浙江大学测试试卷:计科教材练习【06】
浙江大学大学计算机基础课程题库

当前位置: [当前课程:]31 8 0102010830单选教材08-30如果划分子网,需要子网掩码。
C类子网的掩码的前三个字节都是 (______)。
(答案:C )A.253B.254C.255D.256活动修改删除31 9 0102010831单选教材08-31使用IP命令程序Ping可以侦查网络的通信状态,而使用(______)命令可以查看机器的TCP/IP配置参数,包括机器网卡的MAC地址。
(答案:B)A.PingB.IpConfig/allC.IPconfigD.Ping /all活动修改删除32 0 0102010832单选教材08-32通过FTP进行上载文件到FTP服务器,需要使用(______)。
(答案:D )A.用户名B.匿名C.密码D.用户名和密码活动修改删除32 1 0102010833单选教材08-33Telnet时是一种登录因特网服务器的方式,BBS是在网络进行聊天、讨论的因特网服务。
实际上它们是(______)的。
(答案:D )A.概念相同B.协议相同C.完全不同D.功能类似活动修改删除32 2 0102010834单选教材08-34因特网新闻组不是指使用浏览新闻信息,而是通过(______)方法进行交流。
(答案:B )A.浏览新闻B.邮件C.论坛D.BBS活动修改删除32 3 0102010835单选教材08-35因特网即时通信,它是指可以在因特网上在线进行(______)(答案:D )A.语音聊天B.视频对话C.文字交流D.以上都是活动修改删除32 4 0102010836单选教材08-36搜索引擎成为因特网服务的服务,使用搜索引擎主要有分类查询和(______) (答案:C )A.模糊查询B.指定查询C.关键字查询活动修改删除34 0 0102010916单选教材09-16邮递员问题,或者叫做最短路径问题是(______) 。
(答案:B )A.P问题B.NP问题C.P和NP问题D.以上都不是活动修改删除34 1 0102011001单选教材10-01计算机病毒是一种(______)。
浙大计算机网络基础-2004-2005春算机网络基础期末试卷6

浙江大学2004–2005学年春夏季学期 《计算机网络基础》课程期末考试试卷 开课学院:计算机学院 ,考试形式:闭,允许带___________入场 考试时间: 2005 年 7月 5日,所需时间: 120 分钟 考生姓名: 学号: 专业: 题序 一 二 三 四 五 总 分 得分 评卷人 注意事项: 1.请把答案写在答题纸对应的题号内; 2.有关IP地址表达方式,如果没有特别的掩码标明,则均按标准地址分类表示。
一、 Please select the best choice for following questions (50 points)1.What is the advantage of using a layered model of networking?A. Simplified the networkB. For the purpose of standardizationC. Divides the complexity of internetworking into discrete, more easily learned operationsubsetsD. All of the above2.What is the name of protocol data unit (PDU) at the network layer of the OSI referencemodel?A. TransportB. FrameC. PacketD. Segment3.Which is true when a broadcast is sent out in an E thernet 802.3 LAN?A. The broadcast is sent only to the default gateway.B. The broadcast is sent only to the destination hardware address in the broadcast.C. The broadcast is sent to all devices in the collision domain.D. The broadcast is sent to all devices in the broadcast domain.4.Segmentation of a data stream happens at which layer of the OSI model?A. PhysicalB. Data LinkC. NetworkD. Transport5.Which of following international standard defines for Fast Ethernet?A. IEEE 802.3B. IEEE 802.3zC. IEEE 802.3uD. IEEE 802.3ae6.What does the Data Link layer use to find hosts on a local network?A. Logical network addressesB. Port numbersC. Hardware addressesD. Default gateways7.What were the key reasons the ISO released the OSI model?A. To allow companies to charge more for their equipmentB. To help vendors create interoperable network devicesC. To help vendors create and sell specialized software and hardwareD. So the IBM mainframe would be replaced with the PC8.What is used at the Transport layer to stop a receiving host’s buffer from overflowing?A. SegmentationB. PacketsC. AcknowledgmentsD. Flow control9.When data is encapsulated, which is the correct order?A. Data, frame, packet, segment, bitB. Segment, data, packet, frame, bitC. Data, segment, packet, frame, bitD. Data, segment, frame, packet, bit10.What does the term “Base”indicate in 100Base-TX?A. The maximum distanceB. The type of wiring usedC. A LAN switch method using half duplexD. A signaling method for communication on the network11.What is the maximum distance of 100Base-T?A. 100 feetB. 1000 feetC. 100 metersD. 1000 meters12.Which of the following would describe a transport layer connection that would ensure reliabledelivery?A. RoutingB. AcknowledgmentsC. SwitchingD. System authentication13.Which of the following is not considered a reason for LAN congestion?A. Low bandwidthB. Too many users in a broadcast domainC. Broadcast stormsD. Routers14.Which of the following are two basic types of dynamic routing?A. Static and defaultB. TCP and UDP exchangeC. Distance-vector and link-stateD. None of the above15.If your LAN network is currently congested and you are using only hubs in your network, whatwould be the BEST solution to decrease congestion on your network?A. Cascade you r hubs.B. Replace your hubs with switches.C. Replace your hubs with routers.D. Add faster hubs.16.What technology is a used by most switches to resolve topology loops and ensure that dataflows properly through a single network path?A. RIPB. STPC. IGRPD. Store-and-forward17.Which of the following is one of the characteristics of IP?A. reliable and connectionlessB. unreliable and connectionlessC. reliable and connection-orientedD. unreliable and connection-oriented18.What is the valid host range for subnet 172.16.10.16 (Mask 255.255.255.240)?A. 172.16.10.20 through 172.16.10.22B. 172.16.10.16 through 172.16.10.23C. 172.16.10.17 through 172.16.10.31D. 172.16.10.17 through 172.16.10.3019.What range of addresses can be used in the first octet of a Class B network address?A. 1–126B. 128–190C. 128–191D. 129–19220.Which of the following is not true?A. IP is connectionless and provides routing.B. ARP is used to find an IP address of a host.C. UDP is connectionless.D. TCP is connection oriented.21.Which class of IP address provides a maximum of only 254 host addresses per network ID?A. Class AB. Class BC. Class CD. Class D22.Which protocol tool use ICMP?A. TelnetB. PingC. ARPD. FTP23.Which of the following is an IEEE standard for frame tagging?A. 802.1XB. 802.3ZC. 802.1QD. 802.3U24.A client will use ____ to send emails to mail-server.A.POP3B.SMTPC.TELNETD.FTP25.Which protocol used in PPP allows multiple Network layer protocols to be used during aconnection?A. LCPB. NCPC. HDLCD. X.2526.When too many packets are present in the subnet, performance degrades. What is this situationcalled?A. dead lockB. congestionC. network faultD. network busy27.Which language can be used to realize the client-side dynamic web page generation?A. CGIB. ASPC. JavaScriptD. PHP28. The two-wire connections between each subscriber’s telephone and the end office are knownin the trade as the____.A. trunkB. local loopC. linkD. switch29.When web page is transmitted over SSL, the protocol used is _____.A. HTTPB. SHTTPC. HTTPSD. SSL30.Nyquist proved that if an arbitrary signal has been run through a low-pass filter of bandwidth H,the filtered signal can be completely reconstructed by making only ________ (exact) samples per secondA. HB. 0.5HC. 2HD. 4H31.To convert a binary message to an ASCII message in email system, we can use _____ encoding,which break up groups of 24 bits into four 6-bit units, with each unit being sent as a legal ASCII character.A. base64B. quoted-printableC. SMTPD. POP332.A CRC generator polynomial is G(x)= X8+X5+X2+l. How many bits will the checksum be?A. 7B. 8C. 9D. 1033. If the length of sequence is 4 bits, the maximum sending window size should be ____.A. 13B. 14C. 15D. 1634.In 802.11, to solve the _______ station problem and the hidden station problem, we can useCSMA/CA protocol. According this protocol, before the station sending a data, it must send RTS frame and wait a CTS frame back.A. faultB. mobileC. exposedD. wireless35.If the congestion window size is 20KB, and the receive window size is 30KB, what is themaximum bytes can the TCP entity transmit?A. 20KBB. 30KBC. 50KBD. 10KB36.Port numbers below ________ are called well-known ports and are reserved for standardservices.A. 256B. 1024C. 4096D. 100037.________, which are overlay networks on top of public networks but with most of theproperties of private network.A. PBXB. VPNC. CDMA 1XD. GPRS38.The problem of running out of IP addresses is not a theoretical problem that might occur atsome point in the distant future. Some people felt that a quick fix was needed for the short term.This quick fix came in the form of ____________________.A. IP6B. DHCPC. RARPD. NAT39.Public-key algorithms have the property that ____________________ keys are used forencryption and decryption and that the decryption key cannot be derived from the encryption key. These properties make it possible to publish the public key.A. one timeB. randomC. sameD. different40.The main public-key algorithm is ____________________ which derives its strength from thefact that it is very difficult to factor large numbers.A. DESB. AESC. MD5D. RSA41.Various schemes have been devised for digital signatures, using both symmetric-key and________-key algorithms.A. publicB. privateC. one timeD. one way42.Often, authentication is needed but secrecy is not, based on the idea of a one-way hash functionthat takes an arbitrarily long piece of plaintext and from it computes a fixed-length bit string.This hash function, MD, often called a ________.A. message digestB. packet-switchedC. message-detectD. mini data43.URL(Uniform Resource Locator) have three parts: the ________, the DNS name of themachine on which the page is located, and a local name uniquely indicating the specific page.A. protocolB. addressC. port numberD. name44.HTTP1.1, which supports ________ connections. With them, it is possible to establish a TCPconnection, send a request and get a response, and then additional requests and get additional response.A. one timeB. persistentC. stop and waitD. one-way45._______, when it is used, a bad frame that is received is discarded, but the good framesreceived after it are buffered.A. selective repeatB. go back NC. sliding windowD. stop and wait46.How does the FDM multiplexing schemes work like?A. each user having exclusive possession of some bandB. each user take turns, periodically getting the entire bandwidth for a litter burst of timeC. each user transmit over the entire frequency spectrum all the time with different codingD. each user transmit over a shared fiber using different wavelength47.When we use a modem, which use 16 phases signal to modulation, then how much can we getthe maximum data rate in a 2400 baud channel (in noiseless channel)?A. 400bpsB. 2400bpsC. 9.6kbpsD. 14.4kbps48.______ is a small java program that has been compiled into binary instruction running in JVM,and can be embedded into HTML pages, interpreted by JVM-capable browsers.A. JavaScriptB. JavaBeanC. AppletD. JSP49.Which of the following best describes the function of the OSI reference model’s transportlayer?A. It sends data by using flow controlB. It provides the best path for deliveryC. It determines network addressesD. It provides error-correcting50.What is the most efficient subnet mask to use on point-to-point WAN links?A. 255.255.255.0B. 255.255.255.224C. 255.255.255.252D. 255.255.255.248二、 Please choose true(T) or false( F) for the following questions (15 points)1.Error-correcting and error-detecting are two types of technique in error control.2.Link state dynamic routing algorithms operate by having each router maintain a tablegiving the best known distance to each destination and which line to use to get there. These tables are updated by exchanging information with the neighbors.3.With Manchester encoding, each bit period is divided into two equal intervals. A binary 1bit is sent by having the voltage set high during the first interval and low in the second one.A binary 0 is just the reverse: first low and then high.4. A connection is established in TCP by means of the two-way handshake.5.The range of frequencies transmitted without being strongly attenuated is called bandwidth.6.Shannon’s major result is that the maximum data rate of a noisy channel whose bandwidthis H Hz, and whose signal-to-noise ratio is S/N, is given byMaximum number of baud/sec = H log2 (1+S/N)7.Two different switching techniques are widely used nowadays: circuit switching and packetswitching.8.The protocols used to determine who goes next on a multi-access channel belong to asub-layer of the data link layer called the LLC sublayer.9.The b asic function of RTP is to multiplex several real-time data streams onto a singlestream of UDP packets.10.The Internet solution is to realize that two potential problems exist n etwork capacity andreceiver capacity and to deal with each of them separately. To do so, each sender maintains two windows: the window the receiver has granted and a second window, the congestion window.11.Selective repeat, is for the receiver simply to di scard all subsequent frames, sending noacknowledgments for the discarded frames.12.The IPSec is a set of open standards that provides data confidentiality, data integrity, andauthentication between participating peers at the IP layer.13.B2C, the full name i s Business to Company.14.One type of person-to-person communication often goes by the name of end-to-endcommunication, to distinguish it from the client-server model.15.An issue that occurs at every level is how to keep a fast sender from swamping a slowreceived with data. This subject is called flow control.三、 Please answer the following questions briefly.1.What are the principal differences between connectionless communications andconnection-oriented communications? (5 points)2.Data link protocols almost always put the CRC in a trailer rather than in a header. Why? (5points)3.Suppose that the TCP congestion window is set to 18KB and a timeout occurs. How big willthe window be if the next four transmission bursts are all successful? Assume that the maximum size of segment is 1KB. (5 points)四、 A large number of consecutive IP address are available starting at 198.16.0.0. Supposethat four organizations, A, B, C, and D, request 4000,2000,4000, and 8000 addresses, respectively, and in that order. For each of these, give the first IP address assigned, the last IP address assigned, and the mask in the w.x.y.z/s notation. (8 points)(Notice: To start with, all the requests are rounded up to a power of two.)五、 The following figure describes a simple authentication p rotocol. Assume you are Trudy, pleaseuse reflection attack to attack Bob.(1). Draw the attack figure and give clear the steps of the attach(2). What are the differences between authentication and authorization? (12 points)。
浙江大学测试试卷:计科教材练习【06】

A.封装、继承、多态
B.顺序、循环和分支
C.多分支、循环和函数
D.函数、方法和过程
6.高级语言的基本数据类型是(D )。
A.变量、常量、标识符
B.顺序、循环和分支
C.数组、链表和堆栈
D.整型、实型和字符
7.程序设计中常用的运算类型有算术、逻辑和(C )
A.移位 B.复合 C.关系 D.对象
窗体顶端
测试试卷:计科教材练习【06】
一、判断题,共5题, 总分:5分。请直接点击选择True or False.
1.测试是寻找程序中的错误,常用的方法有黑盒测试和白盒测试。(T ) True False
2.Java程序是汇编语言程序。(F ) True False
3.一个CPU所执行的全部指令就是指令系统。(T ) True False
8.HTML语言是属于(C )
A.面向过程 B.面向对象 C.网页编程 D.文字处理
9.通常,for循环语言用于循环次数(C )的程序中。
A.由循环体决定
B. 在循环体外决定
C.确定
D.不确定
10.函数或方法是一段独立的程序代码,也是可以被程序设计者调用的。调用函数或方法时,如果需要在形式参数和实际参数之间做到(D )。
D.常量调用和变量调用
16.程序设计过程,包括了问题的定义、设计方案、(A )、文档以及运行维护等六个步骤。
A.编码和测试 B.语言和算法 C.过程和函数 D.函数或方法
17.软件开发过程使用工程管理的方法,通常有各种开发模型,例如(A )。
A.瀑布模型和增量模型
B.瀑布模型和数学模型
C.RAD模型和数学模型
D.螺旋模型和数学模型
浙大大计基第六章作业

一、填空题1、操作使用2、算法算法3、指令4、数据传输运算5、操作码地址下一条指令的地址6、机器语言程序7、汇编语言源程序8、过程对象过程9、C PASCAL C++ Java10、封装继承多态11、属性行为12、HTML XML13、源程序目标程序14、逐句一次性整体15、算法错误16、运算对象变量常量17、整型实型字符型18、符号常量19、构造数据类型下标20、赋值语句复合语句返回语句21、算术运算22、常量变量23、函数24、Switch25、While for for26、Do……while27、设计方案编码运行维护28、黑盒白盒29、瀑布螺旋30、使用二、选择题1、D2、C3、C4、B5、A6.D 7、A 8、C 9、C 10、D11、B 12、C 13、C 14、C 15、A16、A 17、A 18、A 19、A 20、B三、思考题6、解释程序所谓解释程序是高级语言翻译程序的一种,它将源语言(如BASIC)书写的源程序作为输入,解释一句后就提交计算机执行一句,并不形成目标程序。
就像外语翻译中的“口译”一样,说一句翻一句,不产生全文的翻译文本。
这种工作方式非常适合于人通过终端设备与计算机会话,如在终端上打一条命令或语句,解释程序就立即将此语句解释成一条或几条指令并提交硬件立即执行且将执行结果反映到终端,从终端把命令打入后,就能立即得到计算结果。
这的确是很方便的,很适合于一些小型机的计算问题。
但解释程序执行速度很慢,例如源程序中出现循环,则解释程序也重复地解释并提交执行这一组语句,这就造成很大浪费。
编译程序这是一类很重要的语言处理程序,它把高级语言(如FORTRAN、COBOL、Pascal、C等)源程序作为输入,进行翻译转换,产生出机器语言的目标程序,然后再让计算机去执行这个目标程序,得到计算结果。
编译程序工作时,先分析,后综合,从而得到目标程序。
所谓分析,是指词法分析和语法分析;所谓综合是指代码优化,存储分配和代码生成。
浙江大学05-06秋冬计算机网络考试试卷

浙江⼤学05-06秋冬计算机⽹络考试试卷浙江⼤学2005–2006学年秋季学期《计算机⽹络》课程期末考试试卷开课学院:软件学院,考试形式:闭卷考试时间:_____年____⽉____⽇, 所需时间:120分钟考⽣姓名: ___学号:专业:得分:答案:For every following question, please select your best answer only1.The transmission unit for the physical layer is a/an __________.A.)packetB.)frameC.)bitD.)byte2.Which best describes the structure of an encapsulated data packet?A.)Segment header, network header, data, frame trailerB.)Segment header, network header, data, segment trailerC.)Frame header, network header, data, frame trailerD.)Frame header, segment header, data, segment trailer3.The communication subnet consists of __________.A.)physical layer, data link layer, and network layerB.)physical layer, network layer, transport layerC.)physical layer, data link layer, network layer, transport layerD.)data link layer, network layer, transport layer, session layer4.Which of the following statements best describes a WAN?A.)It connects LANs that are separated by a large geographic area.B.)It connects workstations, terminals, and other devices in a metropolitan area.C.)It connects LANs within a large building.D.)It connects workstations, terminals, and other devices within a building.5.Which is the movement of data through layers?A.)WrappingB.)EncapsulationC.)TravelingD.)Transmission6.Which is the OSI model?A.) A conceptual framework that specifies how information travels through networks.B.) A model that describes how data make its way from one application program to another throughout a network.C.) A conceptual framework that specifies which network functions occur at each layerD.)All of the above7.Which of the OSI layers divides the transmitted bit stream into frames?A.)Physical layerB.)Data link layerC.)Network layerD.)Transport layer8.Which of the following is incorrect?A.)The OSI model is better the TCP/IP model.B.)The OSI model provides more efficient implementation than the TCP/IP model.C.)The OSI model has more layers than the TCP/IP model.D.)The OSI model makes the distinction between services, interfaces, protocols.9.In the TCP/IP model, which layer deals with reliability, flow control, and error correction?A.)ApplicationB.)TransportC.)InternetD.)Network access10.The TCP/IP protocol suite has specifications for which layers of the OSI model?A.) 1 through 3B.) 1 through 4 and 7C.)3,4,and 5 through 7D.)1,3,and 411. A noiseless 4-k Hz channel is sampled every 1 msec. What is the maximum data rate?A.)8000 bpsB.)4000 bpsC.)1000 bpsD.)Can be infinite12.If a binary signal is sent over a 4-k Hz channel, what is the maximum achievable data rate?A.)8000 bpsB.)4000 bpsC.)1000 bpsD.)Can be infinite13.If a binary signal is sent over a 4-k Hz channel whose signal-to-noise ratiois 127:1, what is the maximum achievable data rate?A.)28000 bpsB.)8000 bpsC.)4000 bpsD.)Can be infinite14. A modem constellation diagram has data points at the following coordinates: (1, 1), (1, -1), (-1, 1), and (-1, -1). How many bps can a modem with these parameters achieve at 1200 baud?A.)1200 bpsB.)2400 bpsC.)4800 bpsD.)None of the above15.What is WDM?A.)Multiplexing on fiber-optic cable.B.)Multiplexing using the density of the transmission media.C.) A form of flow control that monitors WAN delays.D.) A form of congestion management for WANs.16.Which technology is not a type of wireless communication?A.)CellularB.)BroadbandC.)InfraredD.)Spread spectrum17.What is one advantage of using fiber optic cable in networks?A.)It is inexpensive.B.)It is easy to install.C.)It is an industry standard and is available at any electronics storeD.)It is capable of higher data rates than either coaxial or twisted-pair cable.18. A telephone switch is a kind of __________.A.)packet-switchingB.)buffer-switchingC.)fabric-switchingD.)circuit-switching.19. A cable TV system has 100 commercial channels, all of them alternating programswith advertising. This kind of multiplexing uses ___________.A.)TDMB.)FDMC.)FDM + TDMD.)None of the above.20. A bit string, 01101111101111110, needs to be transmitted at the data link layer.What is the string actually transmitted after bit stuffing (Whenever the sender’s data link layer encounters five consective 1s in the data, it automatically stuffs a 0 bit into the outgoing bit stream)A.)01101111101111110B.)0110111110011111010C.)011011111011111010D.)None of the above21.When DCF (Distributed Coordination Function) is employed, 802.11 uses a protocolcalled __________.A.)CSMA/CAB.)CSMA/CDC.)ALOHAD.)WDMA22.Which of the following can NOT directly be used for framing?A.)Character count.B.)Flag bytes with byte stuffing.C.)Starting and ending flags, with bit stuffing.D.)Physical layer coding violations.23.Which of the following can a VLAN be considered?A.)Broadcast domainB.)Collision domainC.)Both a broadcast and a collision domainD.)Domain name24.What is the purpose of Spanning Tree Protocol? (Network Bridging)A.)To maintain single loop pathsB.)To maintain a loop-free networkC.)To maintain a multiloop networkD.)To maintain a reduced loop network25.Which uses the twisted pairs?A.)10Base5.B.)10Base2.C.)10Base-F.D.)10Base-T.26.How do switches learn the addresses of devices that are attached to their ports?A.)Switches get the tables from a router.B.)Switches read the source address of a packet that is entering through a port.C.)Switches exchange address tables with other switches.D.)Switches are not capable of building address tables.27.Repeaters can provide a simple solution for what problem?A.)Too many types of incompatible equipment on the networkB.)Too much traffic on a networkC.)Too-slow convergence ratesD.)Too much distance between nodes or not enough cable.28.Which of the following is true of a switch’s function?A.)Switches increase the size of a collision domains.B.)Switches combine the connectivity of a hub with the capability to filteror flood traffic based on the destination MAC address of the frame.C.)Switches combine the connectivity of a hub with the traffic direction ofa router.D.)Switches perform Layer 4 path selection.29.Ethernet MAC addresses are how many bits in length?A.)12B.)24C.)48D.)6430.What is the information that is “burned in ” to a network interface card?A.)NICB.)MAC addressC.)HubD.)LAN31.Which connector does UTP (Unshield Twised Pair) use?A.)STPB.)RJ-45C.)RJ-69D.)BNC/doc/a9251a5077232f60ddcca14b.html ing repeaters does which of the following to the collision domain?A.)ReducesB.)Has no effect onC.)ExtendsD.)None of the above33.Which of the following is not a feature of microsegmentation?A.)It enables dedicated access.B.)It supports multiple conversions at any given time.C.)It increases the capacity for each workstation connected to the network.D.)It increases collisions.34.Which of the following protocols would have the highest channel utilization?A.)0.5-persistent CSMAB.)1-persistent CSMAC.)Pure ALOHAD.)Slotted ALOHA35.Which of the following is true concerning a bridge and its forwarding decisions?A.)Bridges operate at OSI Layer 2 and use IP addresses to make decisions.B.)Bridges operate at OSI Layer 3 and use IP addresses to make decisions.C.)Bridges operate at OSI Layer 2 and use MAC addresses to make decisions.D.)Bridges operate at OSI Layer 3 and use MAC addresses to make decisions.36.Fast Ethernet supports up to what transfer rate?A.) 5 MbpsB.)10 MbpsC.)100 MbpsD.)1000 Mbps37.Media Access Control refers to what?A.)The state in which a NIC has captured the networking medium and is readyto transmitB.)Rules that govern media capture and releaseC.)Rules that determine which computer on a shared-medium environment is allowed to transmit the dataD.) A formal byte sequence that has been transmitted.38.Which best describes a CSMA/CD network?A.)One node’s transmission traverses the entire network and is received and examined by every node.B.)Signals are sent directly to the destination if the source knows both theMAC and IP addressesC.)One node’s transmission goes to the nearest router, which sends it directlyto the destination.D.)Signals always are sent in broadcast mode.39.Which of the following statements about IPv4 header fields is incorrect?A.)An address has 32 bits.B.)The TTL has 4 bits.C.)The version has 4 bits.D.)The identification has 16 bits.40.The subnet mask for a class B network is 255.255.255.192. How many subnetworks are available? (Disregard special addresses)A.) 2B.) 4C.)1024D.)19241.Which of the following can be used to connect a keyboard with a computer?A.)802.3B.)802.11C.)802.15D.)802.1642.Which of the following can be used as the wireless local loop for public switched telephone systems?A.)802.3B.)802.11C.)802.15D.)802.1643.What is the IP address of the internal loopback?A.)10.10.10.1B.)255.255.255.0C.)127.0.0.1D.)192.0.0.144.How does the network layer forward packets from the source to the destination?A.)By using an IP routing tableB.)By using ARP responsesC.)By referring to a name serverD.)By referring to the bridge45.What is one advantage of dynamic routing?A.)Takes little network overhead and reduces network trafficB.)Reduces unauthorized break-ins because security is tightC.)Adjusts automatically to topology or traffic changesD.)Requires little bandwidth to operate efficiently46.Which best describes a default route?A.)Urgent-data route manually entered by a network administratorB.)Route used when part of the network failsC.)Route used when the destination network is not listed explicitly in therouting tableD.)Preset shortest path47.What does ICMP stand for?A.)Internal Control Message PortalB.)Internal Control Message ProtocolC.)Internet Control Message PortalD.)Internet Control Message ProtocolE.)48.What does TTL stand for? (For IP Header fields)A.)Time-To-ListB.)Time-To-LiveC.)Terminal-To-ListD.)Terminal-To-Live49.What is one advantage of distance vector algorithms?A.)They are not likely to count to infinity.B.)You can implement them easily on very large networks.C.)They are not prone to routing loops.D.)They are computationally simple50.Which of the following best describes a link-state algorithm?A.)It recreates the topology of the entire internetwork.B.)It requires numerous computations.C.)It determines distance and direction to any link on the internetwork.D.)It uses litter network overhead and reduces overall traffic.51.What is the minimum number of bits that can be borrowed to form a subnet?A.) 1B.) 2C.) 4D.)None of the above52.In order to find out its IP address, a machine can use __________.A.)ARPB.)RARPC.)ICMPD.)UDP53.Which portion of the Class B address 154.19.2.7 is the network address?A.)154B.)154.19C.)154.19.2D.)154.19.2.754.How many host addresses can be used in a Class C network?A.)253B.)254C.)255D.)25655.Which of the following can NOT be used to traffic shaping?A.)OverprovisioningB.)Leaky bucket algorithmC.)Token bucket algorithmD.)Packet scheduling56.When the congestion is very seriously, which kind of control should be used?A.)Warning bitsB.)Load sheddingC.)Chocke packetsD.)Hop-by-hop chope packets57.Which of the following is most appropriate in order to make the full use of IP addresses?A.)SubnetingB.)CIDRC.)NATD.)All of the above58.How many bits does an IPv6 address have?A.)32B.)64C.)128D.)25659.Which of the following is true for distance vector routing?A.)Useful for nothing.B.)Used in OSPFC.)Used in BGPD.)None of the aboveGiven the subnet shown in (a) and the incomplete routing table shown in (b), please use distance vector routing to answer the next 4 questions.60.What is the new distance and next hop for going to C?A.)28,IB.)28,AC.)12,ID.)12,G61.What is the new distance and next hop for going to F?A.)30,HB.)30,IC.)18,AD.)18,K62.What is the new distance and next hop for going to H?A.)0,AB.)3,IC.)12,HD.)18,K63.What is the new distance and next hop for going to L?A.)6,AB.)13,IC.)14,HD.)15,K64.What does the window field in a TCP segment indicate?A.)Number of 32-bit words in the headerB.)Number of the called portC.)Number used to ensure correct sequencing of the arriving dataD.)Number of octets that the device is willing to accept65.What do TCP and UDP use to keep track of different conversations crossing a network at the same time?A.)Port numbersB.)IP addressesC.)MAC addressesD.)Route numbers66.Which range of port numbers is unregulated?A.)Below 255B.)Between 256 and 512C.)Between 256 and 1023D.)Above 102367.Which of the following is incorrect for the TCP header fields?A.)The source port has 16 bits.B.)The URG has just 1 bit.C.)The Window size has 32 bits.D.)The acknowledgement number has 32 bits.68.How does TCP synchronize a connection between the source and the destination before data transmission?A.)Two-way handshakeB.)Three-way handshakeC.)Four-way handshakeD.)None of the above69.What is true for TCP’s retransmission timer?A.)Fixed value to allow 90% of segments arrive without retransmissionB.)Fixed value to allow 80% of segments arrive without retransmissionC.)Dynamic value based on the past successful transmission historyD.)Dynamic value based on the last successful transmission’s RTT70.UDP segments use what protocols to provide reliability?A.)Network layer protocolsB.)Application layer protocolsC.)Internet protocolsD.)Transmission control protocols71.Which of the following is most appropriate?A.)UDP just provides an interface to the IP protocol with the added feature of demultiplexing multiple processes using the ports.B.)UDP can be used to implement RPC.C.)UDP can be used to implement RTP.D.)All of the above.72.Which of the following is a basic service of the transport layer?A.)Provides reliability by using sequence numbers and acknowledgementsB.)Segments upper-layer application dataC.)Establishes end-to-end operationsD.)All of the above73.The TCP primitives depend on __________.A.)both the operating system and the TCP protocol.B.)the operating system only.C.)the TCP protocol only.D.)the operating system and the TCP protocol and the IP protocol.74.The default port for TELNET is __________.A.)21B.)22C.)23D.)2475.Which of the following is incorrect?A.)DNS stands for Domain Name System.B.)There is only one record associated with every IP.C.)Domain names can be either absolute or relative.D.)Domain names are case insensitive.76.What does MIME stand for?A.)Messages In Multi EncodingB.)Multipurpose Internet Mail ExtensionsC.)Multipurpose Internet Mail EncodingD.)None of the above77.Which of the following is not a protocol for email?A.)SMTPB.)POP3C.)IMAPD.)GOPHER78.Which of the following is incorrect?A.)HTML stands for HyperText Markup Language.B.)XML stands for eXtensible Markup Language.C.)XHTML stands for eXtended HyperText Markup Language.D.) A browser can display HTML documents as well as XML documents.79.Which of the following tags is used to define a hyperlink?A.) …B.) …C.) …D.)…80.Which of the following is not a built-in HTTP request methods?A.)GETB.)POSTC.)PUTD.)FETCH81.Which of the following is not able to generate dynamic content on the server side?A.)CGIB.)JSPC.)ASPD.)JavaScript82.Which of the following is able to generate dynamic content on the client side?A.)Java AppletB.)JavaScriptC.)ActiveXD.)All of the above83.Which of the following is true?A.)WAP 1.0 is successful while I-Mode is not.B.)I-Mode is successful while WAP 1.0 is not.C.)Both WAP 1.0 and I-Mode are successful.D.)Neither WAP 1.0 nor I-Mode is successful.84.Which of the following security policies is hopeless?A.)802.11 WEPB.)Bluetooth securityC.)WAP 2.0 securityD.)None of the above85.Which of the following is incorrect?A.)X.509 can be used to describe the certificates.B.)An organization that certifies public keys is now called a CA.C.)The Diffie-Hellman key exchange allows strangers to establish a shared secret key.D.)The Diffie-Hellman key exchange can be attacked by the bucket brigade or man-in-the-middle attack.86.In a public key encryption system, a sender has encrypted a message with the recipient's public key. What key does the recipient use to decipher the message?A.)The recipient's private key.B.)The recipient's public key.C.)The sender's private key.D.)The sender's public key.87.Which of the following statements is true of ping?A.)The ping command is used to test a device’s network connectivity.B.)The ping stands for packet Internet groperC.)The ping 127.0.0.1 command is used to verify the operation of the TCP/IP stack.D.)All of the above.88.Which of the following can be used to test application protocols?A.)pingB.)tracertC.)netstatD.)telnet89.Which of the following can be used to display TCP connections?A.)pingB.)tracertC.)netstatD.)telnet90.Which of the following system calls is used to create a server socket?A.)socketB.)openC.)requestD.)creat91.Which of the following system calls is to specify queue size for a server socket?A.)bindB.)sizeC.)listenD.)acceptFor the following cipher chaining modes, please answer the following three questions.92.Which mode is most suitable for use with interactive terminals?A.)Cipher chaining AB.)Cipher chaining BC.)Cipher chaining CD.)Cipher chaining D93.Which mode is most suitable for use with real-time streaming?A.)Cipher chaining AB.)Cipher chaining BC.)Cipher chaining CD.)Cipher chaining D94.Which mode is most suitable for use with disk files?A.)Cipher chaining AB.)Cipher chaining BC.)Cipher chaining CD.)Cipher chaining D95.Which of the following is the strongest symmetric-key encryption algorithm?A.)DESB.)AESC.)RSAD.)MD596.Which of the following is the strongest public-key encryption algorithm?A.)DESB.)SHA-1C.)RSAD.)MD5Consider the figure shown below, which takes some plaintext as input and produces signed ciphertext in some ASCII format as output. Please answer the next questions97.Which of the following should be used for blank (I)?A.)DESB.)AESC.)MD5D.)None of the above98.Which of the following should be used for blank (II)?A.)RSA with Alice’s private RSA keyB.)RSA with Alice’s public RSA keyC.)RSA with Bob’s private RSA keyD.)RSA with Bob’s public RSA key99.Which of the following should be used for blank (III)?A.)MD5B.)AESC.)SHA-1D.)Base64 encoding100.Which of the following should be used for blank (IV)?A.)MD5B.)AESC.)SHA-1D.)None of the above。
浙江大学计算机考研真题

牛客网,程序员学求职备考神器
NOWCODER
10、在采用中断 I/O 方式控制打印输出的情况下,CPU 和打印控制接口中的 I/O 端口之间交换的信息不可能是()。(点击查看答案>>>>>>>>) A、打印字符 B、主存地址 C、设备状态 D、控制命令
牛客网,程序员学求职备考神器
NOWCODER
牛在牛客网
测试输入包含若干测试用例。每个测试用例的第 1 行给出评估的道路条数 N、 村庄数目 M (N, M < =100 );随后的 N 行对应村庄间道路的成本,每行给出一 对正整数,分别是两个村庄的编号,以及此两村庄间道路的成本(也是正整数)。 为简单起见,村庄从 1 到 M 编号。当 N 为 0 时,全部输入结束,相应的结果不要 输出。 输出描述:
8、下列有关总线定时的叙述中,错误的是()。(点击查看答案>>>>>>>>) A、异步通信方式中,全互锁协议最慢 B、异步通信方式中,非互锁协议的可靠性最差 C、同步通信方式中,同步时钟信号可由各设备提供 D、半同步通信方式中,握手信号的采样由同步时钟控制
9、若磁盘转速为 7200 转/分,平均寻道时间为 8ms,每个磁道包含 1000 个扇 区,则访问一个扇区的平均延迟时间大约是()。(点击查看答案>>>>>>>>) A、8.1ms B、12.2ms C、16.3ms D、20.5ms
【浙江大学】大学计算机基础教程——习题与参考答案

4. 频率
5. 读数据包并解包、打包并发送
6. 易失性、RAM、被读出
7. FAT
8. 150K
9. RAM
10.用户、计算机
11.通用串行总线
选择题:
1、B 2、C 3、C 4、BCDEF 5、C 6、B 7、D 8、D 9、D 10、A
6.多媒体信息交互处理所需的硬件设备是在普通PC机的基础上,再包括:高性能的CPU(带有多媒体扩展指令MMX);快速、大容量的内存;声卡;显卡;视频卡和质量较高的显示器;CD-ROM或DVD-ROM驱动器;扫描仪;数码相机;数字摄像机等外围设备。多媒体信息处理所需的软件有:多媒体操作系统;多媒体创作软件和应用软件,如图像处理、音乐处理、演示文稿制作、动画制作、视频处理等。
11、D 12、B 13、D 14、B 15、B
第4章 核心:操作系统
简答题:
1.系统软件是指管理、监控和维护计算机软、硬件资源,起到为用户提供友好的交互界面、支持用户运行应用软件、提高计算机的使用效率等的软件。应用软件是人们为了解决某些特定的具体问题而设计开发的各种程序。
选择题:
1、E 2、C 3、B 4、BDFJLE 5、C 6、ABEFH
7、B 8、D 9、A 10、C 11、A 12、B
第2章 信息表示和逻辑基础
简答题:
1.数制又称为“计数(或记数)体制”,一般把多位数码中每一位的构成方法以及实现从低位到高位的进位规则叫做数制。数制的3个基本特点为:(1)一个R进制的数制有R-1个数码;(2)最大的数码为R-1;(3)计数规则为“逢R进一”。
12.一个正数的原码和它的真值相同,负数的原码为这个数真值的绝对值,符号位为1。反码的定义是:一个正数的反码等于它的原码;一个负数的反码,最高位(符号位)为1,其余各位按位求反。补码的定义是:一个正数的补码等于它的原码;一个负数的补码等于它的反码加上1(从最低位上加1,并考虑进位,但进位不改变符号位)。
浙江大学测试试卷:计科教材练习【07】

TrueTrueTrueTrueTrueA.CPUA.个人数据库B.网络数据库C.ERPD.以上都是10.ERP是基于数据库技术的软件产品,它是指( A 010*******)。
A.企业数据库应用系统B.数据库开发工具C.数据库管理系统D.分布式数据库系统11.关系型数据库是目前数据库技术的主流,这里的关系一词的意思是( B 010*******)。
A.在数据之间的关联B.一个没有重复值的集合C.对数据进行逻辑判断D.对数据进行处理12.当前应用最广泛的数据模型是( B 010*******)。
A.ER模型B.关系模型C.网状模型D.层次模型13.下列四项中,不属于数据库特点的是( D 010*******)。
A.数据共享B.数据完整性C.数据冗余较小D.数据独立性低14.数据库中存储的是( D 010*******)。
A.数据B.数据模型C.数据之间的联系D.数据以及数据之间的联系15.反映现实世界中实体及实体间联系的信息模型是( D 010*******)。
A.关系模型B.层次模型C.网状模型D.E-R模型16.一个关系数据库中有一个数据表的记录数为100万,它是指( C 010*******)。
A.属性值B.度数C.基数D.维数行记录基17.一个关系数据库中有一个数据表有15列,它是指( B 010*******)。
列属性度A.属性值B.度数C.基数D.维数18.以下不属于关系的操作是( B 010*******)。
A.插入B.求和C.删除D.并和交19.在关系数据库技术中,行记录的专业名词是( A 010*******)。
A.元组B.元素C.元数据D.元运算A.C/SB.D/SC.B/SA.层次模型的DBMSB.网状模型的DBMSC.关系模型的应用程序D.关系模型的DBMS28.以下( B 010*******)属于数据库管理系统。
A.JavaB.OracleC.Visual BasicD.Fortran29.下列数据模型中,数据独立性最高的是( B 010*******)。
浙大计算机机试历年真题
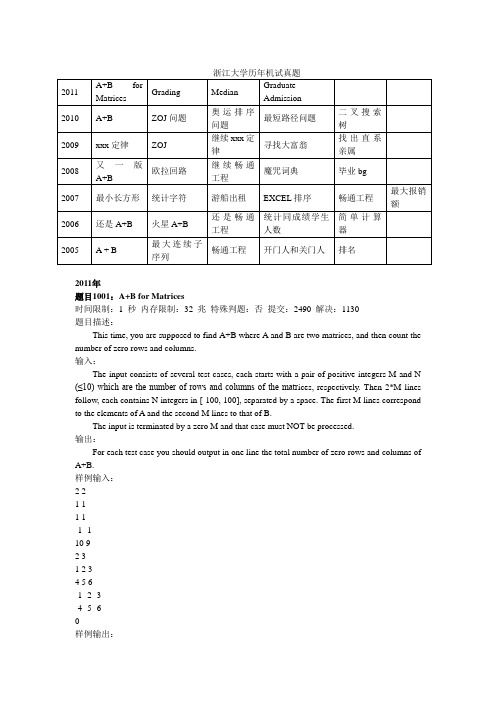
浙江大学历年机试真题2011 A+B forMatricesGrading MedianGraduateAdmission2010 A+B ZOJ问题奥运排序问题最短路径问题二叉搜索树2009 xxx定律ZOJ 继续xxx定律寻找大富翁找出直系亲属2008 又一版A+B欧拉回路继续畅通工程魔咒词典毕业bg2007 最小长方形统计字符游船出租EXCEL排序畅通工程最大报销额2006 还是A+B 火星A+B 还是畅通工程统计同成绩学生人数简单计算器2005 A + B 最大连续子序列畅通工程开门人和关门人排名2011年题目1001:A+B for Matrices时间限制:1 秒内存限制:32 兆特殊判题:否提交:2490 解决:1130题目描述:This time, you are supposed to find A+B where A and B are two matrices, and then count the number of zero rows and columns.输入:The input consists of several test cases, each starts with a pair of positive integers M and N (≤10) which are the number of rows and columns of the matr ices, respectively. Then 2*M lines follow, each contains N integers in [-100, 100], separated by a space. The first M lines correspond to the elements of A and the second M lines to that of B.The input is terminated by a zero M and that case must NOT be processed.输出:For each test case you should output in one line the total number of zero rows and columns of A+B.样例输入:2 21 11 1-1 -110 92 31 2 34 5 6-1 -2 -3-4 -5 -6样例输出:15题目1002:Grading题目描述:Grading hundreds of thousands of Graduate Entrance Exams is a hard work. It is even harder to design a process to make the results as fair as possible. One way is to assign each exam problem to 3 independent experts. If they do not agree to each other, a judge is invited to make the final decision. Now you are asked to write a program to help this process.For each problem, there is a full-mark P and a tolerance T(<P) given. The grading rules are: • A problem will first be assigned to 2 experts, to obtain G1 and G2. If the differenc e is within the tolerance, that is, if |G1 - G2| ≤ T, this problem's grade will be the average of G1 and G2.• If the difference exceeds T, the 3rd expert will give G3.• If G3 is within the tolerance with either G1 or G2, but NOT both, then this p roblem's grade will be the average of G3 and the closest grade.• If G3 is within the tolerance with both G1 and G2, then this problem's grade will be the maximum of the three grades.• If G3 is within the tolerance with neither G1 nor G2, a judge will give the final grade GJ.输入:Each input file may contain more than one test case.Each case occupies a line containing six positive integers: P, T, G1, G2, G3, and GJ, as described in the problem. It is guaranteed that all the grades are valid, that is, in the interval [0, P]. 输出:For each test case you should output the final grade of the problem in a line. The answer must be accurate to 1 decimal place.样例输入:20 2 15 13 10 18样例输出:14.0题目1004:Median题目描述:Given an increasing sequence S of N integers, the median is the number at the middle position. For example, the median of S1={11, 12, 13, 14} is 12, and the median of S2={9, 10, 15, 16, 17} is 15. The median of two sequences is defined to be the median of the non-decreasing sequence which contains all the elements of both sequences. For example, the median of S1 and S2 is 13.Given two increasing sequences of integers, you are asked to find their median.输入:Each input file may contain more than one test case.Each case occupies 2 lines, each gives the information of a sequence. For each sequence, the first positive integer N (≤1000000) is the size of that sequence. Then N integers follow, separated by a space.It is guaranteed that all the integers are in the range of long int.输出:For each test case you should output the median of the two given sequences in a line.样例输入:4 11 12 13 145 9 10 15 16 17样例输出:13题目1005:Graduate Admission题目描述:It is said that in 2011, there are about 100 graduate schools ready to proceed over 40,000 applications in Zhejiang Province. It would help a lot if you could write a program to automate the admission procedure.Each applicant will have to provide two grades: the national entrance exam grade GE, and the interview grade GI. The final grade of an applicant is (GE + GI) / 2. The admission rules are: • The applicants are ranked according to their final grades, and will be admitted one by one from the top of the rank list.• If there is a tied final grade, the applica nts will be ranked according to their national entrance exam grade GE. If still tied, their ranks must be the same.• Each applicant may have K choices and the admission will be done according to his/her choices: if according to the rank list, it is one's turn to be admitted; and if the quota of one's most preferred shcool is not exceeded, then one will be admitted to this school, or one's other choices will be considered one by one in order. If one gets rejected by all of preferred schools, then this unfortunate applicant will be rejected.• If there is a tied rank, and if the corresponding applicants are applying to the same school, then that school must admit all the applicants with the same rank, even if its quota will be exceeded.输入:Each input file may contain more than one test case.Each case starts with a line containing three positive integers: N (≤40,000), the total number of applicants; M (≤100), the total number of graduate schools; and K (≤5), the number of choices an applicant may have.In the next line, separated by a space, there are M positive integers. The i-th integer is the quota of the i-th graduate school respectively.Then N lines follow, each contains 2+K integers separated by a space. The first 2 integers are the applicant's GE and GI, respectively. The next K integers represent the preferred schools. For the sake of simplicity, we assume that the schools are numbered from 0 to M-1, and the applicants are numbered from 0 to N-1.输出:For each test case you should output the admission results for all the graduate schools. The results of each school must occupy a line, which contains the applicants' numbers that school admits. The numbers must be in increasing order and be separated by a space. There must be no extra space at the end of each line. If no applicant is admitted by a school, you must output anempty line correspondingly.样例输入:11 6 32 1 2 2 2 3100 100 0 1 260 60 2 3 5100 90 0 3 490 100 1 2 090 90 5 1 380 90 1 0 280 80 0 1 280 80 0 1 280 70 1 3 270 80 1 2 3100 100 0 2 4样例输出:0 1035 6 72 81 42010题目1003:A+B题目描述:给定两个整数A和B,其表示形式是:从个位开始,每三位数用逗号","隔开。
pta浙大版习题及答案

pta浙大版习题及答案PTA浙大版习题及答案近年来,计算机科学与技术专业的学生们纷纷加入了PTA(浙大版习题)的学习和竞赛中。
PTA作为一种在线编程练习平台,为学生们提供了一个锻炼编程能力的机会。
它的题库涵盖了各个难度级别的题目,从简单的基础题到复杂的高级题,适合不同水平的学生。
在这篇文章中,我们将探讨PTA浙大版习题及答案的一些特点和应用。
首先,PTA浙大版习题的题目设计非常贴近实际编程场景。
这些题目通常模拟了真实的问题,要求学生们运用所学的算法和数据结构知识来解决。
这样的设计使学生们能够更好地理解和应用所学的知识,培养他们的实际编程能力。
其次,PTA浙大版习题的题目涵盖了多个知识点和技能。
学生们在解题过程中需要灵活运用不同的算法和数据结构,如排序算法、图算法、动态规划等。
同时,PTA还提供了一些常见的编程题目,如字符串处理、数组操作等,帮助学生们巩固基础知识和编程技巧。
此外,PTA浙大版习题还提供了详细的答案和解析。
对于每个题目,学生们可以在提交答案后立即得到反馈,包括对答案的正确性进行评估和解析。
这种及时的反馈对于学生们的学习和提高非常有帮助,他们可以根据反馈及时调整自己的学习方法和思路。
对于学生们来说,PTA浙大版习题的学习和竞赛有着多重好处。
首先,通过解题,学生们可以提高自己的编程能力和解决问题的能力。
这对于他们未来的学习和工作都非常重要。
其次,PTA浙大版习题的竞赛形式可以激发学生们的学习兴趣和竞争意识。
在竞赛中,学生们可以与其他同学进行切磋和比拼,相互促进,共同进步。
此外,PTA浙大版习题还提供了一些奖励机制,激励学生们更加努力地学习和参与竞赛。
然而,PTA浙大版习题也存在一些挑战和问题。
首先,由于题目的难度较高,有些学生可能会感到挫败和失望。
他们可能会遇到一些困难,无法解决某些题目。
这时,他们需要保持积极的心态,不断学习和尝试,相信自己能够克服困难。
其次,PTA浙大版习题的学习和竞赛需要较长的时间和精力投入。
大学计算机基础(浙江大学)题库

大学计算机基础(浙江大学)题库测试试卷:计科教材练习【01】--------------------------------------------------------------------------------一、判断题,共10题, 总分:10分。
请直接点击选择True or False.1.计算机文化是指能够理解计算机是什么以及它是如何作为资源被使用的。
( T ) True False2.计算思维的本质是对求解问题的抽象和实现问题处理的自动化。
如果说,数学思维是“抽象和关系”,那么计算思维则是“状态和过程”。
( T ) True False3.我们可以定义计算机系统是指计算机的所有资源。
它包括了计算机硬件和软件。
( T ) True False4.计算机系统结构是研究计算机的硬件互联使得计算机更有效、更高速和更可靠。
( T ) True False5.应用软件是管理计算机所需要的那些软件。
( F ) True False6.程序设计主要有面向文本设计技术和面向对象设计技术。
( F ) True False7.程序是算法的具体实现。
( T ) True False8.计算机被加电后进入工作状态,就开始执行程序,直到关机为止。
( T ) True False9.因特网的开放结构,主要表现在进入网络的机器,属于企业、机构、政府甚至个人的,它们之间的关系是平等地位,没有权限的定义。
( T ) True False10.因特网是一个庞大的计算机互联形成的网络,构建因特网的主要目的是实现各种通信。
( F ) True False--------------------------------------------------------------------------------二、单选题,共11题, 总分:11分。
请四个中选择一个是正确的答案。
1.半导体技术是按一个较高的指数规律发展的。
大学计算机基础(浙江大学)题库

测试试卷:计科教材练习【01】--------------------------------------------------------------------------------一、判断题,共10题, 总分:10分。
请直接点击选择True or False.1.计算机文化是指能够理解计算机是什么以及它是如何作为资源被使用的。
( T ) True False2.计算思维的本质是对求解问题的抽象和实现问题处理的自动化。
如果说,数学思维是“抽象和关系”,那么计算思维则是“状态和过程”。
( T ) True False3.我们可以定义计算机系统是指计算机的所有资源。
它包括了计算机硬件和软件。
( T ) True False4.计算机系统结构是研究计算机的硬件互联使得计算机更有效、更高速和更可靠。
( T ) True False5.应用软件是管理计算机所需要的那些软件。
( F ) True False6.程序设计主要有面向文本设计技术和面向对象设计技术。
( F ) True False7.程序是算法的具体实现。
( T ) True False8.计算机被加电后进入工作状态,就开始执行程序,直到关机为止。
( T ) True False9.因特网的开放结构,主要表现在进入网络的机器,属于企业、机构、政府甚至个人的,它们之间的关系是平等地位,没有权限的定义。
( T ) True False10.因特网是一个庞大的计算机互联形成的网络,构建因特网的主要目的是实现各种通信。
( F ) True False--------------------------------------------------------------------------------二、单选题,共11题, 总分:11分。
请四个中选择一个是正确的答案。
1.半导体技术是按一个较高的指数规律发展的。
根据摩尔定律,当价格不变时,集成电路上可容纳的晶体管数目,约每隔( D )个月便会增加一倍,性能也将提升一倍。
大学计算机基础课后答案(浙大版)

dj dj《计算机科学基础》习题解答第一章一.填空题1.处理处理2.黑盒程序3.输入输出存储运算控制4.运算器控制器中央处理器5.存储器数据6.硬件软件7.电子管晶体管集成电路超大规模集成电路8.处理器子系统存储器子系统输入输出子系统9.输入输出键盘显示器10.更有效更可靠更高速11.过程对象12.图形用户接口13.程序操作系统14.硬件软件数据/信息过程通信15.因特网开放16.Web 万维网超文本置标17.音频动画图片18.资源19.抽象自动化20.计算思维二.选择题1.A2.A3.A4.B5.C6.A7.D8.C9.D10.C11.A12.C13.B14.C15.D16.C 17.D 18.C 19.B 20.C 21.B第二章一.填空题1.进位进制2.十八十六3.补码浮点数整小4.规则ASCII Unicode 特征5.位图矢量6.采样量化7.逻辑或逻辑非异或基本逻辑电路8.与关系或关系非关系9.逻辑函数二值函数10.Ture(1)False(0)11.逻辑函数逻辑变量12.低位半加器13.触发器二.选择题1.B 2.C 3.B 4.A 5.A6.C 7.C 8.C 9.A 10.D11.B 12.B 13.D 14.A 15.B16.C 17.D 18.A 19.D 20.C21.D 22.C 23.C 24.C 25.B26.C 27.C三.综合题4.1100 10001 1110 10000000000 0.01 111.001 10.1017.10 55 93 0.625 0.3125 0.8125 2.25 10.1259.233.1548 9B.3616 1252.1448 2AA.321610.111101.11000101 11001001010.112.原码反码补码0.110010.110010.110010.11001-0.110011.110011.001101.001110.111110.111110.111110.11111-0.111111.111111.000001.0000115.阶码7位,含符号位,因此阶码的最大表示范围为+(25-1)~-2-5,即该浮点数最大表示范围是-2-32~+231第三章一.填空题1.输入输出2.CPU 端口3.4.运算器控制器运算器控制电路数据寄存器5.算术逻辑部件与或非6.数据总线地址总线控制总线7.主频字长缓存8.复杂指令集计算机精简指令集计算机9.存储单元存储单元地址10.存储单元32×102411.随机存储器只读存储器DRAM EPROM EEPROM12.电缆磁道扇区SATA13.CD-R/W CD-R DVD14.固态15.数据外存(磁盘)内存(主存)数据外存(磁盘)16.缓存虚拟17.键盘/鼠标器串/ 并口USB 音频口游戏口18.CRT LCD 像素显示卡(显卡)每英寸点数激光针式3 4 19.笔记本电脑通用串行总线127二.选择题1.D2.B3.C4.A5.BA7.B8.C9.D10.C11.A12.B13.C14.C15.B第四章一.填空题1.接口硬件资源2.实时系统单用户单任务多用户多任务3.多多个4.IOS Windows Mobile SymbianOS Android 5.内核Shell6.进程管理存储器管理设备管理文件管理7.程序作业进程8.外存内存9.块设备驱动10.硬件时钟软件时钟11.注册表程序regedit F5键.COM 文本视频13.文件分配表NTFS 二.选择题1.D2.C3.D4.D5.B6.D7.C8.D9.D10.B11.B12.C13.A14.B15.C16.A17.D第五章一.选择题1.D2.3.C 4.D 5.B 6.C 7.B 8.B 9.C 10.D 11.B 12.B 13.B 14.A 15.D 16.A 17.A 18.B 19.C 20.D 21.A 22.A 23.D 24.第六章一.填空题1.操作使用2.算法算法3.指令4.数据传输运算5.操作码地址下一条指令的地址6.机器语言程序7.汇编语言源程序8.过程对象过程9.C PASCAL C++ Java10.封装继承多态11.属性行为12.HTML XML13.源程序目标程序14.逐句一次性整体15.算法错误16.运算对象17.变量常量18.符号常量19.构造数据类型下标20.赋值语句复合语句返回语句21.算术运算22.常量变量23.函数24.Switch25.While for for26.Do…while27.设计方案编码运行维护28.黑盒白盒29.瀑布螺旋30.使用二.选择题1.D2.C3.C4.B5.A6.B7.C8.C9.C10.D11.D12.C13.C14.C15.A16.A17.A18.A19.A20.B第七章一.选择题1.B2.A3.C4.B5.C6.B7.D8.C9.D10.A11.B12.C13.BB15.A16.B17.C18.D19.B20.C第八章一.选择题1.D2.D3.C4.B5.B6.C7.B8.D9.D10.D11.D12.A13.A14.BA16.A C D F 17.A C D 18.C19.D20.D21.D22.B23.D24.D25.A26.D27.D28.D29.B30.C31.B32.D33.D34.B35.D36.C二.是非题1.×2.×3.×4.√5.×6.√7.×8.×9.√10.√11.√12.√13.√14.√15.√16.×17.√18.√19.×20.√21.√22.23.√24.√25.×26.√27.×28.×29.×30.×31.×32.√33.×34.×35.×36.×37.×38.√39.×40.×41.√第九章一.选择题1.C2.3.C4.D5.C6.A7.D8.A9.C10.B11.A12.C13.B14.A15.B16.A17.D18.B19.A20.B第十章一.单选题1.D2.D3.4.C5.D6.B7.C二.多选题1.A B C2.A B D3.A E I J4.B D 三.是非题1.√2.√3.×4.×5.×6.√7.√8.√9.×10.×11.×12.√13.。
浙江大学数据结构与算法课程自我测试

窗体顶端1. 邻接表是图的一种—。
X正确答案点评厂A顺序存储结构C B链式存储结构C C索引存储结构C D散列存储结构止确答案:B答案讲解:无【试题出处】第6章第3节1窗体底端窗体顶端2. 一组记录的关键字为(46,79,56,38,40,84),则利用快速排序的方法,以第一个记录为基准元素得到的一次划分结果为。
X正确答案点评厂 A 3&40,46,56,79,84f B 40,38,46,79,56,84C C 40,38,46,56,79,84C D 40,38,46,84,56,79止确答案:C窗体底端窗体顶端3. 设深度为h的二叉树上只有度为0和度为2的结点,则此类二叉树中所包含的结点数至多为____ (注意C和D中h是指数)。
X正确答案点评厂 A 2h-lf B 2(h-l)C C2*h-1D2*h窗体底端窗体顶端4. 一个栈的入栈序列是a,b,c,d,则下列序列中不可能的输出序列是X正确答案点评「A acbdB dcba「C acdb「D dbac正确答案:D窗体底端窗体顶端5. 计算机算法是指 _____ oX正确答案点评「A计算方法''B排序方法C C调度方法C D解决问题的有限运算序列正确答案:D窗体底端窗体顶端6. 关于二叉树的三种遍历,下列说法正确的是—。
X正确答案点评C A任意两种遍历序列都不可以唯一决定该二叉树B任意两种遍历序列都可以唯一决定该二叉树C C先序遍历序列和后序遍历序列可以唯一决定该二叉树厂D先序遍历序列和中序遍历序列可以唯一决定该二叉树正确答案:D窗体底端窗体顶端7. 顺序表的特点是 _____ 。
r A逻辑上相邻的结点其物理位置不相邻C B逻辑上相邻的结点其物理位置亦相邻C C顺序表不是随机存储结构厂D在顺序表中插入和删除操作比在链表上方便正确答案:B窗体底端窗体顶端8. 设散列表长为14,散列函数是H(key)=key%ll,表中已有数据的关键字为15, 3& 61, 84共四个,现要将关键字为49的结点加到表中,用二次探测法解决冲突,则放入的位置是X正确答案点评C A8「B 3「C5C D9正确答案:D窗体底端窗体顶端9. 对顺序存储的线性表,设其长度为n,且在任何位置上插入或删除操作都是等概率的。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
F.源程序
G.算法错误
H.对部分程序
窗体底端
A.数量一致 B.类型一致 C.顺序一致 D.以上都是
11.不管循环条件是否满足循环执行的要求,循环体至少被执行一次的语句是(B )。
A.while
B.do/while
C. for
D.以上都是
12.常量有两种,一种是符号常量,一种是(C )。
A.标识符 B.数据类型 C.文字常量 D.数学常量
13.在计算机高级语言中,可以使用诸如a=a+b这种表达式,其中a、b为变量。这里变量的含义是(C )。
D.常量调用和变量调用
16.程序设计过程,包括了问题的定义、设计方案、(A )、文档以及运行维护等六个步骤。
A.编码和测试 B.语言和算法 C.过程和函数 D.函数或方法
17.软件开发过程使用工程管理的方法,通常有各种开发模型,例如(A )。
A.瀑布模型和增量模型
B.瀑布模型和数学模型
C.RAD模型和数学模型
5.面向对象的程序设计具有(A )特点。
A.封装、继承、多态
B.顺序、循环和分支
C.多分支、循环和函数
D.函数、方法和过程
6.高级语言的基本数据类型是(D )。
A.变量、常量、标识符
B.顺序、循环符
7.程序设计中常用的运算类型有算术、逻辑和(C )
A.移位 B.复合 C.关系 D.对象
窗体顶端
测试试卷:计科教材练习【06】
一、判断题,共5题, 总分:5分。请直接点击选择True or False.
1.测试是寻找程序中的错误,常用的方法有黑盒测试和白盒测试。(T ) True False
2.Java程序是汇编语言程序。(F ) True False
3.一个CPU所执行的全部指令就是指令系统。(T ) True False
4.机器语言编写的程序能被计算机直接执行。(T ) True False
5.LISP不是函数型语言。(F ) True False
二、单选题,共18题, 总分:18分。请四个中选择一个是正确的答案。
1.不需要了解计算机内部构造的语言是(D )。
A.机器语言
B.汇编语言
C.操作系统
D.高级程序设计语言
A.使用说明书
B.与程序相关的所有文件
C.算法
D.全部
E.高级语句
F.算术
G.有序
H.测试记录
2.用汇编语言编写的程序叫做“(D)”,是面向计算机硬件的程序。用于网页编程的语言是“(C)”,在不同系统之间进行转换的语言是“(F)”。
A.Java
B.C
C.HTML
D.汇编程序
E.机器语言程序
F.XML
D.螺旋模型和数学模型
18.软件的生命周期是指软件从开发到使用到(B )的全过程。
A.销售出去 B.不再使用 C.更多的使用 D.重新开发
三、选择性填空题,共3题, 总分:9分。先点击要填写的位置,再选择一个正确的答案。
1.软件是程序加上该程序的文档。文档是指该软件的“(B)”。程序是“(C)”的具体实现。按照定义,程序是一组计算机指令的“(G)”集合。
2.能够把由高级语言编写的源程序翻译成目标程序文件的系统软件叫(C )。
A.解释程序 B.汇编程序 C.编译程序 D.编码程序
3.(C )不属于结构化程序设计的控制成分。
A.顺序结构 B.循环结构 C.GOTO结构 D.选择结构
4.一个指令代码通过助记符号表示的语言叫做(D )。
A.目标语言 B.中级语言 C.机器语言 D.汇编语言
8.HTML语言是属于(C )
A.面向过程 B.面向对象 C.网页编程 D.文字处理
9.通常,for循环语言用于循环次数(C )的程序中。
A.由循环体决定
B. 在循环体外决定
C.确定
D.不确定
10.函数或方法是一段独立的程序代码,也是可以被程序设计者调用的。调用函数或方法时,如果需要在形式参数和实际参数之间做到(D )。
A.数学变量 B.标识符 C.内存位置 D.数据类型
14.分支语句有多种名字,例如选择语句、条件语句,以下(C )也是分支语句的一种说法。
A.转移语句 B.复合语言 C. 判断语句 D.返回语句
15.程序设计中,调用过程的参数传递有两种:(A )
A.值调用和引用调用
B.参数调用和无参调用
C.过程调用和函数调用
G.Python
H.Lisp
3.解释程序对源代码中的程序进行“(A)”翻译,翻译过程和执行过程同时进行。而编译程序对源程序是“(E)”翻译为目标程序,产生可执行文件。编译系统能发现不合法的语句和表达,但是,如果是“(G)”,则不能被发现,这是属于逻辑问题。
A.逐句
B.语法错误
C.优化错误
D.词法错误
