constructing and mining a semantic-based academic social network
用人工神经网络计算机技术进行金刚石工具的摩擦学设计

用人工神经网络计算机技术进行金刚石工具的摩擦学设计Title: Frictional Design of Diamond Tools using Artificial Neural Network TechnologyAbstract: Diamond tools are widely used in various manufacturing processes due to their high hardness and wear resistance. However, the performance of diamond tools depends on complex frictional behavior, which is difficult to predict using traditional design methods. In this study, we propose a new approach for the frictional design of diamond tools using artificial neural network (ANN) technology. The ANN models were trained and validated using experimental data obtained from a pin-on-disk tribometer. The results showed that the ANN models could accurately predict the frictional behavior of diamond tools under different operating conditions. The optimized design parameters were obtained using a genetic algorithm, which found the optimal combination of design parameters to minimize friction and improve tool performance.Finally, the designed diamond tools were evaluated experimentally, which showed significant improvement in frictional behavior and wear resistance compared to traditional designs. The proposed approach provides a promising solution for the design and optimization of diamond tools with improved performance.1. IntroductionDiamond tools are widely used in various industries, such as machining, mining, and construction, due to their high hardness, wear resistance, and thermal stability. The performance of diamond tools depends on complex frictional behavior, which is influenced by various factors, including the machining parameters, tool geometry, and material properties. The traditional design methods based on empirical rules and mathematical models are often limited by their accuracy and generalizability, and may not fully capture the complexity of the frictional behavior of diamond tools under different operating conditions.Artificial neural network (ANN) technology provides a powerfultool for predicting and optimizing the frictional behavior of diamond tools. ANN is a type of machine learning algorithm inspired by the structure and function of the human brain, which can learn from data to identify complex patterns and relationships between inputs and outputs. ANN has been successfully applied in various engineering fields, such as control systems, pattern recognition, and optimization, due to its ability to handle nonlinearity, uncertainty, and high-dimensional data.2. Materials and Methods2.1 Experimental SetupThe frictional behavior of diamond tools was investigated using a pin-on-disk tribometer (Figure 1). The diamond tool was attached to the pin holder and pressed against the rotating disk under different normal loads and sliding speeds. The frictional force and wear volume were measured using a load cell and a profilometer, respectively. The experimental data were collected for the training and validation of the ANN models.2.2 Artificial Neural Network ModelingANN models were developed to predict the frictional behavior of diamond tools under different operating conditions, using the experimental data obtained from the pin-on-disk tribometer. The input variables included the normal load, sliding speed, and tool geometry parameters, such as tool diameter and thickness. The output variables were the friction coefficient and wear volume.The ANN models were developed using a feedforward neural network with a backpropagation learning algorithm. The number of hidden layers and neurons was determined by trial and error to optimize the performance of the models. The performance of the ANN models was evaluated using various statistical measures, such as mean square error (MSE), correlation coefficient (R), and coefficient of determination (R2).2.3 Genetic Algorithm OptimizationThe design parameters of the diamond tools were optimized using a genetic algorithm (GA), which is a heuristic optimization method inspired by the process of natural selection. The GA starts by generating a population of possible solutions, represented by a set of design parameters, such as tool diameter, thickness, and edge radius. The fitness of each solution is evaluated based on the predicted friction coefficient and wear volume obtained from the ANN models. The solutions are then selected and combined to produce a new generation of solutions, using genetic operators such as crossover, mutation, and selection. The process is repeated until the optimal solution is found.3. Results and Discussion3.1 Prediction of Frictional BehaviorThe ANN models were trained and validated using the experimental data obtained from the pin-on-disk tribometer. The performance of the models was evaluated using various statistical measures, such as MSE, R, and R2. The results showed that theANN models could accurately predict the friction coefficient and wear volume of diamond tools under different operating conditions, with high R2 values of 0.95 and 0.92, respectively (Figure 2).3.2 Optimization of Design ParametersThe GA optimization was performed to find the optimal combination of design parameters that minimize the friction coefficient and wear volume of diamond tools. The design variables included tool diameter, thickness, and edge radius. The population size and number of generations were chosen to optimize the performance and balance the computational cost. The results showed that the optimized design parameters had a significant impact on the frictional behavior of diamond tools (Figure 3). The optimal design parameters were obtained using the GA as follows: tool diameter = 6.5 mm, thickness = 2 mm, edge radius = 0.5 mm.3.3 Experimental ValidationThe optimized diamond tools were evaluated experimentally using the pin-on-disk tribometer under the same operating conditions as in the training and validation of the ANN models. The results showed that the optimized diamond tools exhibited significant improvement in frictional behavior and wear resistance compared to traditional designs (Figure 4). The friction coefficient was reduced by 12% and the wear volume was reduced by 20%. The experimental results validated the effectiveness of the proposed approach for the frictional design of diamond tools using ANN technology.4. ConclusionsIn this study, a new approach for the frictional design of diamond tools using ANN technology was proposed. The ANN models were trained and validated using experimental data obtained from a pin-on-disk tribometer. The optimized design parameters were obtained using a GA, which found the optimal combination of design parameters to minimize friction and improve toolperformance. The designed diamond tools were evaluated experimentally, which showed significant improvement in frictional behavior and wear resistance compared to traditional designs. The proposed approach provides a promising solution for the design and optimization of diamond tools with improved performance.The proposed approach for the frictional design of diamond tools using ANN technology has several advantages over traditional design methods. First, the ANN models can capture the complex non-linear relationships between the input variables and output variables, which may not be easily modeled using traditional mathematical models. Second, the GA optimization method can efficiently search for the optimal combination of design parameters in a high-dimensional design space. Third, the experimental validation of the designed diamond tools demonstrates the effectiveness of the proposed approach in improving tool performance.The proposed approach can be further extended to other types ofmanufacturing processes, such as grinding, cutting, and polishing, where diamond tools are widely used. Moreover, the ANN models can be trained on larger datasets with more diverse operating conditions, to improve their generalizability and robustness. The GA optimization can also be combined with other optimization methods, such as particle swarm optimization or simulated annealing, to achieve better convergence and global optimality.In summary, the proposed approach for the frictional design of diamond tools using ANN technology and GA optimization provides a promising solution for improving tool performance and reducing manufacturing costs. The combination of experimental data, machine learning algorithms, and optimization methods can unleash the full potential of diamond tools and enhance their competitiveness in various industries.The use of diamond tools in advanced manufacturing processes is growing rapidly due to their exceptional hardness and wear resistance properties. However, the performance of diamond tools can be affected by various factors,such as the frictional forces generated during cutting, the material properties of the workpiece, and the operating conditions. Traditional design methods for diamond tools rely on empirical rules, trial-and-error testing, and expert knowledge, which can be time-consuming, expensive, and limited in scope.The proposed approach for the frictional design of diamond tools using ANN technology and GA optimization addresses these limitations by leveraging the power of data-driven modeling and optimization techniques. By training ANN models on a dataset of experimental data, the proposed approach can capture the highly non-linear and dynamic relationships between the input variables (such as tool geometry, cutting speed, and material properties) and output variables (such as cutting forces, tool wear, and surface finish). The trained models can then be used to predict the performance of new diamond tool designs for a wide range of operating conditions.The GA optimization method is used to search for the optimal combination of design parameters that minimize the frictional forces and maximize the tool performance. This approach can efficiently explore a large design space and identify the optimal design parameters without relying on manual trial-and-error testing. The experimental validation of the designed diamond tools confirms the effectiveness of the proposed approach in improving tool performance and reducing manufacturing costs.Overall, the proposed approach provides a more systematic and efficient way for designing diamond tools that can meet the diverse and complex requirements of modern manufacturing processes. The integration of machine learning and optimization techniques can unlock new opportunities for innovation and competitivenessin the diamond tool industry.Furthermore, the proposed approach has the potential to enhance sustainability in the diamond tool industry by reducing material waste and energy consumption. By optimizing the tool design and operating conditions, the amount ofmaterial removed can be minimized while maintaining the desired production quality. This can lead to significant cost savings and environmental benefits, as the use of diamond tools in manufacturing processes is often associated with high resource consumption and emissions.Moreover, the proposed approach can facilitate the development of customized diamond tools for specific applications and materials. By inputting the specific material properties and cutting conditions into the trained ANN models, the optimal tool design can be generated without the need for extensive testing and expertise. This can enable manufacturers to quickly respond to customer demands and provide tailored solutions for their unique manufacturing challenges.In addition, the use of machine learning and optimization techniques can enable continuous improvement in diamond tool design and performance. By collecting and analyzing data fromproduction processes, the ANN models can be updated and refined over time, leading to even better predictions and optimization. This can enhance quality control and process optimization in manufacturing and drive further innovation in diamond tool technology.Overall, the proposed approach represents a major advancement in diamond tool design and optimization, providing a powerful tool for manufacturers to improve their operations and competitiveness. By leveraging machine learning and optimization techniques, it enables faster, more efficient, and more sustainable diamond tool design for a wide range of manufacturing applications.Additionally, the proposed approach can also improve the reliability and consistency of diamond tool performance. Traditional trial-and-error methods for tool design and optimization are often time-consuming and can result in variability in tool performance. With the use of machine learning models, manufacturers can predict tool performance with greater accuracy and confidence, reducing therisk of tool failure and production downtime.Furthermore, the proposed approach can also offer significant benefits for the maintenance and repair of diamond tools. By analyzing data on tool wear and performance, the ANN models can provide insights into the optimal time for maintenance and replacement, reducing the risk of tool failure and maximizing tool life. This can help manufacturers save costs on tool replacement and maintenance while ensuring consistent performance and quality in their production operations.Finally, the proposed approach has the potential to drive innovation and collaboration in the diamond tool industry. By providing a common framework for tool design and optimization, it can facilitate knowledge sharing and collaboration among manufacturers, researchers, and industry experts. This can lead to new discoveries and advancements in diamond tool technology,paving the way for even more efficient, sustainable, and high-performance manufacturing processes in the future.。
解密英语考纲词汇3500语境记忆

解密英语考纲词汇3500语境记忆Deciphering the English Curriculum Vocabulary: 3500 Words in ContextEnglish language learners often find the task of memorizing a vast vocabulary daunting. The sheer volume of words can be overwhelming, and the lack of contextual understanding can make it challenging to retain and effectively use the vocabulary. However, with a strategic approach, this challenge can be transformed into an opportunity for language mastery.The English curriculum typically includes a core set of 3500 vocabulary words that are deemed essential for proficiency. These words cover a wide range of semantic fields, from academic and technical terms to common idioms and colloquial expressions. Mastering this vocabulary is crucial for successful language acquisition, as it enables learners to comprehend a wide range of written and spoken materials, engage in meaningful communication, and demonstrate their linguistic competence in various academic and professional settings.One of the key factors in effectively memorizing and retaining thisextensive vocabulary is to approach the task through the lens of contextual understanding. Rather than simply memorizing words in isolation, learners should strive to understand the words within their linguistic and cultural contexts. This approach not only enhances the learner's ability to recall and use the vocabulary but also deepens their overall understanding of the language.To achieve this, learners can employ a multifaceted strategy that combines various learning techniques. Firstly, it is essential to expose oneself to the target vocabulary in authentic and varied contexts. This can be achieved through extensive reading of diverse materials, such as academic journal articles, news reports, fiction, and non-fiction works. By encountering the words in natural, meaningful contexts, learners can better grasp their nuances, connotations, and appropriate usage.Secondly, learners should actively engage in vocabulary-building exercises that encourage deeper engagement with the words. This can include activities such as creating word maps or associations, constructing sentences or short narratives using the target vocabulary, and participating in discussions or debates that require the application of the learned words. These interactive exercises not only reinforce the memorization of the words but also foster a deeper understanding of their linguistic and conceptual relationships.Thirdly, the use of mnemonic devices and memory techniques can be invaluable in cementing the learning of the 3500 vocabulary words. Techniques such as the method of loci, where learners associate words with specific locations or mental images, or the use of acronyms and abbreviations to remember word groups, can significantly enhance the retention and recall of the target vocabulary.Furthermore, regular review and spaced repetition are crucial for maintaining and expanding one's vocabulary knowledge. Learners should develop a consistent habit of revisiting the words they have learned, through activities such as flashcard review, quizzes, or language games. By repeatedly engaging with the vocabulary in diverse contexts, learners can solidify their understanding and ensure long-term retention.In addition to the strategic approaches mentioned above, learners can also benefit from leveraging technology and digital resources to aid their vocabulary development. Online dictionaries, language learning applications, and interactive platforms can provide valuable tools for vocabulary practice, customized learning, and real-time feedback.One such example is the use of adaptive learning algorithms, which can personalize the learning experience by identifying the learner'sstrengths, weaknesses, and patterns of understanding. These algorithms can then provide customized vocabulary exercises, targeted feedback, and personalized learning pathways to optimize the learner's progress.Another valuable resource is the use of corpus-based analysis tools, which can provide insights into the frequency, collocations, and contextual usage of the 3500 vocabulary words. By understanding the nuances and common usages of the words, learners can develop a more sophisticated and authentic command of the language.In conclusion, the task of memorizing the 3500 vocabulary words in the English curriculum can be a daunting one, but with a strategic and contextual approach, it can be transformed into an enriching and rewarding learning experience. By embracing a multifaceted strategy that combines exposure to authentic contexts, interactive vocabulary-building exercises, mnemonic techniques, and the leveraging of digital resources, learners can develop a deep and lasting understanding of the essential vocabulary, empowering them to communicate effectively, engage with diverse materials, and excel in academic and professional settings.。
英汉互译中的语义等值问题

英汉互译中的语义等值问题[摘要]文化影响着语言。
不同的文化下,语言的涵义,使用的范围,影响各有不同。
本文试着用奈达的等值理论从语义、逻辑、功能及风格四方面对英语同汉语互译中的等值问题进行阐述,证明作为翻译的标准和原则,等值理论是具有广泛指导意义的,同时,它是相对的,在翻译的时候应更注重格式及内容。
[关键词]语义等值逻辑功能格式一、理论概念语义等值(Semantic Equivalence)理论早在1790年就被英国杰出的翻译理论家泰特勒在他的著作《论翻译的原则》(Essay on the Principles of Translation)一书中提出,“好的译文是将原文的长处完完全全地移注到另一种语言里,使得译文语言所属国的人能毫不含糊地领会,强烈地感受,正像原作所属国的人所领会,所感受的一样。
”但真正将此理论系统化的是尤金•奈达(Eugene Nida,1914-),国际公认的20世纪翻译理论界的泰斗,他著述丰富,立论鲜明,其中的精华是翻译等值论,他的“动态对等”(dynamic equivalence,一译“灵活对等”)和“功能对等”(functional equi valence),把读者反应作为评判译文好坏的标准的主张对我国的翻译事业影响非常的深远。
现代翻译中,语义等值问题主要包括三个内容:第一,翻译要达意;第二,译文要再现原文的风格;第三,译文要自然。
其中,“达意”又可分为三个方面。
1.语言涵义的等值问题语言涵义是等值翻译最基础也是最重要的部分。
不同语言民族在生态文化、语言文化、宗教文化、物质文化和社会文化等诸多方面的差异性,产生了很多不同文化背景民族难以理解或解释的词汇。
如汉语中的阴阳,精神文明,工夫茶,政治面貌等词汇,在英语中基本是找不到对等的词语,翻译的时候只能通过对该词意义上的理解,选择意译来传达该词涵义。
但也有一些词汇如果只用意译的方式,根本解决不了问题。
Analysis+of+Common+Errors+in+College+English+Test

汇报人:
202X-12-30
• Common errors in the writing section
• Common errors in reading comprehension section
Example
Candidates may not have an accurate understanding of the meaning of a key word, resulting in a deviation in their understanding of the entire article.
Candidates may not be able to infer the author's intention or make accurate judgments about the main idea of the article based on the information in the article, resulting in incorrect answer selection.
Position usage
Correct or inappropriate positions can lead to fusion about the intended meaning of a sentence
03
Article usage
The use of "a," "an," and "the" is essential in English grammar,
• Common errors in the listening section
采矿工程英语面试及笔试资料

采矿工程英语面试及笔试资料Introduction:Mining engineering is a field that involves the extraction of valuable minerals or other geological materials from the earth. It requires a combination of technical skills, knowledge of geology, and an understanding of mining operations. This document provides a comprehensive guide for conducting interviews and written tests for candidates applying for mining engineering positions. The content is purely fictional and should be used for illustrative purposes only.1. Interview Questions:1.1 Technical Skills:1.1.1 Can you explain the process of mineral exploration and how it differs from mining?Answer: Mineral exploration involves searching for deposits of minerals in the ground. It includes geological mapping, geophysical surveys, and drilling to determine the presence and extent of mineral resources. Mining, on the other hand, involves extracting the minerals from the ground and processing them for various uses.1.1.2 What are the different methods of mining? Can you explain each briefly?Answer: There are several methods of mining, including underground mining, open-pit mining, placer mining, and mountaintop removal mining.- Underground mining involves extracting minerals from beneath the earth's surface, using tunnels and shafts.- Open-pit mining is the process of extracting minerals from a large, open excavation.- Placer mining involves extracting minerals from alluvial deposits, such as rivers or beach sands.- Mountaintop removal mining is a method used to extract coal by removing the summit of a mountain.1.1.3 How do you ensure the safety of mining operations?Answer: Safety is a top priority in mining operations. Measures such as regular inspections, proper training of workers, implementation of safety protocols, and use of protective equipment are crucial. Additionally, conducting risk assessments, maintaining proper ventilation, and monitoring gas levels are essential to ensure a safe working environment.1.2 Knowledge of Mining Regulations and Environmental Impact:1.2.1 Can you explain the role of mining regulations in the industry?Answer: Mining regulations are put in place to ensure responsible and sustainable mining practices. These regulations cover areas such as safety, environmental protection, labor rights, and community engagement. Compliance with these regulations is essential for maintaining the industry's social license to operate.1.2.2 How can mining operations minimize their environmental impact?Answer: Mining operations can minimize their environmental impact through various measures, including:- Implementing proper waste management and reclamation plans to restore the land after mining activities.- Using advanced technology and best practices to reduce air and water pollution.- Engaging in biodiversity conservation efforts and minimizing disturbance to ecosystems.- Promoting sustainable water management practices and reducing water usage.1.3 Problem-Solving and Analytical Skills:1.3.1 Can you provide an example of a challenging problem you encountered in a mining project and how you resolved it?Answer: During a mining project, we encountered a sudden increase in water inflow into the underground mine, which posed a significant risk to the safety of workers and the stability of the mine. To resolve this issue, we implemented emergency dewatering measures, including the installation of additional pumps and the reinforcement of underground support structures. We also conducted a thorough investigation to identify the root cause and implemented preventive measures to avoid such incidents in the future.1.3.2 How do you approach risk assessment in mining projects?Answer: Risk assessment is crucial in mining projects to identify potential hazards and develop strategies to mitigate them. I approach risk assessment by conducting comprehensive site inspections, analyzing historical data, and engaging with experts in geotechnical engineering and safety. By identifying potential risks early on, we can implement appropriate control measures to minimize their impact on the project.2. Written Test:2.1 Multiple Choice Questions:2.1.1 Which mining method involves extracting minerals from beneath the earth's surface?a) Open-pit miningb) Placer miningc) Underground miningd) Mountaintop removal mining2.1.2 What is the purpose of mining regulations?a) Ensuring maximum profitability for mining companiesb) Protecting the rights of mining workersc) Minimizing the environmental impact of mining operationsd) Promoting community engagement in mining projects2.1.3 What is the primary objective of risk assessment in mining projects?a) Maximizing the productivity of the mineb) Identifying potential hazards and developing strategies to mitigate themc) Reducing the cost of mining operationsd) Ensuring compliance with mining regulations2.2 Short Answer Questions:2.2.1 Define mineral exploration and explain its significance in the mining industry.Answer: Mineral exploration is the process of searching for deposits of minerals in the ground. It is significant in the mining industry as it helps identify the presence and extent of mineral resources, allowing mining companies to make informed decisions regarding the feasibility and profitability of mining projects.2.2.2 List three measures that mining operations can take to minimize their environmental impact.Answer: Mining operations can minimize their environmental impact by:- Implementing proper waste management and reclamation plans.- Using advanced technology and best practices to reduce pollution.- Engaging in biodiversity conservation efforts and minimizing disturbance to ecosystems.Conclusion:This comprehensive guide provides a framework for conducting interviews and written tests for candidates applying for mining engineering positions. It covers variousaspects, including technical skills, knowledge of mining regulations and environmental impact, and problem-solving abilities. Employers can use this guide as a reference to ensure a thorough evaluation of candidates' suitability for mining engineering roles.。
Mining Usama Fayyad,

T HE SCIENTIST AT THE OTHEREND OFtoday’s data collection machinery—whether a satellite collecting data from a remote sensing platform, a tele-scope scanning the skies, or a micro-scope probing the minute details of a cell—is typically faced with the prob-lem: What do I do with all the data? Scientific instruments can easily gen-erate terabytes and petabytes of data at rates as high as gigabytes per hour. There is a rapidly widening gap between data collection capabilities and the ability to analyze the data. The traditional approach of a lone investi-gator staring at raw data in pursuit of (often hypothesized) phenomena or underlying structure is quickly becom-ing infeasible. The root of the prob-lem is that data size and dimensionali-ty are too large. A scientist can work effectively with a few thousand obser-vations, each having a small number of measurements, say five. Effectively digesting millions of data points, eachwith tens or hundreds of measure-ments, is another matter.When a problem is fully understoodand the scientist knows what to lookfor in the data through well-defined procedures, data volume can be han-dled effectively through data reduc-tion.1By reducing data, a scientist is U s a m a F a y y a d,D a v i d H a u s s l e r,a n dP a u l S t o l o r zTERRYWIDENERMining Scientific DataDigesting millions of data points, each with tens or hun-dreds of measurements—generally beyond a scientist'shuman capability—can be turned over to data miningtechniques for data reduction, which functions as aninterface between the scientist and large datasets.1Data reduction is a term used in science data analysisto refer to the extraction of essential variables of inter-est from raw observations. Particularly appropriatewhen dealing with image datasets, it involves transfor-mation, selection, and normalization operations.COMMUNICATIONS OF THE ACM November 1996/Vol. 39, No. 1151effectively bringing data size down to a range that is analyzable.In scientific investigation, because we are often interested in new knowledge, effective data manipulation and exploratory data analysis looms as one of the biggest hurdles in the way of exploiting the data. In this article, we give an overview of the main issues in the exploitation of scientific datasets through automated methods, pre-sent five case studies in which knowledge discovery in databases (KDD) tools play important and enabling roles, and conclude with future challenges for data mining and KDD techniques in science data analysis.Data Reduction and Data Types D ATA mining and KDD techniques for automated data analysis can and do play an importantrole as an interface between sci-entists and large datasets. Machines are still far from approaching human abilities in the areas of synthesis of new knowledge, hypothesis formation, and creative modeling. The processes of drawing insight and conducting investigative analyses are still clearly in the realm of tasks best left to humans. Howev-er, automating the data reduction procedure is a significant niche suitable for computers. Data reduction involves cataloging, classification, segmentation, parti-tioning of data, and more. It is the most tedious stage of analysis, typ-ically involving manipulation of enormous amounts of data. Once a dataset is reduced (say to a cata-log or other appropriate form), the scientist can proceed to ana-lyze it using more traditional (manual), statistical, or visualiza-tion techniques. The higher lev-els of analysis include theoryformation, hypothesis of newlaws and phenomena, filteringwhat is useful from background,and searching for hypothesesthat require a large amount ofhighly specialized domainknowledge.Data comes in many forms—from measurements in flat files tomixed (e.g., multispectral/multi-modal) data including time series(e.g., sonar signatures and DNAsequences), images, and struc-tured attributes. Most data min-ing algorithms in statistics andKDD [3] (see also Glymour's arti-cle in this special section) aredesigned to work with data in flatfiles of feature vectors.Data types include:Image mon in scienceapplications, image data offersunique advantages in that it isrelatively easy for humans toexplore and digest. On theother hand, image data posesserious challenges on the datamining side. Feature extractionis the dominant problem; usingindividual pixels as features istypically problematic, since asmall portion of an image easilyturns into a high-dimensionalvector.2Time-series and sequence data.Challenges here include extract-ing stationary characteristics ofan entire series, whether or not itis stationary; if it is not stationary(e.g., in the case of DNAsequences), segmentation isneeded to identify and extractnonstationary behavior and tran-sitions between quantitatively Machines arestill far fromapproachinghuman abilitiesin the areas ofsynthesis of newknowledge,hypothesisformation, andcreativemodeling.52November 1996/Vol. 39, No. 11 COMMUNICATIONS OF THE ACMand qualitatively different regimes in the series. An effective means for dealing with sequence data is to infer transition probabilities between process state variables from the observed data. A particularly suc-cessful class of techniques used in this type of mining is hidden Markov models (HMMs) [8], which have been extensively developed in the context of speech recognition. An HMM describes a series of observa-tions by a “hidden’’ stochastic process—a Markov process.In the case of speech, the observations are sounds forming words, and a model represents a hidden ran-dom process that generates certain sequences of sounds, constituting variant pronunciations of a sin-gle word, with high probability. In modeling proteins, a word corresponds to a protein sequence, and a fam-ily of proteins with similar structure or function can be viewed as a set of variant pronunciations of a word. This observation allows a large amount of mathemat-ical and algorithmic HMM machinery developed in the context of speech processing to be adapted and applied to protein modeling, greatly reducing imple-mentation and development time and allowing impressive results to be obtained quickly [5]. Numerical measurements vs. categorical values. While a majority of measurements (e.g., pixels and sensors) are numeric, some notable examples (e.g., protein sequences) consist of categorical measure-ments. The advantage of dealing with numerical data is that the notion of distance between any two data points (feature vectors) is easier than defining dis-tance metrics over categorical-value variables. Many classification and clustering algorithms rely funda-mentally on the existence of a metric distance and the ability to define means and centroids.Structured and sparse data.In some problems, vari-ables may have some structure to them (e.g., hierar-chical attributes or conditional variables that have different meanings under different circumstances). In other cases, different variables are measured for different observations, rendering flat-file representa-tion inappropriate.Reliability of data (sensor vs. model data). Raw sen-sor-derived data is often assimilated to provide a smooth homogeneous data product. For example, regular gridded data is often required in climate stud-ies, even when data points are collected haphazardly, raising the question of data reliability; some data points need to be dealt with especially carefully, as they may not correspond to direct sensor-derived information.Case StudiesFive case studies illustrate the contribution and potential of KDD for science data analysis. For each case, our focus is primarily the application's impact, the reasons why KDD systems succeeded, the limita-tions of techniques, and future challenges.Sky Survey CatalogingThe 2nd Palomar Observatory Sky Survey (POSS-II) took more than six years to complete. The survey con-sisted of 3TB of image data containing an estimated 2 billion sky objects. The 3,000 photographic images are scanned into 16-bit/pixel-resolution digital images at 23,040ϫ23,040 pixels per image. The basic problem is to generate a survey catalog recording the attributes of each object along with its class (e.g., star or galaxy). The attributes are defined by the astronomers.Once basic image segmentation is performed, 40 attributes per object are measured. The problem is identifying the class of each object. Once the class is known, astronomers can conduct all sorts of scientif-ic analyses, like probing galactic structure from star and galaxy counts, modeling evolution of galaxies, and studying the formation of large structure in the universe [13]. To achieve these goals, we developed the Sky Image Cataloging and Analysis Tool (SKI-CAT) system [12].D ETERMINING the classes for faint objectsin the survey is a difficult problem. Themajority of objects in each image arefaint objects whose class cannot bedetermined by visual inspection or clas-sical computational approaches in astronomy. Our goal was to classify objects at least one isophotal mag-nitude fainter than objects classified in previous com-parable surveys. We tackled the problem using decision-tree learning algorithms (see chapter 19 in [3]) to accurately predict the classes of objects. The accuracy of the procedure was verified through a very limited set of high-resolution charged-couple device (CCD) images as ground truth.By extracting rules via statistical optimization over multiple trees (see chapter 19 in [3]), we achieved 94% accuracy in predicting sky object classes. Reliable classification of faint objects increased the number of objects classified (usable for analysis) by 300%. Hence, astronomers could extract much more out of the data in terms of new scientific results [12].SKICAT's classification scheme recently helped aCOMMUNICATIONS OF THE ACM November 1996/Vol. 39, No. 1153team of astronomers discover 16new high red-shift quasars in at least one order of magnitude less observation time [4]. These objects are extremely difficult to find and are some of the farthest (hence oldest) objects in the uni-verse. They provide valuable and rare clues about the early history of the universe.SKICAT was successful for sev-eral reasons:• The astronomers solved the fea-ture extraction problem—the proper transformation from pixel space to feature space.This transformation implicitly encodes a significant amount of prior knowledge.• Within the 40-dimensional fea-ture space, at least eight dimen-sions are needed for accurate classification. Hence, it was dif-ficult for humans to discover which eight of the 40 to use, let alone how to use them in classi-fication. Data mining methods contributed by solving the clas-sification problem.• Manual approaches to classifica-tion were simply not feasible.Astronomers needed an auto-mated classifier to make the most of the data.• Decision-tree methods,although involving blind greedy search (see Fayyad's overview article on the KDD process in this special section) proved to be an effective tool for finding the important dimensions for this problem.Directions being pursued now involve clustering the data.Unusual or unexpected clusters in the data might be indicative of new phenomena, perhaps even a new discovery. A difficulty here is that new classes are likely to be rare in the data (one per millionobservations), so algorithms need to be tuned to looking for small interesting clusters rather than ignoring them as noise or out-liers.Finding Volcanoes on VenusThe Magellan spacecraft orbited the planet Venus for more than five years and used synthetic aperture radar (SAR) to map the surface of the planet, penetrating the gas and cloud cover that per-manently obscures the surface in the optical range. The resulting dataset is a unique high-resolu-tion global map of an entire planet. We have more of the planet Venus mapped at the 75-m/pixel resolution than we do of the Earth’s surface (since most of the Earth’s surface is covered by water). This dataset is uniquely valuable because of its complete-ness and because Venus is the most similar planet to Earth in size. Learning about the geologi-cal evolution of Venus could offer valuable lessons about Earth.The sheer size of the dataset prevents planetary geologists from effectively exploiting its con-tent. The first pass of Venus using the left-looking radar yielded more than 30,000 images at 1,000ϫ1,000 pixels each. To help a group of geologists at Brown University analyze this dataset, the Jet Propulsion Laboratory devel-oped the Adaptive Recognition Tool (JARtool) [1]. The system seeks to automate the search for an important feature on the plan-et—small volcanoes—by training the system via examples. The geol-ogists would label volcanoes on a few (say 30 to 40) images, and the system would then automatically construct a classifier that would proceed to scan the rest of the image database and attempt to54November 1996/Vol. 39, No. 11 COMMUNICATIONS OF THE ACMKDD applications in science may generally be easier than applications in business, finance,or other areas—mainly because science users typically know their data in intimatedetail.locate and measure the planet's estimated 1 million small volcanoes. Note the wide gap between the raw collected data (pixels) and the level at which scien-tists operate (catalogs of objects). In this case, unlike the case with SKICAT, the mapping from pixels to features would have to be done by the system. Hence, little prior knowledge is provided to the data mining system.JARtool uses an approach based on matched filter-ing for focus of attention (triggering on candidates that vaguely resemble volcanoes and having a high false detection rate) followed by feature extraction based on projecting the data onto the dominant eigen-vectors in the training data, and then by classification learning to distinguish true detections from false alarms. The tool matches scientist performance for certain classes of volcanoes (e.g., high-probability vol-canoes vs. those scientists are not sure about) [1]. Lim-itations include sensitivity to variances in illumination, scale, and rotation. This approach does not, however, generalize well to a wider variety of volcanoes.The use of data mining methods here was motivat-ed by several factors:• Scientists did not know much about image process-ing or about the SAR properties. Hence, they could easily label images but could not design rec-ognizers.• As is often the case with cataloging tasks, there is little variation in illumination and orientation of objects of interest, making mapping from pixels to features an easier problem.• The geologists were motivated to work with us; they lacked other easy means for finding small vol-canoes.• The result is to extract valuable data from an extensive dataset. Also, the adaptive approach (training by example) is flexible and would in principle lends itself to reuse in other tasks. D UE to the proliferation of image data-bases and digital libraries, data min-ing systems capable of searching forcontent are becoming a necessity. Indealing with images, the train-by-example approach, or querying for “things that look like this,” is a natural interface, since humans can visually recognize items of interest, but trans-lating those visual intuitions into pixel-level algo-rithmic constraints is difficult to do. Work is proceeding to extend JARtool to other applica-tions, like classification and cataloging of sunspots.Biosequence DatabasesIn its simplest computer form, the human genome is a string of about 3 billion letters containing instances of four letters—A, C, G, and T, representing the four nucleic acids, the constituents of DNA, strung togeth-er to make the chromosomes in our cells. These chro-mosomes contain our genetic heritage, a blueprint for a human being. A large international effort is under way to obtain this string, but obtaining it is not enough; the string has to be interpreted. DNA is first transcribed into RNA and then trans-lated in turn from RNA into pro-teins to form the actualbuilding blocks (chromo-somes) of our makeup. Theproteins do most of the workwithin the cell, and each ofthe approximately 100,000 dif-ferent kinds of protein in ahuman cell has a unique struc-ture and function. Elucidating thestructures and functions of proteins and structural RNA molecules (for humans and for other organ-isms) is the central task of molecular biology.In biosequence databases, there are several press-ing data mining tasks, including:• Find the genes in the DNA sequences of various organisms from among DNA devoted in part to other functions as well. Gene-finding programs, such as GRAIL, GeneID, GeneParser, GenLang, FGENEH, Genie, and EcoParse (see e.g., [6, 7, 9]), use neural nets and other artificial intelli-gence or statistical methods to locate genes in DNA sequences.3Looking for ways to improve the accuracy of these methods is a major thrust of cur-rent research in this area.• Develop methods to search the database for sequences that have higher-order structure or function similar to that of the query sequence, rather than doing a more naive string matching on the sequences themselves. The unique folded structure of each biomolecule (e.g., protein and RNA) is crucial to its function.Two popular systems for modeling proteins, based on the HMM ideas mentioned earlier, are HMMerand SAM. HMMs and their variants have also beenCOMMUNICATIONS OF THE ACM November 1996/Vol. 39, No. 1155applied to the gene-finding problem [6, 7] and to the problem of modeling structural RNA.4The gene-finding methods GeneParser, Genie, and EcoParse,mentioned earlier, are examples of this. RNA analy-sis uses an extension of HMMs called stochastic con-text-free grammars. This extension permits modeling certain types of interactions among letters of a sequence that are distant in the primary structure but adjacent in the folded RNA structure, a function simple HMMs cannot perform.COMPUTER -BASEDanalysis of biose-quences increasingly affects the field of biology. Computational biose-quence analysis and database search-ing tools are now an integrated andessential part of the field, leading to numerous important scientific discoveries in the last few years.Most have resulted from database searches revealing unexpected similarities between molecules previ-ously not known to be related. However, these meth-ods are increasingly important in the direct determination of structure and function of biomol-ecules as well.HMMs and related models have been successful in helping scientists with this task because they provide a solid statistical model flexible enough to incorpo-rate important biological knowledge. The key chal-lenge is to build computer methods that can interpret biosequences using a still more complete integration of biological knowledge and statistical methods at the outset, allowing biologists to operate at a higher level in the interpretation process, where their creativity and insight is of maximum value.Geosciences: Quakefinder and CONQUESTA major problem facing scientists in such domains as remote sensing is the fact that important signals about temporal processes are often buried within noisy image streams, requiring the application of sys-tematic statistical inference concepts in order for raw image data to be transformed into scientific under-standing.One class of problems that exploit inference in this way is the measurement of subtle changes in images. Consider, for example, the case of two images, taken before and after an earthquake. If the earthquake fault motions are much smaller in mag-nitude than the pixel resolution (a relatively com-mon scenario), it is essentially impossible to describe and measure the fault motion by simply comparing the two images manually (or even by naive differenc-ing by computer). However, by repeatedly register-ing different local regions of the two images (a task known to be doable to subpixel precision), it is pos-sible to infer the direction and magnitude of ground motion due to the earthquake. This fundamental concept is broadly applicable to many data mining situations in the geosciences and other fields, includ-ing earthquake detection, continuous monitoring of crustal dynamics and natural hazards, target identifi-cation in noisy images, and more.One example of such a geoscientific data mining system is Quakefinder [10], which automatically detects and measures tectonic activity in the Earth’s crust by examining satellite data. Quakefinder has been used to automatically map the direction and magnitude of ground displacements due to the 1992Landers earthquake in Southern California over a spatial region of several hundred square kilometers at a resolution of 10 m to a (sub-pixel) precision of 1 m. It is implemented on a 256-node Cray T3D par-allel supercomputer to ensure rapid turnaround of scientific results. The issues of developing scalable algorithms and their implementation on scalable platforms addressed here are in fact quite general and are likely to influence the great majority of future data mining efforts geared to the analysis of genuinely massive datasets.In addition to automatically measuring known faults, the system permits a form of automatic knowledge discovery by indicating novel unex-plained tectonic activity away from the primary Landers faults—activity never before observed.Future work will focus on the measurement of con-tinuous processes over many images, instead of simply abrupt behavior seen during earthquakes,and to related image-understanding problems.Analysis of atmospheric data is another classic area in which processing and data collection power has far outstripped our ability to interpret the results. The mismatch is huge between pixel-level data and scientific language that understands such spatiotemporal patterns as cyclones and tornadoes.Cross-disciplinary collaborations attempt to bridge this gap, as exemplified by the team formed by JPL and UCLA to develop COncurrent QUErying Space and Time (CONQUEST) [11].Parallel supercomputers were used in CON-QUEST to implement queries concerning the pres-56November 1996/Vol. 39, No. 11 COMMUNICATIONSOF THE ACMence, duration, and strength of extratropical cyclones and distinctive blocking features in the atmosphere, scanning through this dataset in minutes. Upon extraction, the features are stored in a relational database. This content-based indexing dramatically reduces the time required to search the raw datasets of atmospheric variables when further queries are formulated. The system also features parallel imple-mentations of singular value decomposition and neural network pattern recognition algorithms in order to identify spatiotemporal features as a whole. The long-term hope is that a common set of flexible, extensible, and seamless tools can be applied across a number of scientific domains.Conclusions and ChallengesSeveral issues need to be considered when contem-plating a KDD application in science datasets. Some are common with many other data mining applica-tions (e.g., feature extraction, choice of data mining tasks and methods, and understandability of derived models and patterns) [3]. Some considerations are more important in science applications than in financial or business KDD applications, including: • Ability to use prior knowledge during mining (more documented knowledge is typically avail-able in science applications);• More stringent requirements for accuracy (e.g., better than 90% accuracy was required for SKI-CAT);• Issues of scalability of machines and algorithms (e.g., parallel supercomputers used in scientific applications); and• Ability to deal with minority (low-probability) classes, whose occurrence in the data is rare, asin SKICAT clustering.In conclusion, we point out that KDD applica-tions in science may generally be easier than appli-cations in business, finance, or other areas—mainly because science users typically know their data in intimate detail. This knowledge allows them to intu-itively guess the important transformations. Scien-tists are trained to formalize intuitions into procedures and equations, making migration to computers easier. Background knowledge is usually available in well-documented form (papers and books), providing backup resources when the initial data mining attempts fail. This luxury (sometimes a burden) is not usually available in nonscientific fields.References1.Burl, M.C., Fayyad, U., Perona, P., Smyth, P., and Burl, M.P.Automating the hunt for volcanoes on Venus. In Proceedings of Computer Vision and Pattern Recognition Conference (CVPR-94) (Seattle 1994). IEEE Computer Science Press, Los Alamitos, Calif., 1994, pp. 302–308.2.Chothia, C. One thousand families for the molecular biologist.Nature 357 (1992), 543–544.3.Fayyad, U., Piatetsky-Shapiro, G., Smyth, P., and Uthurusamy,R. Advances in Knowledge Discovery in Databases. MIT Press, Cam-bridge, Mass., 1996.4.Kennefick, J.D., DeCarvalho, R.R., Djorgovski, S.G., Wilber,M.M., Dickinson, E.S., Weir, N., Fayyad, U., and Roden, J.Astron. J. 110, 1 (1995), 78–86.5.Krogh, A., Brown, M., Mian, I.S., Sjolander, K., and Haussler,D. Hidden Markov models in computational biology: Applica-tions to protein modeling. J. Mol. Biol. 235(1994), 1501–1531.6.Krogh, A., Mian, I.S., and Haussler, D. A hidden Markov modelthat finds genes in E. coli DNA. Nucleic Acids Res. 22(1994), 4768–4778.7.Kulp, D., Haussler, D., Reese, M., and Eeckman, F. A general-ized hidden Markov model for the recognition of human genes in DNA. In Proceedings of the Conference on Intelligent Systems in Molecular Biology(1996). AAAI Press, Menlo Park, Calif., 1996.8.Rabiner, L.R. A tutorial on hidden Markov models and select-ed applications in speech recognition. Proc. IEEE 77 (1989), 257–286.9.Snyder, E.E., and Stormo, G.D. Identification of coding regionsin genomic DNA sequences: An application of dynamic pro-gramming and neural networks. Nucleic Acids Res. 21 (1993), 607–613.10.Stolorz, P., and Dean, C. Quakefinder: A scalable data miningsystem for detecting earthquakes from space. In Proceedings of the 2nd International Conference on Knowledge Discovery and Data Mining (Portland, Oreg., 1996), AAAI Press, Menlo Park, Calif., 1996.11.Stolorz, P., Nakamura, H. Mesrobian, E., Muntz, R.R., Shek,E.C., Mechoso, C.R., Farrara, J.D. Fast spatiotemporal datamining of large. geophysical datasets. In Proceedings of the 1st International Conference on Knowledge Discovery and Data Mining (Montréal, Aug. 1995), AAAI Press, Menlo Park, Calif. 1995, pp. 300–305.12. Weir, N., Fayyad, U.M., and Djorgovski, S.G. Automatedstar/galaxy classification for digitized POSS-II. Astron. J. 109, 6 (1995), 2401–2412.13.Weir, N., Djorgovski, S.G., and Fayyad, U.M. Initial galaxycounts from digitized POSS-II. Astron. J. 110, 1 (1995), 1–20.Additional references for this article can be found at /research/datamine/CACM-DM-refs/.USA MA FA YYA D is senior researcher at Microsoft and a Distin-guished Visiting Scientist at the Jet Propulsion Laboratory, Califor-nia Institute of Technology. He can be reached at fayyad@.DAVID HAUSSLER is a professor of computer science at the Uni-versity of California, Santa Cruz. He can be reached at haussler@.PAUL STOLORZ is technical group supervisor at the Jet Propul-sion Laboratory, California Institute of Technology. He can be reached at pauls@.Permission to make digital/hard copy of part or all of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage, the copyright notice, the title of the publication and its date appear, and notice is given that copying is by permission of ACM, Inc. To copy otherwise, to republish, to post on servers, or to redistribute to lists requires prior specific permission and/or a fee.© ACM 0002-0782/96/1100 $3.50COMMUNICATIONS OF THE ACM November 1996/Vol. 39, No. 1157。
Quantitative Data Analysis- Questionnaire Design

Professional and Academic Skills(PAS)-2Week-3Quantitative Data Analysis- Questionnaire Design andLevel MeasurementDate: 10/02/2020v Collecting Quantitative Data using Questionnaire v Questionnaire Designv Pilot Questionnairev Level of Measurement: Categorical Variable and Continuous Variablev Identify the main issues that you need to consider when preparing quantitative data for analysisCollecting Primary Data using QuestionnaireØQuestionnaire:“is a method/technique of data collection in which each person is asked to respond to same set of questions in a predetermined order”(De Vaus, 2014)Ø “It also widely used as an instrument” (Ekinci, 2015)ØIt provides efficient way of collecting responses from a large sample prior to quantitative analysisTypes of QuestionnaireSource: Saunders (2016)Advantages and disadvantages of questionnaireAdvantages◦Large sample size – can be collected relatively quickly◦Cost effective- large sample of the population can be contacted at relative cost◦Analysis easier and visualisation – closed questions are easier to analyse◦Anonymity- allows respondents to maintain their anonymity◦If completed anonymously and in private then personal questions may receive more valid answersDisadvantages◦Difficult for respondents to provide deep reasons behind consumers behaviour◦Unanswered questions- some questions will be ignored and left unanswered◦Dishonest answer- they may not be 100% truthful with their answers◦Respondents under no/little pressure to complete and return◦No flexibility re questions posed and no supplementary options available-Things to Consider to Produce a Good QuestionnaireüTo ensure that it will collect precise data that you require to answer your research question(s) and your research objectivesüYou are unlikely to have more than one opportunity to collect the dataüDesign of your questionnaire will affect the response rate and the reliability of the data you collect (clear, specific and unambiguous)üEasy questions at the start and open questions at endüFar more closed than open questionsü Types of questions you need to ask to collect your dataüNumber of questions you need to ask to collect your dataüVisual presentation of the questionnaire- Colourful, artistic appearance of the questionnaireValidity and ReliabilityValidity: refers to the ability of your questionnaire to measure what you intend to measure also know as measurement validity.Reliability- refers to the consistency of the research method used, For example if the same method was used again would it lead to the same data collected.For a questionnaire to be valid it must be reliableValidity and reliability of the data you collect and the response rate you achieve depend largely on the:- Design of your questions- Structure of your questionnaire- and the rigor of your pilot testingFactors that can impact ReliabilityØParticipants errorØParticipants biasØResearcher errorØResearcher biasHow many questions should a questionnaire have?◦For your MA dissertation time taken to complete the questionnaire should not exceed 10 -12 minutes.◦Effective design of the questions should allow you to include all necessary questions for your final project and should consist maximum 15-20 questions.How many need to be collected ?◦Around a minimum of 100 for your MA dissertation when conducting a mono method.Constructing your Questions- Closed and Open questionsOpen questions- refer to as open ended questions, allow respondents to give answers in their own wayFink (2013) Closed questions- refer to closed-ended questions or forced-choice questions, provide a number of alternative answers from which the respondent is instructed to choose. It is easier,quicker and require minimal writingThere are 6 types of closed questions:List question: where the respondent is offered a list of items, any of which may be selectedCategory question: where only one response can be selected from a given set of categoriesRanking question: where the respondent is asked to place something in orderRating question: in which a rating device is used to record responsesQuantity question: to which the response is a number giving the amountMatrix question: where responses to two or more questions can be collected using the same gridSource: Saunders, 2016Rating /Likert Scale questionsCategory questionQuantity questionSemantic differential Rating question- Series of bi-polar adjectives between which underlined spaces areprovided for the recipient to record their views/feelings.Example of Rank questionExample of Matrix QuestionConstructing the QuestionnaireØExplaining the purpose of the questionnairev Covering letter or welcome screen:self-completed questionnaires should be accompanied by a covering letter, email, text or SMS message which explains the purpose of of the surveyv Introducing the questionnaire- explain clearly and concisely why you want the respondents to complete the surveyExample of Introduction for Interviewer-completed questionnaire….Lavrakas, 2016Closing the QuestionnaireØ at the end of the questionnaire you will need to explain clearly what you want your respondents to do with their completed questionnaire.Example:Saunders, 2016Pilot Testing and Assessing ValidityThe purpose of the pilot testing is to refine questionnaire so that the respondents will have no problems in answering the questions and there will be no problem in recording the dataØIt helps you to obtain some assessment of the questions, validity and likely reliability of the dataØTo ensure that the data collected will enable your investigative questions to be answeredØfor student questionnaire minimum number of a pilot is 10 (Flink, 2013)To ensure questionnaire’s face validity, as part of your Pilot you should try to get additional information about (Bell and Waters, 2014)-üHow long the question took to completeüthe clarity of the instructionüWhich, if any, questions were ambiguousüWhich, if any, question the respondents felt uneasyüwhether in the layout was clear and attractiveüany other commentsInternet QuestionnaireFor both Web and Mobile questionnaire:ØIt is important to have clear timetable that identifies the tasks need to be doneØA good response will depend on the recipient being motivated to answer the questionnaire and to send it backØEmail or SMS message and visual appearance will help to ensure a high level of responseØQuestionnaire design must be clear across all display mediaData collection- what to measureIf you intend to undertake quantitative analysis then you should consider:v The number of cases of data (sample size)v Type or types of data (scale of measurement)v Data layout and format required by the analysis softwarev Impact of data coding on subsequent analysis (for different types ofdata)v Process and checking the data error (checking your data for out of range values)When you collect data you need to decide on two thingsv What to measurev How to measureWhat to Measurev Usually we collect several measures on each person or thing of interestv Each thing we collect data about is called an observationv Each observation can be a person or an organisation, a product or a period in time Factual or demographic variables- age, gender, education, occupation, incomeAttitudes or opinion variables- record how respondents feel about something, or what they think is true or falsev Behaviour or event variables- contain data about what people did or what happened in past, happening or will happen in the future.Data collection- what to measure continue …..VariablesObservations Age SexIncome Brand preference 20Female 10,000Zara 30Female 35,000Cartier25Male 25,000 SuperdryLevel of MeasurementLevel of measurement: is the relationship between what is being measured and the numbers that represent what is being measured Variables can take many forms and levels. Quantitative data can be divided into two distinct groups:v Categorical variable◦Descriptive or Nominal data◦Ranked datav Numerical variable◦Continuous data◦Discrete DataCategorical DataCategorical data- refer to data whose values can not be measured numerically but can be classified into sets (categories) according to the characteristics that identify or describe the variable or placed in rank order (Brown and Saunders, 2008)i.e. your species (human, domestic cat, fruit bat), race, sex, age group, and educational levelv Descriptive/Nominal data- these data simply count the number of occurrences in each category of a variable. (a car manufacturer may categorize the types of cars as hatchback, Saloon and estate)Binary/dichotomous variable: a sub-type of nominal scale with only two categories.It names two distinct types of things such as: Male or Female, Dead or Alive; Yes or NoCategorical Data continuous…….v Ranked/ordinal variable- precise form of categorical data. When categories are ordered, the variable is known as an ordinal variable.v Ordinal variables will tell us the things that happenedv The order in which things occurredv But this data will not tell us differences between the values/points on a scaleExample 1- beauty pageant winners- first, second and thirdExample-2 : satisfaction levelUnsatisfied Very unsatisfied Very Satisfied Satisfied Somewhatsatisfied123 45Examples of Nominal and ordinal DataNumerical Variablev Numerical variables are those whose values are measured or counted numerically as quantities . (Brown and Saunders, 2008).v These data are more precise than categorical data as you can assign each data valuea position on a numerical scaleTypes of Numerical variable:v Continuous variable-a variable that has a changing value and it can take on infinitely many, uncountable number. i.e. time, a person’s weight, Age, number of customers etcv Interval data: for data to be interval, we must be certain that data on scalerepresent equal differences in the property being measured. (i.e. measure averageday time temperature during summer in London- 60-70 degrees Fahrenheit, 80-90….)Numerical Data continues ……v Ratio data : a ratio variable has all the properties of an interval variable, and also has an absolute value of 0.v Discrete variable- can take only certain values. Usually the whole number on the scale. i.e.v Example:rating your confidence level on 5 point scale.Number of Customers-12Number of shops- 10Number of friends- 8Stress Level0 1 2 3 4 5 6 7 8 9 10Seminar ActivityActivity-1:Demonstrate your choice of data collection method(s) that you plan to adopt in your study.Activity-2-In small groups, discuss about different types of questionnaire and which one you are likely to use.- What are the main attributes of questionnaires discussed on this PPT?-What scale of measurement questions you are likely to use in you questionnaire, provide at least three examples of Rating scales questions.。
英语中名词的定义

英语中名词的定义Nouns are a fundamental part of speech in the English language, serving as the building blocks for constructing meaningful sentences and conveying ideas. A noun is a word that names a person, place, thing, or idea. Nouns can be singular or plural, common or proper, and can take on various grammatical roles within a sentence. Understanding the definition and function of nouns is crucial for effective communication and comprehension in the English language.At the most basic level, a noun is a word that represents a tangible or intangible entity. Tangible nouns refer to physical objects that can be perceived through the senses, such as a book, a chair, or a mountain. Intangible nouns, on the other hand, represent abstract concepts, emotions, or ideas that cannot be physically touched or seen, such as love, justice, or freedom.Nouns can be classified into several subcategories based on their characteristics and usage. One of the most fundamental distinctions is between common nouns and proper nouns. Common nouns are general names that refer to a class or group of people, places, orthings, such as dog, city, or flower. Proper nouns, on the other hand, are specific names that identify a particular person, place, or thing, such as Fido, New York, or Rose.Another important distinction is between singular and plural nouns. Singular nouns refer to a single entity, while plural nouns refer to more than one of the same entity. In English, the majority of plural nouns are formed by adding an "-s" or "-es" to the end of the singular form, as in "book" becoming "books" or "box" becoming "boxes." However, there are also many irregular plural forms, such as "child" becoming "children" or "mouse" becoming "mice."Nouns can also be classified based on their grammatical function within a sentence. For example, a subject noun is the noun that performs the action of the verb in a sentence, such as "The dog barked." An object noun, on the other hand, receives the action of the verb, as in "The boy threw the ball." Nouns can also serve as the complement of a sentence, providing additional information about the subject or object, as in "She is a teacher."In addition to their grammatical roles, nouns can also be modified by other parts of speech, such as adjectives, which provide additional information about the noun, or possessive pronouns, which indicate ownership or association with the noun. For instance, in the sentence "The large dog chased the small cat," the nouns "dog" and "cat" aremodified by the adjectives "large" and "small," respectively.Nouns also play a crucial role in the formation of compound words, which are words created by combining two or more existing words. Examples of compound nouns include "sunflower," "bookshelf," and "heartache." These compound nouns often represent a single, unified concept that is distinct from the individual words that make up the compound.Furthermore, nouns can be further classified based on their semantic properties, such as abstract or concrete nouns, collective nouns, and mass nouns. Abstract nouns refer to intangible concepts, such as "love" or "justice," while concrete nouns represent tangible objects that can be perceived through the senses. Collective nouns, such as "team" or "herd," refer to a group of individuals or items, while mass nouns, such as "water" or "sand," represent a substance that cannot be easily counted or divided into individual units.The importance of nouns in the English language cannot be overstated. Nouns are the foundation upon which sentences are built, allowing us to name and identify the people, places, things, and ideas that are central to our communication and understanding of the world around us. Without nouns, our ability to express ourselves and convey meaning would be severely limited.In conclusion, the definition of a noun in English encompasses a wide range of words that represent tangible and intangible entities, as well as the various subcategories and grammatical functions that nouns can serve. Mastering the understanding and use of nouns is a crucial aspect of developing proficiency in the English language, as they are the building blocks of effective communication and expression.。
Automatically Constructing a Dictionary for Information Extraction Tasks

Automatically Constructing a Dictionary for InformationExtraction TasksEllen RiloffDepartment of Computer ScienceUniversity of MassachusettsAmherst,MA01003riloff@Proceedings of the Eleventh National Conference on Artificial Intelligence,1993,AAAI Press/MIT Press,pages811–816.AbstractKnowledge-based natural language processing systems have achieved good success with certain tasks but they are of-ten criticized because they depend on a domain-specific dictionary that requires a great deal of manual knowledge engineering.This knowledge engineering bottleneck makes knowledge-based NLP systems impractical for real-world applications because they cannot be easily scaled up or ported to new domains.In response to this problem,we devel-oped a system called AutoSlog that automatically builds a domain-specific dictionary of concepts for extracting infor-mation from ing AutoSlog,we constructed a dictio-nary for the domain of terrorist event descriptions in only5 person-hours.We then compared the AutoSlog dictionary with a hand-crafted dictionary that was built by two highly skilled graduate students and required approximately1500 person-hours of effort.We evaluated the two dictionaries using two blind test sets of100texts each.Overall,the AutoSlog dictionary achieved98%of the performance of the hand-crafted dictionary.On thefirst test set,the Auto-Slog dictionary obtained96.3%of the performance of the hand-crafted dictionary.On the second test set,the over-all scores were virtually indistinguishable with the AutoSlog dictionary achieving99.7%of the performance of the hand-crafted dictionary.IntroductionKnowledge-based natural language processing(NLP)sys-tems have demonstrated strong performance for informa-tion extraction tasks in limited domains[Lehnert and Sund-heim,1991;MUC-4Proceedings,1992].But enthusiasm for their success is often tempered by real-world concerns about portability and scalability.Knowledge-based NLP systems depend on a domain-specific dictionary that must be carefully constructed for each domain.Building this dic-tionary is typically a time-consuming and tedious process that requires many person-hours of effort by highly-skilled people who have extensive experience with the system.Dic-tionary construction is therefore a major knowledge engi-neering bottleneck that needs to be addressed in order for information extraction systems to be portable and practical for real-world applications.We have developed a program called AutoSlog that au-tomatically constructs a domain-specific dictionary for in-formation extraction.Given a training corpus,AutoSlog proposes a set of dictionary entries that are capable of ex-tracting the desired information from the training texts.If the training corpus is representative of the targeted texts,the dictionary created by AutoSlog will achieve strong perfor-mance for information extraction from novel texts.Given a training set from the MUC-4corpus,AutoSlog created a dictionary for the domain of terrorist events that achieved 98%of the performance of a hand-crafted dictionary on2 blind test sets.We estimate that the hand-crafted diction-ary required approximately1500person-hours to build.In contrast,the AutoSlog dictionary was constructed in only 5person-hours.Furthermore,constructing a dictionary by hand requires a great deal of training and experience whereas a dictionary can be constructed using AutoSlog with only minimal training.We will begin with an overview of the informationextrac-tion task and the MUC-4performance evaluation that moti-vated this work.Next,we will describe AutoSlog,explain how it proposes dictionary entries for a domain,and show examples of dictionary definitions that were constructed by AutoSlog.Finally,we will present empirical results that demonstrate AutoSlog’s success at automatically creating a dictionary for the domain of terrorist event descriptions.Information Extraction from Text Extracting information from text is a challenging task for natural language processing researchers as well as a key problem for many real-world applications.In the last few years,the NLP community has made substantial progress in developing systems that can achieve good performance on information extraction tasks for limited domains.As op-posed to in-depth natural language processing,information extraction is a more focused and goal-oriented task.For example,the MUC-4task was to extract information about terrorist events,such as the names of perpetrators,victims, instruments,etc.Our approach to information extraction is based on a tech-nique called selective concept extraction.Selective conceptextraction is a form of text skimming that selectively pro-cesses relevant text while effectively ignoring surrounding text that is thought to be irrelevant to the domain.The work presented here is based on a conceptual sentence analyzer called CIRCUS[Lehnert,1990].To extract information from text,CIRCUS relies on a domain-specific dictionary of concept nodes.A concept node is essentially a case frame that is triggered by a lexical item and activated in a specific linguistic context.Each concept node definition contains a set of enabling condi-tions which are constraints that must be satisfied in order for the concept node to be activated.For example,our dictionary for the terrorism domain contains a concept node called$kidnap-passive$that extracts information about kid-napping events.This concept node is triggered by the word “kidnapped”and has enabling conditions that allow it to be activated only in the context of a passive construction. As a result,this concept node is activated by phrases such as“was kidnapped”,“were kidnapped”,etc.Similarly,the dictionary contains a second concept node called$kidnap-active$which is also triggered by the word“kidnapped”but has enabling conditions that allow it to be activated only in the context of an active construction,such as“terrorists kidnapped the mayor”.In addition,each concept node definition contains a set of slots to extract information from the surrounding context. In the terrorism domain,concept nodes have slots for perpe-trators,victims,instruments,etc.Each slot has a syntactic expectation and a set of hard and soft constraints for its filler.The syntactic expectation specifies where thefiller is expected to be found in the linguistic context.For example, $kidnap-passive$contains a victim slot that expects itsfiller to be found as the subject of the clause,as in“the mayor was kidnapped”.The slot constraints are selectional restrictions for the slotfiller.The hard constraints must be satisfied in order for the slot to befilled,however the soft constraints suggest semantic preferences for the slotfiller so the slot may befilled even if a soft constraint is violated.Given a sentence as input,CIRCUS generates a set of instantiated concept nodes as its output.If multiple trigger-ing words appear in a sentence then CIRCUS can generate multiple concept nodes for that sentence.However,if no triggering words are found in a sentence then CIRCUS will generate no output for that sentence.The concept node dictionary is at the heart of selective concept extraction.Since concept nodes are CIRCUS’only output for a text,a good concept node dictionary is crucial for effective information extraction.The UMass/MUC-4system[Lehnert et al.,1992a]used2dictionaries:a part-of-speech lexicon containing5436lexical definitions, including semantic features for domain-specific words and a dictionary of389concept node definitions for the domain of terrorist event descriptions.The concept node dictionary was manually constructed by2graduate students who had extensive experience with CIRCUS and we estimate that it required approximately1500person-hours of effort to build.The MUC-4Task and CorpusIn1992,the natural language processing group at the Uni-versity of Massachusetts participated in the Fourth Message Understanding Conference(MUC-4).MUC-4was a com-petitive performance evaluation sponsored by DARPA to evaluate the state-of-the-art in text analysis systems.Sev-enteen sites from both industry and academia participated in MUC-4.The task was to extract information about terror-ist events in Latin America from newswire articles.Given a text,each system was required tofill out a template for each terrorist event described in the text.If the text de-scribed multiple terrorist events,then one template had to be completed for each event.If the text did not mention any terrorist events,then no templates needed to befilled out.A template is essentially a large case frame with a set of pre-defined slots for each piece of information that should be extracted from the text.For example,the MUC-4templates contained slots for perpetrators,human targets,physical targets,etc.A training corpus of1500texts and instantiated templates(answer keys)for each text were made available to the participants for development purposes.The texts were selected by keyword search from a database of newswire articles.Although each text contained a keyword associated with terrorism,only about half of the texts contained a specific reference to a relevant terrorist incident.Behind the Design of AutoSlogTwo observations were central to the design of AutoSlog. Thefirst observation is that news reports follow certain stylistic conventions.In particular,the most important facts about a news event are typically reported during the ini-tial event description.Details and secondary information are described later.It follows that thefirst reference to a major component of an event(e.g.,a victim or perpetra-tor)usually occurs in a sentence that describes the event. For example,a story about a kidnapping of a diplomat will probably mention that the diplomat was kidnapped before it reports secondary information about the diplomat’s fam-ily,etc.This observation is key to the design of AutoSlog. AutoSlog operates under the assumption that thefirst refer-ence to a targeted piece of information is most likely where the relationship between that information and the event is made explicit.Once we have identified thefirst sentence that contains a specific piece of information,we must determine which words or phrases should activate a concept node to ex-tract the information.The second key observation behind AutoSlog is that the immediate linguistic context surround-ing the targeted information usually contains the words or phrases that describe its role in the event.For example, consider the sentence“A U.S.diplomat was kidnapped by FMLN guerrillas today”.This sentence contains two impor-tant pieces of information about the kidnapping:the victim (“U.S.diplomat”)and the perpetrator(“FMLN guerrillas”). In both cases,the word“kidnapped”is the key word that relates them to the kidnapping event.In its passive form, we expect the subject of the verb“kidnapped”to be a victim and we expect the prepositional phrase beginning with“by”to contain a perpetrator.The word“kidnapped”specifies the roles of the people in the kidnapping and is therefore the most appropriate word to trigger a concept node. AutoSlog relies on a small set of heuristics to determine which words and phrases are likely to activate useful con-cept nodes.In the next section,we will describe these heuristics and explain how AutoSlog generates complete concept node definitions.Automated Dictionary Construction Given a set of training texts and their associated answer keys,AutoSlog proposes a set of concept node definitions that are capable of extracting the information in the answer keys from the texts.Since the concept node definitions are general in nature,we expect that many of them will be useful for extracting information from novel texts as well. The algorithm for constructing concept node definitions is as follows.Given a targeted piece of information as a string from a template,AutoSlogfinds thefirst sentence in the text that contains the string.This step is based on the observation noted earlier that thefirst reference to an object is likely to be the place where it is related to the event.The sentence is then handed over to CIRCUS which generates a conceptual analysis of the ing this analysis,AutoSlog identifies thefirst clause in the sentence that contains the string.A set of heuristics are applied to the clause to suggest a good conceptual anchor point for a concept node definition.If none of the heuristics is satisfied then AutoSlog searches for the next sentence in the text that contains the targeted information and the process is repeated.The conceptual anchor point heuristics are the most im-portant part of AutoSlog.A conceptual anchor point is a word that should activate a concept;in CIRCUS,this is a triggering word.Each heuristic looks for a specific lin-guistic pattern in the clause surrounding the targeted string. The linguistic pattern represents a phrase or set of phrases that are likely to be good for activating a concept node.If a heuristic successfully identifies its pattern in the clause then it generates two things:(1)a conceptual anchor point and(2)a set of enabling conditions to recognize the com-plete pattern.For example,suppose AutoSlog is given the clause“the diplomat was kidnapped”along with“the diplomat”as the targeted string.The string appears as the subject of the clause and is followed by a passive verb“kid-napped”so a heuristic that recognizes the pattern<subject> passive-verb is satisfied.The heuristic returns the word “kidnapped”as the conceptual anchor point along with en-abling conditions that require a passive construction.To build the actual concept node definition,the concep-tual anchor point is used as its triggering word and the enabling conditions are included to ensure that the concept node is activated only in response to the desired linguistic pattern.For the example above,thefinal concept node will be activated by phrases such as“was kidnapped”,“were kidnapped”,“have been kidnapped”,etc.The current version of AutoSlog contains13heuristics, each designed to recognize a specific linguistic pattern.These patterns are shown below,along with examples that illustrate how they might be found in a text.The bracketed item shows the syntactic constituent where the string was found which is used for the slot expectation(<dobj>is the direct object and<np>is the noun phrase followinga prepo-sition).In the examples on the right,the bracketed item is a slot name that might be associated with thefiller(e.g.,the subject is a victim).The underlined word is the conceptual anchor point that is used as the triggering word.Linguistic Pattern Examplesubject passive-verb victim was murdered subject verb infinitive perpetrator attempted to killpassive-verb dobj killedtargetinfinitive dobj to killtarget gerund dobj killingwas victimnoun prep np bombwith instrument passive-verb prep np was aimedIn principle,passive verbs should not have objects.However, we included this pattern because CIRCUS occasionally confused active and passive constructions.In principle,concept nodes can have multiple slots to extract multiple pieces of information.However,all of the concept nodes generated by AutoSlog have only a single slot.appear in sentences that do not describe the nature of the event(e.g.,“The FMLN claimed responsibility”could refer to a bombing,kidnapping,etc.).Sample Concept Node DefinitionsTo illustrate how this whole process comes together,we will show some examples of concept node definitions gen-erated by AutoSlog.Figure1shows a relatively simple concept node definition that is activated by phrases such as “was bombed”,“were bombed”,etc.AutoSlog created this definition in response to the input string“public buildings”which was found in the physical target slot of a bombing template from text DEV-MUC4-0657.Figure1shows the first sentence in the text that contains the string“public buildings”.When CIRCUS analyzed the sentence,it iden-tified“public buildings”as the subject of thefirst clause. The heuristic for the pattern<subject>passive-verb then generated this concept node using the word“bombed”as its triggering word along with enabling conditions that require a passive construction.The concept node contains a single variable slot which expects itsfiller to be the subject of the clause(*S*)and labels it as a target because the string came from the physical target template slot.The constraints for physical targets are pulled in from the domain specifica-tions.Finally,the concept node is given the type bombing because the input string came from a bombing template. Id:DEV-MUC4-0657Slotfiller:“public buildings”Sentence:(in la oroya,junin department,in the central peruvian mountain range,public buildingsVariable slots are slots that extract information.Constant slots have pre-defined values that are used by AutoSlog only to specify the concept node type.template slot).The constraints associated with perpetra-tors are incorporated and the concept node is assigned the type“perpetrator”because our domain specifications map the perpetrator template slots to perpetrator types in con-cept nodes.Note that this concept node does not extract the direct object of“threatened to murder”as a victim.We would need a separate concept node definition to pick up the victim.Id:DEV-MUC4-0071Slotfiller:“guerrillas”Sentence:(the salvadoran guerrillas1219,son of patricio rodriguez,and17-year-old andres argueta,son of emimesto argueta.)CONCEPT NODEName:victim-active-verb-dobj-took Trigger:tookVariable Slots:(victim(*DOBJ*1))Constraints:(class victim*DOBJ*)Constant Slots:(type kidnapping)Enabling Conditions:((active))Figure3:A bad concept node definition AutoSlog generates bad definitions for many reasons, such as(a)when a sentence contains the targeted string but does not describe the event(i.e.,ourfirst observation mentioned earlier does not hold),(b)when a heuristic pro-poses the wrong conceptual anchor point or(c)when CIR-CUS incorrectly analyzes the sentence.These potentially dangerous definitions prompted us to include a human inthe loop to weed out bad concept node definitions.In the following section,we explain our evaluation procedure and present empirical results.Empirical ResultsTo evaluate AutoSlog,we created a dictionary for the do-main of terrorist event descriptions using AutoSlog and compared it with the hand-crafted dictionary that we used in MUC-4.As our training data,we used1500texts and their associated answer keys from the MUC-4corpus.Our targeted information was the slotfillers from six MUC-4 template slots that contained stringfills which could be eas-ily mapped back to the text.We should emphasize that AutoSlog does not require or even make use of these com-plete template instantiations.AutoSlog needs only an an-notated corpus of texts in which the targeted information is marked and annotated with a few semantic tags denoting the type of information(e.g.,victim)and type of event(e.g., kidnapping).The1258answer keys for these1500texts contained 4780stringfillers which were given to AutoSlog as input along with their corresponding texts.In response to these strings,AutoSlog generated1237concept node definitions. AutoSlog does not necessarily generate a definition for ev-ery stringfiller,for example if it has already created an identical definition,if no heuristic applies,or if the sentence analysis goes wrong.As we mentioned earlier,not all of the concept node definitions proposed by AutoSlog are good ones.Therefore we put a human in the loop tofilter out definitions that might cause trouble.An interface displayed each dictionary definition proposed by AutoSlog to the user and asked him to put each definition into one of two piles:the“keeps”or the“edits”.The“keeps”were good definitions that could be added to the permanent dictionary without alteration. The“edits”were definitions that required additional editing to be salvaged,were obviously bad,or were of questionable value.It took the user5hours to sift through all of the definitions.The“keeps”contained450definitions,which we used as ourfinal concept node dictionary.Finally,we compared the resulting concept node dictionary with the hand-crafted dictionary that we used for MUC-4.To ensure a clean comparison,we tested the AutoSlog dictionary using the official version of our UMass/MUC-4system.The resulting“AutoSlog”system was identical to the official UMass/MUC-4system except that we replaced the hand-crafted concept node dictionary with the new AutoSlog dictionary.We evaluated both sys-tems on the basis of two blind test sets of100texts each.Recall F-measure4650.514348.654441.903941.79Table1:Comparative ResultsThe official UMass/MUC-4system was among the top-performing systems in MUC-4[Lehnert et al.,1992b]and the results in Table1show that the AutoSlog dictionary achieved almost the same level of performance as the hand-crafted dictionary on both test paring F-measures, we see that the AutoSlog dictionary achieved96.3%of the performance of our hand-crafted dictionary on TST3,and 99.7%of the performance of the official MUC-4system on TST4.For TST4,the F-measures were virtually indis-tinguishable and the AutoSlog dictionary actually achieved better precision than the original hand-crafted dictionary. We should also mention that we augmented the hand-crafted dictionary with76concept nodes created by AutoSlog be-fore thefinal MUC-4evaluation.These definitions im-proved the performance of our official system byfilling gaps in its coverage.Without these additional concept nodes,the AutoSlog dictionary would likely have shown even better performance relative to the MUC-4dictionary.ConclusionsIn previous experiments,AutoSlog produced a concept node dictionary for the terrorism domain that achieved90%of the performance of our hand-crafted dictionary[Riloff and Lehnert,1993].There are several possible explanations for the improved performance we see here.First,the previ-ous results were based on an earlier version of AutoSlog. Several improvements have been made to AutoSlog since then.Most notably,we added5new heuristics to recognize additional linguistic patterns.We also made a number of improvements to the CIRCUS interface and other parts of the system that eliminated many bad definitions and gener-ally produced better results.Another important factor was the human in the loop.We used the same person in both experiments but,as a result,he was more experienced the second time.As evidence,hefinished thefiltering task in only5hours whereas it took him8hours thefirst time. AutoSlog is different from other lexical acquisition sys-tems in that most techniques depend on a“partial lexicon”as a starting point(e.g.,[Carbonell,1979;Granger,1977; Jacobs and Zernik,1988]).These systems construct a def-inition for a new word based on the definitions of other words in the sentence or surrounding context.AutoSlog, however,constructs new dictionary definitions completely from scratch and depends only on a part-of-speech lexicon, which can be readily obtained in machine-readable form. Since AutoSlog creates dictionary entries from scratch, our approach is related to one-shot learning.For exam-ple,explanation-based learning(EBL)systems[DeJong and Mooney,1986;Mitchell et al.,1986]create complete con-cept representations in response to a single training instance. This is in contrast to learning techniques that incremen-tally build a concept representation in response to multi-ple training instances(e.g.,[Cardie,1992;Fisher,1987; Utgoff,1988]).However,explanation-based learning sys-tems require an explicit domain theory which may not be available or practical to obtain.AutoSlog does not need any such domain theory,although it does require a few simple domain specifications to build domain-dependent concept nodes.On the other hand,AutoSlog is critically dependent on a training corpus of texts and targeted information.We used the MUC-4answer keys as training data but,as we noted earlier,AutoSlog does not need these complete template instantiations.AutoSlog would be just as happy with an “annotated”corpus in which the information is marked and tagged with event and type designations.NLP systems often rely on other types of tagged corpora,for example part-of-speech tagging or phrase structure bracketing(e.g., the Brown Corpus[Francis and Kucera,1982]and the Penn Treebank[Marcus et al.]).However,corpus tagging for automated dictionary construction is less demanding than other forms of tagging because it is smaller in scope.For syntactic tagging,every word or phrase must be tagged whereas,for AutoSlog,only the targeted information needs to be tagged.Sentences,paragraphs,and even texts that are irrelevant to the domain can be effectively ignored.We have demonstrated that automated dictionary con-struction is a viable alternative to manual knowledge en-gineering.In5person-hours,we created a dictionary that achieves98%of the performance of a hand-crafted dictio-nary that required1500person-hours to build.Since our approach still depends on a manually encoded training cor-pus,we have not yet eliminated the knowledge engineering bottleneck.But we have significantly changed the nature of the bottleneck by transferring it from the hands of NLP ex-perts to novices.Our knowledge engineering demands canRiloff,E.and Lehnert,W.1993.Automated Dictionary Con-struction for Information Extraction from Text.In Proceedings of the Ninth IEEE Conference on Artificial Intelligence for Ap-plications.IEEE Computer Society Press.93–99.Utgoff,P.1988.ID5:An Incremental ID3.In Proceedingsof the Fifth International Conference on Machine Learning.107–120.。
中外翻译理论期末考试点

中外翻译理论考点△重点1.John Fryer(傅兰雅)(British)Translates more practical aspects of Euro-American science and technology into late imperial China.(Editor of The Chinese Scientific Magazine《格致汇编》)Mirroring the Origins of Chemistry《化学鉴原》Chemical Analyse《化学考质》An Introduction to Chemistry《化学初阶》Methods of translating(to establish a systematic nomenclature based on 3 linguistic choices):(1)Using existing nomenclature(系统命名法) from native works on the arts and science;(2)Coining new terms by creating a new character, inventing an descriptive term, or phoneticizing a Western term according to the Mandarin dialect;(3)Constructing a general vocabulary list of terms and proper names.-Why Xu Shou and John Fryer’s translated names for the elements are still in use? -Because their method of translation was quite rational and not simply.2.Lin Shu——famous for introducing the Western literary works into ChineseBorn in Fujian Province in 1852 and received the provincial graduate(举人)The most influential works:La Dame Aux Camelias《巴黎茶花女遗事》;Oliver Twist《贼史》Uncle Tom’s Cabin《黑奴吁天录》The first person to bring many of the important works of Western literature to the attention to the Chinese for the first time and Chinese began to appreciate the value of Western fiction.Translation motives:(1)to cultivate patriotism: his translation intentions were to save the nation from subjugation and ensure its survival;(2)To educate the public: he hopes that the Chinese people could learn the pioneering spirit from reading the translation of the novel.Translation Methods:(1)Omission(considering the Chinese culture and the Chinese reader’s reception): delete some contents for the sake of Chinese literary norms and Chinese reader’staste;(2)Addition(considering reader’s expectation): to publish and improve the original and also to help the readers to understand the original and the Western tradition, making the translation more interesting and attractive and appealing; (3)Alteration(considering the Chinese reader’s aesthetic tendencies): due to the social and cultural differences between the source and target languages, he made some compensation or replacement;(4)Adaptation(considering the feudal Chinese ethics)Criticism of his Translations:(1)the choice of the source text(2)Mistranslation and Incorrect OmissionContributions of his Translation:(1)to reconsider the value of fiction as a genre(2)To change people’s disregard of foreign literature(3)To exert a tremendous influence on later generation3.Fu LeiSome of his translations:Eugenie Grandet《欧也妮·葛朗台》Le Pere Goriot《高老头》Jean Christophe 《约翰·克里斯多夫》Translation Ideas:(1)Spiritual Resemblance Theory: In terms of effect, translation should be the same as copying painting, for what is searched for is spiritual similarity rather than formal similarity; Translation would be easy if breaking the structure, and characteristics of the native language could convey the features of the foreign language and obtain the original spirit; The meaning and spirit of the original, the fluency and integrity of the translation could be combined in one.(2)Translating as a holy career: Those who are not poets should not translate poetry, for what they produce will not only be unpoetic and it will not be like prose either; Measures of our adaptability: our enthusiasm about the original work since emotional interest affects understanding and our artistic insight.Whatever the style of the original, it will always be unified and coherent.(3)Language of translation: paying too much attention to grammar, syntax and style is definitely not conductive to the creation of great works.He can hardly achieve translating it into Chinese to convey the tone of the original text and reproducing the mood and atmosphere in the translation.But it can serve as an important link between what goes before and what comes after in the original text.4.Qian Zhongshu(Fortess Besieged)Works of translation: On the Art of Poetry《谈艺录》;The Pipe-Awl Chapters《管锥编》Translation Ideals:Realm of transformation(化境):describes what an ideal translation is like, differentiates the good translation from the bad, and contains hidden echoes of similar terminology from traditional Chinese poetics and art criticism.(1)The highest standard in literary translation is “化”, transforming a work from the language of one country into that of another, this could be done without betraying ant evidence of artifice by virtue of divergences in language and speech habits, besides, preserving intact the flavor of the original.(2) a translation should cleave to the original with such fidelity that it would not read like a translation, for a literary work in its own language will never read as though it has been through a process of translation.(与奈达的动态对等理论相似)(3)Misrepresentation:讹.The words transmit and entice explain how translation functions in cultural interchange; it acts as a middleman, a liaison as though playing the role of matchmaker and bringing about a “literary romance”between nations.(4)Translation was to save people the trouble of learning foreign languages and reading the original works,but now it entices the readers into doing the very thing. It arouses the reader’s curiosity, causing them to yearn for the original.(5)The Chinese character for “translation”译has etymological and associative connections with the characters for “seduction”诱,“error”讹,“mediator”媒 and “transformation”化(6)Sublimity,化: changing the form and retaining the content and style or spirit at the same time; a translation should be both smooth and idiomatic in the target language; should be faithful to the original in content or spirit and style;is an all but unrealizable ideal.5.JakobsonHe experimented with “supraconscious”(超意识的)poems, the co-founder of both the Moscow Linguistic Circle and the Prague Linguistic Circle.His essay “On Linguistic Aspects of Translation” extends the significance of translation to include intralingual and intersemiotic translation.His emphasis on the functional role of linguistic elements in the translated text had a positive effect on the work of poetry translators3 kinds of translation are to be differently labeled:(1)Intralingual translation or rewording is an interpretation of verbal signs by means of other signs of the same language;(2)Interlingual translation or translation proper is an interpretation of verbal signs by means of some other language;(3)Intersemiotic translation or transmutation is an interpretation of verbal signsby means of signs of nonverbal signs systems.Equivalence in difference is the cardinal problem of language and the pivotal concern of linguistics.(差异对等是语言的基本问题,也是语言学的核心问题)6.CatfordFundamental Problems in PhoneticsTranslation Ideals:(1)The definition of translations: translation is the replacement of textual material in one language (SL)by equivalent textual material in another language(TL).(2)The general types of translationCatford saw language as a set of systems operating at different levels, and described broad translation types using three sets of criteria:A.in terms of the extent of translation, he distinguished between full translationB.In terms of the levels of language involved in translation, a distinction is drawn between total translation and restricted translation(phonological translation and graphological translation)C.In terms of the grammatical or phonological rank at which translation equivalence is established, he distinguished between rank-bound translation and unbounded translation(3)Formal correspondence and textual equivalenceA formal correspondence is “any TL category(units, class, element of structure, etc); a textual equivalent is “any TL text or portion of text which is observed on a particular occasion.In his own words, translation shifts are thus “departures from formal correspondence in the process of going from the SL to the TL.”:1) A level shift would be sth. That is expressed by grammar in one language and lexis in another;2)Category shiftsa.structural shiftsb.Class shiftsc.Unit shifts or rank shifts: rank here refers to the hierarchical linguistic units of sentence, clause, group, word and morpheme.d.Intra-system shifts(4)The limits of translatability(可译性)It fails where the difficulty is linguistic and those where it is cultural(节日,特殊意象)7.Peter Newmark(Englishman)One of the main figures in the founding of translation studies in English-speaking world.Communicative translation and semantic translation(交际翻译和语义翻译)——main contribution to general translation theory Communicative translation:1)responds to the representational and vocative functions;2)Is likely to be smoother, simpler, clearer, more direct, more conventional, conforming to a particular register of language, tending to undertranslate.3)In some sense, communicative translation, by adapting and making the thought and cultural content of the original more accessible to the reader, gives semantic translation another dimension.4)The transition to communicative translation is basically makes the text smoother, lighter, more idiomatic and easier to read.5)“Standardized English”must be translated communicatively, whether a standardized equivalent exists or not, even if it appears in a novel or a quotation, unless the term is used descriptively rather than operatively in the original text.Semantic translation:1)attempts to recreate the precise flavor and tone of the original;2)Tends to be more complex, more awkward, more detailed, more concentrated, and pursues the thought-process rather than the intention of the transmitter to overtranslate, to be more specific than the original3)the transition to semantic translation normally reduces the unit of translation, and brings the text closer to the figurative and formal elements of the original.wrence Venuti(a distinguished American translation theorist, historian and translator) Translation Ideals:(1)Invisibility of the translator(译者的不可见性)The Translator’s Invisibility: A History of TranslationThe absence of any linguistic or stylistic peculiarities makes it reflects the foreign writer’s personality or intention or the essential meaning of the foreign text—the appearance, that the translation is not in fact a translation, but the “original.”The more fluent the translation, the more invisible the translator, and, presumably, the more visible the writer or the foreign text.(2)Foreignizing translation strategy(异化翻译策略)Venuti defined translation as a process by which the chain of signifiers(意符,能指) that constitutes the source-language text is replaced by a chain of signifiers in the target language which the translator provides on the strength of an interpretation.Because meaning is an effect of relations and differences among signifiers along a potentially endless chain(polysemous, intertextual, subject to infinite linkages) “resistancy”(异化、反翻译)Resistancy seeks to free the readers of the translation, as well as the translator, from the cultural constraints that ordinarily govern their reading and writing and threaten to overpower and domesticate the foreign text, annihilating(消灭) its foreignness. Resistance assumes an ideology of autonomy(自主性的意识形态), locating the alien(异己) in a cultural other, pursuing cultural diversity, foregrounding(突出) the linguistic and cultural differences of the source-language text(源语文本) and transforming the hierarchy of cultural values(文化价值层次)in the target languages.The translation of Buddhist scriptures:The initial period:An Shigao; Zhi Qian(Han Dynasty)The period of development:Dao’an (East Jin Dynasty); Kumarajiva(鸠摩罗什)The period of prosperity:Xuanzang(Tang Dynasty)Translation of western science(16—18AD,Ming Dynasty): Matteo Ricci(利玛窦)Italian Jesuit priest, one of the founding of the Jesuit ChinaMission.The first person to translate the Confucian classics into awestern language,Latin with assistance from the scholarXu Guangqi. They translated Euclid’s The Elements(几何原本)into Chinese.Xu Guangqi: he had coin so many new terms and to select carefully the accurateexpressions of mathematical concepts and contexts fromthe wide vocabulary of Chinese.Three Great Pillars of Chinese Catholicism(中国天主教的三大支柱):Matteo Ricci,Xu Guangqi,and Yang Tingyun(Summary of WesternLearning《西学凡》;On Geography《识方外纪》). Translations during Ming Dynasty had 2 distinguished characteristics:(1)the subject of translation shifted from Buddhist scriptures to scientific and technological knowledge;(2)Translators in this period of time were mainly scientists and government officials who were erudite scholars, and the Western missionaries who brought Western knowledge to China.The translation of science in the Late Qing Dynasty:Robert Morrison, Daniel Jerome,Benjamin Hobson, James Legge,Alexander Wylie. John Fryer.Yan Fu1.Famous for introducing Western thoughts, including Darwin’s idea of “natural selection” into China during the late 19th century.2.His heart was indeed not in technical translation but in the transmission of the political ideas which he had discovered in the West so he translated a number of key works of modern Western thought:1)Evolution and Ethics and Other Essays (天演论——赫胥黎)2)The Study of Sociology(群学肄言——斯宾塞)3)The Wealth of Nations(原富——亚当斯密)4)On Liberty(群己权界论——论自由,斯图亚特)Translation Theory: faithfulness, comprehensibility, elegance(信达雅)Hu ShiHu originally emphasized 8 guidelines that all Chinese writers should take to heart in writing:1)Writing with substance(要言之有物)2)Do not imitate the ancients3)Respect grammar4)Reject melancholy(不要无病呻吟)5)Eliminate old cliches(杜绝陈词滥调)6)Do not use allusions(典故)7)Do not use couplets or parallelism(对偶骈文)8)Do not avoid popular expressions(俗话俗字)or forms of characters Translation Ideals:(1)Choosing those masterpieces of famous writers only;(2)Adopting a vernacular prose style in the translation of those dramas of a verse style. He adopted a unity of faithfulness and expressiveness1) a translator should be responsible for the author to keep the spirit of the original and secondly be responsible for the readers and make his version intelligible.2)The literary works that were hard to understand could never succeed in educating people, and thus clearness in meaning is of primary importance in literary translation.Practice: Over the Roofs《关不住了》;Book of Experiments《尝试集》Lu Xun’s translation ideals:he insisted that “he would rather be faithful to the original than be fluent to the translation(宁信而不顺)”, he stressed that it was a special class of readers that his translations were intended for the proletariat literary critics who had special class interests to champion. Extreme faithfulness to the original was a way ensuring that “true” Marxist literary thought be presented to those who wanted the facts as they were.He said “The Chinese language is just too imprecise, and to this ailment, I believe we have to suffer some more pain and embody our thought in wayward syntactical structures——ancient, dialectal, as well as foreign so that one day these structures can become our own.”Practice: From the Earth to the Moon in 97hours 12 minutes.Zhou ZuorenTranslation ideals: prefers straightforward translation, that is : it should convey the original meaning and preserve the original style and express the original meaning as far as our Chinese language can do. In other words, it is faithfulness and expressiveness,Practice: Ali Baba《侠女奴》Liang ShiqiuTranslation ideals:having a book translated is to make it comprehensible, mistranslation is indeed unacceptable. Even though partialmistranslations are mistakes that may really be endlessly harmful,you have nevertheless enjoyed reading them. It would not do anyharm to modify the syntax somewhat and to make it peremptory sothat the text becomes intelligible to the reader because it’s nopleasure to grind through a text while stiff translation can notpreserve the original tone of terseness and conscious.Dead translation is very different, which is bound to be dead frombeginning to end and makes no difference whether it is read or not,also,dead translation might as well involve distorted translation. Major works: Peter Pan《彼得潘》,Wuthering Heights《咆哮山庄》;Meditation《沉思录》Lin YutangWorks of translation:The Chinese Puzzle《国民革命外纪》Women and Knowledge《女子与知识》Pygmalion《卖花女》《庄子》Chuangtse《浮生六记》Six Chapters of a Floating LifeTranslation Theory:On Translation《论翻译》:he pointed out that “translation is an art”.On Poetry Translation《论译诗》He pointed out three “responsibility”and explained the implication.He also proposed three criteria for translation: faithfulness, fluency, and beauty (忠实、通顺和美)He assumed four types of translation concerning the degree of faithfulness: literal, dead, free, and random translation.Words of each language have the beauty of sound,meaning,spirit, form, literary style and literary form.Zhu ShenghaoZhu’s work made up the core of the mainland-Chinese version of The Complete Works of Shakespeare, and the first volume is made up of 9 comedies while the second consists of 8 tragedies.Translation Ideals:(can be revealed from his self-preface of The Complete Plays of Shakespeare.) The preface consists of five paragraphs:(1)the significance of Shakespeare;(2)The situation of Shakespeare translation in China(3)His experience of translating Shakespeare and hardship involved in this process(4)His method of translating Shakespeare: to preserve the original spirit as far as possible; and if not, he made his best to put the original meaning into clear and readable Chinese. He strongly objected was word-to-word stiff translation. After finishing a paragraph, he would pretend to be a reader or a performer.Yang XianyiAccomplishment of translation: A Dream of Red Mansion, Li SaoHe acknowledged his wife’s significance in their translation——Collaborationtranslation.Translation Ideals:(1)Faithfulness: a translation should not be far from the original but not word-to-word translation.(2)Culture and translation: Translation is more than language switching. What more important is the culture behind the words.(3)Poetry translation with or without rhyme: Keeping the rhyme is secondary to keeping the meaning and it is impossible to keep everything in translation because of the differences in the two cultures.Yu GuangzhongHis works often focused upon four fundamental aspects of literature:poetry, prose, translation and commentary.Works: The Old Man and the Sea,Anthology of Modern English and American Poetry.Translation Ideals:1)The fundamental similarities and differences between translation and creative writing: if a writer also translate, his translation style will inevitably be affected by his own creative writing style, conversely, his own writing style will not remain unaffected.2)Translation is a ‘necessary evil’, a substitute we rely on for lack of something better. Not even a good translation can convey the true meaning of the original. In case of bad translations, besides distorting the original meaning, they often have a pernicious impact on indigenous writing styles.Theodore Savory (文艺学派)The Language of Science; Words of ScienceDifficulties in his search for the equivalent of a word:(1)Illusory Correspondence: a word often has several meanings and the translator should take the context into consideration when choosing an appropriate word in the target language.(2)Gaps in languages which cannot be filled in translating: because a word may be quite familiar in one language but there is no equivalent one in another. All kinds of writings where the two nations whose languages are concerned may have different customs, different games and amusements and different degrees of technical development.(3)Idioms, idiomatic phrases and provisional expressions:he suggested that the translator should ask himself 3questions:(a)what does the author say?(b)What does he mean?(c)How does he say it?A good translator’s knowledge of the translated language must be wide and it must also be critically applied so that no detail is likely to be missed. Categories of translation:(1)perfect translation:refers to the translation of all purely informative statements such as are encountered by the traveler or used by the advertiser.(2)Adequate translation:matter is more important than manner(内容比形式更重要)(3)Composite translation:includes the translation of prose into prose, of poetry into prose and of poetry into poetry(4)Translation of learned, scientific, technical and practical matter.The principles of translation:made solely because of the intrinsic importance of the original work, which is strictly confined to the practical business of living; It is almost a necessity that the translator shall have a reasonable knowledge of the science or the technique about which the original was written.The Principle of Translation:(1) A translation must give the words of the original.(2)~must give the ideas of the original(3)~should read like an original work(4)~should read like a translation(5)~should reflect the style of the original(6)~should possess the style of the translator(7)~should read as a contemporary of the original(8)~should read as a contemporary of the translator(9)~may add to or omit from the original(10)~may never add or to omit from the original(11)~of verse should be in prose(12)~of verse should be in verse.We need to choose different words in different contexts.Eugene Nida’s Translation TheoryMain Translation Ideas(1)Two basic orientations in translating:formal and dynamic equivalence.1)D ynamic-equivalence attempts to convey the thought expressed in a source text ;2)F ormal-equivalence attempts to render the text word-for-word.(2)Principles governing a translation oriented toward formal equivalence:1)g rammatical units;2)C onsistency in word usage;3)M eaning in terms of the source context;(3)Principles governing a translation oriented toward dynamic equivalence(动态对等): the most notable contribution; elaborated in “Principles of Correspondence”and it stands to reason that there can be no absolute correspondence between two languages. It’s the closest natural equivalent to the source-language message.But here are some limitations:1)special literary form,2)semantically exocentric expressions(语义外向),3)intraorganismic meaning.(4)Principles governing a translation oriented toward functional equivalence.Terms Explanation1.Five Losses:Dao’an(1)Sanskrit and Chinese are in reversing word order in sentence structure, as far as grammar is concerned.(2)Sanskrit prefers to be simple and straight forward, while Chinese prefers to be complex, polished in writing.(3)Sanskrit tends to be repetitive for important points while Chinese does not.(4)Sanskrit always contains sentences within sentences while Chinese does not.(5)Sanskrit writing is repetitive in subsequent passage, while the repetitiongs are deleted in Chinese translations.2.Five Untranslatables:Xuanzangsecrets,polysemy,none in china,deference to the past,to inspire respect and righteousness:Prajna instead of “wisdom.”3.信达雅(严复)Translation involves three requirements difficult to fulfill:1)Faithfulness2)Comprehensibility:prime importance3)EleganceFaithfulness is difficult enough to attain but a translation that is faithful but not comprehensible is no translation at prehensibility is therefore of prime importance.4.直译(literal translation)Straightforward translation/direct translationFormal correspondenceWorld-to-word translation(逐字译)Stiff translation(硬译)(Lu Xun)5.意译(free translation)Sense-for-sense translation/sense translationSemantic correspondenceFree translation(自由译)Distorted translation(歪译)(Lin Shu)6.Dead transportation: not only putting every word and every sentence in the same order as the original, but also not allowing the addition of a single word or even the change of the same order of any words.7. Three Responsibilities(a)The translator should have a complete understanding of the language and contents of the source text.(b)The translator should have a good command of Chinese so that he can produce a smooth and expressive version.(c)The translator should be trained properly to hold proper opinions on the standards and techniques of translation.9.Three Criteria1)Faithfulness: the first responsibility for the translator to fulfill but it doesn’t mean a word-to-word translation. A faithful version will not only convey the meaning of the source text but also spirit of the words and their implications.It is not possible to achieve absolute faithfulness.2)Fluency: a fluent translation should be based on sentence-to-sentence translation rather than word-for-word translation.3)Beauty: translation is an art and an ideal translator should make translationa fine art. So when we translate the Western literary text such as poetry and fiction into Chinese, we have to take its aesthetic value into consideration.。
采矿工程专业英语

accoustic signal 音响信号 accretion 表土 accumulation 蓄积 accumulator 蓄电池 accumulator capacity 蓄电池容量 accumulator lamp 蓄电池灯 accumulator locomotive 蓄电池机车 accuracy 精度 accuracy degree 精确度 acetate 醋酸盐 acetic acid 醋酸 aceton 丙酮 acetonitrile乙腈 acetyl 乙酰 acetylene 乙炔acetylene lamp 电石灯 achromatic 消色差的 aciculite 针状矿石 acid 酸 acid minewater 酸性矿水 acid number 酸值 acid proof 酎酸的 acid resistance 耐酸性 acid resistant 耐酸的 acid resistant steel 耐酸钢 acid resisting steel 耐酸钢 acid rock 酸性岩 acid treatment of a bore hole 钻孔酸处理 acid value 酸值 acidite 酸性岩acidity 酸度 acidness 酸度 acidproof 耐酸的 actinium 锕 actinolite 阳起石 actionradius 酌半径 activate 活化 activated carbon 活性煤 activated charcoal 活性煤 activating agent 活化剂 activation 活性化 activation energy 活化能 activator 活化剂 active 活化的采矿英语专业词汇Aabandoned workings 废巷道 abandonment 废弃 abelite 阿贝立特炸药 abichite 砷铜矿 ability 能力 ability to flow 怜性 ablation 水蚀 ablution 洗净 abnormality 反常abrasion 磨损 abrasion resistance抗磨蚀能力 abrasive 磨料abruption 断层 abscissa 横座标 absite 钍钛铀矿 absolute error 绝对误差 absolute humidity 绝对温度 absorbability 吸收性 absorbent 吸收剂 absorber 吸收器吸收剂 ;减震器 absorbing ability 吸收性absorption 吸收 absorption factor吸收系数 absorption meter 液体溶气计 absorptivity 吸收性absortion constant 吸收常数 abstraction of pillars 回采煤柱 abundance 丰富 abundant 富有的 abutment 拱座 abutment area 支承压力带 abutment pressure 支承压力 accelerated motion 加速运动 accelerating agent 速凝剂acceptance test 验收试验 acceptor charge 被动装药 accessory equipment 补助设备 accessory minerals 副矿物 accidental explosion 意外爆炸 acclivity 上倾 accompanying bed伴生层active dust 活性尘末active working face 生产工祖activity 活度actual mining 回采工作actuate 驱动actuating roll 导辊actuator 执行机构acuity 敏锐度acute 尖的acute angle 锐角adamantine 冷铸钢粒adamantine boring 冷铸钢粒钻进adamantine drill 金刚石钻adamellite 石英二长石adamic earth 红粘土adaptability 适合性adaptation 适应adapter 插座adaptibility 适合性addition 加法;加添additional tension 附加应力additive 添加剂adelpholite 铌铁锰矿adhere 粘着adherence 粘着adhesion force 粘附力adhesive 胶粘剂adhesive power 粘附力adhesiveness 胶粘性adhesivity 胶粘性adiabatic 绝热的adiabatic compression 绝热压缩adit 平硐adit collar 平硐口adit cut mining 平硐开采adit entrance 平硐口adit mine 平硐开采矿山adit mouth 平硐口adjoining rock 围岩adjust 蝶adjustable prop 伸缩式支柱adjuster 装配工adjusting device 蝶装置adjusting screw 蝶螺丝adjustment 蝶adjutage 喷射管admissible 容许的admission 进入;容许admitting pipe 进入管admixture 掺和物adobe 风干砖adobe blasting 裸露装药爆破adobe shot 裸露装药爆破adsorb 吸附adsorbate 吸附物adsorbent 吸附剂adsorption 吸附adsorption film 吸附膜adsorption isotherm 等温吸附式adular 冰长石adularia 冰长石adulterant 掺杂物adustion 可燃性advance 工祖进尺advance bore 超前钻孔advance borehole 超前钻孔advance cut 超前掏槽advance grouting 超前灌浆advance heading 超前平巷advance mining 前进式开采advance of the face 工祖推进advance rate 掘进速度advance workings 超前工祖advanced face 超前工祖advanced gallery 超前平巷advancement 掘进advancing 掘进advancing along the strike 沿走向掘进advancing long wall 前进式长壁开采advancing longwall 前进式长壁开采advancing mining 前进式开采advancing system 前进式开采法advancing to the dip 俯斜掘进advancing to the rise 仰斜掘进advantage 长处adventure 矿山企业adversary grade 逆坡adverse grade 逆坡aegerite 纯钠辉石aegirine 霓石aegirite 霓石aeolation 风蚀aerated concrete 气孔混凝土aerating chamber 空气混合室aeration 通风aerator 充气器aeremia 沉箱病aerial cableway 架空死aerial conveyer 架空运输机aerial dust 浮尘aerial ropeway 架空死aerial tramway 架空死aerocrete 气孔混凝土aeroembolism 沉箱病aerofloat 黑药aerogel 气凝胶aerolite 陨石aerolith 陨石aerometer 气体表aerophore 氧气呼吸器aerosite 深红银矿aerosol 气溶胶aerotriangulation 航空三角测量aeroview 空中俯瞰图aerugo 铜绿aeschynite 易解石afflux 岭after damp 炮烟after gases 炮烟aftercare 土地复田护理aftercooler 后冷却器二次冷却器afterdamp 爆后气体aftereffect 后效afterexpansion 残余膨胀aftergases 爆后气体aftertreatment 后处理agalite 纤滑石agalmatolite 寿山石agate 玛瑙age 期age of mine 矿山寿命ageing 老化agent 剂agglomerant 粘结剂agglomerate 烧结矿agglomeration 聚集agglutinant 烧结剂agglutination 凝集aggregate thickness 总厚度aggregation 聚集aging 老化agitation 搅拌agitator 搅拌器agnotozoic era 元古代agricolite 硅铋石aikinite 针硫铋铅矿air adit 通风平硐air blast 空气冲击air blast goaf stowing machine 风力充填机air blaster 艾欠道克斯压气爆破筒air blowpipe 炮眼吹洗管air bottle 压气瓶air box 木制风管air brake 空气制动器air brattice 风帘air brick 空心砖air bubble 气泡air bump 空气突出air chamber 空气室air change 换气air channel 空气通路air classifier 空气分级机air cleaner 空气滤净器air cleaning 风力选矿air compartment 通风隔间air composition 空气成分air compressor 空气压缩机air conditioning 空气第air connection 通风联络巷air consumption 空气消耗量air contamination 空气污染air cooler 空气冷却器air cooling 空气冷却air crossing 风桥air current 风流air curtain 风帘air cylinder 空气缸air distribution 风量分配air door 风门air door tender 风门工air drift 通风石巷air drill 风钻air drilling 风动钻眼air driven mine car loader 风动矿车装载机air driven pump 风动泵air driven rockerloader 压气式铲斗后卸装载机air drying 风干air duct 空气通路air ejector 喷气器air escape 空气漏出air feed 气力推进air filter 空气过滤器air float table 气浮式风力摇床air flotation 充气浮选air flow 风流air flow resistance 气凌力air gap 风口air gate 风巷air hammer 气锤air heading 通风平巷air heater 空气加热器air hose 压气软管air humidity 空气湿度air inlet 进气口air intake 进气口air jig 风力跳汰机air leg 风动钻架air level 气泡水准仪air lift 空气提液器air line 空气管air lock 气闸air locomotive 压气机车air measurement 通风测量air moisture 空气湿度air motor 风动发动机air movement 空气怜air network 通风网air opening 风巷air operated machine 风动机air partition 风墙air permeability 透气性air pick 风镐air pipe 风管air pocket 气袋airpollution 空气污染air powered locomotive 压气机车air preheater 空气顸热器air pressure 空气压力air proof 不透气的air pulsated jig 气动跳汰机air pump 抽气泵air receiver 蓄气器air resistance 空气阻力air screw fan 轴两扇风机air separation 风选air separator 风力分离器风力分选机air shaft 风井air splitting 风林支air stopping 风墙air strainer 空气滤清器air supply 空气供应air table 风力淘汰盘air tank 空气箱air trammer 风动机车air trunk 通风隔间air tube 风井air valve 气阀air velocity 风临度air vessel 蓄气器airbridge 风桥aircurrent 风流airdox 艾欠道克斯压气爆破筒airdox blaster 艾欠道克斯压气爆破筒airdox cylinder 压气爆破筒airflow measurement 通风测量airing 通气airleg 气腿airlock 风闸airman 风门工airway 风巷airwinch 风动绞车akerite 光辉正长岩;英辉正长岩akins classifier 螺旋分级机alabandine 硫锰矿alabandite 硫锰矿alabaster 雪花石膏alabastrite 雪花石膏alamosite 铅辉石alarm 警报alarm device 警报装置alarm signal 警报信号alaskaite 白岗岩alaskite 白岗岩alaunstein 茂石albertite 沥清煤albite 钠长石albitite 钠长岩albitophyre 钠长斑岩albronze 铝青铜alcali 碱alcohol 醇alertor 警报信号alidade 指方规aliphatic acid 脂族酸alkali 碱alkalimeter 碱量计alkalimetry 碱量滴定法alkaline 碱的alkaline accumulator 碱性蓄电池alkaline earth metal 碱土金属alkalinity 碱度alkyl 烷基all over work 长壁开采all ups 原煤allactite 砷水锰矿allanite 褐帘石allemontite 砷锑矿alligator 自翻式吊桶allomerism 异质同晶allomorphism 同质异晶allophane 水铝英石allophanite 水铝英石allotrope 同素异形体allotropy 同素异形allowable concentration 许容浓度allowable error 容许误差allowable load 容许负载allowable stress 容许应力allowance 公差alloy 合金alloy bit 合金钻头alloyed steel 合金钢alluvial 冲积的alluvial deposit 冲积矿床alluvial gold 砂金alluvial mining 砂矿开采alluvial soil 冲积土alluvial tin 砂锡矿alluviation 冲积alluvion 冲积层alluvium 冲积层almandine 铁铝榴石almandite 铁铝榴石alnico 铝镍钴合金alnoite 黄长煌斑岩aloxite 铝砂alstonite 碳酸钙钡矿altait 碲铅矿alteration 变蚀酌alternate load 交变负载alternate motion 往复运动alternate stress 交变应力alternating 交替的alternating current 交流alternating current generator 交立电机alternating current motor 交羚动机alternating motion 往复运动alternation 交替altimeter 测高计altimetry 高度测量术altitude 高度alum 茂alum earth 矾土alumel 铝镍合金alumina 矾土alumina cement 高铝水泥aluminate 铝酸盐aluminium 铝aluminium bronze 铝青铜aluminum detonator 铝壳雷管alundum 氧化铝alunite 茂石amalgam 汞齐amalgamating barrel 提金桶amalgamation 汞齐化酌amalgamator 提金器汞齐化器amatol 阿马托炸药amazonite 天河石amazonstone 天河石amber 琥珀ambient 周围的ambient temperature 周围温度ambligonite 磷铝石amblygonite 磷铝石ambulance 急救车americium 镅amethyst 紫晶amide 酰安amine 胺amino acid 氨基酸ammon dynamite 硝安炸药ammon explosive 硝铵炸药ammonal 阿梅那尔ammonia 氨ammonia gelatine dynamite 铵胶炸药ammonite 阿芒炸药ammonium 铵ammonium nitrate 硝安ammonium nitrate dynamite 硝安炸药ammonium nitrate explosives 硝安炸药ammonium nitrate prill 颗粒状硝铵amorphous 无定形的amorphous state 无定形状恙amortization 折旧ampelite 黄铁碳质页岩amphibole 角闪石amphibolite 闪岩amphibolization 闪石化酌amplification 放大amplifier 放大器amplify 放大amplitude 振幅ampole 安瓿amygdaloid 杏仁岩amygdaloidal texture 杏仁状结构analcime 方沸石analcite 方沸石analog digital conversion 模拟数字转换analogy 类似analyser 分析器analysis 分析analyst 化验员analytic 分析的analytical 分析的analytical chemistry 分析化学analyze 分析analyzer 分析器anatase 锐钛矿anbauhobel 快速刨煤机anchor 锚anchor bolt 锚杆ancillary work 辅助工作ancylite 碳酸锶铈矿andalusite 红柱石anderseam 下部煤层andesine 中长石andesite 安山岩andradite 钙铁榴石anemobarometer 风速风压计anemograph 自记风速计anemometer 风速表anemometry 风速测定aneroid barometer 无液气压计anfo explosives 铵油炸药anfo loader 铵油炸药装填器angle 角angle bar 角钢angle face 倾斜工祖angle gauge 角规angle of bedding 层理面倾斜角angle of break 崩落角angle of contact 接触角angle of deflection 偏角angle of dip 倾角angle of draw 落角angle of elevation 仰角angle of emergence 出射角angle of friction 摩擦角angle of incidence 入射角angle of inclination 倾角angle of internal friction 内摩擦角angle of pitch 螺距角angle of repose 休止角angle of rest 休止角angle of rolling friction 滚动摩擦角angle of strike 走向角度angle of subsidence 边界角angle shot mortar test 开槽臼炮试验anglesite 硫酸铅矿angular 角的angular acceleration 角加速度angular hole 斜炮眼angular motion 角动angular velocity 角速度anhydride 酐anhydrite 硬石膏anion 阴离子anisotropy 蛤异性ankerite 铁白云石annabergite 镍华annealing 退火annual advance 年掘进annual output 年产量anode 阳极anomaly 异常anorthite 钙长石anorthoclase 歪长石anorthosite 斜长石antarctic pole 南极antecedent magnetic concentration 储备处理磁选anthracene 葸anthracite 无烟煤anthracite culm 无烟煤粉anthracite mine 无烟煤矿anthracography 煤相学anthracology 煤炭学anthracometer 二氧化碳计anthracosis 煤肺病anthrafine 无烟煤细末anthrakometry 二氧化碳测定法anti acid 耐酸的anticlinal 背斜anticline 背斜anticlinorium 复背斜anticlockwise rotation 反时针旋转antidote 解毒药antifoamer 消泡剂antifoaming agent 消泡剂antifreeze 防冻剂antifreezing agent 防冻剂antimonite 辉锑矿antimony 锑antimony glance 辉锑矿antioxidant 抗氧剂antioxidizer 抗氧剂antiseptic 防腐剂apatite 磷灰石aplite 细晶岩apophyllite 鱼眼石apophyse 岩枝apophysis 岩枝apparatus 频apparent resistance 表观阻力apparent specific gravity 表观此重apparent viscosity 视粘度apple coal 软煤applicable 可以应用的application 应用appreciation 评价approach 接近approved cable 防爆电缆approved lamp 安全灯approved shot firing apparatus 安全放炮器耐爆放炮器approximate 近似的approximate value 近似值approximation 近似法apron conveyor 平板运输机apron coveyor 板式输送机apron feeder 板式给矿机apyrous 耐火的aqua regia 王水aquation 水合酌aqueduct 输水桥aqueous 水的aqueous solution 水溶液aquifer 蓄水层aquiferous 含水的aragonite 霰石arc 弧arch 拱arch lining 拱形支架arch pressure 支承压力arch setting 安设拱形支架arch span 拱跨arch theory 成拱论arch timbering 拱形木支架arch truss 拱式桁架arched support 拱形支架architecture 建筑学archy lining 拱形支架arcose sandstone 长石砂岩arcwall face 弧形工祖area 矿区area blasting 多排列爆破area of explosion 爆炸区arenaceous 砂质的arenarious 砂质的arenology 砂岩学arenous 砂质的areometer 比重计arfvedsonite 钠钙闪石argentite 辉银矿argentum 银argillaceous rock 泥质岩argillaceous sandstone 泥质砂岩argillaceous slate 泥板岩argillite 泥质板岩argon 氩argyrodite 硫银锗矿arkose 长石砂岩arm 杠杆;柄arm mixer 叶片式搅拌机armature 加强armature core 电枢铁心armature winding 电枢绕组armored cable 铠装电缆armored concrete 钢筋混凝土armoure 加强armoured concrete 钢筋混凝土armoured conveyerpanzer conveyer 镫装运输机arrangement 布置arrangements 准备arrester 制动器制止器arrester catch 止动器挡车器arrestor 避雷器arsenic 砷arsenite 砷华arsenolite 砷华arsenopyrite 砷黄铁矿arsensilver blende 淡红银矿articulated roof beam 铰接顶梁articulated yielding arch 铰接可缩性拱形支架articulation 铰链接合artificial caving 人工崩落artificial draught 人工通风artificial petroleum 人造石油artificial respiration 人工呼吸artificial vetilation 人工通风asbestos 石棉asbestos wool 石棉绒asbolane 钴土矿asbolite 钴土矿asbstos cement 石棉水泥ascending working 漏口ascension 上升ascensional ventilation 上向通风ash 灰ash coal 高灰煤ash composition 灰分组成ash content 灰分askew 斜的asparagus stone 黄绿磷灰石asphalt 地沥青asphalt base crude oil 沥青基原油asphalt concrete 地沥青混凝土asphaltite 沥青岩asphyxia 窒息asphyxy 窒息aspirail 通风孔aspirating tube 吸气管aspiration 吸气aspirator 抽风机assay 试金assemblage 装配assemble 装配assimilation 同化酌association缔合assort 分类assortment 分类assurance factor 安全系数astillen 脉壁; 隔墙astriction 收缩astringency 收敛性asymmetric 不对称的asymmetrical 不对称的asymmetry 不对称asymptotic 渐近的asynchronous generator 异步发电机asynchronous motor 异步电动机atacamite 氯铜矿atmoizer 喷雾器atmosphere 大气atmospheric 大气的atmospheric conditions 通风条件;大气条件atmospheric corrosion 大气腐蚀atmospheric moisture 空气湿度atmospheric pressure 大气压力atom 原子atomic 原子的atomic number 原子序atomic ore 放射性矿石atomic volume 原子体积atomization 喷雾atomizer 喷雾器attack 循环; 开始attal 充填物料attenuation 衰减atteration 冲积土attle 充填料attraction 引力attractive force 引力attrition 磨耗attrition mill 盘磨机attrition test 磨损试验auger drill 螺旋钻augering 螺旋钻法auget 雷管augite 辉石aureole 接触带auric 金的auriferous 含金的aurum 金austenite 奥氏体austenitic steel 奥氏体钢autmatic measuring device 自动计量器auto alarm 自动报警auto ignition 自燃autocollimation 自动视准autoconverter 自动变流autocrane 汽车起重机autodumper 自卸汽车autofeed 自动给料autofeeder 自动给矿机autogenous cutting 气割autogenous welding 气焊autoloader 汽车式装载机automated mine 自动化煤矿automated mining 自动化采掘automatic block 自动闭塞automatic brake 自动制动器automatic checking 自动检验automatic circuit breaker 自动断路器automatic control 自动控制automatic controller 自动第器自动蝶器automatic coupler 自动车钩automatic door 自动风门automatic dumper 自动翻车机automatic equipment 自动设备automatic feed 自动给料automatic feeder 自动给矿机automatic installation 自动设备automatic loading device 自动装载设备automatic lubrication 自动润滑automatic lubricator 自动润滑器automatic oiling 自动润滑automatic pressure controller 自动倒器自动压力控制器automatic regulator 自动第器自动蝶器automatic release 自动释放automatic resetting 自动复位automatic sampler 自动取样器automatic sorting 自动选分automatic warning device 自动告警装置automatic weighing device 自动秤automation 自动化automatization 自动化automobile 汽车autotransformer 单卷变压器autotruck 载重汽车auxiliary 辅助的auxiliary adit 辅助平峒auxiliary equipment 辅助设备auxiliary fan 辅助扇风机auxiliary level 辅助平巷auxiliary shaft 辅助竖井auxiliary support 辅助支架auxiliary tools 辅助仪表auxiliary ventilation 局部通气auxilliary winch 辅助绞车aventurine 砂金石average 平均average error 平均误差average life 平均寿命average pressure 平均压力average sample 平均试样average trend 平均走向average value 平均值axe 斧axial 轴性的axial blower 轴寥风机axial compression 轴向压缩axial direction 轴向axial fan 轴两扇凤机axial flow compressor 轴两压缩机axial flow fan 轴寥风机axial piston motor 轴向柱塞马达axial piston pump 轴向活塞泵axial pump 轴两泵axle 车轴axle base 轴距axle bearing 轴承axle box 轴颈箱axle box bearing 轴箱轴承axle journal 轴颈azimuth 方位azimuth angle 方位角azimuth compass 方位测量罗盘azote 氮azurite 蓝铜矿Bbabbit 巴氏合金back bolting 顶板锚杆支护back bone 分水岭back brace 背板back break 超欠挖back brushing 挑顶back coming 后退回采back filler 回填机back filling 充填back filling method 充填法back filling shrinkage 充填物收缩back filling system 分段上向充填开采法back lath 顶板背板back leg bracing 柱腿支撑back lye 井下错车道back pulling 回采煤柱back stope 上向梯段回采工祖back stoping 上向梯段回采back stroke 回程back water 回水back weight 平衡锤backacter 反铲backbye deputy 井下维修工backdigger 反铲backdraught 逆通风backfill 充填backfill material 充填料backfill operations 充填工作backhoe 反铲backlash 轮齿隙backman 辅助工backpressure 顶板压力backstoping 上向梯段回采backwall injection 井壁背后灌浆backweight 平衡锤backwork 辅助工作bacteria leaching 细菌沥滤bactericide 杀菌剂bad top 不稳固顶板baddeleyite 斜锆矿baffle plate 反射板bag filter 袋滤器bag powder 装袋炸药bag type accumulator 皮囊式蓄能器bagger 多斗控掘机bagging 装袋baghouse 囊式集尘窒baikalite 贝钙铁辉石bail 吊桶bailer 铲bailing ring 集水圈bailing tank 戽水斗baking coal 粘结煤bal 矿山balance 平衡balance bob 平衡锤balance bunker 平衡仓balance level 水准仪balance pit 平衡重井筒balance plane 自重滑行坡balance rope 平衡钢丝绳balance rope pulley 平衡绳滑轮balance tail rope 平衡尾绳balance valve 平衡阀balance weight 平衡锤balanced hoist 两容漆升机balanced hoisting 平衡提升balanced load 平衡负载balanced winding 平衡提升balancing 平衡balas 浅红晶石balk 煤层薄ball 球ball and socket joint 球节ball bearing 滚珠轴承ball bushing 球轴套ball cage 球护圈ball charge 磨球装量ball crusher 球磨机ball inclinometer 球式测斜仪ball indentation test 布氏硬度试验ball joint roof bar 球铰顶梁ball mill 球磨机ball retainer 球护圈ball up 钻孔堵塞ball valve 球阀ballas 浅红晶石ballast concrete 石碴混凝土ballast pit 采石场ballast rod 冲唤钻杆balling drum 球磨机滚筒ballistic mortar test 弹道臼炮试验ballistic pendulum test 弹道摆试验ballistite 巴里斯泰特炸药ballstone 球石balsam 香液bamboo tamping rod 竹炮棍band 带band brake 带式制动器带闸band conveyor 带式运输机band iron 带铁band ore 带状矿石banging piece 防险器断绳保险器banging pieces 断绳保险器防坠器banjo 钻车bank 阶段bank coal 原煤bank excavation 阶段采掘bank height 台阶高度bank method of attack 阶段开采法bank shaft mouth 坚井口bank work 阶梯开采bankcoal 原煤banker 掘土工banket 含金砾岩层bankhead 斜井井口出车平台banking 堆积bannock 耐火粘土bar 杆bar cutter 杆式截煤机bar grizzly 棒条筛bar mat reinforcement 网状钢筋bar reinforcement 钢筋bar rigged drifter 架式凿岩机bar screen 棒条筛bare 裸露的bare cable 裸电缆bare log 钻孔柱状图bargh 矿山企业baring 复盖岩层; 剥离barings 截煤粉barite 重晶石barium 钡barkevikite 棕闪石barney 单钩提升上山用的平衡重车barney car 单钩提升上山用的平衡重车barometer 气压表barometric 气压的barometric height 气压高度barrage 堰barrel 桶barren 不含矿物的barren layer 废石层barren rock 废石barricade 隔墙barrier 岩粉棚barrier method 柱式开采法barrier pillar 安全煤柱barrier system 柱式开采法barrierless accumulator 非隔离式蓄能器barring 顶板支护barrow 手推车barrow pit 手车运输的露天矿baryte 重晶石baryum 钡basal cleavage 贮理basal level 基淮面basalt 玄武岩base 基础;碱基base charge 基本装药量;炮眼底部装约base line 基线base plate 底板base road 诛base rock 基岩base unit 基本单位bashing 用废矸石充填采空区basic 基性的basic line 基线basic rock 碱性岩basin 煤田;盆地;贮水池basis 基础bass 炭质页岩basset 露头bast 炭质页岩bastard 夹石bastite 绢石bastnaesite 氟碳铈矿bat 泥质页岩batardeau 隔墙bathoclase 水平节理batholite 基岩batholith 基岩bathometer 深海测深仪bathymeter 深海测深仪bating 井筒延伸;卧底batt 泥质页岩batter 坡度batter level 倾斜仪batter pile 斜桩batter post 斜柱battered prop 斜柱battery 电池组;木隔壁; 工专battery capacity 蓄电池容量battery charger 充电机battery lamp 蓄电池灯battery locomotive 蓄电池机车battery powered haulage 蓄电池机车运输battery shuttle car 蓄电池梭车baulk 煤层薄baum jig 空气跳汰机baum jig washer 空气跳汰机baum wash box 空气跳汰机bauxite 铝土矿bawke 吊桶beach combing 海滨开采砂矿beach placer 海滨漂砂矿床beam 梁bearer 矿柱bearing 煤层走向; 轴承bearing alloy 轴承合金bearing block 矿枉煤柱bearing bush 轴承瓦bearing bushing 轴承瓦bearing cap 轴承盖bearing capacity 承重能力bearing housing 轴承壳bearing indicator 方位指示器bearing load 轴承负载bearing metal 轴承合金bearing pointer 方位指示器bearing position 支点bearing power 承重能力bearing pressure 承压力bearing ring 之框bearing set 之框bearing test 承载力试验bearing up pulley 紧绳轮beat 打击beater 木捣锤beater pulverizer 锤碎机beckelite 方钙饰镧矿bed 地层bed plane 层理面bed series 层系bed succession 层序bed thinning 煤层变薄bed top 矿层顶板bedded iron ore 层状铁矿bedded rock 层状岩bedded vein 层状矿脉bedding 层理bedding rock 基岩bedding surface 层理面bedrock 基岩beetle 大锤; 捣固机belemnite 箭石bell man 信号工bell pit 小探井bell rope 信号铃拉绳belly 煤层变厚belonite 针雏晶belowground 地下的belt 胶带belt bucket elevator 带头式提升机belt cleaner 净带器belt conveyor 带式运输机belt discharging plant 胶带输送机卸料装置belt elevator 带式提升机belt extension 胶带接长belt fastener 带扣belt feeder 带式给矿机belt heading 皮带输送机平巷belt hoister 斜井用胶带输送机belt idler pulley 皮带拉紧滚筒belt incline 胶带输送机斜井belt joint 带接belt lacer 带扣belt lacing 胶带接合belt lacing machine 缝带机belt loader 胶带动载机belt pulley 带式运输机滚筒belt punch 皮带穿孔器belt roller 皮带轮belt screen 带筛belt separator 带式分选机belt slip protection 胶带打滑保护belt stower 抛掷式胶带充填机belt stretcher 紧带器belt tension 皮带张力belt tightener 紧带器belt tightening pulley 皮带拉滚筒belt training idler 胶带导辊belt transport 皮带输送belt type dehydrator 带式干燥机belt type magnetic separator 带式磁选机belting 输送机胶带装置bench 阶段bench cut blasting 阶段爆破bench drilling 阶段钻眼bench face 台阶工祖bench floor 台阶底bench height 台阶高度bench hole 梯段的下向垂直炮眼bench mining 阶梯式开采bench preparation 阶段准备bench stoping 阶梯式开采benched quarry 阶段采石场benching 阶梯式开采benching bank 阶段bend 弯管bimetallic strip relay 双金属片继电器 bin 矿仓 bin gate 贮仓闸门 binder 粘结剂 binding agent 粘结剂 bindingcoal 粘结煤 binding energy 结合能 binding force 结合力 bing 堆 bing hole放矿溜口 binning 装仓biogeochemistry 生物地球化学 biotite黑云母 biquartz 双石英 bismuth 铋bismuth glance 辉铋矿 bismuthinite 辉铋矿 bismuthite 泡铋矿 bisulfate 硫酸氢盐 bisulfite 亚硫酸氢盐 bisulphate 硫酸氢盐 bisulphite 亚硫酸氢盐 bit 钎头 bit dresser 钻头修整机 bit dressing 钻头修整 bit edge 钻刃 bit face 钻头刃面 bit grinder 钻头磨锐机 bit head 钻头 bit life 钎头使用期间 bit shank 钎尾 bitter earth 氧化镁 bitum 沥青bituminous coal 沥青煤 bituminous rock 沥青岩 bituminous shale 沥青页岩 black band 菱铁矿 black blastingpowder 黑色火药 black bog 泥炭沼泽 black diamond 黑金刚石 black earth黑土 black iron ore 磁铁矿 black lead 石黑 black lead ore 黑铅矿bender 弯机 bending force 弯力 bending machine 弯机 bending moment 弯曲矩 bending resistance 抗弯强度 bending rolls 辊子卷板机 bending strength 抗弯强度 bendingstress 弯曲应力 bending test 弯曲试验 benefication 选矿 beneficiating method 选矿法 beneficiation 选矿 benitoite 蓝锥矿 bent 弯曲 bent entry 弯曲平巷 bent face 弯工祖 bent pipe 弯管 bentonite 皂土 benzene 苯 benzine汽油 benzol 苯 beresite 黄铁长英岩 berm 段台 berme 段台 berthierite 辉铁锑矿 bertrandite 硅铍石 beryl 绿柱石 beryllium 铍 beryllonite 磷钠铍石 beton 混凝土 bevel 斜面 bevel gear 伞齿轮 bevel gear drive 伞齿轮传动 bevelgearing 伞齿轮咬合 ;锥齿轮传动装置 bevel wheel 伞齿轮 bevelling 锨 bicable tramway 双线死 bickford fuse 比克福特导爆线 biconetype rolling cutter bit 双圆锥齿轮钻 头 big hole大径钻孔 billot 杆 bimetal 双金属 bimetalthermometer 双金属温度计black manganese 黑锰矿black powder 黑火药black powder train 黑药导火线blackdamp 室息性空气blacksmith 锻工blade 刀片blade grader 推土机blader 推土机blaize 硬砂岩blanch 铅矿石blanket 表层blanket table 平面洗矿台blast 爆炸blast blower 鼓风机blast firing 放炮blast hole 炮眼blast hole drill 凿岩机blast layout 装药布置blast stower 风力充填机blastability 爆炸性blaster 放炮工blaster cap 雷管blasters' permit 爆破技术员blasthole 炮眼blasthole bit 炮眼钻头blasthole collar 炮眼口blasthole method 深孔爆破开采法blasting 爆破blasting accessories 爆破用七blasting agent 炸药blasting cable 放炮电缆blasting cartridge 药包blasting charge 装炸药blasting compound 炸药blasting cone 爆破漏斗blasting device 爆破用具blasting drift 爆破平巷blasting dust 爆破尘末blasting equipment 爆破用具blasting explosive 炸药blasting fume 炮烟blasting fuse 导火线blasting galvanometer 放炮电路试验器blasting gelatine 煤炸药blasting lead 爆破导线blasting machine 电气发爆器blasting material 爆炸物blasting oil 硝化甘油blasting operation 爆破blasting ratio 爆破比blasting supplies 起爆颇blasting switch 爆破开关blasting technician 放炮工blasting tools 爆破工具bleed of gas 瓦斯喷出bleeder entry 通风平巷bleeder hole 放泄孔bleeder off hole 排放钻孔bleeder pipe 排出管blende 闪锌矿blender 掺合器混合器blending 掺合blending bunker 配合仓blending conveyor 掺合输送机blind 暗的blind coal 无焰炭blind drift 独头巷道blind galley 独头巷道blind lead 无露头矿脉blind outcrop 盲露头blind pit 暗井blind shaft 暗井blister 气泡block 采区;块;滑车组block brake 闸块式制动器block caving method 分段崩落采矿法block line 钻井钢丝绳block mining 分块开采blockage 闭塞blockhole 炮眼blockhole blasting 爆破地面大块岩石blockholing 爆破地面大块岩石blocking 闭塞blondin 采掘场架空死blow 放炮blow of gas 瓦斯喷出blow up 爆炸blowcharging 风力装药blowed fill 风力充填blower 吹风机blower fan 吹风机blowing out 吹洗炮眼blowing over 工祖通风blowing ventilation 吹入通风blowlamp 焊灯blowout 突出blowout preventer 防喷器blowpipe 喷焊器喷割器blowtorch 焊灯blue cap 蓝色焰晕blue printing machine 蓝图机blue spar 天蓝石blue vitriol 胆矾blueprint 蓝图blueprint paper 蓝图纸bluestone 胆矾blunt 钝的blunt drill 钝钻board 板board and pillar 房柱式开法board and pillar method 房柱式开采法board and pillar work 房柱式开法board and wall method 房柱式开采法boarding 安装木板boart 工业用圆粒金刚石bob 铅锥bobbin 绕线管bog land 沼地bogie 小车;转向架boiled oil 熟炼油boiler 锅炉boiling 沸腾boiling process 沸腾法boke 小细脉bolt 螺栓bolt connection 螺栓连接bolt joint 螺栓接合bolting 锚杆支护bolting cost 锚杆支架费bonanza 富矿脉bond 结合bond energy 结合能bonding agent 结合剂bonding energy 结合能bonding strength 结合强度bone 可燃性页岩bone char 骨煤bone coal 骨煤bone picker 拣矸工bonnet 盖bonny 矿襄bonstay 暗井bont 提升装置bonze 末精选的铅矿石boom 悬臂boom crane 伸臂起重机boom hoist 悬臂绞车boom ripper 悬臂挑预机boose 矿石内的脉石booster 传爆药booster fan 辅助扇风机booster primer 传爆药booster pump 增压泵boosting 局部通风bootleg 拒爆炮眼booze 铅矿bop 防喷器boracite 方硼石borax 硼砂bord 巷道bord and pillar method 房柱式开采法bord and pillar work 房柱式开法bord and wall method 房柱式开采法border 边缘border pile 边桩bordering 炮泥borderline 界线bore 孔bore bit 钻头bore borings 钻粉bore hole 炮眼bore meal 钻粉bore mining 溶液采矿bore mud 钻泥bore plug 钻孔岩样borehole 钻孔borehole charge 钻孔装药borehole clinometer 钻孔测斜仪borehole diameter 钻孔直径borehole profile 钻孔断面图borehole pump 深井泵borehole seal 镗孔密封垫borehole shooting 钻井爆破borehole survey 钻孔测量borer 钻工boride 硼化物boring 钻进boring bar 钻杆boring bit 钎头boring for oil 石油钻深boring frame 钻塔boring head 钻头boring machine 钻机boring mud 钻泥boring pump 钻眼用泵boring rig 钻塔boring rod 钻杆boring rope 钻机用的钢丝绳boring tool 钻具boring tower 钻塔boring tube 钻管bornite 斑铜矿boron 硼bort bit 金刚石钻头bortz 工业用圆粒金刚石bortz powder 金刚石粉borway bit 齿状钻头boss hammer 大锤bossing 厚层切底bottle coal 瓦斯煤bottom 底板bottom banksman 井底把钩工bottom belt 底部皮带bottom canch 卧底bottom captain 井下组长bottom cutting 底部截槽bottom discharge bucket 底卸式铲斗bottom discharge skip 底卸式箕斗bottom dump bucket 底卸式铲斗bottom dump skip 底卸式箕斗bottom dumping car 底卸式车bottom gangway 底导坑bottom gate 底导坑bottom heading 底导坑bottom hole 底部炮眼bottom installation 井底车场设备bottom kerf 底槽bottom layer 底层bottom layout 井底车场布置bottom level 井底车场标高bottom loading belt 底带装载式胶带输送机bottom man 井底把钓工bottom plate 底板bottom pressure 底部压力bottom priming 底部点火bottom sediment 罐底杂质bottom slice 底分层bottom stope 下向梯段工祖bottom stoping 下向梯段回采bottom taking 卧底bottom wall 下盘bottomer 井底把钓工bottoming bit 可卸式钻头boulangerite 硫锑铅矿boulder 圆石boulder blaster 大块爆破工boulder blasting 二次爆破boulder crusher 粗碎机boundary 边界boundary breakthrough 边界联络横巷boundary condition 边界条件boundary layer 边界层boundary of property 建矿边界boundary of section 采区边界boundary surface 界面boundary surface active agent 界面活性剂boundary value 监界品位boundary ventilation 对边通风bounge 煤的挤出bournonite 车轮矿bouse 矿石内的脉石boutgate 通地面的人行道bow 弧;拱梁bowl classifier 浮槽分级机box 箱box car 棚车box compass 罗盘box floor 溜口底box timbering 板框支护box type scraper 箱形刮斗boxhole 联络小巷brace 撑木bracing 支撑bracket 托架;井口车场bracket crane 悬臂式起重机bradford breaker 勃莱福型破选机brae 斜井braize 煤尘brake 制动器brake application time 制动时间brake band 制动带brake beam 制动杠杆brake block 闸瓦brake drum 制动鼓brake equipment 制动装置brake shoe 塞块brakesman 跟车工braking 制动braking controller 制动控制器braking device 制动装置braking distance 制动距离braking effort 制动力braking energy 制动能braking fluid 制动液braking force 制动力braking incline 轮子坡braking terminal 制动终点站braking time 制动时间branch 支线branch circuit 分支电路branch conduit 支管branch entry 支巷branch roadway 中间平巷branching 分支brannerite 钛铀矿brash 脆的brasil 黄铁矿brass 黄铜brassil 黄铁矿brattice 风布brattice cloth 风幛布brattice way 上部巷道braunite 褐锰矿bravoite 镍黄铁矿brazil 黄铁矿brazing 铜焊breach 缺口break 崩落break in declivity 倾斜变化break in grade 坡度转折点break thrust 背斜上冲断层breakability 可破碎性breakage 崩落breakage face 回采工祖breakdown 破坏;破损breakdown fluid 爆破用压力水breakdown point 强度极限breakdown test 破坏试验breaker 破碎机;落煤工breakerroll 破碎辊breaking 破碎breaking cone 破碎圆锥breaking current 开闸电流断路电流breaking in 磨合breaking load 断裂负载breaking out of fire 发生火灾breaking point 强度极限breaking strength 抗断强度breaking stress 致断应力breaking test 破坏试验breaking up of boulders 大块二次破碎breaking weight 断裂负载breakoff 联络小巷breakthrough 联络小巷breast 工祖前壁breast and pillar 房柱式采煤法breast and pillar method 房柱式采煤法breast mining 扒矿开采breast stoping 扒矿开采breather 通气孔breathing 呼吸breathing apparatus 呼吸器breathing bag 氧气囊breathing mask 防毒面具breccia 角砾岩breeze 粉煤brettis 风帘brick 砖brick earth 砖土brick lining 砖砌支护bricking 砖砌支护bricklayer 砌砖工brickwork 砌砖bridge 桥bridge conveyor 桥式输送机bridge crane 桥式起重机bridging 桥连brigade 工子brigadesman 矿山救护队队员bright coal 辉煤brightness 亮度briight coal 辉煤brine 盐水brine intake 冻结管brinell apparatus 布氏硬度试验器brinell hardness test 布氏硬度试验brinell hardness tester 布氏硬度试验器bring back 后退式回采bringing back 后退回采briquette 煤球briquette press 压煤砖机briquetting 煤砖制造briquetting machine 团压机briquetting press 压煤砖机brisance 猛度brittle 脆的brittle fracture 脆性断裂brittleness 脆性broaching bit 扩孔钻头broad gauge track 宽轨broadwall 长壁开采brochantite 水胆矾broil 露头broken charge 分段装药bromargyrite 溴银矿bromin 溴bromlite 碳酸钙钡矿bromyrite 溴银矿bronchiectasis 支气管扩张bronchitis 支气管炎bronze 青铜bronzite 古铜辉光brookite 板钛矿brow 巷道口brow bin 临时贮石仓brow box 临时贮石仓brow of station 井底车场的标高brown coal 褐煤brown hematite 褐铁矿broyl 露头brucite 水镁石bryle 露头bubble 气泡bubble cell 泡沫浮选槽bucked ore 富矿石bucker 碎矿机bucket 吊桶bucket capacity 抓斗子容量bucket chain 斗链bucket chain dredger 多斗挖掘船bucket conveyor 斗式运输机bucket dredger 多斗挖掘船bucket elevator 提斗机bucket excavator 多斗挖掘机bucket grab 抓斗bucket hook 吊桶钩bucket loader 斗式装载机bucket pump 链斗提水机bucket teeth 铲斗齿bucket trenching machine 多斗控沟机bucket wheel excavator 斗轮式挖掘机buckling 纵向弯曲buckling load 纵弯曲负载buckling strength 纵向弯曲强度buckling stress 纵向弯曲应力bucksaw 架锯buddle 斜面固定淘汰盘buddle jig 动筛跳汰机buffer 缓冲器。
英语作文先后顺序的词

英语作文先后顺序的词The Order of Words in English WritingThe structure and order of words in a sentence are crucial elements in English writing as they convey the intended meaning and ensure clear communication. In the English language the sequence of words typically follows a specific pattern known as the subject-verb-object (SVO) order which is the most common word order used in constructing sentences. This standard arrangement allows the reader to easily identify the subject performing the action the verb describes and the object receiving that action. Maintaining this conventional word order is essential for composing coherent and understandable written passages.Beyond the basic SVO format there are other patterns of word placement that writers can utilize to achieve different rhetorical effects or to emphasize certain aspects of a sentence. Altering the typical sequencing of subject verb and object can alter the focus and nuance of a statement. For instance, placing the object before the verb as in object-verb-subject (OVS) order can highlight the objectand de-emphasize the subject. Inverting the standard word order to verb-subject-object (VSO) can create a sense of immediacy or urgency. Adverbial phrases that describe when where or how an action occurs are often positioned at the beginning or end of a sentence to provide contextual information. The flexibility to manipulate word order allows writers to control the flow of ideas and direct the reader's attention.Understanding the conventions of word order is particularly important when constructing more complex sentence structures. Compound and complex sentences that contain multiple clauses require careful placement of conjunctions subordinate clauses and other modifying elements. Failure to position these components properly can result in ambiguous or confusing phrasing. For example in the sentence "The student who completed the assignment on time received an A" the relative clause "who completed the assignment on time" clearly modifies the subject "the student." However if the clause is moved to the end of the sentence as in "The student received an A who completed the assignment on time" the meaning becomes unclear as it is uncertain whether the clause describes the student or the grade. Maintaining the expected word order helps the reader process the relationship between the different parts of the sentence.In addition to syntactical conventions word order also plays a role inconveying semantic nuance. The placement of adjectives adverbs and other modifiers can alter the emphasis and implication of a statement. Consider the difference between the phrases "the extremely tall woman" and "the tall extremely woman." In the first example the adverb "extremely" intensifies the adjective "tall" whereas in the second example it is unclear whether "extremely" modifies "tall" or the entire noun phrase "tall woman." Carefully arranging modifiers allows writers to precisely communicate their intended meaning.The rules governing word order in English are not absolute and inflexible however. Poets and other creative writers often intentionally deviate from standard syntax to achieve specific stylistic effects. Inverting the typical SVO structure can lend a sense of formality or poetic flair to a passage. Separating a verb from its subject or object through the insertion of other elements can create suspense or emphasize certain words. While these unconventional arrangements may initially seem confusing to readers their purpose is to draw attention to particular words or ideas and evoke an emotional response.Mastering the conventions of word order is an essential skill for any writer composing in English. Understanding how to properly construct sentences and arrange modifying elements is crucial for crafting clear and coherent written work. Yet the flexibility tomanipulate syntax allows writers to experiment with language and craft pieces that are not only informative but also aesthetically compelling. By mindfully controlling the placement of words writers can guide the reader's attention and convey nuanced meaning. Ultimately the order of words is a powerful tool that enables effective communication and artistic expression.。
大学英语大一期末考试重点单词

大学英语大一期末考试重点单词1. Noun:- A noun is a word that represents a person, place, thing, or idea. It is essential to have a strong grasp of nouns as they form the basic structure of sentences and are vital for effective communication.2. Verb:- Verbs are words that describe an action, occurrence, or state of being. They are crucial in constructing sentences and conveying information. Understanding different verb tenses and forms is essential for accurate expression.3. Adjective:- Adjectives are words that describe or modify nouns or pronouns. They add detail, color, and depth to our language. Being able to accurately use adjectives allows for more vivid and engaging descriptions.4. Adverb:- Adverbs modify verbs, adjectives, or other adverbs, providing additional information about time, place, manner, degree, or frequency. Understanding adverbs is essential for expressing precise meanings and adding clarity to sentences.5. Pronoun:- Pronouns are words used in place of nouns, helping to avoid repetition and providing coherence in communication. Understanding different types of pronouns and using them correctly is crucial for effective writing and speaking.6. Preposition:- Prepositions are words that show relationships between nouns, pronouns, and other words in a sentence. They indicate location, direction, time, and manner. Proper usage of prepositions enhances the structure and fluency of sentences.7. Conjunction:- Conjunctions connect words, phrases, or clauses, providing a logical flow to a sentence. They are vital for joining ideas and forming cohesive paragraphs and essays. Understanding different types of conjunctions is fundamental for effective writing.8. Interjection:- Interjections are words used to express strong emotions or sudden reactions. While they are not essential for basic communication, they add depth and emphasis to language. Being aware of interjections enhances one's ability to convey emotions accurately.9. Synonyms:- Synonyms are words that have similar meanings. Knowing synonyms allows for variation in language usage, making written and spoken communication more engaging and sophisticated.10. Antonyms:- Antonyms are words that have opposite meanings. Understanding antonyms helps in expanding vocabulary and expressing nuances in communication.11. Collocations:- Collocations are words that frequently appear together due to their semantic associations. Learning collocations helps in using appropriate word combinations, leading to natural and accurate language usage.12. Idioms:- Idioms are phrases or expressions that have figurative meanings, often not deducible from their literal interpretation. They add color and creativity to language. Understanding idioms is crucial for understanding and effectively using idiomatic expressions in communication.13. Phrasal Verbs:- Phrasal verbs are combinations of a verb and a preposition or adverb that create a new meaning. They are common in spoken English and are essential for understanding native speakers and colloquial language.14. Prefixes:- Prefixes are added to the beginning of words to change their meaning or create new words. Understanding prefixes can help in deciphering the meaning of unfamiliar words and expanding vocabulary.15. Suffixes:- Suffixes are added to the end of words to change their meaning or create new words. Like prefixes, suffixes are important for word analysis and vocabulary development.16. Homophones:- Homophones are words that sound the same but have different meanings and often different spellings. Recognizing homophones is key to avoiding confusion and using words correctly.17. Homographs:- Homographs are words that are spelled the same but have different meanings and sometimes different pronunciations. Understanding homographs helps in interpreting text and using words appropriately.18. Homonyms:- Homonyms are words that are spelled and pronounced the same but havedifferent meanings. Being able to distinguish homonyms is important for clear and precise communication.19. Active Voice:- Active voice is a grammatical voice in which the subject performs the action expressed by the verb. Using active voice generally creates clearer and more direct sentences.20. Passive Voice:- Passive voice is a grammatical voice in which the subject is acted upon by the verb. Passive voice is used when the focus is on the action rather thanthe doer or when the doer is unknown or not important.21. Clauses:- Clauses are groups of words that contain a subject and a verb. Understanding different types of clauses (e.g., main clauses, subordinate clauses) is essential for constructing complex sentences and expressing detailed ideas. 22. Phrases:- Phrases are groups of words that function as a unit within a sentence. They do not contain a subject and a verb. Learning about different types of phrases (e.g., noun phrases, verb phrases) helps in sentence construction and vocabulary development.23. Syntax:- Syntax refers to the rules governing the structure of sentences in a language. Understanding syntax is crucial for creating coherent and grammatically correct sentences.24. Punctuation:- Punctuation marks are symbols used in writing to separate sentences, clauses, and phrases, indicating pauses, tone, and emphasis. Proper punctuation is essential for clear and effective written communication.25. Spelling:- Spelling is the correct arrangement of letters in a word. Good spellingskills are important for clear and professional communication, both in written and digital forms.26. Vocabulary:- Vocabulary refers to the words and phrases known and used by a person. Expanding one's vocabulary is key to effective communication and comprehension.27. Grammar:- Grammar is the system of rules that govern the structure and use of a language. A strong understanding of grammar is essential for speaking and writing correctly and coherently.28. Listening:- Listening is the ability to accurately receive and interpret spoken language. Developing strong listening skills is crucial for understanding others and learning from auditory sources.29. Speaking:- Speaking is the ability to convey information, ideas, and feelings by using spoken language. Good speaking skills are important for effective communication and expression.30. Reading:- Reading is the process of interpreting written language. Developing strong reading skills is essential for comprehension, learning, and gathering information.31. Writing:- Writing is the ability to express thoughts, ideas, and information inwritten form. Strong writing skills are important for effective communication, academic success, and professional advancement.Conclusion:By focusing on and mastering these key vocabulary words, students can significantly improve their English language skills. These words form the foundation for effective communication in reading, writing, listening, and speaking. Regular practice and usage of these words will enhance both fluency and accuracy in English proficiency. Therefore, it is essential for studentsto dedicate time and effort to building a solid vocabulary base as they progress through their college English studies.。
《图式理论在初中英语词汇教学中的应用研究开题报告(英文)》

《图式理论在初中英语词汇教学中的应用研究》开题报告1.Purpose and Significance of the paperBased on psychological model of a learner's background knowledge, schema theory is used by the psychologists to explain the people's understanding process. In light of schema theory, the semantic map, the map which guides the students to intrigue their background knowledge in the mind to understand the current knowledge, can be constructed in the vocabulary teaching.There are significances in theory and practice: in theory, this thesis applies schema theory into the vocabulary teaching in the senior middle school, which enrich the empirical data and support of the schema theory; in practice, this thesis investigates the situation of the vocabulary teaching in the middle school and proposes an teaching method to improve the effectiveness of vocabulary teaching in the senior middle school, which will help the students to enhance their vocabulary capacity, and intrigue teachers to further the studies in the teaching methods.2.The Research status of the paperSchema theory was previously applied in studying human memory in psychology. In recent years, much attention has been paid to use schema theory in second and foreign language teaching. At the beginning, schema theory was widely used in reading and listening .Since 1970s, scholars began to show interest in vocabulary acquisition.In the aspect of vocabulary learning, many scholars analyzed the relationship between schema theory and vocabulary learning. Rumelhart (1980) proposed that a word is just a schema. He thought that schemata were very important in differentiating information. Proficient readers had fully developed word schemata.As for reading comprehension, Hudson (1982) held the idea that schema has a better effect on poor learners than good learners. He pointed that schema is moreeffective in guessing words and comprehension especially to poor learners. V ocabulary guessing will be more successful when the reader’s schemata are in accordance with the reading content.Peng Yanhong (2006), Tangjian Fu (2007) discussed how to improve students’vocabulary memory efficiency based on schema theory and English vocabulary learning strategies, such as associative memory, and so on. Yin mei (2007), and Zhang Xiuqing (2009) discussed the university’s vocabulary teaching and learning from the perspective of the overlap, conflict, and default of schema in culture schema. Ma Yumei (2009) put forward that teachers can improve vocabulary teaching method by constructing a single conceptual schema and contextual schema. Yangshi Sheng (2010) and Yang Haining (2009) proposed that teachers should help students to start their original schema or rebuild a new schema in vocabulary teaching. By assimilation and conformation, the students can complete the learning of new knowledge and incorporate it into the existing cognitive structure.In short, all the scholars above emphasized that both schemata and background knowledge are very important in vocabulary teaching and learning. What’s more, they all agreed that students should acquire new words from context and their previous knowledge. But they neglected to demonstrate the feasibility of using schema theory in vocabulary teaching and learning from the cognitive perspective in detail.3.The main contents of the paperPartⅠIntroduction1.1 General Background1.2 The Significance of the Research1.3 Research MethodPart II Literature Review2.1 Definition of V ocabulary2.2 Previous Studies of V ocabulary TeachingPart III Related Theory3.1 Definition of Schema theory3.2 Classification of Schema Theory3.3 Development of Schema TheoryPart IV Methodology4.1 Subjects4.2 Instrument4.3 Procedures4.4 Data CollectionPart V Result and Disscussion5.1 Result5.2 Disscussion5.3 SummaryPart VI Conclusion6.1 Implications for Pedagogy6.2 Limitations4.The main Research Method of the paperQuestionnaire and interview:The instruments of the study includes questionnaire, test papers on students memory and vocabulary competence. What’s more, the English text book published by foreign language teaching and research press is used as teaching book.V ocabulary competence tests: The two classes were given a vocabulary pre-test to check their vocabulary level. The pre-test paper given before the research aimed at testing the two classes' vocabulary level. The pre-test were held before the experiment without telling students in advance in order to avoid students' preparation beforehand, insuring the reliability and validity.5.References[1]Anderson, R. C. and Pearson, P. D. A. schema-theoretic view of basic processes in reading comprehension[M]. Beijing, Foreign Language Teaching and Research Press, 1984. 42.[2]Batia Laufer, Incidental vocabulary acquisition in a second language: the constructof task-induced involvement[J]. Applied Linguistics. 2001.(3):1-26.[3]Carrell, P. L. Schema theory and ESL reading pedagogy[M]. TESOL Quarterly, 1983. 17.[4]Henriksen, B. Three dimensions of vocabulary development. Studies in second language acquisition[J]. 1995. (21):303-317.[5]Kintsch, Ccomprehension [M]. London: Cambridge University Press, 1998. 217.[6]Laufer, B. Ease and difficulty in vocabulary learning: Some teaching implications. Foreign Language Annuals [J]1990. (23), 147-156.[7]Melka. F. Receptive vs. productive aspects of vocabulary [Eds.], In N.Schmitt and M, Mc Carthy(Eds.) V ocabulary: Descriptions, acquisition and pedagogy, Cambridge University press, 1997.[8]Rumblhart, D.E. et al. The Representation of knowledge in memory. In Anderson, et al (eds). Schooling and the Acquisition of Knowledge. Hillsdale, N.J.: Erlbaum,1977. 99-I,35.[9]麻珍玉.基于图式理论的高中英语词汇教学研究[D].西北师范大学,2003.[10]马玉梅.基于图式的大学英语词汇教学模式[J].河南师范大学学报,2009,(2).[11]师璐.试论意象图式及其在词义延伸中的作用[J].四川外语学院学报,2004,(5).[12]孙晓婷.图式理论与英语词汇习得[J].西安邮电外语学院报,2008, (2)[13]谭茗兮.论图式理论在高中英语词汇教学的应用[J].外语教学与研究.2007,(16)[14]唐建福.认知图式理论与词汇习得策略[J].湖北教育学院学报,2007,(11)[15]杨海宁.皮亚杰图式理论在词汇教学中的应用[J].辽宁行政学院学报,2009,(6)[16]杨世生.词源学与图式理论对英语词汇记忆的启示[J].长江大学学报, 2010.。
湘中地区早寒武世牛蹄塘组黑色岩系地球化学特征与有机质富集机理

第51卷第8期2020年8月中南大学学报(自然科学版)Journal of Central South University (Science and Technology)V ol.51No.8Aug.2020湘中地区早寒武世牛蹄塘组黑色岩系地球化学特征与有机质富集机理吴诗情1,2,郭建华1,2,王玺凯1,2,李智宇1,2,刘辰生1,2,焦鹏1,2,陈广1,2(1.中南大学地球科学与信息物理学院,湖南长沙,410083;2.中南大学有色金属成矿预测与地质环境监测教育部重点实验室,湖南长沙,410083)摘要:中国南方扬子板块寒武纪早期广泛发育一套富有机质黑色岩系,为了研究其有机质富集特征及控制因素,对湘中地区AY −1井牛蹄塘组32件岩芯样品总有机碳质量分数w (TOC)、主微量和稀土元素质量分数等地球化学特征参数进行测试。
研究结果表明:研究区牛蹄塘组黑色页岩有机质丰度高,与热液相关的Ni 和Sb 等微量元素富集以及热液指标w (Co)+w (Ni)较高;w (P 生物)和w (Ba 生物)显示牛蹄塘组生产力在中—高等水平,w (U)/w (Al),w (V)/w (Al),w (Ni)/w (Co),w (V)/w (Cr)和w (U)/w (Th)共同指示水体基本处于缺氧、还原环境;从底部至顶部,页岩受热液作用强度、生产力水平和水体还原性变化均表现为由弱—强—弱的趋势,且与有机质丰度呈现正相关;顶部生产力水平虽然较高且趋于稳定,但沉积时海平面下降使水体还原性减弱,有机质无法良好地保存。
强热液活动、高古生产力和强还原环境使牛蹄塘组中部形成高有机碳丰度的页岩层系,成为页岩气勘探的有利层段。
关键词:湘中地区;牛蹄塘组;黑色岩系;地球化学;有机质富集中图分类号:P595文献标志码:A开放科学(资源服务)标识码(OSID)文章编号:1672-7207(2020)08-2049-12Geochemical characteristics and organic matter enrichment mechanism of the Lower Cambrian Niutitang formation blackrock series in central HunanWU Shiqing 1,2,GUO Jianhua 1,2,WANG Xikai 1,2,LI Zhiyu 1,2,LIU Chensheng 1,2,JIAO Peng 1,2,CHEN Guang 1,2(1.School of Geosciences and Info-Physics,Central South University,Changsha 410083,China;2.Key Laboratory of Metallogenic Prediction of Nonferrous Metals and Geological Environment Monitoring,Ministry of Education,Central South University,Changsha 410083,China)Abstract:During the early Cambrian period,in the Yangtze plate of South China,there widely developed a set ofDOI:10.11817/j.issn.1672-7207.2020.08.001收稿日期:2019−11−08;修回日期:2020−01−22基金项目(Foundation item):中国地质调查局地质调查项目(DD20160183);湖南省科技创新计划项目(2017GK2233);湖南省自然科学基金资助项目(2017JJ1034)(Project(DD20160183)supported by the Geological Survey Program of Geological Survey of China;Project(2017GK2233)supported by the Science and Technology Innovation Program of Hunan Provine;Project (2017JJ1034)supported by the Natural Science Foundation of Hunan Province)通信作者:郭建华,博士,教授,从事沉积学与页岩气研究;E-mail:**************.cn第51卷中南大学学报(自然科学版)organic-rich black rock series.In order to study its features and controlling factors of organic matter(OM) enrichment,32core samples of Niutitang formation from well AY−1in Central Hunan were selected for geochemical tests such as total carbon mass fraction of TOC,major elements,trace elements and rare elements. The results show that the mass fraction of TOC of black shale in Niutitang formation is high.The trace elements related to hydrothermal fluid(HF)such as Ni and Sb were accumulated,while w(Co)+w(Ni)as the HF indicators ishigh.w(Pxs )and w(Baxs)show a middle-high productivity level of Niutitang formation.w(U)/w(Al),w(V)/w(Al),w(Ni)/w(Co),w(V)/w(Cr)and w(U)/w(Th)jointly indicate that the water is basically in anoxic and reducing environment.From bottom to top of Niutitang formation,hydrothermal activity intensity,productivity level and the change of water's reducibility all show a weak−strong−weak tendency.And this tendency has a positive correlation with mass fraction of TOC.Although the productivity of the top of Niutitang formation is relatively high and tends to be stable,sea−level falling weakens the reduction of water during deposition,which makes the OM not able to well preserved.In summary,intense hydrothermal activity,high paleoproductivity and strong reducing environment result in the high TOC shale series in the middle part of Niutitang formation which is also a favorable exploration layer of shale gas in the study area.Key words:Central Hunan Province;Niutitang formation;black rock series;geochemistry;organic matter enrichment震旦纪—寒武纪是一段重要的地质历史时期,在此时期内伴随着全球构造板块变化及火山作用的发生[1],全球古海洋地球化学环境[2]、生物数量及种类均发生了较大变化[3]。
Pragmatic Meaning of Words

(Searl, 1979)
Both the context of culture and the context of situation are necessary for a proper understanding of an utterance or text.
Opposite meaning
The meaning produced is just the opposite to the conceptual meaning of an expression.
It’s very considerate of you to sing so loudly while I was asleep.
Non-linguistic context
Non-linguistic context may extend to include the entire cultural background.
e.g. Have you eaten? Western: an offer to dine together Chinese: a bare greeting
Grammatical context
In some cases, the meaning of a polysemous word may be determined by the grammatical structure in which it appears.
get
get a new book; get a reward get angry; get really frightened I get him to deliver the mail.
西南财经大学拟引进人才基本情况表
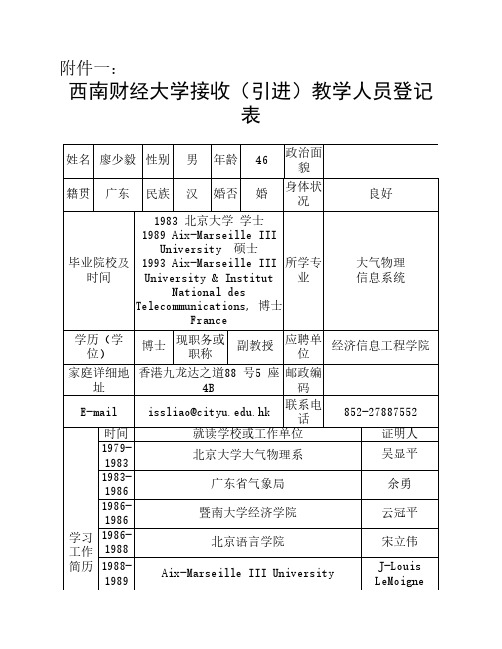
Personalization in M-Commerce
Applications
ห้องสมุดไป่ตู้HKD180,000
Combining the Empirical Approach and
1st
2006
User Modeling Techniques for Personalized Mobile Advertising
附件一:
西南财经大学接收(引进)教学人员登记 表
姓名 廖少毅 性别
男 年龄
46
政治面 貌
籍贯 广东 民族
汉 婚否
婚
身体状 况
良好
1983 北京大学 学士
1989 Aix-Marseille III
University 硕士
毕业院校及 1993 Aix-Marseille III 所学专
时间
University & Institut 业
2008
Techniques: A Design Research Approach for Personalized Mobile
Decision Support System
Advertising Applications
A Functional Dependencies-Based
June Bayesian Networks Learning Method IEEE Transactions
已公 开发 表、
2006
Sept 2005
and Its Application in a Mobile on SMC (Part B),
Commerce System
Constructing Intelligent and Open Mobile Commerce using a Semantic
语言学重点概念总结

Design features(定义特征):the distinctive features of human language that essentially make human language distinguishablefrom languages of animals.Synchronic(共时的):said of an approach that studies language at a theoretical “point” in time.Diachronic(历时的):said of the study of development of language and languages over time.Prescriptive(规定式):to make an authoritarian statement about the correctness of a particular use of language.Descriptive(描写式):to make an objective and systematic account of the patterns and use of a language or variety.Competence(语言能力):unconscious knowledge of the system of grammatical rules in a language.对于一门语言的语法规则系统的无意识获得的知识。
Performance(语言运用):the language actually used by people in speaking or writing.人们说话写作时实际使用的语言。
Langue(语言):the language system shared by a “speech community”.一个“语言社团”共有的语言系统。
goe开头的单词 -回复

goe开头的单词-回复Goe Knowledge Graph: A Comprehensive GuideIntroduction to Goe Knowledge GraphKnowledge graphs have gained significant traction in recent years due to their ability to organize and connect vast amounts of data. A knowledge graph refers to a structured representation of knowledge in a graph format, where entities are represented as nodes, and relationships between entities are represented as edges. Goe is a leading player in the knowledge graph domain, providing powerful solutions for various industries. In this article, we will explore Goe's offerings and delve into its applications in different fields.What is Goe?Goe is a knowledge graph company that specializes in creating and maintaining knowledge graphs for various purposes. With their cutting-edge technology and expertise in data management, Goe aims to revolutionize the way we connect and comprehend information. Their knowledge graph infrastructure, known as theGoe Knowledge Graph, serves as a framework for organizing, querying, and analyzing complex data structures.Understanding Goe Knowledge GraphThe Goe Knowledge Graph is designed to capture and represent information in a multidimensional manner. It allows users to traverse data by exploring interconnected nodes and relationships, providing a holistic view of the underlying information. The graph's nodes represent entities, such as people, organizations, or concepts, while edges signify the relationships between these entities. This semantic approach enables users to discover valuable insights by uncovering hidden connections between seemingly unrelated data points.Building a Goe Knowledge GraphConstructing a Goe Knowledge Graph involves several key steps. Firstly, the data acquisition phase involves gathering relevant data from various sources, such as databases, APIs, or web scraping. Goe supports both structured and unstructured data formats, allowing for flexibility in data integration. Once the data is collected, itundergoes a preprocessing stage, where it is cleaned, standardized, and transformed into a unified format.Next comes the entity recognition and resolution stage. Goe employs advanced natural language processing and machine learning algorithms to identify and disambiguate entities within the data. This process ensures that entities are correctly linked to their corresponding nodes, eliminating any ambiguities that might arise from homonyms or synonyms.After entity resolution, the relationship extraction phase takes place. Goe utilizes various techniques, including dependency parsing and pattern recognition, to extract meaningful relationships between entities. These relationships are then represented as edges, further enriching the knowledge graph structure.Improving Goe Knowledge Graph PerformanceTo enhance the performance and usability of the Goe Knowledge Graph, Goe offers several optimization techniques. One such technique is entity linking, which connects entities in theknowledge graph to external data sources, allowing for real-time updates and enrichment. Additionally, Goe provides query optimization mechanisms that ensure efficient retrieval of information from the graph, even when dealing with large-scale datasets.Applications of Goe Knowledge GraphThe Goe Knowledge Graph finds applications across multiple domains. In the healthcare industry, it enables researchers to discover potential drug interactions, identify disease patterns, and improve patient outcomes. In finance, the knowledge graph assists in fraud detection, risk assessment, and portfolio optimization. Furthermore, Goe's knowledge graph fuels innovation in smart cities by facilitating urban planning, transportation optimization, and resource allocation.ConclusionThe Goe Knowledge Graph offers a powerful solution for organizing and making sense of complex data structures. Throughits sophisticated techniques for data acquisition, entity resolution, and relationship extraction, Goe presents users with a comprehensive understanding of the underlying information. With diverse applications in healthcare, finance, and smart cities, Goe's knowledge graph continues to shape the future of data management and analysis.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Journal of Intelligent&Fuzzy Systems21(2010)197–207197 DOI:10.3233/IFS-2010-0451IOS PressConstructing and mining a semantic-based academic social networkTrong Hai Duong a,Ngoc Thanh Nguyen b,∗and Geun Sik Jo a,∗a School of Computer and Information Engineering,Inha University,Koreab Institute of Informatics and Engineering,Wroclaw University of Technology,PolandAbstract.A number of studies have focused on how to construct an academic social network.The relational ties among researchers are either co-authorship or shared keywords that are captured from scientific journals.The problem with such a network is that researchers are limited within their professional social network.In this paper,we propose a novel method for building a social network explicitly based on researchers’knowledge interests.The researcher’s profile is automatically generated from metadata of scientific publications and homepage.By measuring the similarity between topics of interest,we are able to construct a researcher social network with relational linkages among authors that are produced by matching the their corresponding profiles.A direct loop graph-based social network is proposed.The graph naturally represents such a social network.Interestingly,our results showed that a social network based on profile matching is more representative than network based on publication co-authorship or shared keywords.Researcher mining in the academic social network has been explored via two problems Researcher Ranking and Expert Finding.Keywords:Ontology,researcher profile,ontology-based user profile,ontology integration,social network,social network visualization1.Introduction1.1.Related workSocial networks have recently attracted considerable interest.There are a number of systems for generating social network visualizations and performing statisti-cal analyses for the purpose of sociological research, including UCINet[30],JUNG[19],and GUESS[1]. With the intention of utilizing social networks for the semantic web,several studies have examined automatic extraction of social networks and visualization network applications such as TouchGraph’s Facebook Browser and Vizster.The TouchGraph’s Facebook Browser lets bloggers visualize their friends and photos.Vizster is ∗Corresponding authors.Ngoc Nguyen Thanh and Geun Sik.E-mail:thanh@pwr.wrov.pl(N.T.Ngugen);gsjo@inha.ac.kr (G.S.Jo).built as a visualization system that end-bloggers of so-cial networking services can use to facilitate discovery and increase awareness of their online community[17]. Both of these tools are used to display the network be-tween a blogger and his friends in large communities such as Facebook and Friendster.Takama et al.[28]at-tempted to develop a visualization map that contributed to an interactive blog search.The visualization map was facilitated by linking the keywords of the blogs.Karger and Quan[20]meanwhile presented a visualization sys-tem that displays messages from multiple blogs together as a reply graph,a diagram describing relationships be-tween a message and all comments related to the mes-sage.Their result showed that bloggers were able to understand how the relevant issues are constructed and related.In the academic area,several researchers have at-tempted to conduct a thorough investigate on of the issue of extraction and mining of an academic social1064-1246/10/$27.50©2010–IOS Press and the authors.All rights reserved198T.H.Duong et al./Constructing and mining a semantic-based academic social networknetwork.Harrison and Stephen[15]described the elec-tronic journal as the heart of an online scholarly com-munity where academic journals principally function as channels of communication for practicing scholars. Newman[23,24]constructed a scientist collaboration network based on co-authorship data from journal pa-pers.In this collaboration network,two scientists were considered to connect if they had authored a paper to-gether.The problem with such a network is that re-searchers are limited within their professional social network.Expertfinding is one of the most important sub-jects for mining from social networks.The task of expertfinding entails identifying persons with rele-vant expertise or experience for a given topic.There are many methods that focus on expertfinding,and mainly fall into two categories:profile-based methods and document-based methods.In profile-based meth-ods[2,3,11,22],researchersfirst build a term-based ex-pertise profile(called document reorganization in[11]) for each candidate,and rank the candidate experts based on the relevance scores of their profiles for a given topic by using traditional ad hoc retrieval models.In document-based methods[3,5,25],instead of creat-ing such term-based expertise profiles,researchers use supporting documents as a bridge and rank the candi-dates based on the co-occurrences of topic and candi-date mentions in the supporting documents.However, the number of candidate experts is limited;for example, there are only1092candidate experts in TREC[2,5], but in a network everyone can be a candidate,and thus the number of candidate experts can be in the millions. In addition,on the Web,only unstructured data is avail-able,and candidate names and topics are presented as keywords in plain texts,whereas a social network con-tains not only personal local information but also com-plex relationships.1.2.Our approachFrom a list of researchers’publications,it is possible to get to know the knowledge interests of a researcher, his/her collaborators,and even the latest conferences attended by that researcher.Moreover,other personal information of a researcher such as basic information (e.g.photo,affiliation,and position),contact informa-tion(e.g.address,email,and telephone),and educa-tional history(e.g.graduated university and major) may be extracted from his/her personal sites.There-fore,for each researcher,we can create a profile based on an ontology by extracting the profile information from his/her homepage and journal papers.This in-cludes typical information in the researcher profile(see Fig.1).By measuring the similarity between the inter-esting topics,we are able to construct an academic so-cial network.Relational linkages among authors are not only co-authorship but also are produced by matching their corresponding profiles together.In particular,an academic social network is generated by considering a target researcher who plays a central role.The tar-get’s co-authors are counted as the second level of the network.The complete network is decided by n levels where n>1.Relational linkages among the researchers are produced by matching their corresponding profile together.Moreover,the number of candidate experts that can be utilized will be in the millions,and we can find experts for a given topic by taking into account the contributions from all the researchers in the academic network and the score of his/her research topics.Our approach aims at conducting a thorough investi-gation of the issue of the construction and mining of an academic social network,providing the following main contributions:•We propose a novel method for building an academic social network based explicitly on re-searchers’knowledge interests.In particular,it fo-cuses on how to automatically extract the profile of a researcher from metadata of his/her scientific publications and homepage,and how to identify researchers with interest knowledge that is similar to that of the target.The target profile is further im-proved by learning interest knowledge from sim-ilar profiles.•A direct loop graph-based social network is pro-posed.The graph naturally represents such a social network.It is useful to deduce indirect re-lationships among researchers.The network can be reduced by considering only a specific rela-tion or combining all relations.Interestingly,our results showed that a social network based on profile matching is more representative than the networks based on publication co-authorship or keywords.•Researcher mining in the academic social net-work has been explored.We solved two main problems related to mining:Researcher Ranking and Expert Finding.In the researcher ranking,the researchers are ranked based on an importance weight.The importance measurement for each re-searcher takes into account the contributions from all the other researchers in the academic networkFig.1.Research profile.200T.H.Duong et al./Constructing and mining a semantic-based academic social network•S c=(t1,t2,...,t n)is the collection of all key-objects(terms)in the document collection D c,•−→S c=(w1,w2,...,w n)is a feature vector of the concept c,where w i is the weight distribution of term i in S c,0≤w i≤1.2.3.Researcher profile generationThis section describes the process of building an on-tological user profile based on the techniques described in the previous section.Hierarchical user information in the initial user profile is treated as an ontology.More clearly,we learn and improve the users profile in the form of an ontology.rmation collectionHomepage retrieval.Given a person’s name and possibly an email address,the systemfinds the person’s homepage by the following steps:•Feature Vector Construction:We collect100 homepages and extract keywords for each home-page manually.We then make a consensus among them to obtain the most representative keywords for a given homepage.The keywords are called components of the feature vector.The feature vec-tor can be used to distinguish between a homepage and other webpages.•Query Generation:A set of mentions is generated from a person’s name.For example,for the name John Fitzgerald Kennedy,the corresponding set of mentions may contain Kennedy,J.F.Kennedy and John F.Kennedy.Thefirst query uses the per-son’s name or each mention,and Google’s site:the operator with the most specific domain name ap-pears in their corresponding email address(Trong Hai Duong site:eslab.inha.ac.kr).If no result is returned,increasingly general queries are issued (Trong Hai Duong site:inha.ac.kr).If thefinal re-sult is empty,a simple query containing only the person’s name is used.A none-empty result is sent to Homepage Identification.•Homepage Identification:For each page in the re-sult,the system crawls its internal hyperlinks to collect the user’s entire web home directory.We match the feature vector with this result to choose the correct homepage.Publication Retrieval.Many scholarly publications are currently available on the Internet and in digital is a sub search en-gine that has been proved to be the most effective in searching such publications.We use the Google search to crawl all user’s publications by using ba-sic keyword of the user’s name and propably email as follows:•Feature Vector Construction:Similar to homepage retrieval,we construct a feature vector to representa publication site.By using the feature vector wecould distinguish between a publication site and other webpages.•Query Generation:A set of mentions from a person’name is generated as presented in the homepage retrieval section.The query is the longest name of the person or a corresponding mention.•Publication Collection:Each query is input to to crawl all user’s publi-cations.The result isfiltered by retaining the sites associated with a user’s email.Thefinal result is passed to Publication Identification.•Publication Identification:For each page in the re-sult,we match the feature vector with this result;then,depending on the matching cost,we can se-lect all correct publication sites.rmation extractionPersonal Information Extraction.The method to extract personal information was referred to[21]as follows:•Finding Relevant Web Pages:Given a researcher name and probably an email,Homepage and Pub-lication sites are identified as presented in the above section.•In preprocessing:(A)We separate the text into paragraphs(i.e.,sequences of tokens),(B)we de-termine tokens in the paragraphs,and(C)we as-sign possible tags to each token.•In tagging:Given a sequence of units,we deter-mine the most likely corresponding sequence of tags by using a trained tagging model.In this pa-per,we make use of CRF as the tagging model.It is a conditional probability distribution of a se-quence of labels given a sequence of observations, represented as P(Y/X),where X denotes the ab-servation sequence and Y the label sequence.All components Y i of Y are assumed to range over a finite label letter Y.The conditional probability is formulized as follows:T.H.Duong et al./Constructing and mining a semantic-based academic social network201p(x|y)=1Z(x)expe∈E,jλj t j(e,y|e,x)+v∈V,kµk s k(v,y|v,x)(3)where x is a data sequence,y is a label sequence,and y|e and y|v are the set of components of y asso-ciated with edge e and vertex v in the linear chainrespectively;t j and s k are feature functions;theparametersλj andµk are coefficients correspond-ing to the feature functions t j and s k respectively,and are estimated from the training data;Z(x)isthe normalization factor.The model is used tofindthe sequence of tags Y∗with the highest likelihoodY∗=max y P(Y|X),using the Viterbi algorithm.•In training:The CRF model is built with labeled data and by means of an iterative algorithm basedon Maximum Likelihood Estimation.Paper Mention Information Extraction.We man-ually describe structure paper resource portals such as ACM portal,IEEE Eplore,CiteSeer,etc,to obtain exactly important mentions of paper information such as the authors’name,affiliation and email,paper’s title,abstraction,and content,....For each publication site,we identify the corresponding paper portal.Then, depending on the structure paper portal,we can easily extract useful information from the publication site.If there is no paper portal indexed,we apply a method that is similar to Personal Information Extraction.2.4.Interest knowledge building2.4.1.Document presentationThe t f–idf weight(term frequency-inverse docu-ment frequency)is a weight often used in information retrieval and text mining.This weight is a statistical measure used to evaluate how important a word is to a document in a collection or corpus.Here,we use a tradi-tional vector space model(tf–id f)to define the feature of the documents.Definition2.3(Feature Vector of Document).Let T d=(t1,t2,...,t n)be the collection of all of key-words(or terms)of the document d.Term fre-quency t f(d,t)is defined as the number of occur-rences of term t in document d.A set of term fre-quency pairs,P d={(t,f)|t∈T d,f>threshold},is called the pattern of a document.Given a pattern P d={(t1,f1),(t2,f2),...,(t m,f m)},let d be the fea-ture vector of document d and let td be the collection of corresponding terms to the pattern.Then we have:d=(w1,w2,...,w m)(4) td=(t1,t2,...,t m)(5) wherew i=f imj=1f j∗log|D||d:t i∈d|(6)Definition2.4(Feature Vector of Set of Documents). Let P i={(t1,f1),(t2,f2),...,(t m,f m)}be the pattern of the document i belonging to the set of documentds,i=1,...,n.A set of term frequency pairs,P c=i=1,...,nP i,is called the pattern of the ds.Let−→ds be the feature vector of the ds and let tds be the collection of corresponding terms to the pattern.Then we have:−→ds=(w1,w2,...,w k)(7) tds=(t1,t2,...,t k)(8) wherew i=f imj=1f j∗log|D|i(9)–|D|:the total number of documents in the corpus.–|d:t i∈d|:the number of documents where the term t i appears(that is).If the term is not in the corpus,this will lead to a division-by-zero.It is therefore common to use1+|d:t i∈d|.2.4.2.Training•Building an ontology representing a common user’s profile.•Assigning documents to the ontology.•Computing the feature vector of each category (concept),via the following method:–For each leaf concept,the feature vector is cal-culated as the feature vector of a set of docu-ments:−→S c=−→ds c(10)–For each non-leaf concept c,its feature vec-tor is calculated by taking into consideration202T.H.Duong et al./Constructing and mining a semantic-based academic social network the contributions from the documents(denotedD c)that have been assigned to it and other doc-uments(denoted D c ,for any c is a direct subconcept of c)that have been assigned to directsub concepts of the concept c:−→S c=α−→ds c+β−→ds c (11)where −→ds c and−→ds c correspond to the feature vec-tors of the sets of documents D c and D c ,0≤α,β≤1andα+β=1.2.4.3.Automatically building a user’s profileAfter collecting the relevant document,a number of features are extracted by the fore mentioned equation, which is the general candidate concept of the per-sonal ontology.With these concepts,a general personalAlgorithm1:Automatically building a user’s profileinput:Given a set of key words(keyWord)concernedwith the user and the pre-defined profile(commonProfile),trained as described above output:Corresponding user’s profile/*Collecting use’s information*/ infoUser←−CollectingInfoUser(keyWord);1featureVector←−ExtractingFeatureVector2(infoUser);commonProfile←−AscendingImportantConcept 3(commonProfile);foreach each feature vector d of each document belong to4featureVector doforeach each concept c belonging to commonProfile5do/*Similarity between a concept and document*/sim(d,c)=sim(−→d,−→S c)=(T di,T c2i)∈K(d i∗S c i)ni=1(d i)2∗ni=1(S c i)2(12)where K={(T d i,T c2i)|Sims(T d i,T c2i)=1}6if match≥threshold then7if the concept c does not exist in userProfile 8thencreate a new concept c for the9userProfile;end10add document d into the corresponding11concept c belonging to userProfile;break;end12end13end14Return(userProfile);15ontology can be automatically built,as shown inAlgorithm1.3.Researcher social network visualization3.1.An enrich social network of researchersAn enrich social network of researchers is generatedby considering a target researcher who plays a cen-tral role.The target’s co-authors and referenced au-thors(co-operators)collected from the target’s pub-lications are counted as the second level of the net-work.Continuously,the target’s collaborators are con-sidered as the target researcher.His/her collaboratorsare supplemented on the network as the third level.The complete network is decided by n levels,wheren>1.The researchers’profiles are generated.Rela-tional linkages among the researchers are produced bymatching between the corresponding personal profiles.Notice that there may be numerous edges connectingtwo researchers.The number of the edges is equal tothe number of matches between their correspondingprofiles.Here,we define the researcher social networkas a direct loop graph:Definition3.1A researcher social network is a direct loop graph with the following quadruple:G=(C∗,R∗,N,M)(13) where,•C∗is a set of nodes representing researchers.•R∗is a set of arcs representing relations between researchers:Co-author,Reference-author,and In-teresting topic.Each arc is associated by a nu-merical value being the weight(w)of the relation represented by the arc.–w co ij=(n co ij/N co i),where w co ij is the weight of the co-author relation from the author j to i’s;n co ij is the number of collaborative instances ofthe author j with i,thefirst author;N co i is thenumber of co-authors of i.–r ref ij=(n ref i/N ref i)where w ref ij is the weight of the reference-author relation from the author jto i;n ref ij is the number of reference instancesof the author j in i’s papers;N ref i is the numberof reference-authors of i’s.–Weight of each interesting topic relation isequal to the similarity degree between twofeature vectors representing the correspondingtopics.T.H.Duong et al./Constructing and mining a semantic-based academic social network203•N is an adjacency matrix of G,denoted as N(G), is a n−by−n matrix where n is the number of nodes in G,and entry is the number of arcs in G with endpoints(v i,v j)/v i=v j.•M is an incidence matrix of G,written as M(G), and is a n−by−m matrix where m is the number of edges(relations)in G;if v i is the starting point ofe j,entry m ij is equal to–1;if v i is the second pointof e j,entry m ij is equal to w>0being the weight of a relation that is represented by the arc e j.•If vertex v is a startpoint of edge e,then v and e are incident values.•The degree of vertex v,written as d(v),is the number of incident values of edges.•A local matrix of vertex v i,denoted as L(v i) being M(G)is limited byleft columnv∈(v0,...,v i)d(v)+1andright columnv∈(v0,...,v i)d(v)+d(v i)(14)where v i is a vertex at row i of matrix M(G). The network naturally represents such a social net-work.It is useful to deduce indirect relationships among authors.The network can be reduced by considering only specific relations or combining all relations.For example,a co-author social network is generated from the network by taking only co-author relations.A net-work that combines all the relations(and is thus called a combined social network)is effective tofind a relevant author.3.2.A combined social network of researchersHere,we simply present the combined social network as follows:Definition3.2A combined social network is given by a graph G=(V,E),where V is a set of nodes repre-senting researchers and E is a set of edges(V*V)rep-resenting the relationships between the corresponding researchers.The relationships are combined by all the relations:Co-author,Reference-author,and Interesting topic.In particular,we need to estimate the weight of a given relation to blend all the relations together.Let w(v i,v j)be the relation weight,and w ij= w(v i,v j)be the weight of all relations from v i to v j.The relation weight matrix representation of G,W=(w ij), is a n×n matrix wherew ij=α∗w c+β∗w r+δ∗w i(15)w ij is the combined weight of the researcher social net-work graph,w c is the weight of a co-author relation,w r is the weight of a reference-author,and w i is the weight of an interesting topic.To calibrate the coefficientsα,β,andδ,we can generate the coefficients by taking a consensus among experts’suggestions.Definition3.3(Forward researchers).For any re-searcher v i∈V,the forward researchers of v i are de-fined as F vi={v j|v j∈V,∃r ij∈E}.Definition3.4(Backward researchers).For any re-searcher v i∈V,the forward researchers of v i are de-fined as B vi={v j|v j∈V,∃r ji∈E}.4.Social network mining4.1.Important researchers of an academic network An importance measurement of a researcher must take into account the contributions from all the other researchers in the academic network and the score of his/her research topics.It consists of two steps,Initial-ization and Propagation.In Initialization,first,a combined social network G=(V,E)is composed,where V is a set of nodes representing researchers and E is a set of edges(V∗V) representing the relationship between the correspond-ing researchers.The initial importance score(weight) of each relationship is calculated by eq.(14).Sec-ond,we use the interest knowledge of the researcher’profile to calculate an initial importance score of re-search topics for each person(the weight of the node). Suppose T={t1,t2,...,t m}is a collection of inter-esting topics.Each topic is represented by a descrip-tion t={a1,a2,...,a k}and the corresponding fea-ture vector s={s1,s2,...,s k},where0≤s i≤1is the weight of the term a i.We denote f(t)as a func-tion to compute the score of the feature vector s of the corresponding topic t.The initial importance score of research topics for the researcher c is calculated as follows:W c=mi=1f(t i)nj=1hjl=1f(t l)(16)where m and h j are the number of feature vectors of the corresponding researchers c and j,respectively.n is the number of researchers in the social network.In Propagation,the importance score of each re-searcher is improved by taking into account the contri-204T.H.Duong et al./Constructing and mining a semantic-based academic social network butions from all the other researchers in the academicnetwork via characterization of four features of poten-tially important scores of the researchers and the rela-tions,which drive the drifting stream of consciousness:•A researcher is more important if there are morerelations originating from the researcher.•A researcher is more important if there is a re-lation originating from the researcher to a moreimportant researcher.•A researcher is more important if it has a higherrelation weight to any other researchers.•A relation weight is higher if it originates from amore important researcher.Let r(c i)be a function of an importance weight ofresearcher c i,r i=r(c i)be a importance weight value ofthe researcher c i,w(c i,c j)be a relation weight function,and w i,j=w(c i,c j)be the weight of all relations fromc i to c j.It is possible that there exists more than onerelation from researcher c i to researcher c j.For exam-ple,the researcher Geun Sik Jo may have two relations,Supervisor and Co-author,with the researcher TrongHai Duong.Therefore,r j w i,j is the total importancevalue of all the relations from concept c i to concept c j.In fact,the basic idea underlying Propagation is sim-ilar to the idea of[12];we present a similar recursiveformula that computes the weight of a relation startingfrom researcher c i to researcher c j at the(k+1)th iter-ation(see eq.(17)).The weight is proportional to theimportance of c i and is the inverse ratio of the sum ofall the importance values of c j’s backward concepts atthe k+1th iteration.w k+1(c i,c j)=r k(c i)t i∈B ir k(t i)(17)And the recursive formulae are used to calculate the importance of concept c i at the k+1th iteration.The im-portance consists of two parts;one contributed by all the importance values of c i’s forward researchers and the weight of relations from c i to the forward researchers with probabilityα.The other is contributed by some independent jump probabilities(here1/V)with prob-abilityλ;the formulation is then expressed as follows:r k+1(c i)=α1V+λc j∈F iw k+1(c i,c j)r k(c j),α+λ=1(18)4.2.ExpertfindingThe expertfinding task is generally defined as fol-lows[6,10,27]:given a keyword query,a list of experts and a collection of supporting documents,rank those experts based on the information from the data collec-tion.Expertfinding is similar to the traditional ad-hoc retrieval task,since both tasks targetfinding relevant information items given a user query.This problem has many real-world applications.For example,organizers of a conference need to assign submissions to PC mem-bers based on their research interests and expertise.As a retrieval task,expertfinding has recently attracted much attention mostly due to the launching of the En-terprise track[6,27]of TREC[31].The key challenge in expertfinding is to infer the association between a person(i.e.,candidate expert)and an expertise area (i.e.,topic)from the supporting document collection. Different from previous researches,wefind experts via the academic social network,taking into consider-ation two aspects:if a researcher has authored many papers on a topic or if the topic is mentioned in his/her many papers,then he/she is a candidate expert on the topic;and,if a researcher has relationships(such as co-author,reference,similar topic)with many other re-searchers who are experts on a topic,then he/she also is a candidate expert on the topic.The expertfinding is similar to the above Importance Researcher problem since for both tasks the importance measurement of a re-searcher must take into account the contributions from all the other researchers in the academic network.The major difference is that the expertfinding only considers researchers descending score of importance researcher based on a given topic,but not a combination of all topics.The importance is the consideration of that the relevancy of a candidate expert to the topic.It consists of two steps,Initialization and Propagation.In Initialization:our strategy for calculating the ini-tial expert score is based on the probabilistic model as follows:Formally,suppose T={t1,t2,...,t m}is a collection of interesting topics.Each topic is represented by a de-scription t={a1,a2,...,a k}and the corresponding feature vector s={s1,s2,...,s k}where0≤s i≤1is the weight of the term a i.Let R be a binary random variable to denote the relevance(1for relevant and0 for non-relevant).Given a query t and an expert candi-date c,we are interested in estimating the conditional probability R(R|c,t)indicating whether the candidate c is relevant to topic t or not.Denote oc(c,t,s)as the weight of the term t occurring in the feature vector s of a corresponding topic in T.P(R=1|c,t)=soc(c,t,s)c i∈Vsoc(c i,t,s)P(t)(19)。
