degree in communication and information system from Beijing Jiaotong University in2008.He is currently working toward the Ph.D degree in communication and information system in Beijing Jiaotong University.His current research interests include resource management in heterogeneous wireless network. Email:06120210@。
卡梅伦液压数据手册(第 20 版)说明书
iv
⌂
CONTENTS OF SECTION 1
☰ Hydraulics
⌂ Cameron Hydraulic Data ☰
Introduction. . . . . . . . . . . . . ................................................................ 1-3 Liquids. . . . . . . . . . . . . . . . . . . ...................................... .......................... 1-3
4
Viscosity etc.
Steam data....................................................................................................................................................................................... 6
1 Liquid Flow.............................................................................. 1-4
Viscosity. . . . . . . . . . . . . . . . . ...................................... .......................... 1-5 Pumping. . . . . . . . . . . . . . . . . ...................................... .......................... 1-6 Volume-System Head Calculations-Suction Head. ........................... 1-6, 1-7 Suction Lift-Total Discharge Head-Velocity Head............................. 1-7, 1-8 Total Sys. Head-Pump Head-Pressure-Spec. Gravity. ...................... 1-9, 1-10 Net Positive Suction Head. .......................................................... 1-11 NPSH-Suction Head-Life; Examples:....................... ............... 1-11 to 1-16 NPSH-Hydrocarbon Corrections.................................................... 1-16 NPSH-Reciprocating Pumps. ....................................................... 1-17 Acceleration Head-Reciprocating Pumps. ........................................ 1-18 Entrance Losses-Specific Speed. .................................................. 1-19 Specific Speed-Impeller. .................................... ........................ 1-19 Specific Speed-Suction...................................... ................. 1-20, 1-21 Submergence.. . . . . . . . . ....................................... ................. 1-21, 1-22 Intake Design-Vertical Wet Pit Pumps....................................... 1-22, 1-27 Work Performed in Pumping. ............................... ........................ 1-27 Temperature Rise. . . . . . . ...................................... ........................ 1-28 Characteristic Curves. . ...................................... ........................ 1-29 Affinity Laws-Stepping Curves. ..................................................... 1-30 System Curves.. . . . . . . . ....................................... ........................ 1-31 Parallel and Series Operation. .............................. ................. 1-32, 1-33 Water Hammer. . . . . . . . . . ...................................... ........................ 1-34 Reciprocating Pumps-Performance. ............................................... 1-35 Recip. Pumps-Pulsation Analysis & System Piping...................... 1-36 to 1-45 Pump Drivers-Speed Torque Curves. ....................................... 1-45, 1-46 Engine Drivers-Impeller Profiles. ................................................... 1-47 Hydraulic Institute Charts.................................... ............... 1-48 to 1-52 Bibliography.. . . . . . . . . . . . ...................................... ........................ 1-53
英语题库第二章大管轮要考的题译文

1115.释放阀可用来当排出阀关闭时将液体回流到吸入侧。
1129.系统流量增加时,管路摩擦和阻力将增大。
注意“rise”与“raise”之区别。
1154.潜热能改变水的物理状态。
1155.在同样的温度下,蒸汽变成水时所释放的热量,称为冷凝潜热。
1158.WHR代表废热回收装置。
1163.从燃油中去除杂质和水分,这对柴油机发火燃烧很重要。
1164.离心式分油机高速旋转时产生的离心力比重力大几千倍。
1165.船舶上的油水分离器能保证船舶排放舱底水等污水时木排油。
1166.见上题。
1167.舱底水总管设计用来排放除了压载舱、燃油舱和水舱之外的任何水密空间的污水到旋外Other than =except1168.油与水混合后会产生乳化。
1169.离心式分油机设计用来分离两种液体时,被称为分水机。
1170.离心式分油机设计用来分离油中的杂质和少量水时,被称为分杂机。
1171.分杂机运行时,由于杂质比重较大,积聚在分离筒的四周。
1172.很多年以来,离心式分油机被设计成分批运行。
意即,分油机运行一段时间,固体杂质积聚在分离筒内,当分油机停止运行时,才开始排渣。
1173.对于分水机,使用较大直径的比重环,油水界面会向分离筒四周移动。
1174.对于分水机,使用较小直径的比重环,油水界面会向分离筒中心移动。
1175.在油水分离器中,油是向上运动到集油室的。
1176.油水分离器开始工作时应首先注满清水。
1177.油滴尺寸大,将有助于油、水分离。
1178.液压马达是由油来驱动的。
1179.在液压系统中,安全阀用来防止系统超压。
186.在液压系统中,液压油泵将机械能转变为液压能。
1187.在液压系统中,液压马达将液压能转变为持续的回转运动。
1188.减压阀可用来限制压力,它主要是控制阀后的压力。
1189.液压马达转子的回转速度与油量有关,而与油压无关。
1190.方向控制阀用来引导液压流体的方向。
1191.异常振动、部件过度磨损、油压异常等都会引起液压系统内外泄露。
自动化控制工程外文翻译外文文献英文文献

Team-Centered Perspective for Adaptive Automation DesignLawrence J.PrinzelLangley Research Center, Hampton, VirginiaAbstractAutomation represents a very active area of human factors research. Thejournal, Human Factors, published a special issue on automation in 1985.Since then, hundreds of scientific studies have been published examiningthe nature of automation and its interaction with human performance.However, despite a dramatic increase in research investigating humanfactors issues in aviation automation, there remain areas that need furtherexploration. This NASA Technical Memorandum describes a new area ofIt discussesautomation design and research, called “adaptive automation.” the concepts and outlines the human factors issues associated with the newmethod of adaptive function allocation. The primary focus is onhuman-centered design, and specifically on ensuring that adaptiveautomation is from a team-centered perspective. The document showsthat adaptive automation has many human factors issues common totraditional automation design. Much like the introduction of other new technologies and paradigm shifts, adaptive automation presents an opportunity to remediate current problems but poses new ones forhuman-automation interaction in aerospace operations. The review here isintended to communicate the philosophical perspective and direction ofadaptive automation research conducted under the Aerospace OperationsSystems (AOS), Physiological and Psychological Stressors and Factors (PPSF)project.Key words:Adaptive Automation; Human-Centered Design; Automation;Human FactorsIntroduction"During the 1970s and early 1980s...the concept of automating as much as possible was considered appropriate. The expected benefit was a reduction inpilot workload and increased safety...Although many of these benefits have beenrealized, serious questions have arisen and incidents/accidents that have occurredwhich question the underlying assumptions that a maximum availableautomation is ALWAYS appropriate or that we understand how to designautomated systems so that they are fully compatible with the capabilities andlimitations of the humans in the system."---- ATA, 1989The Air Transport Association of America (ATA) Flight Systems Integration Committee(1989) made the above statement in response to the proliferation of automation in aviation. They noted that technology improvements, such as the ground proximity warning system, have had dramatic benefits; others, such as the electronic library system, offer marginal benefits at best. Such observations have led many in the human factors community, most notably Charles Billings (1991; 1997) of NASA, to assert that automation should be approached from a "human-centered design" perspective.The period from 1970 to the present was marked by an increase in the use of electronic display units (EDUs); a period that Billings (1997) calls "information" and “management automation." The increased use of altitude, heading, power, and navigation displays; alerting and warning systems, such as the traffic alert and collision avoidance system (TCAS) and ground proximity warning system (GPWS; E-GPWS; TAWS); flight management systems (FMS) and flight guidance (e.g., autopilots; autothrottles) have "been accompanied by certain costs, including an increased cognitive burden on pilots, new information requirements that have required additional training, and more complex, tightly coupled, less observable systems" (Billings, 1997). As a result, human factors research in aviation has focused on the effects of information and management automation. The issues of interest include over-reliance on automation, "clumsy" automation (e.g., Wiener, 1989), digital versus analog control, skill degradation, crew coordination, and data overload (e.g., Billings, 1997). Furthermore, research has also been directed toward situational awareness (mode & state awareness; Endsley, 1994; Woods & Sarter, 1991) associated with complexity, coupling, autonomy, and inadequate feedback. Finally, human factors research has introduced new automation concepts that will need to be integrated into the existing suite of aviationautomation.Clearly, the human factors issues of automation have significant implications for safetyin aviation. However, what exactly do we mean by automation? The way we choose to define automation has considerable meaning for how we see the human role in modern aerospace s ystems. The next section considers the concept of automation, followed by an examination of human factors issues of human-automation interaction in aviation. Next, a potential remedy to the problems raised is described, called adaptive automation. Finally, the human-centered design philosophy is discussed and proposals are made for how the philosophy can be applied to this advanced form of automation. The perspective is considered in terms of the Physiological /Psychological Stressors & Factors project and directions for research on adaptive automation.Automation in Modern AviationDefinition.Automation refers to "...systems or methods in which many of the processes of production are automatically performed or controlled by autonomous machines or electronic devices" (Parsons, 1985). Automation is a tool, or resource, that the human operator can use to perform some task that would be difficult or impossible without machine aiding (Billings, 1997). Therefore, automation can be thought of as a process of substituting the activity of some device or machine for some human activity; or it can be thought of as a state of technological development (Parsons, 1985). However, some people (e.g., Woods, 1996) have questioned whether automation should be viewed as a substitution of one agent for another (see "apparent simplicity, real complexity" below). Nevertheless, the presence of automation has pervaded almost every aspect of modern lives. From the wheel to the modern jet aircraft, humans have sought to improve the quality of life. We have built machines and systems that not only make work easier, more efficient, and safe, but also give us more leisure time. The advent of automation has further enabled us to achieve this end. With automation, machines can now perform many of the activities that we once had to do. Our automobile transmission will shift gears for us. Our airplanes will fly themselves for us. All we have to dois turn the machine on and off. It has even been suggested that one day there may not be aaccidents resulting from need for us to do even that. However, the increase in “cognitive” faulty human-automation interaction have led many in the human factors community to conclude that such a statement may be premature.Automation Accidents. A number of aviation accidents and incidents have been directly attributed to automation. Examples of such in aviation mishaps include (from Billings, 1997):DC-10 landing in control wheel steering A330 accident at ToulouseB-747 upset over Pacific DC-10 overrun at JFK, New YorkB-747 uncommandedroll,Nakina,Ont. A320 accident at Mulhouse-HabsheimA320 accident at Strasbourg A300 accident at NagoyaB-757 accident at Cali, Columbia A320 accident at BangaloreA320 landing at Hong Kong B-737 wet runway overrunsA320 overrun at Warsaw B-757 climbout at ManchesterA310 approach at Orly DC-9 wind shear at CharlotteBillings (1997) notes that each of these accidents has a different etiology, and that human factors investigation of causes show the matter to be complex. However, what is clear is that the percentage of accident causes has fundamentally shifted from machine-caused to human-caused (estimations of 60-80% due to human error) etiologies, and the shift is attributable to the change in types of automation that have evolved in aviation.Types of AutomationThere are a number of different types of automation and the descriptions of them vary considerably. Billings (1997) offers the following types of automation:?Open-Loop Mechanical or Electronic Control.Automation is controlled by gravity or spring motors driving gears and cams that allow continous and repetitive motion. Positioning, forcing, and timing were dictated by the mechanism and environmental factors (e.g., wind). The automation of factories during the Industrial Revolution would represent this type of automation.?Classic Linear Feedback Control.Automation is controlled as a function of differences between a reference setting of desired output and the actual output. Changes a re made to system parameters to re-set the automation to conformance. An example of this type of automation would be flyball governor on the steam engine. What engineers call conventional proportional-integral-derivative (PID) control would also fit in this category of automation.?Optimal Control. A computer-based model of controlled processes i s driven by the same control inputs as that used to control the automated process. T he model output is used to project future states and is thus used to determine the next control input. A "Kalman filtering" approach is used to estimate the system state to determine what the best control input should be.?Adaptive Control. This type of automation actually represents a number of approaches to controlling automation, but usually stands for automation that changes dynamically in response to a change in state. Examples include the use of "crisp" and "fuzzy" controllers, neural networks, dynamic control, and many other nonlinear methods.Levels of AutomationIn addition to “types ” of automation, we can also conceptualize different “levels ” of automation control that the operator can have. A number of taxonomies have been put forth, but perhaps the best known is the one proposed by Tom Sheridan of Massachusetts Institute of Technology (MIT). Sheridan (1987) listed 10 levels of automation control:1. The computer offers no assistance, the human must do it all2. The computer offers a complete set of action alternatives3. The computer narrows the selection down to a few4. The computer suggests a selection, and5. Executes that suggestion if the human approves, or6. Allows the human a restricted time to veto before automatic execution, or7. Executes automatically, then necessarily informs the human, or8. Informs the human after execution only if he asks, or9. Informs the human after execution if it, the computer, decides to10. The computer decides everything and acts autonomously, ignoring the humanThe list covers the automation gamut from fully manual to fully automatic. Although different researchers define adaptive automation differently across these levels, the consensus is that adaptive automation can represent anything from Level 3 to Level 9. However, what makes adaptive automation different is the philosophy of the approach taken to initiate adaptive function allocation and how such an approach may address t he impact of current automation technology.Impact of Automation TechnologyAdvantages of Automation . Wiener (1980; 1989) noted a number of advantages to automating human-machine systems. These include increased capacity and productivity, reduction of small errors, reduction of manual workload and mental fatigue, relief from routine operations, more precise handling of routine operations, economical use of machines, and decrease of performance variation due to individual differences. Wiener and Curry (1980) listed eight reasons for the increase in flight-deck automation: (a) Increase in available technology, such as FMS, Ground Proximity Warning System (GPWS), Traffic Alert andCollision Avoidance System (TCAS), etc.; (b) concern for safety; (c) economy, maintenance, and reliability; (d) workload reduction and two-pilot transport aircraft certification; (e) flight maneuvers and navigation precision; (f) display flexibility; (g) economy of cockpit space; and (h) special requirements for military missions.Disadvantages o f Automation. Automation also has a number of disadvantages that have been noted. Automation increases the burdens and complexities for those responsible for operating, troubleshooting, and managing systems. Woods (1996) stated that automation is "...a wrapped package -- a package that consists of many different dimensions bundled together as a hardware/software system. When new automated systems are introduced into a field of practice, change is precipitated along multiple dimensions." As Woods (1996) noted, some of these changes include: ( a) adds to or changes the task, such as device setup and initialization, configuration control, and operating sequences; (b) changes cognitive demands, such as requirements for increased situational awareness; (c) changes the roles of people in the system, often relegating people to supervisory controllers; (d) automation increases coupling and integration among parts of a system often resulting in data overload and "transparency"; and (e) the adverse impacts of automation is often not appreciated by those who advocate the technology. These changes can result in lower job satisfaction (automation seen as dehumanizing human roles), lowered vigilance, fault-intolerant systems, silent failures, an increase in cognitive workload, automation-induced failures, over-reliance, complacency, decreased trust, manual skill erosion, false alarms, and a decrease in mode awareness (Wiener, 1989).Adaptive AutomationDisadvantages of automation have resulted in increased interest in advanced automation concepts. One of these concepts is automation that is dynamic or adaptive in nature (Hancock & Chignell, 1987; Morrison, Gluckman, & Deaton, 1991; Rouse, 1977; 1988). In an aviation context, adaptive automation control of tasks can be passed back and forth between the pilot and automated systems in response to the changing task demands of modern aircraft. Consequently, this allows for the restructuring of the task environment based upon (a) what is automated, (b) when it should be automated, and (c) how it is automated (Rouse, 1988; Scerbo, 1996). Rouse(1988) described criteria for adaptive aiding systems:The level of aiding, as well as the ways in which human and aidinteract, should change as task demands vary. More specifically,the level of aiding should increase as task demands become suchthat human performance will unacceptably degrade withoutaiding. Further, the ways in which human and aid interact shouldbecome increasingly streamlined as task demands increase.Finally, it is quite likely that variations in level of aiding andmodes of interaction will have to be initiated by the aid rather thanby the human whose excess task demands have created a situationrequiring aiding. The term adaptive aiding is used to denote aidingconcepts that meet [these] requirements.Adaptive aiding attempts to optimize the allocation of tasks by creating a mechanism for determining when tasks need to be automated (Morrison, Cohen, & Gluckman, 1993). In adaptive automation, the level or mode of automation can be modified in real time. Further, unlike traditional forms of automation, both the system and the pilot share control over changes in the state of automation (Scerbo, 1994; 1996). Parasuraman, Bahri, Deaton, Morrison, and Barnes (1992) have argued that adaptive automation represents the optimal coupling of the level of pilot workload to the level of automation in the tasks. Thus, adaptive automation invokes automation only when task demands exceed the pilot's capabilities. Otherwise, the pilot retains manual control of the system functions. Although concerns have been raised about the dangers of adaptive automation (Billings & Woods, 1994; Wiener, 1989), it promises to regulate workload, bolster situational awareness, enhance vigilance, maintain manual skill levels, increase task involvement, and generally improve pilot performance.Strategies for Invoking AutomationPerhaps the most critical challenge facing system designers seeking to implement automation concerns how changes among modes or levels of automation will be accomplished (Parasuraman e t al., 1992; Scerbo, 1996). Traditional forms of automation usually start with some task or functional analysis and attempt to fit the operational tasks necessary to the abilities of the human or the system. The approach often takes the form of a functional allocation analysis (e.g., Fitt's List) in which an attempt is made to determine whether the human or the system is better suited to do each task. However, many in the field have pointed out the problem with trying to equate the two in automated systems, as each have special characteristics that impede simple classification taxonomies. Such ideas as these have led some to suggest other ways of determining human-automation mixes. Although certainly not exhaustive, some of these ideas are presented below.Dynamic Workload Assessment.One approach involves the dynamic assessment o fmeasures t hat index the operators' state of mental engagement. (Parasuraman e t al., 1992; Rouse,1988). The question, however, is what the "trigger" should be for the allocation of functions between the pilot and the automation system. Numerous researchers have suggested that adaptive systems respond to variations in operator workload (Hancock & Chignell, 1987; 1988; Hancock, Chignell & Lowenthal, 1985; Humphrey & Kramer, 1994; Reising, 1985; Riley, 1985; Rouse, 1977), and that measures o f workload be used to initiate changes in automation modes. Such measures include primary and secondary-task measures, subjective workload measures, a nd physiological measures. T he question, however, is what adaptive mechanism should be used to determine operator mental workload (Scerbo, 1996).Performance Measures. One criterion would be to monitor the performance of the operator (Hancock & Chignel, 1987). Some criteria for performance would be specified in the system parameters, and the degree to which the operator deviates from the criteria (i.e., errors), the system would invoke levels of adaptive automation. For example, Kaber, Prinzel, Clammann, & Wright (2002) used secondary task measures to invoke adaptive automation to help with information processing of air traffic controllers. As Scerbo (1996) noted, however,"...such an approach would be of limited utility because the system would be entirely reactive."Psychophysiological M easures.Another criterion would be the cognitive and attentional state of the operator as measured by psychophysiological measures (Byrne & Parasuraman, 1996). An example of such an approach is that by Pope, Bogart, and Bartolome (1996) and Prinzel, Freeman, Scerbo, Mikulka, and Pope (2000) who used a closed-loop system to dynamically regulate the level of "engagement" that the subject had with a tracking task. The system indexes engagement on the basis of EEG brainwave patterns.Human Performance Modeling.Another approach would be to model the performance of the operator. The approach would allow the system to develop a number of standards for operator performance that are derived from models of the operator. An example is Card, Moran, and Newell (1987) discussion of a "model human processor." They discussed aspects of the human processor that could be used to model various levels of human performance. Another example is Geddes (1985) and his colleagues (Rouse, Geddes, & Curry, 1987-1988) who provided a model to invoke automation based upon system information, the environment, and expected operator behaviors (Scerbo, 1996).Mission Analysis. A final strategy would be to monitor the activities of the mission or task (Morrison & Gluckman, 1994). Although this method of adaptive automation may be themost accessible at the current state of technology, Bahri et al. (1992) stated that such monitoring systems lack sophistication and are not well integrated and coupled to monitor operator workload or performance (Scerbo, 1996). An example of a mission analysis approach to adaptive automation is Barnes and Grossman (1985) who developed a system that uses critical events to allocate among automation modes. In this system, the detection of critical events, such as emergency situations or high workload periods, invoked automation.Adaptive Automation Human Factors IssuesA number of issues, however, have been raised by the use of adaptive automation, and many of these issues are the same as those raised almost 20 years ago by Curry and Wiener (1980). Therefore, these issues are applicable not only to advanced automation concepts, such as adaptive automation, but to traditional forms of automation already in place in complex systems (e.g., airplanes, trains, process control).Although certainly one can make the case that adaptive automation is "dressed up" automation and therefore has many of the same problems, it is also important to note that the trend towards such forms of automation does have unique issues that accompany it. As Billings & Woods (1994) stated, "[i]n high-risk, dynamic environments...technology-centered automation has tended to decrease human involvement in system tasks, and has thus impaired human situation awareness; both are unwanted consequences of today's system designs, but both are dangerous in high-risk systems. [At its present state of development,] adaptive ("self-adapting") automation represents a potentially serious threat ... to the authority that the human pilot must have to fulfill his or her responsibility for flight safety."The Need for Human Factors Research.Nevertheless, such concerns should not preclude us from researching the impact that such forms of advanced automation are sure to have on human performance. Consider Hancock’s (1996; 1997) examination of the "teleology for technology." He suggests that automation shall continue to impact our lives requiring humans to co-evolve with the technology; Hancock called this "techneology."What Peter Hancock attempts to communicate to the human factors community is that automation will continue to evolve whether or not human factors chooses to be part of it. As Wiener and Curry (1980) conclude: "The rapid pace of automation is outstripping one's ability to comprehend all the implications for crew performance. It is unrealistic to call for a halt to cockpit automation until the manifestations are completely understood. We do, however, call for those designing, analyzing, and installing automatic systems in the cockpit to do so carefully; to recognize the behavioral effects of automation; to avail themselves of present andfuture guidelines; and to be watchful for symptoms that might appear in training andoperational settings." The concerns they raised are as valid today as they were 23 years ago.However, this should not be taken to mean that we should capitulate. Instead, becauseobservation suggests that it may be impossible to fully research any new Wiener and Curry’stechnology before implementation, we need to form a taxonomy and research plan tomaximize human factors input for concurrent engineering of adaptive automation.Classification of Human Factors Issues. Kantowitz and Campbell (1996)identified some of the key human factors issues to be considered in the design of advancedautomated systems. These include allocation of function, stimulus-response compatibility, andmental models. Scerbo (1996) further suggested the need for research on teams,communication, and training and practice in adaptive automated systems design. The impactof adaptive automation systems on monitoring behavior, situational awareness, skilldegradation, and social dynamics also needs to be investigated. Generally however, Billings(1997) stated that the problems of automation share one or more of the followingcharacteristics: Brittleness, opacity, literalism, clumsiness, monitoring requirement, and dataoverload. These characteristics should inform design guidelines for the development, analysis,and implementation of adaptive automation technologies. The characteristics are defined as: ?Brittleness refers to "...an attribute of a system that works well under normal or usual conditions but that does not have desired behavior at or close to some margin of its operating envelope."?Opacity reflects the degree of understanding of how and why automation functions as it does. The term is closely associated with "mode awareness" (Sarter & Woods, 1994), "transparency"; or "virtuality" (Schneiderman, 1992).?Literalism concern the "narrow-mindedness" of the automated system; that is, theflexibility of the system to respond to novel events.?Clumsiness was coined by Wiener (1989) to refer to automation that reduced workload demands when the demands are already low (e.g., transit flight phase), but increases them when attention and resources are needed elsewhere (e.g., descent phase of flight). An example is when the co-pilot needs to re-program the FMS, to change the plane's descent path, at a time when the co-pilot should be scanning for other planes.?Monitoring requirement refers to the behavioral and cognitive costs associated withincreased "supervisory control" (Sheridan, 1987; 1991).?Data overload points to the increase in information in modern automated contexts (Billings, 1997).These characteristics of automation have relevance for defining the scope of humanfactors issues likely to plague adaptive automation design if significant attention is notdirected toward ensuring human-centered design. The human factors research communityhas noted that these characteristics can lead to human factors issues of allocation of function(i.e., when and how should functions be allocated adaptively); stimulus-response compatibility and new error modes; how adaptive automation will affect mental models,situation models, and representational models; concerns about mode unawareness and-of-the-loop” performance problem; situation awareness decay; manual skill decay and the “outclumsy automation and task/workload management; and issues related to the design of automation. This last issue points to the significant concern in the human factors communityof how to design adaptive automation so that it reflects what has been called “team-centered”;that is, successful adaptive automation will l ikely embody the concept of the “electronic team member”. However, past research (e.g., Pilots Associate Program) has shown that designing automation to reflect such a role has significantly different requirements than those arising in traditional automation design. The field is currently focused on answering the questions,does that definition translate into“what is it that defines one as a team member?” and “howUnfortunately, the literature also shows that the designing automation to reflect that role?” answer is not transparent and, therefore, adaptive automation must first tackle its own uniqueand difficult problems before it may be considered a viable prescription to currenthuman-automation interaction problems. The next section describes the concept of the electronic team member and then discusses t he literature with regard to team dynamics, coordination, communication, shared mental models, and the implications of these foradaptive automation design.Adaptive Automation as Electronic Team MemberLayton, Smith, and McCoy (1994) stated that the design of automated systems should befrom a team-centered approach; the design should allow for the coordination betweenmachine agents and human practitioners. However, many researchers have noted that automated systems tend to fail as team players (Billings, 1991; Malin & Schreckenghost,1992; Malin et al., 1991;Sarter & Woods, 1994; Scerbo, 1994; 1996; Woods, 1996). Thereason is what Woods (1996) calls “apparent simplicity, real complexity.”Apparent Simplicity, Real Complexity.Woods (1996) stated that conventional wisdomabout automation makes technology change seem simple. Automation can be seen as simply changing the human agent for a machine agent. Automation further provides for more optionsand methods, frees up operator time to do other things, provides new computer graphics and interfaces, and reduces human error. However, the reality is that technology change has often。
带领外教品尝中国传统美食的英语作文

带领外教品尝中国传统美食的英语作文Trying Traditional Chinese Food with My Foreign TeachersLast weekend was so much fun! My school had a special event where we got to bring our foreign English teachers to experience traditional Chinese food. I was really excited because I love Chinese food and I wanted to share it with my teachers.We all met up at the school on Saturday morning. There were five foreign teachers - Mr. Smith from America, Ms. Gonzalez from Mexico, Mr. Rousseau from France, Ms. Kumari from India, and Mr. Jakobsen from Denmark. I've had them all as my English teachers before and they're really nice.First, we went to a restaurant that specializes in Beijing cuisine. The first dish we tried was jiaozi or dumplings. They are little pouches made of dough stuffed with different fillings like pork and vegetables. You pick them up with your chopsticks and dip them in a vinegar sauce. The teachers seemed to really like them, especially Mr. Jakobsen who ate about twenty!Next, we had a big plate of zhajiangmian, which are thick hand-pulled noodles mixed with a sauce made from fermented soybean paste. It has a very unique and strong flavor. Some of the teachers weren't sure about it at first, but I thought it wasdelicious. My favorite part was the little pieces of cucumber on top that gave it a nice crunch.For the main course, we had the famous Peking duck. It's a whole crispy-skinned duck that the chef slices up right in front of you. You take the sliced duck and wrap it up in a little pancake with some cucumber, green onion and sweet bean sauce. Ms. Kumari from India is vegetarian, so she just ate the pancakes and veggies without the duck. The rest of us really enjoyed the Peking duck though!After finishing up at the Beijing restaurant, we headed over to try some Sichuan food, which is known for being really spicy. We had a hot pot where you cook thin slices of meat and vegetables yourself in a big pot of boiling broth right at your table. We ordered a really spicy broth made with dozen of different chili peppers. Mr. Rousseau from France turned really red and started sweating because it was so spicy for him! I thought it was perfect though.We also had some kung pao chicken which had a sweet and spicy sauce with lots of dried chili peppers and peanuts. The teachers loved all the different flavors and ingredients. For dessert, we had smashed red bean paste buns which are sweetbuns filled with a thick, sweet red bean paste. They went really well with the spicy food.After lunch, we walked around the hutong neighborhood near the Sichuan restaurant. A hutong is a traditional neighborhood with small alleys and courtyard homes. We stopped and watched a game of jianzi which is like a Chinese version of hacky-sack where you use your feet to keep a weighted shuttlecock from hitting the ground. Some of the teachers joined in and tried it themselves which was really funny to watch!Later that evening, we went for a fancier Cantonese-style dinner. We started with some dim sum like har gow shrimp dumplings, char siu bao barbecue pork buns, and danlun rice noodle rolls. Dim sum is a Cantonese tradition of eating lots of small dishes almost like appetizers. My favorite was the custard tarts which are little egg custards in a flaky tart shell.Then for the main courses, we had a whole crispy-skinned chicken chopped up and served with a ginger-scallion sauce on the side. We also tried stir-fried beef ho fun which are thick, chewy rice noodles. And we had sauteed gai lan or Chinese broccoli in a garlic sauce. I was really full by the end but it was all so delicious.The teachers all smiled and thanked me and my classmates for introducing them to the wide variety of flavors and dishes in Chinese cuisine. Mr. Smith from America said he had no idea there were so many different styles and types of Chinese food before trying it himself. Ms. Gonzalez from Mexico said the Sichuan food reminded her of the spicy food from her home country.I felt really proud to be able to share my culture's incredible food with my foreign teachers. They were all so interested and open to trying new and different dishes. I think they have a much better understanding now of just how diverse and delicious Chinese cooking can be. Hopefully they'll remember this amazing culinary experience from their time living in China! I know I'll never forget that fun-filled day exploring the flavors of my favorite traditional cuisines.。
科技英语写作复杂的翻译例句

几个复杂的翻译例句1.The history of the Internet dates to the early days of computer networking in the 1960s. Today, when many workgroups have personal computers linked together in Local Area Networks (LANs), it's somewhat difficult to envision a world when mainframes dominated, and getting those mainframes to talk to one another was a bold new concept.因特网的历史可以追溯到计算机开始联网的六十年代。
今天,当很多工作小组都已拥有自己在局域网中互相联网的个人计算机时,人们也许很难想象,在大型计算机机独霸天下的年代要想让这些大型机互相进行信息交流曾被认为是一种十分大胆而超前的设想。
2.The use of programming languages (compilers) not only results in higher part quality but also allows for more rapid development of machining instructions.In addition,simulations can be run on remote computer terminals,to ensure that the program functions as intended. This method prevents unnecessary occupation of expensive machinery for debugging procedures.采用编程语言(编译程序)不仅能提高零件加工质量而且还可更快地开发出加工指令。
利普希茨空间到有界解析函数空间的加权微分复合算子

利普希茨空间到有界解析函数空间的加权微分复合算子张亮【摘要】Abstrac: Theories of weighted differentiation composition operators are important component parts in operator fields.Boundedness and compactness of the weighted differentiation composition operators between different spaces have been widely studied and a number of results have been given.On this basis,the necessary and sufficient conditions of the boundedness and compactness of the weighted differentiation composition operator from the Lipschitz spaces to bounded analytic function spaces in the unit disk are presented and proved.%加权微分复合算子理论是算子领域的重要组成部分.不同空间的加权微分复合算子的有界性和紧致性被深入地研究并出现了许多成果.在此基础上给出了单位圆盘上从利普希茨空间到有界解析函数空间的加权微分复合算子有界和紧致的性质,并证明了算子有界和紧致的充要条件.【期刊名称】《菏泽学院学报》【年(卷),期】2011(033)005【总页数】3页(P25-27)【关键词】利普希茨空间;有界解析函数空间;加权微分复合算子【作者】张亮【作者单位】天津大学理学院,天津300072【正文语种】中文【中图分类】O174.5记D={z:|z|<1}为复平面上的单位圆盘;H(D)表示D上的解析函数全体;H∞β(D)表示有界解析函数的全体且满足‖f‖H∞β=szupD(1-|z|2)β|f(z)|<∞.对于0 <α <1,Λα(D)表示的是利普希茨空间,满足:对任∈意的f∈H(D),任意的z,w∈D,存在常数C >0,使得|f(z)-f(w)|≤C|z-w|α而且‖f‖Λα=|f(0)|+任意的f∈H(D),满足‖f‖βα=|f(0)|+szupD(1 -|z|2)α|f'(z)|<∞ 的∈函数全体,记为Bα.设φ∈H(D),记Cφ为H(D)上的复合算子:Cφf(z)=f(φ(z)),z∈D ,f∈H(D).设D 为H(D)上的微分算子:Df(z)=f'(z).H(D)上的加权微分复合算子uCφD定义为:uCφDf(z)=u(z)f'(φ(z)).范数A与范数B等价,记:A≈B,如果存在常数C>0,使得B/C≤A≤CB.文献[1~5]已经深入研究了微分复合算子在不同空间的有界性和紧致性.借助文献[1~5]的一些方法,给出了从利普希茨空间到有界解析函数空间的加权微分复合算子的一些性质.引理1[6]设X和Y是Λα或者H∞β空间,则算子uCφD:X→Y是紧算子,当且仅当uCφD:X→Y为有界算子且对任意有界序列{fk}⊂X,当k→∞ 时,若{fk}在单位圆盘的紧子集上一致收敛于0,则uCφDfk在Y上也一致收敛于0.引理2[7]如果0 <α < 1,则B1-α(D)= Λα(D);且任意的f∈ Λα(D)有:定理1 假设0<α<1且φ是单位圆盘上的解析自映射,u∈H(D),则uCφD∶Λα→H∞β是有界算子当且仅当证明微分复合算子有界的充分性证明如下:假设条件(1)成立,则对任意的z∈D且f∈Λα,微分复合算子有界的必要性证明如下:假设uCφD:Λα→H∞β 是有界算子,则对所有f∈ Λα,存在常数C,使得‖uCφDf‖H∞β ≤C‖f‖Λα.则令f(z)=z,有:证明微分复合算子是紧算子的充分性证明如下:假设uCφD:Λα→H∞β 有界且式(8)成立,设{fk}k∈N是Λα上的序列满足sku∈p∈N‖fk‖Λα <∞,且当k→∞ 时,fk在D的紧子集上一致收敛于0.由假设,对任意的ε>0,存在δ∈(0,1),使得下式成立,即:设K={z∈D:|φ(z)|≤δ},结合引理2,则有:微分复合算子是紧算子的必要性证明如下:假设uCφD是紧算子,则uCφD是有界的.设{zk}k∈N是D上的序列且当k→∞ 时,|φ(zk)|→1.设:易证fk∈Λα,sku∈pN‖ fk‖Λα<∞,且当k→∞ 时,fk在D的紧子集上一致收敛于0.因为uCφD是紧的,由引理1,klim→∞ ‖uCφDfk‖H∞β =0.所以:【相关文献】[1]Stevi'c S.Norm of weighted composition operators from Bloch space to on the unit ball[J].Ars Combinatoria,2008,88:125–127.[2]Stevi'c S.On a new operator fromto the Bloch -type space on the unit ball [J].Utilitas Mathematica,2008,77:257 -263.[3]Wulan H ,Zhou J.Type spaces of analytic functions[J].Journal of Function Spaces and Applications,2006,4(1):73 -84.[4]Zhou Z H,Shi J pactness of composition operators on the Bloch space in classical bounded symmetric domains[J].Michigan Math,2002,50:381-405.[5]Hu Z,Wang position operators on Bloch-type spaces[J].Proceedings of the Royal Society of EdinburghA,2005,135(6):1229-1239.[6]Cowen C C,MacCluer B position operators on spaces of analytic functions [M].CRC Press,Boca Raton,FL,1995.[7]Zhu K H.Spaces of holomorphic functions in the unit ball[M].New York:Springer,2005.Abstrac:Theories of weighted differentiation composition operators are important component parts in operator fields.Boundedness and compactness of the weighted differentiation composition operators between different spaces have been widely studied and a number of results have been given.On this basis,the necessary and sufficient conditions of the boundedness and compactness of the weighted differentiation composition operator from the Lipschitz spaces to bounded analytic function spaces in the unit disk are presented and proved.。
从 Zygmund 型空间到- Blochα空间的加权复合算子

从 Zygmund 型空间到- Blochα空间的加权复合算子郭洁婷;谭海鸥【摘要】令ϕ, u 分别是复平面 C 上的单位开圆盘 D 中的解析自映射和解析函数。
加权复合算子定义为()()()()( ())uC f z u z f zϕϕ=,( z D f H D∈∈,讨论了该加权复合算子从 Zygmund 型空间,())到α-Bloch 空间的有界性。
%Let ϕ be an analytic self-map and u be a fixed analytic function in the open unit disk D on the complex plane C . The weighted composition operator is defined by ( )( )( )uC f zϕ =( ) ( ( )) u z f zϕ, ( z D f H D∈ ∈ . This paper studies the boundedness of the weighted composition , ( )) operators from Zygmund type spaces to α -Bloch spaces.【期刊名称】《五邑大学学报(自然科学版)》【年(卷),期】2015(000)002【总页数】6页(P6-11)【关键词】加权复合算子;α -Bloch 空间;Zygmund 型空间;有界性【作者】郭洁婷;谭海鸥【作者单位】五邑大学数学与计算科学学院,广东江门 529020;五邑大学数学与计算科学学院,广东江门 529020【正文语种】中文【中图分类】O174.51 预备知识设为复平面中的开单位圆盘,表示上解析函数全体组成的函数空间. 定义为上解析自映射所诱导的复合算子:,,. 我们知道:若一个线性算子把有界集映为有界集,则称它为有界的. 在解析函数空间中,我们感兴趣的是找出所诱导的有界算子或紧算子的函数理论特征. 对于这方面的研究,相应的结果见文献[1-2].设是上的解析函数,定义上的加权复合算子,,它是乘积算子和复合算子的推广. 记是满足的函数的集合,且由文献[3]的定理5.3和闭图像定理有当且仅当,且则称为Zygmund 类. 容易说明,在下是半范数空间,但在下,我们得到Zygmund类的两个等价的范数. 这个范数将会再一次用来表示,伴随这个范数的Zygmund类称为Zygmund空间.若函数满足:,则称属于小Zygmund 空间,记为. 显然,是的一个闭子空间. 根据式(2)容易得到:其中,是与无关的正常数[4].上的Zygmund型空间是指上满足的函数全体,记为. 在范数下,Zygmund型空间是一个Banach空间. 小Zygmund型空间是满足且的函数全体,记为,显然,是的闭子空间.设,记,称为空间. 记,称为小空间. 当时,空间即为经典的Bloch空间和小Bloch空间.Bloch型空间到其他全纯函数空间的复合算子与加权复合算子的研究成果详见文献[5-12],关于Zygmund空间上的复合算子的有界性的一些特征见文献[13-15]. 本文主要研究从Zygmund型空间到空间的加权复合算子的有界性,可看作是对文献[16-17]中结果的推广.2 主要结果首先给出有用的引理.引理1[18] 若,则1); 2).定理1 设,是单位圆盘上的解析自映射,,则下列表述是等价的:1)是有界的; 2)是有界的;3),且. (4)证明 3)1). 只证明当时的情况,,时的证明类似.因为和成立,对于任意的. 由引理1可以得到:当且式(4)成立,同时,时,我们得到算子是有界的.1)2). 结论显然成立.2)3). 根据引理1,分5种情况讨论.情形1 当时,假设是有界的. 取,则有:另一方面,取,则有,因此,由式(6)、式(7)和函数的有界性,有:情形2 当时,假设是有界的. 令,,则.当时,有:当时,有且,所以. 由式(9)易知,所以对,当时,有:. (10)由式(6)和式(10),有:对于,当时,由式(7),有:由式(8)、式(11)和式(12),得证.情形3 当时,假设是有界的. 令,,,,则有:. (13)由于,所以. 由式(9)易知. 所以对,当时,由式(8),有:. (14)对,当时,由式(8),有:由式(8)、式(14)和式(15),得证.情形4 当时,假设是有界的. 的证明与情形3类似. 现在我们证明. 令,. 则,,易知,则有:. (16)对,当时,由式(8)和式(16),有:对,当时,由式(6),有:由式(6)、式(8)、式(17)和式(18),得证.情形5 当时,假设是有界的. 的证明与情形3类似. 现在我们证明.对,当时,有:对,当时,由式(6),有:由式(19)和式(20),得.推论1 设,,是单位圆盘上的解析自映射,,则下列表述是等价的:1); 2);3),且.[1] ZHU Kehe. Operator Theory in Functions Spaces [M]. New York: Springer, 1990.[2] COWEN C C, MACCLUER B D. Composition Operator on Spaces of Analytic Functions [M]. Boca Rat on: CRC Press, 1995.[3] DUREN P L. Theory of Spaces [M]. New York: Academic Press, 1970.[4] LI Songxiao, STEVIC S. Volterra type operators on Zygmund space [J]. J Inequal Appl, 2007(1): 1-10.[5] OHNO S, STROETHOFF K, ZHAO Ruhan. Weighted composition operators between Bloch-type spaces [J]. Rocky Mountain J Math, 2003,33(1): 191-215.[6] OHNO S. Weighted composition operators between and the Bloch space [J]. Taiwanese J Math, 2001, 5(3): 555-563.[7] ZHU Xiangling. Generalized weighted composition operators from Bloch-type spaces to weighted Bergman spaces [J]. Indian J Math, 2007, 49(2): 139-149.[8] FU Xiaohong, ZHU Xiangling. Weighted composition operators on some weighted spaces in the unit ball [J]. Abstr Appl Anal, 2008(2): 1-8. [9] LI Songxiao, STEVIC S. Weighted composition operators from Bergman-type spaces into Bloch spaces [J]. Proc Indian Acad Sci Math Sci, 2007, 117(3): 371-385.[10] LI Songxiao, STEVIC S. Weighted composition operators from to the Bloch space on the polydisk [J]. Abstr Appl Anal, 2007, 2007: 1-13. [11] STEVIC S. Norm of weighted composition operators from Bloch space to on the unit ball [J]. Ars Combin, 2008, 88: 125-127.[12] ZHU Xiangling. Weighted composition operators between and Bergman type spaces [J]. Commun Korean Math Soc, 2006, 21(4): 719-727.[13] CHOE B, KOO H, SMITH W. Composition operators on small spaces [J]. Integr Equat Oper Th, 2006, 56(3): 357-380.[14] MADIGAN K, MATHESON A. Compact composition operators on the Bloch spaces [J]. TransAmer Math Soc, 1995, 347(7): 2679-2687.[15] LI Songxiao, STEVIC S. Weighted composition operators from Zygmund spaces into Bloch spaces [J]. Applied Mathematics and Computation, 2008, 36(2): 825-831.[16] 邹堃,谭海鸥. 从Zygmund空间到Bloch-type空间的加权复合算子[J]. 青岛理工大学学报,2010, 31(5): 105-108.[17] SANATPOUR A H, HASSANLOU M. Essential norms of weighted composition operators between Zygmund-type spaces and Bloch-type spaces [J]. Turkish Journal of Mathematics, 2014, 38: 872-882.[18] ESMARILI K, LINDSTORM M. Weighted composition operators between Zygmund type spaces and their essential norms [J]. Integr Equ Oper Teory, 2013, 75(4): 473-490.[责任编辑:熊玉涛]。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
������������
1. Introduction
Let ������ = {������ : |������| < 1} be the open unit disk in the complex plane C and ������ = {������ : |������| = 1} its boundary, and ������(������) denotes the set of all analytic functions on ������. An analytic self-map ������ : ������ → ������ induces the composition operator ������������ on ������(������), defined by ������������ (������) = ������(������(������)) for ������ analytic on ������. It is a wellknown consequence of Littlewood’s subordination principle that the composition operator ������������ is bounded on the classical Hardy ������������ (0 < ������ ≤ ∞) spaces, Bergman ������������ (0 < ������ ≤ ∞) spaces, and Bloch spaces (see, e.g., [1–4]). Let ������ be a fixed analytic function on the open unit disk. Define a linear operator ������������������ on the space of analytic functions on ������, called a weighted composition operator, by ������������������ ������ = ������ ⋅ (������ ∘ ������), where ������ is an analytic function on ������. We can regard this operator as a generalization of a multiplication operator and a composition operator. In recent years the weighted composition operator has received much attention and appears in various settings in the literature. For example, it is known that isometries of many analytic function spaces are weighted composition operators (see [5], for instance). Their boundedness and compactness have been studied on various Banach spaces of analytic functions, such as Hardy, Bergman, BMOA, Bloch-type, and Zygmund spaces; see, for example, [6–11]. Also, it has been studied from one Banach space of analytic functions to another; one may see [12–23].
Abstract and Applied Analysis 0 < ������ < 1 and let ������(������) = ������(������) (������������). Then ������(������) is in ������∞ ⊂ ������1 , and ‖������‖������1 ≤ ‖������‖∞ . It follows that ������ ������ ������ ������ ������ (������+1) ������ ������ = (1 − |������|2 ) ������ ������ ������ ������ (1 − |������|2 ) ������ (������������)������ ������ ������ ������ ������ ������ ������������ (������)������ ������������������ ≤ ������ ������ ������ ������ ������ ������������ ������������������ (1 − |������������|2 ) ������ ������ ������ ������ ������ ������������ ������������������ (1 − |������|2 ) ������ ������ ������ ������ ������ ������������ ������������������ (1 − |������|2 )
1/������
For 0 < ������ ≤ ∞, the Hardy space ������������ consists of those functions ������ ∈ ������(������), for which ������ ������ ������ = sup ������������ (������, ������) < ∞. ������ ������ ������������ ������������������
2 For ������ > 0 the ������-Bloch space ������������ consists of all analytic functions ������ defined on ������ such that ������ ������ ������ ������ ������ ������ ������ = sup{(1 − |������|2 )������ ������ ������ ������ : ������ ∈ ������} , ������ ������ ������ ������������������ ������������������ ������ ������������ (������)������ 0 < ������ < +∞. (3)
Hindawi Publishing Corporation Abstract and Applied Analysis Volume 2013, Article ID 365286, 10 pages /10.1155/2013/365286
Research Article Weighted Composition Operators from Hardy to Zygmund Type Spaces
0≤������<1
(2)
It is well known that with norm (2) the ������������ space is a Banach space if 1 ≤ ������ ≤ ∞, for 0 < ������ < 1, ������������ space is a nonlocally convex topological vector space, and ������(������, ������) = ‖������ − ������‖������ ������ is a complete metric for it. For more information about the ������������ space, one may see these books, for example, [24, 25].
Hale Waihona Puke The purpose of this paper is to consider the weighted composition operators from the Hardy space ������������ (0 < ������ < ∞) to the Zygmund type spaces Z������ . Our main goal is to characterize boundedness and compactness of the operators ������������������ from ������������ to Z������ in terms of function theoretic properties of the symbols ������ and ������. Now we give a detailed definition of these spaces. For 0 ≤ ������ < 1, ������(������) ∈ ������(������), we set ������������ (������, ������) = ( 1 2������ ������ ������������ ������ ������������ ������������) , 0 < ������ < ∞, ������ ∫ ������ ������������ (������������ )������ ������ ������ 2������ 0 ������ (1) ������ ������������ ������ ������ ������ ������∞ (������, ������) = max ������ ������������ (������������ )������ ������ ������ . 0≤������≤2������ ������
