Interactive Web Usage Mining with the Navigation Visualizer
文本挖掘

▐
▐
8.1.4文本挖掘与信息检索
▐
信息检索领域一般用查全率和查准率,对检索的效果进行 量化评价。信息检索主要解决文本的标引问题,使用倒排 文本数据结构来表示文本信息。为了提高信息检索的效率, 信息检索系统在不断添加新的功能,如文本分类、文本聚 类、自动摘要和主题词自动抽取等方法,使用户能够更加 方便地从不同途径准确地查找到所需信息。自动摘要能够 减轻用户测览相关文本所需的时间,使用户能够快速地掌 握相关文本中的内容。文本的自动分类和自动聚类能够根 据文本的内容信息将文本集合划分为不同的类或者簇,方 便用户查找所需信息。
8.2.2 Web的特点
Web是一个非常成功的基于超文本的分布式信息系统。Web 的特点如下:
1.庞大性。Web 为全球范围发布和传播信息提供了机会, 它允许任何人在任何地方任何时间传播和获取信息。由于 Web的开放性,使得WCb上的信息与日俱增,呈爆炸性增 长。
2.动态性。Web不仅以极快的速度增长,而且其信息还 在不断地发生更新。新闻、公司广告、股票市场、Web服 务中心等都在不断地更新着各自的页面。链接信息和访问 记录也在频繁更新之中。
▐
8.1.1文本挖掘概述
▐
文本挖掘涵盖多种技术 , 包括信息抽取 , 信息检索 , 自然语 言处理和数据挖掘技术。它的主要用途是从原本未经使用 的文本中提取出未知的知识,但是文本挖掘也是一项非常 困难的工作 , 因为它必须处理那些本来就模糊而且非结构 化的文本数据,所以它是一个多学科混杂的领域,涵盖了信 息技术、文本分析、模式识别、统计学、数据可视化、数 据库技术、机器学习以及数据挖掘等技术。文本挖掘在商 业智能、信息检索、生物信息处理等方面都有广泛的应用。 例如,客户关系管理,自动邮件回复,垃圾邮件过滤,自 动简历评审,搜索引擎等等。
数据与知识工程

数据与知识工程1.对语义Web的理解1)语义Web是以某种方式链接,使全球范围内的计算机均可以处理的信息网,并通过标准、标记语言和处理工具对Web进行扩展。
使得Web不仅是人与人交互的信息空间,而且是语义丰富的数据网络;既能够被人浏览,也能够利用计算机程序执行操作。
2)语义Web的目标是为了解决在不同应用、企业和社区之间的互操作性问题。
(这种互操作性是通过语义来保证的;而互操作的环境是异质、动态、开放的Web。
)3)语义Web力图实现所有网络数据的“无缝”式连接,并使数据能被计算机自动处理和理解。
其最终目标是让计算机可以在这些海量信息中找到真正能满足需要的任何信息,从而将互联网最广泛的应用(万维网中现存的信息)发展成一个巨大的全球信息库、知识库。
4)语义Web技术能够在任何微小的网络数据之间建立连接。
(这种连接不仅仅局限于网页之间,而是在“数据”这个粒度上;任何微小的数据都可以与其他信息进行“沟通”。
)同时,语义Web帮助人们更精确地描述数据的含义,表示为计算机能够理解和处理的形式。
(从而,可以通过信息代理(agent)像搜索引擎采集网页那样采集数据;在推理引擎的帮助下智慧地集成数据,并最终呈现给用户使用。
)2.语义Web主要解决两个问题:1)如何对Web资源进行表示,从而便于让agent进行处理(获取、存储、推理、查询等)。
2)如何重用Web页面、多媒体信息、数据库等遗留资源(legacy resource),以便实现从现有Web到语义Web的过渡。
3.当前知识管理技术的缺陷●Searching information–Keyword-based search engines●Extracting information–human involvement necessary for browsing, retrieving, interpreting, combining●Maintaining information–inconsistencies in terminology, outdated information.●Viewing information–Impossible to define views on Web knowledge4.语义web技术●Explicit Metadata●Ontologies●Logic and Inference●Agents5.语义web模型6.动作描述推理基于谓词逻辑的动作刻画和推理⏹情景演算⏹流演算⏹STRIPS系统采用命题语言的动作刻画和推理⏹基于PDL的动作刻画和推理⏹基于PTL的动作刻画和推理基于描述逻辑的动作刻画和推理⏹基于描述逻辑的动作形式系统⏹情景演算的可判定形式⏹基于动态描述逻辑DDL(X)的动作刻画和推理7.情景演算⏹用常量s0表示初始情景;⏹用二元函数do(a, s)表示在情景s下执行动作a后产生的后继情景。
Web使用挖掘技术的研究

3.Web使用挖掘(Web Usage Mining)
Web使用挖掘又叫Web 日志挖掘或Web用户访问模式挖 掘, 挖掘的对象是Web服务器上的信息, 包括服务 日志、 用户 注册信息等内容, 也有人通过客户端代理收集用户的行为, 这 些记录更准确更详细, 但是有可东西方文化交流与传播的不平 衡, 而且随着东西方文化交流的不断加强, 强势文化势必会逐 渐取得优势, 弱势文化则存在因失去 自 身特点而被同化的危 险。 如果没有构筑起坚实的人文素质基础, 当学生面对巨大的 文化差异时, 就极有可能承受不住文化冲击而发生认识偏差, 其极端的表现形式就是产生民族 自卑感或者盲 目排外 的意 识。所以, 英语教学应结合实际适当介绍我国文化 、 历史 、 地 理、 人文与 自然景观和各地风俗人情及我国改革开放的当代 成就, 有意识地引导学生了解我国源远流长的优秀文化传统、 悠久的灿烂文明史, 培养学生的民族 自尊心, 激发学生的民族
档, 并且是以某种格式(如HTM L(Hypertext M arkup Language, 超文本标识语言)或XM L(Extensible M arkup Language, 可扩展 性标识语言 ))呈现的 非结构化或半结构化数据, 这些数据的 特 点是结构不规则或不完整, 模式信息量大, 模式变化快, 大量
自豪感 。
听、 读、 说、 写的语言能力, 如何在中专英语教学中开展好人文
素质教育 , 既是一道重大的理论课题 , 更是一个迫切的实践课
题。广大中专英语教师不仅要有扎实的专业水平, 也要不断提 高人文素养, 觉对传统中专英语教学进行纠编, 要自 切合实际 在中专英语教学中积极开展人文素质教育, 促进学生素质全
的文档并没有任何排列次序, 也没有分类索引。 这些特征决定 了Web信息处理的难度相当大。
管理学专业英语第四版下Unit 6 Big Data_The Managment Revolution

管理学专业英语教程(第四版·下)
星蓝海学习网
Outlines
1
Introduction
2 Dimensions of Big Data
3 Five Management Challenges
SAS added two additional dimensions to big data: variability and complexity. Variability refers to the variation in data flow rates. Complexity refers to the number of data sources.
❖ Better Pricing Harnessing big data collected from customer interactions allows firms to price appropriately and reap the rewards.
❖ Cost Reduction Big data analytics leads to better demand forecasts, more efficient routing with visualization and real-time tracking during shipments, and highly optimized distribution network management.
Popular Big Data Techniques (1)
❖ As data become cheaper, the complements to data become more valuable.
浅谈Web数据挖掘技术

浅谈Web数据挖掘技术作者:李晓玮来源:《电脑知识与技术》2013年第22期摘要:随着网络的快速发展与普及,大量有用的网络信息给人们生活、工作和学习带来了便利。
与此同时网络中还存在着许多无用的信息,如何从浩如烟海的数据海洋中,快速准确的查找数据,成为了当今社会不可忽视的问题。
Web数据挖掘技术,正是解决这一问题的关键。
该文从Web数据挖掘技术的角度,阐述Web数据挖掘的概念、分类、过程及常见的Web数据挖掘算法。
关键词: Web数据挖掘;PageRank算法;网络数据中图分类号:TP311.12 文献标识码:A 文章编号:1009-3044(2013)22-4992-021 概述当前,人们随时随地都在利用网络获取信息,不断利用网络进行着上传和下载的操作,这些信息数据在网络上传播和储存着。
因此,网络就形成了一个庞大的数据存储集散地。
如何从海量的网络数据中快速有效地对数据进行分析和检索,并在其中发觉潜在有用的信息,是当今社会需要解决的问题。
Web数据挖掘技术正是很好的解决了这个问题,以下将探讨一下Web 数据挖掘技术。
2 Web数据挖掘概念2.1数据挖掘Web数据挖掘是数据挖掘的一个分支,首先需要了解什么是数据挖掘。
数据挖掘(Data Mining, DM),是指从大量数据中提取有效的、新颖的、潜在有用的、最终可被理解的知识的过程。
在数据库系统中称其为知识发现(Knowledge Discovery in Database, KDD)。
Web 数据挖掘技术融合了数据库系统、统计学、信息科学、人工智能、机器学习等,是一个新兴的多学科交叉应用领域。
2.2 Web数据挖掘Web数据挖掘是在数据挖掘技术的基础上,针对网络数据主要是Web文档和服务日志文件进行的数据分析、归纳和汇总并在其中发现和提取潜在有用的信息及知识的技术。
3 Web数据挖掘的分类根据 Web 数据挖掘的对象,可将 Web 数据挖掘划分为三种类型。
社会性软件支持的WebCL中人际交互的研究的开题报告

社会性软件支持的WebCL中人际交互的研究的开题报告一、研究背景目前,社交软件成为了人们日常生活中必不可少的一部分,人们可以通过社交软件交流信息、分享生活和认识新朋友。
现在的社交软件已经不再只是简单的文字聊天,还包括图片、视频、语音等多种表达方式。
同时,WebCL作为一种新的Web技术,可以使得Web应用能够借助GPU等硬件进行高速计算,从而提高应用的性能和响应速度。
因此,将WebCL应用于社交软件的开发中,能够提高社交软件的用户体验和效率。
在社交软件中,人际交互是其中非常重要的一个方面。
人们使用社交软件,除了想要获得信息以外,更希望能够与其他人进行互动,分享感受和交流想法。
因此,如何在WebCL的技术支持下研究社交软件中的人际交互,是非常有意义的。
二、研究内容社会性软件支持的WebCL中人际交互的研究,主要包括以下内容:1. WebCL技术的介绍和应用场景分析对WebCL技术进行介绍,分析其在社交软件开发中的应用场景和优势。
2. 社交软件中人际交互的分析和设计分析社交软件中人际交互的特点,从用户角度出发,设计符合用户需求的社交软件界面和操作方式。
3. WebCL支持下的社交软件开发基于WebCL技术,开发出社交软件,并测试其性能和响应速度。
4. 人际交互的实验研究通过实验研究,探究社交软件中人际交互的影响因素和用户行为特点。
三、研究意义1. 提高社交软件的用户体验和效率通过WebCL技术的应用,可以大幅提高社交软件的性能和响应速度,使得用户能够更加顺畅地使用社交软件。
2. 拓展WebCL技术的应用范围将WebCL技术应用于社交软件的开发中,可以拓展其应用范围,并提高其在Web开发中的实用性。
3. 探究人际交互行为的特点和影响因素通过实验研究,可以深入探究社交软件中人际交互行为的特点和影响因素,为社交软件开发和设计提供参考。
四、研究方法本研究主要应用实验研究方法,通过设计实验,分析社交软件中人际交互的影响因素和用户行为特点。
domexception blocked a frame with -回复

domexception blocked a frame with -回复Title: Understanding DOMException: Blocked a Frame With [...]Introduction:The web development ecosystem has significantly evolved over the years, providing developers with powerful tools and frameworks to create dynamic and interactive websites. However, despite these advancements, developers often encounter challenges while working with the Document Object Model (DOM). DOMException with the message "Blocked a Frame With [...]" is a common error that developers may encounter. This article aims to explain the intricacies of this error and guide readers through the step-by-step process to resolve it effectively.I. Understanding the DOM and the Document Object Model:To comprehend DOMException, it is crucial to have a basic understanding of the Document Object Model (DOM). DOM is a representation of an HTML or XML document that provides developers with a comprehensive set of objects, properties, and methods to manipulate and interact with the respective document.II. Exploring DOMException:DOMException is a standardized mechanism by which DOM interfaces report error conditions. It is an exception object that represents an abnormal event triggered during DOM operations. The "Blocked a Frame With [...]" message specifically indicates that a frame or an iframe is trying to access a resource from another domain, as part of a "Cross-Origin Resource Sharing" (CORS) policy.III. Causes of "Blocked a Frame With [...]" Error:1. Same-Origin Policy Violation: The Same-Origin Policy restricts web pages from making requests to another domain. Any attempt to access resources (such as JavaScript, CSS, or images) from a different origin or protocol triggers this error.2. CORS Misconfiguration: Cross-Origin Resource Sharing (CORS) policy allows controlled access to resources on other domains. If CORS is misconfigured or not enabled on the server-side, a "Blocked a Frame With [...]" error may occur.IV. Troubleshooting and Resolving "Blocked a Frame With [...]" Error:1. Checking for Same-Origin Policy Violation: Ensure that the code is not accessing resources (such as images, scripts, or stylesheets) from a different origin. Cross-origin requests may require the use of server-side techniques like JSONP or CORS.2. Enabling CORS: If your application depends on resources from other domains, enable CORS on the server-side by configuring the appropriate response headers, allowing the cross-origin requests. Consult the server documentation to understand the specific steps for enabling CORS.3. Specifying Appropriate CORS Headers: When accessing resources from another domain, ensure that the server'sAccess-Control-Allow-Origin header allows the requesting domain. Additionally, verify that the Access-Control-Allow-Credentials and the Access-Control-Allow-Methods headers are set correctly.4. Using Relative Paths: Utilize relative paths while referencing different resources within the application. This approach avoidsdomain-specific issues and potential cross-origin errors.5. Validating Certificate and Security Measures: If the error occurs when accessing resources from a secure (HTTPS) domain, ensure that the SSL/TLS certificate is valid and implemented correctly. Invalid or expired certificates can trigger the “Blocked a Frame With [...]" error.6. Debugging and Logging: Implement logging mechanisms to capture relevant information about the error. This helps in diagnosing the root cause and identifying potential solutions.Conclusion:The "Blocked a Frame With [...]" error can be a daunting problem for web developers. However, understanding the concepts behind DOMException and the underlying causes can significantly ease the troubleshooting process. By following the step-by-step guide mentioned in this article, developers can effectively tackle the error and ensure seamless functioning of their web applications. Remember to verify the CORS configuration, adhere to theSame-Origin Policy, and validate security measures to prevent such errors and enhance the overall user experience.。
Web数据挖掘在电子商务中的应用

Web数据挖掘在电子商务中的应用电子商务网站每天都会产生大量的数据,运用数据挖掘技术可以从这些数据中发现对市场分析及预测非常有益的信息。
本文讨论了Web数据挖掘技术在电子商务中的应用。
标签:数据挖掘Web数据挖掘电子商务网络技术和数据库技术飞速发展,电子商务显示出越来越强大的生命力,同时各种基于互联网的商业Web站点也面临越来越激烈的竞争。
如何了解到顾客尽可能多的爱好和价值取向,为顾客提供更优质的服务成为电子商务发展迫切要解决的问题。
而电子商务网站的顾客在Web上的行为都会产生大量数据信息,不仅包括本次交易信息而且还有利用搜索引擎,以及在站点内进行浏览的相关数据。
利用数据挖掘技术可以有效地帮助企业分析这些数据,优化Web站点拓扑结构,指导企业调整营销策略,给客户提供动态的个性化的高效率服务。
一、Web数据挖掘Web数据挖掘(Web Data Mining),是数据挖掘技术在Web环境下的应用,是从大量的Web文档集合和在站点内进行浏览的相关数据中发现潜在的、有用的模式或信息。
它是一项综合技术,涉及到Internet技术、人工智能、计算机语言学、信息学、统计学等多个领域。
对应于不同的Web数据,Web挖掘也分成三类:Web内容挖掘、Web结构挖掘和Web使用模式挖掘。
Web使用模式挖掘(Web Usage Mining)是对用户访问Web时在服务器方留下的访问记录进行挖掘,它通过挖掘Web日志文件及客户交易数据来发现有意义的用户访问模式和相关的潜在用户群。
其主要特点是对用户信息数据进行抽取、转换、分析和其他模型化处理,从中提取辅助商业决策的关键性数据。
尽管Web挖掘的形式和研究方向层出不穷,但随着电子商务的兴起和迅猛发展,Web挖掘的一个重要应用方向将是电子商务系统。
电子商务是数据挖掘技术最恰当的应用领域,因为电子商务可以很容易满足数据挖掘所必需的因素:丰富的数据源、自动收集的可靠数据,并且可将挖掘的结果转化成商业行为,商业投资可以及时评价。
Web Usage Mining在远程教育中的应用研究

发规 则来 帮助 识别 用户 :不 同的I地 址代 表 着不 同的用户 ; P 当 户; P 在I 地址相 同 , 用 户使 用 的操作 系统或 浏览 器也 相 同时 , 而
自 上 个 世 纪 9 年 代 开 始 。 着 Itre的 日 益 普 及 , 络 已 O 随 nen t 网
务 器 记 录 文 件 结 合 起 来 ,其 过 程 可 分 为 以下 4 阶 段 : 数 据 收 个 集 、 据预 处理 、 式发 现 和模式 分析 。 数 模
21 数 据 收 集 .
正 是在 这样 的历史 背景 下,基 于We 挖掘 技术 的现代 远 程 b 教育 的研究 与 应 用在 辅 助 日常教 学 过程 中起 到 了不 可代 替 的 作用 , 但是 却存 在 一个 共 同的 问题 : 少个 性化 的服 务 。学校 只 缺
集 到 的数 据 的数 量 多少 和 质量 好 坏直 接 关 系到 后继 过程 的成
不 完整 的 、 余 的 、 冗 错误 的数 据 , 以如果 不对 原始 We 所 b日志文 件 进行 修改 。 会影 响模 式 发现 和模式 分析 过程 的质量 。对 数 将
据 进 行提 取 、 分解 、 合并 和修 改 , 主要 包含 以下 几 个 阶段 : 据 数 清 洗 、 户识别 、 用 会话 识别 、 径 补充 和事件 识别 。 路 数据 清洗 。 目的是 根据 要求 , 删除 无关 紧要 的数据 , 并某 合
录删 除 。
We 文档 服 务器 中发 现 与抽象 信 息 的过程 。通过 对We 文 档 中 b b 大量 信 息的 分析 , 以记 录和追 踪用 户 的浏览 行 为 , 可 例如 : 哪个
网页最 受 欢迎 , 户 喜欢 使 用 哪类 浏 览 器 ( I浏 览 器 或邀 游 用 如 E 浏 览 器 ) 操 作 系 统 ( n o 或 Ln x ) 等 等 。 以 了解 学 生 学 和 Widw iu 等 ,
计算机英语试题及答案

计算机英语试题及答案一、选择题(每题2分,共20分)1. Which of the following is not a programming language?A. JavaB. C++C. PythonD. Photoshop2. What does CPU stand for?A. Central Processing UnitB. Central Power UnitC. Central Printing UnitD. Central Programming Unit3. What is the full form of HTML?A. Hyper Text Markup LanguageB. Hyper Text Markup LanguageC. Hyper Text Markup LanguageD. Hyper Text Markup Language4. In computer networking, what does IP stand for?A. Internet ProtocolB. Internet ProgrammingC. Internet ProviderD. Internet Processor5. What is the primary function of a router?A. To print documentsB. To store dataC. To connect multiple networksD. To provide internet access6. Which of the following is a type of database management system?A. MS WordB. MS ExcelC. MS AccessD. MS PowerPoint7. What does the acronym RAM stand for?A. Random Access MemoryB. Rapid Access MemoryC. Remote Access MemoryD. Real Access Memory8. What is the term for a collection of data stored in a computer in a structured format?A. FileB. DocumentC. DatabaseD. Folder9. Which of the following is not a type of computer virus?A. TrojanB. WormC. AntivirusD. Ransomware10. What does the term "bandwidth" refer to in the context ofinternet usage?A. The width of the cableB. The speed of data transferC. The number of usersD. The quality of the connection二、填空题(每题2分,共20分)1. The basic unit of data in computing is called a ________.2. A ________ is a type of software that is designed to prevent, detect, and remove malware.3. The process of converting data into a form that can be easily transmitted or stored is known as ________.4. A ________ is a hardware device that allows a computer to connect to a network.5. The term "cybersecurity" refers to the practice of protecting systems, networks, and programs from ________ and other types of cyber attacks.6. A ________ is a collection of related data and the way it is organized.7. The ________ is a type of computer memory that retains data even when the power is off.8. The process of finding and fixing errors in a program is known as ________.9. A ________ is a type of software that allows users to create and edit documents.10. The ________ is a set of rules that define how data is formatted, transmitted, and received.三、简答题(每题10分,共30分)1. Explain the difference between a server and a client in a network.2. Describe the role of an operating system in a computer system.3. What are the key components of a computer system?四、论述题(每题30分,共30分)1. Discuss the importance of data backup and recovery in a computer system.答案:一、选择题1. D2. A3. A4. A5. C6. C7. A8. C9. C10. B二、填空题1. bit2. Antivirus3. Encoding4. Network Interface Card (NIC)5. unauthorized access6. Database7. Hard disk8. Debugging9. Word processor10. Protocol三、简答题1. In a network, a server is a computer system or device that provides resources or services to other computers, known as clients. The server manages network traffic, centralizes data storage, and provides access to shared resources, while the client is a computer that requests and uses these resourcesor services.2. An operating system is the software that manages computer hardware, software resources, and provides services for computer programs. It acts as an intermediary between theuser and the computer hardware, allowing users to interactwith the computer without needing detailed knowledge of the hardware.3. The key components of a computer system include thecentral processing unit (CPU), memory (RAM), storage devices (hard disk, SSD), input devices (keyboard, mouse), output devices (monitor, printer), and peripheral devices (scanner, webcam).四、论述题1. Data backup and recovery are critical in a computer system because they ensure that data is preserved in case ofhardware failure, data loss, or cyber attacks. Regularbackups allow for the restoration of data to a previous state, minimizing downtime and potential loss of information. This process is essential for maintaining business continuity and protecting against data loss.。
Web Usage Mining在电子商务中的应用
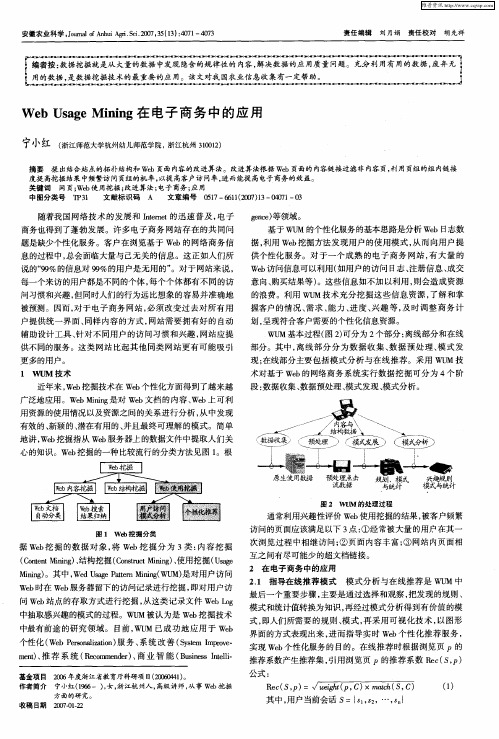
据 W b 掘 的数 据 对 象 , We 掘 分 为 3 : e挖 将 b挖 类 内容 挖 掘 (ot t i n)结构 挖掘 (osut in)使用 挖掘 ( s e Cn nMn g、 e i Cnr n g 、 tc M i Ua g
M n g 。其 中 , dUaePt r nn( M) ii ) n We s aenMi gWU 是对 用户访 问 g t i We 时在 We b b服务器 留下 的访 问记 录进 行挖掘 , 即对 用户访
每一个来访的用户都是不同的个体 , 每个个体都有不同的访
问习惯 和兴趣 , 同时人们 的行为远 比想象 的容 易并准 确地 但
被预测。因而, 对于电子商务网站 , 必须改变过去对所有用
户提 供统 一界 面 、 同样 内容 的方式 , 网站需要 拥 有好 的 自动 辅 助设计 工具 、 对不 同用 户 的访 问习惯 和兴趣 , 针 网站应 提 供不 同的服务 。这类 网站 比起 其 他 同类 网站 更有 可 能吸 引
…
…
)
…
】
We sg nn bU a eMiig在 电子 商 务 中 的应 用
宁小红 浙 师 大 杭 幼 师 学 , 江 州30) (江 范 学 州 儿 范 院 浙 杭 11 02
摘 要 提 出结合站点 的拓 扑结构 和 we b页面 内容的改进 算法。 改进 算法根据 We b页面的 内容链接过 滤非 内容页 , 用页组的组 内链接 利 度提 高挖 掘结 果中频繁访 问 页组 的机 率 , 以提 高客 户访 问率 , 进而 能提 高 电子 商务的效益 。 关键 词 网页 ; b 用挖 掘 ; We 使 改进 算法 ; 电子 商务 ; 应用 中图分 类号 T 3 P 1 文 献标识码 A 文章编号 01 — 612叩) — 47 — 3 57 61(o 1 001 0 3
Web Usage Mining在网络教学中的应用研究

系统 慢 慢 流失 , 而 网络 教 学便 会 最 终失 去 其 应有 的效应 。 从
现 有 的基 于 We b的网 络 教学 系统 仅 仅 注 重 内容 的罗 列 。 没
有把 站 点积 累 下来 的 大量 信 息 进 行 分 析 利 用 , 不 能解 决 个 体 并 化学 习 之需 求 , 以也 就 无法 对 学 习 者 实 施 个 性化 的完 善 的教 所
维普资讯
W b sg in 在网 e ae n g 络教学中的 U M i 应用研究
陶剑文 黄崇本
( 江 工 商 职 业 技 术 学 院 计 算 机 应 用 研 究 所 宁 波 3 5 1 ) 浙 10 2
*
摘 要 随 着 We b的爆炸式增长 , b 用挖掘技 术的研 究与应 用得到 了快速发展 。打追智能化 与个性化 的 网络教 We 使 学环境是 目前 网络教 学研 究的一 个热点 , 论述 了基 于 We 使 用挖 掘的 We b b个性化技 术在 网络教 学中的具体 应用。
学 服务 。
1 We nn bMiig介绍
部 分 主要 是 指模 式 分 析 与在 线推 荐 。具 体 来 说 , 用 W U 技 采 M
术 对基 于 We 的 网络 教 学 系统 实 行数 据 挖 掘 可 分 为 四个 阶 段 : b 数 据 收集 、 据 预 处理 、 式 发 现 、 式分 析 , 图 1所 示 。 数 模 模 如
圈 1 W UM 的 处 理 过 翟
2 1 数 据 收 集 数 据 收集 是 wuM 过 程 的 第 一 步 , 所 收 . 其 集 到 的数 据 质 量 将 直 接 影 响 后 续 过 程 的 成 败 。通 常 意 义 上 来 说 , 基 于 We 网络 教 学 中 可 利 用 的 w e 据 包 括 :. b 在 b的 b数 a we
关联规则 rule generation
关联规则rule generation【释义】rule generation规则生成:一种根据给定的规则和条件自动生成内容或结构的方法。
【短语】1fuzzy rule generation模糊规则的生成2Rule Generation Matrix生成矩阵3decision rule generation决策规则生成4rule generation algorithm规则生成算法5extraction rule generation抽取规则生成6Conditional rule generation条件规则产生7association rule generation关联规则挖掘8generation rule产生规则;计生成规则9gas generation rule燃气生成规律【例句】1In this paper,a method for run time rule generation is introduced.提出一种现场可调整的控制器规则生成方法。
2In this paper,a method for run time rule generation is introduced.本文提出了一种针对网络入侵检测事务流的实时动态规则生成方法。
3The news recommendation rule generation part is based on feature extraction part and it is the complement of the system.新闻推荐规则是建立在用户特征提取算法的基础之上实现的,是对本系统实现的补充和完善。
4In this paper,a novel real-time and dynamical rule generation method for network intrusion detection stream was proposed.本文提出了一种针对网络入侵检测事务流的实时动态规则生成方法。
交互式在线学习APP界面设计研究——以中国大学MOOC(慕课)为例

第34卷第3期 机电卢品开发与创新Vol.34,No.3 2021 年 5 月Development & Innovation of Machinery & Electrical Products May.,2021文章编号:1002-6673 (2021) 03-145-03交互式在线学习APP界面设计研究——以中国大学MOOC(慕课)为例阮晓敏!孙亚云(中国矿业大学建筑与设计学院,江苏徐州221116)摘要:伴随数字媒体技术的快速发展,针对“互联网+教育”理念下高校学生广泛使用交互式在线学习A P P的现状,文章以中国大学M O O C(慕课)学习平台为研究对象,立足当前教学实际着眼于A P P界面设计,分别从界面的布局、图形、色彩三个方面进行分析。
根据研究进行总结梳理,提出主要面向高校学生的 交互式在线学习A P P的界面设计原则,以期为相关设计实践提供参考。
关键词:交互式%在线学习%界面设计中图分类号:T P31 文献标识码:A d〇i:10.3969/j.issn.1002-6673.2021.03.050Research on the Interface Design of Interactive Online Learning Application-----A Case Study of MOOC Platform in ChinaR U A N X iao-M in,S U N Y a-Y u n# School of Architecture &Design,China University of Mining and Technology,Xuzhou Jiangsu 221116,China)Abstract:Along with the rapid development of di g i t a l media technology,interactive online learning apps are widely used by college students under the concept of n Internet+ education” .This paper takes the M O O C platform in China a s the research object and based on the actual teaching analysis interface layout,graphics,color three aspects.The interface design principle of interactive online learning A P P for college students i s proposed according to the research.In order to provide reference for related design practice.Keywords:Interface;Online learning;Interface design0引言伴随着大数据、移动互联、云计算等技术在各个领域 的不断成熟和普及,信息的传递由原先的单向传递向多 向互动传递发展,促使知识量增长、知识更新周期缩短,因而充分利用碎片化时间,灵活运用各种网络手段及技 术渠道即时获取知识便尤为重要。
名著读书笔记英语版

名著读书笔记英语版英语读书笔记篇一To Wang Lun is written by Li Bai who among other poets stands out in the halls of glory.One day, Li Bai goes on abroad. He is about to sail when there’s stamping and singing on shore.Oh! Here comes Wang Lun to see him off, who is Li Bai’s best friend. Li Bai is very excited to see his best friend at this leaving moment. But he is sa d, either. So he can’t say a simple sentence. He knows that words can’t express their friendship. Although the Peach Blossom Pool is one thousand feet deep, it can’t match Wang Lun’s love for him.英语原著读书笔记篇二Abstract The Old Man and the Sea tells the frustrated experience that the old fisherman fishes in the course. The theme is deep, andit is a song of praise of heroism.“But man is not made for defeat. A man can be destroyed but not defeated” has been the classic saying and the old man al so has been the most typical and the most representative of the Hemingway’s “tough guy”。
Research on personalized recommendation system in E-learning

Research on Personalized Recommendation System in E-Iearning
Rong Shan
Zhibin Ren
authoring learning materials and preparing tests or examinations than their classical counter parts. The necessity of mastering technology-intensive teaching tools and the lack of the tutor's computer literacy often make tutors reluctant to participate in online teaching activity. Based on the analysis of the aforementioned limitations existing current e Education systems, it is obvious that on one hand, we need to provide learner with more intelligent learning environment that supports various customized learning services as needed, on the other hand, we need innovative mechanism to all aviate tutor work load in terms of facilitating the development of learning contents and test/exam by hiding as much technique details as possible. Now days more and more educators believe that the above identified factors are a key to the future successful e-Education and thus naturally become the focus and motivation of this dissertation. Now there are some personalized recommendation system [2], but users are asked to fill out registration information or regularly gives certain products (such as PTV) [3] information to build its user interest model by some of it, or the server access logs been analyzed to understand user behavior and interests to achieve the final recommendation. The former relies heavily on the use of the system, and to some extent will affect the user's normal activities; the latter when the user interest changes, recommended effect declined. For the current recommendation system problems, the paper design a personalized recommendation system which based on the browsing behavior (Browsing Behavior Personalized Information Recommendation System,BBIRS). II.
VMware AirWatch移动设备管理说明书

D ATA S HE E TWORKSPACE ONE AIRWATCH SERVICE—GOLDAT A GLANCEThe Workspace ONE AirWatch Service—Gold provides basic assistance to Customers with limited knowledge of VMware AirWatch. This service familiarizes the customer with VMware Enterprise Mobility Management best practices pertaining to use cases and management of devices, email, content, and applications. The goal of this offering is to design and implement an infrastructure and configurations to support the customer’s current mobility initiatives.KEY BENEFITS• Accelerates time-to-deployment• Provides exposure toVMware AirWatch technologies• Encourages adoption of VMware recommended practices for theVMware AirWatch platform• Accelerates mobility strategy adoption and implementation• Provides a first step in partnering with VMware to focus on long term mobility solution delivery IntroductionThe Workspace ONE AirWatch- Gold Service provides guided implementation services to design, configure, and deploy the AirWatch solution. This service drives greater customer adoption of the AirWatch platform through structured delivery of Consulting Services. The Gold level of service provides implementation design, installation and configuration for one (1) UAT environment and one (1) production environment, and pilot and production deployment support. The VMware consultant will assist with solution design to aid in rapid adoption and optimize the time-to-value for the customer’s AirWatch solution. This service is the first step in partnering with customers to focus on long term solution delivery.1. Service OverviewVMware will provide implementation services connected with the purchase of your Workspace One Standard, Workspace One Advanced, or AirWatch License Bundle. Deployment will be conducted in either an AirWatch hosted environment or an AirWatch on-premise environment hosted in the customer’s data center(s). This project will be organized into three phases: 1) Assessment (Kick-Off), 2) Installation & Configuration, and 3) Deploy.The implementation scope includes:1.1. Highly-available production environment installation/configuration ofAirWatch console, device services, database services, API, and AWCM in the customer’s datacenter (applicable only for on-premise environment) 1.2. Highly-available production environment installation/configuration ofAirWatch Cloud Connector (ACC) (if necessary), Secure Email Gateway (SEG) (if necessary), and AirWatch Tunnel OR Mobile Access Gateway(MAG).1.3. Highly-available Disaster Recovery environment installation for AirWatchconsole (if necessary), device services (if necessary), database services (if necessary), ACC (if necessary), SEG (if necessary), and AirWatch Tunnel OR Mobile Access Gateway (MAG) (if necessary)1.4. For on-premise deployments, Test environment installation/configurationof AirWatch console, device services, database services, API, and AWCM in the customer’s datacenter (this is not a highly-available and disasterrecovery configuration)1.5. Test environment installation/configuration of AirWatch Cloud Connector(ACC) (if necessary), Secure Email Gateway (SEG) (if necessary), andAirWatch Tunnel OR Mobile Access Gateway (MAG) if necessary (non-HA, non-DR).1.6. AD/LDAP Integration1.7. Certificate/PKI Integration1.8. Secure email for managed devices via PowerShell integration, Secure Email Gateway (SEG), or Google Apps for Work1.9. AirWatch Browser for internal websites1.10. Content Locker integration with back-end file systems and Content Locker repository1.11. Advanced App Management, internal apps, App Config for Enterprise (ACE), and app wrapping (if necessary)1.12. User/administrator configuration1.13. Configuration of device and enterprise security policies1.14. VMware NSX Integration1.15. VMware Identity Manager Configuration (if required)1.16. Assistance with custom enrollment documentation1.17. Guided two-week pilot rollout (two-week period in which all use-cases are deployed to a subset of users for the purposesof testing EMM configuration prior to full roll-out)1.18. Roll-out support for a period of four (4) weeks after initial deployment of devices (four-week deployment of AirWatchEMM to the first wave of mobile end-users. The number of devices and/or end-users for a roll-out wave will be defined by Customer)2. Service Assumptions2.1. CUSTOMER RESOURCES: Should Customer request VMware to perform tasks that are dependent upon Customerresources or decisions, Customer will make such resource available or decisions final in a timely manner.2.2. HARDWARE PROCUREMENT: Procurement and installation of hardware is the responsibility of Customer. VMware willprovide recommendations and assistance.2.3. WORKSITE: The Consulting Services tasks may be performed on-site or remotely. An approximate travel schedule willbe mutually agreed.2.4. ON-SITE TRAVEL: In weeks where both parties have agreed that an on-site resource is prudent, travel for VMwareconsultants will occur on Mondays and Thursdays unless otherwise agreed. It is expected that consultants will travel to Customer’s facility on Monday morning, arriving on site as early on Monday as possible, as dictated by flight options and travel time. The consultants will work on-site through Thursday and will schedule return travel on Thursday evenings, as available. Travel expenses are not included in this Datasheet. Travel expenses will be quoted separately and agreed mutually between Customer and VMware.2.5. WORKING HOURS: Engagements that require consultants to work in excess of 40 hours per week, to work on weekendsor major national holidays and/or to travel outside of this schedule will be considered exceptions to this policy and will be reviewed and approved by VMware and Customer as required.2.6. EMM POLICY ALIGNMENT: Alignment of all EMM configurations and policy design with Customer’s requirements is theresponsibility of Customer. VMware will provide recommendations and assistance.2.7. PRE-REQUISITES: Pre-requisites must be completed for all installation components before any installation activities willbe performed. Should Customer not purchase the associated software for deployment, the services deliverable line items associated with those software components will not be delivered.2.8. PROJECT MANAGEMENT: VMware and the Customer’s project management will work closely together to ensure thatproject scope remains consistent and issues are resolved on a timely basis.2.9. DELIVERABLE LANGUAGE: All work, documentation and work product(s) will be provided in English.2.10. USE-CASE SCOPE: The scope of the use-cases will be considered locked upon completion of Deliverable 1.5 (SeeService Deliverables Table below), and will be delivered within a single production Deploy phase. Any alteration to the use-case scope thereafter may necessitate a change request.2.11. VMWARE IDENTITY MANAGER: If leveraging an Identity Manager Connector for third-party SAML integration, Customerwill provide a fully functional, cloud-based Identify Manager. VMware will integrate with a maximum of two approved third-party SAML endpoints for Identity Manager integrations. Approved endpoints are limited to those listed in the Identity Manager Cloud Application Catalog. Additional manually configured endpoints are outside the scope of this project. Customer-specific customization for the Identity Manager is out-of-scope of this Datasheet.2.12. THINAPP: VMWare ThinApp integration is out-of-scope of this Datasheet.2.13. X ENAPP: XenApp environment integration is out-of-scope of this Datasheet.3. ResponsibilitiesAll supplier and Customer responsibilities are listed in the Deliverables section. The ownership is defined as follows:3.1. Primary Owner = VMware: VMware is responsible for delivery of the component, with minimal assistance fromCustomer’s project team.3.2. Joint: VMware and Customer’s project team are jointly responsible for delivery of the component.3.3. Primary Owner = CUSTOMER: VMware is responsible for assisting Customer project team as needed to deliverthe component.4. Completion CriteriaThe project will be deemed complete or may require a PCR when any of the criteria below are met:4.1. Completion of all service deliverables included in the Deliverables section4.2. Consumption of three-hundred twenty (320) hours of Consulting Services; effort associated with this allocation of hoursshall only be allocated to tasks defined in Datasheet.4.3. Passage of twenty-eight (28) weeks after project kick-off (Deliverable 1.1)5. Deliverables6. PricingFor pricing, contact your local VMware Sales Representative. VMware SKU: CON-WS1-AW-GOLD7. Terms and ConditionsThis Datasheet is for informational purposes only. VMWARE MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DATASHEET. All VMware service engagements are governed by the VMware Professional Services General Terms and Conditions (see /files/pdf/services/tc.pdf). If you are located in the United States, the VMware contracting entity for the service will be VMware, Inc., and if outside the United States, the VMware contracting entity will be VMware International Limited.If you purchase this packaged service outside of the ELA, the service must be delivered and accepted within the first 12 months of the purchase, or the service will be forfeited.For More InformationFor more information about VMware products and services visit /services or contact your local VMware representative.About VMware Professional ServicesVMware Professional Services transform IT possibilities into business outcomes. Our comprehensive portfolio of services uncovers and exploits the unique opportunities made possible by VMware technology. Drawing on our unparalleled product expertise and customer experience, we collaborate with your team to address the technical, people, process and financial considerations for IT transformation to deliver results that are positive, tangible, and material to IT and your business.Appendix A: Gantt TimelineVMware, Inc. 3401 Hillview Avenue Palo Alto CA 94304 USA T el 877-486-9273 Fax 650-427-5001 。
python 在经济学中的应用

英文回答:Python is extensively utilized within the realm of economics for the purposes of data analysis, forecasting, and modeling. The language's inherent simplicity and user-friendly nature render it an optimal tool for economists necessitating manipulation of large datasets andplex statistical models. Leveraging packages such as Pandas, NumPy, and SciPy, economists can readily manipulate and analyze data, conduct regression analysis, and execute simulations. These capabilities are indispensable for theprehension of economic trends, formulation of policy rmendations, and assessment of the ramifications of diverse factors on the economy. In practical terms, Python can be instrumental in analyzing employment trends, discerning consumer spending patterns, and evaluating the impacts of governmental policies on economic growth. The language's adaptability additionally empowers economists to craft custom models and algorithms tailored to address specific research inquiries or policy challenges.Python在经济学领域被广泛用于数据分析,预测和建模目的。
python helium使用方法

python helium使用方法Helium is a Python library that provides a convenient way to automate web browsers. It enables developers to interact with web pages, perform actions like clicking buttons, filling out forms, and scraping data. In this article, we will explore the different features of Helium and walk through step-by-step instructions on how to use it.What is Helium?Helium is a web automation toolkit written in Python. It aims to simplify the process of interacting with web pages by abstracting the underlying complexities. It wraps the Selenium WebDriver, which is a popular automation tool, and provides a moreuser-friendly API.InstallationTo start using Helium, you first need to install it. You can install the library using pip, the Python package installer. Open your command prompt or terminal and run the following command:pip install heliumMake sure you have Python and pip installed on your system before executing the command.Helium BasicsOnce Helium is installed, you can import it into your Python script using the following line:from helium import *Launching a BrowserTo get started, you need to launch a web browser using Helium. Helium supports multiple browsers, including Chrome, Firefox, and Edge. To open a new instance of Chrome, you can use the`start_chrome()` method like this:start_chrome()By default, Helium will open a new browser window. You can also specify a URL to open in the browser upon launch:start_chrome("Interacting with Web PagesHelium provides several methods to interact with web pages. For example, to click on a button or a link, you can use the `click()` method and pass a text or an attribute value that uniquely identifies the element:click("Sign In") # Click on a button with the text "Sign In"click(S("#button-id")) # Click on a button with the attributeid="button-id"Similarly, to fill out a form input, you can use the `write()` method:write("john@example", into="Email") # Fill out an input with the attribute name="Email"Automating TasksHelium allows you to automate repetitive tasks on web pages. For example, if you need to fill out a form with multiple fields, you can use the `write()` method multiple times:write("John", into="First Name") # Fill out the First Name field write("Doe", into="Last Name") # Fill out the Last Name field write("john@example", into="Email") # Fill out the Email field click("Submit") # Click on the Submit buttonYou can also wait for certain elements to appear on the page using the `wait_until()` method:wait_until(Text("Welcome")) # Wait until an element with the text"Welcome" appearsData ExtractionHelium provides easy-to-use methods for extracting data from web pages. You can retrieve the text of an element using the `Text()` method:text = Text(S("#element-id")).valueprint(text) # Print the text of an element with the attributeid="element-id"You can also extract the values of form inputs using the `Value()` method:value = Value(S("#input-id")).valueprint(value) # Print the value of an input with the attributeid="input-id"Closing the BrowserOnce you have completed your automation tasks, you can close the browser using the `kill_browser()` method:kill_browser()ConclusionIn this article, we have explored the basics of using Helium, a Python library for web automation. We discussed how to install Helium, launch a browser, interact with web pages, automate tasks, extract data, and close the browser. Helium simplifies the process of web automation and provides a convenient API for developers to build powerful automation scripts. With Helium, you can easily automate repetitive tasks, scrape data from web pages, and perform various actions on web elements.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Interactive Web Usage Mining with the Navigation VisualizerEelco Herder Department of Computer Science University of Twente, P.O. Box 217 7500 AE Enschede, The Netherlands herder@cs.utwente.nlHarald WeinreichDepartment of Informatics University of Hamburg, Vogt-Kölln-Straße 30 D-22527 Hamburg, Germanyweinreich@informatik.uni-hamburg.deABSTRACTWeb usage mining, the analysis of user navigation paths through web sites, is a common technique for evaluating site designs or adaptive hypermedia techniques. However, often it is hard to relate aggregated clusters or measures to actual user navigation behavior. By contrast, basic graph-based visualizations of user navigation paths are easier to interpret, but it is difficult to find effective views that convey all the required information. In this paper we present the Navigation Visualizer, a web usage analysis tool that combines the two approaches. The Navigation Visualizer makes use of the rich data set that is collected by the Scone proxy-based web enhancement framework and facilitates dynamic selection of the data and interactive exploration with various layout mechanisms, color codings and markers. Several aggregated measures can be calculated and exported to statistical and data mining packages.Author KeywordsUser navigation, web sites, access tracking, interactive visualization, web usage miningACM Classification KeywordsH5.4. Hypertext/hypermedia: NavigationINTRODUCTIONThe data that can be collected from web usage logs is highly multidimensional, varying from basic statistics – such as the relative amount of back button usage – to more aggregate data, such as the linearity of user navigation paths and semantic similarity of documents to a query [7]. While it is possible to put these data into tables and to analyze the data with statistical software or data mining applications, there is often still the need for visual analysis to enable researchers to interpret the meaning of the available data [3]. Unfortunately, it is hard – if not impossible – to visualize a large number of dimensions of numerous items in a workable manner, as discernability and understandability decrease with the amount of data that is displayed [8]. Several approaches to reduce the amount of data, such as clustering, binding, filtering and hierarchization of documents or usage patterns, have been applied in various systems [2, 3]. However, the resulting abstract views are often too complex to interpret or to compare. By contrast, traditional graph visualization of the node-and-link structure [e.g. 13] is easy to understand, but badly scalable and it hardly allows visualizing additional metadata, such as page view times, back button usage, or page relevancy. Especially when evaluating various possible effects of adaptive hypermedia techniques or site redesigns, the interpretation of the recorded data has to be supported.In this paper we present a graph-based web usage visuali-zation tool – the Navigation Visualizer – that allows re-searchers to dynamically select and match the data to be shown and to interactively explore the visualization. Selection criteria for users, web sites and time slices are used to narrow down or to broaden the number of items; various color codings and markers are available to compare several dimensions side by side; zoom and pan tools [2] are used to explore larger graphs. The tool also offers means to display and export data in a tabular format to be further processed by statistical software.The remainder of this paper is structured as follows:. In the next section we present related work on graphical overviews, web usage mining and web usage visualization. Then we describe the design rationale, followed by an overview of the actual system. We continue with a discussion on the implementation: how data is captured, processed, modeled and represented. In particular, the advanced web logging functionality of the Scone framework is introduced. RELATED WORKGraph drawing is a common technique for information visualization and it has been subject of research since decades [2, 8]. Graphs are a natural means to model the structure of the web, with the pages represented by nodes and the links represented by edges. Many graph algorithms are used, in original or adapted form, to calculate and express properties of web sites and individual pages [1, 7]. Although to a lesser extent, graph theoretic methods have also been applied to the user navigation paths through web sites. Some interesting results include the observation that moreCopyright is held by the author/owner(s).CHI 2005, April 2–7, 2004, Portland, Oregon, USA. ACM 1-59593-002-7/05/0004.successful users navigate sites in a non-linear manner [10] and that the time spent on a web page is a good indicator of the user’s interest in the page [12]. In earlier research we found that more focused patterns of page revisits indicated that users knew about and were better able to use the site structure – and that these patterns can be captured in measures [6, 7].Several systems for visualizing user navigation have been developed, some of which are mentioned in [13], in which the WebQuilt visualization system is introduced. WebQuilt is interactive in the sense that it provides semantic zooming and filtering, given a storyboard. However, this is only useful for predefined, goal-directed tasks. Cockburn and McKenzie [4] mention various issues related to graphical representations of web browsers’ revisitation tools. Although these issues originally are raised from the end user’s point of view, they are valid for researchers examining user logs as well.In short, from the related work it can be observed that the data to inspect is manifold and that graphical representations provide limited views on the data. More interactive graphical representations are expected to perform better in providing researchers with means to find the matters that they are interested in.DESIGN RATIONALEThe idea of an interactive web usage visualization tool arose when we were looking for specific user navigation patterns that indicate users’ disorientation while carrying out tasks on various web sites [6]. After having calculated a large number of measures, we wanted to seewhat these measures reallymeant. Despite the availabilityof several web usagevisualization tools, no tool wasfound that allowed forvisualization and exploration ofthe various patterns in webnavigation.Visual analysis usually startswith getting the ‘big picture’,followed by gradually zoomingin to the interesting details [2].Concretely, this means that itshould be possible to define thedata set that one is interested inby selecting the users, the websites and time slices to bedisplayed. As mentionedbefore, comprehensibility isincreased by limiting thenumber of items to bedisplayed. As mentioned in the preceding section, navigation paths are commonly modeled as directed graphs [1]. These navigation graphs can be regarded as an overlay of the web site’s structure, consisting of the pages visited and the links followed. A tree layout [8], with pages ordered from top to bottom by its shortest distance from the start of any session and from left to right by its first occurrence turned out to provide the most stable and comprehensive layout.The navigation graph should be able to represent various dimensions of the data. Color coding is an obvious candidate for this purpose. As can be observed from the card game Set, it is quite hard to examine three continuous scales at once. Therefore, we opted for a combination of color codings and interactive markers for both nodes and edges. Finally, as it is sometimes easier to notice patterns and outliers by means of statistical analysis, the system should provide means to calculate relevant measures that can be exported to a statistical package or a data mining tool.SYSTEM OVERVIEWThis section provides an overview of the Navigation Visualizer, followed by an example of how the system is used for data analysis.FunctionalityFigure 1 displays the main screen of the Navigation Visualizer. The largest part of the window is occupied by the navigation graph itself. The upper right part offers various manipulation options:Figure 0: The main window of the Navigation Visualizer-powerful way to distinguish between dimensions such as user characteristics, page access statistics and textual similarity;- Marker options: Selection of markers that are used in addition to the color coding, to facilitate comparison between multiple dimensions;- Page identifier options: Neither the page title, url or thumbnail is sufficient for easily distinguishing between pages [4]. Therefore, we allow researchers to change between these options;- Graph layout options: By default, the spanning tree graph layout is used. Several alternatives to build the tree (e.g. depth-first or breadth-first) can be selected.Alternative graph layout mechanisms, such as force-directed layout [8], are available as well.The bottom right part provides details on a selected node. This is either a list of descriptive statistics or a preview of the page, which can be displayed in a separate window on request. A separate dialogue allows selection of relevant statistical information on user navigation paths and site characteristics. At the moment, primarily measures on navigation complexity, page view times and patterns of revisits [6, 7] are calculated. When required, other export options can be easily defined.Example AnalysisIn this subsection we illustrate the use of the Navigation Visualizer with an excerpt from a study on the effect of link annotation on user navigation patterns [6]. Thirty-two subjects were asked to carry out five everyday web tasks, such as planning a weekend trip to London. Half of the subjects were provided with previously defined navigation suggestions. We found significant differences in navigation complexity, use of the back button and home page visits – all measures were lower in the link annotation condition. This could mean that:- either the subjects were simply following the link sug-gestions, which would be a negative effect;- or the subjects were less prone to get stuck and conse-quently visited the home page – to start a new trial – toa lesser extent.Visual exploration of the navigation paths of subjects that scored very high or low on the measures suggested a pattern of random, unexpected visits to pages visited before – see figure 2 – which suggested that the latter was the case. This was confirmed by the results of the post-questionnaires. IMPLEMENTATIONIn this section we explain some implementation aspects of the Navigation Visualizer. In the first subsection we briefly describe the framework Scone that is used to capture the data. In the second subsection we describe the object-oriented graph model and its visualization.Capturing the Data with SconeFor successful web usage mining four datasets are required [3]: the contents of each page visited, the link structure between the pages, the web usage recordings and user characteristics, such as demographics and tasks.In order to avoid common problems associated with processing server logs [5] and to capture additional and more detailed data, we employed and extended Scone, our framework for rapid development of web enhancement and evaluation of web tools [14]. Scone is a Java-based frame-work for rapid development of web enhancement and evaluation of web tools. A core element of the framework is IBM’s intermediary WBI [9] that provides means to moni-Figure2. In the picture above the navigation path of a subject working on a task without link suggestions is displayed. The cycle in the right side part of the graph shows how the subject repeatedly arrives at a page visited before and finally gives up.In the picture on the left the navigation path of a subject working on the same task, but with link suggestions is displayed. After having solved one subtask (left side), she returns to the site’s home page for the next subtask.tor and manipulate any data transferred between web browser and server.Scone also offers an access tracking component that registers the most relevant user actions and records them in a database. This is achieved by adding JavaScript code that captures and submits many browser events, such as a click on a link, a form submission, and the opening and closing of browser windows.A robot component is available for exploring and analyzing web sites. The Navigation Visualizer utilizes the robot to gather pages that have not been visited yet, in order to build a web server’s link topology. In user-adaptive systems the robot can also function as a scout gathering information on the user’s behalf.The data that are collected by the user tracking component and the robot are mapped onto an object model called netObjects. It represents the pages and links relevant for a user session as well as the users’ attributes and their actions. Scone can also automatically store the objects of this model in a relational database in real time.Modeling and Visualizing Data with the Navigation VisualizerThe advantage of the object-oriented data model is that various restrictions on the users, page characteristics and time slices can be specified for building the navigation graph. The graph consists of the pages, which are repre-sented by the nodes, and the links, which are represented by the edges. The page characteristics and page access infor-mation are contained in the nodes, link traversal data in the edges.Each object in the navigation graph has its own visuali-zation object. The graph visualization object keeps track of the aspects that the researcher aims to visualize and instructs the node and edge visualizations to base their appearance on specific attributes in their model counter-parts. The strict separation of model and view facilitates extension of the visualization possibilities without having to change the model.The graph model provides various methods for calculating distances between nodes [1]. Overall graph characteristics that are relevant for navigation path analysis can be calcu-lated as well, among other things its diameter, fan degree, density, stratum and compactness [6].SUMMARYIn this paper we presented the Navigation Visualizer, a web usage analysis tool that combines the mathematical, high level approach of web usage mining with interactive graph-based visualizations. It facilitates tracing and understanding user actions, which would be harder to do with either one of the approaches. Furthermore, the Navigation Visualizer provides means for preprocessing complex user data for further analysis in statistical packages. ACKNOWLEDGMENTSThe first author’s work is carried out in the context of the PALS project, which is sponsored by the Dutch Innovative Research Program IOP-MMI.REFERENCES1. Baldi, P., Frasconi, P. and Smith, P. Modeling the Inter-net and the Web: Probabilistic Methods and Algorithms.Wiley, ISBN 0-470-84906-1, (2003).2. Chen, C. Information Visualisation and Virtual Environ-ments. Springer-Verlag, ISBN 1-85233-136-4, (1999).3. Chi, E.H. Improving Web Usability through Visuali-zation. IEEE Internet Computing 6 (2), (2002), 64-71. 4. Cockburn, A. and McKenzie, B. What Do Web UsersDo? An Empirical Analysis of Web Use. Intl. J. Human-Computer Studies 54 (6), (2000). 903-922.5. Cooley, R. The use of Web structure and content toidentify subjectively interesting Web usage patterns.ACM Trans. Internet Technology 3 (2), (2003), 93-116.6. Herder, E. and Juvina, I. Discovery of IndividualNavigation Styles. Proc. of Workshop on IndividualDifferences in Adaptive Hypermedia at AdaptiveHypermedia 2004 (2004).7. Herder,E. and Van Dijk, B. Site Structure and UserNavigation: Models, Measures and Methods. InAdaptable and Adaptive Hypermedia Systems, edited by S.Y. Chen and G.D. Magoulas, (2004), 19-34.8. Herman, I., Melançon, G. and Marshall, M.S. GraphVisualization and Navigation in Information Visuali-zation: a Survey. IEEE Trans. Visualization andComputer Graphics 6 (1), (2000), 24-43.9. Maglio, P. and Barrett, R. Intermediaries personalizeinformation streams. Communications of the ACM 43(8), (2000), 96-101.10. McEneaney, J.E. Visualizing and Assessing Navigationin Hypertext. Proc. Hypertext ’99, (1999), 61-70.11. Mukherjea, S. and Foley, J.D. Visualizing the World-Wide Web with the Navigational View Builder. Proc. 3rd Intl. WWW Conference on Technology, Tools andApplications (1995), 1075-1087.12. Shahabi, C., Zarkesh, A.M., Adibi, J. and Shah, V.Knowledge Discovery from Users Web-Page Navi-gation. Proc. 7th Intl. Workshop on Research Issues in Data Engineering RIDE '97 (1997), 20-29.13. Waterson, S.J., Hong, J.I., Sohn, T. and Landay, J.A.What Did They Do? Understanding Clickstreams withthe WebQuilt Visualization System. Proc. AdvancedVisual Interfaces (2002).14. Weinreich, H., Buchmann, V., Lamersdorf, W. Scone:Ein Framework zur evaluativen Realisierung vonErweiterungen des Webs. Proc. KiVS ´03, (2003), 31-42. Project website: http://www.scone.de/.。
