川大《Web技术》第二次网上作业及答案
WEB技术(新) 阶段作业二
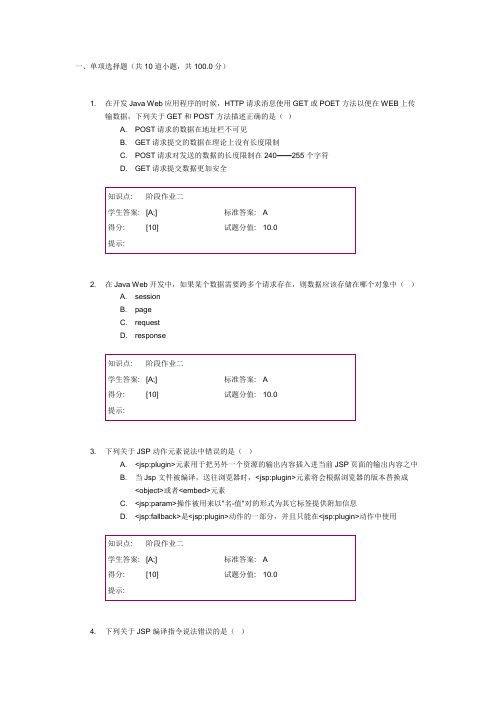
一、单项选择题(共10道小题,共100.0分)1. 在开发Java Web应用程序的时候,HTTP请求消息使用GET或POET方法以便在WEB上传输数据,下列关于GET和POST 方法描述正确的是()A. POST请求的数据在地址栏不可见B. GET请求提交的数据在理论上没有长度限制C. POST请求对发送的数据的长度限制在240——255个字符D. GET请求提交数据更加安全2. 在Java Web开发中,如果某个数据需要跨多个请求存在,则数据应该存储在哪个对象中()A. sessionB. pageC. requestD. response3. 下列关于JSP动作元素说法中错误的是()A. <jsp:plugin>元素用于把另外一个资源的输出内容插入进当前JSP页面的输出内容之中B. 当Jsp文件被编译,送往浏览器时,<jsp:plugin>元素将会根据浏览器的版本替换成<object>或者<embed>元素C. <jsp:param>操作被用来以"名-值"对的形式为其它标签提供附加信息D. <jsp:fallback>是<jsp:plugin>动作的一部分,并且只能在<jsp:plugin>动作中使用4. 下列关于JSP编译指令说法错误的是()A. 编译指令用于从JSP发送一个信息到Servlet容器上B. 编译指令元素为编译阶段提供了全局信息C. 编译指令向客户端产生任何输出D. 编译指令所有的指令都在整个JSP页面内有效5. 在HTML页面中包含如下所示代码,则编写Javascript函数判断是否按下键盘上的回车键正确的编码是()<input name="password" type="text" onkeydown="myKeyDown()">A. function myKeyDown(){ if (window.keyCode==13) alert("你按下了回车键");}B. function myKeyDown(){ if (document.keyCode==13) alert("你按下了回车键");}C. function myKeyDown(){ if (event.keyCode==13) alert("你按下了回车键");}D. function myKeyDown(){ if (keyCode==13) alert("你按下了回车键");}6. 在HTML页面中包含一个按钮控件mybutton,如果要实现点击该按钮时调用已定义的JavaScript函数compute,要编写的HTML代码是()A. <input name="mybutton" type="button" onBlur="compute()"value="计算">B. <input name="mybutton" type="button" onFocus="compute()"value="计算">C. <input name="mybutton" type="button" onClick="function compute()"value="计算">D. <input name="mybutton" type="button" onClick="compute()"value="计算"7. 某网页中有一个表单,其名称是mainForm,该表单的第一个元素是按钮,其名称是myButton,则表述该按钮对象的方法是()A. document.forms.myButtonB. document.mainForm.myButtonC. document.forms[0].element[0]D. document. myButton8. JavaScript产生当前日期的方法是()A. Now()B. Date()C. new Date()D. new Now()9. 下列JavaScript的判断语句中正确的是()A. if(i==0)B. if(i=0)C. if i==0 thenD. if i=0 then10. 如果想在网页显示后动态地改变网页的标题()A. 是不可能的B. 使用JavaScript语句,document.write("新的标题内容");C. 使用JavaScript语句,document.title=("新的标题内容");D. 使用JavaScript语句,document.changeTitle("新的标题内容");。
Review_for_Chapter_2,川大计网部分习题答案第二章

Chapter 2 Review QeustionsR1,R3,R4,R5,R10,R11,R13,R15,R16,R20,R21,R22,R27,R28R1. List five nonproprietary Internet applications and the application-layer protocols that they use.Answer:The Web: HTTP; file transfer: FTP; remote login: Telnet; Network News: NNTP;e-mail: SMTP.R3. What is the difference between network architecture and application architecture?Answer:Network architecture refers to the organization of the communication process into layers (e.g., the five-layer Internet architecture). Application architecture, on the other hand, is designed by an application developer and dictates the broad structure of the application (e.g., client-server or P2P)•R4What information is used by a process running on one host to identify a process running on another host?Answer:The IP address of the destination host and the port number of the destination socket.•R5For a P2P file-sharing application, do you agree with the statement, “There is no notion of client and server sides of a communication session”? Why or why not?Answer:No. As stated in the text, all communication sessions have a client side and a server side. In a P2P file-sharing application, the peer that is receiving a file is typically the client and the peer that is sending the file is typically the server.•R10Recall that TCP can be enhanced with SSL to provide process-to-process security services, including encryption. Does SSL operate at the transport layer or the application layer? If the application developer wants TCP to be enhanced with SSL, what does the developer have to do ?Answer:SSL operates at the application layer. The SSL socket takes unencrypted data from the application layer, encrypts it and then passes it to the TCP socket. If the application developer wants TCP to be enhanced with SSL, she has to include the SSL code in the application.•R11What is meant by a handshaking protocol?Answer:A protocol uses handshaking if the two communicating entities first exchange control packets before sending data to each other. SMTP uses handshaking at the application layer whereas HTTP does not.•R13Telnet into a Web server and send a multiline request message. Include in the request message the If-modified-since: header line to force a response message with the 304 Not Modified status code.Answer:Issued the following command (in Windows command prompt) followed by the HTTP GET message to the “”web server:> telnet 80Since the index.html page in this web server was not modified since Fri, 18 May 2007 09:23:34 GMT, the following output was displayed when the above commands were issued on Sat, 19 May 2007. Note that the first 4 lines are the GET message and header lines input by the user and the next 4 lines (starting from HTTP/1.1 304 Not Modified) is the response from the web server.•R15Suppose Alice, with a Web-based e-mail account (such as Hotmail or gmail), sends a message to Bob, who accesses his mail from his mail server using POP3. Discuss how the message gets from Alice’s host to Bob’s host. Be sure to list the series of application-layer protocols that are used to move the message between the two hosts.Answer:Message is sent from Alice’s host to her mail server over HTTP. Alice’s mail server then sends the message to Bob’s mail server over SMTP. Bob then transfers the message from his mail server to his host over POP3.•R16Print out the header of an e-mail message you have recently received. How many Received: header lines are there? Analyze each of the header lines in the message.Answer: skipped•R20Consider a new peer Alice who joins BitTorrent without possessing any chunks. Without any chunks, she cannot become a top-four uploader for any of the other peers, since she has nothing to upload. How then will Alice get her first chunk?Answer:Alice will get her first chunk as a result of she being selected by one of her neighbors as a result of an “optimistic unchoke,”for sending out chunks to her.•R21In BitTorrent, suppose Alice provides chunks to Bob throughout a 30-second interval. Will Bob necessarily return the favor and provide chunks to Alice in this same interval? Why or why not?Answer:It is not necessary that Bob will also provide chunks to Alice. Alice has to be in the top 4 neighbors of Bob for Bob to send out chunks to her; this might not occur even if Alice is provides chunks to Bob throughout a 30-second interval.•R22What is an overlay network? Does it include routers? What are the edges in the overlay network? How is the query-flooding overlay network created and maintained?Answer:The overlay network in a P2P file sharing systemconsists of the nodes participating in the file sharingsystem and the logical links between the nodes. There is a logical link (an “edge”in graph theory terms) from node A to node B if there is a semi-permanent TCPconnection between A and B. An overlay network does not include routers. With Gnutella, when a node wants to join the Gnutella network, it first discovers the IPaddress of one or more nodes already in the network. It then sends join messages to these nodes. When the node receives confirmations, it becomes a member of the of Gnutella network. Nodes maintain their logical links with periodic refresh messages.•R27For the client-server application over TCP described in section 2.7, why must the server program be executed before the client program? For the client-server application over UDP described in Section 2.8, why may the client program be executed before the server program?Answer:For the TCP application, as soon as the client is executed, it attempts to initiate a TCP connection with the server. If the TCP server is not running, then the client will fail to make a connection. For the UDP application, the client does not initiate connections (or attempt to communicate with the UDP server) immediately upon execution•R28The UDP server described in Section 2.8 needed only one socket, where the TCP server described in Section 2.7 needed two sockets. Why? If the TCP server were to support n simultaneous connections, each from a different client host, how many sockets would the TCP server need?Answer:With the UDP server, there is no welcoming socket, and all data from different clients enters the server through this one socket. With the TCP server, there is awelcoming socket, and each time a client initiates aconnection to the server, a new socket is created. Thus, to support n simultaneous connections, the serverwould need n+1 sockets.ProblemsP1,P4,P5,P7,P8,P16,P24,P25•P1True or false?a. A user requests a Web page that consists of some textand three images. For this page, the client will sendone request message and receive four responsemessages.b.Two distinct Web pages (for example,/research.html and/student.html)can be sent over the same persistent connection.c.With nonpersistent connection between browser andorigin server, it is possible for a single TCP segment to carry two distinct HTTP request messages.d.The Date: header in the HTTP response messageindicates when the object in the response was lastmodified.Answer:a) Fb) Tc) Fd) F•P4Obtain the HTTP/1.1 specification (RFC2616). Answer the following questions: a.Explain the mechanism used forsignaling between the client and serverto indicate that a persistent connection is being closed. Can the client, theserver ,or both signal the close of aconnection?b.What encryption services are providedby HTTP?Answer:a) Persistent connections are discussed in section 8 ofRFC 2616 (the real goal of this question was to getyou to retrieve and read an RFC). Sections 8.1.2 and8.1.2.1 of the RFC indicate that either the client or theserver can indicate to the other that it is going to close the persistent connection. It does so by including theincluding the connection-token "close" in theConnection-header field of the http request/reply.b) HTTP does not provide any encryption services.•P5Read RFC 959 for FTP. List all of theclient commands that are supported by the RFC.Answer:Access control commands:USER, PASS, ACT, CWD, CDUP, SMNT, REIN, QUIT.Transfer parameter commands:PORT, PASV, TYPE STRU, MODE.Service commands:RETR, STOR, STOU, APPE, ALLO, REST, RNFR, RNTO, ABOR, DELE,RMD, MRD, PWD, LIST, NLST, SITE, SYST, STAT, HELP, NOOP.•P7Suppose within your Web browser you click on a link to obtain a Web page. The IP address for the associated URL is not cached in your local host, so a DNS lookup is necessary to obtain the IP address. Suppose that nDNS servers are visited before your host receives theIP address from DNS; the successive visits incur andRTTof RTT1,…RTTn. Further suppose that the Webpage associated with the link contains exactly one object, consisting of a small amount of HTML text. LetRTT0denote the RTT between the local host and theserver containing the object. Assuming zero transmission time of the object, how much time elapses from when the client clicks on the link until the client receives the object?Answer:The total amount of time to get the IPaddress iselapses to set up the Once the IP address is known, RTTTCP connection and another RTTelapses to requestand receive the small object. The total response time is•P8Referring to Problem P7,suppose theHTML file references three very smallobjects on the same server. Neglecting transmission times, how much timeelapses witha.Non-persistent HTTP with no parallelTCP connections?b.Non-persistent HTTP with parallelconnections?c.Persistent HTTP?Answer: a)b)c)•P16Consider distributing a file of F=5 Gbits to N peers. The server has an upload rateof us =20Mbps, and each peer has adownload rate of di =1Mbps and anupload rate of u. For N=10,100, and1,000 and u=100Kbps, 250Kbps,and 500Kbps,prepare a chart giving the minimum distribution time for each of the combinations of N and u for both client-server distribution and P2P distribution.Answer:For calculating the minimum distribution time for client-server distribution, we use the following formula:Similarly, for calculating the minimum distribution time for P2P distribution, we use the following formula:•P24Suppose that in UDPClient.java we replace the LineDatagramSocket clientSocket= new DatagramSocket();withDatagramSocket clientSocket= new DatagramSocket(5432);Will it become necessary to changeUDPServer.java? What are the port numbers for the sockets in UDPClient and UDPServer?What were they before making this change?Answer:•P25Install and compile the Java ProgramsTCPClient and UDPCLient on one hostand TCPServer and UDPServer onanother host.a.Suppose you run TCPClient before yourun TCPServer. What happens? Why?b.Suppose you run UDPCLient before yourun UDPServer. What happens? Why?c.What happens if you use different portnumbers for the client and server sides?Answer:a)If you run TCPClient first, then the client will attempt to make a TCP connection with a non-existent server process.A TCP connection will not be made.b) UDPClient doesn't establish a TCP connection with the server. Thus, everythingshould work fine if you first run UDPClient, then run UDPServer, and then type some input into the keyboard.c) If you use different port numbers, then the client will attempt to establish a TCP connection with the wrong process or a non-existent process. Errors will occur.。
动态网制作(本科)第二次作业_0001-四川电大-课程号:5107703-[参考答案]
![动态网制作(本科)第二次作业_0001-四川电大-课程号:5107703-[参考答案]](https://img.taocdn.com/s3/m/257d6b3d79563c1ec5da71fb.png)
动态网页制作(开放本科)第二次作业_0001
四川形成性测评系统课程代码:5107703 课程复习资料
、单项选择题(共 20 道试题,共 80 分。
)
1. 请问Mid(“I am a student.”,9,2)的返回值是什么?()
A. "tu"
B. "st"
C. "en"
D. "nt"
正确的答案是:A
2. 在VBScript中,下列说法正确的是()。
A. 没有计算数的指数次方的运算符,但可以通过* 运算符实现。
B. &运算符可以强制将任意两个表达式进行字符串链接。
C. 表达式 16/5 的结果是1。
D. 以上都正确
正确的答案是:B
3. 在VBScript中,下列运算符优先级最高的是()。
.
A. 求余运算 (Mod)
B. 负数 (-)
C. 乘法和除法 (*, /)
D. 字符串连接 (&)
正确的答案是:B
4. 执行完 a=5 Mod 3 语句后,a的值为()。
A. 0
B. 2
C. 3
D. 5
正确的答案是:B
5. 下面 a=Trim(" vbscript") & Rtrim(" good") 语句后,a的值为()。
A. " vbscript good"
B. "vbscript good"。
川大《计算机应用基础》第二次作业答案

川大《计算机应用基础》第二次作业答案*单顶爲棒3L亞大案兵to个屮飘・2.0 «■, Hiuo-im.柞毎中孫绐叫的琵吨中”只自一顷启荷合閘目轻卓1 .屯子工停中时申元稱的默认叔?9 ____________ .R、数宇B. 文本仁日酹D.華刖#乙用碣电子二柞卿P的厅号逆行地号萱定__________ <A. 数字#B. TSC. 砖V手圧宾今D. 字母或皈字3.Exce 2010主界五窗口中爺绸栏上时&隹tfl茅来向单元钳人_____________ .4.敌宁氐袁字D W #4.?FExrel 2QLW.鐘AE7宇咋淘W幡用时,需曙辅人的畫訐宇符扉’九逗号氐分号仁甲引总#D.飕引号5.枉Excel工"谢生界面已不包含谶项卡足______________ .C. 睹人D. iM6.Exce XHO_U恵辽件的軸认扛屋名为_____ .A. JjQtR. xlsx VC. ppLXt>. Jpeg7.在Emd 20m 霍定一^单元悟笛存人的公士y=L計2+7:则当发单元框处于舖崔曲舸蟲M丙容为A.13+2+7B.-13*2+7^C.33D.=33S.当跖Extel MID中的分變匸总时「廖季宪按仝经宇段对sae農困孑 ____________ -A. 求诩B. 洁谨U曲D.貝沛宀弘在Excel 201OP, 表讲行排强L存"排序羽话惟中S0瞎權启的排序超字蚀I限制沖—A, 1*TR” 2半C. 孙D”任总扌*量裂艮£E U 第Y典 旧何鱼M-H S &蛊仪W 5LE"怨一I长只・S E 舌徵図播, 观盟一題E 盂餾翼・<ft 空規第«{?•竄Inr 阳 Y担Qir L e K'曲ID .8IQHtecm^-Y®968但I 635床丫B幕佝型,Ga甲喷*H O I O 0CDV<圮離G卷晅览々日4|朋葩HOTON 】u3d 」9M0d 出・9T田盟星奴畐ilz B OLT盘•畐fWU 三S蛊田岁罰期毀柏習・9Q飾事1.IX 貝£&盟舉壽直&早空料fWJK姐 &借畜1K D 9.&&料團姿少s fr半昼诃»床,爸<HOTOCUodJWMOdln To圧半星対-S 5^ I td+七< 、d + _h u 1+ 宅c s d+ 宅x w壬普g y r x fe s 養 w s f i c s f e Z +4I V N ±< > s+suN +E O 珊越妁迅g 父to R W I T Y 棚HBrnoIOZ -u -o d m 、—£00翼・署・t B i s n - k te r w e k % 妖te R 帛第出 15工一:&暑・£住半博 ¥L V 5L et «< od lt ・二o d tti 龙E fe R ・IC is G卷建星也u妙HOIOZ M u一•二ft o ^ 港z・我二-f r o s ^-o vx f i .o ^19•在PowerPoint 2010中,対幻灯片的車新排序,浓!)0删!除等操咋,以及亩视荃休构忠部持別有用的观劇是A. 幻灯片視图B. 幻灯片刘比腿“c. xmsD. 备注页规圉20. ^PowerPoint 2010中,设昌幻灯片背貝格式的填充选项中包含A. 宁体・宁号、做色、风格B・廿模板.幻灯片版式C•纯色.新变.图片和纹理毎“D.壳度对比度和馆和度21•按照网书信号危廊延迟,从<1弓戊排净正昶的星A. 易理网、B. JS硕C. 城域网、广域网、城理网城域冈、广减网7 广域网、局域网局域网、广减网22.以下頑于无经按入旦联网的__________ .A. GPRS/CDMAB. 3GC. WLAND. 肛上都杲723. QQS ____ •A. AD5US?丄网软件B. 即时通(5聊天软件“D. 办公枚件24. 当丽我国的互联网主要以科护和教育为目的.从爭詐经兰性的活动。
川大《WEB技术》18春在线作业2-0001参考答案

试卷总分:100得分:0
一、单选题(共21道试题,共84分)
1.下面不可以用来处理图形的软件是:
A.Fireworks
B.Flash
C.FrontPage
D.Photoshop
正确答案:C
2.以下不属于动态网页技术的是:
A.CGI
C.HTML
正确答案:C
18.常用的网页图像格式有:
A.gif,tiff
B.tiff,jpg
C.gif,jpg
D.tiff,png
正确答案:C
19.下列()表示的不是按钮。
A.type="submit"
B.type="reset"
C.type="image"
D.type="button"
正确答案:C
20.属于静态网页文件扩展名的是:
另一方面,随着社会的发展,人们的就业观念发生了重大变化,更多的人认为工作的目的不仅仅是为了生存,而是为了实现自身的价值,人们不再愿意从事那种传统的束缚于单位的就业形式,而更愿意寻找一种适合自己意愿的、满足自己爱好的、更加自由的就业方式,从而拥有更多属于自己的自由时间和空间来安排自己的生活、实现个人的价值,近年来兴起的SOHO一族就是典型例证。SOHO是Small Office Home Office(小办公室、居家办公室)的缩写,它是指个人以自己的家或小型场所为办公室而从事工作的小型事业体(个体户)。SOHO代表了一种自由的新型就业方式,其工作场所不固定,工作时间自由,收入高低也不确定,特别适合与高新科技、信息技术相关工作的劳动者,如软件程序员、网络工程师、记者、编辑、自由撰稿人、音乐制作人、广告工作者、咨询师等。
《WEB技术》20春在线作业2-0001【四川大学答案49980】

21.一个网站是通过()将很多的网页链接在一起的。 A.文字 B.超媒体 C.超链接 D.图像
多选题 1.在表格元素中,TR元素的VALIGN属性的可能值有 A.TOP B.MIDDLE C.CENTER D.BOTTOM E.BASELINE
3.以下扩展名中不表示网页文件的是: A..htm B..html C..asp D..txt
4.下列()是定义样式表的正确格式。 A.{body:color=black(body)} B.body:color=black C.body {color:black} D.{body;color:black}
14.可以不用发布就能在本地计算机上浏览的页面编写语言是 A.ASP B.HTML C.PHP D.JSP
15.一台装有windows系统的计算机,要上网必须安装()协议。 Beui B.IPX/SPX C.TCP/IP D.FTP
16.要创建一个到UseNet新闻组的链接,下面正确的句法是 A.蓝色新闻网 B.蓝色新闻网 C.蓝色新闻网
《WEB技术》20春在线作业2-0001 红字部分为答案!
单选题 1.浏览网页,是属于 Internet 所提供的()服务。 A.FTP B.Email C.Telnet D.WWW
2.下面不是网页美化工具的是: A.Dreamweaver B.Fireworks C.Photoshop D.Freehand
2.在BODY的属性中,和颜色相关的有 A.ALINK B.BGCOLOR C.LINK D.TEXT E.VLINK
判断题 1.在IE中,通过“查看”菜单下的“源文件”菜单项可查看到HTML网页的源代码。
计算机二级Web练习题及答案(2)

计算机二级Web练习题及答案(2)
计算机二级Web练习题及答案2017
12以下选项中,全部都是表格标记的是( )。
参考答案:B
简答题:
当前主要的 WEB数据库访问技术有哪些?
答:到目前为止,WEB数据库访问技术主要分为两大类:
(1)公共网关接口技术(CGI);
CGI 是 WEB 服务器运行时外部程序的'规范,按照 CGI 编写的程序可以扩展服务器的功
能,完成服务器不能完成的工作,外部程序执行时可以生成HTML 文档,并将文档返回
WEB服务器。
(2)服务器端脚本编程技术。
当前较为流行的几种有代表性的服务器端脚本编程技术是ASP、PHP、JSP。
HTML是什么?简述它的基本结构。
答:HTML(Hypertext Marked Language,超文本标记语言)是一种用来制作 WEB 上超文
本文档的简单标记语言。
对于大多数WEB页面来说,都具有如下所示的基本结构:
……主体内容……
ASP提供的 6个内置全局对象的名称及其主要功能是什么?
(1)Response(响应)对象:它控制在HTTP响应消息中,将消息发送给浏览器
(2)Request(请求)对象:它在一个HTTP请求过程中,获取由浏览器传送给服务器的消息
(3)Server(服务器)对象:它提供对驻留在服务器上的资源的访问
(4)Session(会话期)对象:它用于存储和管理与一个特定的用户会
话有关的信息
Application(应用程序)对象:它用于存储和管理与该Web 应用程序有关的信息
ObjectContext:用来配合 Microsoft Transction Server进行分散式交易处理。
四川大学《WEB技术》20春在线作业2.doc

1.浏览网页,是属于 Internet 所提供的()服务。
A.FTPB.EmailC.TelnetD.WWW【参考答案】: D2.下面不是网页美化工具的是:A.DreamweaverB.FireworksC.PhotoshopD.Freehand【参考答案】: A3.以下扩展名中不表示网页文件的是:A..htmB..htmlC..aspD..txt【参考答案】: D4.下列()是定义样式表的正确格式。
A.{body:color=black(body}B.body:color=blackC.body {color: black}D.{body;color:black}【参考答案】: A5.HTML定义了网页的结构,()决定了浏览器如何显示HTML代码。
A.JavaScriptB.CSSC.XMLD.C#【参考答案】: B6.用于设置文本框显示宽度的属性是:A.SizeB.MaxLengthC.ValueD.Length【参考答案】: A7.若要以加粗宋体、6号字显示“hello”以下用法中,正确的是:A.bfont size=6hello/b/fontB.bfont face=”宋体”size=6hello/font/b C.bfont size=“宋体”size=6hello/b/font D.bfont size=“宋体”fontsize=6hello/b/font【参考答案】: B8.以下不是被称为“网页设计三剑客”的是:A.DreamweaverB.FrontPageC.FireworksD.Flash【参考答案】: B9.下面不是常用的浏览器软件的是:A.Internet ExplorerB.NavigatorC.MosaicD.Word【参考答案】: D10.要创建一个到FTP的链接,下面正确的句法是:A.A HREF=〃news:166.111.136.3〃清华九井站点/AB.A HREF=〃usenet:166.111.136.3〃清华九井站点/AC.A HREF=〃ftp://166.111.136.3〃清华九井站点/AD.A HREF=〃http://166.111.136.3〃清华九井站点/A【参考答案】: C11.Dreamweaver 是()软件。
四川大学《WEB技术与网页制作》在线作业1-00001

《WEB技术与网页制作》在线作业1-00001
下面不是网站的链接结构的是:
A:层状结构
B:分散点集合结构
C:线性结构
D:网状结构
参考选项:B
在HTML语言中,用来定义颜色采用的是:
A:二进制编码系统
B:八进制编码系统
C:十六进制编码系统
D:十进制编码系统
参考选项:C
属于静态网页文件扩展名的是:
A:asp
B:htm
C:aspx
D:jsp
参考选项:B
要创建一个到FTP的链接,下面正确的句法是:
A:A HREF=〃news:166.111.136.3〃清华九井站点/A
B:A HREF=〃usenet:166.111.136.3〃清华九井站点/A
C:A HREF=〃ftp://166.111.136.3〃清华九井站点/A
D:A HREF=〃http://166.111.136.3〃清华九井站点/A
参考选项:C
若要产生一个4行30列的多行文本域,以下方法中,正确的是:
A:Input type=”text” Rows=”4” Cols=”30” Name=”txtintrol”B:TextArea Rows=”4” Cols=”30” Name=”txtintro”
C:TextArea Rows=”4” Cols=”30” Name=”txtintro”/TextArea D:TextArea Rows=”30” Cols=”4” Name=”txtintro”/TextArea
参考选项:C
下面不是 Internet 服务的主要内容的是:
A:WWW 服务
B:电子邮件
C:文件传输
D:文字处理
参考选项:D
1。
川大网考《WEB技术与网页制作》复习题库及答案

《WEB技术与网页制作》复习资料一、单项选择题1、BODY元素可以支持很多属性,其中用于定义文档背景颜色的属性为( C )A、ALINKB、BACKGROUNDC、BGCOLORD、VLINK2、要创建一个到UseNet新闻组的链接,下面正确的句法是( B )A、<A HREF=″usenet:news、blue、com″>蓝色新闻网</A>B、<A HREF=″news:news、blue、com″>蓝色新闻网</A>C、<A HREF=″ftp:news、blue、com″>蓝色新闻网</A>D、<A HREF=″http://news、blue、com″>蓝色新闻网</A>3、互联网项目开发是分阶段进行的,其中在阶段转换时出现的判断点是( D )A、测试点B、投入点C、阶段D、界标4、正确描述创建一个段落的句法是( A )A、<P>Paragraph Text</P>B、<L>Paragraph Text</L>C、<PR>Paragraph Text</PR>D、<PRG>Paragraph Text</PRG>5、若想将窗体中数据发送到服务器,并由服务器脚本处理,应将<INPUT>标记的TYPE属性的值设为( A )A、SUBMITB、RADIOC、PASSWORDD、RESET6、一般来说,Web服务器提供的安全保护措施是( A )A、授权和链接加密B、授权C、链接加密D、不能提供安全保护措施7、互联网项目开发是分阶段进行的,其中在阶段转换时出现的判断点被称为( B )A、阶段B、界标C、测试点D、投入点8、要创建一个到Email地址的链接,下面正确的句法是( A )A、<A HREF=″mailto:zzz_buaa@263、com″>和我联系</A>B、<A HREF=″news: zzz_buaa@263、com″>和我联系</A>C、<A HREF=″usenet: zzz_buaa@263、com″>和我联系</A>D、<A HREF=″http:// zzz_buaa@263、com″>和我联系</A>9、一般来说,Web服务器提供的安全保护措施是( B )A、链接加密B、授权和链接加密C、密钥D、授权10、一个HTML文档所需的最基本的标记对是( D )A、<TITLE>和</TITLE>B、<BODY>和</BODY>C、<HEAD>和</HEAD>D、<HTML>和</HTML>11、当<INPUT>标记的TYPE属性为_______时,代表一个密码框。
福师(2020-2021)《网页设计技术》在线作业二(2)答案

福师(2020-2021)《网页设计技术》在线作业二注:本科有多套试卷,请核实是否为您所需要资料,本资料只做参考学习使用!!!一、单选题(共20题,40分)1、下面关于标记的说法不正确的是()。
A标记要填写在一对尖括号(<>)内B书写标记的时候,英文字母的大、小写或混合使用大小写都是允许的。
C标记内可以包含一些属性,属性名称出现在标记的后面,并且以分号进行分隔。
DHTML对属性名称的排列顺序没有特别的要求。
提示:认真复习课本知识302,并完成以上题目【参考选择】:C2、关于Dreamweaver的操作界面,下列说法不正确的是()。
A工具箱包含了常用的工具,制作网页时用到这些工具。
B对象属性浮动工具栏,对网页制作时选择的对象相适应,用来设置对象的属性。
C状态栏,是表示出被编辑网页的效果。
D状态栏,是表示出被编辑网页中正在被编辑的标记名。
提示:认真复习课本知识302,并完成以上题目【参考选择】:C3、能够返回键盘上的按键对应字符的事件是( )AonKeyDownBonKeyPressConKeyUpDonMouseOver提示:认真复习课本知识302,并完成以上题目【参考选择】:B4、网页在Internet 上是通过URL来指明其所在的位置的,每个不同的网页都应该有不同的URL,比如sina网站主页的URL就是()。
ABhttp:\\CDmailto:提示:认真复习课本知识302,并完成以上题目【参考选择】:A5、要动态改变层中的内容可以使用下列哪些方法?( )A利用层的innerHTML改变内容B利用层的innerText改变内容C可以通过设置层的隐藏和显示来实现D可以通过设置层的样式属性的display属性来实现提示:认真复习课本知识302,并完成以上题目。
川大《Web技术》第二次网上作业及答案

一.单侬:摩睡二小人朋乂40个小款,皿小鼠2,0 W.HSO.Oft,也国小款的出的送城由,口勺一通篇符合篇门装求通1> Rrssm'es^er 拦____ 手fc〔t 口A.经愫处理白.悭。
琼储d匚立画制作D里处维2.Fi t “ n±L)是_士火牛匕A.因像她一VB师揖福C.动]画制作口.字处理X Fl aslx^"_______ J i'fr *A.匿悌#耳B,麻而柒泡匚就画制作/O.车处埋4-下药不是McthW IB第股王弟内唇晌是工"¥承房日电了邮件C.文件传标D.文字处理1区下面T干砥鼾传1弓呻A> Droixvci amx日FtcntFaie卡匚PhotEsrhi^p□. HTHL6-下面不是网?俣化工具的是A.Dreaiva arrer *B.FiraTorksC.PhctEsh.jpD.Fteahanl7.下面不是理占的腱接结构的是工层状结构0-分散点集白名杓”C,线性结构D.网I龙结构出一个碰占是通过_______ 将羽多的网历链接在一起的,A,文字B.超媒体C,超捶接*D,图傀7单击网页中的超道接可以跳转到其他___________ ,A.酿/0.操作系统C.文件D.碘10.下面不是常用的融览器软件的是A. In^exnet Explorer81 NavigatorC, MosaicD. Word/分析下面的Javascript代码,式过运算后M的值为工二11/y.4 uurnLmj,中,力的7七/;*!1L儿llrumber /BL mpriberC< 11D.程序坂错12 . JsriraScHLpI 是运彳丁在 的脚本语言。
A,服务器端B 客总常炉C 补跑器运行后把结果返回到客f D.在容尸端运行后।把结果返回到服芬爵13 .在Bipt 甲裁组的 __________ 属性用于迓回教蛆甲元素的个教。
大工13秋《web技术》在线作业1,2,3

大工13秋《web技术》在线作业1,2,3大工13秋《Web技术》在线作业1试卷总分:100 测试时间:--单选题判断题、单选题(共10 道试题,共50 分。
)1.对远程网站上的文件进行维护,通常采用的手段是()。
A. SMTPB. POP3C. FTPD. HTTP满分:5分2.在HTML语言中,表格的标记是()。
A.B.C.D.满分:5分3.XML的定义表示()。
A. 客户端脚本程序语言B. 文档对象模型C. 级联样式表D. 可扩展标记语言满分:5分4.关于JSP内置对象,下列不属于其内置对象的是()。
A. RequestB. ResponseC. SessionD. Vector满分:5分5.以下关于web概念知识,说法错误的是()。
A. 获取WWW服务时,通常需要使用浏览器作为客户端程序B. WWW服务和电子邮件服务是Internet提供的最常用的两种服务C. 网站就是一系列逻辑上可以视为一个整体的页面的集合D. 所有网页的扩展名都是.htm满分:5分6.()是通用的网关接口,是外部程序和Web服务器之间的标准编程接口。
A. ASPB. JSPC. PHPD. CGI满分:5分7.可以在()文件中修改Tomcat服务器端口号。
A. server.xmlB. web.xmlC. tomcat.xmlD. 不能改满分:5分8.要将JavaScript代码片段嵌入到HTML文档中,使用的HTML标记是()。
A.B.C.D.满分:5分9.完整的HTML文档必须包含三个元素,它们是head、html和()。
A. bodyB. scriptC. titleD. link满分:5分10.表格中设置单元格占几行的属性是()。
A. rowspanB. colspanC. rowD. col满分:5分大工13秋《Web技术》在线作业1试卷总分:100 测试时间:--单选题判断题、判断题(共10 道试题,共50 分。
Review_for_Chapter_2,川大计网部分习题答案第二章

Chapter 2 Review QeustionsR1,R3,R4,R5,R10,R11,R13,R15,R16,R20,R21,R22,R27,R28R1. List five nonproprietary Internet applications and the application-layer protocols that they use.Answer:The Web: HTTP; file transfer: FTP; remote login: Telnet; Network News: NNTP;e-mail: SMTP.R3. What is the difference between network architecture and application architecture?Answer:Network architecture refers to the organization of the communication process into layers (e.g., the five-layer Internet architecture). Application architecture, on the other hand, is designed by an application developer and dictates the broad structure of the application (e.g., client-server or P2P)•R4What information is used by a process running on one host to identify a process running on another host?Answer:The IP address of the destination host and the port number of the destination socket.•R5For a P2P file-sharing application, do you agree with the statement, “There is no notion of client and server sides of a communication session”? Why or why not?Answer:No. As stated in the text, all communication sessions have a client side and a server side. In a P2P file-sharing application, the peer that is receiving a file is typically the client and the peer that is sending the file is typically the server.•R10Recall that TCP can be enhanced with SSL to provide process-to-process security services, including encryption. Does SSL operate at the transport layer or the application layer? If the application developer wants TCP to be enhanced with SSL, what does the developer have to do ?Answer:SSL operates at the application layer. The SSL socket takes unencrypted data from the application layer, encrypts it and then passes it to the TCP socket. If the application developer wants TCP to be enhanced with SSL, she has to include the SSL code in the application.•R11What is meant by a handshaking protocol?Answer:A protocol uses handshaking if the two communicating entities first exchange control packets before sending data to each other. SMTP uses handshaking at the application layer whereas HTTP does not.•R13Telnet into a Web server and send a multiline request message. Include in the request message the If-modified-since: header line to force a response message with the 304 Not Modified status code.Answer:Issued the following command (in Windows command prompt) followed by the HTTP GET message to the “”web server:> telnet 80Since the index.html page in this web server was not modified since Fri, 18 May 2007 09:23:34 GMT, the following output was displayed when the above commands were issued on Sat, 19 May 2007. Note that the first 4 lines are the GET message and header lines input by the user and the next 4 lines (starting from HTTP/1.1 304 Not Modified) is the response from the web server.•R15Suppose Alice, with a Web-based e-mail account (such as Hotmail or gmail), sends a message to Bob, who accesses his mail from his mail server using POP3. Discuss how the message gets from Alice’s host to Bob’s host. Be sure to list the series of application-layer protocols that are used to move the message between the two hosts.Answer:Message is sent from Alice’s host to her mail server over HTTP. Alice’s mail server then sends the message to Bob’s mail server over SMTP. Bob then transfers the message from his mail server to his host over POP3.•R16Print out the header of an e-mail message you have recently received. How many Received: header lines are there? Analyze each of the header lines in the message.Answer: skipped•R20Consider a new peer Alice who joins BitTorrent without possessing any chunks. Without any chunks, she cannot become a top-four uploader for any of the other peers, since she has nothing to upload. How then will Alice get her first chunk?Answer:Alice will get her first chunk as a result of she being selected by one of her neighbors as a result of an “optimistic unchoke,”for sending out chunks to her.•R21In BitTorrent, suppose Alice provides chunks to Bob throughout a 30-second interval. Will Bob necessarily return the favor and provide chunks to Alice in this same interval? Why or why not?Answer:It is not necessary that Bob will also provide chunks to Alice. Alice has to be in the top 4 neighbors of Bob for Bob to send out chunks to her; this might not occur even if Alice is provides chunks to Bob throughout a 30-second interval.•R22What is an overlay network? Does it include routers? What are the edges in the overlay network? How is the query-flooding overlay network created and maintained?Answer:The overlay network in a P2P file sharing systemconsists of the nodes participating in the file sharingsystem and the logical links between the nodes. There is a logical link (an “edge”in graph theory terms) from node A to node B if there is a semi-permanent TCPconnection between A and B. An overlay network does not include routers. With Gnutella, when a node wants to join the Gnutella network, it first discovers the IPaddress of one or more nodes already in the network. It then sends join messages to these nodes. When the node receives confirmations, it becomes a member of the of Gnutella network. Nodes maintain their logical links with periodic refresh messages.•R27For the client-server application over TCP described in section 2.7, why must the server program be executed before the client program? For the client-server application over UDP described in Section 2.8, why may the client program be executed before the server program?Answer:For the TCP application, as soon as the client is executed, it attempts to initiate a TCP connection with the server. If the TCP server is not running, then the client will fail to make a connection. For the UDP application, the client does not initiate connections (or attempt to communicate with the UDP server) immediately upon execution•R28The UDP server described in Section 2.8 needed only one socket, where the TCP server described in Section 2.7 needed two sockets. Why? If the TCP server were to support n simultaneous connections, each from a different client host, how many sockets would the TCP server need?Answer:With the UDP server, there is no welcoming socket, and all data from different clients enters the server through this one socket. With the TCP server, there is awelcoming socket, and each time a client initiates aconnection to the server, a new socket is created. Thus, to support n simultaneous connections, the serverwould need n+1 sockets.ProblemsP1,P4,P5,P7,P8,P16,P24,P25•P1True or false?a. A user requests a Web page that consists of some textand three images. For this page, the client will sendone request message and receive four responsemessages.b.Two distinct Web pages (for example,/research.html and/student.html)can be sent over the same persistent connection.c.With nonpersistent connection between browser andorigin server, it is possible for a single TCP segment to carry two distinct HTTP request messages.d.The Date: header in the HTTP response messageindicates when the object in the response was lastmodified.Answer:a) Fb) Tc) Fd) F•P4Obtain the HTTP/1.1 specification (RFC2616). Answer the following questions: a.Explain the mechanism used forsignaling between the client and serverto indicate that a persistent connection is being closed. Can the client, theserver ,or both signal the close of aconnection?b.What encryption services are providedby HTTP?Answer:a) Persistent connections are discussed in section 8 ofRFC 2616 (the real goal of this question was to getyou to retrieve and read an RFC). Sections 8.1.2 and8.1.2.1 of the RFC indicate that either the client or theserver can indicate to the other that it is going to close the persistent connection. It does so by including theincluding the connection-token "close" in theConnection-header field of the http request/reply.b) HTTP does not provide any encryption services.•P5Read RFC 959 for FTP. List all of theclient commands that are supported by the RFC.Answer:Access control commands:USER, PASS, ACT, CWD, CDUP, SMNT, REIN, QUIT.Transfer parameter commands:PORT, PASV, TYPE STRU, MODE.Service commands:RETR, STOR, STOU, APPE, ALLO, REST, RNFR, RNTO, ABOR, DELE,RMD, MRD, PWD, LIST, NLST, SITE, SYST, STAT, HELP, NOOP.•P7Suppose within your Web browser you click on a link to obtain a Web page. The IP address for the associated URL is not cached in your local host, so a DNS lookup is necessary to obtain the IP address. Suppose that nDNS servers are visited before your host receives theIP address from DNS; the successive visits incur andRTTof RTT1,…RTTn. Further suppose that the Webpage associated with the link contains exactly one object, consisting of a small amount of HTML text. LetRTT0denote the RTT between the local host and theserver containing the object. Assuming zero transmission time of the object, how much time elapses from when the client clicks on the link until the client receives the object?Answer:The total amount of time to get the IPaddress iselapses to set up the Once the IP address is known, RTTTCP connection and another RTTelapses to requestand receive the small object. The total response time is•P8Referring to Problem P7,suppose theHTML file references three very smallobjects on the same server. Neglecting transmission times, how much timeelapses witha.Non-persistent HTTP with no parallelTCP connections?b.Non-persistent HTTP with parallelconnections?c.Persistent HTTP?Answer: a)b)c)•P16Consider distributing a file of F=5 Gbits to N peers. The server has an upload rateof us =20Mbps, and each peer has adownload rate of di =1Mbps and anupload rate of u. For N=10,100, and1,000 and u=100Kbps, 250Kbps,and 500Kbps,prepare a chart giving the minimum distribution time for each of the combinations of N and u for both client-server distribution and P2P distribution.Answer:For calculating the minimum distribution time for client-server distribution, we use the following formula:Similarly, for calculating the minimum distribution time for P2P distribution, we use the following formula:•P24Suppose that in UDPClient.java we replace the LineDatagramSocket clientSocket= new DatagramSocket();withDatagramSocket clientSocket= new DatagramSocket(5432);Will it become necessary to changeUDPServer.java? What are the port numbers for the sockets in UDPClient and UDPServer?What were they before making this change?Answer:•P25Install and compile the Java ProgramsTCPClient and UDPCLient on one hostand TCPServer and UDPServer onanother host.a.Suppose you run TCPClient before yourun TCPServer. What happens? Why?b.Suppose you run UDPCLient before yourun UDPServer. What happens? Why?c.What happens if you use different portnumbers for the client and server sides?Answer:a)If you run TCPClient first, then the client will attempt to make a TCP connection with a non-existent server process.A TCP connection will not be made.b) UDPClient doesn't establish a TCP connection with the server. Thus, everythingshould work fine if you first run UDPClient, then run UDPServer, and then type some input into the keyboard.c) If you use different port numbers, then the client will attempt to establish a TCP connection with the wrong process or a non-existent process. Errors will occur.。
Review_for_Chapter_2,川大计网部分习题答案第二章

Chapter 2 Review QeustionsR1,R3,R4,R5,R10,R11,R13,R15,R16,R20,R21,R22,R27,R28R1. List five nonproprietary Internet applications and the application-layer protocols that they use.Answer:The Web: HTTP; file transfer: FTP; remote login: Telnet; Network News: NNTP;e-mail: SMTP.R3. What is the difference between network architecture and application architecture?Answer:Network architecture refers to the organization of the communication process into layers (e.g., the five-layer Internet architecture). Application architecture, on the other hand, is designed by an application developer and dictates the broad structure of the application (e.g., client-server or P2P)•R4What information is used by a process running on one host to identify a process running on another host?Answer:The IP address of the destination host and the port number of the destination socket.•R5For a P2P file-sharing application, do you agree with the statement, “There is no notion of client and server sides of a communication session”? Why or why not?Answer:No. As stated in the text, all communication sessions have a client side and a server side. In a P2P file-sharing application, the peer that is receiving a file is typically the client and the peer that is sending the file is typically the server.•R10Recall that TCP can be enhanced with SSL to provide process-to-process security services, including encryption. Does SSL operate at the transport layer or the application layer? If the application developer wants TCP to be enhanced with SSL, what does the developer have to do ?Answer:SSL operates at the application layer. The SSL socket takes unencrypted data from the application layer, encrypts it and then passes it to the TCP socket. If the application developer wants TCP to be enhanced with SSL, she has to include the SSL code in the application.•R11What is meant by a handshaking protocol?Answer:A protocol uses handshaking if the two communicating entities first exchange control packets before sending data to each other. SMTP uses handshaking at the application layer whereas HTTP does not.•R13Telnet into a Web server and send a multiline request message. Include in the request message the If-modified-since: header line to force a response message with the 304 Not Modified status code.Answer:Issued the following command (in Windows command prompt) followed by the HTTP GET message to the “”web server:> telnet 80Since the index.html page in this web server was not modified since Fri, 18 May 2007 09:23:34 GMT, the following output was displayed when the above commands were issued on Sat, 19 May 2007. Note that the first 4 lines are the GET message and header lines input by the user and the next 4 lines (starting from HTTP/1.1 304 Not Modified) is the response from the web server.•R15Suppose Alice, with a Web-based e-mail account (such as Hotmail or gmail), sends a message to Bob, who accesses his mail from his mail server using POP3. Discuss how the message gets from Alice’s host to Bob’s host. Be sure to list the series of application-layer protocols that are used to move the message between the two hosts.Answer:Message is sent from Alice’s host to her mail server over HTTP. Alice’s mail server then sends the message to Bob’s mail server over SMTP. Bob then transfers the message from his mail server to his host over POP3.•R16Print out the header of an e-mail message you have recently received. How many Received: header lines are there? Analyze each of the header lines in the message.Answer: skipped•R20Consider a new peer Alice who joins BitTorrent without possessing any chunks. Without any chunks, she cannot become a top-four uploader for any of the other peers, since she has nothing to upload. How then will Alice get her first chunk?Answer:Alice will get her first chunk as a result of she being selected by one of her neighbors as a result of an “optimistic unchoke,”for sending out chunks to her.•R21In BitTorrent, suppose Alice provides chunks to Bob throughout a 30-second interval. Will Bob necessarily return the favor and provide chunks to Alice in this same interval? Why or why not?Answer:It is not necessary that Bob will also provide chunks to Alice. Alice has to be in the top 4 neighbors of Bob for Bob to send out chunks to her; this might not occur even if Alice is provides chunks to Bob throughout a 30-second interval.•R22What is an overlay network? Does it include routers? What are the edges in the overlay network? How is the query-flooding overlay network created and maintained?Answer:The overlay network in a P2P file sharing systemconsists of the nodes participating in the file sharingsystem and the logical links between the nodes. There is a logical link (an “edge”in graph theory terms) from node A to node B if there is a semi-permanent TCPconnection between A and B. An overlay network does not include routers. With Gnutella, when a node wants to join the Gnutella network, it first discovers the IPaddress of one or more nodes already in the network. It then sends join messages to these nodes. When the node receives confirmations, it becomes a member of the of Gnutella network. Nodes maintain their logical links with periodic refresh messages.•R27For the client-server application over TCP described in section 2.7, why must the server program be executed before the client program? For the client-server application over UDP described in Section 2.8, why may the client program be executed before the server program?Answer:For the TCP application, as soon as the client is executed, it attempts to initiate a TCP connection with the server. If the TCP server is not running, then the client will fail to make a connection. For the UDP application, the client does not initiate connections (or attempt to communicate with the UDP server) immediately upon execution•R28The UDP server described in Section 2.8 needed only one socket, where the TCP server described in Section 2.7 needed two sockets. Why? If the TCP server were to support n simultaneous connections, each from a different client host, how many sockets would the TCP server need?Answer:With the UDP server, there is no welcoming socket, and all data from different clients enters the server through this one socket. With the TCP server, there is awelcoming socket, and each time a client initiates aconnection to the server, a new socket is created. Thus, to support n simultaneous connections, the serverwould need n+1 sockets.ProblemsP1,P4,P5,P7,P8,P16,P24,P25•P1True or false?a. A user requests a Web page that consists of some textand three images. For this page, the client will sendone request message and receive four responsemessages.b.Two distinct Web pages (for example,/research.html and/student.html)can be sent over the same persistent connection.c.With nonpersistent connection between browser andorigin server, it is possible for a single TCP segment to carry two distinct HTTP request messages.d.The Date: header in the HTTP response messageindicates when the object in the response was lastmodified.Answer:a) Fb) Tc) Fd) F•P4Obtain the HTTP/1.1 specification (RFC2616). Answer the following questions: a.Explain the mechanism used forsignaling between the client and serverto indicate that a persistent connection is being closed. Can the client, theserver ,or both signal the close of aconnection?b.What encryption services are providedby HTTP?Answer:a) Persistent connections are discussed in section 8 ofRFC 2616 (the real goal of this question was to getyou to retrieve and read an RFC). Sections 8.1.2 and8.1.2.1 of the RFC indicate that either the client or theserver can indicate to the other that it is going to close the persistent connection. It does so by including theincluding the connection-token "close" in theConnection-header field of the http request/reply.b) HTTP does not provide any encryption services.•P5Read RFC 959 for FTP. List all of theclient commands that are supported by the RFC.Answer:Access control commands:USER, PASS, ACT, CWD, CDUP, SMNT, REIN, QUIT.Transfer parameter commands:PORT, PASV, TYPE STRU, MODE.Service commands:RETR, STOR, STOU, APPE, ALLO, REST, RNFR, RNTO, ABOR, DELE,RMD, MRD, PWD, LIST, NLST, SITE, SYST, STAT, HELP, NOOP.•P7Suppose within your Web browser you click on a link to obtain a Web page. The IP address for the associated URL is not cached in your local host, so a DNS lookup is necessary to obtain the IP address. Suppose that nDNS servers are visited before your host receives theIP address from DNS; the successive visits incur andRTTof RTT1,…RTTn. Further suppose that the Webpage associated with the link contains exactly one object, consisting of a small amount of HTML text. LetRTT0denote the RTT between the local host and theserver containing the object. Assuming zero transmission time of the object, how much time elapses from when the client clicks on the link until the client receives the object?Answer:The total amount of time to get the IPaddress iselapses to set up the Once the IP address is known, RTTTCP connection and another RTTelapses to requestand receive the small object. The total response time is•P8Referring to Problem P7,suppose theHTML file references three very smallobjects on the same server. Neglecting transmission times, how much timeelapses witha.Non-persistent HTTP with no parallelTCP connections?b.Non-persistent HTTP with parallelconnections?c.Persistent HTTP?Answer: a)b)c)•P16Consider distributing a file of F=5 Gbits to N peers. The server has an upload rateof us =20Mbps, and each peer has adownload rate of di =1Mbps and anupload rate of u. For N=10,100, and1,000 and u=100Kbps, 250Kbps,and 500Kbps,prepare a chart giving the minimum distribution time for each of the combinations of N and u for both client-server distribution and P2P distribution.Answer:For calculating the minimum distribution time for client-server distribution, we use the following formula:Similarly, for calculating the minimum distribution time for P2P distribution, we use the following formula:•P24Suppose that in UDPClient.java we replace the LineDatagramSocket clientSocket= new DatagramSocket();withDatagramSocket clientSocket= new DatagramSocket(5432);Will it become necessary to changeUDPServer.java? What are the port numbers for the sockets in UDPClient and UDPServer?What were they before making this change?Answer:•P25Install and compile the Java ProgramsTCPClient and UDPCLient on one hostand TCPServer and UDPServer onanother host.a.Suppose you run TCPClient before yourun TCPServer. What happens? Why?b.Suppose you run UDPCLient before yourun UDPServer. What happens? Why?c.What happens if you use different portnumbers for the client and server sides?Answer:a)If you run TCPClient first, then the client will attempt to make a TCP connection with a non-existent server process.A TCP connection will not be made.b) UDPClient doesn't establish a TCP connection with the server. Thus, everythingshould work fine if you first run UDPClient, then run UDPServer, and then type some input into the keyboard.c) If you use different port numbers, then the client will attempt to establish a TCP connection with the wrong process or a non-existent process. Errors will occur.。
Review_for_Chapter_2,川大计网部分习题答案第二章

Review_for_Chapter_2,川大计网部分习题答案第二章Chapter 2 Review QeustionsR1,R3,R4,R5,R10,R11,R13,R15,R16,R20,R21,R22,R27,R28R1. List five nonproprietary Internet applications and the application-layer protocols that they use.Answer:The Web: HTTP; file transfer: FTP; remote login: Telnet; Network News: NNTP;e-mail: SMTP.R3. What is the difference between network architecture and application architecture?Answer:Network architecture refers to the organization of the communication process into layers (e.g., the five-layer Internet architecture). Application architecture, on the other hand, is designed by an application developer and dictates the broad structure of the application (e.g., client-server or P2P) R4What information is used by a process running on one host to identify a process running on another host?Answer:The IP address of the destination host and the port number of the destination socket.R5For a P2P file-sharing application, do you agree with the statement, “There is no notion of client and server sides of a communication session”? Why or why not?Answer:No. As stated in the text, all communication sessions have a client side and a server side. In a P2P file-sharing application, the peer that is receiving a file is typically the client and the peer that is sending the file is typically the server.R10Recall that TCP can be enhanced with SSL to provide process-to-process security services, including encryption. Does SSL operate at the transport layer or the application layer? If the application developer wants TCP to be enhanced with SSL, what does the developer have to do ?Answer:SSL operates at the application layer. The SSL socket takes unencrypted data from the application layer, encrypts it and then passes it to the TCP socket. If the application developer wants TCP to be enhanced with SSL, she has to include the SSL code in the application.R11What is meant by a handshaking protocol?Answer:A protocol uses handshaking if the two communicating entities first exchange control packets before sending data to each other. SMTP uses handshaking at the application layer whereas HTTP does not.R13Telnet into a Web server and send a multiline request message. Include in the request message the If-modified-since: header line to force a response message with the 304 Not Modified status code.Answer:Issued the following command (in Windows commandprompt) followed by the HTTP GET message to the “”web server:> telnet 80Since the index.html page in this web server was not modified since Fri, 18 May 2007 09:23:34 GMT, the following output was displayed when the above commands were issued on Sat, 19 May 2007. Note that the first 4 lines are the GET message and header lines input by the user and the next 4 lines (starting from HTTP/1.1 304 Not Modified) is the response from the web server.R15Suppose Alice, with a Web-based e-mail account (such as Hotmail or gmail), sends a message to Bob, who accesses his mail from his mail server using POP3. Discuss how the message gets from Alice’s host to Bob’s host. Be sure to list the series of application-layer protocols that are used to move the message between the two hosts.Answer:Message is sent from Alice’s host to her mail server over HTTP. Alice’s mail server then sends the message to Bob’s mail server over SMTP. Bob then transfers the message from his mail server to his host over POP3.。
