7506配置
H3C_S7506E维护操作管理守则

精心整理H3C_S7506E维护操作手册配置举例:1、配置设备主机名如:sysnameH3C_S7506E2、3如:4如:5如:6如:7如:authorization-attributelevel38、配置将用户名admin及密码abc应用于telnet登录验证如:service-typetelnet9、开启telnet如:telnetserverenable10、配置E0/0接口描述如:descriptionto_G1/0/1_1.1.1.111、配置E0/0接口IP地址(广域网口IP地址)如:ipaddress2.2.2.212、配置E0/0接口为全双工状态如:13如:14如:15如:16如:17如:18如:19、配置环回地址如:ipaddress3.3.3.25520、配置VLAN端口如:interfaceVlan-interface121、配置VLAN接口的描述如:descriptionServer22、配置VLAN端口IP地址如:ipaddress3.3.3.1.023创建备份组并配置虚拟IP地址如:vrrpvrid1virtual-ip3.3.3.3 24、配置交换机在备份组中的优先级如:25如:26如:27如:2829如:30如:area 0.0.0.1network0.0.0.3network1.1.1.00.0.0.25531、设置OSPF链路开销参考值10000 bandwidth-reference1000032、将该OSPF区域设置为完全末梢区如:stubno-summary33、OSPF的开销如:ospfcost2034、开启SNMP代理如:35如:36如:37如:38如:39如:40如:snmp-agenttrapqueue-size500 41、配置SNMP陷阱报文生存时间如:snmp-agenttraplife60042、配置远程登录接口如:user-interfacevty0443、配置远程登录使用用户名及密码验证。
S7506E三层交换机配置资料讲解

***************************************************************** ************** Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. ** Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ****************************************************************** *************Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902description test#vlan 3985description dhcp for temp guest meetingsupervlansubvlan 36#vlan 3986description dianxin wireless supervlansubvlan 3901#vlan 3987description huisuo vlan 33 supervlansubvlan 33#vlan 3988description wirelesssupervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250#vlan 3991supervlansubvlan 1200 to 1225#vlan 3992supervlansubvlan 100 to 111#vlan 3993supervlansubvlan 1032 to 1150#vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790#vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#vlan 3999description to UTM200#vlan 4000 to 4001#ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator andif-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan#dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0gateway-list 192.168.36.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3990network 192.168.138.0 mask 255.255.254.0gateway-list 192.168.138.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!!service-type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1#interface NULL0#interface Vlan-interface1ip address 192.168.39.2 255.255.255.0 #interface Vlan-interface2ip address 192.168.31.227 255.255.255.0 #interface Vlan-interface30ip address 192.168.30.254 255.255.255.0 #interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 ##interface Vlan-interface3986 (分配网关)ip address 192.168.160.1 255.255.224.0local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0#interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0#interface Vlan-interface3989ip address 192.168.140.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3990ip address 192.168.138.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#local-proxy-arp enable#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3999description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/2port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39#interface GigabitEthernet3/0/3 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/4 port access vlan 1227qos apply policy kefang inbound mirroring-group 2 monitor-port #interface GigabitEthernet3/0/5 port access vlan 3901qos apply policy kefang inbound #interface GigabitEthernet3/0/6 port access vlan 8#interface GigabitEthernet3/0/7 port access vlan 3999description to UTM-200_G 0/0 qos apply policy kefang inbound #interface GigabitEthernet3/0/8 port access vlan 8qos apply policy kefang inbound #interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10qos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/12 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/23 port access vlan 35stp edged-port enableqos apply policy kefang inboundstp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/25port access vlan 2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/26port access vlan 2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundmirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundqos apply policy kefang inbound #interface GigabitEthernet3/0/32 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/33 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/34 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/39#interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound #interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #interface GigabitEthernet3/0/45 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/46 port access vlan 35qos apply policy kefang inbound #interface GigabitEthernet3/0/47port access vlan 34qos apply policy kefang inbound#interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/32port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/38port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253 ip route-static 10.0.18.0 255.255.255.0 192.168.30.253 ip route-static 10.0.24.0 255.255.255.0 192.168.30.253 ip route-static 10.0.25.0 255.255.255.0 192.168.30.253 ip route-static 10.0.29.0 255.255.255.0 192.168.30.253 ip route-static 10.0.97.0 255.255.255.0 192.168.30.253 ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253 ip route-static 10.11.30.0 255.255.255.0 192.168.30.253 ip route-static 10.11.70.0 255.255.255.0 192.168.30.253 ip route-static 10.11.72.0 255.255.255.0 192.168.30.253ip route-static 10.12.41.0 255.255.255.0 192.168.30.253ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253 ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2 #snmp-agentsnmp-agent local-engineid 800063A203000FE22EDA1Csnmp-agent community write q-ideasnmp-agent sys-info version allsnmp-agent target-host trap address udp-domain 192.168.34.120 udp-port 5000 params securityname q-idea#dhcp server detect#dhcp enable#user-interface aux 0idle-timeout 0 0user-interface vty 0 4acl 3011 inboundauthentication-mode schemeuser privilege level 3#return<7506E>。
H3C交换机操作手册

目录H3C以太网交换机的基本操作 (2)1.1 知识准备 (3)1.2 操作目的 (3)1.3 网络拓扑 (3)1.4 配置步骤 (3)1.4.1 串口操作配置 (3)1.4.2 查看配置及日志操作 (6)1.4.3 设置密码操作 (6)1.5 验证方法 (7)H3C以太网交换机VLAN配置 (7)1.6 知识准备 (7)1.7 操作目的 (7)1.8 操作内容 (7)1.9 设备准备 (7)1.10 拓扑 (7)1.11 配置步骤 (8)1.12 验证方法 (8)H3C以太网交换机链路聚合配置 (8)1.13 知识准备 (8)1.14 操作目的 (8)1.15 操作内容 (8)1.16 设备准备 (8)1.17 网络拓扑 (8)1.18 配置步骤 (9)1.19 验证方法 (10)H3C以太网交换机STP配置 (10)1.20 知识准备 (10)1.21 操作目的 (10)1.22 操作内容 (10)1.23 设备准备 (10)1.24 网络拓扑 (11)1.25 配置步骤 (11)1.26 验证方法 (12)H3C以太网交换机VRRP配置 (12)1.27 知识准备 (12)1.28 操作目的 (12)1.29 操作内容 (12)1.30 设备准备 (12)1.31 网络拓扑 (13)1.32 配置步骤 (13)1.33 验证方法 (15)H3C以太网交换机镜像配置 (15)1.34 知识准备 (15)1.35 操作目的 (15)1.36 操作内容 (15)1.37 设备准备 (15)1.38 网络拓扑 (15)1.39 配置步骤 (16)1.40 验证方法 (16)H3C以太网交换机路由配置 (17)1.41 知识准备 (17)1.42 操作目的 (17)1.43 操作内容 (17)1.44 设备准备 (17)1.45 网络拓扑 (17)1.46 配置步骤 (17)1.47 验证方法 (18)H3C以太网交换机ACL配置 (18)1.48 知识准备 (18)1.49 操作目的 (19)1.50 操作内容 (19)1.51 网路拓扑 (19)1.52 配置步骤 (19)1.53 验证方法 (19)实验一H3C以太网交换机的基本操作备注:H3C以太网交换机采用统一软件平台VRP,交换机命令完全相同。
H3C S7506E上配置策略路由
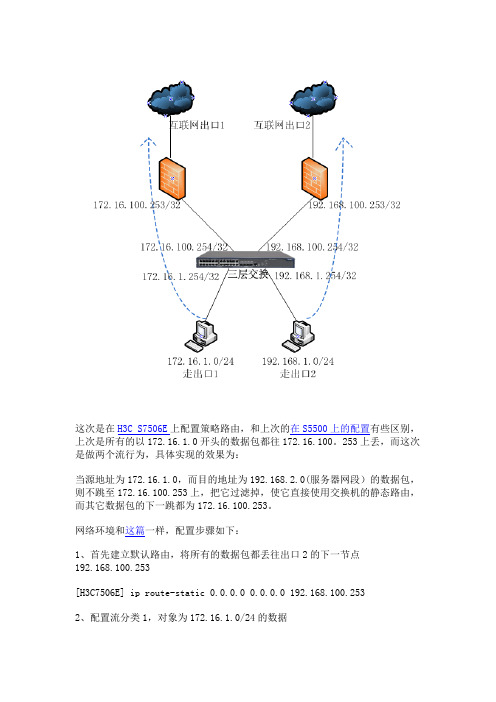
这次是在H3C S7506E上配置策略路由,和上次的在S5500上的配置有些区别,上次是所有的以172.16.1.0开头的数据包都往172.16.100。
253上丢,而这次是做两个流行为,具体实现的效果为:当源地址为172.16.1.0,而目的地址为192.168.2.0(服务器网段)的数据包,则不跳至172.16.100.253上,把它过滤掉,使它直接使用交换机的静态路由,而其它数据包的下一跳都为172.16.100.253。
网络环境和这篇一样,配置步骤如下:1、首先建立默认路由,将所有的数据包都丢往出口2的下一节点192.168.100.253[H3C7506E] ip route-static 0.0.0.0 0.0.0.0 192.168.100.2532、配置流分类1,对象为172.16.1.0/24的数据[H3C7506E]acl number 3001[H3C7506E-acl-adv-3001] rule 0 deny ip source 172.16.1.0 0.0.0.255 dest 192.168.2.0 0.0.0.255[H3C7506E] quit[H3C7506E] traffic classifier 1[H3C7506E-classifier-1] if-match acl 3001[H3C7506E-classifier-1] quit3、配置刚才定义的流分类的行为,定义如果匹配则允许[H3C7506E] traffic behavior 1[H3C7506E-behavior-1] filter permit[H3C7506E-behavior-1] quit4、配置流分类2,对象仍为172.16.1.0、24[H3C7506E]acl number 3002[H3C7506E-acl-adv-3002] rule 0 permit ip source 172.16.1.0 0.0.0.255 [H3C7506E] quit[H3C7506E] traffic classifier 2[H3C7506E-classifier-2] if-match acl 3002[H3C7506E-classifier-2] quit5、配置刚才定义的流分类的行为,定义如果匹配就下一跳至出口1即172.16.100.253[H3C7506E] traffic behavior 2[H3C7506E-behavior-2] redirect next-hop 172.16.100.253[H3C7506E-behavior-2] quit6、将刚才设置的应用至QOS策略中,定义policy 1[H3C7506E] qos policy 1[H3C7506E-qospolicy-2] classifier 1 behavior 1[H3C7506E-qospolicy-2] classifier 2 behavior 2[H3C7506E-qospolicy-2] quit7、在接口上应用定义的QOS策略policy 1[H3C7506E] interface GigabitEthernet 1/0/15[H3C7506E-GigabitEthernet1/0/15] qos apply policy 1 inbound[H3C7506E-GigabitEthernet1/0/15] quit至此,配置已完成。
交换机设置教程图解
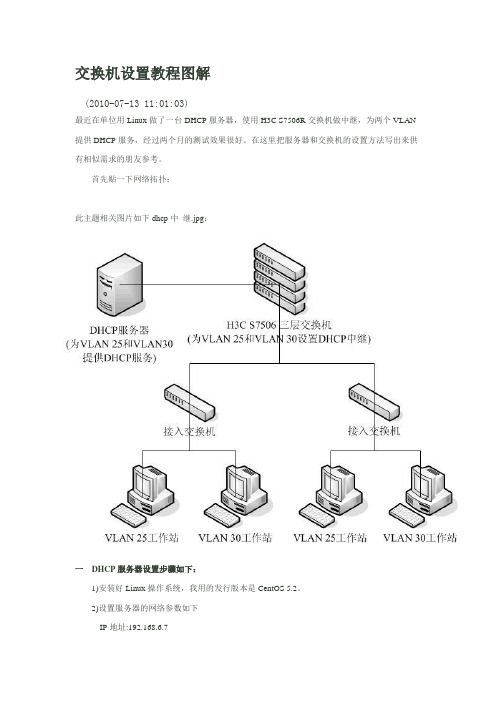
交换机设置教程图解(2010-07-13 11:01:03)最近在单位用Linux做了一台DHCP服务器,使用H3C S7506R交换机做中继,为两个VLAN 提供DHCP服务,经过两个月的测试效果很好。
在这里把服务器和交换机的设置方法写出来供有相似需求的朋友参考。
首先贴一下网络拓扑:此主题相关图片如下dhcp中继.jpg:一DHCP服务器设置步骤如下:1)安装好Linux操作系统,我用的发行版本是CentOS 5.2。
2)设置服务器的网络参数如下IP地址:192.168.6.7子网掩码:255.255.255.0网关:192.168.6.254DNS:192.168.6.103)安装DHCP服务CentOS和Red Hat Enterprise Linux等系统默认并不安装DHCP服务。
可以使用这个命令来检查系统是否已经安装DHCP服务:rpm –q dhcp如果返回提示“package dhcp is not installed”,说明没有安装DHCP服务。
把CentOS安装DVD 光盘放入光驱,执行以下命令:cd /media/CentOS_5.2_Final/CentOSrpm –ivh dhcp-3.0.5-13.el5.i386.rpm系统会显示安装进度,安装成功后再次执行“rpm –q dhcp”命令,系统会返回消息“dhcp-3.0.5-13.el5”,说明DHCP服务已正确安装。
4)把配置文件模板复制为dhcpd.confDHCP服务的配置要靠编辑/etc/dhcpd.conf来进行。
DHCP服务程序默认没有建立dhcpd.conf 配置文件,但自带配置模板,只要稍加修改就可以使用。
执行“cp /usr/share/doc/dhcp-3.0.5/dhcpd.conf.sample /etc/dhcpd.conf”命令,可以把系统自带的配置文件模板复制到/etc目录并重命名为dhcpd.conf。
7506E安全配置指导-ARP攻击防御配置

配置源 MAC 地址固定的 ARP 攻击检测功能
可选 建议在网关设备上配置本功能
防止仿冒用户、 仿冒网关攻击
配置 ARP 主动确认功能
可选 建议在网关设备上配置本功能
配置 ARP Detection 功能
可选 建议在接入设备上配置本功能
详细配置 1.3
1.4 1.5 1.6 1.7
1-1
配置任务 配置 ARP 自动扫描、固化功能
地址进行解析,导致 CPU 负荷过重及网络流量过大。 z 攻击者向设备发送大量 ARP 报文,对设备的 CPU 形成冲击。 关于 ARP 攻击报文的特点以及 ARP 攻击类型的详细介绍,请参见“ARP 攻击防范技术白皮书”。 目前 ARP 攻击和 ARP 病毒已经成为局域网安全的一大威胁,为了避免各种攻击带来的危害,设备 提供了多种技术对攻击进行防范、检测和解决。 下面将详细介绍一下这些技术的原理以及配置。
主机向设备某端口连续发送目标 IP 地址不能解析的 IP 报文,当每 5 秒内由此主机发出 IP 报 文触发的 ARP 请求报文的流量超过设置的阈值,那么对于由此主机发出的 IP 报文,设备不允 许其触发 ARP 请求,直至 5 秒后再处理,从而避免了恶意攻击所造成的危害。 z 如果发送攻击报文的源不固定,可以采用 ARP 黑洞路由功能。开启该功能后,一旦接收到目 标 IP 地址不能解析的 IP 报文,设备立即产生一个黑洞路由,使得设备在一段时间内将去往该 地址的报文直接丢弃。等待黑洞路由老化时间过后,如有报文触发则再次发起解析,如果解 析成功则进行转发,否则仍然产生一个黑洞路由将去往该地址的报文丢弃。这种方式能够有 效地防止 IP 报文的攻击,减轻 CPU 的负担。
i
1 ARP攻击防御配置
H3C网络设备控标参数A
接口
≥24个GE端口,≥4个万兆SFP口
CPU防护
实现CPU保护功能,能限制非法报文对CPU的攻击,保护交换机在各种环境下稳定工作
堆叠
最大堆叠台数≥9台,并要求实配接口的基础上额外满配堆叠带宽所需的接口和互联模块,支持跨设备链路聚合,单一IP管理,分布式弹性路由,支持远程堆叠
1
招标规格:
功能及技术指标
参数要求
产品类型
24口PoE接入交换机
兼容性
与核心交换机同一品牌
交换容量
≥330Gbps(以官网最小值为标准)
转发性能
≥95Mpps(以官网最小值为标准)
供电
支持POE+
接口
≥24个GE端口,≥4个万兆SFP口
CPU防护
实现CPU保护功能,能限制非法报文对CPU的攻击,保护交换机在各种环境下稳定工作
组播协议
支持IGMP v1/v2/v3,MLD v1/v2,支持IGMP Snooping v1/v2/v3,MLD Snooping v1/v2,支持PIM Snooping,支持组播VLAN
路由协议
支持IPv4静态路由、RIP V1/V2、OSPF,支持IPv6静态路由、RIPng,支持IPv4和IPv6环境下的策略路由
1
LSQM2GP24TSSA0
24端口千兆以太网光口(SFP,LC)+4端口万兆以太网光接口模块(SFP+,LC)
1
LSQM2GT24TSSC0
24端口千兆以太网电接口(RJ45)+4端口万兆以太网光接口模块(SFP+,LC)
1
招标规格:
功能及技术指标
参数要求
S7506E设备参数
要求设备采用业务承载母板与接口子卡分离的设计,提高设备可扩展性
★总插槽数
≥4
★业务插槽数
配置主控引擎冗余后,业务插槽数(大槽)>=2,业务子卡槽位数最大支持8
★交换容量
≥240G
★整机包转发率
≥48Mpps
系统可靠性
支持双主控,主备切换“零丢包”
关键部件冗余
支持主控引Байду номын сангаас、电源等关键部件冗余备份
关键部件冗余支持主控板电源模块冗余可支持业务板卡类型防火墙业务板入侵防御系统板无线控制器业务板负载均衡业务板应用控制网关业务板网络流量分析业务板sslvpn业务业务板异常流量检测业务板异常流量清洗业务板虚拟化特性支持h3cirf2技术或ciscovss技术将多台物理设备虚拟化为一台逻辑设备虚拟组内可以实现一致的转发表项统一的管理跨物理设备的链路聚合支持4台设备的虚拟化支持至少三种以上分裂检测功能支持远距离虚拟化距离可达70km提供相关专利证明文件需提供重庆本地相关应用案例不少于3个
支持基于端口、MAC地址、IP地址、IP优先级、DSCP优先级、TCP/UDP端口号、协议类型等方式的流分类;
支持流量整形和流量监管
MPLS特性
支持L3VPN:支持跨域MPLS VPN(Option1/2/3)、嵌套MPLS VPN、支持分层PE(HoPE)、CE双归属、MCE、多角色主机、GRE隧道等;支持L2VPN:Martini、Kompella、CCC和SVC方式;支持MPLS TE、RSVP TE
★资质认证
提供工信部(原信产部)IPv4、IPv6入网证书,提供IPv4、IPv6检验报告,为了保证设备软件的合法性,必须提供中华人民共和国国家版权局颁发的计算机软件著作权登记证书
飞利浦 TAN7506 蓝牙无线耳机 用户手册说明书

用户手册访问以下网站注册您的产品并获取支持/support耳机TAN75067000 系列目录1 重要安全说明 2听力安全 2一般信息 22 蓝牙无线耳机 3包装盒内物品 3其他设备 3蓝牙无线耳机概述 43 使用入门 5电池充电 5将耳机与手机配对 54 使用耳机 6将耳机连接至蓝牙设备 6将耳机连接到您的计算机 6管理通话和音乐 6ANC(主动降噪) 7语音助手 7忙碌模式 7Philips 耳机应用 75 技术数据 86 注意 9符合性声明 9旧产品和电池的处理 9拆除集成式电池 9符合电磁场 (EMF) 法规 9环保信息 10法规遵循注意事项 107 商标 118 常见问题解答 12中文 11 重要安全说明听力安全• 为避免听力受损,应限制以高音量使用耳机的时间,并将音量设定在安全级别。
音量越大,安全收听的时间越短。
使用耳机时请确保遵循以下准则。
• 在合理时间内以合理音量收听。
• 听力适应后,注意不要持续地调高音量。
• 请勿将音量调得太高而使得无法听见周围的声音。
• 在有潜在危险的情况下应谨慎使用或暂停使用。
• 耳机声压过大可导致听力受损。
• 建议在驾车时不要双耳佩戴耳机,而且在某些地区这样做可能属于违法行为。
• 出于安全考虑,在驾车时或其它存在潜在危险的环境下,应避免让音乐或通话分散您的注意力。
危险一般信息为避免损坏或故障:• 切勿将耳机置于高温环境• 切勿摔落耳机• 切勿将耳机置于滴水或溅水环境下。
• 切勿将耳机没入水中。
• 切勿使用任何包含酒精、氨水、苯或研磨剂的清剂清洁产品。
• 如果需要,请使用软布清洁产品,可用少量的水或稀释的中性肥皂水将布打湿进行清洁。
• 切勿将集成式电池置于高温环境,如阳光直射处、明火或类似环境。
• 请换掉可能会破坏安全保护机制的型号不正确的电池;• 如果将电池投入火中或热烤箱中,或将其机械压碎或切割,可能会导致爆炸;• 如果将电池放在极高温度环境中,可能会导致爆炸或易燃液体或气体泄漏;• 如果将电池放在极低气压环境中,可能会导致爆炸或易燃液体或气体泄漏。
S7506E三层交换机配置上课讲义

***************************************************************** ************** Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. ** Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ****************************************************************** *************Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902#vlan 3985description dhcp for temp guest meeting supervlansubvlan 36#vlan 3986description dianxin wirelesssupervlansubvlan 3901#vlan 3987description huisuo vlan 33supervlansubvlan 33#vlan 3988description wirelesssupervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250#vlan 3991subvlan 1200 to 1225#vlan 3992supervlansubvlan 100 to 111#vlan 3993supervlansubvlan 1032 to 1150#vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790 #vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#description to UTM200#vlan 4000 to 4001#ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator and if-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan #dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0 gateway-list 192.168.36.254expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0 gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0 gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3990network 192.168.138.0 mask 255.255.254.0 gateway-list 192.168.138.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!!service-type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1##interface Vlan-interface1ip address 192.168.39.2 255.255.255.0 #interface Vlan-interface2ip address 192.168.31.227 255.255.255.0 #interface Vlan-interface30ip address 192.168.30.254 255.255.255.0 #interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 #interface Vlan-interface3985ip address 192.168.36.254 255.255.255.0 #interface Vlan-interface3986 (分配网关)ip address 192.168.160.1 255.255.224.0local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0#interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0#interface Vlan-interface3989ip address 192.168.140.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3990ip address 192.168.138.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3994ip address 192.168.132.1 255.255.255.128#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128local-proxy-arp enable#interface Vlan-interface3999description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/2port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39qos apply policy kefang inboundmirroring-group 1 mirroring-port both#interface GigabitEthernet3/0/3port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/4port access vlan 1227qos apply policy kefang inboundmirroring-group 2 monitor-port#interface GigabitEthernet3/0/5port access vlan 3901qos apply policy kefang inbound#interface GigabitEthernet3/0/6port access vlan 8#interface GigabitEthernet3/0/7port access vlan 3999description to UTM-200_G 0/0qos apply policy kefang inbound#interface GigabitEthernet3/0/8port access vlan 8qos apply policy kefang inbound#interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/12 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/17 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/23 port access vlan 35stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/24 port access vlan 34stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/25 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/26 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/27 port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundmirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/31port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/32port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/33port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/34port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/39 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound#interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #interface GigabitEthernet3/0/45 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/46 port access vlan 35qos apply policy kefang inbound #interface GigabitEthernet3/0/47 port link-type trunkport trunk permit vlan 1 30qos apply policy kefang inbound #interface GigabitEthernet3/0/48 port access vlan 34qos apply policy kefang inbound #interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/7port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/13port link-type trunkqos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundinterface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/38port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunk#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunk#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet8/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094qos apply policy kefang inbound#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253 ip route-static 10.0.18.0 255.255.255.0 192.168.30.253 ip route-static 10.0.24.0 255.255.255.0 192.168.30.253 ip route-static 10.0.25.0 255.255.255.0 192.168.30.253 ip route-static 10.0.29.0 255.255.255.0 192.168.30.253 ip route-static 10.0.97.0 255.255.255.0 192.168.30.253 ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253 ip route-static 10.11.30.0 255.255.255.0 192.168.30.253 ip route-static 10.11.70.0 255.255.255.0 192.168.30.253 ip route-static 10.11.72.0 255.255.255.0 192.168.30.253 ip route-static 10.12.41.0 255.255.255.0 192.168.30.253 ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253 ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2。
IRF

IRF介绍以太网是广播性质的网络,一旦链路成环路很容易导致广播风暴,耗尽网络链路及设备资源。
然而在传统的数据中心网络部署中,为了保证网络设备和链路的高可靠,往往通过引入双机热备、双链路双归属的冗余方式组网,引入MSTP+VRRP协议来实现链路和设备网关的热备,这种部署方式必然会带来网络环路和复杂度的增加。
IRF(Intelligent Resilient Framework,智能弹性架构)是H3C自主研发的交换机虚拟化技术。
它的核心思想是将多台物理设备虚拟化成一台“虚拟设备”,实现N:1的横向虚拟化整合。
使用这种虚拟化技术可以实现多台设备的协同工作、统一管理和不间断维护。
为了便于描述,这个“虚拟设备”也称为IRF。
所以,本文中的IRF有两层意思,一个是指IRF技术,一个是指IRF设备。
IRF的优点:˙简化管理。
IRF形成之后,用户通过任意成员设备的任意端口均可以登录IRF系统,对IRF 内所有成员设备进行统一管理。
而不用物理连接到每台成员设备上分别对它们进行配置和管理。
˙简化网络运行。
IRF形成的虚拟设备中运行的各种控制协议也是作为单一设备统一运行的,例如路由协议会作为单一设备统一计算。
这样省去了设备间大量协议报文的交互,简化了网络运行,缩短了网络动荡时的收敛时间。
IRF技术的这一特性是常见的集群技术所不具备的,后者仅仅能完成设备管理上的统一,而集群中的设备在网络中仍然分别作为独立节点运行。
˙强大的网络扩展能力。
通过增加成员设备,可以轻松自如的扩展IRF系统的端口数、带宽和处理能力。
˙保护用户投资。
由于具有强大的扩展能力,当用户进行网络升级时,不需要替换掉原有设备,只需要增加新设备既可。
很好的保护了用户投资。
˙高可靠性。
IRF的高可靠性体现在多个方面,例如:成员设备之间IRF物理端口支持聚合功能,IRF系统和上、下层设备之间的物理连接也支持聚合功能,这样通过多链路备份提高了IRF系统的可靠性;IRF系统由多台成员设备组成,Master设备负责IRF系统的运行、管理和维护,Slave设备在作为备份的同时也可以处理业务,一旦Master设备故障,系统会迅速自动选举新的Master,以保证通过IRF系统的业务不中断,从而实现了设备的1:N备份。
S7506E三层交换机配置

****************************************************************************** * Copyright (c) 2004-2008 Hangzhou H3C Tech. Co., Ltd. All rights reserved. * * Without the owner's prior written consent, ** no decompiling or reverse-engineering shall be allowed. ******************************************************************************* Login authenticationUsername:adminPassword:<7506E>di cur#version 5.20, Release 6305#sysname 7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group 1 localmirroring-group 2 local#switch-mode standard#acl number 3010description to UTM200rule 0 permit ip source 192.168.128.0 0.0.15.255 rule 1 permit ip source 192.168.160.0 0.0.31.255 acl number 3011rule 0 permit ip source 192.168.34.0 0.0.0.255 rule 1 permit ip source 192.168.37.0 0.0.0.255 rule 2 permit ip source 192.168.31.0 0.0.0.255 rule 3 permit ip source 192.168.39.0 0.0.0.255 rule 4 permit ip source 192.168.254.0 0.0.0.255 acl number 3500#vlan 1#vlan 2 to 2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902description test#vlan 3985description dhcp for temp guest meeting supervlansubvlan 36#vlan 3986description dianxin wirelesssupervlansubvlan 3901#vlan 3987description huisuo vlan 33supervlansubvlan 33vlan 3988description wireless supervlansubvlan 2222#vlan 3989supervlansubvlan 3 to 29#vlan 3990supervlansubvlan 1226 to 1250 #vlan 3991supervlansubvlan 1200 to 1225 #vlan 3992supervlansubvlan 100 to 111 #vlan 3993supervlansubvlan 1032 to 1150vlan 3994supervlansubvlan 911 to 1031#vlan 3995supervlansubvlan 791 to 910#vlan 3996supervlansubvlan 351 to 421 747 to 790 #vlan 3997supervlansubvlan 231 to 350#vlan 3998supervlansubvlan 112 to 230#vlan 3999description to UTM200#vlan 4000 to 4001ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator and if-match acl 3500#traffic behavior kefangredirect next-hop 192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan #dhcp server ip-pool 3985network 192.168.36.0 mask 255.255.255.0 gateway-list 192.168.36.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3986network 192.168.160.0 mask 255.255.224.0 gateway-list 192.168.160.1dns-list 202.96.128.86 8.8.8.8 202.96.128.166 expired day 0 hour 2#dhcp server ip-pool 3987network 192.168.33.0 mask 255.255.255.0 gateway-list 192.168.33.254dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 8#dhcp server ip-pool 3988network 192.168.142.0 mask 255.255.254.0 gateway-list 192.168.142.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3989network 192.168.140.0 mask 255.255.254.0gateway-list 192.168.140.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3990network 192.168..0 mask 255.255.254.0gateway-list 192.168..1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3991network 192.168.136.0 mask 255.255.254.0gateway-list 192.168.136.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3992network 192.168.134.0 mask 255.255.254.0gateway-list 192.168.134.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3993network 192.168.132.128 mask 255.255.255.128 gateway-list 192.168.132.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3994network 192.168.132.0 mask 255.255.255.128 gateway-list 192.168.132.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3995network 192.168.131.128 mask 255.255.255.128 gateway-list 192.168.131.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3996network 192.168.131.0 mask 255.255.255.128 gateway-list 192.168.131.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3997network 192.168.130.128 mask 255.255.255.128 gateway-list 192.168.130.129dns-list 202.96.128.86 202.96.128.166 8.8.8.8expired day 0 hour 4#dhcp server ip-pool 3998network 192.168.130.0 mask 255.255.255.128 gateway-list 192.168.130.1dns-list 202.96.128.86 202.96.128.166 8.8.8.8 expired day 0 hour 4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!! -type telnetlevel 3#stp instance 0 root primarystp enable#monitor-link group 1#interface NULL0#interface Vlan-interface1ip address 192.168.39.2 255.255.255.0#interface Vlan-interface2ip address 192.168.31.227 255.255.255.0 #interface Vlan-interface30ip address 192.168.30.254 255.255.255.0 #interface Vlan-interface32ip address 192.168.32.254 255.255.255.0 #interface Vlan-interface34ip address 192.168.34.254 255.255.255.0 #interface Vlan-interface35ip address 192.168.35.254 255.255.255.0 #interface Vlan-interface37ip address 192.168.37.254 255.255.255.0 #interface Vlan-interface38ip address 192.168.38.254 255.255.255.0 #interface Vlan-interface3985ip address 192.168.36.254 255.255.255.0 #ip address 192.168.160.1 255.255.224.0 local-proxy-arp enable#interface Vlan-interface3987ip address 192.168.33.254 255.255.255.0 #interface Vlan-interface3988ip address 192.168.142.1 255.255.254.0 #interface Vlan-interface3989ip address 192.168.140.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3990ip address 192.168..1 255.255.254.0local-proxy-arp enable#interface Vlan-interface3991ip address 192.168.136.1 255.255.254.0 local-proxy-arp enable#interface Vlan-interface3992ip address 192.168.134.1 255.255.254.0 local-proxy-arp enableinterface Vlan-interface3993ip address 192.168.132.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3994ip address 192.168.132.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3995ip address 192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address 192.168.131.1 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3997ip address 192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address 192.168.130.1 255.255.255.128 local-proxy-arp enable#description to UTM200ip address 192.168.145.1 255.255.255.0#interface Vlan-interface4000description to f1000-sip address 192.168.254.1 255.255.255.0#interface Vlan-interface4001ip address 192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan 1 to 3984 3999 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundport link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inboundport link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan 4000qos apply policy kefang inbound#port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3 to 29 39 50 to 99 101 to 3984 4001 to 4094 port trunk pvid vlan 39qos apply policy kefang inboundmirroring-group 1 mirroring-port both#interface GigabitEthernet3/0/3port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/4port access vlan 1227qos apply policy kefang inboundmirroring-group 2 monitor-port#interface GigabitEthernet3/0/5port access vlan 3901qos apply policy kefang inbound#interface GigabitEthernet3/0/6port access vlan 8#interface GigabitEthernet3/0/7description to UTM-200_G 0/0 qos apply policy kefang inbound #interface GigabitEthernet3/0/8 port access vlan 8qos apply policy kefang inbound #interface GigabitEthernet3/0/9 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/12 port access vlan 2#interface GigabitEthernet3/0/13 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/17 port access vlan 2#interface GigabitEthernet3/0/18 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan 2#interface GigabitEthernet3/0/23 port access vlan 35stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/24 port access vlan 34stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/25 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/26 port access vlan 2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/27 port link-type trunkmirroring-group 1 monitor-port#interface GigabitEthernet3/0/28port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan 29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet3/0/31port access vlan 4000qos apply policy kefang inbound#interface GigabitEthernet3/0/32port access vlan 2qos apply policy kefang inbound#port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/34 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan 37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/39qos apply policy kefang inbound #interface GigabitEthernet3/0/40 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan 2stp disablestp loop-protectionqos apply policy kefang inbound #interface GigabitEthernet3/0/42 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan 2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan 34qos apply policy kefang inbound #port access vlan 2qos apply policy kefang inbound#interface GigabitEthernet3/0/46port access vlan 35qos apply policy kefang inbound#interface GigabitEthernet3/0/47port link-type trunkport trunk permit vlan 1 30qos apply policy kefang inbound#interface GigabitEthernet3/0/48port access vlan 34qos apply policy kefang inbound#interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/13port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/32port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/38port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunk#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/9port link-type trunk#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan 3901qos apply policy kefang inboundmirroring-group 2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan 30description 到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#port trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan 1 to 3984 4000 to 4094#route-policy kefang permit node 0if-match acl 3010apply ip-address next-hop 192.168.129.1#ip route-static 0.0.0.0 0.0.0.0 192.168.254.2ip route-static 10.0.0.0 255.255.255.0 192.168.30.253ip route-static 10.0.18.0 255.255.255.0 192.168.30.253ip route-static 10.0.24.0 255.255.255.0 192.168.30.253ip route-static 10.0.25.0 255.255.255.0 192.168.30.253ip route-static 10.0.29.0 255.255.255.0 192.168.30.253ip route-static 10.0.97.0 255.255.255.0 192.168.30.253ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0 192.168.30.253ip route-static 10.11.30.0 255.255.255.0 192.168.30.253ip route-static 10.11.70.0 255.255.255.0 192.168.30.253ip route-static 10.11.72.0 255.255.255.0 192.168.30.253ip route-static 10.12.41.0 255.255.255.0 192.168.30.253ip route-static 10.100.1.0 255.255.255.0 192.168.30.253ip route-static 116.6.69.101 255.255.255.255 192.168.30.253 ip route-static 172.16.1.0 255.255.255.0 61.144.43.216ip route-static 172.16.1.0 255.255.255.0 192.168.145.2ip route-static 192.168.0.0 255.255.255.0 192.168.30.253ip route-static 192.168.4.0 255.255.255.0 192.168.30.253ip route-static 192.168.5.0 255.255.255.0 192.168.30.253ip route-static 192.168.7.0 255.255.255.0 192.168.30.253ip route-static 192.168.8.0 255.255.255.0 192.168.30.253ip route-static 192.168.9.0 255.255.255.0 192.168.30.253ip route-static 192.168.19.0 255.255.255.0 192.168.30.253 ip route-static 192.168.21.0 255.255.255.0 192.168.30.253 ip route-static 192.168.22.0 255.255.255.0 192.168.30.253 ip route-static 192.168.23.0 255.255.255.0 192.168.30.253 ip route-static 192.168.24.0 255.255.255.0 192.168.30.253 ip route-static 192.168.26.0 255.255.255.0 192.168.30.253 ip route-static 192.168.28.0 255.255.255.0 192.168.30.253 ip route-static 192.168.29.0 255.255.255.0 192.168.30.253 ip route-static 192.168.41.0 255.255.255.0 192.168.30.253 ip route-static 192.168.46.0 255.255.255.0 192.168.30.253 ip route-static 192.168.68.0 255.255.255.0 192.168.30.253 ip route-static 192.168.76.0 255.255.255.0 192.168.30.253 ip route-static 192.168.82.0 255.255.255.0 192.168.30.253 ip route-static 192.168.84.0 255.255.255.0 192.168.30.253 ip route-static 192.168.86.0 255.255.255.0 192.168.30.253 ip route-static 192.168.88.0 255.255.255.0 192.168.30.253 ip route-static 192.168.91.0 255.255.255.0 192.168.30.253 ip route-static 192.168.96.0 255.255.255.0 192.168.30.253 ip route-static 192.168.103.0 255.255.255.0 192.168.30.253 ip route-static 192.168.202.0 255.255.255.0 192.168.30.253 ip route-static 192.168.253.0 255.255.255.0 192.168.253.1 ip route-static 192.168.254.4 255.255.255.252 192.168.254.2#snmp-agentsnmp-agent local-engineid 800063A203000FE22EDA1Csnmp-agent community write q-ideasnmp-agent sys-info version allsnmp-agent target-host trap address udp-domain 192.168.34.120 udp-port 5000 params securityname q-idea#dhcp server detect#dhcp enable#user-interface aux 0idle-timeout 0 0user-interface vty 0 4acl 3011 inboundauthentication-mode schemeuser privilege level 3#return<7506E>。
H3C_7506交换机主主模式_配置
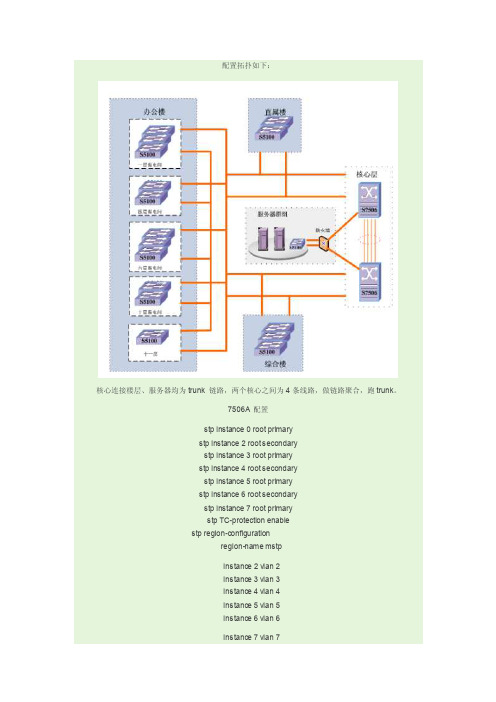
配置拓扑如下:核心连接楼层、服务器均为trunk 链路,两个核心之间为4条线路,做链路聚合,跑trunk。
7506A 配置stp instance 0 root primarystp instance 2 root secondarystp instance 3 root primarystp instance 4 root secondarystp instance 5 root primarystp instance 6 root secondarystp instance 7 root primarystp TC-protection enablestp region-configurationregion-name mstpinstance 2 vlan 2instance 3 vlan 3instance 4 vlan 4instance 5 vlan 5instance 6 vlan 6instance 7 vlan 7active region-configurationstp enablevlan 2vlan 3vlan 4vlan 5vlan 6vlan 7interface Vlan-interface2ip address 192.168.2.251 255.255.255.0 vrrp vrid 2 virtual-ip 192.168.2.254interface Vlan-interface3ip address 192.168.3.251 255.255.255.0 vrrp vrid 3 virtual-ip 192.168.3.254vrrp vrid 3 priority 110interface Vlan-interface4ip address 192.168.4.251 255.255.255.0 vrrp vrid 4 virtual-ip 192.168.4.254interface Vlan-interface5ip address 192.168.5.251 255.255.255.0 vrrp vrid 5 virtual-ip 192.168.5.254vrrp vrid 5 priority 110interface Vlan-interface6ip address 192.168.6.251 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.6.254interface Vlan-interface7ip address 192.168.7.251 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.7.254vrrp vrid 6 priority 110link-aggregation group 1 mode manualvrrp ping-enableinterface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan allport link-aggregation group 17506B 配置stp instance 0 root primarystp instance 2 root primary stp instance 3 root secondarystp instance 4 root primary stp instance 5 root secondarystp instance 6 root primary stp instance 7 root secondary stp TC-protection enablestp region-configuration region-name mstpinstance 2 vlan 2instance 3 vlan 3instance 4 vlan 4instance 5 vlan 5instance 6 vlan 6instance 7 vlan 7active region-configurationstp enablevlan 2vlan 3vlan 4vlan 5vlan 6vlan 7interface Vlan-interface2ip address 192.168.2.252 255.255.255.0 vrrp vrid 2 virtual-ip 192.168.2.254vrrp vrid 2 priority 110interface Vlan-interface3ip address 192.168.3.252 255.255.255.0 vrrp vrid 3 virtual-ip 192.168.3.254interface Vlan-interface4ip address 192.168.4.252 255.255.255.0 vrrp vrid 4 virtual-ip 192.168.4.254vrrp vrid 4 priority 110interface Vlan-interface5ip address 192.168.5.252 255.255.255.0 vrrp vrid 5 virtual-ip 192.168.5.254interface Vlan-interface6ip address 192.168.6.252 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.6.254vrrp vrid 6 priority 110interface Vlan-interface7ip address 192.168.7.252 255.255.255.0 vrrp vrid 6 virtual-ip 192.168.7.254link-aggregation group 1 mode manualvrrp ping-enableinterface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan allport link-aggregation group 1interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan allport link-aggregation group 1楼层交换机配置(S5100)vlan 2 to 7stp bpdu-protectionstp enablestp region-configurationregion-name mstpinstance 2 vlan 2instance 3 vlan 3instance 4 vlan 4instance 5 vlan 5instance 6 vlan 6instance 7 vlan 7active region-configuration所有连接PC机的端口,全部配置边缘端口(stp edged-port enable)楼层连接核心的两条上行链路配置为trunk,这两个端口不能配置边缘端口注:双机做完后,可以用dis stp brief 查看状态1、两个核心上所有连接楼层接入的端口都应该为fordowing状态2、楼层接入交换机主核心线路端口应该为fordowing,从核心线路端口应该为discard核心间的链路聚合,随后有相关日志描述。
华为SW7506R交换机配置文档

华为SW7506R交换机配置文档以下命令适用于SW7506R交换机,其他的H3C交换机应该也没问题1.设备名称配置<H3C>system 进入配置模式[H3C]sysname SW7506R-01 配置设备名称2.telnet配置[SW7506R-01]user-interface vty 0 4 进入vty接口并配置允许并发的连接用户数[SW7506R-01-ui-vty0-4]authentication-mode password 配置认证模式为PSW[SW7506R-01-vty0-4] set authentication password cipher ***** 配置密文密码[SW7506R-01-ui-vty0-4]user privilege level 3 配置用户访问级别3.配置VLANVLAN划分及加入端口[H3C]vlan 2[H3C-vlan2]name test VLAN名称[H3C-vlan2]description conncet to ..... 配置描述,例如连接至防火墙或核心交换机、路由器(有的版本支持字符之间有空格,有的不支持)[H3C-vlan2]port g1/0/1 将g1/0/1端口划入至VLAN2[H3C-vlan2]port g1/0/2 to g1/0/6 批量将端口划分至VLAN2配置VLAN的interface地址interface vlan 1ip addr 192.168.1.254 255.255.255.04.配置TRUNKinterface GigabitEthernet*/*/*port link-type trunk 配置以太网端口的链路类型,开启为Trunk 端口port trunk permit vlan all 将Trunk端口加入到指定的VLAN,此处为允许所有vlan通过Trunk干道5.端口汇聚A.简单端口汇聚<H3C> system-viewSystem View: return to User View with Ctrl+Z[H3C] link-aggregation group 1 mode manual# 将以太网端口Ethernet2/0/1 至Ethernet2/0/3 加入汇聚组1。
S7506E三层交换机配置

***************************************************************** ************** Copyright (c) 2004-2008Hangzhou H3C Tech.Co.,Ltd. All rights reserved. ** Without the owner's prior written consent,** no decompiling or reverse-engineering shall be allowed.****************************************************************** *************Login authenticationUsername:adminPassword:<7506E>di cur#version5.20,Release6305#sysname7506E#domain default enable system#telnet server enable#ip ttl-expires enableip unreachables enable#port-security enable#loopback-detection enable#mirroring-group1 localmirroring-group2 local#switch-mode standard#acl number3010description to UTM200rule0permit ip source 192.168.128.00.0.15.255 rule1permit ip source 192.168.160.00.0.31.255 acl number3011rule0permit ip source192.168.34.00.0.0.255 rule1permit ip source192.168.37.00.0.0.255 rule2permit ip source192.168.31.00.0.0.255 rule3permit ip source192.168.39.00.0.0.255 rule4permit ip source 192.168.254.00.0.0.255 acl number3500#vlan1#vlan2to2221#vlan 2222description wireless_guest#vlan 2223 to 2500#vlan 3000description test#vlan 3901description dianxin ap#vlan 3902description test#vlan 3985description dhcp for temp guest meeting supervlansubvlan 36#vlan 3986description dianxin wirelesssupervlansubvlan3901#vlan 3987description huisuo vlan33supervlansubvlan 33#vlan 3988description wirelesssupervlansubvlan2222#vlan 3989supervlansubvlan 3 to29#vlan 3990supervlansubvlan1226to1250#vlan 3991supervlansubvlan1200to1225#vlan 3992supervlansubvlan 100to111#vlan 3993supervlansubvlan1032to1150#vlan 3994supervlansubvlan 911to1031#vlan 3995supervlansubvlan 791to910#vlan 3996supervlansubvlan 351to421747 to790 #vlan 3997supervlansubvlan 231to350#vlan 3998supervlansubvlan 112to230#vlan 3999description to UTM200#vlan 4000 to 4001#ftth#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier kefang operator andif-match acl 3010traffic classifier denyvlanclass operator andif-match acl 3500#traffic behavior kefangredirect next-hop192.168.145.2traffic behavior dengvlanfilter deny#qos policy kefangclassifier kefang behavior kefangqos policy denyvlanclassifier denyvlanclass behavior dengvlan#dhcp server ip-pool 3985network192.168.36.0mask 255.255.255.0 gateway-list192.168.36.254dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour8#dhcp server ip-pool 3986network192.168.160.0mask255.255.224.0 gateway-list192.168.160.1dns-list202.96.128.868.8.8.8 202.96.128.166 expired day0hour2#dhcp server ip-pool 3987network192.168.33.0mask 255.255.255.0 gateway-list192.168.33.254dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour8#dhcp server ip-pool 3988network192.168.142.0mask255.255.254.0 gateway-list192.168.142.1dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour4#dhcp server ip-pool 3989network192.168.140.0mask255.255.254.0 gateway-list192.168.140.1dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour4#dhcp server ip-pool 3990network192.168.138.0mask255.255.254.0 gateway-list192.168.138.1dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour4#dhcp server ip-pool 3991network192.168.136.0mask255.255.254.0 gateway-list192.168.136.1dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour4#dhcp server ip-pool 3992network192.168.134.0mask255.255.254.0 gateway-list192.168.134.1dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour4#dhcp server ip-pool 3993network192.168.132.128 mask255.255.255.128 gateway-list192.168.132.129dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour4#dhcp server ip-pool 3994network192.168.132.0mask255.255.255.128 gateway-list192.168.132.1dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour4#dhcp server ip-pool 3995network192.168.131.128 mask255.255.255.128 gateway-list192.168.131.129dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour4#dhcp server ip-pool 3996network192.168.131.0mask255.255.255.128 gateway-list192.168.131.1dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour4#dhcp server ip-pool 3997network192.168.130.128 mask255.255.255.128 gateway-list192.168.130.129dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour4#dhcp server ip-pool 3998network192.168.130.0mask255.255.255.128 gateway-list192.168.130.1dns-list202.96.128.86202.96.128.1668.8.8.8 expired day0hour4#dhcp server ip-pool 3999#local-user adminpassword cipher _PW\RO>8';4.[DN#`U3;6Q!! service-type telnetlevel3#stp instance 0root primarystp enable#monitor-link group1#interface NULL0#interface Vlan-interface1ip address192.168.39.2255.255.255.0#interface Vlan-interface2ip address192.168.31.227255.255.255.0#interface Vlan-interface30#interface Vlan-interface32ip address192.168.32.254255.255.255.0 #interface Vlan-interface34ip address192.168.34.254255.255.255.0 #interface Vlan-interface35ip address192.168.35.254255.255.255.0 #interface Vlan-interface37ip address192.168.37.254255.255.255.0 #interface Vlan-interface38ip address192.168.38.254255.255.255.0 #interface Vlan-interface3985ip address192.168.36.254255.255.255.0 #interface Vlan-interface3986(分配网关)ip address192.168.160.1255.255.224.0 local-proxy-arp enable#interface Vlan-interface3987ip address192.168.33.254255.255.255.0 #interface Vlan-interface3988ip address192.168.142.1255.255.254.0 #interface Vlan-interface3989local-proxy-arp enable#interface Vlan-interface3990ip address192.168.138.1255.255.254.0 local-proxy-arp enable#interface Vlan-interface3991ip address192.168.136.1255.255.254.0 local-proxy-arp enable#interface Vlan-interface3992ip address192.168.134.1255.255.254.0 local-proxy-arp enable#interface Vlan-interface3993ip address192.168.132.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3994ip address192.168.132.1255.255.255.128 local-proxy-arp enable#interface Vlan-interface3995ip address192.168.131.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3996ip address192.168.131.1255.255.255.128 local-proxy-arp enable#interface Vlan-interface3997ip address192.168.130.129 255.255.255.128 local-proxy-arp enable#interface Vlan-interface3998ip address192.168.130.1255.255.255.128 local-proxy-arp enable#interface Vlan-interface3999description to UTM200ip address192.168.145.1255.255.255.0#interface Vlan-interface4000description to f1000-sip address192.168.254.1255.255.255.0#interface Vlan-interface4001ip address192.168.254.101 255.255.255.252 #interface GigabitEthernet2/0/1port link-type trunkport trunk permit vlan1 to 39843999to4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/2port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/3port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/4port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/5port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/6port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/7port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/8port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/9port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet2/0/10port link-type trunkport trunk permit vlan1 to 39844000to4094qos apply policy kefang inbound#interface GigabitEthernet2/0/11port link-type trunkport trunk permit vlan1 to 39844000to4094qos apply policy kefang inbound#interface GigabitEthernet2/0/12port link-type trunkport trunk permit vlan1 to 39844000to4094qos apply policy kefang inbound#interface GigabitEthernet3/0/1port access vlan4000qos apply policy kefang inbound#interface GigabitEthernet3/0/2port link-type trunkundo port trunk permit vlan 1port trunk permit vlan3 to 293950to 99 101to 3984 4001 to4094 port trunk pvid vlan 39qos apply policy kefang inboundmirroring-group1 mirroring-port both#interface GigabitEthernet3/0/3port access vlan2qos apply policy kefang inbound#interface GigabitEthernet3/0/4port access vlan1227mirroring-group2 monitor-port #interface GigabitEthernet3/0/5 port access vlan3901qos apply policy kefang inbound #interface GigabitEthernet3/0/6 port access vlan8#interface GigabitEthernet3/0/7 port access vlan3999 description to UTM-200_G0/0 qos apply policy kefang inbound #interface GigabitEthernet3/0/8 port access vlan8qos apply policy kefang inbound #interface GigabitEthernet3/0/9 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/10 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/11 port access vlan2stp edged-port enable#interface GigabitEthernet3/0/12 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/13 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/14 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/15 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/16 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/17 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/18 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/19 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/20 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/21 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/22 port access vlan2stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/23 port access vlan35stp edged-port enableqos apply policy kefang inbound #interface GigabitEthernet3/0/24 port access vlan34stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/25port access vlan2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/26port access vlan2stp edged-port enableqos apply policy kefang inbound#interface GigabitEthernet3/0/27port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound mirroring-group1 monitor-port#interface GigabitEthernet3/0/28port access vlan2qos apply policy kefang inbound#interface GigabitEthernet3/0/29port access vlan29qos apply policy kefang inbound#interface GigabitEthernet3/0/30port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound##interface GigabitEthernet3/0/32 port access vlan2qos apply policy kefang inbound #interface GigabitEthernet3/0/33 port access vlan2qos apply policy kefang inbound #interface GigabitEthernet3/0/34 port access vlan2qos apply policy kefang inbound #interface GigabitEthernet3/0/35 port access vlan2qos apply policy kefang inbound #interface GigabitEthernet3/0/36 port access vlan2qos apply policy kefang inbound #interface GigabitEthernet3/0/37 port access vlan37qos apply policy kefang inbound #interface GigabitEthernet3/0/38 port access vlan2qos apply policy kefang inbound ##interface GigabitEthernet3/0/40 port access vlan2qos apply policy kefang inbound #interface GigabitEthernet3/0/41 port access vlan2stp disablestp loop-protectionqos apply policy kefang inbound #interface GigabitEthernet3/0/42 port access vlan2qos apply policy kefang inbound #interface GigabitEthernet3/0/43 port access vlan2qos apply policy kefang inbound #interface GigabitEthernet3/0/44 port access vlan34qos apply policy kefang inbound #interface GigabitEthernet3/0/45 port access vlan2qos apply policy kefang inbound #interface GigabitEthernet3/0/46 port access vlan35qos apply policy kefang inbound#interface GigabitEthernet3/0/47port link-type trunkport trunk permit vlan1 30qos apply policy kefang inbound#interface GigabitEthernet3/0/48port access vlan34qos apply policy kefang inbound#interface GigabitEthernet4/0/1port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/2port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/3port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/4port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/5port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/6port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/7port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/8port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/9port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/10port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/11port link-type trunkport trunk permit vlan1 to 39844000to4094qos apply policy kefang inbound#interface GigabitEthernet4/0/12port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/13port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/14port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/15port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/16port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/17port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/18port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/19port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/20port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/21port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/22port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/23port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/24port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/25port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/26port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/27port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/28port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/29port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/30port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/31port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/32port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/33port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/34port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/35port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/36port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/37port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/38port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/39port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/40port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/41port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/42port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/43port link-type trunkport trunk permit vlan1 to 39844000to4094qos apply policy kefang inbound#interface GigabitEthernet4/0/44port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/45port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/46port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/47port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet4/0/48port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/1port link-type trunkport trunk permit vlan1 to 39844000to4094 loopback-detection enableqos apply policy kefang inbound#interface GigabitEthernet8/0/2port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/3port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/4port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/5port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/6port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/7port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/8port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/9port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/10port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet8/0/11port link-type trunkundo port trunk permit vlan 1port trunk permit vlan3901qos apply policy kefang inboundmirroring-group2 mirroring-port both#interface GigabitEthernet8/0/12port access vlan30description到集团综合楼qos apply policy kefang inbound#interface GigabitEthernet9/0/1port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/2port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/3port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/4port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/5port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/6port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/7port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/8port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/9port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/10port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/11port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface GigabitEthernet9/0/12port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface M-Ethernet0/0/0#interface Ten-GigabitEthernet5/0/1port link-type trunkport trunk permit vlan1 to 39844000to4094 qos apply policy kefang inbound#interface Ten-GigabitEthernet5/0/2port link-type trunkport trunk permit vlan1 to 39844000to4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/1port link-type trunkport trunk permit vlan1 to 39844000to4094qos apply policy kefang inbound#interface Ten-GigabitEthernet6/0/2port link-type trunkport trunk permit vlan1 to 39844000to4094qos apply policy kefang inbound#route-policy kefang permit node0if-match acl 3010apply ip-address next-hop192.168.129.1#ip route-static0.0.0.00.0.0.0 192.168.254.2ip route-static10.0.0.0 255.255.255.0192.168.30.253ip route-static 10.0.18.0 255.255.255.0192.168.30.253ip route-static 10.0.24.0 255.255.255.0192.168.30.253ip route-static 10.0.25.0 255.255.255.0192.168.30.253ip route-static 10.0.29.0 255.255.255.0192.168.30.253ip route-static 10.0.97.0 255.255.255.0192.168.30.253ip route-static 10.10.0.0 255.255.0.0 192.168.30.253ip route-static 10.11.2.0 255.255.255.0192.168.30.253ip route-static 10.11.30.0 255.255.255.0192.168.30.253ip route-static 10.11.70.0 255.255.255.0192.168.30.253ip route-static 10.11.72.0 255.255.255.0192.168.30.253ip route-static 10.12.41.0 255.255.255.0192.168.30.253ip route-static 10.100.1.0 255.255.255.0192.168.30.253ip route-static116.6.69.101255.255.255.255192.168.30.253ip route-static 172.16.1.0 255.255.255.061.144.43.216ip route-static 172.16.1.0 255.255.255.0192.168.145.2ip route-static 192.168.0.0255.255.255.0192.168.30.253ip route-static 192.168.4.0255.255.255.0192.168.30.253ip route-static 192.168.5.0255.255.255.0192.168.30.253ip route-static 192.168.7.0255.255.255.0192.168.30.253ip route-static 192.168.8.0255.255.255.0192.168.30.253ip route-static 192.168.9.0255.255.255.0192.168.30.253ip route-static192.168.19.0255.255.255.0192.168.30.253ip route-static192.168.21.0255.255.255.0192.168.30.253ip route-static192.168.22.0255.255.255.0192.168.30.253ip route-static192.168.23.0255.255.255.0192.168.30.253ip route-static192.168.24.0255.255.255.0192.168.30.253ip route-static192.168.26.0255.255.255.0192.168.30.253ip route-static192.168.28.0255.255.255.0192.168.30.253ip route-static192.168.29.0255.255.255.0192.168.30.253ip route-static192.168.41.0255.255.255.0192.168.30.253ip route-static192.168.46.0255.255.255.0192.168.30.253ip route-static192.168.68.0255.255.255.0192.168.30.253ip route-static192.168.76.0255.255.255.0192.168.30.253ip route-static192.168.82.0255.255.255.0192.168.30.253ip route-static192.168.84.0255.255.255.0192.168.30.253ip route-static192.168.86.0255.255.255.0192.168.30.253ip route-static192.168.88.0255.255.255.0192.168.30.253ip route-static192.168.91.0255.255.255.0192.168.30.253ip route-static192.168.96.0255.255.255.0192.168.30.253ip route-static192.168.103.0255.255.255.0192.168.30.253 ip route-static192.168.202.0255.255.255.0192.168.30.253 ip route-static192.168.253.0255.255.255.0192.168.253.1ip route-static192.168.254.4255.255.255.252192.168.254.2# snmp-agent33 / 34snmp-agent local-engineid 800063A203000FE22EDA1Csnmp-agent community write q-ideasnmp-agent sys-info version allsnmp-agent target-host trap address udp-domain192.168.34.120udp-port 5000 params securityname q-idea#dhcp server detect#dhcp enable#user-interface aux0idle-timeout0 0user-interface vty04acl 3011inboundauthentication-mode schemeuser privilege level 3#return<7506E>。
网络实践之交换机7506与防火墙配置

中心机房核心交换机与防火墙的配置核心交换机在中心机房安装的核心交换机选用了H3C公司的S7503全模块化多业务核心交换机。
该核心交换机配置为:双冗余电源引擎,3个业务插槽,1个主控插槽;该核心交换机背板带宽:1000Gbps,包转发速率:274Mpps,FLASH内存:64MB,DRAM内存:512MB,网络标准:IEEE802.1d,IEEE802.1x,IEEE802.3,IEEE 802.3u,IEEE802.3x,IEEE802.3z,IEEE802.1Q,IEEE802.1p,传输速率:10/100/1000/10000Mbps,1个Console接口,1个10/100 BASE-TX管理接口,48个千兆以太网电口。
其对应的指示灯含义如下:指示灯灭:表示链路没有连通;指示灯常亮:表示链路已经连通。
指示灯闪烁:表示有数据收发。
防火墙在中心机房安装的防火墙选用了H3C公司的SecPath F1000-S企业级高端防火墙。
该防火墙配置为:双冗余电源引擎,1个CON配置口,1个备份口(AUX),2个10/100/1000M以太网口(支持光口或者电口),2个10/100/1000M以太网口(支持电口),2个MIM插槽,CPU主频:600MHz,FLASH内存:16MB,DDR RAM:512MB。
其对应的指示灯含义如下:指示灯灭:表示链路没有连通;指示灯常亮:表示链路已经连通。
指示灯闪烁:表示有数据收发。
核心交换机配置如下:Login authenticationUsername:adminPassword:<7503>dis curr#version 5.20, Release 6605P06#sysname 7503#domain default enable system#telnet server enable#mirroring-group 1 local#switch-mode standard#time-range web 12:00 to 13:00 daily#acl number 3000rule 0 deny ip source 172.16.6.100 0 destination 172.16.3.103 0 time-range web rule 1 deny ip source 172.16.6.100 0 destination 172.16.3.104 0 time-range web rule 2 deny ip source 172.16.6.100 0 destination 172.16.3.105 0 time-range web acl number 3001rule 0 deny ip#vlan 1description Default#vlan 2description F1000-S#vlan 3description SERVER#vlan 4description SERVER_MANAGER#vlan 5description DAPING#vlan 6description WEBvlan 10description VPN_Line#domain systemaccess-limit disablestate activeidle-cut disableself-service-url disable#traffic classifier web2 operator andif-match acl 3001traffic classifier web operator andif-match acl 3000#traffic behavior web2filter denytraffic behavior webfilter permit#qos policy webclassifier web behavior webclassifier web2 behavior web2#user-group system#local-user adminpassword simple Center!@#authorization-attribute level 3service-type telnet terminallocal-user centerpassword cipher $.T)1&WJ`>-%`DJL.:OE)Q!! authorization-attribute level 3service-type telnet terminal#interface NULL0#interface LoopBack10ip address 172.16.10.1 255.255.255.255#interface Vlan-interface1description VLAN1ip address 172.16.1.254 255.255.255.0#interface Vlan-interface2description connect to Firewallip address 172.16.2.254 255.255.255.0#interface Vlan-interface3description SERVERip address 172.16.3.254 255.255.255.0#interface Vlan-interface4description SERVER_MANAGERip address 172.16.4.254 255.255.255.0#interface Vlan-interface5description DAPINGip address 192.168.1.254 255.255.255.0#interface Vlan-interface6description WEBip address 172.16.6.254 255.255.255.0#interface Vlan-interface10description connect to Local-VPN-Special-Line ip address 172.16.99.1 255.255.255.0#interface GigabitEthernet0/0/1#interface GigabitEthernet0/0/2#interface GigabitEthernet0/0/3#interface GigabitEthernet0/0/4#interface GigabitEthernet0/0/5shutdown#interface GigabitEthernet0/0/6shutdown#interface GigabitEthernet0/0/7shutdown#interface GigabitEthernet0/0/8shutdown##interface GigabitEthernet0/0/10 #interface GigabitEthernet0/0/11 #interface GigabitEthernet0/0/12 #interface GigabitEthernet0/0/13 #interface GigabitEthernet0/0/14 #interface GigabitEthernet0/0/15 #interface GigabitEthernet0/0/16 #interface GigabitEthernet0/0/17 #interface GigabitEthernet0/0/18 #interface GigabitEthernet0/0/19 port access vlan 10#interface GigabitEthernet0/0/20 port access vlan 10#interface GigabitEthernet0/0/21 port access vlan 10#interface GigabitEthernet0/0/22 port access vlan 10#interface GigabitEthernet0/0/23 port access vlan 10#interface GigabitEthernet0/0/24 port access vlan 10#interface GigabitEthernet0/0/25 port access vlan 10#interface GigabitEthernet0/0/26 port access vlan 10##interface GigabitEthernet0/0/28mirroring-group 1 mirroring-port both#interface GigabitEthernet1/0/1port access vlan 3#interface GigabitEthernet1/0/2port access vlan 3#interface GigabitEthernet1/0/3port access vlan 3#interface GigabitEthernet1/0/4port access vlan 3#interface GigabitEthernet1/0/5port access vlan 3#interface GigabitEthernet1/0/6description Connect to Center Monitor PCport access vlan 3#interface GigabitEthernet1/0/7port access vlan 3#interface GigabitEthernet1/0/8description Connect to Center Flag Manage PCport access vlan 3#interface GigabitEthernet1/0/9description connect to Storage System Controller A Port 1 port access vlan 3#interface GigabitEthernet1/0/10port access vlan 3#interface GigabitEthernet1/0/11port access vlan 4#interface GigabitEthernet1/0/12port access vlan 4#port access vlan 4#interface GigabitEthernet1/0/14port access vlan 4#interface GigabitEthernet1/0/15description connect to Storage System Controller B Port 1 port access vlan 4#interface GigabitEthernet1/0/16port access vlan 4#interface GigabitEthernet1/0/17description Connect to WEB_Manage_Interfaceport access vlan 6qos apply policy web outbound#interface GigabitEthernet1/0/18description Connect to WEBport access vlan 6qos apply policy web outbound#interface GigabitEthernet1/0/19port access vlan 3#interface GigabitEthernet1/0/20port access vlan 3#interface GigabitEthernet1/0/21description Connect to DAPING Manage PCport access vlan 5#interface GigabitEthernet1/0/22description Connect to DAPING Control Hostport access vlan 5#interface GigabitEthernet1/0/23description Connect to F1000-Sport access vlan 2#interface GigabitEthernet1/0/24port access vlan 2#interface M-Ethernet0/0/0#ip route-static 0.0.0.0 0.0.0.0 172.16.2.1ip route-static 172.16.21.0 255.255.255.0 172.16.99.2 ip route-static 172.16.22.0 255.255.255.0 172.16.99.3 ip route-static 172.16.23.0 255.255.255.0 172.16.99.4 ip route-static 172.16.24.0 255.255.255.0 172.16.99.5 ip route-static 172.16.25.0 255.255.255.0 172.16.99.6 ip route-static 192.168.0.0 255.255.255.0 172.16.2.1 #load xml-configuration#user-interface aux 0authentication-mode schemeidle-timeout 5 0user-interface vty 0 4authentication-mode schemeuser privilege level 3idle-timeout 5 0#return<7503>防火墙配置如下:Login authenticationUsername:adminPassword:<F1000-S>dis curr#sysname F1000-S#l2tp enable#ike local-name vpn#firewall packet-filter enablefirewall packet-filter default permit#firewall statistic system enable#DNS server 219.150.32.132#radius scheme systemserver-type extended#domain systemip pool 1 172.16.254.1 172.16.254.253#local-user adminpassword cipher $.T)1&WJ`>-%`DJL.:OE)Q!! service-type telnet terminallevel 3local-user btvpnpassword simple 666666service-type ppplocal-user centerpassword cipher $.T)1&WJ`>-%`DJL.:OE)Q!! service-type telnet terminallevel 3#ike proposal 1encryption-algorithm 3des-cbc authentication-algorithm md5#ike peer 1exchange-mode aggressivepre-shared-key 333333id-type nameremote-name vpnclientnat traversal#ipsec proposal p1esp authentication-algorithm sha1esp encryption-algorithm 3des#ipsec policy-template l2tp 1ike-peer 1proposal p1#ipsec policy l2tppolicy 1 isakmp template l2tp #acl number 2000rule 0 permit source 172.16.3.106 0rule 1 permit source 172.16.4.206 0rule 2 permit source 172.16.6.100 0rule 3 permit source 172.16.6.200 0rule 6 permit source 172.16.3.120 0rule 7 permit source 172.16.3.150 0rule 8 permit source 172.16.3.130 0rule 9 permit source 172.16.3.140 0rule 10 permit source 172.16.3.110 0rule 11 permit source 172.16.24.130 0rule 12 permit source 172.16.22.130 0rule 13 permit source 172.16.23.130 0rule 14 permit source 172.16.21.130 0rule 15 permit source 172.16.25.130 0#acl number 3012description L2TP VPN access controlrule 1 permit icmprule 2 permit tcp destination 172.16.3.0 0.0.0.255rule 3 permit udp destination 172.16.3.106 0 destination-port eq dns rule 4 permit tcp destination 172.16.6.100 0 destination-port eq www rule 80 permit udp destination 192.168.2.200 0 destination-port eq 1701 rule 81 permit udp destination 192.168.2.200 0 destination-port eq 500 rule 82 permit udp source-port eq 500rule 83 permit udp destination 192.168.2.200 0 destination-port eq 4500 rule 84 permit udp source-port eq 4500rule 85 permit 50 destination 192.168.2.200 0rule 86 permit 51 destination 192.168.2.200 0rule 100 deny ip#interface Virtual-Template0ppp authentication-mode papppp ipcp dns 172.16.3.106 172.16.4.206ip address 172.16.254.254 255.255.255.0remote address pool 1#interface Aux0async mode flow#interface GigabitEthernet0/0description connect to Switch_7503Eip address 172.16.2.1 255.255.255.0#interface GigabitEthernet0/1description connect to Internetip address 13.65.2.100 255.255.255.0nat outbound 2000#interface GigabitEthernet1/0#interface GigabitEthernet1/1 description Connect to HuanBaoJuip address 192.168.2.200 255.255.255.0 #interface Encrypt2/0#interface NULL0#interface LoopBack10ip address 172.16.10.1 255.255.255.0 #firewall zone localset priority 100#firewall zone trustadd interface GigabitEthernet0/0add interface GigabitEthernet0/1add interface GigabitEthernet1/1add interface Virtual-Template0set priority 85#firewall zone untrustset priority 5#firewall zone DMZset priority 50#firewall interzone local trust#firewall interzone local untrust#firewall interzone local DMZ#firewall interzone trust untrust#firewall interzone trust DMZ#firewall interzone DMZ untrust#l2tp-group 1allow l2tp virtual-template 0tunnel password simple 444444#ip route-static 0.0.0.0 0.0.0.0 13.65.2.1 preference 60ip route-static 172.16.1.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 172.16.2.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 172.16.3.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 172.16.4.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 172.16.6.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 172.16.21.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 172.16.22.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 172.16.23.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 172.16.24.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 172.16.25.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 172.16.99.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 192.168.0.0 255.255.255.0 192.168.2.1 preference 60 ip route-static 192.168.1.0 255.255.255.0 172.16.2.254 preference 60 ip route-static 192.168.2.0 255.255.255.0 192.168.2.1 preference 60 #user-interface con 0authentication-mode schemeidle-timeout 5 0user-interface aux 0user-interface vty 0 4authentication-mode schemeuser privilege level 3set authentication password cipher $.T)1&WJ`>-%`DJL.:OE)Q!! idle-timeout 5 0protocol inbound telnet#return<F1000-S>更多信息请点击进入。
H3C核心交换机S7506E网络维护手册

网络设备维护手册第一章交换机操作手册此部分档使用本项目交换机型号如下:S7506E/S5120/S5130/WX3024E1.1设备登陆1。
1。
1 Console登陆1、通过交换机Console 口进行本地登录是登录交换机的最基本的方式,也是配置通过其他方式登录交换机的基础。
连接示意图如下:2、把电脑和交换机连接好后,交换机上电开机,然后在电脑上进行如下操作,首先点击开始->程序->附件-〉通讯->超级终端打开后出现下面图示,输入名称,可以任意输入。
输入完成点击确定,出现下面界面,连接时使用选择COM口,一般台式机为COM1或COM2,而笔记本经过转接,可能会产生COM3或COM4,也有可能是其他的,你可以在下面的选择项里看到,选择完成后点击确定。
通过上面的选择,现在到了对端口属性进行设置,一般情况下没有进行过修改,默认只要点击还原为默认值就可以了,然后再单击确定。
之后敲回车即可,会出现H3C>提示符,说明已经与交换机连接,可以进行配置了,如果没有可以重启交换机或检查连接是否正确.1.1.2 telnet登陆1、新建用户名密码local-user admin /admin为用户名password cipher h3c@123 /h3c@123为密码authorization—attribute level 3 /授权admin用户的等级为3,3为最高级service—type telnet /授权admin用户的登陆方式,可以为ftp、telnet等#telnet server enable /开启telnet服务使用电脑连接至交换机:开始菜单-输入cmd,如下图,输入telnet 1。
1。
44.254,输入用户名密码admin/h3c@123即可登录交换机1。
2 交换机加电开机显示sarting....。
************************************************************** ** H3C S5510—24P BOOTROM,Version 142 ****************************************************************Copyright (c) 2004—2008 Hangzhou H3C Tech。
H3C交换机操作手册

目录H3C以太网交换机的基本操作 (2)1.1 知识准备 (3)1.2 操作目的 (3)1。
3 网络拓扑 (3)1.4 配置步骤 (3)1.4.1 串口操作配置 (3)1。
4。
2 查看配置及日志操作 (4)1。
4.3 设置密码操作 (4)1.5 验证方法 (5)H3C以太网交换机VLAN配置 (5)1。
6 知识准备 (5)1。
7 操作目的 (5)1。
8 操作内容 (5)1。
9 设备准备 (5)1.10 拓扑 (6)1。
11 配置步骤 (6)1。
12 验证方法 (6)H3C以太网交换机链路聚合配置 (6)1.13 知识准备 (6)1.14 操作目的 (6)1。
15 操作内容 (6)1。
16 设备准备 (6)1。
17 网络拓扑 (7)1.18 配置步骤 (7)1.19 验证方法 (8)H3C以太网交换机STP配置 (8)1.20 知识准备 (8)1。
21 操作目的 (8)1.22 操作内容 (8)1.23 设备准备 (8)1。
24 网络拓扑 (9)1.25 配置步骤 (9)1.26 验证方法 (9)H3C以太网交换机VRRP配置 (10)1.27 知识准备 (10)1.28 操作目的 (10)1.29 操作内容 (10)1。
30 设备准备 (10)1.31 网络拓扑 (10)1.32 配置步骤 (10)1。
33 验证方法 (12)H3C以太网交换机镜像配置 (12)1。
34 知识准备 (12)1.35 操作目的 (12)1.36 操作内容 (12)1。
37 设备准备 (12)1.38 网络拓扑 (12)1.39 配置步骤 (13)1.40 验证方法 (13)H3C以太网交换机路由配置 (13)1。
41 知识准备 (13)1。
42 操作目的 (13)1.43 操作内容 (13)1。
44 设备准备 (13)1。
45 网络拓扑 (14)1。
46 配置步骤 (14)1。
47 验证方法 (14)H3C以太网交换机ACL配置 (15)1。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
acl number 3001 rule 0 permit ip source 172.16.1.0 0.0.0.255
#
interface NULL0
#
interface Vlan-interface1 ip address 192.168.0.254 255.255.255.0
[H3C5500-classifier-1] if-match acl 3001
[H3C5500-classifier-1] quit
3、配置刚才定义的流分类的行为,定义如果匹配就下一跳至出口1即172.16.100.253
[H3C5500] traffic behavior 1
authentication-mode scheme
user privilege level 3
#
[H3C5500-behavior-1] redirect next-hop 172.16.100.253
[H3C5500-behavior-1] quit
4、将刚才设置的应用至QOS策略中,定义policy 1
[H3C5500] qos policy 1
[H3C5500-qospolicy-1] classifier 1 behavior 1
拓扑图:
网络情况如下:
用户1网络:172.16.1.0/24
用户2网络: 192.168.1.0/24
至出口1网络:172.16.100.0/24
至出口2网络:192.168.100.0/24
实现功能:用户1通过互联网出口1,用户2通过互联网出口2。
功能实现:在三层交换台机上配置默认路由,将数据包丢向192.168.100.253,再利用策略路由,凡是用户2网络IP192.168.1.0/24的地址都丢向172.16.100.253。
speed 1000
duplex full
#
interface GigabitEthernet1/0/15
port link-type trunk
port trunk permit vlan 1 101 103
speed 1000
duplex full
qos apply policy 1 inbound
domain default enable system
#
telnet server enable
#
vlan 1
#
vlan 100 to 103
#
traffic classifier 1 operator and if-match acl 3001
#
#
interface Vlan-interface100 ip address 192.168.100.254 255.255.255.0
#
interface Vlan-interface101 ip address 192.168.1.254 255.255.255.0
#
2、配置流分类1,对象为172.16.1.0/24的数据
[H3C5500]acl number 3001
[H3C5500-acl-adv-3001] rule 0 permit ip source 172.16.1.0 0.0.0.255
[H3C5500] quit
[H3C5500] traffic classifier 1
interface Vlan-interface102 ip address 172.16.100.254 255.255.255.0
#
interface Vlan-interface103 ip address 172.16.1.254 255.255.255.0
#
interface GigabitEthernet1/0/1
-------------
配置步骤:
说明:这里接口的配置等操作就不在写了。
1、首先建立默认路由,将所有的数据包都丢往出口2的下一节点192.168.100.253
[H3C5500] ip route-static 0.0.0.0 0.0.0.0 192.168.100.253
#
dhcp server ip-pool 2 network 172.16.1.0 mask 255.255.255.0 gateway-list 172.16.1.254 dns-list 221.228.255.1
#
local-user huawei password cipher .]@USE=B,53Q=^Q`M<1!! service-type telnet terminal level 3
#
interface GigabitEthernet1/0/16
port link-type trunk
port trunk permit vlan 1 101 103
speed 1000
duplex full
qos apply policy 1 inbound
#
traffic behavior 1 redirect next-hop 172.16.100.253
#
qos policy 1 classifier 1 behavior 1
#
dhcp server ip-pool 1 network 192.168.1.0 mask 255.255.255.0 gateway-list 192.168.1.254 dns-list 221.228.255.1
[H3C5500-GigabitEthernet1/0/15] quit
至此,配置已完成。
-----------------------
配置文件(略过一些接口配置信息):
version 5.20, Release 2102P02
#
sysname H3C5500
#
port link-type access
port access vlan 100
speed 1000
duplex full
#
interface GigabitEthernet1/0/2
port link-type access
port access vlan 102
ip route-static 0.0.0.0 0.0.0.0 192.168.100.253
#
dhcp enable
#
load xml-configuration
#
user-interface aux 0
authentication-mode scheme
user-interface vty 0 4
[H3C5500-qospolicy-1] quit
5、在接口上应用定义的QOS策略policy 1
[H3C5500] interface GigabitEthernet 1/0/15
[H3C5500-GigabitEthernet1/0/15] qos apply源自policy 1 inbound
