FortiGate-200D
Fortinet网络安全解决方案 PPT

FortiGate产品特点
深度整合的立体安全防御
• 单点安全部署,集成度低 • 多次处理,效率低 • 成本高 • 部署、管理、维护困难
• 有机结合的安全方案 • 一次处理,效率高 • 高性价比 • 易于部署、管理、维护
技术优势遥遥领先
安全功能全
FortiOS操作系统
FIREWALL
IPSபைடு நூலகம்
VPN
处理器 价格 功耗 防火墙吞吐量 延迟
包转发率(IPv4) 包转发率(IPv6)
Intel Xeon E6 – 2640V2
$$$$$ 95W 8 Gbps ~100 µs
FortiASIC NP 4 FortiASIC NP 6
$$ 10 W 20 Gbps 3 µs
$ 9W 40 Gbps 3 µs
Fortinet网络安全解决方案
Fortinet公司简介
Fortinet公司概况
公司成立:2000年10月 IPO:2009年11月 NASDAQ:FTNT 总部:Sunnyvale, California 2013财年销量:$615M
产品发布:2002年5月
已销售设备数量:130万
用户数量:17万
完善产品线覆盖每个细分市场
MSSP 运营商 数据中心 /云计算 大型企业
分支机构
中小企业
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
✔
(Branch) (Branch) (Branch) (Campus) (Campus)
✔
✔
✔
飞塔产品整体解决方案

18
FortiGate中型设备
适合中型企业和大型企业分支机构的安全设备
FGT-1240B
• 高性能多功能安全 • 更高性价比和同级别更高接口密度
FGT-1000C FGT-800C FGT-600C FGT-300C FGT-200B FGT-200B-POE
主要好处:
✓ 高速防火墙和 IPSec VPN 性能 ✓ 高速应用控制 ✓ 加速的 IPS/AV 性能 ✓ 板载存储器,用于 WAN 优化、本地报 告和归档*
数据库安全
FortiDB
数据库安全审计
安全云服务
FortiGuard 实时安全云 服务网络
终端访问安全
FortiClient
终端访问安全
统一安全管理
FortiAuthenticator
统一认证管理
FortiManager
集中安全管理
FortiAnalyzer
集中安全审计
7
7
Fortinet实现网络安全的全方位立体防御
FGT-240D
4 Gbps 6us 3.2M
FGT-280D (-POE)
4Gbps 2us 3.2M
每秒新建会话 IPSec VPN
IPS (HTTP) 防病毒 (代理/流 )
22k 450 Mbps
950 Mbps 300/700Mbps
22k 450 Mbps
950 Mbps 300/700Mb ps 40 x GE RJ45
300-600 Series Mid Range
800-1000 Series
3000 Series
5000 Series High End
PoE, High Density GE
派克液压密封件说明书

派克汉尼汾公司版权所有未经许可不能摘录,翻印。
保留修改权利2021年6月警告销售条件本样本中产品和/或系统或相关产品出现故障,选型不当或使用不当,均可能导致人身伤亡和财产损失。
本文档以及由派克·汉尼汾公司及其子公司和授权经销商提供的其他资料,为具有技术知识的用户提供进一步研究所需的产品和/或系统选项。
重要的是,用户必须对您的应用进行全面的分析,并对当前产品样本中与产品或系统相关的资料进行评估。
由于工作条件以及产品或系统的多样性,用户必须自行分析和测试,并独自承担一切后果,包括:产品和系统的最终选型以及确保满足应用的所有性能、安全和警告等方面的要求。
派克·汉尼汾及其子公司可能会随时对本样本中的产品,包括但不限于:产品的特性、产品的规格、产品的结构、产品的有效性以及产品的价格作出变更而不另行通知.本样本中的所有产品均由派克·汉尼汾公司及其子公司和援权经销商销售。
与派克签订的任何销售合同均按照派克标准条件和销售条件中规定的条款执行(提供复印件备索)。
本公司的密封件,只能在本公司的文件资料述及的应用参数范围与接触介质、压力、温度和存放时间相一致的情况下才能使用。
在规定的应用参数范围外使用以及错误选用不同的材料都可能导致密封件寿命的缩短以及设备的损坏,甚至更严重的后果(如生命安全,环境污染等)。
样本中所列出的工作压力、温度范围、运动速度是极限值,它们之间相互关联、相互影响;在极端的工况下,建议不要同时把各个参数都同时用到极限值。
对于特殊的要求(压力、温度、速度、介质等),请联系派克汉尼汾公司以咨询合适的密封结构、材料、配置、安装建议等。
由于诸多工作参数会影响到流体传动系统及密封元件,这些设备的制造商必须在实际工作条件下测试、验证并批准密封系统的功能与可靠性。
此外,对于不断出现的新的介质(液压油、润滑脂、清洗剂等),用户特别注意它们与目前所用的密封件弹性体材料的兼容性。
我们建议用户在大批量应用之前,在厂内或现场先做密封材料的兼容性能测试,作为密封产品与系统供应商,我们建议用户遵循我们的这些建议。
Fortinet无线与有线产品速递

FortiWLC-200D
适用于中型企业 4 个千兆电口,1 个 console 口 120GB SSD 支持 200 颗 AP 和 2500 个终端 AP 自动发现 AC 并下载配置 不按 AP 数量授权
FortiWLC-500D
ห้องสมุดไป่ตู้适用于大型企业 4 个千兆电口,4 个千兆光口,2 个万兆光口, 1 个 console 口 480GB SSD 支持 500 颗 AP 和 6250 个终端 不按 AP 数量授权
室内型 802.11ac AP 4 根天线(内置/外置) 双频 2.4GHz 和 5GHz 2X2 MIMO 双网口 POE 供电
室内型 802.11ac AP 6 根天线(内置/外置) 双频 2.4GHz 和 5GHz 3X3 MIMO 双网口 POE 供电
AP1020 i/e
室内型 802.11n AP 2 根天线(内置/外置) 双频 2.4GHz 和 5GHz 2X2 MIMO 单网口 POE 供电
FortiAP S311C/313C
FortiAP S321C/323C
OAP832 e
室外型 802.11ac AP 户外防水等级 IP67 6 根天线(外置) 双频 2.4GHz 和 5GHz 3X3 MIMO 双网口 POE 供电
FortiAP222C 室外型 802.11ac AP 户外防水等级 IP55 4 根天线(外置) 双频 2.4GHz 和 5GHz 2x2 MIMO 单网口 PoE 供电
整合型 WiFi 产品 (由 FortiGate 管理,更安全的无线接入)
FortiAP24D
FortiAP221/223C
室内型 802.11n AP 2 根天线(内置) 双频 2.4GHz 或 5GHz 1x 1 MIMO 5 个千兆网口 PoE 供电
FortiGate+FortiWifi-2014

$20,000,000 $0 2009 2010 2011 2012 2013 2014 2015 FortiAP revenue (annual) FortiWiFi revenue (annual) Controller revenue associated with AP revenue FortiSwitch revenue
512 512 1,024
FG-3040B
FG-3140B FG-3240C FG-3810A FG-3950/51B – FG – VM08 FG-5001A-SW/DW
1,024
1,024 1,024 1,024 1,024 1,024 1,024 1,024
1,024
1,024 1,024 1,024 1,024 1,024 1,024 1,024
全向天线覆盖
21
定向天线覆盖
网络安全基础架构 - FortiGate UTM安全网关
22
引领革命性的安全变化• • Nhomakorabea• •23
单点安全部署,集成度低 多次处理,效率低 成本高 部署、管理、维护困难
• • • •
有机结合的安全方案 一次处理,效率高 高性价比 易于部署、管理、维护
技术优势遥遥领先
供电方式:优选POE供电方式
天线选则:信号穿透损耗较小(如木质门、窗户等),可采用全向天线; 信号穿透损耗较大(如铁质门、实心水泥墙体等),可 采用定向天线
19
无线场景-室内-学校宿舍
某高校宿舍楼: 考虑事项: 1.楼层数量 2.每层宿舍数量 3.上网人数 4.并发用户 5.障碍区分:房间隔断材质(钢筋混凝土结构); 走廊(双边/单边宿舍?) 门窗:(木门?有窗户?) 覆盖设计:平层有2个支路,每支路合路1台500mW 的11n AP,共 采用6个全向吸顶天线,每个天线覆盖4个房间。 信道规划:本层信道1,6,11交错设置 安装方式:安装在走廊的顶部 供电方式:整栋楼由POE交换机集中供电
禧玛诺公路车变速手柄说明书

Manual del distribuidorDM-ST0001-05(Spanish)CARRETERATiagraSORASHIMANO ClarisSHIMANO 2300TourneySin serieMTBRAPIDFIRE PlusEZ-FIRE PlusST-M4000ST-M4050ST-T4000ST-T3000ST-M370ST-EF65ST-EF51ST-EF51-A ST-TX800ST-EF41ST-EF40ST-4600ST-4603ST-3500ST-3503ST-2400ST-2403ST-2300ST-2303ST-A070ST-A073ST-R460ST-R350ST-R353ST-R240ST-R243•Este manual del distribuidor está dirigido principalmente a mecánicos de bicicletas profesionales.Los usuarios que no hayan recibido formación profesional en el montaje de bicicletas no deberán intentar la instalación de componentes usando los manuales del distribuidor.Si tiene dudas en relación con cualquier información de este manual, no proceda con la instalación. Por el contrario, póngase en contacto con el comercio donde hizo la compra o un distribuidor local de bicicletas para solicitar asistencia.•Lea todos los manuales de instrucciones incluidos con el producto.•No desmonte o modifique el producto más allá de lo permitido en la información de este manual del distribuidor.•Puede consultar online todos los manuales del distribuidor y manuales de instrucciones en nuestro sitio web().•Cumpla con la normativa y las reglamentaciones del país o región donde ejerce su trabajo de distribuidor.•D urante la instalación de componentes, asegúrese de seguir las indicaciones de los manuales de instrucciones.S e recomienda utilizar exclusivamente piezas originales de Shimano. Si piezas como tornillos y tuercas se aflojan o se deterioran, la bicicleta puede desmontarse repentinamente, provocando lesiones corporales graves.A demás, si los ajustes no se realizan correctamente, podrían producirse algunos problemas y la bicicleta podría desmontarse repentinamente, provocando lesiones corporales graves.•U tilice gafas de seguridad para proteger los ojos mientras realiza tareas de mantenimiento, como la sustitución de piezas. •D espués de leer detenidamente el manual del distribuidor, guárdelo en un lugar seguro para consultas futuras.A simismo, asegúrese de informar de lo siguiente a los usuarios:•L as palancas de freno ST-EF65/ST-EF51/ST-EF51-A (palancas de freno para 4 dedos) están equipadas con un mecanismo para hacerlas compatibles con los FRENOS V con modulador de potencia o frenos cantilever y de rodillo.S i se selecciona un modo incorrecto puede producirse que la fuerza de frenado sea excesiva o insuficiente, lo que podría causar accidentes peligrosos.A segúrese de seleccionar el modo de acuerdo con las instrucciones que se dan en la tabla de la derecha.P osición C/RVVRCC Rosición de modo para compatibilidad con frenososición de modo para compatibilidad con frenosP osición-VVVRCC Rosición de modo para compatibilidad con FRENOS Vcon modulador de potenciatilice las palancas de freno con el mecanismo de cambio de modo en las combinaciones especificadas anteriormente.•Cada bicicleta puede funcionar de forma diferente dependiendo del producto. Por lo tanto, es importante entender y acostumbrarse al funcionamiento del sistema de frenado de la bicicleta (incluyendo la presión de la maneta del freno y las características de control de la bicicleta). Un uso inadecuado del sistema de frenos podría hacerle perder el control o caer, con la posibilidad de sufrir lesiones de gravedad. Para conseguir un funcionamiento óptimo consulte a su distribuidor de bicicletas o el manual del propietario. Es importante probar la bicicleta y el funcionamiento de los frenos, así como otras funciones básicas, etc.•Si el freno delantero se aplica demasiado fuerte, la rueda puede bloquearse y la bicicleta puede caer hacia delante y causarle lesiones graves.•Asegúrese siempre de que los frenos delanteros y traseros funcionan correctamente antes de montar en la bicicleta.•La distancia de frenado necesaria aumenta con el suelo mojado. Reduzca su velocidad y aplique los frenos de manera suave y anticipada.•Si la superficie de la carretera está mojada, las cubiertas patinarán con mayor facilidad. Si las cubiertas patinan, puede producirse una caída. Para evitarlo, reduzca su velocidad y aplique los frenos de manera suave y anticipada.NOTAAsimismo, asegúrese de informar de lo siguiente a los usuarios:•Asegúrese de mantener la biela girando durante el funcionamiento del cambio. •Lea los manuales del distribuidor del desviador, el cambio y el freno.•Los productos no están garantizados contra el desgaste natural y el deterioro resultante del uso normal y el envejecimiento.Para la instalación en la bicicleta y el mantenimiento:•Cuando monte el tipo de recorrido superior, seleccione un cuadro que disponga de tres soportes de funda exterior como se indica en la ilustración de la derecha.•Utilice una funda exterior que tenga la suficiente longitud para permitir girar el manillar completamente a ambos lados. Además, verifique que la maneta de cambio no toca el cuadro de la bicicleta cuando se gira el manillar completamente. •Utilice el cable especificado y una guía de cable para lograr un funcionamiento suave.•Engrase el cable interior y el interior de la funda exterior antes de utilizarlos, para garantizar que deslizan correctamente. •Se desaconseja el uso de un cuadro con tendido de cable interno, ya que tiende a impedir el funcionamiento del cambio SIS debido a la alta resistencia del cable.•Para el cable del cambio se utiliza una grasa especial. No utilice grasa de alta calidad o de otros tipos, porque podría deteriorar el funcionamiento del cambio.•Si no se pueden realizar ajustes en el cambio, compruebe que los extremos de la horquilla trasera están alineados. Compruebe también si el cable está lubricado y si la funda exterior es demasiado larga o demasiado corta.El producto real puede diferir de la ilustración, ya que este manual está concebido básicamente para explicar los procedimientos de uso del producto.Soporte de la funda exteriorMTBInstalación en el manillarLas herramientas y los pares de apriete varían dependiendo del producto. Realice el apriete a un par adecuado para el tamaño de la herramienta.* Utilice un puño de manillar con un diámetro exterior no mayor de 32 mm.Llave Allen de 5 mm Llave Allen de 3 mm< ST-TX800, ST-EF41 >Llave Allen de 3 mmInstalación del cable de freno* Móntelo tal como se muestra en la figura.123CARRETERAInstalación en el manillarSujete el conjunto con el tornillo de sujeción sobre la parte externa del soporte.Tire hacia atrás de la tapa del soporte y utilice una llave Allen de 5 mm para apretar el tornillo.Utilice un puño de manillar con un diámetro exterior no mayor de 32 mm.Instalación del cable de frenoCARRETERACable usado* Utilice un cable que tenga la suficiente longitud para poder girar el manillar completamente a ambos lados.* Para obtener información sobre cómo instalar el cable del freno, consulte el manual del distribuidor del freno.1. Incline la palanca hacia dentro (como cuando se acciona el cambio) para facilitar el paso del cable a través del gancho del cable.2. Pase el cable interior a través.Nota:No limpie la grasa del cable interior.No permita que se adhiera polvo al cable interior.3. Finalmente, envuelva el manillar con la cinta para manillar.MTB(1)Corte de la funda exteriorAl cortar la funda exterior, corte el extremo opuesto al extremo marcado.Después de cortarla, redondee el extremo para que el interior del orificio tenga un diámetro uniforme.Coloque el mismo terminal exterior para cortar el extremo de la funda exterior.< Palanca trasera >1. Coloque la palanca (B) en la posición superior.2. Compruebe la posición superior en el indicador y monte el cable.3.4. Pase el cable interior a través de la funda exterior.Si el gancho del cable no se alinea con el orificio del cable del cambio, presione la palanca (B) de nuevo hasta que lo haga y, a continuación, instale el cable.Confirmar: Asegúrese de que el extremo interior está firmemente asentado en el gancho del cable.< Palanca delantera >Accione la palanca (B) 2 veces o más, compruebe en el indicador que la posición baja es correcta y, a continuación, sujete el cable interior.1.2. Si el gancho del cable no se alinea con el orificio del cable del cambio, presione la palanca (B) de nuevo hasta que lo haga y, aManeta (B)2< Ajustador de cable >* C 1. * Introduzca un objeto delgado en forma de barra para extraer el separador del soporte exterior.2.Monte el terminal del soporte de la funda exterior (de venta por separado).El margen de ajuste para el ajustador de cable es de cinco vueltas desde su posición de apriete completo.El ajustador se aprieta hasta que falta 1 vuelta para llegar a su posición de apriete completo.exterior (de venta por separado)Nota:Instale después de apretar el tornillo de ajuste.El rango de ajuste para el tornillo de ajuste es de seis vueltas completas.2. Pase el cable interior a través y coloque la funda exterior.* Utilice una funda exterior que tenga la suficiente longitud para permitir girar el manillar completamente a ambos lados.Confirmar : Asegúrese de que la funda exterior está firmementeasentada en el tope exterior.Ajuste del recorrido de la manetaEl ajuste del recorrido de la maneta puede realizarse de las siguientes maneras.Para conocer qué herramientas deben utilizarse y los puntos de ajuste consulte la tabla que encontrará a continuación.(A) Hacia la derecha: El recorrido de la maneta sehace más pequeño.(B) Hacia la izquierda: El recorrido de la maneta sehace más grande.Al utilizar el bloque de ajuste de alcance (separador de zapata)Nota:Al montar el bloque de ajuste de alcance de 8 grados, utilice un manillar de tipo anatómico. Si se utiliza un manillar de tiporedondo, el recorrido del cable puede ser demasiado corto y esto puede producir una fuerza de frenado insuficiente.< ST-4600 / ST-4603 / ST-3500 / ST-3503 / ST-2400 / ST-2403 / ST-R460 / ST-R350 / ST-R353 >separadores de zapata (A)separadores de zapata (A) + (B)Para aumentar el recorrido de la palancaExtraiga el separador de zapata (A) y monte la goma amortiguadora.Para reducir el recorrido de la palancaInserte el separador de zapata (B) todo lo que pueda para que los salientes encajen en los orificios del separador de zapata (A).* Aplique una pequeña cantidad de grasa a los salientes cuando monte el separador de zapata y la goma amortiguadora.Tipo anatómicoTipo redondo4°8°< ST-2300 / ST-2303 >Para reducir el alcance, desmonte la goma amortiguadora y sustitúyalacon el separador de zapata accesorio (dos tipos disponibles: 4° y 8°).Método de sustitución1. Extraiga la goma amortiguadora.2. Aplique una capa fina de grasa a los dos salientes del separador dezapata.3. Presione el separador de zapata para que los salientes entren todo loposible.Ajuste del cable interiorCuando se suministra ajustador de cableEl margen de ajuste para el ajustador de cable es de cinco vueltas desde su posición de apriete completo.El ajustador se aprieta hasta que falta 1 vuelta para llegar a su posición de aprietecompleto.8°Goma amortiguadoraC ómo sustituir el cable interior< En el caso de los tipos con tornillo en la tapa >1. P onga la palanca (B) en el piñón más pequeño.2. D esenrosque los tornillos para retirar la tapa.3. T ire hacia fuera del cable interior y monte un cableinterior nuevo.< En el caso de los tipos con tornillo en la tapa del extremo del cable >1. P onga la palanca (B) en el piñón más pequeño.2. E xtraiga la tapa de enganche del extremo del cable einstale el cable interior nuevo.• P ara obtener información sobre cómo sustituir el cable del cambio, consulte el apartado "Instalación del cable del cambio". • P ara obtener información sobre cómo sustituir el cable del cambio con o sin ajustador de cable, consulte el apartado"Instalación del cable del cambio/ajustador de cable".T apa de enganche del extremo del cable e enganche del o del cableD estornillador n.º 2D esmontaje del soporte y la maneta* L a ilustración muestra la palanca derecha.< ST-4600 / ST-4603 / ST-3500 / ST-3503 / ST-2400 / ST-2403 / ST-R460 / ST-R350 / ST-R353 >1. P rimero utilice la herramienta original Shimano (de venta por separado) para retirar el anillo elástico. Utilice la pieza (B) de laherramienta original Shimano (2) para alinear el anillo elástico con la dirección de desmontaje. A continuación, coloque la pieza(A) contra el anillo elástico y extraiga el anillo elástico.*T ourney no va provisto de un anillo elástico.2. I ntroduzca una llave Allen o una herramienta similar en el orificio del eje de la palanca y, a continuación, golpéelo suavementecon un martillo de plástico para empujar el eje de la palanca hacia fuera, lo que lo desmontará en el cuerpo del soporte y el N ota: A segúrese siempre de extraer el eje de la palanca en esta dirección. Si se extrae en la dirección contraria, el cuerpo del soportepuede sufrir daños.Y6RT66000Y6RT68000(1)H erramienta original Shimano parala extracción de anillos elásticosC uerpo del soporteE je de la palanca< ST-2300 / ST-2303 / ST-A070 / ST-A073 >1. Primero utilice una llave Allen de 2 mm para extraer el tornillo.2. Introduzca una llave Allen o una herramienta similar en el orificio del eje de la palanca y, a continuación, golpéelo suavementecon un martillo de plástico para empujar el eje de la palanca hacia fuera, lo que lo desmontará en el cuerpo del soporte y el cuerpo de la palanca.Nota:Asegúrese siempre de extraer el eje de la palanca en esta dirección. Si se extrae en la dirección contraria, el cuerpo del soporte puede sufrir daños.Cuerpo de la palancaS ustitución del muelle de retorno< ST-3500 / ST-3503 / ST-2400 / ST-2403 / ST-R350 / ST-R353 >1. C on el separador montado en el muelle de retorno,presione la punta del muelle de retorno en el orificio delmiembro del rodamiento y presione para encajar el casquillo del eje.*T enga en cuenta que los muelles de retorno izquierdo y derecho son diferentes.< ST-2300 / ST-2303 >1. C oloque el muelle de retorno en el orificio del miembro delrodamiento del cuerpo de la palanca.*T enga en cuenta que los muelles de retorno izquierdo y derecho son diferentes.MC Coloque el extremo del muelle en el orificio del miembro del rodamiento.O rificio S eparador M Coloque el extremo del muelle en el orificio del miembro del rodamiento.O rificioM ontaje del cuerpo del soporte y del cuerpo de la maneta< ST-4600 / ST-4603 / ST-R460 >1. 1.2. A linee los orificios del espárrago y, a continuación, coloquela herramienta original Shimano (1) en la posición indicada en la ilustración para montar mediante presión el eje de la palanca.• L a dirección correcta del eje de la maneta es con la ranura del anillo elástico orientada hacia arriba.• C ompruebe que la superficie del cuerpo del soporte esplana para que el anillo elástico del eje de la manetapueda encajar correctamente en la ranura.3. E xtraiga la herramienta original Shimano (1) y, acontinuación, utilice la herramienta (2) para montar el anillo elástico.M uelle de retornoM uescaR anura del anillo elástico H erramienta original Shimano para la extracción de anillos elásticos (1):Y 6RT66000 Herramienta original Shimano para la extracción de anillos elásticos (2):Y 6RT68000< ST-3500 / ST-3503 / ST-2400 / ST-2403 / ST-R350 / ST-R353 > 1. C oloque la herramienta original Shimano para el muelle deretorno.2. A linee los orificios del espárrago y, a continuación, coloquela herramienta original Shimano (1) en la posición indicada en la ilustración para montar mediante presión el eje de la palanca.•L a dirección correcta del eje de la maneta es con la ranura del anillo elástico orientada hacia arriba.•C ompruebe que la superficie del cuerpo del soporte esplana para que el anillo elástico del eje de la manetapueda encajar correctamente en la ranura.3. E xtraiga la herramienta original Shimano (1) y, aanillo elástico.4. Econ unos alicates.5. Fmuelle de retorno es correcto.H erramienta original Shimanopara la instalación de muellesde retorno (TL-ST03)anura del anillo elásticoH erramienta original Shimano para la extracción de anillos elásticos (1):Y6RT66000H erramienta original Shimano para la extracción de anillos elásticos (2):Y6RT68000originalShimano para la instalaciónde muelles de retorno< ST-2300 / ST-2303 / ST-A070 / ST-A073 >1. C oloque la herramienta original Shimano para el muelle deretorno.2. A linee los orificios del espárrago y, a continuación, monte el eje de la palanca en la posición indicada en la ilustración.3. E xtraiga la herramienta original Shimano para el muelle deretorno con unos alicates.4. F inalmente, compruebe que el funcionamiento del freno ydel muelle de retorno es correcto.H erramienta original Shimanopara la instalación de muelles de retorno (TL-ST03)je de la palanca a posición correcta es para que el hueco redondo del eje de la palanca se alinee con el tornillo de fijación de la palanca.Fijado mediante un tornillo de fijación de la palanca ar de apriete: 1 - 2 N•m H erramienta original Shimano para lainstalación de muelles deretornoSustitución de la tapa del soporteLas pestañas de la tapa del soporte encajan cada una en una ranura delsoporte.•Introduzca una pequeña goma impregnada en alcohol dentro de la tapa del soporte para efectuar la instalación con más facilidad.Tenga en cuenta que las especificaciones están sujetas a cambios por mejoras sin previo aviso. (Spanish)。
FortiADC-Datasheet-CN-201310

到 100 倍的数据响应加速 L7 内容交换
支持连接池维护及连接复用技术 -HTTP Host,HTTP Request URL,Referrer
TCP 缓存 -Source IP Address
客户端连接保持 URL redirect,HTTP request/response
FAD-VM0 4 FAD-VM0 8
硬件指标
FORTIADC-VM01
FORTIADC-VM02
FORTIADC-VM04
Hypervisor 支持版本 vCPU 支持(最小/最大) 内存支持(最小/最大) 网络接口支持(最小/最大) 存储支持(最小/最大) 处理能力* 最大连接数* L7 RPS* 管理
管理
集群部署,单点管理 CLI 管理接口用于配置及监控 SSH 远程网络安全管理 安全 Web UI 访问管理 SNMP 管理,提供 private MIBs
支持 SNMP traps 阀值设置 支持 Syslog 管理员权限设置管理 内建实用诊断工具 实时数据监控图表
FortiADC-200D
FortiADC-300E
指标
硬件指标
处理能力 最大连接数 7 层 RPS SSL TPS SSL 处理能力 内存 网络接口 存储空间 管理方式 电源
环境
尺寸 输入电压 功耗 最大电流 散热 操作温度 存储温度 湿度
认证
管理标准 安全认证
Dimensions
尺寸(英寸) 尺寸(毫米) 重量
1 512 MB / 2 GB 10 50 MB / 1 TB 基于硬件 基于硬件 基于硬件
* 测试环境:基于 Intel Core i7-2600K CPU ,启用各个平台 License 所支持的最大虚拟 CPU 核数和最大内存
Fortinet安接入解决方案介绍-产品版

2
1
275 Mbps
IPS吞吐量
35 Mbps
SSL 检测(IPS)吞吐量
22.5 Mbps
NGFW吞吐量
① 2x GE RJ45 WAN接口 ② 10x GE RJ45交换接口 ③ 4x GE RJ45 PoE 接口
2 Mil 4,000 1 Gbps 275 Mbps 16 x GE RJ45 32GB
FG-92D UTM
2 Gbps
1.5 Mil 22,000 130 Mbps 950 Mbps 16 x GE RJ45 16 GB
22 Fortinet Internal & Partner Confidential
$5.00 $-
Fortinet
▪ 全球UTM市场占有率第一位 ▪ 增长率超过整个UTM 市场 ▪ 每季度发货量超过10万台 ▪ 连续7年Gartner UTM魔力象限“领导者”
Check Point
Cisco
Dell
Fortinet
Sophos
WatchGuard
Fortinet Internal & Partner Confidential
FortiGate入门级防火墙
高性能防火墙和VPN型号,适用于不开启较多安全功能的 独立中小型企业及总分型企业的总部与远程分支互联
23 Fortinet Internal & Partner Confidential
FortiGate/FortiWiFi 60D
12
1.5 Gbps
防火墙吞吐量
50万
Source : IDC Worldwide Security Appliances Tracker, September 2015 (Based on quarterly revenue)
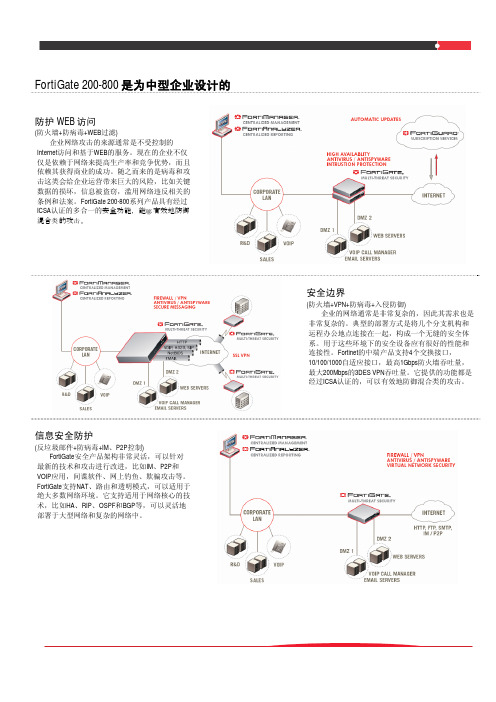
FortiGate 200-800 系列
500Mbps 100Mbps 140Mbps 300Mbps 2,000
600Mbps 120Mbps 150Mbps 400Mbps 3,000
是
是
是
400,000
400,000
400,000
10K
10K
10K
5000Biblioteka 500080001.75inch
1.75inch
1.75inch
16.8inch
Fortinet在ASIC芯片上有强大的优势:
FortiASIC 系列包括内容层处理芯片(CP)和网络层处理器(NP)两种 ASIC 芯片技术。 FortiASIC-CP 系列是专门用来处理内容层数据,与传统的单纯采用 CPU 来处理数据相比性能更为优越。该芯片是 Fortinet 的专利技 术。它的独特的算法可以实现在 VPN 通道上高速扫描病毒,以保 障正常的通讯。 FortiASIC-NP 系列是用来加速网络层的数据处理的。它能够达到极 高的处理性能和安全性,性价比有很强的优势。
FortiOS:专用的安全操作系统
FortiOS 是 FortiGate 多功能安全平台的操作系统。开发该系统时充 分地考虑了安全、性能和可靠性。它充分地发挥了应用层加速和 网络层加速的 ASIC 芯片的性能。FortiOS 集成了状态监测防火墙、 IPS、防病毒、Web 过滤、反垃圾邮件、IM/P2P、虚拟系统和带宽 管理等网络安全功能。FortiOS 提供了全面的 UTM 安全服务、获得 了 EAL4+认证
网络安全平台 FortiGate™安全平台是基于Fortinet公司的FortiASIC™ 内容处理器技术提供的一整套综合性实时安全解决方案。FortiGate™ 200-800系列包
Fortinet Fortigate 200D用户手册说明书

Fortinet fortigate 06, 201201-430-175181-20120706Copyright© 2012 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, and FortiGuard®, are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance metrics contained herein were attained in internal lab tests under ideal conditions, and performance may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Forti
Case Study - 同程旅游网

总部、数据中心和门店的全网状VPN互联
区域中心 区域中心
苏州中心
苏州同城 灾备中心
full mesh
门店
门店
区域中心 区域中心
全网状VPN有利于充分 利用各地的带宽,分支 站点之间的访问不需要 通过中心节点,有效的 降低站点之间访问的时 延。
FortiGate丰富的产品线 让同城网根据不同的网 络规模和互联要求,选 择最合适的型号。
4
Fortinet全网状VPN互联
为满足客户需求,Fortinet公司选用FortiGate-1000C作为总部的网关,在 中心端的FortiGate设备上使用多条ISP的线路进行连接,每个门店放置一 台小型的FortiWIFI-30D的设备。
可以进行VPN的汇结的中心节点,同时支持内网安全管理。采用FortiGate UTM产品作为分公司的安全网关,可以实现对总部的VPN的加密功能,并 可以控制内网用户的使用和保障安全。在门店使用拨号模式的VPN来与总 部的设备建立VPN连接。
12
Fortinet解决方案产品配置列表
部署位置 数据中心出口 支付系统外联区域 小于20人门店 小于30人门店 小于50人门店 小于50人门店 小于50人门店 同程会销场地 同程新收购分公司 门店无线接入 门店有线交换机接入
产品型号 FortiGate-1500D FortiGate-200D FortiWiFi-30E FortiWiFi-50E FortiWiFi-90D-POE FortiGate-90D-POE FortiGate-60D FortiGate-94D-POE FortiGate-140D FortiAP-221C FortiSwitch-124D
SSL VPN的性能卓越, 可以同时支持数千客户 端连入。同城网利用 SSL VPN功能大大提高 了工作效率。
一次语音流量穿越飞塔Gate不通问题的解决过程

一次语音流量穿越飞塔Gate不通的解决过程V 1.0北京超圣信华科技有限公司2016年4月11日问题:一次语音穿越Gate不通的解决过程版本:V1.0日期:2016年4月11日作者:宋泽春摘要:一次语音穿越Gate不通的解决过程关键字:SIP、SDP、SDF、RTP文档记录文档说明本文档描述了一次语音流量穿越飞塔Gate不通的解决过程的说明。
目录文档记录 (33)文档说明 (33)第1章需求 (55)第2章SIP浅析 (55)第3章拓扑结构 (55)第4章配置部分 (66)4.1配置火墙地址 (66)4.2开启负载均衡功能及VOIP高级特性 (66)4.3配置虚拟服务器 (77)4.4配置真实服务器 (77)4.5监控检查 (88)4.6配置虚拟IP (99)4.7策略配置 (1010)第5章分割点 (1212)第6章遇到的问题 (1212)6.1负载均衡回切慢问题 (1212)6.2语音无法建立问题 (1414)6.3语音IPPBX无法回切问题 (1717)第1章需求内部安装两台IPPBX,外部IP分机呼入,通过Fortiner 200D可实现负载均衡功能。
当主设备故障后,呼叫会切换到备用设备。
需求:默认语音网关访问飞塔VIP流量分发到IPPBX A上当IPPBX A异常,语音网关访问飞塔的VIP的流量分发到IPPBX B上当IPPBX A恢复后,语音网关访问飞塔VIP的流量继续分发到IPPBX A上第2章 SIP浅析简单的说SIP有信令流(5060)和媒体流(两个人的通话)两部分组成,信令流主要用作从语音网关到IPPBX管理系统的注册,媒体流用来传输建立好通道的语音流量。
第3章拓扑结构拓扑结构如下:第4章配置部分欲完成上述需求,飞塔防火墙需要启用负载均衡功能。
即,两个IPPBX管理系统作为两台服务器看待,语音网关作为访问者看待,飞塔防火墙通过其负载均衡模块将两台IPPBX管理系统向语音网关发布。
UTM网关综合竞争分析ppt课件

H3C
F100-S,A,E
中端产品
高端产品
Rugged-100C,FG110C,FG-100D(新) ,FG-140D(新),FG200B/POE,FG200D(新),FG-240D(新),FG300C,FG-600C,FG-800C,FG-1000C,FG1240B
FG3016B,FG3040B,FG3140B,FG 3240C(新),FG3600C(新) ,FG3950B,FG5000系列
Rugged-100C,FG110C,FG-100D(新),FG140D(新),FG200B/POE,FG-200D(新) ,FG-240D(新),FG-300C,FG-600C,FG800C,FG-1000C,FG-1240B
高端产品
FG3016B,FG3040B,FG31 40B,FG3240C(新) ,FG3600C(新) ,FG3950B,FG5000系列
Check Point
移动数据保护(MDP)和企业防火墙和UTM等魔术象限报告中均处于领导者地位。今年不论是市场行为还是产品 更迭均未有亮眼的表现。今年Check Point 产品没有大版本更新,产品版本延续使用2012,只是在性能有默默 的升级。新推出了一款R77软刀片,集成了加速、合规检查和其Threat Cloud防0day攻击的功能。
TZ系列,
SonicWALL NSA220,NSA250M,NSA2400
NSA3500,NSA4500,NSA3600,NSA4600,NS SuperMassive E10000系
A5600,NSA6600,E5500,E6500,E7500,E850 列,SuperMassive E9000
0,E8510
品牌 Fortinet
FORTINET FortiGate NIDS 说明书

FortiGate NIDS GuideFortiGate NIDS指南FortiGate 用户手册第四卷版本2.50 MR22003年8月6日© Copyright 2003 美国飞塔有限公司版权所有。
本手册中所包含的任何文字、例子、图表和插图,未经美国飞塔有限公司的许可,不得因任何用途以电子、机械、人工、光学或其它任何手段翻印、传播或发布。
FortiGate NIDS 指南版本2.50 MR22003年8月8日注册商标本手册中提及的产品由他们各自的所有者拥有其商标或注册商标。
服从规范FCC Class A Part 15 CSA/CUS请访问以获取技术支持。
请将在本文档或任何Fortinet技术文档中发现的错误信息或疏漏之处发送到techdoc@。
目录概述 (1)NIDS 模块 (1)使用NIDS检测模块检测入侵企图 (1)使用NIDS预防模块预防入侵 (1)使用NIDS响应模块管理消息 (2)NIDS检测和预防特性 (2)拒绝服务(DoS)攻击 (2)嗅探 (2)权利提升 (3)NIDS躲避 (3)关于本文档 (3)2.50版中的新增内容 (3)文档约定 (4)Fortinet的文档 (5)Fortinet技术文档的注释 (5)客户服务和技术支持 (6)检测攻击 (7)特征组 (7)特征举例 (9)一般配置步骤 (11)NIDS常规配置 (11)选择要监视的网络接口 (11)禁用NIDS (11)配置校验和检验 (12)选择一个特征组 (12)查看特征列表 (12)启用和禁用NIDS攻击特征 (13)更新攻击定义 (14)创建用户定义的特征 (15)创建用户自定义的特征 (15)用户定义特征提示 (17)常规配置步骤 (17)用户定义特征的语法 (17)语法约定 (17)完整的特征语法 (17)特征语法的细节 (19)管理用户定义的特征 (24)上载用户定义特征列表 (24)下载用户定义特征列表 (24)FortiGate NIDS 指南iii预防攻击 (25)一般配置步骤 (26)启用NIDS攻击预防 (26)启用NIDS预防特征 (27)配置特征临界值 (31)配置syn淹没特征值 (32)举例:NIDS配置 (33)预防TCP和UDP攻击 (33)管理NIDS消息 (37)记录攻击消息日志 (37)配置FortiGate设备发送报警邮件 (38)启用FortiGate设备发送入侵报警邮件功能 (38)定制报警邮件消息 (39)减少NIDS攻击日志和邮件消息的数量 (39)自动减少消息 (39)术语表 (41)索引 (43)iv美国飞塔有限公司FortiGate NIDS 指南版本2.50 MR2概述FortiGate NIDS是一个实时的网络入侵探测器,它使用攻击定义库库检测和预防各种各样的可疑的网络数据流和基于网络的直接攻击。
FortiGate 300C 高性能网络安全设备说明书

capabilities for deeper inspection. Rich console views and reports together with a flexible policy engine provide the visibility and control to empower employees yet secure your enterprise.Finally, these features of the FortiGate FortiOS Network Security Platform are routinely validated by independent real-world tests and consistently getting superior ratings in security effectiveness.Features & Benefits§ 5 times faster hardware accelerated next generation firewall offers best-in-class price/performance ratio §Integrated high port density delivers maximum flexibility and scalability§NSS Labs Recommended NGFW and NGIPS with consolidated security delivers top-rated protection§Application control plus identity and device-based policy enforcement provides more granular protection§Intuitive management interface enables broad and deep visibility that scales from a single FortiGate to thousandsHighlightsFirewall Performance IPS Performance Interfaces8 Gbps1.4 GbpsMultiple GE RJ45 and GE RJ45 ManagementDATA SHEETFortiGate ® 300CHigh Performance, Top-rated Network Security for Mid-sized EnterprisesDATA SHEET:HARDWAREInterfaces1. 8x GE RJ45 NP2 Accelerated Ports2. 2x GE RJ45 Ports3. Console Port4. 2x USB Ports5. USB Management Port6. Redundant DC Power ConnectorFortiGate 300CContent ProcessorThe FortiASIC CP6 content processor works outside of the directflow of traffic, providing high-speed cryptography and contentinspection services including:§Signature-based content inspection acceleration§Encryption and decryption offloadingNetwork ProcessorFortiASIC NP2 network processor works inline with FortiOSfunctions delivering:§Superior firewall performance for IPv4 traffic with ultra-lowlatency down to 3 microseconds§VPN accelerationDATA SHEET: FortiGate ® 300CSOFTWAREFortiOS Managment UI — FortiView and Application Control PanelSERVICESFortiGuard ™ Security ServicesFortiGuard Labs offers real-time intelligence on the threat landscape, delivering comprehensive security updates across the full range of Fortinet’s solutions. Comprised of security threat researchers, engineers, and forensic specialists, the team collaborates with the world’s leading threat monitoring organizations, other network and security vendors, as well as law enforcement agencies:§Real-time Updates — 24x7x365 Global Operations research security intelligence, distributed via Fortinet Distributed Network to all Fortinet platforms.§Security Research — FortiGuard Labs have discovered over 170 unique zero-day vulnerabilities to date, totaling millions of automated signature updates monthly.§Validated Security Intelligence — Based on FortiGuard intelligence, Fortinet’s network security platform is tested and validated by the world’s leading third-party testing labs and customers globally.FortiCare ™ Support ServicesOur FortiCare customer support team provides global technical support for all Fortinet products. With support staff in the Americas, Europe, Middle East and Asia, FortiCare offers services to meet the needs of enterprises of all sizes:§Enhanced Support — For customers who need support during local business hours only.§Comprehensive Support — For customers who need around-the-clock mission critical support, including advanced exchange hardware replacement.§Premium Services — For global or regional customers who need an assigned Technical Account Manager, enhancedservice level agreements, extended software support, priority escalation, on-site visits and more.§Professional Services — For customers with more complex security implementations that require architecture and design services, implementation and deployment services, operational services and more.For more information, please refer to the FortiOS data sheet available at For more information, please refer to /careFor more information, please refer to /guardFortiOSFortiOS helps you protect your organization against advanced threats, configure and deploy your network security faster and see deep into what’s happening inside your network. It enables organization to set up policies specific to types of devices, users and applications with industry-leading security capabilities. FortiOS leverages custom FortiASICs and the Optimum Path Processing architecture of FortiGate to deliver 5 times faster throughput performance. In essence, FortiOS delivers:§Comprehensive Security — Control thousands of applications and stop more threats with NSS Labs Recommended IPS, sandboxing, VB100 certified antimalware and more. §Superior Control and Visibility — Stay in control with rich visibility over network traffic, granular policy control, and intuitive, scalable security and network management.§Robust Networking Capabilities — Optimize your network with extensive switching and routing, high availability, WAN optimization, embedded WiFi controller, and a range of virtual options.GLOBAL HEADQUARTERS Fortinet Inc.899 Kifer RoadSunnyvale, CA 94086United StatesTel: +/salesEMEA SALES OFFICE 120 rue Albert Caquot 06560, Sophia Antipolis, FranceTel: +33.4.8987.0510APAC SALES OFFICE 300 Beach Road 20-01The Concourse Singapore 199555Tel: +65.6513.3730LATIN AMERICA SALES OFFICEProl. Paseo de la Reforma 115 Int. 702Col. Lomas de Santa Fe,C.P . 01219Del. Alvaro Obregón México D.F .Tel: 011-52-(55) 5524-8480Copyright© 2015 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, FortiCare® and FortiGuard®, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary and may be significantly less effective than the metrics stated herein. Network variables, different network environments and other conditions may negatively affect performance results and other metrics stated herein. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet and any such commitment shall be limited by the disclaimers in this paragraph and other limitations in the written contract. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests, and in no event will Fortinet be responsible for events or issues that are outside of its reasonable control. Notwithstanding anything to the contrary, Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.DATA SHEET: FortiGate ®300CUp to 2 units: FG-200B, FG-200D, FG-240D and FG-300D, FG-400D, FG-500D, FDD-200B, FDD-400B and FDD-800B. Not supported for: FG-200D-POE/240D-POE.1 GE SFP LX Transceiver Module FG-TRAN-LX 1 GE SFP LX transceiver module for all systems with SFP and SFP/SFP+ slots.1 GE SFP RJ45 Transceiver Module FG-TRAN-GC 1 GE SFP RJ45 transceiver module for all systems with SFP and SFP/SFP+slots..1 GE SFP SX Transceiver ModuleFG-TRAN-SX1 GE SFP SX transceiver module for all systems with SFP and SFP/SFP+ slots.ORDER INFORMATIONFirewall Latency (64 byte, UDP) 2 μs Firewall Throughput (Packet per Second)12 Mpps Concurrent Sessions (TCP) 2 Million New Sessions/Second (TCP)50,000Firewall Policies10,000IPsec VPN Throughput (512 byte) 4.5 Gbps Gateway-to-Gateway IPsec VPN Tunnels 2,000Client-to-Gateway IPsec VPN Tunnels 10,000SSL-VPN Throughput200 Mbps Concurrent SSL-VPN Users (Recommended Maximum)500IPS Throughput 2.8 Gbps Antivirus Throughput200 Mbps Virtual Domains (Default / Maximum)10 / 10Maximum Number of FortiAPs (Total / Tunnel)512 / 256Maximum Number of FortiTokens1,000Maximum Number of Registered FortiClients 2,000High Availability ConfigurationsActive-Active, Active-Passive, ClusteringSPECIFICATIONSStorage Temperature -31–158°F (-35–70°C)Humidity 20–90% non-condensing Operating Altitude Up to 7,400 ft (2,250 m)Compliance FCC Part 15 Class A, C-Tick, VCCI, CE, UL/cUL, CB CertificationsICSA Labs: Firewall, IPsec, IPS, Antivirus, SSL-VPN Note: A ll performance values are “up to” and vary depending on system configuration. Antivirus performance is measuredusing 44 Kbyte HTTP files. IPS performance is measured using 1 Mbyte HTTP files. IPsec VPN performance is based on 512 byte UDP packets using AES-256+SHA. Antivirus Throughput is measured in proxy mode.For complete, up-to-date and detailed feature set, please refer to the Administration Handbook and FortiOS Datasheet.。
fortigate-200b-poe - 快速入门指南说明书

© Copyright 2010 Fortinet Incorporated. All rights reserved.Products mentioned in this document are trademarks or registered trademarks of their respective holders.Regulatory ComplianceFCC Class A Part 15, / CE Mark 07 September 2017Bureau of Standards Metrology and Inspection (BSMI) – TaiwanThe presence conditions of the restricted substance (BMSI RoHS table) are available at the link below:https:///bsmiFortiGate-200B-POE01-420-117374-20170907Visit these links for more information and documentation for your Fortinet product:Technical Documentation - Fortinet Knowledge Center - Technical Support - Training Services - NAT/Route modeYou would typically use NAT/Route mode when the FortiGate unit is deployed as agateway between private and public networks. In its default NAT/Route mode configura-tion, the unit functions as a firewall. Firewall policies control communications through the FortiGate unit.Transparent modeYou would typically use the FortiGate unit in Transparent mode on a private network be-hind an existing firewall or behind a router. In its default Transparent mode configuration, the unit functions as a firewall.Web-based Manager1.Connect the FortiGate MGMT1 interface to a management computer Ethernet inter-face. Use a cross-over Ethernet cable to connect the devices directly. Use straight-through Ethernet cables to connect the devices through a hub or switch.2.Configure the management computer to be on the same subnet as the MGMT1interface of the FortiGate unit. To do this, change the IP address of the management computer to 192.168.1.2 and the netmask to 255.255.255.0.3.To access the FortiGate web-based manager, start a web browser and type the ad-dress http://192.168.1.994.Type admin in the Name field and click Login.NAT/Route modeTo change the administrator password1.Go to System > Admin > Administrators .2.Select Change Password for the admin administrator and enter a new password.To configure interfaces1.Go to System > Network > Interface.2.Select the edit icon for each interface to configure.3.Set the addressing mode for the interface. (See the online help for information.)•For manual addressing, enter the IP address and netmask for the interface.•For DHCP addressing, select DHCP and any required settings.•For PPPoE addressing, select PPPoE, and enter the username and password and any other required settings.To configure the Primary and Secondary DNS server IP addresses1.Go to System > Network > Options, enter the Primary and Secondary DNS IP ad-dresses that you recorded above and select Apply.To configure a Default Gateway1.Go to Router > Static and select Edit icon for the static route.2.Set Gateway to the Default Gateway IP address you recorded above and select OK.Transparent modeTo switch from NAT/route mode to transparent mode1.Go to System > Config > Operation Mode and select Transparent.2.Set the Management IP/Netmask to 192.168.1.99/24.3.Set a default Gateway and select Apply.To change the administrator password1.Go to System > Admin > Administrators.2.Select Change Password for the admin administrator and enter a new password.To change the management interface1.Go to System > Config > Operation Mode.2.Enter the Management IP address and netmask that you recorded above and selectApply.To configure the Primary and Secondary DNS server IP addresses1.Go to System > Network > Options, enter the Primary and Secondary DNS IP address-es that you recorded above and select Apply.Command Line Interfacee the RJ-45 to DB9 serial cable to connect the FortiGate Console port to the man-agement computer serial port.2.Start a terminal emulation program (HyperTerminal) on the management computer.Use these settings: Baud Rate (bps) 9600, Data bits 8, Parity None, Stop bits 1, and Flow Control None.3.At the Login: prompt, type admin and press Enter twice (no password required).NAT/Route mode1.Configure the FortiGate MGMT1 interface.config system interface edit MGMT1set ip <intf_ip>/<netmask_ip>end2.Repeat to configure each interface, for example, to configure the Port 1 interface.config system interface edit port1...3.Configure the primary and secondary DNS server IP addresses.config system dnsset primary <dns-server_ip>set secondary <dns-server_ip>end4.Configure the default gateway.config router static edit 1set gateway <gateway_ip>endTransparent Mode1.Change from NAT/Route mode to Transparent mode and configure the ManagementIP address.config system settingsset opmode transparentset manageip <mng_ip>/<netmask> set gateway <gateway_ip>end 2.Configure the DNS server IP address.config system dnsset primary <dns-server_ip> set secondary <dns-server_ip>endConfiguringAC Power Required 100-240VAC, 60-50 Hz, 5-4 Amp Chassis1UNetwork Interfaces8 10/100 POE ports4 10/100/1000 non-accelerated ports 4 10/100/1000 accelerated ports 1 Console port 2 USB A 1 USB BFSM slots 1 64GB SSD (not included)LED DescriptionPackage ContentsconnectionInterface DescriptionConnectingAdministrator user name adminAdministrator password(none)NAT/Route modePort 1192.168.1.99Port 9192.168.100.99To reset the FortiGate unit to the factory defaults, in the CLI type the command:execute factoryresetStraight-throughEthernet cableAC Power CableRJ-45 toDB-9 Serial CableRack-MountBrackets4 Rubber feetHDD Dummy CardFactory DefaultsEnsure the FortiGate unit is placed on a stable surface. Connect the following tothe FortiGate unit:•Connect the RJ-45 to DB-9 serial cable into the Console port on the unit.Insert the other end into the management computer.•Insert an ethernet cable into Port 1-8. Insert the other end into the POE cli-ent device.•Insert the ethernet cable into Port 9 to 16. Insert the other end to the routerconnected to the Internet, or to the modem.•Connect the AC power cable to the power supply on the back of the unit.•Connect the power cord to a surge protected power bar or power supply.FSM ModulesCaution: When installing the FSM module, ensure that the FORTINET and/or“THIS SIDE UP” labels are orientated upwards when inserting the module intothe unit.To insert the FSM module1.Insert the module into the FSM slot on the unit with the Fortinet and/or “ThisSide Up” labels facing upwards.2.Close the latch.Interface Type Speed Protocol DescriptionConsole RJ-45Ethernet Connection to the man-agement computer.Provides access to thecommand line interface(CLI).Ports 1 to 8RJ-4510/100 Base-TEthernet POE source capableports. Supports up to 15WPOE devices.Ports 9 to12RJ-4510/100/1000Base-TEthernet Non-accelerated ports.Ports 13to 16RJ-4510/100/1000Base-TEthernet ASIC accelerated ports.USB USB A USB Optional connections forthe USB key, modem, orbackup operation.USB Man-agementUSB B For future use.FSM FSM Fortinet Storage Module.One SATA hard disk driveslot supports 64GB 2.5inch solid state drives.Configuration ToolsWeb ConfigWeb Config is an easy to use management tool. Use it to configure the admin-istrator password, the interface and default gateway addresses, and the DNSserver addresses, add devices for log collection and configure reports.Requirements:•An Ethernet connection between the Fortinet unit and management com-puter.• A web browser on the management computer.Command Line Interface (CLI)The CLI is a full-featured management tool. Use it to configure the administratorpassword, the interface addresses, the default gateway address, and the DNSserver addresses. To configure advanced settings, see the Tools and Documen-tation CD-ROM.Requirements:•The RJ-45 to DB-9 serial connection between the Fortinet unit and themanagement computer.• A terminal emulation application (HyperTerminal for Windows) on the man-agement computer.LED State DescriptionPowerGreen The unit is on.Off The unit is off.StatusGreen flashing The unit is starting up.Green The unit is running normally.HAGreen The unit is being used in an HAcluster.AlarmRed A critical error has occurred.Amber A minor error has occurred.Off No errors detected.POEGreen POE is in use at that port.Off POE is not in use at that port.Ready Green Indicates that POE is available.Ports1 to 8Link/Activity Green Port is online.Flashing Port is sending or receiving data.Speed Off Connected at 10 Mbps.Amber Connected at 100 Mbps.Ports9 to16Link/Activity Green Port is online.Flashing Port is sending or receiving data.Speed Green Connected at 1000Mbps.Amber Connected at 100 Mbps.Off Connected at 10 Mbps.。
Fortigate防火墙抓包命令

Fortigate防火墙抓包命令在Fortigate防火墙上Troubleshooting,绝大多数情况下,用好Diagnose Sniffer 和Diagnose debug这两个命令就能解决很多问题。
一般来说,Troubleshooting时,先用Sniffer命令查看数据包到底有没有到达防火墙,然后用Debug命令来查看数据包达到防火墙后是怎样的处理流程。
Sniffer命令格式:Fortigate# diagnose sniffer packet <interface-name> '<filter>'举例:抓包IP地址10.2.22.21与202.103.24.68之间所有的DNS通信FG200D3915807028 # diagnose sniffer packet any 'port 53 and host 10.2.22.21 and 202.103.24.68'输出结果示例:interfaces=[any]filters=[port 53 and host 10.2.22.21 and 202.103.24.68]23.015563 10.2.22.21.53751 -> 202.103.24.68.53: udp 4823.043507 202.103.24.68.53 -> 10.2.22.21.53751: udp 6423.044743 10.2.22.21.53752 -> 202.103.24.68.53: udp 48Sniffer命令支持几种不同详尽程度的输出方式,在输入完抓包命令之后打个问号可以显示输出详尽程度的选项FG200D3915807028 # diagnose sniffer packet any 'port 53 and host 10.2.22.21 and 202.103.24.68' ?<verbose>1: print header of packets2: print header and data from ip of packets3: print header and data from ethernet of packets (if available)4: print header of packets with interface name5: print header and data from ip of packets with interface name6: print header and data from ethernet of packets (if available) with intf name或者直接在抓包命令后加个“空格+数字1-6",例如FG200D3915807028 # diagnose sniffer packet any 'port 53 and host 10.2.22.21 and 202.103.24.68' 6输出的结果示例如下:interfaces=[any]filters=[port 53 and host 10.2.22.21 and 202.103.24.68]21.327456 OA-Zone in 10.2.22.21.61158 -> 202.103.24.68.53: udp 470x0000 0000 0000 0001 18c5 8a1b 3cdc 0800 4500 ..........<...E.0x0010 004b 05d0 0000 7f11 3310 0a02 1615 ca67 .K......3......g0x0020 1844 eee6 0035 0037 daef 0003 0100 0001 .D...5.7........0x0030 0000 0000 0000 0377 7777 0473 6f68 7503 .......www.sohu.0x0040 636f 6d0c 6d69 6372 6f70 6174 7465 726e com.0x0050 0363 6f6d 0000 0100 01 .....21.349692 OA-Zone out 202.103.24.68.53 -> 10.2.22.21.61158: udp 630x0000 0000 0000 0000 906c ac02 5579 0800 4500 .......l..Uy..E.0x0010 005b 0000 4000 3b11 3cd0 ca67 1844 0a02 .[..@.;.<..g.D..0x0020 1615 0035 eee6 0047 82d7 0003 8180 0001 ...5...G........0x0030 0001 0000 0000 0377 7777 0473 6f68 7503 .......www.sohu.0x0040 636f 6d0c 6d69 6372 6f70 6174 7465 726e com0x0050 0363 6f6d 0000 0100 01c0 0c00 0100 0100 ............0x0060 0002 5800 0471 5043 1c ..X..qPC.21.350943 OA-Zone in 10.2.22.21.61159 -> 202.103.24.68.53: udp 470x0000 0000 0000 0001 18c5 8a1b 3cdc 0800 4500 ..........<...E.0x0010 004b 05d3 0000 7f11 330d 0a02 1615 ca67 .K......3......g0x0020 1844 eee7 0035 0037 bfed 0004 0100 0001 .D...5.7........0x0030 0000 0000 0000 0377 7777 0473 6f68 7503 .......www.sohu.0x0040 636f 6d0c 6d69 6372 6f70 6174 7465 726e com0x0050 0363 6f6d 0000 1c00 01 .....21.371071 OA-Zone out 202.103.24.68.53 -> 10.2.22.21.61159: udp 900x0000 0000 0000 0000 906c ac02 5579 0800 4500 .......l..Uy..E.0x0010 0076 0000 4000 3b11 3cb5 ca67 1844 0a02 .v..@.;.<..g.D..0x0020 1615 0035 eee7 0062 f73e 0004 8180 0001 ...5...b.>......0x0030 0000 0001 0000 0377 7777 0473 6f68 7503 .......www.sohu.0x0040 636f 6d0c 6d69 6372 6f70 6174 7465 726e com0x0050 0363 6f6d 0000 1c00 01c0 1900 0600 0100 ............0x0060 0000 3c00 1f07 6465 6661 756c 7400 c03b ..<...default..;0x0070 0000 0007 0000 0384 0000 0258 0001 5180 ...........X..Q.0x0080 0000 003c ...<4 packets received by filterDebug命令用于观察防火墙对数据流的处理,可以得知该数据流被处理后的结果,在命令行下输入一下命令,开启对数据流的监控,然后在客户端上模拟产生触发条件的流量,再返回FortiGate终端查看输出结果。
FortiGate 1500D产品介绍与解决方案指南说明书

Securing Big DataBig Data Security impact, challenges and solutionsSOLUTION GUIDE: SECURING BIG DATAIn the digital age, information is the new currency. And in order to get information, enterprises are mining data – lots of it – for the knowledge that it can yield. Big Data is a broad term for a quantity of raw data (data sets) so large or complex that traditional data processing applications are inadequate.Data sets grow in size in part because they are increasingly being gath devices, such as mobile and wireless devices, software logs, street cameras, microphones, radio-frequency identification (RFID) readers, the Internet of Things (IoT) and many more sources. The world’s technological per-capita capacity to store information has grown significantly with the advance in technology.On the scale of Internet commerce or social networks, the amount of data can be pretty large - think of the hundreds of millions of smartphones and end-user devices. On the scale of consumer, medical, scientific, or research data, it can be even larger, as sensors and instruments can collect vast amounts of raw data, whether from a single source (such as instrumentation of a GE aircraft engine during a flight) or from the projected 26 billion devices that will make up the Internet of Things.The Gold Rush that we currently see for collecting and analyzing Big Data, which in turn is increasingly being fed by the Internet of Things, is creating significant challenges for data center networks and their security in four key areas:Big Data AggregationFact: Increasingly, rather than processing and reducing the raw data at the data source to a more manageable volume, raw datais being transferred and stored centrally – because it now can be – so that it can be analyzed in different ways over time. Today, enterprises are transferring terabytes of data over long distances every day. The sheer quantity of data is forcing core network and data center upgrades, such as 100GbE switching fabric, to deal with individual data transfers at 10Gbps or even higher. Ranked by NSS Labs as having the lowest total cost of ownership per protected-Mbps, the FortiGate 1500D not only gives you the high bandwidth and security your institution needs, it also makes your IT budget go further.The Challenge: This creates challenges for traditional perimeter security products, such as firewalls, since many vendor solutionsare not designed to handle such large inflows and sessions. For example, a firewall that boasts 10 GbE ports or 40 Gbps aggregate throughput may not actually have the internal processing paths to handle an individual 10Gbps flow. LAN congestion from normal enterprise campus traffic may further saturate the CPU or memory resources, causing large flows to stall or even drop.Fortinet’s Solution: FortiGate high performance data center firewalls are based on purpose-built FortiASIC technology that meets the most demanding Big Data performance environments in several aspects:1. Throughput / latency - ranging from 80 Gbps to over 1T bps / smaller than 7 μs2. Port density – from six to hundreds of ports per appliance3. High speed interfaces – support for 10/40/100 GbpsThe FortiGate family of Data Center firewalls provides the range and flexibility to adapt to different sizes and requirements of Big Data and Data Center environments, as outlines in the following table:SOLUTION GUIDE: SECURING BIG DATABig Data ProcessingFact: Big data flows are not symmetrical – the raw data that goes in does not necessarily go out in the same form and volume. Instead, the data kept in storage arrays is typically analyzed by an intermediary set of servers and further reduced and delivered as a reduced set of insights before exiting the data center.The Challenge: What all of this means is that there is a rapidly growing volume of lateral, intra-server traffic , or east-west traffic, which never leaves the data center. Many studies show that east-west traffic now accounts for up more than 70% of data center traffic and is expected to increase even further as the amount of big data analytics continues to increases.East-west traffic needs to be segmented and inspected, not just for blocking lateral movement of advanced persistent threats and insider attacks, but to secure the data itself, some of which can be sensitive if disclosed or leaked. Network security architectures need to evolve from perimeter or security gateway oriented, to a multi-tiered, hybrid architecture that supports an increasingly virtualized and abstracted environment through the adoption of server and network virtualization and cloud computing.Fortinet’s Solution: In order to provide visibility for east-west traffic and the enforcement of security and segmentation between virtual machines (VMs), Fortinet provides a wide range of virtual appliances, from virtual firewalls, through virtual Web Application Firewall (WAF) to Application Delivery Controller (ADC), that integrate into all major virtualized environments as outlines in the below table:Fact: A growing number of companies are using Big Data technology to store and analyze petabytes of data to gain better insights about their customers and their business. As a result, information classification becomes critical and information ownership must be addressed to facilitate any reasonable classification. Enterprises need to identify owners for the outputs of Big Data processes, as well as the raw data. Thus data ownership will be distinct from information ownership – perhaps with IT owning the raw data and business units taking responsibility for the outputs.The Challenge: With data is being archived for long periods the question must be asked, who is authorized to access which data, and for what purposes? Often there is not just a single data set, but rather multiple repositories of data that may be combined and analyzed together. Each set of data may contain sensitive or confidential information and may be subjected to specific regulations or internal controls. Further, there is often not just one group of analysts or researchers but many different constituents seeking to gain different insights over a long period of time. A large pharmaceutical company provided a good example where their Big Data research efforts were open to not just internal employees, but also to contractors, interns, and visiting scholars. However, a separate analytics sandbox needed to be created for each of them with individual access and auditing rights.3 SOLUTION GUIDE: SECURING BIG DATAGLOBAL HEADQUARTERS Fortinet Inc.899 Kifer RoadSunnyvale, CA 94086United StatesTel: +/salesEMEA SALES OFFICE 120 rue Albert Caquot 06560, Sophia Antipolis, FranceTel: +33.4.8987.0510APAC SALES OFFICE 300 Beach Road 20-01The Concourse Singapore 199555Tel: +65.6513.3730LATIN AMERICA SALES OFFICEProl. Paseo de la Reforma 115 Int. 702Col. Lomas de Santa Fe,C.P . 01219Del. Alvaro Obregón México D.F.Tel: 011-52-(55) 5524-8480Copyright © 2015 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, FortiCare® and FortiGuard®, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other resultsmay vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations,and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable. 25 Aug 2015 – 10:37 AM MKT-STORAGE:01_BROCHURES:05_SOLUTION_GUIDES:SG-Securing-Big-data:SG-Securing-Big-Data-CFortinet’s Solution: Fortinet’s physical and virtual firewall appliances provides the ability to enforce segmentation to create trustzones and zero trust zones with related security policies so that access and utilization of applications, data sets and analytic data are restricted based on the organization’s policies and appropriate national and vertical regulations. Granular identification and permissions can be implemented, managed and enforced with FortiAuthenticator or via the integration of FortiGate with 3rd party identity management solutions.FortiGate and FortiMail - Fortinet’s secure mail gateway appliance - also provide for Data Loss Protection (DLP) so that Big Data information will not be sent out to unauthorized sources.Big Data and the CloudFact: Only a limited number of organizations are likely to build a Big Data environment entirely in-house, so the Cloud and Big Data will be inextricably linked. However, storing data in the cloud does not alleviate the enterprise’s responsibility for protecting it - from both a regulatory and a commercial perspective.The Challenge: Storing data in the public cloud, which is outside of the organization’s security infrastructure, still requires the same type of security mechanisms and policies found in the enterprise network. As cloud providers differ in the scope of the security appliances they allow enterprises to deploy within their network, it is of crucial importance that the cloud provider’s security offering meets the enterprise’s requirements and provide full protection and segmentation of the stored data.Fortinet’s Solution: Fortinet’s wide range of physical appliances, and the industry leading performance they provide, is used by cloud providers to secure their cloud environment. The availability of FortiGate and FortiWeb as virtual appliances available on major cloud providers, such as Amazon Web Services (AWS) and Microsoft Azure, allows enterprises to implement a robust and full security implementation to protect their data stored in the cloud.ConclusionIT organizations may need to fundamentally re-think network security instead of taking incremental steps to meet evolving data center security needs. In many cases, data center transformation is happening not just because of Big Data but by cloud computing and SaaS initiatives as well. As part of this transformation, IT should consider an architecture that is:• High performance – able to support the larger volumes of data with higher network throughput and high-speed ports (e.g. 40G/100G fabric) with high port density, but also be scalable and elastic to accommodate ever-growing data sets.• Secure – augment perimeter security with increased internal segmentation to secure east-west movement of data and monitor for advanced and insider threats.• Consolidated – integrate multiple security functions from core security functions like firewalling/VPN, anti-malware and intrusion prevention to advanced threat protection, strong authentication and access control.• Hybrid – deploy security for data stored in the cloud to enforce an enterprise wide security posture.Finally, customers may consider Big Data as an opportunity to improve their security posture. With more control and monitoring points being deployed throughout the network and with SIEM (security information and event management) and log management tools to aggregate security logs and event data, more security analytics and insight are possible using big data techniques and tools to better protect both big data and the data center as a whole.。
FortiSIEM 6.7.2 迪奥电子收集器安装指南说明书

Diode Collector Installation Guide FortiSIEM6.7.2FORTINET DOCUMENT LIBRARYhttps://FORTINET VIDEO GUIDEhttps://FORTINET BLOGhttps://CUSTOMER SERVICE&SUPPORThttps://FORTINET TRAINING&CERTIFICATION PROGRAM https:///training-certificationNSE INSTITUTEhttps://FORTIGUARD CENTERhttps://END USER LICENSE AGREEMENThttps:///doc/legal/EULA.pdfFEEDBACKEmail:********************03/07/2023FortiSIEM6.7.2Diode Collector Installation GuideTABLE OF CONTENTSChange Log4 Diode Collector5 Feature5 Standard Configuration5 Additional Configurations7 Example diode_collector.json File7Change Log02/13/2023Initial version of Diode Collector Installation GuideDiode Collectorl Featurel Standard Configurationl Additional Configurationsl Example diode_collector.json FileFeatureThe diode collector has the following functionalities:1.Ability to install without Internet connectivity2.Ability to work without registering with Supervisor node3.Ability to collect syslog,SNMP trap and Windows log via WMI/OMI protocol using local configuration4.Ability to send events to another Collector or Worker via UDP/514using syslog protocolA diode collector only requires a strictly one-way communication from itself to another Collector or Worker.There are twodeployment modes:1.Diode Collector->Worker2.Diode Collector->Regular Collector->WorkerThe regular Collector can send events to Worker via HTTPS.Standard ConfigurationTo configure a diode collector,there are two general steps.Note that there is a Service Provide case(1),and anEnterprise case(2),in Step1.Step1:Collect Collector Information from Supervisor Node1.For Service Provider case,a Collector is associated with a customer.a.Navigate to Admin>Setup>Organizations.b.Click New,and create an Organization with the Collector.c.Get the Customer Id,which appears in the ID column.This should appear after the Organization is created.d.Navigate to ADMIN >Health>Collector Health.e.From the Collector Health page,get the following information:l Customer Name(From the Organization column)l Collector Name(From the Name column)l Collector Id(From the Collector ID column)2.For Enterprise case(1Organization)a.Navigate to ADMIN > Setup> Collector.b.Click New,and create a Collector.c.Navigate to ADMIN > Health> Collector Health.d.From the Collector Health page,get the following information:l Collector Idl Collector NameStep2:Configure Collector Using the Information in Step11.Download the collector binary from the Fortinet Support Site.2.Run configFSM.sh on the VM(Internet connectivity not needed).Installation steps are provided here.3.Modify the file/opt/phoenix/config/diode_collector.json.See Example diode_collector.json File for anexample file.a.Set custId to Customer Id from Step1(for Enterprise case,set to1).b.Set collectorId to Collector Id from Step1.c.Set orgName to Customer Name from Step1(for Enterprise case,set to super).d.Set collectorName to Collector Name from Step1.e.Set eventUploadServers to the Worker in UDP:<IP1>:514,UDP<IP2:514>format where IP1and IP2areWorker IP addresses.f.Set Windows Server credentials in the Credentials section.4.Run the following command.phProvisionDiodeCollectorSetup is now complete,and events should appear in the FortiSIEM GUI.There are no differences between events from a diode collector and a regular collector.Additional ConfigurationsThe following additional configurations are available.l Adding Windows Servers or Changing WMI/OMI Credentialsl Change ParsersAdding Windows Servers or Changing WMI/OMI CredentialsTo add more Windows servers or change WMI/OMI credentials,take the following step.1.Modify/opt/phoenix/config/diode_collector.jsonThere is no need to restart any process.Change ParsersTo Change Parsers,take the following steps.1.Modify or create parser files under/opt/phoenix/config/xml/2.Edit/opt/phoenix/config/xml/parserOrder.csv3.Restart phParser by running the following command.killall-9phParserExample diode_collector.json FileThis JSON has1WMI example and1OMI example.{"custId":2000,"orgName":"org1","collectorId":10000,"collectorName":"CO1","eventUploadServers":"UDP:192.168.1.100:514,UDP:192.168.1.101:514","eventUploadEpsLimit":1000,"creds":[{"custId":"2000","accessIp":"1.2.3.4","deviceType":{"vendor":"Microsoft","model":"Windows","version":"ANY"},"accessMethod":{"accessProtocol":"MS_WMI","pullInterval":1,"credential":{"username":"Administrator","password":"12345678"},"template":{"name":"Get All Logs","logTypes":[{"type":"SECURITY","include":"",//blank means ALL"exclude":""//blank means ALL },{"type":"APPLICATION","include":"",//blank means ALL"exclude":""//blank means ALL },{"type":"SYSTEM","include":"",//blank means ALL"exclude":""//blank means ALL }]}}},{"custId":"2000","accessIp":"1.2.3.4","deviceType":{"vendor":"Microsoft","model":"Windows","version":"ANY"},"accessMethod":{"accessProtocol":"MS_OMI","pullInterval":1,"credential":{"username":"Administrator","password":"12345678","omiAuth":"ntlm or kerberos","kerberosADServer":"1.2.3.4","kerberosDomain":"abc"},"template":{"name":"Get All Logs","logTypes":[{"type":"SECURITY","include":"","exclude":""},{"type":"APPLICATION","include":"","exclude":""},{"type":"SYSTEM","include":"","exclude":""}]}}}]}Copyright©2023Fortinet,Inc.All rights reserved.Fortinet®,FortiGate®,FortiCare®and FortiGuard®,and certain other marks are registered trademarks of Fortinet,Inc.,and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet.All other product or company names may be trademarks of their respective owners.Performance and other metrics contained herein were attained in internal lab tests under ideal conditions,and actual performance and other results may work variables,different network environments and other conditions may affect performance results.Nothing herein represents any binding commitment by Fortinet,and Fortinet disclaims all warranties,whether express or implied,except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel,with a purchaser that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and,in such event,only。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
系列
FortiASIC 加速技术,FortiGate-100D 可提供业界领先的性能,高密度的千兆网络接口可为日益增长的网络的扩展性提供保证。
大量的本地存储空间更可以为您的网
络提供进行广域网加速必备的Web缓存功能,提升您的用网体验。
关键特性
整合安全架构比部署多台安全设备更强的安全防护能力,并且降低总拥有成本。
高端口密度高达 90个GbE 接口 ,极大提升了网络部署的灵活度和可扩展能力。
单一管理界面 通过单一界面完成所有功能的配置和部署,降低管理复杂度。
以太网供电
将外围设备无缝集成到安全环境中
内容处理器
FortiASIC CP8内容处理器主要工作于外向的流量,可以有效节省宝贵的CPU计算
资。
能够提供高速的复杂计算操作和深度内容检测:
• 对基于签名的内容深度检查进行加速
• 加密和解密网络流量
网络处理器
FortiASIC NP4Lite 网络处理器可以执行众多防火墙和VPN功能:
• 对通过防火墙数据包进行线速转发
• VPN 加速
• 异常流量检测、流量内容检查和数据包重组
• 流量整形和优先转发机制
• 通过使用FortiASIC专用芯片
可以在提供数千兆转发性能的
情况下执行恶意内容的深度检
查,从容应对当今的安全威
胁。
并且通过众多第三方机构
的严苛测试,确保您的网络安
全设备不再是网络瓶颈。
4
12
3
57
6
USB 管理端口
管理端口
Console 端口
USB 端口
2 x 10/100/1000 WAN 接口
52 x 10/100/1000 LAN 接口
32 x 10/100/1000 PoE LAN接口
4 x GbE SFP DMZ 接口
4
125
FortiGate-280D-POE
68
2
3
行业认证
FortiGate家族产品,包括物理设备和虚拟化设备,始终能够满足严苛的第三方测试标准,也因此我们拿到了比其他安全设备提供商更多的行业认证。
我们始终以业界领先的技术为您提供极高的安全保护,FortiGate也是可以让您放心使用并依靠的安全产品。
更多的安全保护、更好的 ROI
FortiGate通过对自身使命的不断进化来提供给用户更多的价值。
比如扩展了对WiFi和二层交换机的控制功能,整合令牌服务器,终端控制和广域网优化以及更多的安全功能,我们其实还增加了很多内容给部署我们产品的用户,除了价格。
完整且实时的安全保护
Fortinet的FortiGuard订阅服务提供自动化、实时、及时更新的安全保护,以帮您抵御最新的安全威胁。
我们遍布全球的威胁研究实验室为您提供全天候的更新。
当您需要我们的时候,我们就在这里。
世界级的技术支持
Fortinet FortiCare可以对Fortinet的所有产品和服务对您进行全球化综合支持。
您可以放心使用我们的产品,有FortiCare 的支持,可以保证我们产品能够全天候高效地保护您的用户、应用、数据免遭威胁的侵扰。
Copyright© 2013 Fortinet, Inc. All rights reserved. Fortinet®, FortiGate®, and FortiGuard®, are registered trademarks of Fortinet, Inc. and other Fortinet names herein may also be trademarks of Fortinet. All other product or company names may be trademarks of their respective owners. Performance metrics contained herein were attained in internal lab tests under ideal conditions, and performance may vary. Network variables, different network environments and other conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser that expressly warrants that the identified product will perform according to the performance metrics herein. For absolute clarity, any such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any guarantees. Fortinet reserves the right to change, modify, transfer, or otherwise revise this publication without notice, and the most current version of the publication shall be applicable.
FST-PROD-DS-GT2HS FG-200D-DAT-R4-201311
Note: All performance values are “up to” and vary depending on system configuration. Antivirus performance is measured using 44 Kbyte HTTP files. IPS performance is measured using 1 Mbyte HTTP files.
规格
ICSA Labs: Firewall, IPSec, IPS, Antivirus, SSL VPN。
