CommUser
Config文件的使用:通过程序修改Config文件

Config⽂件的使⽤:通过程序修改Config⽂件对于config⽂件,⼀般情况下都是使⽤ConfigurationManager加载,然后通过读取相应节点的值来获取想要的数据,但是,有时候需要修改config⽂件的值,这时候就⽤到了OpenExeConfiguration()⽅法。
MSDN上⾯对该⽅法的解释:ConfigurationManager.OpenExeConfiguration⽅法⽤来把指定的客户端配置⽂件作为Configuration对象打开,该⽅法具有两个重载:名称说明ConfigurationManager.OpenExeConfiguration (ConfigurationUserLevel)将当前应⽤程序的配置⽂件作为 Configuration 对象打开。
ConfigurationManager.OpenExeConfiguration (String)将指定的客户端配置⽂件作为 Configuration 对象打开。
⼀、使⽤OpenExeConfiguration(ConfigurationUserLevel)重载设置当前应⽤程序的配置⽂件客户端应⽤程序使⽤应⽤于所有⽤户的全局配置、应⽤于单个⽤户的单独配置以及应⽤于漫游⽤户的配置。
userLevel 参数通过指⽰该配置⽂件是不具有⽤户级别(配置⽂件与应⽤程序位于同⼀⽬录中),还是具有⼀个依每个⽤户⽽定的⽤户级别(配置⽂件位于⽤户级别所确定的应⽤程序设置路径中),从⽽确定所打开的配置⽂件的位置。
通过向 userLevel 传递下列值之⼀来指定要获取的配置:若要获取应⽤于所有⽤户的 Configuration 对象,请将 userLevel 设置为 None。
若要获取应⽤于当前⽤户的本地 Configuration 对象,请将 userLevel 设置为 PerUserRoamingAndLocal。
若要获取应⽤于当前⽤户的漫游 Configuration 对象,请将 userLevel 设置为 PerUserRoaming。
Allen-Bradley DPI External Communications Kit 安装说明

DPI External Communications KitInstallation InstructionsThese Installation Instructions are provided with the DPI External Comms Kit. This document explains how to install a communications adapter (sold separately) into the kit, mount the kit in an enclosure, and connect the required cables.These instructions also describe the accessory AC Power Adapter. See AC Power Adapter (20-XCOMM-AC-PS1) on page3 for details.CompatabilityThis kit is for use with only the following Allen-Bradley communication adapters (sold separately):•20-COMM-E EtherNet/IP•20-COMM-C ControlNet (coax)•20-COMM-Q ControlNet (fiber)•20-COMM-D DeviceNet (Series B or later)•20-COMM-B BACnet MS/TP•20-COMM-M Modbus/TCPThe DPI External Comms Kit is typically used to provide an additional network connection for a drive that already has a 20-COMM-* installed inside. For example, one network may be used for control and a second network may be used for configuration and data collection.Installing the Communications Adapter1.Before you install the communication adapter into theComms Kit, make sure to configure all of the adapter’s switches and/or jumpers, if applicable, to appropriatesettings. Refer to the Communication Adapter UserManual for details.2.Remove the Comms Kit enclosure cover from the baseby unfastening its two screws.3.Fasten the communication adapter into the enclosurecover by using the adapter’s captive screws (Figure 1).This also grounds the adapter.4.The communication adapter is supplied with two InternalInterface (ribbon) cables. Use only the longer 15.24 cm(6 in.) Internal Interface cable. Plug one end of the cableinto the mating connector on the power supply board in the base of the Comms Kit enclosure.Figure 1Mounting and Connecting the Adapter5.Plug the other end of the Internal Interface cable into themating connector on the communication adapter.6.If using an Allen-Bradley I/O Board option (20-XCOMM-IO-OPT*) with the External Comms Kit,install the I/O board into the kit at this time. For details, see the I/O Board Installation Instructions provided with the board. Otherwise, fasten the enclosure cover onto the base using the two screws in the cover.Mounting the External Comms KitPanel or DIN rail mount the Comms Kit before connecting the adapter to the network and drive.External Comms Kit (20-XCOMM-DC-BASE)!ATTENTION: Risk of equipment damage exists.The communications adapter contains ESD(Electrostatic Discharge) sensitive parts that can bedamaged if you do not follow ESD controlprocedures. Static control precautions are requiredwhen handling the adapter. If you are unfamiliar withstatic control procedures, refer to Guarding AgainstElectrostatic Damage, Publication 8000-4.5.2.!ATTENTION: Risk of equipment damage exists.During panel or DIN rail mounting, be sure toprevent any debris (metal chips, wire strands, etc.)from falling into the Comms Kit. Debris that fallsinto the kit could cause damage on power up.Minimum SpacingExternal Comms Kits can be zero-stacked (side-by-sidemounting). Allow 75 mm (3 in.) of space on the bottom of the enclosure for cable entry. Allow at least 75 mm (3.2 in.) of enclosure clearance depth to accommodate the Comms Kit.Panel Mounting Using the Dimensional DrawingMount the Comms Kit to a panel using two M4 or #8 panhead screws (not included). Figure 2 shows mounting dimensions.Figure 2Panel Mounting DimensionsPanel Mounting Procedure Using Comms Kit as a Template The following procedure enables you to use the assembled Comms Kit as a template for drilling holes in the ing the assembled Comms Kit as a template, carefully mark the center of both holes on the panel.2.Remove the Comms Kit to a clean location.3.Drill and tap the mounting holes for the recommended M4 or #8 panhead screws (not included).4.Place the Comms Kit back on the panel, and check for proper hole alignment.5.Attach the Comms Kit to the panel using the mounting screws.DIN Rail MountingThe Comms Kit can be mounted using these DIN rails:•35 x 7.5 mm (EN 50 022 - 35 x 7.5)•35 x 15 mm (EN 50 022 - 35 x 15)Before mounting the Comms Kit on a DIN rail, open the DIN rail latch. Press the DIN rail mounting area of theComms Kit against the DIN rail, and manually lock the DIN rail latch (Figure 3).Figure 3DIN Rail MountingElectrical ConnectionsAfter the communication adapter (and I/O Board option, if used) is installed and the Comms Kit is mounted, connect all required cables. See Figure 4 and its related table showing the connectors and their connection procedures.Figure 4Connecting to the Comms Kit!ATTENTION: Risk of equipment damage, injury or death exists. Unpredictable operation may occur if you fail to verify that parameter settings and switch settings are compatible with yourapplication. Verify that settings are compatible with your application before applying power to the drive.Item DescriptionConnection Procedure➊Network Connector Connection for the network. Insert the network cable plug into the mating connector on the communications adapter.➋Optional I/O T erminal BlockSee the I/O Board option (20-XCOMM-IO-OPT*) Installation Instructions for details.Configuring the Communications AdapterAfter mounting and connecting the Comms Kit, configure the communication adapter. Refer to the communication adapter User Manual for complete details.External Comms Kit SpecificationsCommunicationsElectricalMechanicalEnvironmentalRegulatory ComplianceNOTE: In order to remain CE and CTick compliant, the DPI cable length may not exceed 30 m (98.4 ft.).NOTE: This is a product of category C3 according to IEC 61800-3. It is not intended for operation in a domestic environment.The 20-XCOMM-AC-PS1 is an accessory AC-to-DC converter for use with the External Comms Kit. It is used when only 100-240 V AC power is available inside a control panel. The converter, which comes with interchangeable plugs, is shown below. The converter connects to an AC receptacle inside the control panel. Use the appropriate plug for your region:(1)The DC power source or AC-to-DC converter used to power the Comms Kit must *************************************************,itsconnector must be of “pin and barrel” construction with a 2 mm pin.(2)To power multiple Comms Kits, see Powering Daisy-Chained Comms Kits on page 4.Network Dependent on installed 20-COMM-* adapter Drive Protocol Data RatesDPI125 kbps or 500 kbpsDrive 60 mA at 12 VDC supplied from drive via DPI cable NetworkNone for all network protocols except:DeviceNet 60 mA at 24 VDCDC Power Supply Requirement (1)(1)Since the Comms Kit is powered by a nominal 24 VDC, the current consumption listed in this table differs from the value shown on the label of the communication adapter, which is based on the adapter being powered by 5 VDC from the drive.20-COMM-B 75 mA at 24 VDC 20-COMM-C 105 mA at 24 VDC20-COMM-D 60 mA at 24 VDC 20-COMM-E 140 mA at 24 VDC 20-COMM-Q 135 mA at 24 VDC 20-COMM-M 140 mA at 24 VDCDimensions Width Height Depth 108 mm (4.25 in.)108 mm (4.25 in.) with I/O terminal block attached 75 mm (2.95 in.)Weight340 g (12 oz.)Temperature Operating Storage-10 to 50° (14 to 122° F)-40 to 85° (-40 to 185° F)Relative Humidity 5 to 95% non-condensingAtmosphereImportant: The Comms Kit must not be installed in an area where the ambient atmosphere contains volatile or corrosive gas, vapors or dust. If theComms Kit is not going to be installed for a period of time, it must be stored in an area where it will not be exposed to a corrosive atmosphere.ShockOperationalNon-operational 30g, 11 ms (DIN Rail Mount)50g, 11 ms (Panel Mount)30g, 11 ms (DIN Rail Mount)50g, 11 ms (Panel Mount)Vibration Operational Non-operational 2.5g, 5 to 2000 Hz 5.0g, 5 to 2000 HzUL UL508CCUL CAN / CSA C22.2 No. 14-M91CE EN50178 and EN61800-3CTickEN61800-3AC Power Adapter (20-XCOMM-AC-PS1)For use in the US For use in the UKFor use in EuropeFor use in AustraliaPublication 20COMM-IN001D-EN-P – May 2007P/N 319869-P04Supersedes 20COMM-IN001C-EN-P – July 2006Copyright © 2007 Rockwell Automation, Inc. All rights reserved. Printed in USA.Electrical ConnectionsPowering a Single Comms KitThe DC output plug is connected to the mating DC ADP connector on the 20-XCOMM-DC-BASE.Powering Daisy-Chained Comms KitsAdditional Comms Kits can be powered by daisy-chaining them together. For each Comms Kit in the chain, connect all DC “+” terminals together and all DC “-” terminals together (Figure 5).Figure 5Powering Multiple Comms Kits via Daisy ChainingThe number of Comms Kits that can be daisy-chained together is dependent on:•Total current consumed by all of the communication adapters being daisy-chained. For adapter current consumptions at 24 VDC, see DC Power Supply Requirement on page 3.•Whether or not an I/O Board option is installed. If it is, the I/O Board consumes 60 mA @ 24VDC.•Available current output capacity of the AC-to-DC converter being used.The following two examples explain how to determine the number of daisy-chained Comms Kits that can be powered:Example 1: Suppose the Comms Kits being daisy-chained each have an installed 20-COMM-E EtherNet/IP adapter and I/O Board option, and that the kits will be powered by the 20-XCOMM-AC-PS1 converter which has an output capacity of 830 mA.Since the current consumed by one Comms Kit is 200 mA (140 mA for the 20-COMM-E plus 60 mA for the I/O board), divide the power source’s available output capacity by this consumption (830 mA ÷ 200 mA = 4.15), and round down the result. For this example, 4 daisy-chained Comms Kits can be powered.Example 2: Suppose the Comms Kits being daisy-chained each have an installed 20-COMM-C ControlNet adapter, and that the kits will be powered by the 20-XCOMM-AC-PS1 converter which has an output capacity of 830 mA.Since the current consumed by one Comms Kit is 105 mA, divide the power source’s available output capacity by this consumption (830 mA ÷ 105 mA = 7.90), and round down the result. For this example, 7 daisy-chained Comms Kits can be powered.AC Power Adapter SpecificationsTIP: It is highly recommended to use twisted wire pairs for better noise immunity.TIP: When using the DC power source to also power the additional I/O, subtract the required I/O current from the power source capacity before making the calculation.InputRated Input Voltage Operating Input Voltage AC Input Frequency 100 - 240 VAC 90 - 264 VAC 47 - 63 Hz OutputOutput Voltage Output Current24 VDC 830 mAU.S.Allen-BradleyDrivesTechnicalSupport-Tel:(1)262.512.8176,Fax:(1)262.512.2222,Email:*****************,Online:/support/abdrives。
IGMP协议

IGMP协议概述The Internet Group Management Protocol(IGMP)is a network‑layer protocol used by hosts and ad‑jacent routers on an Internet Protocol(IP)network to report their multicast group memberships.It is an essential component of IP multicast,which enables efficient delivery of data to multiple hosts simultaneously.BackgroundIn traditional IP networks,data packets are typically sent to a unicast address,which means they are delivered to a specific destination host.However,in scenarios where data needs to be sent to multiple recipients simultaneously,such as multimedia streaming or real‑time collaboration applications,the unicast approach becomes inefficient and resource‑consuming.This is where multicast comes into play.What is Multicast?Multicast is a communication method that allows a single sender to transmit data packets to a group of receivers.Instead of sending separate copies of the data to each receiver,the sender multicasts the data once,and it is then replicated and delivered only to the members of the multicast group who have expressed interest in receiving the data.Role of IGMPIGMP plays a crucial role in enabling hosts to join and leave multicast groups dynamically.It allows routers to learn which hosts are interested in receiving multicast traffic for specific groups and effi‑ciently forward the data only to those interested hosts.How IGMP Works1.Host Joins a Multicast Group:When a host wants to receive multicast traffic for a specific group,it sends an IGMP join message to its local router,indicating its interest in joining the group. 2.Router Membership Query:Routers periodically send IGMP membership queries on the networkto discover which hosts belong to multicast groups.These queries elicit IGMP membership re‑ports from the hosts.3.Host Membership Reports:Upon receiving a query,hosts respond with IGMP membership re‑ports,indicating the multicast groups they are interested in.4.Router Forwarding:Routers maintain a list of active multicast groups and their associated hosts.They use this information to forward multicast traffic only to the hosts that have joined the re‑spective groups.Benefits and ApplicationsIGMP enables efficient distribution of multicast traffic,reducing network congestion and bandwidth consumption.It finds applications in various scenarios,including:•Video streaming and IPTV•Online gaming and interactive applications•Software‑defined networking(SDN)•Content delivery networks(CDNs)•Collaborative tools and virtual classroomsSecurity and LimitationsWhile IGMP facilitates multicast communication,it’s important to consider security aspects and im‑plement appropriate measures to prevent unauthorized access or malicious activities.Additionally, IGMP has some limitations,such as scalability challenges in large networks and potential issues with router performance under heavy multicast traffic.In conclusion,IGMP is a critical protocol for managing multicast group memberships in IP networks. By allowing hosts to join and leave multicast groups dynamically,IGMP enables efficient and scalable delivery of multicast traffic,catering to various applications and improving network performance. IGMP协议的工作原理IGMP(Internet Group Management Protocol)是一种网络层协议,用于在Internet协议(IP)网络上的主机和相邻路由器之间报告它们的组播组成员关系。
AT88SC0808C Atmel 密码型存储器数据手册说明书

AT88SC0808CAtmel CryptoMemory, 8-KbitSUMMARY DATASHEETFeatures • One of a family of nine devices with user memories from 1-Kbit to 256-Kbit •8-Kbit (1-Kbyte) EEPROM user memory• Eight 128-byte (1-Kbit) zones • Self-timed write cycle• Single byte or 16-byte page write mode • Programmable access rights for each zone• 2-Kbit configuration zone• 37-byte OTP area for user-defined codes• 160-byte area for user-defined keys and passwords •High security features• 64-bit mutual authentication protocol (under license of ELVA) • Encrypted checksum • Stream encryption• Four key sets for authentication and encryption • Eight sets of two 24-bit passwords • Anti-tearing function• Voltage and frequency monitor•Smart card features• ISO 7816 Class A (5V) or Class B (3V) operation• ISO 7816-3 asynchronous T = 0 protocol (Gemplus ®patent) * • Multiple zones, key sets and passwords for multi-application use • Synchronous 2-wire serial interface for faster device initialization * • Programmable 8-byte answer-to-reset register •ISO 7816-2 compliant modules•Embedded application features• Low voltage operation: 2.7V to 5.5V• Secure nonvolatile storage for sensitive system or user information • 2-wire serial interface• 1.0MHz compatibility for fast operation• Standard 8-lead plastic packages, green compliant (exceeds RoHS) •Same pinout as 2-wire Serial EEPROMs•High reliability• Endurance: 100,000 cycles • Data retention: 10 years • ESD protection: 4,000V min* Note: Modules available with either T=0 / 2-wire modes or 2-wire mode onlyThis is a summary document. The complete document is available on the Atmel website at .AT88SC0808C [SUMMARY DATASHEET]Atmel-2024MS-CryptoMem-AT88SC0808C-Datasheet-Summary_1220132Table 1. Pin AssignmentFigure 1.Pin Configuration1. DescriptionThe Atmel ®AT88SC0808C member of the Atmel CryptoMemory ®family is a high-performance secure memory providing 8-Kbits of user memory with advanced security and cryptographic features built in. The user memory is divided into eight 128-byte zones, each of which may be individually set with different security access rights or effectively combined together to provide space for one to eight data files.1.1 Smart Card ApplicationsThe AT88SC0808C provides high security, low cost, and ease of implementation without the need for a microprocessor operating system. The embedded cryptographic engine provides for dynamic and symmetric mutual authentication between the device and host, as well as performing stream encryption for all data and passwords exchanged between the device and host. Up to four unique key sets may be used for these operations. The AT88SC0808C offers the ability to communicate with virtually any smart card reader using the asynchronous T = 0 protocol (Gemplus Patent) defined in ISO 7816-3.1.2 Embedded ApplicationsThrough dynamic and symmetric mutual authentication, data encryption, and the use of encrypted checksums, theAT88SC0808C provides a secure place for storage of sensitive information within a system. With its tamper detection circuits, this information remains safe even under attack. A 2-wire serial interface running at 1.0MHz is used for fast and efficientcommunications with up to 15 devices that may be individually addressed. The AT88SC0808C is available in industry standard 8-lead packages with the same familiar pinout as 2-wire Serial EEPROMs.V CC =C1RST=C2SCL/CLK=C3NC=C4ISO Smart Card ModuleC5=GND C6=NC C7=SDA/IO C8=NCNC NC NC GND123487658-lead SOIC, PDIP V CC NC SCL SDAV CC =C1NC=C2SCL/CLK=C3NC=C4TWI Smart Card ModuleC5=GND C6=NC C7=SDA/IO C8=NCAT88SC0808C [SUMMARY DATASHEET]Atmel-2024MS-CryptoMem-AT88SC0808C-Datasheet-Summary_1220133Figure 1-1. Block Diagram2.Pin Descriptions2.1Supply Voltage (V CC )The V CC input is a 2.7V to 5.5V positive voltage supplied by the host.2.2 Clock (SCL/CLK)In the asynchronous T = 0 protocol, the SCL/CLK input is used to provide the device with a carrier frequency f . The nominal length of one bit emitted on I/O is defined as an “elementary time unit” (ETU) and is equal to 372/f. When the synchronous protocol is used, the SCL/CLK input is used to positive edge clock data into the device and negative edge clock data out of the device.2.3 Reset (RST)The AT88SC0808C provides an ISO 7816-3 compliant asynchronous answer to reset sequence. When the reset sequence is activated, the device will output the data programmed into the 64-bit answer-to-reset register. An internal pull-up on the RST input pad allows the device to be used in synchronous mode without bonding RST. The AT88SC0808C does not support the synchronous answer-to-reset sequence2.4 Serial Data (SDA/IO)The SDA pin is bidirectional for serial data transfer. This pin is open-drain driven and may be wired with any number of other open drain or open collector devices. An external pull-up resistor should be connected between SDA and V CC . The value of this resistor and the system capacitance loading the SDA bus will determine the rise time of SDA. This rise time will determine the maximum frequency during read operations. Low value pull-up resistors will allow higher frequency operations while drawing higher average power. SDA/IO information applies to both asynchronous and synchronous protocols.When the synchronous protocol is used, the SCL/CLK input is used to positive edge clock data into the device and negative edge clock data out of the device.V CCAT88SC0808C [SUMMARY DATASHEET]Atmel-2024MS-CryptoMem-AT88SC0808C-Datasheet-Summary_12201343.*NOTICE: Stresses beyond those listed under “AbsoluteMaximum Ratings” may cause permanent damage to the device. This is a stress rating only and functional operation of the device at these or any other condition beyond those indicated in the operational sections of this specification is not implied. Exposure to absolute maximum rating conditions for extended periods of time may affect device reliability.Table 3-1.DC CharacteristicsNote:1. V IL min and V IH max are reference only and are not tested2. To prevent latch up conditions from occurring during power up of the AT88SCxxxxC, V CC must be turned onbefore applying V IH . For powering down, V IH must be removed before turning V CC offAT88SC0808C [SUMMARY DATASHEET]Atmel-2024MS-CryptoMem-AT88SC0808C-Datasheet-Summary_1220135Table 3-2.AC CharacteristicsApplicable over recommended operating range from V CC = +2.7 to 5.5V,4. Device Operation for Synchronous ProtocolsClock and Data Transitions:The SDA pin is normally pulled high with an external device. Data on the SDA pin may change only during SCL low time periods (see Figure 4-3 on page 7). Data changes during SCL high periods will indicate a start or stop condition as defined below.Start Condition:A high-to-low transition of SDA with SCL high is a start condition which must precede any other command (see Figure 4-4 on page 7).Stop Condition:A low-to-high transition of SDA with SCL high is a stop condition. After a read sequence, the stop command will place the EEPROM in a standby power mode (see Figure 4-4 on page 7).Acknowledge:All addresses and data words are serially transmitted to and from the EEPROM in 8-bit words. The EEPROM sends a zero to acknowledge that it has received each word. This happens during the ninth clock cycle (see Figure 4-5 on page 7). Memory Reset:After an interruption in protocol, power loss or system reset, any 2-wire part can be reset by following these steps: 1. Clock up to nine cycles2. Look for SDA high in each cycle while SCL is high3. Create a start conditionAT88SC0808C [SUMMARY DATASHEET] Atmel-2024MS-CryptoMem-AT88SC0808C-Datasheet-Summary_1220136 Figure 4-1. Bus Timing for 2-wire Communications:SCL: Serial Clock, SDA – Serial Data I/OFigure 4-2. Write Cycle Timing:SCL: Serial Clock, SDA – Serial Data I/ONote: The write cycle time t WR is the time from a valid stop condition of a write sequence to the end of the internalclear/write cycleSCLSDA INSDA OUTSTOPCONDITIONSTARTCONDITIONSCLSDAAT88SC0808C [SUMMARY DATASHEET]Atmel-2024MS-CryptoMem-AT88SC0808C-Datasheet-Summary_1220137Figure 4-3. Data ValidityFigure 4-4. Start and Stop DefinitionsFigure 4-5. Output AcknowledgeDATA CHANGE ALLOWEDDATA STABLEDATA STABLESDASCLSDASCLSTART STOPSCLDAT A INDAT A OUTEG D E L W O N K C A T R A T S 981AT88SC0808C [SUMMARY DATASHEET]Atmel-2024MS-CryptoMem-AT88SC0808C-Datasheet-Summary_12201385.Device Architecture5.1User ZonesThe EEPROM user memory is divided into eight zones of 1024 bits each. Multiple zones allow for different types of data or files to be stored in different zones. Access to the user zones is allowed only after security requirements have been met. These security requirements are defined by the user during the personalization of the device in the configuration memory. If the same security requirements are selected for multiple zones, then these zones may effectively be accessed as one larger zone.6. Control LogicAccess to the user zones occurs only through the control logic built into the device. This logic is configurable through access registers, key registers and keys programmed into the configuration memory during device personalization. Also implemented in the control logic is a cryptographic engine for performing the various higher-level security functions of the device.AT88SC0808C [SUMMARY DATASHEET]Atmel-2024MS-CryptoMem-AT88SC0808C-Datasheet-Summary_12201397. Configuration MemoryThe configuration memory consists of 2048 bits of EEPROM memory used for storing passwords, keys and codes and defining security levels to be used for each user zone. Access rights to the configuration memory are defined in the control logic and may not be altered by the user.AT88SC0808C [SUMMARY DATASHEET]Atmel-2024MS-CryptoMem-AT88SC0808C-Datasheet-Summary_122013108. Security FusesThere are three fuses on the device that must be blown during the device personalization process. Each fuse locks certain portions of the configuration memory as OTP memory. Fuses are designed for the module manufacturer, card manufacturer and card issuer and should be blown in sequence, although all programming of the device and blowing of the fuses may be performed at one final step.9. Protocol selectionThe AT88SC0808C supports two different communication protocols.• Smart Card Applications:The asynchronous T = 0 protocol defined by ISO 7816-3 is used for compatibility with the industry’s standard smart card readers• Embedded Applications:A 2-wire serial interface is used for fast and efficient communication with logic or controllersThe power-up sequence determines which of the two communication protocols will be used.9.1 Asynchronous T = 0 ProtocolThis power-up sequence complies with ISO 7816-3 for a cold reset in smart card applications.• V CC goes high; RST, I/O-SDA and CLK-SCL are low • Set I/O-SDA in receive mode • Provide a clock signal to CLK-SCL •RST goes high after 400 clock cyclesThe device will respond with a 64-bit ATR code, including historical bytes to indicate the memory density within theCryptoMemory family. Once the asynchronous mode has been selected, it is not possible to switch to the synchronous mode without powering off the device.Figure 9-1. Asynchronous T = 0 Protocol (Gemplus Patent)V cc I/O-SDARSTCLK-SCL9.2 Synchronous 2-wire Serial InterfaceThe synchronous mode is the default after powering up V CC due to an internal pull-up on RST. For embedded applications using CryptoMemory in standard plastic packages, this is the only communication protocol.• Power-up V CC , RST goes high also• After stable V CC , CLK-SCL and I/O-SDA may be drivenFigure 9-2. Synchronous 2-wire ProtocolNote:Five clock pulses must be sent before the first command is issued10. Communication Security ModesCommunications between the device and host operate in three basic modes. Standard mode is the default mode for the device after power-up. Authentication mode is activated by a successful authentication sequence. Encryption mode is activated by a successful encryption activation following a successful authentication. Table 10-1. Communication Security Modes (1)Note:1. Configuration data include viewable areas of the configuration zone except the passwords:• MDC: Modification Detection Code •MAC: Message Authentication CodeV cc I/O-SDARST CLK-SCL1234511. Security Options11.1 Anti-tearingIn the event of a power loss during a write cycle, the integrity of the device’s stored data may be recovered. This function is optional: the host may choose to activate the anti-tearing function, depending on application requirements. When anti-tearing is active, write commands take longer to execute, since more write cycles are required to complete them, and data are limited to eight bytes.Data are written first to a buffer zone in EEPROM instead of the intended destination address, but with the same accessconditions. The data are then written in the required location. If this second write cycle is interrupted due to a power loss, the device will automatically recover the data from the system buffer zone at the next power-up.In 2-wire mode, the host is required to perform ACK polling for up to 8mS after write commands when anti-tearing is active. At power-up, the host is required to perform ACK polling, in some cases for up to 2mS, in the event that the device needs to carry out the data recovery process.11.2 Write LockIf a user zone is configured in the write lock mode, the lowest address byte of an 8-byte page constitutes a write access byte for the bytes of that page.Example: The write lock byte at $080 controls the bytes from $080 to $087The write lock byte may also be locked by writing its least significant (rightmost) bit to “0”. Moreover, when write lock mode is activated, the write lock byte can only be programmed — that is, bits written to “0” cannot return to “1”.In the write lock configuration, only one byte can be written at a time. Even if several bytes are received, only the first byte will be taken into account by the device.12. Password VerificationPasswords may be used to protect read and/or write access of any user zone. When a valid password is presented, it ismemorized and active until power is turned off, unless a new password is presented or RST becomes active. There are eight password sets that may be used to protect any user zone. Only one password is active at a time, but write passwords give read access also..12.1 Authentication ProtocolThe access to a user zone may be protected by an authentication protocol. Any one of four keys may be selected to use with a user zone.The authentication success is memorized and active as long as the chip is powered, unless a new authentication is initialized or RST becomes active. If the new authentication request is not validated, the card loses its previous authentication and itshould be presented again. Only the last request is memorized.Note: Password and authentication may be presented at any time and in any order. If the trials limit has been reached (after four consecutive incorrect attempts), the password verification or authentication process will not be takeninto accountFigure 12-1. Password and Authentication OperationsREAD ACCESS12.2 ChecksumThe AT88SC0808C implements a data validity check function in the form of a checksum, which may function in standard,authentication or encryption modes.In the standard mode, the checksum is implemented as a Modification Detection Code (MDC), in which the host may read an MDC from the device in order to verify that the data sent was received correctly.In the authentication and encryption modes, the checksum becomes more powerful since it provides a bidirectional dataintegrity check and data origin authentication capability in the form of a Message Authentication Code (MAC). Only thehost/device that carried out a valid authentication is capable of computing a valid MAC. While operating in the authentication or encryption modes, the use of a MAC is required. For an ingoing command, if the device calculates a MAC different from the MAC transmitted by the host, not only is the command abandoned but the mode is also reset. A new authentication and/or encryption activation will be required to reactivate the MAC.12.3 EncryptionThe data exchanged between the device and the host during read, write and verify password commands may be encrypted to ensure data confidentiality.The issuer may choose to require encryption for a user zone by settings made in the configuration memory. Any one of four keys may be selected for use with a user zone. In this case, activation of the encryption mode is required in order to read/write data in the zone and only encrypted data will be transmitted. Even if not required, the host may elect to activate encryption provided the proper keys are known.12.4 Supervisor ModeEnabling this feature allows the holder of one specific password to gain full access to all eight password sets, including the ability to change passwords.12.5 Modify ForbiddenNo write access is allowed in a user zone protected with this feature at any time. The user zone must be written during device personalization prior to blowing the security fuses.12.6 Program OnlyFor a user zone protected by this feature, data within the zone may be changed from a “1” to a “0”, but never from a “0” to a “1”.13. Initial Device ProgrammingTo enable the security features of CryptoMemory, the device must first be personalized to set up several registers and load in the appropriate passwords and keys. This is accomplished through programming the configuration memory of CryptoMemory using simple write and read commands. To gain access to the configuration memory, the secure code must first besuccessfully presented. For the AT88SC0808C device, the secure code is $22 E8 3F. After writing and verifying data in the configuration memory, the security fuses must be blown to lock this information in the device. For additional information on personalizing CryptoMemory, please see the application notes Programming CryptoMemory for Embedded Applications and Initializing CryptoMemory for Smart Card Applications (at ).14.Note: 1. Formal drawings may be obtained from an Atmel sales office2. Both the J and P module packages are used for either ISO (T=0 / 2-wire mode) or TWI (2-wire mode only)15. Packaging InformationOrdering Code: MJ or MJTG Ordering Code: MP or MPTGModule Size: M2Dimension*: 12.6 x 11.4 [mm] Glob Top: Round - ∅ 8.5 [mm] Thickness: 0.58 [mm]Pitch: 14.25mm Module Size: M2Dimension*: 12.6 x 11.4 [mm]Glob Top: Square - 8.8 x 8.8 [mm] Thickness: 0.58 [mm]Pitch: 14.25mmNote: *The module dimensions listed refer to the dimensions of the exposed metal contact area. The actual dimensions of the module after excise or punching from the carrier tape are generally 0.4mm greater in both directions (i.e., apunched M2 module will yield 13.0 x 11.8mm)15.1 Atmel AT88SC0808C Package Marking Information15.2 Ordering Code: SH8S1 – 8-lead JEDEC SOIC15.3 Ordering Code: PU8P3 – 8-lead PDIP16. Revision History。
NE5000E 配置指南-广域网接入(V300R007C00_03)

修改记录
修改记录累积了每次文档更新的说明。最新版本的文档包含以前所有文档版本的更新内 容。
文档版本 03 (2012-07-20)
第三次正式发布。
文档版本 02 (2009-12-10)
第二次正式发布。
文档版本 01 (2009-09-05)
第一次正式发布。
文档版本 03 (2012-07-20)
华为专有和保密信息
HUAWEI NetEngine5000E 核心路由器 V300R007C00
配置指南-广域网接入
文档版本 03 发布日期 2012-07-20
华为技术有限公司
版权所有 © 华为技术有限公司 2012。 保留一切权利。 非经本公司书面许可,任何单位和个人不得擅自摘抄、复制本文档内容的部分或全部,并不得以任何形式传播。
[ x | y | ... ]* &<1-n> #
意义
命令行关键字(命令中保持不变、必须照输的部分)采用 加粗字体表示。
命令行参数(命令中必须由实际值进行替代的部分)采用 斜体表示。 表示用“[ ]”括起来的部分在命令配置时是可选的。 表示从两个或多个选项中选取一个。
表示从两个或多个选项中选取一个或者不选。
vБайду номын сангаас
版权所有 © 华为技术有限公司
HUAWEI NetEngine5000E 核心路由器 配置指南-广域网接入
目录
目录
前 言....................................................................................................................................................ii
NetComm Wireless NTC-220或NTC-140W系列无线路由器与Eaton网络卡P

C o n n e c t i n g a N e t C o m m W i r e l e s s R o u t e r t o a n E a t o n N e t w o r k C a r dI n t r o d u c t i o nThis document provides instructions for connecting a NetComm Wireless NTC-220or NTC-140W Serieswireless router to one of the following Eaton connectivity cards:•Industrial Gateway Card(INDGW-M2)•Gigabit Industrial Gateway X2Card(INDGW-X2)•Power Xpert Gateway UPS(PXGX-UPS)•Power Xpert Gateway Minislot UPS(PXGMS)•Gigabit Network(Network-M2)NOTE The Network-M2card has now reached end-of-life(EOL)status.P r e r e q u i s i t e s•Eaton UPS with a INDGW-M2,INDGW-X2,PXGX-UPS,PXGMS,or Network-M2card•USB-to-USB(Type B)cable for PXGX-UPS•USB-to-USB(MiniTypeB)for PXGMS•USB-to-USB(MicroUSB B)for INDGW-M2,INDGW-X2,or Network-M2•Serial COM port or USB-to-serial9-pin male adapter•An existing PredictPulse account(refer to the PredictPulse Quick Start Guide)•Download the latest card firmware and RNDIS driver from the Eaton product site:–For the INDGW-M2card,go tohttps:///us/en-us/catalog/backup-power-ups-surge-it-power-distribution/eaton-industrial-gateway-card.resources.html–For the INDGW-X2card,go tohttps:///us/en-us/catalog/backup-power-ups-surge-it-power-distribution/eaton-gigabit-industrial-gateway-card.html.Go to the Resources page and scroll down to the Software,firmware,and applications section.Clickthe links to download the firmware and RNDIS driver files.NOTE The Netcomm Wireless router must be powered by a120V electrical outlet powered bythe UPS.This ensures that the router is protected during a power outage.If no UPS-protected outlet is available,a Universal Accessory Power(UAP)kit is required.The UAPmust be installed by an Eaton technician.Contact your Eaton service representative for aquote.N e t C o m m W i r e l e s s R o u t e r I n s t a l l a t i o n G u i d e l i n e sRefer to the Quick Start Guide provided with the NetComm Wireless router for instructions on mounting therouter and connecting power.NOTE The router must be powered by a120V electrical outlet powered by the UPS.Thisensures that the router is protected during a power outage.If no UPS-protected outlet isavailable,a Universal Accessory Power(UAP)kit is required.The UAP must be installedby an Eaton technician.Contact your Eaton service representative for a quote.I N D G W -M 2o r I N D G W -X 2C a r d I n s t a l l a t i o nThe hot-swappable INDGW-M2and INDGW-X2cards (see Figure 1and Figure 2)can be installed without turning off the UPS or disconnecting the load.To install the card:1.Ensure that the UPS has logic power.2.Remove the two screws securing the Minislot or X-slot cover and remove the cover from the UPS.Retain the screws.3.Remove the INDGW-M2or INDGW-X2card from its shipping package.4.Slide the card into the open slot.Secure with the screws removed in Step 2.5.Wait for the Warning LED (see Figure 1or Figure 2)to flash only green to indicate that the card is operational.The ON LED also flashes green when the card is ready.6.Connect a USB cable from the SETTINGS port of the INDGW-M2or INDGW-X2card to a USB port on the laptop.•Windows will automatically detect the INDGW-M2or INDGW-X2card connection 7.Open a web browser and enter https://169.254.0.1.You are prompted to log in.Figure 1.INDGW-M2CardFigure 2.INDGW-X2Card8.Log in using the username admin and password admin .9.You are prompted to change your password.Network Connector Network Speed LED Network Link/Activity LED AUX (EMP)ConnectorRESTART ButtonON LED Warning LEDSETTINGS/UPS Data Connector Modbus Connector INDGW-M2or INDGW-X2Card InstallationINDGW-M2or INDGW-X2Card Installation.10.Enter the new password Eaton123!,re-enter the new password,and press Submit11.Read and accept the license agreement.12.The INDGW-M2or INDGW-X2card home page displays(see Figure3).13.The green ON LED should be flashing to indicate that the card is operating normally(see Figure1orFigure2).wait10seconds,plug it back in,and wait3minutes.If the LED still does not flash,contact the Brightlayer DataCenter at800-356-5737,option2,option2to troubleshoot.Figure3.INDGW-M2or INDGW-X2Home Page ArrayI N D G W-M2o r I N D G W-X2C a r d F i r m w a r e U p d a t e1.As noted in the Prerequisites section,the installation requires the latest card firmware.To view thefirmware installed on the INDGW-M2or INDGW-X2card,click the Maintenance(wrench)icon on the cardhome page(see Figure3).The Firmware tab shown in Figure4displays.2.The Version column shows the firmware version of the card.To check the latest firmware for the networkcard:•For an INDGW-M2card,go tohttps:///us/en-us/catalog/backup-power-ups-surge-it-power-distribution/eaton-industrial-gateway-card.html•For an INDGW-X2card,go tohttps:///us/en-us/catalog/backup-power-ups-surge-it-power-distribution/eaton-gigabit-industrial-gateway-card.html3.Click Resources ,then scroll down and expand the Software,firmware,and applications section.Figure4.INDGW-M2or INDGW-X2Card Firmware Tab4.Note the latest available firmware version.If that version is later than the one on the network card,update the card firmware:a.Click the link to download and save that file to a known location.b.Remain connected to the card via the USB cable using the redirected IP address http://169.254.0.1.c.Select Maintenance from the left-hand menu and select Firmware at the top to display the UPDATE FIRMWARE page (see Figure 4).d.Click Upload to load the latest firmware to the card.Click Choose File to navigate to the firmware file saved in Step 4.b.e.Select the firmware file and click Upload .f.When the firmware update is completed,a prompt is displayed.Allow the card to reboot and wait 2–4minutes for completion.g.Log in to the card,return to the Firmware tab,and confirm that the firmware updated was successful.E n v i r o n m e n t a l M o n i t o r i n g P r o b e (E M P )G e n 2I n s t a l l a t i o n1.Remove the EMP and cable from the packaging.2.Install the EMP as directed in theEnvironmental Monitoring Probe Gen2EMPDT1H1C2Installation Instructions .•Set the MODBUS ADDRESS switches on each EMP as appropriate for your application (see Figure 5).For example,for an application with one EMP,set the switches as shown in Figure 5,with switch 1and TER (termination)in the 1position.For a multiple-EMP application,at least one switch must be set on each EMP in in the daisy-chain and the TER switch set on the last EMP in thedaisy-chain.INDGW-M2or INDGW-X2Card InstallationFigure 5.EMP MODBUS ADDRESSSwitches3.Connect the USB end of the cable to the AUX port on the INDGW-M2or INDGW-X2card and the RJ45end to the FROM DEVICE port on the EMP.If possible,route the cable into the battery cabinet and place the EMP in the battery cabinet.4.On the INDGW-M2or INDGW-X2home page (see Figure 3),select Environment from the left-hand menu to display the SENSOR COMMISSIONING page (see Figure 6).Figure 6.Sensor Commissioning Page5.As shown in Figure 6,no sensors have yet been discovered in the system.Click Discover to identify the EMP sensor(s).When discovered,the EMP is displayed as shown in Figure 7.•If no device is found,verify the EMP connections and settings and click Discoveragain.INDGW-M2or INDGW-X2Card InstallationFigure 7.EMP Sensor DiscoveredC o n n e c t i n g t h e R o u t e r t o a n I ND G W -M 2o r I N D G W -X 2C a r dTo connect the NTC-220or NTC-140W Series router to an INDGW-M2or INDGW-X2card:•Connect the Ethernet cable from the LAN port on the router to the Network connector on the INDGW-M2or INDGW-X2card (see Figure 1or Figure 2).•If the INDGW-M2or INDGW-X2card is located inside the UPS chassis,route the cable out of the chassis via a conduit hole that is protected by a rubber grommetOnce connected,the LEDs on the INDGW-M2or INDGW-X2card’s Network port should light and the green LED at the top left of the SETTINGS port should blink.C o n f i g u r i n g a n I ND G W -M 2o r I N D G W -X 2C a r dTo troubleshoot or set up the INDGW-M2or INDGW-X2card,refer to the INDGW-M2User’s Guide or INDGW-X2User’s Guide .The INDGW-M2or INDGW-X2card’s default configuration includes a DHCP network configuration.To configure the INDGW-M2or INDGW-X2card,connect to the card’s SETTINGS port with USB-to-USB (MicroUSB B)cable.Once connected,open an internet browser and navigate to 169.254.0.1to display the Network M2home page (see Figure 3).Log in using the default credentials:Username:adminPassword:adminYou are prompted to change your password.Enter a new password of at least eight characters,including one lowercase letter,one uppercase letter,one numeric character,and one special character.Record the new password.The INDGW-M2or INDGW-X2card will reboot and ask for the new password.Enter the web GUI and click Settings on the left sidebar menu.Click the Network &Protocol tab (see Figure 8).Verify the IPv4Mode is set to DHCP and record the IP address to be used later when configuring the PredictPulseWizard.INDGW-M2or INDGW-X2Card InstallationFigure 8.INDGW-M2or INDGW-X2Card Network &Protocol TabClick the General tab (see Figure 9).In the SMTP SETTINGS section:•Enter in the Server IP/Hostname field •To ensure that e-mails are not marked as spam,enter *************************in the Default sender address fieldScroll down and click Save in the bottom right.Figure 9.INDGW-M2or INDGW-X2Card General TabIn the SYSTEM DETAILS section,select the appropriate time zone and select the Dynamic (NTP)radio button.Enter 192.168.1.1in the NTP server field.For instructions on configuring NTP in the modem,see the Configuring a PXGX-UPS or PXGMS Card section.Also enter the Location ,Contact ,and System Name .Click Save .Proceed to the Run the PredictPulse Wizardsection.INDGW-M2or INDGW-X2Card InstallationP X G X-U P S o r P X G M S I n s t a l l a t i o nC o n n e c t i n g t h e R o u t e r t o a P X G X-U P S o r P X G M S C a r dConnect the NTC-220or NTC-140W Series router and Eaton network e the included Ethernet cable orequivalent.•For a PXGX-UPS card,connect the Ethernet cable from the LAN port on the router to the Upstream port on the card(see Figure10):•For a PXGMS card,connect the Ethernet cable from the LAN part on the router to the Ethernet10/100 port on the card(see Figure11)Route the Ethernet cable into the UPS via the appropriate conduit holes.Once connected,the LEDs on theactive Ethernet port,as well as the green Power LED and Status LEDs should light.Figure10.Power Xpert Gateway UPS(PXGX-UPS)CardFigure11.Power Xpert Gateway Minislot UPS(PXGMS)CardC o n f i g u r i n g a P X G X-U P S o r P X G M S C a r dTo troubleshoot or set up the PXGX-UPS or PXGMS card,refer to Sections3–5of thePXGX-UPS Quick Start Instructions or PXGMS Quick Start Instructions for instructions on connecting aWindows-based computer to the card’s Setup port using a USB cable.To configure the PXGX-UPS or PXGMS card,connect to the card’s Setup port using a USB cable.Onceconnected,open an internet browser and navigate to169.254.0.101.Log in using the default credentials:Username:adminPassword:adminNOTE The PXGX-UPS password may be the MAC address of the card.The PXGMS passwordmay be the card serial number.If installing on an existing PXGX-UPS or PXGMS card,reset the card to factory default settings as follows:•Locate the onboard DIP switch and set switch6to ONPXGX-UPS or PXGMS InstallationPXGX-UPS or PXGMS Installation•Reboot the card to restore the factory defaults•Return switch6to OFF and reboot the cardFor more information on restoring the factory default settings,refer to the PXGX-UPS Card User’s Guide or PXGMS Card User’s Guide.For a new installation,the PXGX-UPS or PXGMS card will use the factory default settings.From the Configuration menu(see Figure12),select E-mail to display the E-mail tab(see Figure13).MenuFigure12.Configuration ArrayEnsure that the SMTP server/IP hostname is and the recipient checkboxes are setup as shown in Figure13,with********************.com as the only e-mail recipient.TabFigure13.E-mailPXGX-UPS or PXGMS InstallationFigure14.E-Mail Event Trigger ConfigurationPageFigure15).Select the Synchronize with NTP server(s)radio button and enter192.168.1.1for the NTP serverIP address.Ensure that the correct time zone is selected for the Time zone for logs,e-mail,and connecteddevice.Click Apply after making any changes.TabFigure15.Date/Timethe network key printed on the back of the modem.Once connected,open an internet browser:•For an NTC-140W router,navigate to192.168.1.1•For an NTC-220router,navigate to https://192.168.1.1Log in using the default credentials(see Figure16):Username:adminPassword:adminFigure Comm Wireless Log-InPageNavigate to the Services tab and select Network Time (NTP).Ensure the correct time zone is selected and the remaining settings are as shown in Figure 17,with 151.110.127.39listed for NTP service.Click Save if any changes were made.Figure Comm Wireless ServicesTabProceed to the Run the PredictPulse Wizard section.PXGX-UPS or PXGMS InstallationN e t w o r k -M 2C a r d I n s t a l l a t i o nFor instructions on installing a Network-M2card,refer to the documentPredict Pulse ™Setup for an Eaton®Gigabit Network (Network-M2)Card .C o n n e c t i n g t h e R o u t e r t o a N e t w o r k -M 2C a r dTo connect the NTC-220or NTC-140W Series router to a Network-M2card:•Connect the Ethernet cable from the LAN port on the router to the Ethernet port on the Network-M2card (see Figure 18).•If the Network-M2card is located inside the UPS chassis,route the cable out of the chassis via a conduit hole that is protected by a rubber grommetOnce connected,the LEDs on the Network-M2card’s Ethernet port should light and the green LED at the top left of the SETTINGS port should blink.Figure work-M2CardC o n f i g u r i n g a N e t w o r k -M 2C a r dTo troubleshoot or set up the Network-M2card,refer to the Network-M2User’s Guide .The Network-M2default configuration includes a DHCP network configuration.To configure the Network-M2card,connect to the card’s SETTINGS port with USB-to-USB (MicroUSB B)cable.Once connected,open an internet browser and navigate to 169.254.0.1to display the Network M2home page (see Figure 19).Log in using the default credentials:Username:adminPassword:adminYou are prompted to change your password.Enter the new password Eaton123!,re-enter the new password,and press Submit.Entering a password other than Eaton123!will cause the PredictPulse activation to fail.Network-M2Card InstallationFigure work-M2Card Home PageThe Network-M2card will reboot and ask for the new password.Enter the web GUI and click Settings on the left sidebar menu.Click the Network &Protocol tab (see Figure 20).Verify the IPv4Mode is set to DHCP and record the IP address to be used later when configuring the PredictPulse Wizard.Figure work-M2Card Network &Protocol TabClick the General tab (see Figure 21).In the SMTP SETTINGS section:•Enter in the Server IP/Hostname field •To ensure that e-mails are not marked as spam,enter *************************in the Default sender addressfieldNetwork-M2Card InstallationFigure work-M2Card General TabScroll down and click Save in the bottom right.In the SYSTEM DETAILS section,select the appropriate time zone and select the Dynamic (NTP)radio button.Enter 192.168.1.1in the NTP server field.For instructions on configuring NTP in the modem,see the Configuring a PXGX-UPS or PXGMS Card section.Also enter the Location ,Contact ,and System Name .Click Save .Proceed to the Run the PredictPulse Wizard section.C o n n e c t i n g a P o w e r X p e r t E t h e r n e t S w i t c hSome installations have multiple UPSs with network cards that must be connected.In these cases,install a four-or six-port Power Xpert Ethernet Switch (see Figure 22).Install an Eaton Power Xpert Ethernet Switch to the DIN rail and apply power.Connect a straight-through Ethernet CAT5cable between the WAN port on the wireless router and port 1on the Power Xpert Ethernet Switch.Connect another straight-through Ethernet cable from the Upstream port on the PXGX-UPS or Ethernet port on the PXGMS or Network-M2to any open port other than 1on the Power Xpert EthernetSwitch.Connecting a Power Xpert Ethernet SwitchFigure 22.Power Xpert EthernetSwitchesR u n t h e P r e d i c t P u l s e W i z a r dTo run the PredictPulse Wizard (ActivatePredictPulse.exe ),connect a laptop or personal computer as follows.For a PXGX-UPS card,using an RJ-45Ethernet cable,connect the laptop or personal computer to the card’s Downstream port.For a PXGMS ,Network-M2,INDGW-M2or INDGW-X2card,using an RJ-45Ethernet cable,connect the laptop or personal computer to the LAN/WAN port on the router.You can also run the PredictPulse wizard while connected to the modem Wi-Fi.For instructions on connecting to the modem Wi-Fi,see the Configuring an INDGW-M2or INDGW-X2Card ,Configuring a PXGX-UPS or PXGMS Card ,or Configuring a Network-M2Card section.Run the PredictPulse Wizard (ActivatePredictPulse.exe ).The Eaton PredictPulse window displays (see Figure 23).Figure 23.PredictPulse Wizard InitialDisplayEnter the Organization Code and customer E-Mail Address and click Begin Registration .The PredictPulse Device Activation window displays (see Figure 24).Run the PredictPulse WizardFigure 24.PredictPulse Device ActivationWindowEnter the IP address or a range of IP addresses to continue.The wizard attempts to connect to a UPS at thataddress.NOTE For a PXGX-UPS or PXGMS card,the IP address assigned by the modem can be foundon the Configuration menu.Select Network ,verify that DHCP Enabled is checked(see Figure 25),and the IP address is listed.If DHCP was not enabled initially,you mayneed to reboot the card to have the modem assign an IP address.Figure 25.DHCPEnabledThe IP address can also be found from the modem GUI.Navigate to the Networking tab,select LAN on the sidebar and DHCP under the drop-down menu (see Figure 26).Scroll down to the Dynamic DHCP client list (see Figure 27)to find the connected devices.The web card IP will have an asterisk as the Computer name.Run the PredictPulse WizardFigure Comm Wireless DHCPTabFigure 27.Dynamic DHCP ClientListNOTE If the wizard displays the configuration error message shown in Figure 28,enter thecard’s username and password and click OK .Figure 28.PredictPulse Wizard Card ConfigurationErrorThe PredictPulse wizard activates each card.Upon completion,the wizard displays a confirmation message (see Figure 29).Run the PredictPulse WizardNOTE If the user is running Microsoft Outlook and it is open,an activation e-mail is sentautomatically to Eaton’s PredictPulse servers.You may need to send the e-mail fromyour Drafts or Outbox folder once you've connected to a LAN if you were connected tothe modem Wi-Fi while running the wizard.If the user does not have Outlook installed,the e-mail components are saved in the user’s My Documents folder and instructionsare provided for sending the activation e-mail manually.Figure29.Activation CompleteWindowNOTE The registration process to activate the unit for PredictPulse may take15minutes ormore.To ensure the PredictPulse activation was successful,call the Brightlayer DataCenter at800-356-5737,option2,option2for assistance.P r e d i c t P u l s e R e m o t e M o n i t o r i n g A c t i v a t i o n C o m p l e t i o n C h e c k l i s t•https:// account enrollment complete•Universal Accessory Power kit installed(if no UPS protected outlet is available for the modem and/or network switch to plug into.Must be installed by an Eaton technician,contact your Eaton servicerepresentative for a quote.)•Network switch installed(if multiple UPS are connected to the same modem)•PredictPulse-compatible network connectivity card installed•Connectivity card upgraded to latest firmware•Connectivity card configured for PredictPulse•Modem NTP configured•Environmental Monitoring Probe connected•PredictPulse activation wizard run from modem connection•Call placed to the Brightlayer Data Center at800-356-5737,option2,option2to confirm portal activation and communication receiptPredictPulse Remote Monitoring Activation Completion ChecklistT r o u b l e s h o o t i n gS i g n a l S t r e n g t hThe biggest risk for the router is low signal quality.As an initial test,observe AT&T cell phone signal strength in the area of installation.To quantify the signal,connect an Ethernet cable to the router.Once connected,open an internet browser and navigate to 192.168.1.1.Log into the router’s Status page (see Figure 30)using the credentials:Username:adminPassword:adminOn the Status page,observe the Signal strength (dBm)and position the router to maximize the value.If the signal is weak,an external antenna may be required.The external antenna replaces the 3G antennas provided with the router.Once connected,position the external antenna to maximize the signal strength.Figure Comm Wireless StatusPageTroubleshootingI n c o r r e c t P r o f i l eThe wireless router can only use the profile stored on the SIM.On the router’s Networking page (see Figure 31),verify that Profile1is selected and that the APN is .attz ,as shown.Figure Comm Wireless NetworkingPageR e b o o t i n g t h e R o u t e rIf the wireless router loses connection to the connectivity card,the router can be rebooted from the router's System page (see Figure 32).The connection will be interrupted momentarily while the SIM data loads.Figure Comm Wireless SystemPageR e m o t e R e b o o t F u n c t i o nAlthough not required,Eaton recommends enabling the remote reboot function of your router to assist Eaton specialists in remotely troubleshooting.To do so,navigate to the router’s Services page (see Figure 33).Remote Reboot FunctionConnecting a NetComm Wireless Router to an Eaton Network Card P-164000722—Rev 1121Figure Comm Wireless ServicesPageScroll down and click SMS Messaging .From the SMS Messaging drop-down menu,select Diagnostics (see Figure 34).Figure Comm Wireless SMS Messaging Drop-DownMenuRemote Reboot Function22Connecting a NetComm Wireless Router to an Eaton Network Card P-164000722—Rev 11Ensure that the selections are set as shown in Figure 35,with:•Enable remote diagnostics and command execution –ON •Only accept authenticated SMS messages –OFF •Send Set command acknowledgement replies –OFF •Access advanced RDB variables –OFF •Allow execution of advanced commands –ON •Send acknowledgement replies –the sender’s number •Send command error replies –OFF •Send error replies to –the sender’s number •Send a maximum number of –100–replies per –day •White list –should be emptyClick Save .Figure Comm Wireless SMS DiagnosticsSettingsA d d i t i o n a l I n f o r m a t i o n a n d S u p p o r tFor additional information about PredictPulse,visit /PredictPulse .For specific questions,call the Brightlayer Data Center at 800-356-5737,option 2,option 2.Additional Information and SupportAdditional Information and Support Connecting a NetComm Wireless Router to an Eaton Network Card P-164000722—Rev1123P-16400072211P-16400072211。
戴尔OptiPlex 3030一体机快速入门指南说明书

2Connect the keyboard and mouse Connectez le clavier et la sourisConecte el teclado y el mouse3Connect the network cable (optional)Connectez le câble réseau (facultatif)Conecte el cable de red (opcional)4Connect the power cableConnectez le câble d’alimentationConecte el cable de alimentación5Turn on your computerMettez votre ordinateur sous tensionEncienda su equipo6Finish Windows setupTerminez l’installation de Windows | Finalizar configuración de WindowsEnable security and updatesActivez la sécurité et les mises à jourActivar seguridad y actualizacionesConnect to your networkConnectez-vous à votre réseauConectar a su redLog in to your Microsoft account orcreate a local accountConnectez-vous à votre compteMicrosoft ou créez un compte localInicie sesión en su cuenta de Microsofto cree una cuenta local1Set up the standInstallez le socleMontaje del apoyoFeaturesCaractéristiques | Funciones1. Microphone (touchscreencomputer only)2. Microphone (non-touchscreencomputer only)3. Camera4. Camera-status light5. Camer-privacy latch6. Optical drive7. On-screen display (OSD) buttons 8. Hard-drive activity light9. Power button/Power-status light 10. Stereo speakers 11. USB 2.0 connectors12. Cable cover screw stub 13. Line-out connector 14. VGA connector 15. Network connector 16. Power-cable connector 17. Power-diagnostic button 18. Power-diagnostic light 19. Security-lock slot 20. Audio connector 21. USB 3.0 connectors 22. Memory card reader1. Microphone (ordinateur à écrantactile uniquement)2. Microphone (ordinateur à écran nontactile uniquement)3. Caméra4. Voyant d’état de la caméra5. Loquet du cache de la caméra6. Lecteur optique7. Boutons de menu à l’écran (OSD)8. Voyant d’activité du disque dur 9. Bouton d’alimentation/Voyantd’alimentation 10. Haut-parleurs stéréo11. Connecteurs USB 2.012. Embout de vis du cache-câbles 13. Connecteur de ligne de sortie 14. Connecteur VGA 15. Connecteur réseau 16. Connecteur d’alimentation17. Bouton de diagnostic d’alimentation 18. Voyant de diagnostic d’alimentation 19. Emplacement pour verrou de sécurité20. Connecteur audio 21. Connecteurs USB 3.022. Lecteur de carte mémoire1. Micrófono (solo equipos conpantalla táctil)2. Micrófono (solo equipos conpantalla que no sea táctil)3. Cámara4. Indicador luminoso de estado dela cámara5. Cierre de privacidad de la cámara6. Unidad óptica7. Botones de visualización enpantalla (OSD)8. Indicador luminoso de actividad dela unidad del disco duro9. Indicador luminoso del botón deencendido y el estado de la alimentación 10. Altavoces estéreo11. Conectores USB 2.012. Tope del tornillo de la cubiertadel cable13. Conector de línea de salida 14. Conector VGA 15. Conector de red16. Conector del cable de alimentación 17. Botón de diagnóstico dela alimentación18. Indicador luminoso de diagnósticode la alimentación19. Ranura del bloqueo de seguridad 20. Conector de audio 21. Conectores USB 3.022. Lector de tarjetas de memoriaProduct support and manuals Support produits et manuelsSoporte técnico de productos y manuales /support/support/manuals /windows8Contact DellContacter Dell | Póngase en contacto con Dell /contactdellRegulatory and safetyRéglementations et sécurité | Normativa y Seguridad /regulatory_compliance Regulatory model and type Modèle et type réglementaires Modelo y tipo normativoW10B W10B001Computer modelModèle de l’ordinateur | Modelo de equipoOptiPlex 3030 AIO© 2014 Dell Inc.© 2014 Microsoft Corporation.Printed in China.Printed on recycled paper.2014-01Información para NOM, o Norma Oficial MexicanaLa información que se proporciona a continuación se mostrará en los dispositivos que se describen en este documento, en conformidad con los requisitos de la Norma Oficial Mexicana (NOM):Importador:Dell México S.A. de C.V.Paseo de la Reforma 2620 - Piso 11.°Col. Lomas Altas 11950 México, D.F.Número de modelo reglamentario:W10B Voltaje de entrada:100 V CA–240 V CA Corriente de entrada (máxima):2,00 A / 2,50 A Frecuencia de entrada:50 Hz–60 HzExplore resourcesExplorez les ressources | Explorar recursosHelp and TipsAide et astuces | Ayuda y consejos My DellMon Dell | Mi DellRegister your computerEnregistrez votre ordinateur | Registre su equipo。
运营商用英语怎么说的单词怎么拼

运营商用英语怎么说的单词怎么拼运营商是指提供网络服务的供应商,如中国联通、中国电信、中国移动这些公司叫运营商。
那么你知道运营商用英语怎么说吗?下面跟着店铺一起来学习一下关于运营商的英语知识吧。
运营商的英语说法Operatorcarrier运营商相关英语表达本地交换运营商 local exchange carrier虚拟网络运营商 Virtual Network Operator移动通信运营商 Mobile telecom carrier主导运营商 incumbent operator通信运营商 Communications Operator运营商管理 Carrier Management运营商的英语例句1. The deal is expected to result in similar tie-ups between big media companies and telecommunications operators.这笔交易可能促成大型传媒公司和电信运营商结成类似的联营关系。
2. A plethora of new operators will be allowed to enter the market.大批新的运营商将获准进入该市场。
3. SELT can reduce operators'costs and thereby the customer's subscription cost.SELT能降低运营商的成本进而是用户的花费.4. Analysis of the managing strategies of Telecommunicaton Service Providers in 3 G.浅析电信运营商在3G中的经营策略.5. This paper proposed an end - to - end authenticationprotocol between two motion operation businesses.提出了一个在不同移动运营商中移动终端的相互认证协议.6. And caps on roaming charges will cause operators to raise prices elsewhere.并且漫游价封顶也会使运营商在其他方面加价.7. But operators are newcomers to the world of television.但是移动运营商毕竟是新近参与到广播电视领域中的.8. The company also recently added new carrier partners in Europe.该公司近期也在欧洲增加了新运营商合作伙伴.9. Table 2 show the SMS charges by GSM Operator in Malaysia.表2列举了马来西亚GSM运营商的SMS短消息收费价格.10. Another attempt at misdirection was foiled by an alert mail carrier.另一个企图被挫败的错误警报邮件运营商.11. The Chinese telecommunication is the present informationization service level highest operator.中国电信是目前信息化服务水平最高的运营商.12. It won so many customers that other operators had to follow suit.这样拉拢来许多顾客,而其他运营商也不得不提高网速.13. Mobile digital television to promote a domestic three main private operators.移动数字电视的推广以国内三家民营运营商为主.14. Operators should, therefore, concentrate on ensuring that entries are the required quality.因此, 旅游运营商应该着重于保证评价的内容达到必需的质量.15. Telecom carriers initiated the service in some trial cities last year.电信运营商去年已在一些城市试点这一服务.运营商相关英文阅读:中国三大运营商流量花招激怒用户Mobile phone users in China expected a pleasant surprise this month. Starting from October 1, a new policy adopted by the three giant cellphone operators - China Mobile, China Telecom and China Unicom - has allowed unused data from individual data packages to be carried over to the next month for use.中国手机用户在本月迎来了惊喜。
Accounting Information System (3)

Learning Objective 2
Describe enterprise architecture and its domains.
2013 Pearson Education, Inc. Publishing as Prentice Hall, AIS, 11/e, by Bodnar/Hopwood
2013 Pearson Education, Inc. Publishing as Prentice Hall, AIS, 11/e, by Bodnar/Hopwood
3–8
eBusiness and Enterprise Architecture
Enterprise Architecture (EA) involves
Mail servers File servers Web servers Commerce servers Application servers and database servers
3–6
2013 Pearson Education, Inc. Publishing as Prentice Hall, AIS, 11/e, by Bodnar/Hopwood
3–7
eBusiness and Enterprise Architecture
The
the joint structure and behavior of the enterprise and its information system. Objectives of an EA:
enterprise architecture (EA) describes
Types of servers:
constantly runs and exchanges information with remote users. Clients are programs that access and exchange information with servers.
用户注册(一)之注册页面以及图形验证码
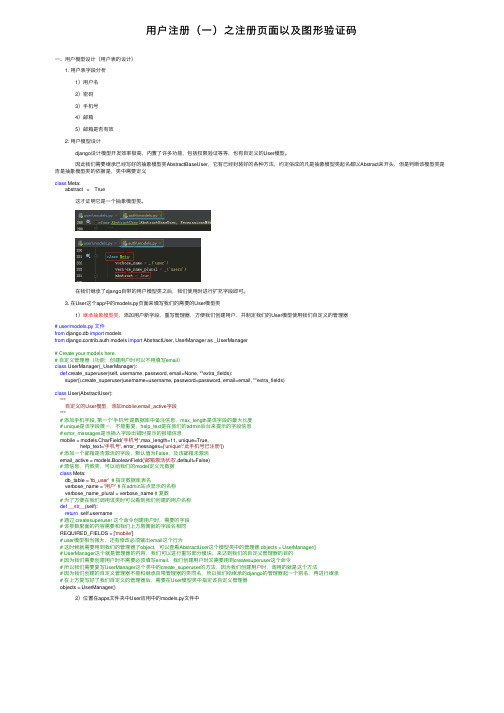
⽤户注册(⼀)之注册页⾯以及图形验证码⼀、⽤户模型设计(⽤户表的设计) 1. ⽤户表字段分析 1)⽤户名 2)密码 3)⼿机号 4)邮箱 5)邮箱是否有效 2. ⽤户模型设计 django设计模型开发效率极⾼,内置了许多功能,包括权限验证等等,也有⾃定义的User模型。
因此我们需要继承已经写好的抽象模型类AbstractBaseUser,它有已经封装好的各种⽅法,约定俗成的凡是抽象模型类起名都以Abstract来开头,但是判断该模型类是否是抽象模型类的依据是,类中需要定义class Meta:abstract = True 这才证明它是⼀个抽象模型类。
在我们继承了django⾃带的⽤户模型类之后,我们使⽤时进⾏扩充字段即可。
3. 在User这个app中的models.py页⾯来填写我们的需要的User模型类 1)继承抽象模型类,添加⽤户新字段,重写管理器,⽅便我们创建⽤户,并制定我们的User模型使⽤我们⾃定义的管理器# user/models.py ⽂件from django.db import modelsfrom django.contrib.auth.models import AbstractUser, UserManager as _UserManager# Create your models here.# ⾃定义管理器(功能:创建⽤户时可以不⽤填写email)class UserManager(_UserManager):def create_superuser(self, username, password, email=None, **extra_fields):super().create_superuser(username=username, password=password, email=email, **extra_fields)class User(AbstractUser):"""⾃定义的User模型,添加moblie,email_active字段"""# 添加⼿机字段, 第⼀个'⼿机号'是数据库中备注信息,max_length是该字段的最⼤长度# unique是该字段唯⼀,不能重复,help_text是在我们的admin后台来提⽰的字段信息# error_messages是当插⼊字段出错时提⽰的报错信息mobile = models.CharField('⼿机号',max_length=11, unique=True,help_text='⼿机号', error_messages={'unique':'此⼿机号已注册'})# 添加⼀个邮箱是否激活的字段,默认值为False,及该邮箱未激活email_active = models.BooleanField('邮箱激活状态',default=False)# 源信息,内嵌类,可以给我们的model定义元数据class Meta:db_table = 'tb_user'# 指定数据库表名verbose_name = '⽤户'# 在admin站点显⽰的名称verbose_name_plural = verbose_name # 复数# 为了⽅便在我们调⽤该类时可以看到我们创建的⽤户名称def__str__(self):return ername# 通过 createsuperuser 这个命令创建⽤户时,需要的字段# 该参数⾥⾯的内容需要和我们上⽅唇膏就的字段名相同REQUIRED_FIELDS = ['mobile']# user模型相当强⼤,还有修改必须输出email这个⾏为# 这时候就需要⽤到我们的管理器了object,可以查看AbstractUser这个模型类中的管理器 objects = UserManager()# UserManager这个就是管理器的内容,我们可以进⾏重写部分模块,来达到我们的⾃定义管理器的⽬的# 因为我们需要创建⽤户时不需要必须填写email,我们创建⽤户时⼜需要⽤到createsuperuser这个命令# 所以我们需要复写UserManager这个类中的create_superuser的⽅法,因为我们创建⽤户时,调⽤的就是这个⽅法# 因为我们创建的⾃定义管理器不能和继承⾃带管理器的类同名,所以我们给继承的django的管理器起⼀个别名,再进⾏继承# 在上⽅复写好了我们⾃定义的管理器后,需要在User模型类中指定该⾃定义管理器objects = UserManager() 2)位置在apps⽂件夹中User应⽤中的models.py⽂件中 3)在主⽬录下的settings⽂件中添加我们⾃定义模型类的地址(告诉整个项⽬我们的⽤户模型类已经修改了,并且位置在XXX)# 注明我们的User模型的导⼊路径AUTH_USER_MODEL = 'er'# er这个地址是因为我们创建的⽤户模型类是在user这个app下的User这个类作为⽤户模型类 4)在pycharm中进⾏远程连接我们的虚拟机 找到菜单栏中的Tools下⾯的start SSH session ,然后选择我们的远程主机地址连接即可。
Linux命令手册大全

3.15寻找文件 命令:find 格式:find pathname [option] expression 功能:在所给的路经名下寻找符合表达式相匹配的文件。 选项:-name 表示文件名 -user 用户名,选取该用户所属的文件 -group 组名,选取该用户组属的文件 -mtime n 选取 n 天内被修改的文件 -newer fn 选取比文件名为 fn 更晚修改的文件 注释: 例如:% find . -name '*abc*' -print 3.16搜索文件中匹配符 命令:grep 格式:grep [option] pattern filenames 功能:逐行搜索所指定的文件或标准输入,并显示匹配模式的每一行。 选项:-v 找出模式失配的行 -c 统计匹配行的数量 -n 显示匹配模式的每一行 注释: 例如:% ps -aux | grep R 3.17比较文件不同 命令:diff (difference) 格式:diff filename1 filename2 功能:显示两文件的不同之处。 选项: 注释: 例如:% diff file1 file2 3.18比较文件 命令:cmp (compare) 格式:cmp [-l] [-s] filename1 filename2 功能:显示比较两文件不同处的信息 选项:-l 给出两文件不同的字节数 -s 不显示两文件的不同处,给出比较结果 注释: 例如:% cmp file1 file2 3.19比较文件共同处 命令:comm (common) 格式:comm [-123] filename1 filename2 功能:选择或拒绝比较两文件出现的共同行 选项:-1 不显示第1列 -2 不显示第2列
奥的斯电梯故障代码

奥的斯电梯故障代码1100 SOFTWARE RESET 软件复位1101 RING SOFTWARE RESET 群控软件复位1200 SIO MESSAGE FRAMING ERROR 从MCSS接受到的数据信息中检测到结构错误1201 SIO TIMEOUT ERROR 与MCSS通讯超时1300 RSL1 LOSS OFSYNCHRONISATION 轿厢通讯收发不同步1301 RSL2 LOSS OF SYNCHRONISATION 厅外通讯收发不同步1302 RSL3 LOSS OF SYNCHRONISATION 群控通讯收发不同步1400 RSL1 TOTAL PARITY ERRORS 轿厢通讯出现奇偶校验错误1401 RSL2 TOTAL PARITY ERRORS 厅外通讯出现奇偶校验错误1402 RSL3 TOTAL PARITY ERRORS 群控通讯出现奇偶校验错误1500 RING1 CHECKSUM ERROR 群控环1通讯有检测故障1501 RING1 TIMEOUT ERROR 群控环1通讯有超时故障1700 MCSS NOT AVAILABLE MCSS通讯故障1701 CAR SHUTDOWN WHILE IN EPO 备用电源操作时出现故障1702 DTC PROTECTION COUNT DTC关门保护1703 DTO PROTECTION COUNT DTO关门保护1704 DELAY CAR PROTECTION DCP保护1800 EFO-P AND EFO-CK ARE INVALID OR DO NOT MATCH 消防楼层参数错误或EFO-P与EFO-CK不一致或该层门被封1801 ASL-P AND ASL-CK ARE INVALID OR DO NOT MATCH 消防可选楼层参数错误或ASL-P与ASL-CK不一致或该层门被封EFS AND EFS-CK ARE INVALID OR DO NOT MATCH 消防类型参数错误或EFS与EFS-CK不一致ASL2-P AND ASL2-CK ARE INVALID OR DO NOT MATCH 消防第二可选楼层参数错误或ASL2-P与ASL2-CK不一致或该层门被封1804 RCBII电池电压不足1805 EQO HOISTWAY SENSOR FAILED 地震井道传感器故障1806 INVALID EQO PARAMETERSETUP 无效的地震参数1807 CAR IS CONFIGURED FOR RANDOMCALLS 电梯由随机内外呼控制运行故障代码服务器显示说明2000 STM softwarereset 电子板软件运行错误,引起CPU复位。
abaqus问答自己总结

abaqus问答自己总结1、Q:预拉钢筋怎样施加预应力,请各位指点~~~~Q:我在文档里看到要在inp文件定义一个rebar,但是rebar只能用于shell, membrane, and solid elements 。
我现在想做的是一个预应力拉索,不是镶嵌在shell, membrane, and solid 这些单元里的,而是独立的一根拉锁。
拉索单元打算用truss,但是怎样在truss上使用rebar啊?请高手指点还有个问题,我看到别人的inp文件,如下:*rebar,element=continuum,material=rebar2,name=ubartop1,1.005e-4,0.15,0.0,0.5,1第二行第一个是setname(top1),第二个是rebar的截面面积(1.005e-4),那第三、第四、第五是指什么?(0.15,0,0.5),最后一个应该是方向,是1方向。
哪位高人指点下第三、四、五项分别代表什么?A:施加预应力*initinial conditions,type=stress,rebarelset,rebar name,所施加预应力的值,另prestress hold 为保持所施加的预应力的值不变,我的理解是防止别的构件吃掉所施加的预应力,造成所施加预应力的损失。
使用了这个命令之后就避免了这种损失,保证所施加的预应力都施加到了钢筋上。
A:谢谢指点,你所说的应该是把预应力加在rebar上面,但我发觉truss单元不能定义成rebar,其实是我多想了,truss本来就可以当拉索,实际工程中加预应力只是为了使钢绞线拉紧,起到张拉作用,而在abaqus里,truss本身就是拉紧的,不用施加预应力A:我知道模拟加强筋的时候需要用rebar,但钢筋确实可以直接用truss来模拟,而lz所说的预应力其实其实只是施工时的张力而并不是真正意义上的预应力,比如螺栓预应力之类的。
如果是索的话可能是要施加预应力的,仅个人看法。
5680t-GPON开局教程

ONU
超级终端登录 或Telnet登录
MA5616
ONU
超级终端登录 或Telnet登录
HG850a
ONT
Web浏览器登录
2.2
如果维护PC已经与主控板SCUL上的控制接口“CON”用串口线连接好,可以通过超级终端登录GPON设备。操作方法如下:
步骤 1在维护PC的Windows环境下,选择“开始> 程序 > 附件 > 通讯 > 超级终端”。
密码:admintelecom
缺省IP地址+子网掩码
IP地址:192.168.100.1
子网掩码:255.255.255.0
----结束
3
3.1
建议不同用户类型的ONU通过不同PON口接入到OLT,保证高价值客户业务的QoS和安全性,避免相互影响;
对于重要局点OLT建议通过上行端口链路聚合保护方式接入上层汇聚设备(如:华为公司的NE40E设备);
设备管理方式
FTTH组网模式下ONU设备通过OMCI进行管理,FTTB组网模式下ONU设备通过SNMP进行管理
3.3
同一型号ONU采用相同的VLAN配置,并统一在OLT进行CS+C’切换;
同一型号ONU采用相同的各种模板:线路模板、DBA模板、业务模板;
在ONU设备上基于VLAN对上网业务报文重标记 Cos(802.1p)为0,以避免上网业务流量影响其他重要业务。
步骤 2在打开的“连接描述”对话框中输入一个用于标识此会话连接的名称,并单击“确定”。
步骤 3选择实际使用的串口(COM1或COM2),串口属性的参数取值配置为与系统缺省值相同(每秒位数:9600,数据位:8,奇偶校验:无,停止位:1,数据流控制:无),并单击“确定”。
FUJITSU Cloud Service K5 COLMINA 平台服务说明书

FUJITSU Cloud Service K5 COLMINA Platform Service DescriptionJanuary 26, 20181. Service OverviewFujitsu provides the following services.(1) Basic ServiceThis Service enables the C ustomer’s factory data to be received, stored, and used.I. Data ReceiveThe Customer can receive CSV files sent via a Web API.Also, the Customer can assign a receive data number to each receive unit, and record the receive results inthe data arrival record table.II. Data StoreThe Customer can convert CSV files received as described in I. above to RDB format, and store them assequential performance data in the data store area.III. Authentication FunctionThe Customer can identify the End User by its user name and password, and authenticate it.IV. COLMINA PortalThe Customer can operate as follows:∙Setting of End User (add/change/delete)∙Data Receive Status Check∙Service Usage Status Check (disk usage amount)∙Calling Data Visualization ApplicationsV. Usage Status CheckThe Customer can check the usage status of this Service (a list of visualized factories) via the Help Desk(*1).(2) Data VisualizationThe Customer can visualize data received and stored by using Data Visualization “powered by Intelligent Dashboard(*2)“.I. VisualizationThe Customer can display data stored as described in (1) II. above layer by layer in graph form on thedashboard screen.Also, the Customer can import its images and graphics and display them on the dashboard screen.∙examples of layer type: country, region, factory/production line/machine∙examples of graph type: by time period, by year, by month, by dayII. Alarm DisplayThe Customer can display alarm information on the dashboard screen based on the data threshold pre-set bythe Customer.III. Master Maintenancei. Screen Design ConfigurationThe Customer can configure contents (templates, graphs, alarm threshold, screen transition layers, etc.)to be displayed on the dashboard screen and register graphics.ii. End User Authority ManagementThe Customer can manage functions and permissions that can be assigned to each End User.iii. Sequential Performance Data OutputThe Customer can download stored data as a CSV file.2. Restrictions and Notes(1) About Basic ServiceI. The following table lists the restrictions that apply to Data Receive:Note: The Customer may fail to receive data correctly if any of above restrictions is applicable. II.The following table lists the notes that apply to data formats:III.If data is registered with the same key items (time, data type, data elements, etc.) in storing, it will be overwritten with the information that is registered later.IV. The transfer protocol in this Service is HTTPS, and the method is POST. V.In the case of the excessive usage that could cause serious damage to the operation of this Service or the usage that regularly exceeds the restrictions that apply to data receive, the access to this Service may be rejected.VI. The Customer may apply for the addition of a disk usage amount under this Service. If Fujitsu consents tosaid application, Fujitsu will separately notify the Customer of the work date for said addition. Once said addition has been completed, Fujitsu will notify the Customer of the use start date for said addition, and the addition will take effect on said use start date. Note that when the Customer applies for the addition of a disk usage amount, the Customer shall cease using this Service by the work date for said addition to be separately notified by Fujitsu, and the Customer cannot use this Service on said work date.VII. The Customer shall be solely responsible for data received and stored while using this Service.The Customer hereby gives Fujitsu its consent to Fujitsu’s use data collected in the “Location of Information Co llection” listed below, in order to improve service quality, improvefunctionality, and collect and disclose statistics from the data. In any event, Fujitsu will not use the Customer's actual resource data without the VIII. If the Customer uses, or provides to Fujitsu, personal information or personal data under this Service, theCustomer shall necessarily give mandatory notification to the subject of said personal information or said personal data, or shall obtain mandatory consent from said subject. The Customer hereby represents and warrants that personal information or personal data provided to Fujitsu, and the use of said personal information or personal data by Fujitsu, shall neither violate any applicable laws, rules or regulations of any country nor prejudice any rights of any third party.IX. If data suspected of containing a virus is detected in the Fujitsu Environment, the data used by the Customerin this Service may be deleted without notice to the Customer in order to protect the Fujitsu Environment. X.Fujitsu will not recover data registered or created in this Service . It is the Customer’s responsibility to take backups of, recover or recreate said data.XI. Data used in this Service shall be prepared by the Customer in CSV format (the format mandatory for thisService) and shall be sent to the URL designated in this Service.XII. In addition to the present Service Description, the detailed service description at the following URL sets forththe license terms and conditions applicable to open source and other software to be separately identified byFujitsu as part of this Service. If the license terms and conditions set forth in said detailed service descriptionare contrary to the provisions of the present Service Description, the license terms and conditions set forth insaid detailed service description shall prevail.https:///doc/en/colminapf/document/manual/servicedetails.pdf(2) About Data VisualizationI. Refer to the following URL for details of client environments that can access this Service.https:///doc/en/colminapf/document/manual/requirements.pdf II. The Customer can add the languages to be displayed on the dashboard screen. Other than Japanese, a total of five (5) languages can be added.III. The Customer shall prepare the graphic images to be displayed on the dashboard screen. These include images of the factory, production line and machinery, as well as alerts and icons.IV. In the Master Maintenance, the linefeed code for uploading and downloading CSV files is CRLF. Note that the CSV files that can be uploaded is only those of the definition information used for screen design configuration.V. In the Master Maintenance, the maximum number of records when using a CSV file to download stored data is 50,000. If the number of records to be downloaded exceeds this limit, the Customer shall divide the recordsinto several instances, for example, by reducing the target time selected in downloading.VI. Regardless of the disk usage amount, the maximum number of sequential performance data items that can be stored is 80,000,000.(3) This Service is available in following regions:・Eastern Japan Region 2Footnotes:*1. Contact the Help Desk to confirm usage status.*2. Intelligent Dashboard means the solution offered by Fujitsu to assist the overall optimization leading to the resolution of problems in the manufacturing industry and IoT-based visualization of entire factory operations.Supplementary Provision (January 26, 2018)The present Service Description is effective from January 26, 2018.。
customer的用法总结大全

customer的用法总结大全(学习版)编制人:__________________审核人:__________________审批人:__________________编制学校:__________________编制时间:____年____月____日序言下载提示:该文档是本店铺精心编制而成的,希望大家下载后,能够帮助大家解决实际问题。
文档下载后可定制修改,请根据实际需要进行调整和使用,谢谢!并且,本店铺为大家提供各种类型的经典范文,如英语单词、英语语法、英语听力、英语知识点、语文知识点、文言文、数学公式、数学知识点、作文大全、其他资料等等,想了解不同范文格式和写法,敬请关注!Download tips: This document is carefully compiled by this editor.I hope that after you download it, it can help you solve practical problems. The document can be customized and modified after downloading, please adjust and use it according to actual needs, thank you!In addition, this shop provides various types of classic sample essays, such as English words, English grammar, English listening, English knowledge points, Chinese knowledge points, classical Chinese, mathematical formulas, mathematics knowledge points, composition books, other materials, etc. Learn about the different formats and writing styles of sample essays, so stay tuned!customer的用法总结大全customer的意思n. 顾客,客户,主顾,customer用法customer可以用作名词customer的基本意思是“顾客”,指具体的人,是可数名词,可加不定冠词或数词修饰,有复数形式。
【跨境电商英文课件】店铺装修

Introduction of the use of the decoration platform
Third. Introduction of the main area of the decoration platform
page management - page editor
Introduction of the use of the decoration platform
Introduction of the use of the decoration platform
Iv. preview and release of the shop 1. shop previews
Introduction of the use of the decoration platform
Introduction of the use of the decoration platform
Third. Introduction of the main area of the 4. style editor - shop color matching
You can click " template download" to download our visual designer to design a good PSD source file to quickly generate some pictures used by the shop.
The Use the shop module
Ii. picture carousel & shop module use
2. what is the picture carousel? The picture carousel is a region where you display a set of pictures in the store. you can set 1 5 pictures ( if you set a picture instead of a carousel ), and you can specify hyperlinks for all pictures. the height range of the picture carousel needs to be between 100 - 600 ( pixels ), and the best width and height of the same set of carousel will be consistent, which will give the buyer a better experience.
customer是什么意思中文翻译

customer是什么意思中文翻译customer是我们在英语中常见的名词,那么customer做名词都表达哪些意思呢?下面店铺为大家带来customer的英语意思和相关例句,欢迎大家学习!customer作名词的意思顾客,客户;主顾;<口>家伙customer的英语音标英 [ˈkʌstəm] 美 [ˈkʌstəm]customer的时态customerscustomer的英语例句1. In some stores we were undermanned and customer service was suffering.有些店我们人手不足,对顾客照顾不周。
2. It does not matter one whit to the customer.这对顾客来说一点关系都没有。
3. Several manufacturers are also nibbling away at Ford's traditional customer base.几家制造商也在蚕食福特公司的传统客户群。
4. As one former customer said cynically, "He's probably pocketed the difference!"正如一位愤世嫉俗的旧主顾所说的那样,“他很可能把差额塞进了自己的腰包!”5. The owners of the store have stepped up customer mailings.店主们加大了对顾客的邮寄宣传力度。
6. If there's anything I can't stand it's an indecisive, wishy-washy customer.如果说我有什么不能容忍的话,那就是犹犹豫豫、挑来挑去的客户。
7. Good customer relations require courtesy, professionalism and effective response.良好的客户关系需要做到礼貌、专业,并提供有效的回复。
