rfc3701.6bone (IPv6 Testing Address Allocation) Phaseout
中移动家庭网关终端技术规范v3.0.0

中国移动通信企业标准家庭网关终端技术规范版本号:3.0.0中国移动通信集团公司发布╳╳╳╳-╳╳-╳╳发布 ╳╳╳╳-╳╳-╳╳实施QB-╳╳-╳╳╳-╳╳╳╳ T e c h n i c a l S p e c i f i c a t i o n f o r H o m e G a t e w a y目录3.术语、定义和缩略语 ....................................................................................... 错误!未指定书签。
USB扩展及管理(可选)................................................................................ 错误!未指定书签。
DLNA(可选)............................................................................................................... 错误!未指定书签。
5.6.硬件要求....................................................................................................... 错误!未指定书签。
设备面板标识要求........................................................................................... 错误!未指定书签。
操作管理 ...................................................................................................................... 错误!未指定书签。
srv6相关标准

SRv6(Segment Routing over IPv6)是一种基于IPv6网络的新型路由技术,它通过在IPv6数据包中添加一个24位的标签来标识不同的路径。
这种技术可以提高网络的可扩展性、灵活性和安全性。
以下是一些与SRv6相关的标准:1. RFC 8210:这是SRv6的基本规范,定义了SRv6的基本概念、操作和实现要求。
2. RFC 8365:这个文档描述了如何使用BGP-LS(Border Gateway Protocol - Link State)协议在IPv6网络中传播SRv6路由信息。
3. RFC 8402:这个文档描述了如何使用MP-BGP(Multiprotocol BGP)协议在IPv6网络中传播SRv6路由信息。
4. RFC 8415:这个文档描述了如何使用IS-IS(Intermediate System to Intermediate System)协议在IPv6网络中传播SRv6路由信息。
5. RFC 8475:这个文档描述了如何使用OSPF(Open Shortest Path First)协议在IPv6网络中传播SRv6路由信息。
6. RFC 8597:这个文档描述了如何使用BFD(Bidirectional Forwarding Detection)协议在IPv6网络中检测SRv6路径的状态。
7. RFC 8795:这个文档描述了如何使用LDP(Label Distribution Protocol)协议在IPv6网络中分发SRv6标签。
8. RFC 8879:这个文档描述了如何使用PCE(Path Computation Element)协议在IPv6网络中计算SRv6路径。
9. RFC 8915:这个文档描述了如何使用SDN(Software-Defined Networking)技术来实现SRv6网络。
10. RFC 9119:这个文档描述了如何使用SRv6技术来实现网络切片。
希尔斯通 S 系列网络入侵防御系统(NIPS)S600 S1060 S1560 S190

Hillstone S-SeriesNetwork Intrusion Prevention System (NIPS)S600 / S1060 / S1560 / S1900 / S2100 / S2160 / S2700 / S2660 / S3560 / S3500 /S3860 / S3900 / S5500 /S5560As the threat landscape continues to evolve aggressively, an increasing number of network pro-tection technologies have quickly emerged. Among these various technologies, Intrusion Preven-tion System (IPS) remains one of the most widely deployed solutions, regardless of platform or form factor.Hillstone Network-based IPS (NIPS) appliance operates in-line, and at wire speed, performing deep packet inspection, and assembling inspection of all network traffic. It also applies rules based on several methodologies, including protocol anomaly analysis and signature analysis to block threats. Hillstone NIPS can be deployed in the network to inspect traffic left undetected by perimeter solutions, and is an integral part of network security systems for its high-performance, no compromise, best-of-breed protection capability and broad and flexible deployment scenarios.Product HighlightsUnparalleled Threat Protection without Performance CompromiseThe Hillstone NIPS platform has the most comprehensive high performance inspection engine, combined with the best-of-breed signature partnering with leading technology part-ners, providing customers the highest threat detection rate with the lowest total cost of ownership (TCO). Hillstone IPS engine has 99.6% blocking rate of static exploits and 98.325% blocking rate of live exploits (reported by NSS Labs).The Hillstone NIPS platform provides high throughput, low latency and maximum availability to maintain efficient secu -rity operations without compromising network performance. NIPS combines protocol analysis, threat reputation and other features that deliver threat protection from Layer 2 to Layer 7, including ARP attack, Dos/DDoS attack, abnormal protocols, malicious URLs, malwares and web attacks.Granular Reporting with User Targeted ViewpointsHillstone NIPS provides comprehensive visibility based on protocol, application, user and content. It can identify more than 4,000 applications, including hundreds of mobile and cloud applications.Bringing multiple sources together, the system can identify contextual information to make proper blocking decisions. With a granular and robust reporting function, it offers visibil-ity across different views:• Unique templates, based on whether you are a business system administrator, a security administrator or the CIO or executive.• Organized Threat Content – whether a security, system risk, network threat or traffic view – in order to help you clearly understand the risk and make the right decision.Product Highlights (Continued) FeaturesIntrusion Prevention• 12,700+ signatures, protocol anomaly detection, rate-based detection, custom signatures, manual, automatic push or pull signature updates, integrated threat encyclopedia• IPS Actions: monitor, block, reset (attackers IP or victim IP, incoming interface) with expiry time• Packet logging option• Filter based selection and review: severity, target, OS, application or protocol • IP exemption from specific IPS signatures• IDS sniffer mode• IPv4 and IPv6 rate based DoS protection with threshold settings against TCP Syn flood, TCP/UDP/SCTP port scan, ICMP sweep, TCP/UDP/SCIP/ICMP session flooding (source/destination)• Active bypass with bypass interfaces• Predefined prevention configuration• Support web server protection, including CC attack, external link attack, iframe, cross-site request forgery (CSRF) attack, etc.• Support protection of brute force attack including FTP, MSRPC, POP3, SMTP, SUNRPC and telnet• Support weak password detection for FTP, MSRPC, POP3, SMTP, SUNRPC and telnet• Threat Details support URI and Attack Data Decoding• Support MPLS frame inspectionThreat Correlation Analytics• Correlation among unknown threats, abnormal behavior and application behavior to discover potential threat or attacks• Multi-dimension correlation rules, automatic daily update from the cloud Advanced Threat Detection• Behavior-based advanced malware detection• Detection of more than 2000 known and unknown malware families including Virus, Worm, Trojan, Spyware, Overflow etc• Real-time, online, malware behavior model database updateAbnormal Behavior Detection• Behavior modeling based on L3-L7 baseline traffic to reveal anomalous network behavior, such as HTTP scanning, Spider, SPAM, SSH/FTP weak password, and spyware• Detection of DDoS including Flood, Sockstress, zip of death, reflect, DNS query, SSL DDos and application DDoS• Supports inspection of encrypted tunneling traffic for unknown applications • Real-time, online, abnormal behavior model database updateAntivirus• Manual, automatic push or pull signature updates• Flow-based antivirus: protocols include HTTP/HTTPS, SMTP, POP3, IMAP, FTP/ SFTP, SMB• Compressed file virus scanning Attack Defense• Abnormal protocol attack defense• Anti-DoS/DDoS, including SYN Flood, DNS Query Flood defense• ARP attack defense• IP scanning and port scanningURL Filtering• Flow-based web filtering inspection• Manually defined web filtering based on URL, web content and MIME header• Dynamic web filtering with cloud-based real-time categorization database: over 140 million URLs with 64 categories (8 of which are security related)• Additional web filtering features:- Filter Java Applet, ActiveX or cookie- Block HTTP Post- Log search keywords- Exempt scanning encrypted connections on certain categories for privacy• Web filtering profile override: allows administrator to temporarily assign different profiles to user/group/IP• Web filter local categories and category rating override• Support allow/block list• Customizable alarmAnti-Spam• Real-time spam classification and prevention• Confirmed spam, suspected spam, bulk spam, valid bulk• Protection regardless of the language, format, or content of the message• Support both SMTP and POP3 email protocols• Inbound and outbound detection• Whitelists to allow emails from trusted domain/email addresses• User-defined blacklistsCloud-Sandbox• Upload malicious files to cloud sandbox for analysis• Support protocols including HTTP/HTTPS, POP3, IMAP, SMTP and FTP• Support file types including PE, ZIP, RAR, Office, PDF, APK, JAR and SWF• File transfer direction and file size control• Provide complete behavior analysis report for malicious files• Global threat intelligence sharing, real-time threat blocking• Support detection only mode without uploading filesData Security• Web content filtering and file content filtering• Support file filtering with over 100 file formats• Support network behavior recordingEase of Deployment and Centralized Management Deploying and managing the Hillstone NIPS is simple, with minimum overhead. It can be deployed in the following modes to meet security requirements and ensure optimal network connectivity:• Active protection (intrusion prevention mode), real time monitoring and blocking.• Passive detection (intrusion detection mode), real time monitoring and alert.The Hillstone NIPS can be managed by the Hillstone Security Management Platform (HSM). Administrators can centrally register, monitor, and upgrade NIPS devices deployed in differ-ent branches or locations, with a unified management policy across the network for maximum efficiency.Features (Continued)Botnet C&C Prevention• Discover intranet botnet host by monitoring C&C connections and block further advanced threats such as botnet and ransomware• Regularly update the botnet server addresses• Prevention for C&C IP and domain• Support TCP, HTTP, and DNS traffic detection• IP and domain whitelistsIP Reputation• Identify and filter traffic from risky IPs such as botnet hosts, spammers, Tor nodes, breached hosts, and brute force attacks• Logging, dropping packets, or blocking for different types of risky IP traffic• Regular IP reputation signature database upgradeApplication Control• Over 4,000 applications that can be filtered by name, category, subcategory, technology and risk• Each application contains a description, risk factors, dependencies, typical ports used, and URLs for additional reference• Actions: block, monitor• Provide multi-dimensional monitoring and statistics for applications running in the cloud, including risk category and characteristics• Support encrypted applicationQuality of Service (QoS)• Support encrypted application• Max/guaranteed bandwidth tunnels or IP/user basis• Tunnel allocation based on security domain, interface, address, user/user group, server/server group, application/app group, TOS, VLAN• Bandwidth allocated by time, priority, or equal bandwidth sharing• Type of Service (TOS) and Differentiated Services (DiffServ) support• Prioritized allocation of remaining bandwidth• Maximum concurrent connections per IP• Bandwidth allocation based on URL category• Bandwidth limit by delaying access for user or IPIPv6• Management over IPv6, IPv6 logging and HA• IPv6 tunneling, DNS64/NAT64 etc• IPv6 routing protocols, static routing, policy routing, ISIS, RIPng, OSPFv3 and BGP4+• IPS, Application identification, Antivirus, Access control, ND attack defense VSYS• System resource allocation to each VSYS• CPU virtualization• Non-root VSYS support IPS, URL filtering, Policy, QoS, etc.• VSYS monitoring and statistics• Support backup of all VSYS configurations at onceSSL Proxy• SSL offload: SSL traffic decryption• SSL require/ exempt: SSL traffic allowed or block based on the policy rules without decryptionFlexible Traffic Analysis and Control• Support 3 operation modes: Route/NAT (layer 3) , Transparent (layer 2) with optional bypass interface, and TAP mode (IDS Mode) with Hillstone Firewall Integration• Traffic analysis and control based on policy rules by source/destination zone, source/destination IP address, users, service or applications High Availability• Redundant heartbeat interfaces• AP and peer mode• Standalone session synchronization• HA reserved management interface• Failover:- Port, local & remote link monitoring- Stateful failover- Sub-second failover- Failure notification• Deployment Options:- HA with link aggregation- Full mesh HA- Geographically dispersed HAVisible Administration• Management access: HTTP/HTTPS, SSH, telnet, console• Central Management: Hillstone Security Manager (HSM), web service APIs • Two-factor authentication: username/password, HTTPS certificates file• System Integration: SNMP, syslog, alliance partnerships• Rapid deployment: USB auto-install, local and remote script execution• Dynamic real-time dashboard status and drill-in monitoring widgets• Storage device management: storage space threshold customization and alarm, old data overlay, stop recording.• Language support: EnglishLogs and Reporting• Logging facilities: local storage for up to 6 months, multiple syslog servers and multiple Hillstone Security Audit (HSA) platforms• Encrypted logging and log integrity with HSA scheduled batch log uploading • Reliable logging using TCP option (RFC 3195)• Detailed traffic logs: forwarded, violated sessions, local traffic, invalid packets • Comprehensive event logs: system and administrative activity audits, routing & networking, VPN, user authentications, WiFi related events• Log aggregation: support aggregation of AV and C&C logs• IP and service port name resolution option• Brief traffic log format option• Granular Reporting with User Targeted Viewpoints- HA Management/C-level View- Business System Owner View- Network Security Administrator ViewStatistics and Monitoring• Application, URL, threat events statistic and monitoring• Real-time traffic statistic and analytics• System information such as concurrent session, CPU, Memory and temperature• iQOS traffic statistic and monitoring, link status monitoring• Support traffic information collection and forwarding via Netflow (v9.0)• Cloud-based threat intelligence push service• Geographical distribution of external network attacksCloudView• Cloud-based security monitoring• 24/7 access from web or mobile application• Device status, traffic and threat monitoring• Cloud-based log retention and reporting500 GB (optional)Dimension (W×D×H, mm)16.9 × 11.8 × 1.7 in(430×300×44mm)17.1×12.6×1.7 in(436x 320x 44mm)16.9 x 14.8 x 1.7 in(430x375x44mm)Weight14.3 lb (6.5 kg)14.33 lb (6.5kg)22.0 lb (10 kg)Temperature32-104°F (0-40°C)32-104°F (0-40°C)32-104°F (0-40°C) Relative Humidity5-85% (no dew)10%~95% (no dew)5-85% (no dew)14 GbpsConsumption 1 + 1 1 + 1 1 + 1Dimension (W×D×H, mm)16.9 × 19.7 × 3.5 in(430×500×88mm)16.9 × 19.7 × 3.5 in(430×500×88mm)17.1×21.3×1.7 in(436x542x44mm)Weight35.3 lb (16 kg)35.3 lb (16 kg)32.6 lb (14.8kg)Temperature32-104°F (0-40°C)32-104°F (0-40°C)32-104°F (0-40°C) Relative Humidity5-85% (no dew)5-85% (no dew)10%~95% (no dew)ModuleIOC-S-4GE-B-LIOC-S-4SFP-LIOC-S-4GE-BIOC-S-4SFPIOC-S-8SFPIOC-S-4GE-4SFPI/O Ports 4 x SFP Ports4 × SFP Ports 4 × GE and 4 × SFP Ports Dimension slot)1U (Occupies 1 generic slot)slot)1U (Occupies 1 generic slot)generic slot) 1U (Occupies 1 generic slot)Weight0.22 lb (0.1 kg)0.22 lb (0.1 kg)0.33 lb (0.15 kg)0.33 lb (0.15 kg)0.55 lb (0.25 kg)0.55 lb (0.25 kg)ModuleIOC-S-2SFP+IOC-S-4SFP+IOC-S-4SFP-BIOC-S-2SFP+-BIOC-S-4SFP+-BIOC-S-4GE-B-HIOC-S-4GE-4SFP-HI/O Ports 2 × SFP+ Ports 4 × SFP+ Ports 4 × SFP Bypass Ports 2 × SFP+ Bypass Ports 4 × SFP+ Bypass Ports 4 × GE Bypass Ports 4 × GE and 4 × SFP Ports Dimension 1U (Occupies 1 generic slot)1U (Occupies 1 generic slot)1U (Occupies 1 generic slot) Weight0.44 lb (0.2 kg)0.88 lb (0.4 kg)0.33 lb (0.15 kg)ModuleIOC-S-8GE-B-HIOC-S-8SFP-HIOC-S-4SFP-HIOC-S-2SFP+-HIOC-S-4SFP+-HIOC-S-4SFP-B-HIOC-S-2SFP+-B-HI/O Ports 8 × GE Bypass Ports 8 × SFP Ports 4 × SFP Ports 2 × SFP+ Ports 4 × SFP+ Ports 4 × SFP Bypass Ports 2 × SFP+ Bypass Ports Dimension 1U (Occupies 1 generic slot)1U (Occupies 1 generic slot)1U (Occupies 1 generic slot) Weight0.55 lb (0.25 kg)0.33 lb (0.15 kg)0.88 lb (0.4 kg)Module OptionsNOTES:(1) IPS throughput data is obtained under HTTP traffic with all IPS rules being turned on;(2) Maximum concurrent connections are obtained under TCP traffic; and it can be upgraded with Additional Enhanced License (AEL);(3) New sessions are obtained under TCP traffic.Unless specified otherwise, all performance, capacity and functionality are based on StoneOS5.5R5. Results may vary based on StoneOS ® version and deployment.ModuleIOC-S-4SFP+-AIOC-S-2MM-BE-AIOC-S-2SM-BE-AIOC-S-2QSFP+-AI/O Ports 4 × SFP , MM bypass (2 pairs of bypass ports) 2 × QSFP+Dimension 1U1UWeight2.09 lb (0.96 kg)2.09 lb (0.96 kg)2.09 lb (0.96 kg)2.09 lb (0.96 kg)。
派克核电门户网站产品说明书

10 CFR 50 • AERB • ASME QME-1* • ASME QSC (NCA-3800) • ASME 第 III 部分 • ASME U核级认证核级认证 • ASN • CNSC CRN-N* HAF 604 • IAEA SC-QA 780 298* • IEEE* • ISO 9001: •E 派克核电门户网站无论您是要建新的发电厂,还是要改进现有电厂,派克都会依照行业统一的质量保证计划,使不同部门的各种产品进入核电市场,提高生产率和利润率。
这些产品包括安全专项和安全相关的核级子系统和组件,以及为非管制工厂区提供的优质的“成熟”商品。
派克门户网站是我们投入数百万美元用于核能研究和发展的承诺之一,是我们承诺提获得越来越多在全球供应且通过认证的核能产品的单一途径。
供行业所要求的高效性、可靠性和成本效益的体现。
我们支持单源购买各种产品系列,通过最新的订购方式提高工厂生产率和利润率。
另外,我们在将近 50 个国家拥有 50,000 名员工,因而门户网站产品在全球都有供应。
有关订购门户网站产品的更多信息,请:拨打电话 256 885 3833(销售)、256 885 3880(技术支持)或 发送电子邮件至 ipdusnuclear@parker .com派克核电门户网站是根据派克现行的 NQA- 1 和 10CFR50 附录 B 规定的质量保证计划开发的,并且采用了行业及规范性文件中规定的最佳实3 级阀门的 ASME N 核级认证外,派克核电门户网站上提供的产品符合 10CFR 第 21 部分中对基本组件的规定,按照认可的质保计划或是商品级物项执行。
专项不会提高质量,而是验证并记录专用项目中已有的的质量。
EU PED*HAF 604*IAEA SC-QA KTA 3507NNSANQA-1Parker Hannifin Ltd.Tachbrook Park DriveTachbrook Park,Warwick, CV34 6TU英国电话:+44 (0) 1926 317 878传真:+44 (0) 1926 317 855********************欧洲、中东和非洲AE – 阿联酋,迪拜电话:+971 4 8127100********************AT – 奥地利,维也纳新城电话:+43 (0)2622 23501-0*************************AT – 东欧,维也纳新城电话:+43 (0)2622 23501 900****************************AZ – 阿塞拜疆,巴库电话:+994 50 2233 458****************************BE/LU – 比利时,尼韦尔电话:+32 (0)67 280 900*************************BY – 白俄罗斯,明斯克电话:+375 17 209 9399*************************CH – 瑞士,埃托瓦电话:+41 (0)21 821 87 00*****************************CZ – 捷克共和国,Klecany电话:+420 284 083 111*******************************DE – 德国,卡尔斯特电话:+49 (0)2131 4016 0*************************DK – 丹麦,巴勒鲁普电话:+45 43 56 04 00*************************ES – 西班牙,马德里电话:+34 902 330 001***********************FI – 芬兰,万塔河电话:+358 (0)20 753 2500parker. ****************FR – 法国,Contamine s/Arve电话:+33 (0)4 50 25 80 25************************GR – 希腊,雅典电话:+30 210 933 6450************************HU – 匈牙利,布达佩斯电话:+36 23 885 470*************************IE – 爱尔兰,都柏林电话:+353 (0)1 466 6370*************************IT – 意大利,Corsico (MI)电话:+39 02 45 19 21***********************KZ – 哈萨克斯坦,阿拉木图电话:+7 7273 561 000****************************NL – 荷兰,奥尔登扎尔电话:+31 (0)541 585 000********************NO – 挪威,阿斯克尔电话:+47 66 75 34 00************************PL – 波兰,华沙电话:+48 (0)22 573 24 00************************PT – 葡萄牙,莱萨·达·帕尔梅拉电话:351 22 999 7360**************************RO – 罗马尼亚,布加勒斯特电话:+40 21 252 1382*************************RU – 俄罗斯,莫斯科电话:+7 495 645-2156************************SE – 瑞典,Spånga电话:+46 (0)8 59 79 50 00************************SK – 斯洛伐克,班斯卡·比斯特里察电话:+421 484 162 252**************************SL – 斯洛文尼亚,新梅斯托电话:+386 7 337 6650**************************TR – 土耳其,伊斯坦布尔电话:+90 216 4997081************************UA – 乌克兰,基辅电话:+380 44 494 2731*************************UK – 英国,沃里克电话:+44 (0)1926 317 878********************ZA – 南非,坎普顿公园电话:+27 (0)11 961 0700*****************************北美地区CA – 加拿大,安大略省米尔顿电话:+1 905 693 3000US – 美国,克利夫兰电话:+1 216 896 3000亚太地区AU – 澳大利亚,城堡山电话:+61 (0)2-9634 7777CN – 中国,上海电话:+86 21 2899 5000HK – 香港电话:+852 2428 8008IN – 印度,孟买电话:+91 22 6513 7081-85JP – 日本,东京电话:+81 (0)3 6408 3901KR – 韩国,首尔电话:+82 2 559 0400MY – 马来西亚,莎阿南电话:+60 3 7849 0800NZ – 新西兰,惠灵顿电话:+64 9 574 1744SG – 新加坡电话:+65 6887 6300TH – 泰国,曼谷电话:+662 186 7000-99TW – 台湾,台北电话:+886 2 2298 8987南美AR – 阿根廷,布宜诺斯艾利斯电话:+54 3327 44 4129BR – 巴西,圣若泽杜斯坎普电话:+55 800 727 5374CL – 智利,圣地亚哥电话:+56 2 623 1216MX – 墨西哥,阿波达卡电话:+52 81 8156 6000核电门户网站手册 M&K 12/10 1M派克授权的本地经销商© 2010 派克汉尼汾公司派克全球办事处联系信息欧洲产品信息中心免费电话:00 800 27 27 5374(AT, BE, CH, CZ, DE, DK, EE, ES, FI, FR, IE,IL, IS, IT, LU, MT, NL, NO, PL, PT, RU, SE,SK, UK, ZA)– 一点的方式。
RFC1006通信协议

M. Rose & D. Cass [Page 1]Network Working Group Marshall T. Rose, Dwight E. Cass Request for Comments: RFC 1006 Northrop Research and Technology Center Obsoletes: RFC 983 May 1987 ISO Transport Service on top of the TCPVersion: 3Status of this MemoThis memo specifies a standard for the Internet community. Hostson the Internet that choose to implement ISO transport serviceson top of the TCP are expected to adopt and implement thisstandard. TCP port 102 is reserved for hosts which implement thisstandard. Distribution of this memo is unlimited.This memo specifies version 3 of the protocol and supersedes[RFC983]. Changes between the protocol as described in Request forComments 983 and this memo are minor, but are unfortunatelyincompatible.M. Rose & D. Cass [Page 1]1. Introduction and PhilosophyThe Internet community has a well-developed, mature set oftransport and internetwork protocols (TCP/IP), which are quitesuccessful in offering network and transport services toend-users. The CCITT and the ISO have defined various session,presentation, and application recommendations which have beenadopted by the international community and numerous vendors.To the largest extent possible, it is desirable to offer thesehigher level directly in the ARPA Internet, without disruptingexisting facilities. This permits users to develop expertisewith ISO and CCITT applications which previously were notavailable in the ARPA Internet. It also permits a moregraceful convergence and transition strategy fromTCP/IP-based networks to ISO-based networks in themedium-and long-term.There are two basic approaches which can be taken when "porting"an ISO or CCITT application to a TCP/IP environment. Oneapproach is to port each individual application separately,developing local protocols on top of the TCP. Although this isuseful in the short-term (since special-purpose interfaces to the TCP can be developed quickly), it lacks generality.A second approach is based on the observation that both the ARPAInternet protocol suite and the ISO protocol suite are bothlayered systems (though the former uses layering from a morepragmatic perspective). A key aspect of the layering principleis that of layer-independence. Although this section isredundant for most readers, a slight bit of background materialis necessary to introduce this concept.Externally, a layer is defined by two definitions:a service-offered definition, which describes the servicesprovided by the layer and the interfaces it provides toaccess those services; and,a service-required definitions, which describes the servicesused by the layer and the interfaces it uses to access thoseservices.Collectively, all of the entities in the network which co-operate to provide the service are known as the service-provider.Individually, each of these entities is known as a service-peer.Internally, a layer is defined by one definition:a protocol definition, which describes the rules which eachservice-peer uses when communicating with other service-peers. M. Rose & D. Cass [Page 2]Putting all this together, the service-provider uses the protocol and services from the layer below to offer the its service to the layer above. Protocol verification, for instance, deals withproving that this in fact happens (and is also a fertile fieldfor many Ph.D. dissertations in computer science).The concept of layer-independence quite simply is:IF one preserves the services offered by the service-provider THEN the service-user is completely naive with respect to the protocol which the service-peers useFor the purposes of this memo, we will use the layer-independence to define a Transport Service Access Point (TSAP) which appearsto be identical to the services and interfaces offered by theISO/CCITT TSAP (as defined in [ISO8072]), but we will in factimplement the ISO TP0 protocol on top of TCP/IP (as defined in[RFC793,RFC791]), not on top of the the ISO/CCITT networkprotocol. Since the transport class 0 protocol is used over theTCP/IP connection, it achieves identical functionality astransport class 4. Hence, ISO/CCITT higher level layers (allsession, presentation, and application entities) can operatefully without knowledge of the fact that they are running on aTCP/IP internetwork.M. Rose & D. Cass [Page 3]2. MotivationIn migrating from the use of TCP/IP to the ISO protocols, thereare several strategies that one might undertake. This memo waswritten with one particular strategy in mind.The particular migration strategy which this memo uses is basedon the notion of gatewaying between the TCP/IP and ISO protocolsuites at the transport layer. There are two strong argumentsfor this approach:1. Experience teaches us that it takes just as long to get goodimplementations of the lower level protocols as it takes to getimplementations of the higher level ones. In particular, it hasbeen observed that there is still a lot of work being done at the ISO network and transport layers. As a result, implementationsof protocols above these layers are not being aggressivelypursued. Thus, something must be done "now" to provide a mediumin which the higher level protocols can be developed. SinceTCP/IP is mature, and essentially provides identicalfunctionality, it is an ideal medium to support this development.2. Implementation of gateways at the IP and ISO IP layers areprobably not of general use in the long term. In effect, thiswould require each Internet host to support both TP4 and TCP.As such, a better strategy is to implement a graceful migrationpath from TCP/IP to ISO protocols for the ARPA Internet when theISO protocols have matured sufficiently.Both of these arguments indicate that gatewaying should occur ator above the transport layer service access point. Further, thefirst argument suggests that the best approach is to perform thegatewaying exactly AT the transport service access point tomaximize the number of ISO layers which can be developed.NOTE: This memo does not intend to act as a migration orintercept document. It is intended ONLY to meet theneeds discussed above. However, it would not beunexpected that the protocol described in this memomight form part of an overall transition plan. Thedescription of such a plan however is COMPLETELYbeyond the scope of this memo.Finally, in general, building gateways between other layers in the TCP/IP and ISO protocol suites is problematic, at best.To summarize: the primary motivation for the standard described in this memo is to facilitate the process of gaining experience with higher-level ISO protocols (session, presentation, andapplication). The stability and maturity of TCP/IP are ideal for M. Rose & D. Cass [Page 4]providing solid transport services independent of actualimplementation.M. Rose & D. Cass [Page 5]3. The ModelThe [ISO8072] standard describes the ISO transport servicedefinition, henceforth called TP.ASIDE: This memo references the ISO specifications ratherthan the CCITT recommendations. The differencesbetween these parallel standards are quite small,and can be ignored, with respect to this memo,without loss of generality. To provide the readerwith the relationships:Transport service [ISO8072] [X.214]Transport protocol [ISO8073] [X.224]Session protocol [ISO8327] [X.225]The ISO transport service definition describes the servicesoffered by the TS-provider (transport service) and the interfaces used to access those services. This memo focuses on how the ARPA Transmission Control Protocol (TCP) [RFC793] can be used to offer the services and provide the interfaces.+-----------+ +-----------+ | TS-user | | TS-user | +-----------+ +-----------+ | || TSAP interface TSAP interface || [ISO8072] || |+----------+ ISO Transport Services on the TCP +----------+ | client |-----------------------------------------| server | +----------+ (this memo) +----------+ | || TCP interface TCP interface || [RFC793] || |For expository purposes, the following abbreviations are used:TS-peer a process which implements the protocol described by this memoTS-user a process talking using the services of a TS-peer M. Rose & D. Cass [Page 6]TS-provider the black-box entity implementing the protocoldescribed by this memoFor the purposes of this memo, which describes version 2 of theTSAP protocol, all aspects of [ISO8072] are supported with oneexception:Quality of Service parametersIn the spirit of CCITT, this is left "for further study". Afuture version of the protocol will most likely support the QOSparameters for TP by mapping these onto various TCP parameters.The ISO standards do not specify the format of a session port(termed a TSAP ID). This memo mandates the use of the GOSIPspecification [GOSIP86] for the interpretation of this field.(Please refer to Section 5.2, entitled "UPPER LAYERS ADDRESSING".) Finally, the ISO TSAP is fundamentally symmetric in behavior.There is no underlying client/server model. Instead of a serverlistening on a well-known port, when a connection is established, the TS-provider generates an INDICATION event which, presumablythe TS-user catches and acts upon. Although this might beimplemented by having a server "listen" by hanging on theINDICATION event, from the perspective of the ISO TSAP, all TS-users just sit around in the IDLE state until they either generate a REQUEST or accept an INDICATION.M. Rose & D. Cass [Page 7]4. The PrimitivesThe protocol assumes that the TCP[RFC793] offers the followingservice primitives:Eventsconnected - open succeeded (either ACTIVE or PASSIVE)connect fails - ACTIVE open faileddata ready - data can be read from the connectionerrored - the connection has errored and is now closed closed - an orderly disconnection has startedActionslisten on port - PASSIVE open on the given portopen port - ACTIVE open to the given portread data - data is read from the connectionsend data - data is sent on the connectionclose - the connection is closed (pending data issent)This memo describes how to use these services to emulate the following service primitives, which are required by [ISO8073]:EventsN-CONNECT.INDICATION- An NS-user (responder) is notified thatconnection establishment is in progressN-CONNECT.CONFIRMATION- An NS-user (responder) is notified thatthe connection has been establishedN-DATA.INDICATION- An NS-user is notified that data can beread from the connectionM. Rose & D. Cass [Page 8]N-DISCONNECT.INDICATION- An NS-user is notified that the connectionis closedActionsN-CONNECT.REQUEST- An NS-user (initiator) indicates that itwants to establish a connectionN-CONNECT.RESPONSE- An NS-user (responder) indicates that itwill honor the requestN-DATA.REQUEST - An NS-user sends dataN-DISCONNECT.REQUEST- An NS-user indicates that the connectionis to be closedThe protocol offers the following service primitives, as definedin [ISO8072], to the TS-user:EventsT-CONNECT.INDICATION- a TS-user (responder) is notified thatconnection establishment is in progressT-CONNECT.CONFIRMATION- a TS-user (initiator) is notified that theconnection has been establishedT-DATA.INDICATION- a TS-user is notified that data can be read from the connectionT-EXPEDITED DATA.INDICATION- a TS-user is notified that "expedited" data can be read from the connectionT-DISCONNECT.INDICATION- a TS-user is notified that the connectionis closedM. Rose & D. Cass [Page 9]ActionsT-CONNECT.REQUEST- a TS-user (initiator) indicates that itwants to establish a connectionT-CONNECT.RESPONSE- a TS-user (responder) indicates that itwill honor the requestT-DATA.REQUEST - a TS-user sends dataT-EXPEDITED DATA.REQUEST- a TS-user sends "expedited" dataT-DISCONNECT.REQUEST- a TS-user indicates that the connectionis to be closedM. Rose & D. Cass [Page 10]5. The ProtocolThe protocol specified by this memo is identical to the protocolfor ISO transport class 0, with the following exceptions:- for testing purposes, initial data may be exchangedduring connection establishment- for testing purposes, an expedited data service issupported- for performance reasons, a much larger TSDU size issupported- the network service used by the protocol is providedby the TCPThe ISO transport protocol exchanges information between peers in discrete units of information called transport protocol data units (TPDUs). The protocol defined in this memo encapsulates theseTPDUs in discrete units called TPKTs. The structure of theseTPKTs and their relationship to TPDUs are discussed in the nextsection.PRIMITIVESThe mapping between the TCP service primitives and the service primitives expected by transport class 0 are quite straight-forward:network service TCP--------------- ---CONNECTION ESTABLISHMENTN-CONNECT.REQUEST open completesN-CONNECT.INDICATION listen (PASSIVE open)finishesN-CONNECT.RESPONSE listen completesN-CONNECT.CONFIRMATION open (ACTIVE open)finishesDATA TRANSFERN-DATA.REQUEST send dataN-DATA.INDICATION data ready followed by M. Rose & D. Cass [Page 11]read dataCONNECTION RELEASEN-DISCONNECT.REQUEST closeN-DISCONNECT.INDICATION connection closes orerrorsMapping parameters is also straight-forward:network service TCP--------------- ---CONNECTION RELEASECalled address server’s IP address(4 octets)Calling address client’s IP address(4 octets)all others ignoredDATA TRANSFERNS-user data (NSDU) dataCONNECTION RELEASEall parameters ignoredCONNECTION ESTABLISHMENTThe elements of procedure used during connection establishment are identical to those presented in [ISO8073], with threeexceptions.In order to facilitate testing, the connection request andconnection confirmation TPDUs may exchange initial user data, using the user data fields of these TPDUs.In order to experiment with expedited data services, theconnection request and connection confirmation TPDUs maynegotiate the use of expedited data transfer using thenegotiation mechanism specified in [ISO8073] is used (e.g.,setting the "use of transport expedited data transfer service" bit in the "Additional Option Selection" variable part). Thedefault is not to use the transport expedited data transferservice.M. Rose & D. Cass [Page 12]In order to achieve good performance, the default TPDU size is 65531 octets, instead of 128 octets. In order to negotiate a smaller (standard) TPDU size, the negotiation mechanismspecified in [ISO8073] is used (e.g., setting the desired bit in the "TPDU Size" variable part).To perform an N-CONNECT.REQUEST action, the TS-peer performsan active open to the desired IP address using TCP port 102.When the TCP signals either success or failure, this resultsin an N-CONNECT.INDICATION action.To await an N-CONNECT.INDICATION event, a server listens onTCP port 102. When a client successfully connects to thisport, the event occurs, and an implicit N-CONNECT.RESPONSEaction is performed.NOTE: In most implementations, a single server willperpetually LISTEN on port 102, handing offconnections as they are madeDATA TRANSFERThe elements of procedure used during data transfer are identical to those presented in [ISO8073], with one exception: expediteddata may be supported (if so negotiated during connectionestablishment) by sending a modified ED TPDU (described below).The TPDU is sent on the same TCP connection as all of the otherTPDUs. This method, while not faithful to the spirit of [ISO8072], is true to the letter of the specification.To perform an N-DATA.REQUEST action, the TS-peer constructs thedesired TPKT and uses the TCP send data primitive.To trigger an N-DATA.INDICATION action, the TCP indicates thatdata is ready and a TPKT is read using the TCP read dataprimitive.CONNECTION RELEASETo perform an N-DISCONNECT.REQUEST action, the TS-peer simply closes the TCP connection.If the TCP informs the TS-peer that the connection has been closed or has errored, this indicates an N-DISCONNECT.INDICATION event.M. Rose & D. Cass [Page 13]6. Packet FormatA fundamental difference between the TCP and the network serviceexpected by TP0 is that the TCP manages a continuous stream ofoctets, with no explicit boundaries. The TP0 expects informationto be sent and delivered in discrete objects termed networkservice data units (NSDUs). Although other classes of transportmay combine more than one TPDU inside a single NSDU, transportclass 0 does not use this facility. Hence, an NSDU is identicalto a TPDU for the purposes of our discussion.The protocol described by this memo uses a simple packetizationscheme in order to delimit TPDUs. Each packet, termed a TPKT, isviewed as an object composed of an integral number of octets, ofvariable length.NOTE: For the purposes of presentation, these objects are shown as being 4 octets (32 bits wide). Thisrepresentation is an artifact of the style of this memo and should not be interpreted as requiringthat a TPKT be a multiple of 4 octets in length.A TPKT consists of two parts: a packet-header and a TPDU. Theformat of the header is constant regardless of the type of packet. The format of the packet-header is as follows:0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | vrsn | reserved | packet length | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+where:vrsn 8 bitsThis field is always 3 for the version of the protocol described in this memo.packet length 16 bits (min=7, max=65535)This field contains the length of entire packet in octets,including packet-header. This permits a maximum TPDU size of65531 octets. Based on the size of the data transfer (DT) TPDU,this permits a maximum TSDU size of 65524 octets.The format of the TPDU is defined in [ISO8073]. Note that onlyTPDUs formatted for transport class 0 are exchanged (differenttransport classes may use slightly different formats).M. Rose & D. Cass [Page 14]To support expedited data, a non-standard TPDU, for expedited data is permitted. The format used for the ED TPDU is nearly identical to the format for the normal data, DT, TPDU. The only difference is that the value used for the TPDU’s code is ED, not DT:0 1 2 30 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | header length | code |credit |TPDU-NR and EOT| user data | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | ... | ... | ... | ... | | ... | ... | ... | ... | | ... | ... | ... | ... | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ After the credit field (which is always ZERO on output and ignored on input), there is one additional field prior to the user data.TPDU-NR and EOT 8 bitsBit 7 (the high-order bit, bit mask 1000 0000) indicates the endof a TSDU. All other bits should be ZERO on output and ignored on input.Note that the TP specification limits the size of an expeditedtransport service data unit (XSDU) to 16 octets.M. Rose & D. Cass [Page 15]7. CommentsSince the release of RFC983 in April of 1986, we have gained much experience in using ISO transport services on top of the TCP. In September of 1986, we introduced the use of version 2 of theprotocol, based mostly on comments from the community.In January of 1987, we observed that the differences betweenversion 2 of the protocol and the actual transport class 0definition were actually quite small. In retrospect, thisrealization took much longer than it should have: TP0 is is meant to run over a reliable network service, e.g., X.25. The TCP can be used to provide a service of this type, and, if no one complainstoo loudly, one could state that this memo really just describes a method for encapsulating TPO inside of TCP!The changes in going from version 1 of the protocol to version 2and then to version 3 are all relatively small. Initially, indescribing version 1, we decided to use the TPDU formats from the ISO transport protocol. This naturally led to the evolutiondescribed above.M. Rose & D. Cass [Page 16]8. References[GOSIP86] The U.S. Government OSI User’s Committee."Government Open Systems Interconnection Procurement(GOSIP) Specification for Fiscal years 1987 and1988." (December, 1986) [draft status][ISO8072] ISO."International Standard 8072. Information ProcessingSystems -- Open Systems Interconnection: TransportService Definition."(June, 1984)[ISO8073] ISO."International Standard 8073. Information ProcessingSystems -- Open Systems Interconnection: TransportProtocol Specification."(June, 1984)[ISO8327] ISO."International Standard 8327. Information ProcessingSystems -- Open Systems Interconnection: SessionProtocol Specification."(June, 1984)[RFC791] Internet Protocol.Request for Comments 791 (MILSTD 1777)(September, 1981)[RFC793] Transmission Control Protocol.Request for Comments 793 (MILSTD 1778)(September, 1981)[RFC983] ISO Transport Services on Top of the TCP.Request for Comments 983(April, 1986)[X.214] CCITT."Recommendation X.214. Transport Service Definitionsfor Open Systems Interconnection (OSI) for CCITTApplications."(October, 1984)[X.224] CCITT."Recommendation X.224. Transport ProtocolSpecification for Open Systems Interconnection (OSI)for CCITT Applications." (October, 1984)M. Rose & D. Cass [Page 17][X.225] CCITT."Recommendation X.225. Session Protocol Specificationfor Open Systems Interconnection (OSI) for CCITTApplications."(October, 1984)M. Rose & D. Cass [Page 18]。
LTE典型信令过程

NAS:PDN connectivity request
Authentication and NAS security procedure
S6a: Update Location request
S11: Modify bearer response S1AP: Path Switch Response
X2AP: UE Context Release
Flush DL Buffer
Data Forwarding End Marker
Switch DL Path
S1 Handover
➢This type of handover takes place when there is no X2 connectivity between source eNB and target eNB.
S10: Forward SRNS Context Notification
UE Detach from old cell and sync to new cell
S10: Forward SRNS Context Ack
S1AP: MME Status Transfer
RRC: Connection Reconfiguration Complete
➢The release of resources at the source side is directly triggered from the target eNB.
UE
S-eNB
RRC: Measurement Control
rfc中常用的测试协议

rfc中常用的测试协议引言在计算机网络领域中,为了确保网络协议的正确性和稳定性,测试协议起到了至关重要的作用。
RFC(Request for Comments)是一系列文件,用于描述互联网相关协议、过程和技术。
在RFC中,也包含了一些常用的测试协议,用于验证和评估网络协议的功能和性能。
本文将介绍RFC中常用的测试协议,并深入探讨其原理和应用。
二级标题1:PING协议三级标题1.1:概述PING协议是一种常用的网络测试协议,用于测试主机之间的连通性。
它基于ICMP (Internet Control Message Protocol)协议,通过发送ICMP Echo Request报文并等待目标主机的ICMP Echo Reply报文来判断目标主机是否可达。
三级标题1.2:工作原理PING协议的工作原理如下: 1. 发送方主机生成一个ICMP Echo Request报文,并将目标主机的IP地址作为目的地。
2. 发送方主机将报文发送到网络中。
3.中间路由器收到报文后,将报文转发到下一跳路由器。
4. 目标主机收到ICMP Echo Request报文后,生成一个ICMP Echo Reply报文,并将其发送回发送方主机。
5. 发送方主机收到ICMP Echo Reply报文后,通过比较报文中的标识符和序列号等字段,判断目标主机是否可达。
三级标题1.3:应用场景PING协议在网络中的应用非常广泛,常用于以下场景: - 测试主机之间的连通性,判断网络是否正常工作。
- 测试网络延迟,通过计算ICMP Echo Request报文的往返时间来评估网络质量。
- 排查网络故障,通过检查ICMP Echo Reply报文中的错误码来定位故障原因。
二级标题2:Traceroute协议三级标题2.1:概述Traceroute协议用于跟踪数据包从源主机到目标主机经过的路径。
它通过发送一系列的UDP报文,并在每个报文中设置不同的TTL(Time to Live)值来实现。
VPN常见错误代码及相应的解决方法

VPN常见错误代码及相应的解决方法VPN(Virtual Private Network)是一种用于在公共网络上建立私密连接的技术。
在使用VPN时,有时会出现一些错误代码,这可能会导致VPN无法正常连接、断开连接或无法访问特定网站等问题。
本文将介绍一些常见的VPN错误代码及相应的解决方法。
1.错误代码619:这是由于无法建立VPN连接引起的错误。
解决方法包括:-确认输入的用户名和密码是否正确。
-检查防火墙设置,并确保VPN协议被允许通过。
-确保VPN服务器正常运行并且可访问。
2.错误代码800:这是由于无法建立远程服务器的VPN连接引起的错误。
解决方法包括:-检查网络连接是否正常。
如果使用无线网络,请尝试连接有线网络进行测试。
-确认防火墙设置是否允许VPN流量通过。
-重新安装VPN客户端,或使用其他VPN客户端进行测试。
3.错误代码806:这是由于VPN服务器和客户端的协议不匹配引起的错误。
解决方法包括:- 确认VPN服务器和客户端使用相同的VPN协议(如PPTP、L2TP、OpenVPN等)。
-检查防火墙设置,确保相应的协议端口被允许通过。
-尝试在不同的操作系统上进行连接,以确定是否是特定操作系统的兼容性问题。
4.错误代码789:这是由于远程服务器的安全层协议设置不正确引起的错误。
解决方法包括:-检查VPN服务器的安全层协议设置,确保与客户端匹配。
-检查客户端的安全层协议设置,确保与服务器匹配。
-尝试禁用防火墙或安全软件,以确定是否是它们引起的问题。
5.错误代码691:这是由于远程服务器拒绝访问引起的错误。
解决方法包括:-确认输入的用户名和密码是否正确。
-检查账号是否被锁定或禁用。
6.错误代码633:这是由于已经在使用的端口被VPN占用引起的错误。
解决方法包括:-重新启动电脑,以释放被占用的端口。
-在网络适配器的属性设置中重新安装VPN协议。
7.错误代码628:这是由于无法连接到远程服务器引起的错误。
山石网科漏洞扫描系统V5.5-1.9.7版本说明说明书

Version V5.5-1.9.7山石网科漏洞扫描系统V5.5-1.9.7发布概述发布日期:2022年9月27日本次发布新增基线配置核查支持RDP协议和支持批量上传Windows离线检查结果,优化漏洞引擎,提升内网存活探测准确率及漏洞检测精度。
平台和系统文件新增功能功能描述新漏洞库信息总数192236条。
在线基线扫描支持RDP协议。
基线配置核查支持批量上传Windows离线检查结果。
增加基线配置核查离线脚本(apache、tomcat、weblogic、webshere、mysql、oracle、sqlserver)。
更新了Apache ActiveMQ、Google Golang、Iteris Apache Velocity、Mozilla Firefox、Sangoma Technologies Asterisk、Linux kernel、Pillow、AdPlug、Gnome gnome-autoar、KDE Discover、wpa_supplicant组件相关的漏洞库。
新增CVE-2019-0630 SMB2远程代码执行漏洞、CVE-2020-1350 域名服务器漏洞信息扫描。
修复了MySQL弱密码漏报。
更新了Adobe Acrobat Reader、 Apache Ambari、 Struts2、Mozilla Firefox、Linux kernel、Dovecot、aiohttp、OpenSSL、OpenLDAP、Oracle Database Server、TYPO3 Core、Python、Oracle Fusion Middleware组件相关的漏洞库。
更新了artifex mupdf、 Linux kernel、 pki-core 、Samba、Caucho Technology Resin、Red Hat Directory Server、Wireshark、Cloud Native Computing CNI、Openvswitch、Google Chrome、GNOME Keyring、GNU Binutils组件相关的漏洞库。
CISCO官方配置手册IPV6-DHCP

Implementing IPv6 for Cisco IOS Software
22
Implementing DHCP for IPv6
Information About Implementing DHCP for IPv6
Client and Server Identification
Each DHCP for IPv6 client and server is identified by a DHCP unique identifier (DUID). The DUID is carried in the client identifier and server identifier options. The DUID is unique across all DHCP clients and servers, and it is stable for any specific client or server. DHCP for IPv6 uses DUIDs based on link-layer addresses for both the client and server identifier. The device uses the MAC address from the lowest-numbered interface to form the DUID. The network interface is assumed to be permanently attached to the device.
中国网通PHS短消息网关技术规范第一分册

中国网络通信集团公司企业标准PHS短消息网关技术规范第一分册短消息网关与服务提供商(SP)接口规范(CNGP)V2.02004-3-12发布 2004-3-12实施中国网络通信集团公司发布目录前言 (1)1.适用范围 (2)2.引用标准 (2)3.缩略语 (2)4.CNGP概述 (3)4.1CNGP功能描述 (3)4.2协议栈 (3)4.3通信方式 (3)4.3.1 长连接 (4)4.3.2 短连接 (6)4.3.3 交互过程中的应答方式 (7)4.3.4 端口号 (7)4.4通信流程 (7)4.4.1 CNGP登录模式 (7)4.4.2 SP发送短消息 (8)4.4.3 SP接收短消息 (8)4.4.4 SMGW转发短消息 (9)4.5编号规则 (10)5.CNGP消息定义 (12)5.1基本数据类型 (12)5.2消息结构 (12)5.3消息头格式 (12)5.4SP与SMGW之间的消息定义 (13)5.4.1 login (13)5.4.2 login_resp (14)5.4.3 submit (15)5.4.4 submit_resp (16)5.4.5 deliver (16)5.4.6 deliver_resp (17)5.4.7 active_test (18)5.4.8 active_test_resp (18)5.4.9 exit (18)5.4.10 exit_resp (18)5.5SMGW与SMGW之间的消息定义 (18)5.5.1 login (19)5.5.2 login_resp (19)5.5.3 active_test (20)5.5.4 active_test_resp (20)5.5.5 forward (20)5.5.6 forward_resp (22)5.5.7 exit (22)5.5.8 exit_resp (23)6.状态报告格式 (24)6.1MO的状态报告 (24)6.2MT的状态报告 (25)7.CNGP编码说明 (26)7.1短消息格式代码表 (26)7.2短消息状态表 (26)7.3E RR错误代码表 (31)7.4STATUS错误代码表 (32)7.5TLV说明表 (33)8.基于CNGP的API函数 (35)附录A 基于CNGP协议的API函数说明 (36)前言本标准描述了PHS短消息网关(SMGW)和服务提供商(SP)之间、短消息网关(SMGW)和短消息网关(SMGW)之间的通信协议。
ipv6测试解决方案

©2006 Ixia. All rights reserved.
总结
双栈路由器带来新功能:
– – – 建立维护隧道 地址和协议转换 完成新的路由协议
一致性测试对于不同厂家的设计产品是至关重要的 验证新的双栈路由器的转发功能是否正确和性能测试也是必须 的 评估路由器在新的路由协议下的性能和扩展性也是十分重要的 在应用层的测试也是必须的,它可以改善最终用户的体验
应用程序的有效吞吐量及响应时间
IXIA公司IPv6测试平台及典型配置 总结
©2006 Ixia. All rights reserved.
IPv6 测试的重要性
IPv6 带来的技术革新
– 与IPv4相比,IPv6在寻址、标记、QoS、多媒体、安全性、移动性和高级 管理等方面有突出增强,是下一代的承载技术 – IPv6不仅涉及三层承载,同时涉及封装、路由、加密、隧道、应用等多个 层面,是一个全方位的革新 – 与此相适应的测试需求,也在二到七层全面展开 – 由IPv6引发的新规范: – RFC 2460, RFC 2461,RFC 2462,RFC 1981,RFC 2675, RFC 2374,RFC 3056, RFC 3122, RFC 2893, RFC 2473, RFC 3056RFC 2766, RFC 2765, RFC 2090, RFC 2740RFC 2545 – 成功的IPv6测试意味着成功的产品研发及生产,成功的网络及业务部署。
©2006 Ixia. All rights reserved.
转发功能和性能
目标
功能
输入
报文头、内容、报 文长 指定负载 报文头、内容、报 文长,IPv6/IPv4 混 合比例
结果
报文头、内容完整 性检查,丢包率
sftp 消息认证算法

sftp 消息认证算法SFTP(Secure File Transfer Protocol)是一种安全的文件传输协议,它在SSH(Secure Shell)上构建。
SFTP使用SSH协议进行身份验证和加密,因此支持多种消息认证算法以确保通信的安全性。
以下是一些常见的SFTP消息认证算法:1. HMAC-SHA-2(HMAC with SHA-2):- SFTP可以使用基于SHA-2系列的HMAC算法,如HMAC-SHA-256和HMAC-SHA-512,来进行消息认证。
这些算法提供了强大的安全性。
2. HMAC-SHA-1:-尽管SHA-1已经被认为是不安全的,但在某些情况下,仍然可能会使用HMAC-SHA-1进行消息认证。
然而,强烈建议使用更安全的算法,如SHA-256或SHA-512。
3. HMAC-MD5:-类似于HMAC-SHA-1,HMAC-MD5也是一种较旧的消息认证算法,不再被推荐用于安全性要求较高的环境。
4. UMAC-64和UMAC-128:- UMAC是一种基于Poly1305的消息认证码算法。
UMAC-64使用64位密钥,而UMAC-128使用128位密钥。
它们提供了高性能和良好的安全性。
5. AES-GCM:- Advanced Encryption Standard Galois/Counter Mode(AES-GCM)是一种组合加密和消息认证码的模式。
它结合了AES加密和GCM认证,提供了高度的安全性和效率。
6. AES-CCM:- Advanced Encryption Standard Counter with Cipher Block Chaining-Message Authentication Code(AES-CCM)也是一种组合加密和消息认证码的模式,类似于AES-GCM。
这些消息认证算法用于验证SFTP通信中传输的数据的完整性,防止数据被篡改。
在配置SFTP 服务器和客户端时,通常可以指定首选的消息认证算法和加密算法。
ISISv6协议测试——信而泰网络测试仪实操

目录前言: (1)一、ISIS协议原理 (1)二、测试用例 (2)三、测试步骤 (3)3.1占用Ports (3)3.2配置IP地址 (4)3.3配置ISIS (4)3.4发布LSP (10)3.5配置流量 (14)3.6启用ISIS (17)3.7发流验证 (18)前言:isis是一种与ospf很相似的网络协议(属于动态路由协议),它被应用在巨大规模网络,如运营商以及银行等。
同样的它也是基于链路状态算法,支持clnp网络,ip网络。
与ospf不同的是,它是基于数据链路层报文传输,而ospf则是在ip层进行计算。
它可以自动的发现远程网络,只要网络拓扑结构发生了变化,路由器就会相互交换路由信息,不仅能够自动获知新增加的网络,还可以在当前网络连接失败时找出备用路径。
一、ISIS协议原理缩略语OSI中的概念IP中对应的概念IS Intermediate System中间系统Router路由器ES End System端系统Host主机DISDesignatedIntermediateSystem指派中间系统Designated Router(DR) OSPF中的选举路由器SysID System ID系统ID OSPF中的Router ID PDU Packet Data Unit报文数据单元IP报文LSPLink state Protocol Data Unit链路状态协议数据单元OSPF中的LSA 用来描述链路状态分层·层次性:IS-IS有两个级别,区分两个层次Level-1:普通区域(Areas)叫Level-1(L1)Level-2:骨干区(Backbone)叫Level-2(L2)·骨干区Backbone是连续的Level2路由器的集合;由所有的L2(含L1/L2)路由器组成,注意必须是连续(连通)的;·L1和L2运行相同的SPF算法;·一个路由器可能同时参与L1和L2为验证ISIS邻居是否能够正常建立、DUT能否学习到全部的10条Routes以及测试仪接收到发送的流量是否有丢包等测试项目,接下来将为您介绍使用信而泰Renix测试软件验证DUT基本的ISIS功能和ISIS路由的流量转发功能,并观察验证能否完成以上测试项目。
中国移动IPv6终端技术要求V100--资料

中国移动I P v6终端技术要求V1.0.0目录1 范围 (1)2 规范性引用文件 (1)3 术语、定义和缩略语 (2)3.1 术语和定义 (2)3.1.1 接入点名称Access Point Name (2)3.1.2 网关GPRS支持节点Gateway GPRS Support Node (2)3.1.3 分组数据协议上下文Packet Data Protocol Context (2)3.1.4 双栈终端Dual stack terminal (2)3.1.5 终端形态 (2)3.2 缩略语 (3)4 总体技术要求 (4)5 终端技术要求 (4)5.1 协议栈 (4)5.1.1 概述 (4)5.1.2 RFC 2460 IPv6协议规范 (4)5.1.3 RFC 4291 IPv6地址结构 (5)5.2 DNS客户端 (5)5.3 DHCP客户端 (5)5.4 IPv4/IPv6协议翻译技术 (5)5.4.1 BIH (5)5.4.2 464XLAT (8)5.5 隧道过渡技术 (9)5.5.1 Teredo技术 (9)5.5.2 6rd (9)6 PDP/PDN连接激活及IPv6地址获取过程 (10)6.1 IPv6地址配置 (10)6.2 PDP/PDN连接的建立和IP地址的获取 (10)6.2.1 3GPP Release 8之前终端PDP上下文的激活和IPv6地址获取过程 (10)6.2.2 3GPP Release 8之后(含Release 8)终端PDP/PDN连接的建立和IPv6地址获取过程 (11)7 终端PDP/PDN连接激活策略 (12)7.1 概述 (12)7.2 双栈终端PDP/PDN连接激活策略一:同时获取IPv4和IPv6地址 (12)7.3 双栈终端PDP/PDN连接激活策略二:按需建立IPv4或IPv6连接 (14)7.4 两种PDP/PDN连接激活策略的选择和使用 (15)8 WLAN网络中的IPv6地址获得 (15)9 DNS解析 (15)9.1 概述 (15)9.2 终端DNS解析流程 (15)9.3 DNS服务器地址的获取 (15)9.4 DNS解析承载类型的选择 (15)9.5 DNS解析目的地址类型的选择 (15)10 终端应用软件系统 (16)11 IP头压缩技术要求 (16)12 安全 (16)13 APN设定 (17)14 不同终端类型要求 (17)14.1 手机/平板电脑类终端 (17)14.2 MiFi/移动CPE终端 (17)14.3 数据卡终端 (17)前言本文档是依据3GPP、IETF发布的IPv6相关标准制定,并结合现阶段IPv6升级改造及试点项目需求所定义的手机、平板电脑、MiFi、移动CPE、数据卡等移动终端IPv6部分技术要求。
浪潮英信安全服务器解析

也 一 直 是 市 场 上 销 售 的 主 流 产 品 。 高
品 质 的 输 出 效 果 ,小 巧 紧 凑 的 机 身 设 计 , 用 户 提 供 了 舒 适 、 捷 的桌 面 打 为 便
印环境 。 i MF 0 0 4 1B 的推 出 ,在 需 C 4 1B/ 0 2
佳能凭借 “ 良机 ” “ 礼 ” 明 显 带 和 好 ,
市 场 透 析
计 算 机 与 网 络 创 新 生 活
7 9
浪潮 英 信 安 全服 务器 解 析
随 着 应 用 的 复 杂 程 度 越 来越 高 , 各
滤 功 能 基 于 高速 功 能 芯 片 实现 , 占 用 不 库 、 容 S 兼 NORT 主 流 规 则 库 、 持 模 支
种 协 议 和 网 络 应 用 越 来 越 多 ,面 对 各
通 过 芯 片 级 别 实 现 。 于 浪 潮 服 务器 硬 基
入 是 来 自网 络 上 的数 据 包 和 流 , 是 内 还
存 中 的 数 据 ,都 能 够 被 CO RE 进 行 高
效 的 处 理 。对 于 来 自 网 络 上 的 数 据 包 和 流 ,核 心 查 找 CORE 能 够 对 数 据 包
度 与强大实力 。
者 ,输 入 包 装 箱 内 附 送 的 密 码 卡 的 验 证 码 与 相 关 信 息 ,即 可 获 得 佳 能 为 用 户 准 备 的 罗 技 无 线 鼠 标 、微 波 炉 和 秋 日恋 曲 床 上 四件 套 等 丰 盛 好 礼 。
用 环 境 、 控 性 等 基 本 需 求 . 合 国 内 操 结
命 中 规 则 发 送 Ree 包 、 st 支持 敏 感 字 段 屏 蔽技术以及支持规 则原单位乱序 等。
《短信名址服务总体技术要求》通信标准发布

《短信名址服务总体技术要求》通信标准发布作者:暂无来源:《计算机世界》 2012年第28期本报讯 7 月18 日,“ 短信名址服务总体技术要求”通信标准在京发布,该标准是中国通信标准化协会的全新尝试,将帮助企业加速实现移动信息化进程,进一步推动我国移动互联网产业的发展。
工信部电信研究院标准所副所长吕军表示:此次行业标准的推出为行业创新探索和发展更多微应用商业模式提供了良好示范作用。
MIPS 抢占数字电视智能化先机本报讯日前,为数字家庭、网络、移动和嵌入式应用提供业界标准处理器架构与内核的美普思科技公司在最新进展通报会上透露,Android 平台与iPPea 公司共同推出数字电视的智能外接器产品iPPeaTV。
据了解,售价50 美元的iPPea仅有一个U 盘大小,可以通过HDMI接口让数字电视运行Android平台,成为一台智能电视。
此外,MIPS 还与炬力、君正等企业联合推出了低价平板电脑。
腾讯网正式启用新版首页本报讯近日,腾讯网正式启用新版首页。
同时,腾讯公司网络媒体事业群宣布启动门户、微博、视频、无线的跨平台深度整合战略,着力将下一代腾讯网打造成大数据时代的智慧门户。
腾讯公司网络媒体事业群总裁刘胜义表示,“此次改版,是基于变革思路构建‘下一代腾讯网’的第一步。
我们会强化新媒体平台的融合与对用户需求的挖掘,构建一个能读懂用户心理的智慧门户。
”ADP 助力HP 打造全球集成式薪酬考勤本报讯近日,人力资源、薪酬、福利管理服务提供商 ADP 与HP 签署合约,向其提供薪酬与考勤/ 劳动力管理应用系统。
据悉,新系统部署完成后,将简化HP 现有人力资源管理平台的数目,同时在整个集团范围内推行日益流行的全球标准化薪酬管理流程。
根据双方合约,新系统将于2013 年上半年开始,并在5 年内部署完毕。
联通金立合推双核智能机本报讯近日,中国联通金立百万合约启动仪式在京举行。
国产手机金立正式发布了其首款千元双核智能手机—“风华”GN700W。
address sanitizer 参数

Address Sanitizer(简称ASan 或AddressSanitizer)是一个用于检测内存错误的开源工具,主要包括以下几种参数:1. --address-sanitizer:启用AddressSanitizer 功能。
2. --no-address-sanitizer:禁用AddressSanitizer 功能。
3. --address-sanitizer-coverage:启用AddressSanitizer 覆盖率报告。
4. --no-address-sanitizer-coverage:禁用AddressSanitizer 覆盖率报告。
5. --address-sanitizer-verify:启用AddressSanitizer 验证模式,该模式会检查程序中的内存访问是否符合预期。
6. --no-address-sanitizer-verify:禁用AddressSanitizer 验证模式。
7. --address-sanitizer-detect-leaks:启用AddressSanitizer 泄漏检测功能。
8. --no-address-sanitizer-detect-leaks:禁用AddressSanitizer 泄漏检测功能。
9. --address-sanitizer- conservative:启用AddressSanitizer 保守模式,该模式会降低误报率,但可能导致检测速度较慢。
10. --no-address-sanitizer-conservative:禁用AddressSanitizer 保守模式。
11. --address-sanitizer-log-path:指定AddressSanitizer 日志文件的路径。
12. --no-address-sanitizer-log-path:指定不生成AddressSanitizer 日志文件。
13. --address-sanitizer-symbol-prefix:设置AddressSanitizer 符号前缀,用于标识检测到的内存错误。
incon-ts-vps-vapor-pressure-sensor-installation-说明

• Small screwdriver (terminal block connection)
• Slip joint pliers (crimping splice connector)
Related Documents
• 000-2058 : Vapor Recovery Monitor Operators Guide
1
ARB Approved IOM - Executive Orders VR-204-P (Vapor Pressure Sensor Install Guide)
Vapor Shear Valve
1" NPT Pipe Connection
Figure 1
Install to Shear Valve
Intrisically Safe Conduit to
VRM Console
Vapor Return Line with Inline Tee
© 2008 FFS 000-2143 Rev. VR-204-N
Preparation
1. Perform a site inspection. Determine how the Vapor Pressure Sensor will be installed. The preferred installation method for this product is to come off the horizontal 1" port of the vapor shear valve. If this is not possible, then a piping tee may need to be installed below the Vapor Flow Meter.
Rsyslog与syslog-ng比较
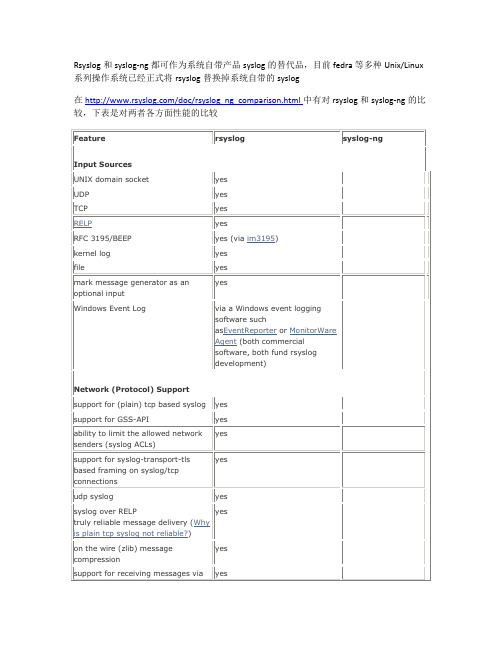
Rsyslog和syslog-ng都可作为系统自带产品syslog的替代品,目前fedra等多种Unix/Linux 系列操作系统已经正式将rsyslog替换掉系统自带的syslog在/doc/rsyslog_ng_comparison.html中有对rsyslog和syslog-ng的比较,下表是对两者各方面性能的比较Rsyslog Features∙native support for writing to MySQL databases∙native support for writing to Postgres databases∙direct support for Firebird/Interbase, OpenTDS (MS SQL, Sybase), SQLLite, Ingres, Oracle, and mSQL via libdbi, a database abstraction layer (almost as good as native) ∙native support for sending mail messages (first seen in 3.17.0)∙support for (plain) tcp based syslog - much better reliability∙support for sending and receiving compressed syslog messages∙support for on-demand on-disk spooling of messages that can not be processed fast enough (a great feature for writing massive amounts of syslog messages to a database) ∙support for selectively processing messages only during specific timeframes and spooling them to disk otherwise∙ability to monitor text files and convert their contents into syslog messages (one per line)∙ability to configure backup syslog/database servers - if the primary fails, control is switched to a prioritized list of backups∙support for receiving messages via reliable RFC 3195 delivery (a bit clumpsy to build right now...)∙ability to generate file names and directories (log targets) dynamically, based on many different properties∙control of log output format, including ability to present channel and priority as visible log data∙good timestamp format control; at a minimum, ISO 8601/RFC 3339 second-resolution UTC zone∙ability to reformat message contents and work with substrings∙support for log files larger than 2gb∙support for file size limitation and automatic rollover command execution∙support for running multiple rsyslogd instances on a single machine∙support for TLS-protected syslog (both natively and via stunnel)∙ability to filter on any part of the message, not just facility and severity∙ability to use regular expressions in filters∙support for discarding messages based on filters∙ability to execute shell scripts on received messages∙control of whether the local hostname or the hostname of the origin of the data is shown as the hostname in the output∙ability to preserve the original hostname in NAT environments and relay chains∙ability to limit the allowed network senders∙powerful BSD-style hostname and program name blocks for easy multi-host support ∙massively multi-threaded with dynamic work thread pools that start up and shut themselves down on an as-needed basis (great for high log volume on multicoremachines)∙very experimental and volatile support for syslog-protocol compliant messages (it is volatile because standardization is currently underway and this is a proof-of-concept implementation to aid this effort)∙world's first implementation of syslog-transport-tls∙the sysklogd's klogd functionality is implemented as the imklog input plug-in. So rsyslog is a full replacement for the sysklogd package∙support for IPv6∙ability to control repeated line reduction ("last message repeated n times") on a per selector-line basis∙supports sub-configuration files, which can be automatically read from directories.Includes are specified in the main configuration file∙supports multiple actions per selector/filter condition∙MySQL and Postgres SQL functionality as a dynamically loadable plug-in∙modular design for inputs and outputs - easily extensible via custom plugins∙an easy-to-write to plugin interface∙ability to send SNMP trap messages∙ability to filter out messages based on sequence of arrival∙support for comma-seperated-values (CSV) output generation (via the "csv" property replace option). The CSV format supported is that from RFC 4180.∙support for arbitrary complex boolean, string and arithmetic expressions in message filtersSyslog Featuressyslog-ng has a much larger scope than merely transporting syslog messages and storing them to plain text log files:▪the ability to format log messages using UNIX shell-like variable expansion;▪the use of this shell-like variable expansion when naming files, thus covering thousands of destination files with a single statement;▪the ability to send log messages to local applications;▪ability to message flow-control in network transport;▪logging directly into a database (since syslog-ng Open Source Edition 2.1);▪rewrite portions of the syslog message with set and substitute primitives (since syslog-ng OSE 3.0);▪classify incoming log messages and at the same time extract structured information from the unstructured syslog message (since syslog-ng OSE 3.0);▪generic name-value support: each message is just a set of name-value pairs, which can be used to store extra information (since syslog-ng OSE 3.0);▪the ability to process structured message formats transmitted over syslog, like extract columns from CSV formatted lines (since syslog-ng OSE 3.0);▪the ability to correlate multiple incoming messages to form a more complex, correlated event (since syslog-ng OSE 3.2);简单来说选择rsyslog的理由如下:1、后端存查日志支持的客户端多,支持 MySQL,PostgresSQL,Oracle 等2、在同一台机器上支持多子rsyslog进程,可以监听在不同端口3、直接兼容系统自带的syslog.conf配置文件4、可将消息过来后再次转发5、配置文件中可以写简单的逻辑判断6、有现成的前端web展示程序当然上面所说的功能syslog-ng也都差不多有,但syslog-ng的免费版本是closed source的。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Network Working Group R. Fink Request for Comments: 3701 R. Hinden Obsoletes: 2471 March 2004 Category: Informational6bone (IPv6 Testing Address Allocation) PhaseoutStatus of this MemoThis memo provides information for the Internet community. It doesnot specify an Internet standard of any kind. Distribution of thismemo is unlimited.Copyright NoticeCopyright (C) The Internet Society (2004). All Rights Reserved. AbstractThe 6bone was established in 1996 by the IETF as an IPv6 Testbednetwork to enable various IPv6 testing as well as to assist in thetransitioning of IPv6 into the Internet. It operates under the IPv6 address allocation 3FFE::/16 from RFC 2471. As IPv6 is beginning its production deployment it is appropriate to plan for the phaseout ofthe 6bone. This document establishes a plan for a multi-yearphaseout of the 6bone and its address allocation on the assumptionthat the IETF is the appropriate place to determine this.This document obsoletes RFC 2471, "IPv6 Testing Address Allocation", December, 1998. RFC 2471 will become historic.1. IntroductionThe 6bone IPv6 Testbed network was established in March 1996,becoming operational during the summer of 1996 using an IPv6 testing address allocation of 5F00::/8 [TEST-OLD] that used the original (and now obsolete) provider based unicast address format. In July 1998, a new IPv6 Addressing Architecture [ARCH] replaced the originalprovider based unicast address format with the now standardizedAggregatable Global Unicast Address Format [AGGR].To allow the 6bone to operate under the revised IPv6 addressarchitecture with the new Aggregatable Global Unicast addressingformat, [TEST-OLD] was replaced with a new IPv6 testing addressFink & Hinden Informational [Page 1]allocation" of 3FFE::/16 in [TEST-NEW]. During the fall of 1998, in anticipation of [AGGR], the 6bone was re-addressed under the3FFE::/16 prefix with little problems.From the fall of 1998, until the issuance of this note, the 6bone has continued to successfully operate with Aggregatable Global UnicastAddress prefixes from the 3FFE::/16 allocation, using a set of 6bone routing practice rules specified in [GUIDE], and later refined to6Bone backbone routing guidelines in [PRACTICE].During its lifetime the 6bone has provided:- a place for early standard developers and implementers to testout the IPv6 protocols and their implementations;- a place for early experimentation with routing and operationalprocedures;- a place to evolve practices useful for production IPv6 prefixallocation;- a place to provide bootstrap qualification for production IPv6address prefix allocation;- a place to develop IPv6 applications;- a place for early users to try using IPv6 in their hosts andnetworks.As clearly stated in [TEST-NEW], the addresses for the 6bone aretemporary and will be reclaimed in the future. It further statesthat all users of these addresses (within the 3FFE::/16 prefix) will be required to renumber at some time in the future.Since 1999 planning for, and allocation of, IPv6 production addressprefixes by the Regional Internet Registry (RIR) community has beenunderway. During 2002 more production IPv6 address prefixes had been allocated than are allocated by the 6bone at the top level. It isgenerally assumed that this is one reasonable indicator that planning for a 6bone phaseout should begin.It is generally assumed that there is still some remaining need forthe 6bone, at least for current usage that will take time to evaluate and possibly move to production IPv6 networks when possible.It is generally viewed that the 6bone is an IETF activity as it wasestablished by IETF participants to assist the IETF in developingIPv6 protocols, and also to assist in the IPv6 transition. To this Fink & Hinden Informational [Page 2]end, the [TEST-NEW] RFC specified that the 6bone testing was to beunder the auspices of the IETF IPng Transition (ngtrans) WorkingGroup 6bone testbed activity. However, during 2002 the ngtransworking group was terminated and replaced to a certain degree by the v6ops working group, which did not include oversight of the 6bone in its charter. Therefore it is assumed that it is appropriate to usethe IETF Informational RFC process to determine a 6bone phaseoutplan, as well as an appropriate way to get community feedback on the specifics of the 6bone phaseout.This plan for a 6bone phaseout specifies a multi-year phaseouttimeline to allow sufficient time for continuing operation of the6bone, followed by a sufficient time for 6bone participants toconvert to production IPv6 address prefixes allocated by the relevant Regional Internet Registry (RIR), National Internet Registry, orLocal Internet Registries (ISPs).It is anticipated that under this phaseout plan the 6bone will cease to operate by June 6, 2006, with all 6bone prefixes fully reclaimedby the IANA.This document obsoletes RFC 2471, "IPv6 Testing Address Allocation", December, 1998. RFC 2471 will become historic.The key words "MUST", "MUST NOT", "REQUIRED", "SHALL", "SHALL NOT","SHOULD", "SHOULD NOT", "RECOMMENDED", "MAY", and "OPTIONAL" in this document are to be interpreted as described in [RFC2119].2. 6bone Phaseout PlanTo provide for the continuing useful operation of the 6bone, to theextent that IETF consensus judges it to be useful, 6bone top leveladdress prefixes known as pseudo TLA’s (pTLAs) MAY continue to beallocated until January 1, 2004.Thus after the pTLA allocation cutoff date January 1, 2004, it isREQUIRED that no new 6bone 3FFE pTLAs be allocated.To provide for sufficient planning time for 6bone participants toconvert to production IPv6 address prefixes, all 6bone prefixesallocated by the cutoff time specified above, except for allocations withdrawn as a matter of 6bone operating procedures, SHALL remainvalid until June 6, 2006.Thus after the 6bone phaseout date June 6, 2006, it is the intentthat no 6bone 3FFE prefixes, of any size/length, be used on theInternet in any form. Network operators may filter 3FFE prefixes on their borders to ensure these prefixes are not misused.Fink & Hinden Informational [Page 3]It should be noted that this RFC does not intend to imply that a6bone prefix holder, whether at the pTLA top level or lower, shouldseek a production IPv6 address prefix at any specific level. It may be entirely reasonable for a 6bone prefix holder to seek a higherlevel, or a lower level, IPv6 prefix as their specific needs dictate.3. References3.1. Normative References[ARCH] Hinden, R. and S. Deering, "Internet Protocol Version 6(IPv6) Addressing Architecture", RFC 3513, April 2003.[AGGR] Hinden, R., Deering, S. and M. O’Dell, "An AggregatableGlobal Unicast Address Format", RFC 2374, July 1998.[RFC2119] Bradner, S., "Keywords for use in RFCs to IndicateRequirement Levels", BCP 14, RFC 2119, March 1997.[TEST-NEW] Hinden, R., Fink, R. and J. Postel, "IPv6 Testing Address Allocation", RFC 2471, December 1998.[TEST-OLD] Hinden, R. and J. Postel, "IPv6 Testing AddressAllocation", RFC 1897, January 19963.2. Informative References[GUIDE] Rockell, R. and R. Fink, "6Bone Backbone RoutingGuidelines", RFC 2772, February 2000.[PRACTICE] Durand, A. and B. Buclin, "6bone Routing Practice", RFC2546, March 1999.5. Security ConsiderationsThis document defines a phaseout plan for the usage of the IPv6Testing Address Allocation [TEST-NEW], which uses addressesconsistent with [AGGR]. It does not have any direct impact onInternet infrastructure security.6. IANA ConsiderationsThis document defines a phaseout plan for the usage of the IPv6Testing Address Allocation [TEST-NEW]. The IANA MUST reclaim the3FFE::/16 prefix upon the date specified in section 2.0.Fink & Hinden Informational [Page 4]When the 6bone Testing Address Allocation is reclaimed by the IANA,it is expected that many network operators will filter it on theirborders to ensure these prefixes are not misused.There is experience from the IPv4 world that such filters may not be removed promptly should this address space be reallocated, and it is recommended that the IANA bears this in mind before reallocating itin a manner that would require it to be routed globally within thecurrent Internet.7. Authors’ AddressesRobert L. FinkEMail: bob@Robert M. HindenNokia313 Fairchild DriveMountain View, CA 94043USPhone: +1 650 625-2004EMail: bob.hinden@Fink & Hinden Informational [Page 5]8. Full Copyright StatementCopyright (C) The Internet Society (2004). This document is subject to the rights, licenses and restrictions contained in BCP 78 andexcept as set forth therein, the authors retain all their rights.This document and the information contained herein are provided on an "AS IS" basis and THE CONTRIBUTOR, THE ORGANIZATION HE/SHEREPRESENTS OR IS SPONSORED BY (IF ANY), THE INTERNET SOCIETY AND THE INTERNET ENGINEERING TASK FORCE DISCLAIM ALL WARRANTIES, EXPRESS ORIMPLIED, INCLUDING BUT NOT LIMITED TO ANY WARRANTY THAT THE USE OFTHE INFORMATION HEREIN WILL NOT INFRINGE ANY RIGHTS OR ANY IMPLIEDWARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Intellectual PropertyThe IETF takes no position regarding the validity or scope of anyIntellectual Property Rights or other rights that might be claimedto pertain to the implementation or use of the technologydescribed in this document or the extent to which any licenseunder such rights might or might not be available; nor does itrepresent that it has made any independent effort to identify anysuch rights. Information on the procedures with respect torights in RFC documents can be found in BCP 78 and BCP 79.Copies of IPR disclosures made to the IETF Secretariat and anyassurances of licenses to be made available, or the result of anattempt made to obtain a general license or permission for the useof such proprietary rights by implementers or users of thisspecification can be obtained from the IETF on-line IPR repositoryat /ipr.The IETF invites any interested party to bring to its attentionany copyrights, patents or patent applications, or otherproprietary rights that may cover technology that may be requiredto implement this standard. Please address the information to theIETF at ietf-ipr@.AcknowledgementFunding for the RFC Editor function is currently provided by theInternet Society.Fink & Hinden Informational [Page 6]。
