FO-007 Guest Security
kaspersky embedded systems security 管理员指南说明书

Kaspersky Embedded Systems Security管理员指南应用程序版本:2.2.0.605尊敬的用户:感谢您选择Kaspersky Lab 作为您的安全软件提供商。
我们希望本文档能帮助您使用我们的产品。
注意!本文档是AO Kaspersky Lab(以下简称Kaspersky Lab)的资产。
本文档的所有权利受俄罗斯联邦版权法和国际条约保护。
根据适用法律,非法复制和分发本文档或部分文档需承担民事、行政或刑事责任。
未经Kaspersky Lab 的书面许可,不得对任何材料进行任何类型的复制或分发,包括译本形式。
本文档和与之相关的图形图像只能用于信息参考、非商业和个人目的。
Kaspersky Lab 保留在没有事先通知的情况下修改本文档的权利。
对于本文档所用第三方所有的任何材料的内容、质量、相关性或准确性,或与使用此类文档相关的任何潜在损害,Kaspersky Lab 不承担任何责任。
本文档使用的注册商标和服务标志属于各自的所有者。
文档修订日期:2018.12.06© 2018 年 AO Kaspersky Lab 版权所有。
保留所有权利。
https://https://内容关于本指南 (10)本文内容 (10)文档约定 (12)有关Kaspersky Embedded Systems Security 2.2 的信息来源 (13)独立检索信息源 (13)在论坛上讨论Kaspersky Lab 应用程序 (14)Kaspersky Embedded Systems Security 2.2 (15)关于Kaspersky Embedded Systems Security 2.2 (15)新增功能 (17)分发包 (18)硬件和软件需求 (19)安装和卸载应用程序 (21)Kaspersky Embedded Systems Security 2.2 软件组件以及它们在Windows Installer 服务中对应的代码 (21)Kaspersky Embedded Systems Security 2.2 软件组件 (22)软件组件的“管理工具”集 (23)安装Kaspersky Embedded Systems Security 2.2 后系统的更改 (24)Kaspersky Embedded Systems Security 2.2 进程 (27)Windows Installer 服务的安装和卸载设置及命令行选项 (27)Kaspersky Embedded Systems Security 2.2 安装和卸载日志 (31)安装计划 (32)选择管理工具 (32)选择安装类型 (33)使用向导安装和卸载应用程序 (34)使用安装向导安装 (35)Kaspersky Embedded Systems Security 2.2 安装 (35)Kaspersky Embedded Systems Security 2.2 控制台安装 (37)在其他计算机上安装应用程序控制台以后的高级设置 (38)在安装Kaspersky Embedded Systems Security 2.2 后执行的操作 (40)修改组件集和恢复Kaspersky Embedded Systems Security 2.2 (42)使用安装向导卸载 (43)Kaspersky Embedded Systems Security 2.2 卸载 (43)Kaspersky Embedded Systems Security 2.2 控制台卸载 (44)从命令行安装和卸载应用程序 (45)关于从命令行安装和卸载Kaspersky Embedded Systems Security 2.2 (45)在安装Kaspersky Embedded Systems Security 2.2 后执行的操作 (47)添加/删除组件。
FO-SOP酒店标准操作程序-前厅部(中英文对照)

STANDARD OPERATING PROCEDURES标准操作程序POLICYNO.ﻩSUBJECT编号标题FO-DM-001 Duty Check List工作检查表FO-DM-002 BombThreatﻫ炸弹威胁FO-DM-003Car Accident交通事故FO-DM-004 VIP Check in重要客人入住FO-DM-005 Accident– Guest意外—客人FO-DM-006GuestComplaints and Disputes客人抱怨和争执FO-DM-007Request for Doctor/ Hospitalization求医要求/住院治疗的要求FO-DM-008 Fights争斗FO-DM-009 Fire火灾FO-DM-022 Lost &Found丢失和发现FO-DM-024 SafetyBox保险箱FO-DM-028IncomingFaxes/Email at night time夜间接受传真/电子邮件FO-DM-030 Valuables贵重物品保管FO-DM-031Guest Birthday客人生日FO-BC-002 Incoming faxes接收传真FO-BC-005MeetingRoomRental会议室租用FO-BC-006 OutgoingFax发送传真FO-BC-007DHL/EMS/Courier Services DHL特快专递FO-CON-002 Baggage Service for Arrivals行李抵达服务FO-CON-003Baggage Service for Departure行李离店服务FO-CON-004Baggage Service for group Arrivals团队行李抵达服务FO-CON-005 BaggageServiceforg roup Departure团队行李离开服务FO-CON-006Baggage Storage行李贮存服务FO-CON-007 Brochures, MapsandDirections指引册,地图,导游册FO-CON-008 Flags旗帜FO-CON-009AllIncoming Itemsﻩﻩﻩﻩ所有收入条款FO-CON-010 Newspapers报纸FO-CON-011Outgoing Items外送物件FO-CON-013 RoomingGuest陪同客人进房间FO-CON-014ShuttleBus班车FO-CON-015Outdated mail, faxes and parcels过期的邮件,传真和包裹FO-CON-016Paging Service呼叫服务FO-CON-017 postal expressservice邮政快递服务FO-CON-018 Taxibooking and arrangement出租车预订及安排FO-CON-019 Trolleyﻩ手推车服务FO-CON-020 Umbrella雨伞服务FO-CON-AR-001 Airport send off机场送行FO-CON-AR-002Airport PickUp机场接客FO-CON-AR-003Airport LostLuggage行李丢失FO-CON-AR-004VIP Arrive-Limousine接重要客人-豪华轿车FO-CON-AR-005 VIP Arrive-(By Taxi)接重要客人(用出租车)FO-CON-AR-006Mobile Phone移动电话FO-CON-DRICER-001HouseUse/ Complimentary Vehicle酒店自用/免费用车FO-CON-DRIVER-002Limousine Availabilityﻩﻩﻩ大型轿车使用率FO-CON-DRIVER-003LimousineCleaning & Maintenanceﻩﻩ大型轿车清洁和保养FO-CON-DRIVER-004 Mileage/ Petrol Controlﻩ运程/汽油控制FO-CON-DRIVER-005 LimousineRequestﻩﻩﻩﻩ用车申请FO-CON-DRIVER-006 The Responsibilityof Driverﻩﻩﻩ司机责任保证FO-EF-007Guest Preference客人爱好FO-EF-008 Executive Floor Check In行政楼层入住FO-EF-009Hosting招待FO-FD-010ComputerDown计算机系统崩溃FO-FD-011Foreign CurrencyExchange外币兑换FO-FD-016Internal Trace Report内部事务报告FO-FD-017 KeyControl钥匙控制FO-FD-018 Lost &Found atCheckIn失物招领FO-EFM-012 VIP CheckIn重要客人入住FO-EFM-016 Alleged Theft偷窃FO-EFM-017 GuestComplaintsand Disputes客人抱怨和争执FO-EFM-018Complimentary/ House Use免费房使用FO-EFM-020 Request forDoctor/ Hospitalization求医要求/住院治疗FO-EFM-023Lost and Found失物招领FO-EFM-024 Safety Deposit BoxesKeyInventory保险箱钥匙清单FO-EFM-025Safety Box保险箱FO-EFM-027 Valuables贵重物品保管FO-EFM-028 In-House Clinic酒店医疗中心FO-EFM-029GuestBirthday客人生日FO-EFM-030Guest Join-In Authorization会员加盟授权FO-EFM-031 Guest Comments客人意见FO-EFM-032 Bookingatother PlazaRoyaleHotel豪廷酒店网络内约定FO-EFM-033 HotelEvents酒店活动FO-TEL-001 Telephone ControlDDD/IDD国际/国内长途电话控制FO-TEL-002Call AccountingSystem电话记费系统FO-TEL-003 Call Barringand Unbarring电话禁呼和解禁FO-TEL-004 Do Not DisturbFeatureﻩ请勿打扰事宜FO-TEL-005Guest Locator Feature为客人接电话至指定地点FO-TEL-006 Incoming Calls接听来电FO-TEL-007Operator Assisted Calls接线员辅助呼叫FO-TEL-008 PABX Adcom Fax System专用交换机传真系统FO-TEL-009 PABX Adcom Mail System专用交换机邮件系统FO-TEL-010 Public Address Paging System公共提示标志FO-TEL-011Wake up Call叫醒服务FO-TEL-012Personal calls私人电话FO-001 Baggage Service行李服务FO-002BusinessCenter Service商务中心FO-003 Engineering Service工程服务FO-004Handling GuestComplaints处理客人投诉FO-005Handling IncomingCalls处理来电FO-006 Housekeeping Service客房服务FO-007Room Service-IncomingCall客房送餐来电FO-008 In-Room Dining Order客房用餐预订FO-009 RunnerService特殊服务FrontOfficeTermstoKnow前厅部须知A.H.&M.A. American Hotel and Motel Association.美国饭店及汽车旅馆协会Accommodate A promiseof a room for a guest–ifnot in th athotel,then a commitment to finda room elsewhere.对客人保证客房的承诺AdjoiningRooms Two or more rooms side byside without a conne ctingdoorbetween them. Inother words, roomscan beadjoining without beingconnecting.两间或两间以上并排的、之间没有房门直接联系的房间。
F007用户手册(中文)

F007指纹门禁一体机使用说明书一、产品简介:F007是一款全金属结构的指纹门禁一体机。
它采用精密的电子线路和优良的生产工艺,高贵典雅,气度非凡。
本产品采用国际领先的指纹识别技术,安全可靠,是对出入安全要求极高的场所应用门禁的理想选择,广泛适用于商务机构、办公室、工厂、住宅小区等。
本产品配合红外遥控键盘和管理员密码进行指纹管理,操作简单方便。
最多可以存储120枚指纹,其中2枚管理员指纹,118枚用户指纹,每枚指纹分配一个ID号。
二、功能简介休眠功能本机配有人体感应装置,当有人接近时,本机即进入待机状态,人离开30秒后,本机自动进入休眠状态,进入休眠状态可以省电,且能延长使用寿命。
管理员遥控操作功能用红外遥控器操作,输入管理员密码进入编程状态,可进行如下操作:修改管理员密码、增加指纹、删除指纹、清空指纹、设置开门时间、设置防拆报警时间、解除防拆报警。
管理员指纹操作功能管理员指纹的ID号为1-2,不能用于开锁,其中ID号为1的指纹用于增加用户指纹和解除防拆报警,ID号为2的指纹用于删除用户指纹和解除防拆报警。
用户指纹操作功能用户指纹的ID号为3-120,仅用于开锁。
出门按钮操作功能外接出门按钮,用于开锁。
参数设置功能开门时间:0~10 秒,出厂时默认设置为5秒,管理员可以通过遥控器设置。
驱动电锁功能NC与COM接线端子控制阴极电锁,采用断电开锁方式,应设置开门时间为1-10秒。
N0与COM接线端子控制阳极电锁,采用通电开锁方式,应设置开门时间为0(实际为50mS)。
防拆报警功能当本机正常工作时被非法拆卸,蜂鸣器会发出连续的报警声,持续1分钟自动关闭。
重要信息请不要私自修理本机,如有问题,请返回厂家修理。
安装在墙上之前如果要打孔,请仔细检查暗线或线管,在钻孔或固定线夹的时候要使用安全眼镜。
如果产品升级,说明书将可能有所不同,恕不另行通知。
三、接口原理及接口参数继电器输出接口本机的NO、COM、NC分别接继电器的常开、公共、常闭输出管脚,与其内部电路完全隔离,开锁时继电器吸合,用于驱动阳极锁或阴极锁,触点输出电流为3A,接口原理,如图1所示。
FO-SOP酒店标准操作程序-前厅部(中英文对照)

STANDARD OPERATING PROCEDURES标准操作程序POLICY NO. SUBJECT编号标题FO-DM-001 Duty Check List工作检查表FO-DM-002 Bomb Threat炸弹威胁FO-DM-003 Car Accident交通事故FO-DM-004 VIP Check in重要客人入住FO-DM-005 Accident – Guest意外—客人FO-DM-006 Guest Complaints and Disputes客人抱怨和争执FO-DM-007 Request for Doctor/ Hospitalization求医要求/住院治疗的要求FO-DM-008 Fights争斗FO-DM-009 Fire火灾FO-DM-022 Lost & Found丢失和发现FO-DM-024 Safety Box保险箱FO-DM-028 Incoming Faxes/ Email at night time夜间接受传真/电子邮件FO-DM-030 Valuables贵重物品保管FO-DM-031 Guest Birthday客人生日FO-BC-002 Incoming faxes接收传真FO-BC-005 Meeting Room Rental会议室租用FO-BC-006 Outgoing Fax发送传真FO-BC-007 DHL / EMS/Courier Services DHL特快专递FO-CON-002 Baggage Service for Arrivals行李抵达服务FO-CON-003 Baggage Service for Departure行李离店服务FO-CON-004 Baggage Service for group Arrivals团队行李抵达服务FO-CON-005 Baggage Serviceforg roup Departure团队行李离开服务FO-CON-006 Baggage Storage行李贮存服务FO-CON-007 Brochures, Maps and Directions指引册,地图,导游册FO-CON-008 Flags旗帜FO-CON-009 All Incoming Items所有收入条款FO-CON-010 Newspapers报纸FO-CON-011 Outgoing Items外送物件FO-CON-013 Rooming Guest陪同客人进房间FO-CON-014 Shuttle Bus班车FO-CON-015 Outdated mail, faxes and parcels过期的邮件,传真和包裹FO-CON-016 Paging Service呼叫服务FO-CON-017 postal express service邮政快递服务FO-CON-018 Taxi booking and arrangement出租车预订及安排FO-CON-019 Trolley手推车服务FO-CON-020 Umbrella雨伞服务FO-CON-AR-001 Airport send off机场送行FO-CON-AR-002 Airport Pick Up机场接客FO-CON-AR-003 Airport Lost Luggage行李丢失FO-CON-AR-004 VIP Arrive-Limousine接重要客人-豪华轿车FO-CON-AR-005 VIP Arrive-( By Taxi )接重要客人(用出租车)FO-CON-AR-006 Mobile Phone移动电话FO-CON-DRICER-001 House Use/ Complimentary Vehicle酒店自用/免费用车FO-CON-DRIVER-002 Limousine Availability大型轿车使用率FO-CON-DRIVER-003 Limousine Cleaning & Maintenance大型轿车清洁和保养FO-CON-DRIVER-004 Mileage/ Petrol Control运程/汽油控制FO-CON-DRIVER-005 Limousine Request用车申请FO-CON-DRIVER-006 The Responsibility of Driver司机责任保证FO-EF-007 Guest Preference客人爱好FO-EF-008 Executive Floor Check In行政楼层入住FO-EF-009 Hosting招待FO-FD-010 Computer Down计算机系统崩溃FO-FD-011 Foreign Currency Exchange外币兑换FO-FD-016 Internal Trace Report内部事务报告FO-FD-017 Key Control钥匙控制FO-FD-018 Lost & Found at Check In失物招领FO-EFM-012 VIP Check In重要客人入住FO-EFM-016 Alleged Theft偷窃FO-EFM-017 Guest Complaints and Disputes客人抱怨和争执FO-EFM-018 Complimentary / House Use免费房使用FO-EFM-020 Request for Doctor / Hospitalization求医要求/住院治疗FO-EFM-023 Lost and Found失物招领FO-EFM-024 Safety Deposit Boxes Key Inventory保险箱钥匙清单FO-EFM-025 Safety Box保险箱FO-EFM-027 Valuables贵重物品保管FO-EFM-028 In-House Clinic酒店医疗中心FO-EFM-029 Guest Birthday客人生日FO-EFM-030 Guest Join-In Authorization会员加盟授权FO-EFM-031 Guest Comments客人意见FO-EFM-032 Booking at other Plaza Royale Hotel豪廷酒店网络内约定3FO-EFM-033 Hotel Events酒店活动FO-TEL-001 Telephone Control DDD/IDD国际/国内长途电话控制FO-TEL-002 Call Accounting System电话记费系统FO-TEL-003 Call Barring and Unbarring电话禁呼和解禁FO-TEL-004 Do Not Disturb Feature请勿打扰事宜FO-TEL-005 Guest Locator Feature为客人接电话至指定地点FO-TEL-006 Incoming Calls接听来电FO-TEL-007 Operator Assisted Calls接线员辅助呼叫FO-TEL-008 PABX Adcom Fax System专用交换机传真系统FO-TEL-009 PABX Adcom Mail System专用交换机邮件系统FO-TEL-010 Public Address Paging System公共提示标志FO-TEL-011 Wake up Call叫醒服务FO-TEL-012 Personal calls私人电话FO-001 Baggage Service行李服务FO-002 Business Center Service商务中心FO-003 Engineering Service工程服务FO-004 Handling Guest Complaints处理客人投诉FO-005 Handling Incoming Calls处理来电FO-006 Housekeeping Service客房服务FO-007 Room Service-Incoming Call客房送餐来电FO-008 In-Room Dining Order客房用餐预订FO-009 Runner Service特殊服务Front Office Terms to Know前厅部须知A.H.&M.A. American Hotel and Motel Association.美国饭店及汽车旅馆协会Accommodate A promise of a room for a guest – if not in that hotel,then a commitment to find a room elsewhere.对客人保证客房的承诺Adjoining Rooms Two or more rooms side by side without a connectingdoor between them. In other words, rooms can be adjoiningwithout being connecting.两间或两间以上并排的、之间没有房门直接联系的房间。
安盟动态口令认证系统产品说明书

安盟动态口令身份认证系统产品说明文档1动态口令身份认证系统原理在传统的静态口令验证系统中,由于口令为“一次设置,重复使用”,由于口令的重复使用而增加了口令丢失和破解的危险性,降低了系统的安全系数,特别是在互联网环境下,黑客、木马和病毒泛滥,使得静态口令更加容易被泄露,造成企业信息系统和资源的非授权访问,导致直接经济损失和间接的信誉和商誉损失。
所以,除了用户记忆的静态口令外,还需要增加一个物理因素,如令牌,这样采用你所知道的(记忆的静态密码)和你所拥有的(令牌)两个要素构成有效密码,实现严格身份信息验证,而你所拥有的要素必须具有不可复制和篡改的性能。
动态口令认证即是依据上述原理实现的双因素强身份认证系统:1)本系统以令牌作为信物,实现双因素认证。
令牌显示依据种子密钥和时间随机计算的动态口令,具有不可复制和篡改的性能,而后台认证系统认为,只有持有令牌才可能输入正确的密码,反过来说,只要输入了当前时间点的正确密码,就可以认为持有可信的要素,即令牌。
用户登录时,必须同时验证静态口令(称之为PIN码)和动态口令,只有两者均正确时才能确认用户身份2)令牌与服务器之间的同步。
令牌和认证服务器一般以密钥和时间为基础,每隔一定时间(常见为60妙)就计算出一个口令,由于令牌和认证服务器双方都共享了对称密钥、时间因子和计算方法,所以计算出来的口令就是同步的和唯一的。
3)一次一密。
令牌上显示的密码只有在当前时间点有效,且使用一次即失效,实现高强度的安全性。
系统的部署结构如下:解决的主要问题:1)密码安全管理问题,实现不依赖于客户端安全意识和安全习惯可控的安全性,用户也免于设置复杂密码、记忆并定期更新之苦。
2)密码每分钟变化,只在当前时间点有效,且使用一次即失效,即使黑客在传输过程当中截获或窃听了,只有在一分钟之内解开,且解开之后,必须先于用户或管理员进入系统才构成威胁,这几乎不可能,大大加强了应用系统的安全性和可靠性。
飞客病毒查杀方法

各位:近期,飞客蠕虫病毒的活动日益活跃,针对用户可能被感染飞客蠕虫病毒,现在提供该木马病毒查杀解决方案如下,供大家参考。
电脑主机在感染飞客蠕虫(Conficker)病毒后,存在远程控制、窃密、泄密等潜在危害,并可能通过发起大范围的网络欺诈和网络攻击等手段危及我省政务信息网及公共互联网安全。
飞客蠕虫主要利用Windows操作系统MS08-067漏洞来传播,同时也能借助任何有USB接口的硬件设备来感染。
这个蠕虫利用的是一个已知的被用于windows 2000,windows xp,windows vista,windows server2003和windows server 2008操作系统的服务器服务漏洞。
Linux和macintosh操作系统不会受到这个病毒的影响。
一、被感染症状:1、帐户锁定策略被自动复位。
2、某些微软Windows服务会自动禁用,如自动更新,后台智能传输服务(BITS ),WindowsDefender和错误报告服务。
3、域控制器对客户机请求回应变得缓慢。
4、系统网络变得异常缓慢。
这可以从检测的网络流量图和windows任务管理器中看出。
5、与杀毒软件,windows系统更新有关的网站无法访问。
6、发射暴力密码破解攻击管理员密码以帮助它穿越并扩散到管理员共享。
二、检测方法:第一种方法:输入:/infection_test/cfeyechart.html网址,打开网页。
若能看到六个图标,说明就没感染“飞客”病毒,若上一排图标左右两个不显示,那么就中了“飞客”病毒A或B变种,若上一排图标三个不显示那就中了“飞客”病毒C变种。
第二种方法:输入:http://four.cs.uni-bonn.de/fileadmin/user_upload/werner/cfdetector/,网址,点击该网页显示绿色的钩说明没有被感染。
三、部分查杀工具:1、卡巴斯基“飞客”专杀(/anti-virus/kidokiller.exe)2、360顽固木马专杀(/anti-virus/superkiller.exe)四、防范措施:1、利用360安全卫士、金山卫士、QQ安全管家等工具及时打好各种漏洞补丁;2、安装杀毒软件,并及时下载更新,对系统进行全盘扫描杀毒;3、在使用U盘前应尽量开启具有U盘防火墙功能的安全软件;4、不要随意执行未知的及存在风险的程序文件;5、不访问有害信息网站,不随意下载/安装可疑插件,并检查IE的安全级别是否被修改。
安盟双因素身份认证管理系统v7.0安装手册(1)

安盟双因素动态口令身份认证管理系统V7.0认证服务器安装手册四川安盟电子信息安全有限责任公司1前言在安盟身份认证解决方案中,安盟身份认证服务器软件是网络中的身份认证引擎,由安全管理员或网络管理员进行维护。
安盟身份认证服务器采用全新的内存数据库及微内核技术,大大提高系统的处理能力和可靠性,支持一主十备的认证服务器集群,支持千万数量级的用户认证需求。
2运行环境2.1支持的操作系统•IBM AIX5L v5.1:APAR IY43694•IBM AIX5L v5.2:APAR IY441732.2安盟认证服务器硬件选型安盟认证服务器的硬件要求:¾Windows平台:z Intel Pentium266MHz处理器或更好(Windows2000Server)z Intel Pentium733MHz处理器或更好(Windows2003Server,Standard 或Enterprise Edition)z256MB内存+1MB/每1,000用户z NTFS格式要想获得更高的认证效率建议采用以下配置:z双Intel Pentium(或者Xeon)4(1.8GHz或更好)处理器。
z每CPU〉256MB内存z硬盘空间:200MB用于认证服务器软件每1000用户增加1MB远程管理软件需要20MB安盟Windows认证代理(Agent)5MB¾Unix平台:z HP-UX11/PA-RISC2.x处理器z IBM AIX5L v5.1or5.2/PowerPC或RISC/6000处理器z Solaris8或Solaris9/UltraSPARC处理器推荐的硬件配置:z HP-UX:HP J2240双236MHz PA-8200处理器z AIX:RS/6000双233MHz处理器z Solaris:Ultra SPARC II双300MHz处理器磁盘空间:z400MB用于认证服务器软件z128MB内存/每CPU+1MB/每1,000用户z1GB硬盘空间用于日志存储3安盟认证服务器安装及配置3.1安盟认证服务器安装前注意事项1)如果操作系统是windows,安盟认证服务器必须安装在NTFS分区上。
SEC--007备用钥匙控制程序

Standard Operating Procedures-Security保安部标准操作程序Subject : Key Control Effective Date :主题:备用钥匙的管理程序执行日期:2011年7月1日Policy No. : SEC--007 Issued by : Security Manager制度编号: SEC--007 发布:保安部经理Page : 1 of 3 Approved by : General Manager页数:第一页批准人:总经理Distribution : Senior Executive Committee Department Heads A&B All associates分发:高级行政委员会、部门经理A&B级、所有员工为加强本部钥匙管理,特制定如下规定。
Security need to record all of keys of hotel, and cautiously keep them , and strictly comply the following policy. 保安部需对整个酒店钥匙进行登记,警慎的保存,并按照以下程序对钥匙进行管理。
Policy & Procedure 政策和程序1.Whoever privately takes the keys will be not allowed.未经允许,任何人不得私自拿取钥匙2.Whoever privately prepares any office key will be not allowed.未经允许任何人不得私配办公室任何钥匙,统一由工程部配制。
3.Earnestly carry out the rule on “who takes it, who must be responsible for it”, and record the details,security guards should be responsible for the key-receiving register.认真贯彻“谁领用,谁负责”的原则,并做好领用登记,登记本由保安员保管。
2010版网络神探宾馆说明书(模式切换版)

网络神探宾馆版使用介绍上海雨人软件技术开发有限公司2011年1月关于使用手册雨人产品上海雨人软件技术开发有限公司,成立于1998 年11 月。
是中国著名的网络安全、审计、监控、管理产品的研发企业。
好泰莱雨人产品的一个产品系列,好泰莱系列主要应用于企业、政府机关、校园、家庭等领域的网络安全监控及审计管理。
一.产品安装1.1 系统需求服务器系统需求操作系统Windows2003 server+SP2 (推荐)系统组件IIS (Internet服务管理器) 版本要求 5.0 以上Internet Explorer (IE 浏览器)版本要求6.0 以上数据库Microsoft SQL Server2000(SQL2000)+SP4硬件需求1.宾馆客房数量在50台与100台之间:CPU:酷睿双核内存:2G硬盘:3202.宾馆客房数量在100 台-200台:CPU:酷睿双核内存:2G硬盘:500G 管理机系统需求操作系统Windows2003 server+SP2 (推荐)Windows2000 server + SP4Windows2000 Pro + SP4Windows XP + SP2系统组件Internet explorer (IE 浏览器) 版本要求6.0 及以上1.2 安装环境配置网络结构为了能够保证好泰莱上网管理系统的稳定运行,并达到管理部门的监控要求,网络结构应符合监控管理的需求,以下提供两种网络拓扑方案,推荐使用网络拓扑一:好泰莱上网管理系统安装在代理服务器上:网络拓扑二:好泰莱上网管理系统安装在与集线器或交换机镜像端口相连的机器上:设置网络防火墙 好泰莱上网管理系统实时与监控管理部门的管理中心进行通信,所需的端口 为 TCP:7878,如果网络中有防火墙需将这些端口开放。
二.产品设置2.1 进入WEB管理界面好泰莱上网管理系统安装好后,便可通过WEB 管理界面来设置及使用好泰莱。
Step1: 打开IE 浏览器,并在IE 浏览器的地址栏中输入WEB 管理的地址:http://好泰莱服务器的IP:7070/ndbrowser 例如,好泰莱服务器的IP 地址是192.168.0.247,则Web管理机地址为:http://192.168.0.247:7070/ndbrowser注:也可以从系统开始菜单中打开该页面地址:开始->程序->好泰莱上网管理系统->管理主页,进入系统后界面如下图:Step2:在账号栏中输入admin(admin 为管理员账号,具有最高的管理权限),并输入密码后点击“确定”进入管理界面。
F-Secure Rescue CD用户指南说明书

When to Use the Rescue CDThere are two main situations when you should use the Rescue CD:•The computer no longer starts, as the operating system has beencorrupted by malware. In this case you can use the Rescue CD to scanthe computer and quarantine the malware. This may allow the operatingsystem to start properly again.•If you suspect that your security software has been compromised bymalware. You can use the Rescue CD to check this, as it is independentof the operating system.If the computer cannot be recovered, you can also use Rescue CD and a USBdrive to save important data. Note that if you copy data from the computer to theUSB drive, this data may contain malware. The Rescue CD cannot scanencrypted disks. This includes for example, Windows Vista BitLocker diskencryption.System Requirements To use the F-Secure Rescue CD, the computer must meet the following minimum requirements:•x86 compatible•at least 512 MB of RAM•startup from a CD•connected to the Internet or be able to use a USB driveUsing the Rescue CD on a working operating system may renameessential system files and so cause your operating system to no longer start. If this happens you can use your operating system repair disk toreinstall the operating system. Note that this may reinstall a freshoperating system and so remove any personal settings and files youhave.Using the Rescue CD 1.Place the F-Secure CD in your CD drive and switch the computer on. After a few seconds you should see a prompt that shows F-Secure Rescue CD.2.Press E NTER within 15 seconds after you see the prompt to start Rescue e the arrow keys to select Next and press E NTER .4.Wait for the latest virus definition database to be downloaded from F-Secure. This is finished when you see the End User License Agreement window.5.Press P AGE D OWN to read the agreement and then select Next and press E NTER .6.Select I Agree and press E NTER if you agree to the terms.7.Select which drives you want to scan.8.Select Proceed to scan and press E NTER .9.When the scan is finished, press E NTER to see the scan report.10.If any malware were found, you can see which files were renamed by the Rescue CD. Select Next and press E NTER when you are ready to continue.11.Select Restart and press E NTER .12.Wait for 5 seconds for the computer to switch off. The computer restarts.13.If you see the same screen as you did in step 1, wait for 15 seconds for thecomputer to start normally.If you do not see the F-Secure Rescue CD screen you should check that the computer can start from CD. To do so:1.Restart the computer .2.Hold the BIOS options key while the computer starts, usually this is one of F1, F2, F10, F12 or DELETE . If none of these work, consult the documentation for the computer.3.Change the option that determines which device the BIOS tries to find the operating system from, so that the CD drive is searched first.4.Save settings and restart the computer.The Master Boot Record is a small section at the start of a disk that can be used to hide malware. You should scan the Master Boot Records.Using a USBdrive You can download the Rescue CD updates to a USB drive using a healthy computer that has an Internet access. This USB drive must be more than 512 MB and less than 16 GB in size for the Rescue CD to recognize it. In addition, the USB drive must have at least 256 MB of free space. You can use this USB drive to fix a computer that cannot connect to the Internet and so cannot download the Rescue CD updates.Recommended method:1.Create a new directory called fsecure to the USB drive.2.Go to the fsecure directory and create a directory called rescuecd under thefsecure directory.3.Start the Rescue CD while the USB drive is still connected to the computer.When the Rescue CD starts, it finds the USB drive you have configured for it.4.Select Next when the Rescue CD notifies you that the memory stick hasbeen found.5.The Rescue CD starts to download the latest databases.The Rescue CD has finished downloading databases when the end-user license agreement appears.6.The memory stick is ready and you can remove the CD and the memorystick.7.Insert the memory stick to the computer you want to fix and use the RescueCD to boot the computer.Alternative method:1.On a healthy computer with Internet access, Insert an empty USB drive.2.Open /latest/fsdbupdate9-packed.run withyour web browser.Your web browser asks you what you want to do with the file in the web site.3.Choose to save the file to your computer.4.After the web browser has finished downloading the file, go to the directorywhere you downloaded the fsdbupdate9-packed.run file and copy it to the USB drive.5.Insert this USB drive in the computer on which you want to use the RescueCD.6.Follow the instructions in Using the Rescue CD.Automate theScanningProcess You can set up a USB drive to make the Rescue CD process almost automatic. This drive must be 256 MB or greater in size. You can:•Preload virus definition database updates to the USB drive to fix a computer without Internet access.•Define proxies that Rescue CD will use to download updates.•Set Rescue CD to skip the wizard and automatically clean the computer.To set up your USB drive:1.Create a new directory called fsecure to the USB drive.2.Go to the fsecure directory and create a directory called rescuecd under thefsecure directory.3.Start the Rescue CD while the USB drive is still connected to the computerand run through the steps described in Using the Rescue CD. This USB drive now contains a virus definition database and is ready to use.Once you have completed the above steps you can also set up the USB drive so that it runs through the scan process automatically:1.Open the file fsecure/rescuecd/config with a text editor.2.Add the text timeout=1 to the file. With this value, you have 1 secondbetween each step of the Rescue CD process before the program selects the default option automatically.To use the USB drive, insert it into the infected computer and use Rescue CD asnormal.If you can access the Internet from the infected computer only through a proxy, you can define proxy settings in the same config file to download updates through the proxies you define. To define a proxy, add thefollowing line to the config file:http_proxies=http://user:password@address:portNote that http://, user, password and port are optional and address is mandatory. For example, the following is a valid proxy setting:http_proxies=sam:********************.com:8090,http://**************,DISCLAIMER"F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure product names and symbols/logos are either trademarks or registered trademarks of F-Secure Corporation. All product names referenced herein are trademarks or registered trademarks of their respective companies. F-Secure Corporation disclaims proprietary interest in the marks and names of others. Although F-Secure Corporation makes every effort to ensure that this information is accurate, F-Secure Corporation will not be liable for any errors or omission of facts contained herein. F-Secure Corporation reserves the right to modify specifications cited in this document without prior notice.Companies, names and data used in examples herein are fictitious unless otherwise noted. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express written permission of F-Secure Corporation.This product may be covered by one or more F-Secure patents, including the following:GB2353372, GB2366691, GB2366692, GB2366693, GB2367933, GB2368233, GB2374260Copyright © 2011 F-Secure Corporation. All rights reserved。
OBIS Series OBD II 检测系统 EEEA134A 产品说明书

OBD II INSPECTION SYSTEMMODEL EEEA134ABID SPECIFICATIONSCERTIFIED TEST MODE•Meets and exceeds Texas OBD II Inspection requirements.•Performs State-specified, software-controlled,automated OBD testing sequence with computer-determined pass/fail results.• Interfaces to SUN dynamometer for driveability testing (future enhancement).• Tamper-resistant, secured PC system• Automatic operation, calibration, communication and printing.• Simple vehicle OBD II interface and testing VEHICLE DIAGNOSTICS• Interfaces to Snap-Link ™ program to display live vehicle data• Interfaces to shop management system (Shopkey Information System)PC MODE• Allows operation of most IBM-compatible software programs running under WINDOWS ™ 2000.STANDARD HOST SYSTEM HARDWARE:• High performance, IBM compatible microprocessor,PENTIUM ® 900 mHz minimum*• 128 MB RAM minimum*• WINDOWS ™ 2000 operating systems • One 3.5” 1.44 MB floppy disk drive• Large-capacity hard drive, 20 GB minimum*• Disk key security • 16X DVD-ROM• 101-key enhanced keyboard• High resolution, 17” color SVGA monitor minimum*• 56,000 baud modem, minimum*STANDARD HOST SYSTEM HARDWARE (Cont’d)•High performance, non-secured laser printer •Custom-designed, easy access, secured host cabinet•Accepts user-loaded software* (Computer host system subject to enhancement as necessary)PERFORMANCE SPECIFICATIONS:•Digital, microprocessor-controlled, OBD testing •Automatic gas cap testing•High performance communication with host •Automated OBD II testing•+35° to +110° F. operating temperature range •+20° to +130° F. storage temperature range •Operates in ambient humidities up to 100%, non-condensing•Complies with SAE J-1850 OBD standard •Complies with EPA 40 CFR PART 51 as interpreted by TNRCC.STANDARD ACCESSORIES•OBD II interface module•Remote control•25’ AC power cord•25’ modem connection cable•2D bar code scanner•Fuel cap pressure tester w/adapters •Laser printerOPTIONAL CAPABILITIES (FUTURE ENHANCEMENTS)•Engine systems analyzer •Dynamometer interface•Gas analysis•Vehicle diagnostic softwarePOWER/WEIGHT/DIMENSIONS:•120V AC 60 hz 5.0 amps •Approximate shipping weight: 300 lbs.•Dimensions: 58” H x 31” W x 27” D* NOTE: Specifications are subject to change as required by various state requirements. Specifications subject to change without notice. Preliminary12/01©2001 Snap-on Tools CompanyOBD II INSPECTION SYSTEM NORTH CAROLINA MODEL EEEA135ABID SPECIFICATIONSCERTIFIED TEST MODE•Meets and exceeds North Carolina OBD II Inspection requirements.•Performs State-specified, software-controlled,automated OBD testing sequence with computer-determined pass/fail results.• Interfaces to SUN dynamometer for driveability testing (future enhancement).• Tamper-resistant, secured PC system• Automatic operation, calibration, communication and printing.• Simple vehicle OBD II interface and testing VEHICLE DIAGNOSTICS• Interfaces to Snap-Link ™ program to display live vehicle data• Interfaces to shop management system (Shopkey Information System)PC MODE• Allows operation of most IBM-compatible software programs running under WINDOWS ™ 2000.STANDARD HOST SYSTEM HARDWARE:• High performance, IBM compatible microprocessor,PENTIUM ® 1000 mHz minimum*• 128 MB RAM minimum*• WINDOWS ™ 2000 operating systems • One 3.5” 1.44 MB floppy disk drive• Large-capacity hard drive, 20 GB minimum*• Disk key security • 16X DVD-ROM• 101-key enhanced keyboard• High resolution, 17” color SVGA monitor minimum*• 56,000 baud modem, minimum*STANDARD HOST SYSTEM HARDWARE (Cont’d)•High performance, non-secured laser printer •Custom-designed, easy access, secured host cabinet•Accepts user-loaded software* (Computer host system subject to enhancement as necessary)PERFORMANCE SPECIFICATIONS:•Digital, microprocessor-controlled, OBD testing •High performance communication with host •Automated OBD II testing•+35° to +110° F. operating temperature range •+20° to +130° F. storage temperature range •Operates in ambient humidities up to 100%, non-condensing•Complies with SAE J-1850 OBD standard •Complies with EPA 40 CFR PART 51 as interpreted by North Carolina STANDARD ACCESSORIES•OBD II interface module•Remote control•25’ AC power cord•25’ modem connection cable•1D bar code scanner•Laser printerOPTIONAL CAPABILITIES (FUTURE ENHANCEMENTS)•Engine systems analyzer •Dynamometer interface•Gas analysis•Vehicle diagnostic softwarePOWER/WEIGHT/DIMENSIONS:•120V AC 60 hz 5.0 amps •Approximate shipping weight: 300 lbs.•Dimensions: 58” H x 31” W x 27” D* NOTE: Specifications are subject to change as required by various state requirements. Specifications subject to change without notice. SS2100 (5/02)©2002 Snap-on Tools CompanyOBD II INSPECTION SYSTEM PENNSYLVANIA MODEL EEEA136ABID SPECIFICATIONSCERTIFIED TEST MODE•Meets and exceeds Pennsylvania OBD II Inspection requirements.•Performs State-specified, software-controlled, automated OBD testing sequence with computer-determined pass/fail results.•Interfaces to SUN dynamometer for driveability testing (future enhancement).•Tamper-resistant, secured PC system •Automatic operation, calibration, communication and printing.•Simple vehicle OBD II interface and testing VEHICLE DIAGNOSTICS•Interfaces to Snap-Link™ program to display live vehicle data•Interfaces to shop management system (Shopkey Information System)PC MODE•Allows operation of most IBM-compatible software programs running under WINDOWS™ 2000. STANDARD HOST SYSTEM HARDWARE:•High performance, IBM compatible microprocessor, PENTIUM® 1000 mHz minimum*•128 MB RAM minimum*•WINDOWS™ 2000 operating systems•One 3.5” 1.44 MB floppy disk drive•Large-capacity hard drive, 20 GB minimum*•Disk key security•16X DVD-ROM•101-key enhanced keyboard•High resolution, 17” color SVGA monitor minimum*•56,000 baud modem, minimum*STANDARD HOST SYSTEM HARDWARE (Cont’d)•High performance, non-secured laser printer •Custom-designed, easy access, secured host cabinet•Accepts user-loaded software* (Computer host system subject to enhancement as necessary)PERFORMANCE SPECIFICATIONS:•Digital, microprocessor-controlled, OBD testing •High performance communication with host •Automated OBD II testing•+35° to +110° F. operating temperature range •+20° to +130° F. storage temperature range •Operates in ambient humidities up to 100%, non-condensing•Complies with SAE J-1850 OBD standard •Complies with EPA 40 CFR PART 51 as interpreted by Pennsylvania STANDARD ACCESSORIES•OBD II interface module•Remote control•25’ AC power cord•25’ modem connection cable•2D bar code scanner•Laser printer•Gas Cap TesterOPTIONAL CAPABILITIES (FUTURE ENHANCEMENTS)•Engine systems analyzer •Dynamometer interface•Gas analysis•Vehicle diagnostic softwarePOWER/WEIGHT/DIMENSIONS:•120V AC 60 hz 5.0 amps •Approximate shipping weight: 300 lbs.•Dimensions: 58” H x 31” W x 27” D* NOTE: Specifications are subject to change as required by various state requirements. Specifications subject to change without notice. SS2101 (5/02)©2002 Snap-on Tools Company。
前厅部 目录索引 FO Index
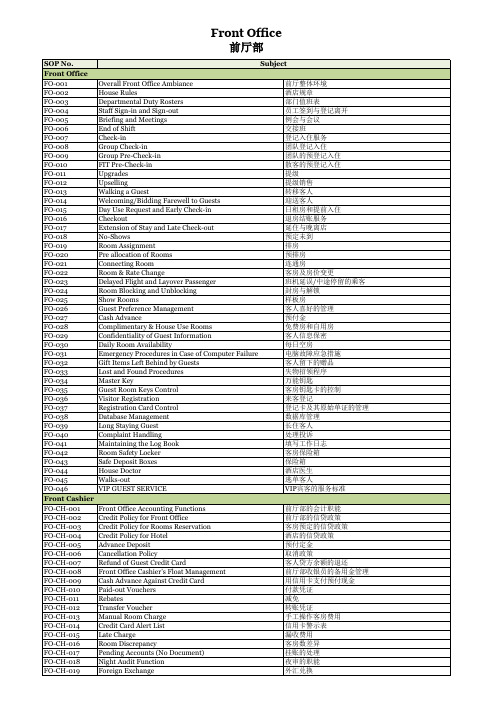
SOP No. Front Office FO-001 FO-002 FO-003 FO-004 FO-005 FO-006 FO-007 FO-008 FO-009 FO-010 FO-011 FO-012 FO-013 FO-014 FO-015 FO-016 FO-017 FO-018 FO-019 FO-020 FO-021 FO-022 FO-023 FO-024 FO-025 FO-026 FO-027 FO-028 FO-029 FO-030 FO-031 FO-032 FO-033 FO-034 FO-035 FO-036 FO-037 FO-038 FO-039 FO-040 FO-041 FO-042 FO-043 FO-044 FO-045 FO-046 Front Cashier FO-CH-001 FO-CH-002 FO-CH-003 FO-CH-004 FO-CH-005 FO-CH-006 FO-CH-007 FO-CH-008 FO-CH-009 FO-CH-010 FO-CH-011 FO-CH-012 FO-CH-013 FO-CH-014 FO-CH-015 FO-CH-016 FO-CH-017 FO-CH-018 FO-CH-019 Subject Overall Front Office Ambiance House Rules Departmental Duty Rosters Staff Sign-in and Sign-out Briefing and Meetings End of Shift Check-in Group Check-in Group Pre-Check-in FIT Pre-Check-in Upgrades Upselling Walking a Guest Welcoming/Bidding Farewell to Guests Day Use Request and Early Check-in Checkout Extension of Stay and Late Check-out No-Shows Room Assignment Pre allocation of Rooms Connecting Room Room & Rate Change Delayed Flight and Layover Passenger Room Blocking and Unblocking Show Rooms Guest Preference Management Cash Advance Complimentary & House Use Rooms Confidentiality of Guest Information Daily Room Availability Emergency Procedures in Case of Computer Failure Gift Items Left Behind by Guests Lost and Found Procedures Master Key Guest Room Keys Control Visitor Registration Registration Card Control Database Management Long Staying Guest Complaint Handling Maintaining the Log Book Room Safety Locker Safe Deposit Boxes House Doctor Walks-out VIP GUEST SERVICE Front Office Accounting Functions Credit Policy for Front Office Credit Policy for Rooms Reservation Credit Policy for Hotel Advance Deposit Cancellation Policy Refund of Guest Credit Card Front Office Cashier’s Float Management Cash Advance Against Credit Card Paid-out Vouchers Rebates Transfer Voucher Manual Room Charge Credit Card Alert List Late Charge Room Discrepancy Pending Accounts (No Document) Night Audit Function Foreign Exchange 前厅整体环境 酒店规章 部门值班表 员工签到与登记离开 例会与会议 交接班 登记入住服务 团队登记入住 团队的预登记入住 散客的预登记入住 提级 提级销售 转移客人 迎送客人 日租房和提前入住 退房结账服务 延住与晚离店 预定未到 排房 预排房 连通房 客房及房价变更 班机延误/中途停留的乘客 封房与解锁 样板房 客人喜好的管理 预付金 免费房和自用房 客人信息保密 每日空房 电脑故障应急措施 客人留下的赠品 失物招领程序 万能钥匙 客房钥匙卡的控制 来客登记 登记卡及其原始单证的管理 数据库管理 长住客人 处理投诉 填写工作日志 客房保险箱 保险箱 酒店医生 逃单客人 VIP宾客的服务标准 前厅部的会计职能 前厅部的信贷政策 客房预定的信贷政策 酒店的信贷政策 预付定金 取消政策 客人贷方余额的退还 前厅部收银员的备用金管理 用信用卡支付预付现金 付款凭证 减免 转账凭证 手工操作客房费用 信用卡警示表 漏收费用 客房数差异 挂账的处理 夜审的职能 外汇兑换
城市漫步守护星007网站使用说明书

守护星007网站使用说明书守护星系列定位器有一个专属的网站。
该网站可以自动识别用户是PC登录还是手机登录,切换到相应界面。
PC版本是个全功能版本,手机版本受手机浏览器的局限,目前只有定位查询功能。
PC登录界面:手机登录界面:1.激活设备当用户第一次拿到定位器的时候,首先要用PC上激活它。
激活后用户将获得用户名和密码,用这些信息登录就可以设置操作设备。
步骤如下:1.用浏览器打开2.按要求输入设备信息和用户信息3.把机器的P/N号填入网站设备IMEI拦内。
(打开机器后盖可以看到)4.如果激活成功,将返回到登录界面,请用刚才你输入的用户名和密码登录系统。
2.PC版本使用由于PC版本采用了WEB2.0技术,请不要使用IE6等过时的浏览器,推荐firefox或者IE7以上。
2.1.1.登录首先请用你设备激活后获得的用户名和密码登录登录成功后显示主界面如下(如果没有显示一下界面,请按F5刷新):2.1.2.添加设备一个用户名下可以有多个设备,请按下图点击添加弹出如下对话框,按提示填入设备信息。
点击确定,添加成功后可以在设备列表上看到新添加的设备。
2.1.3.删除设备在设备列表里面选中要删除的设备,点击设备管理里面的删除出现以上对话框,选中Yes即可删除。
2.1.4.修改昵称点击设备控制面板上的昵称按钮在出现的对话框中修改昵称2.1.5.设置绑定号码守护星007的面板上有4个按键可以用来绑定号码,用户按相应键就会呼出对应的号码。
在网站上设置如下:点击设备控制面板里面的绑定号码按钮在弹出的对话框里面设置相应的号码。
注意设置不是立刻生效的,要等定位器主动来更新,默认是5分钟。
当然你可可以重新开机,那样就立刻生效了。
所有的设置都是这样的。
2.1.6.安全报警功能守护星007拥有超强的安全报警功能:既可以设置安全区域,也可以设置安全路径。
当设备超出你设置的安全区域或者安全路径外,就会向你设定的号码发送你设定的短信。
点击设备控制面板的安全报警按钮。
ATTO Celerity FC Host Adapter Getting Started Guid

ATTO Technology, Inc.155 CrossPoint ParkwayAmherst, New York 14068 USATel (716) 691-1999Fax (716) 691-9353Sales support:****************Technical support: Please visit https:///support/ for hours of operation.*********************Tel (716) 691-1999 ext. 242© 2016 ATTO Technology, Inc. All rights reserved. All brand or product names are trademarks of their respective holders. No part of this document may be reproduced in any form or by any means without the express written permission of ATTO Technology, Inc.4/2016 PRMA-0400-000MDCelerity Fibre Channel Host AdapterGetting Started GuideThank you for purchasing the ATTO Celerity FC HostAdapter. This guide gives you the basics for installing andconfiguring your adapter. For more information, refer to theCelerity Installation and Operation Manual and the ATTOUtilities Manual.Ensure you have the equipment and software youneed for the installation:•Celerity FC adapter• A computer with an available PCIe, PCIe 2.0 orPCIe 3.0 expansion slot•Storage, cables and connectorsInstalling the Latest Celerity 32Gb, 16Gb or 8GbDrivers1Please visit the ATTO website at https:///2Hover over Support and click Downloads.3For returning customers login by entering yourusername and password. For new users pleaseregister to create login.4Select Product: Click on Fibre Channel HBAs5Select Model: Click on 32Gb, 16Gb CelerityHBAs or 8Gb Celerity HBAsInstall DriversConfigure your system to recognize and use yourCelerity adapter by installing drivers for your operatingsystem.Windows1Power on your system and log in as theadministrator or a user with properadministrative privileges.2Go to the ATTO website and login as describedin the Installing the Latest Celerity 32Gb, 16Gbor 8Gb Drivers section3Click on Windows. This will display the mostcurrent Windows drivers available.4Click on Windows XX Driver link based on theoperating system (x86 or x64) in use. If you areunsure which version you are using, pleasecontact your system administrator.5Open the download link and click run.6Follow the on-screen instructions to completethe driver installation.NoteWHQL Certified Drivers are available for selectCelerity Fibre Channel HBAs. If available, thesedrivers will be listed below the default Windowsdrivers.OS XSupport for all Celerity FC models except 164E1Power on your system and log in as theadministrator or a user with properadministrative privileges.2Go to the ATTO website and login as describedin the Installing the Latest Celerity 32Gb, 16Gbor 8Gb Drivers section3Click on Mac. This will display the most currentMac OS X drivers available.4Click on the Mac OS X Driver link based on theoperating system in use. If you are unsure whichversion you are using, please contact your system administrator.5Open the download.6Launch the installer package.7Follow the on-screen instructions.LinuxNoteNote: These steps assume a basic knowledge of Linux terminal commands. You must also have the correct kernel source files for the appropriate kernel already installed.1Power on your system and log in as the administrator or a user with properadministrative privileges.2Go to the ATTO website and login as described in the Installing the LatestCelerity 32Gb, 16Gb or 8Gb Driverssection.3Click on Linux. This will display the most current Linux drivers available.4Click on Linux XX Driver link based on the operating system in use. If you are unsure which version you are using, pleasecontact your system administrator.5Copy the .tgz file to a temporary folder.6Open a terminal window and change to the location of copied tgz from step 5.7Extract the file using the command tar -xfz <filename.tgz>.8Change to the directory created above then run the installer script ./install.sh.9Click on Y to load driver.10Click on Y to install CLI tools.11Confirm location.VMware (ESXi 5.x/6.0)NoteNote: ESXi 5.0 & later: 8Gb Celerity supportESXi 5.1 & later: 16Gb Celerity support1Download the correct Driver Bundle from the VMware or ATTO website.2Within the bundle unzip the Driver VIB file (.vib) for your ATTO Adapter.3Use the Datastore Browser in the vSphere Client to upload the VIB file to your ESXihost.4Log in to the ESXi host on the Local Tech Support Console (ESXi), or through anSSH client.5Install the VIB using the followingcommand on the ESXi host: # esxclisoftware vib install -v <full path to VIB file> 6Once the VIB is installed, reboot the ESXihostFreeBSDNoteRefer to the Celerity Installation and Operation Manual forinstructions on installing FreeBSD driversInstalling the ATTO ConfigToolThe ATTO ConfigTool is a free utility. Visit theATTO website (/downloads.php) for specific operatingsystem support information and downloads.The ATTO ConfigTool includes twocomponents: a GUI Application and a systemservice. Either, or both, of these componentscan be installed on a host, depending on thefunctionality desired. Refer to the Utilitiesmanual for additional details.NoteLogging and other important features are only available if theATTO ConfigTool service is installed. We recommendinstalling the service as a minimum configuration.NoteThe vConfigTool supports VMware VCenter Server. Refer tothe ATTO website for information on downloading and usingthis free utility.Windows Installation Instructions:1Double-click thewin_app_configtool_xxx.exe package file2Click "Unzip" to extract the installer files.The files are put in "C:\ATTO\ConfigTool\4.xx" directory.2.1To install the Full Application orApplication Only:•Navigate to the "C:\ATTO\ConfigTool\4.xx\Service"directory•Double-click on the ConfigTool_xxx.exeinstaller executable•Select Full Installation or ApplicationOnly as desired.•Follow the on-screen instructions2.2To install the System Service only:•Navigate to the"C:\ATTO\ConfigTool\4.xx\Service"directory•Double-click on the "attocfgd.msi"installer executable•Follow the on-screen instructionsOS X Installation Instructions:1Double-click theosx_app_configtool_xxx.exe package file.2 A Finder window appears.2.1To install the Full Application orApplication Only:•In the Finder window that appears,double-click on the ConfigTool_xxx.appinstaller executable.•Select Full Installation or ApplicationOnly as desired.•Follow the on-screen instructions.2.2To install the System Service only:•Navigate to the “Service” folder in theFinder window that appears.•Double-click on the "attocfgd.mpkg"installer executable file.•Follow the on-screen instructions.Linux Installation Instructions:1Extract the package file by running thefollowing command in a terminal: tar -xvzflnx_app_configtool_xxx.tgz2Navigate to the extracted folder“lnx_app_configtool_xxx”2.1To install the Full Application orApplication Only:•Run the ConfigTool_xxx.bin installerexecutable as root or superuser.•Select Full Installation or ApplicationOnly as desired.•Follow the on-screen instructions.2.2To install the System Service only:•Navigate to the “Service” directorylocated inside thelnx_app_configtool_xxx directory•Double-click on the "attocfgd.msi"installer executableRun the “attocfgd.sei” installer executable asroot or superuser using the followingcommand line: ./attocfgd.sei -i.Hardware InstallationBack up your system data before changing orinstalling any hardware.CAUTIONCelerity FC host adapters containcomponents that are sensitive toelectrostatic discharge (ESD). ESDcan Cause damage to the Celerity FChost adapter. Please follow standardmethods to avoid ESD.1Install the latest drivers. Refer to InstallDrivers of your Celerity Fibre Channel HostAdapter Getting Started Guide.2Power down the computer and unplug thecomputer from all power sources.3Open the case.4Install the Celerity FC host adapter in anyopen PCI Express expansion slot. ForCelerity 164E only, install the appropriateexternal power cable (supplied). If youhave questions about how to install anexpansion card in your system, consultyour computer’s documentation.NoteAll Celerity cards fit in x8 or x16 mechanicalslots.CAUTIONCelerity 16Gb Quad Fibre ChannelHost Adapters (FC-164E) requireexternal power supply and adequatecooling to ensure proper systemoperation and prevent data loss.5Connect Fibre Channel devices byinserting a Fibre Channel cable from thedevices to the connectors on the CelerityFC host adapter until you hear a click.6Close the case on the computer and powerit up.Configure your storage and adapterDefault settings are appropriate for mostsystems but you may change settings usingthe ATTO Configuration Tool on the ATTOwebsite.Please see ATTO Utilities Installation andOperations Manual for further information.。
安装梵讯房屋管理系统失败的解决方案

安装梵讯失败的解决方案目录问题一:安装时提示组件错误。
net 4.0未安装 (1)问题二:安装时提示组件错误SQL未安装 (2)问题三:安装梵讯时发生错误 (2)问题四:双击没有反映 (2)问题五:登录梵讯时提示没有找到数据库 (3)问题六:登录梵讯时提示“97427”错误 (3)问题七:登录时提示没有权限 (4)问题八:安装SQL时提示“25541" (4)问题九:安装梵讯时提示写入错误 (5)问题十:让C盘的可用空间大于一个G (5)问题十一:分区工具使用 (5)问题一:安装时提示组件错误.net 4。
0未安装1.现象:安装梵讯房屋管理系统的系统组件发生错误,在成功安装所有的系统组件之前安装程序无法继续进行的解决方法:(单击详细信息后显示:未能安装组件 Microsoft。
NET Ffamework 4(x86和x64)并显示下列错误消息,按照下面的步骤来处理)2.解决方案:第一步:查看系统盘即c盘的可用空间有没有大于一G,如果没有请清理c盘的空间,大于一G后在安装C盘的可用空间小于一个G,请按照这个方法来处理:http://help.fooww。
com/helptopic2158—932。
aspx第二步:下载微软的补丁来安装下,补丁的下载地址如下:http://www。
fooww。
com/download/如果装不了.NET4请安装.zip在安装补丁时,如果有错误,不用管,压缩包里面的两个补丁都单击安装后,在安装下“梵讯房屋管理系统的安装包"如果还是有提示错误请按照第三步来处理。
第三步:修改注册表:下载下面的文件安装下http://www。
fooww。
com/download/tools/fooww_reg.zipxp系统解压出来双击安装win7系统解压出来需要在此文件上右键选择“以管理员身份运行”第四步:完成以上步骤后在双击安装梵讯软件的安装包问题二:安装时提示组件错误SQL未安装1.现象:安装梵讯房屋管理系统的系统组件发生错误,在成功安装所有的系统组件之前安装程序无法继续进行的解决方法(单击详细信息后显示:未能安装组件SQL ServerCompact 3.5 SP2,并显示下列错误消息)2.解决方案:第一步:下载数据库文件安装包下载地址:http://www。
泰勒SafeNet身份验证器产品介绍说明书

Contents3 Diverse Form Factors for Convenient Strong Authentication4 Hardware OTP Tokens4 Certificate-based Virtual Smart Card5 Certificate-based Smart Cards6 Certificate-Based USB Tokens6 FIDO Devices7 Smartphone and Software Tokens7 Tokenless Authentication Solutions8 Card Readers8 About SafeNet Identity and Access Management Solutions 8 About ThalesDiverse Form Factors for Convenient Strong AuthenticationOffering the broadest range of multi-factor authentication methods and form factors, Thales facilitates and empowers enterprise-wide security initiatives for maintaining and improving secure access to enterprise resources.Thales’s SafeNet authenticators include hardware and software OTP tokens, FIDO devices, X.509 certificate-based USB tokens , physical and virtual smart cards, OOB, hybrid tokens, and phone tokens for all mobile platforms. Many Thales SafeNet hardware tokens support physical access control to secure buildings and sites.Allowing you to address numerous use cases, assurance levels and threat vectors, Thales’s authenticators are supported by authentication platforms which offer uniform, centralized policy management—delivered in the cloud or on premises. Supporting software solutions include SafeNet Trusted Access (STA), an access management and authentication service, and SafeNet Authentication Client Middleware, for certificate-based authentication.Thales partners with 3rd-party CMS vendors to offer the most comprehensive identity access and authentication management solutions.To tailor strong authentication to your business and IT needs, choose from the authenticators shown below:Hardware OTP TokensThales’s SafeNet OTP hardware tokens provide a strong and scalable foundation for securing access to enterprise, web-based and cloud applications, and complying with privacy and security regulations.Thales’s SafeNet hardware tokens offer rich case-branding options, and are field-programmable by the customer, enabling organizations to maintain stringent control over their own critical OTP security data.Certificate-based Virtual Smart CardEnable your cloud transformation securely by building on your current PKI authentication framework for cloud access. Increase mobility by allowing users to access enterprise apps with PKI credentials, from any device via VDI.As convenient as another credit card in your wallet, Thales’s SafeNet credit card-size form factors enable enhanced security with PKI Certificate-Based-Authentication (CBA) and enable preboot authentication, disk encryption, file encryption, digital signatures, and secure certificate and key storage.All Thales smart card authenticators can easily double as physical access cards to secure buildings and sites, in addition to offering rich branding options and support for photo-badging. Depending on the configuration, Thales’s certificate-based authenticators are FIPS or CC certified. The dual interface versions of SafeNet IDPrime Smart Cards comply with the ISO 14443 standard which is also compatible with some NFC readers present in smartphones and tablets. SafeNet IDPrime Smart Cards are supported by SafeNet Authentication Client Middleware or SafeNet Minidriver.Thales’s portfolio of certificate-based USB tokens offers strong multi-factor authentication in a traditional USB form factor, enabling organizations to address their PKI security needs. SafeNet PKI USB tokens offer a single solution for strong authentication and applications access control, including remote access, network access, password management, network logon, as well as advanced applications including digital signature, data and email encryption.Depending on their configuration, the certificate-based USB tokens can be FIPS and CC certified.FIDO DevicesFIDO authenticators enable multi-factor authentication to cloud and web services as well as Windows 10 devices. Thales offers a range of FIDO devices, including a combined PKI-FIDO smart card and a FIDO USB token.Smartphone and Software TokensOffering the convenience of phone-as-a-token authentication, Thales offers PUSH OTP software authentication for tablets and mobile phones.Tokenless Authentication SolutionsThales’s tokenless technology enables any user to be authenticated anytime and anywhere. Thales’s context-based authentication offers convenient, frictionless strong authentication while maintaining the flexibility and agility to add protection with stronger methods of security in higher risk situations. Combined with “step-up” authentication, context-based authentication optimizes a layered approach to access security by assessing user login attributes and matching them against pre-defined security policies.Card ReadersInterface devices, or readers, are an essential component of any smart card deployment and ensure communication between smart cards and network services, but they must do so in a convenient yet secure manner. Thales’s full range of smart card readers provide the perfect balance of ease of use, backed by the highest level of security.About SafeNet Identity and Access Management SolutionsThales's industry-leading Access Management and Authentication solutions let enterprises centrally manage and secure access to enterprise IT, web and cloud-based applications. Utilizing policybased SSO and universal authentication methods, enterprises can effectively prevent breaches, migrate to the cloud securely and simplify regulatory compliance.To learn more, visit: /access-managementAbout ThalesThe people you rely on to protect your privacy rely on Thales to protect their data. When it comes to data security, organizations are faced with an increasing number of decisive moments. Whether the moment is building an encryption strategy, moving to the cloud, or meeting compliance mandates, you can rely on Thales to secure your digital transformation.Decisive technology for decisive moments.> <Contact usFor all office locations and contact information, please visit /contact-ush a l e s - N o v e m b e r 2020 • R M v 46。
SOP-Front Office - RS

STANDARD OPERATING PROCEDURES标准操作程序POLICY NO. SUBJECT编号标题FO-RS-001 Reservation Office Hours预定部作息时间FO-RS-002 Reservation Form预定表格FO-RS-003 Making New Reservation新预定FO-RS-004 Amendment Reservation预定的修改FO-RS-005 Reservation Cancellation预定的取消FO-RS-006 Confirmation Letter/Slip确认信/纸条FO-RS-007 Reservation Form Filing预定表格的填写FO-RS-008 Arrival Report到达报告FO-RS-009 No Show预定但未抵达FO-RS-010 Reservation Procedure With Credit Arrangement信用预定程序FO-RS-011 Reservation Procedure Without Pre-approvedCredit Arrangement无事先确认信用的预定FO-RS-012 Guarantee Reservation担保预定FO-RS-013 Guarantee Reservation Policy担保预定政策FO-RS-014 House Use Room And Complimentary Room客用房或免费房STANDARD OPERATING PROCEDURESEffective Date : Jan. 2009Subject : Reservation OfficeHours 预定部作息时间Policy No : FO-RS-001 Issued by : FOMPage : 1 of 1 Approved by :General Manager Distribution : Executive Committee Department Head A&B: All AssociatesObjective 目标The objective of setting this procedure is to maximize the productivity of reservation agent and minimize the manning as well.设置该程序的目的是发挥预定部员工的最大效率以及最大限度降低人力投入。
Pro-Watch系统产品文件说明书

Security Management SystemsF E AT U R E S Pro-Watch provides comprehensive options for audit and reporting to address forensics, compliance and business intelligence data mining needs. The Reporting application includes basic report templates and the capability to generate custom reports. Reports can be exported as XLS, CSV and PDF formats. Pro-Watch provides a solid and proven platform for an intelligent business management solution. It is successfully deployed in enterprises of many sizes and across various vertical applications suchas manufacturing facilities, campuses, government facilities and critical infrastructure.• Web Based Client for Badging, Reporting, Alarm and Event Monitoring• Mobile Client for Badging and Door Control• Supports Windows®Server2008/2012/2012, SQL Server 2008/ 2012/ 2014, Windows 7/8/8.1/ 10 (32-bit and 64-bit)• Single user interfacefor multiple securityand businessfunctions• Add HSDK andPro-Watch can beintegrated with otherbuilding systems suchas secondary fire,lighting and heating,ventilation, and airconditioning• Web Services APIenables IntegrationOptions• CertificationManagement• Custom triggers andprocedures• Associates events toactions includingsending emails,running a storedprocedure, ortriggering a panel I/Opoint. Events may betriggered at thePro-Watch level forpanel-to-panel andpanel-to-softwareactions or within apanel for local actions• Basic Reports• Virtualization supportfor VMWare andMicrosoft® Hyper-V• Compliance Reportsthat offer data andstatistical reporting;auto generatedreports uponschedules• Easy system setupand maintenancewith user definablehardware templates• Database partitioningand definableoperator permissions• IP, serial and modemcommunications• CASI Micro/5 andM2000 ReplacementProgram• Lite, Professional,Corporate andEnterprise editionsPro-Watch® 4.3Security Management SuiteDesigned to meet the challenges of today’s demanding environments, Honeywell’s Pro-Watch security management suite providesthe flexibility, scalability and control required for comprehensive security management. Pro-Watch equips organizations withthe right tools to protect people, secure assets and ensure regulatory compliance by combining access control, digitalvideo, intrusion and other functions into one powerful system.Integration with access control and video systems from Honeywell and third-party manufacturers makes it possible to leverageexisting installed hardware as the system expands. Modular hardware and software options make it easy and cost-effectiveto expand a system to keep up with growing business needs.With Pro-Watch Web Based Client, customers can utilize their existing network infrastructure to provide remote security management for badging, reporting, and alarm and event monitoring. Less software allows for savings on installation costs and time while continuing to provide optimal security protection.Pro-Watch streamlines tasks with a common user interface to improve operator effectiveness and help organizations minimize training costs. Events may be routed to specific workstations and linked to automated system responses such as camera call-ups and outward notifications. Options for integrating intercom and mass notification components provide a vital link to the security dispatch center.2 |The Pro-Watch suite offers base software licenses that address security needs from small sites to global enterprises:Pro-Watch Lite Edition: Basic functionality for the small office with support for up to 32 doors on PW-Series panels.Pro-Watch Professional Edition: Complete security functionality with more options for medium-sizedorganizations with up to 64 doors ororganizations requiring integrated processes or regulatory compliance.Pro-Watch Corporate Edition: Complete security for larger organizations and campuses. Additional high availability options make this edition the optimal choice fororganizations requiring 24/7 business continuity plans for their security system.Pro-Watch Enterprise Edition: Global security system that merges multiple Pro-Watch Corporate Edition systems to efficiently manage badgeholder data and report on events across theorganization.Integrations available using Pro-Watch Professional EditionPro-Watch Lite Edition (PWLE) and Pro-Watch Professional Edition (PWPE) are optimized for the needs of smaller security systems.These editions leverage Microsoft® SQL Express 2012 (included), so the server can be accommodated on either a workstation for a single PC or on a separate server. In either case, additional clients may be connected to the server up to supported limits. Refer to the specifications guide on page 5 for more details.Pro-Watch Lite Edition offers basic functionality for the small office and features Pro-Watch PW Series access controllers. Additional client licenses can be added as needed up to a total of 5.Pro-Watch Professional Edition is ideal for sites requiring more than 32 readers or additional client workstations.Small Systems: Pro-Watch Lite and Pro-Watch Professional EditionsBoth Pro-Watch Professional Edition (PWPE) and Pro-Watch Corporate Edition (PWCE) are targeted for the needs of medium to large installations.An IT topology deployment with a separate server is recommended. Workstations can be connected via LAN or WAN, making it convenient to manage multiple sites on a single server. Pro-Watch Professional Edition features Microsoft SQL Express 2012 (included).Both editions offer numerous options to meet a variety of security needs. For limits on connectivity support in PWPE, refer to the specifications guide on page 5.PWCE is truly the best fit for the largest systems and campuses because it has no restrictions on numbers of add-on readers or workstations. Honeywell also offers redundant solutions on PWCE for organizations requiring 24/7 operations.Medium & Large Systems: Pro-Watch Professional and Pro-Watch Corporate EditionsEnterprise Systems:Pro-Watch Enterprise EditionPro-Watch Enterprise Edition (PWEE) provides a security solution forthe global organization by sharing badgeholder identities and event data across the organization.With a PWEE system, an enterprise server facilitates two-way datasharing among regional servers. This enables single credential solutions across organizations.If equipped with two or more Pro-Watch Corporate Editions (PWCE),an organization may easily upgrade its servers to become part of an Enterprise system. EachCorporate Edition server becomes a regional server and retains regional system control.| 3PR OF E S S ION A L, C O R P OR AT E&E N T E R PR I SE E DI T ION S• Standard Badging and Advanced Badging client• 2-D PDF417 barcode add-on license for badging• Option for Transportation Security Clearinghouse (TSC) background checks in Pro-Watch AP (Airport)• Integration toHoneywell VISTA®panels FBP-128 /250and GX in NorthAmerica and toHoneywell GalaxyDimension GD-48,GD-96, GD-264,GD-520 in Europe• Event Procedurestriggers onconsecutive duplicateevents• Mustering, anti-passback and guardtour• Minimum andmaximum occupancyenforcement• Integrates videodevices added inMAXPRO® VMS• Supports Commendintercom systemservers GE200,GE300, GE700 andGE800• Detailed historicrecords for trackingconfigurationchanges, securityoperations and deviceevents to comply withaudit requirementsfor regulatorycompliance• Intercoms linked toreaders and locationson maps providequick access tospecific units• Supports R14 andlater AutoCAD files(DWFx or XPS) withadd-on license• Options forintegratingbiometrics,third-party hardware,radar-video solutionsand IT convergence• High availability andredundant serversolutions (CorporateEdition)• Support for WirelessLocksets fromAllegion, Assa Abloy,and Salto• Support forDisconnected Locksetsfrom Salto• FICAM PACSInfrastructureAPL Listed4 || 5SPEC IF IC AT IONS1 Must have a standard client license on a machine in order to run an Advanced Badging client license.2 Must order one regional server in an Enterprise system for each PWCE server in the system.3 E nterprise system capabilities align with Corporate for respective regional servers.Enterprise systems link together two or more Corporate Edition systems to share badgeholder identities and events among the Corporate Edition systems.1 Includes RAM required by the client machine to run the Windows operating system.6 |PR O -WATC H SE R V E R 1 R EQ U IR E ME N T S1 F or a system to be considered small, the Pro-Watch system shall have less than 5 clients, no more than 128 online readers, less than 5000 historical events per day, and properdatabase maintenance conducted by the end user or servicing dealer. For a system to be large, it must have between 5000 and 50,000 historical events per day, between 128 and 512 online readers, between 5 and 15 client workstations, and proper database maintenance conducted by the end user or servicing dealer. If the system will have more than 50,000 events per day, exceed 512 online readers, exceed 15 client workstations, or use Pro-Watch server side functions like anti-passback, event triggers and procedures, Real Time Data Transfer Utility, HSDK, etc. please consult Honeywell for custom server sizing.2 R AID technology used for the larger system server – Disk sets 1 and 2. When several physical disks are set up to use RAID technology, the operating system will be installed on a single disk (OS installed on RAID1 mirrored set) and the Database and Storage on a separate disk (RAID 5 or 10 disk set)3 To estimate database storage space, use the following approximations and add to the base DB size of 500MB: • Badgeholder storage = (# of badgeholders) x (75KB)* estimate based on typical captured picture size • Event history storage = (# of events per day) x (2.5 KB) x (# of days to retain in server)• A udit history storage = [(# of cardholder changes per day) + (# of system configuration changes per day)+(# of events per day)+(# of operator system changes per day)]* (1.2KB)x (# of days to retain in server)4 H oneywell highly recommends some type of removable media for daily database backups. Database backups should be removed from the server and stored in a safe, secure location so in the event of system failure this valuable data can be recovered. We recommend two or more removable media per server based upon end user processes. Alternatively, Honeywell system installers can engage the end-user’s IT group to participate in some type of network backup program.• I mportant Notice – These server and workstation hardware guidelines are intended for use as a reference only. The specifications are subject to changes due to marketconditions, software updates, manufacturing changes, and other variables outside of our control. Honeywell recommends for planning based on system growth and expansion, operating system updates and upgrades, database engine updates and upgrades, end user system expansion, historical data retention requirements, and archive data storagerequirements. Please consult with Honeywell as applicable for assistance.OR DE RING| 7For more information/uk Honeywell Security and Fire Honeywell International Middle EastSheikh Zayed Road, EMAAR Business Park Building 2, Level 2, Office 201PO Box 232362, Dubai, U.A.E. Telephone: +971 4 4505800 Facsimile: +971 4 4505900 Pro-Watch® is a registered trademarkof Honeywell International Inc. Microsoft®, Microsoft® BackOffice® and Windows® 2000 are registered trademarks of Microsoft Corporation HSFV-PRW43LTWD-01-ME(0617)DS-E June 2017© 2017 Honeywell International Inc.OR DE R ING8 |。
srvo007的三个基本流程

srvo007的三个基本流程下载温馨提示:该文档是我店铺精心编制而成,希望大家下载以后,能够帮助大家解决实际的问题。
文档下载后可定制随意修改,请根据实际需要进行相应的调整和使用,谢谢!并且,本店铺为大家提供各种各样类型的实用资料,如教育随笔、日记赏析、句子摘抄、古诗大全、经典美文、话题作文、工作总结、词语解析、文案摘录、其他资料等等,如想了解不同资料格式和写法,敬请关注!Download tips: This document is carefully compiled by theeditor. I hope that after you download them,they can help yousolve practical problems. The document can be customized andmodified after downloading,please adjust and use it according toactual needs, thank you!In addition, our shop provides you with various types ofpractical materials,such as educational essays, diaryappreciation,sentence excerpts,ancient poems,classic articles,topic composition,work summary,word parsing,copy excerpts,other materials and so on,want to know different data formats andwriting methods,please pay attention!1. 故障诊断流程:检查机器人系统的电源和连接,确保所有电缆都正确连接。
警惕Guest账号

警惕Guest账号
黄东
【期刊名称】《网管员世界》
【年(卷),期】2005(000)005
【摘要】由于工作的特殊性,笔者负责管理机房的交换路由设备和几台重要的服务器。
其中有两台服务器用做Web,分别安装了Windows2000 Server和Windows2003 Server操作系统.采用NTFS分区.同时使用TOMCAT和IIS对外提供Web服务。
【总页数】1页(P88)
【作者】黄东
【作者单位】山东
【正文语种】中文
【中图分类】TP316.7
【相关文献】
1.外贸商需警惕:黑客盗取账号骗取客户贷款 [J],
2.巧用系统Guest账号提高内网控制效率 [J], 转转
3.用Guest账号应对恶意程序:限制使用最危险的应用 [J], Mark; Burnett; 盛青(译)
4.解决用户账号问题 Windows安全模型的变化帮助您配置用户账号控制和最小权限用户账号 [J], Russell Smith; LYH(译)
5.盗窃商家微信公共账号行骗市民需警惕 [J],
因版权原因,仅展示原文概要,查看原文内容请购买。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
FRONT OFFICE RECEPTION OPERATIONS MANUAL
GENERAL POLICIES & PROCEDURES
Policy Name : Guest Security
Effective Date : 01 June 2006
Revised Date : Nil
Applicable : All Staff
Forms to use : Nil
Refers to :Nil
Purpose
The purpose of this policy is t o ensure our hotel guest’s privacy is not infringed and that all staff must place utmost concern for their safety and security.
Policy
It is the policy of Hyatt Regency Dongguan that staff do not disclose hotel guest’s room numbers or any of their personal details to the public other than the Public Security Bureau (PSB) via the submission of Registration card and through computer link.
Any other requirement to do so must have the approval from the Front Office Manager. Procedure
Whereabouts of In-house guests:
1.When approached by a member of the public, on disclosing the whereabouts of
hotel guest, staff should check the system if there is prior instruction from guest.
Examples like “INCO” –do not disclose, “SCREEN” –screen all calls etc should be strictly adhered to. These scripting should then be used:
- INCO “I am sorry sir, there is no such person registered with the hotel”
-SCREEN “May I have your name and company you work for and I will try to reach Mr xxx” Then go to the back office to contact the guest and
check if he would like to take this call otherwise advise visitor to leave a
message.
Page 1
FRONT OFFICE RECEPTION OPERATIONS MANUAL
GENERAL POLICIES & PROCEDURES
2.If guest is registered with the hotel, the staff can put the call through to his room
but NOT DISCLOSE guest’s room number to the visitor. This scripting should then be used:
-“For security reasons, I am not ab le to disclose the guest room number, however, I can assist by putting you through to his room.” Ensure that
when dialing for the room, the access is not noticeable.
Checking in Single female or elderly guests:
1.Always block room near the lift and nearest to any hotel reception counters if
there is no special request from guest.
2.When explaining guest’s room’s number and location, ensure there is no
strangers loitering nearby who could overhear the conversation.
Request disclosure of guest details or bills
1.Should there be any request to mail / fax guest details or bills to a third party,
authorization should be given from the guest himself via written notice. His signature will then be counterchecked with the one on the registration card prior to any disclosure.
2.If the request is from the guest himself via the telephone the staff must explain
to the guest that a written notice is still needed for security reason. Of course, this practice can be over-ridden based on discretion of the Assistant Manager. 3.S hould a member of the public request to pay for a guest’s bill without any
knowledge from the guest, the cashier must inform the guest to seek his consent first. In the event that the guest cannot be located, then the visitor can leave behind his business card; a signed credit card imprint with written authorization to charge him. The staff will reassure the visitor that once the guest agrees to this arrangement, the bills with the processed charge form will be forwarded to the visitor. No other details e.g. room rates, guest’s details should be revealed at any point.
Page 2
FRONT OFFICE RECEPTION OPERATIONS MANUAL
GENERAL POLICIES & PROCEDURES
Public Area
1.It is every staff’s responsibility to be alert of strangers loitering around the
guests’ floors, lobby area or other public area of the hotel. These sightings should be immediately reported to the security. For safety reasons, at no time should the staff approach or follow these characters.
2.Whenever discussing guest’s stay, ensure room numbers and status of guests is
not mentioned whenever in the public area.
Prepared by James Fan Date 01 Jun 2006 Approved by Date
Page 3。
