35-TPC-E implementation-Mark-Wong-Rilson-Nascimento
艾顿 bypass 隔离自动转换交换器说明书

Unmatched performance and reliabilityBypass isolation ATS Eaton’s bypass isolation automatic transfer switch (ATS) is designed to provide unmatched performance, reliability and versatility for critical standby power applications. Supervisory intelligence is provided by an ATC-900 or ATC-300+ controller, delivering operational simplicity and field adaptability coupled with diagnostic and troubleshooting capabilities. The bypass isolation ATS design is ideal for those applications where the ability to perform maintenance is required without interrupting power to life safety and other critical loads.Product configuration• Automatic operation—ATS and bypass switch• Open and closed transition• 100–1200 A rating• Two-, three- or four-pole• NEMA T 1, 3R• Up to 600 Vac, three- orfour-wire, 60 Hz or 50/60 Hz• Drawout ATS and fixedbypass switch, facilitatingconcurrent maintenance• Service entranceFeatures and benefitsProven performanceand reliability• Automatic and non-automaticoperation modes are availableto provide multiple methods oftransferring the load betweenpower sources• Manual operation allowsunloaded transfer betweenpower sources for allproduct configurations• UL T 1008 Listed short-circuitand short-time (select catalognumbers only) withstandclosing current ratingsmaximize system reliabilitySimplified installationand integration• Factory-configured powersource and load terminalsfor top/bottom cable ingress• Removable enclosure panelsprovide front and rear accessto cable terminal connections• Seismic certified to OSHPD,CBC, IBC and UBCEnhanced safety• Two-door, compartmentalizedconstruction provides steelbarriers, protecting workers• Integral safety interlocksautomatically open the maincontacts prior to the ATSbeing isolated for test orremoved for serviceImproved serviceability• Two-door design eliminatesthe need to scheduleshutdowns for routine test,inspection or maintenanceof the ATS• Drawout design allows theATS to be disconnectedfrom the electrical bus andisolated in cell for regulartesting as prescribed bycode (NFPA T 70, 99, 110)• Testing of the isolated ATScan be performed whilethe bypass switch is in theautomatic or non-automaticmode of operationDesign featuresDual automatic technology Eaton’s bypass isolationtransfer switch design includes an automatic bypass switch and an ATS housed within a single assembly.Regardless of which power switch is actively distributing power, redundant automatic operation provides for a rapid load transfer and restoration of power to life safety and critical loads, eliminating the need for active supervision by qualified personnel.Segmented construction The ATS and automatic bypass switch are housed in separate compartments, with robust steel walls, that isolate the power switches from each other to facilitate ease of maintenance and worker safety. Eachcompartment includes a door with padlockable handle. This design prevents the possibility of inadvertent contact andunnecessary exposure to power cable terminations and energized electrical control components.Drawout ATS and fixed-mounted bypassService personnel can rack-out and isolate the ATS (with compartment door closed) from the electrical bus for routine test or exercise. A Kirk T -key interlock prevents access to the racking mechanism until the load connection has been transitioned to the automatic bypass switch.Opening the compartment door allows the ATS to be completely drawn out of the cell for inspection or maintenance.Safety interlocks prevent rack-out or rack-in of the ATS from the electrical bus with the main contacts closed. The automatic bypass switch is fixed mounted to the electrical bus and stands ready to initiate an automatic load transfer when the ATS is undergoing maintenance.Multi-tap control power transformerSystem voltage can be fieldconfigured via a multi-tap control power transformer (CPT) with quick-disconnect plugs.T ransition to bypass mode When maintenance or testing of the ATS needs to be performed, qualified personnel can easily and quickly transition the load connection between the ATS and automatic bypass switch using door-mounted operator controls fitted with indication lights. The transition occurs in a make-before-break fashion, ensuring continuous power flow to loads.Multiple operation modes Operation is possible in the following modes:• Automatic • Non-automatic •Manual AIn automatic mode, the transfer switch is self-acting, and atransfer is automatically initiated by the intelligent logic controller.In non-automatic mode(optional), a transfer is initiated by the operator using a door-mounted selector switch.In manual mode, a transfer is initiated by the operator using controls mounted directly on the automatic bypass switch or ATS.Alternatively, a transfer can be initiated remotely via an HMi remote annunciator controller.A Manual operation (unloaded) is provided forall product configurations.for top and bottom cable terminationFixed-mounted automatic Drawout ATS can be isolated for test within compartment orand automatic bypassswitch compartments600–1200 A rating (480 V), NEMA 1 enclosure100–400 A rating (480 V), NEMA 1 enclosureFixed-mounted automatic Drawout ATS can within compartmentor completely removedRemoveable optionpanels allow front access for top and bottom cableterminationDrawout ATS removed for bench level inspection/Automatic bypass switch stands ready to transfer load2EATON Bypass isolation automatic transfer switchesStandard enclosure dimensions and weightsDimensions and weights shown are approximate and subject to change. Reference product outline drawings for the latest information.NEMA 1 enclosure NEMA 3R enclosureNEMA 12/4X enclosureTransferswitch rating Device Dimensions in inches (mm)Normal,emergency, loadNeutral A Weight ABCA Neutral connection size listed is for product configuration with a solid neutral. For product configurations with a switched neutral (four-pole), reference the size listed in theEmergency/Load Connection column.B Three-pole product configuration.C Four-pole product configuration.3EATON Bypass isolation automatic transfer switchesEaton is a registered trademark.All other trademarks are property of their respective owners.Eaton1000 Eaton Boulevard Cleveland, OH 44122United States © 2022 EatonAll Rights Reserved Printed in USAPublication No. PA01602019E / Z25954March 2022Product selectionCatalog numbering systemote: N Some catalog number combinations may not be available. For additional information, please contact your local Eaton sales representative.Bypass isolation ATS schematic diagramUL 1008 withstand and closing current ratings (kA)Ampere Device Up to 480 VUp to 600 V Short-circuit (specific circuit Short-circuit (specific circuit SpecificFollow us on social media to get the latest product and support information.。
c-tpat 计划的承诺书

c-tpat 计划的承诺书英文回答:C-TPAT (Customs-Trade Partnership Against Terrorism) is a voluntary supply chain security program led by U.S. Customs and Border Protection. The program aims to enhance the security of global trade and prevent terrorism by collaborating with businesses to implement best practices and secure supply chains.As a participant in the C-TPAT program, I am committed to fulfilling the requirements and obligations outlined in the C-TPAT agreement. This commitment involves implementing and maintaining effective security measures throughout my supply chain, from the point of origin to the point of distribution.One of the key commitments of the C-TPAT program is conducting a comprehensive risk assessment of my supply chain. This involves identifying potential vulnerabilitiesand implementing appropriate security measures to mitigate those risks. For example, I may conduct background checkson employees, secure cargo and facilities, and establish protocols for handling and inspecting shipments.Another commitment is to maintain a high level of awareness and vigilance within my organization. This includes providing security training to employees, establishing reporting mechanisms for suspicious activities, and regularly reviewing and updating security procedures.By fostering a culture of security consciousness, I canhelp prevent and detect potential security threats.Furthermore, I am committed to cooperating with U.S. Customs and Border Protection and other government agencies to support their efforts in securing the international supply chain. This may involve sharing information, participating in joint security exercises, and facilitating inspections and audits.In addition to these commitments, I understand the importance of ongoing monitoring and continuous improvement.I will regularly review and assess the effectiveness of my security measures, identify areas for improvement, and take necessary actions to enhance the security of my supply chain.中文回答:C-TPAT(海关贸易反恐伙伴计划)是由美国海关和边境保护局领导的自愿供应链安全计划。
中英文技能对照表
3gpp Service Systems Aspects

TS 32.312 TS 32.313 TS 32.314 TS 32.316 TS 32.317 TS 32.321 TS 32.322 TS 32.323 TS 32.324 TS 32.325 TS 32.326 TS 32.327 TS 32.331 TS 32.332 TS 32.333 TS 32.334 TS 32.335 TS 32.336 TS 32.337 TS 32.341 TS 32.342 TS 32.343 TS 32.344 TS 32.345 TS 32.346 TS 32.347 TS 32.351 TS 32.352 TS 32.353 TS 32.354 TS 32.355 TS 32.356 TS 32.357 TS 32.361 TS 32.362 TS 32.363 TS 32.364 TS 32.365 TS 32.366 TS 32.367 TS 32.371 TS 32.372 TS 32.373 TS 32.375 TS 32.376 TS 32.381 TS 32.382 TS 32.383
TS 32.503 TS 32.505 TS 32.506 TS 32.507 TS 32.511 TS 32.521 TS 32.522 TS 32.523 TS 32.525 TS 32.531 TS 32.532 TS 32.533 TS 32.535 TS 32.536 TS 32.537 TS 32.541 TS 32.542 TS 32.543 TS 32.551 TS 32.571 TS 32.572 TS 32.581 TS 32.582 TS 32.583 TS 32.584 TS 32.591 TS 32.592 TS 32.593 TS 32.594 TS 32.600 TS 32.601 TS 32.602 TS 32.603 TS 32.604 TS 32.606 TS 32.607 TS 32.611 TS 32.612
HCIE笔试datacom题库H12-891

1.CE1和CE2属于同一个VPN,VPN实例的名字为vpna。
通过OptionC方式一实现CE1和CE2互通。
为实现该需求,ASBR-PE1配置了两条路由策略,针对1.[ASBR-PE1-bgp]peer route-policy policy2 export(仅填写IP地址)。
【答案】:(10.0.34.4/10.0.4.4)1.telemetry两种订阅方式,其中订阅时间较短的方式是_____?(全称)【答案】:(动态订阅)1.<rpc xm/ns ="xxxx"message-id="1024“属于netconf中的_____层(中文全称)【答案】:(消息)1.请将以下命令与其作用对应起来_______。
【答案】:(Arp br adcast-Suppress enable ---- ARP广播抑制Arp c llect h st enable ---- 主机信息搜集Arp-pr xy l cal enable ---- ARP本地代理Arp distribute-gateway enable ---- 分布式网关)1.Q S在执行时有一定的顺序,请将以下的几个Q S功能模块按照正确的顺序排序。
1-复杂流分类、2-拥塞避免、3-拥塞管理、4-简单流分类、5-流量整形1.CE1 和CE2 属于同一个WPN,VPN 实例的名字为vpna。
通过OptionC 方式一实现CE1 和CE2 互通。
为实现该需求,请将以下命令行与设备编号进行匹配。
1.HQoS 一共有三级队列: Leve1l, Level2, Level3。
请将以下队列名称与队列等级一一对应。
【答案】:1. NETC NE内容层为设备配置数据,针对以下NETC NEF信息,描述正确的有哪些项?A、该配置采用了Huawei-YANG方式B、该配置为在设备上创建VLAN 10C、该配置采用了NETC NF <edit-c nfig>操作,把配置数据加载到启动配置库D、<c nfig>中包含了“perati n”属性,为merge操作【答案】:ABCD1.SR-MPLS P licy可以借助BGP扩展来传递隧道信息,其信息如图所示。
亚马逊CSR审核文件清单

# LABOR DOCUMENTS
1 考勤记录 Attendance Records (_______年_____月到_______年_____月)
2 员工加班申请表(如有) Overtime Application Form (if any)
3 综合计时工作制批文(如有) Comprehensive Working Hours System Approval (if any)
4 工资表 Payroll Records (_______年_____月到_______年_____月)
5 当地政府最低工资标准文件 Local Minimum Wage Notice
6 人事档案, 员工花名册 Personnel Files, Employee Roster
7 招聘政策, 招聘程序文件 Recruitment Policy &Recruitment Procedure
A) 社会保险参保收据(最近三个月); B) 社会保险参保名单(最近一个月); C) 当地社会保险参保计算方法 15
A) Social Insurance Contribution Receipts (Most recent three months); B) Social Insurance Enrollment Name List (Most recent month); C) Local Social Insurance Calculation Formula 16 投诉程序和相关记录 Grievance Procedure and Records
8 员工离职记录(最近 3 个月) Worker Resignation Records (Most recent 3 months) 员工手册,工厂休假政策 (带薪年假,产假,病假等)
InteractX 3.X Driver Guide
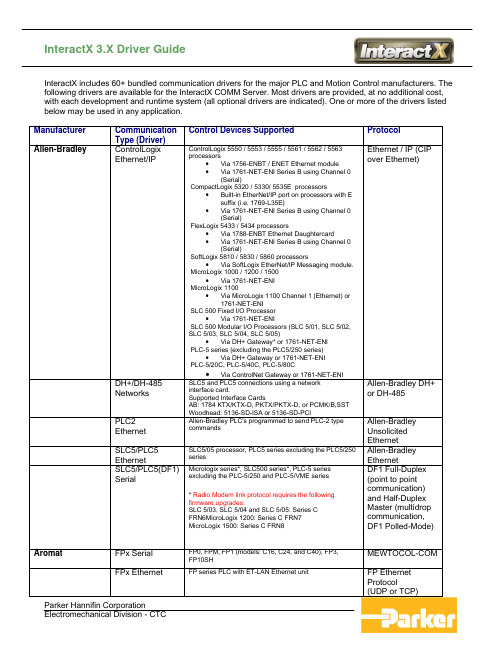
InteractX includes 60+ bundled communication drivers for the major PLC and Motion Control manufacturers. The following drivers are available for the InteractX COMM Server. Most drivers are provided, at no additional cost, with each development and runtime system (all optional drivers are indicated). One or more of the drivers listed below may be used in any application.Manufacturer CommunicationType (Driver)Control Devices Supported ProtocolAllen-Bradley ControlLogixEthernet/IP ControlLogix 5550 / 5553 / 5555 / 5561 / 5562 / 5563processors•Via 1756-ENBT / ENET Ethernet module•Via 1761-NET-ENI Series B using Channel 0(Serial)CompactLogix 5320 / 5330/ 5535E processors•Built-in EtherNet/IP port on processors with Esuffix (i.e. 1769-L35E)•Via 1761-NET-ENI Series B using Channel 0(Serial)FlexLogix 5433 / 5434 processors•Via 1788-ENBT Ethernet Daughtercard•Via 1761-NET-ENI Series B using Channel 0(Serial)SoftLogix 5810 / 5830 / 5860 processors•Via SoftLogix EtherNet/IP Messaging module.MicroLogix 1000 / 1200 / 1500• Via1761-NET-ENIMicroLogix 1100•Via MicroLogix 1100 Channel 1 (Ethernet) or1761-NET-ENISLC 500 Fixed I/O Processor• Via1761-NET-ENISLC 500 Modular I/O Processors (SLC 5/01, SLC 5/02,SLC 5/03, SLC 5/04, SLC 5/05)•Via DH+ Gateway* or 1761-NET-ENIPLC-5 series (excluding the PLC5/250 series)•Via DH+ Gateway or 1761-NET-ENIPLC-5/20C, PLC-5/40C, PLC-5/80C•Via ControlNet Gateway or 1761-NET-ENIEthernet / IP (CIPover Ethernet)DH+/DH-485 Networks SLC5 and PLC5 connections using a networkinterface card.Supported Interface CardsAB: 1784 KTX/KTX-D, PKTX/PKTX-D, or PCMK/B,SSTWoodhead: 5136-SD-ISA or 5136-SD-PCIAllen-Bradley DH+or DH-485PLC2 Ethernet Allen-Bradley PLC's programmed to send PLC-2 typecommandsAllen-BradleyUnsolicitedEthernetSLC5/PLC5 Ethernet SLC5/05 processor, PLC5 series excluding the PLC5/250seriesAllen-BradleyEthernetSLC5/PLC5(DF1) Serial Micrologix series*, SLC500 series*, PLC-5 seriesexcluding the PLC-5/250 and PLC-5/VME series* Radio Modem link protocol requires the followingfirmware upgrades:SLC 5/03, SLC 5/04 and SLC 5/05: Series CFRN6MicroLogix 1200: Series C FRN7MicroLogix 1500: Series C FRN8DF1 Full-Duplex(point to pointcommunication)and Half-DuplexMaster (multidropcommunication,DF1 Polled-Mode)Aromat FPx Serial FP0, FPM, FP1 (models: C16, C24, and C40), FP3,FP10SHMEWTOCOL-COMFPx Ethernet FP series PLC with ET-LAN Ethernet unit FP EthernetProtocol(UDP or TCP)Automation Direct205/405 ECOMEthernet DL-05, DL-06, DL-230, DL-240, DL-250, DL-260, DL-430,DL-440 and DL-450 PLCs via an Hx-ECOM module.Koyo Ethernet205/305/405 DirectNet Serial DL-05, DL-06, DL-230, DL-240, DL-250, DL-260, DL-330, DL-340, DL-430, DL-440 and DL-450 PLCsDirectNet HexMode205/405 K Sequence Serial SG Series PLCsSL Series PLCsD1-105,D2-05, D2-06, D2-230, D2-240, D2-250, D2-260D4-430, D4-440, D4-450Koyo K SequenceBusware BuswareEthernet BUSWARE Ethernet I/O modules models: E200-FB00,E201-8B00, E290-FB00, E151-FB00, E190-8B00, E250-FB00, E300-FB00, and E191-CB00BUSWARE RS-485 I/O connected through an EthernetI/O module models: M200-FB00, M290-FB00, M151-FB00, M190-8B00, M181-4B00, M250-8B00, and M300-8B00Modbus OpenProtocol overEthernet usingWinsock V1.1 orhigher.Compumotor Example applications provided on CTC’s web site for Compumotor products See ListingUnder ParkerSee Listing Under Parker See Listing UnderParkerContrex Contrex CX-Series Serial. Contrex CX-1000 Motion Controller CX-Series SerialCommunicationsBinary Data-LinkProtocol.Contrex M – Series M-Cut, M-Drive, M-Rotary, M-Shuttle, M-Track, M-Traverse, M-Trim, ML-Drive, ML-TrimM-Series Data-LinkProtocol (4 byte/ 8byte).Control Technology Inc. CTi 2500EthernetCTi 2500 Series Processors (Use Siemens/TI 505Driver)CTi 2500 Serial CTi 2500 Series Processors (Use Siemens/TI 505Driver)Cutler – Hammer Cutler – HammerSerial D50 and D300 Programmable Controllers Cutler-HammerHex Mode ProtocolFuji Fuji Flex NB/NS/NJ series serial communications Fuji Computer Link GE Fanuc CCM Serial Series 90-30 311/313, 331/341Series 90-70 731/732, 771/772, 781/782Series Six CCM2Series FiveGE CCMGE Ethernet Series 90-30 311/313, 331/341, 350,360Series 90-70 731/732, 771/772, 781/782GE OPEN (Wide range model support)Horner OCS (Horner's Operator Control Stations)GE EthernetGE Ethernet Global Data Series 90-30 CPU-364 or higher equipped to handleEGD transactionsAny device that supports EGD protocol.EGD TransactionsGE Fanuc continued.SNP Serial Series GE MicroSeries 90-30 311/313, 331/341, 350,360Series 90-70 731/732, 771/772, 781/782GE OPEN Wide range model supportGE SNPSNPX Serial Series GE MicroSeries 90-30 311/313, 331/341, 350,360Series 90-70 731/732, 771/772, 781/782GE-OPEN Wide range model supportGE SNPXGeneral DDE Client DDE Client Driver is capable of standard "CF TEXT" DDEdata format "CF TEXT" DDE data formatODBC Database Client Retrieves data records from ODBC compliantdatabases such as using the Microsoft Data AccessComponents (MDAC) including• Microsoft Access• Microsoft SQL• Oracle• SybaseODBC Databaseusing MDACSimulator Live data simulation including Boolean, ramp, wave,sineand string values-General (Cont’d) AdvancedSimulator Provides data simulation by returning valuessequentially on a timed basis from an ODBC record set-OPC Client InteractX tags may be served to 3rd party OPCClients.-OPC Server 3rd party OPC Servers can be used to interface to multiplecontrol devices-User Configurable Driver Serial and Ethernet devices Master andunsolicitedmessaging forASCII and Binaryprotocols. EthernetDevices viaEthernet SerialEncapsulationHilscher DeviceNet andProifibus DP Use with Hilscher Communications Interface (CIF)cards forDeviceNet and Profibus DP connectivity.DeviceNet Master: CIF50-DNMDeviceNet Slave: CIF50-DNSProfibus DP Master: CIF50-PBProfibus DP Slave: CIF50-DPSUniversal DeviceDriver for CIFCardsHoneywell UDC Serial Honeywell UDC 3000UDC 3300 MODB3K mode Modbus RTU with Honeywell UDC extensionsIntelligent Actuator IA Super SELSerialIA Super SEL Controllers (Type E & G)X-Sel ControllersSuper SEL and X-Sel Controllers:SerialCommunicationProtocolsIDEC Serial Micro1, Micro3, MicroSmart, OpenNet, FA2J, FA2,FA3S-CP11 and FA3S-CP12 PLCsIdec ASCII ProtocolIOTech PointScanModBus TCPIOtech PointScan 100 modulesIOtech PointScan 200 modules connected through aPointScan 100 module. Modbus Open Protocol over Ethernet using Winsock V1.1 or higher.Micro-DCI Micro-DCISerial 53MC1000, 53MC2000, 53MC2002, 53MC4000, 53MC5000 Micro-DCI DataLinkProtocol. Binarymode switchingthrough theconfiguration port issupported.Mitsubishi A and Q SeriesEthernet All A Series PLCs via AJ71E71 ModuleAll Q Series PLCs via A1SJ71QE71 ModuleMitsubishi EthernetA Series Serial All A Series PLCs Format 1 withChecksum Enabled FX Net Serial FX, FX2C, FX0N, FX2N Format 1,ChecksumFX SeriesSerialFX, FX0, FX0N, FX2N Direct SerialModicon ModbusEthernet Modbus Ethernet compatible devices, both Master andSlave.Modus Master andSlave (Mailbox)Modbus Plus Modbus Plus compatible devices, both Master and Slave. Modbus Plus viaSA85 cardModbus Serial ASCII Modbus ASCII compatible devices, Flow Computers usingthe Daniels/Omni/Elliot register addressingModbus ASCIIModbus Serial RTU Modbus compatible devicesElliott Flow ComputerMagnetek GPD 515 DriveOmni Flow ComputerModbus RTUModbus SerialRTU SLAVE -UnsolicitedModbus compatible devices Modbus RTUOmron Fins Ethernet C200H/C200HE/C200HE-Z/C200HG/C200HGZ/C200HS/C200HX/C200HX-Z,C500, C1000H,C2000/C2000H, CV500, CV1000,CV2000, CVM1/CVM1-V2(CPU01/CPU11/CPU21), CS1H/CS1GOmron FINSFins Serial C200H/C200HE/C200HE-Z/C200HG/C200HGZ/C200HS/C200HX/C200HX-Z,C500, C1000H,C2000/C2000H, CV500, CV1000,CV2000, CVM1/CVM1-V2(CPU01/CPU11/CPU21),CS1H/CS1GOmron FINS Host Link C20H, C200H, CQM1 Omron Host LinkOptimation OptilogicEthernet OL2208, OL2211, OL2201; OL2108, OL2109, OL2111;OL2408, OL2418; OL2252; OL3406, OL3420, OL3440,OL3850Ethernet usingWinsock V1.1 orhigher.Parker AcroloopACR9000 ACR9000 Series EhterNet/IP Ethernet/ IP(ACRCIP)AcroloopPC Bus Cards ISA and PCI ACR1500, ACR2000, ACR8010, and ACR8020PC CardsBus InterfaceAcroloopGeneral SerialACR9000 RS-232 Serial User Config. Driver(*Note: The 6K OPC Server is an extra Cost Option) 6K Serial andEthernet6K Series of Universal Motion Controllers6K2, 6K4, 6K6 and 6K8Compumotor 6KOPC ServerParker (Cont’d)Compax3SerialRS-232 and RS-422 serial connectivity Compax 3 SerialGemini and Gemini6K Serial and Ethernet connectivity CompumotorActiveX Control(*Note: The 3S OPC Server is NOT bundled with InteractX) PLmC Ethernet connectivity 3S OPC ServerProvided withPLmCAries CE Aries CE via Ethernet Ethernet (ACREN)Partlow Partlow ASCIISerialPartlow ASCII Devices Partlow ASCIIPhilips PhilipsP8/PC20 Serial PC20 (using the CI21 or VI21 card), MC30 (using the CI30card), MC31, MC41, ISCOS 10, ISCOS 60, ISCOS 70PhilipsProgrammableControllerCommunicationProtocol(PPCCOM)Siemens MPI Network Siemens S7-300 and S7-400 devices via MPI PCAdapter:Siemens Part: 6ES7-972-OCA23-OXAO Version 5.1Siemens Part: 6ES7-972-OCA22-OXAO Version 5.0 Multi Point Interface (MPI) via PC AdapterEthernet to MPI Ethernet to MPI serial connection using NETLink adapterfrom Systeme HelmholzSiemens EthernetDriver.Siemens Ethernet Siemens S7-300/400 PLCs via an Industrial Ethernetinterface communication processor (CP)S7-200 via CP243 ModuleS7-300 via CP343 ModuleS7-400 via CP443 ModuleS7 Messaging onIndustrial Ethernet(ISO 8073 Class 0)over TCP/IPS5 - RK512 Any device that supports 3964 or 3964R protocol and usesthe RK 512 computer link program. 3964R and 3964 (The 3964 variant is identical to 3964 except it does not use a Byte Check Character)S5 Programming Port Siemens S5 - 90U, 95U, 100U – 100, 100U – 101,100U –103, 101U, 115U – 941, 115U – 942, 115U –943, 115U –944, 115U – 945, 135U – 921, 135U –922, 135U – 928,155U – 946, 155U - 947AS511 CurrentLoopSiemens (Cont’d) S7-200 PPI Siemens S7-200 devices Point-to-Point (PPI)S7-200CommunicationsProtocolSimatic 505 Ethernet TI Series 505 processors including 525, 545, 565 Simatic 505-CP2572Ethernet module orthe ControlTechnology Inc.505-CP2572 card.User DatagramProtocol (UDP) orTransfer ControlProtocol (TCP)Simatic 505 Serial TI Series 500/505 processors - 520, 525, 535, 545, 555,565, 575Non-IntelligentTerminal Protocol(NITP)Transparent Byteprotocol (TB)TIWAY UNLINK (Serial) TIWAY Secondary Devices via TIWAY 1 HostAdapter or TIWAY 1 UNILINK Host Adapterconnection to TIWAY compatible PLCsNITP protocolSixnet SixnetEthertrakEthernet SIXNET EtherTRAK I/O modules (firmware version 2.10 orlater), SIXNET RemoteTRAK I/O connected through anEtherTRAK I/O module. (Both the RemoteTRAK andEtherTRAK must have firmware version 2.01 or later.),SIXNET VersaTRAK RTUs (firmware version 2.12 or later),SIXNET SIXTRAK gateways (firmware version 2.12 or later)Modbus OpenProtocol overEthernet usingWinsock V1.1 orhigher.SoftPLC DF1 Serial SoftPLC based Controllers. (Use Allen BradleySLC5/PLC5 DF1 SerialDriver)DF1 Ethernet SoftPLC based Controllers. (Use Allen BradleyEthernet Driver) SquareD SY/MAX Serial SY/MAX PLCs and PowerLogic power line monitors SY/MAX Point-to-PointTelemecanique Uni-TelwaySerial TSX Controllers including the TSX Micro/Premium PLCs Small and LargeFrame Uni-TelewayThermo Westronics ThermoWestronicsSerialSeries 1200 Recorder, Series 1600 Recorder, Series 3000Recorder, SM 100 Smart Multiplexer, SV 100, SV 180, SV180 (2.0) - version 2.0A or laterModbus RTU SerialThermoWestronicsEthernetSV 100, SV 180, SV 180 (2.0) - version 2.0A or later Modbus TCPEthernetToshiba T Series Serial EX100, EX200,T1, T1 Super, T2 PLCs, and T3 PLCs Toshiba ASCIIComputer LinkProtocol Toyopuc Computer LinkSerialPC2 Series PLC or any Computer Link compatible device Computer Link PC2 Ethernet PC2 Series PLCs via EN-I/F Module Computer LinkPC2/PC3EthernetPC2 and PC3 Series PLCs via EN-I/F Module Computer LinkWAGO EthernetTCP/IP Wago 750 Bus Couplers Wago SpecificModbus EthernetYaskawa Memobus Plus Yasakawa controllers via Memobus Plus using the ModiconSA85 Network card.Memobus PlusMP Ethernet MP 920 Series controllers using 2181F Ethernetcommunication modulesEthernet TCP/IPYaskawa (Cont’d) Memobus Plus MP 900 Series controllers using serial Connection withnative tag addressingModbus RTUYokogawa DarwinEthernet DA100-1, DA100-2, DR131, DR231, DR232, DR241,DR242, DC100-1, DC100-2Yokagawa DarwinEthernetDarwin Serial DA100-1, DA100-2, DR131, DR231, DR232, DR241,DR242, DC100-1, DC100-2 Yokogawa Darwin SerialYokogawa (Cont’d)DX EthernetSupported Yokogawa Devices: DX102, DX204, DX104, DX208, DX106, DX210, DX112, DX220, DX230, MV100, MV200,DXAdvanced Models: DX1002, DX2004, DX1004, DX2008, DX1006, DX2010, DX1012, DX2020, DX2030, DX2040, DX2048Yokogawa DX Ethernet TCPDX SerialDX102, DX210, DX104, DX220, DX106, DX230, DX112, MV100, DX204, MV200, DX208Yokogawa DX SerialDXP EthernetDXP100, DXP200Yokogawa DXP Ethernet TCP。
Edexcel INSET培训07-08技术支持指南说明书
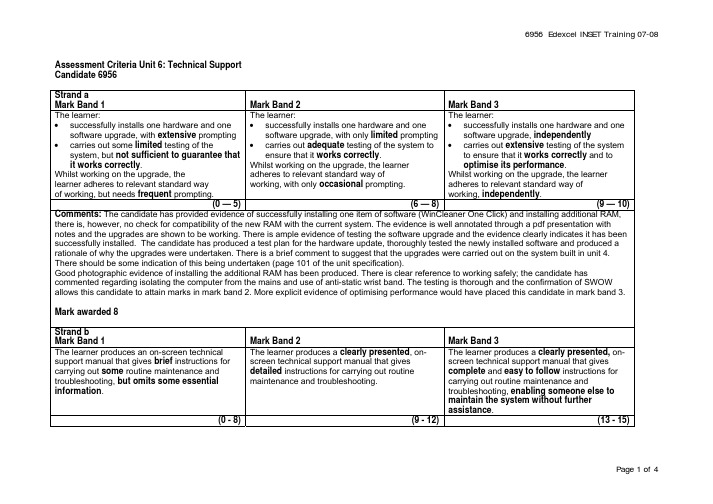
Assessment Criteria Unit 6: Technical SupportCandidate 6956Strand aMark Band 1 Mark Band 2 Mark Band 3The learner:•successfully installs one hardware and one software upgrade, with extensive prompting •carries out some limited testing of the system, but not sufficient to guarantee that it works correctly.Whilst working on the upgrade, thelearner adheres to relevant standard wayof working, but needs frequent prompting. The learner:•successfully installs one hardware and onesoftware upgrade, with only limited prompting• carries out adequate testing of the system toensure that it works correctly.Whilst working on the upgrade, the learneradheres to relevant standard way ofworking, with only occasional prompting.The learner:•successfully installs one hardware and onesoftware upgrade, independently• carries out extensive testing of the systemto ensure that it works correctly and tooptimise its performance.Whilst working on the upgrade, the learneradheres to relevant standard way ofworking, independently.(0 — 5)(6 — 8)(9 — 10) Comments: The candidate has provided evidence of successfully installing one item of software (WinCleaner One Click) and installing additional RAM, there is, however, no check for compatibility of the new RAM with the current system. The evidence is well annotated through a pdf presentation with notes and the upgrades are shown to be working. There is ample evidence of testing the software upgrade and the evidence clearly indicates it has been successfully installed. The candidate has produced a test plan for the hardware update, thoroughly tested the newly installed software and produced a rationale of why the upgrades were undertaken. There is a brief comment to suggest that the upgrades were carried out on the system built in unit 4. There should be some indication of this being undertaken (page 101 of the unit specification).Good photographic evidence of installing the additional RAM has been produced. There is clear reference to working safely; the candidate has commented regarding isolating the computer from the mains and use of anti-static wrist band. The testing is thorough and the confirmation of SWOW allows this candidate to attain marks in mark band 2. More explicit evidence of optimising performance would have placed this candidate in mark band 3.Mark awarded 8Strand bMark Band 1 Mark Band 2 Mark Band 3The learner produces an on-screen technical support manual that gives brief instructions for carrying out some routine maintenance and troubleshooting, but omits some essential information. The learner produces a clearly presented, on-screen technical support manual that givesdetailed instructions for carrying out routinemaintenance and troubleshooting.The learner produces a clearly presented, on-screen technical support manual that givescomplete and easy to follow instructions forcarrying out routine maintenance andtroubleshooting, enabling someone else tomaintain the system without furtherassistance.(0 - 8)(9 - 12)(13 - 15)Comments: The candidate has produced a well presented and detailed technical manual which is in a format suitable for on-screen display. However, the manual needs to be easy to read on screen which should involve good navigation so that the reader can locate the information required quickly and easily. Whilst there is a link to each major section and it contains sufficient information relating to routine maintenance i.e. Defrag, backup and restore, the manual does not have an index to all the topics without having to explore each section to see what they contain. Trouble shooting is also included together with suggestions of the less obvious solutions to routine maintenance which might be required to be undertaken. The candidate has attempted to include many of the sections indicated in 6.1 and 6.2 of the unit specification.Each item is introduced and for many of the routines there are screen shots which help the reader follow the instructions. There is a maintenance schedule included together with internet connectivity and security issues.The candidate has presented a manual which can be read on screen with sufficient audience awareness to meet the requirements of the top of Mark Band 2.Although the manual is well presented, to access mark band 3, the reader must be able to locate the information required quickly and easily and there should be a recommended procedure for recording any maintenance work carried out. The candidate has suggested that all work undertaken be recorded but has not produced any details relating to a procedure for recording this work.Mark Awarded 12.Strand cMark Band 1 Mark Band 2 Mark Band 3The presentation includes:• a brief description of the key features of at least four web-based tools for collaborativeworking• a description of the capabilities andlimitations of each tool, but with little or nocomparison• a demonstration of aspects of the setup and use of a web-based tool, but not detailedenough to give a clear picture of what isinvolved. The presentation includes:• a detailed description — supported byexamples — of the key features of at leastfour web-based tools for collaborative working• a detailed description and comparison of thecapabilities and limitations of each tool• a clear demonstration of the setup and use ofa web-based tool, giving an accurate pictureof what is involved.The presentation includes:• a comprehensive description — supportedby a range of well-chosen examples — ofthe key features of at least four web-basedtools for• collaborative working• a detailed description and comparison ofthe capabilities and limitations of each tool,assessing their suitability for particulartasks•an effective demonstration of the setup anduse of a web-based tool, giving a full andaccurate picture of what is involved.(0 - 8)(9 - 11)(12 - 15)Comments: A series of good explanations with comparisons of four tools used for collaborative working with well chosen examples and comprehensive descriptions of the capabilities and limitations of each tool, assessing their suitability for particular tasks. Setting up and managing a ‘Sharepoint’ site has been fully and carefully explained. The candidate has used a range of well-chosen examples to illustrate the key features of each chosen web-based too which is sufficient for the bottom of mark band 3.l There is possibly too much text on some of the slides which could distract from the primary purpose of the presentation which is to illustrate the functions of the software. It is not really designed to be delivered to an audience it lends itself more to be read on-screen. The slides should be designed to convey key messages only; the details should appear in the speaker notes and/or handouts. This combination should then enable the audience to make an informed decision based upon the presentation. Holistically there is enough technical evidence within the presentation to meet the requirements of mark band 3 but the construction of the actual presentation stops the awarding of high marks in this band.Mark Awarded 12.Strand dMark Band 1 Mark Band 2 Mark Band 3The report:•identifies some of the communication needs of a small business (SME)• makes some recommendations, for internet connectivity, security procedures, an internet access policy and use of email• is written in simple, non-technical language. The report:•describes most of the communication needsof a small business (SME)• makes detailed recommendations, with somejustification, for internet connectivity, securityprocedures, an internet access policy and useof email• is clearly presented in simple, non-technicallanguage.The report:•describes all the communication needs ofa small business (SME), both current andfuture• makes detailed and appropriaterecommendations, with full justification,for internet connectivity, securityprocedures, an internet access policy anduse of email•is effectively presented in simple, non-technical language, demonstrating fullawareness of audience and purpose.(0 - 10)(11 - 15)(16 - 20) Comments: The candidate has produced a very well detailed report in simple non-technical language which investigates many of the communications options available to an SME. Within the report, the candidate discusses the communication needs in specific terms and includes sensible recommendations for the four elements which need to be covered.The candidate has covered all the requirements of Mark Band 2 and has included both current and future needs but has not submitted the additional evidence of fully justifying each recommendation in order to move into Mark Band 3.Mark Awarded 15Overall CommentsThe eportfolio is relatively easy to access. The candidate has used folders and a sensible link (index.htm) to start the eportfolio. The Index page contains the links to supporting evidence but it is sometimes difficult to return to the main index from some of the sections.The candidate is clearly working at AS level for this qualification with much of the evidence being of a high standard.The end mark reflects a candidate working at the A/B grade boundary area and is clearly capable of achieving a higher grade A mark. Note – the boundaries can change each year at Awarding.Overall Mark Awarded 47/60。
Implementation of a Reliable Multicast Protocol

Implementation of a Reliable Multicast Protocol
Department of Computer Science, City University of Hong Kong, 83 Tat Chee Avenue, Kowloon, Hong Kong (e-mail: wjiaȰ.hk) SUMMARY A reliable multicast protocol (RMP) based on a logical token ring approach can achieve agreement of a group of operational processes in distributed systems. The structure of RMP is modulated into component protocols that achieve total ordering, atomicity of multicast messages; dynamic group configuration and fault-tolerance cooperatively. RMP uses a virtual token to order multicast messages in a logical process ring. It is highly efficient over networks and its algorithm design and implementation are presented. The use of a state machine approach simplifies this complex system implementation. Experience and lessons drawn from RMP and general techniques applied to group communication protocol are also described. Ȱ1997 by John Wiley & Sons, Ltd.
rfc4210.Internet X.509 Public Key Infrastructure Certificate Management Protocol (CMP)

Network Working Group C. Adams Request for Comments: 4210 University of Ottawa Obsoletes: 2510 S. Farrell Category: Standards Track Trinity College Dublin T. Kause SSH T. Mononen SafeNet September 2005 Internet X.509 Public Key InfrastructureCertificate Management Protocol (CMP)Status of This MemoThis document specifies an Internet standards track protocol for the Internet community, and requests discussion and suggestions forimprovements. Please refer to the current edition of the "InternetOfficial Protocol Standards" (STD 1) for the standardization stateand status of this protocol. Distribution of this memo is unlimited. Copyright NoticeCopyright (C) The Internet Society (2005).AbstractThis document describes the Internet X.509 Public Key Infrastructure (PKI) Certificate Management Protocol (CMP). Protocol messages aredefined for X.509v3 certificate creation and management. CMPprovides on-line interactions between PKI components, including anexchange between a Certification Authority (CA) and a client system. Table of Contents1. Introduction (5)2. Requirements (5)3. PKI Management Overview (5)3.1. PKI Management Model (6)3.1.1. Definitions of PKI Entities (6)3.1.1.1. Subjects and End Entities (6)3.1.1.2. Certification Authority (7)3.1.1.3. Registration Authority (7)3.1.2. PKI Management Requirements (8)3.1.3. PKI Management Operations (10)4. Assumptions and Restrictions (14)4.1. End Entity Initialization (14)Adams, et al. Standards Track [Page 1]4.2. Initial Registration/Certification (14)4.2.1. Criteria Used (15)4.2.1.1. Initiation of Registration/Certification ..15 4.2.1.2. End Entity Message Origin Authentication ..15 4.2.1.3. Location of Key Generation (15)4.2.1.4. Confirmation of Successful Certification ..16 4.2.2. Mandatory Schemes (16)4.2.2.1. Centralized Scheme (16)4.2.2.2. Basic Authenticated Scheme (17)4.3. Proof-of-Possession (POP) of Private Key (17)4.3.1. Signature Keys (18)4.3.2. Encryption Keys (18)4.3.3. Key Agreement Keys (19)4.4. Root CA Key Update (19)4.4.1. CA Operator Actions (20)4.4.2. Verifying Certificates (21)4.4.2.1. Verification in Cases 1, 4, 5, and 8 (22)4.4.2.2. Verification in Case 2 (22)4.4.2.3. Verification in Case 3 (23)4.4.2.4. Failure of Verification in Case 6 (23)4.4.2.5. Failure of Verification in Case 7 (23)4.4.3. Revocation - Change of CA Key (23)5. Data Structures (24)5.1. Overall PKI Message (24)5.1.1. PKI Message Header (24)5.1.1.1. ImplicitConfirm (27)5.1.1.2. ConfirmWaitTime (27)5.1.2. PKI Message Body (27)5.1.3. PKI Message Protection (28)5.1.3.1. Shared Secret Information (29)5.1.3.2. DH Key Pairs (30)5.1.3.3. Signature (30)5.1.3.4. Multiple Protection (30)5.2. Common Data Structures (31)5.2.1. Requested Certificate Contents (31)5.2.2. Encrypted Values (31)5.2.3. Status codes and Failure Information forPKI Messages (32)5.2.4. Certificate Identification (33)5.2.5. Out-of-band root CA Public Key (33)5.2.6. Archive Options (34)5.2.7. Publication Information (34)5.2.8. Proof-of-Possession Structures (34)5.2.8.1. Inclusion of the Private Key (35)5.2.8.2. Indirect Method (35)5.2.8.3. Challenge-Response Protocol (35)5.2.8.4. Summary of PoP Options (37)Adams, et al. Standards Track [Page 2]5.3. Operation-Specific Data Structures (38)5.3.1. Initialization Request (38)5.3.2. Initialization Response (39)5.3.3. Certification Request (39)5.3.4. Certification Response (39)5.3.5. Key Update Request Content (40)5.3.6. Key Update Response Content (41)5.3.7. Key Recovery Request Content (41)5.3.8. Key Recovery Response Content (41)5.3.9. Revocation Request Content (41)5.3.10. Revocation Response Content (42)5.3.11. Cross Certification Request Content (42)5.3.12. Cross Certification Response Content (42)5.3.13. CA Key Update Announcement Content (42)5.3.14. Certificate Announcement (43)5.3.15. Revocation Announcement (43)5.3.16. CRL Announcement (43)5.3.17. PKI Confirmation Content (43)5.3.18. Certificate Confirmation Content (44)5.3.19. PKI General Message Content (44)5.3.19.1. CA Protocol Encryption Certificate (44)5.3.19.2. Signing Key Pair Types (45)5.3.19.3. Encryption/Key Agreement Key Pair Types ..45 5.3.19.4. Preferred Symmetric Algorithm (45)5.3.19.5. Updated CA Key Pair (45)5.3.19.6. CRL (46)5.3.19.7. Unsupported Object Identifiers (46)5.3.19.8. Key Pair Parameters (46)5.3.19.9. Revocation Passphrase (46)5.3.19.10. ImplicitConfirm (46)5.3.19.11. ConfirmWaitTime (47)5.3.19.12. Original PKIMessage (47)5.3.19.13. Supported Language Tags (47)5.3.20. PKI General Response Content (47)5.3.21. Error Message Content (47)5.3.22. Polling Request and Response (48)6. Mandatory PKI Management Functions (51)6.1. Root CA Initialization (51)6.2. Root CA Key Update (51)6.3. Subordinate CA Initialization (51)6.4. CRL production (52)6.5. PKI Information Request (52)6.6. Cross Certification (52)6.6.1. One-Way Request-Response Scheme: (52)6.7. End Entity Initialization (54)6.7.1. Acquisition of PKI Information (54)6.7.2. Out-of-Band Verification of Root-CA Key (55)6.8. Certificate Request (55)Adams, et al. Standards Track [Page 3]6.9. Key Update (55)7. Version Negotiation (56)7.1. Supporting RFC 2510 Implementations (56)7.1.1. Clients Talking to RFC 2510 Servers (56)7.1.2. Servers Receiving Version cmp1999 PKIMessages (57)8. Security Considerations (57)8.1. Proof-Of-Possession with a Decryption Key (57)8.2. Proof-Of-Possession by Exposing the Private Key (57)8.3. Attack Against Diffie-Hellman Key Exchange (57)9. IANA Considerations (58)Normative References (58)Informative References (59)A. Reasons for the Presence of RAs (61)B. The Use of Revocation Passphrase (61)C. Request Message Behavioral Clarifications (63)D. PKI Management Message Profiles (REQUIRED) (65)D.1. General Rules for Interpretation of These Profiles (65)D.2. Algorithm Use Profile (66)D.3. Proof-of-Possession Profile (68)D.4. Initial Registration/Certification (BasicAuthenticated Scheme) (68)D.5. Certificate Request (74)D.6. Key Update Request (75)E. PKI Management Message Profiles (OPTIONAL) (75)E.1. General Rules for Interpretation of These Profiles (76)E.2. Algorithm Use Profile (76)E.3. Self-Signed Certificates (76)E.4. Root CA Key Update (77)E.5. PKI Information Request/Response (77)E.6. Cross Certification Request/Response (1-way) (79)E.7. In-Band Initialization Using External IdentityCertificate (82)F. Compilable ASN.1 Definitions (83)G. Acknowledgements (93)Adams, et al. Standards Track [Page 4]1. IntroductionThis document describes the Internet X.509 Public Key Infrastructure (PKI) Certificate Management Protocol (CMP). Protocol messages aredefined for certificate creation and management. The term"certificate" in this document refers to an X.509v3 Certificate asdefined in [X509].This specification obsoletes RFC 2510. This specification differsfrom RFC 2510 in the following areas:The PKI management message profile section is split to twoappendices: the required profile and the optional profile. Someof the formerly mandatory functionality is moved to the optionalprofile.The message confirmation mechanism has changed substantially.A new polling mechanism is introduced, deprecating the old polling method at the CMP transport level.The CMP transport protocol issues are handled in a separatedocument [CMPtrans], thus the Transports section is removed.A new implicit confirmation method is introduced to reduce thenumber of protocol messages exchanged in a transaction.The new specification contains some less prominent protocolenhancements and improved explanatory text on several issues.2. RequirementsThe key words "MUST", "MUST NOT", "REQUIRED", "SHOULD", "SHOULD NOT", "RECOMMENDED", "MAY", and "OPTIONAL" in this document (in uppercase, as shown) are to be interpreted as described in [RFC2119].3. PKI Management OverviewThe PKI must be structured to be consistent with the types ofindividuals who must administer it. Providing such administratorswith unbounded choices not only complicates the software required,but also increases the chances that a subtle mistake by anadministrator or software developer will result in broadercompromise. Similarly, restricting administrators with cumbersomemechanisms will cause them not to use the PKI.Adams, et al. Standards Track [Page 5]Management protocols are REQUIRED to support on-line interactionsbetween Public Key Infrastructure (PKI) components. For example, amanagement protocol might be used between a Certification Authority(CA) and a client system with which a key pair is associated, orbetween two CAs that issue cross-certificates for each other.3.1. PKI Management ModelBefore specifying particular message formats and procedures, we first define the entities involved in PKI management and their interactions (in terms of the PKI management functions required). We then groupthese functions in order to accommodate different identifiable types of end entities.3.1.1. Definitions of PKI EntitiesThe entities involved in PKI management include the end entity (i.e., the entity to whom the certificate is issued) and the certificationauthority (i.e., the entity that issues the certificate). Aregistration authority MAY also be involved in PKI management.3.1.1.1. Subjects and End EntitiesThe term "subject" is used here to refer to the entity to whom thecertificate is issued, typically named in the subject orsubjectAltName field of a certificate. When we wish to distinguishthe tools and/or software used by the subject (e.g., a localcertificate management module), we will use the term "subjectequipment". In general, the term "end entity" (EE), rather than"subject", is preferred in order to avoid confusion with the fieldname. It is important to note that the end entities here willinclude not only human users of applications, but also applicationsthemselves (e.g., for IP security). This factor influences theprotocols that the PKI management operations use; for example,application software is far more likely to know exactly whichcertificate extensions are required than are human users. PKImanagement entities are also end entities in the sense that they are sometimes named in the subject or subjectAltName field of acertificate or cross-certificate. Where appropriate, the term "end- entity" will be used to refer to end entities who are not PKImanagement entities.All end entities require secure local access to some information --at a minimum, their own name and private key, the name of a CA thatis directly trusted by this entity, and that CA’s public key (or afingerprint of the public key where a self-certified version isavailable elsewhere). Implementations MAY use secure local storagefor more than this minimum (e.g., the end entity’s own certificate or Adams, et al. Standards Track [Page 6]application-specific information). The form of storage will alsovary -- from files to tamper-resistant cryptographic tokens. Theinformation stored in such local, trusted storage is referred to here as the end entity’s Personal Security Environment (PSE).Though PSE formats are beyond the scope of this document (they arevery dependent on equipment, et cetera), a generic interchange format for PSEs is defined here: a certification response message MAY beused.3.1.1.2. Certification AuthorityThe certification authority (CA) may or may not actually be a real"third party" from the end entity’s point of view. Quite often, the CA will actually belong to the same organization as the end entities it supports.Again, we use the term "CA" to refer to the entity named in theissuer field of a certificate. When it is necessary to distinguishthe software or hardware tools used by the CA, we use the term "CAequipment".The CA equipment will often include both an "off-line" component and an "on-line" component, with the CA private key only available to the "off-line" component. This is, however, a matter for implementers(though it is also relevant as a policy issue).We use the term "root CA" to indicate a CA that is directly trustedby an end entity; that is, securely acquiring the value of a root CA public key requires some out-of-band step(s). This term is not meant to imply that a root CA is necessarily at the top of any hierarchy,simply that the CA in question is trusted directly.A "subordinate CA" is one that is not a root CA for the end entity in question. Often, a subordinate CA will not be a root CA for anyentity, but this is not mandatory.3.1.1.3. Registration AuthorityIn addition to end-entities and CAs, many environments call for theexistence of a Registration Authority (RA) separate from theCertification Authority. The functions that the registrationauthority may carry out will vary from case to case but MAY includepersonal authentication, token distribution, revocation reporting,name assignment, key generation, archival of key pairs, et cetera. Adams, et al. Standards Track [Page 7]This document views the RA as an OPTIONAL component: when it is notpresent, the CA is assumed to be able to carry out the RA’s functions so that the PKI management protocols are the same from the end-entity’s point of view.Again, we distinguish, where necessary, between the RA and the tools used (the "RA equipment").Note that an RA is itself an end entity. We further assume that all RAs are in fact certified end entities and that RAs have private keys that are usable for signing. How a particular CA equipmentidentifies some end entities as RAs is an implementation issue (i.e., this document specifies no special RA certification operation). Wedo not mandate that the RA is certified by the CA with which it isinteracting at the moment (so one RA may work with more than one CAwhilst only being certified once).In some circumstances, end entities will communicate directly with a CA even where an RA is present. For example, for initialregistration and/or certification, the subject may use its RA, butcommunicate directly with the CA in order to refresh its certificate.3.1.2. PKI Management RequirementsThe protocols given here meet the following requirements on PKImanagement1. PKI management must conform to the ISO/IEC 9594-8/ITU-T X.509standards.2. It must be possible to regularly update any key pair withoutaffecting any other key pair.3. The use of confidentiality in PKI management protocols must bekept to a minimum in order to ease acceptance in environmentswhere strong confidentiality might cause regulatory problems.4. PKI management protocols must allow the use of differentindustry-standard cryptographic algorithms (specificallyincluding RSA, DSA, MD5, and SHA-1). This means that any given CA, RA, or end entity may, in principle, use whicheveralgorithms suit it for its own key pair(s).5. PKI management protocols must not preclude the generation of key pairs by the end-entity concerned, by an RA, or by a CA. Keygeneration may also occur elsewhere, but for the purposes of PKI management we can regard key generation as occurring whereverthe key is first present at an end entity, RA, or CA.Adams, et al. Standards Track [Page 8]6. PKI management protocols must support the publication ofcertificates by the end-entity concerned, by an RA, or by a CA. Different implementations and different environments may choose any of the above approaches.7. PKI management protocols must support the production ofCertificate Revocation Lists (CRLs) by allowing certified endentities to make requests for the revocation of certificates.This must be done in such a way that the denial-of-serviceattacks, which are possible, are not made simpler.8. PKI management protocols must be usable over a variety of"transport" mechanisms, specifically including mail, http,TCP/IP and ftp.9. Final authority for certification creation rests with the CA.No RA or end-entity equipment can assume that any certificateissued by a CA will contain what was requested; a CA may altercertificate field values or may add, delete, or alter extensions according to its operating policy. In other words, all PKIentities (end-entities, RAs, and CAs) must be capable ofhandling responses to requests for certificates in which theactual certificate issued is different from that requested (for example, a CA may shorten the validity period requested). Note that policy may dictate that the CA must not publish orotherwise distribute the certificate until the requesting entity has reviewed and accepted the newly-created certificate(typically through use of the certConf message).10. A graceful, scheduled change-over from one non-compromised CAkey pair to the next (CA key update) must be supported (notethat if the CA key is compromised, re-initialization must beperformed for all entities in the domain of that CA). An endentity whose PSE contains the new CA public key (following a CA key update) must also be able to verify certificates verifiable using the old public key. End entities who directly trust theold CA key pair must also be able to verify certificates signed using the new CA private key (required for situations where the old CA public key is "hardwired" into the end entity’scryptographic equipment).11. The functions of an RA may, in some implementations orenvironments, be carried out by the CA itself. The protocolsmust be designed so that end entities will use the same protocol regardless of whether the communication is with an RA or CA.Naturally, the end entity must use the correct RA of CA publickey to protect the communication.Adams, et al. Standards Track [Page 9]12. Where an end entity requests a certificate containing a givenpublic key value, the end entity must be ready to demonstratepossession of the corresponding private key value. This may be accomplished in various ways, depending on the type ofcertification request. See Section 4.3 for details of the in-band methods defined for the PKIX-CMP (i.e., CertificateManagement Protocol) messages.3.1.3. PKI Management OperationsThe following diagram shows the relationship between the entitiesdefined above in terms of the PKI management operations. The letters in the diagram indicate "protocols" in the sense that a defined setof PKI management messages can be sent along each of the letteredlines.Adams, et al. Standards Track [Page 10]+---+ cert. publish +------------+ j| | <--------------------- | End Entity | <-------| C | g +------------+ "out-of-band"| e | | ^ loading| r | | | initial| t | a | | b registration/| | | | certification| / | | | key pair recovery| | | | key pair update| C | | | certificate update| R | PKI "USERS" V | revocation request| L | -------------------+-+-----+-+------+-+-------------------| | PKI MANAGEMENT | ^ | ^| | ENTITIES a | | b a | | b| R | V | | || e | g +------+ d | || p | <------------ | RA | <-----+ | || o | cert. | | ----+ | | || s | publish +------+ c | | | || i | | | | || t | V | V || o | g +------------+ i| r | <------------------------| CA |------->| y | h +------------+ "out-of-band"| | cert. publish | ^ publication| | CRL publish | |+---+ | | cross-certificatione | |f cross-certificate| | update| |V |+------+| CA-2 |+------+Figure 1 - PKI EntitiesAt a high level, the set of operations for which managementmessages are defined can be grouped as follows.1. CA establishment: When establishing a new CA, certain steps arerequired (e.g., production of initial CRLs, export of CA publickey).2. End entity initialization: this includes importing a root CApublic key and requesting information about the options supported by a PKI management entity.Adams, et al. Standards Track [Page 11]3. Certification: various operations result in the creation of newcertificates:1. initial registration/certification: This is the processwhereby an end entity first makes itself known to a CA or RA, prior to the CA issuing a certificate or certificates forthat end entity. The end result of this process (when it is successful) is that a CA issues a certificate for an endentity’s public key, and returns that certificate to the end entity and/or posts that certificate in a public repository. This process may, and typically will, involve multiple"steps", possibly including an initialization of the endentity’s equipment. For example, the end entity’s equipment must be securely initialized with the public key of a CA, to be used in validating certificate paths. Furthermore, an end entity typically needs to be initialized with its own keypair(s).2. key pair update: Every key pair needs to be updated regularly(i.e., replaced with a new key pair), and a new certificateneeds to be issued.3. certificate update: As certificates expire, they may be"refreshed" if nothing relevant in the environment haschanged.4. CA key pair update: As with end entities, CA key pairs needto be updated regularly; however, different mechanisms arerequired.5. cross-certification request: One CA requests issuance of across-certificate from another CA. For the purposes of this standard, the following terms are defined. A "cross-certificate" is a certificate in which the subject CA and the issuer CA are distinct and SubjectPublicKeyInfo contains averification key (i.e., the certificate has been issued forthe subject CA’s signing key pair). When it is necessary to distinguish more finely, the following terms may be used: across-certificate is called an "inter-domain cross-certificate" if the subject and issuer CAs belong todifferent administrative domains; it is called an "intra-domain cross-certificate" otherwise.1. Note 1. The above definition of "cross-certificate"aligns with the defined term "CA-certificate" in X.509.Note that this term is not to be confused with the X.500 "cACertificate" attribute type, which is unrelated. Adams, et al. Standards Track [Page 12]2. Note 2. In many environments, the term "cross-certificate", unless further qualified, will beunderstood to be synonymous with "inter-domain cross-certificate" as defined above.3. Note 3. Issuance of cross-certificates may be, but isnot necessarily, mutual; that is, two CAs may issuecross-certificates for each other.6. cross-certificate update: Similar to a normal certificateupdate, but involving a cross-certificate.4. Certificate/CRL discovery operations: some PKI managementoperations result in the publication of certificates or CRLs:1. certificate publication: Having gone to the trouble ofproducing a certificate, some means for publishing it isneeded. The "means" defined in PKIX MAY involve the messages specified in Sections 5.3.13 to 5.3.16, or MAY involve other methods (LDAP, for example) as described in [RFC2559],[RFC2585] (the "Operational Protocols" documents of the PKIX series of specifications).2. CRL publication: As for certificate publication.5. Recovery operations: some PKI management operations are used when an end entity has "lost" its PSE:1. key pair recovery: As an option, user client key materials(e.g., a user’s private key used for decryption purposes) MAY be backed up by a CA, an RA, or a key backup systemassociated with a CA or RA. If an entity needs to recoverthese backed up key materials (e.g., as a result of aforgotten password or a lost key chain file), a protocolexchange may be needed to support such recovery.6. Revocation operations: some PKI operations result in the creation of new CRL entries and/or new CRLs:1. revocation request: An authorized person advises a CA of anabnormal situation requiring certificate revocation.7. PSE operations: whilst the definition of PSE operations (e.g.,moving a PSE, changing a PIN, etc.) are beyond the scope of this specification, we do define a PKIMessage (CertRepMessage) thatcan form the basis of such operations.Adams, et al. Standards Track [Page 13]Note that on-line protocols are not the only way of implementing the above operations. For all operations, there are off-line methods of achieving the same result, and this specification does not mandateuse of on-line protocols. For example, when hardware tokens areused, many of the operations MAY be achieved as part of the physical token delivery.Later sections define a set of standard messages supporting the above operations. Transport protocols for conveying these exchanges indifferent environments (file-based, on-line, E-mail, and WWW) arebeyond the scope of this document and are specified separately.4. Assumptions and Restrictions4.1. End Entity InitializationThe first step for an end entity in dealing with PKI managemententities is to request information about the PKI functions supported and to securely acquire a copy of the relevant root CA public key(s).4.2. Initial Registration/CertificationThere are many schemes that can be used to achieve initialregistration and certification of end entities. No one method issuitable for all situations due to the range of policies that a CAmay implement and the variation in the types of end entity which can occur.However, we can classify the initial registration/certificationschemes that are supported by this specification. Note that the word "initial", above, is crucial: we are dealing with the situation where the end entity in question has had no previous contact with the PKI. Where the end entity already possesses certified keys, then somesimplifications/alternatives are possible.Having classified the schemes that are supported by thisspecification we can then specify some as mandatory and some asoptional. The goal is that the mandatory schemes cover a sufficient number of the cases that will arise in real use, whilst the optional schemes are available for special cases that arise less frequently.In this way, we achieve a balance between flexibility and ease ofimplementation.We will now describe the classification of initialregistration/certification schemes.Adams, et al. Standards Track [Page 14]4.2.1. Criteria Used4.2.1.1. Initiation of Registration/CertificationIn terms of the PKI messages that are produced, we can regard theinitiation of the initial registration/certification exchanges asoccurring wherever the first PKI message relating to the end entityis produced. Note that the real-world initiation of theregistration/certification procedure may occur elsewhere (e.g., apersonnel department may telephone an RA operator).The possible locations are at the end entity, an RA, or a CA.4.2.1.2. End Entity Message Origin AuthenticationThe on-line messages produced by the end entity that requires acertificate may be authenticated or not. The requirement here is to authenticate the origin of any messages from the end entity to thePKI (CA/RA).In this specification, such authentication is achieved by the PKI(CA/RA) issuing the end entity with a secret value (initialauthentication key) and reference value (used to identify the secret value) via some out-of-band means. The initial authentication keycan then be used to protect relevant PKI messages.Thus, we can classify the initial registration/certification schemeaccording to whether or not the on-line end entity -> PKI messagesare authenticated or not.Note 1: We do not discuss the authentication of the PKI -> end entity messages here, as this is always REQUIRED. In any case, it can beachieved simply once the root-CA public key has been installed at the end entity’s equipment or it can be based on the initialauthentication key.Note 2: An initial registration/certification procedure can be secure where the messages from the end entity are authenticated via someout-of-band means (e.g., a subsequent visit).4.2.1.3. Location of Key GenerationIn this specification, "key generation" is regarded as occurringwherever either the public or private component of a key pair firstoccurs in a PKIMessage. Note that this does not preclude acentralized key generation service; the actual key pair MAY have been Adams, et al. Standards Track [Page 15]。
Eaton Universal TR Series定时器说明书

Eaton’s Universal TR Series timers are a versatile and cost-competitive family of timing relays. The compact IEC-style housing installs easily onto a standard DIN rail, and the direct-wire design eliminates the need for additional sockets and accessories. Each timer has multiple user-selectable timing functions and timing ranges, and a universal input voltage of either 12 or 24 V to 240 Vac or Vdc, depending on the model.TR timing relaysReducing your inventory costsWith up to seven selectabletiming functions and sevenselectable time ranges from50 milliseconds to 100 hours,you can meet the needs ofalmost any application withjust one or two stock items.Do you need 24 Vdc control insome cases and 120 Vac controlin others? Y ou are covered withthe Universal TR Series timer, asit has a universal, self-selectingcontrol voltage input range fromeither 12 or 24 V (depending onmodel) to 240 Vac or Vdc. Areyou tired of buying minimumquantities of sockets andaccessories for your plug-intiming relays? The direct wiredesign of the Universal TR Seriesgives you everything you need ina single item.Reducing your labor costsDuring initial installation, thelarge terminals on the UniversalTR Series make wiring quickand easy. The offset designeven allows easy access to thebottom terminals when the topwires are installed. The easy-to-read set point markings improvethe accuracy of setup, therebyreducing your startup time. Areyou spending too much timetroubleshooting and replacingtimers? The dual LED indicatorson the Universal TR Series usemultiple modes to signal inputpower, relay state and timingstatus. The Universal TR Seriesalso features a high-qualitydesign with twice the relay lifeof many competitors.For more information,please visit/timersEaton is a registered trademark.All other trademarks are property of their respective owners.Eaton1000 Eaton Boulevard Cleveland, OH 44122United States © 2019 EatonAll Rights Reserved Printed in USAPublication No. PA04910001E / Z23622December 2019SpecificationsUniversal TR timing relays A Check data sheet for more detailed information.Timer function descriptionsFunction #1—Asymmetrical Flasher,Pause First (lp)Function #2—Asymmetrical Flasher, Pulse First (li)Function #3— ON Delay and OFF Delay with Control Contact (ER)Function #4—ON Delay and Single Shot Leading Edge Voltage Controlled (EWu)Function #5—ON Delay and Single Shot Leading Edge Control Contact (EWs)Function #6—Single Shot Leading and Single Shot T railing Edge with Control Contact (WsWa)Function #7—Pulse Sequence Monitoring (Wt)Function #8—ON Delay, Power T riggered (E)Function #9—Single Shot Leading Edge Voltage Controlled (Wu)Function #10—OFF Delay/Signal OFF Delay (R)Function #11—Single Shot Leading Edge with Control Input (Ws)Function #12—Single Shot T railing Edge with Control Input (Wa)Function #13—ON Delay Control Signal Start, T railing Edge OFF (Es)Function #14—Flasher,Pause First (Bp)Input Power (U)LED U/t*Output LED**Output Relay (R)Input Power (U)LED U/t*Output LED**Output Relay (R)Input Power (U)LED U/t*Trigger Signal (S)Output LED**Output Relay (R)Input Power (U)LED U/t*Output LED**Output Relay (R)Input Power (U)LED U/t*Trigger Signal (S)Output LED**Output Relay (R)Input Power (U)LED U/t*Trigger Signal (S)Output LED**Output Relay (R)Input Power (U)LED U/t*Trigger Signal (S)Output LED**Output Relay (R)Input Power (U)LED U/t*Output LED**Output Relay (R)Input Power (U)LED U/t*Output LED**Output Relay (R)Input Power (U)LED U/t*Trigger Signal (S)Output LED**Output Relay (R)Input Power (U)LED U/t*Trigger Signal (S)Output LED**Output Relay (R)Input Power (U)LED U/t*Trigger Signal (S)Output LED**Output Relay (R)Input Power (U)LED U/t*Trigger Signal (S)Output LED**Output Relay (R)Input Power (U)LED U/t*Output LED**Output Relay (R)Follow us on social media to get the latest product and support information.。
Workmanship and Specifications Manual

Workmanship and Specifications Manual (WSM)Level I DocumentL3 TECHNOLOGIES, COMMUNICATION SYSTEMS – WEST RESTRICTED INFORMATION: THIS DOCUMENT CONTAINS RESTRICTED INFORMATION OF L3 TECHNOLOGIES, COMMUNICATION SYSTEMS – WEST (CSW). RECIPIENT AGREES IN CONSIDERATION FOR RECEIPT OF THIS DOCUMENT, TO USE IT SOLELY FOR THE LIMITED PURPOSE FOR WHICH IT IS MADE AVAILABLE AND NOT TO TRANSMIT IT AND/OR THE INFORMATION THEREIN CONTAINED, IN WHOLE OR PART, OR TO SUFFER SUCH ACTION BY OTHERS, FOR ANY PURPOSE, EXCEPT WITH THE WRITTEN PERMISSION, FIRST OBTAINED, FROM L3 TECHNOLOGIES (CSW). THE RECIPIENT FURTHER AGREES TO SURRENDER THE DOCUMENT AND ALL COPIES OR CERTIFY DESTRUCTION OF SAME TO L3 TECHNOLOGIES (CSW). WHEN THE REASON FOR ITS RECEIPT HAS TERMINATED. FURTHER DISSEMINATION ONLY AS DIRECTED BY L3 TECHNOLOGIES (CSW) (06401).APPROVAL*DATEMO/DAY/YRL3 Technologies, Inc.Communication Systems-West640 North 2200 WestP.O. Box 16850Salt Lake City, UT 84116Written by (Mechanical Engineer)Jenson Schenk 2-12-2019 Approved by (Mechanical DesignEngineering)Chris Lott 2-12-2019 Approved by (Mfg. Process Engineer)Logan Moen2-12-2019 Approved by (EngineeringManagement)Brady Davies 2-12-2019Approved by (OperationsManagement)Merrill Stoddard 2-12-2019DOCUMENT NUMBER:WSMApproved by (Product Assurance)Tom Benedict2-12-2019CAGE CODE:06401REV.:B*All signatures stored electronically in Teamcenter.Revision Release Date Summary of Changes Name[A] 10-6-2014 Initial release Workmanship, SpecificationsManual[B] 2-12-2019Integrate standalone partmarking spec and IS-015.Update terms and definitionsthroughout.Workmanship and SpecificationsManual for L3T, CommunicationSystems - WestTable of Contents1.Scope/Purpose: (1)2.Internal Specifications (IS) Definitions (1)3.Workmanship Standards (WS) Definitions (2)4. Engineering Specification Definitions (2)mercial Off The Shelf (COTS) Definitions ............................. E rror! Bookmark not defined.6.Inspection Terms and Definitions (3)7.Drawing Definitions (3)1. Scope/PurposeThe Workmanship and Specifications Manual (WSM) invokes CSW Workmanship Standards (WS), Internal Specifications (IS), and miscellaneous Engineering Specifications as required design, manufacturing, and acceptance criteria when identified on the Purchase Order, Product Definition Data Set (Drawing, Parts List, CAD model, etc.), or Statement of Work. This manual may be identified as the Workmanship and Specifications Manual, WSM or S01, within a Product Definition Data Set. The WSMis also applicable to all CSW procurements unless otherwise specified in the Purchase Order, Drawing,or Subcontractor Statement of Work (SSOW). The only exception to this requirement are Commercial Off the Shelf (COTS) parts purchased on a CSW Vendor Item Control Drawing (VICD) or Procurement Control Drawing (PCD), or other parts with a CSW approved Assertion of Commerciality.This WSM is to support Communication Systems- West (CSW) products and associated processes. This manual is a comprehensive set of Internal Specifications, Workmanship Standards, and Specifications that support business needs and products through their lifecycle.This document is to be used at L3 Technologies Inc., Communication Systems – West (CSW), Salt Lake City facility, and is applicable to internal manufacture of product and product delivered to CSW when identified in Purchase Order documentation. This includes demonstration equipment that is deliverable. The Workmanship and Specifications Manual is a Level I document and considered policy.2. Internal Specification (IS) DefinitionInternal Specifications (IS) are internally generated documents that include design and manufacturing requirements, permissions, or allowable technical variations and alternatives to drawing requirements which are global in nature. The specifications are a Level I document that define acceptable workmanship practices and substitutions to processes or the Bill of Materials, while still maintaining compliance toworkmanship requirements. Designs that take exception to any IS allowance shall include a comment in the Product Definition Data Set (commonly a note on the drawing). Notes that disallow an IS permission shall take precedence and serve to maintain unique customer or contractual requirements.Internal Specifications (IS) direct and govern in the Level 1 hierarchy over CSW drawings, BOM (Parts List), Workmanship Standards and Specifications by default until tailored out by exception on the drawing or Quality Assurance Program Plan (QAPP).Internal Specifications are maintained and approved through a formal Product Configuration Control Board (PCCB) comprised of representatives of applicable functions/organizations. The PCCB, chaired by the Manager of Configuration Management, is responsible to assemble the necessary representatives (including DCMA customer representatives, for notification only) for review and approval.3. Workmanship Standard (WS) DefinitionThe intent for Workmanship Standards is to establish minimum quality requirements by which product should be built, inspected and tested for manufacture of electronic and mechanical assemblies. Workmanship Standards have been established as separate documents to provide minimum acceptance criteria when CSW design authority drawings are silent on unique characteristics. Some examples of silent characteristics are: A drawing calls out paint with no visual or cosmetic accept/reject criteria. Wire is noted on a BOM; however, wire routing or securing criteria are not called out on the drawing. Fastening hardware, such as flat/split washers, are noted on the BOM and Drawing without explicit washer placement/hardware stacking shown.The acceptance criteria established in the WS are not intended to define design intent, nor are they intended to authorize repair/modification or design change. The WS is a collection of visual acceptability requirements for product designed by CSW.Users of this standard should be knowledgeable of the applicable requirements of this document and how to apply them to CSW design authority drawings. If a conflict occurs between an IS, Drawings and a WS, the IS and drawings take precedence over the WS.The graphic illustrations and dimensions shown may not be exact, but general acceptance criteria are provided. In case of conflict between the Workmanship Standard written text criteria and graphic illustrations, the written text criteria shall take precedence over the graphic illustrations.NOTEWorkmanship criteria should be used as a supplement to IPC-A-610,Acceptability of Electronic Assemblies and IPC-A-620, Requirementsand Acceptance for Cable and Wire Harness Assemblies.Quality Engineering, Design Engineering, and Operations Engineering Committees will be responsible for creating and updating existing Workmanship Standards. Workmanship Standards require approval through a formal Product Configuration Control Board (PCCB) comprised of representatives of applicable functions/organizations. The PCCB, chaired by the Manager of Configuration Management, is responsible to assemble the necessary representatives (including DCMA customer representatives, for notification only) for review and approval.4. Engineering Specifications DefinitionEngineering Specifications define the types of documents and engineering artifacts to be used as design processes, documentation, description, performance specifications, interfaces, and/or characteristics of such items as part marking, torque retention, Molded Connector Backshells, etc. Specifications require approval through a formal Product Configuration Control Board (PCCB) comprised of representatives of applicable functions/organizations. The PCCB, chaired by the Manager of Configuration Management, is responsible to assemble the necessary representatives (including DCMA customer representatives, for notification only) for review and approval.5. Inspection Terms and DefinitionsThis paragraph and the following subparagraphs provide terms and definitions to guide inspection on the configuration hierarchy of the following documents. Inspection shall use the following documents in the order listed to accept and reject product subject to CSW design authority:•Internal Specifications, Specifications, Drawings•IPC-A-610•IPC/WHMA-620•J-STD-001•Workmanship Standards (WS)•Quality Assurance Program Plan (QAPP) and Quality Bulletins (QB)6. Terms and DefinitionsCOTS Commercial-Off-The-Shelf, See FAR 2.101CSW L3 Technologies Inc., Communication Systems - WestDCMA Defense Contract Management AgencyFAR Federal Acquisition RegulationMOTS Modified-Off-The-ShelfPCD Procurement Control DrawingQAPP Quality Assurance Program PlanQB Quality BulletinVICD Vendor Item Control DrawingGoverning Document: Y-001, Quality Management SystemRelated Documents:IS-001, Use of Non-Specified Hardware/Material and Drawing NotesIS-002, Alternate Piece Marking MethodIS-003, Workmanship Acceptability of Electronic AssembliesIS-004, Base Materials for Rigid and Multilayer Printed Wiring BoardsIS-005, Printed Wiring Board Workmanship & Design CriteriaIS-006, Drawing StandardsIS-007, Elimination and Replacement of Obsolete and Cancelled SpecificationsIS-008, Part Number/Suffix ConfigurationIS-009, Immersion Gold – Electroless Nickel SpecificationIS-010, Unique Identification Number (UID)IS-011, Elimination and Replacement of Primer and Paint Part NumbersIS-012, Minimizing the Use of Hexavalent Chromium Conversion CoatingsIS-013, Substitution of Alternate Size and Shape MaterialsIS-014, Contract Number Required on Identification PlateIS-015, Acceptance of Product from Vendors due to Name Change/Acquisition/Merger 60083155, Specification of Torque and Retention Requirements for Threaded Hardware 1000154383, Specification of Part Marking RequirementsWS-000, Workmanship Standards Introduction。
EPC系统原理-业务功能详细介绍复习过程

EPC系统原理-业务功能详细介绍R1.0版本鲜枣课堂目录EPC系统原理-业务功能详细介绍 (2)1LTE的背景 (2)2EPC系统的网络结构 (2)3EPC系统的业务功能介绍 (4)3.1基本功能 (4)3.1.1标识管理 (4)3.1.2节点选择 (7)3.1.3移动性管理 (8)3.1.4切换管理 (10)3.1.5会话管理 (10)3.2特性功能 (11)3.2.1安全功能 (11)3.2.2与现有网络的互通功能 (11)3.2.3支持多PDN接入功能 (12)3.2.4负荷均衡功能 (12)4名词术语及缩略语 (13)EPC系统原理-业务功能详细介绍1 L TE的背景随着移动通信技术的不断成熟和用户需求的不断提升,宽带无线接入的概念开始被越来越多的运营商和用户关注。
相比较于WiFi(Wireless Fidelity,无线保真)和WiMAX(Worldwide Interoperability for Microwave Access,全球微波接入互操作性)等无线接入方案的迅猛发展,3GPP(3rd Generation Partnership Project,第三代合作伙伴计划)组织制定的WCDMA (Wideband Code Division Multiple Access,宽带码分多址)、HSDPA(HighSpeed Downlink Packet Access,高速下行分组接入)、HSUPA(High Speed Uplink PacketAccess,高速上行分组接入)虽然在支持移动性和QoS(Quality of Service,服务质量)方面有较大优势,但是在无线频谱利用率和传输时延等方面有所落后。
此外,一方面目前的数据类业务种类繁多且数据量大,对空口的数据传输数率提出了更高的要求;另一方面OFDM(Orthogonal Frequency Division Multiplexing,正交频分复用技术)技术为核心的无线接入技术逐渐成熟,大幅度提升空口速率可以变为现实。
IRmark 生成指南说明书

IRmark Generation Step By Step Guide for SOAP based services1. Generating the IRmark (3)1.1 Preparing the XML file (3)1.2 Canonicalisation (4)1.3 SHA-1 Hash (4)1.4 Base64/32 encoding (4)2. General Advice (5)2.1 White Space (5)2.2 Comments in the payload (5)2.3 If you are using the sample Java code (5)1. Generating the IRmarkIf you are generating an IRmark for a Gateway Protocol based service please see the step by step guide for Gateway Protocol services.The IRmark process can be split down into a few main steps. This document will attempt to give clear guidelines on these steps. This document will not cover the response schema and the legislative requirements around the IRmark.This document uses EMCS for its examples; this is for illustrative purposes only. These steps can be applied to any SOAP based service that supports IRmark.The element name contained in the SOAP Header that the IRmark has to be supplied in may differ slightly per service; this has no effect on the process for calculating the IRmark. The element name is usually: BinarySecurityToken1.1 Preparing the XML fileThe IRmark is generated from the payload of the submission so this part of the XML must be extracted first. The payload is everything inside and including the <Body></Body> node. When you extract the body you must “inherit” any and all namespace declarations in the <Envelope> node and place them in the <Body> node. See Fig 1.Fig 1.<Envelope xmlns="/2003/05/soap-envelope"> <Body xmlns="/2003/05/soap-envelope">N.B. This is just for the generation of the IRmark and the namespace should not be present in the <Body> on submission. The above is for illustrative purposes only, if you have other namespaces declared in the Envelope these will also need to be inherited.1.2 CanonicalisationThe extracted XML must then be canonicalised. The W3C spec for canonicalisation can be found here:/TR/2001/REC-xml-c14n-20010315It is not advisable to try and write your own component to achieve this. Most popular development environments will already have C14n components that will do this work for you. It is also possible to prepare your XML up front when it is generated so that it is essentially already canonicalised, however care should be taken when doing this to make sure you cater for character references and so forth. There are examples of canonical XML in the tech pack.1.3 SHA-1 HashOnce the XML is in canonical form a SHA-1 digest must be created from it. Again nearly every environment should have several components available that handle this. The important thing to remember is that your resulting SHA-1 hash must be in binary (160 bits long or in other words an array of 20 bytes)1.4 Base64/32 encodingThe SHA-1 hash can then be Base64 and Base32 encoded. As with the other two processes this should be done using already available components and the results should be printable/readable strings that can be inserted into the XML (Base64) and displayed to the user (Base32)2. General Advice2.1 White SpaceThe C14n specification does not require removal of white space from inside your <Body> node (apart from normalising line-endings to line feed characters). So the XML that you extract to generate the IRmark should be formatted in exactly the same way as the XML that is eventually submitted. We advise that your XML should have no extra spacing at all, it is not needed and will cut down on some of the problems you may find while implementing the IRmark, as well as reducing file size and processing time.2.2 Comments in the payloadDo not use comments in the body of your submission. It may be impossible to avoid the use of comments for Corporation Tax submissions that include iXBRL, in which case we advise that you Base64 encode the iXBRL before IR mark calculation and file transmission.2.3 If you are using the sample Java codeIf you are using the sample code, everything is handled for you, so you do not need to replicate any of the processes in this document.If you have any suggestions for information that could go into this document to help with the understanding of the IRmark process please forward them to:****************。
Eaton Addressable 3 Channel I O Unit ULCIO351 用户指南
Technical DataSignalling Line Circuit Style 7, Class A Supervised, Power LimitedCurrent1.14mA (nom) 1.36mA (Max)Operating Voltage (nom)24VDC (nom)Line Impedance50Ω (nom)Inputs 1, 2, 3 Contact Only Initiating Circuit Style C, Class B Supervised power limitedVoltage 8.4VDC (Max)Current 1mA (Max)Line Impedance 16Ω (Max)Trigger Resistance 5.6kΩ (nom)End Of Line Resistor22kΩ (nom)Output 1, 2, 33 Contact Set ProgrammableVoltage 24VDC (nom) 30VDC (Max) Contact Rating 1 (Max) A Resistive, PF1Switching Power 33kΩ (min)Power factor1 (nom)EnvironmentalOperating Temperature 0°C - 49 °C Humidity (Non Condensing)93% RHStandardsUL864 9th EditionCompatibilitySuitable for use with Eaton Addressable Fire SystemsPhysical CharacteristicsDimensions 180mm x 129mm x 60mmWeight0.28kg Ingress ProtectionIP65Installation1. Separate the two halves of the unit.2. Drill out (or knock out) the required cableentries in the surface mounting back-box.3. Fit the back-box in position and pass the wires into it.4. Connect the unit according to the diagram below.5. Recommended cable Type FPLP (plenum cable), Type FPLR(riser cable), or Type FPLNotes:N No addressing of the interface is required. See control panel operation for details.DescriptionSLC Field Wiring (input)Input 1, 2, 3Output 1, 2, 3Wiring Gauge 12 Max AWG 12 Max AWG 12 Max AWG Wiring ClassClass A Style 7Class B Style C NA Ground Fault Impedance0.1Ω0.1Ω0.1ΩSupervised, power limited YesYesProgrammableInpuo 1, 2, 3 Operation :Normal Standby (Default), Alarm, NAC Silenced, Alarm Reset, Trouble, supervisory ,Drill (Features programmable using PC site installer)Ouopuo 1, 2, 3 Operations: Normal Standby. AlarmNots:N 1. The end of line resistor must always be fitted, even if theinputs are unused. Installer / Service Engineer must ensure it is fitted.2. Monitored inputs can detect open circuit, short circuit orground faults3. Output relays are volt-free contacts and are not monitored,but must be connected to power limited source.4. Each I/O channel consumes a separate address and has thefacility for separate text for each channel.Soandard CNnntcoiNneTeChNICal DaTa 25-16303-A December 2018eaoNnEMEA Headquarters Route de la Longeraie 71110 Morges, Switzerland Eaton.euTEL: +44 (0) 1302 321541FAX: +44 (0) 1302 303220********************************************© 2018 EatonAll Rights ReservedEaton is a registered trademark.All trademarks are property of their respective meaoNn eltcorical Syeotme lod.Wheatley Hall Road Doncaster DN2 4NBTEL: +44 (0) 1302 303303 FAX: +44 (0) 1302 367155。
Creating Deal Velocity--Deal Terms that Really Matter

The Future = The Past
$25
Venture Capital Median Amount Raised By Round Type
$25
$20 Median Amount Raised ($ M)
investors: Turbine ($15m, Highland & Polaris); Polaris ($16M investment in Meridio, Northern Ireland); TD Capital ($5m investment in Contour Semiconductor); Powerspan ($30m, Rockport, Beacon Energy, First Energy Corp.); Highland ($20M in AMP Resources) company against IBM, Microsoft, AOL, Tandem, Compaq, HP, Apple, Samsung, EMC, Allied Signal, Pratt & Whitney, GE, Lucent, Alcatel Mainspring, Integrated Genetics, Focus Enhancements, Netegrity, Tecogen, Astea International, Alloy Systems, DynaGen,
($4.2B merger with Kana); Excel Switching ($2B sale to Lucent); ($50M, bought by Aegis plc); Eigner ($22M, bought by Agile); Netlink ($185M, by Cabletron); Mainspring (bought by IBM); Feanix ($50M earn out to Axon plc); Apama UK (bought by Progress)
从尼克李森巴林银行倒闭案谈企业内部控制制度

能是业界创新的积极分子。
4.年轻企业急需重视核心能力的构建作为年轻的企业,工作效率严重不足(3.75),因此进一步优化各业务操作流程中各部门之间的衔接与配合,加强绩效考核与战略的强关联性,确保绩效能驱动战略的实施,让员工更有全局思维,经营思维尤为重要。
面对以上竞争力特征,港企如何定位出竞争力盲点,制定配套的改进策略突破呢?三、企业竞争力提升之道:重点突破、环环紧扣调研发现,港企在客户关系管理上表现尤为突出,但在其他环节不同类型企业有不同表现,其中跨界学习能力缺失对企业的创新有显著影响,战略未能与员工达成共识,经营上会影响效率。
如此环环紧扣的竞争力元素,需重点突破、配套改进的提升策略(Porter,1996)。
借鉴Dave Ulrich 教授对提升竞争力的建议,结合港企的表现。
笔者建议致力于自我竞争能力提升的企业,可以透过以下几步寻求突破:第一步:进行全面内外部评估。
构建一个全面的竞争力评估工具(如《企业竞争力评估》工具),并且将自身实际情况评估,自我预期评判、主要竞争对手对比评估,标杆对标评估,发现自身的优势与不足。
第二步:对评估结果进行DNA 元素影响链分析。
这些DNA 元素往往由因果或连带关系,例如跨界学习与创新有一定关系,有时候评估出来最弱的环节并一定是直接突破的环节。
因此企业对这些关系进行影响链分析,找到突破点。
第三步:制定改进目标、计划。
根据突破口,明确提升目标,或对标对象,尽可能让目标可视化,制定环环紧扣改善计划,避免单向推进,实现重点与全面的平衡。
第四步:匹配资源投入,定期进行评估纠偏,避免急功近利。
竞争力的提升不是一朝一夕的事情,资源的配套是必须的;同时及时进行改进效果的评估、改进计划的纠偏等,确保投入能对竞争力全局起作用。
四、结论本文借鉴Dave Ulrich 的《企业竞争力评估》调研工具,20多家企业的管理者与核心人员对香港企业的竞争能力从11个维度进行评估,发现当前香港企业在竞争力上出现关注客户维护,但创新能力不足等问题,通过对问题的分析,文章最后针对香港企业竞争力现状提出香港企业需要采取重点突破、环环紧扣的建设思路。
保护自身权益的3s原则英文

保护自身权益的3s原则英文The 3S principle for protecting one's own rights and interests is a set of guidelines that can be applied in various situations to ensure that individuals are adequately protected. The principles are: Self-awareness, self-education, and self-action. By adhering to these principles, individuals can make informed decisions and take appropriate actions to safeguard their rights and interests. This essay will explore the 3S principle in detail and discuss its application in different scenarios.The first principle of the 3S principle is self-awareness. This involves understanding one's rights and knowing what actions can be taken to protect them. It is crucial for individuals to be aware of their legal rights in various aspects of life, such as employment, housing, and consumer rights. By knowing their rights, individuals can identify when these rights are being violated and take appropriate actions to rectify the situation. For example, if an individual believes they have been wrongfully terminated from their job, they need to be aware of applicable labor laws and seek legal advice if needed. Self-awareness also extends to recognizing potential threats and knowing how to mitigate them. By being alert to signs of potential rights infringement, individuals can take proactive measures to prevent harm.。
TPC,TPCC,TPMC

第一章什么是TPC和tpmC?1 TPCTPC(Transaction Processing Performance Council,事务处理性能委员会)是由数10家会员公司创建的非盈利组织,总部设在美国。
该组织对全世界开放,但迄今为止,绝大多数会员都是美、日、西欧的大公司。
TPC的成员主要是计算机软硬件厂家,而非计算机用户,它的功能是制定商务应用基准程序(Benchmark)的标准规范、性能和价格度量,并管理测试结果的发布。
TPC的出版物是开放的,可以通过网络获取()。
TPC不给出基准程序的代码,而只给出基准程序的标准规范(Standard Specification)。
任何厂家或其它测试者都可以根据规范,最优地构造出自己的系统(测试平台和测试程序)。
为保证测试结果的客观性,被测试者(通常是厂家)必须提交给TPC一套完整的报告(Full Disclosure Report),包括被测系统的详细配置、分类价格和包含五年维护费用在内的总价格。
该报告必须由TPC授权的审核员核实(TPC本身并不做审计)。
现在全球只有几个审核员,全部在美国。
TPC已经推出了四套基准程序,被称为TPC-A、TPC-B、TPC-C和TPC-D。
其中A和B已经过时,不再使用了。
TPC-C是在线事务处理(OLTP)的基准程序,TPC-D是决策支持(Decision Support) 的基准程序。
TPC即将推TPC-E,作为大型企业(Enterprise)信息服务的基准程序。
2 tpmCtpmC值在国内外被广泛用于衡量计算机系统的事务处理能力。
但究竟什么是tpmC值呢?作者曾向一些用户、推销人员乃至某些国外大公司的技术人员问过这个问题,但回答的精确度与tpmC值的流行程度远非相称。
tpmC这一度量也常被误写为TPM或TPMC。
TPC-C模拟一个批发商的货物管理环境。
该批发公司有N个仓库,每个仓库供应10个地区,其中每个地区为3000名顾客服务。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
3
Question Policy Interrupt us if something is unclear Keep long generic questions to the end Approach us during the conference Write us
markwkm@ rilson.nascimento@
10
TPC-E Overview (5) Business Model – Comparison with TPC-C
TPC-C Wholesale supplier Organized by Warehouses Districts Customers
TPC-E Brokerage House Organized by Customers Accounts Securities Companies
B ro k e r
BROKER C A S H _ T R A N S A C T IO N CHARGE C O M M IS S IO N _ R A T E SETTLEM EN T TRADE T R A D E _ H IS T O R Y TRA D E_REQ U EST TRA D E_TY PE F ix e d T a b le s
% ----10.21 9.59 8.08 1.96 19.03 12.89 4.84 14.43 0.96 17.99 n/a -----
Response Time (s) Average : 90th % ----------------0.021 : 0.043 0.040 : 0.083 0.346 : 0.945 0.313 : 0.677 0.006 : 0.010 0.005 : 0.009 0.003 : 0.004 0.014 : 0.018 0.055 : 0.090 0.009 : 0.017 0.036 : 0.122 -----------------
C u s to m e r
A C C O U N T _ P E R M IS S IO N CUSTOM ER CU STO M ER_A C CO U N T CU STO M ER_TA X R A TE H O L D IN G H O L D IN G _ H IS T O R Y H O L D IN G _ S U M M A R Y W A T C H _ IT E M W A T C H _ L IS T L egend:
15
TPC-E Overview (10) Sample Test Configuration
16
TPC-E Overview (11) Sample Test Configuration, Variation I
17
TPC-E Overview (12) Sample Test Configuration, Variation II
20
DBT-5 Architecture
21
DBT-5 Architecture - Loader Database creation is vendor specific, but... Database population can be vendor neutral TPC-E includes a data generator for database loading
M a rk e t
COM PANY C O M P A N Y _ C O M P E T IT O R D A IL Y _ M A R K E T EXCHANGE F IN A N C IA L IN D U S T R Y LA ST_TRA D E N E W S _ IT E M N EW S_X REF G ro w in g T a b le s SECTOR S E C U R IT Y
11
TPC-Ema – Comparison with TPC-C
C h a r a c t e r is t ic
T a b le s C o lu m n s M in C o ls / T a b le M a x C o ls / T a b le D ata Type Cou n t D ata Types P r im a r y K e y s F o r e ig n K e y s T a b le s w / F o r e ig n Keys C h e c k C o n s t r a in t s R e f e r e n t ia l I n t e g r it y
Rilson Nascimento
MSc Candidate in the Federal University of Pernambuco, Brazil Previously worked at Itautec Performance Lab
2
Table of Contents TPC-E Overview Workload Architecture Experimental Results Research Future Work
OLTP Database-centric workload Comparability of results Familiar business model – easy to understand Reduce cost of running benchmark Enhance schema complexity Be more representative to what customers do
4
Why TPC-E? /tpce/spec/TPCEpresentation.ppt TPC-C is over 14 years old Not practical to modify existing workload Transaction are too lightweight by today's standards CPU performance grew according to Moore's Law Disk latency did not Reduce cost/complexity of running benchmark Encourage DB uses which is more representative of what customer do
TPC-E
33 188 2 24 M any UID , CH AR, N UM , D ATE, BO O L, LO B 33 50 27 22 Yes
TPC-C
9 92 3 21 4 UID , CH AR, N UM , DATE 8 9 7 0 N o
12
TPC-E Overview (7) Database Tables and Scaling
18
TPC-E Overview (13) Sample Test Configuration, Variation III
19
TPC-E Overview – Highlights and Benefits Financial business model Rich transaction set Diverse, realistic schema Server-centric workload with DB focus Realistic application model Rebalanced hardware configuration Specification provides code where sponsor creativity is not being tested
Processor: Intel(R) Xeon(TM) CPU 2.80GHz w/HT Memory: 3 GB Disk: 14 disks in hw RAID 0 (data) Operating System: Linux 2.6.20-gentoo-r4 Database Engine: PostgreSQL 8.2.3 Database Size: 2806 MB (1000 customers, 50 ITD)
D im e n s io n
AD DRESS ST A TU S_T Y PE TAXRATE Z IP _ C O D E S c a lin g T a b le s
13
TPC-E Overview (8) Transactions
14
TPC-E Overview (9) Metrics
Performance (throughput), expressed in tpsE Price/Performance, expressed in price/tpsE Availability Date, when all products necessary to achieve the stated performance will be available
Total ----------3869 3635 3063 743 7212 4885 1835 5467 363 6817 9 -----------
Rollbacks ----------38 0 0 0 0 0 0 0 0 0 0 -----------
% -----0.99 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 0.00 ------
5
TPC-E vs. DBT-5 TPC-E is a benchmarking specification for generating marketing collateral DBT-5 a test kit to help improve PostgreSQL
6
TPC-E Overview TPC-E Goals
