CCNA(640-802)题库V104.3 拖图题
思科认证考试题库

CCNA640-802 V13题库试题分析题库讲解:吴老师(艾迪飞CCIE实验室首发网站:1. What are two reasons that a network administrator would use access lists? (Choose two.)A. to control vty access into a routerB. to control broadcast traffic through a routerC. to filter traffic as it passes through a routerD. to filter traffic that originates from the routerE. to replace passwords as a line of defense against security incursionsAnswer: AC解释一下:在VTY线路下应用ACL,可以控制从VTY线路进来的telnet的流量。
也可以过滤穿越一台路由器的流量。
2. A default Frame Relay WAN is classified as what type of physical network?A. point-to-pointB. broadcast multi-accessC. nonbroadcast multi-accessD. nonbroadcast multipointE. broadcast point-to-multipointAnswer: C解释一下:在默认的情况下,帧中继为非广播多路访问链路。
但是也可以通过子接口来修改他的网络的类型。
3.Refer to the exhibit. How many broadcast domains exist in the exhibited topology?A. oneB. twoC. threeD. fourE. fiveF. sixAnswer: C解释一下:广播域的问题,在默认的情况下,每个交换机是不能隔离广播域的,所以在同一个区域的所有交换机都在同一个广播域中,但是为了减少广播的危害,将广播限制在一个更小的范围,有了VLAN的概念,VLAN表示的是一个虚拟的局域网,而他的作用就是隔离广播。
Cisco CCNA 认证考试最新真题

Cisco CCNA 认证考试最新真题体验1. The command frame-relay map ip 10.121.16.8 102 broadcast was entered on the router. Which of the following statements is true concerning this command?A.This command should be executed from the global configuration mode.B.The IP address 10.121.16.8 is the local router port used to forward data.C.102 is the remote DLCI that will receive the information.D.The broadcast option allows packets, such as RIP updates, to be forwarded across the PVC2. While troubleshooting a network connectivity problem, a technician observes steady link lights on both the workstation NIC and the switch port to which the workstation is connected. However, when the ping command is issued from the workstation, the output message "Request timed out." is displayed. At which layer of the OSI model does the problem most likely exist?A.the session layerB.the network layerC.the data link layerD.the access layer3. In order to allow the establishment of a Telnet session with a router, which set of commands must be configured?A.router(config)# line console 0router(config-line)# enable password ciscoB.router(config)# line console 0router(config-line)# enable secret ciscorouter(config-line)# loginC.router(config)# line console 0router(config-line)# password ciscorouter(config-line)# loginD.router(config)# line vty 0router(config-line)# password cisco router(config-line)# login4. On point-to-point networks, OSPF hello packets are addressed to which address?A.127.0.0.1B.192.168.0.5C.224.0.0.5D.254.255.255.2555. What should be part of a comprehensive network security plan?A.Allow users to develop their own approach to network security.B.Physically secure network equipment from potential access by unauthorized individualsC.Encourage users to use personal information in their passwords to minimize the likelihood of passwords being forgottenD.Delay deployment of software patches and updates until their effect on end-user equipment is well known and widely reported6. During startup, the router displays the following error message:boot: cannot open "flash:" What will the router do next?A.Because of damaged flash memory, the router will fail the POST.B.It will attempt to locate the IOS from a TFTP server. If this fails, it will initiate the setup dialogC.It will attempt to locate the IOS from a TFTP server. If this fails, it will load a limited IOS from ROM.D.It will attempt to locate the configuration file from a TFTP server. If this fails, it will initiate the setup dialog7. At which OSI layer is a logical path created between two host systems?A.sessionB.transportworkD.physical8. A routing protocol is required that supports:1) routing update authentication2) an addressing scheme that conserves IP addresses3) multiple vendors4) a network with over 50 routersWhich routing protocol fulfills these requirements?A.RIPv1B.RIPv2C.EIGRPD.OSPF9. When a new trunk is configured on a 2950 switch, which VLANs by default are allowed over the trunk link?A.no VLANsB.all VLANsC.only VLANs 1 - 6D.only the VLANs that are specified when creating the trunk10. Which protocol provides a method of sharing VLAN configuration information between switches?A.VTPB.STPC.ISLD.802.1QDBDCB CCDBA博主的更多文章>>CCNA第一学期《Final Examination》2009-02-27 08:58:47 标签:CCNA[推送到技术圈]1请参见图示。
完整版CCNA测试题库及答案

完整版CCNA测试题库及答案描述载波侦听多路由访问/冲突检测(CSMA/CD)的工作原理。
CSMA/CD是一种帮助设备均衡共享带宽的协议,可避免两台设备同时在网络介质上传输数据。
虽然他不能消除冲突,但有助于极大的减少冲突,进而避免重传,从而提高所的设备的数据传输效率。
区分半双工和全双工通信。
并指出两种方法的需求。
与半双工以太网使用一对导线不同,全双工以太网使用两队导线,全双工使用不同的导线来消除冲突,从而允许同时发送和接收数据,而半双工可接收或发送数据,但不能同时接收和发送数据,且仍会出现冲突。
要使用全双工,电缆两端的设备都必须支持全双工,并配置成一全双模式运行。
描述MAC地址的组成部分以及各部分包含的信息。
MAC(硬件)地址时一种使用十六进制表示的地址,长48位(6B)。
其中前24位(3B)称为OUI(Organizationally Unique Idebtifier,组织唯一表示符),有IEEE分配给NIC制造商;余下的部分呢唯一地标识了NIC识别十进制数对应的二进制值和十六进制值。
用这三种格式之一表示的任何数字都可以转换为其他两种格式,能够执行这种转换对理解IP地址和子网划分至关重要。
识别以太网帧中与数据链路层相关的字段。
在以太网中,与数据链路层相关的字段包括前导码,帧其实位置分隔符,目标MAC地址,源MAC地址,长度或者类型以及帧校验序列。
识别以太网布线相关的IEEE标准。
这些标准描述了各种电缆类型的功能和物理特征,包括(但不限于)10Base2、10Base5和10BaseT。
区分以太网电缆类型及其用途。
以太网电缆分3种:直通电缆,用于将PC或路由器的以太网接口连接到集线器或交换机;交叉电缆。
用于将集线器连接到集线器,集线器连接到交换机,交换机连接到交换机以及PC连接到PC;反转电缆,用于PC和路由器或交换机之间建立控制台连接。
描述数据封装过程及其在分组创建中的作用。
数据封装指的是在OSI模型各层给数据添加信息的过程,也成为分组创建。
CCNA题库V104.2 补充新题 64Q(题库改版后新题目)

学网络技术去鸿鹄论坛命运的改变从技术开始鸿鹄团队致力于为每一位网络技术爱好者提供帮助有事您发帖,斑竹为您跑腿,给您答疑。
CCNA题库战报交流群:82327397欢迎备考CCNA的朋友加入,一起讨论交流,通过CCNA考试!CCNA最新题库/最新战报发布区:/forum-261-1.htmlCCNA考试代号:640-802考试时间:中文110分钟英文110+30=140分钟通过分数:825题库版本:V104.2Exam AQUESTION 1Which two commands correctly verify whether port security has been configured on port FastEthernet 0/12on a switch?(choose two)A.SW1#show swithport port-security interface FastEthernet 0/12B.SW1# show swithport port-secure interface FastEthernet 0/12C.SW1# show port-secure interface FastEthernet 0/12D.SW1#show running-configAnswer: CDQUESTION 2Which component of VPN technology ensures that data can be read only by its intended recipient?A.data integrity B.encryption C.key exchange D.authenticationAnswer: DQUESTION 3Refer to the exhibit.What is the effect of the configuration that is shown?A.It tells the router or switch to try establish an SSH connection first and if that fail to use telnet.B.Itconfigures a cisco network device to use the SSH protocol on incoming communications via the virtualterminal ports.C.It allows seven failed login attempts before the VTY lines are temporarily shutdown.D.It configures the virtual terminal lines with the password 030752180500.E.It configures SSH globally for all logins.Answer: BQUESTION 4Which IPV6 routing protocol uses multicast group FFO2::8 to send updates?A.RIPng B.OSPFv3C.IS-IS for IPv6D.staticAnswer: Cb b s .h h 010.co mWhich of the following are true regarding the debug output shown in the graphic?(choose two)A.This router was configured with the commands:RtrA(config)#router ripRtrA(config-router)#version 2RtrA(config-router)#network 172.16.0.0RtrA(config-router)#network 10.0.0.0B.This router was configured with the commands:RtrA(config)#router ripRtrA(config-router)#network 172.16.0.0RtrA(config-router)#network 10.0.0.0C.etwork 10.0.0.0 will be displayed in the routing table.work 192.168.168.0 will be displayed in the routing table.E.This router was configured with the commands:RtrA(config)#router ripRtrA(config-router)#network 192.168.1.0RtrA(config-router)#network 10.0.0.0RtrA(config-router)#network 192.168.168.0F.split-horizon was disabled on this router.Answer: BCQUESTION 6The network administrator is asked to configure 113 point-to-point links.Which IP addressing scheme best defines the address range and subnet mask that meet the requirement and waste the fewest subnet and host addresses?A.10.10.0.0/18 subnetted with mask 255.255.255.252B.10.10.0.0/25 subnetted with mask 255.255.255.252C.10.10.0.0/24 subnetted with mask 255.255.255.252D.10.10.0.0/23 subnetted with mask 255.255.255.252E.10.10.0.0/16 subnetted with mask 255.255.255.252Answer: Db b s .h h 010.co mVLAN 3 is not yet configured on your switch.What happens if you set the switchport access vlan 3commmand interface configuration mode?A.The command is accepted and the respective VLAN is added to vlan dat.B.The command is rejected.C.The command is accepted and you must configure the VLAN manually.D.The port turns amber.Answer: AQUESTION 8Which parameter can be tuned to affect the selection of a static route as a backup.when a dynamic protocol is also being used?A.link bandwidth B.hop count C.link costD.administrative distanceE.link delayAnswer: DQUESTION 9Refer to the exhibit. In the Frame Relay network, which ip address would be assigned to the interfaces with point-to-poin PVCs?A.DLCI 16:192.168.10.1/24DLCI 17:192.168.10.2/24DLCI 99:192.168.10.3/24DLCI 28:192.168.10.4/24b b s .h h 010.co mB.DLCI 16:192.168.10.1/24DLCI 17:192.168.11.1/24DLCI 99:192.168.10.2/24DLCI 28:192.168.11.2/24C.DLCI 16:192.168.10.1/24DLCI 17:192.168.11.1/24DLCI 99:192.168.12.1/24DLCI 28:192.168.13.1/24D.DLCI 16:192.168.10.1/24DLCI 17:192.168.10.1/24DLCI 99:192.168.10.2/24DLCI 28:192.168.10.3/24Answer: BQUESTION 10Why will a switch never learn a broadcast address?A.Broadcast frames are never sent to swiches.B.Broadcast addresses use an incorrect format for the switching table.C. A broadcast address will never be the source address of a frame.D.Broadcasts only use network layer addressing.E.A broadcast frame is never forwarded by a switch.Answer: CQUESTION 11Wich command can you use to manually assign a static IPV6 address to a muter interface?A.ipv6 address PREFIX_1::1/64B.ipv6 autoconfig 2001:db8:2222:7272::72/64C.ipv6 autoconfigD.ipv6 address 2001:db8:2222:7272::72/64Answer: DQUESTION 12The EIGRP configuration in the Glencoe router uses a single network statement.From the output shown in the graph would advertise these networks in EIGRP?b b s .h h 010.co mwork 172.26.168.0 area 478work 172.26.0.0work 172.26.168.128 0.0.0.127work 172.26.168.128 area 478Answer: BQUESTION 13Which IPsec security protocol should be used when confidentiality is required?A.AH B.MD5C.PSK D.ESPAnswer: DQUESTION 14What is the function of the command switchport trunk native vlan 999 on a…(此处文字不清楚).?A.It designates VLAN 999 for untagged traffic.B.It blocks VLAN 999 traffic from passing on the trunk.C.It creates a VLAN 999 interface.D.It designates VLAN 999 as the default for all unkown tagged traffic.Answer: DQUESTION 15Which command can be used from a PC to verfy the connectivity between host that connect thro…(字体不清)…?A.tracert address B.ping address C.arp addressD.traceroute addressAnswer: AQUESTION 16In which solution is a router ACL used?A.protecting a server frome unauthorized accesB.controlling path selection,based on the route metricC.reducing router CPU utilizationD.filterring packets that are passing through a routerAnswer: DQUESTION 17Which statement is true, as relates to classful or classless routing?b b s .h h 010.co mA.RIPV1 and OSPF are classless routing protocols.B.Classful routing protocols send the subnet mask in routing updates.C.Automatic summarization at classful boundaries can cause problems on disc……D.EIGRP and OSPF are classful routing protocols and summarize routes by def……Answer: CQUESTION 18A router has two FastEthernet interfaces and needs to connect to four vlans in the local network.How can you accomplish this task,using the fewest physical interfaces and without decreasing network performance?A.Add two more FastEthernet interfaces.B.Add a second router to handle the vlan traffic.e a hub to connect the four vlans with a FastEthernet interface on router.D.Implement a router-on-a-stick configuration.Answer: DQUESTION 19Refer to the exhibit.How many broadcast domains are configured on switch2?A.5B.20C.4D.1Answer: CQUESTION 20What is the effect of using the service password-encryption command?A.nly passwords configured after the command has been entered will be encrypted.B.Only the enable password will be encrypted.C.Only the enable secret password will be encryptedD.It will encrypt the secret password and remove the enable secret password from the configuration.E.It will encrypt all current and future passwords.Answer: Eb b s .h h 010.co mQUESTION 21Refer to the exhibit.A technician has installed SwithchB and needs to configure it for remote access from the management workstation connected SwitchA Which set of commands is required to accomplish this task?A.SwitchB(config)#interface FastEthernet 0/1SwitchB(config)#ip address 192.168.8.252 255.255.255.0SwitchB(config)#no shutdownB.SwitchB(config)#ip default-gateway 192.168.8.254SwitchB(config)#interface vlan 1SwitchB(config)#ip address 192.168.8.252 255.255.255.0SwitchB(config)#no shutdown C.SwitchB(config)#interface vlan 1SwitchB(config)#ip address 192.168.8.252 255.255.255.0SwitchB(config)#ip default-gateway 192.168.8.254 255.255.255.0SwitchB(config)#no shutdownD.SwitchB(config)#ip default-network 192.168.8.254SwitchB(config)#interface vlan 1SwitchB(config)#ip address 192.168.8.252 255.255.255.0SwitchB(config)#no shutdownAnswer: BQUESTION 22Refer to the exhibit.The speed of all serial links is E1 and the speed of the all Ethernet links is 100Mb/s.A static route will be established on the Manchester router to the direct traffic toward the internet over the most direct path available.What configuration on the Manchester router will establish a router toward the internet for traffic that originates from workstation on the Manchester LAN?b b s .h h 010.co mA.ip route 0.0.0.0 255.255.255.0 172.16.100.2B.ip route 0.0.0.0 255.255.255.252 128.107.1.1C.ip route 0.0.0.0 0.0.0.0 128.107.1.1D.ip route 0.0.0.0 0.0.0.0 172.16.100.1E.ip route 0.0.0.0 255.255.255.255 172.16.100.2F.ip route 0.0.0.0 0.0.0.0 172.16.100.2Answer: FQUESTION 23What Frame Relay mechanism is used to build the map illustrated in the accompanying graphic?A.inverse multiplexingB.LMI mapingC.Inverse ARPD.ARPE.Proxy ARPAnswer: CQUESTION 24Refer to the exhibit.A network engineer is troubleshooting an internet connectivity problem on the computer.What is causing the problem?b b s .h h 010.co mA.wrong DNS serverB.wrong default gatewayC.incorrect IP addressD.incorrect subnet maskAnswer: CQUESTION 25How many broadcast domains are shown in the graphic assuming only the default vlan is configured on the switches?b b s .h h 010.co mA.oneB.sixC.twelveD.twoAnswer: AQUESTION 26How dose a DHCP server dynamically assign IP address to host?A.Addresses are allocated after a negotiation between the server and the host to determine the length ofthe agreement.B.Addresses are assigned for a fixed period of time.At the end of period,a newquest for an address mustbe made ,and another address is then assigned.C.Addresses are leased to host.A host will usually keep the same address by periodically contacting theDHCP sever to renew the lease.D.Addresses are permanently assigned so that the host uses the same address at all times.Answer: CQUESTION 27Which type of EIGRP route entry describes a feasible successor?A. a primary route,stored in the routing table B. a backup route,stored in the routing table C. a backup route,stored in the topology table D.a primary route,stored in the topology tableAnswer: CQUESTION 28What is the purpose of the inverse ARP?A.to map a known DLCI to an IP addressB.to map a known IP address to a MAC addressC.to map known SPID to a MACaddressD.to map a known DLCI to a MAC addressE.to map a known IP address to a SPID.F.to map a known MAC address to an IP addressAnswer: AQUESTION 29What is the default maximum number of equal-cost paths that can be placed into the routing of a cisco OSPF router?A.16B.2C.unlimitedD.4Answer: Db b s .h h 010.co mQUESTION 30Which IPV6 routing protocol uses multicast group FF02::9 to send updates?A.RIPng B.OSPFv3C.staticD.IS-IS for IPv6Answer: AQUESTION 31What are two benefits of using NAT?(choose two)A.NAT protects network security because private networks are not advertised.B.NAT accelerates the routing process because no modifications are made on the packets.C.Dynamic NAT facilitates connections from the outside of the network.D.NAT facilitates end-to-end communication when IPsec is enable.E.NAT eliminates the need to re-address all host that require extemal access.F.NAT conserves addresses through host MAC-level multiplexing.Answer: AEQUESTION 32Which three statements about RSTP are true?(choose three)A.RSTP significantly reduces topology reconverging time after a link failure.B.RSTP expends the STP port roles by adding the alternate and backup roles.C.RSTP port atates are blocking,discarding,learing,or forwarding.D.RSTP also uses the STP proprsal-agreement sequence.E.RSTP use the same timer-baseed process as STP on point-to-point links.F.RSTP provides a faster transition to the forwarding state on point-to-point links than STP does.Answer: ABFQUESTION 33Refer to the exhibit.The serial0/0 interface of the Tampa router connects the Oriando router.Which two statements are true about the connection between these two routers?(choose two)b b s .h h 010.co mA.The only device with which the Tampa router will negotiate a data link is the Orlando router.B.The link is addressed on the *zero*subnet 10.0.0.0 network.C.The link uses a three-way handshake for authentication.D.The link uses a two-way handshake for authentication.E.Data exchanges between the Oriando and Tampa routers are encrypted.Answer: BCQUESTION 34A switch is configured as a vtp sever with a domain name of CCNA.Which cisco ios privileged modecommand,followed by a reload of the swith,will reset the VTP management domain name of the switch to a NULL value?A.#vtp domain unset B.#delete vlan.dat C.#no vtp domain D.#vtp domain nullAnswer: BQUESTION 35If an Ethernet port on a router was assigned an IP address of 172.1.1.1/20,what is the maximum number of hosts allowed on this subnet?A.4094B.1024C.8190D.2046b b s .h h 010.co mE.4096Answer: AQUESTION 36Which two statements about static NAT translations are true?(choose two)A.They are always present in the NAT table.B.They allow connection to be initiated from the outside.C.They can be configured with access lists, to allow two or more connections to be initiated from theoutside.D.They require no inside or outside interface markings because addresses are statically defined.Answer: ABQUESTION 37Which of these represents an IPv6 link-local address?A.FE08::280e:611:a:f14f:3d69B.FE81::280f:512b:e14f:3d69C.FE80::380e:611a:e14f:3d69D.FEFE:0345:5f1b::e14d:3d69Answer: CQUESTION 38What are three features of the IPV6 protocol?(choose three)plicated header B.plug-and-play C.no broadcasts D.checksums E.optional IPsec F.autoconfigurationAnswer: BCFQUESTION 39Assuming default setting,how can you erase the VTP database of VLANs on a CISCO IOS switch running in VTP server mode?A.Enable VTP pruningB.From privileged mode ,erase the startup configuration file,then reload.C.From privileged mode ,erase the vlan date file, then reload.D.Cycle the switch power.Answer: CQUESTION 40Refer to the exhibit.which address and mask combination a summary of the routes learned by EIGRP?b b s .h h 010.co mA.192.168.25.0 255.255.255.240B.192.168.25.16 255.255.255.252C.192.168.25.0 255.255.255.252D.192.168.25.28 255.255.255.240E.192.168.25.16 255.255.255.240F.192.168.25.28 255.255.255.240Answer: EQUESTION 41Refer to the exhibit A frame on vlan 1on switch s1 is sent to switch s2 when the frame is received on vlan 2,what causes this behavior?A.trunk mode mismatchesb b s .h h 010.co mB.vlans that do not correspond to a unique IP subnetC.native vlan mismatchesD.allowing only vlan 2 on the destination.Answer: CQUESTION 42Refer to the exhibit.The network administrator normally establishes a telnet session with the switch from host A.However,host A is unavailable.The administrator ′s attempt to the switch from host B fails,but pings to the other two hosts are successful.what is the issue?A.Host B and the switch need to be in the same subnet.B.The switch needs and appropriate default gateway assigned.C.The switch interface connected to the router is down.D.Host B need to be assigned an IP address in vlan 1.Answer: BQUESTION 43What value is primarily used to determine which port becomes the root port on each nonroot switch in a spanning-tree topology?A.lowest port MAC addressB.port priority number and MAC address.C.VTP revision numberD.highest port priority number.E.path costAnswer: EQUESTION 44Refer to the exhibit.Router 1 was just successfully rebooted.identify the current OSPF router ID for Router 1.b b s .h h 010.co mA.208.149.23.194B.220.173.149.10C.208.149.23.162D.190.172.32.10Answer: AQUESTION 45Why do large OSPF networks use a hierarchical design?(choose three)A.to confine network instability to single areas of the network.B.to reduce the complexity of router configuration C.to speed up convergenceD.to lower costs by replacing routers with distribution layer switchesE.to decrease latency by increasing bandwidthF.to reduce routing overheadAnswer: ACFQUESTION 46A network administrator receives an error message while tring to configure the Ethernet interface of a router with IP address 10.24.24.24/29.which statement explains the reason for this issue?A.The address is a broadcast address B.The Ehernet interface is faultyC.VLSM-capable routing protocols must be enable first on the router.D.This address is a network address.Answer: DQUESTION 47Which two are advantages of static routing when compared to dynamic routing?(choose two)A.Security increases because only the network administrator may change the routing tables.B.Configuration complexity decreases as network size increases.C.Routing updates are automatically sent to neighbors.D.Route summarization iscompued automatically by the router.E.Routing traffic load is reduced when used in stub network linksF.An efficient algorithm is used to build routing tables,using automatic updates.G.Routing tables adapt automatically to topology changes.b b s .h h 010.co mAnswer: AEQUESTION 48A company has a small network,consisting of a single switch and a single router.The switch has been configured with two vlans,and route-on-a-stick is being configured on the router for inter-vlan routing.A trunk is configured to connect the switch to the router.What is the minimum number of router subinterfaces that are required for all the vlans to communicate?A.one B.three C.two D.zeroAnswer: CQUESTION 49Which command can be a router to verify the layer 3 path to a host?A.traceroute address B.tracert address C.ssh address D.telnet addressAnswer: AQUESTION 50Which dose the frame-relay interface-dlc i command configure?A.remote DLCI on the main interface B.local DLCI on the main interface C.local DLCI on the subinterface D.remote DLCI on the subinterfaceAnswer: CQUESTION 51What is the OSPF default frequency,in seconds,at which a cisco router sends hello packets on a multi-access network?A.10B.40C.30D.20Answer: AQUESTION 52Refer to the exhibt.Host A has tested connectivity to a remote network.What is the default gateway for host A?b b s .h h 010.co mA.172.16.182.1B.192.168.1.1C.10.16.176.1D.192.168.1.6Answer: AQUESTION 53Which commands is necessary to permit SSH or Telnet access to a cisco switch that is otherwise configured for these vty line protocols?A.transport type allB.transport output allC.transport preferred allD.transport input allAnswer: DQUESTION 54Which command shows your active Telnet connections?A.show sessionB.show cdp neighborsC.show usersD.show queueAnswer: AQUESTION 55Which two states are the port states when RSTP has converged?(choose two)A.blocking B.learning C.disabled D.forwarding E.listeningAnswer: ADb b s .h h 010.co mQUESTION 56There are no boot system commands in a router configuration in NVRAM.What is the fallback sequence that router will use to find an ios during reload?A.Flash,TFTP server,ROM B.Flash,NVRAM,ROMC.ROM,NVRAM,TFTP serverD.NVRAM,TFTP server,ROME.TFTP server,Flash,NVRAMAnswer: A QUESTION 57Refer to the graphic.A host is connected to switch port Fa0/3 with a crossover cable.The host and switch have…as shown.However,the port indicator on switch port Fa0/3 is not on,and the host can notcommunicate with…to vlan 2 on the same switch.Based on the information given.what is the problem?A.The switch has been assigned an incorrect subnet mask.B.Switch port FA0/3 is not configured as a trunk port C.Switch port FA0/3 has been blocked by STPD.The switch and the hosts must be in the same subnetE.The cable is the wrong typeAnswer: E QUESTION 58Refer to the exhibit.Which user-mode password has just been set?A.Telnet B.Auxiliary C.SSH D.Consoleb b s .h h 010.co mAnswer: AQUESTION 59DNS servers provide what service?A.they run a spell check on host names to ensure accurate routingB.they map individual hosts to their specific IP addressC.they convert domain names into IP addressD.Given an IP address,they determine the name of the host that is…Answer: CQUESTION 60Which command enables RSTP on a switch?A.spanning-tree mode rapid-pvstB.spanning-tree uplinkfastC.spanning-tree backbonefastD.spanning-tree mode mst Answer: A QUESTION 61Which two are features of IPv6?(choose two)A.multicast B.broadcast C.allcastD.podcastE.anycast Answer: AE QUESTION 62Which statement about access lists that are applied to an interface is true?A.you can apply multiple access lists with the same protocol or in different…B.you can config one access list,per direction,per layer 3 protocolC.you can place as many access lists as you want on any interfaceD.you can apply ony one access list on any interfaceAnswer: DQUESTION 63Which item represents the standard IP ACL?A.access-list 50 deny 192.168.1.1 0.0.0.255B.access-list 110 permit ip any anyC.access-list 2500 deny tcp any host 192.168.1.1 eq 22D.access-list 101 deny tcp any host 192.168.1.1bbs.hh1.c o mAnswer: AQUESTION 64What is one benefit of PVST+?A.PVST+reduces the CPU cycles for all the switches in the networkB.PVST+automatically selects the root bridge location,to provide optimiz…C.PVST+allow the root switch location to be optimized per vlan.D.PVST+supports Layer 3 load balancing without loops.Answer: Cmoc.1hh.sbb。
CISCO_CCNA网络工程师题库

培训大讲堂官方YY 频道:3660mCCNA题库考试代号: 640-802考试时间:英文110+30=140分钟通过分数: 825题库版本: V104.4鸿鹄论坛招募CCNA、CCNP答疑讲师答疑地点:鸿鹄官方YY频道3660鸿鹄大讲堂:bbs.hh010./thread-46172-1-1.htmlCCNA题库战报交流QQ群:144288127 (500人超级群)CCNA题库战报交流区: bbs.hh010./forum-261-1.html1000 G视频教程免费下载:bbs.hh010./forum-228-1.htmlCCNA(640-802)题库V104.4CCNA(640-802)题库V104.4(情人节版)CCNA 题库战报500人超级QQ群 144288127V104系列是官方的终结版本,以后不会再出V105 V106 V108等等CCNA 最新题库/最新战报发布区: bbs.hh010./forum-261-1.html下载官方正版题库、看最新考试战报,请随时关注鸿鹄论坛 bbs.hh010.CCNA考试报名1900,详情请联系鸿鹄全国区十七名客服 QQ 71202306========================================更新容:V104.1修正V104中错误题目,确定经典争议题目答案;V104.2增加拖图题并可完美模拟考试,VCE题库增加中文注释;V104.3针对思科CCNA考试变题,更新考试新增题目93Q,更新V104.2实验题;V104.4增加全文中文注释,汇总V104.3九次更新,删除部分旧题目,为目前最新官方正版题库;2011.8.1 增加每日新题,修订部分错误。
2012.2.14 情人节版增加5道新题,分别是519、520、521、522、523题修改176题、375题、443题、482题答案错误修改59题、88题、453题、107题、270题注释错误增加个别疑难拖图题注释,优化实验题=============================================QUESTION 1When you are logged into a switch, which prompt indicates that you are in privileged mode?(当您登录到交换机,哪种提示表明你在特权模式?)A. %B.C. >D. $E. #Answer: ESection: Chapter 4: Introduction to Cisco IOSExplanation/Reference:特权模式就是#提示符QUESTION 2Which command shows system hardware and software version information?(哪些命令显示系统硬件和软件的版本信息?)A. show configurationB. show environmentC. show inventoryD. show platformE. show versionAnswer: ESection: Chapter 4: Introduction to Cisco IOSExplanation/Reference:查看系统的软件和硬件信息使用的命令是show versionQUESTION 3Cisco Catalyst switches CAT1 and CAT2 have a connection between them using ports FA0/13. An 802. 1Q trunk is configured between the two switches. On CAT1, VLAN 10 is chosen as native, but on CAT2 the native VLAN is not specified.What will happen in this scenario?(思科 Catalyst 交换机 CAT1 和 CAT2 有它们之间的连接使用端口FA0/13。
CCNA论坛最新题库TK640-802 v201 v31 v101实验题
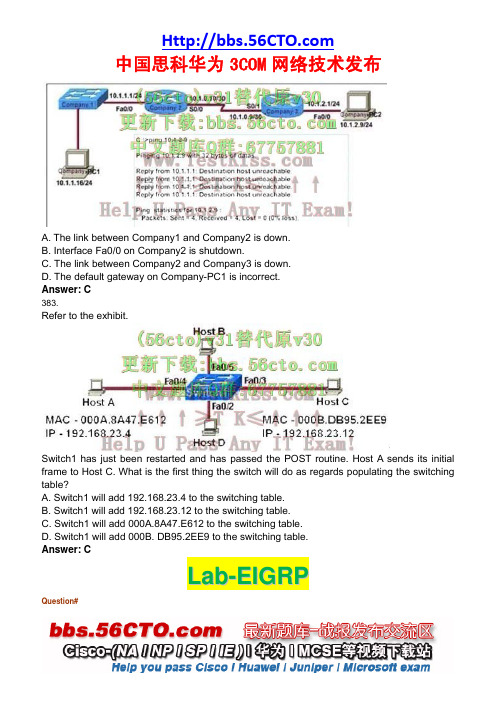
A. The link between Company1 and Company2 is down.B. Interface Fa0/0 on Company2 is shutdown.C. The link between Company2 and Company3 is down.D. The default gateway on Company-PC1 is incorrect.Answer: C383.Refer to the exhibit.Switch1 has just been restarted and has passed the POST routine. Host A sends its initial frame to Host C. What is the first thing the switch will do as regards populating the switching table?A. Switch1 will add 192.168.23.4 to the switching table.B. Switch1 will add 192.168.23.12 to the switching table.C. Switch1 will add 000A.8A47.E612 to the switching table.D. Switch1 will add 000B. DB95.2EE9 to the switching table.Answer: CL a b-E I G R PQuestion#After adding RTR_2 router, no routing updates are being exchanged between RTR_1 and the new location. All other inter connectivity and internet access for the existing locations of thecompany are working properly.The task is to identify the fault(s) and correct the router configuration to provide full connectivity between the routers. Access to the router CLI can be gained by clicking on the appropriate host.All passwords on all routers are cisco .IP addresses are listed in the chart below.RTR_A#show run!!interface FastEthernet0/0ip address 192.168.60.97 255.255.255.240!interface FastEthernet0/1ip address 192.168.60.113 255.255.255.240!interface Serial0/0ip address 192.168.36.14 255.255.255.252clockrate 64000!router eigrp 212network 192.168.36.0network 192.168.60.0no auto-summary!RTR_A#show ip route192.168.36.0/30 is subnetted, 1 subnetsC 192.168.36.12 is directly connected, Serial 0/0192.168.60.0/24 is variably subnetted, 5 subnets, 2 masksC 192.168.60.96/28 is directly connected, FastEthernet0/0C 192.168.60.112/28 is directly connected, FastEthernet0/1D 192.168.60.128/28 [ 90/21026560 ] via 192.168.36.13, 00:00:57, Serial 0/0 D 192.168.60.144/28 [ 90/21026560 ] via 192.168.36.13, 00:00:57, Serial 0/0 D 192.168.60.24/30 [ 90/21026560 ] via 192.168.36.13, 00:00:57, Serial 0/0 D* 198.0.18.0 [ 90/21026560 ] via 192.168.36.13, 00:00:57, Serial 0/0********************************************************************************RTR_2#show run!!interface FastEthernet0/0ip address 192.168.77.34 255.255.255.252!interface FastEthernet0/1ip address 192.168.60.65 255.255.255.240!interface FastEthernet1/0ip address 192.168.60.81 255.255.255.240!!router eigrp 22network 192.168.77.0network 192.168.60.0no auto-summary!RTR_2#show ip route192.168.60.0/28 is variably subnetted, 2 subnetsC 192.168.60.80 is directly connected, FastEthernet1/0C 192.168.60.64 is directly connected, FastEthernet0/1192.168.77.0/30 is subnetted, 1 subnetsC 192.168.77.32 is directly connected, FastEthernet0/0**********************************************************RTR_B#show run!interface FastEthernet0/0ip address 192.168.60.129 255.255.255.240!interface FastEthernet0/1ip address 192.168.60.145 255.255.255.240!interface Serial0/1ip address 192.168.60.26 255.255.255.252!router eigrp 212network 192.168.60.0!RTR_B#show ip route192.168.60.0/24 is variably subnetted, 5 subnets, 2 masksC 192.168.60.24/30 is directly connected, Serial0/1C 192.168.60.128/28 is directly connected, FastEthernet0/0C 192.168.60.144/28 is directly connected, FastEthernet0/1D 192.168.60.96/28 [ 90/21026560 ] via 192.168.60.25, 00:00:57, Serial 0/1 D 192.168.60.112/28 [ 90/21026560 ] via 192.168.60.25, 00:00:57, Serial 0/1 192.168.36.0/30 is subnetted, 1 subnetsD 192.168.36.12 [ 90/21026560 ] via 192.168.60.25, 00:00:57, Serial 0/1 D* 198.0.18.0 [ 90/21026560 ] via 192.168.60.25, 00:00:57, Serial 0/1**************************************************************************RTR_1#show run!!interface FastEthernet0/0ip address 192.168.77.33 255.255.255.252!interface Serial1/0ip address 198.0.18.6 255.255.255.0!!interface Serial0/0ip address 192.168.36.13 255.255.255.252clockrate 64000!interface Serial0/1ip address 192.168.60.25 255.255.255.252clockrate 64000!!router eigrp 212network 192.168.36.0network 192.168.60.0network 192.168.85.0network 198.0.18.0no auto-summary!ip classlessip default-network 198.0.18.0ip route 0.0.0.0 0.0.0.0 198.0.18.5ip http serverRTR_1#show ip route192.168.36.0/30 is subnetted, 1 subnetsC 192.168.36.12 is directly connected, Serial 0/0192.168.60.0/24 is variably subnetted, 5 subnets, 2 masksC 192.168.60.24/30 is directly connected, Serial0/1D 192.168.60.128/28 [ 90/21026560 ] via 192.168.60.26, 00:00:57, Serial 0/1D 192.168.60.144/28 [ 90/21026560 ] via 192.168.60.26, 00:00:57, Serial 0/1D 192.168.60.96/28 [ 90/21026560 ] via 192.168.36.14, 00:00:57, Serial 0/0192.168.77.0/30 is subnetted, 1 subnetsC 192.168.77.32 is directly connected, FastEthernet0/0C 192.0.18.0/24 is directly connected, Serial 1/0*S 0.0.0.0 via 198.0.18.5Explanation:Step1:Identify the faults in configuration on RTR_1 and RTR_2. As the SIM specifies all other inter connectivity and internet access for the existing locations of the company are working properly.Routing Protocols used in the SIM is EIGRP with AS 212 as provided by exhibit.Faults Identified:1. Wrong AS (EIGRP 22) provided at RTR_2 (New router)2. RTR_1 does not advertise the new network between RTR_1 and RTR_2 into EIGRP.We need to correct the above two configuration mistakes to have full connectivityStep2:Correcting the EIGRP AS to 212Wrong AS (EIGRP 22) provided at RTR_2 (New router)All routers that want to exchange routes within EIGRP needs to be in same Autonomous System.Step 2.1:First we need to remove the current wrong EIGRP AS 22 from Router RTR_2Click on Host-F to get CLI of RTR_2RTR_2>enablePassword : cisco(Provided by SIM Q )RTR_2#conf tRTR_2(conf)#Step 2.2:Removing the wrong EIGRP routing process with AS 22RTR_2(conf)#no router eigrp 22The above statement removes all the EIGRP configuration configured for AS 22 .Step 2.3:Adding the correct EIGRP configurationStart the EIGRP routing process with AS 212RTR_2(conf)#router eigrp 212Step 2.4:Advertise the directly connected networks into EIGRP on RTR_2Fa 0/0 - 192.168.77.34Fa 1/0 - 192.168.60.81Fa 0/1 - 192.168.60.65RTR_2(config-router)#network 192.168.60.0RTR_2(config-router)#network 192.168.77.0RTR_2(config-router)#no auto-summaryRTR_2(config-router)#endStep 2.5:Important save the changes made to router RTR_2RTR_2#copy run startStep 3:RTR_1 does not advertise the new network between RTR_1 and RTR_2 into EIGRP. Click on Host-G to get CLI of RTR_1The network192.168.77.0 is used between RTR_1Fa0/0- RTR_2Fa 0/0This network needs to be advertise into EIGRP routing process at RTR_1RTR_1>enablePassword : cisco(Provided by SIM Q )RTR_1#conf tRTR_1(conf)#Step 3.1:Enter EIGRP routing process for AS 212RTR_1(conf)#router eigrp 212Step 3.2:The network192.168.77.0is used between RTR_1 Fa0/0- RTR_2 Fa 0/0 . Advertise this network into EIGRPRTR_1(config-router)#network 192.168.77.0RTR_1(config-router)#endStep 3.3:Important save the changes made to router RTR_1RTR_1#copy run startVerification:From RTR_2 CLIping RTR_1 Serial 1/0 IP address 198.0.18.6RTR_2#ping 198.0.18.6!!!!!A successful ping shows the new RTR_2 will have full connectivity with other routers. Any Questions are welcomed!!!!!L a b-A C LCorp1>enable (you may enter "cisco" as it passwords here)We should create an access-list and apply it to the interface which is connected to the Server LAN because it can filter out traffic from both Sw-2 and Core networks. The Server LAN network has been assigned addresses of 172.22.242.17 -172.22.242.30 so we can guess the interface connected to them has an IP address of 172.22.242.30 (.30 is the number shown in the figure). Use the "show running-config" command to check which interface has the IP address of 172.22.242.30. Corp1#show running-configWe learn that interface FastEthernet0/1 is the interface connected to Server LAN network. It is the interface we will apply our access-list (for outbound direction).Corp1#configure terminalOur access-list needs to allow host C - 192.168.33.3 to the Finance Web Server 172.22.242.23 via web (port 80)Corp1(config)#access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80Deny other hosts access to the Finance Web Server via webCorp1(config)#access-list 100 deny tcp any host 172.22.242.23 eq 80All other traffic is permittedCorp1(config)#access-list 100 permit ip any anyApply this access-list to Fa0/1 interface (outbound direction)Corp1(config)#interface fa0/1Corp1(config-if)#ip access-group 100 outNotice: We have to apply the access-list to Fa0/1 interface (not Fa0/0 interface) so that the access-list can filter traffic coming from the Core network.Click on host C and open its web browser. In the address box type http://172.22.242.23 to check if you are allowed to access Finance Web Server or not. If your configuration is correct then you can access it.Click on other hosts (A, B and D) and check to make sure you can't access Finance Web Server from these hosts.Finally, save the configurationCorp1(config-if)#endCorp1#copy running-config startup-configL a b-V T PThis task requires you to use the CLI of Sw-AC3 to answer five multiple-choice questions. This does not require any configuration.To answer the multiple-choice questions, click on the numbered boxes in the right panel.There are five multiple-choice questions with this task. Be sure to answer all five questions before leaving this item.Question 1:What interface did Sw-AC3 associate with source MAC address 0010.5a0c.ffba ?a) Fa0/1b) Fa0/3c) Fa0/6d) Fa0/8e) Fa0/9f) Fa0/12Answer: Fa 0/8Explanation: to find out which interface associated with a given MAC address, use the show mac-address-table command. It shows the learned MAC addresses and their associated interfaces. After entering this command, you will see a MAC address table like this:From this table we can figure out that the MAC address 0010.5a0c.ffba is associated with interface Fa0/8 Question 2:What ports on Sw-AC3 are operating has trunks (choose three)?a) Fa0/1b) Fa0/3c) Fa0/4d) Fa0/6e) Fa0/9f) Fa0/12Answer: Fa0/3, Fa0/9 and Fa0/12Explanation: Use the show interface trunk command to determine the trunking status of a link and VLAN status. This command lists port, its mode, encapsulation and whether it is trunking. The image below shows how it works:(This image is used for demonstration only)Question 3:What kind of router is VLAN-R1?a) 1720b) 1841c) 2611d) 2620Answer: 2620Explanation: VLAN-R1 is the router directly connected to Sw-Ac3 switch, so we can use the show cdp neighbors command to see:1. Neighbor Device ID : The name of the neighbor device;2. Local Interface : The interface to which this neighbor is heard3. Capability: Capability of this neighboring device - R for router, S for switch, H for Host etc.4. Platform: Which type of device the neighbor is5. Port ID: The interface of the remote neighbor you receive CDP information6. Holdtime: Decremental hold time in secondsSample output of show cdp neighbors command:One thing I want to notice you is "Local Intrfce" in the image above refers to the local interface on the device you are running the "show cdp neighbors" commandQuestion 4: Which switch is the root bridge for VLAN 1?Answer: Sw-DS1Explanation: First we use the show spanning-tree vlan 1 to view the spanning-tree information of VLAN 1From the "Cost 19", we learn that the root switch is directly connected to the Sw-Ac3 switch over a 100Mbps Ethernet linkNotice that if you see all of the interface roles are Desg (designated) then you can confirm Sw-Ac3 switch is the root bridge for this VLAN (VLAN 1).If you see there is at least one Root port in the interface roles then you can confirm Sw-Ac3 is not the root bridge because root bridge does not have root port. In this case, we notice that the root port on Sw-Ac3 switch is FastEthernet0/12, so we have to figure out which switch is associated with this port -> it is the root bridge. You can verify it with the show cdp neighbors command:The "Local Intrfce" column refers to the interface on the switch running "show cdp neighbors" command. In this case, Sw-DS1 is associated with interface FastEthernet0/12 -> Sw-DS1 is the root bridgeQuestion 5: What address should be configured as the default-gateway for the host connected to interface fa 0/4 of SW-Ac3?Answer: 192.168.44.254Explanation:First we have to identify which VLAN interface Fa0/4 belongs to by the show vlan commandFrom the exhibit we know that VLAN 44 is configured on router using sub-interface Fa0/0.44 with IP address 192.168.44.254/24Therefore the default gateway of the host should be 192.168.44.254Question 6: From which switch did Sw-Ac3 receive VLAN information ?Answer: Sw-AC2Explanation: to view the VTP configuration information, use the show vtp status commandSo we knew Sw-Ac3 received VLAN information from 163.5.8.3 (notice:the IP address may be different). Finally we use the show cdp neighbors detail to find out who 163.5.8.3 is:Question 7: Refer to the exibit, SwX was taken out of the production network for maintenance. It will be reconnected to the Fa 0/16 port of Sw-Ac3. What happens to the network when it is reconnected and a trunk exists between the two switches?A - All VLANs except the default VLAN win be removed from all switchesB - All existing switches will have the students, admin, faculty, Servers, Management, Production, and no-where VLANsC - The VLANs Servers, Management, Production and no-where will replace the VLANs on SwXD - The VLANs Servers, Management, Production and no-where will be removed from existing switchesAnswer and Explanation:First we should view the VTP configuration of switch Sw-Ac3 by using the show vtp status command on Sw-Ac3Notice that its configuration revision number is 5 and VTP Domain Name is home-officeNext, from the exhibit we know that SwX has a revision number of 6, which is greater than that of Sw-Ac3 switch, and both of them have same VTP Domain Name called "home-office".Therefore SwX will replace vlan information on other switches with its own information. We should check vlan information of Sw-Ac3 switch with show vlan commandSo the correct answer is D - The VLANs Servers, Management, Production and no-where will be removed from existing switchesPlease notice that in the real CCNA exam you may see a different configuration revision of Sw-Ac3 or of SwX. In general, which switch has a higher revision number it will become the updater and other switches will overwrite their current databases with the new information received from the updater (provided that they are on the same domain and that switch is not in transparent mode). Also, some recent comments have said that the new switch's VTP Operating Mode is Server but the answer is still the same.Question 8:Out of which ports will a frame be forwarded that has source mac-address 0010.5a0c.fd86 and destination mac-address 000a.8a47.e612? (Choose three)A - Fa0/8B - Fa0/3C - Fa0/1D - Fa0/12Answer: B C DExplanation:First we check to see which ports the source mac-address and the destination mac-address belong to by using show mac-address-table commandWe notice that the source mac-address 0010.5a0c.fd86 is listed in the table and it belongs to Vlan 33 but we can't find the destination mac-address 000a.8a47.e612 in this table. In this case, the switch will flood to all ports of Vlan 33 and flood to all the trunk links, except the port it received this frame (port Fa0/6). Therefore from the output above, we can figure out it will flood this frame to Fa0/1, Fa0/3 and Fa0/12.Please notice that the "show mac-address-table" command just lists information that was learned by the switch, it means that there can be other ports besides Fa0/1, Fa0/3 and Fa0/12 belong to Vlan 33. You can use the show vlan command to see which ports belong to vlan 33And we found other ports which belong to vlan 33, they are Fa0/2, Fa0/5 and Fa0/7. Our switch will flood the frame to these ports, too.And we can check which trunk ports will receive this frame by the show interface trunk command-> Port Fa0/9 will also receive this frame!Question 9:If one of the host connected to Sw-AC3 wants to send something for the ip 190.0.2.5 (or any ip that is not on the same subnet) what will be the destination MAC addressAnswer and Explanation:Because the destination address is not on the same subnet with the switch, it will forward the packet to its default gateway. So we have to find out who is the default gateway of this switch by using the show running-config commandFrom the output, we notice that its default-gateway is 192.168.1.254. In fact, we can easily guess that its default gateway should be a layer 3 device like a router; and in this case, the VLAN-R1 router. To verify our theory, use the show cdp neighbor detail command and focus on the description of VLAN-R1 routerFrom this output, we can confirm the switch's default gateway is VLAN-R1 router (with the IP address of 192.168.1.254). And "the interface: FastEthernet0/3" tells us that the switch is connected to VLAN-R1 router through Fa0/3 port (Fa0/3 is the port on the switch).Finally we just need to use the show mac-address-table command to find out which MAC address is associated with this interface(Notice that in the real CCNA exam the MAC address or port may be different)And we find out the corresponding MAC address is 000a.b7e9.8360. Although there are some entries of port Fa0/3 with different Vlans but they have the same MAC addressL a b-R I P(o l d-l a b)Answer:Router>enableRouter#config terminalRouter(config)#hostname GothaGotha(config)#enable secret mi222keGotha(config)#line console 0Gotha(config-line)#password G8tors1Gotha(config-line)#exitGotha(config)#line vty 0 4Gotha(config-line)#password dun63labGotha(config-line)#loginGotha(config-line)#exitGotha(config)#interface fa0/0Gotha(config-if)#ip address 209.165.201.1 255.255.255.224Gotha(config)#interface s0/0/0Gotha(config-if)#ip address 192.0.2.176 255.255.255.240Gotha(config-if)#no shutdownGotha(config-if)#exitGotha(config)#router ripGotha(config-router)#version 2Gotha(config-router)#network 209.165.201.0Gotha(config-router)#network 192.0.2.176Gotha(config-router)#endGotha#copy run start ——————————————————————————————————————————————————————————LAB: RIP V2Question#Central Florida Widgets recently installed a new router in their office (NEW_RTR). Complete the network installation by performing the initial router configurations and configuring RIP V2 routing using the router Command Line Interface (CLI) on the NEW_RTR .Click on image for larger pictureConfigure the router per the following requirements:1) Name of the router is NEW_RTR2) Enable-secret password is cisco3) The password to access user EXEC mode using the console is class4) The password to allow telnet access to the router is class5) IPV4 addresses must be configured as follows:5.1) Ethernet network 209.165.202.128 /27 – Router has the last assignable hostaddress in subnet.5.2) Serial Network is 192.0.2.16 /28 - Router has the last assignable hostaddress in subnet.6) Interfaces should be enabled.7) Router protocol is RIPv2Explanation:Step1:Click on the console host, you will get a pop-up screen CLI of Router.Router>Configure the new router as per the requirements provided in Lab questionRequirement 1:Name of the router is NEW_RTRStep2:To change the hostname of the router to NEW_RTR follow the below stepsRouter>Router>enableRouter# configure terminalRouter (config)# hostname NEW_RTRNEW_RTR(config)#Requirement 2:Enable-secret password is ciscoStep3:To set the enable secret password to cisco use the following commandNEW_RTR(config)#enable secret ciscoRequirement 3:The password to access user EXEC mode using the console is classStep 4:We need to configure the line console 0 with the password classAlso remember to type login command after setting up the password on line con 0 which allows router to accept logins via console.NEW_RTR(config)# line con 0NEW_RTR(config-line)#password classNEW_RTR(config-line)#loginNEW_RTR(config-line)# exitNEW_RTR(config)#Requirement 4:The password to allow telnet access to the router is classStep 5:To allow telnet access we need to configure the vty lines 0 4 with the password classAlso remember to type login command after setting up the password on line vty 0 4 which allows router to accept logins via telnet.NEW_RTR(config)# line vty 0 4NEW_RTR(config-line)#password classNEW_RTR(config-line)#loginNEW_RTR(config-line)# exitNEW_RTR(config)#Requirement 5:5.1) Ethernet network 209.165.202.128 /27 – Router has the last assignable hostaddress in subnet.5.2) Serial Network is 192.0.2.16 /28 - Router has the last assignable hostaddress in subnet.Step 6:Ethernet network 209.165.202.128 /27 – Router has the last assignable host address in subnet.Ethernet Interface on router NEW_RTR is Fast Ethernet 0/0 as per the exhibitFirst we need to identify the subnet maskNetwork: 209.165.202.128 /27Subnet mask: /27: 27 bits = 8 + 8 + 8 + 3=8(bits).8(bits).8(bits) .11100000 (3bits)=255.255.255.11100000=11100000 = 128+64+32+0+0+0+0+0= 224Subnet mask: 255.255.255.224Different subnet networks and there valid first and last assignable host address range for above subnet mask are Subnet Networks :::::: Valid Host address range :::::: Broadcast address209.165.202.0 :::::: 209.165.202.1 - 209.165.202.30 ::::: 209.165.202.31209.165.202.32 :::::: 209.165.202.33 - 209.165.202.62 ::::: 209.165.202.63209.165.202.64 :::::: 209.165.202.65 - 209.165.202.94 :::::: 209.165.202.95209.165.202.96 :::::: 209.165.202.97 - 209.165.202.126 :::::: 209.165.202.127209.165.202.128 :::::: 209.165.202.129 - 209.165.202.158 :::::: 209.165.202.159209.165.202.160 :::::: 209.165.202.161 - 209.165.202.190 :::::: 209.165.202.191209.165.202.192 :::::: 209.165.202.193 - 209.165.202.222 :::::: 209.165.202.223209.165.202.224 :::::: 209.165.202.225 - 209.165.202.254 :::::: 209.165.202.255Use above table information for network 209.165.202.128 /27 to identifyFirst assignable host address: 209.165.202.129Last assignable host address: 209.165.202.158This IP address (209.165.202.158) which we need to configure on Fast Ethernet 0/0 of the router using the subnet mask 255.255.255.224NEW_RTR(config)#interface fa 0/0NEW_RTR(config-if)#ip address 209.165.202.158 255.255.255.224Requirement 6:To enable interfacesUse no shutdown command to enable interfacesNEW_RTR(config-if)#no shutdownNEW_RTR(config-if)#exitStep 7:Serial Network is 192.0.2.16 /28 - Router has the last assignable host address in subnet.Serial Interface on NEW_RTR is Serial 0/0/0 as per the exhibitFirst we need to identify the subnet maskNetwork: 192.0.2.16 /28Subnet mask: /28: 28bits = 8bits+8bits+8bits+4bits=8(bits).8(bits).8(bits) .11110000 (4bits)=255.255.255.11100000=11100000 = 128+64+32+16+0+0+0+0= 240Subnet mask: 255.255.255.240Different subnet networks and there valid first and last assignable host address range for above subnet mask are Subnet Networks ::::: Valid Host address ::::::::::: Broadcast address192.0.2.0 :::::: 192.0.2.1 - 192.0.2.14 ::::::: 192.0.2.15192.0.2.16 ::::::: 192.0.2.17 - 192.0.2.30 ::::::: 192.0.2.31192.0.2.32 :::::::: 192.0.2.33 - 192.0.2.46 :::::: 192.0.2.47and so on ….Use above table information for network 192.0.2.16 /28 to identifyFirst assignable host address: 192.0.2.17Last assignable host address: 192.0.2.30We need to configure Last assignable host address (192.0.2.30) on serial 0/0/0 using the subnet mask 255.255.255.240NEW_RTR(config)#interface serial 0/0/0NEW_RTR(config-if)#ip address 192.0.2.30 255.255.255.240Requirement 6:To enable interfacesUse no shutdown command to enable interfacesNEW_RTR(config-if)#no shutdownNEW_RTR(config-if)#exitRequirement 7:Router protocol is RIPv2Step 8:Need to enable RIPv2 on router and advertise its directly connected networksNEW_RTR(config)#router ripTo enable RIP v2 routing protocol on router use the command version 2NEW_RTR(config-router)#version 2Optional:no auto-summary (Since LAB networks do not have discontinuous networks)RIP v2 is classless, and advertises routes including subnet masks, but it summarizes routes by default.So the first things we need to do when configuring RIP v2 is turn off auto-summarization with the router command noauto-summary if you must perform routing between disconnected subnets.NEW_RTR (config-router) # no auto-summaryAdvertise the serial 0/0/0 and fast Ethernet 0/0 networks into RIP v2 using network commandNEW_RTR(config-router)#network 192.0.2.16NEW_RTR(config-router)#network 209.165.202.128NEW_RTR(config-router)#endStep 9:Important please do not forget to save your running-config to startup-configNEW_RTR# copy run startAny questions are welcomed on above LAB... Best of Luck!!!!!L a b-N A T(o l d-l a b) NAT-LABAnswers:Bomar(Config)#access-list 1 permit 192.168.16.33 0.0.0.15Bomar(Config)#access-list 1 deny anyBomar(Config)#ip nat pool TestKiss 198.18.237.225 198.18.237.230 prefix-length 29Bomar(Config)#ip nat inside source list 1 pool TestKiss overloadBomar(Config)#interface fa0/0BomarConfig-if)#ip nat insideBomar(Config)#interface S0/0Bomar(Config-if)#ip nat outsideBomar(Config-if)#exitBomar#Copy run start-------------------------------------------------------------------------------Question:A network associate is configuring a router for the weaver company to provide internet access. The ISP has provided the company six public IP addresses of 198.18.184.105 198.18.184.110. The company has 14 hosts that need to access the internet simultaneously. The hosts in the company LAN have been assigned private space addresses in the range of 192.168.100.17 – 192.168.100.30 .CLICK ON IMAGE TO VIEWClick Knowledge Base for NAT SIM to learn the concepts before attempting or learning this SIM QuestionNAT SIM Configuration:The following configuration translates between inside hosts (Weaver LAN) addressed from 192.168.100.16 /28 network (192.168.100.17 – 192.168.100.30) to the globally unique pool of address provided by ISP 198.18.184.105 – 198.18.184.110 /29.Weaver>enableWeaver#configure terminalBefore starting the NAT configuration verify that router hostname currently configured is weaver. If not change hostname to Weaver using the commandRouter(config)#hostname WeaverStep1:Create an access-list to match all the Weaver LAN address that need to be the candidates for NAT translationsWeaver(config)#access-list 10 permit 192.168.100.16 0.0.0.15Step2:Create a NAT Pool with pool name isp_adr and specify the pool address range provided by ISP with their netmask.Weaver(config)#ip nat pool TestKiss 198.18.184.105 198.18.184.110 netmask 255.255.255.248Step3:Packets that match access-list 10 will be translated to an address from the pool called "TestKiss".Overload keyword specify to use Port based NATing to support all the Weaver LAN address range.Weaver(config)#ip nat inside source list 10 pool TestKiss overloadSIM Question already provides that appropriate interfaces have been configured for NAT Inside and NAT Outside statements.For your information configuration would have been like thisWeaver(config)#interface fastethernet 0/0Weaver(config-if)#ip nat insideWeaver(config)#interface serial 0/0Weaver(config-if)#ip nat outsideWeaver#copy run start。
CCNA考试题目及答案640-802_2008_10_6
Exam CISCO-640-8021.Which two methods are examples of implementing Layer 2 security on a Cisco switch? (Choose two.) A:disable trunk negotiation on the switchB:enable Cisco Discovery Protocol globally to monitor for malicious devicesC:configure a switch port host where appropriateD:enable HTTP access to the switch for security troubleshootingE:use only protected Telnet sessions to connect to the Cisco deviceF:install a modem on the auxiliary port for emergency accessCorrect Answers: A, C2.Which type of attack is characterized by a flood of packets that are requesting a TCP connection to a server?A: denial of service B: brute forceC: reconnaissance D: Trojan horseCorrect Answers: A3.Refer to the exhibit. S0/0 on R1 is configured as a multipoint interface to communicate with R2 and R3 in this hub-and-spoke Frame Relay topology. While testing this configuration, a technician notes that pings are successful from hosts on the 172.16.1.0/24 network to hosts on both the 172.16.2.0/25 and 172.16.2.128/25 networks. However, pings between hosts on the 172.16.2.0/25 and 172.16.2.128/25 networks are not successful. What could explain this connectivity problem?A: The ip subnet-zero command has been issued on the R1 router.B: The RIP v2 dynamic routing protocol cannot be used across a Frame Relay network.C: Split horizon is preventing R2 from learning about the R3 networks and R3 from learning about the R2 networks.D: The 172.16.2.0/25 and 172.16.2.128/25 networks are overlapping networks that can be seen by R1, but not between R2 and R3.E: The 172.16.3.0/29 network used on the Frame Relay links is creating a discontiguous network between the R2 and R3 router subnetworks.Correct Answers: C4.Which of the following are true regarding the command output shown in the display? (Choose two.) A:There are at least two routers participating in the RIP process.B:A ping to 192.168.168.2 will be successful.C:A ping to 10.0.15.2 will be successful.D:RtrA has three interfaces participating in the RIP process.Correct Answers: A, C5.Refer to the exhibit. What is the effect of the configuration that is shown?A: It configures SSH globally for all logins.B: It tells the router or switch to try to establish an SSh connection first and if that fails to use Telnet.C: It configures the virtual terminal lines with the password 030752180500.D: It configures a Cisco network device to use the SSH protocol on incoming communications via the virtual terminal ports.E: It allows seven failed login attempts before the VTY lines are temporarily shutdown.Correct Answers: D6.Refer to the exhibit. The two connected ports on the switch are not turning orange or green. What would be the most effective steps to troubleshoot this physical layer problem? (Choose three.)A:Ensure that the Ethernet encapsulations match on the interconnected router and switch ports. B:Ensure that cables A and B are straight-through cables.C:Ensure cable A is plugged into a trunk port.D:Ensure the switch has power.E:Reboot all of the devices.F:Reseat all cables.Correct Answers: B, D, F7.Refer to the exhibit. PC_1 is sending packets to the FTP server. Consider the packets as they leave RouterA interface Fa0/0 towards RouterB. Drag the correct frame and packet address to their place in the table.Drag and drop question. Drag the items to the proper locations.Correct Answers:8.Refer to the exhibit. The FMJ manufacturing company is concerned about unauthorized access to the Payroll Server. The Accounting1, CEO, Mgr1, and Mgr2 workstations should be the only computers withaccess to the Payroll Server. What two technologies should be implemented to help prevent unauthorized access to the server? (Choose two.)A:access lists B:encrypted router passwordsC:STP D:VLANsE:VTP F:wireless LANsCorrect Answers: A, D9.An administrator is configuring a router that will act as the hub in a Frame Relay hub-and-spoke topology. What is the advantage of using point-to-point subinterfaces instead of a multipoint interface on this router?A: It avoids split-horizon issues with distance vector routing protocols.B: Only one IP network address needs to be used to communicate with all the spoke devices.C: Point-to-point subinterfaces offer greater security compared to a multipoint interface configuration.D: Only a single physical interface is needed with point-to-point subinterfaces, whereas a multipoint interface logically combines multiple physical interfaces.Correct Answers: A10.Which statement is correct about the internetwork shown in the diagram?A: Switch 2 is the root bridge.B: Spanning Tree is not running.C: Host D and Server 1 are in the same network.D: No collisions can occur in traffic between Host B and Host C.E: If Fa0/0 is down on Router 1, Host A cannot access Server 1.F: If Fa0/1 is down on Switch 3, Host C cannot access Server 2.Correct Answers: E11.Which two values are used by Spanning Tree Protocol to elect a root bridge? (Choose two.)A:amount of RAMB:bridge priorityC:IOS versionD:IP addressE:MAC addressF:speed of the linksCorrect Answers: B, E12.Refer to the graphic. It has been decided that Workstation 1 should be denied access to Server1. Which of the following commands are required to prevent only Workstation 1 from accessing Server1 while allowing all other traffic to flow normally? (Choose two.)A:RouterA(config)# interface fa0/0RouterA(config-if)# ip access-group 101 outB:RouterA(config)# interface fa0/0RouterA(config-if)# ip access-group 101 inC:RouterA(config)# access-list 101 deny ip host 172.16.161.150 host 172.16.162.163RouterA(config)# access-list 101 permit ip any anyD:RouterA(config)# access-list 101 deny ip 172.16.161.150 0.0.0.255 172.16.162.163 0.0.0.0 RouterA(config)# access-list 101 permit ip any anyCorrect Answers: B, C13.How many subnets can be gained by subnetting 172.17.32.0/23 into a /27 mask, and how many usable host addresses will there be per subnet?A: 8 subnets, 31 hostsB: 8 subnets, 32 hostsC: 16 subnets, 30 hostsD: 16 subnets, 32 hostsE: A Class B address can't be subnetted into the fourth octet.Correct Answers: C14.Which spread spectrum technology does the 802.11b standard define for operation?A: IRB: DSSSC: FHSSD: DSSS and FHSSE: IR, FHSS, and DSSSCorrect Answers: B15.What is the maximum data rate specified for IEEE 802.11b WLANs?A: 10 MbpsB: 11 MbpsC: 54 MbpsD: 100 MbpsCorrect Answers: B16.Refer to the output from the show running-config command in the exhibit. What should the administrator do to allow the workstations connected to the FastEthernet 0/0 interface to obtain an IP address?A: Apply access-group 14 to interface FastEthernet 0/0.B: Add access-list 14 permit any any to the access list configuration.C: Configure the IP address of the FastEtherent 0/0 interface to 10.90.201.1.D: Add an interface description to the FastEthernet 0/0 interface configuration.Correct Answers: C17.Which additional configuration step is necessary in order to connect to an access point that has SSID broadcasting disabled?A: Set the SSID value in the client software to public.B: Configure open authentication on the AP and the client.C: Set the SSID value on the client to the SSID configured on the AP.D: Configure MAC address filtering to permit the client to connect to the AP.Correct Answers: C18.What is the function of the Cisco IOS command ip nat inside source static 10.1.1.5 172.35.16.5?A: It creates a global address pool for all outside NAT transactions.B: It establishes a dynamic address pool for an inside static address.C: It creates dynamic source translations for all inside local PAT transactions.D: It creates a one-to-one mapping between an inside local address and an inside global address. E: It maps one inside source address to a range of outside global addresses.Correct Answers: D19.What three pieces of information can be used in an extended access list to filter traffic? (Choose three.)A:protocolB:VLAN numberC:TCP or UDP port numbersD:source switch port numberE:source IP address and destination IP addressF:source MAC address and destination MAC addressCorrect Answers: A, C, E20.Given the partial router configuration in the graphic, why does the workstation with the IP address 192.168.1.153/28 fail to access the Internet? (Choose two.)A:The NAT inside interfaces are not configured properly.B:The NAT outside interface is not configured properly.C:The router is not properly configured to use the access control list for NAT.D:The NAT pool is not properly configured to use routable outside addresses.E:The access control list does not include the IP address 192.168.1.153/28 to access the Internet. Correct Answers: A, C21.A network administrator wants to add a line to an access list that will block only Telnet accessby the hosts on subnet 192.168.1.128/28 to the server at 192.168.1.5. What command should be issued to accomplish this task?A: access-list 101 deny tcp 192.168.1.128 0.0.0.15 192.168.1.5 0.0.0.0 eq 23access-list 101 permit ip any anyB: access-list 1 deny tcp 192.168.1.128 0.0.0.15 host 192.168.1.5 eq 23access-list 1 permit ip any anyC: access-list 1 deny tcp 192.168.1.128 0.0.0.255 192.168.1.5 0.0.0.0 eq 21access-list 1 permit ip any anyD: access-list 101 deny tcp 192.168.1.128 0.0.0.240 192.168.1.5 0.0.0.0 eq 23access-list 101 permit ip any anyE: access-list 101 deny ip 192.168.1.128 0.0.0.240 192.168.1.5 0.0.0.0 eq 23access-list 101 permit ip any anyF: access-list 101 deny ip 192.168.1.128 0.0.0.15 192.168.1.5 0.0.0.0 eq 23access-list 101 permit ip any anyCorrect Answers: A22.HotspotHotspot question. Click on the correct location or locations in the exhibit. Correct Answers:23.What functions do routers perform in a network? (Choose two.)A:packet switchingB:access layer securityC:path selectionD:VLAN membership assignmentE:bridging between LAN segmentsF:microsegmentation of broadcast domainsCorrect Answers: A, C24.Refer to the exhibit. Each of these four switches has been configured with a hostname, as well as being configured to run RSTP. No other configuration changes have been made. Which switch will have only one forwarding interface?A: SwitchAB: SwitchBC: SwitchCD: SwitchDCorrect Answers: B25.Refer to the exhibit. All of the routers in the network are configured with the ip subnet-zero command. Which network addresses should be used for Link A and Network A? (Choose two.)A:Network A - 172.16.3.48/26B:Network A - 172.16.3.128/25C:Network A - 172.16.3.192/26D:Link A - 172.16.3.0/30E:Link A - 172.16.3.40/30F:Link A - 172.16.3.112/30Correct Answers: B, D26.Which destination addresses will be used by Host A to send data to Host C? (Choose two.)A:the IP address of Switch 1B:the MAC address of Switch 1C:the IP address of Host CD:the MAC address of Host CE:the IP address of the router's E0 interfaceF:the MAC address of the router's E0 interfaceCorrect Answers: C, F27.Refer to the graphic. Host A is communicating with the server. What will be the source MAC address of the frames received by Host A from the server?A: the MAC address of router interface e0B: the MAC address of router interface e1C: the MAC address of the server network interfaceD: the MAC address of host ACorrect Answers: AB28.Click the console of the HOME router . Input the folling command into CLI on the right side Home> enableHome # show runHome # show cdp neighborexamine the configuration informations related to problem solution.Drag and drop question. Drag the items to the proper locations.Correct Answers:29.When a new trunk is configured on a 2950 switch, which VLANs by default are allowed over the trunk link?A: no VLANsB: all VLANsC: only VLANs 1 - 64D: only the VLANs that are specified when creating the trunkCorrect Answers: B30.Which of the following is true regarding the use of switches and hubs for network connectivity?A: Switches take less time to process frames than hubs take.B: Switches do not forward broadcasts.C: Hubs can filter frames.D: Using hubs can increase the amount of bandwidth available to hosts.E: Switches increase the number of collision domains in the network.Correct Answers: E31.Why does the data communication industry use the layered OSI reference model? (Choose two.)A:It divides the network communication process into smaller and simpler components, thus aiding component development, design, and troubleshooting.B:It enables equipment from different vendors to use the same electronic components, thus saving research and development funds.C:It supports the evolution of multiple competing standards, and thus provides business opportunities for equipment manufacturers.D:It encourages industry standardization by defining what functions occur at each layer of the model. E:It provides a means by which changes in functionality in one layer require changes in other layers.Correct Answers: A, D 32.HotspotHotspot question. Click on the correct location or locations in the exhibit. Correct Answers:33.Which of the following statements describe the network shown in the graphic? (Choose two.)A:There are two broadcast domains in the network.B:There are four broadcast domains in the network.C:There are six broadcast domains in the network.D:There are four collision domains in the network.E:There are five collision domains in the network.F:There are seven collision domains in the network.Correct Answers: A, FBPlease Input correct Answer here:35.Refer to the exhibit. The network shown in the exhibit is running the RIPv2 routing protocol. The network has converged, and the routers in this network are functioning properly. The FastEthernet0/0 interface on R1 goes down. In which two ways will the routers in this network respond to this change? (Choose two.)A:All routers will reference their topology database to determine if any backup routes to the 192.168.1.0 network are known.B:Routers R2 and R3 mark the route as inaccessible and will not accept any further routing updates from R1 until their hold-down timers expire.C:Because of the split-horizon rule, router R2 will be prevented from sending erroneous information to R1 about connectivity to the 192.168.1.0 network.D:When router R2 learns from R1 that the link to the 192.168.1.0 network has been lost, R2 will respond by sending a route back to R1 with an infinite metric to the 192.168.1.0 network.E:R1 will send LSAs to R2 and R3 informing them of this change, and then all routers will send periodic updates at an increased rate until the network again converges.Correct Answers: C, D36.What is the media access method used by Gigabit Ethernet?A: CSMA/CAB: CSMA/CDC: token passingD: point-to-pointE: logical link controlCorrect Answers: B37.DropDrag and drop question. Drag the items to the proper locations.Correct Answers:38.Why will a switch never learn a broadcast address?A: Broadcasts only use network layer addressing.B: A broadcast frame is never forwarded by a switch.C: A broadcast address will never be the source address of a frame.D: Broadcast addresses use an incorrect format for the switching table.E: Broadcast frames are never sent to switches.Correct Answers: C39.An inbound access list has been configured on a serial interface to deny packet entry for TCP andUDP ports 21, 23 and 25. What types of packets will be permitted by this ACL? (Choose three.)A:FTPB:TelnetC:SMTPD:DNSE:HTTPF:POP3Correct Answers: D, E, F40.Refer to the exhibit. After HostA pings HostB, which entry will be in the ARP cache of HostA to support this transmission?Please Input correct Answer here:switch port fa0/1 to establish a link with router R1 using the IEEE standard protocol? (Choose three.)A:Switch(config)# interface fastethernet 0/1B:Switch(config-if)# switchport mode accessC:Switch(config-if)# switchport mode trunkD:Switch(config-if)# switchport access vlan 1E:Switch(config-if)# switchport trunk encapsulation islF:Switch(config-if)# switchport trunk encapsulation dot1qCorrect Answers: A, C, F42.Refer to the exhibit. What kind of cable should be used to make each connection that is identified by the numbers shown?A: 1 - Ethernet crossover cable2 - Ethernet straight-through cable3 - fiber optic cable4 - rollover cableB: 1 - Ethernet straight-through cable2 - Ethernet straight-through cable3 - serial cable4 - rollover cableC: 1 - Ethernet rollover cable2 - Ethernet crossover cable3 - serial cable4 - null modem cableD: 1 - Ethernet straight-through cable2 - Ethernet crossover cable3 - serial cable4 - rollover cableE: 1 - Ethernet straight-through cable2 - Ethernet crossover cable3 - serial cable4 - Ethernet straight-through cableCorrect Answers: B43.At which layers of the OSI model do WANs operate? (Choose two.)A:application layerB:session layerC:transport layerD:network layerE:datalink layerF:physical layerCorrect Answers: E, FBPlease Input correct Answer here:Central1(config)#router eigrp 23Central1(config-router)#network 192.168.33.045.The network security policy requires that only one host be permitted to attach dynamically to each switch interface. If that policy is violated, the interface should shut down. Which two commands must the network administrator configure on the 2950 Catalyst switch to meet this policy? (Choose two.)A:Switch1(config-if)# switchport port-security maximum 1B:Switch1(config)# mac-address-table secureC:Switch1(config)# access-list 10 permit ip hostD:Switch1(config-if)# switchport port-security violation shutdownE:Switch1(config-if)# ip access-group 10Correct Answers: A, D46.Refer to the exhibit. A problem with network connectivity has been observed. It is suspected that the cable connected to switch port Fa0/9 on Switch1 is disconnected. What would be an effect of this cable being disconnected?A: Host B would not be able to access the server in VLAN9 until the cable is reconnected.B: Communication between VLAN3 and the other VLANs would be disabled.C: The transfer of files from Host B to the server in VLAN9 would be significantly slower.D: For less than a minute, Host B would not be able to access the server in VLAN9. Then normal network function would resume.Correct Answers: D47.Refer to the exhibit. The FMJ manufacturing company is concerned about unauthorized access to the Payroll Server. The Accounting1, CEO, Mgr1, and Mgr2 workstations should be the only computers with access to the Payroll Server. What two technologies should be implemented to help prevent unauthorized access to the server? (Choose two.)A:access listsB:encrypted router passwordsC:STPD:VLANsE:VTPF:wireless LANsCorrect Answers: A, D48.Refer to the exhibit. NAT has been used to convert all the IP addresses on the internal network to the single address 128.107.1.1 as traffic is routed toward the Internet. Which of these statements accurately describes what will happen when the IP traffic returns from the Internet destined for hosts on the internal network?A: ExternalRouter will require a route to 172.16.0.0/16 in its routing table to properly direct the traffic.B: InternalRouter will convert the source IP addresses of all packets before forwarding them onto the internal network.C: ExternalRouter will translate the destination IP addresses of all packets before forwarding them to InternalRouter.D: As InternalRouter will be receiving traffic from ExternalRouter, the destination IP addresses will already have been converted to 172.16.0.0/16 addresses.E: ExternalRouter can use the directly connected interface on the 128.107.0.0/27 network to route return traffic to its originators.Correct Answers: E49.Refer to the exhibit. A network associate needs to configure the switches and router in the graphic so that the hosts in VLAN3 and VLAN4 can communicate with the enterprise server in VLAN2. Which two Ethernet segments would need to be configured as trunk links? (Choose two.)A:AB:BC:CD:DE:EF:FCorrect Answers: C, F50.Which statement is correct regarding the operation of DHCP?A: A DHCP server uses a ping to detect address conflicts.B: A DHCP server uses a gratuitous ARP to detect DHCP clients.C: A DHCP client uses a ping to detect address conflicts.D: A DHCP client uses a gratuitous ARP to detect a DHCP server.E: If and address conflict is detected, the address is removed from the pool for an amount of time configurable by the administrator.Correct Answers: A51.A Cisco router that was providing Frame Relay connectivity at a remote site was replaced with a different vendor's frame relay router. Connectivity is now down between the central and remote site. What is the most likely cause of the problem?A: mismatched LMI typesB: incorrect DLCIC: mismatched encapsulation typesD: incorrect IP address mappingCorrect Answers: C52.Which additional configuration step is necessary in order to connect to an access point that has SSID broadcasting disabled?A: Set the SSID value in the client software to public.B: Configure open authentication on the AP and the client.C: Set the SSID value on the client to the SSID configured on the AP.D: Configure MAC address filtering to permit the client to connect to the AP.Correct Answers: C53.What is the default routing update period for RIPv2?A: 15 secondsB: 30 secondsC: 180 secondsD: 240 secondsCorrect Answers: B54.Acknowledgements, sequencing, and flow control are characteristics of which OSI layer?A: Layer 2B: Layer 3C: Layer 4D: Layer 5E: Layer 6F: Layer 7Correct Answers: C55.An access list has been designed to prevent HTTP traffic from the Accounting Department from reaching the HR server attached to the Holyoke router. Which of the following access lists will accomplish this task when grouped with the e0 interface on the Chicopee router?A: permit ip any anydeny tcp 172.16.16.0 0.0.0.255 172.17.17.252 0.0.0.0 eq 80B: permit ip any anydeny tcp 172.17.17.252 0.0.0.0 172.16.16.0 0.0.0.255 eq 80C: deny tcp 172.17.17.252 0.0.0.0 172.16.16.0 0.0.0.255 eq 80permit ip any anyD: deny tcp 172.16.16.0 0.0.0.255 172.17.17.252 0.0.0.0 eq 80permit ip any anyCorrect Answers: D56.Which of the following are key characteristics of PPP? (Choose three.)A:can be used over analog circuitsB:maps Layer 2 to Layer 3 addressC:encapsulates several routed protocolsD:supports IP onlyE:provides error correctionCorrect Answers: A, C, E57.Refer to the exhibit. The network administrator must complete the connection between the RTA of the XYZ Company and the service provider. To accomplish this task, which two devices could be installed at the customer site to provide a connection through the local loop to the central office of the provider? (Choose two.)A:WAN switchB:PVCC:ATM switchD:multiplexerE:CSU/DSUF:modemCorrect Answers: E, F58.What is the maximum data rate specified for IEEE 802.11b WLANs?A: 10 MbpsB: 11 MbpsC: 54 MbpsD: 100 MbpsCorrect Answers: B59.Refer to the exhibit. A technician is troubleshooting a host connectivity problem. The host is unable to ping a server connected to Switch_A. Based on the results of the testing, what could be the problem?A: A remote physical layer problem exists.B: The host NIC is not functioning.C: TCP/IP has not been correctly installed on the host.D: A local physical layer problem exists.Correct Answers: D60.When a router is connected to a Frame Relay WAN link using a serial DTE interface, how is the interface clock rate determined?A: It is supplied by the CSU/DSU.B: It is supplied by the far end router.C: It is determined by the clock rate command.D: It is supplied by the Layer 1 bit stream timing.Correct Answers: A61.Refer to the exhibit. RouterA is configured to use NAT in overload mode PC_A is sending packets to Web Server. Drag the addresses to fill in the NAT terminology table with their associated IP address values. Note: Addresses may be used, none, once or more.Drag and drop question. Drag the items to the proper locations. Correct Answers:62.Refer to the exhibit. The network shown in the exhibit is running the RIPv2 routing protocol. The network has converged, and the routers in this network are functioning properly. The FastEthernet0/0 interface on R1 goes down. In which two ways will the routers in this network respond to this change? (Choose two.)A:All routers will reference their topology database to determine if any backup routes to the 192.168.1.0 network are known.B:Routers R2 and R3 mark the route as inaccessible and will not accept any further routing updates from R1 until their hold-down timers expire.C:Because of the split-horizon rule, router R2 will be prevented from sending erroneous information to R1 about connectivity to the 192.168.1.0 network.D:When router R2 learns from R1 that the link to the 192.168.1.0 network has been lost, R2 will respond by sending a route back to R1 with an infinite metric to the 192.168.1.0 network.E:R1 will send LSAs to R2 and R3 informing them of this change, and then all routers will send periodic updates at an increased rate until the network again converges.Correct Answers: C, D63.The Ethernet networks connected to router R1 in the graphic have been summarized for router R2 as192.1.144.0/20. Which of the following packet destination addresses will R2 forward to R1, according to this summary? (Choose two.)A:192.1.159.2B:192.1.160.11C:192.1.138.41D:192.1.151.254E:192.1.143.145F:192.1.1.144Correct Answers: A, D64.Refer to the exhibit. Host B is actively communicating by Ethernet with the server. Host A has frames to send to the Internet. How will host A proceed?A: Host A will listen and transmit when there is no traffic on the segment.B: Host A will immediately begin transmitting because the destination is different.C: Host A must wait for the server to reply to host B before transmitting.D: Host A will immediately begin transmitting because it has priority based on its MAC address. E: Host A can send its frames at any time because it will be sending them through the router. Correct Answers: A65.Why would a network administrator configure port security on a switch?A: to prevent unauthorized Telnet access to a switch portB: to limit the number of Layer 2 broadcasts on a particular switch portC: to prevent unauthorized hosts from accessing the LAND: to protect the IP and MAC address of the switch and associated portsE: to block unauthorized access to the switch management interfaces over common TCP portsCorrect Answers: C66.What is the effect of using the service password-encryption command?A: Only the enable password will be encrypted.B: Only the enable secret password will be encrypted.C: Only passwords configured after the command has been entered will be encrypted.D: It will encrypt the secret password and remove the enable secret password from the configuration. E: It will encrypt all current and future passwords.Correct Answers: E67.Which two devices can interfere with the operation of a wireless network because they operate on similar frequencies? (Choose two.)A:copierB:microwave ovenC:toasterD:cordless phoneE:IP phoneF:AM radioCorrect Answers: B, D68.Which type of attack is characterized by a flood of packets that are requesting a TCP connection to a server?A: denial of serviceB: brute forceC: reconnaissanceD: Trojan horseCorrect Answers: A69.Refer to the exhibit. A technician is investigating a problem with the network that is shown. The router is a 2800 model and all switches are 2950 models. These symptoms have been observed:- All of the user hosts can access the Internet.- None of the user hosts can access the server located in VLAN 9.- All of the hosts can ping each other.What could cause these symptoms?。
CCNA(640-802)题库V104.4(2012.11.11)

CCNA(640-802)题库V104.4(2012.11.11)Exam AQUESTION 1When you are logged into a switch, which prompt indicates that you are in privileged mode?A. %B. @C. >D. $E. #Answer: ESection: Chapter 4: Introduction to Cisco IOSExplanation/Reference:当你登陆一台交换机的时候,登陆到特权模式时,怎么显示的?考点分析:登入交换机,进去用户模式是使用>作为提示符,进入特权模式是使用#号提示符.QUESTION 2Which command shows system hardware and software version information?A. show configurationB. show environmentC. show inventoryD. show platformE. show versionAnswer: ESection: Chapter 4: Introduction to Cisco IOSExplanation/Reference:那一条命令显示系统的硬件和软件版本信息?考点分析:这道题考的是show version这个基本的命令的作用。
show version此命令的作用能显示系统的硬件和软件版本信息。
QUESTION 3Cisco Catalyst switches CA T1 and CA T2 have a connection between them using ports FA0/13. An 802. 1Q trunk is configured between the two switches. On CA T1, VLAN 10 is chosen as native, but on CA T2 the native VLAN is not specified.What will happen in this scenario?A. 802.1Q giants frames could saturate the link.B. VLAN 10 on CA T1 and VLAN 1 on CA T2 will send untagged frames.C. A native VLAN mismatch error message will appear.D. VLAN 10 on CA T1 and VLAN 1 on CA T2 will send tagged frames.Answer: CSection: Chapter 10: VLANExplanation/Reference:交换机CA T1和CA T2通过F0/13端口连接,交换机之间封装是的802.1q,在VLAN10中本征VLAN被修改成了VLAN10,在CA T2上没有指定。
思科认证考试题库

CCNA640-802 V13题库试题分析题库讲解:吴老师(艾迪飞CCIE实验室首发网站:1. What are two reasons that a network administrator would use access lists? (Choose two.)A. to control vty access into a routerB. to control broadcast traffic through a routerC. to filter traffic as it passes through a routerD. to filter traffic that originates from the routerE. to replace passwords as a line of defense against security incursionsAnswer: AC解释一下:在VTY线路下应用ACL,可以控制从VTY线路进来的telnet的流量。
也可以过滤穿越一台路由器的流量。
2. A default Frame Relay WAN is classified as what type of physical network?A. point-to-pointB. broadcast multi-accessC. nonbroadcast multi-accessD. nonbroadcast multipointE. broadcast point-to-multipointAnswer: C解释一下:在默认的情况下,帧中继为非广播多路访问链路。
但是也可以通过子接口来修改他的网络的类型。
3.Refer to the exhibit. How many broadcast domains exist in the exhibited topology?A. oneB. twoC. threeD. fourE. fiveF. sixAnswer: C解释一下:广播域的问题,在默认的情况下,每个交换机是不能隔离广播域的,所以在同一个区域的所有交换机都在同一个广播域中,但是为了减少广播的危害,将广播限制在一个更小的范围,有了VLAN的概念,VLAN表示的是一个虚拟的局域网,而他的作用就是隔离广播。
CCNA考试题

C C N A考试题(总9页) -CAL-FENGHAI.-(YICAI)-Company One1-CAL-本页仅作为文档封面,使用请直接删除第一部分:选择题1:提供可靠数据传输、流控的是OSI的第几层()A、表示层B、网络层C、传输层D、会话层E、链路层2:子网掩码产生在那一层()A、表示层B、网络层C、传输层D、会话层3:当路由器接收的IP报文的目的地址不是本路由器的接口IP地址,并且在路由表中未找到匹配的路由项,采取的策略是()A、丢掉该分组B、将该分组分片C、转发该分组D、以上答案均不对4:当一台主机从一个网络移到另一个网络时,以下说法正确的是()A、必须改变它的IP地址和MAC地址B、必须改变它的IP地址,但不需改动MAC地址C、必须改变它的MAC地址,但不需改动IP地址D、MAC地址、IP地址都不需改动5:ISO提出OSI的关键是()A、系统互联B、提高网络速度C、为计算机制定标准D、经济利益6:OSI参考模型按顺序有哪些层()A、应用层、传输层、网络层、物理层B、应用层、表示层、会话层、网络层、传输层、数据链路层、物理层C、应用层、表示层、会话层、传输层、网络层、数据链路层、物理层D、应用层、会话层、传输层、物理层7:LAN的拓扑形式一般以()为主。
A、总线型B、环型C、令牌环D、载波侦听与冲突检测CSMA/CD8:网段地址154.27.0.0的网络,若不做子网划分,能支持()台主机A、254B、1024C、65,534D、16,777,2069:路由器网络层的基本功能是()。
A、配置IP地址B、寻找路由和转发报文C、将MAC地址解释成IP地址10:选出基于TCP协议的应用程序()。
A、PINGB、TFTPC、TELNETD、OSPF11:某公司申请到一个C类IP地址,但要连接6个的子公司,最大的一个子公司有26台计算机,每个子公司在一个网段中,则子网掩码应设为()。
A、255.255.255.0B、255.255.255.128C、255.255.255.192D、255.255.255.22412:B类地址的缺省掩码是()。
CCNA认证指南(640 802)

3 8.3 OSPF高级
配置**
4 8.4真题精选
***
5 8.5真题解答
***
9.1局域网设计** 9.2交换机分类*
9.3交换机基本配置 **
9.4交换机的安全.6真题解答 ***
10.1 VLAN介绍** 10.2 VLAN干线***
10.3配置VLAN***
读书笔记
中国人写的网络技术书,总体不错,有些细节提示比较到位,可以结合经典教材一起看,4星推荐。
精彩摘录
数据链路层的主要功能是如何在不可靠的物理线路上进行数据的可靠传输。数据链路层完成的是网络中相邻 结点之间可靠的数据通信。为了保证数据的可靠传输,发送方把用户数据封装成帧
路由器有两大典型功能,即数据通道功能和控制功能。
19.3 VPN**
19.4真题精 选*
19.5真题解 答*
20.1 DHCP** 20.2 NAT***
20.3真题精选*** 20.4真题解答***
21.2 IPv6地址*
21.1 IPv6的重要 性*
21.3 IPv6路由
21.5真题精选*
21.4 IPv6过渡策 略*
21.6真题解答*
12.5真题精 选***
12.6真题解 答***
13.1无线网络介绍 **
13.2无线局域网安 全***
13.3配置无线局域 网*
13.4无线故障排除 **
13.5真题精 选***
13.6真题解 答***
14.1广域网 概述**
14.2广域网 技术**
14.3真题精 选***
14.4真题解 答***
17.5复杂ACL
17.6真题精选*** 17.7真题解答***
CCNA640-802实验题

Answer:Bomar(Config)#interface fa0/0Bomar(Config-if)#ip nat insideBomar(Config)#interface S0/0Bomar(Config-if)#ip nat outsideBomar(Config-if)#exitBomar(Config)#access-list1permit192.168.16.330.0.0.15Bomar(Config)#access-list1deny anyBomar(Config)#ip nat pool nat_test198.18.237.225198.18.237.230prefix-length29 Bomar(Config)#ip nat inside source list1pool nat_test overloadAnswer:3.After adding Interior router,no routing updates are being exchanged between Perimeter and the new location.All other interconnectivity and Internet access for the existing locations of the company are working properly.The task is to identify the fault(s)and correct the router configurations to provide full connectivity between the routers.Access to the router CLI can be gained by clicking on the appropriate host.All passwords on all routers are cisco.Answer:1.Click terminal-server"E",input commands like this:Central2>enablepassword:ciscoCentral2#config tCentral2(config)#no router eigrp22Central2(config)#router eigrp23Central2(config-router)#network192.168.33.0Central2(config-router)#network192.168.72.02.Click terminal-server"G",input commands like this:Central1>enablePassword:ciscoCentral1#config tCentral1(config)#router eigrp23Central1(config-router)#network192.168.33.04.Answer:E Question#2Answer:B Question#3Answer:A6.The Pass4sure network topology and the output of Pass4sure1are shown below:Please study the exhibit shown above carefully,and answer the following questions. Question#1What destination Layer2address will be used in the frame header containing a packet for host172.30.4.4?A.704B.196C.702D.344Answer:CQuestion#2A static map to the Pass4sureB location is required.Which command should be used to create this map?A.frame-relay map ip172.30.0.3704broadcastB.frame-relay map ip172.30.0.3196broadcastC.frame-relay map ip172.30.0.3702broadcastD.frame-relay map ip172.30.0.3344broadcastAnswer:BQuestion#3Which connection user the default encapsulation for serial interfaces on Cisco routers?A.The serial connection to the Pass4sure2branch office.B.The serial connection to the Pass4sure3branch office.C.The serial connection to the Pass4sure4branch office.D.The serial connection to the Multination Core.Answer:AQuestion#4If required,what password should be configured on the router in the Pass4sure2branch office to allow a connection to be established with the Pass4sure1router?A.No password is required.B.EnableC.SecretD.TelnetE.ConsoleAnswer:A7.A user is unable to connect to the Internet.Based on the layered approach to troubleshooting and beginning with the lowest layer,drag each procedure on the left to its proper category on the right.Answer:8.Drag the security features on the left to the specific security risks they help protect against on the right.(Not all options are used.)Answer:9.Drag the cable type on the left to the purpose for which it is best suited on the right.(Not all options are used.)Answer :10.Refer to the exhibit.PC_1is sending packets to the FTP server.Consider the packets as they leave RouterA interface Fa0/0towards RouterB.Drag the correct frame and packet address to their place in thetable.Answer:11.If a Cisco router has learned about network 10.1.1.0from multiple sources,the router will select and install only one entry into the routing table.Indicate the order of preference that the router will use by dragging the routes on the left to the order of preference category on the right.Answer:12.Drag the options on the left under the type of switch port that they describe on the right.Answer:13.Match the terms on the left with the appropriate OSI layer on the right.(Not all options are used.)Answer:14.Drag the appropriate 5steps of the boot sequence on the left to their correct slots on the right.(Not all options apply.)Answer:15.Drag the Cisco default administrative distance to the appropriate routing protocol or route.(Not all options are used.)Answer:16.Routing has been configured on the local router with these commands:Local(config)#ip route 0.0.0.00.0.0.0192.168.1.1Local(config)#ip route 10.1.0.0255.255.255.0192.168.2.2Local(config)#ip route10.1.0.0255.255.0.0192.168.3.3Drag each destination IP address on the left to its correct next hop address on the right.Answer:17.Drag the term on the left to its definition on the right.(Not all options are used.)Answer:18.Drag each category on the left to its corresponding router output line on the right.Each router output line is the result of a show ip interface command.Not all categories are used.Answer:19.Drag each feature on the left to the appropriate routing protocol on the right.Answer:20.Drag the connection types on the left to the appropriate type of cable used on the right.(Not all options are used.)Answer:21.Drag the description on the left to the routing protocol on the right.(Not all options are used.)Answer:22.Place the Spanning-Tree Protocol port state on its function by dragging the state on the left to the correct target on the right.(Not all options on the left are used.)Answer:23.Answer:。
CCNA640-802拖图题
Answer:
Section: Drag n Drop Explanation/Reference:
QUESTION 563
Answer:
Section: Drag n Drop Explanation/Reference:
QUESTION 553
Answer:
Section: Drag n Drop Explanation/Reference:
Answer:
Section: Drag n Drop Explanation/Re
QUESTION 566
Answer:
Section: Drag n Drop
Explanation/Reference: QUESTION 567
哪哪如那当当周周链为中中
split horizon水水删水 prevent information about a route form being sent in the direction from which the route 哪哪链为那那哪发送当官是不环
defining a maximum上是最它值 prevent invalid update form looping the internetwork indefinitely 哪哪配输当更最能哪分位环链。
Answer:
Section: Drag n Drop
Explanation/Reference: QUESTION 577
CCNA考试流程及注意事项

CCNA考试流程及注意事项1,CCNA考试代号640—802,考试时间140分钟,总分1000分,通过分数825分,最新题库版本v104。
考试题型,选择、拖图题、实验题。
(1)选择题,是原题,看题库的时候要达到秒杀的地步。
(2)拖图题,计算子网掩码的有的拖图题,是把左边IP地址拖到右边图中相应的位置上,考试时IP地址肯定会有变化,题型是完全一样的,看题库的时候要理解掌握。
(3)实验题,题型跟题库一样,IP什么的会有变化。
注:一般考友的经验,用一到两周看四五遍题库是可以顺利通过考试的,但是题库一定要看到秒杀的程度,在鸿鹄报名考试,考前辅导是不收费的,只要报名考试就可以加入VIP群,有问题直接提,有讲师答疑。
考前有冲刺辅导,详情咨询鸿鹄客服。
2,考试报名流程(提前1-30天报名):(1).考生填完考试报名表后,传给客服。
(2).考生拍下淘宝链接并且付款到淘宝。
(3).我们安排考试,安排好了通知考生去考点查询预约情况。
(4).考生去查询考试情况,打电话或者是亲自去考点查询都可以。
(这样说就可以:你好,是XX考点吗?我叫XX,我预约了咱考点X月X日的考试,你看看安排好了没有?)(5).考生确认没问题了,考试当天去考试。
(6).考试后确认收货并付款给卖家,考后的注册我们都协助考生完成。
3,考试的时候需要携带两个证件:第一证件:身份证军官证护照港澳通行证第二证件:学生证(带钢印)信用卡医保卡暂住证工作证驾驶证注:最好提前半个小时就到达考点!4,考前问卷调查,题目就是问问你准备考试多长时间,你看的什么教材,你是怎么知道cisco,你是自学还是培训,你家离考点路程多远,你文化程度,这些无所谓。
但问满不满18周岁,一定选YES,问同不同意CISCO协议,一定选“同意”。
有不明白的可以直接问考官。
协议过后,调查问卷页面右下角点END选项,考试系统自动开始从服务器抽取题目,题目前一天已由考试中心从澳洲下载完毕,暂存于服务器中。
CCNA640-802V13+题库51-100题

51.What can a network administrator utilize by using PPP Layer 2 encapsulation? (Choose three.)A. VLAN supportB. compressionC. authenticationD. sliding windowsE. multilink supportF. quality of service52.Refer to the exhibit. What is the meaning of the term dynamic as displayed in the output of the show frame-relay map command shown?A. The Serial0/0 interface is passing traffic.B. The DLCI 100 was dynamically allocated by the router.C. The Serial0/0 interface acquired the IP address of 172.16.3.1 from a DHCP server.D. The DLCI 100 will be dynamically changed as required to adapt to changes in the Frame Relay cloud.E. The mapping between DLCI 100 and the end station IP address 172.16.3.1 was learned through Inverse ARP.53. What is the function of the Cisco IOS command ip nat inside source static 10.1.1.5 172.35.16.5?A. It creates a global address pool for all outside NAT transactions.B. It establishes a dynamic address pool for an inside static address.C. It creates dynamic source translations for all inside local PAT transactions.D. It creates a one-to-one mapping between an inside local address and an inside global address.E. It maps one inside source address to a range of outside global addresses.54.Refer to the exhibit. What is the effect of the configuration that is shown?A. It configures SSH globally for all logins.B. It tells the router or switch to try to establish an SSh connection first and if that fails to use Telnet.C. It configures the virtual terminal lines with the password 030752180500.D. It configures a Cisco network device to use the SSH protocol on incoming communications via the virtual terminal ports.E. It allows seven failed login attempts before the VTY lines are temporarily shutdown.55.Refer to the exhibit. When PC1 sends an ARP request for the MAC address of PC2, network performance slows dramatically, and the switches detect an unusually high number of broadcast frames. What is the most likely cause of this?A. The portfast feature is not enabled on all switch ports.B. The PCs are in two different VLANs.C. Spanning Tree Protocol is not running on the switches.D. PC2 is down and is not able to respond to the request.E. The VTP versions running on the two switches do not match.56. An administrator issues the command ping 127.0.0.1 from the command line prompt on a PC. Ifa reply is received, what does this confirm?A. The PC has connectivity with a local host.B. The PC has connectivity with a Layer 3 device.C. The PC has a default gateway correctly configured.D. The PC has connectivity up to Layer 5 of the OSI model.E. The PC has the TCP/IP protocol stack correctly installed.57.Host 1 has just started up and requests a web page from web server 2. Which two statements describe steps in the process Host 1 uses to send the request to web server 2 (choose two)?A. Host 1 addresses the frames to the MAC address of router R1B. Host 1 looks in its ARP cache for the MAC address of router R1C. Host 1 addresses the frames to the MAC address of web server 2D. Host 1 sends the packets to router R1 to be forwarded to web server 2E. Host 1 sends a broadcast ARP request to obtain the MAC address of webserver2.58.Refer to the exhibit.Which two statements about the configuration of the switch interface are correct? (Choose two)A. The switchport belongs only to VLAN 2B. Interface fa0/0 will be in both VLAN 1 (by default) and VLAN 2C. The exhibit shows interface fa0/0 to be dynamically mapped to VLAN 2D. A network host can be connected to this interface.59.Refer to the exhibit. The network administrator requires easy configuration options and minimal routing protocol traffic. What two options provide adequate routing table information for traffic that passes between the two routers and satisfy the requests of the network administrator? (Choose two.)A. a dynamic routing protocol on InternetRouter to advertise all routes to CentralRouter.B. a dynamic routing protocol on InternetRouter to advertise summarized routes to CentralRouter.C. a static route on InternetRouter to direct traffic that is destined for 172.16.0.0/16 to CentralRouter.D. a dynamic routing protocol on CentralRouter to advertise all routes to InternetRouter.E. a dynamic routing protocol on CentralRouter to advertise summarized routes to InternetRouter.F. a static, default route on CentralRouter that directs traffic to InternetRouter.60.What are some of the advantages of using a router to segment the network? (Choose two.)A. Filtering can occur based on Layer 3 information.B. Broadcasts are eliminated.C. Routers generally cost less than switches.D. Broadcasts are not forwarded across the router.E. Adding a router to the network decreases latency.61. Refer to the exhibit. What is the meaning of the output MTU 1500 bytes?A. The maximum number of bytes that can traverse this interface per second is 1500.B. The minimum segment size that can traverse this interface is 1500 bytes.C. The maximum segment size that can traverse this interface is 1500 bytes.D. The minimum packet size that can traverse this interface is 1500 bytes.E. The maximum packet size that can traverse this interface is 1500 bytes.F. The maximum frame size that can traverse this interface is 1500 bytes.62. There are no boot system commands in a router configuration in NVRAM. What is the fallback sequence that the router will use to find an IOS during reload?A. TFTP server, Flash, NVRAMB. ROM, NVRAM, TFTP serverC. NVRAM, TFTP server, ROMD. Flash, TFTP server, ROME. Flash, NVRAM, ROM63.Host 1 receives a file from remote server 1. Which MAC address appears as the source address in the header of the frames received by Host 1?A. The MAC address of the NIC in Host 1 .B. The MAC address of the NIC in server 1.C. The MAC address of the Fa0/0 interface of router R1D. The MAC address of the s0/0/0 interface of the router R264.In which circumstance are multiple copies of the same unicast frame likely to be transmitted in a switched LAN?A. during high traffic periodsB. after broken links are re-establishedC. when upper-layer protocols require high reliabilityD. in an improperly implemented redundant topologyE. when a dual ring topology is in use65.Which of the following describe private IP addresses? (Choose two.)A. addresses chosen by a company to communicate with the InternetB. addresses that cannot be routed through the public InternetC. addresses that can be routed through the public InternetD. a scheme to conserve public addressesE. addresses licensed to enterprises or ISPs by an Internet registry organization66.Refer to the exhibit. A network administrator is adding two new hosts to SwitchA. Which three values could be used for the configuration of these hosts? (Choose three.)A. host 1 IP address: 192.168.1.79B. host 1 IP address: 192.168.1.64C. host 1 default gateway: 192.168.1.78D. host 2 IP address: 192.168.1.128E. host 2 default gateway: 192.168.1.129F. host 2 IP address: 192.168.1.19067.Which of the following statements are true regarding bridges and switches? (Choose 3.)A. Switches are primarily software based while bridges are hardware based.B. Both bridges and switches forward Layer 2 broadcasts.C. Bridges are frequently faster than switches.D. Switches have a higher number of ports than most bridges.E. Bridges define broadcast domains while switches define collision domains.F. Both bridges and switches make forwarding decisions based on Layer 2 addresses.68. Which of the following describes the roles of devices in a WAN? (Choose three.)A. A CSU/DSU terminates a digital local loop.B. A modem terminates a digital local loop.C. A CSU/DSU terminates an analog local loop.D. A modem terminates an analog local loop.E. A router is commonly considered a DTE device.F. A router is commonly considered a DCE device.69.A router receives information about network 192.168.10.0/24 from multiple sources. What will the router consider the most reliable information about the path to that network?A. a directly connected interface with an address of 192.168.10.254/24B. a static route to network 192.168.10.0/24C. a RIP update for network 192.168.10.0/24D. an OSPF update for network 192.168.0.0/16E. a default route with a next hop address of 192.168.10.1F. a static route to network 192.168.10.0/24 with a local serial interface configured as the next hop70.Which three Layer 2 encapsulation types would be used on a W AN rather than a LAN? (Choose three.)A. HDLCB. EthernetC. Token RingD. PPPE. FDDIF. Frame Relay71.What can be determined from the router output shown in the graphic?A. 200.1.1.64 is a default route.B. The output shows that there are three default routes.C. The output came from router R2.D. The output came from a router that has four physical interfaces.E. EIGRP is in use in this network.72.Which additional configuration step is necessary in order to connect to an access point that has SSID broadcasting disabled?A. Set the SSID value in the client software to public.B. Configure open authentication on the AP and the client.C. Set the SSID value on the client to the SSID configured on the AP.D. Configure MAC address filtering to permit the client to connect to the AP.73.Why will a switch never learn a broadcast address?A. Broadcasts only use network layer addressing.B. A broadcast frame is never forwarded by a switch.C. A broadcast address will never be the source address of a frame.D. Broadcast addresses use an incorrect format for the switching table.E. Broadcast frames are never sent to switches.74.Refer to the graphic. Host A has established a connection with the HTTP server attached to interface E0 of the xyz router. Which of the following statements describe the information contained in protocol data units sent from host A to this server? (Choose three.)A. The destination port number in a segment header will have a value of 80.B. The destination port number in a segment header will have a unique value greater than or equal to 1023.C. The destination address of a frame will be the MAC address of the HTTP server interface.D. The destination address of a frame will be the MAC address of the E0 interface of the abc router.E. The destination IP address of a packet will be the IP address of the E0 interface of the abc router.F. The destination IP address of a packet will be the IP address of the network interface of the HTTP server.75.What are two reasons a network administrator would use CDP? (Choose two.)A. to verify the type of cable interconnecting two devicesB. to determine the status of network services on a remote deviceC. to obtain VLAN information from directly connected switchesD. to verify Layer 2 connectivity between two devices when Layer 3 failsE. to obtain the IP address of a connected device in order to telnet to the deviceF. to determine the status of the routing protocols between directly connected routers76.What is the purpose of the command shown below?vtp password Fl0r1daA. It is used to validate the sources of VTP advertisements sent between switches.B. It is used to access the VTP server to make changes to the VTP configuration.C. It allows two VTP servers to exist in the same domain, each configured with different passwords.D. It is the password required when promoting a switch from VTP client mode to VTP server mode.E. It is used to prevent a switch newly added to the network from sending incorrect VLAN information to the other switches in the domain.77.R1 forwards a packet from Host 1 to remote Server 1. Which statement describes the use of aMAC as the frame carrying this packet leaves the s0/0/0 interface of R1?A.The frame does not have MAC addresses.B.The source MAC address in the frame is the MAC address of the NIC of Host 1.C.The source MAC address in the frame is the MAC address of the s0/0/0 interface of R1.D. The destination MAC address in the frame is the MAC address of the NIC of server 1.E. The destination MAC address in the frame is the MAC address of the s0/0/0 interface of R278.A network administrator needs to force a high-performance switch that is located in the MDF to become the root bridge for a redundant path switched network. What can be done to ensure that this switch assumes the role as root bridge?A. Establish a direct link from the switch to all other switches in the network.B. Assign the switch a higher MAC address than the other switches in the network have.C. Configure the switch so that it has a lower priority than other switches in the network.D. Configure the switch for full-duplex operation and configure the other switches for half-duplex operation.E.Connect the switch directly to the MDF router, which will force the switch to assume the role of root bridge.79.Refer to the exhibit. Given the output of the Floor3 switch, what statement describes the operation of this switch?A. VTP is disabled on this switch.B. The switch can create, change, and delete VLANs.C. The switch learns VLAN information but does not save it to NVRAM.D. The switch can create VLANs locally but will not forward this information to other switches.E. The switch learns VLAN information and updates the local VLAN data base in NVRAM.80.What is the effect of the following access list condition?access-list 101 permit ip 10.25.30.0 0.0.0.255 anyA. permit all packets matching the first three octets of the source address to all destinationsB. permit all packets matching the last octet of the destination address and accept all source addressesC. permit all packets from the third subnet of the network address to all destinationsD. permit all packets matching the host bits in the source address to all destinationsE. permit all packets to destinations matching the first three octets in the destination address81.Refer to the exhibit. Hosts on the same VLAN can communicate with each other but are unable to communicate with hosts on different VLANs. What is needed to allow communication between VLANs?A. a switch with a trunk link that is configured between the switchesB. a router with an IP address on the physical interface that is connected to the switchC. a switch with an access link that is configured between the switchesD. a router with subinterfaces configured on the physical interface that is connected to the switch82.Why would a network administrator configure port security on a switch?A. to prevent unauthorized Telnet access to a switch portB. to limit the number of Layer 2 broadcasts on a particular switch portC. to prevent unauthorized hosts from accessing the LAND. to protect the IP and MAC address of the switch and associated portsE. to block unauthorized access to the switch management interfaces over common TCP ports83.The show interfaces serial 0/0 command resulted in the output shown in the graphic. What are possible causes for this interface status? (Choose three.)A. The interface is shut down.B. No keepalive messages are received.C. The clockrate is not set.D. No loopback address is set.E. No cable is attached to the interface.F. There is a mismatch in the encapsulation type.84.Host 1 sends an ICMP echo request to remote sever1. Which destination address does Host 1 place in the Layer2 header of the frame containing the ping packet?A. The IP address of sever 1.B. The MAC address of NIC in sever 1.C. The IP address of F0/0 interface of router R1.D. The MAC address of the Fa0/0 interface of router R1.E. The IP address of the s0/0/0 interface of router R2F. The MAC address of the s0/0/0 interface of router R285.A network administrator is troubleshooting the OSPF configuration of routers R1 and R2. The routers cannot establish an adjacency relationship on their common Ethernet link. The graphic shows the output of the show ip ospf interface e0 command for routers R1 and R2. Based on the information in the graphic, what is the cause of this problem?A. The OSPF area is not configured properly.B. The priority on R1 should be set higher.C. The cost on R1 should be set higher.D. The hello and dead timers are not configured properly.E. A backup designated router needs to be added to the network.F. The OSPF process ID numbers must match.86.On which types of network will OSPF elect a backup designated router?A. point-to-point and multiaccessB. point-to-multipoint and multiaccessC. point-to-point and point-to-multipointD. nonbroadcast and broadcast multipointE. nonbroadcast and broadcast multiaccess87.This graphic shows the results of an attempt to open a Telnet connection to router ACCESS1 from router Remote27. Which of the following command sequences will correct this problem?A. ACCESS1(config)# line console 0ACCESS1(config-line)# password ciscoB. Remote27(config)# line console 0Remote27(config-line)# loginRemote27(config-line)# password ciscoC. ACCESS1(config)# line vty 0 4ACCESS1(config-line)# loginACCESS1(config-line)# password ciscoD. Remote27(config)# line vty 0 4Remote27(config-line)# loginRemote27(config-line)# password ciscoE. ACCESS1(config)# enable password ciscoF. Remote27(config)# enable password cisco88.Refer to the exhibit. Subnet 10.1.3.0/24 is unknown to router RTB. Which router command will prevent router RTB from dropping a packet destined for the 10.1.3.0/24 network if a default route is configured?A. ip classlessB. ip default-networkC. network 10.1.1.0D. network 10.1.1.0 0.0.0.255 area 089.Host 1 sends a request for a file to remote sever1. Which destination address does Host 1 place f the packet containing the request?A. The Mac address of the NIC in Sever1B. The IP address of Server 1.C. The MAC address of the s0/0/0 interface of router R2D. The IP address of the s0/0/0 interface of router R1E. The IP address of the Fa0/0 interface of router R190.Which statement accurately describes a benefit provided by VTP?A. VTP allows routing between VLANs.B. VTP allows a single port to carry information to more than one VLAN.C. VTP allows physically redundant links while preventing switching loops.D. VTP allows switches to share VLAN configuration information.91.Refer to the exhibit. What kind of cable should be used to make each connection that is identified by the numbers shown?A. 1 - Ethernet crossover cable2 - Ethernet straight-through cable3 - fiber optic cable4 - rollover cableB. 1 - Ethernet straight-through cable2 - Ethernet straight-through cable3 - serial cable4 - rollover cableC. 1 - Ethernet rollover cable2 - Ethernet crossover cable3 - serial cable4 - null modem cableD. 1 - Ethernet straight-through cable2 - Ethernet crossover cable3 - serial cable4 - rollover cableE. 1 - Ethernet straight-through cable2 - Ethernet crossover cable3 - serial cable4 - Ethernet straight-through cable92.Refer to the exhibit. A network administrator attempts to ping Host2 from Host1 and receives the results that are shown. What is a possible problem?A. The link between Host1 and Switch1 is down.B. TCP/IP is not functioning on Host1C. The link between Router1 and Router2 is down.D. The default gateway on Host1 is incorrect.E. Interface Fa0/0 on Router1 is shutdown.F. The link between Switch1 and Router1 is down.93.What does the "Inside Global" address represent in the configuration of NAT?A. the summarized address for all of the internal subnetted addressesB. the MAC address of the router used by inside hosts to connect to the InternetC. a globally unique, private IP address assigned to a host on the inside networkD. a registered address that represents an inside host to an outside network94.During startup, the router displays the following error message:boot: cannot open "flash:"What will the router do next?A. Because of damaged flash memory, the router will fail the POST.B. It will attempt to locate the IOS from a TFTP server. If this fails, it will initiate the setup dialog.C. It will attempt to locate the IOS from a TFTP server. If this fails, it will load a limited IOS from ROM.D. It will attempt to locate the configuration file from a TFTP server. If this fails, it will initiate the setup dialog.E. It will attempt to locate the configuration file from a TFTP server. If this fails, it will load a limited configuration from ROM.95.Refer to the exhibit. S0/0 on R1 is configured as a multipoint interface to communicate with R2 and R3 in this hub-and-spoke Frame Relay topology. While testing this configuration, a technician notes that pings are successful from hosts on the 172.16.1.0/24 network to hosts on both the 172.16.2.0/25 and 172.16.2.128/25 networks. However, pings between hosts on the 172.16.2.0/25 and 172.16.2.128/25 networks are not successful. What could explain this connectivity problem?A. The ip subnet-zero command has been issued on the R1 router.B. The RIP v2 dynamic routing protocol cannot be used across a Frame Relay network.C. Split horizon is preventing R2 from learning about the R3 networks and R3 from learning about the R2 networks.D. The 172.16.2.0/25 and 172.16.2.128/25 networks are overlapping networks that can be seen by R1, but not between R2 and R3.E. The 172.16.3.0/29 network used on the Frame Relay links is creating a discontiguous network between the R2 and R3 router subnetworks.96.Refer to the exhibit. Hosts in network 192.168.2.0 are unable to reach hosts in network 192.168.3.0. Based on the output from RouterA, what are two possible reasons for the failure? (Choose two.)A. The cable that is connected to S0/0 on RouterA is faulty.B. Interface S0/0 on RouterB is administratively down.C. Interface S0/0 on RouterA is configured with an incorrect subnet mask.D. The IP address that is configured on S0/0 of RouterB is not in the correct subnet.E. Interface S0/0 on RouterA is not receiving a clock signal from the CSU/DSU.F. The encapsulation that is configured on S0/0 of RouterB does not match the encapsulation that is configured on S0/0 of RouterA.97.When upgrading the IOS image, the network administrator receives the exhibited error message. What could be the cause of this error?A.The new IOS image is too large for the router flash memory.B.The TFTP server is unreachable from the router.C.The new IOS image is not correct for this router platform.D. The IOS image on the TFTP server is corrupt.E. There is not enough disk space on the TFTP server for the IOS image.98. You and a co-worker have established wireless communication directly between your wireless laptops. What type of wireless topology has been created?A. BSSB. ESSC. IBSSD. SSID99.The Frame Relay network in the diagram is not functioning properly. What is the cause of the problem?A. The Gallant router has the wrong LMI type configured.B. Inverse ARPis providing the wrong PVC information to the Gallant router.C. The S3 interface of the Steele router has been configured with the frame-relay encapsulation ietf command.D. The frame-relay map statement in the Attalla router for the PVC to Steele is not correct.E. The IP address on the serial interface of the Attalla router is configured incorrectly.100. Which of the following statements describe the network shown in the graphic? (Choose two.)A. There are two broadcast domains in the network.B. There are four broadcast domains in the network.C. There are six broadcast domains in the network.D. There are four collision domains in the network.E. There are five collision domains in the network.F. There are seven collision domains in the network.。
CCNA考试题

Cisco 640-802Cisco Certified Network Associate (CCNA)Q&A 192 v13 & v 3.21TestInside ,help you pass any IT exam!CopyrightTestInside reserves the right to take legal action against you according to the International Copyright Laws if the pdf file is being distributed by you.w ww .c is co hu aw ei .c om1. What are two reasons that a network administrator would use access lists? (Choose two.)A. to control vty access into a routerB. to control broadcast traffic through a routerC. to filter traffic as it passes through a routerD. to filter traffic that originates from the routerE. to replace passwords as a line of defense against security incursionsAnswer: AC2. A default Frame Relay WAN is classified as what type of physical network?A. point-to-pointB. broadcast multi-accessC. nonbroadcast multi-accessD. nonbroadcast multipointE. broadcast point-to-multipointAnswer: C3. Refer to the exhibit. How many broadcast domains exist in the exhibited topology?A. oneB. twoC. threeD. fourE. fiveF. six www.ciscohuawei.comAnswer: C4. A single 802.11g access point has been configured and installed in the center of a square office. A few wireless users are experiencing slow performance and drops while most users are operating at peak efficiency. What are three likely causes of this problem? (Choose three.) A. mismatched TKIP encryption B. null SSID C. cordless phonesD. mismatched SSIDE. metal file cabinetsF. antenna type or direction Answer: CEF5. Refer to the exhibit. What two facts can be determined from the WLAN diagram? (Choose two.)A. The area of overlap of the two cells represents a basic service set (BSS).B. The network diagram represents an extended service set (ESS).C. Access points in each cell must be configured to use channel 1.D. The area of overlap must be less than 10% of the area to ensure connectivity.E. The two APs should be configured to operate on different channels. Answer: BEw ww .c is co hu aw ei .c om6. The command frame-relay map ip 10.121.16.8 102 broadcast was entered on the router. Which of the following statements is true concerning this command?A. This command should be executed from the global configuration mode.B. The IP address 10.121.16.8 is the local router port used to forward data.C. 102 is the remote DLCI that will receive the information.D. This command is required for all Frame Relay configurations.E. The broadcast option allows packets, such as RIP updates, to be forwarded across the PVC. Answer: E7. Which type of attack is characterized by a flood of packets that are requesting a TCP connection to a server?A. denial of serviceB. brute forceC. reconnaissanceD. Trojan horse Answer: A8. Which of the following are associated with the application layer of the OSI model? (Choose two.) A. ping B. Telnet C. FTP D. TCP E. IP Answer: BC9. For security reasons, the network administrator needs to prevent pings into the corporate networks from hosts outside the internetwork. Which protocol should be blocked with access control lists? A. IP B. ICMP C. TCP D. UDP Answer: Bw ww .c is co hu aw ei .c om10. Refer to the exhibit. The network administrator has created a new VLAN on Switch1 and added host C and host D. The administrator has properly configured switch interfaces FastEthernet0/13 through FastEthernet0/24 to be members of the new VLAN. However, after the network administrator completed the configuration, host A could communicate with host B, but host A could not communicate with host C or host D. Which commands are required to resolve this problem?A. Router(config)# interface fastethernet 0/1.3Router(config-if)# encapsulation dot1q 3Router(config-if)# ip address 192.168.3.1 255.255.255.0 B. Router(config)# router ripRouter(config-router)# network 192.168.1.0 Router(config-router)# network 192.168.2.0Router(config-router)# network 192.168.3.0 C. Switch1# vlan database Switch1(vlan)# vtp v2-mode Switch1(vlan)# vtp domain cisco Switch1(vlan)# vtp serverD. Switch1(config)# interface fastethernet 0/1 Switch1(config-if)# switchport mode trunkSwitch1(config-if)# switchport trunk encapsulation isl Answer: Aw ww .c is co hu aw ei .c om11. What are two recommended ways of protecting network device configuration files from outside network security threats? (Choose two.)A. Allow unrestricted access to the console or VTY ports.B. Use a firewall to restrict access from the outside to the network devices.C. Always use Telnet to access the device command line because its data is automatically encrypted.D. Use SSH or another encrypted and authenticated transport to access device configurations.E. Prevent the loss of passwords by disabling password encryption. Answer: BD12. Refer to the exhibit.The access list has been configured on the S0/0 interface of router RTB in the outbound direction. Which two packets, if routed to the interface, will be denied? (Choose two.)access-list 101 deny tcp 192.168.15.32 0.0.0.15 any eq telnet access-list 101 permit ip any anyA. source ip address: 192.168.15.5; destination port: 21B. source ip address:, 192.168.15.37 destination port: 21C. source ip address:, 192.168.15.41 destination port: 21D. source ip address:, 192.168.15.36 destination port: 23E. source ip address: 192.168.15.46; destination port: 23F. source ip address:, 192.168.15.49 destination port: 23 Answer: DEw ww .c is co hu aw ei .c om13. Refer to the exhibit. Switch1 has just been restarted and has passed the POST routine. Host A sends its initialframe to Host C. What is the first thing the switch will do as regards populating the switching table?A. Switch1 will add 192.168.23.4 to the switching table.B. Switch1 will add 192.168.23.12 to the switching table.C. Switch1 will add 000A.8A47.E612 to the switching table.D. Switch1 will add 000B.DB95.2EE9 to the switching table. Answer: C14. The user of Host1 wants to ping the DSL modem/router at 192.168.1.254. Based on the Host1 ARP table thatis shown in the exhibit, what will Host1 do?A. send a unicast ARP packet to the DSL modem/routerB. send unicast ICMP packets to the DSL modem/routerC. send Layer 3 broadcast packets to which the DSL modem/router respondsD. send a Layer 2 broadcast that is received by Host2, the switch, and the DSL modem/router Answer: B15. What are two security appliances that can be installed in a network? (Choose two.) A. ATMw ww .c is co hu aw ei .c omC. IOSD. IOXE. IPSF. SDM Answer: BE16. Refer to the exhibit. What is the most efficient summarization that R1 can use to advertise its networks to R2?A. 172.1.0.0/22B. 172.1.0.0/21C. 172.1.4.0/22D. 172.1.4.0/24 172.1.5.0/24 172.1.6.0/24 172.1.7.0/24E. 172.1.4.0/25172.1.4.128/25 172.1.5.0/24 172.1.6.0/24 172.1.7.0/24 Answer: C17. Which spread spectrum technology does the 802.11b standard define for operation? A. IRw ww .c is co hu aw ei .c omC. FHSSD. DSSS and FHSSE. IR, FHSS, and DSSS Answer: B18. Refer to the exhibit. Assume that all router interfaces are operational and correctly configured. In addition, assume that OSPF has been correctly configured on router R2. How will the default route configured on R1 affectthe operation of R2?A. Any packet destined for a network that is not directly connected to router R1 will be dropped.B. Any packet destined for a network that is not directly connected to router R2 will be dropped immediately.C. Any packet destined for a network that is not directly connected to router R2 will be dropped immediately because of the lack of a gateway on R1.D. The networks directly connected to router R2 will not be able to communicate with the 172.16.100.0, 172.16.100.128, and 172.16.100.64 subnetworks.E. Any packet destined for a network that is not referenced in the routing table of router R2 will be directed to R1. R1 will then send that packet back to R2 and a routing loop will occur. Answer: E19. A network interface port has collision detection and carrier sensing enabled on a shared twisted pair network. From this statement, what is known about the network interface port?w w w .c is co hu aw ei .c omA. This is a 10 Mb/s switch port.B. This is a 100 Mb/s switch port.C. This is an Ethernet port operating at half duplex.D. This is an Ethernet port operating at full duplex.E. This is a port on a network interface card in a PC. Answer: C20. Refer to the topology and router configuration shown in the graphic. A host on the LAN is accessing an FTPserver across the Internet. Which of the following addresses could appear as a source address for the packetsforwarded by the router to the destination server?A. 10.10.0.1B. 10.10.0.2C. 199.99.9.33D. 199.99.9.57E. 200.2.2.17F. 200.2.2.18 Answer: D21. A company is installing IP phones. The phones and office computers connect to the same device. To ensure maximum throughput for the phone data, the company needs to make sure that the phone traffic is on a different network from that of the office computer data traffic. What is the best network device to which to directly connect the phones and computers, and what technology should be implemented on this device? (Choose two.)w w w .c is co hu aw ei .c omA. hubB. routerC. switchD. STPE. subinterfacesF. VLAN Answer: CF22. Refer to the exhibit. Which statement describes DLCI 17?A. DLCI 17 describes the ISDN circuit between R2 and R3.B. DLCI 17 describes a PVC on R2. It cannot be used on R3 or R1.C. DLCI 17 is the Layer 2 address used by R2 to describe a PVC to R3.D. DLCI 17 describes the dial-up circuit from R2 and R3 to the service provider.Answer: C23. Which routing protocol by default uses bandwidth and delay as metrics? A. RIP B. BGP C. OSPF D. EIGRP Answer: D24. Refer to the output from the show running-config command in the exhibit. What should the administrator do to allow the workstations connected to the FastEthernet 0/0 interface to obtain an IP address?w ww .c is co hu aw ei .c omA. Apply access-group 14 to interface FastEthernet 0/0.B. Add access-list 14 permit any any to the access list configuration.C. Configure the IP address of the FastEtherent 0/0 interface to 10.90.201.1.D. Add an interface description to the FastEthernet 0/0 interface configuration. Answer: C25. In the implementation of VLSM techniques on a network using a single Class C IP address, which subnet mask is the most efficient for point-to-point serial links? A. 255.255.255.0 B. 255.255.255.240 C. 255.255.255.248 D. 255.255.255.252 E. 255.255.255.254w ww .c is co hu aw ei .c omAnswer: D26. Refer to the exhibit. The networks connected to router R2 have been summarized as a 192.168.176.0/21 routeand sent to R1. Which two packet destination addresses will R1 forward to R2? (Choose two.)A. 192.168.194.160B. 192.168.183.41C. 192.168.159.2D. 192.168.183.255E. 192.168.179.4F. 192.168.184.45 Answer: BE27. Refer to the exhibit. Switch-1 needs to send data to a host with a MAC address of 00b0.d056.efa4. What will Switch-1 do with this data?A. Switch-1 will drop the data because it does not have an entry for that MAC address.B. Switch-1 will flood the data out all of its ports except the port from which the data originated.w ww .c is co hu aw ei .c omC. Switch-1 will send an ARP request out all its ports except the port from which the data originated.D. Switch-1 will forward the data to its default gateway. Answer: B28. Two routers named Atlanta and Brevard are connected by their serial interfaces as shown in the exhibit, but there is no data connectivity between them. The Atlanta router is known to have a correct configuration. Given the partial configurations shown in the exhibit, what is the problem on the Brevard router that is causing the lack of connectivity?A. A loopback is not set.B. The IP address is incorrect.C. The subnet mask is incorrect.D. The serial line encapsulations are incompatible.E. The maximum transmission unit (MTU) size is too large.F. The bandwidth setting is incompatible with the connected interface. Answer: B29. Which two values are used by Spanning Tree Protocol to elect a root bridge? (Choose two.) A. amount of RAM B. bridge priority C. IOS version D. IP address E. MAC address F. speed of the linksw w w .c i s c o hu aw ei .c om30. Refer to the exhibit. Which switch provides the spanning-tree designated port role for the network segment that services the printers?A. Switch1B. Switch2C. Switch3D. Switch4 Answer: C31. While troubleshooting a network connectivity problem, a technician observes steady link lights on both theworkstation NIC and the switch port to which the workstation is connected. However, when the ping command is issued from the workstation, the output message "Request timed out." is displayed. At which layer of the OSI model does the problem most likely exist? A. the session layer B. the protocol layer C. the data link layer D. the access layer E. the network layer F. the application layerw ww .c is co hu aw ei .c om32. Refer to the exhibit. Why would the network administrator configure RA in this manner?A. to give students access to the InternetB. to prevent students from accessing the command prompt of RAC. to prevent administrators from accessing the console of RAD. to give administrators access to the InternetE. to prevent students from accessing the InternetF. to prevent students from accessing the Admin network Answer: B33. In order to allow the establishment of a Telnet session with a router, which set of commands must beconfigured?A. router(config)# line console 0router(config-line)# enable password cisco B. router(config)# line console 0 router(config-line)# enable secret cisco router(config-line)# login C. router(config)# line console 0 router(config-line)# password ciscow ww .c is co hu aw ei .c omrouter(config-line)# login D. router(config)# line vty 0router(config-line)# enable password cisco E. router(config)# line vty 0router(config-line)# enable secret cisco router(config-line)# login F. router(config)# line vty 0router(config-line)# password ciscorouter(config-line)# loginAnswer: F34. Refer to the exhibit. The two exhibited devices are the only Cisco devices on the network. The serial networkbetween the two devices has a mask of 255.255.255.252. Given the output that is shown, what three statementsare true of these devices? (Choose three.)A. The Manchester serial address is 10.1.1.1.B. The Manchester serial address is 10.1.1.2.C. The London router is a Cisco 2610.D. The Manchester router is a Cisco 2610.E. The CDP information was received on port Serial0/0 of the Manchester router.F. The CDP information was sent by port Serial0/0 of the London router. Answer: ACEw ww .c is co hu aw ei .c om35. A network administrator has configured two switches, named London and Madrid, to use VTP. However, the switches are not sharing VTP messages. Given the command output shown in the graphic, why are these switches not sharing VTP messages?A. The VTP version is not correctly configured.B. The VTP operating mode is not correctly configured.C. The VTP domain name is not correctly configured.D. VTP pruning mode is disabled.E. VTP V2 mode is disabled.F. VTP traps generation is disabled. Answer: C36. Host 1 is trying to communicate with Host 2. The e0 interface on Router C is down. Which of the followingare true? (Choose two.)A. Router C will use ICMP to inform Host 1 that Host 2 cannot be reached.B. Router C will use ICMP to inform Router B that Host 2 cannot be reached.C. Router C will use ICMP to inform Host 1, Router A, and Router B that Host 2 cannot be reached.D. Router C will send a Destination Unreachable message type.w ww .c is co hu a w ei .c o mE. Router C will send a Router Selection message type.F. Router C will send a Source Quench message type. Answer: AD37. Refer to the exhibit. Assuming that the router is configured with the default settings, what type of routerinterface is this?A. EthernetB. FastEthernetC. Gigabit EthernetD. asynchronous serialE. synchronous serial Answer: B38. On point-to-point networks, OSPF hello packets are addressed to which address? A. 127.0.0.1 B. 172.16.0.1 C. 192.168.0.5 D. 223.0.0.1 E. 224.0.0.5F. 254.255.255.255 Answer: E39. While troubleshooting a connectivity problem, a network administrator notices that a port status LED on a Cisco Catalyst series switch is alternating green and amber. Which condition could this indicate? A. The port is experiencing errors. B. The port is administratively disabled.w ww .c is co hu aw ei .c omC. The port is blocked by spanning tree.D. The port has an active link with normal traffic activity. Answer: A40. Refer to the exhibit. The network shown in the exhibit is running the RIPv2 routing protocol. The network has converged, and the routers in this network are functioning properly. The FastEthernet0/0 interface on R1 goes down. In which two ways will the routers in this network respond to this change? (Choose two.)A. All routers will reference their topology database to determine if any backup routes to the 192.168.1.0 networkare known.B. Routers R2 and R3 mark the route as inaccessible and will not accept any further routing updates from R1 until their hold-down timers expire.C. Because of the split-horizon rule, router R2 will be prevented from sending erroneous information to R1 about connectivity to the 192.168.1.0 network.D. When router R2 learns from R1 that the link to the 192.168.1.0 network has been lost, R2 will respond by sending a route back to R1 with an infinite metric to the 192.168.1.0 network.E. R1 will send LSAs to R2 and R3 informing them of this change, and then all routers will send periodic updatesat an increased rate until the network again converges. Answer: CD41. What is the maximum data rate specified for IEEE 802.11b WLANs? A. 10 Mbps B. 11 Mbps C. 54 Mbps D. 100 Mbps Answer: B42. Which of the following describe the process identifier that is used to run OSPF on a router? (Choose two.) A. It is locally significant.w ww .c is co hu aw ei .c omB. It is globally significant.C. It is needed to identify a unique instance of an OSPF database.D. It is an optional parameter required only if multiple OSPF processes are running on the router.E. All routers in the same OSPF area must have the same process ID if they are to exchange routing information. Answer: AC43. Refer to the exhibit. The FMJ manufacturing company is concerned about unauthorized access to the Payroll Server. The Accounting1, CEO, Mgr1, and Mgr2 workstations should be the only computers with access to thePayroll Server. What two technologies should be implemented to help prevent unauthorized access to the server?(Choose two.)A. access listsB. encrypted router passwordsC. STPD. VLANsE. VTPF. wireless LANs Answer: AD44. Which two statements are true about the command ip route 172.16.3.0 255.255.255.0 192.168.2.4? (Choose two.)A. It establishes a static route to the 172.16.3.0 network.B. It establishes a static route to the 192.168.2.0 network.C. It configures the router to send any traffic for an unknown destination to the 172.16.3.0 network.D. It configures the router to send any traffic for an unknown destination out the interface with the addressw ww .c is co hu aw ei .c om192.168.2.4.E. It uses the default administrative distance.F. It is a route that would be used last if other routes to the same destination exist. Answer: AE45. The network shown in the diagram is experiencing connectivity problems. Which of the following will correct the problems? (Choose two.)A. Configure the gateway on Host A as 10.1.1.1.B. Configure the gateway on Host B as 10.1.2.254.C. Configure the IP address of Host A as 10.1.2.2.D. Configure the IP address of Host B as 10.1.2.2.E. Configure the masks on both hosts to be 255.255.255.224.F. Configure the masks on both hosts to be 255.255.255.240. Answer: BD46. Which three statements are correct about RIP version 2? (Choose three.) A. It has the same maximum hop count as version 1. B. It uses broadcasts for its routing updates. C. It is a classless routing protocol.D. It has a lower default administrative distance than RIP version 1.E. It supports authentication.F. It does not send the subnet mask in updates. Answer: ACEw w w .c is c o h u aw ei .c om47. What should be part of a comprehensive network security plan? A. Allow users to develop their own approach to network security.B. Physically secure network equipment from potential access by unauthorized individuals.C. Encourage users to use personal information in their passwords to minimize the likelihood of passwords being forgotten.D. Delay deployment of software patches and updates until their effect on end-user equipment is well known and widely reported.E. Minimize network overhead by deactivating automatic antivirus client updates.Answer: B48. How should a router that is being used in a Frame Relay network be configured to avoid split horizon issues from preventing routing updates?A. Configure a separate sub-interface for each PVC with a unique DLCI and subnet assigned to the sub-interface.B. Configure each Frame Relay circuit as a point-to-point line to support multicast and broadcast traffic.C. Configure many sub-interfaces on the same subnet.D. Configure a single sub-interface to establish multiple PVC connections to multiple remote router interfaces.Answer: A49. Refer to the exhibit. Router1 was just successfully rebooted. Identify the current OSPF router ID for Router1.A. 190.172.32.10B. 208.149.23.162C. 208.149.23.194D. 220.173.149.10 Answer: Cw ww .c is co hu aw ei .c om50. Which two statements best describe the wireless security standard that is defined by WPA? (Choose two.) A. It specifies use of a static encryption key that must be changed frequently to enhance security. B. It requires use of an open authentication method.C. It specifies the use of dynamic encryption keys that change each time a client establishes a connection.D. It requires that all access points and wireless devices use the same encryption key.E. It includes authentication by PSK. Answer: CE51. What can a network administrator utilize by using PPP Layer 2 encapsulation? (Choose three.)A. VLAN supportB. compressionC. authenticationD. sliding windowsE. multilink supportF. quality of service Answer: BCE52. Refer to the exhibit. What is the meaning of the term dynamic as displayed in the output of the show frame-relay map command shown?A. The Serial0/0 interface is passing traffic.B. The DLCI 100 was dynamically allocated by the router.C. The Serial0/0 interface acquired the IP address of 172.16.3.1 from a DHCP server.D. The DLCI 100 will be dynamically changed as required to adapt to changes in the Frame Relay cloud.E. The mapping between DLCI 100 and the end station IP address 172.16.3.1 was learned through Inverse ARP. Answer: E53. What is the function of the Cisco IOS command ip nat inside source static 10.1.1.5 172.35.16.5? A. It creates a global address pool for all outside NAT transactions.w ww .c is co hu aw ei .c omB. It establishes a dynamic address pool for an inside static address.C. It creates dynamic source translations for all inside local PAT transactions.D. It creates a one-to-one mapping between an inside local address and an inside global address.E. It maps one inside source address to a range of outside global addresses. Answer: D54. Refer to the exhibit. What is the effect of the configuration that is shown?A. It configures SSH globally for all logins.B. It tells the router or switch to try to establish an SSh connection first and if that fails to use Telnet.C. It configures the virtual terminal lines with the password 030752180500.D. It configures a Cisco network device to use the SSH protocol on incoming communications via the virtualterminal ports.E. It allows seven failed login attempts before the VTY lines are temporarily shutdown. Answer: D55. Refer to the exhibit. When PC1 sends an ARP request for the MAC address of PC2, network performanceslows dramatically, and the switches detect an unusually high number of broadcast frames. What is the most likelycause of this?w ww .c is co hu aw ei .c omA. The portfast feature is not enabled on all switch ports.B. The PCs are in two different VLANs.C. Spanning Tree Protocol is not running on the switches.D. PC2 is down and is not able to respond to the request.E. The VTP versions running on the two switches do not match. Answer: C56. An administrator issues the command ping 127.0.0.1 from the command line prompt on a PC. If a reply isreceived, what does this confirm?A. The PC has connectivity with a local host.B. The PC has connectivity with a Layer 3 device.C. The PC has a default gateway correctly configured.D. The PC has connectivity up to Layer 5 of the OSI model.E. The PC has the TCP/IP protocol stack correctly installed. Answer: E57. Host 1 has just started up and requests a web page from web server 2. Which two statements describe steps in the process Host 1 uses to send the request to web server 2 (choose two)?A. Host 1 addresses the frames to the MAC address of router R1B. Host 1 looks in its ARP cache for the MAC address of router R1C. Host 1 addresses the frames to the MAC address of web server 2D. Host 1 sends the packets to router R1 to be forwarded to web server 2w ww .c is co hu aw ei .c omE. Host 1 sends a broadcast ARP request to obtain the MAC address of webserver2. Answer: CE58. Refer to the exhibit.Which two statements about the configuration of the switch interface are correct? (Choose two) A. The switchport belongs only to VLAN 2B. The switchport belongs only to VLAN 2C. Interface fa0/0 will be in both VLAN 1 (by default) and VLAN 2D. The exhibit shows interface fa0/0 to be dynamically mapped to VLAN 2E. A network host can be connected to this interface. Answer: AE59. Refer to the exhibit. The network administrator requires easy configuration options and minimal routingprotocol traffic. What two options provide adequate routing table information for traffic that passes between thetwo routers and satisfy the requests of the network administrator? (Choose two.)A. a dynamic routing protocol on InternetRouter to advertise all routes to CentralRouter.w ww .c is co hu aw ei .c om。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Explanation/Reference:
QUESTION 462
Answer:
Explanation/Reference:
QUESTION 463
Answer:
Explanation/Reference:
QUESTION 464
Answer:
Explanation/Reference:
QUESTION 483
Answer:
Explanation/Reference:
QUESTION 484
Answer:
Explanation/Reference:
QUESTION 485
Answer:
Explanation/Reference:
QUESTION 486
Answer:
Answer:
Explanation/Reference:
QUESTION 466
பைடு நூலகம்nswer:
Explanation/Reference:
QUESTION 467
Answer:
Explanation/Reference:
QUESTION 468
Answer:
Explanation/Reference:
QUESTION 458
Answer:
Explanation/Reference:
QUESTION 459
Answer:
Explanation/Reference:
QUESTION 460
Answer:
Explanation/Reference:
QUESTION 461
Answer:
Answer:
Explanation/Reference:
QUESTION 482
Match the items on the left with appropriate OSI layer on the right. (Not all options are used.)
Answer:
Explanation/Reference:
QUESTION 465 Refer to the exhibit. Complete the network diagram by dragging the correct device name or description to the correct location. Not all the names or descriptions will be used.
Answer:
Explanation/Reference:
QUESTION 470
Answer:
Explanation/Reference:
QUESTION 471
Answer:
Explanation/Reference:
QUESTION 472
Answer:
Explanation/Reference:
QUESTION 480 Drag the description on the left to the routing protocol on the right.
Answer:
Explanation/Reference:
QUESTION 481 Drag the options on the left under the type of switch port that they describe on the right.
Explanation/Reference:
QUESTION 477
Answer:
Explanation/Reference:
QUESTION 478
Answer:
Explanation/Reference:
QUESTION 479
Answer:
Explanation/Reference:
Explanation/Reference:
QUESTION 487
Answer:
Explanation/Reference:
QUESTION 488
Answer:
Explanation/Reference:
QUESTION 469 Refer to the exhibit. PC_1 is sending packets to the FTP server. Consider the packets as they leave RouterA interface Fa0/0 towards RouterB. Drag the correct frame and packet address to their place in the table.
QUESTION 473
Answer:
Explanation/Reference:
QUESTION 474
Answer:
Explanation/Reference:
QUESTION 475
Answer:
Explanation/Reference:
QUESTION 476
Answer:
