Operational Semantics of UML 2.0 Interactions
参考的英语单词

参考的英语单词参考,指参证有关材料来帮助研究和了解;在研究或处理某些事情时,把另外的资料或数据拿来对照。
那么你知道参考的英语单词是什么吗?下面来学习一下吧。
参考英语单词1reference参考英语单词2refer to参考的英语例句:我喜欢同时参考好几页书,这在电脑上难以实现。
这本参考书对我们的研究很有用。
This reference book is very useful to our study.这份资料是从各种参考书中摘出的。
The information is culled from various reference books.这本参考书对我有用处吗?Is this reference book of any use to me?本阅览室的参考书不得私自带出。
No reference books are to be taken out of the reading room without permission.他有大量的参考书可供使用。
He has a large number of reference books at his disposal.他在文章中引用大量参考资料。
He loaded his pages with references.参考编号将会于登记完成后即时提供,以作参考。
A reference number will be provided instantly after the lucky draw registration.S3支持许多选项;请参考文档看看是否可以使用它们。
Amazon:: S3 supports many options; you should consult the documentation if you think you can use them.关于在生产环境中使用Encrypted File Container的方法,请参考SLES文档和版本说明。
UML专业术语翻译
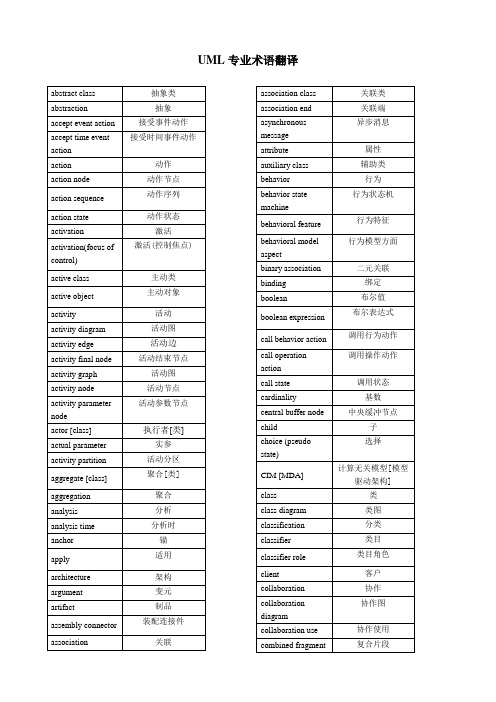
析构事件
development process
开发过程
diagram
图
disjoint substate
互斥子状态
distribution unit
分布单元
domain
领域
Domain Facility[MDA]
领域设施[模型驱动架构]
duration constraint
primitive type
基本类型
procedure
规程
process
过程
profile
外廓
profile application
外廓应用
projection
投影
property
特性
property value
特性值
protocol state machine
协议状态机
protocol transition
动作状态
activation
激活
activation(focus of control)
激活(控制焦点)
active class
主动类
active object
主动对象
acபைடு நூலகம்ivity
活动
activity diagram
活动图
activity edge
活动边
activity final node
活动结束节点
局部前置条件
loop node
循环节点
lost message
丢失的消息
manifestation
显现
mapping
映射
marked PIM [MDA]
A UML Virtual Machine for Embedded Systems

A UML Virtual Machine for Embedded SystemsTim Schattkowsky, Wolfgang MuellerC-LAB, Paderborn University{tim|wolfgang}@c-lab.deAbstractStateCharts are well accepted for embedded systems specification for various applications. However, for the specification of complex systems they have several limitations. In this article, we present a novel approach to efficiently execute an UML 2.0 subset for embedded real-time systems implementation with focus on hardware interrupts, software exceptions, and timeouts. We introduce a UML Virtual Machine, which directly executes sequence diagrams, which are embedded into hierarchically structured state transition diagrams. Whereas state diagrams are directly executed as Embedded State Machines (ESMs), sequence diagrams are translated into UVM Bytecode. The final UVM execution is performed by the interaction of the ESM and the Bytecode Interpreter. Due to our completely model-based approach, the UVM runtime kernel is easily adaptable and scalable to different scheduling and memory management strategies.Keywords: UML, Executable Models, Hardware/Software Co-design, Virtual Machine, Embedded Systems1.IntroductionEmbedded systems design comes in different variations and is most often due to the specific application or project [7]. Sometimes, graphical means like StateCharts or Matlab/Simulink are applied for graphical specification. The different tools come with different plugins for code generation. Different code generators for different micro controllers such as C166 and different Real-Time Operating Systems (RTOSs) like OSEK are available [6]. There have been efforts to investigate retargetable compilers to easily adopt them to different hardware platforms [4]. Other investigations concern different scheduling and timing analysis technologies [3]. Most recently, the Model-Driven Architecture (MDA) approach [14] became also recognized in the domain embedded systems design. MDA is based on the idea that specification and development is based on a platform-independent model (PIM). The PIM has to be mapped to a platform-specific model (PSM) in some undefined way. This PSM is used for the actual implementation. Executable UML seems to become a major role here, as it enables the PSM itself to be executable. However, current approaches mostly target towards platform-specific code generation. In addition, they the limitations and real-time requirements of embedded systems are not considered.A different approach to portable code comes from the idea of using a Virtual Machine (VM). A VM is a virtual computer defining the runtime environment for the executed software. Thus, the VM functions as a low level abstraction layer defined by its behavior and the format of the executed software program. The VM programs consist often of bytecode similar to the machine code executed by a microprocessor. Examples for the use of bytecode are the P-Code used by UCSD Pascal and the Java Bytecode. One of the main advantages of a VM is the portability of the code. Once the VM is ported to a specific platform, any available bytecode should instantly run on that VM. Any VM improvement with respect to runtime, stability, and security is immediately beneficial to existing software. This highly reduces costs for development and testing.We introduce a novel approach to efficiently execute an UML 2.0 subset for embedded microcontrollers. In order to support real-time system implementation our approach explicitly focus on hardware interrupts, software exceptions, and timeouts. For efficient execution, we define a UML virtual machine, which directly executes UML 2.0 [16] state diagrams and embedded sequence diagrams. The combination of both overcomes the limitations of purely state-oriented modeling means. The computation of UVM is defined by the close interaction of the ESM (Executable State Machine) Interpreter and the Bytecode interpreter. The first one processes direct binary representation of state diagrams whereas the second one manages the execution of the Bytecode, which is generated from the embedded sequence diagrams. The UVM execution starts from an initial ESM, the Adaptive Runtime Kernel, which controls scheduling and memory management of the different ESMs. Since our approach is completely model-based, the kernel and it subcomponents (scheduler, memory manager, ESM loader) are implemented as ESMs, so that the kernel can be easilyreconfigured by reloading application-specific schedulers or memory managers, respectively.The paper is structured as follows. The next section discusses related works. Section 3 introduces our executable UML 2.0 subset combining state and sequence diagrams to executable models. Section 4 the UVM architecture and its components as well as the UVM Bytecode. Section 5 provides a detailed example before Section 6 closes with conclusions.2.Related WorksWith respect to embedded systems design methodologies, there are very few approaches, which are frequently applied for real systems like the one from IMEC, COSYMA, OCTOPUS [7], or the SpecC methodology [2] . All except OCTOPUS are based on specific design environments and/or languages. OCTOPUS was one of the first methodologies, which followed a straight object-oriented approach including HW/SW partitioning already considering a hardware abstraction layer (hardware wrapper).Meanwhile, in the context of the OMG Model Driven Architecture [14], the notion of executable UML became of wider interest [10]. Based on Starr’s approach to executable UML [13], which is mainly based on class and state diagrams, Project Technology developed X T UML [9] as an executable and translatable UML subset for embedded real-time systems in the areas of flight-critical systems, performance-critical and fault-tolerant telecom systems, and resource-constrained consumer electronics. The corresponding tool integrates a plugin-interface to adopt different code generators. A similar approach to executable UML is xUML [17] which also relies on a language-specific code generation, e.g., for Ada or C [15].The most prominent approach to portable code was introduced by Java and its VM [5]. Though Java was originally designed for embedded systems, due to the large footprint of its runtime environment and the garbage collection memory management, it is less suited for small micro controllers and real-time applications. The Java compiler generates low-level bytecode, which is executed on a Java Virtual Machine (VM). Therefore, the compiled Java program runs on each platform where a Java VM is available.There also exists a proposal for a UML VM [12]. However, this does not cover the use of a true VM for UML models. Instead, the authors present in their approach mainly a Java data model for representing the four-layer metamodel of the UML. To allow the executionof a model by an interpreter, the authors mainly attach state diagrams to classes. Detailed behavior has to be implemented manually in Java.Our approach presents a VM designed to directly execute UML models. The underlying design methodology resembles the structure of well-established concepts for embedded system specification by using an executable UML 2.0 subset. In contrast to other approaches, our concepts combine a completely model-based approach focusing on the specific requirements of embedded systems including interrupts and timeouts.3.MethodologyStateCharts are frequently applied in embedded systems design. UML has introduced the State Transition Diagrams (STDs, also known as StateMachine Diagrams) as a variation of Harel’s StateCharts [1]. However, several behavioral aspects like concurrent objects and simple data-oriented algorithms (e.g., sorting) cannot be easily expressed. The UML 2.0 sequence diagrams (SDs) have several extensions for loops etc, which make them an ideal compliment for the use of STDs. We can overcome these drawbacks of using STDs through the integration of SDs with STDs.Our approach enables object-oriented development using STDs and SDs for the specification and execution of real-time embedded systems. We cover interrupt/exception handling and hard real-time constraints through timeouts since they are of key importance for safety and reliability [3]. The remainder of this paper focuses on the use of SDs and STDs in our approach, since the use of class diagrams for type definition is quite straightforward.In our approach, an STD describes behavior of a method (Operation) at the topmost level. This enables state-oriented modeling within an object-oriented system and is crucial for the integration with existing designs. Furthermore, it enables consistent declarative timeout-, interrupt- and exception handling. Such exceptions may include software exceptions like runtime exceptions and user-defined exceptions as well as external exception, i.e., interrupts.We support STDs consisting of composite and simple states. Concurrent States are intentionally unsupported, as we support concurrency through asynchronous operation calls. However, introducing an operation for each region of a concurrent State and interconnecting these with communication channel objects can resemble concurrent States. These Operations can then be run concurrently. However, additional synchronization may be necessary to resemble the semantics of a concurrent State.State transitions are triggered by different events. In our approach, these are state completion, explicit, timeout, hardware interrupt, and software exception, i.e., division by zero. Interrupts and exceptions are processed immediately and cause the current state to be exited. Thewhole Operation is completed when the associated state machine reaches a final state.In our approach, an integration mechanism is provided to incorporate additional Events from an Operation. Each StateMachine may have an attached EventGenerator Operation, which can produce additional EventObjects. The EventObject Class defines a member operation that can be used to retrieve the actual event identifier as an integer. Additionally, an action Operation can be assigned, that will be called for all compatible actions on transitions within the StateMachine. Together, this allows having individual action/event semantics per StateMachine and enables a much broader use of StateMachines than other approaches. Finally, it enables the reuse of existing state charts in our methodology. In this context, care has to be taken as the execution semantics may differ.The SDs used in our approach have a limited set of necessary features compared to what is allowed by the UML 2.0 specification (cf. Figure 3). This reflects the properties of the supposed execution environment. All messages in the diagrams have to be synchronous. The CombinedFragment as defined in UML 2.0 is used to resemble control structures. Thus, in our approach it is limited to be an Alternative, Option, or Loop.The STDs hierarchically embed STDs (StateMachines) and/or SDs (Interactions), which may again integrate other STDs or SDs (Behaviour as in the UML metamodel). Which combination of diagrams is used is mainly due to the individual application and system’s complexity. To achieve the arbitrary composition of both diagrams, we had to define interfaces between sequential parts represented as UML sequence and state diagrams. Those interfaces allow the integration of both into composite models.When integrating a SD into a STD, the SD has to expose state-like behavioral semantics. The sequential end of the sequence diagram is equivalent to a completion transition. Furthermore, SDs can directly trigger transitions in the containing StateMachine. In the model, this is depicted by a call to the transition() operation of the Runtime class. Finally, exceptions raised by the sequence diagram have to consistently map to transitions in the containing state machine.4.The UML Virtual MachineThe UML Virtual Machine (UVM) is a virtual computer for executing UML models based on our approach using the previously introduced combination of STDs and SDs. In order to enable simple and efficient execution of such models, we use a transformation to equivalent executable state-oriented binary models. A StateMachine from an STD is translated to the binary encoding of an Executable State Machine (ESM). An embedded SD defining an Activity of a State or Transition is translated to executable UVM bytecode.The next section outlines the UVM basic principles. Thereafter, we introduce Executable State Machine (ESM) and bytecode details.4.1UVM ExecutionThe UVM consists of two major components: the Model Execution Unit (MEU) and the Runtime Kernel (RK) (see Figure 1).Figure 1. UML Virtual Machine ArchitectureThe MEU executes the RK and the UML models, i.e., STDs and the embedded SDs. The MEU thus has two interacting interpreters, one for the Executable State Machine (ESM) generated from an STD and another one for the Bytecode compiled from an SD.The ESM Interpreter keeps track of the current state and performs transitions between States. After a Transition, it invokes the Bytecode Interpreter to execute the Activity associated with the current state and waits until this Activity finishes or an interrupt or timeout occurs. The Bytecode Interpreter executes the Bytecode in a microprocessor-like manner using an instruction pointer and a stack for program control. However, stack frames also include State information.A Timer in the MEU enforces Timeouts. The ESM interpreter manages such timeouts just like interrupts from external sources and unexpected Exceptions (i.e, ‘division by zero’ or exceptions from the host platform). Such events are mapped to the respective Triggers in the ESM. In such a case, the ESM Interpreter immediately stops the Bytecode Interpreter and the current state is pushed to thestack while the ESM Interpreter switches to a transition for handling the event and gives control to the Bytecode Interpreter for executing the Bytecode of the Activity.Nested external interrupts from the environment, like from a sensor, are processed corresponding to traditional interrupts by firing the corresponding event when the current interrupt processing has finished. Note here, that the sequence of multiple different interrupts is not preserved and the multiple occurrence of an interrupt may result in a single event.As introduced in the previous section, the UVM is based on the execution a hierarchical StateMachine. Thus, an initial model has to be provided. That initial machine is denoted as the Adaptive Runtime Kernel (ARK) und is contained in predefined operations of special class. The ARK implements the basic runtime environment of the UVM like memory manager, scheduler, and the (optional) dynamic ESM loader.Since the ARK is implemented along the concepts of a hierarchical ESM itself, it can be easily adapted to the individual application. The ARK scheduler and the memory manager control the different applications given as ESMs. The memory manager is implemented as a set of operations on the ARK class that perform the actual allocation and deallocation. Those operations are invoked by the Bytecode Interpreter whenever object instances are created and destroyed. The scheduler is implemented as an operation computing the next model to be scheduled for execution. The scheduler implementation is likely to rely on external events (i.e., timer interrupts) for its implementation. Through this, different algorithms can be adapted for both functionalities to achieve the desired real-time properties. In the simplest case, only has to manage one ESM, which gives a trivial implementation of the scheduler. Simple implementations for the management of multiple ESMs can be given by round-robin scheduling and buddy-style memory management.4.2Executable StateMachinesAs introduced before, the STD StateMachine is translated to an equivalent Executable StateMachine (ESM) that is based on a simplified metamodel where States have only a doActivity and Transitions have no Activities at all and just a single Trigger. The design model will be transformed accordingly by introducing additional States and Transitions to resemble the defined behavior. This is also used to resolve deferred Triggers and conflicting Transitions. Consequently, there is no need for an event queue at runtime, as at most one transition can be enabled by an event. This simplifies the UVM implementation, as the handling of conflicting events is one of the most critical issues when executing StateChart variants, as it is usually complex and has several semantic variants.Furthermore, each state may have a timeout value. This value is derived from the transition timeouts for the state in the design model. As there may be multiple transitions containing expressions, these expressions will be combined and evaluated when entering the state to compute a definitive timeout value. If that timeout is less then the pending timeout (from an embedded state), it is pushed on the UVM timeout stack and becomes the pending timeout. A timer in the UVM triggers the corresponding transition if the state is not exited before the timeout. The timeout is finally removed from the timeout stack when the state is exited, e.g., by completion.4.3UVM BytecodeAs introduced before, the encoding of an SD results in Bytecode, which is equivalent to statements of the SD. This Bytecode is created based on the instruction set of the UVM. However, since the SD may include severally nested expressions and invocations, those have to be resolved and mapped to the instruction set. The code of the nested diagrams is transformed by decomposition of the expressions into an equivalent flattened version composed of executable UVM instructions. Parameters are passed to and from Interactions through a stack, like it is given in other compiled high-level languages. Table 1 gives an overview of the most important instructions.As a basic concept, the UVM has no registers, as this implies several limitations. However, UVM hardware implementations could make transparent use of registers to optimize their performance. In general, the lack of registers allows flexible use of the available hardware resources and enables simple scalable implementation in both hard- and software.The UVM instruction set has instructions similar to those of common microprocessors. The syntax is derived from the Motorola syntax [11], as the explicit operand size declaration is convenient for the register-free approach. Most instructions in the UVM equal their counterparts in common microprocessor instruction sets like those of the Intel x86 family and Motorola 68k family (see Table 1). This includes the typical instructions for moving data, integer and floating point math and bit manipulations. The UVM directly supports classes and primitive types. We support the Boolean type, 32-bit Integers, Strings (as byte arrays), and 64 bit Floating-Point Numbers.Furthermore, the control instructions differ to reflect the ESM approach. Instructions for managing and invoking objects are introduced. In addition, instructions for state transitions are required. Unconditional branches are not available, as these are not possible at the model level. Subroutine calls remain, but are interpreted asoperation calls. As Operations are compiled to ESMs, the complete instruction marks the state completion and replaces the usual return instruction. The major difference however lies in the stack handling, which had to be changed to the StateMachine behavior. The event and trans instructions enable immediate changes in the control flow through an explicit event or transition, respectively. This may cause an immediate exit from the current State implementation. The event command can be regarded as an ESM-compatible replacement for the traditional int/trap instruction.Concurrency is supported through asynchronous operations calls using the invokea instruction. Such a call creates a new thread which is implicitly terminated by the completion of the operation.Furthermore, the UVM supports explicit switching between different threads of execution through the continue operation. it causes the UVM to save to current thread state to its stack, restore the state of the thread specified by the operand and continue execution in that thread. This operation used by the scheduler.Table 1. UVM Instruction Set (excerpt) Mnemonic DstSrc SemanticsData Movement & Stack Instructionsmove.[b,l,d] mem mem/im Dst← Srcpush.[b,l,d] mem [-sp]← Dstpop.[b,l,d] mem Dst← [sp+]enter imm (Initialize local frame)Math Instructionsadd.[b,l,d] mem mem/im Dst← Dst + Srccmp.[b,l,d] mem mem/im [Flags according]...Logical InstructionsNot.[b,l,d] mem Dst← ~DstAnd.[b,l,d] mem mem/im Dst← Dst ∧ Src ...Shift InstructionsAsl.[b,l,d] mem mem/im Dst← Dst << Src Lsl.[b,l,d] mem mem/im Dst←Dst <<< Src...Control InstructionsbCC disp Conditional branchbra disp Unconditionalbranch OO Control Instructionsnew memmem/imDst← (instanceof Src)destroy mem (destroy instance Dst)interface memmem Dst← Dst as Srcinvoke mem Im (invoke Src on Dst)fork mem Im (fork Src on Dst)invokes mem Im (invoke static Src on Dst) invokei mem Im (interface op Src on Dst) ...Synchronization Instructionsjoin mem (join thread Dst)sync mem (obtain instance lock)trysync mem (lock if possible)release mem (release instance lock)ESM Control Instructionstrans mem (transition to Dst)event mem (event Dst will becomplete (return)Thread Control Instructionscontinue Mem (continue Thread Dst) 5.ExampleAs an example, we outline the implementation of the well-known ZMODEM protocol [8] for file transfers, i.e., used in Telnet sessions. We focus on the significant partsof the receiver implementation to demonstrate the basic concepts of our approach.The implementation is presumed to be contained in a class ZModem with operations for sending and receiving files. Figure 2 shows a cutout of the state diagram for the receive() operation. The operation is returning a set of File objects representing the received files. The implementation closely resembles the ZMODEM state machine and thus demonstrates nicely the use of an existing StateMachine design in our approach. The provided tags define the event and action processing in this StateMachine as consuming ZMODEM Frames (data packets) using the frame type as the triggering event. The corresponding action is sending back response ZMODEM FrameHeader objects. This leads to a complete implementation of the StateMachine based on the protocol frame types.The StateMachine starts by sending a ZRINIT headerto initiate the file transfer and waiting for a ZFILE frame header response with as a trailing subpacket containing the name and size of the file to be received. It retries this up to MaxZRININT times before giving up. This illustrates the use of timeouts in our approach.Once a ZFILE frame header has been successfully received, the transition to the CheckFile state takes place. This state is implemented by the SD (Interaction) shownin Figure 3.。
UML名词中英对照表
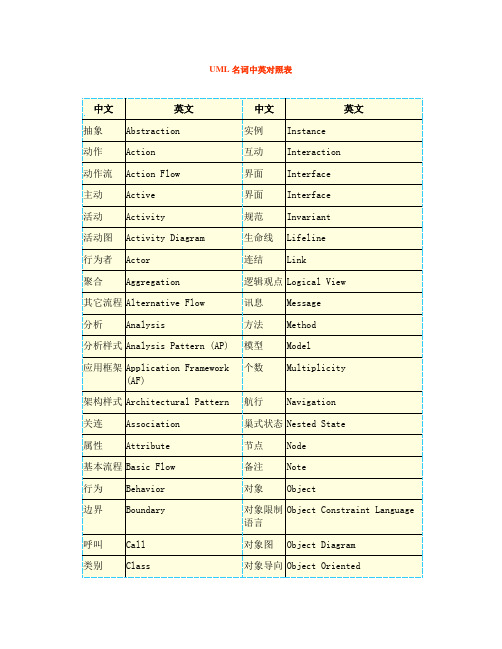
UML 名词中英对照表中文 抽象 动作 动作流 主动 活动 活动图 行为者 聚合英文 Abstraction Action Action Flow Active Activity Activity Diagram Actor Aggregation中文 实例 互动 界面 界面 规范 生命线 连结 Instance Interaction Interface Interface Invariant Lifeline Link英文逻辑观点 Logical View 讯息 方法 模型 个数 航行 Message Method Model Multiplicity Navigation其它流程 Alternative Flow 分析 Analysis分析样式 Analysis Pattern (AP) 应用框架 Application Framework (AF) 架构样式 Architectural Pattern 关连 属性 Association Attribute巢式状态 Nested State 节点 备注 对象 Node Note Object基本流程 Basic Flow 行为 边界 呼叫 类别 Behavior Boundary Call Class对象限制 Object Constraint Language 语言 对象图 Object Diagram对象导向 Object Oriented类别图 合作 合作图 沟通 组件 组件图Class Diagram Collaboration Collaboration Diagram Communicate Component Component Diagram操作 过载 覆盖 套件 参数 被动Operation Overloading Overriding Package Parameter Passive Pattern Polymorphism组件框架 Component Framework (CF) 样式 组件式开 Component-Based 发 Development 组合 具体 限制 建构 建构元 控制 建立 Composition Concrete Constraint Construction Constructor Control Creation 多型后续条件 Post-Condition 前置条件 Pre-Condition 程序观点 Process View 特性 限定 关系 需求 回传 角色 情节 循序图 Property Qualifier Relationship Requirement Return Role Scenario Sequence Diagram资料型态 Datatype 相依 部署图 Dependency Deployment Diagram部署观点 Deployment View 设计 Design方法规格 Signature 状态 状态机 State State Machine设计样式 Design Pattern (DP) 解构 解构元 Destruction Destructor状态转移 State Transition Diagram图 区别 动态 封装 实体 事件 延伸 外观 Discriminator Dynamic Encapsulation Entity Event Extend Facade 静态 型别 结构 子系统 Static Stereotype Structure Subsystem责任区线 Swimlane 标注值 模板 测试 追溯 转移 类型 Tagged Value Template Test Trace Transition Type结束状态 Final State 事件流程 Flow Of Event 控制焦点 Focus of Control 框架 框架 Framework Framework统一模塑 Unified Modeling Language 语言 使用 Use门槛条件 Guard 实作 Implementation使用个案 Use Case 使用个案 Use Case Diagram 图 使用个案 Use-Case View 观点 View Virtual Visibility实作观点 Implementation View 包含 Include基础框架 Infrastructure Framework 观点 (IF) 继承 Inheritance 虚拟 可见度初始状态 Initial State。
On the Description of Communications Between Software Components with UML

On the Description of Communications Between SoftwareComponents with UMLZhiwei An Dennis PetersFaculty of Engineering and Applied ScienceMemorial University of NewfoundlandSt.John’s NL A1B3X5zhiwei@engr.mun.ca dpeters@engr.mun.caNovember12,2003AbstractFor the purpose of analysis and verification,in software design,architecture of the software system and communications between software components should be specified.Unified Modeling Language(UML)isa standard software design notation that includes Sequence diagrams and Collaboration diagrams,whichdescribe the interaction between objects.They also can be used to describe communications betweencomponents.In this paper,we discuss what should be modeled in the communication and how theelements in UML can be adopted to model the communication.A formalism of UML design models thatcan be used for design analysis is also proposed.1IntroductionSoftware systems are often composed of several components each of which is a computational entity that realizes a particular ponents interact with each other by communications between them. Documenting communications is one part of software design and the design models should be verifiable to ensure the correctness of the design.In software systems,synchronous and asynchronous communication could exist.To describe different types of communications between components,several methodologies have been proposed.Two kinds of methods are1)Architectural Description Languages(ADL)[1]and2)UML in architecture description [3,4].The Unified Modeling Language(UML)[6]is a standard modeling language with rich diagrams to model static and dynamic aspects of a system.Sequence diagrams and collaboration diagrams are two types of UML diagrams widely used in communication description.In a sequence diagram,the horizontal dimension represents different objects and the vertical dimension represents time.Each object has a lifeline with activation bars.The bar begins with the invocation of a method and stops when the method ends.Arrows represent messages transmitted between the objects.The life line could have a branch at a time point and the two or more lines could merge at a later time.The branch means conditional branch or concurrency.Sequence diagrams specify time explicitly.In a sequence diagram,objects interact with each other via messages.A message may specify several different time points such as sending time and receiving time.One message links two events and the order of events is specified.A collaboration diagram presents a set of roles to be played by instances as well as required relationships between them.It also presents a set of messages specifying the interaction between the instances playing the roles to achieve the desired result.In collaboration diagrams,message order is described by adding numbers to arrow labels.To verify the UML design models,the idea of model checking[2]is proposed.Typically,a model checking algorithm checks properties of a system description based on a(finite)state machine model with parallel composition.To generate the automata based model,sequence diagrams should be analyzed and translated into state machines.A sequence diagram describes time explicitly so the timing relation of the events can be derived from it.In UML design models for a software system there are usually several sequence diagrams.Analysis of all of these diagrams could generate a state machine based model for model checking.The rest of this paper is organized as follows:In Section2,we discuss types of communications between software components and what should be modeled in the communication.Section3uses an simplified elevator example to show how to use UML diagrams to describe interactions.In Section4,we propose one behavior model of the software system and illustrate how information in Sequence diagrams could be mapped to the behavior model.In Section5,we draw some conclusions.2Types of CommunicationsCommunications between software components are either asynchronous or synchronous.The difference be-tween these two classes of communications is that synchronous communications involves blocking operations in the communication.In synchronous communication,the component is suspended after the send operation until it is unblocked by the other partner in the communication.In asynchronous communication,nonblock-ing operations are used which means that the components will proceed without waiting for the completion of the communication.The following classes of communications are possible.Shared Variable A variable that can be accessed by more than one component is a means of communi-cation.The basic operations on a shared variable are read and write so mutual exclusion is the main problem in this type.Asynchronous Message Passing(AMP)In this type of communication,there are two events1)the sender sends out the message and continues running,2)the receiver receives the message.If the receiver is available and the processes are co-located,1and2happen at essentially the same time and could be considered as the same event.If the receiver is not available,the message is stored in a buffer until the receiver is available.The sender is not blocked at any time.Synchronous Message Passing(SMP)In Synchronous Message Passing,the sender cannot send the message until the receiver is available to receive it.There is no buffer in this type of communication. Procedure Call In Procedure Call,there are four events1)the caller calls an access program in the callee,2)the access program is invoked,3)the access programfinishes,and4)the caller knows that the calleefinishes.In Procedure Call1and2happen at the same time and they could be considered as one event.3and4are also the same event.Between the events of2and3,the caller is blocked. Remote Procedure Call When there are more than one process and a process calls a function in another process,this type of communication is called Remote Procedure Call(RPC).The mechanism of RPC is almost the same as procedure call except that the function in another process may be unavailable because that function is called by another component and it can not be called twice at the same time.Asynchronous communication and synchronous communication have the similar semantics and can be modeled in a similar way.For example,synchronous message passing is a special case of asynchronous message passing without a buffer and asynchronous message passing between two components could be modeled as two synchronous messages:from one component to a buffer and then from the buffer to the other component.Table1:Concepts in Communication and UMLCommunication Concepts UML NotationsComponent ObjectComponent’s Life LifelineRunning Access Program Activation BarMessages or Calls Message Arrow(Operations)Message Name or Call Name Arrow LabelEvent Two Ends of an ArrowTwo ends of an Activation Bar3Description of Communications in UMLThe techniques for denoting communication types in UML are defined in UML1.4.To describe communi-cations with UML,thefirst step is to map concepts in communication to the elements in UML diagram. Table1illustrates the relations of UML notations and concepts of communication in this work.Operations and events should be distinguished here:operations have time duration and they are often composed of several events which are points in time.Some concepts in communication cannot be represented by UML notations.For example,the data state is not in UML at all and control state may be represented implicitly.After mapping concepts of communications to elements of UML,we need to model communications with the semantics of collaboration diagrams and sequence diagrams.To describe the whole system,thefirst step is to use collaboration diagrams to describe relations between objects,the second step is to use sequence diagrams to describe interactions.3.1Collaboration Diagrams in CommunicationBecause a collaboration diagram presents a collection of instances and their relationships,we can use it to describe the relations between components,as illustrated in Figure1.The arrows between components represent messages and calls.Since this diagram only illustrates the static relations between components no number is used in the arrow label.Figure1:Elevator System in Collaboration Diagram3.2Sequence Diagrams in CommunicationA sequence diagrams describes several aspects of the communication.First,it can describe the phenomenon of when one access program is invoked,what other events could be generated during the run time of theaccess programs.Second,it can illustrate the mechanism of communication.When one access program is invoked,it may send messages to or call access programs in other components.Messages and calls are distinguished by different types of arrows.For example,Figure 2shows that when the access program schedule is invoked,three operations,getFloor ,getDirection and nextStop happen.Figure 3illustrates the order of the events in the case of AMP.Figure 2:Stimulus in UML,IFigure 3:Stimulus in UML,IISince there are a finite number of access programs in the system and we can draw one sequence diagram for each access program,the number of sequence diagrams is equal to the number of access programs and hence the number of sequence diagrams will not grow too rapidly as the system size increases.Figure 2and Figure 3only illustrate the behaviour when one access program is invoked.More sequence diagrams are needed to completely describe the communications between components,including conflict resolution.Figure 4illustrates all types of communications discussed in Section 2.In I,a procedure call is illustrated:component P calls an access program in component Q (operation a ).The access program in Q is invoked at the same time as the component P calls it and P is blocked.After the access program in Q ends,P is unblocked.In II,P calls Q (operation a )first and it is blocked until the operation b .If Q is unavailable and R wants to call Q,R is blocked and should wait until the operation b is over.R will be unblocked only after the operation d .In III,P sends a message (operation a )to Q and P is not blocked.If Q is not available before it finishes serving the message form P and R sends a message to it (operation b ),a buffer is used to store the message and re-send the message to Q (operation c )after Q is available.In this type of communication,no component is blocked.In IV,P sends a message to Q (operation a ),R sends a message to Q (operation b )when Q is not available and Ris blocked,this operation can finish only after Q finishes serving the message from P.When the operation b ends,R is unblocked and Q begins to serve the message from R.In V,read andwrite are two basic operations and they should obey the rules of mutual exclusion.I. Procedure Call II. Remote Procedure CallIV. Synchronous Message Passing P,Q,R are componentsa, b, c, d are messages or callsvar is shared variable Figure 4:Types of Communication in UMLFigure4only illustrates some basic types of communications.In a realistic system mixtures and variants of these communications exist.In Figure5,the communication are AMP.In this example,the coordinator can access two messages from two schedulers so we can draw two lifelines for coordinator.A buffer is necessary when message delete cannot be processed immediately after being sent.Figure5:Communication Mechanism4Analysis TechniqueTo verify UML design models,we need a formalism to accept all sequences of events described by the model. In software systems,components are modeled as state machines and most model checking algorithms accept automata based specification as the input,so parallel composition of state machines is the model in this research work.4.1From UML to State Machine ModelSequence diagrams describe the relative order of events.In communications,there are several possible orders of events so the events are not totally ordered.The best description of the relationship of events is a partial order .In[5],relations of messages in Message Sequence Charts(MSC)are translated into a partial order. Because sequence diagrams come from MSCs with extension,a similar process can be used to extract the partial order from sequence diagrams.UML Sequence diagrams do not have state variables in them so they do not represent component state precisely.UML Statecharts have the ability to describe the behavior of the component but Module Interface Specifications(MIS)[7]make better use of abstraction and are more amenable to machine processing.A discussion of the process for generating a formal behaviour model from component MIS is beyond the scope of this paper.From the discussion above,we can propose that the problem of synthesizing concurrent automata from Sequence diagrams can be divided into two steps.1)Describe partial order relation in sequence diagrams formally and2)synthesizing concurrent automata model from the partial order relations and component MIS. 5ConclusionUML interaction diagrams have the ability to describe the communication between software components. Collaboration diagrams describe the relations between components and sequence diagrams describe two aspects of the interaction:1)when one event happens,what other events could happen,and2)what communications mechanisms represent the communication types.To verify software design,an automata based behavior model could be derived from the sequence diagrams and used for model checking.References[1]Robert Allen and David Garlan.A formal basis for architectural connection.ACM Trans.Software Eng.and Methodology,July1997.[2]E.M.Clark,O.Grumberg,and D.Peled.Model Checking.MIT Press,2000.[3]Hassan Gomaa.Designing Concurrent,Distributed,and Real-Time Applications with UML.Addison-Wesley,2000.[4]Christine Hofmeister,Robert Nord,and Dilip Soni.Applied Software Architecture.Addison-Wesley,2000.[5]Madhavan Mukund,K.Narayan Kumar,and Milind Sohoni.Synthesizing distributedfinite-state systemsfrom MSCs.In Proc.Int’l Conf.Concurrency Theory(CONCUR),number1877in Lecture Notes in Computer Science,pages521–535,University Park,PA,2000.Springer-Verlag.[6]Rational Software Inc.,et al.OMG Unified Modelling Language Specification,version1.5edition,March2003.[7]Yabo Wang.Formal and abstract software module specifications—a survey.CRL Report238,Commu-nications Research Laboratory,Hamilton,Ontario,Canada,November1991.。
The Elements of UML 2.0 style

The Elements of UML 2.0 style作者 : Scott W.Ambler(1)General Diagramming Guidelines1. Avoid Crossing Lines2. Depict Crossing Lines as a Jump3. Avoid Diagonal or Curved Lines4. Apply Consistently Sized Symbols5. Attach Lines to the Middle of Bubbles6. Align Labels Horizontally7. Arrange Symbols Symmetrically8. Don’t Indicate “Exploding” Bubbles9. Minimize the Number of Bubble Types10. Include White Space in Diagrams11. Organize Diagrams Left to Right, Top to Bottom12. Avoid Many Close Lines13. Provide a Notation Legend14. Show Only What You Have to Show15. Prefer Well-Known Notation over Esoteric Notation16. Reorganize Large Diagrams into Several17. Prefer Single-Page Diagrams18. Focus on Content First, Appearance Second19. Apply Consistent, Readable Fonts20. Set and Follow Effective Naming Conventions21. Apply Common Domain Terminology in Names22. Apply Language Naming Conventions on Design Diagrams23. Name Common Elements Consistently Across Diagrams24. Indicate Unknowns with a Question Mark25. Consider Applying Color to Your Diagrams26. Apply Color or Different Fonts Sparingly(2)Guidelines for Common UML Modeling Elements 27. Describe Diagrams with Notes28. Set a Convention for Placement of Diagram Legends29. Left-Justify Text in Notes30. Prefer Notes over OCL or ASL to Indicate Constraints31. Follow Common Coding Conventions for OCL and ASL32. Name Stereotypes in <<user interface>>and <<UI>> Format33. List Stereotypes Last34. Don’t Indicate Assumed Stereotypes35. Prefer Naming Conventions over Stereotypes36. Tagged Values Follow Stereotypes37. Align Classifier Stereotypes with Names38. Introduce New Stereotypes Sparingly39. Apply Stereotypes Consistently40. Apply Visual Stereotypes Sparingly41. Deemphasize Frame Borders42. Avoid Diagram Frames43. Apply Standard Labels to Descriptors44. Use Interaction Occurrences over Part Decompositions45. Fully Specify Operation Names in References46. Depict One Interface per Port47. Depict One Port per Realizing Class48. Provided Interfaces on the Left49. Required Interfaces on the Right50. Apply Realizes Relationships for Ports51. Reflect Implementation Language Constraints in Interface Definitions52. Name Interfaces According to Language-Naming Conventions53. Prefer “Lollipop” Notation to Indicate Realization of an Interface54. Define Interfaces Separately from Your Classifiers55. Do Not Depict the Operations and Attributes of Interfaces in Your Classes56. One Label per Interface Connection57. Place Interface Labels above the Interface(3)UML Use-Case Diagrams58. Begin Use-Case Names with a Strong Verb以“强动词”作为用例名称的开头59. Name Use Cases Using Domain Terminology使用领域术语作为用例名称60. Imply Timing Considerations by Stacking Use Cases以用例的堆放顺序“暗示”其发生时间61. Place Your Primary Actor(s) in the Top Left Corner of the Diagram把主要参与者放置于图标的左上角62. Draw Actors on the Outside Edges of a Use-Case Diagram将参与者放置于用例图的边框外63. Name Actors with Singular, Domain-Relevant Nouns用单数的、领域相关的名称来为参与者命名64. Associate Each Actor with One or More Use Cases每个参与者关联到一个或者多个用例65. Name Actors to Model Roles, Not Job Titles以角色命名参与者,不以职务头衔命名66. Use <<system>> to indicate System Actors使用<<system>>表示系统参与者67. Don’t Allow Actors to Interact with One Another不允许参与者之间有互动68. Introduce an Actor Called “Time” to Initiate Scheduled Events用“时间”参与者标示预定事件69. Indicate an Association between an Actor and a Use Case if the Actor Appears Within The Use-Case Logic如果参与者出现在用例中,则可以在参与者和用例之间放置关联70. Avoid Arrowheads on Actor–Use-Case Relationships在参与者与用例之间的关联中,避免出现箭头71. Apply <<include>> When You Know Exactly When to Invoke the Use Case用例“一定”会启动,适用包含关系72. Apply <<extend>> When a Use Case May Be Invoked Across Several Use Case Steps用例“可能”会启动,适用扩展关系73. Apply Extend Associations Sparingly谨慎地使用扩展关系74. Generalize Use Cases When a Single Condition Results in Significantly New Business Logic描述相似的业务逻辑时,适用泛化关系75. Do Not Apply <<uses>>, <<includes>>, or <<extends>>不要使用<<uses>>, <<includes>>,或<<extends>>76. Avoid More Than Two Levels of Use-Case Associations用例之间的包含关系或扩展关系,避免达到两层以上77. Place an Included Use Case to the Right of the Invoking Use Case把被包含用例放置于基础用例的右方78. Place an Extending Use Case below the Parent Use Case把扩展用例放置于基础用例的下方79. Apply the “Is Like” Rule to Use-Case Generalization应用“就像是”规则来判断用例之间的泛化关系80. Place an Inheriting Use Case below the Base Use Case把子用例放置于父用例的下方81. Apply the “Is Like” Rule to Actor Inheritance应用“就像是”规则来判断参与者之间的泛化关系82. Place an Inheriting Actor below the Parent Actor把子参与者放置于父参与者的下方83. Avoid Modeling Extension Points避免使用扩展点84. Model Extension Conditions Only When They Aren’t Clear只有在不清楚的情况下,才使用扩展条件85. Indicate Release Scope with a System Boundary Box在系统范围方框内指出发布范围86. Avoid Meaningless System Boundary Boxes避免无意义的系统范围方框(4)UML Class Diagrams87. Identify Responsibilities on Domain Class Models88. Indicate Visibility Only on Design Models89. Indicate Language-Dependent Visibility with Property Strings90. Indicate Types on Analysis Models Only When the Type Is an Actual Requirement91. Be Consistent with Attribute Names and Types92. Model Association Classes on Analysis Diagrams93. Do Not Name Associations That Have Association Classes94. Center the Dashed Line of an Association Class95. Use Common Terminology for Class Names96. Prefer Complete Singular Nouns for Class Names97. Name Operations with Strong Verbs98. Name Attributes with Domain-Based Nouns99. Do Not Model Scaffolding Code100. Center Class Names101. Left-Justify Attribute Operation and Names102. Do Not Model Keys103. Never Show Classes with Just Two Compartments104. Label Uncommon Class Compartments105. Include an Ellipsis (. . .) at the End of an Incomplete List106. List Static Operations/Attributes before Instance Operations/Attributes107. List Operations/Attributes in Order of Decreasing Visibility108. For Parameters That Are Objects, List Only Their Types109. Develop Consistent Operation and Attribute Signatures110. Avoid Stereotypes Implied by Language Naming Conventions111. Indicate Exceptions in an Operation’s Property String112. Model Relationships Horizontally113. Draw Qualifier Rectangles Smaller than Classes114. Model Collaboration between Two Elements Only When They Have a Relationship 115. Model a Dependency When the Relationship Is Transitory116. Tree-Route Similar Relationships to a Common Class117. Always Indicate the Multiplicity118. Avoid a Multiplicity of “*”119. Replace Relationship Lines with Attribute Types120. Do Not Model Implied Relationships121. Do Not Model Every Dependency122. Center Names on Associations123. Write Concise Association Names in Active Voice124. Indicate Directionality to Clarify an Association Name125. Name Unidirectional Associations in the Same Direction126. Word Association Names Left to Right127. Indicate Role Names When Multiple Associations between Two Classes Exist128. Indicate Role Names on Recursive Associations129. Make Associations Bidirectional Only When Collaboration Occurs in Both Directions 130. Indicate Direction Only on Unidirectional Associations131. Avoid Indicating Non-Navigability132. Redraw Inherited Associations Only When Something Changes133. Question Multiplicities Involving Minimums and Maximums134. Apply the Sentence Rule for Inheritance135. Place Subclasses below Superclasses136. Beware of Data-Based Inheritance137. A Subclass Should Inherit Everything138. Differentiate Generalizations between Associations139. Indicate Power Types on Shared Generalization140. Apply the Sentence Rule for Aggregation141. Be Interested in Both the Whole and the Part142. Place the Whole to the Left of the Part143. Apply Composition to Aggregates of Physical Items144. Apply Composition When the Parts Share Their Persistence Life Cycle with the Whole 145. Don’t Worry About the Diamonds(5)UML Package Diagrams146. Create Class Package Diagrams to Logically Organize Your Design147. Create UML Component Diagrams to Physically Organize Your Design148. Place Inheriting Packages below Base Packages149. Vertically Layer Class Package Diagrams150. Create Use-Case Package Diagrams to Organize Your Requirements151. Include Actors on Use-Case Package Diagrams152. Arrange Use-Case Package Diagrams Horizontally153. Give Packages Simple, Descriptive Names154. Make Packages Cohesive155. Indicate Architectural Layers with Stereotypes on Packages156. Avoid Cyclic Dependencies between Packages157. Reflect Internal Relationships in Package Dependencies(6)UML Sequence Diagrams158. Strive for Left-to-Right Ordering of Messages159. Layer Object Lifelines160. Give an Actor the Same Name as a Class, If Necessary161. Include a Prose Description of the Logic162. Place Proactive System Actors on the Leftmost Side of Your Diagram163. Place Reactive System Actors on the Rightmost Side of Your Diagram164. Avoid Modeling Object Destruction165. Avoid Activation Boxes166. Name Objects Only When You Reference Them in Messages167. Name Objects When Several of the Same Type Exist168. Apply Textual Stereotypes to Lifelines Consistently169. Focus on Critical Interactions170. Justify Message Names beside the Arrowhead171. Create Objects Directly172. Apply Operation Signatures for Software Messages173. Apply Prose to Messages Involving Human and Organization Actors174. Prefer Names over Types for Parameters175. Indicate Types as Parameter Placeholders176. Apply the <<include>> Stereotype for Use Case Invocations177. Do Not Model Obvious Return Values178. Model a Return Value Only When You Need to Refer to It Elsewhere in a Diagram 179. Justify Return Values beside the Arrowheads180. Model Return Values as Part of a Method Invocation181. Indicate Types as Return-Value Placeholders182. Indicate the Actual Value for Simple Return Values(7)UML Communication Diagrams183. Create Instance-Level Diagrams to Explore Object Design Issues184. Create Specification-Level Diagrams to Explore Roles185. Apply Robustness Diagram Visual Stereotypes186. Do Not Use Communication Diagrams to Model Process Flow187. Create a Sequence Diagram When Sequence Is Important188. Apply Sequence Diagram Guidelines to Instance-Level Communication Diagrams 189. Indicate Parameters Only When They Aren’t Clear190. Depict an Arrow for Each Message191. Consolidate Getter Invocations192. Indicate Concurrent Threads with Letters193. Model “Bare” Links on Instance-Level Communication Diagrams194. Show Role-Pertinent Information in Specification-Level Diagrams195. Prefer Roles on Links Instead of Within Classes196. Indicate Navigability Sparingly197. Use Links to Reflect Consistent Static Relationships(8)UML State Machine Diagrams198. Create a State Machine Diagram When Behavior Differs Based on State199. Place the Initial State in the Top Left Corner200. Place the Final State in the Bottom Right Corner201. State Names Should Be Simple but Descriptive202. Question “Black-Hole” States203. Question “Miracle” States204. Model Substates for Targeted Complexity205. Aggregate Common Substate Transitions206. Create a Hierarchy of State Machine Diagrams for Very Complex Entities 207. Always Include Initial and Final States in Top-Level State Machine Diagrams 208. Name Software Actions Using Implementation-Language Naming Conventions 209. Name Actor Actions Using Prose210. Indicate Entry Actions Only When Applicable to All Entry Transitions211. Indicate Exit Actions Only When Applicable to All Exit Transitions212. Model Recursive Transitions Only When You Want to Exit and Reenter the State 213. Name Transition Events in Past Tense214. Place Transition Labels near the Source States215. Place Transition Labels on the Basis of Transition Direction216. Do Not Overlap Guards217. Introduce Junctions to Visually Localize Guards218. Use Guards Even If They Do Not Form a Complete Set219. Never Place a Guard on an Initial Transition220. Use Consistent Language for Naming Guards(9)UML Activity Diagrams221. Place the Starting Point in the Top Left Corner222. Include an Ending Point223. Simplify Operations Requiring Flow Charts224. Apply Connectors to Avoid Unwieldy Activity Edges225. Connectors Should Match226. Label Connectors with Numbers227. Question “Black-Hole” Activities228. Question “Miracle” Activities229. Reflect the Previous Activity by Using Decision Points230. Avoid Superfluous Decision Points231. Ensure That Each Activity Edge Leaving a Decision Point Has a Guard232. Do Not Overlap Guards233. Ensure That Guards on Decision Points Form a Complete Set234. Ensure That Exit Guards and Activity Invariants Form a Complete Set235. Apply an [Otherwise] Guard for “Fall-Through” Logic236. Model Guards Only If They Add Value237. Indicate Decision Logic over Complex Guards238. Simplify Guards By Indicating Decisions Within Diamonds239. Ensure That Forks Have Corresponding Joins240. Ensure That a Fork Has Only One Entry241. Ensure That a Join Has Only One Exit242. Avoid Superfluous Forks243. Activity Edges Should Enter Joins and Forks from the Same Side244. Model Joinspecs Only When the Join Isn’t Clear245. Align Fork and Join Bars246. Order Swim Lanes in a Logical Manner247. Apply Swim Lanes to Linear Processes248. Have Fewer than Five Swim Lanes249. Replace Swim Lanes with Swim Areas in Complex Diagrams250. Reorganize into Smaller Activity Diagrams When Swim Areas Include Several Activities 251. Consider Horizontal Swim Lanes for Business Processes252. Model the Key Activities in the Primary Swim Lane253. Model Action Objects as Names on Activity Edges254. Depict Input Pins on the Left255. Depict Output Pins on the Right256. Pins Should Have Names Describing the Parameter(s)257. Avoid Superfluous Pins258. Model Action Objects only when they are not obvious259. Place Shared Action Objects on Swim Lane Separators260. Apply State Names When an Object Appears Several Times261. Reflect the Life-Cycle Stage of an Action Object in Its State Name262. Show Only Critical Inputs and Outputs263. Depict Action Objects as Smaller than Activities(10)UML Component Diagrams264. Apply Descriptive Names to Architectural Components265. Apply Environment-Specific Naming Conventions to Detailed Design Components 266. Apply Consistent Textual Stereotypes267. Avoid Modeling Data and User Interface Components268. Apply One Component Stereotype Consistently269. Show Only Relevant Interfaces270. Model Dependencies from Left to Right271. Place Inheriting Components below Base Components272. Make Components Dependent Only on Interfaces273. Avoid Modeling Compilation Dependencies(11)UML Deployment Diagrams274. Indicate Software Components on Project-Specific Diagrams275. Assume That Nodes Are Devices276. Use Concise Notation277. Apply Drum Notation for Data Stores278. Focus on Nodes and Communication Associations in Enterprise-Level Diagrams 279. Group Common Nodes280. Put Detail into Installation Scripts281. Use Descriptive Terms to Name Nodes282. Model Only Vital Software Components283. Apply Consistent Stereotypes to Components284. Apply Visual Stereotypes to Nodes285. Indicate Communication Protocols via Stereotypes286. Model Only Critical Dependencies between Components(12)UML Object Diagrams287. Indicate Attribute Values to Clarify Instances288. Prefer Object Names over Attribute Values289. Indicate Roles to Distinguish Different Relationships(13)UML Composite Structure Diagrams290. Focus on Object Roles in Collaboration-Style Composite Structure Diagrams 291. Focus on Collaborations in Detailed-Style Composite Structure Diagrams 292. Create Detailed-Style Composite Structure Diagrams over Collaboration Style 293. Create UML Object Diagrams Instead of Composite Structure Diagrams(14)UML Interaction Overview Diagrams294. Reference Other Diagrams, Don’t Depict Them295. Don’t List Lifelines(15)UML Timing Diagrams296. Draw a Continuous Timing Diagram for Analog Values297. Draw a Value Change Timing Diagram to Explore High-Level Life Cycles 298. Draw State Machine Diagrams to Explore Detailed Life Cycles299. Order the States Intelligently300. Model Time along the X Axis301. Don’t Label the Time Axis “Time”302. Center the X Axis Heading303. Place the Y Axis Heading at the Top Left304. Use Time Observations to Depict Specific Times305. Use Timing Marks to Depict a Time Series306. You Don’t Need to Label All Timing Marks307. Use Time Durations to Depict a Specific Period of Time308. Use Time Constraints to Bound a Specific Period of Time。
SA描述语言和UML

各种结构性、行为性事务都可放入一个包内。 一个包构成一个命名空间 包仅是一个概念,存在于开发阶段;而组件于运行时 真实存在 包的几种变形:frameworks, models, and subsystems
注记性事物——UML的说明性部分
dog-eared corner
Notes
Note依附于某个或多个UML元素, 对它们进行解释和说明
- 一系列的信息交互。
由具 体的 上下 文来 区分
State machine
- 一个对象或一个交互在其生命期内所处状态,及其对外部事件
的反应
Activity
- 一个计算过程所进行的一系列步骤action
群组性事物——UML的组织
主要的群组事物: 包
Name and/or Contents
图的层次结构
用例图
类图
行为图
状态图
活动图
交互图
- 顺序图 - 交流图
实现图
组件图 部署图
类图
类图表示一系列的类、接 口、协作、它们之间的关 系 类图是属于静态图
牢记:体系架构的建立是一个连续的、迭代的 过程,我们可能需要反复地重复上述基本步骤
IEEE 1471
A Brief History of the UML (0) 面向对象技术
面向对象语言
面向对象技术的发展历史
A Brief History of the UML (1)
第一个面向对象语言
使用面向对象技术,对系统建模(概念和实施)
对人和机器来说,都有用的语言
外文翻译--UML 2.0 序列图组合碎片

中文2270字UML2.0 Sequence Diagram Combined fragmentsThe diagram's purposeThe sequence diagram is used primarily to show the interactions between objects in the sequential order that those interactions occur. Much like the class diagram, developers typically think sequence diagrams were meant exclusively for them. However, an organization's business staff can find sequence diagrams useful to communicate how the business currently works by showing how various business objects interact. Besides documenting an organization's current affairs, a business-level sequence diagram can be used as a requirements document to communicate requirements for a future system implementation. During the requirements phase of a project, analysts can take use cases to the next level by providing a more formal level of refinement. When that occurs, use cases are often refined into one or more sequence diagrams.An organization's technical staff can find sequence diagrams useful in documenting how a future system should behave. During the design phase, architects and developers can use the diagram to force out the system's object interactions, thus fleshing out overall system design. One of the primary uses of sequence diagrams is in the transition from requirements expressed as use cases to the next and more formal level of refinement. Use cases are often refined into one or more sequence diagrams. In addition to their use in designing new systems, sequence diagrams can be used to document how objects in an existing (call it "legacy") system currently interact. This documentation is very useful when transitioning a system to another person or organization.The notationSince this is the first article in my UML diagram series that is based on UML 2, we need to first discuss an addition to the notation in UML 2 diagrams, namely a notation element called a frame. The frame element is used as a basis for many other diagram elements in UML 2, butthe first place most people will encounter a frame element is as the graphical boundary of a diagram. A frame element provides a consistent place for a diagram's label, while providing a graphical boundary for the diagram. The frame element is optional in UML diagrams; as you can see in Figures 1 and 2, the diagram's label is placed in the top left corner in what I'll call the frame's "namebox," a sort of dog-eared rectangle, and the actual UML diagram is defined within the body of the larger enclosing rectangle.In most sequence diagrams, however, the UML 1.x "in-line" guard is not sufficient to handle the logic required for a sequence being modeled. This lack of functionality was a problem in UML 1.x. UML 2 has addressed this problem by removing the "in-line" guard and adding a notation element called a Combined Fragment. A combined fragment is used to group sets of messages together to show conditional flow in a sequence diagram. The UML 2 specification identifies 11 interaction types for combined fragments.AlternativesAlternatives are used to designate a mutually exclusive choice between two or more message sequences. 3 Alternatives allow the modeling of the classic "if then else" logic (e.g., if I buy three items, then I get 20% off my purchase; else I get 10% off my purchase).As you will notice in Figure 8, an alternative combination fragment element is drawn using a frame. The word "alt" is placed inside the frame's namebox. The larger rectangle is then divided into what UML 2 calls operands. 4 Operands are separated by a dashed line. Each operand is given a guard to test against, and this guard is placed towards the top left section of the operand on top of a lifeline. 5 If an operand's guard equates to "true," then that operand is the operand to follow.Figure 8: A sequence diagram fragment that contains an alternative combination fragment As an example to show how an alternative combination fragment is read, Figure 8 shows the sequence starting at the top, with the bank object getting the check's amount and the account's balance. At this point in the sequence the alternative combination fragment takes over. Because of the guard "[balance >= amount]," if the account's balance is greater than or equal to the amount, then the sequence continues with the bank object sending the addDebitTransaction and storePhotoOfCheck messages to the account object. However, if the balance is not greater than or equal to the amount, then the sequence proceeds with the bank object sending the addInsuffientFundFee and noteReturnedCheck message to the account object and the returnCheck message to itself. The second sequence is called when the balance is not greater than or equal to the amount because of the "[else]" guard. In alternative combination fragments, the "[else]" guard is not required; and if an operand does not have an explicit guard on it, then the "[else]" guard is to be assumed.Alternative combination fragments are not limited to simple "if then else" tests. There can be as many alternative paths as are needed. If more alternatives are needed, all you must do isadd an operand to the rectangle with that sequence's guard and messages.OptionThe option combination fragment is used to model a sequence that, given a certain condition, will occur; otherwise, the sequence does not occur. An option is used to model a simple "if then" statement (i.e., if there are fewer than five donuts on the shelf, then make two dozen more donuts).The option combination fragment notation is similar to the alternation combination fragment, except that it only has one operand and there never can be an "else" guard (it just does not make sense here). To draw an option combination you draw a frame. The text "opt" is placed inside the frame's namebox, and in the frame's content area the option's guard is placed towards the top left corner on top of a lifeline. Then the option's sequence of messages is placed in the remainder of the frame's content area. These elements are illustrated in Figure 9.Figure 9: A sequence diagram fragment that includes an option combination fragment Reading an option combination fragment is easy. Figure 9 is a reworking of the sequence diagram fragment in Figure 7, but this time it uses an option combination fragment because more messages need to be sent if the student's past due balance is equal to zero. According to the sequence diagram in Figure 9, if a student's past due balance equals zero, then the addStudent, getCostOfClass, and chargeForClass messages are sent. If the student's past duebalance does not equal zero, then the sequence skips sending any of the messages in the option combination fragment.The example Figure 9 sequence diagram fragment includes a guard for the option; however, the guard is not a required element. In high-level, abstract sequence diagrams you might not want to specify the condition of the option. You may simply want to indicate that the fragment is optional.LoopsOccasionally you will need to model a repetitive sequence. In UML 2, modeling a repeating sequence has been improved with the addition of the loop combination fragment.The loop combination fragment is very similar in appearance to the option combination fragment. You draw a frame, and in the frame's namebox the text "loop" is placed. Inside the frame's content area the loop's guard 6 is placed towards the top left corner, on top of a lifeline. Then the loop's sequence of messages is placed in the remainder of the frame's content area. In a loop, a guard can have two special conditions tested against in addition to the standard Boolean test. The special guard conditions are minimum iterations written as "minint = [the number]" (e.g., "minint = 1") and maximum iterations written as "maxint = [the number]"(e.g., "maxint = 5"). With a minimum iterations guard, the loop must execute at least the number of times indicated, whereas with a maximum iterations guard the number of loop executions cannot exceed the number.Figure 10: An example sequence diagram with a loop combination fragmentThe loop shown in Figure 10 executes until the reportsEnu object's hasAnotherReport message returns false. The loop in this sequence diagram uses a Boolean test to verify if the loop sequence should be run. To read this diagram, you start at the top, as normal. When you get to the loop combination fragment a test is done to see if the value hasAnotherReport equals true. If the hasAnotherReport value equals true, then the sequence goes into the loop fragment. You can then follow the messages in the loop as you would normally in a sequence diagramUML 2.0 序列图组合碎片图的目的序列图主要用于按照交互发生的一系列顺序,显示对象之间的这些交互。
SA03 - 架构描述语言(ADL)--UML概述

软件架构Software Architecture叶红星博士技术总监yehx@神州数码系统集成服务有限公司培训中心架构描述语言(ADL)统一建模语言(UML)概述目标当完成这一章时,你应能:•熟练掌握统一建模语言(UML)的定义•熟练掌握UML的结构•熟练掌握UML的元模型UML的定义The UML is a language for•visualizing•specifying•constructing•documentingthe artifacts of software systems.UML是一种用于可视化、详述、构造、记录软件系统的制品的语言。
UML 的发展历史-1Booch method OMT Unified Method 0.8OOPSLA ´95OOSEOther methods UML 0.9Web -June ´96public feedbackFinal submission to OMG, Sep ‘97First submission to OMG, Jan ´97UML 1.1OMG Acceptance, Nov 1997UML 1.0UML partners UML 1.409/2001UML 1.3June 1999UML 1.503/2003UML 2.007/2005UML 的发展历史-2March 20001.3September 2001 1.4July 2004 1.4.2(ISO/IEC 19501:2005)March 20031.5 July 20052.0August 20072.1.1November 20072.1.2(ISO/IEC DIS 19505:2008)February 20092.2发布日期版本UML的结构UML的建筑块UML的建筑块——事物1.结构性事物(Structural things)UML模型的静态的部件,UML的名词2.行为性事物(Behavioral things)UML模型的动态的部件,UML的动词3.分组事物(Grouping things)UML模型的组织性的部件4.注释事物(Annotational things)UML模型的解释性的部件结构性的事物1.Class(类)2.Active C lass(主动类)3.Interface(接口)ponent(组件/构件)e Case(用例)6.Colloboration(协作)7.Artifact(制品/工件)8.Node(节点)所有的结构性的事物统称为类元(Classifier)用例•A use case is a description of a set of sequence of actions a system performs that yields an observable result of value to a particular actor.•用例是对一组动作序列的描述,系统执行这些动作,它们对一个特定的参与者产生一个有价值的可观察的结果。
DoDAF 2.0 可靠性建模方法论:基于设备系统的运营观点说明书

Mission Reliability Modeling for Equipment System Based on the Operational Viewpoint ofDoDAF 2.0Lin Shaoyang,College of Information System and Management National University of Defense TechnologyChangsha, P. R. China***************************Wu XiaoyueCollege of Information System and Management National University of Defense TechnologyChangsha, P. R. ChinaAbstract—Currently, Department of Defense Architecture Framework (DoDAF) 2.0 is widely used in many aspects of the architecture-related modeling fields. Due to the highly complex structure of architecture, its reliability became a pivotal issue. However, DoDAF 2.0 is lack of a specific viewpoint to model the reliability of the architecture. This paper introduces an approach to deal with reliability modeling method related missions posed by Equipment System (ES), which is an obvious characterized architecture. OV-1, OV-5a and OV-6c of DoDAF 2.0's operational viewpoint are extracted and extended as the modeling framework. Use case diagram, class diagram and sequence diagram of Unified Modeling Language (UML) are picked to present the products mentioned. The study also regulates a series of standards for each extended product in detail, in order to collect requisite reliability-related parameters for further analysis and calculation. Later, the proposed model is applied to an ES as an example to verify its availability.Keywords-reliability modeling; equipment system; mission reliability; equipment system; operational viewpoint; DoDAF2.0I.I NTRODUCTIONEquipment System (ES) is made up of wide ranges of correlative and function-complementary equipment, which integrate into an organic integrity of diverse categories, structures and scales, according to the claim of optimal placement and operational capability, thus making up a large high-level system, namely System of Systems (SoS) or architecture.Reliability is a key performance parameter in system design, so has become a basis factor affecting mission success [1]. Mission is the foundation of ES, since all member of ES are related with each other as a whole by the same target—achieving the specific destination. Mission reliability refers to the probability that a system will perform its specified mission in its mission section [2]. Therein, mission section is the profile to the events and time sequence the mission has to follow. Mission reliability reflects the ability of fulfilling the task successfully, thus playing a big part in ES operational effectiveness.On the basis of multi-view method, Architecture Framework (AF) provides a collection of normalized modeling process and description method, which standardizes the contents contained to ensure the unified understanding and comparing principal from all stakeholders [3]. Currently DoDAF 2.0 of U.S. is often adopted as descriptive model in military field [4-6]. Nonetheless, no specialized reliability modeling viewpoint or product arises in DoDAF 2.0.Several reliability modeling methods have been used in the mission reliability analysis. Fault tree analysis is suitable in describing non-repairable systems in [7–9], but its limitations become apparent when conducted to quantitative issues. Bayesian Networks were developed as a logic graphical representation [10–11], and it has shown its agile computation efficiency. This approach is also applied in the proposed methodology. Later, state-space models, namely Markov chains and Petri nets, appear as main methods for analyzing system's dynamic reliability [12-14]. However, it has the state space growth explosion problem.Yet, methods mentioned above show weakness on describing ES, since ES usually has great amount of units of different levels and complicated logical relations. On the other hand, product sets of DoDAF 2.0 do not supply all sufficient data for ES reliability analysis. In the paper, we propose a reliability modeling framework based on the operational viewpoint of DoDAF 2.0, viewing to probe into a reliability modeling framework to ES.For the rest of the paper, section II introduces DoDAF 2.0 and its operational viewpoint. Section III demonstrates the processed reliability modeling product set and its UML description in detail. Section IV describes the application of this approach to an ES as a case study. Section V summarizes the paper and gives a perspective to further research.II.D O DAF2.0A ND I TS O PERATIONAL V IEWPOINTDoDAF 2.0 is a graphical and tabular description for SoS. It provides general guidance for development, usage and management of DoD architectures with an emphasis on interoperability and integration between constituentInternational Conference on Logistics Engineering, Management and Computer Science (LEMCS 2014)systems in SoS [15]. In total, 8 viewpoints and 52 products are built in DoDAF 2.0.Viewpoint replaces "view" of antecedent versions, in order to coordinate with ISO. These viewpoints are further classified for describing the overarching aspects for every viewpoint (All Viewpoint, AV), requirements and deployments (Capability Viewpoint, CV), data relationships and alignment structure (Data and Information Viewpoint, DIV), operation scenarios and activities (Operational Viewpoint, OV), relationships between OV&CV and projects being implemented (Project Viewpoint, PV), performers, activities services and their exchanges (Service Viewpoint, SvcV), applicable principals (Standard Viewpoint, StdV), and the composition, interconnectivity and context (System Viewpoint, SV),as Fig.1 demonstrating. Each of these views has a well-defined product set in accordance with different perspectives.The DoDAF 2.0 viewpoints reside in a presentation layer, underlying which there is a data layer where defining attributes and relationships of the architecture can be documented [16]. There is a natural and straight correspondence between AF and UML [3]. Additionally, DoDAF 2.0 formalism is increasingly being supported by other commercially available architecting tools, in which documents, sheets, matrices and such structured presentations are employed to narrow development cycle, e.g. DOORs of Telelogic, Requisite Pro of Rational and Caliber RM of Borland. One of the advantages UML possesses is that not only does it allow capturing DoDAF 2.0's data layer but also supports modeling and simulation on purpose of verification.OV describes the missions and activities, operational elements, and resource flow exchanges required to conduct operations [16]. OV is adept at tracing system's dynamic behaviors and transformation, and just such character makes it quiet suitable for modeling ES mission reliability. OV has 9 products in total, involved capturing organization relationships, resource flows, state transition and other architecture's characters. For mission reliability modeling, this paper provides a tailored product set, including OV-1, OV-5a and OV-6c to model ES's mission reliability, and it would be elaborately discussed in nextFigure 1. DoDAF 2.0 eight viewpoints.III.M ISSION R ELIABILITY M ODEL U NDER OVProduct SetThe clipped product set of ES mission reliability model is shown in Fig. 1.OV-1 aims at describing the contents and processes of the mission(s) that ES has to fulfill. Graph of jpg is recommended as the storage format. Its visualized representation enables further reliability modeling, meanwhile offering information particularly concerned by high-level decision makers during their decision process. OV-1's contents depend on the unique objective and application of specific ES. In general, it may involve operation processes, organization hierarchy, geographical distribution and operational expectations including what missions will emerge, which unit(s) will undertake, what sequences should be complied with et al, and also the interaction with external environment and systems. The links between two elements are suggested but not limited as one of the follows:∙Control: Control link from A to B means B's activity is managed by A's instructions.∙TrackInfo: TrackInfo link represents the information flow movements.∙Assistance: Assistance link from A to B indicates that if B gets failed, A would make up.∙Affirm: Affrim link reports the lower equipment's being- state and attack-complete state from lowerlevel to the command center.The relationships of the elements on the diagram sometimes convey their relative position, although this is not specifically captured in the semantics. Since each ES differs, we do not set specific rules for OV-1.OV-5a is a newly created product in DoDAF 2.0, in order to describe mission constituents and their hierarchical structure. Through the decomposition it can be cleared that the duty each mission should accomplish and unnecessary redundancy that can be eliminated. Thus the model could be simplified and efficiency may be improved as well. To clarify the affect that lower-level failure brought about to higher missions, logic connections are introduced into OV-5a. Currently 'AND' gate and 'OR' gate are mainly considered. They can be defined as follows.Def. 1AND gate: Only when all nodes under AND gate succeed does mission above the gate succeed, as Fig. 2(a).Def. 2OR gate: As long as at least one of the nodes under OR gate succeeds will mission above the gate succeed, as Fig. 2(b).OV-6c depicts the sequence and information exchanges between phases. Through constant refining to the mission process, execution order and rules would be gradually precise and accurate. UML sequence diagram is adopted as representation standard. Sequence division is consistent with divided layered graph of OV-5a. On top of the graph is ES' object, accompanied by its relevant lifeline. Specific time points are labeled on left of the lifeline labels. Bars on the lifeline stand for its duration time. Solid arrow line is message transiting between objects.In each phase's sequence diagram, time propels in terms of lifeline. In reality, lifeline is finite and does not fit for long-time phase. Thus object's lifeline should be regulated in more details. As Fig. 3 shows, on left of the object A's lifeline, t11represents A's start time and similarly t12 end time, while t21 is the time message 1 from another object arrives. t22 on the right indicates message 2 leaving time.A N DP 1P 2AO RP 1P 2BFigure 2. (a) AND gate example. (b) OR gate examplemessage 2O bj ect A t 11t12t 22message 1t 21Figure 3. OV-5a UML sequence diagram representationIV. UML D EFINITIONa. OV-5a UML normalizationOV-5a describes the operations that are normally conducted in the different nodes. The extended use-case and class diagram provides a means of breaking down activities to lower level activities as well as indicating the nodes that perform the activities. It includes node, activity, link and logic relation. Their normalized data definition is shown in table 2 (a)-(d).b. OV-5a UML normalizationThe OV-6c is used to define time based behavioral scenarios between operational elements. The interactions can be service operations as well as the interactions defined on OV-5a diagrams. There are three types of elements in OV-6c: node, lifeline and message transit. Therein, node data definition is the same as OV-5a. Lifeline can be potentially described by the messageArrivingTime and messageLeavingTime attributes of message transit. Table 3 illustrates the data definition for message transit.TABLE I.ES M ISSION R ELIABILITY M ODELTABLE II.(A)D ATA D EFINITION F OR N ODETABLE III. (A) D ATA D EFINITION M ESSAGE TRANSITV.C ASE S TUDYAn ES is presented in this part as a detailed illustration to the proposed model. The system basically consists of five parts: Ground Based Interceptor (GBI), X band Ground Based Rader (GBR), Battle Management and Command, Control & Communications (BM/C3) system, Upgraded Early Warning Radar (UEWR), and Defense Support Program/Space-Based Infrared System (DSP/SBIRS) [17].GBI is an up-to-date kinetic energy antipersonnel weapon intercepting ballistic missile warheads in its midcourse outside the atmosphere and destroying it through straightly impact. Traditional GBI consists of Exoatmospheric Kill Vehicle (EKV) and two booster rockets.GBR is X band phased array radar, and it is the main fire control radar of the system, deployed at the same place with GBI. It mainly involves surveillance, capture, trace, identification, fire control assistance and damage evaluation.BM/C3 is the brain of system, connecting all constituent systems organically. It mainly involves in receiving data from each detector to analyze the striking missile's parameters (like speed, trajectory, point of fall et. al), calculating "sweet point", directing UEWR and GBR to trace and capture the target, giving launch orders to GBI, offering revised target information to the flying interceptor, evaluation intercepting effect, and so on. BM/C3 is also deployed with GBI and GBR.UWER is upgraded phased array radar used to detect and track ballistic missile and provide early warnings. It detects and traces ballistic missile initial flight and provides GBR rough azimuth information.DSP supplies early warnings for the system. Via merging data from two or more DSPs, ballistic trajectory can be forecasted. Furthermore, compared with foregone missiles' infrared characteristics, the ballistic version can be confirmed. Currently, DSP is gradually replaced by SBIRS, which consists of two kinds satellites: Lower Earth Orbit (LEO) and High Earth Orbit (HEO). Highly flexible infrared sensor technique of HEO conveys strategy, the launch and flight of theatre ballistic missile, global theatre infrared data and processed intelligence. LEO satellites are equipped with two kind sensors: the capture one is to observe flame during the rocket launch phase; the other trace one could keep in track with the locked target from its midcourse until back into the atmosphere.Fig. 4 is the OV-1 model of the system. Substantially the system functions in such procedures:1: Early warning phase1) DSP/SBIRS detects the booster's plume when the striking ballistic missiles launches, and traces until its booster rocker turning off. Via repeater satellite or earth station, DSP/SBIRS sends trackinfo back to BM/C3for predicting the striking missile's incoming direction as well as impact area. Pertinent data would also be sent to UEWR.2) After gets information of ballistic position, UEWR will search and detect associative airspace to trace the striking missile. When discovering missile warhead, it will track robustly and send trackinfo to BM/C3.2: Interception decision phase1) BM/C3formulates operations management plan, including intercepting pattern, interceptor quantity, calculating effective acting distance, thus preliminarily ascertaining GBI's launch direction and moment. Meanwhile BM/C3should send control information to GBI and receive affirm to get its authorization.2) BM/C3 sends trackinfo got from UEWR to GBR to guide its search. Through detecting and tracing ballistic warhead, GBR would retrieve more precise information for BM/C3decision. Meanwhile, GBR would generate warhead image by sufficient data it has collected.3) BM/C3conducts target identification and threat evaluation to verify the warhead version, the trajectory and the impact point. On this basis, interception decision about GBI's launch moment and estimated interception point is made. When the accuracy of the estimated interception point is within the appointed scope (20km), BM/C3 would give GBI launching orders targeting on the estimated interception point.3:Interception implementation phase1) As soon as receiving orders, GBI launches immediately. After that, GBR precisely tracks GBI and warhead, returns revised objective data back to BM/C3 to update GBI's flight.2) When GBI reaches the estimated airspace, EKV separates with the booster rocket. Then EKV compares the target information detected with former images provided by GBR to verify and target objective, thus destroying it through straight collision.4: Interception effectiveness evaluation1) During the GBI collision, GBR collects interception data sending back to BM/C3.2) BM/C3evaluated the interception effectiveness. If failed, BM/C3 has to decide whether to conduct a second interception.According to the procedure, its operational activities decomposition can be depicted like Fig. 5(a). Furthermore, Fig. 5(b) shows the class diagram for the case "EKV attack". On purpose of saving space, some of the class attribute values and operations have been omitted. For the proposed model of OV-6c, the above mentioned interception decision phase is hired as an example, and it is shown in Fig. 6.VI.C ONCLUSIONDoDAF 2.0 is a rife model framework for ES. The paper proposes a mission reliability modeling method based on the operational viewpoint of DoDAF 2.0 and illustrates the UML normalization. An ES is an example of highly complex and adaptive ES characterized by a loosely coupled federation of constituent systems. The proposed model succeeds in describing ES reliability structure, proving the methods validity. For further research, transition mechanism between OV-5a and OV-5b can be investigated in terms of enriching the product set and heterogeneous representation. Besides, UML entities can be enlarged for more abundant and convenient details. More importantly, system view's product can also be used on mission reliability modeling.A CKNOWLEDGMENTThe paper is partly supported by National Natural Science Foundation of China under grant no. 71071159.Figure 4.OV-1 modelD S P /S B I R Sdet ect pl um et racem i ssi l est ore dat asend i nf o.recei ve com m andU E W Rsearchw arheadG B IG B Rl aunch gi ve orders<extends><extends>revi se fli ghtseparat eboost ersE K V at t ack<extends><extends><extends>recei vei nf o.cal cul at edeci degenerat ei m ageFigure 5. (a) OV-5a modelactivityIDnodeContained activityDescription successrulesE K VA t t acknodeId ofActivity linkIn linkToprerequisitesuccessProbability startTime endTimeE K V S eparat enodeId ofActivity linkIn linkToprerequisitesuccessProbability startTime endTimeA t t ackO rdermessageType messageIdmessageFrom: GBR, UEWR messageArrivingTime Fl i ght P osi t i onE K V posi t i oni ngmessageType messageIdmessageFrom: GBR messageArrivingTimeR evi sed Fl i ght ANDmessageType messageId messageFrom messageTomessageArrivingTime messageLeavingTimeTarget V eri ficat i on ANDFigure 5. (b) OV-5a class diagram for the case "EKV attack"U E W RG B RB M /C 31: controlAuthorizationG B I6: launch decision order(position,time)3: traceMessage5: traceMessagewarhead image4: traceMessage 2: af f i r m at i onFigure 6. OV-6c Sequence diagram for interception decision phaseR EFERENCES[1] Reliability primer for command, control, communications,computer, intelligence, surveillance, and reconnaisssance (C4ISR) facilities. available at: http: // www. usace. ary. mil /publications/ armytm/tm5-698-3/entire.pdf.2005a.[2] Chul Kim, “Analysis for mission reliability of a combat tank ,”IEEE Transactions on Reliability, vol. 38, no. 2, pp 242-245, 1989. [3] Robert K. Garrett, Steve A., Neil T Baron, “Managing theinterstitials, a system of systems framework suited for the ballistic missile defense system ,” Systems Engineering, vol 14,no. 1, pp. 87-108,2011.[4] Yang Kewei and Tan Yuejin, Architecture RequirementsTechnique and Method. Peking: Science Press, 2010.[5] Shu Yu, Research on weapon equipment architecture modelingmethod and application based on the capability requirements, Ph.D. Dissertation, National University of Defense Technology, 2009. [6] Jiang Zhiping, Research on architecture verification method andkey technique for C4ISR system based on CADM, Ph.D. Dissertation, National University of Defense Technology, 2007. [7] Bobbio A., Portinale L, “Improving the analysis of dependablesystems by mapping fault trees into Bayesian networks ,” Reliability Engineering & System Safety, vol. 71, no. 5, pp 249-260, 2001.[8] Hichem Boudali, Joanne,Bechta Dugan, “Dynamic fault treemodels for fault tolerant computer systems ,” IEEE Transaction On Reliability, vol. 41, no. 3, pp 363-377, 1992.[9] Huang Chin-Yu, Chang Yung-Ruei, “An improved decompositionscheme for assessing the reliability of embedded systems by using dynamic fault trees,” Reliability Engineering & System Safety, vol 92, no. 10, pp 1403-1412, 2007.[10] Boudali H., Dugan J. B, “A discrete-time Bayesian networkreliability modeling and analysis framework ,” Reliability Engineering & System Safety, vol 87, no. 6, pp 337-349, 2005. [11] Hichem Boudali, Joanne Bechta Dugan, “A continuous-timeBayesian network reliability modeling and analysis framework ,” IEEE Transaction On Reliability, vol 55, no. 1, pp 34-41, 2006. [12] Jau-Yeu Menq, Pan-Chio Tuan, “Discrete Markov ballistic missiledefense system modeling ,” European Journal of Operational Research, vol 178, no. 1, pp 560-578, 2007.[13] Kim K, Park S, “Phased-mission system reliability under Markovenvironment ,” IEEE Transaction On Reliability, vol 43, no. 5, pp 301-309, 1994.[14] Abidin E.Olmez, “Mission centric reliability analysis of C4ISRarchitectures using petri net ,” In Proceedings of IEEE International Conference on Systems, Man and Cybernetics, pp 587-592, 2003. [15] Department of Defense Architecture Working Group, DoDArchitecture Framework 2.0, Volume 2: Architecture and Models, available at: /Portals/0/Documents/DODAF/DoDAF_v2-02_web.pdf[16] Biswas, A, Hayden, J, Phillips, MS, Bhasin, KB, Putt, C, &Sartwell, T, “Applying DoDAF to NASA orion mission communication and navigation architecture. In Proceedings of IEEE Aerospace Conference, pp 1-9, 2008.[17] Wang Minle and Li Yong, Ballistic Missile PenetrationEffectiveness Analysis. Peking: National Defense Industry Press, 2010.。
TU Munich

A Compositional Approach to Statecharts SemanticsGerald L¨uttgen ICASE,NASA Langley Research Center Hampton,VA23681–2199USA luettgen@ Michael von der BeeckDepartment of Comp.Sc.TU MunichD–80290M¨unchenGermanybeeck@in.tum.deRance CleavelandDepartment of Comp.Sc.SUNY at Stony BrookStony Brook,NY11794–4400USArance@ABSTRACTStatecharts is a visual language for specifying reactive system be-havior.The formalism extends traditionalfinite–state machines with notions of hierarchy and concurrency,and it is used in many popular software design notations.A large part of the appeal of Statecharts derives from its basis in state machines,with their in-tuitive operational interpretation.The classical semantics of State-charts,however,suffers from a serious defect:it is not composi-tional,meaning that the behavior of system descriptions cannot be inferred from the behavior of their positionality is a prerequisite for exploiting the modular structure of Statecharts for simulation,verification,and code generation,and it also provides the necessary foundation for reusability.This paper suggests a new compositional approach to formaliz-ing Statecharts semantics asflattened labeled transition systems in which transitions represent system steps.The approach builds on ideas developed for timed process calculi and employs structural operational rules to define the transitions of a Statecharts expres-sion in terms of the transitions of its subexpressions.It isfirst pre-sented for a simple dialect of Statecharts,with respect to a vari-ant of Pnueli and Shalev’s semantics,and is illustrated by means of a small example.To demonstrate itsflexibility,the proposed approach is then extended to deal with practically useful features available in many Statecharts variants,namely state references,his-tory states,and priority concepts along state hierarchies. Categories and Subject DescriptorsD.2.1[Requirements/Specifications]:[languages];D.3.1[Pro-gramming Languages]:Formal Definitions and Theory;F.3.2[Se-mantics of Programming Languages]:[operational semantics]The aim of this paper is to present a new approach to defining State-charts semantics which combines all three abovementioned fea-tures in a formal,yet operationally intuitive,fashion.Our semantic account borrows ideas from timed process calculi[13],which also employ the synchrony hypothesis[2]and which allow one to rep-resent ordinary system behavior and clock ticks using labeled tran-sition systems.These transition systems are defined via structural operational rules[28]—i.e.,rules in SOS format—along the state hierarchy of the Statechart under consideration.Our semantics ex-plicitly represents macro steps as sequences of micro steps which begin and end with the ticking of a global clock.Thereby,compo-sitionality is achieved on the explicit micro–step level and causality and synchrony on the implicit macro–step level.The current work builds on previous research by the authors[20],which developed a compositional timed process algebra that was then used to em-bed a simple variant of Statecharts introduced in[21].That work indirectly yielded a compositional operational semantics for State-charts.In this paper,we re–develop the semantics of[20]with-out reference to a process algebra,thereby eliminating the rather complicated indirection.Our intention is to make the underlying semantic issues and design decisions for Statecharts more apparent and comprehensible.The paper also argues for theflexibility and elegance of our approach by extending our semantics to cope with popular Statecharts features used in practice,such as state refer-ences,history states,and priority concepts.Organization of this paper.The next section gives a brief overview of Statecharts,including our notation and its classical semantics. Section3presents our new compositional approach to Statecharts semantics.It also establishes a coincidence result with respect to the traditional step semantics and illustrates our approach by means of an example.Section4shows how our framework can be ex-tended to include various features employed in many Statecharts dialects.Finally,Section5discusses related work,while Section6 contains our concluding comments as well as some directions for future research.2.AN OVERVIEW OF STATECHARTS Statecharts is a specification language for reactive systems,i.e., systems characterized by their ongoing interaction with their en-vironment.The notation enriches basicfinite–state machines with concepts of hierarchy,concurrency,and priority.In particular,one Statechart may be embedded within the state of another Statechart, and a Statechart may be composed of several simultaneously ac-tive sub–Statecharts which communicate via broadcasting events. Transitions are labeled by pairs of event sets,where thefirst com-ponent is referred to as trigger and may include negated events, and the second is referred to as action.Intuitively,if the environ-ment offers all the positive but none of the negated events of the trigger,then the transition is enabled and can be executed,thereby generating the events in the label’s action.As an example,consider the Statechart depicted in Figure1.It consists of an and–state,labeled by,which denotes the paral-lel composition of the two Statecharts labeled by and,both of which are or–states describing a sequential state machine.Or–state is further refined by or–state and basic state,which are connected via transition labeled by.The label specifies that is triggered by the occurrence of event;its execution does not generate any new event as its action is empty.Or–state con-tains the basic states and,connected by transition with trigger and empty action;hence,is enabled if event occurs but event does not.Or–state consists of two basicFigure1:Example Statechart.states and connected via transition with label,so that upon occurrence of trigger event,transition can be executed and generate event.In this paper,wefirst consider a simple dialect of Statecharts that supports a basic subset of the popular features present in many Statecharts variants.In particular,it considers hierarchy and con-currency.However,it ignores interlevel transitions(i.e.,transitions crossing borderlines of states),state references(i.e.,triggers of the form in,where is the name of a state),and history states(re-membering the last active sub–state of an or–state).In addition, it does not attach any implicit priorities to transitions at different levels in the state hierarchy.To illustrate theflexibility of our approach,we show in Section4how it can be extended to deal with state references,history states,and the abovementioned pri-ority concepts.Interlevel transitions,however,cannot be brought in accordance with a compositional semantics,as they represent an unstructured“goto”behavior(cf.Section5).2.1Term–based SyntaxFor our purposes it is convenient to represent Statecharts not visu-ally but by terms,as is done in[20,21].Formally,let be a count-able set of names for Statecharts states,be a countable set of names for Statecharts transitions,and be a countable set of State-charts events.For technical convenience,we assume that and are disjoint.With every event we associate a negated coun-terpart and define df as well as df, for.The set SC of Statecharts terms is then defined by the following inductive rules.1.Basic state:If,then is a Statecharts term.2.Or–state:Suppose that and that are State-charts terms for,with df.Also letdf and,with.Then is a Statecharts term.Hereare the sub–states of,set contains the tran-sitions connecting these states,is the default state of, and is the currently active sub–state of.The transitions in are of the form df,where(a)is the name of,(b)source df is the source state of,(c)trg df is the trigger of,(d)act df is the action of,and(e)target df is the target state of.In the sequel,trg stands for trg and trg for trg.Since we assume that all state names and tran-sition names are mutually disjoint,we may uniquely referto states and transitions by using their names,e.g.,we may write for.We also assume that no transition produces an event which appears negated in its trigger.3.And–state:If,if are Statecharts terms for,and if df,then is a State-charts term,where are the(parallel)sub–states of.The Statecharts term corresponding to the Statechart depicted in Figure1is term which is defined as follows.dfdfdfdfdfdfdfdfdfNote that components two andfive of a transition in some or–state refer to the indexes of the source and target state in the sequence,respectively,and not to the states’names.2.2Classical SemanticsIn this section,we sketch the semantics of Statecharts terms adopted in[21],which is a slight variant of the“classical”Statecharts se-mantics as proposed by Pnueli and Shalev[29].We refer the reader to[21]for a detailed discussion of the underlying semantic issues.As mentioned before,a Statechart reacts to the arrival of some ex-ternal events by triggering enabled micro steps in a chain–reaction manner.When this chain reaction comes to a halt,a complete macro step has been performed.More precisely,a macro step comprises a maximal set of micro steps,or transitions,that(i)are relevant,(ii)are mutually consistent,(iii)are triggered by events offered by the environment or generated by other mi-cro steps,(iv)are mutually compatible,and(v)obey the princi-ple of causality.These notions may be defined as follows.Let SC,let be a transition in,let be a set of transitions in,and let.Transition is relevant for Statecharts term,in signs relevant,if the source state of is cur-rently active.Transition is consistent with all transitions in,in signs consistent,if is not in the same parallel com-ponent as any transition in.Transition is triggered by event set,in signs triggered,if the positive but not the negative trigger events of are in.Transition is compatible with all transitions in,in signs compatible,if no event produced by appears negated in a trigger of a transition in.Finally,we say that transition is enabled in with re-spect to event set and transition set,if enabled, where enabled df relevant consistent triggered act compatible.A macro step is a subset of transitions in enabled that is causally well-founded.Technically,causality holds if there exists an order-ing among the transitions in a macro step such that no transition depends on events generated by transitions occurring after in the macro step.In[21],an operational approach for causally justifying the triggering of each transition of a macro step is given.It em-ploys the nondeterministic step–construction function presented inTable1:Step–construction functionTable1,which is adapted from Pnueli and Shalev[29].Given aStatecharts term and a set of environment events,the step–construction function nondeterministically computes a set of transitions.In this case,Statecharts term may evolve in the single macro step to Statecharts term,thereby executing the transitions in and producing the events df act.Term can be derived from by updating the index in everyor–state of satisfying for some .Observe that once one has constructed a macro step,all information about how the macro step was derived at is discarded.This is the source for the compositionality defect of this semanticsfor Statecharts:when two Statecharts are composed in parallel,thecombination of the causality orderings may introduce newly en-abled transitions(cf.[19]).Let us illustrate a couple of macro steps of the example State-chart depicted in Figure1.For convenience,we abbreviate a State-charts term by its active basic states,e.g.,term is abbreviatedby.Moreover,we let df and assume that the environment only offers event.Then,both transitions and are enabled,and the execution of results in macro step,i.e.,a macro step in which only a single tran-sition takes part.Although is also enabled,it cannot be executed together with in the same macro step.Otherwise,global con-sistency is violated since generates event whose negated coun-terpart is contained in the trigger of.However,transitions and can take part in the same macro step,as is located in a dif-ferent parallel component than and is triggered by event which is generated by.This leads to macro step. All macro steps of our example Statechart can be found in Figure3.3.A COMPOSITIONAL SEMANTICSWhile Pnueli and Shalev’s semantics has the advantage of simplic-ity,it is not compositional:it relies on a global analysis of an entire Statecharts expression in order to infer its macro steps.In particu-lar,it does not compute the macro steps of a Statechart in terms of the macro steps of its subcomponents.When the Statechart in ques-tion is large,the procedure can therefore be slow,since the macro steps of subcomponents cannot be“precomputed”and reused.It also means that the semantics cannot be used as a basis for modu-lar reasoning about Statecharts.In the following,we present our approach to defining a composi-tional semantics for Statecharts.Our framework is based onflatlabeled transition systems and is defined in the SOS style,i.e.,via structural operational rules[28].Each such rule is of the formnamepremisesynchrony hypothesismacro stepFigure 2:Illustration of our operational semantics.and should be read as follows:Rule (name )is applicable if boththe statements in its premise and its side condition hold;in this case,one might infer the conclusion .The benefits of employing SOS –style semantics are manifold.Most tools for the formal analy-sis and verification of systems rely on compilers which translate a textual system specification,e.g.,a Statechart term,into a la-beled transition system or a Kripke structure [5].Examples of such tools are those offering equivalence checkers and/or model check-ers,including the CONCURRENCY WORKBENCH [6],SPIN [14],and SMV [24].In addition,several meta–theories regarding SOS –style semantics have been developed.Of most relevance to our work are results which infer the compositionality of a semantics from the syntactical structure of the premises,conclusions,and side conditions of the SOS rules defining it [35].3.1Our approachIn contrast to related work,we develop an operational semantics on the micro–step level rather than the macro–step level and represent macro steps as sequences of micro steps.Within such a setting,compositionality is easy to achieve.The challenge is to identify the states at which macro steps start and end so that Statecharts’tradi-tional,non–compositional macro–step semantics can be recovered.Our solution is based on the observation that since Statecharts is a synchronous language,ideas from timed process calculi may be adapted.In particular,we use explicit global clock ticks to denote the boundaries of macro steps.Our flat labeled transition systems therefore possess two kinds of transitions:those representing the execution of a Statecharts tran-sition and those representing global clock ticks.In timed pro-cess calculi such transitions are referred to as action transitions and clock transitions ,respectively.The ideas behind our seman-tics are illustrated in Figure 2,where clock transitions are labeled by .The other transitions are action transitions and actually carry pairs of event sets as labels.An action transition stands for a single Statechart transition which is enabled if the system en-vironment offers all events in but none in .The states of our transition systems are annotated with (extended)Statecharts terms from which one may infer the events generated at any point of execution of the considered Statechart.Accordingly,the clas-sical macro–step semantics of Statecharts can be recovered from our semantics as follows:assume that the global clock ticks,sym-bolizing the beginning of a macro step,when the system environ-ment offers the events in .Starting from a clock transition,followTable 2:Functions out (top)and default (bottom)default df default df defaultdefaultdfdefaultSCSC andSCSC ,are defined via SOS rules.Table3:Operational rules:action transitionstrgANDoutcBASdefaulttarget cOR3The operational rules for action transitions are given in Table3,where the subscript of the transition relation should be ignored fornow;the subscript will only be needed in Section4.3.For conve-nience,we write.More-over,we let stand for the sequence and write for.Rule(OR1)states that or–state can evolve to if transition is enabled,i.e.,if(i)the source state of is the currently active state,(ii)all its positive trigger events trg are offered by the environment,(iii)the positive counterparts of all its negated trigger events trg are not offered by the envi-ronment,and(iv)the negated events corresponding to act are not offered by the environment,i.e.,no transition within the same macro step has alreadyfired due to the absence of such an event. The latter is necessary for implementing global consistency in our semantics.Rules(OR2)and(OR3)deal with the case that an in-ner transition of the active sub–state of the considered or–state is executed.Hence,sub–state needs to be updated accordingly. The resulting micro term also reflects—via the double colons—that a transition originating within the or–state has been executed,in which case the or–state may no longer en-gage in a transition in during the same macro step,i.e.,before executing the next clock transition.Finally,Rule(AND)deals with and–states.If sub–statefires a transitionholds, which stands forholds—,a clock tick can be accepted and does not result in any change of state(cf.Rule(cOR2)).Rule(cOR3)formalizes the be-havior that an or–state can engage in a clock transition if its active sub–state can engage in one.Finally,Rule(cAND)states that an and–state can engage in a clock transition if all its sub–states can, provided that there is no action transition whose execution cannot be prevented,i.e.,provided that6t (6)69n , t 29(75n (6n ), t 5n 2ba 6)(5n ab σFigure 3:Our semantics (left)and the macro–step semantics (right)for the Statechart in Figure 1.with inputand outputto,if there existSC ,,and,for some,such that 1.,,and.While Conds.(2)and (3)guarantee that all considered action tran-sitions are enabled by the environment,Cond.(5)ensures the max-imality of the macro step,i.e.,it implements the synchrony hy-pothesis.Now,we can establish the desired result,namely that our macro–step semantics coincides with the classical macro–step se-mantics of Statecharts.T HEOREM 3.1(C OINCIDENCE RESULT ).Let SC aswell as.Then,if and only if.P ROOF .(Sketch .)Consider the following construction.Ifis a sequence of Statecharts transitions of SCgenerated by the step–construction function relative to environmentand satisfying out ,then there exists a se-quence ofaction transitions as described in Def.1,such that the -th action transition corresponds to the execution of in .Vice versa,assume that the conditions of Def.1are satisfied for some and that is the sequence of State-charts transitions which can be identified with the considered se-quence of action transitions starting in .Then,can be generated by the step–construction function relative to and ,where the transitions fire in the order indicated by sequence .3.4ExampleWe now return to our example Statechart of Figure 1.Our seman-tics of this Statechart and its classical macro–step semantics are depicted on the left and right in Figure 3,respectively.In both dia-grams,we represent a transition of the formout df inout df out in out df outinout df outinoutdfacttrgin,whereout,and the second macro step is encoded bythe sequence,where out.4.EXTENSIONSWe now illustrate the flexibility of our approach by adapting it to incorporate features offered by many popular Statecharts variants,namely state references ,history mechanisms ,and priority concepts along the or–state hierarchy.4.1State ReferencesMany Statecharts variants permit trigger events of the form in ,for,which are satisfied whenever state is active.In our setting,we may encode this feature via the employed communica-tion scheme.To do so,we first extend the set of events by the dis-tinguished events in ,for all.Moreover,the sets out ,for SC ,need to be re–defined —as shown in Table 5—such that they include the events in ,for any active state in .It is easy to see that the resulting semantics handles state references as expected.4.2History StatesUpon entering or–states,their initial states are activated.However,in practice it is often convenient to have the option to return to the sub–state which was active when last exiting an or–state,e.g.,aftercompleting an interrupt routine.In Statecharts’visual syntax thisis done by permitting distinguished history states in or–states to which transitions from the outside of the considered or–states may point.Such history states can have twoflavors:deep and shallow. Deep means that the‘old’active state of the or–state and the‘old’active states of all its sub–states are restored.Shallow means that only the active state of the or–state is restored and that its sub–statesare reinitialized as usual.In our term–based setting,we may model history states and transitions traversing to history states as follows. For each transition pointing to some or–state,we additionally record a historyflag none deep shallow.If none, then transition is interpreted in the standard way,otherwise it is interpreted to point to the deep—if deep—or shallow—if shallow—history state in.In the light of this formalization,it is easy to integrate a history mechanism in our operational semantics.One just has to replace function default in Rule(cOR1)by function default, where none deep shallow is the historyflag of transi-tion.The terms default none and default deep are sim-ply defined by default and,respectively.The definition of default shallow can be done along the structure of Statecharts terms as follows1.default shallow df,2.default shallow dfdefault, 3.default shallow df default shallow.Here,default shallow,where,stands for default shallow default shallow.Observe that default needs only to be defined for Statecharts terms SC and not also for micro terms SC SC.4.3Priority ConceptsSome Statecharts dialects consider an implicit priority mechanism along the hierarchy of or–states.In UML Statecharts[3],for exam-ple,inner transitions of an or–state have priority over outer transi-tions,while this is the other way around in STATEMATE[10].Let us provide aflexible scheme for encoding both priority concepts,for which we introduce the notion of addresses which are built accord-ing to the BNF,for.The set of all such addresses is denoted by ddr.Each action transi-tion is then labeled with an address pointing to the sub–term of the considered Statecharts term,from which the transition originates (cf.the subscripts of the transitions in Table3).Intuitively,the symbol encodes that the transition originates from the considered state,i.e.,this state must be an or–state and the transition leaves the or–state’s active sub–state.Address also requires the state to be an or–state and the transition to originate from address of the currently active sub–state of the or–state.Finally,address indicates that the considered state is an and–state having at least sub–states and that the transition originates from address of the -th sub–state.Given an address ddr,we can now define the set MI of addresses which are considered more important than according to the chosen priority concept.The definitions of MI for the priority concepts of UML Statecharts and STATEMATE can be done straightforwardly along the structure of and are given in Table6. They do not require any extra explanation.Now,we can define a Table6:Priority Structure`a la UML(top)and`a la STATEMATE (bottom)MI dfMI df MIMI df MIfor action transitions,which coincides with the original transition relation given in Section3,except that low–priority action transitions arefiltered out.PrioThis rule states that an action transition located at address may be executed if there exists no action transition at some more important address,which cannot be prevented in any system environment. The justification for the fact that only action transitions with empty sets as labels have pre–emptive power over lower prioritized ac-tion transition is similar to the one regarding the pre–emption of clock transitions in Section3.One might wonder why this“two–level”definition of Statecharts semantics is still compositional,as the above side condition concerns a global property.In order to see this,one may again employ meta–theoretic results about the compositionality of semantics defined via SOS rules[35].Alterna-tively,one can distribute the side condition among the original rules for action transitions,such that compositionality becomes obvious, as is done in approaches to priority in process algebras[4].Some details on this issue can be found in the appendix.5.RELATED WORKWe categorize related work along the three dimensions of State-charts semantics:causality,synchrony,and compositionality.This classification wasfirst considered by Huizing and Gerth[15]who demonstrated that these dimensions cannot be trivially combined within a simple semantic framework.The original Statecharts semantics,as presented by Harel et al.[11], obeys causality and synchrony.However,it ignores compositional-ity and the concept of global ter,Huizing et al.[16] provided a compositional denotational semantics for this variant, while Pnueli and Shalev[29]suggested the introduction of global consistency for improving the practicality of the variant.How-ever,Pnueli and Shalev’s formalization is again not compositional. Its compositionality defect has recently been analyzed by adapting ideas from intuitionistic logic,as it can be shown that the logic un-derlying Pnueli and Shalev’s semantics does not respect the Law of the Excluded Middle[19].Other researchers have developed languages whose semantics obey the synchrony hypothesis and compositionality but violate causal-ity.Prominent representatives of such languages include Berry’s ESTEREL[2],to which recently some dialect of Statecharts has been interfaced as graphical front–end[32],and Maraninchi’s AR-GOS[22].Both languages are deterministic and treat causalityrather conservatively in a pre–processing step,before determining the semantics of the considered program as Mealy automaton via structural operational rules[23].Moreover,ARGOS semantics sig-nificantly differs from Statecharts semantics by allowing sequential components tofire more than once within a macro step.Another approach to formalizing Statecharts,whichfits into this category, is the one of Scholz[30]who uses streams as semantic domain for defining a non–causalfixed point semantics.The popular synchronous version of STATEMATE[10]neglects the synchrony hypothesis.Events generated in one step may not be consumed within the same step but in the next step only.The oper-ational semantics of this dialect has been compositionally formal-ized by Damm et al.[7].It was also considered by Mikk et al.[25] who translated STATEMATE specifications to input languages of model–checking tools by using hierarchical automata[26]as in-termediate language.This intermediate language was employed by Latella et al.[17],too,for formalizing the semantics of UML Statecharts[3]in terms of Kripke structures.However,UML State-charts discard not only the synchrony hypothesis but additionally negated events and,thereby,make the notion of global consistency obsolete.Their semantics was also investigated by Paltor and Lil-ius[27],who developed a semantic framework on the basis of a term–rewriting system.Our work is,however,most closely related to approaches which aim at combining all three dimensions—causality,synchrony,and compositionality—within a single formalism.These approaches may be split into two classes.Thefirst class adapts a process–algebraic approach,where Statecharts languages are embedded in process algebras,for which structured operational semantics based on labeled transition systems are defielton and Smolka[34] have pioneered this approach which was then refined by Levi[18]. Their notion of transition system involves complex labels of the form,where is a set of events and is a transitive, irreflexive order on encoding causality.The second class is characterized by following essentially the same ideas but avoid-ing the indirection of process algebra.Research by Uselton and Smolka[33]again employs the mentioned partial order,whereas Maggiolo–Schettini et al.[21]require even more complex and in-tricate information about causal orderings,global consistency,and negated events.While our present work alsofits into this class, although it originated in the former[20],it avoids complex la-bels by representing causality via micro–step sequences and by adding explicit clock transitions to retrieve macro–step informa-tion.Thereby,our semantics is not only simple and concise but also comprehensible and suited for interfacing Statecharts to exist-ing analysis and verification tools.In addition,our approach is very flexible as we demonstrated by adding several prominent features, namely state references,history states,and priority concepts,to our initially rather primitive Statecharts dialect.An alternative compositional semantics for Statecharts is presented by von der Beeck in[37].That account is based on the one pre-sented here,although its practical utility is compromised by the inclusion of unnecessary syntactic information in the semantic re-lation.In particular,the inclusion of transition names into the labels of execution steps allows Statecharts exhibiting the same observa-tional behavior but differing in the naming of transitions to be dis-tinguished.Finally,we briefly comment on interlevel transitions which prohibit a compositional Statecharts semantics as they are based on the idea of“goto–programming.”First of all,interlevel transitions jeopar-dize a strictly structural definition of Statecharts terms,which is a prerequisite for deriving any compositional semantics.Hence,for modeling interlevel transitions,the syntax of Statecharts must be changed in a way such that interlevel transitions may be represented by several intralevel transitions which are connected via dedicated ports.This can be done either explicitly,as in the Communicating Hierarchical State Machine language introduced by Alur et al.[1], or implicitly via a synchronization scheme along the hierarchy of or–states,as in Maraninchi’s ARGOS[22].6.CONCLUSIONSThis paper presented a new approach to formalizing Statecharts se-mantics,which is centered around the principle of compositionality and borrows from ideas developed for timed process algebras.In contrast to related work,our approach combines all desired features of Statecharts semantics,namely causality,synchrony,and compo-sitionality,within a single formalism,while still being simple and comprehensible.Its foundation on structural operational rules guar-antees that our semantics is easy to implement in specification and verification tools and that it can be adapted to several Statecharts dialects.The proposed semantic framework also permits the inte-gration of many features desired in practice,as we demonstrated by extending it to dealing with state references,history states,and pri-ority st,but not least,we hope that this paper testifies to the utility of applying knowledge from thefield of Concurrency Theory to formalizing practical specification languages rigorously yet clearly.7.ACKNOWLEDGMENTSWe would like to thank the anonymous referees for their valuable comments and suggestions.8.REFERENCES[1]R.Alur,S.Kannan,and municatinghierarchical state machines.In ICALP’99,volume1644ofLNCS,pages169–178.Springer-Verlag,1999.[2]G.Berry and G.Gonthier.The ESTEREL synchronousprogramming language:Design,semantics,implementation.SCP,19(2):87–152,1992.[3]G.Booch,J.Rumbaugh,and I.Jacobson.The UnifiedModeling Language User Guide.Addison Wesley,1998. [4]R.Cleaveland and M.Hennessy.Priorities in processrm.&Comp.,87(1/2):58–77,1990.[5]R.Cleaveland,E.Madelaine,and S.Sims.Generatingfront-ends for verification tools.In TACAS’95,volume1019 of LNCS,pages153–173.Springer-Verlag,1995.[6]R.Cleaveland and S.Sims.The NCSU CONCURRENCYWORKBENCH.In CAV’96,volume1102of LNCS,pages394–397.Springer-Verlag,1996.[7]W.Damm,B.Josko,H.Hungar,and A.Pnueli.Acompositional real-time semantics of STATEMATE designs.In de Roever et al.[8],pages186–238.[8]W.-P.de Roever,ngmaack,and A.Pnueli,editors.Compositionality:The Significant Difference,volume1536of LNCS.Springer-Verlag,1997.。
Modeling the ODP Computational Viewpoint with UML 2.0 The Templeman Library Example

Modeling the ODP Computational Viewpoint with UML2.0: The Templeman Library ExampleJos´e Ra´u l Romero and Antonio VallecilloDpto.de Lenguajes y Ciencias de la Computaci´o nUniversidad de M´a laga,Spain{jrromero,av}@lcc.uma.esAbstractThe advent of UML2.0has provided a new set of con-cepts more apt for modeling the structure and behavior of distributed systems.These concepts and mechanisms can be effectively used for representing the ODP concepts,in particular those from the Computational Viewpoint.In this paper we present an example that uses the UML2.0profile for the ODP computational viewpoint to illustrate its bene-fits and limitations.1IntroductionThe computational viewpoint describes the functionality of an ODP system and its environment through the decom-position of the system,in distribution transparent terms,into objects which interact at interfaces.In the computational viewpoint,applications and ODP functions consist of con-figurations of interacting computational objects.Although the ODP reference model provides abstract languages for the relevant concepts,it does not prescribe particular notations to be used in the individual viewpoints. The viewpoint languages defined in the reference model are abstract languages in the sense that they define what con-cepts should be used,not how they should be represented. Several notations have been proposed for the different view-points by different authors,which seem to agree on the need to represent the semantics of the ODP viewpoints con-cepts in a precise manner[2,4,8,12,10,11].For exam-ple,formal description techniques such as Z and Object-Z have been proposed for the information and enterprise viewpoints[21],and LOTOS,SDL or Z for the computa-tional viewpoint[8,20].Lately,rewriting logic and Maude have also shown their adequacy for modeling the ODP lan-guages[6,5,19].However,the formality and intrinsic difficulty of most formal description techniques have encouraged the quest for more user-friendly notations.In this respect,the general-purpose modeling notation UML(Unified Modeling Lan-guage)is clearly the most promising candidate,since it is familiar to developers,easy to learn and to use by non-technical people,offers a close mapping to implementa-tions,and has commercial tool support.Until the advent of UML version2.0,both the lack of precision in the UML definition and the semantic gap be-tween the ODP concepts and the UML constructs hindered its application in this context.The UML(1.4)Profile for EDOC[13]tried to bridge this gap.But from our perspec-tive,the gap was so big that the Profile ended up being too large and difficult to understand and use by both ODP and UML users.With the advent of UML2.0the situation may have changed,since not only its semantics have been more precisely defined,but it also incorporates a whole new set of concepts more apt for modeling the structure and behavior of distributed systems.In addition,the wide adoption of UML by industry,the number of available UML tools,and the increasing interest for model-driven development and the MDA initiative,mo-tivated ISO/IEC and ITU-T to launch a joint project in2004, which aims to define the use of UML for ODP system speci-fications(ITU-T Rec.X.906—ISO/IEC19793[9]).Thus, ODP modellers could use the UML notation for express-ing their ODP specifications in a standard graphical way, and UML modellers could use the RM-ODP concepts and mechanisms to structure their UML system specifications.In this paper we explore the use of the UML2.0profile for modeling the ODP computational viewpoint concepts presented in[17]and detailed in[18].More specifically,we show how this profile can be used to model operational ODP systems by representing,as an example,the Templeman’s library management system.The structure of this document is as follows.First,sec-tions2and3serve as a brief introduction to the compu-tational viewpoint and UML2.0,respectively.Section4 presents a summary of the UML2.0Profile for the ODP Computational Viewpoint,describing how to model compu-tational specifications in UML.This profile is used in Sec-tion5for specifying the Templeman’s library system.Fi-nally,Section6draws some conclusions and outlines some future research activities.2Computational Viewpoint in RM-ODP The computational viewpoint is directly concerned with the distribution of processing but not with the interaction mechanisms that enable distribution to occur.The computa-tional specification decomposes the system into objects per-forming individual functions and interacting at well-defined interfaces.The heart of the computational language is the object model which defines the form of interface that an object can have;the way that interfaces can be bound and the forms of interaction which can take place at them;the actions an ob-ject can perform,in particular the creation of new objects and interfaces;and the establishment of bindings.The computational object model provides the basis for ensuring consistency between engineering and technology specifications(including programming languages and com-munication mechanisms)thus allowing open interworking and portability of components in the resulting implementa-tion.2.1Computational language conceptsIn the ODP Reference Model,the computational lan-guage uses a basic set of concepts and structuring rules, including those from ITU-T Recommendation X.902, ISO/IEC10746-2,and several concepts specific to the com-putational viewpoint.Objects and interfaces.ODP systems are modeled in terms of objects.An object contains information and of-fers services.A system is composed as a configuration of interacting objects.In the computational viewpoint we talk about computational objects,which model the entities de-fined in a computational specifiputational ob-jects are abstractions of entities that occur in the real world, in the ODP system,or in other viewpoints[8].Computational objects have state and can interact with their environment at interfaces.An interface is an abstrac-tion of the behavior of an object that consists of a subset of the interactions of that object together with a set of con-straints on when they may occur.ODP objects may have multiple interfaces.Computational putational objects and interfaces can be specified by templates.In ODP,an<X> template is“the specification of the common features of a collection of<X>s in sufficient detail that an<X>can be instantiated using it”.<X>can be anything that has a type.Thus,an interface of a computational object is usually specified by a computational interface template,which is an interface template for either a signal interface,a stream in-terface or an operation interface.A computational interface template comprises a signal,stream or operation interface signature as appropriate;a behavior specification;and an environment contract specification.An interface signature consists of a name,a causality role(producer,consumer,etc.),and set of signal signa-tures,operation signatures,orflow signatures as appropri-ate.Each of these signatures specify the name of the inter-action and its parameters(names and types). Interactions.RM-ODP prescribes three particular types of interactions:signals,operations,andflows.A signal may be regarded as a single,atomic action between com-putational objects.Signals constitute the most basic unit of interaction in the computational viewpoint.Operations are used to model object interactions as represented by most message passing object models,and come in twoflavors: interrogations and announcements.An interrogation is a two-way interaction between two objects:the client object invokes the operation(invocation)on one of the server ob-ject interfaces;after processing the request,the server ob-ject returns some result to the client object,in the form of a termination.An announcement is a one-way interaction between a client object and a server object.In contrast to an interrogation,after invocation of an announcement op-eration on one of its interfaces,the server object does not return a termination.Terminations model every possible outcome of an operation.Flows model streams of infor-mation,i.e.,aflow represents an abstraction of a sequence of interactions from a producer to a consumer,whose ex-act semantics depends on the specific application domain. In the ODP computational viewpoint,operations andflows can be expressed in terms of signals[8].Environment putational object templates may have environment contracts associated with them. These environment contracts may be regarded as agree-ments on behaviors between the object and its environ-ment,including Quality of Service(QoS)constraints,us-age and management constraints,etc.These QoS con-straints involve temporal,volume and dependability con-straints,amongst others,and they can imply other usage and management constraints,such as location and distribution transparency constraints.An environment constraint can thus describe both re-quirements placed on an object’s environment for the cor-rect behavior,and constraints on the object behavior in the correct environment.2.2Structure of ODP computational specifica-tionsA computational specification describes the functional decomposition of an ODP system,in distribution transpar-ent terms,as:(a)a configuration of computational objects;(b)the internal actions of those objects;(c)the interactions that occur among those objects;(d)environment contracts for those objects and their interfaces.A computational specification also defines an initial set of computational objects and their behavior.The configu-ration will change as the computational objects instantiate further computational objects or computational interfaces; perform binding actions;effect control functions upon bind-ing objects;delete computational interfaces;or delete com-putational objects.3Unified Modeling Language2.0UML is a visual modeling language that provides a wide number of graphical elements for modeling systems,which are combined in diagrams according to a set of given rules. The purpose of such diagrams is to show different views of the same system or subsystem and indicate what the system is supposed to do.There are mainly two types of diagrams:structural and behavioral.The former ones focus on the organization of the system.Structural diagrams include package diagrams, object diagrams,deployment diagrams,class diagrams and composite structure diagrams.Behavioral diagrams reflect the system response to inner and outer requests and its evo-lution in time,and include activity diagrams,use cases,stat-echarts and interaction diagramsOne of the major improvements of UML2.0[15,16]is the addition of new diagrams and the enhancements made to existing ones:UML2.0structure,composite,commu-nication,timing and interaction overview diagrams allow solving many of the UML1.x limitations.Most of these im-provements have been influenced by the integration of the mature SDL language within UML.In addition,UML2.0 now provides better constructs for modeling the software ar-chitecture of large distributed systems,with concepts such as components and connectors,and has promoted the use of OCL(Object Constraint Language),now fully aligned with UML2.0[14].Finally,the language extension mech-anisms have been greatly enhanced too,with the more pre-cise definition of UML Profiles to allow the customization of UML constructs and semantics for given application do-mains.These new concepts and mechanisms of UML2.0 constitute the basis of our proposal.4Modeling Computational Viewpoint Con-cepts in UML2.0The UML2.0Profile for the ODP Computational View-point(which is fully described in[18])consists of three main parts.First,it defines the ODP computational view-point metamodel,which is an evolution of the metamodel presented in[19],and defines the semantics,properties and related elements of each metaclass.Second,ODP concepts are mapped to UML elements.This mapping contains infor-mation about every ODP computational concept,the UML base element that represents each concept,and the stereo-type that extends the metaclass so that the specific domain terminology can be used.This section summarizes how the main concepts of the ODP computational language are mapped to UML2.0con-cepts.4.1Computational objects and interfaces Computational object templates and objects.A key concept of the ODP computational viewpoint is the compu-tational object.Each computational object is instantiated from its corresponding computational object template.A computational object template will be mapped to a UML component,which represents autonomous system units,that encapsulate state and behavior and interacts with their environment in terms of provided and required inter-faces.In UML,components are classifiers.A UML classi-fier can have a set of features,that characterize its instances.ODP computational objects will then be mapped to UML component instances.Computational putational objects inter-act with their environment at interfaces.These are instan-tiated from computational interface templates,which com-prise the interface signature(signal,operation or stream as appropriate),a behavior specification and an environment contract specification.There are no exact terms in UML2.0to provide one-to-one mappings for these ODP concepts.However,the se-mantics provided by other modeling elements can be used with slight customizations.If we consider computational interfaces as interaction points at which computational objects interact,wefind that this concept corresponds to the UML concept of interaction point,i.e.,a port at the instance level.In ODP,a computational interface template comprises an interface signature,which is defined as the set of action templates associated with the interactions of an interface. Each of these action templates comprises the name for the interaction,the number,names and types of the parametersand an indication of causality with respect to the object that instantiates the template.Then,an ODP computational interface signature will be mapped to a set of UML interfaces,each of which is de-fined as a kind of classifier that represents a declaration of a set of coherent public features and obligations.This means that each interface can be considered as the specification of a contract that must be fulfilled by any instance of a clas-sifier that realizes the interface(e.g.,the UML component instance that represents the computational object,through its corresponding interaction point).Different stereotypes will be used to distinguish the in-terfaces that represent the different kinds of computational interface signatures.4.2InteractionsIn ODP,the basic one-way communication mechanism from an initiating object to a responding object is the signal, which represents a single basic interaction between them. Operations andflows are also interactions,although they can be handled in terms of signals,as previously mentioned in Section2.1.An ODP signal will be mapped to a UML message, which is the specification of the conveyance of information from one instance to another.In UML,a message can spec-ify either the raising of a UML signal or the call of an UML operation.In ODP,in order to specify a signal we need to provide its signature and its behavior.An interaction signature will be represented by an UML reception,which consists of a declaration stating that the interface classifier is prepared to react to the receipt of a sig-nal.In ODP,each interface signature comprises a set of in-teraction signatures that conform to the interface type.This means that we need to define the proper set of ODP inter-actions as public features of the appropriate UML interface classifier.The behavior of interactions refers to the communication process between computational objects,which will be ex-pressed in UML with behavioral diagrams[3]:(a)Interac-tion models describe how messages are passed between ob-jects and cause invocations of other behaviors;(b)Activity models focus on the sequence,input/outputs and conditions for invoking other behaviors;and(c)Finally,state machine models show how events(e.g.,signal events)cause changes to the object state and invoke other behaviors.Which of them to choose is a matter of the system per-spective that the modeler needs to specify,since each of these models is focused on a different aspect of the sys-tem dynamics.For instance,timing diagrams could be also useful to represent the interactions among computational objects when some timed simple constraints need to be ob-served or applied.4.3Environment contractsEnvironment contracts place constraints on the behavior of computational objects,and usually include QoS,usage, and management aspects.The ODP Reference Model does not prescribe how an environment contract must be speci-fied;it just defines this concept and its basic contents.Each system modeler might like to specify their own constraints in the way that best suits their particular appli-cation,and therefore the UML elements(and their seman-tics)required to model different environment contracts can change from one application to another.Thus,instead of in-corporating these kind of concepts into our UML Profile,we have decided to use separate profiles for representing QoS and other extra-functional aspects of environment contracts. The possibility offered by UML2.0to apply multiple pro-files to a package—as long as they do not have conflicting constraints—will allow the specifier use the QoS profile(s) of his preference.4.4Computational specificationsAs described in2.2,a computational specification de-scribes the functional decomposition of an ODP system,in distribution transparent terms.In UML,the computational specification will be represented by a set of diagrams that model both structural and behavioral aspects of the system. These diagrams will use the elements provided by the ap-plied profiles(using their specified semantics).A configuration of computational objects and their inter-acting interfaces will be modeled by component diagrams (at the instance level).The internal actions of those objects will be represented by behavioral diagrams associated to the UML components that represent those objects.4.5Summary of the mappingsThe fact that most ODP concepts can be represented by UML2.0concepts without changing their original seman-tics(maybe imposing some additional constraints on them, at most)enables the use of a UML Profile as the right kind of mechanism for our purposes[7].Note that the profile mech-anism does not allow for modifying existing metamodels. Rather,a profile is intended to provide a straightforward mechanism for adapting an existing metamodel with con-structs that are specific to a particular domain.As a summary,Table1shows the most important stereo-types defined in the UML Profile for the ODP Computa-tional Viewpoint[18].Table1.Summary of the Computational Viewpoint ProfileODP Concept UML Base Element StereotypeComputational object template Component CV CompObjectTemplate Computational interface template Port CV CompInterfaceT emplate Signal interface signature Interface(s) CV SignalInterfaceSignature Operation interface signature Interface(s) CV OperationInterfaceSignature Stream interface signature Interface(s) CV StreamInterfaceSignature Announcement signature Reception CV AnnouncementSignature Interrogation signature Reception CV InterrogationSignature Termination signature Reception CV TerminationSignature Signal signature Reception CV SignalSignatureFlow signature Reception CV FlowSignature Computational object InstanceSpecification CV ObjectSignal interface Port(interaction point) CV SignalInterfaceOperation interface Port(interaction point) CV OperationInterfaceStream interface Port(interaction point) CV StreamInterfaceSignal Message CV SignalFlow Interaction/Message CV FlowAnnouncement Message CV AnnouncementInvocation Message CV InvocationTermination Message CV Termination5A Case StudyWe will illustrate the use of the UML Profile for the ODP Computational Viewpoint by modeling the comput-erized system that supports the operations of a Templeman Library at the University of Kent at Canterbury,in particu-lar those operations related to the borrowing process of the Library items.The system should keep track of the items of the Uni-versity Library,its borrowers,and their outstanding loans. The library system will be used by the library staff(librarian and assistants)to help them record loans,returns,etc.The borrowers will not interact directly with the library system.The basic rules that govern the borrowing process of that Library are as follows:1.Borrowing rights are given to all academic staff,andto postgraduate and undergraduate students of the Uni-versity.2.Library books and periodicals can be borrowed.3.The librarian may temporarily withhold the circulationof Library items,or dispose them when they are no longer apt for loan.4.There are prescribed periods of loan and limits on thenumber of items allowed on loan to a borrower at any one time.5.Items borrowed must be returned by the due day andtime which is specified when the item is borrowed.6.Borrowers who fail to return an item when it is duewill become liable to a charge at the rates prescribed until the book or periodical is returned to the Library, and may have borrowing rights suspended.7.Borrowers returning items must hand them in to an as-sistant at the Main Loan Desk.Any charges due on overdue items must be paid at this time.8.Failure to pay charges may result in suspension by theLibrarian of borrowing facilities.Despite they leave many details of the system unspeci-fied,these textual regulations will be the starting point for the ODP specifications below.5.1Computational objects and interfacesIn order to represent the computational specification for the Templeman Library,we need to identify the computa-tional elements that participate in the borrowing process. Each of these elements(i.e.,computational objects and in-terfaces)are instantiated from their corresponding compu-tational templates.In UML,we represent the system struc-ture using a component diagram,that describes the compu-tational object templates and the computational interfaces at which these objects interact.As shown in Figure1,there are four different kinds of computational objects:(a)a manager(UserMgr)for each user(i.e.,borrower);(b)the system that managesponent Diagram representing ODP Computational Templatesthefines applied to users who exceed the borrowing pe-riod(FineSystem);(c)the system that manages the library items(ItemMgr);and(d)the borrowing process coordina-tor(BorrowingSystem).These objects interact with each other and with their en-vironment at computational interfaces,which are instanti-ated from their corresponding interface templates.In this case,we usefive computational interfaces,all of them op-erational interfaces.As shown in Figure1,each interface is modeled by a UML port feature and its provided and re-quired UML interfaces,whose receptions represent the in-dividual interaction signatures.For readability reasons,we have shown interface signatures as balls and sockets in Fig-ure1.An extended notation for the signature of the IUser-Mgnt interface is shown in Figure2,where UML receptions are explicitly depicted.In this example,only operation computational interfaces have been defined.Therefore,just two causalities are pos-sible:client or server.This implies that the tag object-Role can be omitted because the causality is implicitly rep-resented by the kind of dependency existing between the UML port and the UML interface—e.g.,an usage depen-dency(required interface)represents that the computational interface will interact as a client.There are also cases in which the system designer might prefer to adopt an oper-ational object-oriented approach,which represents the ex-change of information between objects in terms of oper-ation interactions between computational objects.In this case,modeling these interactions as UML operations might probably be simpler,as shown in Figure3.Figure2.Interface signature forIUserMgnt ponent diagram following anoperational OO approach5.2Behavioral specificationWe need to specify different behavior aspects of the com-putational elements.In fact,activity,communication,inter-action and sequence diagrams might be useful to representFigure4.Activity diagram for the Borrowing Processboth the internal actions of the computational objects,and the interactions that occur between them.In case we want to specify how object interactions are performed,activities can be useful because they are an abstraction of the many ways that messages are exchanged between objects[3].This makes activities useful at the stage of development where the primary concern is dependency between tasks,rather than interaction protocols.The activity diagram for the bor-rowing process is shown in Figure4.Alternatively,when messages and interaction protocols are the focus of development,UML interaction diagrams are more appropriate,as shown in Figure5.6ConclusionsIn this paper we have shown with an example how the ODP computational specifications can be expressed in UML2.0,using the Profile for the Computational viewpoint described in[17].Wefind results to be encouraging,since the profile has proved to be expressive enough to describe the system functionality and processes,in a natural way.It is still to be proved whether ODP and UML modelersfind it natural,too,but we hope this example can help these two kinds of audiences understand better the proposal.There are some lines of work that we plan to address shortly.In particular,once we count with a graphical no-tation to model the ODP computational viewpoint,we per-ceive that its connection to formal notations and tools might bring along many real advantages.For instance,formal analysis of the system can be achieved from the UML en-vironment(such as model checking or theorem proving), freeing the system analyst from most formal technicalities. In this sense,we are working in the provision of bridges be-tween the UML2.0specification and the Maude language, so that the Maude formal toolkit can be used with the UML models produced for the ODP system.In addition,the computational viewpoint is just one of thefive ODP viewpoints.Defining and analyzing the corre-spondences between the different viewpoint specifications is also required.The aforementioned ITU-T Rec.X.906—ISO/IEC19793standard is defining UML profiles for all viewpoints[9].The example presented here tries to serve as input to this work,both to illustrate the use of the Compu-tational Profile and to provide with examples that help tack-ling how to define and analyze viewpoint correspondences. Acknowledgements This work has been supported by Spanish Research Project TIC2002-04309-C02-02.References[1] D.H.Akehurst,J.Derrick,and A.G.Waters.Addressingcomputational viewpoint design.In Proc.of EDOC2003, pages147–159,Brisbane,Australia,Sept.2003.[2] C.Bernardeschi,J.Dustzadeh,A.Fantechi,E.Najm,A.Ni-mour,and F.Olsen.Transformations and consistent seman-tics for ODP viewpoints.In Proc.of FMOODS’97,pages 371–386,Canterbury,1997.Chapman&Hall.[3] C.Bock.UML2activity and action models part2:Actions.Journal of Object Technology,2(5):41–56,2003.[4]H.Bowman,J.Derrick,P.Linington,and M.W.Steen.FDTs for puter Standards&Interfaces,17:457–479,Sept.1995.[5] F.Dur´a n,M.Rold´a n,and ing maude towrite and execute ODP Information Viewpoint specifiputer Standards&Interfaces,2005.[6] F.Dur´a n and A.Vallecillo.Formalizing ODP Enterprisespecifications in puter Standards&Interfaces, 25(2):83–102,June2003.[7]L.Fuentes and A.Vallecillo.An introduction to UML pro-files.UPGRADE,The European Journal for the Informatics Professional,5(2):5–13,Apr.2004.[8]ISO/IEC.RM-ODP.Reference Model for Open DistributedProcessing.Geneva,Switzerland,1997.International Stan-dard ISO/IEC10746-1to10746-4,ITU-T Recommenda-tions X.901to X.904.[9]ISO/e of UML for ODP System Specification.Geneva,Switzerland,(to appear in2006).International Standard ISO/IEC19793,ITU-T Recommendation X.906.[10] D.R.Johnson and H.Kilov.Can aflat notation be used tospecify an OO system:using Z to describe RM-ODP con-structs.In Proc.of FMOODS’96,pages407–418,Paris, Mar.1996.Chapman&Hall.[11] D.R.Johnson and H.Kilov.An approach to a Z toolkit forthe Reference Model of Open Distributed -puter Standards&Interfaces,21(5):393–402,Dec.1999.[12]P.Linington.RM-ODP:The architecture.In osevicand L.Armstrong,editors,Open Distributed Processing II, pages15–33.Chapman&Hall,Feb.1995.[13]OMG.A UML Profile for Enterprise Distributed ObjectComputing V1.0.Object Management Group,Aug.2001.OMG document ad/2001-08-19.[14]OMG.OCL2.0,Oct.2003.Final Adopted Specificationptc/03-10-04.[15]OMG.Unified Modeling Language Specification(version2.0):Infrastructure,2003.ptc/03-12-01.[16]OMG.Unified Modeling Language Specification(version2.0):Superstructure,2003.Draft Adopted Specificationptc/03-08-02.[17]J.R.Romero and A.Vallecillo.Modeling the ODP Compu-tational Viewpoint with UML2.0.In Proc.of EDOC2005, Enschede,Netherlands,Sept.2005.IEEE CS Press. [18]J.R.Romero and A.Vallecillo.UML2.0Profile forthe ODP Computational Viewpoint.Technical Report TR-05-03,Universidad de M´a laga,Mar.2005.Available from http://www.lcc.uma.es/˜jrromero[19]J.R.Romero and A.Vallecillo.Formalizing ODP computa-tional specifications in Maude.In Proc.EDOC2004,pages 212–233,Monterey,California,Sept.2004.IEEE CS Press.[20]R.Sinnot and K.J.Turner.Specifying ODP computationalobjects in Z.In Proc.of FMOODS’96,pages375–390,Can-terbury,1997.Chapman&Hall.[21]M.W.Steen and J.Derrick.ODP Enterprise View-point Specifiputer Standards&Interfaces, 22(2):165–189,Sept.2000.。
UMLS

语义网络的54种语义关系不能表达语义类型 之间可能存在的所有关系,但比常规叙词表 的“属分”、“相关”关系细致得多。 例如: MeSH中,“基因靶效应(Gene Targeting)” 是“遗传技术”的一个下位词 在UMLS中,其语义类型是“分子生物研究技 术” :
和“精神过程”之间存在影响关系 和“生理功能”之间存在测量关系等等
物理上相关(physically related to):
包含(contains) …的分支(branch of) 等9种关系 时间上相关(temporally related to): 与…同时发生(co-occurs) 先于…发生(precedes) 共3种关系 功能上相关(functionally related to): 影响(affects) 引起(brings about) 执行(performs) 等21种关系
Event 事 Phenomenon or Process 现象或过程 Natural Phenomenon or Process 自然现象或过程 Biologic Function 生物学功能 Pathologic Function 病理学功能 Disease or Syndrome 疾病或综合征 Neoplastic Process 肿瘤发生 每种语义类型都有其定义及语义关系 列举出该语义类型可标识的超级叙词表中的概念(超级叙词表 中的每个概念至少被标识为一种语义类型)
语义类型
节点 语义关系 将节点连成网络 每种语义关系都有其定义,并规定了可 链接的语义类型。 最基本的语义关系是“isa”,表示语义 类型间的等级隶属关系。 如:肿瘤发生 isa 疾病或综合征
除“isa”关系外,其余53种语义关系均为相关 关系(associated with),主要分为5大类:
The Production Cell An Exercise in the Formal Verification of a UML Model

The Production Cell:An Exercise in the Formal Verification of a UML ModelJohan Lilius and Ivan Porres PaltorTurku Centre for Computer Science(TUCS),Lemmink¨a isenkatu14A,FIN-20520Turku,FinlandJohan.Lilius,Ivan.Porres@abo.fiAbstractWe show how to model the Production Cell,a standard example for evaluating design notations for embedded sys-tems,using the Unified Modelling Language(UML).Then, we use the vUML tool,developed by the authors,to verify our model of the Production Cell.The input model and the results from the verification are expressed using the UML notation,thus hiding the model-checking formalism from the user.We also show how to use the object-oriented de-composition of the model,that is given by a UML class dia-gram,to reduce the complexity of the model-checking prob-lem.We conclude that the vUML tool helps the designer to verify the software of distributed object-oriented embedded systems,without learning all the details of a model checker. 1IntroductionThe Unified Modelling Language(UML)is a standard-ised notation for specifying object-oriented[1]software systems.A UML model is a set of diagrams describing and documenting the structure,behaviour and usage of a software system.The UML notation and semantics are de-scribed in[12].UML is used to model all kinds of software systems,including concurrent and distributed systems for embedded applications.There are commercial modelling tools available on the market to help the designer to cre-ate UML models,and some of these tools can also generate program code from a model.The UML standard defines several kinds of diagrams that are used to describe different aspects or views of a system. Class diagrams,e.g.,show the object-oriented structure of the system while Use case diagrams show the users and their requirements for the system.A Statecharts diagram is a graphical representation of a state machine.A state ma-chine describes the behaviour of an object as changes in its internal state resulting from receiving external events.UML Statecharts use a notation similar to Harel’s Statecharts[3],but the interpretation of the diagrams is considerable dif-ferent.UML state machines are usually implemented in software,and their semantics reflect this fact:there are no assumptions on the speed of the computational nodes and communication links.Another important difference is that events are queued and dispatched one by one,so only one event is present at a certain time.This paper is both a case study in UML and a case study in the use of a verification tool.We show how to use UML to model the Production Cell case study[6]and we apply a model-checking tool during the design process to gain a high confidence in the correctness of the model.The model-checker we use is vUML,a tool developed by the authors and particularly suited to the verification of UML models. The main contributions of the paper are thus:1)we show how to use UML to model and verify control software for non-trivial applications,2)we show how to use the vUML verification tool in a iterative model-based design process.We proceed as follows:In section two,we briefly present the vUML tool and how it works.Section three explains the semantics used by the tool to interpret the models during the verification.Section four shows how we use UML and vUML to model and verify the Production Cell case study. The properties that can be verified in a model are explained in sectionfive.Wefinish the paper with some conclusions and discussion of related work.2Using a verification tool during the design phaseUML is an expressive and rich language.Most UML models are highly descriptive and easy to understand,but UML models must be verified since they may exhibit be-haviours not expected by the designer.We propose to use a model checker to exhaustively verify a UML model.A model checker is a tool that automatically searches the com-plete set of states of a model for a given incorrect behaviour. Model checking(cf.[2]for a survey)has been successfully applied in industrial verification projects.By verifying theUML model,we can ensure that the software is free of de-sign errors before implementing it.vUML is a tool that automatically verifies UML mod-els provided that the behaviour of the objects is describedusing Statecharts diagrams.The target user of the tool is the designer of object-oriented software systems.vUMLhas been specifically designed to verify concurrent and dis-tributed models containing active objects.Yet,it can also be used with sequential designs,since it also supports syn-chronous communication(i.e.procedure calls).The main design decision behind vUML is to be as au-tomatic and transparent to the designer as possible.How-ever,the designer must add some extra information into thedesign so the tool can extract the properties that must be verified.The vUML tool uses two new stereotypes to de-fine behavioural constraints to be satisfied by the model: progress an invalid states.These stereotypes are not part of the UML standard,but they help the designer tointroduce safety and liveness requirements into the model without using a complex formulae in a temporal logic.Their role in the verification is explained in more detail in section four.It is also possible to restrict the behaviour of an object by defining a contraint over a class or over an association of classes.A constraint over a class is usually called a class invariant.It is a predicate over the attributes and states of the instances of the class.The invariant of an object must hold in any moment after the creation of the object.It is also possible to define a constraint involving two objects.This is a constraint over an association:it restricts the behaviour of the objects that are collaborating together.Again,there is a more detailed discussion of about constraints in section four.Figure1shows how vUML works.The tool uses in-ternally the SPIN[5]model checker to perform the verifi-cation,but the designer does not have to know how to use SPIN or the PROMELA[4]language in order to use vUML.A normal session with vUML is as follows:After cre-ating the model,the designer invokes vUML to verify it.The tool automatically converts the UML model into a PROMELA specification and invokes SPIN.Then,the ver-ification is performed by SPIN without interaction from the designer.If the verification fails,vUML generates a counter-example that shows how to reproduce the error in the model.vUML reports the errors using UML sequence diagrams.The designer can study these diagrams andfix the error in the model.This process can be repeated until the model is correct.The vUML tool is described in more detail in[8].We can use vUML in a iterative and incremental designprocess,where the model is constructed and verified con-tinuously until it is complete and correct.The verification process is automatic and it can be repeated as manytimesManual modeling step perfomed by the designerAutomatic verification step performed by a tooling vUMLas needed with little or no effort from the designer.Also, the vUML tool can verify an open model,where the envi-ronment is not defined completely.This feature allows the designer to use the vUML tool from the beginning of the design process.3Operational Semantics of UML State Ma-chinesThe vUML tool can verify UML models only if the be-haviour of the objects is described using UML Statecharts diagrams.A UML Statechart diagram is a graphical repre-sentation of a UML state machine.The semantics of UML States Machines are described in[11].A state machine re-ceives events from the environment and reacts to them.The reactions include sending new events to other objects and executing internal methods on the object.UML Statecharts diagrams use the same notation as Harel’s Statecharts,but the semantics of UML state machines differ considerably. The execution semantics of a UML state machine is de-fined in terms of a hypothetical machine whose key com-ponents are:an event queue that holds incoming event in-stances until they are dispatched,an event dispatch mech-anism for selecting and de-queueing event instances from the event queue,and an event processor that processes dis-patched events.Events are queued and dispatched one by one.Each ob-ject will execute an algorithm,the run-to-completion(rtc) step that dispatches and executes events on its event queue until the top state generates a completion event and the state machine exits.The semantics presented in[11]is described in plain en-glish and is too informal to be used as the basis of a model checking tool.We propose a more formal description of the UML state machines in[7].Our formalistation closelyfollows the descriptions of the UML standard,but it is also suitable for a model checking tool.The UML standard does not define the semantics of the input queue.As we do not know of any practical proposal from other authors in this aspect we shall assume a FIFO policy for the event dispatcher.The main task of the event processor is tofind out which transitions are enabled,e.g.can befired based on thefirst event in the queue A transition is enabled if its source state is active,its trigger matches the current event,and its guard holds.It is possible that an event enables multiple transi-tions and that these transitions can be in conflict,i.e.they may have the same source state but different targets.Only one of the conflicting transitions canfire,and this decision is taken by the event processor based on the priority of the transition or,if they have the same priority,nondeterministi-cally.The set offiring transitions is then grouped into a step. The transitions in the step are executed in sequence and the event processor will only consider the next event in the queue after all transitions in the step have beenfired.This is also another important difference between UML Statecharts and Harel’s Statecharts.The idea of the run-to-completion step is to ensure that an event can only be dequeued and dispatched after the previous current event has been fully completed.A more detailed description of the semantics of UML state machines used in the vUML tool can be found in[7].4The Production Cell case studyThe Production Cell[6]is a standard example for eval-uating methodologies for designing embedded systems.It is a model of an actual industrial installation in a metal-processing plant in Karlsruhe,Germany.Figure2shows a top view of the plant.The model in-cludes several machines that must be coordinated in order to forge metal blanks.The machines should process the metal blanks as fast as possible,but they should also avoid dropping the blanks to thefloor or colliding against each other.There is a conveyor belt that feeds the blanks into a rotary table.The table rotates and lifts the blanks so they can be picked by the robot.The robot has two arms,one for feeding the press with blanks and another to extract the forged blanks from the press.The robot is very efficient and it can use an arm to place a forged blank into the deposit belt while the other arm carries a new blank to the press.4.1Modelling the pressWe decided to modelfirst the central element of the sys-tem:the press.The task of the press is to forge metal blanks. The mobile part of the press is initially in the middle posi-tion until the robot places a blank into the press.After theFigure2.Top view of the production cell press is loaded,the press moves upwards until the blank is forged and then it moves downwards to the unloading po-sition.The robot gets the forged piece and the cycle starts again.Figure3represents these steps graphically.UnloadingFigure3.Robot and pressWe decide to split the model of the press in two parts: the plant and the controller.These elements are represented using two classes:PressPlant and PressController.Figure4 is the class diagram of the Press.A factory with many simi-lar presses can be modeled as many object instances of these classes.The instances of the PressPlant and PressController are active objects.An active object maintains its own thread of control and runs concurrently with other active objects.PressControllerCtrl Plant<<active>>PressPlant<<active>>engineforgeunloadedpressToppressMiddlepressLowerFigure4.Class diagram of the press The class diagram shows the structure of the press,itsclasses and their associations,but it does not describe the behaviour of the class instances.We use UML Statecharts to model the behaviour of the instances of the PressCon-troller and PressPlant.Figure5shows the Statecharts di-agram for the controller of the press,while Figure6is a model of the plant of the press.Thefirst action performed by the controller is to enter the“Loading”state.There is an entry action associated to this state.Each time that the controller enters this state,the action is executed.In this case,it informs to the robot that the press is ready to be loaded.When the robot places a new blank into the press,it sends the“forge”event to the press controller.The“forge”event is the trigger of a tran-sition from the“Loading”state to the“Pressing”state.As soon as the press receives the“forge”event,it will leave the “Loading”state and it will enter the“Pressing”state.The transition contains an action.It commands the plant to start the engine to lift the press.The“Pressing”state is exited when the mobile part of the press arrives at the top.Then the controller switches to the“GoingBottom”state and it commands the engines to go down.The“GoingBottom”state has an internal transition,a transition where the set of source and target states is the same.It captures an event from the plant indicating that the press is in the middle po-sition and it instructs the plant to continue moving down. When the mobile part is at the bottom of the press,the con-troller enters the“Unloading”state.It stops the engine and it signals the robot to indicate that the press is ready to be unloaded.After taking the forged blank,the robot sends an“Unloaded”event so the press can move to the loading position.4.1.1Adding user requirements to the modelThe Unloading state is marked with the progress stereotype.Every time that the machine has processed one piece,the controller enters this state.The progress stereotype indicates the fact that the object has made a unit of work.It is a liveness requirement for the press.It states that the“Unloading”state should be visited infinitely of-ten in a normal execution of the object.It is equivalent to the following linear temporal logic(LTL)[10]formula:.The square or sym-bol is read as“always”and the diamond or is read as “eventually”.The formula can be read as:always the press will eventually be in the unloading state and eventually in a different state.We have chosen to annote the“Unloading”state as a progress state beacuse entering this state means that the press has completely processed a request from an external client.If the press is fed with an unlimited amount of blanks,the controller should enter and exit the“Unload-ing”state an infinite amount of times.Figure6shows a model of the plant of the press.Theunloaded ^ Plant.engine(UP)Figure5.Controller of the pressstate machine is divided into two orthogonal regions.The left region keeps the state of the engine,while the right re-gion models the position of the mobile part of the press. The press is initially in the middle position and the engine is stopped.If the engine is set to“Forward”,the mobile part will start moving and,eventually,it will enter the“AtTop”state.The transition from the“AtMiddle”to the“AtTop”state does not have a trigger.It is a completion transition and it willfire as soon as the movement is complete.The guard ensures that the activity associated with the state and the completion transition is only carried out while the guard holds.A guard is a predicate over the attributes and states of the object.The term is true when the state named is active.In this case,the guard is true while the“Forward”state is active.If the mobile part is in the top of the press and the en-gine is set to forward,the press can break itself by mov-ing the plate past its physical limit.This is modeled with the“TopCrash”state,that is marked with the invalid stereotype.This stereotype is used to capture a safety re-quirement:An invalid state should never be entered.The requirement can be interpreted in terms of a LTL formula as:.An invalid state is similar to an as-sertion statement of a program,it does not add more be-haviour to the system,but it captures a requirement for the system.The model also contains the“LowerCrash”state that captures the requirement that the mobile part should not be moved past its lower limit.The complete require-ment for the object isFigure6.Plant of the press.4.1.2Instanciating objectsA UML Statecharts describes the behaviour of all the ob-jects instantiated from a given class,but it does not cre-ate the objects.Instead,we can use a UML collaboration diagram to instantiate and link together the objects of our model.The main model elements of a collaboration dia-gram are objects and links between objects.An object is an instance of a class,and a link is an instance of an association of a class.In our semantics,each object in the collaboration di-agram runs in a different process.Each process is an instance of a run-to-completion step,and it is scheduled asynchronously.Processes communicate by sending events trough links,which are instances of associations of a class. This means that if link goes from object to objectin the collaboration diagram,then any message sent along from will automatically be routed to.Note that a link can introduce arbitrary delays when transmitting an event, but it cannot loose events.Figure7is a simple collaboration diagram showing an instance of the press controller and the plant.It shows the collaboration in its initial state where the objects have not exchanged any message yet.Since these objects are active and run concurrently,it is not always easy to determine how these objects will collaborate,i.e,which messages will be exchanged and in which order.We can use the vUML tool to automatically generate all possible evolutions of the col-laboration diagram and to check whether our model holds the safety and liveness requirements that we have intro-duced in it.:PressPlant:PressControllerCtrl PlantFigure7.Press collaboration diagram4.1.3Open modelsIt is important to note that the collaboration diagram does not include an object representing the robot.The press con-troller sends the“pressReadyLoad”and“pressReadyUn-load”trough a link named“robot”,and it expects the “forge”and“unload”events from any of its links.However, we have not modelled the robot yet.The model is open.Open models that react to messages sent by external en-tities,cannot be verified with a model checker.They have to be closed or verified by hand.However,vUML can convert an open model into a closed one,where no external event instances are needed,if the external events do not carry pa-rameters.vUML automatically determines when the source of an event is not defined within the model and creates an event generator for those events.Since the model does not contain any information about the generation of these events,the event generator is nondeterministic.vUML au-tomatically discards events directed to a missing link.The vUML tool detects that the diagram in Fig.7is an open model and creates an event generator for the“forge”and“unloaded”events.This allows us to verify the compo-sition of the press controller and the plant while abstracting from the robot.The event generator is demonic,it generates the events trying to reveal an error in the model.The twokey characteristics of the event generator are:it will eventu-ally produce an event and it will not send an event to an ob-ject,if the event will not trigger a transition.Thefirst con-straint ensures that the model will never deadlock because the event generator would have decided not to send an event to an object.The second constraint has been introduced to speed up the verification.As defined in the semantics,the state of an object does not change when the object receives an unexpected event.By not sending events that will notfire a transition we can reduces the verification problem osten-sibly and avoid a possile livelock situation where the event generatorfloods an object with unexepected events.4.1.4Verification of the pressBy running the verification,we can observe that it is possi-ble to reach the TopCrash state.Figure8shows the output of the vUML tool for the previous model.It is a counter-example,a sequence of events that leads to an error in the model.The right part of the Fig.8is a sequence diagram derived from Fig.7that shows one of the sequences of mes-sages exchanged between the press and the plant that lead to the crash.The left part of thefigure is a textual descrip-tion of the counter-example,also generated by the tool.The textual description contains both the internal and externally observable activity of the objects,while the UML sequence diagram only shows the externaly observable and consumed events.The interpretation of the counter-example is as follows: Initially,the Controller receives a forge event from an object placed outside of the diagram(1).The controller sends a message to the press to start the engine(2)and it enters the“Pressing”state(3).The plant receives the message (4),and the engine is set to forward(5).Eventually,the mobile part of the press reaches the top of the press(6,8) and the plant sends the“pressTop”event to the controller (7),but the plant continues its movement.If the reaction of the controller is too slow,the lower plate can reach the top plate(9)and the machines crashes(10).Step7is not shown in the sequence diagram because the execution tracefinish before the controller receives and consumes the pressStop event.The link between the plant and the controller can intro-duce arbitrary delays and the processor executing the con-troller object can use a significant amount of time to pro-cess the events.The model checker explores exhaustively all possible behaviours of the system,including all possi-ble ways to schedule the execution of the objects.Although the model does not contain any time information and nei-ther vUML nor SPIN handle real-time model,the analysis of the counter-example from the model checker reveals a time constraint in the implementation of the model.In the final implementation,the reaction time of the controller for the“pressTop”must be bounded.Unfortuanetelly,we can not use vUML tofind the upper bound for this time con-straint.It depends on may factors:the speed of the engine of the press,the distance from the sensor to the real end of the press,the latency of the communication link between the sensor and the controller,the speed of the processor ex-ecuting the controller object and the presence of other real-time threads on the processor.We can use the vUML tool to search for other errors in the model and check that the “LowerCrash”state is also reachable.In order tofix these errors,we modify the model of the plant so it captures the notion that the implementation of the controller is much faster than the plant.Figure9shows the redesigned model of the plant.We can verify that the new model preserves the requirements for the press for all possible executions of thesystem.Figure9.Second model of the plant of press4.1.5Constraining an association of objectsIn order to fulfill all the requirements from the specification of the press,we must check whether the press is always in the right position during the load and unload phases to avoid a collision with the robot arms.We formulate this require-ment using the following constraint:.A term of the form is true when the state is active in the object associated to the role.A constraint is inter-preted as the LTL formula during the verification.Fig-ure10shows the new collaboration diagram for the press. We place this new safety requirement over a link since it is a constraint affecting two different objects.Every time that the Controller or the Plant will change its internal state,the verifier will check if the constraint holds.We can use the vUML tool to perform the verification1Ctrl accepts forge from outside 2Ctrl sends engine(UP)to Plant3Ctrl enters in pressing4Plant accepts engine(UP)from Ctrl5Plant enters in Forward6Plant advances7Plant sends pressTop to Ctrl 8Plant enters in AtTop 9Plant advances10Plant enters in TopCrashObject Plant has entered the invalid state TopCrash Figure 8.Sequence diagram showing an error trace:PressPlantPlant:PressControllerCtrl{ Ctrl.Loading => Plant.AtMiddle ^ Ctrl.Unloading => Plant.AtLower}Figure 10.Constrained pressagain and observe that the model is correct.We can con-clude that the revised model of the press does not contain deadlocks,the machine cannot crash,the lower part of the press is always in the correct position during the loading and unloading operations and that the press always forges all the metal blanks.These verifications have been performed as-suming that the robot loads and unloads the press correctly.4.2Modelling the robotThe most complex object in the production cell is the robot.It has five actuators and eight sensors.A normal work cycle of the robot can be described in four main steps:1.The robot rotates clockwise until Arm 1is faced to the table.Arm 1extends and picks up a metal blank from the table.2.The robot rotates counterclockwise until Arm 2points towards the press.Arm 2extends and picks up a forged piece from the press.3.The robot rotates counterclockwise until Arm 2points towards the deposit belt.Arm 2extends and drops the piece into the conveyor belt.4.The robot rotates counterclockwise until Arm 1points towards the press.Arm 1extends and places the blank into the press.The robot controller must coordinate the execution of these steps with the other objects of the model.As we can observe in Fig.3,the controller of the robot and the con-troller of the press must synchronise their operation duringthe loading and unloading phases in order to avoid a colli-sion.This is a normal design requirement in models con-taining active objects that evolute independently.We can synchronise the activity of two objects by us-ing call events and deferred events .Call events are special events that represent a synchronous invocation of a specific operation.A call event is generated by a method call ac-tion.Although the standard does not make this explicit,we have assumed that each call event has a corresponding re-turn event.On the level of a single state machine,when a method call is executed as an action,the whole transi-tion step is only completed when the invoked objects com-plete their own run-to-completion steps.The sender of a call event is blocked until the receiver consumes the event.When an event is consumed,it dissapears from the ob-ject,independently of it has trigger a transition or not.In order to avoid this situatuation,it is possible to define a set of deferred events to each state.If an object receives an event and the event does not enable any transition and the event is contained in the set of deferred events of the cur-rent state configuration,the object will place the event in the input queue again.If the receiver is not always ready to process a call event,it should defer it.If a call event does not enable any tran-sition on the receiver and it is not deferred,the event will be discharged.In this case,the caller will wait indefinitely since the call event will never be processed.This situation can be avoided by deferring the call events until the receiver is in a state where it can process them.This synchronisation mechanism is used between the robot and the press.The press sends the “pressReadyUn-load”event to the robot to indicate that,effectively,the press is ready to be unloaded.If the robot cannot process the re-quest of the press,i.e.because it is taking a piece from the table,the event will be deferred.Actually,the robot must also coordinate its activity with the table and the deposit conveyor belt.Figure 11shows a Statecharts diagram describing the behaviour of the con-troller of the robot.It is divided in four main composite states ,corresponding to the four main tasks of the robot.。
uml序列图(条件)

UML 序列图来自: IBM Rational Edge现在是二月,而且到如今你或许已经读到、或听到人们谈论UML 2.0 ——包括若干进步的UML 的新规范,所做的变化。
考虑到新规范的重要性,我们也正在修改这个文章系列的基础,把我们的注意力从OMG 的UML 1.4 规范,转移到OMG 的已采纳UML 2.0草案规范(又名UML 2)。
我不喜欢在一系列文章的中间,把重点从 1.4 变为2.0 ,但是UML 2.0 草案规范是前进的重要一步,我感觉需要扩充文字。
由于一些理由,OMG 改良了UML 。
主要的理由是,他们希望UML 模型能够表达模型驱动架构(MDA),这意味着UML 必须支持更多的模型驱动的符号。
同时,UML 1.x 符号集合有时难以适用于较大的应用程序。
此外,为了要使图变成更容易阅读,需要改良符号元件。
(举例来说,UML 1.x 的模型逻辑流程太复杂,有时不可能完成。
对UML 2 中的序列图的符号集合的改变,已经在序列化逻辑建模方面取得巨大的进步)。
注意我上面所述的文字:“已采纳UML2.0草案规范。
”确实,规范仍然处于草案状态,但是关键是草案规范已经被OMG 采用,OMG是一个直到新标准相当可靠,才会采用它们的组织。
在UML 2 完全地被采用之前,规范将会有一些修改,但是这些改变应该是极小的。
主要的改变将会是在UML 的内部——包括通常被实施UML 工具的软件公司使用的功能。
本文的主要目的是继续把我们的重点放在基础UML图上;这个月,我们进一步了解序列图。
再次请注意,下面提供的例子正是以新的UML 2 规范为基础。
图的目的序列图主要用于按照交互发生的一系列顺序,显示对象之间的这些交互。
很象类图,开发者一般认为序列图只对他们有意义。
然而,一个组织的业务人员会发现,序列图显示不同的业务对象如何交互,对于交流当前业务如何进行很有用。
除记录组织的当前事件外,一个业务级的序列图能被当作一个需求文件使用,为实现一个未来系统传递需求。
UML术语中英对照表
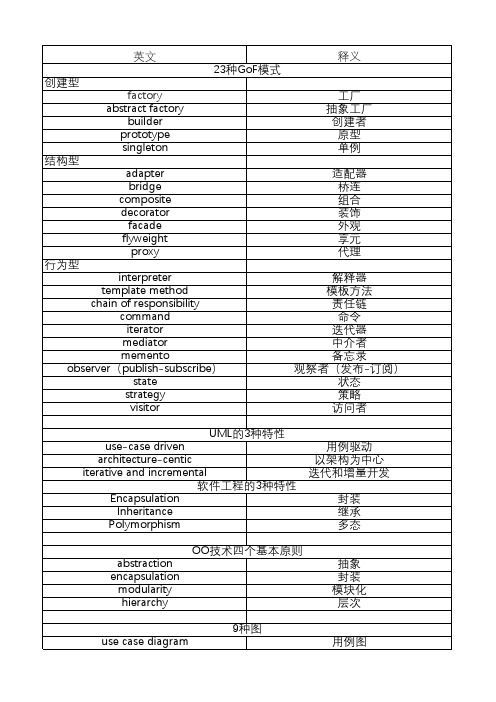
UML的3种特性 use-case driven architecture-centic iterative and incremental
软件工程的3种特性
Encapsulation Inheritance
Polymorphism
用例驱动 以架构为中心 迭代和增量开发
封装 继承 多态
英文 23种GoF模式
创建型 factory
abstract factory builder
prototype singleton 结构型 adapter
bridge composite decorator
facade flyweight
proxy 行为型
interpreter template method chain of responsibility
command iterator mediator
memento observer(publish-subscribe)
state strategy visitor
释义
工厂 抽象工厂 创建者
原型 单例
适配器 桥连 组合 装饰 外观 享元 代理
解释器 模板方法 责任链
命令 迭代器 中介者 备忘录 观察者(发布-订阅)
façade framwork general ordering generalizable element generation granularity graphic marker group transition guillemets hibernate hyperlink implementation indeterminacy indirect instance indirect substate inheritance instantiation
On Generalization and Overriding in UML 2.0

On Generalization and Overriding in UML2.0Fabian B¨u ttner and Martin GogollaUniversity of Bremen,Computer Science Department,Database Systems Group Abstract.In the upcoming Unified Modeling Language specifica-tion(UML2.0),subclassing(i.e.,generalization between classes)has amuch more precise meaning with respect to overriding than it had in ear-lier UML versions.Although it is not expressed explicitly,UML2.0has acovariant overriding rule for methods,attributes,and associations.In thispaper,wefirst precisely explain how overriding is defined in UML2.0.We relate the UML approach to the way types are formalized in pro-gramming languages and we discuss which consequences arise when im-plementing UML models in programming languages.Second,weaknessesof the UML2.0metamodel and the textual explanations are addressedand solutions,which could be incorporated with minor efforts are pro-posed.Despite of these weaknesses we generally agree with the UML2.0way of overriding and provide supporting arguments for it.1IntroductionThe Unified Modeling Language(UML)[OMG03b,OMG04]is a de-facto stan-dard for modeling and documenting software systems.Generalization in class diagrams(i.e.,subclassing)is one of the key concepts in the object-oriented methodology and in UML:It allows us to express that one class is a specializa-tion of another one.The more special class is described as a set of changes and extensions to the more general class.However,the concrete interpretation of subclassing in an executable envi-ronment was rather undefined with respect to overriding(see[Beu02,Pon02]) in previous UML versions(namely,1.x).In UML2.0,along many other major changes,generalization is defined much more precisely than in1.x.Although it is never mentioned explicitly on640pages,UML2.0introduces a covariant overriding rule for operations and properties.Hence,a subclass over-riding a superclass operation may replace the parameter types by subtypes of them.The same rule applies for attributes(the attribute type can be replaced by a subtype)and associations(the association end types can be replaced by subtypes),which can be redefined in UML2.0as well.The UML2.0provides a meaning for specialization which is consistent across operations,attributes,and associations.There has been a never ending discussion about whether covariance is a good meaning for overriding in the areas of programming languages and type theory. There has been nofinal agreement,but a general conclusion was that subclassing in the presence of covariant overriding cannot be used to define subtyping(fora formal explanation see[AC96],a good overview can be found in[Bru96]). Thus on the one hand,statically type checked programming languages cannot have a sound type system when covariant subclassing is generally allowed.On the other hand,it is argued that many situations in the real world are better modeled covariantly,a good argument for this is made,for example in[Duc02].A more formal comparison of both concepts which does not advocate either of them can be found in[Cas95].Commonly,UML models arefinally implemented in a statically typed pro-gramming languages such as Java,C++,and C#.Most of these programming languages do not permit covariant method overriding for the aforementioned type safety reasons(Eiffel[Mey88]is one of the few exceptions).Hence,there is a gap between subclassing semantics in UML and common OO programming languages,which must be considered during implementation of UML models. Nevertheless,we support the UML2.0view of subclassing as we think that the richer expressiveness outweighs the typing problems.This paper precisely explains how overriding is defined in UML2.0.We relate the UML approach to the way types are formalized in programming languages and we discuss which consequences arise when implementing UML models in programming languages.Despite of the mentioned typing problems we generally agree with the UML2.0way of overriding and provide supporting arguments.However,we have some concerns regarding overriding and subclassing in the final adopted UML2.0specification,which could be corrected with minor ef-forts:(i)There are two inconsistencies in the metamodel parts which deal with redefinition and subclassing.(ii)The definition of subclassing in UML2.0is scat-tered over a large number of class diagrams,several textual semantics sections, and a couple of additional interdependent OCL operations.Thus understanding how subclassing works in UML is a complex task.Since subclassing is such an important concept in object-oriented analysis and design,an explaining section is definitely missing in order to carry the meaning of UML subclassing to the broader audience.This is especially important in the context of Model Driven Architecture[KWB03,OMG02].(iii)Different from earlier versions,UML2.0 uses the term‘subtyping’at various locations where‘subclassing’is intended. Because of the mentioned covariant overriding rule in subclassing,the term‘sub-typing’should be used more carefully in the specification.This paper is structured as follows:Section2explains our notions of class, type,subtyping,variance,and subclassing used in this paper and relates sub-classing to subtyping.Section3shows how subclassing and overriding is han-dled in UML2.0.Section3also illustrates the consequences of having covariant overriding when implementing object models in statically typed programming languages.In Section4,we justify the existence of a covariant overriding rule in UML and address the mentioned concerns with regard to the technical realiza-tion in the specification.We close the paper with a conclusion in Section5.2BackgroundIn this section we shortly explain our notions for type,subsumption(subtype polymorphism),covariance,and contravariance,following[CW85,AC96].We re-late the notions of subclassing and subtyping.The section is designed to summa-rize central relevant notions in programming languages and type theory employ-ing minimal formalization overhead.Readers familiar with these notions may skip this section.2.1Type,Subsumption,and VarianceIn a programming language,a type represents a set of values and the operations that are applicable to them.For example the type Integer may denote the set of natural numbers N and the operations1,+,and−.In object-oriented pro-gramming,an object type represents a set of objects and the messages that can be sent to the objects.Types can be used to form a membership predicate over expressions:If an expression e evaluates to a result of type T we say e has type T, denoted as e:T.A strongly typed programming language provides mechanisms to ensure that only appropriate operations are applied to values.For example, "Hello"-5would be rejected,because a String type typically does not include a’-’operation for strings and numbers.In statically typed programming lan-guages like C++,Pascal,Java,C#and many others,expressions are assigned static types by a type checker before actual execution.The type checker guar-antees that if an expression has the static type T,its evaluation at runtime will always be a value of type T.A powerful typing rule which is implemented in nearly all common program-ming languages and in modeling languages like UML is the subsumption rule, also known as subtype polymorphism.The subsumption rule states that if an expression e has type S and S is a subtype of a type T,denoted as S<:T, then e has also type T.if e:S and S<:T then e:TAs a consequence,expressions may have more than one type.In order to have a sound type system(i.e.,no wrong types can be derived for expressions),only certain types can be related by the subtype relation<:.Typically,subtyping for complex types(i.e.,for function types and object types)is derived from simpler types(e.g.,for function types,<:is derived from the parameter types and return types of a function).Several sound type systems exist,with varying rules for subtyping,including virtual types,higher-order type systems(generic types)and other more elaborated concepts.The following general considerations hold for these systems as well.For languages with functions,the→type constructor can be used to con-struct function types.For example,Integer→String denotes the type of a function from Integer to String.As explained in[CW85],for given function types X→Y and Z→W the subtype relation X→Y<:Z→W can be defined as follows: X→Y<:Z→W iffZ<:X and Y<:WFor example the function type Real→Integer is a subtype of the function type Integer→Real,assuming Integer<:Real.Because the argument types X and Z are related by<:in the opposite direction as X→Y and Z→W,this subtyping rule for function types is contravariant w.r.t.to the argument type,and covariant w.r.t.the return type.Strictly speaking,we must always specify to which part of a complex type we refer to when using the term variance.Formally,variance is defined as follows:Let T{−}denote a type T with some‘hole’(i.e.,a missing type expression in it).Let T{A}denote the type T when the hole isfilled with a type A.T{−}is:covariant if A<:B implies T{A}<:T{B}and contravariant if A<:B implies T{B}<:T{A}.However,some‘default’references for variance have been established in the literature,such as the parameter type for a function type,so the subtype rule for functions is generally known as the contravariance rule for functions.In object-oriented languages,the most important concept is sending a mes-sage to an object(i.e.,invoking an operation).Thus in a statically typed pro-gramming language,the type checker prevents that inappropriate messages are sent to objects.We denote an object type as follows:T=[l1:T1,...,l n:T n],where l i are the elements(labels)of T(i.e.,methods andfields).In the case of afield l i,which is actually a method without parameters,T i is simply another object type(or a basic type).In the case of a method l i,T i is a function type.For example,a simple Point type may be modeled as follows:Point=[x:Integer,y:Integer,distanceTo:Point→Integer] Obviously,an object type T for which T <:T holds must contain the labels l1,...,l n since an object of type T must understand all methods andfield access operations that an object of the supertype T understands.Furthermore, in general we cannot allow that the individual label types T1,...,T n change in T .Subtyping for object types is sound,if we require T i=T i for i=1..n: [l1:T 1,...,l n+m:T n+m]<:[l1:T1,...,l n:T n]if T i=T i,i=1..n Formal proofs for this can be found in[AC96].The basic idea is as follows: Let o be an object of type T .If we allowed T i<:T i for some i in the above subsumption rule for object types then we could derive o.l i:T i.Thus the type checker would accept an assignment o.l i:=x for a value x:T i.But this as-signment would be valid only if T i<:T i(contradiction).The other way round, if we allowed T i<:T i,a similar contradiction occurs for a selection operation x:T i:=o.l i.Hence,type systems having a general co-or contravariant subtyp-ing rule for object types cannot be sound.However,in class based languages,where all methods of an object are de-clared statically(at compile-time),the types for method labels may change in subtypes in a covariant way(both,the object type and the method label type become more special).Thus for S=[l:X→Y]and T=[l:Z→W],S is a subtype of T(S<:T) iffZ<:X and Y<:W and l cannot be updated.Although the type of thelabel l varies covariantly with the object type,this rule is commonly known as the contravariance rule for method overriding,because the parameter type varies contravariantly with respect to the object type.Also common in the literature is the(unsound)covariance rule for method overriding which also refers to the parameter types.2.2Classes and SubclassesClasses describe objects with same implementations[Mey97].A class serves as a generator for objects.It specifies which state(i.e.,which attributes)and which behavior(i.e.,which methods)objects generated by the class have.Subclassing is a technique for reusing object descriptions(classes).A new class(the subclass)is described as a set of changes to an existing one(the superclass).The partial order denotes if a class is a direct or indirect subclass of another class.There is no general agreement about the exact semantics of subclassing(see e.g.,[CHC90,PS92,Bru96]).Common definitions of subclassing in programming languages involve the following mechanisms to describe how a new class is de-rived from an existing one:(i)Inheritance,properties of the superclass become properties of the subclass(often,this is the default),(ii)Overriding,properties of the superclass are redefined in the subclass(in typical OO languages,over-riding is restricted to methods),(iii)Extension,new properties are added to the subclass.Classes can be used to define types(a class c defines a type type(c)).Then, the subclass relationship can be used to define subtyping.This is done in most common statically typed OO programming languages as follows:type(s)<:type(c)iffs cTo achieve this behavior,types must be extended and distinguished by names (i.e.,c=c implies type(c)=type(c )).Thus,two distinct classes can have completely identical definitions but do not create the same type.This is known as name subtyping in the literature and is used,for example,in Java,C++,and C#.Other languages allow distinct classes to create the same type.However, having name subtyping or not has no impact on the variance aspects of overriding when subclassing is subtyping.While defining subtyping as subclassing has no consequences for inheritance and extension,it restricts the way overriding can be applied in subclassing. Especially,as explained above,method overriding cannot be covariant(i.e.,the parameter types of an overriding method cannot be subtypes of the parameter types of the overridden method)as explained above.After having discussed programming languages let us now turn to modeling languages.3How UML Handles Subclassing and OverridingIn this section,we explain how subclassing and overriding is handled in the UML 2.0metamodel using a simple example.We focus on overriding of methods,although the same principles apply to attributes and associations ends.3.1The Animals ExampleFig.1shows an example of a class diagram containing a generalization relation-ship.The class Animal generalizes the classes Cow and Rat.Read the other way,we say Cow and Rat are specializations or simply subclasses of Animal.Rat beep()CowAnimaleat(food)eat(food)makeMilk()Fig.1.Example class diagramAs said above,along with generalization comes inheritance and overriding.The eat(food)operation defined in Animal is inherited by Rat.Thus,instances of class Rat do not only have the operation beep(),but also eat(food).In class Cow,we have repeatedly defined eat(food)to indicate that the class provides a new definition of the eat(food)operation.In this case,we say Cow overrides,or,in UML 2.0terms,redefines eat(food)from Animal.Rat beep()FoodGrassCowAnimalmakeMilk()eat(food : Food)eat(food : Grass)Fig.2.Example class diagram with parameter typesHowever,the reader may notice that we have omitted the parameter types in Fig.1.If we fully specified our operations,the class diagram may look as in Fig.2.We now have clarified the fact that Cows shall only eat a certain kind of food:Grass.But,is this still overriding?Earlier UML versions left the wayoperations(methods)override intentionally undefined:The way methods override each other is a semantic variation point.[OMG03b,p.2-74].The upcoming UML2.0specification[OMG04]is more precise:An operation may be redefined in a specialization of the featured clas-sifier.This redefinition may specialize the types of the formal parame-ters or return results,add new preconditions or postconditions,add new raised exceptions,or otherwise refine the specification of the operation.[OMG04,p.78]Thus,in UML2.0,Cow::eat(food:Grass)may override Animal::eat(food:Food) if Grass is a specialization(i.e.,a subclass)of Food.As we explained in Section2, this kind of overriding is covariant.The following subsection shows how this restriction is modeled in the UML2.0metamodel.3.2Relevant Excerpts of the UML2.0MetamodelThe metamodel elements relevant for generalization and redefinition are scat-tered overfive class diagrams in the specification.Furthermore,constraints and additional operations are defined separately in the textual part.Thus,the de-scription is distributed over more than20(!)locations.The class diagrams in Figs.3and4combine all relevant aspects.Constraints and additional opera-tions are attached either in-place or as comments.We have given names to the invariants(which do not occur in the UML2.0specification)in order to refer to them in the following.Three invariant constraints occur in Figs.3and4.Two of them,RedefinitionContextValid and RedefinedElementsConsistent,belong to the metaclass RedefinableElement.The third,SpecializeValidType,belongs to the metaclass Classifier.Wefirst look at RedefinitionContextValid.This constraint is straightforward. Its meaning is,that for an element e which redefines another element e,e must belong to some subclass of the class in which e is defined.The additional operation isRedefinitionContextValid(e:RedefinableElement)must yield true for each redefined element.The second constraint,RedefinedElementsConsistent,is more subtle and has a lot of impact on the UML2.0semantics:Its meaning is that all redefined ele-ments must be consistent with the redefining element.The concrete meaning of ‘is consistent’is deferred to subclasses of RedefinableElement,e.g.,to Operation. To illustrate this constraint,we consider our animals example from Fig.2.On the metamodel level,it looks like the object diagram in Fig.5(we have omitted the operation makeMilk()and the class Rat for simplicity).isRedefinitionContextValid(r:RedefinableElement) =redefinitionContext−>exists( c1 |r.redefinitionContext−>exists( c | c.allParents−>includes(c1)))/redefinedElement {union}RedefinableElement isConsistentWith(e:RedefinableElement) = falseisRedefinitionContextValid(r:RedefinableElement)=...TypeconformsTo(o:Type)=false Class ClassifierinheritableMembers(c:Classifier)=member−>select(m|c.hasVisOf(m))general specific 11/redefinitionContext {union}redefinedElement−>forAll(e | isRedefinitionContextValid(e))inv RedefinitionContextValid [1]:redefinedElement−>forAll(e | e.isConsistentWith(self))inv RedefinedElementsConsistent [2]:parents−>forAll(c | maySpecializeType(c))inv SpecializeValidType [3]:conformsTo(o:Classfier)=(self=o) or allParents()−>includes(o)inherit(inhs:Set(NamedElement)=inhsmaySpecializeType(c:Classifier)=oclIsKindOf(c.oclType)Generalization isSubstitutable:BooleanFig.3.Condensed UML 2.0Facts about Generalization and Redefinition -Part AFig.4.Condensed UML 2.0Facts about Generalization and Redefinition -Part BformalParameter formalParameter type typegeneralspecificfeature feature redefinedElement general specific food :Parameter food’:Parameter :Generalization Grass :ClassFood :Class eat’:Operation Cow :Class :GeneralizationAnimal :Classeat :Operation Fig.5.Example as metamodel object diagramFor this object diagram,the invariant RedefinedElementsConsistent can be written out as follows:eat .redefinedElement →forAll(e |e .isConsistentWith(eat ))=eat .isConsistentWith(eat )=eat .formalParameter[1].type .conformsTo(eat .formalParameter[1])=food .type .conformsTo(food .type)=Grass .conformsTo(Food)=(Grass =Food)or Grass .allParents →includes(Food)RedefinedElementsConsistent is responsible for the mentioned covariant overrid-ing rule in UML 2.0.If one operation redefines (i.e.,overrides)another,all formal argument and return types of the redefining operation must be specializations of the formal argument and return types of the redefined operation.Finally,the third invariant SpecializeValidType intends that a classifier may specialize each of its superclasses.We show in Section 4that the operation maySpecializeType(c:Classifier)involved in the constraint depends on the OCL definition of subtyping in an ill-defined way.3.3Interpretation of UML Models using Covariant OverridingLet us consider again our animals class diagram from Fig.2.The following piece of program (pseudo code)illustrates the problem which arises when eat is covariantly overridden in class Cow.declare x :Animaldeclare y :Foodx :=someAnimaly :=someFoodx .eat(y)If we assume that instances of type Cow can be substituted for instances of type Animal (i.e.,by subsumption),then the expression someAnimal may evaluate to an object of type Cow and the result of someAnimal can be still safely assigned to the variable x .Further,x.eat (y )would be statically type safe,because the static type of x is Animal.Nevertheless,if the expression someFood evaluates to an instance which has type Food (i.e.,which has not type Grass),theevaluation of x.eat (y )will produce an error because Cow::eat is not defined for the parameter type Food.This consideration exemplifies why subclassing cannot be subtyping when the parameter types of a method are covariantly redefined,for the reasons given in Section 2.However,class based programming languages like Java,C++,or C#have (more or less)sound type systems and prohibit covariant method overriding.Actually,they only support invariant overriding,although covariant overrid-ing would be sound for methods (i.e.,parameter types could vary contravari-antly and return types could vary covariantly w.r.t.the object type).Newer versions of C++and Java allow at least covariant redefinition of return types[Str97][BCK +01].If a class diagram containing covariant overriding is to be translated into such a programming language,the inherent typing problem be-comes obvious.A pragmatic solution may look like the one in Fig.6.Rat beep()CowAnimalmakeMilk()eat(food : Food)eat(food : Grass)Rat beep()Cow Animal makeMilk()eat(food : Food)eat(food : Food)if (not food.oclIsKindOf(Grass))raise type errorelseeat food.oclAsType(Grass)Fig.6.Transformation to invariant overridingAlthough the animals example is now statically type safe,it still produces an error if cows shall eat food which is not grass.We have only deferred the error from compile time to runtime.It is important to see that this (potential)error is inherent to the UML class diagram and not a consequence of the implementation.The designer of the class diagram expresses that cows must not eat inappropriate food,for example to avoid mad cow diseases.Multi-methods [ADL91,BC97,CL95,DCG95]provide an alternative interpre-tation of covariant specialization.Instead of simply failing a dispatch (i.e.,a method call),one of the overridden base class methods may be called instead.Actually,a multi-method based semantics could have been chosen for overriding in UML 2.0.However,we feel that multi-methods are a less intuitive meaning for specialization than ‘simple’overriding.Furthermore,multi-method seman-tics are difficult to realize in common OO languages and,in general,can lead to ambiguities in the context of multiple inheritance.At least one commonly known OO programming language exists,in which covariant overriding as it is realized in UML2.0is directly available:Eiffel [Mey88,Mey97].Eiffel,aware of the mentioned typing problems,supports covari-ant overriding as a fundamental design aspect and thus is close to the UML2.0 understanding of subclassing.Our animals example could be directly imple-mented in Eiffel.A runtime error would be raised by Eiffel when a cow tries to eat food which is not grass.Although Eiffel is not statically type safe,ongoing work proposes that many runtime type errors could be eliminated by compilers by using more elaborated analysis and type-checking techniques[HBM+03].4Concerns with the UML2.0SpecificationDespite the subclassing resp.subtyping problem explained in the last section, we generally agree with the UML2.0way of defining redefinition for operations, attributes,and associations.Why do we agree?Even sound statical type systems such as in Java,cannot guarantee real substitutability for subtypes.A more special object may violate semantic contracts(e.g.,invariants)which a more general object fulfills.Type systems guaranteeing real substitutability would require a behavioral notion of subtyping(e.g.,the‘Liskov Substitution Principle’[LW94]).However,it seems that very few real world examples[Duc02]exist where objects of one class are generally substitutable for objects of another class.If subclassing must be subtyping when modeling real world aspects,very few subclassing relations can exist.On the other hand,it is a basic desire of designers to model set inclusion by subclassing(i.e.,the set of cows is a subset of the set of animals).Hence,although identifying subclassing and subtyping is desirable for programming languages to achieve reasonable statical safe type checking,it is not adequate for intuitive object-oriented modeling on a higher level of abstraction.Therefore,we agree with the covariant way of overriding in UML2.0.Nevertheless,we have a couple of concerns with the upcoming specification, which are not fundamental but regard the technical realization of how subclass-ing and overriding(redefinition)is described.4.1Concerns with the MetamodelWe have found two errors in the metamodel parts that model subclassing and overriding.These errors can befixed with minor efforts.Ill-defined operation Classifier::maySpecializeType Consider the third invariant constraint of the metaclass Classifier(named SpecializeValidType in Fig.3).For each instance c of Classifier,c.parents→forAll(c |c.maySpecializeType(c ))must hold.This can be rewritten using the definition of maySpecializeType toc.parents→forAll(c |c.oclIsKindOf(c .oclType))The built-in OCL operation o.oclIsKindOf(t)is defined as follows:‘The oclIsKindOf property determines whether t is either the direct type or one of the supertypes of an object’[OMG03a].Since subtyping in OCL requires sub-classing,the definition of maySpecializeType is circular:c may subclass c only if c is a subtype of c and if c is a subtype of c then c must be a subclass of c .Hence,maySpecializeType is not well-defined.As a proposal for solving this problems we argue for simply omitting Special-izeValidType from the UML 2.0specification,as it does not make any further restrictions to UML models.Operation Property::isConsistentWith contradicts textual semantics Another inconsistency can be found in Property::isConsistentWith .Consider the example in Fig.7.It is similar to the previous one,except that animals and cows now have a ‘food’attribute (i.e.,a property)instead of an ‘eat’operation.The (textual)specification states,in the covariant specialization manner,that an attribute type must be redefined by the same or a more specific type.However,if we write out the operation isConsistentWith we obtainfood .redefinedElement →forAll(e |e .isConsistentWith(food ))=food .isConsistentWith(food )=food .type .conformsTo(food .type)=Food .conformsTo(Grass)=(Food =Grass)or Food .allParents →includes(Grass)which obviously yields false.If we used this definition of maySpecializeType for Property,we gained a contravariant overriding rule for properties,which is not intended according to the explaining text and which does not match the general idea behind redefinition in UML 2.0.Apparently,the subterm type .conformsTo(p .type)must be flipped (i.e.,be rewritten to p .type .conformsTo(self .type))to achieve the intended covariant overriding rule for properties.Animalfood : Food general specific type typegeneralspecific feature feature redefinedElement food : Grass Cow:Generalization Food :Class Grass :Class:Generalizationfood :Property food’:Property Animal :Class Cow :Class Fig.7.Example with Properties。
转换 名词解释 uml中的意思

转换名词解释 uml中的意思UML是Unified Modeling Language的缩写,意为统一建模语言。
它是一种用于软件系统设计、建模和文档化的图形语言。
1. Use Case Diagram: A UML diagram that represents the interactions between a system and its users or external systems.用例图:表示系统和用户或外部系统之间交互的UML图示。
2. Class Diagram: A UML diagram that represents the structure and relationships of the classes in a system.类图:表示系统中类的结构和关系的UML图示。
3. Object Diagram: A UML diagram that represents the instances of classes and their relationships at a specific point in time.对象图:表示特定时间点上类的实例及其关系的UML图示。
4. Sequence Diagram: A UML diagram that represents the interactions between objects in a chronological order.顺序图:按照时间顺序表示对象之间交互的UML图示。
5. Activity Diagram: A UML diagram that represents the flow of activities or processes in a system.活动图:表示系统中活动或流程的流程示意图的UML图示。
6. State Machine Diagram: A UML diagram that represents the possible states and transitions of an object or system.状态图:表示对象或系统可能的状态和转换的UML图示。
形式语义-操作语义

表达式的语义
逻辑表达式的求值
求值规则(2)
b, true b, false b, false b, true b0 , t0 b1 , t1 b0 b1 , t b0 , t0 b1 , t1 b0 b1 , t
积 其中n是n 0 与n1的
表达式的语义
逻辑表达式的求值
求值规则(1) true, true false, false a0 , n0 a1 , n1 如果n0 等于n1 a0 a1 , true a0 , n0 a1 , n1 如果n0 不等于n1 a0 a1 , false a0 , n0 ( a1 , n1 如果n0小于等于n1 a0 a1 , true a0 , n0 a1 , n1 如果n0大于n1 a0 a1 , false
操作语义
操作语义概述(2) 传统的操作语义的顶峰是VDL(维也纳定义语言),IBM 的维也纳实验室,形式化定义PL/1语言 与此同时,英国赫斯利实验室对PL/1语言 的形式化被 ANSI接受为标准(形式化程度较低,规范的自然语言描述) 操作语义的另一个变种是变换语义。用分而治之的思想降 低复杂度(抽象复杂度+翻译复杂度)。德国CIP小组提出 的广谱语言。M5,M4,M3,M2,M1 1981,Plotkin提出结构化的操作语义。把公理化方法引入 操作语义中,基本思想是:复合成分的操作语义可以归结 为其各个组成部分的操作语义。
表达式的语义
状态下布尔表达式((x*y)<z) ∧+(z+x=0)的求值, (x)=3, (y)=5, (z)=7
TTCN3 关键字介绍
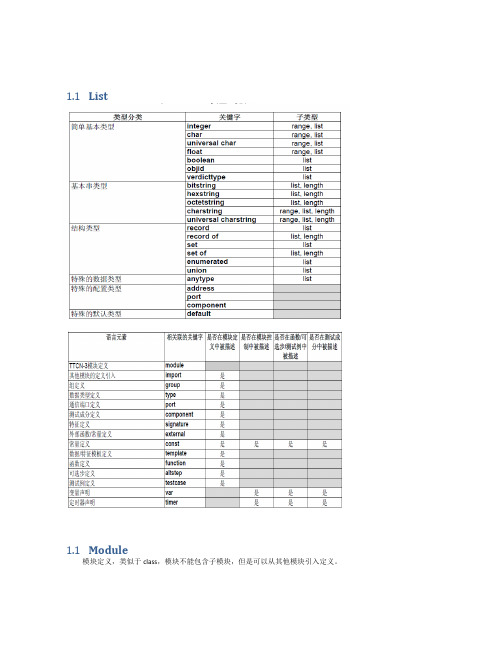
1.1List1.1Module模块定义,类似于class,模块不能包含子模块,但是可以从其他模块引入定义。
定义部分:定义测试成分、通信端口、数据类型、常数、测试数据模板、函数、测试端口上调用的过程特征(signatures)、测试例等等。
控制部分:分调用测试例并控制它们的执行。
控制部分也可以声明(局部)变量等,程序语句(如ifelse和do-while)可以用于各个测试例的选择和执行顺序。
TTCN-3不支持全局变量的概念。
1.2Type用户自定义数据类型type float pi (3.1415926);type set MySetType{integer field1,charstring field2}1.3Template模板(Templates)用于传送一个特定值的集合或是测试接收的值的集合是否与模板说明匹配。
a) 模板提供了一种组织和重复使用测试数据的方法b) 模板能够被参数化;c) 模板允许匹配机制;d) 模板既能够用于基于消息的通信,也能用于基于过程的通信1.4ComponentThe component type defines which ports are associated with a component.•It is also possible to declare constants, variables and timers local to a particular component type.•These declarations are visible to all testcases, functions and altsteps that run on an instance of the given component type. This shall be explicitly stated using the runs on keyword (see clause 16) in the testcase, function or altstep header.1.5Port && messagePort:端口可以基于消息(message标识),和基于过程(procedure)的,甚至是二者混合(mixed)的。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Operational Semantics of UML2.0InteractionsMar´ıa Victoria Cengarle1and Alexander Knapp21Technische Universit¨a t M¨u nchencengarle@in.tum.de2Ludwig-Maximilians-Universit¨a t M¨u nchenknapp@pst.ifi.lmu.deAbstract.An operational semantics for UML2.0Interactions is defined thatforfinite traces is compliant with the trace-based denotational semantics of aprevious work.To this end,the notion of interactions in the classical sense is used.That is,the operational semantics of UML2.0Interactions is given by composingtheir translation into interactions in the classical sense and the reduction relationsbelow.1PreliminariesWe briefly review the basic definitions on partially ordered,labelled multisets as intro-duced by Pratt[3]for modelling concurrency.In particular,we define sequential and parallel composition operators and the notion of traces and processes.A partially ordered,labelled multiset,or pomset,is the isomorphism class[(X,≤X,λX)]of a labelled partial order(X,≤X,λX)w.r.t.monotone,label-preserving maps.A trace is a pomset whose ordering is total.We write p↓for all possible linearisa-tions of a pomset p,i.e.,all traces that extend the ordering of p:[(X ,≤X ,λX )]∈[(X,≤X,λX)]↓if,and only if X =X,λX =λX,and≤X⊆≤X where x1≤X x2 or x2≤X x1for all x1,x2∈X .The empty pomset,represented by(∅,∅,∅),is denoted byε.Let p=[(X,≤X,λX)] and q=[(Y,≤Y,λY)]be pomsets such that X∩Y=∅.The concurrence of p and q, written as p q,is given by[(X∪Y,≤X∪≤Y,λX∪λY)].The concatenation of p and q, written as p;q,is given by[(X∪Y,(≤X∪≤Y∪(X×Y))∗,λX∪λY)].Given a binary, symmetric relation<>on labels,the<>-concatenation of p and q,written as p;<>q,is given by[(X∪Y,(≤X∪≤Y∪{(x,y)∈X×Y|λX(x)<>λY(y)})∗,λX∪λY)].We write p n for the n-fold iteration of pomset concatenation with n a natural number,i.e.,p0=εand p n+1=p;p n.Furthermore we let p∗denote n≥0p n.Analogously,we write p n<> for the n-fold iteration of<>-concatenation with p0<>=εand p(n+1)<>=p;<>p n<>.Note that concatenation and<>-concatenation are associative,and concurrence is associative and commutative.A process is a set of pomsets.An n-ary function f on pomsets is lifted to processes P1,...,P n by defining f(P1,...,P n)={f(p1,...,p n)|p1∈P1,...,p n∈P n}.2Abstract SyntaxWe define the abstract syntax of a fragment of the language of UML2.0interactions of[2].We assume two primitive domains for instances I and messages M.An event e isInteraction::=None|Empty|Basic|CombinedFragmentCombinedFragment::=strict(Interaction,Interaction)|seq(Interaction,Interaction)|par(Interaction,Interaction)|loop(Nat,(Nat|∞),Interaction)|ignore(Messages,Interaction)|restr(Instances,Interaction)|alt(Interaction,Interaction)|not(Interaction)Table1.Abstract syntax of interactions(fragment).either of the form snd(s,r,m)or of the form rcv(s,r,m),representing the dispatch and the arrival of message m from sender instance s to receiver instance r,respectively. The set E comprises all events over I and M.The message of an event e is denoted byµ(e).We say that the instance s is active for snd(s,r,m)and,similarly,that the instance r is active for rcv(s,r,m);the(singleton)set of instances active for an event e is denoted byα(e).We define a binary,symmetric conflict relation<>on events: e<>e ⇔α(e)∩α(e )=∅.A basic interaction is given by an event-labelled pomset[(E,≤E,λE)]such that conflicting events do not occur concurrently,i.e.,if e1,e2∈E withλE(e1)<>λE(e2), then e1≤E e2or e2≤E e1.The abstract syntax of interactions is given by the grammar in Tab.1.Therein,Basic ranges over the basic interactions,Nat ranges over the natural numbers,Messages over the subsets of M,and Instances over the subsets of I.Note that the interaction constants None and Empty as well as the interaction oper-ators restr and not are not part of the specification of UML2.0interactions as defined in[2].The operator not results from the translation of UML2.0interactions(including the negative operators neg and assert)into“interactions in the classical sense”;see[1]. The operator restr and the constants None and Empty simplify the definition of the op-erational semantics.Interactions of the form seq(alt(B1,B2),B2)motivate the operator restr,where B i are the basic interactions{snd(s i,r i,m i)≤rcv(s i,r i,m i)}(i=1,2) with m1=m2.In case the second operand of the weak sequencing operator seq makes progress by sending the message m2from instance s2to instance r2,then thefirst op-erator of the seq,which is a disjunction,may only choose itsfirst operator;we call that progress a non-local choice.3Denotational Semantics3.1Semantic DomainsThe domain P comprises all basic interactions.The subdomain T of P comprises all pomsets in P that are traces.In particular,the empty pomsetεis in T;also all eventscan be identified with traces of length one.The notion of the set of active instances of an event e ∈E is extended to an event-labelled pomset p =[(X,≤X ,λX )]by setting α(p )= x ∈X α(λX (x )).For a pomset p =[(X,≤X ,λX )]∈P and an event e ∈E we write e ∈min p ,if there is an x ∈X with x ∈min ≤X X and λX (x )=e ;note that x is unique defined,if it exists.If e ∈min p ,we write p \{e }for [(X \{x }),≤X ∩(X \{x })2,λX (X \{x })]with x ∈min ≤X X and λX (x )=e .On pomsets in P and for a set of messages M ,the filtering relation filter (M ):P →℘P removes some elements of a pomset whose labels show a message in M .More pre-cisely,we first define filter (M )on event-labelled sets:Let X be a set and λ:X →E a labelling function;then X ∈filter (M )(X,λ)if X ⊆X and,if x ∈X \X ,then µ(λ(x ))∈M .For an event-labelled partial order (X,≤X ,λX )we set (X ,≤X ∩(X ×X ),λX X )∈filter (M )(X,≤X ,λX )if X ∈filter (M )(X,λX ).Finally,we extend these definitions to event-labelled pomsets by setting [(X ,≤X ,λX )]∈filter (M )([(X,≤X ,λX )])if (X ,≤X ,λX )∈filter (M )(X,≤X ,λX ),which is ob-viously well-defined.For a pomset p ∈P ,we write p M for filter (M )−1(p );and,consequently,for a process P ⊆P ,we write P M for filter (M )−1(P ).Finally,on processes in ℘P and for a set of instances L ,the restriction function restr (L ):℘P →℘P removes all those pomsets from a process which show an event that is active for an instance in L ,i.e.,restr (L )(P )={p ∈P |α(p )∩L =∅}.We also write P [L ]for restr (L )(P ).The process building operators are transferred to traces using the following identi-ties:Lemma 1.Let P,P 1,P 2⊆P be processes,M ⊆M a set of messages,and L ⊆I a set of instances.1.(P 1;P 2)↓=(P 1↓);(P 2↓)2.(P 1;<>P 2)↓=((P 1↓);<>(P 2↓))↓3.(P 1 P 2)↓=((P 1↓) (P 2↓))↓4.(P M )↓=((P ↓) M )↓5.(P [L ])↓=(P ↓)[L ]6.(P 1∪P 2)↓=(P 1↓)∪(P 2↓)7.(P \P )↓=(P \(P ↓))↓3.2Trace-Based SemanticsThe trace-based,denotational semantics of the authors [1]can be rendered as a function P :Interaction →℘T defined as follows:P None =∅P Empty ={ε}P B =B ↓P strict(S ,S )=P S ;P SP seq(S ,S )=(P S ;<>P S)↓P par(S,S )=(P S P S )↓P loop(m,n,S)= m≤i<n+1((P S)i<>)↓P ignore(M,S)=((P S) M )↓P restr(L,S)=(P S)[L]P alt(S,S )=P S∪P SP not(S)=T\P Swhere S and S are interactions,M⊆M,L⊆I,and n a natural number or infinity, where∞+1=∞.In particular,a trace t is positive for an interaction S,written t|=p S if,and only if, t∈P S.We make use of the following syntactical identifications:strict(Empty,S)≡Sseq(Empty,S)≡Spar(Empty,S)≡par(S,Empty)≡Sloop(0,0,S)≡Emptyrestr(L,Empty)≡Emptyignore(∅,Empty)≡Emptyalt(Empty,Empty)≡Empty4ProcessesFor a process P⊆P and an event e∈E,we define the left quotient P/e of P by e to be the process{p∈P|e;p∈P}.This operation is right-adjoined to prefixing pomsets by e with respect to set inclusion,as e;P⊆P if,and only if P⊆P /e. Lemma2.Let P,P1,P2⊆P be processes,e∈E an event,M⊆M a set of messages, and L⊆I a set of instances.1.(P1;P2)/e=((P1/e);P2)∪((P1∩{ε});(P2/e))2.(P1;<>P2)/e=((P1/e);<>P2)∪(P1[α(e)];<>(P2/e))3.(P1 P2)/e=((P1/e) P2)∪(P1 (P2/e))4.(P M )/e=(P/e) M ∪{ε|µ(e)∈M};P M5.(P[L])/e={ε|α(e)∩L=∅};(P/e)[L]6.(P1∪P2)/e=(P1/e)∪(P2/e)7.(P\P)/e=P\(P/e)Proof.By calculation,we have:(1)(P1;P2)/e={p|∃p1,p2.p1∈P1∧p2∈P2∧e;p=p1;p2}={p|∃p 1,p2.e;p 1∈P1∧p2∈P2∧p=p 1;p2∨∃p1,p 2.ε=p1∈P1∧e;p 2∈P2∧p=p1;p 2}=(P1/e);P2∪(P1∩{ε});(P2/e)(2)(P1;<>P2)/e={p|∃p1,p2.p1∈P1∧p2∈P2∧e;p=p1;<>p2}={p|∃p 1,p2.e;p 1∈P1∧p2∈P2∧p=p 1;<>p2∨∃p1,p 2.p1∈P1∧α(p1)∩α(e)=∅∧e;p 2∈P2∧p=p1;<>p 2} =(P1/e);<>P2∪(P1[α(e)];<>(P2/e))(3)(P1 P2)/e={p|∃p1,p2.p1∈P1∧p2∈P2∧e;p=p1 p2}={p|∃p 1,p2.e;p 1∈P1∧p2∈P2∧p=p 1 p2∨∃p1,p 2.p1∈P1∧e;p 2∈P2∧p=p1 p 2}=((P1/e) P2)∪(P1 (P2/e))(4)(P M )/e={p|∃p .e;p ∈P∧p∈p M∨p∈P M ∧µ(e)∈M}=(P/e) M ∪{ε|µ(e)∈M};P M(5)(P[L])/e={p|∃p .e;p ∈P∧α(p )∩α(L)=∅∧α(e)∩α(L)=∅∧p=p }={ε|α(e)∩L=∅};(P/e)[L](6)(P1∪P2)/e={p|e;p∈P1}∪{p|e;p∈P2}=(P1/e)∪(P2/e)(7)(P\P)/e={p|¬(e;p∈P)}=P\(P/e)The following lemma summarises an obvious characterisation of when the empty pomset can result from a process expression:Lemma3.Let P,P1,P2⊆P be processes,M⊆M a set of messages,and L⊆I a set of instances.1.ε∈(P1;P2)⇐⇒(ε∈P1)∧(ε∈P2)2.ε∈(P1;<>P2)⇐⇒(ε∈P1)∧(ε∈P2)3.ε∈(P1 P2)⇐⇒(ε∈P1)∧(ε∈P2)4.ε∈(P M )⇐⇒ε∈P5.ε∈(P[L])⇐⇒ε∈P6.ε∈(P1∪P2)⇐⇒(ε∈P1)∨(ε∈P2)7.ε∈(P\P)⇐⇒ε/∈PProcess expressions satisfy some obvious monotonicity conditions:Lemma4.Let P,P ,P1,P 1,P2,P 2⊆P be processes,M,M ⊆M a set of messages, and L,L ⊆I sets of instances.1.P1⊆P 1∧P2⊆P 2⇒(P1;P2)⊆(P 1;P 2)2.P1⊆P 1∧P2⊆P 2⇒(P1;<>P2)⊆(P 1;<>P 2)3.P1⊆P 1∧P2⊆P 2⇒(P1 P2)⊆(P 1 P 2)4.P⊆P ∧M⊆M ⇒(P M )⊆(P M )5.P⊆P ∧L⊇L ⇒(P[L])⊆(P [L ])6.P1⊆P 1∧P2⊆P 2⇒(P1∪P2)⊆(P 1∪P 2)7.P⊇P ⇒(P\P)⊆(P\P )All these observations can be extended straightforwardly to P n<>/e:P0<>/e=∅P(n+1)<>/e=((P/e);<>P n<>)∪(P[α(e)];<>(P n<>/e))ε∈P n<>⇐⇒(ε∈P)∨(n=0)P⊆P ⇒P n<>⊆P n<>5Operational SemanticsWe define the domain Eτof events and the silent eventτas E∪{τ}.Analogously, Pτis the domain of all pomsets labelled with events from Eτ,and Tτthe subdomain comprising all pomsets in Pτthat are traces.We define the set of active instances ofτasα(τ)=∅.Based on the observations in Lemma3,we define a predicateε(−)on interactions which determines whether an interaction contains the empty trace:ε(None)⇐⇒ffε(Empty)⇐⇒ttε(B)⇐⇒B=εε(strict(S,S ))⇐⇒ε(S)∧ε(S )ε(seq(S,S ))⇐⇒ε(S)∧ε(S )ε(par(S,S ))⇐⇒ε(S)∧ε(S )ε(loop(m,n,S))⇐⇒ε(S)∨(m=0)ε(ignore(M,S))⇐⇒ε(S)ε(restr(L,S))⇐⇒ε(S)ε(alt(S,S ))⇐⇒ε(S)∨ε(S )ε(not(S))⇐⇒¬ε(S)The operational semantics of interactions is given by two ternary relations between interactions S and S and an event e∈Eτ:The positive reduction relation,denoted byS e−→p S ,is defined by the rules in Tab.2.The negative reduction relation,denoted by S e−→n S ,is defined by the rules in Tab.3.In these rules,the variously decoratedmeta-variables range as follows:S over interactions,B over basic interactions,e over Eτ,e over E,m over the natural numbers,n over the natural numbers or infinity.(basic p)B e−→p B\{e}if e∈min B(strict p)S1e−→p S 1strict(S1,S2)e−→p strict(S 1,S2)(seq1p)S1e−→p S 1seq(S1,S2)e−→p seq(S 1,S2)(seq2p)S2e−→p S 2seq(S1,S2)e−→p seq(restr(α(e),S1),S 2)(par1p)S1e−→p S 1par(S1,S2)e−→p par(S 1,S2)(par2p)S2e−→p S 2par(S1,S2)e−→p par(S1,S 2)(loop1p)loop(0,n,S)τ−→p Empty(loop2p)S e−→p Sloop(m,n+1,S)e−→p seq(S ,loop(m˙−1,n,S))(ignore1p)ignore(M,Empty)τ−→p Empty(ignore2p)S e−→p Signore(M,S)e−→p ignore(M,S )(ignore3p)ignore(M,S)e−→p ignore(M,S)ifµ(e)∈M (restr p)S e−→p Srestr(L,S)e−→p restr(L,S )ifα(e)∩L=∅(alt1p)S1e−→p S 1alt(S1,S2)e−→p S 1(alt2p)S2e−→p S 2alt(S1,S2)e−→p S 2(not1p)S e−→n Snot(S)e−→p not(S )(not2p)not(S)τ−→p Empty if¬ε(S) Table2.Positive reduction relation of the operational semantics.6CorrectnessIf S e1−→p S1,S1e2−→p S2,...,S n−1e n−→p S ,we write S t−→p S ,where t= e1;e2;···;e n∈Tτis afinite trace possibly containing one or more occurrences of(empty n)Empty e−→n None(none n)None e−→n None(basic1n)B e−→n B\{e}if e∈min B(basic2n)B e−→n None if e/∈min B (strict n)S1e−→n S 1S2e−→n S 2strict(S1,S2)e−→n alt(strict(S 1,S2),strict(restr(I,S1),S 2))(seq n)S1e−→n S 1S2e−→n S 2seq(S1,S2)e−→n alt(seq(S 1,S2),seq(restr(α(e),S1),S 2))(par n)S1e−→n S 1S2e−→n S 2par(S1,S2)e−→n alt(par(S 1,S2),par(S1,S 2))(loop1n)loop(0,∞,S)e−→n not(None)(loop2n)S e−→n S loop(m˙−1,n,S)e−→n Sloop(m,n+1,S)e−→n alt(seq(S ,loop(m˙−1,n,S)),seq(restr(α(e),S),S ))(ignore1n)S e−→n Signore(M,S)e−→n alt(ignore(M,S ),ignore(M,S))ifµ(e)∈M(ignore2n)S e−→n Signore(M,S)e−→n ignore(M,S )if e=τ∨µ(e)/∈M(restr1n)S e−→n Srestr(L,S)e−→n restr(L,S )ifα(e)∩L=∅(restr2n)restr(L,S)e−→n None ifα(e)∩L=∅(alt n)S1e−→n S 1S2e−→n S 2alt(S1,S2)e−→n alt(S 1,S 2)(not n)S e−→p Snot(S)e−→n not(S )Table3.Negative reduction relation of the operational semantics.the silent eventτ.Given a trace t∈Tτ,we let t denote the trace obtained from t by removing every occurrence of the silent eventτ.The above introduced operational semantics of interactions is correct w.r.t.the de-notational one,that is,given an interaction,traces that lead the interaction to Empty are positive for the interaction:Lemma5.Let S,S be interactions and e∈E.1.If S e−→p S ,then P S ⊆P S/e.2.If Sτ−→p S ,then P S ⊆P S.3.If S e−→n S ,then P S ⊇P S/e.4.If Sτ−→n S ,then P S ⊇P S.Proof.Claims(1)and(3)follow immediately from Lemma2,claims(2)and(4)from Lemma4.Proposition6.Let S be an interaction and t be a trace in Tτ.If S t−→p Empty,then t |=p S.Proof.From Lemma5,and by induction on the length of t,follows that if S t−→p Empty, then t ;P Empty⊆P S,i.e., t ∈P(S).7CompletenessLemma7.Let S be an interaction and e∈E.Then1.(P S)/e= {P(S )|Sτ∗;e−−→p S }2.(T\P S)/e= {T\P(S )|Sτ∗;e−−→n S }−→p Empty3.ε∈P S⇐⇒Sτ∗Proof.Claims(1)and(2)follow by mutual induction on the term structure of the inter-action S from Lemma2.Claim(3)follows by induction on the term structure of the interaction S from the syntactical identifications,the definition ofε(−)and theτ-rules.Proposition8.Let S be an interaction and t∈T be afinite trace.If t∈P(S),then there is a t∈Tτwith t= t and S t−→p Empty.Proof.From Lemma7(1)and by induction follows that for everyfinite trace t∈T and for every interaction S with t∈P(S),there are a t∈Tτwith t= t and an interaction S t such that S t−→p S t andε∈P S t.Thus,by Lemma7(3),for an interaction S and afinite trace t∈T,there is a t∈Tτwith t= t and S t−→p Empty.References1.Mar´ıa Victoria Cengarle and Alexander Knapp.UML2.0Interactions:Semantics and Refine-ment.In Jan J¨u rjens,Eduardo B.Fernandez,Robert France,and Bernhard Rumpe,editors, Proc.3rd Int.Wsh.Critical Systems Development with UML(CSDUML’04),pages85–99.Technical Report TUM-I0415,Institut f¨u r Informatik,Technische Universit¨a t M¨u nchen,2004.2.Object Management Group.UML2.0Superstructure Specification.Final adopted specifica-tion,OMG,2003./cgi-bin/doc?ptc/03-08-02.3.Vaughan Pratt.Modeling Concurrency with Partial Orders.Int.J.Parallel Program.,15(1):33–71,1986.。
