ACSAR Software Model Checking with Transfinite Refinement
关于ADAMS与Matlab联合仿真的讨论
发表于 2006-3-12 19:56 资料 个人空间 短消息 加为好友请教:在CAR 中进行联合仿真的问题!!请教:如何直接使用标准模块中的整车模型进行联合仿真控制? 我研究的重点是操纵稳定性控制(ADAMS 和matlab/simulink 联合控制),而标准模块中的车辆模型已经很成熟,更接近实际汽车模型,所以想直接引用。
根据VIEW 中的“雷达”这一例子,是需要定义输入和输出状态变量(要用build —system elements —state variable 进行定义),而CAR 中是没有这一选项的,既然能将Control 模块装到CAR 中,为什么就不能定义状态变量? 通过修改acar.cfg 文件,已经能使view 和car 互通了,在car 中的view 界面下已有build —system elements —state variable 选项,请问,可以在这里进行定义吗?期望您的指教!引用 报告 回复honeyjuneni 新手会员UID 75478 精华 0 积分 1 帖子 80 贡献积分 2 阅读权限 10 注册 2004-10-13 状态 离线#2 大 中 小使用道具发表于 2006-3-13 12:45 资料 个人空间 短消息 加为好友Re:请教:在CAR 中进行联合仿真的问题!! 怎么每人理我啊?到底能不能直接在standard interface 中利用shared 的整车模型与matlab 进行联合仿真?引用 报告 回复summitxu 新手会员UID 42325 精华 0 积分 1 帖子 48 贡献积分 0 阅读权限 10注册 2004-3-30状态 离线 #3 大 中 小使用道具发表于 2006-3-13 18:39 资料 个人空间 短消息 加为好友Re:请教:在CAR 中进行联合仿真的问题!!你必须在template 下先定义输入输出变量,那样才可以联合仿真。
(完整版)项目测试规范

3.1.5 设计测试用例 在需求分析文档确立基线以后, 测试组需要针对项目的测试需求编写测试用例,
3.1.1 成立测试团队 .......................................................................................................... 5 3.1.2 测试预通知 .............................................................................................................. 5 3.1.3 召开测试启动会议 .................................................................................................. 5 3.1.4 编写测试计划文档 .................................................................................................. 6 3.1.5 设计测试用例 .......................................................................................................... 6 3.2 实施测试阶段 ..................................................................................................................... 7 3.2.1 实施测试用例 .......................................................................................................... 7 3.2.2 提交报告 .................................................................................................................. 7 3.2.3 回归测试 .................................................................................................................. 8 3.3 总结阶段 ............................................................................................................................. 8 3.3.1 编写测试报告 .......................................................................................................... 8 3.3.2 测试工作总结 .......................................................................................................... 9 3.3.3 测试验收 .................................................................................................................. 9 3.3.4 测试归档 ................................................................................................................ 10 3.4 缺陷跟踪 ........................................................................................................................... 10 4 缺陷类型定义 .............................................................................................................................. 11 5 测试标准 ...................................................................................................................................... 12 6 争议处理 ...................................................................................................................................... 12 7 标准文档 ...................................................................................................................................... 12
HP Color LaserJet Enterprise MFP M776用户指南说明书
Legal informationCopyright and License© Copyright 2019 HP Development Company, L.P.Reproduction, adaptation, or translation without prior written permission is prohibited, except as allowedunder the copyright laws.The information contained herein is subject to change without notice.The only warranties for HP products and services are set forth in the express warranty statementsaccompanying such products and services. Nothing herein should be construed as constituting anadditional warranty. HP shall not be liable for technical or editorial errors or omissions contained herein.Edition 1, 10/2019Trademark CreditsAdobe®, Adobe Photoshop®, Acrobat®, and PostScript® are trademarks of Adobe Systems Incorporated.Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries.macOS is a trademark of Apple Inc., registered in the U.S. and other countries.AirPrint is a trademark of Apple Inc., registered in the U.S. and other countries.Google™ is a trademark of Google Inc.Microsoft®, Windows®, Windows® XP, and Windows Vista® are U.S. registered trademarks of MicrosoftCorporation.UNIX® is a registered trademark of The Open Group.iiiT able of contents1 Printer overview (1)Warning icons (1)Potential shock hazard (2)Printer views (2)Printer front view (2)Printer back view (4)Interface ports (4)Control-panel view (5)How to use the touchscreen control panel (7)Printer specifications (8)T echnical specifications (8)Supported operating systems (11)Mobile printing solutions (12)Printer dimensions (13)Power consumption, electrical specifications, and acoustic emissions (15)Operating-environment range (15)Printer hardware setup and software installation (16)2 Paper trays (17)Introduction (17)Load paper to Tray 1 (multipurpose tray) (17)Load Tray 1 (multipurpose tray) (18)Tray 1 paper orientation (19)Use alternative letterhead mode (24)Enable Alternative Letterhead Mode by using the printer control-panel menus (24)Load paper to Tray 2 (24)Load Tray 2 (24)Tray 2 paper orientation (26)Use alternative letterhead mode (29)Enable Alternative Letterhead Mode by using the printer control-panel menus (29)Load paper to the 550-sheet paper tray (30)Load paper to the 550-sheet paper tray (30)550-sheet paper tray paper orientation (32)Use alternative letterhead mode (35)Enable Alternative Letterhead Mode by using the printer control-panel menus (35)ivLoad paper to the 2 x 550-sheet paper trays (36)Load paper to the 2 x 550-sheet paper trays (36)2 x 550-sheet paper tray paper orientation (38)Use alternative letterhead mode (41)Enable Alternative Letterhead Mode by using the printer control-panel menus (41)Load paper to the 2,700-sheet high-capacity input paper trays (41)Load paper to the 2,700-sheet high-capacity input paper trays (41)2,700-sheet HCI paper tray paper orientation (43)Use alternative letterhead mode (45)Enable Alternative Letterhead Mode by using the printer control-panel menus (45)Load and print envelopes (46)Print envelopes (46)Envelope orientation (46)Load and print labels (47)Manually feed labels (47)Label orientation (48)3 Supplies, accessories, and parts (49)Order supplies, accessories, and parts (49)Ordering (49)Supplies and accessories (50)Maintenance/long-life consumables (51)Customer self-repair parts (51)Dynamic security (52)Configure the HP toner-cartridge-protection supply settings (53)Introduction (53)Enable or disable the Cartridge Policy feature (53)Use the printer control panel to enable the Cartridge Policy feature (54)Use the printer control panel to disable the Cartridge Policy feature (54)Use the HP Embedded Web Server (EWS) to enable the Cartridge Policy feature (54)Use the HP Embedded Web Server (EWS) to disable the Cartridge Policy feature (55)Troubleshoot Cartridge Policy control panel error messages (55)Enable or disable the Cartridge Protection feature (55)Use the printer control panel to enable the Cartridge Protection feature (56)Use the printer control panel to disable the Cartridge Protection feature (56)Use the HP Embedded Web Server (EWS) to enable the Cartridge Protection feature (56)Use the HP Embedded Web Server (EWS) to disable the Cartridge Protection feature (57)Troubleshoot Cartridge Protection control panel error messages (57)Replace the toner cartridges (58)T oner-cartridge information (58)Remove and replace the cartridges (59)Replace the imaging drums (62)Imaging drum information (62)Remove and replace the imaging drums (63)Replace the toner-collection unit (66)T oner-collection unit information (66)vRemove and replace the toner-collection unit (67)Replace the staple cartridge (M776zs model only) (70)Staple cartridge information (70)Remove and replace the staple cartridge (71)4 Print (73)Print tasks (Windows) (73)How to print (Windows) (73)Automatically print on both sides (Windows) (74)Manually print on both sides (Windows) (74)Print multiple pages per sheet (Windows) (75)Select the paper type (Windows) (75)Additional print tasks (76)Print tasks (macOS) (77)How to print (macOS) (77)Automatically print on both sides (macOS) (77)Manually print on both sides (macOS) (77)Print multiple pages per sheet (macOS) (78)Select the paper type (macOS) (78)Additional print tasks (79)Store print jobs on the printer to print later or print privately (79)Introduction (79)Create a stored job (Windows) (79)Create a stored job (macOS) (80)Print a stored job (81)Delete a stored job (81)Delete a job that is stored on the printer (81)Change the job storage limit (82)Information sent to printer for Job Accounting purposes (82)Mobile printing (82)Introduction (82)Wi-Fi, Wi-Fi Direct Print, NFC, and BLE printing (82)Enable wireless printing (83)Change the Wi-Fi Direct name (83)HP ePrint via email (83)AirPrint (84)Android embedded printing (85)Print from a USB flash drive (85)Enable the USB port for printing (85)Method one: Enable the USB port from the printer control panel (85)Method two: Enable the USB port from the HP Embedded Web Server (network-connectedprinters only) (85)Print USB documents (86)Print using high-speed USB 2.0 port (wired) (86)Method one: Enable the high-speed USB 2.0 port from the printer control panel menus (86)Method two: Enable the high-speed USB 2.0 port from the HP Embedded Web Server (network-connected printers only) (87)vi5 Copy (88)Make a copy (88)Copy on both sides (duplex) (90)Additional copy tasks (92)6 Scan (93)Set up Scan to Email (93)Introduction (93)Before you begin (93)Step one: Access the HP Embedded Web Server (EWS) (94)Step two: Configure the Network Identification settings (95)Step three: Configure the Send to Email feature (96)Method one: Basic configuration using the Email Setup Wizard (96)Method two: Advanced configuration using the Email Setup (100)Step four: Configure the Quick Sets (optional) (104)Step five: Set up Send to Email to use Office 365 Outlook (optional) (105)Introduction (105)Configure the outgoing email server (SMTP) to send an email from an Office 365 Outlookaccount (105)Set up Scan to Network Folder (108)Introduction (108)Before you begin (108)Step one: Access the HP Embedded Web Server (EWS) (108)Step two: Set up Scan to Network Folder (109)Method one: Use the Scan to Network Folder Wizard (109)Method two: Use Scan to Network Folder Setup (110)Step one: Begin the configuration (110)Step two: Configure the Scan to Network Folder settings (111)Step three: Complete the configuration (118)Set up Scan to SharePoint (118)Introduction (118)Before you begin (118)Step one: Access the HP Embedded Web Server (EWS) (118)Step two: Enable Scan to SharePoint and create a Scan to SharePoint Quick Set (119)Scan a file directly to a SharePoint site (121)Quick Set scan settings and options for Scan to SharePoint (122)Set up Scan to USB Drive (123)Introduction (124)Step one: Access the HP Embedded Web Server (EWS) (124)Step two: Enable Scan to USB Drive (124)Step three: Configure the Quick Sets (optional) (125)Default scan settings for Scan to USB Drive setup (126)Default file settings for Save to USB setup (126)Scan to email (127)Introduction (127)Scan to email (127)Scan to job storage (129)viiIntroduction (129)Scan to job storage on the printer (130)Print from job storage on the printer (132)Scan to network folder (132)Introduction (132)Scan to network folder (132)Scan to SharePoint (134)Introduction (134)Scan to SharePoint (134)Scan to USB drive (136)Introduction (136)Scan to USB drive (136)Use HP JetAdvantage business solutions (138)Additional scan tasks (138)7 Fax (140)Set up fax (140)Introduction (140)Set up fax by using the printer control panel (140)Change fax configurations (141)Fax dialing settings (141)General fax send settings (142)Fax receive settings (143)Send a fax (144)Additional fax tasks (146)8 Manage the printer (147)Advanced configuration with the HP Embedded Web Server (EWS) (147)Introduction (147)How to access the HP Embedded Web Server (EWS) (148)HP Embedded Web Server features (149)Information tab (149)General tab (149)Copy/Print tab (150)Scan/Digital Send tab (151)Fax tab (152)Supplies tab (153)Troubleshooting tab (153)Security tab (153)HP Web Services tab (154)Networking tab (154)Other Links list (156)Configure IP network settings (157)Printer sharing disclaimer (157)View or change network settings (157)Rename the printer on a network (157)viiiManually configure IPv4 TCP/IP parameters from the control panel (158)Manually configure IPv6 TCP/IP parameters from the control panel (158)Link speed and duplex settings (159)Printer security features (160)Introduction (160)Security statements (160)Assign an administrator password (160)Use the HP Embedded Web Server (EWS) to set the password (160)Provide user access credentials at the printer control panel (161)IP Security (161)Encryption support: HP High Performance Secure Hard Disks (161)Lock the formatter (161)Energy-conservation settings (161)Set the sleep timer and configure the printer to use 1 watt or less of power (161)Set the sleep schedule (162)Set the idle settings (162)HP Web Jetadmin (163)Software and firmware updates (163)9 Solve problems (164)Customer support (164)Control panel help system (165)Reset factory settings (165)Introduction (165)Method one: Reset factory settings from the printer control panel (165)Method two: Reset factory settings from the HP Embedded Web Server (network-connectedprinters only) (166)A “Cartridge is low” or “Cartridge is very low” message displays on the printer control panel (166)Change the “Very Low” settings (166)Change the “Very Low” settings at the control panel (166)For printers with fax capability (167)Order supplies (167)Printer does not pick up paper or misfeeds (167)Introduction (167)The printer does not pick up paper (167)The printer picks up multiple sheets of paper (171)The document feeder jams, skews, or picks up multiple sheets of paper (174)Clear paper jams (174)Introduction (174)Paper jam locations (174)Auto-navigation for clearing paper jams (175)Experiencing frequent or recurring paper jams? (175)Clear paper jams in the document feeder - 31.13.yz (176)Clear paper jams in Tray 1 (13.A1) (177)Clear paper jams in Tray 2 (13.A2) (182)Clear paper jams in the fuser (13.B9, 13.B2, 13.FF) (188)ixClear paper jams in the duplex area (13.D3) (194)Clear paper jams in the 550-sheet trays (13.A3, 13.A4) (199)Clear paper jams in the 2 x 550 paper trays (13.A4, 13.A5) (206)Clear paper jams in the 2,700-sheet high-capacity input paper trays (13.A3, 13.A4, 13.A5, 13.A7) (213)Resolving color print quality problems (220)Introduction (220)Troubleshoot print quality (221)Update the printer firmware (221)Print from a different software program (221)Check the paper-type setting for the print job (221)Check the paper type setting on the printer (221)Check the paper type setting (Windows) (221)Check the paper type setting (macOS) (222)Check toner-cartridge status (222)Step one: Print the Supplies Status Page (222)Step two: Check supplies status (222)Print a cleaning page (222)Visually inspect the toner cartridge or cartridges (223)Check paper and the printing environment (223)Step one: Use paper that meets HP specifications (223)Step two: Check the environment (223)Step three: Set the individual tray alignment (224)Try a different print driver (224)Troubleshoot color quality (225)Calibrate the printer to align the colors (225)Troubleshoot image defects (225)Improve copy image quality (233)Check the scanner glass for dirt and smudges (233)Calibrate the scanner (234)Check the paper settings (235)Check the paper selection options (235)Check the image-adjustment settings (235)Optimize copy quality for text or pictures (236)Edge-to-edge copying (236)Improve scan image quality (236)Check the scanner glass for dirt and smudges (237)Check the resolution settings (238)Check the color settings (238)Check the image-adjustment settings (239)Optimize scan quality for text or pictures (239)Check the output-quality settings (240)Improve fax image quality (240)Check the scanner glass for dirt and smudges (240)Check the send-fax resolution settings (242)Check the image-adjustment settings (242)Optimize fax quality for text or pictures (242)Check the error-correction setting (243)xSend to a different fax machine (243)Check the sender's fax machine (243)Solve wired network problems (244)Introduction (244)Poor physical connection (244)The computer is unable to communicate with the printer (244)The printer is using incorrect link and duplex settings for the network (245)New software programs might be causing compatibility problems (245)The computer or workstation might be set up incorrectly (245)The printer is disabled, or other network settings are incorrect (245)Solve wireless network problems (245)Introduction (245)Wireless connectivity checklist (245)The printer does not print after the wireless configuration completes (246)The printer does not print, and the computer has a third-party firewall installed (246)The wireless connection does not work after moving the wireless router or printer (247)Cannot connect more computers to the wireless printer (247)The wireless printer loses communication when connected to a VPN (247)The network does not appear in the wireless networks list (247)The wireless network is not functioning (247)Reduce interference on a wireless network (248)Solve fax problems (248)Checklist for solving fax problems (248)What type of phone line are you using? (249)Are you using a surge-protection device? (249)Are you using a phone company voice-messaging service or an answering machine? (249)Does your phone line have a call-waiting feature? (249)Check fax accessory status (249)General fax problems (250)The fax failed to send (250)No fax address book button displays (250)Not able to locate the Fax settings in HP Web Jetadmin (250)The header is appended to the top of the page when the overlay option is enabled (251)A mix of names and numbers is in the recipients box (251)A one-page fax prints as two pages (251)A document stops in the document feeder in the middle of faxing (251)The volume for sounds coming from the fax accessory is too high or too low (251)Index (252)xiPrinter overview1Review the location of features on the printer, the physical and technical specifications of the printer,and where to locate setup information.For video assistance, see /videos/LaserJet.The following information is correct at the time of publication. For current information, see /support/colorljM776MFP.For more information:HP's all-inclusive help for the printer includes the following information:●Install and configure●Learn and use●Solve problems●Download software and firmware updates●Join support forums●Find warranty and regulatory informationWarning iconsUse caution if you see a warning icon on your HP printer, as indicated in the icon definitions.●Caution: Electric shock●Caution: Hot surface●Caution: Keep body parts away from moving partsPrinter overview1●Caution: Sharp edge in close proximity●WarningPotential shock hazardReview this important safety information.●Read and understand these safety statements to avoid an electrical shock hazard.●Always follow basic safety precautions when using this product to reduce risk of injury from fire orelectric shock.●Read and understand all instructions in the user guide.●Observe all warnings and instructions marked on the product.●Use only a grounded electrical outlet when connecting the product to a power source. If you do notknow whether the outlet is grounded, check with a qualified electrician.●Do not touch the contacts on any of the sockets on the product. Replace damaged cordsimmediately.●Unplug this product from wall outlets before cleaning.●Do not install or use this product near water or when you are wet.●Install the product securely on a stable surface.●Install the product in a protected location where no one can step on or trip over the power cord.Printer viewsIdentify certain parts of the printer and the control panel.Printer front viewLocate features on the front of the printer.2Chapter 1 Printer overviewPrinter front view3Printer back viewLocate features on the back of the printer.Interface portsLocate the interface ports on the printer formatter. 4Chapter 1 Printer overviewControl-panel viewThe control panel provides access to the printer features and indicates the current status of the printer.NOTE:Tilt the control panel for easier viewing.The Home screen provides access to the printer features and indicates the current status of the printer.screens.NOTE:The features that appear on the Home screen can vary, depending on the printerconfiguration.Control-panel view5Figure 1-1Control-panel view?i 12:42 PM6Chapter 1 Printer overviewHow to use the touchscreen control panelPerform the following actions to use the printer touchscreen control panel.T ouchT ouch an item on the screen to select that item or open that menu. Also, when scrolling T ouch the Settings icon to open the Settings app.How to use the touchscreen control panel 7SwipeT ouch the screen and then move your finger horizontally to scroll the screen sideways.Swipe until the Settings app displays.Printer specificationsDetermine the specifications for your printer model.IMPORTANT:The following specifications are correct at the time of publication, but they are subject to change. For current information, see /support/colorljM776MFP .T echnical specificationsReview the printer technical specifications.Product numbers for each model ●M776dn - #T3U55A ●Flow M776z - #3WT91A ●Flow M776zs - #T3U56APaper handling specificationsPaper handling features Tray 1 (100-sheet capacity)Included Included Included Tray 2 (550-sheet capacity)IncludedIncludedIncluded8Chapter 1 Printer overview550-sheet paper trayOptional Included Not included NOTE:The M776dn models accept one optional550-sheet tray.Optional Included Included2 x 550-sheet paper tray and standNOTE:The M776dn models accept one optional550-sheet tray that may be installed on top of thestand.Optional Not included Not included2,700-sheet high-capacity input (HCI) paper trayand standNOTE:The M776dn models accept one optional550-sheet tray that may be installed on top of theoptional printer stand.Printer standOptional Not included Not included NOTE:The M776dn models accept one optional550-sheet tray that may be installed on top of theoptional printer stand.Inner finisher accessory Not included Not included Included Automatic duplex printing Included IncludedIncludedIncluded Included Included10/100/1000 Ethernet LAN connection with IPv4and IPv6Hi-Speed USB 2.0Included Included IncludedIncluded Included IncludedEasy-access USB port for printing from a USBflash drive or upgrading the firmwareIncluded Included Included Hardware Integration Pocket for connectingaccessory and third-party devicesHP Internal USB Ports Optional Optional OptionalOptional Optional OptionalHP Jetdirect 2900nw Print Server accessory forWi-Fi connectivity and an additional Ethernet portOptional IncludedIncludedHP Jetdirect 3100w accessory for Wi-Fi, BLE, NFC,and proximity badge readingPrints 45 pages per minute (ppm) on Letter-sizepaper and 46 ppm on A4-size paperEasy-access USB printing for printing from a USBIncluded Included Includedflash driveT echnical specifications9Included Included Included Store jobs in the printer memory to print later orprint privatelyScans 100 pages per minute (ppm) on A4 andIncluded Included Included letter-size paper one-sidedIncluded Included Included 200-page document feeder with dual-headscanning for single-pass duplex copying andscanningNot included Included Included HP EveryPage T echnologies including ultrasonicmulti-feed detectionNot included Included Included Embedded optical character recognition (OCR)provides the ability to convert printed pages intotext that can be edited or searched using acomputerIncluded Included Included SMART Label feature provides paper-edgedetection for automatic page croppingIncluded Included Included Automatic page orientation for pages that haveat least 100 characters of textIncluded Automatic tone adjustment sets contrast,Included Includedbrightness, and background removal for eachpageIncluded Included Includedfolders on a networkIncludedSend documents to SharePoint®Included IncludedIncluded Included Included NOTE:Memory reported on the configurationpage will change from 2.5 GB to 3 GB with theoptional 1 GB SODIMM installed.Mass storage: 500 GB hard disk drive Included Included IncludedSecurity: HP Trusted Platform Module (TPM)Included Included IncludedT ouchscreen control panel Included Included IncludedRetractable keyboard Not included Included Included 10Chapter 1 Printer overviewFax Optional Included IncludedSupported operating systemsUse the following information to ensure printer compatibility with your computer operating system.Linux: For information and print drivers for Linux, go to /go/linuxprinting.UNIX: For information and print drivers for UNIX®, go to /go/unixmodelscripts.The following information applies to the printer-specific Windows HP PCL 6 print drivers, HP print driversfor macOS, and to the software installer.Windows: Download HP Easy Start from /LaserJet to install the HP print driver. Or, go tothe printer-support website for this printer: /support/colorljM776MFP to download the printdriver or the software installer to install the HP print driver.macOS: Mac computers are supported with this printer. Download HP Easy Start either from /LaserJet or from the Printer Support page, and then use HP Easy Start to install the HP print driver.1.Go to /LaserJet.2.Follow the steps provided to download the printer software.Windows 7, 32-bit and 64-bit The “HP PCL 6” printer-specific print driver is installed for this operating system aspart of the software installation.Windows 8.1, 32-bit and 64-bit The “HP PCL-6” V4 printer-specific print driver is installed for this operating systemas part of the software installation.Windows 10, 32-bit and 64-bit The “HP PCL-6” V4 printer-specific print driver is installed for this operating systemas part of the software installation.Windows Server 2008 R2, SP 1, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2012, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2012 R2, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2016, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Windows Server 2019, 64-bit The PCL 6 printer-specific print driver is available for download from the printer-support website. Download the driver, and then use the Microsoft Add Printer tool toinstall it.Supported operating systems11macOS 10.13 High Sierra, macOS 10.14 MojaveDownload HP Easy Start from /LaserJet , and then use it to install the print driver.NOTE:Supported operating systems can change.NOTE:For a current list of supported operating systems and HP’s all-inclusive help for the printer, go to /support/colorljM776MFP .NOTE:For details on client and server operating systems and for HP UPD driver support for this printer, go to /go/upd . Under Additional information , click Specifications .●Internet connection●Dedicated USB 1.1 or 2.0 connection or a network connection● 2 GB of available hard-disk space ●1 GB RAM (32-bit) or2 GB RAM (64-bit)●Internet connection●Dedicated USB 1.1 or 2.0 connection or a network connection●1.5 GB of available hard-disk spaceNOTE:The Windows software installer installs the HP Smart Device Agent Base service. The file size is less than 100 kb. Its only function is to check for printers connected via USB hourly. No data is collected. If a USB printer is found, it then tries to locate a JetAdvantage Management Connector (JAMc) instance on the network. If a JAMc is found, the HP Smart Device Agent Base is securelyupgraded to a full Smart Device Agent from JAMc, which will then allow printed pages to be accounted for in a Managed Print Services (MPS) account. The driver-only web packs downloaded from for the printer and installed through the Add Printer wizard do not install this service.T o uninstall the service, open the Control Panel , select Programs or Programs and Features , and then select Add/Remove Programs or Uninstall a Programto remove the service. The file name isHPSmartDeviceAgentBase.Mobile printing solutionsHP offers multiple mobile printing solutions to enable easy printing to an HP printer from a laptop, tablet, smartphone, or other mobile device.T o see the full list and to determine the best choice, go to /go/MobilePrinting .NOTE:Update the printer firmware to ensure all mobile printing capabilities are supported.●Wi-Fi Direct (wireless models only, with HP Jetdirect 3100w BLE/NFC/Wireless accessory installed)●HP ePrint via email (Requires HP Web Services to be enabled and the printer to be registered with HP Connected)●HP Smart app ●Google Cloud Print12Chapter 1 Printer overview。
NetMRI网络设备自动化管理与配置命令脚本(CCS)教程说明书

Dave SignoriSenior Director, Product ManagementNetwork Insight and NetMRISif Baksh Systems EngineerJohn BelamaricSoftware ArchitectCloud and Network AutomationCustomizing NetMRI NetworkChanges with ConfigurationCommand Scripting (CCS)Agenda•Why script and what scripting options are available in NetMRI •CCS Script Sections•Variables•Lists•Triggers•Filters•Operators•Other CCS Commands and Statements•Viewing, Adding, and Running CCS Scripts•Community Site and TABWhy Use Scripting?•Scripts:•Automate changes to infrastructure devices•Ensure consistent changes•Can be scheduled to run at specific times•Can be triggered to respond to specific events•Scripting reduces the risk of errors being made during execution •No fat fingering•No instant mistakes•Other features to consider before you script …•Config Templates•Config Search•RulesScripting Languages Supported •Focus of this tutorial:•CCS (Change Control Scripting)•Is a proprietary, high-level scripting language designed for network admins •Primary goal is to convert device-specific commands into repeatable tasks •Also supported:•Perl:•Is a general purpose, high-level scripting language•It has a large collection of 3rd party libraries and modules•It has powerful pattern matching and text processing featuresCCS SectionsSection MandatoryScript-Filter XAction XAction-FilterAction-Commands XScript-VariablesOutput-TriggersTriggerTrigger-FilterTrigger-VariablesTrigger-TemplateTrigger-CommandsCCS Sections -SampleSection MandatoryScript-Filter XAction XAction-FilterAction-Commands XScript-VariablesOutput-TriggersTriggerTrigger-Filter Trigger-Variables Trigger-Template Trigger-Commands Using these sectionsSample: Reset Password•Reset Password commands can be written as a CCS script as follows: Script-Filter:$Vendor eq "Cisco" and $sysDescr like /IOS/Script-Variables:$username word "User Name"$password password "New Password"# # # # # # # # # ## This is a commentAction:Set IOS User PasswordAction-Commands:config terminalusername $username password 0 $passwordexitwrite memory Prompt user to type in anusername and passwordOnly run on Cisco IOS devicesExecute commandsSample: Reset Password •The mandatory sections are highlighted in Red •The optional sections are highlighted in BlueScript-Filter:$Vendor eq "Cisco" and $sysDescr like /IOS/ Script-Variables:$username word "User Name"$password password "New Password" # # # # # # # # # ## This is a commentAction:Set IOS User PasswordAction-Commands:config terminalusername $username password 0 $passwordexitwrite memory RequiredRequired Required OptionalVariables•Temporary holding place•Declared using a dollar sign ($) e.g. $username•The value can change during the life of the script•Are global in scope. Available in all sections.•Are updated using the SET: directive•Three types of variables:•Script-Variables: prompt the user at runtime•Trigger-Variables: populated from output of a previous section•Well-Known variables: bundled with NetMRI like $Vendor, $Model, and $Version •When declaring a variable, you must specify a data type•i.e. number (integer), text (string), true/false (boolean)•Regex•$one_digit/^[1-9]$/•Predefined Regex•word, ipaddress, url, phoneno, zipcode, emailLists•CCS Scripts can reference a built-in file called a List. Think of it as a light-weight database.•Use the command getListValue to get the content of the List.•Lists can be created (or imported) under: Config Management -> Job Management -> ListsReading from a List•We use getListValue() to read from the List.SET: $reset= getListValue (Authorized_Users,username,“alice ”,default_passwd,NULL)•Look up from the List Authorized_Users , where username equals “alice ”, and return the corresponding password.•If the user “alice ” cannot be found, return NULL as the password.•Based on the List we defined, we expect to get the password “inW0nderl@nd ” for the user “alice ”.role username default_passwdnew_hire alice inW0nderl@nd new_hireNeoT@keTheRedPillSample with List: Reset Password Script-Filter:$Vendor eq "Cisco" and $sysDescr like /IOS/Script-Variables:$user word “Enter username to reset password"Action:Get default password of a single user from List Authorized_UsersAction-Commands:SET: $reset = getListValue(Authorized_Users,username,$user,default_passwd, “Nope”) Action-Commands: {$reset ne “Nope”}config terminalusername $user password 0 $resetendwr memTriggers•Mini script that only handles a single iteration of a loop•Action section runs, produces output, send it to the Trigger •Trigger section runs, reading in information as input, uses Trigger-Template to extract what’s necessary.•Runs commands in Trigger-Commands using the information extractedCCS Sections –Trigger SampleSection MandatoryScript-Filter XAction XAction-FilterAction-Commands XScript-VariablesOutput-TriggersTriggerTrigger-Filter Trigger-Variables Trigger-Template Trigger-Commands Using these sectionsTriggers•Action-Commands generates a list of output, and calls the Trigger to process the entire list, one item at a time.•Trigger-Commands defines what specific commands are run against each item of the list.•Take the familiar CLI commands sh run | inc username for example, “sh run”is like the Action-Commands, and sends the output to “inc username” to filter out just the usernames.Script-Filter:$Vendor eq "Cisco" and $sysDescr like /IOS/Script-Variables:$user word“Enter username to reset password”Action:Get existing usernamesAction-Commands:show run | inc usernameOutput-Triggers:Update Password# # # # # # # # # # #Trigger:Update PasswordTrigger-Variables:$existing_user wordTrigger-Template:username [[$existing_user]].+password 0.+Trigger-Commands:SET $reset = getListValue(Authorized_Users,username,$existing_user,default_passwd,NULL) conf tusername $existing_user password 0 $resetendwr mem Action, sends output to “Update Password” TriggerTrigger-Template extracts actual username from “show run “ inc username”Execute commands on theusernameScript-Filter:$Vendor eq "Cisco" and $sysDescr like /IOS/Script-Variables:$user word“Enter username to reset password”Action:Get existing usernamesAction-Commands:show run | inc usernameOutput-Triggers:Update Password# # # # # # # # # # #Trigger:Update PasswordTrigger-Variables:$existing_user wordTrigger-Template:username [[$existing_user]].+password 0.+Trigger-Commands:SET $reset = getListValue(Authorized_Users,username,$existing_user,default_passwd,NULL) Trigger-Commands:{$reset ne NULL}conf tusername $existing_user password 0 $resetendwr mem Action, sends output to “Update Password” TriggerTrigger-Template extracts actual username from “show run “ inc username”Execute commands on theusernameFilters•The {} is used as a filter to restrict execution.•Action-Commands and Trigger-Commands can be extended to specify optional filter criteria, restricting execution to cases where specific conditions exist.Example 1:Action-Commands: { $Vendor eq“Cisco” }show interfacesExample 2:Trigger-Commands: { $existing_user eq“Neo” }config tusername $existing_user password 0 $resetFilter Sections•Action-Filter and Trigger-Filter sections can also be used to apply the filter to the entire Action or Trigger section.Example 1:Action-Filter:$Vendor eq“Cisco” show interfacesExample 2:Trigger-Filter:$existing_user eq“Neo”Filters•Filters grant more flexibility and help optimize your code:•They work like an if-then, unless, or case statement•They can be written in two ways:Action:Show Running Config Action-Filter:$Vendor eq“Cisco”Action-Commands:show run | inc username Action:Update Logging DestinationAction-Commands {$sysDescr like /IOS/} logging 205.201.59.69Action-Commands {$sysDescr like /NX-OS/} logging server 205.201.59.69Action-Commands {$sysDescr like /SRX/} set system syslog host 205.201.59.69 any anyOperators•There are several ways to compare two variables•Here are four common approaches:Expressioneq ne in like Definition A equal to B A not equal to B A in list that follows A is similar to BExample Trigger-Commands:{$user eq“Neo”}Action-Commands:{$user ne “admin”}Action-Commands:{$user in[“Neo”,”alice”,”Morpheus”]}Trigger-Commands:{$user like /lic/}Notes Will execute if useris “Neo”Will execute if user isnot “admin”Will execute if user isNeo, alice, or MorpheusWill execute if theusername contains“lic”: either “alice”or “click”Assignment vs. Comparison•The =symbol is NOT the same as the eq comparison operator.•Assignment:•When we use =, we are taking whatever is B and copying it to A:Example: SET: $A = “no”•Comparison:•When we use eq, we are making an evaluation that ends in true or false, by comparing A to B:Example: { $A eq“no” }Putting It All Together -State Variable SampleScript-Filter:$Vendor eq "Cisco" and $sysDescr like /IOS/Script-Variables:$role word “Enter the role, such as new_hire ”Action:Get existing usernamesAction-Commands:show run | inc usernameSET: $ChangesMade = “no”Output-Triggers:Delete user# # # # # # # # # # #Trigger:Delete userTrigger-Variables:$existing_user wordTrigger-Filter:$existing_user ne “admin”Trigger-Template:username [[$existing_user]].+password 0.+Trigger-Commands:SET: $user_role = getListValue(Authorized_Users,username,$existing_user,role,NULL)Trigger-Commands: { $ChangesMade eq “no” and $user_role eq $role }conf tSET: ChangesMade = “yes”Initialize $ChangesMade to “no”Set $ChangesMade to “yes”State Variable Sample (continued)Trigger-Commands: { $user_role eq $role }no username $existing_userIterations# # # # # # # # # # #Action:Write to memory if changes were madeAction-Commands: { $ChangesMade eq “yes” }endwr memOnly execute if$ChangesMade is “yes”Other CCS Commands•Table below summarizes other CCS commands. For more details, refer to the Network Automation CSS Scripting Guide.Command DescriptionDEBUG Provides a mechanism to check whether or not a loop is entered or a statement is executed. Place DEBUG statement in front of the operation to check, and a debug icon will appear next to it if it would be executed.GET-CONFIGS Provides a mechanism to ensure Network Automation has the most up-to-date configurations from the network devices.LOG-INFOGenerates log messages to be sent to the appropriate log facilities, and goes into the standard Network Automation logging.LOG-WARNINGLOG-ERRORLOG-DEBUGPRINT Allows the printing of simple text strings (similar to the C “printf” command) and the printing of values within variables in CCS scripts to output text files.SKIPERROR Turns off error handling for script attributes when an error may appear from the acted-upon device, potentially preventing further job execution.SLEEP Pauses script execution for a specified number of seconds.EXPR Evaluate expressions, discussed next.Comments•Anything after the #symbol is ignored by the script•Use this to add human-readable comments so people reading the script (could be yourself later) understand the code.•For example:Action-Commands:# get current list of network interfaces to decide# which ones to disable# -Neo 04/25/2015DEBUG: Statement•Placing the DEBUG: directive in front of any statement will cause CCS to only print it out in the session log, but not execute the command.•For example:Action-Commands:DEBUG: conf tDEBUG: no username $usernameDEBUG: endDEBUG: wr memOperatorsOperator DescriptionA| B A if it is neither null nor 0, otherwise BA& B A if neither argument is null or 0, otherwise 0A <B A is less than BA <=B A is less than or equal to BA =B A is equal to BA !=B A is not equal to BA >=B A is greater than or equal to BA >B A is greater than BA +B Arithmetic sum of A and BA –B Arithmetic difference of A and BA *B Arithmetic product of A and BA /B Arithmetic quotient of A divided by BA %B Arithmetic remainder of A divided by BEXPR Command•EXPR performs more advanced comparison and evaluations •For example, increase $A by 1 (useful for iterating) EXPR: $A = $A + 1•Or compute the product of $A times $BEXPR: $A = $A * $BViewing, Adding, and Running CCS Scripts •Config Management -> JobManagement -> Scripts•Click Add to createAdding New CCS Script Levels Low, Medium, and High, indicatethe permission level needed to executethe scriptCategory is anything you want totype in that helps you organizescriptsName of scriptBody of CCS scriptRunning CCS Scripts•Config Management -> Job Management -> Scripts -> Run nowViewing Status and Job Details •Config Management -> Job Management -> Job HistoryViewing Status and Job DetailsCustomer Participation OpportunitiesTechnical Advisory Boards•10 TABs including NetMRI and Network Insight•Roadmap and early look at pre-releasedfeatures•Input for future enhancements•Best practices•First NetMRI session held on May 12th•Request membership at the Infoblox CommunitySite。
402 1 电动门用户手册说明书
1FAAC S.p.A.Via Benini, 140069 Zola Predosa (BO) - ITALIATel.: 051/61724 - Fax: 051/758518www.faac.it732143 Rev.A.EC DECLARATION OF CONFORMITY FOR MACHINES ....................................................................................p. 2 WARNINGS FOR THE INSTALLER .......................................................................................................................p. 2 1.DESCRIPTION AND TECHNICAL SPECIFICATIONS ....................................................................................p. 31.1.DIMENSIONS ................................................................................................................................p. 32.ELECTRIC DEVICES (standard system) ....................................................................................................p. 33.INSTALLING THE AUTOMATED SYSTEM ......................................................................................................p. 43.1.PRELIMINARY CHECKS ................................................................................................................p. 43.2.INSTALLATION DIMENSIONS ........................................................................................................p. 43.2.1.GENERAL RULES FOR DETERMINING THE INSTALLATION DIMENSIONS ............................p. 43.3.INSTALLATION OF THE OPERATORS .............................................................................................p. 44.START-UP ....................................................................................................................................................p. 64.1.ADJUSTING THE ANTI-CRUSHING SYSTEM ..................................................................................p. 65.FINAL OPERATIONS ...................................................................................................................................p. 76.AUTOMATED SYSTEM TEST .........................................................................................................................p. 77.MANUAL OPERATION ...............................................................................................................................p. 78.RESTORING NORMAL OPERATION MODE ................................................................................................p. 79.MAINTENANCE ..........................................................................................................................................p. 710.REPAIRS .....................................................................................................................................................p. 711.TROUBLE SHOOTING .................................................................................................................................p. 821)ATTENTION! To ensure the safety of people, it is important that you readall the following instructions. Incorrect installation or incorrect use of the product could cause serious harm to people.2)Carefully read the instructions before beginning to install the product.3)Do not leave packing materials (plastic, polystyrene, etc.) within reachof children as such materials are potential sources of danger.4)Store these instructions for future reference.5)This product was designed and built strictly for the use indicated in thisdocumentation. Any other use, not expressly indicated here, could compromise the good condition/operation of the product and/or be a source of danger.6)FAAC declines all liability caused by improper use or use other than thatfor which the automated system was intended.7)Do not install the equipment in an explosive atmosphere: the presenceof inflammable gas or fumes is a serious danger to safety.8)The mechanical parts must conform to the provisions of Standards EN12604 and EN 12605.For non-EU countries, to obtain an adequate level of safety, the Standards mentioned above must be observed, in addition to national legal regulations.9)FAAC is not responsible for failure to observe Good Technique in theconstruction of the closing elements to be motorised, or for any deformation that may occur during use.10)The installation must conform to Standards EN 12453 and EN 12445.For non-EU countries, to obtain an adequate level of safety, the Standards mentioned above must be observed, in addition to national legal regulations.11)Before attempting any job on the system, cut out electrical power .12)The mains power supply of the automated system must be fitted with anall-pole switch with contact opening distance of 3mm or greater. Use of a 6A thermal breaker with all-pole circuit break is recommended.13)Make sure that a differential switch with threshold of 0.03 A is fittedupstream of the system.14)Make sure that the earthing system is perfectly constructed, andconnect metal parts of the means of the closure to it.15)The safety devices (EN 12978 standard) protect any danger areasagainst mechanical movement Risks , such as crushing, dragging,and shearing.16)Use of at least one indicator-light (e.g. FAACLIGHT ) is recommendedfor every system, as well as a warning sign adequately secured to the frame structure, in addition to the devices mentioned at point “15”.17)FAAC declines all liability as concerns safety and efficient operationof the automated system, if system components not produced by FAAC are used.18)For maintenance, strictly use original parts by FAAC.19)Do not in any way modify the components of the automated system.20)The installer shall supply all information concerning manual operationof the system in case of an emergency, and shall hand over to the user the warnings handbook supplied with the product.21)Do not allow children or adults to stay near the product while it isoperating.22)Keep remote controls or other pulse generators away from children,to prevent the automated system from being activated involuntarily.23)Transit through the leaves is allowed only when the gate is fully open.24)The user must not attempt any kind of repair or direct action whateverand contact qualified personnel only.25)Maintenance: check at least every 6 months the efficiency of thesystem, particularly the efficiency of the safety devices (including,where foreseen, the operator thrust force) and of the release devices.26)Anything not expressly specified in these instructions is not permitted.WARNINGS FOR THE INSTALLERGENERAL SAFETY OBLIGATIONSEC DECLARATION OF CONFORMITY FOR MACHINES(DIRECTIVE 98/37/EC)Manufacturer:FAAC S.p.A.Address:Via Benini, 1 - 40069 Zola Predosa BOLOGNA - ITALY Declares that:402 mod. operator,•is built to be integrated into a machine or to be assembled with other machinery to create a machine under the provisions of Directive 98/37/EC;•conforms to the essential safety requirements of the following EEC directives:73/23/EEC and subsequent amendment 93/68/EEC.89/336/EEC and subsequent amendment 92/31/EEC and 93/68/EECand also declares that it is prohibited to put into service the machinery until the machine in which it will be integrated or of which it will become a component has been identified and declared as conforming to the conditions of Directive 98/37/EC.Bologna, 01 January 2005The Managing DirectorA. Bassi3These instructions apply to the following models:402 CBC - 402 SBSThe FAAC 402 automated system for swing leaf gates consists of an enbloc composed of an electric pump and a hydraulic piston which transmits drive to the leaf.The model with a hydraulic locking does not require installation of electric locks, as it guarantees mechanical locking of the leaf when the motor is not operating.The model without a hydraulic locking, requires the installation of electric locks to ensure the leaf is mechanically locked.The 402 automated systems were designed and built to automate swing leaf gates. Do not use for any other purpose.Tab. 1: Technical specifications of “402 Operator”MODEL402 CBC402 SBSPower supply voltage 230 Vac(+6%-10%) 50 (6o) Hz Rod extension speed 1.3 cm/s 1 cm/s Pump flow rate1 l/min 0.75 l/min Traction and thrust force 0-500 daN0-690 daNOperating ambient temperature -40°C - +55°CAbsorbed power 220 W Absorbed current 1 A Motor rotation speed 1400 rpm Motor winding temperature 120°C Weight 6.5 kg Type of oil FAAC HP OILProtection class IP 55Single leaf max length 1,80 m3,00 mUse frequency55 (cycles/hour)4To ensure a correctly operating automated system, the structure of the existing gate or gate to be built must satisfy the following requirements:•Max length of leaves according to the dimensions of Table 1 on page 3.• A strong and rigid leaf structure.•Smooth, uniform leaves movement, without any irregular friction during the entire travel;•Existing hinges in good condition.•Travel limit mechanical stops must be provided.We advise you to carry out the metalwork jobs before installing the automated system.The condition of the structure directly influences the reliability and safety of the automated system.Table A : Recommended dimensions for standard operatorsc = The effective rod stroke is shorter than the maximum stroke, inorder to prevent the rod from reaching its stop point internally, during the opening and closing stages.(*) Rod effective stroke (**) maximum dimension1)Fasten the rear attachment on the pilaster, following the indications in Table A . Modify, if necessary, the length of the supplied attachment.Attention : To avoid compromising good operator functionality, we recommend you to respect the indicated dimensions.• For iron pilasters, accurately weld the rear attachment (ref.ባ, Fig. 6) directly on the pilaster.• For masonry pilasters, select one of the following solutions:A)appropriately lay a walling-in plate and then accurately weld the rear attachment.B)secure, with screws and expansion plugs, the rear attachment plate (ref. a, Fig.6) to the pilaster and then accurately weld the rear attachment to theplate as shown in Fig. 6.If the dimensions indicated in table A or B cannot be executed,the following must be considered in order to determine different measurements:-to obtain 90° opening of the leaf: a + b = c.-to obtain over 90° opening of the leaf: a + b < c.-lower a and b dimensions will result in higher speeds . We advise you to observe the current legal regulations;-limit the difference of the a and b dimensions to within 40 mm :higher differences will considerably vary speed during the opening and closing motion;-for reasons of operator dimensions, the minimum Z dimension is 50 mm (Fig. 4);-if the pilaster dimensions or the position of the hinge (dimension d ) do not make it possible to contain dimension a to the required size, a niche must be made in the pilaster as shown in Opening angle 90°110°a (mm)120100b (mm)120100c(*)(mm)240240d(**)(mm)705056-Lastly, remove the key and restore the power supply to the system.For any repairs, contact FAAC’s authorised Repair Centres.78The following table will help you identify and solve some particular conditions.CONDITIONGate not moving.Gate moving slowly.Gate moving jogwise.The operator is losing oil from the breather screw.The leaves stop at slow-down.Gate speed not constant.A B CD E FSUGGESTION-Check if mains power is supplied.-Make sure that the operator is not unlocked. (chapter 8.).-Check the adjustment of the anti-crushing system (paragraph 4.1).-Check oil level inside the tank. (chapter 9 - Fig. 16).-Check the connection and operation of the thrust capacitor.-Check the efficiency of the electronic control unit.-Check the adjustment of the anti-crushing system (paragraph 4.1).-Make sure that you have removed the breather screw (chapter 5).-Run some complete gate opening and closing cycles, in order to release any air inside the piston.-An initial, minimum oil leak is normal. A larger leak may occur if the operator is not fitted in a perfectly horizontal plane. If the oil leak does not stop soon, weadvise you to visit an authorised repair centre.-Check the adjustment of the anti-crushing system (paragraph 4.1).-Incorrect installation dimensions (paragraph 3.2).Notes919M A I N T E N A N C E R E G I S T E R.o N e t a D b o j f o n o i t p i r c s e D se r u t a n g i S 1_______________________________________________________________________________________________________________________________________na i c i n h c e T re m o t s u C 2_______________________________________________________________________________________________________________________________________na i c i n h c e T re m o t s u C 3_______________________________________________________________________________________________________________________________________na i c i n h c e T re m o t s u C 4_______________________________________________________________________________________________________________________________________na i c i n h c e T re m o t s u C 5_______________________________________________________________________________________________________________________________________na i c i n h c e T re m o t s u C 6_______________________________________________________________________________________________________________________________________na i c i n h c e T re m o t s u C 7_______________________________________________________________________________________________________________________________________na i c i n h c e T re m o t s u C 8_______________________________________________________________________________________________________________________________________na i c i n h c e T re m o t s u C 9_______________________________________________________________________________________________________________________________________na i c i n h c e T re m o t s u C 01_______________________________________________________________________________________________________________________________________na i c i n h c e T re m o t s u C I n s t a l l a t i o n t e c h n i c i a n ________________________________________________C u s t o m e r ___________________________________________________________________T y p e of s y s t e m ________________________________________________________S e r i a l n u m b e r _________________________________________________________I n s t a l l a t i o n d a t e ______________________A c t i v a t i o n ________________________S y s t e m c o n f ig u r a t i o nT R A P L E D O M RE B M U N L A I R E S e r o t a u t t A 402C A A F 1e c i v e d y t e f a S 2e c i v e d y t ef a S 1s l l e c o t o h p f o r i a P 2s l l e c o t o h p f o r i a P 1e c i v e d l o r t n o C 2e c i v e d l o r t n o C lo r t n o c o i d a R pm a l g n i h s a l F ec i v ed re h t O ec i v ed re h t O I n d i c a t i o n of r e s i d u a l r i s k s a n d o f f o r e s e e a b l e i m p r o p e r u s e_________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________Read the instructions carefully before using the product and store them for future useIf correctly installed and used, the 402 automated system ensures a high degree of safety.Some simple rules on behaviour can prevent accidental trouble:-Do not pass between the leaves when they are moving. Waitfor the leaves to open fully before passing through them.-Do not, on any account stay in between the leaves.-Do not stand near the automated system, and do not allowchildren, persons or things to do so, especially when it is operating.-Keep remote controls or other pulse generators away fromchildren, to prevent the automated system from being activated involuntarily.-Do not allow children to play with the automated system.-Do not willingly obstruct leaves movement.-Prevent any branches or shrubs from interfering with leavesmovement.-Keep indicator-lights efficient and easy to see.-Do not attempt to activate the leaves by hand unless you havereleased them.-In the event of malfunctions, release the leaves to allow accessand wait for qualified technical personnel to do the necessary work.-When you have set manual operation mode, cut power to thesystem before restoring normal operation.-Do not in any way modify the components of the automatedsystem.-Do not attempt any kind of repair of direct action whateverand contact qualified personnel only.-At least every six months: arrange a check by qualifiedpersonnel of the automated system, safety devices and earth connection.These instructions apply to the following models:402 CBC - 402 SBS.The FAAC 402 automated system for swing leaf gates consists of a hydraulic enbloc composed of an electric pump and a hydraulic piston which transmits drive to the leaf.The models with a hydraulic locking do not require installation of an electric lock, as they guarantee mechanical locking of the leaf when the motor is not operating.The other models, without a hydraulic locking always require one or more electric locks to ensure the leaf is mechanically locked.Leaves of up to 3 mt can be automated depending on the selected model.The functioning of the operators is controlled by an electronic control unit, housed in an enclosure with adequate degree of protection against atmosphere agents.The leaves are normally closed.When the electronic control unit receives an opening command from the radio control or any other pulse generator, it activates the hydraulic appliance which rotates the leaves until they reach the opening position to allow access.If automatic mode was set, the leaves close automatically after selected pause time has elapsed.If the semi-automatic mode was set, a second pulse must be sent to close the leaf again.A stop pulse (if supplied) always stops movement.For details on the behaviour of the automated system in different function logics, consult the installer.Automated systems include safety devices (photocells) that prevent the leaves from moving when there is an obstacle in the area they protect.The 402 automated system is supplied standard with a hydraulic anti-crush protection safety device (BY-PASS) which limits the torque transmitted to the leaves.The warning-light indicates the current leaf movement.If the gate has to be moved manually due to a power cut or fault of the automated system, use the release device as follows:-Insert the triangular key on the release screw located in the lower part of the flange (Fig.1).-Turn the release key anti-clockwise for about two turns.-Open or close the leaf manually.To prevent an involuntary pulse from activating the operator during the manoeuvre, cut power to the system before re-locking the operator.-To re-lock the operator, turn the key clockwise until it stops (Fig.1).-Release the operator from the front and rear attachments.732143 - Rev. A。
Model checking large software specifications

large system requirements specification using symbolic model checking. In our experiment, we translated (Sections 3 and 4) a significant portion of a preliminary version of the Traffic Alert and Collision Avoidance System II (TCAS II) System Requirements Specification from the Requirements State Machine Language (RSML) [44] into input to the Symbolic Model Verifier (SMV) [45]. TCAS II is an aircraft collision avoidance system required on many commercial aircraft and has been described as “the most complex system to be incorporated into the avionics of commercial aircraft” [44, p. 685]. We were able to control the size of the BDDs representing the specification (Section 5) so that we could analyze a number of properties (Section 6). These include general robustness properties as well as some safety-critical properties specific to the domain. Our objective was to test the effectiveness of model checking on software systems, so our experiences in applying the technology are more important than the individual results. One intent is to convey how we overcame some key obstacles, with the hope that most or all of these techniques are applicable to other situations. We stress two approaches that we found crucial in overcoming the complexity and size of the specification, making it more amenable to symbolic model checking: the use of nondeterministic modeling primarily to abstract nonlinear arithmetic and to allow checking part of the specification, and the use of an iterative process to analyze the specification. We discuss related work (Section 7), as well as point out some limitations of the current model-checking techniques and tools, and suggest some future research directions (Section 8). Our analysis was based on preliminary versions of the specification, mainly on the version 6.00, dated March 1993. We
Model Checking说明书

$#
Given an abstraction function h : S Sh, the concrete states are grouped and mapped into abstract states :
Mh
h
h h Preservation Theorem ?
M
27
%
If M has partial behavior of N, we say that “N simulates M”: M N
generate initial abstraction
Mh
model check
Mh |=
Mh |=
generate counterexample Th
stop
Th check if counterexample spurious Th is not spurious
35
$*
Counterexample-Guided Abstraction Refinement C, SpecC, Verilog
11
Determines Patterns on Infinite Traces
Atomic Propositions a
a
a
a
a
Boolean Operations
Temporal operators
a Xa Fa Ga aUb
“a is true now” “a is true in the neXt state” “a will be true in the Future” “a will be Globally true in the future” “a will hold true Until b becomes true”
ABB 测量与分析 Contrac 电子单元客户特定设置说明书

—ABB MEASUREMENT & ANALYTICS | DATA SHEET Contrac electronic unitCustomer specific settings2 CONTRAC ELECTRONIC UNIT CUSTOMER SPECIFIC SETTINGS | DS/CONTRAC/SETTING-EN REV. ACONTRAC ELECTRONIC UNIT CUSTOMER SPECIFIC SETTINGS | DS/CONTRAC/SETTING-EN REV. A 3—Ordering InformationContrac electronic unit Code Bus tagNo bus tag (standard) –Bus tag HART / FSK Bus (max. 8 characters) 146 Bus address fieldbus (max. 3 characters) 147 Torque / Force setting100 % torque / force to + direction (standard) –75 % torque / force to + direction 149 50 % torque / force to + direction 150 100 % torque / force to - direction –75 % torque / force to - direction 152 50 % torque / force to - direction 153 Speed (°/s - mm/s)Standard see data sheet of actuator –AUT speed + direction (...................................) 154 AUT speed − direction (...................................) 155 MAN speed (...................................) 156 Rapid traverse speed (...................................) 157 Behavior in 100 % end positionKeep toght with 1x rated torque / force (standard) –Position dependent switch-off 161 Limit for position dependent switch-off (...................................) (permitted 80 % to 100 %) 162 Torque dependent switch-off with 1x rated torque / force 163 Torque dependent switch-off with 2x rated torque / force 164 Behaviour in 0 % end positionKeep toght with 1x rated torque / force (standard) –Position dependent switch-off 166 Limit for position dependent switch-off (...................................) (permitted 0 % to 20 %) 167 Torque dependent switch-off with 1x rated torque / force 168 Torque dependent switch-off with 2x rated torque / force 169 Breakaway with increased torque / force in end positionsNo breakaway (Standard) –Breakaway in 0 % end position 170 Breakaway in 100 % end position 171 Breakaway in 0 % and 100 % end position 172 Position to switch back to rated value (...........%) (permitted 0 % to 5 %) 173 Close tight (no positioning close to end position)Positioning close to end position (standard) –Close tight 175 Position limit to close tight (...........%) (permitted 1 % to 10 % or 90% to 99 %) 176 Digital input (not available with PROFIBUS DP communication)OFF 177 Manual override (standard) –Rapid traverse mode 179 Stepp controller commands 1804 CONTRAC ELECTRONIC UNIT CUSTOMER SPECIFIC SETTINGS | DS/CONTRAC/SETTING-EN REV. A—... Ordering InformationContrac electronic unit CodeDigital output (one signal each for 1 output; not available with PROFIBUS DP communication)BA1 (..........) ready for operation 181 BA2 (..........) signal end position 0 % 182 BA3 (..........) signal end position 100 % 183 Collective disturbance message 184 Collective alarm 185 Local operation 186 Signal limit 1; rising 187 Signal limit 1; falling limit = (..... %) (permitted % to 10%; stand. 10 %) 188 Signal limit 2; rising 189 Signal limit 2; falling limit = (.....%) (permitted % to 10 %; standard 90 %)190 Hysteresis for 1 + 2 = (..... %) (permitted % to 10 %; standard 90 %)Control of external rapid traverse motor (+ direction) 191 Control of external rapid traverse motor (- direction) 192 Set point selectionAnalogue set point (not available with PROFIBUS DP communication) –Digital set point 211 Set point range (not available with PROFIBUS DP communication)Set point start (standard: 4.0 mA) start < end ...... mA permitted 0 to 20 mA 212 Set point end (standard: 20.0 mA) start > end ...... mA permitted 0 to 20 mA 213 Set point monitoring (not available with PROFIBUS DP communication)Without monitoring of analogue set point (standard) –215 With monitoring of analogue set point 215Upper limit ..... mA (permitted 20 to 25 mA)Lower limit ..... mA (permitted 1 to 5 mA)Behaviour in case of set point or communication failureLocking in last position (standard) –Positioning / closed loop control with last set point 219 Drive to safety position 220 Safety position: ............% (permitted 0 to 100 %) 221 Actual value range (not available with PROFIBUS DP communication)Actual value 4 to 20 mA (standard) –Actual value 0 to 20 mA 230 Failure message via actual value (not available with PROFIBUS DP communication)No failure message via actual value (standard) –Failure message via actual value ‘signal high’ 232 Failure message via actual value ‘signal low’ 233 Upper signal limit (standard 21.5 mA) ........ mA (permitted 20 mA to 25 mA) 234 Lower signal limit (standard 3.5 mA) ........ mA (permitted 1 mA to 5 mA) 235 Positioning loop monitoringPositioning loop monitoring OFF (standard) –Positioning loop monitoring ON 237 Positioning / ControllerOperation as positioner (standard) –Operation as process controller 239 Conventional process controller operation 240 Reciprocal process controller operation 241 No integrating end position behavior 242 Integrating end position behavior 243CONTRAC ELECTRONIC UNIT CUSTOMER SPECIFIC SETTINGS | DS/CONTRAC/SETTING-EN REV. A 5Contrac electronic unit CodeRe-start behaviorAUT after voltage recovery (standard) –MAN after voltage recovery 237 Rapid traverseNo rapid traverse (standard) –Rapid traverse with servo motor 418 Monitoring of process transmitter signalPerm upper limit (standard 21.0 mA) ...... mA (permitted 20 mA to 25 mA) 246 Perm lower limit (standard 21.0 mA) ...... mA (permitted 1 mA to 5 mA) 247 Non-standard version(standard: no remark) 68-................ / ................Non-standard no of electronic unit 248 Non-standard no of actuator 249 Setpoint characteristic selectionLinear (standard) –Equal percentage 25 % 223 Equal percentage 50 % 224 Programmable characteristic (see table below for values) 225 Split Range 226 Values for split range (only with Code No. 226)Start value for split range 227 End value for split range 2286CONTRAC ELECTRONIC UNIT CUSTOMER SPECIFIC SETTINGS | DS/CONTRAC/SETTING-EN REV. A—... Ordering InformationNoticeThe pairs of values 0 % / 100 % and 100 % / 100% are pre-set. All other entered values for set point and actual value must be higher than the previous one.—TrademarksPROFIBUS and PROFIBUS DP are registered trademarks of PROFIBUS & PROFINET International (PI)Sales ServiceSet point (%)Action value (%) 1 002 3 45678 91011 12 131415 16 17 18 19 20 2122 100100CONTRAC ELECTRONIC UNIT CUSTOMER SPECIFIC SETTINGS | DS/CONTRAC/SETTING-EN REV. A 7—ABB LimitedMeasurement & Analytics Howard Road, St. Neots Cambridgeshire, PE19 8EU UKTel: +44 (0)870 600 6122 Fax: +44 (0)1480 213 339Mail:**********************.comABB Inc.Measurement & Analytics 125 E. County Line Road Warminster, PA 18974 USATel: +1 215 674 6000 Fax: +1 215 674 7183/actuatorsABB Automation Products GmbH Measurement & Analytics Schillerstr. 72 32425 Minden GermanyTel: +49 571 830-0 Fax: +49 571 830-1806D S /C O N T R A C /SE T T I N G -E N R e v . A 11.2018—We reserve the right to make technical changes or modify the contents of this document without prior notice.With regard to purchase orders, the agreed particulars shall prevail. ABB does not accept anyresponsibility whatsoever for potential errors or possible lack of information in this document. We reserve all rights in this document and in the subject matter and illustrations contained therein. Any reproduction, disclosure to third parties or utilization of its contents – in whole or in parts – is forbidden without prior written consent of ABB. Copyright© 2018 ABB All rights reserved 3KXE181011R1001。
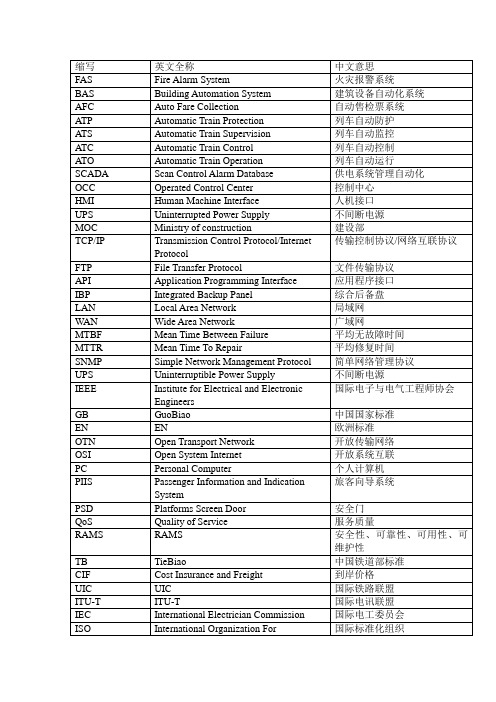
轨道交通行业常用英文缩写对照表
●TDT Train Depart Timer 列车发车计时器设于各车站,为列车运行提供车站发车时机,列车到站晚点情况的时间指示,提示列车按计划时刻表运行。
正常情况下,在列车整列进入站台后,按系统给定站停时间倒计时显示距计划时刻表的发车时间,为零时指示列车发车;若列车晚点发车,则TDT增加停站时间的计时。
在特殊情况下,若实施了站台扣车控制,TDT给出"H"显示;如有提前发车命令,TDT立即显示零;列车通过车站时TDT显示"="。
●城市轨道交通专业词汇缩写AC:信标/计轴Axle Counter●ACS:计轴系统Axle Counter System●ADC:自动关门Auto Door Close●ADO:自动开门Auto Door OpenADM:系统管理器ADU:特征显示单元AF:音频●AFC:自动售检票系统Auto Fare CollectionAM:列车自动运行驾驶模式Automatic ModelAMU:ATO匹配单元AP:接入点、轨旁无线单元/应用模块Application P……APAM:ATO功率放大板块API:应用程序接口APR:绝对位置参考应答器、信标AR:自动折返驾驶/列车自动折返模式ARS:列车进路设定AS:管理服务器/接入交换机Access SwitchASK:数字调幅、幅移键控●ATB:自动折返按钮Automatic Turnback ButtonATC:列车自动控制系统ATI:列车到达时刻显示器ATO:列车自动运行ATP:列车自动防护ATR:列车自动调整‘ATS:列车自动监控Automatic Train SupervisionAXC:计轴器B&A:操作和显示BAS:环境与设备监控系统Bd:波特bond:棒●BS:骨干交换机Backbone SwitchBUMA:总线控制板CA:控制中心自动控制模、中央自动模式CAN:现场总线CAZ:冲突防护区域’CBI:计算机联锁Computer Based InterlockingCBN:通信系统CBTC:基于通信的列车控制Communication Based Train Control ●CC:车载控制器Carborne Controller●CCTE:车载安全计算机(包括ATP/ATO子系统)CCTV:闭路电视/电视监视器CD:载频检测模块CDM:电码检测模块CDTA:中央数据传输系统CE:控制设备CENELEC:欧洲电工标准委员会CESB:中央紧急停车按钮CER:控制室CG:编码发生器CH:校核信号CI:计算机联锁Computer Based InterlockingCLC:线路控制器●CLOW:中央联锁工作站Center Locking WorkstationCM:编码人工驾驶模式●COAST:惰行COM:通信服务器●COTS:可购买的商用产品●CPL:耦合器模块CouplerCPISA:通信处理器CPS:条件电源块CPU:中央处理单元CRC:循环冗余校验CRT:阴极射线显示器CS:中央服务器Center ServerCSEX:电码系统模拟器扩展CTC:调度集中CTS:光数据传输系统●DAB:报警按钮(为了及时处理意外或临时事故而设置在车厢里的乘客报警按钮)●DB:轨道数据库Data BaseDCC;元件接口模块/车辆段、停车场控制中心Depot Contral CenterDCS:数据通信系统Data Communication SubsystemDCU:数据储存单元DCR:车站综合控制室●DDS:数字频率合成技术、DDU:诊断和数据上载单元、诊断和数据更新单元DEBLIMO:闪光元件接口模块DEM:调节器DESIMO:信号机元件接口模块DEWEMO:道岔元件接口模块DI:列车发车时刻显示器●DID:目的地号Destination IdentificationDIOM:离散输入、输出板块DOC:驱动输出模块DOT:倒换方向DPU:车辆段程序单元DS:模拟MMI、演示系统、数据服务器DSP:数字信号处理技术DSIT:接口控制模块●DSU:数据服务单元Data Service UnitDT:VCC数据传输DTC:数字轨道电路DTI:发车计时器、发车时间表示显示器Departure Time IndicatorDTM:现场LDTS分机●DTRO:无人驾驶列车折返运行DTS:光纤网、数据传输系统、光纤通信系统读点EBR:紧急制动继电器EB:紧急制动ECC:元件接口模块EFAST:列车控制元件接口模块EFID:入口馈电设备EPROM:只读储存器●ERC:人工取消进路E……Route CancelESB、ESP:紧急关闭按钮Emergency Stop ButtonESS:紧急车站停车系统ESIT:电子元件接口模块EU:电子单元FAS:火灾自动报警系统FEC:非向前纠错FEP:前端处理器FFT:快速傅立叶变换FID:馈电设备FOTL:光纤传输线●FRONTAM:数据存储单元●FSB:全常用制动Full Service BrakingFSK:数字调频、频移键控FTGS:西门子公司的遥供无绝缘音频轨道电路/音频无绝缘轨道电路●GEBR:可保证的紧急制动率Guaranteed Emergency Brake RateGO:ATP速度命令选择和核准电路HMI:人机接口/人机界面Human-Machine Interface●IBP:综合后备盘Integrated Backup PanelI/O:输入/输出Input/OutputICM:输入控制模板、输入模块ICU:区域控制中心、控制单元、计算模块ID:识别IEC:国际电工委员会●IFS:接口服务器Interface Server●ILC:联锁控制器InterLocking ControllerIRU:接口继电器单元JTC;无绝缘轨道电路KOMDA:开关量输出板LAN:局域网Local area NetLC:车站控制LCC:本地控制台LCD:液晶显示器Liquid Crystal DisplayLCP:局域控制板(设于站控室内墙LCP控制盘上,需要扣车或取消时,按压按钮扣车或取消扣车,当站台的紧急停车按钮被按动时,在LCP上报警应按取消报警按钮)●LCW:本地控制工作站Local Control WorkstationLDTS:现场数据传输系统LED:发光二极管Light Emitting DiodeLEU:轨旁电子单元、信号接口LFU:环路馈送单元LISTE:信号机元件接口板块LIU:环线调谐单元LMM:环路调制解调器板块LOM:逻辑输出板块LPU;车站程序单元LZB:连续式列车自动控制系统●MAL:移动授权Movement Authority Limit●MAZ:移动授权区域Movement Authority ZoneMD:调频检测板块●MDC:手动关门Manual Door Close●MDO:手动开门Manual Door Open●ME:存储互换模块Memory ExchangeMELDE:开关量输入板MI:联锁单元●MicroLok:微机联锁/联锁设备MMI:人机界面MMS;维护管理系统MODEM:调制解调器MPM:主处理器板块●MR:车载无线设备MSK:最小移频键控MSS:最大安全速度●MWS:维护工作站Maintenance Work StationMT:轨道联锁、城市轨道交通、MTIB:移动列车初始化信标MTO:无人驾驶MUX:接口电机NDO:非安全数字输出板NFS:网络文件系统NIC:网络接口卡NISAL:数字集成安全保障逻辑NMS:网管系统/网络管理工作站NRM:非限制人工驾驶模式NRZI:不归零倒置NSS:网络支撑系统NVI:非安全型输入NVLE:非安全逻辑模拟器工作站NVO:非安全型输出OBE:车载设备OCC:运营控制中心Operational Contral Center OCM:输出控制模块ODI:操作/显示接口OLM;通信模块、光连接模块OLP:光连接插头OPG:速度脉冲发生器●OTN:开放的传输网OVW:全线表示盘子系统PAC:环路调制解调器PAL:逻辑处理模块PAS:车站广播系统PB:停车制动PC:道岔控制PCB:控制器、印路电路板PCU:协议传输单元PD:多项式除法器PEB:站台紧急按钮、PF:工频PI:站台显示器PID:乘客导向系统PIIS:乘客信息显示器PIS:乘客导向系统●PL:运行等级/站到站的运行时间PM:道岔转辙机PROFI BUS:过程现场总线PROM:课编程计数器●PSA:远方报警盘●PSC:远台屏蔽门中央控制盘PSD:站台屏蔽门●PSL:就地控制盘PSU:电源单元PTI:列车识别系统PVID:永久性车辆标识Permernent Vehicle IdentificationPWD:梯形波调幅RAMS:安全性RB:重定位信标RC:进路控制RCC;远程通信控制器RCM:远程通信控制模块●RI:继电器接口Relay Interface/接口设备RM:限制人工驾驶RMO:限速模式RTOS:实时操作系统RTU:车站远程终端单元Remote Terminal UnitRX:接收器●SAN:存储区域网络SB:脚踏阀、常用闸,行驶制动器Servicebrake/常用制动Service Braking ●SBD:安全制动距离Safe Braking DistanceSBO:安全型单断输出SC;运行图编辑子系统SCADA:电力监控系统SCC:车站控制计算机/车站引导控制计算机SCEG:车站控制器紧急通路SCI:计算机联锁SCR:车站控制室S&D:诊断服务、检修和诊断SD:安全装置SDM:联锁系统维护工作站●SDT:站停时间Station Dwell TimeSER:信号设备室SICAS:西门子计算机辅助信号/微机联锁设备SIL:安全完整度等级SIOM:串行输入、输出模块SIR:安全联锁继电器SISIG:烙断器板SLC:同步环线盒SLM:速度和位置模块SM:列车自动防护驾驶、系统维护台、系统维护模块SMC:系统管理中心●SMSS:维护监测子系统●SNMP:简单网络管理协议SNOOPER:列车和事件监控器SO:维护操作台S—PC:模拟PCSPDI:瞬间接触开关SQL:结构化查询语言SRS:运行图STA;天线STC:车站控制器STEKOP:现场接口计算机STIB:静态列车初始化信标STS:厂家测试成套设备SYN:同步天线TAC;测速电机出来模块TC:轨道区段、轨道电路TCM:轨道编码模块TCP/IP;远程控制协议/国际协议TD:列车位置检测TDB:线路数据库TDT;列车发车计时器TID:列车输入数据模块/列车追踪号Tracking Identification TM:室内控制柜TMT:列车监督和追踪TOD:司机显示盘、列车输出数据模块/司机操作显示单元●TR:分线柜/接口设备TRC:列车进路计算机TS:目标速度Target Speed/终端服务器Terminal Server●TSR:临时限速Temporary Speed RestrictionTTE:时刻表编辑器TTF:时刻表●TTT:列车跟踪Train Tracking T……TU:调谐单元、轨道电路控制单元TVP:轨道空闲处理TWC:车-地通信Traffic Wayside CommunicationTX:发送器●UPS:不间断电源URM:非限制人工驾驶模式V AS:车辆报告系统VCC;车辆控制中心VCS:车辆通信系统VDI:安全数字输入板VDO:安全数字输出板VENUS:处理器板中断板VESUV:同步比较板VHM:车况监视器VICOS:车辆和基础集中控制操作系统●VO:表决器模块V oterVOBC:车载计算机、车载控制设备VPI:安全型计算机联锁●VR:列车调整Vehicle RegulationVRD:安全继电器驱动器VSC:安全型串行控制器WEEZ Bond:小型调谐阻抗连接变压器WCC:轨旁通信控制器WE;轨旁设备WESTE:道岔接口模块●ZC:区域控制器Zone Controler●●●名称全称中文意义●FAS 1.1 Fire Alarm System 火灾报警系统BAS Building Automation System 建筑设备自动化系统AFC Auto Fare Collection 自动售检票系统ATP Automatic Train Protection 列车自动防护ATS Automatic Train Supervision 列车自动监控ATC Automatic Train Control 列车自动控制ATO Automatic Train Operation 列车自动运行●SCADA Scan Control Alarm Database 供电系统管理自动化OCC Operated Control Center 控制中心MMI Man Machine Interface 人机接口UPS Uninterrupted Power Supply 不间断电源供给MOC Ministry Of construction 建设部IDC Intermodality Data Center 清结算数据中心LAN Local Area Network 局域网WAN Wide Area Network 广域网OTN Open Transport Network 开放传输网络Tc (A) Trailer Car 拖车Mp (B) Motor Car With Pantograph 带受电弓的动车M (C) Motor Car 动车AW0 空载●AW1 每位乘客都有座位●AW2 每平方米6人●AW3 每平方米9人●CSC Contactless Smart Card 非接触智能卡CST Contactless Smart Token 非接触智能筹码EOD Equipment Operating Data 设备运行参数专业:车辆专业●名称全称中文意义LRU Line Replaceable Unit 线路可替换单元TBD To be Defined 待定义,待规定TBEx Trailer Bogie -External 拖车外转向架TBIn Train Bogie -Intermediate 拖车中间转向架TBU Tread Brake Unit 踏面制动单元WSP Wheel Speed Sensor 轮速传感器PB Powered Bogie 动车转向架FDU Frontal Display Unit 前部显示单元IDU Internal Display Unit 内部显示单元TIMS Train Integrated Management System 列车综合管理系统DVA Digital and Audio Announcements 数字语音广播器MPU Main Processor Unit 主控单元APU Audio Power Unit 放大器单元VPI Visual Passenger Information 可视乘客信息VVVF Variable voltage Variable Frequency 变压变频专业:信号系统●名称全称中文意义●PTI Positive Train Identification 列车自动识别SICAS Siemens Computer Aided Signaling 西门子计算机辅助信号DTI Departure Time Indicator 发车计时器PIIS Passenger Information and Indication System 旅客向导系统ADM Administrator Workstation 系统工作管理站RM Restricted Manual Mode ATP限制允许速度的人工驾驶AR Automatic Reversal 自动折返ATT Automatic Train Tracking 列车自动跟踪SIC Station Interface Case 车站接口箱LCP Local Control Panel 局部控制台ARS Automatic Route Setting 列车自动进路排列ATR Automatic Train Regulation 列车自动调整专业:通信系统●名称全称中文意义●MDF Multiplex Distribution Frame 综合配线架TBS TETRA Base Station TETRA基站PABX Private Automatic Branch Exchange 专用自动小交换机DDF Digital Distribution Frame 数字配线架ODF Optical Distribution Frame 光配线架VDF Audio Distribution Frame 音频配线架DxTiP Digital Exchange for TETRA TETRA数字交换机ISDN Integrated Services Digital Network 综合业务数字网OMS OTN Management System OTN管理系统NCC Network Control Center 网络控制中心名称全称中文意义●PCM Pulse Code Modulation 脉冲编码调制TETRA Terrestial trunked Radio 欧洲数字集群标准TDM Time Division Multiplexing 时分复用PSTN Public Switched Telephone Network 公用电话交换网CDD Configuration and Data Distribution Server 配置及数字分配服务器专业:自动售检票系统●名称全称中文意义● 2 2.1 File Transfer Protocol 文件传输协议TCP/IP Transmission Control Protocol/ Internet Protocol传输控制/网络协议CPS Central Processing System 中央计算机系统SPS Station Processing System 车站计算机系统PIN Personal Identification Number 个人身份号码MCBF Mean Cycles Between Failure 运行设备两次损坏之间的次数MTTR Mean Time To Repair 维修耗时平均值TVM Ticket Vending Machine 自动售票机SEMI-TVM Manually Operated Ticket Vending Machine 半自动售票机PVU Portable Verifying Unit 便携式验票机GATE 闸机专业:火灾报警●名称全称中文意义GCC Graphic Control Computer 图形监视计算机MTBF Mean Time Between Failures 平均无故障运行时间EMC Electro Magnetic Compliance 电磁兼容性FAC 消防专项合格证书●I/O Input/Output 输入/输出专业:环境监控●名称全称中文意义EMCS Electrical and Mechanical Control System 车站设备监控系统ECS Environment Control System 环境控制系统DDC Dircct Digital Controller 数字直接控制器PLC Programmable Logic Controller 可编程逻辑控制器API Application Programming interfac 应用程序接口●Tc (A) Trailer Car 拖车Mp (B) Motor Car With Pantograph 带受电弓的动车M (C) Motor Car 动车AW0 空载AW1 每位乘客都有座位AW2 每平方米 6人AW3 每平方米 9人●SIV:系统信息显示(System Information Viewer)车辆PCA:Personal Call Assistant 个人呼叫助理。
Efficient model checking of safety properties

Helsinki University of Technology Laboratory for Theoretical Computer ScienceResearch Reports76Teknillisen korkeakoulun tietojenka¨sittelyteorian laboratorion tutkimusraportti76Espoo2002HUT-TCS-A76ON MODEL CHECKING SAFETY PROPERTIESTimo LatvalaB TEKNILLINEN KORKEAKOULUTEKNISKA HÖGSKOLANHELSINKI UNIVERSITY OF TECHNOLOGYTECHNISCHE UNIVERSITÄT HELSINKIUNIVERSITE DE TECHNOLOGIE D’HELSINKIHelsinki University of Technology Laboratory for Theoretical Computer Science Research Reports76Teknillisen korkeakoulun tietojenka¨sittelyteorian laboratorion tutkimusraportti76Espoo2002HUT-TCS-A76ON MODEL CHECKING SAFETY PROPERTIESTimo LatvalaHelsinki University of TechnologyDepartment of Computer Science and EngineeringLaboratory for Theoretical Computer ScienceTeknillinen korkeakouluTietotekniikan osastoTietojenka¨sittelyteorian laboratorioDistribution:Helsinki University of Technology Laboratory for Theoretical Computer Science P.O.Box5400FIN-02015HUTTel.+358-0-4511Fax.+358-0-4513369E-mail:lab@tcs.hut.fic Timo LatvalaISBN951-22-6265-7ISSN1457-7615Otamedia OyEspoo2002A BSTRACT:Safety properties are an interesting subset of general temporal properties for systems.In the linear time paradigm,model checking of safety properties is simpler than the general case,because safety properties can be captured byfinite automata.This work discusses the theoretical and some of the practical issues related to model checking LTL properties.Ourfirst contribution is a theorem relating abstraction for Coloured Petri nets as defined by Lakos[36]and preservation of safety properties.We show that a subset of the safety properties are preserved for this abstraction frame-work.Our other contribution is an efficient algorithm for translating LTL safety properties tofinite automata.Minor contributions include new proofs for some old complexity results regarding LTL and safety properties.The implementation of the translation algorithm is also experimentally evaluated.Experiments support the feasibility of the approach.In many tests the implementation is quite competitive when compared to algorithms trans-lating full LTL to Büchi automata.The implementation can also check if an LTL formula is pathologic.The check performs well according to experi-ments.K EYWORDS:Computer aided verification,model checking,LTL,safety properties,abstraction,Coloured Petri netsCONTENTS1Introduction11.1Contributions and Results (2)1.2Related Work (2)1.3Outline (3)2Preliminaries4 3Automata Theoretic Foundations6 4Linear Temporal Logic94.1Syntax and Semantics of LTL (9)4.2Expressiveness and Complexity (11)4.3Safety and Liveness Properties (12)4.4Deciding safety (15)5Abstraction and Safety Properties185.1Coloured Petri Nets (18)5.2Abstraction and Petri Nets (20)5.3Temporal Logic and Refinement (23)5.4An Example (25)6Model Checking Safety Properties286.1Detecting Bad Prefixes (29)6.2Informativeness (31)6.3Translation Algorithm (34)6.4Finite Trace Semantics for LTL (40)7Implementation427.1Translation (42)7.2Checking Pathologic Safety (44)8Translation Experiments468.1Random Formulae (47)Syntactically Safe Formulae (47)General Formulae (49)8.2Model Checking Case Studies (50)9Discussion53 References551INTRODUCTIONDeveloping reliable systems is not an easy task.If the system has concurrencyit is even harder.When concurrency is introduced in a system,phenomenawhich are not present in sequential systems manifest themselves.The in-herent non-determinism of concurrent systems can give rise to subtle errorswhich are very hard to understand and can be difficult to reproduce.Concurrency is a devious source of complexity.Even a simple system can exhibit complex behaviour when concurrency is allowed.This is alsoobvious from many examples in concurrency theory.Determining if afiniteautomaton accepts any string or a given string can be decided with simplelinear-time algorithms.In the concurrent case,i.e.deciding if the intersec-tion of kfinite automata accept any string or a given string,the best knownalgorithms decide the problem in exponential-and linear-time respectively.One of the ways introduced to aid designers in designing correct concur-rent systems is model checking[8,51].Introduced roughly20years ago,model checking has already revolutionised the way hardware systems are de-signed,and can be considered industry practice today[23].The basic idea of model checking is simple.Both the system and the properties the system should have,are expressed as mathematical models.Special algorithms allow comparison of the system against the properties andif the system model violates a property,a violating execution can be displayed.If the model and the properties have been specified correctly,no error will gounnoticed.In the ideal case,all of these stages are automatic and very littlehuman intervention is required.Unsurprisingly,model checking has its limitations.The perhaps most acute problem is how to enable model checking to cope with the ever increas-ing size and complexity of systems.For some classes of systems,the methodsscale quite well.This has made possible the success of model checking inhardware systems.Finding methods which scale for systems which are asyn-chronous and data intensive seems to be more challenging.Consequently,concurrent software systems are still debugged mostly using traditional meth-ods.The problems related to scaling in model checking are referred to as thestate explosion problem[60].In this work we focus on efficient model checking of safety properties,us-ing the automata theoretical approach[62,34,63].Safety properties describeproperties of the system which havefinite counterexamples or,more infor-mally,properties requiring that“nothing bad happens”.A typical safety prop-erty requires e.g.that the value of x always is greater than three.Many com-mon properties such as invariants are safety properties which makes safetyproperties very interesting.In the automata theoretic approach to model checking both the system and the property to be verified are described as automata.The property holdsif all of the executions of the system automaton also are executions of theproperty ually the property is not given as an automaton butin some temporal logic such as linear temporal logic(LTL).There are alsoother logics such as CTL which can be used for specification.In this workwe will mostly restrict ourselves to properties expressed using LTL.This work discusses the theoretical and some of the practical issues of1INTRODUCTION1model checking LTL safety properties.The most relevant complexity resultare presented and analysed.Coloured Petri Nets are one of the formalismsused to describe concurrent systems.We investigate which properties,espe-cially safety properties,are preserved when abstractions defined in[36]areused.Most of this work is dedicated to investigating how to efficiently com-pile an LTL formula into an automaton,when the given formula describes asafety property.Efficient compilation of the formulas facilitates the verifica-tion of larger and more complex systems.1.1Contributions and ResultsWe develop an efficient translation of safety LTL formulae tofinite automata,based on the algorithm presented by Kupferman and Vardi[32].The al-gorithm has been implemented and extensive experiments have been per-formed.Our results show that the algorithm scales better than algorithms fortranslating general LTL formulae to automata.Currently,the implementa-tion is not the fastest of the available translators.However,the experimentsindicate that usingfinite automata for safety model checking results in a realdifference in performance for practical models,especially when the propertydoes not hold.The implementation also includes thefirst implementationto our knowledge of an algorithm for deciding if a formula is a pathologicsafety formula.The work also has some strictly theoretical contributions.Minor contribu-tions include new proofs for some of the complexity results related to safetymodel checking.A more significant contribution is that we show that the ab-straction/refinement framework introduced by Lakos can be used to aid theabstraction when model checking safety properties.We prove that the ab-stractions in the framework preserve a subset of the safety properties in LTL.We also extend the result to some branching time properties.The feasibilityof the approach is argued with a small example.1.2Related WorkModel checking of safety properties has been investigated by number of au-thors.Alpern and Schneider[2]were thefirst to give a formal definitions ofsafety and liveness.The work of Sistla[53]on characterising safety of LTLformulas syntactically continues this work and adds to it significantly.Mostof the automata theoretic insight into safety and liveness comes from Kupfer-man’s and Vardi’s[32]paper.Many important notions are defined there forthefirst time,among them the notions of informativeness for prefixes andclassification of LTL formulae into intentionally,accidentally and patholog-ically safe.The paper also introduces a translation from LTL formulae tofinite automata,which is the basis for the algorithm in this work.Many com-plexity results are also due to them.Geilen[21]also considers translatingLTL intofinite automata.His approach reformulates some of the results ofKupferman and Vardi using their notion of informativeness.The focus ofthe paper is on presenting a tableau algorithm for run-time monitors of LTLproperties.Havelund and Rosu[25]also focus on monitoring executionsof systems.They present a dynamic programming algorithm which checks 21INTRODUCTIONsequences against properties specified in a linear temporal logic with past op-erators.An algorithm for model checking past temporal logic specificationsis also presented in[3].Lakos[36]has defined and introduced most of the concepts related to abstraction and refinement used in this work.He also proved that the refine-ments used are in some sense behaviour respecting.Lewis[41]continuedLakos work and investigated refinement especially in the context of incre-mental development.Lewis also proves that given certain conditions,therefined net is weakly bisimilar to the original net.The approach of Padberget al.[49]is close to the results presented in this paper.They show how arule-based approach for morphisms can be used to stepwise refine nets whilepreserving invariants.1.3OutlineWe begin in Section2by introducing Kripke structures,the system modelused in this work,and by defining some fundamental concepts.Section3gives the automata theoretic foundations,while setting the stage for the au-tomata theoretic approach to model checking employed in this work.Sec-tion4defines LTL and presents the relevant complexity theoretical resultsand clarifies the connection between LTL and automata on infinite words.The important concepts of safety and liveness are also defined and discussedin this section.In Section5abstraction for Coloured Petri Nets w.r.t.modelchecking safety properties is investigated.The translation algorithm fromLTL tofinite automata is given in Section5.Section6discusses imple-mentation issues while Section7focuses on experimentally evaluating theperformance of the algorithm.Section8discusses the results and speculateson possible future work.1INTRODUCTION32PRELIMINARIESFormal languages.A very important concept in this work is the concept oflanguages.LetΣbe afinite set called the alphabet.Afinite word of lengthn overΣis a mapping w:{1,2,...,n}→Σ.Words are also in many casespresented as strings w=σ0σ1...σn,whereσi∈Σ.A language offinitewords overΣis a set L offinite words.We can also talk about infinite words.They are mappings w:N→Σ.Languages are defined as in thefinite wordcase.Regular expressions.One way we will define languages in this work is using regular expressions.We define the syntax of regular expressions w.r.t.an alphabet.•Every letter from the alphabet is a regular expression.•Ifαandβare regular expressions,then so are ,(α∪β),(αβ)andα∗Every regular expression defines a language.The letterσ∈Σdefines theone-word language{σ}.By we denote the empty string and(α∪β)is theunion of the languages ofαandβ.With(αβ)we denote the concatenationof the languages ofαandβ.In some cases the shorthandαi=αα···α,i.e.αi times,is used.The Kleene star,α∗is defined through the union:α∗= ∪ i∈N+αiIn many cases our alphabet will be2Σ.In this case we will use booleanterms overΣto define sets of letters.IfΣ={a,b},then a∨b denotes{{a},{b},{a,b}}while¬a denotes{∅,{b}}.The expression can be seenas a shorthand for2Σ.Formal models.All formal reasoning requires a formal model of the sys-tem under inspection.In this work we will consider the common modelwhere time is discrete and no concept of duration exists.This means thatthe ordering between events is relevant,but time between events is not.Ateach point in time,the system can be described by its state.The behaviour ofthe system is the possible sequences of states of the system.All behaviours ofthe system are considered infinite.For the class of systems we are especiallyfocusing on,reactive systems,this assumption is easy to justify.Reactive sys-tems continuously react to inputs from the environment and they have nonatural terminating state.Abstractly,their behaviour can be seen as infinite.It is of course possible that the system,e.g.due to a programming error,en-ters a state from which it cannot proceed.This can,however,be simulatedby having the system loop in the same state.The notions above can be formalised using the Kripke structure model.The model is very simple and abstract,but it will be sufficient for our pur-poses most of the ter we will also introduce higher-level formalismswhich are closer to programming languages.These mainly function as gen-erators of Kripke structures.Definition1A Kripke structure is a tuple M= S,δ,s0,π ,where•S is a set of states,42PRELIMINARIES•δ⊆S×S is the transition relation obeying the condition that∀s∈S:∃s ∈S:(s,s )∈δ,•s0is the initial state of the system,and•π:S→2AP is a labelling function which assigns a set of atomicpropositions to each state.An execution of a Kripke structure M is an infinite sequence of statesσ=s0s1s2...,where s0is the initial state of M and(s i,s i+1)∈δ.The set of states S can be eitherfinite or infinite.Most definitions in thiswork are oblivious to this,however,a few of the algorithms requirefinitenessfor termination.We can also define the language of a Kripke structure.An executionσcan be projected onto the alphabet2AP by using the labelling functionπ.This projected sequence can be considered a word in(2AP)ω.The set of exe-cutions of the Kripke structure generates a set of infinite words,the languageof the Kripke structure,denoted L(M).The relation between executions and infinite words will allow us to use automata theory to specify behaviours of systems.This is one of the fun-damental ideas which underlies the automata theoretic approach to modelchecking.2PRELIMINARIES53AUTOMATA THEORETIC FOUNDATIONSFinite automata onfinite an infinite words are essential constructs for the au-tomata theoretic approach to verification.This section introduces alternatingautomata and non-deterministic automata.Just asfinite automata onfinite words are equivalent to regular languages finite automata on infinite words are equivalent to omega-regular langua-ges(c.f.[59]).Omega-regular languages are like the normal regular lan-guages but an additional operator,ω,is allowed for omega-regular expres-sions.The expression(a∪b)(ba)ωcharacterises all strings which start witha orb and are followed by infinitely many ba:s.In the following we considerwords defined over an alphabetΣ.Let X be afinite set and B+(X)the set of all positive Boolean formulas over X including the abbreviations true and false.A set Y⊆X satisfies aformulaθ∈B+(X)iffθis satisfied by setting all the elements in Y to trueand all elements in X\Y to false.For the familiar non-deterministic automaton,if Q is a set of states,a tran-sition relationδcan be defined asδ⊆Q×Σ×Q.A transitionδ(q,σ)={q1,q2,q3}maps a state and a letterσ∈Σto a set of states.The non-deterministic nature of the automaton allows it to move to several states inone transition.Alternating automata generalise this by allowing the automa-ton use a bounded number of copies of itself which work non-determinis-tically.Formally,transitions are mapped to arbitrary positive formulas inB+(Q).As an example,if we have the transitionδ(q,σ)=q1∧(q2∨q3),theautomaton moves to the states q1and non-deterministically to q2or q3.Letw=σ0σ1...be a word and let w i=σiσi+1...denote the suffix of w startingfrom the i:th position.The automaton above accepts a suffix w l from q if itaccepts w l+1both from q1and from either q2or q3.In this framework thenon-deterministic transition above is expressed asδ(q,σ)=q1∨q2∨q3Non-deterministic automata are thus automata where only the or-connective is al-lowed in the transition relation.Non-determinism captures existential choicewith the perfect guessing capability of the automata.Non-determinism caneasily capture existential style questions such as“accept any word which hasthe property p”.Alternating automata can succinctly express both universaland existential choice.When a word w=σ0σ1...is read by an automaton it induces runs of the automaton.For a non-deterministic automaton a run can be seen as afunction r:N→Q,where r(0)is an initial state and for every i≥0,r(i+1)is inδ(r(i),σi).Each position is mapped to a state of the automatonand the run must respect the transition relation of the automaton.Due tonon-determinism,one word induces several runs.Runs for an alternating automaton are not so simple.An alternating au-tomaton can be seen as making copies of it self,when“and”appears in atransition.A run of an alternating automaton is thus better viewed as a la-belled tree rather than as a path as for non-deterministic automata.A tree isa non-empty set T⊆N∗,where for every x·c∈T with x∈N∗and c∈N wehave x∈T.The elements of T are called nodes and the empty word is theroot of T.For x·c∈T,x∈T is the unique parent of x·c,and respectivelyall x·c∈T are the children x.A node without children is called a leaf.The 63AUTOMATA THEORETIC FOUNDATIONSlevel of a node is its distance from the root .A pathπ=x0x1...of a treeis a maximal sequence of nodes such that x0is the root and x i is the parentof x i+1for all i≥0.AΣ-labelled tree is a pair T,V ,where T is a tree andV:T→Σmaps each node of T to a letter inΣ.Definition2An alternating automaton is tuple A= Σ,Q,δ,Q0,F where•Σis the input alphabet,•Q is afinite set of states,•δ:Q×Σ→B+(Q)is a transition function,•Q0⊆Q is a set of initial states and,•F⊆Q is a set offinal states.A run of A over an infinite word w=σ0σ1...is a Q-labelled tree T r,r ,where T⊆N∗and r( )∈Q0.For every node x∈T r withδ(r(x),σ|x|+1)=θthere is a possibly empty set{r(x·c)|x·c∈T r}which satisfiesθ.Withthe Büchi accepting condition,A accepts a run T r,r if all infinite pathsπ⊆T r visit at least one state in F infinitely often.A word is accepted if thereexists an accepting run for it.Ifδ(r(x),σi)=true,then x does not need to have any children.Thus allbranches of the tree need not be infinite in the run.On the other hand falsemust not appear in a run,since false is not satisfiable.The special cases of non-deterministic and deterministic are easy to de-fine.An automaton A is non-deterministic iffδ(q,σ)uses only disjunctions.A is deterministic iffδ(q,σ)∈(Q∪false)and|Q0|=1.The Büchi ac-cepting condition is the obvious:a run r:N→Q is accepted if at least onestate in F is visited infinitely often in the run and a word is accepted if hasan accepting run.Alternating automata can also acceptfinite words.A run on afinite word w=σ0σ1...σn is afinite Q-labelled tree T r,r with T⊆N≤n,where N≤nis set of N-words not longer than n.Otherwise,a run is defined in the sameway as in the infinite word case.A run is accepted iff for all nodes x of leveln we have that r(x)∈F.The set of words an automaton A accepts is denoted L(A)and is called the language of A.If L(A)=∅the automaton is called empty.Alternation does not increase the expressive power offinite automata.Al-ternating automata onfinite words define a regular language and alternatingautomata on infinite words an omega-regular language(c.f.[63]).However,both in thefinite and the infinite word case,alternating automata can beexponentially more succinct than non-deterministic automata.The transla-tion of an alternating automaton to afinite automaton constructs an non-deterministic automaton which is exponentially larger.In the general case,the blow-up is unavoidable.The intuitive idea behind the translation is thatthefinite automaton guesses a run tree of the alternating automaton.At agiven point of a run,thefinite automaton keeps a whole level in memory.When it reads the next symbol it guesses the next level.3AUTOMATA THEORETIC FOUNDATIONS7Allfinite automata are closed under union,intersection and complemen-tation.While complementing non-deterministic automata involves an ex-ponential penalty,alternating automata on infinite words can be comple-mented with only a quadratic blow up[31]and alternating automata onfinitewords complemented in linear time(c.f.[63]).In many applications it is important to determine if the automaton is empty.For a non-deterministic automaton onfinite words,determining ifthe automaton is empty can be done in linear time simply by checking if anyfinal state is reachable from an initial state using the normal graph traversalalgorithms.The problem can be shown to be NLOGSPACE-complete usingthe reachability method(c.f.[63]).An automaton on infinite words is non-empty if there exists a path from an initial state to afinal state,and thefinal state can be reached from itself.Despite the algorithmically more challenging task,the linear time bound canbe maintained in the following way.The strongly connected components(SCC)of the automaton can be computed in linear time[56].If a non-trivial SCC contains afinal state the automaton is ing thereachability method this problem can also be shown to be NLOGSPACE-complete.Unsurprisingly emptiness checking for alternating automata is much more challenging.For both thefinite word and infinite word case,it is in factPSPACE-complete.Proposition3([6])The non-emptiness problem for alternating automata isPSPACE-completeProof:An alternating automaton can be translated into a non-deterministic automa-ton with an exponential blow-up[6].Non-deterministic automata can betested for emptiness in logarithmic space and thus if we do the translationand the emptiness checking on-the-fly,we get a polynomial space algorithm.To prove PSPACE-hardness of the emptiness problem we can reduce, as we later shall see,the validity problem for LTL to the emptiness prob-lem(c.f.[63]). 83AUTOMATA THEORETIC FOUNDATIONS4LINEAR TEMPORAL LOGICTemporal logic[50]is a popular way of specifying properties of reactive sys-tems.There are two basic variants of temporal logic,linear and branch-ing[37].In linear temporal logic(LTL),introduced to the verification settingby Pnueli[50],any given point in time has only one future,while branch-ing time logics[37]allows several possible futures.The perhaps most knownbranching time logic is computation tree logic(CTL),introduced in[15].There has been a two decade long debate,albeit currently not so in-tense,among researchers in the concurrency community which paradigm,the branching or the linear,is superior in reasoning about concurrency.Tothe author’s knowledge,the most recent contribution to this debate is[64].In this work,we almost exclusively focus on the linear paradigm.The primary reason is that current research indicates[32]that the concept ofsafety does not seem to be as fruitful in the branching time paradigm.LTL allows properties of systems be specified easily,especially compared to e.g.first order logic.The great innovation of Pnueli[50]was that thismodal logic was suitable for this mon properties like invariants,fairness and causal relationships can be concisely expressed without the hor-de of quantifiers thatfirst order logic would require.LTL also enjoys a complexity advantage compared to fullfirst order logic.It is expressive enough in most cases.In contrast,solving thefirst order logicmodel checking problem is non-elementary(c.f.[9]).4.1Syntax and Semantics of L TLThe syntax of LTL consists of atomic propositions,the normal boolean con-nectives,and temporal operators.Let AP be a set of atomic propositions.Well-formed formulae of LTL are constructed in the following way:•true,false and every p∈AP are well-formed formulae•Ifψandϕare well-formed formulae,then so areψ∧ϕ,ψ∨ϕ,ψUϕ,ψVϕ,¬ϕand Xϕ.LTL is interpreted over infinite sequences of atomic propositions,i.e.infinitewords in(2AP)ω.A model(or word)π=σ0σ1σ2...,whereσi⊆AP,is amappingπ:N→2AP.Byπi we denote the suffixπi=σiσi+1σi+2...andπi denotes the prefixπi=σ0σ1...σi.For an LTL formulaψand a modelπ,we writeπi|=ψ,“the suffixπi is a model ofψ”.The semantics of themodels relation|=is defined inductively in the following way.•For allπi we have thatπi|=true andπi|=false.•For atomic propositions p∈AP,πi|=p iff p∈σi•πi|=ψ1∨ψ2iffπi|=ψ1orπi|=ψ2.•πi|=ψ1∧ψ2iffπi|=ψ1andπi|=ψ2.•πi|=Xψiffπi+1|=ψ.•πi|=¬ψiffπi|=ψ.4LINEAR TEMPORAL LOGIC9•πi|=ψ1Uψ2iff there exists k≥i such thatπk|=ψ2and for alli≤j<kπj|=ψ1.•πi|=ψ1Vψ2iff for all k≥i,ifπk|=ψ2,then there is i≤j<k suchthatπj|=ψ1.Usually we do not writeπ0|=ψbut simplyπ|=ψ.Other commonlyused abbreviations are Fψ=true Uψ,Gψ=false Vψ,and the normalabbreviations for the boolean connectives⇒,⇔.Of interest is also the un-less-operator W which is defined by the equivalenceψ1Wψ2≡ψ1Uψ2∨Gψ1.A sufficient set of operators which can express all LTL-properties is∨,U,X,¬.Note also the duality between until and release,¬(ψ1Uψ1)≡¬ψ1V¬ψ2.The operator X is the so called next-operator which requires that a formula is true in the next position of the execution.The binary operator U is calledthe until-operator.ψ1Uψ2means that eventuallyψ2will be true,and untilthenψ1is true.This version of the until-operator is called reflexive becausethe operator is satisfied ifψ2is true immediately.The dual of until,V,iscalled the release-operator.The formulaψ1Vψ2requires thatψ2is true ifψ1has not been true at an earlier point of time.In this caseψ1andψ2must besimultaneously true at some point.Note thatψ1is not required to eventuallybecome true.The operator G has the meaning“globally”or“henceforth”.It requires that a formula is true in all positions from the current onward.The dual of G is F,called“finally”or“eventually”.The meaning of Fψisthatψmust be true at the current point or at some point in the future.Theunless-operator,W,also known as the weak until operator,says that thefirstargument holds at least up until the second argument.The second argumentis never required to hold though.An LTL formulaψspecifies a language L(ψ)={π∈(2AP)ω|π|=ψ}.The connection between the executions of a Kripke structure and the mod-els of an LTL formula is now clear.The executions generate words over2AP,which can also be interpreted as models of an LTL formula.Thus,given aKripke structure M and an LTL formulaψ,we write M|=ψiff the pro-jection to the atomic propositions of the LTL formula of each execution ofthe Kripke structure M is a model ofψ.Sometimes this is referred to as theuniversal model checking problem.The dual of the universal model check-ing problem is the existential model checking problem where we ask if anyexecution of the Kripke structure satisfies the given formula.Example4Writing simple properties in LTL is fairly straightforward.Speci-fying an invariant is easy.Let p be the atomic proposition having the meaningthat the variable x is greater than zero.Claiming that this is an invariant iseasy:G pRequiring that x will always return to state where it is greater than zero is notmuch more difficult:GF pCausal relationships are also easily expressed.If p is an atomic propositionmeaning that“A goes up”and q means“A comes down”formalising“if A 104LINEAR TEMPORAL LOGIC。
Software Model Checkingfor Embedded Systems

Gap Model Description
Line Line Line Line Line Line … Line Line
5: … 12: … 15:… 21:… 25:… 27:… 41:… 47:…
Program
Error trace
Raw error trace may be 1000’s of steps long Must map line listing onto model description Mapping to source is made difficult by
Using the pattern system: 2-bounded existence forall[v: Vehicle]. between {keyIn(v)} and {keyRem(v)} {activate(v)} exists at most {2} times;
What makes model-checking modelsoftware difficult?
OK
Finite-state model Model Checker
or
Error trace
Line Line Line Line 5: … 12: … 15:… 21:…
(Φ
Ω)
Temporal logic formula
Static Analyses Abstract Interpretation Slicing Optimizations
Java Source
Model Compiler
Model Description
Model extraction: compiling to model checker inputs:
SINAMICS S120 基本参数,非常有用

r899.2 r2139.3 r899.4 r899.5 r899.6 r2139.7 r2684.8 r899.9 r2684.10 r2684.11 r2684.12 r2199.0 r2670 r2670.0 r2670.1 r2670.2 r2670.3 r2670.4 r2670.5 r2670.15 r2683 r2683.0 r2683.1 r2683.2 r2683.4 r2683.5 r2683.6 r2683.7 r2683.8 r2683.9 r2683.10 r2683.11 2089[1] r51.0 r51.1 r51.2 r51.3 r51.4 r896.0 r1406.8 r835.0 2089[2] r2521
Pபைடு நூலகம்D2
PZD3
0 1 2 3 4
PZD5 PZD6 PZD7 PZD8 PZD9 PZD10 PZD11 PZD12 PZD13 PZD14 PZD15 PZD16
p820[0] p821[0] p822[0] p823[0] p824[0] p897 p1545[0] p828[0] p2646 p2642 p2643 p2644 p2645 p2654
ZSW1.2 ZSW1.3 ZSW1.4 ZSW1.5 ZSW1.6 ZSW1.7 ZSW1.8 ZSW1.9 ZSW1.10 ZSW1.11 ZSW1.12 ZSW1.13 AKTSATZ AKTSATZ.0 AKTSATZ.1 AKTSATZ.2 AKTSATZ.3 AKTSATZ.4 AKTSATZ.5 AKTSATZ.15 PosZSW PosZSW.0 PosZSW.1 PosZSW.2 PosZSW.4 PosZSW.5 PosZSW.6 PosZSW.7 PosZSW.8 PosZSW.9 PosZSW.10 PosZSW.11 ZSW2 ZSW2.0 ZSW2.1 ZSW2.2 ZSW2.3 ZSW2.4 ZSW2.7 ZSW2.8 ZSW2.11 MELDW XistP
西门子数字工业软件 - 自动驾驶汽车开发辅助功能验证与验证说明书

Nico Nagl –Portfolio Development Autonomous DrivingValidation & VerificationADAS-Fahrfunktionen effizient validieren und verifizierenWhere today meets tomorrow.Nico Nagl –Portfolio DevelopmentConnectivityAutonomous VehiclesShared MobilityVehicle ElectrificationDisruptive InnovationKey to sustained businessEngineering the NEXT product not just the best product for the futureAddressing challenges for autonomous driving vehicle developmentFROM ADAS TO AUTONOMOUS DRIVING“+25% CAGR (through 2030) for Sensors”Roland Berger , on “Autonomous Driving”, 2014…“14.2 billion kilometers of testing is needed”Akio Toyoda, CEO of ToyotaParis Auto Show 2016“Design validation will be a major –if not thelargest –cost component”Roland Berger“Autonomous Driving” 2014Engineering implications of the AV development challengeIncreasing software and hardware complexityMassive validation and verification cyclesGrowing number and variety of sensorsComplex interactions between systems Rethinkthe vehicle development processesWhile balancing safety, comfort and efficiency performancesGrowing number and variety of sensorsMassive validation and verification cycles Reconciling agility with better traceabilityIncreased hardware and software complexityADAS/AV systems virtual V&V Automotive industry needsVirtual validation(MiL, SiL)Semi virtual validation(HiL, DiL, VehiL)Real validationvehicle testing(proving ground, public road)~106test cases~103test cases~102test cases~102test cases~102test cases~102test casesSAE level 1 to 5SAE level 1 to 5SAE level 1 to 5Need for efficient and automated simulation orchestrationFAILING IN SIMULATION DOES NOT KILL PEOPLEDo Things Right-Doing the Right ThingsEfficiency and EffectivenessADAS/AV systems virtual V&VAutomotive industry needs•Take not ideal world into account•Need for realistic and non-idealenvironments•Need for more vehicle physics than before •Simulation of appropriate scenarios is essentialDesign, Validation & Verification framework for ADAS and AVMiL / SiL / ClusterHiL / DiL / ViLProving ground /field testV&V environmentsDigital Twin “World”Digital Twin “Vehicle”Design adaptations(HW/SW)1M –10M scenariosRequirementsMultiple variantsCertification -HomologationSimulation definitionRequirements & system architectures Real worldVehicle under developmentMassive Verification and Validation of ADAS and AVsRequirementsCertification -HomologationSimulation definitionRequirements & system architectures Real worldVehicle under developmentDigital Twin “World”Digital Twin “Vehicle”Multiple variants1M –10M scenariosMiL / SiL / ClusterV&V environmentsHiL / DiL / ViLProving ground /field testChallenge:From thousands of scenarios (or millions of miles) to the relevant critical representationClosed loop automated process for generating critical scenariosOrchestration of virtual test scenarios“Falsification”Identify critical scenariosDigital Twin of the World1000’s of scenarios(weather, light, road types, …)(sensors, controls,powertrain, chassis)…Data Mining, AnalyticsOptimize vehicleonly againstrelevant criticalscenariosDigital Twin of theTest VehicleSimcenter Prescan Virtual testing of autonomous driving functions Complete sensor models library:Camera, Radar, LIDAR, Ultrasone, Infrared, V2X, GPS Scenario 1 -Adaptive Cruise Control ACC Scenario 2 –Advanced Emergency Braking SystemAEBSSimcenter Prescan: camera simulation Ground truth: depth camera exampleWorld modelling solutionsScenario import Scripted scenario generation Ready to use scenariosGUIWorld modelling: non-ideal environmentRealistic bumped asphalt Faded, dirty lane markersNon-perfect lane markers Lane markers with snow Mud, water puddles on the roadSimcenter Prescan–Scenario generation From real data to simulationSimcenterPrescan World modelling: custom data source importKITTI DatasetEgoGPS DataTarget GPS Data Ego state Prescan APIRoadnetwork TargetstatesTarget typesWorld modelling: DataModel APIExplore critical scenarios Prepare for certification •Prescan DataModel API→programmatic creation of scenarios→Repeatability•All important assets can be created viascripting:•Roads•Actors•Traffic signs•Nature elements•Trajectories•Environmental conditions •Etc.Parameter variationV 2X &U l t r a s o n i c R a d a r & L i d a r C a m e r a Ready to use sensor modelsSensor simulationV2N V2VV2P V2ISensors models: the right fidelity level for scaled-up simulationBalancing accuracy andcomputation time ofsensor simulationsLidar (spinning and solid-state)Physics-based Radar simulationExample: during night-time driving Example: Realistic lighting conditionsSimcenter Prescan Physics Based Camera (PBC) simulationRadar simulation exampleDevelopment with model validation in mindTwo projects for radar models validation performed in close collaboration withmajor Dutch Tier2 and Japanese Tier1From a lab… To a test track… To the real world…Radar SimulationValidating simulation results against measured dataReal World Testing•Vehicle with radar•Range-doppler measurementsSimulation Testing•Simulated vehicle using thephysics-based radar model•Range-doppler data generatedbased on the simulated scenarioWhen higher fidelity vehicle dynamics makes the difference!For AEBS,ESC pump dynamics is critical.For level 4-5,redundancy will be ensured by the ESC,the EPB and the eBooster.When level 4-5,we will probably work with steer by wire and motor redundancy.Powertrain and braking systemsmodels for ACC casesPick the relevant fidelity level fromSimcenter Amesim scalable modeling offerFull vehicle dynamics models forAEB safety casesWhen higher fidelity vehicle dynamics makes the difference!45 Libraries / 4,000 Multi-physics Models •Validated and maintained•Supporting multiple levels of complexity •No need for details physics expertise•Hydraulic, hydraulic component design •Hydraulic resistance, filling•Pneumatic, pneumatic component design •Gas Mixture, moist airFluids•Signal and control•Engine signal generator •Real time, MIL –SIL –HILControl•1D –2D –3D mechanical,•Transmission, cam and followers •Finite-elements import •Vehicle dynamicsMechanics•IFP drive, IFP engine •IFP exhaust •CFD-1DIC Engine•Electrical basics, electromechanical •Electrical motors and drives •Electrical static conversion•Automotive electrics, electrochemicalElectrics•Fuel cell •Battery•Power generationEnergy•Thermal, thermal hydraulics•Thermal-hydraulic component design •Cooling, air-conditioning •Two-phase flowThermalSimcenter Prescan360Scenario authoringModels integration environment Sensors and environment simulationSimcenter PrescanProcess automation Simulation plan orchestrator Results analysis and reportingHEEDSThird partyVehicle dynamicsOff-the-shelf validation scenarios, metrics anddashboardsVehicle dynamicsSimcenter AmesimORSimulation production: overall workflow and AEBS exampleNumerous results analysisReportingSimulation plan definitionSimulation plan executionScenariosEgo modelsAzureKubernetesScripted scenario generation automates the process of creating scenarios at scale Test Automation /Design Optimization ToolOrchestration •HEEDS•Prescan APIs •3rd party toolingScenario Change •Parametric sweeping •Design of Experiments •OptimizationHow to run •Single machine •Distributed•Cloud and clusterResults•Local•Cluster•Test automation InterfaceCreate wide variability with on cloud and clusterDo not simulate any scenario.Simulate critical scenarios related toyour application!BUTHow do we identify critical scenarios?Should this scenario be simulated?Simcenter Prescan360 BenefitsPlan Execute Report •Process Automation: avoidance of manual errors•No manual creation of scenarios saves time•Multiple scenario testing for algorithms•Identify critical scenarios for each individual application •Deep insight in highly complex correlations•Realistic simulations•Verification traceability: ready for regulations •SAFE TIME•REDUCE COSTS •ENSURE HIGHEST QUALITY •BE INNOVATIVESpeed Up the Development of Autonomous Vehicles with Simcenter Prescan360Nico Nagl -E-Mail:*********************Where today meets tomorrow.。
自动特征分析套件(ACS)测试系统将圆片级——可靠性测试速度提高五倍

己口 口 晦 5月 第2 卷 第 5期 7
业
SL 横 河 电机 发 布 新 一 代 高 速 数 据 采 集 仪
数 据采集 仪既 可 以与 P C连 接 使用 也 可 以独 立工 作 , 活 灵
方 便 的模 块化 结构 能够 让 客 户 自由构 建属 于 自己的测 试
美 国吉 时利 ( e he) K i l 仪器 公 司 ( Y E代 码 : I, t y N S KE )
日前 宣 布 增 强 了 其 AC a tmae c aatr ain S( uo td h rcei t z o
si , u e 自动 特征分 析套 件 ) t 软件 , 入 了面 向半 导体 可靠 性 纳
服务 体系 。东方 集成 还 成 立 了 由该 领域 专 家 组 成 的顾 问 咨询 团 队 , 能够随 时为 电子制 造企业 提供 包括 设计 、 生产 、 制造 各个 环节 的测试 解决 方案及 仪器仪 表设 备 。
自动 特征 分 析套 件 ( S AC )测试 系统 将 圆片级 可 靠 性 测试 速 度 提 高五 倍
系统 。集高速 采集 、 高速 传 输 、 高速 存 储 和 快速 启 动 于一
体 的 S 10 , L 0 0 特别 适合 机 电 、 电力 电 子 、 电等行 业 的产 家 品评价 和耐 久性试 验等 。
S 10 L 00的主要 特点 :1高速 采 集 ;2高 速传 输 并高 () ()
与 寿命预测 测试 应用 的 W L wae vl ei it , R( frl e rl bly 圆片 e a i
级 可靠性 ) 选测 试工 具 。4 0 以 A S软件 已有 的单 点 备 .版 C 和多 点并行 测试 功能 为 基 础 , 加 了对数 据 库 的 支持 , 增 以
OXYMAT 6 气体分析仪安全手册说明书

Trademarks
All names identified by ® are registered trademarks of the Siemens AG. The remaining trademarks in this publication may be trademarks whose use by third parties for their own purposes could violate the rights of the owner.
Danger
indicates that death or severe personal injury will result if proper precautions are not taken.
Warning indicates that death or severe personal injury may result if proper precautions are not taken.
Acyba GLS模块安装与配置指南说明书

1.Installation1.1 Manual installation (via zip file)To manually install the module, you have to extract the zip file under app/code/Acyba/GLS directory.The module run with dependencies to others modules, that you need to install. You can find them in the composer.json file of the module. To install them, you have to use the following command : composer require vendor_name/module_name:X.X.XWarning : to install the dependencies, you have to use the above command with module names and version numbers as declared in the composer.json file of GLS module.Once the GLS module and its dependencies are installed, please run the followings Magento commands :php magento setup:upgradephp magento setup:di:compile2. Configuration2.1 Shipping methodsThe module created a new GLS shipping method in Stores > Configuration > Sales > Shipping Methods.To activate the GLS shipping method on the website, it’s necessary to switch the “Enable”parameter on and fill up the fields “GLS webservice login” and “GLS webservice password” whose values are provided by GLS.Warning : to use the official GLS module for Magento 2, you have to be a GLS customer. The use of the different GLS shipping methods is subject to the acceptance of GLS general terms and conditions. The activation of the GLS shipping methods of this module have to match with the prices lists signed with GLS. For more information, please get in touch with your GLS commercial contact.If you’re not a GLS customer, please connect to www.gls-group.eu to discover all the GLS services and contact GLS.The module is provided with a default configuration and all these parameters are editable in the menu Stores > Configuration > Sales > Shipping Methods > GLS, your transport partner :Title: Label of the GLS shipping method group displayed on the websiteEnable: By default disabled when installing the module. Switch on to see GLS shippingmethods on the websiteGLS webservice login: Provided by GLSGLS webservice password: Provided by GLSMaximum package weight : Maximum package weight that GLS can carryGLS Chez vous : Enable or disable the “at home” shipping methodThis service match the following GLS offers:- Business Parcel for your national shipments- Euro Business Parcel for your European shipments- Global Business Parcel for your international shipmentsGLS Chez Vous setup: Configuration field, please see more explanations and examplesbelowGLS Chez Vous order: Set the order of appearance of the “at home” shipping method amongGLS shipping methodsGLS Chez Vous +: Enable or disable the “at home” shipping methodThis service match the GLS offer : Flex Delivery ServiceGLS Chez Vous + setup: Configuration field, please see more explanations and examplesbelowGLS Chez Vous + order: Set the order of appearance of the “at home” shipping methodamong GLS shipping methodsGLS Point Relais: Enable or disable the relay shipping methodThis service match the GLS offer: Shop Delivery ServiceGoogle Maps API Key: API key to use the relay shipping method to locate the relays on aGoogle Maps (See: 5.1 Generation of the Google Maps API Key to learn how to generate this key)GLS Point Relais setup: Configuration field, please see more explanations and examplesbelowGLS Point Relais order: Set the order of appearance of the relay shipping method amongGLS shipping methodsOnly XL shop search: Enable the display of XL relays only (disabled by default)GLS Avant 13H: Enable or disable the express shipment before 1pmThis service match the GLS offer: Express Parcel GuaranteedGLS Avant 13H setup: Configuration field, please see more explanations and examplesbelowGLS Avant 13H order: Set the order of appearance of the express shipping method amongGLS shipping methodsTracking URL: Used to generate shipment tracking URLDebug: Allow to enable the module debugging function for the shipping costs calculation(Advanced function for developer)GLS module order: set the order of appearance of the GLS shipping methods group amongother shipping methodsThe configuration fields use a PHP format syntax used by the OWEBIA module for Magento 2, whose documentation is here.For example, here is the provided configuration for at home shipment:1. title : label displayed on the website for this shipping method2. enabled : activation conditions for this method. In this example, the method will be displayedonly if the destination country is France3. price : shipping fees for this method. In this example, if the cart total weight is less than or equalto 150, the fees will be 5, if the cart total weight is less than or equal to 160, the fees will be 3 and in other cases, it will be 0It’s possible to add filters on customer group, product categories etc … (for more informations, please check documentation)Many methods can be created for one configuration field. To do that, you have to duplicate the addMethod function by defining others rules.Warning: in the method name (ex: tohome_fr above), only the part before the underscore can be edit2.2 GLS Advanced Setup2.2.1 General ConfigurationAgency code: GLS agency code you are linked to. Information provided by GLS2.2.2 Import/export configurationThis section contains the configuration to manage the import and export of GLS orders. For more information about import and export, please check 4. Import/Export.Active: Activation of automatic import/export through a cron taskFrequency: Cron task frequency in minutes (every X minutes)Cron expression: Cron expression generated from frequency field (if the you can't see themodification after saving, please refresh Magento configuration cache)Import folder: Folder in which there are the orders to importExport folder: Folder in which the exported orders are downloadedStatus of orders to export: Status of orders to export for automatic export through the crontask3. DisplayAfter the shipping methods configuration, here is an example of the display of these methods on the website:If the user choose the shipping method “Point Relais”, a popup to choose the relay to deliver to will be displayed:This way he can choose the relay by clicking the button “Choose this relay”.By clicking on markers on the map, the user can see relay opening hours:A confirmation popup will ask the user to confirm his choice:After confirmation, the relay details will be displayed below the shipping method:4. Import/Export4.1 Export to WinExpéThe module allows to export orders files to the GLS WinExpé software.The exports configuration is done in Stores > Configuration > Sales > GLS Advanced Setup (check 2.2.2 Import/export Configuration).This feature is reachable through a new menu entry “GLS IMPORT/EXPORT > Export orders”.In the configuration, the “Export Folder” parameter have to be well set.The export screen lists all orders whose shipping method is a GLS one. It’s possible to either download or export one or several orders. To do this, you have to check orders that you want to export, then choose in the “Actions” menu what you want to do.The “Download” option will download the generated file on your computer.The “Export” option will put the generated file in the directory set in configuration (Stores > Configuration > Sales > GLS Advanced Setup > Import / Export Configuration).You have to create a FTP access on this directory and configure it in WinExpé so the software can automatically recovers the files. For any question about the WinExpé software configuration, please get in touch with your GLS IT contact.4.2 Import from WinExpéThe module allows to import files from the GLS WinExpé software, to save tracking numbers in Magento.The imports configuration is done in Stores > Configuration > Sales > GLS Advanced Setup (check 2.2.2 Import/export Configuration).This feature is reachable through a new menu entry “GLS IMPORT/EXPORT > Import tracking numbers”.In the configuration, the “Import folder” parameter have to be well set.In the import screen you will find a button to import files that are in the folder set in the configuration (Stores > Configuration > Sales > GLS Advanced Setup > Import / Export Configuration). With these files, the tracking numbers will be added to the matching orders, then files will be deleted.You have to create a FTP access on this directory and configure it in WinExpé for the software can automatically upload the files to import.4.3 Automatic Import/ExportIt’s possible to automate orders import and export. It can be configured in Stores > Configuration > Sales > GLS Advanced Setup (check 2.2.2 Import/export Configuration).To enable this, you have to switch on the “Active” parameter in configuration (Stores > Configuration > Sales > GLS Advanced Setup > Import / Export Configuration > Active) and fill up the wanted frequency in minutes (Stores > Configuration > Sales > GLS Advanced Setup > Import / Export Configuration > Frequency).Then, Magento will export orders that have the defined status (Stores > Configuration > Sales > GLS Advanced Setup > Import / Export Configuration > Status of orders to export) and import orders at the defined frequency.5. Miscellaneous5.1 Generation of the Google Maps API KeyTo use the GLS Point Relais shipping method, it’s necessary to define an API key. Indeed, the module uses a Google Map to locate the relays, and this service require an API key.You have to generate this API Key and set it in the configuration (check 2.1 Shipping Methods). Here are the different steps to generate this API key:Go to https://Connect with a Google accountGo to “Credentials” sectionClick on “Create credentials” > “API Key” (It’s possible to configure restriction for this key)Copy the keyGo to “Library” sectionSearch “Google Maps JavaScript API” and click on the corresponding resultClick on “Enable”Back in the GLS configuration, paste the key in Stores > Configuration > Sales > ShippingMethods > GLS, your transport partner > Google Maps API Key5.2 SupportIf you need some help with the configuration or installation of our module, please contact yout GLS advisor。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
ACSAR:Software Model Checking withTransfinite RefinementMohamed Nassim Seghir and Andreas PodelskiUniversit¨a t Freiburg1IntroductionACSAR(Automatic Checker of Safety properties based on Abstraction Refine-ment)is a software model checker for C programs in the spirit of Blast[5], F-Soft[6],Magic[4]and Slam[1].It is based on the counterexample-guided abstraction refinement(CEGAR)paradigm.Its specificity lies in the way it overcomes a problem common to all tools based on this paradigm.The problem arises from creating more and more spurious counterexamples by unfolding the same(while-or for-)loop over and over again;this leads to an infinite or at least too large sequence of refinement steps.The idea behind ACSAR is to ab-stract not just states but also the state changes induced by structured program statements,including for-and while-statements.The use of the new abstraction allows one to shortcut such a“transfinite”sequence of refinement steps.The divergence of the abstraction refinement loop is not just a theoretical problem but one that hits us in our practical use of software model checker. ACSAR is integrated in a higher order theorem prover,namely Isabelle[3].It is called,from within Isabelle,for discharging automatically generated verification obligations.Thus,another specificity of ACSAR as a software model checker lies in the way that it is used.We report on our experience of using ACSAR at the end of the paper.2A motivating exampleLet us illustrate the need of abstracting loops through the example in Figure1(a). This example is taken from the list of benchmarks that were used by McMillan and Jhala[7].It represents the concatenation of two strings.The key word assume does not exist in the C language but it is used for the model checker to express additional assumptions.A classical refinement generates predicates i≥200,j<100,i+1≥200,j+ 1<100,i+2≥200,j+2<100...i+99≥200,j+99<100.The loop is unrolled as many times as the number of loop iterations in a real execution. Moreover,if we want to perform a generic verification for arbitrary string length, by substituting size for100in line12and21,and size∗2for200in line25,the refinement process completely diverges.The problem is inherent to the CEGAR scheme in its present form(based on state abstraction)where the loop(15,16,17, 18,19,15)is unfolded over and over again.In this case,neither the interpolation approach nor the split prover method seem to help[7].next−j)==(inext;18j=j(a)(b)Fig.1.Example in C code before and after the abstraction3Loop abstraction approachAs alternative to the iterative unfolding of loops,ACSAR approximates state changes induced by the execution of the loop.The idea of abstracting transi-tions was previously used to prove the termination of programs[2].Our use of transition abstraction is in the context of checking safety properties.3.1How does ACSAR abstract loops?ACSAR extracts the list of transition constraints corresponding to the program. Bellow is the transition constraints corresponding to the loop(15,16,17,18,19, 15)from the example in Figure1(a).pc=15∧y[j]=0∧z [i]=y[j]∧i =i+1∧j =j+1∧pc =15(1) pc=15∧y[j]=0∧pc =21(2)A transition constraint is a conjunction of atomic formulas,it expresses a binary relation between a starting state and an arrival state of the program.In atomic formulas,variables marked with primes are evaluated in the arrival state of the transition,otherwise they are evaluated in the starting state.The special variable pc represents the program counter.When an atomic formula does not contain any variable marked with a prime it is called a guard.An atomic formula that contains variables with primes is called an update.If a variable does not appear marked with a prime in any atomic formula,then it means implicitly that its value does not change when the transition is performed.The next step is the abstraction phase.In this phase non relevant guards are removed and constraints expressing relations between old and new values of the variables are extracted.For example:the expression(i −i)=(j −j)is automatically extracted by ACSAR as both variables i and j increase by the same constant number within the loop.Transition constraints(1)and(2)are replaced by their abstractions(1’)resp.(2’).To the difference of transition(1) its abstraction(1’)does not loop but it approximates the effect of the loop over the program variables.With this abstraction ACSAR succeeds to prove that the program is safe.pc=15∧i −i=j −j∧pc =21(1’)pc=15∧pc =21(2’)Question:How can one express the above abstraction of a loop in terms of a source-to-source transformation on the C program?The problem is that a tran-sition constraint expresses a constraint on the after-value of a transition,but a program statement defines the after-value by the value of an expression.As of-ten,the solution is very simple.We write the transition constraint as a program expression(using an uninitialized auxiliary variable xnext.See Figure1(b). The loop(15,16,17,18,19,15)is replaced by a nondeterministic’if’block(the ‘nondeterministic’expression is denoted*).What do we gain with loop abstraction?The benefit is two folds:–We obtain better performance in terms of time and space.Table1illustratesa comparison between the loop abstraction approach and a simple approachbased on the weakest precondition for refinement.We apply both approaches on different instances of the example offigure1(a).Column size contains different values of the size of input array variables x and y.Implicitly,the size of z is2∗ing the simple approach,we clearly notice a nonlinear increase of the verification time in function of instance size.With the loop abstraction approach,the execution time is the same and relatively small for all the instances.–Using the loop abstraction approach,we can verify a generic version(sec-tion2)of the previous example.The abstract transition represents a param-eterization of all paths corresponding to loop unfolding of different instances of the example program.instance timesimple loop abstraction1 1.190.292 2.77/333.59/4127.72/5336.56/1http://www.verisoft.deinteraction between the verification engineer and Isabelle.In the(ongoing)in-teractive verification effort for the Vamos micro-kernel(which is being developed within the Verisoft project),ACSAR automatically discharges about75%of the (automatically generated)verification obligations(the remaining25%concern properties that require variable quantification).Outlook:We are planning to carry over methods for the generation of linear invariants[8]to our approach for abstracting loops.We want also to handle simple array assertions that involve quantifiers;e.g.,∀i(0≤i<n)⇒a[i]=0. References1.Thomas Ball and Sriram K.Rajamani.The Slam project:debugging system softwarevia static analysis.In POPL,pages1–3,2002.2.Byron Cook,Andreas Podelski,and Andrey Rybalchenko.Abstraction refinementfor termination.In SAS,pages87–101,2005.3.Matthias Daum,Stefan Maus,Norbert Schirmer,and M.Nassim Seghir.Integrationof a software model checker into Isabelle.In LPAR,pages381–395,2005.4.Sagar Chaki et al.Modular verification of software components in C.In ICSE,pages385–395,2003.5.Thomas A.Henzinger et al.Software verification with BLAST.In SPIN,pages235–239,2003.6.Franjo Ivancic,Ilya Shlyakhter,Aarti Gupta,and Malay K.Ganai.Model checkingc programs using F-soft.In ICCD,pages297–308,2005.7.Ranjit Jhala and Kenneth L.McMillan.A practical and complete approach topredicate refinement.In TACAS,pages459–473,2006.8.Michael Karr.Affine relationships among variables of a program.Acta Inf.,6:133–151,1976.9.Norbert Schirmer.A verification environment for sequential imperative programsin Isabelle/HOL.In LPAR,pages398–414,2004.APPENDIXA ACSAR the toolA.1EnvironmentACSAR is written in Gnu C++under the Linux operating system.It was tested with success under the following versions of Linux:Debian,Suse and Gentoo.A.2AvailabilityA package containing the binary of ACSAR can be downloaded from the follow-ing address:http://www.mpi-inf.mpg.de/∼seghir/ACSAR/ACSAR-web-page.html.A.3ApplicationACSAR is used in the Verisoft project as a back-end for the higher order in-teractive theorem prover Isabelle.Its role is to discharge runtime error guards, mainly for:overflows and underflows,array out of bounds and NULL pointer dereferences.Among the applications that we verified:the Vamos micro-kernel. We are actually verifying a string library and the C0compiler(C0is a subset of the C language).25%of the functions constituting the C0compiler were already verified.Figure2shows program representation within the Isabelle proof envi-ronment.Guards are given between’{’’}’.The result of the verification after calling ACSAR is shown in Figure3.Figure4shows the case when a guard does not hold,in this situation a counter example is generated.B DemoIn this section we describe our demonstration plan.First,we consider exampleof Figure5to show how to specify a property and verify whether it holds using ACSAR.This example represents a routine from Linux-2.4.0CD-ROM interface device driver.For readability concerns,portions of the code that are not relevantto the property that we want to check are omitted.As verifier,one does not require to understand the functionality of the codeto be verified,however,one should know what to verify and how to specify it. Fortunately,for our example of Figure5,the developer documented his code by adding the following comment:Fig.2.Program representation in IsabelleFig.3.Result of Isabelle after calling ACSARFig.4.Case of counter exampleThe result register can be read10bytes at a time,a wait for result to be asserted must be done between every10bytesThis constitutes for us an informal description of a behavioral property that the implementation should fulfill.A formalization of this assertion is required so that we can check it with ACSAR.For this,we use functions called by the routine as stubs and exploit them to define a monitor for the property to be checked.The function read register is the one that reads the result register and is ready is the one that is called to wait for the result. The specification can then be stated as follows:between every ten calls of func-tion read register we must call the function is ready at least once.We introduce the variable monitor,it is incremented each time the func-tion read register is called,this is illustrated in Figure6.If monitor becomes greater than ten then error label ERRORresultresult--file linux driver.c Option’reach’specifies that we want to check reachability,’mainproc’spec-ifies the root procedure and’file’refers to the sourcefile of the program that we want to verify.As result,ACSAR returns a counter example.See Figure7. Local variables are renamed by concatenating their names with the name of the function in which they are declared.Numbers at the beginning of lines represent pc internal values(not line numbers in the sourcefile).The counter example says that variable monitor becomes greater than ten after it is incremented once and we jump to ERRORresultconcat1.c--loopsumr The’loopsumr’option tells ACSAR to abstract a loop if it is unfolded more than twice during the verification.This time ACSAR is able to prove the safety of the program.To see the transformation occurring to the program,we use the option’printloopsumr’that displays transition constraints constituting the loop and the abstraction of the loop as a single transition constraint.See Fig-ure8.pcthe occurrence of pc1represents the update.We notice in the abstraction that new variables temp1and temp2are introduced.They correspond respec-tively to the values of i and j after executing the loop.Transition constraints constituting the original loop are disabled.result(unsigned char∗resultsize)4{5unsigned char a,b;6int i,res;7unsigned int retryresult1;11if((a&0xf0)!=0x20)12{13if(b>8)14{15for(i=0;i<8;i++)16{17∗result result1;19//..........20}21b=b−8;22while(b>10)23{24res=is ready();25while((retryresultresultbuffer=read register(); 37if(ERROR==1)goto ERRORresultbuffer=read register();50if(ERROR==1)goto ERROR1:;56end:;57}1int is ready()2{3monitor=0;4if(ACSARresultFig.6.Monitor corresponding to the CD-ROM driverFig.7.Counter example generated by ACSARFig.8.Loop abstraction computed by ACSAR。
