天津理工大学计算机网络试验三
计算机网络技术实验报告四
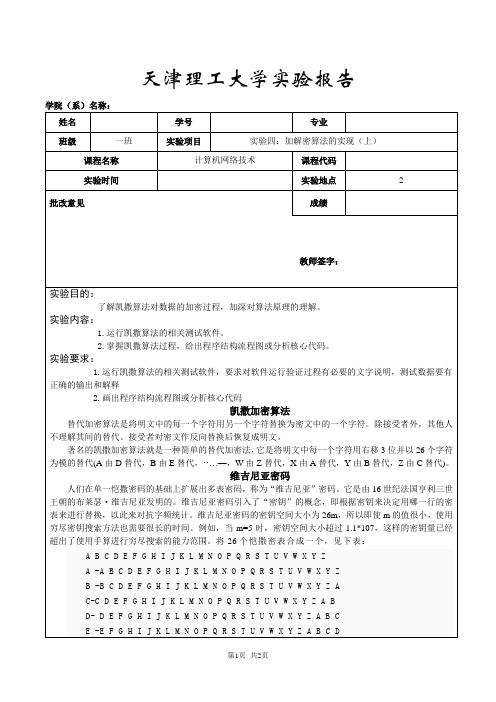
天津理工大学实验报告学院(系)名称:F -FGHIJKLMNOPQRSTUVWXYZ A B C D EG- G H I J K L M N O P Q R S T U V W X Y Z A B C D E FH -H I J K L M N O P Q R S T U V W X Y Z A B C D E F GI- I J K L M N O P Q R S T U V W X Y Z A B C D E F G HJ -J K L M N O P Q R S T U V W X Y Z A B C D E F G H IK -K L M N O P Q R S T U V W X Y Z A B C D E F G H I JL -L M N O P Q R S T U V W X Y Z A B C D E F G H I J KM -M N O P Q R S T U V W X Y Z A B C D E F G H I J K LN -N O P Q R S T U V W X Y Z A B C D E F G H I J K L MO -O P Q R S T U V W X Y Z A B C D E F G H I J K L M NP -P Q R S T U V W X Y Z A B C D E F G H I J K L M N OQ -Q R S T U V W X Y Z A B C D E F G H I J K L M N O PR -R S T U V W X Y Z A B C D E F G H I J K L M N O P QS -S T U V W X Y Z A B C D E F G H I J K L M N O P Q RT -T U V W X Y Z A B C D E F G H I J K L M N O P Q R SU -U V W X Y Z A B C D E F G H I J K L M N O P Q R S TV -V W X Y Z A B C D E F G H I J K L M N O P Q R S T UW -W X Y Z A B C D E F G H I J K L M N O P Q R S T U VX -X Y Z A B C D E F G H I J K L M N O P Q R S T U V WY -Y Z A B C D E F G H I J K L M N O P Q R S T U V W XZ -Z A B C D E F G H I J K L M N O P Q R S T U V W X Y加密方法:维吉尼亚密码引入了“密钥”的概念,即根据密钥来决定用哪一行的密表来进行替换,以此来对抗字频统计。
天津理工大学——计算机网络——实验一
参数: -a 显示所有连接和侦听端口。服务器连接通常不显示。 -e 显示以太网统计。该参数可以与 -s 选项结合使用。 -n 以数字格式显示地址和端口号(而不是尝试查找名称)。 -s 显示每个协议的统计。默认情况下,显示 TCP、UDP、ICMP 和 IP 的统计。-p 选项可以
图六
S3.查看当前目录下的文件,如图七。
图七
S4.将 file2.txt 下载到本地的 E:\,如图八。
图八
(3) ipconfig 命令作用:该诊断命令显示所有当前的 TCP/IP 网络配置值。该命令在运行 DHCP 系统上的特殊 用途,允许用户决定 DHCP 配置的 TCP/IP 配置值。 使用格式: ipconfig [/? | /all | /release [adapter] | /renew [adapter]
实验记录: S1. Net stat -as
第 6 页 共 11 页
图 十八
(7) ping 验证与远程计算机的连接。该命令只有在安装了 TCP/IP 协议后才可以使用。
ping [-t] [-a] [-n count] [-l length] [-f] [-i ttl] [-v tos] [-r count] [-s count] [[-j computer-list] | [-k computer-list]] [-w timeout] destination-list
interface whose address translation table should be modified.
If not present, the first applicable interface will be used.
天津理工大学数据结构实验报告3

实验(三)实验名称二叉树的遍历软件环境 Windows98/2000, VC++6.0或turbo C硬件环境PⅡ以上微型计算机实验目的 理解二叉树的逻辑特点,掌握二叉链表存储结构,掌握二茬树遍历算法的递归与非递归实现实验内容(应包括实验题目、实验要求、实验任务等)二叉树的遍历利用二叉链表作为存储结构建立一棵二叉树,每个结点中存放一种水果名(例如apple、orange、banana等,并要求从键盘输入),结点数不少于5个。
要求分别以先序、中序和后序进行遍历,输出遍历结果。
并编写一递归算法,交换该二叉树中所有结点的左、右孩子。
实验过程与实验结果(可包括实验实施的步骤、算法描述、流程、结论等)实验步骤及算法描述和流程:1. 创建二叉链表的结点存储结构及数据的输入输出函数因为每个结点所存储的数据类型为字符串,却无法使用字符串和String等数据类型,所以使用单链表作为结点所存储的数据类型。
1.1 数据的输入函数indata( )当输入的字符不为'0'时,以尾插法将数据插入单链表。
1.2 数据的输出函数直接输出单链表。
2. 生成二叉链表利用先序遍历生成二叉链表:2.1 用单链表s记录输入的数据2.2 若单链表s为空,则二叉链表结点为空,否则根节点=s,利用递归调用分别生成根节点的左子树和右子树2.3 返回二叉链表3. 先序遍历、中序遍历、后序遍历二叉链表3.1 先序遍历:访问根节点,左子树,右子树的顺序3.2 中序遍历:访问左子树,根节点,右子树的顺序3.3 后序遍历:访问左子树,右子树,根节点的顺序利用递归调用分别用以上三种顺序遍历二叉链表。
4. 交换二叉链表的左右孩子当二叉链表的结点左孩子或者右孩子都不为空时,利用递归调用,分别交换左子树很右孩子的左右孩子,最后将根节点的左右孩子指针交换。
5. 主函数5.1 调用生成二叉链表的函数,从键盘输入二叉链表的各个结点5.2 分别调用先序遍历、中序遍历、后序遍历二叉链表函数,输出所有结点5.3 交换二叉链表的左右孩子5.4 重复5.2结论: 输入各个结点:apple、pear、orange、banana、peach、grape、watermelon 先序遍历输入与输入一致 中序遍历输出:orange、pear、banana、apple、grape、peach、watermelon 后序遍历输出:orange、banana、pear、grape、watermelon、peach、apple 交换二叉树的左右孩子后 先序遍历输出:apple、peach、watermelon、grape、pear、banana、orange编程中出现的问题:输入的二叉链表左右子树必须对称,如果不对称,交换二叉树的左右子树后,程序出错,不知道出错在哪,没有调试成功。
天津理工大学 计算机网络题库

PART Ⅰ: ChoiceB 1. Which of the following services does not the transport layer provide for the application layer?A.In-order delivery of data segments between processesB.Best effort delivery of data segments between communicating hostsC.Multiplexing and demultiplexing of transport layer segmentsD.Congestion controlA 2. What are the two of the most important protocols in the Internet?A. TCP and IPB. TCP and UDPC. TCP and SMTPD. ARP and DNSC 3. The Internet provides two services to its distributed applications: a connection oriented reliable service and a ( ).A. connection oriented unreliable serviceB. connectionless reliable serviceC. connectionless unreliable serviceD. In order data transport serviceD 4. Processes on two different end systems communicate with each other by exchanging ( ) across the computer network.A. packetsB. datagramC. framesD. messagesA 5. The job of delivering the data in a transport-layer segment to the correct socket is called ( ).A. demultiplexingB. multiplexingC. TDMD. FDMC 6. Two important reasons that the Internet is organized as a hierarchy of networks for the purposes of routing are:A.Least cost and maximum free circuit availabilityB.Message complexity and speed of convergenceC.Scale and administrative autonomyD.Link cost changes and link failureB 7. Which of characters is not distance-vector algorithm’s characters?()A. iterativeB. globalC. asynchronousD. distributedD 8. The length of IPV6 address is ()bits.A. 32B. 48C. 64D. 128C 9. The host component of a CIDR address of the form a.b.c.d/25 can contain addresses for:A.225 hosts (minus “special” hosts)B.512 hosts (minus “special” hosts)C.2(32-25) hosts (minus “special” hosts)D.25 hosts (minus “special” hosts)C 10. The primary function of the address resolution protocol (ARP) that resides in Internet hosts androuters is:A.To provide LAN router functionsB.To translate between LAN addresses and physical interface addressesC.To translate IP addresses to LAN addressesD.To calculate the shortest path between two nodes on a LANA 11. The POP3 protocol runs over ____ and uses port ____.A. TCP 110B. UDP 110C. UDP 25D. TCP 25D 12.When a destination host transport layer receives data from the network layer, it unambiguouslyidentifies the appropriate process to pass the data to by using a triplet consisting of:A. Source port #, destination IP address, and source IP addressB. Destination port #, source port #, process ID#C. Destination port #, source port #, destination IP addressD. Destination port #, source port #, source IP addressD 13. From the list below, select the items found in the TCP segment structure that are not found in theUDP segment structure:A. Application Generated DataB. Destination Port #C. Source Port #D. Sequence #A 14. The RIP routing protocol is based on an algorithm that is:A. Based on information received only from link “neighbors”B. A link state algorithmC. An OSPF algorithmD. A centralized routing algorithmB 15. With an exterior routing protocol, which of the following issues generally dominates the routing decisions?A. Geographical distance between AS’sB. PolicyC. Number of AS’s traversedD. Current congestion levels in the AS’sA 1. End system are connected together by ____.A. communication linksB. application layerC. transport layerD. the network layerC 2. Which application’s NOT using TCP?A. SMTPB. HTTPC. DNSD. All of themB 3. In the polling protocols, the master node polls each of the nodes in a/an ____ fashion.A. randomB. appointedC. round-robinD. uncirculatedC 4. The DNS protocol runs over ____ and uses port ____.A. UDP 36B. TCP 36C. UDP 53D. TCP 53A 5. TCP provides a ____ service to its applications to eliminate the possibility of the sender over-flowingthe receiver’s buffer.A. flow-controlB. congestion controlC. reliability controlD. data connectionD 6. We can classify just about any multiple access protocol as belonging to one of three categories: channel partitioning protocols, random access protocols, and ____.A. address resolution protocolsB. Dynamic host configuration protocolsC. link-control protocolsD. taking-turns protocolsB 8. The maximum transfer unit(MTU) in Ethernet frame structure is ()byte .A. 1000B. 1500C. 800D. 2000B 9. The socket of UDP is identified by _____ and _______.A. source IP address and source port numberB. destination IP address and destination port number.C. source IP address and destination port number.D. destination IP address and source IP address.C 10. Which is not plug and play in the following four items?A. DHCPB. HubsC. RoutersD. SwitchesD 11.Which of routers is not default routers ?A. first-hop routerB. source routerC. destination routerD. second-hop routerB 13. ICMP is_____.A. the protocol of Application layerB. the protocol of network layerC. the protocol of transport layerD. not a part of TCP/IP protocolsB 14. As general, we has following channel partitioning protocols except ____.A. TDMB. CSMAC. FDMD.CDMAD 15. ____ is most used for error reporting.A. UDPB. SMTPC. FTPD. ICMPB 16. The header of IPV6 is ____byte.A. 20B. 40C. 60D. 80B 17. In the network layer these service are host-to-host service provided by ____. (B)A. the transport layer to the network layerB. the network layer to the transport layerC. the network layer to the network layerD. the transport layer to the transport layerA 18. If there is not enough memory to buffer an incoming packet , a policy that drop the arriving packet called ____.A. drop-tailB. packet lossC. protocolD. encapsulationC 19. In either case, a ____ receives routing protocol messages, which are used to configure its forwarding table.A. serverB. hostC. routerD. ModemD 20. Which of the following functions does not belong to PPP___.A. framingB. link-control protocolsC. network-control protocolsD. error correctionB 1. Which of the following services does the Internet network layer provide for the Internet transport layer?A.In-order delivery of data segments between processesB.Best effort delivery of data segments between communicating hostsC.Multiplexing and demultiplexing of transport layer segmentsD.Congestion controlD 2. The main task of the Internet’s Domain Name System (DNS) is to:A.Translate port numbers to IP addressesB.Specify the standards for Internet domain namesC.Provide an authority for registering domain namesD.Translate mnemonic(记忆的)names to IP addressesA 10. The FTP protocol runs over ____ and uses port ____.A. TCP 21B. TCP 80C. UDP 20D. TCP 110C 3.RDT3.0’s receiver FSM is same to:a) RDT1.0 b) RDT2.1 c) RDT2.2 d) RDT2.0B 4.The Transmission Control Protocol (TCP) provides which of the following services?a)End-to-end station addressingb)Application multiplexingc)Inter network routingd)Medium access control (MAC)D 6.Given that the requested information is not available at any intermediate databases, a non-iterated DNS query from a requesting host would follow the path:a)Root name server, local name server, authoritative name serverb)Authoritative name server, root name server, host name serverc)Local name server, root name server, local name server, authoritative name servere)Local name server, root name server, authoritative name serverA 8.lect the four essential steps, briefly described, for terminating a TCP connection between a client and a server, assuming that the initiating host is the client:(1)Client sends TCP segment with ACK0 and final sequence number(2)Client sends TCP segment with FIN =1 and goes into FIN_WAIT state(3)Server sends TCP segment to ACK the client’s FIN request and enters CLOSE_WAIT state(4)Server sends TCP segment with FIN=0(5)Server sends TCP segment with FIN=1(6)Client sends TCP segment with to ACK server’s FIN and enters second FIN_WAIT state(7)Client sends TCP segment with FIN=0a) 2,3,5,6 b) 5,1,2,3 c) 1,3,5,7 d) 2,3,4,6B 10.When compensating for link cost changes in the distance vector algorithm, it can generally be said that:a)Increased costs are propagated quickly, i.e., “bad news” travels fastb)Decreased costs are propagated rapidly, i.e., “good news” travels fastc)Decreased costs do not converged)None of the aboveB 14.As an IP datagram travels from its source to its destination:a)the source IP address is changed at each router to identify the sending routerb)the router uses the destination IP address to consult its routing tablec)the router does not use the IP addresses in the datagramd)the destination IP address is changed at each router to reflect the next hopC 15.From the list below, choose the bit pattern which could be a valid generator value for the CRC code (R) 11010:a)1110b)011010c)100101d)10011A 16.Consider sending a 1300 byte IPv4 datagram into a link that has an MTU of 500 bytes:a)Three fragments are created.b)Four fragments are created.c)Three fragments are created with offsets 0, 500 1000d)The last fragment consists of exactly 300 bytes of data from the original datagramC 17.Suppose one IPv6 router wants to send a datagram to another IPv6 router, but the two are connected together via an intervening IPv4 router. If the two routers use tunneling, then:a)The sending IPv6 router creates an IPv4 datagram and puts it in the data field of an IPv6datagram.b)The sending IPv6 router creates one or more IPv6 fragments, none of which is larger than themaximum size of an IPv4 datagram.c)The sending IPv6 router creates an IPv6 datagram and puts it in the data field of an IPv4datagram.d)The sending IPv6 router creates an IPv6 datagram and intervening IPv4 router will reject theIPv6 datagramD 18.Which of the following was an important consideration in the design of IPv6a)fixed length 40-byte header and specified options to decrease processing time at IPv6 nodesb)128-bit addresses to extend the address spacec)different types of service (flows) definedd)all of the aboveD 19.A network bridge table is used to perform the following:a)Mapping MAC addresses to bridge port numbersb)Forwarding frames directly to outbound ports for MAC addresses it handlesc)Filtering (discarding) frames that are not destined for MAC addresses it handlesd)All of the abovePART Ⅱ: True / False (1 points per question – total:20 points)1. The DNS server can update the records. (T)2. The TCP connection is a direct virtual pipe between the client’s socket and the server’s connection socket. (T)3. SMTP protocol connect the sender’s mail server and receiver’s mail server (T)4. Whereas a transport-layer protocol provides logical communication between processes running on different hosts, a network-layer protocol provides logical communication between hosts. (T)5. UDP and TCP also provide integrity checking by including right-detection fields in their headers. (F)6. If the application developer chooses UDP instead of TCP, then the application is not directly talking with IP. ( F )7. When we develop a new application, we must assign the application a port number. ( T )8. Real-tine applications, like Internet phone and video conferencing, react very poorly to TCP’s congestion control. ( T )9. The sender knows that a received ACK or NAK packet was generated in response to its most recently transmitted data packet. (T)10. To simplify terminology, when in an Internet context, we refer to the 4-PDU as a unit. (F)11. DV algorithm is essentially the only routing algorithm used in practice today in the Internet。
大工春计算机网络实验实验报告完整版

大工春计算机网络实验实验报告Document serial number【NL89WT-NY98YT-NC8CB-NNUUT-NUT108】姓名:报名编号:学习中心:层次:专升本(高起专或专升本)专业:网络工程实验一:交换机的登录与配置实验目的:1、掌握Console口登录交换机和使用Telnet方式登录交换机的方法;2、Comware平台的基本使用。
实验问题讨论:1.使用Telnet方式登录交换机:(1)在交换机上做出必须的预先配置,例如配置交换机的IP地址和子网掩码,配置登录交换机的用户密码,配置登录用户的权限级别等。
请把你为完成这些预先配置所执行的配置命令写到实验报告中。
答:配备IP:<Quidway>sytem→<Quidway>interfaceVLAN-interfacel→配置权限:<Quidway>user-inerfacevty04→[QW-vi-vty0-4]authentication?→[QW-vi-vtu0-4]setauthenticationsample123456→[QW]userprivilege3(2)配置PCA的IP地址和子网掩码,注意要把PCA的IP地址与交换机的IP地址设在同一网段。
请把你所做的配置写到实验报告中。
答:将PC机IP实验二:交换机VLAN间路由配置实验实验目的:1、掌握交换机VLAN间路由的配置方法;2、掌握VLAN间路由配置命令。
实验问题讨论:1.“resetsaved-configuration”命令和“reboot”命令的功能是什么?答:“reset?saved-configuration”命令的功能是擦除旧的配置文件。
“reboot”命令的功能是用来复位单板。
2.SwitchA中VLAN1的端口都包括哪几个端口VLAN2的端口包括哪几个端口VLAN3的端口都包括哪几个端口答:VLAN1:Fa0/1-6和Fa0/9-24VLAN2:Fa0/7?VLAN3:Fa0/8实验三:路由器的登录与基础配置实验目的:1、掌握路由器两种登录方式;2、掌握路由器基础命令功能。
2022年天津理工大学网络工程专业《计算机网络》科目期末试卷A(有答案)

2022年天津理工大学网络工程专业《计算机网络》科目期末试卷A(有答案)一、选择题1、TCP/IP模型中的网络接口层对应OSI参考模型的()。
I.物理层Ⅱ.数据链路层Ⅲ.网络层Ⅳ.传输层A. I、IIB. II、III.C. I、ⅢD.Ⅱ、Ⅳ2、()是计算机网络中的OSI参考模型的3个主要概念。
A.服务、接口、协议B.结构、模型、交换C.子网、层次、端口D.广域网、城域网、局域网3、下面有关BGP4的描述中,不正确的是()。
A.BGP4是自治系统之间的路由协议B.BGP4不支持CIDR技术C.BGP4加入路由表的路由并不一定是最佳路由D.BGP4封装在TCP段中传送4、在IP首部的字段中,与分片和重组无关的是()。
注:假设现在已经分片完成。
A.总长度B.标识C.标志D.片偏移5、信道速率为4kbit/s,采用停止-等待协议。
传播时延t=20ms,确认帧长度和处理时间均可忽略。
问帧长()才能使信道的利用率达到至少50%。
A.40bitB.80bitC.160bitD.320bit6、下列关于交换机的叙述中,正确的是()A.以太网交换机本质上是一种多端口网桥B.通过交换机互连的一组工作站构成一个冲突域C.交换机每个端口所连网络构成一个独立的广播域D.以太网交换机可实现采用不同网络层协议的网络互连7、一个UDP用户数据报的数据字段为8192B。
在链路层要使用以太网来传输,那么应该分成()IP数据片。
A.3个B.4个C.5个D.6个8、假设某时刻接收端收到有差错的UDP用户数据报,其动作为()。
A.将其丢弃B.请求重传C.纠错D.忽略差错9、如果用户程序使用UDP进行数据传输,那么()协议必须承担可靠性方面的全部工作。
A.数据链路层B.网络层C.传输层D.应用层10、当客户端请求域名解析时,如果本地DNS服务器不能完成解析,就把请求发送给其他服务器,当某个服务器知道了需要解析的IP地址,把域名解析结果按原路返回给本地DNS服务器,本地DNS服务器再告诉客户端,这种方式称为()。
第二学期计算机网络试卷A

2005 ~2006 学年度第2 学期《计算机网络技术》期末考试试卷课程代码:0600100 试卷编号: 1-A命题日期:2006 年 5 月20 日答题时限:120 分钟考试形式:闭卷笔试PART Ⅰ: Single Choice (1 point per question – total: 20 points)1. Which of the following services does the Internet network layer provide for the Internet transport layer?a)In-order delivery of data segments between processesb)Best effort delivery of data segments between communicating hostsc)Multiplexing and demultiplexing of transport layer segmentsd)Congestion control2. The main task of the I nternet’s Domain Name System (DNS) is to:a)Translate port numbers to IP addressesb)Specify the standards for Internet domain namesc)Provide an authority for registering domain namesd)Translate mnemonic names to IP addresses3.RDT3.0’s receiver FSM is same to:a) RDT1.0 b) RDT2.1 c) RDT2.2 d) RDT2.04. The Transmission Control Protocol (TCP) provides which of the following services?a)End-to-end station addressingb)Application multiplexingc)Inter network routingd)Medium access control (MAC)5.When a destination host transport layer receives data from the network layer, it unambiguouslyidentifies the appropriate process to pass the data to by using a triplet consisting of:a)Source port #, destination IP address, and source IP addressb)Destination port #, source port #, process ID#a)Destination port #, source port #, destination IP addressc)Destination port #, source port #, source IP address6.Given that the requested information is not available at any intermediate databases, anon-iterated DNS query from a requesting host would follow the path:a)Root name server, local name server, authoritative name serverb)Authoritative name server, root name server, host name serverc)Local name server, root name server, local name server, authoritative name servera)Local name server, root name server, authoritative name server7.From the list below, select the items found in the TCP segment structure that are not found inthe UDP segment structure:a)Application Generated Datab)Destination Port #c)Source Port #a)Sequence #8.Select the four essential steps, briefly described, for terminating a TCP connection between aclient and a server, assuming that the initiating host is the client:(1)Client sends TCP segment with ACK0 and final sequence number(2)Client sends TCP segment with FIN =1 and goes into FIN_WAIT state(3)Server sends TCP segment to ACK the client’s FIN request and enters CLOSE_WAITstate(4)Server sends TCP segment with FIN=0(5)Server sends TCP segment with FIN=1(6)Client sends TCP segment with to ACK server’s FIN and enters second FIN_WAIT state(7)Client sends TCP segment with FIN=0a) 2,3,5,6 b) 5,1,2,3 c) 1,3,5,7 d) 2,3,4,69.The RIP routing protocol is based on an algorithm that is:a)Based on information received only from link “neighbors”b) A link state algorithmc)An OSPF algorithmd) A centralized routing algorithm10.When compensating for link cost changes in the distance vector algorithm, it can generally besaid that:a)Increased costs are propagated quickly, i.e., “bad news” travels fastb)Decreased costs are propagated rapidly, i.e., “good news” trave ls fastc)Decreased costs do not converged)None of the above11.Two important reasons that the Internet is organized as a hierarchy of networks for thepurposes of routing are:a)Least cost and maximum free circuit availabilityb)Scale and administrative autonomyc)Message complexity and speed of convergenced)Link cost changes and link failure12.With an exterior routing protocol, which of the following issues generally dominates therouting decisions?a)Geographical distance between AS’sb)Policyc)Number of AS’s traversedd)Cu rrent congestion levels in the AS’s13.The host component of a CIDR address of the form a.b.c.d/22 can contain addresses for:a)2(32-22) hosts (minus “special” hosts)b)512 hosts (minus “special” hosts)c)d times 22 hostsd)10 hosts (minus “special” hosts)14.As an IP datagram travels from its source to its destination:a)the source IP address is changed at each router to identify the sending routerb)the router uses the destination IP address to consult its routing tablec)the router does not use the IP addresses in the datagramd)the destination IP address is changed at each router to reflect the next hop15.From the list below, choose the bit pattern which could be a valid generator value for the CRCcode (R) 11010:a)1110b)011010c)100101d)1001116.The primary function of the address resolution protocol (ARP) that resides in Internet hostsand routers is:a)To provide LAN router functionsb)To translate between LAN addresses and physical interface addressesc)To translate between IP addresses and LAN addressesd)To calculate the shortest path between two nodes on a LAN17.Consider sending a 1300 byte IPv4 datagram into a link that has an MTU of 500 bytes:a)Three fragments are created.b)Four fragments are created.c)Three fragments are created with offsets 0, 500 1000d)The last fragment consists of exactly 300 bytes of data from the original datagram18.Suppose one IPv6 router wants to send a datagram to another IPv6 router, but the two areconnected together via an intervening IPv4 router. If the two routers use tunneling, then:a)The sending IPv6 router creates an IPv4 datagram and puts it in the data field of an IPv6datagram.b)The sending IPv6 router creates one or more IPv6 fragments, none of which is largerthan the maximum size of an IPv4 datagram.c)The sending IPv6 router creates an IPv6 datagram and puts it in the data field of an IPv4datagram.d)The sending IPv6 router creates an IPv6 datagram and intervening IPv4 router will rejectthe IPv6 datagram19.Which of the following was an important consideration in the design of IPv6a)fixed length 40-byte header and specified options to decrease processing time at IPv6nodesb)128-bit addresses to extend the address spacec)different types of service (flows) definedd)all of the above20. A network bridge table is used to perform the following:a)Mapping MAC addresses to bridge port numbersb)Forwarding frames directly to outbound ports for MAC addresses it handlesc)Filtering (discarding) frames that are not destined for MAC addresses it handlesd)All of the abovePART Ⅱ: True / False (1 points per question – total:15 points)Instructions: Mark the symbol “√” (for True) if the statement is correct, or the symbol “χ” (for1.The Internet’s Transport Layer protocol provides reliable data transfer between end systems.works should be designed such that the Traffic Intensity value for each network node is less than 1.3.The maximum size of a single UDP segment is limited to 216 –1 bits.4.two separate TCP connections, one to port 20 and one to port 21, and is said to send its commands “out of band”.5.During the first step of a TCP connection handshake between a client and a server, the server receives a TCP segment with a null sequence number and the SYN bit set to 1.6.TCP congestion control is designed to prevent buffer overflow in network end-systems.7.Due to the characteristics of its congestion avoidance algorithm, TCP can be said to be a “fair” protocol with regard to sharing available bandwidth among users of a common transmission link. 8.In the Internet, interior routers in the same autonomous system execute the same routing algorithm to compute routing paths.9.All link layer protocols that support IP have the same frame structure (i.e., length of frame, number and length of header fields).10.Routers sometimes use transport layer protocols, such as TCP or UDP, to exchange routing table information with each other.11.Any node in the IP network defined by 192.118.15.0/24 would be required to have an IP address of the form 192.118.15.xxx.12.Pure Aloha is more efficient than Slotted-Aloha.13.The entries in a bridge table need to be configured by the network administrator.yer-2 switches can be used to isolate one LAN segment’s collision domain from that of another LAN segment.15.The Time Division Multiplexing (TDM) channel partitioning protocol is appealing because it eliminates collisions and is perfectly fair with regard to bandwidth availability.PART Ⅲ: Briefly answer each of the following questions. (1 points per question –total: 20 points)messaging service.2. Explain the difference between go-back-N and selective repeat.3. Where can queuing occur in a router? Briefly explain the conditions that lead to such queuing.4. Satellite links often exhibit high propagation times and low transmission speed. What does this mean?5. The difference between UDP and IP packets is minimal. Why shouldn’t applications use IP directly?6. Can two computers that have a different implementation of the same protocol exchange messages? Explain your answer.7. What are the differences between routing and forwarding? Briefly explain each of them.8. Briefly explain the formula “l astByteSent-lastByteAcked≤min {CongWin ,RcvWin}”. If necessary, you can draw a figure to describe your answer.9. Ethernet follows a CSMA/CD protocol scheme. Explain how this scheme works.10. For a sliding window protocol, it is necessary to have the window size at most half of the range of sequence numbers. Why?PART Ⅳ: Answer each of the following questions. (Total: 55 points)1. (total: 6 points) Consider the network shown below. Run Dijkstra’s algorithm to compute the shortest paths from A to all other nodes in the network. While selecting the next node, if several nodes have the same min cost, select the one with lowest id, (e.g., if B and D have the same min cost, then select B).Determine the routing table (destination, next-node, and cost) at node A.2. (total: 6 points)Consider TCP Reno (the one that uses both timeout and 3 duplicate ACKs to detect packet losses). Remember the receiver sends cumulative ACK whenever a segment is received and assume that our TCP implementation discards out-of-order segments, so as in Go-Back-N, the sender shouldre-transmit all packets starting from base when a packet loss is detected. Remember congestion window needs to be adjusted before retransmission.A server application has 26 TCP segments (packets) (that are numbered as 1, 2, 3… 26) to send to the receiver site. Assume that the sender started from slow start with a congestion window of 1 and continued according to TCP Reno congestion control algorithm. The initial Threshold value was 4. The timeout duration at the sender is set to RTT.Assume that the sender sends a number of TCP segments and receives all ACKs just before the next RTT (ignore the time between back-to-back sent segments). Finally, assume that 15th and 21st segments got lost during their first transmission. Now, by using the above information, your task is to complete the blank entries in the below table until all the segments are sent and all the ACKs are successfully received. If you want, you can use the chart below to work out your solution before filling in the table below.Cong. Win.0 1 2 3 4 5 6 7 8 9 10 11 RTT3.together with lines.SYN,ACK A layer 4 protocolSpanning Tree Algorithm One of their primary jobs involves RFCsrepeater Techniques to efficiently use IP addressesIETF This model lacks a setup and tear down phase VLSM,CIDR This layer 2 technology helps prevent bridge loops inEthernet LANs and also in token ring LANsconnectionless You might this layer 2 technology in token ring LANs,but not in Ethernet LANsFull-duplex Something you might find in the 3-way handshakeUDP An example of a wire link technology Source route bridging The ability to talk and listen at the same timeOptical fiber cabling This device moves bits from one data link network toanother without inspecting the frame’s contents4. (total: 8 points) Caching and delays.Consider the networks shown in the figure below. There are two user machines and in the network . Suppose the user at types in the URL into a browser to retrieve a 1Gbit (1000 Mbit) .Authoritativea)(5points)List the sequence of DNS and HTTP messages sent/received from/by as well as any other messages that leave/enter the network that are not directly sent/received by from the point that the URL is entered into the browser until the completely received. Indicate the source and destination of each message. You can assume that every HTTP requestby is first directed to the HTTP cache in and that the cache is initially empty, and that all DNS requests are iterated queries.b) (3points) Now assume that machine makes a request to exactly the same URL that made. List the sequence of DNS and HTTP messages sent/received from/by as well as any other messages that leave/enter the network that are not directlysent/received by from the point that the URL is entered into the browser until the completely received. Indicate the source and destination of each message. [Hint: make sure you consider caching here]5. (total: 11 points) Addressing, and following the dataConsider the simple network shown below:a) Write down an IP address for all interfaces at all hosts and routers in the network. The IPaddresses for A and E are as given. You should assign IP addresses so that interfaces on the same network have the same network-part of their IP address. Indicate the number of bits in the B R1C R2DA EB R1C R2Dc) Now focus on the actions taken at both the network and data link layers at sender A, the intervening router, and destination E in moving an IP datagram from A to E:①How do A, E and the router determine the IP addresses needed for the IP datagram?Source IP Destination IPSource IP Destination IPBC DR2R1④How do A, E and the router determine the physical (LAN) addresses needed for the data link layer frame?d) Suppose that the router in the figure below is replaced by a bridge.①How would the IP addresses change in this case?②How would the physical (LAN) addresses change in this case?③How would does a learning bridge learn the physical addresses of the attached hostsPART Ⅴ: (total: 6 points) About the labs.The following transcript is a mail transfer session between hosts A and B using TCP/IP. According to the session, answer the questions.Questions:1. What is the whole name of the sender’s host? What is the user name of the sender?2. How many users does the sender want to send the E-mail?3. What is the whole name of the receiver’s host?4. Which users can receive the E-mail?5. For receiving the mail, what is the port number waiting for the connection on the receiver host?6. What is the name of the transport layer protocol?Optional Question (No Points for this exam):This final examination was: a. Easier than I expected b. About what I expected c. Harder than I expected。
天津理工大学 计算机网络实验二

}
/****************************************************************************** * Send data * ***************************************************************************/ void MainWindow::sendMessage() { QString textEdit = ui->lineEdit->text(); QString strData =QString::fromLocal8Bit("Time: ") + QTime::currentTime().toString() + "\n" + textEdit.toLocal8Bit() + "\n"; QByteArray sendMessage = strData.toLocal8Bit(); mChat += ("Send " + sendMessage); ui->textEdit->setText(mChat); tcpSocket->write(sendMessage); ui->lineEdit->clear(); } /****************************************************************************** * Receive data * ***************************************************************************/ void MainWindow::onReciveData() { QString data = tcpSocket->readAll(); qDebug()<<data; mChat +=("Recv " + data); ui->textEdit->setText(mChat); } /****************************************************************************** * Create new listen * ***************************************************************************/ void MainWindow::newListen() { if(!tcpServer->listen(QHostAddress::Any,6666)) { qDebug()<<tcpServer->errorString(); tcpServer->close(); } } /****************************************************************************** * Accept connection
计算机网络技术实验报告二

(1)专门设有“BBS控制”工具栏,用于阅读和发文(2)引入了“最喜爱的站点”功能,只要在地址簿设置好,以后就可以方便快捷地连接这些最喜爱的站点(3)有大量的快捷键,在右手使用鼠标的时候可以使用左手操作一批Alt键为主的快捷键(4)通过增强的F5-F8快捷键功能,简化了文章发表、回复、写完发表、快速发文等操作(5)URL识别功能很强,可以识别含中文的URL、折行URL,可以把选中文字作为URL打开,甚至把BBS页面上的“发表文章”等功能识别为URL而点击使用(6)有单篇文章下载、讨论区批量文章下载、精华区文章全部下载等特殊功能。
4.练习实现文件上传下载的各种方法:
(1)利用cuteFTP软件实现信息传输功能(2)网站资源的直接下载(3)使用专门下载工具
CuteFTP是小巧强大的FTP工具之一,友好的用户界面,稳定的传输速度,FlashFXP传输速度比较快,但有时对于一些教育网FTP站点却无法连接;LeapFTP传输速度稳定,能够连接绝大多数FTP站点;CuteFTP虽然相对来说比较庞大,但其自带了许多免费的FTP站点,资源丰富。上传文件注意事项:
FTP登陆后目录结构如下:|- wwwroot网站根目录,网页文件请上传到这个目录。|- logfiles网站日志文件,系统自动产生,不占用您的空间。|- database Access数据库文件可以存放在这个目录下。
注意:(1)您的网页必需存放在wwwroot目录下才能被访问,缺省网站的文档按优先顺序为index.htm,index.asp,default.htm,default.asp(2)本网页文件名为index.htm是您的主机自动开设后系统生成的,您可以删除掉或用自己的覆盖(3)推荐您使用CUTEFTP或者LEAFTP等软件进行上传,如果在上传中碰到无法列出目录等情况,请尝试着把上传软件的PASV模式关掉(或者设置为port)。
天津理工大学计算机网络

天津理工大学计算机科学与技术学院《编译原理》上机指导《编译原理》课程组实验一词法分析器一实验目的1掌握手工生成词法分析器的方法,了解词法分析器的内部工作原理。
2通过设计编制调试一个具体的词法分析程序,加深对词法分析原理的理解。
并掌握在对程序设计语言源程序进行扫描过程中将其分解为各类单词的词法分析方法。
3掌握根据程序的伪代码来编写程序模块程序源代码。
二实验涉及到的知识要点词法分析器的功能输入是源程序,输出单词符号。
词法分析可以采用如下两种处理结构:(1)把词法分析程序作为主程序;(2)把词法分析程序作为语法分析程序调用的子程序。
三实验预习(以把词法分析程序作为主程序为例)程序语言的单词符号通常可以分以下五种:保留字、标识符、常数、运算符、界符。
语法分析程序输出的单词符号通常以二元式的形式表示:(单词种别,单词自身的值)四实验程序流程(仅供参考)五程序结构(仅供参考)Token=‘’; /*对token数组初始化*/S=getch( ); /*读入一个字符*/Getbc( ); /*滤除空白*/Switch(s){case ‘a’:case ‘b’:…case ‘z’:while (letter( ) || digit( )){concat(); /*将当前读入的字符送token数组*/getch();}retract(); /*非字母或数字则扫描指针回退一个字符*/c=reserve(); /*判断token是否为关键字,把返回值给c*/ if(c==0) /*若token是标识符*/{buildlist(); /*将标识符登录到符号表中*/return(id,指向符号表入口指针);}else /*若token不是标识符*/return(保留字,null);break;case ‘0’:case ‘1’:…case ‘9’:while (digit()) /*若当前读入的字符是数字*/ {concat(); /*将当前读入的数字送token数组*/getch();}retract(); /*非数字则扫描指针回退一个字符*/buildlist(); /*将常数登录到常数表*/return(num,num的常数表入口指针);break;case ‘+’:return(‘+’,null);break;case ‘-’:return(‘-’,null);break;case ‘*’:return(‘*’,null);break;case ‘<’:getch();if(ch==‘=’)return(relop,LE);else{retract(); /*扫描指针回退一个字符*/return(relop,LT)} break;case ‘;’:return(‘;’,null);break;default:error();}六实验内容题目:用以下语言词法构造规则,来构造词法分析器。
天津理工大学优秀教案

一、教学目标1. 知识目标:使学生掌握计算机网络的基本概念、组成、工作原理和应用。
2. 能力目标:培养学生分析问题和解决问题的能力,提高学生的动手操作能力。
3. 情感目标:激发学生对计算机网络的兴趣,培养学生严谨、求实的科学态度。
二、教学重难点1. 教学重点:计算机网络的基本概念、组成、工作原理。
2. 教学难点:计算机网络的工作原理和应用。
三、教学过程1. 导入新课教师简要介绍计算机网络的发展历程,激发学生的学习兴趣。
2. 讲授新课(1)计算机网络的基本概念讲解计算机网络的定义、分类、拓扑结构等基本概念。
(2)计算机网络的组成介绍计算机网络的硬件设备(如路由器、交换机、网卡等)和软件系统(如操作系统、网络协议等)。
(3)计算机网络的工作原理讲解计算机网络的数据传输、路由选择、网络通信协议等基本原理。
3. 课堂练习教师布置相关练习题,让学生巩固所学知识。
4. 案例分析选取一个实际案例,分析计算机网络在实际应用中的问题和解决方案。
5. 总结归纳教师总结本节课的重点内容,强调计算机网络在实际生活中的应用。
6. 布置作业布置课后作业,巩固所学知识。
四、教学反思1. 教学方法:本节课采用讲授法、案例分析法等多种教学方法,提高学生的学习兴趣。
2. 教学效果:通过本节课的学习,学生对计算机网络的基本概念、组成、工作原理有了较为全面的认识。
3. 改进措施:在今后的教学中,将更加注重理论与实践相结合,提高学生的动手操作能力。
五、教学评价1. 学生评价:学生对本节课的学习效果表示满意,认为教学内容丰富,易于理解。
2. 教师评价:教师对本节课的教学效果表示肯定,认为学生能够积极参与课堂活动,掌握所学知识。
总之,本节课的教学目标达成,教学效果良好。
在今后的教学中,将继续优化教学方法,提高教学质量。
计算机网络管理实验报告

计算机网络管理实验报告
实验目的:
本次实验旨在掌握计算机网络管理的基本原理和方法,以及学习使用网络管理工具来监控和维护网络系统的运行状态,提高网络的可靠性和安全性。
实验内容:
1. 学习网络管理的基本概念和原理;
2. 熟悉网络管理工具的使用方法;
3. 进行网络性能监测和故障排除;
4. 分析和总结网络管理实验结果。
实验步骤:
1. 网络管理基本原理学习:通过阅读相关教材和资料,了解网络管理的定义、分类、作用和原则等基本概念。
2. 网络管理工具学习:掌握常见的网络管理工具如Wireshark、Zabbix等的使用方法,包括安装、配置和操作步骤。
3. 网络性能监测:利用网络管理工具对网络进行性能监测,包括带宽利用率、延迟、丢包率等指标的检测和分析。
4. 网络故障排除:通过分析网络管理工具的监测结果,找出网络故障的原因并进行相应的处理和修复。
5. 实验总结:对实验过程中遇到的问题和解决方法进行总结,提出改进建议,为今后网络管理工作提供参考。
实验结果:
通过本次实验,我深刻理解了网络管理的重要性和必要性,掌握了一定的网络管理基本技能和工具的使用方法。
在实验中,我成功监测并解决了网络中出现的性能问题,提高了网络的可靠性和安全性。
同时,通过实验总结,我进一步完善了自己的网络管理知识体系,为今后的网络管理工作打下了坚实的基础。
结论:
网络管理是计算机网络运行维护的关键环节,只有有效地进行网络管理,才能保证网络系统的正常运行和安全稳定。
通过本次实验,我对网络管理有了更深入的了解,相信在今后的学习和工作中能更好地运用网络管理知识,提升自己的技能水平。
天津理工大学实验报告填写示例1 (1)

局域网、PC机连入Internet
(三)实验学时:
2学时,必做,验证实验
(四)实验内容:
根据每次实验内容自行填写
(五)实验要求:
可以根据每次实验逐条简单书写实验要求
(六)实验步骤:
前三个实验手工抄写各自源程序代码,不允许雷同,如发现,二者均做零分处理!
(七)实验中遇到的问题及解决方法:
天津理工大学实验报告
学院(系)名称:计算机科学与技术学院
姓名
学号专业ຫໍສະໝຸດ 计算机科学与技术(中加)班级
实验项目
(根据每次实验内容自行填写)类和对象的定义和实现
课程名称
课程代码
实验时间
实验地点
批改意见
成绩
教师签字:
(一)实验目的:
(根据每次实验内容自行填写)
(二)实验环境:
软件环境:Windows 2000/XP
将实验中的问题及解决办法简单概括,字数不限!问题及解决办法好的实验报告给予加分!
目前的三次实验项目
实验一:Java程序设计初步
实验二:Java面向对象机制(1)
实验二:Java面向对象机制(2)
634121948@
网络实验

C:\Documents and Settings\stud>netstat -as
IPv4 Statistics
Packets Received = 132187
Received Header Errors = 0
Received Address Errors = 2004
Datagrams Forwarded = 0
Unknown Protocols Received = 0
Received Pቤተ መጻሕፍቲ ባይዱckets Discarded = 4160
Received Packets Delivered = 126026
Output Requests = 2444
Routing Discards = 0
Discarded Output Packets = 0
Bluetooth网络连接:
节点IP址址: [0.0.0.0]范围ID: []
缓存中没有名称
无线网络连接:
节点IP址址: [0.0.0.0]范围ID: []
缓存中没有名称
结果解读
列出本地NetBIOS名称,类型,状态
问题解决
无
命令
-c
功能
列出远程[计算机]名称及其IP地址
执行结果
C:\Documents and Settings\Administrator>nbtstat -c
Record Name . . . . . : localhost
Record Type . . . . . : 1
Time To Live . . . . : 602420
Data Length . . . . . : 4
天津理工大学C++实验三

string color;
public:
wardrobe(float &p ,int &c ,string &pl ,string &w ,string &co ):base(p,c,pl)
{
wood=w; color=co;
}Байду номын сангаас
void print()
{
cout<<"\n立柜"<<"\t产地:"<<place<<"\t颜色:"<<color<<"\t木料:"<<wood<<"\n库存量:"
{d=z; cout<<"Derived Constructor\n";}
~Derived( )
{cout<<"Derived Destructor\n";}
void Show( )
{cout<<data1<<','<<data2<<','<<d<<endl;}
};
void main( )
{Derived c(1, 2, 3);
}
};
void main( )
{
Circle c(1, 1, 1);
c.ShowCircle( );
c.Move(1, 2);
c.ShowCircle( );
c.Setxy(4, 5);
c.Setr(2);
天津理工大学计算机专业UML面向对象分析与建模实验报告三

天津理工大学实验报告学院(系)名称:计算机与通信工程学院
【实验过程记录(源程序、测试用例、测试结果及心得体会等)】用户用传真机发送文件的成功情况顺序图:
用户用传真机发送文件的失败情况顺序图:
测试结果及心得体会:
通过画交互模型顺序图,更能清晰的理解一个事件发生的全过程,中的各种细节,可能发生的问题,并进行实时处理,更好的掌握事件的脉络。
大学啊不错啊,好好学习,不要耽误了青春,但是是这个专业坑爹啊,,找好自己的方向,不要被这个专业误导了啊,,
理工的学妹,学弟们,你说呢,,哈哈哈哈,嘿嘿联系/。
天津理工大学计算机网络实验三
实验报告
学院(系)名称:计算机与通信工程学院
姓名学号专业
班级实验名称实验三:路由器配置
课程名称计算机网络课程代码
实验时间实验地点7#219批改意见成绩
教师签字:
1.实验目的
理解路由器工作原理和配置方法,掌握路由器的接线方法,登录方式,静态路由和动态路由的配置。
2.实验环境
Windows
3.实验要求
进行网络地址规划,配置路由器;检查路由器配置。
掌握路由协议的种类和特点。
掌握静态路由、默认路由的配置方法。
掌握查看路由条目的方法。
并验证路由的作用。
4.实验过程记录(源程序、测试用例、测试结果及心得体会等)
(1)静态路由:
配置路由器 1 和各个端口 ip:
验证:
(2)Rip 路由配置路由器 1:
验证:
(3)Ospf 路由验证:
心得体会:
通过此次实验,我不仅学会了配置静态、动态路由的方法,还掌握了查看路由条目的方法、验证路由的作用,收获颇多。
【本文档内容可以自由复制内容或自由编辑修改内容期待
你的好评和关注,我们将会做得更好】。
网络管理基本命令实验 报告

天津理工大学实验报告学院(系)名称:管理学院
ping -l +数值:所发送缓冲区大小。
ping -t :继续执行ping命令,直到用户按ctrl+c终止。
①ping命令
②ping -t :继续执行ping命令,直到用户按ctrl+c终止。
③ping -n +(数据包个数):发出的测试包个数。
二、使用ipconfig命令:
三、使用netstat命令:
①netstat 用于显示与IP 、TCP 、UDP 和ICMP 协议相关的统计数据,一般用于检验本机各端口的网络连接情况。
②netstat -a 本选项显示一个所有的有效连接信息列表,包括已建立的连接,也包括监听连接请求,断开连接或者处于联机等待状态等
③netstat -e ——本选项用于显示关于以太网的统计数据。
四、使用route,tracert,arp命令:①route命令
②route print 打印路由表
③tracert+网址
arp -a显示所有接口的 ARP 缓存表
⑥其他相关命令arp -s、arp -d、arp -g。
《计算机网络原理》实验指导书

《计算机网络原理》实验指导书课程代码:0660086天津理工大学计算机计算机科学与工程学院2007年9月目录一、实验指导书的选用范围............................ 错误!未定义书签。
二、计算机网络技术课程简介.......................... 错误!未定义书签。
三、实验的地位、作用和目的及学生能力标准............ 错误!未定义书签。
四、实验方式与基本要求.............................. 错误!未定义书签。
五、考核方式与实验报告要求.......................... 错误!未定义书签。
六、实验项目........................................ 错误!未定义书签。
实验一:验证常用网络命令........................ 错误!未定义书签。
实验验证常用的网络命令...................... 错误!未定义书签。
实验用telnet方式收发邮件................... 错误!未定义书签。
实验二:基于TCP/UDP的Socket编程............... 错误!未定义书签。
实验:基于TCP and UDP的socket编程.......... 错误!未定义书签。
实验:基于TCP的Web Server .................. 错误!未定义书签。
实验:基于TCP/UDP的Daytime的客户端和服务器端错误!未定义书签。
实验:基于TCP/UDP的Echo的客户端和服务器端.. 错误!未定义书签。
实验 SOCKET编程实现聊天程序................ 错误!未定义书签。
实验 SOCKET编程实现mini FTP Client/ Server程序错误!未定义书签。
附录1 参考程序............................ 错误!未定义书签。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
)静态路由:(1ip1配置路由器和各个端口:
验证:
(2)Rip路由
配置路由器1:
验证:
(3)Ospf路由
验证:
心得体会:
通过此次实验,我不仅学会了配置静态、动态路由的方法,还掌握了查看路由条目的方法、验证路由的作用,收获颇多。
实验报告计算机与通信工程学院学院(系)名称:
姓名
学号
专业
班级
实验名称
实验三:路由器配置
课程名称
计算机网络
课程代码
实验时间
实验地点7#219批意见成绩教师签字:
实验目的1.
理解路由器工作原理和配置方法,掌握路由器的接线方法,登录方式,静态路由和动态路由的配置。实验环境2.
Windows
实验要求3.
进行网络地址规划,配置路由器;检查路由器配置。掌握路由协议的种类和特点。掌握静态路由、默认路由的配置方法。掌握查看路由条目的方法。并验证路由的作用。
