Asa配置大全
ASA防火墙的基本配置
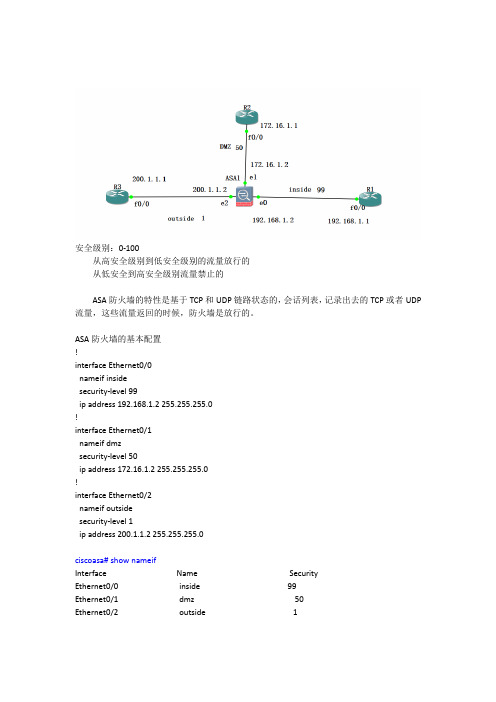
安全级别:0-100从高安全级别到低安全级别的流量放行的从低安全到高安全级别流量禁止的ASA防火墙的特性是基于TCP和UDP链路状态的,会话列表,记录出去的TCP或者UDP 流量,这些流量返回的时候,防火墙是放行的。
ASA防火墙的基本配置!interface Ethernet0/0nameif insidesecurity-level 99ip address 192.168.1.2 255.255.255.0!interface Ethernet0/1nameif dmzsecurity-level 50ip address 172.16.1.2 255.255.255.0!interface Ethernet0/2nameif outsidesecurity-level 1ip address 200.1.1.2 255.255.255.0ciscoasa# show nameifInterface Name SecurityEthernet0/0 inside 99Ethernet0/1 dmz 50Ethernet0/2 outside 12、路由器上配置配置接口地址路由--默认、静态配置VTY 远程登录R3:interface FastEthernet0/0ip address 200.1.1.1 255.255.255.0no shutdown配置去内网络的路由ip route 192.168.1.0 255.255.255.0 200.1.1.2配置去DMZ区域的路由ip route 172.161.0 255.255.255.0 200.1.1.2配置远程登录VTYR3(config)#line vty 0 2R3(config-line)#password 666R3(config-line)#loginR2:interface FastEthernet0/0ip address 172.16.1.1 255.255.255.0no shutdown配置默认路由IP route 0.0.0.0 0.0.0.0 172.16.1.2配置远程登录VTYR3(config)#line vty 0 2R3(config-line)#password 666R3(config-line)#loginR2:interface FastEthernet0/0ip address 192.168.1.1 255.255.255.0no shutdown配置默认路由IP route 0.0.0.0 0.0.0.0 192.168.1.2配置远程登录VTYR3(config)#line vty 0 2R3(config-line)#password 666R3(config-line)#loginR1可以Telnet R3 ,反过来不行R1不可以ping通R3防火墙放行流量防火墙能放行R3低安全级别的---R1高安全级别区域--Telnet流量ciscoasa(config)# access-list 100 permit tcp host 200.1.1.1 host 192.168.1.1 eq 23应用列表到接口ciscoasa(config)# access-group 100 in interface outside验证:防火墙能放行R3低安全级别的---R1高安全级别区域--ICMP流量ciscoasa(config)# access-list 100 permit icmp host 200.1.1.1 host 192.168.1.1验证。
ASA配置

vpdn group dx ppp authentication pap //启用验证方式
vpdn username 051211077922 password 983980 //就是ISP给你的帐号和密码
interface GigabitEthernet0/2
route inside 192.168.0.0 255.255.0.0 192.168.4.1 1 *指向三层交换机路由接口的vlan静态路由
: end
lybenet#
vpdn group dx request dialout pppoe //为ADSL拨号创建虚拟专用拨号网络组(VPDN Group),ChengDu为组名,随便填你自己喜欢的
!
nat-control * 定义T的第一步,启动NAT
global (outside) 1 interface *定义PAT的第三步,复用外部端口做PAT
nat (inside) 1 0.0.0.0 0.0.0.0 * 定义PAT的第二步,局域网用户都可以使用PAT
!
route outside 0.0.0.0 0.0.0.0 123.100.1.1 1 * 指向互联网的默认路由
ip address 192.168.100.1 255.255.255.0
!
interface Ethernet0/2 *定义ASA的DMZ接口 (用来连接服务器)
nameif dmz
security-level 50
ip address 192.168.1.3 255.255.255.0
ssh 0.0.0.0 0.0.0.0 dxoutside
教程:ASA配置(三个区域)
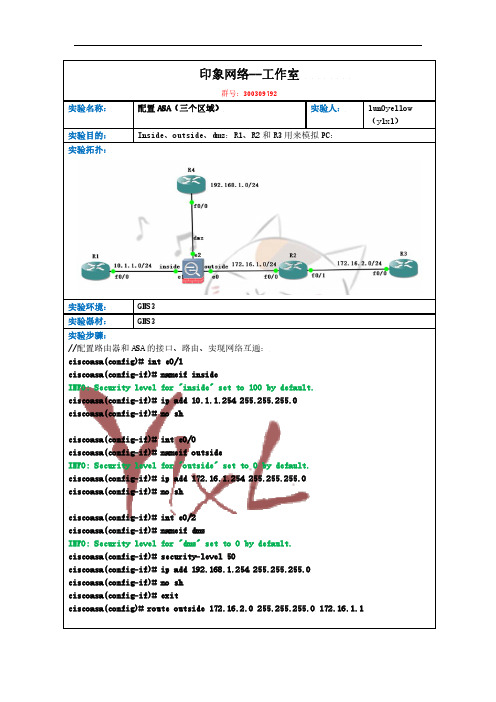
印象网络--工作室群号:300309792实验名称: 配置ASA(三个区域) 实验人:lun0yellow(ylxl) 实验目的: Inside、outside、dmz:R1、R2和R3用来模拟PC:实验拓扑:实验环境: GNS3实验器材: GNS3实验步骤://配置路由器和ASA的接口、路由、实现网络互通:ciscoasa(config)# int e0/1ciscoasa(config-if)# nameif insideINFO: Security level for "inside" set to 100 by default.ciscoasa(config-if)# ip add 10.1.1.254 255.255.255.0ciscoasa(config-if)# no shciscoasa(config-if)# int e0/0ciscoasa(config-if)# nameif outsideINFO: Security level for "outside" set to 0 by default.ciscoasa(config-if)# ip add 172.16.1.254 255.255.255.0ciscoasa(config-if)# no shciscoasa(config-if)# int e0/2ciscoasa(config-if)# nameif dmzINFO: Security level for "dmz" set to 0 by default.ciscoasa(config-if)# security-level 50ciscoasa(config-if)# ip add 192.168.1.254 255.255.255.0ciscoasa(config-if)# no shciscoasa(config-if)# exitciscoasa(config)# route outside 172.16.2.0 255.255.255.0 172.16.1.1//在R1、R2、R3、R4上配置:R1(config)#int f0/0R1(config-if)#ip add 10.1.1.1 255.255.255.0R1(config-if)#no shR1(config-if)#exitR1(config)#ip route 0.0.0.0 0.0.0.0 10.1.1.254R1(config)#do wrR2(config)#int f0/0R2(config-if)#ip add 172.16.1.1 255.255.255.0R2(config-if)#no shR2(config-if)#int f0/1R2(config-if)#int f0/1R2(config-if)#ip add 172.16.2.2 255.255.255.0R2(config-if)#no shR2(config-if)#exitR2(config)#ip route 10.1.1.0 255.255.255.0 172.16.1.254R2(config)#ip route 192.168.1.0 255.255.255.0 172.16.1.254 R2(config)#do wrR3(config)#int f0/0R3(config-if)#ip add 172.16.2.1 255.255.255.0R3(config-if)#no shR3(config-if)#exitR3(config)#ip route 0.0.0.0 0.0.0.0 172.16.2.2R3(config)#do wrR4(config)#int f0/0R4(config-if)#ip add 192.168.1.1 255.255.255.0R4(config-if)#no shR4(config-if)#exitR4(config)#ip route 0.0.0.0 0.0.0.0 192.168.1.254R4(config)#do wr//配置R1/R2/R3/R4的vty密码。
配置ASA

防火墙技术实验报告实验名称:防火墙技术实验内容一、拓扑图:二、实验步骤:1.分别在ASA1和ASA2上配置ip地址和命名。
ASA1:ciscoasa(config)# host ASA1ASA1(config)# int e0/0ASA1(config-if)# ip add 192.168.1.3 255.255.255.0 ASA1(config-if)# no shASA1(config-if)# nameif insideASA1(config-if)# int e0/1ASA1(config-if)# ip add 120.3.2.21 255.255.255.252 ASA1(config-if)# no shASA1(config-if)# nameif outsideASA1(config-if)# exitASA2:ASA2(config)# int e0/0ASA2(config-if)# ip add 192.168.1.3 255.255.255.0 ASA2(config-if)# no shASA2(config-if)# nameif insideASA2(config-if)# exitASA2(config)# int e0/1ASA2(config-if)# ip address 120.3.2.22 255.255.255.252ASA2(config-if)# no shASA2(config-if)# nameif outsideASA2(config-if)# exit2.分别在ASA1和ASA2上配置NAT和映射,还有ACL。
ASA1:ASA1(config)# nat (inside) 1 0.0.0.0 0.0.0.0ASA1(config)# global (outside) 1 interfaceASA1(config)# route outside 0.0.0.0 0.0.0.0 120.3.2.22ASA1(config)# route inside 192.168.0.0 255.255.0.0 192.168.1.3ASA1(config)# access-list 101 extended permit icmp any anyASA1(config)# access-list 101 extended permit ip any anyASA1(config)# access-group 101 in interface outsideASA2:ASA2(config)# nat (inside) 1 0.0.0.0 0.0.0.0ASA2(config)# global (outside) 1 interfaceASA2(config)# route inside 192.168.0.0 255.255.0.0 192.168.1.1ASA2(config)# route outside 0.0.0.0 0.0.0.0 120.3.2.21ASA2(config)# access-list 101 extended permit icmp any anyASA2(config)# access-list 101 extended permit ip any anyASA2(config)# access-group 101 in interface outsideASA2(config)# static (inside,outside) tcp 120.3.2.22 www 192.168.140.254 www 3.在SW1和SW2上配置ip地址后配置默认路由。
asa配置手册

asa配置手册一些基础配置,个人工作学习中的一点整理,如有错误请指正,谢谢。
#设置主机名:(config)#hostname dust#设置时区:dust(config)#clock timezone EST 7#设置时钟:dust#clock set 15:45:30 28 FEB 2008#配置内接口 IPdust(config)#int Ethernet 0/0dust(config-if)#nameif insidedust(config-if)#security-level 100dust(config-if)#ip address 192.168.88.254 255.255.255.0#配置外部接口IPdust(config)#int Ethernet 0/1dust(config-if)#nameif outsidedust(config-if)#security-level 0dust(config-if)#ip address 210.X.X.X 255.255.255.248#配置用户名和密码dust(config)#username admin password ********* privilege 15 注:15 表示有最高权限#配置HTTP 和TELNETdust(config)#aaa authentication telnet console LOCALdust(config)#http server enabledust(config)#http 192.168.88.0 255.255.255.0 insidedust(config)#telnet 192.168.88.0 255.255.255.0 inside#配置SSH接入:dust(config)#crypto key generate rsa modulus 1024dust(config)#aaa authentication ssh console LOCALdust(config)#ssh 192.168.88.0 255.255.255.0 insidedust(config)#ssh 0 0 outsidedust(config)#ssh timeout 30dust(config)#ssh version 2#配置ASDM(自适应安全设备管理器)接入:dust(config)#http server enable 8080dust(config)#http 192.168.88.0 255.255.255.0 insidedust(config)#http 0 0 outsidedust(config)#asdm image disk0:/asdm-621.bindust(config)#username dust password ccie privilege 15#动态NAT:dust(config)#nat-controldust(config)#nat (inside) 1 192.168.10.0 255.255.255.0dust(config)#nat (inside) 1 0 0dust(config)#global (outside) 1 interfacedust(config)#global (dmz) 1 192.168.202.100-192.168.202.110#静态NATdust(config)#static (dmz.outside) 210.10.10.253 192.168.202.1dust(config)#access-list ccie extended permit tcp any host 210.10.10.253 eq wwww dust(config)#access-group ccie in interface outside#配置ACLdust(config)#access-list ccie extended deny ip 192.168.201.0 255.255.255.240 any dust(config)#access-list ccie extended permit ip any anydust(config)#access-group ccie in interface inside#ICMP协议dust(config)#icmp deny any echo outsidedust(config)#icmp permit any outsidedust(config)#access-list 111 permit icmp any any echo-reply dust(config)#access-list 111 permit icmp any any unrechable dust(config)#access-list 111 permit icmp any any time-exceededdust(config)#access-group 111 in interface outside#配置默认路由dust(config)#route ouside 0.0.0.0 0.0.0.0 220.1.1.1 1#配置DHCP服务器dust(config)#dhcpd address 192.168.10.50-192.168.10.100 insidedust(config)#dhcpd enable insidedust(config)#dhcpd dns 202.102.192.68 insidedust(config)#dhcpd lease 86400 interface insidedust(config)#dhcpd option xx ip 192.168.10.10#保存配置dust#write memory 或copy running-config startup-config #清除配置dust(config)#clear configure alldust(config)#clear configure xxx xxxasa remote vpn#在outside接口上启用isakampdust#configure terminaldust(config)#crypto isakmp enable outside#创建一个isakmp策略dust(config)#crypto isakmp policy 1dust(config-isakmp-policy)#authentication pre-sharedust(config-isakmp-policy)#encryption desdust(config-isakmp-policy)#hash md5dust(config-isakmp-policy)#group 2dust(config-isakmp-policy)#lifetime 86400#配置组策略dust(config)#group-policy mypolicy internaldust(config)#group-policy mypolicy attributesdust(config-group-policy)#vpn-tunnel-protocol ipsecdust(config-group-policy)#split-tunnel-policy tunnelspecifieddust(config-group-policy)#nem enable#定义地址池dust(config)#ip local pool vpn-pool 192.168.88.110-192.168.88.120#定义隧道组dust(config)#tunnel-group cisco type remote-accessdust(config)#tunnel-group cisco general-attributesdust(config-tunnel-general)#address-pool vpn-pooldust(config-tunnel-general)#authentication-server-group (outside) LOCAL dust(config-tunnel-general)#default-group-policy mypolicydust(config-tunnel-general)#tunnel-group cisco ipsec-attributesdust(config-tunnel-ipsec)#pre-shared-key cisco#配置转换集dust(config)#crypto ipsec transform-set ccsp esp-des esp-md5-hmacdust(config)#crypto ipsec transform-set cisco esp-des esp-md5-hmac#添加本地帐户dust(config)#username user01 password adminabcdust(config)#username user02 password admindec#定义映射集,并应用到外部接口dust(config)#crypto dynamic-map dyn-map 10 set transform-set ccsp ciscodust(config)#crypto dynamic-map dyn-map 10 set reverse-routedust(config)#crypto map cisco 60001 ipsec-isakmp dynamic dyn-mapdust(config)#crypto map cisco interface outside#配置分离隧道dust(config)#access-list split_list standard permit 192.168.88.0 255.255.255.0 dust(config)#group-policy mypolicy attributesdust(config-group-policy)#split-tunnel-policy tunnelspecifieddust(config-group-policy)#split-tunnel-network-list value split_listdust(config-group-policy)#dns-server value 202.102.192.68 8.8.8.8#放行访问列表dust(config)#access-list 100 extended permit ip 192.168.88.0 255.255.255.0 192.168.88.0 255.255.255.0dust(config)#access-list 111 extended permit icmp any any echo-replydust(config)#access-list 111 extended permit icmp any any unreachabledust(config)#access-list 111 extended permit icmp any any time-exceededdust(config)#nat (inside) 0 access-list split_listdust(config)#access-group 111 in interface outsidedust(config)#access-group 100 in interface outsidedust(config)#access-group 100 in interface inside#查看被asp和acl drop的包dust(config)# show asp drop frame acl-drop客户端连接时,地址为outside的IP,组名为cisco 密码为cisco。
asa配置步骤

思科防火墙已经从PIX发展到ASA了,IOS也已经从早期的6.0发展到7.2。
但总体的配置思路并没有多少变化。
只是更加人性化,更加容易配置和管理了。
下面是我工作以来的配置总结,有些东西是6.3版本的,但不影响在7.*版本的配置。
一:6个基本命令: nameif、 interface、 ip address 、nat、 global、 route。
二:基本配置步骤:step1: 命名接口名字nameif ethernet0 outside security0nameif ethernet1 inside security100nameif ethernet2 dmz security50**7版本的配置是先进入接口再命名。
step2:配置接口速率interface ethernet0 10full autointerface ethernet1 10full autointerface ethernet2 10fullstep3:配置接口地址ip address outside 218.106.185.82ip address inside 192.168.100.1 255.255.255.0ip address dmz 192.168.200.1 255.255.255.0step4:地址转换(必须)* 安全高的区域访问安全低的区域(即内部到外部)需NAT和global;nat(inside) 1 192.168.1.1 255.255.255.0global(outside) 1 222.240.254.193 255.255.255.248*** nat (inside) 0 192.168.1.1 255.255.255.255 表示192.168.1.1这个地址不需要转换。
直接转发出去。
* 如果内部有服务器需要映射到公网地址(外网访问内网)则需要static和conduit或者acl.static (inside, outside) 222.240.254.194 192.168.1.240static (inside, outside) 222.240.254.194 192.168.1.240 10000 10后面的10000为限制连接数,10为限制的半开连接数。
ASA防火墙基本配置

一、基本配置#hostname name //名字的设置#interface gigabitethernet0/0 //进入接口0/0#nameif outside //配置接口名为outside#security-level 0 //设置安全级别。
级别从0--100,级别越高安全级别越高#ip address 218.xxx.xxx.xxx 255.255.255.248 //设置外部ip地址#no shutdown#interface ethernet0/1 //进入接口0/1#nameif inside //配置接口名为inside#security-level 100 //设置安全级别。
级别从0--100,级别越高安全级别越高#ip address 192.168.10.1 255.255.255.0 //设置ip地址#duplex full //全双工#speed 100 //速率#no shutdown#interface ethernet0/2 //进入接口0/2#nameif dmz //配置接口名为dmz#security-level 50 //设置安全级别。
级别从0--100,级别越高安全级别越高#ip address 192.168.9.1 255.255.255.0 //设置dmz接口ip地址#no shutdown#interface Management0/0 //进入管理接口# nameif guanli //接口名# security-level 100 //安全级别#ip address 192.168.1.1 255.255.255.0 //IP地址注意:security-level 配置安全级别。
默认外网接口为0/0 安全级别默认为0内网接口为0/1 安全级别默认为100dmz 接口为0/2 安全级别默认为50默认情况下,相同安全级别接口之间不允许通信,可以使用以下命令:#same-security-traffic permit interface //允许相同安全级别接口之间互相通信。
ASA型号及配置命令

ASA型号及配置命令asa复习笔记一、cisco防火墙1.软件防火墙它用于基于IOS软件的设备。
一般来说,客户端上具有应用层智能的状态检测防火墙引擎占CPU和内存资源的2.5%(可以定期欣赏)硬件防火墙(更多优势)应用在一般企业外部网络:pix500系列安全设备、asa5500系列自适应安全设备、catalyst6500系列交换机和cisco7600系列路由器的防火墙服务模块(不可以定期升值)二、 Ciscosa1常见型号:型号asa5505asa5510asa5520asa5540asa5550asa5580规模作用交换机接小型企业、分公司和企业设备成本低,易于部署、集成8个10/100端口快速口远程办公环境以太网交换机中型企业、分公司企业环设备成本低,易于部署,具有高级安全和网络服务境中型企业具有模块化、高性能网络中的高可用性主动/主动服路(小凡模拟器)务,并能连接千兆以太网设备由大中型企业,服务提供商提供高密度,主动/主动高可用性服务和千兆以太网连器接,设备具有高可靠性和高性能接大型企业、服务提供商网千兆级提供高达1.2gb/s的防火墙吞吐量,具有主动口络的高性能设备/主动高可用性服务、光纤和千兆位以太网连接性大型企业、数据中心、和提供王兆位以太网连接运营商网络型号为asa5580-20、asa5580-402.基本配置配置主机名:ciscoasa>enciscoasa#cinft思科ASA(配置)#主机名ASA802域名:asa802(config)#enablepassword123telnet或ssh密码:Asa802(配置)#passwdciscoasa接口名称和安全级别asa802(config-if)#nameifinside(不起名,ping不通)Asa802(如果配置)#安全级别100(值为0-100,值越大,安全级别越高)//默认情况下,outside口安全级别为0,inside口安全级别为100,防火墙允许数据从高安全级别流向低安全级别的接口,但不允许流量从低安全级别流向高安全级别的接口,若要放行,必须做策略,acl放行;若接口的安全级别相同,那么它们之间不允许通信,绝对不允许,但有时有这个需要,故意把它们设成一样。
ASA配置实例
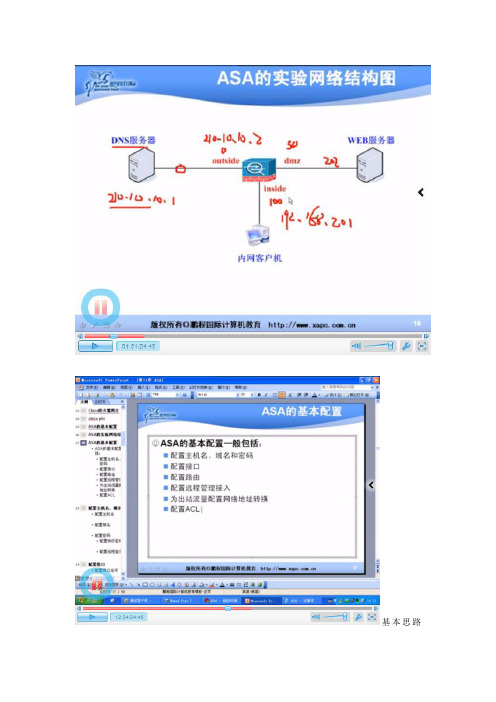
基本思路如图所示1、配置DNS外网那个服务器注意网关是为了实验方便,实际不会设置防火墙outside口的IP地址的2、DMZ区的web服务器IP地址192.168.202.2 网关为192.168.202.13、inside 区则放了一台PC机,pc机的IP:192.168.201.2网关为192.168.201.1DNS就用拓扑图中的DNS地址4、首先要将防火墙的主机名域名路由配置好这样才可以PC机ping通192.168.201.1通过三个配置你会发现DNS PC DMZ去ping自己所在的网关都是通的但是如果想pc 想pingDmz会发现无法ping通的这个是时候要做一个ACL 让他们两两ping通其中111是一个扩展访问ACL 但因为后面接了一个permit 所以不写extend也可以这个时候你用netstat -an 你会发现在outside的DNS 可以看到内网的IP 这个就不符合要求了。
也就是防火墙现在单单是一个路由器的功能所以这个时候要做的是1、将DNS服务器的网关去掉因为实际就这样不可能配置好网关的。
2、为内网的出站做一个网络地址转换----NAT 做一个PAT 其中命令中的1表示一个标记这个时候你会发现PC机又可以重新ping通外网了。
用netstat –an 可以看到地址已转换3、新问题:这时你会发现内网访问DMZ区不行也就是说如果要访问DMZ区要做一个针对DMZ区的地址转换这个时候你去DMZ区用netstat –an 可以看到地址已转换。
3、以上就是NAT的DMZ与outside的做好了要求:外网的DNS 可以访问到内网的DMZ区:这个时候做一个静态NAT 将DMZ区的服务器发布出去这个时候要考虑与前面的111extended想对应这个时候最好show run 看看。
做一个远程管理接入:开启telnet ssh 等SSH这里弄了一个钥匙对。
第8章拓展篇-ASA高级配置

dhcpd dns 202.106.0.20 202.106.46.151 –配置DNS服务器地址dhcpd wins 10.1.1.20 –配置WINS服务器dhcpd address 10.1.1.100-10.1.1.200 inside 分配地址100-200在inside接口dhcpd enable inside --开启inside接口上的DHCPdhcpd address 172.16.1.10-172.16.1.20dhcpd enable dmzasacisco(config)# interface Ethernet0/0 --进入接口asacisco(config-if)# nameif outsideasacisco(config-if)# security-level 0asacisco(config-if)# pppoe client vpdn group ADSL 开启pppoeasacisco(config-if)# ip address pppoe setroute 自动创建一个缺省路由asacisco(config)# vpdn group ADSL request dialout pppoe --请求pppoe拨号asacisco(config)# vpdn group ADSL localname fs87829050–ADSL用户名asacisco(config)# vpdn group ADSL ppp authentication pap --认证方式asacisco(config)# vpdn username fs87829050password ********* -adsl用户名密码定义安全策略ACL(访问控制列表)分为标准和扩展,区别在与标准的只基于源,而扩展的基于源和目的ACL号标准的1-99 扩展100-199asacisco(config)# access-list (word) (permit/deny)(源网络,源主机)asacisco(config)# access-list 10 standard permit 153.31.53.0 255.255.255.0扩展ACLasacisco(config)# access-list (word) (permit/deny) (协议tcp/udp/ip) (源网络,源主机) (目的网络,目的主机) asacisco(config)# access-list 101 permit ip 172.16.1.0 255.255.255.0 10.1.1.0 255.255.255.0(--允许172.16.1.0/24网段访问,10.1.1.0/24网段)asacisco(config)# access-list 100 permit tcp any(源) host 211.1.1.3(目的) eq 80--any 所有源地址host 只针对主机ep就是= 211.1.1.3 80端口asacisco(config)# access-list 100 extended permit tcp any host 211.1.1.3 eq 80--允许外部所有主机访问211.1.1.3的80端口asacisco(config)# access-group 100 in interface outside --将100 ACL应用到outside接口上asacisco(config)# access-group 101 in interface inside –将101 ACL 应用到inside接口上对象分组asacisco(config)# object-group service对象分组名字tcp/udp协议object-group service yongyou tcp(例子)port-object eq 5872 开启的端口port-object eq 1872 开启的端口Exit 退出asacisco(config)# access-list out extended permit tcp any host 211.1.1.3 object-group yongyou(写一个ACL命名为out 协议为tcp允许外部所有主机访问211.1.1.3 的5872\1872)asacisco(config)# access-group out in interface outside(将ACL应该在outside接口上)设置透明模式•转换模式•定义接口•设置管理IP(211.1.1.2/24)•透明模式下安全策略的定义和路由模式的设置是一样的VPN借助IPSec,用户可以通过互联网等不受保护的网络传输敏感信息。
ASA基本配置与实验环境搭建

扩展ACL:asa802(config)#access-list acl-name extended {permit | deny} protocol src-ip-add src-mask dst-ip-add dst-mask [operator port]
NETSCREEN防火墙:通过对外网端口MIP和访问策略(set policy)来实现外网对内网及DMZ专项服务的访问限制。
ASA防火墙: 通过静态映射(static
(inside,outside))和策略(access-list)来实现外网对内网及DMZ专项服务的访问限制。
3、
内网地址转换
Telnet或SSH密码:
asa802(config)#passwd cisco
ASA接口名字和安全级别
asa802(config-if)#nameif inside(不起名,ping不通)
asa802(config-if)#security-level 100(取值0—100 ,值越大,安全级越高)
5、
路由的实现
PIX防火墙:通过route outside 、route inside来实现内外网的访问路由。
NETSCREEN防火墙:通过set route来实现内外网的访问路由。
ASA防火墙:通过route outside 、route inside来实现内外网的访问路由。
6、
管理地址的定义
定义一个全局地址池:
asa802(config)#global (outside) 1 200.1.1.100-200.0.0.110
ASA的配置

清除配置信息:
conf t
clear configure all
clear configure command[level2 command]
end
=======================================================================
exit
regex url1 \.sina\.com
class-map type regex match-any url-class1
match regex url1
exit
class-map type inspect http http-url-class1
match not request header host regex class url-class1
access-list 111 permit icmp any any
access-list 111 permit ip any any
access-group 111 in int outside
access-group 111 in int inside
access-group 111 in int dmz
http 192.168.201.0 255.255.255.0 inside
http 0 0 outside
asdm image disk0:/asdm-615.bin
username lgs password cisco privlege 15
-----------------------------------------------------------------------
ASA基本配置

ASA命令介绍:一、基本配置1、显示ASA版本信息ciscoasa# show version2、配置主机名ciscoasa(config)# hostname asa8023、配置域名asa802(config)# domain-name 4、配置密码a、配置特权密码asa802(config)# enable password asa802b、配置远程登陆(telnet、SSH)密码asa802(config)# passwd cisco5、配置接口a、配置接口IP地址asa802(config-if)# ip address 192.168.1.1 255.255.255.0b、配置接口名字asa802(config-if)# nameif namec、配置接口安级级别asa802(config-if)# security-level number6、查看接口信息asa802(config-if)# show run interface(不必要在特权下)7、查看IP信息asa802(config-if)# show ip address(show ip)8、配置静态路由asa802(config)# route interface-name network mask next-hop-address 9、查看路由表asa802# show route10、配置远程管理接入a、配置Telnet接入----明文传输asa802(config)# telnet {network|ip-address} mask interface-name 注:ASA不允许telnet流量从安全级别为0的接口进入b、配置SSH(安全的telnet加密传输)接入(3个步骤)步骤1:配置主机名和域名步骤2:生成RSA密钥对(公钥和私钥)asa802(config)# crypto key generate rsa modulus 1024步骤3:配置防火墙允许SSH接入asa802(config)# ssh 192.168.0.0 255.255.255.0 insideasa802(config)# ssh 0 0 outside配置空闲超时时间与版本(可选)asa802(config)# ssh timeout 30asa802(config)# ssh version 2c、配置ASDM(ASA安全设备管理器)接入asa802(config)# http server enableasa802(config)# http 192.168.0.0 255.255.255.0 insideasa802(config)# asdm image disk0:/asdm-602.binasa802(config)# username benet password cisco privilege 1511、配置网络地址转换(NAT)a、配置PAT(2个步骤)---把多个私网地址转换成1个公网地址,多对少的转换步骤1:定义什么流量需要被转换asa802(config)# nat (interface_name) nat-id local-ip mask 步骤2:定义全局地址池(也可转到外部接口)asa802(config)# global (interface_name) nat-id {global-ip [-global-ip] |interface}b、配置Staticasa802(config)# static (real_interface,mapped_interface) mapped_ip real_ip注:从低到高需要通过ACL放行相应的流量c、查看NAT的转换条目asa802(config)#show xlate12、配置ACLa、标准ACLasa802(config)#access-list acl_name standard {permit | deny}ip_addr maskb、扩展ACLasa802(config)# access-list acl_name extended {permit | deny}protocol src_ip_addr src_mask dst_ip_addr dst_mask [operator port]c、将ACL应用到接口asa802(config)# access-group acl_name {in | out} interface interface_name12、清空当前ASA相关协议配置asa802(config)#clear config route|static|nat|global13、清空当前ASA所有配置asa802(config)#clear config all--------------------------------------------------------二、ASA的高级应用1、配置URL(统一资源定位符)过滤(4个步骤)步骤1:定义Regex(正则表达式)-定义URL匹配的字符串asa802(config)# regex url1 "\.sohu\.com"---""步骤2:创建class-map(类映射)-识别传输流量,分类流量asa802(config)# access-list tcp_filter permit tcp 192.168.10.0255.255.255.0 any eq wwwasa802(config)# class-map tcp_filter_classasa 802(config-cmap)# match access-list tcp_filter-------------------------------------------------------------------------------------------------asa802(config)# class-map type inspect http http_class--------把字符串划分类asa802(config-cmap)# match request header host regex url1 步骤3:创建policy-map(策略映射)-针对不同的类执行不同的操作 asa802(config)# policy-map type inspect http http_url_policy-----带http 检测类型的策略映射asa802(config-pmap)# class http_classasa802(config-pmap-c)# drop-connection log ---同时产生日志信息-----------------------------------------------------------------------------------------------------asa802(config)# policy-map inside_http_url_policy ---标准的策略映射asa802(config-pmap)# class tcp_filter_classasa802(config-pmap-c)# inspect http http_url_policy步骤4:应用policy-map应用接口上asa802(config)# service-policy inside_http_url_policy interface inside2、配置日志管理服务器(三种方式)第一种:本地Buffer保存日志asa802(config)# logging enableasa802(config)# logging buffered informational 第二种:配置ASDM日志asa802(config)# logging enableasa802(config)# logging asdm informational 第三种:配置日志服务器asa802(config)# logging enableasa802(config)# logging trap informationalasa802(config)# logging host inside 192.168.10.13、配置ASA安全特性a、基本威胁检测asa802(config)# threat-detection basic-threatb、防范IP分攻击asa802(config)# fragment chain 1c、启用IDS(入侵检测系统)功能(可选)。
ASA_8.3基本配置

ASA_8.3基本配置1.ASDM图形界面基本配置步骤:1)在asa上面开启hhtps服务,命令如下:ciscoasa(config)# http server enable(开启http服务)ciscoasa(config)# http 10.10.0.0 255.255.0.0 inside(指定可网管的地址,必须配置,不然无法网管)ciscoasa(config)# aaa authentication http console LOCAL(为asdm网管启用AAA认证,LOCAL为内建的AAA服务器的名字,采用本地认证,名字区分大小写;console只是一个关键字不是console口) 2)给asa配置管理地址,命令如下:ciscoasa(config)# interface e 0/1ciscoasa(config-if)# nameif insideciscoasa(config-if)# ip add 10.10.10.10 255.255.255.0ciscoasa(config-if)# no shutdown3)配置管理asa的用户名密码,命令如下:ciscoasa(config)#username admin password admin privilege 15 4)使用火狐浏览器在地址栏输入asa的管理地址,如下:https://10.10.10.10根据提示安装java,进入asdm管理界面。
注意:java安装完后,重新输入上面地址,运行asdm可能会提示java安全阻止该程序运行的问题。
解决办法是到java安全设置里面把上述地址加入可信任站点里面。
步骤:控制面板→程序→java→安全→编辑站点列表→输入https://10.10.10.10→添加。
2.ASA初始化配置1)配置SSH远程登录命令:ciscoasa(config)#crypto key generate rsa modulus 1024 //指定rsa系数的大小,这个值越大,产生rsa的时间越长,cisco推荐使用1024.ciscoasa(config)#write mem //保存刚刚产生的密钥ciscoasa(config)#ssh 0.0.0.0 0.0.0.0 outside //0.0.0.0 0.0.0.0 表示任何外部主机都能通过SSH访问outside接口ciscoasa(config)username admin password admin privilege 15 //为SSH登录配置账密ciscoasa(config)#aaa authentication ssh console LOCAL //为ssh登录启用aaa认证采用本地数据库认证2)给接口命名并指定ip地址和安全级别说明:①安全级别相同接口之间的流量默认不通,可配置放行,命令如下:ciscoasa(config)# same-security-traffic permit inter-interface(放行安全级别相同接口之间的流量)ciscoasa(config)# same-security-traffic permit intra-interface (放行从一个接口先进然后又从同一个接口出的流量)②从安全级别高的到低的流量为outbound流量,默认放行;从低安全级别到高安全级别的流量为inbound流量,默认阻塞。
ASA配置命令

要想配置思科的防火墙得先了解这些命令:常用命令有:nameif、interface、ip address、nat、global、route、static等。
global指定公网地址范围:定义地址池。
Global命令的配置语法:global (if_name) nat_id ip_address-ip_address [netmarkglobal_mask]其中:(if_name):表示外网接口名称,一般为outside。
nat_id:建立的地址池标识(nat要引用)。
ip_address-ip_address:表示一段ip地址范围。
[netmark global_mask]:表示全局ip地址的网络掩码。
nat地址转换命令,将内网的私有ip转换为外网公网ip。
nat命令配置语法:nat (if_name) nat_id local_ip [netmark]其中:(if_name):表示接口名称,一般为inside.nat_id:表示地址池,由global命令定义。
local_ip:表示内网的ip地址。
对于0.0.0.0表示内网所有主机。
[netmark]:表示内网ip地址的子网掩码。
routeroute命令定义静态路由。
语法:route (if_name) 0 0 gateway_ip [metric]其中:(if_name):表示接口名称。
0 0 :表示所有主机Gateway_ip:表示网关路由器的ip地址或下一跳。
[metric]:路由花费。
缺省值是1。
static配置静态IP地址翻译,使内部地址与外部地址一一对应。
语法:static(internal_if_name,external_if_name) outside_ip_addr inside_ ip_address其中:internal_if_name表示内部网络接口,安全级别较高,如inside。
external_if_name表示外部网络接口,安全级别较低,如outside。
asa配置文档

asa5520# show running-config: Saved:ASA Version 8.0(4)!hostname asa5520enable password 8Ry2YjIyt7RRXU24 encryptedpasswd oP3HIfiDhQjsmEWl encryptednamesdns-guard!interface GigabitEthernet0/0speed 10duplex fullnameif outsidesecurity-level 0ip address 61.50.145.82 255.255.255.252!interface GigabitEthernet0/1nameif insidesecurity-level 100ip address 10.1.1.2 255.255.255.0!interface GigabitEthernet0/2nameif dmzsecurity-level 50ip address 10.1.18.1 255.255.255.0!interface GigabitEthernet0/3shutdownno nameifno security-levelno ip address!interface Management0/0nameif managementsecurity-level 100ip address 192.168.1.1 255.255.255.0management-only!regex ""boot system disk0:/asa804-k8.binftp mode passiveaccess-list 101 extended permit ip 132.147.0.0 255.255.0.0 anyaccess-list out_in extended permit ip any 61.50.145.72 255.255.255.248access-list out_in extended permit icmp any anyaccess-list dmz_in extended permit ip any anyaccess-list 200 extended permit ip host 132.147.160.221 anyaccess-list 200 extended permit ip host 132.147.160.18 anyaccess-list 200 extended permit ip host 132.147.160.29 anyaccess-list 200 extended permit ip host 132.147.160.30 anyaccess-list 200 extended permit ip host 132.147.160.62 anypager lines 24logging asdm informationalmtu outside 1500mtu inside 1500mtu dmz 1500mtu management 1500no failovericmp unreachable rate-limit 1 burst-size 1asdm image disk0:/asdm-508.binno asdm history enablearp timeout 14400global (outside) 1 interfaceglobal (dmz) 1 interfacenat (inside) 1 access-list 101nat (dmz) 1 10.1.18.0 255.255.255.0static (inside,outside) tcp 61.50.145.77 www 132.147.160.186 www netmask 255.255.255.255static (inside,outside) tcp 61.50.145.77 ssh 132.147.160.186 ssh netmask 255.255.255.255static (inside,outside) tcp 61.50.145.77 https 132.147.160.186 https netmask 255.255.255.255static (inside,outside) tcp 61.50.145.77 8820 132.147.160.186 8820 netmask 255.255.255.255static (inside,outside) tcp 61.50.145.77 8821 132.147.160.186 8821 netmask 255.255.255.255static (inside,outside) tcp 61.50.145.77 8830 132.147.160.186 8830 netmask 255.255.255.255static (inside,outside) udp 61.50.145.77 8830 132.147.160.186 8830 netmask 255.255.255.255static (inside,outside) udp 61.50.145.77 8820 132.147.160.186 8820 netmask 255.255.255.255static (inside,outside) udp 61.50.145.77 8821 132.147.160.186 8821 netmask 255.255.255.255static (inside,outside) tcp 61.50.145.77 ftp-data 132.147.160.186 ftp-data netmask 255.255.255.255static (inside,outside) tcp 61.50.145.77 ftp 132.147.160.186 ftp netmask255.255.255.255static (inside,outside) tcp 61.50.145.74 81 132.147.160.185 81 netmask 255.255.255.255static (inside,outside) tcp 61.50.145.74 telnet 10.1.1.1 telnet netmask 255.255.255.255static (inside,outside) tcp 61.50.145.74 www 132.147.160.185 www netmask 255.255.255.255static (inside,outside) tcp 61.50.145.78 www 132.147.160.5 www netmask 255.255.255.255static (inside,outside) tcp 61.50.145.78 citrix-ica 132.147.160.5 citrix-ica netmask 255.255.255.255static (inside,outside) tcp 61.50.145.76 www 132.147.160.8 www netmask 255.255.255.255static (inside,outside) tcp 61.50.145.76 5000 132.147.160.8 5000 netmask 255.255.255.255static (dmz,outside) tcp 61.50.145.74 880 10.1.18.2 880 netmask 255.255.255.255 static (inside,outside) 61.50.145.73 132.147.161.2 netmask 255.255.255.255 static (inside,outside) 61.50.145.75 132.147.160.163 netmask 255.255.255.255 static (inside,dmz) 10.1.18.8 132.147.160.8 netmask 255.255.255.255static (inside,dmz) 10.1.18.6 132.147.160.6 netmask 255.255.255.255static (inside,dmz) 10.1.18.5 132.147.160.5 netmask 255.255.255.255static (inside,dmz) 10.1.18.186 132.147.160.186 netmask 255.255.255.255static (inside,dmz) 10.1.18.73 132.147.161.2 netmask 255.255.255.255static (inside,dmz) 10.1.18.18 132.147.160.18 netmask 255.255.255.255access-group out_in in interface outsideaccess-group dmz_in in interface dmzroute outside 0.0.0.0 0.0.0.0 61.50.145.81 1route inside 132.147.0.0 255.255.0.0 10.1.1.1 1timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolutedynamic-access-policy-record DfltAccessPolicyaaa authentication ssh console LOCALhttp server enablehttp 192.168.1.0 255.255.255.0 managementno snmp-server locationno snmp-server contactsnmp-server enable traps snmp authentication linkup linkdown coldstartcrypto ipsec security-association lifetime seconds 28800crypto ipsec security-association lifetime kilobytes 4608000telnet 0.0.0.0 0.0.0.0 insidetelnet timeout 5ssh 0.0.0.0 0.0.0.0 outsidessh timeout 5console timeout 0dhcpd address 192.168.1.2-192.168.1.254 management dhcpd enable management!threat-detection basic-threatthreat-detection statistics access-listno threat-detection statistics tcp-intercept username gssnet password 2BObWO62u/Y2Tp.4 encrypted username greenman password Serm7uFhgKKjoFt2 encrypted !class-map inspection_defaultmatch default-inspection-trafficclass-map type regex match-any thundermatch regex class-map type inspect http match-all cm_h_badrequest match request header host regex class thunderclass-map 200match access-list 200!!policy-map type inspect dns migrated_dns_map_1parametersmessage-length maximum 512policy-map type inspect http pm_denybadhttpparametersclass cm_h_badrequestreset logpolicy-map global_policyclass inspection_defaultinspect dns migrated_dns_map_1inspect ftpinspect h323 h225inspect h323 rasinspect rshinspect rtspinspect esmtpinspect sqlnetinspect skinnyinspect sunrpcinspect xdmcpinspect sipinspect netbiosinspect tftpinspect http pm_denybadhttppolicy-map xiansuclass 200police input 4500000 2250police output 4500000 2250!service-policy global_policy globalservice-policy xiansu interface insideprompt hostname contextCryptochecksum:354fea9c2de7638155d42ecbea4bd056 : endasa5520#asa5520#。
ASA型号及配置命令

ASA复习笔记一、 Cisco防火墙1. 软件防火墙用在基于IOS软件的设备上,一般客户机上具有应用层智能的状态检测防火墙引擎占CPU、内存资源(可以定期升值)2. 硬件防火墙(更有优势)应用在一般企业外部网络:PIX 500系列安全设备、ASA 5500系列自适应安全设备、Catalyst 6500系列交换机和Cisco 7600 系列路由器的防火墙服务模块(不可以定期升值)二、 Cisco ASA1常见型号:2.基本配置配置主机名:ciscoasa>enciscoasa#cinf tciscoasa(config)#hostname asa802域名:asa802(config)#domain-name 特权密码:asa802(config)#enable password 123Telnet或SSH密码:asa802(config)#passwd ciscoASA接口名字和安全级别asa802(config-if)#nameif inside(不起名,ping不通)asa802(config-if)#security-level 100(取值0—100 ,值越大,安全级越高)//默认情况下,outside口安全级别为0,inside口安全级别为100,防火墙允许数据从高安全级别流向低安全级别的接口,但不允许流量从低安全级别流向高安全级别的接口,若要放行,必须做策略,ACL 放行;若接口的安全级别相同,那么它们之间不允许通信,绝对不允许,但有时有这个需要,故意把它们设成一样。
#show interface inside接口地址:asa802(config-if)#ip address 10.0.0.0.1 255.255.255.0asa802(config-if)#no shut查看接口地址:asa802(config)#show ip address(备注:在5505中不支持在物理接口上直接进行配置,必须将将接口加入vlan,进vlan配置,在vlan没no shu时,接口也不可以no shu)配置路由:asa802(config)#route outside(端口名称) 0.0.0.0 0.0.0.0 (目的网段)20.0.0.1(下一跳)可简写asa802(config)#route outside(端口名称)0 0(目的网段) 20.0.0.1(下一跳)asa802#show route 查看路由表3. ASA支持3种主要的远程管理接入方式:Telnet、SSH和ASDM。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
1、ASA基本配置静态路由:route outside 192.168.100.0 255.255.255.0 192.168.1.99配置允许telnet:telnet 192.168.10.0 255.255.255.0 inside配置telnet超时时间:telnet timeout 5配置本地认证telnet与console:aaa authentication telnet console LOCAL配置SSH生成密钥对:aaa authentication ssh console LOCALciscoasa(config)# crypto key generate rsaINFO: The name for the keys will be: <Default-RSA-Key>Keypair generation process begin. Please wait...ciscoasa(config)#配置允许SSH:ssh 192.168.10.0 255.255.255.0 inside配置允许ASDM管理:http server enablehttp 192.168.10.0 255.255.255.0 insideasdm image disk0:/asdm-602.binusername cisco password cisco privilege 15配置PAT:nat (inside) 1 192.168.10.0 255.255.255.0global (outside) 1 interface配置端口映射:access-list to_server extended permit tcp any host 192.168.1.99 eq wwwaccess-group to_server in interface outsidestatic (inside,outside) tcp interface www 192.168.10.98 www netmask 255.255.255.255配置ACL:access-list to_server extended permit tcp any host 192.168.1.99 eq wwwaccess-group to_server in interface outside配置允许ICMP穿越:policy-map global_policyclass inspection_defaultinspect icmp配置URL过滤:url-server (outside) vendor websense host 192.168.1.100 timeout 30 protocol TCP version 1 connections 5filter url http 192.168.10.0 255.255.255.0 0.0.0.0 0.0.0.0 allow日志管理:开启logging:logging enable开启console日志:logging console 7将日志发送到日志服务器:logging trap 7logging host inside 192.168.10.98配置IPS:ip audit name zxd info action alarmip audit name cisco attack action alarmip audit interface outside zxdip audit interface outside cisco2、VPN配置ASA IPSec L2L配置:access-list nonat extended permit ip 192.168.10.0 255.255.255.0 192.168.100.0 255.255.255.0 nat (inside) 0 access-list nonatcrypto ipsec transform-set cisco esp-des esp-nonecrypto map cisco 10 match address nonatcrypto map cisco 10 set peer 192.168.1.96crypto map cisco 10 set transform-set ciscocrypto map cisco interface outsidecrypto isakmp enable outsidecrypto isakmp policy 1authentication pre-shareencryption deshash shagroup 1tunnel-group 192.168.1.96 type ipsec-l2ltunnel-group 192.168.1.96 ipsec-attributespre-shared-key ciscoASA Remote VPN Server配置:ip local pool vpnpool 192.168.2.250-192.168.2.254group-policy vpntest internalgroup-policy vpntest attributesvpn-tunnel-protocol IPSecusername zhong password xiaodongtunnel-group vpntest type remote-accesstunnel-group vpntest general-attributesaddress-pool vpnpooldefault-group-policy vpntesttunnel-group vpntest ipsec-attributespre-shared-key ciscocrypto ipsec transform-set cisco esp-des esp-md5-hmac crypto dynamic-map vpntest 1 set transform-set cisco crypto dynamic-map vpntest 1 set reverse-route crypto map cisco 1 ipsec-isakmp dynamic vpntest crypto map cisco interface outsidecrypto isakmp enable outsidecrypto isakmp policy 10authentication pre-shareencryption aeshash shagroup 2RADIUS认证用户:aaa-server vpntest protocol radiusaaa-server vpntest (outside) host 192.168.1.100key ciscotunnel-group vpntest general-attributes authentication-server-group (outside) vpntestASA SSL VPN配置ip local pool vpnpool 192.168.2.200-192.168.2.210 username zhong password xiaodongwebvpnenable outsidesvc image disk0:/sslclient-win-1.1.3.173.pkgsvc enabletunnel-group-list enablegroup-policy webvpn internalgroup-policy webvpn attributesvpn-tunnel-protocol svc webvpnwebvpnsvc ask enabletunnel-group webvpn type remote-accesstunnel-group webvpn general-attributesaddress-pool vpnpooldefault-group-policy webvpntunnel-group webvpn webvpn-attributesgroup-alias hnebony enableIOS SSL VPN配置aaa new-modelaaa authentication login vpnauthen localusername zhong password xiaodongip local pool vpnpool 192.168.20.200 192.168.20.254interface loopback 0ip address 192.168.20.1 255.255.255.0exitwebvpn install svc disk0:/webvpn/svc.pkgwebvpn gateway outip address 192.168.1.99inservicewebvpn context vpntestpolicy group vpntestfunctions svc-enabledsvc address-pool vpnpoolsvc split include 192.168.0.0 255.255.0.0exitdefault-group-policy vpntestaaa authentication list vpnauthengateway outinserviceIOS Easy VPN Server配置:aaa new-modelaaa authentication login vpnauthen localaaa authorization network vpnauthor localusername zhong password xiaodongip local pool vpnpool 192.168.20.200 192.168.20.254ip access-list extended splitpermit ip 192.168.0.0 0.0.255.255 192.168.20.0 0.0.0.255 crypto isakmp policy 1authentication pre-sharehash md5group 2crypto isakmp client configuration group vpntestkey ciscopool vpnpoolacl splitcrypto ipsec transform-set cisco esp-aes esp-sha-hmac crypto dynamic-map vpndymap 1set transform-set ciscoreverse-routecrypto map vpntest client authentication list vpnauthen crypto map vpntest client configuration address respond crypto map vpntest isakmp authorization list vpnauthor crypto map vpntest 10 ipsec-isakmp dynamic vpndymap inter f0/0crypto map vpntest使用ACS认证与授权:aaa authentication login vpnauthen group radiusaaa authorization network vpnauthor group radiusradius-server host 192.168.1.100 auth-port 1645 acct-port 1646 key ciscoRADIUS (IETF)选中6、64、65、69、81.建立用户:vpntest(vpn组路由器配置crypto isakmp client configuration group vpntest可以取消)然后建立用户IOS Easy VPN Client配置:crypto ipsec client ezvpn vpntestmode clientconnect autopeer 192.168.10.1group vpntest key ciscousername zhong password xiaodonginterface f0/0crypto ipsec client ezvpn vpntestinterface f1/0crypto ipsec client ezvpn vpntest inside R1#crypto ipsec client ezvpn xauthUsername: zhongPassword:3、802.1X认证aaa new-modelaaa authentication dot1x default group radius aaa authorization network default group radius radius-server host 192.168.1.100 key cisco dot1x system-auth-controlinterface f0/1dot1x port-control auto指定VLAN:4、RSTPAlternate port—Offers an alternate path toward the root switch to that provided by the current root port.Backup port—Acts as a backup for the path provided by a designated port toward the leaves of the spanning tree. A backup port can exist only when two ports are connected in a loopback by a point-to-point link or when a switch has two or more connections to a shared LAN segment.Edge ports—If you configure a port as an edge port on an RSTP switch by using the spanning-tree portfast interface configuration command, the edge port immediately transitions to the forwarding state. An edge port is the same as a Port Fast-enabled port, and you should enable it only on ports that connect to a single end station.Root ports—If the RSTP selects a new root port, it blocks the old root port and immediately transitions the new root port to the forwarding state.Point-to-point links—If you connect a port to another port through a point-to-point link and the local port becomes a designated port, it negotiates a rapid transition with the other port by using the proposal-agreement handshake to ensure a loop-free topology. As shown in Figure 18-4, Switch A is connected to Switch B through a point-to-point link, and all of the ports are in the blocking state. Assume that the priority of Switch A is a smaller numerical value than the priority of Switch B. Switch A sends a proposal message (a configuration BPDU with the proposal flag set) to Switch B, proposing itself as the designated switch. After receiving theproposal message, Switch B selects as its new root port the port from which the proposalmessage was received, forces all nonedge ports to the blocking state, and sends an agreement message (a BPDU with the agreement flag set) through its new root port. After receiving Switch B’s agreement message, Switch A also immediately transitions its designated port to the forwarding state. No loops in the network are formed because Switch B blocked all of its nonedge ports and because there is a point-to-point link between Switches A and B. When Switch C is connected to Switch B, a similar set of handshaking messages are exchanged.Switch C selects the port connected to Switch B as its root port, and both ends immediately transition to the forwarding state. With each iteration of this handshaking process, one more switch joins the active topology. As the network converges, this proposal-agreement handshaking progresses from the root toward the leaves of the spanning tree. The switch learns the link type from the port duplex mode: a full-duplex port is considered to have a point-to-point connection; a half-duplex port is considered to have a shared connection. You can override the default setting that is controlled by the duplex setting by using the spanning-tree link-type interface configuration command.5、时间访问列表time-range zxdabsolute start 08:30 24 August 2009 end 18:00 01 September 2009time-range ciscoperiodic daily 8:00 to 18:00access-list 110 permit ip any any time-range cisco6、QOSCAR:rate-limit input access-group 101 1000000 3000 4000 conform-action transmit exceed-action dropGTS:class-map match-all ciscomatch access-group 101!!policy-map ciscoclass ciscopolice cir 500000 bc 10000 pir 1000000 be 10000conform-action transmitexceed-action set-prec-transmit 2violate-action dropinterface f1/0service-policy output ciscoCBWFQ:class-map match-all cbwfqmatch access-group 101policy-map cbwfqclass cbwfqpriority percent 60interface f1/0service-policy output cbwfq7、NA T-T8、标准化产品特色:1定位准确,以就业为导向。
