TEMPLATE_3+1+1IAPD-Agmt_ASU_1510106
tp-link ac控制器主要功能配置实例说明书

声明Copyright © 2021 普联技术有限公司版权所有,保留所有权利未经普联技术有限公司明确书面许可,任何单位或个人不得擅自仿制、复制、誊抄或转译本手册部分或全部内容,且不得以营利为目的进行任何方式(电子、影印、录制等)的传播。
为普联技术有限公司注册商标。
本手册提及的所有商标,由各自所有人拥有。
本手册所提到的产品规格和资讯仅供参考,如有内容更新,恕不另行通知。
除非有特殊约定,本手册仅作为使用指导,所作陈述均不构成任何形式的担保。
目录第1章前言 (1)目标读者 (1)本书约定 (1)第2章设备管理 (3)如何修改Web登录密码 (3)2.1.1应用介绍 (3)2.1.2需求介绍 (3)2.1.3设置方法 (3)第3章基础联网设置 (5)如何配置连接互联网 (5)3.1.1应用介绍 (5)3.1.2需求介绍 (5)3.1.3设置方法 (5)第4章AP管理 (8)AP管理设置指南 (8)4.1.1应用介绍 (8)4.1.2需求介绍 (8)4.1.3设置方法 (9)4.1.4配置注意事项 (15)AP批量升级如何使用 (16)4.2.1应用介绍 (16)4.2.2需求介绍 (16)4.2.3设置方法 (17)4.2.4配置注意事项 (19)射频调优功能如何使用 (20)4.3.1应用介绍 (20)4.3.2需求介绍 (21)4.3.3设置方法 (21)4.3.4配置注意事项 (26)智能漫游功能如何使用 (27)4.4.1应用介绍 (27)4.4.2需求介绍 (27)4.4.3设置方法 (27)4.4.4配置注意事项 (31)如何设置AP定时重启与条目固化? (32)4.5.1应用介绍 (32)4.5.2需求介绍 (32)4.5.3设置方法 (32)4.5.4配置注意事项 (34)跨网络发现AP的几种方式及配置方法 (35)4.6.1应用介绍 (35)4.6.2需求介绍 (35)4.6.3设置方法 (35)第5章易展管理 (45)AC控制器搭配易展AP设置指南 (45)5.1.1应用介绍 (45)5.1.2需求介绍 (45)5.1.3设置方法 (46)5.1.4配置注意事项 (49)第6章认证管理 (50)无线控制器中MAC认证上网使用方法 (50)6.1.1应用介绍 (50)6.1.2需求介绍 (50)6.1.3设置方法 (50)6.1.4配置注意事项 (54)AC Portal认证设置指南—使用内置WEB服务器和内置认证服务器 (55)6.2.1应用介绍 (55)6.2.2需求介绍 (55)6.2.3设置方法 (56)6.2.4配置注意事项 (58)AC Portal认证设置指南—使用内置WEB服务器和外部认证服务器 (59)6.3.1应用介绍 (59)6.3.2需求介绍 (59)6.3.3设置方法 (60)6.3.4配置注意事项 (65)AC Portal认证设置指南—使用外置WEB服务器和内部认证服务器 (66)6.4.1应用介绍 (66)6.4.2需求介绍 (66)6.4.3设置方法 (67)6.4.4配置注意事项 (71)AC Portal认证设置指南—使用外置WEB服务器和外部认证服务器 (72)6.5.1应用介绍 (72)6.5.2需求介绍 (72)6.5.3设置方法 (73)6.5.4配置注意事项 (77)短信认证设置指南 (78)6.6.1应用介绍 (78)6.6.2需求介绍 (78)6.6.3设置方法 (78)6.6.4配置注意事项 (87)一键上网使用方法 (88)6.7.1应用介绍 (88)6.7.2需求介绍 (88)6.7.3设置方法 (89)6.7.4配置注意事项 (93)微信认证使用方法 (94)6.8.1应用介绍 (94)6.8.2需求介绍 (94)6.8.3设置方法 (95)6.8.4配置注意事项 (106)免认证策略的使用方法 (107)6.9.1应用介绍 (107)6.9.2需求介绍 (107)6.9.3设置方法 (108)6.9.4配置注意事项 (110)Portal认证中外部WEB服务器建立规范 (111)6.10.1应用介绍 (111)6.10.2认证流程 (111)6.10.3流程及规范要求 (112)第7章安全管理 (116)广播风暴抑制配置指南 (116)7.1.1应用介绍 (116)7.1.2需求介绍 (116)7.1.3设置方法 (117)DHCP防护配置指南 (118)7.2.1应用介绍 (118)7.2.2需求介绍 (118)7.2.3设置方法 (119)ARP防护配置指南 (121)7.3.1应用介绍 (121)7.3.2需求介绍 (121)7.3.3设置方法 (121)第8章双链路备份 (124)双链路备份设置方法 (124)8.1.1应用介绍 (124)8.1.2需求介绍 (124)8.1.3设置方法 (125)8.1.4配置注意事项 (129)第9章其他功能 (130)连云配置指南 (130)9.1.1应用介绍 (130)9.1.2需求介绍 (131)9.1.3设置方法 (131)远程管理配置指导 (138)9.2.1应用介绍 (138)9.2.2需求介绍 (138)9.2.3设置方法 (138)9.2.4配置注意事项 (145)第1章前言本手册旨在帮助您正确使用ER 2/3/5/6/7/8系列企业级路由器。
华美商桥 Premier 手机 App 用户指南说明书

华美商桥® Premier(business Bridge®Premier)手机App用户指南2022 年 4月目录企业网上银行手机App概览 (3)支持的设备 (3)IBM Security® Trusteer® (3)下载手机App (3)登录页面及系统菜单 (4)账户资料 (5)核准付款及模版 (7)转账 (9)支票服务 (10)支付账单 (11)用户管理 (12)其他仪表板小工具 (13)手机App功能 (14)保安编码器核准 (15)激活保安编码器App (15)企业网上银行手机App 概览本指南介绍了华美商桥® Essentials (business Bridge®Essentials )及华美商桥® Premier (business Bridge®Premier )企业网上银行手机App 的主要功能,方便您随时在手机上查看账户、交易、通知,发起和核准转账与付款,以及查询银行地址等。
支持的设备Apple iPhones® 及 iPads®操作系统: iOS 11 及更新的版本。
Android™ 设备操作系统: Android 9.0 及更新的版本。
IBM Security ® Trusteer ®Trusteer 是一款轻量级软件,可保护您的设备免受恶意软件攻击。
当您通过手机App 登录华美商桥® Premier (business Bridge®Premier )时,您的网上银行账号和登录凭证会受到保护。
下载手机App在手机或其他移动设备上,请在 Google Play™ 或 Apple App Store™ 中查找“East West Bank ”,并选择蓝色的 East West Bank Business Mobile App 下载。
Aruba IAP-VPN产品说明书

OUR COMMITMENT TO YOUGENERAL INSTRUCTIONSStep 1: Choose your Access Points (APs)For all options below, first i dentify existing in-house inventory of Aruba Central-manageable Aruba APs or purchase new APs to meet the quantity that needs to be deployed. All IAP and UAP models can all be used. Learn more about the models at:https:///products/networking/ac cess-points/Step 2: Choose AP Evaluation LicensesThe following table lists the AP evaluation license (or 1-year license for purchase) required for Aruba Central management. For licens ing questions, please contact TAC.Any IAP/UAP 90-Day EvalLicense 1-Year License (for purchase)DeviceManagement JW450-EVALS JY925AAE ServiceManagement JY928-EVALS JY928AAECONTACT USPlease contact your designated Aruba representative to learn more or to obtain a quote for Aruba APs.manage, configure and monitor Virtual Gateways: https://portal-/platform/signup/regist ration#/SIGNUPStep 2: Deploy your Headend Gateway (physical VPNC) In order to connect end-users to enterprise services in your data center or campus network, an Aruba Headend Gateway (HG) acting as a VPNC needs to be deployed. Please select a HG Eval license or HG 1-year license (for purchase) for the VPNC based on your throughput and concurrent user requirements using the Aruba IAP-VPN Solution Guide. Please contact TAC for any licensing questions.Headend GatewayHG Lic.EvaluationHG 1yr Lic.Subscription7010 or 7024JZ121-EVALS JZ118AAE 70307205JZ198-EVALS JZ195AAE 721072207240/7240XM/ 7280There may also be other selection factors for your deployment, such as form factor, client count, and required encrypted throughput. Learn more at:https:// /products/networking/ gateways-and-controllers/CONTACT USPlease contact your designated Aruba representative to learn more or to obtain a quote for Aruba Mobility Controllers.SPECIAL PROGRAMEVALUATION LICENSES FOR UP TO 90 DAYS ADDITIONAL INFORMATIONImportant Note on Evaluation LicensesThis applies to EVL-PEFV-xxxx, EVL-VIA, EVL-AP and EVL-PEFlicenses.Good through June 30, 2020, customers can contact the account partner or Aruba TAC to request the specific Eval licenses. The licenses would be generated on behalf of the customer and the customer would be notified via email regarding the license details and how to activate on a particular Mobility Controller.These Eval licenses are good for up to 90 days (3x 30) in increments of 30 days. Before the first period expires, the customer MUST reapply the license for the next 30 days and then repeat the process one more time. The first 30-day period starts from the time the license is installed on the Controller. An alert shown via the Controller GUI will inform when the license is due to expire. If this alert is not TAC.your business needs the backing of Services.GLOSSARY:1: VPNC = VPN Concentrator.Central or Mobility Master.configured by Mobility Master. To learn more on VMC, view the datasheet:https:///assets/ds/DS_VMC.pdf4: vmore info on vGW, please view the SD-WAN datasheet.APPENDIX A: SETTING UP VIRTUAL GATEWAYSFor AWS: Request whitelisting for an Amazon Machine Image or AMI using the following form: https://bit.ly/2QB8q1X A notification is sent once the whitelisting is done, and the AMI is visible in the AWS Console. Then, follow the deploy the gateway: https://bit.ly/2wrumFNNote:download the product here:https:///marketplace/pp/B081Y65W5MFor Azure: Download the required VHD image from the Aruba Support Portal (here: https://bit.ly/33L9VAdFollow the instructions here to upload to Azure and deploy the Virtual Gateway using Aruba Central:APPENDIX B: CHOOSING THE BEST-FIT SOLUTIONIAP-VPN, Aruba VIA, and RAP deploymentsThere are many considerations when choosing a WFH solution. We have narrowed it down to a handful of decision factors that can simplify your choice, especially if you are new to Aruba WFH offerings.For the deployment of an Aruba WFH solution, virtualized head-end gateways can offer the fastest time to operation, removing the need to ship and handle devices onsite. For example, the Aruba vGW available in AWS today can be installed and deployed remotely in an AWS account, then managed entirely through Aruba Central. The Decision tree below will help you decide on a solution.Fully Cloud-managed with Aruba Central.Other considerations:•Multi AP roaming •VRRP redundancy;stateless L2 failover •Subscription licenses •Supported AP type:RAP , IAP , UAP•Supported VPNCs*:HW GW, vGW (AWS)Other considerations:•Cloud Managed with Aruba Central •Users download the VIA client•No need to ship AP hardware•Supported VPNCs*:HW GW, vGW (AWS)WFH SolutionsDeployVirtual Intranet Access Solution managed on-prem by Mobility Master.Other considerations:•Single AP•Controller cluster;stateful L2 failover •Perpetual licenses •Supported AP type:CAP , RAP , IAP , UAP •Supported VPNCs*:HW MC, VMC (ESXi,Hypervisor)Choose implementation. Prefer Cloud or on-prem mgmt?DeployIAP-VPN & SD-WAN VPNC DeployArubaOS 8.X Remote AP Prefer client VPN or hardware VPN?HardwareClientOn-premCloud© Copyright 2020 Hewlett Packard Enterprise Development LP. The information contained herein is subject to change without notice. The only warranties for Hewlett Packard Enterprise products and services are set forth in the express warranty statementsaccompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Hewlett Packard Enterprise shall not be liable for technical or editorial errors or omissions contained herein.Contact Us Share。
Door King 2600-264 Pad Mount 和 6300-089 NIPB-Model

131133Shown for Reference in Outline Form Pad Mount 2600-264Callout = PM (PM includes parts also used in Post Mount 2600-263)PMPMPMPMPM111127121113115117119123125Not Shown2XShown for Reference Pad Mount 2600-264121Ref1162XEOREV DESCRIPTION Drawn APPR ---N Added Item 116; Items 151, 153, 180, 211 Was: 2616-016, 2904-002, 2620-019,2902-007,2340-065; Deleted 166 Was: 2620-019.Sal 09/22/08 D.C.09/22/08N IPB-Model 6300-089,1/2HP,230 V, Primary,Convenient Open PROPRIETARY AND CONFIDENTIAL COMMENTS:SHEET 1 OF 6CHECKED DRAWN DATENAME REV A DWG. NO.SIZE Scale: None 6300-889Sal 06/23/082. Items 200-211 Not Shown for Clarity.1. See attached reference sheet for BOM; Reference Movex 6300-089 Rev N.Notes: Unless Otherwise Specified.THE INFORMATION CONTAINED IN THIS DRAWING IS THE SOLE PROPERTY OF Door King. ANY REPRODUCTION IN PART OR AS A WHOLE WITHOUT THE WRITTEN PERMISSION OF Door King IS PROHIBITED.Item Part Number Qty UM Description Rev 16300-8891EA IPB-230V 1/2HP, Convenient Open, Swing Gate Optr N 32600-7051EA Bracket Panel Base Model 63052600-8691EA Motor Base 610/605 Battery Bk62600-1241EA Motor Assembly 1/2 HP Dual Pul81215-0182EA Wire Nut #71B92600-6881EA Belt - 17" 4L170 Cogged102600-1971EA Motor 24VDC For BB112600-5691EA Pulley 10" Cast Iron AC100X5/8131601-0191EA Keyway 3/16 x 3/16 x 1152600-4281EA Belt-Cogged, AX-34192600-4691EA Marker Strip 230V 1Phase213130-0081EA Terminal Block 5 pin233129-0051EA Terminal Block Cover 5 Position252600-8301EA Jumper- Ring Tongue272599-0141EA Decal Copper Wire Only292600-4391EA Washer Cup - Brass312599-0061EA Decal SUPPLY GND322600-6192EA Wire Clp-5/8" Concord 770-1209332600-6651EA Battery Tray 610351801-0092EA Battery 12V 3.0 AmpHour PS1230372600-6381EA Bracket Radio 610 Battery Bkup396300-0421EA Housing Assembly 6300412600-6131EA Bracket Magnetic Ctr Potted433004-0101EA Magnetic Counter Threaded453004-0512EA Nut Panel 1/4-18472600-7791EA Swing Crank Arm Extended492600-0611EA Collar 2 OD x 1 1/4 ID x 5/8 L572600-1741EA Main Shaft Assy Model 630592630-0101EA Snap Ring 1.25"612600-0731EA Magnet Counter Ring632600-6812EA Clutch Plate 9" Die Cast652801-0032EA Clutch Pad 9" OD620/25,630,630672600-6441EA Worm Gear 100 Teeth Delrin712600-7731EA Bracket Board Mtg Panel 630722600-8751EA Capacitor Mounting Clamp732600-5331EA Switch Cover Doorking Lockable742600-1021EA Capacitor 50uf 370VAC752600-7311EA Gasket Switch Cover771506-0711EA Tone Generator Loud791812-0051EA Switch Push Button N.O.811601-0411EA Switch Toggle SPST 2POS831601-1401EA Switch Toggle 2 Pole On-Off852599-0081EA Label Patent871200-0282EA Outlet Snap-In Leviton 1306882600-7492EA Wire Connector STA-KON RC6892600-82012EA Bushing 1/2914001-0961EA Transformer 460/230/208-115V932340-0101EA PCB Battery Backup954502-0101EA PCB Gate Operator974001-0201EA Terminal 20 Pin992600-8402EA Jumper- Ring Tongue #8 Screw 1012600-9451EA Cover Plastic Insulator1112600-7251EA Cover-Model 63001132600-7321EA Nameplate Plastic DKS1152802-0402EA Washer Push on Clamp1161897-0522EA Gasket, Microphone Support 1171702-5071EA Cam "J" Hook1194001-0351EA Lock N16058BDxSFx2K Key 16120 1212600-7201EA Crank Arm Joint Assembly Blk 1232600-6301EA Joint Cover Swinger Left1252600-6311EA Joint Cover Swinger Right 1272600-7111EA Bracket 3/16 x 2 x 121312599-0341EA Label Gate Operator1332599-1991EA Label Universal1402615-0523EA Bolt Hex Head 3/8-16 x 1 1412615-0081EA Bolt Hex Head 1/4-20 x 1 1/2 1502616-0194EA Screw Phillips Head 8-32 x 3/4 1512616-0181EA Screw Phillips Head 8-32 x 1/2 1522616-0175EA Screw Phillips Head 8-32 x 3/8 1532616-0012EA Screw Phillips Head 6-32 x 3/8 1542616-0512EA Screw Phillips 10-32 x 3/8 1552616-0526EA Screw Phillips Head 10-32 x1/2 1562616-0017EA Screw Phillips Head 6-32 x 3/8 1572600-8872EA Screw Nylon Phillips 6-32 x 1/4 1582616-0032EA Screw Phillips Head 6-32 x 3/4 1602620-2202EA Washer 1.25 x 2 x .06251612620-1312EA Washer 1 7/8 OD x 1/2 ID 1/8 T 1622620-0442EA Lockwasher #81632600-1838EA Washer Bellville 1.5 OD x .5 ID 1642620-0212EA Washer 1/2 SAE1652620-0024EA Washer 1/4 USS1702620-0104EA Washer #10 SAE1802620-4118EA Nut Hex Flange Lock 5/16-18 1812902-0086EA Nut Keps 1/4-201822620-3201EA Nut Center Lock 1/2-131832620-4202EA Nut Hex 1/2-131842620-4091EA Nut Hex Flange Lock 1/4-20 1852620-4011EA Nut Hex 8-322001804-03115EA Tie Wrap 4"2012600-6981EA Wire Set Model 6050,6100,6300 2032340-1641EA Wire Set BB 6100,6300,9150 2057082-0521EA Wire 8" Green 16 AWG Stranded 2077082-1371EA Wire 5" Green Stranded 14AWG 2092599-1002EA Sign Warning2116300-0651EA Manual Installation。
IS104GPS-2F 6-port Gigabit managed PoE switch User

User ManualIS104GPS-2F6-port Gigabit managed PoE switchInstallation Manual Introduction<User Manual>mainly introduces the hardware features, installation methods,and precautions during the installation of IS104GPS-2F.This manual includes the following sections:Chapter1:Product introduction.Briefly describe the basic functions and features of the switch,detailed hardware and software specifications and appearance information.Chapter2:Hardware Connections.Guide the connection of switch with other devices and precautions.Chapter3:Product Installation.Guide the hardware installation method and precautions.Chapter4:Product Packaging and Use Recommendations.Chapter1Product Introduction1.1Product introductionThe IS104GPS-2F is a6-port Gigabit-managed industrial PoE switch that provides4Gigabit ports and2Gigabit SFP ports.Each PoE port can provide up to46W for IEEE802.3af/at compatible powered devices(PDs).It is especially suitable for applications where AC power is not easily available or high wiring costs.It support EMC industrial grade4protection;corrugated high-strength aluminum profile housing,IP40grade,low power design,seismic rail mounting,-40°C-75°C operating temperature, can work in harsh environments;IS104GPS-2F also supports Apollo cloud one-stop management platform for status checking and management monitoring,to make it become a reliable solution for Intelligent transportation,video surveillance and other harsh industrial environments.21.2FeaturesFull Gigabit Ethernet port4full Gigabit RJ45PoE network port,and2Gigabit SFP ports, breaking the traditional100M limitation,data transmission will not stuckBroadcom high performance industrial grade chip for more stable performanceBroadcom high-performance industrial-grade chips that dramatically increase network data processing ratesPowerful working environmentEMC industrial grade4protection;corrugated high-strength aluminum profile housing,IP40grade,low power design,seismic rail mounting,-40°C-75°C operating temperature,can work in harsh environments3Support Apollo cloud platform one-stop management Support cloud platform to visualize management of switches and attached power devices,making operation and maintenance management easier1.3Software and hardware specificationsHardware specificationChipBroadcom high performance chipFlash16MBRAM64MBDDRPort410/100/1000M RJ45Port21000M SFP PortPoE Power supply 410/100/1000MbpsRJ45Port support 802.3af/atPoE power supplyThe maximum power per port is46W4Indicator 6Link/Act indicator4POEindicatorALM Alarm indicatorP1、P2Power Indicator1SYS indicatorPerformance Forward mode:store and forward Backplane bandwidth:12Gbps Packet forwarding rate:8.9Mpps Support8K MAC address table depthStandard protocol IIEEE802.3:Ethernet Media Access Control (MAC)ProtocolIEEE802.3i:10BASE-T EthernetIEEE802.3u:100BASE-TX Fast EthernetIEEE802.3ab:1000BASE-T Gigabit Ethernet IEEE802.3z:1000BASE-X Gigabit Ethernet (optical fiber)5IEEE802.3ad:Standard method for performing link aggregationIEEE802.3x:Flow ControlIEEE802.1p:LAN Layer2Qos/Cos protocol for traffic prioritization(multicast filtering)IEEE802.1q:VLAN Bridge OperationIEEE802.1d:STP spanning treeIEEE802.1s:MSTP Spanning TreeIEEE802.1w:RSTP Spanning TreeIEEE802.3afIEEE802.3atIndustry Standard EMI:FCCCFR47Part15,EN55022/CISPR22, Class AEMS:IEC61000-4-2(ESD):±8kV(contact),±15kV6(air)IEC61000-4-3(RS):10V/m(80MHz-2GHz)IEC61000-4-4(EFT):Power Port:±4kV;Data Port:±2kVIEC61000-4-5(Surge):Power Port:±2kV/DM,±4kV/CM;Data Port:±6kVIEC61000-4-6(CS):3V(10kHz-150kHz);10V (150kHz-80MHz)IEC60068-2-6(Vibration)IEC60068-2-27(Shock)IEC60068-2-32(Free Fall)Operation environment Working temperature:-40~75°CStorage temperature:-40to75°CRelative humidity:5%to95%(no condensation)7Certification CE,FCC,RoHSMean timebetweenfailures(MTBF)100,000hrsWarranty3yearsLightningprotectionNetwork port:±6KV power port:±4KV ESD Contact:±8KV Air:±15KVPhysical specification Input:48-56VDCHousing:IP40grade protection,corrugated high strength metal housingInstallation:DIN rail mountingSize:163mm×46.5mm×110mm,Weight:1kg8Software specification101112131.4AppearanceIndicator StatusDescriptionP1、P2On The corresponding power supply working normally.Off The corresponding power supply is not connected or working abnormal.SYS Blink System is running normally14ingOff/ alwa ys brig ht System operation is abnormal/start unsuccessfulALM On Alarm start upOff Alarm not triggeredLink/ACT F1-F4BlinkingSFP port is working normalOff SFP port is working abnormally/port is not connected1516Chapter 2.Hardware Connection2.1Connect to RJ45portUse the network cable to connect the switch to the RJ45port of network device.Normally,the switch's downlink port has POE power supply enabled by default.It can support POE power supply to AP ,bridge,network camera and other PDs which comply with IEEE802.3af and IEEE802.3atstandards.2.2Connect to the SFP portThe SFP port of the IS104GPS-2F supports only Gigabit fiber modules.It is recommended to use standard SFP module products. The process of installing a fiber module on a switch is as follows:1.Grasp the fiber module from the side and insert it smoothly along the SFP port slot of the switch until the fiber module is in close contact with the switch;2.Confirm the Rx and Tx ports of the fiber module when connecting.Insert one end of the fiber into the Rx and Tx ports to ensure that the Tx and Rx ends of the interface are correctly connected,and the other end of the fiber is connected to another device.3.After power-on,check the status of the corresponding indicator.If the indicator is on,the link is up.If not,please check the line and confirm that the peer device is enabled.1718Attention:It is not allowed to excessively bend the fiber,and its radius of curvature should be no less than 10cm;Ensure the cleanliness of the fiber end face;Please do not look directly into the fiber optic connector with your eyes,as this may cause eye damage.2.3Check before power-onCheck that the power supply of the power outlet meets the switch specifications.Check that the power supply,switch,and rack are properly grounded.Check whether the switch is connected to other network devices.2.4Device initializationThe switch will automatically initialize after the power is turnedonand the power switch is turned on.The indicator light will appear as follows:After the power is turned on,the power indicator remains steady, the SYS light enters the blinking state,and the system runs normally.The indicator of each port indicates the connection status of each port,indicating that the switch has started to work normally.Chapter3,Product InstallationBefore installation,confirm the operating environment of the equipment:power supply voltage,installation space,installation method,etc.Please carefully confirm the following installation requirements:-Check for cables and connectors required for19installation♦-Check whether the cable is in place(not more than100m)according to reasonable configuration requirements.♦-The product does not provide mounting components,the user must prepare the components of the selected installation type:screws,nuts and tools to ensure reliable installationPower requirements:12-56V DC(12-48V nonsupportPoE,support date exchange only)Environmental requirements:Working temperature:-40~75°CStorage temperature:-40to75°CRelative humidity:5%to95%(no condensation) Power input20215pin 5.08mmterminalInput range:12-56VDCP1&P2dual redundant power supply,Support reverse connection protectionGround protectionGroundprotectionConnect to groundRail mountingChapter4,Packing list and use recommendations 4.1Product packagingItem Quantity Description Switch1set\Phoenix terminal1*5,1*2eachper one unit Connect to power and alarm switchWarranty card1piece For after-sales maintenance User Manual1copy Used to guide users to installswitches4.2Recommendations1.For safety reasons,non-professionals should not open the product casing;2.Pay attention to the danger of strong electricity and safe protection when the product is powered on;223.Do not use the switch in a humid environment to prevent water from entering the fuselage through the casing,resulting in damage to the machine;4.In the state of power-on of the product,please do not plug and unplug the cable if non special case;5.Please do not place heavy objects on the switch to avoid accidents;6.It is recommended to use the switch indoors.It is recommended to add a waterproof box when using it outdoors. Note:The pictures in the manual are for reference only,whichever is subject to the actual product.23。
aruba配置手册

wlan ssid-profile "default"wpa-passphrase 1234567890 ---tkip设置provision-ap copy-provisioning-params ip-addr 192.168.102.250 provision-ap no ipaddrprovision-ap a-ant-gain 2provision-ap g-ant-gain 2provision-ap a-antenna 1provision-ap g-antenna 1provision-ap external-antennaprovision-ap master 192.168.102.100provision-ap server-ip 192.168.102.100provision-ap ap-group "default"provision-ap ap-name "00:0b:86:cb:bd:62"provision-ap no syslocationprovision-ap fqln ""provision-ap reprovision ip-addr 192.168.102.250interface loopback ip address "192.168.30.200"apboot> helpboot - run bootcmd or boot AP image or elf file or from flashcd - cfg register displaycw - cfg register writedis - disassemble instructionsdhcp - invoke DHCP client to obtain IP/boot paramseloop - loopback received ethernet framesflash - FLASH sub-systemgo - start application at address 'addr'help - print online helpmc - memory copymd - memory displaymii - MII sub-systemmtest - simple RAM testnetstat - net statisticsmw - memory writeping - ping net hostprintenv - env displaypurgeenv - purge envregs - display various regsreset - reset processorrun - run commands in an environment variablesaveenv - save environment variables to persistent storagesetenv - set variable in env (ipaddr/netmask/gatewayip/master/serverip) setenv ipaddr x.x.x.xsetenv netmask x.x.x.xsetenv gatewayip x.x.x.xsetenv serverip x.x.x.xsetenv master x.x.x.xtcpdump - dump received packetstcpsend - send TCP packettftpboot - boot via tftptlb - dump TLBtrace - dump trace bufferversion - print monitor versionwdog - stop refreshing watchdog timerapboot>No spanning-tree 关闭spanning-treeAdp discover disable 关闭ADPAdp imgp-join disable 关闭im-j一、WEB页面认证1、wlan ssid-profile (staff-ssid-profile) :定义ssid配置文件1.1 essid staff :定义ssid下的essid—显示出来的ssid2、wlan virtual-ap (staff-vap-profile) :定义virtual-ap的配置文件2.1 ssid-profile (staff-ssid-profile) :在virtual-ap下引用定义过SSID2.2 vlan ID aa,bb :把virtual-ap加入到要ssid所属VLAN3、aaa profile staff-aaa-profile :定义AAA认证配置文件4、aaa server-group (staff-servergroup) :定义server-group配置文件4.1 auth-server internal :定义认证服务器为本地认证4.2 set role condition role value-of 设置角色set role condition <condition> set-value <role> position <number>5、aaa authentication captive-portal (staff-auth-profile) :captive-portal配置5.1 server-group staff-servergroup :在下面引用定义过的server-group6、user-role staff-logon :定义用户登陆前权限的配文件6.1 access-list session logon-control position 1定义用户登陆前的权限--位置16.2 access-list session captiveportal position 2 定义用户登陆前的权限--26.3 Captive-Portal staff-auth-profile position 3定义过captive-portalRe-authentication interval 480 再次认证间隔480秒默认3600秒7、user-role vip-role :定义用户成功登陆后的配置文件7.1session-acl allowall 赋予所有允许权限session-acl http-acl 只有http8、wlan virtual-ap staff-vap-profile :进入定义过的virtual-ap配置文件8.1 aaa-profile staff-aaa-profile :引用定义过的AAA配置文件9、ap-group default :定义ap-group,最好用默认的9.1 virtual-ap staff-vap-profile :引用定义过的Virtual-ap配置文件10、aaa profile staff-aaa-profile :进入定义过的AAA配置文件10.1 initial-role staff-logon :把initial-role改为定义过用户登陆前配置11、aaa authentication-server internal use-local-switch :定义认证SERVER为本地交换机12、local-userdb add username staff password 123456 role vip-role :定义用户的登陆的用户名和密码及权限二、MAC 地址认证配置1、wlan ssid-profile (staff-ssid-profile) :定义ssid配置文件1.1 essid staff :定义ssid下的essid2、wlan virtual-ap (staff-vap-profile) :定义virtual-ap的配置文件2.1 ssid-profile (staff-ssid-profile) :virtual-ap下引用定义过的SSID配置文件2.2 vlan ID :把virtual-ap加入到要ssid所属的VLAN3、aaa profile staff-aaa-mac-profile :定义AAA认证配置文件4、aaa authentication mac staff-mac-profile :定义mac配置文件4.1 Delimiter dash :定义mac地址的格式4.2 Case upper (upper/lower):定义mac地址的大/小写备注:aaa authentication mac staff-mac-profileclone <profile>delimiter {colon|dash|none}max-authentication-failures 数字aaa authentication mac mac-blacklist MAC黑名单max-authentication-failures 5 最多认证失败次数5、aaa server-group (staff-macservergroup) :定义server-group配置文件5.1 auth-server internal :定义认证服务器为本地认证5.2 set role condition role value-of6、user-role staff-logon :定义用户登陆前权限的配文件6.1 access-list session logon-control :定义用户登陆前的权限6.2 access-list session captiveportal :定义用户登陆前的权限7、user-role vip-role :定义用户成功登陆后的配置文件7.1session-acl allowall :赋予权限8、wlan virtual-ap staff-vap-profile :进入定义过的virtual-ap配置文件8.1 aaa-profile staff-aaa-mac-profile :引用定义过的AAA配置文件9、ap-group default :定义ap-group,最好用默认的9.1 virtual-ap staff-vap-profile :引用定义过的Virtual-ap配置文件10、aaa profile staff-aaa-mac-profile :进入定义过的AAA配置文件10.1 initial-role staff-logon :把initial-role改为定义过的用户登陆前的配置文件10.2 authentication-mac staff-mac-profile :把定义的authentication mac文件引用10.3 mac-server-group staff-macservergroup :把定义的servergroup加入11、aaa authentication-server internal use-local-switch :定义认证SERVER为本地交换机12、local-userdb add username mac地址password mac地址 role vip-role :定义用户的登陆的用户名和密码及权限注意:如果是有线直接连在端口上的话要进行认证必须把连接口设为UNTRUSTED.同时在设定:进入aaa authentication wired 后设定:profile (staff-aaa-profile) 为你设定认证的AAA profileBlacklist:5次错误就拒绝访问show aaa authentication captive-portal default:Max authentication failures 改为5次show aaa authentication dot1x default:Max authentication failures 改为5次1、aaa bandwidth-contract "256" kbits "256"2、aaa bandwidth-contract "256" kbits 256ip access-list session "pass"any any any permit queue low!user-role "ap512"access-list "pass" position 1bw-contract "256" per-user upstreambw-contract "256" per-user downstreamaaa bandwidth-contract "2M-BW" mbits "2" 带宽2M控制aaa bandwidth-contract 128_up kbits 128 带宽128k控制aaa bandwidth-contract 512 kbits 512aaa bandwidth-contract 64 kbits 64aaa bandwidth-contract 256 kbits 256aaa bandwidth-contract 1 mbits 1 带宽1M控制aaa bandwidth-contract 128_up kbits 128user-role 128bw-contract 128_up per-user upstreamuser-role ap-rolesession-acl controlsession-acl ap-acl!user-role pre-employeesession-acl allowallMaster mobility controller configuration1Initial setup of Aruba-master2Core VLAN configuration and IP addressing3Core VLAN port assignment4Loopback IP address ----- interface loopback ip address 设置环回地址Deploy APs5配置AP VLAN6配置 AP VLAN DHCP Server7Connect Aruba APs8Provisioning Aruba APs(Aruba-master) (config-if)#write mSaving Configuration...ip dhcp pool "userpool" 定义pool的名字default-router 192.168.11.254 定义默认路由网关—loopback地址dns-server 192.168.11.254---202.106.0.20 定义DNS网关lease 8 0 0network 192.168.11.0 255.255.255.0service dhcp 启动dhcpinterface gigabitethernet 1/1no muxportswitchport mode trunkip default-gateway 192.168.0.254interface vlan 1no ip addressno ip igmpinterface gigabitethernet 1/1no switchport access vlaninterface loopback ip address "192.168.0.100"(Aruba800-4) (config) # show ip interface briefInterface IP Address / IP Netmask Admin Protocolvlan 1 172.16.0.254 / 255.255.255.0 up upvlan 10 192.168.0.1 / 255.255.255.0 up upvlan 30 192.168.30.200 / 255.255.255.0 up uploopback unassigned / unassigned up up(Aruba800-4) (config) # rf arm-profile default ----------关闭ARM后调整channel---ok (Aruba800-4) (Adaptive Radio Management (ARM) profile "default") #assignment disable (Aruba800-4) (Adaptive Radio Management (ARM) profile "default") #no scan(Aruba800-4) (Adaptive Radio Management (ARM) profile "default") #write memoryrf dot11g-radio-profile "default"tx-power 20 ------------------------发射功率调整rf dot11g-radio-profile "default"channel 11 ------------------------调整AP信道interface vlan 20ip address 192.168.0.1 255.255.255.0ip nat insideno ip igmp存配置:24 (Aruba2400) #configure t25(Aruba2400) (config) #copy tftp: 172.16.0.100 aruba2400-0904.cfg flash: 2400.bak 26(Aruba2400) (config) #copy flash: 2400.bak flash: 2400.cfg27(Aruba2400) # copy running-config tftp: 192.168.4.100 aruba2400-0904.cfgRadius配置:aaa authentication-server radius Radius1host <ipaddr>key <key>enableaaa server-group corpnetauth-server Radius1dot1x配置:aaa authentication dot1x corpnetaaa profile corpnetauthentication-dot1x corpnetdot1x-default-role employeedot1x-server-group corpnetvirtual AP:wlan ssid-profile corpnetessid Corpnetopmode wpa2-aeswlan virtual-ap corpnetvlan 1aaa-profile corpnetssid-profile corpnetap-group defaultvirtual-ap corpnet时间设定:time-range workhours periodic周期weekday 09:00 to 17:00ip access-list session restricted 受限制any any svc-http permit time-range workhoursany any svc-https permit time-range workhoursuser-role guestsession-acl restrictedmesh设置:ap mesh-radio-profile <profile-name>11a-portal-channel <11a-portal-channel>11g-portal-channel <11g-portal-channel>a-tx-rates [6|9|12|18|24|36|48|54]beacon-period <beacon-period>children <children>clone <source-profile-name>g-tx-rates [1|2|5|6|9|11|12|18|24|36|48|54]heartbeat-threshold <count>hop-count <hop-count>link-threshold <count>max-retries <max-retries>metric-algorithm {best-link-rssi|distributed-tree-rssimpv <vlan-id>rts-threshold <rts-threshold>tx-power <tx-power>ap mesh-radio-profile <profile-name>clone <source-profile-name>ap-group <group>mesh-radio-profile <profile-name>ap-name <name>mesh-radio-profile <profile-name>wlan ssid-profile <profile>essid <name>opmode <method> 方式wpa-passphrase <string> (if necessary)wlan virtual-ap <name>ssid-profile <profile>vlan <vlan>forward-mode bridgeaaa-profile <name>rap-operation {always|backup|persistent}ap-group <name>virtual-ap <name># ip access-list session "Employee-Policy"any any any permit queue lowRemote AP配置The firewall must be configured to pass NAT-T traffic (UDP port 4500) to the controller.)1、Configure a public IP address for the controller.2、Configure the VPN server on the controller. The remote AP will be a VPN client to the server.3、Configure the remote AP role.4、Configure the authentication server that will validate the username and password for the remote AP.5、Provision the AP with IPSec settings, including the username and passwordfor the AP, before you install it at the remote location.1、Cli:vlan <id>interface fastethernet <slot>/<port>switchport access vlan <id>interface vlan <id>ip address <ipaddr> <mask>2、Using the CLI to configure VPN server:vpdn group l2tpppp authentication PAPip local pool <pool> <start-ipaddr> <end-ipaddr>crypto isakmp key <key> address <ipaddr> netmask <mask>3、Using the CLI to configure the user role:(table1) (config) # user-role remote(table1) (config-role) #session-acl allowallip access-list session <policy>any any svc-papi permitany any svc-gre permitany any svc-l2tp permitany alias mswitch svc-tftp permitany alias mswitch svc-ftp permit4、Using the CLI to configure the VPN authentication profile:4.1 aaa server-group <group>auth-server <server>4.2 aaa authentication vp ndefault-role <role>server-group <group>5、Using the CLI to enable double encryption:ap system-profile <profile>double-encryptap-name <name> 需要插上远端AP后配置ap-system-profile <profile>Using the CLI to enable double encryption:ap system-profile <profile>double-encryptap-name <name>ap-system-profile <profile>Using the CLI to configure the AAA profile:aaa profile <name>initial-role <role>authentication-dot1x <dot1x-profile>dot1x-default-role <role>dot1x-server-group <group>Using the CLI to define the backup configuration in the virtual AP profile: wlan ssid-profile <profile>essid <name>opmode <method>wpa-passphrase <string> (if necessary)wlan virtual-ap <name>ssid-profile <profile>vlan <vlan>forward-mode bridgeaaa-profile <name>rap-operation {always|backup|persistent}ap-group <name>virtual-ap <name>orap-name <name>virtual-ap <name>Using the CLI to configure the DHCP server on the AP:ap system-profile <name>lms-ip <ipaddr>master-ip <ipaddr>rap-dhcp-server-vlan <vlan>wlan virtual-ap <name>ssid-profile <profile>vlan <vlan>forward-mode bridgeaaa-profile <name>rap-operation {always|backup|persistent}ap-group <name>ap-system-profile <name>virtual-ap <name>orap-name <name>ap-system-profile <name> virtual-ap <name>。
ipage返回参数

ipage返回参数
iPage是一个网站托管服务提供商,它提供了许多不同的功能
和服务来帮助用户建立和管理他们的网站。
当你使用iPage服务时,可能会遇到各种不同的返回参数。
这些返回参数可能涉及到网站的
性能、安全性、访问统计、付款信息等方面。
以下是一些可能的返
回参数:
1. 网站性能参数,这些参数可能包括网站的加载速度、响应时间、带宽使用情况等。
这些参数可以帮助你了解你的网站在iPage
服务器上的表现如何。
2. 安全性参数,iPage可能会返回有关你网站安全性的参数,
比如SSL证书的状态、防火墙设置、恶意软件扫描结果等。
这些参
数对于保护你的网站和访问者的信息非常重要。
3. 访问统计参数,iPage可能会提供有关网站访问量、访问来源、流量分布等统计数据。
这些数据可以帮助你了解网站的受欢迎
程度和访问者行为。
4. 付款信息参数,如果你使用iPage的付费服务,可能会涉及
到付款信息的返回参数,比如付款状态、账单明细等。
总的来说,iPage返回的参数可能涉及到网站性能、安全性、访问统计和付款信息等多个方面。
这些参数可以帮助你更好地了解和管理你的网站。
希望这些信息能够帮助到你。
padlocal服务规则

padlocal服务规则
PadLocal是一个提供微信个人号API接口的服务。
其服务规则
主要包括以下几个方面:
1. 注册和认证规则,用户需要通过官方渠道注册并提供真实有
效的个人信息进行认证,以确保服务的安全和合法性。
2. 使用规则,用户在使用PadLocal服务时,需遵守相关法律
法规,不得用于违法、违规或侵犯他人权益的活动,包括但不限于
传播淫秽、暴力信息,进行赌博、诈骗等违法行为。
3. 隐私保护规则,PadLocal承诺严格遵守相关的隐私保护法
律法规,保护用户的个人隐私信息,不会未经用户授权将其信息提
供给第三方。
4. 费用规则,用户在使用PadLocal服务时,需要按照相关的
收费标准支付费用,同时需要注意服务的有效期和续费规定。
5. 安全规则,用户在使用PadLocal服务时,需要保管好自己
的账号信息,不得将账号信息泄露给他人,以免造成不必要的损失。
总的来说,PadLocal的服务规则主要是为了保障用户的合法权益、维护服务的安全稳定运行以及遵守相关的法律法规。
希望以上回答能够满足你的要求。
Sophos UTM 产品说明说明书

Sophos UTM Feature ListGeneral ManagementÌCustomizable dashboardÌRole-based administration: Auditor, read-only and manager for all functionsÌNo-charge, centralized management of multipleUTMs via Sophos UTM Manager (SUM)ÌConfigurable update serviceÌReusable system object definitions for networks, services, hosts, time periods, users and groups, clients and servers ÌPoint & Click IPS rule managementÌSelf-service user portal for one-click VPN setupÌConfiguration change trackingÌManual or fully automated backup and restore optionsÌEmail or SNMP trap notification optionsÌSNMP supportÌOne-time password (OTP) / Two-factor authentication(2FA) supports OATH protocol for WebAdmin, User Portal, SSL VPN, IPSec VPN, HTML5 Portal and SSH Login*ÌOne-click secure access for Sophos customer support** Network Routing and ServicesÌRouting: static, multicast (PIM-SM)and dynamic (BGP, OSPF)ÌNAT static, masquerade (dynamic)ÌP rotocol independent multicast routing with IGMP snooping ÌBridging with STP support and ARP broadcast forwarding ÌW AN link balancing: 32 Internet connections, auto-link health check, automatic failover, automatic andweighted balancing and granular multipath rulesÌZ ero-config active/passive high- availabilityÌA ctive/active clustering for up to 10 appliancesÌ802.3ad interface link aggregationÌQoS with full control over bandwidth pools anddownload throttling using Stochastic Fairness Queuingand Random Early Detection on inbound trafficÌF ull configuration of DNS, DHCP and NTPÌS erver load balancingÌI Pv6 supportÌR ED supportÌVLAN DHCP support and tagging**ÌMultiple bridge support**Network ProtectionÌStateful deep packet inspection firewallÌIntrusion protection: Deep packet inspectionengine, 18,000+ patternsÌSelective IPS patterns for maximumperformance and protectionÌIPS pattern aging algorithm for optimal performance*ÌFlood protection: DoS, DDoS and portscan blockingÌCountry blocking by region or individual country(over 360 countries) with separate inbound/outbound settings and exceptionsÌSite-to-site VPN: SSL, IPSec, 256- bit AES/3DES,PFS, RSA, X.509 certificates, pre-shared keyÌRemote access: SSL, IPsec, iPhone/iPad/Cisco VPN client supportÌVoIP handling for SIP and H.323 connectionsÌConnection tracking helpers: FTP, IRC, PPTP, TFTPÌIdentity-based rules and configuration withAuthentication Agent for usersAdvanced Threat Protection*ÌDetect and block network traffic attempting tocontact command and control servers usingDNS, AFC, HTTP Proxy and firewallÌIdentify infected hosts on the network Sandstorm Protection***ÌCloud-based sandbox to detect, block and gain visibility into evasive zero-day targeted attacks in active content such as executables, PDFs, Office Documents, and more ÌPreviously unseen suspicious files aredetonated in the cloud-sandbox and monitoredbefore being released to the end-userÌComplete reporting on all suspicious file activityincluding detailed sandbox analysis results AuthenticationÌTransparent, proxy authentication (NTLM/Kerberos) or client authenticationÌAuthentication via: Active Directory, eDirectory,RADIUS, LDAP and TACACS+ÌSingle sign-on: Active directory, eDirectoryÌSophos Transparent Authentication Suite (STAS)provides AD agent for transparent reliable SSOauthentication with Microsoft Active Directory***ÌSSL supportÌTools: server settings check, username/passwordtesting and authentication cache flushÌGraphical browser for users and groupsÌAutomatic user creationÌScheduled backend synchronization prefetchÌComplex password enforcementWeb ProtectionÌURL Filter database with 35 million+ sitesin 96 categories and 65+ languagesÌApplication Control: Accurate signatures andLayer 7 patterns for thousands of applicationsÌDynamic application control based onproductivity or risk thresholdÌView traffic in real-time, choose to block or shapeÌMalware scanning: HTTP/S, FTP and web-based email via dual independent antivirus engines (Sophos & Avira) block all forms of viruses, web malware, trojans and spywareÌFully transparent HTTPS filtering of URLs*ÌOption for selective HTTPS Scanning of untrusted sites**ÌAdvanced web malware protectionwith JavaScript emulation*ÌLive Protection real-time in-the-cloud lookupsfor the latest threat intelligenceÌPotentially unwanted application (PUA) download blocking*ÌMalicious URL reputation filtering backed by SophosLabs ÌReputation threshold: set the reputation threshold awebsite requires to be accessible from internal networkÌActive content filter: File extension, MIME type,JavaScript, ActiveX, Java and FlashÌTrue-File-Type detection/scan within archive files**ÌYouTube for Schools enforcementÌSafeSearch enforcementÌGoogle Apps enforcement*Web PolicyÌAuthentication: Active Directory, eDirectory,LDAP, RADIUS, TACACS+ and local databaseÌSingle sign-on: Active Directory,eDirectory, Apple Open DirectoryÌProxy Modes: Standard, (Fully) Transparent, Authenticated, Single sign-on and Transparent with AD SSO*ÌTransparent captive portal with authenticationÌSupport for separate filtering proxies in different modesÌTime, user and group-based access policiesÌBrowsing quota time policies and quota reset option**ÌAllow temporary URL filter overrides with authentication ÌClient Authentication Agent for dedicated per-user tracking ÌCloning of security profilesÌCustomizable user-messages for events in local languages ÌCustom HTTPS verification CA supportÌSetup wizard and context sensitive online helpÌCustomizable block pagesÌCustom categorization to override categoriesor create custom categories*ÌSite tagging for creating custom site categories**ÌAuthentication and filtering options by device typefor iOS, Android, Mac, Windows and others*ÌPolicy testing tool for URLs, times,users and other parameters*Email ProtectionÌReputation service with spam outbreak monitoring based on patented Recurrent-Pattern-Detection technologyÌAdvanced spam detection techniques: RBL, heuristics,SPF checking, BATV, URL scanning, grey listing, RDNS/HELO checks, expression filter and recipient verification ÌBlock spam and malware during the SMTP transaction ÌDetects phishing URLs within e-mailsÌGlobal & per-user domain and address black/white lists ÌRecipient Verification against Active Directory accountÌE-mail scanning with SMTP and POP3 supportÌDual antivirus engines (Sophos & Avira)ÌTrue-File-Type detection/scan within archive files**ÌScan embedded mail formats: Block maliciousand unwanted files with MIME type checkingÌQuarantine unscannable or over-sized messagesÌFilter mail for unlimited domains and mailboxesÌAutomatic signature and pattern updatesÌSophos Live Anti-Virus real-time cloud lookups** Email Encryption and DLPÌPatent-pending SPX encryption for one-way message encryption*ÌRecipient self-registration SPX password management**ÌAdd attachments to SPX secure replies**ÌTransparent en-/decryption and digitalsigning for SMTP e-mailsÌCompletely transparent, no additionalsoftware or client requiredÌSupports S/MIME, OpenPGP, and TLS standardsÌPGP key server supportÌAllows content/virus scanning even for encrypted e-mails ÌCentral management of all keys and certificates- no key or certificate distribution requiredÌDLP engine with automatic scanning of emailsand attachments for sensitive data*ÌPre-packaged sensitive data type contentcontrol lists (CCLs) for PII, PCI, HIPAA, andmore, maintained by SophosLabs*Email ManagementÌUser-quarantine reports mailed outdaily at customizable timesÌLog Management service supportÌCustomizable User Portal for end-usermail management, in 15 languagesÌAnonymization of reporting data to enforce privacy policy ÌOver 50 Integrated reportsÌPDF and CSV exporting of reportsÌCustomizable email footers and disclaimersÌSetup wizard and context sensitive online helpÌEmail header manipulation support**End-User PortalÌSMTP quarantine: view and releasemessages held in quarantineÌSender blacklist/whitelistÌHotspot access informationÌDownload the Sophos Authentication Agent (SAA)ÌDownload remote access clientsoftware and configuration filesÌHTML5 VPN portal for opening clientless VPN connections to predefined hosts using predefined servicesÌDownload HTTPS Proxy CA certificatesVPNÌPPTP, L2TP, SSL, IPsec, HTML5-based and Ciscoclient-based remote user VPNs, as well as IPsec, SSL,Amazon VPC-based site-to-site tunnels and SophosRemote Ethernet Device (RED) plug-and-play VPNÌIPv6 SSL VPN support***VPN IPsec ClientÌAuthentication: Pre-Shared Key (PSK), PKI(X.509), Smartcards, Token and XAUTHÌEncryption: AES (128/192/256), DES, 3DES(112/168), Blowfish, RSA (up to 2048 Bit), DHgroups 1/2/5/14, MD5 and SHA-256/384/512ÌIntelligent split-tunneling for optimum traffic routingÌNAT-traversal supportÌClient-monitor for graphical overview of connection status ÌMultilingual: German, English and FrenchÌIPsec Tunnel BindingVPN SSL ClientÌProven SSL-(TLS)-based securityÌMinimal system requirementsÌProfile support for varying levels of accessÌSupports MD5, SHA, DES, 3DES and AESÌWorks through all firewalls, regardless of proxies and NAT ÌSupport for iOS and AndroidClientless VPNÌTrue clientless HTML5 VPN portal for accessingapplications securely from a browser on any device VPN One-ClickÌEasy setup and installations of every client within minutes ÌDownload of client-software, individual configurationfiles, keys and certificates one click away fromthe Security Gateway end-user portalÌAutomatic installation and configuration of the clientÌNo configuration required by end userVPN REDÌCentral Management of all REDappliances from Sophos UTMÌNo configuration: Automatically connectsthrough a cloud-based provisioning serviceÌSecure encrypted tunnel using digital X.509certificates and AES256- encryptionÌRED sites are fully protected by the Network, Weband Mail security subscriptions of the Central UTM.ÌVirtual Ethernet for reliable transfer ofall traffic between locationsÌIP address management with centrally definedDHCP and DNS Server configurationÌRemotely de-authorize RED devicesafter a select period of inactivityÌCompression of tunnel traffic* (RED50, RED 10 revision 2, 3)ÌVLAN port configuration options* (RED 50)ÌSupport for RED 15w with integrated 802.11n WiFi AP*** Secure Wi-FiÌSimple plug-and-play deployment,automatically appearing in the UTMÌCentral monitor and manage all access points (APs) and wireless clients through the built-in wireless controller ÌIntegrated security: All Wi-Fi traffic isautomatically routed through the UTMÌWireless 802.11 b/g/n at 2.4 GHz and 5GHz (AP 50)ÌPower-over-Ethernet 802.3af (AP 30/50)ÌMultiple SSID support: Up to 8ÌStrong encryption supports state-of-the-artwireless authentication including WPA2-Enterpriseand IEEE 802.1X (RADIUS authentication)ÌWireless guest Internet access with customizablesplash pages on your captive portalÌVoucher-based guest access for daily or weekly access ÌTime-based wireless network accessÌWireless repeating and bridging meshednetwork mode with AP 50ÌHotspot backend authentication support*(RADIUS, TACACS, LDAP, AD)ÌAutomatic channel selection background optimization**ÌMulti-tenant hotspot administration**ÌSupport for HTTPS login support**Web Application Firewall ProtectionÌReverse proxyÌURL hardening engineÌForm hardening engineÌDeep-linking controlÌDirectory traversal preventionÌSQL injection protectionÌCross-site scripting protectionÌDual-antivirus engines (Sophos & Avira)ÌHTTPS (SSL) encryption offloadingÌCookie signing with digital signaturesÌPath-based routingÌOutlook anywhere protocol supportÌReverse authentication (offloading) for form-basedand basic authentication for server access*ÌPersistent session cookie support***Web Application Firewall ManagementÌAuto server discovery scans attachednetworks and identifies web serversÌIntegrated load balancer spreadsvisitors across multiple serversÌPredefined firewall profiles for MicrosoftOutlook Web Access (OWA)ÌQuick server switch allows easy maintenanceÌSkip individual checks in a granular fashion as required ÌMatch requests from source networksor specified target URLsÌSupport for logical and/or operatorsÌAssists compatibility with various configurationsand non-standard deploymentsÌOptions to change WAF performance parameters**ÌUpload custom WAF rules**ÌScan size limit option**ÌAllow/Block IP ranges**ÌWildcard support for server paths**ÌAutomatically append a prefix/suffix for authentication** UTM Endpoint ProtectionÌWindows endpoint protection with SophosAntivirus and device controlÌOn-access, on-demand or scheduled scanningfor malware, viruses, spyware and TrojansÌPUA scanningÌLive Protection Antivirus provides real-time, in-the-cloud lookups for the latest threat intelligenceÌHIPS with suspicious behavior detectionÌWeb protection with malicious site protectionÌDownload scanningÌDevice control including removable storage, optical media, modems, Bluetooth, wireless, infrared and more * New in UTM Accelerated (9.2)** New in UTM Advantage (9.3)*** New in UTM Elevated (9.4)ÌWeb in Endpoint enforcement of web policy and webmalware scanning on the endpoint with full policyand reporting synchronization with the UTMUTM Endpoint ManagementÌFully managed within the UTMÌEasy deployment from the UTM using using our installer ÌMonitor connected endpoints, threat statusand device utilization with full log accessÌAlerts for infected endpoints*SEC Endpoint Integration*ÌI ntegration with Sophos Enterprise ConsoleEndpoint Management provides UTM webpolicy and reporting for Web in EndpointLogging and ReportingÌLogging: Remote syslog, nightly rotation, email/ftp/SMB/SSH archiving and log management serviceÌOn-box reporting: Packet filter, intrusion protection,bandwidth and day/week/month/year scalesÌIdentity-based reportingÌPDF or CSV report exportingÌE xecutive report scheduling and archivingÌR eactive reporting engine crafts reports as you click on data ÌS ave, instantly email or subscribe recipients to any reports ÌP DF and CSV exporting of reportsÌN ightly compression and rotation of logsÌL og file archiving: On-box, FTP, SMB, SSH, Email and Syslog ÌH undreds of on-box reportsÌD aily activity reportingÌU RL filter override reportÌP er-user tracking and auditingÌA nonymization of reporting data to enforce privacy policy ÌF ull transaction log of all activity in human-readable formatUnited Kingdom and Worldwide Sales Tel: +44 (0)8447 671131Email:****************North American SalesToll Free: 1-866-866-2802Email:******************Australia and New Zealand SalesTel: +61 2 9409 9100Email:****************.auAsia SalesTel: +65 62244168Email:********************Oxford, UK | Boston, USA© Copyright 2016. Sophos Ltd. All rights reserved.Registered in England and Wales No. 2096520, The Pentagon, Abingdon Science Park, Abingdon, OX14 3YP, UK Sophos is the registered trademark of Sophos Ltd. All other product and company names mentioned are trademarks or registered trademarks of their respective owners.1129-02.13DD.dsna.simple。
iaptops意思解释 -回复

iaptops意思解释-回复"iaptops"并不是一个常见的词汇,也无法在现有的英语词典中找到它的确切定义。
鉴于此,下面将为你提供两种可能的理解意思,希望能够帮助你更好地理解该词。
1. "iaptops" 是潜在的拼写错误考虑到"iaptops"是一个比较生僻的词汇,很可能是作者写错了单词。
从类似于"laptop"的词形式可以推测,"iaptops"可能是"laptops"的拼写错误。
因此,我们可以将"iaptops"的理解意思定为"laptops"。
在这种情况下,"laptops"指的是便携式电脑。
2. "iaptops" 是一个新的词汇或隐喻另一种理解"iaptops"的方式是将其视为一个新的词汇,或者在文学作品、科技领域或社交媒体上的一个隐喻。
以下是一些可能的意义:a) "iaptops"可能指的是具有智能功能的笔记本电脑。
随着技术的发展,智能设备变得越来越普遍,人们对于在电子设备上进行各种操作的需求也变得更高。
"iaptops"可能代表具有高度智能化的笔记本电脑,可以通过语音识别、手势控制等方式与用户进行交互。
b) "iaptops"也可能指的是科技公司Apple的笔记本电脑产品。
苹果公司生产的笔记本电脑(例如MacBook系列)广受全球用户的喜爱。
"iaptops"可能是一种缩写或简写方式,将"Apple"和"laptops"合并在一起,突出强调苹果公司的电脑产品。
c) 在社交媒体上,"iaptops"可能是独特的、自创的词汇,用于指代一种新的电脑使用方式或者某个特定的社交群体。
ios项目的bundle identifier的申请 -回复

ios项目的bundle identifier的申请-回复iOS项目的Bundle Identifier的申请一、什么是Bundle Identifier?在iOS开发中,Bundle Identifier是一个项目的唯一标识符,用于在App Store中唯一标识一个应用程序。
它是一个类似于域名的字符串,通常采用逆序的域名格式,例如com.example.appname。
二、为什么需要申请Bundle Identifier?1. 唯一性:每个iOS应用程序必须有一个独特的Bundle Identifier。
这样可以确保在App Store中,每个应用程序都有一个唯一的标识符。
2. 应用程序关联:Bundle Identifier还用于应用程序与其他应用程序或操作系统的关联,例如通过URL Scheme进行相互跳转等。
3. 数据共享:Bundle Identifier还用于应用程序间共享数据,例如使用分享扩展或共享的Keychain等。
三、如何申请Bundle Identifier?1. Apple开发者账号:首先,开发者需要拥有一个有效的Apple开发者账号。
如果没有账号,可以前往developer.apple网站进行注册。
2. 登录开发者账号:登录开发者账号后,进入Developer Account界面。
3. 创建App ID:在Developer Account界面,点击左侧导航栏中的"Certificates, Identifiers & Profiles"选项,然后选择"Identifiers"。
点击页面右上方的"+"按钮,选择"App IDs"。
4. 命名Bundle Identifier:在创建App ID页面,输入你的应用程序的名称。
在Bundle ID栏目中,输入一个唯一的Bundle Identifier。
reportlab basedoctemplate -回复

reportlab basedoctemplate -回复[ReportLab based Octemplate],以中括号内的内容为主题,写一篇1500-2000字文章,一步一步回答ReportLab 是一个用于生成丰富且可定制的电子文档的Python 库。
它具有强大的功能,可以用于创建报告、表格、图表等各种类型的文档。
而Octemplate 是ReportLab 的一个扩展,用于创建模板化的文档。
本文将一步一步地介绍如何使用ReportLab 和Octemplate 创建模板化的电子文档。
第一步:安装ReportLab 和Octemplate首先,确保已经安装了Python 解释器。
然后,打开命令行界面,并通过以下命令安装ReportLab:pip install reportlab接下来,通过以下命令安装Octemplate:pip install octemplate安装完成后,我们就可以开始使用ReportLab 和Octemplate 了。
第二步:创建一个模板首先,创建一个名为"template.odt" 的空白OpenDocument 文档。
这将作为我们的模板。
打开一个文本编辑器,将以下内容复制到"template.odt" 中:Hello, [name]!Today is [date].Here is a list of your tasks for the day:1. [task1]2. [task2]3. [task3]Have a great day!在该模板中,我们使用了占位符(用方括号括起来的内容),这些占位符将在后续步骤中被替换为实际的值。
第三步:创建一个Python 脚本现在,我们需要创建一个Python 脚本,用于生成基于模板的文档。
打开一个文本编辑器,将以下内容复制到脚本中,并将文件保存为"generate_document.py":pythonfrom octemplate import Renderer# 创建一个Renderer 对象renderer = Renderer("template.odt")# 填充占位符data = {"name": "Alice","date": "2022-01-01","task1": "完成报告","task2": "开会讨论","task3": "编写代码"}renderer.set_vars(data)# 生成文档renderer.render("output.docx")在以上脚本中,我们首先导入了Octemplate 的Renderer 类。
VesseLINK

INTRODUCTIONThis Quick Start Guide (QSG) provides instructions for initial start-up of the system up to and including making a basic phone call and accessing the internet. This QSG is only for use onVesseLINK™ systems that have been successfully installed per the Installation guide (Document # 84464). After initial start-up, for more detailed operational procedures, reference the VesseLINK™ User Manual (Document # 84469) located on the Thales website and is also accessible through the VesseLINK™ Management Portal.BDU Front Panel DetailPOTS Phone connectionBy default the POTS phone(s) are pre-configured to use the Iridium voice lines without any additional configuration. The BDU can accept up to 2 POTS phones (with RJ-14 Splitter).VoIP or Thales IP Phone connectionBy default the BDU has (3) extensions preconfigured for use with POTS phones, VoIP phones, or Thales IP handsets as shown in the table below. If using a VoIP phone, Thales recommends CISCO SPA504G and Grand Stream GXP2140 models for ease of use with VesseLINK™. Other brands and models may be supported but functionality cannot be guaranteed. Follow your VoIP phone configuration guide to connect using the following parameters. THALES MANAGEMENT PORTALWhen you first log into the Thales Management Portal, you will notice menu choices down the left hand side of the screen. Each of these menu options are discussed in more detail in the VesseLINK ™ User Manual.• Status – Provides status of each of the Devices, GPS, LAN, Phones, Services, and the SIM card.Thales VesseLINK ™Quick Start GuideIMPORTANT: DOWNLOAD INSTRUCTIONS MANUALS NOW(included)Wi-Fi Antenna (included)BDU or Terminal Unit10ft Ethernet cable (included)Power Switch(Note: System () and/or Satellite () LEDs may be red since the antenna is not 12V Power adapter to AC MainsSIM CARDWi-Fi AntennaADU or AntennaBDU or Terminal UnitPOTS PhoneVOIP Phone(s) or HandsetWAN Port for Network orCellular ModemVesseLINK™ IMEI and IMSI from mobile deviceInstall SIM card from Air-time provider as below. Insert card with contacts down as shown until it clicks into place. Be sure to engage the lock for the SIM Card and secure the SIM Cover once the SIM Card has been locked into place.Installing SIM card and engaging the lockSTEP 4: Power the VesseLINK™ Unit.Before powering the unit, make sure the AC/DC supply is plugged in and connected to the TU.System, Satellite and Wi-Fi status LED’sSystem Solid GREEN Satellite Solid BLUE Wi-FiOFFAll custom configuration settings will be lost.VesseLINK™ User Interface Login5。
Neo-Flex Mobile Media Center, LD Installation Guid

| USA: 1-800-888-8458 | Europe: +31 (0)33-45 45 600 | China: 400-120-3051 | Japan:*************************English, Español, Français, Deutsch, Nederlands, Italiano, Svenska, 日本語, 汉语Neo-Flex™ Mobile Media Center, LDwith 90˚ Portrait/Landscape rotation• 100 x 100 mm • 200 x 200 mm • 200 x 300 mm • 300 x 200 mm • 300 x 300 mm • 400 x 200 mm • 400 x 300 mm • 500 x 200 mm • 500 x 300 mm • 600 x 200 mm • 600 x 300 mm • 200 x 400 mm • 300 x 400 mm • 400 x 400 mm • 500 x 400 mm • 600 x 400 mmTools NeededUser's GuideEnglishFor the latest User Installation Guide please visit: Holds displays with the following VESA mounting hole pattern:• 100 x 100 mm • 200 x 200 mm • 200 x 300 mm • 300 x 200 mm • 300 x 300 mm • 400 x 200 mm • 400 x 300 mm • 500 x 200 mm • 500 x 300 mm• 600 x 200 mm • 600 x 300 mm • 200 x 400 mm • 300 x 400 mm • 400 x 400 mm • 500 x 400 mm • 600 x 400 mmHolds displays with the following VESA mounting hole pattern:Features & Speci fi cationsCAUTION: DO NOT EXCEED MAXIMUM LIST-ED WEIGHT CAPACITY . SERIOUS INJURY OR PROPERTY DAMAGE MAY OCCUR!SafetyImportant! You will need to adjust this product after installation is complete. Make sure all your equipment is properly installed on the product before attempting adjustments. This product should move smoothly and easily through the full range of motion and stay where you set it. If movements are too easy or dif fi cult or if product does not stay in desired positions, follow the adjustmentinstructions to create smooth and easy movements. Depending on your product and the adjustment, it may take many turns to notice a difference. Any time equipment is added or removed from thisproduct, resulting in a change in the weight of the mounted load, you should repeat these adjustment steps to ensure safe and optimum operation.Stored Energy Hazard: The lift mechanism in the tower is under tension and will move up rapidly, on its own, as soon as attached equipment is removed. For this reason, DO NOT remove equipment or make adjustments to lift tension unless the front assembly has been moved to the highest position on the tower! Failure to follow this instruction may result in serious personal injury and/or equipmentdamage!A B 12345 67 8 9 104x4x4x4x2x1x1x4x1x1x8x M3.5 x 6mm2xM4x20mmM4x40mmM5x20mmM5x40mm4x4x4x4xM6x20mmM6x45mmM8x25mmM8x50mm4x4x4x4x4x4x4x4x1x4x1xM5x8mm1x1x2x1xM10 x 60mmLeg Mounting HardwareLeg Cover Mounting ScrewsShelf Mounting HardwarePower Strip HardwareCable Management Support HardwareTop Cap HardwareTM Mounting Hardware400mm Extension HardwareLarge Display Cart Hardware100x100mm VESA Plate HardwareM5 x 16mm 1x1x8x M3 x 39mm1x2x2xM8 x 14mm2xM5 x 16mm1x2x2x8x4x5.1(ID) x 10(OD) x 6mm8.1(ID) x 16(OD) x 6mm5.1(ID) x 10(OD) x 18mm8.1(ID) x 16(OD) x 24mm5.3(ID) x 16(OD) x 1.0mm6.3(ID) x 14(OD) x 1.0mm4x1xM5x9mm1x1x4x2xM5x8mmM6x8mm1x4x M5 x 10mm4x1x1x1x4xM5 x 8mmM6 x 8mm25 - 36 lbs(11.3 - 16 kg)4x4x 5.1(ID) x 10(O D) x 12m m8.1(ID) x 16(O D) x 12m mM4 x 12mm4x4x4x4x4x4x4xM5 x 12mmM5 x 20mmM5 x 7mmM6 x 12mmComponentsM8M5 Converter445625 - 50 lbs(11.3 - 22.7 kg)1xM5 x 8mm4xM6 x 8mm25 - 36 lbs(11.3 - 16 kg)• 100 x 100 mm • 200 x 200 mm • 200 x 300 mm • 300 x 200 mm • 300 x 300 mm • 400 x 200 mm • 400 x 300 mm • 500 x 200 mm • 500 x 300 mm • 600 x 200 mm • 600 x 300 mm • 200 x 400 mm • 300 x 400 mm • 400 x 400 mm • 500 x 400 mm • 600 x 400 mm• 75 x 75 mm • 100 x 100 mm • 200 x 100 mm • 200 x 200 mm144Holds displays with the following VESA mounting hole pattern:Holds displays with the following VESA mounting hole pattern:775x75mm 200x100mmVESA Adapter Confi gurationsTV/Monitor Hole Pattern Sizes7Mount Type A TV/Monitor to Arm A75x75mm200mm (7-7/8”)200mm (7-7/8”)B C D 7a100x200mm200x200mm200x100mm7bMount VESA Adapters to Arm based on TV/Monitor hole pattern size (B, C, or D) .Mount Type B, C, or D TV/Monitor to ArmM8M5 KIT Instructions8Adjustment Stepfi cult or if product does not stay in desired Increase Lift StrengthIf the mounted weight is too heavy or this product does not stay up when raised, then you'll need to increase Lift Strength:Decrease Lift StrengthIf the mounted weight is too light or this product does not stay down when lowered, then you'll need to decrease Lift Strength:MINIMUM THREAD ENGAGEMENT screw. For instance, if the screw diameter is 8mm,the minimum thread engagement is also 8mm.)8abc2xM5 x 16mmTM Mounting Hardwarea b1xTM Mounting Hardware25 - 50 lbs(11.3 - 22.7 kg)9Adjustment Stepfi cult or if product does not stay in desired optimum operation.Increase Lift StrengthIf the mounted weight is too heavy or this product does not stay up when raised, then you'll need to increase Lift Strength:Decrease Lift StrengthIf the mounted weight is too light or this product does not stay down when lowered, then you'll need to decrease Lift Strength:12ab1xM5x8mm1x10abdc2xM5x9mm2x2xPower Strip HardwareCable Management Support HardwareCable Management Support Hardware21 of 21888-24-073-W-03 rev. T • 01/19 © 2015 Ergotron, Inc. All rights reserved. NeoFlex ™ is a registered trademark of Ergotron, Inc. | USA: 1-800-888-8458 | Europe: +31 (0)33-45 45 600 | China: 400-120-3051 | Japan:*************************Learn more about ergonomic computer use at:Set Your Workstation to Work For YOU!Height Position top of screen slightly below eye level.Position keyboard at about elbow height with wrists fl at.Distance Position screen an arm's length from face—at least 20” (508mm).Position keyboard close enough to create a 90˚ angle in elbow.Angle Tilt screen to eliminate glare. Tilt the keyboard back 10° so that your wrists remain fl at.To Reduce FatigueBreathe - Breathe deeply through your nose.Blink - Blink often to avoid dry eyes.Break • 2 to 3 minutes every 20 minutes • 15 to 20 minutes every 2 hours.For local customer care phone numbers visit: For Service visit: For Warranty visit: /warranty。
requesttemplate 使用
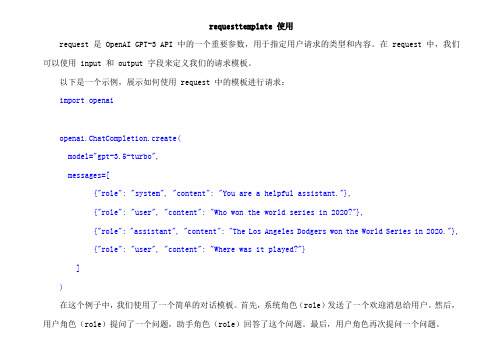
requesttemplate 使用request 是 OpenAI GPT-3 API 中的一个重要参数,用于指定用户请求的类型和内容。
在 request 中,我们可以使用 input 和 output 字段来定义我们的请求模板。
以下是一个示例,展示如何使用 request 中的模板进行请求:import openaiopenai.ChatCompletion.create(model="gpt-3.5-turbo",messages=[{"role": "system", "content": "You are a helpful assistant."},{"role": "user", "content": "Who won the world series in 2020?"},{"role": "assistant", "content": "The Los Angeles Dodgers won the World Series in 2020."}, {"role": "user", "content": "Where was it played?"}])在这个例子中,我们使用了一个简单的对话模板。
首先,系统角色(role)发送了一个欢迎消息给用户。
然后,用户角色(role)提问了一个问题,助手角色(role)回答了这个问题。
最后,用户角色再次提问一个问题。
我们可以根据需要扩展或修改这个模板。
每个消息都由 role 和 content 字段组成,role 指定了消息的发送者,content 则是消息的内容。
homedepot前台链接规则

homedepot前台链接规则Homedepot前台链接规则一、前言在Homedepot的前台工作中,链接是我们与客户进行沟通和交流的重要工具。
为了确保信息的准确传达和顺畅流转,Homedepot 制定了一系列前台链接规则。
本文将详细介绍这些规则,以帮助前台员工更好地理解和遵守。
二、链接规则概述1. 链接的目的和内容应与客户的需求和问题相关,不应随意发起无关链接。
2. 链接应准确、简洁、明了,避免使用复杂的技术术语或行业术语,以免给客户造成困扰。
3. 链接应尽量避免使用缩写词或简写,以确保客户能够准确理解链接的含义。
4. 链接中的信息应准确无误,不得包含任何虚假、误导性或不当的内容。
5. 链接应具有可操作性,即客户能够通过链接直接进入相关页面或资源,而不需要进行额外的操作或搜索。
三、具体链接规则1. 链接的格式在链接中,应将相关信息放在方括号[]内,并在方括号后面紧接着链接的标题。
例如:[退货政策]、[产品查询]等。
2. 链接的位置链接应放置在与客户需求相关的对话或讨论中,以便客户能够直接点击链接查看相关信息。
3. 链接的使用时机链接应在客户提出相关问题或表达需求后立即提供。
不应过早或过晚提供链接,以免给客户造成困扰或延误解决问题的时间。
4. 链接的更新链接中的信息应及时更新,确保客户获取到的是最新的、准确的信息。
5. 链接的分类根据不同的需求和问题,链接可以分为产品链接、退货链接、支付链接、促销链接等,以便客户能够快速找到所需信息。
四、链接规则的重要性1. 提高工作效率:链接规则的制定可以帮助前台员工快速找到相关资源和信息,减少搜索和确认的时间,提高工作效率。
2. 提升客户满意度:通过提供准确、及时的链接,可以满足客户的需求,解决客户的问题,提升客户的满意度。
3. 统一信息传达:链接规则的制定可以确保前台员工在信息传达方面保持一致性,避免出现不同员工给出不同链接的情况,给客户造成困扰。
4. 降低错误率:链接规则的使用可以减少因信息错误或不准确而引发的问题和纠纷,降低工作中的错误率。
平板ua代码大全

平板ua代码大全平板电脑是一种便携式电子设备,它具有触摸屏功能,能够更直观地与用户进行交互,并且它拥有与电脑相似的功能,但是更加轻便、便于携带。
随着科技的不断进步,平板电脑已经成为了现代人生活中必不可少的工具之一,深受广大消费者的喜爱。
平板电脑的UA代码,即用户代理代码,是一种用于标识和识别设备的字符串,它描述了设备的硬件、软件以及操作系统的信息,帮助网站、应用程序和服务根据设备的特点进行优化和适配。
以下是一些常见的平板UA代码:1.苹果iPad UA代码:Mozilla/5.0(iPad;CPU OS12_0like Mac OS X) AppleWebKit/605.1.15(KHTML,like Gecko)Version/12.0Mobile/15E148Safari/604.12.三星Galaxy Tab UA代码:Mozilla/5.0(Linux;Android9.0;SM-T835)AppleWebKit/537.36(KHTML,like Gecko)Chrome/80.0.3987.99 Safari/537.363.微软Surface UA代码:Mozilla/5.0(Windows NT10.0;Win64;x64)AppleWebKit/537.36(KHTML,like Gecko)Chrome/87.0.4280.88 Safari/537.36Edg/87.0.664.66通过分析这些UA代码,我们可以了解到不同平板电脑的硬件、操作系统和浏览器等信息。
这对于开发者和网站管理员来说非常重要,因为他们可以根据用户的设备特征和浏览器功能进行网站优化和适配,提供更好的用户体验。
同时,对于普通用户来说,了解平板UA代码也是有益的。
首先,通过UA代码可以判断一个网站或者应用程序是否对不同设备进行了适配,如果发现访问某个网站的时候出现了排版错乱或者功能无法正常使用等问题,可以尝试更换浏览器或者更改UA代码以解决问题。
iap支付验证流程

iap支付验证流程下载温馨提示:该文档是我店铺精心编制而成,希望大家下载以后,能够帮助大家解决实际的问题。
文档下载后可定制随意修改,请根据实际需要进行相应的调整和使用,谢谢!并且,本店铺为大家提供各种各样类型的实用资料,如教育随笔、日记赏析、句子摘抄、古诗大全、经典美文、话题作文、工作总结、词语解析、文案摘录、其他资料等等,如想了解不同资料格式和写法,敬请关注!Download tips: This document is carefully compiled by theeditor. I hope that after you download them,they can help yousolve practical problems. The document can be customized andmodified after downloading,please adjust and use it according toactual needs, thank you!In addition, our shop provides you with various types ofpractical materials,such as educational essays, diaryappreciation,sentence excerpts,ancient poems,classic articles,topic composition,work summary,word parsing,copy excerpts,other materials and so on,want to know different data formats andwriting methods,please pay attention!IAP(In-App Purchase)支付验证流程是指在应用内购买商品或服务时,进行支付验证的过程。
python isotp 参数

python isotp 参数一、概述ISOTP(Internet Standard Token Profiles)是一种用于描述网络协议参数的标准框架,Python中的ISOTP库提供了用于创建和解析ISOTP参数的函数。
本文档将介绍如何使用Python ISOTP库以及一些常见的ISOTP参数。
二、安装Python ISOTP库要使用Python ISOTP库,需要先安装该库。
可以通过以下命令使用pip安装:```shellpip install isotp```三、ISOTP参数的使用ISOTP参数可以通过Python ISOTP库进行创建和解析。
以下是一些常见的ISOTP参数及其用法示例:1. 端口号参数:isotp_portisotp_port参数用于指定网络连接的端口号。
可以使用以下代码创建一个ISOTP端口号参数:```pythonfrom isotp import IsotpParameterport = IsotpParameter(parameter_type="port", value=80)```在上面的代码中,我们创建了一个名为port的ISOTP端口号参数,其值为80。
2. 协议版本参数:isotp_versionisotp_version参数用于指定网络协议的版本。
可以使用以下代码创建一个ISOTP协议版本参数:```pythonfrom isotp import IsotpParameterversion = IsotpParameter(parameter_type="version", value="1.0")```在上面的代码中,我们创建了一个名为version的ISOTP协议版本参数,其值为"1.0"。
3. 认证参数:isotp_auth_infoisotp_auth_info参数用于指定网络连接的认证信息。
iap快速使用手册

iap快速使用手册
IAP(In-App Purchase)是应用程序内购买,是一种在应用程序内部购买
虚拟商品或服务的机制。
以下是IAP快速使用手册:
1. 确定需要销售的商品或服务:首先,您需要确定您想要销售的商品或服务。
这可以包括游戏道具、扩展功能、订阅服务等。
2. 配置IAP:在您的应用程序中,您需要配置IAP。
这通常涉及到在应用程序的设置中添加商品信息,包括商品ID、名称、描述和价格等。
3. 实现购买逻辑:在您的应用程序中,您需要实现购买逻辑。
当用户想要购买商品时,您的应用程序会向苹果或谷歌等平台发起购买请求。
4. 处理购买回调:当用户成功购买商品后,您的应用程序会收到一个回调。
您需要在您的应用程序中实现这个回调,以便处理购买结果。
5. 验证交易:为了确保交易的安全性,您需要在您的应用程序中验证交易。
这通常涉及到检查交易状态、验证签名等。
6. 更新用户界面:当用户成功购买商品后,您可能需要更新用户界面以反映购买结果。
例如,您可以显示一个消息告诉用户已经成功购买了商品。
7. 处理退款和报告:为了遵守苹果和谷歌的政策,您需要处理退款和报告。
这通常涉及到向苹果或谷歌报告销售数据和退款信息。
以上是IAP快速使用手册的基本步骤。
请注意,具体的实现细节可能会因平台和开发工具而有所不同。
因此,您应该参考苹果和谷歌等平台的文档来了解更多关于IAP的详细信息。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
International Accelerated Degree Program AgreementBetweenThe Arizona Board of Regents for and on behalf ofArizona State University (“ASU”)and(Name of the Partner University) (“SCHOOLXXX”)ASU school/college represented: …………………XXX school/college represented: …………………Graduate degree(s) being offered through this Program Agreement: …………………This International Accelerated Degree Program (IADP) Agreement (this “Program Agreement”) is made between Partner University (“XXX”), (Country of University), and the Arizona Board of Regents (“ABOR”) for and on behalf of Arizona State University, USA (“ASU”). This Program Agreement is subject to the terms of the General Collaboration Agreement between the parties (the “General Agreement”), the terms of which are incorporated herein by reference and shall prevail in the event of a conflict with the terms of this Program Agreement. The parties agree as follows:1.Agreement and variation1.1.XXX and ASU agree to establish a collaborative education program known as the“XXX-ASU International Accelerated Degree Program”(the “Program”) in whichqualified undergraduate students enrolled at XXX, after successfully completing thefirst three (3) years of their curriculum, will apply for admission to selected fields ofstudy at ASU (subject to all applicable ABOR and ASU policies of admissionprocedures and standards) for the next two (2) years to finish a required trainingcurriculum to qualify f or their bachelor’s degree awarded at XXX and a Master’sdegree to be awarded by ASU.1.2.The parties have agreed that the Program will be conducted in accordance with theterms and conditions set forth in this Program Agreement.1.3.No agreement or understanding amending or varying the terms of this ProgramAgreement shall be legally binding on either party unless made in writing and signedby both parties.2.The Program2.1.The academic component of the Program will be implemented and administered intwo phases. During Phase I, XXX will select students as candidates for study at ASUunder the Program. These students will study at XXX and complete the first three years of a four-year Bachelor’s Degree p rogram in disciplines mutually agreed to by XXX and ASU (each discipline has to establish a curriculum approved by both parties which will be attached as a separate addendum to this Program Agreement).XXX will recommend qualified students to ASU. ASU will evaluate these students in accordance with ASU’s admission procedures and standards and will accept such students solely at its discretion. The students accepted by ASU will enter Phase II of the Program. During Phase II, the students will continue their studies in the chosen discipline at ASU for the next two years following the approved curricula. Each successful student will receive a Bachelor’s Degree from XXX following completion of the degree requirements, and a Master’s Degree from ASU following completion of all respective degree requirements.2.2.XXX and ASU have agreed that the following schools, colleges and academic unitsshall initially participate in the Program (each, a “Participating Unit” and together, the “Participating Units”):2.2.1.For ASU: Name of the School/College2.2.2.For XXX: _____________________________2.2.3.After commencement of the Program, the parties will assess the Program’sdevelopment and determine whether sufficient demand exists to expand theProgram to include additional Participating Units.2.3.Each Participating Unit will identify the degree program or degree programs whichthey will offer under this Program Agreement. Each Participating Unit will require a program of study approved by both XXX and ASU containing required courses and elective courses satisfying the B achelor’s Degree requirement at XXX and the Master’s D egree requirement at ASU. The program of study for each Participating Unit will detail the course sequences to guide students’ progression through the Program. Each party may amend its respective program of study as it deems necessary or appropriate.2.4.Set forth below is a description of each phase of the Program and the requirements forstudents participating in the Program.Phase I2.4.1.Three years of undergraduate study at XXX during which time the studentswill complete courses required by their own disciplines as well as extraEnglish language classes for which they must achieve the languageproficiency required by ASU for admission.2.4.2.English language proficiency for admission to ASU shall be at least TOEFL550/IBT TOEFL 80 or IELTS 6.5. XXX will teach English language coursesto assure language proficiency.2.4.3.Students who wish to proceed to Phase II will be assessed by ASU todetermine their qualification for admission to ASU in the same manner thatASU assesses other international students wishing to enroll at ASU.2.4.4.Students who pass the assessment process described in 2.4.3 will be admittedto study at ASU under the Program and will receive an official admissionletter to assist their application for an F-1 visa to continue their education atASU. Students are responsible for applying for the student visa andaddressing all immigration matters with the appropriate authorities.2.4.5.Once the F-1 visa is issued and all ASU requirements of enrollment aresatisfied, students will be permitted to enroll in ASU.Phase II2.4.6.ASU will perform an assessment of all the applicants recommended by XXXat the end of Phase I and offer admission to students meeting ASU’sadmission standards. Students who fail the assessment or who are unable toobtain an F-1 visa to the USA will continue their studies at XXX.2.4.7.Students who successfully complete Phase I and who obtain an F-1 visa willbe provided provisional graduate admission to ASU under this ProgramAgreement to start Phase II. Students will begin at ASU as undergraduatestudents. Upon completion of their first year of full time study at ASU, eachstude nt’s academic performance will be evaluated by the School/College’sfaculty.2.4.8.Students in Phase II will be afforded all of the usual privileges of full timeinternational students studying at ASU in accordance with all applicable lawsand regulations.2.4.9.Each student who has successfully completed one year of degree-specificcourse work specified by the Participating Unit at ASU will be reviewed andevaluated by XXX. If approved, XXX will award a diploma or a certificateindicating that the student has fulfilled all of the course requirements for aBachelor’s Degree at XXX.2.4.10.Upon issuance of the diploma or certificate described in 2.4.9, XXX willforward an official copy of the diploma/certificate and the student’s transcriptto the ASU Graduate Admissions Office. Upon ASU’s receipt of thediploma/certificate and transcript, the graduate program, the Participating Unitand the Division of Gr aduate Studies will evaluate the student’s qualifications.If the student meets ASU’s graduate admission standards, the student will beadmitted into one of the following School/College Masters Programs: MS- (orany other program approved by ASU and identified to XXX).2.5.Tuition and Fees2.5.1.Student tuition and fees for Phase I studies will be established and collectedby XXX and ASU shall have no claim against those fees.2.5.2.Students in Phase II who have not graduated from XXX must register withXXX and pay tuition and fees to XXX.2.5.3.Students in Phase II are liable for all costs to study at ASU. The cost shallinclude travel between (Partner University Country) and the United States,room and board, insurance coverage and all tuition and prescribed fees to becollected by ASU. The base tuition and fees for Phase II are those publishedby ASU for international students. Tuition and fees may be adjusted at thesole discretion of ASU.2.5.4.XXX will have no claim against tuition and fees collected by ASU. XXXwaives any and all rights to any commission on student tuition and fees paidto ASU.3.Term and Termination3.1.The initial term of the Program and this Program Agreement shall commence on thelast date noted in the signature blocks of this Program Agreement and shall continuefor a period ending three (3) years thereafter. The Program and this ProgramAgreement shall earlier terminate: (A) in the event of a breach by either party of thisProgram Agreement or the General Agreement which is not cured within thirty (30)days of receipt of written notice from the non-breaching party; (B) in the event oftermination of the General Agreement; or (iii) as described in Section 3.3.3.2.In the third year after commencement of this Program Agreement, the parties willundertake a joint evaluation and determine whether to extend the Program Agreementfor another term of 3 years.3.3.Either party may terminate this Program Agreement by giving the other party at leastsix (6) months prior written notice. Upon either party’s notice to the other of itsintention to terminate this Program Agreement, no additional students will beaccepted into the Program, but the commitments and obligations of each partyhereunder shall continue until all students enrolled in the Program complete theProgram.3.4.Without prejudice to any other remedy for breach of this Program Agreement, upontermination of this Program Agreement, no party will be released from anyobligations which have accrued prior to the effective date of such termination.This Program Agreement shall take effect when signed by the authorized representatives of the parties.The Arizona Board of Regents Name of Partner Universityfor and on behalf ofArizona State University____________________________________ ____________________________________ Robert E. Page, Jr. NameUniversity Provost TitleArizona State University Name of Partner UniversityDate Signed:__________________________ Date Signed:______________________________________________________________ ____________________________________ Andrew N. Webber NameVice Provost for Graduate Education Titleof Arizona State University Name of Partner UniversityDate Signed:__________________________ Date Signed:______________________________________________________________Name of ASU DeanTitleArizona State UniversityDate Signed:__________________________。
