SRX办事处系列分支网关(精)
juniper瞻博网络公司简介

行业领导者瞻博网络[NASDAQ:JNPR]成立于1996年,总部位于美国加利福尼亚州桑尼维尔,目前在全球近50个国家和地区设有办事处。
自成立之初,公司就一直帮助客户不断超越网络用户和终端数量飞速增长所引发的需求,同时满足对高性能、可靠性和绝对安全性的业务要求。
凭借我们在架构、芯片设计方面的核心能力,以及拥有业界唯一的电信级专用“纯IP”模块化网络操作系统“JUNOS® 软件”,瞻博网络一直保持着行业领先地位。
瞻博网络提供广泛的产品组合,涵盖了路由、交换、安全、应用加速、身份识别策略和控制以及管理等方面,旨在为客户提供无与伦比的性能、更出色的选择和灵活性,同时帮助降低总体拥有成本。
在每个涉入领域,瞻博网络的市场份额均位居前三甲,同时,也创造了很多个第一:第一个基于ASIC的路由器平台;第一个基于ASIC的防火墙;第一个入侵检测与防护(IDP)产品,以及最全面且最具远见的SSL VPN 产品。
企业愿景瞻博网络基于“连接一切,人人有能 (connecting everything and empowering everyone)”的理念,从根本上采用有别于竞争对手的方法来构建网络,致力于提供解决最棘手、最复杂的网络问题的解决方案,以实现“连接一切”的承诺。
背景Pradeep Sindhu在Xerox PARC的计算机科学实验室工作的11年中注意到了互联网的爆炸式增长和其重要性。
Sindhu也发现路由器的巨大潜力。
就这样,瞻博网络于1996年2月6日在加利福尼亚州成立了。
与很多新创立的公司不同,瞻博网络并没有从简单的问题着手,而是一开始就确定了它的标志性行事作风:应对最棘手的问题立即解决。
公司的首款产品,创新型M40路由器于1998年9月发售。
M40远远超越了市场上的所有其它路由产品,确立了瞻博网络在硬件市场上的创新型厂商的重要地位。
在开发M40的期间,瞻博网络开发了JUNOS软件。
该软件后来成为公司的主要优势,并为未来的一切创新奠定了强大的基础。
推荐-JuniperSRX系列新一代业务网关 精品

10+ 年研发, TL-9000 认证
kernel
JUNOS
J2300/ J4350/ J6350
M7i M10i MX960 M20 M40e M120 M320 T320 T640
集成的业界最好的解决方案
满足服务提供商需求的性能以及可靠性,还有企业的安全特性 在单一的OS中,提供简化的操作,可靠的/性能以及增强的功能
▪ 2008年9月发布 ▪ 革命性的架构 ▪ 集成的服务 ▪ 可伸缩的性能 ▪ 简化的操作 ▪ 世界上最高速的安全解决方案 ▪ ScreenOS的历史,在 JUNOS
里面延续
基于动态服务的架构,加速了新服务的部署
SRX5000 世界最快的安全解决方案
世界最大容量的防火墙 集成式的服务 可扩展的性能 简化的操作 以JUNOS和Juniper动态服务架 构(DSA)驱动
RE
服务
FW/VPN/IDP NAT/路由
Fabric Fabric
出流包
输入输出卡
QoS/Shaping
服务处理卡
Juniper 完整的中低端UTM产品系列
SRX 650 防火墙性能(最大) 7 Gbps IPS性能 900 Mbps VPN性能 1.5 Gbps 最大的并发会话数 512 k
电信级路由操作系统JUNOS和安全操作系统 ScreenOS的完美融合
▪ 来自JUNOS的MPLS/NSF/NSR等高级 功能
▪ 来自JUNOS的层次化CLI配置风格 ▪ 来自ScreenOS的安全特性: 安全域
/NAT/IPsec VPN/Screen/深度检测 /UTM ▪ Commit/JUNOS Scripts等高级管理特 性
Juniper SRX

DATASHEETProduct DescriptionThe Juniper Networks ® SRX Series Services Gateways for the branch joins Juniper Networks SRX Series for the data center, EX Series Ethernet Switches, M Series Multiservice Edge Routers, MX Series 3D Universal Edge Routers, and T Series Core Routers. This provides a single Juniper Networks Junos ® operating system-based portfolio of unprecedented scale. With Junos OS, enterprises and service providers can lower deployment and operational costs across their entire distributed workforce.• SRX Series for the branch runs Junos OS, the proven operating system that is used by core Internet routers in all of the top 100 service providers around the world. The rigorously tested carrier-class routing features of IPv4/IPv6, OSPF, BGP, and multicast have been proven in over 15 years of worldwide deployments.• SRX Series for the branch provides perimeter security, content security, access control, and network-wide threat visibility and control. Using zones and policies, network administrators can configure and deploy branch SRX Series gateways quickly and securely. The SRX Series also includes wizards for firewall, IPsec VPN, NAT, and initial setup to simplify configurations out of the box.• Policy-based VPNs support more complex security architectures that require dynamic addressing and split tunneling. For content security, SRX Series for the branch offers a complete suite of Unified Threat Management (UTM) services consisting of: intrusion prevention system (IPS), on-box and cloud-based antivirus, antispam, Web filtering, and data loss prevention to protect your network from the latest content-borne threats. Select SRX Series models feature Content Security Accelerator for high-performance IPS and antivirus scanning. The branch SRX Series integrates with other Juniper security products to deliver enterprise-wide unified access control (UAC) and adaptive threat management. These capabilities give security professionals powerful tools in the fight against cybercrime and data loss.• SRX Series for the branch are secure routers that bring high performance and proven deployment capabilities to enterprises that need to build a worldwide network of thousands of sites. The wide variety of options allow configuration of performance, functionality, and price scaled to support from a handful to thousands of users. Ethernet, serial, T1/E1, DS3/E3, xDSL, DOCSIS3, Wi-Fi, and 3G/4G/LTE wireless are all available options for WAN or Internet connectivity to securely link your sites. Multiple form factors allow you to make cost-effective choices for mission-critical deployments. Managing the network is easy using the proven Junos OS command-line interface (CLI), scripting capabilities, a simple-to-use Web-based GUI, or Network and Security Manager (NSM) for large scale deployments.Product OverviewJuniper Networks SRX Series Services Gateways for the branch are secure routers that provide essential capabilities that connect, secure, and manage workforce locations sized from handfuls to hundreds of users. By consolidating fast, highly available switching, routing, security, and applications capabilities in a single device, enterprises can economically deliver new services, safe connectivity, and a satisfying end user experience. All SRX Series Services Gateways, including products scaled for the branch, campus, and data center applications, are powered by Juniper Networks Junos OS—the proven operating system that provides unmatched consistency, better performance with services, and superior infrastructure protection at a lower total cost of ownership.SRX SERIES SERVICES GATEWAYS FOR THE BRANCHSRX100, SRX210, SRX220, SRX240 AND SRX650Architecture and Key ComponentsKey Hardware Features of the Branch SRX Series Productsnetwork DeploymentsThe SRX Series Services Gateways for the branch are deployed at remote and branch locations in the network to provide all-in-one secure WAN connectivity, IP telephony, and connection to local PCs and servers via integrated Ethernet switching.Features and Benefitssecure routingShould you use a router and a firewall to secure your network? By building the branch SRX Series with best-in-class routing, switching and firewall capabilities in one product, enterprises don’t have to make that choice. Why forward traffic if it’s not legitimate?SRX Series for the branch checks the traffic to see if it is legitimate and permitted, and only forwards it on when it is. This reduces the load on the network, allocates bandwidth for all other mission-critical applications, and secures the network from malicious users.The main purpose of a secure router is to provide firewall protection and apply policies. The firewall (zone) functionality inspects traffic flows and state to ensure that originating and returning information in a session is expected and permitted fora particular zone. The security policy determines if the sessioncan originate in one zone and traverse to another zone. This architectural choice receives packets from a wide variety of clients and servers and keeps track of every session, of every application, and of every user. It allows the enterprise to make sure that only legitimate traffic is on its network and that traffic is flowing in the expected direction.Figure 1: Firewalls, zones, and policiesFigure 2: High availabilityTo ease the configuration of a firewall, SRX Series for the branch uses two features—“zones” and “policies.” While these can be user-defined, the default shipping configuration contains, at a minimum, a “trust” and “untrust” zone. The trust zone is used for configuration and attaching the internal LAN to the branch SRX Series. The untrust zone is commonly used for the WAN or untrusted Internet interface. To simplify installation and make configuration easier, a default policy is in place that allows traffic originating from the trust zone to flow to the untrust zone. This policy blocks all traffic originating from the untrust zone to the trust zone. A traditional router forwards all traffic without regard to a firewall (session awareness) or policy (origination and destination of a session).By using the Web interface or CLI, enterprises can create a series of security policies that will control the traffic from within and in between zones by defining policies. At the broadest level, all types of traffic can be allowed from any source in security zones to any destination in all other zones without any scheduling restrictions. At the narrowest level, policies can be created that allow only one kind of traffic between a specified host in one zone and another specified host in another zone during a scheduled time period.High AvailabilityJunos OS Services Redundancy Protocol (JSRP) is a core feature of the SRX Series for the branch. JSRP enables a pair of SRX Series systems to be easily integrated into a high availability network architecture, with redundant physical connections between the systems and the adjacent network switches. With link redundancy, Juniper Networks can address many common causes of system failures, such as a physical port going bad or a cable getting disconnected, to ensure that a connection is available without having to fail over the entire system. This is consistent with a typical active/standby nature of routing resiliency protocols.When SRX Series Services Gateways for the branch areconfigured as an active/active HA pair, traffic and configuration is mirrored automatically to provide active firewall and VPN session maintenance in case of a failure. The branch SRX Series synchronizes both configuration and runtime information. As a result, during failover, synchronization of the following information is shared: connection/session state and flow information, IPSec security associations, Network Address Translation (NAT) traffic, address book information, configuration changes, and more. InHigh AvailabilityActive /StandbyActiveActive /StandbyActive /ActiveActiveActive /Activecontrast to the typical router active/standby resiliency protocols such as Virtual Router Redundancy Protocol (VRRP), all dynamic flow and session information is lost and must be reestablished in the event of a failover. Some or all network sessions will have to restart depending on the convergence time of the links or nodes. By maintaining state, not only is the session preserved, but security is kept intact. In an unstable network, this active/active configuration also mitigates link flapping affecting session performance.session-Based Forwarding Without the Performance Hit In order to optimize the throughput and latency of the combined router and firewall, Junos OS implements session-based forwarding, an innovation that combines the session state information of a traditional firewall and the next-hop forwarding of a classic router into a single operation. With Junos OS, a session that is permitted by the forwarding policy is added tothe forwarding table along with a pointer to the next-hop route. Established sessions have a single table lookup to verify that the session has been permitted and to find the next hop. This efficient algorithm improves throughput and lowers latency for session traffic when compared with a classic router that performs multiple table lookups to verify session information and then to find a next-hop route. Figure 3 shows the session-based forwarding algorithm. When a new session is established, the session-based architecture within Junos OS verifies that the session is allowed by the forwarding policies. If the session is allowed, Junos OS will look up the next-hop route in the routing table. It then inserts the session and the next-hop route into the session and forwarding table and forwards the packet. Subsequent packets for the established session require a single table lookup in the session and forwarding table, and are forwarded to the egress interface.Figure 3: Session-based forwarding algorithmPolicy: DroppedFigure 4: The distributed enterprisesrX100srX220 srX240specificationsProtocols• IPv4, IPv6, ISO Connectionless Network Service (CLNS) routing and Multicast• Static routes• RIPv2 +v1• OSPF/OSPFv3• BGP• BGP Router Reflector3• IS-IS• Multicast (Internet Group Management Protocol (IGMPv1/2/3), PIM-SM/DM, Session Description Protocol (SDP), DistanceVector Multicast Routing Protocol (DVMRP), source-specific), MSDP• MPLS (RSVP, LDP)5iP Address Management• Static• Dynamic Host Configuration Protocol (DHCP)(client and server)• DHCP relayencapsulations• Ethernet (MAC and VLAN tagged)• Point-to-Point Protocol (PPP) (synchronous)– Multilink Point-to-Point Protocol (MLPPP)• Frame Relay– Multilink Frame Relay (MLFR) (FRF.15, FRF.16), FRF.12, LFI • High-Level Data Link Control (HDLC)• Serial (RS-232, RS-449, X.21, V.35, EIA-530)• 802.1q VLAN support• Point-to-Point Protocol over Ethernet (PPPoE)switching• 802.1D, RSTP, MSTP, 802.3adtraffic Management• 802.1p, DSCP, EXP• Marking, policing, and shaping• Class-based queuing with prioritization• Weighted random early detection (WRED)• Queuing based on VLAN, data-link connection identifier (DLCI), interface, bundles, or multi-field (MF) filterssecurity• Firewall, zones, screens, policies• Stateful firewall, stateless filters• Screens denial of service (DoS) and provides distributed denial of service (DDoS) protection (anomaly-based)• Prevent replay attack; Anti-Replay• Unified Access Control• UTM1 (SRX220, SRX650 and high memory versions of SRX240, SRX210, and SRX100 only)– Antivirus1, antispam1, Web filtering1, IPS1– C ontent Security Accelerator in SRX210 high memory, SRX220 high memory, SRX240 high memory, and SRX6501– E xpressAV option in SRX210 high memory, SRX220 highmemory, SRX240 high memory, and SRX6501– Content filteringVPn• Tunnels (GRE, IP-IP, IPsec)• IPsec, Data Encryption Standard (DES) (56-bit), triple Data Encryption Standard (3DES) (168-bit), Advanced Encryption Standard (AES) (128-bit+) encryption• Message Digest 5 (MD5),SHA-1 , SHA-128, SHA-256 authentication• Access Manager: Dynamic VPN Client. Browser-based remote access feature requiring a license.Multimedia transport• Compressed Real-Time Transport Protocol (CRTP)High Availability• VRRP• JSRP• Stateful failover and dual box clustering• SRX650:– Redundant power (optional)– GPIM hot swap on SRX650– Future internal failover and SRE hot swap (OIR)• Backup link via 3G wireless or other WANiPv65• OSPFv3• RIPng• IPv6 Multicast Listener Discovery (MLD)• BGP• ISISWireless• CX111 Cellular 3G/4G/LTE Broadband Data Bridge supported on all branch SRX Series devices• 3G ExpressCards supported on SRX210 with built-in ExpressCard slot• AX411 Wireless LAN (Wi-Fi 802.11 a/b/g/n) Access Point supported on all6 branch SRX Series devices• WLA Series Wireless LAN Access Points and WLC Series Wireless LAN Controllers are supported on branch SRX Series devicessrX650srX210sLA, Measurement, and Monitoring• Real-time performance monitoring (RPM)• Sessions, packets, and bandwidth usage• Juniper J-Flow monitoring and accounting servicesLogging• Syslog• Traceroute• Extensive control- and data-plane structured and unstructured syslogAdministration• Juniper Networks Network and Security Manager support (NSM)• Juniper Networks STRM Series Security Threat Response Managers support• Juniper Networks Advanced Insight Solutions support• External administrator database (RADIUS, LDAP, SecureID)• Auto-configuration • Configuration rollback• Rescue configuration with button • Commit confirm for changes • Auto-record for diagnostics • Junos OS upgrade with button • Software upgrades• Juniper J-Web, USB, HTTP, FTP, SSHCertifications• Common Criteria (CC) EAL3• FIPS-140 Level 2• Supported hardware versions of the FIPS 140-2•Gateways: SRX100B, SRX210B, SRX240B and SRX650-BASE-SRE6-645AP with JNPR-FIPS-TAMPER-LBLS -Roles, Services, and Authentication: Level 3 -EMI/EMC: Level 3-Design Assurance: Level 3-FIPS-approved algorithms: Triple-DES; AES; DSA; SHS; -RNG; RSA; HMAC• NEBS Compliance for SRX240, SRX650• Department of Defense (DoD) Certification for SRX Series Services Gateways, including testing and certification by the Department of Defense Joint Interoperability Test Command (JITC) for interoperability with DoD networks and addition of the SRX Series Services Gateways to the Unified Capabilities Approved Product List (UC APL)• DOCSIS3 mini-PIM certification by CableLabsJunos OS version testedJunos OS 10.4Junos OS 11.1Junos OS 10.4Junos OS 10.4Junos OS 10.4specifications (continued)BGP instances51016206410*There are several models available for the SRX210. Please contact your Juniper or partner account representative for more information.1. Unified Threat Management—antivirus, antispam, Web filtering, and IPS require a subscription license and the high memory system option to use the feature. UTM is not supported on the low memory version. Please see the ordering section for options. Content Filtering and UAC are part of the base software with no additional license.2. SRX100B installed with 1 GB DRAM, with 512 MB accessible. Optional upgrade to 1 GB DRAM is available with purchase of memory software license key.3. BGP Route Reflector supported on SRX650. See ordering section for more information.4. 3G USB modem support planned for availability Q4 2011.5. Supported in packet mode with services.6. SRX100 supports AX411 in 2H 2011.7. When UTM is enabled capacities supported are low memory specifications, on high memory system options.8. When UTM is enabled concurrent sessions supported is 50% 0f value shown. 9. SRX650 supports a single Services and Routing Engine (SRE).10. SRX210H-POE is Class A.Juniper networks services and supportJuniper Networks is the leader in performance-enabling services that are designed to accelerate, extend, and optimize your high-performance network. Our services allow you to maximize operational efficiency while reducing costs and minimizing risk, achieving a faster time to value for your network. Juniper Networks ensures operational excellence by optimizing the network to maintain required levels of performance, reliability, and availability. For more details, please visit /us/en/products-services.Ordering informationSRX650-BASE-SRE6-645APSRX650 Services Gateway with 1 ServicesRouting Engine (SRE), 4 x 10/100/1000BASE-T ports, 2 GB DRAM, 2 GB CF, fan tray, 645 W AC PoE power supply unit for SRX650. Provides 397 W system power @ 12 V and 247 W PoE power @ 50 VDC. Works with 90-250 VAC input. Includes power cord and rack mount kit.srX650 interface ModulesProduct Comparison (continued)SRX650-K-AV One year subscription for Juniper-KasperskyAbout Juniper networksJuniper Networks is in the business of network innovation. From devices to data centers, from consumers to cloud providers, Juniper Networks delivers the software, silicon and systems that transform the experience and economics of networking. The company serves customers and partners worldwide. Additional information can be found at .1000281-013-EN Aug 2011Copyright 2011 Juniper Networks, Inc. All rights reserved. Juniper Networks, the Juniper Networks logo, Junos, NetScreen, and ScreenOS are registered trademarks of Juniper Networks, Inc. in the United States and other countries. All other trademarks, service marks, registered marks, or registered service marks are the property of their respective owners. Juniper Networks assumes no responsibility for any inaccuracies in this document. Juniper Networks reserves the right to change, modify, transfer, or otherwise revise this publication without notice.eMeA Headquarters Juniper Networks Ireland Airside Business ParkSwords, County Dublin, Ireland Phone: 35.31.8903.600 EMEA Sales: 00800.4586.4737 Fax: 35.31.8903.601APAC HeadquartersJuniper Networks (Hong Kong) 26/F, Cityplaza One 1111 King’s RoadTaikoo Shing, Hong Kong Phone: 852.2332.3636 Fax: 852.2574.7803Corporate and sales Headquarters Juniper Networks, Inc. 1194 North Mathilda Avenue Sunnyvale, CA 94089 USAPhone: 888.JUNIPER (888.586.4737) or 408.745.2000 Fax: 408.745.2100 Printed on recycled paperTo purchase Juniper Networks solutions, please contact your Juniper Networks representative at 1-866-298-6428 or authorized reseller.。
Juniper Networks SRX4100 和 SRX4200 服务网关数据表说明书

Data SheetTable 1. SRX4100 and SRX4200 Statistics¹The SRX4100 and SRX4200 recognize more than 4,275 applications and nested applications in plain-text or SSL-encrypted transactions. The firewalls also integrate with Microsoft Active Directory and combine user information with application data to provide network-wide application and user visibility and control.Features and BenefitsTable 2. SRX4100 and SRX4200 Features and BenefitsSRX4100 and SRX4200 Services Gateways Specifications Software SpecificationsFirewall Services•Stateful and stateless firewall•Zone-based firewall•Screens and distributed denial of service (DDoS) protection •Protection from protocol and traffic anomalies•Unified Access Control (UAC)Network Address Translation (NAT)•Source NAT with Port Address T ranslation (PAT)•Bidirectional 1:1 static NAT•Destination NAT with PAT•Persistent NAT•IPv6 address translationVPN Features•Tunnels: Site-to-site, hub and spoke, dynamic endpoint,AutoVPN, ADVPN, Group VPN (IPv4/ IPv6/Dual Stack)•Juniper Secure Connect: Remote access/SSL VPN •Configuration payload: Yes•IKE Encryption algorithms: Prime, DES-CBC, 3DES-CBC, AEC-CBC, AES-GCM, Suite B•IKE authentication algorithms: MD5, SHA-1, SHA-128,SHA-256, SHA-384•Authentication: Pre-shared key and public key infrastructure(PKI) (X.509)•IPsec (Internet Protocol Security): Authentication Header(AH) / Encapsulating Security Payload (ESP) protocol •IPsec Authentication Algorithms: hmac-md5, hmac-sha-196,hmac-sha-256•IPsec Encryption Algorithms: Prime, DES-CBC, 3DES-CBC,AEC-CBC, AES-GCM, Suite B•Perfect forward secrecy, anti-reply•Internet Key Exchange: IKEv1, IKEv2•Monitoring: Standard-based dead peer detection (DPD)support, VPN monitoring•VPNs GRE, IP-in-IP, and MPLS High Availability Features•Virtual Router Redundancy Protocol (VRRP) – IPv4 and IPv6•Stateful high availability:-Dual box clustering-Active/passive-Active/active-Configuration synchronization-Firewall session synchronization-Device/link detection-In-Service Software Upgrade (ISSU)•IP monitoring with route and interface failoverApplication Security Services3•Application visibility and control•Application-based firewall•Application QoS•Advanced/application policy-based routing (APBR)•Application Quality of Experience (AppQoE)•Application-based multipath routing•User-based firewallThreat Defense and Intelligence Services3•Intrusion prevention system•Antivirus•Antispam•Category/reputation-based URL filtering•SSL proxy/inspection•Protection from botnets (command and control)•Adaptive enforcement based on GeoIP•Juniper Advanced Threat Prevention, a cloud-based SaaSoffering, to detect and block zero-day attacks•Adaptive Threat Profiling•Encrypted T raffic Insights•SecIntel to provide threat intelligence•Juniper ATP Appliance, a distributed, on-premises advancedthreat prevention solution to detect and block zero-day attacks Offered as advanced security subscription license.Routing Protocols•IPv4, IPv6, static routes, RIP v1/v2•OSPF/OSPF v3•BGP with route reflector•IS-IS•Multicast: Internet Group Management Protocol (IGMP) v1/v2;Protocol Independent Multicast (PIM) sparse mode (SM)/source-specific multicast (SSM); Session Description Protocol(SDP); Distance Vector Multicast Routing Protocol (DVMRP);Multicast Source Discovery Protocol (MSDP); reverse pathforwarding (RPF)•Encapsulation: VLAN, Point-to-Point Protocol over Ethernet(PPPoE)•Virtual routers•Policy-based routing, source-based routing•Equal-cost multipath (ECMP)QoS Features•Support for 802.1p, DiffServ code point (DSCP), EXP •Classification based on VLAN, data-link connection identifier(DLCI), interface, bundles, or multifield filters•Marking, policing, and shaping•Classification and scheduling•Weighted random early detection (WRED)•Guaranteed and maximum bandwidth•Ingress traffic policing•Virtual channels Network Services•Dynamic Host Configuration Protocol (DHCP) client/server/relay•Domain Name System (DNS) proxy, dynamic DNS (DDNS)•Juniper real-time performance monitoring (RPM) and IPmonitoring•Juniper flow monitoring (J-Flow)Advanced Routing Services•Packet Mode•MPLS (RSVP, LDP)•Circuit cross-connect (CCC), translational cross-connect (TCC)•L2/L2 MPLS VPN, pseudo-wires•Virtual private LAN service (VPLS), next-generation multicast VPN (NG-MVPN)•MPLS traffic engineering and MPLS fast re-routeManagement, Automation, Logging, and Reporting•SSH, T elnet, SNMP•Smart image download•Juniper CLI and Web UI•Juniper Networks Junos Space Security Director•Python•Junos events, commit and OP scripts•Application and bandwidth usage reporting•Debug and troubleshooting toolsHardware SpecificationsTable 3. SRX4100 and SRX4200 Hardware SpecificationsJuniper Networks Services and SupportJuniper Networks is the leader in performance-enabling services designed to accelerate, extend, and optimize your high-performance network. Our services allow you to maximize operational efficiency while reducing costs and minimizing risk, achieving a faster time to value. Juniper Networks ensures operational excellence by optimizing the network to maintain required levels of performance, reliability, and availability. For more details, please visit https:///us/en/products.html.Ordering InformationT o order Juniper Networks SRX Series Services Gateways, and to access software licensing information, please visit the How to Buy page at https:///us/en/how-to-buy/form.html.Base System AccessoriesSRX4100 Performance Upgrade License Advanced Security Services Subscription LicensesRemote Access/Juniper Secure Connect VPN LicensesAbout Juniper NetworksAt Juniper Networks, we are dedicated to dramatically simplifyingnetwork operations and driving superior experiences for end users.Our solutions deliver industry-leading insight, automation, securityand AI to drive real business results. We believe that poweringconnections will bring us closer together while empowering us all tosolve the world’s greatest challenges of well-being, sustainabilityand equality.Corporate and Sales HeadquartersJuniper Networks, Inc.1133 Innovation WaySunnyvale, CA 94089 USAPhone: 888.JUNIPER (888.586.4737)or +1.408.745.2000APAC and EMEA HeadquartersJuniper Networks International B.V.Boeing Avenue 240 1119 PZ Schiphol-RijkAmsterdam, The NetherlandsPhone: +31.207.125.700Copyright 2022 Juniper Networks, Inc. All rights reserved. Juniper Networks, the Juniper Networks logo, Juniper, and Junos are registered trademarks of Juniper Networks, Inc. in the United States and other countries. All other trademarks, service marks, registered marks, or registered service marks are the property of their respective owners. Juniper Networks assumes no。
JuniperSRX中文配置手册及图解

前言、版本说明 (2)一、界面菜单管理 (4)2、WEB管理界面 (4)(1)Web管理界面需要浏览器支持Flash控件。
(4)(2)输入用户名密码登陆: (4)(3)仪表盘首页 (5)3、菜单目录 (7)二、接口配置 (12)1、接口静态IP (12)2、PPPoE (13)3、DHCP (14)三、路由配置 (16)1、静态路由 (16)2、动态路由 (16)四、区域设置Zone (18)五、策略配置 (20)1、策略元素定义 (20)2、防火墙策略配置 (22)3、安全防护策略 (25)六、地址转换 (26)1、源地址转换-建立地址池 (26)2、源地址转换规则设置 (27)七、VPN配置 (30)1、建立第一阶段加密建议IKE Proposal (Phase 1) (或者用默认提议) (30)2、建立第一阶段IKE策略 (31)3、建立第一阶段IKE Gateway (32)4、建立第二阶段加密提议IKE Proposal (Phase 2) (或者用默认提议) (33)5、建立第一阶段IKE策略 (34)6、建立VPN策略 (35)八、Screen防攻击 (38)九、双机 (39)十、故障诊断 (39)前言、版本说明产品:Juniper SRX240 SH版本:JUNOS Software Release [9.6R1.13]注:测试推荐使用此版本。
此版本对浏览速度、保存速度提高了一些,并且CPU占用率明显下降很多。
9.5R2.7版本(CPU持续保持在60%以上,甚至90%)9.6R1.13版本(对菜单操作或者保存配置时,仍会提升一部分CPU)一、界面菜单管理1、管理方式JuniperSRX系列防火墙出厂默认状态下,登陆用户名为root密码为空,所有接口都已开启Web管理,但无接口地址。
终端连接防火墙后,输入用户名(root)、密码(空),显示如下:root@srx240-1%输入cli命令进入JUNOS访问模式:root@srx240-1% cliroot@srx240-1>输入configure进入JUNOS配置模式:root@srx240-1% cliroot@srx240-1> configureEntering configuration mode[edit]root@srx240-1#防火墙至少要进行以下配置才可以正常使用:(1)设置root密码(否则无法保存配置)(2)开启ssh/telnet/http服务(3)添加用户(root权限不能作为远程telnet帐户,可以使用SHH方式)(4)分配新的用户权限2、WEB管理界面(1)Web管理界面需要浏览器支持Flash控件。
SRX100服务网关快速入门-JuniperNetworks

注意: 接通电源后,必须等待色常亮,再执行下一部分。
第 2 部分:连接管理设备
使用以下任一方法将管理设备连接到服务网关:
按照第 2 页中的图示,将 RJ-45 电缆 (以太网电缆)从前面板上 fe-0/0/1 至 fe-0/0/7 端口中的任何一个连接到管理设备 (工作站或便携式计算机)上的以太网端口。我们 建议使用这种连接方法。如果您使用此方法进行连接,请继续第 3 部分。 将 RJ-45 电缆(以太网电缆)从标有 CONSOLE 的端口连接到提供的 DB-9 适配器, 然后将其连接到管理设备上的串行端口。 (串行端口设置:9600 8-N-1。 ) 如果使用此方法进行连接,请继续执行 Branch SRX Series Services Gateways Golden Configurations 中提供的 CLI 配置说明,该文档的网址为 /us/en/local/pdf/app-notes/3500153-en.pdf。
第 6 部分:访问 J-Web 界面
1. 2. 3. 4. 在管理设备上启动 Web 浏览器。 在 URL 地址字段中输入 http://192.168.1.1。将显示 J-Web 登录页面。 指定缺省用户名为 root。不要在 Password 字段中输入任何值。 单击 Log In。将显示 J-Web Initial Setup 页面。
SRX100 服务网关型号
提供以下两种型号的 SRX100 服务网关:
SRX100 服务网关前面板
设备
SRX100B SRX100H
DDR 内存
512 MB 1 GB
连接和配置 SRX100 服务网关
J-SRX100
按照下面的说明连接和设置 SRX100 服务网关以保护网络。参照设备前面板上的 LED 来 帮助您确定设备的状态。
Juniper Networks SRX5400、SRX5600和SRX5800服务网关产品说明说明

The SRX5400, SRX5600, and SRX5800 are supported by Juniper Networks Junos®Space Security Director, which enables distributed security policy management through an intuitive, centralized interface that enables enforcement across emerging and traditional risk vectors. Using intuitive dashboards and reporting features, administrators gain insight into threats, compromised devices, risky applications, and more.Based on Juniper’s Dynamic Services Architecture, the SRX5000 line provides unrivaled scalability and performance. Each services gateway can support near linear scalability with the addition of Services Processing Cards (SPCs) and I/O cards (IOCs), enabling a fully equipped SRX5800 to support up to 1.2 Tbps firewall throughput. The SPCs are designed to support a wide range of services, enabling future support of new capabilities without the need for service-specific hardware. Using SPCs on all services ensures that there are no idle resources based on specific services being used—maximizing hardware utilization.The scalability and flexibility of the SRX5000 line is supported by equally robust interfaces. The SRX5000 line employs a modular approach, where each platform can be equipped with a flexible number of IOCs that offer a wide range of connectivity options, including 1GbE, 10GbE, 40GbE, and 100GbE interfaces. With the IOCs sharing the same interface slot as the SPCs, the gateway can be configured as needed to support the ideal balance of processing and I/O. Hence, each deployment of the SRX Series can be tailored to specific network requirements. The scalability of both SPCs and IOCs in the SRX5000 line is enabled by the custom-designed switch fabric. Supporting up to 960 Gbps of data transfer, the fabric enables realizationof maximum processing and I/O capability available in any particular configuration. This level of scalability and flexibility enables future expansion and growth of the network infrastructure, providing unrivaled investment protection.The tight service integration on the SRX Series is enabled by Juniper Networks Junos® operating system. The SRX Seriesis equipped with a robust set of services that include stateful firewall, intrusion prevention system (IPS), denial of service (DoS), application security, VPN (IPsec), Network Address Translation (NAT), unified threat management (UTM), quality of service (QoS), and large-scale multitenancy. In addition to the benefit of individual services, the SRX5000 line provides a low latency solution.Junos OS also delivers carrier-class reliability with six nines system availability, the first in the industry to achieve independent verification by Telcordia. Furthermore, the SRX Series enjoys the benefit of a single source OS, and single integrated architecture traditionally available on Juniper’s carrier-class routers and switches.SRX5800The SRX5800 Services Gateway is the market-leading security solution supporting up to 1.2 Tbps firewall throughput and latency as low as 32 microseconds for stateful firewall. The SRX5800 also supports 1 Tbps IPS and 395 million concurrent sessions. Equipped with the full range of advanced security services, the SRX5800 is ideally suited for securing large enterprise, hosted, or colocated data centers, service provider core and cloud provider infrastructures, and mobile operator environments. The massive performance, scalability, and flexibility of the SRX5800 make it ideal for densely consolidated processing environments, and the service density makes it ideal for cloud and managed service providers.SRX5600The SRX5600 Services Gateway uses the same SPCs and IOCsas the SRX5800 and can support up to 570 IMIX Gbps firewall throughput, 180 million concurrent sessions, and 460 Gbps IPS. The SRX5600 is ideally suited for securing enterprise data centers as well as aggregation of various security solutions. The capability to support unique security policies per zone and its ability to scale with the growth of the network infrastructure make the SRX5600 an ideal deployment for consolidation of services in large enterprise, service provider, or mobile operator environments. SRX5400The SRX5400 Services Gateway uses the same SPCs and IOCs as the SRX5800 and can support up to 285 Gbps IMIX firewall, 90 million concurrent sessions, and 230 Gbps IPS. The SRX5400 is a small footprint, high-performance gateway ideally suited for securing large enterprise campuses as well as data centers, either for edge or core security deployments. The ability to support unique security policies per zone and a compelling price/performance/footprint ratio make the SRX5400 an optimal solution for edge or data center services in large enterprise, service provider, or mobile operator environments. Service Processing Cards (SPC)As the “brains” behind the SRX5000 line, SPCs are designedto process all available services on the platform. Without the need for dedicated hardware for specific services or capabilities, there are no instances in which a piece of hardware is taxedto the limit while other hardware is sitting idle. SPCs are designed to be pooled together, allowing the SRX5000 line to expand performance and capacities with the introduction of additional SPCs, drastically reducing management overhead and complexity. The high-performance SPC3 cards are supported on the SRX5400, SRX5600, and SRX5800 Services Gateways.I/O Cards (IOCs)To provide the most flexible solution, the SRX5000 line employs the same modular architecture for SPCs and IOCs. The SRX5000 line can be equipped with one or several IOCs, supporting the ideal mix of interfaces. With the flexibility to install an IOC or an SPC on any available slot, the SRX5000 line can be equipped to support the perfect blend of interfaces and processing capabilities, meeting the needs of the most demanding environments while ensuring investment protection. Juniper offers the IOC2, a second-generation card with superior connectivity options. The IOC2 offers 100GbE as well as 40GbE and high-density 10GbE and 1GbE connectivity options. These options reduce the need for link aggregation when connecting high throughput switches to the firewall, as well as enabling increased throughput in the firewall itself. The IOC2 is supported on all three platforms in the SRX5000 line of services gateways.The third generation of IOCs from Juniper, the IOC3, delivers the highest throughput levels yet, along with superior connectivity options including 100GbE, 40GbE, and high-density 10GbE interfaces. The IOC2 or IOC3 operates with the Express Path optimization capability, delivering higher levels of throughput—up to an industry-leading 2 Tbps on the SRX5800. The IOC3 cards are supported on the SRX5400, SRX5600, and SRX5800.Routing Engine (RE2) and Enhanced System Control Board (SCB3)The SRX5K-RE-1800X4 Routing Engine (RE2) is the latest in the family of REs for the SRX5000 line with a multicore processor running at 1800 MHz. It delivers improved performance, scalability, and reliability with 16 GB DRAM and 128 GB solid-state drive (SSD). The SRX5K-SCB3 Enhanced System Control Board (SCB3) enables 240 Gbps per slot throughput with intra as well as interchassis high availability and redundancy.Features and BenefitsNetworking and SecurityThe Juniper Networks SRX5000 line of Services Gateways has been designed from the ground up to offer robust networking andsecurity services.*Requires Junos OS 15.1x49-D10 or greater.**Requires Junos OS 18.2R1-S1 or greater.IPS CapabilitiesJuniper Networks IPS capabilities offer several unique features that assure the highest level of network security.Content Security UTM CapabilitiesThe UTM services offered on the SRX5000 line of Services Gateways include industry-leading antivirus, antispam, content filtering,and additional content security services.Advanced Threat PreventionAdvanced threat prevention (ATP) solutions that defend against sophisticated malware, persistent threats, and ransomware are available for the SRX5000 line. Two versions are available: Juniper Sky ATP, a SaaS-based service, and the Juniper ATP Appliance, anon-premises solution.More information about Juniper Sky ATP can be found at /us/en/products-services/security/sky-advanced-threat-prevention/. Additional information about the Juniper ATP Appliance can be found at /us/en/products-services/ security/advanced-threat-prevention-appliance/.Centralized ManagementJuniper Networks Junos Space Security Director delivers scalable and responsive security management that improves the reach, ease, and accuracy of security policy administration. It lets administrators manage all phases of the security policy life cycle through a single web-based interface, accessible via standard browsers. Junos Space Security Director centralizes application identification, firewall, IPS, NAT, and VPN security management for intuitive and quick policy administration. Security Director runs on the Junos Space Network Management Platform for highly extensible, network-wide management functionality, including ongoing access to Juniper and third-party Junos Space ecosystem innovations.Specifications1SRX5600Services GatewaySRX5800Services GatewaySRX5400Services Gateway Performance, capacity and features listed are based on systems running Junos OS 18.2R1 and are measured under ideal testing conditions. Actual results may vary based on Junos OS releases and by deployments.Firewall* Session capacity differs based on UTM/AppSecure/IPS features enabled.* Session capacity differs based on UTM/AppSecure/IPS features enabled.Maximum number of BGP and OSPF routes recommended is 100,000.Please consult the technical publication documents and release notes for a list of compatible ISSU features.T o enable dual control links on the SRX5000 line, two SRX5K-RE-1800X4 modules must be installed on each cluster member.SRX5000 line of gateways operating with Junos OS release 10.0 and later are compliant with the R6, R7, and R8 releases of 3GPP TS 20.060 with the following exceptions (not supported on the SRX5000 line): - Section 7.5A Multimedia Broadcast and Multicast Services (MBMS) messages- Section 7.5B Mobile Station (MS) info change messages- Section 7.3.12 Initiate secondary PDP context from GGSNShort term is not greater than 96 consecutive hours, and not greater than 15 days in 1 year.WarrantyFor warranty information, please visit /support/warranty/.Juniper Networks Services and SupportJuniper Networks is the leader in performance-enabling services that are designed to accelerate, extend, and optimize yourhigh-performance network. Our services allow you to maximize operational efficiency while reducing costs and minimizing risk, achieving a faster time to value for your network. Juniper Networks ensures operational excellence by optimizing the network to maintain required levels of performance, reliability, and availability. For more details, please visit /us/en/products-services .Ordering Information*These products require Junos OS 12.1X47-D15 or greater.**Requires Junos OS 15.1X49-D10 or greater.Corporate and Sales Headquarters Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, CA 94089 USAPhone: 888.JUNIPER (888.586.4737)or +Copyright 2019 Juniper Networks, Inc. All rights reserved. Juniper Networks, the Juniper Networks logo, Juniper, and Junos are registered trademarks of Juniper Networks, Inc. in the United States and other countries. All other trademarks, service marks, registered marks, or registered service marks are the property of their respective owners. Juniper Networks assumes no responsibility for any inaccuracies in this document. Juniper Networks reserves the right to change, modify, transfer, or otherwise revise this publication without notice.APAC and EMEA Headquarters Juniper Networks International B.V.Boeing Avenue 2401119 PZ Schiphol-Rijk Amsterdam, The Netherlands Phone: +31.0.207.125.700EXPLORE JUNIPERAbout Juniper NetworksJuniper Networks brings simplicity to networking with products, solutions and services that connect the world. Through engineering innovation, we remove the constraints and complexities of networking in the cloud era to solve the toughest challenges our customers and partners face daily. At Juniper Networks, we believe that the network is a resource for sharing knowledge and human advancement that changes the world. We are committed to imagining groundbreaking ways to deliver automated, scalable and secure networks to move at the speed of business.* I n 12.3X48-D10, the Services Offload feature was renamed Express Path and is included withoutrequiring a license for Junos OS X48 releases and beyond. With the X48 release, the Express Path feature is supported on all SRX5000 Services Gateways including the SRX5400. For versions prior to the X48 release, the Services Offload license is still required and supports only SRX5600 and SRX5800 products. Express Path is available on the SRX5400, SRX5600, and SRX5800 Services Gateways. No separate license required.。
Juniper Networks SRX Series Services Gateway Trans

SRX Series Services Gateway Transceiver ReferenceApril2016Contents SRX Series Services Gateway Transceivers (2)SRX Series Services Gateway Transceiver Interfaces (9)Installing Transceivers (13)Documentation and Release Notes (14)Requesting T echnical Support (14)Self-Help Online T ools and Resources (15)Opening a Case with JTAC (15)Revision History (15)SRX Series Services Gateway TransceiversYou can install transceivers of the following types in sockets in various cards or modules in SRX Series Services Gateways:•Small form-factor pluggable (SFP)•Enhanced small form-factor pluggable (SFP+)•10-Gigabit SFP (XFP)•100-Gbps form-factor pluggable (CFP)•Quad 40-Gbps form-factor pluggable plus (QSFP+)This guide describes all of the transceivers applicable to the SRX Series Services Gateways.The transceiver types are not interchangeable,with one exception:SFP+transceivers can be used in SFP interfaces.However,an SFP+transceiver installed in an SFP interface will be limited to the 1Gbps maximum data rate of the interface in which it isinstalled.NOTE:Modular Interface Cards (MICs)with SFP interfaces do not support SFP+transceivers.WARNING:Do not look directly into a fiber-optic transceiver or into the ends of fiber-optic cables.Fiber-optic transceivers and fiber-optic cable connected to a transceiver emit laser light that can damage youreyes.WARNING:Do not leave a fiber-optic transceiver uncovered except when inserting or removing cable.The safety cap keeps the port clean and prevents accidental exposure to laserlight.CAUTION:Avoid bending fiber-optic cable tighter than its minimum bend radius.An arc smaller than a few inches in diameter can damage the cable and cause problems that are difficult todiagnose.CAUTION:If you are having a problem running a Juniper Networks device that is using a third-party optic or cable,the Juniper Networks Technical Assistance Center (JTAC)can help you diagnose the source of the problem.Your JTAC engineer might recommend that you check the third-party optic or cable and potentially replace it with an equivalent Juniper Networks optic or cable that is qualified for the device.SRX Series Services Gateway Transceiver ReferenceT able 1on page 3describes the SFP transceivers applicable to SRX Series Services Gateway SFP interfaces.Table 1:SFP Gigabit Ethernet Transceivers2km62.5/125µm LCMMF1300100BASE-FXSFP 100BASE-FX Fast Ethernet optic moduleSRX-SFP-FE-FX2km50/125µm70km9/125µm LC SMF 15501000BASE-ZX SFP1000BASE-LH Gigabit Ethernet optic module SRX-SFP-1GE-LH70km9/125µm LC SMF 15501000BASE-ZX SFP1000BASE-LH Gigabit Ethernet optic module,extended temperature range (see note below)SRX-SFP-1GE-LH-ET 10km 9/125µm LC SMF 13101000BASE-LX SFP1000BASE-LH Gigabit Ethernet optic moduleSRX-SFP-1GE-LX 550m50/125µm LCMMF550m62.5/125µm10km 9/125µm LC SMF 13101000BASE-LX SFP1000BASE-LH Gigabit Ethernet optic module,extended temperature range (see note below)SRX-SFP-1GE-LX-ET550m50/125µm LCMMF550m62.5/125µm550m50/125µm LCMMF 8501000BASE-SX SFP1000BASE-SX Gigabit Ethernet optic moduleSRX-SFP-1GE-SX 275m62.5/125µmSRX Series Services Gateway TransceiversTable 1:SFP Gigabit Ethernet Transceivers (continued)550m50/125µm LCMMF8501000BASE-SXSFP1000BASE-SX Gigabit Ethernet optic module,extended temperature range (see note below)SRX-SFP-1GE-SX-ET275m62.5/125µm100m4twisted pair,category 5shieldedRJ-45Copper 1000BASE-T SFP1000BASE-T Gigabit Ethernet module (uses Cat 5cable)SRX-SFP-1GE-T 100m4twisted pair,category 5shieldedRJ-45Copper 1000BASE-T 1000BASE-T Gigabit Ethernet module (uses Cat 5cable),extendedtemperture range SRX-SFP-1GE-T-ET 20km9/125µm LC SMF(single-strand fiber)15501310100BASE-BX-U 100BASE-BX Fast Ethernet optic module SFP-FE20KT13R15EX-SFP-FE20KT13R1520km9/125µm LC SMF(single-strand fiber)131********BASE-BX-D 100BASE-BX Fast Ethernet optic module SFP-FE20KT15R13EX-SFP-FE20KT15R1310km9/125µm LC SMF(single-strand fiber)149013101000BASE-BX-U 1000BASE-BX10optic moduleSFP-GE10KT13R14EX-SFP-GE10KT13R1410km9/125µm LC SMF(single-strand fiber)155013101000BASE-BX-U 1000BASE-BX10optic moduleSFP-GE10KT13R15EX-SFP-GE10KT13R1510km9/125µm LC SMF(single-strand fiber)131014901000BASE-BX-D 1000BASE-BX10optic moduleSFP-GE10KT14R13EX-SFP-GE10KT14R1310km9/125µm LC SMF(single-strand fiber)131015501000BASE-BX-D 1000BASE-BX10optic moduleSFP-GE10KT15R13EX-SFP-GE10KT15R1340km9/125µm LC SMF(single-strand fiber)155013101000BASE-BX-U 1000BASE-BX optic moduleSFP-GE40KT13R15EX-SFP-GE40KT13R15SRX Series Services Gateway Transceiver ReferenceTable 1:SFP Gigabit Ethernet Transceivers (continued)Max.Core and SizeMediaλ (nm)ModelRXTX40km9/125µmLCSMF(single-strand fiber)131015501000BASE-BX-D1000BASE-BX optic moduleSFP-GE40KT15R13EX-SFP-GE40KT15R13NOTE:For SRX3400and SRX3600Services Gateways to meet NEBS and ETSI standards,all transceivers installed in the services gateway must be of extended temperature (ET)type.T able 2on page 5describes the SFP+10-Gigabit Ethernet transceivers applicable to SRX Series Services Gateway SFP and SFP+interfaces.Table 2:SFP+10-Gigabit Ethernet TransceiversMax.Core and SizeMediaλ (nm)SKURX TX40km9/125µmLCSMF155010GBASE-ERSFP+10-Gigabit Ethernet optic module.Meets extended temperature rangerequirements (see note below)SRX-SFP-10GE-ER10km9/125µm LC SMF 131010GBASE-LR SFP+10-Gigabit Ethernet optic module.Meets extended temperature rangerequirements (see note below)SRX-SFP-10GE-LR EX-SFP-10GE-LR300m (OM3)400m (OM4)50/125µm LCMMF 85010GBASE-SR SFP+10-Gigabit Ethernet optic moduleSRX-SFP-10GE-SR EX-SFP-10GE-SR33m62.5/125µmSRX Series Services Gateway TransceiversTable 2:SFP+10-Gigabit Ethernet Transceivers (continued)Max.Core and SizeMediaλ (nm)SKURX TX220m50/125µm LCMMF126010GBASE-LRMSFP+10GBase-LRM 10-Gigabit Ethernet optic moduleSFPP-10GE-LRM220m62.5/125µm300m50/125µmLCMMF 85010GBASE-SR SFP+10-Gigabit Ethernet optic moduleSRX-SFPP-10G-SR-ET10km9/125µm LC SMF 131010GBASE-LR SFP+10-Gigabit Ethernet optic moduleSRX-SFPP-10G-LR NOTE:For SRX3400and SRX3600Services Gateways to meet NEBS and ETSI standards,all transceivers installed in the services gateway must be of extended temperature (ET)type.T able 3on page 6describes the SFP+10-Gigabit Ethernet,Direct Attach Cables (DAC)transceivers applicable to SRX Series Services Gateway SFP+interfaces.Table 3:SFP+10-Gigabit Ethernet DAC TransceiversMax.Core and SizeMediaλ (nm)SKURX TX 1mSFP+passive Twinaxcopper cable assembly Direct Attached 30AWG10GBASE-DAC10-Gbps full-duplex serialtransmissionSRX-SFP-10GE-DAC-1M EX-SFPP-10GE-DAC-1M3mSFP+passive Twinaxcopper cable assembly Direct Attached 30AWG10GBASE-DAC10-Gbps full-duplex serialtransmissionSRX-SFP-10GE-DAC-3M EX-SFP-10GE-DAC-3M5mSFP+passive Twinaxcopper cable assemblyDirect Attached 24AWG10GBASE-DAC10-Gbps full-duplex serialtransmissionEX-SFP-10GE-DAC-5MSRX Series Services Gateway Transceiver ReferenceTable 3:SFP+10-Gigabit Ethernet DAC Transceivers (continued)7mSFP+passive Twinaxcopper cable assemblyDirect Attached 24AWG10GBASE-DAC10-Gbps full-duplex serialtransmissionEX-SFP-10GE-DAC-7MT able 4on page 7describes the XFP 10-Gigabit Ethernet transceivers applicable to SRX Series Services Gateway XFP interfaces.Table 4:XFP 10-Gigabit Ethernet Transceivers40km9/125µmLCSMF155010GBASE-ER10-Gigabit Ethernet single-mode optic moduleSRX-XFP-10GE-ER40km9/125µm LC SMF 155010GBASE-ER 10-Gigabit Ethernet single-mode optic module,extended temperature range (see note below)SRX-XFP-10GE-ER-ET 10km9/125µm LC SMF 131010GBASE-LR 10-Gigabit Ethernet single-mode optic moduleSRX-XFP-10GE-LR 10km9/125µm LC SMF 131010GBASE-LR 10-Gigabit Ethernet single-mode optic module,extended temperature range (see note below)SRX-XFP-10GE-LR-ET 10km9/125µm LC SMF 85010GBASE-SR 10-Gigabit Ethernet short-reachmultimode optic moduleSRX-XFP-10GE-SR 10km9/125µm LC SMF 85010GBASE-SR 10-Gigabit Ethernet short-reachmultimode optic module,extended temperature range (see note below)SRX-XFP-10GE-SR-ET SRX Series Services Gateway TransceiversNOTE:For SRX3400and SRX3600Services Gateways to meet NEBS and ETSI standards,all transceivers installed in the services gateway must be of extended temperature (ET)type.T able 5on page 8describes the CFP 100-Gigabit Ethernet transceivers applicable to SRX Series Services Gateway CFP interfaces.Table 5:CFP 100-Gigabit Ethernet TransceiversMax.Mediaλ (nm)SKURX TX10kmDual SCSMF1310100GBASE-LR4100-Gigabit Ethernet single-mode optic module SRX-CFP-100G-LR4100m (OM3)150m (OM4)Ribbon cable,24multimode fibersMMF850100GBASE-SR10100-Gigabit Ethernet single-mode optic moduleSRX-CFP-100G-SR10100m24-fiber MPO MMF860860100GBASE-SR10100-Gigabit Ethernet CFP2-100GBA SE-SR1010kmLCSMF 131********GBASE-LR4100-Gigabit EthernetCFP2-100GBASE-LR4T able 6on page 8describes the QSFP+40-Gigabit Ethernet transceivers applicable to SRX Series Services Gateway QSFP+interfaces.Table 6:QSFP+40-Gigabit Ethernet TransceiversMax.C onnect orMediaλ (nm)SKURX TX100m (OM3)150m (OM4)OM3,OM4,12fiber MPOconnector MMF85040GBASE-SR440-Gigabit Ethernet single-mode optic moduleSRX-QSFP-40G-SR410kmLCSMF131040GBASE-LR440-Gigabit Ethernet single-mode optic module SRX-QSFP-40G-LR4150m (OM3)OM4duplex MMFMMF131040GBASE-LX440-Gigabit Ethernet pluggableJNP-QSFP-40G-LX4SRX Series Services Gateway Transceiver ReferenceSRX Series Services Gateway Transceiver InterfacesT able 7on page 9,T able 8on page 9,T able 9on page 9,and T able 10on page 10show the different types of transceiver interfaces available on the various types of SRX Series Services Gateways.Table 7:SRX210,SRX220,and SRX240Services Gateway Transceiver Interface Types11-Port SFP Mini-PIM (not supported on SRX220)SRX-MP-1SFPSFP11-Port Gigabit Ethernet SFP Mini-PIMSRX-MP-1SFP-GE SFP Table 8:SRX550and SRX650Services Gateway Transceiver Interface Types11-Port Gigabit Ethernet SFP Mini-PIM SRX-MP-1SFP-GE (SRX550only)SFP88-Port Gigabit Ethernet SFP XPIM SRX-GP-8SFP22-Port 10-Gigabit Ethernet XPIMSRX-GP-2XE-SFPP-TXSFP+Table 9:SRX1400,SRX3400,and SRX3600Services Gateway Transceiver Interface Types16IOC SRX3K-16GE-SFPSFP6SYSIOC SRX1K-SYSIO-GE (SRX1400only)2NP-IOC SRX1K3K-NP-2XGE-SFPPSFP+3SYSIOC SRX1K-SYSIO-XGE (SRX1400only)2IOCSRX3K-2XGE-XFPXFP SRX Series Services Gateway Transceiver InterfacesTable 10:SRX5400,SRX5600,and SRX5800Services Gateway Transceiver Interface Types40IOCSRX5K-40GE-SFP SFP16Flex IOC Port Module SRX-IOC-16GE-SFP 2SPC SRX5K-SPC-2-10-402SPC SRX5K-SPC-4-15-32020MIC SRX-MIC-20GE-SFP10MIC SRX-MIC-10XG-SFPP SFP+4IOCSRX5K-4XGE-XFP XFP4Flex IOC Port Module SRX-IOC-4XGE-XFP1MIC SRX-MIC-1X100G-CFP CFP 2MICSRX-MIC-2X40G-QSFPQSFP+The following is a list of transceivers supported on the SRX300Series,SRX550High Memory,and SRX1500Services Gateways.√√√SRX-SFP-1GE-LH √√√SRX-SFP-1GE-LX √√√SRX-SFP-1GE-SX √√√SRX-SFP-1GE-T √√SRX-SFP-FE-FX √EX-SFP-10GE-LR √EX-SFP-10GE-SR √√EX-SFP-FE20KT13R15√√EX-SFP-FE20KT15R13SRX Series Services Gateway Transceiver Reference√√EX-SFP-GE10KT13R14√√EX-SFP-GE10KT13R15√√EX-SFP-GE10KT14R13√√EX-SFP-GE10KT15R13√√EX-SFP-GE40KT13R15√√EX-SFP-GE40KT15R13√EX-SFPP-10GE-DAC-1M√EX-SFPP-10GE-DAC-3M The following is a list of all the cards and supported transceivers for the SRX1400ServicesGateway.SRX Series Services Gateway Transceiver InterfacesThe following is a list of all the cards and supported transceivers for the SRX3400andSRX3600ServicesGateways.SRX Series Services Gateway Transceiver ReferenceFollowing is a list of transceivers supported on all cards,along with the Junos OS releasein which they were introduced,for the SRX5000line of ServicesGateways.Installing TransceiversTransceivers are hot-insertable and hot-removable.Removing a transceiver does notinterrupt the functioning of the card or module.T o install a transceiver:1.Attach an ESD grounding strap to your bare wrist,and connect the strap to one of theESD points on the chassis.2.T ake each transceiver to be installed out of its electrostatic bag,and identify thesocket on the card or module where you will installit.WARNING:Do not leave a fiber-optic transceiver uncovered except wheninserting or removing cable.The safety cap keeps the port clean andprevents accidental exposure to laser light.Installing TransceiversSRX Series Services Gateway Transceiver Reference3.For each fiber interface transceiver,verify that the interface port is covered by a rubbersafety cap.If it is not,cover the interface port with a safety cap.The safety cap preventsthe release of laser light that can damage your eyes.4.Carefully align the transceiver with the socket in the services gateway card or module.The connector should face the socket.5.Slide the transceiver into the socket until the connector is seated in the componentslot.If you are unable to fully insert the transceiver,make sure the connector is orientedcorrectly.See the hardware documentation for your services gateway for moreinformation about LEDs.6.Close the ejector handle of the transceiver.7.Remove the rubber safety caps from both the transceiver and from the end of thecable.Insert the cable into the transceiver.8.Verify that the status LEDs on the component faceplate indicate that the transceiveris functioning correctly.Documentation and Release NotesT o obtain the most current version of all Juniper Networks®technical documentation,see the product documentation page on the Juniper Networks website at/techpubs/.If the information in the latest release notes differs from the information in thedocumentation,follow the product Release Notes.Juniper Networks Books publishes books by Juniper Networks engineers and subjectmatter experts.These books go beyond the technical documentation to explore thenuances of network architecture,deployment,and administration.The current list canbe viewed at /books.Requesting Technical SupportT echnical product support is available through the Juniper Networks T echnical AssistanceCenter(JTAC).If you are a customer with an active J-Care or Partner Support Servicesupport contract,or are covered under warranty,and need postsales technical support,you can access our tools and resources online or open a case with JTAC.•JTAC policies—For a complete understanding of our JTAC procedures and policies,review the JTAC User Guide located at/us/en/local/pdf/resource-guides/7100059-en.pdf.•Product warranties—For product warranty information,visit/support/warranty/.•JTAC Hours of Operation—The JTAC centers have resources available24hours a day,7days a week,365days a year.Requesting T echnical SupportSelf-Help Online Tools and ResourcesFor quick and easy problem resolution,Juniper Networks has designed an onlineself-service portal called the Customer Support Center(CSC)that provides you with thefollowing features:•Find CSC offerings:/customers/support/•Find product documentation:/techpubs/•Find solutions and answer questions using our Knowledge Base:/•Download the latest versions of software and review release notes:/customers/csc/software/•Search technical bulletins for relevant hardware and software notifications:https:///alerts/•Join and participate in the Juniper Networks Community Forum:/company/communities/•Open a case online in the CSC Case Management tool:/cm/T o verify service entitlement by product serial number,use our Serial Number Entitlement(SNE)T ool:https:///SerialNumberEntitlementSearch/Opening a Case with JTACYou can open a case with JTAC on the Web or by telephone.•Use the Case Management tool in the CSC at /cm/.•Call1-888-314-JTAC(1-888-314-5822toll-free in the USA,Canada,and Mexico).For international or direct-dial options in countries without toll-free numbers,visit us at/support/requesting-support.htmlRevision HistoryJune2015—Added information about DAC and CFP2optics.August2015—Updated core and cladding size for SRX-SFP-FE-FX.October2015—Added information about DAC optics.November2015—Added OM4detail for SRX-SFP-10GE-SR.April2016—Added transceiver support information for the SRX300Series,SRX550HighMemory,and SRX1500Services Gateways.SRX Series Services Gateway Transceiver ReferenceCopyright©2016,Juniper Networks,Inc.All rights reserved.Juniper Networks,Junos,Steel-Belted Radius,NetScreen,and ScreenOS are registered trademarks of Juniper Networks,Inc.in the United States and other countries.The Juniper Networks Logo,the Junos logo,and JunosE are trademarks of Juniper Networks,Inc.All other trademarks,service marks,registered trademarks,or registered service marks are the property of their respective owners.Juniper Networks assumes no responsibility for any inaccuracies in this document.Juniper Networks reserves the right to change,modify, transfer,or otherwise revise this publication without notice.。
Juniper Networks SRX300 Services Gateway说明书

Quick Start GuideMount the SD-WAN Edge CPE1.Attach the brackets to the SD-WAN Edge CPE.e the screws and cage nuts supplied with the rack to securethe SD-WAN Edge CPE in the rack.Ground the SD-WAN Edge CPE1.Ensure the rack on which the SD-WAN Edge CPE is to bemounted is properly grounded and in compliance withinternational and local standards. Verify that there is a good electrical connection to the grounding point on the rack. (no paint or isolating surface treatment)2.Attach a lug (not provided) to a #18 AWG minimum groundingwire (not provided), and connect it to the grounding point on the device’s rear panel. Then connect the other end of the wire to rack ground.Connect Power1.Plug the power cord into a 100-240 VAC, 50-60 Hz AC powersource.2.Insert the other end of the power cord directly into the AC inputsocket on the back of the device.Caution: Risk of explosion if battery is replaced by anincorrect type. Dispose of used batteries according to the manufacturer’s instructions.Attention: Risque d’explosion si la batterie est remplacée par un type incorrect. Éliminez les piles usagées conformément auxinstructions.12121Caution: The earth connection must not be removed unlessall supply connections have been disconnected.Attention: Le raccordement à la terre ne doit pas être retiré sauf si toutes les connexions d’alimentation ont été débranchées.Caution: The device must be installed in a restricted-accesslocation. It should have a separate protective earthing terminal on the chassis that must be permanently connected to earth to adequately ground the chassis and protect the operator from electrical hazards.Attention: L'appareil doit être installé dans un emplacement à accès restreint. Il doit comporter une borne de terre de protection distincte sur le châssis, qui doit être connectée en permanence à la terre pour assurer une mise à la terre adéquate du châssis et protéger l'opérateur des risques électriques.Caution: Use the AC power cord supplied with the device .For International use, you may need to change the AC line cord. You must use line cord sets that have been approved for the socket type in your country.Attention: Utilisez le cordon d’alimentation secteur fourniavec l’appareil. Pour une utilisation internationale, vous devrez peut-être changer le cordon d’alimentation secteur. Vous devez utiliser des jeux de cordons d’alimentation qui ont étéapprouvés pour le type de prise dans votre pays.321SD-WAN Edge CPESDW1001.SDW100 SD-WAN Edge CPE2.Rack Mounting Kit—2 brackets and 8 screws3.Power cord—either Japan, US, Continental Europe or UK4.Console cable—RJ-45 to DB-95.Documentation—Quick Start Guide (this document)25143Package ContentsCheck the System LEDs1.Verify basic operation by checking the system LEDs. Whenoperating normally, the Power LED should be on green and the Status LED should be either on blue or blinking when the device is booting up.Connect Network Cables1.For the 1000BASE-T RJ-45 ports, connect 100-ohm Category 5,5e or better twisted-pair cable.2.For the SFP slots, first install SFP transceivers and then connectfiber optic cabling to the transceiver ports.The following transceivers are supported:⏹1000BASE-SX (ET4201-SX)⏹1000BASE-LX (ET4201-LX)⏹1000BASE-ZX (ET4201-ZX)⏹1000BASE-LHX (ET4201-LHX)3.As connections are made, check the port status LEDs to be surethe links are valid.⏹On/Blinking Green — Port has a valid link. Blinking indicates network activity.Make Initial Configuration Changes1.Connect a PC to one of the SD-WAN Edge CPE’s LAN ports.2.Log in to the web interface using the default management IPaddress 192.168.100.1 (there is no user name or password).3.Configure the Barrista controller IP address and port throughone of the following methods.⏹DHCP: Automatic configuration.⏹Static: Manually set the IP address, subnet mask, default gateway, and DNS servers.⏹PPPoE: Set the PPPoE username and password.4.Click “Save” to confirm the configuration and enable the SD-WAN Edge CPE to communicate with the Barrista controller.Hardware Specifications41153126Chassis Size (WxDxH)42.6 x 27.0 x 4.4 cm (16.8 x 10.6 x 1.7 in.)Weight 2.64 kg (5.81 lb)Temperature Operating: 0 °C to 40 °C (32 °F to 104 °F)Storage: -20 °C to 70 °C (-4 °F to 158 °F)Humidity Operating: 10% to 90% (non-condensing)InterfacesNetwork Ports 3-10: RJ-45 10/100/1000BASE-TPorts 1-2 RJ-45 10/100/1000BASE-T or SFP USB 1 USB 3.0ConsoleRS-232 serial, RJ-45 portPower AC Input100-240 VAC 50-60 Hz 2.5 APower Consumption 65 Watts Maximum Maximum Current0.9 ARegulatory Compliances EmissionsCE MarkEN 55032, Class A EN 61000-3-2, Class A EN 61000-3-3FCC Class A CNS 1343847 CPR FCC Part 15:2016, Subpart B, Class A ANSI C63.4:2014CISPR 32.2015 + COR1:2016, Class A AS/NZS CISPR 32:2015, Class ACanada Std. ICES-003:2016 Issue 6, Class A Immunity IEC 61000-4-2/3/4/5/6/8/11SafetyUL 62368-1 & CAN/CSA C22.2 No. 62368-1-14CB IEC/EN 60950-1 & IEC/EN 62368-1 2nd. BSMI Safety Standard CNS14336-1Taiwan RoHSCNS 15663Safety and Regulatory InformationFCC Class AThis equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful interference in which case the user will be required to correct the interference at his own expense.You are cautioned that changes or modifications not expressly approved by the party responsible for compliance could void your authority to operate the equipment.You may use unshielded twisted-pair (UTP) for RJ-45 connections - Category 3 or better for 10 Mbps connections, Category 5 or better for 100 Mbps connections, Category 5, 5e, or 6 for 1000 Mbps connections. For fiber optic connections, you may use 50/125 or 62.5/ 125 micron multimode fiber or 9/125 micron single-mode fiber.CE MarkCE Mark Declaration of Conformance for EMI and Safety (EEC)This information technology equipment complies with the requirements of the Council Directive 2014/30/EU on the Approximation of the laws of the Member States relating to Electromagnetic Compatibility and 2014/ 35/EU for electrical equipment used within certain voltage limits. For the evaluation of the compliance with these Directives, the following standards were applied:RFI Emission:⏹Limit according to EN 55032:2012+AC:2013, Class A⏹Limit for harmonic current emission according to EN 61000-3-2:2014, Class A⏹Limitation of voltage fluctuation and flicker in low-voltage supplysystem according to EN 61000-3-3:2013Immunity:⏹Product family standard according to EN 55024:2010⏹Electrostatic Discharge according to IEC 61000-4-2:2008⏹Radio-frequency electromagnetic field according to IEC 61000-4-3:2010⏹Electrical fast transient/burst according to IEC 61000-4-4:2012⏹Surge immunity test according to IEC 61000-4-5:2014⏹Immunity to conducted disturbances, Induced by radio-frequencyfields: IEC 61000-4-6:2013⏹Power frequency magnetic field immunity test according to IEC61000-4-8:2009⏹Voltage dips, short interruptions and voltage variations immunity testaccording to IEC 61000-4-11:2004LVD:⏹EN 62368-1:2014/A11: 2017The Declaration of Conformity (DoC) can be obtained from -> support -> download.Japan - VCCI Class ALaser SafetyWarning: Fiber Optic Port Safety:Avertissment: Ports pour fibres optiques - sécurité sur le plan optique: Warnhinweis: Faseroptikanschlüsse - Optische Sicherheit:Battery SafetyPower Cord SafetyPlease read the following safety information carefully before installing the device:Warning:Installation and removal of the unit must be carried out by qualified personnel only.⏹The unit must be connected to an earthed (grounded) outlet tocomply with international safety standards.⏹Do not connect the unit to an A.C. outlet (power supply) without anearth (ground) connection.⏹The appliance coupler (the connector to the unit and not the wallplug) must have a configuration for mating with an EN 60320/IEC 320 appliance inlet.⏹The socket outlet must be near to the unit and easily accessible. Youcan only remove power from the unit by disconnecting the powercord from the outlet.⏹This unit operates under SELV (Safety Extra Low Voltage) conditionsaccording to IEC 60950. The conditions are only maintained if the equipment to which it is connected also operates under SELVconditions.When using a fiber optic port, never look at thetransmit laser while it is powered on. Also, never lookdirectly at the fiber TX port and fiber cable ends whenthey are powered on.Ne regardez jamais le laser tant qu'il est sous tension.Ne regardez jamais directement le port TX(Transmission) à fibres optiques et les embouts decâbles à fibres optiques tant qu'ils sont sous tension.Niemals ein Übertragungslaser betrachten, währenddieses eingeschaltet ist. Niemals direkt auf den Faser-TX-Anschluß und auf die Faserkabelenden schauen,während diese eingeschaltet sind.Warning: If your device uses a lithium battery, do not attemptto replace the battery yourself. Return the device to themanufacturer for battery replacement.Avertissement: Si votre appareil utilise une batterie aulithium, n’essayez pas de remplacer la batterie vous-même.Renvoyez l’appareil au fabricant pour le remplacement de labatterie.If the device contains lithium batteries that are encased in asealed chassis, do not attempt to open the sealed chassis underany circumstances.Si l’appareil contient des piles au lithium logées dans unchâssis scellé, n’essayez en aucun cas d’ouvrir le châssis scellé.Risk of explosion if the battery is replaced by an incorrect type.Dispose of used batteries according to the instructions.Risque d’explosion si la batterie est remplacée par un typeincorrect. Éliminez les piles usagées conformément auxinstructions.CLASS ILASER DEVICEDISPOSITIF LASERDE CLASSE ILASERGERDER KLASSE IÄTFrance and Peru onlyThis unit cannot be powered from IT† supplies. If your supplies are of IT type, this unit must be powered by 230 V (2P+T) via an isolation transformer ratio 1:1, with the secondary connection point labeled Neutral, connected directly to earth (ground).† Impédance à la terreImportant! Before making connections, make sure you have the correct cord set. Check it (read the label on the cable) against the following:Veuillez lire à fond l’information de la sécurité suivante avant d’installer l’appareil:Avertissement: L’installation et la dépose de ce groupe doivent être confiés à un personnel qualifié.⏹Ne branchez pas votre appareil sur une prise secteur (alimentationélectrique) lorsqu’il n’y a pas de connexion de mise à la terre (mise à la masse).⏹Vous devez raccorder ce groupe à une sortie mise à la terre (mise àla masse) afin de respecter les normes internationales de sécurité.⏹Le coupleur d’appareil (le connecteur du groupe et non pas la prisemurale) doit respecter une configuration qui permet unbranchement sur une entrée d’appareil EN 60320/IEC 320.⏹La prise secteur doit se trouver à proximité de l’appareil et son accèsdoit être facile. Vous ne pouvez mettre l’appareil hors circuit qu’en débranchant son cordon électrique au niveau de cette prise.⏹L’appareil fonctionne à une tension extrêmement basse de sécuritéqui est conforme à la norme IEC 60950. Ces conditions ne sontmaintenues que si l’équipement auquel il est raccordé fonctionne dans les mêmes conditions.France et Pérou uniquement:Ce groupe ne peut pas être alimenté par un dispositif à impédance à la terre. Si vos alimentations sont du type impédance à la terre, ce groupe doit être alimenté par une tension de 230 V (2 P+T) par le biais d’un transformateur d’isolement à rapport 1:1, avec un point secondaire de connexion portant l’appellation Neutre et avec raccordement direct à la terre (masse).Bitte unbedingt vor dem Einbauen des Geräts die folgenden Sicherheitsanweisungen durchlesen:Warnung: Die Installation und der Ausbau des Geräts darf nur durch Fachpersonal erfolgen.⏹Das Gerät sollte nicht an eine ungeerdete Wechselstromsteckdoseangeschlossen werden.⏹Das Gerät muß an eine geerdete Steckdose angeschlossen werden,welche die internationalen Sicherheitsnormen erfüllt.⏹Der Gerätestecker (der Anschluß an das Gerät, nicht derWandsteckdosenstecker) muß einen gemäß EN 60320/IEC 320konfigurierten Geräteeingang haben.⏹Die Netzsteckdose muß in der Nähe des Geräts und leichtzugänglich sein. Die Stromversorgung des Geräts kann nur durch Herausziehen des Gerätenetzkabels aus der Netzsteckdoseunterbrochen werden.⏹Der Betrieb dieses Geräts erfolgt unter den SELV-Bedingungen(Sicherheitskleinstspannung) gemäß IEC 60950. Diese Bedingungen sind nur gegeben, wenn auch die an das Gerät angeschlossenen Geräte unter SELV-Bedingungen betrieben werden.电源线安全安装交换机前,请仔细阅读以下安全信息。
Juniper Networks

Data Sheet攻击缓解:入侵防御系统瞻博网络的入侵防御系统 (IPS) 已与瞻博网络的 NGFW 紧密集成,可减少威胁并防范各种攻击和漏洞。
与瞻博网络 Sky™ Advanced Threat Prevention (Sky ATP) 结合后,IPS 可对已知和未知的威胁提供全面的防御,在零日攻击袭击网络之前就开始防范。
该解决方案会持续监控对新近发现漏洞的新攻击,不断更新对新网络攻击方法的网络防护。
经由网络,针对客户端和服务器系统上的漏洞发起的攻击在造成任何损坏之前就会被阻止。
未知恶意软件:瞻博网络 Sky ATP瞻博网络 Sky ATP 是基于云的服务,可以提供全面的高级恶意软件防护。
通过与 SRX 系列防火墙集成,瞻博网络 Sky ATP 可提供动态反恶意软件解决方案来适应不断变化的威胁环境。
该解决方案提供基于云的服务来通过强大的机器学习算法动态分析 Web 和电子邮件文件,从而迅速识别新的、未知的恶意软件。
一旦得出结论,相关决策就会发送至 SRX 系列 NGFW,以供实施。
瞻博网络 Sky ATP 支持所有主流文件类型,包括Microsoft(.docx、.xls和 .ppt)、pdf 和 Android 应用程序 (APK)。
阻止已知威胁:反恶意软件保护来自多种攻击途径的恶意活动在持续激增,这种情况下,企业外围就成为了阻拦威胁进入网络的第一道防线。
反恶意软件保护将基于云的声誉情报与 SRX 系列 NGFW 的本机处理相结合,提供轻便快捷的安全保护。
其成果则是能够抵御众多已知威胁的高效外围防御,而且不会降低用户或业务的速度。
浏览防御:恶意 URL 过滤钓鱼攻击是一种流行的攻击方法,通常会导致企业内部出现严重漏洞。
毫无戒备的用户单击恶意 URL 后,就会安装利用漏洞的根程序病毒包,而此病毒包作为高级持续攻击的前导,为有价值的企业数据遭窃取创造了条件。
攻击者通常会破坏热门网站,引诱用户无意中提供其用户密码。
Junipe SRX1400业务网关 说明书

产品简介产品说明瞻博网络SRX1400业务网关是市场领先的SRX 系列数据中心产品线的最新成员。
SRX1400整合了多种安全服务和网络功能,具有极高的可用性,主要为10GbE 网络环境提供保护。
它采用了模块化设计,其通用尺寸的模块可以从前面板进行维护和更换。
SRX1400利用创新的技术,增加了可靠性和网络的可用性,并提供极高的并发安全服务性能。
凭借瞻博网络的动态服务架构和Junos OS ,以及基于SRX3000业务网关成熟的电信级特性,SRX1400确立了新的价值标准,扩展了SRX 系列数据中心产品线,能够经济高效地满足更小网络环境的安全需求。
每台SRX1400业务网关都整合了多种安全服务,并执行全面的安全策略,其性能完全能满足当今10GbE 高性能网络环境的需要。
面向网络安全专业人员SRX1400是按照电信级标准从底层开始设计的高可靠设备,能够在严格的高性能数据中心网络环境中,长时间无故障地连续运行。
SRX1400的设计和生产过程都采用了TL 9000质量管理体系,无论是软件、支持服务还是硬件(包括能够分离控制和用户平面的创新芯片组)都100%由瞻博网络提供,同时,SRX1400还将性能提升到一种新的水平,能够满足高性能网络的需要。
动态服务架构利用瞻博网络的动态服务架构,高端SRX 系列能够在处理器的多个核心之间动态、快速地分配数据会话。
动态服务架构不是像其他供应商那样,将网络流量和服务固定或严格捆绑到专门的CPU 核心和处理资源,而是动态地平衡流量会话,在由所有可用资源构成的一个共享池中动态地处理工作负载。
这就避免了在一般的安全计算平台上经常出现的情况,即一些资源全负荷或接近全负荷地运行,而其它资源却闲置或低负荷地运行。
产品概述SRX1400业务网关作为专业级的安全平台,非常适合部署在中小型的数据中心、企业和电信运营商网络。
在这些环境中,客户主要考虑的问题是功能整合、10Gbps 性能、空间节省和经济性。
SRX配置

SRX 100 SRX 210 SRX 220
J2320
J2350
SSG520 SSG520M SSG350M SSG550 SSG550M
Packet Forwarding Engine (aka ―PFE‖)
Programmable
ASIC(s)
Forwarding Table
Switch Fabric
PIC PIC
分离式设计是GR/NSR等高级特性的物理基础, 保证路由协议重启或路由引擎故障切换时,零丢 包!
15
工程师目前经常面临的问题
13
NetScreen架构(2K/5K series)
Integrated Security Applications Integrated Security Applications Security -Specific, Real -Time OS Security Real Time OS High Speed Backplane CPU In Out GigaScreen ASIC
VoIP—Avaya Integ. Gway
VoIP
– Juniper 开放式通信 – POE
FW, VPN, NAT, UAC
统一威胁管理
– 入侵防御 – 反病毒—Kaspersky – 网页过滤—Websense – 反垃圾邮件-Symantec
SSG20 Wireless SSG5 Wireless SSG320M SSG140
12
传统防火墙及NS构架
控制/转发层面不完全分离 Slow Path in RISC CPU Fast Path in GigaScreen ASIC 迄今为止GigaScreen3 (Born in Oct 2003)仍然是最快的防火墙SPU (Security Process Unit) 之一 3Mpps per GigaScreen3 1.4M PPS per Cisco FWSM (IBM 4GS3 Power NP) 2M PPS per MS-DPC NP or 1M PPS per SRX5K SPU
juniperSRX系列防火墙srx210-240-650

面向分支办事处的SRX系列 业务网关
SRX0、SRX0和SRX0
产品概述
面向分支办事处的瞻博网络SRX系 列业务网关提供多项基本功能,能 够连接、保护和管理用户数量从几 名到数百名的办公机构。通过在单 一设备中整合快速且高度可用的交 换、路由、安全和应用功能,企业 将能够经济地提供多项新型服务, 确保安全的连接,并为最终用户带 来满意的体验。包括面向分支办事 处、园区和数据中心应用而扩展 的产品在内的所有SRX系列业务网 关,均采用了经过实践检验的瞻博 网络JUNOS软件操作系统,能够以 更低的总体拥有成本,带来无与伦 比的一致性、更出色的服务性能, 以及卓越的基础架构保护能力。
● 个固定端口0/00/000以太局域网端口,个千兆以太网背板物理接口模块 (GPIM) 插槽 ● 支持T、E、千兆以太局域网端口;支持最多个可转换为可选PoE的端口 (包括0.at) ,PoE+,后向兼容0.af ● 可提高IPS与ExpressAV性能的内容安全加速器 ● 完整的UTM;防病毒、防垃圾邮件、Web过滤和入侵防御系统 ● 统一接入控制和内容过滤 ● 模块化服务与路由引擎;未来内部故障切换与热插拔 ● 默认 GB DRAM,默认 GB紧凑型闪存,支持添加额外存储的外部紧凑型闪存插槽 ● 可选冗余AC电源;PoE就绪的标准AC电源;高达0瓦冗余PoE电源,或00瓦非冗余。
在不影响性能的情况下实现基于会话的转发
为了优化路由器与防火墙组合的吞吐量和延迟,JUNOS软件提供 了基于会话的转发能力。这一创新将传统防火墙的会话状态信息与 普通路由器的下一跳转发能力完美结合到单一操作之中。通过使用 JUNOS软件,转发策略所准许的会话将会添加到转发表中,同时还 会添加一个指向下一跳路由的指针。已建立的会话可对单一路由表 进行查找,来确认会话已经获得准许,并搜索下一跳地址。相比需 要执行多次路由表查找以确认会话信息、并搜索下一跳路由地址的 传统路由器,这种算法大大提高了执行效率,能够显著改进会话流 量的吞吐量并降低延迟。
SRX办事处系列分支网关

1
架构和关键组件
分支办事处 SRX 系列产品的关键硬件特性
产品
SRX100 业务网关 SRX210 业务网关
SRX220 业务网关
SRX240 业务网关
SRX650 业务网关
说明
• 8 个 10/100 以太局域网端口 • 全面 UTM2;防病毒2、防垃圾邮件2、网页过滤2、入侵防护系统2(大内存版本) • 统一接入控制 (UAC) 和内容过滤 • 1GB8 DRAM、1GB 闪存标准配置(在小内存版本中可使用 512MB DRAM) • 2 个 10/100/1000 以太网端口和 6 个 10/100 以太局域网端口,1 个 Mini-PIM 插槽、1 个 ExpressCard 插槽和 2 个 USB 端口 • 出厂时可选择 4 个 动态以太网供电 (PoE) 端口 802.3af • 支持 T1/E1、串行、ADSL/2/2+、VDSL、G.SHDSL、DOCSIS3、以太网小封装可插拔收发器 (SFP) 和千兆以太网接口 • 内容安全加速器硬件,用于提高 IPS 和 ExpressAV 的性能 • 全面 UTM2;防病毒2、防垃圾邮件2、网页过滤2、入侵防护系统2(大内存版本) • 统一接入控制 (UAC) 和内容过滤 • 512MB DRAM 标准配置(出厂时可选 1GB DRAM)、1GB 闪存标准配置 • 8 个 10/100/1000 以太局域网端口、2 个 Mini-PIM 插槽 • 出厂时可选择 8 个 PoE 端口;PoE +803.3at,与 802.3af 后向兼容 • 支持 T1/E1、串行、ADSL/2/2+、VDSL、G.SHDSL、DOCSIS3、以太网小封装可插拔收发器 (SFP) 和千兆以太网接口 • 内容安全加速器硬件,用于提高 IPS 和 ExpressAV 的性能 • 全面 UTM2;防病毒2、防垃圾邮件2、网页过滤2、入侵防防御系统2(大内存版本) • 统一接入控制和内容过滤 • 1GB DRAM、1GB 闪存标准配置 • 16 个 10/100/1000 以太局域网端口、4 个 Mini-PIM 插槽 • 出厂时可选择 16 个 PoE 端口;PoE +803.3at,与 802.3af 后向兼容 • 支持 T1/E1、串行、ADSL/2/2+、VDSL、G.SHDSL、DOCSIS3、以太网小封装可插拔收发器 (SFP) 和千兆以太网接口 • 内容安全加速器硬件,用于提高 IPS 和 ExpressAV 的性能 • 全面 UTM2;防病毒2、防垃圾邮件2、网页过滤2、入侵防护系统2(大内存版本) • 统一接入控制和内容过滤 • 512MB DRAM 标准配置(出厂时可选 1GB DRAM)、1GB 闪存标准配置 • 4 个固定 10/100/1000 以太局域网端口、8 个 GPIM 插槽或多个 GPIM 和 XPIM 的组合 • 支持 T1、E1、千兆以太局域网端口;采用可选 PoE 时支持多达 48 端口交换,包括 802.3at、PoE+,与 802.3af 后向兼容 • 内容安全加速器硬件,用于提高 IPS 和 ExpressAV 的性能 • 全面 UTM2;防病毒2、防垃圾邮件2、网页过滤2、以及入侵防护系统2 • 统一接入控制和内容过滤 • 模块化服务和路由引擎;将来将支持内部故障切换和热插拔 • 2GB DRAM 标准配准、2GB compact flash 标准配置、用于增加存储的外部 compact flash 插槽 • 可选冗余交流电源;支持 PoE 的标准交流电源;PoE 电源具有 250 瓦冗余能力或 500 瓦非冗余能力
Juniper Networks SRX1500服务网关产品说明说明书

Data SheetSRX1500 与瞻博网络 Contrail 服务编排结合使用,可以向企业和服务提供商提供完全自动化的 SD-WAN。
其全自动部署 (ZTP) 功能极大地简化了分支机构网络连接的初始部署和持续管理。
SRX1500的高性能和可扩展性使它可以用作 VPN 集线器,在各种 SD-WAN 拓扑结构中端接 VPN/安全叠加连接。
SRX1500 服务网关运行 Juniper Networks Junos®操作系统,这是一个已得到实践验证并且运营商可以定制加强的网络操作系统,目前在为全球前 100 强服务提供商网络提供支持。
IPv4/IPv6、OSPF、BGP 和组播经过严格测试的运营商级路由功能已在超过 15年的全球部署中久经验证。
功能与优势SRX1500 服务网关规格软件规格防火墙服务•有状态和无状态防火墙•基于区域的防火墙•筛选和分布式拒绝服务 (DDoS) 保护•抵御协议和流量异常•与 Pulse 统一访问控制 (UAC) 集成•与 Aruba Clear Pass Policy Manager 集成•基于用户角色的防火墙•SSL 检测网络地址转换 (NAT)•带有端口地址转换 (PAT) 的源 NAT•双向 1:1 静态 NAT•带有 PAT 的目标 NAT•持久 NAT•IPv6 地址转换VPN 功能•隧道:通用路由封装 (GRE)1、IP-IP1、IPsec•站点-站点 IPsec VPN、自动 VPN、组 VPN•IPsec 加密算法:数据加密标准 (DES)、三重 DES (3DES)、高级加密标准 (AES-256)、AES-GCM•IPsec 身份验证算法:MD5、SHA-1、SHA-128、SHA-256•预共享密钥和公钥基础架构 (PKI) (X.509)•完全向前保密,防重播•IPv4 和 IPv6 IPsec VPN•站点-站点 VPN 的多代理 ID•互联网密钥交换(IKEv1、IKEv2),NAT-T•虚拟路由器和服务质量 (QoS) 感知•基于标准的失效对等方检测 (DPD) 支持•VPN 监控高可用性功能•虚拟路由器冗余协议 (VRRP)•有状态的高可用性- 双机箱集群- 主动/被动- 主动/被动- 配置同步- 防火墙会话同步- 设备/链路检测- 不中断服务的软件升级 (ISSU)•采用路由与接口故障转移的 IP 监控应用程序安全性服务2•应用程序可见性和控制•基于应用程序的防火墙•应用程序 QoS•高级/基于应用程序策略的路由 (APBR)•应用程序体验质量 (AppQoE)•基于应用程序的多路径路由威胁防御和情报服务3•入侵防御•防病毒•反垃圾邮件•类别/基于信誉的 URL 过滤•SecIntel 提供威胁情报•防范僵尸网络(命令和控制)•基于 GeoIP 的自适应实施•瞻博网络 Advanced Threat Prevention(一种基于云的 SaaS产品),可检测并阻止零日攻击•瞻博网络 ATP 设备,是一种内部部署的分布式高级威胁防御解决方案,可用于检测并阻止零日攻击路由协议•IPv4、IPv6•静态路由•RIP v1/v2•OSPF/OSPF v3•具有路由反射器的 BGP•IS-IS•组播:Internet 组管理协议 (IGMP) v1/v2;协议无关组播(PIM) 稀疏模式 (SM)/密集模式 (DM)/源特定组播 (SSM);会话描述协议 (SDP);距离矢量组播路由协议 (DVMRP);组播源发现协议 (MSDP);逆向路径转发 (RPF)•封装:VLAN、通过以太网传输的点对点协议 (PPPoE)•虚拟路由器•基于策略的路由,基于源的路由•等价多路径 (ECMP)QoS 功能•支持 802.1 p、DiffServ代码点 (DSCP)、EXP•按 VLAN、数据链路连接标识符 (DLCI)、接口、束或多域过滤器分类•标记、监管和整形•分类和计划•加权随机早期检测 (WRED)•保证带宽和最大带宽•入口流量监管•虚拟通道•层次结构整形和策略制定交换功能•基于 ASIC 的第 2 层转发•MAC 地址学习•VLAN 寻址以及集成路由与桥接 (IRB) 支持•链路聚合与 LACP•LLDP 和 LLDP-MED•STP、RSTP、MSTP•MVRP•802.1X 身份验证网络服务•动态主机配置协议 (DHCP) 客户端/服务器/中继•域名系统 (DNS) 代理、动态 DNS (DDNS)•瞻博网络实时性能监控 (RPM) 和 IP 监控•瞻博网络流量监控(J 流)•双向转发检测 (BFD)•双向主动测量协议 (TWAMP)•IEEE 802.3ah 链路默认管理 (LFM)•IEEE 802.1ag 连接故障管理 (CFM)高级路由服务•分组模式•MPLS(RSVP、LDP)•电路交叉连接 (CCC)、平移交叉连接 (TCC)•L2/L2 MPLS VPN、伪线•虚拟专用 LAN 服务 (VPLS)、下一代组播 VPN (NG-MVPN)•MPLS 流量工程和 MPLS 快速重新路由管理、自动化、日志记录和报告•SSH、T elnet、SNMP•智能图像下载•瞻博网络 CLI 和 Web UI•瞻博网络 Junos Space 和 Security Director•Python•Junos OS 事件、提交和 OP 脚本•应用程序和带宽使用情况报告•自动安装•调试和故障排除工具GRE、IP-IP 和 VRRP 在有状态高可用性模式下不受支持。
Juniper SRX防火墙配置手册

Juniper SRX防火墙简明配置手册Juniper Networks, Inc.北京市东城区东长安街1号东方经贸城西三办公室15层1508室邮编:100738电话:65288800目录一、JUNOS操作系统介绍 (3)1.1 层次化配置结构 (3)1.2 JunOS配置管理 (3)1.3 SRX主要配置内容 (4)二、SRX防火墙配置对照说明 (5)2.1 初始安装 (5)2.1.1 登陆 (5)2.1.2 设置root用户口令 (5)2.1.3 设置远程登陆管理用户 (5)2.1.4 远程管理SRX相关配置 (6)2.2 Policy (6)2.3 NAT (6)2.3.1 Interface based NAT............................................................. 错误!未定义书签。
2.3.2 Pool based Source NAT......................................................... 错误!未定义书签。
2.3.3 Pool base destination NAT................................................. 错误!未定义书签。
2.3.4 Pool base Static NAT (7)2.4 IPSEC VPN (7)2.5 Application and ALG (8)2.6 JSRP ........................................................................................................ 错误!未定义书签。
三、SRX防火墙常规操作与维护 (9)3.1 设备关机 (9)3.2 设备重启 (9)3.3 操作系统升级 (10)3.4 密码恢复 (10)3.5 常用监控维护命令 (11)Juniper SRX防火墙简明配置手册SRX系列防火墙是Juniper公司基于JUNOS操作系统的安全系列产品,JUNOS集成了路由、交换、安全性和一系列丰富的网络服务。
Juniper SRX Branch系列防火墙J-WEB配置手册

一、J-WEB管理系统简介 (3)1.1SRX系列防火墙J-WEB界面使用注意事项 (3)二、SRX防火墙J-WEB操作应用场景一 (4)2.1固定公网IP地址上网应用场景拓扑及需求说明 (4)2.1.1应用场景一拓扑图 (4)2.1.2拓扑图介绍及需求说明 (4)2.1.3应用场景一需求分解与配置思路说明 (5)2.2初始化安装 (5)2.2.1设备登陆 (5)2.2.2系统基线配置指引 (5)2.3应用场景一生产配置实施步骤介绍 (7)2.3.1WEB界面登录到防火墙 (7)2.3.2配置接口IP地址 (8)2.3.3配置安全区域 (9)2.3.4配置路由协议 (11)2.3.5配置NAT地址转换 (11)2.3.6配置安全策略 (14)2.3.7应用场景一验证测试结果 (15)2.3.8应用场景一测试配置CLI(生产配置) (16)三、SRX防火墙J-WEB操作应用场景二 (18)3.1PPPOE拨号上网应用场景拓扑及需求说明 (18)3.1.1应用场景二拓扑图 (18)3.1.2拓扑介绍及需求说明 (18)3.1.3应用场景二需求分解与配置思路说明 (18)3.2初始化安装 (19)3.2.1设备登陆 (19)3.2.2系统基线配置指引 (19)3.3应用场景二生产配置实施步骤介绍 (20)3.3.1配置PPPOE拨号 (20)3.3.2配置DHCP服务器 (29)3.3.3配置目标地址转换 (30)3.3.4配置源地址转换 (32)3.3.5配置安全策略 (32)3.3.6应用场景二验证测试结果 (33)四、SRX防火墙J-WEB操作应用场景三 (34)4.1远程动态VPN应用场景拓扑及需求说明 (34)4.1.1应用场景三拓扑图 (34)4.1.2拓扑介绍及需求说明 (34)4.1.3应用场景三需求分解与配置思路说明 (35)4.2初始化安装 (35)4.2.1设备登陆 (35)4.2.2系统基线配置指引 (35)4.3应用场景三生产配置实施步骤介绍 (36)4.3.1动态VPN配置思路及过程介绍和验证 (36)Juniper SRX Branch系列防火墙J-WEB配置手册说明SRX系列防火墙是Juniper公司基于JUNOS操作系统的安全系列产品,JUNOS集成了路由、交换、安全性和一系列丰富的网络服务。
SRX 5600 Services Gateway 硬体指南

SRX5600Services Gateway 硬體指南Juniper Networks,Inc.1194North Mathilda Avenue Sunnyvale,California94089USA408-745-2000產品編號:000000,修訂本01This product includes the Envoy SNMP Engine,developed by Epilogue Technology,an Integrated Systems Company.Copyright©1986-1997, Epilogue Technology Corporation.All rights reserved.This program and its documentation were developed at private expense,and no part of them is in the public domain.This product includes memory allocation software developed by Mark Moraes,copyright©1988,1989,1993,University of Toronto.This product includes FreeBSD software developed by the University of California,Berkeley,and its contributors.All of the documentation and software included in the 4.4BSD and 4.4BSD-Lite Releases is copyrighted by the Regents of the University of California.Copyright ©1979,1980,1983,1986,1988,1989,1991,1992,1993,1994.The Regents of the University of California.All rights reserved.GateD software copyright©1995,the Regents of the University.All rights reserved.Gate Daemon was originated and developed through release 3.0by Cornell University and its collaborators.Gated is based on Kirton’s EGP,UC Berkeley’s routing daemon(routed),and DCN’s HELLO routing protocol.Development of Gated has been supported in part by the National Science Foundation.Portions of the GateD software copyright©1988,Regents of the University of California.All rights reserved.Portions of the GateD software copyright©1991, D.L.S.Associates.This product includes software developed by Maker Communications,Inc.,copyright©1996,1997,Maker Communications,Inc.Juniper Networks,the Juniper Networks logo,JUNOS,NetScreen,ScreenOS,and Steel-Belted Radius are registered trademarks of Juniper Networks,Inc.in the United States and other countries.JUNOSe is a trademark of Juniper Networks,Inc.All other trademarks,service marks,registered trademarks,or registered service marks are the property of their respective owners.Juniper Networks assumes no responsibility for any inaccuracies in this document.Juniper Networks reserves the right to change,modify, transfer,or otherwise revise this publication without notice.Products made or sold by Juniper Networks or components thereof might be covered by one or more of the following patents that are owned by or licensed to Juniper Networks:U.S.Patent Nos.5,473,599,5,905,725,5,909,440,6,192,051,6,333,650,6,359,479,6,406,312,6,429,706,6,459,579,6,493,347,6,538,518,6,538,899,6,552,918,6,567,902,6,578,186,and6,590,785.SRX5600Services Gateway Hardware GuideCopyright©2008,Juniper Networks,Inc.All rights reserved.Printed in USA.修訂歷程March2009—Revision01Initial release.The information in this document is current as of the date listed in the revision history.2000年通告Juniper Networks hardware and software products are Year2000compliant.The JUNOS software has no known time-related limitations through the year2038.However,the NTP application is known to have some difficulty in the year2036.ii■END USER LICENSE AGREEMENTREAD THIS END USER LICENSE AGREEMENT(“AGREEMENT”)BEFORE DOWNLOADING,INSTALLING,OR USING THE SOFTWARE.BY DOWNLOADING,INSTALLING, OR USING THE SOFTWARE OR OTHERWISE EXPRESSING YOUR AGREEMENT TO THE TERMS CONTAINED HEREIN,YOU(AS CUSTOMER OR IF YOU ARE NOT THE CUSTOMER,AS A REPRESENTATIVE/AGENT AUTHORIZED TO BIND THE CUSTOMER)CONSENT TO BE BOUND BY THIS AGREEMENT.IF YOU DO NOT OR CANNOT AGREE TO THE TERMS CONTAINED HEREIN,THEN(A)DO NOT DOWNLOAD,INSTALL,OR USE THE SOFTWARE,AND(B)YOU MAY CONTACT JUNIPER NETWORKS REGARDING LICENSE TERMS.1.The Parties.The parties to this Agreement are(i)Juniper Networks,Inc.(if the Customer’s principal office is located in the Americas)or Juniper Networks(Cayman)Limited(if the Customer’s principal office is located outside the Americas)(such applicable entity being referred to herein as“Juniper”),and(ii)the person or organization that originally purchased from Juniper or an authorized Juniper reseller the applicable license(s)for use of the Software(“Customer”)(collectively,the“Parties”).2.The Software.In this Agreement,“Software”means the program modules and features of the Juniper or Juniper-supplied software, for which Customer has paid the applicable license or support fees to Juniper or an authorized Juniper reseller,or which was embedded by Juniper in equipment which Customer purchased from Juniper or an authorized Juniper reseller.“Software”also includes updates, upgrades and new releases of such software.“Embedded Software”means Software which Juniper has embedded in or loaded onto the Juniper equipment and any updates,upgrades,additions or replacements which are subsequently embedded in or loaded onto the equipment.3.License Grant.Subject to payment of the applicable fees and the limitations and restrictions set forth herein,Juniper grants to Customer a non-exclusive and non-transferable license,without right to sublicense,to use the Software,in executable form only,subject to the following use restrictions:a.Customer shall use Embedded Software solely as embedded in,and for execution on,Juniper equipment originally purchased by Customer from Juniper or an authorized Juniper reseller.b.Customer shall use the Software on a single hardware chassis having a single processing unit,or as many chassis or processing units for which Customer has paid the applicable license fees;provided,however,with respect to the Steel-Belted Radius or Odyssey Access Client software only,Customer shall use such Software on a single computer containing a single physical random access memory space and containing any number of e of the Steel-Belted Radius or IMS AAA software on multiple computers or virtual machines(e.g., Solaris zones)requires multiple licenses,regardless of whether such computers or virtualizations are physically contained on a single chassis.c.Product purchase documents,paper or electronic user documentation,and/or the particular licenses purchased by Customer may specify limits to Customer’s use of the Software.Such limits may restrict use to a maximum number of seats,registered endpoints,concurrent users,sessions,calls,connections,subscribers,clusters,nodes,realms,devices,links,ports or transactions,or require the purchase of separate licenses to use particular features,functionalities,services,applications,operations,or capabilities,or provide throughput,performance,configuration,bandwidth,interface,processing,temporal,or geographical limits.In addition,such limits may restrict the use of the Software to managing certain kinds of networks or require the Software to be used only in conjunction with other specific Software.Customer’s use of the Software shall be subject to all such limitations and purchase of all applicable licenses.d.For any trial copy of the Software,Customer’s right to use the Software expires30days after download,installation or use of the Software.Customer may operate the Software after the30-day trial period only if Customer pays for a license to do so.Customer may not extend or create an additional trial period by re-installing the Software after the30-day trial period.e.The Global Enterprise Edition of the Steel-Belted Radius software may be used by Customer only to manage access to Customer’s enterprise network.Specifically,service provider customers are expressly prohibited from using the Global Enterprise Edition of the Steel-Belted Radius software to support any commercial network access services.The foregoing license is not transferable or assignable by Customer.No license is granted herein to any user who did not originally purchase the applicable license(s)for the Software from Juniper or an authorized Juniper reseller.e Prohibitions.Notwithstanding the foregoing,the license provided herein does not permit the Customer to,and Customer agrees not to and shall not:(a)modify,unbundle,reverse engineer,or create derivative works based on the Software;(b)make unauthorized copies of the Software(except as necessary for backup purposes);(c)rent,sell,transfer,or grant any rights in and to any copy of the Software,in any form,to any third party;(d)remove any proprietary notices,labels,or marks on or in any copy of the Software or any product in which the Software is embedded;(e)distribute any copy of the Software to any third party,including as may be embedded in Juniper equipment sold in the secondhand market;(f)use any‘locked’or key-restricted feature,function,service, application,operation,or capability without first purchasing the applicable license(s)and obtaining a valid key from Juniper,even if such feature,function,service,application,operation,or capability is enabled without a key;(g)distribute any key for the Software provided by Juniper to any third party;(h)use the Software in any manner that extends or is broader than the uses purchased by Customer from Juniper or an authorized Juniper reseller;(i)use Embedded Software on non-Juniper equipment;(j)use Embedded Software (or make it available for use)on Juniper equipment that the Customer did not originally purchase from Juniper or an authorized Juniper reseller;(k)disclose the results of testing or benchmarking of the Software to any third party without the prior written consent of Juniper;or(l)use the Software in any manner other than as expressly provided herein.■iii5.Audit.Customer shall maintain accurate records as necessary to verify compliance with this Agreement.Upon request by Juniper, Customer shall furnish such records to Juniper and certify its compliance with this Agreement.6.Confidentiality.The Parties agree that aspects of the Software and associated documentation are the confidential property of Juniper.As such,Customer shall exercise all reasonable commercial efforts to maintain the Software and associated documentation in confidence,which at a minimum includes restricting access to the Software to Customer employees and contractors having a need to use the Software for Customer’s internal business purposes.7.Ownership.Juniper and Juniper’s licensors,respectively,retain ownership of all right,title,and interest(including copyright) in and to the Software,associated documentation,and all copies of the Software.Nothing in this Agreement constitutes a transfer or conveyance of any right,title,or interest in the Software or associated documentation,or a sale of the Software,associated documentation,or copies of the Software.8.Warranty,Limitation of Liability,Disclaimer of Warranty.The warranty applicable to the Software shall be as set forth in the warranty statement that accompanies the Software(the“Warranty Statement”).Nothing in this Agreement shall give rise to any obligation to support the Software.Support services may be purchased separately.Any such support shall be governed by a separate,written support services agreement.TO THE MAXIMUM EXTENT PERMITTED BY LAW,JUNIPER SHALL NOT BE LIABLE FOR ANY LOST PROFITS,LOSS OF DATA,OR COSTS OR PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES,OR FOR ANY SPECIAL,INDIRECT,OR CONSEQUENTIAL DAMAGES ARISING OUT OF THIS AGREEMENT, THE SOFTWARE,OR ANY JUNIPER OR JUNIPER-SUPPLIED SOFTWARE.IN NO EVENT SHALL JUNIPER BE LIABLE FOR DAMAGES ARISING FROM UNAUTHORIZED OR IMPROPER USE OF ANY JUNIPER OR JUNIPER-SUPPLIED SOFTWARE.EXCEPT AS EXPRESSLY PROVIDED IN THE WARRANTY STATEMENT TO THE EXTENT PERMITTED BY LAW,JUNIPER DISCLAIMS ANY AND ALL WARRANTIES IN AND TO THE SOFTWARE(WHETHER EXPRESS,IMPLIED,STATUTORY,OR OTHERWISE), INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY,FITNESS FOR A PARTICULAR PURPOSE,OR NONINFRINGEMENT.IN NO EVENT DOES JUNIPER WARRANT THAT THE SOFTWARE,OR ANY EQUIPMENT OR NETWORK RUNNING THE SOFTWARE,WILL OPERATE WITHOUT ERROR OR INTERRUPTION,OR WILL BE FREE OF VULNERABILITY TO INTRUSION OR ATTACK.In no event shall Juniper’s or its suppliers’or licensors’liability to Customer,whether in contract,tort(including negligence),breach of warranty,or otherwise,exceed the price paid by Customer for the Software that gave rise to the claim,or if the Software is embedded in another Juniper product,the price paid by Customer for such other product.Customer acknowledges and agrees that Juniper has set its prices and entered into this Agreement in reliance upon the disclaimers of warranty and the limitations of liability set forth herein,that the same reflect an allocation of risk between the Parties(including the risk that a contract remedy may fail of its essential purpose and cause consequential loss),and that the same form an essential basis of the bargain between the Parties.9.Termination.Any breach of this Agreement or failure by Customer to pay any applicable fees due shall result in automatic termination of the license granted herein.Upon such termination,Customer shall destroy or return to Juniper all copies of the Software and related documentation in Customer’s possession or control.10.Taxes.All license fees payable under this agreement are exclusive of tax.Customer shall be responsible for paying Taxes arising from the purchase of the license,or importation or use of the Software.If applicable,valid exemption documentation for each taxing jurisdiction shall be provided to Juniper prior to invoicing,and Customer shall promptly notify Juniper if their exemption is revoked or modified.All payments made by Customer shall be net of any applicable withholding tax.Customer will provide reasonable assistance to Juniper in connection with such withholding taxes by promptly:providing Juniper with valid tax receipts and other required documentation showing Customer’s payment of any withholding taxes;completing appropriate applications that would reduce the amount of withholding tax to be paid;and notifying and assisting Juniper in any audit or tax proceeding related to transactions hereunder.Customer shall comply with all applicable tax laws and regulations,and Customer will promptly pay or reimburse Juniper for all costs and damages related to any liability incurred by Juniper as a result of Customer’s non-compliance or delay with its responsibilities herein. Customer’s obligations under this Section shall survive termination or expiration of this Agreement.11.Export.Customer agrees to comply with all applicable export laws and restrictions and regulations of any United States and any applicable foreign agency or authority,and not to export or re-export the Software or any direct product thereof in violation of any such restrictions,laws or regulations,or without all necessary approvals.Customer shall be liable for any such violations.The version of the Software supplied to Customer may contain encryption or other capabilities restricting Customer’s ability to export the Software without an export license.mercial Computer Software.The Software is“commercial computer software”and is provided with restricted e, duplication,or disclosure by the United States government is subject to restrictions set forth in this Agreement and as provided in DFARS227.7201through227.7202-4,FAR12.212,FAR27.405(b)(2),FAR52.227-19,or FAR52.227-14(ALT III)as applicable.13.Interface Information.To the extent required by applicable law,and at Customer's written request,Juniper shall provide Customer with the interface information needed to achieve interoperability between the Software and another independently created program,on payment of applicable fee,if any.Customer shall observe strict obligations of confidentiality with respect to such information and shall use such information in compliance with any applicable terms and conditions upon which Juniper makes such information available.14.Third Party Software.Any licensor of Juniper whose software is embedded in the Software and any supplier of Juniper whose products or technology are embedded in(or services are accessed by)the Software shall be a third party beneficiary with respect to this Agreement,and such licensor or vendor shall have the right to enforce this Agreement in its own name as if it were Juniper.In addition, certain third party software may be provided with the Software and is subject to the accompanying license(s),if any,of its respective owner(s).To the extent portions of the Software are distributed under and subject to open source licenses obligating Juniper to make the source code for such portions publicly available(such as the GNU General Public License(“GPL”)or the GNU Library General Publiciv■License(“LGPL”)),Juniper will make such source code portions(including Juniper modifications,as appropriate)available upon request for a period of up to three years from the date of distribution.Such request can be made in writing to Juniper Networks,Inc.,1194 N.Mathilda Ave.,Sunnyvale,CA94089,ATTN:General Counsel.You may obtain a copy of the GPL at/licenses/gpl.html,and a copy of the LGPL at /licenses/lgpl.html.15.Miscellaneous.This Agreement shall be governed by the laws of the State of California without reference to its conflicts of laws principles.The provisions of the U.N.Convention for the International Sale of Goods shall not apply to this Agreement.For any disputes arising under this Agreement,the Parties hereby consent to the personal and exclusive jurisdiction of,and venue in,the state and federal courts within Santa Clara County,California.This Agreement constitutes the entire and sole agreement between Juniper and the Customer with respect to the Software,and supersedes all prior and contemporaneous agreements relating to the Software,whether oral or written(including any inconsistent terms contained in a purchase order),except that the terms of a separate written agreement executed by an authorized Juniper representative and Customer shall govern to the extent such terms are inconsistent or conflict with terms contained herein.No modification to this Agreement nor any waiver of any rights hereunder shall be effective unless expressly assented to in writing by the party to be charged.If any portion of this Agreement is held invalid,the Parties agree that such invalidity shall not affect the validity of the remainder of this Agreement.This Agreement and associated documentation has been written in the English language,and the Parties agree that the English version will govern.(For Canada:Les parties aux présentés confirment leur volontéque cette convention de même que tous les documents y compris tout avis qui s'y rattaché,soient redigés en langue anglaise. (Translation:The parties confirm that this Agreement and all related documentation is and will be in the English language)).■vvi■目錄關於本指南xxi目標 (xxi)目標讀者 (xxi)文件慣例 (xxi)J系列服務路由器與SRX系列服務閘道的JUNOS軟體文件 (xxiii)取得文件 (xxiv)文件意見回饋 (xxv)要求技術支援 (xxv)第1部分SRX5600服務閘道綜述第1章服務閘道綜述3服務閘道說明 (3)元件冗餘 (4)第2章硬體元件5服務閘道機箱 (5)中間背板 (7)I/O卡(IOC) (8)IOC元件 (9)服務處理卡 (10)SPC元件 (12)主機子系統 (13)開關控制板 (14)SCB插槽 (14)SCB冗餘 (15)SCB元件 (15)SCB LED (15)路由引擎 (16)路由引擎元件 (16)路由引擎介面連接埠與狀態指示燈 (17)路由引擎啟動順序 (18)纜線管理系統 (18)精密介面 (19)警示LED與警示切斷/亮起測試按鈕 (20)主機子系統LED (21)目錄■viiSRX5600服務閘道硬體指南電源供應器LED (21)IOC與SPC LED (21)SCB LED (22)風扇LED (22)線上按鈕 (22)警示轉接接點 (23)電源供應器 (23)電源供應器安裝與替換 (23)AC電源供應器 (24)AC電源供應器組態 (24)AC電源供應器LED (25)DC電源供應器 (25)DC電源供應器組態 (26)DC電源供應器LED (26)冷卻系統 (27)第2部分設定服務閘道第3章為安裝服務閘道準備場地31場地準備核對清單 (31)機櫃需求 (32)機櫃大小與空間需求 (32)機櫃空氣流通需求 (32)機架需求 (32)機架尺寸與強度 (33)裝載托架孔的間距 (34)連接至建築結構 (34)空氣流通與硬體維護的空間需求 (34)第4章安裝概觀37第5章拆開服務閘道的包裝39必要工具及零件 (39)拆開服務閘道的包裝 (39)確認收到的零件 (40)第6章安裝裝載硬體43為機架或機櫃安裝裝載硬體 (43)卸除安裝托架以在中央裝載裝置 (45)viii■目錄目錄第7章安裝服務閘道47安全需求、警告與準則 (47)使用機械起重機安裝服務閘道 (47)所需工具 (47)使用起重機安裝服務閘道 (48)安裝纜線管理系統 (49)第8章連接服務閘道51必要工具及零件 (51)將服務閘道連接到管理與警示裝置 (51)連線到網路以進行超出頻寬的管理 (52)連接到管理主控台或附屬裝置 (52)連接到外部警示報告裝置 (53)連接IOC纜線 (53)第9章將服務閘道接地並為其供電55必要工具及零件 (55)將服務閘道接地 (55)將電源連接到AC供電的服務閘道 (56)開啟AC供電服務閘道的電源 (57)將電源連接到DC供電的服務閘道 (58)開啟DC供電服務閘道的電源 (59)關閉服務閘道電源 (61)第10章組態JUNOS軟體63第3部分硬體維護、替換及疑難排解步驟第11章維護硬體元件71必要工具及零件 (71)例行維護程序 (71)維護冷卻系統元件 (72)維護空氣濾網 (72)維護風扇架 (72)維護主機子系統 (73)維護IOC與SPC (75)維護IOC纜線 (77)目錄■ixSRX5600服務閘道硬體指南搬運及存放卡 (78)手持卡片 (79)存放卡 (81)維護電源供應器 (82)第12章硬體元件疑難排解83資源疑難排解的綜述 (83)指令行介面 (83)LED (84)精密介面LED (84)元件LED (84)機箱與介面警示訊息 (85)Juniper Networks技術支援中心 (85)冷卻系統疑難排解 (85)IOC疑難排解 (86)SPC疑難排解 (87)電源系統疑難排解 (88)第13章替換硬體元件91現場可替換單元(FRU) (91)必要工具及零件 (92)替換精密介面 (93)移除精密介面 (93)安裝精密介面 (94)替換警示轉接線 (95)拔除警示轉接連接線 (95)連接警示轉接連接線 (96)替換冷卻系統元件 (96)替換風扇架 (96)移除風扇架 (96)安裝風扇架 (97)替換空氣濾網 (98)移除空氣濾網 (98)安裝空氣濾網 (99)替換主機子系統元件 (100)使主機子系統離線 (100)替換SCB (101)操作及定位SCB頂出器 (101)移除SCB (102)安裝SCB (102)替換路由引擎 (104)移除路由引擎 (104)安裝路由引擎 (105)替換路由引擎介面連接埠的連接 (106)替換管理乙太網路纜線 (107)替換主控台或附屬纜線 (107)x■目錄目錄替換IOC (107)移除IOC (108)安裝IOC (109)替換SPC (111)移除SPC (111)安裝SPC (113)移除SFP或XFP收發機 (115)安裝SFP或XFP收發機 (116)替換電源系統元件 (116)移除AC電源供應器 (117)安裝AC電源供應器 (119)移除DC電源供應器 (119)安裝DC電源供應器 (121)替換AC電線 (123)拔下AC電線 (123)連接AC電源供應線 (124)替換DC電源供應纜線 (124)拔下DC電纜 (124)安裝DC電纜 (125)替換纜線管理系統 (126)移除纜線管理系統 (126)安裝纜線管理系統 (126)第4部分附錄附錄A安全與法規遵從性資訊129安全警告層級的定義 (129)安全準則與警告 (130)一般安全準則與警告 (131)合格人員警告 (131)受限制存取區域警告 (132)防止靜電傷害 (134)防火安全需求 (134)滅火 (135)滅火設備 (135)安裝安全準則與警告 (135)機箱抬起準則 (135)安裝指示警告 (136)機架裝載的要求與警告 (136)傾斜警告 (140)雷射與LED安全準則與警告 (140)一般雷射安全準則 (141)第1類雷射產品警告 (141)第1類LED產品警告 (141)雷射光束警告 (142)開放式光學連接埠孔隙的雷射光警告 (142)目錄■xiSRX5600服務閘道硬體指南維護與操作安全準則與警告 (143)電池處理警告 (144)摘除首飾警告 (145)閃電活動警告 (146)操作溫度警告 (146)產品棄置警告 (148)電力安全準則與警告 (148)發生電力意外時 (149)一般電力安全準則與警告 (149)AC電源電力安全準則 (153)DC電源電力安全準則與警告 (154)管理單位核准與遵從性陳述 (159)管理單位核准 (159)EMC需求之遵從性陳述 (161)加拿大 (161)歐洲共同體 (161)日本 (161)美國 (161)環保需求的遵從性陳述 (161)鋰電池 (161)聽覺噪音的遵從性陳述 (162)附錄B實體規格163實體規格 (163)附錄C服務閘道環境規格165服務閘道環境規格 (165)附錄D電源準則、需求與規格167機箱接地 (167)接地纜線插孔規格 (167)接地纜線規格 (168)DC電源規格與需求 (168)DC電源系統電力規格 (168)DC電源斷路器規格 (169)DC電源供應器電力規格 (169)DC供電服務閘道的電源需求 (169)DC電纜規格 (171)DC電纜插孔規格 (172)DC電纜規格 (172)AC電源規格與準則 (172)AC電源系統電力規格 (172)AC電源供應器電力規格 (173)AC電源斷路器規格 (173)xii■目錄目錄AC供電服務閘道的電源需求 (173)AC電線規格 (175)現場電力接線準則 (177)發訊距離限制 (177)無線電頻率干擾 (177)電磁相容性 (177)附錄E纜線與電線準則與規格179網路纜線規格與準則 (179)在多模式與單一模式光纖纜線中損失訊號 (179)光纖纜線中的衰減與消散 (179)計算光纖纜線的功率預算 (180)計算光纖纜線的功率限度 (180)路由引擎介面纜線與電線規格 (182)附錄F不使用機械起重機安裝服務閘道183必要工具及零件 (183)從機箱中移除元件 (183)移除電源供應器 (184)移除風扇架 (184)移除SCB (185)移除IOC與SPC (186)將機箱手動安裝到機架中 (187)將元件重新安裝到機箱中 (189)重新安裝電源供應器 (189)重新安裝風扇架 (190)重新安裝SCB (191)重新安裝IOC與SPC (192)安裝纜線管理系統 (193)附錄G聯絡客戶支援並退還硬體195找到元件序號 (195)SRX5600機箱序號標籤 (196)SCB序號標籤 (197)IOC與SPC序號標籤 (198)電源供應器序號標籤 (198)路由引擎序號標籤 (199)聯繫客戶支援 (200)您可能需要提供給JTAC的資訊 (200)退還程序 (200)必要工具及零件 (201)將服務閘道包裝好,以用於運輸 (202)包裝元件以用於運輸 (203)目錄■xiiiSRX5600服務閘道硬體指南附錄H纜線連接器接腳配置205路由引擎ETHERNET連接埠的RJ-45連接器接腳配置 (205)路由引擎AUX和CONSOLE連接埠的RJ-45連接器接腳配置 (205)第5部分索引索引 (209)xiv■目錄圖清單第1部分SRX5600服務閘道綜述第2章硬體元件5圖1:完全組態的服務閘道機箱的前視圖 (6)圖2:完全組態的AC電源服務閘道機箱的後視圖 (6)圖3:完全組態的DC電源服務閘道機箱的後視圖 (7)圖4:中間背板 (8)圖5:SRX5600上支援的IOC (9)圖6:水平安裝在SRX5600中的IOC (9)圖7:典型SPC (11)圖8:水平安裝在SRX5600服務閘道中的SPC (12)圖9:SCB (14)圖10:路由引擎 (16)圖11:路由引擎中的USB記憶體裝置 (17)圖12:纜線管理分隔板 (19)圖13:安裝在裝置上的纜線管理系統 (19)圖14:精密介面的前面板 (20)圖15:警示轉接接點 (23)圖16:AC電源供應器 (24)圖17:DC電源供應器 (25)圖18:通過機箱的氣流 (27)圖19:風扇架 (28)圖20:空氣濾網 (28)第2部分設定服務閘道第3章為安裝服務閘道準備場地31圖21:典型開放式框架機架 (34)圖22:機箱尺寸與空間需求 (35)第5章拆開服務閘道的包裝39圖23:運輸板條箱內的內容 (40)第6章安裝裝載硬體43圖24:為四柱式機架或機櫃安裝前裝載硬體 (44)圖25:為開放式框架機架安裝裝載硬體 (45)第7章安裝服務閘道47圖26:將服務閘道安裝到機架中 (49)圖27:安裝纜線管理系統 (50)第8章連接服務閘道51圖28:路由引擎管理連接埠 (52)圖29:路由引擎乙太網路纜線連接器 (52)圖30:主控台與附屬纜線連接器 (53)圖清單■xvSRX5600服務閘道硬體指南圖31:警示轉接接點 (53)圖32:將纜線連接至IOC (54)第9章將服務閘道接地並為其供電55圖33:將AC電源連接到服務閘道 (57)圖34:將DC電源連接到服務閘道 (59)第3部分硬體維護、替換及疑難排解步驟第11章維護硬體元件71圖35:卡邊 (79)圖36:請勿握住連接器邊 (80)圖37:請勿用一條邊來支撐整塊卡 (81)第12章硬體元件疑難排解83圖38:通過機箱的氣流 (85)第13章替換硬體元件91圖39:移除精密介面 (94)圖40:安裝精密介面 (95)圖41:警示轉接接點 (95)圖42:移除風扇架 (97)圖43:安裝風扇架 (98)圖44:移除空氣濾網 (99)圖45:安裝空氣濾網 (100)圖46:移除SCB (102)圖47:安裝SCB (104)圖48:移除路由引擎 (105)圖49:安裝路由引擎 (106)圖50:路由引擎介面連接埠 (106)圖51:纜線連接器 (107)圖52:移除IOC (109)圖53:安裝IOC (111)圖54:將纜線連接至IOC (111)圖55:移除SPC (113)圖56:安裝SPC (114)圖57:將纜線連接至SPC (114)圖58:移除SFP或XFP (116)圖59:移除AC電源供應器 (118)圖60:安裝AC電源供應器 (119)圖61:移除DC電源供應器 (120)圖62:安裝DC電源供應器 (122)圖63:連接DC電源 (123)圖64:將電纜連接至DC電源供應器 (125)圖65:移除或安裝纜線管理系統 (126)第4部分附錄附錄A安全與法規遵從性資訊129圖66:將元件放置於靜電袋中 (134)附錄D電源準則、需求與規格167圖67:接地纜線插孔 (168)xvi■圖清單圖清單圖68:服務閘道的典型DC來源佈線 (171)圖69:DC電纜插孔 (172)圖70:AC插頭類型 (176)附錄F不使用機械起重機安裝服務閘道183圖71:安裝服務閘道前先移除電源供應器 (184)圖72:移除風扇架 (185)圖73:移除SCB (186)圖74:移除IOC或SPC (187)圖75:將服務閘道機箱安裝到機架中 (189)圖76:重新安裝電源供應器 (190)圖77:安裝風扇架 (191)圖78:安裝SCB (192)圖79:安裝IOC或SPC (193)圖80:安裝纜線管理系統 (193)附錄G聯絡客戶支援並退還硬體195圖81:序號ID標籤 (196)圖82:SRX5600機箱序號標籤 (197)圖83:SCB序號標籤 (197)圖84:IOC與SPC序號標籤 (198)圖85:AC電源供應器序號標籤 (199)圖86:DC電源供應器序號標籤 (199)圖87:路由引擎序號標籤 (200)圖清單■xviiSRX5600服務閘道硬體指南xviii■圖清單表格清單關於本指南xxi表1:通告圖示 (xxii)表2:文字與語法慣例 (xxii)表3:J系列服務路由器與SRX系列服務閘道的JUNOS軟體文件 (xxiii)第1部分SRX5600服務閘道綜述第2章硬體元件5表4:4連接埠100億位元乙太網路IOC LED (10)表5:40連接埠10億位元乙太網路IOC LED (10)表6:SPC LED (12)表7:開關控制板LED (15)表8:路由引擎LED (17)表9:警示LED與警示切斷/亮起測試按鈕 (20)表10:主機子系統LED (21)表11:精密介面上的電源供應器LED (21)表12:IOC與SPC LED (21)表13:SCB LED (22)表14:風扇LED (22)表15:AC電源供應器LED (25)表16:電源供應器冗餘與配電 (26)表17:DC電源供應器LED (26)第2部分設定服務閘道第3章為安裝服務閘道準備場地31表18:場地準備核對清單 (31)第5章拆開服務閘道的包裝39表19:完全組態的服務閘道的零件清單 (41)表20:附件盒零件清單 (41)第6章安裝裝載硬體43表21:四柱式機架或機櫃裝載孔位置 (43)第3部分硬體維護、替換及疑難排解步驟第13章替換硬體元件91表22:現場可替換單元 (92)表23:必要工具及零件 (92)表格清單■xixSRX5600服務閘道硬體指南第4部分附錄附錄B實體規格163表24:實體規格 (163)附錄C服務閘道環境規格165表25:服務閘道環境規格 (165)附錄D電源準則、需求與規格167表26:DC電源系統電力規格 (168)表27:DC電源供應器電力規格 (169)表28:DC供電的基礎系統需求 (170)表29:元件電源需求 (170)表30:DC電纜規格 (172)表31:AC電源系統規格 (173)表32:AC電源供應器電力規格 (173)表33:基礎系統AC電源需求 (174)表34:元件電源需求 (174)表35:AC電線規格 (175)附錄E纜線與電線準則與規格179表36:導致連結損失的因素的估計值 (181)表37:路由引擎管理與警示介面的纜線與電線規格 (182)附錄H纜線連接器接腳配置205表38:路由引擎ETHERNET連接埠的RJ-45連接器接腳配置 (205)表39:AUX和CONSOLE連接埠的RJ-45連接器接腳配置 (206)xx■表格清單關於本指南此前言為您使用SRX5600服務閘道硬體提供以下指導方針:■目標(第xxi頁)■目標讀者(第xxi頁)■文件慣例(第xxi頁)■J系列服務路由器與SRX系列服務閘道的JUNOS軟體文件(第xxiii頁)■取得文件(第xxiv頁)■文件意見回饋(第xxv頁)■要求技術支援(第xxv頁)目標本手冊介紹Juniper Networks SRX5600服務閘道的硬體元件、安裝、基本組態以及基本疑難排解程序。
SRX安全网关操作手册

SRX安全网关操作手册神州数码(中国)有限公司二零一零年六月目录1.总体概述 (7)1.1.文档术语 (7)2.SRX基本操作 (8)2.1.通过Console线缆连接路由器 (8)2.2.设备关闭 (10)2.3. 设备重启 (10)2.4.JUNOS升级 (11)2.5.密码恢复 (11)3.SRX基本管理配置介绍 (12)3.1.JUNOS CLI (12)4.SRX开机配置过程 (14)4.1.SRX硬件设备简介 (14)4.1.1 SRX 240面板图 (14)4.1.2 SRX 210面板图 (15)4.1.3 SRX 100面板图 (15)4.2.SRX安装流程 (15)4.3.开始配置 (15)4.3.1开机登录 (16)4.3.2清空默认配置 (16)4.3.3从所有配置清空后开始配置 (17)5.常用故障诊断命令 (20)查看端口状态 (20)查看路由表 (20)查看OSPF邻居关系 (20)Ping (21)Traceroute (21)监控接口流量 (21)监控RE CPU利用率 (22)监控并发会话数 (22)冷却系统故障检查 (22)机箱硬件组件故障检查 (23)6. 设备日常维护 (24)日常维护步骤 (24)配置文件查看 (24)配置文件提交 (24)7.SRX常用功能及典型配置 (25)7.1 SRX常用功能配置 (25)7.2 SRX一个典型配置 (28)6.硬件返修及CASE信息 (34)一般性免责说明:神州数码(中国)有限公司力求确保《Juniper SRX防火墙快速安装手册》中信息的准确性,但不对信息的准确性承担任何责任。
神州数码(中国)有限公司可能随时更改本《手册》中提到的产品或调试命令等技术,恕不另行通知。
神州数码(中国)有限公司及其供应商不对因使用本《手册》或任何Juniper网络公司产品或服务而导致的任何间接、特殊、引致或意外损失而承担任何责任,包括但不限于利润或收入损失、替换产品或服务的成本、数据丢失或破坏,或使用或依赖使用本文提供的信息而造成的损失,即使Juniper 网络公司或其供应商事先已得知发生此类损失的可能性。
SRX基本配置
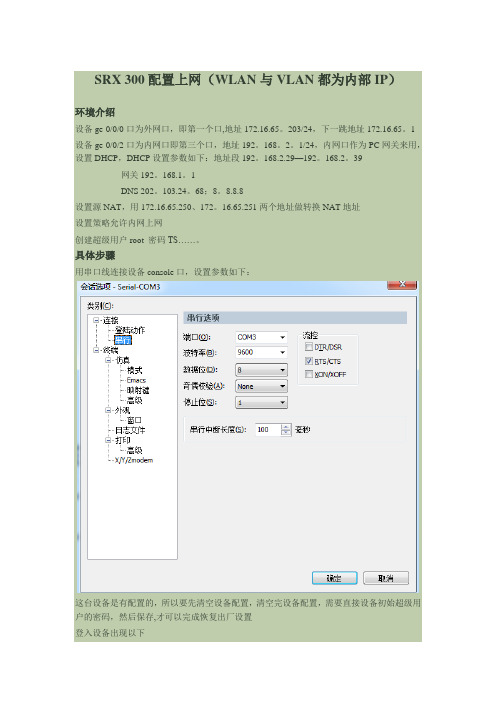
SRX 300配置上网(WLAN与VLAN都为内部IP)环境介绍设备ge-0/0/0口为外网口,即第一个口,地址172.16.65。
203/24,下一跳地址172.16.65。
1 设备ge-0/0/2口为内网口即第三个口,地址192。
168。
2。
1/24,内网口作为PC网关来用,设置DHCP,DHCP设置参数如下:地址段 192。
168.2.29—192。
168.2。
39网关 192。
168.1。
1DNS 202。
103.24。
68;8。
8.8.8设置源NAT,用172.16.65.250、172。
16.65.251两个地址做转换NAT地址设置策略允许内网上网创建超级用户root 密码TS……。
具体步骤用串口线连接设备console口,设置参数如下:这台设备是有配置的,所以要先清空设备配置,清空完设备配置,需要直接设备初始超级用户的密码,然后保存,才可以完成恢复出厂设置登入设备出现以下root@root〉root@root>configure 进入配置模式Entering configuration mode[edit]root@root# load factory-default 恢复出厂设备warning:activating factory configuration[edit]root@root# set system root-authentication plain—text-password 设置超级用户密码New password:Retype new password:[edit]root@root# commitcommit complete[edit] 此时回复出厂设置完成,下一步开始配置login: root 输入默认用户名rootPassword: 输入重置设备前输入的密码root@root%cli 敲入cli进入执行模式root@root> configure 敲入configure进入配置模式,执行模式代表符号“〉”Entering configuration mode[edit]root@root# 配置模式“#”root@root# set system login user lvlin class super—user authentication plain-text—password 建立用户名为“wangjian”的超级用户New password:为用户“root"设置密码Retype new password: 重复输入密码[edit]root@root#delete interfaces ge—0/0/0。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
网络部署 SRX 系列分支办事处业务网关部署在网络中的远程和分支办事处 场所,提供一体化安全广域网连接、网络电话、以及通过集成以 太网交换连接到本地计算机和服务器的能力。
特性和优势
安全路由 您是否应使用路由器和防火墙来保证网络安全?通过把分支办 事处 SRX 系列与一流的路由和防火墙能力整合为一个产品,企 业不必采用这样的选择。如果流量不合法,那么为什么要转发 它呢?
3Байду номын сангаас
相反的是,如果发生故障切换,全部动态流和会话信息都会丢 失,必须重建。部分或全部应用会话必须重启,这取决于链接 或节点的会聚时间。通过保持状态,不仅可保持会话,而且安 全性也毫发无损。在不稳定网络中,这种活跃/活跃配置还能够 减轻影响会话性能的链路摆动。
无损性能的基于会话的转发 为了优化组合路由器和防火墙的处理能力和延迟,Junos 操作系 统实现了基于会话的转发机制,这是把传统防火墙的会话状态信 息和传统路由器的下一跳转发整合为单个操作的一种创新。采用 Junos 操作系统,被转发策略允许的会话与下一跳路由的指针一 起被添加到转发表中。对于已建立的会话,只需进行一次查表, 以验证该会话已经获得许可,并查找下一跳。与执行多次查表来 验证会话信息然后查找下一跳路由的传统路由器相比,这种高效 算法提高了会话处理能力,并缩短了会话延迟。
图 3 表示出了基于会话的转发算法。当建立一个新会话时,在 Junos 操作系统内的基于会话的架构会验证转发策略是否允许该 会话。如果允许该会话,Junos 操作系统会在路由表中查找下一 跳路由。然后,它把会话和下一跳路由插入到会话和转发表中, 并转发信息包。对于已建立会话的后续信息包,只需在会话和转 发表中进行一次查找,并转发到出口接口。
• SRX 系列分支办事处网关采用 Junos 操作系统,该操作系统是在全球 100 强服务提 供商的核心互联网路由器中普遍采用的成熟操作系统。在过去 10 年的全球推广应用 中,经过严格测试的电信运营商级 IPv4/IPv6、OSPF、BGP 和多播路由特性已得 到证明。
• SRX 系列分支办事处业务网关提供周界安全、内容安全、接入控制以及整个网络范围 的威胁能见度和控制能力。一流的防火墙和虚拟专用网 (VPN) 技术能够以最低的配置 和一致的性能保证周界安全性。通过运用分区和策略,即使是没有经验的网络管理员 也能够快速安全地为分支办事处部署和配置 SRX 系列产品。基于策略的 VPN 支持需 要动态地址分配和分离隧道的更复杂安全架构。对于内容安全,SRX 系列分支办事处 产品提供一整套统一威胁管理 (UTM) 服务,包括:入侵防护系统 (IPS)、防病毒、防 垃圾邮件、通过内容过滤实现的网页过滤以及数据丢失防护,从而保护您的网络,防 止最新的内容威胁。精选型号的产品具有内容安全加速器以提供高性能 IPS 和防病毒 性能。分支办事处 SRX 系列产品与其它的瞻博安全产品集成,从而提供企业级的统一 接入控制和自适应威胁管理。这些能力为安全专家提供了与网络犯罪和数据丢失斗争 的强大工具。
主用
EX 系列
主用 / 主用
互联网
SRX240
故障
EX 系列
SRX240
主用
EX 系列
图 2:高可用性
为了便于防火墙的配置,SRX 系列分支办事处网关采用两个特 性 -- “区域”和“策略”。虽然这些可由用户定义,但默认出 厂配置包含至少一个信任区域和一个非信任区域。信任区域用 于配置以及把局域网连接到分支办事处 SRX 系列产品。非信 任区域用于广域网或互联网接口。为了简化安装并使配置更容 易,有默认策略可以让从信任区域发起的流量能够流转到非信 任区域。此策略阻挡从非信任区域发起并流向信任区域的全部 流量。传统路由器转发全部流量,不考虑防火墙(会话感知) 或策略(会话的源点和目的地)。
当把 SRX 系列分支办事处业务网关配置为一对活跃网关时,会 自动对流量和配置进行镜像,从而在发生故障时保持活跃的防 火墙和 VPN 会话。此时,分支办事处 SRX 系列产品可同步配 置和运行时信息。结果是,在故障切换期间,下列信息的同步 是共享的:连接/会话状态和流量信息、IPsec 安全关联、网络 地址转换 (NAT) 流量、地址薄信息、配置变更等。与典型的路 由器活跃/备用弹性协议(例如虚拟路由器冗余协议 (VRRP))
产品说明
瞻博网络® 的 SRX 系列分支办事处业务网关综合了瞻博网络公司的高端 SRX 系列、EX 系列以太网交换机、M 系列多服务边缘路由器、MX 系列三维通用边缘路由器以及 T 系 列核心路由器,从而提供基于瞻博网络的 Junos® 操作系统的、规模空前的产品系列。 采用 Junos 操作系统,企业和服务提供商能够在其整个分布式员工队伍中降低部署和运 营成本。
会话初始包处理
安全策略评估和下一跳查找
表 更新
会话和转发表
入口 接口
被策略禁止: 丢弃
允许业务流的 转发
出口 接口
图 3:基于会话的转发算法
小型办公机构
固定移动站点 (移动 – 3G)
SRX210
移动
蜂窝
DSL
EX4200/EX2200 EX3200/EX2200
高可用性 Junos 操作系统服务冗余协议 (JSRP) 是分支办事处 SRX 系列 的一个核心特性。JSRP 支持把一对安全系统方便地集成为高效 的网络架构,在系统和相邻网络交换机之间采用冗余物理连接。 通过链接冗余,瞻博网络可解决许多常见的系统故障原因,例如 物理端口恶化或电缆松脱,从而保证连接的可用性,而不需要整 个系统进行故障切换。这与路由弹性协议的典型活跃/备用特点 一致。
“不信任”区域 互联网
“信任”区域
内部网 “来宾”区域
“DMZ” 区域
图 1:防火墙、区域和策略
2
主用 / 备用
高可用性
主用 / 备用
互联网
互联网
SRX240
主用
EX 系列
SRX240
备用
EX 系列
SRX240
故障
EX 系列
SRX240
主用
EX 系列
主用 / 主用
互联网
SRX240
主用
EX 系列
SRX240
产品简介
SRX 系列分支
办事处业务网关
SRX100、SRX210、SRX220、 SRX240 和 SRX650
产品概述
瞻博网络公司的 SRX 系列分支办事 处业务网关是一种安全路由器,它为 从少量用户到成百上千用户规模的工 作场所提供必要的连接、安全和管理 能力。通过在单个设备中整合快速、 高可用性的交换、路由、安全和应用 能力,企业能够以经济高效的方式提 供新服务、安全连接,并且使最终用 户获得满意的体验。所有 SRX 系列 业务网关(包括针对分支办事处、园 区和数据中心应用量身定制的产品) 都由瞻博网络公司的 Junos 操作系统 支持 -- 该操作系统是一个成熟产品, 它以较低的总拥有成本提供无与伦比 的一致性、更好的性能和服务、以及 优异的基础设施保护。
• SRX 系列分支办事处网关是一种安全路由器,它为需要建立具有成千上万站点的全球 网络的企业提供高性能和成熟的部署能力。众多的选项允许根据规模配置性能、功能 和价格,从而支持从少量用户到成千上万用户的环境。以太网、串行线路、T1/E1、 xDSL、DOCSIS3、城域以太网和第三代 (3G) 蜂窝无线技术都是广域网或互联网连 接的可用选项,从而安全地链接您的站点。多种外形尺寸使您能够针对关键性事务 部署做出经济高效的选择。使用成熟的 Junos 操作系统命令行接口 (CLI) 和脚本能 力,或者仅使用基于浏览器的图形用户界面,能够方便地管理网络。
SRX 系列分支办事处产品检查流量是否合法,并且仅转发合法的 流量。这能够降低网络的负载,为所有其它的关键性事务应用分 配带宽,并防止网络受到攻击。
安全路由器的主要作用是提供防火墙保护并应用策略。防火墙 (区域)功能检查流量和状态,以保证在会话中发起和返回信
息对特定区域而言有所预期并经过允许。安全策略决定在某个 区域中是否可以发起会话以及是否可以穿越到另一个区域。这 种架构选择从各种客户机和服务器接收信息包,并跟踪每个应 用和每个用户的任何会话。它使企业能够确保网络中只有合法 的流量,并且使流量按预期的方向流动。
1
架构和关键组件
分支办事处 SRX 系列产品的关键硬件特性
产品
SRX100 业务网关 SRX210 业务网关
SRX220 业务网关
SRX240 业务网关
SRX650 业务网关
说明
• 8 个 10/100 以太局域网端口 • 全面 UTM2;防病毒2、防垃圾邮件2、网页过滤2、入侵防护系统2(大内存版本) • 统一接入控制 (UAC) 和内容过滤 • 1GB8 DRAM、1GB 闪存标准配置(在小内存版本中可使用 512MB DRAM) • 2 个 10/100/1000 以太网端口和 6 个 10/100 以太局域网端口,1 个 Mini-PIM 插槽、1 个 ExpressCard 插槽和 2 个 USB 端口 • 出厂时可选择 4 个 动态以太网供电 (PoE) 端口 802.3af • 支持 T1/E1、串行、ADSL/2/2+、VDSL、G.SHDSL、DOCSIS3、以太网小封装可插拔收发器 (SFP) 和千兆以太网接口 • 内容安全加速器硬件,用于提高 IPS 和 ExpressAV 的性能 • 全面 UTM2;防病毒2、防垃圾邮件2、网页过滤2、入侵防护系统2(大内存版本) • 统一接入控制 (UAC) 和内容过滤 • 512MB DRAM 标准配置(出厂时可选 1GB DRAM)、1GB 闪存标准配置 • 8 个 10/100/1000 以太局域网端口、2 个 Mini-PIM 插槽 • 出厂时可选择 8 个 PoE 端口;PoE +803.3at,与 802.3af 后向兼容 • 支持 T1/E1、串行、ADSL/2/2+、VDSL、G.SHDSL、DOCSIS3、以太网小封装可插拔收发器 (SFP) 和千兆以太网接口 • 内容安全加速器硬件,用于提高 IPS 和 ExpressAV 的性能 • 全面 UTM2;防病毒2、防垃圾邮件2、网页过滤2、入侵防防御系统2(大内存版本) • 统一接入控制和内容过滤 • 1GB DRAM、1GB 闪存标准配置 • 16 个 10/100/1000 以太局域网端口、4 个 Mini-PIM 插槽 • 出厂时可选择 16 个 PoE 端口;PoE +803.3at,与 802.3af 后向兼容 • 支持 T1/E1、串行、ADSL/2/2+、VDSL、G.SHDSL、DOCSIS3、以太网小封装可插拔收发器 (SFP) 和千兆以太网接口 • 内容安全加速器硬件,用于提高 IPS 和 ExpressAV 的性能 • 全面 UTM2;防病毒2、防垃圾邮件2、网页过滤2、入侵防护系统2(大内存版本) • 统一接入控制和内容过滤 • 512MB DRAM 标准配置(出厂时可选 1GB DRAM)、1GB 闪存标准配置 • 4 个固定 10/100/1000 以太局域网端口、8 个 GPIM 插槽或多个 GPIM 和 XPIM 的组合 • 支持 T1、E1、千兆以太局域网端口;采用可选 PoE 时支持多达 48 端口交换,包括 802.3at、PoE+,与 802.3af 后向兼容 • 内容安全加速器硬件,用于提高 IPS 和 ExpressAV 的性能 • 全面 UTM2;防病毒2、防垃圾邮件2、网页过滤2、以及入侵防护系统2 • 统一接入控制和内容过滤 • 模块化服务和路由引擎;将来将支持内部故障切换和热插拔 • 2GB DRAM 标准配准、2GB compact flash 标准配置、用于增加存储的外部 compact flash 插槽 • 可选冗余交流电源;支持 PoE 的标准交流电源;PoE 电源具有 250 瓦冗余能力或 500 瓦非冗余能力
