rfc5981.Authorization for NSIS Signaling Layer Protocols
authorization加密规则

授权加密规则是指在信息传输和使用过程中,为了保护数据的安全性和完整性,采用各种加密算法和安全协议进行加密和认证的一系列规则和措施。
在现代网络环境下,随着信息技术的快速发展和普及,数据的安全性日益成为人们关注的焦点,特别是在金融、电子商务等领域,安全性更是至关重要。
制定和实施有效的授权加密规则显得尤为重要。
一、授权加密规则的基本原则1. 数据的机密性授权加密规则的首要目标是保护数据的机密性,确保数据在传输和存储过程中不被未经授权的第三方所获取和窃取。
采用强大的加密算法对数据进行加密处理是保障数据机密性的基本手段。
2. 数据的完整性授权加密规则还要求保证数据的完整性,即在数据传输和接收的过程中能够有效地检测数据是否被篡改,防止数据在传输过程中被恶意篡改以及确保数据的真实性。
3. 数据的可用性授权加密规则还需要保证数据的可用性,即在数据传输和存储过程中,能够确保数据的有效传输和使用,避免因加密算法的复杂性导致数据的无法正常使用。
二、授权加密规则的具体措施1. 使用全球信息站安全证书 (SSL/TLS)为了保证数据传输安全,全球信息站需要使用SSL/TLS安全证书来加密用户和服务器之间的通信,防止数据在传输过程中被窃取和篡改。
2. 使用双因素认证在授权过程中,采用双因素认证可以提高用户身份认证的安全性,不仅仅需要用户提供密码,还需要提供其他识别信息,如验证码、生物特征等,以增加认证的可靠性。
3. 使用强加密算法为了保障数据的安全性,采用强大的加密算法如AES、RSA等进行数据加密,确保数据在传输和存储过程中不易被破解。
4. 完善的访问控制机制建立完善的访问控制机制,对用户进行严格的身份认证和授权管理,确保只有经过授权的用户才能访问和使用数据,避免未经授权的访问和使用。
5. 加强数据的备份和恢复为了保障数据的可用性,及时备份重要数据,并建立完善的数据恢复机制,以应对意外数据丢失或损坏的情况。
6. 定期安全审计定期对系统和数据进行安全审计,发现和修复安全隐患,确保系统和数据的安全。
Extreme Networks SLX 9640高性能固定路由器商品介绍说明书

ExtremeRouting? SLX 9640
Built to Suit Your Business Needs Ext rem e Elem ent s are t he b uild ing b locks t hat allow you t o t ailor your net w ork t o your sp ecific b usiness environm ent , g oals, and ob ject ives. They enab le t he creat ion of an A ut onom ous Net w ork t hat d elivers t he p osit ive exp eriences and b usiness out com es m ost im p ort ant t o your org anizat ion.
W W W.EXTREMENETW
1
Flexib le Bo rd er Ro ut ing w it h Int ernet Scale, Ult ra-Deep Buffers,
MPLS and EVPN
The SLX 964 0 is a very p ow erful com p act d eep b uffer Int ernet b ord er rout er, p rovid ing a cost -efficient solut ion t hat is p urp ose-b uilt for t he m ost d em and ing service p rovid er and ent erp rise d at a cent ers and MA N/ WA N ap p licat ions. The rob ust syst em archit ect ure sup p ort ed by SLX-OS and a versat ile feat ure set includ ing IPv4 , IPv6, and MPLS/ VPLS w it h Carrier Et hernet 2.0 and OA M cap ab ilit ies t o p rovid e d ep loym ent flexib ilit y.
sip authorization 原理

sip authorization 原理SIP(Session Initiation Protocol)是一种用于建立、修改和终止多媒体会话的协议。
在SIP中,SIP授权(SIP Authorization)是一种用于验证用户身份的机制,它通过SIP消息头中的Authorization字段来实现。
SIP授权的原理是基于HTTP Digest认证协议的。
在SIP授权中,客户端向服务器发送一个请求,服务器返回一个401 Unauthorized响应,要求客户端提供用户名和密码。
客户端将用户名和密码使用MD5算法进行加密,并将结果放入Authorization字段中,然后再次向服务器发送请求。
服务器收到请求后,使用相同的算法对用户名和密码进行加密,并将结果与客户端提供的结果进行比较。
如果两者相同,则认为客户端是合法的,否则认为客户端是非法的。
SIP授权的过程如下:1. 客户端向服务器发送一个请求。
2. 服务器返回一个401 Unauthorized响应,要求客户端提供用户名和密码。
3. 客户端将用户名和密码使用MD5算法进行加密,并将结果放入Authorization字段中。
4. 客户端再次向服务器发送请求,并在请求头中包含Authorization字段。
5. 服务器收到请求后,使用相同的算法对用户名和密码进行加密,并将结果与客户端提供的结果进行比较。
6. 如果两者相同,则认为客户端是合法的,否则认为客户端是非法的。
SIP授权的优点是可以保护SIP网络免受未经授权的访问和攻击。
它可以防止未经授权的用户访问SIP网络,并保护SIP网络中的用户信息和通信内容。
此外,SIP授权还可以提高SIP网络的可靠性和安全性,确保SIP网络的正常运行。
总之,SIP授权是一种用于验证用户身份的机制,它通过SIP消息头中的Authorization字段来实现。
它的原理是基于HTTP Digest认证协议的,可以保护SIP网络免受未经授权的访问和攻击,提高SIP网络的可靠性和安全性。
RFC3261 中文

SIP即时消息RFC3428目录SIP即时消息RFC3428 (1)1、SIP协议介绍 (13)2、SIP协议功能概况 (13)3、术语 (15)4、实施概览 (15)5、协议的结构 (25)6、协议的定义 (27)7、SIP消息: (35)7.1 请求 (36)7.2应答 (37)7.3 头域 (38)7.3.1 头域格式。
(38)7.3.2 头域分类。
(42)7.3.3 缩写格式 (42)7.4包体 (42)7.4.1 消息正文类型(MessageBodyType) (42)7.4.2 消息体长度 (43)7.5 分帧的SIP消息(Framing SIP Messages) (43)8 一般用户代理行为 (43)8.1 UAC特性 (44)8.1.1 产生一个请求 (44)8.1.1.1 Request-URI (45)8.1.1.2 TO (45)8.1.1.3 From (46)8.1.1.4 Call-ID (47)8.1.1.5 Cseq (48)8.1.1.6 Max-Forwards (48)8.1.1.7 Via (48)8.1.1.8 Contact (49)8.1.1.9 Supported 和 Require (50)8.1.1.10 附加信息部分 (50)8.1.2 发送一个请求 (50)8.1.3 处理应答 (51)8.1.3.1: transaction 层的错误 (52)8.1.3.2 未知的应答 (52)8.1.3.3 Vias (52)8.1.3.4 处理3xx应答 (52)8.1.3.5 处理4xx应答 (54)8.2 UAS特性 (55)8.2.1 方法判定 (56)8.2.2 包头判断 (56)8.2.2.1 TO 和Request-URI (56)8.2.2.2 合并的请求 (57)8.2.2.3 Require (57)8.2.3 内容处理 (58)8.2.4 应用扩展 (58)8.2.5 处理请求 (59)8.2.6 产生应答 (59)8.2.6.1 发送一个临时应答 (59)8.2.6.2 包头和Tags (60)8.2.7 无状态UAS行为 (60)8.3 重定向服务器 (61)9.1 客户行为(Client Behavior) (63)9.2 服务端行为(Server Behavior) (65)10 注册(Registrations) (66)10.1 概览 (66)10.2 构造一个REGISTER请求 (67)10.2.1 增加绑定 (69)10.2.1.1 设置Contact地址的过期参数 (70)10.2.2 删除绑定 (71)10.2.3 访问绑定 (71)10.2.4 刷新绑定 (72)10.2.5 设置内部时钟 (72)10.2.6 寻找注册服务器 (72)10.2.7 传送一个请求 (73)10.2.8 错误响应 (73)10.3 处理REGISTER请求 (73)11 查询能力 (76)11.1 构造OPTIONS请求 (77)11.2 处理OPTIONS请求 (78)12 对话(Dialog) (80)12.1 创建一个对话 (81)12.1.1 UAS行为 (81)12.1.2 UAC行为 (82)12.2 对话中的请求 (83)12.2.1 UAC行为 (84)12.1.1.1 产生请求 (84)12.2.1.2 处理应答 (86)12.2.2 UAS行为 (87)13 初始化一个会话 (88)13.1 概览 (88)13.2 UAC处理 (89)13.2.1 创建一个初始化的INVITE (89)13.2.2 处理INVITE应答 (92)13.2.2.1 1xx应答 (92)13.2.2.2 3xx应答 (92)13.2.2.3 4xx,5xx,6xx应答 (93)13.2.2.4 2xx 应答 (93)13.3 UAS处理 (94)13.3.1 处理INVITE (94)13.3.1.1 提示进度 (95)13.3.1.2 INVITE请求转发 (96)13.3.1.3 INVITE请求的拒绝 (96)13.3.1.4 接受INVITE请求 (96)14 更改已经存在的会话 (97)14.1 UAC行为 (98)14.2 UAS行为 (99)15 结束一个会话 (101)15.1 使用BYE请求终止一个会话 (102)15.1.1 UAC行为 (102)15.1.2 UAS行为 (103)16 proxy行为 (103)16.1 概述 (103)16.2 有状态的proxy (104)16.3 验证请求 (106)16.4 路由信息预处理 (108)16.6 请求转发 (111)16.7 应答的处理 (120)16.8 处理定时器C (128)16.9 处理通讯层的错误 (129)16.10 CANCEL处理 (129)16.11 无状态的proxy (130)16.12 Proxy Route处理的总结 (132)16.12.1例子 (133)16.12.1.1 基本SIP四边形 (133)16.12.1.2 穿越一个严格路由proxy (135)17事务 (137)17.1 客户端事务 (139)17.1.1 INVITE客户事务 (140)17.1.1.1 INVITE事务概述 (140)17.1.1.2 正式的描述 (141)17.1.1.3 构造ACK请求 (145)17.1.2 非INVITE客户端事务 (146)17.1.2.2 正式的描述 (146)17.1.3 客户端事务匹配应答 (148)17.1.4 处理通讯错误 (148)17.2 服务端事务 (150)17.2.1 INVITE服务端事务 (150)17.2.2 非INVITE服务端事务 (153)17.2.3 为服务端事务匹配请求。
RFC959

RFC-959标准中文版备忘录状态本备忘录描述了文件传输协议(FTP)的官方规范。
对本备忘录的发布没有限制。
本规范新包括了如下可选命令:CDUP (返回父目录), SMNT (结构装备), STOU(唯一保存),RMD (删除目录), MKD (新建目录), PWD(打印目录), and SYST (系统)。
本规范与前一个版本兼容目录1. 介绍2. 概述2.1. 历史2.2. 术语2.3. FTP模型3. 数据传输功能3.1. 数据表示和存储3.1.1. 数据类型3.1.1.1. ASCII类型3.1.1.2. EBCDIC类型3.1.1.3. 图像类型3.1.1.4. 本地类型3.1.1.5. 格式控制3.1.1.5.1. 非打印(NON PRINT)3.1.1.5.2. TELNET格式控制3.1.1.5.2. CARRIAGE CONTROL(ASA)3.1.2. 数据结构3.1.2.1. 文件结构3.1.2.2. 记录结构3.1.2.3. 页结构3.2. 建立数据连接3.3. 数据连接管理3.4. 传输模式3.4.1. 流模式3.4.2. 块模式3.4.3. 压缩模式3.5. 错误恢复和重新开始4. 文件传送功能4.1. FTP命令4.1.1. 访问控制命令4.1.2. 传输参数命令4.1.3. FTP服务命令4.2. FTP响应4.2.1. 按功能分组的响应代码4.2.2. 按数字顺序排列的响应代码1. 介绍FTP的目标是:1)促进程序/数据文件的共享;2)鼓励(通过程序)使用远程计算机;3)使用户不必面对不同主机上不同文件系统的差异;4)对数据进行高效可靠的传输。
FTP尽管可以直接在终端上应用,但它主要被设计通过程序来使用。
本规范通过设计简单易实现的协议来试图满足大型机、小型机、个人工作站、TAC等用户的需要。
本文需要文件传输协议(TCP)[2]以及Telnet协议[3]的知识。
关于它们的文档可以在ARPA-互联网协议手册[1]中找到。
sftp 消息认证算法

sftp 消息认证算法SFTP(Secure File Transfer Protocol)是一种安全的文件传输协议,它在SSH(Secure Shell)上构建。
SFTP使用SSH协议进行身份验证和加密,因此支持多种消息认证算法以确保通信的安全性。
以下是一些常见的SFTP消息认证算法:1. HMAC-SHA-2(HMAC with SHA-2):- SFTP可以使用基于SHA-2系列的HMAC算法,如HMAC-SHA-256和HMAC-SHA-512,来进行消息认证。
这些算法提供了强大的安全性。
2. HMAC-SHA-1:-尽管SHA-1已经被认为是不安全的,但在某些情况下,仍然可能会使用HMAC-SHA-1进行消息认证。
然而,强烈建议使用更安全的算法,如SHA-256或SHA-512。
3. HMAC-MD5:-类似于HMAC-SHA-1,HMAC-MD5也是一种较旧的消息认证算法,不再被推荐用于安全性要求较高的环境。
4. UMAC-64和UMAC-128:- UMAC是一种基于Poly1305的消息认证码算法。
UMAC-64使用64位密钥,而UMAC-128使用128位密钥。
它们提供了高性能和良好的安全性。
5. AES-GCM:- Advanced Encryption Standard Galois/Counter Mode(AES-GCM)是一种组合加密和消息认证码的模式。
它结合了AES加密和GCM认证,提供了高度的安全性和效率。
6. AES-CCM:- Advanced Encryption Standard Counter with Cipher Block Chaining-Message Authentication Code(AES-CCM)也是一种组合加密和消息认证码的模式,类似于AES-GCM。
这些消息认证算法用于验证SFTP通信中传输的数据的完整性,防止数据被篡改。
在配置SFTP 服务器和客户端时,通常可以指定首选的消息认证算法和加密算法。
rfc中常用的测试协议

rfc中常用的测试协议摘要:1.RFC 简介2.RFC 中常用的测试协议a.网络协议测试1.网络数据包抓取和分析2.网络仿真和测试工具b.应用层协议测试1.HTTP 和HTTPS 测试2.FTP 和FTPS 测试3.SMTP 和SMTPS 测试c.安全协议测试1.TLS 和SSL 测试2.IPsec 测试d.传输协议测试1.TCP 和UDP 测试e.无线网络协议测试1.802.11 无线网络测试正文:RFC(Request for Comments)是一个用于讨论和记录互联网协议的标准文档系列。
在RFC 中,有许多常用的测试协议,这些协议用于确保互联网协议在实际应用中能够正常工作。
本文将详细介绍这些测试协议。
首先,RFC 中包含了大量的网络协议测试。
网络数据包抓取和分析是网络协议测试的基础,这对于诊断网络问题和优化网络性能至关重要。
此外,网络仿真和测试工具也是必不可少的,例如,网络模拟器(如NS-3)和测试平台(如Ixia)可以帮助工程师在实验室环境中模拟实际网络状况,从而对协议进行更严格的测试。
其次,应用层协议测试在RFC 中也占据重要地位。
HTTP 和HTTPS 是Web 应用中最常用的协议,有许多测试工具可以对它们的性能和安全性进行测试,例如,JMeter 和Locust 等负载测试工具。
此外,FTP 和FTPS、SMTP 和SMTPS 等传输协议也是常用的测试对象。
在安全协议方面,RFC 中包含了TLS 和SSL、IPsec 等协议的测试方法。
这些协议对于保护互联网数据传输的安全至关重要,因此需要进行严格的测试以确保其性能和安全性。
传输协议方面,TCP 和UDP 是互联网中最常用的传输协议,它们的测试方法也是RFC 中的重要内容。
TCP 测试关注可靠性和流量控制等方面,而UDP 测试则更注重数据传输速率和丢包率等指标。
最后,无线网络协议测试在RFC 中也有一定的比重。
例如,802.11 无线网络测试是评估无线局域网性能的关键。
.net core iauthorizationhandler 自定义返回

.net core iauthorizationhandler 自定义返回在 `.NET Core` 中,`IAuthorizationHandler` 用于处理授权请求并返回授权决策。
如果需要自定义返回结果,可以重写 `HandleRequirementAsync` 方法,并在其中根据授权决策执行相应的操作。
例如,下面是一个简单的示例,演示如何在授权失败时返回自定义的 JSON 响应:```csharpusing Microsoft.AspNetCore.Authorization;using Microsoft.AspNetCore.Authorization.Policy;using Microsoft.AspNetCore.Http;using System.Threading.Tasks;namespace CustomAuthorizationHandler{public class CustomAuthorizationHandler : AuthorizationHandler<CustomRequirement>{protected override async Task HandleRequirementAsync(AuthorizationHandlerContext context, CustomRequirement requirement){if (!requirement.IsAuthorized){context.Fail();// 设置响应状态码为 401(未经授权)context.HttpContext.Response.StatusCode = 401;// 使用 JSON 序列化返回对象awaitcontext.HttpContext.Response.WriteAsync(JsonConvert.SerializeObject(new { Code = 401, Message = "未经授权" }));}else{context.Succeed(requirement);}}}}```在上述示例中,首先继承了 `AuthorizationHandler<CustomRequirement>` 类,并在构造函数中接受 `IHttpContextAccessor`、`ILogger<CustomAuthorizationHandler>` 和`IPermissionWatchDog` 实例作为参数。
请求头authorization 认证原理
请求头authorization 认证原理请求头authorization 认证原理背景介绍在进行网络通信时,身份认证是非常重要的一环。
而HTTP请求头的Authorization字段旨在提供一种安全的方式来验证请求的发送者身份。
本文将深入探讨Authorization认证的原理和相关应用。
什么是请求头AuthorizationAuthorization是HTTP请求头的一部分,用于向服务器提供身份验证信息。
当我们向服务器发送请求时,可以在请求头中包含Authorization字段来提供身份验证凭据。
认证原理的基础概念1. 客户端和服务器的通信在进行身份验证过程中,存在一个客户端(通常是浏览器、应用程序等)和一个服务器(存储用户信息和处理验证请求)之间的通信过程。
2. 用户名和密码为了证明用户的身份,需要用户提供正确的用户名和密码组合。
3. 加密算法为了保证身份验证信息的安全性,加密算法是必不可少的。
常见的加密算法包括MD5、SHA1等。
基本认证流程基本的Authorization认证流程如下:1.客户端向服务器发送请求。
2.服务器返回需要进行身份验证的响应。
3.客户端将用户名和密码进行Base64编码,并将编码后的字符串放入请求头的Authorization字段中。
4.服务器验证身份凭据,并返回相应的响应结果。
常见的Authorization认证方案1. Basic认证Basic认证是最简单和最常见的认证方案之一。
其基本流程如下:1.客户端将用户名和密码使用:连接,并进行Base64编码。
2.客户端将编码后的字符串放入请求头的Authorization字段中,格式为Basic 编码后的字符串。
3.服务器将请求头中的Authorization字段进行解码并验证身份凭据。
2. Bearer认证Bearer认证是OAuth 中使用的一种认证方案,主要用于API访问的身份验证。
其基本流程如下:1.客户端通过OAuth 协议获取访问令牌(Access Token)。
authorizationserver issuer

渭河“119”洪水特点及分析
赵彩君
【期刊名称】《陕西水利》
【年(卷),期】2012(000)002
【摘要】本文从雨水工情方面分析了渭河“11·9”洪水的特点,全面总结抗洪抢险工作的经验和体会,提出治理建议,对做好渭河防汛工作具有积极意义。
【总页数】3页(P111-113)
【作者】赵彩君
【作者单位】陕西省防汛抗旱总指挥部办公室,陕西西安710004
【正文语种】中文
【中图分类】TV122.1
【相关文献】
1.渭河中下游“11·9”暴雨洪水分析 [J], 宋淑红
2.渭河2012“11·9”暴雨洪水探析 [J], 张纪周
3.渭河“11·9”洪水防汛启示 [J], 梁林江;雷文青;张广林
4.渭河宝鸡段7·11洪水对滩区景观工程影响分析 [J], 吕跃;潘凤莉
5.渭河“11·9”洪水特性及其河道影响分析 [J], 石长伟;杨宁;陈乃联;包岁利;薛亚莉
因版权原因,仅展示原文概要,查看原文内容请购买。
authorization bearer 解析

一、什么是Authorization Bearer 解析在网络通信中,授权(Authorization)是一个重要的概念,用于验证用户或客户端是否有权限访问指定的资源。
而Bearer是Authorization请求头的一种类型,通常用于向服务器传递令牌(Token)以进行身份验证和授权。
Authorization Bearer解析即是对Bearer令牌在请求头中的解析和处理过程的描述和分析。
二、为什么需要进行Authorization Bearer解析1. 安全性需求:在开放的网络环境中,对用户身份进行验证和授权是保障系统安全性的重要手段。
通过对Bearer令牌的解析,可以有效地确认请求的合法性和用户的身份。
2. 访问控制需求:许多Web服务和API接口都需要对访问进行限制和控制,Bearer令牌的解析可以帮助系统进行精确的访问控制。
3. 用户体验需求:对Bearer令牌的灵活解析和处理,可以使得用户在使用系统时更加方便和便捷,提升用户体验。
三、Authorization Bearer解析的流程1. 提取Bearer令牌:服务器需要从请求头中的Authorization字段中提取Bearer令牌,这通常涉及到对HTTP请求头的解析和处理。
2. 验证令牌合法性:接下来,服务器需要对提取到的Bearer令牌进行验证,包括对令牌的有效期、签名等进行检查。
这一步需要使用相应的加密算法和验证逻辑。
3. 根据令牌进行授权:验证通过后,服务器根据令牌中包含的信息进行授权判断,确定用户是否有权限访问请求的资源。
这包括对用户角色、权限等信息的判断和处理。
四、Authorization Bearer解析的常见问题和解决方案1. 令牌安全性问题:Bearer令牌的泄露可能导致用户身份被盗用,因此需要采取相应的安全措施来保障令牌的安全性,比如使用HTTPS协议传输令牌,定期更换令牌等。
2. 令牌有效性验证问题:服务器需要对令牌的有效性进行验证,包括检查令牌的签名、时效性等,因此需要建立相应的验证机制和算法。
authorizationfilter

authorizationfilter
Authorization Filter是 用于安全性检查的过滤器,它在用户请求访问资源之前进行验证,检查用户是否有权限访问这项资源。
Authorization Filter由一个过滤器的抽象类IAuthorizationFilter实现,它提供在用户客户端发送请求之前允许或禁止访问资源所需的所有方法。
当一个用户尝试访问一个控制器或操作方法时,Authorization Filter会执行以下动作:
(1)检测当前用户是否有权访问此资源;
(2)决定是否允许用户访问资源;
(3)如果不允许用户访问,则抛出HTTP错误403(拒绝访问),以拒绝用户的访问。
Authorization Filter可以被应用在整个控制器或单独的操作方法上,它可以让我们轻松确保每个用户请求访问资源之前都有权限去访问。
许多可用的过滤器提供不同类型的授权,例如,基于角色的授权,基于特定用户或用户组的授权,还有自定义授权等,它们允许我们根据需要为用户控制访问权限。
authorizationverificationr -回复

authorizationverificationr -回复什么是授权验证(Authorization Verification)?授权验证(Authorization Verification)是指在计算机系统中,对用户或程序的授权信息进行验证的过程。
它主要用于确认用户或程序的身份和权限,以确保只有合法的用户或程序能够访问特定资源或执行特定操作。
授权验证通常是通过比较用户或程序提供的身份验证信息与系统存储的授权信息来完成的。
在计算机系统中,授权验证是安全性和访问管理的关键组成部分。
它帮助保护系统免受未经授权的访问、信息泄露和数据损坏等威胁。
通过对用户或程序的身份进行验证,系统可以控制其访问权限,并对其进行追踪和审计。
这是一种非常重要的安全措施,特别是对于那些存储敏感数据或提供关键服务的系统。
授权验证的主要步骤是什么?授权验证的过程通常包括以下几个步骤:1. 用户身份验证(User Authentication):这是验证用户身份的第一步。
用户通常需要提供用户名和密码等凭据,以证明他们是合法的用户。
这些凭据可以与系统中存储的已注册用户信息进行比较,以确认用户的合法性。
2. 访问权限验证(Access Rights Verification):一旦用户的身份被验证通过,系统将根据用户的权限配置对其进行访问权限验证。
这通常涉及检查用户是否具有执行所请求操作所需的权限。
例如,如果用户试图访问受限资源或执行管理员操作,系统将检查其权限并相应地授权或拒绝访问。
3. 会话管理(Session Management):为了确保安全性,系统通常会为每个用户分配一个会话,并为其生成一个会话令牌或标识符。
这个会话令牌将与用户相关联,并用于跟踪用户的活动和验证其访问权限。
会话管理涉及对会话令牌的生成、维护和注销等操作。
4. 审计与日志记录(Audit and Logging):授权验证完成后,系统通常会记录相关的审计日志,以便跟踪和追溯用户的活动。
sip authorization 原理

SIP authorization 原理什么是SIP authorizationSIP(Session Initiation Protocol)是一种用于建立、维护和终止通信会话的协议。
在SIP中,授权(authorization)是一项重要的功能,用于验证和控制用户身份和权限,以确保通信会话的安全性和合法性。
SIP授权的作用SIP授权的主要作用是验证用户的身份和权限,以确保通信会话的合法性和安全性。
具体来说,SIP授权可以实现以下功能:1.验证用户身份:通过验证用户的身份信息,如用户名和密码,确定用户是否有权进行通信。
2.控制权限:根据用户的身份和权限,控制其可以进行的操作和访问的资源。
3.保护通信会话:通过验证和控制,确保通信会话的安全性,防止非法访问和欺诈行为。
SIP授权的原理SIP授权的原理主要包括用户身份的验证和权限的控制。
用户身份的验证用户身份的验证是SIP授权的第一步,在用户发起通信会话时进行。
常见的用户身份验证方式有:1.基本认证(Basic Authentication):用户在请求消息中携带用户名和密码,服务器根据这些信息进行验证。
2.摘要认证(Digest Authentication):用户在请求消息中携带用户名、密码的哈希值和其他相关信息,服务器根据这些信息进行验证。
3.TLS(Transport Layer Security)认证:通过使用SSL/TLS协议,在传输层对通信进行加密和认证。
用户身份的验证可以通过以下步骤进行:1.用户发起请求:用户发起一个SIP请求,如邀请(INVITE)或注册(REGISTER)。
2.服务器响应:服务器收到请求后,对用户进行身份验证。
3.身份验证:服务器根据用户身份提供的验证信息,进行身份验证。
4.验证结果:服务器根据身份验证的结果,发送相应的响应消息给用户,如成功(200 OK)或失败(401 Unauthorized)。
权限的控制用户身份验证通过后,在通信会话中还需要进行权限的控制。
authorizationcodeissuedat -回复

authorizationcodeissuedat -回复什么是授权码(Authorization Code),它是如何产生和使用的。
同时,本文将深入探讨授权码的重要性和安全性问题。
授权码是认证和授权流程中的一种凭证,通常用于客户端(例如Web浏览器,移动设备或台式机应用程序)向资源服务器请求访问授权。
授权码是一种临时令牌,通常在认证成功后颁发,有效期通常为几分钟到几个小时不等。
在OAuth 2.0体系中,授权码由授权服务器发放,用于交换访问令牌(Access Token)。
当客户端需要访问受保护资源时,首先需要将用户重定向到授权服务器,以进行身份验证和授权。
如果用户身份验证和授权成功,授权服务器将返回授权码。
授权码的生成由授权服务器负责。
在交换请求中,客户端必须使用先前获得的客户端ID和客户端密钥进行身份验证,并附加由授权服务器生成的回调URI。
授权服务器将验证客户端ID和密钥并确定回调URI是否与之前验证的一致。
如果检查成功,则授权服务器将发出授权码。
授权码可以保证OAuth 2.0体系中的安全,因为它不会在未授权的客户端之间流通。
授权码只能在受到保护的回调URI中交换,这可以保护资源服务器和客户端之间的通信。
此外,授权码只被颁发一次,而且是临时的,有效期短暂。
这确保了在安全性方面更高的控制级别。
总之,授权码在OAuth 2.0体系中扮演着至关重要的角色。
授权码的存在保护了客户端和资源服务器之间的通信安全,防止了未授权的流通,这是一个强大的安全措施。
同时,授权码的有效期限制了它的使用范围,进一步增强了安全性。
当然,这并不是说授权码是完美的,恶意攻击仍然可以通过其他方式突破授权码的防御,但授权码仍然是授权和认证流程中不可或缺的要素之一。
authorizationcodecallbackhandler -回复

authorizationcodecallbackhandler -回复Authorization Code Callback Handler是什么?Authorization Code Callback Handler是一种在OAuth 2.0授权流程中用于处理授权码回调的机制。
在使用OAuth 2.0进行认证和授权时,应用程序通常需要跳转到认证服务器上的登录页面,并获取用户的授权,以便访问其受保护资源。
当用户成功登录并授权后,认证服务器会生成一个授权码,然后将用户重定向回应用程序的回调URL,并将该授权码作为查询参数传递给回调URL。
应用程序在收到回调请求后,需要进行处理,并使用该授权码进行进一步的授权流程。
为什么需要Authorization Code Callback Handler?使用Authorization Code Callback Handler可以实现更安全和可靠的授权流程。
它与将授权码直接返回给客户端的方式相比,提供了额外的安全层。
通过使用回调URL,可以确保授权码只能返回给预先注册的重定向URL,并且可以防止授权码被恶意截获。
回调URL还允许应用程序执行额外的操作,例如将授权码从URL中提取出来,并在后续请求中使用它来获取访问令牌。
因此,Authorization Code Callback Handler为OAuth 2.0授权提供了更好的控制和安全性。
如何实现Authorization Code Callback Handler?实现Authorization Code Callback Handler涉及以下几个步骤:1. 注册回调URL:在开始实现之前,应用程序需要先向认证服务器注册回调URL。
这通常是在认证服务器的开发者控制台或管理界面上完成的。
回调URL是一个公开可访问的URL,它将在用户完成授权后被认证服务器重定向到。
2. 处理回调请求:当认证服务器将用户重定向回应用程序的回调URL时,应用程序的服务器将接收到该请求。
邮件错误代码说明信息
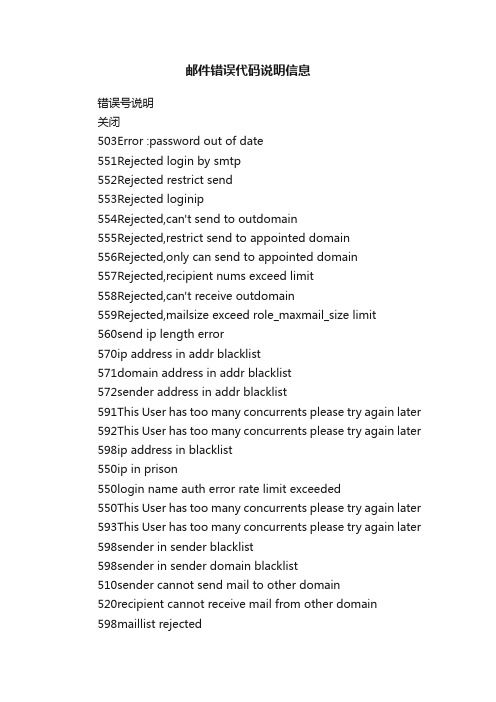
邮件错误代码说明信息错误号说明关闭503Error :password out of date551Rejected login by smtp552Rejected restrict send553Rejected loginip554Rejected,can't send to outdomain555Rejected,restrict send to appointed domain556Rejected,only can send to appointed domain557Rejected,recipient nums exceed limit558Rejected,can't receive outdomain559Rejected,mailsize exceed role_maxmail_size limit560send ip length error570ip address in addr blacklist571domain address in addr blacklist572sender address in addr blacklist591This User has too many concurrents please try again later 592This User has too many concurrents please try again later 598ip address in blacklist550ip in prison550login name auth error rate limit exceeded550This User has too many concurrents please try again later 593This User has too many concurrents please try again later 598sender in sender blacklist598sender in sender domain blacklist510sender cannot send mail to other domain520recipient cannot receive mail from other domain598maillist rejected594This User has too many concurrents please try again later 595This User has too many concurrents please try again later 596This User has too many concurrents please try again later 597Licence account exceed598mail size exceeds limit598mail rejected by keyword554Sender address rejected Access denied598|ip|address|in|blacklist|for|more|details|Please|see|http:// 211.150.100.59:8083/blacklist/blacklist.htm?ip= 598mail from and data from mismatch598rate of recurrent pattern exceeded598spam detected598virus detected503Error :password out of date551Rejected login by smtp552Rejected restrict send553Rejected loginip554Rejected,can't send to outdomain555Rejected,restrict send to appointed domain556Rejected,only can send to appointed domain557Rejected,recipient nums exceed limit558Rejected,can't receive outdomain559Rejected,mailsize exceed role_maxmail_size limit560send ip length error570ip address in addr blacklist571domain address in addr blacklist572sender address in addr blacklist591This User has too many concurrents please try again later 592This User has too many concurrents please try again later 598ip address in blacklist550ip in prison550login name auth error rate limit exceeded550This User has too many concurrents please try again later 593This User has too many concurrents please try again later 598sender in sender blacklist598sender in sender domain blacklist510sender cannot send mail to other domain520recipient cannot receive mail from other domain598maillist rejected594This User has too many concurrents please try again later 595This User has too many concurrents please try again later 596This User has too many concurrents please try again later 597Licence account exceed598mail size exceeds limit598mail rejected by keyword554Sender address rejected Access denied598|ip|address|in|blacklist|for|more|details|Please|see|http:// 211.150.100.59:8083/blacklist/blacklist.htm?ip= 598mail from and data from mismatch598rate of recurrent pattern exceeded598spam detected598virus detected503Error :password out of date551Rejected login by smtp552Rejected restrict send553Rejected loginip554Rejected,can't send to outdomain555Rejected,restrict send to appointed domain556Rejected,only can send to appointed domain557Rejected,recipient nums exceed limit558Rejected,can't receive outdomain559Rejected,mailsize exceed role_maxmail_size limit560send ip length error570ip address in addr blacklist571domain address in addr blacklist572sender address in addr blacklist591This User has too many concurrents please try again later 592This User has too many concurrents please try again later 598ip address in blacklist550ip in prison550login name auth error rate limit exceeded550This User has too many concurrents please try again later 593This User has too many concurrents please try again later 598sender in sender blacklist598sender in sender domain blacklist510sender cannot send mail to other domain520recipient cannot receive mail from other domain598maillist rejected594This User has too many concurrents please try again later 595This User has too many concurrents please try again later 596This User has too many concurrents please try again later 597Licence account exceed598mail size exceeds limit598mail rejected by keyword554Sender address rejected Access denied598|ip|address|in|blacklist|for|more|details|Please|see|http:// 211.150.100.59:8083/blacklist/blacklist.htm?ip= 598mail from and data from mismatch598rate of recurrent pattern exceeded598spam detected598virus detected503Error :password out of date551Rejected login by smtp552Rejected restrict send553Rejected loginip554Rejected,can't send to outdomain555Rejected,restrict send to appointed domain556Rejected,only can send to appointed domain557Rejected,recipient nums exceed limit558Rejected,can't receive outdomain559Rejected,mailsize exceed role_maxmail_size limit560send ip length error570ip address in addr blacklist571domain address in addr blacklist572sender address in addr blacklist591This User has too many concurrents please try again later 592This User has too many concurrents please try again later 598ip address in blacklist550ip in prison550login name auth error rate limit exceeded550This User has too many concurrents please try again later 593This User has too many concurrents please try again later 598sender in sender blacklist598sender in sender domain blacklist510sender cannot send mail to other domain520recipient cannot receive mail from other domain598maillist rejected594This User has too many concurrents please try again later 595This User has too many concurrents please try again later 596This User has too many concurrents please try again later597Licence account exceed598mail size exceeds limit598mail rejected by keyword554Sender address rejected Access denied598|ip|address|in|blacklist|for|more|details|Please|see|http:// 211.150.100.59:8083/blacklist/blacklist.htm?ip= 598mail from and data from mismatch598rate of recurrent pattern exceeded598spam detected598virus detected503Error :password out of date551Rejected login by smtp552Rejected restrict send553Rejected loginip554Rejected,can't send to outdomain555Rejected,restrict send to appointed domain556Rejected,only can send to appointed domain557Rejected,recipient nums exceed limit558Rejected,can't receive outdomain559Rejected,mailsize exceed role_maxmail_size limit560send ip length error570ip address in addr blacklist571domain address in addr blacklist572sender address in addr blacklist591This User has too many concurrents please try again later 592This User has too many concurrents please try again later 598ip address in blacklist550ip in prison550login name auth error rate limit exceeded550This User has too many concurrents please try again later593This User has too many concurrents please try again later 598sender in sender blacklist598sender in sender domain blacklist510sender cannot send mail to other domain520recipient cannot receive mail from other domain598maillist rejected594This User has too many concurrents please try again later 595This User has too many concurrents please try again later 596This User has too many concurrents please try again later 597Licence account exceed598mail size exceeds limit598mail rejected by keyword554Sender address rejected Access denied598|ip|address|in|blacklist|for|more|details|Please|see|http:// 211.150.100.59:8083/blacklist/blacklist.htm?ip= 598mail from and data from mismatch598rate of recurrent pattern exceeded598spam detected598virus detected密码过期登陆方式限制禁用发送登录ip限制禁止给外域邮箱发送邮件禁止用户发送邮件到指定域只允许用户发送邮件到指定域最多收件人数限制禁止接收外域发来的邮件最大邮件大小加速器传递MUA IP有误发件人IP在地址本系统黑名单中发件人域名在地址本系统黑名单中发件人邮箱在地址本系统黑名单中ip connect并发超限ip connect频率超限ip黑名单ip 在监狱中登陆失败数超限sender频率超限sender并发超限sender黑名单sender domain黑名单禁止发外域禁止收外域禁止发listip rcpt频率超限ip rcpt error 超限sender rcpt error 超限Licence账户超限邮件大小超限关键字拒信在access中拒信ip 黑名单伪造发件人拒信复发率超限拒信abs检测垃圾拒信病毒邮件拒信密码过期登陆方式限制禁用发送登录ip限制禁止给外域邮箱发送邮件禁止用户发送邮件到指定域只允许用户发送邮件到指定域最多收件人数限制禁止接收外域发来的邮件最大邮件大小加速器传递MUA IP有误发件人IP在地址本系统黑名单中发件人域名在地址本系统黑名单中发件人邮箱在地址本系统黑名单中ip connect并发超限ip connect频率超限ip黑名单ip 在监狱中登陆失败数超限sender频率超限sender并发超限sender黑名单sender domain黑名单禁止发外域禁止收外域禁止发listip rcpt频率超限ip rcpt error 超限sender rcpt error 超限Licence账户超限邮件大小超限关键字拒信在access中拒信ip 黑名单伪造发件人拒信复发率超限拒信abs检测垃圾拒信病毒邮件拒信密码过期登陆方式限制禁用发送登录ip限制禁止给外域邮箱发送邮件禁止用户发送邮件到指定域只允许用户发送邮件到指定域最多收件人数限制禁止接收外域发来的邮件最大邮件大小加速器传递MUA IP有误发件人IP在地址本系统黑名单中发件人域名在地址本系统黑名单中发件人邮箱在地址本系统黑名单中ip connect并发超限ip connect频率超限ip黑名单ip 在监狱中登陆失败数超限sender频率超限sender并发超限sender黑名单sender domain黑名单禁止发外域ip rcpt频率超限ip rcpt error 超限sender rcpt error 超限Licence账户超限邮件大小超限关键字拒信在access中拒信ip 黑名单伪造发件人拒信复发率超限拒信abs检测垃圾拒信病毒邮件拒信密码过期登陆方式限制禁用发送登录ip限制禁止给外域邮箱发送邮件禁止用户发送邮件到指定域只允许用户发送邮件到指定域最多收件人数限制禁止接收外域发来的邮件最大邮件大小加速器传递MUA IP有误发件人IP在地址本系统黑名单中发件人域名在地址本系统黑名单中发件人邮箱在地址本系统黑名单中ip connect并发超限ip connect频率超限ip黑名单ip 在监狱中登陆失败数超限sender频率超限sender并发超限sender黑名单sender domain黑名单禁止发外域禁止收外域禁止发listip rcpt频率超限ip rcpt error 超限sender rcpt error 超限Licence账户超限邮件大小超限关键字拒信在access中拒信ip 黑名单伪造发件人拒信复发率超限拒信abs检测垃圾拒信登陆方式限制禁用发送登录ip限制禁止给外域邮箱发送邮件禁止用户发送邮件到指定域只允许用户发送邮件到指定域最多收件人数限制禁止接收外域发来的邮件最大邮件大小加速器传递MUA IP有误发件人IP在地址本系统黑名单中发件人域名在地址本系统黑名单中发件人邮箱在地址本系统黑名单中ip connect并发超限ip connect频率超限ip黑名单ip 在监狱中登陆失败数超限sender频率超限sender并发超限sender黑名单sender domain黑名单禁止发外域禁止收外域禁止发listip rcpt频率超限ip rcpt error 超限sender rcpt error 超限Licence账户超限邮件大小超限关键字拒信在access中拒信ip 黑名单伪造发件人拒信复发率超限拒信abs检测垃圾拒信病毒邮件拒信。
authorizationerror error 1000

authorizationerror error 1000怎么解决
"Authorization Error 1000" 通常是指在进行某种身份验证或授权操作时发生的错误。
解决这个问题可能涉及到与身份验证、授权服务或应用程序配置相关的一些步骤。
以下是一些建议:
1. 检查API密钥或令牌:如果你的应用程序使用API密钥或令牌进行身份验证,确保它们是有效的、未过期的,并且正确配置在你的应用程序中。
2. 验证权限:确保你的应用程序具有执行所需操作的正确权限。
有时,错误可能是由于缺少必要权限而引起的。
3. 检查授权服务:如果你的应用程序与外部授权服务(例如OAuth)集成,确保你的应用程序正确地与授权服务进行通信,并且授权服务的配置是正确的。
4. 查看文档或错误消息:查阅相关的文档或错误消息,以获取更多关于错误的信息。
有时候,错误消息中包含了详细的说明,可以帮助你更好地理解问题的根本原因。
5. 日志调试:启用详细的日志记录,以便捕获更多关于错误的信息。
这可以帮助你跟踪到错误发生的具体位置。
6. 检查网络连接:确保你的应用程序能够访问所需的身份验证或授权服务。
网络问题有时可能导致授权错误。
7. 联系服务提供商:如果你的应用程序与外部服务集成,例如第三方API或身份验证服务,考虑联系服务提供商获取支持。
他们可能能够提供更具体的解决方案或帮助你解决问题。
authorizationcodecallbackhandler -回复

authorizationcodecallbackhandler -回复什么是[authorizationcodecallbackhandler]?[authorizationcodecallbackhandler]是一个用于授权码回调处理的工具或程序。
在开发Web应用程序过程中,常常需要与第三方身份验证服务进行交互,以获得用户的授权并获取相关的用户信息。
回调处理是其中的一种常见方式,而[authorizationcodecallbackhandler]则是用来处理这种回调的工具或程序。
授权码回调是一个通用的授权协议,它通过将用户重定向到授权服务器来进行身份验证,并在成功授权后将用户重定向回应用程序的方式来完成授权流程。
回调处理程序的作用是接收从授权服务器返回的授权码,并将其用于获取访问令牌。
授权码一般具有时限,在有效期内使用授权码获取访问令牌并进行后续的用户信息获取等操作。
[authorizationcodecallbackhandler]的功能和使用方式可以根据具体的开发需求而有所不同。
一般来说,它需要具备以下功能:1. 接收授权服务器的回调:[authorizationcodecallbackhandler]需要监听某个URL或端口,以接收来自授权服务器的回调请求。
这个URL或端口可以在应用程序的配置中进行指定。
2. 提取授权码:在接收到授权服务器的回调请求后,[authorizationcodecallbackhandler]需要从请求中提取授权码。
授权码通常作为请求参数的一部分,并且可能需要根据具体的协议规范进行解析和提取。
3. 获取访问令牌:提取到授权码后,[authorizationcodecallbackhandler]需要使用该授权码向授权服务器发起请求,以获取访问令牌。
这个请求一般需要在请求头中包含应用程序的身份信息,以及用于证明授权码的有效性的相关凭证。
4. 处理访问令牌:[authorizationcodecallbackhandler]在获取到访问令牌后,可以对其进行处理和保存,以便在应用程序中后续的操作中使用。
oauth1.0 签名原理

oauth1.0 签名原理OAuth 1.0 签名原理OAuth(Open Authorization)是一种开放的授权协议,用于互联网资源的授权访问。
它允许用户通过授权向第三方应用程序提供访问其资源的权限,而无需将用户名和密码直接提供给第三方应用程序。
在OAuth 1.0版本中,签名机制是保证身份验证的关键。
签名机制基于密钥和哈希算法,确保请求参数在传输过程中不被篡改,从而保证请求的合法性和完整性。
下面将详细解释OAuth 1.0签名原理。
1. 获取临时凭证(Temporary Credential Request)在OAuth 1.0中,用户通过向第三方应用程序发出请求来获取临时凭证。
这个请求包括一些必要的参数:服务提供商的URL、应用程序的消费者密钥(Consumer Key)和消费者密钥的签名方法。
2. 生成签名基本字符串(Signature Base String)接下来,为了生成签名,需要创建签名基本字符串(Signature Base String)。
签名基本字符串是由五个部分组成:HTTP方法、URL、参数排序后的查询字符串、用户令牌(在临时凭证响应中收到的)以及临时令牌(在临时凭证响应中收到的)。
3. 生成签名密钥(Signing Key)签名密钥(Signing Key)由消费者密钥和令牌秘钥组成。
消费者密钥是在向服务提供商注册应用程序时获得的。
令牌秘钥包括用户令牌和临时令牌,由服务提供商提供。
4. 生成签名(Signature)通过使用签名密钥和签名基本字符串,可以生成签名(Signature)。
签名是通过将签名密钥与签名基本字符串进行哈希算法计算的结果得到的。
5. 发送请求(Send Request)最后,将签名和其他必要参数添加到请求中,向服务提供者发送请求。
请求参数包括消费者密钥、签名方法、签名、时间戳以及一些其他可能需要的参数。
服务提供商将验证请求的签名和参数,如果验证通过,则返回访问令牌(Access Token)和访问令牌密钥(Access Token Secret),以便在未来的请求中进行身份验证和授权。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Internet Engineering Task Force (IETF) J. Manner Request for Comments: 5981 Aalto University Category: Experimental M. Stiemerling ISSN: 2070-1721 NEC H. Tschofenig Nokia Siemens Networks R. Bless, Ed. KIT February 2011 Authorization for NSIS Signaling Layer ProtocolsAbstractSignaling layer protocols specified within the Next Steps inSignaling (NSIS) framework may rely on the General Internet Signaling Transport (GIST) protocol to handle authorization. Still, thesignaling layer protocol above GIST itself may require separateauthorization to be performed when a node receives a request for acertain kind of service or resources. This document presents ageneric model and object formats for session authorization within the NSIS signaling layer protocols. The goal of session authorization is to allow the exchange of information between network elements inorder to authorize the use of resources for a service and tocoordinate actions between the signaling and transport planes.Status of This MemoThis document is not an Internet Standards Track specification; it is published for examination, experimental implementation, andevaluation.This document defines an Experimental Protocol for the Internetcommunity. This document is a product of the Internet EngineeringTask Force (IETF). It represents the consensus of the IETFcommunity. It has received public review and has been approved forpublication by the Internet Engineering Steering Group (IESG). Notall documents approved by the IESG are a candidate for any level ofInternet Standard; see Section 2 of RFC 5741.Information about the current status of this document, any errata,and how to provide feedback on it may be obtained at/info/rfc5981.Manner, et al. Experimental [Page 1]Copyright NoticeCopyright (c) 2011 IETF Trust and the persons identified as thedocument authors. All rights reserved.This document is subject to BCP 78 and the IETF Trust’s LegalProvisions Relating to IETF Documents(/license-info) in effect on the date ofpublication of this document. Please review these documentscarefully, as they describe your rights and restrictions with respect to this document. Code Components extracted from this document must include Simplified BSD License text as described in Section 4.e ofthe Trust Legal Provisions and are provided without warranty asdescribed in the Simplified BSD License.Table of Contents1. Introduction . . . . . . . . . . . . . . . . . . . . . . . . . 32. Conventions Used in This Document . . . . . . . . . . . . . . 43. Session Authorization Object . . . . . . . . . . . . . . . . . 4 3.1. Session Authorization Object format . . . . . . . . . . . 5 3.2. Session Authorization Attributes . . . . . . . . . . . . . 6 3.2.1. Authorizing Entity Identifier . . . . . . . . . . . . 7 3.2.2. Session Identifier . . . . . . . . . . . . . . . . . . 9 3.2.3. Source Address . . . . . . . . . . . . . . . . . . . . 9 3.2.4. Destination Address . . . . . . . . . . . . . . . . . 11 3.2.5. Start Time . . . . . . . . . . . . . . . . . . . . . . 12 3.2.6. End Time . . . . . . . . . . . . . . . . . . . . . . . 13 3.2.7. NSLP Object List . . . . . . . . . . . . . . . . . . . 133.2.8. Authentication Data . . . . . . . . . . . . . . . . . 154. Integrity of the SESSION_AUTH Object . . . . . . . . . . . . . 15 4.1. Shared Symmetric Keys . . . . . . . . . . . . . . . . . . 15 4.1.1. Operational Setting Using Shared Symmetric Keys . . . 16 4.2. Kerberos . . . . . . . . . . . . . . . . . . . . . . . . . 17 4.3. Public Key . . . . . . . . . . . . . . . . . . . . . . . . 18 4.3.1. Operational Setting for Public-Key-BasedAuthentication . . . . . . . . . . . . . . . . . . . . 194.4. HMAC Signed . . . . . . . . . . . . . . . . . . . . . . . 215. Framework . . . . . . . . . . . . . . . . . . . . . . . . . . 23 5.1. The Coupled Model . . . . . . . . . . . . . . . . . . . . 23 5.2. The Associated Model with One Policy Server . . . . . . . 23 5.3. The Associated Model with Two Policy Servers . . . . . . . 245.4. The Non-Associated Model . . . . . . . . . . . . . . . . . 246. Message Processing Rules . . . . . . . . . . . . . . . . . . . 25 6.1. Generation of the SESSION_AUTH by an Authorizing Entity . 25 6.2. Processing within the QoS NSLP . . . . . . . . . . . . . . 25 6.2.1. Message Generation . . . . . . . . . . . . . . . . . . 25 6.2.2. Message Reception . . . . . . . . . . . . . . . . . . 26 Manner, et al. Experimental [Page 2]6.2.3. Authorization (QNE or PDP) . . . . . . . . . . . . . . 26 6.2.4. Error Signaling . . . . . . . . . . . . . . . . . . . 27 6.3. Processing with the NATFW NSLP . . . . . . . . . . . . . . 27 6.3.1. Message Generation . . . . . . . . . . . . . . . . . . 28 6.3.2. Message Reception . . . . . . . . . . . . . . . . . . 28 6.3.3. Authorization (Router/PDP) . . . . . . . . . . . . . . 28 6.3.4. Error Signaling . . . . . . . . . . . . . . . . . . . 296.4. Integrity Protection of NSLP Messages . . . . . . . . . . 297. Security Considerations . . . . . . . . . . . . . . . . . . . 308. IANA Considerations . . . . . . . . . . . . . . . . . . . . . 319. Acknowledgments . . . . . . . . . . . . . . . . . . . . . . . 3410. References . . . . . . . . . . . . . . . . . . . . . . . . . . 34 10.1. Normative References . . . . . . . . . . . . . . . . . . . 34 10.2. Informative References . . . . . . . . . . . . . . . . . . 351. IntroductionThe Next Steps in Signaling (NSIS) framework [RFC4080] defines asuite of protocols for the next generation in Internet signaling.The design is based on a generalized transport protocol for signaling applications, the General Internet Signaling Transport (GIST)[RFC5971], and various kinds of signaling applications. Twosignaling applications and their NSIS Signaling Layer Protocol (NSLP) have been designed, a Quality of Service application (QoS NSLP)[RFC5974] and a NAT/firewall application (NATFW NSLP) [RFC5973].The basic security architecture for NSIS is based on a chain-of-trust model, where each GIST hop may choose the appropriate securityprotocol, taking into account the signaling application requirements. For instance, communication between two directly adjacent GIST peers may be secured via TCP/TLS. On the one hand, this model isappropriate for a number of different use cases and allows thesignaling applications to leave the handling of security to GIST. On the other hand, several sessions of different signaling applications are then multiplexed onto the same GIST TLS connection.Yet, in order to allow for finer-grain per-session or per-useradmission control, it is necessary to provide a mechanism forensuring that the use of resources by a host has been properlyauthorized before allowing the signaling application to commit theresource request, e.g., a QoS reservation or mappings for NATtraversal. In order to meet this requirement, there must beinformation in the NSLP message that may be used to verify thevalidity of the request. This can be done by providing the host with a Session Authorization Object that is inserted into the message and verified by the respective network elements.Manner, et al. Experimental [Page 3]This document describes a generic NSLP-layer Session AuthorizationObject (SESSION_AUTH) used to convey authorization information forthe request. "Generic" in this context means that it is usable byall NSLPs. The scheme is based on third-party tokens. A trustedthird party provides authentication tokens to clients and allowsverification of the information by the network elements. Therequesting host inserts the authorization information (e.g., a policy object) acquired from the trusted third party into the NSLP messageto allow verification of the network resource request. Networkelements verify the request and then process it based on admissionpolicy (e.g., they perform a resource reservation or change bindings or firewall filter). This work is based on RFC 3520 [RFC3520] andRFC 3521 [RFC3521].The default operation when using NSLP-layer session authorization is to add one authorization policy object. Yet, in order to supportend-to-end signaling and request authorization from differentnetworks, a host initiating an NSLP signaling session may add morethan one SESSION_AUTH object in the message. The identifier of theauthorizing entity can be used by the network elements to use thethird party they trust to verify the request.2. Conventions Used in This DocumentThe key words "MUST", "MUST NOT", "REQUIRED", "SHALL", "SHALL NOT","SHOULD", "SHOULD NOT", "RECOMMENDED", "MAY", and "OPTIONAL" in this document are to be interpreted as described in BCP 14, RFC 2119[RFC2119].The term "NSLP node" (NN) is used to refer to an NSIS node running an NSLP protocol that can make use of the authorization object discussed in this document. Currently, this node would run either the QoS NSLP [RFC5974] or the NAT/Firewall NSLP [RFC5973] service.3. Session Authorization ObjectThis section presents a new NSLP-layer object called sessionauthorization (SESSION_AUTH). The SESSION_AUTH object can be used in the currently specified and future NSLP protocols.The authorization attributes follow the format and specificationgiven in RFC3520 [RFC3520].Manner, et al. Experimental [Page 4]3.1. Session Authorization Object formatThe SESSION_AUTH object contains a list of fields that describe thesession, along with other attributes. The object header follows the generic NSLP object header; therefore, it can be used together withany NSLP.0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+|A|B|r|r| Type |r|r|r|r| Length |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-++ +// Session Authorization Attribute List //+ ++---------------------------------------------------------------+The value for the Type field comes from shared NSLP object typespace. The Length field is given in units of 32-bit words andmeasures the length of the Value component of the TLV object (i.e.,it does not include the standard header).The bits marked ’A’ and ’B’ are extensibility flags and are used tosignal the desired treatment for objects whose treatment has not been defined in the protocol specification (i.e., whose Type field isunknown at the receiver). The following four categories of objecthave been identified, and are described here for informationalpurposes only (for normative behavior, refer to the particular NSLPdocuments, e.g., [RFC5974] [RFC5973]).AB=00 ("Mandatory"): If the object is not understood, the entiremessage containing it MUST be rejected, and an error message sent back (usually of class/code "Protocol Error/Unknown objectpresent").AB=01 ("Ignore"): If the object is not understood, it MUST bedeleted, and the rest of the message processed as usual.AB=10 ("Forward"): If the object is not understood, it MUST beretained unchanged in any message forwarded as a result of message processing, but not stored locally.AB=11 ("Refresh"): If the object is not understood, it should beincorporated into the locally stored signaling application statefor this flow/session, forwarded in any resulting message, andalso used in any refresh or repair message which is generatedlocally. This flag combination is not used by all NSLPs, e.g., it is not used in the NATFW NSLP.Manner, et al. Experimental [Page 5]The remaining bits marked ’r’ are reserved. The extensibility flags follow the definition in the GIST specification. The SESSION_AUTHobject defined in this specification MUST have the AB bits set to"10". An NSLP Node (NN) may use the authorization information if it is configured to do so, but may also just skip the object.Type: SESSION_AUTH_OBJECT (0x016)Length: Variable, contains length of session authorization objectlist in units of 32-bit words.Session Authorization Attribute List: variable lengthThe session authorization attribute list is a collection ofobjects that describes the session and provides other information necessary to verify resource request (e.g., a resourcereservation, binding, or firewall filter change request). Aninitial set of valid objects is described in Section 3.2.3.2. Session Authorization AttributesA session authorization attribute may contain a variety ofinformation and has both an attribute type and sub-type. Theattribute itself MUST be a multiple of 4 octets in length, and anyattributes that are not a multiple of 4 octets long MUST be padded toa 4-octet boundary. All padding bytes MUST have a value of zero.0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Length | X-Type | SubType |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+// Value ... //+---------------------------------------------------------------+Length: 16 bitsThe Length field is two octets and indicates the actual length of the attribute (including Length, X-Type, and SubType fields) innumber of octets. The length does NOT include any padding of the value field to make the attribute’s length a multiple of 4 octets. X-Type: 8 bitsSession authorization attribute type (X-Type) field is one octet. IANA acts as a registry for X-Types as described in Section 8,IANA Considerations. This specification uses the followingX-Types:Manner, et al. Experimental [Page 6]1. AUTH_ENT_ID: The unique identifier of the entity thatauthorized the session.2. SESSION_ID: The unique identifier for this session, usuallycreated locally at the authorizing entity. See also RFC 3520 [RFC3520]; not to be confused with the SESSION-ID of GIST/NSIS.3. SOURCE_ADDR: The address specification for the signalingsession initiator, i.e., the source address of the signalingmessage originator.4. DEST_ADDR: The address specification for the signaling session endpoint.5. START_TIME: The starting time for the session.6. END_TIME: The end time for the session.7. AUTHENTICATION_DATA: The authentication data of the SessionAuthorization Object.SubType: 8 bitsSession authorization attribute sub-type is one octet in length.The value of the SubType depends on the X-Type.Value: variable lengthThe attribute-specific information.3.2.1. Authorizing Entity IdentifierThe AUTH_ENT_ID is used to identify the entity that authorized theinitial service request and generated the Session AuthorizationObject. The AUTH_ENT_ID may be represented in various formats, andthe SubType is used to define the format for the ID. The format for AUTH_ENT_ID is as follows:0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Length | X-Type | SubType |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+// OctetString ... //+---------------------------------------------------------------+ Manner, et al. Experimental [Page 7]Length: Length of the attribute, which MUST be > 4.X-Type: AUTH_ENT_IDSubType:The following sub-types for AUTH_ENT_ID are defined. IANA acts as a registry for AUTH_ENT_ID SubTypes as described in Section 8,IANA Considerations. Initially, the registry contains thefollowing SubTypes of AUTH_ENT_ID:1. IPV4_ADDRESS: IPv4 address represented in 32 bits.2. IPV6_ADDRESS: IPv6 address represented in 128 bits.3. FQDN: Fully Qualified Domain Name as defined in [RFC1034] as an ASCII string.4. ASCII_DN: X.500 Distinguished name as defined in [RFC4514] as an ASCII string.5. UNICODE_DN: X.500 Distinguished name as defined in [RFC4514] as a UTF-8 string.6. URI: Universal Resource Identifier, as defined in [RFC3986].7. KRB_PRINCIPAL: Fully Qualified Kerberos Principal namerepresented by the ASCII string of a principal, followed bythe @ realm name as defined in [RFC4120] (e.g.,johndoe@nowhere).8. X509_V3_CERT: The Distinguished Name of the subject of thecertificate as defined in [RFC4514] as a UTF-8 string.9. PGP_CERT: The OpenPGP certificate of the authorizing entityas defined as Public-Key Packet in [RFC4880].10. HMAC_SIGNED: Indicates that the AUTHENTICATION_DATA attribute contains a self-signed HMAC signature [RFC2104] that ensures the integrity of the NSLP message. The HMAC is calculatedover all NSLP objects given in the NSLP_OBJECT_LIST attribute that MUST also be present. The object specifies the hashalgorithm that is used for calculation of the HMAC asTransform ID from Transform Type 3 of the IKEv2 registry[RFC5996].OctetString: Contains the authorizing entity identifier.Manner, et al. Experimental [Page 8]3.2.2. Session IdentifierSESSION_ID is a unique identifier used by the authorizing entity toidentify the request. It may be used for a number of purposes,including replay detection, or to correlate this request to a policy decision entry made by the authorizing entity. For example, theSESSION_ID can be based on simple sequence numbers or on a standardNTP timestamp.0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Length | X-Type | SubType |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+// OctetString ... //+---------------------------------------------------------------+Length: Length of the attribute, which MUST be > 4.X-Type: SESSION_IDSubType:No sub-types for SESSION_ID are currently defined; this field MUST be set to zero. The authorizing entity is the only network entity that needs to interpret the contents of the SESSION_ID; therefore, thecontents and format are implementation dependent.OctetString: The OctetString contains the session identifier.3.2.3. Source AddressSOURCE_ADDR is used to identify the source address specification ofthe authorized session. This X-Type may be useful in some scenarios to make sure the resource request has been authorized for thatparticular source address and/or port. Usually, it corresponds tothe signaling source, e.g., the IP source address of the GIST packet, or flow source or flow destination address, respectively, which arecontained in the GIST MRI (Message Routing Information) object.0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Length | X-Type | SubType |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+// OctetString ... //+---------------------------------------------------------------+ Manner, et al. Experimental [Page 9]Length: Length of the attribute, which MUST be > 4.X-Type: SOURCE_ADDRSubType:The following sub-types for SOURCE_ADDR are defined. IANA acts as a registry for SOURCE_ADDR SubTypes as described in Section 8,IANA Considerations. Initially, the registry contains thefollowing SubTypes for SOURCE_ADDR:1. IPV4_ADDRESS: IPv4 address represented in 32 bits.2. IPV6_ADDRESS: IPv6 address represented in 128 bits.3. UDP_PORT_LIST: list of UDP port specifications, represented as 16 bits per list entry.4. TCP_PORT_LIST: list of TCP port specifications, represented as 16 bits per list entry.5. SPI: Security Parameter Index, represented in 32 bits.OctetString: The OctetString contains the source address information. In scenarios where a source address is required (see Section 5), atleast one of the sub-types 1 or 2 MUST be included in every SessionAuthorization Object. Multiple SOURCE_ADDR attributes MAY beincluded if multiple addresses have been authorized. The sourceaddress of the request (e.g., a QoS NSLP RESERVE) MUST match one ofthe SOURCE_ADDR attributes contained in this Session AuthorizationObject.At most, one instance of sub-type 3 MAY be included in every Session Authorization Object. At most, one instance of sub-type 4 MAY beincluded in every Session Authorization Object. Inclusion of a sub- type 3 attribute does not prevent inclusion of a sub-type 4 attribute (i.e., both UDP and TCP ports may be authorized).If no PORT attributes are specified, then all ports are consideredvalid; otherwise, only the specified ports are authorized for use.Every source address and port list must be included in a separateSOURCE_ADDR attribute.Manner, et al. Experimental [Page 10]3.2.4. Destination AddressDEST_ADDR is used to identify the destination address of theauthorized session. This X-Type may be useful in some scenarios tomake sure the resource request has been authorized for thatparticular destination address and/or port.0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Length | X-Type | SubType |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+// OctetString ... //+---------------------------------------------------------------+Length: Length of the attribute in number of octets, which MUST be > 4.X-Type: DEST_ADDRSubType:The following sub-types for DEST_ADDR are defined. IANA acts as a registry for DEST_ADDR SubTypes as described in Section 8, IANAConsiderations. Initially, the registry contains the followingSubTypes for DEST_ADDR:1. IPV4_ADDRESS: IPv4 address represented in 32 bits.2. IPV6_ADDRESS: IPv6 address represented in 128 bits.3. UDP_PORT_LIST: list of UDP port specifications, represented as 16 bits per list entry.4. TCP_PORT_LIST: list of TCP port specifications, represented as 16 bits per list entry.5. SPI: Security Parameter Index, represented in 32 bits.OctetString: The OctetString contains the destination addressspecification.In scenarios where a destination address is required (see Section 5), at least one of the sub-types 1 or 2 MUST be included in everySession Authorization Object. Multiple DEST_ADDR attributes MAY beincluded if multiple addresses have been authorized. The destination Manner, et al. Experimental [Page 11]address field of the resource reservation datagram (e.g., QoS NSLPReserve) MUST match one of the DEST_ADDR attributes contained in this Session Authorization Object.At most, one instance of sub-type 3 MAY be included in every Session Authorization Object. At most, one instance of sub-type 4 MAY beincluded in every Session Authorization Object. Inclusion of a sub- type 3 attribute does not prevent inclusion of a sub-type 4 attribute (i.e., both UDP and TCP ports may be authorized).If no PORT attributes are specified, then all ports are consideredvalid; otherwise, only the specified ports are authorized for use.Every destination address and port list must be included in aseparate DEST_ADDR attribute.3.2.5. Start TimeSTART_TIME is used to identify the start time of the authorizedsession and can be used to prevent replay attacks. If theSESSION_AUTH object is presented in a resource request, the networkSHOULD reject the request if it is not received within a few seconds of the start time specified.0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Length | X-Type | SubType |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+// OctetString ... //+---------------------------------------------------------------+Length: Length of the attribute, which MUST be > 4.X-Type: START_TIMESubType:The following sub-type for START_TIME is defined. IANA acts as aregistry for START_TIME SubTypes as described in Section 8, IANAConsiderations. Initially, the registry contains the followingSubType for START_TIME:1 NTP_TIMESTAMP: NTP Timestamp Format as defined in RFC 5905[RFC5905].OctetString: The OctetString contains the start time.Manner, et al. Experimental [Page 12]3.2.6. End TimeEND_TIME is used to identify the end time of the authorized sessionand can be used to limit the amount of time that resources areauthorized for use (e.g., in prepaid session scenarios).0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+| Length | X-Type | SubType |+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+// OctetString ... //+---------------------------------------------------------------+Length: Length of the attribute, which MUST be > 4.X-Type: END_TIMESubType:The following sub-type for END_TIME is defined. IANA acts as aregistry for END_TIME SubTypes as described in Section 8, IANAConsiderations. Initially, the registry contains the followingSubType for END_TIME:1 NTP_TIMESTAMP: NTP Timestamp Format as defined in RFC 5905[RFC5905].OctetString: The OctetString contains the end time.3.2.7. NSLP Object ListThe NSLP_OBJECT_LIST attribute contains a list of NSLP object typesthat are used in the keyed-hash computation whose result is given in the AUTHENTICATION_DATA attribute. This allows for an integrityprotection of NSLP PDUs. If an NSLP_OBJECT_LIST attribute has beenincluded in the SESSION_AUTH object, an AUTHENTICATION_DATA attribute MUST also be present.The creator of this attribute lists every NSLP object type whose NSLP PDU object was included in the computation of the hash. The hashcomputation has to follow the order of the NSLP object types asspecified by the list. The receiver can verify the integrity of the NSLP PDU by computing a hash over all NSLP objects that are listed in this attribute (in the given order), including all the attributes of the authorization object. Since all NSLP object types are uniqueover all different NSLPs, this will work for any NSLP.Manner, et al. Experimental [Page 13]Basic NSIS Transport Layer Protocol (NTLP) / NSLP objects like thesession ID, the NSLPID, and the MRI MUST be always included in theHMAC. Since they are not carried within the NSLP itself, but onlywithin GIST, they have to be provided for HMAC calculation, e.g.,they can be delivered via the GIST API. They MUST be normalized totheir network representation from [RFC5971] again before calculating the hash. These values MUST be hashed first (in the order sessionID, NSLPID, MRI), before any other NSLP object values that areincluded in the hash computation.A summary of the NSLP_OBJECT_LIST attribute format is describedbelow.0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+---------------+---------------+---------------+---------------+| Length | NSLP_OBJ_LIST | zero |+---------------+---------------+-------+-------+---------------+| # of signed NSLP objects = n | rsv | NSLP object type (1) |+-------+-------+---------------+-------+-------+---------------+| rsv | NSLP object type (2) | ..... //+-------+-------+---------------+---------------+---------------+| rsv | NSLP object type (n) | (padding if required) |+--------------+----------------+---------------+---------------+Length: Length of the attribute, which MUST be > 4.X-Type: NSLP_OBJECT_LISTSubType: No sub-types for NSLP_OBJECT_LIST are currently defined.This field MUST be set to 0 and ignored upon reception.# of signed NSLP objects: The number n of NSLP object types thatfollow. n=0 is allowed; in that case, only a padding field iscontained.rsv: reserved bits; MUST be set to 0 and ignored upon reception.NSLP object type: the NSLP 12-bit object type identifier of theobject that was included in the hash calculation. The NSLP objecttype values comprise only 12 bits, so four bits per type value arecurrently not used within the list. Depending on the number ofsigned objects, a corresponding padding word of 16 bits must besupplied.Manner, et al. Experimental [Page 14]。
