最新CCNA第一学期第七章答案
计算机网络-课后答案第七章

问题7-1:用一个例子说明置换密码的加密和解密过程。
假定密钥为CIPHER,而明文为attack begins at four,加密时明文中的空格去除。
答:在英文26个字母中,密钥CIPHER这6个字母在26个英文字母中出现的位置用红色a b然后按行问题7-2答:(1)向一个特定服务器非常快地发送大量任意的分组,使得该服务器过负荷因而无法正常工作。
(2)向一个特定服务器发送大量的TCP SYN报文段(即建立TCP连接的三次握手中的第一个报文段)。
服务器还误以为是正常的因特网用户的请求,于是就响应这个请求,并分配了数据结构和状态。
但攻击者不再发送后面的报文段,因而永远不能够完成TCP连接的建立。
这样可以浪费和耗尽服务器的大量资源。
这种攻击方式又称为SYN flooding(意思是使用同步标志进行洪泛)。
(3)重复地和一个特定服务器建立TCP连接,然后发送大量无用的报文段。
(4)将IP数据报分片后向特定服务器发送,但留一些数据报片不发送。
这就使得目的主机永远无法组装成完整的数据报,一直等待着,浪费了资源。
(5)向许多网络发送ICMP回送请求报文(就是使用应用层的PING程序),结果使许多主机都向攻击者返回ICMP回送回答报文。
无用的、过量的ICMP报文使网络的通信量急剧增加,甚至使网络瘫痪。
这种攻击方式被称为smurf攻击。
Smurf就是能够对网络自动发送这种ICMP报文攻击的程序名字。
分布式拒绝服务DDOS的特点就是攻击者先设法得到因特网上的大量主机的用户账号。
然后攻击者设法秘密地在这些主机上安装从属程序(slave program),如图所示。
一时刻在拒绝服务和分布式拒绝服务都是很难防止的。
使用分组过滤器并不能阻止这种攻击,因为攻击者的IP地址是事先不知道的。
当主机收到许多攻击的数据报时,很难区分开哪些是好的数据报,而哪些是坏的数据报。
例如,当服务器收到请求建立TCP连接的SYN报文时,很难区分这是真的请求建立TCP连接,还是恶意消耗服务器资源的连接请求。
CCNA在线练习答案第七章

1设计师如何确定原型测试需包括的功能?设计师如何确定原型测试需包括的功能?他们选择符合业务需求的功能。
他们选择符合业务需求的功能。
他们选择符合业务需求的功能。
他们选择在网络核心出现的功能。
他们选择在网络核心出现的功能。
他们选择现有网络中没有的功能。
他们选择现有网络中没有的功能。
他们从常见网络运行情况列表中选择功能。
他们从常见网络运行情况列表中选择功能。
2.请参见图示。
请参见图示。
针对网络设计中圈出的缺陷,针对网络设计中圈出的缺陷,可采取哪两项措施来弥补?可采取哪两项措施来弥补?可采取哪两项措施来弥补? (选择两项。
)两项。
)为所有最终用户提供冗余连接。
为所有最终用户提供冗余连接。
为所有最终用户提供冗余连接。
另外添加一个核心交换机来增大冗余度。
另外添加一个核心交换机来增大冗余度。
在用于将服务器群连接到每台核心交换机的服务器块中添加一台交换机。
在用于将服务器群连接到每台核心交换机的服务器块中添加一台交换机。
向DMZ 另外添加一台交换机,并将新交换机与核心交换机直接连接。
另外添加一台交换机,并将新交换机与核心交换机直接连接。
提供一台冗余防火墙路由器,并将其连接到另一个提供一台冗余防火墙路由器,并将其连接到另一个 ISP 、核心交换机和、核心交换机和DMZ 。
3.网络工程师在设计网络安全性原型时可实施哪项网络工程师在设计网络安全性原型时可实施哪项 OSI 模型第模型第 2 层安全措施?层安全措施?网络边缘的防火墙网络边缘的防火墙接入设计层的端口安全性接入设计层的端口安全性接入设计层的端口安全性分布设计层的端口安全性分布设计层的端口安全性接入设计层的接入设计层的 IP 访问控制列表访问控制列表 4.请参见图示。
请参见图示。
在对图示的在对图示的 Cisco 网络进行原型测试时,必须检验连通性。
网络进行原型测试时,必须检验连通性。
假设所有连接均工作正常且在所有设备和接口上启用了设所有连接均工作正常且在所有设备和接口上启用了CDP ,则该命令是从哪台设备上发出的?设备上发出的?R 1 R1 S 1 R3 S 2 R5S35.请参见图示。
CCNA认证基础课程-课后作业.习题答案

CCNA认证基础-习题分析讲义第一部分第一章1. Convert the binary number 10111010 into its hexadecimal equivalent. Select thecorrect answer from the list below. (3)1) 852) 903) BA4) A15) B36) 1C2. Convert the Hexadecimal number A2 into its Base 10 equivalent. Select thecorrect answer from the list below. (4)1) 1562) 1583) 1604) 1625) 1646) 1663. Which binary number is a representation of the decimal number 248? (3)1) 111010002) 111101003) 111110004) 111110104. Which of the following will test the internal loopback of a node? (3)1) ping 10.10.10.12) ping 192.168.1.13) ping 127.0.0.14) ping 223.223.223.2235) ping 255.255.255.2555. What can be verified by successfully pinging the reserved loopback address ona host? (2)1) Connectivity exists between two hosts on the LAN.2) The TCP/IP stack of the local host is configured correctly.3) A connection exists between a host and the default gateway.4) The route a packet takes from the local host to a remote host is valid.6. Which of the following commands could be used on a Windows-basedcomputer to view the current IP configuration of the system? (Choose two.) (3,4)1) configip2) ifconfig3) ipconfig4) winipcfg5) Winipconfig7.Refer to the exhibit. What must be configured on Host B to allow it to communicate withthe Host C? (Choose three.) (2,4,6)1)the MAC address of RTA router interface connected to Switch 12) a unique host IP address3)the IP address of Switch 14)the default gateway address5)the MAC address of Host C6)the subnet mask for the LAN8. What are important characteristics to consider when purchasing a networkinterface card? (Choose two.) (2,3)1) security used on the network2) media used on the network3) system bus used on the computer4) software installed on the network5) diagnostic tools installed on the network第二章1. Select the necessary information that is required to compute the estimated timeit would take to transfer data from one location to another. (Choose two.) (1,5)1) file size2) data format3) network in use4) type of medium5) bandwidth of the link2. Using the data transfer calculation T=S/BW, how long would it take a 4MB file tobe sent over a 1.5Mbps connection? (2)1) 52.2 seconds2) 21.3 seconds3) 6.4 seconds4) 2 seconds5) 0.075 seconds6) 0.0375 seconds3. What are features of the TCP/IP Transport layer? (Choose two.) (3,5)1) path determination2) handles representation, encoding and dialog control3) uses TCP and UDP protocols4) packet switching5) reliability, flow control and error correction4. Which of the following is the Layer 4 PDU? (4)1) bit2) frame3) packet4) Segment5. What is important to remember about the data link layer of the OSI model whenconsidering Peer to Peer communication? (Choose three.) (3,4,5)1) It links data to the transport layer.2) It encapsulates frames into packets.3) It provides a service to the network layer.4) It encapsulates the network layer information into a frame.5) Its header contains a physical address which is required to complete the datalink functions.6) It encodes the data link frame into a pattern of 1s and 0s (bits) for transmissionon the medium.6. Which statement describes a star topology? (2)1) Each host in the network is connected to a backbone cable that is terminated atboth ends.2) Each host is connected to a hub or switch, either of which acts as a central pointfor all network connections.3) Each host is directly connected to two other hosts to form a long chain of hosts.4) Each host has a connection to all other hosts in the network.7. Which statements describe the logical token-passing topology? (Choose two.)(2)1) Network usage is on a first come, first serve basis.2) Computers are allowed to transmit data only when they possess a token.3) Data from a host is received by all other hosts. Electronic tokens are passedsequentially to each other.4) Token passing networks have problems with high collision rates.8. Which technologies are considered to be LAN technologies? (Choose two.) (2,5)1) DSL2) Token Ring3) Frame Relay4) ISDN5) Ethernet9.Refer to the exhibit. Host A wants to send a message to host B. Place the following stepsin the correct order so that the message can be sent. (4)A - add network layer addressesB - transmit bitsC - create application dataD - add data link layer addresses1) B, A, D, C2) D, A, C, B3) A, D, A, B4) C, A, D, B5) C, D, A, B6) C, B, A, D10.After an uns u ccessful ping to the local router, the technician decides to investigate therouter. The technician observes that the lights and fan on the router are not operational.In which layer of the OSI model is the problem most likely occurring? (4)1) transport2) network3) data link4) physical11. Refer t o the exhibit. What is the order of the TCP/IP Protocol Data Units as datais moved as indicated through the OSI model? (3)1) data, segments, frames, packets, bits2) data, packets, segments, frames, bits3) data, segments, packets, frames, bits4) data, packets, frames, segments, bits第三章1. Which combinations of charges will be repelled by electric force? (Choose two.)(4,6)1) neutral and neutral2) neutral and positive3) neutral and negative4) positive and positive5) positive and negative6) negative and negative2. Which of the following are considered the best media for use in data networkcommunications? (Choose three.) (2,3,6)1) glass2) fibers3) copper4) gold5) plastic6) silicon7) Silver3. Which of the following wireless standards increased transmission capabilitiesto 11 Mbps? (2)1) 802.11a2) 802.11b3) 802.11c4) 802.11d4. What is attenuation? (3)1) opposition to the flow of current2) measurement of electrical signals relative to time3) degradation of a signal as it travels along the medium4) amount or volume of traffic that is flowing on the medium5. Which cable specifications are indicated by 10BASE-T? (3)1) 10 Mbps transmission speed, baseband signal, 500 meter cable length, coaxialcable2) 10 Mbps transmission speed, broadband signal, 100 meter cable length, coaxialcable3) 10 Mbps transmission speed, baseband signal, 100 meter cable length,twisted-pair cable4) 10 Gbps transmission speed, broadband signal, 500 meter cable length,twisted-pair cable6. For which Ethernet installations would fiber optic rather than Cat5 UTP be abetter media choice? (Choose two.) (2,4)1) a 3 meter connection between two 10BASE-T hubs2) an environment with many potential sources of EMI and RFI3) a peer to peer connection between two NICs with RJ45 connectors4) an installation between two buildings that are located 500 meters apart5) a single building installation where installation costs are the major concern7. Refer to the exhibit. Which type of UTP cable should be used to connect Host Ato Switch1? (4)1) rollover2) console3) crossover4) straight-through8. Refer to the exhibit. Which type of Category 5 cable is used to make an Ethernetconnection between Host A and Host B? (3)1) coax cable2) rollover cable3) crossover cable4) straight-through cable第四章1. During cable testing, which of the following are used to calculate theinformation carrying capacity of a data cable? (Choose two.) (2,5)1) bit speed2) attenuation3) wire map4) saturation limit5) analog bandwidth2. What type of wiring problem is depicted in this sample of a cable tester? (3)1) a fault2) a short3) an open4) a split a good map3. In a new network installation, the network administrator has decided to use amedium that is not affected by electrical noise. Which cable type will best meet this standard? (5)1) coaxial2) screened twisted pair3) shielded twisted pair4) unshielded twisted pair5) fiber optic4. How does network cable length affect attenuation? (3)1) Category 5 cable that is run in metal conduit has the highest attenuation in theshortest distance.2) Shorter cable lengths have greater signal attenuation.3) Longer cable lengths have greater signal attenuation.4) The length of the cable has no effect on signal attenuation.第五章1. The highest capacity Ethernet technologies should be implemented in whichareas of a network? (Choose three.) (3,4,5)1) between workstation and backbone switch2) between individual workstations3) between backbone switches4) between enterprise server and switch5) on aggregate access links2. What device must be used between an AUI port of a networking device and themedia to which it is being connected? (3)1) a transducer2) a transmitter3) a transceiver4) a transponder5) a port replicator3. An ISDN Basic Rate Interface (BRI) is composed of how many signalingchannels? (1)1) 12) 23) 34) 44. Which layer of the OSI model covers physical media? (1)1) Layer 12) Layer 23) Layer 34) Layer 45) Layer 56) Layer 65. What type of network cable is used between a terminal and a console port? (3)1) cross-over2) straight-through3) rollover4) patch cable6. What is the recommended maximum number of workstations configured on apeer-to-peer network? (3)1) 252) 153) 104) 55) 27. Which of the following increases the potential for a collision to occur? (4)1) the use of an active hub instead of an intelligent hub2) the use of an intelligent hub instead of an active hub3) a reduction in the number of devices attached to the hub4) an increase in the number of devices attached to the hub8. What is the maximum length of a media segment used for 100BASE-TX? (1)1) 100 meters2) 185 meters3) 400 meters4) 500 meters9. Which cable diagram displays the end to end pinout for a crossover cable usedwith Cisco devices? (3)1) Cable A2) Cable B3) Cable C4) Cable D第六章1. What does the "10" in 10Base2 indicate about this version of Ethernet? (2)1) The version uses Base10 numbering within the frames.2) The version operates at a transmission rate of 10 Mbps.3) Frames can travel 10 meters unrepeated.4) The maximum frame length is 10 octets.2. How is a MAC address represented? (4)1) four groups of eight binary digits separated by a decimal point2) four Base10 digits separated by a decimal point3) six hexadecimal digits4) twelve hexadecimal digits5) twenty-four Base10 digits3. Which of the following statements are correct about CSMA/CD? (Choose three.)(1,3,6)1) It is a media access method used in LANs.2) It is a media access method used in FDDI WANs.3) When a device needs to transmit, it checks to see if the media is available.4) A device sends data without checking media availability because all deviceshave equal access.5) Multiple devices can successfully transmit simultaneously.6) Only one device can successfully transmit at a time.4. Which devices shown in the graphic must have a MAC address? (5)1) only PC2) only router3) PC and router4) PC, hub, and router5) PC, printer, and router第七章1. Which of the following items are common to all 100BASE technologies?(Choose three.) (1,4,5)1) frame format2) media3) connectors4) timing5) multi-part encoding2. Which of the following does 1000BASE-T use to accomplish gigabit speeds onCat 5e cable? (4)1) the use of four conductors in full-duplex mode2) the use of two multiplexed pairs of wires, simultaneously3) the use of three pairs of wires for data and the fourth for stabilization andforward error correction4) the use of all four pairs of wires in full-duplex mode, simultaneously3. For which of the following is Ethernet considered the standard? (Choose three.)(1,4,5)1) inter-building connection2) mid-length voice3) video conferencing4) vertical wiring5) horizontal wiring6) diagonal wiring4. To make sure timing limitations are not violated when implementing a 10 MbpsEthernet network involving hubs or repeaters, a technician should adhere to which rule? (4)1) the 4-5-3 rule2) the 6-4-2 rule3) the 3-4-5 rule4) the 5-4-3 rule5. What is the maximum distance that 10BASE-T will transmit data before signalattenuation affects the data delivery? (1)1) 100 meters2) 185 meters3) 300 meters4) 500 meters6. When using Category 5 UTP cable, which RJ-45 pin pairs are used to exchangedata between hosts on an Ethernet network? (2)1) 1 and 2; 4 and 52) 1 and 2; 3 and 63) 3 and 6; 7 and 84) 4 and 5; 7 and 8第八章1. John has been hired as the network administrator of a local company and hasdecided to add more hubs to the company's existing network. Which of the following has been caused by John's inexperience? (1)1) collision domain extended2) an increased number of collision domains3) increased network performance4) increased bandwidth5) extended bandwidth2. "CompA" is trying to locate a new computer named "CompB" on the network.Which of the following does "CompA" broadcast to find the MAC address of "CompB"? (2)1) MAC request2) ARP request3) ping4) Telnet5) proxy ARP3. Which of the following is a term associated with replacing hubs with switchesto increase the number of collision domains? (3)1) encapsulation2) latency3) segmentation4) layered model5) broadcast domain6) Extended4. The accumulation of traffic from which of the following can cause a networkcondition called broadcast radiation? (Choose three.) (3,5,6)1) anonymous FTP servers2) telnet sessions3) video over IP applications4) NAS services5) ARP requests6) RIP updates5. Which of the following describes the use of Spanning Tree Protocol (STP)? (4)1) resolve routing loops2) eliminate Split Horizon errors3) limit collisions4) resolve switching loops6. Which term describes the delay in time that occurs when a frame leaves itssource device and reaches its destination? (4)1) collision2) backoff3) attenuation4) latency5) broadcast7. Based on the graphic above, which of the following occurs as each host systemcomes on line in the topology? (2)1) The switch sends its MAC address to each host.2) The switch adds MAC address to the bridge table as each host sends a frame.3) Each host exchanges MAC addresses with each other.4) The switch listens for data traffic to block since the switch lacks an IP address. 8. Which devices segment collision domains? (Choose two.) (2,3)1) transceiver2) router3) switch4) hub5) media9. Which protocol is used to eliminate switching loops? (3)1) Transmission Control Protocol2) Routing Information Protocol3) Spanning Tree Protocol4) Interior Gateway Routing Protocol5) Internetworking Protocol10. Refer to the exhibit. A network associate needs to establish an Ethernetconnection between Host A and Host B. However, the distance between the two hosts is further than the cabling standards allow. Which two devices that operate at the physical layer of the OSI can be used to allow Host A and Host B to communicate? (2,5)1) switch2) hub3) bridge4) router5) repeater第九章1. Which term describes an ARP response by a router on behalf of a requestinghost? (3)1) ARP2) RARP3) Proxy ARP4) Proxy RARP2. Which protocol functions at the internet layer of the TCP/IP protocol suite? (4)1) File Transfer Protocol (FTP)2) Trivial File Transfer Protocol (TFTP)3) Transmission Control Protocol (TCP)4) Internet Protocol (IP)5) User Datagram Protocol (UDP)6) Simple Mail Transport Protocol (SMTP)3. Which of these workstation installation and setup tasks are concerned withnetwork access layer functions? (Choose two.) (2,4)1) configuring the e-mail client2) installing NIC drivers3) configuring IP network settings4) connecting the network cable5) using FTP to download application software updates4. Which part of an IP address identifies a specific device on a network? (4)1) first two octets2) third and fourth octets3) network portion4) host portion5) only the fourth octet5. Which of the following are features of the Internet Protocol (IP)? (Choose two.)(1,3)1) It is the most widely implemented global addressing scheme.2) It allows two hosts to share a single address on a local area network.3) It is a hierarchical addressing scheme allowing addresses to be grouped.4) It is only locally significant, used primarily on local area networks.6. Which of the following are useable Class A IP addresses with a default subnetmask? (Choose three.) (2,3,5)1) 127.0.39.12) 111.9.28.303) 123.1.2.1324) 128.50.38.25) 105.1.34.16) 0.23.92.37. Which application layer protocols use UDP at the transport layer? (Choose two.)(2,4)1) FTP2) SNMP3) Telnet4) DHCP5) SMTP第十章1. Which OSI layer encapsulates data into packets? (3)1) session2) transport3) network4) data link2. Which OSI layer defines the functions of a router? (3)1) physical2) data link3) network4) transport5) session3. Which of the following are Cisco proprietary routing protocols? (Choose two.)(2,6)1) RIPv22) IGRP3) OSPF4) BGP5) RIPv16) EIGRP4. A company with a Class B license needs to have a minimum of 1,000 subnetswith each subnet capable of accommodating 50 hosts. Which mask below is the appropriate one? (4)1) 255.255.0.02) 255.255.240.03) 255.255.255.04) 255.255.255.1925) 255.255.255.2245. A small company has a class C network license and needs to create five usablesubnets, each subnet capable of accommodating at least 20 hosts. Which of the following is the appropriate subnet mask? (3)1) 255.255.255.02) 255.255.255.1923) 255.255.255.2244) 255.255.255.2406. When a network administrator applies the subnet mask 255.255.255.248 to aClass A address, for any given subnet, how many IP addresses are available to be assigned to devices? (6)1) 10222) 5103) 2544) 1265) 306) 67. Host A is assigned the IP address 10.18.97.55 /21. How many more networkdevices can be assigned to this subnetwork if Host A is the only one that has an IP address assigned so far? (4)1) 2542) 5093) 10214) 20455) 40946) 81908.Refe r to the exhibit. The network administrator wants to create a subnet for thepoint-to-point connection between the two routers. Which subnetwork mask would provide enough addresses for the point-to-point link with the least number of wasted addresses?1) 255.255.255.1922) 255.255.255.2243) 255.255.255.2404) 255.255.255.2485) 255.255.255.2529. What is the correct number of usable subnetworks and hosts for the IP networkaddress 192.168.35.0 subnetted with a /28 mask?1) 6 networks / 64 hosts2) 14 networks / 32 hosts3) 14 networks / 14 hosts4) 30 networks / 64 hosts10. Which subnet masks would be valid for a subnetted Class B address? (Choosetwo.) (5,6)1) 255.0.0.02) 255.254.0.03) 255.224.0.04) 255.255.0.05) 255.255.252.06) 255.255.255.19211. Refer to the exhibit. How will the Fohi router dynamically learn routes to the192.168.16.16/28, 192.168.16.32/28, and 192.168.16.48/28 subnetworks? (3)1) with a static route2) with a routed protocol3) with a routing protocol4) with a directly connected route12. How many broadcast domains are shown in the diagram? (1)1) three2) four3) five4) six5) seven6) eight13. How many collision domains are shown in the diagram? (5)1) three2) four3) five4) six5) seven6) eight14. A router interface has been assigned an IP address of 172.16.192.166 with amask of 255.255.255.248. To which subnet does the IP address belong?1) 172.16.0.02) 172.16.192.03) 172.16.192.1284) 172.16.192.1605) 172.16.192.1686) 172.16.192.17615. Refer to the exhibit. Host A is sending data to Host B. Once R2 determines thatdata from Host A must be forwarded to R1 to reach Host B, which layer of the OSI model will R2 use to address and build the frames destined for R1?1) physical2) data link3) network4) transport5) session6) presentation16. Which type of address is 192.168.170.112/28?1) host address2) subnetwork address3) broadcast address4) multicast address17. Which type of address is 223.168.17.167/29?1) host address2) multicast address3) broadcast address4) subnetwork address18. Which combination of network id and subnet mask correctly identifies all IPaddresses from 172.16.128.0 through 172.16.159.255?1) 172.16.128.0 255.255.255.2242) 172.16.128.0 255.255.0.03) 172.16.128.0 255.255.192.04) 172.16.128.0 255.255.224.05) 172.16.128.0 255.255.255.19219. Refer to the exhibit. The internetwork in the exhibit has been assigned the IPaddress 172.20.0.0. What would be the appropriate subnet mask to maximize the number of networks available for future growth?1) 255.255.224.02) 255.255.240.03) 255.255.248.04) 255.255.252.05) 255.255.254.06) 255.255.255.0第十一章1. If a network administrator needed to download files from a remote server, whichprotocols could the administrator use to remotely access those files? (Choose two.) (3,5)1) NFS2) ASCII3) TFTP4) IMAP5) FTP6) UDP2. What is established during a connection-oriented file transfer betweencomputers? (Choose two.) (2,5)1) a temporary connection to establish authentication of hosts2) a connection used for ASCII or binary mode data transfer3) a connection used to provide the tunnel through which file headers aretransported4) a command connection which allows the transfer of multiple commands directlyto the remote server system5) a control connection between the client and server3. Which of the following protocols are used for e-mail transfer between clientsand servers? (Choose three.) (3,4,5)1) TFTP2) SNMP3) POP34) SMTP5) IMAP46) postoffice4. Which type of institution does the domain suffix .org represent? (4)1) government2) education3) network4) non-profit5. Which of the following services is used to translate a web address into an IPaddress? (1)1) DNS2) WINS3) DHCP4) Telnet6. Which part of the URL http://www.awsb.ca/teacher gives the name of thedomain? (4)1) www2) http://3) /teacher4) awsb.ca7. Which protocols are TCP/IP application layer protocols? (Choose two.) (2,4)1) UDP2) FTP3) IP4) SMTP5) TCP8. What are three characteristics of the TCP protocol? (Choose three.) (3,4,6)1) has less overhead than UDP2) is used for IP error messages3) forces the retransmission undelivered packets4) creates a virtual session between end-user applications5) carries the IP address of destination host in the TCP header6) is responsible for breaking messages into segments and reassembling9. Two peer hosts are exchanging data using TFTP. During the current session, adatagram fails to arrive at the destination. Which statement is true regarding the retransmission of the datagram? (2)1) Datagram retransmission requires user authentication.2) Datagram retransmission is controlled by the application.3) Datagram retransmission relies on the acknowledgements at transport layer.4) Datagram retransmission occurs when the retransmission timer expires in thesource host.案例学习1. 子网计算练习:Answer2. 子网号及广播地址计算练习Answer3. 子网规划练习:已知:给定一个C类地址201.16.5.0/24。
最新最新CCNA第一学期第七章答案

最新CCNA第一学期第七章答案套接字是源IP 地址与源端口号的组合,或者目的IP 地址与目的端口号的组合。
2、主机设备需要通过网络发送大型视频文件,同时为其他用户提供数据通信。
下列哪种功能可以让不同通信流同时发生,而不会让一个数据流使用所有可用带宽?多路复用对交替发送多个通信流很有用。
窗口大小用于降低数据通信速率。
端口号用于将数据流传送到正确的应用程序。
确认用于通知发送设备数据包流已收到或未收到。
3、主机设备通过HTTP 协议向Web 服务器发送数据包。
传输层使用下列哪项来将数据流传送到服务器上的正确应用程序?目的端口号用于将数据流传输到正确的应用程序,而源端口号由源设备随机生成并进行跟踪。
序列号用于指示如何重组和重新排序收到的数据段。
确认用于通知发送设备数据包流已收到或未收到。
源和目的端口号用于识别正确的应用程序和应用程序中的窗口。
客户端在注册端口范围内随机选择可用的源端口。
TCP 执行的所有额外控制任务会使通信产生延迟和开销,例如排列数据段、跟踪序列号、请求重新传输以及许多其他任务。
TCP 使用三次握手。
UDP 不使用该功能。
三次握手可以确保传输之前源和目的设备之间存在连接。
10、TCP 报头中的哪两个标志用于在TCP 三次握手中建立两台网络设备之间的连接?(请选择两项。
)TCP 使用SYN 和ACK 标记来建立两个网络设备之间的连接。
窗口大小是指发送方在收到目的设备的确认之前可以发送的字节数。
通过源和目标之间的三次握手,会话开始时即可确定初始窗口。
这取决于TCP 会话的目的设备一次可以接受和处理的数据量。
13、一台PC 从服务器下载一个大文件。
TCP 窗口大小为1000 字节。
服务器使用100 字节的数据段发送文件。
服务器发送多少个数据段后会要求PC 确认?对于有1000 个字节的窗口,目的主机会接受数据段直至1000 个字节的数据全部收到。
然后目的主机发送确认。
17、技术人员想使用TFTP 来将大型文件从文件服务器传输到远程路由器。
第七章课后习题参考答案

2. 试简单说明下列协议的作用:IP、ARP、RARP和ICMP。
答:IP协议:实现网络互连。
使参与互连的性能各异的网络从用户看起来好像是一个统一的网络。
ARP协议:完成IP地址到MAC地址的映射。
RARP:使只知道自己硬件地址的主机能够知道其IP地址。
ICMP:允许主机或路由器报告差错情况和提供有关异常情况的报告。
5. 试说明IP 地址与硬件地址的区别。
为什么要使用这两种不同的地址?答:IP地址在IP数据报的首部,而硬件地址则放在MAC帧的首部。
在网络层以上使用的是IP地址,而链路层及以下使用的是硬件地址。
在IP层抽象的互连网上,我们看到的只是IP数据报,路由器根据目的站的IP地址进行选路。
在具体的物理网络的链路层,我们看到的只是 MAC 帧,IP 数据报被封装在 MAC 帧里面。
MAC帧在不同的网络上传送时,其MAC帧的首部是不同的。
这种变化,在上面的IP层上是看不到的。
每个路由器都有IP 地址和硬件地址。
使用IP地址与硬件地址,尽管连接在一起的网络的硬件地址体系各不相同,但IP层抽象的互连网却屏蔽了下层这些很复杂的细节,并使我们能够使用统一的、抽象的IP地址进行通信。
6.(1)子网掩码为255.255.255.0代表什么意思?(2)一网络的子网掩码为255.255.255.248,问该网络能够连接多少台主机?(1)一A类网络和一B类网络的子网号subnet-id分别为16bit的8bit,问这两个网络的子网掩码有何不同?(2)一个B类地址的子网掩码是255.255.240.0。
试问在其中每一个子网上的主机数最多是多少?(3)一个A类地址的子网掩码为255.255.0.255。
它是否为一个有效的子网掩码?(4)某个IP地址的十六进制表示是C22F1481,试将其转换为点分十进制的形式.这个地址是哪一类IP 地址?(5)C类网络使用子网掩码有无实际意义?为什么?答:(1)C类地址对应的子网掩码值。
CCNA学习指南(第7版)_提要

文体说明斜体且下划线表示该字段应被替换蓝色中括号表示该字段可选;蓝色双竖线表示选择其一,蓝色花括号表示选择范围。
除非特别说明,命令行中的所有字符、符号均为半角。
表示速率时,b代表位(bit),B代表字节。
“接口号”表示不带关键字interface,“接口”表示带除非特别说明,本文不严格区分“接口”与“端口”,可以认为二者等同。
传输层端口一般会注明。
×——— ×——— ×——— ×——— ×反掩码=255.255.255.255 –子网掩码IOS命令中,自定义的名称、用户名、密码等区分大小写,命令关键字不区分大小写。
在NA考试中,必须保存配置,且只能用copy run start,不允许用write实验环境推荐配置:(全局) no ip domain-lookup //关闭名称查询,也可用快捷键Ctrl+Shift+6line con 0 //根据实际情况进入线路,vty的具体范围可用show run查看exec-timeout 0 0 //控制台永不超时logg sync //开启显示同步,避免在命令行输入时被显示信息打断exit若不是通过console口连接设备,则需用terminal monitor命令使debug信息回显到非console口。
开启debug会使设备CPU负载大幅上升,输出信息较多也会占用输出带宽,因此使用前先看看设备负载(show process),不要在负载重的设备上启用,会死机。
尽量缩小debug内容范围。
命令undebug all关闭所有debug。
show run的结果可以复制到记事本等纯文本编辑器,用作配置信息,但是show run 的结果中已开启的端口没写no shutdown命令,需手动添加!一般情况下,除了非模块化的交换接口外,其他接口默认都是关闭状态,需手动启用。
一次选中多个接口,可以在interface关键字后加range关键字,【例】选中g0/0到2接口:interface range g0/0 - 2 //横线前后最好带空格,以适用大多数版本IOS选中g0/0和2接口:interface range g0/0,g0/2也可以上二者同时使用:inte range g0/0 - 1,g0/2在交换机上配置默认网关,用来跨网段管理该设备:(全局) ip default-gateway IP第一章网络互联交换机通过MAC地址作为通讯标识,每个端口都是一个冲突域。
数字集成电路分析与设计 第七章答案

CHAPTER 7P7.1. Assume that all nodes start at 0V. The first row outputs will be at DD T V V -. Since thesenodes are also the gate nodes of the second row of transistors, their source nodes will be at 2DD T V V -. Likewise, the last row of transistors have voltages of 3DD T V V -. However, this value is below 0V so we leave them at 0V.1.2V1.2V0.73V 0.73V 0.73V0.33V0.33V0.33V0V0V0VP7.2. (a)(b)(c)(d)P7.3. (a) First calculate V Q .()01.80.51.15Q DD T DD T V V V V V Vγ=-=-+=--=Since this is slightly below 1.3V (voltage at which the PMOS turns on), we assume that the PMOS is slightly on. Since the PMOS’s V GS is quite low (because Q is high) and its V DS is quite high (because Q is low), the transistor is very likely in saturation. Similarly for the NMOS, because its V GS is high and its V DS is low, it’s likely in the linear region. Equating the two currents:()()()()()()()()22,,222211DSNDSN CN NQ Q CN NSDP sat DSN linV N N OX GSN T DSN P sat OX GSP T V GSP T CP PN V N N OX Q T Q P sat OX DD Q T V DD Q T CP PE L N I I W C V V V W v C V V V V E L L W C V V V W v C V V V V V V E L L μμ=---=-++----=--++For simplicity we shall assume that 11Q CN NV E L +≈ and220QV ≈.()()()2N N OX Q T QP sat OX DD Q T DD Q T CP P NW C V V V W v C V V V V V V E L L μ---≈--+Solve to produce:0.0080V Q V ≈When the CLK goes low, the intermediate output suffers from clock feedthough. To calculate the effects of clock feedthrough, let us first compute the capacitances involved. The capacitance from the clock signal to Q is:(.2/)(.2)0.0.4fF GS OL C C fF um um ===The capacitance from the Q to ground is:()()()(),310.2320.2 1.4fF Q DN IN inv d g C C C C W C W =+=+=+=The capacitive feedthrough equation is:()210.04 1.80.05V 0.04 1.41.150.05 1.1VGS CLK Q GS Q Q Q Q C V V C C V V V -∆∆===-++=+∆=-=To get the new value of Q V , first determine the determine the regions of operation of the transistors in the inverter by calculating V S . Then, once again, use the currentequations to determine Q V .Since the new voltage of V Q is still greater than the switching voltage, the transistors are in the same regions:()()()()()()2000460.4100.2810P N sat OX DD Q T Q N N OX Q T DD Q T CP P OXW L v C V V V V W C V V V V V E L C μ---≈---+⨯⨯≈()()()21.8 1.10.50.2270OX C --()()0.016V1.10.5 1.8 1.10.5 4.8≈---+(b) In this case 1.8Q DD V V V == and 0Q V =. Clock feedthrough has no effect since the transmission gate CLK signals cancel each other out.()()()()()()()(),3151515315(23)312.5102100.2110(2)0.23(210)(0.2)312.5101100.2257.532.5pass pass inv d inv eqn g eff g eqn d t R C R C R C W C W C W R C Wps ps ps----=+=+++⎡⎤=⨯⨯+⨯+⨯+⎣⎦⨯⨯=+=P7.4.a. Out A BC =+BBOutb. Out AB BC C =++Outc. ()Out A B C AB ABC AB =+++=+BBOutd. ()()1Out A B C AB ABC AB AB C AB A B =+++=+=+==+OutP7.5.a. ()Out A B C =+b. ()()Out A B C D E =+++ P7.6.a. Out A BC =+c bclkclkV DDb. Out AB BCC =++a bclkclkV DDc.()Out A B C AB ABC AB =+++=+V DDd.()()()Out A B C AB A B C A B AB=+++=+++=+aclkclkV DDP7.7.Assuming that one of the transistors in each transmission gate is being driven by a min-sized inverter:a.()()()()122333passinvRC R R RLERC R R+====b.()()()()()()()()313133313133AAinvCCinvRRC RLERC R RRRC RLERC R R========()()()()339333BBinvRRC RLERC R R====P7.8.a. Out A sel B sel =⋅+⋅b.R inv 6.25k ΩC inv,diff 1.2fF C pass,gate 0.8fF C pass,diff0.8fFR pass 6.25k ΩCpass,diff0.8fFCpass,gate0.8fFfC inv,gate2.4f fFCpass,diff0.8fFc. ()()(),,,,,,2A C inv inv diff pass gate pass diff inv pass inv gate pass gate pass diff t R C C C R R fC C C -=++++++ d. (),,inv inv LOADC out inv diff LOAD inv inv diffR R C t fC C R C f f-=+=+ e.()()()()(),,,,,,,,220inv inv diff pass gate pass diff inv pass inv gate pass gate pass diff inv LOADinv inv diff inv LOAD inv pass inv gate t R C C C R R fC C C R C R C fR C dtR R C df f f =++++++++=+-===3.2=P7.9. In both of these cases, the logical effort is the same due to the fact that the longest pathfrom output to ground is three transistors long. Assume that the CLK arrives ahead of the signals. Then,12()26663R R LE R λλ+== P7.10. We will use 0.18um technology and the node names below:W=4W=4OutFor the two inverter inputs:()()()3230.2 1.2fF inv g C C W ===For the pass gate inputs:()0.4fF pass g C C W ==At node x:()(3)(2) 1.4x eff eff g C C W C W C W fF =++=At node y:()2((2))(2)2y eff g eff C C W C W C W fF =++=At node Out:()((2))(2) 1.2out eff g eff C C W C W C W fF =++=The shortest path is through the one of the G ND input nodes to the output:()()()()min 212.5 1.4212.5 1.247.5x out t RC RC k fF k fF ps =+=+=The longest path is through one of the inverters to the output.()()()()()()max 2312.5 1.4212.52312.5 1.2112.5sx y out t RC RC RC k fF k fF k fF p =++=++=P7.11. At 0t =: DD F V =0X =?Y =.When the a goes high the first time, the voltage at X would be computed using the charge-sharing formula:()101.21V 210F DDX X F C V V C C ===++But because the maximum allowable voltage at node x is 0.734V, set 0.734V X V = Then recomputed V F :()()()()10 1.220.734 1.05V 10F DD X X F F C V C V V C --===When Phi goes down, F DD V V = and V X and V Y remains the same. The next time the Phi goes up, all the internal nodes are 0. When Phi goes down, F DD V V = and V X and V Y remains at 0. P7.12.P7.13.a. The input settings that give you the worst-case charge sharing are any of 1a c e === and both of 0b d ==. Essentially, what you are doing it trying to create the greatest amount of parasitic capacitances without creating a path to G ND .b. Assuming that transistors share nodes to reduce capacitance.()()()()()()()12*11125(3)(5) 5.2fF 333190.2 1.8fF 5.2 1.8 1.34V 5.2 1.8g d g d C C W C W C W C C W W W C V V C C =++==++=====++ The actual voltage would be larger than this since the internal node cannot rise above V DD -V T .c. This circuit fails if the worse case voltage falls below the switching voltage which can be computed to be V S =0.92V. Therefore, the circuit will operate properly. P7.14. Both of these circuits act as latches. When EN is on, there is a path from the output toeither V DD or G ND . The first latch is better than the second because the second latch suffers from charge sharing. When EN is off, there is no path from the output to either of the sources, if IN is switching it is possible for whatever charge that is held on OUT to be shared with the internal nodes between the two NMOS’s or the two PMOS’s. Therefore, the second one is not as good as the first one. P7.15.a.OUT OL X DD TV V V V V ==-b. First, let ’s find the required change in voltage:()()2OUT DD OLX DD T DD T TV V V V V V V V V ∆=-∆=+--=Now, let’s set up the clock feedthrough equation and solve for C b :22b OUT X b XX X T Xb OUT X DD OL TC V V C C V C V C C V V V V V ∆∆=+∆==∆-∆--。
CCNA第一学期各章习题及答案

诶了我累了目录第二章网络通信P2-8第三章应用层功能及协议P9-14第四章OSI传输层P15-20第五章OSI网络层P21-27第六章网络编址-IPv4 P28-34第七章数据链路层P35-40第八章OSI物理层P41-45第九章以太网P46-51第十章网络规划和布线P52-61第十一章配置和测试网络P62-70第一学期末考试P71-91文档末尾返回目录第二章网络通信001 TCP/IP 网络接入层有何作用路径确定和数据包交换数据表示、编码和控制可靠性、流量控制和错误检测详细规定构成物理链路的组件及其接入方法将数据段划分为数据包002下列哪些陈述正确指出了中间设备在网络中的作用(选择三项)确定数据传输路径发起数据通信重新定时和重新传输数据信号发送数据流管理数据流数据流最后的终止点003下列哪三项陈述是对局域网(LAN) 最准确的描述(选择三项)LAN 通常位于一个地域内。
此类网络由由一个组织管理。
LAN 中的不同网段之间一般通过租用连接的方式连接。
此类网络的安全和访问控制由服务提供商控制。
LAN 为同一个组织内的用户提供网络服务和应用程序访问。
此类网络的每个终端通常都连接到电信服务提供商(TSP)。
004 什么是PDU传输期间的帧损坏在目的设备上重组的数据因通信丢失而重新传输的数据包特定层的封装005 OSI 模型哪两层的功能与TCP/IP 模型的网络接入层相同(选择两项)网络层传输层物理层数据链路层会话层006请参见图示。
所示网络属于哪一类型WANMANLANWLAN007 以下哪种特征正确代表了网络中的终端设备管理数据流发送数据流重新定时和重新传输数据信号确定数据传输路径008 第4 层端口指定的主要作用是什么标识本地介质中的设备标识源设备和目的设备之间的跳数向中间设备标识通过该网络的最佳路径标识正在通信的源终端设备和目的终端设备标识终端设备内正在通信的进程或服务009 请参见图示。
下列哪组设备仅包含终端设备A、C、DB、E、G、HC、D、G、H、I、JD、E、F、H、I、JE、F、H、I、J010 选择关于网络协议的正确陈述。
思科答案CCNA4-7

1.请参见图示。
网络技术人员确定DHCP 客户端工作不正常。
客户端从作为DHCP 服务器的路由器上接收了IP 配置信息,但无法访问Internet。
根据图中所示的输出,问题最可能出在哪里?4 未启用HTTP 服务器服务。
未定义DCHP 的内部接口。
未将DHCP 地址池绑定到接口。
地址池中没有为客户端定义默认路由器。
DHCP 地址池中排除了所有主机地址。
2.请参见图示。
根据图中所示的配置,应该如何为网络中的关键主机(例如路由器接口、打印机和服务器)分配排除地址池?1地址由网络管理员静态分配。
DHCP 服务器动态分配地址。
地址必须先列在DHCP 地址池中,才能用于静态分配。
地址必须先列在DHCP 地址池中,才能用于动态分配。
3.请参见图示。
请参见图示。
根据图中所示的输出,此DHCP 服务器成功分配或更新了多少个地址?4167894.使用NAT 的两个好处是什么?(选择两项。
)12它可节省公有IP 地址。
它可增强网络的私密性和安全性。
它可增强路由性能。
它可降低路由问题故障排除的难度。
它可降低通过IPsec 实现隧道的复杂度。
5.有关NAT 与PAT 之间的差异,下列哪一项正确?4PAT 在访问列表语句的末尾使用"overload" 一词,共享单个注册地址。
静态NAT 可让一个非注册地址映射为多个注册地址。
动态NAT 可让主机在每次需要外部访问时接收相同的全局地址。
PAT 使用唯一的源端口号区分不同的转换。
6.网络管理员应该使用哪种NAT 来确保外部网络一直可访问内部网络中的web 服务器?2NAT 过载静态NAT静态NATPAT7.请参见图示。
哪个或哪些地址是内部全局地址?310.1.1.2192.168.0.100209.165.20.25网络10.1.1.0 中的任意地址8.请参见图示。
下列关于图中所示配置的说法中哪两项正确?(选择两项。
)13来自网络10.1.1.0 的流量将被转换。
CCNA第一学期第7章章节考试题答案100%
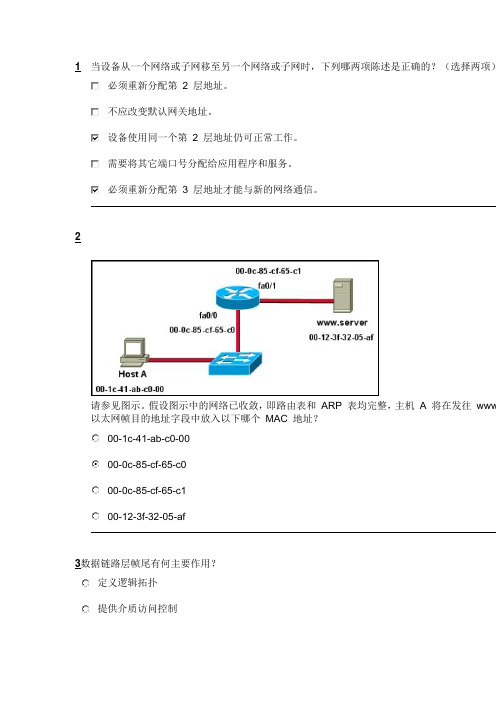
1当设备从一个网络或子网移至另一个网络或子网时,下列哪两项陈述是正确的?(选择两项)必须重新分配第 2 层地址。
不应改变默认网关地址。
设备使用同一个第 2 层地址仍可正常工作。
需要将其它端口号分配给应用程序和服务。
必须重新分配第 3 层地址才能与新的网络通信。
2请参见图示。
假设图示中的网络已收敛,即路由表和ARP 表均完整,主机 A 将在发往www 以太网帧目的地址字段中放入以下哪个MAC 地址?00-1c-41-ab-c0-0000-0c-85-cf-65-c000-0c-85-cf-65-c100-12-3f-32-05-af3数据链路层帧尾有何主要作用?定义逻辑拓扑提供介质访问控制支持帧错误检测传送帧的路由信息4请参见图示。
PC 正在向笔记本电脑发送帧。
离开RouterB 时,帧中包括的源MAC 地址和源MAC - PC源MAC - RouterA 的S0/0源MAC - RouterB 的Fa0/1源IP - PC源IP - RouterA 的S0/0源IP - RouterB 的Fa0/15在网络中实现第2 层协议时应该考虑哪三个因素?(选择三项)所选的第 3 层协议网络的地址范围传输层定义的PDU物理层实现要连接的主机数量网络层编址?介质共享应用进程逻辑拓扑中间设备的功能7以太网帧中的前导码有何作用?作为数据的填充位用于同步计时用于标识源地址。
用于标识目的地址。
8请参见图示。
流量从PC 路由到笔记本电脑时,会进行多少次CRC 计算?12468169有关物理拓扑和逻辑拓扑的陈述,下列哪一项正确?逻辑拓扑始终与物理拓扑相同。
物理拓扑与网络传输帧的方法有关。
物理信号路径是按数据链路层协议定义的。
逻辑拓扑由节点之间的虚拟连接组成。
10网络管理员有责任以图形精确表示公司网络线路和设备在建筑内的位置。
这种图是什么?逻辑拓扑物理拓扑电缆路径线路网接入拓扑11请参见图示。
下列哪项陈述描述了图示网络使用的介质访问控制方法?三个网络全部采用CSMA/CA。
思科CCNA考试答案(全)

CCNA思科考试答案(全)第 1 章考试1一家拥有10 名员工的小型公司使用单个LAN 在计算机之间共享信息。
哪种类型连接适合此公司?由当地电话服务提供商提供的拨号连接能够使公司方便且安全地连接员工的虚拟专用网络通过当地服务提供商建立的私有专用线路通过当地服务提供商提供的宽带服务(如DSL)答案:4解析:对于这种小型办公室,比较适合通过被称为数字用户线路(DSL) 的常见宽带服务实现Internet 连接,这种服务由当地的电话服务提供商提供。
由于员工人数很少,带宽的问题并不突出。
如果公司较大,在远程站点有分支机构,则专用线路会更加适合。
如果公司员工需要通过Internet 与公司联系,则采用虚拟专用网。
2哪种网络情况需要使用WAN?员工工作站需要获取动态分配的IP 地址。
员工在出差时需要通过VPN 连接到公司电子邮件服务器。
分支机构的员工需要与同一园区网络上的另一座建筑物内的公司总部共享文件。
员工需要访问托管在其建筑物内DMZ 中的公司Web 服务器上的网页。
答案:2解析:当出差的员工需要通过WAN 连接到公司电子邮件服务器时,VPN 将通过WAN 连接在员工笔记本电脑与公司网络之间创建一个安全隧道。
通过DHCP 获取动态IP 地址是LAN 通信的功能。
在企业园区的不同建筑物之间共享文件可通过LAN 基础设施来实现。
DMZ 是企业LAN 基础设施内一个受保护的网络。
3以下哪项描述了WAN 的特征?WAN 和LAN 在同一地理范围内运行,但有串行链路。
WAN 网络归运营商所有。
所有串行链路均被视为WAN 连接。
WAN 可提供到园区主干网的终端用户网络连接。
答案:2解析:WAN 可用于将企业LAN 互连到远程分支机构站点LAN 和远程工作人员站点。
WAN 归运营商所有。
虽然WAN 连接一般通过串行接口实现,但并不是所有串行链路均连接至WAN。
LAN(而非WAN)可在组织中提供终端用户网络连接。
4电路交换WAN 技术的两个常见类型是什么?(请选择两项。
ccna1章节与期末答案

第一章:正确答案:2.4.5•解析:由于不需要使用网络设备和专用服务器,对等网络易于创建,复杂性更低,且成本更少。
而且对等网络也没有集中管理。
这种网络安全性更低,不可扩展,而且那些同时充当客户端和服务器的设备可能性能更差正确答案:1解析:正确答案: 3.5解析:选择网络介质的条件包括:所选介质可以成功传送信号的距离、要安装所选介质的环境、必须传输的数据量和速度以及介质和安装的成本。
正确答案:3和4解析:终端设备上的应用程序可以生成数据,更改数据内容并且负责启动封装过程。
正确答案:1和4解析:终端设备会发出通过网络传输的数据。
中间设备会在链路发生故障时通过备用路径传输数据,并且会过滤数据传输以增强安全性。
网络介质提供网络消息的传输通道。
正确答案:4解析:外联网是公司外部的人或企业合作伙伴访问数据的网络区域。
内部网只描述通常仅供内部人员访问的网络区域。
当设备连接到有线网络时,有线LAN 会受BYOD(自带设备)影响。
使用大学无线LAN 的设备多为平板电脑和智能手机。
大学生主要使用无线WAN 来访问他们的手机运营商网络。
.正确答案:2解析:由于通过Internet 可以联系在线供应商,所以家庭用户通过Internet 进行网上购物。
内联网基本上是仅供内部使用的局域网。
外联网是外部合作伙伴访问组织内部特定资源的网络。
家庭用户并不一定使用LAN 来访问Internet。
例如,PC 可以通过调制解调器直接连接到ISP。
正确答案:1解析:内部网这个术语用于表示一个组织的私有局域网和广域网连接。
内部网的设计旨在仅允许该组织的成员、员工或其他获得授权的人员进行访问。
正确答案:2和4解析:电缆和DSL 均能实现高带宽、始终联网,并提供到主机计算机或LAN 的以太网连接。
10正确答案:2和3解析:移动电话连接需要使用移动电话网络。
卫星连接通常用于家庭或企业外部不便使用物理布线的位置。
11正确答案:2解析:当对网络资源的请求超出了可用容量时,网络就会变得拥堵。
CCNA第一学期各章习题和参考答案.doc

CCNA第一学期各章习题和参考答案第二章网络通信1、TCP/IP网络接入层有何作用?A路径确定和数据包交换B数据表示、编码和控制C可靠性、流量控制和错误检测E将数据段划分为数据包2、下列哪些陈述正确指出了中间设备在网络中的作用?(选择三项)B发起数据通信D发送数据流F数据流最后的终止点3、下列哪三项陈述是对局域网(LAN) 最准确的描述?(选择三项)C LAN 中的不同网段之间一般通过租用连接的方式连接。
D此类网络的安全和访问控制由服务提供商控制。
F此类网络的每个终端通常都连接到电信服务提供商(TSP)。
004 什么是PDU?A传输期间的帧损坏B在目的设备上重组的数据C因通信丢失而重新传输的数据包005 OSI 模型哪两层的功能与TCP/IP 模型的网络接入层相同?(选择两项)018哪个应用层协议通常用于支持客户端与服务器之间的文件传输?A HTMLB HTTP D Telnet019哪个应用层协议中规定了Microsoft 网络中用于文件共享的服务?A DHCPB DNS D SMTP E Telnet020服务器上的应用层通常如何处理多客户端服务请求?A终止与服务的所有连接B拒绝与单一守护程序的多个连接C暂停当前连接,建立新连接第四章OSI传输层001下列哪两项是用户数据报协议(UDP) 的功能?(选择两项)A流量控制 D 面向连接E 序列和确认002请参见图示。
此Wireshark 捕获输出的第7 行中执行的是哪一项TCP 操作?A会话创建B 数据段重传C 数据传输D 会话断开003数据段的TCP 报头中为什么包含端口号?A指示转发数据段时应使用的正确路由器接口B 标识接收或转发数据段时应使用的交换机端口C确定封装数据时应使用的第3 层协议让接收主机转发数据到适当的应用程序E让接收主机以正确的顺序组装数据包004OSI 模型哪一层负责规范信息从源设备到目的设备准确可靠地流动?A应用层 B 表示层 C 会话层传输层 E 网络层005请参见图示。
CCNA第一学期各章知识题及答案解析

诶了我累了目录第二章网络通信P2-8第三章应用层功能及协议P9-14 第四章OSI传输层P15-20第五章OSI网络层P21-27第六章网络编址-IPv4 P28-34第七章数据链路层P35-40第八章OSI物理层P41-45第九章以太网P46-51第十章网络规划和布线P52-61 第十一章配置和测试网络P62-70 第一学期末考试P71-91文档末尾返回目录第二章网络通信001 TCP/IP 网络接入层有何作用?路径确定和数据包交换数据表示、编码和控制可靠性、流量控制和错误检测详细规定构成物理链路的组件及其接入方法将数据段划分为数据包002下列哪些陈述正确指出了中间设备在网络中的作用?(选择三项)确定数据传输路径发起数据通信重新定时和重新传输数据信号发送数据流管理数据流数据流最后的终止点003下列哪三项陈述是对局域网(LAN) 最准确的描述?(选择三项)LAN 通常位于一个地域内。
此类网络由由一个组织管理。
LAN 中的不同网段之间一般通过租用连接的方式连接。
此类网络的安全和访问控制由服务提供商控制。
LAN 为同一个组织内的用户提供网络服务和应用程序访问。
此类网络的每个终端通常都连接到电信服务提供商(TSP)。
004 什么是PDU?传输期间的帧损坏在目的设备上重组的数据因通信丢失而重新传输的数据包特定层的封装005 OSI 模型哪两层的功能与TCP/IP 模型的网络接入层相同?(选择两项)网络层传输层物理层数据链路层会话层006请参见图示。
所示网络属于哪一类型?WANMANLANWLAN007 以下哪种特征正确代表了网络中的终端设备?管理数据流发送数据流重新定时和重新传输数据信号确定数据传输路径008 第4 层端口指定的主要作用是什么?标识本地介质中的设备标识源设备和目的设备之间的跳数向中间设备标识通过该网络的最佳路径标识正在通信的源终端设备和目的终端设备标识终端设备内正在通信的进程或服务009 请参见图示。
思科CCNA1第七章试题及答案英文版

25. QuestionWhat is the binary equivalent of the decimal number 232?o 11101000o 11000110o 10011000o 1111001026. QuestionWhat is the decimal equivalent of the binary number 10010101?o149o 157o 168o 1921. QuestionHow many bits are in an IPv4 address?o32o 64o 128o 2562. QuestionWhich two parts are components of an IPv4 address? (Choose two.)o subnet portiono network portiono logical portiono host portiono physical portiono broadcast portion3. QuestionWhat does the IP address 172.17.4.250/24 represent?o network addresso multicast addresso host addresso broadcast address4. QuestionWhat is the purpose of the subnet mask in conjunction with an IP address?o to uniquely identify a host on a networko to identify whether the address is public or privateo to determine the subnet to which the host belongso to mask the IP address to outsiders5. QuestionWhat subnet mask is represented by the slash notation /20?o 255.255.255.248o 255.255.224.0o 255.255.240.0o 255.255.255.0o 255.255.255.1926. QuestionA message is sent to all hosts on a remote network. Which type of message isit?o limited broadcasto multicasto directed broadcasto unicast7. QuestionWhat are three characteristics of multicast transmission? (Choose three.)o The source address of a multicast transmission is in the range of 224.0.0.0 to 224.0.0.255.o A single packet can be sent to a group of hosts.o Multicast transmission can be used by routers to exchange routing information.o The range of 224.0.0.0 to 224.0.0.255 is reserved to reach multicast groups on a local network.o Computers use multicast transmission to request IPv4 addresses.o Multicast messages map lower layer addresses to upper layer addresses.8. QuestionWhich three IP addresses are private ? (Choose three.)o 10.1.1.1o 172.32.5.2o 192.167.10.10o 172.16.4.4o 192.168.5.5o 224.6.6.69. QuestionWhich two IPv4 to IPv6 transition techniques manage the interconnection of IPv6 domains? (Choose two.)o trunkingo dual stacko encapsulationo tunnelingo multiplexing10. QuestionWhich of these addresses is the shortest abbreviation for the IP address:3FFE:1044:0000:0000:00AB:0000:0000:0057?o 3FFE:1044::AB::57o 3FFE:1044::00AB::0057o 3FFE:1044:0:0:AB::57o 3FFE:1044:0:0:00AB::0057o 3FFE:1044:0000:0000:00AB::57o 3FFE:1044:0000:0000:00AB::005711. QuestionWhat type of address is automatically assigned to an interface when IPv6 is enabled on that interface?o global unicasto link-localo loopbacko unique local12. QuestionWhat are two types of IPv6 unicast addresses? (Choose two.)o multicasto loopbacko link-localo anycasto broadcast13. QuestionWhat are three parts of an IPv6 global unicast address? (Choose three.)o an interface ID that is used to identify the local network for a particular hosto a global routing prefix that is used to identify the network portion of the address that has been provided by an ISPo a subnet ID that is used to identify networks inside of the local enterprise siteo a global routing prefix that is used to identify the portion of the network address provided by a local administratoro an interface ID that is used to identify the local host on the network14. QuestionAn administrator wants to configure hosts to automatically assign IPv6 addresses to themselves by the use of Router Advertisement messages, but also to obtain the DNS server address from a DHCPv6 server. Which address assignment method should be configured?o SLAACo stateless DHCPv6o stateful DHCPv6o RA and EUI-6415. QuestionWhich protocol supports Stateless Address Autoconfiguration (SLAAC) for dynamic assignment of IPv6 addresses to a host?o ARPv6o DHCPv6o ICMPv6o UDP16. QuestionWhich two things can be determined by using the ping command? (Choose two.)o the number of routers between the source and destination deviceo the IP address of the router nearest the destination deviceo the average time it takes a packet to reach the destination and for theresponse to return to the sourceo the destination device is reachable through the networko the average time it takes each router in the path between source and destination to respond17. QuestionWhat is the purpose of ICMP messages?o to inform routers about network topology changeso to ensure the delivery of an IP packeto to provide feedback of IP packet transmissionso to monitor the process of a domain name to IP address resolution 18. QuestionWhat is indicated by a successful ping to the ::1 IPv6 address?o The host is cabled properly.o The default gateway address is correctly configured.o All hosts on the local link are available.o The link-local address is correctly configured.o IP is properly installed on the host.19. QuestionA user is executing a tracert to a remote device. At what point would a router,which is in the path to the destination device, stop forwarding the packet?o when the router receives an ICMP Time Exceeded messageo when the RTT value reaches zeroo when the host responds with an ICMP Echo Reply messageo when the value in the TTL field reaches zeroo when the values of both the Echo Request and Echo Reply messages reach zero20. QuestionWhat field content is used by ICMPv6 to determine that a packet has expired?o TTL fieldo CRC fieldo Hop Limit fieldo Time Exceeded field21. QuestionFill in the blank.The decimal equivalent of the binary number 10010101is 149 .22. QuestionFill in the blank.The binary equivalent of the decimal number 232 is 1110100023. QuestionFill in the blank.What is the decimal equivalent of the hex number 0x3F? 63。
ccna1章节与期末答案
第一章:ccna1章节与期末答案正确答案:2.4.5•解析:由于不需要使用网络设备和专用服务器,对等网络易于创建,复杂性更低,且成本更少。
而且对等网络也没有集中管理。
这种网络安全性更低,不可扩展,而且那些同时充当客户端和服务器的设备可能性能更差正确答案:1解析:正确答案: 3.5解析:选择网络介质的条件包括:所选介质可以成功传送信号的距离、要安装所选介质的环境、必须传输的数据量和速度以及介质和安装的成本。
正确答案:3和4解析:终端设备上的应用程序可以生成数据,更改数据内容并且负责启动封装过程。
正确答案:1和4解析:终端设备会发出通过网络传输的数据。
中间设备会在链路发生故障时通过备用路径传输数据,并且会过滤数据传输以增强安全性。
网络介质提供网络消息的传输通道。
正确答案:4解析:外联网是公司外部的人或企业合作伙伴访问数据的网络区域。
内部网只描述通常仅供内部人员访问的网络区域。
当设备连接到有线网络时,有线LAN 会受BYOD(自带设备)影响。
使用大学无线LAN 的设备多为平板电脑和智能手机。
大学生主要使用无线WAN 来访问他们的手机运营商网络。
.正确答案:2解析:由于通过Internet 可以联系在线供应商,所以家庭用户通过Internet 进行网上购物。
内联网基本上是仅供内部使用的局域网。
外联网是外部合作伙伴访问组织内部特定资源的网络。
家庭用户并不一定使用LAN 来访问Internet。
例如,PC 可以通过调制解调器直接连接到ISP。
正确答案:1解析:内部网这个术语用于表示一个组织的私有局域网和广域网连接。
内部网的设计旨在仅允许该组织的成员、员工或其他获得授权的人员进行访问。
正确答案:2和4解析:电缆和DSL 均能实现高带宽、始终联网,并提供到主机计算机或LAN 的以太网连接。
10正确答案:2和3解析:移动电话连接需要使用移动电话网络。
卫星连接通常用于家庭或企业外部不便使用物理布线的位置。
11正确答案:2解析:当对网络资源的请求超出了可用容量时,网络就会变得拥堵。
CCNA7 题库复习资料

Chapter7 Virtual LANs(VLANs)VLAN Basics如何在1个交换性的网络里,分割广播域呢?答案是创建VLAN.VLAN是连接到定义好了的switch的端口的网络用户和资源的逻辑分组.给不同的子网分配不同的端口,就可以创建更小的广播域.默认情况下,在某个VLAN中的主机是不可以与其他VLAN通信的,除非你使用router来创建VLAN间的通信VLAN的一些特点:1.网络的增加,移动和改变,只需要在适当的VLAN中配置合适的端口2.安全,因为不同VLAN的用户不能互相通信,除非依靠router来做VLAN间的通信3.因为VLAN可以被认为是按功能划分的逻辑分组,所以VLAN和物理位置,地理位置无关4.VLAN增加安全性5.VLAN增加广播域的数量,而减小广播域的大小Broadcast Control每种协议都会有广播的现象发生,至于发生不频率,次数,一般由以下几点决定:1.协议类型2.在网络上运行的应用程序3.这些服务如何的被使用Security安全性是VLAN的1大特点,不同VLAN的用户不能互相通信,除非依靠router来做VLAN 间的通信Flexibility and ScalabilityVLAN的灵活性和可扩展性:1.可以不管物理位置如何,把适当的端口分配到适当的 VLAN中就可以了.可以把VLAN 理解正下面的样子:2.当VLAN增加的太大以后,你可以划分更多的VLAN,来减少广播消耗掉更多带宽的影响,在VLAN中的用户越少,被广播影响的就越少,来比较下下面2个图,明显可以发现,图2,即VLAN的具有更高的灵活性和可扩展性,如下:VLAN Memberships手动由管理员分配端口划分的VLAN叫静态VLAN(static VLAN);使用智能管理软件,动态划分VLAN的叫动态VLAN(dynamic VLAN)Static VLANs静态VLAN:静态VLAN安全性较高,手动划分端口给VLAN,和设备的物理位置没什么关系.而且,每个VLAN中的主机必须拥有正确的IP地址信息,如VLAN2配置为172.16.20.0/24Dynamic VLANs动态VLAN:使用智能管理软件,可以基于MAC地址,协议,甚至应用程序来动态创建VLAN.Cisco设备管理员可以使用VLAN管理策略服务器(VLAN Management Policy Server,VMPS)的服务来建立个MAC地址数据库,来根据这个动态创建VLAN,VMPS数据库把MAC地址映射VLAN上Identifying VLANs当帧在网络中被交换,switches根据类型对其跟踪,加上根据硬件地址来判断如何对它们进行操作.有1点要记住的是:在不同类型的连接中,帧被处理的方式也不一样要交换环境中的2种连接类型:1.access links:指的是只属于一个VLAN,且仅向该VLAN转发数据帧的端口,也叫做native VLAN.switches把帧发送到access-link设备之前,移去任何的VLAN信息.而且access-link设备不能与VLAN外通信,除非数据包被路由。
计算机网络自顶向下第七版第七章答案

计算机⽹络⾃顶向下第七版第七章答案Computer Networking: A Top-Down Approach,7th Edition计算机⽹络⾃顶向下第七版Solutions to Review Questions and ProblemsChapter 7 Review Questions1.In infrastructure mode of operation, each wireless host is connected to the largernetwork via a base station (access point). If not operating in infrastructure mode, a network operates in ad-hoc mode. In ad-hoc mode, wireless hosts have noinfrastructure with which to connect. In the absence of such infrastructure, the hosts themselves must provide for services such as routing, address assignment, DNS-like name translation, and more.2.a) Single hop, infrastructure-basedb) Single hop, infrastructure-lessc) Multi-hop, infrastructure-basedd) Multi-hop, infrastructure-less3.Path loss is due to the attenuation of the electromagnetic signal when it travelsthrough matter. Multipath propagation results in blurring of the received signal at the receiver and occurs when portions of the electromagnetic wave reflect off objects and ground, taking paths of different lengths between a sender and receiver. Interference from other sources occurs when the other source is also transmitting in the samefrequency range as the wireless network.4.a) Increasing the transmission powerb) Reducing the transmission rate5.APs transmit beacon frames. An AP’s beacon frames will be transmitted over one ofthe 11 channels. The beacon frames permit nearby wireless stations to discover and identify the AP.6.False7.APs transmit beacon frames. An AP’s beacon frames will be transmitted over one ofthe 11 channels. The beacon frames permit nearby wireless stations to discover and identify the AP.8.False9.Each wireless station can set an RTS threshold such that the RTS/CTS sequence isused only when the data frame to be transmitted is longer than the threshold. This ensures that RTS/CTS mechanism is used only for large frames.10.No, there wouldn’t be any advantage. Suppose there are two stations that want totransmit at the same time, and they both use RTS/CTS. If the RTS frame is as long asa DATA frames, the channel would be wasted for as long as it would have beenwasted for two colliding DATA frames. Thus, the RTS/CTS exchange is only useful when the RTS/CTS frames are significantly smaller than the DATA frames.11.Initially the switch has an entry in its forwarding table which associates the wirelessstation with the earlier AP. When the wireless station associates with the new AP, the new AP creates a frame with the wireless station’s MAC address and broadcasts the frame. The frame is received by the switch. This forces the switch to update itsforwarding table, so that frames destined to the wireless station are sent via the new AP.12.Any ordinary Bluetooth node can be a master node whereas access points in 802.11networks are special devices (normal wireless devices like laptops cannot be used as access points).13.False14.“Opportunistic Scheduling” refers to matching the physical layer protocol to channelconditions between the sender and the receiver, and choosing the receivers to which packets will be sent based on channel condition. This allows the base station to make best use of the wireless medium.15.UMTS to GSM and CDMA-2000 to IS-95.16.The data plane role of eNodeB is to forward datagram between UE (over the LTEradio access network) and the P-GW. Its control plane role is to handle registration and mobility signaling traffic on behalf of the UE.The mobility management entity (MME) performs connection and mobility management on behalf of the UEs resident in the cell it controls. It receives UE subscription information from the HHS.The Packet Data Network Gateway (P-GW) allocates IP addresses to the UEs and performs QoS enforcement. As a tunnel endpoint it also performs datagram encapsulation/decapsulation when forwarding a datagram to/from a UE.The Serving Gateway (S-GW) is the data-plane mobility anchor point as all UE traffic will pass through the S-GW. The S-GW also performs charging/billing functions and lawful traffic interception.17.In 3G architecture, there are separate network components and paths for voice anddata, i.e., voice goes through public telephone network, whereas data goes through public Internet. 4G architecture is a unified, all-IP network architecture, i.e., both voice and data are carried in IP datagrams to/from the wireless device to several gateways and then to the rest of the Internet.The 4G network architecture clearly separates data and control plane, which is different from the 3G architecture.The 4G architecture has an enhanced radio access network (E-UTRAN) that is different from 3G’s radio access network UTRAN.18.No. A node can remain connected to the same access point throughout its connectionto the Internet (hence, not be mobile). A mobile node is the one that changes its point of attachment into the network over time. Since the user is always accessing theInternet through the same access point, she is not mobile.19.A permanent address for a mobile node is its IP address when it is at its homenetwork. A care-of-address is the one its gets when it is visiting a foreign network.The COA is assigned by the foreign agent (which can be the edge router in theforeign network or the mobile node itself).20.False21.The home network in GSM maintains a database called the home location register(HLR), which contains the permanent cell phone number and subscriber profileinformation about each of its subscribers. The HLR also contains information about the current locations of these subscribers. The visited network maintains a database known as the visitor location register (VLR) that contains an entry for each mobile user that is currently in the portion of the network served by the VLR. VLR entries thus come and go as mobile users enter and leave the network.The edge router in home network in mobile IP is similar to the HLR in GSM and the edge router in foreign network is similar to the VLR in GSM.22.Anchor MSC is the MSC visited by the mobile when a call first begins; anchor MSCthus remains unchanged during the call. Throughout the call’s duration and regardless of the number of inter-MSC transfers performed by the mobile, the call is routed from the home MSC to the anchor MSC, and then from the anchor MSC to the visited MSC where the mobile is currently located.23.a) Local recoveryb) TCP sender awareness of wireless linksc) Split-connection approachesChapter 7 ProblemsProblem 1Output corresponding to bit d 1 = [-1,1,-1,1,-1,1,-1,1]Output corresponding to bit d 0 = [1,-1,1,-1,1,-1,1,-1]Problem 2Sender 2 output = [1,-1,1,1,1,-1,1,1]; [ 1,-1,1,1,1,-1,1,1]Problem 3181111)1()1(111111)1()1(1112=?+?+-?-+?+?+?+-?-+?=d 181111)1()1(111111)1()1(1122=?+?+-?-+?+?+?+-?-+?=dProblem 4Sender 1: (1, 1, 1, -1, 1, -1, -1, -1)Sender 2: (1, -1, 1, 1, 1, 1, 1, 1)Problem 5a) The two APs will typically have different SSIDs and MAC addresses. A wirelessstation arriving to the café will associate with one of the SSIDs (that is, one of the APs). After association, there is a virtual link between the new station and the AP. Label the APs AP1 and AP2. Suppose the new station associates with AP1. When the new station sends a frame, it will be addressed to AP1. Although AP2 will alsoreceive the frame, it will not process the frame because the frame is not addressed to it. Thus, the two ISPs can work in parallel over the same channel. However, the two ISPs will be sharing the same wireless bandwidth. If wireless stations in different ISPs transmit at the same time, there will be a collision. For 802.11b, the maximum aggregate transmission rate for the two ISPs is 11 Mbps.b) Now if two wireless stations in different ISPs (and hence different channels) transmitat the same time, there will not be a collision. Thus, the maximum aggregatetransmission rate for the two ISPs is 22 Mbps for 802.11b.Problem 6Suppose that wireless station H1 has 1000 long frames to transmit. (H1 may be an AP that is forwarding an MP3 to some other wireless station.) Suppose initially H1 is the onlystation that wants to transmit, but that while half-way through transmitting its first frame, H2 wants to transmit a frame. For simplicity, also suppose every station can hear every other station’s signal (that is, no hidden terminals). Before transmitting, H2 will sense that the channel is busy, and therefore choose a random backoff value.Now suppose that after sending its first frame, H1 returns to step 1; that is, it waits a short period of times (DIFS) and then starts to transmit the second frame. H1’s second frame will then be transmitted while H2 is stuck in backoff, waiting for an idle channel. Thus, H1 should get to transmit all of its 1000 frames before H2 has a chance to access the channel. On the other hand, if H1 goes to step 2 after transmitting a frame, then it too chooses a random backoff value, thereby giving a fair chance to H2. Thus, fairness was the rationale behind this design choice.Problem 7A frame without data is 32 bytes long. Assuming a transmission rate of 11 Mbps, the time to transmit a control frame (such as an RTS frame, a CTS frame, or an ACK frame) is (256 bits)/(11 Mbps) = 23 usec. The time required to transmit the data frame is (8256 bits)/(11 Mbps) = 751DIFS + RTS + SIFS + CTS + SIFS + FRAME + SIFS + ACK= DIFS + 3SIFS + (3*23 + 751) usec = DIFS + 3SIFS + 820 usecProblem 8a) 1 message/ 2 slotsb) 2 messages/slotc) 1 message/slota)i) 1 message/slotii) 2 messages/slotiii) 2 messages/slotb)i) 1 message/4 slotsii) slot 1: Message A→ B, message D→ Cslot 2: Ack B→ Aslot 3: Ack C→ D= 2 messages/ 3 slotsiii)slot 1: Message C→ Dslot 2: Ack D→C, message A→ BRepeatslot 3: Ack B→ A= 2 messages/3 slotsProblem 10a)10 Mbps if it only transmits to node A. This solution is not fair since only A is gettingserved. By “fair” it m eans that each of the four nodes should be allotted equal number of slots.b)For the fairness requirement such that each node receives an equal amount of dataduring each downstream sub-frame, let n1, n2, n3, and n4 respectively represent the number of slots that A, B, C and D get. Now,data transmitted to A in 1 slot = 10t Mbits(assuming the duration of each slot to be t)Hence,Total amount of data transmitted to A (in n1 slots) = 10t n1Similarly total amounts of data transmitted to B, C, and D equal to 5t n2, 2.5t n3, and t n4 respectively.Now, to fulfill the given fairness requirement, we have the following condition:10t n1 = 5t n2 = 2.5t n3 = t n4Hence,n2 = 2 n1n3 = 4 n1n4 = 10 n1Now, the total number of slots is N. Hence,n1+ n2+ n3+ n4 = Ni.e. n1+ 2 n1 + 4 n1 + 10 n1 = Ni.e. n1 = N/17Hence,n2 = 2N/17n3 = 4N/17n4 = 10N/17The average transmission rate is given by:(10t n1+5t n2+ 2.5t n3+t n4)/tN= (10N/17 + 5 * 2N/17 + 2.5 * 4N/17 + 1 * 10N/17)/N= 40/17 = 2.35 Mbpsc)Let node A receives twice as much data as nodes B, C, and D during the sub-frame.Hence,10tn1 = 2 * 5tn2 = 2 * 2.5tn3 = 2 * tn4i.e. n2 = n1n3 = 2n1n4 = 5n1Again,n1 + n2 + n3 + n4 = Ni.e. n 1+ n1 + 2n1 + 5n1 = Ni.e. n1 = N/9Now, average transmission rate is given by:(10t n1+5t n2+ 2.5t n3+t n4)/tN= 25/9 = 2.78 MbpsSimilarly, considering nodes B, C, or D receive twice as much data as any other nodes, different values for the average transmission rate can be calculated.Problem 11a)No. All the routers might not be able to route the datagram immediately. This isbecause the Distance Vector algorithm (as well as the inter-AS routing protocols like BGP) is decentralized and takes some time to terminate. So, during the time when the algorithm is still running as a result of advertisements from the new foreign network, some of the routers may not be able to route datagrams destined to the mobile node.b)Yes. This might happen when one of the nodes has just left a foreign network andjoined a new foreign network. In this situation, the routing entries from the oldforeign network might not have been completely withdrawn when the entries from the new network are being propagated.c)The time it takes for a router to learn a path to the mobile node depends on thenumber of hops between the router and the edge router of the foreign network for the node.Problem 12If the correspondent is mobile, then any datagrams destined to the correspondent would have to pass through the correspondent’s home agent. The foreign agent in the network being visited would also need to be involved, since it is this foreign agent thatnotifies the correspondent’s home agent of the location of the correspondent. Datagrams received by the correspondent’s home agent would need to be encapsulated/tunneled between the correspondent’s home agent and for eign agent, (as in the case of the encapsulated diagram at the top of Figure 6.23.Problem 13Because datagrams must be first forward to the home agent, and from there to the mobile, the delays will generally be longer than via direct routing. Note that it is possible, however, that the direct delay from the correspondent to the mobile (i.e., if the datagram is not routed through the home agent) could actually be smaller than the sum of the delay from thecorrespondent to the home agent and from there to the mobile. It would depend on the delays on these various path segments. Note that indirect routing also adds a home agent processing (e.g., encapsulation) delay.Problem 14First, we note that chaining was discussed at the end of section 6.5. In the case of chaining using indirect routing through a home agent, the following events would happen: ?The mobile node arrives at A, A notifies the home agent that the mobile is now visiting A and that datagrams to the mobile should now be forwarded to thespecified care-of-address (COA) in A.The mobile node moves to B. The foreign agent at B must notify the foreign agent at A that the mobile is no longer resident in A but in fact is resident in Band has the specified COA in B. From then on, the foreign agent in A willforward datagrams it receives that are addressed to the mobile’s COA in A to t he mobile’s COA in B.The mobile node moves to C. The foreign agent at C must notify the foreign agent at B that the mobile is no longer resident in B but in fact is resident in C and has the specified COA in C. From then on, the foreign agent in B will forwarddatagrams it receives (from the foreign agent in A) that are addressed to themobile’s COA in B to the mobile’s COA in C.Note that when the mobile goes offline (i.e., has no address) or returns to its home network, the datagram-forwarding state maintained by the foreign agents in A, B and C must be removed. This teardown must also be done through signaling messages. Note that the home agent is not aware of the mobile’s mobility beyond A, and that the correspondent is not at all aware of the mobil e’s mobility.In the case that chaining is not used, the following events would happen: ?The mobile node arrives at A, A notifies the home agent that the mobile is now visiting A and that datagrams to the mobile should now be forwarded to thespecified care-of-address (COA) in A.The mobile node moves to B. The foreign agent at B must notify the foreign agent at A and the home agent that the mobile is no longer resident in A but infact is resident in B and has the specified COA in B. The foreign agent in A can remove its state about the mobile, since it is no longer in A. From then on, thehome agent will forward datagrams it receives that are addressed to the mobile’sCOA in B.The mobile node moves to C. The foreign agent at C must notify the foreign agent at B and the home agent that the mobile is no longer resident in B but in fact is resident in C and has the specified COA in C. The foreign agent in B canremove its state about the mobile, since it is no longer in B. From then on, thehome agent will forward datagrams it receives that are addressed to the mobile’sCOA in C.When the mobile goes offline or returns to its home network, the datagram-forwarding state maintained by the foreign agent in C must be removed. This teardown must also bedone through signaling messages. Note that the home agent is always aware of the mobile’s cu rrent foreign network. However, the correspondent is still blissfully unaware of the mobile’s mobility.Problem 15Two mobiles could certainly have the same care-of-address in the same visited network. Indeed, if the care-of-address is the address of the foreign agent, then this address would be the same. Once the foreign agent decapsulates the tunneled datagram and determines the address of the mobile, then separate addresses would need to be used to send the datagrams separately to their different destinations (mobiles) within the visited network.Problem 16If the MSRN is provided to the HLR, then the value of the MSRN must be updated in the HLR whenever the MSRN changes (e.g., when there is a handoff that requires the MSRN to change). The advantage of having the MSRN in the HLR is that the value can be provided quickly, without querying the VLR. By providing the address of the VLR Rather than the MSRN), there is no need to be refreshing the MSRN in the HLR.。
最新CCNA认证试题及答案「中文版」

最新CCNA认证试题及答案「中文版」1、对于这样一个地址,192.168.19.255/20,下列说法正确的是: ( )(A) 这是一个广播地址(B) 这是一个网络地址(C) 这是一个私有地址(D) 地址在192.168.19.0网段上(E) 地址在192.168.16.0网段上(F) 这是一个公有地址答案:CE注:IP地址中关键是看她的主机位,将子网掩码划为二进制,1对应上面的地址是网络位,0对应的地址是主机位192.168.19.255/20划为二进制为:11000000.10101000.00010011.1111111111111111.11111111.11110000.00000000主机位变成全0表示这个IP的网络地址主机槐涑扇?表示这个IP的广播地址RFC1918文件规定了保留作为局域网使用的私有地址:10.0.0.0 - 10.255.255.255 (10/8 prefix)172.16.0.0 - 172.31.255.255 (172.16/12 prefix)192.168.0.0 - 192.168.255.255 (192.168/16 prefix)2、目前,我国应用最为广泛的LAN标准是基于()的以太网标准.(A) IEEE 802.1(B) IEEE 802.2(C) IEEE 802.3(D) IEEE 802.5答案:C参考知识点:现有标准:IEEE 802.1 局域网协议高层IEEE 802.2 逻辑链路控制IEEE 802.3 以太网IEEE 802.4 令牌总线IEEE 802.5 令牌环IEEE 802.8 FDDIIEEE 802.11 无线局域网记住IEEE802.1-------IEEE802.5的定义以太网是一种计算机局域网组网技术。
IEEE制定的IEEE 802.3标准给出了以太网的技术标准。
它规定了包括物理层的连线、电信号和介质访问层协议的内容。
