ICRP110Adult Refeerence Computationl Phantoms2Abstract
病案信息学第十四章电子病案

世界性的浪潮:加速EHR系统的发展 -------美国
p 美国总统乔治.W.布什在对众议院的2004年度国 情咨文中提倡升级医疗信息技术建设. 他说: 将 健康记录计算机化,我们可以避免严重的医疗事故 ,降低费用,提高医疗水平.
n 布什总统已经制定了一份计划,以确保大多数美国人 在今后10 年内拥有电子健康记录;
病案信息学第十四章电子病案
一、概述
p EMR更多强调在医疗机构内部医疗记录的电子化 和业务过程的计算机化;EPR和CPR则强调医疗 机构内部以病人为中心医疗信息的集成,包括病 人历次的就诊和住院记录的集成;EHR则进一步 将EPR扩展到医疗机构之间,包括医疗机构之间 以个人为中心的信息集成。
p 尽管不同的机构对电子病历的定义有所不同,但 基本上都从电子病历应当包括的信息内容和电子 病历系统应当具备的功能两个方面进行了描述。
病案信息学第十四章电子病案
•世界性的浪潮:加速EHR系统的发展 -------美国
p IHE组织定义的标准的数字化医院框架如下图,EHR的外 围是标准接口群,通过接口标准组织起各种各样独立运 行的临床软件,再将这些软件运行的结果信息分别记录 到EPR,就实现了电子病历的核心地位。
病案信息学第十四章电子病案
病案信息学第十四章电 子病案
2023/12/27
病案信息学第十四章电子病案
一、概述
p 美国医学研究所(IOM)1991:电子病案是基于一 个特定系统的电子化病人记录,该系统具有提供用 户访问完整准确的数据、警示、提示和临床决策支 持系统、连接医疗知识源和其他帮助的能力。
p 美国电子病案学会(CPRI)1997年修订:电子病案 内容包含了纸质病案的所有信息,但它决不只是利 用计算机将纸质病案移植为电子载体,而是将纸质 病案中文字的、图表的信息变为计算机能够识别和 理解的格式化数据予以输入、存储、处理、查询。 他不仅包括静态的病案信息,还可以利用信息技术 将文本、图像、声音结合起来,进行多媒体的信息 综合处理。
GE Vernova Flexipad 产品说明书

FLEXIPADEasier Maintenance, Higher Robustness & Reliability and Better Performance &Compactness thanks to a unique patented pads design and superior PEEK material properties.PEEK shell easily dismountable &replaceableHIGH PERFORMANCE THRUST & GUIDE BEARING PADSADVANCED BEARING TECHNOLOGY•GE Vernova’s Flexipad thrust & guide bearing pads have a sliding surface with a long lasting and high-performance thermoplastic coating.•They advantageously replace conventional babbitt pads, thanks to higher resistance to temperature and pressure, higher dimensional integrity and a lower friction co-efficient.•GE Vernova can upgrade existing babbitt pads to Flexipad by remachining the pads and installing a Flexipad PEEK shell instead of the babbitt coating.Pad repair in less than 1 hour on site Reduction of spare parts inventory: Only thin PEEK shells to be kept as spares5x less wear than PTFE coatings (*)Safe operation without injectionUp to 30% reduction in bearing losses(*) wear measured on our test rig by operating PEEK and PTFE pads in similar conditionsFLEXIPAD BENEFITSEasily & quickly repairable on site:in case of coating damage, one only has to dismount the pad from the bearing, dismount the Flexipad PEEK shell and install a spare one and remount the pad. The pad repair can be done on site in less than 1 hour. There is no need anymore to ship the pads to an external supplier for rebabbittingMore robust & reliable bearings: due to the low thermal conductivity of the Flexipad coating, the bearing pads have smaller thermal deformations compared to conventional materials, allowing a fast unit re-start after a stop. Low friction properties keep units with ageing hydraulic jacking systems operational, despite more starts and stops.More compact, more efficient bearings: with higher thermal and mechanical strengths, new bearings can be downsized and work with significantly higher loads.Reduced upgrade cost: Flexipad’shigh load carrying properties allow to keep existing thrust bearing arrangements and civil works, thus reducing upgrade costs if unit power and weight are increased.Improved peace of mind by solvinghot or problem bearings : Flexipad is more resistant to temperature and pressure, meaning it is less likely to seize up or trip a machine.HIGH PERFORMANCE THRUST & GUIDE BEARING PADSFEATURESFlexipad has a composite coating made from PEEK which improves pad characteristics. The coating is easily dismountable –see picture on the first page –with no need for any specific tooling.GE Vernova recommends the use of Flexipad pads for all Guide & Thrust bearings in vertical and horizontal arrangements. In particular Flexipad is particularly suited •To solve bearing issues such as overheating of the bearing: as it allows for higher specific pressure and reduced oil temperature increase•In refurbishment in case of increase of rotation speed or thrust load•For new bearings to reduce friction lossesFLEXIPADCONTACT US************************+ 1855 522 0755PEEK COATING SUPERIOR CHARACTERISTICS•High temperature resistance and maintenance of characteristics at higher temperatures •Tough material with lowdeformation, low wear and creep for a longer life-time•Very high load carrying capacity •Low friction co-efficient improves sliding propertiesMain CharacteristicsPEEK*Babbitt**PTFE***Melting point (°C)341240327Tensile strength room temp. (MPa)24022Tensile strength at 100°C. (MPa)15015Seizure, max. load (MPa)≥25 3.5w orking pressure 14Friction coefficient in oil0.0510.20.043Wear (based on comparative wear test)~2µm ~11µm Elongation2%300%Hardness (Rockwell)12620* PolyEtherEtherKetone ** or ‘White Metal’ *** PolyTetraFluoroEthylene, or Teflon®FEEDBACK FROM THE FIELD20 years experience with PEEK coated pads. Flexipad itself was first installed on a hydro unit in 2018. 14 thrust bearings & 3 guide bearings have been equipped worldwide with Flexipad pads for units from 4 MW to 188 MW, 75 rpm to 600 RPM. Examples:•Thrust bearing failure on Swiss unit in 2017. Due to low-speed rotation of the rotor for several hours after a guide vane failure. The mechanism got locked and was not able to close completely due to debris that entered between the blades. GE Vernova a solution based on PEEK material. •Test simulated bearing seizure due to lack of lubricating oil. In this scenario during operation with 4 MPa and 800 rpm the oil was removed from thebearing housing. The bearing continued to operate for 15 minutes. The surface was only slightly worn without any catastrophic damage visible.。
Quantum Computing for Computer Scientists

More informationQuantum Computing for Computer ScientistsThe multidisciplinaryfield of quantum computing strives to exploit someof the uncanny aspects of quantum mechanics to expand our computa-tional horizons.Quantum Computing for Computer Scientists takes read-ers on a tour of this fascinating area of cutting-edge research.Writtenin an accessible yet rigorous fashion,this book employs ideas and tech-niques familiar to every student of computer science.The reader is notexpected to have any advanced mathematics or physics background.Af-ter presenting the necessary prerequisites,the material is organized tolook at different aspects of quantum computing from the specific stand-point of computer science.There are chapters on computer architecture,algorithms,programming languages,theoretical computer science,cryp-tography,information theory,and hardware.The text has step-by-stepexamples,more than two hundred exercises with solutions,and program-ming drills that bring the ideas of quantum computing alive for today’scomputer science students and researchers.Noson S.Yanofsky,PhD,is an Associate Professor in the Departmentof Computer and Information Science at Brooklyn College,City Univer-sity of New York and at the PhD Program in Computer Science at TheGraduate Center of CUNY.Mirco A.Mannucci,PhD,is the founder and CEO of HoloMathics,LLC,a research and development company with a focus on innovative mathe-matical modeling.He also serves as Adjunct Professor of Computer Sci-ence at George Mason University and the University of Maryland.QUANTUM COMPUTING FORCOMPUTER SCIENTISTSNoson S.YanofskyBrooklyn College,City University of New YorkandMirco A.MannucciHoloMathics,LLCMore informationMore informationcambridge university pressCambridge,New York,Melbourne,Madrid,Cape Town,Singapore,S˜ao Paulo,DelhiCambridge University Press32Avenue of the Americas,New York,NY10013-2473,USAInformation on this title:/9780521879965C Noson S.Yanofsky and Mirco A.Mannucci2008This publication is in copyright.Subject to statutory exceptionand to the provisions of relevant collective licensing agreements,no reproduction of any part may take place withoutthe written permission of Cambridge University Press.First published2008Printed in the United States of AmericaA catalog record for this publication is available from the British Library.Library of Congress Cataloging in Publication dataYanofsky,Noson S.,1967–Quantum computing for computer scientists/Noson S.Yanofsky andMirco A.Mannucci.p.cm.Includes bibliographical references and index.ISBN978-0-521-87996-5(hardback)1.Quantum computers.I.Mannucci,Mirco A.,1960–II.Title.QA76.889.Y352008004.1–dc222008020507ISBN978-0-521-879965hardbackCambridge University Press has no responsibility forthe persistence or accuracy of URLs for external orthird-party Internet Web sites referred to in this publicationand does not guarantee that any content on suchWeb sites is,or will remain,accurate or appropriate.More informationDedicated toMoishe and Sharon Yanofskyandto the memory ofLuigi and Antonietta MannucciWisdom is one thing:to know the tho u ght by which all things are directed thro u gh allthings.˜Heraclitu s of Ephe s u s(535–475B C E)a s quoted in Dio g ene s Laertiu s’sLives and Opinions of Eminent PhilosophersBook IX,1. More informationMore informationContentsPreface xi1Complex Numbers71.1Basic Definitions81.2The Algebra of Complex Numbers101.3The Geometry of Complex Numbers152Complex Vector Spaces292.1C n as the Primary Example302.2Definitions,Properties,and Examples342.3Basis and Dimension452.4Inner Products and Hilbert Spaces532.5Eigenvalues and Eigenvectors602.6Hermitian and Unitary Matrices622.7Tensor Product of Vector Spaces663The Leap from Classical to Quantum743.1Classical Deterministic Systems743.2Probabilistic Systems793.3Quantum Systems883.4Assembling Systems974Basic Quantum Theory1034.1Quantum States1034.2Observables1154.3Measuring1264.4Dynamics1294.5Assembling Quantum Systems1325Architecture1385.1Bits and Qubits138viiMore informationviii Contents5.2Classical Gates1445.3Reversible Gates1515.4Quantum Gates1586Algorithms1706.1Deutsch’s Algorithm1716.2The Deutsch–Jozsa Algorithm1796.3Simon’s Periodicity Algorithm1876.4Grover’s Search Algorithm1956.5Shor’s Factoring Algorithm2047Programming Languages2207.1Programming in a Quantum World2207.2Quantum Assembly Programming2217.3Toward Higher-Level Quantum Programming2307.4Quantum Computation Before Quantum Computers2378Theoretical Computer Science2398.1Deterministic and Nondeterministic Computations2398.2Probabilistic Computations2468.3Quantum Computations2519Cryptography2629.1Classical Cryptography2629.2Quantum Key Exchange I:The BB84Protocol2689.3Quantum Key Exchange II:The B92Protocol2739.4Quantum Key Exchange III:The EPR Protocol2759.5Quantum Teleportation27710Information Theory28410.1Classical Information and Shannon Entropy28410.2Quantum Information and von Neumann Entropy28810.3Classical and Quantum Data Compression29510.4Error-Correcting Codes30211Hardware30511.1Quantum Hardware:Goals and Challenges30611.2Implementing a Quantum Computer I:Ion Traps31111.3Implementing a Quantum Computer II:Linear Optics31311.4Implementing a Quantum Computer III:NMRand Superconductors31511.5Future of Quantum Ware316Appendix A Historical Bibliography of Quantum Computing319 by Jill CirasellaA.1Reading Scientific Articles319A.2Models of Computation320More informationContents ixA.3Quantum Gates321A.4Quantum Algorithms and Implementations321A.5Quantum Cryptography323A.6Quantum Information323A.7More Milestones?324Appendix B Answers to Selected Exercises325Appendix C Quantum Computing Experiments with MATLAB351C.1Playing with Matlab351C.2Complex Numbers and Matrices351C.3Quantum Computations354Appendix D Keeping Abreast of Quantum News:QuantumComputing on the Web and in the Literature357by Jill CirasellaD.1Keeping Abreast of Popular News357D.2Keeping Abreast of Scientific Literature358D.3The Best Way to Stay Abreast?359Appendix E Selected Topics for Student Presentations360E.1Complex Numbers361E.2Complex Vector Spaces362E.3The Leap from Classical to Quantum363E.4Basic Quantum Theory364E.5Architecture365E.6Algorithms366E.7Programming Languages368E.8Theoretical Computer Science369E.9Cryptography370E.10Information Theory370E.11Hardware371Bibliography373Index381More informationPrefaceQuantum computing is a fascinating newfield at the intersection of computer sci-ence,mathematics,and physics,which strives to harness some of the uncanny as-pects of quantum mechanics to broaden our computational horizons.This bookpresents some of the most exciting and interesting topics in quantum computing.Along the way,there will be some amazing facts about the universe in which we liveand about the very notions of information and computation.The text you hold in your hands has a distinctflavor from most of the other cur-rently available books on quantum computing.First and foremost,we do not assumethat our reader has much of a mathematics or physics background.This book shouldbe readable by anyone who is in or beyond their second year in a computer scienceprogram.We have written this book specifically with computer scientists in mind,and tailored it accordingly:we assume a bare minimum of mathematical sophistica-tion,afirst course in discrete structures,and a healthy level of curiosity.Because thistext was written specifically for computer people,in addition to the many exercisesthroughout the text,we added many programming drills.These are a hands-on,funway of learning the material presented and getting a real feel for the subject.The calculus-phobic reader will be happy to learn that derivatives and integrals are virtually absent from our text.Quite simply,we avoid differentiation,integra-tion,and all higher mathematics by carefully selecting only those topics that arecritical to a basic introduction to quantum computing.Because we are focusing onthe fundamentals of quantum computing,we can restrict ourselves to thefinite-dimensional mathematics that is required.This turns out to be not much more thanmanipulating vectors and matrices with complex entries.Surprisingly enough,thelion’s share of quantum computing can be done without the intricacies of advancedmathematics.Nevertheless,we hasten to stress that this is a technical textbook.We are not writing a popular science book,nor do we substitute hand waving for rigor or math-ematical precision.Most other texts in thefield present a primer on quantum mechanics in all its glory.Many assume some knowledge of classical mechanics.We do not make theseassumptions.We only discuss what is needed for a basic understanding of quantumxiMore informationxii Prefacecomputing as afield of research in its own right,although we cite sources for learningmore about advanced topics.There are some who consider quantum computing to be solely within the do-main of physics.Others think of the subject as purely mathematical.We stress thecomputer science aspect of quantum computing.It is not our intention for this book to be the definitive treatment of quantum computing.There are a few topics that we do not even touch,and there are severalothers that we approach briefly,not exhaustively.As of this writing,the bible ofquantum computing is Nielsen and Chuang’s magnificent Quantum Computing andQuantum Information(2000).Their book contains almost everything known aboutquantum computing at the time of its publication.We would like to think of ourbook as a usefulfirst step that can prepare the reader for that text.FEATURESThis book is almost entirely self-contained.We do not demand that the reader comearmed with a large toolbox of skills.Even the subject of complex numbers,which istaught in high school,is given a fairly comprehensive review.The book contains many solved problems and easy-to-understand descriptions.We do not merely present the theory;rather,we explain it and go through severalexamples.The book also contains many exercises,which we strongly recommendthe serious reader should attempt to solve.There is no substitute for rolling up one’ssleeves and doing some work!We have also incorporated plenty of programming drills throughout our text.These are hands-on exercises that can be carried out on your laptop to gain a betterunderstanding of the concepts presented here(they are also a great way of hav-ing fun).We hasten to point out that we are entirely language-agnostic.The stu-dent should write the programs in the language that feels most comfortable.Weare also paradigm-agnostic.If declarative programming is your favorite method,gofor it.If object-oriented programming is your game,use that.The programmingdrills build on one another.Functions created in one programming drill will be usedand modified in later drills.Furthermore,in Appendix C,we show how to makelittle quantum computing emulators with MATLAB or how to use a ready-madeone.(Our choice of MATLAB was dictated by the fact that it makes very easy-to-build,quick-and-dirty prototypes,thanks to its vast amount of built-in mathematicaltools.)This text appears to be thefirst to handle quantum programming languages in a significant way.Until now,there have been only research papers and a few surveyson the topic.Chapter7describes the basics of this expandingfield:perhaps some ofour readers will be inspired to contribute to quantum programming!This book also contains several appendices that are important for further study:Appendix A takes readers on a tour of major papers in quantum computing.This bibliographical essay was written by Jill Cirasella,Computational SciencesSpecialist at the Brooklyn College Library.In addition to having a master’s de-gree in library and information science,Jill has a master’s degree in logic,forwhich she wrote a thesis on classical and quantum graph algorithms.This dualbackground uniquely qualifies her to suggest and describe further readings.More informationPreface xiii Appendix B contains the answers to some of the exercises in the text.Othersolutions will also be found on the book’s Web page.We strongly urge studentsto do the exercises on their own and then check their answers against ours.Appendix C uses MATLAB,the popular mathematical environment and an es-tablished industry standard,to show how to carry out most of the mathematicaloperations described in this book.MATLAB has scores of routines for manip-ulating complex matrices:we briefly review the most useful ones and show howthe reader can quickly perform a few quantum computing experiments with al-most no effort,using the freely available MATLAB quantum emulator Quack.Appendix D,also by Jill Cirasella,describes how to use online resources to keepup with developments in quantum computing.Quantum computing is a fast-movingfield,and this appendix offers guidelines and tips forfinding relevantarticles and announcements.Appendix E is a list of possible topics for student presentations.We give briefdescriptions of different topics that a student might present before a class of hispeers.We also provide some hints about where to start looking for materials topresent.ORGANIZATIONThe book begins with two chapters of mathematical preliminaries.Chapter1con-tains the basics of complex numbers,and Chapter2deals with complex vectorspaces.Although much of Chapter1is currently taught in high school,we feel thata review is in order.Much of Chapter2will be known by students who have had acourse in linear algebra.We deliberately did not relegate these chapters to an ap-pendix at the end of the book because the mathematics is necessary to understandwhat is really going on.A reader who knows the material can safely skip thefirsttwo chapters.She might want to skim over these chapters and then return to themas a reference,using the index and the table of contents tofind specific topics.Chapter3is a gentle introduction to some of the ideas that will be encountered throughout the rest of the ing simple models and simple matrix multipli-cation,we demonstrate some of the fundamental concepts of quantum mechanics,which are then formally developed in Chapter4.From there,Chapter5presentssome of the basic architecture of quantum computing.Here one willfind the notionsof a qubit(a quantum generalization of a bit)and the quantum analog of logic gates.Once Chapter5is understood,readers can safely proceed to their choice of Chapters6through11.Each chapter takes its title from a typical course offered in acomputer science department.The chapters look at that subfield of quantum com-puting from the perspective of the given course.These chapters are almost totallyindependent of one another.We urge the readers to study the particular chapterthat corresponds to their favorite course.Learn topics that you likefirst.From thereproceed to other chapters.Figure0.1summarizes the dependencies of the chapters.One of the hardest topics tackled in this text is that of considering two quan-tum systems and combining them,or“entangled”quantum systems.This is donemathematically in Section2.7.It is further motivated in Section3.4and formallypresented in Section4.5.The reader might want to look at these sections together.xivPrefaceFigure 0.1.Chapter dependencies.There are many ways this book can be used as a text for a course.We urge instructors to find their own way.May we humbly suggest the following three plans of action:(1)A class that provides some depth might involve the following:Go through Chapters 1,2,3,4,and 5.Armed with that background,study the entirety of Chapter 6(“Algorithms”)in depth.One can spend at least a third of a semester on that chapter.After wrestling a bit with quantum algorithms,the student will get a good feel for the entire enterprise.(2)If breadth is preferred,pick and choose one or two sections from each of the advanced chapters.Such a course might look like this:(1),2,3,4.1,4.4,5,6.1,7.1,9.1,10.1,10.2,and 11.This will permit the student to see the broad outline of quantum computing and then pursue his or her own path.(3)For a more advanced class (a class in which linear algebra and some mathe-matical sophistication is assumed),we recommend that students be told to read Chapters 1,2,and 3on their own.A nice course can then commence with Chapter 4and plow through most of the remainder of the book.If this is being used as a text in a classroom setting,we strongly recommend that the students make presentations.There are selected topics mentioned in Appendix E.There is no substitute for student participation!Although we have tried to include many topics in this text,inevitably some oth-ers had to be left out.Here are a few that we omitted because of space considera-tions:many of the more complicated proofs in Chapter 8,results about oracle computation,the details of the (quantum)Fourier transforms,and the latest hardware implementations.We give references for further study on these,as well as other subjects,throughout the text.More informationMore informationPreface xvANCILLARIESWe are going to maintain a Web page for the text at/∼noson/qctext.html/The Web page will containperiodic updates to the book,links to interesting books and articles on quantum computing,some answers to certain exercises not solved in Appendix B,anderrata.The reader is encouraged to send any and all corrections tonoson@Help us make this textbook better!ACKNOLWEDGMENTSBoth of us had the great privilege of writing our doctoral theses under the gentleguidance of the recently deceased Alex Heller.Professor Heller wrote the follow-ing1about his teacher Samuel“Sammy”Eilenberg and Sammy’s mathematics:As I perceived it,then,Sammy considered that the highest value in mathematicswas to be found,not in specious depth nor in the overcoming of overwhelmingdifficulty,but rather in providing the definitive clarity that would illuminate itsunderlying order.This never-ending struggle to bring out the underlying order of mathematical structures was always Professor Heller’s everlasting goal,and he did his best to passit on to his students.We have gained greatly from his clarity of vision and his viewof mathematics,but we also saw,embodied in a man,the classical and sober ideal ofcontemplative life at its very best.We both remain eternally grateful to him.While at the City University of New York,we also had the privilege of inter-acting with one of the world’s foremost logicians,Professor Rohit Parikh,a manwhose seminal contributions to thefield are only matched by his enduring com-mitment to promote younger researchers’work.Besides opening fascinating vis-tas to us,Professor Parikh encouraged us more than once to follow new directionsof thought.His continued professional and personal guidance are greatly appre-ciated.We both received our Ph.D.’s from the Department of Mathematics in The Graduate Center of the City University of New York.We thank them for providingus with a warm and friendly environment in which to study and learn real mathemat-ics.Thefirst author also thanks the entire Brooklyn College family and,in partic-ular,the Computer and Information Science Department for being supportive andvery helpful in this endeavor.1See page1349of Bass et al.(1998).More informationxvi PrefaceSeveral faculty members of Brooklyn College and The Graduate Center were kind enough to read and comment on parts of this book:Michael Anshel,DavidArnow,Jill Cirasella,Dayton Clark,Eva Cogan,Jim Cox,Scott Dexter,EdgarFeldman,Fred Gardiner,Murray Gross,Chaya Gurwitz,Keith Harrow,JunHu,Yedidyah Langsam,Peter Lesser,Philipp Rothmaler,Chris Steinsvold,AlexSverdlov,Aaron Tenenbaum,Micha Tomkiewicz,Al Vasquez,Gerald Weiss,andPaula Whitlock.Their comments have made this a better text.Thank you all!We were fortunate to have had many students of Brooklyn College and The Graduate Center read and comment on earlier drafts:Shira Abraham,RachelAdler,Ali Assarpour,Aleksander Barkan,Sayeef Bazli,Cheuk Man Chan,WeiChen,Evgenia Dandurova,Phillip Dreizen,C.S.Fahie,Miriam Gutherc,RaveHarpaz,David Herzog,Alex Hoffnung,Matthew P.Johnson,Joel Kammet,SerdarKara,Karen Kletter,Janusz Kusyk,Tiziana Ligorio,Matt Meyer,James Ng,SeverinNgnosse,Eric Pacuit,Jason Schanker,Roman Shenderovsky,Aleksandr Shnayder-man,Rose B.Sigler,Shai Silver,Justin Stallard,Justin Tojeira,John Ma Sang Tsang,Sadia Zahoor,Mark Zelcer,and Xiaowen Zhang.We are indebted to them.Many other people looked over parts or all of the text:Scott Aaronson,Ste-fano Bettelli,Adam Brandenburger,Juan B.Climent,Anita Colvard,Leon Ehren-preis,Michael Greenebaum,Miriam Klein,Eli Kravits,Raphael Magarik,JohnMaiorana,Domenico Napoletani,Vaughan Pratt,Suri Raber,Peter Selinger,EvanSiegel,Thomas Tradler,and Jennifer Whitehead.Their criticism and helpful ideasare deeply appreciated.Thanks to Peter Rohde for creating and making available to everyone his MAT-LAB q-emulator Quack and also for letting us use it in our appendix.We had a gooddeal of fun playing with it,and we hope our readers will too.Besides writing two wonderful appendices,our friendly neighborhood librar-ian,Jill Cirasella,was always just an e-mail away with helpful advice and support.Thanks,Jill!A very special thanks goes to our editor at Cambridge University Press,HeatherBergman,for believing in our project right from the start,for guiding us through thisbook,and for providing endless support in all matters.This book would not existwithout her.Thanks,Heather!We had the good fortune to have a truly stellar editor check much of the text many times.Karen Kletter is a great friend and did a magnificent job.We also ap-preciate that she refrained from killing us every time we handed her altered draftsthat she had previously edited.But,of course,all errors are our own!This book could not have been written without the help of my daughter,Hadas-sah.She added meaning,purpose,and joy.N.S.Y.My dear wife,Rose,and our two wondrous and tireless cats,Ursula and Buster, contributed in no small measure to melting my stress away during the long andpainful hours of writing and editing:to them my gratitude and love.(Ursula is ascientist cat and will read this book.Buster will just shred it with his powerful claws.)M.A.M.。
执行时间latency等待时间

SSppeeededuupFpPFSPQSQRR(((1(10.02.)21) 01.002.2) )1.12.222 ImprSoSpvpeieendegduuptFhpPFePp((e(1(r1f0o.0r51.m)51)a10n..1065c..6e5) )1o01f.12t.h323e FP operations overall is slightly better because
10
AAmddaahhl’ls’sLaLwawcacnaanlsaolsboe baeppalipedpltioedpatroeptwaroeCPU
tdwesoigCnPaUltedrensaitgivnesa;ltfoerrnexaatimvpelse; :
fIrIspsoommqirgrooupnpcetalileefrxeviesmcaamsarmoernoeyrntospnltystaltdFeitaigePinot:sSnniipQogisfennRirocesffaoidsornflmfrfotoelaafrsyltnpoginicoranegant;ppspinoihebeiisgnlcreppsfteFofocoPrSiirmsnauql2tplauyF0pnaP%oarcsmeseeoqo;rfoFnuPotgahtreveary eesxpeceuctiiaolnlytiamme oonf ga cprritoiccaelsgsroarpshidces sbiegnncehdmfaorkr
Performance Measurement 1
Performance
Execution time 时间latency等待时间: Time between the start and the pletion of an
ICRP报告名称(至112号)

ICRP 01号出版物—— Recommendations of the International Commission on Radiological Protection (Superseded by ICRP 26).ICRP 02号出版物—— Report of Committee II on Permissible Dose for Internal Radiation (Superseded by ICRP 30).ICRP 03号出版物—— Report of Committee III on Protection Against X-rays up to Energies of 3 MeV and Beta- and Gamma-rays from Sealed Sources ICRP 04号出版物—— Report of Committee IV on Protection Against X-rays Electromagnetic Radiation Above 3 MeV and Electrons, Neutrons and Protons ICRP 05号出版物—— Report on Committee V in the Handling and Disposal of Radioactive Materials in Hospitals and Medical Research Establishments (Superseded by ICRP 25).ICRP 06号出版物—— Recommendations of the ICRP (Revision to ICRP 1) (Superseded by ICRP 26).ICRP 07号出版物—— Principals of Environmental Monitoring Related to the Handling of Radioactive MaterialICRP 08号出版物—— The Evaluation of Risks from RadiationICRP 09号出版物—— Recommendations of the International Commission on Radiological Protection (Revision of ICRP 6) (Superseded by ICRP 26) ICRP 10A号出版物—— The Assessment of Internal Contamination Resulting from Recurring of Prolonged Uptakes (Superseded by ICRP 54)ICRP 10号出版物—— Evaluation of Radiation Doses to Body Tissues from Internal Contamination due to Occupational Exposure (Superseded by ICRP 54)ICRP 11号出版物—— A Review of the Radiosensitivity of the Tissues in BoneICRP 12号出版物—— General Principles of Monitoring for Radiation Protection of Workers (Superseded by ICRP 35)ICRP 13号出版物—— Radiation Protection in Schools for Pupils up to the Age of 18 Years (Superseded by ICRP 36)ICRP 14号出版物—— Radiosensitivity and Spatial Distribution of DoseICRP 15号出版物—— Protection Against Ionizing Radiation from External Sources(Superseded by ICRP 33).ICRP 16号出版物—— Protection of the Patient in X-ray Diagnosis (Superseded by ICRP 34).ICRP 17号出版物—— Protection of the Patient in Radionuclide Investigations (Superseded by ICRP 52).ICRP 18号出版物—— The RBE for High-LET Radiations with Respect to MutagenesisICRP 19号出版物—— The Metabolism of Compounds of Plutonium and Other Actinides (See also ICRP 48).ICRP 20号出版物—— Alkaline Earth Metabolism in Adult ManICRP 21号出版物—— Data for Protection Against Ionizing Radiation from External Sources - Supplement to ICRP Publication 15 (Superseded by ICRP 33 & 51).ICRP 22号出版物—— Implication of Commission Recommendations that Doses be Kept as Low as Readily AchievableICRP 23号出版物—— Reference Man: Anatomical, Physiological and Metabolic CharacteristicsICRP 24号出版物—— Radiation Protection in Uranium and Other MinesICRP 25号出版物—— The Handling, Storage, Use and Disposal of Unsealed Radionuclides in Hospitals and Medical Research Establishments (Supersedes ICRP 5).ICRP 26号出版物—— Recommendations of the International Commission on Radiological Protection (Superseded by ICRP 60)(Supersedes ICRP 1, 6 & 9) ICRP 27号出版物—— Problems Involved in Developing an Index of HarmICRP 28号出版物—— The Principles and General Procedures for Handling Emergency and Accidental Exposure of WorkersICRP 29号出版物—— Radionuclide Release into the Environment - Assessment of Doses to ManICRP 30号出版物—— Limits for Intakes of Radionuclides by WorkersICRP 31号出版物—— Biological Effects of Inhaled RadionuclidesICRP 32号出版物—— Limits for Inhaled Radionuclides by WorkersICRP 33号出版物—— Protection Against Ionizing Radiation from External Sources Used in Medicine (Supersedes ICRP 15 & 21)ICRP 34号出版物—— Protection of the Patient in Diagnostic RadiologyICRP 35号出版物—— General Principles of Monitoring for Radiation Protection of Workers (Supersedes ICRP 12)ICRP 36号出版物—— Protection Against Ionizing Radiation in the Teaching of ScienceICRP 37号出版物—— Cost-Benefit Analysis in the Optimization of Radiation ProtectionICRP 38号出版物—— Radionuclide Transformations: Energy and Intensity of EmissionsICRP 39号出版物—— Principles of Limiting Exposure of the Public to Natural Sources of RadiationICRP 40号出版物—— Protection of the Public in the Event of Major Radiation Accidents:Principles for Planning (Superseded by ICRP 63)ICRP 41号出版物—— Nonstochastic Effects of Ionizing RadiationICRP 42号出版物—— A Compilation of the Major Concepts and Quantities in Use by the ICRPICRP 43号出版物—— Principles of Monitoring for the Radiation Protection of the PublicICRP 44号出版物—— Protection of the Patient in Radiation TherapyICRP 45号出版物—— Quantitative Bases for Developing a Unified Index of HarmICRP 46号出版物—— Radiation Protection Principles for the Disposal of Solid Radioactive WasteICRP 47号出版物—— Radiation Protection of Workers in MinesICRP 48号出版物—— The Metabolism of Plutonium and Related ElementsICRP 49号出版物—— Developmental Effects of Irradiation on the Brain of the Embryo and FetusICRP 50号出版物—— Lung Cancer Risk from Indoor Exposures to Radon DaughtersICRP 51号出版物—— Data for Use in Protection Against External Radiation (Supersedes ICRP 21)ICRP 52号出版物—— Protection of the Patient in Nuclear Medicine (Supersedes ICRP 17).ICRP 53号出版物—— Radiation Dose to Patients from RadiopharmaceuticalsICRP 54号出版物—— Individual Monitoring for Intakes of Radionuclides by Workers: Design and InterpretationICRP 55号出版物—— Optimization and Decision-Making in Radiological ProtectionICRP 56号出版物—— Age-dependent Doses to Members of the Public from Intake of RadionuclidesICRP 57号出版物—— Radiological Protection of the Worker in Medicine and DentistryICRP 58号出版物—— RBE for Deterministic EffectsICRP 59号出版物—— The Biological Basis for Dose Limitation in the SkinICRP 60号出版物—— 1990 Recommendations of the International Commission on Radiological ProtectionICRP 61号出版物—— Annual Limits on Intake of Radionuclides by Workers Based on the 1990 RecommendationsICRP 62号出版物—— Radiological Protection in Biomedical ResearchICRP 63号出版物—— Principles for Intervention for Protection of the Public in a Radiological EmergencyICRP 64号出版物—— Protection from Potential Exposure: A Conceptual FrameworkICRP 65号出版物—— Protection Against Radon-222 at Home and at WorkICRP 66号出版物—— Human Respiratory Tract Model for Radiological ProtectionICRP 67号出版物—— Age-dependent Doses to Members of the Public from Intake of RadionuclidesICRP 68号出版物—— Dose Coefficients for Intakes of Radionuclides by WorkersICRP 69号出版物—— Age-dependent Doses to Members of the Public from Intake of Radionuclides: Part 3 Ingestion Dose CoefficientsICRP 70号出版物—— Basic Anatomical & Physiological Data for use in Radiological Protection: The SkeletonICRP 71号出版物—— Age-dependent Doses to Members of the Public from Intake of Radionuclides: Part 4 Inhalation Dose CoefficientsICRP 72号出版物—— Age-dependent Doses to the Members of the Public from Intake of Radionuclides Part 5, Compilation of Ingestion and Inhalation CoefficientsICRP 73号出版物—— Radiological Protection and Safety in MedicineICRP 74号出版物—— Conversion Coefficients for use in Radiological Protection against External RadiationICRP 75号出版物—— General Principles for the Radiation Protection of WorkersICRP 76号出版物—— Protection from Potential Exposures: Application to Selected Radiation SourcesICRP 77号出版物—— Radiological Protection Policy for the Disposal of Radioactive WasteICRP 78号出版物—— Individual Monitoring for Internal Exposure of WorkersICRP 79号出版物—— Genetic Susceptibility to CancerICRP 80号出版物—— Radiation dose to patients from radiopharmaceuticalsICRP 81号出版物—— Radiation Protection Recommendations as Applied to the Disposal of Long-lived Solid Radioactive WasteICRP 82号出版物—— Protection of the Public in Situations of Prolonged Radiation ExposureICRP 83号出版物—— Risk Estimation for Multifactorial DiseasesICRP 84号出版物—— Pregnancy and Medical RadiationICRP 85号出版物—— Avoidance of Radiation Injuries from Medical Interventional ProceduresICRP 86号出版物—— Prevention of Accidents to Patients Undergoing Radiation TherapyICRP 87号出版物—— Managing Patient Dose in Computed TomographyICRP 88号出版物—— Doses to the Embryo and Fetus from Intakes of Radionuclides by the MotherICRP 89号出版物—— Basic Anatomical and Physiological Data for Use in Radiological Protection: Reference ValuesICRP 90号出版物—— Biological Effects after Prenatal Irradiation (Embryo and Fetus)ICRP 91号出版物—— A Framework for Assessing the Impact of Ionising Radioation on Non-Human SpeciesICRP 92号出版物—— Relative Biological Effectiveness (RBE), Quality Factor (Q), and Radiation Weighting Factor (wR)ICRP 93号出版物—— Managing Patient Dose in Digital RadiologyICRP 94号出版物—— Release of patients after therapy with unsealed radionuclidesICRP 95号出版物—— Doses to Infants from Ingestion of Radionuclides in Mother's MilkICRP 96号出版物—— Protecting People Against Radiation Exposure in the Event of a Radiological AttackICRP 97号出版物—— Prevention of High-dose-rate Brachytherapy AccidentsICRP 98号出版物—— Radiation Aspects of Brachytherapy for Prostate CancerICRP 99号出版物—— Low-Dose Extrapolation of Radiation Related Cancer RiskICRP 100号出版物—— Human Alimentary Tract Model for Radiological ProtectionICRP 101号出版物—— Assessing Dose of the Representative Person for the Purpose of Radiation Protection of the Public and the Optimisation of Radiological ProtectionICRP 102号出版物—— Managing Patient Dose in Multi-Detector Computed Tomography(MDCT)ICRP 103号出版物—— The 2007 Recommendations of the International Commission on Radiological ProtectionICRP 104号出版物—— Scope of Radiological Protection Control MeasuresICRP 105号出版物—— Radiological Protection in MedicineICRP 106号出版物—— Radiation Dose to Patients from Radiopharmaceuticals - A third amendment to ICRP Publication 53ICRP 107号出版物—— Nuclear Decay Data for Dosimetric CalculationsICRP 108号出版物—— Environmental Protection: the Concept and Use of Reference Animals and PlantsICRP 109号出版物—— Application of the Commission's Recommendations for the Protection of People in Emergency Exposure SituationsICRP 110号出版物—— Adult Reference Computational PhantomsICRP 111号出版物——Application of the Commission’s Recommendations to the Protection of People Living in Long-term Contaminated Areas After a Nuclear Accident or a Radiation EmergencyICRP 112号出版物—— Preventing Accidental Exposures from New External Beam Radiation TherapyICRP Supporting Guidance 2—— Radiation and Your Patient: A Guide for Medical PractitionersICRP Supporting Guidance 3—— Guide for the Practical Application of the ICRP Human Respiratory Tract ModelICRP Supporting Guidance 4—— Development of the Draft 2005 Recommendations of the ICRP——A Collection of PapersICRP Supporting Guidance 5——Analysis of the Criteria Used by the International Commission on Radiological ProtectionICRP 01号出版物——Recommendations of the International Commission on Radiological Protection (Superseded by ICRP 26).国际放射防护委员会01号出版物 - 关于国际放射防护委员会建议(取代了国际放射防护委员会26)。
伦敦大学学院科学和数据密集型计算授课型研究生申请要求

伦敦大学学院科学和数据密集型计算授课型研究生申请要求伦敦大学学院简介学校名称伦敦大学学院学校英文名称University College London学校位置英国 | 英格兰 | 伦敦2020 QS 世界排名8伦敦大学学院概述伦敦大学学院(University CollegeLondon),英文简称UCL,建校于1826年,位于英国伦敦,世界著名的顶尖高等学府,为享有顶级声誉的综合研究型大学,其排名稳居世界各类权威榜单英国前五。
伦敦大学学院位居2020QS世界大学排名世界第8,2020泰晤士高等教育世界大学排名世界第15,2020USNews世界大学排名世界第21 ,2019软科世界大学学术排名(ARWU)世界第15 ,在REF 2014英国大学官方排名中科研实力以及影响力均位列全英第1。
同时位列2018ARWU学科排名医疗技术世界第2,心理学、人体生命科学世界第3;2019QS学科排名中教育学、建筑学世界第1,人类学、考古学、解剖生理学世界前5 ,科学和数据密集型计算专业简介该项目旨在提供严格的计算科学的正式培训,培养具有高度计算能力的科学家和工程师,使他们能够将数值方法和对其结果的批判性评价应用于其科学或工程领域。
它将计算领域的最佳实践与前沿科学结合在一起,并提供了相对于传统科学、工程和数学课程的计算优势。
科学和数据密集型计算专业相关信息专业名称科学和数据密集型计算专业英文名称Scientific and Data Intensive Computing MSc隶属学院数理科学学院学制1年语言要求雅思6.5(6)托福92(读写24听说20)GMAT/GRE 要求不需要2020 Fall 申请时间11月学费(当地货币)28,930科学和数据密集型计算课程内容序号课程中文名称课程英文名称1计算与仿真方法Computational and Simulation Methods2数值方法Numerical Methods3数值优化Numerical Optimisation4 C ++研究计算Research Computing with C++5Python研究软件工程Research Software Engineering with Python 6高性能计算技术Techniques of High-Performance Computing 7大数据机器学习Machine Learning with Big-Data8统计数据分析Statistical Data Analysis* 伦敦大学学院科学和数据密集型计算研究生申请要求由 Mastermate 收集并整理,如果发现疏漏,请以学校官网为准。
临床药师参与1例心衰终末期合并利尿剂抵抗患者容量管理的体会

临床药师参与1例心衰终末期合并利尿剂抵抗患者容量管理的体会杨 贤1,兰 希2,严思敏1,王文晓3,葛卫红1(1.南京大学医学院附属鼓楼医院药学部,江苏 南京 210008;2.南京大学医学院附属鼓楼医院心内科,江苏 南京 210008;3.青岛大学附属医院药学部,山东 青岛 266000)[摘要] 1例72岁男性患者,因“反复胸痛7年,胸闷气喘3年,加重1个月”入院,入院诊断为慢性心功能不全急性失代偿,陈旧性广泛前壁心肌梗死,冠状动脉支架植入后,急性肾功能不全。
临床药师评估后,认为患者存在容量超负荷并且合并利尿剂抵抗,建议将托拉塞米注射液由静脉滴注改为静脉持续输注。
同时联合小剂量多巴胺改善肾血流。
后患者存在低钠血症,药师建议加用托伐普坦片(15 mg ,qd )纠正电解质紊乱。
出院前患者心衰症状好转,体质量较入院时有明显下降,血钠、血钾均恢复至正常范围。
[关键词] 临床药师;心力衰竭;容量管理;利尿剂抵抗;电解质;药学监护[中图分类号] R969.4 [文献标识码] A [文章编号] 1672 – 8157(2021)01 – 0017 – 04Experience of clinical pharmacists participating in the capacity management of a heart failure patient with diuretic resistanceYANG Xian 1, LAN Xi 2, YAN Si-min 1, WANG Wen-xiao 3, GE Wei-hong 1(1. Department of Pharmacy, Nanjing Drum TowerHospital, the Affiliated Hospital of Nanjing University Medical School, Nanjing 210008, China; 2. Department of Cardiology, Nanjing Drum Tower Hospital, the Affiliated Hospital of Nanjing University Medical School, Nanjing 210008, China; 3. Department of Pharmacy, the Affiliated Hospital of Qingdao University, Qingdao 266000, China )[ABSTRACT] One 72-year-old male patient was hospitalized because of repeated chest pain for 7 years, chest tightness andasthma for 3 years and aggravation for 1 month. The patient was diagnosed as acute decompensation for chronic heart failure, old extensive anterior myocardial infarction, post coronary stent implantation and acute renal insufficiency. After evaluation by the clinical pharmacist, the patient was considered to have capacity overload and diuretic resistance. Pharmacist suggested to use torasemide injection by continuously intravenous infusion instead of intravenous drip. At the same time, small doses of dopamine was also suggested to be used combined with torasemide to improve renal blood flow. And then tolvaptan tablets (15 mg, qd) were also advised to be given to him for correcting electrolyte turbulence. The patient's symptoms of heart failure improved, the body weight decreased significantly compared with that of admission, and the level of blood sodium and blood potassium all returned to the normal range before discharge.[KEY WORDS] Clinical pharmacist; Heart failure; Capacity management; Diuretic resistance; Electrolyte; Pharmaceutical care·临床药师园地·[通信作者] 葛卫红,女,主任药师,研究方向:临床药学。
Patient Safety 患者安全

4
Evolution of Patient Safety
‘Will we put the methods of science to work in the evaluation of our practices, or must we admit that no matter how much we read, study, practice and take pains, when it comes to a show-down of the results of our treatment, no one could tell the difference between what we have accomplished and results of some genial charlatan…?”
6
8
What We Know
Canadian Institute for Health Information (2004) • One in nine adults contract infection in hospital. • One in nine patients receive wrong medication or wrong dose. • More deaths after experiencing adverse events in hospital than deaths from breast cancer, motor vehicle and HIV combined.
2001-3 2001 2002 2004 2006
Halifax Symposia on Medical Error RCPSC National Steering Committee on Patient Safety RCPSC Report: Building a Safer System Canadian Patient Safety Institute 6th Canadian Symposium on Patient Safety (Vancouver)
Cradlepoint COR IBR1100系列3G 4G LTE网络解决方案说明说明书

1Cradlepoint COR IBR1100/IBR1150 SpecificationsFigure 1: COR IBR1100Highly Available, Cloud-Managed Networking for Extreme ConditionsThe Cradlepoint COR IBR1100 Series is a compact, ruggedized 3G/4G/LTE networking solution designed for mission critical connectivity in the most challenging environments.Ideal for in-vehicle networks including police cars, ambulances, and mass transit, this cloudmanaged solution provides organizations the ability to scale deployments quickly and manage their vehicle networks easily in real-time.With an extensive list of safety and hardening certifications, the COR IBR1100 is engineered to protect against extreme temperatures, humidity, shocks, vibrations, dust, water splash, reverse polarity and transient voltage.Key Features• Cloud-managed for zero-touch deployment and intelligent management • Internal 3G/4G modem with secured SIM card access and dual SIM slots• LTE support for all major U.S. carriers and Europe/international operators (failover to HSPA+ or EVDO) • Software-defined radio supports multiple carriers (Gobi)• WiFi (IBR1100) and non-WiFi versions (IBR1150) available: IBR1100 includes dual-band dual-concurrent 2.4/5 GHz 802.11 a/b/g/n/ac WiFi; 2 x 2 MIMO with two external dualband antenna connectors • Ignition sensingRuggedized: protects against vibration, shock, dust, splash, & humidityBuilt-in transient and reverse polarity voltage protection; 9–36 DC voltage input range• Integrated temperature sensor• Three 10/100 Ethernet ports (LAN/WAN configurable)2• Antenna connectors for external cellular modem (two) and active GPS (one) • RS-232 serial portFigure 2: COR IBR1100 FrontFigure 3: COR IBR1100 BackFeaturesWAN• 4G LTE/HSPA+/EVDO (multi-carrier)• WiFi as WAN¹, with WPA2 Enterprise Authentication for WiFi-as-WAN³ • Failover/Failback • Load Balancing• Advanced Modem Failure Check • WAN Port Speed Control • WAN/LAN Affinity • IP PassthroughLAN• VLAN 802.1Q• DHCP Server, Client, Relay DNS and DNS Proxy DynDNS • UPnP • DMZ3• Multicast/Multicast Proxy• QoS (DSCP and Priority Queuing) • MAC Address FilteringWiFi¹• Dual-Band Dual-Concurrent • 802.11 a/b/g/n/ac• Up to 128 connected devices (64 per radio – 2.4 GHz and 5 GHz) • Multiple SSIDs: 2 per radio (4 total) • WPA2 Enterprise (WiFi) • Hotspot/Captive Portal • SSID-based PriorityManagement• Cradlepoint Enterprise Cloud Manager² • Web UI, API, CLI• Active GPS support on all models • Data Usage Alerts (router and per client) • Advanced Troubleshooting (support) • Device Alerts • SNMP • SMS control • Serial RedirectorVPN and Routing• IPsec Tunnel – up to 5 concurrent sessions • L2TP³ • GRE Tunnel • OSPF/BGP/RIP³ • Per-Interface Routing • Routing Rules • NAT-less Routing• Virtual Server/Port Forwarding • NEMO/DMNR³ • IPv6 • VRRP³ STP³ NHRP³Security4• RADIUS and TACACS+• 802.1x authentication for Ethernet • Zscaler integration³ • Certificate support • ALGs• MAC Address Filtering• Advanced Security Mode (local user management only) • Per-Client Web Filtering • IP Filtering• Content Filtering (basic) • Website FilteringCloud Optimized IP Communications• Automated WAN Failover/Failback support• WAN Affinity and QoS allow prioritization of VoIP services • Advanced VPN connectivity options to HQ• SIP ALG and NAT to allow VoIP and UC communications to traverse firewall • MAC Address Filtering• 802.1p/q for LAN QoS segmentation and treatment of VoIP on LAN • Private Network support (wired and 4G WAN) • Cloud-based management²1 – WiFi-related functions are only supported on IBR1100 models2 – Enterprise Cloud Manager requires a subscription3 – Requires an Extended Enterprise LicenseSpecificationsWAN• Integrated 4G LTE modem (with 3G failover)• Three LAN/WAN switchable 10/100 Ethernet ports – one default WAN (cable/DSL/T1/satellite/Metro Ethernet) • WiFi as WAN, Metro WiFi; 2x2 MIMO “N” 2.4 GHz or 5 GHz; 802.11 a/b/g/n/ac (IBR1100 only)5LAN• Dual-band dual-concurrent WiFi; 802.11 a/b/g/n/ac (IBR1100 only) • Three LAN/WAN switchable 10/100 Ethernet ports – two default LAN • Serial console support for out-of-band management of a connected device PORTS• Power • 2-wire GPIO • USB 2.0• 3 Ethernet LAN/WAN• 2 cellular antenna connectors (SMA) • 1 active GPS antenna connector (SMA) • 2 WiFi antenna connectors (R-SMA)• Serial DE-9 (commonly called “DB -9”) connector – RS-232 (out-of-band management of an external device requires a null modem adapter/cable) TEMPERATURE• −30° C to 70° C (−22 °F to +158 °F) operating • −40 °C to 85 °C (−40 °F to +185 °F) storage• Includes temperature sensor with options for alerts and automatic shutoff HUMIDITY (non-condensing)• 5% to 95% operating • 5% to 95% storage POWER• DC input steady state voltage range: 9–36 VDC (requires inline fuse for vehicle installations)– For 9–24 VDC installations, use a 3 A fuse – For > 24 VDC installations, use a 2.5 A fuse• Reverse polarity and transient voltage protection per ISO 7637-2 • Ignition sensing (automatic ON and time-delay OFF) • Power consumption:– idle: typical=400mA@12VDC (4.8W); worst case=800mA@12VDC (9.6W) – Tx/Rx: typical=650mA@12VDC (7.8W); worst case=1300mA@12VDC (15.6W) – 12VDC 2A adapter recommendedSIZE – 5.3 in x 4.4 in x 1.4 in (134 mm x 112 mm x 35 mm)6WEIGHT – 16.1 oz (457 g) CERTIFICATIONS• FCC, CE, IC• WiFi Alliance (IBR1100 only) – 802.11a/b/g/n certified, 802.11ac supported • Safety: UL/CUL, CB Scheme, EN60950-1 • Hazardous Locations: Class I, Div. 2 (pending)• Shock/Vibration/Humidity: compliant with MIL STD 810G and SAEJ1455• Ingress Protection: compliant with IP64 (includes protection from dust and splashing water) • Materials: WEEE, RoHS, RoHS-2, California Prop 65 • Vehicle: E-Mark, compliant with ISO 7637-2 • Telecom: PTCRB/CTIA, GCF-CC GPS• GPS Protocols: TAIP and NMEA 0183 V3.0 • Satellite channels: 12 channel, continuous tracking • 1 Hz refresh rate • Accuracy:– < 2m: 50% – < 5m: 90% • Acquisition:– Hot start: 1 second – Warm start: 29 seconds – Cold start: 32 seconds • Sensitivity– Tracking: −161 dBm (tracking sensitivity is the lowest GNSS signal level for which the device can still detect an in-view satellite 50% of the time when in sequential tracking mode) – Acquisition (standalone): −145 dBm (acquisition sensitivity is the lowest GNSS signal level for which the device can still detect an in-view satellite 50% of the time) • Operational limits: altitude < 6000 m or velocity < 100 m/s (either limit may be exceeded, but not both)What’s In The Box• Ruggedized router with integrated business-class 3G/4G modem; includes integrated mounting plate • Two meter locking power and GPIO cable (direct wire) Quick Start Guide with warranty informationNOTE: Due to the diverse needs of customers, the COR IBR1100/IBR1150 package does not include a power adapter or antennas. See the Accessories section below for several power and antenna options.7Feature Details• WAN Security – NAT, SPI, ALG, inbound filtering of IP addresses, port blocking, service filtering (FTP, SMTP, HTTP, RPL, SNMP, DNS, ICMP, NNTP, POP3, SSH), protocol filtering, WAN ping (allow/ignore) • Redundancy and Load Balancing – Failover/failback with 4G, 3G, Ethernet with rule selection, advanced load balancing options (round robin, spillover, data usage, rate), WAN failure detection, VRRP • Intelligent Routing – UPnP, DMZ, virtual server/port forwarding, routing rules, NATless routing, wired or wireless WAN-to-LAN IP passthrough, route management, perinterface routing, content filtering, IP filtering, website filtering, per-client Web filtering, local DHCP server, DHCP client, DHCP relay, DNS, DNS proxy; ALGs: PPTP, SIP, TFTP, FTP, IRC; MAC address filtering, Dynamic DNS, LAN/WAN affinity, VLAN 802.1Q (coming Q4), STP, enterprise routing protocols: BGP/OSPF/RIP, multicast proxy support, IP setting overrides, IPv6 support • Management – Enterprise Cloud Manager: cloud-enabled management and application platform (subscription-based); web-based GUI (local management), optional RADIUS or TACACS+ username/password; remote WAN web-based management w/ access control (HTTP, HTTPS); SNMP v1, v2c, & v3; CLI over SSH, SSH to serial, SSH to telnet; API; one-button firmware upgrade; modem configuration, update, and management; modem data usage w/ alerts, per-client data usage; custom AT scripting to modems • Performance & Health Monitoring – Advanced QoS with traffic shaping, with DSCP/DiffServe QoS, Modem Health Management (MHM) improves connectivity of modem, SSID-based priority, WAN port speed control, several levels of basic and advanced logging for troubleshooting • VPN (IPsec) – Tunnel, NAT-T, and transport modes; connect to Cradlepoint, Cisco/Linksys, CheckPoint, Watchguard, Juniper, SonicWall, Adtran and others; certificate support; Hash (MD5, SHA128, SHA256, SHA384, SHA512), Cipher (AES, 3DES, DES); support for 5 concurrent connections, GRE tunneling, L2TP support, multiple networks supported in a single tunnel, site-to-site dynamic VPN with NHRP • GPS – Active GPS antenna port; GUI mapping; multiple server reporting (coming Q4) with LAN and WAN options; TAIP and NMEA; custom intervals based on time and/or velocity (coming Q4)Support and Warranty∙ CradleCare Support Agreement available with technical support, software upgrades, and advanced hardware exchange – 1, 3, and 5 year optional.∙One-year limited hardware warranty available in the US and Canada; two-year limited hardware warranty for integrated EU products when purchased from an authorized EU distributor – extend warranty to 2, 3, or 5 yearsAccessoriesBecause of the diversity of customer needs, the COR IBR1100/IBR1150 does NOT include a power adapter or antennas in the box (it does include a direct wire power/GPIO cable for vehicle installation). Cradlepoint offers several accessory options for power adapters or antennas. Please see an associate for details.8Business-Grade Modem SpecificationsCOR IBR1100/IBR1150 models include an integrated 4G LTE modem – specific model names include a specific modem.Please note that LPE models are flexible and support bands for multiple cellular providers; however, only the frequency bands in bold below are supported by the listed provider.COR IBR1100LPE-VZ, COR IBR1150LPE-VZ – 4G LTE/HSPA+/EVDO• Technology : LTE , HSPA+, EVDO Rev A• Downlink Rates : LTE 100 Mbps, HSPA+ 21.1 Mbps, EVDO 3.1 Mbps (theoretical) • Uplink Rates : LTE 50 Mbps, HSPA+ 5.76 Mbps, EVDO 1.8 Mbps (theoretical) • Frequency Bands :– LTE Band 2 (1900 MHz), Band 4 – AWS (1700/2100 MHz), Band 5 (850 MHz), Band 13 (700 MHz), Band 17 (700 MHz), Band 25 (1900 MHz) – HSPA+/UMTS (850/900/1900/2100 MHz, AWS) – GSM/GPRS/EDGE (850/900/1800/1900 MHz) – CDMA EVDO Rev A/1xRTT (800/1900 MHz)• Power : LTE 23 dBm +/− 1, HSPA+ 23 dBm +/− 1, EVDO 24 dBm +0.5/−1 (typical conducted) • Antennas : two SMA male (plug), finger tighten only (maximum torque spec is 7 kgfcm) • GPS : active GPS support• Industry Standards & Certs : FCC。
国际放射防护委员会(ICRP)出版物一览表(2021 版)
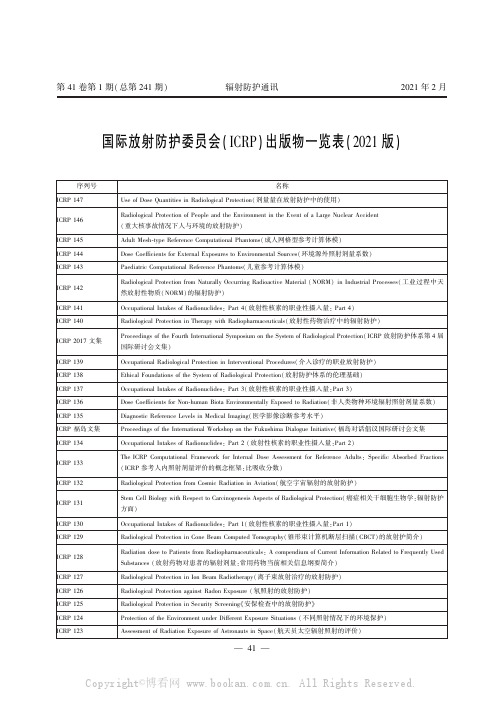
The ICRP Computational Framework for Internal Dose Assessment for Reference Adults: Specific Absorbed Fractions
声明:辐射防护中组织反应的阈剂量)
Radiological Protection in Fluoroscopically Guided Procedures outside the Imaging Department( 影像科外部透视引导程
ICRP 117
序中的放射防护)
Conversion Coefficients for Radiological Protection Quantities for External Radiation Exposures( 外照射放射防护量的转
Radiation dose to Patients from Radiopharmaceuticals: A compendium of Current Information Related to Frequently Used
Substances ( 放射药物对患者的辐射剂量:常用药物当前相关信息纲要简介)
ICRP 2017 文集
Proceedings of the Fourth International Symposium on the System of Radiological Protection( ICRP 放射防护体系第 4 届
国际研讨会文集)
ICRP 139
Occupational Radiological Protection in Interventional Procedures( 介入诊疗的职业放射防护)
电脑发明 英语作文

The invention of the computer is arguably one of the most significant milestones in the history of technology.It has revolutionized the way we live,work,and communicate. Here is an essay on the invention of the computer,highlighting its origins,development, and impact on society.The Birth of the ComputerThe concept of a computer dates back to ancient times,with devices like the abacus used for simple calculations.However,the modern computer as we know it today was born in the mid20th century.The first electronic generalpurpose computer,the ENIAC Electronic Numerical Integrator and Computer,was developed during World War II by J.Presper Eckert and John W.Mauchly.It was a massive machine that filled a room and was primarily used for military calculations.The Evolution of ComputingFollowing the ENIAC,the development of the computer accelerated rapidly.The invention of the transistor in1947by John Bardeen,Walter Brattain,and William Shockley at Bell Labs marked a significant breakthrough,leading to smaller and more efficient computers.The1960s saw the emergence of mainframe computers,which were large,powerful machines used by businesses and universities.The1970s brought the advent of the microprocessor,with Intels4004being the first commercially available microprocessor in1971.This development paved the way for personal computers PCs,which became accessible to the general public in the1980s. Companies like IBM and Apple played pivotal roles in popularizing PCs,with Apples Macintosh,introduced in1984,being a significant milestone in userfriendly computing. The Internet and BeyondThe invention of the World Wide Web by Tim BernersLee in1989further transformed the role of computers.The web made information accessible to anyone with a computer and an internet connection,democratizing knowledge and communication.The1990s saw the rise of the internet,email,and online services,which have become integral parts of modern life.In the21st century,the computer has evolved from a tool for calculations and data processing to a multifaceted device that supports a wide range of activities,from entertainment to complex scientific research.The development of mobile computing, with smartphones and tablets,has further extended the reach of computing power.Impact on SocietyThe invention of the computer has had a profound impact on society.It has transformed industries,from manufacturing to healthcare,by automating processes and providing tools for analysis and decisionmaking.In education,computers have become essential tools for learning and research,offering access to vast resources of information and facilitating global collaboration.The computer has also reshaped social interactions,with social media platforms connecting people across the globe and changing the way we communicate.However,it has also raised concerns about privacy,security,and the digital divide,highlighting the need for responsible use and regulation.ConclusionThe invention of the computer has been a catalyst for change,driving technological advancements and shaping the modern world.As we continue to innovate and develop new technologies,it is crucial to consider the ethical implications and ensure that the benefits of computing are accessible to all.The future of computing holds great promise, with artificial intelligence,quantum computing,and other emerging technologies poised to redefine our relationship with machines.。
ic3简介

“IC3计算机综合应用能力考核∙全球标准认证”简介一、全球信息通信技术(Information Communication Technology ,ICT)专业能力考试管理中心-思递波(Certiport)简介(一)基本情况●成立于1997年,总部位于美国●是全球性三大IT测验与教学研究中心之一●是微软办公软件全球考试管理中心(二)目前使命●运用高仿真的模拟技术与全球标准国际认证,成功提升个人生活品质与升学、就业、职场竞争力。
●配合联合国科技善用者计划(Power Users of Technology),推动全球计算机综合能力的标准教学与考核。
(三)全球统计成果资料●全球参加认证考试的人次已超过1,100万人次(截止2012年1月)(11+ millionValidate Exams Delivered)●全球已有15,000以上的考试中心(15,000+ testing center world-wide)●全球每月超过150,000考试人次(150,000 exams monthly)●通行132个国家和地区(132 countries in operation)●IC3已经被翻译成24种语言(24 languages)●在全球19个国家聘请270位主题式专家制定全球标准与命题二、IC3是什么?为何要引入IC3全球标准?(一)IC3发展背景计算机综合应用能力考核∙全球标准认证(Internet and Computing Core Certification,简称IC3)是根据联合国科技善用者计划,由全球性ICT专业能力考试管理中心—思递波(Certiport)与全球数字素养咨询委员会(Global Digital Literacy Council,GDLC)共同提供的国际权威认证。
IC3的宗旨是根据全球国际协议的技能标准开发考试认证,目标是提升全球计算机与网络科技信息知识水平,提高信息软件应用知能与技术,使学生及社会人员具备一般ICT应用的核心知识与技能,获得政府、企业和教育机构等社会部门的广泛认可。
oscp考试内容

OSCP的考试内容涵盖了渗透测试的大部分领域,包括但不限于:被动信息收集、主动信息收集、漏洞扫描、缓冲区溢出(Win32和Linux)、漏洞利用、文件传输、提权、客户端攻击、WEB应用攻击、密码攻击、端口重定向和隧道、Metasploit框架、免杀、渗透测试实战演练等。
具体来说,OSCP考试由6个机器组成,考生需要在24小时内拿到70分(满分100)及以上的分数才能获得证书。
每台机器不止一个flag,低权限shell对应local.txt,root或者admin shell,对应proof.txt。
考生必须提交flag到的Control Panel才能获得分数。
其中还包括一个由3个机器组成的Active Directory(AD)环境,只有拿下AD,考试才有过的可能。
建议考生在参加考试前进行充分的准备,包括熟悉相关知识和技能,以及进行模拟练习等。
除了以上提到的内容,OSCP考试还涉及到一些其他重要的知识点,例如:1. 漏洞扫描和修复:OSCP考生需要了解如何使用各种漏洞扫描工具,如Nmap、Nessus等,对目标系统进行扫描和识别潜在的安全漏洞。
同时,他们也需要了解如何修复这些漏洞,以增强目标系统的安全性。
2. 密码攻击:OSCP考试中可能涉及到各种密码攻击方式,如字典攻击、暴力破解等。
考生需要了解如何使用各种工具和方法来破解密码,并理解如何保护密码安全。
3. WEB应用攻击:OSCP考生需要了解各种WEB应用攻击方式,如跨站脚本攻击(XSS)、跨站请求伪造(CSRF)等。
他们需要熟悉如何利用这些攻击方式对WEB应用程序进行攻击,并了解如何防御这些攻击。
4. 渗透测试实战演练:OSCP考试中可能包括一些实战演练,要求考生在模拟的真实环境中进行渗透测试。
这些演练可能包括对目标系统进行侦查、漏洞扫描、攻击等操作,以评估目标系统的安全性。
总之,OSCP考试内容非常广泛和深入,要求考生具备扎实的网络安全知识和技能。
IC3介绍

IC3世界上首张针对计算机和网络基本技能考核的认证First Global Certification for Computer Digital LiteracyIC³国际考试分三个科目,所有教学大纲与能力项目的发展与研制都是根据29个学习目标、271个技能项目研制而成。
(在全球20个国家汇集270位题材的国际专家(Subject Matter Expert)订定全球标准与命题。
)IC³计算机综合能力考核国际认证考试科目【注1】*正式考试成绩将依照全球参加考试者的成绩,采取动态式及格标准。
以上数据仅供参考,最新信息请随时上Certicenter网站()或向相关业务代理单位查询。
【注2】本简章若有修正,以网站()公告为准,不另通知。
*本表示依照IC³--2005年规划的教学与评估内容整理。
IC3的优势根源证明此国际计算机使用执照证书已获全球超过60个国家及国际机构等采认支持。
确保每位计算机用户获得认可的信息应用能力及基本知识,从而具有立足于信息社会的能力。
全球标准国际认证,成功提升个人生活质量与升学、就业、职场竞争力。
企业人才技能认证证照互相采认凭证准则之一。
提供核心技能和知识必要使用一些计算机应用和因特网。
有效地测试计算的知识并且技能保证精通达到。
提供进一步基础提高生产力与其它桌面有特殊用途的证明。
IC3的优势根源:·根据市场要求,不断变更的考试试题库·试题的命题组是由来自20个国家,汇集270个题材的国际专家组成·每年试题都得到国际计算机行业的第三方专家鉴定,保证每道试题的质量获得IC3证书的好处:获得世界60多个国家的认可(美国、加拿大、英国、日本等),有大量的国际性机构对该认证给予支持(详见链接),确保通过IC3考试的人才可以通行世界。
美国1500多所大学对通过IC3认证考试的学生打开方便之门,通过该认证考试的学生可以在世界任何一地来申请免修美国大学的部分学分。
计算机技术中的人脑机接口技术应用指南

计算机技术中的人脑机接口技术应用指南人脑机接口技术(Brain-Computer Interface,简称BCI)是一种连接人类大脑和计算机系统的技术,它使得人类可以通过直接与计算机进行交互来控制外部设备或者获取信息。
BCI技术在计算机技术领域具有广泛的应用前景,正逐渐改变着人类与计算机之间的交互方式。
一、人脑机接口技术在医学领域的应用1. 康复治疗:BCI技术可以帮助中风、脊髓损伤等病患重建运动功能。
通过BCI技术,病患可以直接控制机器臂或者轮椅,实现肢体的运动,提高生活质量。
2. 神经反馈治疗:BCI技术可以帮助治疗注意力缺陷多动障碍(ADHD)、抑郁症等心理疾病。
通过监测脑电波,BCI技术可以进行神经反馈训练,促进病患脑部活动的调整,从而改善病情。
3. 脑机接口控制假肢:BCI技术可以实现与假肢的无缝连接,使截肢者能够通过思维指令来控制假肢的运动。
这种技术不仅提高了截肢者的生活质量,还可以让其重新融入社会。
二、人脑机接口技术在游戏和娱乐领域的应用1. 脑电游戏:通过监测脑电波,BCI技术可以将玩家的思维指令转化为游戏中的操作,实现人与游戏的真实互动。
玩家可以通过集中注意力或放松大脑等方式来控制游戏角色的行动,提升游戏体验。
2. 脑控VR技术:结合虚拟现实技术,BCI技术可以实现用户通过思维指令来控制虚拟环境中的角色或场景。
用户可以通过想像自己在飞机上,脑机接口识别飞行指令后,虚拟现实场景中的角色会飞行,增强了VR游戏的沉浸感。
3. 脑机音乐互动:通过BCI技术,用户可以通过思维指令来创作音乐或者进行音乐互动。
例如,用户可以通过想像特定的旋律或乐器来控制计算机生成的音乐,或者通过思维指令改变音乐的节奏和音调。
三、人脑机接口技术在安全领域的应用1. 脑电密码学:BCI技术可以通过识别个体的脑电波模式来验证身份,实现脑电密码学。
这种身份验证方式更为安全,可以防止密码被盗用或破解,保护个人隐私。
2. 情感识别:BCI技术可以通过监测人的脑电波,识别情绪变化。
菲利普斯密码提示码l-10

菲利普斯密码提示码l-10
菲利普斯密码提示码L-10是一种复杂的密码系统,用于保护和加密生物学实验数据。
它是由Thomas Philips博士提出的,包括以下几个主要组件:DNA和RNA序列:分子生物学实验的关键步骤是在DNA中提取特定的序列,作为一种可以用来产生理想的RNA序列的模板。
称为“菲利普斯序列提供者(FSP)”的机器人将被招募,以确保DNA序列的精确性,这样就可以使用DNA来指导RNA的合成。
借助菲利普斯代码,微生物可以被安全地加以保护,避免不可预知的外部因素因素的影响。
计算机技术也会被用来帮助菲利普斯密码提示码L-10。
为了使机器人能够正确识别DNA序列,通常会使用经过培训的人工智能算法来分析输入信息以及特定基因的相似性。
这样,任何破坏DNA序列的错误就会被发现和消除。
联合使用人工智能算法和机器人可以帮助生物学实验数据更加可靠可信。
当然,菲利普斯密码提示码L-10还有另一个重要组成部分,即密码生成器。
该密码生成器可以使用对特定基因的研究结果来生成独特的密码,以帮助保护和加密实验数据。
如果再次破解密码,实验数据就会无法识别。
菲利普斯密码提示码L-10的应用越来越广泛,从全球研究组织到大型医药公司,都开始采用这一技术,以提高实验过程的安全性和准确性。
未来,随着人工智能技术的进一步深入研究,菲利普斯密码提示码L-10可能会得到更多的应用,以确保生物学实验数据的安全和准确。
pi mpi lcp介电常数值

pi mpi lcp介电常数值pi(圆周率)是一个无理数,约等于3.14159。
它在数学和科学领域中广泛应用,具有重要的意义和价值。
mpi(介电常数)是描述介质电性质的物理量,反映了电场中电荷受力的强弱。
lcp(液晶聚合物)是一种特殊的聚合物材料,具有液晶相和聚合物相的特性,被广泛应用于光电显示技术中。
圆周率(pi)作为一个无理数,其数值是无限不循环的。
它的精确计算一直是数学家们努力追求的目标,但迄今为止,只能通过近似方法来计算。
然而,尽管它的计算方法可能很复杂,但pi的应用却非常广泛。
它是圆的周长与直径之比,不仅在数学几何中有着重要的作用,还在物理学、工程学和计算机科学等领域中扮演着重要的角色。
介电常数(mpi)是描述介质电性质的物理量,是介质相对真空的电容性质的度量。
它反映了电场中电荷受力的强弱,是衡量介质对电场响应的重要参数。
不同介质的介电常数不同,可以在一定程度上决定介质的电性质和应用效果。
在电子技术、电力系统和通信领域中,mpi的准确测量和控制对于设备的设计和性能优化至关重要。
液晶聚合物(lcp)是一种特殊的聚合物材料,具有液晶相和聚合物相的特性。
液晶相是介于固态和液态之间的有序相,具有流动性和定向性。
聚合物相是由大量聚合物链构成的固态结构。
将这两种相结合,可以制备出具有液晶性质的聚合物材料。
lcp在光电显示技术中得到广泛应用,如液晶显示器、液晶电视和液晶投影仪等。
它的优点包括低功耗、高对比度和视角宽等,使得其在电子产品的设计和制造中具有重要地位。
pi、mpi和lcp分别在数学、物理和材料科学领域中发挥着重要作用。
它们的研究和应用不仅推动了科学技术的发展,也为人类创造了更多的便利和可能性。
通过深入了解它们的特性和应用,我们能更好地理解和应用它们,为人类的进步和发展做出更大的贡献。
脑机接口概述

美国Smith-Kettlewell视觉科学研究所 Sutter等人设计的脑反应接口以对视觉刺激
反应中所产生的视觉诱发电位作为BCI信号 输入,通过诱发电位选择计算机显示屏上 某一特定部分,进而可以实现选择的功能 。
28
我国清华大学 高上凯等人深入分析了稳态视觉诱发电位 (SSVEP)的特征和提取方法,设计了具有
6
BCI分类
基于视觉诱发电位的BCI 基于P300信号的BCI 基于皮层慢电位的BCI 基于感知运动节律的BCI
7受到一个固定频率的视觉刺 激的时候,人的大脑视觉皮层会产生一个 连续的与刺激频率有关( 刺激频率的基频或 倍频处) 的响应。这个响应被称为稳态视觉 诱发电位( Steady-State Visual Evoked Potentials,SSVEP),它可以可靠的应用于脑 -机接口系统( BCIs) 。
脑-机接口概述
研究背景
肌萎缩性脊髓 侧索 硬化症
脑中风 脑或脊髓损伤 脑瘫 其他疾病
2
脑-机接口的定义
脑机接口(英语:brain-computer interface,简称 BCI;有时也称作direct neural interface或者brainmachine interface),是在人或动物脑与外部设备 间创建的直接连接通路。
31
脑电信息的解析
信号的实时在线处理 个体参数优化的问题 脑-机交互适应学习的问题 异步的BCI系统工作模式
32
实用化的系统设计
系统工作稳定可靠 用户在使用中方便舒适 系统可便携且价格便宜
33
脑-机接口产品
34
35
36
37
38
我们BCI所作的工作
脑疲劳 基于ALPHA波的BCI 基于运动想象的BCI 基于视觉稳态刺激的BCI
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Adult Reference
Computational Phantoms
ICRP PUBLICATION 110
Approved by ICRP in October 2007and
adopted by ICRU in October 2008
Abstract –This report describes the development and intended use of the computational phan-toms of the Reference Male and Reference Female.In its 2007Recommendations,ICRP adopted these computational phantoms for forthcoming updates of organ dose coefficients for both internal and external radiation sources (ICRP,2007).The phantoms are based on medical image data of real people,yet are consistent with the data given in Publication 89(ICRP,2002)on the reference anatomical and physiological parameters for both male and female subjects.The reference phantoms are constructed after modifying the voxel models (Golem and Laura)of two individuals whose body height and mass resembled the reference data.The organ masses of both models were adjusted to the ICRP data on the adult Reference Male and Reference Female,without compromising their anatomic realism.This report describes the methods used for this process and the characteristics of the resulting computa-tional phantoms.
Chapter 1summarises the main reasons for constructing these phantoms –voxel phan-toms being the state of the art,and the necessity for compliance with the anatomical char-acteristics of the Reference Male and Reference Female given in Publication 89(ICRP,2002).Chapter 2summarises the specifications of the computational phantoms with respect to external dimensions and the source and target regions that are required.Chapter 3char-acterises the previously segmented voxel models (Golem and Laura)that are the origins of the reference phantoms.Chapter 4sketches the modifications that had to be applied to these models to create voxel models of the Reference Male and Reference Female.Chapter 5is a description of the resulting reference computational phantoms of the Reference Male and Reference Female.Finally,Chapter 6indicates their applications and highlights their limitations.
The phantoms’technical descriptions are contained in Annexes A–H,which represent the larger part of this report.The numerical data representing the phantoms are contained on an electronic data storage medium (CD-ROM)that accompanies the printed publication.One of the aims of this report is to assist those who wish to implement the phantoms for their own calculations.
Furthermore,to illustrate the uses of these phantoms,graphical illustrations of conver-sion coefficients for some external and internal exposures are included in Annexes I–L.
ICRP Publication
110
ICRP Publication110
A comprehensive set of recommended values will be published in separate reports.Finally, Annex M presents a description of the datafiles on the CD-ROM.
Ó2009ICRP.Published by Elsevier Ltd.
Keywords:Computational phantoms;Voxel models;Reference Male;Reference Female
References
ICRP,2002.Basic anatomical and physiological data for use in radiological protection:reference values.
ICRP Publication89.Ann.ICRP32(3–4).
ICRP,2007.The2007Recommendations of the International Commission on Radiological Protection.
ICRP Publication103.Ann.ICRP37(2–4).。
