Progresses_in_Synthetic_Methods_of_Carbazole_and_Its_Derivatives
rapid verification method for the trajectory optimation of reentry vehicles

Rapid Veri cation Method forthe Trajectory Optimizationof Reentry VehiclesScott Josselyn¤and I.Michael Ross†Naval Postgraduate School,Monterey,California93943IntroductionT HE trajectory optimization of path-constrained nonlinear dy-namic systems such as those arising in the guidanceand design of reentry vehicles has long been considered a dif cult problem.1¡3 Of the many methods to solve such problems,the direct collocation method with sparse nonlinear programming(NLP)has proved to be quite effective.3Because direct methods do not tie the resulting solutions to the Pontryagin maximum principle4(PMP),a two-step direct–indirect approach has been used successfullyfor nding ex-tremal solutions.5One major drawback of the direct–indirect ap-proach is that a signi cant amount of labor is necessary to derive all of the necessary conditions including complex switching and junc-tion conditions for state-constrainedproblems.Even with estimates of the adjoint arcs,solving the multipoint boundary-valueproblem is an elaborate task.Over the past few years,a new approach to solving complex tra-jectory optimizationproblems has been proposed.6¡9The Legendre pseudospectralmethod is a particularlyeffective method because it providesspectrallyaccuratesolutionsfor the costatesand other cov-ectors without the use of any analyticaldifferentialequationsfor theReceived15August2002;revision received20November2002;accepted for publication21November2002.This material is declared a work of the ernment and is not subject to copyright protection in the United States.Copies of this paper may be made for personal or internal use,on condition that the copier pay the$10.00per-copy fee to the Copyright Clear-ance Center,Inc.,222Rosewood Drive,Danvers,MA01923;include the code0731-5090/03$10.00in correspondence with the CCC.¤Graduate Research Assistant,Department of Aeronautics and Astronau-tics;sbjossel@.Student Member AIAA.†Associate Professor,Department of Aeronautics and Astronautics; imross@.Associate Fellow AIAA.adjoints.7;8The software package,DIDO9(named after Queen Dido of Carthage),is a realization of the many advances made in solving complex trajectory optimization problems including an implemen-tation of the symmetric covectormapping theorem(CMT).7;8In this Note,we focus on an application of the CMT to the veri cation of the rst-order optimality conditions arising in the path-constrained trajectory optimization of reentry vehicles.The particular problem chosen is the standard benchmark problem of maximizing cross range.1¡3Overview of the Veri cation MethodThe CMT may be articulated as follows:Given an optimal con-trol problem,P,let P N denote its Legendre pseudospectralapprox-imation,where N is the order of the Legendre polynomial used in the approximation.Let P¸denote the boundary-value problem (BVP)arising from an application of the PMP to problem P,and let P N¸denote the generalized root- nding problem obtained by applying the Karush–Kuhn–Tucker(KKT)conditions to problem P N.The CMT asserts that if P¸is discretized by a Legendre pseu-dospectral method,that is,an indirect method,then there exists an order-preserving map between these discretized covectors and the KKT multipliers associated with problem P N¸.Hence,from the KKT multipliers,one can nd covectors by the direct Legendre pseudospectralmethod as if one solved the problem by the indirect method.This is the CMT;more details are provided in Refs.7and 8.Clearly,one main advantage of the CMT is that it obviates the need for a two-tier direct–indirect approach and provides a quicker way to verify the optimality of the computed trajectory.The reentry problem is solved using DIDO,9which implements a particular version of the Legendre pseudospectral method that exploits a sparsity pattern of the discrete Jacobian by way of the NLP solver SNOPT.10Feasibility is declared when the state his-tories obtained by a Runge–Kutta(R–K)propagation(ode45rou-tine in MA TLAB®that implements the Dormand–Prince pair)of the initial conditions using the interpolated controls obtained from DIDO(DIDO controls)match the states obtained from DIDO (DIDO states)within a prescribed tolerance.Convergence is de-clared when DIDO controlsmatch the Pontryagin-extremalcontrols (withinsome prescribedtolerance)computedthroughan application of the CMT(CMT controls)using the DIDO states and DIDO cov-ectors.In the following sections,we provide details of our approach by way of the reentry problem.Reentry Dynamic ModelThe state of the vehicle is represented by the six-dimensional vector(r,µ,Á,v,Ã,°)consisting of radial position,longitude, latitude,speed,heading angle,and ight-path angle,respectively. The equations of motion are given by1¡3P r D v sin°(1) PµD v cos°cosÃ(2) PÁD v cos°sinÃ(3) P v D a s¡g sin°CÄ2r cosÁ.sin°cosÁ¡cos°sinÁsinÃ/(4) PÃD a w¡v cos°cosÃtanÁ¡Ä2r sinÁcosÁcosÃC2Ä.tan°cosÁsinásinÁ/(5) P°D a n¡g cos°C v cos°CÄ2r cosÁ.cos°cosÁC sin°sinÁsinÃ/C2ÄcosÁcosÃ(6) where g D¹©=r2is the inverse-square gravitational acceleration with¹©D0:14076539£1017ft3/s2andÄis the Earth’s angular velocity,7:2722£10¡5rad/s.The aerodynamic accelerations,a s,a n,and a w,resolved in the tangential,normal,and binormal direc-tions area s D¡D=m;a n D L cos±=m;a w D L sin±=m(7)where±is the bank angle and m D7008slugs is the mass of the vehicle.The aerodynamic lift and drag forces are given byL D q d AC L.®/;D D q d AC D.®/(8) where A D2690ft2is a reference area and q d is the dynamic pressure,q d D1½.r/v2(9) and½is the atmospheric density.The lift and drag coef cients are modeled asC L.®/D C L0C C L®®(10)C D.®/D C D0C C D®®C C D®2®2(11) where the coef cients C L0D¡0:2070,C L a D1:676,C D0D 0:07854,C Da D¡0:3529,and C D a2D2:040are adaptedfrom Ref.3 with®,the angle of attack,in radians.An exponential atmosphericmodel½.r/D½0e¡¯.r¡r0/(12) is used with½0D0:002378slug/ft3,r0D20,902,900ft,and¯D 4:20168£10¡5/ft.Problem De nitionFor an initialequatorialorbit,maximizingthe crossrangeis equiv-alent to maximizing or minimizingthe nal latitude.Thus,the prob-lem is to nd a control history u.t/D[±.t/®.t/]T that minimizes the nal latitudeJ DÁ.t f/(13) subject to the dynamic model of the preceding section,the initial conditions,h D260;000ft,v D24,061ft/s,ÁD0deg,ÃD0deg,µD0deg,and°D¡1:064deg;the nal conditions[term termi-nal area energy management(TAEM)3interface]h D80;000ft, v D2500ft/s,and°D¡5deg;and the heating-rateconstraint q·70 Btu/ft2/s,where q is modeled as1¡3q D q a q r;q a D h0C h1®C h2®2C h3®3;q r D C½N v M(14) with N D0:5,M D3:07,C D9:289£10¡9Btu¢s2:07/ft3:57/slug0:5 andh0D1:067;h1D¡1:101;h2D0:6988h3D¡0:1903Note that this heating-rate model is a mixed state-control constraint11whose implications are discussed in the following section.Theoretical Optimal Controls and Junction Conditions Analytic expressions for the Pontryagin-extremal controls are easily derived by a straightforwardapplicationof the PMP.4;11Bank angle is given by±D tan¡1.¸Ã=¸°cos°/(15) and the angle of attack must satisfy the transcendentalequation,¡¸v¡C D0C2C D®2®¢C C L®v¸Ãsin±C¸°cos±´C¹h mq rd¡h1C2h2®C3h3®2¢D0(16)where¸v,¸Ã,and¸°are the costates associated with the states v,Ã,and°,respectively,and¹h is the covector associated with the mixed state-control heating-rate constraint.If we set q a D1so that q D q r,we get a pure state constraint,q D C½N v M(17)where C D7:357£10¡9Btu¢s2:07/ft3:57/slug0:5roughly equates the two heating rates.If this heating-ratemodel is chosen,then Eq(16) can be solved as®DC L®2D®2v¸vµ¸Ãsin±cos°C¸°cos±¶¡C D®2D®2(18)However,in the presence of a pure state variable constraint,the radius and velocity costates must satisfy the junction conditions,11¸r ¡t¡e¢D¸r¡t C e¢¡´¯Nq e(19)¸v ¡t¡e¢D¸v¡t C e¢C´Mq e=v(20)where´is the covector associated with the implicitly imposed con-straint q e D70Btu/ft2/s at the entry(exit)point of the heating-rate constraint.Note that,in DIDO,this point constraint is not explicitlyimposed but is simply part of the inequalityconstraintspeci cation, q·70Btu/ft2/s.All other costates are continuous.ResultsAn80-node solution corresponding to the mixed state-control heating-rate constraint formulation is shown in Fig.1.The solid lines representthe state historiesof an R–K propagationas explained earlier.It is apparent that the results are in excellent agreement. The errors in the target states are2.7652ft of altitude(0.0035%), 0.4063ft/s of velocity(0.0163%),and0.0166deg in ight-path angle(0.3314%).This solution was computed in7.58min on a 1.8-GHz,512-MB(RAM)Pentium4.If solution speed is desired over terminal point accuracy,a20-node solution can be obtained in32.75s with target state errors of2934ft of altitude(3.67%), 127.6ft/s of velocity(5.11%),and0.45deg in ight-path angle (8.9%).In any case,the extremality of the80-node solution is demonstrated in Fig.2.It is apparent that there is close agreement between the DIDO-control histories and the CMT controls calcu-lated from Eqs.(15)and(16)using the DIDO covectors.Figure3 shows that the Hamiltonian is constant,that is,veri cation of the rst integral,4to within10¡3in magnitude and equal to zero(time-free problem).Thus,the DIDO solution satis es quite accurately the rst-order necessary conditions for optimality.Note that these conditions have been veri ed without the tedium of indirect meth-ods.For completion,Fig.4is provided to show that the constraint on the heating rate of the vehicle was maintained throughouttheFig.1State histories from a DIDO run:——,R–K propagationand,DIDO solutions for80nodes.Fig.2Application of theCMT.Fig.3First integral(time-free problem),Hamiltonian=0.Fig.4Heating-rate pro le with and without a heating-rateconstraint.Fig.5Jump discontinuities in costates by way of the CMT.trajectory.The unconstrainedheating-rate pro le is also shown for comparative purposes.Figure5shows the costates associated with radius and velocity when the heating rate is modeled as a pure state constraint[see Eq.(17)].Note the large jump in the radius costate. When´is computed from Eq.(18)and its value is substituted in Eq.(19),the velocity costate is predicted to drop to¡2.48at(near, numerically)the entry point.The actual value of this costate is ap-proximately¡2.42,which is in close agreementwith the prediction. This agreement demonstrates that the junction conditions are also satis ed reasonably accurately.ConclusionsAccurate extremal solutions for the path-constrained reentry problemcan be obtainedin an ef cientmannerusing pseudospectral methods that exploit sparsity patterns.The CMT facilitates a rapid procedure for the veri cation of various optimality tests.This obvi-ates a need for the labor-intensive two-tier direct–indirect method. Computational time for the reentry problem reveals that results can be obtained within a few minutes for high accuracy and less than a minute for reduced accuracy.Further reduction in computational time is possible,for example,by way of analytic Jacobians,but it is clear that pseudospectral methods offer new possibilities in solving optimal control problems.It appears that accurate real-time solutions to complex optimal control problems are possible in the very near future.Thus,solutions to dif cult problems,such as onboard trajectory generation for abort guidance,appear to be within reach.AcknowledgmentWe thank Arthur E.Bryson of Stanford University for providing suggestions and valuable insights into this problem.References1Bryson,A. E.,Mikami,K.,and Battle, C.T.,“Optimal Lateral Turns for a Re-Entry Glider,”Aerospace Engineering,Vol.21,No.3, 1962.2Vinh,N.X.,Optimal Trajectories in Atmospheric Flight,Elsevier,New York,1981,pp.1–52.3Betts,J.T.,Practical Methods for Optimal Control Using Nonlinear Programming,Society for Industrial and Applied Mechanics,Philadelphia, 2001.4Pontryagin,L.S.,Boltyanskii,V.G.,Gamkrelidze,R.V.,and Mischenko, E.F.,The Mathematical Theory of Optimal Processes,Wiley-Interscience, New York,1962.5Kreim,H.,Kugelmann,B.,Pesch,H.J.,and Breitner,M.H.,“Mini-mizing the Maximum Heating of a Reentering Space Shuttle:An Optimal Control Problem with Multiple Control Constraints,”Optimal Control Ap-plications and Methods,V ol.17,1996,pp.45–69.6Elnagar,J.,Kazemi,M.A.,and Razzaghi,M.,“The Pseudospec-tral Legendre Method for Discretizing Optimal Control Problems,”IEEE Transactions on Automatic Control,Vol.40,No.10,1995, pp.1793–1796.7Ross,I.M.,and Fahroo,F.,“A Pseudospectral Transformationofthe Cov-ectors of Optimal Control Systems,”Proceedings of the First International Federation on Automatic Control(IF AC)Symposium on Systems Structure and Control,International Federation on Automatic Control,Laxenburg, Austria,2001.8Ross,I.M.,and Fahroo,F.,“Convergence of Pseudospectral Ap-proximations for Optimal Control Problems,”Proceedings of the2001 IEEE Conference on Decision and Control,IEEE Press,Piscataway,NJ, 2001.9Ross,I.M.,and Fahroo,F.,“User’s Manual for DIDO2002:A MA TLAB Application Package for Dynamic Optimization,”Dept.of Aeronautics and Astronautics,NPS Technical Rept.AA-02-002,Naval Postgraduate School, Monterey,CA,June2002.10Gill,P.E.,Murray,W.,and Saunders,M.A.,“SNOPT:An SQP Al-gorithm for Large-Scale Constrained Optimization,”Numerical Analysis Rept.97-1,Dept.of Mathematics,Univ.of California,San Diego,La Jolla, CA,1997.11Hartl,R.F.,Sethi,S.P.,and Vickson,R.G.,“A Survey of the Maxi-mum Principles for Optimal Control Problems with State Constraints,”SIAM Review,V ol.37,No.2,1995,pp.181–218.。
迈瑞笔试题 软件开发
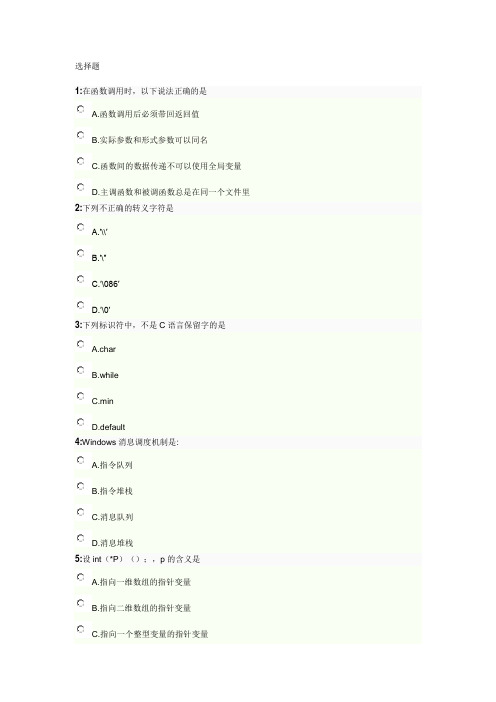
选择题1:在函数调用时,以下说法正确的是A.函数调用后必须带回返回值B.实际参数和形式参数可以同名C.函数间的数据传递不可以使用全局变量D.主调函数和被调函数总是在同一个文件里2:下列不正确的转义字符是A.′\\′B.′\″C.′\086′D.′\0′3:下列标识符中,不是C语言保留字的是A.charB.whileC.minD.default4:Windows消息调度机制是:A.指令队列B.指令堆栈C.消息队列D.消息堆栈5:设int(*P)();,p的含义是A.指向一维数组的指针变量B.指向二维数组的指针变量C.指向一个整型变量的指针变量D.指向整型函数的指针变量6:常数的书写格式决定了常数的类型和值,0x1011 是A.8 进制整型常量B.字符常量C.16 进制整型常数D.2 进制整型常数7:表达式10%2 值是A.0B.1C.5D.5.08:下列关于C语言的叙述错误的是A.英文字母大小写不加以区分B.不同类型的变量可以出现在同一个表达式中C.在赋值表达式中赋值号两边的类型可以不同D.某些运算符在不同的场合可以有不同的含义9:在下述选项时,没有构成死循环的程序是A.int i=100 while (1) { i=i%100+1; if (i>100) break; }B.for (;;);C.int k=1000; do { ++k; }while(k>=10000);D.int s=36; while (s);--s;10:以下不能看作一条C 语句的是A.{;}B.a=5,b=5,c=5;C.if(x>=0&&y=0);D.if(x= =0)a=5;b=10;11:表达式5&2||5|2的值是A.0B.1C.2D.312:下列数据中,不是C语言常量的是A.′\n′B.″a″C.e-2D.01213:设int a=9,b=20;则printf(″%d,%d\n″,a--,--b);的输出结果是A.9,19B.9,20C.10,19D.10,2014:若变量定义时未初始化,则其值不确定的是A.静态全局变量B.局部变量C.静态局部变量D.全局变量15:错误的转义字符是A.'\091'B.'\\'C.'\0'D.'\''16:若变量A 的类型为T,则在程序中A.可以通过NEW(A),得到指向A且类型为T的指针B.可以有多个类型为T的指针变量指向AC.只能有一个类型为T的指针变量指向AD.可以通过NEW(A),得到指向T类型变量的指针A17:结构型变量占用内存的字节数是A.各成员占用内存字节数之和B.第一个成员占用的内存字节数C.占用内存最大成员所需的字节数D.最后一个成员占用的内存字节数18:在某文件中,若全局变量与局部变量同名,则A.视为同一个变量B.变量作用域不确定C.不允许D.允许19:1. 若定义了enum color{yellow,green,blue=5,red,brone};2. 则枚举常量yellow和red的值分别是A.0,3B.0,6C.1,6D.3,620:下列不属于C语言保留字的是A.charB.whileC.typedefD.look简答题21:写一个病毒。
REPSOL_VETTING_PROCESS_AND_CRITERIA_2014_tcm11-689923

III. Effective Date
01 Aug 2014
Page 2 of 31
REPSOL VETTING PROCESS AND CRITERIA
IV. DEFINITIONS For the purpose of these procedures, the following definitions apply: Acceptable means the vessel can be used within the scope described above, and is the only rating that allows such use. This rating results from a favourable assessment based on information that we have deemed positive and sufficient. The rating of the vessel may be affected by relevant modifications concerning safety and operational systems, changes of name, technical operator, crew, flag, etc., as well as any incident, casualty or terminal negative feedback report, PSC detention or Memoranda or condition of Class. (See also “Vetting Assessment”.) Barge, for the purpose of these procedures, means a vessel carrying goods in rivers, inland navigation, lakes and ports, not sailing on open sea or bays and restricted by Flag Administration to inland water navigations. EBIS Barge: for the purpose of these procedures, means a vessel carrying goods in European rivers, not sailing on open sea or bay CAP (Condition Assessment Programme).- Independent and thorough scheme of inspections of the actual condition of a vessel. It is applicable as established in the present Vetting Process and Criteria and as defined in the Rules of the Classification Societies members of IACS. Cargo means any kind of material subject to a contract of transportation, mainly crude oil, oil products, chemical products, LPG, LNG, Lubricants, Liquid fertilizers and dry bulk cargoes. Charter Party means contract of affreightment signed between shipowner and charterer when hiring a vessel for the carriage of goods. Chief Officer and 2nd. Engineer terminology considered equivalent to 1st. Officer and 1st. Asst. Engineer for the purpose of these procedures. COA vessel means vessels included in a contract of affreightment to lift a fixed or determinable quantity of cargo of a specified type over a given period of time. EBIS the European Barge Inspection Scheme, is used to evaluate barges, tugs and dumb barges used to distribute oil and chemicals within Europe ESP (Enhanced Survey Programme).- It is applicable as established in SOLAS XI1/2 and as defined in Resolution A.744 (18). Heavy grade Oil: o o o crude oils, having a density at 15º C higher than 900 kg/m3; oils, other than crude oils, having either a density at 15º C higher than 900 kg/m3 or a kinematic viscosity at 50 º C higher than 180 mm2/s; or; bitumen, tar and their emulsions.
斑马技术公司DS8108数字扫描仪产品参考指南说明书

Practical Lock_Unlock Pairing for Concurrent Programs

Practical Lock/Unlock Pairing for Concurrent ProgramsHyoun Kyu Cho University of Michigan netforce@Yin WangHewlett-Packard Labsyin.wang@Hongwei LiaoUniversity of Michiganhwliao@Terence Kelly Hewlett-Packard Labs terence.p.kelly@ St´e phane LafortuneUniversity of Michiganstephane@Scott MahlkeUniversity of Michiganmahlke@AbstractIn the multicore era,developers face increasing pressure to parallelize their programs.However,building correct and ef-ficient concurrent programs is substantially more difficult than building sequential ones.To address the multicore chal-lenge,numerous tools have been developed to assist multi-threaded programmers,including static and dynamic bug de-tectors,automated bugfixers,and optimization tools.Many of these tools rely on or benefit from the precise identifica-tion of critical sections,i.e.,sections where the thread of ex-ecution holds at least one lock.For languages where critical sections are not lexically scoped,e.g.,C/C++,static analysis often fails to pair up lock and unlock calls correctly.In this paper,we propose a practical lock/unlock pairing mechanism that combines static analysis with dynamic in-strumentation to identify critical sections in POSIX multi-threaded C/C++programs.Our methodfirst applies a con-servative inter-procedural path-sensitive dataflow analysis to pair up all lock and unlock calls.When the static analysis fails,our method makes assumptions about the pairing us-ing common heuristics.These assumptions are checked at runtime using lightweight instrumentation.Our experiments show that only one out of891lock/unlock pairs violates our assumptions at runtime and the instrumentation imposes negligible overhead of3.34%at most,for large open-source server programs.Overall,our mechanism can pair up98.2% of all locks including7.1%of them paired speculatively. Permission to make digital or hard copies of all or part of this work for personal orclassroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on thefirst page.To copy otherwise,to republish,to post on servers or to redistributeto lists,requires prior specific permission and/or a fee.CGO’1323-27February2013,Shenzhen China.978-1-4673-5525-4/13/$31.00c 2013IEEE...$15.00Categories and Subject Descriptors F.3.2[Logics and Meanings of Programs]:Semantics of Programming Lan-guages–Program analysisGeneral Terms Algorithms,Languages,Verification Keywords Program analysis,Critical section,Concurrent programs,Static analysis,Dynamic monitoring1.IntroductionMost performance-aware programmers are experiencing ever growing pressure to parallelize their programs because uniprocessor performance hasflattened out and multicore processors promise more cores in each successive hard-ware generation.Parallel programming,however,remains a daunting task for a variety of reasons.First of all,reasoning about concurrent events and synchronization is inherently challenging for human programmers,who think sequen-tially.In addition,concurrency bugs such as deadlocks,data races,and atomicity violations require global knowledge of the program.Finally,the nondeterministic execution of par-allel programs makes these bugs hard to detect,reproduce, andfix.There has been much effort to relieve the burden of par-allel programming.For example,many automatic concur-rency bug detection tools have been developed[9,19,28]. Automated bugfixing tools are also available[15,31].In addition,researchers are exploring ways to adapt classical compiler optimization techniques for sequential programs to parallel programs[17,30].if(x)lock(L)...if(x)unlock(L)illustrated in Figure1are a major source of false posi-tives[9].Automated bugfix tools often add locks to avoid deadlock[31]or restore atomicity[15],which may intro-duce new deadlocks if the usage of existing locks is un-known.Finally,it is well known that many compiler opti-mization techniques cannot be directly applied to concurrent programs[30].Currently compilers only optimize code sec-tions that do not involve any lock operation,which can be quite conservative[17].Correct identification of critical sec-tions allows better optimization for concurrent programs.Numerous static analysis approaches have been devel-oped and many can be adapted to infer critical sections.In general,model checking based tools are precise but do not scale to practical programs[14],while scalable tools using specially designed algorithms are often imprecise[4,6,7]. For example,Saturn[7]is a scalable static analysis engine that is both sound and complete with respect to the user-provided analysis script.Writing a script that is sound and complete with respect to the target program,however,is as difficult as writing an analysis engine itself.The lock analy-sis script bundled with Saturn is neither sound nor complete, most notably because it lacks global alias analysis.In this paper,we propose a practical lock/unlock pairing mechanism that combines dataflow analysis with dynamic instrumentation.Our interprocedural path-sensitive dataflow analysis is a variant of existing tools[4,6].It conservatively identifies lock acquisition and release pairs.When the anal-ysis is uncertain,we use heuristics such as those based on structure types and location proximity to determine the pair. Finally,we instrument the target program with light-weight checking instructions to monitor whether the pairing is cor-rect at run-time.When a violation occurs,feedback informa-tion is provided to revise the pairing.This paper makes several contributions.We present a static lock/unlock pairing analysis algorithm which yields accurate results in most cases.We develop a lightweight dy-namic checking mechanism to ensure our analysis is correct. We demonstrate the effectiveness of our lock/unlock pair-ing mechanism including both static analysis and dynamic checking with real-world multithreaded programs such as OpenLDAP,Apache,and MySQL.The remainder of the paper is organized as follows.We first present the challenges with motivating examples in Sec-tion2.Next,Section3describes how our static lock/unlock pairing analysis works,and Section4discusses how to ex-tend the analysis for inter-procedural cases.We explain the dynamic checking mechanism in Section5.Section6 presents the experimental results and Section7outlines re-lated work.Finally,we summarize the contributions and conclude in Section8.2.Background and MotivationWhile our approach can help any tool that needs accurate static information about critical sections,we show its effec-BenchmarksOpenLDAPMySQLApacheTable1.Number of annotations needed to modeltiveness in the context of deadlock avoidance.In this sec-tion,we briefly provide some background on dynamic dead-lock avoidance in Gadara[31]and explain what kind of chal-lenges exist for lock/unlock pairing.2.1GadaraGadara is a tool that enables multithreaded programs to avoid circular-mutex-wait deadlocks at runtime.The basic idea is to intelligently postpone lock acquisition attempts when necessary to ensure that deadlock cannot occur.It proceeds in the following phases.First,Gadara constructs a Petri net model from program source code using com-piler techniques.Based on structural analysis of the model, Gadara synthesizes feedback control logic for each structural construct in the model that contributes to a potential dead-lock.Finally,it instruments the control logic into the target program.Given that the model is correct,Gadara automatically synthesizes maximally permissive controllers that delay lock acquisitions only if the program model indicates that dead-lock might later result if the lock were granted immedi-ately.Due to lack of accurate information about critical sec-tions,however,Gadara’s program analysis or control synthe-sis could fail.In such cases,Gadara requires programmers to provide annotations.These annotations specify which un-locks match and that no mutex can be held at certain program points.Table1shows the number of annotations needed to model the benchmarks for Gadara.Providing annotations can be tedious,difficult,and error-prone even for program-mers familiar with both the target program and Gadara.2.2Challenges for Lock/Unlock PairingThis subsection discusses the major challenges that a static lock/unlock pairing analysis should address in order to model programs accurately in the context of deadlock avoid-ance.We illustrate the challenges via simplified code exam-ples.2.2.1Infeasible PathOne of the challenges for static lock/unlock pairing is the ambiguity caused by infeasible paths.The traditional way in which compilers abstract programs’control path is to represent programs with controlflow graphs(CFGs).Each vertex in a CFG represents a basic block and each edge corresponds to a branch from one basic block to another. Thus,a sequence of basic blocks connected with edges in a CFG represents a control path.Not all sequences,however, are actually possible control paths in program execution; some are infeasible paths.1:if(flag)lock(node->mutex);2:while(condition){3:...4:if(flag)unlock(node->mutex); 5:...6:node=node->next;7:...8:if(flag)lock(node->mutex); 9:...10:}11:if(flag)unlock(node->mutex);(a)1:void callee(task*ptr){2:unlock(ptr->mutex);3:...4:lock(ptr->mutex);5:}6:7:void caller(task*ptr){8:lock(ptr->mutex);9:...10:callee(ptr);11:...12:unlock(ptr->mutex);13:}(b)1:lock(parent->mutex);2:...3:if(condition1){4:lock(child->mutex);5:...6:unlock(child->mutex);7:}8:...9:unlock(parent->mutex);(c)1:int handle_task(task*job){ 2:if(job->has_mutex)3:lock(job->mutex);4:if(job->is_special){5://Handle special case 6:if(job->has_mutex){ 7:unlock(job->mutex); 8:return result; 9:}10:}11://Handle normal cases12:if(job->has_mutex)13:unlock(job->mutex); 14:return result;15:}task()returns by ei-ther the unlock in line7or the unlock in line13.However, directly translating the CFG of this example to Petri net vi-olates the semiflow property due to infeasible paths as de-scribed in Section2.2.Our analysis rules out the infeasible paths and gives accurate lock/unlock pairing results through the following process.After pruning the CFG,the corresponding unlock set mapping decides that both the unlock in line7and the unlock in line13can release the mutex acquired by the lock in line3.Then,the path condition calculation step determines the Boolean expressions that represent path conditions for each lock and unlock.In this example,path condition(job→hasspecial=0)∧(job→hasspecial=0)∧(job→hasFigure4.Finding unlock set corresponding to lock ysis then translates them into Boolean expressions by as-signing a Boolean variable to each branch condition.In or-der to encode the branch correlations into the expressions, this assignment process assigns the same Boolean variable to branch conditions that must have the same value.As a result,the Boolean expression of the lock is(x1),and the unlock in line7and the unlock in line13receive(x2∧x1) and(¬x2∧x1),respectively.Thefinal step of the analysis is to check whether the lock and the corresponding unlocks pair up for all feasible paths. This can be done by determining whether the statement“if the path condition for the lock is true,then the disjunction of the path conditions for corresponding unlocks is true”is al-ways true or not.In this example,the statement is interpreted as the Boolean expression(¬x1)∨(x2∧x1)∨(¬x2∧x1).In order to verify if it is always true,we apply a SAT solver on the negation of the Boolean expression.If it is unsatisfiable, then the statement is always true,and the lock and the corre-sponding unlocks are paired.Otherwise,they are not paired up.In this example,the negation of the Boolean expression is unsatisfiable and the lock is paired up with the unlock in line7and line13.3.2Mapping Lock to Set of Corresponding Unlocks Before applying the infeasible path analysis,this step groups corresponding locks and unlocks.More specifically,it maps a set of corresponding unlocks to each lock.We say an unlock corresponds to a lock if it can release the mutex acquired by the lock on any path.Since the mutex acquired by a lock can be released at different program points,we map a set of corresponding unlocks and not just a single unlock.This step is necessary because the same mutex can be acquired and released multiple times.This analysis algorithm traverses the CFG in a depthfirst manner while managing a stack of locks for each mutex.The core analysis algorithm is given in Figure4.Although we only show it for one mutex in this version,the actual analysis simultaneously works on all mutexes.The underlying idea is to add an unlock to the correspond-ing unlock set of a lock,if there is a path in which the unlock follows the lock but there is no path in which there is an-other lock of the same mutex between the lock and unlock. The top element of the lock stack is the most recent lock that the traversal encountered,so it adds the unlock to the GEN set of the top element.Other elements in the lock stack are the locks that the traversal met before the last lock along the traversal,so it adds the unlock to the KILL sets of them. Ultimately,the corresponding unlocks of each lock are the unlocks that are in the GEN set but not in the KILL set.3.3Path Condition CalculationThis step calculates the Boolean expressions for path condi-tions that must be true for each lock and unlock to execute.It first calculates path conditions and translates them by assign-ing a Boolean variable for each branch condition.We define the path condition of a statement as the Boolean combina-tion,i.e.,AND(∧),OR(∨),NOT(¬),of branch conditions, which must be true for the statement to be executed.The core path condition calculation algorithm is illus-trated in Figure5.With this algorithm,the path condition of a statement is the path condition from the entry basic block to the basic block that the statement belongs to.The under-lying idea of this algorithm is that the path condition from the CFG node‘src’to‘dest’is the disjunction(OR)of the conditions along the paths which go through‘child’, for all children of‘src’.This idea is reflected in line18.This algorithm uses caching and post dominator informa-tion for computational efficiency.Since there can be an ex-ponential number of paths to the number of basic blocks,the naive recursive algorithm is not feasible for real programs. In order to avoid repetitive computation for the same path, it uses a path condition cache indexed by(src,dest)pair. In addition,it uses post dominator(PDOM)information as a shortcut,to simplify the resulting conditions.After path condition calculation,the analysis translates the path conditions to Boolean expressions by assigning a Boolean variable to each branch condition.To reveal the branch correlations in the Boolean expressions,our analysis assigns the same Boolean variable to the branch conditions that must have the same value.This is possible by using global value numbering(GVN)and hashing them to map to Boolean variables.3.4Checking Lock/Unlock PairingUsing the analysis results of the previous steps,this stepfi-nally verifies whether all locks are paired up with the cor-responding unlocks on every feasible path.To achieve this goal,we use an open source SAT solver MiniSAT[8].For 1://Recursively calculates path condition from2://src to dest3:condition calculate_path_cond(CFG,src,dest)4://Consult path condition cache for efficiency 5:if(src,dest)is in cache6:return condition from cache;7://Always reaches dest if it post-dominate src 8:if dest PDOM src9:return TRUE;10://Dead end11:if src has no successor12:return FALSE;13://The control can reach dest following14://each successor15:for(each successor c of src)16:cond1=branch condition of branch(src->c); 17:cond2=calculate_path_cond(CFG,c,dest); 18:condition=condition OR(cond1AND cond2); 19:put condition in cache with index(src,dest); 20:return condition;21:end1:Connection*c=NULL;2:for(;index<tblsize;index++){3:...4:if(connections[index].state==C_USED){5:c=&connections[index];6:lock(&c->c_mutex);7:break;8:}9:}10:...11:if(c!=NULL)unlock(&c->c_mutex);Figure8.Instrumentation wrapper for lock and unlockanalysis can map the unlock in line11as the correspondingunlock of the lock in line6.However,it cannot guaranteethe lock is paired up for all feasible paths due to the lackof understanding about program semantics.A human pro-grammer can easilyfigure out that the variable c is not NULLwhen the lock in line6is executed,thus the lock is paired upwith the unlock in line11if the value of c is not modified inbetween.However,it is difficult for a static analysis to un-derstand such program semantics.In this case,our analysisprovides the mapping for the modeling as the best effort re-sult.However,this type of best effort analysis result mightbe incorrect for other cases.For these reasons,our lock/unlock pairing mechanismneeds a way to verify whether all of the analysis results arecorrect or there exists any violation of the assumptions itmade.In order to do that,we need to check two types ofconditions.First,the mapping of unlocks to each lock shouldbe checked.If the mutex acquired by a lock is released byan unlock that is not in the corresponding unlock set,itshould be detected.Second,the semiflow requirement has tobe checked.In other words,whether each lock is paired upwith an unlock for all feasible paths or not is to be checked.In the following subsections,we discuss these two types ofchecking in detail.5.1Checking Lock-to-Unlocks MappingWe instrument all locks and unlocks to check whether themapping of each lock to corresponding unlocks is correct ornot.Wefirst assign a unique ID to each lock and unlock.Atruntime,the instrumented code manages a thread-local datastructure that keeps the acquiring lock’s ID of each mutex.Since the data structure is thread local,it does not need tosynchronize with other threads to access the data structure.When an unlock releases the mutex,the instrumented codelooks up the acquiring lock’s ID of the mutex and checkswhether its own ID is in the corresponding unlock set of thelock.The IDs of locks and unlocks can be simply assignedas a unique number to each calling instruction for intra-procedural cases.However,if they are paired up by the inter-Benchmarks Number DFT Speculatively UnpairedPaired Paired Analysis 271,546110319353152.7%926,111147463489211.8%224,8840171733.9%4,01102323.4%7528101150.0%83522243.8%mutex[FID]set(kept in line6 of Figure8)is empty when the root node function(FID)re-turns.6.Experimental ResultsWe have implemented the lock/unlock pairing mechanism including both the static analysis and checking instrumen-tation as a pass of the LLVM compiler infrastructure[18]. Our implementation operates on the LLVM intermediate representation and provides both analysis results and in-strumented code.For the aggressive refinement of LLVM’s memory dependency analysis,we use Gadara’s type-based method for mutex pointers and memory profiling for other variables.All of our experiments were executed on a2.50GHz Intel Core2Quad machine with8GB of memory running Linux 2.6.32.We evaluate the effectiveness of our lock/unlock pairing with Apache2.2.11web server[1],MySQL5.0.91 database server[24],OpenLDAP2.4.21lightweight direc-tory access protocol server[26],pbzip21.1.4,pfscan1.0, and aget0.4.6.1Effectiveness of Static AnalysisTable2shows the effectiveness of our static lock/unlock pairing analysis.The third column is the total number of locks and the fourth column is the number of locks trivially paired up in a basic block.We also compare our approach against depthfirst traversal(DFT)of controlflow graph, which is used by previous static lockset-based tools such as RacerX[9].Statically paired locks mean the number of locks that could be paired up with infeasible path analysis. Speculatively paired locks are the ones that our analysis could successfully map the corresponding unlock sets but could not guarantee pairing for all feasible paths due to the limitation described in Section5.Thus the sums of the sixth and seventh columns are the numbers of locks that our static analysis could pair up with unlocks.As can be seen in the table,our static analysis works effectively for nearly all of the cases.Overall,trivial pairing fails to handle70%of locks and DFT fails to handle20.5%of locks.By contrast, our approach handles all but1.8%of locks—an eleven-fold improvement compared with DFT.There are still unpaired locks,although the number of such cases is relatively small.There are three types of causes for these cases.First,there are inherently unpaired locks in the programs.Three unpaired locks of OpenLDAP are from one function,ldap connection(),and in this category.When the function is called in certain contexts, these locks are paired up and our analysis can catch those cases.In other contexts,however,they are not paired up and thus our analysis cannot pair them up.The second category of unpaired locks is due to the type-based memory dependency analysis refinement that we use for mutex pointers.This refinement assumes that two mutex pointers do not alias if the types of wrapper structures en-closing the mutex variables are different.With this assump-tion our analysis cannot pair up a lock and unlocks if they1:class THD{2:struct st_my_thread_var*mysys_var;3:...4:char*enter_cond(mutex_t*mutex){5:...6:mysys_var->current_mutex=mutex;7:...8:}9:void exit_cond(char*old_msg){10:...11:unlock(mysys_var->current_mutex);12:...13:}14:};15:...16:bool wait_for_relay_log_space(RELAY_LOG_INFO*rli){17:THD*thd=rli->mi->io_thd;18:char*save_proc_info;19:...20:lock(&rli->log_space_lock);21:save_proc_info=thd->enter_cond(&rli->log_space_lock); 22:...23:thd->exit_cond(save_proc_info);24:...25:}cond()in line21saves the mutex ina pointer and passes it to exitLOGmy var for the unlock.The type based memory dependency refinement would consider them not to alias,and consequently our lock/unlock pairing analysis can-not pair them.Among the unpaired locks of MySQL,eightof them are in this category.The last cause of unpaired unlocks is function pointers.The current implementation of our lock/unlock pairing anal-ysis cannot track the inter-procedural cases in which a func-tion is called via a function pointer,since it uses the call-graph information which only puts edges for direct function calls.One of OpenLDAP’s locks,two of MySQL’s locks,and two of Apache’s locks could not be paired up for this reason.Static analysis time as a percentage of compilation time is presented in the last column of Table2.Analyzing MySQLand OpenLDAP takes considerably longer than analyzing other benchmarks because they have more complex controlflows and include more lock/unlock function calls.Table3 presents the number of basic blocks in a function before and after CFG pruning,as described in Section3.5.Our CFG pruning significantly reduces both average and maximum number of basic blocks,which is essential for the scalabilityof our static analysis procedure.Benchmarks After PruningAverage AverageOpenLDAP818805.88 1.18Apache465136.16 1.06pfscan483312.11 1.83Table3.Number of Basic Blocks before/after Pruning6.2Runtime Overhead of Dynamic CheckingFigure10presents the runtime overheads of the dynamic checking instrumentation.For server programs,it is mea-sured as the comparison of average response time to clients on the same machine.For pbzip2,pfscan,and aget,the execution times are compared.Four parallel clients and worker threads are used for the servers and the other pro-grams,respectively.As can be seen in the graph,our check-ing instrumentation imposes very small overheads for the programs.The runtime overheads range from0.5%to3.4% and the average is1.6%.As discussed in Section6.1,our static analysis yields three types of results:statically paired,speculatively paired, and unpaired.For both statically and speculatively paired locks,our framework instruments the checking mechanism presented in Section5,whose major overhead comes from the executions of locks and unlocks.Therefore,even if our analysis does not work well so that it yields more specu-latively paired locks,the runtime overhead would not be drastically increased.For unpaired locks,the current im-plementation of our framework falls back to programmer annotations and does not add checking instrumentation.It is possible to add more heuristics to make guesses for un-paired locks,but the dynamic checking overhead would be still roughly proportional to the number of the executions of locks and unlocks even for those cases.Compared to the native implementation of lock and un-lock,our instrumentation slows down a pair of lock and un-lock by roughly18×.Thus,it is possible that our dynamic checking incurs excessive overhead if the target program locks and unlocks too many times without doing much work. However,it is not a common practice to make programs lock and unlock too often,and such programs would already suf-fer poor performance.Furthermore our current instrumen-tation implementation is a simple un-optimized use of the C++STL library,and overheads can be further reduced by optimizing the implementation of instrumented code.6.3Assumption ViolationAlthough the frequency is very low,our static lock/unlock pairing analysis can potentially yield incorrect results due to the assumptions and heuristics it uses as described in Section5.Once the instrumented dynamic checking de-tects a problem,the information is fed back to the analyzer and the underlying client system revises the model.WhileFigure11.Incorrectly paired lock due to pointer problem.Software model checking has a long history.We recom-mend an excellent survey for the background on this sub-ject[14].Here we summarize several results relevant to this paper.Classical model checking techniques model systems as labeled transition systems and verify properties specified in temporal logic.These techniques scale poorly for soft-ware verification due to the state explosion problem.Most software model checking tools are execution based and state-less.These tools systematically explore all program paths in hope tofind bugs more quickly than stress testing[3,22].Abstract model checking scales to real software by map-ping program states to an abstract domain[5].As abstrac-tion may not capture all the information needed to verify a property,when a counter-example is discovered,it is unclear whether it is genuine or spurious due to abstraction.In this case,the abstraction can be refined tofilter out spurious ex-amples.Automated program abstraction and refinement are difficult,and the iterative process may not converge.In prac-tice,automated abstract model checking methods are limited to small or special-purpose programs[12,13].In the area of static program analysis,many scalable dataflow analysis algorithms have been developed,which can be viewed as model checking with manually defined ab-straction[29].For example,Saturn[7]is a scalable anal-ysis engine that is both sound and complete with respect to the user-provided abstraction,written in its Calypso lan-guage.This framework enables the programmer to manually refine and optimize the abstraction for each specific analysis task.Other scalable algorithms use carefully tuned heuristics that can be viewed as predefined abstraction.For example, ESP[6]is a path-sensitive analysis tool that scales to large programs by merging branches that lead to the same analy-sis state.The analysis is sound but incomplete with respect to this abstraction.Regarding the original program,however, manually defined abstractions are often unsound.For example,the locking patterns in Figure1(a)often confuses standard dataflow analysis algorithms integrated in tools designed for higher level applications[9,31].Both the locking analysis script bundled in Saturn and the ESP al-gorithm would identify the branch correlations easily if the。
Refactoring an Automotive Embedded Software Stack using the Component-Based Paradigm

Refactoring an Automotive Embedded Software Stack using the Component-Based Paradigm Thomas M.Galla∗,Dietmar Schreiner†‡,Wolfgang Forster∗,Christof Kutschera†,Karl M.G¨o schka‡,and Martin Horauer†∗DECOMSYSDependable Computer Systems GmbHStumpergasse48/28,A-1060Vienna,AustriaEmail:wolfgang.forster@Email:thomas.m.galla@†University of Applied Sciences Technikum ViennaDepartment of Embedded SystemsH¨o chst¨a dtplatz5,A-1200Vienna,AustriaEmail:kutschera@technikum-wien.atEmail:horauer@technikum-wien.at‡Vienna University of TechnologyInstitute of Information Systems,Distributed Systems GroupArgentinierstrasse8/184-1,A-1040Vienna,AustriaEmail:d.schreiner@infosys.tuwien.ac.atEmail:k.goeschka@infosys.tuwien.ac.atAbstract—The number of electronic systems in cars is con-tinuously growing.Electronic systems,consisting of so-called electronic control units(ECUs)interconnected by a communi-cation network,account for up to30%of a modern car’s worth. Consequently,software plays an ever more important role,both for the implementation of functions and the infrastructure.In order to benefit from the reuse of software modules,the major automotive companies have standardized a large number of these modules in the context of the AUTOSAR consortium.In this paper we propose the refactoring of the AUTOSAR stack of system software modules by applying the component-based paradigm in order to increase the scalability of the software stack according to the particular requirements of the application. We demonstrate the feasibility of this approach by performing the refactoring of the modules FlexRay Driver and FlexRay Interface as an example and by deploying the resulting refactored components in a sample automotive application.Finally,we measure the execution time as well as the memory consumption of the refactored components and compare these measures to the measures obtained from the corresponding ordinary AUTOSAR modules.I.I NTRODUCTION AND R ELATED W ORKIn the last decade the percentage of electronic components in today’s cars has been ever increasing.According to[1]the new S-Class Mercedes for example utilizes seven communi-cation buses and72microcontrollers.Since1993major automotive companies have been striving for the deployment of standard software modules in their appli-cations since the potential benefits are huge[2].This trend has been a key motivation for the formation of the AUTOSAR[3] consortium in2002.Important issues in this context are safety (increased test depth of standard software modules),software reuse,for the possibility to combine software modules supplied by different vendors due to standardized interfaces,and—last but not least—cost reasons in order to cope with shorter development cycles.The software stack proposed by AUTOSAR follows a lay-ered architecture of basic software modules comprising com-munication modules,operating system,and modules providing access to the microcontroller’s integrated peripheral devices (e.g.,A/D converters,digital I/O).In this paper we will reason that a layered architecture as proposed by AUTOSAR is inefficient as far as resource usage is concerned(especially memory consumption)due to limited adaptivity to the needs of the application software. In order to overcome this drawback,we will propose a refactored version of the AUTOSAR stack of basic software modules by applying the component-based paradigm[4],[5] to the AUTOSAR stack.Hereby we will focus on a well-defined part of the AUTOSAR software stack namely the software modules related to the FlexRay communication sys-tem[6],[7].This approach is fundamentally different to most component-based approaches which,as far as communication is concerned,rely on the existence of a(non component-based)middleware.The approach presented in this paper,on the contrary,addresses communication in a component-based fashion as well,by modeling this communication by means of explicit connectors[8].This approach gives the possibility to choose the type of connector best suited for the given application and thus reduces the memory footprint as well as the communication overhead compared to a monolithic non component-based middleware.This selection of the best-suitedconnector is based on so-called contracts which govern the selection during a model transformation process[9].Finally, by means of a sample application,we will show that the refactored version of the AUTOSAR software modules into a set offiner grained software components provides better scalability and thus reduces the overall resource consumption of the software stack for a specific application.The paper is structured as follows:Section II illustrates the AUTOSAR hard-and software architecture.Section III describes how the component-based approach is applied to the AUTOSAR FlexRay communication modules.In Section IV the refactored component-based AUTOSAR FlexRay commu-nication stack is deployed in a sample application.The result-ing memory footprint and the execution time of the refactored stack is analyzed and compared to an ordinary AUTOSAR stack applied to the very same application.Section V gives a short summary of the results and concludes the paper.II.S YSTEM A RCHITECTUREA.Hardware ArchitectureThe hardware architecture of automotive systems can be viewed at different levels of abstraction.On the highest level of abstraction,the system level,an automotive system consists of a number of networks interconnected via gateways.In general these networks correspond to the different functional domains that can be found in today’s cars(i.e.,chassis domain,power train domain,body domain).The networks themselves comprise a number of electronic control units(ECUs)which are interconnected via a com-munication media.The physical topology used for the inter-connection is basically arbitrary;however,bus,star,and ring topologies are the most common topologies in today’s cars.–This network level represents the medium level of abstraction. On the lowest level of abstraction,the ECU level,the major parts of an ECU are of interest.An ECU comprises one or more micro controller units(MCUs)as well as one or more communication controllers(CCs).In most cases,exactly one MCU and one CC are used to build up an ECU.In order to be able to control physical processes in the car(e.g.,control the injection pump of an engine)the ECU’s MCU is connected to actuators via the MCU’s analogue or digital output ports.To provide means to obtain environmental information,sensors are connected to the MCU’s analogue or digital input ports. We call this interface the ECU’s environmental interface.The CC(s)facilitate(s)the physical connectivity of the ECU to the respective network(s).We call this interface of an ECU the ECU’s network interface.B.Software ArchitectureThe AUTOSAR software architecture makes a rather strict distinction between application software and basic or system software.While the basic(or system)software provides func-tionality like communication protocol stacks for automotive communication protocols(e.g.,FlexRay[6],[7]),an operat-ing system and diagnostic modules,the application software comprises all application specific software items(i.e.,control loops,interaction with sensor and actuators).This way,the ba-sic or system software provides the fundament the application software is built upon.The Runtime Environment(RTE)provides the interface be-tween application software components and the basic software modules as well as the infrastructure services that enables communication to occur between application software com-ponents.1)Application Software Architecture:Application software in AUTOSAR consists of application software components, which are ECU and location independent and sensor-actuator components that are dependent on ECU hardware and there-fore location dependent.Whereas instances of application software components can easily be deployed to and relo-cated among different ECUs,instances of sensor-actuator components must be deployed to a specific ECU for per-formance/efficiency reasons.Deploying multiple instances of the same component to a single ECU is supported by the AUTOSAR component standard.Application software components as well as sensor-actuator components are interconnected via connectors.These connec-tors represent the exchange of signals or the remote method invocations among the connected components.2)System Software Architecture:In addition to the applica-tion software components,AUTOSAR also defines a layered architecture of system software modules,which provide a basic platform for the execution of the application software components.Figure1gives a coarse grained overview of the major categories of system software modules.Fig.1.AUTOSAR–System Software Stack OverviewThe Input/Output Services are software modules that pro-vide standardized access to sensors,actuators and ECU on-board peripherals(e.g.,D/A or A/D converters etc.).The Mem-ory Services comprise software modules that facilitate the stan-dardized access to internal and external non-volatile memory for means of persistent storage.The Communication Services category,which is of primary interest for the remainder of this paper,contains software modules that provide standardized ac-cess to vehicle networks(i.e.,the Local Interconnect Network (LIN)[10],the Controller Area Network(CAN)[11],[12],and FlexRay).Last but not least,the System Services encompass all software modules that provide standardized(e.g.,operating system,timer support,error loggers)and ECU specific(ECU state management,watchdog management)system services and library functions.The structure of the Communication Services for the FlexRay communication system are depicted in Figure2.Fig.2.AUTOSAR –FlexRay Communication ServicesThe FlexRay Transport Protocol module (FrTp)is used to perform segmentation and reassembly of large protocol data units (PDUs)—also termed “messages”—transmitted and received by the Diagnostic Communication Manager (see below).This protocol is rather similar or even compatible (in certain configuration settings)to the ISO TP for CAN [13]specified in ISO/DIS 15765-2.2.The PDU Router module (PduR)provides two major ser-vices.On the one hand it dispatches PDUs received via the underlying interfaces (e.g.,FlexRay Interface)to the different higher layers (COM,Diagnostic Communication Manager).On the other hand the PDU router performs gateway func-tionalities between different communication networks by for-warding PDUs from one interface to another of either the same (e.g.,FlexRay to FlexRay)or of different type (e.g.,CAN to FlexRay).The COM module provides signal-based communication to the higher layers (RTE).The signal-based communication service of COM can be used for intra-ECU communication as well as for inter-ECU communication.In the former case,COM mainly uses shared memory for this intra-ECU commu-nication,whereas for the latter case at the sender side COM packs multiple signals into a PDU and forwards this PDU to the PDU router in order to issue the PDU’s transmission via the respective interface.—On the receiver side,COM obtains a PDU from the PDU router,extracts the signals contained in the PDU and forwards the extracted signals to the higher software layers.The Diagnostic Communication Manager module (Dcm)provides services which allow a tester device to control diag-nostic functions in an ECU via the communication network (i.e.,CAN,LIN,FlexRay).Hereby the Dcm supports the Keyword Protocol 2000(KWP2000)[14]standardized in ISO/DIS 14230-3and the Unified Diagnostic Services (UDS)protocol [15]standardized in ISO/DIS 14229-1.Network management modules provide means for the coor-dinated transition of the ECUs in a network into and out of a low-power (or even power down)sleep mode.AUTOSAR NM is hereby divided into two modules:a communication protocol independent module named Generic NM (Nm)anda communication protocol dependent module named FlexRay NM (FrNm).Based on the frame-based services provided by the FlexRay Driver (see below)the FlexRay Interface module (FrIf)fa-cilitates the sending and the reception of protocol data units (PDUs).Hereby multiple PDUs can be packed into a single frame at the sending ECU and have to be extracted again at the receiving ECU.The point in time when this packing and extracting of PDUs takes place is governed by the temporal scheduling of so-called communication jobs of the FlexRay Interface.The instant when the frames containing the packed PDUs are handed over to the FlexRay Driver for transmission or retrieved from the FlexRay Driver upon reception is trig-gered by communication jobs of the FlexRay Interface as well.Hereby each communication job can consist of one or more communication operations,each of these communication op-erations handling exactly one communication frame (including the PDUs contained in this frame).Just like the FlexRay Interface module,the FlexRay Driver module (Fr)is protocol specific as well.The FlexRay Driver module provides the basis for the FlexRay Interface module,by facilitating the transmission and the reception of frames via the respective communication controller.III.A PPLYING THE C OMPONENT -B ASED A PPROACH Components may interact at runtime if their related provided and required interfaces are validly associated at composition time.This association,namely the connector,is an abstract representation of any interaction occurring between the con-nected components.In most component models the process of component interaction is covered within some middleware,therefore we consider those kinds of connectors to be implicit.An explicit connector on the other hand is an architectural entity that is used to represent component composition and interaction and owns its unique implementation of interaction operators.Therefore,an explicit connector encapsulates all communication logic for one specific type of interaction.In addition an explicit connector specifies properties of the con-nected components’interaction and provides contracts [16],[17]regarding communication channels and resource require-ments.These contracts define guarantees about the behavior of the associated elements,by specifying requirements and pro-visions of associated elements.In general a contract consists of two obligations:1)A client,requiring a service from a provider,has to satisfy the provider’s preconditions.2)A provider of that required service has to fulfill its postcondition,if the client’s precondition is met.Hereby we distinguish five types of contracts [8]that are named after the model element they are associated with:1)Component-contracts deal with a component’s resource requirements or deployment restrictions like required memory or required ECU type.2)Interface-contracts specify services and properties of the components’interfaces like operation signatures,interface type or temporal properties like worst-case execution time(WCET)at operation level.3)Port-contracts deal with the relation between componentports and interfaces.Behavioral protocols are typically contained within port-contracts.4)Connector-contracts specify constraints related to theused communication channels like worst-case propaga-tion delays,but also regarding resource requirements of the connector implementation.5)Platform-contracts specify properties of platform ele-ments like ECUs or communication systems e.g.ECU type,available memory or timing information.These contracts,when associated with explicit connec-tors introduced previously,govern the model transformation process,where explicit connectors are transformed into com-ponents representing so-called connector fragments.—This transformation process is described in Section III-C in more detail.Applying the component-based paradigm to the AUTOSAR system software,however,is not feasible without performing an adequate refactoring of the AUTOSAR system software modules in advance.This refactoring yieldsfiner-grained sys-tem software components exhibiting a well-defined function-ality and thus provides the basis for an application dependent selection of only those components needed by a specific appli-cation.This refactoring consist of two steps—namely vertical layer slicing and combining of the module slices of adjacent layers—which are discussed in the following subsections. Note that this approach is fully compliant with AUTOSAR, since AUTOSAR defines different conformance classes,and allows(in certain conformance classes)the grouping of several modules into module groups,where the interfaces of the module group with other AUTOSAR modules(which are not a member of this group)have to adhere to the AUTOSAR specification,whereas those interfaces which are only module group internal(intra module group interfaces)do not have to adhere to the AUTOSAR specification.A.Vertical Layer SlicingThefirst step of transforming the AUTOSAR layered mod-ule software architecture into a component based software architecture is the vertical slicing of the different modules into module slices.We hereby assume that each module comprises a number of rather independent functional units.The process of slicing must be governed by the following premises:•Related functional units shall be located in the same module slice.•The number of interactions between the functional units of different module slices must be minimized.•The functional units within a single module slice shall exhibit a large amount of inter functional unit interaction. This way,we arrive at a defined set of module slices,each slice consisting of one or more functional units,where the module slices exhibit a low number of inter-unit interaction but a high number of intra-unit interactions.The key idea behind this slicing is that each of the resulting module slices is afirst class candidate for becoming(a part of)a dedicated system software component.1)Slicing of the AUTOSAR FlexRay Interface and Driver Module:When applying the slicing step to the AUTOSAR FlexRay Driver,we identified the following module slices for the AUTOSAR FlexRay Driver:A base slice containing all the functional units that provide some kind of basic functionality to the module(e.g.,module initialization).—This slice is always required(and thus must be deployed)when using any of the other slices of the module.All functional units dealing with FlexRay’s global time(e.g.,alarm timer services based on this global time)have been allocated into a time services slice.Functional units dealing with FlexRay’s wakeup service have been grouped into a wakeup slice,all functional units related to the handling of FlexRay’s media test symbols have been combined in a media test symbol slice, and functional units for querying the operational status of the FlexRay communication controller(e.g.,checking whether the communication controller is synchronous with the other controllers in the FlexRay network)have been combined in a status slice.The functional units dealing with the transmission of PDUs(in the FlexRay Interface)or frames(in the FlexRay Driver)have been combined in a transmission slice whereas the functional units dealing with reception have been allocated in a reception slice.2)Slicing of the AUTOSAR FlexRay Transport Protocol: Aside from the obligatory base slice which provides basic functionality of the module the AUTOSAR FlexRay Transport protocol mainly consists offive almost orthogonal functional units,namely a unit dealing with segmentation and reassembly if the data to be transmitted exceeds the maximum transfer unit of the underlying communication protocol,a functional unit dealing with acknowledgment,a functional unit forflow control handling,and last but not least,functional units for reception and transmission.Since these functional units implement to a large degree orthogonal functionality,almost all25possible combinations of the functional units are feasible.One possible combination(which is a typical use case in diagnostic communication using ISO/DIS14229-1)is non-segmented,non-acknowledged1,communication withoutflow control.–In this combination it is obvious that the functional units dealing withflow control,segmentation,and acknowl-edgment are not required and can thus be omitted from the system software stack.Furthermore,if an ECU is only a receiver in diagnostic communication,the sending functional unit can be eliminated as well.bining Module Slices of Different LayersAfter the slicing of the modules has been performed,further improvements with respect to execution time and memory 1No acknowledgment on transport layer level is used,since acknowledg-ment takes place on the diagnostic layer level(which is one layer above the transport layer)anyway.consumption can be achieved,when combining related slices of vertically adjacent modules into a single component. Again this combination shall be guided by the premises already stated in Section III-A.Reasonable candidates for such a combination are the re-ception and the transmission slices of the FlexRay Driver with those of the FlexRay Interface,since every time,a higher layer of the system software stack used the transmit functionality of the FlexRay Interface,the transmit functionality of the FlexRay Driver is required as well.When looking at the AUTOSAR FlexRay Transport Proto-col however,the situation gets a little bit more complex.—For the transmission of transport layer messages,the transmit slices of FlexRay Driver and FlexRay Interface are required. Furthermore,if acknowledgment orflow control is required by the higher layer,the respective slices(namely theflow control and/or the acknowledgment slice)of the FlexRay Transport Protocol are required.Since both functionalities require communication from the receiving to the sending ECU, the reception slices of FlexRay Interface and FlexRay Driver are needed as well.C.Model TransformationAs already stated,we build component based applications using a model driven development approach.Interaction be-tween application components is expressed by explicit con-nectors.Therefore,thefirst required step in developing a com-ponent based application is to define a platform independent model(PIM)of the desired component architecture:All used components and all their interdependencies modeled,by means of explicit connectors,are specified within a composition spec-ification.At this phase of development,the explicit connector is an abstract representation of communication and interaction requirements that provides little information on the runtime properties of the process of interaction.In the second step,a platform specific model(PSM)of the deployment specification for the application has to be defined.Now that information on the target platform and the component’s physical location is specified,the nature of available communication channels becomes visible.At this step one can see,for example,if interaction is distributed or local.By applying model transformations,the abstract explicit connectors from the platform independent composition speci-fication get replaced by a composite structure of component-like model entities.This is done by splitting the abstract connector up into two associated pieces,the connector frag-ments that are composed elements themselves.Each fragment is attached to exactly one of the components,the original explicit connector was bound to and has to be deployed along with it.The fragment’s internal structure is determined by all contracts applied to the explicit connector and to system specifications within the application models.It is obvious that explicit connectors for local compositions may be as simple as local procedure calls and therefore would not require an explicit representation.On the contrary,connectors between components deployed in a distributed manner are represented by rather complex composite structures dealing with matters of concurrency and distributed communication.The whole transformation is recursively applied to the composition model until the resulting model contains no other connectors than local procedural ones(that represent local procedure calls) connecting components or connector fragments.Beside the additional contracts,that arise by introducing new model elements,the connector fragments respectively their internals,that can be used to improve the verification of the application model,our approach also issues great potential for optimization of the application’s communication subsystem.As mentioned before,a connector fragment is a composite structure itself and contains only that communica-tion primitives it requires to fulfill operations specified within the application model.Therefore,all features provided by a generic communication stack that are not required for a specific application can be eliminated from the system.As an example(see Figure3)consider an explicit data broadcast connector(C)for distributed deployment that con-nects two application software components(A and B),where the interface of the sending application software component has a contract assigned that the amount of data sent by this component is smaller than the maximum transfer unit (MTU)of the underlying communication protocol(FlexRay). Consider further that the direction of data exchange is strictly unidirectional and that the contracts of the sending and the receiving application software component’s interface state that neither acknowledgment norflow control is required. Therefore,the connector fragment at the sending application’s component side has to contain a request handler and a sender component(for sending access to the FlexRay communication controller)only,whereas the receiving side’s fragment has to contain a receiver and a data buffer component only.The selection of the sender and receiver component can be done ac-cording to the system specification(e.g.,communication media type)and to the interface contract.Therefore,only the com-ponents containing the transmission slice of the AUTOSAR FlexRay Transport Protocol are needed.—All other slices of the transport protocol can be eliminated.The remaining slice (the transmission slice)of the AUTOSAR FlexRay Transport Protocol depends on the transmission component of FlexRay Interface and FlexRay Driver.There are further possible use cases where a large number of module slices can be eliminated during model transformation:•Most diagnostic services do not require the exchange of data which exceeds the maximum transfer unit of the underlying communication protocol.—Therefore,the segmentation and reassembly module slice of the trans-port protocol can be eliminated.•When looking at a simple sensor node which only broad-casts sensor value in signals,one realizes that such a sensor node does not require any transport protocol at all.—From the FlexRay Driver and FlexRay Interface functionality,only the transmission component and the base component is needed.<< component >>A << component >>B<< component >>A<< component >>BC<< connector >>CDeployment Boundary<< component >>Request Handler<< component >>Sender<< component >>Buffer<< component >>Receiver<< fragment >>C’<< fragment >>C’’<<contract>>data < MTUFig.3.Example TransformationIV.P ROOF OF C ONCEPTA.Sample ApplicationIn order to demonstrate the feasibility of the presented ap-proach,we implemented a sample application.This application is based on a typical automotive use case:A central locking system including a speed sensor to provide automatic locking of the doors when the car has reached a certain speed.The application was specified to contain a central logic for controlling the status of the doors.Inputs are lock and unlock requests(initiated by the user)and the actual speed of the car.Normally the doors are locked and unlocked according to the requests by the user.If,however,the speed of the car exceeds a certain value,the doors are locked automatically by the control logic.As long as the car’s speed exceeds the certain value,unlock requests of the user are ignored.The doors are not unlocked automatically when the car slows down below the mentioned speed value;another unlock request has to be received.Every time the doors have to be locked or unlocked, the control logic transmits an according order to each door lock.1)Composition:The distributed system for the door lock application consists of a sensor which transmits unlock and lock requests as well as a sensor providing the actual speed status.Further,a control logic for processing the sensor data and triggering unlock or lock commands is present.Finally,the distributed system contains actuators locking and unlocking the doors according to the commands of the central control logic.The key sensors may be implemented at the door lock to detect the turning of a key,at infrared or radio receivers to recognize the usage of a remote control,at buttons in the interior of the car,and so on.I.e.,it must be possible to connect more than one key sensor to the system.The requests generated by the key sensors are intended to be used by the lock control logic only.The speed sensor is considered to provide speed data to every subsystem in need,i.e.,one sensor broadcasting the actual speed throughout the car.The actuators for opening and closing the doors may—obviously—have a couple of instances.Therefore the system has to be designed in a way which allows multiple door lock actuators.The functionality of the application was divided into the following four components:Two sensor components(“key sensor”and“speed sensor”),one controlling component(“lock control”)and one actuator component(“door lock”). Multiple instances of the“key sensor”and“door lock”components may be available,i.e.,more than one“key sensor”may use the interface to“lock control”as well as“lock control”may use more then one interface instance to door lock components.While designing the example application we focusedon one“key sensor”and one“door lock”component instance for reasons of simplicity.position of the Door Lock ApplicationAs one can see in Figure4,two procedure call(≪PC≫) and one broadcast(≪Broadcast≫)interfaces have been cho-sen.Procedural interfaces may be used if the receiver of the information is explicitly addressed by the sender and the communications purpose is a procedure call(as it is the case in。
DNA的生物合成和损伤修复DNA Biosynthesis and DNA Damage Repair

The hybrid DNA became less and less..
summary
DNA replicates in a semiconservative manner. When the two parental strands separate, each serves as the template for making a new , complementary strand.
The DNA band position was recorded.
There was one band of 15N DNA.
The bacteria were transferred to an 14NH4Cl medium and grown for one generation.
The DNA density was determined again.
The two replication forks proceed bidirectionally away from the origin and the strands are copied as they separate until the terminus is reached.
4. DNA replication is semidiscontinuous.
In contrast eukaryotic chromosomes consist of multiple replicons.
⑵. Origin: The initiation within a replicon always occurs at a fixed point known as the origin.
ECE_94

ORIGINAL :UNITED NATIONS of March 20, 1995E/ECE/324 )Rev.1/Add.93/Amend.4E/ECE/TRANS/505 )April 1, 2003STATUS OF UNITED NATIONS REGULATIONECE 94UNIFORM PROVISIONS CONCERNING THE APPROVAL OF:VEHICLES WITH REGARD TO THE PROTECTION OF THEOCCUPANTS IN THE EVENT OF A FRONTAL COLLISIONIncorporating:00 series of amendments Date of Entry into Force: 01.10.95 Supplement 1 to the 00 series of amendments Date of Entry into Force: 12.08.96 01 series of amendments Date of Entry into Force: 12.08.98 Supplement 1 to the 01 series of amendments Date of Entry into Force: 21.02.02 Supplement 2 to the 01 series of amendments Date of Entry into Force: 31.01.03 Corr. 1 to the 01 series of amendments Date of Entry into Force: 26.06.02ORIGINAL :UNITED NATIONS of March 20, 1995 E/ECE/324)E/ECE/TRANS/505 )Rev.1/Add.93/Amend.4April 1, 2003TITLE:Frontal Collision - ISSUE:4 Regulation No. 94Protection Apr/2003PAGE: IUNITED NATIONS AGREEMENTCONCERNING THE ADOPTION OF UNIFORM TECHNICAL PRESCRIPTIONS FOR WHEELED VEHICLES, EQUIPMENT AND PARTS WHICH CAN BE FITTED AND/OR BE USED ON WHEELED VEHICLES AND THE CONDITIONS FOR RECIPROCAL RECOGNITION OFAPPROVALS GRANTED ON THE BASIS OF THESE PRESCRIPTIONS (*)Revision 2, including the amendments which entered into force on October 16, 1995)Addendum 93: Regulation No. 94Amendment 4Supplement 2to the 01 series of amendments – Date of entry into force: January 31, 2003UNIFORM PROVISIONS CONCERNING THE APPROVAL OF VEHICLES WITH REGARD TO THEPROTECTION OF THE OCCUPANTS IN THE EVENT OF A FRONTAL COLLISION(*)Former title of the Agreement:Agreement Concerning the Adoption of Uniform Conditions of Approval and Reciprocal Recognition of Approval for Motor Vehicle Equipment and Parts, done at Geneva on March 20, 1958.ORIGINAL :UNITED NATIONS of March 20, 1995Regulation No. 94UNIFORM PROVISIONS CONCERNING THE APPROVAL OF VEHICLES WITH REGARD TO THE PROTECTION OF THE OCCUPANTS IN THE EVENT OF A FRONTAL COLLISION CONTENTSREGULATION1. Scope2. Definitions3. Application for approval4. Approval5. Specifications6. Instructions for users of vehicles equipped with airbags7. Modification and Extension of approval of the vehicle type8. Conformity of production9. Penalties for non-conformity of production10. Production definitely discontinued11. Transitional provisions12. Names and addresses of technical services responsible for conducting approval tests, and ofadministrative departmentsANNEXESAnnex 1 - Communication concerning the approval or extension or refusal or withdrawal of approval or production definitely discontinued of a vehicle type with regard to the protection of theoccupants in the event of a frontal collision, pursuant to Regulation No. 94Annex 2 - Arrangements of the approval markAnnex 3 - Test procedureAnnex 4 - Determination of performance criteriaAnnex 5 - Arrangement and installation of dummies and adjustment of restraint systemsTITLE:Frontal Collision - ISSUE:1 Regulation No. 94 Protection Jan/1999PAGE: IIORIGINAL :UNITED NATIONS of March 20, 1995Regulation No. 94Annex 6 - Procedure for determining the "H" point and the actual torso angle for seating positions in motor vehiclesAppendix 1 - Description of the three-dimensional "H" point machineAppendix 2 - Three-dimensional reference systemAppendix 3 - Reference data concerning seating positionsAnnex 7 - Test procedure with trolleyAppendix - Equivalence curve - Tolerance band for curve _V = f (t)Annex 8 - Technique of measurement in measurement tests: instrumentationAnnex 9 - Definition of the deformable barrierAnnex 10 - Certification procedure for the dummy lower leg and foot.TITLE:Frontal Collision - ISSUE:1 Regulation No. 94 Protection Jan/1999PAGE: IIIORIGINAL :UNITED NATIONS of March 20, 1995TITLE:Frontal Collision - ISSUE:1 Regulation No. 94Protection Jan/1999PAGE: 1Regulation No. 941.SCOPE1.1.This regulation applies to power-driven vehicles of Category M 1(1)of a total permissible mass not exceeding 2.5 tonnes; heavier vehicles may be approved at the request of the manufacturer;1.2.It shall apply at the request of the manufacturer for the approval of a vehicle type with regard to the protection of the occupants of the front outboard seats in the event of a frontal collision. 2.DEFINITIONSFor the purposes of this Regulation:2.1."Protective system" means interior fittings and devices intended to restrain the occupants and contribute towards ensuring compliance with the requirements set out in Paragraph 5 below;2.2."Type of protective system" means a category of protective devices which do not differ in such essential respects as: Their technology; Their geometry;Their constituent materials;2.3."Vehicle width" means the distance between two planes parallel to the longitudinal median plane (of the vehicle) and touching the vehicle on either side of the said plane but excluding the rear-view mirrors, side marker lamps, tyre pressure indicators, direction indicator lamps, position lamps, flexible mud-guards and the deflected part of the tyre side-walls immediately above the point of contact with the ground;2.4. "Overlap" means the percentage of the vehicle width directly in line with the barrier face; 2.5. "Deformable barrier face" means a crushable section mounted on the front of a rigid block;2.6."Vehicle type" means a category of power-driven vehicles which do not differ in such essential respects as:2.6.1. The length and width of the vehicle, in so far as they have a negative effect on the results of the impact test prescribed in this Regulation,2.6.2.The structure, dimensions, lines and materials of the part of the vehicle forward of the transverse plane through the "R" point of the driver's seat, in so far as they have a negative effect on the results of the impact test prescribed in this Regulation,(1)As defined in the Consolidated Resolution on the Construction of Vehicles (R.E.3), Annex 7 (document TRANS/SC1/WP29/78/Amend.3), i.e., motor vehicles used for the carriage of passengers and comprising not more than eight seats in addition to the driver's seat.ORIGINAL :UNITED NATIONS of March 20, 19952.6.3.The lines and inside dimensions of the passenger compartment and the type of protectivesystem, in so far as they have a negative effect on the results of the impact test prescribedin this Regulation,2.6.4.The siting (front, rear or centre) and the orientation (transversal or longitudinal) of theengine,2.6.5.The unladen mass, in so far as there is a negative effect on the result of the impact testprescribed in this Regulation,2.6.6.The optional arrangements or fittings provided by the manufacturer, in so far as they have anegative effect on the result of the impact test prescribed in this Regulation,2.7."Passenger compartment"means the space for occupant accommodation, bounded bythe roof, floor, side walls, doors, outside glazing and front bulkhead and the plane of the rearcompartment bulkhead or the plane of the rear-seat back support;2.8."R point" means a reference point defined for each seat by the manufacturer in relation thevehicle's structure, as indicated in Annex 6;2.9."H point"means a reference point determined for each seat by the testing serviceresponsible for approval, in accordance with the procedure described in Annex 6;2.10."Unladen kerb mass"means the mass of the vehicle in running order, unoccupied andunladen but complete with fuel, coolant , lubricant, tools and spare wheel (if these areprovided as standard equipment by the vehicle manufacturer).2.11."Airbag"means a device installed to supplement safety belts and restraint systems inpower-driven vehicles, i.e. systems which, in the event of a severe impact affecting thevehicle, automatically deploy a flexible structure intended to limit, by compression of the gascontained within it, the gravity of the contacts of one or more parts of the body of anoccupant of the vehicle with the interior of the passenger compartment.2.12."Passenger airbag"means an airbag assembly intended to protect occupant(s) in seatsother than the driver's in the event of a frontal collision.2.13."Child restraint"means an arrangement of components which may comprise acombination of straps or flexible components with a securing buckle, adjusting devices,attachments, and in some cases a supplementary chair and/or an impact shield, capable ofbeing anchored to a power driven vehicle. It is so designed as to diminish the risk of injuryto the wearer, in the event of a collision or of abrupt deceleration of the vehicle by limitingthe mobility of the wearer's body.2.14."Rearward-facing" means facing in the direction opposite to the normal direction of travelof the vehicle.TITLE:Frontal Collision - ISSUE:1 Regulation No. 94 Protection Jan/1999PAGE: 2ORIGINAL :UNITED NATIONS of March 20, 19953.APPLICATION FOR APPROVAL3.1.The application for approval of a vehicle type with regard to the protection of the occupantsof the front seats in the event of a frontal collision shall be submitted by the vehiclemanufacturer or by his duly accredited representative.3.2.It shall be accompanied by the undermentioned documents in triplicate and followingparticulars;3.2.1. A detailed description of the vehicle type with respect to its structure, dimensions, lines andconstituent materials;3.2.2.Photographs, and/or diagrams and drawings of the vehicle showing the vehicle type in front,side and rear elevation and design details of the forward part of the structure;3.2.3.Particulars of the vehicle's unladen kerb mass;3.2.4.The lines and inside dimensions of the passenger compartment;3.2.5. A description of the interior fittings and protective systems installed in the vehicle.3.3.The applicant for approval shall be entitled to present any data and results of tests carriedout which make it possible to establish that compliance with the requirements can beachieved with a sufficient degree of confidence.3.4. A vehicle which is representative of the type to be approved shall be submitted to thetechnical service responsible for conducting the approval tests.3.4.1. A vehicle not comprising all the components proper to the type may be accepted for testprovided that it can be shown that the absence of the components omitted has nodetrimental effect on the results of the test in so far as the requirements of this Regulationare concerned.3.4.2.It shall be the responsibility of the applicant for approval to show that the application ofParagraph 3.4.1. is compatible with compliance with the requirements of this Regulation. TITLE:Frontal Collision - ISSUE:1 Regulation No. 94 Protection Jan/1999PAGE: 3ORIGINAL :UNITED NATIONS of March 20, 1995 TITLE:Frontal Collision - ISSUE:3 Regulation No. 94Protection Apr/2003PAGE: 44.APPROVAL4.1. If the vehicle type submitted for approval pursuant to this Regulation meets the requirements of this Regulation , approval of that vehicle type shall be granted.4.1.1. The technical service appointed in accordance with Paragraph 10 below shall check whether the required conditions have been satisfied.4.1.2.In case of doubt, account shall be taken, when verifying the conformity of the vehicle to the requirements of this Regulation, of any data or test results provided by the manufacturer which can be taken into consideration in validating the approval test carried out by the technical service.4.2.An approval number shall be assigned to each type approved. Its first two digits (at present 01 corresponding to the 01 series of amendments), shall indicate the series of amendments incorporating the most recent major technical amendments made to the Regulation at the time of issue of the approval. The same Contracting Party may not assign the same approval number to another vehicle type.4.3.Notice of approval or of refusal of approval of a vehicle type pursuant to this Regulation shall be communicated by the Parties to the Agreement which apply this Regulation by means of a form conforming to the model in Annex 1 to this Regulation and photographs and/or diagrams and drawings supplied by the applicant for approval, in a format not exceeding A4 (210 X 297 mm) or folded to that format and on an appropriate scale.4.4.There shall be affixed, conspicuously and in a readily accessible place specified on the approval form, to every vehicle conforming to a vehicle type approved under this Regulation, an international approval mark consisting of:4.4.1. A circle surrounding the Letter "E" followed by the distinguishing number of the country which has granted approval (1)4.4.2.The number of this Regulation, followed by the Letter "R", a dash and the approval number, to the right of the circle prescribed in Paragraph 4.4.1.(1)1 for Germany,2 for France,3 for Italy,4 for the Netherlands,5 for Sweden,6 for Belgium,7 for Hungary,8 for the Czech Republic,9 for Spain, 10 for Yugoslavia, 11 for the United Kingdom, 12 for Austria, 13 for Luxembourg, 14 for Switzerland, 15 (vacant), 16 for Norway, 17 for Finland, 18 for Denmark, 19 for Romania, 20 for Poland, 21 for Portugal, 22 for the Russian Federation, 23 for Greece, 24 for Ireland, 25 for Croatia, 26 for Slovenia, 27 for Slovakia, 28 for Belarus, 29 for Estonia, 30 (vacant), 31 for Bosnia and Herzegovina, 32 for Latvia, 33 (vacant), 34 for Bulgaria, 35 (vacant), 36 for Lithuania,37 for Turkey, 38 (vacant), 39 for Azerbaijan, 40 for The former Yugoslav Republic of Macedonia, 41 (vacant), 42 for the European Community (Approvals are granted by its Member States using their respective ECE symbol), 43 for Japan, 44 (vacant), 45 for Australia, 46 for Ukraine, 47 for South Africa and 48 for New Zealand. Subsequent numbers shall be assigned to other countries in the chronological order in which they ratify to the Agreement concerning the Adoption of Uniform Technical Prescriptions for Wheeled Vehicles, Equipment and Parts which can be Fitted and/or be Used on Wheeled Vehicles and the Conditions for Reciprocal Recognition of Approvals Granted on the Basis of these Prescriptions, for Motor Vehicle Equipment and Parts, or in which they accede to that Agreement, and the numbers thus assigned shall be communicated by the Secretary-General of the United Nations to the Contracting Parties to the Agreement.ORIGINAL :UNITED NATIONS of March 20, 19954.5.If the vehicle conforms to a vehicle type approved, under one or more other Regulationsannexed to the Agreement, in the country which has granted approval under thisRegulation, the symbol prescribed in Paragraph 4.4.1. need not be repeated; in such a casethe Regulation and approval numbers and the additional symbols of all the Regulationsunder which approval has been granted in the country which has granted approval underthis Regulation shall be placed in vertical columns to the right of the symbol prescribed inParagraph 4.4.1.4.6.The approval mark shall be clearly legible and be indelible.4.7.The approval mark shall be placed close to or on the vehicle data plate affixed by themanufacturer.4.8.Annex 2 to this Regulation gives examples of approval marks.5.SPECIFICATIONS5.1.General specifications applicable to all tests5.1.1.The "H" point for each seat shall be determined in accordance with the procedure describedin Annex 6.5.1.2.When the protective system for the front seating positions includes belts, the beltcomponents shall meet the requirements of Regulation No. 16.5.1.3.Seating positions where a dummy is installed and the protective system includes belts, shallbe provided with anchorage points conforming to Regulation No. 14.5.2.SpecificationsThe test of the vehicle carried out in accordance with the method described in Annex 3 shallbe considered satisfactory if all the conditions set out in Paragraphs 5.2.1. to 5.2.6. beloware all satisfied at the same time.5.2.1.The performance criteria recorded, in accordance with Annex 8, on the dummies in the frontoutboard seats shall meet the following conditions:5.2.1.1. The head performance criterion (HPC) shall not exceed 1000 and the resultant headacceleration shall not exceed 80 g for more than 3 ms. The latter shall be calculatedcumulatively, excluding rebound movement of the head;TITLE:Frontal Collision - ISSUE:1 Regulation No. 94 Protection Jan/1999PAGE: 5ORIGINAL :UNITED NATIONS of March 20, 1995 TITLE:Frontal Collision - ISSUE:1 Regulation No. 94Protection Jan/1999PAGE: 65.2.1.2.The neck injury criteria (NIC) shall not exceed the values shown in Figures 1 and 2(1);Figure 1Neck Tension CriterionFigure 2 Neck Shear Criterion(1)Until October 1, 1998, the values obtained for the neck shall not be pass/fail criteria for the purposes of granting approval.The results obtained shall be recorded in the test report and be collected by the approval authority. After this date, the values specified in this paragraph shall apply as pass/fail criteria unless or until alternative values are adopted.ORIGINAL :UNITED NATIONS of March 20, 1995 TITLE:Frontal Collision - ISSUE:1 Regulation No. 94Protection Jan/1999PAGE: 75.2.1.3. The neck bending moment about the y axis shall not exceed 57 Nm in extension (1);5.2.1.4. The thorax compression criterion (ThCC) shall not exceed 50 mm; 5.2.1.5. The viscous criterion (V * C) for the thorax shall not exceed 1,0 m/s;5.2.1.6.The femur force criterion (FFC) shall not exceed the force-time performance criterion shownin Figure 3;Figure 3Femur Force Criterion5.2.1.7. The tibia compression force criterion (TCFC) shall not exceed 8 kN;5.2.1.8. The tibia index (TI), measured at the top and bottom of each tibia, shall not exceed 1,3 at either location;5.2.1.9. The movement of the sliding knee joints shall not exceed 15 mm.5.2.2.Residual steering wheel displacement, measured at the centre of the steering wheel hub, shall not exceed 80 mm in the upwards vertical direction and 100 mm in the rearward horizontal direction.(1)Until October 1, 1998, the values obtained for the neck shall not be pass/fail criteria for the purposes of granting approval.The results obtained shall be recorded in the test report and be collected by the approval authority. After this date, the values specified in this paragraph shall apply as pass/fail criteria unless or until alternative values are adopted.ORIGINAL :UNITED NATIONS of March 20, 19955.2.3.During the test no door shall open;5.2.4.During the test no locking of the locking systems of the front doors shall occur;5.2.5.After the impact, it shall be possible, without the use of tools, except for those necessary tosupport the weight of the dummy:5.2.5.1. To open at least one door, if there is one, per row of seats and, where there is no such door,to move the seats or tilt their backrests as necessary to allow the evacuation of all theoccupants; this is, however, only applicable to vehicles having a roof of rigid construction; 5.2.5.2. To release the dummies from their restraint system which, if locked, shall be capable ofbeing released by a maximum force of 60 N on the centre of the release control;5.2.5.3. To remove the dummies from the vehicle without adjustment of the seats.5.2.6.In the case of a vehicle propelled by liquid fuel, no more than slight leakage of liquid fromthe fuel feed installation shall occur on collision;5.2.7.If there is continuous leakage of liquid from the fuel-feed installation after the collision, therate of leakage shall not exceed 30 g/min; if the liquid from the fuel-feed system mixes withliquids from the other systems and the various liquids cannot easily be separated andidentified, all the liquids collected shall be taken into account in evaluating the continuousleakage.6.INSTRUCTIONS FOR USERS OF VEHICLES EQUIPPED WITH AIRBAGS6.1.The vehicles shall carry information to the effect that it is equipped with airbags for seats. 6.1.1.For a vehicle fitted with an airbag assembly intended to protect the driver, this informationshall consist of the inscription "AIRBAG" located in the interior of the circumference of thesteering wheel; this inscription shall be durably affixed and easily visible.6.1.2.For a vehicle fitted with a passenger airbag intended to protect occupants other than thedriver, this information shall consist of the warning label described in Paragraph 6.2. below.6.2. A vehicle fitted with one or more passenger frontal protection airbags shall carry informationabout the extreme hazard associated with the use of rearward-facing child restraints onseats equipped with airbag assemblies.TITLE:Frontal Collision - ISSUE:2 Regulation No. 94 Protection Apr/2003PAGE: 8ORIGINAL :UNITED NATIONS of March 20, 1995 TITLE:Frontal Collision - ISSUE:2 Regulation No. 94Protection Apr/2003PAGE: 96.2.1.As a minimum, this information shall consist of a label containing a pictogram and text warningas indicated below.The overall dimensions shall be 120 x 60 mm or the equivalent area, as a minimum. The label shown above may be adapted in such a way that the layout differs from the example above; however, the text content shall meet the above prescriptions.6.2.2.At the time of type approval, the label shall be in at least one of the languages of the Contracting Party where the application for approval is submitted. The manufacturer shall declare his responsibility for ensuring the warning is provided at least in one of the languages of the country in which the vehicle is to be sold.6.2.3.In the case of a frontal protection airbag on the front passenger seat, the warning shall be durably affixed to each face of the passenger front sun visor in such a position that at least one warning on the sun visor is visible at all times, irrespective of the position of the sun visor. Alternatively, one warning shall be on the visible face of the stowed sun visor and a second warning shall be on the roof behind the visor, so, at least one warning is visible at all times. The text size must allow the label to be easily read by a normal sighted user seated on the seat concerned.In the case of a frontal protection airbag for other seats in the vehicle, the warning must be directly ahead of the relevant seat, and clearly visible at all times to someone installing a rear-facing child restraint on that seat. The text size must allow the label to be easily read by a normal sighted user seated on the seat concerned.This requirement does not apply to those seats equipped with a device which automatically deactivates the frontal protection airbag assembly when any rearward-facing child restraint is installed.ORIGINAL :UNITED NATIONS of March 20, 1995 TITLE:Frontal Collision - ISSUE:2 Regulation No. 94Protection Apr/2003PAGE: 106.2.4.Detailed information, making reference to the warning, shall be contained in the owner's manual of the vehicle; as a minimum the following text in the official languages of the country where the vehicle is to be registered, must include:"Do not use a rearward facing child restraint on a seat protected by an airbag in front of it!"The text shall be accompanied by an illustration of the warning to be found in the vehicle.7.MODIFICATION AND EXTENSION OF APPROVAL OF THE VEHICLE TYPE7.1.Any modification affecting the structure, the number of seats, the interior trim or fittings, or the position of the vehicle controls or of mechanical parts which might affect the energy-absorption capability of the front of the vehicle shall be brought to the notice of the administrative department granting approval. The department may then either:7.1.1. Consider that the modifications made are unlikely to have an appreciable adverse effect and that in any case the vehicle still complies with the requirements; or7.1.2. Require the technical service responsible for conducting the tests to carry out a further test, among those described below, according to the nature of the modifications;7.1.2.1.Any modification of the vehicle affecting the general form of the structure of the vehicle and/or any increase in mass greater than 8% which in the judgement of the authority would have a marked influence on the results of the tests shall require a repetition of the test as described in Annex 3;7.1.2.2.If the modifications concern only the interior fittings, if the mass does not differ by more than 8 percent and if the number of front seats initially provided in the vehicle remains the same, the following shall be carried out:7.1.2.2.1. A simplified test as provided for in Annex 7 and/or,7.1.2.2.2. A partial test as defined by the technical service in relation to the modifications made. 7.2.Confirmation or refusal of approval, specifying the alterations, shall be communicated by the procedure specified in Paragraph 4.3. above to the Parties to the Agreement which apply this Regulation.7.3.The competent authority issuing the extension of approval shall assign a series number for such an extension and inform thereof the other Parties to the 1958 Agreement applying this Regulation by means of communication form conforming to the model in Annex 1 to this Regulation.8.CONFORMITY OF PRODUCTIONThe conformity of production procedures shall comply with those set out in the Agreement, Appendix 2 (E/ECE/324-E/ECE/TRANS/505/Rev.2) with the following requirements: 8.1.Every vehicle approved under this Regulation shall conform to the vehicle type approved, as regards features contributing to the protection of the occupants of the vehicle in the event of a frontal collision.8.2. The holder of the approval shall ensure that for each type of vehicle at least the tests concerning the taking of measurements are carried out;8.3.The authority which has granted type approval may at any time verify the conformity control methods applied in each production facility. The normal frequency of these verifications shall be once every two years.ORIGINAL :UNITED NATIONS of March 20, 19959.PENALTIES FOR NON-CONFORMITY OF PRODUCTION9.1.The approval granted in respect of a vehicle type pursuant to this Regulation may bewithdrawn if the requirement laid down in Paragraph 8.1. above is not complied with or if thevehicle or vehicles selected have failed to pass the checks prescribed in Paragraph 8.2.above.9.2.If a Contracting Party to the Agreement applying this Regulation withdraws an approval ithas previously granted, it shall forthwith so notify the other Contracting Parties applying thisRegulation, by means of a communication form conforming to the model in Annex 1 to theRegulation.10.PRODUCTION DEFINITELY DISCONTINUEDIf the holder of the approval completely ceases to manufacture the type of vehicle approvedin accordance with the Regulation, he shall so inform the authority which granted theapproval. Upon receiving the relevant communication that authority shall inform thereof theother Parties to the 1958 Agreement applying this Regulation by means of a communicationform conforming to the model in Annex 1 to this Regulation.11.TRANSITIONAL PROVISION11.1.As from the official date of entry into force of Supplement 1 to the 01 series of amendments,no Contracting Party applying this Regulation shall refuse to grant ECE approval under thisRegulation as amended by Supplement 1 to the 01 series of amendments.11.2.As from October 1, 2002Contracting Parties applying this Regulation shall grantECE approvals only to those types of vehicles which comply with the requirements of thisRegulation as amended by Supplement 1 to the 01 series of amendments.11.3.As from October 1, 2003 Contracting Parties applying this Regulation may refuse firstnational registration (first entry into service) of vehicles which do not meet the requirementsof this Regulation as amended by the 01 series of amendments.S AND ADDRESSES OF TECHNICAL SERVICES RESPONSIBLE FORCONDUCTING APPROVAL TESTS, AND OF ADMINISTRATIVE DEPARTMENTSThe Contracting Parties to the Agreement applying this Regulation shall communicate to theUnited Nations secretariat the names and addresses of the technical services responsiblefor conducting approval tests, of manufacturers authorised to carry out tests and of theadministrative departments which grant approval and to which forms certifying approval orrefusal or withdrawal of approval, issued in other countries, are to be sent.TITLE:Frontal Collision - ISSUE:2 Regulation No. 94 Protection June/2002PAGE: 11。
synthetic division method -回复

synthetic division method -回复Synthetic division is a method used in algebra to perform division of polynomials. It is particularly useful in dividing a polynomial by a linear factor, as it provides a straightforward and efficient approach. In this article, we will explore the concept of synthetic division, step by step, to understand the process and how it can be applied in various mathematical problems.Step 1: Understanding the BasicsTo begin with, let's have a brief overview of the key terms related to synthetic division. A polynomial is an algebraic expression comprising of variables, coefficients, and exponents. Division, in this context, refers to dividing one polynomial by another. Finally, synthetic division is a simplified method to perform polynomial division. It is often used when we need to find the quotient and remainder of dividing one polynomial by a linear factor.Step 2: Identify the DivisorIn synthetic division, the first step is to identify the divisor. The divisor is a linear factor of the polynomial we wish to divide. A linear factor is an expression of the form (ax+b), where 'a' and 'b' are constants. For example, consider the polynomial (3x^3 - 4x^2+ 2x + 1) and the linear factor (x - 2). Here, (x - 2) is the divisor.Step 3: Arrange the PolynomialNext, we arrange the polynomial in descending order, based on the exponent of the variable. In our example, the polynomial (3x^3 - 4x^2 + 2x + 1) is already arranged in descending order. However, if the polynomial is not in the desired order, we may need to rearrange it before proceeding.Step 4: Determine the Synthetic Division TableThe synthetic division table is a tabular representation that helps us perform the division efficiently. The table starts with a row representing the coefficients of the polynomial and an empty space to the right for the synthetic division steps. In our example, the synthetic division table would appear as follows:2 3 -4 2 1 -> (coefficients)Step 5: Perform the Synthetic DivisionNow we are ready to perform the synthetic division. Starting from the left, we take the first coefficient (3) and bring it down directlybelow the line in the synthetic division table. Then we multiply the divisor (2) by the number we just brought down and write the result in the next column. In this case, 2 multiplied by 3 is 6, so we write 6 below the next column.2 3 -4 2 16________Next, add the value in the second column (6) to the coefficient in the second column (-4). The sum is 2, which we write below the line in the same column.2 3 -4 2 16________2Repeat this process for each subsequent column. Multiply the result from the previous step (2) by the divisor (2) and write the product below the next column. Then add the value in the newcolumn to the coefficient in the corresponding column of the polynomial.2 3 -4 2 16 8________2 4Continue this process until you reach the last column of the polynomial.Step 6: Interpret the ResultsOnce we have completed the synthetic division, we can interpret the results. The numbers in the last row of the synthetic division table represent the coefficients of the quotient polynomial. In our example, the coefficients are 2 and 4. Therefore, the quotient polynomial is represented as (2x + 4).Step 7: Analyze the RemainderLastly, the number in the bottom-right cell of the synthetic division table represents the remainder of the division. In our example, the remainder is 1. Hence, the entire synthetic division can beexpressed as (3x^3 - 4x^2 + 2x + 1) = (2x + 4) + (1/(x - 2)).Synthetic division is an effective method for dividing polynomials, especially when dealing with linear factors. By following these step-by-step instructions, you can confidently apply synthetic division to solve various polynomial division problems.。
英语技术写作试题及答案

英语技术写作试题及答案一、选择题(每题2分,共20分)1. The term "API" stands for:A. Application Programming InterfaceB. Artificially Programmed IntelligenceC. Advanced Programming InterfaceD. Automated Programming Interface答案:A2. Which of the following is not a common data type in programming?A. IntegerB. StringC. BooleanD. Vector答案:D3. In technical writing, what is the purpose of using the term "shall"?A. To indicate a requirement or obligationB. To suggest a recommendationC. To express a possibilityD. To denote a future action答案:A4. What does the acronym "GUI" refer to in the context of computing?A. Graphical User InterfaceB. Global User InterfaceC. Generalized User InterfaceD. Graphical Unified Interface答案:A5. Which of the following is a correct statement regarding version control in software development?A. It is used to track changes in software over time.B. It is a type of software testing.C. It is a method for encrypting code.D. It is a way to compile code.答案:A6. What is the primary function of a compiler in programming?A. To debug codeB. To execute codeC. To translate code from one language to anotherD. To optimize code for performance答案:C7. In technical documentation, what does "RTFM" commonly stand for?A. Read The Frequently Asked QuestionsB. Read The Full ManualC. Read The File ManuallyD. Read The Final Message答案:B8. Which of the following is a common method for organizing code in a modular fashion?A. LoopingB. RecursionC. EncapsulationD. Inheritance答案:C9. What is the purpose of a "pseudocode" in programming?A. To provide a detailed step-by-step guide for executing codeB. To serve as a preliminary version of code before actual codingC. To act as an encryption for the codeD. To be used as a substitute for actual code in production答案:B10. What does "DRY" stand for in software development?A. Don't Repeat YourselfB. Data Retrieval YieldC. Database Record YieldD. Dynamic Resource Yield答案:A二、填空题(每空2分,共20分)1. The process of converting a high-level code into machine code is known as _______.答案:compilation2. In programming, a _______ is a sequence of characters that is treated as a single unit.答案:string3. The _______ pattern in object-oriented programming is a way to allow a class to be used as a blueprint for creating objects.答案:prototype4. A _______ is a type of software development methodology that emphasizes iterative development.答案:agile5. The _______ is a set of rules that defines how data is formatted, transmitted, and received between software applications.答案:protocol6. In technical writing, the term "should" is used toindicate a _______.答案:recommendation7. The _______ is a type of software that is designed to prevent, detect, and remove malicious software.答案:antivirus8. A _______ is a variable that is declared outside the function and hence belongs to the global scope.答案:global variable9. The _______ is a programming construct that allows you to execute a block of code repeatedly.答案:loop10. In software development, the term "branch" in version control refers to a _______.答案:separate line of development三、简答题(每题10分,共40分)1. Explain the difference between a "bug" and a "feature" in software development.答案:A "bug" is an unintended behavior or error in a software program that causes it to behave incorrectly or crash. A "feature," on the other hand, is a planned and intentional part of the software that provides some functionality or capability to the user.2. What is the significance of documentation in technical writing?答案:Documentation in technical writing is significant as it serves to provide detailed information about a product or system, making it easier for users, developers, and other stakeholders to understand its workings, usage, and maintenance. It is crucial for training, troubleshooting, and future development.3. Describe the role of a software architect in a software development project。
On the unusual effectiveness of Logic in computer science

On the Unusual Effectiveness of Logic in Computer ScienceJoseph Y.Halpern Robert Harper Neil Immerman Phokion G.KolaitisMoshe Y.Vardi Victor VianuJanuary20011Introduction and OverviewIn1960,E.P.Wigner,a joint winner of the1963Nobel Prize for Physics,published a paper titled On the Un-reasonable Effectiveness of Mathematics in the Natural Sciences[Wig60].This paper can be construed as an examination and affirmation of Galileo’s tenet that“The book of nature is written in the language of mathe-matics”.To this effect,Wigner presented a large number of examples that demonstrate the effectiveness of mathematics in accurately describing physical phenomena.Wigner viewed these examples as illustrations of what he called the empirical law of epistemology,which asserts that the mathematical formulation of the laws of nature is both appropriate and accurate,and that mathematics is actually the correct language for formulating the laws of nature.At the same time,Wigner pointed out that the reasons for the success of mathematics in the natural sciences are not completely understood;in fact,he went as far as asserting that“...the enormous usefulness of mathematics in the natural sciences is something bordering on the mysterious and there is no rational explanation for it.”In1980,R.W.Hamming,winner of the1968ACM Turing Award for Computer Science,published a follow-up article,titled The Unreasonable Effectiveness of Mathematics[Ham80].In this article,Hamming provided further examples manifesting the effectiveness of mathematics in the natural sciences.Moreover, he attempted to answer the“implied question”in Wigner’s article:“Why is mathematics so unreasonably effective?”Although Hamming offered several partial explanations,at the end he concluded that on balance this question remains“essentially unanswered”.Since the time of the publication of Wigner’s article,computer science has undergone a rapid,wide-ranging,and far-reaching development.Just as in the natural sciences,mathematics has been highly effective in computer science.In particular,several areas of mathematics,including linear algebra,number theory, probability theory,graph theory,and combinatorics,have been instrumental in the development of computer science.Unlike the natural sciences,however,computer science has also benefitted from an extensive and continuous interaction with logic.As a matter of fact,logic has turned out to be significantly more effective in computer science than it has been in mathematics.This is quite remarkable,especially since much of the impetus for the development of logic during the past one hundred years came from mathematics.This paper summarizes a symposium,by the same title,which was held at the1999Meeting of the American Association for the Advancement of Science.The authors wrote the following:Section1and7–Kolaitis,Section2–Immerman,Section3–Vianu,Section4-Harper,Section5-Halpern,and Section6–Vardi.Cornell University.Work partially supported by NSF Grant IRI-96-25901.Carnegie-Mellon University Work partially supported by NSF Grant CCR-9502674and DARPA Contract F19628-95-C-0050.University of Massachusetts,Amherst.Work partially supported by NSF grant CCR-9877078.University of California,Santa Cruz.Work partially supported by NSF Grant CCR-9610257.Rice University.Work partially supported by NSF Grants CCR-9700061,CCR-9988322,IIS-9978135,and CCR-9988322.University of California,San Diego.Work partially supported by NSF Grant IIS-9802288.Indeed,let us recall that to a large extent mathematical logic was developed in an attempt to confront the crisis in the foundations of mathematics that emerged around the turn of the20th Century.Between1900 and1930,this development was spearheaded by Hilbert’s Program,whose main aim was to formalize all of mathematics and establish that mathematics is complete and rmally,completeness means that all“true”mathematical statements can be“proved”,whereas decidability means that there is a mechanical rule to determine whether a given mathematical statement is“true”or“false”.Hilbertfirmly believed that these ambitious goals could be achieved.Nonetheless,Hilbert’s Program was dealt devastating blows during the1930s.Indeed,the standardfirst-order axioms of arithmetic were shown to be incomplete by G¨o del in his celebrated1931paper[G¨o d31].Furthermore,A.Turing,A.Church,and A.Tarski demonstrated the undecidability offirst-order logic.Specifically,the set of all validfirst-order sentences was shown to be undecidable[Chu36,Tur37],whereas the set of allfirst-order sentences that are true in arithmetic was shown to be highly undecidable[Tar35].Today,mathematical logic is a mature and highly sophisticated research area with deep results and a number of applications in certain areas of mathematics.All in all,however,it is fair to say that the interaction between logic and mathematics has been rather limited.In particular,mathematical logic is not perceived as one of the mainstream area of mathematics,and the“typical”mathematician usually knows little about logic.Along these lines,R.W.Hamming’s judgment[Ham80]is not uncommon,albeit perhaps severe:“...we have had an intense study of what is called the foundations of mathematics...It is an interesting field,but the main results of mathematics are impervious to what is found there.”In contrast,logic has permeated through computer science during the past thirty years much more than it has through mathematics during the past one hundred years.Indeed,at present concepts and methods of logic occupy a central place in computer science,insomuch that logic has been called“the calculus of computer science”[MW85].Our goal in this article is to illustrate the effectiveness of logic in computer science by focusing on just a few of the many areas of computer science on which logic has had a definite and lasting impact.Specifically,the connections between logic and computational complexity will be high-lighted in Section2,the successful use offirst-order logic as a database query language will be illustrated in Section3,the influence of type theory in programming language research will be addressed in Section4,the deployment of epistemic logic to reason about knowledge in multi-agent systems will be covered in Section 5,and the connections between logic and automated design verification will be presented in Section6.2Descriptive ComplexityA fundamental issue in theoretical computer science is the computational complexity of problems.How much time and how much memory space is needed to solve a particular problem?Let DTIME be the set of problems that can be solved by algorithms that perform at moststeps for inputs of size.The complexity class Polynomial Time(P)is the set of problems that are solvable in time at most some polynomial in.Formally,P DTIME.Some important computational problems appear to require more than polynomial time.An interesting class of such problems is contained in nondeterministic polynomial time(NP).A nondeterministic compu-tation is one that may make arbitrary choices as it works.If any of these choices lead to an accept state,then we say the input is accepted.The three-colorability problem—testing whether an undirected graph can have its vertices colored with three colors so that no two adjacent vertices have the same color—as well as hundreds of other well-known combinatorial problems are NP-complete.(See[GJ79]for a survey of many of these.)This means that not only are they in NP,but they are the“hardest problems”in NP:all problems in NP are reducible(in polynomial time)to each NP-complete problem.At present,the fastest known algorithm for any of these problems is exponential.An efficient algorithm for any one of these problems would translate to an efficientalgorithm for all of them.The P NP question,which asks whether P and NP coincide,is an example of our inability to determine what can or cannot be computed in a certain amount of computational resource: time,space,parallel time,etc.Complexity theory typically considers yes/no problems.This is the examination of the difficulty of computing a particular bit of the desired output.Yes/no problems are properties of the input.The set of all inputs to which the answer is“yes”have the property in question.Rather than asking the complexity of checking if a certain input has a property,in Descriptive Complexity we ask how hard is it to express the property in some logic.It is plausible that properties that are harder to check might be harder to express. What is surprising is how closely logic mimics computation:descriptive complexity exactly captures the important complexity classes.In Descriptive Complexity we view inputs asfinite logical structures,e.g.,a graph is a logical structurewhose universe is the set of vertices and is the binary edge relation. Proviso:We will assume unless otherwise stated that a total ordering relation on the universe()is avail-able.Infirst-order logic we can express simple properties of our input structures.For example the following says that there are exactly two edges leaving every vertex.In second-order logic we also have variables that range over relations over the universe.These variables may be quantified.A second-order existential formula(SO)begins with second order existential quantifiers and is followed by afirst-order formula.As an example,the following second-order existential sentence says that the graph in question is three-colorable.It does this by asserting that there are three unary relations,Red(R),Yellow(Y),and Blue(B),defined on the universe of vertices.It goes on to say that every vertex has some color and no two adjacent vertices have the same color.Descriptive Complexity began with the following theorem of R.Fagin.Observe that Fagin’s Theorem characterizes the complexity class NP purely by logic,with no mention of machines or time,Theorem1([Fag74])A set of structures is in NP iff there exists a second-order existential formula, such that.Formally,NP SO.Define CRAM to be the set of properties checkable by concurrent-read,concurrent-write,parallel random-access machines using polynomially many processors in parallel time.FO,the set offirst-order expressible properties,exactly captures the complexity class CRAM[1],i.e.,constant parallel time.It is possible to increase the power of FO by allowing longer descriptions for longer inputs.Let FO be those properties describable by a block of restricted quantifiers that may be iterated times for inputs of size.Theorem2([Imm88])For all constructible1,FO CRAM.1“Constructible”means that the function can be computed in space.All but very bizarre functions are con-structible.Another proviso of this theorem is that for,thefirst-order formulas may have access not only to ordering but to the addition and multiplication relations on the-element universe.Thus,parallel time corresponds exactly tofirst-order iteration,i.e.,quantifier-depth.Rather than iterating blocks of quantifiers,a natural way to increase the power offirst-order logic is by allowing inductive defini-tions.This is formalized via a least-fixed-point operator(LFP).As an example,the reflexive,transitive closure of the edge relation can be defined via the following inductive definition,Equivalently,this can be expressed using the least-fixed-point operator,LFPIt is exciting that the natural descriptive class FO(LFP)—first-order logic extended with the power to define new relations by induction—precisely captures polynomial time.Theorem3([Imm82,Imm86,Var82])A problem is in polynomial time iff it is describable infirst-order logic with the addition of the least-fixed-point operator.This is equivalent to being expressible by afirst-order formula iterated polynomially many times.Formally,P FO LFP FO.Theorems1and3cast the P NP question in a different light.(In the following we are using the fact that if P were equal to NP,then NP would be closed under complementation.It would then follow that every second-order formula would be equivalent to a second-order existential one.)Corollary4P is equal to NP iff every second-order expressible property overfinite,ordered structures is al-ready expressible infirst-order logic using inductive definitions.In symbols,P NP FO LFP SO.The following theorem considers the arbitrary iteration offirst-order formulas,which is the same as iterating them exponentially,and is more general than monotone iteration offirst-order formulas.Such iteration defines the partial-fixed-point operator.The theorem shows that this allows the description of exactly all properties computable using a polynomial amount of space.Theorem5([Imm81,Imm82,Var82])A problem is in polynomial space iff it is describable infirst logic with the addition of the partial-fixed-point operator.This is equivalent to being expressible by afirst-order formula iterated exponentially.Formally,PSPACE FO PFP FO.A refinement of Theorem5shows that the precise amount of space used can be characterized via the number of distinct variables in the relevantfirst-order formula,i.e.,the number of descriptive variables captures space,for,DSPACE V AR,[Imm91].Combinatorial games due to Ehrenfeucht and Fra¨ıss´e have been used to prove many inexpressibility results.These bounds provide useful insights but they do not separate relevant complexity classes because they are proved without the ordering relation[Ehr61,Fra54,Imm99].No such lower bounds were known for separating the classes corresponding to P and PSPACE.Abiteboul and Vianu showed why,thus proving another fundamental relationship between logic and complexity.In the following,FO(wo)meansfirst-order logic without a given ordering relation.Theorem6([A V91])The following conditions are equivalent:1.FO(wo)LFP FO(wo)PFP2.FO LFP FO PFP3.P PSPACEDescriptive complexity reveals a simple but elegant view of computation.Natural complexity classes and measures such as polynomial time,nondeterministic polynomial time,parallel time,and space have natural descriptive characterizations.Thus,logic has been an effective tool for answering some of the basic questions in complexity.23Logic as a Database Query LanguageThe database area is an important area of computer science concerned with storing,querying and updating large amounts of data.Logic and databases have been intimately connected since the birth of database systems in the early1970’s.Their relationship is an unqualified success story.Indeed,first-order logic (FO)lies at the core of modern database systems,and the standard query languages such as Structured Query Language(SQL)and Query-By-Example(QBE)are syntactic variants of FO.More powerful query languages are based on extensions of FO with recursion,and are reminiscent of the well-knownfixpoint queries studied infinite-model theory(see Section2).The impact of logic on databases is one of the most striking examples of the effectiveness of logic in computer science.This section discusses the question of why FO has turned out to be so successful as a query language. We will focus on three main reasons:FO has syntactic variants that are easy to use.These are used as basic building blocks in practical languages like SQL and QBE.FO can be efficiently implemented using relational algebra,which provides a set of simple operations on relations expressing all FO queries.Relational algebra as used in the context of databases was introduced by Ted Codd in[Cod70].It is related to Tarski’s Cylindric Algebras[HMT71].The algebra turns out to yield a crucial advantage when large amounts of data are concerned.Indeed,the realization by Codd that the algebra can be used to efficiently implement FO queries gave the initial impetus to the birth of relational database systems3.FO queries have the potential for“perfect scaling”to large databases.If massive parallelism is avail-able,FO queries can in principle be evaluated in constant time,independent of the database size.A relational database can be viewed as afinite relational structure.Its signature is much like a relational FO signature,with the minor difference that relations and their coordinates have names.The name of a coordinate is called an attribute,and the set of attributes of a relation is denoted.For example,a “beer drinker’s”database might consist of the following relations:frequents drinker barJoe King’sJoe Molly’sSue Molly’s serves bar beerKing’s BassKing’s BudMolly’s BassThe main use of a database is to query its data,e.g.,find the drinkers who frequent only bars serving Bass.It turns out that each query expressible in FO can be broken down into a sequence of simple subqueries.2This section is based in part on the article[Imm95].See also the books[EF95,Imm99]for much more information about descriptive complexity.3Codd received the ACM Turing Award for his work leading to the development of relational systems.Each subquery produces an intermediate result,that may be used by subsequent subqueries.A subquery isof the form:where is a literal or,is in the input or is on the left-hand side of a previous subquery inthe sequence,and is not in the input and does not occur previously in the sequence.The meaning of sucha subquery is to assign to the result of the FO query on the structure resulting from the evaluation of the previous subqueries in the sequence.The subqueries provide appealing building blocks forFO queries.This is illustrated by the language QBE,in which a query is formulated as just described.Forexample,consider the following query on the“beer drinker’s”database:Find the drinkers who frequent some bar serving Bass.This can be expressed by a single query of the above form:answer frequents serves BassIn QBE,the query is formulated in a visually appealing way as follows:answer drinker frequents drinker bar serves bar beerBassSimilar building blocks are used in SQL,the standard query language for relational database systems.Let us consider again the query.The naive implementation would have us check,for each drinker and bar,whether holds.The number of checks is then the product of the number of drinkers and the number of bars in the database,which can be roughly in the size of the database.This turns out to be infeasible for very large databases.A better approach,and the one used in practice,makes use of relational algebra.Before discussing how this works,we informally review the algebra’s operators.There are two set operators,(union)and(difference).The selection operator, denoted extracts from the tuples satisfying a condition cond involving(in)equalities of attribute values and constants.For example,beer Bass serves produces the tuples in serves for which the beer is Bass.The projection operator,denoted,projects the tuples of relation on a subset of its attributes.The join operator,denoted by,consists of all tuples over such that and.A last unary operator allows to rename an attribute of a relation without changing its contents.Expressions constructed using relational algebra operators are called relational algebra queries.Thequery is expressed using relational algebra as follows:A result of crucial importance is that FO and relational algebra express precisely the same queries.The key to the efficient implementation of relational algebra queries is twofold.First,individual algebraoperations can be efficiently implemented using data structures called indexes,providing fast access to data.A simple example of such a structure is a binary search tree,which allows locating the tuples with a givenattribute value in time,where is the number of tuples.Second,algebra queries can be simplifiedusing a set of rewriting rules.The query above can be rewritten to the equivalent but more efficient form:drinker frequents bar beer Bass servesThe use of indexes and rewriting rules allows to evaluate the above query at cost roughly in thesize of the database,which is much better than.Indeed,for large databases this can make the differencebetween infeasibility and feasibility.The FO queries turn out to be extremely well-behaved with respect to scaling.Given sufficient resources,response time can in principle be kept constant as the database becomes larger.The key to this remarkableproperty is parallel processing.Admittedly,a lot of processors are needed to achieve this ideal behaviour:polynomial in the size of the database.This is unlikely to be feasible in practice any time soon.The keypoint,however,is that FO query evaluation admits linear scaling;the speed-up is proportional to the numberof parallel processors used.Once again,relational algebra plays a crucial role in the parallel implementation of FO.Indeed,thealgebra operations are set oriented,and thus highlight the intrinsic parallelism in FO queries.For example,consider the projection.The key observation is that one can project the tuples in independently of each other.Given one processor for each tuple in,the projection can be computed in constant time,independent of the number of tuples.As a second example,consider the join.This can be computedby joining all pairs of tuples from and,independently of each other.Thus,if one processor is availablefor each pair,the join can be computed in constant time,independent on the number of tuples in and.Since each algebra operation can be evaluated in constant parallel time,each algebra query can also beevaluated in constant time.The constant depends only on the query and is independent of the size of thedatabase.Of course,more and more processors are needed as the database grows.In practice,the massive parallelism required to achieve perfect scaling is not available.Nevertheless,there are algorithms that can take optimal advantage of a given set of processors.It is also worth noting thatthe processors implementing the algebra need not be powerful,as they are only required to perform veryspecific,simple operations on tuples.In fact,it is sufficient to have processors that can implement the basicBoolean circuit operations.This fact is formalized by a result due to Immerman[Imm87]stating that FOis included in AC,the class of problems solvable by circuits of constant depth and polynomial size,withunbounded fan-in.In conclusion,logic has proven to be a spectacularly effective tool in the database area.FO provides thebasis for the standard query languages,because of its ease of use and efficient implementation via relationalalgebra.FO can achieve linear scaling,given parallel processing resources.Thus,its full potential as a querylanguage remains yet to be realized.A good introduction to the database area may be found in[SKS97],while[Ull88]provides a morein-depth presentation.Thefirst text on database theory is[Mai83],followed more recently by[AHV95].The latter text also described database query languages beyond FO,includingfixpoint logics.An excellentsurvey of relational database theory is provided in[Kan91].The relationship betweenfinite-model theoryand databases is discussed in[Via].4Type Theory in Programming Language ResearchIn the1980’s and1990’s the study of programming languages was revolutionized by a remarkable confluenceof ideas from mathematical and philosophical logic and theoretical computer science.Type theory emergedas a unifying conceptual framework for the design,analysis,and implementation of programming languages.Type theory helps to clarify subtle concepts such as data abstraction,polymorphism,and inheritance.Itprovides a foundation for developing logics of program behavior that are essential for reasoning aboutprograms.It suggests new techniques for implementing compilers that improve the efficiency and integrityof generated code.Type theory is the study of type systems.Reynolds defines a type system to be a“syntactic disciplinefor enforcing levels of abstraction”[Rey85].A type system is a form of context-sensitive grammar thatimposes restrictions on the formation of programs to ensure that a large class of errors,those that arise frommisinterpretation of values,cannot occur.Examples of such errors are:applying a function on the integersto a boolean argument;treating an integer as a pointer to a data structure or a region of executable code;int booltrue false=if then elsefun(:):is()true false fun(:):isThe operator ranges over the arithmetic operations,,and.The variable ranges over numerals for the natural numbers.The variables and are bound in the expression fun(:):is.Figure1:Abstract Syntax of MinMLint int intinttrue bool false boolint int =bool boolif then elsefun(:):is()Figure2:Type System of MinMLover-writing a program’s memory without regard to its purpose or validity;violating the assumptions of a procedure by calling it with too few arguments or arguments of the wrong type.A type system is typically defined by an inductive definition of a typing judgement of the form. Here is an expression,is its type,and assigns types to the global variables that may occur within. The typing judgement is defined to be the least three-place relation closed under a given collection of typing rules that determine whether or not an expression is well-typed.The abstract syntax of an illustrative fragment of the ML language is given in Figure1.Its type system is given in Figure2.Note that the language constructs are grouped according to their type.Each type comes with expressions to denote its values together with operations for manipulating those values in a computation.The rules governing the function type constructor exhibit an intriguing similarity to the introduction and elimination rules for implication in Gentzen’s system of natural deduction.This similarity is not accidental: according to the propositions-as-types principle[CF58,CHS72,How80]there is an isomorphism between propositions and types with the property that the natural deduction proofs of a proposition correspond to the elements of its associated type.This principle extends to the full range of logical connectives and quantifiers, including those of second-and higher-order logic.An operational semantics defines how to execute programs.It is useful to define the operational se-mantics of a language as a transition relation between states of an abstract machine,with certain states=====true false()()()()fun(:):is ()The notation stands for the result of substitution for free occurrences of and for freeoccurrences of in the expression.Figure3:Operational Semantics of MinMLdesignated asfinal states.For the illustrative language of Figure2the states of the abstract machine are closed expressions;thefinal states are the fully-evaluated expressions.The transition relation is given in Figure3using Plotkin’s technique of structured operational semantics[Plo81].These rules constitute an inductive definition of the call-by-value evaluation strategy,in which function arguments are evaluated prior to application,and for which function expressions are fully evaluated.One role of a type system is to preclude execution errors arising from misinterpretation of values. Theorem1:[Type Soundness]If,then either is fully evaluated or there exists such thatand.A type error is an expression such that is not a value,yet there is no such that.In practice type errors correspond to illegal instructions or memory faults;the type soundness theorem ensures that well-typed programs never incur such errors.The structure of more realistic programming languages can be described using very similar techniques. According to the type-theoretic viewpoint programming language“features”correspond to types.The fol-lowing chart summarizes some of the main correspondences:Concept Type Values Operationsbooleans bool true,false conditionalintegers int integer numerals integer arithmeticfloating point float f.p.numerals f.p.arithmetictuples ordered pairs component projectiondisjoint union tagged values case analysisprocedures procedure definition procedure callrecursive types heap pointers traversalpolymorphism templates,generics instantiationdata abstraction packages,modules opening a packagemutable storage ref storage cells update,retrievetagging any tagged values dynamic dispatch Organizing programming languages by their type structure has a number of benefits.We mention a few salient ones here.First,language concepts are presented modularly,avoiding confusion or conflation。
专八英语阅读

英语专业八级考试TEM-8阅读理解练习册(1)(英语专业2012级)UNIT 1Text AEvery minute of every day, what ecologist生态学家James Carlton calls a global ―conveyor belt‖, redistributes ocean organisms生物.It’s planetwide biological disruption生物的破坏that scientists have barely begun to understand.Dr. Carlton —an oceanographer at Williams College in Williamstown,Mass.—explains that, at any given moment, ―There are several thousand marine species traveling… in the ballast water of ships.‖ These creatures move from coastal waters where they fit into the local web of life to places where some of them could tear that web apart. This is the larger dimension of the infamous无耻的,邪恶的invasion of fish-destroying, pipe-clogging zebra mussels有斑马纹的贻贝.Such voracious贪婪的invaders at least make their presence known. What concerns Carlton and his fellow marine ecologists is the lack of knowledge about the hundreds of alien invaders that quietly enter coastal waters around the world every day. Many of them probably just die out. Some benignly亲切地,仁慈地—or even beneficially — join the local scene. But some will make trouble.In one sense, this is an old story. Organisms have ridden ships for centuries. They have clung to hulls and come along with cargo. What’s new is the scale and speed of the migrations made possible by the massive volume of ship-ballast water压载水— taken in to provide ship stability—continuously moving around the world…Ships load up with ballast water and its inhabitants in coastal waters of one port and dump the ballast in another port that may be thousands of kilometers away. A single load can run to hundreds of gallons. Some larger ships take on as much as 40 million gallons. The creatures that come along tend to be in their larva free-floating stage. When discharged排出in alien waters they can mature into crabs, jellyfish水母, slugs鼻涕虫,蛞蝓, and many other forms.Since the problem involves coastal species, simply banning ballast dumps in coastal waters would, in theory, solve it. Coastal organisms in ballast water that is flushed into midocean would not survive. Such a ban has worked for North American Inland Waterway. But it would be hard to enforce it worldwide. Heating ballast water or straining it should also halt the species spread. But before any such worldwide regulations were imposed, scientists would need a clearer view of what is going on.The continuous shuffling洗牌of marine organisms has changed the biology of the sea on a global scale. It can have devastating effects as in the case of the American comb jellyfish that recently invaded the Black Sea. It has destroyed that sea’s anchovy鳀鱼fishery by eating anchovy eggs. It may soon spread to western and northern European waters.The maritime nations that created the biological ―conveyor belt‖ should support a coordinated international effort to find out what is going on and what should be done about it. (456 words)1.According to Dr. Carlton, ocean organism‟s are_______.A.being moved to new environmentsB.destroying the planetC.succumbing to the zebra musselD.developing alien characteristics2.Oceanographers海洋学家are concerned because_________.A.their knowledge of this phenomenon is limitedB.they believe the oceans are dyingC.they fear an invasion from outer-spaceD.they have identified thousands of alien webs3.According to marine ecologists, transplanted marinespecies____________.A.may upset the ecosystems of coastal watersB.are all compatible with one anotherC.can only survive in their home watersD.sometimes disrupt shipping lanes4.The identified cause of the problem is_______.A.the rapidity with which larvae matureB. a common practice of the shipping industryC. a centuries old speciesD.the world wide movement of ocean currents5.The article suggests that a solution to the problem__________.A.is unlikely to be identifiedB.must precede further researchC.is hypothetically假设地,假想地easyD.will limit global shippingText BNew …Endangered‟ List Targets Many US RiversIt is hard to think of a major natural resource or pollution issue in North America today that does not affect rivers.Farm chemical runoff残渣, industrial waste, urban storm sewers, sewage treatment, mining, logging, grazing放牧,military bases, residential and business development, hydropower水力发电,loss of wetlands. The list goes on.Legislation like the Clean Water Act and Wild and Scenic Rivers Act have provided some protection, but threats continue.The Environmental Protection Agency (EPA) reported yesterday that an assessment of 642,000 miles of rivers and streams showed 34 percent in less than good condition. In a major study of the Clean Water Act, the Natural Resources Defense Council last fall reported that poison runoff impairs损害more than 125,000 miles of rivers.More recently, the NRDC and Izaak Walton League warned that pollution and loss of wetlands—made worse by last year’s flooding—is degrading恶化the Mississippi River ecosystem.On Tuesday, the conservation group保护组织American Rivers issued its annual list of 10 ―endangered‖ and 20 ―threatened‖ rivers in 32 states, the District of Colombia, and Canada.At the top of the list is the Clarks Fork of the Yellowstone River, whereCanadian mining firms plan to build a 74-acre英亩reservoir水库,蓄水池as part of a gold mine less than three miles from Yellowstone National Park. The reservoir would hold the runoff from the sulfuric acid 硫酸used to extract gold from crushed rock.―In the event this tailings pond failed, the impact to th e greater Yellowstone ecosystem would be cataclysmic大变动的,灾难性的and the damage irreversible不可逆转的.‖ Sen. Max Baucus of Montana, chairman of the Environment and Public Works Committee, wrote to Noranda Minerals Inc., an owner of the ― New World Mine‖.Last fall, an EPA official expressed concern about the mine and its potential impact, especially the plastic-lined storage reservoir. ― I am unaware of any studies evaluating how a tailings pond尾矿池,残渣池could be maintained to ensure its structural integrity forev er,‖ said Stephen Hoffman, chief of the EPA’s Mining Waste Section. ―It is my opinion that underwater disposal of tailings at New World may present a potentially significant threat to human health and the environment.‖The results of an environmental-impact statement, now being drafted by the Forest Service and Montana Department of State Lands, could determine the mine’s future…In its recent proposal to reauthorize the Clean Water Act, the Clinton administration noted ―dramatically improved water quality since 1972,‖ when the act was passed. But it also reported that 30 percent of riverscontinue to be degraded, mainly by silt泥沙and nutrients from farm and urban runoff, combined sewer overflows, and municipal sewage城市污水. Bottom sediments沉积物are contaminated污染in more than 1,000 waterways, the administration reported in releasing its proposal in January. Between 60 and 80 percent of riparian corridors (riverbank lands) have been degraded.As with endangered species and their habitats in forests and deserts, the complexity of ecosystems is seen in rivers and the effects of development----beyond the obvious threats of industrial pollution, municipal waste, and in-stream diversions改道to slake消除the thirst of new communities in dry regions like the Southwes t…While there are many political hurdles障碍ahead, reauthorization of the Clean Water Act this year holds promise for US rivers. Rep. Norm Mineta of California, who chairs the House Committee overseeing the bill, calls it ―probably the most important env ironmental legislation this Congress will enact.‖ (553 words)6.According to the passage, the Clean Water Act______.A.has been ineffectiveB.will definitely be renewedC.has never been evaluatedD.was enacted some 30 years ago7.“Endangered” rivers are _________.A.catalogued annuallyB.less polluted than ―threatened rivers‖C.caused by floodingD.adjacent to large cities8.The “cataclysmic” event referred to in paragraph eight would be__________.A. fortuitous偶然的,意外的B. adventitious外加的,偶然的C. catastrophicD. precarious不稳定的,危险的9. The owners of the New World Mine appear to be______.A. ecologically aware of the impact of miningB. determined to construct a safe tailings pondC. indifferent to the concerns voiced by the EPAD. willing to relocate operations10. The passage conveys the impression that_______.A. Canadians are disinterested in natural resourcesB. private and public environmental groups aboundC. river banks are erodingD. the majority of US rivers are in poor conditionText CA classic series of experiments to determine the effects ofoverpopulation on communities of rats was reported in February of 1962 in an article in Scientific American. The experiments were conducted by a psychologist, John B. Calhoun and his associates. In each of these experiments, an equal number of male and female adult rats were placed in an enclosure and given an adequate supply of food, water, and other necessities. The rat populations were allowed to increase. Calhoun knew from experience approximately how many rats could live in the enclosures without experiencing stress due to overcrowding. He allowed the population to increase to approximately twice this number. Then he stabilized the population by removing offspring that were not dependent on their mothers. He and his associates then carefully observed and recorded behavior in these overpopulated communities. At the end of their experiments, Calhoun and his associates were able to conclude that overcrowding causes a breakdown in the normal social relationships among rats, a kind of social disease. The rats in the experiments did not follow the same patterns of behavior as rats would in a community without overcrowding.The females in the rat population were the most seriously affected by the high population density: They showed deviant异常的maternal behavior; they did not behave as mother rats normally do. In fact, many of the pups幼兽,幼崽, as rat babies are called, died as a result of poor maternal care. For example, mothers sometimes abandoned their pups,and, without their mothers' care, the pups died. Under normal conditions, a mother rat would not leave her pups alone to die. However, the experiments verified that in overpopulated communities, mother rats do not behave normally. Their behavior may be considered pathologically 病理上,病理学地diseased.The dominant males in the rat population were the least affected by overpopulation. Each of these strong males claimed an area of the enclosure as his own. Therefore, these individuals did not experience the overcrowding in the same way as the other rats did. The fact that the dominant males had adequate space in which to live may explain why they were not as seriously affected by overpopulation as the other rats. However, dominant males did behave pathologically at times. Their antisocial behavior consisted of attacks on weaker male,female, and immature rats. This deviant behavior showed that even though the dominant males had enough living space, they too were affected by the general overcrowding in the enclosure.Non-dominant males in the experimental rat communities also exhibited deviant social behavior. Some withdrew completely; they moved very little and ate and drank at times when the other rats were sleeping in order to avoid contact with them. Other non-dominant males were hyperactive; they were much more active than is normal, chasing other rats and fighting each other. This segment of the rat population, likeall the other parts, was affected by the overpopulation.The behavior of the non-dominant males and of the other components of the rat population has parallels in human behavior. People in densely populated areas exhibit deviant behavior similar to that of the rats in Calhoun's experiments. In large urban areas such as New York City, London, Mexican City, and Cairo, there are abandoned children. There are cruel, powerful individuals, both men and women. There are also people who withdraw and people who become hyperactive. The quantity of other forms of social pathology such as murder, rape, and robbery also frequently occur in densely populated human communities. Is the principal cause of these disorders overpopulation? Calhoun’s experiments suggest that it might be. In any case, social scientists and city planners have been influenced by the results of this series of experiments.11. Paragraph l is organized according to__________.A. reasonsB. descriptionC. examplesD. definition12.Calhoun stabilized the rat population_________.A. when it was double the number that could live in the enclosure without stressB. by removing young ratsC. at a constant number of adult rats in the enclosureD. all of the above are correct13.W hich of the following inferences CANNOT be made from theinformation inPara. 1?A. Calhoun's experiment is still considered important today.B. Overpopulation causes pathological behavior in rat populations.C. Stress does not occur in rat communities unless there is overcrowding.D. Calhoun had experimented with rats before.14. Which of the following behavior didn‟t happen in this experiment?A. All the male rats exhibited pathological behavior.B. Mother rats abandoned their pups.C. Female rats showed deviant maternal behavior.D. Mother rats left their rat babies alone.15. The main idea of the paragraph three is that __________.A. dominant males had adequate living spaceB. dominant males were not as seriously affected by overcrowding as the otherratsC. dominant males attacked weaker ratsD. the strongest males are always able to adapt to bad conditionsText DThe first mention of slavery in the statutes法令,法规of the English colonies of North America does not occur until after 1660—some forty years after the importation of the first Black people. Lest we think that existed in fact before it did in law, Oscar and Mary Handlin assure us, that the status of B lack people down to the 1660’s was that of servants. A critique批判of the Handlins’ interpretation of why legal slavery did not appear until the 1660’s suggests that assumptions about the relation between slavery and racial prejudice should be reexamined, and that explanation for the different treatment of Black slaves in North and South America should be expanded.The Handlins explain the appearance of legal slavery by arguing that, during the 1660’s, the position of white servants was improving relative to that of black servants. Thus, the Handlins contend, Black and White servants, heretofore treated alike, each attained a different status. There are, however, important objections to this argument. First, the Handlins cannot adequately demonstrate that t he White servant’s position was improving, during and after the 1660’s; several acts of the Maryland and Virginia legislatures indicate otherwise. Another flaw in the Handlins’ interpretation is their assumption that prior to the establishment of legal slavery there was no discrimination against Black people. It is true that before the 1660’s Black people were rarely called slaves. But this shouldnot overshadow evidence from the 1630’s on that points to racial discrimination without using the term slavery. Such discrimination sometimes stopped short of lifetime servitude or inherited status—the two attributes of true slavery—yet in other cases it included both. The Handlins’ argument excludes the real possibility that Black people in the English colonies were never treated as the equals of White people.The possibility has important ramifications后果,影响.If from the outset Black people were discriminated against, then legal slavery should be viewed as a reflection and an extension of racial prejudice rather than, as many historians including the Handlins have argued, the cause of prejudice. In addition, the existence of discrimination before the advent of legal slavery offers a further explanation for the harsher treatment of Black slaves in North than in South America. Freyre and Tannenbaum have rightly argued that the lack of certain traditions in North America—such as a Roman conception of slavery and a Roman Catholic emphasis on equality— explains why the treatment of Black slaves was more severe there than in the Spanish and Portuguese colonies of South America. But this cannot be the whole explanation since it is merely negative, based only on a lack of something. A more compelling令人信服的explanation is that the early and sometimes extreme racial discrimination in the English colonies helped determine the particular nature of the slavery that followed. (462 words)16. Which of the following is the most logical inference to be drawn from the passage about the effects of “several acts of the Maryland and Virginia legislatures” (Para.2) passed during and after the 1660‟s?A. The acts negatively affected the pre-1660’s position of Black as wellas of White servants.B. The acts had the effect of impairing rather than improving theposition of White servants relative to what it had been before the 1660’s.C. The acts had a different effect on the position of white servants thandid many of the acts passed during this time by the legislatures of other colonies.D. The acts, at the very least, caused the position of White servants toremain no better than it had been before the 1660’s.17. With which of the following statements regarding the status ofBlack people in the English colonies of North America before the 1660‟s would the author be LEAST likely to agree?A. Although black people were not legally considered to be slaves,they were often called slaves.B. Although subject to some discrimination, black people had a higherlegal status than they did after the 1660’s.C. Although sometimes subject to lifetime servitude, black peoplewere not legally considered to be slaves.D. Although often not treated the same as White people, black people,like many white people, possessed the legal status of servants.18. According to the passage, the Handlins have argued which of thefollowing about the relationship between racial prejudice and the institution of legal slavery in the English colonies of North America?A. Racial prejudice and the institution of slavery arose simultaneously.B. Racial prejudice most often the form of the imposition of inheritedstatus, one of the attributes of slavery.C. The source of racial prejudice was the institution of slavery.D. Because of the influence of the Roman Catholic Church, racialprejudice sometimes did not result in slavery.19. The passage suggests that the existence of a Roman conception ofslavery in Spanish and Portuguese colonies had the effect of _________.A. extending rather than causing racial prejudice in these coloniesB. hastening the legalization of slavery in these colonies.C. mitigating some of the conditions of slavery for black people in these coloniesD. delaying the introduction of slavery into the English colonies20. The author considers the explanation put forward by Freyre andTannenbaum for the treatment accorded B lack slaves in the English colonies of North America to be _____________.A. ambitious but misguidedB. valid有根据的but limitedC. popular but suspectD. anachronistic过时的,时代错误的and controversialUNIT 2Text AThe sea lay like an unbroken mirror all around the pine-girt, lonely shores of Orr’s Island. Tall, kingly spruce s wore their regal王室的crowns of cones high in air, sparkling with diamonds of clear exuded gum流出的树胶; vast old hemlocks铁杉of primeval原始的growth stood darkling in their forest shadows, their branches hung with long hoary moss久远的青苔;while feathery larches羽毛般的落叶松,turned to brilliant gold by autumn frosts, lighted up the darker shadows of the evergreens. It was one of those hazy朦胧的, calm, dissolving days of Indian summer, when everything is so quiet that the fainest kiss of the wave on the beach can be heard, and white clouds seem to faint into the blue of the sky, and soft swathing一长条bands of violet vapor make all earth look dreamy, and give to the sharp, clear-cut outlines of the northern landscape all those mysteries of light and shade which impart such tenderness to Italian scenery.The funeral was over,--- the tread鞋底的花纹/ 踏of many feet, bearing the heavy burden of two broken lives, had been to the lonely graveyard, and had come back again,--- each footstep lighter and more unconstrained不受拘束的as each one went his way from the great old tragedy of Death to the common cheerful of Life.The solemn black clock stood swaying with its eternal ―tick-tock, tick-tock,‖ in the kitchen of the brown house on Orr’s Island. There was there that sense of a stillness that can be felt,---such as settles down on a dwelling住处when any of its inmates have passed through its doors for the last time, to go whence they shall not return. The best room was shut up and darkened, with only so much light as could fall through a little heart-shaped hole in the window-shutter,---for except on solemn visits, or prayer-meetings or weddings, or funerals, that room formed no part of the daily family scenery.The kitchen was clean and ample, hearth灶台, and oven on one side, and rows of old-fashioned splint-bottomed chairs against the wall. A table scoured to snowy whiteness, and a little work-stand whereon lay the Bible, the Missionary Herald, and the Weekly Christian Mirror, before named, formed the principal furniture. One feature, however, must not be forgotten, ---a great sea-chest水手用的储物箱,which had been the companion of Zephaniah through all the countries of the earth. Old, and battered破旧的,磨损的, and unsightly难看的it looked, yet report said that there was good store within which men for the most part respect more than anything else; and, indeed it proved often when a deed of grace was to be done--- when a woman was suddenly made a widow in a coast gale大风,狂风, or a fishing-smack小渔船was run down in the fogs off the banks, leaving in some neighboring cottage a family of orphans,---in all such cases, the opening of this sea-chest was an event of good omen 预兆to the bereaved丧亲者;for Zephaniah had a large heart and a large hand, and was apt有…的倾向to take it out full of silver dollars when once it went in. So the ark of the covenant约柜could not have been looked on with more reverence崇敬than the neighbours usually showed to Captain Pennel’s sea-chest.1. The author describes Orr‟s Island in a(n)______way.A.emotionally appealing, imaginativeB.rational, logically preciseC.factually detailed, objectiveD.vague, uncertain2.According to the passage, the “best room”_____.A.has its many windows boarded upB.has had the furniture removedC.is used only on formal and ceremonious occasionsD.is the busiest room in the house3.From the description of the kitchen we can infer that thehouse belongs to people who_____.A.never have guestsB.like modern appliancesC.are probably religiousD.dislike housework4.The passage implies that_______.A.few people attended the funeralB.fishing is a secure vocationC.the island is densely populatedD.the house belonged to the deceased5.From the description of Zephaniah we can see thathe_________.A.was physically a very big manB.preferred the lonely life of a sailorC.always stayed at homeD.was frugal and saved a lotText BBasic to any understanding of Canada in the 20 years after the Second World War is the country' s impressive population growth. For every three Canadians in 1945, there were over five in 1966. In September 1966 Canada's population passed the 20 million mark. Most of this surging growth came from natural increase. The depression of the 1930s and the war had held back marriages, and the catching-up process began after 1945. The baby boom continued through the decade of the 1950s, producing a population increase of nearly fifteen percent in the five years from 1951 to 1956. This rate of increase had been exceeded only once before in Canada's history, in the decade before 1911 when the prairies were being settled. Undoubtedly, the good economic conditions of the 1950s supported a growth in the population, but the expansion also derived from a trend toward earlier marriages and an increase in the average size of families; In 1957 the Canadian birth rate stood at 28 per thousand, one of the highest in the world. After the peak year of 1957, thebirth rate in Canada began to decline. It continued falling until in 1966 it stood at the lowest level in 25 years. Partly this decline reflected the low level of births during the depression and the war, but it was also caused by changes in Canadian society. Young people were staying at school longer, more women were working; young married couples were buying automobiles or houses before starting families; rising living standards were cutting down the size of families. It appeared that Canada was once more falling in step with the trend toward smaller families that had occurred all through theWestern world since the time of the Industrial Revolution. Although the growth in Canada’s population had slowed down by 1966 (the cent), another increase in the first half of the 1960s was only nine percent), another large population wave was coming over the horizon. It would be composed of the children of the children who were born during the period of the high birth rate prior to 1957.6. What does the passage mainly discuss?A. Educational changes in Canadian society.B. Canada during the Second World War.C. Population trends in postwar Canada.D. Standards of living in Canada.7. According to the passage, when did Canada's baby boom begin?A. In the decade after 1911.B. After 1945.C. During the depression of the 1930s.D. In 1966.8. The author suggests that in Canada during the 1950s____________.A. the urban population decreased rapidlyB. fewer people marriedC. economic conditions were poorD. the birth rate was very high9. When was the birth rate in Canada at its lowest postwar level?A. 1966.B. 1957.C. 1956.D. 1951.10. The author mentions all of the following as causes of declines inpopulation growth after 1957 EXCEPT_________________.A. people being better educatedB. people getting married earlierC. better standards of livingD. couples buying houses11.I t can be inferred from the passage that before the IndustrialRevolution_______________.A. families were largerB. population statistics were unreliableC. the population grew steadilyD. economic conditions were badText CI was just a boy when my father brought me to Harlem for the first time, almost 50 years ago. We stayed at the hotel Theresa, a grand brick structure at 125th Street and Seventh avenue. Once, in the hotel restaurant, my father pointed out Joe Louis. He even got Mr. Brown, the hotel manager, to introduce me to him, a bit punchy强力的but still champ焦急as fast as I was concerned.Much has changed since then. Business and real estate are booming. Some say a new renaissance is under way. Others decry责难what they see as outside forces running roughshod肆意践踏over the old Harlem. New York meant Harlem to me, and as a young man I visited it whenever I could. But many of my old haunts are gone. The Theresa shut down in 1966. National chains that once ignored Harlem now anticipate yuppie money and want pieces of this prime Manhattan real estate. So here I am on a hot August afternoon, sitting in a Starbucks that two years ago opened a block away from the Theresa, snatching抓取,攫取at memories between sips of high-priced coffee. I am about to open up a piece of the old Harlem---the New York Amsterdam News---when a tourist。
英文版计算机试题及答案

英文版计算机试题及答案一、选择题(每题2分,共20分)1. Which of the following is not a function of an operating system?A. Process managementB. Memory managementC. Data storageD. File management2. In a computer network, what does the term "bandwidth" refer to?A. The width of the network cableB. The maximum rate of data transferC. The number of users connectedD. The speed of the network processor3. What is the primary purpose of a firewall?A. To prevent unauthorized access to a networkB. To encrypt dataC. To manage network trafficD. To store user passwords4. Which of the following is a type of software used for creating and editing documents?A. Spreadsheet softwareB. Database softwareC. Word processing softwareD. Graphics software5. What is the term used to describe the process of converting data from one format to another?A. Data migrationB. Data transformationC. Data conversionD. Data translation6. What does the acronym "CPU" stand for in computing?A. Central Processing UnitB. Central Processing UnitC. Computer Processing UnitD. Computing Processing Unit7. What is the function of a router in a network?A. To connect multiple networksB. To store dataC. To provide power to devicesD. To print documents8. What is the process of finding and fixing errors in software called?A. DebuggingB. PatchingC. UpdatingD. Patching9. Which of the following is a type of computer virus that replicates itself by attaching to other programs?A. TrojanB. WormC. RansomwareD. Spyware10. What is the term for the graphical representation of data on a computer screen?A. Data visualizationB. Data representationC. Data graphingD. Data mapping二、填空题(每题2分,共20分)1. The _________ is the primary memory used by a computer to store data and instructions that are currently being processed.2. A _________ is a type of software that allows users to create and edit images.3. The process of converting analog signals to digital signals is known as _________.4. A _________ is a collection of data stored in a structured format.5. The _________ is a hardware component that connects a computer to a network.6. In computer programming, a _________ is a sequence of statements that perform a specific task.7. The _________ is a type of malware that hides its presence and waits for a trigger to activate.8. A _________ is a type of software that is designed to protect a computer from unauthorized access.9. The _________ is the process of organizing and managing data in a database.10. A _________ is a type of software that allows users tocreate and edit spreadsheets.三、简答题(每题10分,共30分)1. Describe the role of a server in a computer network.2. Explain the difference between a compiler and an interpreter in programming.3. Discuss the importance of data backup and recovery in a computing environment.四、编程题(每题15分,共30分)1. Write a simple program in Python that calculates the factorial of a given number.2. Create a function in Java that takes an array of integers and returns the largest number in the array.答案:一、选择题1. C2. B3. A4. C5. C6. A7. A8. A9. B10. A二、填空题1. RAM (Random Access Memory)2. Graphics software3. Analog-to-digital conversion4. Database5. Network interface card (NIC)6. Function or procedure7. Trojan8. Antivirus software9. Database management10. Spreadsheet software三、简答题1. A server in a computer network is a powerful computer or system that manages network resources, including hardware and software, and provides services to other computers on the network, such as file storage, web hosting, and print services.2. A compiler is a program that translates source codewritten in a programming language into machine code that a computer can execute. An interpreter, on the other hand, reads and executes the source code line by line without the need for a separate compilation step.3. Data backup and recovery are crucial in a computing environment to prevent data loss due to hardware failure, software bugs, or malicious attacks. Regular backups ensure that data can be restored to a previous state in case of corruption or deletion.四、编程题1. Python Program for Factorial Calculation:```pythondef factorial(n):if n == 0:return 1 else:。
Chapter1 Computer System Overview

C HAPTER 1C OMPUTER S YSTEM O VERVIEWR EVIEW Q UESTIONS1.1 List and briefly define the four main elements of a computer.1.2 Define the two main categories of processor registers.1.3 In general terms, what are the four distinct actions that a machine instruction can specify?1.4 What is an interrupt?1.5 How are multiple interrupts dealt with?1.6 What characteristics distinguish the various elements of a memory hierarchy?1.7 What is cache memory?1.8 List and briefly define three techniques for I/O operations.1.9 What is the distinction between spatial locality and temporal locality?1.10 In general, what are the strategies for exploiting spatial locality and temporal locality?P ROBLEMS1.1 Suppose the hypothetical processor of Figure 1.3 also has two I/O instructions:0011 = Load AC from I/O0111 = Store AC to I/OIn these cases, the 12-bit address identifies a particular external device. Show theprogram execution (using format of Figure 1.4) for the following program:1. Load AC from device 5.2. Add contents of memory location 940.3. Store AC to device 6.Assume that the next value retrieved from device 5 is 3 and that location 940contains a value of 2.1.2 The program execution of Figure 1.4 is described in the text using six steps.Expandthis description to show the use of the MAR and MBR.1.3 Consider a hypothetical 32-bit microprocessor having 32-bit instructionscomposed of two fields. The first byte contains the opcode and the remainder animmediate operand or an operand address.a. What is the maximum directly addressable memory capacity (in bytes)?b. Discuss the impact on the system speed if the microprocessor bus has1. a 32-bit local address bus and a 16-bit local data bus, or2. a 16-bit local address bus and a 16-bit local data bus.c. How many bits are needed for the program counter and the instructionregister?1.4 Consider a hypothetical microprocessor generating a 16-bit address (for example,assume that the program counter and the address registers are 16 bits wide) andhaving a 16-bit data bus.a. What is the maximum memory address space that the processor can accessdirectly if it is connected to a “16-bit memory”?b. What is the maximum memory address space that the processor can accessdirectly if it is connected to an “8-bit memory”?c. What architectural features will allow this microprocessor to access a separate“I/O space”?d. If an input and an output instruction can specify an 8-bit I/O port number, howmany 8-bit I/O ports can the microprocessor support? How many 16-bit I/O ports?Explain.1.5 Consider a 32-bit microprocessor, with a 16-bit external data bus, driven by an8-MHz input clock.Assume that this microprocessor has a bus cycle whose minimum duration equals four input clock cycles.What is the maximum data transfer rate across the bus that this microprocessor can sustain in bytes/s? To increase its performance, would it be better to make its external data bus 32 bits or to double the external clock frequency supplied to the microprocessor? State any other assumptions you make and explain. Hint: Determine the number of bytes that can be transferred per bus cycle.1.6 Consider a computer system that contains an I/O module controlling a simplekeyboard/printer Teletype.The following registers are contained in the CPU and connected directly to the system bus:INPR: Input Register, 8 bitsOUTR: Output Register, 8 bitsFGI: Input Flag, 1 bitFGO: Output Flag, 1 bitIEN: Interrupt Enable, 1 bitKeystroke input from the Teletype and output to the printer are controlled by the I/O module.The Teletype is able to encode an alphanumeric symbol to an 8-bit word and decode an 8-bit word into an alphanumeric symbol.The Input flag is set when an 8-bit word enters the input register from the Teletype. The Output flag is set when a word is printed.a. Describe how the CPU, using the first four registers listed in this problem, canachieve I/O with the Teletype.b. Describe how the function can be performed more efficiently by also employingIEN.1.7 In virtually all systems that include DMA modules, DMA access to main memoryis given higher priority than processor access to main memory.Why?1.8 A DMA module is transferring characters to main memory from an externaldevice transmitting at 9600 bits per second (bps).The processor can fetchinstructions at the rate of 1 million instructions per second. By how much will the processor be slowed down due to the DMA activity?1.9 A computer consists of a CPU and an I/O device D connected to main memory Mvia a shared bus with a data bus width of one word.The CPU can execute a maximum of106 instructions per second. An average instruction requires five processor cycles,three of which use the memory bus. A memory read or write operation uses one processor cycle. Suppose that the CPU is continuously executing “background”programs that require 95% of its instruction executionrate but not any I/O instructions.Assume that one processor cycle equals one bus cycle. Now suppose that very large blocks of data are to be transferred between M and D.a. If programmed I/O is used and each one-word I/O transfer requires the CPU toexecute two instructions, estimate the maximum I/O data transfer rate, in words per second, possible through D.b. Estimate the same rate if DMA transfer is used.1.10 Consider the following code:for (i = 0; i < 20; i++)for (j = 0; j<10; j++)a[i] = a[i] * ja. Give one example of the spatial locality in the code.b. Give one example of the temporal locality in the code.1.11 Generalize Equations (1.1) and (1.2) in Appendix 1 A to n-level memory hierarchies.1.12 Consider a memory system with the following parameters:Tc = 100 ns Cc = 0.01 cents/bitTm = 1200 ns Cm = 0.001 cents/bita. What is the cost of 1 MByte of main memory?b. What is the cost of 1 MByte of main memory using cache memorytechnology?c. If the effective access time is 10% greater than the cache access time, what isthe hit ratio H?1.13 A computer has a cache, main memory, and a disk used for virtual memory. If areferenced word is in the cache, 20 ns are required to access it. If it is in mainmemory but not in the cache, 60 ns are needed to load it into the cache (thisincludes the time to originally check the cache), and then the reference is startedagain. If the word is not in main memory, 12 ms are required to fetch the wordfrom disk, followed by 60 ns to copy it to the cache, and then the reference isstarted again. The cache hit ratio is 0.9 and the main-memory hit ratio is 0.6.What is the average time in ns required to access a referenced word on this system?1.14 Suppose a stack is to be used by the processor to manage procedure calls andreturns. Can the program counter be eliminated by using the top of the stack as a program counter?A NSWERS TO Q UESTIONS1.1 List and briefly define the four main elements of a computer.A main memory, which stores both data and instructions: an arithmetic and logicunit (ALU) capable of operating on binary data; a control unit, which interpretsthe instructions in memory and causes them to be executed; and input and output(I/O) equipment operated by the control unit.1.2 Define the two main categories of processor registers.User-visible registers: Enable the machine- or assembly-language programmer tominimize main memory references by optimizing register use. For high-levellanguages, an optimizing compiler will attempt to make intelligent choices ofwhich variables to assign to registers and which to main memory locations. Somehigh-level languages, such as C, allow the programmer to suggest to the compilerwhich variables should be held in registers. Control and status registers: Used bythe processor to control the operation of the processor and by privileged,operating system routines to control the execution of programs.1.3 In general terms, what are the four distinct actions that a machine instruction can specify?These actions fall into four categories: Processor-memory: Data may betransferred from processor to memory or from memory to processor.Processor-I/O: Data may be transferred to or from a peripheral device bytransferring between the processor and an I/O module. Data processing: Theprocessor may perform some arithmetic or logic operation on data. Control: Aninstruction may specify that the sequence of execution be altered.1.4 What is an interrupt?An interrupt is a mechanism by which other modules (I/O, memory) may interruptthe normal sequencing of the processor.1.5 How are multiple interrupts dealt with?Two approaches can be taken to dealing with multiple interrupts. The first is todisable interrupts while an interrupt is being processed. A second approach is todefine priorities for interrupts and to allow an interrupt of higher priority to causea lower-priority interrupt handler to be interrupted.1.6 What characteristics distinguish the various elements of a memory hierarchy?The three key characteristics of memory are cost, capacity, and access time.1.7 What is cache memory?Cache memory is a memory that is smaller and faster than main memory and that is interposed between the processor and main memory. The cache acts as a buffer for recently used memory locations.1.8 List and briefly define three techniques for I/O operations.Programmed I/O: The processor issues an I/O command, on behalf of a process, to an I/O module; that process then busy-waits for the operation to be completed before proceeding. Interrupt-driven I/O: The processor issues an I/O command on behalf of a process, continues to execute subsequent instructions, and isinterrupted by the I/O module when the latter has completed its work. Thesubsequent instructions may be in the same process, if it is not necessary for that process to wait for the completion of the I/O. Otherwise, the process is suspended pending the interrupt and other work is performed. Direct memory access (DMA):A DMA module controls the exchange of data between main memory and an I/Omodule. The processor sends a request for the transfer of a block of data to theDMA module and is interrupted only after the entire block has been transferred.1.9 What is the distinction between spatial locality and temporal locality?Spatial locality refers to the tendency of execution to involve a number ofmemory locations that are clustered. Temporal locality refers to the tendency fora processor to access memory locations that have been used recently.1.10 In general, what are the strategies for exploiting spatial locality and temporallocality?Spatial locality is generally exploited by using larger cache blocks and byincorporating prefetching mechanisms (fetching items of anticipated use) intothe cache control logic. Temporal locality is exploited by keeping recently used instruction and data values in cache memory and by exploiting a cachehierarchy.Answers to Problems1.1 Suppose the hypothetical processor of Figure 1.3 also has two I/O instructions:0011 = Load AC from I/O0111 =Store AC to I/OIn these cases, the 12-bit address identifies a particular external device. Show the program execution (using format of Figure 1.4) for the following program:1. Load AC from device 5.2. Add contents of memory location 940.3. Store AC to device 6.Assume that the next value retrieved from device 5 is 3 and that location 940 contains a value of 2.Memory (contents in hex): 300: 3005; 301: 5940; 302: 7006Step 1: 3005 IR; Step 2: 3 ACStep 3: 5940 IR; Step 4: 3 + 2 = 5 ACStep 5: 7006 IR; Step 6: AC Device 61.2 The program execution of Figure 1.4 is described in the text using six steps.Expand this description to show the use of the MAR and MBR.1. a. The PC contains 300, the address of the first instruction. This value isloaded in to the MAR.b. The value in location 300 (which is the instruction with the value 1940 inhexadecimal) is loaded into the MBR, and the PC is incremented.These two steps can be done in parallel.c. The value in the MBR is loaded into the IR.2. a. The address portion of the IR (940) is loaded into the MAR.b. The value in location 940 is loaded into the MBR.c. The value in the MBR is loaded into the AC.3. a. The value in the PC (301) is loaded in to the MAR.b. The value in location 301 (which is the instruction with the value 5941)is loaded into the MBR, and the PC is incremented.c. The value in the MBR is loaded into the IR.4. a. The address portion of the IR (941) is loaded into the MAR.b. The value in location 941 is loaded into the MBR.c. The old value of the AC and the value of location MBR are added andthe result is stored in the AC.5. a. The value in the PC (302) is loaded in to the MAR.b. The value in location 302 (which is the instruction with the value 2941)is loaded into the MBR, and the PC is incremented.c. The value in the MBR is loaded into the IR.6. a. The address portion of the IR (941) is loaded into the MAR.b. The value in the AC is loaded into the MBR.c. The value in the MBR is stored in location 941.1.3 Consider a hypothetical 32-bit microprocessor having 32-bit instructionscomposed of two fields. The first byte contains the opcode and the remainder an immediate operand or an operand address.a. What is the maximum directly addressable memory capacity (in bytes)?b. Discuss the impact on the system speed if the microprocessor bus has1. a 32-bit local address bus and a 16-bit local data bus, or2. a 16-bit local address bus and a 16-bit local data bus.c. How many bits are needed for the program counter and the instructionregister?a. 224 = 16 MBytesb. (1) If the local address bus is 32 bits, the whole address can be transferred atonce and decoded in memory. However, since the data bus is only 16 bits, itwill require 2 cycles to fetch a 32-bit instruction or operand.(2) The 16 bits of the address placed on the address bus can't access thewhole memory. Thus a more complex memory interface control is needed tolatch the first part of the address and then the second part (since themicroprocessor will end in two steps). For a 32-bit address, one may assumethe first half will decode to access a "row" in memory, while the second halfis sent later to access a "column" in memory. In addition to the two-stepaddress operation, the microprocessor will need 2 cycles to fetch the 32 bitinstruction/operand.c. The program counter must be at least 24 bits. Typically, a 32-bitmicroprocessor will have a 32-bit external address bus and a 32-bit programcounter, unless on-chip segment registers are used that may work with asmaller program counter. If the instruction register is to contain the wholeinstruction, it will have to be 32-bits long; if it will contain only the op code(called the op code register) then it will have to be 8 bits long.1.4 Consider a hypothetical microprocessor generating a 16-bit address (for example,assume that the program counter and the address registers are 16 bits wide) and having a 16-bit data bus.a. What is the maximum memory address space that the processor can accessdirectly if it is connected to a “16-bit memory”?b. What is the maximum memory address space that the processor can accessdirectly if it is connected to an “8-bit memory”?c. What architectural features will allow this microprocessor to access a separate“I/O space”?d. If an input and an output instruction can specify an 8-bit I/O port number,how many 8-bit I/O ports can the microprocessor support? How many 16-bit I/O ports?Explain.In cases (a) and (b), the microprocessor will be able to access 216 = 64K bytes;the only difference is that with an 8-bit memory each access will transfer a byte, while with a 16-bit memory an access may transfer a byte or a 16-byte word. For case (c), separate input and output instructions are needed, whose execution will generate separate "I/O signals" (different from the "memory signals" generated with the execution of memory-type instructions); at a minimum, one additional output pin will be required to carry this new signal. For case (d), it can support 28 = 256 input and 28 = 256 output byte ports and the same number of input and output 16-bit ports; in either case, the distinction between an input and an output port is defined by the different signal that the executed input or output instruction generated.1.5 Consider a 32-bit microprocessor, with a 16-bit external data bus, driven by an8-MHz input clock.Assume that this microprocessor has a bus cycle whose minimum duration equals four input clock cycles.What is the maximum data transfer rate across the bus that this microprocessor can sustain in bytes/s? To increase its performance, would it be better to make its external data bus 32 bits or to double the external clock frequency supplied to the microprocessor? State any other assumptions you make and explain. Hint: Determine the number of bytes that can be transferred per bus cycle.Clock cycle =18MHz=125nsBus cycle = 4 ⨯ 125 ns = 500 ns2 bytes transferred every 500 ns; thus transfer rate = 4 MBytes/secDoubling the frequency may mean adopting a new chip manufacturing technology (assuming each instructions will have the same number of clock cycles); doubling the external data bus means wider (maybe newer) on-chip data bus drivers/latches and modifications to the bus control logic. In the first case, the speed of the memory chips will also need to double (roughly) not to slow down the microprocessor; in the second case, the "wordlength" of the memory will have to double to be able to send/receive 32-bit quantities.1.6 Consider a computer system that contains an I/O module controlling a simplekeyboard/printer Teletype.The following registers are contained in the CPU and connected directly to the system bus:INPR: Input Register, 8 bitsOUTR: Output Register, 8 bitsFGI: Input Flag, 1 bitFGO: Output Flag, 1 bitIEN: Interrupt Enable, 1 bitKeystroke input from the Teletype and output to the printer are controlled by the I/O module.The Teletype is able to encode an alphanumeric symbol to an 8-bit word and decode an 8-bit word into an alphanumeric symbol.The Input flag is set when an 8-bit word enters the input register from the Teletype. The Output flag is set when a word is printed.a. Describe how the CPU, using the first four registers listed in this problem, canachieve I/O with the Teletype.b. Describe how the function can be performed more efficiently by also employingIEN.a. Input from the Teletype is stored in INPR. The INPR will only accept datafrom the Teletype when FGI=0. When data arrives, it is stored in INPR, andFGI is set to 1. The CPU periodically checks FGI. If FGI =1, the CPUtransfers the contents of INPR to the AC and sets FGI to 0.When the CPU has data to send to the Teletype, it checks FGO. If FGO = 0, the CPU must wait. If FGO = 1, the CPU transfers the contents of theAC to OUTR and sets FGO to 0. The Teletype sets FGI to 1 after the word isprinted.b. The process described in (a) is very wasteful. The CPU, which is muchfaster than the Teletype, must repeatedly check FGI and FGO. If interruptsare used, the Teletype can issue an interrupt to the CPU whenever it is readyto accept or send data. The IEN register can be set by the CPU (underprogrammer control)1.7 In virtually all systems that include DMA modules, DMA access to main memoryis given higher priority than processor access to main memory.Why?If a processor is held up in attempting to read or write memory, usually nodamage occurs except a slight loss of time. However, a DMA transfer may be to or from a device that is receiving or sending data in a stream (e.g., disk or tape), and cannot be stopped. Thus, if the DMA module is held up (denied continuing access to main memory), data will be lost.1.8 A DMA module is transferring characters to main memory from an externaldevice transmitting at 9600 bits per second (bps).The processor can fetch instructions at the rate of 1 million instructions per second. By how much will the processor be slowed down due to the DMA activity?Let us ignore data read/write operations and assume the processor only fetches instructions. Then the processor needs access to main memory once every microsecond. The DMA module is transferring characters at a rate of 1200 characters per second, or one every 833 µs. The DMA therefore "steals" every 833rd cycle. This slows down the processor approximately 1⨯100%=0.12%8331.9 A computer consists of a CPU and an I/O device D connected to main memory Mvia a shared bus with a data bus width of one word.The CPU can execute a maximum of106 instructions per second. An average instruction requires five processor cycles,three of which use the memory bus. A memory read or write operation uses one processor cycle. Suppose that the CPU is continuously executing “background”programs that require 95% of its instruction execution rate but not any I/O instructions.Assume that one processor cycle equals one bus cycle. Now suppose that very large blocks of data are to be transferred between M and D.a. If programmed I/O is used and each one-word I/O transfer requires the CPU toexecute two instructions, estimate the maximum I/O data transfer rate, in words per second, possible through D.b. Estimate the same rate if DMA transfer is used.a. The processor can only devote 5% of its time to I/O. Thus the maximum I/Oinstruction execution rate is 106⨯ 0.05 = 50,000 instructions per second. TheI/O transfer rate is therefore 25,000 words/second.b. The number of machine cycles available for DMA control is106(0.05⨯ 5 + 0.95⨯ 2) = 2.15⨯ 106If we assume that the DMA module can use all of these cycles, and ignoreany setup or status-checking time, then this value is the maximum I/Otransfer rate.1.10 Consider the following code:for (i = 0; i < 20; i++)for (j = 0; j<10; j++)a[i] = a[i] * ja. Give one example of the spatial locality in the code.b. Give one example of the temporal locality in the code.a. A reference to the first instruction is immediately followed by a reference tothe second.b. The ten accesses to a[i] within the inner for loop which occur within a shortinterval of time.1.11 Generalize Equations (1.1) and (1.2) in Appendix 1 A to n-level memoryhierarchies.DefineC i = Average cost per bit, memory level iS i = Size of memory level iT i = Time to access a word in memory level iH i = Probability that a word is in memory i and in no higher-level memoryB i = Time to transfer a block of data from memory level (i + 1) to memory level iLet cache be memory level 1; main memory, memory level 2; and so on, for atotal of N levels of memory. ThenC s =C i S i i =1N∑S ii =1N ∑ The derivation of T s is more complicated. We begin with the result from probability theory that:Expected Value of x = i Pr x =1[]i =1N∑We can write:T s = T i H i i =1N ∑We need to realize that if a word is in M 1 (cache), it is read immediately. If it is in M 2 but not M 1, then a block of data is transferred from M 2 to M 1 and then read.Thus:T 2 = B 1 + T 1Further T 3 = B 2 + T 2 = B 1 + B 2 + T 1Generalizing:T i = B j +T 1j =1i -1∑SoT s = B j H i ()j =1i -1∑i =2N ∑+T 1H i i =1N ∑But H i i =1N ∑=1Finally T s = B j H i ()j =1i -1∑i =2N ∑+T 11.12 Consider a memory system with the following parameters:Tc = 100 ns Cc = 0.01 cents/bitTm = 1200 ns Cm = 0.001 cents/bita. What is the cost of 1 MByte of main memory?b. What is the cost of 1 MByte of main memory using cache memory technology?c. If the effective access time is 10% greater than the cache access time, what is thehit ratio H ?a. Cost = C m ⨯ 8 ⨯106 = 8 ⨯103 ¢ = $80b. Cost = C c ⨯ 8 ⨯106 = 8 ⨯104 ¢ = $800c. From Equation 1.1 : 1.1 ⨯ T 1 = T 1 + (1 – H)T 2(0.1)(100) = (1 – H)(1200)H = 1190/12001.13 A computer has a cache, main memory, and a disk used for virtual memory. If areferenced word is in the cache, 20 ns are required to access it. If it is in mainmemory but not in the cache, 60 ns are needed to load it into the cache (thisincludes the time to originally check the cache), and then the reference is startedagain. If the word is not in main memory, 12 ms are required to fetch the wordfrom disk, followed by 60 ns to copy it to the cache, and then the reference isstarted again. The cache hit ratio is 0.9 and the main-memory hit ratio is0.6.What is the average time in ns required to access a referenced word on thissystem?There are three cases to consider:Avg = (0.9)(20) + (0.06)(80) + (0.04)(12000080) = 480026 ns1.14 Suppose a stack is to be used by the processor to manage procedure calls andreturns. Can the program counter be eliminated by using the top of the stack as a program counter?Yes, if the stack is only used to hold the return address. If the stack is also used to pass parameters, then the scheme will work only if it is the control unit that removes parameters, rather than machine instructions. In the latter case, the processor would need both a parameter and the PC on top of the stack at the same time.。
改进水平集的车辆检测算法

1 视 频 车辆 检 测技 术
基于 视频 的车 辆检 测方 法主 要有 背景 差分 法 、 计模 型检 测算 法 、 于主动 轮廓 的方 法等 。 统 基
1 1 背 景 差 分 法 .
背景差 分法 是 目前运 动 目标检 测 中最 常用 的方法 之一 [ 。这种 方 法 利用 当前 帧 图像 ( ) 背 z, 与
第3 3卷 第 5 期
21 O O年 1 月 0
பைடு நூலகம்
辽 宁 科 技 大 学 学 报
J u n l fUnv r iyo ce c n c n lg a nn o r a ie st fS in ea d Te h o o y Lio ig o
Vo _ 3 NO 5 I3 .
O c ., 01 t 2 0
改进 水 平集 的车 辆 检 测 算 法
赵 莹 , 学 东 张
( 宁科 技 大 学 电 子 与 信 息 工 程 学 院 , 宁 鞍 山 1 4 5 ) 辽 辽 1 0 1
摘 要 : 对视频序 列的车辆检 测 , 究 了常用的车辆检 测算 法。提 出一种 改进的基 于水平集 函数 的车辆 针 研
景 图像 B ( ) z, 的差 分检 测运 动车 辆 。得到 前景 二值 图像 DB ( . y , )
)一 () 1
式 中 阈值 适 当选 择 , 得 到较好 的前 景二 值 图像 。 可 1 2 混合高 斯分 布背 景模 型 . 混合 高斯 分 布背景 模 型( xu e f a sinmo e , Mit r u s d l MO ) og a s GS 由于具 有 良好 的鲁棒 性 、 定性 而在 稳 图像 序列 处理 中得 到广 泛应 用 ] 。在 高斯 分 布背 景 模 型 中 , 图像 中的 每一 个 像 素 点 都 被 看作 一 个 过 程 ,{ , , , } { ( 。 Y ,) 1 ≤ t , 每 一 个像 素 点 建立 一个 有 k个 高斯 分 布组 成 的 混合 高 。 … 一 I x , 。 i : ≤i }对
《大学英语过程写作》网课答案

文档基本上包括了所有课后问题的答案不过因为是乱序,所以只好下载下来然后通过word关键词搜索法,方法如下,把题目复制到word 搜索框,就会弹出。
如果搜索不到可以删除若干个修饰词,只留下几个名词再次搜索大学英语过程写作林娟(排错版)Week 11Why is brainstorming important?A、It allows writers to analyze the writing prompt and organize their thoughts.B、It contributes to unity and coherence of writing because i t allows writers to map out their ideas.C、all of the aboveD、none of the above我的答案:C2At what point in the writing process should we brainstorm?A、at the beginningB、at the beginningC、at the endD、in the middleE、always我的答案:A3What are 6 types of brainstorming?A、listing, clustering, t-chart, freewritingB、listing, clustering, cubing, freewriting, looping, t-chartC、freewriting, mapping, cubing, q-chart, looping, listingD、organizing, listing, looping, freecharting, cubing, t-chartE、organizing, cubing, researching, q-chart, freelisting, looping我的答案:A4In which situation would a T Chart be the most effective form of brainstorming?A、when creating formulating an argumentB、when showing the cause and effect of a situationC、when comparing two thingsD、both answers a and cE、Do not judge your ideas at the beginning. Simply just get your ideas out.我的答案:DWeek 21Outlining is ( ) in the writing process.A、the first stageB、the second stageC、the third stageD、the fourth stage我的答案:B2Among the following choices, which one can not be used as major supporting ideas?A、Points of comparisonB、ReasonsC、ExamplesD、Steps in a process我的答案:C3How is a major supporting idea different from a minor one?A、Major supporting ideas are more important than the minor ones.B、Major supporting ideas are general while the minor ones are specific.C、Major supporting ideas outnumber minor ones in a paper.D、Major supporting ideas provide more convincing evidences than minor ones.我的答案:B4Among the following choices, which one can not be used as minor supporting ideas?A、QuotesB、StatisticsC、InstancesD、Arguments我的答案:D5What are the three features of a thesis statement?A、It should have a narrow focus,B、It can be a fact,C、It should be an opinion,D、it can forecasts the body paragraphs我的答案:ACD6The parallel structure is the most important thing in outline.我的答案:√7An outline is thoughts, rather than a paragraph. So we can just write down ideas rather than supporting sentences.我的答案:√Week 31Can you identify the logical fallacy in this claim? “My roommate saidphilosophy class is boring, and I felt the same too. All philosophy classesmust be boring.”A、hasty generalizationB、post hocC、guilt by associationD、oversimplification我的答案:A2Can you identify the logical fallacy in this claim? “Even though it the first day, I can tell this is going to be a boring course”.A、hasty generalizationB、post hocC、guilt by associationD、oversimplification我的答案:A3Can you identify the logical fallacy in this claim? “Traffic jam can besolved by traffic control in the downtown area.”A、post hocB、guilt by associationC、oversimplificationD、begging the question我的答案:C4Which one is not one of the three appeals of an argument that Aristotle postulated:( )A、logical appealB、Ethical appealC、Emotional appealD、Emphatic appeal我的答案:D5What is the difference between the major and minor premises?A、The major premise is usually a more important and lengthy claim while the minor one is less important and lengthy.B、The major premise is usually a broad and generally recognized truth, while the minor one is a more specific and narrowly applicable fact.C、Major claim connotes minor claim.D、The major premise major is usually a more specific and narrowly applicable fact while the minor one is a broad and generally applicable truth.我的答案:B6Syllogism is a kind of deductive reasoning.A、Deductive reasoning (from general to specific)B、Inductive reasoning (from specific to general)我的答案:A7All fragile things are breakable things. Some glasses a re fragile things.Therefore,A、Some Glasses will break.B、Some Glasses are breakable things.C、Some things are breakable.D、None of the above.我的答案:B8Can you identify the logical fallacy in this claim? “Xiao Ming alwayscheats in exams. Xiao Ming is your friend. You always cheat in exams.A、hasty generalizationB、post hocC、guilt by associationD、oversimplification我的答案:C9Can you identify the logical fallacy in this claim? “We have a new Math teacher. And my Math turns out to be a disaster this semester. The newMath teacher is responsible for my poor performance. ”A、post hocB、guilt by associationC、oversimplificationD、begging the question我的答案:A10Can you identify the logical fallacy in this claim? “we shouldn’t liar like Zhao Zhi to represent us in this competition.A、post hocB、guilt by associationC、oversimplificationD、begging the question我的答案:D11How to convert logical syllogism into written argument ?A、Provide evidence for each premise.B、Lay out each premise clearly.C、Draw a clear connection to the conclusion.D、Support the conclusion with new evidence.我的答案:ABC12What’s the structure of introduction?A、Background informationB、Hookc.C、Thesis statementD、Evidence of Thesis statement我的答案:ABCWeek 41What is one advantage of the block style of writing?A、It allows the writer to fully present two of the aspects of a subject in one paragraph without any interruption or influence from other ideas or topics.B、It allows the writer to fully present all of the aspects of a subject in one paragraph with many interruptions or influences from other ideas or topics.C、It allows the writer to fully present all of the aspects of a subject in one paragraph without any interruption or influence from other ideas or topics.D、It allows the writer to fully present four ideas or topics in one paragraph without any interruption or influence from the subject.我的答案:C 得分:20.0分2How is a point-by-point style argumentative essay different from a block style argumentative essay regarding how they disprove opposing pointsof view?A、Whereas only one paragraph in a block style argumentative essay will present a strong argument against an opposing view, all three paragraphs in a point-by-point style argumentative essay seek to disprove opposing points of view.B、Whereas only one paragraph in a point-by-point style argumentative essay will present a strong argument against an opposing view, all three paragraphs in a block style argumentative essay seek to disprove opposing points of view.C、Whereas all three paragraphs in a block style argumentative essay seek to disprove opposing points of view, only one paragraph in an argumentative point-by-point style essay will present a strong argument against an opposing view.D、Whereas all three paragraphs in a point-by-point style argumentative essay seek to disprove opposing points of view, in a block style argumentative essay there are no strong arguments against an opposing view.我的答案:B\C 得分:0.0分3What are two ways that we can organize paragraphs a ccording to thispresentation?A、introduction, body, and conclusionB、block style and point-by-point styleC、summative and narrativeD、point-by-point style and comparative style我的答案:B 得分:20.0分4What is a characteristic of point by point style writing? A、Writers can focus on comparing things through unique lenses or perspectives in each paragraph.B、The writer can focus on completely explaining one subject in each paragraph.C、The writer will personalize or reflect on the comparison made in the third paragraph.D、The use of an introduction and conclusion are unique to this style of writing.我的答案:A 得分:20.0分5 When looking at our writing, we should ask ourselves if we are ________ two things from a certain perspective or ________ one subject.A、ComparingB、ExplainingC、EngagingD、ElaboratingE、InvigilatingF、ConflatingG、Initiating我的答案:AG\BG 得分:0.0分Week 51What are the two locations where citations can be found in a paper?A、After quotes and summarizingB、At the beginning of the paper and at the end of the paperC、In text or at the end of the textD、To support your writing and to avoid plagiarism我的答案:B 得分:0.0分2Which of the following is not a reason to provide proper citation?A、To show our hard wo rk and all of the research that we’ve doneB、To plagiarize (using another person’s words or ideas without giving them proper credit)C、To establish our credibility as a writerD、To allow readers to find more information about our ideas我的答案:A\C 得分:0.0分3What does procrastination mean?A、Supporting the efforts of othersB、Getting things done earlyC、Writing down referencesD、leaving things until the last moment我的答案:D 得分:12.5分4What are the two most commonly used citation styles?A、Modern Language Association & American Psychological AssociationB、Social Sciences & Liberal Arts and HumanitiesC、Citation and PlagiarismD、Multiple Language Association & American Physiology Association 我的答案:B\C 得分:0.0分5Which of these is an example of MLA Citation?A、(Stone 15)B、(Stone, 2014, p. 15) is an example of MLA Citation我的答案:A6When making citations at the end of a text, which lines must be indented?A、All lines except the first lineB、All lines except the last lineC、The first lineD、The second line我的答案:C 得分:0.0分7Which style of citation is the most specific and why?A、MLA requires the date of publication because they focus more on the Liberal arts and Humanities, and research in this field is only catalogued by year.B、APA because they focus more on the Liberal arts, and research in this field is only catalogued by year.C、APA requires the date of publication because they focus more on the scientific realm, and research in this field is always changing.D、These two popular styles of citation are pretty much the same, and one does not require more details than the other.我的答案:A\B 得分:0.0分8In which situations should we use citation?A、Quoting, Summarizing, ProverbsB、Paraphrasing, Quoting, Common KnowledgeC、Common Knowledge, Quoting, Better safe than sorryD、Summarizing, Paraphrasing, Quoting我的答案:D 得分:12.5分Week 61Why is it better to use a strong verb than to use a noun?A、Nouns show actionB、Nouns are informal.C、Verbs show actionD、Verbs are informal.我的答案:C 得分:16.6分2How do we tighten sentences?(排序)1、reflect on the logical relationship among sentence and ideas. 2、look for words that don’t do their share of the work 3、use strong verbs 4、Keep it clear and simpleA、2341B、1234C、3214D、4321我的答案:D 得分:0.0分3What are three synonyms for the word “say” (use a thesaurus)?A、mention, denigrate, proclaimB、enunciate, exhume, clarifyC、inculcate, state, pontificateD、allege, opine, verbalize我的答案:B 得分:0.0分4Why should we be careful of the word be?A、“Be” allows for the use of adjectives which are not descriptive.B、“Be” is rarely used in written English.C、“Be” is often confused for “bee”.D、“Be” is often used in a passive manner and does not show action. 我的答案:D 得分:16.6分5What are the three ways to create powerful descriptive language?A、use of adjecitvesB、parallel structureC、varied sentence structureD、theme and rheme我的答案:ACD 得分:0.0分6 When we say “sentence variety”, what can we vary?A、sentence lengthB、sentence openingC、sentence endingD、sentence structure我的答案:AD 得分:8.5分Week 71Which thematic progression pattern has been used in this paragraph?Hemp’s environmental credentials are indisputable. It grows better inorganic systems than in conventional ones. It smothers weeds andcontrols pests, clearing the land for other crops. It improves the structureof the soil, with strong roots to prevent erosion. If processed in the field,it returns nutrients to the land and purports to ‘clean up’ soil co with heavy metals. It is one of a minority of textile-fibre crops that can begrown in temperate climates. So why, given its potential, is so little hempused today? (New Internationalist, June 1998, p. 14)A、simple linear progressionB、split progressionC、constant progressionD、derived hyperthematic progression我的答案:A 得分:0.0分2Which lexical cohesion strategy has been used in the following paragraph?A big tree with a thick trunk and outspread branches was nearby, andtaking care to leave not the slightest mark, he climbed up into the crotch,and stretching out on one of the broad limbs, after a fashion, rested…Something was coming through the bush, slowly, carefully, thesame winding way Rainsford had come. He flattened himself down on the limb and through a screen of leaves, saw it was a man.A、synonymyB、hyponymyC、repetitionD、metonymy我的答案:B 得分:10.0分3Which one is more coherent?(仅填A或B即可)A、The most striking example of value rigidity I can think of is the old south Indian Monkey Trap, which depends on value rigidity for its effectiveness.A hollowed-out coconut chained to a stake makes the trap.A monkey can put its hand though a small hole in the coconut and grab some rice inside. The monkey can put its hand into the hole but cannot take its fist out with rice in it. The monkey's value rigidity traps it when it reaches in. The rice cannot be revalued. He cannot see that freedom without rice is more valuable than capture with it.B、The most striking example of value rigidity I can think of is the old south Indian Monkey Trap, which depends on value rigidity for its effectiveness. The trap consists of a hollowed-out coconut chained to a stake. The coconut has some rice inside which can be grabbed through a small hole. The hole is big enough so that the monkey's hand can go in,but too small for his fist with rice in it to come out. The monkey reachesin and is suddenly trapped - by nothing more than his own value rigidity.He can't revalue the rice. He cannot see that freedom without rice is morevaluable than capture with it.我的答案:B 得分:10.0分4Which lexical cohesion strategy has been used in the following paragraph?‘NOW, what I want is, Fact s. Teach these boys and girls nothing but Facts.Facts alone are wanted in life. Plant nothing else, and root out everythingelse. You can only form the minds of reasoning animals upon Facts:nothing else will ever be of any service to them. …Stick to Facts, Sir!A、hyponymyB、repetitionC、antonymyD、metonymy我的答案:B5Which lexical cohesion strategy has been used in the following paragraph?He fell asleep. What woke him was a loud crash.A、metonymyB、repetitionC、hyponymyD、antonymy我的答案:D6Which thematic progression pattern has been used in this paragraph? The inventor of the diode valve was Fleming. He made use of the fact, first noticed by Edison, that an electric current could be made to flow across the empty space between the hot filament of an electric lamp and another metal electrode placed inside the evacuated bulb. This effect depends upon the thermionic emission of electrons from the heated metal filament. (W. P. Jolly, (1972). Electronics, p. 61)A、simple linear progressionB、split progressionC、constant progressionD、derived hyperthematic progression我的答案:C\D 得分:0.0分7Which grammatical cohesion strategy has been used in the following paragraph? I see traces of the turtle soup, and vension, and gold spoon in this. Yes, I do! Cried Mr. Bounderby, shaking his head with obstinate cunning. ‘By the Lord Harry, I do.’ A、ellipsisB、conjunctionC、referenceD、substitution我的答案:D 得分:10.0分8Which one is not a grammatical cohesion strategy?A、referenceB、substitutionC、metonymyD、ellipsisE、conjunction我的答案:C 得分:10.0分9Which paragraph in the following is more coherent? (仅填A或B即可) A、Nauru is so small that the plane lands in what is best described as the capital's main street. To stop cars when planes are landing the seaward side of the runway has traffic lights at each end. Well-fed and brightly clothed Naurans cowd the tiny air terminal with their smart cars. The only hotel, the luxurious Menen, is a 10-minute drive half way round the island and is where new arrivals are driven off in Japanese m inibuses. The well-paved road passes rows of neat, modern houses, set among the trees.B、Nauru is so small that the plane lands in what is best described as thecapital's main street. The seaward side of the runway has traffic lights at each end to stop cars when planes are landing. The tiny air terminal is crowded with well-fed and brightly clothed Naurans with their smart cars. New arrivals are driven off in Japanese minibuses for the 10-minute drive half way round the island to the only hotel, the luxurious Menen. The well-paved road passes rows of neat, modern houses, set among the trees. (David Lascelles, The Financial Times)我的答案:B 得分:10.0分10What is the purpose of using cohesion strategies?A、to connect the writing as a wholeB、to flow smoothly from one idea to the next oneC、to ensure the accuracy of writingD、to bring out more ideas as inspiration我的答案:AB 得分:10.0分Week 81Which one is more formal? (请从A和B里选择即可)A、This is to inform you that your book has been rejected by our publishing company as it was not up to the required standard. In case you would like us to reconsider it, we would suggest that you go over it and make some necessary changes.B、You know that book I wrote? Well, the publishing company rejected it. They thought it was awful. But hey, I did the best I could, and I think it was great. I’m not gonna redo it the way they said I should.我的答案:A 得分:33.3分2Which ones have used nominalization?A、I do not understand either her meaning or his intention.B、I do not understand either what she means or what he intends.C、The fact that I denied what he accused me of impressed the jury.D、My denial of his accusations impressed the jury.我的答案:A 得分:33.3分3Nominalization is to turn a verb or an adjective into a noun.我的答案:√ 得分:33.4分。
progress in electromagnetics research latex 模板

progress in electromagnetics research latex模板模板的主要目的是帮助研究者在撰写学术文章时能够更加便捷和规范地使用LaTeX 进行排版。
LaTeX 是一种专业的排版系统,由于其强大的排版能力和丰富的功能扩展,广泛应用于科学、技术和工程领域。
在电磁学研究中,研究者常常需要撰写包含复杂数学符号、图表和公式的文章。
传统的文字处理软件往往难以满足这些专业需求,而LaTeX 则为研究者提供了一种简单而高效的解决方案。
下面,我们将一步一步回答您关于"progress in electromagnetics research LaTeX 模板" 的问题。
问题1:有没有成熟的"progress in electromagnetics research" LaTeX 模板可供使用?答案:是的,有很多成熟的"progress in electromagnetics research" LaTeX 模板可供使用。
这些模板通常包含了常见的科技期刊排版要求,如页边距、字体、行距等,并提供了额外的宏包和命令,以便于引用文献、排版图表和公式。
一些知名的模板包括IEEE Transactions on Antennas and Propagation (IEEE TAP) 模板和Applied Computational Electromagnetics Society (ACES) 模板等。
问题2:如何选择适合的模板?答案:选择适合的模板取决于您期望发表的期刊。
许多期刊都提供官方的LaTeX 模板,您可以在期刊的官方网站或投稿系统中找到下载链接。
如果您的目标期刊没有提供官方模板,您可以选择符合同领域期刊排版风格的开源模板。
通过谷歌学术或在GitHub 上搜索关键词"progress in electromagnetics research LaTeX 模板",通常可以找到大量可供选择的模板。
基于人脸识别和RFID技术的智能车辆管理系统

信 息 技 术DOI:10.16661/ki.1672-3791.2104-5042-1225基于人脸识别和rFID技术的智能车辆管理系统①管中华 戚颖(四川中电启明星信息技术有限公司 四川成都 610041)摘 要:随着社会的经济发展,在企业运营过程中需要管控的车辆数量逐年增加,特别是企业经营地域的覆盖面广阔的大型企业,如电力、石油、化工、交通等行业相关企业。
车辆和驾驶员的数量增加,给传统的车队管理方式带来了挑战。
电话调度和驾驶员随身携带车钥匙等传统方式已经难以适应车队的高效率调度、驾驶授权的安全可控和行驶数据的精准采集等核心诉求。
为此,该文提出了一种基于人脸识别和RFID技术的智能车辆管理系统设计思路,该系统由调度系统、人脸识别系统、钥匙柜及其系统、短信系统以及OCR组件组成。
为企业构建了全时空的(任何人、任何时间、任何地点)企业用车环境,保障高效用车和车辆驾驶授权的安全可控。
关键词:车钥匙 RFID 人脸识别 OCR 调度中图分类号:U463.6 文献标识码:A文章编号:1672-3791(2021)03(c)-0034-05Intelligent Vehicle Management System Based on Facerecognition and rFID TechnologyGUAN Zhonghua QI Ying(Aostar Information Technologies Co., Ltd., Chengdu, Sichuan Province, 610041 China )Abstract : With the economic development of the society, in the process of enterprise operation, the number of vehicles to be controlled is increasing year by year, especially for large enterprises with a wide geographical range, such as electric power, petroleum, chemical industry, transportation and other industries. The increase in the number of vehicles and drivers brings challenges to the traditional f leet management. Traditional methods such as telephone scheduling and drivers carrying car keys have been diff icult to adapt to the core demands of eff icient f leet scheduling, safe and controllable driving authorization and accurate collection of driving data. Therefore, this paper proposes a design idea of intelligent vehicle management system based on face recognition and RFID technology. The system is composed of scheduling system, face recognition system, key cabinet and its system, SMS system and OCR components. It builds a full space-time (anyone, anytime, anywhere) vehicle use environ-ment for enterprises, ensure the eff iciency of vehicle use and the safety and controllability of vehicle driving authorization.Key Words : Car key; RFID; Face recognition; OCR; Scheduling①作者简介:管中华(1985—),男,本科,中级工程师,研究方向为企业数字化建设。
科学文献

Debashish Chowdhury ;y, Ludger Santeny, Andreas Schadschneidery , Shishir Sinha 1, and Abhay Pasupathy 2
Abstract: The spatio-temporal organizations of vehicular tra c in cellular-automata models with "slow-to-start" rules are qualitatively di erent from those in the NagelSchreckenberg (NaSch) model of highway tra c. Here we study the e ects of such a slow-to-start rule, introduced by Benjamin, Johnson and Hui (BJH), on the the distributions of the distance-headways, time-headways, jam sizes and sizes of the gaps between successive jams by a combination of approximate analytical calculations and extensive computer simulations. We compare these results for the BJH model with the corresponding results for the NaSch model and interpret the qualitative di erences in the nature of the spatio-temporal organizations of tra c in these two models in terms of a phase separation of the tra c caused by the slow-to-start rule in the BJH model.
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
有机化学Chinese Journal of Organic ChemistryREVIEW* E-mail: sgou@; lei.fang@Received September 3, 2011; revised January 10, 2012; accepted February 8, 2012.Project supported by the National Natural Science Foundation of China (No. 81001361) and the Ph.D. Programs Foundation of Ministry of Education of China (No. 20100092120046).国家自然科学基金(No. 81001361)和教育部博士点基金青年教师(Nos. 20100092120046)资助项目.Chin. J. Org. Chem. 2012, 32, 1217~1231 © 2012 Chinese Chemical Society & SIOC, CAS/ 1217DOI: 10.6023/cjoc1109031咔唑及其衍生物合成方法研究进展房旭彬a ,b 房 雷*,a ,b 苟少华*,a ,b(a 东南大学药物研究中心 南京 211189)(b 江苏省生物药物高技术研究重点实验室 南京 211189)摘要 咔唑及其衍生物是一类重要的含氮芳杂环化合物, 具有许多独特的理化性质及生物活性, 分析、归纳、总结了近5年来发表的文献, 选取具有代表性的实例, 并按照中间体的不同将合成方法分为四类, 分别讨论了咔唑及其衍生物合成方法的进展情况, 对咔唑及其衍生物成环的新方法给予重点关注. 关键词 咔唑; 衍生物; 合成方法; 研究进展Progresses in Synthetic Methods of Carbazole and Its DerivativesFang, Xubin a ,b Fang, Lei *,a ,b Gou, Shaohua *,a ,b(a Pharmaceutical Research Center , Southeast University , Nanjing 211189)(b Jiangsu Province Hi-Tech Laboratory for Bio-medical Research , Southeast University , Nanjing 211189)Abstract Carbazole and its derivatives are a class of important nitrogen-containing heterocyclic compounds possessing various unique properties and biological activity. Herein the current progress of their synthetic strategies reported in the past 5 years is reviewed. The representative examples, which have been divided into four categories according to the usage of differ-ent key intermediates, are selected and discussed in detail. Special emphasis is put on the newly developed cyclization reac-tions which may be useful for the construction of the tricyclic backbone of carbazoles. Keywords carbazole; derivatives; synthetic methods; progress咔唑是一种含氮的杂环化合物, 是许多精细化学品的中间体, 可用于制作塑料、农药、杀虫剂、医药以及新型聚合物材料等. 在咔唑分子特定位置引入各种取代基团或官能团对其进行化学修饰, 可以获得多类结构新颖的咔唑衍生物, 目前已有多个被当作药物或药物中间体被加以开发, 例如许多的咔唑衍生物显示出良好抗肿瘤活性和抗惊厥活性, 这也体现了咔唑类化合物在医药方面的应用潜力[1~4]. 近年来, 随着研究和生产需求的不断增长, 对咔唑及其类似物的需求量呈逐年上升的趋势, 传统方法合成的化合物虽然比较经济, 但是产品单一, 不能满足多样性需要. 因此, 研究咔唑的合成方法并使之便于工业化生产具有相当重要的意义.1 传统方法咔唑的传统合成方法主要包括Graebe-Ullmann 反应、Bucherer 咔唑合成和Borsche-Drechsel 环化反应. Graebe-Ulmann 反应, 由氨基二苯胺经重氮化反应, 加热脱掉氮气得到咔唑, 如Scheme 1a 所示. 该反应由Graebe 和Ullmann [1a]于1896年报道, Ullmann 通过该方法合成了几个咔唑化合物, 但是其他研究人员发现不饱和基团的存在对该反应会产生不利影响. Preston, Tucker 和Cameron [2]首次通过该方法获得了硝基咔唑(微量)、乙酰基咔唑(22%)和氰基咔唑(34%), 但收率都不是很理想. Bucherer 咔唑合成方法是Bucherer [3a]于1904年报道, 由芳肼与萘酚在亚硫酸氢钠存在下共热反应合成了苯并咔唑, 如Scheme 1b 所示. Borsche- Drechsel 环化反应是Drechsel 和Borsche 分别于1868年和1904年报道[1b,3b], 以苯肼与环己酮缩合成腙, 后者在酸性条件下环化生成四氢咔唑, 再经催化脱氢制得咔 唑[4], 如Scheme 1c 所示. 得益于催化脱氢方法的发展, Borsche 方法已经成为一条操作简便、条件温和、成本有机化学1218 / © 2012 Chinese Chemical Society & SIOC, CASChin. J. Org. Chem. 2012, 32, 1217~1231低廉、产率高的咔唑合成路线, 具有较高的工业化生产价值.N HNH 2O N HOHNHNH 23N HNHNH 2H NNN HRa-NiN H+(a)(b)+(c)Scheme 1此外, 工业上也常常采用2-氨基联苯氧化脱氢或2,2'-二氨基联苯脱氨制备咔唑[5], 如Scheme 2所示.NH 2O (空气)N HHCl, 200NHNH 2H 2N-NH 3V 2O 5, 600Co CScheme 22 新方法20世纪最后10年中, 大量新颖的贵金属和过渡金属催化剂被应用于咔唑及其衍生物的合成中, 极大地丰富了合成手段, 为合成更为复杂的咔唑衍生物奠定了基础. 如今已不仅仅局限于简单地合成咔唑, 数以万计的咔唑衍生物通过新的方法被合成出来, 并广泛应用于医药和染料工业中. 按照中间体的不同, 本文将咔唑及其衍生物的合成方法分为四类: 联苯、二苯胺、吲哚和其它.2.1 以联苯为中间体的方法以联苯为中间体的合成方法得益于Suzuki-Miyaura 偶联反应的发现. 该方法的基本合成策略是利用Suzuki-Miyaura 偶联反应首先合成带有不同取代基的联苯中间体, 然后利用不同的含氮基团以及使用相应的催化剂环合得到目标物(Scheme 3). Suzuki-Miyaura 偶联与Ullmann 等方法相比, 其反应温度通常不超过100 ℃, 而且在水、醇和醚的混合物体系中即可进行反应, 反应条件及收率上都具有显著优势, 有着广阔的应用前景. 例如, 咔唑心安(用于高血压)的重要中间体4-羟基咔唑在合成中依然采用大大过量的铜粉作为催化剂, 高温185 ℃反应, 制备联苯收率仅为50%~60%, 若采用Pd 催化Suzuki-Miyaura 偶联则收率可提高至95%~100%, 催化剂用量也缩小至5 mol%, 温度降至90 ℃左右, 这样可以大量节约能源, 减少环境污染, 提高效率.HN R''R'H 2N R''+cat.cat.(a)(b)Z=Br, I, OTfScheme 3在环合步骤中, 可以利用成环的基团主要有NO 2, N 3, NHR 等, 相应的催化剂见表 1. 当X 和Y 是卤素或OTf 时, 则需要外加氨基化合物, 作为咔唑的氮源.表1 X, Y, Z 取代基及催化剂a Table 1 X, Y, Z -substituent and the catalystsX Y Z Cat. Yield/%NO 2 H — MoO 2Cl 2(dmf)2 87 N 3 H — Rh 2(O 2CC 3F 7)4 98NHR H — Pd(OAc)2 96 — — Br Pd 2(dba)3 59 — — I CuI 98 — — OTf Pd(dba)2 97adba =dibenzylideneacetone.在各种环合反应中, 以硝基为环合基团的应用最为广泛. Arnáiz 小组[6]以各种二取代的硝基联苯为原料, 利用MoO 2Cl 2(dmf)2为催化剂在PPh 3存在的条件下合成了一系列的咔唑及咔唑衍生物1~9, 其收率达70%~87% (Eq. 1), 该方法以MoO 2Cl 2(dmf)2为催化剂, 价格相对低廉, 与贵金属催化剂相比具有明显的成本优势, 极具应用价值. 2007年, Carter 等[7]报道了使用Diels-Alder 反应同样可以获得多取代硝基联苯中间体, 收率达58%~78%, 比Suzuki 偶联方法(22%~98%)表现出更好的稳定性. 以硝基联苯为关键中间体, 经PPh 3/二氯苯体系环合, 同样可合成一系列咔唑衍生物,Chinese Journal of Organic ChemistryChin. J. Org. Chem. 2012, 32, 1217~1231© 2012 Chinese Chemical Society & SIOC, CAS/ 1219如Siamenol 等(Scheme 4).NO 2R 1R 2H NR 1R 2MoO Cl (dmf) (5 mol%)PPh 3 (2.4 equiv.)toluene,1: R 1 = H, R 2 = H2: R 1 = t -Bu, R 2 = 3: R 1 = OMe, R 2 = H 4: R 1 = CHO, R 2 = H 5: R 1 = COMe, R 2 = H 6: R 1 = F, R 2 = H7: R 1 = CO 2Et, R 2 = H 8: R 1 = OH, R 2 = H9: R 1 = CO 2H, R 2 = H 70% ~ 87%Δ(1)t -Bu22PG'O/PGO/Diels-Alder 58% ~ 78%Scheme 4通常情况下, 硝基联苯的环合反应需要高温长时间反应(5~12 h)才能反应完全, 2009年, Creencia 等[8]报道, 以硝基联苯为原料, 在P(OEt)3或PPh 3存在下, 使用微波辅助合成了咔唑, 在微波功率为200 W 条件下, 反应仅2 min 就获得环合产物, 收率高达96% (Eq. 2).NO 2MWH NP(OEt) or PPh 96%(2)以叠氮基为环合基团同样是合成咔唑的有效手段. 2007年, Sapi 等[9]通过Suzuki-Miyaura 偶联反应得到叠氮基联苯, 后者加热释放出氮气, 最终得到咔唑(Scheme 5). 试验结果显示叠氮联苯上的取代基的不同, 收率上存在很大差异, 波动范围在51%~71%. 研究发现, 当联苯中间体一端为苯并吲哚时, 产物具有良好的选择性, 提示取代基的电性特点对环合位点具有重要影响. 2009年, Driver 等[10]以叠氮基联苯为原料, 分别以Rh 2(O 2CC 3F 7)4 (5 mol%), 4 Å MS (100 wt%), PhMe, 60 ℃和Rh 2(O 2CC 7H 15)4 (5 mol%), 4 Å MS (100 wt%), (CH 2Cl)2, 60 ℃两个条件合成了23个咔唑衍生物, 该方法收率较高, 达到65%~98% (Scheme 6), 提示铑催化反应具有明显优势. 同时该研究还讨论了环合时的区域选择性(14∶15), 结果显示, 其中R'为氯或三氟甲基时14∶15>95∶5, R 为氟时比例也高达89∶11, 然而当R 为甲基比例仅为66∶34, 为甲氧基时几乎没有选择性(Scheme 6, 表2), 这一发现进一步补充了Sapi 等的关于取代基与环合位点关系的理论.H3N H H NN H NHN 3NH3BrN 3ArB(OH)234+3DME, 10016010: R = 3-H, 71%11: R = 3-CN, 70%12: R = 3-CHO, 51%13: 65%160o Co Co C0% ~ 5%+Scheme 52R R 2HN 3H R R'N H RN H R'RRh (O CC F )Rh 2(O 2CC 3F 7)4or Rh 2(O 2CC 7H 15)4 (5 mol%)A PhMe, 60 ℃+14154。
