计算机网络概论 英文版
计算机网络(第四版)英文原版1.1 Uses of Computer Networks

1.1.1 Business Applications
Many companies have a substantial number of computers. For example, a company may have separate computers to monitor production, keep track of inventories, and do the payroll. Initially, each of these computers may have worked in isolation from the others, but at some point, management may have decided to connect them to be able to extract and correlate information about the entire company.
专业计算机网络简介英语作文

专业计算机网络简介英语作文English:Computer networks are an essential part of our modern world, enabling communication and data transfer between devices and users across the globe. As a professional field, computer networking involves the design, implementation, and management of networks, including local area networks (LANs), wide area networks (WANs), and the internet. This field encompasses a range of technologies and protocols, including Ethernet, TCP/IP, wireless networking, and network security. Professionals in this field work to ensure efficient and secure communication between devices, as well as the availability and reliability of network resources. Computer networking also plays a crucial role in supporting various industries and applications, such as e-commerce, telecommunication, online services, and cloud computing. The demand for skilled network professionals continues to grow as our reliance on technology and connectivity increases, making computer networking a valuable and dynamic field of study and practice.Translated content:计算机网络是我们现代世界的必要组成部分,它使得设备和用户在全球范围内能够进行通信和数据传输。
计算机网络基础知识ppt课件 英文版

sketch map
Main function: to achieve the communication and resource sharing1. Basic function: data communication Main features: resource sharing
data
Classification: wide area network (WAN):Tens to thousands of kilometers local area network (ALN) A few meters to a few kilometers metropolitan area network(MAN) (Between WAN and LAN)
1.2
The basis of computertion -- in the form of an electrical signal to the data transmitted from one end to the other end. 2、 The m ai n technol ogy -- "t he maxi m um transmission rate index of data communication" 3、Modulation, demodulation (Modem): converting the data signals and analog signals.
批注本地保存成功开通会员云端永久保存去开通
What is a computer network
? ?
The computer network is the computer system in different geographical location and function of independent by communication lines are interconnected, the system realizes the sharing and communication of cyber source in the network management software
计算机网络英文教材ppt第二章

Chapter 2 The Physical Layer
30
2.5.3 The Local Loop: Modems, ADSL, and Wireless
Figure 2-23. The use of both analog and digital transmission for a computer to computer call. Conversion is done by the modems and codecs.
3
Chapter 2 The Physical Layer
DTE
DCE
传输介质 DCE
DTE
用户环境
通信系统
Chapter 2 The Physical Layer
用户环境
4
Chapter 2 The Physical Layer
DTE: Equipment that hopes to connect the network. Such as computer, terminal, etc.
2
Chapter 2 The Physical Layer
The definition of physical layer:
the interface between DTE(Data
Terminal Equipment) and
DCE(Data Communications
Equipment)
Chapter 2 The Physical Layer
Chapter 2 The Physical Layer
27
2.5.1 Structure of the Telephone System
(a) Fully-interconnected network. (b) Centralized switch. (c) Two-level hierarchy.
全套英文版《计算机网络》电子课件教案-part i introduction
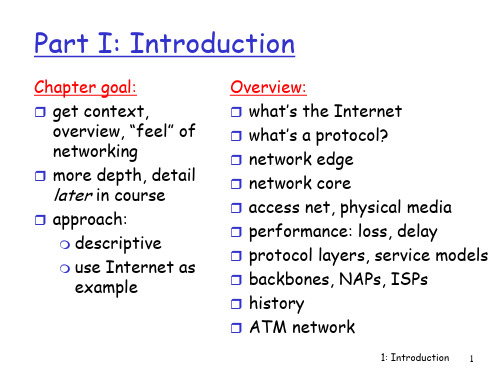
Overview: what’s the Internet what’s a protocol? network edge network rmance: loss, delay protocol layers, service models backbones, NAPs, ISPs history ATM network
1: Introduction 7
The network edge:
end systems (hosts):
run application programs e.g., WWW, email at “edge of network”
client/server model
client host requests, receives service from server
protocols define format, order of msgs sent and received among network entities, and actions taken on msg transmission, receipt
1: Introduction 5
What’s a protocol?
router server
local ISP
workstation mobile
regional ISP
company network
1: Introduction 3
What’s the Internet: a service view
communication
infrastructure enables
Internet: “network of
networks”
loosely hierarchical
计算机网络英文版课件1
Development of computer network
T
T
HOST
T
T
T
T
T
HOST
TTT
T
T
HOST CCP
T
T
H
T
T
C
CCP
T
HOST
T
T
CCP
C CommunicaCt
T
HOST
T T
ion subnet
H
H
T
T
T
T
Resource subnet
T
computer network vs. distributed system
Wide Area Networks(2)
❖A stream of packets from sender to receiver. ❖Store-and-forward (packet-switched): a packet
is stored in an intermediate router in its entirety, stored there until the required output line is free, and then forwarded.
❖ Software: This is what actually makes computer networks–not the hardware!
➢ Protocols: describe how two communicating parties exchange
information.
➢ Services: describe what a network offers to parties that want
计算机网络基础知识课件英文版

Discover the world of computer networks, from their definition and significance to their classification and protocols. Explore the fascinating concepts of OSI and TCP/IP models, network topologies, devices, security, performance optimization, applications, and management.
Network Performance Optimization
Data Transmission Rate
Learn about factors that influence transmission speeds, such as bandwidth, latency, and throughput.
Star
A network topology where devices are connected to a central hub or switch.
Ring
A network topology where devices are connected in a circular manner, forming a
Reducing Latency
Discover techniques to minimize latency, ensuring faster response times and smoother network performance.
Increasing Bandwidth
计算机网络(第四版)英文原版1.9 Summary

A factor in the delay of a store-and-forward packet-switching system is how long it takes to store and forward a packet through a switch. If switching time is 10 μsec, is this likely to be a major factor in the response of a client-server system where the client is in New York and the server is in California? Assume the propagation speed in copper and fiber to be 2/3 the speed of light in vacuum.
Well-known networks include the Internet, ATM networks, Ethernet, and the IEEE 802.11 wireless LAN. The Internet evolved from the ARPANET, to which other networks were added to form an internetwork. The present Internet is actually a collection of many thousands of networks, rather than a single network. What characterizes it is the use of the TCP/IP protocol stack throughout. ATM is widely used inside the telephone system for long-haul data traffic. Ethernet is the most popular LAN and is present in most large companies and universities. Finally, wireless LANs at surprisingly high speeds (up to 54 Mbps) are beginning to be widely deployed.
计算机网络简介英语作文

计算机网络简介英语作文Introduction to Computer Networks.In today's world, computer networks have become an integral part of our lives, connecting people, devices, and information across vast distances. These networks enable seamless communication, information sharing, and collaboration, powering everything from personal email to global businesses and research institutions.1. Definition of Computer Networks.Computer networks are interconnected collections of devices that can exchange data and share resources. These devices can range from personal computers and laptops to servers, routers, switches, and even mobile phones and tablets. Networks can be classified based on their size, topology, and purpose.2. Types of Computer Networks.Local Area Networks (LANs): These are networks that cover a small geographical area, such as an office building or a school campus. LANs typically connect computers and devices within a close proximity, enabling fast andefficient data transfer.Wide Area Networks (WANs): WANs span a much larger geographical area, connecting LANs or other networks across cities, states, or even countries. The internet is an example of a global WAN.Metropolitan Area Networks (MANs): These networkscover a geographical area larger than a LAN but smallerthan a WAN, typically connecting multiple buildings or locations within a city or metropolitan region.Personal Area Networks (PANs): PANs connect devices within a personal space, such as a room or on a person's body. They are commonly used for wireless communication between devices like smartphones, headphones, and wearables.3. Components of Computer Networks.Hardware: This includes devices like computers, routers, switches, servers, and cables that form the physical infrastructure of the network.Software: Network software manages and controls the flow of data, enabling devices to communicate with each other effectively.Protocols: Protocols define the rules and formats for data communication on the network. They ensure that devices can understand and interpret the information being transmitted.4. Functions of Computer Networks.Data Communication: Networks enable the transmission of data between devices, allowing users to send and receive emails, access websites, or share files.Resource Sharing: Networks allow devices to access andshare resources like printers, scanners, and servers.Distributed Processing: By dividing tasks between multiple devices, networks can improve processing speed and efficiency.Information Retrieval: Networks provide access to vast repositories of information, enabling users to search and retrieve information from various sources.5. Technologies Used in Computer Networks.Wired vs. Wireless: Networks can be wired, using cables to connect devices, or wireless, using radio waves for communication. Wireless networks, such as Wi-Fi and Bluetooth, provide greater flexibility and convenience.Networking Protocols: Protocols like TCP/IP, HTTP, SMTP, and FTP govern how devices communicate with each other on the network.Networking Hardware: Routers, switches, servers, andfirewalls are essential hardware components that enable network connectivity, manage traffic, and provide security.6. Security Considerations in Computer Networks.With the increasing interconnectedness of computer networks, security has become a paramount concern. Measures like firewalls, antivirus software, and encryption techniques are used to protect networks from unauthorized access, data breaches, and malicious attacks.Conclusion.Computer networks have revolutionized the way we live and work, connecting people and resources across the globe. Understanding the basics of computer networks is crucial in today's interconnected world, as it enables us to leverage their power and address the challenges posed by ever-evolving technologies and security threats.。
计算机网络第五版(英文版)
• Co-operator: EPFL • 正申请上海市科委项目
This is a Bilingual Course
• Why we give this bilingual course?
– To meet the needs of excellent engineer training program and internationalization
– Final exam (40%), middle exam (20%), experiments (20%), reports/problems (10%), and others (10%) – After study Chapter 4, there will be mid-term exam
– Deployment Models
• • • • Private Cloud Community Cloud Public Cloud Hybrid Cloud
Source: Wikipedia
1.2 Uses of Computer Networks (5)
• Client-server module
Source: David Lazer et al., “Computational Social Science”, SCIENCE, 323, 721-724 (2009)
Exploring Study (1)
1. Use complex network theory and dynamics of human behavior (DHB) to analyze social networks and optimize social networking service (SNS). 2. Research on opinion evolution and interference model on Internet, specially on social networking service (SNS).
计算机网络(第四版)英文原版1.7MetricUnits

计算机网络(第四版)英文原版1.7MetricUnits [ Team LiB ]1.7 Metric UnitsTo avoid any confusion, it is worth stating explicitly that in this book, as in computer science in general, metric units are used instead of traditional English units (the furlong-stone-fortnight system). The principal metric prefixes are listed in Fig. 1-39. The prefixes are typically abbreviated by their first letters, with the units greater than 1 capitalized (KB, MB, etc.). One exception (for historical reasons) is kbps for kilobits/sec. Thus, a 1-Mbps communication line transmits 106 bits/sec and a 100 psec (or 100 ps) clock ticks every 10-10 seconds. Since milli and micro both begin with the letter ''m,'' a choice had to be made. Normally, ''m'' is for milli and ''μ'' (the Greek letter mu) is for micro.Figure 1-39. The principal metric prefixes.It is also worth pointing out that for measuring memory, disk, file, and database sizes, in common industry practice, the units have slightly different meanings. There, kilo means 210 (1024) rather than 103 (1000) because memories are always a power of two. Thus, a 1-KB memory contains 1024 bytes, not 1000 bytes. Similarly, a 1-MB memory contains 220 (1,048,576) bytes, a 1-GB memory contains 230 (1,073,741,824) bytes, and a 1-TB database contains 240 (1,099,511,627,776) bytes. However, a 1-kbps communication line transmits 1000 bits per second and a 10-Mbps LAN runs at 10,000,000 bits/sec because these speeds are not powers of two. Unfortunately, many people tend to mix upthese two systems, especially for disk sizes. To avoid ambiguity, in this book, we will use the symbols KB, MB, and GB for 210, 220, and 230 bytes, respectively, and the symbols kbps, Mbps, and Gbps for 103, 106, and 109 bits/sec, respectively.[ Team LiB ]。
计算机网络(第四版)英文原版1.2 Network Hardware

Broadcast networks have a single communication channel that is shared by all the machines on the network. Short messages, called packets in certain contexts, sent by any machine are received by all the others. An address field within the packet specifies the intended recipient. Upon receiving a packet, a machine checks the address field. If the packet is intended for the receiving machine, that machine processes the packet; if the packet is intended for some other machine, it is just ignored.
计算机网络英文版课件-第2章 The Physical Layer

Amplitude Amplitude
••• Time
f
3f
9f
Frequency
b. Frequency-domain decomposition of the composite signal
Computer Networks, Chapter 2 The Physical Layer
18
Time and frequency domain of a nonperiodic composite signal
Computer Networks, Chapter 2 The Physical Layer
6
Units of period and frequency
Computer Networks, Chapter 2 The Physical Layer
7
Simplex, half-duplex, or full-duTransmission
• The timing of a signal is unimportant. • Information is received and translated by agreed upon patterns.
Computer Networks, Chapter 2 The Physical Layer
Computer Networks, Chapter 2 The Physical Layer
3
Type of Data
计算机网络英文课件:1-2 Introduction

Computer Networks -1-Part 2
4
The Data Link Layer
• Data link layer is to transform a raw transmission facility into a line that appears free of undetected transmission errors to the network layer
Add a checksum (cyclic redundancy check) that should match the bits before it
Also: Provide the mechanisms so that fast senders don’t overwhelm slow receivers (flow control)
2020/12/7
Computer Networks -1-Part 2
5
Data Link Layer
• Observation: We also need to specify how a number of computers can share a common channel (e.g. wire), that is medium access control sublayer (MAC):
– How many nanoseconds a bit lasts
– whether transmission may proceed simultaneously in both directions
– how the initial connection is established
– how it is torn down when both sides are finished
计算机网络英文课件

Resource sharing, high reliability, saving money Powerful communication medium(electronic mail, videoconference) e-commerce (electronic commerce)
Introduction and Overview
Uses of Computer Networks Mobile Users
Mobile computers, such as notebook computers and personal digital assistants (PDAs), are one of the fastest-growing segments of the computer industry. merger of cell phones and PDAs into tiny wireless computers, WAP (Wireless Application Protocol) portable office wireless networks on campus wireless networks on military Privacy Freedom of speech Copyright ……
Two computers are said to be interconnected if they are able to exchange information. The connection need not be via a copper wire; fiber optics, microwaves, infrared, and communication satellites can also be used. Networks come in many sizes, shapes and forms.
计算机网络英语课件(第一章)

The Important Concepts (9)
Network. Two or more computers linked by communication lines. 网络:用一些通信线路链接起来两个或更多的计算机。 Noise. In data communication,electronic interference. 噪音:在数据通信中的电子干扰。 Polling. Asking a series of terminals,or checking a series of buffers,one by one,to see if they have data to transmit. A technique for determining who gets to transmit data next. 查询:逐个地询问一组终端或检查一组缓冲寄存器,看看它们 是否有数据要发送。一种确定下一个该谁发送数据的技术。
The Important Concepts (5)
Modem. An acronym for MOdulator— DEModulator. A de-vice that converts data from the computer’s internal digital form to analog wave form,and back again. Used to link computer equipment to a telephone line. 调制解调器:调制器和解调器的缩写词。一种能把 数据从计算机内部的数字量形式转换成模拟量形式, 并且还能转换回来的设备。该设备用于链接计算机 设备与电话线路。
The Important Concepts (2)
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
– However, understanding network protocols and technologies allows them to write efficient and reliable code that enables applications to scale across many sites
© 2009 Pearson Education Inc., Upper Saddle River, NJ. All rights reserved. 9
3.2.2 Message Transport in the Internet
• Message service does not make any guarantees • So messages may be
© 2009 Pearson Education Inc., Upper Saddle River, NJ. All rights reserved. 5
3.1 Introduction
• Internet application programmers can get started easily • It is possible to create Internet applications without knowing how networks operate
6
3.2 Two Basic Internet Communication Paradigms
• The Internet supports two basic communication paradigms:
– 3.2.1 Stream Transport in the Internet – 3.2.2 Message Transport in the Internet
– Lost (i.e., never delivered) – Duplicated (more than one copy arrives) – Delivered out-of-order
• A programmer who uses the message paradigm must insure that the application operates correctly
3.2.2 Message Transport in the Internet
• In a message paradigm, the network accepts and delivers messages • Each message delivered to a receiver corresponds to a message that was transmitted by a sender
– Multicast
• a message can be multicast to some of the computers on a network, 1-tomany
– Broadcast
• a message can be broadcast to all computers on a given network, 1-to-all
• Later parts of the text provide the necessary information by explaining data communications and protocols used to form the Internet
© 2009 Pearson Education Inc., Upper Saddle River, NJ. All rights reserved.
Chapter 3
Internet Applications and Network Programming
© 2009 Pearson Education Inc., Upper Saddle River, NJ. All rights reserved.
2
Topics Covered
• • • • • • • • • • • • • 3.1 Introduction 3.2 Two Basic Internet Communication Paradigms 3.3 Connection-Oriented Communication 3.4 The Client-Server Model of Interaction 3.5 Characteristics of Clients and Servers 3.6 Server Programs and Server-Class Computers 3.7 Requests, Responses, and Direction of Data Flow 3.8 Multiple Clients and Multiple Servers 3.9 Server Identification and Demultiplexing 3.10 Concurrent Servers 3.11 Circular Dependencies Among Servers 3.12 Peer-to-Peer Interactions 3.13 Network Programming and the Socket API
– the network never delivers part of a message, nor does it join multiple messages together – if a sender places exactly n bytes in an outgoing message, the receiver will find exactly n bytes in the incoming message
© 2009 Pearson Education Inc., Upper Saddle River, NJ. All rights reserved.
4
3.1 Introduction
• The Internet offers users a rich diversity of services
– none of the services is part of the underlying communication infrastructure
• Internet provides a general purpose mechanism on which
– all services are built – and individual services are supplied by application programs that run on computers attached to the Internet
• The message paradigm allows delivery in different forms:
– Unicast
• a message can be sent from an application on one computer directly to an application on another, 1-to-1
• It is possible to devise new services without changing the Internet • Chapter covers two key concepts of Internet applications:
– describes the conceptual paradigm that applications follow when they communicate over the Internet – presents the details of the socket Application Programming Interface (socket API) that Internet applications use
– the network can choose to combine smaller blocks into one large block or can divide a large block into smaller blocks
© 2009 Pearson Education Inc., Upper Saddle River, NJ. All rights reserved. 8
• Figure 3.1 summarizes the differences
