INFO1003_Foundamental of IT_2012 Semester 2_tutorial week 5 Solution_Week 5 - JavaScript Answers
2025届高考英语一轮复习仿真模拟试卷能力检测一含解析新人教版

高考仿真模拟试卷(一)(时间:120分钟满分:120分得分:________)第一部分阅读理解(共两节,满分40分)第一节(共15小题;每小题2分,满分30分)阅读下列短文,从每题所给的A、B、C和D四个选项中,选出最佳选项。
A(2025届“皖南八校”高三第一次联考)The Code of Visiting Yellowstone National Park The following regulations have been sorted for your convenience.Emergency Phone: Dial 911Yellowstone is a wilderness filled with natural wonders that also have potential dangers.There is no guarantee of your safety.Regulations are strictly enforced to protect you and the park's resources.WildlifeDo not approach wildlife, no matter how calm they appear.Always obey instructions from park staff on the scene.You must stay at least 100 yards away from bears and wolves and at least 25 yards away from other large animals—bison, elk, bighorn sheep, deer, moose, and coyotes.Do not feed any animal.It harms them and it is illegal.Geothermal (地热的) DangersBoardwalks and trails protect you.You must stay on boardwalks and designated (指定的) trails.Pools may be near or above the boiling temperatures and can cause severe, possibly even deadly burns.●Keep your children close to you at all times; make sure they understand the danger.●Pets are prohibited in thermal areas.●Swimming or bathing in thermal pools or streams is prohibited.Where swimming is allowed, swim at your own risk.●Poisonous gases may exist at dangerous levels.If you feel sick, leave immediately.WeatherYellowstone's weather can change quickly and bring cold temperatures, high winds, rain and falling snow.●Be prepared for changing temperatures, storms, and emergencies.●Carry adequate clothing.Driving●Unless otherwise posted, the top speed throughout the park is 45 mph.●If you see wildlife while driving, do not stop or pause in the roadway.1.What do we know about Yellowstone National Park?A.It allows visitors to feed some animals.B.It gives visitors a free ride in the park.C.It will punish visitors if they bring their pets.D.It not only offers visitors pleasure but also there may be dangers.2.When visiting Yellowstone, what are you advised to do?A.Swim in the designated places.B.Tap those calm animals gently.C.Pull up to take photos of animals.D.Bring some cloths to avoid poisonous gases.3.Why is the text written?A.To explain the facilities of the park.B.To introduce the features of the park.C.To offer some guidance to visit the park.D.To attract more people to visit the park.B(2025届四川省天府名校高三上学期联合质量测评)Imagine a small group of people with a shared passion for the same craft.They all have different skills and approaches, but they come together to share skills, share stories, and share in the joy of making something.Modern maker culture is filling headlines and lab spaces all over the world.The way makers communicate with each other has changed over time.In the past, skills mainly came from personal sitdowns with members of the group.But sometimes a teacher wasn't available, or the one available didn't know how to do the skill others wanted to learn.Today a teacher doesn't even have to be in the same country or occupy the same decade as the students.Thanks to the work of people who take the time to break down and share the details of their craft, an interested individual can learn anything.Guides may range from videos to diagrams and text.Regardless of the media, maker resources are meant to be shared.One of the features of the maker movement is the crossover between different interests.Perhaps a passion for cars and for leathercraft can result in a truly custom interior (定制的内饰).Perhaps a love of knitting (编织) and robotics will result in a tiny—but very mobile—robotic furry cat.And once you have started your creation, finding a community to share with is no longer limited to the people nearby.Modern makers have been sharing videos of their progress online for years, contributing greatly to the rapid spread of the maker movement.As different as the participants might be, they share enthusiasm, support, and a willingness to try.Imagine making a pingpong table together with your makers' team.One group builds the basic frame.Another group takes on the responsibility of painting.You knit the net.There is joy in just giving it a try.It will remind you of childhood creations.Whether you are an experienced programmer or just picking up a hammer for the first time, it is never a bad time to come up with an idea, try something, and share the results.4.How did makers communicate with each other in the past?A.By meeting face to face.B.By asking personal questions.C.By visiting a teacher together.D.By sitting together in a classroom.5.What does the underlined word “crossover” in Paragraph 4 mean?A.Exchange.B.Difference.C.Combination.D.Independence.6.What greatly speeds up the spread of modern maker culture?A.The sharing of videos on the Internet.B.The development of education.C.The increasing willingness to share.D.The increasing number of participants.7.Why does the author mention making a pingpong table in the last paragraph?A.To advise us to start small.B.To inspire some creative ideas.C.To stress the importance of childhood creations.D.To encourage us to join in the maker movement.C(2025届贵州省安顺市高三上学期第一次联考)Holding hands, people jumped into the water, and floated around in Boston's Charles River recently.That is something that would not have been possible years ago because the river was so polluted.In the 1960s, the music group The Standells even sang about the river in their popular song—“Dirty Water”.The swimmers were getting their onceayear chance to cool off from the summer heat in the Charles River.It is called “City Splash”.For a few days each year, the state of Massachusetts allows public swimming on Boston's part of the nearly 130kilometer Charles River.The event is in its fifth year.It is a chance for the nonprofit Charles River Conservancy to show its efforts to build a “swim park”.Their idea is to build floating docks where swimmers can jump safely into the river—without touching the risky bottom.These docks would be in areas where the water quality would be tested repeatedly.Boston is one of the cities hoping to follow the model of Copenhagen, Denmark.That city opened the first of its three floating harbor baths in the early 2000s.On sunny days, people swim in the harbor baths surrounded by tall buildings and cars on the highways.At night, the area is filled with people enjoying music and food.Just recently Paris opened public swimmin g in a oncepolluted canal.New York, London, Berlin and other cities are planning similar features for their waterways.In Boston, the Charles River Conservancy still needs to raise several million dollars.It also needs to get approvals from city, state and federal agencies.The groups spokeswoman S.J.Port, said the__biggest__problem has already been taken care of: The Charles is now one of the cleanest city rivers in America.The U.S.Environmental Protection Agency announced this month that the riverearned a “B” grade for water quality last year—an “A” being the best grade.It means the Charles River met the requirement for swimming 55 percent of the time.8.What is the function of floating docks?A.They are places for swimmers to rest.B.They let swimmers get into the river safely.C.They surround swimmers in a safe area of the river.D.They are used to test the water quality repeatedly.9.Which of the following has set a good example for others in offering floating harbor baths?A.Paris.B.Boston.C.Copenhagen.D.Berlin.10.What does the underlined part “the biggest problem” refer to?A.The pollution of Charles River.B.Lack of money to treat pollution.C.Getting approvals from governments.D.Meeting the requirement of “A” grade.11.What can be inferred from the text?A.The water in Charles River reaches drinking standard.B.People can swim in Charles River at any time.C.This summer is the hottest in Boston.D.Charles River flows through Boston.D(2024年安徽省合肥市巢湖市高考英语模拟试卷)Angel Garcia Crespo is a computer engineer at Carlos Ⅲ University of Madrid in Spain.His group has invented a new way for deafblind people to “watch” TV.The idea for the technology grew out of previous work by his group.The team had already worked on making audiovisual (视听的) materials accessible to people with either vision or hearing disabilities.But the group wanted to help people with both challenges.So they asked some deafblind people what would help.In addition to relying on their sense of touch to communicate, deafblind people can also get and send information with a Braille line.The Braille system uses patterns of raised dots to stand for letters and numbers.A Braille line is an electronic machine with a changeable Braille display.Dots rise up or drop down based on the information sent to the machine.Now the new system changes TV signals to data a Braille line can use.“The key to the system is the possibility of using subtitles (字幕) to collect TV information,”Garcia Crespo explains.“Subtitles travel with the image (影像) and the audio in electromagnetic waves we don't see.But an electronic system can keep those waves.”First,a computer program,or app,pulls out the subtitles and visual descriptions from the broadcast signal.The system then combines the information and changes both into data for Braille.Now another app gets to work, which sends the data out to people's Braille lineson demand.“This is done in real time,in less than a second,” Garcia Crespo says.This lets a deafblind person “watch” TV as it's broadcast.The system will work with various Braille lines,as long as there's a bluetooth connection available.Now,the system is only used in Europe,and it should soon be available in the US.12.What inspired Garcia Crespo's group to work on the new technology?A.Deafblind people's poor life.B.Their pity on the disabled people.C.The challenges they face in work.D.Their group's previous research.13.Why can the electronic system collect TV information?A.It can combine all kinds of broadcast signals.B.It can keep the waves with subtitles travelling.C.It can work together with a variety of Braille lines.D.It can pull out the subtitles and visual descriptions.14.What does the author think of the future of the new technology?A.Challenging. B.Bright.C.Rewarding. D.Hopeless.15.What should be a suitable title for the text?A.New Technology Is Improving Deafblind People's LifeB.A New Braille Line Is Applied to Disabled People's LifeC.A Spanish Group Makes TV Accessible to Blind PeopleD.New Technology Helps Deafblind People “Watch” TV其次节(共5小题;每小题2分,满分10分)依据短文内容,从短文后的选项中选出能填入空白处的最佳选项。
2024-2025学年人教版高一英语上册期中同步自测试卷及答案

2024-2025学年人教版高一英语上册期中同步自测试卷班级:________________ 学号:________________ 姓名:______________一、听力题(每题3分)1.Question: What is the woman’s favorite sport?A. Basketball.B. Swimming.C. Volleyball.Answer: BExplanation: The recording mentions that the woman enjoys swimming, indicating that swimming is her favorite sport.2.Question: Where is the man planning to go for his vacation?A. Paris.B. Rome.C. London.Answer: AExplanation: The man says he is looking for travel packages to Paris, indicating his vacation destination is Paris.3.Question: What time does the train leave for New York?A. 8:30 am.B. 9:15 am.C. 10:00 am.Answer: BExplanation:The recording states that the train to New York departs at 9:15 am.4.Question: How many apples did the boy buy?A. Two.B. Three.C. Four.Answer: AExplanation: The boy says he only has enough money for two apples.5.Question: What is the weather like today?A. Sunny.B. Rainy.C. Cloudy.Answer: BExplanation:The recording mentions that it’s raining heavily outside, indicating that today’s weather is rainy.二、单选题(每题3分)1.— What do you think of the concert last night?Wonderful! It couldn’t have been _________.A. a better oneB. a worse oneC. the best oneD. the worst oneAnswer: A2.The teacher_________the students to hand in their homework on time.A. requestedB. hopedC. wishedD. suggestedAnswer: A3.It was the third time that he_________to the Summer Palace.A. had goneB. had beenC. wentD. has beenAnswer: B4.The young man insisted that he_________nothing wrong and_________free.A. did; should be setB. had done; must be setC. had done; should be setD. did; must be setAnswer: C5.The old man_________in the small village for more than 50 years.A. has livedB. had livedC. livedD. livesAnswer: A三、多选题(每题4分)Question 1:Which of the following sentences are correct in grammar? (Choose two.)A. He said that he had finished his homework.B. She will have been studying for three hours by then.C. They had been married for twenty years before they separated.D. We will have to finish the project in the next two weeks.Answers: A, CExplanation:A. Uses the past perfect tense correctly to refer to an action that wascompleted before another past action.C. Uses the past perfect continuous tense correctly to refer to an actionthat had been ongoing for a period of time before another past action.Question 2:Match the following definitions with their respective words. (Choose two.)A. A long and serious illness.B. To prevent something from happening.C. A strong feeling of anger or hatred.D. A person who studies the stars and planets.1) Resentment2) Chronic3) Astronomer4) PreventAnswers: 1) C, 2) A, 3) D, 4) BExplanation:1) Resentment - A strong feeling of anger or hatred.2) Chronic - A long and serious illness.3) Astronomer - A person who studies the stars and planets.4) Prevent - To prevent something from happening.Question 3:Identify the parts of speech of the underlined words in the sentences. (Choose two.)A. The cat is playing with its ball.B. She sang beautifully at the concert.C. I am reading a book about history.D. He quickly finished his homework.Answers: B (verb), C (verb)Explanation:B. “Sang” is a verb (past tense of “sing”).C. “Reading” is a verb (present continuous tense of “read”). Question 4:Complete the sentence with the correct idiom. (Choose two.)A. To put offB. To call offC. To take offD. To set offThe match was_______due to bad weather.Answers: B, DExplanation:B. “To call off” can mean to cancel an event or appointment.D. “To set off” can also be used in the context of canceling or postponing an event, especially due to bad weather. However, it is less common than “to call off” in this sense. Both are accept able answers.Question 5:Identify the subject-verb agreement errors in the sentences. (Choose two.)A. The committee has made a decision.B. He have gone to the market.C. They is ready for the exam.D. She doesn’t likes the color.Answers: B, CExplanation:B. “He” is a singular subject, so the verb should be “has” instead of“have”.C. “They” is a plural subject, so the verb should be “are” instead of“is”.四、阅读理解(每题4分)Title: The Benefits of Reading for High School StudentsReading is a crucial activity for high school students, not only for academic success but also for personal growth. With the increasing demands of the modern world, it hasbecome even more important to cultivate a strong reading habit. Here are somebenefits of reading for high school students.Firstly, reading improves vocabulary and language skills. By reading various texts,students encounter new words and expressions, which they can then use in their own writing and speaking. This not only enriches their language but also makes them more confident in expressing themselves.Secondly, reading enhances comprehension abilities. As students read more, they learn to analyze and interpret text, understanding the author’s perspective and the intended message. This skill is crucial in all academic subjects and for everyday life.Thirdly, reading fosters critical thinking. When reading, students are challenged toquestion, evaluate, and analyze the information presented. This process sharpens theirability to think critically, an essential skill for problem-solving and decision-making. Lastly, reading provides a window to different cultures and perspectives. Through books, students can travel to faraway places, meet diverse characters, and gain insights into different ways of life. This broadens their horizons and cultivates empathy and understanding.Questions1.What is the main purpose of the passage? (4 points)Answer: To discuss the benefits of reading for high school students.2.According to the passage, what is one of the key benefits of reading forhigh school students? (4 points)Answer: It improves vocabulary and language skills.3.How does reading enhance comprehension abilities? (4 points)Answer: By learning to analyze and interpret text, understanding the author’s perspective and the intended message.4.What skill does reading foster that is essential for problem-solving anddecision-making? (4 points)Answer: Critical thinking.5.What does reading provide high school students with according to thepassage? (4 points)Answer: A window to different cultures and perspectives.五、作文(30分)Section V: Writing (30 points)Topic: The Importance of Perseverance in Achieving GoalsDirections: Write an essay of at least 150 words on the importance of perseverance in achieving goals. You may use your own experiences or examples from others to illustrate your point.Example Essay:In today’s fast-paced world, perseverance often serves as the key to unlocking the door to success. Achieving goals, whether academic,professional, or personal, requires unwavering dedication and resilience.I personally have witnessed the power of perseverance in my journey to mastera foreign language. Initially, the task seemed daunting, with its complexgrammar rules and vast vocabulary. However, through consistent effort and perseverance, I gradually overcame these challenges. Each day, I dedicated myself to reading, listening, and speaking, never giving up despite the difficulties. Over time, my efforts paid off, and I found myself fluent in the language.This experience taught me that perseverance is not just about enduring hardship; it’s about turning challenges into opportunities. It’s about believing in oneself, even when the going gets tough. In conclusion, perseverance is a vital trait for anyone aspiring to achieve their goals, as it transforms dreams into realities.(Note: This is a sample essay to illustrate the structure and content of the writing task. Students should write their own essays based on their own experiences and insights.)。
Analysis of a predator–prey model with modified Leslie–Gower

Nonlinear Analysis:Real World Applications7(2006)1104–1118/locate/naAnalysis of a predator–prey model with modified Leslie–Gower and Holling-type II schemes with time delayA.F.Nindjin a,M.A.Aziz-Alaoui b,∗,M.Cadivel ba Laboratoire de Mathématiques Appliquées,Universitéde Cocody,22BP582,Abidjan22,Côte d’Ivoire,Franceb Laboratoire de Mathématiques Appliquées,Universitédu Havre,25rue Philippe Lebon,B.P.540,76058Le Havre Cedex,FranceReceived17July2005;accepted7October2005AbstractTwo-dimensional delayed continuous time dynamical system modeling a predator–prey food chain,and based on a modified version of Holling type-II scheme is investigated.By constructing a Liapunov function,we obtain a sufficient condition for global stability of the positive equilibrium.We also present some related qualitative results for this system.᭧2005Elsevier Ltd.All rights reserved.Keywords:Time delay;Boundedness;Permanent;Local stability;Global stability;Liapunov functional1.IntroductionThe dynamic relationship between predators and their prey has long been and will continue to be one of dominant themes in both ecology and mathematical ecology due to its universal existence and importance.A major trend in theoretical work on prey–predator dynamics has been to derive more realistic models,trying to keep to maximum the unavoidable increase in complexity of their mathematics.In this optic,recently[2],see also[1,5,6]has proposed afirst study of two-dimensional system of autonomous differential equation modeling a predator prey system.This model incorporates a modified version of Leslie–Gower functional response as well as that of the Holling-type II.They consider the following model⎧⎪⎪⎨⎪⎪⎩˙x=a1−bx−c1yx+k1x,˙y=a2−c2yx+k2y(1)with the initial conditions x(0)>0and y(0)>0.This two species food chain model describes a prey population x which serves as food for a predator y.The model parameters a1,a2,b,c1,c2,k1and k2are assuming only positive values.These parameters are defined as follows:a1is the growth rate of prey x,b measures the strength of competition among individuals of species x,c1∗Corresponding author.Tel./fax:+133232744.E-mail address:Aziz-Alaoui@univ-lehavre.fr(M.A.Aziz-Alaoui).1468-1218/$-see front matter᭧2005Elsevier Ltd.All rights reserved.doi:10.1016/j.nonrwa.2005.10.003A.F.Nindjin et al./Nonlinear Analysis:Real World Applications7(2006)1104–11181105 is the maximum value of the per capita reduction rate of x due to y,k1(respectively,k2)measures the extent to which environment provides protection to prey x(respectively,to the predator y),a2describes the growth rate of y,and c2 has a similar meaning to c1.It wasfirst motivated more by the mathematics analysis interest than by its realism as a model of any particular natural dynamical system.However,there may be situations in which the interaction between species is modelized by systems with such a functional response.It may,for example,be considered as a representation of an insect pest–spider food chain.Furthermore,it is afirst step towards a predator–prey model(of Holling–Tanner type)with inverse trophic relation and time delay,that is where the prey eaten by the mature predator can consume the immature predators.Let us mention that thefirst equation of system(1)is standard.By contrast,the second equation is absolutely not standard.This intactness model contains a modified Leslie–Gower term,the second term on the right-hand side in the second equation of(1).The last depicts the loss in the predator population.The Leslie–Gower formulation is based on the assumption that reduction in a predator population has a reciprocal relationship with per capita availability of its preferred food.Indeed,Leslie introduced a predator prey model where the carrying capacity of the predator environment is proportional to the number of prey.He stresses the fact that there are upper limits to the rates of increase of both prey x and predator y,which are not recognized in the Lotka–V olterra model.In case of continuous time,the considerations lead to the following:d y d t =a2y1−yx,in which the growth of the predator population is of logistic form,i.e.d y d t =a2y1−yC.Here,“C”measures the carry capacity set by the environmental resources and is proportional to prey abundance,C= x, where is the conversion factor of prey into predators.The term y/ x of this equation is called the Leslie–Gower term.It measures the loss in the predator population due to the rarity(per capita y/x)of its favorite food.In the case of severe scarcity,y can switch over to other population,but its growth will be limited by the fact that its most favorite food,the prey x,is not available in abundance.The situation can be taken care of by adding a positive constant to the denominator,hence the equation above becomes,d y d t =a2y1−yand thus,d y d t =y⎛⎜⎝a2−a2.yx+d⎞⎟⎠that is the second equation of system(1).In this paper,we introduce time delays in model(1),which is a more realistic approach to the understanding of predator–prey dynamics.Time delay plays an important role in many biological dynamical systems,being particularly relevant in ecology,where time delays have been recognized to contribute critically to the stable or unstable outcome of prey densities due to predation.Therefore,it is interesting and important to study the following delayed modified Leslie–Gower and Holling-Type-II schemes:⎧⎪⎪⎨⎪⎪⎩˙x(t)=a1−bx(t)−c1y(t)x(t)+k1x(t),˙y(t)=a2−c2y(t−r)x(t−r)+k2y(t)(2)for all t>0.Here,we incorporate a single discrete delay r>0in the negative feedback of the predator’s density.1106 A.F .Nindjin et al./Nonlinear Analysis:Real World Applications 7(2006)1104–1118Let us denote by R 2+the nonnegative quadrant and by int (R 2+)the positive quadrant.For ∈[−r,0],we use the following conventional notation:x t ( )=x( +t).Then the initial conditions for this system take the formx 0( )= 1( ),y 0( )= 2( )(3)for all ∈[−r,0],where ( 1, 2)∈C([−r,0],R 2+),x(0)= 1(0)>0and y(0)= 2(0)>0.It is well known that the question of global stability of the positive steady state in a predator–prey system,with a single discrete delay in the predator equation without instantaneous negative feedback,remains a challenge,see [3,5,7].Our main purpose is to present some results about the global stability analysis on a system with delay containing modified Leslie–Gower and Holling-Type-II terms.This paper is organized as follows.In the next section,we present some preliminary results on the boundedness of solutions for system (2)–(3).Next,we study some equilibria properties for this system and give a permanence result.In Section 5,the analysis of the global stability is made for a boundary equilibrium and sufficient conditions are provided for the positive equilibrium of both instantaneous system (1)and system with delay (2)–(3)to be globally asymptotically stable.Finally,a discussion which includes local stability results for system (2)–(3)is given.2.PreliminariesIn this section,we present some preliminary results on the boundedness of solutions for system (2)–(3).We consider (x,y)a noncontinuable solution,see [4],of system (2)–(3),defined on [−r,A [,where A ∈]0,+∞].Lemma 1.The positive quadrant int (R 2+)is invariant for system (2).Proof.We have to show that for all t ∈[0,A [,x(t)>0and y(t)>0.Suppose that is not true.Then,there exists 0<T <A such that for all t ∈[0,T [,x(t)>0and y(t)>0,and either x(T )=0or y(T )=0.For all t ∈[0,T [,we havex(t)=x(0)expt0a 1−bx(s)−c 1y(s)x(s)+k 1d s (4)andy(t)=y(0)expt0a 2−c 2y(s −r)x(s −r)+k 2d s .(5)As (x,y)is defined and continuous on [−r,T ],there is a M 0such that for all t ∈[−r,T [,x(t)=x(0)expt0a 1−bx(s)−c 1y(s)x(s)+k 1d s x(0)exp (−T M)andy(t)=y(0)expt0a 2−c 2y(s −r)x(s −r)+k 2d sy(0)exp (−T M).Taking the limit,as t →T ,we obtainx(T ) x(0)exp (−T M)>0andy(T ) y(0)exp (−T M)>0,which contradicts the fact that either x(T )=0or y(T )=0.So,for all t ∈[0,A [,x(t)>0and y(t)>0.A.F.Nindjin et al./Nonlinear Analysis:Real World Applications7(2006)1104–11181107 Lemma2.For system(2)–(3),A=+∞andlim supt→+∞x(t) K(6) andlim supt→+∞y(t) L(7) where K=a1/b and L=a2/c2(K+k2)e a2r.Proof.From thefirst equation of system(2)–(3),we have for all t∈[0,A[,˙x(t)<x(t)(a1−bx(t)).A standard comparison argument shows that for all t∈[0,A[,x(t) ˜x(t)where˜x is the solution of the following ordinary differential equation˙˜x(t)=˜x(t)(a1−b˜x(t)),˜x(0)=x(0)>0.As lim t→+∞˜x(t)=a1/b,then˜x and thus x is bounded on[0,A[.Moreover,from Eq.(5),we can define y on all interval[kr,(k+1)r],with k∈N,and it is easy to see that y is bounded on[0,A[if A<+∞.Then A=+∞,see [4,Theorem2.4].Now,as for all t 0,x(t) ˜x(t),thenlim sup t→+∞x(t) lim supt→+∞˜x(t)=K.From the predator equation,we have˙y(t)<a2y(t),hence,for t>r,y(t) y(t−r)e a2r,which is equivalent,for t>r,toy(t−r) y(t)e−a2r.(8) Moreover,for any >1,there exists positive T ,such that for t>T ,x(t)< K.According to(8),we have,fort>T +r,˙y(t)<y(t)a2−c2e−a2rK+k2y(t),which implies by the same arguments use for x that,lim supt→+∞y(t) L ,where L =a2/c2( K+k2)e a2r.Conclusion of this lemma holds by letting →1.3.EquilibriaIn this section we study some equilibria properties of system(2)–(3).These steady states are determined analytically by setting˙x=˙y=0.They are independent of the delay r.It is easy to verify that this system has three trivial boundary equilibria,E0=(0,0),E1=(a1/b,0)and E2(0,a2k2/c2).1108 A.F .Nindjin et al./Nonlinear Analysis:Real World Applications 7(2006)1104–1118Proposition 3.System (2)–(3)has a unique interior equilibrium E ∗=(x ∗,y ∗)(i.e.x ∗>0and y ∗>0)if the following condition holdsa 2k 2c 2<a 1k 1c 1.(9)Proof.From system (2)–(3),such a point satisfies(a 1−bx ∗)(x ∗+k 1)=c 1y ∗(10)andy ∗=a 2(x ∗+k 2)c 2.(11)If (9)holds,this system has two solutions (x ∗+,y ∗+)and (x ∗−,y ∗−)given by ⎧⎪⎪⎨⎪⎪⎩x ∗±=12c 2b (−(c 1a 2−a 1c 2+c 2bk 1)± 1/2),y ∗±=a 2(x ∗±+k 2)c 2,where =(c 1a 2−a 1c 2+c 2bk 1)2−4c 2b(c 1a 2k 2−c 2a 1k 1)>0.Moreover,it is easy to see that,x ∗+>0and x ∗−<0. Linear analysis of system (2)–(3)shows that point E 0is unstable (it repels in both x and y directions)and point E 1is also unstable (it attracts in the x -direction but repels in the y -direction).For r >0,the characteristic equation of the linearized system at E 2takes the formP 2( )+Q 2( )e − r =0,whereP 2( )= 2−A ,Q 2( )=a 2( −A),andA =a 1−c 1a 2k 2c 2k 1.Let us defineF 2(y)=|P 2(iy)|2−|Q 2(iy)|2.It is easy to verify that the equation F 2(y)=0has one positive root.Therefore,if E 2is unstable for r =0,it will remain so for all r >0,and if it is stable for r =0,there is a positive constant r 2,such that for r >r 2,E 2becomes unstable.It is easy to verify that for r =0,E 2is asymptotically stable if a 2k 2/c 2>a 1k 1/c 1,stable (but not asymptotically)if a 2k 2/c 2=a 1k 1/c 1and unstable if a 2k 2/c 2<a 1k 1/c 1.4.Permanence resultsDefinition 4.System (2)–(3)is said to be permanent,see [4],if there exist , ,0< < ,independent of the initial condition,such that for all solutions of this system,min lim inf t →+∞x(t),lim inf t →+∞y(t)A.F .Nindjin et al./Nonlinear Analysis:Real World Applications 7(2006)1104–11181109andmaxlim sup t →+∞x(t),lim sup t →+∞y(t).Theorem 5.System (2)–(3)is permanent ifL <a 1k 1c 1.(12)Proof.By Lemma (2),there is a =max {K,L }>0independent of the initial condition such thatmax lim sup t →+∞x(t),lim sup t →+∞y(t) .We only need to show that there is a >0,independent of the initial data,such thatmin lim inf t →+∞x(t),lim inf t →+∞y(t) .It is easy to see that,for system (2)–(3),for any >1and for t large enough,we have y(t)< L .Thus,we obtain˙x >xa 1−bx −c 1 Lk 1 .By standard comparison arguments,it follows thatlim inf t →+∞x(t)1ba 1−c 1 L k 1 and letting →1,we obtainlim inf t →+∞x(t)1ba 1−c 1Lk 1.(13)Let us denote by N 1=1/b(a 1−c 1L/k 1).If (12)is satisfied,N 1>0.From (13)and Lemma 2and for any >1,there exists a positive constant,T ,such that for t >T ,x(t)>N 1/ and y(t)< L .Then,for t >T +r ,we have˙y(t)>y(t)a 2−c 2N 1+ k 2y(t −r) .(14)On the one hand,for t >T +r ,these inequalities lead to˙y(t)>−2c 2LN 1+ k 2y(t),which involves,for t >T +r ,y(t −r)<y(t)exp2c 2LN 12r .(15)On the other hand,from (14)and (15),we have for t >T +r ,˙y(t)>y(t)a 2−c 2N 1+ k 2exp 2c 2LN 1+ k 2r y(t) which yieldslim inf t →+∞y(t)a 2(N 1+ k 2)2exp − 2c 2LN 12r =y .1110 A.F .Nindjin et al./Nonlinear Analysis:Real World Applications 7(2006)1104–1118Letting →1,we getlim inf t →+∞y(t) a 2(N 1+k 2)c 2exp −c 2LN 1+k 2r=y 1.Let be =min {N 1,y 1}>0.Then we have shown that system (2)–(3)is permanent.5.Global stability analysis 5.1.Stability of E 2Theorem 6.If a 1−c 1y 1(k 1<0,then E 2is globally asymptotically stable for system (2)–(3).Proof.As lim inf t →+∞y(t) y 1and lim sup t →+∞x(t) K ,from the prey’s equation we obtain:∀ 1,∃T >0,∀t >T ,˙x(t)<x(t)a 1−bx −c 1y 1(k 1+ K).Asa 1−c 1y 1(k 1+K)<0,there exists >1such thata 1−c 1y 1(k 1<0.Then,by standard comparison arguments,it follows that lim sup t →+∞x(t) 0and thus,lim t →+∞x(t)=0.The -limit set of every solution with positive initial conditions is then contained in {(0,y),y 0}.Now from (7),we obviously obtain ⊂{(0,y),0 y L }.As E 0/∈ ,(E 0is unstable is repels in both x and y directions)and as is nonempty closed and invariant set,therefore ={E 2}. 5.2.Stability of E ∗without delayFirst,we give some sufficient conditions which insure that the steady state in the instantaneous system,i.e.without time delay,is globally asymptotically stable.Theorem 7.The interior equilibrium E ∗is globally asymptotically stable ifa 1+c 1<b(k 1+x ∗),(16)a 1a 2<bk 2(c 2−a 2).(17)Proof.The proof is based on constructing a suitable Lyapunov function.We defineV (x,y)=(x −x ∗)−x ∗ln x x ∗ + (y −y ∗)−y ∗ln yy ∗ ,where =k 2c 1/k 1a 2.A.F .Nindjin et al./Nonlinear Analysis:Real World Applications 7(2006)1104–11181111This function is defined and continuous on int(R 2+).It is obvious that the function V is zero at the equilibrium E∗and is positive for all other values of x and y ,and thus,E ∗is the global minimum of V .The time derivative of V along a solution of system (2)–(3)is given byd V d t =(x −x ∗) a 1−bx −c 1y x +k 1 + (y −y ∗) a 2−c 2y x +k 2.Centering d V /d t on the positive equilibrium,we getd V d t =−b +a 1−bx ∗x +k 1 (x −x ∗)2−c 2x +k 2(y −y ∗)2+a 2 x +k 2−c 1x +k 1 (x −x ∗)(y −y ∗)= −b +a 1−bx ∗x +k 1(x −x ∗)2−c 2x +k 2(y −y ∗)2(18)+a 2x +k 2+c 1x +k 1 (x −x ∗)2+(y −y ∗)22. −b +a 1−bx ∗k 1+c 1k1(x −x ∗)2+−c 2 x +k 2+c 1k 1(y −y ∗)2 −b +a 1−bx ∗k 1+c 1k 1(x −x ∗)2+c 1k 1(x +k 2)x +k 2−c 2k 2a 2 (y −y ∗)2.(19)From (16),we obtain−b +a 1−bx ∗k 1+c 1k 1<0.From (6)and (17),there exists >1and T >0,such thatK +k 2−c 2k 2a 2<0,and for t >T ,d V d t−b +a 1−bx ∗k 1+c 1k 1(x −x ∗)2+c 1k 1(x +k 2)K +k 2−c 2k 2a 2(y −y ∗)2.Thus,d V /d t is negative definite provided that (16)and (17)holds true.Finally,E ∗is globally asymptoticallystable.If in particular,we suppose that environment provides the same protection to both prey and predator (i.e.k 1=k 2)then Theorem 7can be simplified as follows.Corollary 8.The interior equilibrium E ∗is globally asymptotically stable ifk 1=k 2(20)anda 1<b(k 1+x ∗).(21)1112 A.F .Nindjin et al./Nonlinear Analysis:Real World Applications 7(2006)1104–1118Proof.From (18),we haved Vd t =−b +a 1−bx ∗x +k 1 (x −x ∗)2−c 2 x +k 2(y −y ∗)2+c 1(k 2−k 1)xk 1(x +k 2)(x +k 1) (x −x ∗)(y −y ∗) −b +a 1−bx ∗k 1(x −x ∗)2−c 2x +k 2(y −y ∗)2+c 1(k 2−k 1)xk 1(x +k 2)(x +k 1)(x −x ∗)(y −y ∗),which is negative definite provided that (20)and (21)holds true and thus E ∗is globally asymptotically stable.5.3.Stability of E ∗with delayIn this subsection we shall give a result on the global asymptotic stability of the positive equilibrium for the delayed system.Theorem 9.Assume that parameters of system (2)–(3)satisfya 1k 1c 1>maxa 12c 2,32a 2k 2c 2.(22)Then ,for b large enough ,there exists r 0>0such that ,for r ∈[0,r 0],the interior equilibrium E ∗is globally asymp-totically stable in R 2+.Proof.First of all,we rewrite Eqs.(2)to center it on its positive equilibrium.By using the following change of variables,X(t)=lnx(t)x ∗ andY (t)=lny(t)y ∗,the system becomes⎧⎪⎨⎪⎩˙X(t)=x ∗ −b +a 1−bx ∗x(t)+k 1 (e X(t)−1)−c 1y ∗x(t)+k 1(e Y (t)−1),˙Y (t)=−c 2y ∗x(t −r)+k 2(e Y (t −r)−1)+a 2x ∗x(t −r)+k 2(e X(t −r)−1).(23)According to the global existence of solutions established in Lemma 2,we can assume that the initial data exists on [−2r,0](this can be done by changing initial time).Now,let >1be fixed and let us define the following Liapunov functional V :C ([−2r ;0],R 2)→R ,V ( 1, 2)= 1(0)0(e u −1)d u + 2(0)(e u−1)d u +a 2x ∗2k 2 0−r (e 1(u)−1)2d u+c 2y ∗2k 2 0−r 0v e 2(s) c 2y ∗k 2(e 2(s −r)−1)2+a 2x ∗k 2(e 1(s −r)−1)2 d s d v +c 22k 2r L 0−r c 2y ∗k 2(e 2(s)−1)2+a 2x ∗k 2(e 1(s)−1)2 d s .Let us define the continuous and nondecreasing function u :R +→R +byu(x)=e x −x −1.A.F .Nindjin et al./Nonlinear Analysis:Real World Applications 7(2006)1104–11181113We have u(0)=0,u(x)>0for x >0andu(| (0)|) u( 1(0))+u( 2(0)) V ( 1, 2),where =( 1, 2)and |·|denotes the infinity norm in R 2.Let v :R +→R +be define byv(x)=2u(x)+(e x −1)2 a 2x ∗r 2k 2+ c 2y ∗k 2+a 2x ∗k 2 c 2y ∗r 24k 2e x +c 22k 2r 2 L .It is clear that v is a continuous and nondecreasing function and satisfies v(0)=0,v(x)>0andV ( 1, 2) v( ),where · denotes the infinity norm in C ([−2r ;0],R 2).Now,let (X,Y )be a solution of (23)and let us compute˙V(23),the time derivative of V along the solutions of (23).First,we start with the functionV 1( 1, 2)= 1(0)0(e u −1)d u + 2(0)0(e u −1)d u +a 2x ∗2k 2 0−r (e 1(u)−1)2d u .We haveV 1(X t ,Y t )=X(t)(e u−1)d u +Y (t)(e u−1)d u +a 2x ∗2k 2t t −r(e X(u)−1)2d u .Then,˙V1|(23)=(e X(t)−1)˙X(t)+(eY (t)−1)˙Y (t)+a 2x ∗2k 2((e X(t)−1)2−(e X(t −r)−1)2).System (23)gives us˙V 1|(23)=x ∗ −b +a 1−bx ∗x(t)+k 1 (e X(t)−1)2−c 1y ∗x(t)+k 1(e Y (t)−1)(e X(t)−1)−c 2y∗x(t −r)+k 2(e Y (t)−1)(e Y (t −r)−1)+a 2x ∗x(t −r)+k 2(e Y (t)−1)(e X(t −r)−1)+a 2x ∗2k 2((e X(t)−1)2−(e X(t −r)−1)2).By using several times the obvious inequalities of type−c 1y ∗x(t)+k 1(e Y (t)−1)(e X(t)−1) c 1y ∗x(t)+k 1 (e Y (t)−1)22+(e X(t)−1)22c 1y ∗2k 1((e Y (t)−1)2+(e X(t)−1)2),we get˙V1|(23)x ∗−b +a 1−bx ∗k 1+a 22k 2 +c 1y ∗2k 1 (e X(t)−1)2+c 1y ∗2k 1+a 2x ∗2k 2 (e Y (t)−1)2−c 2y ∗x(t −r)+k 2(e Y (t)−1)(e Y (t −r)−1).As,e Y(t−r)=e Y(t)− tt−re Y(s)˙Y(s)d s,we obtain˙V1|(23)x∗−b+a1−bx∗k1+a22k2+c1y∗2k1(e X(t)−1)2+c1y∗2k1+a2x∗2k2−c2y∗x(t−r)+k2(e Y(t)−1)2+c2y∗x(t−r)+k2(e Y(t)−1)tt−re Y(s)˙Y(s)d s.(24)From(23),we have(e Y(t)−1) tt−re Y(s)˙Y(s)d s= tt−re Y(s)−c2y∗x(s−r)+k2(e Y(t)−1)(e Y(s−r)−1)d s +tt−re Y(s)a2x∗x(s−r)+k2(e Y(t)−1)(e X(s−r)−1)d sc2y∗2k2+a2x∗2k2tt−re Y(s)d s.(e Y(t)−1)2+c2y∗2k2tt−re Y(s)(e Y(s−r)−1)2d s+a2x∗2k2tt−re Y(s)(e X(s−r)−1)2d sand as y∗e Y(s) L for s large enough,we obtain,for t large enough,(e Y(t)−1) tt−re Y(s)˙Y(s)d s Lrc22k2+a2x∗2k2y∗(e Y(t)−1)2+ tt−re Y(s)c2y∗2k2(e Y(s−r)−1)2+a2x∗2k2(e X(s−r)−1)2d sand as x(s−r) L for s large enough,(24)becomes,for t large enough,˙V1|(23)x∗−b+a1−bx∗k1+a22k2+c1y∗2k1(e X(t)−1)2+c1y∗2k1+a2x∗2k2−c2y∗x(t−r)+k2+c2Lrk2c2y∗2k2+a2x∗2k2(e Y(t)−1)2+c2y∗k2tt−re Y(s)c2y∗2k2(e Y(s−r)−1)2+a2x∗2k2(e X(s−r)−1)2d s.(25)The next step consists in computation of the time derivative along the solution of(23),of the termV2( 1, 2)=c2y∗2k2−rve 2(s)c2y∗k2(e 2(s−r)−1)2+a2x∗k2(e 1(s−r)−1)2d s d v+c22k2r L−rc2y∗k2(e 2(s)−1)2+a2x∗k2(e 1(s)−1)2d s.We haveV2(X t,Y t)=c2y∗2k2tt−rtve Y(s)c2y∗k2(e Y(s−r)−1)2+a2x∗k2(e X(s−r)−1)2d s d v+c22k2r Ltt−rc2y∗k2(e Y(s)−1)2+a2x∗k2(e X(s)−1)2d s.Then,˙V2|(23)=c2y∗2k2e Y(t)c2y∗k2(e Y(t−r)−1)2+a2x∗k2(e X(t−r)−1)2r−c2y∗2k2tt−re Y(s)c2y∗k2(e Y(s−r)−1)2+a2x∗k2(e X(s−r)−1)2d s+c22k2r Lc2y∗k2(e Y(t)−1)2+a2x∗k2(e X(t)−1)2−c22k2r Lc2y∗k2(e Y(t−r)−1)2+a2x∗k2(e X(t−r)−1)2=c2r2k2c2y∗k2(e Y(t−r)−1)2+a2x∗k2(e X(t−r)−1)2(y∗e Y(t)− L)−c2y ∗2k2 tt−re Y(s)c2y∗k2(e Y(s−r)−1)2+a2x∗k2(e X(s−r)−1)2d s+c22k2r Lc2y∗k2(e Y(t)−1)2+a2x∗k2(e X(t)−1)2.For t large enough,we have y∗e Y(t)− L<0and thus,˙V2|(23) −c2y∗2k2tt−re Y(s)c2y∗k2(e Y(s−r)−1)2+a2x∗k2(e X(s−r)−1)2d s+c22k2r Lc2y∗k2(e Y(t)−1)2+a2x∗k2(e X(t)−1)2.This inequality and(25)lead to,for t large enough,˙V| (23)x∗−b+a1−bx∗k1+a22k2+c1y∗2k1(e X(t)−1)2+c1y∗2k1+a2x∗2k2−c2y∗x(t−r)+k2+c2Lrk2c2y∗2k2+a2x∗2k2(e Y(t)−1)2+c22k2r Lc2y∗k2(e Y(t)−1)2+a2x∗k2(e X(t)−1)2−bx∗(k1+x∗)k1+a1x∗k1+a2x∗2k2+c1y∗2k1+c2a2x∗r L2k22(e X(t)−1)2+c1y∗2k1+a2x∗2k2−c2y∗x(t−r)+k2+c2Lrk2c2y∗k2+a2x∗2k2(e Y(t)−1)2.Now,if−bx ∗(k1+x∗)k1+a1x∗k1+a2x∗2k2+c1y∗2k1<0(26)andc1y∗2k1+a2x∗2k2−c2y∗x(t−r)+k2<0(27)then,for r small enough,we can conclude that ˙V|(23)is negative definite.Hence V satisfies all the assumptions of Corollary 5.2in [4]and the theorem follows.We now study when inequalities (26)and (27)hold.From (10),we have −bx ∗(k 1+x ∗)=c 1(y ∗−a 1(k 1+x ∗)/c 1)and using (11),(26)becomes32c 1k 1a 2(x ∗+k 2)c 2−a 1+a 2x ∗2k 2<0which is rewritten as x ∗a 2k 1c 1k 2+3a 2c 2<2a 1k 1c 1−3a 2k 2c 2.(28)As x ∗ a 1b ,then the following inequalitya 1a 2k 1c 1k 2+3a 2c 2 <b 2a 1k 1c 1−3a 2k 2c 2(29)implies (28).Now,if the following inequality holdsc 1y ∗2k 1+a 2x ∗2k 2−c 2y ∗a 1b+k 2<0,(30)then,for t large enough,(27)holds ing (11),(30)is reformulated asc 1y ∗2k 1+c 2y ∗−a 2k 22k 2<c 2y ∗a1b+k 2c 12k 1+c 22k 2<c 2a 1b+k 2+a 22y ∗c 12k 1+c 22k 2<c 2a 1b +k 2+c 22(x ∗+k 2)c 1k 1<c 2⎛⎜⎝2a 1b +k 2+1x ∗2−1k 2⎞⎟⎠.As x ∗ a 1/b ,then the last inequality is satisfied ifc 1k 1<c 2⎛⎜⎝3a 1b +k 2−1k 2⎞⎟⎠(31)that is ifa 1c 1k 2k 1+a 1c 2<b k 2k 1(2c 2k 1−c 1).(32)In conclusion,ifa 1k 1c 1>maxa 12c 2,32a 2k 2c 2and for b large enough,there exists a unique interior equilibrium and for r small enough it is globally asymptoticallystable.6.DiscussionIt is interesting to discuss the effect of time delay r on the stability of the positive equilibrium of system (2)–(3).We assume that positive equilibrium E ∗exists for this system.Linearizing system (2)–(3)at E ∗,we obtain˙X(t)=A 11X(t)+A 12Y (t),˙Y (t)=A 21X(t −r)+A 22Y (t −r),(33)whereA 11=−bx ∗+c 1x ∗y ∗(x ∗+k 1)2,A 12=−c 1x ∗x ∗+k 1,A 21=c 2(y ∗)2(x ∗+k 2)2=a 22c 2andA 22=−c 2y ∗x ∗2=−a 2.The characteristic equation for (33)takes the formP ( )+Q( )e − r =0(34)in whichP ( )= 2−A 11 andQ( )=−A 22 +(A 11A 22−A 12A 21).When r =0,we observe that the jacobian matrix of the linearized system isJ = A 11A 12A 21A 22 .One can verify that the positive equilibrium E ∗is stable for r =0provided thata 1<bk 1.(35)Indeed,when (35)holds,then it is easy to verify thatT r(J )=A 11+A 22<0andDet (J )=A 11A 22−A 12A 21>0.By denotingF (y)=|P (iy)|2−|Q(iy)|2,we haveF (y)=y 4+(A 211−A 222)y 2−(A 11A 22−A 12A 21)2.If (35)holds,then =0is not a solution of (34).It is also easy to verify that if (35)holds,then equation F (y)=0has at least one positive root.By applying standard theorem on the zeros of transcendental equation,see [4,Theorem4.1],we see that there is a positive constant r0(which can be evaluated explicitly),such that for r>r0,E∗becomes unstable.Then,the global stability of E∗involves restrictions on length of time delay r.Therefore,it is obvious that time delay has a destabilized effect on the positive equilibrium of system(2)–(3).References[1]M.A.Aziz-Alaoui,Study of Leslie–Gower-type tritrophic population,Chaos Solitons Fractals14(8)(2002)1275–1293.[2]M.A.Aziz-Alaoui,M.Daher Okiye,Boundeness and global stability for a predator–prey model with modified Leslie–Gower and Holling-typeIIschemes,Appl.Math.Lett.16(2003)1069–1075.[3]E.Beretta,Y.Kuang,Global analyses in some delayed ratio-depended predator–prey systems,Nonlinear Anal.Theory Methods Appl.32(3)(1998)381–408.[4]Y.Kuang,Delay Differential Equations,with Applications in Population Dynamics,Academic Press,New York,1993.[5]R.K.Upadhyay,V.Rai,Crisis-limited chaotic dynamics in ecological systems,Chaos Solitons Fractals12(2)(2001)205–218.[6]R.K.Upadhyay,S.R.K.Iyengar,Effect of seasonality on the dynamics of2and3species prey–predator system,Nonlinear Anal.:Real WorldAppl.6(2005)509–530.[7]R.Xu,M.A.J.Chaplain,Persistence and global stability in a delayed predator–prey system with Michaelis–Menten type functional response,put.130(2002)441–455.。
高考试卷英语及答案

第一部分:听力理解(共两节,满分30分)第一节(共5小题;每小题2分,满分10分)听下面5段对话或独白,每段对话或独白后有一个小题,从题中所给的A、B、C三个选项中选出最佳选项,并标在试卷的相应位置。
1. A. He has been to China twice. B. He is a Chinese teacher. C. He is a Chinese student.2. A. They are planning a trip to the mountains. B. They are discussing the weather. C. They are preparing for a science project.3. A. She wants to study medicine. B. She is interested in art. C. She is going to be a teacher.4. A. They are discussing the best way to get to the airport. B. They are planning a party. C. They are talking about their weekend plans.5. A. He enjoys playing soccer. B. He is a good basketball player. C. He prefers to play chess.第二节(共5小题;每小题2分,满分10分)听下面5段对话或独白,每段对话或独白后有几个小题,从题中所给的A、B、C三个选项中选出最佳选项,并标在试卷的相应位置。
6. What does the man mean when he says "Let's not keep her waiting"?A. They should wait for her.B. They should not keep her waiting.C. They should go somewhere else.7. Why does the woman want to change her job?A. She is not happy with her current job.B. She wants to work closer to home.C. She wants to travel more.8. What does the man suggest doing next?A. Going to the movies.B. Visiting a museum.C. Having a picnic.9. Why does the woman want to buy a new car?A. Her old car is too old.B. She needs a car for work.C. She wants a more comfortable car.10. What is the main topic of the conversation?A. Traveling to different countries.B. The benefits of learning a new language.C. The challenges of living in a foreign country.第二部分:阅读理解(共两节,满分40分)第一节(共15小题;每小题2分,满分30分)阅读下面短文,从短文后各题所给的A、B、C、D四个选项中,选出可以填入空白处的最佳选项。
操作系统名词解释整理

==================================名词解释======================================Operating system: operating system is a program that manages the computer hardware. The operating system is the one program running at all times on the computer (usually called the kernel), with all else being systems programs and application programs.操作系统:操作系统一个管理计算机硬件的程序,他一直运行着,管理着各种系统资源Multiprogramming: Multiprogramming is one of the most important aspects of operating systems. Multiprogramming increases CPU utilization by organizing jobs (code and data) so that the CPU always has one to execute.多程序设计:是操作系统中最重要的部分之一,通过组织工作提高CPU利用率,保证了CPU始终在运行中。
batch system: A batch system is one in which jobs are bundled together with the instructions necessary to allow them to be processed without intervention.批处理系统:将许多工作和指令捆绑在一起运行,使得它们不必等待插入,以此提高系统效率。
中海油英语试题及答案

中海油英语试题及答案一、选择题(每题1分,共10分)1. The company is known for its _______ in the oil industry.A) innovationB) traditionC) reputationD) regulation答案:A2. The project is expected to _______ in the next quarter.A) commenceB) concludeC) deteriorateD) escalate答案:A3. The manager _______ the proposal and asked for revisions.A) approvedB) rejectedC) postponedD) scrutinized答案:B4. The team is working on _______ the new technology.A) implementingB) replicatingC) discardingD) researching答案:A5. The report _______ the environmental impact of the project.A) underestimatesB) overestimatesC) ignoresD) assesses答案:D6. The company aims to _______ its market share.A) diminishB) expandC) stabilizeD) monopolize答案:B7. The _______ of the oil spill was immediately reported tothe authorities.A) incidentB) occurrenceC) eventD) episode答案:B8. The _______ of the drilling equipment is crucial for the project's success.A) maintenanceB) installationC) operationD) design答案:A9. The _______ of the meeting has been postponed due to unforeseen circumstances.A) commencementB) conclusionC) cancellationD) agenda答案:A10. The _______ of the company's profits has been a topic of discussion.A) allocationB) fluctuationC) maximizationD) reduction答案:B二、填空题(每空1分,共10分)1. The _______ of the company's new policy has been well received by the employees.答案:implementation2. The _______ of the drilling site is a critical factor in ensuring safety.答案:inspection3. The _______ of the project was completed ahead of schedule.答案:construction4. The _______ of the environmental report is essential for compliance with regulations.答案:accuracy5. The _______ of the drilling process requires specialized knowledge.答案:management6. The _______ of the oil reserves is a key consideration for future investments.答案:assessment7. The _______ of the company's assets is a complex process.答案:valuation8. The _______ of the new technology will revolutionize the industry.答案:introduction9. The _______ of the company's strategy has led to significant growth.答案:execution10. The _______ of the oil spill was contained within hours.答案:impact三、阅读理解(每题2分,共10分)阅读以下短文,回答下列问题。
Polycom RealPresence Collaboration Server 8.8.1.30

Patch NotesPolycom® RealPresence® Collaboration ServerBuild ID: 8.8.1.3015Released File: OVA, ISO, BIN, QCOW2, Upgrade FileRelease Date: June 26, 2020PurposeThis patch includes fixes for the following issues when applied over the RealPresence Collaboration Server 8.8.1.3 release.EN-171810 Stability15 minutes in the call.EN-166867 Stability A user was unable to make ISDN calls to an RMX 2000 system.EN-159667 General An RMX 1800 system could not display the Global Address Book after aRealPresence Resource Manager failover. The issue resolved after a reboot.EN-178695 Stability An RMX 2000 system became unreachable by RMX Manger while upgrading itto an 8.8.1.x build.These Patch Notes document only the changes from the prerequisite generally available (GA) release. Refer to the Release Notes for that GA release for the complete release documentation.KVM DistributionThe RealPresence Collaboration Server now offers a Kernel-based Virtual Machine (KVM) option for virtual environments. KVM is built into Linux and allows users to turn Linux into a hypervisor that can run multiple virtual machines (VMs).Hardware configuration required for KVM deployment is the same as specified for VMware deployment (Please refer to the Polycom RealPresence Collaboration Server v8.8.1 Release Notes for more details).Prerequisites and Configuration ConsiderationsFor information on prerequisites and configuration considerations, please see the Polycom RealPresence Collaboration Server v8.8.1 Release Notes and the Polycom RealPresence Collaboration Server 8.8.1 Administrator Guide.Installation and Upgrade NotesThe procedure to deploy all of the software components is documented here.Deploying a KVM ImageTo deploy a new server instance on a KVM server:1Obtain the software component image files from your Poly support representative.2For each software component, create a new volume on your KVM server and import the image file.For more on this task, see Create a new volume on the KVM server.3Optionally, set the server to automatically startup.Create a new volume on the KVM serverYou can create a new volume on the KVM server using the Virtual Machine Manager or Virsh command line depending on the toolset available to you.Using Virtual Machine ManagerTo create a new volume on the KVM server using Virtual Machine Manager:1Go to Applications > System Tools > Virtual Machine Manager and click to create a new virtual machine.2Choose Import existing disk image and click Forward.3Enter or browse to the location of the software component image file.4Choose the OS type (Linux) and Version number (CentOS 6.9) and click Forward.5Enter the Memory (RAM) and CPUs required for the chosen software component image as identified in the Prerequisites and Configuration Considerations section and click Forward.6Enter a meaningful name for the VM instance.7Click Network selection and select the network on which the KVM host is defined.8Click Finish.Using Virsh command line toolThe commands in the following procedure can be run to remote KVM servers.When connecting to remote instances, the option --connect qemu://<hostname>/system can be used, where <hostname> is the hostname or IP address of the remote KVM server.Virsh is a command line tool for managing hypervisors and guests. The tool is built on the libvirt management API and can be used as an alternative to other tools like the graphical guest manager (virt-manager) and xm.To create a new volume on the KVM server using Virsh1Determine which storage pool you would like to use:virsh pool-list2Create a new volume on the server:NOTE: We recommend using a raw disk image as it offers increased performance over the qcow2 format.virsh vol-create-as <storage_pool> <volume> <size>GB --format rawWhere:<storage_pool> is the pool determined in step 1.<volume> is the name of the raw disk volume.3Upload the image to the volume:virsh vol-upload --pool <storage_pool> <volume> <path-to-image>4Get the path of the raw disk:virsh vol-path --pool <storage_pool> <volume>Upgrade Information for the RealPresence Collaboration ServerThe following sections provide important general information about upgrading RealPresence Collaboration Servers to this release.Upgrade Package ContentsThe RealPresence® Collaboration Server 8.8.1.4 software upgrade package includes:●The *.upg file for upgrading RealPresence Collaboration Server, Virtual Edition on KVM●The *.qcow2file for deploying RealPresence Collaboration Server, Virtual Edition on KVM. Supported Upgrade PathsUpgrade of RealPresence Collaboration Server from 8.7.4.360 to 8.8.1.4 and subsequent downgrade to 8.7.4.360 has been verified.Resource CapacitiesThe benchmarks for Conferencing and Resource Capacities with KVM deployment is the same as specified for VMware deployment. For information on Resource Capacities, please refer to the Polycom RealPresence Collaboration Server v8.8.1 Release Notes.。
英语作文互联网的利弊

The Internet has become an integral part of modern life,offering a myriad of benefits as well as some drawbacks.Here is a detailed look at both the advantages and disadvantages of the Internet.Advantages of the Internet:1.Access to Information:The Internet provides a vast repository of information on virtually any topic.It allows users to access news,research,and educational materials with just a few clicks.munication:It has revolutionized the way we communicate.With email,social media,and instant messaging,people can stay in touch with friends and family across the globe instantly.cation:Online learning platforms and resources make education more accessible. Students can take courses,attend lectures,and participate in discussions from anywhere in the world.4.Ecommerce:The Internet has transformed shopping,making it possible to purchase goods and services from the comfort of ones home.It has also opened up opportunities for small businesses to reach a global market.5.Telecommuting:Many jobs can now be done remotely,reducing the need for daily commutes and contributing to a better worklife balance.6.Entertainment:From streaming movies and music to playing online games,the Internet offers endless forms of entertainment.working:Professional networking sites make it easier to connect with colleagues and find job opportunities.Disadvantages of the Internet:1.Cybersecurity Threats:The Internet is fraught with risks such as hacking,identity theft, and online scams,which can lead to significant financial and personal losses.2.Privacy Concerns:Many websites and apps collect personal data,sometimes without users explicit consent,leading to privacy invasions and potential misuse of information.3.Misinformation:The ease of publishing content online has led to the spread of fakenews and misinformation,which can have serious societal implications.4.Addiction:Excessive use of the Internet,especially social media,can lead to addiction, affecting mental health and social interactions.5.Isolation:While the Internet connects people,it can also lead to social isolation as individuals may prefer online interactions over facetoface communication.6.Health Issues:Prolonged screen time can cause physical health problems such as eye strain,poor posture,and sedentary lifestylerelated issues.7.Digital Divide:Not everyone has equal access to the Internet,leading to a digital divide where some populations are left behind in terms of access to information and opportunities.In conclusion,while the Internet offers numerous benefits that enhance our lives,it is crucial to be aware of and mitigate the potential risks it poses.A balanced approach to using the Internet,with an emphasis on digital literacy and safety,can help maximize its advantages while minimizing its disadvantages.。
高考英语试卷打印版

一、听力(共两节,满分30分)第一节(共15小题,每小题1.5分,满分22.5分)听力材料:1. A. I have a headache.B. I have a toothache.C. I have a stomachache.D. I have a backache.2. A. I think you should study hard.B. I think you should take a break.C. I think you should go to the doctor.D. I think you should go to the library.3. A. The weather is sunny.B. The weather is cloudy.C. The weather is rainy.D. The weather is windy.4. A. He is a teacher.B. He is a doctor.C. He is a lawyer.D. He is a student.5. A. She is a doctor.B. She is a teacher.C. She is a lawyer.D. She is a student.6. A. I have a meeting.B. I have a flight.C. I have a test.D. I have a party.7. A. I like reading books.B. I like watching movies.C. I like playing sports.D. I like eating out.8. A. I will go to the park.B. I will go to the beach.C. I will go to the mountains.D. I will go to the library.9. A. I will buy a new car.B. I will buy a new phone.C. I will buy a new house.D. I will buy a new computer.10. A. I will go to the gym.B. I will go to the pool.C. I will go to the beach.D. I will go to the park.11. A. She is happy.B. She is sad.C. She is angry.D. She is surprised.12. A. He is tired.B. He is hungry.C. He is thirsty.D. He is bored.13. A. The movie is good.B. The movie is bad.C. The movie is boring.D. The movie is exciting.14. A. The restaurant is good.B. The restaurant is bad.C. The restaurant is expensive.D. The restaurant is cheap.15. A. The school is big.B. The school is small.C. The school is new.D. The school is old.第二节(共5小题,每小题3分,满分15分)听力材料:16. What are the speakers mainly talking about?A. The weather forecast.B. A new restaurant.C. A school event.D. A vacation plan.17. Why does the man ask the woman to help him?A. He needs advice on a school project.B. He wants to borrow a book from her.C. He needs help with his homework.D. He wants to go to the movies with her.18. What does the woman suggest the man do?A. Go to the gym.B. Go to the library.C. Go to the beach.D. Go to the park.19. What is the man's plan for the weekend?A. To go hiking.B. To go camping.C. To go swimming.D. To go shopping.20. How does the woman feel about the man's suggestion?A. She is interested.B. She is not interested.C. She is worried.D. She is angry.二、单选题(共20小题,每小题1分,满分20分)21. My brother _______ (be) a doctor, but he works as a teacher now.B. wasC. wereD. will be22. _______ (not) sunny today, so we can't go swimming.A. It isB. There isC. It wasn'tD. There wasn't23. _______ (be) a good idea to invite your friends to the party.A. It isB. It wasC. It wereD. It will be24. _______ (be) the best way to improve your English.A. It isB. It wasC. It wereD. It will be25. _______ (do) you like this movie?A. WhatB. WhoC. Why26. _______ (be) my first time to visit this city.A. It isB. It wasC. It wereD. It will be27. _______ (be) a great opportunity for us to learn from each other.A. It isB. It wasC. It wereD. It will be28. _______ (do) you think about the new teacher?A. WhatB. WhoC. WhyD. When29. _______ (be) a good idea to take a break after a long day of studying.A. It isB. It wasC. It wereD. It will be30. _______ (be) a wonderful day for a picnic.A. It isC. It wereD. It will be31. _______ (be) my favorite season.A. It isB. It wasC. It wereD. It will be32. _______ (be) a good time to visit the museum.A. It isB. It wasC. It wereD. It will be33. _______ (be) a great day for a hike.A. It isB. It wasC. It wereD. It will be34. _______ (be) a perfect day for a beach trip.A. It isB. It wasC. It wereD. It will be35. _______ (be) a good idea to take a walk in the park.A. It isB. It wasC. It wereD. It will be三、完形填空(共15小题,每小题1分,满分15分)阅读下面短文,从短文后各题所给的A、B、C、D四个选项中,选出可以填入空白处的最佳选项。
年轻人如何分辨网络虚假信息英语作文

年轻人如何分辨网络虚假信息英语作文全文共6篇示例,供读者参考篇1Title: How to Spot Fake Information on the InternetHey guys, today we're gonna talk about how to tell if the information we see on the internet is real or fake. It's super important to be smart and careful when we're looking at stuff online!First of all, we should check the source of the information. If it's from a reliable website or a trusted news outlet, then it's more likely to be true. But if it's from a random blog or a sketchy website, then we should be careful and double-check the facts.Next, we need to look at the date of the information. Sometimes old news or outdated facts can be spread around on the internet, making us think they're new. So always check when the information was published to make sure it's still relevant.Another thing to watch out for is sensational headlines or clickbait. If something sounds too crazy or too good to be true, it might just be fake. So don't believe everything you see rightaway, and always do some research before sharing it with your friends.Lastly, it's important to use our common sense and critical thinking skills. If something doesn't quite add up or if it's too extreme, then it's probably not true. So trust your instincts and don't fall for fake news or misinformation!Remember, guys, it's up to us to be smart and responsible internet users. Let's always double-check our sources, verify the facts, and think critically about the information we see online. Stay safe and stay informed!篇2Yo, guys! Today I wanna talk about how us young peeps can tell if some info we see online is fake or not. It's super important to know the difference, ‘cause there's a ton of fake stuff out there tryna fool us. Here are a few tips to help you spot those sneaky lies:First off, check the source. If the info is coming from a reliable and trusted website or news outlet, you're probably good to go. But if it's from some random blog or sketchy site you've never heard of, you might wanna do some more digging to make sure it's for real.Next up, look at the facts. If the info sounds too crazy orfar-fetched to be true, it might be a big ol' lie. Take a sec tofact-check by doing a quick search or asking a grown-up for help. Don't just believe everything you see online, ‘cause some people out there are just tryna mess with you.Another thing to watch out for is clickbait. If a headline or post seems really dramatic or over-the-top, it's probably just trying to get you to click on it. Remember, not everything online is as exciting or shocking as it seems.And finally, use your common sense. If something seems fishy or not quite right, trust your gut. Don't share or spread info that you're not sure about, ‘cause you don't wanna be spreading fake news yourself.So there you have it, young peeps! Stay smart, stay safe, and keep on rockin' in the digital world. Let's show those fake news creators that we're too smart to fall for their tricks! Peace out!篇3Hey guys, do you know how to tell if the information you see online is real or fake? It's super important to be able to spot fake news so we don't get tricked or believe in something that isn'ttrue. Here are some tips for young people on how to tell if online information is fake:1. Check the source: Make sure the information is coming from a reliable and trustworthy source. If it's from a website you've never heard of, it might not be accurate.2. Look for multiple sources: If you see a news story or information that seems fishy, try to find other sources that confirm it. If only one source is reporting it, it might not be true.3. Fact-check: Take the time to fact-check the information you see online. Look up the information on trusted websites to see if it's accurate.4. Beware of clickbait: Be cautious of flashy headlines or sensational stories that are meant to get your attention. They might not always be true.5. Use your common sense: If something seems too good to be true or doesn't sound right, it's probably fake. Trust your gut instincts.Remember, it's important to be critical thinkers and question the information we see online. By being smart and savvy, we can protect ourselves from falling for fake news. Stay safe out there, guys!篇4Yo guys, do you know how to tell if the info you see online is real or fake? It's super important to be able to spot fake news so you don't get tricked! Here are some tips for all you cool young dudes out there:1. Check the source: Before you believe something you read online, make sure it's coming from a reliable source. Look for well-known websites or news outlets that you trust. If you've never heard of the site before, it might be best to double check the info.2. Look for evidence: Real news stories usually have facts and evidence to back them up. If you see a claim online but there's no proof to support it, be suspicious. Don't just believe everything you read without doing some research.3. Watch out for clickbait: Sometimes websites use flashy headlines or pictures to grab your attention, even if the story isn't true. If something seems too crazy or unbelievable, it could be fake news.4. Fact check: If you're not sure if something is true or not, take a few minutes to look it up. There are fact-checking websites out there that can help you verify if the info is legit.5. Be skeptical: In the wild world of the internet, it's important to approach everything with a critical eye. Don't believe everything you see right away, and don't share stories unless you're sure they're real.So remember, dudes and dudettes, stay sharp and always question what you see online. Don't get fooled by fake news - you're way too cool for that!篇5Title: How Can Young People Tell If Information on the Internet Is Fake?Hey guys! Today I want to talk to you about how to spot fake information on the internet. With so much information out there, it can be hard to know what is true and what is fake. But don't worry, I've got some tips to help you out!First, you can check the source of the information. Is it from a reliable website or news outlet? If you're not sure, you can do a quick search to see if the website is known for spreading fake news. Remember, just because something looks professional doesn't mean it's true!Second, look at the date of the information. Is it recent or is it old news that has been circulating for years? Fake news often resurfaces, so make sure you're getting the most up-to-date information.Third, check if other reliable sources are reporting the same information. If only one website is sharing the news, it might not be true. Look for multiple sources to confirm the information.Lastly, use your critical thinking skills. Does the information sound too good to be true? Is it trying to make you angry or scared? Fake news often plays on our emotions, so be wary of any information that seems too sensational.Remember, it's important to be a smart consumer of information on the internet. Don't believe everything you read and always double-check before sharing with others. Stay safe and stay smart online!篇6Hey guys, do you know how to tell if the information you see online is fake? Today I am going to tell you some ways to spot fake information on the internet.First of all, you should always check the source of the information. If the source is a reliable and well-known website or organization, then the information is more likely to be true. But if you have never heard of the source before, you should be cautious and double-check the information.Secondly, you should look for supporting evidence. If the information is true, there should be other sources or evidence to back it up. Don't just believe something because it sounds good or because a lot of people are sharing it.Another way to spot fake information is to check the date of the article or post. Sometimes fake news is old news that has been recycled and presented as new. So always make sure the information is up to date.Also, be skeptical of information that is too good to be true. Fake news often plays on people's emotions or desires, so if something seems too perfect or unbelievable, it might be fake.Lastly, always fact-check the information before sharing it with others. You can use fact-checking websites or ask a teacher or parent for help if you are not sure about something.Remember, it is important to be a smart and responsible internet user. Don't believe everything you see online and alwaysquestion the information before sharing it with others. Stay safe and be smart!。
missing the point,逻辑 -回复

missing the point,逻辑-回复"Missing the Point: The Importance of Logic"Introduction:In today's world, where information overload is the norm, it is essential to develop skills that allow us to think critically and navigate through a sea of ideas and opinions. One of the fundamental skills that can help us achieve this is logic. Logic is the backbone of rational thinking, enabling us to formulate valid arguments and sound conclusions. However, many individuals often fail to grasp the significance of logic in their daily lives, often falling victims to fallacies, misinformation, and irrational thinking. This article aims to shed light on the importance of logic, step by step, debunking common misconceptions and highlighting its significance.Step 1: Defining LogicFirst and foremost, it is essential to define what logic is. In simple terms, logic is the systematic study of reasoning. It is a tool that allows us to analyze arguments and determine their validity and soundness. Logic provides us with a set of rules and principles that help structure our thinking, enabling us to form solid conclusionsbased on evidence and reason. Understanding this basic definition is crucial for grasping the significance of logic in our lives.Step 2: Identifying FallaciesOne of the primary reasons why people often miss the point and fail to grasp the importance of logic is the prevalence of fallacious reasoning in everyday discourse. Fallacies are errors in reasoning that can lead to wrong conclusions and flawed arguments. Common fallacies include ad hominem attacks, appeal to authority, and strawman arguments. By learning to recognize these fallacies, individuals can separate sound arguments from faulty ones, fortify their critical thinking skills, and avoid being misled by fallacious reasoning.Step 3: Critical Thinking and Problem-SolvingLogic is inseparable from critical thinking, as it provides the foundation for effective problem-solving. The ability to think critically is a valuable skill that allows individuals to analyze and evaluate information objectively. By utilizing logical reasoning, individuals can identify assumptions, evaluate evidence, and draw conclusions based on valid deductions. Critical thinking combined with logic helps individuals approach issues with a systematic andrational mindset, enabling them to find creative solutions and make informed decisions.Step 4: Avoiding Manipulation and MisinformationIn today's digital age, where misinformation spreads like wildfire, logic serves as a shield against manipulation. By understanding logic, individuals can discern valid arguments from mere persuasive tactics. They can separate well-substantiated claims supported by evidence from baseless assertions. Logic empowers individuals to question information critically, fact-check sources, and reach informed conclusions. In an era plagued by fake news and disinformation, logic is indispensable in helping individuals navigate the complex landscape of information.Step 5: Personal and Professional SuccessDeveloping logical thinking skills has far-reaching implications, both personally and professionally. Inductive and deductive reasoning, critical analysis, and problem-solving abilities are highly valued in today's job market. Employers seek individuals who possess the ability to think logically and make sound decisions. Moreover, logic is essential for effective communication, enabling individuals to present their ideas clearly and concisely, persuadingothers based on reasoned arguments. Both in personal pursuits and career aspirations, logic plays a crucial role in achieving success.Conclusion:In a world inundated with information, misinformation, and fallacious reasoning, logic becomes the lighthouse that guides us through the storm. Its importance cannot be overstated. By embracing logic, individuals can sharpen their critical thinking skills, avoid fallacious reasoning, and navigate the complex maze of ideas and information. Logic allows us to think rationally, discern fact from fiction, and make informed decisions. Embracing logic is not merely an intellectual exercise but a practical necessity in today's world. So, let us not miss the point; let us embrace logic and empower ourselves to become more informed, rational, and logical thinkers.。
山东省东营市2023-2024学年高一下学期期末考试英语试题

山东省东营市2023-2024学年高一下学期期末考试英语试题一、阅读理解Campus ResourcesBookstoreThe bookstores supply required and recommended textbooks, reference materials, and college sportswear. You can buy or rent textbooks. Access more details about the bookstore on My Macomb.Locations:South Campus K Building 586.445.7385Center Campus P Building 586.286.2093LibraryMacomb Community College’s Library collections contain print and multimedia materials covering a wide range of topics. Each campus library features resources in the program areas offered at that location. Center Campus focuses on Nursing, Public Safety, and Early Childhood Education. The South Campus Library highlights Applied Technology, Media and Communication Arts, and Engineering Technology.Locations:South Campus J Building 586.445.7401Center Campus C Building 586.286.2104College Success Skills-CSSK-1200CSSK is a three-credit-hour course that is open to all students. You will learn what it takes to be a successful college student, explore campus resources, and connect with other students. You will also learn goal setting, study strategies, time management and educational planning.Career (职业) Development and Decision Making-LIFE-1010LIFE is a three-credit-hour course. It will guide you to explore your interests, personality and values as they’re late to the world of work. This course is suggested if you are undecided on a job path, or have ideas about what you want to do but are unsure how to get there. In this class you will tour companies and talk to professionals in different industries.1.Where can you get multimedia materials in Engineering Technology?A.South Campus K Building586.445.7385B.Center Campus PBuilding586.286.2093C.South Campus J Building586.445.7401D.Center Campus C Building586.286.2104 2.Why is the course LIFE established?A.To guide students to explore campus resources.B.To inspire students to develop research interests.C.To encourage students to set educational plans.D.To help students make suitable career choices.3.Where is this text probably taken from?A.A course plan.B.A student guide.C.An academic article.D.A college newspaper.I used to behave like a superhero with my family. But talking with a stranger was very difficult for me. I stayed like this for a long time. But conditions seemed to change after I attended college.One day when I was doing some research on the Internet for my college project, I found a video on how to deal with shyness. The person in the video explained everything about shyness and said something that inspired me. He said, “No one is born with confidence. They develop it with time. It is a learnable skill. Anyone can learn it.”Due to my newly found motivation (动机), I watched hundreds of personal development videos in 2 to 3 days. I also ordered some personal development books and read online articles. Only consuming information was not going to change my life. I knew I would have to perform it.I wanted to change very much. So, I created a proper list of how to meet with people. In the list, I mentioned everything from eye contact to smile, handshake, asking questions, etc. I tried to talk with a stranger every day and got mixed up even more with my classmates.Now I wanted to change my life completely. That’s why I tried to conquer my biggest fear: stage fear. Luckily, there was a public speaking competition at my college. I asked every classmate to give me company. But not even one student was ready.I wanted to do it so badly that I ended up doing it alone, which was a fearless move for me. On the competition day, I was very scared. I knew that if I didn’t conquer this fear, it would stay with me for my whole life. After stepping on stage I found it was not that frightening. I did my best and I got 3rd prize out of 31 students. My teachers were congratulating me. I was so happythat I finally made it.4.What stirred up the author’s determination to change?A.An inspiring video.B.A college project.C.Articles on shyness.D.Books on personal development.5.What does the underlined word “consuming” mean in paragraph 3?A.Taking in.B.Taking advantage of.C.Using up.D.Being addicted to.6.What can be inferred about the speaking competition?A.31 students were awarded 3rd prize.B.It helped the author remove stage fear.C.It was the biggest challenge for the author.D.Teamwork was required in thecompetition.7.What can we learn from the author’s experience?A.The early bird catches the worm.B.Actions speak louder than words.C.Nothing is impossible to a willing heart.D.All things are difficult before they are easy.Sea level is rising due to climate change, which threatens the future of millions of people around the world. Also, it threatens our cultural past. “It’s really the history of our species that’s at risk in a lot of ways,” says Meghan Howey, an archaeologist at the University of New Hampshire in Durham. Another archaeologist Anderson recently used online data to look at the dangers caused by rising seas to cultural sites in the southeastern United States. He found a one-meter rise in sea level could des troy more than 13,000 of those places.So how are we going to protect the important places? Efforts to limit the worst impacts from climate change, including sea level rise, will require cutting greenhouse-gas emissions (排放) or maybe taking steps to limit flooding in important areas. Another approach might be to move cultural treasures. But projects like that are often very expensive. It’s unlikely that funds to do that will be available (可用的) for every site. And some treasures simply can’t be moved.But high-tech tools might help preserve knowledge of those treasures before physical sites are lost, says Mark McCoy, an archaeologist at Southern Methodist University in Dallas, Texas. For example, scanning and imaging tools can help. LIDAR is a type of system that uses lasers to make exact 3-D scans of objects. High-resolution digital photography can make detailed images.Computer technologies can also create 3-D virtual reality models.Rising seas are likely to eventually bury a lot of archaeological treasures. And in some cases, the old techniques (技术) that archaeologists have long used may also help. “I still use traditional methods out on a site when the conditions call for it,” McCoy notes. For example, he says, “Paper and pencil do not require batteries and don’t break when I drop them on rocks.”8.Why does the author mention two archaeologists in Paragraph 1?A.To stress the risk to cultural sites.B.To prove the value of online data.C.To explain the reason of sea level rise.D.To show the impact of climate change. 9.What does Paragraph 3 mainly talk about?A.How to make exact 3-D scans of objects.B.How to save the endangered cultural treasures.C.Scanning and imaging tools can help save the treasures.D.High-tech tools may play a part in preserving knowledge of the sites.10.What’s McCoy’s attitude towards traditional methods?A.Supportive.B.Doubtful.C.Objective.D.Puzzled. 11.Which of the following shows the structure of the whole text?(P: Paragraph)A.B.C.D.News companies are increasingly using video and images from social media to report on the ongoing conflict(冲突) between Israel and Hamas. This has led some media organizations to increase their efforts to identify false or misleading information.Reporters covering the war are limited by the government on how they can document the conflict. But they can use a flood of video and pictures published online. Therefore, reports of thewar have included many images and video that appeared on social media. News content has also been recorded by satellite equipment and cameras placed around Israel and Gaza.Using this kind of content in news shows has become very common for major media companies. Wendy McMahon, president of CBS News and Stations, told The Associated Press that many people watching news reports today expect to be part of “a shared viewing experience.” This way, they can feel like they are learning what is going on right along with the reporters, McMahon said.In order to create this kind of experience, news reporters have to search through a huge online supply of images and video, which comes from services like YouTube, Instagram, and Facebook.Checking this material, however, can be difficult. With so much material, it is easy for people or organizations to create false images and video using artificial intelligence (AI). Reuters news agency uncovered several images published online that turned out to be false.McMahon, from CBS, said the Israel-Hamas war has in many ways confirmed a big fear among news reporters: “News companies would see a flood of misinformation to an extent that was never seen before.”12.What can we learn about the reports on the war between Israel and Hamas?A.They are free from government limits.B.They take advantage of online content.C.They document all the conflicts in detail.D.They are mainly recorded by satelliteequipment.13.What is a challenge for news reporters according to the passage?A.Editing news materials.B.Removing fear of misinformation.C.Identifying false content.D.Creating images and video with AI. 14.Why are online video and images commonly used by media companies?A.They are easily accessible to people.B.They offer a better viewing experience.C.They record what is going on faithfully.D.They are in good supply on social media. 15.Which is the most suitable title for the text?A.How to Publish Online News B.How to Identify False InformationC.How Social Media Affects News Reports D.How Social Media Helps to Cover theConflictWorld Wildlife Day is celebrated each year on March 3rd. This is a day that has the goal of informing the general public about the plants and wild animals in the world. So you can do many things to celebrate this day.As we all know, litter can be harmful to birds, fish, and other wildlife. Therefore, make an effort to pick up any litter that you see. 16You can visit an aquarium or zoo near you, because aquariums and zoos help a lot with endangered species, allowing their populations to increase. 17 Thus, World Wildlife Day is the perfect day to pay a local aquarium or zoo a visit.If possible, try to learn about the plants and wild animals near you. You can do some research about local wildlife. You can also research some of the threats to these plants and wild animals. 18 For example, if one of the primary threats an animal faces is litter, be sure to deal with it properly, and pick up any litter you see.If you like, you can plant a garden with native tree, bush and flower species. 19 To plant them in the garden accordingly, it is necessary to do some research beforehand on trees, bushes and flowers that are native to your area and where they would grow best.20 There are a variety of organizations that help wildlife in different ways. If you have a specific species that you’d like to support, or even if you’d just like to help wildlife in general, there might be an organization somewhere that you can join and assist with their efforts. A.Every year, there is a theme for World Wildlife Day.B.If the threat they face is caused by human, try to help reduce it.C.These may be the only places to find certain endangered animals.D.Additionally, it’s a good way to join an organization that helps wildlife.E.These can help provide wild animals with a place where they can shelter.F.Databases online can help us find the plants which are native to our area.G.And you’d better make sure that you reduce the amount of litter you create.二、完形填空Two seconds were left on the clock, we were down by one point, and I was at thefree-throw line. If I 21 the first shot, I would take a second shot. If we 22 , we were out. It was the finals.I like playing basketball very much, though I’m not a(n) 23 athlete. I started playing basketball in the sixth grade. I practiced outside for hours and hours, days and days and my 24 had become very good. In every game I played as hard as I could. I was 25 able to make the team in the eighth grade, and even worked my way up to being a starter. Although I could not run as fast or jump as high as my naturally athletic teammates, that never 26 me. I strongly believed that my effort would 27 .Now this was my 28 , all eyes on me. I was a good free-throw shooter. I’d 29 a thousands of times. 30 , on that day, on that shot, I missed. I 31 jumped up for the rebound. Someone from the other team 32 it, though, and the game was over. We were out.After the game, our coach 33 everyone for a great season. Then he turned to me, saying, “Excellent!” And everyone present clapped.I learned that day that there is no such thing as “your moment”. Who you are does not come down to one success or one 34 . What you do and how hard you work every single day do 35 .21.A.threw B.recorded C.made D.demanded 22.A.managed B.lost C.agreed D.succeeded 23.A.flexible B.determined C.intelligent D.natural 24.A.shot B.personality C.will D.shape 25.A.directly B.eventually C.personally D.equally 26.A.failed B.struck C.upset D.injured 27.A.pay off B.break out C.make up D.fall apart 28.A.focus B.affair C.moment D.attempt 29.A.missed B.counted C.reflected D.practiced 30.A.Besides B.However C.Therefore D.Otherwise 31.A.probably B.blindly C.finally D.immediately 32.A.got B.blocked C.tracked D.moved 33.A.admired B.defined C.praised D.appreciated 34.A.survival B.failure C.honour D.example35.A.differ B.happen C.impact D.matter三、语法填空阅读下面短文,在空白处填入1个适当的单词或括号内单词的正确形式。
researched analysis英语写作 -回复

researched analysis英语写作-回复Research Analysis: [Smartphone Usage Among Teenagers]Introduction:Smartphone usage among teenagers has become a topic of great interest and concern in recent years. With the increasing accessibility and affordability of smartphones, teenagers are spending more time engaging with these devices. This research analysis aims to explore the patterns and impact of smartphone usage among teenagers, considering factors such as social media, academic performance, mental health, and physical well-being.1. Current Trends in Smartphone Usage Among Teenagers:To begin the analysis, it is important to understand the current trends in smartphone usage among teenagers. According to recent studies, an overwhelming majority of teenagers (around 95) own a smartphone. These devices are primarily used for communication, entertainment, and accessing social media platforms. Teenagers spend an average of 7-9 hours per day on their smartphones, with a significant portion of this time dedicated to social mediaengagement.2. Impact on Social Media Usage:Social media has become an integral part of teenagers' lives, and their smartphone usage plays a vital role in this. Various studies have shown a direct correlation between smartphone usage and social media consumption among teenagers. Excessive use of social media can lead to negative effects, such as increased feelings of loneliness, depression, and low self-esteem. Additionally, smartphone dependency on social media can hinder teenagers' ability to develop and maintain real-life interpersonal relationships.3. Academic Performance:Smartphone usage can also have an impact on teenagers' academic performance. While smartphones provide access to educational resources and information, they also serve as a significant distraction. Frequent notifications, social media engagements, and gaming temptations can divert students' attention away from their studies, resulting in reduced productivity and lower academic achievements. Researchers suggestestablishing boundaries and time management strategies to mitigate these negative effects.4. Mental Health Implications:The intensive use of smartphones among teenagers has raised concerns about its impact on mental health. The constant exposure to social media can generate feelings of anxiety, body dissatisfaction, and fear of missing out (FOMO). Moreover, cyberbullying through social media platforms can significantly impact teenagers' mental well-being, leading to increased stress levels and even depression. It is crucial to promote digital literacy and create safer online spaces to address these mental health concerns.5. Physical Well-being:Teenagers' excessive smartphone usage often results in sedentary behaviors, contributing to a sedentary lifestyle and physical health issues. Spending hours sitting while engrossed in smartphone activities limits physical activity and exercise opportunities. This can lead to various health problems, such as obesity, diabetes, andcardiovascular diseases. Encouraging teenagers to engage in outdoor activities, sports, and exercise can help counteract the negative effects of prolonged smartphone usage.Conclusion:Smartphone usage among teenagers has become a growing concern due to its influence on various aspects of their lives. The analysis highlights the impact of smartphone usage on social media consumption, academic performance, mental health, and physical well-being. Parents, educators, and policymakers must work together to promote responsible smartphone usage, establish healthy habits, and create a balanced environment that allows teenagers to benefit from technology while mitigating its potential negative consequences.。
The design space of register renaming techniques

Register renaming is a technique to remove false data dependencies—write after read (WAR) and write after write (WAW)—that occur in straight line code between reg-ister operands of subsequent instructions.1-3 By eliminating related precedence require-ments in the execution sequence of the instructions, renaming increases the average number of instructions that are available for parallel execution per cycle. This results in increased IPC (number of instructions exe-cuted per cycle).The identification and exploration of the design space of register-renaming lead to a com-prehensive understanding of this intricate tech-nique. As this article shows, the design space of register renaming is spanned by four main dimensions: the scope of register renaming, the layout of the rename buffers, the method of register mapping, and the rename rate. Rele-vant aspects of the design space give rise to eight basic alternatives for register-renaming. In addi-tion, the kind of operand fetch policy signifi-cantly affects how the processor carries out the rename process, which duplicates the eight basic alternatives to 16 possible implementa-tion schemes. The article indicates which basic implementation scheme is used in relevant superscalar processors.As register renaming is usually implement-ed in conjunction with shelving, the under-lying microarchitecture is assumed to employ shelving. (See the “Instruction shelving prin-ciple” box for a discussion of this technique.)Register renamingThe principle of register renaming is straightforward. If the processor encounters an instruction that addresses a destination reg-ister, it temporarily writes the instruction’s result into a dynamically allocated rename buffer rather than into the specified destina-tion register. For instance, in the case of the following WAR dependency:i1:add …, r2, …; [… ←(r2) +(…)]i2:mul r2, …, …; [r2 ← (…) ∗(…)] the destination register of i2 (r2) is renamed, say to r33. Then, instruction i2 becomesi2′:mul r33, …, …; [r33 ←(…) * (…)] Its result is written into r33 instead of into r2. This resolves the previous WAR dependency between i1 and i2. In subsequent instructions, however, references to source registers must be redirected to the rename buffers allocated to them as long as this renaming remains valid.3A precursor to register renaming was intro-duced for floating-point instructions in 1967 by Tomasulo in the IBM 360/91,4a scalar supercomputer of that time that pioneered both pipelining and shelving (dynamic instruction issue). The 360/91 renamed float-ing-point registers to preserve the logical con-sistency of the program execution rather than to remove false data dependencies.Dezsö Sima Budapest Polytechnic T O BOOST PROCESSOR AND SYSTEM PERFORMANCE, VIRTUALLY ALL RECENT SUPERSCALARS RENAME REGISTERS.0272-1732/00/$10.00 2000 IEEET HE D ESIGN S PACE OF R EGISTER R ENAMING T ECHNIQUES70Tjaden and Flynn5first suggested the use of register renaming for removing false data dependencies for a limited set of instructions that corresponds more or less to the load instructions. However, they didn’t use the term “register renaming.” Keller6introduced this designation in 1975 and extended renam-ing to cover all instructions including a desti-nation register. He also described how to implement register renaming in processors. Even so, due to the complexity of this tech-nique almost two decades passed after its con-ception before register renaming came into widespread use in superscalars at the begin-ning of the 1990s.Early superscalars such as the HP PA 7100, Sun SuperSparc, DEC Alpha 21064, MIPS R8000, and Intel Pentium typically didn’t use renaming. Renaming appeared gradually—first in a restricted form called partial renam-ing (to be discussed in the next section) —in the early 1990s in the IBM RS/6000 (Power1), Power2, PowerPC 601, and the NextGen Nx586 processors. See Figure 1. Full renaming emerged later, beginning in 1992,first in the high-end models of the IBM main-frame ES/9000, then in the PowerPC 603. Subsequently, renaming spread into virtually all superscalar processors with the notable exception of Sun’s UltraSparc line. At present,register renaming is considered to be a stan-dard feature of performance-oriented super-scalar processors.Design space of register-renamingtechniquesThe main dimensions of register renamingare as follows:•scope of register renaming,•layout of the renamed registers,71SEPTEMBER–OCTOBER2000Figure 1. Chronology of register renaming in commercial superscalar processors. The introduction date indicates the first year of volume production. Following the model designation is the issue rate of the processors (in parentheses). Note that for the issue rate of CISC processors, one x86 instruction is considered to be the equivalent of 1.3 to 1.9 RISC instructions.34•method of register mapping and,•rename rateas indicated in subsequent sections. Due to volume restrictions we ignore additional dimensions that are related to the renaming process such as recovery from a misprediction. Scope of register renamingTo indicate how extensively the processor makes use of renaming, I distinguish between partial and full renaming. Partial renaming is restricted to one or only a few instruction types, for instance, only to floating-point instructions. Early processors typically employed this incom-plete form of renaming; the Power1 (RS/6000), Power2, PowerPC 601, and the Nx586 are examples, as shown in Figure 2. Of these, the Power1 (RS/6000) renames only floating-point loads. As the Power1 has only a single floating-point unit, it executes floating-point instruc-tions in sequence. Thus there’s no need for renaming floating-point register instructions. The Power2 processor introduces multiple floating-point units and for this reason it extends renaming to all floating-point instruc-tions. The Power PC 601 renames only the link and count register. The Nx586, which has an integer core, obviously restricted renaming to fixed-point instructions.Full renaming covers all instructions includ-ing a destination register. As Figure 1 demon-strates, virtually all recent superscalar processors employ full renaming. Notewor-thy exceptions are the Sun UltraSparc line and Alpha processors preceding the Alpha 21264. Rename buffer layoutRename buffers establish the actual frame-work for renaming. There are three essential design aspects in their layout:•type of rename buffers,•number of rename buffers, and •number of read and write ports. Rename buffer typesThe choice of which type of rename buffers to use in a processor has far-reaching impact on the implementation of the rename process. Given its importance, designers must consid-er the various design options. T o simplify this presentation, I initially assume a common architectural register file for all processed data types, and then extend the discussion to the split-register scenario that is commonly employed.As Figure 3 illustrates, there are four fun-damentally different ways to implement rename buffers. The range of choices includes a) using a merged architectural and rename register file, b) employing a stand-alone rename register file, c) keeping renamed val-ues either in the reorder buffer (ROB), or d) in the shelving buffers.In the first approach, rename buffers are implemented along with the architectural reg-isters in the same physical register file called the merged architectural and rename register file or the merged register file for short. Here, both architectural and rename registers are dynamically allocated to particular registers of the same physical file.Each physical register of the merged archi-tectural and rename register file is at any time in one of four possible states.27These states reflect the actual use of a physical register as follows:•uncommitted (available) state,•used as an architectural register (archi-72R ENAMING R EGISTERSIEEE MICROFigure 2. Register renaming scope: partial (a) and full (b).tectural register state),•used as a rename buffer—but this register doesn’tyet contain the result ofthe associated instruction(rename buffer, not-validstate), and•used as a rename buffer—this register already con-tains the result of theassociated instruction(rename buffer, validstate).During instruction pro-cessing, the states of the phys-ical registers are changed as described in the following and indicated in the state transi-tion diagram in Figure 4. As part of the initializationthe first n physical registers are assigned to the architectural registers, where n is the number of the registers declared by the instruction set architecture (ISA). These registers are set to be in the architectural register (AR) state; the remaining physical registers take on the avail-able state. When an issued instruction includes a destination register, a new rename buffer is needed. For this reason, one physical register is selected from the pool of the available registers and allocated to the concerned destination reg-ister. Accordingly, its state is set to the renamebuffer, not-valid state, and its valid bit is reset.After the associated instruction finishes execu-tion, the produced result is written into the allo-cated rename buffer. Its valid bit is set, and itsstate changes to rename buffer, valid. Later,when the associated instruction completes, theallocated rename buffer will be declared to bethe architectural register that implements the73SEPTEMBER–OCTOBER2000Figure 3. Generic types of rename buffers. Shaded boxes indicate the rename buffers.Figure 4. State transition diagram of a particular register of the merged architectural andrename register file.27AR: architectural register, RB: rename buffer.destination register specified in the just-completed instruction. Its state then changes to the architectural register state to reflect this. Note that in contrast to other rename buffer types, no data transfer is required for updat-ing the architectural registers in merged archi-tectural and rename register files. Instead, only the status of the related registers needs to be changed.Finally, when an old architectural register is reclaimed, it is set to the available state. Assuming dispatch-bound operand fetching, a possibility for reclaiming such old architec-tural registers is to keep track of the physical registers that have been the previous instances of the same architectural register, and reclaim the previous instance when the instruction incorporating the new instance completes. Also, not-yet-completed instructions must be canceled for exceptions or faulty executed speculative instructions. Then allocated rename buffers in a) the rename buffer, not-valid and b) the rename buffer, valid states are deallocated and changed to available states. In addition, the corresponding mappings—kept in either the mapping table or the rename buffer (as discussed later)—must be canceled. Merged architectural and rename register files are employed, for instance, in the high-end models (520-based models) of the IBM ES/9000 mainframes, Power and R1x000 processors, and Alpha 21264s.All other alternatives separate rename buffers from architectural registers.In the first “separated” variant, a stand-alone rename register file (or rename register file for short) is used exclusively to implement rename buffers. The PowerPC 603/620 and PA8x00 processors are examples of using rename register files.Alternatively, renaming can also be based on the reorder buffer (ROB); see “ROB prin-ciple” box. The ROB has recently been wide-ly used to preserve the sequential consistency of instruction execution. When using a ROB, an entry is assigned to each issued instruction for the duration of its execution. It’s quite nat-ural to use this entry for renaming as well—basically by extending it with a new field that will hold the result of that instruction. Exam-ples of processors using the ROB for renam-ing are the Am29000 superscalar, K5, K6, Pentium Pro, Pentium II, and Pentium III. The ROB can even be extended further to serve as a central shelving buffer as well. In this case, the ROB is also occasionally desig-nated as the DRIS (deferred scheduling reg-ister renaming instruction shelf). The Lightning processor proposal36and the K6 made use of this solution. Because the Light-ning proposal—which dates back to the beginning of the 1990s—was too ambitious in the light of the technology available at that time, it couldn’t be economically implement-ed and never reached the market.The last conceivable implementation alter-native of rename buffers is to use the shelving buffers for renaming (see the “Instruction shelving principle” box again). In this case, each shelving buffer must be extended func-tionally to also perform the task of a rename buffer. But this alternative has a drawback resulting from the different deallocation mech-anisms of the shelving and rename buffers. While shelving buffers can be reclaimed as soon as the instruction has been dispatched, rename buffers can be deallocated only at a later time, not earlier than the instruction has been completed. Thus, a deeper analysis is needed to reveal the appropriateness of using shelving buffers for renaming. To date, no processor has chosen this alternative.Split rename register filesFor simplicity’s sake, I’ve so far assumed that all data types are stored in a common archi-tectural register file. But usually, processors provide distinct architectural register files for fixed-point and floating-point data. Conse-quently, they typically employ distinct rename register files, as shown in Figure 5.As depicted in this figure, when the proces-sor employs the split-register principle, dis-74R ENAMING R EGISTERSIEEE MICROtinct fixed-point and floating-point register files are needed for merged files and stand-alone rename register files. In this case separate data paths are also needed to access the fixed-point and the floating-point registers. Recent processors typically incorporate split rename registers. When renaming takes place within the ROB, usually a single mech-anism is maintained for the preservation of the sequential consistency of instruction exe-cution. Then all renamed instructions are kept in the same ROB queue despite using split architectural register files for fixed-point and floating-point data. In this case, clearly, each ROB entry is expected to be long enough to hold either fixed-point or floating-point data.Number of rename buffersRename buffers keep register results tem-porarily until instructions complete. By tak-ing into account that not every instruction produces a register result, we can state that in a processor up to as many rename buffers are needed as the maximum number of instruc-tions that are in execution; that is, issued but not yet completed. Issued but not yet com-pleted instructions are either•held in shelving buffers waiting for exe-cution (if shelving is employed),•just been processed in execution units,•in the load queue waiting for cache access(if there is a load queue), or•in the store queue waiting for comple-tion, then forwarded to the cache to exe-cute the required store operation (if thereis a store queue).Thus, the maximal number of instructionsthat may have been issued but not yet com-pleted in the processor (npmax) isnpmax= wdw+ nEU+ nLq+ nSq(1)wherewdw is the width of the dispatch window(total number of shelving buffers),nEU is the number of the execution unitsthat may operate in parallel,nLq is the number of the entries in the loadqueue, andnSq is the number of the entries in the storequeue.Assuming a worst-case design approach,from this formula we can determine that thetotal number of rename buffers required(nrmax) isnrmax= wdw+ nEU+ nLq,(2)since instructions held in the store queue don’trequire rename buffers.Furthermore, if the processor includes aROB, based on Equation 1 we can say thatthe total number of ROB entries required(nROBmax) isnROBmax= npwax.(3)Nevertheless, if the processor has fewerrename buffers or fewer ROB entries thanexpected, according to the worst-caseapproach (as given by Equations 2 and 3) issueblockages can occur due to missing free75SEPTEMBER–OCTOBER2000Figure 5. Using split registers in the case of (a) merged register files, and (b) a stand-alone rename register file. FX indicates fixed point; FP indicates floating point.rename buffers or ROB entries. With a decreasing number of entries provided, we expect a smooth, slight performance degra-dation. Hence, a stochastic design approach is also feasible. There, the required number of entries is derived from the tolerated level of performance degradation.Based on Equations 1 to 3, the following relations are typically valid concerning the width of the processor’s dispatch window (wdw), the total number of the rename buffers (nr), and the reorder width (nROB), which equals the total number of ROB entries available:wdw< nr≤nROB(4) Table 1 summarizes the type and the num-ber of rename buffers provided in recent RISC and x86 superscalar processors. In addi-tion, Table 1 shows four key parameters of the enlisted processors: the issue rate, width of the dispatch window (wdw), total number of rename buffers provided (nr), and the reorder width (nROB).As the data in Table 1 indicates, the designs of most processors have taken into account the four interrelations. There are, however, two obvious exceptions. First, the PowerPC 604 provides 20 rename buffers, more than the processor’s reorder width of 16. In the sub-sequent PowerPC 620, Intel decreased the number to 16. Second, the R10000 provides only 32 ROB entries. This number is far too low compared to the dispatch width (48) and to the number of available rename buffers (64). MIPS addressed this disproportion in the R12000 by increasing the reorder width of the processor to 48.Number of read and write portsBy taking into account current practice, in the following discussion I assume split regis-ter files.Clearly, as many read ports are required in the rename buffers as there are data items that76R ENAMING R EGISTERS IEEE MICROthe rename buffers may need to supply in any one cycle. Note that rename buffers supply required operands for the instructions to be executed and also forward the results of the completed instructions to the addressed archi-tectural registers.The number of operands that need to be delivered in the same cycle depends first of all on whether the processor fetches operands dur-ing instruction issue or during instruction dis-patch. (See the “Operand fetch policies” box.)If operands are fetched issue bound, the rename buffers need to supply the operands for all instructions that are issued into the shelving buffers in the same cycle. Thus, both the fixed-point and floating-point rename buffers are expected to deliver in each cycle all required operands for up to as many instruc-tions as the issue rate. This means that in recent four-way superscalar processors the fixed-point and the floating-point rename buffers typically need to supply 8 and 12 operands respectively, assuming up to two fixed-point and three floating-point operands in each fixed-point and floating-point instruc-tion, respectively. If, however, there are some issue restrictions, the required number of read ports is decreased accordingly.In contrast, if the processor uses the dis-patch-bound fetch policy, the rename buffers should provide the operands for all instruc-tions that are forwarded from the dispatch window (instruction window) for execution in the same cycle. In this case, the fixed-point rename buffers need to supply the required fixed-point operands for the integer and load-store units (including register operands for the specified address calculations and fixed-point data for the fixed-point store instructions). The floating-point rename buffers need to deliver operands for the floating-point units (floating-point register data) and also for the load-store units (floating-point operands of the floating-point store instructions). In the Power3, for instance, this implies the follow-ing read port requirements. The fixed-point rename buffers need to have 12 read ports (up to 3 ×2 operands for the 3 integer-units as well as 2 ×2 address operands and 2 ×1 data operands for the 2 load-store units). On the other hand, the floating-point rename regis-ters need to have 8 read ports (up to 2 ×3 operands for the 2 floating-point units and 2 ×1 operands for the 2 load-store units).In addition, if rename buffers are imple-mented separately from the architectural reg-isters, the rename buffers must forward in eachcycle as many result values to the architectur-al registers as the completion rate (retire rate)of the processor. Since recent processors usu-ally complete up to four instructions per cycle,this task typically increases the required num-ber of read ports in the rename buffers by four.T oo many read ports in a register file mayunduly increase the physical size of the datapath and consequently the cycle time. Toavoid this problem, a few high-performanceprocessors (such as the Power2, Power3, andAlpha 21264) implement two copies of par-ticular register files. The Power2 duplicatesthe fixed-point architectural register file, thePower3 doubles both the fixed-point renameand the architectural file, and the Alpha21264 provides two copies of the fixed-pointmerged architectural and rename register file.As a result, fewer read ports are needed ineach of the copies. For example, with twocopies of the fixed-point merged register file,the Power3 needs only 10 read ports in eachfile, instead of 16 read ports in a fixed-pointregister file. A drawback of this approach is,however, that a scheme is also required to keepboth copies coherent.Now let’s turn to the required number ofwrite ports (input ports). Since in each cyclerename buffers need to accept all results pro-duced by the execution units, these buffersmust provide as many write ports as results theexecution units may produce per cycle. Thefixed-point rename buffers receive results fromthe available integer-execution units and fromthe load-store units (fetched fixed-point data).In contrast, the floating-point rename buffershold the results of the floating-point executionunits and the load-store units (fetched float-77SEPTEMBER–OCTOBER2000ing-point data). Most results are single data items requiring one write port. However, there are a few exceptions. When execution units generate two data items, they require two write ports as well, similar to the PowerPC proces-sor load-store units. After execution of the LOAD-WITH-UPDATE instruction, these units return both the fetched data value and the updated address value.Register mapping methodsDuring renaming, the processor needs to allocate rename buffers to the destination reg-isters of the instructions (or usually to every instruction to simplify logic). It also must keep track of the mappings actually used and deallocate rename buffers no longer used. Accordingly, the related aspect of the design space has three components:•allocation scheme of the rename buffers,•method of keeping track of actual map-pings, and•deallocation scheme of rename buffers. As far as the allocation scheme of rename buffers is concerned, rename buffers are usu-ally allocated to instructions during instruc-tion issue. If rename buffers are assigned to the instructions as early as during instruction issue, rename buffer space is wasted, since rename buffers are not needed until the results become available in the last execution cycle. Delaying the allocation of rename buffers to the instructions37saves rename buffer space. Various schemes have been proposed for this, such as virtual renaming37-40 and others.41In fact, a virtual allocation scheme has already been introduced into the Power3.37 Established mappings must be maintained until their invalidation. There are two possi-bilities for keeping track of the actual map-ping of particular architectural registers to allocated rename buffers. The processor can use a mapping table for this or can track the actual register mapping within the rename buffers themselves. See Figure 6.A mapping table has as many entries as there are architectural registers provided by the instruction set architecture (usually 32). Each entry holds a status bit (called the entry valid bit in F igure 6a), which indicates whether the associated architectural register is renamed. Each valid entry supplies the index of the rename buffer, which is allocat-ed to the architectural register belonging to that entry (called the RB index). For instance, Figure 6a shows that the mapping table holds a valid entry for architectural register r7, which contains the RB index of 12. This indi-cates that architectural register r7 is actually renamed to rename buffer 12.Each entry is set up during instruction issue, while new rename buffers are allocated78R ENAMING R EGISTERS IEEE MICROFigure 6. Methods for keeping track of the actual mapping of architectural registers to rename buffers: using a mapping table (a) and mapping within rename buffers (b).to the issued instructions. A valid mapping is updated when the architectural register belonging to that entry is renamed again. It will be invalidated when the related mapping is no longer needed and the allocated rename buffer is reclaimed. In this way, the mapping table continuously provides the latest alloca-tions. Source registers are renamed by access-ing the mapping table with the register numbers as indices and fetching the associat-ed rename buffer identifiers (RB indices), as Figure 6a shows.Obviously, for split architectural register files, separate fixed-point and floating-point mapping tables are needed.As discussed earlier, mapping tables should provide one read port for each source operand that may be fetched in any one cycle and one write port for each rename buffer that may be allocated in any one cycle.The other fundamentally different alterna-tive for keeping track of actual register map-pings relies on an associative mechanism (see Figure 6b). In this case no mapping table exists, but each rename buffer holds the iden-tifier of the associated architectural register (usually the register number of the renamed destination register) and additional status bits. These entries are set up during instruction issue when a particular rename buffer is allo-cated to a specified destination register. As Fig-ure 6b shows, in this case each rename buffer holds the following five pieces of information:• a status bit, which indicates that thisrename buffer is actually allocated (calledthe entry valid bit in the figure),•the identifier of the associated architec-tural register (Dest. Reg. No.),• a further status bit, called the latest bit,whose role will be explained later,•another status bit, called the value validbit, which shows whether the actual valueof the associated architectural register hasalready been generated, and•the value itself, provided that the valuevalid bit signifies an already producedresult.The latest bit marks the last allocation of a given architectural register if it has more than one valid allocation due to repeated renam-ing. For instance, in our example architectur-al register r7 has two subsequent allocations.From these, entry 12 is the latest one as its lat-est bit has been set. Thus, in Figure 6b, renam-ing source register r7 would yield the RBindex of 12. This method of renaming sourceregisters requires an associative lookup in allentries searching for the latest allocation ofthe given source register.With issue-bound operand fetching, sourceregisters are both renamed and accessed duringthe issue process. For this reason, in this case,processors usually integrate renaming andoperand accessing, and therefore keep track ofthe register mapping within the renamebuffers. For dispatch-bound operand fetching,however, these tasks are separated. Source reg-isters are renamed during instruction issue,whereas the source operands are accessed whilethe processor dispatches the instructions to theexecution units. Therefore, in this case, proces-sors typically use mapping tables.If rename buffers are no longer needed, theyshould be reclaimed (deallocated). Thescheme of deallocation depends on key aspectsof the overall renaming process. In particular,they depend on the allocation scheme of therename buffers, the type of rename buffersused, the method of keeping track of actualallocations, and even whether issue-bound ordispatch-bound operands are fetched. How-ever, lack of space restricts discussion of thisaspect of the design space in detail here.Rename rateAs its name suggests, the rename rate standsfor the maximum number of renames that aprocessor can perform in a cycle. Basically, theprocessor should rename all instructionsissued in the same cycle to avoid performancedegradation. Thus, the rename rate shouldequal the issue rate. This is easier said thandone, since it is not at all an easy task to imple-ment a high rename rate (four or higher). T woreasons make it difficult.First, for higher rename rates the detectionand handling of interinstruction dependenciesduring renaming becomes a more complextask. Second, higher rename rates require alarger number of read and write ports on reg-ister files and mapping tables. For instance, thefour-way superscalar R10000 can issue anycombination of four fixed-point and floating-point instructions. Accordingly, its fixed-point79SEPTEMBER–OCTOBER2000。
Foundamental analysis
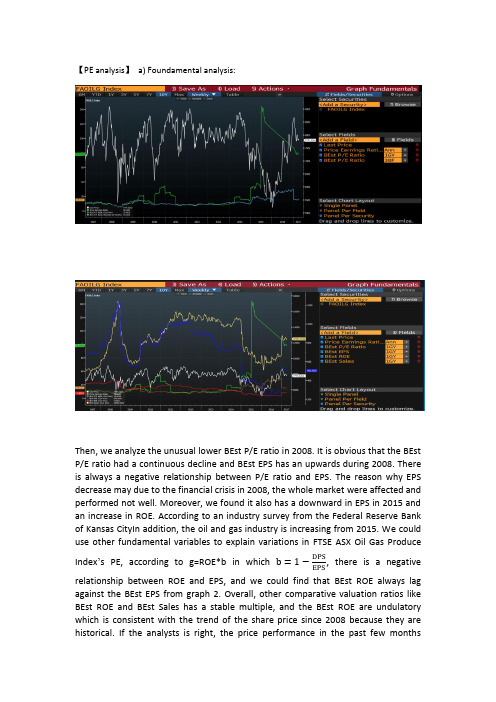
【PE analysis】a) Foundamental analysis:Then, we analyze the unusual lower BEst P/E ratio in 2008. It is obvious that the BEst P/E ratio had a continuous decline and BEst EPS has an upwards during 2008. There is always a negative relationship between P/E ratio and EPS. The reason why EPS decrease may due to the financial crisis in 2008, the whole market were affected and performed not well. Moreover, we found it also has a downward in EPS in 2015 and an increase in ROE. According to an industry survey from the Federal Reserve Bank of Kansas CityIn addition, the oil and gas industry is increasing from 2015. We could use other fundamental variables to explain variations in FTSE ASX Oil Gas Produce, there is a negative Index’s PE, according to g=ROE*b in which b=1−DPSEPSrelationship between ROE and EPS, and we could find that BEst ROE always lag against the BEst EPS from graph 2. Overall, other comparative valuation ratios like BEst ROE and BEst Sales has a stable multiple, and the BEst ROE are undulatory which is consistent with the trend of the share price since 2008 because they are historical. If the analysts is right, the price performance in the past few monthswould accompany improving fundamentals, which could have an upward revision in the FTSE ASX Oil Gas Produce Index’s fundamentals.b) Contrarian analysis:Graph3: The market dada of the FAOILG Index and the calculation of market returnAccording to Lakonishok et al.’s contrarian strategy, we assume that the FTSE ASX Oil Gas Produce Index’s average market returns is the expected market return. Through the calculation, the Average Market Return=[(-29.44%)+29.21%+(-7.90%)+(-0.95%)+(-12.13%)+6.76%+7.82%+0.05%+55.56%+(-8. 44%)]/10=4.054% We suppose g=0and beta=1, Since g=ROE∗b,b=0.=1/E(Rm)= 1/4.054% = 24.6670 for all firms in this sector.So PE ratio =1−bk−gWe can see from above calculations that the PE ratio is lower than the average PE ratio in graph1 (24.6670<78.1202), thus the sector may be undervalued.c) RecommendationIn summary, after the P/E analysis, the FAOILG have an outperform than ASX Index, Thus, I recommend investors to invest the sector and to buy, because it is undervalued and the price will be increased based on the prediction.。
Dell

Dell™ PowerEdge™ 2850 Systems Installation and Troubleshooting Guide IntroductionIndicators, Messages, and CodesFinding Software SolutionsRunning System DiagnosticsTroubleshooting Your SystemInstalling System OptionsInstalling DrivesGetting HelpJumpers and ConnectorsI/O ConnectorsNotes, Notices, and CautionsAbbreviations and AcronymsFor a complete list of abbreviations and acronyms, see the "Glossary" in the User's Guide .Information in this document is subject to change without notice.© 2004 Dell Inc. All rights reserved.Reproduction in any manner whatsoever without the written permission of Dell Inc. is strictly forbidden.Trademarks used in this text: Dell , the DELL logo, Inspiron , Dell Precision , Dimension , OptiPlex , PowerApp , PowerEdge , PowerConnect , PowerVault , DellNet , Axim , and Latitude are trademarks of Dell Inc.; Microsoft , MS-DOS , and Windows are registered trademarks of Microsoft Corporation.Other trademarks and trade names may be used in this document to refer to either the entities claiming the marks and names or their products. Dell Inc. disclaims any proprietary interest in trademarks and trade names other than its own.June 2004NOTE: A NOTE indicates important information that helps you make better use of your computer.NOTICE: A NOTICE indicates either potential damage to hardware or loss of data and tells you how to avoid the problem.CAUTION: A CAUTION indicates a potential for property damage, personal injury, or death.Back to Contents PageJumpers and ConnectorsDell™ PowerEdge™ 2850 Systems Installation and Troubleshooting GuideJumpers —A General ExplanationSystem Board JumpersSystem Board ConnectorsExpansion-Card Riser-Board Components and PCI BusesSCSI Backplane Board ConnectorsDisabling a Forgotten PasswordThis section provides detailed information about the system jumpers. It also provides some basic information on jumpers and switches and describes the connectors on the various boards in the system.Jumpers —A General ExplanationJumpers provide a convenient and reversible way of reconfiguring the circuitry on a printed circuit board. When reconfiguring the system, you may need to change jumper settings on circuit boards or drives.JumpersJumpers are small blocks on a circuit board with two or more pins emerging from them. Plastic plugs containing a wire fit down over the pins. The wire connects the pins and creates a circuit. To change a jumper setting, pull the plug off its pin(s) and carefully fit it down onto the pin(s) indicated. Figure A -1 shows an example of a jumper.Figure A-1. Example JumpersA jumper is referred to as open or unjumpered when the plug is pushed down over only one pin or if there is no plug at all. When the plug is pushed down over two pins, the jumper is referred to as jumpered. The jumper setting is often shown in text as two numbers, such as 1-2. The number 1 is printed on the circuit board so that you can identify each pin number based on the location of pin 1.Figure A -2 shows the location and default settings of the system jumper blocks. See Table A -1 for information about the system jumper designations, default settings, and functions.System Board JumpersFigure A -2 shows the location of the configuration jumpers on the system board. Table A -1 lists the settings for the jumpers.Figure A-2. System Board JumpersCAUTION: Ensure that the system is turned off before you change a jumper setting. Otherwise, damage to the system or unpredictable results may occur.NOTE: Lift up the memory module airflow shroud for easy access to the jumpers.Table A-1. System Board Jumper SettingsJumperSettingDescriptionPASSWD(default)The password feature is enabled.The password feature is disabled.NVRAM_CLR(default)The configuration settings are retained at system boot.Table A-2. System Board ConnectorsConnectorDescriptionBACKPLANE 2U5U Backplane connectorBATTERY System batteryDIMM nX Memory modules (6), where n is the slot in the bank and X is the bank FAN_n Cooling fans:l 1 — optional microprocessor 2l 2, 3, 4 — microprocessor 1l 5, 2U_6 — system fansPROC n Microprocessors (2)Figure A-5 shows the components on the optional PCI-X/PCIe expansion-card riser board, including the expansion-card slots and buses. Table 6-2 lists the PCI bus and operating speed for each expansion-card slot.Figure A-5. Optional PCI-X/PCIe Expansion-Card Riser Board ComponentsSCSI Backplane Board ConnectorsFigure A -6 shows the location of the connectors on the SCSI backplane board.Figure A-6. SCSI Backplane Board ComponentsDisabling a Forgotten PasswordThe system's software security features include a system password and a setup password, which are discussed in detail in "Using the System Setup Program" in the User's Guide . The password jumper enables these password features or disables them and clears any password(s) currently in use.1.Turn off the system, including any attached peripherals, and disconnect the system from the electrical outlet.2.Open the system. See "Opening the System " in "Troubleshooting Your System."NOTICE: See "Protecting Against Electrostatic Discharge" in the safety instructions in your Product Information Guide .3.Lift up the memory module shroud.4.Remove the jumper plug from the password jumper.See Figure A -2 to locate the password jumper (labeled "PASSWD") on the system board.5.Close the system. See "Closing the System " in "Troubleshooting Your System."6.Reconnect your system and peripherals to their electrical outlets, and turn on the system.The existing passwords are not disabled (erased) until the system boots with the password jumper plug removed. However, before you assign a new system and/or setup password, you must install the jumper plug.7.Turn off the system, including any attached peripherals, and disconnect the system from the electrical outlet.8.Open the system. See "Opening the System " in "Troubleshooting Your System."9.Install the jumper plug on the password jumper.10.Lower the memory module shroud.11.Close the system. See "Closing the System " in "Troubleshooting Your System."12.Reconnect your system and peripherals to their electrical outlets, and turn on the system.13.Assign a new system and/or setup password.To assign a new password using the System Setup program, see "Assigning a System Password" in the User's Guide .Back to Contents PageNOTE: If you assign a new system and/or setup password with the jumper plug still removed, the system disables the new password(s) the nexttime it boots.Table B-1 shows the icons used to label the connectors on the system. Table B-1. I/O Connector IconsTable B-2. Serial Connector Pin AssignmentsTable B-3. Keyboard and Mouse Connector Pin Assignments Table B-4. Video Connector Pin AssignmentsTable B-5. USB Connector Pin Assignments Table B-6. NIC Connector Pin AssignmentsNetwork Cable RequirementsThe NIC supports a UTP Ethernet cable equipped with a standard RJ45-compatible plug. Observe the following cabling restrictions. lUse Category 5 or greater wiring and connectors. l Do not exceed a cable run length (from a workstation to a hub) of 100 m (328 ft).For detailed guidelines on operation of a network, see "Systems Considerations of Multi-Segment Networks" in the IEEE 802.3 standard. Back to Contents PageNOTICE: To avoid line interference, voice and data lines must be in separate sheaths.Back to Contents PageIntroductionDell™ PowerEdge™ 2850 Systems Installation and Troubleshooting Guide Other Documents You May Need Obtaining Technical AssistanceYour high-speed system offers significant service and upgrade features. The system includes the following service features to make troubleshooting and repair easy and effective:lEmbedded remote access hardware, which monitors temperatures and voltages throughout the system and notifies you if the system overheats, if a system cooling fan malfunctions, or if a power supply failsl Redundant, hot-pluggable cooling fansl Redundant, hot-pluggable power supplieslSystem diagnostics, which checks for hardware problems (if the system can boot)System upgrade options are offered, including:l An additional microprocessorl Additional system memoryl A variety of PCI, PCI Express (PCIe), and PCI-X expansion-card options (including RAID controller cards)lAn integrated RAID controller that can be activated with an additional memory module, key, and batteryOther Documents You May Needl The Rack Installation Guide or Rack Installation Instructions included with your rack solution describes how to install your system into a rack.l The Getting Started Guide provides an overview of initially setting up your system.l The User's Guide provides information about system features and technical specifications.l The Installation and Troubleshooting Guide describes how to troubleshoot the system and install or replace system components.l Systems management software documentation describes the features, requirements, installation, and basic operation of the software.l Operating system documentation describes how to install (if necessary), configure, and use the operating system software.l Documentation for any components you purchased separately provides information to configure and install these options.lUpdates are sometimes included with the system to describe changes to the system, software, and/or documentation.lRelease notes or readme files may be included to provide last-minute updates to the system or documentation or advanced technical reference material intended for experienced users or technicians.Obtaining Technical AssistanceIf at any time you do not understand a procedure described in this guide or if your system does not perform as expected, a number of tools are provided to help you. For more information on these help tools, see "Getting Help ."Back to Contents PageThe Product Information Guide provides important safety and regulatory information. Warranty information may be included within this document or as a separate document.NOTE: Always read the updates first because they often supersede information in other documents.NOTE: Hard drives bays are numbered 0 through 5 starting at the lower leftmost drive bay. Table 2-2. Front-Panel LED Indicators, Buttons, and Connectorsidentification buttonTable 2-3 lists the drive indicator patterns. Different patterns are displayed as drive events occur in the system. For example, if a hard-drive fails, the "drive failed" pattern appears. After the drive is selected for removal, the "drive being prepared for removal" pattern appears, followed by the "drive ready for insertion or removal" pattern. After the replacement drive is installed, the "drive being prepared for operation" pattern appears, followed by the "drive online" pattern.Table 2-3. Hard-Drive Indicator PatternsTable 2-4. Back-Panel FeaturesNOTE: If RAID is not activated, only the "drive online" indicator pattern appears. The drive-activity indicator also blinks when the drive is being accessed.ComponentDescriptionPower supply indicators Provides information on power status. See "Power Indicator CodesTable 2-6. Power-Supply Indicator CodesIndicatorIndicator CodeTable 2-7. NIC Indicator CodesBack to Contents PageRunning System DiagnosticsDell™ PowerEdge™ 2850 Systems Installation and Troubleshooting Guide Using Server Administrator Diagnostics System Diagnostics FeaturesWhen to Use the System Diagnostics Running the System Diagnostics System Diagnostics Testing Options Using the Advanced Testing Options Error MessagesIf you experience a problem with your system, run the diagnostics before calling for technical assistance. The purpose of the diagnostics is to test yoursystem's hardware without requiring additional equipment or risking data loss. If you are unable to fix the problem yourself, service and support personnel can use diagnostics test results to help you solve the problem.Using Server Administrator DiagnosticsTo assess a system problem, first use the online Server Administrator diagnostics. If you are unable to identify the problem, then use the system diagnostics. To access the online diagnostics, log into the Server Administrator home page, and then click the Diagnostics tab. For information about using diagnostics, see the online help. For additional information, see the Server Administrator User's Guide .System Diagnostics FeaturesThe system diagnostics provides a series of menus and options for particular device groups or devices. The system diagnostics menus and options allow you to:l Run tests individually or collectively.l Control the sequence of tests.l Repeat tests.l Display, print, or save test results.l Temporarily suspend testing if an error is detected or terminate testing when a user-defined error limit is reached.l View help messages that briefly describe each test and its parameters.l View status messages that inform you if tests are completed successfully.lView error messages that inform you of problems encountered during testing.When to Use the System DiagnosticsIf a major component or device in the system does not operate properly, component failure may be indicated. As long as the microprocessor and the system's input/output devices (monitor, keyboard, and diskette drive) are functioning, you can use the system diagnostics to help identify the problem.Running the System DiagnosticsThe system diagnostics can be run either from the utility partition on your hard drive or from a set of diskettes that you create using the Dell OpenManage Server Assistant CD.From the Utility Partition1.As the system boots, press <F10> during POST.2.From the utility partition main menu under Run System Utilities , select Run System Diagnostics .From the Diagnostics DiskettesNOTICE: Use the system diagnostics to test only your system. Using this program with other systems may cause invalid results or error messages. In addition, use only the program that came with your system (or an updated version of that program).Probleml Monitor is not working properly.l Video memory is faulty.Action1.Check the system and power connections to the monitor.2.Run the appropriate online diagnostic test. See "Using Server Administrator Diagnostics" in "Running System Diagnostics."If the tests run successfully, the problem is not related to video hardware. See "Finding Software Solutions."If the tests fail, see "Getting Help."Troubleshooting the KeyboardProbleml System message indicates a problem with the keyboard.l Keyboard is not functioning properly.Action1.Ensure that the keyboard is properly connected to the system.2.Run the appropriate online diagnostic test. See "Using Server Administrator Diagnostics" in "Running System Diagnostics."3.Press each key on the keyboard, and examine the keyboard and its cable for signs of damage.4.Swap the faulty keyboard with a working keyboard.If the problem is resolved, replace the faulty keyboard. See "Getting Help."If the problem is not resolved, see "Getting Help."Troubleshooting the MouseProbleml System message indicates a problem with the mouse.l Mouse is not functioning properly.Action1.Ensure that the mouse is properly connected to the system.2.Run the appropriate online diagnostic test. See "Using Server Administrator Diagnostics" in "Running System Diagnostics."If the test fails, continue to the next step.3.Examine the mouse and its cable for signs of damage.If the mouse is not damaged, go to step 5.If the mouse is damaged, continue to the next step.4.Swap the faulty mouse with a working mouse.If the problem is resolved, replace the faulty mouse. See "Getting Help."5.Enter the System Setup program and ensure that the mouse controller is enabled. See "Using the System Setup Program" in your User's Guide.If the problem is not resolved, see "Getting Help."Troubleshooting Basic I/O FunctionsProbleml Error message indicates a problem with the serial port.l Device connected to the port is not operating properly.Action1.Enter the System Setup program and ensure that the serial port is enabled. See "Using the System Setup Program" in the User's Guide.2.If the problem is confined to a particular application, see the application documentation for specific port configuration requirements that the programmay require.3.Run the appropriate online diagnostic test. See "Using Server Administrator Diagnostics" in "Running System Diagnostics."If the tests run successfully but the problem persists, see "Troubleshooting a Serial I/O Device."Troubleshooting a Serial I/O DeviceProbleml Device connected to the serial port is not operating properly.Action1.Turn off the system and any peripheral devices connected to the serial port.2.Swap the serial interface cable with a working cable, and turn on the system and the serial device.If the problem is resolved, replace the interface cable. See "Getting Help."3.Turn off the system and the serial device, and swap the device with a comparable device.4.Turn on the system and the serial device.If the problem is resolved, replace the serial device. See "Getting Help."If the problem persists, see "Getting Help."Troubleshooting a USB DeviceProbleml System message indicates a problem with a USB device.l Device connected to a USB port is not operating properly.Action1.Enter the System Setup program, and ensure that the USB ports are enabled. See "Using the System Setup Program" in your User's Guide.2.Turn off the system and any USB devices.3.Disconnect the USB devices, and connect the malfunctioning device to the other USB connector.4.Turn on the system and the reconnected device.If the problem is resolved, the USB connector might be defective. See "Getting Help."5.If possible, swap the interface cable with a working cable.If the problem is resolved, replace the interface cable. See "Getting Help."6.Turn off the system and the USB device, and swap the device with a comparable device.7.Turn on the system and the USB device.If the problem is resolved, replace the USB device. See "Getting Help."If the problem persists, see "Getting Help."Troubleshooting a NICProbleml NIC cannot communicate with network.Action1.Run the appropriate online diagnostic test. See "Using Server Administrator Diagnostics" in "Running System Diagnostics."2.Check the appropriate indicator on the NIC connector. See "NIC Indicator Codes" in "Indicators, Messages, and Codes."l If the link indicator does not light, check all cable connections.l If the activity indicator does not light, the network driver files might be damaged or missing.Remove and reinstall the drivers if applicable. See the NIC's documentation.l Change the autonegotiation setting, if possible.l Use another connector on the switch or hub.If you are using a NIC card instead of an integrated NIC, see the documentation for the NIC card.3.Ensure that the appropriate drivers are installed and the protocols are bound. See the NIC's documentation.4.Enter the System Setup program and confirm that the NICs are enabled. See "Using the System Setup Program" in your User's Guide.5.Ensure that the NICs, hubs, and switches on the network are all set to the same data transmission speed. See the network equipment documentation.6.Ensure that all network cables are of the proper type and do not exceed the maximum length. See "Network Cable Requirements" in your User's Guide.Responding to a Systems Management Software Alert MessageSystems management software monitors critical system voltages and temperatures, fans, and hard drives in the system. Alert messages appear in the Alert Log window. For information about the Alert Log window, see the systems management software documentation.Inside the SystemCAUTION: Only trained service technicians are authorized to remove the system cover and access any of the components inside the system. See your Product Information Guide for complete information about safety precautions, working inside the computer, and protecting againstelectrostatic discharge.In Figure 5-1, the covers and bezel are removed to provide an interior view of the system.Figure 5-1. Inside the SystemThe system board holds the system's control circuitry and other electronic components. Several hardware options, such as the microprocessors and memory, are installed directly on the system board. The expansion-card cage accommodates up to three full-length PCI, PCIe, or PCI-X expansion cards.The system provides space for a 3.5-inch diskette drive and an optical drive. The optical drive and the diskette drive trays connect to the controllers on the system board through the SCSI backplane board. For more information, see "Installing Drives."The hard-drive bays provide space for up to six 1-inch SCSI hard drives. The hard drives connect to a controller on the system board or a RAID controller card through the SCSI backplane board. For more information, see "Installing Drives."During an installation or troubleshooting procedure, you may be required to change a jumper setting. For more information, see "Jumpers and Connectors."Removing the BezelThe bezel has a system status indicator. A lock on the bezel restricts access to the power button, diskette drive, optical drive, hard drive(s), and the interior of the system.ing the system key, unlock the bezel.2.Press the tab at the left end of the bezel.3.Rotate the left end of the bezel away from the system to release the right end of the bezel.4.Pull the bezel away from the system. See Figure 5-2.Figure 5-2. Removing the BezelReplacing the Bezel1.Fit the tabs on the right end of the bezel into the corresponding slots in the front panel.2.Rotate the left end of the bezel toward the system to secure the left end of the bezel.ing the system key, lock the bezel.Opening the SystemTo upgrade or troubleshoot the system, remove the system cover to gain access to internal components.1.Remove the bezel. See "Removing the Bezel ."2.Loosen the two thumbscrews that secure the cover to the chassis. See Figure 5-3.3.Slide the top cover backward and grasp the cover at both sides.4.Carefully lift the cover away from the system.Figure 5-3. Removing the CoverClosing the System1.Ensure that no tools or parts are left inside the system and that any cables are routed so that they will not be damaged by the cover.2.Align the cover with the cover alignment hooks on the sides of the chassis, and slide the cover forward. See Figure 5-3.When the cover is properly closed, the back alignment tab protrudes from the slot on the back of the cover.3.Tighten the two thumbscrews that secure the cover to the chassis.4.Replace the bezel. See "Replacing the Bezel ."Troubleshooting a Wet SystemProbleml Liquid spilled on the system.CAUTION: Only trained service technicians are authorized to remove the system cover and access any of the components inside the system. See your Product Information Guide for complete information about safety precautions, working inside the computer, and protecting againstelectrostatic discharge.l Excessive humidity.Action1.Turn off the system and attached peripherals, and disconnect the system from the electrical outlet.2.Open the system. See "Opening the System ."3.Remove all expansion cards installed in the system. See "Removing an Expansion Card " in "Installing System Options."4.Let the system dry thoroughly for at least 24 hours.5.Close the system. See "Closing the System ."6.Reconnect the system to the electrical outlet, and turn on the system and attached peripherals.If the system does not start properly, see "Getting Help ."7.If the system starts properly, shut down the system and reinstall all of the expansion cards that you removed. See "Installing an Expansion Card " in"Installing System Options."8.Run the appropriate online diagnostic test. See "Using Server Administrator Diagnostics " in "Running the System Diagnostics."If the tests fail, see "Getting Help ."Troubleshooting a Damaged SystemProbleml System was dropped or damaged.Action1.Open the system. See "Opening the System ."2.Ensure that the following components are properly installed:l Expansion cardsl Power suppliesl Fansl Drive-carrier connections to the SCSI backplane board, if applicable3.Ensure that all cables are properly connected.4.Close the system. See "Closing the System ."5.Run the system board tests in the system diagnostics. See "Running System Diagnostics ."If the tests fail, see "Troubleshooting Your System ."Troubleshooting the System BatteryCAUTION: Only trained service technicians are authorized to remove the system cover and access any of the components inside the system. See your Product Information Guide for complete information about safety precautions, working inside the computer, and protecting againstelectrostatic discharge.CAUTION: Only trained service technicians are authorized to remove the system cover and access any of the components inside the system. See your Product Information Guide for complete information about safety precautions, working inside the computer, and protecting againstelectrostatic discharge.ProblemlSystem message indicates a problem with the battery. lSystem Setup program loses system configuration information. l System date and time do not remain current.Action1.Re-enter the time and date through the System Setup program. See "Using the System Setup Program" in your User's Guide .2.Turn off the system and disconnect it from the electrical outlet for at least one hour.3.Reconnect the system to the electrical outlet and turn on the system.4.Enter the System Setup program.If the date and time are not correct in the System Setup program, replace the battery. See "System Battery " in "Installing System Options."If the problem is not resolved by replacing the battery, see "Getting Help ."Troubleshooting Power SuppliesProblemlSystem-status indicators are amber. lPower-supply fault indicators are amber. l Front-panel status LCD indicates a problem with the power supply.Action1.Run the appropriate online diagnostics test. See "Using Server Administrator Diagnostics " in "Running the System Diagnostics."2.Locate the faulty power supply.The power supply's fault indicator is lit. See "Redundant Power-Supply Indicator Codes " in "Indicators, Messages, and Codes."3.Ensure that the power supply is properly installed by removing and reinstalling it. See "Power Supplies " in "Installing System Options."4.If reseating the power supply did not resolve the problem, remove the faulty power supply. See "Removing a Power Supply " in "Installing SystemOptions."5.Install a new power supply. See "Replacing a Power Supply " in "Installing System Options."If the problem persists, see "Getting Help ."Troubleshooting System Cooling ProblemsNOTE: If the system is turned off for long periods of time (for weeks or months), the NVRAM may lose its system configuration information. This situation is caused by a defective battery.NOTE: Some software may cause the system time to speed up or slow down. If the system seems to operate normally except for the time kept in the System Setup program, the problem may be caused by software rather than by a defective battery.NOTICE: You can hot-plug the power supplies. One power supply must be installed for the system to operate. The system is in the redundant mode when two power supplies are installed. Remove and install only one power supply at a time in a system that is powered on. Operating the system with only one power supply installed and without a power supply blank installed for extended periods of time can cause the system to overheat.NOTE: After installing a power supply, allow several seconds for the system to recognize the power supply and to determine if it is workingproperly. The power indicator turns green to signify that the power supply is functioning properly. See "Redundant Power-Supply Indicator Codes "in "Indicators, Messages, and Codes."。
英语高考试卷原卷

Section I: Listening Comprehension (25 points)Directions: In this section, you will hear 10 short conversations and 3 long conversations. After each conversation, one or more questions will be asked about what was said. Both the conversation and the questions will be spoken only once. After each question, there will be a pause. During the pause, you must read the four choices marked A), B), C), and D), and decide which is the best answer. Then mark the corresponding letter on Answer Sheet 1 with a single line through the centre.1. A) He is a teacher. B) He is a student. C) He is a doctor. D) He is a writer.2. A) She will go to the library. B) She will go to the cinema. C) She will go to the supermarket. D) She will go to the post office.3. A) She is interested in sports. B) She is good at playing chess. C) She is passionate about painting. D) She is fond of reading books.4. A) The man will buy a new car. B) The man will sell his old car. C) The man will take the bus. D) The man will walk to work.5. A) She will cook dinner. B) She will go shopping. C) She will watch a movie. D) She will go to bed early.6. A) He is a lawyer. B) He is a doctor. C) He is a teacher. D) He is a journalist.7. A) The woman will go to the beach. B) The woman will go to the park.C) The woman will go to the museum. D) The woman will go to the cinema.8. A) He is going to study abroad. B) He is going to find a job. C) Heis going to travel. D) He is going to retire.9. A) She is a doctor. B) She is a teacher. C) She is a nurse. D) She isa student.10. A) He is a student. B) He is a teacher. C) He is a doctor. D) He isa writer.Section II: Structure and Vocabulary (25 points)Directions: There are 10 incomplete sentences in this section. For each sentence there are four choices marked A), B), C), and D). Choose the one that best completes the sentence. Then mark the corresponding letter on Answer Sheet 1 with a single line through the centre.11. I am going to ________ (go) to the party tonight.A) go B) went C) going D) gone12. She ________ (not be) able to come because she is sick.A) doesn't B) isn't C) hasn't D) won't13. The teacher said that the test ________ (be) difficult for us.A) would B) will C) is D) was14. If I ________ (know) the answer, I would have helped you.A) know B) knew C) have known D) had known15. She ________ (not like) to go out in the rain.A) doesn't B) didn't C) hasn't D) won't16. He ________ (be) late for work every day.A) always B) usually C) often D) seldom17. The book ________ (be) very interesting.A) is B) was C) will be D) would be18. She ________ (not go) to the party because she is too busy.A) doesn't B) isn't C) hasn't D) won't19. I ________ (not see) him for a long time.A) haven't B) didn't C) won't D) wouldn't20. ________ (be) careful when you cross the road.A) You must B) You are C) You were D) You willSection III: Reading Comprehension (30 points)Directions: There are 3 passages in this section. Each passage is followed by some questions or unfinished statements. For each of them there are four choices marked A), B), C), and D). You should decide on the best choice and mark the corresponding letter on Answer Sheet 1 with a single line through the centre.Passage 1When it comes to exercise, many people believe that they need to spend hours at the gym to get in shape. However, recent studies have shownthat short bursts of high-intensity exercise can be just as effective. This type of exercise, known as High-Intensity Interval Training (HIIT), involves short periods of intense exercise followed by short rest periods.The benefits of HIIT are numerous. It can help improve cardiovascular health, increase muscle strength, and burn fat more efficiently than traditional long-duration exercise. Additionally, HIIT can be more convenient for people with busy schedules, as it can be completed in as little as 20 minutes.Questions 21-25:21. What is the main idea of the passage?A) The importance of exercise for health.B) The benefits of high-intensity interval training.C) The disadvantages of traditional exercise.D) The reasons why people avoid exercise.22. Which of the following is NOT a benefit of HIIT?A) Improved cardiovascular health.B) Increased muscle strength.C) Longer rest periods.D) Efficient fat burning.23. What is the advantage of HIIT for people with busy schedules?A) It requires less time.B) It is more enjoyable.C) It is less intense.D) It is more effective.24. How long does a typical HIIT session last?A) 20 minutesB) 30 minutesC) 45 minutesD) 1 hour25. What is the tone of the passage?A) NegativeB) PositiveC) NeutralD) CriticalPassage 2The internet has revolutionized the way we communicate and access information. While it has brought numerous benefits, it has also introduced several challenges. One of the most significant challenges is the spread of misinformation. With the vast amount of information available online, it can be difficult to discern what is true and whatis false.Misinformation can have serious consequences. It can lead to misunderstandings, harm reputations, and even influence elections. To combat this problem, it is important for individuals to develop criticalthinking skills and verify the accuracy of the information they encounter.One way to do this is by checking the sources of information. Reliable sources are more likely to provide accurate information. Additionally, individuals should be cautious of information that is presented without evidence or is from unknown sources.Questions 26-30:26. What is the main topic of the passage?A) The benefits of the internet.B) The challenges of the internet.C) The role of critical thinking in the digital age.D) The impact of misinformation on society.27. What is the main challenge mentioned in the passage?A) The lack of access to information.B) The spread of misinformation.C) The difficulty of finding reliable sources.D) The lack of internet connectivity.28. What can individuals do to combat the spread of misinformation?A) They should avoid using the internet.B) They should rely on their intuition.C) They should develop critical thinking skills.D) They should ignore the information they find online.29. Why is it important to check the sources of information?A) To save time.B) To ensure accuracy.C) To avoid boredom.D) To impress others.30. What is the tone of the passage?A) NegativeB) PositiveC) NeutralD) CriticalPassage 3Climate change is one of the most pressing issues of our time. It is caused by human activities, such as the burning of fossil fuels and deforestation, which release greenhouse gases into the atmosphere. These gases trap heat, leading to a rise in global temperatures and a range of negative impacts, including extreme weather events, rising sea levels, and the loss of biodiversity.To address climate change, it is important to take action at both the individual and global levels. Individuals can reduce their carbon footprint by adopting sustainable practices, such as reducing energy consumption, using public transportation, and consuming less meat. On a global scale, governments and organizations need to work together to implement policies that reduce greenhouse gas emissions and promote renewable energy.Questions 31-35:31. What is the main topic of the passage?A) The causes of climate change.B) The effects of climate change.C) The solutions to climate change.D) The importance of sustainable practices.32. What are the human activities that contribute to climate change?A) The use of renewable energy.B) The reduction of energy consumption.C) The burning of fossil fuels and deforestation.D) The promotion of public transportation.33. What are some of the negative impacts of climate change?A) Improved agricultural productivity.B) Increased biodiversity.C) Extreme weather events and rising sea levels.D) Lower global temperatures.34. What can individuals do to help address climate change?A) They should consume more meat.B) They should reduce their carbon footprint.C) They should stop using electricity.D) They should travel by plane more often.35. What is the tone of the passage?A) NegativeB) PositiveC) NeutralD) CriticalSection IV: Writing (20 points)Directions: Write an essay of about 150 words on the following topic: The Importance of Learning a Second Language. You should start your essay with a brief introduction, develop your ideas in the bodyparagraphs, and conclude with a summary of your main points. Remember to use appropriate vocabulary and sentence structures.---This is a simplified example of an English high school entrance examination paper. Actual exam papers may include more complex questions and a wider variety of content.。
技能高考英语_试卷

一、选择题(每题2分,共40分)1. The teacher asked us to ________ our homework before the class began.A. finishB. finishingC. finishedD. finishing up2. She ________ her breakfast in the kitchen this morning.A. hadB. haveC. hasD. had had3. If I ________ you, I would take a train instead of a bus.A. wasB. wereC. amD. be4. The students were all ________ when the teacher came into the classroom.A. satB. sittingC. sitD. to sit5. ________ the weather is so bad, we have to cancel the picnic.A. BecauseB. Because ofC. AsD. Since6. I ________ to the library every weekend to read books.A. goB. goesC. wentD. going7. The book ________ on the table is mine.A. layingB. laidC. layD. laying down8. ________ you are, I will never leave you alone.A. WhoB. WhomC. WhoeverD. Whomever9. The teacher said, "You ________ all the exercises before the class is over."A. have doneB. have to doC. had doneD. have to have done10. I ________ my phone at home, but I don't know where it is now.A. leaveB. leftC. am leavingD. have left二、完形填空(每题2分,共20分)One day, Tom was walking in the street when he saw a cat. The cat was sitting on the ground, looking very hungry. Tom felt sorry for the cat and decided to take it home. He picked up the cat and put it in his bag.Tom walked for a while and then stopped at a small shop. He bought some food for the cat and some water. When he got home, he put the food and water in front of the cat. The cat ate the food and drank the water. It looked very happy.The next day, Tom went to the shop again to buy more food and water for the cat. While he was buying the things, he saw a man sitting on the ground with a cat in his arms. The man was looking at the cat with love and care.Tom asked the man, "Is that your cat?"The man smiled and said, "Yes, it is. I found her on the street a few days ago and she's been living with me ever since."Tom felt happy that he had helped both the cat and the man. He realized that helping others can bring happiness to both of them.11. Tom saw a ________ on the ground.A. dogB. catC. birdD. mouse12. Tom ________ the cat home.A. tookB. broughtC. carriedD. fetched13. The cat looked very ________.A. hungryB. tiredC. happyD. angry14. Tom bought some ________ for the cat.A. food and waterB. toys and ballsC. clothes and shoesD. books and papers15. The cat ate the food and drank the water, and it looked very________.A. sadB. tiredC. happyD. hungry16. Tom saw a man sitting on the ground with a ________ in his arms.A. dogB. catC. birdD. mouse17. The man said he ________ the cat on the street.A. foundB. lostC. boughtD. sold18. Tom realized that helping others can bring ________ to both of them.A. moneyB. foodC. happinessD. love三、阅读理解(每题2分,共20分)Passage 1The Internet has become an important part of our lives. We use it to communicate with others, to find information, and to entertain ourselves. However, the Internet also has some negative effects.One of the biggest problems with the Internet is that it can be addictive. Many people spend too much time online, which can lead to problems with their health, relationships, and work. Another problem is that the Internet can be a source of misinformation. It is easy to find false information on the Internet, and this can be harmful.Despite these problems, the Internet is still a valuable tool. We just need to be careful about how we use it.19. What is the main idea of the passage?A. The Internet is a valuable tool.B. The Internet has negative effects.C. The Internet is addictive.D. The Internet is a source of misinformation.20. Which of the following is NOT mentioned in the passage?A. The Internet can be addictive.B. The Internet can be a source of misinformation.C. The Internet can improve our health.D. The Internet can lead to problems with relationships.Passage 2Traveling is one of the best ways to learn about different cultures. When you travel, you can see how people live in different parts of the world. You can also learn about their traditions and customs.One of the most interesting things about traveling is trying new foods. Every culture has its own unique dishes, and it's exciting to taste them. You can also learn a lot about a culture by the way people dress.Another benefit of traveling is that it can help you grow as a person.It can teach you to be more open-minded and to appreciate different perspectives.21. What is the main idea of the passage?A. Traveling is a good way to learn about different cultures.B. Traveling is a good way to learn about food.C. Traveling is a good way to learn about fashion.D. Traveling is a good way to grow as a person.22. Which of the following is NOT mentioned as a benefit of traveling?A. Learning about different cultures.B. Trying new foods.C. Improving your health.D. Gaining a new perspective.四、短文改错(每题1分,共10分)In a small town, there was a library that had been closed for many years. The townspeople were sad because they could not borrow books. They decided to open the library again, and they raised money to repair it.The library was open again, and the townspeople were very happy. They brought their children to read books. The children were excited to seeso many books. They chose books about animals, and they spent hours reading them.One day, a man came to the library and asked if he could volunteer. He said he loved reading and he wanted to help the library. The librarian agreed, and the man began to work in the library every day.The library became a place where people could come to read and learn. It was a place where people could meet and talk. It was a place wherepeople could find peace and quiet.23. In a small town __________ (change: was)24. The townspeople were sad __________ (change: because)25. They decided to open __________ (change: the)26. The library was open __________ (change: again)27. The children were excited __________ (change: to)28. They chose books __________ (change: about)29. The man began to work __________ (change: in)30. It was a place __________ (change: where)五、书面表达(20分)Write an essay of about 150 words on the topic "The Importance of Learning a Second Language." You should include the following points:1. The benefits of learning a second language.2. How learning a second language can improve one's career opportunities.3. The role of technology in language learning.Remember to use your own words and include appropriate vocabulary and grammar.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Now let’s log our output to the console as a means of debugging: console.log("The subtotal is: " + subtotal); console.log('The total cost is $' + total); As you can see in the console, the subtotal variable has a value of 500500. Now, the problem is clearer. JavaScript is appending 500 with 500 giving us 500500. Looking back at our code, we notice that the line product2='500'. The '500' in single quotes indicates a String, thus, when we perform the operation product1 + product2, it appends (or concatenates) the two Strings together. To fix this problem, remove the single quotes from 500 and run the program again. Next, log the total and subtotal variable into the console. Your program should now produce the correct result.
Exercise 2: Understanding Pop Up Boxes
a. Let’s now play with a few pop up boxes, one line at a time alert("Thank you for visiting"); confirm("Do you accept the terms and conditions?"); var name = prompt("What's your name"); Now after you enter a name for the prompt box, let’s see what value is stored in the name variable, by typing in the variable name: name b. This time, we want our prompt to take in a number. var age = prompt("How old are you?");
Question 4: Understanding console.log
Displaying alerts can be quite annoying. Let's now suppress the alert, and just print things out to the console (instead of to a pop up box via console.log)
Exercise 3: Understanding Arrays
Let’s familiarise ourselves with arrays in order to store more than one value per variable. There are three ways to create arrays as described in page 75 of the reference book. Let’s try one technique: // Declaring the array var planets = new Array(); // Initialising the array planets[0] = "Mercury"; planets[1] = "Venus"; planets[2] = "Earth"; a. Retrieve the first element by calling the variable and the index position: planets[0] b. Overwrite the third element by assigning it a different value: planets[2] = "Mars"; c. Print out what is stored in the planet variable by calling the variable name: planets
JavaScript Exercises
1. JavaScript Concept Questions
1. Given the following JavaScript statement (or line of code), which part is the declaration, and which part is the initialisation? var chicken = 12; Declaration: var chicken Initialisation: chicken = 12; 2. Initially, var x = 10. What is the final value of x = x + 5? Or is this statement even valid? It is valid whereby anything on the right hand side is equated to the variable on the left hand side. Thus, x = 15 3. Does all JavaScript statements need to end with a semi-colon? No, but it is good practice to do so. 4. What is the final value for each variable? var x var y var z x = x x++; a = x z = x = = = + 6; "INFO1003"; 30; z;
+ y; % z;
x 6 36 37
y INFO1003
z 30 7
a 37INFO1003
2. JavaScript Practical Exercise
Exercise 1: Understanding Variables and Operators
Before you start this exercise, you need to open up the JavaScript console (either the Chrome console or Firefox’s Firebug) a) From page 72 of the reference book, to differentiate the difference between Numbers and Strings, notice what is the console output when you type: 40 + 5; // Compared with "40" + "5"; Notice the "+" operator joins the two strings together (called concatenation) b) To prove we’re not lying to you, try out the following statements: var x = 10; x = x + 5;
INFO1003 | FOUNDATIONS OF INFORMATION TECHNOLOGY
3
JavaScript Exercises
var var var var var
product1 = 500; product2 = '500'; subtotal = product1 + product2; tax = .1 * subtotal; total = subtotal + tax;
INFO1003 | FOUNDATIONS OF INFORMATION TECHNOLOGY
2
JavaScript Exercises
However, notice what happens when we try to add an integer with our variable: age + 10; The reason you will see this concatenation is because by default, the prompt saves any input from the user as a String. We therefore want to extract out the integer value from the prompt variable. We achieve this with a parseInt() function: age = parseInt(age); Now let’s try our addition again: age + 10; c. Let’s concatenate this Number with a String, to say, "You are [INSERT AGE] years old", and define this as a new variable, ageText var ageText = "You are " + age + " years old" Remember, the "+" operator acts as a concatenation operator to join all Strings. Also notice, the space before and after the double quotation mark so that the age number is not printed directly after the text with no space. age + 10;
