suspicious process
托业语法词汇200题(含每句精译)

1.T here has been a lot of prejudice in American .A)realistic B) racial C) recycled D) rebellious美国一直都有种族偏见。
答案: racial.B)realistic B) racial C) recycled D) rebellious他是个无可救药的理想主义者;很难将他拉回现实、让他更实际点。
答案: realistic2.The relations between my mother and brother were getting worse as my brother grew olderand more.A)realistic B) racial C) recycled D) rebellious随着哥哥年纪渐长也更叛逆,他与母亲的关系变得更糟。
答案: rebelliousonce they 3.Ecological vehicles are made of materials that canbe easilyaredumped.A)realistic B) racial C) recycled D) rebellious环保车使用的材料使它们在被丢弃后还可以轻易地回收使用。
答案: recycled4.T om goes to that pub every night to have a bottle of beer. Heis acustomer.A)reliable B) regular C) reluctant D) religiousTom每晚都去那家酒吧喝瓶啤酒。
他是常客。
答案: regular5.T o keep health, we haveto keep hours.A)reliable B) regular C) reluctant D) religious为了保持健康,我们必须生活有规律。
六级高频词汇7

Suspicious(5次)1. A ________ official is one who is irresponsible in his work. (05/1)A) timid B) tedious C) suspicious D) slack2. We can’t help being ____of Bob who bought a luxurious sports car just after the money was stolen from the office. (03/9)A) skeptical B) appreciative C) suspicious D) tolerant3. After several nuclear disasters, a ________ has raged over the safety of nuclearenergy.?(01/1)A) quarrel B) suspicion C) verdict D) controversy ?4. Rumours are everywhere, spreading fear, damaging reputations, and turning calm situations into ______ ones. (00/6)A) turbulent B) tragic C) vulnerable D) suspicious5. Some criminals were printing __________ dollar bills until they were arrested. (98/1)A) decent B) fake C) patent D) suspiciousSubtle(3次)1. Diamonds have little ____ value and their price depends almost entirely on their scarcity. (03/6)A) intrinsic B) eternal C) subtle D) inherent2. The glass vessels should be handled most carefully since they are _______.(02/12)A) intricate B) fragile C) subtle D) crisp3. There is a _______ difference in meaning between the words surroundings and environment. (98/6)A) gentle B) subtle C) feeble D) humbleSuperiority(3次)1. Giving a gift can convey a wealth of meaning about your appreciation of their ____ and the importance you place upon the relationship. (02/6)A) solidarity B) priority C) superiority D) hospitality2. There is no doubt that the ________ of these goods to the others is easy to see. (02/1)A) prestige B) superiority C) priority D) publicity3. David tends to feel useless and unwanted in a society that gives so much ______ to those who compete well. (99/6)A) prestige B) regime C) superiority D) legislationPropel(2次)1. Many types of rock are _______ from volcanoes as solid, fragmentary material. (02/12)A) flung B) propelled C) ejected D) injected2. Under the guidance of their teacher, the pupils are building a model boat _______ by steam.(00/1)A) towed B) pressed C) tossed D) propelledReassure(2次)1. As we know, computers are used to store and ________ information efficiently. (04/6)A) reclaim B) reconcile C) reassure D) retrieve2. The woman was worried about the side effects of taking aspirins. but her doctor ____her that it is absolutely harmless. (03/9)A) retrieved B) released C) reassured D) revivedRecession(2次)1. At that time, the economy was still undergoing a _____ and job offers were hard to get. (05/12)A) recession B)concession C)supervision D)deviation2. It is hard to tell whether we are going to have a boom in the economy or a ________. (01/6)A)concession B)recession C)submission D)transmission答案:Suspicious:DCDABSubtle:ABBSuperiority:DBAPropel:CDReassure:DCRecession:AB高频词讲解,Suspiciousadj. 猜疑的,可疑的辨析:suspicious, doubtful这组词都有“怀疑”的意思。
武汉市2023年9月高三质量检测英语试题

2023-2024学年度武汉市部分学校高三年级九月调研考试第一部分听力(共两节,满分30分)做题时,先将答案标在试卷上。
录音内容结束后,你将有两分钟的时间将试卷上的答案转涂到答题卡上。
第一节(共5小题;每小题1.5分,满分7.5分)听下面5段对话。
每段对话后有一个小题,从题中所给的A、B、C三个选项中选出最佳选项。
听完每段对话后,你都有10秒钟的时间来回答有关小题和阅读下一小题。
每段对话仅读一遍。
例:How much is the shirt?A. £19.15.B. £9.18.C. £9.15.答案是C。
1. How will the man get to Alaska?A. By train.B. By plane.C. By boat.2. Why is the woman in a hurry?A. To answer a call.B. To search for a store.C. To look for a washroom.3. What does the mother think of her son?A. Bad-tempered.B. Warm-hearted.C. Absent-minded.4. What is wrong with the man’s laptop?A. Its screen is unclear.B. Its network is down.C. Its mouse is missing.5. Why is Maria calling the man?A. To recheck a schedule.B. To extend an invitation.C. To cancel an appointment.第二节(共15小题;每小题1.5分,满分22.5分)听下面5段对话或独白。
每段对话或独白后有几个小题,从题中所给的A、B、C三个选项中选出最佳选项。
山东省潍坊市大联考2024-2025学年高三上学期10月月考英语试题

山东省潍坊市大联考2024-2025学年高三上学期10月月考英语试题一、阅读理解Mathematics for Computer ScienceThis subject offers an introduction to discrete mathematics(离散数学)oriented toward computer science and engineering.Course Meeting TimesLectures:3 sessions/week, 1. 5 hour/session Problem Sets (psets)Problem sets account for 20% of the final grade. Making a reasonable effort on the problem sets is, for most students, crucial for mastering the course material. Problem sets are designed to be completed in at most 3 hours; the time is monitored through student reports. Online Feedback ProblemsOnline problems to be completed before most class meetings are posted on the class website. These consist of straightforward questions that provide useful feedback about the assigned material. Some students prefer to try the online problems before reading the text or watching videos as an advance guide to going over the material; that’s fine. Watching designated videos, or at least looking at the lecture-slide handouts, is generally helpful but optional.Like team problem-solving in class, online problems are graded only on participation: Students receive full credit as long as they try the problem, even if their answer is wrong. Online feedback problems account for 10% of the final grade. Midterm ExamsThree 80-minute midterm exams will be given. The midterm exams each account for 15%of the final grade.Midterm questions will typically be variations of prior problems from class and psets, and the best way to prepare is to review on the published solutions to these problems. The first exam covers all previous weeks’ material;subsequent exams focus on the material after the previous exam. Final ExamThere will be a three-hour final exam. This exam is worth 25% of the final class grade. The final exam will cover the entire subject with somewhat greater emphasis on material from after Midterm 3. Most exam questions will be variants of problems assigned during the term(psets,class, midterm, and online). It may include a few questions which combine topics that were originally covered separately.1.What determines students’ grade in Online Feedback Problems?A.Active involvement.B.Submission time.C.Accuracy of answers.D.Completion of assignments2.What is the main focus of the final exam?A.Variants of problem sets.B.Combined topics in class.C.The content after midterm exams.D.The whole-term course materials. 3.Which of the following weighs the most in the final grade?A.Final Exam.B.Midterm Exams.C.Problem Sets.D.Online Feedback ProblemsIt all started with a simple question;“Can I paint your portrait (肖像)?”In the summer of 2015, Brian Peterson was reading the book Love Does, about the power of love in action, when his quiet was disturbed by a homeless man. Inspired by the book, Peterson made an unexpected decision: He was going to introduce himself. In that first conversation, Peterson learned that the man’s name was Matt Faris who failed to pursue a career in music and ended up being homeless.“I saw beauty on the face of a man who hadn’t shaved in probably a year, had overgrown fingernails, and probably hadn’t had a shower in close to a year. ”Even though Peterson hadn’t pioked up a paintbrush in about eight years, he asked if he could paint Faris’s portrait. Faris said yes.Peterson’s connection with Faris led him to form Faces of Santa Ana, a nonprofit organization focused on befriending and painting portraits of members of the community who are unhoused. Working from a black-and-white photo of the subject, Peterson chooses colors inspired by the subject’s personality and life story, creating an impressive portrait.Peterson sells the striking artwork, signed by both subject and artist, dividing the proceeds and putting half into what he calls a“love account”for his model. He then helps people use the money to get back on their feet. Many of Peterson’s new friends use the donations to secure immediate necessities. But Peterson has learned not to make assumptions about what a personneeds most. “I’ve made a mistake thinking I knew what people wanted, ” he says, “but why don’t we just ask them?”Peterson has discovered that there’s more to the finished products than the money they bring to someone who’s down and out. The buyers tend to connect to the story of the person in the painting, finding similarities and often friendship with someone they might have otherwise overlooked. “People often tell me, ‘I was the one that would cross the street. But I see homeless people differently now, ’ ”Peterson says.4.What brought Peterson and Faris together?A.Beauty on Faris’ face.B.Inspiration from a book.C.Peterson’s passion for art.D.Faris’ suffering in his life.5.What does the underlined word “mistake” in paragraph 5 refer to?A.Selling the homeless’ portraits for profits.B.Giving instant necessities to the homeless.C.Asking the homeless for their needs directly.D.Taking what the homeless want for granted.6.What does Peterson imply in the last paragraph?A.The homeless are gaining more concern.B.The life of the homeless is different now.C.Buyers value friendship with the homeless.D.Figures in Peterson’s paintings are popular.7.What can we learn from this text?A.A good model is key to a fine artwork.B.An expected decision makes a great artist.C.A picture really is worth a thousand words.D.Each unfortunate person has his own misfortune.The Malagasy baobab tree, whose thick trunks and tiny branches dot Madagascar’s landscape, should not, by rights, have survived to the present day. Scientists believe that its large seeds were once spread by the giant tortoises and lemur monkeys that wandered the island. When these species went extinct over one thousand years ago owing to human activity, the baobab treeshould have disappeared too. It did not. Seheno Andriantsaralaza at the University of Antananarivo and Onja Razafindratsima at the University of California, now think they may know the reason why.Together with their colleagues, the scientists monitored 15 tree canopies (树冠) in a western region of Madagascar, to identify any animals that might have claimed the role of baobab-seed spread. The researchers also set up camera traps around seed-containing fruits lying on the ground, and searched any faeces (粪便) that they encountered along the way for the presence of seeds.They report in the journal Biotropica that a native rodent (啮齿动物) known as the western bunch-tailed rat was caught on camera handling whole fruits on four occasions. Although there was no footage of the rat breaking the fruits open, the team did chance upon 13 fruits that had been chewed into and had their seeds removed. Though the bite marks were not clear enough to identify an initiator, this was clear evidence that a seed- distributing animal was out there. They then found the ecological equivalent of a smoking gun:baobab seeds in seven different piles of bush-pig faces.While the finding is important in its own right, it also provides valuable evidence that introduced species may not be entirely harmful. Madagascar’s pigs, for example, though not native, have made themselves essential to the survival of truly native species. Similar relationships are suspected to hold in South America between rabbits native to Europe and plants with no seed distributors. For Dr Andriantsaralaza, that suggests the full ecological role of introduced species should be considered before talk of extinction begins.8.What made scientists think the baobab tree should have disappeared?A.The extinction of its seed spreader.B.The destruction of human activitiesC.The inadaptation of the baobab tree.D.The increase of its natural enemies. 9.What are camera traps used for?A.Seeking seed-containing fruits.B.Tracking the footprints of seeds.C.Recording the animals’ activities.D.Monitoring the baobab tree canopies. 10.Which is most probably the seed-eater according to the report?A.The giant tortoise B.The bunch-tailed rat.C.The European rabbit.D.The bush-pig.11.What is the author’s purpose in writing the text?A.To introduce a new way to protect the baobab tree.B.To show non-native species are not always harmful.C.To compare different kinds of seed-distributing methods.D.To explain the importance of protecting endangered species.The concepts of delayed satisfaction, self-control, and self-regulation are often used interchangeably and inconsistently. The ability to delay an impulse (冲动) for an immediate reward to receive a more favorable reward at a later time is the standard definition of delayed satisfaction.Studies show that delayed satisfaction is one of the most effective personal characteristics of successful people. People who learn how to manage their need to be satisfied in the moment develop more in their careers, relationships, health, and finances than people who give in to it.Being able to delay satisfaction isn’t the easiest skill to acquire. It involves feeling dissatisfied, which is why it seems impossible for people who haven’t learned to control their impulses. Choosing to have something now might feel good, but making the effort to have discipline and manage your impulses can result in bigger or better rewards in the future. Over time, delayed satisfaction will improve your self-control and ultimately help you achieve your long-term goals faster.The Seinfeld Strategy is one of several helpful self-satisfaction techniques you can use to put off satisfaction for longer periods of time. Every day that you delay satisfaction and avoid temptation (诱惑) , you cross it off your calendar. After a few days, this creates a chain. This strategy works well for people who enjoy gamification (游戏化). If you find it satisfying to keep the chain going, you’re less likely to give in to temptation.Do you find yourself going back to your temptations without thinking about it?If this is the case, you can practice mindfulness to become more aware of what you do. When you notice yourself doing something out of habit, stop for a moment. Ask yourself why you’re doing what you’re doing. Take some time to analyze how you’re feeling. Pay attention to the details. Take a moment of mindulness to interrupt your autopilot every time this happens. The more you practice this, the more you’ll break the habit of going for instant satisfaction.12.What is delayed satisfaction?A.Making quick decisions.B.Giving in to desires instantly.C.Immediate rewards for impulses.D.Postponing rewards for better outcomes. 13.Why is delayed satisfaction hard to attain?A.It can lead to missed opportunities B.It’s bad for achieving long-term goals.C.It’s impossible to resist the inner needs D.It’s a comfort to possess something at once. 14.What does paragraph 4 mainly talk about?A.The complexity of the Seinfeld Strategy B.An example of self-discipline techniques.C.A method of practicing delayed satisfaction.D.The effectiveness of keeping the chain going.15.What does the author suggest people do for returning temptations?A.Ignore useless details.B.Get rid of old bad habits.C.Concentrate on true inner wants.D.Cancel temptations from the calendar.Facing hard things is, well, hard. Sometimes we are forced to simply shift, such as with a loss or failure; however, much of the time, we may recognize the difficulties underneath that need attention but feel too overwhelmed to address them. 16 The difficulties might be an outdated habit, a troubling memory or a long- ignored conflict.Some individuals fool themselves into thinking there really is not a problem. It’s like someone trying to hold active mice under a blanket by holding down the edges of the moving blanket. Pulling back the blanket to let the mice out is needed, despite being terrifying. Once the mice are released, there may be further challenges to get them out of the house. 17 People often encounter similar problems. Avoiding or leaving the situation appears to fix the problem but fails to tackle the underlying cause. Rather than repeatedly cutting weeds, getting down on the ground and pulling the roots is more effective. Facing issues is like uncovering roots for new beginnings to blossom. 1819 It feels like a balled-up mess of wires. Pulling hard at only one wire actually tightens the knot. We have to take a calmer look and pull apart each wire one at a time. We can’t expect the wires to loosen or unwind themselves. 20 Nevertheless, once they have been freed, they can sometimes be separated, put aside, and used as needed. A.They are just there and part of the chaos.B.And humans are masters of avoidance and denial.C.The overall benefits from tough work enable growthD.Making changes in one’s life is hard and complicated.E.Sadly, it often worsens when we approach it with anger.F.However, problems cannot be faced if they are not first recognized.G.Quick fixes might provide relief in the short term but often not in the long term.二、完形填空Madeline sat on her bed and tried to write. Tears dropped onto the page, making the ink 21 . Her best friend was moving, and her heart 22 as she penned how much she would miss him.She heard her mother speaking downstairs, but the words were 23 . This was a 24 , as her mother said, “Kids her age don’t know what love is!”Uncle Joe responded in a low tone. 25 , Madeline couldn’t catch what was said. She continued to write until she reached the end and 26 , she laid her head on the pillow and sobbed. Then, she felt a 27 hand on her shoulder. “It’s going to be okay. You can 28 each other, right?” Madeline 29 her head. “Mom says I’m not old enough for a phone.”Uncle Joe answered 30 , “But I’m friends with Leo’s dad. Your mom said you can talk to Leo on my phone. Plus, I gave her his number.” He didn’t tell her that her mom had thought it all silly and unnecessary.Madeline 31 , throwing her arms around Uncle Joe’s neck. “Thank you!”“No problem.” His eyes fell on the 32 . “Want me to ensure this gets to Leo?” Madeline nodded “Feel like playing a game? I promise I won’t mess around.”Madeline smiled — small but 33 .Uncle Joe wouldn’t read the letter; she 34 him. A sure thing was that his sister was mistaken. Though only eight, Madeline and Leo shared a pure, innocent bond — untouched by 35 .21.A.emerge B.bleed C.leak D.escape 22.A.raced B.hesitated C.ached D.melted23.A.indistinct B.sharp C.pale D.impolite 24.A.burden B.warning C.bonus D.blessing 25.A.Instead B.Anyway C.Again D.Moreover 26.A.worried B.confused C.bored D.exhausted 27.A.comforting B.firm C.smooth D.trembling 28.A.greet B.call C.miss D.visit 29.A.dropped B.shook C.covered D.touched 30.A.proudly B.slowly C.quietly D.casually 31.A.sat up B.turned over C.looked up D.bent down 32.A.toy B.phone C.note D.pen 33.A.friendly B.genuine C.unique D.tight 34.A.refused B.begged C.respected D.trusted 35.A.romance B.doubt C.mood D.status三、语法填空阅读下面短文,在空白处填入1个适当的单词或括号内单词的正确形式。
有关可疑品处理流程考试题

有关可疑品处理流程考试题Handling suspicious items is a complex process that requires attention to detail, quick thinking, and a thorough understanding of safety protocols. When encountering a suspicious item, the first step is to assess the situation calmly and rationally. It is important not to panic, as this can lead to hasty decisions that may compromise the safety of yourself and others. Instead, take a moment to observe the item from a safe distance and assess any potential risks it may pose.处理可疑物品是一个复杂的流程,需要注意细节,迅速思考,并对安全规程有透彻的了解。
当遇到可疑物品时,第一步是冷静理性地评估情况。
重要的是不要恐慌,因为这可能会导致仓促的决定,可能会危及您和他人的安全。
相反,花一点时间从安全距离观察物品,评估它可能带来的任何潜在风险。
Once you have assessed the situation, it is important to report the suspicious item to the appropriate authorities. This could be security personnel, law enforcement, or emergency services, depending on the location and nature of the item. Providing as much detail as possible about the item, its location, and any other relevant information will help responders determine the best course of action.Remember, it is always better to be safe than sorry when dealingwith suspicious items.一旦评估了情况,就重要报告可疑物品给适当的当局。
天津市静海区北京师范大学静海附属学校2024-2025学年高一上学期第一次月考英语试题

天津市静海区北京师范大学静海附属学校2024-2025学年高一上学期第一次月考英语试题一、听力选择题1.What are the speakers going to do this afternoon?A.Play tennis.B.See a movie.C.Arrange a party. 2.What is most probably the man?A.A postman.B.A policeman.C.A repairman.3.Where does the conversation take place?A.On a bus.B.On a plane.C.On a train.4.How do the Scots feel about moving to Paris?A.Nervous.B.Happy.C.Uncertain.5.What does the man think of his cake?A.It’s not soft.B.It’s not fresh.C.It’s not sweet.听下面一段较长对话,回答以下小题。
6.How long was the man in the shower?A.For about 10 minutes.B.For about 30 minutes.C.For about 60 minutes. 7.What do we know about the man?A.He tried to save water.B.He is out of work now.C.He paid the water bill last month.8.What is the most probable relationship between the speakers?A.Brother and sister.B.Host and guest.C.Teacher and student.听下面一段较长对话,回答以下小题。
可疑币鉴别流程

可疑币鉴别流程Detecting and identifying suspicious coins is a process that requires careful attention to detail and a keen eye for potential fraud. Coin authentication is a crucial aspect of numismatics and the broader financial world, as counterfeit coins can severely impact the value and trustworthiness of currency systems. As such, it is important to establish a robust and comprehensive coin authentication process to safeguard against fraudulent activity. 鉴别和识别可疑的硬币是一个需要仔细注意细节和对潜在欺诈有犀利眼光的过程。
硬币鉴定是货币学和更广泛的金融世界中至关重要的一个方面,因为假冒硬币会严重影响货币系统的价值和信誉。
因此,建立一个健全和全面的硬币鉴别过程对抗欺诈活动至关重要。
The first step in the coin authentication process is to conduct a visual inspection of the coin. This involves examining the coin for any irregularities in its design, minting marks, and overall appearance. Additionally, it is important to compare the coin to known authentic examples to look for discrepancies. By conducting a thorough visual inspection, numismatists and coin collectors can identify potential counterfeit coins and take the necessary steps to further authenticatethem.硬币鉴别过程的第一步是对硬币进行视觉检查。
2024届高考英语一轮复习说明文阅读理解讲解课件

结此论处:添加标题文本
遇This到is aCg,oDod篇sp说ace 明for a文sho,rt s尤ubti其tle 是离生活比较远的社科类文本,一定不要着急做题, 或者直接像做A篇应用文那样直接按着题目回原文找答案。 ①应先有大局观,一定读懂第一段,因为第一段是说明文的“魂”,第一段 里有说明文的主旨大意。然后快速浏览找到每段的大意(找每段的主题句, 不是段首就是断尾),看看是下面的哪一类【背景(background)、定义 (definition)、研究实验过程(study)、原理或原因(principle/reason)、 优缺点(advantages and disadvantages)、未来前景(prospect)等 】 ②得到了文章结构,下面就可以读题,也就能又快又准地获取原文答题区 间。
②A bat scientist, Eklof works in the night shadows in western Sweden. His work requires an absolute kind of darkness unpolluted by light. But this category of darkness is threatened. In the 1980s, Eklof tells readers, two-thirds of the churches in Sweden housed bat caves. Not any longer. “Today, this number has been reduced by a third due to light pollution, because the churches all glow brightly in the night.” he writes. ③We have all noticed it when driving through any city at night. Empty places are floodlit. The night sky in Hong Kong is 1200 times brighter than an unlit one. Citizens of some large cities, writes Eklof, have never allowed their eyes to adapt to true night vision. But we are only now beginning to understand the effects. ④Too much light is incredibly destructive to the complex eco-systems many animals inhabit. It scares away the bats that Eklof studies; reef fish eggs go unhatched; birds forget to even sing. ⑤So how can we deal with the too much light? In 2019, France passed laws limiting how much light can be sent into the sky. In Vienna, Austria, the city’s lights are turned off at 11 p.m. Some measures, like artificial lights that do not reflect light upward, are already within our grasp. “We could just turn it all off, but I guess we don’t want to, because darkness is not safe for everyone.” said Eklof in a recent interview. “So it’s vital we find a middle way.” ⑤Right now, it’s hard to know what that middle way might look like. In 50 years, every city could be lit by
suspicious的用法

suspicious的用法Suspicious这个词汇通常被用来形容那些引起怀疑或有可疑动机的事物、行为或人。
它源自拉丁语“suspicere”,意思是“怀疑”。
在英语中,suspicious有多种用法,下面将详细介绍其常见用法及例句。
一级标题:Situations to Use Suspicious二级标题:1. 描述可疑行为和举止当我们遇到某人的行为看起来很奇怪或令人怀疑时,我们可以使用suspicious来形容这种情况。
比如:"He gave a suspicious look and quickly walked away without saying a word."(他神色紧张地向我投以一瞥,然后迅速离开了,什么也没说。
)"She found a mysterious package hidden under the bed, which made her feel suspicious about its content."(她发现床底下藏着一个神秘的包裹,这让她对其内容感到可疑。
)二级标题:2. 怀疑某事真相当我们对某个事件或情况存在怀疑时,可以使用suspicious来表达此观点。
例如:"The police found some suspicious activities near the crime scene, leading them to believe that there may be multiple culprits involved."(警方在案发现场附近发现了一些可疑活动,这使他们相信可能有多个罪犯参与其中。
)"There were suspicious details in the witness's testimony that raised doubts about his credibility."(目击者的证词中有可疑之处,这引发了人们对他的可信度产生了怀疑。
关于烹饪的英语作文

Cooking is an art that involves the preparation of food by heating.It is a skill that many people enjoy mastering,and it can be a great way to express creativity and share culture.Here is an essay about the joys and benefits of cooking in English:The Art of Cooking:A Journey of Flavor and CreativityCooking is not merely a necessity it is an art form that allows individuals to create culinary masterpieces that not only satisfy the palate but also evoke emotions and memories.The process of cooking is a blend of science,technique,and creativity,where ingredients are transformed into dishes that can be shared with family and friends.The Beginning:Ingredients and TechniquesThe journey of cooking starts with the selection of fresh,highquality ingredients.A visit to the local farmers market can be an inspiring experience,as the vibrant colors and aromas of fresh produce can spark ideas for new recipes.Understanding the properties of each ingredient is crucial for instance,the acidity of lemon juice can balance the sweetness of a dessert,while the umami of soy sauce can enhance the flavor of a savory dish.Techniques in cooking range from the simple act of boiling to the complex art of sauce making.Each technique serves a purpose,such as searing meat to lock in the juices or kneading dough to develop gluten for a chewy texture.Mastery of these techniques is essential for elevating the quality of the final dish.The Process:From Preparation to PresentationThe process of cooking is a dance of preparation,where ingredients are measured, chopped,and combined in a harmonious sequence.The cook must be attentive to the timing and temperature,ensuring that each component is cooked to perfection.This requires patience and practice,as well as an understanding of the desired outcome.Presentation is the final act in the culinary performance.A beautifully plated dish can enhance the dining experience,making the meal more enjoyable and memorable.The art of plating involves considering color,texture,and balance,creating a visual symphony that complements the flavors on the plate.The Benefits:Health,Economy,and ConnectionCooking at home offers numerous benefits.It allows for control over the ingredients used, ensuring that meals are healthy and tailored to individual dietary needs.It is also an economical choice,as homemade meals can be more costeffective than dining out.Moreover,cooking is a social activity that fosters connection.Preparing a meal for loved ones is an act of love and care,and sharing a meal together is a timehonored tradition that strengthens bonds.Cooking can also be a communal activity,with friends and family members gathering in the kitchen to share in the process,creating a sense of camaraderie and joy.The Cultural Exchange:Culinary DiversityCooking is a window into different cultures,offering a way to explore and appreciate the diversity of global cuisines.Learning to cook dishes from around the world can be an enriching experience,as it involves not only the acquisition of new cooking techniques but also an understanding of the history and traditions behind each recipe.Conclusion:The Joy of CookingIn conclusion,cooking is a multifaceted activity that offers a wealth of benefits and joys. It is a skill that can be developed and refined over time,providing a sense of accomplishment and satisfaction.Whether it is for the love of creating,the pursuit of health,or the desire to connect with others,cooking is a journey worth embarking on.This essay highlights the various aspects of cooking,from the initial selection of ingredients to the final presentation of the dish,and emphasizes the cultural and social significance of this universal activity.。
2023考研英语一真题及答案解析

【20】A.ruins前面提到……remain today与之在同义语域的只有in ruins“毁灭,消失”。
SectionⅡReading Comprehension
Part A
Text 1
【14】B.influencing前面提到sharing their cultures, ideas and beliefs, as well as talking knowledge with them,动作the development of several civilizations.带入只有influence符合语义。
2023
SectionⅠUse of English
Caravanserais were roadside inns that were built along the Silk Road in areas including China, North Africa and the Middle East.They were typically __1_ outside the walls of a city or village and were usuallyfunded by governments of _2__.
1.A.displayed B.occupied C.located D.equipped
2.A.privately B.regularly C.respectively D.permanently
3.A.definition B.transition C.substitution bination
【17】D.stock up on and前面讲到商人卖货,后面空格又接了supplies供给只有stock up on储存符合文义。
Fortinet AVLab 文件分析指南说明书

OverviewThis guide describes how to use Windows utilities to identify suspicious sample files and send them to the AVLab at Fortinet.The AVLab can further analyze the suspicious sample file,and provide you with the most appropriate solution.When files are infected with ransomware,it is almost always impossible to reliably restore theaffected files.After a device has been victim to a successful or undetected Zero Day infectionor intrusion,it is highly recommended to restore the entire affected system from a cleanbackup.It is nearly impossible without proper forensic procedures to determine whether othercomponents might have been installed during the breach because successfully executedmalware can download and install additional components from a remote site.It is highly recommend to obtain the third-party tools referenced in this guide from the Microsoft Sysinternals site at https:///en-us/sysinternals/.The third-party tools referenced in this guide have been tested on a device running a Windows10operating system.This guide contains the following topics:l Installing and using Process Explorer to locate suspicious files on page1l Installing and using Process Monitor to locate suspicious files on page3l Installing and using Autoruns to locate suspicious files on page5l Revealing hidden,suspicious files on page7l Ending tasks or killing running processes to enable copying of suspicious files on page8Installing and using Process Explorer to locate suspicious filesYou can use the Process Explorer utility to view currently running processes on a host.Process Explorer is similar to Task Manager,but provides more detail about the current running process.Process Explorer can be used to search for and locate suspicious files.A suspicious process can be any processes that are unfamiliar to you or your system administrator.The process name often indicates the name of the runningapplication.You can consider any unfamiliar processes or applications suspicious.To install Process Explorer:1.Download the Process Explorer utility from Microsoft at https:///en-us/sysinternals/downloads/process-explorer.2.Install Process Explorer.To use Process Explorer:1.Open the Process Explorer utility,and search for suspicious processes.2.If you cannot determine whether processes are suspicious,save the list of processes to a text file,and send the fileto the AVLab:a.In Process Explorer,select File>Save As,and save the file as a.txt file.b.Attach the log text file to the FortiCare ticket.c.Skip the last step in this procedure.3.If you locate a suspicious process,use the Process Monitor utility to further analyze the file.See Installing and usingProcess Monitor to locate suspicious files on page3.Installing and using Process Monitor to locate suspicious filesYou can use the Process Monitor utility to monitor in any registry,process,or thread activity in real-time.If you locate a potentially suspicious process by using the Process Explorer utility,you can use the Process Monitor utility to further analyzer the suspicious process.To install Process Monitor:1.Download the Process Monitor utility from Microsoft at https:///en-us/sysinternals/downloads/procmon.2.Install Process Monitor.To use Process Monitor:1.Open the Process Monitor utility.2.Go to Filter>Filter.3.Monitor a process:a.Select Process Name,contains,and then type the name of suspicious process.b.Click Add,Apply,and OK.Results for the process are displayed.4.Review the process results:You can check the API functions being used by the suspicious process.Depending on the type of malware,various samples may indicate various suspicious API calls.Common calls that might be considered suspicious include:l Unpack/Decrypt-VirtualAlloc VirtualProtect RtlMoveMemoryl Ransomware-GetLogicalDrives GetDriveType FindFirstFile FindNextFile EncryptFilel Virus Infector-WriteFile SetFilePointer CreateFileMappingl Process Injector-GetTempPath CreateFile CopyFilel Backdoor-ReadFile WinHttpOpenIn the following example,the Operation column displays example processes for a test sample notepad application.5.Once you have confirmed the suspicious process,right-click the process,and select Properties to view the FilePath.6.Note the file path,and use Windows Explorer to locate the suspicious file.7.In Windows Explorer,add the suspicious file to a ZIP archive with the password:infected.8.Attach the ZIP archive to the FortiCare ticket for the FortiCare team to analyze,or email to************************.Installing and using Autoruns to locate suspicious filesYou can use the Autoruns utility to view all applications or programs within the host that automatically start.An application or program that uses the autorun feature isn't necessarily suspicious.Some clean or legitimate applications or programs can employ autorun.Nonetheless malware uses the autorun feature to ensure persistence upon system reboot.To install Autoruns:1.Download Autoruns from Microsoft at https:///en-us/sysinternals/downloads/autoruns.2.Install Autoruns.To use Autoruns to locate suspicious files:1.Open the Autoruns utility,and go to the Everything tab to view the Autoruns Entry list.2.Search for any unusual,suspicious entries in the Autoruns Entry list.A suspicious autorun entry can be any unfamiliar or unknown application or program that you or your systemadministrator may not be aware ually the entry in the list indicates the name of the application currently running.3.If you cannot determine a suspicious entry in the Autoruns Entry list,save an Autoruns file:a.Go to File>Save.Autorun generates and saves a file with an.arn extension.The following example shows the DESKTOP-I.arn file:b.Attach the log text file to the FortiCare ticket.c.Skip the remaining steps in the procedure.4.If you locate a suspicious entry in the Autoruns Entry list,right click the process,and select Jump to Image..to go tothe file location.The following example shows how to use the Autoruns Entry list to locate a sample test file for Microsoft Edge.5.In Windows Explorer,add the suspicious file to a ZIP archive with the password:infected.6.Attach the ZIP archive to the FortiCare ticket for the FortiCare team to analyze,or email to************************.Revealing hidden,suspicious filesSometimes suspicious files are hidden from view in Windows Explorer.You can use this procedure to display hidden files.This procedure presumes that you have already identified the suspicious file or process.To reveal hidden,suspicious files:1.Press Win+R,type cmd,and press Enter.The Command Prompt window is displayed.2.At the prompt,enter attrib-s-h followed by the<File_Path_of_Suspicious_File>,and press Enter.For example,enter attrib-s-h C:\suspicious\file.exe.The file is unhidden.3.In Windows Explorer,add the suspicious file to a ZIP archive with the password:infected.4.Attach the ZIP archive to the FortiCare ticket for the FortiCare team to analyze,or email to************************.Ending tasks or killing running processes to enable copying of suspicious filesWhen the suspicious sample file is locked by a running process,you cannot obtain the file.This topic describes how to use the following tools to end the task or kill the running process,so you can copy the file.l Windows Task Managerl Process Explorerl Resource MonitorThis procedure presumes that you have already identified the suspicious file or process.To end tasks or kill running processes:1.Open Task Manager or Process Explorer.2.In the list,search for the process that is using the file.3.End or kill the process:l If you are using Task Manager,right-click the file,and select End Task.l If you are using Process Explorer,right-click the file and select Kill Process.4.If you cannot find the suspicious process by using Windows Task Manager or Process Explorer,try using ResourceMonitor:a.Press Win+R,enter resmon,and press Enter to open Resource Monitor.The Resource Monitor window is displayed.b.Go to the CPU tab.c.In the Associated Handles section,enter the filename in the Search box,and press Enter.The process is displayed.d.In the Search Results list,right-click the process,and select End Process.In the following example,a process called cmd.exe is ended.Overview5.In Windows Explorer,add the suspicious file to a ZIP archive with the password:infected.6.Attach the ZIP archive to the FortiCare ticket for the FortiCare team to analyze,or email to************************.Change Log2022-05-26Initial release.。
八年级英语文学作品赏析单选题40题

八年级英语文学作品赏析单选题40题1.In the novel "Oliver Twist", Oliver is known for being _____.A.cunningB.braveC.timidD.arrogant答案:B。
Oliver 在小说《雾都孤儿》中以勇敢著称。
选项A“cunning”意为狡猾的,不符合Oliver 的人物特点;选项C“timid”意为胆小的,也与Oliver 的形象不符;选项D“arrogant”意为傲慢的,同样不是Oliver 的特点。
2.The main character in "Pride and Prejudice", Elizabeth Bennet, is often described as _____.A.shyB.intelligentC.naiveD.snobbish答案:B。
《傲慢与偏见》中的女主角伊丽莎白·贝内特通常被描述为聪明。
选项A“shy”意为害羞的,不符合伊丽莎白的性格;选项C“naive”意为天真的,也不是她的特点;选项D“snobbish”意为势利的,与伊丽莎白的形象相悖。
3.In "Jane Eyre", Jane is characterized by her _____.A.vainnessB.passivityC.independenceD.cowardice答案:C。
在《《简·爱》中,简的特点是独立。
选项A“vainness”意为虚荣,简并不虚荣;选项B“passivity”意为被动,简不是被动的人;选项D“cowardice”意为胆小,简很勇敢,不是胆小之人。
4.The hero in "The Adventures of Tom Sawyer" is _____.zyB.cleverC.stupidD.cruel答案:B。
中考英语阅读理解作者意图与态度分析题50题

中考英语阅读理解作者意图与态度分析题50题1. In the passage, the author mainly wants to _.A. tell a storyB. give some adviceC. describe a placeD. introduce a person答案:B。
本题主要考查对文章主旨的理解。
通过阅读全文,可以发现作者在文中提出了一些建议,而不是单纯讲故事、描述地点或介绍人物。
A 选项讲故事在文章中未体现;C 选项描述地点文章中没有着重强调;D 选项介绍人物也不是文章重点。
2. What can we know from the author's attitude in the passage?A. Optimistic.B. Pessimistic.C. Neutral.D. Angry.答案:A。
从文章中的描述和用词可以看出作者的态度是积极乐观的,而非悲观、中立或生气。
B 选项悲观不符合;C 选项中立也不对;D 选项生气在文章中没有体现。
3. The author writes this passage to _.A. show his love for somethingB. express his dislike for somethingC. explain a conceptD. persuade readers to do something答案:D。
通过对文章内容的分析,可以看出作者的目的是说服读者去做某件事情,而不是单纯表达对某物的喜爱或厌恶,也不是解释一个概念。
A 选项表达喜爱不准确;B 选项表达厌恶不符合;C 选项解释概念不是重点。
4. What is the author's main purpose in writing this passage?A. To amuse readers.B. To inform readers.C. To warn readers.D. To educate readers.答案:B。
批判需要谨慎的英文作文

批判需要谨慎的英文作文"English:"Criticism is an essential aspect of growth and progress, but it indeed requires caution and sensitivity. Whenoffering criticism, it's crucial to balance honesty with tact, as the way we deliver feedback can greatly impact how it's received and its effectiveness in fostering improvement.For instance, imagine you're a manager providing feedback to a team member on their performance. Instead of bluntly pointing out their flaws, you might choose to start with praise for what they've done well, such as, "I really appreciate the effort you put into meeting deadlines." This sets a positive tone and makes the criticism feel less like an attack. Then, you can gently address areas for improvement, like, "However, I've noticed some inconsistencies in your work quality lately."Moreover, it's important to be specific when giving criticism. Vague or general feedback can leave therecipient feeling confused or frustrated, not knowing exactly what they need to change. For example, instead of saying, "Your presentation was okay," you could say, "Your presentation content was thorough, but your delivery lacked enthusiasm, which made it less engaging for the audience." This way, the person knows exactly what aspect of their performance needs improvement.Additionally, empathy plays a crucial role in effective criticism. Before delivering feedback, it's helpful to put yourself in the other person's shoes and consider how they might perceive your words. This can prevent unintentional harm and foster a more constructive dialogue. For instance, if you're critiquing a colleague's proposal, you might say, "I understand the amount of work you've put into this, but I believe we can strengthen the argument by providing more data to support our claims."Furthermore, it's essential to offer constructive suggestions for improvement rather than just pointing outflaws. Criticism should be accompanied by guidance on howto rectify the issues identified. For example, if you're reviewing a student's essay, instead of merely stating, "Your thesis is unclear," you could offer suggestions on how to refine it, such as, "Try to make your thesis statement more concise and specific to provide a clearer direction for your argument."In conclusion, criticism, when delivered thoughtfully and constructively, can be a powerful tool for growth and development. By balancing honesty with tact, being specific, practicing empathy, and offering constructive suggestions, we can ensure that our criticism motivates positive change rather than causing harm or resentment."中文,"批评是成长和进步中必不可少的一部分,但确实需要谨慎和敏感。
读后续写:委婉语+课件-2025届高三英语上学期一轮复习专项

英汉委婉语的一般表现方法
委婉语作为一种修辞格,既是一种“手段”,也是一种目的。大量的 英汉委婉语运用了各种各样的表现手段来达到“委婉”这个目的。
Outside the window, the clouds had rolled over the sun. The room felt darker. “Bad things come in threes,” said Hazel. “No outdoor break is number one. What will be the second thing?” The class didn’t have to wait long to find out.
③(承上启下)Fein和Emma合作,hazel在 one on the painting?” Fein
asked Hazel. ①(衔接)Hazel的反应:犹豫,不确定,但还是尝试了 ②(过渡)完成的画作很赞,阳光也正好出来了,美好 的事情发生了 ③(收尾)呼应前文:Fein鼓励Hazel抛弃“坏事成三”, 看到积极的一面。
1. Euphemisms for Death 讨论死亡可能令人不舒服,因此委婉语常被用来使谈话变得轻松一些。 诸如 "passed away"(去世)或 “gone to a better place”(去了一个更好的 地方)这样的短语比直接说某人死了要温和。例如:
Direct: John died last night. Euphemism: John passed away last night. 2. Euphemisms for Bodily Functions 某些身体功能的讨论可能会显得尴尬。委婉语帮助保持一定的体面:
When things went wrong, Fein always had something nice to say.
Bitdefender GravityZone Elite Suite说明书
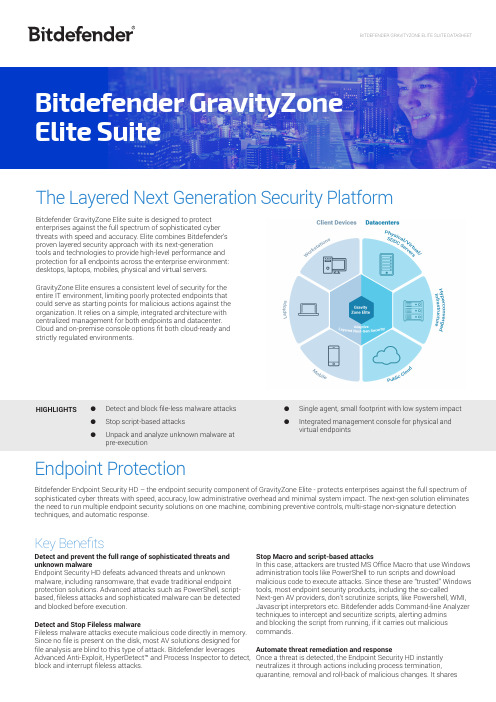
The Layered Next Generation Security Platform Bitdefender GravityZone Elite suite is designed to protectenterprises against the full spectrum of sophisticated cyberthreats with speed and accuracy. Elite combines Bitdefender’sproven layered security approach with its next-generationtools and technologies to provide high-level performance andprotection for all endpoints across the enterprise environment:desktops, laptops, mobiles, physical and virtual servers.GravityZone Elite ensures a consistent level of security for theentire IT environment, limiting poorly protected endpoints thatcould serve as starting points for malicious actions against theorganization. It relies on a simple, integrated architecture withcentralized management for both endpoints and datacenter.Cloud and on-premise console options fit both cloud-ready andstrictly regulated environments.●Detect and block file-less malware attacks ●Stop script-based attacks●Unpack and analyze unknown malware atpre-execution ●Single agent, small footprint with low system impact ●Integrated management console for physical andvirtual endpointsHIGHLIGHTSEndpoint ProtectionBitdefender Endpoint Security HD – the endpoint security component of GravityZone Elite - protects enterprises against the full spectrum of sophisticated cyber threats with speed, accuracy, low administrative overhead and minimal system impact. The next-gen solution eliminates the need to run multiple endpoint security solutions on one machine, combining preventive controls, multi-stage non-signature detection techniques, and automatic response.Key BenefitsDetect and prevent the full range of sophisticated threats and unknown malwareEndpoint Security HD defeats advanced threats and unknown malware, including ransomware, that evade traditional endpoint protection solutions. Advanced attacks such as PowerShell, script-based, fileless attacks and sophisticated malware can be detected and blocked before execution.Detect and Stop Fileless malwareFileless malware attacks execute malicious code directly in memory. Since no file is present on the disk, most AV solutions designed for file analysis are blind to this type of attack. Bitdefender leverages Advanced Anti-Exploit, HyperDetect™ and Process Inspector to detect, block and interrupt fileless attacks.Stop Macro and script-based attacksIn this case, attackers are trusted MS Office Macro that use Windows administration tools like PowerShell to run scripts and download malicious code to execute attacks. Since these are “trusted” Windows tools, most endpoint security products, including the so-calledNext-gen AV providers, don’t scrutinize scripts, like Powershell, WMI, Javascript interpretors etc. Bitdefender adds Command-line Analyzer techniques to intercept and securitize scripts, alerting adminsand blocking the script from running, if it carries out malicious commands.Automate threat remediation and responseOnce a threat is detected, the Endpoint Security HD instantly neutralizes it through actions including process termination,quarantine, removal and roll-back of malicious changes. It shares2threat information in real time with GPN, Bitdefender’s cloud-based threat intelligence service, preventing similar attacks worldwide. Gain threat context and visibilityBitdefender Endpoint Security HD’s unique capability to identify and report suspicious activities gives admins early warning of malicious behavior such as dubious operating system requests, evasive actions and connections to command and control centers.Boost operational efficiency with single agent and integrated console Bitdefender’s single, integrated endpoint security agent eliminates agent fatigue. The modular design offers maximum flexibility and lets administrators set security policies. GravityZone automatically customizes the installation package and minimizes the agent footprint. Architected from the ground up post-virtualization and post-cloud security architectures, GravityZone provides a unified security management platform to protect physical, virtualized and cloud environments.FeaturesMachine LearningMachine learning techniques use well-trained machine models and algorithms to predict and block advanced attacks. Bitdefender’smachine learning models use 40,000 static and dynamic features and are continuously trained on billions of clean and malicious file samples gathered from over 500 million endpoints globally. This dramatically improves the effectiveness of malware detection and minimizes false positives.HyperDetectThis new defense layer in the pre-execution phase features local machine learning models and advanced heuristics trained to spot hacking tools, exploits and malware obfuscation techniques toblock sophisticated threats before execution. It also detects deliverytechniques and sites that host exploit kits and blocks suspicious web traffic.HyperDetect lets security administrators adjust defense to best counter the specific risks the organization likely faces. With the “Report only” option, security administrators can stage and monitor their new defense policy before rolling it out, eliminating business interruption. In a combination of high visibility and threat blockingunique to Bitdefender, users can set HyperDetect to block at normal or permissive level but continue to report at the aggressive level exposing early indicators of compromise.Endpoint Integrated Sandbox AnalyzerThis powerful layer of protection against advanced threats analyzessuspicious files in depth, detonates payloads in a contained virtual3Protected EndpointsSuspiciousFileThreatControl CenterReportsBehavioral AnalysisPolicy ForensicsDashboardDetonation NotificationsMachine LearningResultsPolicySubmissionVerdictBlockingMonitoring environment hosted by Bitdefender, analyzes their behavior and reports malicious intent.Integrated with GravityZone Endpoint agent, the Sandbox Analyzer automatically submits suspicious files for analysis. With a malicious verdict from the Sandbox Analyzer, the Endpoint Security HDautomatically blocks the malicious file on all systems enterprise-wide immediately. The automatic submission function allows enterprise security administrators to choose “monitor” or “block” mode, which prevents access to a file until a verdict is received. Administrators can also manually submit files for analysis. Sandbox Analyzer’s rich forensic information gives clear context on threats and helps them understand threat behavior.Advanced Anti-ExploitExploit prevention technology protects the memory and vulnerable applications such as browsers, document readers, media files and runtime (ie. Flash, Java). Advanced mechanisms watch memory access routines to detect and block exploit techniques such as API caller verification, stack pivot, return-oriented-programming (ROP) and others.Process InspectorProcess Inspector operates in zero-trust mode, continuouslymonitoring all processes running in the operating system. It hunts for suspicious activities or anomalous process behavior, such as attempts to disguise the type of process, execute code in another process’s space (hijack process memory for privilege escalation), replicate, drop files, hide from process enumeration applications and more. It takes appropriate remediation actions, including process termination and undoing changes the process made. It is highly effective indetecting unknown, advanced malware and fileless attacks, including ransomware.Anti-phishing and web security filteringWeb Security filtering enables scanning of incoming web traffic, including SSL, http and https traffic, in real time to prevent thedownload of malware to the endpoint. Anti-phishing protection automatically blocks phishing and fraudulent web pages.Full Disk EncryptionGravityZone-managed full disk encryption using Windows BitLocker and Mac FileVault, taking advantage of the technology built into the operating systems.Endpoint control and hardeningPolicy-based endpoint controls include the firewall, device control with USB scanning, and web content control with URL categorization.Response and containmentGravityZone offers the best clean-up technology on the market. It automatically blocks/contains threats, kills malicious processes and roll backs changes.Datacenter ProtectionGravityZone Security for Virtualized Environments (SVE) leverages Bitdefender Endpoint Security HD’s layered next-generation defenses to provide enterprises best-in-class security for server, VDI and cloud workloads, while maximizing infrastructure performance and operational efficiency. GravityZone SVE is designed as an enterprise solution that can support even the largest datacenters.Key BenefitsAgilitySVE enables security automation across the datacenter lifecycle at rollout as well as during day-to-day security operations of a highly dynamic virtual environment. It integrates with VMware (vCenter, vShield, NSX), Citrix XenCenter and the Nutanix Enterprise Cloud Platform and enables fast automated provisioning.Operational efficiency The unified GravityZone Control Center management console simplifies security deployment, maintenance and upgrades, providing centralized visibility into all virtual and physical servers and workstations. Itsupports centralized creation and automatic administration of security policies to help streamline IT operations while improving compliance.Improved infrastructure utilization Centralized scanning and a small footprint agent greatly reduce the use of memory, disk space, CPU and I/O activity on host servers, increasing VM density and ROI on IT infrastructure.Universal compatibilityCompatible with all virtualization platforms (such as VMware® ESXiTM, Microsoft® Hyper-VTM, Citrix® XenServer®, Red Hat®Enterprise Virtualization®, KVM, and Nutanix® Acropolis), Microsoft Active Directory, and both Windows® and Linux® guest operating systems, GravityZone simplifies deployment, endpoint discovery and policy administration.Unlimited linear scalabilityMultiple SVAs can be used to increase scanning capacity as theDatacenter grows and more VMs are created. As an existing SVA reaches a certain load threshold, new ones can be deployed to accommodate growth. Layered next-gen defenses GravityZone Security for Virtualized Environments incorporates all keysecurity layers of Endpoint Security including HyperDetect, SandboxAnalyzer and fileless attack-detection methods to provide leading protection for enterprise digital assets stored or processed in the datacenter.B D -N G Z -M a r .07.2018-T k #:B i t d e f e n d e r -N G Z -E l i t e -D a t a s h e e t -c r e a t 1973-A 4-e n _E NBitdefender is a global security technology company that provides cutting edge end-to-end cyber security solutions and advanced threat protection to more than 500 million users in more than 150 countries. Since 2001, Bitdefender has consistently produced award-winning business and consumer security technology, and is a provider of choice in both hybrid infrastructure security and endpoint protection. Through R&D, alliances and partnerships, Bitdefender is trusted to be ahead and deliver robust security you can rely on. More information is available at .All Rights Reserved. © 2017 Bitdefender. All trademarks, trade names, and products referenced herein are property of their respective owners. FOR MORE INFORMATION VISIT: /businessSecurity for iOS and Android Mobile DevicesThis solution is designed to support controlled adoption of the bring-your-own-device (BYOD) concept by enforcing security policies consistently on all users’ devices. As a result, mobile devices are controlled, and sensitive business information on them is protected. The administrative burden is reduced with the always-up-to-date status of compliant and non-compliant devices.Security for Exchange ServersIt provides multiple layers of security for messaging: antispam, antiphishing, antivirus and antimalware with behavioral analysis and zero-day threat protection and e-mail traffic filtering, including attachment and content filtering. Antimalware scanning can be offloaded to centralized security servers from protected mail servers. Management and reporting are centralized, allowing unified policies for endpoints and messaging.GravityZone Control CenterGravityZone Control Center is an integrated and centralized management console that provides a single pane of glass view for all the security management components including endpoint security, datacenter security, security for Exchange and mobile devices security. It can be cloud-hosted or deployed locally. GravityZone management center incorporates multiple roles and contains the database server, communication server, update server and web console. For larger enterprises, it can be configured to use multiple virtual appliances with multiple instances of specific roles with built-in load balancer for scalability and high availability.GravityZone Elite Security protects desktops, servers (physical or virtual), mobile devices and e-mail boxes. Servers should account for less than 35% of all units.For detailed system requirements, please refer to https:///business/elite-security.html。
英语GRE核心词汇梳理suspicion

英语GRE核心词汇梳理suspicion[səˈspɪʃn]n. 怀疑,嫌疑(doubt)记来自suspect(v. 怀疑)例She worked for recognition and fame, yet she felt a deep suspicion and respect for the worldin which recognition and fame are granted, the world of money and opinion and power.insanity[ɪnˈsænəti]n. 疯狂(derangement);愚昧(great folly)同a madnessfrigidity[frɪˈʤɪdəti]n. 寒冷;冷淡(the quality or state of being frigid)记来自frigid(adj. 寒冷的)pundit[ˈpʌndɪt]n. 权威人士,专家(one who gives opinions in an authoritative manner)记pandit(n. 学者,专家)变体sentinel[ˈsentɪnl]n. 哨兵,岗哨(sentry; lookout)搭stand sentinel 站岗,守卫overthrow[ˌoʊvərˈθroʊ]v. 推翻;终止(to throw over; overturn)n. 推翻;终止(an instance of overthrowing)dejected[dɪˈʤektɪd]adj. 沮丧的,失望的,灰心的(in low spirits; depressed; disheartened)记词根记忆:de+ject(扔)+ed→被扔掉的→沮丧的,失望的,灰心的mortification[ˌmɔːrtɪfɪˈkeɪʃn]n. 耻辱,屈辱(shame; humiliation)记来自mortify(v. 使难堪)marshal[ˈmɑːrʃl]v. 整理,安排,排列(to arrange in good or effective order)记联想记忆:为行军(march)而作安排(marshal)fitful[ˈfɪtfl]adj. 间歇的,不规则的记联想记忆:fit(一阵)+ful(充满…的)→一阵阵的→间歇的[ˈrelɪk]n. 遗物,遗迹,遗风(a survivor or remnant left after decay, disintegration, or disappearance)sear[sɪr]v. 烧焦(to burn or scorch with intense heat)vaporous[ˈveɪpərəs]adj. 空想的(unsubstantial);多蒸汽的记来自vapor(n. 蒸汽)comedienne[kəˌmiːdɪˈen]n. 喜剧女演员(a woman who is a comedian);滑稽人物记来自comedy(n. 喜剧)[ɡɔːrʤ]n. 峡谷(a narrow steep-walled canyon or part of a canyon)搭the Rhine Gorge 莱茵峡谷dalliance[ˈdæliəns]n. 虚度光阴;调情(an act of dallying)记来自dally(v. 闲荡,嬉戏)munch[mʌntʃ]v. 用力咀嚼,出声咀嚼(to eat with a chewing action)记和lunch(n. 午餐)一起记luscious[ˈlʌʃəs]adj. 美味的(delicious);肉感的(voluptuous)condole[kənˈdoʊl]v. 同情,哀悼(to express sympathy; commiserate)记词根记忆:con(一起)+dole(痛苦)→一起痛苦→哀悼ignorant[ˈɪɡnərənt]adj. 无知的,愚昧的(knowing little or nothing)记词根记忆:ig(不)+nor(=gnor 知道)+ant→不知道的→无知的搭be ignorant of 对…无知overflow[ˌoʊvərˈfloʊ]v. 溢出(to flow over the edges);充满(to be very full)记组合词:over(出)+flow(流)→溢出percolate[ˈpɜːrkəleɪt]v. 过滤出(to cause to pass through a permeable substance);渗透(to penetrate; seep)记词根记忆:per(贯穿)+col(过滤)+ate→过滤出emote[ɪˈmoʊt]v. 激动地表达感情(to act in an emotional or theatrical manner)记词根记忆:e(出)+mote(动)→感动地说出来→激动地表达感情tramp[træmp]v. 重步走(to walk, tread, or step heavily)同plod, stomp, tromplamentable[ləˈmentəbl]adj. 令人惋惜的,悔恨的(expressing grief)记来自lament(n./v. 悔恨;悲叹)prelude[ˈpreljuːd]n. 序幕,前奏(an introductory performance, action, or event)记词根记忆:pre(在…之前)+lud(表演)+e→表演之前→序幕,前奏excruciate[ɪkˈskruːʃieɪt]v. 施酷刑;折磨(to subject to intense mental distress)记联想记忆:ex+cruci(看作crude,残忍的)+ate→给人施酷刑是很残忍的→施酷刑depressed[dɪˈprest]adj. 消沉的(sad and without enthusiasm);凹陷的(flattened downward)记来自depress(v. 消沉,沮丧)alleviate[əˈliːvieɪt]v. 减轻,缓和(to lighten or relieve)记词根记忆:al(加强)+lev(轻)+iate(使…)→使…轻→减轻,缓和contumacious[ˌkɑːntuˈmeɪʃəs]adj. 违抗的,不服从的(unreasonably disobedient, esp. to an order made by a court)记词根记忆:con+tum(肿胀;骄傲)+acious(…的)→坚持自己的骄傲,不受欺压→违抗的,不服从的frolic[ˈfrɑːlɪk]n. 嬉戏(a lively party or game);雀跃(gaiety; fun)v. 嬉戏例The young lambs were frolicing in the fieldintrude[ɪnˈtruːd]v. 把(思想等)强加于;闯入(to thrust or force in or upon someone or sth. especially withoutpermission or fitness)记词根记忆:in(进入)+trud(推;刺)+e→推进去→闯入morsel[ˈmɔːrsl]n. (食物的)一小口,一小块(a small bite or portion of food);小量,一点(a small piece oramount)记词根记忆:mors(咬)+el→咬一口→一小口verbal[ˈvɜːrbl]adj. 口头的(spoken);言语的记词根记忆:verb(字,词)+al→口头的,言语的例Many philosophers agree that the verbal aggression of profanity in certain radical newspapersis not trivial or childish, but an assault on decorum essential to the revolutionaries purpose.glisten[ˈɡlɪsn]v. 闪烁,闪耀(to shine or sparkle with reflected light)记来自glist(n. 闪光);联想记忆:g+listen(听)→因为善于倾听,所以智慧闪耀→闪烁,闪耀tarry[ˈtæri]v. 耽搁(to delay in starting or going; dawdle; linger)同dally, procrastinate, temporizeswipe[swaɪp]n. 猛击(a sweeping blow or stroke)v. 猛击(to hit with a sweeping motion)记联想记忆:s+wipe(擦)→起了摩擦后大打出手→猛击cult[kʌlt]n. 异教,教派(a system of religious beliefs and ritual);狂热的崇拜(worship)记联想记忆:culture(文化)去掉ure→没文化,搞崇拜→狂热的崇拜oath[oʊθ]n. 誓言(a formal promise to fulfill a pledge, especially one made in a court of law);咒骂,诅咒(swearword)wean[wiːn]v. (孩子)断奶;戒掉(to free from an unwholesome habit or interest)搭wean sb. off/from 逐渐戒除恶习(或避免依赖)stooge[stuːʤ]n. 配角,陪衬(one who plays a subordinate or compliant role to a principal);傀儡(puppet)blade[bleɪd]n. 刀刃,刀口(the cutting part of a tool)scutter[ˈskʌtər]v. 疾走,急跑(to move in or as if in a brisk pace)measly[ˈmiːzli]adj. 患麻疹的;少得可怜的,微不足道的(contemptibly small; meager)记来自measles(n. 麻疹)skyrocket[ˈskaɪrɑːkɪt]v. 突升,猛涨(to shoot up abruptly)记组合词:sky(天空)+rocket(火箭)→火箭冲向天空,突然升高→突升gratuity[ɡrəˈtuːəti]n. 赏钱,小费(sth. given voluntarily or beyond obligation usually for some service; tip)记词根记忆:grat(感激)+uity→表示感激的小费→小费forum[ˈfɔːrəm]n. 辩论的场所,论坛(a public meeting place for open discussion)记词根记忆:for(门)+um→门外→广场→论坛demote[ˌdiːˈmoʊt]v. 降级,降职(to reduce to a lower grade)记词根记忆:de+mote(动)→动下去→降级[səˈbɔːrn]v. 收买,贿赂(to induce secretly to do an unlawful thing)记词根记忆:sub(下面)+orn(装饰)→在下面给人好处→贿赂wroth[rɔːθ]adj. 暴怒的,非常愤怒的(intensely angry)搭be wroth with 非常生气countrified[ˈkʌntrifaɪd]adj. 乡村的(rural);粗俗的记词根记忆:countri(=country 乡下)+fied→来自乡下的→乡村的kangaroo[ˌkæ ɡəˈruː]记发音记忆:“看加入”→看着袋鼠宝宝进入妈妈的口袋→袋鼠interjection[ˌɪntərˈʤekʃn]n. 插入语(sth. that is interjected);感叹词(words used as an exclamation)记来自interject(v. 插入)aerial[ˈeriəl]adj. 空中的,空气的(of, relating to, or occurring in the air or atmosphere)记词根记忆:aer(空气)+ial(…的)→空中的croak[kroʊk]n. 蛙鸣声(a croaking sound)v. 发牢骚,抱怨(to grumble)记联想记忆:童话故事里,披着斗篷(cloak)的一群青蛙发出一阵蛙鸣声(croak)incubus[ˈɪkjʊbəs]n. 梦魇(a nightmare);沉重的负担(an oppressive burden)记词根记忆:in+cub(躺)+us→躺在某物内→梦魇abstemious[əbˈstiːmiəs]adj. 有节制的,节俭的(moderate in eating and drinking; temperate)记词根记忆:abs(脱离)+tem(酒)+ious→不喝酒→有节制的charity[ˈtʃærəti]n. 慈善(benevolence);施舍(a voluntary giving of money)记联想记忆:cha(音似:茶)+rity →请喝茶→施舍peel[piːl]v. 削去…的皮(to strip off an outer layer of);剥落(to come off in sheets or scales, as bark, skin,or paint)n. 外皮simonize[ˈsaɪmənaɪz]v. 给…打蜡,把…擦亮(to polish with or as if with wax)vertigo[ˈvɜːrtɪɡoʊ]n. 眩晕,晕头转向(a dizzy, confused state of mind)记词根记忆:vert(转)+igo→眩晕,晕头转向expatiate[ɪkˈspeɪʃieɪt]v. 细说,详述(to speak or write in detail)记词根记忆:ex(出)+pat(走)+iate→走出去→细说,详述howler[ˈhaʊlər]n. 嚎叫的人或动物;滑稽可笑的错误(a ludicrous blunder)记来自howl(v. 嚎叫)roundabout[ˈraʊndəbaʊt]adj. 绕道的,迂回的(indirect; circuitous)记组合词:round(迂回地,围绕地)+about(各处,附近)→迂回的limnetic[lɪmˈnetɪk]adj. 淡水的,湖泊的(of, relating to, or inhabiting the open water of a body of freshwater)reversion[rɪˈvɜːrʒn]n. 恢复,复原(an act of returning);逆转(an act of turning the opposite way)记词根记忆:re(回)+vers(转)+ion→转回去,返回→逆转monsoon[ˌmɑːnˈsuːn]n. 季风(a wind system that influences large climatic regions and reverses direction seasonally);雨季terminus[ˈtɜːrmɪnəs]n. (火车、汽车的)终点站(terminal)记词根记忆:termin(结束)+us→结束地→终点站callow[ˈkæloʊ]adj. (鸟)未生羽毛的(unfledged);(人)未成熟的(immature)记联想记忆:call+(l)ow→叫做低的东西→未成熟的anthem[ˈænθəm]n. 圣歌(a religious choral song);赞美诗(a song of praise);国歌记联想记忆:an+them→一首他们一起唱的歌→圣歌interlard[ˌɪntərˈlɑːrd]v. 使混杂,混入(to vary by intermixture; intersperse)同interlace, intertwinesuffocate[ˈsʌfəkeɪt]v. (使)窒息,把…闷死(to die from being unable to breathe)记词根记忆:suf+foc(喉咙)+ate→在喉咙下面→(使)窒息bruit[bruːt]v. 散布(谣言)(to spread a rumor)记联想记忆:br(看作bring)+u(看作you)+it→把它带给你→散布(谣言)implode[ɪmˈploʊd]v. 内爆(to burst inward);剧减(to undergo violent compression)记词根记忆:im(向内)+plod(打击;撞击)+e→在内部横冲直撞→内爆drenched[drentʃd]adj. 湿透的(soaked or saturated in liquid)boom[buːm]n. 繁荣(prosperity)v. 发出隆隆声(to make a deep hollow sound)记联想记忆:原来是象声词:“嘣”的一声misrepresentation[ˌmɪsˌreprɪzenˈteɪʃn]n. 误传,不实的陈述记联想记忆:mis(错的)+represent(表达)+ation→错误的表达→误传nimble[ˈnɪmbl]adj. 敏捷的,灵活的(moving quickly and lightly)记联想记忆:偷窃(nim)需要手脚灵活(nimble)peep[piːp]n./v. 瞥见,偷看(to look cautiously or slyly);初现(to show slightly)记联想记忆:偷看颠倒过来(peep→peep)还是偷看settle[ˈsetl]v. 安排(to place);决定(to decide on);栖息(to come to rest)记联想记忆:set(放置)+tle→安放,放置→安排ballyhoo[ˈbælihuː]n. 喧闹,呐喊(noisy shouting or uproar)v. 大肆宣传,大吹大擂(to publicize by sensationalmethods)slice[slaɪs]n. 薄片v. 切成片(to cut into pieces)calibrate[ˈkælɪbreɪt]v. 量…口径(to determine the calibre of);校准(to adjust precisely)记来自calibre(n. 口径)sunder[ˈsʌndər]v. 分裂,分离(to separate by violence or by intervening time or space)记发音记忆:“散的”→分离anonymity[ˌænəˈnɪməti]n. 无名,匿名(the quality or state of being anonymous)记词根记忆:an(没有)+onym(名称)+ity→无名,匿名proceeds[ˈproʊsiːdz]n. 收入(the total amount brought in);实收款项(the net amount received after deduction of anydiscount or charges)arrant[ˈærənt]adj. 完全的,彻底的(thoroughgoing);极坏的,臭名昭著的(being notoriously withoutmoderation)prehensile[prɪˈhensl]adj. 能抓住东西的,缠绕的(capable of grasping or holding)记词根记忆:prehens(=prehend 抓住)+ile(能…的)→能抓住东西的rustle[ˈrʌsl]v. 发出沙沙声(to make slight sounds like silk moving or being rubbed together)记联想记忆:可能来自rush(n. 匆促)orthodox[ˈɔːrθədɑːks]adj. 正统的(conforming to the usual beliefs of established doctrines)记词根记忆:ortho(正的,直的)+dox(观点)→正统观点→正统的belongings[bɪˈlɔːɪz]n. 所有物,财产(possessions; property)同estate, holdinghorticulture[ˈhɔːrtɪkʌltʃər]n. 园艺学记词根记忆:horti(花园)+cult(种植;培养)+ure→园艺学scraggly[ˈskræɡli]adj. 凹凸不平的(irregular in form or growth);散乱的(unkempt)crusade[kruːˈseɪd]n. 为维护理想、原则而进行的运动或斗争(vigorous, concerted action for some cause or idea, oragainst some abuse)记词根记忆:crus(十字)+ade→十字军东征→为维护理想、原则而进行的运动或斗争jolt[ʤoʊlt]v. (使)颠簸(to cause jerky movements)n. 震动,摇晃(jerk)记联想记忆:防止颠簸(jolt)用门闩(bolt)固定tweak[twiːk]v. 扭,拧,揪(to pinch and pull with a sudden jerk and twist);调节,微调(to make usually small adjustments in or to)lore[lɔːr]n. 知识(knowledge);特定的知识或传说(a particular body of knowledge or tradition)记参考:folklore(n. 民间传说)cartoon[kɑːrˈtuːn]n. 漫画(amusing drawing that comments satirically on current events)记发音记忆:“卡通”→漫画plank[plæ k]n. 厚木板(a heavy thick board);要点(a principal item of a policy or program)v. 铺板(to cover, build, or floor with planks)rehearse[rɪˈhɜːrs]v. 排练,预演(to practice in order to prepare for a public performance);详述(to tell fully)forgery[ˈfɔːrʤəri]n. 伪造(物)(something forged)记来自forge(v. 伪造)ashen[ˈæʃn]adj. 灰色的,苍白的(resembling ashes (as in color), especially deadly pale)brattish[ˈbrætɪʃ]adj. (指小孩)讨厌的,被宠坏的,无礼的((of a child) ill-mannered; annoying)记联想记忆:brat(小孩)+tish→小孩有时候有点讨厌→讨厌的ardent[ˈɑːrdnt]adj. 热心的,热烈的(intensely enthusiastic or devoted; passionate)记词根记忆:ard(热)+ent→热心的,热烈的flutter[ˈflʌtər]v. 拍翅((of the wings) to move lightly and quickly)同flapnasaladj. 鼻的(pertaining to the nose);有鼻音的记词根记忆:nas(鼻)+al→鼻的ravening[ˈrævənɪ]adj. 狼吞虎咽的(to devour greedily);贪婪的同rapaciousequable[ˈekwəbl]adj. 稳定的,不变的(not varying or fluctuating; steady);(脾气)温和的(tranquil; serene)记词根记忆:equ(平等)+able→能够平等的→稳定的coagulation[koʊˌæɡjuˈleɪʃn]n. 凝结记来自coagulate(v. 使凝结)[hiːv]v. 用力举(to raise or lift with an effort)记联想记忆:heaven(天堂)去掉n→想把天堂举起,却掉了个n→用力举perishing[ˈperɪʃɪ]adj. 严寒的(very cold)spew[spjuː]v. 呕吐(to vomit);大量喷出(to come forth in a flood or gush)narcissism[ˈnɑːrsɪsɪzəm]n. 自恋,自爱(inordinate fascination with oneself)记来自Narcissus,希腊神话中的美少年,因过于爱恋自己水中的影子而溺水身亡,化为水仙花(narcissus)chaffing[ˈtʃæfɪ]adj. 玩笑的,嘲弄的(of, relating to jest, banter)记来自chaff(v. 开玩笑)illiberal[ɪˈlɪbərəl]adj. 偏执的,思想狭隘的(intolerant; bigoted)记联想记忆:il(不)+liberal(开明的)→不开明的→偏执的sour[ˈsaʊər]adj. 酸的(having the acid taste or smell of or as if of fermentation)记发音记忆:“馊啊”→酸的blather[ˈblæðər]v. 喋喋不休地胡说,唠叨(to talk foolishly at length)同babble, blether, blither, smatterrefectory[rɪˈfektri]n. (学院等的)餐厅,食堂(a large room in a school or college in which meals are served)记来自refection(n. 食品,小吃)peruse[pəˈruːz]v. 细读,精读(to read sth. in a careful way)记词根记忆:per(始终)+us(用)+e→反复用→细读,精读seafaring[ˈsiːferɪ]adj. 航海的,跟航海有关的(of or relating to the use of the sea for travel or transportation)记来自seafarer(n. 水手,海员);sea(海)+fare(过日子)+(e)r (人)→靠海生活的人→水手,海员civilian[səˈvɪliən]n. 百姓,平民(any person not an active member of the armed forces or police)记词根记忆:civil(市民的)+ian→百姓,平民daft[dæft]adj. 傻的,愚蠢的(silly; foolish)prank[præ k]n. 恶作剧,玩笑(a trick)记注意不要和plank(n. 厚木板)相混hearsay[ˈhɪrseɪ]n. 谣传,道听途说(rumor; gossip)记组合词:hear(听到)+say(说)→道听途说observance[əbˈzɜːrvəns]n. (对法律、习俗等的)遵守,奉行记词根记忆:ob(加强)+serv(保持)+ance→遵守collate[kəˈleɪt]v. 对照,核对(to compare critically in order to consolidate)记词根记忆:col(共同)+late(放)→放到一起→核对quirk[kwɜːrk]n. 奇事(accident; vagary);怪癖(a strange habit)例An obvious style, easily identified by some superficial quirk, is properly decried as a meremannerism, whereas a complex and subtle style resists reduction to a formula.ballot[ˈbælət]n./v. 投票记联想记忆:ball(球)+(l)ot(签)→用球抽签→投票scissor[ˈsɪzər]n. 剪刀记词根记忆:sciss(切)+or→切开时所借助的工具→剪刀incorrigibility[ɪnˌkɔrɪʤəˈbɪləti]n. 无可救药(incapability of being corrected or amended)记词根记忆:in(不)+cor(=com 一起)+rig(直的)+ibility →无法一起拉直→无可救药redoubtable[rɪˈdaʊtəbl]adj. 令人敬畏的,可怕的(causing fear or alarm; formidable)记联想记忆:re(反复)+doubt(怀疑,疑虑)+able→行动时产生疑虑,说明对手是可怕的,可敬畏的→令人敬畏的,可怕的ennui[ɑːnˈwiː]n. 倦怠(weariness of mind);无聊v. 使无聊同boredomimpregnable[ɪmˈpreɡnəbl]adj. 固若金汤的,无法攻破的(not capable of being captured or entered by force)记词根记忆:im(不)+pregn(拿住)+able(能…的)→拿不住的→无法攻破的junction[ˈʤʌkʃn]n. 交叉路口(an intersection of roads);连接(an act of joining)记词根记忆:junct(连接)+ion→连接;交叉路口mast[mæst]n. 船桅,桅杆(a vertical spar for supporting sails)记联想记忆:与mat(n. 垫子)一起记jarring[ˈʤɑːrɪ]adj. 声音刺耳的(of sounds that have a harsh or an unpleasant effect)记来自jar(v. 发出刺耳声)foppish[ˈfɑːpɪʃ]adj. (似)纨绔子弟的(of or like a fop);浮华的,俗丽的记来自fop(n. 纨绔子弟)construct[kənˈstrʌkt]v. 建造,构造(to build sth.)记词根记忆:con(加强)+struct(建立)→建造,构造yowl[jaʊl]v. 嚎叫,恸哭(to utter a loud long cry of grief, pain, or distress)同howl, wailalter[ˈɔːltər]v. 改变,更改(to change)记alter本身就是词根,意为“改变”ample[ˈæmpl]adj. 富足的(abundant);充足的(enough; adequate)记联想记忆:apple(苹果)很ample(充足)precocious[prɪˈkoʊʃəs]adj. 早熟的(premature)记词根记忆:pre(预先)+coc(煮)+ious→提前煮好的→早熟的plenary[ˈpliːnəri]adj. 全体出席的;完全的,绝对的,无限的记词根记忆:plen(满)+ary→满的→完全的denude[dɪˈnuːd]v. 脱去(to make bare or naked);剥蚀(to lay bare by erosion);剥夺(to deprive of sth. important)记词根记忆:de+nude(赤裸的)→完全赤裸→脱去empirical[ɪmˈpɪrɪkl]adj. 经验的,实证的(based on observation or experience)记来自empiric(n. 经济主义者)flatulent[ˈflætʃələnt]adj. 自负的,浮夸的(pompously overblow; bloated)记词根记忆:fla(吹)+tul+ent→吹嘘的→自负的aver[əˈvɜːr]v. 极力声明;断言;证实(to state positively; affirm)记词根记忆:a(向)+ver(真实的)→向人们说出真相→证实convoke[kənˈvoʊk]v. 召集;召开(会议)(to summon to assemble; convene)记词根记忆:con(一起)+vok(喊)+e→喊到一起→召集loosen[ˈluːsn]v. 变松,松开(to become less firmed or fixed)记来自loose(adj. 宽松的)plead[pliːd]v. 辩护(to offer as a plea in defense);恳求(to appeal)记来自plea(n. 恳求;辩护)例In their preface, the collection's editors plead that certain of the important articles they omittedwere published too recently for inclusion, but in the case of many such articles, this excuse is not valid.lethargy[ˈleθərʤi]n. 昏睡(abnormal drowsiness);呆滞,懒散(the state of being lazy, sluggish)记词根记忆:leth(死)+a(不)+rg(=erg 工作)+y→像死了一样不动的状态→昏睡abscond[əbˈskɑːnd]v. 潜逃,逃亡(to run away and hide in order to escape the law)记词根记忆:abs(脱离)+cond(藏起来)→潜逃Trouble is only opportunity in work clothes.困难只是穿上工作服的机遇。
《新英汉翻译教程》第四章课后答案

How to explain that I was not a proud owner seeking admiration for his vehicle, but a tourist who had broken down如何解释,我不是一个骄傲的主人寻求佩服他的汽车,但游客坏了吗Special equipment assures that the computers will not be disturbed by power interruptions that last less than two hours.特种设备确保计算机就不会被打断,力量持续不到两个小时。
It is actually very, very old and was not always as beautiful as it is now. It is not certain how the Earth began. Probably it began as a huge globe of gas and dust. The globe became smaller and denser. Today the outer layer or crust is cool and hard,它实际上是非常非常老的,并不总是像现在这样美丽。
这都是不确定的地球就开始了。
可能起源于一个由气体和尘埃组成的庞大球体。
地球变得更小且致密。
今天的外层或地壳是凉爽且硬,It was not anger, nor surprise, nor disapproval, not horror, nor any of the other emotions that she had been prepared for.那表情不是生气,不是惊讶,不是不满,不是嫌恶,也不是她原先准备应付的任务一种感情。
Modern geology has for its aim the deciphering of the whole evolution of the earth from the time of the earlier records that can be recognized in the rocks to the present day.当代地质解释为其目标的整体演化的地球早期的时间记录,可以识别岩石到当代。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Fixed vs.variable-length patterns for detectingsuspicious process behaviorAndreas Wespi∗,Herv´e Debar,Marc Dacier and Mehdi NassehiIBM Research Division,Zurich Research Laboratory,S¨a umerstrasse4,CH-8803R¨u schlikon,Switzerland{anw,dac,mmn}@herve.debar@May11,2004AbstractThis paper addresses the problem of creating patterns to model the normal behavior of UNIX processes.The pattern model can be used for intrusion-detection purposes.First,we present methods to generate input data sets that enable us to observe thenormal behavior of a process in a secure environment.Second,we propose varioustechniques to derive eitherfixed-length or variable-length patterns from the input datasets.We show the advantages and drawbacks of each technique,based on the resultsof the experiments we have run on our testbed.1IntroductionIn[6]Forrest et al.introduced a change-detection algorithm which is based on the way natural immune systems distinguish“self”from“nonself”.In[5]they reported preliminary results aimed at establishing such a definition of self for Unix processes.This technique mod-els the way an application or service running on a machine normally behaves by registering the sequences of system calls invoked.An intrusion is assumed to exercise abnormal paths in the executable code,and is detected when new sequences are observed(see also[3,4,7,8]).Like every behavior-based technique,an intrusion-detection system needs to be trained to learn what the“normal”behavior of a process is.This is usually done by recording the activity of the process running in a real environment during a given period.This procedure has several drawbacks:∗Corresponding author.1•It has the potential to produce false alarms if not all possible normal behaviors have been exercised during the recording period,for example when users execute“new”,i.e.previously unseen,commands;•It has the potential to produce no alarm when an attack is performed if the application was hacked during the recording period and the attack pattern was learned by the system;•The observed behavior is a function of the environment in which it is running and thus prevents the distribution of an“initialized”intrusion-detection system that could be immediately plugged in and activated.Another approach consists of artificially creating input data sets that exercise all normal modes of operation of the process.For example,Forrest et al.[5]use a set of112messages to study the behavior of the sendmail daemon.This method eliminates the risk of obtaining false positives but not that of obtaining false negatives.Furthermore,it is an extremely complex and time-consuming task to come up with a good input data set.We make use of the functionality verification test(FVT)suites provided by application developers to observe all the specified behaviors of an application[1].Not only are we able to eliminate the risk of obtaining false positives with this approach,we also dramatically reduce the risk of obtaining false negatives because,by design,our input data set exercises all the normal(in the sense of having been tested by the designer of the application)modes of operation of the application under study.We present the results of experiments we have been running with this technique.Besides the use of the FVT suites,our work differs from that of Forrest et al.in three main ways:•The algorithm used to createfixed-length patterns is slightly different and results in shorter tables of patterns.•We consider in addition the opportunity of using variable-length patterns[14]and various ways of doing this.•The decision to raise an alarm is based on a new paradigm that is simpler than the Hamming distance described in[5],thus allowing possible real-time countermeasure.The structure of the paper is as follows.Section2presents the principles of the intrusion detection method we are working with.It explains how patterns are generated and used to cover sequences.Section3shows how we create the reference information by either recording and replaying user sessions or by using the FVT suites.Section4presents the experimental results obtained when applying afixed-length pattern-generation algorithm. Section5does the same for a variable-length pattern-generation algorithm.These two sections also highlight advantages and disadvantages of each technique.Section6concludes the paper by offering a comparison of the results as well as ideas for future work.22Principles of the approachIn our approach,UNIX processes are described by the sequences of audit events 1[15]that they generate,from start (fork )to finish (exit ).Their normal behavior is modeled by a table of patterns which are sub-sequences extracted from these sequences.The detection process relies on the assumption that when an attack exploits vulnerabilities in the code,new (i.e.not included in the model)sub-sequences of audit events will appear.Figure 1describes the complete chain used to configure the detecting tool.AECFG -> alarmFILE_closeFILE_closeFILE_openS_PASSWORD_READTCPIP_connect ABCD -> matched Figure 1:Intrusion-detection system.2.1Off-line treatmentThe upper part of Fig.1represents how the model of normal behavior is created off-line.Audit events are recorded from the ftp daemon,which has been triggered by an experiment process,and translated as letters for easier handling.Such a letter in our system actually represents the combination of the audit event and the name of the process generating it,both 1Note that Forrest et al.[5,6]use sequences of system calls instead of audit events.Obtaining system calls constitutes a more intrusive technique than the one we present here.3pieces of information being provided by the Unix C2audit trail.This recording runs through afiltering and reduction process whose purpose is explained below.When the experiment has been completed,the entire audit information is used to generate the table of patterns that constitute our model of the normal behavior of the system.The purpose of thefiltering/reduction/aggregation box is threefold(explained in more detail in the remainder of the section):filtering to eliminate irrelevant events(processes that are not related to the services we monitor)and to sort the remaining ones by process number;reduction to remove duplicate sequences due to processes generating exactly the same stream of audit events from start(fork)tofinish(exit)2;andaggregation to remove consecutive occurrences of the same system calls.Sorting prevents the introduction of arbitrary context switches into the audit stream by the operating system.Processes are sorted so that the intrusion-detection process is applied to each process individually.The events inside the process remain in the order in which they have been written to the audit trail.The reduction keeps only unique process images for model extraction.We use test suites to record the normal behavior of the ftp daemon.These test suites carry many repetitive actions and therefore result in many instances of the same process image(see[1]for a complete explanation of this issue).We remove these duplicates because they are not used by the current algorithm extracting the patterns from the reference audit data.The aggregation comes from the observation that strings of N consecutive audit events (N>20)are quite frequent for certain events,with N exhibiting small variations.A good example is the“ftp login”session,where the ftp daemon closes severalfile handles inherited from inetd.The number of these closes changes for no apparent reason.Therefore,we have simplified the audit trail to obtain a model that contains fewer and shorter patterns,and have observed no differences in experiments that do or do not use the aggregation.There is no claim that the reduced(simplified)audit trail and the original one are equivalent;the new one possibly has less semantic content.This is an experimental choice,and we would remove the aggregation part if the true/false alarm performance of the intrusion-detection system were not satisfactory.This aggregation phase would also be omitted if the intrusion-detection technique requires redundancy,e.g.neural networks.The most obvious aggregation consists of replacing identical consecutive audit events with an extra“virtual”audit event.However,doing so enriches the vocabulary(the number of registered audit events)and possibly the number of patterns,which we want to keep small.Our solution simply aggregates these identical consecutive audit events.Therefore, any audit event represents“one or more”such events(i.e.,A=A+in regular expression formalism)at the output of the aggregation box.The pattern-extraction procedure is discussed in detail in Sections4and5.2This is not used in the on-line version because of the memory cost and algorithmic complexity of keeping all known process images.42.2Real-time detectionThe lower part of Fig.1shows the real-time intrusion-detection process.Audit events are again generated by the ftp daemon,and go through the same sorting and reduction mecha-nism in real time.Then,we apply a pattern-matching algorithm (Section 2.3)to cover the sequences on the fly.When no known pattern appropriately matches the current stream of audit events,a decision has to be taken whether to raise an alarm (see Section 2.4).2.3Pattern-matching algorithmThe pattern-matching algorithm is quite critical for the performance of the intrusion-detection system.We wish to maximize both its speed and detection capabilities.Therefore,we require that patterns match exactly,i.e.,that they cannot be matched as regular expres-sions using wildcards.We use a two-step algorithm:the first step looks for an exact match,and the second step looks for the best partial match possible.These two steps are illustrated with the examples presented in Figs.2and 3.String:ABCABCDXYZGHI ABCDXYZGHI XYZGHI GHI ABC validated: 3 consecutive patterns yield exact matchABCD XYZD ABC Remainder of string:ABCD ABCD XYZD ABC GHI ABC ValidatedABC Selectable ABCDABCGHIXYZHF TableXYZDABCD XYZD ABC GHI XYZ Remainder of string:Remainder of string:Figure 2:Exact pattern-matching sequence.The first step of the algorithm is illustrated in Fig.2.A pattern that matches the beginning of the string is selected from the pattern table.If no pattern matches the beginning of the string,then the first event is counted as uncovered and removed.The algorithm is subsequently applied to the remainder of the string.Once a selectable pattern has been found,the algorithm will recursively look for other patterns that exactly cover the continuation of the string up to a given depth D or to the end of the string,which ever comes first (D =3in Fig.2).This means that,for a selectable pattern to be chosen,we must find D other patterns that also completely match the events following that pattern in the sequence.If such a sequence of D patterns does not exist,step 2of the algorithm is used.The rationale behind this is that we want to know whether the selected pattern has a positive influence on the coverage of the audit events that are in its vicinity.When such a D -pattern sequence has been found,the algorithm removes the head pattern from the sequence and continues with the remainder of the string.5String:ABCABCDKMWHF ABCDKMWHF ABC ABCD ABCD XYZD ABC length 6length 7Remainder of string:K Shifted MW Shifted Shifted SELECTEDUncovered sequence KMWABCDXYZDABCGHIXYZHF TableFigure 3:Approximate pattern-matching sequence.If we cannot find three other patterns that match the sequence after the selected pattern,we deselect it and try the next selectable pattern in the table.The fact that there were selectable patterns –but none that fulfill the depth requirement –triggers the second phase of the algorithm.The second step of the algorithm deals with failure cases and is illustrated in Fig.3.The algorithm looks for the sequence of N patterns that covers the largest number of audit events.This sequence is removed from the string and the algorithm goes back to its first part,looking again for a selectable pattern,and shortening the string as long as one is not found.2.4Intrusion detectionFor each string,the algorithm extracts both the number of groups of audit events that were not covered and the length of each of these groups.The decision whether to raise an alarm is based on the length of the uncovered sequences.It is worth noting that this is different from the measures used for the same purpose by Forrest et al.,namely the amount and the percentage of uncovered events in a string [5].There are three reasons for this:•Processes can generate a large number of events.An attack can be hidden in the midst of a set of normal ing the percentage of uncovered characters would fail to detect the attack in this case.•Small processes could be falsely flagged as anomalous because of a few uncovered events if we use the percentage of uncovered characters.•Long processes could be falsely flagged as anomalous because of many isolated uncov-ered events if we use the amount of uncovered characters.6During our experiments we observed that the trace of the attacks was represented by a number of consecutive uncovered characters.This is consistent with thefindings of Kosore-sow and Hofmeyr[8],who note that mismatches due to intrusions occur in fairly distinct bursts in the sequences of system calls that they monitored.This means that an attack cannot be carried out in fewer than T consecutive characters.Our experiments led us to choose the value7for T.In other words,each group of more than six consecutive uncovered events is considered anomalous and isflagged as an attack.This amounts to defining an intrusion as any event that generates a sequence of at least T consecutive events not covered by the algorithm defined above.To validate the concepts presented here,we have developed an intrusion-detection testbed [2].It is used to compare various strategies to build the pattern table used in the detector. Before reporting the results of the experiments performed on the testbed,we address the problem of generating the input data sequences for the intrusion-detection system.We focus on the ftp service,which is widely used,is known to contain many vulnerabilities(either due to softwareflaws or configuration errors),and provides rich possibilities for user interaction. 3Generating the reference dataThe most commonly practiced method for training behavior-based intrusion-detection sys-tems is to record the activity of the users on a normal workday.This recording is used as the reference information from which the process model is extracted during the training phase. In Section3.1we present an improvement of this method.On our testbed we can reproduce the reference information and record it under varying external conditions.Our recording procedure ensures that the reference information is attack-free.Section3.2describes various methods to systematically generate all possible user activities.We concentrate on a method that uses the functionality verification test(FVT)suite to exercise all subcommands of a given process.3.1Experimental reference data generationThefirst approach we present to create the reference data is to simulate user sessions.We wish to do the recording in a closed environment to ensure that no attacks against the ftp server take place.We achieve this goal by asking several participants in our laboratory to record ftp sessions against an internal ftp server supporting users and anonymous connec-tions.The ftp server is then reconfigured inside a closed network to prevent interactions with the outside world.Once this recording process is complete,we automatically transform the recordings into simple expect[9]scripts,which recreate the interactive er-related information such as username,password,and target ftp server is variable to allow the parallelization of the scripts.Additional scripts are added to the database to perform specific actions,such as using tar and compress to transferfiles,that were not in the original configuration of the recordings.7This need comes from the attack simulator.As some attacks involve the use of tar and compression programs to create setuid shells,our normal user activity also has to invoke these commands.We performed a number of experiments to record the reference behavior from which the model is extracted.These experiments involve(1)varying the load on the server(number of simultaneous connections),(2)changing the network interface(Ethernet or Token-Ring), and(3)selecting different subsets of scripts.We separate our user scripts into four groups:all the scripts that we have in the database; the scripts involving normal user behavior;the scripts involving anonymous user behavior; and the scripts involving normal user behavior but without those that have been added to include the usage of tar and compress(via the site exec command).The experimentation results are presented in Table1.Thefirst column describes the experiment,the second gives the total number of scripts run,the third the total number of audit events generated,the fourth the total number of processes created(output of the filtering),thefifth the number of unique processes generated(output of the reduction),and columns six to eight the number of unique processes generated with aggregation levels of3,2, and1,respectively.An aggregation level of N,N=1,2,3,means that N or more identical audit events are aggregated to exactly N such events(e.g.,AAA=AAA+for N=3).Table1:Collection of user data.No.audit events and reduction Experiment description of in the and aggregationscripts ref.set321All scripts on Ethernet interface5511152143070707069All scripts on Token-Ring interface5510506443070707069All scripts simultaneously on both11020135786070707069 Simulation of light load200494126160470707069 Simulation of heavy load6001082548458370707069All scripts500849095393172727271 Normal user scripts500299048400825252524 Anonymous user scripts5001038129376449494949 Normal user scripts w/o“site exec”5001118403417840404040 Table1shows that the number of processes generated is in direct proportion to the number of scripts run.When we look for unique processes,we alwaysfind the same number of different processes(70).Aggregation does not reduce this number significantly.This is radically different from observations(in the LINUX environment)made using the strace command which monitors at the system call level.There,we observed variances in the number of different processes generated from experiment to experiment,mainly because of operating system context switches and signals.This shows that even a low-level information8source such as the C2audit trail gives some abstraction to the data,such as eliminating context switches,signals,and interrupts.3.2Systematic reference data generationEmploying user-“controlled”manipulations to generate the reference behavior of the service is not optimal.One requirement is that in addition to being attack-free and reproducible, the reference behavior must contain all the possible legitimate commands supported by the ftp service,and that these commands must be received by the ftp server from the network interface.A second requirement is that these commands are either generated by an ftp client or directly“manufactured”,for example,by a packet-spoofing tool.3.2.1Software engineering and source-code analysisThefirst possibility to generate the reference data is to extract the complete call graph[10] of the code considered.This process is very costly,and is only possible by acquiring source code for the service investigated.Given the increasing complexity of programs and the fact that many system calls would actually happen inside the libraries for which source-code may not be available,we have eliminated this course of action because it is too cumbersome. Moreover,this technique does notfit our client-side requirement.3.2.2Macroscopic simulation as afinite-state automatonThis second approach is based on afinite-state automaton that implements all possible actions that can be performed by a user.Generating normal behavior simply means running the automaton.However,only a very limited subset of these commands is actually known to users and used by them.Therefore,it would make sense to enrich the automaton with transition probabilities.This approach is very difficult to implement for three main reasons:•The values of the transition probabilities are difficult to determine,and specific to the experimental environment.•This approach is only suitable when the set of commands is limited.It can simulate an ftp client but not a normal user shell session.•Even in simple cases such as ftp clients,implementation problems can arise.Indeed, ftp clients on different platforms sometimes have a different syntax,and the commands they generate make the ftp server react in different ways.These difficulties encountered in modeling ftp activity also apply to other services.There-fore,this approach was dropped from the current implementation of the workbench.93.2.3Approximating user behavior with test suitesA simpler approach consists of using the test suites provided by the operating-system de-velopment laboratories.In our case,we obtained access to the test suite used by the AIX development team.This test suite,called functionality verification tests(FVT),tests the compliance of the implementation of the TCP/IP services with their specification from the functional point of view,i.e.it tests the server functionality using the client in the case of ftp.The FVTs exercise all possible commands a user can send to an ftp server.These FVTs do not offer a realistic view of what users usually do,but at least they show how the system should behave when responding to normal requests.Actually,these test cases implement very simple scripts to test one command at a time.In that sense,they can be considered as traveling a subgraph of the user sessions where the length of the path would not exceed one or two commands between login and logout.This approach is also interesting to evaluate the false-alarm rate of knowledge-based intrusion-detection systems.Because the FVT will make the network daemons generate all sorts of events that do not(or very infrequently)occur in real-life systems,these events can be confused with attack scenarios.In this case,every alarm generated by a knowledge-based intrusion-detection system is a false alarm.If the intrusion-detection system has rules governing the normal behavior of the network service,running such a test suite allows us to check the completeness of the normal behavior model and also to interpret alarms generated by the intrusion-detection system as false alarms.However,the capability to fully train a behavior-based intrusion-detection system on this kind of data is still an open issue,as the profiles may contain behavior rarely exercised by the users.3.3Experimentations with the FVTThis section shows how to use the FVT data to record different reference information sets, from which process models are then generated.Recording the FVT sessions was done by simply running all available tests.Table2 presents the same results as Table1does,but for the FVT data collection.Three separate runs of the FVT were made to compare the resulting reference information.Data collec-tion took place on an isolated network,with as little interference as possible from other applications.Thefirst observation drawn from Table2is that77unique process images for487tests is very small.In fact,many of these tests are redundant,i.e.they transfer exactly the samefile in different modes(e.g.ascii,ebcdic,struct,record).The basic sequence(login, set parameters,transfer,logout)is repeated several times,but the parameter changes affect only the network level,and not the system.Therefore,we do not observe changes in the audit trail.The second observation is that,contrary to the user-simulation case,aggregation reduces the number of different processes in a significant way.Even with these very similar processes, the recording of audit events is sometimes still not completely identical.In particular,the10Table2:Collection of FVT data.Experiment description:Number of No.of processes afterfilteringNo.audit events and reductionSequential run of of in the and aggregationall available FVT tests scripts ref.set321Run14878779340177736557Run24878781340173686258Run34878912840171676156login sequence depends on the number of openfile handles handed to the ftpd daemon by the inetd daemon.We extract the model of behavior from these process images,which we regard as our reference information.4Generatingfixed-length patterns4.1Pattern generationFixed-length patterns are the most immediate approach to generate the table of patterns. We have evolved four ways of obtaining these patterns.For each of them,we use a parameter L,the length of the patterns.Technique1is an exhaustive generation of all possible patterns by sliding a window of size L across the sequence,thus recording each unique L-event sequence.This technique is easy to implement,but it has obvious drawbacks.First,a large number of patterns in the reference table will not be used by the matching algorithm on the reference data set. Moreover,the covering algorithm generates boundary mismatches when the length of the process image is not a multiple of L,because it uses a juxtaposing window instead of a sliding one(which would not make sense in this context).It is worth noting that this is the technique used to run the experiments described in[4,5,8].To solve thefirst problem,technique2is introduced,which shifts the string by L events, thus creating juxtaposed patterns instead of overlapping ones.In other words,the events in positions1to L constitute thefirst pattern,events in the positions L+1to2L constitute the second one,and so on...The table we obtain is thus much shorter than the table generated by technique1,which makes the pattern-matching algorithm faster.Technique2drops the remainder of the sequence of events when its length is not a multiple of L,therefore the second problem mentioned remains.To solve it,we have introduced techniques3and4.They are similar to technique2but keep the events remaining at the end of the string as a stand-alone pattern or concatenated to the last generated pattern,respectively.Techniques3and4both result in100%coverage of the test sets.As they are the ones that were most promising during the experiments,we11focus on them for the remainder of this paper.Note that some of the patterns are smaller or larger than the specified size,and these can only match at the end of the process execution, as they necessarily contain the end-of-process event.4.2Experimental resultsWe have used three test sets in our experiments.Thefirst test is solely based on the FVT. The second test set includes additional information on tools that are used by ftp users,but are not in the testing of the ftp daemon per se.The third data set is based on the recording of several hundred real user sessions.The experimental results are presented for the second test set.The reference table generated from thefirst set does not contain patterns for commands like tar,which are used by normal ing the third set breaks the rulefixed in the introduction of the paper(no user recording for training),thus this set has only been used to evaluate the false negative rates obtained with our approach.The output of the intrusion-detection system is shown in Fig.4.Each line reports the analysis for one process related to the ftp service.|Number of|Number of|Percentage|Number of|Average|Number of|Length of|audit|uncovered|of covered|patterns|size of|groups of|each group|events|events|events|needed|pattern|uncovered|||||||events|||||||||569|4|99.30|188| 3.01|4|1111|97|0|100.00|32| 3.03|0||928|3|99.68|308| 3.00|3|111|735|3|99.59|244| 3.00|3|111|6|0|100.00|2| 3.00|0||878|8|99.09|290| 3.00|8|11111111|839|4|99.52|278| 3.00|4|1111|8|6|25.00|1| 2.00|1|6|963|2|99.79|320| 3.00|1|2|168|2|98.81|55| 3.02|2|11|476|1|99.79|158| 3.01|1|1|366|3|99.18|121| 3.00|3|111Figure4:Output of the intrusion-detection system.Table3shows the results of the experiments to monitor our ftp server under various conditions using the intrusion-detection system loaded with several reference tables.The first column identifies the experiment.The second column lists the number of audit events in the experiment.The third column indicates the two parameters corresponding to the reference table used in the intrusion-detection system,t denotes the generation technique(3 or4)and s the size of the patterns(2,3and4).The fourth column lists the overall number of uncovered characters.Thefifth column lists the number of patterns used for the coverage. The sixth column lists the average size of patterns3,and the seventh column indicates the number of false alarms triggered by the intrusion-detection system.As described in Section 2.4,alarms are raised if there are more than6uncovered events in a row.3This value is truncated to two places after the decimal point.12。
