klausur-web-mining-ss08
DBL_7381_2008-10
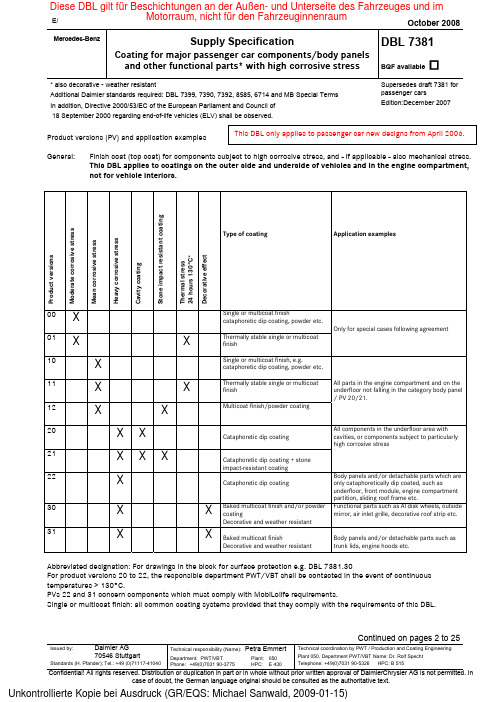
E/ October 2008Mercedes-BenzSupply SpecificationCoating for major passenger car components/body panels and other functional parts* with high corrosive stressDBL 7381BQF available* also decorative - weather resistantAdditional Daimler standards required: DBL 7399, 7390, 7392, 8585, 6714 and MB Special Terms In addition, Directive 2000/53/EC of the European Parliament and Council of 18 September 2000 regarding end-of-life vehicles (ELV) shall be observed.Supersedes draft 7381 for passenger cars Edition:December 2007Continued on pages 2 to 25Issued by:Daimler AG70546 StuttgartStandards (H. Pfander); Tel.: +49 (0)71117-41040Technical responsibility (Name): Petra Emmert Department: PWT/VBTPlant: 050 Phone: +49(0)7031 90-3775HPC: E 430Technical coordination by PWT / Production and Coating Engineering Plant 050, Department PWT/VBT Name: Dr. Rolf SpechtTelephone: +49(0)7031 90-5326 HPC: B 515Confidential! All rights reserved. Distribution or duplication in part or in whole without prior written approval of DaimlerChrysler AG is not permitted. Incase of doubt, the German language original should be consulted as the authoritative text.Product versions (PV) and application examplesGeneral: Finish coat (top coat) for components subject to high corrosive stress, and - if applicable - also mechanical stress.This DBL applies to coatings on the outer side and underside of vehicles and in the engine compartment, not for vehicle interiors.P r o d u c t v e r s i o n sM o d e r a t e c o r r o s i v e s t r e s sM e a n c o r r o s i v e s t r e s sH e a v y c o r r o s i v e s t r e s sC a v i t y c o a t i n gS t o n e i m p a c t r e s i s t a n t c o a t i n gT h e r m a l s t r e s s 24 h o u r s 130°C *D e c o r a t i v e e f f e c tType of coatingApplication examples00 X Single or multicoat finishcataphoretic dip coating, powder etc.01 X X Thermally stable single or multicoatfinishOnly for special cases following agreement10XSingle or multicoat finish, e.g.cataphoretic dip coating, powder etc.11 X X Thermally stable single or multicoatfinish12 X X Multicoat finish/powder coatingAll parts in the engine compartment and on the underfloor not falling in the category body panel / PV 20/21.20 X XCataphoretic dip coating21 X X XCataphoretic dip coating + stone impact-resistant coating All components in the underfloor area with cavities, or components subject to particularly high corrosive stress22XCataphoretic dip coatingBody panels and/or detachable parts which are only cataphoretically dip coated, such asunderfloor, front module, engine compartment partition, sliding roof frame etc.30 X X Baked multicoat finish and/or powder coatingDecorative and weather resistant Functional parts such as Al disk wheels, outside mirror, air inlet grille, decorative roof strip etc. 31X XBaked multicoat finishDecorative and weather resistantBody panels and/or detachable parts such as trunk lids, engine hoods etc.Abbreviated designation: For drawings in the block for surface protection e.g. DBL 7381.30For product versions 20 to 22, the responsible department PWT/VBT shall be contacted in the event of continuous temperatures > 130°C.PVs 22 and 31 concern components which must comply with MobiLolife requirements.Single or multicoat finish: all common coating systems provided that they comply with the requirements of this DBL. Diese DBL gilt für Beschichtungen an der Außen- und Unterseite des Fahrzeuges und imMotorraum, nicht für den Fahrzeuginnenraum1Field of application, general requirementsProduct versions with light alloys as base material1.1.1 Aluminum alloys1.1.1.1 Extruded aluminum parts / Rolled aluminumThe CASS test and/or the filiform test according to 4.17 shall be performed as approval-relevant corrosion test.1.1.1.2 Aluminum die castingThe CASS test without scribe shall be performed as approval-relevant corrosion test.1.1.1.3 Aluminum sand casting/Aluminum chill castingThe CASS test shall be performed as approval-relevant corrosion test.1.1.1.4 Mirror-turned / polished aluminum wheelsThe filiform corrosion test according to Section 4.17 shall be performed as approval-relevant corrosion test for the mirror-turned section, and the CASS test for the three-layer structure.1.1.2Magnesium die casting / Zinc die castingThe corrosion cycle test shall be performed as the approval-relevant corrosion test .To check the coverage of the whole surface, the CASS test can be used as accelerated test.(This test is performed without scratching the surface).1.1.3Other substratesApproval-relevant corrosion tests shall be agreed with the responsible department.2General properties of the materials, raw materials and supply conditionAll product versionsThe materials (cleaning and phosphating agents) used for pretreatment before coating, the binder types and pigments used for the paintwork structure as well as the coating methods and the drying types shall be disclosed to the receiving Daimler AG plant for initial samples and in the event of changes. This stipulation is intended to facilitate, in particular within the framework of development processes, the general material assessment and compliance with any necessary technical and/or personal protective measures for the processing of painted components (e.g. grinding, welding). The pretreatments and coatings shall be free of heavy metals such as arsenic, cadmium, chromium-VI, lead or their compounds. In addition, DBL 7399, Section1.2.1, DBL 8585 and DBL 6714 as well as directive 2000/53/EC of the European Parliament and Council of 18 September 2000 regarding end-of-life vehicles (ELV) or the latest version of the ELV directive shall be observed.Pretreatment, coating material and coating processes shall be selected by the part supplier so as to fulfill the requirements of this DBL. Residues which could promote corrosion and/or impair adhesion of the coating (flux, scale or similar) shall be removed chemically or mechanically, in particular on weld seams or on laser-cut edges.Edges, corners, overlaps and points accessible only with difficulty which are subject to the risk of corrosion shall be treated particularly carefully.The surface shall be free of any visible roughness, craters, dust inclusions etc.2.1.1PV 22/31All materials used in the coating must have been approved according to the applicable material DBL.e.g. cataphoretic dip coating in accordance with DBL 7292.2.2 InitialsamplingThe corrosion-relevant documents of the initial sample inspection report (ISIR) to PWT/VBT or the responsible department of the receiving MB plant shall be attached in the SQMS system (if available) under ISIR plants – surfaces/corrosion testing, and include the following information:Indication of the production and coating location. If the component is produced or coated at several locations, these locations shall be listed separately including the following data for each location. In addition, one component shall be submitted for sampling for each production/coating location.- Pretreatment materials, product name with product code, supplier- Coating materials, product name with product code (for cataphoretic dip coats also binder and pigment paste), supplier- Process description (flow chart)- Process parameters, test frequency- Layer thickness, layer thickness measuring points and layer thickness window (illustrated documentation), test frequency - Object stoving temperature (ideal, minimum, maximum)- Object temperature curves (at full load), object temperature measuring points (illustrated documentation), test frequency - Test frequency requalification measures according to MB Special Terms (corrosion tests, technical-mechanical coating test in analogy with Section 6.2 of this DBL)- Corrosion test report (illustrated)- Repair paint : work instructions, coating materials with product and name of supplierCorrosion test report for this repair concept (illustrated)(material,process)2.3 ChangesAny changes shall be notified to the Daimler AG receiving plant in good time according to VDA volume 2 and MB Special Terms No. 13 and subjected to initial sampling and approval before application in production.2.4 AssembliesNote that this DBL applies to the testing of individual components. If these components are installed with other components which might have an influence on the overall corrosion result after exposure (e.g. conductive rubber components, material combinations which run the risk of creating contact corrosion etc.), relevant corrosion tests in the corresponding assembly condition shall be agreed.2.5 MAG weld seams / heat-affected zoneMAG weld seams shall be pretreated so that silicate and slag residues are removed to an extent that allows proper pretreatment (e.g. phosphating). The heat-affected zone shall be treated in the same way, if it is accessible. Options: ceramic blasting, vibratory finishing ("Trowalisation"), dry ice blasting etc. In individual cases, an additional coating on the weld seams is also possible. It depends on the component which of these possibilities mentioned makes sense, and it shall therefore be selected following discussions with the responsible Daimler AG department.Pickling of components with cavities is not permissible; exceptions can only be allowed in individual cases for small production series following discussions with PWT/VBT. For such components, a cavity preservation shall then always be provided. Precoated components (e.g. with zinc) shall not be pickled in principle.2.6 Punched and cut edgesPunched and cut edges shall be designed such that compliance with the edge protection required in the relevant PV is reliably ensured. The following rework possibilities are available to improve edge protection: grinding, brushing, vibratory finishing ("Trowalisation"), shot peening etc. If freedom from burrs is specified on the drawing, embossing of the edges, where possible, is recommended. If the parts are laser cut, an oxygen-free cut shall be chosen. Where this is not possible, the edges shall be finished as described above.2.7 Cataphoretic dip coating material and pretreatmentThe supplier shall ensure that the phosphate content in the cataphoretic dip coating bath does not exceed 100 ppm as corrosion protection deteriorates significantly with increasing phosphate content. PWT/VBT and/or the materials engineering department of the relevant Daimler AG receiving plant shall be notified in writing if the cataphoretic dip coating materials are changed following sampling with regard to binder / solids ratio, or if measures are taken which might impact on the flow.In addition, care shall be taken to ensure that an Ni content of 0,8 - 1,2 g/l is maintained in the phosphating when zinc-coated sheets are used.coating2.8 CavityThe minimum layer thickness of cataphoretic dip coatings in cavities shall be 12 µm. A complete flow through the parts shall be ensured for cataphoretic dip coatings of cavities. If air bubbles cannot be avoided, these air bubbles shall be shifted to areas which are non-critical with regard to corrosion and functionality by suspending the parts appropriately. If required, additional measures (e.g. waxing) shall be taken.2.8.1 Cavity preservationIf the flange corrosion exceeds the requirements specified in Sections 4.11.7 and 4.12.7, cavity preservation shall be provided. Also, if the adhesion test in the heat-affected zone of cavities is worse than that required in Sections 4.11.8 and 4.12.8, cavity preservation shall be performed.paintwork2.9 RepairFor repair paintwork, the supplier's repair instructions and the coating materials used shall be indicated according to 2.1.2. If repair paintwork is carried out, the relevant components shall also comply with the requirements of the specified PV. The relevant department is responsible for requesting a component repaired in line with these instructions and for testing it according to the specified PV.The following process is required for rewelded, cataphoretically coated components:Completely remove any weld residues from the weld.- Use angle grinder to remove weld flash.- Resand using 80 grit sanding paper.- Clean using commercially available silicone remover.- Apply 2-component repair primer 4075 manufactured by Spies Hecker.Mixing ratio, layer thickness and drying according to manufacturer's specifications.Refinish using MB 7 167, MB spray can (1-component) MB Art. No. 00 986 29 50/7 167 2 spray applications, air drying. 2.10 CoatingthicknessesFor the paints used, the coating thicknesses specified by the paint supplier, at which the requirements of this DBL are fulfilled, shall be maintained.3Dimensions and tolerances / Form of supplyIn accordance with drawing and approved sample.4Technical dataPreliminary remark:Since in addition to the quality of the coating material itself, the material, the pretreatment and the shape of the parts to be coated may also be crucial to compliance with the following requirements, the tests shall be conducted on finished parts. If, due to their size, components are sawn into pieces, the cut edges shall be protected (by waxing, masking with Jaband No. 92402 supplied by Jaband, www.jaband.de).A test angle between 30° and 70° shall be maintained. For components intended for the underfloor, the underside of the components in the intended installation position in the vehicle shall form the upper side in the test chamber.All values indicated are maximum values.FPT ... Focal point test, refer to Section 6.2 of this DBL.n.r. no requirementFrom Section 4.11, either cross cuts or scratch tests can be performed. The values indicated shall always apply.Affected PVs and their requirementsProperties00/01 10/11/12 20/21/22 30/31 Test method4.1 Color Deviation with respect to standard panel not greater than degree of deviation3-4Section 5.16 of this DBL4.2 GlossIn accordance with drawing or approved sample.Deviation with respect to standard panel not greater than degree of deviation2-3Section 5.15 of this DBL4.3 Layer thickness (FPT) According to drawing or approved sample with the tolerances typical of thematerial, as documented in the ISIR.Section 5.1 of this DBL4.4 Cross-cut (FPT) Gt 1Section 5.3 of this DBL4.5 Mandrel bending test,conical mandrelDocument resultNo requirement at presentSection 5.17 of this DBL4.6 CuppingDocument resultNo requirement at presentSection 5.18 of this DBL4.7 Scratch test (FPT) K2 Section5.2 of this DBLAffected PVs and their requirementsProperties 01 11 Test method4.8 Temperatureresistance The coating shall attain the characteristic values of Section 4.4/4.6 and 4.11 or 4.12 (corrosion cycle test) following exposure to temperature24h 130°C Affected PVs and their requirementsProperties Test method4.9 4.9.1 Multiple stone impact testOriginal conditiononly PVs 30/31Chipping area rating 2Degree of corrosion 0,5Section 5.19 of this DBLSection 5.19.1 of this DBL4.9.2 With salt spray fogExposure time in hRequirementonly PV 12/2172Chipping area rating 2Degree of corrosion 1Section 5.19.2 of this DBL4.10 4.10.1 4.10.2 Steam jet teston St Andrews crosson multiple stone impactonly for PV 30/31No loss of adhesion on St Andrew's crossD1, minor wash-out of existing damageSection 5.20 of this DBLAffected PVs and their requirementsProperties 00/01 10/11/12 20/21/22 30/31 Test method4.11 Constant condensation wateratmosphereSection 5.8 of this DBL Exposure time in h 120 240 360 3604.11.1 Blistering/degree of blistering(S) < 2 (S 2) 0Section 5.6 of this DBL4.11.2 Scratch testK21/24 h minutes after removal on the undamaged surface Section 5.2 of this DBL4.11.3 Cross-cutGt 11/24 h minutes after removal on the undamaged surface Section 5.3 of this DBLAffected PVs and their requirementsProperties 00/01 10/11/12 20/21/22 30/31 Test method4.12 Corrosion cycle testSteel substrates(FPT)Assessment after 1, 3 cycles and at the end of the test period.PVs 00/10 shall only be assessed at the end of the test period.Section 5.10 of this DBLExposure time in cycles 3 6 10 104.12.1 Surface corrosion No clusters or accumulations4.12.1.1 Intermediate assessment1 cycleRi 0 Ri 0 Ri 04.12.1.2 Intermediate assessment3 cyclesRi 0 Ri 0 Ri 04.12.1.3 Final assessment 3 cycles Ri 14.12.1.4 Final assessment 6 cycles Ri 14.12.1.5 Final assessment 10 cycles Ri 1 Ri 0Section 5.5 of this DBL 4.12.2 Edgecorrosion The values indicated refer to one edge length.No integration across the whole component is made.4.12.2.1 Intermediate assessment1 cycle KR 0 KR 0 KR 04.12.2.2 Intermediate assessment3 cycles KR 1 (5%) KR 1 (5%) KR 04.12.2.3 Final assessment 3 cycles KR 2 (30%)4.12.2.4 Final assessment 6 cycles KR 2 (30%)4.12.2.5 Final assessment 10 cycles KR 2 (30%) KR 1 (5 %)Section 5.7 of this DBL 4.12.3 Weld corrosion4.12.3.1 Intermediate assessment1 cycle SR 0 SR 0 SR 04.12.3.2 Intermediate assessment3 cycles SR 1 (5%) SR 1 (5%) SR 1 (5%)4.12.3.3 Final assessment 3 cycles SR 1,5 (20%)4.12.3.4 Final assessment 6 cycles SR 1,5 (20%)4.12.3.5 Final assessment 10 cycles SR 1,5 (20%) SR 1,5 (20%)Section 5.14 of this DBL4.12.4 Subsurface corrosionU/2 in mm at end of test 1,5 2 1,5 1,5Section 5.4 of this DBL 4.12.5 Scratch test K 2 Section 5.2 of this DBL 4.12.6 Cross-cutGt1 Section 5.3 of this DBL4.12.7 Blistering/degree of blistering(S)< 2 (S 2) 0 Section 5.6 of this DBL4.12.8 Flange corrosionAssessment after 3 cyclesNo flange corrosion (no red rust) visible to customer Section 5.22 of this DBL4.12.9 CavitiesAssessment at end of testonly PV 20/21Complete coating in cavities with at least 12µmscratch adhesion in the heat-affected zone K 2. Surface corrosion Ri 0Affected PVs and their requirementsProperties 00/01 10/11/12 20/21/22 30/31 Test method 4.13 Corrosion cycle testZinc-coated and zinc-coated + organically coated / hot-dip aluminized substrates (FPT)Assessment after 1, 3 cycles and at the end of the test period.PVs 00/01 shall only be assessed at the end of the test period.The values indicated refer to white rust. No red rust shall occur in any case.Section 5.10 of this DBLExposure time in cycles 3 6 10 10 4.13.1 Surface corrosion No clusters or accumulations4.13.1 .1 Intermediate assessment1 cycle Ri 0 Ri 0 Ri 04.13.1.2 Intermediate assessment3 cycles Ri 0 Ri 0 Ri 04.13.1.3 Final assessment 3 cycles Ri 14.13.1.4 Final assessment 6 cycles Ri 14.13.1.5 Final assessment 10 cycles Ri 1 Ri 0Section 5.5 of this DBL4.13.2 Edge corrosionThe values indicated refer to one edge length. No integration across the whole component is made.4.13.2.1 Intermediate assessment1 cycle KR 0 KR 0 KR 04.13.2.2 Intermediate assessment3 cycles KR 1 (5%) KR 1 (5%) KR 04.13.2.3 Final assessment 3 cycles KR 3 (50%)4.13.2.4 Final assessment 6 cycles KR 3 (50%)4.13.2.5 Final assessment 10 cycles KR 3 (50%) KR 2 (30%)Section 5.7 of this DBL 4.13.3 Weld corrosion4.13.3.1 Intermediate assessment1 cycleSR 0 SR 0 SR 04.13.3.2 Intermediate assessment3 cycles SR 1 (5%) SR 1 (5%) SR 1 (5%)4.13.3.3 Final assessment 3 cycles SR 1,5 (20%)4.13.3.4 Final assessment 6 cycles SR 1,5 (20%)4.13.3.5 Final assessment 10 cycles SR 1,5 (20%) SR 1,5 (20%)Section 5.14 of this DBL4.13.4 Subsurface corrosionU/2 in mm at end of test4 4 4 4 Section 5.4 of this DBL 4.13.5 Scratch test K 2 Section 5.2 of this DBL 4.13.6 Cross-cut Gt 1 Section 5.3 of this DBL4.13.7 Blistering/degree of blistering(S)< 2 (S 2) 0 Section 5.6 of this DBL4.13.8 4.13.8.1 4.13.8.2 Flange corrosionAssessment after 3 cyclesEnd of testonly PV 20/21/22/31No flange corrosion (no red rust) visible to customerOpen flanges max. Ri 4 white rust (no red rust)Section 5.22 of this DBL4.13.9 CavitiesAssessment at end of testonly PV 20/21/22/31Complete coating in cavities with at least 12µm cataphoretic dip coating scratch adhesion in the heat-affected zone K 2. Surface corrosion Ri 0Affected PVs and their requirementsProperties 00/01 10/11/12 20/21/22 30/31 Test method4.14 Salt spray testonly steel substrates This test can be used to obtain a quick assessment of running series parts forsteel substrates without zinc coatingSection 5.9 of this DBLExposure time in h 168 240 504 5044.14.1 Subsurface corrosionU/2 in mm1 Section 5.4 of this DBL4.14.2 Surface corrosion Ri 1 Section5.5 of this DBL4.14.3 Blistering/degree of blistering(S)< 2 (S 2) 0 Section 5.6 of this DBL 4.14.4 Edge corrosion KR 1 Section 5.7 of this DBL 4.14.5 Scratch test K 2 Section 5.2 of this DBL 4.14.6 Cross-cut Gt1 Section 5.3 of this DBLAffected PVs and their requirementsProduct version 00/01 10/11/12 20/21/22 30/314.15 CASS testAluminumThis test shall be used for aluminum as base material. Section 5.11 of this DBL Exposure time in h 96 168 240 2404.15.1 Subsurface corrosionU/2 in mm2 1 Section 5.4 of this DBL 4.15.2 Surface corrosion Ri 0 Section 5.5 of this DBL4.15.3 Blistering/degree of blistering(S)< 2 (S 2) 0 Section 5.6 of this DBL 4.15.4 Edge corrosion KR 2 (30%) KR 1 (5%) Section 5.7 of this DBL 4.15.4.1 Edge corrosion Al wheels KR 1 Section 5.7 of this DBL 4.15.5 Scratch test K 2 Section 5.2 of this DBL 4.15.6 Cross-cut Gt1 Section 5.3 of this DBLAffected PVs and their requirementsProperties 30/31 Test method4.16 Filiform testAluminumThis test shall be used for aluminum as base material. Section 5.12 of this DBLExposure timeCass test 24 hours28 days at 40°C ±1°C / 82°% ±2% rel. humidity4.16.1 4.16.1.1 Subsurface corrosion around ascribe U/2 in mmMaximum filament length inmm24Section 5.13.1 of this DBL4.16.2 Surface corrosion Ri 0Section 5.5 of this DBL4.16.3 Blistering/degree of blistering(S) 0 (S 0)Section 5.6 of this DBL4.16.4 Edge corrosion Ri 1 (5%) Section5.7 of this DBL 4.16.5 Scratch test K 2 Section 5.2 of this DBL 4.16.6 Cross-cut Gt 1 Section 5.3 of this DBLAffected PVs and their requirementsProperties 30 Test method4.17 Filiform corrosionAluminumThis test shall only be used for mirror turned/polished aluminum wheels.Section 5.13 of this DBLExposure timeCass test 24 hours28 days at 60°C ±1°C / 82°% ±2% rel. humidity4.17.1 4.17.1.1 Subsurface corrosion around ascribe U/2 in mmMaximum filament length inmm24Section 5.13.1 of this DBL4.17.2 Surface corrosion Ri 0 Section5.5 of this DBL 4.17.3 Blistering/degree of blistering(S)0 Section 5.6 of this DBL 4.17.4 Edge corrosion KR 0 Section 5.7 of this DBLAffected PVs and their requirementsProperties 00/0110/11/12 20/21/2230/31Test method 4.18 Corrosion cycle testMagnesium/ZincSection 5.10 of this DBL Exposure time in cycles 104.18.1Subsurface corrosion U/2 in mm 1,5 Section 5.4 of this DBL 4.18.2Surface corrosionRi 0Section 5.5 of this DBL4.18.3 Blistering/degree of blistering (S)0 Section 5.6 of this DBL4.18.4 Edge corrosionKR 2 Section 5.7 of this DBL4.18.5 Scratch test K 2 Section5.2 of this DBL4.18.6 Cross-cut Gt 1Section 5.3 of this DBL Affected PVs and their requirementsProperties 00/01 10/11/12 20/21/22 30/31Test method 4.19 CASS testMagnesium/ZincIn principle, this test is only intended to check the complete coverage of thesurface. This test is performed without scratching the surface.Section 5.11 of this DBLExposure time in h 2404.19.1Surface corrosionSection 5.5 of this DBL4.19.2Edge corrosionSection 5.7 of this DBL4.19.3Blistering/degree ofblistering (S)Only to be used as comparative test.Surface corrosion, edge corrosion and blistering shall comply with the values of the alternating VDA test.The values of the original sample from the CASS test are then a constituent part of the ISIR.Section 5.6 of this DBLAffected PVs and their requirementsProperties 00/01 10/11/12 20/21/22 30/31 Test method4.20 Process and operatingfluid test Proof of compliance with these requirements by the paint supplier shall be sufficient (test results are part of ISIR)4.20.1 Hydraulic fluids The coating shall not demonstrate any changes VDA test sheet 621-412Section 4.1.4 Exposure time4 h at 50 °C4.20.2 Standard gasoline Temporary softening is still permitted provided that the adhesion testrequirements in accordance with Section 4.7. are fulfilled again after aregeneration time of 16 hours VDA test sheet 621-412 Section 4.1.1 Exposure time 10 min at 23°C ± 2°C4.20.3 Preservatives After an exposure time of 60 minutes at 23 ± 2°C, wipe off the preservativewith standard gasoline in accordance with DIN 51 604 Part 1.The coating shall neither be swollen nor discolored. VDA test sheet 621-412 Section 4.2.44.20.4 Cold cleaning solvent Temporary softening is permitted provided that the adhesion test requirementsin accordance with Section 4.7. are fulfilled again after a regeneration time of16 hours VDA test sheet 621-412 Section 4.2.3 Exposure time 10 min at 23°C ± 2°C4.20.5 Brake fluid Temporary softening is permitted provided that the adhesion test requirementsin accordance with Section 4.7. are fulfilled again after a regeneration time of16 hours VDA test sheet 621-412 Section 4.2.1 Exposure time 10 min at 23°C ± 2°CAffected PVs and their requirementsProperties 30/31 Test method4.21 Resistance to chemicals Proof of compliance with these requirements by the paint supplier shall besufficient (test results are part of ISIR)Section 5.21 of this DBL 4.21.1 Sulfuric acid4.21.2 Tree pitch4.21.3 Pancreatin4.21.4 Water4.21.5 Caustic soda solution No discoloration. No change in surface with regard to gloss and adhesionSection 5.21 of this DBL4.21.6 Wheel cleaner Only for Al wheels Section5.21 of this DBL For wheel MB No.A 001 986 34 71Affected PVs and their requirementsProperties30/31 Test method 4.22 Cold resistance No cracks 1 hour at –40°CAffected PVs and their requirementsProperties 30 31 Test method4.23 Weathering Proof of compliance with thisrequirement by the paint suppliershall be sufficient (reference samplepart of ISIR) The coating materials used require a separate DBL approval with regard to the compliance with this item.4.23.1 4.23.1.14.23.1.2 Florida testExposure time withoutaluminum wheelsExposure timeAl wheelsAt least 3 yearsAt least 2 yearsChange in color and gloss compared to unexposed reference sample notgreater than assessment figure 3-4 (color) / 2-3 (gloss).No cracks, no chalking.DBL 7399,Section 7.8.2 under 5°South。
kuebler 一般操作手册

kuebler 一般操作手册Kubernetes(简称Kuebler)是一个开源的容器编排系统,用于自动化容器化应用程序的部署、扩展和管理。
以下是Kuebler的一般操作手册:1. 安装和配置:首先,您需要在您的环境中安装和配置Kubernetes。
您可以从Kubernetes的官方网站上下载适合您操作系统的安装包,并按照说明进行安装。
安装完成后,您需要配置网络和存储等基础设施。
2. 创建集群:在安装和配置好Kubernetes后,您需要创建一个集群。
集群是Kubernetes中的一个基本概念,它由一组节点组成,节点上运行着容器。
您可以使用kubeadm等工具来创建一个新的集群。
3. 部署应用程序:一旦集群创建完成,您就可以开始部署应用程序了。
在Kubernetes中,应用程序由一组容器组成,这些容器共同运行并协作。
您可以使用Kubernetes提供的各种API和工具来部署应用程序,例如kubectl命令行工具或Kubernetes的自定义资源定义(CRD)。
4. 管理和监控:一旦应用程序部署完成,您需要对其进行管理和监控。
Kubernetes提供了许多工具和API来监视和管理集群和应用程序的状态。
例如,您可以使用kubectl命令行工具来获取集群和应用程序的状态信息,使用Prometheus等工具来收集和存储监控数据。
5. 扩展和升级:随着应用程序的需求增加或变化,您可能需要扩展或升级应用程序。
Kubernetes提供了许多工具和策略来帮助您实现这一目标,例如自动缩放和滚动更新等。
6. 故障排查:如果集群或应用程序出现问题,您需要进行故障排查。
Kubernetes提供了许多工具和日志来帮助您找到问题所在并解决它们。
例如,您可以使用kubectl命令行工具来获取容器的日志或诊断信息。
以上是Kuebler的一般操作手册,希望对您有所帮助。
请注意,这只是一个概述,具体的操作步骤和细节可能因您的环境和需求而有所不同。
AS-PS02 AS-PS02A 安裝說明说明书
AS-PS02AS-PS02AEN Instruction SheetTR Bilgi DökümaniTW安裝說明CN安装说明EN This is an OPEN TYPE module and therefore should be installed in an enclosure free of airborne dust, humidity, electric shock and vibration. The enclosure should prevent non-maintenance staff from operating the device (e.g. key or specific tools are required for operating the enclosure) in casedanger and damage on the device may occur.FR Ceci est un module ouvert et il doit donc être installé dans u n coffret à l’abri des poussières, des vibrations et ne pas être exposé aux chocs électriques. Le boitier ou l’armoire doit éviter toute action d’un personnel autre que celui affecté à la maintenance de l’appareil (par exemple, clefs, outils spécifiques po url’ouverture du coffret), ceci afin d’éviter tout accident corporel ou endommagement du produit).TR Bu ürün AÇIK TİP bir modül olup toz, rutubet, elektrik şoku ve titreşimden uzak kapalı yerlerde muhafaza edilmelidir. Yanlış kullanım sonucu ürünün zarar görmesini önlemek için yetkili olmayan kişiler tarafındanürüne müdahale edilmesini önleyecek koruyucu önlemler alınmalıdır. (Ürünün bulunduğu panoya kilitkonulması gibi).TW 本機為開放型(OPEN TYPE)機種,因此使用者使用本機時,必須將之安裝於具防塵、防潮及免於電擊∕衝擊意外之外殼配線箱內。
计算机科学重要国际会议

1.2计算机科学与技术重要国际学术会议一、A类会议二、B类会议1.3自动化重要国际学术会议一、A类会议二、B类会议数据挖掘相关的权威期刊和会议-----------------------------------------------[Journals]1.ACM Transactions on Knowledge Discovery from Data (TKDD)2.IEEE Transactions on Knowledge and Data Engineering (TKDE)3.Data Mining and Knowledge Discovery4.Knowledge and Information Systems5.Data & Knowledge Engineering[Conferences]1.SIGMOD:ACM Conference on Management of Data (ACM)2.VLDB:International Conference on Very Large Data Bases (Morgan Kaufmann/ACM)3.ICDE:IEEE International Conference on Data Engineering (IEEE Computer Society)4.SIGKDD:ACM Knowledge Discovery and Data Mining (ACM)5.WWW:International World Wide Web Conferences (W3C)6.CIKM:ACM International Conference on Information and Knowledge Management (ACM)7.PKDD:European Conference on Principles and Practice of Knowledge Discovery in Databases (Springer-Verlag LNAI)JournalsACM TKDD /DMKD/content/1573-756X/?p=859c3e83455d41679ef1be783 e923d1d&pi=0IEEE TKDE /organizations/pubs/transactions/tkde.htm ACM TODS /tods/VLDB Journal /ACM Tois /pubs/tois/ConferencesSigKDD /ICDM /~icdm/SDM /meetings/sdm08/PKDD /VLDB /SigMod /sigmod/ICDE http://www.ipsi.fraunhofer.de/tcde/conf_e.htmlWWW /conferencesOnline Resources网址集合/Computers/Software/Databases/Data_Mining// A google co-op search engine for Data Mining/coop/cse?cx=006422944775554126616%3Aixcd3tdxkke Data Mining, University of Houston/boetticher/CSCI5931%20Data%20Mining.htmlData Mining Program, University of Central Florida / Data Mining Group, University of Dortmundhttp://www-ai.cs.uni-dortmund.de/index.htmlData Mining, MIT OCW/OcwWeb/Sloan-School-of-Management/15-062Data-MiningSpri ng2003/CourseHome/Data Mining Group, Tsinghua /dmg.html KDD oral presentations video Data Mining Events Feed /DataMiningEvents ToolsWeka /ml/weka/Rapid Miner(Yale) /content/view/3/76/lang,en/IlliMine /Alpha Miner http://www.eti.hku.hk/alphaminerPotter's Wheel A-B-C /abc/。
Infoprint 250 導入と計画の手引き 第 7 章ホスト
SUBNETMASK
255.255.255.128
Type of service...............: TOS
*NORMAL
Maximum transmission unit.....: MTU
*LIND
Autostart.....................:
AUTOSTART
*YES
: xx.xxx.xxx.xxx
: xx.xxx.xxx.xxx
*
(
)
IEEE802.3
60 1500
: xxxx
48 Infoprint 250
31. AS/400
IP
MTU
1
1
IPDS TCP
CRTPSFCFG (V3R2)
WRKAFP2 (V3R1 & V3R6)
RMTLOCNAME RMTSYS
MODEL
0
Advanced function printing............:
AFP
*YES
AFP attachment........................:
AFPATTACH
*APPC
Online at IPL.........................:
ONLINE
FORMFEED
*CONT
Separator drawer......................:
SEPDRAWER
*FILE
Separator program.....................:
SEPPGM
*NONE
Library.............................:
GAMING SYSTEM FOR TRACKING PLAYER ACTIVITY DURING

专利名称:GAMING SYSTEM FOR TRACKING PLAYER ACTIVITY DURING VIRTUAL SESSIONS AT AGAMING MACHINE发明人:KAMMLER, Keith, Donald,MCNAMEE, J.,Christopher,SHELDON, Alan,Gael,O'DONNELL, Robert, L.申请号:US2004029353申请日:20040907公开号:WO05/026906P1公开日:20050324专利内容由知识产权出版社提供摘要:A gaming system (11) has a central authority (21) connected to a plurality of gaming machines (13,15,17). Player activity is tracked at the gaming machines (13,15,17) during regular gaming sessions and during virtual gaming sessions. Such data is transmitted to the central authority (21) for providing player points in a player account file of a central database (25). Regular gaming sessions occur between player card insertion as well as after player card insertion. For example, a coin-in event prior to player card insertion will establish a virtual session, and credits remaining on the credit meter at a card-out event will establish a virtual gaming session.申请人:KAMMLER, Keith, Donald,MCNAMEE, J., Christopher,SHELDON, Alan,Gael,O'DONNELL, Robert, L.地址:71 Longueville Road Lane Cove, NSW AU,9179 Sangria Lane Las Vegas, NV 89147 US,7897 Nookfield Drive Las Vegas, NV 89147 US,265 Powerbilt Avenue Las Vegas, NV 89148 US,5055 W. Hacienda Ave. #1220 Las Vegas, NV 89118 US国籍:AU,US,US,US,US代理机构:CARROLL , Christopher, R.更多信息请下载全文后查看。
首钢秘鲁铁矿浮选工艺及设备

首钢秘鲁铁矿浮选工艺及设备
金永涛;董干国;王志国;史帅星
【期刊名称】《有色金属(选矿部分)》
【年(卷),期】2011(000)0z1
【摘要】首钢秘鲁铁矿是首钢集团重要的海外铁矿基地,简要介绍选矿厂的选矿工艺流程,重点介绍浮选作业中采用的浮选机型号及配置.BGRIMM浮选机在首钢秘鲁铁矿的成功应用为我国浮选机进入南美洲市场,参与国际竞争打下了良好的基础.【总页数】4页(P198-201)
【作者】金永涛;董干国;王志国;史帅星
【作者单位】首钢秘鲁铁矿股份有限公司;北京矿冶研究总院,北京100070;北京矿冶研究总院,北京100070;北京矿冶研究总院,北京100070
【正文语种】中文
【中图分类】TD456
【相关文献】
1.关于开发首钢秘鲁铁矿碱性球团的探讨 [J], 陈汉宇
2.首钢秘鲁铁矿转让僵局:一场持续10年的利益博弈 [J], 郭芳
3.首钢秘鲁铁矿马尔科纳矿区9-10号矿体地质特征及成矿模式 [J], 尚潞君;滕正双;张平
4.首钢秘鲁马尔科纳铁矿区磁异常的数据处理 [J], 李文成
5.首钢秘鲁铁矿浮选工艺及设备 [J], 金永涛;董干国;王志国;史帅星
因版权原因,仅展示原文概要,查看原文内容请购买。
基于电磁波的煤岩识别技术研究进展

基于电磁波的煤岩识别技术研究进展柳圆, 司垒, 王忠宾, 魏东, 顾进恒(中国矿业大学 机电工程学院,江苏 徐州 221116)摘要:将电磁波应用于煤岩识别中,可有效提高煤岩界面分辨能力。
结合煤岩界面模型,阐述了运用电磁波技术进行煤岩识别的原理;介绍了γ射线法、雷达探测法、太赫兹信号法、电子共振法、X 射线法和红外热成像法6种具体的煤岩识别方法,分析了各方法的原理,对各方法的优缺点及煤矿井下适用性进行了对比,并结合实际工业应用分析了各方法的研究现状。
γ射线法在探测距离上具有显著优势,但存在放射性问题,基本被淘汰;雷达探测法具有识别准确的优点,但由于其信号衰减严重,探测距离短,目前一般应用于薄煤层测厚;太赫兹信号法探测距离短,只有在井下环境组成稳定时才能应用;电子共振法信号衰减严重,探测距离较短且难度较大,所以目前矿井基本摒弃;X 射线法穿透性强,成像较清晰,但危害性极大;红外热成像法中,主动红外激励法需耗费大量时间对煤岩进行激励,且在处于高瓦斯的矿井环境中,存在极大的安全隐患;截割闪温法虽耗时较短,但对于截齿多、排布复杂的情况很难实现有效的煤岩识别。
指出电磁波回波信息决定着电磁波煤岩识别的准确性,后续应对其进行深层次挖掘。
关键词:煤岩识别;电磁波;γ射线法;雷达探测法;太赫兹信号法;电子共振法;X 射线法;红外热成像法中图分类号:TD823 文献标志码:AResearch progress on coal rock recognition technology based on electromagnetic wavesLIU Yuan, SI Lei, WANG Zhongbin, WEI Dong, GU Jinheng(School of Mechatronic Engineering, China University of Mining and Technology, Xuzhou 221116, China)Abstract : Applying electromagnetic waves to coal rock recognition can effectively improve the resolution capability of coal rock interfaces. Based on the coal rock interface model, the principle of using electromagnetic wave technology for coal rock recognition is explained. The paper introduces six methods for coal rock recognition, including γ–ray method, radar detection method, Terahertz signal method, electron resonance method,X-ray method, and infrared thermal imaging method. The principles of each method are analyzed, and the advantages and disadvantages of each method are compared as well as their applicability in coal mines underground. The research status of each method is analyzed in combination with practical industrial applications.The γ–ray method has significant advantages in detection distance, but it has radiation problems. It is basically eliminated. The radar detection method has the advantage of accurate recognition, but due to its severe signal attenuation and short detection distance, it is currently generally used for thickness measurement in thin coal seams. The Terahertz signal method has a short detection distance and can only be applied when the composition of the underground environment is stable. The electronic resonance method has severe signal attenuation, short收稿日期:2023-07-26;修回日期:2024-01-10;责任编辑:胡娴。
Ubuntu 12.04 Virutal Machine User Manual

User Manual of the Pre-built Ubuntu12.04Virutal MachineCopyright c 2006-2014Wenliang Du,Syracuse University.The development of this document is/was funded by three grants from the US National Science Foundation: Awards No.0231122and0618680from TUES/CCLI and Award No.1017771from Trustworthy Computing.Permission is granted to copy,distribute and/or modify this document under the terms of the GNU Free Documentation License,Version1.2or any later version published by the Free Software Foundation.A copy of the license can be found at /licenses/fdl.html.1OverviewUsing VirtualBox,we have created a pre-built virtual machine(VM)image for UbuntuLinux(version 12.04).This VM can be used for all our SEED labs that are based on Linux.In this document,we describe the configuration of this VM,and give an overview of all the software tools that we have installed.The VM is available online from our SEED web page.Updating the VM is quite time-consuming,because not only do we need to udpate the VM image,we have to make sure that all our labs are consistent with the newly built VM.Therefore,we only plan to update our VM image once every two years,and of course update all our labs once the VM is changed.2VM Configurations2.1Configuration of the VMThe main configuration of this VM is summarized in the following.If you are using VirtualBox,you can adjust the configuration according to the resources of your host machine(e.g.,you can assign more memory to this VM if your host machine has enough memory):•Operating system:Ubuntu12.04with the Linux kernel v3.5.0-37-generic.•Memory:1024M RAM.•Disk space:Maximum80G disk space.We have created two accounts in the VM.The usernames and passwords are listed in the following:er ID:root,Password:seedubuntu.Note:Ubuntu does not allow root to login directly from the login window.You have to login asa normal user,and then use the command su to login to the root account.er ID:seed,Password:dees2.2Network setupCurrently the“Network connection”is set to“NAT”,i.e.,your VM is put in a private network,which uses your host machine as the router.The VMs in such a setting can connect to the Internet via the NAT mechanism,and they are not visible to the outside(their IP addresses are not routable from the outside,e.g., VirtualBox assigns10.0.2.15to each VM under NAT configuration).This setting is sufficient for most of our SEED labs.If you want your VMs to be visible to the outside(e.g.,you want to host a HTTP server in a VM, and you want to access it through the Internet),then,you can refer to the instruction“Network Configu-ration in VirtualBox for SEED Labs”under the following link:/˜wedu/ seed/Documentation/Ubuntu11_04_VM/VirtualBox_MultipleVMs.pdf.The instruction was written for Ubuntu11.04,however,it also works for the updated Ubuntu12.04Virtual Machine as well.3Libraries and Software3.1Libraries and Applications InstalledBesides the packages coming with the Ubuntu12.04installation,the following libraries and applications are additionally installed using the"apt-get install"command.libnet1,libnet1-dev,libpcat-dev,libpcap-dev,libattr1-dev,vim,apache2,php5,libapache2-mod-php5,mysql-server,wireshark,bind9,nmap,netwox/netwag,openjdk-6-jdk,snort,xpdf,vsftpd,telnetd,zsh,ssh,dpkg-dev,openssl,The libcap 2.21and libpcap1.2.0have been compiled and installed from the source down-loaded from the Internet.3.2Softwares configurationNetlib/netwox/wox is a network toolbox;netwag is a GUI of netwox.They can be foundin/usr/bin/.The ICMP spoofing bug of netwox has beenfixed.It should be noted that running netwox/netwag requires the root privilege.Wireshark.Wireshark is a network protocol analyzer for Unix and Windows.It is located in/usr/bin/. Wireshark requires the root privilege to run.Nmap.Nmap is a free security scanner for network exploration and hacking.It is located in/usr/bin/. Some functions of nmap require root privilege.Firefox extensions.Firefox is installed by default in Ubuntu12.04.We have installed some useful extensions,including LiveHTTPHeaders,Tamper Data,and Firebug.They can be launched in the “Tools”menu in Firefox.Elgg web application.Elgg is a very popular open-source web application for social network,and we use it as the basis for some of Web security labs.It should be noted that to access Elgg,the apache2http server and the MySQL database server must be running.Collabtive web application.For some labs,especially those related to web security,we need a non-trivial web application.For that purpose,we have installed the Collabtive web application.Several versionsof Collabtive are installed;most of them were modified from the original version to introduce different vulnerabilities.It should be noted that to access Collabtive,the apache2http server and the MySQL database server must be running.Java.We have installed openjdk-6-jdk,the OpenJDK Development Kit(JDK)6for Java.The com-mands javac and java are available to compile and run java source code.4Pre-Installed ServersSome of the SEED labs may need additional services that are not installed or enabled in the standard Ubuntu distribution.We have included them in our pre-built VM.Note:You need root privilege to start a server.4.1The MySQL ServerThe database server MySQL is installed.It can be started by running"service mysql start".Cur-rently,there are two accounts in the MySQL server.The usernames and passwords are listed below.1.root:seedubuntu2.apache:apache(web applications use this account to connect to the mysql server)You can access the MySQL database server by running the client-side application/usr/bin/mysql. The following is a simple demo on how to use mysql.$mysql-u root-pseedubuntumysql>show databases;mysql>use db_name;mysql>show tables;mysql>select username,user_email from table_name;mysql>quit4.2The Apache2Http ServerThe apache2http server was installed using"apt-get install".It can be started by issuing the "service apache2start"command.The apache2server is configured to listen on both80and 8080ports.All the web pages hosted by the server can be located under the/var/www/directory.For each SEED lab that uses the apache2http server,we have created one or several URLs.Basically, in the pre-built VM image,we use Apache server to host all the web sites used in the lab.The name-based virtual hosting feature in Apache could be used to host several web sites(or URLs)on the same machine.A configurationfile named default in the directory"/etc/apache2/sites-available"contains the necessary directives for the configuration.The following is a list of URLs that we have pre-configured; their corresponding directories are also listed:/var/www/CSRF/Collabtive//var/www/CSRF/Attacker//var/www/SQL/Collabtive//var/www/XSS/Collabtive//var/www/SOP//var/www/SOP/attacker//var/www/SOP/Collabtive/:8080/var/www/SOP/Configuring DNS.The above URL is only accessible from inside of the virtual machine,because we have modified the/etc/hostsfile to map each domain name to the virtual machine’s local IP address (127.0.0.1).You may map any domain name to a particular IP address using the/etc/hosts.For example you can map to the local IP address by appending the following entry to/etc/hostsfile:Therefore,if your web server and browser are running on two different machines,you need to modify the/etc/hostsfile on the browser’s machine accordingly to map the target domain name to the web server’sIP address.4.3Other ServersDNS server The DNS server bind9is installed.It can be started by running"service bind9 start".The configurationfiles are under/etc/bind/.Ftp server.The vsftpd(very secure ftp daemon)server is installed.It can be started by running "service vsftpd start".Telnet server.The telnetd server is installed.It can be started by running"service openbsd-inetd start".SSH server.The openssh server is installed.It can be started by running"service ssh start".5Miscellanious ConfigurationTime zone Currently the time zone is set to be New York,adjust that to the time zone of your location. Display resolution In order to adjust the display resolution in VirtualBox,we have installed guest addi-tions from the terminal(not from the menu in VirtualBox).This is done with the following3commands: sudo apt-get install virtualbox-ose-guest-utilssudo apt-get install virtualbox-ose-guest-x11sudo apt-get install virtualbox-ose-guest-dkmsAfter installing the required additions,you can adjust the display resolution at“System Settings→Dis-plays→Monitor”.6Configure Your VM securely6.1Change the passwordFor the sake of security and your own convenience,we suggest that you change the account password.To change the Ubuntu’s account password.You need to login as root and issue the"passwd username" command.To change MySQL’s root password.You can do it as following:$mysql-u root-pseedubuntuOnce in the prompt do this:mysql>update user set User=’NewRootName’,Password=’NewPassword’where user=’root’;mysql>flush privileges;6.2Configure automatically start serviceIt’s more convenient to start some commonly used service automatically during the system boot up,although most people do not want to start some server that they do not use.Currently,most of the service(except the Apache and MySQL servers)we need for SEED labs are configured not to start automatically.You can use chkconfig to get the current configuration.You can also use chkconfig to modify the configuration.For example,to start the server XYZ automatically during the system bootup,run"chkconfig XYZ on".。
IJWA sample paper

ABSTRACT: Data mining is a part of a process called KDD-knowledge discovery in databases. This process consists basically of steps that are performed before carrying out data mining, such as data selection, data cleaning, pre-processing, and data transformation. Association rule techniques are used for data mining if the goal is to detect relationships or associations between specific values of categorical variables in large data sets. There may be thousands or millions of records that have to be read and to extract the rules for, but the question is what will happen if there is new data, or there is a need to modify or delete some or all the existing set of data during the process of data mining. In the past user would repeat the whole procedure, which is time-consuming in addition to its lack of efficiency. From this, the importance of dynamic data mining process appears and for this reason this problem is going to be the main topic of this paper. Therefore the purpose of is study is to find solution for dynamic data mining process that is able to take into considerations all updates (insert, update, and delete problems) into account. Key words: Static data mining process, dynamic data, data mining, data mining process, dynamic data mining process. Received: 11 July 2009, Revised 13 August 2009, Accepted 18 August 2009 © 2009 D-line. All rights reserved. 1. Introduction Data mining is the task of discovering interesting and hidden patterns from large amounts of data where the data can be stored in databases, data warehouses, OLAP ( on line analytical process ) or other repository information [1]. It is also defined as knowledge discovery in databases (KDD) [2]. Data mining involves an integration of techniques from multiple disciplines such as database technology, statistics, machine learning, neural networks, information retrieval, etc [3]. According [4]: “Data mining is the process of discovering meaningful patterns and relationships that lie hidden within very large databases”. Also [5] defines Data mining as “the analysis of observational data sets to find unsuspected relationships and to summarize the data in novel ways that are both understandable and useful to the data owner”. Data mining is a part of a process called KDD-knowledge discovery in databases [3]. This process consists basically of steps that are performed before carrying out data mining, such as data selection, data cleaning, pre-processing, and data transformation [6]. The architecture of a typical data mining system may have the following major components [3]: database, data warehouse, or other information repository; a server which is responsible for fetching the relevant data based on the user’s data mining request, knowledge base which is used to guide the search. Data mining engine consists of a set of functional modules, Pattern evaluation module which interacts with the data mining modules so as to focus the search towards interesting patterns and graphical user interface which communicates between users and the data mining system, allowing the user interaction with system.
常用端口作用

端口号 | 说明0|无效端口,通常用于分析操作系统1|传输控制协议端口服务多路开关选择器2|管理实用程序3|压缩进程5|远程作业登录7|回显9|丢弃11|在线用户13|时间17|每日引用18|消息发送协议19|字符发生器20|FTP文件传输协议(默认数据口)21|FTP文件传输协议(控制)22|SSH远程登录协议23|telnet(终端仿真协议),木马Tiny Telnet Server开放此端口24|预留给个人用邮件系统25|SMTP服务器所开放的端口,用于发送邮件27|NSW 用户系统 FE29|MSG ICP31|MSG验证,木马Master Paradise、HackersParadise开放此端口33|显示支持协议35|预留给个人打印机服务37|时间38|路由访问协议39|资源定位协议41|图形42|主机名服务43|who is服务44|MPM(消息处理模块)标志协议45|消息处理模块46|消息处理模块(默认发送口)47|NI FTP48|数码音频后台服务49|TACACS登录主机协议50|远程邮件检查协议51|IMP(接口信息处理机)逻辑地址维护52|施乐网络服务系统时间协议53|dns域名服务器54|施乐网络服务系统票据交换55|ISI图形语言56|施乐网络服务系统验证57|预留个人用终端访问58|施乐网络服务系统邮件59|预留个人文件服务60|未定义61|NI邮件62|异步通讯适配器服务63|whois++64|通讯接口65|TACACS数据库服务66|Oracle SQL*NET67|引导程序协议服务端68|引导程序协议客户端69|小型文件传输协议70|信息检索协议71|远程作业服务72|远程作业服务73|远程作业服务74|远程作业服务75|预留给个人拨出服务76|分布式外部对象存储77|预留给个人远程作业输入服务78|修正TCP79|查询远程主机在线用户等信息80|http,用于网页浏览,木马Executor开放此端口81|HOST2名称服务82|传输实用程序83|模块化智能终端ML设备84|公用追踪设备85|模块化智能终端ML设备86|Micro Focus Cobol编程语言87|预留给个人终端连接88|Kerberros安全认证系统89|SU/MIT telnet(终端仿真网关)90|DNSIX 安全属性标记图91|MIT Dover假脱机92|网络打印协议93|设备控制协议94|Tivoli对象调度96|DIXIE协议规范97|快速远程虚拟文件协议98|TAC新闻协议99|后门程序ncx99开放此端口100|未知用途101|NIC 主机名称服务102|消息传输代理103|Genesis 点对点传输网络105|信箱名称服务106|3COM-TSMUX开放端口107|远程Telnet服务108|SNA 网关访问服务109|POP2服务器开放此端口,用于接收邮件110|POP3服务器开放此端口,用于接收邮件111|SUN公司的RPC服务所有端口112|McIDAS 数据传输协议113|认证服务,用于鉴别TCP连接的用户114|音频新闻多点服务115|简单文件传输服务116|ANSA REX 通知117|UUCP 路径服务118|SQL 服务119|NEWS新闻组传输协议,承载USENET通信121|木马BO jammerkillahV开放端口122|SMAKY网络123|网络时间协议,蠕虫病毒会利用,一般关闭128|GSS X许可认证129|密码生成器协议130|Cisco软件开放端口131|Cisco软件开放端口132|Cisco软件开放端口133|统计服务134|INGRES-网络服务135|DCOM服务,冲击波病毒利用,不能关闭136|命名系统137|NETBIOS协议应用,为共享开放138|NETBIOS协议应用,为共享开放139|NETBIOS协议应用,为共享开放140|EMFIS数据服务141|EMFIS控制服务143|Interim邮件访问协议144|UMA软件开放端口145|UAAC协议149|AED 512仿真服务150|SQL(结构化查询语言)-网络152|后台文件传输协议156|SQL(结构化查询语言)服务158|PC邮件服务器159|NSS-路由160|SGMP-陷阱161|简单网络管理协议162|SNMP陷阱163|CMIP/TCP 管理164|CMIP/TCP 代理166|Sirius系统169|发送170|网络附言177|x显示管理控制协议,入侵者通过它访问X-windows操作台178|NextStep Window 服务179|边界网关协议180|图表181|统一184|OC服务器185|远程-KIS186|KIS 协议187|应用通信接口189|队列文件传输190|网关进入控制协议191|Prospero 目录服务192|OSU 网络监视系统193|Spider 远程控制协议194|多线交谈协议197|目录地址服务198|目录地址服务监视器200|IBM系统资源控制器201|AppleTalk(Mac机所用的网络协议)路由保证202|AppleTalk(Mac机所用的网络协议)Name Binding203|AppleTalk(Mac机所用的网络协议)未用端口204|AppleTalk(Mac机所用的网络协议)回显205|AppleTalk(Mac机所用的网络协议)未用端口206|AppleTalk(Mac机所用的网络协议)区信息207|AppleTalk(Mac机所用的网络协议)未用端口208|AppleTalk(Mac机所用的网络协议)未用端口209|快速邮件传输协议210|ANSI(美国国家标准协会)Z39.50211|Texas Instruments 914C/G终端213|IPX(以太网所用的协议)218|Netix消息记录协议219|Unisys ARPs220|交互邮件访问协议 v3223|证书分发中心224|masq拨号器241|预留端口 (224-241)245|链接246|显示系统协议257|安全电子交易系统258|Yak Winsock 个人聊天259|有效短程遥控260|开放端口261|IIOP 基于TLS/SSL的命名服务266|SCSI(小型计算机系统接口)on ST267|Tobit David服务层268|Tobit David复制281|个人连结282|Cable端口A/X286|FXP通信308|Novastor备份313|Magenta逻辑318|PKIX时间标记333|Texar安全端口344|Prospero数据存取协议345|Perf分析工作台346|Zebra服务器347|Fatmen服务器348|Cabletron管理协议358|Shrink可上网家电协议359|网络安全风险管理协议362|SRS发送363|RSVP隧道372|列表处理373|Legend公司374|Legend公司376|AmigaEnvoy网络查询协议377|NEC公司378|NEC公司379|TIA/EIA/IS-99调制解调器客户端380|TIA/EIA/IS-99调制解调器服务器381|hp(惠普)性能数据收集器382|hp(惠普)性能数据控制节点383|hp(惠普)性能数据警报管理384|远程网络服务器系统385|IBM应用程序386|ASA信息路由器定义文件.387|Appletalk更新路由.389|轻型目录访问协议395|网络监视控制协议396|Novell(美国Novell公司)Netware(网络操作系统)over IP 400|工作站解决方案401|持续电源402|Genie协议406|交互式邮件支持协议408|Prospero资源管理程序409|Prospero资源节点管理.410|DEC(数据设备公司)远程调试协议411|远程MT协议412|陷阱协定端口413|存储管理服务协议414|信息查询415|B网络423|IBM操作计划和控制开端424|IBM操作计划和控制追踪425|智能计算机辅助设计427|服务起位置434|移动ip代理435|移动ip管理443|基于TLS/SSL的网页浏览端口,能提供加密和通过安全端口444|简单网络内存分页协议445|Microsoft-DS,为共享开放,震荡波病毒利用,一般应关闭446|DDM-远程关系数据库访问447|DDM-分布式文件管理448|DDM-使用安全访问远程数据库456|木马HACKERS PARADISE开放此端口458|apple quick time软件开放端口459|ampr-rcmd命令464|k密码服务469|广播控制协议470|scx-代理472|ljk-登陆481|Ph服务487|简单异步文件传输489|nest-协议491|go-登陆499|ISO ILL协议500|Internet密钥交换,Lsass开放端口,不能关闭509|陷阱510|FirstClass协议512|远程进程执行513|远程登陆514|cmd命令515|spooler516|可视化数据518|交谈519|unix时间520|扩展文件名称服务器525|时间服务526|新日期529|在线聊天系统服务530|远程过程调用531|聊天532|读新闻533|紧急广播端口534|MegaMedia管理端537|网络流媒体协议542|商业543|Kerberos(软件)v4/v5544|krcmd命令546|DHCPv6 客户端547|DHCPv6 服务器552|设备共享554|Real Time Stream控制协议555|木马PhAse1.0、Stealth Spy、IniKiller开放此端口556|远距离文件服务器563|基于TLS/SSL的网络新闻传输协议564|plan 9文件服务565|whoami查询566|streettalk567|banyan-rpc(远程过程调用)568|DPA成员资格569|MSN成员资格570|demon(调试监督程序)571|udemon(调试监督程序)572|声纳573|banyan-贵宾574|FTP软件代理系统581|Bundle Discovery 协议582|SCC安全583|Philips视频会议584|密钥服务器585|IMAP4+SSL (Use 993 instead)586|密码更改587|申请589|Eye连结595|CAB协议597|PTC名称服务598|SCO网络服务器管理3599|Aeolon Core协议600|Sun IPC(进程间通讯)服务器601|可靠系统登陆服务604|通道606|Cray统一资源管理608|发送人-传递/提供 文件传输器609|npmp-陷阱610|npmp-本地611|npmp-gui( 图形用户界面)612|HMMP指引613|HMMP操作614|SSL(加密套接字协议层)shell(壳)615|Internet配置管理616|SCO(Unix系统)系统管理服务器617|SCO桌面管理服务器619|Compaq(康柏公司)EVM620|SCO服务器管理623|ASF远程管理控制协议624|Crypto管理631|IPP (Internet打印协议)633|服务更新(Sterling软件)637|局域网服务器641|repcmd命令647|DHCP(动态主机配置协议)Failover648|注册登记协议(RRP)649|Cadview-3d软件协议666|木马Attack FTP、Satanz Backdoor开放此端口808|ccproxy http/gopher/ftp (over http)协议1001|木马Silencer,WebEx开放端口1011|木马Doly开放端口1024|动态端口的开始,木马yai开放端口1025|inetinfo.exe(互联网信息服务)木马netspy开放端口1026|inetinfo.exe(互联网信息服务)1027|应用层网关服务1030|应用层网关服务1031|BBN IAD1033|本地网络信息端口1034|同步通知1036|安全部分传输协议1070|木马Psyber Stream,Streaming Audio开放端口1071|网络服务开放端口1074|网络服务开放端口1080|Socks这一协议以通道方式穿过防火墙,允许访问1110|卡巴斯基反病毒软件开放此端口1125|卡巴斯基反病毒软件开放此端口1203|许可证生效端口1204|登陆请求监听端口1206|Anthony数据端口1222|SNI R&D网络端口1233|普遍的附录服务器端口1234|木马SubSeven2.0、Ultors Trojan开放此端口1243|木马SubSeven1.0/1.9开放此端口1245|木马Vodoo,GabanBus,NetBus,Vodoo开放此端口1273|EMC-网关端口1289|JWalk服务器端口1290|WinJa服务器端口1333|密码策略(网络服务)(svchost.exe)1334|网络服务(svchost.exe)1335|数字公正协议1336|即时聊天协议(svchost.exe)1349|注册网络协议端口1350|注册网络协议端口1371|富士通配置协议端口1372|富士通配置协议端口1374|EPI软件系统端口1376|IBM个人-个人软件端口1377|Cichlid许可证管理端口1378|Elan许可证管理端口1380|Telesis网络许可证管理端口1381|苹果网络许可证管理端口1386|CheckSum 许可证管理端口1387|系统开放端口(rundll32.exe)1388|数据库高速缓存端口1389|文档管理端口1390|存储控制器端口1391|存储器存取服务器端口1392|打印管理端口1393|网络登陆服务器端口1394|网络登陆客户端端口1395|PC工作站管理软件端口1396|DVL活跃邮件端口1397|音频活跃邮件端口1398|视频活跃邮件端口1399|Cadkey许可证管理端口1433|Microsoft的SQL服务开放端口1434|Microsoft的SQL服务监视端口1492|木马FTP99CMP开放此端口1509|木马Psyber Streaming Server开放此端口1512|Microsoft Windows网络名称服务1524|许多攻击脚本安装一个后门SHELL于这个端口1600|木马Shivka-Burka开放此端口1645|远程认证拨号用户服务1701|第2层隧道协议1731|NetMeeting音频调用控制1801|Microsoft消息队列服务器1807|木马SpySender开放此端口1900|可被利用ddos攻击,一般关闭1912|金山词霸开放此端口1981|木马ShockRave开放此端口1999|木马BackDoor,yai开放此端口端口号 | 说明2000|木马GirlFriend 1.3、Millenium 1.0开放此端口2001|木马Millenium 1.0、Trojan Cow,黑洞2001开放此端口2003|GNU 查询2023|木马Pass Ripper开放此端口2049|NFS程序常运行于此端口2115|木马Bugs开放此端口2140|木马Deep Throat 1.0/3.0,The Invasor开放此端口2500|应用固定端口会话复制的RPC客户2504|网络平衡负荷2565|木马Striker开放此端口2583|木马Wincrash 2.0开放此端口2801|木马Phineas Phucker开放此端口2847|诺顿反病毒服务开放此端口3024|木马WinCrash开放此端口3128|squid http代理服务器开放此端口3129|木马Master Paradise开放此端口3150|木马The Invasor,deep throat开放此端口3210|木马SchoolBus开放此端口3306|MySQL开放此端口3333|木马Prosiak开放此端口3389|WINDOWS 2000终端开放此端口3456|inetinfo.exe(互联网信息服务)开放端口,VAT默认数据3457|VAT默认控制3527|Microsoft消息队列服务器3700|木马Portal of Doom开放此端口3996|木马RemoteAnything开放此端口4000|腾讯QQ客户端开放此端口4060|木马RemoteAnything开放此端口4092|木马WinCrash开放此端口4133|NUTS Bootp服务器4134|NIFTY-Serve HMI协议4141|Workflow服务器4142|文档服务器4143|文档复制4145|VVR控制4321|远程Who Is查询4333|微型sql服务器4349|文件系统端口记录4350|网络设备4351|PLCY网络服务4453|NSS警报管理4454|NSS代理管理4455|PR聊天用户4456|PR聊天服务器4457|PR注册4480|Proxy+ HTTP代理端口4500|Lsass开放端口,不能关闭4547|Lanner许可管理4555|RSIP端口4590|木马ICQTrojan开放此端口4672|远程文件访问服务器4752|简单网络音频服务器4800|Icona快速消息系统4801|Icona网络聊天4802|Icona许可系统服务器4848|App服务器-Admin HTTP4849|App服务器-Admin HTTPS4950|木马IcqTrojan开放5000端口5000|木马blazer5,Sockets de Troie开放5000端口,应关闭5001|木马Sockets de Troie开放5001端口5006|wsm服务器5007|wsm服务器ssl5022|mice服务器5050|多媒体会议控制协议5051|ITA代理5052|ITA管理5137|MyCTS服务器端口5150|Ascend通道管理协议5154|BZFlag游戏服务器5190|America-Online(美国在线)5191|AmericaOnline1(美国在线)5192|AmericaOnline2(美国在线)5193|AmericaOnline3(美国在线)5222|Jabber客户端连接5225|HP(惠普公司)服务器5226|HP(惠普公司)5232|SGI绘图软件端口5250|i网关5264|3Com网络端口15265|3Com网络端口25269|Jabber服务器连接5306|Sun MC组5321|木马Sockets de Troie开放5321端口5400|木马Blade Runner开放此端口5401|木马Blade Runner开放此端口5402|木马Blade Runner开放此端口5405|网络支持5409|Salient数据服务器5410|Salient用户管理5415|NS服务器5416|SNS网关5417|SNS代理5421|网络支持25423|虚拟用户5427|SCO-PEER-TTA(Unix系统)5432|PostgreSQL数据库5550|木马xtcp开放此端口5569|木马Robo-Hack开放此端口5599|公司远程安全安装5600|公司安全管理5601|公司安全代理5631|pcANYWHERE(软件)数据5632|pcANYWHERE(软件)数据5673|JACL消息服务器5675|V5UA应用端口5676|RA管理5678|远程复制代理连接5679|直接电缆连接5720|MS-执照5729|Openmail用户代理层5730|Steltor's日历访问5731|netscape(网景)suiteware5732|netscape(网景)suiteware5742|木马WinCrash1.03开放此端口5745|fcopy-服务器5746|fcopys-服务器5755|OpenMail(邮件服务器)桌面网关服务器5757|OpenMail(邮件服务器)X.500目录服务器5766|OpenMail (邮件服务器)NewMail服务器5767|OpenMail (邮件服务器)请求代理曾(安全) 5768|OpenMail(邮件服务器) CMTS服务器5777|DALI端口5800|虚拟网络计算5801|虚拟网络计算5802|虚拟网络计算HTTP访问, d5803|虚拟网络计算HTTP访问, d5900|虚拟网络计算机显示05901|虚拟网络计算机显示15902|虚拟网络计算机显示25903|虚拟网络计算机显示36000|X Window 系统6001|X Window 服务器6002|X Window 服务器6003|X Window 服务器6004|X Window 服务器6005|X Window 服务器6006|X Window 服务器6007|X Window 服务器6008|X Window 服务器6009|X Window 服务器6010|X Window 系统6011|X Window 系统6012|X Window 系统6013|X Window 系统6014|X Window 系统6015|X Window 系统6016|X Window 系统6017|X Window 系统6018|X Window 系统6019|X Window 系统6020|X Window 系统6021|X Window 系统6022|X Window 系统6023|X Window 系统6024|X Window 系统6025|X Window 系统6026|X Window 系统6027|X Window 系统6029|X Window 系统6030|X Window 系统6031|X Window 系统6032|X Window 系统6033|X Window 系统6034|X Window 系统6035|X Window 系统6036|X Window 系统6037|X Window 系统6038|X Window 系统6039|X Window 系统6040|X Window 系统6041|X Window 系统6042|X Window 系统6043|X Window 系统6044|X Window 系统6045|X Window 系统6046|X Window 系统6047|X Window 系统6048|X Window 系统6049|X Window 系统6050|ARCserve 代理6051|X Window 系统6052|X Window 系统6053|X Window 系统6054|X Window 系统6055|X Window 系统6056|X Window 系统6057|X Window 系统6058|X Window 系统6059|X Window 系统6060|X Window 系统6061|X Window 系统6062|X Window 系统6063|X Window 系统6267|木马广外女生开放此端口6400|木马The tHing开放此端口6401|seagate(美国希捷公司) 6455|SKIP证书接受6456|SKIP证书发送6471|LVision许可管理器6505|BoKS管理私人端口6506|BoKS管理公共端口6507|BoKS Dir服务器,私人端口6508|BoKS Dir服务器,公共端口6509|MGCS-MFP端口6510|MCER端口6566|SANE控制端口6580|Parsec主服务器6581|Parsec对等网络6582|Parsec游戏服务器6588|AnalogX HTTP代理端口6631|Mitchell电信主机6668|Internet多线交谈6670|木马Deep Throat开放此端口6671|木马Deep Throat 3.0开放此端口6699|Napster文件(MP3)共享服务6701|KTI/ICAD名称服务器6788|SMC软件-HTTP6789|SMC软件-HTTPS6841|Netmo软件默认开放端口6842|Netmo HTTP服务6883|木马DeltaSource开放此端口6939|木马Indoctrination开放此端口6969|木马Gatecrasher、Priority开放此端口6970|real音频开放此端口7000|木马Remote Grab开放此端口7002|使用者& 组 数据库7003|音量定位数据库7004|AFS/Kerberos认证服务7005|音量管理服务7006|错误解释服务7007|Basic监督进程7008|服务器-服务器更新程序7009|远程缓存管理服务7011|Talon软件发现端口7012|Talon软件引擎7013|Microtalon发现7014|Microtalon通信7015|Talon网络服务器7020|DP服务7021|DP服务管理7100|X字型服务7121|虚拟原型许可证管理7300|木马NetMonitor开放此端口7301|木马NetMonitor开放此端口7306|木马NetMonitor,NetSpy1.0开放此端口7307|木马NetMonitor开放此端口7308|木马NetMonitor开放此端口7323|Sygate服务器端7511|木马聪明基因开放此端口7588|Sun许可证管理7597|木马Quaz开放此端口7626|木马冰河开放此端口7633|PMDF管理7674|iMQ SSL通道7675|iMQ通道7676|木马Giscier开放此端口7720|Med图象入口7743|Sakura脚本传递协议7789|木马ICKiller开放此端口7797|Propel连接器端口7798|Propel编码器端口8000|腾讯QQ服务器端开放此端口8001|VCOM通道8007|Apache(类似iis)jServ协议1.x8009|Apache(类似iis)JServ协议1.38010|Wingate代理开放此端口8011|木马way2.4开放此端口8022|OA-系统8080|WWW代理开放此端口8081|ICECap控制台8082|BlackIce(防止黑客软件)警报发送到此端口8118|Privoxy HTTP代理8121|Apollo数据端口8122|Apollo软件管理端口8181|Imail8225|木马灰鸽子开放此端口8311|木马初恋情人开放此端口8351|服务器寻找8416|eSpeech Session协议8417|eSpeech RTP协议8473|虚拟点对点8668|网络地址转换8786|Message客户端8787|Message服务器8954|Cumulus管理端口9000|CS监听9001|ETL服务管理9002|动态id验证9021|Pangolin验证9022|PrivateArk远程代理9023|安全网络登陆-19024|安全网络登陆-29025|安全网络登陆-39026|安全网络登陆-49101|Bacula控制器9102|Bacula文件后台9103|Bacula存储邮件后台9111|DragonIDS控制台9217|FSC通讯端口9281|软件传送端口19282|软件传送端口29346|C技术监听9400|木马Incommand 1.0开放此端口9401|木马Incommand 1.0开放此端口9402|木马Incommand 1.0开放此端口9594|信息系统9595|Ping Discovery服务9800|WebDav源端口9801|Sakura脚本转移协议-29802|WebDAV Source TLS/SSL9872|木马Portal of Doom开放此端口9873|木马Portal of Doom开放此端口9874|木马Portal of Doom开放此端口9875|木马Portal of Doom开放此端口9899|木马InIkiller开放此端口9909|域名时间9911|SYPECom传送协议9990|OSM Applet程序服务器9991|OSM事件服务器10000|网络数据管理协议10001|SCP构造端口10005|安全远程登陆10008|Octopus多路器10067|木马iNi-Killer开放此端口10113|NetIQ端点10115|NetIQ端点10116|NetIQVoIP鉴定器10167|木马iNi-Killer开放此端口11000|木马SennaSpy开放此端口11113|金山词霸开放此端口11233|木马Progenic trojan开放此端口12076|木马Telecommando开放此端口12223|木马Hack'99 KeyLogger开放此端口12345|木马NetBus1.60/1.70、GabanBus开放此端口12346|木马NetBus1.60/1.70、GabanBus开放此端口12361|木马Whack-a-mole开放此端口13223|PowWow 客户端,是Tribal Voice的聊天程序13224|PowWow 服务器,是Tribal Voice的聊天程序16959|木马Subseven开放此端口16969|木马Priority开放此端口17027|外向连接19191|木马蓝色火焰开放此端口20000|木马Millennium开放此端口20001|木马Millennium开放此端口20034|木马NetBus Pro开放此端口21554|木马GirlFriend开放此端口22222|木马Prosiak开放此端口23444|木马网络公牛开放此端口23456|木马Evil FTP、Ugly FTP开放此端口25793|Vocaltec地址服务器26262|K3软件-服务器26263|K3软件客户端26274|木马Delta开放此端口27374|木马Subseven 2.1开放此端口30100|木马NetSphere开放此端口30129|木马Masters Paradise开放此端口30303|木马Socket23开放此端口30999|木马Kuang开放此端口31337|木马BO(Back Orifice)开放此端口31338|木马BO(Back Orifice),DeepBO开放此端口31339|木马NetSpy DK开放此端口31666|木马BOWhack开放此端口31789|Hack-a-tack32770|sun solaris RPC服务开放此端口33333|木马Prosiak开放此端口33434|路由跟踪34324|木马Tiny Telnet Server、BigGluck、TN开放此端口36865|KastenX软件端口38201|Galaxy7软件数据通道39681|TurboNote默认端口40421|木马Masters Paradise开放此端口40422|木马Masters Paradise开放此端口40423|木马Masters Paradise开放此端口40426|木马Masters Paradise开放此端口40843|CSCC 防火墙43210|木马SchoolBus 1.0/2.0开放此端口43190|IP-PROVISION44321|PCP服务器(pmcd)44322|PCP服务器(pmcd)代理44334|微型个人防火墙端口44442|ColdFusion软件端口44443|ColdFusion软件端口44445|木马Happypig开放此端口45576|E代时光专业代理开放此端口47262|木马Delta开放此端口47624|Direct Play服务器47806|ALC协议48003|Nimbus网关50505|木马Sockets de Troie开放此端口50766|木马Fore开放此端口53001|木马Remote Windows Shutdown开放此端口54320|木马bo2000开放此端口54321|木马SchoolBus 1.0/2.0开放此端口61466|木马Telecommando开放此端口65000|木马Devil 1.03开放此端口65301|PC Anywhere软件开放端口。
Mettler Toledo 软件激活指南说明书
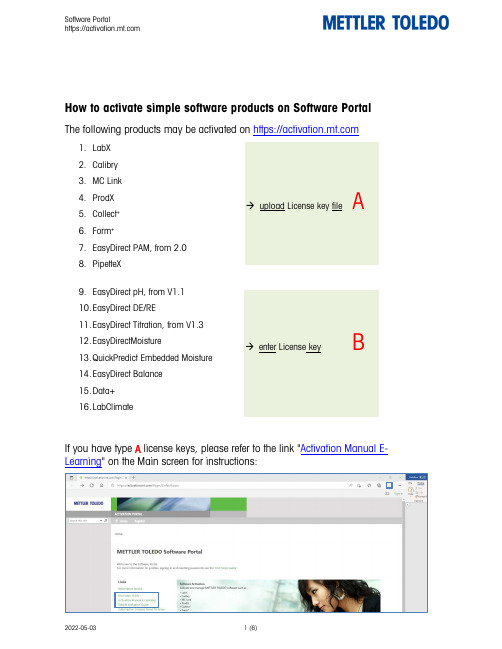
Software Portalhttps://How to activate simple software products on Software PortalThe following products may be activated on https://1. LabX2. Calibry3. MC Link4. ProdX5. Collect +6. Form +7. EasyDirect PAM, from 2.0 8. PipetteX9. EasyDirect pH, from V1.1 10. EasyDirect DE/RE11. EasyDirect Titration, from V1.3 12. EasyDirectMoisture13. QuickPredict Embedded Moisture 14. EasyDirect Balance 15. Data+ 16. LabClimateIf you have type A license keys, please refer to the link "Activation Manual E-Learning " on the Main screen for instructions:→ upload License key fileA→ enter License keyBThis guide describes how to activate a type B license key. Preconditions: -You have an installed type B SW product.-You have a license key for the same type B product.-You have registered for a user account. Please refer to the First Step Guide on the main screen for instructions.Steps to activate a type B product:1.Start your installed type B software product and note / copy the LicenseRegistration Information (LRI)2.Sign in to https:// and refer to "Activation"3.Enter your type B license key and enter / paste the LRI and submitAdd License key + License Registration Information (LRI)Add a single license key for a simple software product plus the LRI out of the installed software.LRI: Add Transfer keyAdd a Transfer key to receive an activated system from another user account.3)2) 1)4.The Software Portal provides a Short Activation Code (SAC) in a pop-up box.Note / copy the Short Activation Code (SAC)4)5.Enter / paste the Short Activation key (SAC) into your Type B software andregister.5)Your type B SW is now activated!View your activated system on Software Portal:Add License key + License Registration Information (LRI)Add a single license key for a simple soft ware product plus the LRI out of the installed software.LRI:Add Transfer keyAdd a Transfer key to receive an activated system from another user account.Add / edit system information (optional)1.Select an activated system and click the magnifierAdd License key + License Registration Information (LRI)Add a single license key for a simple soft ware product plus the LRI out of the installed software.LRI:Add Transfer keyAdd a Transfer key to receive an activated system from another user account.1)2.Select Edit System in License overview and add/change system information2)3.View activated systems including system informationAdd License key + License Registration Information (LRI)Add a single license key for a simple soft ware product plus the LRI out of the installed software.LRI:Add Transfer keyAdd a Transfer key to receive an activated system from another user account.3)。
cowabungalite使用方法

一、背景介绍Cowabungalite是一款用于网络安全测试和渗透测试的工具集,由Python编写,具有简单易用、功能强大等特点。
它包含了许多常用的安全测试工具,如nmap、metasploit、sqlmap等,可以帮助用户快速进行安全测试和漏洞挖掘。
二、安装方法1. 在Linux系统上,可以通过Git来进行安装,首先打开终端,输入以下命令:```bashgit clone xxx```2. 然后切换至cowabunga目录,输入以下命令:```bashcd cowabunga```3. 最后运行安装脚本,输入以下命令:```bashbash cowabunga.sh```4. 安装完成后,可以输入以下命令来启动Cowabungalite:```bashpython3 cowabunga.py```5. 如果想在Windows系统上使用Cowabungalite,可以先安装Python环境,然后按照以上步骤进行安装。
三、使用方法1. 打开Cowabungalite后,可以看到一个命令行界面,界面上列出了可用的工具和选项。
2. 您可以使用help命令查看帮助信息,了解各个工具的用法和参数设定。
3. 使用nmap进行端口扫描时,可以输入以下命令:```bashnmap -sS target_ip```其中target_ip是目标主机的IP位置区域。
nmap将会扫描目标主机的开放端口,并将结果显示出来。
4. 使用metasploit进行渗透测试时,可以输入以下命令:```bashmsfconsole```然后进入metasploit的交互式命令行界面,可以执行各种渗透测试命令,如扫描漏洞、利用漏洞等。
5. 使用sqlmap进行SQL注入测试时,可以输入以下命令:```bashsqlmap -u "xxx"```其中target_url是目标全球信息站的URL位置区域。
sqlmap将会对目标全球信息站进行SQL注入测试,并将测试结果输出。
Door King 6300-084 Electric Strike 说明书

131133Shown for Reference in Outline Form Pad Mount 2600-264Callout = PM (PM includes parts also used in Post Mount 2600-263)PMPMPMPMPM111127121113115117119123125121Not Shown2XShown for Reference Pad Mount 2600-264Ref1162XEOREV DESCRIPTION Drawn APPR ---K Added Item 116; Deleted I66 Was: 2620-019; Revised Items 151, 153, 180, 211 Was: 2616-016, 2904-002, 2902-007, 2340-065.Sal 09/19/08 D.C.09/19/08KIPB-Model 6300-084,1HP, 115 V, Primary PROPRIETARY AND CONFIDENTIAL COMMENTS:SHEET 1 OF 6CHECKED DRAWN DATENAME REV A DWG. NO.SIZEScale: None 6300-884Sal 06/09/082. Items 200-211 Not Shown for Clarity.1. See attached reference sheet for BOM; Reference Movex 6300-084 Rev K.Notes: Unless Otherwise Specified.THE INFORMATION CONTAINED IN THIS DRAWING IS THE SOLE PROPERTY OF Door King. ANY REPRODUCTION IN PART OR AS A WHOLE WITHOUT THE WRITTEN PERMISSION OF Door King IS PROHIBITED.Item Part Number Qty UM Description Rev 16300-8841EA IPB-115V 1HP, Swing Gate Optr, Primary K 32600-7051EA Bracket Panel Base Model 63052600-1621EA Motor Assembly 1HP Model 63081215-0182EA Wire Nut #71B112600-5691EA Pulley 10" Cast Iron AC100X5/8131601-0191EA Keyway 3/16 x 3/16 x 1152600-4281EA Belt-Cogged, AX-34192600-4101EA Marker Strip Silkscn Both Side212600-4141EA Terminal Block-2 Position233129-0021EA Terminal Block Cover 2 Position244001-0931EA MOV Assembly 130VAC272599-0141EA Decal Copper Wire Only292600-4391EA Washer Cup - Brass312599-0061EA Decal SUPPLY GND322600-6192EA Wire Clp-5/8 Concord 770-1209372600-6381EA Bracket Radio 610 Battery Bkup396300-0421EA Housing Assembly 6300412600-6131EA Bracket Magnetic Ctr Potted433004-0101EA Magnetic Counter Threaded453004-0512EA Nut Panel 1/4-18472600-7791EA Swing Crank Arm Extended492600-0611EA Collar 2 OD x 1 1/4 ID x 5/8 L572600-1741EA Main Shaft Assy Model 630592630-0101EA Snap Ring 1.25"612600-0731EA Magnet Counter Ring632600-6812EA Clutch Plate 9" Die Cast652801-0032EA Clutch Pad 9" OD620/25,630,630672600-6441EA Worm Gear 100 Teeth Delrin712600-7731EA Bracket Board Mtg Panel 630732600-5331EA Switch Cover Doorking Lockable752600-7311EA Gasket Switch Cover771506-0711EA Tone Generator Loud791812-0051EA Switch Push Button N.O.811601-0411EA Switch Toggle SPST 2POS852599-0081EA Label Patent871200-0282EA Outlet Snap-In Leviton 1306882600-7492EA Wire Connector STA-KON RC6892600-82012EA Bushing 1/2954502-0101EA PCB Gate Operator974001-0201EA Terminal 20 Pin992600-8402EA Jumper- Ring Tongue #8 Screw1012600-9451EA Cover Plastic Insulator1112600-7251EA Cover-Model 63001132600-7321EA Nameplate Plastic DKS1152802-0402EA Washer Push on Clamp1161897-0522EA Gasket, Microphone Support1171702-5071EA Cam "J" Hook1194001-0351EA Lock N16058BDxSFx2K Key 16120 1212600-7201EA Crank Arm Joint Assembly Blk 1232600-6301EA Joint Cover Swinger Left1252600-6311EA Joint Cover Swinger Right 1272600-7111EA Bracket 3/16 x 2 x 121312599-0341EA Label Gate Operator1332599-1991EA Label Universal1402615-0523EA Bolt Hex Head 3/8-16 x 1 1412615-0081EA Bolt Hex Head 1/4-20 x 1 1/2 1422615-8701EA Bolt Button Socket 3/8-16 x 3/4 1502616-0192EA Screw Phillips Head 8-32 x 3/4 1512616-0181EA Screw Phillips Head 8-32 x 1/2 1522616-0172EA Screw Phillips Head 8-32 x 3/8 1532616-0012EA Screw Phillips Head 6-32 x 3/8 1542616-0512EA Screw Phillips 10-32 x 3/8 1552616-0526EA Screw Phillips Head 10-32 x 1/2 1562616-0012EA Screw Phillips Head 6-32 x 3/8 1572600-8872EA Screw Nylon Phillips 6-32 x 1/4 1582616-0032EA Screw Phillips Head 6-32 x 3/4 1602620-2202EA Washer 1.25 x 2 x .06251612620-1312EA Washer 1 7/8 OD x 1/2 ID 1/8 T 1632600-1838EA Washer Bellville 1.5"OD x .5"ID 1642620-0212EA Washer 1/2 SAE1702620-0102EA Washer #10 SAE1802620-4116EA Nut Hex Flange Lock 5/16-18 1822620-3201EA Nut Center Lock 1/2-131832620-4202EA Nut Hex 1/2-131842620-4091EA Nut Hex Flange Lock 1/4-20 2001804-03115EA Tie Wrap 4"2012600-6981EA Wire Set Model 6050,6100,6300 2057082-1371EA Wire 5" Green Stranded 14AWG 2092599-1002EA Sign Warning2116300-0651EA Manual Installation。
SITRANS FM TRANSMAG 2 电磁流量计传感器 SITRANS FM MAG 911

SITRANS FM (electromagnetic)OverviewAC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 withSITRANS FM MAG 911/E SITRANS FM (electromagnetic) AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/ESITRANS FM TRANSMAG 2 with the SITRANS FM MAG 911/E sensor is an AC pulsed alternating field magnetic flowmeter where the magnetic field strength is much higher than conventional DC pulsed magnetic flowmeters.•Wide range of sizes DN 15 to DN 1000 (½" to 40")•Broad range of liner and electrode materials for extreme process medias•Fully welded construction provides a ruggedness that suits the toughest applications and environments.•Automatic reading of SmartPLUG for easy commissioning •Simple menu operation with two-line display •Comprehensive self-diagnostic with self-monitoring and internal simulationThe main applications of the SITRANS FM transmitter TRANSMAG 2 can be found in the following sectors:•Pulp and Paper industry•Mining industryThe patented pulse alternating field technology is ideal for difficult applications like:•High concentrated paper stock > 3 %•Heavy mining slurries up to 70 % solid concentration •Mining slurries with magnetic particles•Low conductive medias ≥1 μS/cm•Available for remote mounting•PROFIBUS PA (profile 2.0) / HART communication•Analog output and digital outputs for pulses, device status, limits,flow direction, frequency outputThe flow measuring principle is based on Faraday’s law of electromagnetic induction according to which the sensor converts the flowinto an electrical voltage proportional to the velocity of the flow.The TRANSMAG 2 is a microprocessor-based transmitter with abuilt-in alphanumeric display in several languages. The transmittersevaluate the signals from the associated electromagnetic sensorsand also fulfill the task of a power supply unit which provides themagnet coils with a constant current.The magnetic flux density in the sensor is additionally monitored byreference coils.Further information on connection, mode of operation and installation can be found in the data sheets for the sensors.Displays and keypadsOperation of the transmitter can be carried out using:•Keypad and display unit•HART communicator•PC/laptop and SIMATIC PDM software via HART communication•PC/laptop and SIMATIC PDM software using PROFIBUS PA communicationHART communicationPROFIBUS PA communicationFlow Measurement© Siemens AG 2023Flow MeasurementSITRANS FM (electromagnetic)AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/EFlow MeasurementSITRANS FM (electromagnetic) AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/E1)20 °C (68 °F), max. 19.6 bar (285 psi) for steel flanges and max. 15.9 bar (231 psi) for stainless seel flanges2)20 °C (68 °F), max. 51.1 bar (741 psi) for steel flanges and max. 41.4 bar (600 psi) for stainless seel flangesFlow MeasurementSITRANS FM (electromagnetic)AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/EFlow MeasurementSITRANS FM (electromagnetic) AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/EAccessoriesSpare partsFlow MeasurementSITRANS FM (electromagnetic)AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/EFlow MeasurementSITRANS FM (electromagnetic) AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/EFlow MeasurementSITRANS FM (electromagnetic)AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/ESensor cables between sensor and transmitterSufficient shielding must be provided, as well as fixed routing of the signal cables (electrode and coil cable).Signal cables must be routed free of vibration, and protected against strong magnetic and stray fields. In case of doubt, the sensor cables must be routed in grounded steel conduit. The cable length between the sensor and transmitter must not exceed 100 m (328 ft).Flow MeasurementSITRANS FM (electromagnetic) AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/EProtection ringFlow MeasurementSITRANS FM (electromagnetic)AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/EGrounding ringImportant:The rings must be ordered together with the sensor. Gaskets are not included. In case of replacement please include the sensor MLFB code on the order.Classification according to pressure equipment directive (PED 2014/68/EU)SITRANS FM (electromagnetic)AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/E3/153Notes on pressure equipment directiveThe devices are designed for liquids of danger group "Gases of fluid group 1". The categories differ according to the version, and are listed in the table below.Siemens FI 01 · 2023Flow MeasurementSITRANS FM (electromagnetic)AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/E3/154SITRANS FM transmitter TRANSMAG 2 with wall-mounting bracket, dimensions in mm (inch)SITRANS FM transmitter TRANSMAG 2 with special wall-mounting bracket, dimensions in mm (inch)SITRANS FM flow sensor MAG 911/E, compact version, dimensions in mm (inches)Siemens FI 01 · 2023Flow MeasurementSITRANS FM (electromagnetic)AC powered alternating field flowmeters / SITRANS FM TRANSMAG 2 with SITRANS FM MAG 911/E3/155Built-in length MAG 911/E1)Tolerance for built-in lenght: L + 0.0 mm/-4.0 mm (-0.00/-0.157 inches). With protection rings for > DN 25 +6.0 mm, > DN 200 +10.0 mm (> 1" +0.236 inches,> 8" +0.394 inches)Siemens FI 01 · 2023Flow Measurement。
伊朗霍尔木兹海峡沿岸钾盐矿地质特征、成因分析及提取技术

伊朗霍尔木兹海峡沿岸钾盐矿地质特征、成因分析及提取技术胡刚;刘爽;周宾;王永生;缪向亮;钟豫
【期刊名称】《矿产综合利用》
【年(卷),期】2024(45)1
【摘要】这是一篇地球科学及矿物加工工程领域的论文。
伊朗霍尔木兹海峡沿岸
钾盐矿赋存于寒武系Hormuz组盐层内,矿体受褶皱构造控制,形态复杂,形成的“S”形、顶厚、平卧等褶皱形态,矿石类型为氯化物型钾石盐矿石,主要矿石矿物为钾石盐,KCl含量2.5%~35.20%。
研究区寒武系为泻湖相沉积,波斯湾含钾卤水持续蒸
发形成一套含钾石盐海相蒸发岩序列,受阿尔卑斯早期构造活动影响,含钾盐层受挤
压作用,形成盐底辟构造。
采用一次粗选一次扫选二次精选及浮选精矿加洗涤的实
验流程,可以获得了含KCl(湿基87.44%,干基91.14%)或KCl(湿基88.97%,干基93.69%)两种的氯化钾产品,KCl回收率分别为85.93%、81.70%,钾盐选矿指标良好。
【总页数】7页(P8-14)
【作者】胡刚;刘爽;周宾;王永生;缪向亮;钟豫
【作者单位】江西省地质局生态地质大队
【正文语种】中文
【中图分类】TD983;F409.1
【相关文献】
1.可溶性固体钾镁盐矿工程地质特征分析及钻探技术探索
2.可溶性固体钾镁盐矿工程地质特征分析及钻探技术
3.老挝甘蒙钾盐矿床钾镁盐矿层中裂隙水的地球化学特征及其成因探讨
4.他们的任务从缉毒到封锁霍尔木兹海峡——伊朗空中力量概览:1988-2004
因版权原因,仅展示原文概要,查看原文内容请购买。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Semestralklausur zur VorlesungWeb MiningProf.J.F¨u rnkranzTechnische Universit¨a t Darmstadt—Sommersemester2008Termin:4.7.2008Name:Vorname:Matrikelnummer: Fachrichtung:Punkte:(1)....(2)....(3)....(4)....(5)....Summe:Wichtig!•Aufgaben:Diese Klausur enth¨a lt auf den folgenden Seiten5Aufgaben zu insgesamt100Punkten.Jede Aufgabe steht auf einem eigenen Blatt.Kontrollieren Sie sofort,ob Sie alle sechs Bl¨a tter erhalten haben!•Zeiteinteilung:Die Zeit ist knapp bemessen.Wir empfehlen Ihnen,daßSie sich zuerst einen kurzen ¨Uberblick¨u ber die Aufgabenstellungen verschaffen,und dann mit den Aufgaben beginnen,die Ihnen am meisten liegen.•Papier:Verwenden Sie nur Papier,das Sie von uns ausgeteilt bekommen.Sie k¨o nnen Ihre L¨o sungen beliebig auf die sechs Bl¨a tter verteilen,solange klar ersichtlich ist,welche L¨o sung zu welcher Aufgabe geh¨o rt.Sollten sich allerdings mehrere L¨o sungen zu derselben Aufgabefinden,suchen wir uns eine aus.Insbesondere k¨o nnen Sie auch auf den R¨u ckseiten schreiben!Brauchen Sie zus¨a tzlich Papier(auch Schmierpaper),bitte melden.•Hilfsmittel:Als Hilfsmittel darf ein handbeschriebenes DIN-A4-Blatt benutzt werden.Ausl¨a ndische Stu-denten d¨u rfen dar¨u ber hinaus gedruckte W¨o rterb¨u cher verwenden.Elektronische W¨o rterb¨u cher sind nicht erlaubt.•Fragen:Sollten Sie Teile der Aufgabenstellung nicht verstehen,bitte fragen Sie!•Abschreiben:Sollte es sich(wie in den letzten Jahren leider immer wieder)herausstellen,daßIhre L¨o sung und die eines Kommilitonen¨u ber das zu erwartende Maßhinaus¨u bereinstimmen,werden beide Arbeiten negativ beurteilt(ganz egal wer von wem und egal in welchem Umfang abgeschrieben hat).•Ausweis:Legen Sie Ihren Studentenausweis sichtbar auf Ihren Platz.•Aufr¨a umen:Sonst darf außer Schreibger¨a t,Essbarem,von uns ausgeteiltem Papier und eventuell W¨o rter-b¨u chern nichts auf Ihrem Platz liegen.Taschen bitte unter den Tisch!Wer bei diesen Temperaturen einen Mantel mithat,wird gebeten,ihn anzubehalten.Gutes Gelingen!Aufgabe120Punkte(4/4/4/4/4)Sie wollen einen Comparison Shopping Site f¨u r Studenten der TU Darmstadt aufbauen,der automatisch von verschiedenen Anbietern im Web Angebote zu Lehrb¨u chern sammelt,diese vergleicht,und die jeweils g¨u nstigen Angebote zur Verf¨u gung stellt.Beantworten Sie die folgenden Fragen und begr¨u nden Sie mit mindestens einem Satz.1–a Jeder Anbieter hat f¨u r jedes Buch eine eigene Seite,auf der sich unter anderem der Titel des Lehr-buchs,eine vom Verlag zur Verf¨u gung gestellte kurze Inhaltsangabe,der Name des Autors und der Preis bei diesem Anbieterfinden.Sie m¨o chten diese Informationen in einer Datenbank-Relation angebot(Autor,Titel,Inhalt,Anbieter,Preis)sammeln.Wie w¨u rden Sie vorgehen?1–b Leider stellen Sie fest,daßdieser Automatisierungsschritt nicht100%verl¨aßliche Ergebnisse bietet.Sie m¨u ssen nun erkennen,welche Seiten verschiedener Anbieter sich auf die gleichen B¨u cher beziehen,um die Daten angleichen zu k¨o nnen.Wie w¨u rden Sie dieses Problem l¨o sen?1–c Sie wollen das Angebot an Lehrb¨u chern strukturieren und versuchen,automatisch Gruppen von Fach-b¨u chern zufinden,die¨a hnliche Themen behandeln.Welche Technik w¨u rden Sie hier einsetzen?1–d Viele Anbieter bieten den Benutzern die M¨o glichkeit,ihre Meinung zu den B¨u chern in Form eines kurzen Texts zu¨a ußern.Bei einigen dieser Anbieter hat der Benutzer zus¨a tzlich noch die M¨o glichkeit, diese Bewertung auf einer Skala von eins bis f¨u nf zusammenzufassen.Wie w¨u rden Sie vorgehen,wenn Sie so eine numerische Zusammenfassung der schriftlichen Bewertungen auch f¨u r die restlichen Sites nachtr¨a glich automatisch erg¨a nzen m¨o chten?1–e Sie wollen außerdem Ihren Kunden B¨u cher empfehlen,die sie vielleicht interessieren k¨o nnen.Sie haben aber¨u ber die Kunden keinerlei Informationen außer welche B¨u cher sie bisher bei Ihnen gekauft haben.Wie w¨u rden Sie vorgehen?Aufgabe224Punkte(8/6/6/4)Sie betreiben eine Web-Site,die Empfehlungen f¨u r bestimmte Produkte abgibt,basierend auf bisherigen Be-wertungen dieser Produkte.Im Moment gibt es5Benutzer,die8Artikel auf einer Skala von0bis3bewertet haben(0ist am schlechtesten,3ist am besten,bei leeren Eintr¨a gen liegt noch keine Bewertung vor).Benutzer P1P2P3P4P5P6P7P8Adalbert13132Berta02233C¨a sar0332Dorian2220?Emil313122–a Sch¨a tzen Sie mit Hilfe dem in der Vorlesung besprochenen Verfahren die Bewertung,die Benutzer Dorian f¨u r das Produkt P7abgeben w¨u rde.i.ohne Ber¨u cksichtigung der Durchschnittsbewertungen m(u)ii.mit Ber¨u cksichtigung der Durchschnittsbewertungen m(u).Berechnen Sie die¨Ahnlichkeit zwischen den Benutzern dabei nicht mit den in der Vorlesung ange-gebenen Korrelations bzw.Kosinus-Maßen,sondern ziehen Sie die durschnittliche Abweichungen aller gemeinsamen Empfehlungen von3ab,also(in der Terminologie der Vorlesungsfolien):w(u1,u2)=3−1|I u1∩I u2|i∈I u1∩I u2|v(u1,i)−v(u2,i)|2–b Nehmen Sie an,daßalle Benutzer Produkte,die sie mit einer Bewertung>0bewertet haben,auch gekauft haben(und daßsie keine anderen Produkte gekauft haben).Wenn ein neuer Benutzer nun P6 kauft,welches andere Produkt w¨u rden Sie ihm aufgrund von Item-to-Item Korrelationen empfehlen?Stellen Sie die entsprechende Item-to-Item Matrix wie in der Vorlesung auf.2–c Geben Sie an,welche Zerlegung in zwei Cluster die folgenden Methoden auf der oben angegebenen Matrix jeweilsfinden sollten(Sie brauchen sich dabei nicht auf einen konkreten Clustering-Algorithmus zu beziehen):er-Clusteringii.Item-Clusteringiii.Co-Clustering2–d Geben Sie ein Beispiel f¨u r eine gute Assoziations-Regel,die man aus den Kaufdaten aus Aufgabe b) lernen k¨o nnte,und begr¨u nden Sie,warum Sie die Regel f¨u r gut halten.Aufgabe318Punkte(6/4/5/3)Gegeben seien die Web-Dokumente d1,d2,d3,d4,d5,d6und folgende Hyperlinks zwischen diesen Dokumenten: d2→d1d2→d5d3→d5d4→d3d4→d2d5→d1d5→d4d6→d4Sie erhalten als Antwort auf eine Query Q die Dokumente d1und d2zur¨u ck.3–a Berechnen Sie die Hub und Authority Scores f¨u r die Query Q anhand des in der Vorlesung vorgestellten HITS-Algorithmus(F¨u hren Sie maximal drei Iterationen durch).3–b Berechnen Sie die erste Iteration des PageRank-Algorithmus auf allen Knoten.Verwenden Sie dabeiund initialisieren Sie die Werte gleichverteilt.einen Damping-Faktor von233–c Um eine endg¨u ltige Reihung der Suchresultate vorzunehmen,kombiniert Google den PageRank noch mit Merkmalen,die sich auf den Inhalt der Seiten beziehen.1.Nennen Sie drei verschiedene Arten von Informationen,die hier ber¨u cksichtigt werden.2.Was w¨u rde passieren,wenn man nur den PageRank einer Seite zur Reihung der Suchresultateheranziehen w¨u rde?3–d Nehmen Sie an,daßdie Dokumente d2,d4,d6f¨u r die Query Q relevant gewesen w¨a ren.Berechnen Sie den F1-Wert f¨u r das oben angegebene Query-Resultat.Aufgabe416Punkte(2/3/4/3/4)Textklassifikation4–a Der Term-Frequency-Vektor eines Dokumentes bezieht sich auf eine bestimmte Termmenge.In die Term-menge sollte man nur W¨o rter aufnehmen,die vorkommen inder Trainingsmengeder Testmengeder Trainingsmenge und in der Testmengekeine der beiden Mengen4–b Welche der folgenden Techniken werden eingesetzt,um die Grundmenge der Terme zu verkleinern?ShinglingStemmingSparse EncodingDelta EncodingCase Folding4–c Wir sagen,ein bin¨a rer Klassifierer C ist bilinear,wenn es einen Vektor v und eine Zahl b gibt,so dass die Vorhersage C(x)∈{−1,+1}sich f¨u r jeden Eingabvektor x schreiben l¨a sst als C(x)=sign( v,x +b).Welche der folgenden Lernverfahren erzeugen bilineare Klassifizierer,wenn sie auf ein bin¨a res Klassifi-kationsproblem angewandt werden?RocchioNaive-Bayesk-NNlineare SVM4–d Erkl¨a ren Sie die Grundidee der TF-IDF-Gewichtung.4–e Bestimmen Sie,wie viele bin¨a re arithmetische Rechenoperationen ein Naive-Bayes Klassifizierer ben¨o tigt, um die Klassenwahrscheinlichkeiten f¨u r ein Testdokument zu berechnen,das als TF-Vektor(nicht spar-se)gegeben ist,wenn die Termmenge die Gr¨oße m hat und K Klassen zu Auswahl stehen.Aufgabe522Punkte(5/6/5/6)Gegeben sei folgende(symmetrische)Matrix von paarweisen Distanzen zwischen Dokumenten.Die letzte Zeile gibt dabei die Klassenzugeh¨o rigkeit der Dokumente an.d1d2d3d4d5d6d7d8d9d1—2743412591887770d2—23684211811510496d3—8166133129119105d4—3154483934d5—71705864d6—121452d7—1341d8—42d9—Klasse A A A B B C C C CHinweis:Sie k¨o nnen sich vorstellen,daßes sich dabei um euklidische Abst¨a nde handelt.Ein kleiner Wert bedeutet demnach eine hohe¨Ahnlichkeit und ein großer Wert steht f¨u r un¨a hnliche Dokumente.5–a Klassifizieren Sie jedes Dokument anhand eines k-NN Klassifizierers,der jeweils auf den restlichen Do-kumenten trainiert wurde.Trainieren Sie z.B.um d5zu klassifizieren auf{d1,d2,d3,d4,d6,d7,d8,d9}.Geben Sie die Vorhersage f¨u r jedes Dokument an und die daf¨u r verantwortlichen Nachbarn.Verwenden Sie k=1.5–b Erstellen Sie f¨u r die Resultate aus a)die Multiclass-Konfusionsmatrix.Berechnen Sie anhand dieser die Gesamt-Accuracy der Vorhersagen und f¨u r jede Klasse getrennt jeweils Precision und Recall.5–c Berechnen Sie die durchschnittlichen Recall-und Precision-Werte der Vorhersagen unter Verwendung von Micro-Averaging und Macro-Averaging.5–d Beim Micro-Averaging von Mehr-Klassen-Konfusionsmatrizen sind Recall und Precision allgemein gleich.Wie l¨aßt sich das erkl¨a ren?。
