IKE配置
MSR系列路由器IKEDPD功能的配置举例

MSR系列路由器IKEDPD功能的配置举例MSR系列路由器IKE DPD功能的配置举例Copyright ? 2014杭州华三通信技术有限公司版权所有,保留⼀切权利。
⾮经本公司书⾯许可,任何单位和个⼈不得擅⾃摘抄、复制本⽂档内容的部分或全部,并不得以任何形式传播。
本⽂档中的信息可能变动,恕不另⾏通知。
⽬录1 简介 (1)2 配置前提 (1)3 配置举例 (1)3.1 组⽹需求 (1)3.2 使⽤版本 (1)3.3 配置注意事项 (1)3.4 配置步骤 (1)3.4.1 Router A的配置 (1)3.4.2 Router B的配置 (2)3.5 验证配置 (3)3.6 配置⽂件 (6)4 相关资料 (7)1 简介本⽂档介绍MSR系列路由器IKE DPD功能的典型配置举例。
2 配置前提本⽂档不严格与具体软、硬件版本对应,如果使⽤过程中与产品实际情况有差异,请参考相关产品⼿册,或以设备实际情况为准。
本⽂档中的配置均是在实验室环境下进⾏的配置和验证,配置前设备的所有参数均采⽤出⼚时的缺省配置。
如果您已经对设备进⾏了配置,为了保证配置效果,请确认现有配置和以下举例中的配置不冲突。
本⽂档假设您已了解IPsec特性。
3 配置举例3.1 组⽹需求如图1所⽰,Router A和Router B之间建⽴IPsec连接。
要求:在Router A和Router B上都配置DPD 功能进⾏对等体存活状态检测。
图1MSR系列路由器IKE DPD功能的配置组⽹图3.2 使⽤版本本举例是在Release 2317版本上进⾏配置和验证的。
3.3 配置注意事项DPD实验不要采⽤2台设备直连⽅式,因为在这种⽅式下把⽹线、链路层Down,不会有路由,所以⽤于触发IPsec的包不会发送到接⼝,因⽽也不能触发任何IPsec模块。
3.4 配置步骤3.4.1 Router A的配置# 配置接⼝Ethernet0/0的IP地址。
system-view[RouterA] interface ethernet 0/0[RouterA-Ethernet0/0] ip address 1.2.0.2 255.255.255.252[RouterA-Ethernet0/0] quit# 配置ACL,定义由1.2.0.2/30到1.2.0.1/30的数据流。
配置采用IKE方式建立SA示例

配置采用IKE方式建立SA示例(预共享密钥)组网需求如图7-2所示,组网需求如下:●Host1与Host2之间进行安全通信,在SRG A与SRG B之间使用IKE自动协商建立安全通道。
●IKE验证方式为预共享密钥。
图7-2 采用IKE方式建立SA配置示例组网图(预共享密钥)配置步骤步骤1配置SRG A# 进入系统视图。
<SRG> system-view# 配置本端设备的名称。
[SRG] sysname SRG A# 创建编号为2的VLAN。
[SRG A] vlan 2[SRG A-vlan2] quit# 配置Ethernet 1/0/0的链路类型并加入VLAN。
[SRG A] interface Ethernet 1/0/0[SRG A-Ethernet1/0/0] port link-type access[SRG A-Ethernet1/0/0] port access vlan 2[SRG A-Ethernet1/0/0] quit# 配置VLAN接口。
[SRG A] interface vlanif 2[SRG A-Vlanif2] ip address 200.39.1.1 24# 关闭VLAN接口的快速转发功能。
[SRG A-Vlanif2] undo ip fast-forwarding qff[SRG A-Vlanif2] quit# 配置VLAN 2加入Trust区域。
[SRG A] firewall zone trust[SRG A-zone-trust] add interface Vlanif 2[SRG A-zone-trust] quit# 进入Ethernet 0/0/0视图。
[SRG A] interface Ethernet 0/0/0# 配置Ethernet 0/0/0的IP地址。
[SRG A-Ethernet0/0/0] ip address 202.39.160.1 16# 关闭接口的快速转发功能。
IKE协议的安全策略配置

IKE协议的安全策略配置IKE(Internet Key Exchange)协议是一种用于建立VPN连接的安全协议,它通过交换密钥和认证信息来确保网络通信的安全性。
在部署VPN网络时,配置正确的IKE安全策略至关重要,这将直接影响到网络的安全性和性能。
本文将介绍如何对IKE协议进行安全策略配置。
一、制定安全策略在开始配置之前,首先需要明确网络的安全需求。
根据实际情况,制定相应的IKE策略。
以下是一些常见的安全策略:1. 密钥长度:选择合适的密钥长度是确保IKE安全性的关键。
常见的密钥长度有128位和256位,选择更长的密钥长度能提供更高的安全性,但在一些旧的硬件设备上可能会影响性能。
因此,根据实际情况和需求,选择适当的密钥长度。
2. 加密算法:IKE支持多种加密算法,如DES、3DES、AES等。
要选择强大且安全性好的加密算法,以确保数据的机密性。
AES是当前最常用的加密算法,推荐选择AES。
3. 认证算法:IKE支持多种认证算法,如预共享密钥、数字证书等。
预共享密钥是一种简单且易于部署的方法,但安全性相对较低。
数字证书基于公钥基础设施(PKI)提供了更高的安全性。
根据实际需求选择适当的认证算法。
4. Diffie-Hellman密钥交换算法:Diffie-Hellman密钥交换算法用于在IKE中协商共享密钥。
IKE支持多种不同长度的Diffie-Hellman密钥交换算法,如DH Group 1、2、5等。
选择适当的Diffie-Hellman密钥交换算法以确保安全性和性能之间的平衡。
二、配置IKE协议的安全策略在了解了安全策略之后,将其应用到IKE协议的配置中。
以下是一些常见的配置步骤:1. 配置IKE策略集:在VPN设备上创建IKE策略集,定义所需的安全策略。
在配置时,需要提供如下信息:密钥长度、加密算法、认证算法和Diffie-Hellman密钥交换算法等。
2. 配置IKE策略:在IKE策略集中创建IKE策略,指定对等方和本地设备之间的策略。
IPsec VPNs Internet Key Exchange (IKE)配置说明书

Configuring Internet Key Exchange for IPsec VPNsThis module describes how to configure the Internet Key Exchange(IKE)protocol for basic IP Security (IPsec)Virtual Private Networks(VPNs).IKE is a key management protocol standard that is used in conjunction with the IPsec standard.IPsec is an IP security feature that provides robust authentication and encryption of IP packets.IPsec can be configured without IKE,but IKE enhances IPsec by providing additional features,flexibility, and ease of configuration for the IPsec standard.IKE is a hybrid protocol,that implements the Oakley key exchange and Skeme key exchange inside the Internet Security Association Key Management Protocol(ISAKMP)framework.(ISAKMP,Oakley,andSkeme are security protocols implemented byIKE.)Security threats,as well as the cryptographic technologies to help protect against them,are constantly changing.For more information about the latest Cisco cryptographic recommendations,see the Next GenerationEncryption(NGE)white paper.Note•Creating IKE Policies,on page1•Configuring IKE Authentication,on page2•Configuring IKE Mode Configuration,on page3•Configuration Examples for an IKE Configuration,on page4•Verifying IKE Policies,on page6•Additional References,on page7Creating IKE PoliciesRestrictions for configuring AES IKE policy•IPsec and long keys(the“k9”subsystem)must be supported.•AES cannot encrypt IPsec and IKE traffic if an acceleration card is present.enableconfigure terminalcrypto isakmp policy10encryption aes256hash shaauthentication pre-sharegroup14endTroubleshooting Tips•Clear(and reinitialize)IPsec SAs by using the clear crypto sa EXEC command.Using the clear crypto sa command without parameters will clear out the full SA database,which will clearout active security sessions.You may also specify the peer,map,or entry keywords to clear out only a subsetof the SA database.For more information,see the clear crypto sa command in the Cisco IOS SecurityCommand Reference.•The default policy and default values for configured policies do not show up in the configuration whenyou issue the show running-config command.To display the default policy and any default values withinconfigured policies,use the show crypto isakmp policy command.•Any IPsec transforms or IKE encryption methods that the current hardware does not support should bedisabled;they are ignored whenever an attempt to negotiate with the peer is made.If a user enters an IPsec transform or an IKE encryption method that the hardware does not support,a warningmessage will be generated.These warning messages are also generated at boot time.When an encrypted cardis inserted,the current configuration is scanned.If any IPsec transforms or IKE encryption methods are foundthat are not supported by the hardware,a warning message will be generated.Configuring IKE AuthenticationAfter you have created at least one IKE policy in which you specified an authentication method(or acceptedthe default method),you need to configure an authentication method.IKE policies cannot be used by IPsecuntil the authentication method is successfullyconfigured.Before configuring IKE authentication,you must have configured at least one IKE policy,which is where the authentication method was specified(or RSA signatures was accepted by default).NoteTo configure IKE authentication,you should perform one of the following tasks,as appropriate:Configuring RSA Keys Manually for RSA EncryptedNoncesThis task can be performed only if a CA is not in use. Noteenableconfigure terminalcrypto key generate rsa general-keys modulus360crypto key generate ec keysize256label Router_1_Key end Configuring Internet Key Exchange for IPsec VPNsTroubleshooting TipsOptional Configuration using Named Keyenableconfigure terminalcrypto key pubkey-chain rsanamed-key address 10.5.5.1key-string003020174A7D385B 1234EF29335FC9732DD50A37C4F4B0FD 9DADE748429618D518242BA32EDFBDD34296142A DDF7D3D8084076852F2190A00B43F1BD 9A8A26DB 0795*******FCDE9A98420F06A82045B 90288A26DBC644687789F76E EE21quitOptional Configuration using Addresses Keyenableconfigure terminalcrypto key pubkey-chain rsaaddressed-key 10.1.1.2encryption address 10.5.5.1key-string003020174A7D385B 1234EF29335FC9732DD50A37C4F4B0FD 9DADE748429618D518242BA32EDFBDD34296142A DDF7D3D8084076852F2190A00B43F1BD 9A8A26DB 0795*******FCDE9A98420F06A82045B 90288A26DBC644687789F76E EE21quitConfiguring PresharedKeysPreshared keys do not scale well with a growing network.Restrictoins for Mask Preshared Keys•The SA cannot be established between the IPsec peers until all IPsec peers are configured for the same preshared key.•The mask preshared key must be distinctly different for remote users requiring varying levels ofauthorization.A new preshared key should be configured for each level of trust and correct keys must be assigned to the correct parties.Otherwise,an untrusted party may obtain access to protected data.Noteenableconfigure terminalcrypto isakmp identity addresscrypto isakmp key sharedkeystring address 192.168.1.33no-xauth crypto isakmp key sharedkeystring address 10.0.0.1endConfiguring IKE Mode Configurationenableconfigure terminalConfiguring Internet Key Exchange for IPsec VPNsConfiguring Preshared Keysip local pool pool1172.16.23.0172.16.23.255crypto isakmp client configuration address-pool local pool1endConfiguration Examples for an IKE ConfigurationExample:Creating IKE PoliciesThis section contains the following examples,which show how to configure an AES IKE policy and a 3DES IKEpolicy.Cisco no longer recommends using 3DES;instead,you should use AES.For more information about the latest Cisco cryptographic recommendations,see the Next Generation Encryption (NGE)white paper.NoteExample:Creating an AES IKE PolicyThe following example is sample output from the show running-config command.In this example,the AES 256-bit key is enabled.Current configuration :1665bytes !version 12.2service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption !hostname "Router1"!!ip subnet-zero !!no ip domain lookup !ip audit notify logip audit po max-events 100!crypto isakmp policy 10encryption aes 256authentication pre-share lifetime 180crypto isakmp key cisco123address 10.0.110.1!!crypto ipsec transform-set aesset esp-aes 256esp-sha-hmac mode transport ...Configuring Internet Key Exchange for IPsec VPNsConfiguration Examples for an IKE ConfigurationConfiguring Internet Key Exchange for IPsec VPNsExample:Creating3DES IKE PoliciesExample:Creating3DES IKE PoliciesThis example creates two IKE policies,with policy15as the highest priority,policy20as the next priority,and the existing default priority as the lowest priority.It also creates a preshared key to be used with policy20with the remote peer whose IP address is192.168.224.33.crypto isakmp policy15encryption3deshash md5authentication rsa-siggroup2lifetime5000!crypto isakmp policy20authentication pre-sharelifetime10000!crypto isakmp key1234567890address192.168.224.33In the example,the encryption DES of policy default would not appear in the written configuration becausethis is the default value for the encryption algorithm parameter.If the show crypto isakmp policy command is issued with this configuration,the output is as follows:Protection suite priority15encryption algorithm:3DES-Triple Data Encryption Standard(168bit keys)hash algorithm:Message Digest5authentication method:Rivest-Shamir-Adleman SignatureDiffie-Hellman group:#2(1024bit)lifetime:5000seconds,no volume limitProtection suite priority20encryption algorithm:DES-Data Encryption Standard(56bit keys)hash algorithm:Secure Hash Standardauthentication method:preshared KeyDiffie-Hellman group:#1(768bit)lifetime:10000seconds,no volume limitDefault protection suiteencryption algorithm:DES-Data Encryption Standard(56bit keys)hash algorithm:Secure Hash Standardauthentication method:Rivest-Shamir-Adleman SignatureDiffie-Hellman group:#1(768bit)lifetime:86400seconds,no volume limitNote that although the output shows“no volume limit”for the lifetimes,you can configure only a time lifetime(such as86,400seconds);volume-limit lifetimes are not configurable.Example:Configuring IKE AuthenticationThe following example shows how to manually specify the RSA public keys of two IPsec peer--the peer at10.5.5.1uses general-purpose keys,and the other peer uses special-usage keys:crypto key pubkey-chain rsanamed-key address10.5.5.1key-string005C300D06092A864886F70D0101010500034B003048024100C5E23B55D6AB2204AEF1BA A54028A69ACC01C5129D99E464CAB820847EDAD9DF0B4E4C73A05DD2Configuring Internet Key Exchange for IPsec VPNs Verifying IKE PoliciesBD62A8A9FA603DD2E2A8A6F898F76E28D58AD221B583D7A4710203010001quitexitaddressed-key10.1.1.2encryptionkey-string003020174A7D385B1234EF29335FC9732DD50A37C4F4B0FD9DADE748429618D518242BA32EDFBDD34296142A DDF7D3D8084076852F2190A00B43F1BD9A8A26DB0795*******FCDE9A98420F06A82045B90288A26DBC644687789F76E EE21quitexitaddressed-key10.1.1.2signaturekey-string0738BC7A2BC3E9F0679B00FE53987BCC010*******DD06AF E228D24C458AD22858BB5DDD F48364012A2D7163219F882E64CE69D4B583748A241BED0F6E7F2F160DE0986E DF02031F4B0B0912F68200C4C625C3890BFF3321A2598935C1B1quitexitexitVerifying IKE PoliciesRouter#show crypto isakmp policyGlobal IKE policyProtection suite of priority1encryption algorithm:Three key triple DEShash algorithm:Secure Hash Standardauthentication method:Pre-Shared KeyDiffie-Hellman group:#5(1536bit)lifetime:86400seconds,no volume limitVerifying RSA KeysRouter#show crypto key pubkey-chain rsaCodes:M-Manually configured,C-Extracted from certificateCode Usage IP-Address/VRF Keyring NameC Signing default cn=Cisco Licensing Root CA,o=CiscoC Signing default cn=CAC Signing default cn=Cisco Root CA M1,o=CiscoC Signing default cn=Cisco Root CA2048,o=CiscoSystemsC Signing default cn=Cisco Manufacturing CA,o=CiscoSystemsC Signing default ou=Class3Public PrimaryCertification Authority,o=VeriSign,Inc.,c=USC Signing default cn=Cisco Root CA M2,o=CiscoC Signing default cn=Cisco Manufacturing CASHA2,o=CiscoC Signing default cn=Licensing Root-DEV,o=CiscoAdditional ReferencesRelated Documents Document TitleRelated Topic Cisco IOS Master Commands List,All Releases Cisco IOS commands•Cisco IOS Security Command Reference Commands A to C•Cisco IOS Security Command Reference Commands D to L•Cisco IOS Security Command Reference Commands M to R•Cisco IOS Security Command Reference Commands S to ZSecurity commands:complete command syntax,command mode,command history,defaults,usage guidelines,and examplesConfiguring Security for VPNs with IPsec IPsec configuration Configuring Internet Key Exchange Version 2IKE Version 2Deploying RSA Keys Within a PKI Configuring RSA keys to obtain certificates from a CAConfiguring Security for VPNs with IPsecSuite-B ESP transformsConfiguring Certificate Enrollment for a PKI Suite-B support for certificate enrollment for a PKIStandards Title Standards --None MIBsMIBs LinkMIBs To locate and download MIBs for selected platforms,Cisco IOS software releases,and feature sets,use Cisco MIB Locator found at the following URL:/go/mibsNone Configuring Internet Key Exchange for IPsec VPNsAdditional ReferencesRFCs TitleRFCsInternet Security Association and Key Management Protocol (ISAKMP)RFC 2408The Internet Key Exchange (IKE)RFC 2409The OAKLEY Key Determination Protocol RFC 2412Technical Assistance LinkDescription/cisco/web/support/index.html The Cisco Support and Documentation website provides online resources to download documentation,software,and e these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies.Access to most tools on the Cisco Support and Documentation website requires a user ID and password.Configuring Internet Key Exchange for IPsec VPNsAdditional References。
IPSEC(IKE)穿透nat的典型组网和配置
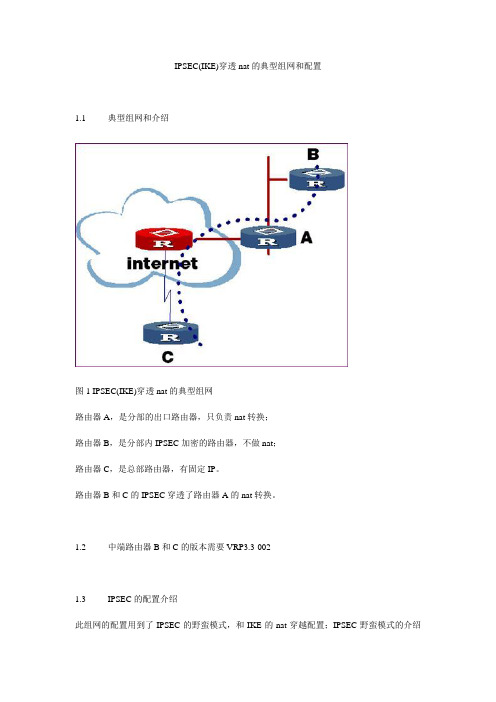
IPSEC(IKE)穿透nat的典型组网和配置1.1 典型组网和介绍图1 IPSEC(IKE)穿透nat的典型组网路由器A,是分部的出口路由器,只负责nat转换;路由器B,是分部内IPSEC加密的路由器,不做nat;路由器C,是总部路由器,有固定IP。
路由器B和C的IPSEC穿透了路由器A的nat转换。
1.2 中端路由器B和C的版本需要VRP3.3-0021.3 IPSEC的配置介绍此组网的配置用到了IPSEC的野蛮模式,和IKE的nat穿越配置;IPSEC野蛮模式的介绍和配置详见《配置手册》。
IKE的nat穿越配置仅一条命令:nat traversal1.4 配置1.4.1 总部路由器C的配置<Center>disp cur#sysname Center#tcp window 8#ike local id Center#ike peer otherexchange-mode aggressivepre-shared-key abcid-type nameremote-id P2nat traversallocal single-subnetpeer single-subnet#ipsec proposal center-1esp authentication-algorithm sha1 #ipsec policy center_1 2 isakmp security acl 100ike-peer otherproposal center-1#controller E1 3/0channel-set 0 timeslot-list 1#controller E1 3/1#interface Aux0async mode flowlink-protocol ppp#interface Ethernet1/0ip address 169.254.0.1 255.255.0.0 #interface Ethernet1/1#link-protocol pppip address 61.1.1.2 255.255.255.0nat outbound 102ipsec policy center_1#interface NULL0#interface LoopBack1ip address 192.168.2.1 255.255.255.0#acl number 100rule 0 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.0.0 0.0.0.255 rule 2 deny ipacl number 102rule 0 deny ip source 192.168.0.0 0.0.255.255 destination 192.168.0.0 0.0.255.255 rule 1 permit ip source 192.168.2.0 0.0.0.255#ip route-static 0.0.0.0 0.0.0.0 61.1.1.1#user-interface con 0user-interface aux 0authentication-mode noneuser privilege level 3set authentication password simple a #return<Center>1.4.2 分部路由器B的配置<P2-1760> disp cur#sysname P2-1760#tcp window 8#ike local id P2#ike peer part-1exchange-mode aggressivepre-shared-key abcid-type nameremote-id Centerremote-address 61.1.1.2nat traversallocal single-subnetpeer single-subnet#ipsec proposal part-1esp authentication-algorithm sha1 #ipsec policy part_1 1 isakmp security acl 100ike-peer part-1proposal part-1#interface Aux0async mode protocollink-protocol ppp#interface Ethernet0/0ip address 16.1.1.2 255.255.255.252 ipsec policy part_1#interface Serial0/0clock DTECLK1link-protocol ppp#interface NULL0#interface LoopBack0ip address 192.168.0.1 255.255.255.0#acl number 100rule 1 permit ip source 192.168.0.0 0.0.0.255 destination 192.168.2.0 0.0.0.255 rule 2 deny ip#ip route-static 0.0.0.0 0.0.0.0 16.1.1.1#user-interface con 0user-interface aux 0user-interface vty 0 4user privilege level 3set authentication password simple a#return1.4.3 分部路由器A的nat配置<P1>disp cur#sysname P1#super password level 3 simple a#local-user a password simple a local-user a level 3#tcp window 8#controller E1 1/0#controller E1 1/1#interface Aux0async mode flowlink-protocol ppp#interface Ethernet0/0ip address 16.1.1.1 255.255.255.252 ##interface Serial2/0clock DTECLK1link-protocol pppip address ppp-negotiatenat outbound 101#interface Serial2/1clock DTECLK1link-protocol ppp#interface NULL0#acl number 101rule 0 permit ip source 192.168.0.0 0.0.0.255rule 1 permit ip source 16.1.1.0 0.0.0.3rule 2 deny ip#ip route-static 0.0.0.0 0.0.0.0 Serial 2/0ip route-static 192.168.0.0 255.255.255.0 16.1.1.2 #user-interface aux 0user-interface vty 0 4authentication-mode localset authentication password simple a#return此处必须注意的一点是:acl中必须包括路由器B的上行口地址网段,文中是16.1.1.0/30网段。
H3C IPV6之ipsec(ike预共享)典型组网配置案例

组网说明:本案例采用H3C HCL模拟器来模拟IPV6 IPSEC+IKE预共享密钥典型组网配置。
为了保证数据传输安全,在R1与R2建立Ipsec vpn隧道。
全网采用OSPFv3协议互通。
配置思路:1、按照网络拓扑图正确配置IP地址。
2、R1与R2建立IPSEC VPN隧道配置过程:第一阶段调试(基础网络配置:)R1:<H3C>sysSystem View: return to User View with Ctrl+Z.[H3C]sysname R1[R1]int loopback 0[R1-LoopBack0]ip address 1.1.1.1 32[R1-LoopBack0]quit[R1]ospfv3 1[R1-ospfv3-1]import-route direct[R1-ospfv3-1]router-id 1.1.1.1[R1-ospfv3-1]quit[R1]int gi 0/0[R1-GigabitEthernet0/0]ipv6 address 1::1 64[R1-GigabitEthernet0/0]ospfv3 1 area 0[R1-GigabitEthernet0/0]quit[R1]int gi 0/1[R1-GigabitEthernet0/1]des <connect to R2>[R1-GigabitEthernet0/1]ipv6 address 2::1 64[R1-GigabitEthernet0/1]ospfv3 1 area 0[R1-GigabitEthernet0/1]quitR2:<H3C>sysSystem View: return to User View with Ctrl+Z. [H3C]sysname R2[R2]int loopback 0[R2-LoopBack0]ip address 2.2.2.2 32[R2-LoopBack0]quit[R2]ospfv3 1[R2-ospfv3-1]router-id 2.2.2.2[R2-ospfv3-1]import-route direct[R2-ospfv3-1]quit[R2]int gi 0/1[R2-GigabitEthernet0/1]des <connect to R1> [R2-GigabitEthernet0/1]ipv6 address 2::2 64 [R2-GigabitEthernet0/1]ospfv3 1 area 0[R2-GigabitEthernet0/1]quit[R2]int gi 0/0[R2-GigabitEthernet0/0]des <connect to SW1> [R2-GigabitEthernet0/0]ipv6 address 3::1 64 [R2-GigabitEthernet0/0]ospfv3 1 area 0[R2-GigabitEthernet0/0]quitSW1:<H3C>sysSystem View: return to User View with Ctrl+Z. [H3C]sysname SW1[SW1]int loopback 0[SW1-LoopBack0]ip address 3.3.3.3 32[SW1-LoopBack0]quit[SW1]ospfv3 1[SW1-ospfv3-1]import-route direct[SW1-ospfv3-1]router-id 3.3.3.3[SW1-ospfv3-1]quit[SW1]int gi 1/0/1[SW1-GigabitEthernet1/0/1]port link-mode route [SW1-GigabitEthernet1/0/1]des <connect to R2> [SW1-GigabitEthernet1/0/1]ipv6 address 3::2 64 [SW1-GigabitEthernet1/0/1]ospfv3 1 area 0 [SW1-GigabitEthernet1/0/1]quit第一阶段测试:物理机填写IP地址:物理机能PING通SW1:第二阶段调试(IPSEC预共享密钥关键配置点):R1:[R1]acl ipv6 advanced 3000[R1-acl-ipv6-adv-3000]rule 0 permit ipv6 source 1::/64 destination 3::/64 [R1-acl-ipv6-adv-3000]quit[R1]ike keychain james[R1-ike-keychain-james]pre-shared-key address ipv6 2::2 64 key simple james [R1-ike-keychain-james]quit[R1]ike proposal 1[R1-ike-proposal-1]quit[R1]ike profile james[R1-ike-profile-james]keychain james[R1-ike-profile-james]proposal 1[R1-ike-profile-james]match remote identity address ipv6 2::2 64[R1-ike-profile-james]local-identity address ipv6 2::1[R1-ike-profile-james]quit[R1]ipsec transform-set james[R1-ipsec-transform-set-james]protocol esp[R1-ipsec-transform-set-james]encapsulation-mode tunnel[R1-ipsec-transform-set-james]esp authentication-algorithm md5[R1-ipsec-transform-set-james]esp encryption-algorithm des-cbc[R1-ipsec-transform-set-james]quit[R1]ipsec ipv6-policy james 1 isakmp[R1-ipsec-ipv6-policy-isakmp-james-1]security acl ipv6 3000[R1-ipsec-ipv6-policy-isakmp-james-1]ike-profile james[R1-ipsec-ipv6-policy-isakmp-james-1]transform-set james[R1-ipsec-ipv6-policy-isakmp-james-1]remote-address ipv6 2::2[R1-ipsec-ipv6-policy-isakmp-james-1]quit[R1]int gi 0/1[R1-GigabitEthernet0/1]ipsec apply ipv6-policy james[R1-GigabitEthernet0/1]quitR2:[R2]acl ipv6 advanced 3000[R2-acl-ipv6-adv-3000]rule 0 permit ipv6 source 3::/64 destination 1::/64 [R2-acl-ipv6-adv-3000]quit[R2]ike keychain james[R2-ike-keychain-james]pre-shared-key address ipv6 2::1 key simple james [R2-ike-keychain-james]quit[R2]ike proposal 1[R2-ike-proposal-1]quit[R2]ike profile james[R2-ike-profile-james]keychain james[R2-ike-profile-james]proposal 1[R2-ike-profile-james]local-identity address ipv6 2::1[R2-ike-profile-james]match remote identity address ipv6 2::1 64[R2-ike-profile-james]quit[R2]ipsec transform-set james[R2-ipsec-transform-set-james]protocol esp[R2-ipsec-transform-set-james]encapsulation-mode tunnel[R2-ipsec-transform-set-james]esp authentication-algorithm md5 [R2-ipsec-transform-set-james]esp encryption-algorithm des-cbc [R2-ipsec-transform-set-james]quit[R2]ipsec ipv6-policy james 1 isakmp[R2-ipsec-ipv6-policy-isakmp-james-1]security acl ipv6 3000[R2-ipsec-ipv6-policy-isakmp-james-1]transform-set james[R2-ipsec-ipv6-policy-isakmp-james-1]ike-profile james[R2-ipsec-ipv6-policy-isakmp-james-1]remote-address ipv6 2::1 [R2-ipsec-ipv6-policy-isakmp-james-1]quit[R2]int gi 0/1[R2-GigabitEthernet0/1]ipsec apply ipv6-policy james[R2-GigabitEthernet0/1]quit第二阶段测试:查看R1的IPSEC显示信息:查看R2的IPSEC显示信息:物理机依然能PING通SW1:SW1也可以PING通物理机:至此,IPV6之IPSEC预共享密钥典型组网配置案例已完成!。
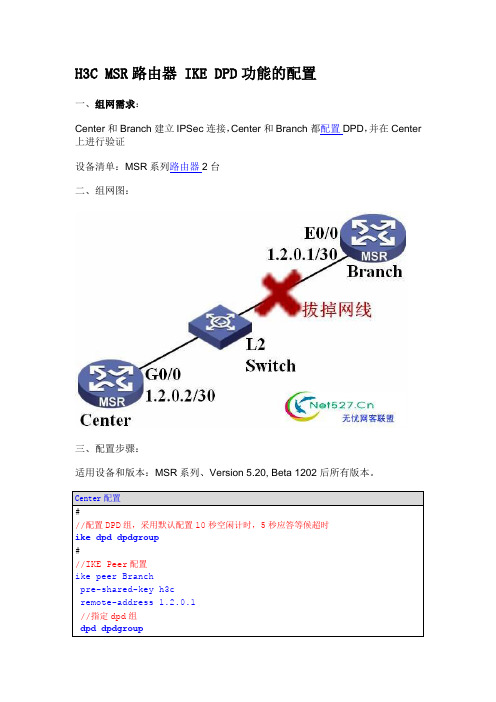
H3C MSR路由器 IKE DPD功能的配置
H3C MSR路由器 IKE DPD功能的配置
一、组网需求:
Center和Branch建立IPSec连接,Center和Branch都配置DPD,并在Center 上进行验证
设备清单:MSR系列路由器2台
二、组网图:
三、配置步骤:
适用设备和版本:MSR系列、Version 5.20, Beta 1202后所有版本。
四、配置关键点:
1) DPD实验不要采用2台设备直连方式,在这种方式下把网线,链路层Down,不会有路由,所以用于触发IPSec的包不会发送到接口,因而也不能触发任何IPSec模块。
2) DPD并不是自始至终地周期性发送,而是通过空闲定时器机制,在每接收到一个IPSec加密的包后就重置这个包对应IKE SA的空闲定时器,如果空闲定时器计时开始到计时结束过程都没有接收到该SA对应的加密包,那么下一次有IP 包要被这个SA加密发送或接收到加密包之前就需要使用DPD来检测对方是否存活。
3) DPD检测主要靠超时计时器,超时计时器用于判断是否再次发起请求,一般来说连续发出3次请求(请求->超时->请求->超时->请求->超时)都没有收到任何DPD应答就应该删除SA,后续如需继续发送加密数据包就需要重新协商SA,如果此时收到加密数据包表明是原来SA的会通知对端重新协商SA。
IPSEC 配置详解

敏感流量由访问列表所定义,并且通过crypto map(保密图)集被应用到接口上。
配置
1、为密钥管理配置IKE
2、(可选)定义SA的全局生命期
(global)crypto ipsec security-association lifetime seconds seconds
(global)crypto ipsec security-association lifetime killobytes kilobytes
(可选)选择IP压缩变换
--comp-lzs
(2)(可选)选择变换集的模式
(crypto-transform)mode {tunnel | transport}
5、使用IPSec策略定义保密映射
保密图(crypto map)连接了保密访问列表,确定了远程对等端、本地地址、变换集和协商方法。
变换集必须和远程对等端上使用的相同
--(可选)如果SA生命期和全局默认不同,那么定义它:
(crypto-map)set security-association lifetime seconds seconds
(crypto-map)set security-association lifetime kilobytes kilobytes
IPSEC 配置详解
IPSec 使用加密、数据完整性、源发鉴别以及拒绝重演分组来保护和认证网络层对等端之间的IP分组
IPSec对于构建内因网、外因网以及远程用户接入VPN来说非常有用处
IPSec支持以下标准
--Internet协议的安全体系结构
--IKE(Internet密钥交换)
(crypto-map)set security-association lifetime kilobytes kilobytes
如何配置IKEv2 VPN隧道:Digi Transport路由器14型号之间的配置说明书

Application NoteHow to Configure an IKEv2 VPN Tunnel Between Two Digi Transport Routers14 March 20171INTRODUCTION (5)1.1Outline (5)1.2Assumptions (5)1.3Corrections (6)1.4Version (6)2DIGI CONFIGURATION – INITIATOR (7)2.1LAN Settings (7)2.2WAN Settings (8)2.2.1ETH 1 configuration (8)2.2.2Default Route configuration (10)2.3IKEv2 Configuration (10)2.4IPsec tunnel Configuration (12)2.5Preshared Key Configuration (14)3DIGI CONFIGURATION - RESPONDER (16)3.1LAN Settings (16)3.2WAN Settings (17)3.2.1Cellular module configuration (17)3.2.2WAN Interface Configuration (PPP1) (19)3.2.3Default Route Configuration (20)3.3IKEv2 Configuration (21)3.4IPsec Tunnel Configuration (22)3.5Preshared Key Configuration (24)4TESTING (26)4.1Analyser Settings (26)4.2Setting the tunnel UP (29)4.3Testing Traffic on the tunnel (31)5CONFIGURATION FILES (36)5.1Initiator Configuration (36)5.2Responder Configuration (39)Figure 1-1-1: Overview Diagram (5)Figure 2-1: LAN Settings (7)Figure 2-2 ETH 1 Configuration (8)Figure 2-3 ETH 1 Configuration – Advanced (9)Figure 2-4 Default Route (10)Figure 2-5 IKE v2 configuration (11)Figure 2-6 IPsec Tunnel Configuration (12)Figure 2-7 Preshared Key Configuration - Initiator user (14)Figure 2-8 Preshared Key Configuration - Responder user (15)Figure 3-1 LAN Settings (16)Figure 3-2: Mobile settings (17)Figure 3-3 PPP 1 settings (19)Figure 3-4 Default Route (20)Figure 3-5 IKEv2 Configuration (21)Figure 3-6 IPsec Tunnel Configuration (22)Figure 3-7 Preshared Key Configuration - Initiator user (24)Figure 3-8 Preshared Key Configuration - Responder user (25)Figure 4-1 Analyser Settings - Initiator (26)Figure 4-2 Analyser Settings – Responder (27)Page | 51.1OutlineThis application note will consider the following scenario:Figure 1-1-1: Overview DiagramInternet Protocol Security (IPsec) is a set of protocols providing cryptographic security services and allows creation of encrypted tunnel between two private networks (VPN). In order to set up and maintain the IPsec VPN, Internet Key Exchange Protocol (IKE) is used. In the last few years, a new version has been designed for IKE protocol (IKEv2), that has the basic outcome as IKEv1 but introduces many improvements as decreased latency (only 4 messages need to be exchanged for set up the VPN) and reliability (all messages are acknowledge and sequenced).This Application Note gives a guide on configuring an IPsec VPN with IKEv2 between two TransPort routers.1.2 AssumptionsThis guide has been written for use by technically competent personnel with a good understanding of the communications technologies used in the product and of the requirements for their specific application. It also assumes a basic ability to access and navigate a Digi Transport router and configure it with basic routing functions.This application note applies only to:Model: Digi Transport WR44Other Compatible Models: Digi Transport VC7400 VPN Concentrator, WR, SR or DR.Firmware versions: 5.077 and laterConfiguration: This Application Note assumes the devices are set to their factory default configurations. Most configuration commands are only shown if they differ from the factory default.For the purpose of this application note the following applies:Preconditions: This guide assumes that two Digi TransPort are reachable to each other via an Internet connection.1.3CorrectionsRequests for corrections or amendments to this application note are welcome and should be addressed to: *********************Requests for new application notes can be sent to the same address.1.4VersionPage | 6Page | 72.1 LAN SettingsIn this AN the LAN interface of the Transport that acts as Initiator is configured on ETH 0 and left as default (192.168.1.1). The configuration can be checked going to the WEB UI:CONFIGURATION – NETWORK > INTERFACES > ETHERNET > ETH 0Figure 2-1: LAN SettingsPage | 82.2 WAN SettingsFirst of all, the Digi TransPort acting as Initiator must have an Internet connection, in this Application note we will configure the ETH WAN in the WR44 as follows.2.2.1 ETH 1 configurationIn this Application note we will configure the ETH 1 as DHCP Client:CONFIGURATION – NETWORK > INTERFACES > ETHERNET > ETH 1Figure 2-2 ETH 1 ConfigurationThen, IPsec must be enabled under the interface, going into the advanced section:Page | 9Figure 2-3 ETH 1 Configuration – AdvancedPage | 102.2.2 Default Route configurationIn the scenario considered in this AN, the default gateway for the TransPort that acts as Initiator is 10.10.1.3, so a default route need to be configured:CONFIGURATION - NETWORK > IP ROUTING/FORWARDING > STATIC ROUTES > DEFAULT ROUTE 0:Figure 2-4 Default Route2.3 IKEv2 ConfigurationIn order to configure the IKEv2 part for the initiator, set the parameters as indicated below: CONFIGURATION – NETWORK > VPN > IPSEC > IKE > IKEV2 > IKEV2 0Page | 11Figure 2-5 IKE v2 configurationClick apply to temporarily save the changes.Page | 122.4 IPsec tunnel ConfigurationThe following section describes how to configure the Digi TransPort’s IPsec Tunnel settings on the initiator.Refer to the following picture and table for the settings of parameters: CONFIGURATION – NETWORK > VPN > IPSEC > IPSEC TUNNELS > IPSEC 0Figure 2-6 IPsec Tunnel ConfigurationPage | 13Page | 142.5 Preshared Key ConfigurationIn IKEv2 for the configuration of Preshared Key, two users need to be configured, one for the local peer and one for the remote. The key for the two users can be different (but each has to match the one configured on the other peer for the same user).Note that any user can be used as the user for the Preshared Key, but best practice recommends using a user in the upper range of users because these users have the (router management) Access Level already set to ‘None’. If a lower User number is configured, the Access Level should be changed to be ‘None’.Refer to the following pictures and tables for the configuration of the users: CONFIGURATION – SECURITY > USERS > USER 10-14 > USER 10Figure 2-7 Preshared Key Configuration - Initiator userPage | 15CONFIGURATION – SECURITY > USERS > USER 10-14 > USER 10Figure 2-8 Preshared Key Configuration - Responder userPage | 16As done for the initiator, in order to configure the Digi TransPort, connect a PC to the ETH0 of the TransPort and log into the Web User Interface (WebUI) with a browser at the default address 192.168.1.1. Then follow the sections below.3.1 LAN SettingsIn this AN the LAN interface of the Transport that acts as Responder is configured on ETH 0, so that need to be changed from the default settings, going to the WEB UI at the section CONFIGURATION – NETWORK > INTERFACES > ETHERNET > ETH 0:Figure 3-1 LAN SettingsPage | 17Please note that having changed the LAN address, you will need to connect again to the router with the browser pointing at the new address 172.16.0.1 (this implies a change also in the IP address of your laptop).3.2 WAN SettingsFirst of all, the Digi TransPort acting as responder must have an Internet connection, in this Application note we will configure the Cellular WAN in the WR44 as follows.3.2.1 Cellular module configurationRefer to the following picture and table for the settings of parameters. Note that the SIM PIN, username and password fields may or may not be required.CONFIGURATION INTERFACES MOBILE MOBILE SETTINGSFigure 3-2: Mobile settingsClick Apply.Note: The APN is dependent on the mobile operator, check with the service provider to obtain the correct APN.Page | 18Page | 193.2.2 WAN Interface Configuration (PPP1)The following section configures the Digi TransPort to use PPP 1 for the cellular interface. Leave all the default settings, except for what is indicated in the following. The username and password fields may or may not be required by the SIMCONFIGURATION INTERFACES ADVANCED PPP1Figure 3-3 PPP 1 settingsPage | 20Click apply, then go to ADMINISTRATIONSAVE CONFIGURATION and save.3.2.3 Default Route ConfigurationIn the scenario considered in this AN the default gateway for the TransPort that acts as Responder is 10.10.2.3, so a default route need to be configured:CONFIGURATION - NETWORK > IP ROUTING/FORWARDING > STATIC ROUTES > DEFAULT ROUTE 0:Figure 3-4 Default RoutePage | 213.3 IKEv2 ConfigurationIn order to configure the IKEv2 part for the responder, set the parameters as indicated below. In order to have the TransPort to be able to respond to IKE request for every authentication/encryption/PRF/group algorithm, check all the options as shown below (by default may not be all already selected). Leave the rest of the settings as default. CONFIGURATION – NETWORK > VPN > IPSEC > IKE > IKEV2 > IKEV2 RESPONDERFigure 3-5 IKEv2 ConfigurationPage | 223.4 IPsec Tunnel ConfigurationThe following section describes how to configure the Digi TransPort’s IPsec Tunnel settings on the responder.Refer to the following picture and table for the settings of parameters: CONFIGURATION – NETWORK > VPN > IPSEC > IPSEC TUNNELS > IPSEC 0Figure 3-6 IPsec Tunnel ConfigurationPage | 23Page | 243.5 Preshared Key ConfigurationAs done for the initiator, also in the responder two users need to be configured for the two peers. Refer to the following pictures and tables for the configuration of the users: CONFIGURATION – SECURITY > USERS > USER 10-14 > USER 10Figure 3-7 Preshared Key Configuration - Initiator userPage | 25CONFIGURATION – SECURITY > USERS > USER 10-14 > USER 11Figure 3-8 Preshared Key Configuration - Responder userPage | 264.1 Analyser SettingsIn many cases is very useful configure the analyser in order to have a debug trace for the IKE negotiation in case of issues of setting up the VPN and for check that the traffic is correctly tunnelled. On both initiator and responder change the settings of the Analyser as shown below (uncheckeverything else):MANAGEMENT - ANALYSER > SETTINGS Initiator (WR44):Figure 4-1 Analyser Settings - InitiatorPage | 27Responder (WR21):Figure 4-2 Analyser Settings – ResponderPage | 28Page | 294.2 Setting the tunnel UPAs soon as the initiator is configured to set up a VPN, it will try to connect to the responder. For a successful negotiation we should see the following logs in the eventlog of the devices: MANAGEMENT - EVENT LOG Initiator:10:55:41, 03 Jan 2017,(69) IKEv2 Negotiation completed pe,Initiator 10:55:41, 03 Jan 2017,Eroute 0 VPN up peer: responder 10:55:41, 03 Jan 2017,New IPSec SA created by responder10:55:41, 03 Jan 2017,(69) New IKEv2 Negotiation peer 37.80.102.65,Initiator (Create Child)10:55:41, 03 Jan 2017,IKE Request Received From Eroute 010:55:41, 03 Jan 2017,Par change by username, eroute 0 autosa to 2 10:55:38, 03 Jan 2017,(69) IKEv2 Negotiation completed pe,Initiator 10:55:38, 03 Jan 2017,PPP 1 down,LL disconnect10:55:37, 03 Jan 2017,(69) New IKEv2 Negotiation peer 37.80.102.65,Initiator (Info)Responder:10:50:51, 03 Jan 2017,(154) IKEv2 Negotiation completed pe,Responder 10:50:51, 03 Jan 2017,Eroute 0 VPN up peer: initiator 10:50:51, 03 Jan 2017,New IPSec SA created by initiator10:50:51, 03 Jan 2017,(154) New IKEv2 Negotiation peer 217.151.242.15,Responder (Create Child)10:50:49, 03 Jan 2017,Telnet session closed10:50:48, 03 Jan 2017,(154) IKEv2 Negotiation completed pe,Responder10:50:48, 03 Jan 2017,(154) New IKEv2 Negotiation peer 217.151.242.15,Responder (Info)The status of the IPsec and IKEv2 SAs can also be seen in the WEB UI:MANAGEMENT - CONNECTIONS > VIRTUAL PRIVATE NETWORKING (VPN) > IPSEC Initiator:Page | 30Responder:4.3Testing Traffic on the tunnelOnce the VPN is UP, in order to test if LAN to LAN traffic is tunnelled as configured, do a ping from a host on initiator LAN to a host in responder LAN. In this AN the two hosts have 192.168.1.100 and 172.16.1.100 as ip addresses.Looking at the trace on the initiator (MANAGEMENT - ANALYSER > TRACE):1)An ICMP ECHO REQUEST arrives on ETH 0 form 192.168.1.100, with destination addressthe host at Responder LAN side (172.16.0.100):------- 3-1-2017 13:06:43.230 -------45 00 00 3C 11 8B 00 00 80 01 BA B5 C0 A8 01 64 E..<...........dAC 10 00 64 08 00 4D 4C 00 01 00 0F 61 62 63 64 ...d..ML....abcd65 66 67 68 69 6A 6B 6C 6D 6E 6F 70 71 72 73 74 efghijklmnopqrst75 76 77 61 62 63 64 65 66 67 68 69 uvwabcdefghiIP (In) From REM TO LOC IFACE: ETH 045 IP Ver: 4Hdr Len: 2000 TOS: RoutineDelay: NormalThroughput: NormalReliability: Normal00 3C Length: 6011 8B ID: 449100 00 Frag Offset: 0Congestion: NormalMay FragmentLast Fragment80 TTL: 12801 Proto: ICMPBA B5 Checksum: 47797C0 A8 01 64 Src IP: 192.168.1.100AC 10 00 64 Dst IP: 172.16.0.100ICMP:08 Type: ECHO REQ00 Code: 04D 4C Checksum: 19533----------Page | 312)The packet matches the eroute 0 and is encrypted and sent through the tunnel withsource 10.104.1.121 (initiator WAN address) and destination 37.80.102.65 (responder WANaddress)----- 3-1-2017 13:06:43.230 -------45 00 00 3C 11 8B 00 00 7F 01 BB B5 C0 A8 01 64 E..<...........dAC 10 00 64 08 00 4D 4C 00 01 00 0F 61 62 63 64 ...d..ML....abcd65 66 67 68 69 6A 6B 6C 6D 6E 6F 70 71 72 73 74 efghijklmnopqrst75 76 77 61 62 63 64 65 66 67 68 69 uvwabcdefghiER 0-responder From LOC TO REMIFACE: ETH 145 IP Ver: 4Hdr Len: 2000 TOS: RoutineDelay: NormalThroughput: NormalReliability: Normal00 3C Length: 6011 8B ID: 449100 00 Frag Offset: 0Congestion: NormalMay FragmentLast Fragment7F TTL: 12701 Proto: ICMPBB B5 Checksum: 48053C0 A8 01 64 Src IP: 192.168.1.100AC 10 00 64 Dst IP: 172.16.0.100ICMP:08 Type: ECHO REQ00 Code: 04D 4C Checksum: 19533--------------- 3-1-2017 13:06:43.230 -------45 00 00 80 00 0C 00 00 FA 11 28 EF 0A 68 01 79 E.........(..h.y25 50 66 41 11 94 11 94 00 6C 00 00 83 82 E0 3A %PfA.....l.....:00 00 00 07 C1 D6 9B 1F E3 49 48 40 7C 9B 3F 51 .........IH@|.?QB8 B9 14 05 1B 04 E4 0C C6 BB AF 6A 1A CB 12 E7 ...........j....6F 42 2E CB 8F AA 7D A7 3F 51 48 84 ED 1B 9B 13 oB....}.?QH.....A0 1B DF E1 67 31 1E 8F 3B 91 0E 27 CB 16 C8 7E ....g1..;..'...~9C 27 D2 FC 56 E6 68 1E E2 F1 9F 92 34 8F 9C DB .'..V.h.....4...8B 50 CC CF 19 6E FF 76 16 85 2B B3 91 FC B4 79 .P...n.v..+....yIP (Final) From LOC TO REM IFACE: ETH 145 IP Ver: 4Hdr Len: 2000 TOS: RoutineDelay: NormalThroughput: NormalReliability: Normal00 80 Length: 128Page | 3200 0C ID: 1200 00 Frag Offset: 0Congestion: NormalMay FragmentLast FragmentFA TTL: 25011 Proto: UDP28 EF Checksum: 104790A 68 01 79 Src IP: 10.104.1.12125 50 66 41 Dst IP: 37.80.102.65UDP:11 94 SRC Port: IKE FLOAT (4500)11 94 DST Port: IKE FLOAT (4500)00 6C Length: 10800 00 Checksum: 0----------3)The reply arrives on ETH1 through the tunnel:----- 3-1-2017 13:06:44.480 -------45 00 00 80 00 0B 00 00 E9 11 39 F0 25 50 66 41 E.........9.%PfA0A 68 01 79 11 94 11 94 00 6C 00 00 76 41 2D C2 .h.y.....l..vA-.00 00 00 07 6A DA 9C E0 8A E4 81 8F B7 03 BB 76 ....j. (v)46 A1 2A EB D1 52 98 6F 42 89 83 83 13 AE 0F 6E F.*..R.oB......n77 3F 2E 7C BC 94 D7 15 88 57 BE B3 8F 8C 55 37 w?.|.....W....U767 41 A2 5C 9B 11 5E 62 E8 AF 51 8C BF 2B A5 C1 gA.\..^b..Q..+..CD 48 5A BE E4 90 74 7E 2B 9D 68 86 10 C5 CA 63 .HZ...t~+.h....c57 FD 33 1C 7E 86 E5 1D 1B 40 EE 98 1F 98 AA DF W.3.~....@......IP (In) From REM TO LOC IFACE: ETH 145 IP Ver: 4Hdr Len: 2000 TOS: RoutineDelay: NormalThroughput: NormalReliability: Normal00 80 Length: 12800 0B ID: 1100 00 Frag Offset: 0Congestion: NormalMay FragmentLast FragmentE9 TTL: 23311 Proto: UDP39 F0 Checksum: 1483225 50 66 41 Src IP: 37.80.102.650A 68 01 79 Dst IP: 10.104.1.121UDP:11 94 SRC Port: IKE FLOAT (4500)11 94 DST Port: IKE FLOAT (4500)00 6C Length: 108Page | 3300 00 Checksum: 0----------4)The packet is decrypted and the ICMP ECHO REPLY is revealed and sent to the destinationhost via ETH 0:----- 3-1-2017 13:06:44.480 -------45 00 00 3C 54 BC 00 00 7F 01 78 84 AC 10 00 64 E..<T.....x....dC0 A8 01 64 00 00 55 4C 00 01 00 0F 61 62 63 64 ...d..UL....abcd65 66 67 68 69 6A 6B 6C 6D 6E 6F 70 71 72 73 74 efghijklmnopqrst75 76 77 61 62 63 64 65 66 67 68 69 uvwabcdefghiIP (Cont) From REM TO LOC IFACE: ETH 145 IP Ver: 4Hdr Len: 2000 TOS: RoutineDelay: NormalThroughput: NormalReliability: Normal00 3C Length: 6054 BC ID: 2169200 00 Frag Offset: 0Congestion: NormalMay FragmentLast Fragment7F TTL: 12701 Proto: ICMP78 84 Checksum: 30852AC 10 00 64 Src IP: 172.16.0.100C0 A8 01 64 Dst IP: 192.168.1.100ICMP:00 Type: ECHO REPLY00 Code: 055 4C Checksum: 19541--------------- 3-1-2017 13:06:44.480 -------45 00 00 3C 54 BC 00 00 7E 01 79 84 AC 10 00 64 E..<T...~.y....dC0 A8 01 64 00 00 55 4C 00 01 00 0F 61 62 63 64 ...d..UL....abcd65 66 67 68 69 6A 6B 6C 6D 6E 6F 70 71 72 73 74 efghijklmnopqrst75 76 77 61 62 63 64 65 66 67 68 69 uvwabcdefghiIP (Final) From LOC TO REM IFACE: ETH 045 IP Ver: 4Hdr Len: 2000 TOS: RoutineDelay: NormalThroughput: NormalReliability: Normal00 3C Length: 6054 BC ID: 21692Page | 3400 00 Frag Offset: 0Congestion: NormalMay FragmentLast Fragment7E TTL: 12601 Proto: ICMP79 84 Checksum: 31108AC 10 00 64 Src IP: 172.16.0.100C0 A8 01 64 Dst IP: 192.168.1.100ICMP:00 Type: ECHO REPLY00 Code: 055 4C Checksum: 19541----------Page | 355.1Initiator ConfigurationThis is the config.da0 file used for the purpose of this Application Note on the Initiator side:eth 0 IPaddr "192.168.1.1"eth 0 ipanon ONeth 1 dhcpcli ONeth 1 ipsec 1eth 1 ipanon ONlapb 0 ans OFFlapb 0 tinact 120lapb 1 tinact 120lapb 3 dtemode 0lapb 4 dtemode 0lapb 5 dtemode 0lapb 6 dtemode 0ip 0 cidr ONdef_route 0 ll_ent "ETH"def_route 0 ll_add 1eroute 0 descr "IKEv2 IPsec Tunnel"eroute 0 peerip "37.80.102.65"eroute 0 peerid "responder"eroute 0 ourid "initiator"eroute 0 locip "192.168.1.0"eroute 0 locmsk "255.255.255.0"eroute 0 remip "172.16.0.0"eroute 0 remmsk "255.255.255.0"eroute 0 ESPauth "SHA1"eroute 0 ESPenc "AES"eroute 0 authmeth "PRESHARED"eroute 0 nosa "TRY"eroute 0 autosa 2eroute 0 ikever 2eroute 0 dhgroup 2eroute 0 enckeybits 128dhcp 0 IPmin "192.168.1.100"dhcp 0 respdelms 500dhcp 0 mask "255.255.255.0"dhcp 0 gateway "192.168.1.1"dhcp 0 DNS "192.168.1.1"sntp 0 server ""dyndns 0 ifent "default"ppp 0 timeout 300ppp 1 name "W-WAN (HSPA 3G)"ppp 1 phonenum "*98*1#"ppp 1 IPaddr "0.0.0.0"ppp 1 timeout 0ppp 1 use_modem 1ppp 1 aodion 1ppp 1 autoassert 1Page | 36ppp 1 r_chap OFFppp 3 name "DSL"ppp 3 l1iface "AAL"ppp 3 username "Enter ADSL Username"ppp 3 r_addr OFFppp 3 IPaddr "0.0.0.0"ppp 3 l_addr ONppp 3 timeout 0ppp 3 do_nat 2ppp 3 aodion 1ppp 3 autoassert 1ppp 3 immoos ONppp 3 echo 10ppp 3 echodropcnt 5ppp 3 l_pap OFFppp 3 l_chap OFFppp 3 defpak 16ppp 4 defpak 16web 0 prelogin_info ONftpcli 0 hostname ""ftpcli 0 directory "support/firmware/transport/radio_module_firmware/he910d"ike2 0 iencalg "AES"ike2 0 ienckeybits 128ike2 0 idhgroup 2modemcc 0 info_asy_add 6modemcc 0 init_str "+CGQREQ=1"modemcc 0 init_str1 "+CGQMIN=1"modemcc 0 apn "Your.APN.goes.here"modemcc 0 link_retries 10modemcc 0 stat_retries 30modemcc 0 sms_interval 1modemcc 0 sms_access 1modemcc 0 sms_concat 0modemcc 0 init_str_2 "+CGQREQ=1"modemcc 0 init_str1_2 "+CGQMIN=1"modemcc 0 apn_2 "Your.APN.goes.here"modemcc 0 link_retries_2 10modemcc 0 stat_retries_2 30modemcc 0 sms_access_2 1modemcc 0 sms_concat_2 0ana 0 anon ONana 0 l2on OFFana 0 xoton OFFana 0 lapdon 0ana 0 lapbon 0ana 0 ikeon ONana 0 maxdata 1500ana 0 logsize 180cmd 0 unitid "ss%s>"cmd 0 cmdnua "99"cmd 0 hostname "digi.router"cmd 0 asyled_mode 2cmd 0 anonftp ONcmd 0 tremto 1200Page | 37cmd 0 rcihttp ONcmd 4 cmd_processor OFFuser 0 access 0user 1 name "username"user 1 epassword "KD5lSVJDVVg="user 1 access 0user 2 access 0user 3 access 0user 4 access 0user 5 access 0user 6 access 0user 7 access 0user 8 access 0user 9 access 0user 10 name "initiator"user 10 epassword "PDZxU0FFQFU="user 10 access 4user 11 name "responder"user 11 epassword "PDZxU0FFQFU="user 11 access 4local 0 transaccess 2sslcli 0 verify 10sslsvr 0 certfile "cert01.pem"sslsvr 0 keyfile "privrsa.pem"ssh 0 hostkey1 "privSSH.pem"ssh 0 nb_listen 5ssh 0 v1 OFFtemplog 0 mb_autooff ONtemplog 0 mo_autooff ONcloud 0 ssl ONPage | 385.2Responder ConfigurationThis is the config.da0 file used for the purpose of this Application Note on the Responder side:eth 0 IPaddr "172.16.0.1"eth 0 ipanon ONaddp 0 enable ONlapb 0 ans OFFlapb 0 tinact 120lapb 1 tinact 120lapb 3 dtemode 0lapb 4 dtemode 0lapb 5 dtemode 0lapb 6 dtemode 0ip 0 cidr ONdef_route 0 ll_ent "ppp"def_route 0 ll_add 1eroute 0 descr "IKEv2 IPsec Tunnel"eroute 0 peerid "initiator"eroute 0 ourid "responder"eroute 0 locip "172.16.0.0"eroute 0 locmsk "255.255.255.0"eroute 0 remip "192.168.1.0"eroute 0 remmsk "255.255.255.0"eroute 0 ESPauth "SHA1"eroute 0 ESPenc "AES"eroute 0 authmeth "PRESHARED"eroute 0 ikever 2eroute 0 dhgroup 2eroute 0 enckeybits 128dhcp 0 IPmin "192.168.1.100"dhcp 0 respdelms 500dhcp 0 mask "255.255.255.0"dhcp 0 gateway "192.168.1.1"dhcp 0 DNS "192.168.1.1"sntp 0 server ""snmpuser 0 eCommunity "KCp0VkxP"ppp 0 timeout 300ppp 1 name "W-WAN"ppp 1 phonenum "*98*1#"ppp 1 IPaddr "0.0.0.0"ppp 1 timeout 0ppp 1 ipsec 1ppp 1 use_modem 1ppp 1 aodion 1ppp 1 autoassert 1ppp 1 ipanon ONppp 1 r_chap OFFppp 3 defpak 16ppp 4 defpak 16web 0 prelogin_info ONike 0 deblevel 4ike2 0 rencalgs "DES,3DES,AES"ike2 0 renckeybits 128Page | 39ike2 0 rauthalgs "MD5,SHA1"ike2 0 rprfalgs "MD5,SHA1"modemcc 0 asy_add 4modemcc 0 info_asy_add 2modemcc 0 init_str "+CGQREQ=1"modemcc 0 init_str1 "+CGQMIN=1"modemcc 0 apn "Internet.t-d1.de"modemcc 0 link_retries 10modemcc 0 stat_retries 30modemcc 0 sms_interval 1modemcc 0 sms_access 1modemcc 0 sms_concat 0modemcc 0 init_str_2 "+CGQREQ=1"modemcc 0 init_str1_2 "+CGQMIN=1"modemcc 0 apn_2 "Your.APN.goes.here"modemcc 0 link_retries_2 10modemcc 0 stat_retries_2 30modemcc 0 sms_access_2 1modemcc 0 sms_concat_2 0ana 0 anon ONana 0 l2on OFFana 0 xoton OFFana 0 lapdon 0ana 0 lapbon 0ana 0 ikeon ONana 0 maxdata 1500ana 0 logsize 180cmd 0 unitid "ss%s>"cmd 0 cmdnua "99"cmd 0 hostname "digi.router"cmd 0 asyled_mode 2cmd 0 tremto 1200cmd 0 rcihttp ONuser 0 access 0user 1 name "username"user 1 epassword "KD5lSVJDVVg="user 1 access 0user 2 access 0user 3 access 0user 4 access 0user 5 access 0user 6 access 0user 7 access 0user 8 access 0user 9 access 0user 10 name "initiator"user 10 epassword "PDZxU0FFQFU="user 10 access 4user 11 name "responder"user 11 epassword "PDZxU0FFQFU="user 11 access 4local 0 transaccess 2sslsvr 0 certfile "cert01.pem"sslsvr 0 keyfile "privrsa.pem"Page | 40How to Configure an IKEv2 VPN Tunnel Between Two Digi Transport RoutersPage | 41ssh 0 hostkey1 "privSSH.pem" ssh 0 nb_listen 5 ssh 0 v1 OFF templog 0 mo_autooff ON cloud 0 ssl ON。
h3c Web 配置手册 IKE

Web配置手册 IKE 目录目录第1章 IKE配置.......................................................................................................................1-11.1 概述....................................................................................................................................1-11.1.1 IKE的安全机制.........................................................................................................1-11.1.2 IKE的交换过程.........................................................................................................1-21.1.3 IKE在IPSec中的作用...............................................................................................1-21.1.4 IPSec与IKE的关系..................................................................................................1-31.2 配置IKE..............................................................................................................................1-31.2.1 配置概述..................................................................................................................1-31.2.2 配置IKE全局参数.....................................................................................................1-51.2.3 配置IKE安全提议.....................................................................................................1-61.2.4 配置IKE DPD...........................................................................................................1-71.2.5 配置IKE对等体.........................................................................................................1-81.2.6 查看IKE安全联盟.....................................................................................................1-91.3 IKE典型配置举例..............................................................................................................1-11第1章 IKE配置1.1 概述在实施IPSec的过程中,可以使用IKE(Internet Key Exchange,因特网密钥交换)协议来建立SA,该协议建立在由ISAKMP(Internet Security Association and KeyManagement Protocol,互联网安全联盟和密钥管理协议)定义的框架上。
IKE配置命令

IKE配置命令ike配置命令包括:1 authentication2 clear crypto isakmp3 crypto isakmp enable4 crypto isakmp key address5 crypto isakmp policy6 encryption7 group8 hash9 lifetime10 show crypto isakmp sa11 show crypto isakmp policy12 debug crypto isakmp1 authentication pre-share命令:authentication pre-share功能:为一个ike策略选择认证方法,目前dcr只支持预共享密钥的认证方法;参数:pre-share指定预共享密钥作为认证方法。
缺省情况:系统缺省选择的认证方法为预共享密钥签名。
命令模式:ike策略配置模式。
使用指南:指定的认证方法是pre-share,两端就必须分别配置自己的预共享密钥。
举例:创建一个优先级为15的ike策略,并为此策略选择pre-share作为认证方法。
router#configrouter(config)#crypto isakmp policy 15router(config-crypto-ike-policy-15)#authentication per-share2 clear crypto isakmp命令:clear crypto isakmp [[connection-id]]功能:删除ike安全策略。
参数:[connection-id]为ike安全联盟的连接标识号。
命令模式:特权用户模式。
使用指南: [connection-id]为可选项,若使用,则只删除连接标识号为[connection-id]的ike安全联盟。
若不使用,则删除所有存在的ike安全联盟。
dst src state conn-id100.1.1.2 100.1.1.1 qm_idle 0110.1.1.2 110.1.1.1 qm_idle 1130.1.1.2 130.1.1.1 qm_idle 2router#configrouter(config)#clear crypto isakmp 2router(config)#exitrouter#show crypto isakmp sadst src state conn-id100.1.1.2 100.1.1.1 qm_idle 0110.1.1.2 110.1.1.1 qm_idle 1router#configrouter(config)#clear crypto isakmprouter(config)#exitrouter#show crypto isakmp sadst src state conn-id3 crypto isakmp enable命令:crypto isakmp enableno crypto isakmp enable功能:启用ike;本命令的no操作是关闭ike。
18 IKE配置

VRP配置指南安全目录目录6 IKE配置 ....................................................................................................................................... 6-16.1 IKE概述 ....................................................................................................................................................... 6-26.1.1 IKE协议简介...................................................................................................................................... 6-26.1.2 IPSec的NAT穿越 ............................................................................................................................. 6-36.1.3 IKE在VRP上的实现 ........................................................................................................................ 6-46.2 配置IKE协商时的本地ID ........................................................................................................................ 6-56.2.1 建立配置任务..................................................................................................................................... 6-56.2.2 配置IKE协商时的本地ID ............................................................................................................... 6-56.3 配置IKE安全提议 ..................................................................................................................................... 6-66.3.1 建立配置任务..................................................................................................................................... 6-66.3.2 创建IKE安全提议并进入IKE安全提议视图................................................................................ 6-76.3.3 选择加密算法..................................................................................................................................... 6-76.3.4 选择验证方法..................................................................................................................................... 6-76.3.5 选择验证算法..................................................................................................................................... 6-86.3.6 选择Diffie-Hellman组标识 .............................................................................................................. 6-86.3.7 配置ISAKMP SA生存周期.............................................................................................................. 6-86.3.8 检查配置结果..................................................................................................................................... 6-96.4 配置IKE对端属性 ..................................................................................................................................... 6-96.4.1 建立配置任务..................................................................................................................................... 6-96.4.2 创建IKE Peer并进入IKE Peer视图 ............................................................................................. 6-106.4.3 配置IKE协商模式.......................................................................................................................... 6-106.4.4 配置IKE安全提议.......................................................................................................................... 6-116.4.5 配置本地ID类型 ............................................................................................................................ 6-116.4.6 配置IPSec的NAT穿越.................................................................................................................. 6-116.4.7 配置身份验证字............................................................................................................................... 6-116.4.8 配置对端IP地址或地址段 ............................................................................................................. 6-126.4.9 配置对端名称................................................................................................................................... 6-126.4.10 配置VPN实例与安全联盟关联的MPLS VPN接入.................................................................. 6-126.4.11 检查配置结果................................................................................................................................. 6-126.5 配置IKE的微调 ....................................................................................................................................... 6-13目录VRP配置指南安全6.5.1 建立配置任务................................................................................................................................... 6-13 6.5.2 配置发送Keepalive报文的时间间隔............................................................................................. 6-14 6.5.3 配置等待Keepalive报文的超时时间............................................................................................. 6-14 6.5.4 配置发送NAT更新报文的时间间隔 ............................................................................................. 6-146.6 维护............................................................................................................................................................ 6-156.6.1 显示 .................................................................................................................................................. 6-156.6.2 清除 .................................................................................................................................................. 6-156.6.3 调试 .................................................................................................................................................. 6-16 6.7 采用IKE协商方式建立安全联盟举例 ................................................................................................... 6-16VRP配置指南安全插图目录插图目录图6-1 安全联盟建立过程................................................................................................................................. 6-3图6-2 IPSec配置组网图 ................................................................................................................................. 6-17VRP配置指南安全 6 IKE配置6 IKE配置关于本章本章描述内容如下表所示。
配置采用IKE方式建立SA示例

配置采用IKE方式建立SA示例(预共享密钥)组网需求如图7-2所示,组网需求如下:●Host1与Host2之间进行安全通信,在SRG A与SRG B之间使用IKE自动协商建立安全通道。
●IKE验证方式为预共享密钥。
图7-2 采用IKE方式建立SA配置示例组网图(预共享密钥)配置步骤步骤1配置SRG A# 进入系统视图。
<SRG> system-view# 配置本端设备的名称。
[SRG] sysname SRG A# 创建编号为2的VLAN。
[SRG A] vlan 2[SRG A-vlan2] quit# 配置Ethernet 1/0/0的链路类型并加入VLAN。
[SRG A] interface Ethernet 1/0/0[SRG A-Ethernet1/0/0] port link-type access[SRG A-Ethernet1/0/0] port access vlan 2[SRG A-Ethernet1/0/0] quit# 配置VLAN接口。
[SRG A] interface vlanif 2[SRG A-Vlanif2] ip address 200.39.1.1 24# 关闭VLAN接口的快速转发功能。
[SRG A-Vlanif2] undo ip fast-forwarding qff[SRG A-Vlanif2] quit# 配置VLAN 2加入Trust区域。
[SRG A] firewall zone trust[SRG A-zone-trust] add interface Vlanif 2[SRG A-zone-trust] quit# 进入Ethernet 0/0/0视图。
[SRG A] interface Ethernet 0/0/0# 配置Ethernet 0/0/0的IP地址。
[SRG A-Ethernet0/0/0] ip address 202.39.160.1 16# 关闭接口的快速转发功能。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
-----------IKE配置----------------
IPSec VPN对等端为了建立信任关系,必须交换某种形式的认证密钥。
Internet 密钥交换(Internet Key Exchange,IKE)是一种为IPSec管理和交换密钥的标准方法。
一旦两个对等端之间的IKE协商取得成功,那么IKE就创建到远程对等端的安全关联(security association,SA)。
SA是单向的;在两个对等端之间存在两个SA。
IKE使用UDP端口500进行协商,确保端口500不被阻塞。
配置的完整过程:(注:命令行前的文字用于标明当前的配置模式)
红色字体为必须进行的配置
1、(可选)启用或者禁用IKE
(global)crypto isakmp enable或者(global)no crypto isakmp enable
默认在所有接口上启动IKE
2、创建IKE策略
(1)定义策略
(global)crypto isakmp policy priority
注释:policy 1表示策略1,假如想多配几个VPN,可以写成policy 2、policy3┅(2)(可选)定义加密算法
(isakmp)encryption {des | 3des}
加密模式可以为56位的DES-CBC(des,默认值)或者168位的3DES(3des)
(3)(可选)定义散列算法
(isamkp)hash {sha | md5}
默认sha
(4)(可选)定义认证方式
(isamkp)authentication {rsa-sig | rsa-encr | pre-share}
rsa-sig 要求使用CA并且提供防止抵赖功能;默认值
rsa-encr 不需要CA,提供防止抵赖功能
pre-share 通过手工配置预共享密钥
(5)(可选)定义Diffie-Hellman标识符
(isakmp)group {1 | 2}
注释:除非购买高端路由器,或是VPN通信比较少,否则最好使用group 1长度的密钥,group命令有两个参数值:1和2。
参数值1表示密钥使用768位密钥,参数值2表示密钥使用1024位密钥,显然后一种密钥安全性高,但消耗更多的CPU时间。
(6)(可选)定义安全关联的生命期
(isakmp)lifetime seconds
注释:对生成新SA的周期进行调整。
这个值以秒为单位,默认值为86400,也就是一天。
值得注意的是两端的路由器都要设置相同的SA周期,否则VPN在正常初始化之后,将会在较短的一个SA周期到达中断。
3、配置认证方式(三种选其一)
1)、 (rsa-sig)使用证书授权(CA)
(1)确保路由器有主机名和域名
(global)hostname hostname
(global)ip domain-name domain
(2)产生RSA密钥
(global)crypto key generate rsa
(3)使用向IPSec对等端发布证书的CA
--设定CA的主机名
(global)crypto ca identity name
--设定联络CA所使用的URL
(ca-identity)enrollment url url
URL应该采用http://ca-domain-nameort/cgi-bin-location的形式
--(可选)使用RA模式
(ca-identity)enrollment mode ra
(ca-identity)query url url
--(可选)设定注册重试参数
(ca-identity)enrollment retry period minutes
(ca-identity)enrollment retry count number
minutes(1到60;默认为1) number(1到100;默认为0,代表无穷次)
--(可选)可选的证书作废列表
(ca-identity)crl optional
(4)(可选)使用可信的根CA
--确定可信的根CA
(global)crypto ca trusted-root name
--(可选)从可信的根请求CRL
(ca-root)crl query url
--定义注册的方法
(ca-root)root {CEP url | TFTP server file | PROXY url}
(5)认证CA
(global)crypto ca authenticate name
(6)用CA注册路由器
(global)crypto ca enroll name
2)、(rsa-encr)手工配置RSA密钥(不使用CA)
(1)产生RSA密钥
(global)crypto key generate rsa
(2)指定对等端的ISAKMP标识
(global)crypto isakmp identity {address | hostname}
(3)指定其他所有对等端的RSA密钥
--配置公共密钥链
(global)crypto key pubkey-chain rsa
--用名字或地址确定密钥
(pubkey-chain)named-key key-name [encryption | signature]
(pubkey-chain)addressed-key key-name [encryption | signature]
--(可选)手工配置远程对等端的IP地址
(pubkey-key)address ip-addr
--指定远程对等端的公开密钥
(pubkey-key)key-string key-string
3)、(preshare)配置预共享密钥
(global)crypto isakmp key key-string {addrss | hostname} {peer-address | peer-hostname}
注释:返回到全局设置模式确定要使用的预先共享密钥和指定VPN另一端路由器IP 地址,即目的路由器IP地址。
相应地在另一端路由器配置也和以上命令类似
4、(可选)使用IKE模式
(1)定义要分发的“内部”或者受保护IP地址库
(global)ip local pool pool-name start-address end-address
(2)启动IKE模式协商
(global)crypto isakmp client configuration address-pool local pool-name。
