Connecting Wireless Sensornets with TCPIP Networks
国际自动化与计算杂志.英文版.

国际自动化与计算杂志.英文版.1.Improved Exponential Stability Criteria for Uncertain Neutral System with Nonlinear Parameter PerturbationsFang Qiu,Ban-Tong Cui2.Robust Active Suspension Design Subject to Vehicle Inertial Parameter VariationsHai-Ping Du,Nong Zhang3.Delay-dependent Non-fragile H∞ Filtering for Uncertain Fuzzy Systems Based on Switching Fuzzy Model and Piecewise Lyapunov FunctionZhi-Le Xia,Jun-Min Li,Jiang-Rong Li4.Observer-based Adaptive Iterative Learning Control for Nonlinear Systems with Time-varying DelaysWei-Sheng Chen,Rui-Hong Li,Jing Li5.H∞ Output Feedback Control for Stochastic Systems with Mode-dependent Time-varying Delays and Markovian Jump ParametersXu-Dong Zhao,Qing-Shuang Zeng6.Delay and Its Time-derivative Dependent Robust Stability of Uncertain Neutral Systems with Saturating ActuatorsFatima El Haoussi,El Houssaine Tissir7.Parallel Fuzzy P+Fuzzy I+Fuzzy D Controller:Design and Performance EvaluationVineet Kumar,A.P.Mittal8.Observers for Descriptor Systems with Slope-restricted NonlinearitiesLin-Na Zhou,Chun-Yu Yang,Qing-Ling Zhang9.Parameterized Solution to a Class of Sylvester MatrixEquationsYu-Peng Qiao,Hong-Sheng Qi,Dai-Zhan Cheng10.Indirect Adaptive Fuzzy and Impulsive Control of Nonlinear SystemsHai-Bo Jiang11.Robust Fuzzy Tracking Control for Nonlinear Networked Control Systems with Integral Quadratic ConstraintsZhi-Sheng Chen,Yong He,Min Wu12.A Power-and Coverage-aware Clustering Scheme for Wireless Sensor NetworksLiang Xue,Xin-Ping Guan,Zhi-Xin Liu,Qing-Chao Zheng13.Guaranteed Cost Active Fault-tolerant Control of Networked Control System with Packet Dropout and Transmission DelayXiao-Yuan Luo,Mei-Jie Shang,Cai-Lian Chen,Xin-Ping Guanparison of Two Novel MRAS Based Strategies for Identifying Parameters in Permanent Magnet Synchronous MotorsKan Liu,Qiao Zhang,Zi-Qiang Zhu,Jing Zhang,An-Wen Shen,Paul Stewart15.Modeling and Analysis of Scheduling for Distributed Real-time Embedded SystemsHai-Tao Zhang,Gui-Fang Wu16.Passive Steganalysis Based on Higher Order Image Statistics of Curvelet TransformS.Geetha,Siva S.Sivatha Sindhu,N.Kamaraj17.Movement Invariants-based Algorithm for Medical Image Tilt CorrectionMei-Sen Pan,Jing-Tian Tang,Xiao-Li Yang18.Target Tracking and Obstacle Avoidance for Multi-agent SystemsJing Yan,Xin-Ping Guan,Fu-Xiao Tan19.Automatic Generation of Optimally Rigid Formations Using Decentralized MethodsRui Ren,Yu-Yan Zhang,Xiao-Yuan Luo,Shao-Bao Li20.Semi-blind Adaptive Beamforming for High-throughput Quadrature Amplitude Modulation SystemsSheng Chen,Wang Yao,Lajos Hanzo21.Throughput Analysis of IEEE 802.11 Multirate WLANs with Collision Aware Rate Adaptation AlgorithmDhanasekaran Senthilkumar,A. Krishnan22.Innovative Product Design Based on Customer Requirement Weight Calculation ModelChen-Guang Guo,Yong-Xian Liu,Shou-Ming Hou,Wei Wang23.A Service Composition Approach Based on Sequence Mining for Migrating E-learning Legacy System to SOAZhuo Zhang,Dong-Dai Zhou,Hong-Ji Yang,Shao-Chun Zhong24.Modeling of Agile Intelligent Manufacturing-oriented Production Scheduling SystemZhong-Qi Sheng,Chang-Ping Tang,Ci-Xing Lv25.Estimation of Reliability and Cost Relationship for Architecture-based SoftwareHui Guan,Wei-Ru Chen,Ning Huang,Hong-Ji Yang1.A Computer-aided Design System for Framed-mould in Autoclave ProcessingTian-Guo Jin,Feng-Yang Bi2.Wear State Recognition of Drills Based on K-means Cluster and Radial Basis Function Neural NetworkXu Yang3.The Knee Joint Design and Control of Above-knee Intelligent Bionic Leg Based on Magneto-rheological DamperHua-Long Xie,Ze-Zhong Liang,Fei Li,Li-Xin Guo4.Modeling of Pneumatic Muscle with Shape Memory Alloy and Braided SleeveBin-Rui Wang,Ying-Lian Jin,Dong Wei5.Extended Object Model for Product Configuration DesignZhi-Wei Xu,Ze-Zhong Liang,Zhong-Qi Sheng6.Analysis of Sheet Metal Extrusion Process Using Finite Element MethodXin-Cun Zhuang,Hua Xiang,Zhen Zhao7.Implementation of Enterprises' Interoperation Based on OntologyXiao-Feng Di,Yu-Shun Fan8.Path Planning Approach in Unknown EnvironmentTing-Kai Wang,Quan Dang,Pei-Yuan Pan9.Sliding Mode Variable Structure Control for Visual Servoing SystemFei Li,Hua-Long Xie10.Correlation of Direct Piezoelectric Effect on EAPap under Ambient FactorsLi-Jie Zhao,Chang-Ping Tang,Peng Gong11.XML-based Data Processing in Network Supported Collaborative DesignQi Wang,Zhong-Wei Ren,Zhong-Feng Guo12.Production Management Modelling Based on MASLi He,Zheng-Hao Wang,Ke-Long Zhang13.Experimental Tests of Autonomous Ground Vehicles with PreviewCunjia Liu,Wen-Hua Chen,John Andrews14.Modelling and Remote Control of an ExcavatorYang Liu,Mohammad Shahidul Hasan,Hong-Nian Yu15.TOPSIS with Belief Structure for Group Belief Multiple Criteria Decision MakingJiang Jiang,Ying-Wu Chen,Da-Wei Tang,Yu-Wang Chen16.Video Analysis Based on Volumetric Event DetectionJing Wang,Zhi-Jie Xu17.Improving Decision Tree Performance by Exception HandlingAppavu Alias Balamurugan Subramanian,S.Pramala,B.Rajalakshmi,Ramasamy Rajaram18.Robustness Analysis of Discrete-time Indirect Model Reference Adaptive Control with Normalized Adaptive LawsQing-Zheng Gao,Xue-Jun Xie19.A Novel Lifecycle Model for Web-based Application Development in Small and Medium EnterprisesWei Huang,Ru Li,Carsten Maple,Hong-Ji Yang,David Foskett,Vince Cleaver20.Design of a Two-dimensional Recursive Filter Using the Bees AlgorithmD. T. Pham,Ebubekir Ko(c)21.Designing Genetic Regulatory Networks Using Fuzzy Petri Nets ApproachRaed I. Hamed,Syed I. Ahson,Rafat Parveen1.State of the Art and Emerging Trends in Operations and Maintenance of Offshore Oil and Gas Production Facilities: Some Experiences and ObservationsJayantha P.Liyanage2.Statistical Safety Analysis of Maintenance Management Process of Excavator UnitsLjubisa Papic,Milorad Pantelic,Joseph Aronov,Ajit Kumar Verma3.Improving Energy and Power Efficiency Using NComputing and Approaches for Predicting Reliability of Complex Computing SystemsHoang Pham,Hoang Pham Jr.4.Running Temperature and Mechanical Stability of Grease as Maintenance Parameters of Railway BearingsJan Lundberg,Aditya Parida,Peter S(o)derholm5.Subsea Maintenance Service Delivery: Mapping Factors Influencing Scheduled Service DurationEfosa Emmanuel Uyiomendo,Tore Markeset6.A Systemic Approach to Integrated E-maintenance of Large Engineering PlantsAjit Kumar Verma,A.Srividya,P.G.Ramesh7.Authentication and Access Control in RFID Based Logistics-customs Clearance Service PlatformHui-Fang Deng,Wen Deng,Han Li,Hong-Ji Yang8.Evolutionary Trajectory Planning for an Industrial RobotR.Saravanan,S.Ramabalan,C.Balamurugan,A.Subash9.Improved Exponential Stability Criteria for Recurrent Neural Networks with Time-varying Discrete and Distributed DelaysYuan-Yuan Wu,Tao Li,Yu-Qiang Wu10.An Improved Approach to Delay-dependent Robust Stabilization for Uncertain Singular Time-delay SystemsXin Sun,Qing-Ling Zhang,Chun-Yu Yang,Zhan Su,Yong-Yun Shao11.Robust Stability of Nonlinear Plants with a Non-symmetric Prandtl-Ishlinskii Hysteresis ModelChang-An Jiang,Ming-Cong Deng,Akira Inoue12.Stability Analysis of Discrete-time Systems with Additive Time-varying DelaysXian-Ming Tang,Jin-Shou Yu13.Delay-dependent Stability Analysis for Markovian Jump Systems with Interval Time-varying-delaysXu-Dong Zhao,Qing-Shuang Zeng14.H∞ Synchronization of Chaotic Systems via Delayed Feedback ControlLi Sheng,Hui-Zhong Yang15.Adaptive Fuzzy Observer Backstepping Control for a Class of Uncertain Nonlinear Systems with Unknown Time-delayShao-Cheng Tong,Ning Sheng16.Simulation-based Optimal Design of α-β-γ-δ FilterChun-Mu Wu,Paul P.Lin,Zhen-Yu Han,Shu-Rong Li17.Independent Cycle Time Assignment for Min-max SystemsWen-De Chen,Yue-Gang Tao,Hong-Nian Yu1.An Assessment Tool for Land Reuse with Artificial Intelligence MethodDieter D. Genske,Dongbin Huang,Ariane Ruff2.Interpolation of Images Using Discrete Wavelet Transform to Simulate Image Resizing as in Human VisionRohini S. Asamwar,Kishor M. Bhurchandi,Abhay S. Gandhi3.Watermarking of Digital Images in Frequency DomainSami E. I. Baba,Lala Z. Krikor,Thawar Arif,Zyad Shaaban4.An Effective Image Retrieval Mechanism Using Family-based Spatial Consistency Filtration with Object RegionJing Sun,Ying-Jie Xing5.Robust Object Tracking under Appearance Change ConditionsQi-Cong Wang,Yuan-Hao Gong,Chen-Hui Yang,Cui-Hua Li6.A Visual Attention Model for Robot Object TrackingJin-Kui Chu,Rong-Hua Li,Qing-Ying Li,Hong-Qing Wang7.SVM-based Identification and Un-calibrated Visual Servoing for Micro-manipulationXin-Han Huang,Xiang-Jin Zeng,Min Wang8.Action Control of Soccer Robots Based on Simulated Human IntelligenceTie-Jun Li,Gui-Qiang Chen,Gui-Fang Shao9.Emotional Gait Generation for a Humanoid RobotLun Xie,Zhi-Liang Wang,Wei Wang,Guo-Chen Yu10.Cultural Algorithm for Minimization of Binary Decision Diagram and Its Application in Crosstalk Fault DetectionZhong-Liang Pan,Ling Chen,Guang-Zhao Zhang11.A Novel Fuzzy Direct Torque Control System for Three-level Inverter-fed Induction MachineShu-Xi Liu,Ming-Yu Wang,Yu-Guang Chen,Shan Li12.Statistic Learning-based Defect Detection for Twill FabricsLi-Wei Han,De Xu13.Nonsaturation Throughput Enhancement of IEEE 802.11b Distributed Coordination Function for Heterogeneous Traffic under Noisy EnvironmentDhanasekaran Senthilkumar,A. Krishnan14.Structure and Dynamics of Artificial Regulatory Networks Evolved by Segmental Duplication and Divergence ModelXiang-Hong Lin,Tian-Wen Zhang15.Random Fuzzy Chance-constrained Programming Based on Adaptive Chaos Quantum Honey Bee Algorithm and Robustness AnalysisHan Xue,Xun Li,Hong-Xu Ma16.A Bit-level Text Compression Scheme Based on the ACW AlgorithmHussein A1-Bahadili,Shakir M. Hussain17.A Note on an Economic Lot-sizing Problem with Perishable Inventory and Economies of Scale Costs:Approximation Solutions and Worst Case AnalysisQing-Guo Bai,Yu-Zhong Zhang,Guang-Long Dong1.Virtual Reality: A State-of-the-Art SurveyNing-Ning Zhou,Yu-Long Deng2.Real-time Virtual Environment Signal Extraction and DenoisingUsing Programmable Graphics HardwareYang Su,Zhi-Jie Xu,Xiang-Qian Jiang3.Effective Virtual Reality Based Building Navigation Using Dynamic Loading and Path OptimizationQing-Jin Peng,Xiu-Mei Kang,Ting-Ting Zhao4.The Skin Deformation of a 3D Virtual HumanXiao-Jing Zhou,Zheng-Xu Zhao5.Technology for Simulating Crowd Evacuation BehaviorsWen-Hu Qin,Guo-Hui Su,Xiao-Na Li6.Research on Modelling Digital Paper-cut PreservationXiao-Fen Wang,Ying-Rui Liu,Wen-Sheng Zhang7.On Problems of Multicomponent System Maintenance ModellingTomasz Nowakowski,Sylwia Werbinka8.Soft Sensing Modelling Based on Optimal Selection of Secondary Variables and Its ApplicationQi Li,Cheng Shao9.Adaptive Fuzzy Dynamic Surface Control for Uncertain Nonlinear SystemsXiao-Yuan Luo,Zhi-Hao Zhu,Xin-Ping Guan10.Output Feedback for Stochastic Nonlinear Systems with Unmeasurable Inverse DynamicsXin Yu,Na Duan11.Kalman Filtering with Partial Markovian Packet LossesBao-Feng Wang,Ge Guo12.A Modified Projection Method for Linear FeasibilityProblemsYi-Ju Wang,Hong-Yu Zhang13.A Neuro-genetic Based Short-term Forecasting Framework for Network Intrusion Prediction SystemSiva S. Sivatha Sindhu,S. Geetha,M. Marikannan,A. Kannan14.New Delay-dependent Global Asymptotic Stability Condition for Hopfield Neural Networks with Time-varying DelaysGuang-Deng Zong,Jia Liu hHTTp://15.Crosscumulants Based Approaches for the Structure Identification of Volterra ModelsHouda Mathlouthi,Kamel Abederrahim,Faouzi Msahli,Gerard Favier1.Coalition Formation in Weighted Simple-majority Games under Proportional Payoff Allocation RulesZhi-Gang Cao,Xiao-Guang Yang2.Stability Analysis for Recurrent Neural Networks with Time-varying DelayYuan-Yuan Wu,Yu-Qiang Wu3.A New Type of Solution Method for the Generalized Linear Complementarity Problem over a Polyhedral ConeHong-Chun Sun,Yan-Liang Dong4.An Improved Control Algorithm for High-order Nonlinear Systems with Unmodelled DynamicsNa Duan,Fu-Nian Hu,Xin Yu5.Controller Design of High Order Nonholonomic System with Nonlinear DriftsXiu-Yun Zheng,Yu-Qiang Wu6.Directional Filter for SAR Images Based on NonsubsampledContourlet Transform and Immune Clonal SelectionXiao-Hui Yang,Li-Cheng Jiao,Deng-Feng Li7.Text Extraction and Enhancement of Binary Images Using Cellular AutomataG. Sahoo,Tapas Kumar,B.L. Rains,C.M. Bhatia8.GH2 Control for Uncertain Discrete-time-delay Fuzzy Systems Based on a Switching Fuzzy Model and Piecewise Lyapunov FunctionZhi-Le Xia,Jun-Min Li9.A New Energy Optimal Control Scheme for a Separately Excited DC Motor Based Incremental Motion DriveMilan A.Sheta,Vivek Agarwal,Paluri S.V.Nataraj10.Nonlinear Backstepping Ship Course ControllerAnna Witkowska,Roman Smierzchalski11.A New Method of Embedded Fourth Order with Four Stages to Study Raster CNN SimulationR. Ponalagusamy,S. Senthilkumar12.A Minimum-energy Path-preserving Topology Control Algorithm for Wireless Sensor NetworksJin-Zhao Lin,Xian Zhou,Yun Li13.Synchronization and Exponential Estimates of Complex Networks with Mixed Time-varying Coupling DelaysYang Dai,YunZe Cai,Xiao-Ming Xu14.Step-coordination Algorithm of Traffic Control Based on Multi-agent SystemHai-Tao Zhang,Fang Yu,Wen Li15.A Research of the Employment Problem on Common Job-seekersand GraduatesBai-Da Qu。
Wireless sensor network

The Greenhouse Environment Monitoring System Based on Wireless Sensor Network TechnologyΙ..INTRODUCTIONПZIGBEE TECHNOLOGYWireless sensor network(WSN) integrates the sensor network techonology, information processing technology and network communication technology with the feature of small size, low cost and easy maintenance, which has a wide application in the area of environment data collection,security monitoring and target tracking.无线传感器网络(WSN)集成了传感器网络的技术,信息处理技术和网络通信技术,具有体积小,成本低,维护方便的特点,在环境数据采集,安全监控和跟踪目标领域具有广泛的应用。
It comprises a great many wireless sensor nodes deployed in the monitoring region, and through wireless communication a multi-hop self-organizing network system is formed.它包括许多部署在监测区域的无线传感器节点,并且通过无线通信一个多跳的自组织网络系统形成了。
Its role is to coordinate the perception , acquisition and process of the information of its perceptual objects within the area covered by the network, and returned data to the observer.At present, large amount of widely-distributed electronic detection devices and implementing facilities are greatly used in greenhouse production , resulting in intertwining cables(相互交织的电缆)in the greenhouse production .目前,大量分布广泛的电子检测设备和执行设备被广泛地运用在温室生产中,导致了温室生产中存在相互交织的电缆。
通信专业英语复习

南京工程学院通信工程学院专业英语复习P40Signal ProcessingSignals commonly need to be processed in a variety of ways. For example,the output signal from a transducer may well be contaminated with unwanted electrical “noise”. The electrodes attached to a patient’s chest when an ECG is taken measure tiny electrical voltage changes due to the activity fo the heart and other muscles. The signal is often strongly affected by “mains pickup”due to electrical interference from the mains supply. Processing the signal using a filter circuit can remove or at least reduce the unwanted part of the part of the signal. Increasing nowadays, the filtering of signals to improve signal quality or to extract important information is done by DSP techniques rather than by analog electronics.信号通常需要有各种不同的方式处理。
例如,来自变压器的输出信号,很可能会受到有害电气“噪声”的污染。
当测量由于心脏和其他肌肉活动引起的微小电压变化的心电图时,需要把电极贴在病人的胸部。
PlayStation 无线耳机说明书
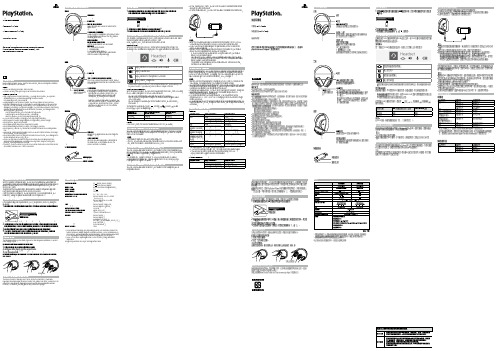
For more instructions about the use of this product (including the Headset Companion app), visit /helpme.ENPrecautionsBefore using this product, carefully read this manual and any manuals for compatible hardware. Retain instructions for future reference.SafetyˎObserve all warnings, precautions, and instructions.ˎCHOKING HAZARD - Small parts. Keep out of the reach of small children.Use and handlingˎStop using the wireless headset immediately if you begin to feel tired or if you experiencediscomfort or pain in your head while operating the wireless headset. If the condition persists, consult a doctor.ˎAvoid prolonged use of the wireless headset. Take a break at about 30-minute intervals. ˎPermanent hearing loss may occur if the headset is used at high volume. Set the volume to asafe level. Over time, increasingly loud audio may start to sound normal but can actually be damaging your hearing. If you experience ringing in your ears or muffled speech, stop listening and have your hearing checked. The louder the volume, the sooner your hearing could be affected. To protect your hearing:ˋLimit the amount of time you use the headset at high volume. ˋAvoid raising the volume to block out noisy surroundings.ˋLower the volume if you can’t hear people speaking near you.ˎIf you feel that the headset is irritating your skin, stop using it immediately. ˎDo not expose the headset to high temperatures, high humidity or direct sunlight. ˎDo not put heavy objects on the headset.ˎDo not allow liquid or small particles to get into the headset.ˎDo not throw or drop the headset, or subject it to strong physical shock.ˎDo not place any rubber or vinyl materials on the headset exterior for an extended period oftime.ˎUse a soft, dry cloth to clean the headset. Do not use solvents or other chemicals. Do not wipewith a chemically treated cleaning cloth.ˎDo not disassemble or insert anything into the headset because this may cause damage to theinternal components or cause injury to you.ˎObserve all signs and instructions that require an electrical device or radio product to beswitched off in designated areas, such as gas/refueling stations, hospitals, blasting areas, potentially explosive atmospheres or aircraft.ˎThe battery used in this device may present a risk of fire or chemical burn if mistreated. Do notdisassemble, heat above 60 °C / 140 °F, or incinerate.Wireless headsetHeadset: CUHYA-0080Wireless Adaptor: CUHYA-0081Instruction Manual Part names and functionsPower/audio mode switchSets the audio mode or turns off headset.Positions:OFF - turns off the headset 1 - Standard Mode2 - Bass Boost Mode (default)This mode can be replaced with audio modes from the Headset Companion app.Adjusts the volume of the headset.MUTE buttonˎPress to switch microphone MUTE on and off. ˎTo engage the sidetone feature, hold down the MUTE button until a beep is heard. Then cycle through the sidetone volume settings (high, medium, off) by holding the MUTE button.Sidetone is a feature that allows you to hear your own voice from the headset. The sidetone volume is adjusted here, and not on the PS4™ system or other devices. When MUTE is on, the sidetone feature is turned off.L markingWhen the included audio cable is connected to the headset for use with mobile devices, the wireless function is turned off.Wireless adaptorReset button Status indicatorˎOn PlayStation®Vita systems, you can listen to audio in standard stereo formatand use the voice chat feature.ˎOn other mobile devices, you can listen to audio in standard stereo format only.HintsˎWhen the included audio cable is connected to the headset, the VSS (Virtual Surround Sound) button and the SOUND/CHAT buttons cannot be used. ˎOutput volume varies depending on the portable device that is connected. Adjust volume accordingly.ˎYou can use the supplied audio cable to connect the headset to your mobile device to listen to audio content and talk on the phone. ˋ I f you are unable to hear audio content using the cable with your mobile device, turn off headset power. ˋ Y our device may only support use of a standard audio cable (not included) to listen to audio content using the headset. Note that standard audio cables do not support voice communication. ˋ T his product is not compatible with all mobile devices. Some features may not work on all mobile devices.Charging the headsetWhen remaining battery level is low, the status indicator flashes red and a beep is heard. Charge the battery by connecting the headset to a supported USB device such as a PC. While the battery is charging, the status indicator lights up red. The status indicator light turns off when the battery is fully charged.HintsˎYou can view the remaining battery charge on a PS4™ system. It is shown on the status display that appears when you change the headset settings.ˎYou might not be able to charge the battery if the USB device or the USB hub does not provide enough power for charging. Try connecting the headset to a different USB device or a different USB connector on the device.ˎCharging takes approximately 3.5 hours when starting with no battery charge left. ˎWhen the remaining battery charge is low, the headset beeps while it is connected and receiving an audio signal.ˎIt is recommended that you charge the battery in an environment with atemperature of 5 °C - 35 °C / 41 °F - 95 °F. Charging in other environments might not be as effective.ˎIf you do not plan to use the wireless headset for an extended period of time, it is recommended that you fully charge it at least once a year to help maintain battery functionality.Status indicator displayHeadset1 F or repair options, visit /helpme.2 I f you see the flashing error light, retry the steps to Restore Headset again. If you continue to see the error after the Restore attempt, then visit /support/wirelessstereoheadset.Wireless adaptorInitial setup1 Charge the headset by connecting it to a USB port with a USB cable.The headset may need up to 3.5 hours to charge fully.2 Insert the wireless adaptor into the USB port.3 Slide the power switch on the headset to position “1” or “2”.Using the headset with PlayStation ®4 systemsThis headset is compatible with PS4™ system software version 5.00 or later. More than one headset can be used with a PS4™ system.Always update your system software to the latest version.Status displayWhen first connecting to a PS4™ system or when changing the settings, thefollowing status information is displayed in the upper left corner of the screen:Stereo Headset Audio Extension is a system setting that controls the type of audio output to the wireless headset. It is available only when the wireless adaptor is inserted.Audio output selectionWith the wireless headset you can listen to audio from the PS4™ system—including music, videos, and games—in Virtual Surround Sound.ˋYou can listen to both game audio and chat audio simultaneously.Use the SOUND/CHAT buttons to adjust the relative volume of game audio versus chat audio.ˋYou can change the audio output to the headset so that you can hear only chat audio.To change the audio output select (Settings)(Devices)[AudioDevices] [Output to Headphones]. NOTE:O n a PS4™ system, the wireless headset defaults to “ON” [All Audio].Using the headset with a computerYou can use the headset with a PC (with Windows® or macOS) that has a USB port. Insert the wireless adaptor into a USB port on the computer you want to use and then turn on the headset.HintsˎThe headset might not work with some computers.ˎThe VSS (Virtual Surround Sound) button and SOUND/CHAT buttons can be used only when the headset is connected to a PS4™ system .Using your headset with PlayStation ®VRYou can use an audio cable to connect your headset to the stereo headphone jack of PlayStation ®VR. This will output all game audio processed by the PlayStation ®VR,including 3D audio if supported by the game title.NoteThis headset only supports stereo or 7.1 virtual surround sound. 3D audio is supported on this headset only when plugged into the PS VR, while playing a PS VR game that supports 3D audio.Using the headset with a portable deviceYou can use an audio cable to connect your headset to the headphone jack of compatible devices.Headset Companion appWith the Headset Companion app, you can select an additional audio mode for your headset. There are several modes to choose from, each optimized to enhance different audio characteristics. These modes are developed exclusively for use with PS4™ systems.To get one of these audio modes, download the Headset Companion app from PlayStation™Store and follow the on-screen instructions.Once this process is complete, you can experience your selected mode on your headset by sliding the power/audio mode switch to position “2”.Resetting the headsetIf the headset does not respond when you try to operate it, reset it by doing the following:1Connect the wireless adaptor to a PS4™ system or other powered USB port.2 Insert a small pin or similar object (not included) into the hole surrounding the reset button in the wireless adaptor, and push in for at least one second.3 On the headset, hold down the MUTE button and the VSS button.4 While still holding down the MUTE button and the VSS button, slide thepower/audio mode switch to position “1” or “2”.Rating labelThe rating label contains specific model, manufacture and compliance information. It is located under the right earpad.To remove the earpad and access the rating label:1 Use one hand to hold the headset in place.2 With your other hand, grip the earpad frame.3 P ull the earpad out.To replace the earpad, align the earpad with the inner frame. Push it back onto the frame until it clicks.End of life product recyclingThe wireless headset is made of plastics, metals, and a lithium-ion battery. Follow localregulations when disposing of the wireless headset. Sony products can be recycled for free in the United States and Canada by dropping the product off at a number of nationwide locations. For details, visit /SonyInfo/csr/SonyEnvironment/spotlight/.VSS (Virtual Surround Sound) buttonThe Virtual Surround Sound effect is on by default. Press and hold for more than one second to turn the VSS on or off.繁體中文使用前須知事項使用本產品前,請先詳細閱讀本說明書及對應裝置的說明書,並妥善保存,以備將來參考之用。
Armacost Lighting Wi-Fi LED Lighting Controller Mo
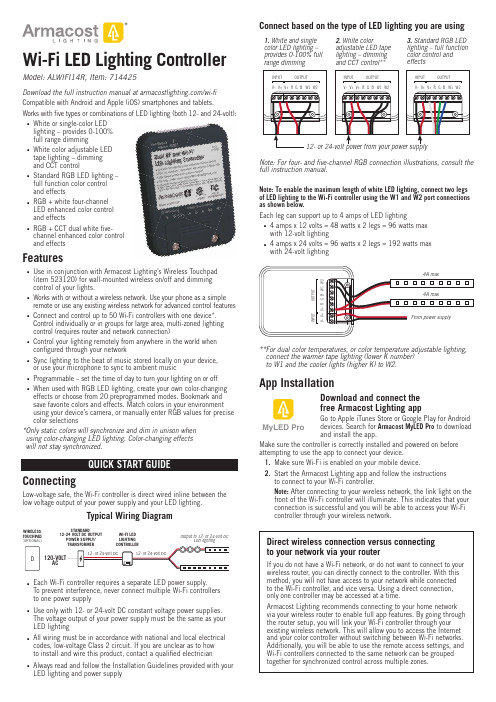
Wi-Fi LED Lighting Controller Model: ALWIFI14R, Item: 714425Download the full instruction manual at /wi-fiCompatible with Android and Apple (iOS) smartphones and tablets. Works with fi ve types or combinations of LED lighting (both 12- and 24-volt): White or single-color LEDlighting – provides 0-100%full range dimmingWhite color adjustable LEDtape lighting – dimmingand CCT controlStandard RGB LED lighting –full function color controland effectsRGB + white four-channelLED enhanced color controland effectsRGB + CCT dual white fi ve-channel enhanced color controland effectsFeaturesUse in conjunction with Armacost Lighting’s Wireless Touchpad(item 523120) for wall-mounted wireless on/off and dimmingcontrol of your lights.Works with or without a wireless network. Use your phone as a simple remote or use any existing wireless network for advanced control features Connect and control up to 50 Wi-Fi controllers with one device*.Control individually or in groups for large area, multi-zoned lightingcontrol (requires router and network connection)Control your lighting remotely from anywhere in the world whenconfi gured through your networkSync lighting to the beat of music stored locally on your device,or use your microphone to sync to ambient musicProgrammable – set the time of day to turn your lighting on or offWhen used with RGB LED lighting, create your own color-changing effects or choose from 20 preprogrammed modes. Bookmark andsave favorite colors and effects. Match colors in your environmentusing your device’s camera, or manually enter RGB values for precise color selections* O nly static colors will synchronize and dim in unison whenusing color-changing LED lighting. Color-changing effectswill not stay synchronized.ConnectingLow-voltage safe, the Wi-Fi controller is direct wired inline between the low voltage output of your power supply and your LED lighting.Typical Wiring DiagramWIRELESSTOUCHPAD(OPTIONAL)ACSTANDARD12-24 VOLT DC OUTPUTPOWER SUPPLY/WI-FI LEDLIGHTINGOutput to 12- or 24-volt DCLED lightingEach Wi-Fi controller requires a separate LED power supply.To prevent interference, never connect multiple Wi-Fi controllersto one power supplyUse only with 12- or 24-volt DC constant voltage power supplies.The voltage output of your power supply must be the same as yourLED lightingAll wiring must be in accordance with national and local electricalcodes, low-voltage Class 2 circuit. If you are unclear as to howto install and wire this product, contact a qualifi ed electricianAlways read and follow the Installation Guidelines provided with yourLED lighting and power supplyfull instruction manual.Note: To enable the maximum length of white LED lighting, connect two legsof LED lighting to the Wi-Fi controller using the W1 and W2 port connectionsas shown below.Each leg can support up to 4 amps of LED lighting4 amps x 12 volts = 48 watts x 2 legs = 96 watts maxwith 12-volt lighting4 amps x 24 volts = 96 watts x 2 legs = 192 watts maxwith 24-volt lighting** F or dual color temperatures, or color temperature adjustable lighting,connect the warmer tape lighting (lower K number)to W1 and the cooler lights (higher K) to W2.App InstallationDownload and connect thefree Armacost Lighting appGo to Apple iTunes Store or Google Play for Androiddevices. Search for Armacost MyLED Pro to downloadand install the app.Make sure the controller is correctly installed and powered on beforeattempting to use the app to connect your device.1. Make sure Wi-Fi is enabled on your mobile device.2. Start the Armacost Lighting app and follow the instructionsto connect to your Wi-Fi controller.Note: After connecting to your wireless network, the link light on thefront of the Wi-Fi controller will illuminate. This indicates that yourconnection is successful and you will be able to access your Wi-Ficontroller through your wireless network.Direct wireless connection versus connectingto your network via your routerIf you do not have a Wi-Fi network, or do not want to connect to yourwireless router, you can directly connect to the controller. With thismethod, you will not have access to your network while connectedto the Wi-Fi controller, and vice versa. Using a direct connection,only one controller may be accessed at a time.Armacost Lighting recommends connecting to your home networkvia your wireless router to enable full app features. By going throughthe router setup, you will link your Wi-Fi controller through yourexisting wireless network. This will allow you to access the Internetand your color controller without switching between Wi-Fi networks.Additionally, you will be able to use the remote access settings, andWi-Fi controllers connected to the same network can be groupedtogether for synchronized control across multiple zones.MyLED ProYou are required to create an Armacost Lighting account upon initial setup. This account registration is used only to protect your devices and to permit remote usage. Next, you will be prompted to select the type of lighting you are connecting. Choose the mode that applies to the type of lighting you are using. For example, if you are using single color or white LED lighting, select “DIM,” and your app will then be confi gured as an LED dimmer.DIM: White/Single Color DimmerCCT: Color Temperature AdjustableRGB: RGB MulticolorRGBW: RGB + Single ColorRGBWW: RGB + Dual ColorNext, you will see a list of all Wi-Fi controllers confi gured on this network. Here, you can access settings and controller properties as well as turn your lighting on/off. Tap the controller name to begin using your lighting, or press and hold to change basic device properties. It is recommendedthat you rename each controller for its location or use.or press and hold to modify controller propertiesTap the powerbutton to toggle the IMPORTANT: If the app displays the error message below, pull downto refresh the controller list.Cannot find any LED controller(s). Please check your device Wi-Fi setting and confirm that the LED controller(s) are plugged inIf the Wi-Fi controller still does not appear, turn your device Wi-Fi connection off and back on and check your network settings.Connect to Smart Speaker/Virtual AssistantBefore beginning use with the following third-party devices, make sure you have setup your Wi-Fi controller through the MyLED Pro app and signed into your Armacost Lighting cloud account. Remote authorization is also required (enabled by default on initial setup).Amazon AlexaIn your Amazon Alexa App, search the skills database for “Magic Home”, then tap enable.Link your Armacost account with the Magic Home Skill. Enter the user name and password that you created in the Armacost MyLED Pro app. Next, discover your Wi-Fi controllers by pressing the Discover Devices button on your app. You can also say, “Alexa, discover devices.” Wi-Fi controllers confi gured on the same wireless network will automatically populate.After your Wi-Fi controller(s) have been discovered, you can rename them in the Alexa app to your preferred names. It is recommended to name them for their location or use, e.g. “Offi ce lights” or “Countertop lights.” Now your lights are ready to control.For a list of additional commands, see the Amazon skill page. Different functions will be available depending on the type of lighting connected to your Wi-Fi controller. Here are some examples:“Alexa, turn on bedroom lights to 20 percent”“Alexa, turn off kitchen counter lights”“Alexa, change accent lights to red”Google HomeIn your Google Home App, navigate to the main menu, then Home control. Press the plus icon to add a device and select “Magic Home Wi-Fi”. All app permissions for Google Home must be granted to complete the setup.Link your Armacost account with the Magic Home Action. Enter the user name and password that you created in the Armacost MyLED Pro app. Google Home will automatically detect compatible devices on the linked home network, and will ask you to assign a room.Press “Done” when you have selected a room and your setup will be complete. You can now assign a nickname to your device. It is recommended to name them for their location or use, e.g. “Offi ce lights” or “Countertop lights.”Now your lights are ready to control. Different functions will be availabledepending on the type of lighting connected to your Wi-Fi controller. Here are some examples:“Hey Google, turn on offi ce lights to 100 percent”“Ok Google, turn bedroom lights to blue”IFTTTIn your IFTTT app or online account, search for the “MagicHue” Service and connect to it.You will then be prompted to link your Armacost Account with the MagicHue Applet. Please enter the user name and password that you created in the Armacost MyLED Pro app.Next, simply enable the applet(s) of your choice. Some applets may require downloading of the IFTTT app to your smartphone. Different functions will be available depending on the type of lighting connected to your Wi-Fi controller.Factory ResetIf you incorrectly entered your network password or have anotherincorrect setting, the link light will not turn on. You will not be able to access the Wi-Fi controller and you will need to do a factory reset. 1. Locate the pinhole on the front of the unit, labeled RESET.2. Using the included straight pin, or a paper clip, insert straight into the pinhole to depress the reset button.3. Continue to press and hold the reset button for ten seconds, then release.The unit will power off and back on and cycle the lighting to indicate the reset has been successful. You can now connect back to your Wi-Fi controller using its default settings. Return to step 1 under “App Installation.”For the full app manual and how-to videos, visit /wifi .mountingTo buy online, or to learn more, visit /dimmers.SPECIFICATIONSInput voltage ................................................................................12-volt or 24-volt DC Output channels .......................................................................................................5Maximum lighting load ....................................................................4 amps per channel Working temperature ..............................................................-5 to 130°F (-20 to 55°C)Wireless working frequency ..............................................................................2.4 GHz FCC ID ..............................................................................................2AIPIALWIFI14R Country of origin .................................................................................................China Limited one-year warranty. This product is for dry location use only. Improper installation,improper powering, abuse, or failure to use this device for its intended purpose will void warranty. Proofofpurchaseisrequiredforallreturns.Questions?*********************************.This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. Changes or modifi cations to this unit not expressly approved by the party responsible for compliance could void the user authority to operate the equipment.Designer-style switch plate and allmounting screws included.© 2018 Armacost Lighting. All rights reserved.180103。
无线传感器网络RBS的优化算法

662009,30(1)计算机工程与设计Computer Engineering and Design0引言无线传感器网络(wireless sensor network ,WSN )是一种全新的数据采集和处理模式,集成了传感器、微机电系统和网络3大技术[1]。
WSN 属于分布式系统,时间同步作为分布式系统的一项重要技术,在无线传感器网络中有着极其重要的地位。
特别是在强实时性系统中,高精度的时钟技术是一个难点和一项关键技术。
传感器网络的协议和应用,例如基于TDMA 的MAC 协议和敏感时间的监测任务等,要求节点间的时间必须保持同步;传感器内的数据融合及传感器读出数据融合等需要时间同步的支持;在作为传感器网络核心技术的节能技术研究中,传感器节点在睡眠模式与工作模式之间切换也需要有精确的节点间时间同步。
无线传感器网络的时间同步是指使网络中所有或部分节点拥有相同的时间基准,即不同节点保持相同的时钟,或者是可以彼此将对方的时钟转换成本地时钟[2]。
由于无线传感器网络特有的属性和设计要求,在WSN 的应用中,传感器节点对功耗有严格要求,并且部署环境经常是常人难以接近的恶劣环境,这使得传统的时间同步技术,如NTP (network time pro-tocol )协议和GPS (global position system )等,无法在WSN 中使用。
因此WSN 中的时间同步技术就成为一个研究热点。
首先会对现已存在的WSN 中的时间同步技术进行分析和比较,并且总结它们的优缺点、能量开销以及同步精度,并由此提出一种时间同步的优化算法。
在贝叶斯估计的支持下,优化RBS 算法。
最后对优化后的算法进行仿真验证。
1相关时间同步算法时间同步机制在传统网络中已经得到广泛应用,但在WSN 中还处于研究阶段。
J.Elson 和K.Romer 在2002年8月的HotNets-I 国际会议上首次提出和阐述了WSN 中的时间同步机制研究课题,在WSN 研究领域引起了关注。
Connecting Wireless Sensornets with TCPIP Networks 翻译

基于TCP/IP网络的无线传感网连接Adam Dunkels1, Juan Alonso1, Thiemo Voigt1, Hartmut Ritter, Jochen SchillerSICS Technical Report T2003: 20ISSN 1100-3154ISRN:SICS-T--2003/20-SE摘要:无线传感器网络是由许多小的无线传感器节点共同组成的,该网络内的各个小节点共同收集信息。
通常这样的网络不能完全孤立地运作,必须连接到外部网络,进行监测和控制连接。
在TCP/IP协议中,该互联网协议组合,已用于标准的大型网络,而且传感器网络能够连接到TCP/IP 网络中。
在本文中,我们讨论三种方式用于连接TCP/IP网络的传感器网络:代理服务器体系结构、容迟网络和TCP/IP传感器网络。
最后我们得出结论,该方法在某种程度上的正交和组合是可行的。
但对于TCP / IP传感器网络,除了目前有些问题仍需要进一步研究之外,TCP/IP网络是一个可行的协议传感器网络。
一. 引言无线传感器网络是一种基于多个小型无线传感器节点共同组成的信息采集模式。
这种传感器节点,体积小而且价格低廉,通常由一个或多个传感器、短程无线电收发器和一个小的微控制器组成,在电池供电的情况下就可以工作。
传感器网络部署设计方案都比较大,其中每个网络由数百甚至数千个传感器节点组成。
在这种部署方案中,每个传感器单独配置节点通常是不可行的,因此节点的自身配置是很重要的。
节能也很关键,尤其是在几乎很难更换传感器电池的情况下。
因此电池的保养也很重要,应该尽量避免更换电池。
大多数传感器网络程序的目标是监测或检测异常现象。
比如建筑环境控制、野生生物栖息地监测[17]和森林火灾监测[ 24 ]。
对于这样的应用,传感器网络不能在完全隔离的环境中工作,必须有一个监测实体的方式,以获得所产生的数据的传感器网络。
通过连接传感器网络现有的网络基础设施,如全球互联网,局域网,或私人网络,远程访问的传感器网络可以实现。
爱默生智能无线网关-产品数据表说明书

Product Data SheetApril 201300813-0200-4420, Rev FA⏹Gateway connects wireless self-organizing networks with any host system ⏹Easy configuration and management of self-organizing networks⏹Easy integration into control systems and data applications through serial and Ethernet LAN connections⏹Seamless integration into AMS Device Manager and DeltaV™ automation system ⏹Greater than 99% reliability with industry proven security⏹Smart Wireless capabilities extends the full benefit of PlantWeb ® architecture to previously inaccessible locationsSmart Wireless GatewaySmart Wireless Gateway April 2013Emerson Smart Wireless GatewayGain real-time process information with greater than 99% wireless data reliability⏹The Smart Wireless Gateway automatically manages wireless communications in constantly changing environments⏹Native integration with DeltaV and Ovation automation systems provides simple and fast commissioning for wireless field networks⏹Connect to data historians, legacy host systems, and other via a LAN applications through Ethernet, Modbus, Serial, OPC, EtherNet/IP, and HART outputsGuarantee system availability withredundant Smart Wireless Gateways⏹Never lose the wireless network with hot standby capabilityand automatic fault detection⏹Smart Wireless Gateways function as a single system,eliminating the need for duplicate host integration⏹One click configuration and plug-and-play architectureComplete wireless network configuration toolsprovided with each Gateway⏹The integrated web interface allows easy configuration of thewireless network and data integration without the need to installadditional software⏹Complimentary AMS Wireless Configurator software providesEmerson Device Dashboards to configure devices and viewdiagnostic dataDrag and Drop device provisioning enables asecure method to add new wireless devices tothe wireless field networkContentsEmerson’s Smart Wireless Solution .. . . . . . . . . page3IEC 62591 (WirelessHART®)... The Industry Standard page3Ordering Information . . . . . . . . . . . . . . . . . . . . . page4Accessories and Spare parts . . . . . . . . . . . . . . . . page5 Specifications . . . . . . . . . . . . . . . . . . . . . . . . . . . . page6 Product certifications . . . . . . . . . . . . . . . . . . . . . page8 Dimensional drawings . . . . . . . . . . . . . . . . . . . . . page9Smart Wireless Gateway April 2013Emerson’s Smart Wireless SolutionIEC 62591 (Wireless HART®)... The Industry StandardSelf-Organizing, Adaptive Mesh Routing⏹No wireless expertise required, network automatically finds the best communication paths⏹The self-organizing, self-healing network manages multiple communication paths for any given device. If an obstruction is introduced into the network, data will continue to flow because the device already has other established paths. The network will then lay in more communication paths as needed for that device.Reliable Wireless Architecture⏹Standard IEEE 802.15.4 radios⏹2.4 GHz ISM band sliced into 15 radio-channels⏹Time Synchronized Channel Hopping to avoid interference from other radios, WiFi, and EMC sources and increase reliability⏹Direct sequence spread spectrum (DSSS) technology delivers high reliability in challenging radio environment Emerson’s Smart WirelessSeamless Integration via a LAN to All Existing Host Systems ⏹Native integration into DeltaV and Ovation is transparent and seamless⏹Gateways interface with existing host systems via a LAN, using industry standard protocols including OPC, Modbus TCP/IP, Modbus RTU, and EtherNet/IPLayered Security Keeps Your Network Safe⏹Ensures that data transmissions are received only by the Smart Wireless Gateway⏹Network devices implement industry standard Encryption, Authentication, Verification, Anti-Jamming, and Key Management⏹Third party security verification including Achilles andFIPS197- User based login and enforced password strength. Password strength monitoring, user based log in, password reset requirements, automatic lockout, password expiration requirements. Based on guidelines from ISA99.03.03 standard approved level two. SmartPower™ Solutions⏹Optimized Emerson instrumentation, both hardware and software, to extend power module life⏹SmartPower technologies enable predictable power lifeSmart Wireless Gateway April 2013 Ordering InformationTable 1. Smart Wireless Gateway Ordering Information★ The Standard offering represents the most common options. The starred options (★) should be selected for best delivery.The Expanded offering is subject to additional delivery lead time.Model Product Description1420Smart Wireless GatewayPower InputStandard StandardA24 VDC Nominal (10.5-30 VDC)★Ethernet Communications - Physical ConnectionStandard Standard1(1)(2)Ethernet★2(3)(4)Dual Ethernet★Wireless Update Rate, Operating Frequency, and ProtocolStandard StandardA3User Configurable Update Rate, 2.4 GHz DSSS, Wireless HART★Serial Communication]Standard StandardN None★A(5)Modbus RTU via RS485★Ethernet Communication - Data ProtocolsStandard Standard2Webserver, Modbus TCP/IP, AMS Ready, HART-IP★4Webserver, Modbus TCP/IP, AMS Ready, HART-IP, OPC★5(6)DeltaV Ready★6(6)Ovation Ready ★8Webserver, EtherNet/IP, AMS Ready, HART-IP★9Webserver, EtherNet/IP, Modbus TCP/IP, AMS Ready, HART-IP★Options (Include with selected model number)Product CertificationsStandard StandardN5FM Division 2, Non-incendive★N6CSA Division 2, Non-incendive★N1ATEX Type n★ND ATEX Dust★N7IECEx Type n★NF IECEx Dust★KD FM & CSA Division 2, Non-incendive and ATEX Type n★N3China Type n★N4TIIS Type n★Redundancy OptionsStandard Standard RD(7)(8)(9)Gateway Redundancy★AdaptersStandard StandardJ1CM 20 Conduit Adapters★J2PG 13.5 Conduit Adapters★J33/4 NPT Conduit Adapters★Antenna Options(10)Standard Standard WL2Remote Antenna Kit, 50 ft. (15.2 m) cable, Lightning Arrestor★Smart Wireless GatewayApril 2013Accessories and Spare partsWL3Remote Antenna Kit, 20 ft. (6.1 m) and 30 ft. (9.1 m) cables, Lightning Arrestor ★WL4Remote Antenna Kit, 10 ft. (3.0 m) and 40 ft. (12.2 m) cables, Lightning Arrestor ★Expanded WN2(11)High-Gain, Remote Antenna Kit, 25 ft. (7.6m) cable, Lightning ArrestorTypical Model Number:1420A2A3 A 2 N5(1)Single active 10/100 baseT Ethernet port with RJ45 connector.(2)Additional ports disabled.(3)Dual active 10/100 baseT Ethernet ports with RJ45 connectors.(4)Multiple active ports have separate IP addresses, firewall isolation, and no packet forwarding.(5)Convertible to RS232 via adaptor, not included with Gateway.(6)Includes Webserver, Modbus TCP, AMS Ready, HART-IP, and OPC.(7)Requires the selection of Dual Ethernet option code 2.(8)Not available with DeltaV Ready option code 5.(9)Not available with EtherNet/IP option codes 8 and 9(10)The WL2, WL3, WL4, and WN2 options require minor assembly.(11)Not available in all countriesTable 1. Smart Wireless Gateway Ordering Information★ The Standard offering represents the most common options. The starred options (★) should be selected for best delivery.The Expanded offering is subject to additional delivery lead time. Table 2. AccessoriesItem DescriptionPart Number AMS® Wireless SNAP-ON™, 1 Gateway License 01420-1644-0001AMS Wireless SNAP-ON, 5 Gateway Licenses 01420-1644-0002AMS Wireless SNAP-ON, 10 Gateway Licenses 01420-1644-0003AMS Wireless SNAP-ON, 5-10 Upgrade Licenses 01420-1644-0004Serial Port HART Modem and Cables only 03095-5105-0001USB Port HART Modem and Cables only03095-5105-0002Table 3. Spare PartsItem DescriptionPart Number Spare Kit, WL2 Replacement (1), Remote Antenna, 50 ft. (15.2 m) Cable, and Lightning Arrestor01420-1615-0302Spare Kit, WL3 Replacement (1), Remote Antenna, 20/30 ft. (6.1/9.1 m) Cables, and Lightning Arrestor01420-1615-0303Spare Kit, WL4 Replacement (1), Remote Antenna, 10/40 ft. (3.0/12.2 m) Cables, and Lightning Arrestor 01420-1615-0304Spare Kit, WN2 Replacement (1), High Gain, Remote Antenna, 25 ft. (7.6 m) Cable, and Lightning Arrestor (2)01420-1615-0402(1)Can not upgrade from integral to remote antenna.(2)Not available in all countries.Smart Wireless GatewayApril 2013SpecificationsFunctional SpecificationsInput Power10.5 - 30 VDCCurrent DrawRadio Frequency Power Output from AntennaMaximum of 10 mW (10 dBm) EIRPMaximum of 40 mW (16 dBm) EIRP for WN2 High Gain optionEnvironmentalOperating Temperature Range: -40 to 158 °F (-40 to 70 °C)Operating Humidity Range: 10-90% relative humidityEMC PerformanceComplies with EN61326-1:2006.Antenna OptionsIntegrated Omnidirectional AntennaOptional remote mount Omnidirectional AntennaPhysical SpecificationsWeight10 lb (4.54 kg)Material of ConstructionHousingLow-copper aluminum, NEMA 4X PaintPolyurethaneCover GasketSilicone Rubber AntennaIntegrated Antenna: PBT/PC Remote Antenna: Fiber Glass CertificationsClass I Division 2 (U.S.)Equivalent WorldwideCommunication SpecificationsIsolated RS4852-wire communication link for Modbus RTU multidrop connectionsBaud rate: 57600, 38400, 19200, or 9600Protocol: Modbus RTUWiring: Single twisted shielded pair, 18 AWG. Wiring distance up to 4,000 ft. (1,524 m)Ethernet10/100base-TX Ethernet communication portProtocols: EtherNet/IP Modbus TCP, OPC, HART-IP, HTTPS (for Web Interface)Wiring: Cat5E shielded cable. Wiring distance 328 ft. (100 m).ModbusSupports Modbus RTU and Modbus TCP with 32-bit floating point values, integers, and scaled integers.Modbus Registers are user-specified.OPCOPC server supports OPC DA v2, v3EtherNet/IPSupports EtherNet/IP protocol with 32 bit Floating Point values and Integers.EtherNet/IP Assembly Input-Output instances are user configurable.EtherNet/IP specifications are managed and distributed by ODVA.Self-Organizing Network SpecificationsProtocolIEC 62591 (Wireless HART), 2.4 - 2.5 GHz DSSS.Maximum Network Size100 wireless devices @ 8 sec or higher.50 wireless devices @ 4 sec.25 wireless devices @ 2 sec.12 wireless devices @ 1 sec.Supported Device Update Rates1, 2, 4, 8, 16, 32 seconds or 1 - 60 minutesNetwork Size/Latency100 Devices: less than 10 sec.50 Devices: less than 5 sec.Data Reliability>99%C u r r e n t (m A )Operating Current Draw is based on 3.6 Watts average powerconsumption. Momentary startup Current Draw up to twice Operating Current Draw.Smart Wireless Gateway April 2013System Security SpecificationsEthernetSecure Sockets Layer (SSL)- enabled (default) TCP/IPcommunicationsSmart Wireless Gateway AccessRole-based Access Control (RBAC) including Administrator,Maintenance, Operator, and Executive. Administrator hascomplete control of the gateway and connections to hostsystems and the self-organizing network.Self-Organizing NetworkAES-128 Encrypted Wireless HART, including individual sessionkeys. Drag and Drop device provisioning, including unique joinkeys and white listing.Internal FirewallUser Configurable TCP ports for communications protocols,including Enable/Disable and user specified port numbers.Inspects both incoming and outgoing packets.Third Party CertificationWurldtech: Achilles Level 1 certified for network resiliency.National Institute of Standards and Technology (NIST):Advanced Encryption Standard (AES) Algorithm conforming toFederal Information Processing Standard Publication 197(FIPS-197)Smart Wireless Gateway April 2013 Product certificationsApproved Manufacturing LocationsRosemount Inc. – Chanhassen, Minnesota, USAEmerson Process Management GmbH & Co. - Karlstein, GermanyEmerson Process Management Asia Pacific Private Limited - SingaporeBeijing Rosemount Far East Instrument Co., Limited - Beijing, ChinaTelecommunication ComplianceAll wireless devices require certification to ensure that they adhere to regulations regarding the use of the RF spectrum. Nearly every country requires this type of product certification. Emerson is working with governmental agencies around the world to supply fully compliant products and remove the risk of violating country directives or laws governing wireless device usage.FCC and ICThis device complies with Part 15 of the FCC Rules. Operation is subject to the following conditions. This device may not cause harmful interference. This device must accept any interference received, including interference that may cause undesired operation. This device must be installed to ensure a minimum antenna separation distance of 20 cm from all persons. Ordinary Location Certification for FMAs standard, the Gateway has been examined and tested to determine that the design meets basic electrical, mechanical, and fire protection requirements by FM, a nationally recognized testing laboratory (NRTL) as accredited by the Federal Occupational Safety and Health Administration (OSHA).North American CertificationsN5FM Division 2, Non-IncendiveCertificate Number: 3028321Nonincendive for Class I, Division 2, Groups A, B, C, and D.Suitable for Class II, III, Division 1,Groups E, F, and G; Indoors/outdoor locations;Type 4XTemperature Code: T4 (-40 °C < T a < 60 °C)Canadian Standards Association (CSA)N6CSA Division 2, Non-IncendiveCertificate Number: 1849337Suitable for Class I, Division 2, Groups A, B, C, and D.Dust Ignition-proof for Class II, Groups E, F, and G;Suitable for Class III Hazardous Locations.;Install per Rosemount drawing 01420-1011.Temperature Code: T4 (-40 °C < T a < 60 °C)CSA Enclosure Type 4X European Union Directive InformationThe EC declaration of conformity for all applicable European directives for this product can be found on the Rosemount websiteat . A hard copy may be obtained by contacting your local sales representative.European CertificationN1ATEX Type nEx nA nL IIC T4 (-40 °C < T a< 60 °C)Special condition for safe use (X):The surface resistivity of the antenna is greater than onegigaohm. To avoid electrostatic charge build-up, it mustnot be rubbed or cleaned with solvents or a dry cloth.The Apparatus is not capable of withstanding the 500Vinsulation test required by Clause 9.4 of EN 60079-15:2005. This must be taken into account when installing the apparatus.ND ATEX DustCertificate Number: Baseefa 07ATEX0057Ex tD A 22 IP66 T135 (-40 °C < T a < 60 °C)Maximum working Voltage = 28 VN7IECEx Type nCertificate Number: IECEx BAS 07.0012XEx nA nL IIC T4 (-40 °C < T a < 60 °C)Maximum working voltage = 28 VSpecial condition for safe use (X):The surface resistivity of the antenna is greater than onegigaohm. To avoid electrostatic charge build-up, it mustnot be rubbed or cleaned with solvents or a dry cloth.The Apparatus is not capable of withstanding the 500 Vinsulation test required by Clause 9.4 of EN 60079-15:2005. This must be taken into account when installing the apparatus.NF IECEx DustCertification Number: IECEx BAS 07.0013Ex tD A22 IP66 T135 (-40 °C < T a < 60 °C)Maximum working voltage = 28 VCombinations of CertificationsKD Combination of N5, N6, and N1.Smart Wireless Gateway April 2013Dimensional drawingsFigure 1. Smart Wireless Gateway Dimensions are in inches (millimeters)Smart Wireless Gateway April 2013 Remote Antenna KitThe Remote Antenna kit includes sealant tape for remote antenna connection, as well as mounting brackets for the antenna, Lightning Arrestor, and the Smart Wireless Gateway.Lightning protection is included on all the options.*Note that the cables lengths on the remote antenna options WL3 and WL4 are interchangeable for installation convenience.Smart Wireless Gateway April 201311Standard Terms and Conditions of Sale can be found at \terms_of_sale The Emerson logo is a trade mark and service mark of Emerson Electric Co.Rosemount and the Rosemount logotype are registered trademarks of Rosemount Inc.PlantWeb is a registered trademark of one of the Emerson Process Management group of companies.HART and WirelessHART are registered trademarks of the HART Communication Foundation Modbus is a trademark of Modicon, Inc.All other marks are the property of their respective owners.© 2012 Rosemount Inc. All rights reserved.Emerson Process Management Rosemount Inc.8200 Market Boulevard Chanhassen, MN 55317 USA T (U.S.) 1-800-999-9307T (International) (952) 906-8888F (952) Emerson Process Management Blegistrasse 23P.O. Box 1046CH 6341 Baar Switzerland T +41 (0) 41 768 6111F +41 (0) 41 768 Emerson Process Management Asia Pacific Pte Ltd 1 Pandan Crescent Signapore 128461T +65 6777 8211F +65 6777 0947Service Support Hotline: +65 6770 8711Email:***************************.comSmart Wireless Gateway00813-0200-4420, Rev FAProduct Data Sheet April 2013Emerson Process Management Latin America 1300 Concord Terrace, Suite 400Sunrise Florida 33323 USA Tel + 1 954 846 5030。
特斯拉电动汽车用户手册说明书

visit /zonedrooftopsystemsEf fi cient system operationTrane® Zoned Rooftop Systems take advantage of the newest technologies to improve comfort and increase ef fi ciency in small buildings.Trane rooftop units are available in a range of ef fi ciency tiers to match your budget and energy use goals. Variable-speed technologies areavailable to adjust compressor and fan speeds to more precisely match load requirements. This improves comfort in the space while reducing energy use at the same time. Zoned Rooftop Systems also offer integrated demand-controlled ventilation and economizer free cooling, further reducing energy use.To fully capitalize on the performance bene fi ts offered by these advanced technologies, integrated system control is a vital part of the solution. The Tracer® Concierge™ control system provides advanced optimization strategies to reduce energy use while improving occupant comfort, and is smart enough to let you know when service is needed to sustain optimal performance.Cost-effective, superior comfort for small buildingsTrane® Zoned Rooftop Systems are available in single- or multiple-zone con fi gurations to provide cost-effective comfort control for different areas of the building with varying comfort needs.The Tracer® Concierge™ control system offers the bene fi ts of a building automation system—without the complexity—and goes beyond managing individual rooms by operating the building smartly and ef fi ciently. It provides advanced capabilities for multiple-zone systems, is easy to use, and offers worry-free operation.Easy to design, install, and operatePackaged rooftop units provide cooling, heating, and ventilation in a single piece of equipment, simplifying system design, installation, and maintenance.Trane® Zoned Rooftop Systems use pre-engineered components and factory-installed controls that are designed to work together, contributing to on-time and on-budget installation. They use familiar components and are easy to recon fi gure if the space use changes in the future.The pre-packaged Tracer® Concierge™ system control panel, with its auto-discovery and con fi guration capabilities, allows for easier and faster installation. It includes an intuitive, easy-to-use operator interface on a 10-inch touchscreen display, along with mobile apps that allow the operator or service provider to manage the building from anywhere.The use of Air-Fi® Wireless controls results in faster project completion, increased sensor location fl exibility, greater reliability due to self-healing mesh networking, and easier relocation to accommodate future space use changes.ZO N E D R O O F TO P S YS T E M SLight commercial rooftop systems from TraneTrane® Zoned Rooftop Systems provide customers with affordable options for small buildings, to increase comfort and ef fi ciency, whilesimplifying maintenance.VAV terminal units (200 to 8000 cfm)• Trane fl ow ring provides unmatched air fl ow measurement accuracy and control • Durable, heavy-gauge air valve cylinder• modulating control• Air-Fi® Wireless communications • Retro fit dampers available for upgrading existing systemsTrane - by Trane Tech nologies (NYSE: TT), a global climate innovator - creates comfortable, energy efficient indoor environments for commercial and residential applications. For more information, please visit or .Trane h as a policy of continuous product and product data improvement and reserves th e righ t to ch ange design and specifications without notice. We are committed to using environmentally conscious print practices.All trademarks referenced are the trademarks of their respective owners.©2020 Trane. All Rights Reserved. ENV-SLB024C-ENNovember 5, 2020•single piece of equipment• able-speed fan control• Three tiers of effi ciency: standard, high, or ultra-high•••Pre-programmed, factory-installed ReliaT el™ DDC controls with wired or Air-Fi® Wireless communicationsAir-Fi® Wireless controls• Eliminates wires between equipment controllers and zone sensors, and between equipment and system controllers, allowing for faster installation, increased location fl exibility, and easier relocation• Self-healing wireless mesh and extended signal range maximize reliability• Supports open communication protocols through conformance with ASHRAE® Standard 135 (BACnet®/ZigBee®)• Up to four sensing functions in one zone sensor: temperature, humidity, occupan-cy, and CO 2• 15-year lifetime batteries。
TiS系列红外热像仪使用说明书

Performance Series Thermal Imagers
用户手册
July 2015 (Simplified Chinese)
© 2015 Fluke Corporation. All rights reserved. Specifications are subject to change without notice. All product names are trademarks of their respective companies.
有限保证和责任限制 在正常使用和维护条件下,Fluke 公司保证每一个产品都没有材料缺陷和制造工艺问题。保证期为从产品发货之日起二(2)年。部件、产品 修理和服务的保证期限为 90 天。本项保证仅向授权零售商的原始买方或最终用户提供,并且不适用于保险丝和一次性电池或者任何被 Fluk e 公司认定由于误用、改变、疏忽、意外非正常操作和使用所造成的产品损坏。Fluke 公司保证软件能够在完全符合性能指标的条件下至少 操作 90 天,而且软件是正确地记录在无缺陷的媒体上。Fluke 公司并不保证软件没有错误或无操作中断。 Fluke 公司仅授权零售商为最终客户提供新产品或未使用过产品的保证。但并未授权他们代表 Fluke 公司提供范围更广或内容不同的保证。 只有通过 Fluke 授权 的销售商购买的产品,或者买方已经按适当的国际价格付款的产品,才能享受 Fluke 的保证支持。在一个国家购买的 产品被送往另一个国家维修时,Fluke 公 司保留向买方收取修理/更换零部件的进口费用的权利。 Fluke 公司的保证责任是有限的,Fluke 公司可以选择是否将依购买价退款、免费维修或更换在保证期内退回到 Fluke 公司委托服务中心的 有缺陷产品。 要求保修服务时,请与就近的 Fluke 授权服务中心联系,获得退还授权信息;然后将产品连同问题描述寄至该服务中心,并预付邮资和保险 费用(目的地离岸价格)。Fluke 对运送途中发生的损坏不承担责任。在保修之后,产品将被寄回给买方并提前支付运输费(目的地交货)。 如果 Fluke 认定产品故障是由于疏忽、误用、污染、修改、意外或不当操作或处理状况而产生,包括未在产品规定的额定值下使用引起的过 压故障;或是由于机件日常使用损耗,则 Fluke 会估算修理费用,在获得买方同意后再进行修理。在修理之后,产品将被寄回给买方并预付 运输费;买方将收到修理和返程运输费用(寄发地交货)的帐单。 本保证为买方唯一能获得的全部赔偿内容,并且取代所有其它明示或隐含的保证,包括但不限于适销性或适用于特殊目的的任何隐含保证。F LUKE 对任何特殊、间接、偶发或后续的损坏或损失概不负责,包括由于任何原因或推理引起的数据丢失。 由于某些国家或州不允许对隐含保证的期限加以限制、或者排除和限制意外或后续损坏本保证的限制和排除责任条款可能并不对每一个买方都 适用。如果本保证的某些条款被法院或其它具有适当管辖权的裁决机构判定为无效或不可执行,则此类判决将不影响任何其它条款的有效性或 可执行性。
fenix3 中英文对照说明书

Owner’s Manual
翻译仅供参考,如有错误之处,请不吝指出,联系QQ:12594065 (SUNG),随时交流修正
February 2015
Printed in Taiwan
190-01840-00_0B
Table of Contents
Setting a Training Target .设...定....训...练...目...标........................................... 7 Cancelling a Training Target .取...消...训...练...目....标................................. 7
Setting up Garmin express 设...置.... G...a..r.m..i.n.. .e..x.p..r.e..s.s....................... 1
Activities .运...动..................................................................... 1 Starting an Activity .开...始...活...动............................................................ 2 Stopping an Activity .停...止...活...动.......................................................... 2 Skiing .滑...雪...................................................................................... 2
Wireless Sensor Networks and Applications

Wireless Sensor Networks andApplicationsWireless Sensor Networks (WSNs) have gained significant attention in recent years due to their potential to revolutionize various industries and applications. These networks consist of small, low-cost sensor nodes that are wirelessly connected to collect and transmit data from the environment. The applications of WSNs are diverse, ranging from environmental monitoring, healthcare, smart homes, industrial automation, agriculture, and more. However, despite their promising potential, WSNs also face several challenges and limitations that need to be addressed for their widespread adoption and success. One of the primarychallenges of WSNs is their limited power supply. Most sensor nodes are powered by batteries, which have a finite lifespan and need to be replaced or recharged periodically. This limitation poses a significant constraint on the deployment and maintenance of WSNs, especially in remote or inaccessible areas. Researchers and engineers are actively working on developing energy-efficient protocols, algorithms, and hardware designs to prolong the battery life of sensor nodes and enable self-sustainability through energy harvesting techniques such as solar, kinetic, or thermal energy. Another critical issue facing WSNs is their vulnerability to security threats and attacks. Since WSNs are often deployed in unattended or hostile environments, they are susceptible to various security risks, including eavesdropping, data tampering, node impersonation, and denial-of-service attacks. Ensuring the confidentiality, integrity, and availability of data in WSNs is a complex and ongoing research area, requiring the development of robust encryption, authentication, key management, and intrusion detection mechanisms to protect against malicious activities and safeguard sensitive information. Furthermore, the scalability and reliability of WSNs are significant concerns, particularly as the number of deployed sensor nodes increases. As WSNs grow insize and complexity, it becomes challenging to maintain efficient communication, data aggregation, and network management. The dynamic nature of wireless communication, environmental interference, and node failures can lead to packet loss, latency, and network congestion, affecting the overall performance andreliability of WSNs. Addressing these scalability and reliability issues requires the design of adaptive routing protocols, fault-tolerant mechanisms, and quality-of-service optimizations to ensure seamless and dependable operation in diverse WSN applications. In addition to technical challenges, the real-world deployment and commercialization of WSNs also face economic, regulatory, and societal barriers. The high initial deployment costs, interoperability with existing infrastructure, compliance with industry standards, and privacy concerns are all factors that impact the widespread adoption and acceptance of WSNs in various domains. Moreover, the ethical implications of collecting and analyzing large volumes of data from WSNs, such as personal health information or environmental surveillance, raise important questions about consent, transparency, and accountability in the use of sensor-generated data. Despite these challenges, the potential benefits of WSNs in enabling smart, connected, and sustainable systems are driving continued research, innovation, and investment in this field. The development of advanced sensor technologies, wireless communication protocols, data analytics, and edge computing capabilities is unlocking new opportunities for WSNs to enhance efficiency, productivity, and quality of life in diverse applications. By addressing the technical, operational, and ethical challenges, WSNs can realize their full potential as a foundational infrastructure for the Internet of Things (IoT) and contribute to a more interconnected and intelligent world.。
传感器相关英语文献

DiMo:Distributed Node Monitoring in WirelessSensor NetworksAndreas Meier†,Mehul Motani∗,Hu Siquan∗,and Simon Künzli‡†Computer Engineering and Networks Lab,ETH Zurich,Switzerland∗Electrical&Computer Engineering,National University of Singapore,Singapore‡Siemens Building T echnologies,Zug,SwitzerlandABSTRACTSafety-critical wireless sensor networks,such as a distributed fire-or burglar-alarm system,require that all sensor nodes are up and functional.If an event is triggered on a node, this information must be forwarded immediately to the sink, without setting up a route on demand or having tofind an alternate route in case of a node or link failure.Therefore, failures of nodes must be known at all times and in case of a detected failure,an immediate notification must be sent to the network operator.There is usually a bounded time limit,e.g.,five minutes,for the system to report network or node failure.This paper presents DiMo,a distributed and scalable solution for monitoring the nodes and the topology, along with a redundant topology for increased robustness. Compared to existing solutions,which traditionally assume a continuous data-flow from all nodes in the network,DiMo observes the nodes and the topology locally.DiMo only reports to the sink if a node is potentially failed,which greatly reduces the message overhead and energy consump-tion.DiMo timely reports failed nodes and minimizes the false-positive rate and energy consumption compared with other prominent solutions for node monitoring.Categories and Subject DescriptorsC.2.2[Network Protocols]:Wireless Sensor NetworkGeneral TermsAlgorithms,Design,Reliability,PerformanceKeywordsLow power,Node monitoring,Topology monitoring,WSN 1.INTRODUCTIONDriven by recent advances in low power platforms and protocols,wireless sensor networks are being deployed to-day to monitor the environment from wildlife habitats[1] Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on thefirst page.To copy otherwise,to republish,to post on servers or to redistribute to lists,requires prior specific permission and/or a fee.MSWiM’08,October27–31,2008,Vancouver,BC,Canada.Copyright2008ACM978-1-60558-235-1/08/10...$5.00.to mission-criticalfire-alarm systems[5].There are,how-ever,still some obstacles in the way for mass application of wireless sensor networks.One of the key challenges is the management of the wireless sensor network itself.With-out a practical management system,WSN maintenance will be very difficult for network administrators.Furthermore, without a solid management plan,WSNs are not likely to be accepted by industrial users.One of the key points in the management of a WSN is the health status monitoring of the network itself.Node failures should be captured by the system and reported to adminis-trators within a given delay constraint.Due to the resource constraints of WSN nodes,traditional network management protocols such as SNMP adopted by TCP/IP networks are not suitable for sensor networks.In this paper,we con-sider a light-weight network management approach tailored specifically for WSNs and their unique constraints. Currently,WSN deployments can be categorized by their application scenario:data-gathering applications and event-detection applications.For data-gathering systems,health status monitoring is quite straight forward.Monitoring in-formation can be forwarded to the sink by specific health status packets or embedded in the regular data packets.Ad-ministrators can usually diagnose the network with a helper program.NUCLEUS[6]is one of the network management systems for data-gathering application of WSN.Since event-detection deployments do not have regular traffic to send to the sink,the solutions for data-gathering deployments are not suitable.In this case,health status monitoring can be quite challenging and has not been discussed explicitly in the literature.In an event-detection WSN,there is no periodic data trans-fer,i.e.,nodes maintain radio silence until there is an event to report.While this is energy efficient,it does mean that there is no possibility for the sink to decide whether the net-work is still up and running(and waiting for an event to be detected)or if some nodes in the network have failed and are therefore silent.Furthermore,for certain military ap-plications or safety-critical systems,the specifications may include a hard time constraint for accomplishing the node health status monitoring task.In an event-detection WSN,the system maintains a net-work topology that allows for forwarding of data to a sink in the case of an event.Even though there is no regular data transfer in the network,the network should always be ready to forward a message to the sink immediately when-ever necessary.It is this urgency of data forwarding that makes it undesirable to set up a routing table and neighborlist after the event has been detected.The lack of regular data transfer in the network also leads to difficulty in de-tecting bad quality links,making it challenging to establish and maintain a stable robust network topology.While we have mentioned event-detection WSNs in gen-eral,we accentuate that the distributed node monitoring problem we are considering is inspired by a real-world ap-plication:a distributed indoor wireless alarm system which includes a sensor for detection of a specific alarm such as fire(as studied in[5]).To illustrate the reporting require-ments of such a system,we point out that regulatory speci-fications require afire to be reported to the control station within10seconds and a node failure to be reported within 5minutes[9].This highlights the importance of the node-monitoring problem.In this paper,we present a solution for distributed node monitoring called DiMo,which consists of two functions: (i)Network topology maintenance,introduced in Section2, and(ii)Node health status monitoring,introduced in Sec-tion3.We compare DiMo to existing state-of-the-art node monitoring solutions and evaluate DiMo via simulations in Section4.1.1Design GoalsDiMo is developed based on the following design goals:•In safety critical event monitoring systems,the statusof the nodes needs to be monitored continuously,allow-ing the detection and reporting of a failed node withina certain failure detection time T D,e.g.,T D=5min.•If a node is reported failed,a costly on-site inspectionis required.This makes it of paramount interest todecrease the false-positive rate,i.e.,wrongly assuminga node to have failed.•In the case of an event,the latency in forwarding theinformation to the sink is crucial,leaving no time toset up a route on demand.We require the system tomaintain a topology at all times.In order to be robustagainst possible link failures,the topology needs toprovide redundancy.•To increase efficiency and minimize energy consump-tion,the two tasks of topology maintenance(in par-ticular monitoring of the links)and node monitoringshould be combined.•Maximizing lifetime of the network does not necessar-ily translate to minimizing the average energy con-sumption in the network,but rather minimizing theenergy consumption of the node with the maximal loadin the network.In particular,the monitoring shouldnot significantly increase the load towards the sink.•We assume that the event detection WSN has no reg-ular data traffic,with possibly no messages for days,weeks or even months.Hence we do not attempt to op-timize routing or load balancing for regular data.Wealso note that approaches like estimating links’perfor-mance based on the ongoing dataflow are not possibleand do not take them into account.•Wireless communications in sensor networks(especially indoor deployments)is known for its erratic behav-ior[2,8],likely due to multi-path fading.We assumesuch an environment with unreliable and unpredictablecommunication links,and argue that message lossesmust be taken into account.1.2Related WorkNithya et al.discuss Sympathy in[3],a tool for detect-ing and debugging failures in pre-and post-deployment sen-sor networks,especially designed for data gathering appli-cations.The nodes send periodic heartbeats to the sink that combines this information with passively gathered data to detect failures.For the failure detection,the sink re-quires receiving at least one heartbeat from the node every so called sweep interval,i.e.,its lacking indicates a node fail-ure.Direct-Heartbeat performs poorly in practice without adaptation to wireless packet losses.To meet a desired false positive rate,the rate of heartbeats has to be increased also increasing the communication cost.NUCLEUS[6]follows a very similar approach to Sympathy,providing a manage-ment system to monitor the heath status of data-gathering applications.Rost et al.propose with Memento a failure detection sys-tem that also requires nodes to periodically send heartbeats to the so called observer node.Those heartbeats are not directly forwarded to the sink node,but are aggregated in form of a bitmask(i.e.,bitwise OR operation).The ob-server node is sweeping its bitmask every sweep interval and will forward the bitmask with the node missing during the next sweep interval if the node fails sending a heartbeat in between.Hence the information of the missing node is disseminated every sweep interval by one hop,eventually arriving at the sink.Memento is not making use of ac-knowledgements and proactively sends multiple heartbeats every sweep interval,whereas this number is estimated based on the link’s estimated worst-case performance and the tar-geted false positive rate.Hence Memento and Sympathy do both send several messages every sweep interval,most of them being redundant.In[5],Strasser et al.propose a ring based(hop count)gos-siping scheme that provides a latency bound for detecting failed nodes.The approach is based on a bitmask aggre-gation,beingfilled ring by ring based on a tight schedule requiring a global clock.Due to the tight schedule,retrans-missions are limited and contention/collisions likely,increas-ing the number of false positives.The approach is similar to Memento[4],i.e.,it does not scale,but provides latency bounds and uses the benefits of acknowledgements on the link layer.2.TOPOLOGY MAINTENANCEForwarding a detected event without any delay requires maintaining a redundant topology that is robust against link failures.The characteristics of such a redundant topology are discussed subsequently.The topology is based on so called relay nodes,a neighbor that can provide one or more routes towards the sink with a smaller cost metric than the node itself has.Loops are inherently ruled out if packets are always forwarded to relay nodes.For instance,in a simple tree topology,the parent is the relay node and the cost metric is the hop count.In order to provide redundancy,every node is connected with at least two relay nodes,and is called redundantly con-nected.Two neighboring nodes can be redundantly con-nected by being each others relay,although having the same cost metric,only if they are both connected to the sink. This exception allows the nodes neighboring the sink to be redundantly connected and avoids having a link to the sinkas a single point of failure.In a(redundantly)connected network,all deployed nodes are(redundantly)connected.A node’s level L represents the minimal hop count to the sink according to the level of its relay nodes;i.e.,the relay with the least hop count plus one.The level is infinity if the node is not connected.The maximal hop count H to the sink represents the longest path to the sink,i.e.,if at every hop the relay node with the highest maximal hop count is chosen.If the node is redundantly connected,the node’s H is the maximum hop count in the set of its relays plus one, if not,the maximal hop count is infinity.If and only if all nodes in the network have afinite maximal hop count,the network is redundantly connected.The topology management function aims to maintain a redundantly connected network whenever possible.This might not be possible for sparsely connected networks,where some nodes might only have one neighbor and therefore can-not be redundantly connected by definition.Sometimes it would be possible tofind alternative paths with a higher cost metric,which in turn would largely increase the overhead for topology maintenance(e.g.,for avoiding loops).For the cost metric,the tuple(L,H)is used.A node A has the smaller cost metric than node B ifL A<L B∨(L A=L B∧H A<H B).(1) During the operation of the network,DiMo continuously monitors the links(as described in Section3),which allows the detection of degrading links and allows triggering topol-ogy adaptation.Due to DiMo’s redundant structure,the node is still connected to the network,during this neighbor search,and hence in the case of an event,can forward the message without delay.3.MONITORING ALGORITHMThis section describes the main contribution of this paper, a distributed algorithm for topology,link and node monitor-ing.From the underlying MAC protocol,it is required that an acknowledged message transfer is supported.3.1AlgorithmA monitoring algorithm is required to detect failed nodes within a given failure detection time T D(e.g.,T D=5min).A node failure can occur for example due to hardware fail-ures,software errors or because a node runs out of energy. Furthermore,an operational node that gets disconnected from the network is also considered as failed.The monitoring is done by so called observer nodes that monitor whether the target node has checked in by sending a heartbeat within a certain monitoring time.If not,the ob-server sends a node missing message to the sink.The target node is monitored by one observer at any time.If there are multiple observer nodes available,they alternate amongst themselves.For instance,if there are three observers,each one observes the target node every third monitoring time. The observer node should not only check for the liveliness of the nodes,but also for the links that are being used for sending data packets to the sink in case of a detected event. These two tasks are combined by selecting the relay nodes as observers,greatly reducing the network load and maximiz-ing the network lifetime.In order to ensure that all nodes are up and running,every node is observed at all times. The specified failure detection time T D is an upper bound for the monitoring interval T M,i.e.,the interval within which the node has to send a heartbeat.Since failure detec-tion time is measured at the sink,the detection of a missing node at the relay needs to be forwarded,resulting in an ad-ditional maximal delay T L.Furthermore,the heartbeat can be delayed as well,either by message collisions or link fail-ures.Hence the node should send the heartbeat before the relay’s monitoring timer expires and leave room for retries and clock drift within the time window T R.So the monitor-ing interval has to be set toT M≤T D−T L−T R(2) and the node has to ensure that it is being monitored every T M by one of its observers.The schedule of reporting to an observer is only defined for the next monitoring time for each observer.Whenever the node checks in,the next monitoring time is announced with the same message.So for every heartbeat sent,the old monitoring timer at the observer can be cancelled and a new timer can be set according the new time.Whenever,a node is newly observed or not being observed by a particular observer,this is indicated to the sink.Hence the sink is always aware of which nodes are being observed in the network,and therefore always knows which nodes are up and running.This registration scheme at the sink is an optional feature of DiMo and depends on the user’s requirements.3.2Packet LossWireless communication always has to account for possi-ble message losses.Sudden changes in the link quality are always possible and even total link failures in the order of a few seconds are not uncommon[2].So the time T R for send-ing retries should be sufficiently long to cover such blanks. Though unlikely,it is possible that even after a duration of T R,the heartbeat could not have been successfully for-warded to the observer and thus was not acknowledged,in spite of multiple retries.The node has to assume that it will be reported miss-ing at the sink,despite the fact it is still up and running. Should the node be redundantly connected,a recovery mes-sage is sent to the sink via another relay announcing be-ing still alive.The sink receiving a recovery message and a node-missing message concerning the same node can neglect these messages as they cancel each other out.This recov-ery scheme is optional,but minimizes the false positives by orders of magnitudes as shown in Section4.3.3Topology ChangesIn the case of a new relay being announced from the topol-ogy management,a heartbeat is sent to the new relay,mark-ing it as an observer node.On the other hand,if a depre-cated relay is announced,this relay might still be acting as an observer,and the node has to check in as scheduled.How-ever,no new monitor time is announced with the heartbeat, which will release the deprecated relay of being an observer.3.4Queuing PolicyA monitoring buffer exclusively used for monitoring mes-sages is introduced,having the messages queued according to a priority level,in particular node-missing messagesfirst. Since the MAC protocol and routing engine usually have a queuing buffer also,it must be ensured that only one single monitoring message is being handled by the lower layers atthe time.Only if an ACK is received,the monitoring mes-sage can be removed from the queue(if a NACK is received, the message remains).DiMo only prioritizes between the different types of monitoring messages and does not require prioritized access to data traffic.4.EV ALUATIONIn literature,there are very few existing solutions for mon-itoring the health of the wireless sensor network deployment itself.DiMo is thefirst sensor network monitoring solution specifically designed for event detection applications.How-ever,the two prominent solutions of Sympathy[3]and Me-mento[4]for monitoring general WSNs can also be tailored for event gathering applications.We compare the three ap-proaches by looking at the rate at which they generate false positives,i.e.,wrongly inferring that a live node has failed. False positives tell us something about the monitoring pro-tocol since they normally result from packet losses during monitoring.It is crucial to prevent false positives since for every node that is reported missing,a costly on-site inspec-tion is required.DiMo uses the relay nodes for observation.Hence a pos-sible event message and the regular heartbeats both use the same path,except that the latter is a one hop message only. The false positive probability thus determines the reliability of forwarding an event.We point out that there are other performance metrics which might be of interest for evaluation.In addition to false positives,we have looked at latency,message overhead, and energy consumption.We present the evaluation of false positives below.4.1Analysis of False PositivesIn the following analysis,we assume r heartbeats in one sweep for Memento,whereas DiMo and Sympathy allow sending up to r−1retransmissions in the case of unac-knowledged messages.To compare the performance of the false positive rate,we assume the same sweep interval for three protocols which means that Memento’s and Sympa-thy’s sweep interval is equal to DiMo’s monitoring interval. In the analysis we assume all three protocols having the same packet-loss probability p l for each hop.For Sympathy,a false positive for a node occurs when the heartbeat from the node does not arrive at the sink in a sweep interval,assuming r−1retries on every hop.So a node will generate false positive with a possibility(1−(1−p r l)d)n,where d is the hop count to the sink and n the numbers of heartbeats per sweep.In Memento,the bitmask representing all nodes assumes them failed by default after the bitmap is reset at the beginning of each sweep interval. If a node doesn’t report to its parent successfully,i.e.,if all the r heartbeats are lost in a sweep interval,a false positive will occur with a probability of p l r.In DiMo the node is reported missing if it fails to check in at the observer having a probability of p l r.In this case,a recovery message is triggered.Consider the case that the recovery message is not kept in the monitoring queue like the node-missing messages, but dropped after r attempts,the false positive rate results in p l r(1−(1−p l r)d).Table1illustrates the false positive rates for the three protocols ranging the packet reception rate(PRR)between 80%and95%.For this example the observed node is in afive-hop distance(d=5)from the sink and a commonPRR80%85%90%95% Sympathy(n=1) 3.93e-2 1.68e-2 4.99e-3 6.25e-4 Sympathy(n=2) 1.55e-3 2.81e-4 2.50e-5 3.91e-7 Memento8.00e-3 3.38e-3 1.00e-3 1.25e-4 DiMo 3.15e-4 5.66e-5 4.99e-67.81e-8Table1:False positive rates for a node with hop count5and3transmissions under different packet success rates.number of r=3attempts for forwarding a message is as-sumed.Sympathy clearly suffers from a high packet loss, but its performance can be increased greatly sending two heartbeats every sweep interval(n=2).This however dou-bles the message load in the network,which is especially substantial as the messages are not aggregated,resulting in a largely increased load and energy consumption for nodes next to the paring DiMo with Memento,we ob-serve the paramount impact of the redundant relay on the false positive rate.DiMo offers a mechanism here that is not supported in Sympathy or Memento as it allows sending up to r−1retries for the observer and redundant relay.Due to this redundancy,the message can also be forwarded in the case of a total blackout of one link,a feature both Memento and Sympathy are lacking.4.2SimulationFor evaluation purposes we have implemented DiMo in Castalia1.3,a state of the art WSN simulator based on the OMNet++platform.Castalia allows evaluating DiMo with a realistic wireless channel(based on the empiricalfindings of Zuniga et al.[8])and radio model but also captures effects like the nodes’clock drift.Packet collisions are calculated based on the signal to interference ratio(SIR)and the radio model features transition times between the radio’s states (e.g.,sending after a carrier sense will be delayed).Speck-MAC[7],a packet based version of B-MAC,with acknowl-edgements and a low-power listening interval of100ms is used on the link layer.The characteristics of the Chipcon CC2420are used to model the radio.The simulations are performed for a network containing80 nodes,arranged in a grid with a small Gaussian distributed displacement,representing an event detection system where nodes are usually not randomly deployed but rather evenly spread over the observed area.500different topologies were analyzed.The topology management results in a redun-dantly connected network with up to5levels L and a max-imum hop count H of6to8.A false positive is triggered if the node fails to check in, which is primarily due to packet errors and losses on the wireless channel.In order to understand false positives,we set the available link’s packet reception rate(PRR)to0.8, allowing us to see the effects of the retransmission scheme. Furthermore,thisfixed PRR also allows a comparison with the results of the previous section’s analysis and is shown in Figure1(a).The plot shows on the one hand side the monitoring based on a tree structure that is comparable to the performance of Memento,i.e.,without DiMo’s possibil-ity of sending a recovery message using an alternate relay. On the other hand side,the plot shows the false positive rate of DiMo.The plot clearly shows the advantage of DiMo’s redundancy,yet allowing sending twice as many heartbeats than the tree approach.This might not seem necessarily fair atfirst;however,in a real deployment it is always possible(a)Varying number of retries;PRR =0.8.(b)Varying link quality.Figure 1:False positives:DiMo achieves the targeted false positive rate of 1e-7,also representing the reliability for successfully forwarding an event.that a link fails completely,allowing DiMo to still forward the heartbeat.The simulation and the analysis show a slight offset in the performance,which is explained by a simulation artifact of the SpeckMAC implementation that occurs when the receiver’s wake-up time coincides with the start time of a packet.This rare case allows receiving not only one but two packets out of the stream,which artificially increases the link quality by about three percent.The nodes are observed every T M =4min,resulting in being monitored 1.3e5times a year.A false positive rate of 1e-6would result in having a particular node being wrongly reported failed every 7.7years.Therefore,for a 77-node net-work,a false positive rate of 1e-7would result in one false alarm a year,being the targeted false-positive threshold for the monitoring system.DiMo achieves this rate by setting the numbers of retries for both the heartbeat and the recov-ery message to four.Hence the guard time T R for sending the retries need to be set sufficiently long to accommodate up to ten messages and back-offtimes.The impact of the link quality on DiMo’s performance is shown in Figure 1(b).The tree topology shows a similar performance than DiMo,if the same number of messages is sent.However,it does not show the benefit in the case of a sudden link failure,allowing DiMo to recover immedi-ately.Additionally,the surprising fact that false positives are not going to zero for perfect link quality is explained by collisions.This is also the reason why DiMo’s curve for two retries flattens for higher link qualities.Hence,leaving room for retries is as important as choosing good quality links.5.CONCLUSIONIn this paper,we presented DiMo,a distributed algorithm for node and topology monitoring,especially designed for use with event-triggered wireless sensor networks.As a de-tailed comparative study with two other well-known moni-toring algorithm shows,DiMo is the only one to reach the design target of having a maximum error reporting delay of 5minutes while keeping the false positive rate and the energy consumption competitive.The proposed algorithm can easily be implemented and also be enhanced with a topology management mechanism to provide a robust mechanism for WSNs.This enables its use in the area of safety-critical wireless sensor networks.AcknowledgmentThe work presented in this paper was supported by CTI grant number 8222.1and the National Competence Center in Research on Mobile Information and Communication Sys-tems (NCCR-MICS),a center supported by the Swiss Na-tional Science Foundation under grant number 5005-67322.This work was also supported in part by phase II of the Embedded and Hybrid System program (EHS-II)funded by the Agency for Science,Technology and Research (A*STAR)under grant 052-118-0054(NUS WBS:R-263-000-376-305).The authors thank Matthias Woehrle for revising a draft version of this paper.6.REFERENCES[1] A.Mainwaring et al.Wireless sensor networks for habitatmonitoring.In 1st ACM Int’l Workshop on Wireless Sensor Networks and Application (WSNA 2002),2002.[2] A.Meier,T.Rein,et al.Coping with unreliable channels:Efficient link estimation for low-power wireless sensor networks.In Proc.5th Int’l worked Sensing Systems (INSS 2008),2008.[3]N.Ramanathan,K.Chang,et al.Sympathy for the sensornetwork debugger.In Proc.3rd ACM Conf.Embedded Networked Sensor Systems (SenSys 2005),2005.[4]S.Rost and H.Balakrishnan.Memento:A health monitoringsystem for wireless sensor networks.In Proc.3rd IEEE Communications Society Conf.Sensor,Mesh and Ad Hoc Communications and Networks (IEEE SECON 2006),2006.[5]M.Strasser,A.Meier,et al.Dwarf:Delay-aware robustforwarding for energy-constrained wireless sensor networks.In Proceedings of the 3rd IEEE Int’l Conference onDistributed Computing in Sensor Systems (DCOSS 2007),2007.[6]G.Tolle and D.Culler.Design of an application-cooperativemanagement system for wireless sensor networks.In Proc.2nd European Workshop on Sensor Networks (EWSN 2005),2005.[7]K.-J.Wong et al.Speckmac:low-power decentralised MACprotocols for low data rate transmissions in specknets.In Proc.2nd Int’l workshop on Multi-hop ad hoc networks:from theory to reality (REALMAN ’06),2006.[8]M.Zuniga and B.Krishnamachari.Analyzing thetransitional region in low power wireless links.In IEEE SECON 2004,2004.[9]Fire detection and fire alarm systems –Part 25:Componentsusing radio links.European Norm (EN)54-25:2008-06,2008.。
基于认证的移动网络中的信任模型——英文翻译

Certification-based trust models in mobile ad hoc networks:A survey and taxonomyMawloud Omar,nUniversite A/Mira,ReSyD,Bejaia,AlgeriaYachne Challal,Abdelmadjid BouabdallahUniversite de Technologie de Compiegne,Heudiasyc-UMR CNRS 6599,Compiegne,France AbstractA mobile ad hoc network is a wireless communication network which does not rely on a pre-existing infrastructure or any centralized management. Securing the exchanges in such network is compulsory to guarantee a widespread development of services for this kind of networks. The deployment of any security policy requires the definition of a trust model that defines who trusts who and how. There is a host of research efforts in trust models framework to securing mobile ad hoc networks. The majority of well-known approaches is based on public-key certificates,and gave birth to miscellaneous trust models ranging from centralized models to web-of-trust and distributed certificate authorities. In this paper,we survey and classify the existing trust models that are based on public-key certificates proposed for mobile ad hoc networks,and then we discuss and compare them with respect to some relevant criteria. Also,we have developed analysis and comparison among trust models using stochastic Petri nets in order to measure the performance of each one with what relates to the certification service availability.Keywords: mobile ad hoc network,trust models,certificates1. IntroductionMobile ad hoc networking is emerging as an important area for new developments in the field of wireless communication. The premise of forming a mobile ad hoc network is to provide wireless communication between heterogeneous devices,anytime and anywhere,with no infrastructure. These devices,such as cell phones,laptops,palmtops,etc. carry out communication with other nodes that come in their radio range of connectivity. Each participating node provides services such as message forwarding,providing routing information,authentication,etc. to form a network with other nodes spread over an area. With the proliferation of mobile computing,mobile ad hoc networking is predicted to be a key technology for the next generation of wireless communications. They are mostly desired in military applications where their mobility is attractive,but have also a high potential for use in civilian applications such as coordinating rescue operations in infrastructure-less areas ,sharing content and network gaming in intelligent transportation systems,surveillance and control using wireless sensor networks,etc.Inherent vulnerability of mobile ad hoc networks introduces new security problems,which are generally more prone to physical security threats. The possibility of eavesdropping,spoofing,denial-of-service,and impersonation attacks increases. Similar to fixed networks,security of mobile ad hoc networks is considered from different points such as availability,confidentiality,integrity,authentication,non repudiation,access control and usage control. However,security approaches used to protect the fixed networks are not feasible due to the salient characteristics of mobile ad hoc networks. New threats,such as attacks raised from internal malicious nodes,are hard to defend. The deployment of any security service requires the definition of a trust model that defines who trusts who and how. There are recent research efforts in trust models framework to securing mobile ad hoc networks. There exist two main approaches: (1) cooperation enforcement trust models,and,(2) certification- based trust models. In Table 1,we present the major differences between cooperation enforcement trust models and certification-based trust models.Table 1Cooperation enforcement vs. certification-based trust modelsThe first trust models category is based basically on reputation among nodes. The reputation of a node increases when it carries out correctly the tasks of route construction and data forwarding. The models of this category support effective mechanisms to measure the reputation of other nodes of the network. They also incorporate techniques that isolate the misbehaving nodes that are those that show a low reputation value. Trust models based on cooperation enforcement are well surveyed in the literature. Marias et al. provided such a thorough survey of cooperation enforcement trust models. In this paper,we are interested in the category of certification-based trust models. Indeed,in this category,the trust relationship among users is performed in a transitive manner,such that if A trusts B,and B trusts C,then A can trust C. In this relationship,the principal B is called Trusted Third Party (TTP). The latter could be a central authority (like CA –Certification Authority) or a simple intermediate user. Both points of view gave birth to two categories of models: (a) Authoritarian models,and (b) Anarchic models. In this paper,we review and classify the existing certification-based trust models belonging to each category. Moreover,to determine the efficiency of a given trust model,it is very important to estimate the certification service availability with respect to mobile ad hoc networks configuration. Therefore,we have modeled the certification process of each surveyed trust model using stochastic Petri nets (SPN). As you will see in the following sections,this allows a better understanding of the performances of the different models and how to leverage some parameters forhigher certification service availability.While a number of surveys covering the issues of key management in mobile ad hoc networks,have provided some insightful overviews of the different schemes proposed in the literature,none of them focuses on issues related to certificates management thoroughly (the scheme architecture,how the certificates are stored and managed,the complexity evaluation of the certification protocol,etc.). To complement those efforts,this work provides detailed taxonomy of certification-based trust models,and illustrates in depth the different schemes by providing the advantages and drawbacks of each one with respect to relevant criteria. The careful examination and analysis has allowed us to carry out a comparative study of the proposed schemes based on an analytic evaluation. The ultimate goal of this paper is to identify the strengths and weaknesses of each scheme in order to devise a more effective and practical certificate-based trust models which can achieve a better trade-off between security and performance.The remaining of this paper is structured as follows. In Section 2,we recall background material relating to basic concepts on cryptography and threshold cryptography. Then,in Section 3,we identify requirements relating to certificates management with respect to mobile ad hoc networks environment and constraints,and in Section 4 we propose a tax on o my of the existing certification-based trust models. Respectively,in Sections 5 and 6,we review the authoritarian models,and anarchic models. For each solution,we provide a brief description and discuss its advantages and short- comings. We model the different solutions using stochastic Petri nets and provide analytical results and conclusions. Then,we make a general analysis and comparison against some important performance criteria. We finally conclude this paper in Section 7 with the sender. Each public-key is published,and the corresponding private-key is kept secret by the sender. Message encrypted with the sender’s public-key can be decrypted only wit h the sender’s private-key. In general,to send encrypted message to someone,the sender encrypts the message with that receiver’s public-key,and the receiver decrypts it with the corresponding private-key authentication is a service related to identification. This function applies to both entities and information itself. Two parties entering into a communication should identify each other.The public-key certificate is a digital data structure issued by a trusted third party to certify a public-key’s ownership. Among other information a public-key certificate contains: (1) certificate number; (2) issuer’s identity; (3) owner’s identity;(4) owner’s public-key; (5) signature algorithm; (6) period of validity; and (7) the issuer’s signature,and eventually other extensions. CA (Certification Authority) is a trusted third party,which is usually a trustworthy entity for issuing certificates. If the same CA certifies two users,then they would have the same CA in common as a third trust party. The two users would then use the CA’s public-key to verify their exchanged certificates in order to authenticate the included public-keys and use them for identification and secure communication. Each CA might also certify public-keys of other CAs,and collectively forms a hierarchical structure. If different CAs certification two users,they must resort to higher-level CAs until they reach a common CA (cf. Fig. 1).Web-of-trust model does not use CAs. Instead,every entity certifies the binding of identities and public- keys for other entities. For example,an entity u might think it has good knowledge of an entity v and is willing to sign’s public-key certificate. All the certificates issued in the system forms a graph of certificates,named web-of-trust (cf. Fig. 2).2. BackgroundIn this section we recall the definition of some security services using cryptographic mechanisms.2.1. Security services and basic cryptography mechanismsConfidentiality is a service used to keep the content of information from all,but those authorized to have it. Confidentiality is guaranteed using encryption. Encryption is a cryptographic transformation of the message into a form that conceals the message original meaning to prevent it from being known or used. If the transformation is reversible,the corresponding reversal process is called decryption,which is a transformation that restores the encrypted message to its original state. With most modern cryptography,the ability to keep encrypted information secret is based not on the cryptographic encryption algorithm,which is widely known,but on a piece of information called a key that must be used with the algorithm to produce an encrypted result or to decrypt previously encrypted information. Depending on whether the same or different keys are used to encrypt and to decrypt the information We distinguish between two types of encryption systems used to assure confidentiality: Symmetric-key encryption: a secret key is shared between the sender and the receiver and it is used to encrypt the message by the sender and to decrypt itby the receiver. The encryption of the message produces a non-intelligible piece of information; the decryption reproduces the original message. Public-key encryption: also called asymmetric encryption,involves a pair of keys (public and private keys)3. Design issuesThe distribution of public-keys and management of certificates have been widely studied in the case of infrastructure-based networks. In the latter,several issues have been well discussed. However,the certificates management in mobile ad hoc networks addresses additional new issues appeared from the constraints imposed,in particular,by the ad hoc network environment. These issues can be resumed in the following points:Certification service availability issue: In mobile ad hoc networks,due to the frequent link failures,nodes mobility,and limited wireless medium,it is typically not feasible to maintain a fixed centralized authority in the network. Further,in networks requiring high security,such a server could become a single point of failure. One of the primary requirements is to distribute the certification service amongst a set of special nodes (or all nodes) in the network.Resources consumption issue: Since the nodes in mobile ad hoc network typically run on batteries with high power consumption and low memory capacity,the certification service must be resource-aware. That means the time and space complexity of the underlying protocols must be acceptably low in terms of computation,communication,and storage overheads.Scalability issue: Many applications in mobile ad hoc networks involve a large number of nodes. When the certificates management is handled through a centralized authority,the latter may become overloaded due to the number of nodes request. Otherwise,if the certification service is designed in a fully distributed way among several nodes in the network,each participant to the service must maintain a local repository,which contains a maximum number of certificates concerning the other nodes in the network. Hence,the storage overhead will be linear to the network size,which may compromise the system scalability to large ad hoc networks.Handling heterogeneity issue: As in the case of wired networks,the certifying authorities might be heterogeneous even in mobile ad hoc networks. This means that two or more nodes belonging to different domains (mainly in term of certification policy) may try to authenticate each other. In such a case,there must be some kind of trust relationship between the two domains.4. TaxonomyIn Fig. 4,we propose a tax on o my of the existing certification-based trust models for mobile ad hoc networks. We divide existing solutions into two categories depending on the existence or not of central authorities.4.1 Authoritarian modelsIn this category,there exist one or more authorities that are trusted by the whole community of ad hoc nodes. Depending on the number of authorities,this category can be further divided into monopolist models and oligopolist models:1.Monopolist models. In this subcategory,the system is ensured by acertification authority. To cope with the spontaneous nature of mobile ad hoc networks,the service is distributed among several servers,which ensure collectively the CA’s role using a (k,n) threshold cryptography scheme. The CA’s private key is divided into n private-shares,such that each server holds one private-share. In order to deliver a certificate to a given client node,each server creates a partial certificate (certificate signed using a private-share). The system processes the client request,such that the combination of any k partial certificates gives as a result a valid certificate signed by the CA’s private-key.This subcategory is divided into:(a) Single distributed CA,where the certification service,in the whole system,is ensured by only one CA,which is distributed among several servers.(b) Hierarchical CAs,where the certification service is ensured by several homogeneous CAs organized into a hierarchy. Each or some CAs in the system is distributed among several servers. A trust relationship should be established among the different CAs in this case.2.Oligopolist models. In this subcategory,the system is composed ofseveral heterogeneous CAs. Each CA has its own policy of certification. Each or some CAs in the system are distributed among several servers.4.2. Anarchic modelsIn this category of models,there is no central authority. Or in other words,each user acts as an authority independently of other users in the network. The propagation of trust in the network forms what is commonly called web-of-trust. As previously outlined,the web-of-trust is managed by users themselves. This model isdecentralized in nature,and so very adequate for mobile ad hoc networks. In this category of trust models,two main operations are addressed: (1) the initial web-of-trust construction and (2) the certificates chain discovery. This subcategory can be further divided into proactive models and reactive models:1. Proactive models. In this subcategory,the protocol of certificates collection is executed systematically among neighboring nodes. Thus,when the node needs to verify a certificate,it is done instantly since the required chain of certificates would have been already retrieved from the network.2. Reactive models. In this subcategory,the certificates collection protocol is executed on-demand. When the node needs to verify a certificate,it collects in a distributed manner the appropriate chain of certificates from the network. This prolongs the delays of certificates verification.In the following sections,we give detailed descriptions of certification-based trust models belonging to each category. We give for each trust model an overview,advantages,drawbacks,and eventually the proposed extensions. Then,for each category,we give an analytical modeling and an overall comparison with respect to the criteria presented in Section 3.5. Authoritarian modelsIn this section we present and discuss certification-based trust models belonging to the authoritarian models category.5.1. Monopolist modelsIn this class of trust models,the certification service is ensured by a single or several homogeneous CA.5.2. Oligopolist modelsIn this class of trust models,the certification service is composed of several heterogeneous CAs,which each one has its own policy of certification.5.3. Modeling and discussionIn order to measure the degree of the possibility to get a successful certification process,we have opted to model trust models using SPN (Stochastic Petri Network). This model is adequate in the sense that the availability of servers at a given moment for a given node requester is probabilistic and depends on many parameters such as mobility,nodes availability,radio links failure,etc. Then,the servers must collaborate collectively to generate a public-key certificate which requires the synchronization of at least k servers. Indeed,SPNs consist of places and transitions as well as a number of functions. Enabled transitions fire according to exponential distributions; characteristic of Markov processes. It allows the quick construction of a simplified abstract model that is numerically solved for different model parameters. In Fig. 10,we present SPNs corresponding to each trust model belonging to this category,and we note in Table 3 the most used terminology in this subsection.Description……7. ConclusionsIn this paper we focused on certification-based trust models in mobile ad hocnetworks. We provided an overview of the objectives and requirements relating to certificates managements with respect to mobile ad hoc networks environments: service availability,resources awareness,scalability,and handling the heterogeneity. We have classified existing solutions into two approaches: (1) Authoritarian models,where the certification service is provided through one or several certification authorities. In order to take into consideration the above-mentioned requirements,and especially availability and resources awareness,the certification service is distributed among a set of special nodes cooperation to provide the service through threshold cryptography. (2) Anarchic models,where each user in the network considers itself as a certification authority and establishes its own trust relationships according to some rules that may require the cooperation of other users in the network. Again,to take into consideration the above-mentioned requirements,some techniques are used to make certificates chain verification fasterwith low certificates storage overhead. We have further divided these two categoriesinto fine grained sub-categories to illustrate the different organizational and performance aspects of the proposed solutions in the literature. We believe that the proposed taxonomy provides a global and precise insight over existing solutions,with a better understanding of the design choices decided by their authors.In order to measure the service availability degree,we have modeled the reviewed certification-based trust models using SPNs(Stochastic Petri Nets),followed by comparisons and analytical discussions of each trust model. We have showed,in the authoritarian models,that there are two criteria that influence on the certification system availability. The first criterion is the coalition of servers providing the certification service: how to choose the servers? And how many servers can be available to respond to a certification requests? The second criterion is the choice of the threshold value (k). We have studied the impact of these two parameters on the successful certification rate of the existing trust models. This allowed us to further categorize the solutions into performance classes depending on the variation of these parameters dictated by the design of each trust model. In the other category of anarchic models,we have showed that there are two significant criteria that influence on the authentication service availability. The first criterion relates to the management of certificates repository servers,and especially their availability to respond to client nodes requests. The second criterion is the policy nature of certificates chain recovery,and especially,the induced length of certificates chain requiring verification during the certification process. We have then studied the impact of these parameters on the rate of successful service of authentication. This culminated to the categorization of existing solutions into performance classes depending on the design of each trust model.This survey should help shed some light on certification-based trust models in mobile ad hoc networks. It should be especially useful to get a global and precise insight of existing solutions through a fine grained taxonomy and a thorough performance modeling,evaluation and comparison.Journal of Network and Computer Applications2011 Elsevier Ltd.中文译文基于认证的移动网络中的信任模型:调查及分类奥玛拉.马洛德阿尔及利亚倍及亚热赛德巴黎米拉大学亚森.查拉,阿伯丁伊德德·堪培根科技大学,法国国家科学研究院摘要:移动网是一种无线通信网络,不依赖于已有的基础设施或任何的集中管理。
感知中国

}
WSN系列讲座(一)
3、结果输出:有TKENV和CMDENV两种界面。TKENV是图形用户界面
接口,其中包括动画自动生成、模块输出窗口和对象监测器。CMDENV 是纯命令行的界面。
WSN系列讲座(一)
随着无线网络的应用越加广泛,相信 相关的技术还会不断地改进。例如现在快 速发展的人工智能技术。
• M2M, Smart Grid, Telematics, Telehealth
WSN系列讲座(一)
感知政务
• 警务通 • 城管通 • 智能公交 • 智能路灯 • 环境监控 • 噪声监控 • 掌上110 • 居民应急疏散信息系统 • 防汛综合平台 • 无线抄表系统
WSN系列讲座(一)
感知企业
• 现代农业 • 工业智能管理网及仓储物流 • 气象监测 • 无线港区 • EMS短信服务平台 • 企业办公综合解决方案 • 电子车票 • 手机实时招车系统 • 位置信息服务 • 图书馆应用
WSN系列讲座(一)
物联网的未来
让地球成为数据世界并充满智慧 我们能充分地感知中国、感知世界
我们能够享受世界并且服务世界
这就是未来的物联网世界
WSN系列讲座(一)
由无线传感器网络和互联WS网N系组列成讲:座(一)
WSN系列讲座(一)
全面感知 无缝互联 高度智能
WSN系列讲座(一)
物联网技术--WSN技术
◆7.数据管理 ◆8.无线通信技术 ◆9.嵌入式操作系统 ◆10.应用技术
5.WSN的应用现状
随着计算成本的下降以及微处理器体积越来越小,已 经为数不少的无线传感器网络开始投入使用。目前无 线传感器网络的应用主要集中在以下领域:
◆1. 环境的监测和保护
随着人们对于环境问题的关注程度越来越高,需要采集 的环境数据也越来越多,无线传感器网络的出现为随机 性的研究数据获取提供了便利,并且还可以避免传统数 据收集方式给环境带来的侵入式破坏。无线传感器网络 还可以跟踪候鸟和昆虫的迁移,研究环境变化对农作物 的影响,监测海洋、大气和土壤的成分等。此外,它也 可以应用在精细农业中,来监测农作物中的害虫、土壤 的酸碱度和施肥状况等。
3.WSN的网络体系结构:
◆网络结构
结构入上图所示,传感器网络系统通常包括传感器节点 (sensor node),汇聚节点(sink node),和管理节点。大量传 感器节点随机的部署在检测区域内部或附近,能够通过自组织方 式构成网络。传感其节点检测的数据沿着其它节点逐跳的进行传 输,其传输过程可能经过多个节点处理,经过多跳后到达汇集节 点,最后通过互联网和卫星达到管理节点,用户通过管理节点对 传感器网络进行配置和管理,发布检测任务以及收集检测数据。
◆4其他用途
无线传感器网络还被应用于其他一些领域。比如 一些危险的工业环境如井矿、核电厂等,工作人员可 以通过它来实施安全监测。也可以用在交通领域作为 车辆监控的有力工具。此外和还可以在工业自动化生 产线等诸多领域,英特尔正在对工厂中的一个无线网 络进行测试,该网络由40台机器上的210个传感器组 成,这样组成的监控系统将可以大大改善工厂的运作 条件。它可以大幅降低检查设备的成本,同时由于可 以提前发现问题,因此将能够缩短停机时间,提高效 率,并延长设备的使用时间。尽管无线传感器技术目 前仍处于初步应用阶段,但已经展示出了非凡的应用 价值,相信随着相关技术的发展和推进,一定会得到 更大的应用。
Instructionsforusingbottles(奶瓶使用说明)

Instructions for using bottles(奶瓶使用说明)Seen on the network BT4 posts or so fire, and BT4 is a famous hacker tool, to crack wireless key is a bit for us and put fine timber to petty use, 1 points, several G BT4 download is really uncomfortable, Beini (bottle) was born to solve this problem, Beini is to break the radio the key, only the size of the 44M itself. I'd like to introduce myself to you.Introduction (Description):With the popularity of domestic wireless network (IEEE 802.11) devices, the security of wireless networks has gradually become the focus of attention. Beini is a system for evaluating wireless network security.Beini: a wireless network security test system based on Tiny Core Linux.FeedingBottle: GUI for the Aircrack-ng toolkit running on the Beini system.For more information and tutorials, please refer to the "readme" file in the CD-ROM (very detailed).Beini is a disk ISO file, you can burn it to a CD, U disk, or VMware. But note that the built-in wireless card notebook mostly PCI device is not recognized by the VMware, so I want to use this experience of a friend with UltraISO burn to U disk, the process is very simple, such as:/view/0756fe6527d3240c8447ef26.html, there is no longer the.As we all know, WEP is much easier than WPA's crack, WEP generally can be done, WPA can only rely on luckBreak time to find the best client, and the router is using wireless communication with computer target hack, Chinanet wireless telecommunications cats are sent to home users, do not use a wireless network, you can also break out break.Tips: rub nets to civilization Oh ~!Video tutorials:/beini_system/swf/feedingbottle-2.0-rc 1.swfBeini: a wireless network security test system based on Tiny Core Linux.FeedingBottle: GUI for the Aircrack-ng toolkit running on the Beini system.For more information about Tiny Core Linux, please visit:For more information about Beini, please visit:/prince_vegeta/prince_vegetaZhao Chunsheng, Tianjin, China2009-09-14---History:2010-06-04 Beini-1.2.1The software program that comes with this release comes from Beini-1.2.--- wireless network card driver: fixes RT3070 driver compatibility issues (LED works normally).- firmware: wireless-fw-2010-06-04.tce, non independent software package.2010-06-02 Beini-1.2The software program that comes with this release comes from Beini-1.1.- upgrading the Linux kernel to 2.6.34.--- wireless network card driver: supports RT3070 and some Broadcom chips.- firmware: wireless-fw-2010-05-27.tce, non independent software package.Hint: for RTL8187 chips, this version does not support RTL8187B, supports only RTL8187L, uses the ieee80211 driver; non RT3070 and Broadcom chip users, please continue to use Beini-1.1.2010-05-20 Beini-1.1This version is based on Beini-1.0-RC5.2 kernel and driver production.- Open FTP service (the default user name: TC, password: empty, the current system default user login TC home; user name: BEINI, password: empty, the current system /tmp directory, minidwep and FeedingBottle of the temporary data stored in this.) The service is provided by the program vsftpd.- shut up - Aircrack update to 1.1.- provide support for airgraph psycho 1.6.tcz, graphviz.tcz, and join related software: libgd.tcz.- shut up - support for airdrop. Join related software: Python.- added Python software: python.tcz, lib.tcz, sqlite3.tcz, bzip2 - TCL tk.tcz, pylorcon.tcz _.- join fcicq's carefully crafted Dictionary:fcicq-dict-unidict-20100410.tce.- firmware: wireless-fw-2010-05-03.tce.Thank you daddy - provide wallpaper, blog: HTTP:/ / / bang37480115 @ 126.- update minidwep - GTK to: minidwep - GTK - 20510.The feedingbottle update to N 3.1: the creation of advanced user interface for the WPA mode; provide support to OPN mode; when continuous capture 6 seconds to obtain WPA handshake packet information, in order to obtain the possible deauthentication packets information, provide an important basis for the manual analysis of information is generated for handshake by client.Provide a new logout program: logout.tcz for easy shutdown and restart.2010 02 beini-1.0-final - 12 -- update the automated test scripts produced by minileaf: minidwep-gtk-20208-original.tce- update the feedingbottle to the optimizations and corrections section code final: 3Pack the NIC driver into the tinycore.gz, and fix the RC version that doesn't support Broadcom chips- upgrading the Linux kernel to 2.6.32.2 enhances system compatibilityIncrease Bib - 1, BEINI, similar to network stumbler tools- IW upgrade to 0.9.192010 - 01 - 22-1 rc5.2 BEINI- update the automated test scripts produced by minileaf: minidwep-gtk-20119.tce- updating feedingbottle to 3 RC3: increased violence pseudo connection function is pseudo connection (aireplay - 1) is not successful can try to use this function; (4) attack chopchop, will show the generated file change schedule XOR attack command edit box of light color in the status bar in the acquisition; AP list interface set up a "AP" option to ignore exceptions (such as: 133ch AP / client list font width font);- shut up - modify the aireplay code to support the pseudo connectivity of the Chinese SSID (aireplay - 1)- IW upgrade to 0.9.18- adds cowpatty.tcz (ver:4.6) to break WPA / WPA2 handshake packagesWPA _ - increased tcpdump.tcz, supplicant.tcz, wl.tcz- firmware: wireless-fw-2010-01-05.tcz, added iwlwifi - 6000- drive: compat-wireless-2.6.32.2-2010-01-05.tcz, zd1211 normal display signal value; support part of Broadcom chip- this version is the last beta version of beini-1.0-final2009-12 - 24-1 rc5.1 BEINI- update the automated test scripts produced by minileaf: minidwep-gtk-1223.tce, this release will bring you a fresh and refreshing feeling!- updating feedingbottle to 3 RC2: to improve the compatibility, support BT3 finals, automatically shut down Aircrack - program exit procedures, the default scanning time from 15 seconds to 30 seconds, after the failure to obtain AP list will be related tips- screen resolution defaults to 1024x768 (24):- BEINI provides support for wireless channels 12, 13, and 14- add libpci.tczl, pci-utils.tcz to support command lspci to view the PCI card information- drive: compat - Wireless - 2.6.32.2- drive: rt3070usb (rt307x) 2009-11 - 10 (test)- change wallpaper,Thanks to Cai Jing (Handan) for making2009-11-30 Beini-1.0-RC5- update the automated test script produced by minileaf:minidwep-wpa-1129.tce, which now supports WPA/WPA2- update FeedingBottle to 3 RC1:1: the creation of an advanced user interface, the equivalent of a command generator, this feature can be removed from the input and output Aircrack-ng get complicated command details (Note: 1, only for WEP; 2, you can customize the parameters; 3, if you do not want to always press [Run] to execute the program, you can try [Auto Run] the function, of course, so only by default parameters to execute commands)2: scanning AP will appear detailed information; scanning AP time is set to: 5sec/15sec/30sec/1min/5min/15min; scanning process can be interrupted at any time- increase rox-filer_root.tcz, ROX-Filer is a very small file manager, she used to manage the dictionary file and WPA/WPA2 handshake packet should be very simple, not familiar with the command line friend recommended (occupies 8MB space, please be careful operation root permissions to run.)- add flit.tcz to display system time and system power supply- add mdk3-v6.tcz, the famous wireless security testing tool - MDK3--- drive: compat-wireless-2009-11-30- firmware: wireless-fw-2009-11-27.tce adds the driver for the Broadcom network cardMost software packages have been changed to TCZ2009-11-15 Beini-1.0-RC4.2Update Tiny Core Linux to 2.5The FeedingBottle update to 2 RC2.1: strengthen their compatibility, add aterm to support bt4-pre-final; Default scan time from 10 seconds to 15 seconds to change the color of the window; aterm; repair -4/-5 attack to get the XOR file name errors BUG repair; click the blank area APs Information ", will appear abnormal client information in the" Clients Information "BUG; an additional 14 channel selection; when the WEP password is ASCII, display the corresponding ASCII information update; BEINI interface; AP Clients Information scanning repair" in the client list will not clear the problem--- increase the mimayin written in crunch.tcz, a command line dictionary generation tools, in line with FeedingBottle's WPA/WPA2 security testing capabilities--- add macchanger-1.5.0.tcz to modify the MAC address of the network card--- drive: compat-wireless-2009-11-15- change some of the package files to TCZ2009-10-30 Beini-1.0-RC4.1- update the automated test scripts produced by minileaf: minidwep-0.11-1029.tce- - update the FeedingBottle to 2 RC2, support WPA/WPA2, and attach a small dictionary; fix the program overflow when you get the AP exception PWR value--- drive: compat-wireless-2009-10-27- change some of the package files to TCZ--- add libusb.tczl, usb-utils.tcz to support command lsusb, to view USB card information--- increase the kernel boot parameter waitusb=6, and solve the problem that the USB boot disk produced by unetbootin can't load the package automatically2009-10-17 Beini-1.0-RC4- update FeedingBottle to 2 RC1, fully updated!- firmware: wireless-fw-2009-10-13.tce, added ar9271.fw--- drive: compat-wireless-2009-10-17- - IW upgrade to 0.9.17- - add nano.tcz to edit files2009-09-23 Beini-1.0-RC3- add an automated test script produced by minileaf: minidwep-0.11-910- - adding support for NTFS format (read only), hard disk boot Beini is more convenient and flexibleAdjust the disc structure- - update the FeedingBottle to 1 RC2.1 to adjust the scan AP time and complete some of the code2009-09-16 Beini-1.0-RC2- update wireless-fw.tce, added two firmware:isl3887usb,isl3887usb_bare (thanks to minileaf (Sichuan, Chengdu) test)- add bash.tce, dosfstools-3.tce, syslinux.tce, and the latter two to make the U disk version systemUpdate the Tiny Core Linux to 2.3.1- - update the FeedingBottle to 1 RC2, adding deauth (-0), fakeauth (-1) and interactive (-2) functions, and refining some of the code- replaced the softer wallpaper2009-09-14 Beini-1.0-RC1- - version 1---Beini:A, wireless, network, security, testing, system, it, is, based, on,, Tiny, Core, Linux.FeedingBottle:Aircrack-ng's GUI on Beini.More, about, Tiny, Core, Linux, please, visit:More, about, Beini, please, visit:/prince_vegeta/prince_vegetaZhaoChunsheng, Tianjin, China14 September 2009---。
Wireless Communication Connecting the World

Wireless Communication Connecting the World Wireless communication has revolutionized the way people connect with each other and the world around them. It has enabled instant communication across vast distances, allowing people to stay in touch with friends and family, conduct business, and access information from virtually anywhere. The impact of wireless communication on society has been profound, shaping the way we live, work, and interact with one another.From a personal perspective, wireless communication has greatly enhanced my ability to stay connected with loved ones. Whether it's through text messages, phone calls, or video chats, I can easily reach out to friends and family members, no matter where they are in the world. This has made it possible to maintain strong relationships despite physical distance, fostering a sense of closeness and connection that would have been much more difficult to achieve in the past.In addition to its impact on personal relationships, wireless communication has also transformed the way we conduct business. Mobile devices and wireless networks have made it possible for professionals to work remotely, collaborate with colleagues in different locations, and access important information on the go. This has led to increased flexibility and productivity in the workplace, as well as the ability to conduct business on a global scale with ease.Furthermore, wireless communication has had a significant impact on education and access to information. With the rise of mobile devices and wireless internet, students and learners of all ages can access a wealth of knowledge and educational resources from anywhere with an internet connection. This has democratized access to information, allowing people from all walks of life to pursue learning and personal growth in ways that were previously unimaginable.On a broader societal level, wireless communication has also played a crucial role in emergency response and disaster relief efforts. During natural disasters or other emergencies, wireless communication networks have been vital in coordinating rescue andrelief operations, as well as keeping affected populations informed and connected. This has undoubtedly saved lives and mitigated the impact of disasters in countless situations.However, it's important to acknowledge that the widespread adoption of wireless communication has also raised concerns about privacy and security. As people increasingly rely on wireless devices to store and transmit sensitive information, the risk of data breaches and cyber attacks has become a significant issue. This has led to ongoing debates about the balance between convenience and security in the digital age, as well as the need for robust measures to protect personal and sensitive information.In conclusion, wireless communication has had a profound and far-reaching impact on society, transforming the way we connect with one another, conduct business, access information, and respond to emergencies. While it has undoubtedly brought about many positive changes, it has also raised important questions about privacy and security in the digital age. As we continue to navigate the evolving landscape of wireless communication, it will be crucial to prioritize the responsible use of technology while harnessing its potential for positive impact.。
wireless receiver感叹号

wireless receiver感叹号Wireless Receiver: The Ultimate Solution for a Tangle-Free ConnectionWireless technology has revolutionized the way we connect and communicate in the modern world. With the increasing popularity of wireless devices, the demand for efficient and reliable wireless receivers has also soared. In this article, we will explore the wonders of wireless receiver technology and its impact on our daily lives.1. Introduction: Embracing the Wireless RevolutionThe growth of wireless devices such as smartphones, tablets, and smartwatches has paved the way for a wire-free lifestyle. Wireless receivers play a crucial role in enabling seamless connectivity between these devices and other peripherals, creating a hassle-free user experience. By eliminating the need for cables and wires, wireless receivers offer flexibility, convenience, and freedom.2. How Wireless Receivers WorkWireless receivers, also known as wireless transceivers, utilize radio frequency (RF) technology to establish a connection between devices. They receive signals wirelessly and convert them into usable data, allowing devices to communicate and transfer information without physical connections.These receivers employ various wireless communication protocols, including Bluetooth, Wi-Fi, and NFC (Near Field Communication), to achieve reliable and efficient data transmission. Each protocol offers uniqueadvantages in terms of range, speed, and power consumption, catering to different connectivity needs.3. Applications of Wireless ReceiversWireless receivers find extensive applications across a wide range of industries and everyday scenarios. Let's explore some of the most prominent applications:a. Entertainment Industry: Wireless audio receivers have revolutionized the way we experience music and entertainment. Bluetooth-enabled speakers, headphones, and soundbars provide a seamless audio experience without the hassle of tangled wires.b. Home Automation: Wireless receivers, when integrated with home automation systems, allow us to control various household appliances remotely. From smart thermostats to security cameras, these receivers offer a convenient and connected home experience.c. Automotive Industry: Wireless technology plays a vital role in modern vehicles. Wireless receivers enable hands-free calling, audio streaming, and even wireless charging, enhancing driver convenience and safety.d. Healthcare: Wireless receivers have transformed the healthcare industry, enabling remote patient monitoring and telemedicine. Medical devices equipped with wireless technology ensure real-time data transmission for accurate diagnosis and treatment.4. Advantages of Wireless ReceiversWireless receivers bring numerous benefits that enhance our daily lives. Let's delve into some of the key advantages:a. Mobility and Flexibility: Wireless receivers enable unrestricted movement, allowing us to connect and communicate with devices without being tied down by cables. This freedom of movement enhances productivity and convenience.b. Decluttered Spaces: Say goodbye to the tangle of wires! Wireless receivers eliminate the need for cables and wires, reducing clutter and creating a clean and organized environment.c. Enhanced User Experience: With wireless receivers, connecting devices becomes effortless, streamlining interactions and improving user experience. Quick and easy pairing of devices ensures a seamless connection every time.d. Improved Connectivity: Wireless receivers offer reliable and stable connections, ensuring uninterrupted data transmission. This is particularly crucial for video streaming, online gaming, and other bandwidth-intensive applications.5. Challenges and Future DevelopmentsWhile wireless receivers have come a long way, there are still some challenges that need to be addressed. These include limited range, potential interference, and security concerns. However, continuous advancements in wireless technology are pushing these boundaries, offering promising solutions for a more connected future.In the near future, we can expect further improvements in wireless receiver technology, such as increased range, faster data transfer speeds, and enhanced security measures. This will open up new possibilities and revolutionize industries even further.6. Conclusion: Empowering Wireless ConnectivityWireless receivers have transformed the way we connect and interact with devices, providing unparalleled convenience and freedom. From entertainment to healthcare, these receivers have become an integral part of our daily lives, enabling seamless connectivity and enhancing user experience. As technology continues to evolve, wireless receiver technology will play a pivotal role in shaping our wireless future. Embrace the wireless revolution and experience the wonders of wireless receivers!。
Wi-Fi Connection Guide

Wi-Fi Connection GuideHigh Definition Video CameraModel No. HC-X920/HC-X920MHC-V720/HC-V720M HC-V520/HC-V520MVQC9464It is required to install the “Image App” on your smartphone/tablet to connect this unit.1[Android ™]: Select “Google Play™ Store”.[iOS]: Select “App Store SM ”.2Enter “Image App” into the search box.3Select “Image App” and install it.Install the “Image App” on your smartphone/tablet Confirm the Wi-Fi ® connection method Connect to Wi-FiStep.1Install the “Image App” on your smartphone/tabletAn environment that can connect to the network is required.Step.2Confirm the Wi-Fi ® connection methodConfirm the wireless access point and smartphone used.When connecting to a wireless access point (wireless LAN router)When connecting to a smartphone1Check if the wireless access point is compatible with IEEE802.11b/g/n.≥Proceed to step 2 once the compatibility is confirmed.2Check if the wireless access point is compatible with WPS*.Compatible with WPS:Proceed to A [Easy Connection (WPS)] of Step.3Not compatible with WPS:Proceed to B [Manual Connection] of Step.3*WPS is an abbreviation for Wi-Fi Protected Setup™.Proceed to C [Direct Connection] of Step.3≥Android and Google Play are trademarks or registered trademarks of Google Inc.≥App Store is a service mark of Apple Inc.≥“Wi-Fi”, “Wi-Fi Protected Setup”, “WPA” and “WPA2” are marks or registered marks of the Wi-Fi Alliance.≥QR Code is a registered trademark of DENSO WAVE INCORPORATED.A [Easy Connection (WPS)]1Press the Wi-Fi button on this unit to setup the Wi-Fi.2Touch a Blank row to register a new wireless network.3Touch [Easy Connection (WPS)].4Press the WPS button on the wireless access point.≥When the connection is complete, a message is displayed on this unit.5Touch [Link to Cell] and start up the smartphone application “Image App”.≥When the connection is complete, images from this unit are displayed on the smartphone screen.B [Manual Connection]≥Please refer to the operating instruction of the device in use for details about the setting and display of the wireless access point.1Press the Wi-Fi button on this unit to setup the Wi-Fi.2Touch a Blank row to register a new wireless network.3Touch [Manual Connection].4Touch [Search for wireless network].≥For more details about [Manual Setting], please refer to the owner’s manual (PDF format) of this unit.5Touch the wireless access point to connect.6Touch [ENTER].≥If an Encryption key (Password) is not set on your router, the connection is complete and a message is displayed.7(When there is an Encryption key (Password))Touch [INPUT], then enter the Encryption key (Password) of the wireless access point.≥For details on how to enter characters, refer to the owner’s manual (PDF format).≥When the entry is complete, touch [Enter].8(When there is an Encryption key (Password))Touch [NEXT].≥A message is displayed when the connection is complete.9Touch [Link to Cell] and start up the smartphone application “Image App”.≥When the connection is complete, images from this unit are displayed on the smartphone screen.C [Direct Connection]1Press the Wi-Fi button on this unit to setup the Wi-Fi.2Touch [Change connection type].3Touch [QR code].≥The QR code is displayed on this unit screen.4Start up the smartphone application “Image App”.5Scan QR code displayed on this unit with the smartphone.≥When using an iOS device, the profile install screen will be displayed on the smartphone. After installing, close the displayed screen by pressing the Home button and start up “Image App” again.≥When the connection is complete, images from this unit are displayed on the smartphone screen.This function can be used with the NFC compatible device with Android (OS version 2.3.3 or later). (Except for some models)NFC is an abbreviation for Near Field Communication.≥When this unit and the smartphone are connected to the same wireless access point, the result is a wireless access point connection. All others are direct connections.1Start up the smartphone application “Image App”.2Touch the smartphone on displayed on the smartphone screen.≥Proceed with the connection by following the smartphone screen instructions.≥When the connection is complete, images from this unit are displayed on the smartphone screen.≥The NFC function cannot be used on the smartphone when a message to touch the NFC mark of the device is not displayed. Try other connection methods.The setting screen for the wireless access point is displayed when the Wi-Fi button is pressed for the first time.When connecting to a wireless access point (wireless LAN router)[Wi-Fi Setup] # [Wireless Settings][Wi-Fi Setup] # [Wireless Settings]A [Delete]B[ENTER]A [Delete]B[ENTER]When connecting to a smartphone[Wi-Fi Setup] # [Direct Connection]Connect with using NFCHC-V720/HC-V720M/HC-V520/HC-V520M。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Connecting Wireless Sensornets with TCP/IP NetworksAdam Dunkels1,2,Juan Alonso1,Thiemo V oigt1,Hartmut Ritter3,Jochen Schiller3 1Swedish Institute of Computer Science,Box1263,SE-16429Kista,Sweden{adam,alonso,thiemo}@sics.se2Department of Computer Science and Engineering,M¨a lardalen University,Box883,SE-72123V¨a ster˚a s,Sweden.3Institute of Computer Science,Freie Universit¨a t Berlin,Takustr.9,D-14195Berlin,Germany {hritter,schiller}@inf.fu-berlin.deAbstract.Wireless sensor networks are based on the collaborative efforts ofmany small wireless sensor nodes,which collectively are able to form networksthrough which sensor information can be gathered.Such networks usually can-not operate in complete isolation,but must be connected to an external networkthrough which monitoring and controlling entities can reach the sensornet.AsTCP/IP,the Internet protocol suite,has become the de-facto standard for large-scale networking,it is interesting to be able to connect sensornets to TCP/IP net-works.In this paper,we discuss three different ways to connect sensor networkswith TCP/IP networks:proxy architectures,DTN overlays,and TCP/IP for sen-sor networks.We conclude that the methods are in some senses orthogonal andthat combinations are possible,but that TCP/IP for sensor networks currently hasa number of issues that require further research before TCP/IP can be a viableprotocol family for sensor networking.1IntroductionWireless sensor networks is an information gathering paradigm based on the collective efforts of many small wireless sensor nodes.The sensor nodes,which are intended to be physically small and inexpensive,are equipped with one or more sensors,a short-range radio tranciever,a small micro-controller,and a power supply in the form of a battery.Sensor network deployments are envisioned to be done in large scales,where each network consists of hundreds or even thousands of sensor nodes.In such a deploy-ment,human configuration of each sensor node is usually not feasible and therefore self-configuration of the sensor nodes is important.Energy efficiency is also critical, especially in situations where it is not possible to replace sensor node batteries.Battery replacement maintenance is also important to minimize for deployments where battery replacement is possible.Most sensor network applications aim at monitoring or detection of phenomena.Ex-amples include office building environment control,wild-life habitat monitoring[17], and forestfire detection[24].For such applications,the sensor networks cannot operate in complete isolation;there must be a way for a monitoring entity to gain access to the data produced by the sensor network.By connecting the sensor network to an existing network infrastructure such as the global Internet,a local-area network,or a private2Adam Dunkels,Juan Alonso,Thiemo V oigt,Hartmut Ritter,Jochen Schiller intranet,remote access to the sensor network can be achieved.Given that the TCP/IP protocol suite has become the de-facto networking standard,not only for the global Internet but also for local-area networks,it is of particular interest to look at methods for interconnecting sensor networks and TCP/IP networks.In this paper,we discuss a number of ways to connect sensor networks to TCP/IP networks.Sensor networks often are intended to run specialized communication protocols, thereby making it impossible to directly connect the sensor network with a TCP/IP network.The most commonly suggested way to get the sensor network to communicate with a TCP/IP network is to deploy a proxy between the sensor network and the TCP/IP network.The proxy is able to communicate both with the sensors in the sensor network and hosts on the TCP/IP network,and is thereby able to either relay the information gathered by the sensors,or to act as a front-end for the sensor network.Delay Tolerant Networking(DTN)[9]is a recently proposed communication model for environments where the communication is characterized by long or unpredictable delays and potentially high bit-error rates.Examples include mobile networks for inac-cessible environments,satellite communication,and certain forms of sensor networks. DTN creates an overlay network on top of the Internet and uses late address binding in order to achieve independence of the underlying bearer protocols and addressing schemes.TCP/IP and sensor network interconnection could be done by using a DTN overlay on top of the two networks.Finally,by directly running the TCP/IP protocol suite in the sensor network,it would be possible to connect the sensor network and the TCP/IP network without re-quiring proxies or gateways.In a TCP/IP sensor network,sensor data could be sent using the best-effort transport protocol UDP,and the reliable byte-stream transport pro-tocol TCP would be used for administrative tasks such as sensor configuration and binary code downloads.Due to the power and memory restrictions of the small8-bit micro-controllers in the sensor nodes,it is often assumed that TCP/IP is not possible to run in sensor networks. In previous work[8],we have shown that this is not true;even small micro-sensor nodes are able to run a full instance of the TCP/IP protocol stack.We have also successfully implemented our small uIP TCP/IP stack[7]on the small sensor nodes developed at FU Berlin[1].There are,however,a number of problems that needs to be solved before TCP/IP can be a viable alternative for sensor network communication.The rest of the paper is structured as follows.We discuss proxy architectures in Section2,followed by a discussion of the DTN architecture in Section3.TCP/IP for sensor networks is presented in Section4,and a comparison of the three methods is given in Section5.Finally,the paper is concluded in Section6.2Proxy ArchitecturesDeploying a special proxy server between the sensor network and the TCP/IP network is a very simple and straightforward way to connect the two networks.In its simplest form, the proxy resides as a custom-made program running on a gateway computer which has access to both the sensor network and the TCP/IP network.Since all interactionConnecting Wireless Sensornets with TCP/IP Networks 3between clients in the TCP/IP network and the sensor nodes is done through the proxy,the communication protocol used in the sensor network may be chosen freely.protocolsProxyFig.1.Proxy architectureThe proxy can operate in either of two ways:as a relay,or as a front-end.In the first case,the proxy will simply relay data coming from the sensor network to clients on the TCP/IP network.The clients must register a particular data interest with the proxy,and the proxy will then relay data from the sensor network to the registered clients.In the second case,where the proxy acts as a front-end for the sensor network,the proxy pro-actively collects data from the sensors and stores the information in a database.The clients can query the proxy for specific sensor data in a variety of ways,such as through SQL-queries or web-based interfaces.One advantage of the proxy based approach to interconnect sensor and TCP/IP net-works is that the proxy completely decouples the two networks.This naturally allows for specialized communication protocols to be implemented in the sensor network.A front-end proxy can also be used to implement security features such as user and data authentication.Among the drawbacks of the proxy approach are that it creates a single point of failure.If the proxy fails,all communication to and from the sensor network is effec-tively made impossible.One possible solution would be to deploy redundancy in the form of a set of back-up proxies.Unfortunately,such a solution reduces the simplic-ity of the proxy approach.Other drawbacks are that a proxy implementation usually is specialized for a specific task or a particular set of protocols.Such a proxy implemen-tation requires special proxies for each application.Also,no general mechanism for inter-routing between proxies exist.Proxies have previously been used for connecting devices to TCP/IP networks in order to overcome limitations posed by the devices themselves,or limitations caused by the communication environment in which the devices are located.The Wireless Ap-plication Protocol (W AP)stack [15]is intended to be simpler than the TCP/IP protocol stack in order to run on smaller devices,and to be better suited to wireless environ-ments.W AP proxies are used to connect W AP devices with the Internet.Similarly,the Remote Socket Architecture [23]exports the BSD socket interface to a proxy in order to outperform ordinary TCP/IP for wireless links.4Adam Dunkels,Juan Alonso,Thiemo V oigt,Hartmut Ritter,Jochen Schiller3Delay Tolerant NetworksThe Delay Tolerant Network architecture[9]is intended for so-called challenged envi-ronments.Properties of such environments include long and variable delays,frequent network partitioning,potentially high bit-error rates and asymmetrical data rates.DTN is based on the observation that the TCP/IP protocol suite is built around a number of implicit assumptions that do not hold true in challenged communication environments. In particular,the underlying assumptions of TCP/IP are:–An end-to-end path must exist between source and destination during the whole data exchange.–The maximum round trip-time for packets must be relatively small and stable.–The end-to-end packet loss is relatively small.The DTN architectural design contains several principles to provide service in these environments:–DTN uses an overlay architecture based on store-and-forward message switching.The messages,called bundles,that are transmitted contain both user data and rele-vant meta-data.A message-switched architecture provides the advantage of a priori knowledge of the size and performance requirements of the data transfer.The bun-dle layer works as an application layer on top the TCP/IP protocol stack.–The base transfer between nodes relies on store-and-forward techniques,i.e.,a packet is kept until it can be sent to the next hop.This requires that every node has storage available in the network.Furthermore,this allows to advance the point of retransmission towards the destination.A DTN consists a set of regions which share a common layer called the bundle layer that resides above the transport layer.The bundle layer stores messages in persistent storage if there is no link available,fragments messages if necessary,and optionally implements end-to-end reliability.The layers below the bundle layer are not specified by the architecture,but are chosen dynamically based on the specific communication characteristics and the available protocols in each region.One or more DTN gateways exist in each DTN region.The DTN gateway forwards bundles between regions,and takes care of delivering messages from other regions to hosts within the local region.The DTN architecture has been designed with the sensor network paradigm in mind. In sensor networks,the network may be partitioned frequently when nodes go into sleep mode or because of node failure.This will disrupt any end-to-end paths through the network.Also,packet loss rates in sensor networks can be very high[28]and routes may be asymmetric.When connecting sensor networks to a TCP/IP network using the DTN architecture, we have at least two regions as depicted in Figure2:one TCP/IP region where the TCP/IP protocol suite is used and one sensor network region where specialized sensor network protocols are implemented.A DTN gateway node is put in between the two networks,similar to where a proxy would have been placed.The DTN gateway acts much as a relay proxy as discussed in the previous section, and the relay proxy approach can be viewed as a specific instance of the DTN architec-ture.The DTN architecture is much more general than a simple proxy based approach,Connecting Wireless Sensornets with TCP/IP Networks5Protocols ApplicationBundle layerProtocols InternetSensor Net.DTN−GatewayFig.2.Connecting using the DTN architecturehowever,as the DTN architecture even allows mapping the sensor network into more than one DTN region,with DTN gateways located within the sensor network.For sensor networks where network partitioning is frequent,or where end-to-end communication is impossible,such a network design would be appropriate.A fully DTN enabled sensor network would easily be extended to a TCP/IP network,simply by connecting one or more of the DTN gateways to the TCP/IP network.4TCP/IP for Sensor NetworksDirectly employing the TCP/IP protocol suite as the communication protocol in the sen-sor network would enable seamless integration of the sensor network and any TCP/IP network.No special intermediary nodes or gateways would be needed for connecting a sensor network with a TCP/IP network.Rather,the connection would simply be done by connecting one or more sensor nodes to the TCP/IP network.TCP/IP in the sensor network would also provide the possibility to route data to and from the sensor net-work over standard technologies such as General Packet Radio Service (GPRS)[4].This leads to an architecture as shown in Figure3.IPTCP/IP TCP/IPTCP/Fig.3.Connecting using TCP/IP in the sensor network6Adam Dunkels,Juan Alonso,Thiemo V oigt,Hartmut Ritter,Jochen Schiller Until recently,many believed that tiny sensor nodes would lack the necessary mem-ory and computational resources to be able to run a full instance of the TCP/IP protocol stack.Therefore,the idea of using TCP/IP for sensor networks has not been given much research attention.We have showed that a full TCP/IP stack indeed can be run even on very limited devices[8],and have implemented our small uIP TCP/IP implementa-tion[7]on the sensor nodes developed at FU Berlin[1].These nodes are equipped with an8-bit Texas Instruments MSP430low-power micro-controller with a built-in mem-ory of2048bytes.Our TCP/IP implementation requires only a few hundreds bytes of memory to operate,which leaves plenty of memory for the actual sensor node applica-tions.The fact that we are able to run the TCP/IP stack even on tiny sensor nodes suggest that TCP/IP for sensor networks may be within reach.Sensor networks running the TCP/IP protocol suite would be very easy to connect to existing TCP/IP networks,and would also able to benefit from the wealth of readily available applications such asfile transfers using FTP or HTTP and possibly time synchronization with NTP.There are, however,a number of problems with using TCP/IP for wireless sensor networks that need to be addressed before TCP/IP is a viable alternative for sensor networks:–The addressing and routing schemes of IP are host-centric.–The header overhead in TCP/IP is very large for small packets.–TCP does not perform well over links with high bit-error rates,such as wireless links.–The end-to-end retransmissions used by TCP consumes energy at every hop of the retransmission path.IP is designed so that every network interface connected to a network has its own IP address.The prefix of the address is the same for all network interfaces in the same physical network and routing is done based on the network prefixes.This does notfit well with the sensor network paradigm,where the main interest is the data generated by the sensors and the individual sensor is of minor importance.Most of the proposed com-munication protocols for sensor networks use data centric routing and addressing[10, 12]and even though similar mechanisms have been developed as overlay networks on top of IP[21],these usually require too much state to be kept in the participating nodes to be feasible to run on limited sensor nodes.The size of TCP/IP packet headers is between28and40bytes,and when sending a few bytes of sensor data in a datagram the headers constitute nearly90%of each packet.Energy efficiency is of prime importance for sensor networks,and since ra-dio transmission often is the most energy consuming activity in a sensor node[20],a header overhead of90%is not acceptable.Hence,most protocols developed for sen-sor networks strive to keep the header overhead as low as possible.For example,the TinyOS[11]message header overhead is only5%.The header overhead in TCP/IP can be reduced using various forms of header compression[13,6,16,5].These mechanisms are commonly designed to work only over a single-hop link,but work is currently being done in trying to adopt these mechanisms to the multi-hop case[19].Furthermore,since TCP was designed for wired networks where bit-errors are un-common and where packet drops nearly always are due to congestion,TCP always interprets packet drops as a sign of congestion and reduces its sending rate in responseConnecting Wireless Sensornets with TCP/IP Networks7 to a dropped packet.This leads to bad performance over wireless links where pack-ets frequently are dropped because of bit-errors.TCP misinterprets the packet loss as congestion and lowers the sending rate,even though the network is not congested.Also,TCP uses end-to-end retransmissions,which in a multi-hop sensor network re-quires a transmission by every sensor node on the path from the sender to the receiver. Such a retransmission consumes more energy than a retransmission scheme where the point of retransmission is moved closer to the receiver.Protocols using other mecha-nisms to implement reliability,such as reliable protocols especially developed for sen-sor networks[22,27,26],are typically designed to be energy conserving.Methods for improving TCP performance in wireless networks have been pro-posed[2,3,14],but these are often targeted towards the case where the wireless link is the last-hop,and not for wireless networks with multiple wireless hops.In addition, traditional methods assume that the routing nodes have significantly larger amounts of resources than what limited sensor nodes have.5Comparison of the MethodsThe three methods for connecting sensor networks to TCP/IP networks presented here are in some respects orthogonal—it is possible to make combinations such as a partially TCP/IP-based sensor network with a DTN overlay connected to the global Internet using an front-end proxy.It is therefore not possible to make a direct comparison of the methods.Instead,we will state the merits and drawbacks of each of the methods and comment on situations in which each method is suited.A pure proxy method works well when the sensor network is deployed relatively close to a place where a proxy server can be safely placed.Since the proxy server by design must have more processing power and more memory than the sensors,it is likely to require an electrical power supply rather than a battery.Also,the proxy may need to be equipped with a stable storage media such as a hard disk,which may make the proxy physically larger than the sensor nodes.One example of a situation where these criteria are met is an office building environment.Here,a proxy server can be placed close to the sensor network,perhaps even in the same room as the sensors,and have immediate access to electrical power.Another example would be a nautical sensor network where the proxy could be equipped with a large battery pack and placed in the water with a buoy such that the significance of the physical size of the proxy node would be reduced.Front-end proxies can also be used for a number of other things,besides for achiev-ing interconnectivity,such as sensor network status monitoring,and generation of sen-sor failure reports to human operators.The DTN architecture can be viewed as a generalization of the proxy architecture and indeed a DTN gateway shares many properties with a proxy server.A DTN gate-way in the sensor network region will be placed at the same place as a proxy server would have been placed,and also requires more memory and stable storage media than the sensor nodes.There are,however,a number of things that are gained by using the DTN architecture rather than a simple proxy architecture.First,DTN inherently allows for multiple DTN gateways in a DTN region,which removes the single-point-of-failure problem of the simple proxy architecture.Second,while a proxy architecture usually is8Adam Dunkels,Juan Alonso,Thiemo V oigt,Hartmut Ritter,Jochen Schiller specialized for the particular sensor network application,DTN provides general mech-anisms and an interface that can be used for a large number of occasions.Also,if the sensor network is deployed in a place with a problematic communication environment, the DTN architecture provides a set of features which can be used to overcome the communication problems.Examples of such situations would be deep-sea exploration or places where seismic activity can disrupt communication.From an interconnectivity perspective,running native TCP/IP in the sensor net-works is the most convenient way to connect the sensor network with a TCP/IP net-work.One or more sensor nodes would simply be attached to the TCP/IP network,and the two networks could exchange information through any of those nodes.The attach-ment can be done either using a direct physical link,such as an Ethernet cable,or over a wireless technology like GPRS.While a TCP/IP enabled sensor network may provide the easiest way to interconnect the networks,it is usually not a complete solution,but must be integrated into a larger architecture.The proxy and DTN architectures discussed here are examples of such an architecture.We can e.g.imagine an office building TCP/IP sensor network that is connected to a front-end proxy located in the cellar of the building.The connection between the proxy and the sensor network would be made using the regular TCP/IP local-area network in the building.Another example would be a TCP/IP sensor network for monitoring the in-door environment in a train.A DTN gateway would be placed in the same train,and the sensor network and the gateway would communicate using TCP/IP over the train’s local area network.The DTN gateway would be able to transmit the gathered information over the global Internet at places where the train has Internet access.Finally,from a security perspective,the front-end proxy architecture provides a good place to implement user and data authentication,since all access to the sensor network goes through the proxy.The DTN architecture is inherently designed for se-curity and uses asymmetric cryptography to authenticate both individual messages and routers.TCP/IP as such does not provide any security,so security must be implemented externally either by using a front-end proxy,DTN,or any of the existing security mech-anisms for TCP/IP networks such as Kerberos.It should also be noted that security methods developed especially with wireless sensor networks in mind[18,25]can be implemented as application layer security in TCP/IP sensor networks.6ConclusionsWe have presented three methods for connecting wireless sensornets with TCP/IP net-works:proxy architectures,Delay Tolerant Networking(DTN)overlays,and TCP/IP for sensor networks.The three methods are orthogonal in that it is possible to form combinations,such as a DTN overlay on top of a TCP/IP sensor network behind a front-end proxy.The proxy architectures are simple and make it possible to use specialized com-munication protocols in the sensor network,but are application specific and creates a single point of failure.The DTN architecture also allows for specialized protocols,butConnecting Wireless Sensornets with TCP/IP Networks9 provides a much more general communication architecture.DTN is also useful if the sensor network itself is deployed in a challenged communication environment.Finally,by using the TCP/IP protocol suite for the sensor network,connecting the sensor network with another TCP/IP network is simply done by attaching one or more sensor nodes to both networks.However,attaching the sensor nodes to the TCP/IP network may not always be ideal,and a combination of either a proxy architecture and TCP/IP,or DTN and TCP/IP,may be beneficial.TCP/IP for sensor networks currently has a number of problems,and therefore fur-ther research in the area is needed before TCP/IP can be a viable alternative for sensor networking.References1.CST Group at FU Berlin.Scatterweb Embedded Sensor Board.Web page.2003-10-21.URL:/2.H.Balakrishnan,S.Seshan,E.Amir,and R.Katz.Improving TCP/IP performance overwireless networks.In Proceedings of thefirst ACM Conference on Mobile Communications and Networking,Berkeley,California,November1995.3.K.Brown and S.Singh.M-TCP:TCP for mobile cellular networks.ACM Computer Com-munications Review,27(5):19–43,October1997.4.J.Cai and D.Goodman.General packet radio service in GSM.IEEE CommunicationsMagazine,35:122–131,October1997.5.S.Casner and pressing IP/UDP/RTP headers for low-speed serial links.RFC2508,Internet Engineering Task Force,February1999.6.M.Degermark,M.Engan,B.Nordgren,and S.Pink.Low-loss TCP/IP header compressionfor wireless networks.ACM/Baltzer Journal on Wireless Networks,3(5),1997.7.A.Dunkels.uIP-a TCP/IP stack for8-and16-bit microcontrollers.Web page.2003-10-21.URL:/adam/uip/8.A.Dunkels.Full TCP/IP for8-bit architectures.In Proceedings of The First InternationalConference on Mobile Systems,Applications,and Services(MOBISYS‘03),May2003. 9.K.Fall.A delay-tolerant network architecture for challenged internets.In Proceedings ofthe SIGCOMM’2003conference,2003.10.J.S.Heidemann,F.Silva,C.Intanagonwiwat,indan,D.Estrin,and D.Ganesan.Building efficient wireless sensor networks with low-level naming.In Symposium on Oper-ating Systems Principles,pages146–159,2001.11.J.Hill,R.Szewczyk,A.Woo,S.Hollar,D.Culler,and K.Pister.System architecture direc-tions for networked sensors.In Proceedings of the9th International Conference on Archi-tectural Support for Programming Languages and Operating Systems,November2000. 12.C.Intanagonwiwat,indan,and D.Estrin.Directed diffusion:a scalable and robustcommunication paradigm for sensor networks.In Mobile Computing and Networking,pages 56–67,2000.pressing TCP/IP headers for low-speed serial links.RFC1144,InternetEngineering Task Force,February1990.14.J.Liu and S.Singh.ATCP:TCP for mobile ad hoc networks.IEEE Journal on SelectedAreas in Communications,19(7):1300–1315,2001.15.Wireless Application Protocol Forum Ltd.Official Wireless Application Protocol:The Com-plete Standard.Wiley Computer Publishing,2000.16.S.Pink M.Degermark,B.Nordgren.IP header compression.RFC2507,Internet Engineer-ing Task Force,February1999.10Adam Dunkels,Juan Alonso,Thiemo V oigt,Hartmut Ritter,Jochen Schiller17.A.Mainwaring,J.Polastre,R.Szewczyk,D.Culler,and J.Anderson.Wireless sensor net-works for habitat monitoring.In First ACM Workshop on Wireless Sensor Networks and Applications(WSNA20029,Atlanta,GA,USA,September2002.18.A.Perrig,R.Szewczyk,V.Wen,D.E.Culler,and J.D.Tygar.SPINS:security protocols forsensor netowrks.In Mobile Computing and Networking,pages189–199,2001.19.S.Mishra R.Sridharan,R.Sridhar.A robust header compression technique for wireless adhoc networks.In MobiHoc2003,Annapolis,MD,USA,June2003.20.V.Raghunathan,C.Schurgers,S.Park,and M.Srivastava.Energy aware wireless microsen-sor networks.IEEE Signal Processing Magazine,19(2):40–50,March2002.21.S.Ratnasamy,P.Francis,M.Handley,R.Karp,and S.Shenker.A scalable content address-able network.In Proceedings of ACM SIGCOMM2001,2001.22.Y.Sankarasubramaniam,O.Akan,and I.Akyildiz.ESRT:Event-to-Sink Reliable Transportin Wireless Sensor Networks.In Proceedings of the4th ACM international symposium on Mobile ad hoc networking and computing(MobiHOC2003),2003.23.M.Schl¨a ger,B.Rathke,A.Wolisz,and S.Bodenstein.Advocating a remote socket architec-ture for internet access using wireless lans.Mobile Networks and Applications,6(1):23–42, 2001.ISSN:1383-469X24.S.N.Simic and S.Sastry.Distributed environmental monitoring using random sensor net-works.In Proceedings of the2nd International Workshop on Information Processing in Sensor Networks,pages582–592,Palo Alto,California,2003.25.F.Stajano.Security for Ubiquitous Computing.John Wiley and Sons,February2002.ISBN:0-470-84493-026.F.Stann and J.Heidemann.RMST:Reliable Data Transport in Sensor Networks.In Pro-ceedings of the First International Workshop on Sensor Net Protocols and Applications, pages102–112,Anchorage,Alaska,USA,April2003.IEEE.27.C.Y.Wan,A.T.Campbell,and L.Krishnamurthy.PSFQ:A Reliable Transport ProtocolFor Wireless Sensor Networks.In First ACM International Workshop on Wireless Sensor Networks and Applications(WSNA2002),Atlanta,September2002.28.J.Zhao and indan.Understanding packet delivery performance in dense wirelesssensor networks.In The First ACM Conference on Embedded Networked Sensor Systems (SenSys2003),Los Angeles,California,November2003.。
