霍尼韦尔实时数据库PHD说明书pim3501
Honeywell Pro-Watch集成保安系统教程说明书

Focus more on business outcomes, worry less about security needs with Honeywell Pro-Watch software.PRO-WATCH INTEGRATED SECURITY SUITE combines the power of Pro-Watch Access Control, Pro-Watch Intelligent Command with Pro-Watch VMS to create information-driven insights that are delivered in a unified dashboard. System tools such as system health dashboards and bulk firmware and password updates lower operational costs and improve operator efficiency. A unified view of alarms in maps and allowing for customized salvo views enhances situational awareness. Automated operating procedure workflows reduce compliance costs and everyday operational costs. Pro-Watch Integrated Security suite also reduces total cost of ownership by leveraging existing infrastructureAdditionally, Pro-Watch Integrated Security Suite uses data from the customer's system to provide proactive diagnostics – allowing the user to accurately budget for maintenance costs. Regional regulations create everyday challenges for security teams. By automating compliance, Pro-Watch reduces the risks of potential fines that could be levied for non-compliance. Automated workstreams allow the security operator to focus on daily needs, instead of on compliance activities.Pro-Watch Integrated Security Suite's flexible architecture achieves 24x7 availability with the industry’s lowest installation and lifecycle costs. The user-friendly design blends functional richness and configurability with an intuitive design requiring minimal operational training. Embedded system tours guide new operators through the basics of system operation, enabling them to be effective within 10 minutes – eliminating the need for costly on-site training.Situational awareness is a core concept in security systems. Pro-Watch Integrated Security Suite uses artificial intelligence to make sense of the mountain of data from multiple systems as it looks for abnormal situations. When detected, the location of the incident is represented on a building map and an incident workflow is created while SOP is executed. All actions related to an incident are archived for later analysis and packaged for external review.Pro-Watch delivers comprehensive options for audit and reporting to address forensics, compliance and business intelligence data mining needs.PRO-WATCH ®5.5Integrated Security SuiteHoneywell Pro-Watch 5.5, part of the Pro-Watch Integrated Security Suite platform, provides robust, global integrated access control, video surveillance and intrusion detection in a single view to protect staff,property, optimize productivity and comply with strict industry regulations all while reducingoperational costs.• Web Based Client for Badging, Reporting, Alarm and Event Monitoring • Mobile Client for Badging, Badging Verification, and Door Control•Server support including Windows® Server 2012/2016/2019, Windows 10 (32-bit and 64-bit), SQL Server 2014/ 2016/2019• Single user interface for multiple security and business functions•Honeywell Software Development Kit(HSDK) and Pro-Watch can be integrated with other building systems such as secondary fire, lighting and heating, ventilation, and air conditioningPERFORMANCE FEATURES AT A GLANCE• Web Services API enables Integration to third-party systems and Active Directory • Certification Management•Event/action associations including sending emails, running a storedprocedure, or triggering a panel I/O point •Pro-Watch-level triggered events for panel-to-panel and panel-to-software actions or within a panel for local actions • Advanced Reports• Support for Microsoft Azure•Virtualization support for VMWare and Microsoft® Hyper-V• HID Origo™ Integration•Compliance Reports that offer data and statistical reporting; auto generated reports upon schedules• Easy system setup and maintenance with user definable hardware templates •Database partitioning and definable operator permissions• Mercury Series 3 Controller •Mercury M5 (CASI) and MS Bridge (Software House) Controller • Lite, Professional, Corporate and Enterprise editionsSMALL SYSTEMS:PRO-WATCH LITE ANDPRO-WATCH PROFESSIONAL EDITIONSPro-Watch Lite Edition (PWLT) and Pro- Watch Professional Edition (PWPE) are optimized for the needs of smaller security systems.These editions leverage Microsoft SQL Express 2019, so the server can be accommodated on either a workstation for a single PC or on a separate server. In either case, additional clients may be connected to the server up to supported limits. Refer to the specifications guide on page 5 for more details.Pro-Watch Lite Edition offers basic functionality for the small office and features Pro-Watch PW Series access controllers. Up to four total client licenses can be added as needed.Pro-Watch Professional Edition is ideal for sites requiring more than 32 readers or up to 6 client workstations.MEDIUM & LARGE SYSTEMS: PRO-WATCH PROFESSIONAL AND PRO-WATCH CORPORATE EDITIONSBoth Pro-Watch Professional Edition(PWPE) and Pro-Watch Corporate Edition (PWCE) are targeted for the needs of medium to large installations.Figure 1. Integrations available using Pro-WatchCameraPrinterBadging workstationLite,Professional and Corporate editions MAXPRO® Workstationand server with Pro-Watch ClientVideo wallDVRNVR Analogmatrix switchPro-Watch workstation and serverMAXPRO® NVR IP camerasVISTA® and Galaxy* Dimension intrusion integrationFacial recognition reader Smart card readerPW-7000PW-7000Prox card readerFingerprint readerWith the exception of Badging and Vista,integration to these systems is not available on Pro-Watch Lite Edition*Galaxy is not available in the USThe reporting application includes basic report templates and the capability to generate custom reports exported as XLS, CSV and PDF formats.Pro-Watch provides a solid and proven security management solution. It is successfully deployed in enterprises of many sizes and across various vertical platform for intelligent campuses, government facilities and critical infrastructure.Additional licensed features include:• Alarm roll-up on maps • GIS maps implementation• System health dashboards for accessdevices• Exporting incidents as PDF• Bulk firmware and password updatesfor non-Honeywell camerasCorporate edition Corporate editionCorporate editionCorporate edition Pro-WatchEnterpriseeditionENTERPRISE SYSTEMS:PRO-WATCH ENTERPRISE EDITIONPro-Watch Enterprise Edition (PWEE) provides a security solution for the global organization by sharing badge holder identities and event data across the organization.With a PWEE system, an enterprise server facilitates two-way data sharing among regional servers. This enables single credential solutions across organizations. If equipped with two or more Pro-Watch Corporate Editions (PWCE), an organization may easily upgrade its servers to become part of an Enterprise system. Each corporate edition server becomes a regional server and retains regional system control.Table 1. Pro-Watch 5.5 specifications1 Must have a standard client license on a machine in order to run an Advanced Badging client license. 2Must order one regional server in an Enterprise system for each PWCE server in the system.Enterprise systems link together two or more Corporate edition systems to share badgeholder identities and events among the Corporate edition systems.PROFESSIONAL, CORPORATE AND ENTERPRISE EDITIONS• Standard badging and advancedbadging client • 2D PDF417 barcode add-on licensefor badging • Option for Transportation SecurityClearinghouse (TSC) background checks in Pro-Watch AP (Airport) and Vendor Management Portal • Integration to Honeywell VISTA®panels 128 /250 FBP, FBPT, BPE, and BPT, and GX in North America and to Honeywell Galaxy® Dimension GD-48, GD-96, GD-264, GD-520 in Europe • Event procedures triggers onconsecutive duplicate events • Mustering, anti-passback and guardtour • Minimum and maximum occupancyenforcement • Integrates video devices added inMAXPRO VMS • Supports Commend® intercomsystem servers GE200, GE300, GE700 and GE800• Detailed historic records for trackingconfiguration changes, security operations and device events to comply with audit • Intercoms linked to readers andlocations on maps provide quick access to specific units • Options for integrating biometrics,third-party hardware, radar-video solutions and IT convergence • High availability and redundantserver solutions (Corporate and Enterprise Edition)• Support for wireless locksets fromAllegion, Assa Abloy and Salto • Support for disconnected locksetsfrom Salto • Direct support for biometric readersfrom Morpho™ and Iris ID™• FICAM PACS Infrastructure APLlistedTable 2. Pro-Watch 5.5 SpecificationsIncludes RAM required by the customer's computer to run the Windows operating system.12RAID technology used for the larger system server – disk sets 1 and 2. When several physical disks are set up to use RAID technology, the operating system will be installed on a single disk(OS installed on RAID1 mirrored set) and the database and storage on a separate disk (RAID 5 or 10 disk set)3To estimate database storage space, use the following approximations and add to the base database size of 500MB:• Badgeholder storage = (number of badgeholders) x (75 KB)* estimate based on typical captured picture size• Event history storage = (number of events per day) x (2.5 KB) x (number of days to retain in server)• Audit history storage = [(number of cardholder changes per day) + (number of system configuration changes per day)+(number of events per day)+(number of operator system changes per day)]* (1.2 KB) x (number of days to retain in server)4Honeywell highly recommends some type of removable media for daily database backups. Database backups should be removed from the server and stored in a safe, secure location so in the event of system failure, this valuable data can be recovered. Honeywell recommends two or more removable media per server based upon end-user processes. Alternatively, Honeywell system installers can engage the end-users' IT group to participate in some type of network backup program.• Important Notice – These server and workstation hardware guidelines are intended for use as a reference only. The specifications are subject to changes due to market conditions, software updates, manufacturing changes and other variables outside of our control. Honeywell recommends for planning based on system growth and expansion, operating system updates and upgrades, database engine updates and upgrades, end-user system expansion, historical data retention requirements and archive data storage requirements. Please consult with Honeywell as applicable for assistance.Table 3. Pro-Watch 5.5 Part Number and DescriptionsMicrosoft®, Windows™, Azure®, Hyper-V®, Windows Server®, SQL Server® are trademarks or registered trademarks of Microsoft, Inc. in the United States and other countries.VMware® is a registered trademark of VMware, Inc. in the United States and other countries.HID® and Mercury™ are trademarks or registered trademarks of HID Global Corporation in the United States and other countries.Intel®, Xeon® , and Core™ are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States or other countries.AutoCAD is a trademark or registered trademark of Autodesk, Inc., in the United States and other countries.Stentofon is a trademark or registered trademark of Zenitel Norway ASA in the United States and other countries.HID Origo™ is a trademark or registered trademark of HID Global Corporation/ASSA ABLOY AB.COMMEND is a trademark or registered trademark of Commend International GmbH in the United States and other countries.MORPHO™ is a trademark or registered trademark of Idemia Identity & Security France in the United States and other countries.IRIS ID™ is a trademark or registered trademark of Datastrip, Inc. in the United States and other countries.Neverfail® is a trademark or registered trademark of Hierholzer Holdings Inc. in the United States and other countries.Pro-Watch®, VISTA®, Galaxy®, LobbyWorks® and MAXPRO® are trademarks or registered trademark of Honeywell International Inc. in the United States and other countries.Honeywell reserves the right, without notification, to make changes in product design or specifications.HIS-PRW55-02-US-EN(1121)DS-IL © 2021 Honeywell International Inc.For More Information/security Honeywell Commercial Security 715 Peachtree St NE Atlanta, GA 303081.800.323.4576。
Aeroflex DT350H Honeywell ASCB Analyzer 产品说明书

FEATURES • ASCB-A, B, and C in one unit • Two receive and one transmit port • Easy menu-driven setup allows intuitive control of unit • Reprogrammable scaling database • Powerful RECORD and BREAKPOINT modes • Four hours of operation from internal battery or operation
PHYSICAL CHARACTERISTICS
Weight 3.8 lbs (1.7 kg)
Height 6.5" (16.5 cm)
Width 9.75" (24.7 cm)
Depth 2.0" (5.0 cm)
Display Super-twist, back-lit LCD; 16-line x 40 characters, 240 x 128 dot graphics
Receive words may be displayed in their predefined scale format from the database or in HEX, Binary, bcd, or a user defined format.
The DT350H has a very powerful breakpoint feature. Receive data can be captured based on up to two breakpoint words which can be programmed to occur independently or in a specific sequence.
A D Medlcal 医用PLUSCONNECT无线体重秤UC-350BLE使用手册说明书

UC-350BLE weight scale
E-5
Pair-Up
• Turn on Bluetooth® and the app. Make sure both are ON when pair-up is proceeding.
• Press and hold “UNIT” button in the back of the scale to start pair-up.
marked inside the compartment.
* The digits “
” will be shown on the LCD.
• Close the battery door and wait until the digits “ ” are shown on the LCD.
CAUTION
If SUCCEED, symbol will be shown on the scale LCD.
If FAIL, symbol “E1” will be shown on the LCD. (Please refer to Troubleshooting for more details.)
Honeywell Black 解码器使用说明书

高清解码器用户手册2安全使用注意事项此内容的目的是确保用户正确使用本产品,以避免危险或财产损失。
在使用此产品之前,请认真阅读此说明手册并妥善保存以备日后参考。
如下所示,预防措施分为“警告”和“注意”两部分: 警告:无视警告事项,可能会导致死亡或严重伤害。
注意:无视注意事项,可能会导致伤害或财产损失。
警告1.在本产品安装使用中,必须严格遵守国家和使用地区的各项电气安全规程。
2.请使用正规厂家提供的电源适配器。
3.请不要将多个编码器连接至同一电源(超过适配器负载量,可能会产生过多热量或导致火灾)。
4.在接线、拆装等操作时请一定要将编码器电源断开,切勿带电操作。
5.如录编码器中出现冒烟现象,或产生恶臭,或发出杂音,请立即关掉电源并且将电源线拔掉,并同经销商或服务中心联系。
6.如果编码器工作不正常,请联系购买设备的商店或最近的服务中心,不要以任何方式拆卸或修改设备。
(对未经认可的修改或维修所导致的问题,本公司不承担责任)。
注意1.请不要使物体摔落到设备上或大力震动编码器,并使设备远离存在磁场干扰的地点。
避免将设备安装到表面震动或容易受到冲击的地方(忽视此项可能会损坏设备)。
2.不能暴露安装于可能淋到雨或非常潮湿的地方。
3.避免将设备放在阳光直射地点、或通风不良的地点,或如加热器或暖气等热源附近(忽视此项可能会导致火灾危险)。
4.为了避免编码器损坏,切勿把编码器设置在有油烟或水蒸气、温度过高或有很多灰尘的场所5.清洁时,用软布擦拭掉机壳上的污垢。
清理污垢时,应以干布清理,污垢不易清除时,可用中性清洗剂轻拭干净,切勿使用碱性清洁剂洗涤。
声明:非常感谢您购买我公司的产品,如果您有什么疑问或需要请随时联系我们。
本手册为编码器产品安装使用手册,支持功能由于型号不同而有所区别,请以实物和随机快速使用说明为准。
本手册旨在供您作为操作和编程系统时的参考工具。
您可以在本手册中找到有关功能和命令的信息,以及详细的菜单树和快速操作指南。
Honeywell HumidIcon数字湿度温度传感器操作指南说明书

Technical NoteSPI Communication with the Honeywell HumidIcon™ Digital Humidity/Temperature SensorsSensing and Control1.0 IntroductionThe Serial Peripheral Interface (SPI) is a simple bus system for synchronous serial communication between one Master and one or more Slaves. It operates in either full-duplex mode or half-duplex mode, allowing simultaneous communication in both directions, or in one direction only. The Master device initiates an information transfer on the bus and generates clock and control signals. Slave devices are controlled by the Master through individual Slave select lines and are active only when selected.Honeywell HumidIcon ™ digital humidity sensors with SPI output operate in half-duplex mode only, with data transfer from the Slave to the Master. Three data lines are required for data transmission:Slave Select (SS)Signal Clock (SCLK)Master-In-Slave Out (MISO)All three of these bus lines are unidirectional. SS and SCLK are controlled by the Master while MISO is controlled by the Slave (see Figure 1).2.0 Data Transfer with SPI Output Humidity SensorsHoneywell’s digital output humidity sensors are design ed to work as Slaves and will therefore only respond when the SS line is asserted. Once the SS line is asserted, the sensor will begin sending data once a clock is received. By default, Honeywell digital humidity sensors are configured to change data on the MISO line with the falling edge of SCLK. This means the Master device should sample MISO on the rising (opposite edge) of SCLK.Honeywell digital humidity sensors can handle high and low SCLK polarity without configuration change. Please contact Honeywell Customer Service with questions regarding SCLK polarity and sampling MISO.Figure 2 shows an example of a 1 byte data transfer from the Slave to the Master. In this example, the data 101 (01100101 binary, or 65 hex) would be read.Figure 2. Example of a 1 Byte SPI Data Transfer with aOnce the clocking begins, Honeywell digital humidity sensors are designed to output up to four bytes of data, depending on the sensor options and the needs of the application. In all cases, the first two data bytes are the compensated humidity output, along with sensor status bits. The third and fourth bytes are for optional compensated temperature output. 2.1 Making a Measurement RequestBy default, the digital output humidity sensor performs humidity measurement and temperature measurement conversions whenever it receives a measurement request (MR) command; otherwise, the sensor is always powered down. The results are stored after each measurement in output registers to be read using a data fetch (DF) command.Detecting whether data is ready to be fetched can be handled by testing the status bits in the fetched data. Refer to Section 2.5 for details of the status bits.SPI Communication with the Honeywell HumidIcon™ Digital Humidity/Temperature Sensors2 Honeywell Sensing and Control2.2 Humidity and Temperature Measurement Request To wake up the humidity sensor and complete a measurement cycle, an MR command is used. The complete measurement cycle performs a humidity measurement and a temperature measurement and stores the results. As shown in Figure 3, an MR command is a read of eight or more bits, ignoring the data that is returned.A DF (Data Fetch) command must be completed before sending another measurement request command to start a new measurement cycle.2.3 Humidity Data FetchTo receive a compensated humidity reading, the Master generates the necessary clock signal after activating thesensor with the Slave select line. The sensor will transmit up to four bytes of data: the first two bytes contain the compensated humidity output, and the second two bytes contain the compensated temperature output.If only the compensated humidity value is required, the Master can terminate communication by stopping the clock and deactivating the slave select line after the second byte. An example of the communication is shown in Figure 4.2.4 Humidity and Temperature Data FetchThe optional corrected temperature data is read out with 14 bitresolution. By reading out the third and fourth bytes of data from the sensor, the complete 14 bit optional compensated temperature value can be read, as shown in Figure 5.When reading the full 14 bit resolution temperature output, the two least significant bits of the fourth data byte are “Do Not Care” and should be ignored.Figure 5. SPI Humidity and Temperature Data FetchPacket = [ {S(1:0),C(13:8)}, {C(7:0)}, {T(13:6)},{T(5:0),xx} ]Where:S(1:0) = Status bits of packetC(13:8) = Upper six bits of 14-bit humidity data C(7:0) = Lower eight bits of 14-bit humidity data T(13:6) = Corrected temperature dataT(5:0),xx = Remaining bits of corrected temperature data forfull 14-bit resolutionHiZ = High impedance 2.5 Status BitsHoneywell digital output humidity sensors offer status bits to ensure robust system operation in critical applications. The sensor status is indicated by the first two most significant bits of data byte 1 (See Table 1).Note 1: Command Mode is used for programming the sensor. This mode should not be seen during normal operationWhen the status bits read “01”, “s tale” data is indicated. This means that the data in the output buffer of the sensor has already been fetched by the Master, and has not yet beenupdated with the new data from the current measurement cycle. This can happen when the Master polls the data quicker than the sensor can update the output buffer.SPI Communication with the Honeywell HumidIcon™ Digital Humidity/Temperature SensorsHoneywell Sensing and Control 33.0 Measurement CycleFigure 6 shows the measurement cycle for the humidity sensor. The measurement cycle time is typically 36.65 ms fortemperature and humidity readings. It is recommended that the user wait until the measurement cycle has completed rather than polling for data to reduce current consumption and noise.Figure 6. Measurement Cycle for Humidity and4.0 Calculation of the Humidity Value from the Digital OutputFor Honeywell humidity sensors, the output of the device is simply a 14 bit number representing between 0 %RH and 100 %RH (see Equation 1):0 %RH = 0 counts100 %RH = 214- 2 counts5.0 Calculation of Optional Temperature from the Digital OutputFor Honeywell Humidity Sensors with the optionalcompensated temperature output, the output of the device is simply a 14 bit number representing between -40 ºC and 125 ºC (see Equation 2):-40 ºC = 0 counts125 ºC = 214– 2 counts6.0 Timing and Level Parameters (See Figure7.)SPI Communication with the Honeywell HumidIcon™ Digital Humidity/Temperature SensorsSensing and ControlHoneywell1985 Douglas Drive NorthGolden Valley, MN 55422 /sensing 009071-1-ENJuly 2012Copyright © 2012 Honeywell International Inc. All rights reserved.WARRANTY/REMEDYHoneywell warrants goods of its manufacture as being free of defective materials and faulty workmanship. Honeywell’s standard product warranty applies unless agreed to otherwise by Honeywell in writing; please refer to your order acknowledgement or consult your local sales office for specific warranty details. If warranted goods are returned to Honeywell during the period of coverage, Honeywell will repair or replace, at its option, without charge those items it finds defective. The foregoin g is buyer’s sole remedy and is in lieu of all other warranties, expressed or implied, including those of merchantability and fitness for a particular purpose. In no event shall Honeywell be liable for consequential, special, or indirect damages.While we provide application assistance personally, through our literature and the Honeywell web site, it is up to the customer to determine the suitability of the product in the application.Specifications may change without notice. The information we supply is believed to be accurate and reliable as of this printing. However, we assume no responsibility for its use. SALES AND SERVICEHoneywell serves its customers through a worldwide network of sales offices, representatives and distributors. For application assistance, current specifications, pricing or name of the nearest Authorized Distributor, contact your local sales office or:E-mail:*********************Internet: /sensingPhone and Fax:Asia Pacific +65 6355-2828+65 6445-3033 FaxEurope +44 (0) 1698 481481+44 (0) 1698 481676 FaxLatin America +1-305-805-8188+1-305-883-8257 FaxUSA/Canada +1-800-537-6945+1-815-235-6847+1-815-235-6545 Fax。
Honeywell PHD实时数据库结构浅析

基于高级程序语言 的应用开发和功能强大 的趋势分析功
能。
其接 口形式主要有 : a ) S h a d o w接 口。S h a d o w接 口可 以将远 程P H D与主 P HD 连 接起来 ,远程P HD 是 一个完 整的P H D系统 ,主
二 、P HD 系统 的构成 及接 口形式
据 的压缩可 以实现大量数据 的长期存储 。系统的虚拟位
3 4 信 息 系统1 程 【2 0 1 3 . 5 2 0
三 、结束 语
P H D 实 时数据库 和O r a c l e 关系数据库搭建的数据平 台,能够确保数据交流通 畅,并将实时数据纳入管理系 统 中 ,进行深层次挖掘和分析 ,管理者可以利用实 时数 据 动态 地监控 生产成 本 ,使 成本控 制发 生在生 产过程
P H D服 务器从 实时系统 中收集 并存储 在 自己的P H D数 据库 中,主P H D J ]  ̄ 务器定期 的获取这些信 息并提供给用
户 。如 果 由于某 种原 因 主P HD J ]  ̄ 务 器 和远 程 P H D H  ̄ 务 器
b ) 数据 的处理和储 存。P H D作为一 体化数据库应用
P H D 系统是由霍尼韦尔公司推出的生产信息集成平 台 ,为流程工业提供 了一个用于生产管理的统一 的信息
化数据库 。它将生产过程数据 、物料移动数据 、设备状
态 、产 品质量指标 等各种数据采集 、存储并 加工成新 的 信息 资源 ,提供给管理 、销售 、技术 、操作 等各层次人 员 ,从而解决 了企业各个部 门信息不一致的问题 ,帮助 他们做 出及时有效 的决策 。
a ) 数据 的采 集 。P H D系统 具有 统一 的数据 采集 基 础 结 构 和 连接 多种 系 统 的 实 时数 据 库 的 产 品化 接 口 R D I ( R e a l T i me Da t a b a s e I n t e r f a c e ) ,其能够像D c s 一样长
Honeywell 35 Series Embedded NVR支持说明书
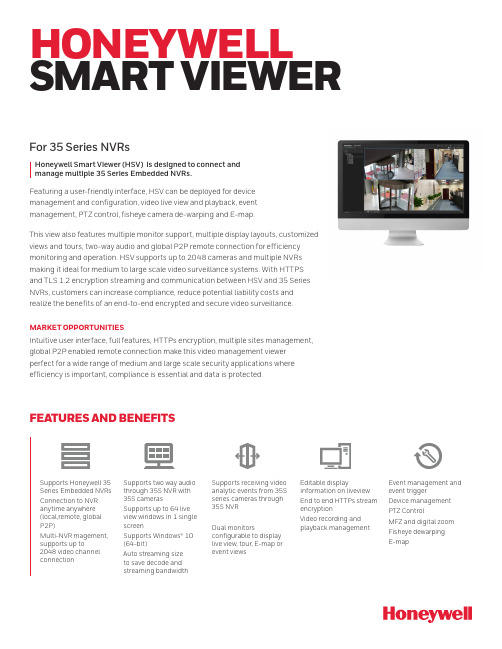
FEATURES AND BENEFITSSupports Honeywell 35 Series Embedded NVRs Connection to NVR anytime anywhere (local,remote, global P2P)Multi-NVR magement, supports up to2048 video channel connectionSupports two way audio through 35S NVR with 35S camerasSupports up to 64 live view windows in 1 single screenSupports Windows® 10 (64-bit)Auto streaming size to save decode and streaming bandwidthSupports receiving video analytic events from 35S series cameras through 35S NVRDual monitorsconfigurable to display live view, tour, E-map or event viewsEditable displayinformation on liveview End to end HTTPs stream encryptionVideo recording and playback managementEvent management and event trigger Device management PTZ ControlMFZ and digital zoom Fisheye dewarping E-mapHONEYWELL SMARTVIEWERHoneywell Smart Viewer (HSV) is designed to connect and manage multiple 35 Series Embedded NVRs.For 35 Series NVRsFeaturing a user-friendly interface, HSV can be deployed for device management and configuration, video live view and playback, event management, PTZ control, fisheye camera de-warping and E-map.This view also features multiple monitor support, multiple display layouts, customized views and tours, two-way audio and global P2P remote connection for efficiency monitoring and operation. HSV supports up to 2048 cameras and multiple NVRs making it ideal for medium to large scale video surveillance systems. With HTTPS and TLS 1.2 encryption streaming and communication between HSV and 35 Series NVRs, customers can increase compliance, reduce potential liability costs and realize the benefits of an end-to-end encrypted and secure video surveillance.MARKET OPPORTUNITIESIntuitive user interface, full features, HTTPs encryption, multiple sites management, global P2P enabled remote connection make this video management viewer perfect for a wide range of medium and large scale security applications where efficiency is important, compliance is essential and data is protected.SYSTEM DIAGRAM35 Series NVRs InternetHoneywell Smart ViewerIP Cameras * For more hardware and integration details, please refer to user manualTECHNICAL SPECIFICATIONSComputer version available onhttps://Android™ is a trademark or registered trademark of Google Inc. in the United States and/or other countries.Apple® is a trademark or registered trademark of Apple, Inc. in the United States and/or other countries.Intel® and Core™ are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and/or other countries.Microsoft® and Windows®are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.ONVIF and the ONVIF logo are trademarks of ONVIF Inc.HEVC Advance logo is a trademark of HEVC Advance .Honeywell reserves the right, without notification, to make changes in product design or specifications.HVS-35HSV-02-US(0123)DS-Y© 2023 Honeywell International Inc.For more information:/securityHoneywell Commercial Security 715 Peachtree St. NE Atlanta, GA 。
(完整版)霍尼韦尔-实时数据库PHD-介绍

Uniformance PHD R310霍尼韦尔工厂过程历史数据库管理系统将数据转化为知识Uniformance PHD过程历史数据库管理系统采集、存储、重现历史及实时工厂数据,提高数据安全和利用率,提升业务绩效PHD为企业的今天及未来,提供完整的历史数据解决方案Uniformance PHD 采集、存储、重现历史及实时工厂数据,使得在生产车间、工厂乃至全公司范围内均能及时了解相关数据信息。
PHD强大的实时数据处理能力确保了企业员工更方便高效地协作、制定并执行生产计划,从而提升业务绩效。
Uniformance PHD支持跨越多个工厂和现场的多控制系统及多应用程序的大规模集成,提供无缝的数据集成接口、自动故障恢复的数据采集、自动历史数据恢复功能,保证大型长周期历史数据库的数据安全与可靠性,确保用户能随时访问数据以及与各类应用的有效集成。
除了采集和整合潜在的大量过程数据之外,PHD还具备强大的历史数据处理功能,可以将繁杂的数据转换成有用的信息。
如“虚拟位号”数学计算功能允许用户将工程和业务知识应用至当前和历史数据中,而内置的工程单位自动转换功能可以帮助用户以其熟悉的方式查看相关数据。
过程数据与业务数据的紧密整合使得用户可以全面了解整个企业的运营情况。
PHD的效益Uniformance PHD为用户带来如下效益:•可扩展性: PHD的分布式结构保证可以从不同的数据源采集数据并汇总到单一而一致的数据库系统中。
PHD数据库的初建规模可以很小,但随着应用需要可以很方便地扩展到处理成千上万个用户和数百万个位号的规模(可以更多)•安全性: PHD提供常用的防火墙配置支持,能够对历史数据进行保护,阻止未授权的访问•可靠性: PHD具有数据采集和历史记录恢复的功能,即使数据采集出现中断,也能保证数据记录的完整性,从PHD R300版本开始,PHD提供利用集群技术部署PHD服务器的选项来满足用户全天候可用性的需求•开放性: PHD具有各类开放的产品化接口,可以与众多霍尼韦尔公司及第三方数据源进行连接。
Honeywell智能设备手册:esome Features to Look for When Ch

For industrial organizations, it is imperative to increase uptime and improve reliability. Plants seek to boost the effectiveness of their operations teams, and also require faster and more accurate engineering and greater maintenance efficiency. In addition, there is a need for higher speed processing and better control in manufacturing applications. Although Distributed Control System (DCS) technology offers significant advantages for modern industrial operations, the right solution should be purpose-built with the latest technology for your industry and application needs.IntroductionAre These Questions on Your Mind?•H ow do you ensure your plant hasan uninterrupted process execution?•W hat if you could maintainsteady and efficientoperation to ensure productsare manufactured accordingto your customer’s qualityand delivery standards?•H ow do youensure your plantpersonnel have thetools to optimizeproduction?•W hat if you could quicklyrespond to changes in themarket that may requireshifts in production typeor volume, or the start-upof new manufacturingfacilities?FPO If yes, what you’re really looking for is a reliable and flexible DCS with features tailored to your control applications...Five Features to Look for When Choosing a Perfect Fit Distributed Control SystemA DCS should be proven in the most demanding automation environments. It should alsooffer innovative solutions vital to improved plant operations in a fiercely competitive climate. Characteristics of a Proven and Innovative SolutionFeature 1:Proven and Innovative Solutions•S table and time-tested controller and I/O design protecting customer investment•P roven communication networks for fault tolerance, performance and security•V ersatile and robust control environment with proven control algorithm •S88-compliant batch control in controller enables faster, more reliable batch execution •D istributed server architecture optimizing system integrationWith the increasing demand for reliability, safety and production yield, DCS has become the preferred choice of today’s plant manager, thanks to its inherent overall system approach with integrity of process data over a high-performance and deterministic network, minimizing the downtime associated with servers, HMI and applications. Advantages of a Robust Distributed Control SystemFeature 2:Greater Robustness than a PLCBuilt-in Redundancy: True redundancy at all levels of the system from the I/O all the way up through the I/O link, the controller, the network and the servers, no single point of failure. One Data Ownership: Shared singular database across controllers and HMIs, maintaining global data consistency while enabling greater usability and operability. Integrated Station Environment: Allows direct access to controllers for process data, alarms and messages for constant view and control of the process.ASM®-compliant Safe Operator Functions: Provides integrated, interactive instructions to reduce incidents, as well as alarm handling and display layouts to improve overall operator response to abnormal conditions.Purpose-built DCS for Your Specific Requirements• P re-built template and rich function libraries enabling rapid implementation of best practices• B uilt-in function blocks specific for power applications• A dvanced batch control capability supporting chemical manufacturing • C FR21 Part 11 compliant system for pharmaceutical needs • F lexible and compact IO design simplifies project execution and reduces maintenance costT oday, there is a growing demand for a flexible distributed control solution designed to meet the diverse requirements of industrial sites around the world. What this means is a solution enabling users to achieve the performance advantages of a true DCS at a more affordable price than alternative approaches.Feature 3:T echnology to Meet Your Specific RequirementsThe DCS you choose shouldn’t just provide sophisticated process control and SCADA functionality; it should also simplify the use and configuration of these capabilities. This will allow you to elevate your automation performance without disrupting your existing operations or changing your normal work practices.Feature 4:Ease of Configuration and UseKeys to Simplifying Engineering and Operations• S tandardized display library with highest ASM compliance • M ulti-level hierarchy windows with single click navigation • P re-built equipment templates for easy configuration and maintenance• C lass-based recipes for faster implementation• B ulk configuration tools that eliminate repetitive manual tasks • D ynamic alarm suppression that simplifies plant operations.Now, more than ever, your industrial facility needs the confidence of a secure path forward for its process control system. Wouldn’t it make sense to decide the level of automation that’s appropriate for you today, and then expand the system at your own pace as your business grows?Grow to Fit Your NeedsA state-of-the-art DCS should be very flexible, from a single controller, engineering/operator station or server for the system— all residing in one PC or redundant pair of PCs. The system can then expand to many controllers, stations and redundant servers, and even beyond. Deploy Automationon Your T ermsA modern distributed systemarchitecture ensures separate DCSclusters that can be independentlyinstalled and maintained, simplifyingthe overall support. It also providesmaximum flexibility for geographicallydistributed control areas, orcontrol areas in different periodsof construction.Reach FirstProduction SoonerWith the right DCS, your processcontrol personnel can reduce the timespent getting ready for first productionby utilizing features such as drag-and-drop configuration, prebuilt algorithms,a global database, and integrated tagconfiguration. They can also developASM-compliant, preconfigured displaysand objects.Feature 5: Flexibility to Expand ControlDiscover a Perfect FitControl SystemIntroducing PlantCruise by Experion—a Distributed Control System which has beendesigned with all the features mentioned above.This makes it the right DCS for all types of manufacturersand industrial enterprises.Based on Honeywell’s award-winning Experion ProcessKnowledge System (PKS), PlantCruise by Experionefficiently answers the automation demands of differentlysized operations and leverages Honeywell’s track recordas a recognized leader in the field of process control.PlantCruise by ExperionProven. Purpose-Built. Easy-to-Use.Five Features to Look for When Choosing a Perfect Fit Distributed Control System ©2015 Honeywell International Inc.All Rights Reserved.Rely on HoneywellAround the world, Honeywell’s control systems areemployed in the most demanding industrial applicationsto improve process safety, reliability and efficiency.You can rely on our proven, advanced DCS technologyto improve your operational and business performance.For More InformationT o learn more about Honeywell’s PlantCruise by Experionsolution, visit or contact yourHoneywell account manager in your country/region orwrite to us at **************************ASM ® and Experion ® are registered trademarks of Honeywell International Inc.* A ll other trademarks are the property of their respective owners.July 2015。
Honeywell的PPTR智能高精度压力传感器说明书

APPLICATIONS:Engine Test StandsFlight Testing Water DepthUnmanned Underwater VehiclesInstrumentation and Analytical Equipment Process ControlResearch and DevelopmentHoneywell’s PPTR offers a rugged, smart pressure transducer for use in harsh environments. It combines proven silicon sensor technology with microprocessor-based signal conditioning to provide an extremely smart pressure transducer. Designed with a hermetically sealed, stainless steel construction, the PPTR operates in severe vibration, thermal and mechanical shock environments. The PPTR has many software features that support a wide range of applications.Digital and AnalogHermeticallySealed±0.20%Accuracy from -40 to 85°C► High Accuracy±0.20% FS Total Error from -40 to 85°C►Simplifies System Design - No additional signal compensation needed to gain the benefits of a very accurate sensor.► Smart, Digital Sensing and Control ►Efficient Data Acquisition - Connect up to 89 units on a network with either RS-232 or RS-485.Easy Interface - Connects to a PC via communication ports.► Versatile and Configurable ►Works with existing and new systems. - All units have 0-5V analog and either RS-232 or RS-485 digital outputs.Isolation diaphragms handle most media - harsh gases or liquids. Optimizes Output - User-configurable pressure units, sampling, update rate.Flags Problems - Internal diagnostics set flags, provide alarms.► User Selectable Software Features ►Baud Rate, Parity Setting, Continuous Broadcast, ASCII or BinaryOutput, Deadband, Sensitivity, Tare Value, Configurable Analog OutputPrecision Pressure Transducer-Ruggedized PPTR AS9100 ISO-9001 ISO-14001PPTRTotal Error: (from -40 to 85°C) Digital: ±0.20% FS Max. (2)Analog: ±0.24% FS Max. (2) Temperature Range:Operating: -40 to 85°C (-40 to 185°F) Storage: -55 to 90°C (-67 to 194°F) Reading Rate (5): 8.33ms to 51.2 min Resolution:Digital: Up to 0.001% FSAnalog: 1.22mV steps (12 bits) Response Delay:(1000/update rate) +1ms, minimum 17ms Pressure Ranges and Type: See Ordering InformationPressure Units (5) : atm, bar, cmwc, ftwc, hPa, inHg, inwc, kg/cm², KPa, mBar, mmHg, MPa, mwc, psi, user, Icom, pfsMedia Compatibility: Liquids and gases com-patible with 316 stainless steel.Typical Weight: 14 oz. (400 gm) 6-pin connector 22 oz. (625 gm) NPT w/pigtail style Output:RS-232 Digital w/0-5V Analog (5) RS-485 Digital w/0-5V Analog (5) Power Requirements:Supply Voltage: 6 to 30 VDC Operating Current: 19 - 27 mABaud Rate (5): 1200, 2400, 4800, 9600, 14400, 19200, 28800Bus Addressing (5): Address up to 89 unitsOverpressure: 3x FS, maximum 6000psi Burst Pressure: 3x FS, maximum 8500psi Mechanical Shock: 1500G, 0.5ms half sine Temp Shock: 24 1-hour cycles, -40 to 85ºC Vibration: 0.5in or 20G’s, 20Hz – 2K HzSPECIFICATIONS CASE OUTLINEORDERING INFORMATIONFULL SCALE PRESSURE RANGEAbsolute Gauge0015 15 PSI N/A 0020 20 PSI 20 PSI 0040 40 PSI 40 PSI 0100 100 PSI 100 PSI 0300 300 PSI 300 PSI 0500 500 PSI 500 PSI 1000 1000 PSI 1000 PSI 1500 1500 PSI 1500 PSI30003000 PSI3000 PSIP1 Pressure P2 PressureA Absolute 0 (vacuum) to FS N/AGGauge Reference to FS ReferenceP1 PRESSURE CONNECTIONP ¼ - 18 NPT (internal)OUTPUTS2V RS-232 digital, 0-5V analog5VRS-485 digital, 0-5V analogELECTRICAL CONFIGURATION AND CONNECTIONB 6-pin connector (4)D½ - 14 NPT external w/4ft pigtail cableOPTIONSA Demonstration Kit (6)B Mating Connector - for 6-pin connector versionC Power Supply/Data Cable - for 6-pin connector (7) E Certificate of ConformanceFCalibration Certificate0500 A P 2V B -BEFTYPE(1) Total Error is the sum of worst case linearity, repeatability, hysteresis, thermal effects and calibra-tion errors from -40 to 85ºC. Calibration is traceable to NIST. (2) Tighter accuracy available on some models. Consult factory. (3) Exposure to overpressure will not permanently affect calibration or accu-racy of unit. Exceeding burst pressure may result in media escape. Mechanical Shock tested per MIL-STD-883D, M2002.3, Cond. B., Vibration tested per MIL-STD-883D, M2007.2, Cond. A. (4) Connect-or MIL-C-26482 Style, Shell Size #10, 6-pin #20 size. (5) User configurable. (6) Demonstration kit includes unit, power supply/data cable, demonstration software, and user manual. (7) Power Supply/Data Cable requires USB port and is available for both RS-232 and RS-485 versions of the PPTR.ESD (electrostatic discharge) sensitive device. Damage may occur when subjected to high energy ESD. Proper ESD precautions should be taken to avoid performance degradation or loss of functionality.EOS (electrical overstress) sensitive device. Damage may occur when subjected to EOS. Do not exceed specified ratings to avoid performance degradation or loss of functionality.Find out more.CustomerServiceEmail:********************Honeywell reserves the right to make changes to improve reliability, function or design. Honeywell does not assume any liability arising out of the application or use of any product or circuit described herein; neither does it convey any license under its patent rights nor the rights of others.Honeywell International 12001 Highway 55 Plymouth, MN 55441ADS-14180December 2016© 2016 Honeywell International Inc.European EMC Directive: Compliant- 6-Pin Connector Model Only RoHS Directive:Non-Compliant。
Honeywell 精密载力传感器(Model 31 Mid)说明书
Mid Range Precision Miniature Load CellsModel 31 MidDESCRIPTIONThe Model 31 mid range, precision miniature load cells measure both tension and compression with options covering 10N to 5 KN / 1000 g to 1000 lb.The Model 31 is a durable miniature load cell with capability of high accuracies of 0.15 % to 0.2 % full scale. Welded, stainless steel construction is designed to minimize or eliminate the effects of off-axis loads.Each bonded strain gage unit is built of welded 17-4 PH stainless steel for additional durability. This, combined with a reliable internal design provides enhanced long-term stability. Further optional modification can permit this model to be completely welded for potential use in underwater applications.VALUE TO CUSTOMERS• Enhanced accuracy of 0.15 % to 0.2 %• Newton, gram, and pound force ranges availableFEATURES• 10 N to 5 kN /1000 g to 1000 lb • mV/V output • Stainless steel• Male thread attachments • Miniature designPOTENTIAL APPLICATIONS• Cable tension• Industrial process control • Medical control systems • Medical equipment testing• Pharmeceutical process or product control • Semiconductor/electronics testing • Aerospace testingPORTFOLIOHoneywell’s miniature and subminiature load cells are designed to fit into systems and applications with limited space or tight clearances. Constructed of rugged stainless steel for precise measurements and excellent long termstability and reliability under harsh operating conditions, these load cells are designed to eliminate or reduce to a minimum the effect of off-axis loads. To view the entire product portfolio, click here .Safety and Productivity Solutions008630Issue 22 Safety and Productivity Solutions 3Table 8. Mounting DimensionsFigure 1. Mounting Dimensions for10 N to 50 N / 1 kg to 10 lb (6AM termination required)Figure 2. Mounting Dimensions for100 N to 5 kN / 25 lb to 1000 lb (6E termination required)Figure 3. Product Nomenclature AL311LoadTypeModel 31Mid Precision Miniature Load CellMHRangeTemperatureCompensation1AInternalAmplifiers2UElectricalTermination6AMAdditionalPoint CalibrationElectrical Conn.Orientation15CSpecialCalibration3MountingThreads632BCalibrationMemory74 Warranty/RemedyHoneywell warrants goods of its manufacture as being free of defective materials and faulty workmanship. Honeywell’s standard product warranty applies unless agreed tootherwise by Honeywell in writing; please refer to your order acknowledgement or consult your local sales office for specific warranty details. If warranted goods are returned to Honeywell during the period of coverage, Honeywell will repair or replace, at its option, without charge those items it finds defective. The foregoing is buyer’s sole remedy and is in lieu of all other warranties, expressed or implied, including those of merchantability and fitness for a particular purpose. In no event shall Honeywell be liable for consequential, special, or indirect damages.While we provide application assistance personally, through our literature and the Honeywell web site, it is up to the customer to determine the suitability of the product in the application.Specifications may change without notice. The information we supply is believed to be accurate and reliable as of this printing. However, we assume no responsibility for its use.008630-2-EN IL50 GLO October 2016© 2016 Honeywell International Inc. All rights reserved.Teflon ® is a registered trademark of E.I. duPont de Nemoursm WARNINGPERSONAL INJURYDO NOT USE these products as safety or emergency stop devices or in any other application where failure of the product could result in personal injury.Failure to comply with these instructions could result in death or serious injury.m WARNINGMISUSE OF DOCUMENTATION• The information presented in this product sheet is for reference only. Do not use this document as a product installation guide.•Complete installation, operation, and maintenanceinformation is provided in the instructions supplied with each product.Failure to comply with these instructions could result indeath or serious injury.Find out moreHoneywell serves its customers through a worldwide network of sales offices, representatives and distributors. For application as-sistance, current specifications, pricing or name of the nearest Authorized Distributor, contact your local sales office.To learn more about Honeywell’s test and measurement products, call +1-815-235-6847 or 1-800-537-6945,visit , or e-mail inquiries to *********************Honeywell Safety and Productivity Solutions 9680 Old Bailes Road Fort Mill, SC 29707 NOTES1. Allowable maximum loads - maximum load to be applied withoutdamage.22. Without damage - loading to this level will not cause excessivezero shift or performance degradation. The user must consider fatigue life or long term use and structural integrity. All structurally critical applications (overhead loading, etc.) should always be designed with safety redundant load paths.3. Standard calibration for tension/compression load cells is intension only.4. Consult factory for extended operation above 125 °C [257 °F].5. Option 6i may increase the load cell height and/or diameter.Consult factory.6. See Figures 1 and 2 to match the mounting interface option withthe range code.7. Maximum operating temperature for options 53s and 53t is 85 °C[185 °F].8. TEDS IEEE 1451.4 module installed at end of cable.Figure 4. Typical System DiagramModel 31Customer supplied Chart recorder Alarm panel Data acquisition Computer PLCDisplay units SC500 SC2000SC2001SC3004GM NK HHIn-line amplifiers (used with unamplified units only)Amplifier OutputUniversal in-line amplifiers UV ±5 Vdc UV-10 ±10 Vdc UBP 0 ±5 Vdc U3W 4 mA to 20 mA (3-wire)DIN rail mount in-line amplifiers DV-05 0 ±5 Vdc (3-wire)DA-05 4 mA to 20 mA (3-wire)DV-10 0 ±10 Vdc (3-wire)。
Honeywell 感应和控制互动目录说明书
If you need detailed product information, or help choosing the right product for your application, see our Interactive Catalog . Use the Interactive Catalog to access the most complete and up-to-date information available.The Interactive Catalog provides an extensive collection of product specifications, application data, and technical literature that can be searched based on criteria you select.This PDF catalog information was published in November 2000.Sensing and ControlHoneywell Inc.11 West Spring StreetFreeport, IL /sensingSensing and Control Interactive Catalog...Click this icon to try the Interactive Catalog.Interactive Catalog Supplements Catalog PDFsBZG/BZH switches have a neoprene seal gasket between the housing halves, elas-tomer boot actuators, sealed conduit con-nectors, and die cast aluminum housing. Mounting holes are located outside the switch cavity and accept No. 10 screws. A neon pilot light can be added to switches having two conduit openings to indicate contact status.FEATURESɀPilot light (optional)ɀCast aluminum housingɀSide or flange mountACCESSORIESPilot Light 110-220 VAC (complete with seal) ............................................15LT1 Wiring Seal (for No. 14 type ‘‘S’’ rubber jacketed cord) ....................................2PA1 ELECTRICAL RATINGCircuitry Electrical RatingA UL Rating15 amp, 125, 250 or 480 VAC;2 amp, 600 VAC;MOUNTING DIMENSIONS(For reference only)PLUNGERSide mount Flange mount Roller plunger ROLLER LEVERSide mountFlange mount(2 conduit openings)RODFlange mount Side mount。
Honeywell 35 Series IP摄像头网络安全指南说明书

Honeywell 35 SeriesIP CamerasNetwork Security GuideRecommendedFind the latest version of this and other Honeywell documents on our website: https:///security.Copy Right© 2022 Honeywell International Inc. All rights reserved. No part of this publication may be reproduced by any means without written permission from Honeywell. The information in this publication is believed to be accurate in all respects. However, Honeywell cannot assume responsibility for any consequences resulting from the use thereof. The information contained herein is subject to change without notice. Revisions or new editions to this publication may be issued to incorporate such changes. For patent information, see https:///us/en/support/legal/patents.RevisionIssue Date RevisionsA 02/2022 New document.Table of Contents1Scope (1)2Application Scenarios (1)3Software Updates (3)Upgrade (3)Downgrade (3)4Removable Storage (3)5Password Management (3)6Port Management (3)7Account Management (4)8Lockout Function (4)9Session Timeout Mechanism (4)10HTTPS Secure Communication (4)Installing a Security Certificate (4)Customized Certificate Info (8)11TLS 1.2 (10)12Backup and Recovery (10)13Decommissioning / Disposal Management (10)14Vulnerability Reporting (11)FiguresFigure 2-1 Internet Connection with Firewall (Recommended) (1)Figure 10-1 Security Certificate Problem (Google Chrome) (5)Figure 10-2 Login Interface (5)Figure 10-3 Certificate Tab (6)Figure 10-4 Install Certificate (6)Figure 10-5 Certificate Import Wizard 1 (7)Figure 10-6 Certificate Import Wizard 2 (7)Figure 10-7 Certificate Import Wizard 3 (8)Figure 10-8 Create Certificate Request (9)Figure 10-9 Upload the Certificate (9)Figure 10-10 Upload Files (10)1 ScopeThis document describes network security features of Honeywell’s 35 Series IP cameras and provides guidelines for improving the security of your video surveillance system.2 Application ScenariosSurveillance systems are commonly set up on a standalone network, consisting of cameras,NVRs/DVRs, and a headend.To minimize security risks introduced during deployment, please make sure the camera isdeployed in a trusted network. If the network connection to the Internet, regardless of itsdirectness or indirectness, there should have a firewall, network-based IDS (Intrusion Detection System) or IPS (Intrusion Prevention System) in place, and configure firewall to block all ports that are enabled in the camera except for HTTPS (443 or user-defined) or there are explicitspecial access requests that get approval from your CIO or similar position.In an intranet environment, Honeywell strongly recommends to use a dedicated router / switch to connect to the cameras and use whitelists of IP / MAC addresses to restrict access to this router / switch, which will effectively reduce the possibility of attack cameras from the intranet.In an intranet environment, Honeywell recommends enabling the camera’s IP/MAC filter bygoing to Setup > System Setup > Access List to configure Allowed IP Address (The menu path for some special models may be different, so please refer to the user guides.) to prevent denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks.Figure 2-1 Internet Connection with Firewall (Recommended)Note: This guide only introduces how to secure the data and communication of 35Series IP cameras. Honeywell strongly recommends that you should follow ourrecommended scenes to deploy camera in a secure environment due to reasonsbelow.•RTSP/RTP is today the most popular live stream transmission protocol, which is widely used in almost all IP cameras, however, it has some security risks which can cause the sensitive data disclosure. RTSP over multicast is the same. RTSP over HTTPS is supported andrecommended on our device.•SNMP is widely used in network management for network monitoring, default we are disable this function because not everyone need it. And if you want to use it, V3 is therecommended for 35 Series IP cameras, you can modify it to V1 / V2 if it needs to becompatible with existing SNMP agent, which has some known security risks that can cause the sensitive data disclosure.•ONVIF is a standard for how IP products within video surveillance and other physical security areas can communicate with each other, however, it has some security risks which can cause the sensitive data disclosure. Default we disable ONVIF, if you want to use it, ONVIF over HTTPS is recommended on our device. You can modify it to ONVIF over HTTP if you need camera to compatible with exist VMS/NVR, which has some known security risks that can cause the sensitive data disclosure.•SMTP is an Internet standard network protocol for email transmission, with which the TLS is used by default for 35 Series IP cameras. You can set the device as non-TLS mode to make the device compatible with the existing SMTP server, however, which has some knownsecurity risks that can cause the sensitive data disclosure.•IEEE 802.1X is an IEEE Standard for port-based Network Access Control (PNAC). It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN. Honeywell 35 Series IP camera also support to connect to IEEE802.1X authentication network. Although the IEEE802.1X server is out of scope, Honeywell recommends you should deployIEEE802.1X Server in secure environment if you enable the IEEE 802.1x client.NTP /SMTP servers are out of scope, Honeywell strongly recommends that you should deploy them in the same secure environment.Note: •It is recommended that you should do physical protection regularly for IP camera.•It is strongly recommended that you should follow local law to legitimately use the IP camera. When you need to collect some video recordings orsnapshot data, especially some personal data, follow the data minimizationprinciple and post up proper statement in the collected zone according tothe local law.Please contact our technical support on how to deploy and configure firewall or configure Honeywell NVR.3 Software UpdatesUpgradeEnsure that your camera firmware is up-to-date and that you are running the latest version of Unified Tool (refer to User manual).DowngradeDowngrade may pose security risk to IP camera as old firmware may not necessary securityupdates or security controls.4 Removable StorageAlways scan SD cards and USB flash drives for viruses before using them with your camera. 5 Password ManagementWhen you log in to your camera for the first time, you will be required to initial the default admin password. The new password must be at least 8 characters in length, contain a mix of uppercase and lowercase characters, and include at least one number and at least one special character (taken from the following set: -_!@%^.~?#$=+*:,& ).Honeywell recommends that you change your password every 90 days.Note: The strong password rule can’t be enforced on ONVIF server due to the camera needs to be complied with the ONVIF standard and pass the ONVIF tool’s test.It is recommended that you should follow the above Honeywell password ruleson ONVIF client when setting/changing your password.6 Port ManagementHoneywell has implemented strict port management on 35 Series IP cameras, disablingunused or unsecured network services such as Telnet, SSH, and FTP.The following ports are enabled by default, you can manually disable them according to your practical application•80 (HTTP) •554 (RTSP) •443 (HTTPS)•3702 (ONVIF) •4096 (Unified tool•5353 (Bonjour)discovery)7 Account ManagementThe admin user can assign different levels of access to different user accounts. “Viewer” usermay only be allowed to monitor and change their own password, while “Administrator” user may also be allowed to access various setup functions.It is recommended that you should apply different account to different user and entitle specific right to a designated account.8 Lockout FunctionBy default, user accounts are locked after five consecutive failed login attempts. The defaultlockout time is 5 minutes. The lock will also release if the camera is restarted.9 Session Timeout MechanismSystem will logout after 30 minutes without operation on web interface, then you need to log in again. System will close the session after 60s when web be closed abnormally.10 HTTPS Secure CommunicationHoneywell has enabled HTTPS by default on 35 Series IP cameras. For example, if you enter"http://171.2.1.32" in your web browser, the address will redirect to "https://171.2.1.32." Installing a Security CertificateWhen you log in to your camera for the first time, you will be prompted to download and installa signed security certificate.To download and install a signed security certificate, follow these steps:1.Enter the IP address of the camera into your browser’s address bar. You will see thefollowing warning message:Figure 10-1 Security Certificate Problem (Google Chrome)2.Click Advanced.3.Click Proceed to 159.99.251.208 (unsafe).4.If you haven’t initialized your camera, in the initial page, Set the default admin usernameand password, and then click SAVE.5.If you have initialized your camera, in the login page, input your username and password,then LOGIN.Figure 10-2 Login Interface6.Go to Setup > System Setup > Maintenance > IMPORT/ EXPORT FILES page, and then findCA certificate row, click EXPORT, and save the root certificate ca.crt.Figure 10-3 Certificate Tab7.Double-click the ca.crt file, then click Open to open the certificate.8.In the Certificate window, on the General tab, click Install Certificate.Figure 10-4 Install Certificate9.The Certificate Import Wizard opens. Click Next to continue.10.Select Place all certificates in the following store, select Trusted Root CertificateAuthorities as the certificate store, and then click Next.Figure 10-6 Certificate Import Wizard 211.Click Finish to import the certificate.You should now be able to reopen the web browser without receiving a warning about the website security.Note: •Your Honeywell Camera/NVR requires a secure connection (HTTPS) toconnect to the network to ensure your privacy. If you change the IP address,you will need to reboot the device for the warning messages to disappear.•Do not configure a security exception as it will leave you vulnerable tophishing sites.Customized Certificate InfoThe self-signed certificate, which is not secure enough, is used as default for 35 Series IP Cameras. To increase the security of HTTPS communication, it is recommended that youshould customize the certificate information and import the Well-known certificate.User can fill in certificate information he wants, and the certificate request file is provided to the certificate issuing authority for signing, then import to camera.1.Go to Setup > Network Setup > HTTPS > CERTIFICATE REQUEST page.2.Enter the required information, then click CREATE button.3.Click EXPORT to export your customized certificate request file.Figure 10-9 Upload the Certificatee this request file to generate the Well-Known certificate from the Well-Known CA.5.Click the CHOOSE FILE and UPLOAD button in Figure 12-11 to upload the Well-Knowncertificate file.6.Then the Well-known certificate will be used instead of the original self-signed certificate. The following interface for importing the Well-known certificate and key file directly is also provided on 35 Series IP Cameras.1.Navigate to Setup → Network Setup → HTTPS → UPLOAD FILES page.2.Select the Well-known certificate and key file that got from the Well-Known CA, then ClickUPLOAD to import them to camera.Figure 10-10 Upload FilesThen the Well-known certificate will be used instead of the original self-signed certificate.Note: If the certificate requirement file is exported from a device, only thecertificate file needs to be imported; but if the certificate requirement file isexported from user self-signed or Well-known CA, both the certificate fileand the key file need to be imported.11 TLS 1.2All Honeywell 35 Series IP cameras use “TLS 1.2 only” to enhance “data transportation security”.12 Backup and RecoveryKeep a backup of your camera’s configuration settings so that, if necessary, you can quicklyrecover your device.13 Decommissioning / Disposal ManagementHoneywell recommends that you should do factory default to clear the configuration / private data and reset it to factory default setting before the camera is decommissioned or resold(Please refer to the “Restoring the Camera” chapter in the user guide).If there is a SD card in the camera, please remove and format it as well.14 Vulnerability ReportingHoneywell encourage coordinated disclosure of security vulnerabilities. Security researchers, industry groups, government organizations and vendors can report potential securityvulnerabilities to Honeywell by choosing one of the two vulnerability types in the form below or by emailing us with below details mentioned.If the vulnerability affects a product, service or solution, email us at*******************, with the following instructions/details.Please encrypt using Honeywell’s public PGP key and include the following:•Product and version•Description of the potential vulnerability•Any special configuration required to reproduce the issue•Step by step instructions to reproduce the issue•Proof of concept or exploit code, if available•Potential ImpactFor all other security issues, email us at**********************with the following instructions.Please encrypt using Honeywell’s public PGP key and include the following:•Website URL or location•Type of vulnerability (XSS, Injection, etc.)•Instructions to reproduce the vulnerability•Proof of concept or exploit code, including how an attacker could exploit the vulnerability •Potential impactTo encrypt your message to our PGP key, please download it from here:https:///en-us/product-security#items_1555827156/Honeywell Building Technologies – Security Americas (Head Office) Honeywell Commercial Security715 Peachtree St. NEAtlanta, GA 30308/Tel: +1 800 323 4576Honeywell Building Technologies – Security MexicoMexico: Av. Santa Fe 94, Torre A, Piso 1, Col. Zedec,CP 0121, CDMX, Mexico.Colombia: Edificio Punto 99, Carrera 11a.98-50, Piso 7, Bogota, Colombia.Tel: 01.800.083.59.25Honeywell Colombia SASCarrera 11A # 98-50, Edificio Punto 99, Piso 7Bogotá DC, ColombiaHoneywell Building Technologies – Security Middle East/N. Africa Emaar Business Park, Building No. 2, Sheikh Zayed RoadP.O. Box 232362Dubai, United Arab Emirates***************************/meTel: +971 4 450 5800Honeywell Building Technologies – Security Europe/South Africa 140 Waterside Road, Hamilton Industrial ParkLeicester, LES 1TN, United Kingdom/ukTel: +44 (0) 1928 378005Honeywell Building Technologies – Security Northern Europe Stationsplein Z-W 961, 1117 CE Schiphol-Oost, Netherlands/nlTel: +31 (0) 299 410 200Honeywell Building Technologies – SecurityDeutschlandJohannes-Mauthe-Straße 14,72458 Albstadt, Germanywww.security.honeywell.deTel: +49 (0) 7431 801-0Honeywell Building Technologies – Security FranceImmeuble LavoisierParc de Haute Technologie3-7 rue Georges Besse92160 Antony, France/frTel: +33 (0) 1 40 96 20 50Honeywell Building Technologies – Security Italia SpAVia Achille Grandi 22, 20097 San Donato Milanese (MI), Italy/itHoneywell Building Technologies – Security EspañaJosefa Valcárcel, 2428027 – Madrid, España/esTel.: +34 902 667 800 Honeywell Building Technologies – Security РоссияиСНГ121059 Moscow,UI, Kiev 7 Russia/ruTel: +7 (495) 797-93-71Honeywell Building Technologies – Security Asia Pacific Building #1, 555 Huanke Road,Zhang Jiang Hi-Tech Park Pudong New Area,Shanghai, 201203, ChinaTel: 400 840 2233Honeywell Building Technologies – Security and Fire (ASEAN) Honeywell International Sdn BhdLevel 25, UOA Corp Tower, Lobby BAvenue 10, The Vertical, Bangsar South City59200, Kuala Lumpur, MalaysiaVisit Partner Connect: Email:*****************************Technical support (Small & Medium Business):Vietnam: +84 4 4458 3369Thailand: +66 2 0182439 Indonesia: +62 21 2188 9000Malaysia: +60 3 7624 1530Singapore: +65 3158 6830Philippines: +63 2 231 3380Honeywell Home and Building Technologies (India)HBT India BuildingsUnitech Trade Centre, 5th Floor,Sector – 43, Block C, Sushant Lok Phase – 1,Gurgaon – 122002, Haryana, IndiaVisit Partner Connect: Email:********************************Toll Free No: 1-800-103-0339Tel: +91 124 4975000Honeywell Building Technologies – Security and Fire (Korea) Honeywell Co., Ltd. (Korea)5F SangAm IT Tower,434, Worldcup Buk-ro, Mapo-gu,Seoul 03922, KoreaVisit: Email:***************************Customersupport:***********************;+821522-8779Tel: +82-2-799-6114Honeywell Building Technologies – Security & Fire (Pacific) Honeywell Ltd9 Columbia WayBAULKHAM HILLS NSW 2153Visit: /Email:*******************************Technical support:Australia: 1300 220 345New Zealand: +64 9 623 5050https:///security +1 800 323 4576 (North America only) Document 800-26989 Rev A –02/2022。
霍尼韦尔中文说明书

霍尼韦尔honeywell VISTA120中文说明书(上)1.产品以及系统的技术指标以及功能VISTA-120可以划分为8个子系统,最多支持128个由有线、总线或无线设备组成的防区,主要性能如下:· 对于5800EU系列无线设备,可以监测无线干扰,支持无线警号,监测时间缩短。
·通过对4101SN 和 4208UXM Mk3 的支持,继电器数量从32个增加到96个。
·增加了和PASSPOINT门禁系统的互动功能。
·支持自驱动警号。
·支持最终触发布防。
·系统布防时可选下载限制。
·防区9可用于电话线监测处理。
·可选择布撤防期间键盘的不同显示。
·对于序列号式总线设备支8倍的数据处理速度。
·防区列表数量从8个扩展到15个。
·可选择每个子系统可以被旁路的防区数量。
基础接线防区•防区2-8可选末端电阻监测,支持NO或 NC探测器•可以划分到任一子系统•防区1可以支持最多16个烟感探测器•防区1-8都可以使用4线烟感探测器•防区 8最多支持50个玻璃破碎探测器总线防区扩展:支持119个总线防区,最大电流128mA:•必须使用总线模块(RPM)•受主机监视•可以划分到任一子系统无线防区扩展:用5800系列无线设备最多可以有128个无线防区(若同时接有有线或总线防区,无线防区相应减少):•发射器发送安全信号供主机监视•可以监测发射器的电池状态•可以划分给任意一个子系统特殊监视防区J7 触发器输出防区 973无线接收机防区988, 990总线回路防区 997 外围设备支持最多32 和6139/5839EU 键盘混合连接的可编址设备,如无线接收机、继电器模块、4285电话模块等:•与键盘接在同一接线柱•每个设备一个唯一的地址•在设备编程中编程使用某个设备可选语音接口模块支持4286模块,以允许通过音频电话监控系统•获得系统状态信息•布撤防系统•控制系统继电器8个子系统整个主机分为8个子系统,每个子系统相当于一台主机•其中最多可以划分3个公共子系统,这3个公共子系统随相关子系统的布撤防状态而布撤防•主控子系统9可以通过一只键盘察看所有子系统状态•每个键盘可以指定给任意子系统•继电器也可以划分到子系统中•特定系统选项也可以按子系统分别设定用户密码整个系统可以设定150个密码,并且一个密码可以指定给多个子系统。
霍尼霍尔(Honeywell)重用性APR(自主气囊)产品说明书

United KingdomIndustryReference Number1788005Product TypeRespiratory ProtectionRangeReusable APRBrand HoneywellBrand formerly known asFERNEZ by WillsonIndustryProduct Use• For use with full-face mask and half-mask equipped with an RD40 connector• For protection against organics gasses and vapours with a boiling point greater than 65°C and solid and liquid particlesOverviewFeature• Light and resistant plastic casing.Feature• Suitable for use in specific zone as free-metal zone and/or nuclear industryFeature• Performance requirements for gas and particles significantly above standard for excellent filtration efficiency over extensive period of time.Feature• Canister made of high-grade charcoal, additionally treated for optimal gas absorption.Features & BenefitsRD40 Plastic Filters A2P3PRODUCT NUMBER: 1788005Honeywell offers a broad choice of plastic canisters. Itsplastic filter range covers many hazardous gases, vapors and/or particulates in many applications.The Honeywell plastic filter range provides a cost-effectiveprotection, without compromise on its quality.This plastic filter is tested according to the EN14387 and theEN143 standard.Feature• Specific canister structure for low breathing resistance and more comfort for the userFeature• Low profile so as not to obstruct the field of visionFeature• Multipurpose and can be used with existing respirators.Feature• Safe storage between periods of use (plastic cover)Filters CartridgesStandardParticle filters efficiency (EN143) EN14387 (Gas/vapours and combined filters for respiratory with negative pressure) -Conformed to the requirements of the European Community Directive 89/686/EEC (Personnal Protective Equipment), belongs to the EC Category III and is CE marked, followed by the identification of the certification body (0194), which assure the quality control (according to the article 11B).Protection TypeCombinationConnection TypeRD40MaterialABS material with plastic cover High Activated charcoal Ø106mm - 285grE.C. Declaration of ConformityEC Category PPE3Quality AssuranceISO 9001 / 2000EC Certificate Number0070-236-079-03-03-0027EC AttestationEC AttestationEC Attestation Number0070-236-079-03-03-0027Declaration of conformity APAVE - 1788005/supplementary/documents_and_downloads/secured/pic_sku_-_certificates/4294989352/1033.aspx1788005 A2P3 tested substances/supplementary/documents_and_downloads/respiratory_protection/reusable_respirators/4294974294/1033.aspxPIC SKU - Pictures/assets/0/324/500/51887/06368eb7e1b74b558a1fc0a53876b865.jpgUser ManualUser Manual FiltersLife CycleDepends on absorption capacity, concentration of contaminant, humidity and user breathingStorage Information5 years after date of manufacturing6 months after opening- Store the filters in a cool, dry, location with the caps attached- The maximum permissible storage period is specified on the filter- Storage temperature range: -20°C / +50°C- Maximum humidity during storage: 80%Care InstructionsControls before useUsers must• Ensure that the level of protection offered by the respirator is sufficient for the type and concentration of contaminant(s) in the work area• Respect the shelf life figuring on the filter• Check the seal pointsLimitations of use• For use only by trained and qualified personal• Do not use where the oxygen level or the atmosphere is less than 17%• Do not use with organic gases and vapours with a boiling point below 65°C• After use, an opened canister must be repacked properly with its caps if it is likely to be re-used. It must be replaced no later than within 6 months after opening.• If a user identifies the break through of the canister by the smell or taste of a gas, the canister must bereplaced immediately• If the breathing resistance of the canister increased significantly, it must be changed.• Filter with a mass over 300 g may not be used fitted directly onto half-masksDisposal• Canister must be disposed in accordance with the local waste disposal regulationsEAN Code7312557880053Packaging Specs Individual Box31 x 26 x 12cmUnit of MeasureCMQuantity per Box/Pack/CaseSales unit per boX of 5 units of 1,580kg© Honeywell International Inc.。
Honeywell 快速入门手册

3820, 3820i, 4820, 4820i Cordless Imaging Systems快速入門手冊附註: 如需有關清潔裝置的資訊,請參閱您的使用手冊。
事前準備關閉電腦後連接基座,基座連接完畢後再度啟動電腦。
基座連接完畢且電源開啟後,將成像器置於基座以建立連線。
基座的綠色 LED 會閃爍,表示成像器的電池正在充電。
USB 連接1Keyboard Wedge 連接序列埠連接RS-23223條碼讀取方式取景窗發出的光束應該位於條碼正中間。
(4820/4820i的方向可任意調整以便讀取。
)握住成像器並對準條碼,扣動扳機。
成像器離條碼越近,光束越細。
反之,若離條碼越遠,則光束越粗。
如果所要掃描的條碼較小,請將成像器靠近條碼,若條碼較大則請將成像器拿遠一點。
如果條碼表面反光度高 (例如加護貝),必須適當地傾斜成像器以便讀取條碼。
附註:如果成像器在掃描條碼時發出三次嗶聲,表示尚未建立連線。
如果成像器只發出一次嗶聲,表示已建立連線。
4820/4820i可從任何方向讀取光束置於條碼中央4產品標準預設設定這個條碼會重設所有的產品標準預設設定。
PC 介面請掃描符合您所用的 PC或介面之條碼。
產品標準預設設定RS-232USB鍵盤 (PC)日本DOS/VAT/PS2 Keyboard Wedge (預設)5PC 介面 (續上頁)鍵盤的國家/地區設定掃描下面的「鍵盤的國家/地區設定」條碼,再掃描 ðƒ 12 ¦¹上合適的數字條碼,然後「儲存」條碼,即可將鍵盤設定成您想要的國家/地區。
一般而言,只有美國的成像器能支援下列字元,其他國家/地區的則不予以支援:@ | $ # { } [ ] = / ' \ < > ~。
國家/地區掃描項目國家/地區掃描項目比利時1義大利5丹麥8挪威9芬蘭2西班牙10法國3瑞士6德國/奧地利4美國 (預設)0英國7模擬外接鍵盤鍵盤的國家/地區設定儲存附註:如需完整的國家/地區清單,請參閱本公司網站上的產品使用手冊,網址為/aidc。
英国Honeywell生产的智能上锁管理系统说明书

Installation12-24V AC/DC:Connect 12 or 24V (AC or DC, 50 or 60Hz) to these two terminals to provide the powernecessary to operate the keypad. For most installations, the keypad and electric lock will share thesame power supply.Output 1: Electric locking device control relay (3 terminals). Connect the positive (+) lead from thepower supply that is being used to power the locking device to the (COM)terminal. If the locking deviceis a Fail Safe (power to lock) type, connect the positive lead of the locking device to the NormallyClosed (N.C.)terminal. If the locking device is a Fail Secure (power to unlock) type, connect thepositive lead of the locking device to the Normally Open (N.O.)terminal. Connect the negative wire ofthe locking device to the negative (-) lead of the power supply that is being used to power the lockingdeviceEG.: This terminal is for connection to an Request-To-Exit Egress device. Connect one lead from theegress button to the EG terminal, and the other lead to the negative power supply output that ispowering the keypad. The egress device must provide a N/O momentary contact. Multiple devices canbe wired in parallel.T amper N.C.: These terminals are not used.Inductive Kickback Protection: Inductive Kickback is a strong electric pulse (up to 500v) generatedby electric locks when power is removed. It is strong enough to destroy the relay contacts in the 917keypad, unless a protective device is added to the circuit. Included with the 917 keypad is a diode thatcan provide this protection for DC-powered electric locks (except magnetic locks). For magnetic locksand all AC-powered locks, use an MOV instead. Wire it into the circuit as seen in the diagram to theleft, taking note of the polarity for the diode (identified by the silver band) and locating it as close aspossible to the electric lock.Featuresprotect against inductivekickback.SECURITY DOOR CONTROLS3580 Willow Lane, Westlake Village, CA 91361-4921 • (805) 494-0622 • Fax: (805) 494-8861•E-mail:***********************P:\INSTALLATION INST\ACCESS CONTRLS\INST-917 Stand Alone.vsd Rev G 03-10 Page 1INSTALLATION INSTRUCTIONS917 EntryCheck Stand-Alone KeypadTMThe SDC 917 Entrycheck Standalone Keypad is designed to control electric locking devices such aselectric door strike, magnetic locks or electrified locksets.Up to 99 different user codes may be programmed into the 917, making it possible to allow or denyentry to any one user, without affecting the codes used by the other 98.Choice of latching or timed output;Timed output:When an authorized PIN code is entered, the relay is activated, unlocking the door perprogrammed time from 1 to 999 seconds. A momentary dry contact connected to the (EG) Request-to-Exit input activates the timed output. PIN codes will not activate the latching function when the keypadis programmed for timed operation.Latching Output:Entering an authorized PIN codes latches the relay output ON or OFF.A momentary dry contact connected to the (EG) Request-to-Exit input will also activate the latchingoutput. The lock is maintained in the ON or OFF mode until a PIN code is re-entered or (EG)Request-to-Exit input is actuated. PIN codes will not activate timed output when the keypad isprogrammed for latching operation.Request-To-Exit Input:A Request-to-Exit device with a momentary, N/O dry contact can be used fortimed egress operation without entering an access code. The device may be an Exit Switch, Sense Baror Request-to-Exit PIR sensor and is typically located within the secured area. When latching operationis chosen, a maintained or momentary, N/O dry contact switching device located remotely or adjacent tothe door may be used for ON/OFF latching without entering an access code.Installation ExamplesThe examples below represent common installation methods.This example uses a single 12VDC power supply to power both the 917 keypad and a 12VDC Fail Secure electric door strike. The N.O. output terminal is used to connect a fail secure device such as a fail secure electric strike.Example #1This example uses separate power supplies for the 917 keypad and two electric locks. This is the preferred method when there are multiple locks being controlled, to help protect the keypad from increased inductive kickback surges caused by the multiple locks.Example #3This example uses a single 24VDC power supply to power both the 917 keypad and a 24VDC Fail Safe magnetic lock. The N.C. output terminal is used to connect this device. Connection of a N.O. egress device is also included in the circuit.Example #2input120VAC input120VAC inputCode Compliant Fixed Time Egress of Entrance Egress Doors. For KeypadsProgrammed for Timed Entry or On/Off Latching:The two following devices are requiredto comply with National, State andLocal Code Criteria per Code Section Titled “Access Controlled EgressDoors” Both device contacts are wired in series with the failsafe lock powerinput. Loss of power to either egress device unlocks door.SDC 423MU or 413MNU Failsafe exit switch with fixed 30 sec. timerSDC 42MD-31DW Failsafe PIR sensor.ASSOCIATED PRODUCTS – TIMED EGRESS CONTROLS Adj. timed Egress for ON/OFF latching Keypads:Wire contacts in series with lock power.SDC MSB55V-10TD or PSB560V-10TD Egress Bars with timer moduleSDC 423U or 413NU Exit Switch withadjustable timer.SDC 2MD-31D-W Timed PIR ExitSensor with adjustable timer .SDC 10TD Mini Timer Module for REXdevices without timers.Adj. Timed Egress for TimedEntry Keypads:Keypads programmed for timed entry,connect to (EG) REX input.SDC MD-31D-W PIR Exit SensorSDC MSB55V or PSB560V Egress Bar SDC 423U or 413NU Exit Switches.inputElectric Strike12VDCFor Keypads Programmed for ON/OFF Latching:Connect momentary contacts to (EG) REX input Pulse on, Pulse off.SDC 423MU or 413NU Exit Switches.For Keypads Programmed for ON/OFF Latching or Timed Entry:Wire contacts in series with lock power.SDC 491or 492Blue Emergency Release Stations.SDC 14-2or 492 7 Day Timer, Scheduled Daily Locking/UnlockingAccess Control Power Supplies1 Amp Class2 Power Supply/Chargers621PJ Power Supply, with Enclosure and Plug-In Transformer.621J Power Supply, with Enclosure, less Transformer.602RF UL 294, Power Supply, 12"x12"x4" Cabinet, built-in Transformer.ASSOCIATED PRODUCTS – REMOTE ON/OFF CONTROLProgrammingAll program settings are protected by a Master Code, to prevent unauthorized changes.When setting up the 917 keypad for the first time (or if the Master Code has been lost) the first step is to program the Master Code you’d like to use.Master Code, Initial Setup:1) Disconnect power from the keypad.2) Set the DAP jumper to “ON”3) Connect power to the keypad. The keypad should start beeping continuously, and the yellow LED flashing continuously.4) Move the DAP jumper to “OFF”. The keypad should stop beeping, and the yellow LED lit steady.5) Enter: 0 MMMM # into the keypad, where “MMMM” is the four-digit Master Code you’d like to use.Example: 0 1234 # would set the Master Code to “1234”Other Programming:Note: All of the programming examples use a Master Code of “1234” but that’s not advisable in actual practice, because it’s too easy for unauthorized personnel to guess.Programming Pattern:As you can see, all programming entries follow the same pattern:[Master Code ] + [number ] + [information to enter, if any ] + [# ][Master Code ] sets the keypad into programming mode. Programming mode is identified by the keypad’s yellow LED being lit steady.[Number ] tells the keypad which feature to change. 0=Master Code; 1=User Code; etc.[# ] completes the programming sequence.User OperationThe yellow LED will flash to indicate that the 917 is ready to accept a command.To release the lock, simply enter one of the User Codes programmed into the keypad, followed by the pound symbol (#):UUUU #Where “UUUU” is a 4-8 digit User CodeExample : if a valid User Code were “7890”, then entering “7890#” would activate the relay to release the lock. The green LED is lit while the relay is activated.If an invalid code is entered , the keypad will return 5 beeps and 5 flashes of the yellow LED. After 10 invalid codes have been entered, the keypad will not allow any more entries for 30 seconds.SpecificationsKeypad Power Requirements:Voltage:12 or 24 volts, DC or AC (50/60hz).Amperage:Standby: 10mA @ 12/24VdcDuring key press: < 30mA @ 12/24VdcDuring relay activation: < 80mA @ 12/24VdcOutput 1: SPDT RelayRelay Contact Rating: (Output 1) 5A@ 28Vdc (Resistive) Factory Default Settings:Master Code: 0000Relay Time: 1 secondUser Codes: None --All are cleared.Access Code WorksheetMaster Code: ____ ____ ____ ____User Codes:120VAC inputThis example uses two 917 keypads to operate the same electric locking device. 917 #1 is considered the master unit and should be located within in the secured area. 917 #2 is the considered a remote egress device and is connected remote egress device terminal (EG) of the master unit.When programming 917 #2, set the Relay Time (programming option 40) to 1 second. Use the Set Relay Time (programming option 40) on 917 #1 to set the unlock time when accessed by either keypad. The latching function (programming option 41) is only available at the master keypad.Example #4Keypad #1 (Master)Keypad #2 (Remote)Keypad #1 Keypad #2 This example uses two 917 keypads to operate the same electric locking device. Power for the electric locking device is wired through both keypads.All programming functions of each keypad are independent from each other. Set Relay Time (programming option 40) must be set on each keypad. The latching function (programming option 41) is available at both keypads.Example #5。
霍尼韦尔实时数据库PHD说明书rdi3301

Uniformance® FILEACCESS and FTP Real-Time Data InterfaceInstallation GuideR310Copyright, Notices, and Trademarks© Honeywell Inc. 2012. All Rights Reserved.While this information is presented in good faith and believed to be accurate, Honeywell disclaims the implied warranties of merchantability and fitness for a particular purpose and makes no express warranties except as may be stated in its written agreement with and for its customers.In no event is Honeywell liable to anyone for any indirect, special or consequential damages. The information and specifications in this document are subject to change without notice.Honeywell, Experion PKS, PlantScape, TotalPlant, Uniformance PHD, and Business FLEX are U.S. registered trademarks of Honeywell International Inc.Other brand or product names are trademarks of their respective owners.Release InformationUniformance 310Document Revision 10Document Revision Date: February, 2012Document ID : rdi3301Document Revisions :PAR DescriptionDocumentRevision9 n/a Revised the document for R300.10 n/a Revised the document for R310Honeywell Process Solutions1860 W. Rose Garden LnPhoenix, Arizona 85027-2708 USAii Uniformance - FILEACCESS and FTP RDI Installation GuideSupport and Other ContactsUnited States and CanadaC Contact: Honeywell Solution Support CenterPhone: 1-800 822-7673.Calls are answered by dispatcher between 6:00 A.M. and 4:00 P.M.Mountain Standard Time. Emergency calls outside normal working hoursare received by an answering service and returned within one hour.Mail: Honeywell HPS TAC, MS L171860 W Rose Garden LnPhoenix, Arizona 85027-2708EuropeContact: HoneywellTAC-EMEAPhone: +32-2-728-2732Facsimile: +32-2-728-2696Mail: TAC-BE02HermesPlaza1HHermeslaan,BelgiumDiegem,B-1831PacificContact: Honeywell Global TAC – PacificPhone: 1300-300-4822 (toll free within Australia)Australia)+61-8-9362-9559(outsideFacsimile: +61-8-9362-9564Mail: Honeywell Limited Australia5 Kitchener WayBurswood 6100, Western AustraliaEmail: GTAC@IndiaContact: Honeywell Global TAC – India66039400Phone: +91-20-Facsimile: +91-20- 66039800Mail: Honeywell Automation India Ltd.56 and 57, Hadapsar Industrial EstateHadapsar, Pune –411 013, IndiaEmail: Global-TAC-India@Uniformance - FILEACCESS and FTP RDI Installation Guide iiiSupport and Other Contactsiv Uniformance - FILEACCESS and FTP RDI Installation GuideKoreaContact: Honeywell Global TAC – KoreaPhone: +82-80-782-2255 (toll free within Korea)Facsimile: +82-2-792-9015Mail: Honeywell Co., Ltd4F, Sangam IT Tower B4-4 Block1590, DMC Sangam-dong, Mapo-gu,Seoul, 121-835, KoreaEmail: Global-TAC-Korea@People’s Republic of ChinaContact: Honeywell Global TAC – ChinaPhone: +86- 21-52574568Mail: Honeywell (China) Co., Ltd33/F, Tower A, City Center, 100 Zunyi Rd.Shanghai 200051, People’s Republic of ChinaEmail: Global-TAC-China@SingaporeContact: Global TAC – South East AsiaPhone: +65-6580-3500Facsimile: +65-6580-3501+65-6445-3033Mail: Honeywell Private LimitedHoneywell Building17, Changi Business Park Central 1Singapore 486073Email: GTAC-SEA@TaiwanContact: Global TAC – TaiwanPhone: +886- 7- 536 2567Facsimile: +886-7-536 2039Mail: Honeywell Taiwan Ltd.17F-1, No. 260, Jhongshan 2nd Road.Cianjhen DistrictKaohsiung, Taiwan, ROCEmail: Global-TAC-Taiwan@Support and Other ContactsUniformance - FILEACCESS and FTP RDI Installation Guide vJapanContact: Global TAC – JapanPhone: +81-3-6730-7160Facsimile: +81-3-6730-7228Mail: Honeywell Japan Inc.New Pier Takeshiba, South Tower Building,20th Floor, 1-16-1 Kaigan, Minato-ku,Tokyo 105-0022, JapanEmail: Global-TAC-JapanJA25@ElsewhereCall your nearest Honeywell office.World Wide WebHoneywell Solution Support Online: /psTraining ClassesHoneywell Automation College: Support and Other Contactsvi Uniformance - FILEACCESS and FTP RDI Installation GuideContents1.Introduction to FILEACCESS RDI and FTP RDI (9)1.1RDI Description (9)Tag Capacity Limitations (9)Concurrent Interface Limitations (10)Data Throughput and Constraints (10)Required Support Files (10)Required Hardware and Software (10)2.Installation of FILEACCESS RDI and FTP RDI (11)2.1Installation Checklist (11)2.2To Define Source System Tag Attributes and Data Types (13)2.3To Complete the RDI Parameter Configuration Form (14)2.4To Complete the Interfaces (RDI’s & Links) Form (15)RDIs participating in an RDC scheme (19)2.5To Increase the Maximum Tags (PhdParams.Dat) (20)2.6To Run RDISetup (21)Interfaces_CustomConfig.Dat (24)2.7To Define and Start RDIs on a Running PHD System (26)2.8Modify Registry Settings (27)To Set the Polled Mode Stamping Option (27)To Set the RDI Startup Option (28)To Prevent Duplicate Bad Tag Messages (31)3.Configure PHD Tags for FILEACCESS RDI (33)3.1Tag Field Usage (33)Tag Type and Tag Attribute (33)Source Index A (33)4.Configure PHD Tags for FTP RDI (35)4.1Tag Field Usage (35)Tag Type and Tag Attribute (35)Uniformance - FILEACCESS and FTP RDI Installation Guide viiContents4.2Values for ST Type Tags (36)5.Format of Configuration File and Input Data File for FILEACCESS RDI (41)5.1Input Data File Format – Exception Mode Tags (41)5.2Configuration File Format – Exception Mode Tags (42)Additional Considerations (45)Warnings (46)Comment Lines (46)6.Format of Configuration File and Input Data File for FTP RDI (47)6.1Input Data File Format – Polled Mode Tags (47)6.2Configuration File – Polled Mode Tags (48)6.3Line Formatting Option (51)6.4Comment Lines (52)7.TCP/IP Configuration File Format (53)8.Troubleshoot RDI (55)8.1Common Installation Problems (55)8.2Problem Diagnosis (55)Glossary (57)Index 59viii Uniformance - FILEACCESS and FTP RDI Installation Guide1. Introduction to FILEACCESS RDI and FTP RDI 1.1 RDI DescriptionThe FILEACCESS RDI and the FTP RDI are used to read data from text files eitherdropped at a local directory or pulled from an FTP server on the network.RDI Type RDI Mode RDI FunctionFILEACCESS RDI Exception Reads files on the local system. Each filehas one or more lines and each linerepresents a single value for a different tag.The files can be:∙Placed in the directory by a remote system,∙Pulled from an FTP server, or∙Pulled from a mapped network drive.FTP RDI Polled Pulls a different file for each tag (as specifiedin the 'Source Tag Name' field), Each filecontains one or more lines, representing thecurrent value and some history.The system uses standard file I/O to read the files associated with each tag, and standardTCP/IP using the FTP protocol. Standard file I/O and TCP/IP sockets provide thefunctionality of the RDIs.You configure each RDI in the Interfaces (RDI’s & Links) form through the PHDConfiguration Tool (previously named TPI).Tag Capacity LimitationsFILEACCESS RDIThe capacity of the RDI is limited by access speed of the file system.FTP RDIThe capacity of the system is limited by the access speed of the network. File retrievalfrom the FTP Server by the FTP RDI can take anywhere from a few seconds to a numberof minutes using FTP. This can put a severe limit on the RDI throughput. As long asFTP requests are not too frequent, then the number of tags is not limited; however, therate of input is limited.Uniformance - FILEACCESS and FTP RDI Installation Guide ∙ 91 Introduction to FILEACCESS RDI and FTP RDI1.1 RDI DescriptionConcurrent Interface LimitationsThere are no concurrent interface limitations for these interfaces.Data Throughput and ConstraintsData throughput is governed by the transfer times of the FTP access or networkconnection.Required Support FilesThe following items are delivered as part of the interface:∙RDIFTP.DLL∙RDITCPIP.DLL∙RDIUTILS.DLLThe FTP RDI and the FILEACCESS RDI use the same .dll files.Required Hardware and SoftwareA hardware connection must exist in the form of a LAN connection providing file access.If access to remote FTP sites is required, then the necessary network access must beavailable.For the FILEACCESS RDI, the default is to just read the files from the local directory;however, the RDI can be configured to pull files from an FTP server or a mappednetwork drive, and place the files into the local directory.10 ∙ Uniformance - FILEACCESS and FTP RDI Installation Guide2. Installation of FILEACCESS RDI and FTP RDI 2.1 Installation ChecklistTask GotoNotes1. Prepare the System EnvironmentTCP/IP must be configured. This guide – sectionRequired Hardware andSoftware2. Enter Database DataIn the PHD Configuration Tool, modify the Tag Source Configuration form, if necessary. This guide – section ToDefine Source SystemTag Attributes and DataTypesIf parameters to behistorized by PHD are notspecified in the standard list(such as parameters withlarger fields), then you mustadd them to this form.In the PHD Configuration Tool, complete the RDI Parameter Configuration form, if necessary This guide – section ToComplete the RDIParameter ConfigurationFormNo modifications to thisform are required.In the PHD Configuration Tool, complete the Interfaces (RDI’s & Links) form. This guide – section To Complete the Interfaces (RDI’s & Links) Form(Optional) In the PHD Configuration Tool, configure additional copies of the Interfaces (RDI’s & Links) form if the RDI is to participate in a Robust Data Collection scheme. Robust Data CollectionUser Guide (pim3501)To support RDC, two orthree copies of each RDImust be configured,depending on the RDCmode of the RDI.(Optional) In the PHD Configuration Tool, complete the RDC Configuration form if the RDI is to participate in a Robust Data Collection scheme. Robust Data CollectionUser Guide (pim3501)Port numbers must beassigned to each RDI thatis to participate in an RDCscheme.Uniformance - FILEACCESS and FTP RDI Installation Guide 112 Installation of FILEACCESS RDI and FTP RDI 2.1 Installation Checklist12 Uniformance - FILEACCESS and FTP RDI Installation GuideTask Go to Notes3. Verify PHD System Configuration Modify the PhdParams.Dat file,if necessary, to ensure that tags to be built against the new RDI will not exceed the specified maximum. This guide – section To Increase the Maximum Tags (PhdParams.Dat)MAX_TAGS and MAX_TAGNO4. Create RDIRun RDISetup to create the appropriate RDI files. This guide – section To Run RDISetupStart>Programs>Uniforman ce>PHD Server>PHD RDI Configuration In a running PHD system, use PHDMAN to define and start the RDI.This guide – section To Define and Start RDIs on a Running PHD SystemPHDMAN EXECUTE Interfaces.Dat PHDMAN STA INT5. Modify Registry Settings (Optional) If appropriate, add the "NewPolledModeStamping" parameter to the registry for the new RDI.This guide – section To Set the Polled Mode Stamping OptionEnable this option if you want the RDI to defer its next scan if it falls behind, instead of starting it immediately after the current scan.(Optional) If appropriate, add the RDIDependency parameter to the registry for the new RDI. This guide – section To Set the RDI Startup OptionEnable this option if you want to startup RDIs in dependency order. (Optional) If appropriate, add the PreventBadTagMessages parameter to the registry for the new RDI.This guide – section To Prevent Duplicate Bad Tag MessagesEnable this option if you want only one record for a tag's bad value to be output to the PHD_EVENT.log.6. Configure PHD Tags In the PHD Configuration Tool, configure PHD tags.This guide – section Configure PHD TagsPHD ConfigurationTool>Tag Configuration form2 Installation of FILEACCESS RDI and FTP RDI2.2 To Define Source System Tag Attributes and Data Types 2.2 To Define Source System Tag Attributes and Data TypesThe Tag Source Configuration form defines the data mapping between a source systemand PHD. Perform the following steps to add attributes for the source system type to theTag Source Configuration form, if necessary.Perform the following procedure only if parameters to be historized are not alreadyspecified in the RDBMS, such as user-defined parameters.Step Action1 Open the PHD Configuration Tool.2 Under Interfaces menu select ‘Source Systems’.3 Select FILEACCESS or FTP in the ‘Current list of Source System records’window.4 In an empty record at the bottom of the form, add the information foradditional parameter(s), as necessary and click the ‘Save’ button.REFERENCE: For definitions of the PHD data types, refer to the PHD System Manual(pim0301), section Understanding the Tag Source Definitions.Uniformance - FILEACCESS and FTP RDI Installation Guide 132 Installation of FILEACCESS RDI and FTP RDI2.3 To Complete the RDI Parameter Configuration Form14 Uniformance - FILEACCESS and FTP RDI Installation Guide2.3 To Complete the RDI Parameter Configuration FormNo modifications are required to the RDI Parameter Configuration form. Perform the following steps to view the form.Step Action 1 Open the PHD Configuration Tool.2 Under Interfaces menu select ‘RDI Types ’.3 Select FILEACCESS or FTP in the ‘Current list of RDI Type records ’ window.4 See Table 1 for the description of each field. 5Close the form.Table 1 – RDI Parameter Configuration FormFieldDescriptionRDI Type Name FILEACCESS or FTP Description Description of the RDI Type Parameter NameName of the parameterFor definitions of the parameters:See Table 3 for FILEACCESS RDI See Table 4 for FTP RDI SeqThe position of the parameter in the RDI program command line.Mandatory Parameter Designates whether parameter is always required. Default Include Specifies that for new RDI’s that this parameter should be included by default.Command Line Prefix The prefix text for the specific parameter. This is usually the fixed portion of a parameter.Default Value Specifies the default value to be transferred to the Interfaces (RDI’s & Links) form Description Description of the parameter.Validation TextThe validation to apply when a value is entered in2 Installation of FILEACCESS RDI and FTP RDI2.4 To Complete the Interfaces (RDI’s & Links) FormField Descriptionthe Interfaces (RDI’s & Links) form.2.4 To Complete the Interfaces (RDI’s & Links) FormThe File Access and FTP RDIs require the activation mode and, conditionally, a path,search mask, and file deletion command specified in the Interfaces (RDI’s & Links)form.Perform the following steps to configure a specific RDI.Step Action1 Open the PHD Configuration Tool.2 Under Interfaces menu select ‘Interfaces (RDI’s and Links)’.3 Fill in the RDI Name, Hostname, Description, and select the Enabled checkbox.4 Select FILEACCESS or FTP as the Source System and then click the‘Retrieve Parameters’ button.The parameters for the RDI will be populated in the table at the bottom of thedisplay.5 After entering the required data, close the form.Table 2 – Interfaces (RDI’s & Links) Form – FILEACCESS and FTP RDIsField Description *RDI/Link Name Enter the PHD Real-time Data Interface name (interfaceinstance name).The RDI Name and Hostname combination must be aunique identifier that will be used to identify data parametersto be collected from the interface.*Host Name Enter the name of the host on which the interface executes.When the user runs RDISetup, the utility only processes theinterfaces defined in the database for the host on whichRDISetup is executing.For PHD systems with buffered PHD Servers, the sameinterface name can be defined on two different hosts.Uniformance - FILEACCESS and FTP RDI Installation Guide 152 Installation of FILEACCESS RDI and FTP RDI 2.4 To Complete the Interfaces (RDI’s & Links) Form16 Uniformance - FILEACCESS and FTP RDI Installation GuideField DescriptionPrimary TDA HostSpecifies that the host running this RDI acts as the primary system that should be queried by other PHD Servers using Transparent Data Access (TDA). *Description Enter the description of the RDI.Enabled Select whether the interface is enabled. If this flag is not set, the RDISetup utility does not process this interface. *RDI Type Name Set to FILEACCESS or FTP *Remote RDI Type NameLeave blankSource System Select FILEACCESS or FTP . Parameter Name ValueFor FILEACCESS RDI parameters, refer to Table 3. For FTP RDI parameters, refer to Table 4.Table 3 – RDI Parameters – FILEACCESS RDIParameter NameValueDescription*MODE SERVER SERVER specifies that the RDI is toexecute in FILE ACCESS mode.Tip:FILEACCESS mode expects files to be placed on its local drives, and FTP mode fetches the files. Since the FILEACCESS RDI expects others to place the files, Honeywell named itSERVER mode; and since the FTP RDI retrieves the files, Honeywell named it CLIENT mode.*CONFIGFILE /c<ConfigFile> Specifies the file that details theconfiguration information. HISTORYMODE /h/h enables history recovery. This can cause excess memory usage and file I/O if many files are being read.2 Installation of FILEACCESS RDI and FTP RDI 2.4 To Complete the Interfaces (RDI’s & Links) FormUniformance - FILEACCESS and FTP RDI Installation Guide ∙ 17Parameter Name Value DescriptionNOINITTAG/i/i disables the insertion of a zero (0) value with –1 confidence at RDI startup, shutdown, or every 24 hours when the RDI resynchronizes its clock.TAGLOOKUP /n<TagFile> Specifies a file containing a list ofnames that will be received as theincoming tag name and the name that is to be checked against the source tagname configured in PHD. Thisallows longer incoming tag names to be matched against shorter PHD tag names. Tag names are matched on a case-insensitive basis.Tag Lookup File Format:<LongTagName> = <ShortTagName>VALUELOOKUP /m<MacroFile> Specifies the name of a file thatcontains a list of replacements for received values.For example, if a value of ‘TRUE’ is received, it needs to be replaced with ‘1’.The macro file can contain many lines. Each line contains a lookup value (case-insensitive) and a replacement value. Examples:∙ TRUE = 1 ∙ YES = 1 ∙ FALSE = 0 ∙ NO = 0TRANSFERMODE /t<mode> Specifies whether to transfer the file inBINARY or ASCII mode during FTP transfers.Where <mode > is BINARY or ASCII. Default is BINARY.2 Installation of FILEACCESS RDI and FTP RDI 2.4 To Complete the Interfaces (RDI’s & Links) Form18 ∙ Uniformance - FILEACCESS and FTP RDI Installation GuideTable 4 – RDI Parameters – FTP RDIParameter NameValueDescription*MODE CLIENT CLIENT specifies that the RDI is to executein FTP mode.Tip:FILEACCESS mode expects files to be placed on its local drives, and FTP mode fetches the files. Since the FILEACCESS RDI expects others to place the files, Honeywell named it SERVER mode; and since the FTP RDI retrieves the files, Honeywell named it CLIENT mode.DEBUGLEVEL/v<number> or VERBOSE/V<number> or VERBOSE sets the tracing information level for client mode. Where <number> is a value from 0 to 2: 0 = None 2 = Full Default is 0.NOINITTAG /i/i disables the insertion of a zero (0) value with –1 confidence at RDI startup,shutdown, or every 24 hours when the RDI resynchronizes its clock.VALUELOOKUP /m<MacroFile> Specifies the name of a file that contains alist of replacements for received values.For example, if a value of ‘TRUE’ isreceived, it needs to be replaced with ‘1’. The macro file can contain many lines. Each line contains a lookup value (case-insensitive) and a replacement value. Examples:∙ TRUE = 1 ∙ YES = 1 ∙ FALSE = 0 ∙ NO = 02 Installation of FILEACCESS RDI and FTP RDI2.4 To Complete the Interfaces (RDI’s & Links) FormParameter Name Value DescriptionTRANSFERMODE /t<mode> Specifies to transfer file in BINARY orASCII mode during FTP transfers.Where <mode > is BINARY or ASCII.Default is BINARY.RDIs participating in an RDC schemeIf the RDI is to participate in a Robust Data Collection (RDC) scheme, then two or threecopies of the Interfaces (RDI’s & Links) form must be configured, depending on whether the RDC scheme is for a single or dual buffer system.In addition, after the Interfaces (RDI’s & Links) forms are completed, the RDCConfiguration form must be completed.REFERENCE: For RDC configuration details refer to the Robust Data Collection UserGuide (pim3501).Uniformance - FILEACCESS and FTP RDI Installation Guide 192 Installation of FILEACCESS RDI and FTP RDI2.5 To Increase the Maximum Tags (PhdParams.Dat)2.5 To Increase the Maximum Tags (PhdParams.Dat)Perform the following steps to view or modify the maximum number of tags configuredfor the PHD System, to ensure that tags built against the new RDI do not exceed thespecified maximum.Step Action1 Open the file <install directory>PHDServer\NtSite\PhdParams.Dat.2 If necessary, increase the values of the following parameters:∙MAX_TAGS - Maximum number of defined tags.∙MAX_TAGNO - Maximum possible tag numbers.3 Save the file.4 If you modified the above parameters, then you need to Stop and Cold Startthe PHD Server in order to resize its global memory sections.To restart the PHD Server, execute the following commands at a commandprompt:PHDCTL STOPPHDCTL START COLD20 ∙ Uniformance - FILEACCESS and FTP RDI Installation Guide2 Installation of FILEACCESS RDI and FTP RDI2.6 To Run RDISetupUniformance - FILEACCESS and FTP RDI Installation Guide 212.6 To Run RDISetupPerform the following steps to run the RDISetup utility, which creates the files for aparticular RDI.REFERENCE: For more information about how RDISetup works, refer to the Basic RDI Installation Guid e (in0701).Attention: The following steps must be performed on the PHD Server machine onwhich the RDI is to run.Attention: Do NOT delete "127.0.0.1 localhost" from the Hosts file. This entry (which is created when Windows is installed) is used by PHD functions. If it is deleted, PHD will not function properly.Prerequisite: Log on to the operating system as a user that is member of the Product Administrators group. Tip: If you change local rights, you must logon again to establish the change.Step Action 1 Make a backup copy of the following files located at <install directory>\PHDServer\NtSite\:Interfaces.Dat and Start_Interfaces.Dat .2 If the RDI was previously created in error, execute the PHDMAN command tostop the interface.PHDMAN SHUT INT <rdiname >TIP:Later, when you execute the 'Save RDI/Link Configuration' command throughRDISetup, the utility may attempt to copy new dlls for every interfaceconfigured for this node. If you choose to leave any existing interfacesrunning on this node, then when RDISetup attempts to copy the dll for arunning interface, the copy fails and an error message is output.3 On the PHD Server where the RDI is to run, open the RDISetup utility:Start>Programs>Uniformance>PHD Server>PHD RDI Configuration4Select the RDI of interest in the left pane.RESULT: The RDI parameters appear in the right pane.5 Verify/modify the values of the items listed Table 5, as needed.2 Installation of FILEACCESS RDI and FTP RDI2.6 To Run RDISetup22 ∙ Uniformance - FILEACCESS and FTP RDI Installation Guide Step Action 6To run RDISetup, select File and choose Save RDI/Link Configuration . 7 Verify that RDISetup accomplished the following for the new RDI:∙ Rewrote the Interfaces.Dat file to add commands that define the new RDI.∙ Rewrote the Start_Interfaces.Dat file to add commands for starting the newRDI.∙ It may have copied the DLL for the interface type as RDI<rdiname>.DLL tothe RDI directory. This will NOT occur for those RDI’s distributed with thePHD Server.Note: RDISetup never writes data to the database.8Verify that the Interfaces.Dat and the Start_Interfaces.Dat files contain the appropriate parameters. 9 Verify that the GO file or registry reflects the correct RDI parameters enteredthrough the Interfaces (RDI’s & Links) form.Registry location: HKLM \ SYSTEM \ CurrentControlSet \ Services\ <RDIServer> \ Parameters \ RDIList \ <rdiname >Table 5 – Parameters Entered Through the RDISetupThis parameter…Sets this… RDIServer Instance If the PHD Server has more than one RDIServer, then thisparameter represents the RDIServer to which this RDI is associated.RDIServer Port If the PHD Server has more than one RDIServer, then thisparameter represents the port number of the RDIServer towhich this RDI is associated.MIN_HISTRECMNAttention: The meaning of the history recovery limitvalues is different for RDIs participating in an RDCscheme than it is for normal RDIs. Normal RDIs (D) This is the minimum duration (minutes)of system outage for invocation of history recovery fromthe real-time system. No history recovery is performed ifthis value and the MAX_HISTRECMN are set to zero (0).Note: For the FILEACCESS RDI and the FTP RDI, theMIN_HISTRECMN value is usually set to 0 for historyrecovery.2 Installation of FILEACCESS RDI and FTP RDI2.6 To Run RDISetupUniformance - FILEACCESS and FTP RDI Installation Guide 23This parameter… Sets this… RDC RDIs (D) The following table shows the meaning ofthe limit values for RDC RDIs. REFERENCE: RobustData Collection Configuration Guide (pim3501).If <limit > is…Then… Both 0 (zero) All history is recovered.Note: The opposite is true for non-RDC RDIs, where no history isrecovered if both parameters are set to zero.Both 1 History recovery is disabled.This setting applies only to RDIsrunning on Shadow RDC nodes.Note: If MIN_HISTRECMN is set toany non-zero value greater than orequal to MAX_HISTRECMN, thenRDC history recovery is disabled.MIN_HISTRECMN 0MAX_HISTRECMN 2 History recovery is minimized (limited to one minute of history). MAX_HISTRECMN For normal RDIs: (D) This is the maximum recoverablehistory duration (minutes).Note: For the FILEACCESS RDI and the FTP RDI, theMAX_HISTRECMN value can be set to a value thatspecifies the maximum amount of history to be recoveredfrom an input file. For RDC RDIs: Refer to the previous table forMIN_HISTRECMN.XSCANSECS (D) Exception interface scan wait interval (scan interval inexception mode). The real-time system will be queried forvalues at this interval (seconds).Use Remote ClockREMCLOCK(D) For the FTP RDI to pass the time from the input file into the tag queue, the REMCLOCK value must be set to 1.The FILEACCESS RDI does not use this parameter.REMSYNCH The FILEACCESS RDI and the FTP RDI do not use thisparameter.。
霍尼韦尔 智能感測等IDENT相关使用者指南说明书
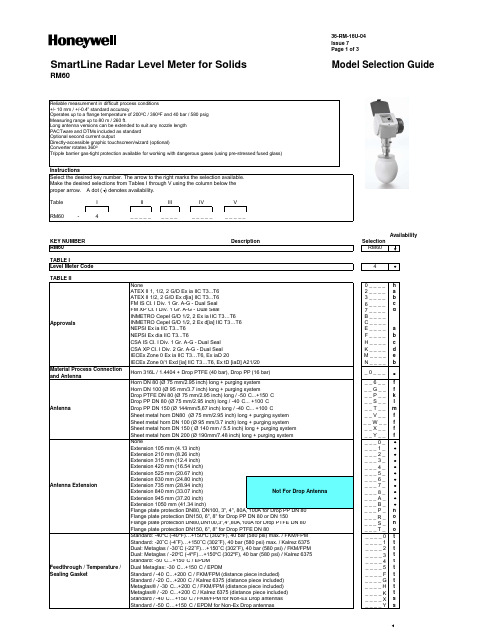
Sheet metal horn DN80 (Ø 75 mm/2.95 inch) long + purging system
Sheet metal horn DN 100 (Ø 95 mm/3.7 inch) long + purging system
Sheet metal horn DN 150 ( Ø 140 mm / 5.5 inch) long + purging system
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Uniformance®Robust Data CollectionUser GuideR310Copyright, Notices, and Trademarks© Honeywell International Inc. 1998 – 2012 All Rights Reserved.While this information is presented in good faith and believed to be accurate, Honeywell disclaims the implied warranties of merchantability and fitness for a particular purpose and makes no express warranties except as may be stated in its written agreement with and for its customers.In no event is Honeywell liable to anyone for any indirect, special or consequential damages. The information and specifications in this document are subject to change without notice.Honeywell, Experion, PlantScape, TotalPlant, Uniformance PHD, and Business FLEX are U.S. registered trademarks of Honeywell International Inc.Other brand or product names are trademarks of their respective owners.Release InformationUniformanceDocument Revision: 14Document Revision Date: February, 2012Document ID: pim3501Document Revisions:DocumentPAR DescriptionRevision13 n/a Revised the document for R300.14 n/a Revised the document for R310.Honeywell Process Solutions1860 W. Rose Garden LnPhoenix, Arizona 85027-2708 USA/psii Uniformance - Robust Data Collection User GuideSupport and Other ContactsUnited States and CanadaContact: Honeywell Solution Support CenterPhone: 1-800 822-7673.Calls are answered by dispatcher between 6:00 A.M. and 4:00 P.M. Mountain StandardTime. Emergency calls outside normal working hours are received by an answeringservice and returned within one hour.Mail: Honeywell HPS TAC, MS L171860 W Rose Garden LnPhoenix, Arizona 85027-2708EuropeTAC-EMEAContact: HoneywellPhone: +32-2-728-2732Facsimile: +32-2-728-2696Mail: TAC-BE02PlazaHermes1HHermeslaan,B-1831 Diegem, BelgiumPacificContact: Honeywell Global TAC – PacificPhone: 1300-300-4822 (toll free within Australia)Australia)(outside+61-8-9362-9559Facsimile: +61-8-9362-9564Mail: Honeywell Limited Australia5 Kitchener WayBurswood 6100, Western AustraliaEmail: GTAC@IndiaContact: Honeywell Global TAC – India66039400Phone: +91-20-Facsimile: +91-20- 66039800Mail: Honeywell Automation India Ltd.56 and 57, Hadapsar Industrial EstateHadapsar, Pune –411 013, IndiaEmail: Global-TAC-India@Uniformance Robust Data Collection User Guide iiiSupport and Other Contacts iv Uniformance - Robust Data Collection User GuideKoreaContact: Honeywell Global TAC – KoreaPhone: +82-80-782-2255 (toll free within Korea)Facsimile: +82-2-792-9015Mail: Honeywell Co., Ltd4F, Sangam IT Tower B4-4 Block1590, DMC Sangam-dong, Mapo-gu,Seoul, 121-835, KoreaEmail: Global-TAC-Korea@People’s Republic of ChinaContact: Honeywell Global TAC – ChinaPhone: +86- 21-52574568Mail: Honeywell (China) Co., Ltd33/F, Tower A, City Center, 100 Zunyi Rd.Shanghai 200051, People’s Republic of ChinaEmail: Global-TAC-China@SingaporeContact: Global TAC – South East AsiaPhone: +65-6580-3500Facsimile: +65-6580-3501+65-6445-3033Mail: Honeywell Private LimitedHoneywell Building17, Changi Business Park Central 1Singapore 486073Email: GTAC-SEA@TaiwanContact: Global TAC – TaiwanPhone: +886- 7- 536 2567Facsimile: +886-7-536 2039Mail: Honeywell Taiwan Ltd.17F-1, No. 260, Jhongshan 2nd Road.Cianjhen DistrictKaohsiung, Taiwan, ROCEmail: Global-TAC-Taiwan@Support and Other ContactsJapanContact: Global TAC – JapanPhone: +81-3-6730-7160Facsimile: +81-3-6730-7228Mail: Honeywell Japan Inc.New Pier Takeshiba, South Tower Building,20th Floor, 1-16-1 Kaigan, Minato-ku,Tokyo 105-0022, JapanEmail: Global-TAC-JapanJA25@ElsewhereCall your nearest Honeywell office.World Wide WebHoneywell Solution Support Online: /psTraining ClassesHoneywell Automation College: Uniformance - Robust Data Collection User Guide vSupport and Other Contactsvi Uniformance - Robust Data Collection User GuideContents1.ABOUT THIS DOCUMENT (11)1.1Who Should Use this Guide (11)1.2What is in this Guide (11)1.3Contact Us (11)2.INTRODUCING ROBUST DATA COLLECTION (13)2.1RDC Functionality (13)2.2RDC Configuration Overview (14)RDI/Link Configuration Requirements (14)RDC Port Number Usage (15)RDI Setup Utility (15)Interface.Dat File Requirements (15)Interfaces_CustomConfig.Dat File (15)Time Synchronization Requirements (16)2.3Single Collector Node to Shadow Configuration (16)2.4Dual Collector Node to Shadow Configuration (16)2.5Summary of RDC Features (19)2.6Real-time System Description (20)2.7Required Software Components (20)2.8History Recovery (21)Data Collection During History Recovery (21)History Recovery for RDC Scheme without a Standby Collector (22)Duration of History Recovery (22)RDC Caching during History Recovery (22)3.ROBUST DATA COLLECTION - DUAL COLLECTOR MODE (23)3.1Dual Collector RDC Architecture (23)3.2Fail-over Functionality (25)Uniformance Robust Data Collection User Guide viiContentsAutomatic Fail-over (25)Manual Fail-over (26)3.3Short Duration Data Loss (26)4.CONFIGURING ROBUST DATA COLLECTION (27)4.1General Guidelines (27)4.2Determine the Port Numbers (27)4.3RDC Configuration Checklist (28)4.4RDI-Specific Documents (30)4.5Prepare the System Environment (30)Update Hosts File on PHD Servers (30)Update Services File to Reserve RDC Ports (31)4.6To Define Source System Tag Attributes and Data Types (32)4.7Complete the RDI Type Configuration Form (32)4.8Complete the Interfaces (RDI’s & Links) Form (33)4.9Complete the RDC configuration Form (37)4.10Verify PHD Configuration on Each RDC Node (40)To Increase Maximum Tags (PhdParams.Dat) (40)5.INSTALL INTERFACES ON RDC NODES (41)5.1Run RDISetup (41)To Run RDISetup for RDC Nodes (41)5.2History Recovery on RDC Nodes (45)5.3Interpret Interfaces.Dat File on RDC Nodes (46)5.4Define and Start interfaces on a Running PHD System (47)6.CONFIGURING PHD TAGS (49)6.1Tags on RDC Shadow Interfaces (49)Tag Field Usage (49)6.2Tags on RDC Collector Interfaces (49)6.3Implement an RDC Watch Dog Tag (Optional) (50)WATCHDOG_TIMER parameter (50)viii Uniformance - Robust Data Collection User GuideContents Watch Dog Tag Configuration Guidelines (50)To Implement a Watch Dog Tag (51)7.MODIFY RDC REGISTRY SETTINGS (53)7.1Enable RDC Disk Caching (Optional) (53)7.2Enable Interface to Execute in Standby and Active Modes (54)8.MONITOR RDC STATUS (55)8.1Access RDC Status Display (55)8.2RDC Status Display Examples (56)8.3Use NSCAN Parameter To Monitor Status (58)9.TROUBLESHOOT RDC (59)9.1Watchdog-related Symptoms (59)APPENDIX A – RDC CONFIGURATION EXAMPLE (61)Example – RDC Topology (61)RDC Data specification form (62)Example – RDC Data Specification Form (63)Example – RDC Entries in Interfaces.Dat File (64)Interfaces.Dat – RDC Shadow node S37 (64)Interfaces.Dat – Collector node APP49 (64)Interfaces.Dat – Collector node APP50 (65)APPENDIX B – RDC FLOW CHARTS (67)RDC Flow Charts (67)Active RDI Flow (67)Standby RDI Flow (68)Shadow RDI Flow (69)GLOSSARY (71)INDEX (73)Uniformance - Robust Data Collection User Guide ixContentsx Uniformance - Robust Data Collection User Guide1. About This Document1.1 Who Should Use this GuideThis guide is intended for those experienced in the configuration and commissioningof PHD.1.2 What is in this GuideThe following table shows the information in each section of this guide:This section… Contains this information…Introducing Robust Data Collection Detailed description of what Robust Data Collection accomplishes when operating in single or dual collector mode.Robust Data Collection - Dual Collector Mode Additional details about an RDC scheme operating in dual collector mode.Configuring Robust DataCollectionInstructions on how to configure Robust Data Collection.Install Interfaces on RDC Nodes Instructions on how to install Robust Data Collection onthe shadow and collector nodes.Monitor RDC Status How to access and interpret the RDC status display.Appendix A – RDC Configuration Example An example RDC topology with associated PHD Configuration Tool forms and Interfaces.Dat files.Appendix B – RDC Flow Charts Flow charts of RDC operation.1.3 ContactUsIf you have any comments or concerns about this documentation, please e-mail us at: support@. Ensure that you type Uniformance Documentation in the subject line of your e-mail message.1 About This Document 1.3 Contact Us2. Introducing Robust DataCollectionFunctionality2.1 RDCRobust Data Collection (RDC) can be referred to as the methodology used to transferdata from a collector node PHD server to the shadow PHD server. A shadow server isa remote PHD node used to gather and store process information from one or morePHD collector node.RDIs and Links (interfaces) on the collector system send the real-time values directlyto the shadow server. The shadow and collector nodes use the same RDBMSdatabase and, therefore, share the same tags. The shadow node provides a bufferbetween the client environment and the process environment. The PHD collectornodes collect real-time data while the PHD Shadow nodes serve process history datato end users. The end user has access to process data without having to connect to anode on the real-time system.On a per-interface basis, Robust Data Collection provides the ability to configuredata collection in the following modes:∙single collector to shadow server∙dual collector to shadow server (not available for Links)When dual collector nodes are implemented, one collector acts as a primary collector,sending data to both the standby and the shadow servers. The standby collector actsas a warm backup node. If a standby collector detects that the primary is not in anACTIVE state, the standby will take over data collection.Note: Links can only be configured to use RDC in single collector to shadow servermode.2 Introducing Robust Data Collection2.2 RDC Configuration Overview2.2 RDC Configuration OverviewRDI/Link Configuration RequirementsThe ability to implement RDC is provided for all interfaces supported by PHD. Each interface must be configured to use RDC behavior for collector and shadowfunctionality. Each of the interfaces must be configured to act in collection or shadow operation. This behavior is available in the common base interface definitionstructures used by all RDIs and Links.You use the PHD Configuration Tool (previously named TPI) to enter the SQLServer data:∙Parameters must exist in the RDI Types configuration form. ∙ Interfaces must exist in the Interface (RDI’s & Links) configuration form for both collector and shadow nodes.∙An entry must exist in the Robust Data Collection configuration form to provide the port numbers for each interface that is to participate in an RDC scheme. The RDC configuration form contains a graphic diagram similar to the following figure for entry of the RDC data. You use the form to identify the behavior forcollector and shadow functionality. The form contains fields for each machine that is to run a copy of the RDI in an RDC scheme.An RDC scheme uses either two or three machines, depending on the functionality required by the site:∙SHADOW ∙ACTIVE ∙ STANDBY (only required for dual collector systems) Figure 1 – RDC Configuration Form – Single Collector Example2 Introducing Robust Data Collection2.2 RDC Configuration OverviewRDC Port Number UsagePHD 150 and prior releases had the Shadow node query (or poll) the collector node for historical and current data.PHD 201 and later now use a push technology for transferring data from the collector node to the shadow node.Communication from the collector computer to the shadow computer requires the configuration and use of unique TCP/IP port addresses between the computers. The ports used must not be used by any other applications resident on or accessing the computers.The receiving-end computer (which, for simple configurations, is the shadow computer) listens on the identified port. The sending-end computer (which, for simple configurations, is the collector computer) transmits data to the identified port. All subsequent communications for the interface between the affected computers use this identified port.Even during a period of History Recovery, the collector node continues to transmit current tag values to the shadow node. The shadow accumulates these values and processes them only after completing the processing of all historical values associated with the interface on the collector node.RDI Setup UtilityAfter entering the SQL Server data on the systems, you run the RDISetup utility (the replacement for the RDI_Services program) on each PHD Server to automatically configure the required SET commands in the Interfaces.Dat file. It may also have to copy the RDI DLL file.Interface.Dat File RequirementsAfter running RDISetup, the Interfaces.Dat file will contain the required RDC SET commands.Interfaces_CustomConfig.Dat FilePrior to Uniformance 210, the RDC SET commands were manually entered by the user into the Interfaces_CustomConfig.Dat file.On pre-210 systems, manual modifications to the Interfaces_CustomConfig.Dat file were required for any environment where RDC configuration was employed, because RDI_Services did not provide the extended configuration requirements for RDC configuration.2 Introducing Robust Data Collection2.3 Single Collector Node to Shadow ConfigurationOn 210 and greater systems, the Interfaces_CustomConfig.Dat file is used only forcustom interface configurations (for example, the WATCHDOG_TIMER parameter)and RDI_Services is replaced by the RDISetup utility.Time Synchronization RequirementsHoneywell highly recommends Time Synchronization across nodes if Robust DataCollection is being implemented.REFERENCE: Refer to Microsoft documentation for information about Windowstime synchronization mechanisms.2.3 Single Collector Node to Shadow ConfigurationIn the example form shown in Figure 1, the shadow computer is being told to listenon port 54200 for incoming communication; and the collector computer is being toldto send communications to port 54200 on the shadow computer. For thisconfiguration, the RDISetup utility inserts the following commands into theInterfaces.Dat file:On Shadow computer:SET MYRDI1:MODE SHADOWSET MYRDI1:ACTIVENODE COLLECTR1/54200On Collector computer:SET MYRDI1:MODE ACTIVESET MYRDI1:ACTIVENODE MYSHADOW/54200For each additional configured interface using RDC, the user must add another porton the shadow and collector computer.Note: Honeywell recommends that when configuring single collector/shadowconfigurations, the user increment the port number on the shadow computer by twofor each RDI.SET MYRDI1:ACTIVENODE COLLECTR1/54200SET MYRDI2:ACTIVENODE COLLECTR1/54202SET MYRDI3:ACTIVENODE COLLECTR2/542042.4 Dual Collector Node to Shadow ConfigurationIn the example in Figure 2, the user added a second collector (standby) computer tothe collection environment, and has set up the shadow computer to listen on port54201 for data from the standby computer COLLECTR1B. For this configuration,RDISetup will insert the following commands into the Interfaces.Dat file:On Shadow computer:2 Introducing Robust Data Collection2.4 Dual Collector Node to Shadow ConfigurationSET MYRDI1:ACTIVENODE COLLECTR1/54200SET MYRDI1:STANDBYNODE COLLECTR1B/54201Figure 2 – RDC Configuration Form – Dual Collector ExampleThe steps identified must be followed for each and every interface running on the collector computer for which the data collected is to be replicated to the shadow computer.For each interface running on any computer, a unique port must be used such that, should two separate collectors be replicating collected data to the same shadow computer, each interface on the shadow has a unique port.The forms in Figure 3 set up the following configuration for the shadow computer: ∙Listen on port 54203 for data from standby computer COLLECTR1B for RDIMYRDI2∙Listen on port 54205 for data from standby computer COLLECTR2B for RDIMYRDI3.For this configuration, RDISetup inserts the following commands into the Interfaces.Dat file.On Shadow computer:SET MYRDI2:ACTIVENODE COLLECTR1/54202SET MYRDI2:STANDBYNODE COLLECTR1B/54203SET MYRDI3:ACTIVENODE COLLECTR2/54204SET MYRDI3:STANDBYNODE COLLECTR2B/542052 Introducing Robust Data Collection2.4 Dual Collector Node to Shadow ConfigurationFigure 3 – RDC Configuration Forms – Additional Dual Collector Examples2 Introducing Robust Data Collection2.5 Summary of RDC Features The following figure summarizes the SET commands generated for RDIs in the previous examples.Figure 4 – Dual Collector to Shadow Server – Topology2.5 Summary of RDC FeaturesThe following is a list of the main features of Robust Data Collection.∙Configuration of a Standby Server for redundancy.∙Automatic fail-over to the Standby Server upon failure of the Active Server.∙Manual fail-over to Standby Server due to software maintenance on Active Server. ∙Automatic data recovery by the Active Server from the Standby Server.∙Standard access to PHD data from the Standby Server while in Standby Mode.∙No dual collection of data from the source system by the Standby Server while in Standby Mode.∙Interface type independent.2 Introducing Robust Data Collection2.6 Real-time System Description2.6 Real-time System DescriptionThe critical element is the ability of the source system to provide a lost connectivityindication to the interface. In general, most interfaces rely on a connectivity state,which is maintained by the interface layer to the source system. The capabilities ofthe interface layer may vary. As an example, the File Access RDI does not connectdirectly to a source system and, therefore, does not have a connectivity state. Thus, itdoes not support the switchover capability. Honeywell can provide furtherclarification upon request.2.7 Required Software ComponentsIn all cases, the collector computer uses an interface that communicates to the rawdata provider (it is a source system collector node).Example: RDILXS.dll, RDIOPC.dll, or PHDEXPInterface.dllIn all cases, the shadow computer will use either RDIShadow.dll orPHDEXPInterface.dll.From R310 and up RDI’s can be reentrant. In some cases this may not be the case. Ifa non-reentrant RDI is being used then each interface defined on a collectioncomputer must have a unique name. It is recommended this name be different fromthe supplied rdiXXX.dll name.Example (where 'rdiname' is identical on both nodes):RDIShadow.dll is copied to RDI<rdiname>.dll on the shadow node.RDILXS.dll is copied to RDI<rdiname>.dll on the collector node.2 Introducing Robust Data Collection2.8 History RecoveryFigure 5 – RDC Software Components Diagram2.8 HistoryRecoveryData Collection During History RecoveryWhen using Robust Data Collection with active/standby collectors, history recovery occurs concurrently with data collection. During the history recovery, the collected data is buffered and then applied to the archives once history recovery has completed. Continuation of real-time data collection during history recovery alleviates the problem with data gaps.The RDI Server buffers the real-time data that is collected while history recovery is in progress. The data is buffered until the history recovery is complete. Upon completion, the real-time data collected during history recovery is transferred to the PHD archives. When the interface retrieves real-time data during a history recovery, it records the data in the PHD archives in the correct time-sequenced order.2 Introducing Robust Data Collection2.8 History RecoveryHistory Recovery for RDC Scheme without a Standby CollectorWith 210 and later (and 201.1.6 or later and 202.1.2 or later), history recovery occursfrom the source system through the Collector node to the Shadow server, even if asecondary (Standby) collector is NOT configured in RDC.In previous releases under RDC, history recovery occurred from the secondarycollector only. When RDC history recovery was required in previous releases with asingle collector, a Gateway RDI on the shadow was used with the Remote Peer RDIon the collector.With release 310, history recovery may occur from the source system through theBuffer to the Shadow server, even if a secondary (Standby) collector is notconfigured in Robust Data Collection.In RDC, you can implement a shadow server and a single collector as a PHD to PHDtype of interface - a shadow interface runs on the Shadow RDC node and a historyrecoverable interface runs on the buffer node.Duration of History RecoveryFor systems running PHD 200 and later software, the interfaces on the Shadow RDCnode automatically perform full history recovery (all collected history is recovered).The default configuration may be modified if the site requires history recovery to bedependent on the amount of data being collected by the collector node or the durationof an outage.If full history recovery is not a site requirement, then parameters MIN_HISTRECMNand MAX_HISTRECMN (with appropriate settings) must be configured.For instructions on adding these parameters, refer to the section History Recovery onRDC Nodes.RDC Caching during History RecoveryDuring history recovery, simultaneously collected data is buffered. By default thevalues are buffered in memory. On a system with a large number of tags, orinterfaces, history recovery could take a long time. The longer history recovery takes,the more collected values need to be buffered.To minimize the amount of memory required by the RDI Server to buffer values, amechanism exists to cache the values to a disk file; thus, memory overhead isreduced and larger systems are supported.This requires a modification to the registry.For instructions for modifying the registry, refer to the section 7.1, Enable RDC DiskCaching (Optional).3. Robust Data Collection - DualCollector Mode3.1 Dual Collector RDC ArchitectureDual collector RDC mode is only available for RDI’s. Links do not support this modeof operation.The following Figure illustrates the architecture for RDI support of the fail-overcapability.Attention: The concept of 'Active' and 'Standby' is RDI-based, not node-based. Acomputer node can host both Active and Standby RDIs; this is beneficial for loadbalancing. For simplicity, the following examples segregate Active and StandbyRDIs on separate computer nodes.On the Active system, the RDIs collect data directly from the source system. Theysend the data to the Active PHD Server and to the partner RDIs on the StandbyServer.The RDIs on the Standby Server initialize, but do not communicate with the sourcesystem for the tag values. They rely on the RDIs on the Active system for the tagvalues. The values are pushed to the Standby Server so that the values are always upto date.Figure 6 – Dual Collector Fail-over ArchitectureIf the Active system goes down (loss of network connectivity or RDI shutdown), theStandby RDIs begin collecting data from the source system and provide these valuesto the Standby PHD Server. It continues to collect these values until the Activesystem comes back up and begins collecting.3 Robust Data Collection - Dual Collector Mode3.1 Dual Collector RDC ArchitectureWhen the Active system comes back up, it initiates a history recovery from theStandby Server and simultaneously begins collecting from the source system. See theActive RDI Flow in Appendix B – RDC Flow Charts.Similarly, when a Standby system has been down, and comes back up, it does ahistory recovery and begins receiving real-time values from the Active system. TheStandby always has a full history of the data collected on the Active Server. When afail-over condition occurs, any application that re-directs to the Standby has access tothe history data in addition to the real-time data. See the Standby RDI Flow inAppendix B – RDC Flow Charts.The mechanism for transferring data from the Active to the Standby RDIs is alsoused to transfer data between the collector and shadow systems (see the followingfigure).Upon Active collector fail-over, RDIs on the Standby system send the real-timevalues directly to the shadow server.Figure 7 – Dual Collector to Shadow Server RDC ArchitectureWhen a Shadow Server is receiving from a collector system consisting of anActive/Standby pair, the Shadow Server is able to receive data from the Standbysystem on failure of the Active Server. See the Shadow RDI Flow in Appendix B –RDC Flow Charts.3 Robust Data Collection - Dual Collector Mode3.2 Fail-over FunctionalityFunctionality3.2 Fail-overThe Standby system∙provides data storage,∙provides data collection,∙provides data transfer to a shadow, and∙is accessible to client applications.The fail-over functionality is available on all source systems supported by PHD. Automatic Fail-overIf the Active server is no longer in an ACTIVE state, or if network communication is lost, the Standby server takes over collection of data from the source system and continues the collection/storage of this data in PHD.For automatic fail-over to occur, there must exist at least one collected tag on the RDI (with a frequency as slow as one minute) to ensure that RDC is aware that the RDI on the primary went down.Automatic Failure Detection by Standby SystemRDC provides the ability for the Standby system to detect the failure of the Active RDI collection system and automatically begin the collection of data.Fail-over will occur only when∙the primary RDI is down or inaccessible, and∙the watchdog tag test has failed (if configured).Note: External errors such as node isolation, DCS errors, or bad data will not trigger an RDC fail-over unless they cause the RDI to fail.Optional Watchdog TagA watchdog tag is an optional feature of RDC, intended to protect the user from duplicate data collection between the primary and standby server in case of a network communication failure. During a network failure, the standby PHD server will check the state of the watchdog tag to see if the primary is continuing to operate normally. If the watchdog tag is being updated, the standby will not start collection, thus avoiding duplicate data collection.Note: A watchdog tag failure on its own will not cause RDC to fail-over. An RDC fail-over occurs only when∙the primary RDI is not ACTIVE, or∙the primary RDI cannot be reached over the network, and∙the watchdog tag is not current.。
