Questions--Chapter 3- Internet Protocols
基于netfilter的tcp网络包的过滤与修改

/1.%6D%70%33 就可以跳过网关的检测
//nf_nat_mangle_tcp_packet 是 netfilter nat 模块里面的导出函数,所以需要 nat 模块加载之后才能进行的。 //如果你没有配置内核自动加载这个模块,好像执行一下“sudo iptables -t nat --list” 命令就会加载起来。 if (ct && nf_nat_mangle_tcp_packet(skb, ct, ctinfo, (char*) head - (char *)payload -3 , 3, (char *) "%6D%70%33", sizeof("%6D%70%33")-1 )) { printk("-----------------nf_nat_mangle_tcp_packet--------------------\n%20s\n", payload); return NF_ACCEPT; } //wineshark 抓包说明后续 tcp 包的序号依然不对,原因是修改后,tcp 的需要加上 增加的字节,但系统不知道这个改变,所以下次还 是用以前的 序号来发送数据, //所以后面的包的序号就不对了. 在/net/ipv4/tcp_output.c 中的 tcp_transmit_skb 函数中,可以看到系统是如何填写这个数据的。但 在 hook 的时候无法 //得到 tcp 层的信息,本来想一劳永逸的把初始序号改正确的但无法做到。只好 hook 没个包的时候都把序号改正过来了。 //nf_nat_mangle_tcp_packet 修改 tcp 包后,会记录下需要调整的 seq 的序列(参考内核源代码/net/ipv4/netfilter/nf_nat_helper.c 文 件爱你里面的 //adjust_tcp_sequence 函数,他把需要调整的信息记录在两个 struct nf_nat_seq 结构里面了。)但没有看到自动对后续的网络国包 进行处理了。 //所以需要在另外的 hook 里面把标识出来的需要修复序号的包都,调用一下 seq 修复函数 nf_nat_seq_adjust,把后面所有 tcp 包的 seq 都进行修复。 //这个工作如果你的修改导致包的长度改变的都需要作。conntrack 模块里面会调用 helper module 的 //nf_nat_seq_adjust_hook 函数来作这个工作的。参考 内核源代码的 /net/ipv4/netfilter/nf_conntrack_l3proto_ipv4.c 中的 ipv4_confirm 函数 //但没看到调用 nf_nat_seq_adjust 函数的地方,所以我自己又加了两个 hook 来捕获后续网络包,显示的调用 nf_nat_seq_adjust 函 数。 //nf_nat_seq_adjust 函数在 net/ipv4/netfilter/nf_nat_helper.c 文件的里面有,但没有导出,所以我把他复制过来了,不过 注意不同 的内核扳本有所不同 //如果编译有问题,就去把对应的内核源代码中的几个函数复制出来吧。
CCNA_ERouting_Chapter_3
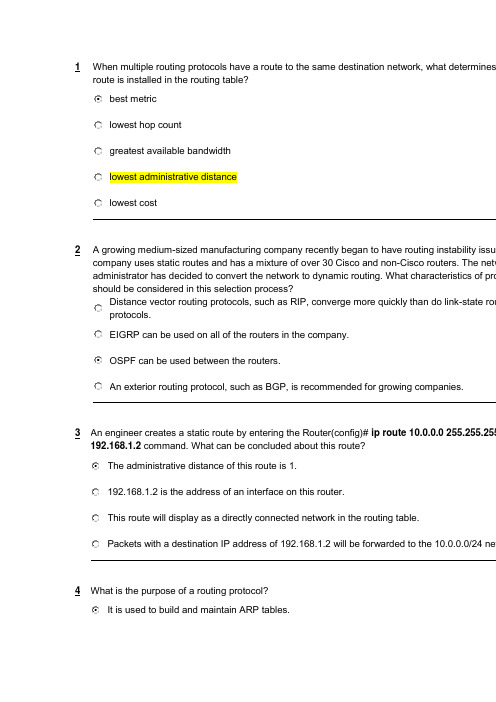
1When multiple routing protocols have a route to the same destination network, what determines route is installed in the routing table?best metriclowest hop countgreatest available bandwidthlowest administrative distancelowest cost2A growing medium-sized manufacturing company recently began to have routing instability issue company uses static routes and has a mixture of over 30 Cisco and non-Cisco routers. The netw administrator has decided to convert the network to dynamic routing. What characteristics of pro should be considered in this selection process?Distance vector routing protocols, such as RIP, converge more quickly than do link-state rou protocols.EIGRP can be used on all of the routers in the company.OSPF can be used between the routers.An exterior routing protocol, such as BGP, is recommended for growing companies.3An engineer creates a static route by entering the Router(config)# ip route 10.0.0.0 255.255.25 192.168.1.2 command. What can be concluded about this route?The administrative distance of this route is 1.192.168.1.2 is the address of an interface on this router.This route will display as a directly connected network in the routing table.Packets with a destination IP address of 192.168.1.2 will be forwarded to the 10.0.0.0/24 ne 4W hat is the purpose of a routing protocol?It is used to build and maintain ARP tables.It provides a method for segmenting and reassembling data packets.It allows an administrator to devise an addressing scheme for the network.It allows a router to share information about known networks with other routers.It provides a procedure for encoding and decoding data into bits for packet forwarding.5Which two conditions would create a setting where the use of a distance-vector routing protocol efficient? (Choose two.)the network requires a special hierarchical designfast convergence of the network is crucialthe network is using a hub and spoke topologythe network is using a flat designthere are more than 15 hops between the most distant routers6Which command would the network administrator issue to determine if load balancing is in effect on a router?show ip protocolsshow ip routeshow ip interface briefshow ip interface7W hich of the following best describes the operation of distance vector routing protocols?They use hop count as their only metric.They only send out updates when a new network is added.They send their routing tables to directly connected neighbors.They flood the entire network with routing updates.8Which two statements correctly describe the concepts of administrative distance and metric? (Choose two.)Administrative distance refers to the trustworthiness of a particular route.A router first installs routes with higher administrative distances.The value of the administrative distance can not be altered by the network administrator.Routes with the smallest metric to a destination indicate the best path.The metric is always determined based on hop count.The metric varies depending which Layer 3 protocol is being routed, such as IP or IPX.9T he following line of code is present in the routing table:O 10.16.1.0/27 [110/129] via 192.168.1.5, 00:00:05, Serial0/0/1What does the number 129 indicate in this output?The cost for this link has a value of 129.The clock rate on this serial interface is set to 129,000.The next-hop router is 129 hops away from this router.This route has been updated 129 times in this routing table.10Which of the following conditions must be met in order for a network to have converged?The routers in the network are operating with dynamic routing protocols.The routers in the network are operating with compatible versions of IOS.The routers in the network are operating with the same routing tables.The routers in the network are operating with consistent routing knowledge.11Refer to the exhibit. Router1 and Router2 are running EIGRP. All interfaces are operational and packets can be forwarde networks. What information will be found in the routing table for Router1?Router1 will have 6 directly connected networks.The administrative distance of the route to network 172.16.0.0 will be 90.The metric for routes to 172.16.0.0 will be 1.The interface that is used to forward packets to 172.16.0.0 will always be the S0/1 interface.12W hich two statements are true regarding the advantages of the use of static routes? (Choose two).increased securityreduced effort in configuring routesthe administrator maintains control over routingeasier to implement in a growing networkreduces the chance of routing errorsincreased router resource usage13The following line of code is displayed in a routing table:R 209.165.201.0/24 [120/2] via 192.168.252.2, 00:00:16, S0/0/0What can be concluded from this output?A packet destined for host 192.168.252.2 will be forwarded out the interface connected to network 209.165.201.0/24The value, 120, is used to determine the best path when a router has more than one routing protocol configured for t destination network.This route was manually configured using the ip route command.192.168.252.2 is an interface on the router that produced this output.14W hat will be the result of the following commands?ORL(config)# interface fastethernet 0/0ORL(config-if)# ip address 172.16.3.1 255.255.255.0ORL(config-if)# no shutdownThe 172.16.3.0 network will be routed by any dynamic routing protocol automatically.A routing table entry is made to the 172.16.3.0 network with a code of "C".A static route is required to route traffic to the 172.16.3.0 network.The commands will be saved to the startup-configuration automatically.15Which two statements are true regarding classless routing protocols? (Choose two.)sends subnet mask information in routing updatessends complete routing table update to all neighborsis supported by RIP version 1allows for use of both 192.168.1.0/30 and 192.168.1.16/28 subnets in the same topologyreduces the amount of address space available in an organization16Which two statements are true regarding metrics? (Choose two.)RIP uses bandwidth as a metric.OSPF uses delay as a metric.EIGRP uses bandwidth as a metric.OSPF uses cost based on bandwidth as a metric.RIP uses delay as a metric.EIGRP uses hop count only as a metric.17W hy is fast convergence desirable in networks that use dynamic routing protocols?Routers will not allow packets to be forwarded until the network has converged.Hosts are unable to access their gateway until the network has converged.Routers may make incorrect forwarding decisions until the network has converged.Routers will not allow configuration changes to be made until the network has converged.18Refer to the exhibit. Which statement correctly describes how R1 will determine the best path to R2?R1 will install a RIP route using network A in its routing table because the administrative distance of RIP is higher thaR1 will install a RIP route using network A in its routing table because the path cost from RIP is lower than EIGRP.R1 will install an EIGRP route using network B in its routing table because the administrative distance of EIGRP is loR1 will install an EIGRP route using network B in its routing table because the path cost from EIGRP is lower than RR1 will install an EIGRP route and a RIP route in its routing table and load balance between them.19Refer to the exhibit. If RIP is the routing protocol, what is the value of the metric from router A to network 192.168.5.0/24?345662472420 A router learns two paths with equal metrics to a destination network via the RIP routing protocol. How will the router handlthe destination network?The router will install the first route it learned into the routing table.The router will install both routes in the routing table and load balance between the two.The router will put the first route in the routing table, and denote the second route as a backup route.The router will pick the path with the higher bandwidth and will place it in the routing table.。
计算机网络第七版答案

计算机网络第七版答案第一章概述1-01 计算机网络向用户可以提供那些服务?答:连通性和共享1-02 简述分组交换的要点。
答:(1)报文分组,加首部(2)经路由器储存转发(3)在目的地合并1-03 试从多个方面比较电路交换、报文交换和分组交换的主要优缺点。
答:(1)电路交换:端对端通信质量因约定了通信资源获得可靠保障,对连续传送大量数据效率高。
(2)报文交换:无须预约传输带宽,动态逐段利用传输带宽对突发式数据通信效率高,通信迅速。
(3)分组交换:具有报文交换之高效、迅速的要点,且各分组小,路由灵活,网络生存性能好。
1-04 为什么说因特网是自印刷术以来人类通信方面最大的变革?答:融合其他通信网络,在信息化过程中起核心作用,提供最好的连通性和信息共享,第一次提供了各种媒体形式的实时交互能力。
1-05 因特网的发展大致分为哪几个阶段?请指出这几个阶段的主要特点。
答:从单个网络APPANET向互联网发展;TCP/IP协议的初步成型建成三级结构的Internet;分为主干网、地区网和校园网;形成多层次ISP结构的Internet;ISP首次出现。
1-06 简述因特网标准制定的几个阶段?答:(1)因特网草案(Internet Draft) ——在这个阶段还不是RFC 文档。
(2)建议标准(Proposed Standard) ——从这个阶段开始就成为RFC 文档。
(3)草案标准(Draft Standard)(4)因特网标准(Internet Standard)1-07小写和大写开头的英文名internet 和Internet在意思上有何重要区别?答:(1)internet(互联网或互连网):通用名词,它泛指由多个计算机网络互连而成的网络。
;协议无特指(2)Internet(因特网):专用名词,特指采用TCP/IP 协议的互联网络。
区别:后者实际上是前者的双向应用1-08 计算机网络都有哪些类别?各种类别的网络都有哪些特点?答:按范围:(1)广域网W AN:远程、高速、是Internet的核心网。
elins协议内容

elins协议内容Elin's Protocol: A Tale of Connection and EmpathyChapter 1: A Chance EncounterIt was a crisp autumn morning, and the city was abuzz with the hustle and bustle of everyday life. Among the crowd, Elin found herself lost in a sea of unfamiliar faces. With a heavy heart and a longing for connection, she yearned for someone to understand her.Chapter 2: The Curious NotebookAs fate would have it, Elin stumbled upon a small, dusty bookstore tucked away on a quiet street corner. Intrigued, she stepped inside and her eyes were immediately drawn to an old notebook lying on a shelf. Its worn-out cover beckoned her to unravel its mysteries.Chapter 3: The Power of WordsWith trembling hands, Elin opened the notebook and discovered a collection of heartfelt letters. Each one told a unique story, filled with emotions and vulnerabilities. As she read through them, a profound realization dawned upon her - the power of words to bridge the gap between souls.Chapter 4: A Journey of UnderstandingInspired by the stories in the notebook, Elin embarked on a personal journey to connect with others. Through heartfelt conversations and shared experiences, she discovered the beauty in embracing diversity and celebrating the uniqueness of every individual.Chapter 5: The Ripple EffectElin's newfound understanding and empathy began to have a ripple effect on those around her. With each connection she made, she witnessed the transformative power of genuine human interaction. Differences ceased to be barriers, and instead, became opportunities for growth and mutual understanding.Chapter 6: A World UnitedWord of Elin's remarkable journey spread far and wide, inspiring others to embrace the principles of the Elin's Protocol. Communities started to come together, breaking down the walls of prejudice and fostering a sense of unity and compassion.Chapter 7: The Legacy Lives OnYears passed, but the impact of Elin's Protocol continued to shape the world. Empathy became the cornerstone of society, and genuine human connections thrived. Elin's Protocol became a living testamentto the enduring power of compassion and understanding.Epilogue: A Call to ActionAs we reflect upon Elin's Protocol, let us remember that each and every one of us has the power to make a difference. By embracing empathy and actively seeking connection, we can create a world that is truly united. Let us carry the torch of Elin's Protocol and inspire others to join us on this remarkable journey.Note: This creative piece follows the guidelines provided and aims to convey the essence of Elin's Protocol through storytelling and emotional connection.。
思科第2学期第3章答案

1下列有关实施 VLAN 的说法中,哪两项正确?(选择两项。
)冲突域的大小会减小。
网络中所需交换机的数量会减少。
VLAN 会对主机进行逻辑分组,而不管它们的物理位置如何。
由于增加了中继信息,网络负载会显著增加。
某一 VLAN 中的设备不会收到其它 VLAN 中的设备所发出的广播。
答案 答案 最高分值correctness of response Option 3 and Option 5 are correct.22下列哪三项陈述准确描述了 VLAN 类型?(请选择三项。
)管理 VLAN 是指经过配置可以访问交换机管理功能的任何 VLAN 。
数据 VLAN 用于传输 VLAN 管理数据和用户生成的流量。
未经配置的交换机初始启动后,所有端口都属于默认 VLAN 。
已分配本地 VLAN 的 802.1Q 中继端口同时支持标记流量和无标记流量。
语音 VLAN 用于支持网络中的用户电话和电子邮件流量。
VLAN 1 总是用作管理 VLAN 。
答案答案最高分值 correctness ofresponse Option 1, Option 3, and Option 4 are correct.33网络管理员正在确定 VLAN 中继链路的最佳位置。
哪两种类型的点对点连接会使用 VLAN 中继两项。
)使用多个 VLAN 的两台交换机之间交换机和客户端 PC 之间交换机和带有 802.1Q 网卡的服务器之间交换机和网络打印机之间共享同一 VLAN 的两台交换机之间答案 答案 最高分值correctness of response Option 1 and Option 3 are correct.24请参见图示。
某帧在 PC-A 与 PC-B 之间传输。
下列有关此帧 VLAN 标记的说法中,哪项是正确的?当此帧离开 PC-A 时,会被添加 VLAN 标记。
当交换机接收此帧时,此帧会被添加 VLAN 标记。
当此帧从端口转出至 PC-B 时,会被添加 VLAN 标记。
计算机网络英文题库附答案chapter3解析

计算机网络英文题库(附答案)chapter3解析-CAL-FENGHAI.-(YICAI)-Company One 1Chapter 3 Transport Layer1.A transport-layer protocol provides for logical communication between ____________・A Application processesB HostsC RoutersD End systems2.Tran sport-layer protocols run in _______ ・A ServersB ClientsC RoutersD End systems3.In transport layer, the send side breaks application messages into ___________ , passes to network layer.A FramesB SegmentsC Data-gramsD bit streams4.Services provided by transport layer inelude _________ ・A HTTP and FTPB TCP and IPC TCP and UDPD SMTP5.Which of the following services is not provided by TCPA Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers6.These two minimal transport-layer services——_______ and ______ ——are the only two services that UDP provides!A process-to-process data delivery, error checkingB congestion control, reliable data transferC flow control, congestion controlD In-order data transfer, error checking7.Port number's scope is _______ t o _______ ・A 0, 1023B 0. 65535C 0, 127D 0,2558.The port numbers ranging from _______ t o _____ are called well-known port numberand are restricted・A 0,1023B 0, 65535C 0, 127D 0,2559.UDP socket identified by two components, they are _________ ・A source IP addresses and source port numbersB source IP addresses and destination IP addressesC destination IP address and destination port numbersD destination port numbers and source port numbers10.TCP socket identified by a (an) _________ ・A 1-tupleB 2-tupleC 3-tupleD 4-tuple11.Which of the following applications normally uses UDP servicesA SMTPB Streaming multimediaC FTPD HTTP12.Reliable data transfer protocol over a perfectly reliable channel is __________ ・A rdt 1.0B rdt2.0C rdt3.0D rdt2.113.Reliable data transfer protocol over a channel with bit errors and packet losses isA rdt 1.0B rdt2.0C rdt3.0D rdt2.114.Which of Hie following about reliable data transfer over a channel with bit errors i s not correct?A RDT2.0: assuming ACK and NAK will not be corniptedB RDT2.1: assuming ACK and NAK can be corruptedC RDT2.2: only use ACK-sD RDT2.2: use both ACK-s and NAK-s15.Which of the following protocols is not pipelining protocols?A TCPB rdt3.0C GO-BACK-ND selective repeat16.Which of the following is not correct about GBN protocol?A Only using ACK-sB Using cumulative ACK-sC Receiver discards all out-of-order packetsD It is not pipelined protocol17.Which of the following is not correct about SR protocol?A receiver individually acknowledges all correctly received packetsB sender only resends packets for which ACK not receivedC It limits sequence number of sent but un-ACK-ed packetsD It is not a pipelined protocol18.Which of the following about TCP connection is not correctA It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection19.The SYN segment is used for ______ ・A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection20.The FIN segment is used for _______ ・A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP conn ection21 ・ How does TCP sender perceive congestionA Through a timeout eventB Through a receiving duplicate ACK-s eventC Both A and BD Either A or B22.Extending host-to-host delivery to process-to-process delivery is called transportlayerand _.A multiplexing and de-multiplexingB storing and forwardingC forwarding and filteringD switching and routing23.UDP is a ______ sendee while TCP is a connection-oriented service・A ConnectionlessB ReliableC Connection-orientedD In-order24.The UDP header has only four fields, they are _________ ・A Source port numbei; destination port number, length and checksumB Source port number, destination port number, source IP and destination IPC source IP, destination IP, source MAC address and destination MAC addressD source IP, destination IP, sequence number and ACK sequence number25.There are two 16七it integers: 1110 0110 0110 0110, 1101 0101 0101 0101. Their checksum is _______ ・A 0100010001000011B 1011101110111100C 1111111111111111D 100000000000000026.The maximum amount of data that can be grabbed and placed in a segment is limited by the _____ ・A Maximum segment size (MSS)B MTUC ChecksumD Sequence number27.The MSS is typically set by first determining the length of the largest linklayer frame that can be sent by the local sending host——the so-called ____________________ ・A Maximum transmission unit (MTU)B MSSC ChecksumD Sequence number2& A File size of 500,000bytes5 MSS equals lOOObytes. When we want to transmit this file with TCP, the sequence number of the first segment is 0, and the sequence number of the second segment is _______________________ ・A 1000B 999C 1001D 50000029.Because TCP only acknowledges bytes up to the first missing byte in thestream, TCP is said to provide _______ ・A Cumulative acknowledgementsB Selective acknowledgementsC 3 duplicate ACKsD positive ACKs30.Provided a=0・125, current value of Estimated-RTT is 0.4s, Saniple-RTT is 0.8s,then the new value of Estimated-RTT is __________ s.A 0.45B 0.6C 0.7D 0.831.Provided RcvBuffer=20,LastByteRcvd=20,LastByteRead= 15, thenRev Window 二・A 14B 15C 16D 1032.TCP service does not provide _______ ・A Reliable data transferB Flow controlC Delay guaranteeD Congestion control33.There are two states in TCP congestion control, which are __________ ・A slow start and congestion avoidanceB safe start and congestion avoidanceC slow start and congestion abandonD safe start and congestion abandon34.The transport-layer protocol provides logical communication between __________ , and the network-layer protocol provides logical communication __________ ・A hosts, processesB processes, hostsC threads, processesD processes, threads35.To implement the multicast services the Internet employs the _________ protocol.A FTPB TCPC IGMPD UDP36.If an application developer chooses ________ protocol, then the application process is almost directly talking with IP.A HTTPB RIPC CSMA/CDD UDP37. ____ maintains connection-state in the end systems. This connection stateincludes receive and send buffers, congestion-control parameters, and sequence and acknowledgment number parameters・A UDPB TCPC DNSD HTTP38.The host that initiates the session in the Internet is labeled as__________ .A serverB user agentC clientD router39.With TCP there is no _________ b etween sending and receiving transport-layer entities ・A flow controlB handshakingC・ congestion control D VC setup40.Tlie Internet's ______ s ervice helps prevent the Inteniet fi*om entering a state of gridlock ・A datagramB congestion controlC sliding windowD timeout event41 ・ Connection setup at the transport layer involves _______ ・A serverB only the two end systemsC clientD router42. A _____ layer protocol provides for logical communication between applications.A transportB applicationC networkingD MAC43.In static congestion window, if it satisfies W*S/R > RTT + S/R, the Latency isA W*S/R-( RTT+ S/R)B 2RTT + O/RC 2RTT + O/R + (k-1 )[W* S/R- (RTT + S/R)]D 2RTT + S/R44.The receive side of transport layer reassembles segments into messages, passes to l ayer.A ApplicationB NetworkingC PhysicalD MAC45.In the following four options, which one is correct?A The variations in the SampIeRTT are smoothed out in the computation of the Esti mated RTTB The timeout should be less than the connection's RTTC Suppose that the last SampIeRTT in a TCP connection is equal to 1 sec. Then the current value of Timeoutinterval will necessarily be>l secD Suppose that the last SampIeRTT in a TCP connection is equal to 1 sec. Then the current value of Timeoutinterval will necessarily be<l sec46.The port number used by HTTP is ________ .A 80B 25C 110D 5347.The port number used by SMTP is ________ .A 80B 25C 110D 534& The port number used by pop3 is _________A 80B 25C 110D 5349.The port number used by DNS is _________A 80B 25C 110D 5350.The port number used by FTP is ________ .A 20 and 21B 20C 21D 5351. A UDP socket identified by a ________ tuple(s).A 2B 4C 1D 352. A TCP socket identified by a _________ tuple(s).A 2B 4C 1D 353. A TCP socket does not include ______ .A Source MAC addressB Source port numberC Destination IP addressD Destination port number54.Which of following about UDP is not correct.A It is a reliable data transfer protocolB It is connectionlessC no handshaking between UDP sender, receiverD it is a best effort service protocol55.DNS uses ______ service・A TCPB UDPC Both TCP and UDPD None of above56.Which of following about UDP is correctA Finer application-level control over what data is sent, and whenB No connection establishment (which can add delay), so no delay for establish a connectionC No connection state (so, UDP can typically support many active clients)D Large packet header overhead (16・B)57.Streaming media uses a ______ service normally・A TCPB UDPC Both TCP and UDPD None of above58.The UDP header has only ________fields.A 2B 4C 1D 359.Which of the following does not included in UDP header.A Source port numberB Destination port numberC ChecksumD Sequence number60.Which of Hie following is not a pipelining protocol.A Rdtl.OB Go-Back-NC Selective repeatD TCP61.In the following four descriptions about MSS and MTU, which one is not correctA The MSS is the maximum amount of application-layer data in the segmentB The MSS is the maximum size of the TCP segment including headersC The MSS is typically set by MTUD The MTU means the largest link-layer frame62.The job of gathering data chunks, encapsulating each data chunk with header information to create segments and passing Hie segments to the network is called___________A multiplexingB de-multiplexingC forwardingD routing63.In the following four descriptions about the relationship between the transport layer and the network layer, which one is not correctA The transport-layer protocol provides logical communication between hostsB The transport-layer protocol provides logical communication between processesC The services that a transport-layer protocol can provide are often constrained by the service model of the network-layer protocolD A computer network may make available multiple transport protocols64.Suppose the following three 8-bit bytes: 01010101, 01110000, 01001100. Whaf s the Is complement of the sum of these 8-bit bytesA 00010001B 11101101C 00010010D 1000100065.The following four descriptions about multiplexing and de-multiplexing, which one is correctA A UDP socket is identified by a two-tuples consisting of a source port number and a destination port number・B If two UDP segment have different source port number, they may be directed to the same destination process・C If two TCP segments with different source port number, they may be directed to the same destination process・D If two TCP segments with same destination IP address and destination port number, they must be the same TCP connection・66.UDP and TCP both have the fields except _________ ・A source port numberB destination port numberC checksumD receive window67.If we define N to be the window size, base to be the sequence number of theoldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [nextseqnum.base+N-1 ] corresponds to packet that __________ ・A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged68.Which of the following about TCP is not correctA It is a connectionless protocolB Point-to-point protocolC Reliable, in-order byte steam protocolD Pipelined protocol69.Which of the following about TCP is not correctA It is a connectionless protocolB full duplex data transfer protocolC connection-oriented protocolD flow controlled protocol70.The maximum amount of data that can be grabbed and placed in a segment is limited by the ______ ・A Maximum segment size (MSS)B MTUC Sequence numberD Check sum71.The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host (the so-called _________ ), and then will fit into a single link-layer frame・A Maximum segment size (MSS)B MTUC Sequence numberD Check sum72.The MSS is the maximum amount of _________ l ayer data in the segment, not the maximum size of the TCP segment including headers・A ApplicationB TransportC NetworkingD Link73.Which of the following field is not used for connection setup and teardownA Sequence numberB TSTC SYND FIN74. ____ is the byte stream number of first byte in the segment・A Sequence numberB ACK numberC ChecksumD port number75. ____ is the byte sequence numbers of next byte expected from odier side・A Sequence numberB ACK numberC ChecksumD port number76.Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide ________ acknowledgements・A CumulativeB SelectiveC SingleD Negative77.Fast retransmit means in the case that _______ duplicate ACK-s are received, the TCP sender resend segment before timer expires・A 3B 4C 5D 67& TCP ______ means sender won't ov©rflow receivei^s buffer by transmitting too much, too fast.A Flow controlB Congestion controlC Reliable data transferD Connection-oriented service79.TCP provides flow control by having the sender maintain a variable called theA Receive windowB Congestion windowC Sliding windowD buffer80.How does TCP sender perceive congestionA TimeoutB 3 duplicate ACK-sC Both A and BD None of above81 ・ Transport protocols run in ______・A ServersB ClientsC RoutersD End systems82.Which of the following services is not provided by TCPA Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers83.Which service does UDP not provideA multiplexingB de-multiplexingC error-detectionD error-correction84.There are three major events related to data transmission and retransmission in the TCP sender, which one is not in it?A data received from application aboveB de-nmltiplexing segmentC timer timeoutD ACK receipt85.Which of the following applications normally uses UDP services?A SMTPB Streaming multimediaC FTPD HTTP86.Which of the following about TCP connection is not correct?A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection87.The SYN segment is used for _______ ・A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection8& Which service helps prevent the internet from entering a state of gridlockA reliable data transferB flow controlC congestion controlD handshaking procedure89.Tlie Internet's ________ is responsible fbr moving packets from one host to another.A application layerB transport layerC network layerD link layer90.In the following applications, which one is a bandwidth-sensitive application?A E-mailB web applicationC real-time audioD file transfer91.In the following applications, which one uses UDP?A E-mailB web applicationC file transferD DNS92.In the following four descriptions, which one is correct?A If one host's transport layer uses TCP, then its network layer must use \-iitiial- circuit network・B Datagram network provides connection serviceC The transport-layer connection service is implemented in the routerD The network-layer connection service is implemented in the router as well as in the end system.93.____ is a speeding-matching service一-matching the rate which the sender is sending against the rate at which the receiving application is reading・A congestion controlB flow controlC sliding-window controlD variable control94.In the following four descriptions about Rev-Window, which one is correct?A The size of the TCP RcvWindow never changes throughout the duration of the connectionB The size of the TCP RcvWindow will change with the size of the TCP RcvBufferC The size of the TCP RcvWindow must be less than or equal to the size of the TCP RcvBufferD Suppose host A sends a file to host B over a TCP connection, the number of unacknowledged bytes that A sends cannot exceed the size of the size of the RcvWindow. 95.There are 6 flag fields. Which one is to indicate that the receiver should pass the data to the upper layer immediately?A PSHB URGC ACKD RST96.Suppose the TCP receiver receives the segment that partially or completely fills ingap in received data, it will ________ .A immediately send ACKB immediately send duplicate ACKC wait some time for arrival of another in-order segmentD send single cumulative97. _____ imposes constrain on the rate at which a TCP sender can send traffic intothe network・A sliding windowB congestion windowC receive windowD variable window98.Flow control and congestion control are same at that they all limit the rate of the sender, but differ in that _______ ・A flow control limits its rate by the size of RcvWindow, but congestion control by the traffic on the linkB congestion control limits its rate by the size of RcvWindow, but flow control by the traffic on the linkC flow control mainly is accomplished by the sender, but congestion control by the receiver.D flow control mainly is accomplished by the receiver, but congestion control by the link.99.This job of delivering the data in a transport-layer segment to the correct socket is called ______ ・A multiplexingB de-muitiplexingC forwardingD routing100.If we define N to be the window size, base to be the sequence number of theoldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [base, nextseqnunvl] corresponds to packet 什lat ____________ ・A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged101.____ are the two types of transport services that the Internet provides to the applications.A TCP and UDPB connection-oriented and connectionless serviceC TCP and IPD reliable data transfer and flow control102.In the following descriptions about persistent connection, which one is not correct?A The server leaves the TCP connection open after sending a responseB Each TCP connection is closed after the server sending one objectC There are two versions of persistent connection: without pipelining and with pipeliningD The default mode of HTTP uses persistent connection with pipelining103.The field of Length in UDP segment specifies the length of __________ ・A the UDP segment, not including the headerB the UDP segment, including the headerC the UDP seginenf s headerD the Length field104.In TCP segment header, which field can implement the reliable data transfer?A source port number and destination port numberB sequence nuniber and ACK numberC urgent data pointerD Receive window105.In the following four descriptions about TCP connection management, which one is not correct?A Either of the two processes participating in a TCP connection can end the connectionB If the FIN bit is set to 1, it means that it wants to close the connectionC In the first two step of the three-way handshake, the client and server randomly choose an initial sequence numberD In the three segments of the three-way handshake, the SYN bit must be set to 1106.Suppose host A sends two TCP segments back to back to host B over a TCP connection. The first segment has sequence number 42, and the second has sequence number 110. If the l sl is lost and 2nd arrives at host B. What will be the acknowledgment number?A 43 C 109B ACK42 D ACK110Choices:1 〜5 ADBCA 6-10 ABACD11〜15 BACDB16〜20 DDAAD 21~25DAAAA 26 〜30 AAAAA31 〜35 BCABC 36-40DBCDB 41V5 BACAA46 〜50 AB CD A 51 〜55ABAAB 5640 DBBDA6145 BAABB 66 〜DAAAA 71-75 BAAAB76-80 AAAAC 81 〜85DADBB 86®AACCC91 〜95 DDBCB 95 〜CBABD 101-106 ABABDB1.Consider sending an object of size 0=500,OOObytes from server to client. Let S=500bytes and RTT=0.2s. Suppose the transport protocol uses static windows with window size 5. For a transmission rate of 100Kbps, determine the latency for sending the whole object. Recall the number of windows K=O/ WS), and there is K-l stalled state (that is idle time gaps).1- SolutionK=0/'(\VS)=500*8* 1000/(5 * 5 000*8)=200Latency=2RTT+ORKK-l )(S,R+RTT-WS‘R)=0.4+500*1000*8'100000+(200-1>(5 00*8/100000+02-5*500*8/1000QQ)=48.36s2.Consider the following plot of TCP congestion window size as a function of time.Fill in the blanks as follow:a) The initial value of Threshold at the first transmission round is ____________ b) The value of Threshold at the 11st transmission round is __________ ・ c) The value of Threshold at the 21st transmission round is __________ ・ d) After the 9th transmission round, segment loss detected by __________ ・(A) Timeout(B) Triple duplicate ACKe) After the 19lh transmission round, segment loss detected by _________ ・(A) Timeout(B) Triple duplicate ACKf) During_______ t ransmission round, the 18lh segment is sent ・2. Solutiona) 12 b) Sc) 7d)Ae)Bf)53. Consider the TCP reliable data transfer in the given graph ・ If in Segment l ,s Sequence number =10,data=u AC'\ please fill in the following blanks ・ a) In Segment 2, ACK number 二 :b) In Segment 3, Sequence number =_______ ; data=u 0123456789^c) If there are some bits corrupted in segment 3 when it arrives Host B, then the ACKnumber in Segment 5 is : and the ACK number in Segment 6 is ,Transmission roundb n 8congestion、f4. The client A wants to request a Web page from Server B ・ Suppose the URL of the page is 172.16.0.200/experiment, and also it wants to receive French version of object. The time-sequence diagram is shown below, please fill in the blanks ・Packet® to Packet③ are TCP connection's segment, then: Packet ①:SYN flag bit 二 aACK flag bit=_b Sequence number= 92 Packet ®: SYN flag bit=l3. Solution:a) 12b)12 c) 12; 22ACK flag bit=_cSequence number= 100 Packet ®: SYN flag bit=_dACK flag bit=l Sequence number= e 4. Solution:a)l b)0 c)l d)0 e)935・ Consider sending an object of size 0=100 Kbytes from server to client. Let S=536 bytes and RTT= 100msec ・ Suppose the transport protocol uses static windows with window size W ・(1) For a transmission rate of 25 kbps, determine the minimum possible latency. Determine the minimum window size that achieves this latency. (2) Repeat (1) for 100 kbps. 5. Solution:(1) Latency=2RTT + OR =2*0.1+100*8/25= 0.2+32=32.2 (s)W* S R > S.R+RTT —- W>L6= so W=2 (2)Latency =2RTT+ O,R=2«0.1+100*8/'100=0.2+8=82 (s) W* S,R> SR+RTT —-W3.3, so W=46. Consider the following plot of TCP congestion window size as a function of time. Please fill in the blanks as below.Aa) The initial value of Threshold at the first transmission round is b) The value of Threshold at die 11th transmission round is ___________ ・ c) The value of Threshold at the 21st transmission round is・congestion window﹃4︱TITIT丄|︱rlrL ︱lrlrL ︱︱LILILIklklrlrlrL ︱IL ︱﹂︱﹂︱ J.IJ.1/Transmission roundd)After the 9th transmission round, _________e)After the 19th transmission round, ________6. Solution:a) 12 b) 8 c) 7 d) timeouttriple ACK occurs・ are detected.e) 321。
[全]国开大学形考计算机第三章 Internet基础练习题库含答案
![[全]国开大学形考计算机第三章 Internet基础练习题库含答案](https://img.taocdn.com/s3/m/9d27f4384afe04a1b171de3a.png)
国开形考计算机第三章Internet基础练习题库含答案选择1.计算机病毒是指_____/特制的具有破坏性的程序2.用户要想在网上查询WWW信息,必须安装并运行一个被称为________的软件。
/浏览器3.计算机网络最突出的优点是________。
/资源共存4.下面对BBS描述正确的是________。
/可以匿名登录也可以注册登录5.计算机网络是计算机与________结合的产物。
/通信技术6.一座办公大楼内各个办公室中的微机进行联网,这个网络属于________。
/LAN7.以下______是4G通信标准之一?/LTE-Advanced8.从可以看出,它是中国的一个________的站点。
/教育部门9.我们将鼠标移到网页上面部分的内容上,发现鼠标的形状变成了一个手型,在网页上这种文字或图标我们称为________。
/超链接10.我们如果要将自己使用的计算机上的文件传送到远处的服务器上,称为________。
/上传11.以下_____不是计算机病毒的发作症状?/USB接口故障12.下列四项中,合法的电子邮件地址是________。
/*************13.Web上每一个页都有一个独立的地址,这些地址称作统一资源定位器,即_______。
/URL14.Internet采用域名是因为__________。
/IP地址不便于记忆15.Foxmail软件的作用是________。
/邮件管理16.万维网简称__________。
/WWW17.以下关于物联网说法错误的是_____。
/将物体连接起来形成的因特网, 不会使用到无线网络技术18.Internet上最重要的信息资源是Web网页,浏览网页最常用的软件是_______。
/Internet Explorer19.根据计算机网络覆盖地理范围的大小, 网络可分为局域网、城域网和______./广域网20.文件传送协议的缩写是________。
/FTP21.下列有关因特网的叙述,________的说法是错误的。
计算机网络(第1~3章习题及答案)

第一章概述(P33)1-02 简述分组交换的要点答:(1)采用存储--转发技术,信道可以为多对会话动态复用,比电路交换资源利用率高。
(2)限制通过网络的数据分组的大小,如果发送报文超出限制,则发送方将报文分割成一个个小分组,每个分组以存储--转发方式独立传输。
当所有分组到达接收方后,接收方将它们重新拼接成报文。
(3)传输特点:延迟较小,且相对稳定,适合计算机应用。
1-03 试从多个方面比较电路交换、报文交换和分组交换的主要优缺点。
答:(1)电路交换电路交换就是终端之间通信时,一方首先发起呼叫,途径的交换机完成转接,直到目的端对方收到发起端的信号,即首先将收发双方的通路完全打通,然后才进行通信。
在整个通信过程中双方一直占用该电路。
它的特点是实时性强,时延小,交换设备成本较低。
但同时也带来线路利用率低,电路接时间长,不同类型用户之间不能通信等缺点。
电路交换比较适用于信息量大、持续时间长的用户通信。
(2)报文交换将用户的报文存储在交换机的存储器中。
当所需要的输出电路空闲时,再将该报文发向接收交换机或终端,它以“存储—转发”方式在网内传输数据。
报文交换的优点是中继电路利用率高,可以多个用户同时在一条线路上传送,可实现不同速率、不同规程的终端间互通。
但它的缺点也是显而易见的。
以报文为单位进行存储转发,占用大量的交换机内存和外存,传输延时大且不确定,不能满足对实时性要求高的用户。
报文交换适用于传输的报文较短、实时性要求较低的网络用户之间的通信,如公用电报网。
(3)分组交换分组交换实质上是在“存储—转发”基础上发展起来的。
它限定通过网络的数据长度,因此发送端必须将长报文分割成一个个小分组,每个带有目的地标识的分组以“存储-转发”技术独立通过网络,到达接收端后,再去掉分组头将各数据字段按顺序重新装配成完整的报文。
分组交换使多路会话的数据共享线路,因此线路利用率比电路交换高;同时,由于分组在每个交换机上的处理时间和等待时间减少以及分组的并行传输,传输性能(传输时延、稳定性)比报文交换好,适合交互式应用。
计算机网络基础(段标第6版) 第3章 习题参考答案

填空1同轴电缆;光纤;双绞线;2物理特性,・传输特性;连通特性;地理范围;抗干扰性;相对价格3电磁干扰(EMI)和射频干扰(RFI)4屏蔽双绞线;非屏蔽双绞线;5绝缘实心电缆;金属丝;6超五类双绞线7计算机-集线器、计算机-交换机、路由器-集线器、路由器-交换机8单模光纤、多模光纤9无线电波;红外线;微波;10光纤;11无线电波、红外线、微波、光波12电视机;空调;键盘;鼠标;13电视机、空调、便携计算机、个人数字代理14堆叠;级联;151AN管理部分;微处理器部分;曼彻斯特编码器;发送和发送控制部分;接收和接收部分组成;16工作组交换机;部门级交换机;企业级交换机17直通式交换;存储转发式;碎片隔离方式18转换网桥;封装网桥;源路由选择网桥;19过滤、存储、转发、流量管理、媒体转换20电子邮件网关;因特网网关;局域网网关;简答:1 .传输介质的评价主要需要考虑哪些因素?1 .带宽需求;2、传输距离;3、铺设环境(如:室内、室外);4、物理拓扑/逻辑拓扑设计;5、可扩展性;6、兼容性(如:现有端接设备);7、安全性(如:有线、无线、屏蔽系统、非屏蔽系统等)2 .屏蔽双绞线和非屏蔽双绞线的主要差异是什么?屏蔽双绞线有屏蔽层,非屏蔽双绞线没有屏蔽层3 .10BASE-T中的各段内容表示含义是什么?IObase-T各部分的含义-简称双绞线以太网10”代表传播速率为IOmbps;"base"代表"基带传输"t"代表双绞线,适用于基带局域网(Ian)的以太网标准,采用双绞线缆,在星形拓扑结构中速度为每秒10兆比特.4 .单模光纤与多模光纤在性能上的主要区别是什么?多模光纤(Mu1tiModeFiber,MMF):纤芯较粗(纤芯直径约为50或62.5μm),可传多种模式的光源。
但其模间色散较大,这就限制了传输数字信号的频率,而且随距离的增加会更加严重,因此,多模光纤传输的距离比较近,一般只有几公里。
(完整版)计算机网络英文题库(附答案)chapter3

Chapter 3 Transport Layer1. A transport-layer protocol provides for logical communication between ____.A Application processesB HostsC RoutersD End systems2. Transport-layer protocols run in ____.A ServersB ClientsC RoutersD End systems3. In transport layer, the send side breaks application messages into ____, passes to network layer.A FramesB SegmentsC Data-gramsD bit streams4. Services provided by transport layer include ____.A HTTP and FTPB TCP and IPC TCP and UDPD SMTP5. Which of the following services is not provided by TCP?A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers6. These two minimal transport-layer services----____ and ____----are the only two services that UDP provides!A process-to-process data delivery, error checkingB congestion control, reliable data transferC flow control, congestion controlD In-order data transfer, error checking7. Port number’s scop e is ____ to ____.A 0, 1023B 0, 65535C 0, 127D 0,2558. The port numbers ranging from ____to ____ are called well-known port number and are restricted.A 0, 1023B 0, 65535C 0, 127D 0,2559. UDP socket identified by two components, they are ____.A source IP addresses and source port numbersB source IP addresses and destination IP addressesC destination IP address and destination port numbersD destination port numbers and source port numbers10. TCP socket identified by a (an) ____.A 1-tupleB 2-tupleC 3-tupleD 4-tuple11. Which of the following applications normally uses UDP services?A SMTPB Streaming multimediaC FTPD HTTP12. Reliable data transfer protocol over a perfectly reliable channel is____.A rdt1.0B rdt2.0C rdt3.0D rdt2.113. Reliable data transfer protocol over a channel with bit errors and packet losses is _ ___.A rdt1.0B rdt2.0C rdt3.0D rdt2.114. Which of the following about reliable data transfer over a channel with bit errors i s not correct?A RDT2.0: assuming ACK and NAK will not be corruptedB RDT2.1: assuming ACK and NAK can be corruptedC RDT2.2: only use ACK-sD RDT2.2: use both ACK-s and NAK-s15. Which of the following protocols is not pipelining protocols?A TCPB rdt3.0C GO-BACK-ND selective repeat16. Which of the following is not correct about GBN protocol?A Only using ACK-sB Using cumulative ACK-sC Receiver discards all out-of-order packetsD It is not pipelined protocol17. Which of the following is not correct about SR protocol?A receiver individually acknowledges all correctly received packetsB sender only resends packets for which ACK not receivedC It limits sequence number of sent but un-ACK-ed packetsD It is not a pipelined protocol18. Which of the following about TCP connection is not correct?A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection19. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection20. The FIN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection21.How does TCP sender perceive congestion?A Through a timeout eventB Through a receiving duplicate ACK-s eventC Both A and BD Either A or B22. Extending host-to-host delivery to process-to-process delivery is called transport-layer ____ and .A multiplexing and de-multiplexingB storing and forwardingC forwarding and filteringD switching and routing23. UDP is a ____ service while TCP is a connection-oriented service.A ConnectionlessB ReliableC Connection-orientedD In-order24. The UDP header has only four fields, they are____.A Source port number, destination port number, length and checksumB Source port number, destination port number, source IP and destination IPC source IP, destination IP, source MAC address and destination MAC addressD source IP, destination IP, sequence number and ACK sequence number25. There are two 16-bit integers: 1110 0110 0110 0110, 1101 0101 0101 0101. Their checksum is____.A 0100010001000011B 1011101110111100C 1111111111111111D 100000000000000026.The maximum amount of data that can be grabbed and placed in a segment is limited by the____.A Maximum segment size (MSS)B MTUC ChecksumD Sequence number27.The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host----the so-called____.A Maximum transmission unit (MTU)B MSSC ChecksumD Sequence number28. A File size of 500,000bytes, MSS equals 1000bytes. When we want to transmit this file with TCP, the sequence number of the first segment is 0, and the sequence number of the second segment is ____.A 1000B 999C 1001D 50000029.Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide____.A Cumulative acknowledgementsB Selective acknowledgementsC 3 duplicate ACKsD positive ACKs30. Provided α=0.125, current value of Estimated-RTT is 0.4s, Sample-RTT is 0.8s, then the new value of Estimated-RTT is ____s.A 0.45B 0.6C 0.7D 0.831.Provided RcvBuffer=20,LastByteRcvd=20,LastByteRead=15, thenRcvWindow=____.A 14B 15C 16D 1032. TCP service does not provide____.A Reliable data transferB Flow controlC Delay guaranteeD Congestion control33. There are two states in TCP congestion control, which are ____.A slow start and congestion avoidanceB safe start and congestion avoidanceC slow start and congestion abandonD safe start and congestion abandon34. The transport-layer protocol provides logical communication between ____, and the network-layer protocol provides logical communication ____.A hosts, processesB processes, hostsC threads, processesD processes, threads35. To implement the multicast services the Internet employs the ____ protocol.A FTPB TCPC IGMPD UDP36. If an application developer chooses ____ protocol, then the application process is almost directly talking with IP.A HTTPB RIPC CSMA/CDD UDP37. ____ maintains connection-state in the end systems. This connection state includes receive and send buffers, congestion-control parameters, and sequence and acknowledgment number parameters.A UDPB TCPC DNSD HTTP38. The host that initiates the session in the Internet is labeled as ____.A serverB user agentC clientD router39. With TCP there is no _____ between sending and receiving transport-layer entities.A flow controlB handshakingC. congestion control D VC setup40. The Internet’s ____service helps prevent the Internet from entering a state of gridlock.A datagramB congestion controlC sliding windowD timeout event41. Connection setup at the transport layer involves ____.A serverB only the two end systemsC clientD router42. A ____layer protocol provides for logical communication between applications.A transportB applicationC networkingD MAC43. In static congestion window, if it satisfies W*S/R > RTT + S/R, the Latency is ____.A W*S/R – ( RTT+ S/R)B 2RTT + O/RC 2RTT + O/R + (k-1)[W* S/R- (RTT + S/R)]D 2RTT + S/R44. The receive side of transport layer reassembles segments into messages, passes to ____layer.A ApplicationB NetworkingC PhysicalD MAC45. In the following four options, which one is correct?A The variations in the SampleRTT are smoothed out in the computation of the EstimatedRTTB The timeout should be less than the connection’s RTTC Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≥1 secD Suppose that the last SampleRTT in a TCP connection is equal to 1 sec. Then the current value of TimeoutInterval will necessarily be≤1 sec46. The port number used by HTTP is ____.A 80B 25C 110D 5347. The port number used by SMTP is ____.A 80B 25C 110D 5348. The port number used by pop3 is ____.A 80B 25C 110D 5349. The port number used by DNS is ____.A 80B 25C 110D 5350. The port number used by FTP is ____.A 20 and 21B 20C 21D 5351. A UDP socket identified by a ____ tuple(s).A 2B 4C 1D 352. A TCP socket identified by a ____ tuple(s).A 2B 4C 1D 353. A TCP socket does not include____.A Source MAC addressB Source port numberC Destination IP addressD Destination port number54. Which of following about UDP is not correct.A It is a reliable data transfer protocolB It is connectionlessC no handshaking between UDP sender, receiverD it is a best effort service protocol55. DNS uses ____ service.A TCPB UDPC Both TCP and UDPD None of above56. Which of following about UDP is correct?A Finer application-level control over what data is sent, and whenB No connection establishment (which can add delay), so no delay for establish a connectionC No connection state (so, UDP can typically support many active clients)D Large packet header overhead (16-B)57. Streaming media uses a ____ service normally.A TCPB UDPC Both TCP and UDPD None of above58. The UDP header has only ____ fields.A 2B 4C 1D 359. Which of the following does not included in UDP header.A Source port numberB Destination port numberC ChecksumD Sequence number60. Which of the following is not a pipelining protocol.A Rdt1.0B Go-Back-NC Selective repeatD TCP61. In the following four descriptions about MSS and MTU, which one is not correct?A The MSS is the maximum amount of application-layer data in the segmentB The MSS is the maximum size of the TCP segment including headersC The MSS is typically set by MTUD The MTU means the largest link-layer frame62. The job of gathering data chunks, encapsulating each data chunk with header information to create segments and passing the segments to the network is called ____.A multiplexingB de-multiplexingC forwardingD routing63. In the following four descriptions about the relationship between the transport layer and the network layer, which one is not correct?A The transport-layer protocol provides logical communication between hostsB The transport-layer protocol provides logical communication between processesC The services that a transport-layer protocol can provide are often constrained by the service model of the network-layer protocolD A computer network may make available multiple transport protocols64. Suppose the following three 8-bit bytes: 01010101, 01110000, 01001100. What’s the 1s complement of the sum of these 8-bit bytes?A 00010001B 11101101C 00010010D 1000100065. The following four descriptions about multiplexing and de-multiplexing, which one is correct?A A UDP socket is identified by a two-tuples consisting of a source port number and a destination port number.B If two UDP segment have different source port number, they may be directed to the same destination process.C If two TCP segments with different source port number, they may be directed to the same destination process.D If two TCP segments with same destination IP address and destination port number, they must be the same TCP connection.66. UDP and TCP both have the fields except ____.A source port numberB destination port numberC checksumD receive window67. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [nextseqnum,base+N-1] corresponds to packet that ____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged68. Which of the following about TCP is not correct?A It is a connectionless protocolB Point-to-point protocolC Reliable, in-order byte steam protocolD Pipelined protocol69. Which of the following about TCP is not correct?A It is a connectionless protocolB full duplex data transfer protocolC connection-oriented protocolD flow controlled protocol70. The maximum amount of data that can be grabbed and placed in a segment is limited by the ____.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum71. The MSS is typically set by first determining the length of the largest link-layer frame that can be sent by the local sending host (the so-called____), and then will fit into a single link-layer frame.A Maximum segment size (MSS)B MTUC Sequence numberD Check sum72. The MSS is the maximum amount of ____layer data in the segment, not the maximum size of the TCP segment including headers.A ApplicationB TransportC NetworkingD Link73. Which of the following field is not used for connection setup and teardown?A Sequence numberB TSTC SYND FIN74. ____ is the byte stream number of first byte in the segment.A Sequence numberB ACK numberC ChecksumD port number75. ____ is the byte sequence numbers of next byte expected from other side.A Sequence numberB ACK numberC ChecksumD port number76. Because TCP only acknowledges bytes up to the first missing byte in the stream, TCP is said to provide ____ acknowledgements.A CumulativeB SelectiveC SingleD Negative77. Fast retransmit means in the case that ____ duplicate ACK-s are received, the TCP sender resend segment before timer expires.A 3B 4C 5D 678. TCP____ means sender won’t overflow receiver’s buffer by tran smitting too much, too fast.A Flow controlB Congestion controlC Reliable data transferD Connection-oriented service79. TCP provides flow control by having the sender maintain a variable called the ____.A Receive windowB Congestion windowC Sliding windowD buffer80. How does TCP sender perceive congestion?A TimeoutB 3 duplicate ACK-sC Both A and BD None of above81. Transport protocols run in ____.A ServersB ClientsC RoutersD End systems82. Which of the following services is not provided by TCP?A Delay guarantees and bandwidth guaranteesB Reliable data transfers and flow controlsC Congestion controlsD In-order data transfers83. Which service does UDP not provide?A multiplexingB de-multiplexingC error-detectionD error-correction84. There are three major events related to data transmission and retransmission in the TCP sender, which one is not in it?A data received from application aboveB de-multiplexing segmentC timer timeoutD ACK receipt85. Which of the following applications normally uses UDP services?A SMTPB Streaming multimediaC FTPD HTTP86. Which of the following about TCP connection is not correct?A It is a broadcast connectionB It is a point-to-point connectionC It is a pipelined connectionD It is a full duplex connection87. The SYN segment is used for____.A TCP connection setupB TCP flow controlC TCP congestion controlD Closing a TCP connection88. Which service helps prevent the internet from entering a state of gridlock?A reliable data transferB flow controlC congestion controlD handshaking procedure89. The Internet’s _____is responsible for moving packets from one host to another.A application layerB transport layerC network layerD link layer90.In the following applications, which one is a bandwidth-sensitive application?A E-mailB web applicationC real-time audioD file transfer91. In the following applications, which one uses UDP?A E-mailB web applicationC file transferD DNS92. In the following four descriptions, which one is correct?A If one host’s transport layer uses TCP, then its network layer must use virtual-circuit network.B Datagram network provides connection serviceC The transport-layer connection service is implemented in the routerD The network-layer connection service is implemented in the router as well as in the end system.93.____ is a speeding-matching service---matching the rate which the sender is sending against the rate at which the receiving application is reading.A congestion controlB flow controlC sliding-window controlD variable control94. In the following four descriptions about Rcv-Window, which one is correct?A The size of the TCP RcvWindow never changes throughout the duration of the connectionB The size of the TCP RcvWindow will change with the size of the TCP RcvBufferC The size of the TCP RcvWindow must be less than or equal to the size of the TCP RcvBufferD Suppose host A sends a file to host B over a TCP connection, the number of unacknowledged bytes that A sends cannot exceed the size of the size of the RcvWindow.95. There are 6 flag fields. Which one is to indicate that the receiver should pass the data to the upper layer immediately?A PSHB URGC ACKD RST96. Suppose the TCP receiver receives the segment that partially or completely fills in gap in received data, it will ____.A immediately send ACKB immediately send duplicate ACKC wait some time for arrival of another in-order segmentD send single cumulative97. _____ imposes constrain on the rate at which a TCP sender can send traffic into the network.A sliding windowB congestion windowC receive windowD variable window98. Flow control and congestion control are same at that they all limit the rate of the sender, but differ in that ____.A flow control limits its rate by the size of RcvWindow, but congestion control by the traffic on the linkB congestion control limits its rate by the size of RcvWindow, but flow control by the traffic on the linkC flow control mainly is accomplished by the sender, but congestion control by the receiver.D flow control mainly is accomplished by the receiver, but congestion control bythe link.99. This job of delivering the data in a transport-layer segment to the correct socket is called ____.A multiplexingB de-multiplexingC forwardingD routing100. If we define N to be the window size, base to be the sequence number of the oldest unacknowledged packet, and next-seq-num to be the smallest unused sequence number, then the interval [base, nextseqnum-1] corresponds to packet that ____.A can be sent immediatelyB have already been transmitted and acknowledgedC cannot be usedD have been sent but not yet acknowledged101. ____ are the two types of transport services that the Internet provides to the applications.A TCP and UDPB connection-oriented and connectionless serviceC TCP and IPD reliable data transfer and flow control102. In the following descriptions about persistent connection, which one is not correct?A The server leaves the TCP connection open after sending a responseB Each TCP connection is closed after the server sending one objectC There are two versions of persistent connection: without pipelining and with pipeliningD The default mode of HTTP uses persistent connection with pipelining103. The field of Length in UDP segment specifies the length of ____.A the UDP segment, not including the headerB the UDP segment, including the headerC the UDP segment’s headerD the Length field104. In TCP segment header, which field can implement the reliable data transfer?A source port number and destination port numberB sequence number and ACK numberC urgent data pointerD Receive window105. In the following four descriptions about TCP connection management, which one is not correct?A Either of the two processes participating in a TCP connection can end the connectionB If the FIN bit is set to 1, it means that it wants to close the connectionC In the first two step of the three-way handshake, the client and server randomly choose an initial sequence numberD In the three segments of the three-way handshake, the SYN bit must be set to 1 106. Suppose host A sends two TCP segments back to back to host B over a TCP connection. The first segment has sequence number 42, and the second has sequence number 110. If the 1st is lost and 2nd arrives at host B. What will be the acknowledgment number?A 43B ACK42C 109D ACK1101.Consider sending an object of size O=500,000bytes from server to client. LetS=500 bytes and RTT=0.2s. Suppose the transport protocol uses static windows with window size 5. For a transmission rate of 100Kbps, determine the latency for sending the whole object. Recall the number of windows K=O/ WS), and there is K-1 stalled state (that is idle time gaps).2.Consider the following plot of TCP congestion window size as a function of time.Fill in the blanks as follow:a) The initial value of Threshold at the first transmission round is ____. b) The value of Threshold at the 11st transmission round is ____. c) The value of Threshold at the 21st transmission round is ____. d) After the 9th transmission round, segment loss detected by ____.(A) Timeout(B) Triple duplicate ACKe) After the 19th transmission round, segment loss detected by ____.(A) Timeout(B) Triple duplicate ACKf) During ____ transmission round, the 18th segment is sent.3.Consider the TCP reliable data transfer in the given graph. If in Segment 1’s Sequence number =10,data=“AC”, please fill in the following blanks. a) In Segment 2, ACK number=____;b) In Segment 3, Sequence number =____; data=“0123456789”c) If there are some bits corrupted in segment 3 when it arrives Host B, then the ACK number in Segment 5 is ____; and the ACK number in Segment 6 is ____.14 180 26 3000 2 6 4 8 10 12 16 20 22 240 28 32Congestion window sizeTransmission round48121612345674. The client A wants to request a Web page from Server B. Suppose the URL of the page is 172.16.0.200/experiment, and also it wants to receive French version of object. The time-sequence diagram is shown below, please fill in the blanks.12345Packet① to Packet③are TCP connection’s segment, then:Packet ①: SYN flag bit= aACK flag bit= bSequence number= 92Packet ②: SYN flag bit=1ACK flag bit= c Sequence number=100 Packet ③: SYN flag bit= d ACK flag bit=1Sequence number= e5. Consider sending an object of size O=100 Kbytes from server to client. Let S=536 bytes and RTT=100msec. Suppose the transport protocol uses static windows with window size W.(1) For a transmission rate of 25 kbps, determine the minimum possible latency. Determine the minimum window size that achieves this latency. (2) Repeat (1) for 100 kbps.6. Consider the following plot of TCP congestion window size as a function of time. Please fill in the blanks as below.a) The initial value of Threshold at the first transmission round is____. b) The value of Threshold at the 11th transmission round is_____. c) The value of Threshold at the 21st transmission round is_____.14 18 26 30 0 2 6 4 8 10 12 16 20 22 24 28 32 Congestion window sizeTransmission round481216d) After the 9th transmission round, _____ occurs.e) After the 19th transmission round, ____ are detected.。
思科计算机概论第三章ITE答案-互联网类

思科计算机概论第三章ITE答案-互联网类思科计算机概论第三章 ITE 答案——互联网类在如今这个数字化的时代,互联网就像是一张无形的大网,把我们所有人都紧紧地联系在了一起。
要说这互联网啊,那可真是有说不完的奇妙之处。
我想起之前有一次,我家小侄子拿着他的平板电脑,一脸疑惑地问我:“叔叔,为什么我在这上面能看到世界各地的东西呀?”我笑着告诉他:“这就是互联网的魔力呀,它能把信息瞬间传递到你的眼前。
”咱们先来说说这第三章里提到的互联网基础知识。
就拿 IP 地址来说吧,它就像是互联网世界里每台设备的“家庭住址”。
想象一下,如果互联网是一个巨大的城市,每台电脑、每部手机都是城市里的居民,那 IP 地址就是它们的门牌号。
没有这个门牌号,信息就找不到它们的“家”,也就没法传递啦。
再来说说域名系统(DNS),这就像是互联网里的电话簿。
当我们在浏览器里输入一个网址,比如,DNS 就会帮我们找到对应的 IP 地址,然后我们才能顺利访问网站。
就好像我们要找一个朋友,不知道他家具体在哪,但是通过电话簿查到了地址一样。
还有网络协议,像 TCP/IP 协议,这可是互联网通信的规则。
如果把互联网上的信息传递比作一场接力赛,那协议就是规定每个运动员怎么交接棒,往哪儿跑的规则。
要是没有这些规则,这场接力赛肯定乱套,信息也没法准确快速地传递。
说到这里,我又想起有一回我去朋友家,他正为电脑连不上网发愁。
我帮他检查了一下,发现是网络设置出了问题,IP 地址和 DNS 配置不对。
我给他调整好之后,看着网页一下子就刷出来了,他那高兴的样子,我到现在都还记得。
在这第三章里,关于互联网的安全问题也不能忽视。
就像我们现实生活中要锁好家门一样,在互联网上我们也得保护好自己的信息。
比如设置强密码,不随意点击不明链接,定期更新软件等等。
不然,就可能被黑客“钻了空子”,造成损失。
还有网络拓扑结构,什么星型、总线型、环型等等。
这就好比不同的城市规划,有的是中心辐射型,有的是一条大路贯穿到底。
人民邮电信管英语第三版参考答案

Unit 1【Ex1.】根据课文内容,回答以下问题。
1.In human terms and in the broadest sense, information is anything that you are capable of perceiving. 2.It includes written communications, spoken communications, photographs, art, music, and nearly anything that is perceptible.3.If we consider information in the sense of all stimuli as information, then we can’t really find organization in all cases.4.No.5.Traditionally, in libraries, information was contained in books, periodicals, newspapers, and other types of recorded media. People access it through a library’s catalog and with the assistance of indexes, in the case of periodical and newspaper articles.6.Computerized “information systems”.7.The problem for most researchers is that they have yet to discover the organizing principles that are designed to help them find the information they need.8.For library materials, the organizing principle is a detailed subject classification system available for searching in an online “catalog”.9.The one thing common to all of these access systems is organization.10.No, it isn’t.【Ex2.】根据给出的汉语词义和规定的词类写出相应的英语单词。
Chapter3章课件

Transparent bridges(透明网桥)
In 1987, ISO approved it as an international standard. IEEE subdivided the data link layer into two sublayers:
LLC (Logical Link Control) MAC (Media Access Control)
Forwarding Learning(static forwarding tables, dynamic forwarding tables) :
How to build the dynamic forwarding tables? flooding、adding entries
Router (路由器)
Chapter 3 Underlying Technologies
— Network Protocol Analysis
School of Computer and Communication Engineering
Objectives
To discuss the need and use of connecting devices such as repeaters (hubs), bridges (two-layer switches), and routers (threelayer switches).
CCNA第3章测验答案

Introduction to Networks
3.1.1规则
哪个过程用于将一个消息放入另一消息内以从源传输到目
的地?
正确 您的
响应 响应
流量控制
封装
访问控制
解码
封装是将一种消息格式放入另一种消息格式的过程。 例如,一个数据包在封装成帧时如 何将其完整放入数据字段中。
此试题参考以下领域的内容:
网络协议在硬件或软件或两者中实施。它们在协议栈的不同层中交互。协议与网络设备 的安装情况无关。本地和远程网络中的源设备和目的设备之间交换信息时需要使用网络 协议。
此试题参考以下领域的内容:
Introduction to Networks
3.2.1协议
列有关
正确 您的
响应 响应
前三个OSI层描述TCP/IP网络层提供的相同常规服务。
4.以太网从IP获取数据包,并将其格式化以供传输。
此试题参考以下领域的内容:
Introduction to Networks
3.2.1协议
只有在远程网络中的设备之间交换消息时才需要使用网络协议。
网络协议定义了所用硬件类型及其如何在机架中安装。
网络协议都是在TCP/IP的网络接入层发挥作用。
网络协议定义了消息在源地址和目的地址之间如何交换。
TCP/IP网络接入层与OSI网络层具有类似的功能。
TCP/IP传输层与OSI第4层提供类似的服务和功能。
OSI第7层和TCP/IP应用层提供相同的功能。
TCP/IP网络层的功能与OSI网络层相同。TCP/IP模型和OSI模型的传输层具有相同 的功能。TCP/IP应用层包括OSI第5、6和7层的相同功能。
此试题参考以下领域的内容:
计算机网络第1-3章部分课后习题参考答案

第一章概述1-03 试从多个方面比较电路交换、报文交换和分组交换的主要优缺点。
答:(1)电路交换的优点:适用于连续传送大量数据。
电路交换的缺点:电路建立时间长,线路利用率低。
(2)报文交换的优点:采用了存储转发技术,线路使用率高。
报文交换的缺点:延迟长。
(3)分组交换的优点:高效——动态分配传输带宽,对通信链路是逐段占用。
灵活——以分组为传送单位和查找路由。
迅速——不必先建立连接就能向其他主机发送分组。
可靠——保证可靠性的网络协议;分布式的路由选择协议使网络有很好的生存性。
分组交换的缺点:分组在各结点存储转发时需要排队,这就会造成一定的时延。
同时分组必须携带的首部(里面有必不可少的控制信息)也造成了一定的开销。
1-12 因特网的两大组成部分(边缘部分与核心部分)的特点是什么?它们的工作方式各有什么特点?答:边缘部分:由所有连接在因特网上的主机组成。
由用户直接使用。
核心部分:由大量网络和连接这些网络的路由器组成。
为边缘部分提供服务。
工作方式:(1)边缘部分:采用客户服务器方式和对等通信方式。
(2)核心部分:采用电路交换、分组交换。
1-13 客户服务器方式与对等通信方式的主要区别是什么?有没有相同的地方?答:相同之处:两者所描述的都是进程之间服务和被服务的关系。
1-18 假设信号在媒体上的传播速度为2×108m/s.媒体长度L分别为:(1)10cm(网络接口卡)(2)100m(局域网)(3)100km(城域网)(4)5000km(广域网)试计算出当数据率为1Mb/s和10Gb/s时在以上媒体中正在传播的比特数。
解:即求传播时延带宽积。
结果见书上课后参考答案。
1-25 试举出日常生活中有关“透明”这种名词的例子。
答:这种例子有很多。
比如日常家用电器,我们并不知道家用电器具体工作原理,但只要清楚某按钮可以完成什么功能,就可以使用家用电器为日常生活服务。
第二章物理层2-04 试解释以下名词:数据,信号,模拟数据,模拟信号,基带信号,带通信号,数字数据,数字信号,码元,单工通信,半双工通信,全双工通信,串行传输,并行传输。
网络科学导论课后题答案

网络科学导论课后题答案
1. What is the purpose of the OSI reference model?
答:OSI参考模型的目的是为了提供一种标准的方法来描述网络通信的过程,以便不同的网络设备之间可以互相通信。
它将网络通信过程分解为7个不同的层,每个层都有自己的功能,从而使网络通信更加有效和可靠。
2. What is the purpose of the TCP/IP protocol suite?
答:TCP/IP协议套件的目的是为了提供一种标准的方法来实现网络通信,它包括了一系列的协议,比如IP协议、TCP协议、UDP协议等,它们可以帮助计算机之间进行数据传输和通信。
它还可以帮助计算机之间进行路由选择,以及控制网络流量。
3. What is the purpose of the Internet Protocol (IP)?
答:Internet协议(IP)的目的是为了提供一种标准的方法来实现网络通信,它可以帮助计算机之间进行数据传输和通信。
它还可以帮助计算机之间进行路由选择,以及控制网络流量。
它还可以帮助计算机之间进行地址分配,以及提供一种机制来确保数据包能够从一台计算机发送到另一台计算机。
2007英语一text3 -回复

2007英语一text3 -回复题目:生活中的互联网[2007英语一text3]是关于生活中的互联网的一篇文章。
互联网在过去的几十年里,对人们的生活方式和社会发展产生了深远的影响。
本文将以互联网的发展、应用和影响为主线,一步一步回答题目。
第一部分:互联网的发展互联网最初是冷战时期美国军方为了实现信息的快速通信而建立的。
随后互联网开始融入到学术界和商业领域,并逐渐发展成为了人们日常生活中不可或缺的一部分。
1. 互联网的起源和发展- 在20世纪60年代末,美国军方为了在冷战中维持高效的信息传输系统而开发了互联网。
- 经过几十年的发展,互联网的使用者逐渐从军方和学术界扩大到了普通大众。
2. 互联网的普及- 随着计算机的普及和互联网技术的不断进步,互联网已经成为全球数十亿人的日常生活和工作必需品。
- 我们可以通过互联网获取信息、进行在线购物、社交媒体互动等。
第二部分:互联网的应用3. 互联网的娱乐应用- 互联网为人们提供了丰富多样的娱乐活动,如在线游戏、影视娱乐、音乐、电子书等。
- 人们可以通过互联网轻松找到他们感兴趣的娱乐内容,并与朋友分享。
4. 互联网的商业应用- 互联网为企业提供了广阔的发展机会,如电子商务、在线支付、数字营销等。
- 很多传统企业转型为互联网企业,改变了商业模式和消费者购物方式。
5. 互联网的教育应用- 互联网已经成为教育领域的重要工具,帮助人们获取知识、提升技能。
- 学生可以通过在线课程、教育平台等方式进行远程学习,并与老师和同学进行交流。
第三部分:互联网对生活的影响6. 互联网的便利性- 互联网让人们的生活更加方便。
我们可以随时随地通过手机或电脑上网,完成各种任务,如购物、学习、娱乐等。
- 互联网为人们提供了更多的选择和可能性,节省了时间和精力。
7. 互联网的社交影响- 互联网极大地改变了人们之间的交流方式。
社交媒体使得人们可以随时联系朋友和家人,分享生活中的点滴。
- 互联网也提供了一个平台,让人们可以参与到更广泛的社交活动中,结识新朋友,扩展社交圈。
DUT-Chapter3

router 1
LAN1
WAN
IP TCP , UDP
router 2 LAN2
host B
AP3 AP4
Chapter 3 outline
3.1 Transport-layer services
3.2 Multiplexing and demultiplexing
3.3 Connectionless transport: UDP
more than one transport protocol available to apps
Internet: TCP and UDP
application transport network data link physical
application transport network data link physical
Chapter 3: Transport Layer
Our goals:
understand principles behind transport layer services:
multiplexing/demultipl exing
reliable data transfer
flow control
Transport Layer 3-3
Transport vs. network layer
network layer: logical
communication between hosts
transport layer: logical
communication between processes
transport protocols run in end systems
计算机网络第3版课后题参考答案

第1章计算机网络的基本概念一、填空题(1)按照覆盖的地理范围,计算机网络可以分为局域网、城域网、和广域网。
(2)ISO/OSI参考模型将网络分为物理层、数据链路层、网络层、传输层、会话层、表示层和应用层。
(3)建立计算机网络的主要目的是:资源共享和在线通信。
二、单项选择题(1)在TCP/IP体系结构中,与OSI参考模型的网络层对应的是:(B )A.主机-网络层B.互联层C.传输层D.应用层(2)在OSI参考模型中,保证端-端的可靠性是在哪个层次上完成的( C )A.数据链路层B.网络层C.传输层D.会话层三、问答题计算机网络为什么采用层次化的体系结构【要点提示】采用层次化体系结构的目的是将计算机网络这个庞大的、复杂的问题划分成若干较小的、简单的问题。
通过“分而治之”,解决这些较小的、简单的问题,从而解决计算机网络这个大问题(可以举例加以说明)。
第2章以太网组网技术一、填空题(1)以太网使用的介质访问控制方法为CSMA/CD。
(2)计算机与10BASE-T集线器进行连接时,UTP电缆的长度不能超过100米。
在将计算机与100BASE-TX集线器进行连接时,UTP电缆的长度不能超过100米。
(3)非屏蔽双绞线由4对导线组成,10BASE-T用其中的2对进行数据传输,100BASE-TX用其中的2对进行数据传输。
二、单项选择题(1)MAC地址通常存储在计算机的( B )A.内存中B.网卡上C.硬盘上D.高速缓冲区(2)关于以太网中“冲突”的描述中,正确的是( D )A.冲突时由于电缆过长造成的B.冲突是由于介质访问控制方法的错误使用造成的C.冲突是由于网络管理员的失误造成的D.是一种正常现象(3)在以太网中,集线器的级联( C )A.必须使用直通UTP电缆B.必须使用交叉UTP电缆C.必须使用同一种速率的集线器D.可以使用不同速率的集线器(4) 下列哪种说法是正确的( A )A.集线器可以对接收到的信号进行放大B.集线器具有信息过滤功能C.集线器具有路径检测功能D.集线器具有交换功能第3章交换与虚拟局域网一、填空题(1)以太网交换机的数据转发方式可以分为直接交换、存储转发交换、和改进的直接交换3类。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Review Questions1. If a router interface is congested, which protocol in the IP suite is used to tell neighbor routers?A. RARPB. ARPC. ICMPD. IPE. TCP2. What valid host range is the IP address 172.16.10.22 255.255.255.240 a part of?A. 172.16.10.20 through 172.16.10.22B. 172.16.10.1 through 172.16.10.255C. 172.16.10.16 through 172.16.10.23D. 172.16.10.17 through 172.16.10.31E. 172.16.10.17 through 172.16.10.303. What range of addresses can be used in the first octet of a Class B network address?A. 1–126B. 1–127C. 128–190D. 128–191E. 129–192F. 192–2204. Which of the following is true? (Choose all that apply.)A. IP is connectionless and provides routing.B. ARP is used to find an IP address of a host.C. UDP is connectionless.D. TCP is connection oriented.E. TCP uses windowing as a flow control method.F. ICMP is used to manage data to routers.G. ARP is used to find a hardware address from a known IP address.5. Assuming a default mask, which two pieces of information can be derived from the IP address 172.16.25.11?A. It is a Class C address.B. It is a Class B address.C. The network address is 172.D. The network address is 172.16.25.E. The host portion is 25.11.6. What protocol is used to find the hardware address of a local device?A. RARPB. ARPC. IPD. ICMPE. BootP7. What are the two most common elements of a request/reply pair with ICMP messages when using the Ping program?A. Echo replyB. Echo requestC. Destination unreachableD. Source quench8. Which class of IP address provides a maximum of only 254 host addresses per network ID?A. Class AB. Class BC. Class CD. Class DE. Class E9. What is the broadcast address of the subnet address 172.16.8.159 255.255.255.192?A. 172.16.255.255B. 172.16.8.127C. 172.16.8.191D. 172.16.8.25510. What is the broadcast address of the subnet address 172.16.99.99 255.255.192.0?A. 172.16.99.255B. 172.16.127.255C. 172.16.255.255D. 172.16.64.12711. If you wanted to have 12 subnets with a Class C network ID, which subnet mask would you use?A. 255.255.255.252B. 255.255.255.248C. 255.255.255.240D. 255.255.255.25512. Which two protocol tools use ICMP?A. TelnetB. PingC. ARPD. Traceroute13. Which of the following is a true statement?A. MAC address broadcasts are all zeros.B. MAC addresses are defined at the Physical layer.C. MAC address are used by bridges and switches to make forwarding/filtering decisions.D. IP addresses allow a flat address scheme, whereas MAC addresses are hierarchal.14. What is the protocol and what is the second part of the network address 172.16.0.1 255.255.0.0?A. IPX, MAC addressB. IP, private Class C directed broadcastC. Private IP address, node numberD. Private IP address, directed broadcast15. What is the result of using a hierarchical addressing scheme?A. Increased number of addressesB. Decreased amount of routers neededC. Increased memory usage on routersD. No routing tables needed on routers16. If you need to have a Class B network address subnetted into exactly 510 subnets, what subnet mask would you assign?A. 255.255.255.252B. 255.255.255.128C. 255.255.0.0D. 255.255.255.19217. Which of the following is a correct ping to a host?A. Router>ping 172.16.0.0B. Router#ping 172.16.25.255C. Router>ping 172.16.10.2D. Router#ping 172.16.2.25618. If you have a 12-bit subnet mask, which of the following is a valid host range for the IP address 172.16.10.33?A. 1–63B. 33–46C. 33–47D. 1–25419. If you are using a Class C network ID with two subnets and need 31 hosts per network, which of the following masks should you use?A. 255.255.255.0B. 255.255.255.192C. 255.255.255.224D. 255.255.255.24820. Which of the following are true? (Choose two.)A. TCP is connection-oriented but doesn’t use flow control.B. IP is not necessary on all hosts that use TCP.C. ICMP must be implemented by all TCP/IP hosts.D. ARP is used to find a hardware address from a known IP address.21. Which of the following are the Internet Protocol (IP) protocols used at the Application layer of the OSI model? (Choose three.)A. IPB. TCPC. TelnetD. FTPE. TFTPF. Ping22. How many subnets and hosts can you get from the network 192.168.254.0/26?A. 4 networks with 64 hostsB. 2 networks with 62 hostsC. 254 networks with 254 hostsD. 1 network with 254 hosts23. You have the network 172.16.10.0/24. How many subnets and hosts are available?A. 1 subnet with 10 hostsB. 1 subnet with 254 hostsC. 192 subnets with 10 hostsD. 254 subnets with 254 hosts24. What mask would you assign to the network ID of 172.16.0.0 if you needed more than 300 hosts with each subnet but fewer than 500?A. 255.255.255.0B. 255.255.254.0C. 255.255.252.0D. 255.255.0.025. You are the network administrator for , and a user cannot reach the corporate server from their remote office. The IP address of the host is 192.168.254.10/24, the default gateway of the host is 192.168.254.1, and the server is 192.168.10.10/24. You have the user type the following from a DOS prompt: ping 192.168.254.1; this is unsuccessful. You then have the user type: ping 127.0.0.1; this is also unsuccessful. What could the problem be?A. The router is down.B. The server is down.C. TCP/IP is not initialized on the host.D. The Ethernet cable is unplugged from the host.Answers to Review Questions1. C. Internet Control Message Protocol (ICMP) is used to send redirects back to an originating router.2. E. First start by using the 256 mask, which in this case is 256 240 16.The first subnet is 16; the second subnet is 32. This host must be in the 16 subnet; the broadcast address is 31, and the valid host range is 17 30.3. D. A Class B network is defined in the first octet with the numbers 128–191.4. A, C, D, E, G. UDP is connectionless, TCP is connection-oriented and uses windowing, and ARP is used to find a hardware address from a known IP address.5. B, E. 172.16.25.11 is a Class B address, and the host portion is 25.11.6. B. Address Resolution Protocol (ARP) is used to find the hardware address from a known IP address.7. A, B. The Ping program uses ICMP echo request and echo replies to check a host on an internetwork.8. C. A Class C network address only has 8 bits for defining hosts. 28 2 254.9. C. The two subnets provided by this Class B mask are 64 and 128. The broadcast address for the 128 subnet is 191.10. B. First start with 256 mask or, in this case, 256 192 64. 64 is the first subnet; 128 is the second subnet. This host is in the 64–subnet range, the broadcast address is 127.255, and the valid host range is 64.1–127.254.11. C. Take a look at the answers and see which subnet mask will give you what you need for subnetting. 252 gives you 62 subnets, 248 gives you 30 subnets, 240 gives you 14 subnets, and 255 is invalid. Only the third option (240) gives you what you need.12. B, D. ICMP is used by both Ping and Traceroute.13. C. MAC addresses are a flat address scheme and used by bridges/switches to make forwarding/filtering decisions. Routers use IP addresses, which is a hierarchical addressscheme, to make routing decisions.14. C. 172.16–31.0.0 is a private IP address that cannot be routed through the Internet. 172.16.0.1 is a host address, not a broadcastaddress. The network broadcast address for this address would be 172.16.255.255.15. A. The designers created a hierarchical addressing scheme when they created the IP address so that more addresses would be available to each network.16. B. If you use the mask 255.255.255.0, that only gives you eight subnet bits, or 254 subnets. You are going to have to use one subnet bit from the fourth octet, or255.255.255.128. This is 9 subnet bits (29 2 510).17. C. The only valid host address listed is 172.16.10.2.18. B. The question is nothing short of stupid (I didn’t think of it!). What Cisco wants you to do is to add “12 bits” to a default mask. Since this is a Class B address, the default mask is 255.255. Adding 12 bits would make the mask 255.255.255.240. The host is located in the 10.32 subnet with the next subnet being 10.48. The valid host range is then 33–46 because 47 is the broadcast address.19. B. The Class C mask of 255.255.255.192 provides two subnets (four if you are using subnet-zero), each with 62 hosts. 255.255.255.224 only provides 30 hosts per subnet. 20. C, D. ICMP must be implemented by all TCP/IP hosts, and ARP is used to find a hardware address from a known IP address.21. C, D, E. Telnet, File Transfer Protocol (FTP), and Trivial FTP are all Application layer protocols. IP is a Network layer protocol, as well as Ping. Transmission Control Protocol (TCP) is a Transport layer protocol.22. B. I bet you struggled with this one, although it isn’t difficult. But the answers will make you think. First, the 254-host answers are not even close, so you have a 50/50 chance between the four-network and two-network options. The part you probably thought about the most is whether Cisco is using subnet-zero. This would provide four networks instead of two. Makes sense. However, Cisco does not consider subnet-zero valid on any of their exams. In addition, you cannot get 64 hosts with this mask, only 62 hosts per subnet, regardless of whether you are using subnet-zero or not, which makes the fournetwork answer completely wrong.23. D. Easy question, easy answer. The third octet is used for all subnets, and the fourth octet is used only for hosts. 8 bits for subnetting, 8 bits for hosts.24. B. This one takes some thought. 255.255.255.0 would give you 254 hosts each with 254 subnets. Doesn’t work for this question. 255.255.254.0 would provide 126 subnets, each with 510 hosts; the second option looks good. 255.255.252.0 is 62 subnets, each with 1022 hosts. So 255.255.254.0 is the only correct answer.25. C. 127.0.0.1 is called the loopback address and is used for diagnostics on a host. If you cannot ping this address, then you have a problem with the IP stack on the host.。
