PLC英文文献
英文文献-可编程逻辑控制器(PLC)英语

Programmable Logic ControllersProgrammable logic controller (plc) is a solid-state device used to control machine motion or process operation by means of a stored program. The PLC sends output control signals and receives input signals through input/output (I/O) devices. A PLC controls outputs in response to stimuli at the inputs according to the logic prescribed by the stored program. The inputs are made up of limit switches, pushbuttons, thunbwheels. Switches, pulses, analog signals, ASCLL serial data, and binary or BCD data from absolute position encoders. The outputs are voltage or current levels to drive end devices such as solenoids, motor starters, relays, lights, and so on. Other output devices include analog devices, digital BCD displays, ASCII compatible devices, servo variable-speed drives, and even computers.Programmable controllers were developed (circa in 1968) when General Motors Corp, and other automobile manufacturers were experimenting to see if there might be an alternative to scrapping all their hardwired control panels of machine tools and other production equipment during a model changeover. This annual tradition was necessary because rewiring of the panels was more expensive than buying new ones.The automotive companies approached a number of control equipment manufacturers and asked them to develop a control system that would have a longer productive life without major rewiring, but would still be understandable to and repairable by plant personnel. The new product was named a “pr ogrammable controller”.The processor part of the PLC contains a central processing unit and memory。
(完整版)PLC英文文献

ONE、PLC overviewProgrammable controller is the first in the late 1960s in the United States, then called PLC programmable logic controller (Programmable Logic Controller) is used to replace relays。
For the implementation of the logical judgment, timing, sequence number, and other control functions. The concept is presented PLC General Motors Corporation. PLC and the basic design is the computer functional improvements,flexible, generic and other advantages and relay control system simple and easy to operate, such as the advantages of cheap prices combined controller hardware is standard and overall。
According to the practical application of target software in order to control the content of the user procedures memory controller, the controller and connecting the accused convenient target。
In the mid-1970s,the PLC has been widely used as a central processing unit microprocessor, import export module and the external circuits are used, large-scale integrated circuits even when the PLC is no longer the only logical (IC) judgment functions also have data processing, PID conditioning and data communications functions. International Electro technical Commission (IEC) standards promulgated programmable controller for programmable controller draft made the following definition : programmable controller is a digital electronic computers operating system, specifically for applications in the industrial design environment。
电气工程及其自动化专业_外文文献_英文文献_外文翻译_plc方面.
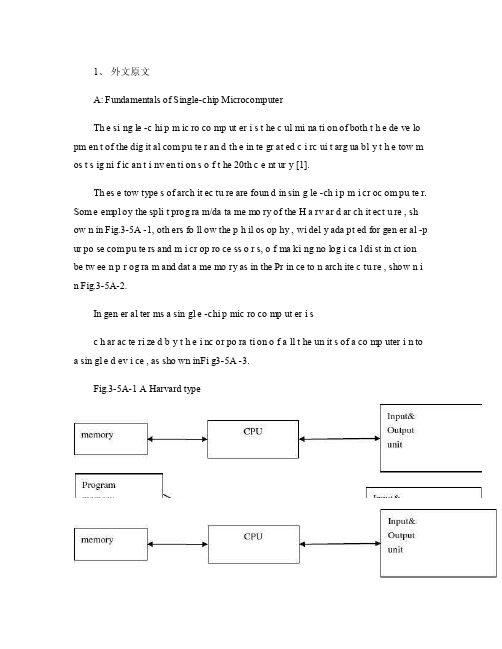
1、外文原文A: Fundamentals of Single-chip MicrocomputerTh e si ng le -c hi p m ic ro co mp ut er i s t he c ul mi na ti on of both t h e de ve lo pm en t of the dig it al com pu te r an d th e in te gr at ed c i rc ui t arg ua bl y t h e tow m os t s ig ni f ic an t i nv en ti on s o f t he 20th c e nt ur y [1].Th es e tow type s of arch it ec tu re are foun d in sin g le -ch i p m i cr oc om pu te r. Som e empl oy the spli t prog ra m/da ta me mo ry of the H a rv ar d ar ch it ect u re , sh ow n in Fig.3-5A -1, oth ers fo ll ow the p h il os op hy , wi del y ada pt ed for gen er al -p ur po se com pu te rs and m i cr op ro ce ss o r s, o f ma ki ng no log i ca l di st in ct ion be tw ee n p r og ra m and dat a me mo ry as in the Pr in ce to n arch ite c tu re , show n i n Fig.3-5A-2.In gen er al ter ms a sin gl e -chi p mic ro co mp ut er i sc h ar ac te ri zed b y t he i nc or po ra ti on of a ll t he un it s of a co mp uter i n to a sin gl e d ev i ce , as sho wn inFi g3-5A -3.Fig.3-5A-1 A Harvard typeFig.3-5A-2. A conventional Princeton computerFig3-5A-3. Principal features of a microcomputerRead only memory (ROM.R OM is usua ll y for the pe rm an ent,n o n-vo la ti le stor a ge of an app lic a ti on s pr og ra m .M an ym i cr oc om pu te rs and m are inte nd e d for high -v ol um e ap pl ic at ions a n d he nc e t h e eco n om ic al man uf act u re of th e de vic e s re qu ir es t h at t he cont en t s o f t he prog ra m me m or y be co mm it t ed perm a ne ntly d u ri ng the man ufa c tu re of ch ip s .Cl ea rl y, thi s im pl ie s a r i go ro us app ro ach to ROM cod e deve l op me nt sin ce cha ng es can not b e mad e afte r manu f a c tu re .Th is dev e lo pm en t proc ess may invo lv e e m ul at io n us in g aso ph is ti ca te d de ve lo pm en t sy ste m wit h a h a rd wa re emu la tio n cap ab il it y as w el l as the use o f po we rf ul s o ft wa re too ls.So me man uf act u re rs pro vi de add it io na l RO M opt i on s by i n cl ud in g in their ra n ge dev ic es wit h (or int en de d fo r use wit h u s er pro gr am ma ble me mo ry. Th e sim p le st of th es e is usu al ly d e vi ce whi ch can op er at e in a micro p ro ce ssor mod e by usi ng som e o f the inp ut /outp u t li ne s as an ad dr es s an d da ta b us fora c ce ss in g ex te rna l mem or y. Thi s t y pe of de vi ce can beh av ef u nc ti on al ly as th e sing le chip mi cr oc om pu te r from whi ch it is d e ri ve d al be it wit h re st ri ct ed I/O and a mod if ied ex te rn al c i rc ui t. The use of thes e d ev ic es is com mo n eve n in prod uc ti on c i rc ui ts wher e t he vo lu me does no tj us ti f y t h e d ev el o pm en t c osts o f c us to m o n -ch i p R OM [2];t he re c a n s ti ll bea s ignif i ca nt saving i n I /O and o th er c h ip s com pa re d to a conv en ti on al mi c ro pr oc es sor b a se d ci rc ui t. Mor e ex ac t re pl ace m en t fo r RO M dev i ce s ca n be o b ta in ed in th e fo rm of va ri an ts w it h 'p ig gy -b ack 'E P RO M(Er as ab le pro gr am ma bl e ROM s oc ke ts or dev ic e s with EPROM i n st ea d o f RO M 。
电气工程及其自动化专业 外文文献 英文文献 外文翻译 plc方面
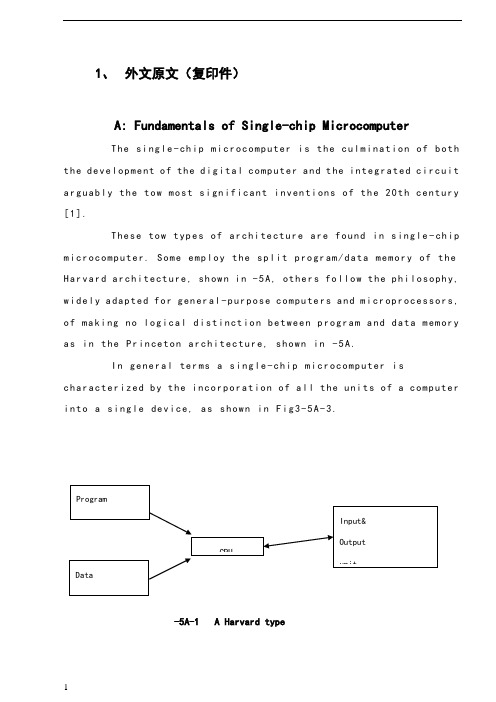
1、外文原文(复印件)A: Fundamentals of Single-chip MicrocomputerTh e si ng le-ch i p mi cr oc om pu ter is t he c ul mi nat i on o f bo th t h e d ev el op me nt o f th e d ig it al com p ut er an d t he int e gr at ed ci rc ui ta r gu ab ly th e t ow m os t s i gn if ic ant i nv en ti on s o f t h e 20t h c en tu ry[1].Th es e to w typ e s of a rc hi te ctu r e ar e fo un d i n s in gl e-ch ip m i cr oc om pu te r. So m e em pl oy t he sp l it p ro gr am/d ata me mo ry o f th e H a rv ar d ar ch it ect u re, sh ow n i n -5A, ot he rs fo ll ow th e ph i lo so ph y, w i de ly a da pt ed fo r g en er al-p ur pos e c om pu te rs an d m i cr op ro ce ss or s, o f m a ki ng no lo gi c al di st in ct io n b e tw ee n p ro gr am a n d da t a m em ory a s i n th e Pr in cet o n ar ch it ec tu re,sh ow n in-5A.In g en er al te r ms a s in gl e-chi p m ic ro co mp ut er i sc h ar ac te ri zed b y the i nc or po ra tio n of al l t he uni t s o f a co mp ut er i n to a s in gl e dev i ce, as s ho wn in Fi g3-5A-3.-5A-1 A Harvard type-5A. A conventional Princeton computerFig3-5A-3. Principal features of a microcomputerRead only memory (ROM).R OM i s u su al ly f or th e p er ma ne nt, n o n-vo la ti le s tor a ge o f an a pp lic a ti on s pr og ra m .M an ym i cr oc om pu te rs an d mi cr oc on tr ol le r s a re in t en de d fo r h ig h-v ol ume a p pl ic at io ns a nd h en ce t he e co nom i ca l ma nu fa ct ure of t he d ev ic es r e qu ir es t ha t the co nt en ts o f the pr og ra m me mo ry b e co mm it te dp e rm an en tl y d ur in g th e m an uf ac tu re o f c hi ps . Cl ear l y, th is im pl ie sa ri g or ou s a pp roa c h t o R OM co de d e ve lo pm en t s in ce c ha ng es ca nn otb e m ad e af te r man u fa ct ur e .T hi s d e ve lo pm en t pr oce s s ma y in vo lv e e m ul at io n us in g a s op hi st ic at ed deve lo pm en t sy st em w i th a ha rd wa re e m ul at io n ca pa bil i ty a s we ll a s th e u se of po we rf ul so ft wa re t oo ls.So me m an uf act u re rs p ro vi de ad d it io na l RO M opt i on s byi n cl ud in g i n th ei r ra ng e de vi ce s wi th (or i nt en de d fo r us e wi th) u s er pr og ra mm ab le m em or y. Th e s im p le st of th es e i s us ua ll y d ev ice w h ic h ca n op er ate in a m ic ro pr oce s so r mo de b y usi n g so me o f th e i n pu t/ou tp ut li ne s as a n ad dr es s an d da ta b us f or acc e ss in g e xt er na l m e mo ry. T hi s t ype o f d ev ic e c an b e ha ve fu nc ti on al l y a s t he si ng le c h ip mi cr oc om pu te r fr om wh ic h i t i s de ri ve d a lb eit w it h r es tr ic ted I/O an d a mo di fie d e xt er na l ci rcu i t. T he u se o f t h es e RO Ml es sd e vi ce s is c om mo n e ve n in p ro du ct io n c ir cu it s wh er e t he v ol um e do es n o t ju st if y th e d e ve lo pm en t co sts of c us to m on-ch i p RO M[2];t he re c a n st il l b e a si g ni fi ca nt s a vi ng in I/O a nd ot he r c hi ps co mp ar ed t o a c on ve nt io nal mi cr op ro ce ss or b as ed c ir cu it. M o re e xa ctr e pl ac em en t fo r RO M d ev ic es c an b e o bt ai ne d in t he f o rm o f va ri an ts w i th 'pi gg y-ba ck'EP RO M(Er as ab le p ro gr am ma bl e ROM)s oc ke ts o rd e vi ce s w it h EP ROM i ns te ad o f R OM 。
PLC相关的外文英语文献与翻译

RelaysThe Programmable Logic ControllerEarly machines were controlled by mechanical means using cams, gears, levers and other basic mechanical devices. As the complexity grew, so did the need for a more sophisticated control system. This system contained wired relay and switch control elements. These elements were wired as required to provide the control logic necessary for the particular type of machine operation. This was acceptable for a machine that never needed to be changed or modified, but as manufacturing techniques improved and plant changeover to new products became more desirable and necessary, a more versatile means of controlling this equipment had to be developed. Hardwired relay and switch logic was cumbersome and time consuming to modify. Wiring had to be removed and replaced to provide for the new control scheme required. This modification was difficult and time consuming to design and install and any small "bug" in the design could be a major problem to correct since that also required rewiring of the system. A new means to modify control circuitry was needed. The development and testing ground for this new means was the U.S. auto industry. The time period was the late 1960's and early 1970's and the result was the programmable logic controller, or PLC. Automotive plants were confronted with a change in manufacturing techniques every time a model changed and, in some cases, for changes on the same model if improvements had to be made during the model year. The PLC provided an easy way to reprogram the wiring rather than actually rewiring the control system.The PLC that was developed during this time was not very easy to program. The language was cumbersome to write and required highly trained programmers. These early devices were merely relay replacements and could do very little else. The PLC has at first gradually, and in recent years rapidly developed into a sophisticated and highly versatile control system component. Units today are capable of performing complex math functions including numerical integration and differentiation and operate at the fast microprocessor speeds now available. Older PLCs were capable of only handling discrete inputs and outputs (that is, on-off type signals), while today's systems can accept and generate analog voltagesand currents as well as a wide range of voltage levels and pulsed signals. PLCs are also designed to be rugged. Unlike their personal computer cousin, they can typically withstand vibration, shock, elevated temperatures, and electrical noise to which manufacturing equipment is exposed.As more manufacturers become involved in PLC production and development, and PLC capabilities expand, the programming language is also expanding. This is necessary to allow the programming of these advanced capabilities. Also, manufacturers tend to develop their own versions of ladder logic language (the language used to program PLCs). This complicates learning to program PLC's in general since one language cannot be learned that is applicable to all types. However, as with other computer languages, once the basics of PLC operation and programming in ladder logic are learned, adapting to the various manufacturers’ devices is not a complicated process. Most system designers eventually settle on one particular manufacturer that produces a PLC that is personally comfortable to program and has the capabilities suited to his or her area of applications.It should be noted that in usage, a programmable logic controller is generally referred to as a “PLC” or “programmable controller”. Although the term “programmable controller” is generally accepted, it is not abbreviated “PC” because the abbreviation “PC” is usually used in reference to a personal computer. As we will see in this chapter, a PLC is by no means a personal computer.Programmable controllers (the shortened name used for programmable logic controllers) are much like personal computers in that the user can be overwhelmed by the vast array of options and configurations available. Also, like personal computers, the best teacher of which one to select is experience. As one gains experience with the various options and configurations available, it becomes less confusing to be able to select the unit that will best perform in a particular application.The typical system components for a modularized PLC are:1. Processor.The processor (sometimes call a CPU), as in the self contained units, is generally specified according to memory required for the program to beimplemented. In themodularized versions, capability can also be a factor. This includes features such as higher math functions, PID control loops and optional programming commands. The processor consists of the microprocessor, system memory, serial communication ports for printer, PLC LAN link and external programming device and, in some cases, the system power supply to power the processor and I/O modules.2. Mounting rack.This is usually a metal framework with a printed circuit board backplane which provides means for mounting the PLC input/output (I/O) modules and processor. Mounting racks are specified according to the number of modules required to implement the system. The mounting rack provides data and power connections to the processor and modules via the backplane. For CPUs that do not contain a power supply, the rack also holds the modular power supply. There are systems in which the processor is mounted separately and connected by cable to the rack. The mounting rack can be available to mount directly to a panel or can be installed in a standard 19" wide equipment cabinet. Mounting racks are cascadable so several may be interconnected to allow a system to accommodate a large number of I/O modules.3. Input and output modules.Input and output (I/O) modules are specified according to the input and output signals associated with the particular application. These modules fall into the categories of discrete, analog, high speed counter or register types.Discrete I/O modules are generally capable of handling 8 or 16 and, in some cases 32, on-off type inputs or outputs per module. Modules are specified as input or output but generally not both although some manufacturers now offer modules that can be configured with both input and output points in the same unit. The module can be specified as AC only, DC only or AC/DC along with the voltage values for which it is designed.Analog input and output modules are available and are specified according to the desired resolution and voltage or current range. As with discrete modules, these are generally input or output; however some manufacturers provide analog input and output in the same module. Analog modules are also available which can directly accept thermocouple inputsfor temperature measurement and monitoring by the PLC.Pulsed inputs to the PLC can be accepted using a high speed countermodule. This module can be capable of measuring the frequency of an inputsignal from a tachometer or other frequency generating device. These modules can also count the incoming pulses if desired. Generally, both frequency and count are available from the same module at the same time if both are required in the application.Register input and output modules transfer 8 or 16 bit words of information to and from the PLC. These words are generally numbers (BCD or Binary) which are generated from thumbwheel switches or encoder systems for input or data to be output to a display device by the PLC.Other types of modules may be available depending upon the manufacturer of the PLC and it's capabilities. These include specialized communication modules to allow for the transfer of information from one controller to another. One new development is an I/O Module which allows the serial transfer of information to remote I/O units that can be as far as 12,000 feet away.4. Power supply.The power supply specified depends upon the manufacturer's PLC being utilized in the application. As stated above, in some cases a power supply capable of delivering all required power for the system is furnished as part of the processor module. If the power supply is a separate module, it must be capable of delivering a current greater than the sum of all the currents needed by the other modules. For systems with the power supply inside the CPU module, there may be some modules in the system which require excessive power not available from the processor either because of voltage or current requirements that can only be achieved through the addition of a second power source. This is generally true if analog or external communication modules are present since these require ± DC supplies which, in the case of analog modules, must be well regulated.5. Programming unit.The programming unit allows the engineer or technician to enter and edit the program to be executed. In it's simplest form it can be a hand held device with a keypad for programentry and a display device (LED or LCD) for viewing program steps or functions, as shown. More advanced systems employ a separate personal computer which allows the programmer to write, view, edit and download the program to the PLC. This is accomplished with proprietary software available from the PLC manufacturer. This software also allows the programmer or engineer to monitor the PLC as it is running the program. With this monitoring system, such things as internal coils, registers, timers and other items not visible externally can be monitored to determine proper operation. Also, internal register data can be altered if required to fine tune program operation. This can be advantageous when debugging the program. Communication with the programmable controller with this system is via a cable connected to a special programming port on the controller. Connection to the personal computer can be through a serial port or from a dedicated card installed in the computer.A Programmable Controller is a specialized computer. Since it is a computer, it has all the basic component parts that any other computer has; a Central Processing Unit, Memory, Input Interfacing and Output Interfacing.The Central Processing Unit (CPU) is the control portion of the PLC. It interprets the program commands retrieved from memory and acts on those commands. In present day PLC's this unit is a microprocessor based system. The CPU is housed in the processor module of modularized systems.Memory in the system is generally of two types; ROM and RAM. The ROM memory contains the program information that allows the CPU to interpret and act on the Ladder Logic program stored in the RAM memory. RAM memory is generally kept alive with an on-board battery so that ladder programming is not lost when the system power is removed. This battery can be a standard dry cell or rechargeable nickel-cadmium type. Newer PLC units are now available with Electrically Erasable Programmable Read Only Memory (EEPROM) which does not require a battery. Memory is also housed in the processor module in modular systems.Input units can be any of several different types depending on input signals expected as described above. The input section can accept discrete or analog signals of various voltage and current levels. Present day controllers offer discrete signal inputs of both AC and DCvoltages from TTL to 250 VDC and from 5 to 250 V AC. Analog input units can accept input levels such as ±10 VDC, ±5 VDC and 4-20 ma. current loop values. Discrete input units present each input to the CPU as a single 1 or 0 while analog input units contain analog to digital conversion circuitry and present the input voltage to the CPU as binary number normalized to the maximum count available from the unit. The number of bits representing the input voltage or current depends upon the resolution of the unit. This number generally contains a defined number of magnitude bits and a sign bit. Register input units present the word input to the CPU as it is received (Binary or BCD).Output units operate much the same as the input units with the exception that the unit is either sinking (supplying a ground) or sourcing (providing a voltage) discrete voltages or sourcing analog voltage or current. These output signals are presented as directed by the CPU. The output circuit of discrete units can be transistors for TTL and higher DC voltage or Triacs for AC voltage outputs. For higher current applications and situations where a physical contact closure is required, mechanical relay contacts are available. These higher currents, however, are generally limited to about 2-3 amperes. The analog output units have internal circuitry which performs the digital to analog conversion and generates the variable voltage or current output.The first thing the PLC does when it begins to function is update I/O. This means that all discrete input states are recorded from the input unit and all discrete states to be output are transferred to the output unit. Register data generally has specific addresses associated with it for both input and output data referred to as input and output registers. These registers are available to the input and output modules requiring them and are updated with the discrete data. Since this is input/output updating, it is referred to as I/O Update. The updating of discrete input and output information is accomplished with the use of input and output image registers set aside in the PLC memory. Each discrete input point has associated with it one bit of an input image register. Likewise, each discrete output point has one bit of an output image register associated with it. When I/O updating occurs, each input point that is ON at that time will cause a 1 to be set at the bit address associated with that particular input. If the input is off, a 0 will be set into the bit address. Memory in today's PLC's is generallyconfigured in 16 bit words. This means that one word of memory can store the states of 16 discrete input points. Therefore, there may be a number of words of memory set aside as the input and output image registers. At I/O update, the status of the input image register is set according to the state of all discrete inputs and the status of the output image register is transferred to the output unit. This transfer of information typically only occurs at I/O update. It may be forced to occur at other times in PLC's which have an Immediate I/O Update command. This command will force the PLC to update the I/O at other times although this would be a special case.Before a study of PLC programming can begin, it is important to gain a fundamental understanding of the various types of PLCs available, the advantages and disadvantages of each, and the way in which a PLC executes a program. The open frame, shoebox, and modular PLCs are each best suited to specific types of applications based on the environmental conditions, number of inputs and outputs, ease of expansion, and method of entering and monitoring the program. Additionally, programming requires a prior knowledge of the manner in which a PLC receives input information, executes a program, and sends output information. With this information, we are now prepared to begin a study of PLC programming techniques.When writing programs for PLCs, it is beneficial to have a background in ladder diagramming for machine controls. This is basically the material that was covered in Chapter 1 of this text. The reason for this is that at a fundamental level, ladder logic programs for PLCs are very similar to electrical ladder diagrams. This is no coincidence.The engineers that developed the PLC programming language were sensitive to the fact that most engineers, technicians and electricians who work with electrical machines on a day-to-day basis will be familiar with this method of representing control logic. This would allow someone new to PLCs, but familiar with control diagrams, to be able to adapt very quickly to the programming language. It is likely that PLC programming language is one of the easiest programming languages to learn.可编程序控制器早期的机器用机械的方法采用凸轮控制、齿轮、杠杆和其他基本机械设备。
自动化专业-外文文献-英文文献-外文翻译-plc方面

1、外文原文(复印件)A: Fundamentals of Single-chip MicrocomputerTh e si ng le-ch i p mi cr oc om pu ter is t he c ul mi nat i on o f bo th t h e d ev el op me nt o f th e d ig it al com p ut er an d t he int e gr at ed ci rc ui ta r gu ab ly th e t ow m os t s i gn if ic ant i nv en ti on s o f t h e 20t h c en tu ry[1].Th es e to w t ype s o f a rc hi te ct ur e a re fo un d i n s i ng le—ch ip m i cr oc om pu te r。
S o me em pl oy th e s p li t p ro gr am/d at a me mo ry of t he H a rv ar d ar ch it ect u re, sh ow n in Fi g.3-5A—1,ot he r s fo ll ow t hep h il os op hy, wi del y a da pt ed f or ge n er al—pu rp os e c o mp ut er s an dm i cr op ro ce ss or s, of ma ki ng no lo gi c al di st in ct io n be tw ee n p ro gr am a n d da ta m em or y a s i n th e Pr in cet o n ar ch it ec tu re,sh ow n in F ig。
3-5A-2.In g en er al te r ms a s in gl e—ch i p mi cr oc om pu ter isc h ar ac te ri zed b y the i nc or po ra tio n of al l t he uni t s o f a co mp ut er i n to a s in gl e de v i ce,as s ho wn i n F ig3—5A—3。
plc英文文献

1. CONVEYOR SYSTEMS Conveyor systems are often modular in nature and can be built up from basic units (or primitives) such as linear conveyor modules, either belt or roller type, and connecting devices such as lift stations and conveyor junction modules. Complex conveyor systems can easily be configured from combinations of these standard modules. Modules are available from a range of vendors in a wide portfolio of styles and varieties [1]. Conventional conveyor systems are typically installed as simple straight assembly lines and a number of workplaces are set on each side of the conveyor for manual and/or automated operations. For simple configurations of this type, the design and implementation is a relatively trivial task. Control programs are easily designed and coded using conventional Ladder Logic Diagrams (LLDs) which can be executed by Programmable Logic Controllers (PLCs) [2]. However, today's demands for multi-product mixes and flexibility for quick system reconfiguration can require more complex conveyor systems. Traditional types of sequentially controlled conveyor installations are often found to be too rigid for such demanding operational requirements. Conveyor systems which support multiple product mixes and variable product 799
plc英文文献.pdf

Plc SynopsisCentral Processing Unit(CPU)is the brain of a PLC controller.CPU itself is usually one of the microcontrollers.Aforetime these were8-bit microcontrollers such as8051,and now these are16-and32-bit microcontrollers.Unspoken rule is that you’ll find mostly Hitachi and Fujicu microcontrollers in PLC controllers by Japanese makers,Siemens in European controllers,and Motorola microcontrollers in American ones.CPU also takes care of communication,interconnectedness among other parts of PLC controllers,program execution,memory operation,overseeing input and setting up of an output.PLC controllers have complex routines for memory checkup in order to ensure that PLC memory was not damaged(memory checkup is done for safety reasons).Generally speaking,CPU unit makes a great number of check-ups of the PLC controller itself so eventual errors would be discovered early.You can simply look at any PLC controller and see that there are several indicators in the form.of light diodes for error signalization. System memory(today mostly implemented in FLASH technology)is used by a PLC for a process control system.Aside form.this operating system it also contains a user program translated forma ladder diagram to a binary form.FLASH memory contents can be changed only in case where user program is being changed.PLC controllers were used earlier instead of PLASH memory and have had EPROM memory instead of FLASH memory which had to be erased with UV lamp and programmed on programmers.With the use of FLASH technology this process was greatly shortened.Reprogramming a program memory is done through a serial cable in a program for application development.User memory is divided into blocks having special functions.Some parts of a memory are used for storing input and output status.The real status of an input is stored either as “1”or as“0”in a specific memory bit/each input or output has one corresponding bit in memory.Other parts of memory are used to store variable contents for variables used in used program.For example,time value,or counter value would be stored in this part of the memory.PLC controller can be reprogrammed through a computer(usual way),but also through manual programmers(consoles).This practically means that each PLC controller can programmed through a computer if you have the software needed for programming. Today’s transmission computers are ideal for reprogramming a PLC controller in factory itself.This is of great importance to industry.Once the system is corrected,it is also important to read the right program into a PLC again.It is also good to check from time to time whether program in a PLC has not changed.This helps to avoid hazardous situations in factory rooms(some automakers have established communication networks which regularly check programs in PLC controllers to ensure execution only of good programs).Almost every program for programming a PLC controller possesses various useful options such as:forced switching on and off of the system input/outputs(I/O lines), program follow up in real time as well as documenting a diagram.This documenting is necessary to understand and define failures and malfunctions.Programmer can add remarks,names of input or output devices,and comments that can be useful when finding errors,or with system maintenance.Adding comments and remarks enables anytechnician(and not just a person who developed the system)to understand a ladder diagram right ments and remarks can even quote precisely part numbers if replacements would be needed.This would speed up a repair of any problems that come up due to bad parts.The old way was such that a person who developed a system had protection on the program,so nobody aside from this person could understand how it was done.Correctly documented ladder diagram allows any technician to understand thoroughly how system functions.Electrical supply is used in bringing electrical energy to central processing unit.Most PLC controllers work either at24VDC or220VAC.On some PLC controllers you’ll find electrical supply as a separate module.Those are usually bigger PLC controllers,while small and medium series already contain the supply er has to determine how much current to take from I/O module to ensure that electrical supply provides appropriate amount of current.Different types of modules use different amounts of electrical current.This electrical supply is usually not used to start external input or er has to provide separate supplies in starting PLC controller inputs because then you can ensure so called“pure”supply for the PLC controller.With pure supply we mean supply where industrial environment can not affect it damagingly.Some of the smaller PLC controllers supply their inputs with voltage from a small supply source already incorporated into a PLC二Opening and based on the industry PC controlThe PLC manufacturer already started to gaze at the formidable impact which brings based on the industry PC control technology.Some experts even believed that the new commercial activity brings new technical and the opening technology standard will bury traditional PLC.The PLC manufacturer believed that although has the massive PLC control device in the industry field installation,but they still needed to unite the labor to control the software company,with the aim of developing them based on the industry PC process control software.Indeed,several years ago have the new old PLC mix use obviously in the industry scene the situation,the industrial user can not but simultaneously study the related new old knowledge,even each other profits from the study.The majority PLC manufacturers have provided the soft logic and one kind of service platform merely for the industrial user.In the high-end application aspect,very difficult to further differentiate the PLC control system and between the industry PC control system's difference,because this both have used the similar type microprocessor and the memory chip.Makes an analogy vividly,if you forget industry PC and in the PLC these words and expressions wording meaning,then can observe in the box is some basic computer hardware technology exactly,we observe are actually these basic strokes complication and the mixture,these technologies are combined effectively in the control systemMoreover,uses the opening control the reason is the system function integration need at the same time,on the other hand is also because some industrial user makes excessive demands the result excessively to the function.If can give the high value,can obtain the more basic strokesknowledge.The PLC manufacturer concentrates the system functionalization,but the industrial user concentrates the system application.The people may see that future trend of development will be further integrates more functions to a control box.Will therefore look like the sequential control and process control such event will select the functionalization method to carry on processing,other elephant motion control and so on can also share in the same control structure system.May believe that the PLC technology will continue to the open style control system direction to shift,particularly based on industry PC control system.The latter except,in the flexible aspect has outside the entirely different superiority compared to traditional PLC,but also has other merits, like can reduce the system to put in the market the cycle,reduces the system investment expenses, enhances from the factory first floor to the enterprise office automation data message mobile efficiency and so on.Already obtained the very good solution about the industry PC control system's real-time response question,perhaps its main thing still hid behind the technology,but lacks the corresponding track record.As for PLC,ruggedness is one of its main features,this already had the quite many track records to confirm.The industrial user still very carefully treated PLC,they are doing the different technical test work to PLC.When uses one kind of new technology,the industrial user needs to consider the question is must take the big risk,simultaneously needs to consider that can bring how many opportunities and the income to its commercial activity.But the industrial user believed not completely the open style control system brings advantage.Along with the technical further development,they start to downplay these ideological concept gradually.The industrial user is being balanced uses the risk which the new technology exists and the income which brings for theirs commercial activity,in order to will provide the effective safeguard for present's decision-making.The industry PC technology has provided many functions,can strengthen PLC the function characteristic,cooperates the processor including the Inner Tibet video frequency and the high speed floating point digit.Although Microsoft Corporation has not promoted further this function characteristic plan,but new Windows CE3.0can definitely satisfy the process control well the need.Some time ago,Siemens Corporation announced a set newly based on the open style control system's software product,namely3.0edition SIMATIC WinAC(Windows automation center). WinAC is based on Windows NT,with SIMATIC S7PLC compatible suiting in industry PC control system solution.WinAC3.0provided had the high integration rate Profibus field bus local area network's connection performance,as well as long-distance programming.In addition,it also integrated for the scene control device localization has provided one kind of new DeviceNet the I/O device driver,uses in DeviceNet which connected installs I/O equipment.The Steeplechase software company has also promoted set of supports are sturdy and healthy when process control embedded Windows the NT operating system interface unit.This part further unified Steeplechase Corporation to use the SBS technology and to move was sturdy and healthy in Windows NT environment industry Compact PCI when the control software.Now,the Steeplechase Corporation's visualization logic controller already promoted to5.0editions.This controller suits in Windows NT4.0and the Windows20,002kind of operating systems,itsreal-time engine can direct and ordinary Ethernet and TCP/IP integrates in together.5.0edition's controllers have used one kind of enlargement mode OPC server driver,thus has the quicker running rate compared to the beforehand edition.Other characteristics also include the new OI network characteristic,as well as can let industrial user design the richly colorful dynamic graph picture and so on.Transysoft Corporation had promoted the new edition ISaGRAF series industrial control configuration software package recently,namely ISaGRAF PRO,it is based on the IEC61131-3 international standards,and independence in any hardware platform soft logical automation control software package.In a network process control system environment,this software package can apply in many kinds of configurations and the distributional control system's development,it has contained a set of development kit,the application procedure working platform,as well as corresponding“hypothesized machine”when movement goal.When this movement the goal can move in various hardware platform.The CTC automation Engineering firm had already issued set of new control software package MachineLogic PCLC(industry PC logic controller),this software may let industry PC act PLC the role,and was still maintaining the industry PC function characteristic.This software can complete the control task which PLC determined,and the program time is equally quick,in1ms; Can also the simultaneous working multi-duty work,but cannot simultaneously surpass16control duties.One kind has the priority and the multitasking essence mechanism is maintaining to each control duty track,guaranteed that the control duty can obtain the highest priority.This software can move the complete5kind of IEC61131-3standard program design language and the PID control procedure,supports two types the I/O control devices.One kind is looks like Profibus and DeviceNet and so on such field bus I/O equipment;Another kind is looks like ISA and PC/104 such industry PC the I/O template.Moreover,this software has also provided to control system's online edition configuration function.The procedure may95/98and under Windows NT develops in Windows and moves,but can also carry out under RTXDOS.SoftPLC Corporation also provided one kind of labor to control software product Tealware, some people were called as very vividly this kind of software product are putting on industry PC clothes'PLC.These installed on support's control system already had the small PLC form factor, but the SoftPLC Corporation's control software was already inserted to CPU.The Tealware software can satisfy each type industrial user the need,from small,single plane system to large-scale,scattered multi-control workstation application.Its characteristic including entire series I/O module,Inner Tibet Ethernet and industry serial communication connection.Recently,Tealware the software already promoted to2.3editions.And,the control software has provided in fact the infinite trapezoidal chart logical control step the foreword,simultaneously allows to have surpasses1,000,000characters the data sheets;Many OI/SCADA application connection;The Inner Tibet Java engine and the FTP server use in the long-distance maintenance and the management;Support user compile C,C,Java procedure and device driver;Suits uses in the embedded Web server;Programming online movement pattern;Firm I/O module support ability and many other standard PLC function;May move,or is A-B Corporation's PLC-which the process which inputs transforms。
plc外文文献译文

Programmable logic controllerA programmable logic controller(PLC)is a digital computer used for automation of electromechanical processes,such as control of machinery on factory assembly lines,amusement rides,or lighting fixtures.PLC is used in many industries and machines.1.HistoryThe PLC was invented in response to the needs of the American automotive manufacturing industry.Before the PLC,control,sequencing,and safety interlock logic for manufacturing automobiles was accomplished using hundreds or thousands of relays,cam timers,and drum sequencers and dedicated closed-loop controllers. In1968GM Hydramatic issued a request for proposal for an electronic replacement for hard-wired relay systems.The first PLC,designated the084because it was Bedford Associates'eighty-fourth project,was the result.Bedford Associates started a new company dedicated to developing,manufacturing,selling,and servicing this new product:Modicon,which stood for MOdular DIgital CONtroller.The Modicon brand was sold in1977to Gould Electronics,and later acquired by German Company AEG and then by French Schneider Electric,the current owner.One of the very first084 models that was presented to Modicon by GM,when the unit was retired after nearly twenty years of uninterrupted service.Modicon used the84moniker at the end of its product range until the984made its appearance.2.DevelopmentEarly PLCs were designed to replace relay logic systems.These PLCs were programmed in"ladder logic",which strongly resembles a schematic diagram of relay logic.Other early PLCs used a form of instruction list programming,based on a stack-based logic solver.Modern PLCs can be programmed in a variety of ways,from ladder logic to more traditional programming languages such as BASIC and C.Another method is State Logic,a very high-level programming language designed to program PLCs based on state transition diagrams.3.FunctionalityThe functionality of the PLC have sequential relay control,motion control, process control,distributed control systems and networking.Regarding the practicality of these desktop computer based logic controllers,it is important to note that they have not been generally accepted in heavy industry because the desktop computersrun on less stable operating systems than do PLCs,and because the desktop computer hardware is typically not designed to the same levels of tolerance to temperature, In more recent years,small products called PLRs(programmable logic relays), are used in light industry where only a few points of I/O(i.e.a few signals coming in from the real world and a few going out)are involved,and low cost is desired. Popular names include PICO Controller,NANO PLC,and other names implying very small controllers.the PLRs are usually not modular or expandable,but their price can be two orders of magnitude less than a PLC and they still offer robust design and deterministic execution of the logic.4.PLC compared with other control systemsPLCs are well-adapted to a range of automation tasks.These are typically industrial processes in manufacturing where the cost of developing and maintaining the automation system is high relative to the total cost of the automation,and where changes to the system would be expected during its operational life.PLCs contain input and output devices compatible with industrial pilot devices and controls;little electrical design is required,and the design problem centers on expressing the desired sequence of operations.PLC applications are typically highly customized systems so the cost of a packaged PLC is low compared to the cost of a specific custom-built controller design.On the other hand,in the case of mass-produced goods,customized control systems are economic due to the lower cost of the components,which can be optimally chosen instead of a"generic"solution,and where the non-recurring engineering charges are spread over thousands or millions of units.A microcontroller-based design would be appropriate where hundreds or thousands of units will be produced and so the development cost(design of power supplies,input/output hardware and necessary testing and certification)can be spread over many sales,and where the end-user would not need to alter the control. Automotive applications are an example;millions of units are built each year,and very few end-users alter the programming of these controllers.However,some specialty vehicles such as transit busses economically use PLCs instead of custom-designed controls,because the volumes are low and the development cost would be uneconomic.Programmable controllers are widely used in motion control,positioning control and torque control.Some manufacturers produce motion control units to be integrated with PLC so that G-code(involving a CNC machine)can be used to instruct machinemovements.PLCs may include logic for single-variable feedback analog control loop,a "proportional,integral,derivative"or"PID controller".A PID loop could be used to control the temperature of a manufacturing process,for example.Historically PLCs were usually configured with only a few analog control loops;where processes required hundreds or thousands of loops,a distributed control system(DCS)would instead be used.As PLCs have become more powerful,the boundary between DCS and PLC applications has become less distinct.PLCs have similar functionality as Remote Terminal Units.An RTU,however, usually does not support control algorithms or control loops.As hardware rapidly becomes more powerful and cheaper,RTUs,PLCs and DCSs are increasingly beginning to overlap in responsibilities,and many vendors sell RTUs with PLC-like features and vice versa.The industry has standardized on the IEC61131-3functional block language for creating programs to run on RTUs and PLCs,although nearly all vendors also offer proprietary alternatives and associated development environments.5.The prospects for PLC.5.1.FeaturesThe main difference from other computers is that PLCs are armored for severe conditions(such as dust,moisture,heat,cold)and have the facility for extensive input/output(I/O)arrangements.PLCs read limit switches,analog process variables (such as temperature and pressure),and the positions of complex positioning systems. Some use machine vision.On the actuator side,PLCs operate electric motors, pneumatic or hydraulic cylinders,magnetic relays,solenoids,or analog outputs.The input/output arrangements may be built into a simple PLC,or the PLC may have external I/O modules attached to a computer network that plugs into the PLC.5.2System scaleA small PLC will have a fixed number of connections built in for inputs and outputs.Typically,expansions are available if the base model has insufficient I/O. Modular PLCs have a chassis(also called a rack)into which are placed modules with different functions.The processor and selection of I/O modules is customised for the particular application.Several racks can be administered by a single processor,and may have thousands of inputs and outputs.A special high speed serial I/O link is used so that racks can be distributed away from the processor,reducing the wiring costs for large plants.5.3User interfacePLCs may need to interact with people for the purpose of configuration,alarm reporting or everyday control.A simple system may use buttons and lights to interact with the user.Text displays are available as well as graphical touch screens.More complex systems use a programming and monitoring software installed on a computer, with the PLC connected via a communication interface.5.4CommunicationsPLCs have built in communications ports,usually9-pin RS-232,but optionally EIA-485or Ethernet.Modbus,BACnet or DF1is usually included as one of the communications protocols.Other options include various fieldbuses such as DeviceNet or Profibus.Other communications protocols that may be used are listed in the List of automation protocols.Most modern PLCs can communicate over a network to some other system,such as a computer running a SCADA(Supervisory Control And Data Acquisition)system or web browser.PLCs used in larger I/O systems may have peer-to-peer(P2P)communication between processors.This allows separate parts of a complex process to have individual control while allowing the subsystems to co-ordinate over the communication link.These communication links are also often used for HMI devices such as keypads or PC-type workstations.可编程逻辑控制器可编程逻辑控制器(PLC)或可编程序控制器是用于机电过程自动化的数字计算机,例如控制机械厂生产线、游乐设施或照明的装置。
PLC-外文文献+翻译

Programmable logic controllerA programmable logic controller (PLC) or programmable controller is a digital computer used for automation of electromechanical processes, such as control of machinery on factory assembly lines, amusement rides, or lighting fixtures. PLCs are used in many industries and machines。
Unlike general—purpose computers,the PLC is designed for multiple inputs and output arrangements, extended temperature ranges, immunity to electrical noise, and resistance to vibration and impact. Programs to control machine operation are typically stored in battery—backed or non-volatile memory. A PLC is an example of a real time system since output results must be produced in response to input conditions within a bounded time, otherwise unintended operation will result。
1。
HistoryThe PLC was invented in response to the needs of the American automotive manufacturing industry。
PLC相关的外文英语文献及翻译

PLC有关的外文英语文件及翻译RelaysThe Programmable Logic ControllerEarly machines were controlled by mechanical means using cams, gears, levers andother basic mechanical devices. As the complexity grew, so did the need for a more sophisticated control system. This system contained wired relay and switch control elements. These elements were wired as required to provide the control logic necessary for the particular type of machine operation. This was acceptable for a machine that never needed to be changed or modified, but as manufacturing techniques improved and plant changeover to new products became more desirable and necessary,a more versatile means of controlling this equipment had to be developed. Hardwired relay and switch logic was cumbersome and time consuming to modify. Wiring had to be removed and replaced to provide for the new control scheme required. This modification was difficult and time consuming to design and install and any small "bug" in the design could be a major problem to correct since that also required rewiring of the system. A new means to modify control circuitry was needed. The development and testing ground for this new means was the U.S. auto industry. The time period was the late 1960's and early 1970's and the result was the programmable logic controller, or PLC. Automotive plants were confronted with a change in manufacturing techniques every time a model changed and, in some cases, for changes on the same model if improvements had to be made during the model year. The PLC provided an easy way to reprogram the wiring rather than actually rewiring the control system.The PLC that was developed during this time was not very easy to program. The language was cumbersome to write and required highly trained programmers. These early devices were merely relay replacements and could do very little else. The PLC has at first gradually, and in recent years rapidly developed into a sophisticated and highly versatile control system component. Units today are capable of performing complex math functions including numerical integration and differentiation and operate at the fast microprocessor speeds now available. Older PLCs were capable of only handling discrete inputs and outputs (that is, on-off type signals), while today's systems can accept and generate analog voltagesPLC有关的外文英语文件及翻译and currents as well as a wide range of voltage levels and pulsed signals. PLCs arealso designed to be rugged. Unlike their personal computer cousin, they can typicallywithstand vibration, shock, elevated temperatures, and electrical noise to whichmanufacturing equipment is exposed.As more manufacturers become involved in PLC production and development, and PLC capabilities expand, the programming language is also expanding. This is necessary to allow the programming of these advanced capabilities. Also, manufacturers tend to develop their own versions of ladder logic language (the language used to program PLCs). This complicates learning to program PLC's in general since one language cannot be learned that is applicable to all types. However, as with other computer languages, once the basics of PLC operation and programming in ladder logic are learned, adapting to the various manufacturers ’ devices is not a complicated process. Most system designers eventually settle on one particular manufacturer that produces a PLC that is personally comfortable to program and has the capabilities suited to his or her area of applications.It should be noted that in usage, a programmable logic controller is generally referred toas a “ PLC” or “ programmable controller ” . Although the term “ programmable contr generally accepted, it is not abbreviated “ PC”becausethe abbreviation “ PC” is usuallyused in reference to a personal computer. As we will see in this chapter, a PLC is by nomeans a personal computer.Programmable controllers (the shortened name used for programmable logic controllers) are much like personal computers in that the user can be overwhelmed by the vast array of options and configurations available. Also, like personal computers, the best teacher of which one to select is experience. As one gains experience with the various options and configurations available, it becomes less confusing to be able to select the unit that will best perform in a particular application.The typical system components for a modularized PLC are:1. Processor.The processor (sometimes call a CPU), as in the self contained units, is generally specified according to memory required for the program to be In the rmodularizeversions,capability can also be a factor. This includes features such as highe math functions, PID control loops and optional programming commands. The processor consists of the microprocessor, system memory, serial communication ports for printer, PLC LAN link and external programming device and, in some cases, the system power supply to power the processor and I/O modules.2. Mounting rack.This is usually a metal framework with a printed circuit board backplane which provides means for mounting the PLC input/output (I/O) modules and processor. Mounting racks are specified according to the number of modules required to implement the system. The mounting rack provides data and power connections to the processor and modules via the backplane. For CPUs that do not contain a power supply, the rack also holds the modular power supply. There are systems in which the processor is mounted separately and connected by cable to the rack. The mounting rack can be available to mount directly to a panel or can be installed in a standard 19" wide equipment cabinet. Mounting racks are cascadable so several may be interconnected to allow a system to accommodate a large number of I/O modules.3. Input and output modules.Input and output (I/O) modules are specified according to the input and output signals associated with the particular application. These modules fall into the categories of discrete, analog, high speed counter or register types.Discrete I/O modules are generally capable of handling 8 or 16 and, in some cases 32, on-off type inputs or outputs per module. Modules are specified as input or output but generally not both although some manufacturers now offer modules that can be configured with both input and output points in the same unit. The module can be specified as AC only, DC only or AC/DC along with the voltage values for which it is designed.Analog input and output modules are available and are specified according to the desired resolution and voltage or current range. As with discrete modules, these are generally input or output; however some manufacturers provide analog input and output in the same module. Analog modules are also available which can directly accept thermocouple inputsfor temperature measurement and monitoring by the PLC.Pulsed inputs to the PLC can be accepted using a high speed countermodule. This module can be capable of measuring the frequency of an inputsignal from a tachometer or other frequency generating device. These modules can also count the incoming pulses if desired. Generally, both frequency and count are available from the same module at the same time if both are required in the application.Register input and output modules transfer 8 or 16 bit words of information to and from the PLC. These words are generally numbers (BCD or Binary) which are generated from thumbwheel switches or encoder systems for input or data to be output to a display device by the PLC.Other types of modules may be available depending upon the manufacturer of thePLC and it's capabilities. These include specialized communication modules to allow for the transfer of information from one controller to another. One new development is an I/O Module which allows the serial transfer of information to remote I/O units that can be as far as 12,000 feet away.4. Power supply.The power supply specified depends upon the manufacturer's PLC being utilized in the application. As stated above, in some cases a power supply capable of delivering all required power for the system is furnished as part of the processor module. If the power supply is a separate module, it must be capable of delivering a current greater than the sum of all the currents needed by the other modules. For systems with the power supply inside the CPU module, there may be some modules in the system which require excessive power not available from the processor either because of voltage or current requirements that can only be achieved through the addition of a second power source. This is generally true if analog or external communication modules are present since these require DC supplies which,± in the case of analog modules, must be well regulated.5. Programming unit.The programming unit allows the engineer or technician to enter and edit the programto be executed. In it's simplest form it can be a hand held device with a keypad for programentry and a display device (LED or LCD) for viewing program steps or functions, as shown. More advanced systems employ a separate personal computer which allows the programmer to write, view, edit and download the program to the PLC. This is accomplished with proprietary software available from the PLC manufacturer. This software also allows the programmer or engineer to monitor the PLC as it is running the program. With this monitoring system, such things as internal coils, registers, timers and other items not visible externally can be monitored to determine proper operation. Also, internal register data can be altered if required to fine tune program operation. This can be advantageous when debugging the program. Communication with the programmable controller with this system is via a cable connected to a special programming port on the controller. Connection to the personal computer can be through a serial port or from a dedicated card installed in the computer.A Programmable Controller is a specialized computer. Since it is a computer, it has all the basic component parts that any other computer has; a Central Processing Unit,Memory, Input Interfacing and Output Interfacing.The Central Processing Unit (CPU) is the control portion of the PLC. It interprets the program commands retrieved from memory and acts on those commands. In present day PLC's this unit is a microprocessor based system. The CPU is housed in the processor module of modularized systems.Memory in the system is generally of two types; ROM and RAM. The ROM memory contains the program information that allows the CPU to interpret and act on the Ladder Logic program stored in the RAM memory. RAM memory is generally kept alive with an on-board battery so that ladder programming is not lost when the system power is removed. This battery can be a standard dry cell or rechargeablenickel-cadmium type. Newer PLC units are now available with Electrically Erasable Programmable Read Only Memory (EEPROM) which does not require a battery. Memory is also housed in the processor module in modular systems.Input units can be any of several different types depending on input signals expected as described above. The input section can accept discrete or analog signals of various voltage and current levels. Present day controllers offer discrete signal inputs of both AC and DCvoltages from TTL to 250 VDC and from 5 to 250 VAC. Analog input units can accept input levels such as ±10 VDC, ±5 VDC and 4-20 ma. current loop values. Discrete input units present each input to the CPU as a single 1 or 0 while analog input units contain analog to digital conversion circuitry and present the input voltage to the CPU as binary number normalized to the maximum count available from the unit. The number of bits representing the input voltage or current depends upon the resolution of the unit. This number generally contains a defined number of magnitude bits and a sign bit. Register input units present the word input to the CPU as it is received (Binary or BCD).Output units operate much the same as the input units with the exception that the unit is either sinking (supplying a ground) or sourcing (providing a voltage) discrete voltages or sourcing analog voltage or current. These output signals are presented as directed by the CPU. The output circuit of discrete units can be transistors for TTL and higher DC voltage or Triacs for AC voltage outputs. For higher current applications and situations where a physical contact closure is required, mechanical relay contacts are available. These higher currents, however, are generally limited to about 2-3 amperes. The analog output units have internal circuitry which performs the digital to analog conversion and generates the variable voltage or current output.The first thing the PLC does when it begins to function is update I/O. This means that all discrete input states are recorded from the input unit and all discrete states to be output are transferred to the output unit. Register data generally has specific addresses associated with it for both input and output data referred to as input and output registers. These registers are available to the input and output modules requiring them and are updated with the discrete data. Since this is input/output updating, it is referred to as I/O Update. The updating of discrete input and output information is accomplished with the use of input and output image registers set aside in the PLC memory. Each discrete input point has associated with it one bit of an input image register. Likewise, each discrete output point has one bit of an output image register associated with it. When I/O updating occurs, each input point that is ON at that time will cause a 1 to be set at the bit address associated with that particular input. If the input is off, a 0 will be set into the bit address. Memory in today's PLC's is generallyconfigured in 16 bit words. This means that one word of memory can store the states of 16 discrete input points. Therefore, there may be a number of words of memory set aside asthe input and output image registers. At I/O update, the status of the input image register isset according to the state of all discrete inputs and the status of the output image register is transferred to the output unit. This transfer of information typically only occurs at I/O update.It may be forced to occur at other times in PLC's which have an Immediate I/O Update command. This command will force the PLC to update the I/O at other times although this would be a special case.Before a study of PLC programming can begin, it is important to gain a fundamental understanding of the various types of PLCs available, the advantages and disadvantagesof each, and the way in which a PLC executes a program. The open frame, shoebox, and modular PLCs are each best suited to specific types of applications based on the environmental conditions, number of inputs and outputs, ease of expansion, and method of entering and monitoring the program. Additionally, programming requires a prior knowledgeof the manner in which a PLC receives input information, executes a program, and sends output information. With this information, we are now prepared to begin a study of PLC programming techniques.When writing programs for PLCs, it is beneficial to have a background in ladder diagramming for machine controls. This is basically the material that was covered in Chapter 1 of this text. The reason for this is that at a fundamental level, ladder logic programs for PLCs are very similar to electrical ladder diagrams. This is no coincidence.The engineers that developed the PLC programming language were sensitive to the fact that most engineers, technicians and electricians who work with electrical machines on a day-to-day basis will be familiar with this method of representing control logic. This would allow someone new to PLCs, but familiar with control diagrams, to be able to adapt very quickly to the programming language. It is likely that PLC programming language is one of the easiest programming languages to learn.可编程序控制器初期的机器用机械的方法采纳凸轮控制、齿轮、杠杆和其余基本机械设施。
关于PLC英文文献(最新整理)

Security in OPERA Specification based PLC SystemsGuiomar Corral, Josep M. Selga, AgustínZaballos, David González-TarragóEnginyeria i Arquitectura La Salle-Universitat RamonLlull (URL)Barcelona-Spain{jmselga, guiomar, zaballos, dgonzalez}@Luis M. TorresDesign of Systems on Silicon (DS2) SAValencia, SpainBerthold HaberlerLinz Strom GmbhLinz, AustriaAbstract— Power Line Communication (PLC) is a broadband telecommunication technology that enables the use of the existing electricity networks for high speed data transmission purposes. European project OPERA (Open PLC European Research Alliance) is a project whose strategic objective is to push PLC technology in all the different and relevant aspects. Within this framework, security is an important aspect thatshould be taken into account and integrated into thespecifications from the very beginning. The project was scheduled in two phases with a duration of two years each. Phase1 produced a first PLC specification, including security.Phase2 produced an improved specification which was submitted to the IEEE as the OPERA PLC proposal within thecontest organized by WG P1901. The paper presents the studies related to security in the PLC access technology made within this process that led to the second security specification of OPERA. Finally, an analysis of this specification isperformed.Keywords- access technologies; PLC; communications network security;OPERA project.I. INTRODUCTIONPower Line Communication (PLC) is a broadband telecommunication technology able to use the existing electricity networks for data transmission purposes, allowing any user connected to the power grid to benefit from Information Technology based services easily. The strategic objective of project OPERA (Open PLC European Research Alliance) [1] is to push PLC technology in all the different and relevant aspects (standardization, technology improvement, installation tools and processes, telecom services, dissemination,..) so as to allow the technology to become a competitive alternative to offer broadband access service to all European citizens using the most ubiquitous infrastructure, the electrical grid, which covers not only the last mile but also in-building and in-home spaces.Security has been sometimes neglected when defining standards. In fact, the initial specifications of many existing standards in related areas such as wireless [2] have been shown to have many vulnerabilities that have had to be fixedin further specifications, not without trouble for the market. Unfortunately OPERA is not different. The specification produced in OPERA Phase1 [1][3] presented also several vulnerabilities that have been fixed in OPERA Phase2 specification [4]. The writing of this second specification by OPERA was inscribed in some way in the process created by the IEEE WG P1901 with the intention of producing an IEEE standard for PLC access and in-home networks. In fact, deliverable D27 [4] is the proposal submitted by OPERA to the IEEE within the mentioned process.The presentation of the OPERA Phase2 specification and the related security analysis are the objectives of this paper.The contents of the present paper is organized as follows. Section II introduces the security requirements to be complied by the specification; Section III succinctly describes the OPERA Phase1 specification; Section IV analyzes the level of compliance of this specification; Section V outlines the basic ideas forcreating a new specification; Section VI contains a security analysis of the new specification and, finally, there is a conclusions section.II. SECURITY REQUIREMENTSThe basic objectives of any security specification are to achieve confidentiality, integrity, mutual authentication and availability. These objectives can be threatened by a series of attacks.Confidentiality is interpreted as the privacy of transactions between two nodes from all other nodes. It is made possible by the techniques of cryptography. The most relevant known attacks against confidentiality are [5]: brute force attack, dictionary attack, eavesdropping attack and precomputation attack.Data integrity refers to ensuring that data has not been altered during the transmission process. Malicious manipulation and forging of messages are different attacks against data integrity. It can be prevented by the use of Message Integrity Checks (MIC).The function of admission control is to guarantee that network resources are only accessed by authorized devices which are who claim to be. Thus, it contains two aspects, one is authentication of the stations and the other is authorization to access the resources. Normally both functions are combined in a single access protocol. Different attacks against admission control are the following: identity usurpation, replay attacks, man-in-the-middle attacks, hijack of MAC addresses, session hijacking, masquerading, malicious device and message interception. Availability refers to the prevention from accessing and using the network by some unauthorized party. Attacks to availability are called Denial of Service (DoS) attacks. The security requirement demands that the specificationmust be robust against these attacks as well as to any other possible attack.III. SUCCINCT DESCRIPTION OF OPERA PHASE 1 SECURITY SPECIFICATION OPERA1 Specification [2][3] is aimed for PLC access networks and defines three types of devices, Head-End (HE), Repeaters (TDR, Time Division Repeaters) and Customer Premises Equipment (CPE). They typically form amulti-hop system like the one depicted in Figure 1.Confidentiality in OPERA1 is achieved by the use of DES[6] and 3DES[7] encryption systems. The admission control process involves three messages: an Access Frame that invites nodes to join the network, a contention Access Reply Frame that is an answer to the Access Frame and arequest to join the network and, finally, an Access Protocol Packet that basically informs about the success or failure of the admission control process. It is, thus, a 3-wayhandshake.The MAC layer is based on token passing controlled by the HE. The HE organizes and controls the downlink data frame for all data transmission from the HE to the CPEs. It also assigns the access duration for each CPE, which allows the uplink transmissions from the CPEs to the HE [2][8].The data frame structure used in the uplink and downlink transmissions is illustrated in Figure 2 [8]. Each frame begins with a “token announce” (TA). The TA is broadcasted in the clear over the network to inform the other stations about the upcoming transmission. The TA is followed by a number of bursts, each one addressing a specific CPE. Each burst consists of a burst header followed by several OPERA packets (basically similar to Ethernet packets). An interpacket header is inserted to separate two continuous packets or fragments of packets in a burst. The last symbol of the data frame carries a “Data Token” (DT).IV. OPERA PHASE 1 SPECIFICATION SECURITY ANALYSISThe most relevant vulnerabilities of OPERA Phase1 specification that have been detected are the following:Vulnerability 1: It uses DES [6] with a 56/64 bit key which has been reported to be breakable. It has even been phased out by FIPS (Federal Information Processing Standards). Brute force attacks as well as other attacks are feasible. Vulnerability 2: Admission control is only based on MAC addresses. Since these addresses are necessarily sent in the clear over the PLC channel, they can be supplanted. Hijacking and identity usurpation are easy to deploy.Vulnerability 3: There is no mutual authentication. There is no provision to authenticate masters. A malicious masterand man-in-the-middle attacks are possible.Vulnerability 4: The OPERA1 proposal does not contain any security Message Integrity Check (MIC) that could preserve data against tampering. Vulnerability 5: Channel Estimation MPDUs are never encrypted and include no MIC. Thus they can be manipulated to cause a DoS attack.Vulnerability 6: Another possible data integrity attack is just to change the position of different blocks in the payload. This would be unnoticed due to the independent ciphering of each block. It is a permutation attack.Vulnerability 7: It uses Diffie-Hellman algorithm without any protection against Man-in-the Middle attack. Although this may seem a big number of vulnerabilities of the OPERA Phase1 specification, the situation is common with other technologies, the most relevant of them being the early IEEE802.11 security specification [1].V. OUTLINE FOR A NEW OPERA SECURITY SPECIFICATIONUpon the view of the previous vulnerabilities it was clear that a new specification was needed and that it should provide stronger encryption,stronger integrity and a new admission control method really securing authentication and authorization.A- Stronger encryption.It can be obtained by the use of AES [9] or 3DES [7] ciphering algorithms. Neither of both has been reported to be cracked until today. For the new security specification the option chosen has been AES. The reason is that upon a careful comparison with 3DES it was clear that under many scenarios AES is less costly than 3DES. Another fact is that AES is recommended by IEEE and that it is believed to be more robust than 3DES.AES is a block cipher. To achieve confidentiality in messages of arbitrary length there are five options [10] called modes of operation. From these possible modes of operation the one chosen was the CTR mode because it can be performed in parallel (CFM and OFM modes do not allow this). Also it avoids some problems from the simpler ECB mode, it is well known and trusted (it has been used for more than 20 years) and does not raise Intellectual Property Rights (IPR) concerns as OCB does.B- Stronger integrity.From the variety of mechanisms generating a Message Integrity Check (MIC) the ones that support integrated confidentiality and integrity are specially interesting because they use one algorithm for both functions, thing that may avoid hardware and software costs. So the decision was to use AES for both functions: confidentiality and MIC generation. The chosen method to performintegrated encryption and authentication was CCM (Counter with CBCMAC) as defined in RFC 3610 [11]. CCM combines CTR mode of encryption with the CBC-MAC mode of authentication. CCM has been used and studied for a longtime and has well-understood cryptographic properties. CCM uses the same encryption key for both processes but, in conjunction with other parameters, it leads to two separated keys.The chosen values of the M and L parameters of CCM are:M = 8; indicating that the MIC is 8 octets long.L = 2; indicating that the length field is 2 octets.The length of the MIC was chosen to be 64 bits since this is the minimum length recommended by [11]. Figure 3: Construction of an Encrypted Burst The previous selections are coincident with those made in standardIEEE802.11i [12] for Wireless LANs. The main difference is that encryption and integrity are not applied over the same message. Encryption is performed over data bursts, which may contain several OPERA packets, while a MIC is generated for each OPERA packet (see Figure 3). The Burst header is authenticated but not encrypted. The OPERA packet header is authenticated and encrypted. This is done to improve efficiency in the very noisy environments typical to PLC channels. In case of error it is not necessary to retransmit the whole burst but only one packet. Another difference with [12] is that the OPERA specification does not support non robust options such as WEP or TKIP. This is possible because OPERA does not have to take into account IEEE802.11 legacy systems. C-Admission controlWith respect to admission control, the open possibilities were to define a specific protocol for OPERA or to use an existing standard. If such a standard existed it seems wiser the option to use it. Fortunately this standard exists and is IEEE 802.1X [13], an IEEE standard for port-based Network Access Control in LAN, based on the EAP (Extensible Authentication Protocol) [14], that has been adapted to be used in other environments such as wireless and which today is part of IEEE802.11i. Due to the adequacy and long time experience of thisstandard the decision was to make use of it in OPERA.IEEE 802.1X defines three entities, Supplicant, Authenticator and Authentication Sever (AS) and allows foran authentication dialog after the two opening messages (EAP-Request and EAP-Response) and before the closing message (EAP-Success or Failure). The three messages of the three-way handshake of OPERA Phase1 commented in Section III have similar functionality to the three EAP messages just mentioned. The approach taken in the new OPERA specification has been to keep the three messagesas defined in OPERA Phase1 for backwards compatibility.The Authenticator is in charge of converting betweenboth formats. The process has been represented in Figure 4. The Authenticator translates messages B and D into the corresponding Radius over EAP messages anddecapsulates/encapsulates messages C, those belonging to the authentication protocol of choice.A much major difference is that the Authenticator in IEEE802.11i is the Access Point while in OPERA can be the HE but also a Repeater.This creates the difference that in OPERA the communication between the Authenticator, when it is a Repeater, and the Authentication Server (Which can be located at the HE or beyond it) is also transmitted over the PLC channel. This fact implies the need to send the messages encrypted, protected with a MIC, with the same rules as in the dialog between Supplicant and Authenticator, and encapsulated into OPERA packets.Another difference is that the Supplicant can be a CPE or Repeater. So, aRepeater can be first a Supplicant and later Authenticator. A smaller difference is that the Access Protocol Packet may convey not only success or failure information but also indication of a failed dialog. The authentication dialog allowed by IEEE802.1X/EAP allows for the use of both shared secrets and certificates. This solves the problem of OPERA1 Phase1 of authenticating only on a MAC address basis.The new specification of OPERA is quite similar to the IEEE 802.11i and it complies with the RSNA (Robust Secure Network Association) defined in it. Nevertheless, the multihop nature of PLC, as shown in Figure 1, is a major difference with respect to wireless. In fact IEEE802.11i does not take into account the possible existence of repeaters.What the OPERA specification does, is to apply recursively the dialog between Supplicant and Authenticator.A node is first Supplicant and, once admitted into the network, may become Authenticator for another Supplicant. This creates a chain of trust among devices onto which security relies upon. What happens is that the messages sent by the Authenticator to the AS are transmitted over the PLC network and, thus, should be protected with encryption and integrity mechanisms as well as the data messages.In agreement with IEEE802.11i, OPERA Phase 2 uses the EAPOL 4-way handshake for key management. The objective of this handshake is to prove mutual knowledge of the PMK (Pairwise Master Key). But prior to this handshake, the PMK has to be transferred to the Authenticator and this again has to be done by means of the secure channel formed by the mentioned chain of trust.VI. SECURITY ANALYSIS OF THE NEW SPECIFICATIONThe new OPERA security specification is quite similar to IEEE 802.11i. Although this standard was developed to overcome vulnerabilities of previous standards, it has still potential vulnerabilities [15]. A first vulnerability is the so called rollback attack, an attack that does not seem possible in the newspecification because it does not include the WEP and TKIP options ofIEEE802.11i. The reflection attack described in the same reference is also not possible because it is not allowed for a device to have simultaneously both roles supplicant and authenticator.The previously mentioned chain of trust should not be subject of concern because there is a chain of trust from the source authority to the supplicant and chains are of limited length. Nevertheless it is reasonable to think that there would be some slight degradation of security in very long chains. Another possible source of vulnerabilities in chains could come in relation to the rerouting of messages due to failures or transient situations but we have not been able to find any.Still there remain some possible DoS attacks in layer 2. Forging of management messages is possible. The solution is to authenticate management frames but here there is atrade-off between security and efficiency. Access Request and Access Reply Frames cannot be authenticated but OPERA is not vulnerable to attacks such as flooding of requests because the access process in OPERA is completely controlled by the Authenticator. A special DoS attack for OPERA Phase1 is forging bit loading messages which in the current specification are sent unencrypted. The proposal is to also encrypt these messages.Also the DoS attacks against the 4-way handshake indicated in [15] are also worth considering. Another possible attack in PLC comes from the manipulation of the impedance of the electrical line or the line itself. This may cause lead to message deletion or, worse, message interception. The implementation of suchan attack seems difficult and requires specific topologies that do not seem to be common. In any case the attack would be a Man in the Middle attackfrom which the specification is already protected because it provides for mutual authentication. Another aspect being improved is the computation burden created by the need to change the key at every hop. One mechanism to improve this aspect is to use a single key to manage the HE and the Repeaters. Another is to define a protocol to agree a single key for transmission between pairs of CPE. VII. CONCLUSIONSThe earlier OPERA Phase1 PLC specification has been detected to be vulnerable to many known security attacks.This led to the definition of a new OPERA PLC specification able to overcome the known attacks. This new OPERA specification was submitted to the IEEE as the proposal of the OPERA consortium for the IEEE standard on PLC access systems. The proposal is based on the principles of standard IEEE802.11i. This is good for many reasons. One is compatibility with wireless in hybrid systems and devices. Another is to use known and proved standards. Nevertheless there are several differences to adapt the specification to the nature of PLC. The main ones are the following:-Instead of applying Encryption and MIC computation to the same block of data, Encryption is applied to Bursts while the MIC is appended to OPERA packets. This makes the system stronger against the very noisy PLC channels.-Admission control protocol is based on IEEE 802.1X except for three messages (Access Frame, Access Reply Frame and Access Protocol Packet) which have a different format but the same functionality.-The multihop nature of PLC is a major difference. IEEE802.11i does not take into account the possible existence of repeaters while OPERA do take them into account. It applies the dialog between Supplicant and Authenticator recursively so as to create a chain of trust among devices. Messages sent by the Authenticator to the Authentication Server may have to be transmitted over the PLC network and, in this case, they are to be protected following the same mechanisms as for the rest of messages. Finally aspects that deserve moreattention have been identified and several new vulnerabilities have been taken into account to provide ideas for a refined version of the OPERA specification. ACKNOWLEDGMENTThis work is supported by FP6 project OPERA (Open PLC European Research Alliance), and by “Enginyeria I Arquitectura La Salle”, DS2 and Linz Strom Gmbh. REFERENCES[1] OPERA Specification-Part 1-Technology-Version 1.0; 31/01/2006./_files/whitepapers/opera_wp2.pdf.. . Last access: 22/02/2010 [2] Todor Cooklev, “Wireless Communication Standards”, IEEE Standards Wireless Networks Series; IEEE, 2004.[3] OPERA Specification Part 2-System-Version 1.0, 31/01/2006./_files/whitepapers/opera_wp2.pdf. Last access: 22/02/2010. [4] OPERA Deliverable D27: OPERA Specification Version 2, 2007. . Last access: 21/02/2010[5] Jon Edney and William A. Arbaugh, “Real 802.11 Security Wi-Fi Protected Access and 802.11i”, Addison-Wesley, 2004.[6] FIPS 46-3, Data Encryption Standard (DES), October, 1999.[7] NIST SP 800-67, “Triple Data Encryption Algorithm (TDEA), including its primary component cryptographic engine, the Data Encryption Algorithm (DEA)”.[8] Le Phu Do, Halid Hrasnica and Ralf Lehnert, “Performance Evaluation of the PLC-MAC Protocol in Accordance with the OPERA Specification”. Proceedings of ISPLC07, pp 447-452, Pisa, Italy, 2007.[9] Federal Information Processing Standards Publication 197:Specification for the Advanced Encryption Standard (AES) -November 26, 2001 (FIPS-97 (2002)).[10] National Institute of Standards and Technology Special Publication 800-38A, December, 2001 Edition: Recommendation for Block Cipher Modes of Operation, Methods and Techniques.[11] IETF, Request for Comments: 3610, “Counter with CBC-MAC (CCM)”,September 2003[12] IEEE P802.11i/D10.0. Medium Access Control (MAC) Security Enhancements, Amendment 6 to IEEE Standard for Information technology – Telecommunications and information exchange between systems – Local and metropolitan area networks – Specific requirements – Part 11: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications. April, 2004. [13] IEEE Standard 802.1X-2001. IEEE Standard for Local andmetropolitan area networks – Port-Based Network Access [14] IETF, Request for Comments: 3748. Extensible Authentication Protocol (EAP), June 2004.[15] Changhua He and John C Mitchell, “Security Analysis and Improvements fro IEEE 802.11i”. The 12th Annual Network and Distributed System Security Symposium (NDSS'05), pages 90-110. Feb. 2005. 4778。
PLC及变频器技术中英文对照外文翻译文献

(文档含英文原文和中文翻译)中英文资料对照外文翻译PLC and inverter technology trends1. The development trend of the programmable controller“PLC is one kind specially for the digital operation operation electronic installation which applies under the industry environment designs. It uses may the coding memory, uses for in its internal memory operation and so on actuating logic operation, sequence operation, time, counting and arithmetic operation instructions, and can through digital or the simulation-like input and the output, controls each type the machinery or the production process. PLC and the related auxiliary equipment should according to form a whole easy with the industrial control system, easy to expand its function the principle to design.”In the 21st century, PLC will have a bigger development. Technologically speaking, computer technology's new achievement more will apply in the programmable controller's design and the manufacture, will have the operating speed to be quicker, the storage capacity to be bigger, an intelligent stronger variety to appear; Looked from the product scale that further develops to subminiature and the ultra-large direction; Looked from the product overcoatability that the product variety will be richer, the specification to be more complete, the perfect man-machine contact surface, the complete communication facility will adapt eachindustrial control situation demand well; Looked from the market that various countries will produce the multi-variety product the situation to break respectively along with the international competition aggravating, will present the minority several brand monopoly international market the aspect, will present the international general programming language; Looking from the network state of play, the programmable controller and other industrial control computer network constitution large-scale control system is the programmable controller technology development direction. Present computer collection and distribution control system DCS (Distributed Control System) had the massive programmable controller application. Is following computer network's development, the programmable controller takes the automation directed net and the international universal network important component, outside industry and industry numerous domain display more and more major function.2. Inverter technology development trendsInverter into the practical phase of more than 1 / 4 century during this period, the frequency converter technology as the basis of power electronics technology and microelectronics technology manager of a leap in the development, as the new power electronic devices and high-performance microprocessor The application of control technologyand the development of increasingly high cost performance of the inverter, more and more small size, but manufacturers are still in constant frequency converter to achieve the further miniaturization and doing new efforts. From a technical point of view, with the frequency converter to further expand the market of the future, with the converter and inverter technology will be on the development of technologies in the following areas further development:(1) large capacity and small size;(2) high-performance and multi-function;(3) enhance the ease-of-use;(4) increase in life expectancy and reliability;(5) of pollution-free.Large capacity and small size of the power semiconductor devices will be with the development of continuous development. In recent years, driven by a voltage power semiconductor devices IGBT (Isolated Gate Bipolar Transistor, isolation gate bipolar transistors) has developed very rapidly and quickly into the traditional use of BJT (bipolar power transistor) and power MOSFET (FET) The various fields. In addition, the IGBT switching device for the IPM (Intelligent Power Module, IPM) and Monolithic Power IC chip will power switching devices and driving circuit,such as the protection of integrated circuits in the same package, with high performance and reliability The merits, with their high current and high pressure of the development of small and medium-sized converter will certainly be more widely used.With micro-electronics technology and semiconductor technology development, for Inverter CPU and semiconductor devices and a variety of sensors of getting higher and higher. With the frequency converter technology and the development of the growing maturity of the exchange governor, modern control theory are constantly new applications. These have further improved the performance of inverter provided the conditions. In addition, with the frequency converter to further promote the use and support are also constantly made new demands, the frequency converter manufacturers to continuously improve the performance and frequency converter functions in Inverter new efforts to meet user And the need for the fierce competition in the market in an invincible position.With the frequency converter market continues to expand, how to further enhance the ease-of-use inverter, so that the technical staff and even ordinary non-technical staff can quickly master the use of frequency converter technology has become manufacturers must consider the issue. Because only easy-to-use products can continue to acquire new customersand further expand the market, so the future of the new converter will be more easy to operate.With the development of semiconductor technology and the development of power electronics technology, the frequency converter used in the various components of the life and reliability are constantly improving, they will make their own life and the frequency converter to further increase reliability.In recent years, people have attached great importance to environmental issues, and thus a "green products" name. Therefore, the inverter, must also consider its impact on the surrounding environment.Promote the use of the frequency converter in the early stages of the noise problem was once a big problem. With the low-noise converter IGBT the emergence of this issue has basically been resolved. However, with the noise problem to solve, people's looks and a converter to the surrounding environment and the impact of other continuously explore new solutions. For example, the use of a diode-voltage converter and PWM inverter circuit converter, the frequency converter itself the high harmonics will bring supply voltage and current distortion, and at the same power to affect the other equipment. However, through the use of the frequency converter Rectifier circuit PWM, we can basically solve the problem. Althoughbecause of price and control technology and other aspects of the reasons for the current PWM converter has not been promoting the inverter, but, with the frequency converter technology development and the people of the importance of environmental issues.PLC及变频器技术的发展趋势1.可编程控制器的发展趋势可编程控制器是一种数字运算操作的电子系统,专为在工业环境下应用而设计。
plc英文参考文献_论文格式_

plc英文参考文献a water pumping control system with a programmable logic controller (plc) and industrial wireless modules for industrial plants—an experimental setupisa transactions, in press, corrected proof, available online 3 december XXramazan bayindir, yucel cetince《电气控制与plc》参考文献参考文献[1] 张凤珊.电气控制及可编程序控制器.2版 [m].北京: 中国轻工业出版社,XX.[2] 《工厂常用电气设备手册》编写组.工厂常用电气设备手册.2版[m].北京: 中国电力出版社,1998.[3] 马志溪.电气工程设计 [m].北京: 机械工业出版社,XX.[4] 刘增良,刘国亭.电气工程cad [m].北京: 中国水利水电出版社,XX.[5] 齐占庆,王振臣.电气控制技术 [m].北京: 机械工业出版社,XX.[6] 史国生.电气控制与可编程控制器技术 [m].北京: 化学工业出版社,XX.[7] 郁汉琪.电气控制与可编程序控制器应用技术 [m].南京: 东南大学出版社,XX.[8] 张万忠.可编程控制器应用技术 [m].北京: 化学工业出版社,XX.[9] 王兆义.小型可编程控制器实用技术 [m].北京: 机械工业出版社,XX.[10] 三菱微型可编程控制器手册 [m].mitsubishi socio-tech,XX.[11] 吴晓君,杨向明.电气控制与可编程控制器应用[m].北京: 中国建材工业出版社,XX.[12] 李道霖.电气控制与plc原理及应用[m].北京: 电子工业出版社,XX.[13] s7-200 cn可编程序控制器手册 [m].西门子(中国)有限公司自动化与驱动集团,XX.[14] siemens wincc手册[m].西门子(中国)有限公司自动化与驱动集团,XX.[15] 魏艳君.多功能屋面sp板切割机[j].机电一体化,XX,(4):47-48.。
关于PLC的英文文献

关于PLC的英文文献1. PROGRAMMABLE LOGIC CONTROLLERS1.1 INTRODUCTIONControl engineering has evolved over time. In the past humans wasthe main method for controlling a system. More recently electricity has been used for control and early electrical control was based on relays. These relays allow power to be switched on and off without a mechanical switch. It is common to use relays to make simple logical control decisions. The development of low cost computer has brought the most recent revolution, the Programmable Logic Controller (PLC). The advent of the PLC began in the 1970s, and has become the most common choice for manufacturing controls. PLC have been gaining popularity on the factory floor and will probably remain predominant for some time to come. Most of this is because of the advantages they offer. . Cost effective for controlling complex systems.. Flexible and can be reapplied to control other systems quickly and easily.. Computational abilities allow more sophisticated control. .Trouble shooting aids make programming easier and reduce downtime. . Reliable components make these likely to operate for years before failure.1.2 Ladder LogicLadder logic is the main programming method used for PLC. As mentioned before, ladder logic has been developed to mimic relay logic. The decision to use the relay logic diagrams was a strategic one. By selecting ladder logic as the main programming method, the amount of retraining needed for engineers and trades people was greatly reduced. Modern control systems still include relays, but these are rarely usedfor logic. A relay is a simple device that uses a magnetic field to control a switch, as pictured in Figure 2.1. When a voltage is appliedto the input coil, the resulting current creates a magnetic field. The magnetic fieldpulls a metal switch (or reed) towards it and the contacts touch, closing the switch. The contact that closes when the coil is energizedis called normally open. The normally closed contacts touch when the input coil is not energized. Relays are normally drawn in schematic form using a circle to represent the input coil. The output contacts are shown with two parallel lines. Normally open contacts are shown as two lines, and will be open (non-conducting) when the input is not energized. Normally closed contacts are shown with two lines with a diagonal line through them. When the input coil is not energized the normally closed contacts will be closed (conducting).Relays are used to let one power source close a switch for another (often high current) power source, while keeping them isolated. An example of a relay in a simple control application is shown in Figure2.2. In this system the first relay on the left is used as normallyclosed, and will allow current to flow until a voltage is applied to the input A. The second relay is normally open and will not allow current to flow until avoltage is applied to the input B. If current is flowing through the first two relays then current will flow through the coil in the third relay, and close the switch for output C. This circuit would normally be drawn in the ladder logic form. This can be read logically as C will be on if A is off and B is on.1.3 ProgrammingThe first PLC were programmed with a technique that was based on relay logic wiring schematics. This eliminated the need to teach the electricians, technicians and engineers how to program a computer - but, this method has stuck and it is the most common technique for programming PLC today. An example of ladder logic can be seen in Figure 2.5. To interpret this diagram imagines that the power is on thevertical line on the left hand side, we call this the hot rail. On the right hand side is the neutral rail. In the figure there are two rungs, and on each rung there are combinations of inputs (two vertical lines) andoutputs (circles). If the inputs are opened or closed in the right combination the power can flow from the hot rail, through the inputs, to power the outputs, and finally to the neutral rail. An input can comefrom a sensor, switch, or any other type of sensor. An output will be some device outside the PLC that is switched on or off, such as lights or motors. In the top rung the contacts are normally open and normally closed, which means if input A is on and input B is off, then power will flow through the output and activate it. Any other combination of input values will result in the output X being off.The second rung of Figure 2.5 is more complex, there are actually multiple combinations of inputs that will result in the output Y turning on. On the left most part of the rung, power could flow through the top if C is off and D is on. Power could also (and simultaneously) flow through the bottom if both E and F are true. This would get power half way across the rung, and then if G or H is true the power will be delivered to output Y. In later chapters we will examine how tointerpret and construct these diagrams. There are other methods forprogramming PLC. One of the earliest techniques involved mnemonic instructions.These instructions can be derived directly from the ladder logic diagrams and entered into the PLC through a simple programming terminal. An example of mnemonics is shown in Figure 2.6. In this example the instructions are read one line at a time from top to bottom. The first line 00000 has the instruction LDN (input load and not) for input 00001. This will examine the input to the PLC and if it is off it will remember a 1 (or true), if it is on it will remember a 0 (or false). The nextline uses an LD (input load) statement to look at the input. If theinput is off it remembers a 0, if the input is on it remembers a 1 (note: this is the reverse of the LD). The AND statement recalls the last two numbers remembered and if they are both true the result is a 1;otherwise the result is a 0. This result now replaces the two numbersthat were recalled, and there is only one number remembered. The process is repeated for lines 00003 and 00004, but when these are done there are now three numbers remembered. The oldest number is from the AND, the newer numbers are from the two LD instructions. The AND in line 00005 combines the results from the last LD instructions and now there are two numbers remembered. The OR instruction takes the two numbers now remaining and if either one is a 1 the result is a 1, otherwise theresult is a 0. This result replaces the two numbers, and there is now a single number there. The last instruction is the ST (store output) thatwill look at the last value stored and if it is 1, the output will be turned on; if it is 0 the output will be turned off.The ladder logic program in Figure 2.6, is equivalent to the mnemonic program. Even if you have programmed a PLC with ladder logic, it will be converted to mnemonic form before being used by the PLC. In the past mnemonic programming was the most common, but now it is uncommon for users to even see mnemonic programs.Sequential Function Charts (SFC) have been developed toaccommodate the programming of more advanced systems. These are similar to flowcharts, but much more powerful. The example seen in Figure 2.7 is doing two different things. To read the chart, start at the top where is says start. Below this there is the double horizontal line that says follow both paths. As a result the PLC will start to follow the branch on the left and right hand sides separately and simultaneously. On the left there are two functions the first one is the power up function. This function will run until it decides it is done, and the power down function will come after. On the right hand side isthe flash function; this will run until it is done. These functions look unexplained, but each function, such as power up will be a small ladder logic program. This method is much different from flowcharts because it does not have to follow a singlepath through theflowchart.Structured Text programming has been developed as a more modern programming language. It is quite similar to languages such as BASIC. A simple example is shown in Figure 2.8. This example uses a PLC memory location N7:0. This memory location is for an integer, as will be explained later in the book. The first line of the program sets the value to 0. The next line begins a loop, and will be where the loop returns to. The next line recalls the value in location N7:0, adds 1 to it and returns it to the same location. The next line checks to see if the loop should quit. If N7:0 is greater than or equal to 10, then theloop will quit, otherwise the computer will go back up to the REPEAT statement continue from there. Each time the program goes through this loop N7:0 will increase by 1 until the value reaches 10.N7:0 := 0;REPEATN7:0 := N7:0 + 1;UNTIL N7:0 >= 10END_REPEAT;2. PLC ConnectionsWhen a process is controlled by a PLC it uses inputs fromsensors to make decisions and update outputs to drive actuators, as shown in Figure 2.9. The process is a real process that will change over time. Actuators will drive the system to new states (or modes of operation). This means that the controller is limited by the sensors available, if an input is not available, the controller will haveno way to detect a condition.The control loop is a continuous cycle of the PLC reading inputs, solving the ladder logic, and then changing the outputs. Like any computer this does not happen instantly. Figure 2.10 shows the basic operation cycle of a PLC. When power is turned on initially the PLC does a quick sanity check to ensure that the hardware is working properly. If there is a problem the PLC will halt and indicate there is an error. For example, if the PLC backup battery is low and power was lost, the memory will be corrupt and this will result in a fault. If the PLC passes the sanity checks it will then scan (read) all the inputs. After the inputs values are stored in memory the ladder logic will be scanned (solved) using the stored values - not the current values. This is done to prevent logic problems when inputs change during the ladder logic scan. When the ladder logic scan is complete the outputs will be scanned (the output values will be changed). After this the system goes back to do a sanity check, and the loop continues indefinitely. Unlike normal computers, the entire program will be run every scan. Typical times for each of the stages are in the order of milliseconds.3. SUMMARY. Normally open and closed contacts.. Relays and their relationship to ladder logic.. PLC outputs can be inputs, as shown by the seal in circuit. . Programming can be done with ladder logic, mnemonics, SFC, and structured text.. There are multiple ways to write a PLC program.。
关于PLC英文文献

Security in OPERA Specification based PLC SystemsGuiomar Corral, Josep M. Selga, AgustínZaballos, David González-TarragóEnginyeria i Arquitectura La Salle-Universitat RamonLlull (URL)Barcelona-Spain{jmselga, guiomar, zaballos, dgonzalez}@Luis M. TorresDesign of Systems on Silicon (DS2) SAValencia, SpainBerthold HaberlerLinz Strom GmbhLinz, AustriaAbstract— Power Line Communication (PLC) is a broadband telecommunication technology that enables the use of the existing electricity networks for high speed data transmission purposes. European project OPERA (Open PLC European Research Alliance) is a project whose strategic objective is to push PLC technology in all the different and relevant aspects. Within this framework, security is an important aspect thatshould be taken into account and integrated into thespecifications from the very beginning. The project was scheduled in two phases with a duration of two years each. Phase1 produced a first PLC specification, including security.Phase2 produced an improved specification which was submitted to the IEEE as the OPERA PLC proposal within thecontest organized by WG P1901. The paper presents the studies related to security in the PLC access technology made within this process that led to the second security specification of OPERA. Finally, an analysis of this specification isperformed.Keywords- access technologies; PLC; communications network security;OPERA project.I. INTRODUCTIONPower Line Communication (PLC) is a broadband telecommunication technology able to use the existing electricity networks for data transmission purposes, allowing any user connected to the power grid to benefit from Information Technology based services easily. The strategic objective of project OPERA (Open PLC European Research Alliance) [1] is to push PLC technology in all the different and relevant aspects (standardization, technology improvement, installation tools and processes, telecom services, dissemination,..) so as to allow the technology to become a competitive alternative to offer broadband access service to all European citizens using the most ubiquitous infrastructure, the electrical grid, which covers not only the last mile but also in-building andin-home spaces.Security has been sometimes neglected when defining standards. In fact, the initial specifications of many existing standards in related areas such as wireless [2] have been shown to have many vulnerabilities that have had to be fixedin further specifications, not without trouble for the market. Unfortunately OPERA is not different. The specification produced in OPERA Phase1 [1][3] presented also several vulnerabilities that have been fixed in OPERA Phase2 specification [4]. The writing of this second specification by OPERA was inscribed in some way in the process created by the IEEE WG P1901 with the intention of producing an IEEE standard for PLC access and in-home networks. In fact, deliverable D27 [4] is the proposal submitted by OPERA to the IEEE within the mentioned process.The presentation of the OPERA Phase2 specification and the related security analysis are the objectives of this paper.The contents of the present paper is organized as follows. Section II introduces the security requirements to be complied by the specification; Section III succinctly describes the OPERA Phase1 specification; Section IV analyzes the level of compliance of this specification; Section V outlines the basic ideas forcreating a new specification; Section VI contains a security analysis of the new specification and, finally, there is a conclusions section.II. SECURITY REQUIREMENTSThe basic objectives of any security specification are to achieve confidentiality, integrity, mutual authentication and availability. These objectives can be threatened by a series of attacks.Confidentiality is interpreted as the privacy of transactions between two nodes from all other nodes. It is made possible by the techniques of cryptography. The most relevant known attacks against confidentiality are [5]: brute force attack, dictionary attack, eavesdropping attack and precomputation attack.Data integrity refers to ensuring that data has not been altered during the transmission process. Malicious manipulation and forging of messages are different attacks against data integrity. It can be prevented by the use of Message Integrity Checks (MIC).The function of admission control is to guarantee that network resources are only accessed by authorized devices which are who claim to be. Thus, it contains two aspects, one is authentication of the stations and the other is authorizationto access the resources. Normally both functions are combined in a single access protocol. Different attacks against admission control are the following: identity usurpation, replay attacks, man-in-the-middle attacks, hijack of MAC addresses, session hijacking, masquerading, malicious device and message interception. Availability refers to the prevention from accessing and using the network by some unauthorized party. Attacks to availability are called Denial of Service (DoS) attacks. The security requirement demands that the specificationmust be robust against these attacks as well as to any other possible attack.III. SUCCINCT DESCRIPTION OF OPERA PHASE 1 SECURITY SPECIFICATION OPERA1 Specification [2][3] is aimed for PLC access networks and defines three types of devices, Head-End (HE), Repeaters (TDR, Time Division Repeaters) and Customer Premises Equipment (CPE). They typically form a multi-hopsystem like the one depicted in Figure 1.Confidentiality in OPERA1 is achieved by the use of DES[6] and 3DES[7] encryption systems. The admission control process involves three messages: an Access Frame that invites nodes to join the network, a contention Access Reply Frame that is an answer to the Access Frame and arequest to join the network and, finally, an Access Protocol Packet that basically informs about the success or failure of the admission control process. It is, thus, a 3-wayhandshake.The MAC layer is based on token passing controlled by the HE. The HE organizes and controls the downlink data frame for all data transmission from the HE to the CPEs. It also assigns the access duration for each CPE, which allows the uplink transmissions from the CPEs to the HE [2][8].The data frame structure used in the uplink and downlink transmissions is illustrated in Figure 2 [8]. Each frame begins with a “token announce” (TA). The TA is broadcasted in the clear over the network to inform the other stations about the upcoming transmission. The TA is followed by a number of bursts, each one addressing a specific CPE. Each burst consists of a burst header followed by several OPERA packets (basically similar to Ethernet packets). An interpacket header is inserted to separate two continuous packets or fragments of packets in a burst. The last symbol of the data frame carries a “Data Token” (DT).IV. OPERA PHASE 1 SPECIFICATION SECURITY ANALYSISThe most relevant vulnerabilities of OPERA Phase1 specification that have been detected are the following:Vulnerability 1: It uses DES [6] with a 56/64 bit key which has been reported to be breakable. It has even been phased out by FIPS (Federal Information Processing Standards). Brute force attacks as well as other attacks are feasible. Vulnerability 2: Admission control is only based on MAC addresses. Since these addresses are necessarily sent in the clear over the PLC channel, they can be supplanted. Hijacking and identity usurpation are easy to deploy.Vulnerability 3: There is no mutual authentication. There is no provision to authenticate masters. A malicious masterand man-in-the-middle attacks are possible.Vulnerability 4: The OPERA1 proposal does not contain any security Message Integrity Check (MIC) that could preserve data against tampering. Vulnerability 5: Channel Estimation MPDUs are never encrypted and include no MIC. Thus they can be manipulated to cause a DoS attack.Vulnerability 6: Another possible data integrity attack is just to change the position of different blocks in the payload. This would be unnoticed due to the independent ciphering of each block. It is a permutation attack.Vulnerability 7: It uses Diffie-Hellman algorithm without any protection against Man-in-the Middle attack. Although this may seem a big number of vulnerabilities of the OPERA Phase1 specification, the situation is common with other technologies, the most relevant of them being the early IEEE802.11 security specification [1].V. OUTLINE FOR A NEW OPERA SECURITY SPECIFICATIONUpon the view of the previous vulnerabilities it was clear that a new specification was needed and that it should provide stronger encryption,stronger integrity and a new admission control method really securing authentication and authorization.A- Stronger encryption.It can be obtained by the use of AES [9] or 3DES [7] ciphering algorithms. Neither of both has been reported to be cracked until today. For the new security specification the option chosen has been AES. The reason is that upon a careful comparison with 3DES it was clear that under many scenarios AES is less costly than 3DES. Another fact is that AES is recommended by IEEE and that it is believed to be more robust than 3DES.AES is a block cipher. To achieve confidentiality in messages of arbitrary length there are five options [10] called modes of operation. From these possible modes of operation the one chosen was the CTR mode because it can be performed in parallel (CFM and OFM modes do not allow this). Also it avoids some problems from the simpler ECB mode, it is well known and trusted (it has been used for more than 20 years) and does not raise Intellectual Property Rights (IPR) concerns as OCB does.B- Stronger integrity.From the variety of mechanisms generating a Message Integrity Check (MIC) the ones that support integrated confidentiality and integrity are specially interesting because they use one algorithm for both functions, thing that may avoid hardware and software costs. So the decision was to use AES for both functions: confidentiality and MIC generation. The chosen method to performintegrated encryption and authentication was CCM (Counter with CBCMAC) as defined in RFC 3610 [11]. CCM combines CTR mode of encryption with the CBC-MAC mode of authentication. CCM has been used and studied for a long time and has well-understood cryptographic properties. CCM uses the same encryption key for both processes but, in conjunction with other parameters, it leads to two separated keys.The chosen values of the M and L parameters of CCM are:M = 8; indicating that the MIC is 8 octets long.L = 2; indicating that the length field is 2 octets.The length of the MIC was chosen to be 64 bits since this is the minimum length recommended by [11]. Figure 3: Construction of an Encrypted BurstThe previous selections are coincident with those made in standardIEEE802.11i [12] for Wireless LANs. The main difference is that encryption and integrity are not applied over the same message. Encryption is performed over data bursts, which may contain several OPERA packets, while a MIC is generated for each OPERA packet (see Figure 3). The Burst header is authenticated but not encrypted. The OPERA packet header is authenticated and encrypted. This is done to improve efficiency in the very noisy environments typical to PLC channels. In case of error it is not necessary to retransmit the whole burst but only one packet. Another difference with [12] is that the OPERA specification does not support non robust options such as WEP or TKIP. This is possible because OPERA does not have to take into account IEEE802.11 legacy systems. C-Admission controlWith respect to admission control, the open possibilities were to define a specific protocol for OPERA or to use an existing standard. If such a standard existed it seems wiser the option to use it. Fortunately this standard exists and is IEEE 802.1X [13], an IEEE standard for port-based Network Access Control in LAN, based on the EAP (Extensible Authentication Protocol) [14], that has been adapted to be used in other environments such as wireless and which today is part of IEEE802.11i. Due to the adequacy and long time experience of thisstandard the decision was to make use of it in OPERA.IEEE 802.1X defines three entities, Supplicant, Authenticator and Authentication Sever (AS) and allows foran authentication dialog after the two opening messages (EAP-Request and EAP-Response) and before the closing message (EAP-Success or Failure). The three messages of the three-way handshake of OPERA Phase1 commented in Section III have similar functionality to the three EAP messages just mentioned. The approach taken in the new OPERA specification has been to keep the three messagesas defined in OPERA Phase1 for backwards compatibility.The Authenticator is in charge of converting betweenboth formats. The process has been represented in Figure 4. The Authenticator translates messages B and D into the corresponding Radius over EAP messages anddecapsulates/encapsulates messages C, those belonging to the authentication protocol of choice.A much major difference is that the Authenticator in IEEE802.11i is the Access Point while in OPERA can be the HE but also a Repeater.This creates the difference that in OPERA the communication between the Authenticator, when it is a Repeater, and the Authentication Server (Which can be located at the HE or beyond it) is also transmitted over the PLC channel. This fact implies the need to send the messages encrypted, protected with a MIC, with the same rules as in the dialog between Supplicant and Authenticator, and encapsulated into OPERA packets.Another difference is that the Supplicant can be a CPE or Repeater. So, aRepeater can be first a Supplicant and later Authenticator. A smaller difference is that the Access Protocol Packet may convey not only success or failure information but also indication of a failed dialog. The authentication dialog allowed by IEEE802.1X/EAP allows for the use of both shared secrets and certificates. This solves the problem of OPERA1 Phase1 of authenticating only on a MAC address basis.The new specification of OPERA is quite similar to the IEEE 802.11i and it complies with the RSNA (Robust Secure Network Association) defined in it. Nevertheless, the multihop nature of PLC, as shown in Figure 1, is a major difference with respect to wireless. In fact IEEE802.11i does not take into account the possible existence of repeaters.What the OPERA specification does, is to apply recursively the dialog between Supplicant and Authenticator.A node is first Supplicant and, once admitted into the network, may become Authenticator for another Supplicant. This creates a chain of trust among devices onto which security relies upon. What happens is that the messages sent by the Authenticator to the AS are transmitted over the PLC network and, thus, should be protected with encryption and integrity mechanisms as well as the data messages.In agreement with IEEE802.11i, OPERA Phase 2 uses the EAPOL 4-way handshake for key management. The objective of this handshake is to prove mutual knowledge of the PMK (Pairwise Master Key). But prior to this handshake, the PMK has to be transferred to the Authenticator and this again has to be done by means of the secure channel formed by the mentioned chain of trust.VI. SECURITY ANALYSIS OF THE NEW SPECIFICATIONThe new OPERA security specification is quite similar to IEEE 802.11i. Although this standard was developed to overcome vulnerabilities of previous standards, it has still potential vulnerabilities [15]. A first vulnerability is the so called rollback attack, an attack that does not seem possible in the newspecification because it does not include the WEP and TKIP options ofIEEE802.11i. The reflection attack described in the same reference is also not possible because it is not allowed for a device to have simultaneously both roles supplicant and authenticator.The previously mentioned chain of trust should not be subject of concern because there is a chain of trust from the source authority to the supplicant and chains are of limited length. Nevertheless it is reasonable to think that there would be some slight degradation of security in very long chains. Another possible source of vulnerabilities in chains could come in relation to the rerouting of messages due to failures or transient situations but we have not been able to find any.Still there remain some possible DoS attacks in layer 2. Forging of management messages is possible. The solution is to authenticate management frames but here there is atrade-off between security and efficiency. Access Request and Access Reply Frames cannot be authenticated but OPERA is not vulnerable to attacks such as flooding of requests because the access process in OPERA is completely controlled by the Authenticator. A special DoS attack for OPERA Phase1 is forging bit loading messages which in the current specification are sent unencrypted. The proposal is to also encrypt these messages.Also the DoS attacks against the 4-way handshake indicated in [15] are also worth considering. Another possible attack in PLC comes from the manipulation of the impedance of the electrical line or the line itself. This may cause lead to message deletion or, worse, message interception. The implementation of suchan attack seems difficult and requires specific topologies that do not seem to be common. In any case the attack would be a Man in the Middle attackfrom which the specification is already protected because it provides for mutual authentication. Another aspect being improved is the computation burden created by the need to change the key at every hop. One mechanism to improve this aspect is to use a single key to manage the HE and the Repeaters. Another is to define a protocol to agree a single key for transmission between pairs of CPE. VII. CONCLUSIONSThe earlier OPERA Phase1 PLC specification has been detected to be vulnerable to many known security attacks.This led to the definition of a new OPERA PLC specification able to overcome the known attacks. This new OPERA specification was submitted to the IEEE as the proposal of the OPERA consortium for the IEEE standard on PLC access systems. The proposal is based on the principles of standard IEEE802.11i. This is good for many reasons. One is compatibility with wireless in hybrid systems and devices. Another is to use known and proved standards. Nevertheless there are several differences to adapt the specification to the nature of PLC. The main ones are the following:-Instead of applying Encryption and MIC computation to the same block of data, Encryption is applied to Bursts while the MIC is appended to OPERA packets. This makes the system stronger against the very noisy PLC channels.-Admission control protocol is based on IEEE 802.1X except for three messages (Access Frame, Access Reply Frame and Access Protocol Packet) which have a different format but the same functionality.-The multihop nature of PLC is a major difference. IEEE802.11i does not take into account the possible existence of repeaters while OPERA do take them into account. It applies the dialog between Supplicant and Authenticator recursively so as to create a chain of trust among devices. Messages sent by the Authenticator to the Authentication Server may have to be transmitted over the PLC network and, in this case, they are to be protected following the same mechanisms as for the rest of messages. Finally aspects that deserve moreattention have been identified and several new vulnerabilities have been taken into account to provide ideas for a refined version of the OPERA specification. ACKNOWLEDGMENTThis work is supported by FP6 project OPERA (Open PLC European Research Alliance), and by “Enginyeria I Arquitectura La Salle”, DS2 and Linz Strom Gmbh. REFERENCES[1] OPERA Specification-Part 1-Technology-Version 1.0; 31/01/2006./_files/whitepapers/opera_wp2.pdf.. . Last access: 22/02/2010 [2] Todor Cooklev, “Wireless Communication Standards”, IEEE Standards Wireless Networks Series; IEEE, 2004.[3] OPERA Specification Part 2-System-Version 1.0, 31/01/2006./_files/whitepapers/opera_wp2.pdf. Last access: 22/02/2010.[4] OPERA Deliverable D27: OPERA Specification Version 2, 2007.. Last access: 21/02/2010[5] Jon Edney and William A. Arbaugh, “Rea l 802.11 Security Wi-Fi Protected Access and 802.11i”, Addison-Wesley, 2004.[6] FIPS 46-3, Data Encryption Standard (DES), October, 1999.[7] NIST SP 800-67, “Triple Data Encryption Algorithm (TDEA), including its primary component cryptographic engine, the Data Encryption Algorithm (DEA)”.[8] Le Phu Do, Halid Hrasnica and Ralf Lehnert, “Performance Evaluation of the PLC-MAC Protocol in Accordance with the OPERA Specification”. Proceedings of ISPLC07, pp 447-452, Pisa, Italy, 2007.[9] Federal Information Processing Standards Publication 197:Specification for the Advanced Encryption Standard (AES) -November 26, 2001 (FIPS-97 (2002)).[10] National Institute of Standards and Technology Special Publication 800-38A, December, 2001 Edition: Recommendation for Block Cipher Modes of Operation, Methods and Techniques.[11] IETF, Request for Comments: 3610, “Counter with CBC-MAC (CCM)”,September 2003[12] IEEE P802.11i/D10.0. Medium Access Control (MAC) Security Enhancements, Amendment 6 to IEEE Standard for Information technology –Telecommunications and information exchange between systems – Local and metropolitan area networks – Specific requirements – Part 11: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications. April, 2004. [13] IEEE Standard 802.1X-2001. IEEE Standard for Local andmetropolitan area networks – Port-Based Network Access [14] IETF, Request for Comments: 3748. Extensible Authentication Protocol (EAP), June 2004.[15] Changhua He and John C Mitchell, “Security Analysis and Improvements fro IEEE 802.11i”. The 12th Annual Network and Distributed System Security Symposium (NDSS'05), pages 90-110. Feb. 2005. 4778。
PLC控制系统英文文献+翻译

PLC控制系统英文文献+翻译PLC控制系统英文文献+翻译Beer filling, Gland machine PLC control system 1.Intorduction Malt beer production process is divided into manufacturing, manufacturing wort, before fermentation, after fermentation, filtration sterilization, packaging, and so few procedures. Beer filling, Gland part of a packaging machine processes. The membrane filtration of beer after the pipeline into the rotary Jiugang, then the valve into the bottle of wine, Gland, was bottled beer. Beer filling, Gland machine's efficiency and degree of automation direct impact on the level of beer production.China's beer industry to meet the increasing scale of production and the demand for beer modern high-speed filling machinery filling the requirements of domestic beer manufacturers are actively seeking to transform the unit or the filling of beer production equipment, making it a good use Performance, advanced technology and high production efficiency and operating a safe and secure, low maintenance costs of the modernization of beer filling machine. 2. Filling beer, Gland principle and control aircraft partsLiquid filling machine by filling principle can be divided into atmospheric filler,filling machines and vacuum pressure on the filling machine. Beer filling,Gland-filling method used pressure is higher than the atmospheric pressure under the filling, storage of the cylinder pressure than the pressure of the bottle, beer bottle into the liquid on pressure.Technology at home and abroad to achieve the filling line is basically: The Rotary Jiugang the rotating movement, placed in Jiugang slots on the empty bottles through the machinery will befixed at the upper Jiugang vacuum valve to open, closed Vacuum bottles for good treatment, Bozhuan stem from operating, open the valve of the bottle filling CO2 gases, vacuum convex .Round to open the vacuum valve, the bottle will air mixed with CO2 out of gas, open the valve again, the CO2 gas bottle filling, the filling valve on the pressure valve in the bottle close to back-pressure gas pressure at the open-Jiuye Pingbi into the bottle, through pneumatic or electrical control filling valve to achieve the filling of beer.Today's advanced international beer filling, Gland machine control system mainly by the photoelectric switch position detection part and take the bottles with, Jiugang speed part, dominated by the PLC, touch screen and other components. Filling, Gland of the mechanical structure and PLC programmable control devices, frequency stepless speed regulation, human-computer interface, and other modern means of complete automatic control technology, the combination of a mechanical and electrical integration.3. Controlled part of the programmeMany domestic beer manufacturers are now using the filling, Gland of the control system of uneven degree of automation; button and all the manual switch technology have set up operations in a box on the panel, PLC controller for the majority of Japanese companies or OMRON Mitsubishi's early products, equipment chain of control, less protection settings, plus the beer filling the scene poor environment, humidity, such as contact with the switch contacts serious corrosion, the system's signal detection of the high failure rate, resulting in equipment control system Operation of low reliability, the normal operation of equipment, such as short-cycle phenomenon.To the actual transformation of the Dandong Yalu River Brewery Co., Ltd. of filling, Gland machine control system as an example, the transformation of methods to clarify the control of such equipment thinking and ideas, according to the scene of the actual process conditions, to prepare the operation of the PLC Procedures. For beer filling, Gland control system of the actual situation and in accordance with the actual process conditions at the scene, re-design of the equipment of the PLC control system. This transformation of the same methods and ideas can be applied to other liquids and the transformation of filling equipment. 3.1 system hardware configurationJapan's Mitsubishi Corporation to use the FX2N128MRPLC use the system to replace the original 2-OMRON's C60P PLC, the original system of the PLC is due to old models, and computer on-line communications need to configure special converters, the system need to increase the external I / O input points , The extension of spare parts more difficult to find. FX2N128MRPLC is an integrated 128-point I / O controller of the box, a computing speed, command rich, high-cost performance, on-line programming simple and easy extension of the advantages of the Mitsubishi FX series, features the strongest small controller .(1) by the Mitsubishi 900 series of 970 GOT human-computer touch screen system to replace the original use of the button panel display equipment and monitor the operation of operating parameters. 970GOT HMI for the 16-color high-brightness significantly, through the convergence of connectivity and FX2N128MRPLC directly connected to the CPU, achieving rapid response. Has many maintenance features, such as the list-editing features, ladder monitoring (troubleshooting) function, the system monitoring functions to find fault and maintenanceof PLC Systems.(2) filling, Gland of the frequency converter in the transformation of no replacement, on-site detection signal means-testing is still used switch, switch for detecting long-term work in the humidity of the great occasions, the choice of capacitive proximity switches, according to PLC I / O terminal of the connection mode, select the type of close PNP switch, the control system of Figure 1. 3.2 Systems Programming PLC controller programming focus and the core is around Jiugang the rotation speed control and Jiugang on 60 bottles of detecting the location of the displaced, broken bottles, empty bottles at the location of testing and related displacement filling Such as control valves. The bottles displacement of testing procedures, using a Mitsubishi PLC in the left command.Figure 1 control system structure diagram .Bottles displacement of detection, using the left-PLC command, which commands the whole of one of the core control procedures, the main electrical switch detection and bottles at the bottle simultaneously detect mobile, the main motor to every week, just to the corresponding Jiugang Have a bottle of, PLC unit within the internal correspondence that 60 bottles of the unit for the M500 ~ M559, the number of units by the first letter K is set to K60, with each change in a second letter K is set to K1, M50 Reaction of the empty bottles in the short position, and detect the location of the motor speed to go on the frequency shift in the corresponding unit within the built-in "1" or "0", control valves and the corresponding mixing caps The motor stopped and opened. Continuous detection system in place after the 90 empty bottles, stop stirring caps the motor running, testing the number of bottles in accordance with the user's requirements canbe arbitrary.A bottle of detection. Rotary Jiugang through pressure to back pressure with the bottle of liquor in the process of empty bottles in the back-pressure, because the bottle itself may crack and other reasons leading to a sudden burst bottles, which need to detect the location of unexploded bottle bottle, in this bottle - The position opened purge solenoid valves, compressed air out, broken bottles at the bottle-blowing from the position in a row after the purge and several bottles of the electromagnetic valve open jet, a high-pressure spray Shuizhu, in the break Bottle position around a few bottles of spray bottles in a row.Detection of broken bottles and bottle-detection switch simultaneously detect movement of breaking bottles, to the main motor of each week, precisely corresponding Jiugang passed a bottle of, PLC unit within the internal correspondence that 20 broken bottles at the unit for the M600 ~ M619, unit With the number of the first letter K is set to K20, with each change in a second letter K is set to K1, M52 response to the location of the broken bottles and detected the location of the motor speed to the frequency shift continue, In the corresponding unit within the built-in "1" or "0", control and the corresponding jet purge solenoid valve opened and stopped. Continuous Spray and purge solenoid valve open to listen, time stopped in accordance with technological requirements can be arbitrary.System security is to control access to the caps simultaneously tracking, not only accurately detect the electrical switching speed detection, the broken bottles into the bottle and detection switch detection switch three conditions.970GOT human-computer touch-screen terminals operated by the software company's Mitsubishi GT WORKS package, whichis a GT Designer with the entire GOT9000 series of graphics software packages. The package is simple, prior to a personal computer simulation on the configuration and debug, after the man-machine operators to download terminals. At the same time, because the man-machine interface and a touch-screen role, will set common switch on the screen to facilitate the operation. And also to increase the number of features, such as setting alarm information. 4.After transformation control systemSystem at the normal operation of the machine for automatic control, in accordance with bottles into and out of the bottle for lack or slow pace set by running into the bottle stall bottles, no less than a bottle cap, automatic washing bottles burst, filling automatic back-pressure position , Covered under the system automatically lose covered a stop and safety protection, such as the coordination of action interlock. All the original button after the operation of the touch screen on. 5.Detection of the state control system monitoringDetection switch into the bottle and break bottles detection switch bottles of pressure by testing each part of the small metal plates above the location of a photoelectric pulse output, a further PLC acquisition, as each bottle of the pressure above the small metal plates is the location of activities , In the machine running after some time, some pressure above the small bottles of iron tablets and detection switch in the location of displacement, resulting in detection switch mistaken judgement, if not for the judgement of bottles of bottles, bottle explosion Lou Jian, misuse, such as the seizure of output errors So that the PLC have mistaken action, such as a back-pressure, unexploded bottle blowing, washing, stirring cap control system malfunction, such as failure phenomenon.Before the transformation of the daily production process, encountered this phenomenon, the operatives could only switch to the various functional or manual control buttons reach the stall so that the equipment work in the absence of monitoring state, the machine lost control function. Caused a lot of production of raw materials such as gas, water, wine waste. Only in the production of intermittent, can be fitter and maintenance electrician in accordance with the detection of small switch on the light-emitting diodes and anti-displacement by adjusting the distance only 5 ~ 8 mm detection switch installation location, and switch to fix detection of small metal plates Gap. This means of detection is very backward, after adjustment reaction to the results, timely response can not be adjusted results.In view of this testing situation, after the transformation of the filling, Gland control system configuration, this part of a new detection and integration in human-computer touch screen, complete bottle of detection.In human-computer touch screen interface on the page display, respectively, at customs, such as electromagnetic motor mixing valve switch state are in different colors to show, very intuitive.Increase the system's functions is to ensure the irrigation of the machine-Gland normal operation of automated control system specifically designed to. 6 Concluding remarks After the transformation of the control system will greatly simplify the complicated mechanical structure, the running and control of inspection, the degree of automation systems meet the design requirements, greatly reducing the operational strength of the labor so that the shrub-like beer output than in the past Raising more than 30 percent, greatly reduce the failure rate.Embodies the modern equipment of automatic control technology. In the digestion and absorption of today's industrial control on the basis of advanced technology innovation, development of domestic technology from the most advanced filling control system.啤酒灌装、压盖机PLC控制系统1、引言啤酒生产过程分为麦芽制造、麦芽汁制造、前发酵、后发酵、过滤灭菌、包装等几道工序。
plc英文参考文献(30个最新范例)

在写作plc论文时,参考文献是必不可少的,作者在选取参考文献时,应兼顾中文文献和英文文献的比例,本文整理了几十个最新的"plc英文参考文献范例",以供参考。
plc英文参考文献范例一:[1]LIANG Ning.Development of Automatic Sorting Device for Dried Jujube Appearance Quality Based on Machine Vision [D].Yangling:Northwest A & F University,2019.[2]ZHANG Pengpeng,ZHOU Min.Design of Handling Control System for LCD Substrate Production Line [J].Combined Machine Tool and Automatic Machining Technology,2019,(9):111-113,123.[3]CHEN Xing.Design of the Appearance Detection System of Electrolytic Capacitor Based on Machine Vision [J].Manufacturing Technology & Machine Tools,2018,674(8):153-157.[4]SU Chaoyang.Research and Development on Capacitor Appearance Defects Based on Image Processing Technology [D].Nanjing:Nanjing University of Aeronautics and Astronautics,2018.[5]HUANG Xinbing,LIU Xiaojuan.Design of Pneumatic Household Elevator Based on PLC Control [J].Chinese Hydraulics & Pneumatics,2019,(10):129-134.[6]WU Hanjiang,ZHANG Fengshou,ZHANG Jiaqi.Design of Honey Pomelo Sorting System Based on PLC [J].Packaging and Food Machinery,2019,37(4):28-30.[7]LIN Zhongxing,ZENG Xianjie,ZHANG Zongshuo.Design of Automatic Pad Printing Machine for Lamp Cap Logo Based on Pneumatic Transmission [J].Chinese Hydraulics & Pneumatics,2019,(1):117-121.[8]LI Yingjue,WEI Kexiang.Design of Automatic Measuring Machine for Wall-thickness of Flange Parts [J].Machine Tool & Hydraulics,2019,(17):93-97.[9]LI Jibo,HUANG Yuanzheng,XUN Jiyong.The Design of Cigarette Box Appearance Detecting System Based on Machine Vision [J].China Instrumentation,2018,(6):68-71.[10]WANG Tao,GUO Jinliang.Design and Implementation of Robot Precise Grasp Based on Image Processing [J].Manufacturing Technology and Machine Tools,2018,(12):47-51.[11]TAO Wencai.Design of Vision Inspection System for Mobile Shell Surface Defects [D].Shenyang:Shenyang University of Technology,2018.[12]JIA Zhenzhen,ZHANG Tao,CAO Xingqiang,et al.Design and Realization of theFood Inner Packaging Detection Device Based on the Machine Vision [J].Food & Machinery,2018,34(7):111-114.[13]LU Minzhi,WANG Zhiwei,WANG Wei.Control System Design of Automatic Laminator Based on Machine Vision Locating [J].Machine Tool & Hydraulics,2017,45(11):59-63.[14]ZHANG Shuzhen.PLC Control in the Implementation of Surface Defect Detection Experiment Device [D].Hefei:Hefei University of Technology,2017.[15]LIU Yunjun,LIU Jinguo,LI Yangmin.Design of Automatic Docking Gripper for Pipe Joints Based on PLC Control [J].Chinese Hydraulics & Pneumatics,2018,(9):44-48.plc英文参考文献范例二:[16]ROMIJNDERS L N G.The development of a new segmented deepwater wave generator[C]// Fourth International Symposium on Ocean Wave Measurement and Analysis.San Francisco,US:ASCE,2002:1209-1217.DOI:10.1061/40604(273)122.[17] HMIDA U B, HAMDI U, MOUNIR S. Design of wireless power and data transmission circuits for im-Plantablc biomicrosystcm[J].Biotechnology, 2007,6(2):153-164.[18] STRASSNER B, CHANU K. Microwave power trans-mission: historical milestones and system components[J].Proceedings of the IEEE, 2013,101(6):1379-1396.[19]WANG Y Z,GONG W,CHI L H.Numerical simulation on oscillation-sliding-uplift rock coupled motion of caisson breakwater under wave excition [J].China Ocean Engineering,2010,24(2):207-218.[20]NOHARA B T,YAMAMOTO I,MATSUURA M.The organized motion control of multi-directional wave maker[C]//Proceedings of 4th IEEE International Workshop on Advanced Motion Control.Mie,Japan:IEEE,1996:470-475.DOI:10.1109/AMC.1996.509294.[21] Chu Liang,Chao Libo,Ou Yang,et al.Hardware-in-the-loop simulation of traction control algorithm based on fuzzy PID[J].Energy Procedia,2012,16(3):1685.[22]LAOUAR A,GUERZIZ A,BOUSSAHA A.Calculation of eigenvalues of Sturm-Liouville equation for simulating hydrodynamic soliton generated by a piston wave maker [J].Springer Plus,2016:1369-1385.DOI:10.1186/s40064-016-2911-0.[23]Cheded.Al-Mulla. Control of a four-level elevator system using a programmable logic controller. International Journal of Electrical Engineering Education.,2003[24]Matsushita Electric Works Ltd., Automation Control Group. FPO programming manual [EB/OL]. (2004-10-05)[2008-09-10][25]He yong yi. A Control System of Material Handling in FMS. Journal of shanghai university. Vol.1.No.1.1997[26]Ren Sheng-le. Development of PLC-based Tension Control System.Chinese Journal of Aeronautics20 (2007) 266-271[27]M. Paredes, M. Sartor, C. Masclet. An optimization process for extension spring design. Computer Methods in Applied Mechanics and Engineering. 2001, 191(8): 783-797[28]Siemens AG.Working with STEP7 V5.2 Getting Started.2002[29]Michel Gilles.Programmabe Logic Controllers:Architecture and Application Wiley.1990.[30]G.L.Batten. Programmabe Controllers:hardware.software and ApplicationNew York:MC Graw-Hill.1994.。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Keywords: Programmable logic controller; VMEbus; PLC processor module
I. Introduction Programmable logic controllers (PLCs) are being used increasingly in instrumentation and control systems in the process industry, as well as in traditional factory automation environments. They offer industrial ruggedness not found with computers, and a flexibility not found in hardwired control systems. In the early days, the PLC was an expensive electronic relay replacer [1]. Although expensive, it was very beneficial to those who could afford the cost associated with equipment purchase and installation. For this reason, early PLCs were more likely to be found in large manufacturing plants, such as General Motors, General Electric and many others. The design criteria for the first PLC were specified in 1968 by the Hydramatic division of the General Motors Corporation [2]. Since their introduction in 1968, PLCs have steadily gained in popularity in industry. From 1970 to 1974, early innovations in microprocessor technology added greater flexibility and intelligence to the PLCs [2]. Capabilities of operator interfaces (CRT terminals and hand-held programming devices), added new dimensions to the PLC applications. An 8-bit microprocessor-based
D,~,
Pro~a~m.h g
Fig. 1. General PLC system parts.
compiled BASIC. Dudeck [10] used an IBM-PC as a programming device to an industrial PLC manufactured by the Allen-Bradley Company. He illustrated a controlled diffusion pumped vacuum evacuation sequence as a ladder diagram program example for this PC-controlled PLC. Muth [11] showed how an IBM-PC can be used to emulate a PLC, and as an off-line device for control program development and debugging. He also indicated the suitability of the Turbo Pascal as a programming language for the control program as well as for simulation software. Recently, research has been directed towards translating ladder diagram language to other forms of PLC languages. Welch [12] described an algorithm for translating unrestricted relay ladder logic into Boolean form. Krogh and Falcione [13] introduced an algorithm for converting relay ladder logic into a sequential function chart (SFC). Further development in the user interface PC-station with literal languages has been carried out recently. Asmaa [14] designed a literal language compiler (called LitSTAT) for IBM-PC machines which depends on the standard literal statements of many PLC manufacturers. The compiler was written using standard C-language. The PLC is composed primarily of three parts as illustrated in Fig. 1. These parts are: the PLC processor module (PLCPM), the input/output (I/O) modules, and the programming device. The PLCPM and the I/O modules require a housing or a framework to hold and support them. This metal assembly is called the 'rack' or 'crate', which provides a means of supplying power and signals to the PLCPM and I/O modules.
Abstract This paper presents an overall view of the architecture and design of a programmable logic controller (PLC). The main objectives of the work are to design, develop, and implement a versatile PLC processor module (PLCPM) based on an industrial open bus architecture called VMEbus (IEEE 1014 Versa Module Euro-standard). The controller is inserted inside the VME crate and controls the industrial process via input and output modules that reside in the crate. The PLCPM is designed to be an intelligent module through the use of a Motorola MC68000 CPU. A method of distributed arbitration protocol, based on an algorithmic state-machine design approach, is added to the design of this module. This facility makes PLCPM suitable to work inside a VMEbus environment. The PLCPM therefore becomes adequate for use in multiprocessing PLC systems. The controller uses a host personal computer (IBM-PC) as a versatile and indispensable system component for process development, monitoring, control and supervision. Software and firmware programs are developed and written for both host-PC and PLCPM using standard C-language and 68000 assembly language, respectively. This results in a sequential control algorithm for the PLCPM and windowing user interface for the host-PC. Ladder diagram programming language is supported by this user interface. © 1998 Elsevier Science B.V.
Taha F. A1-Khudairy*, Bakir A.R. A1-Hashemy, Munqith A.J. A1-Baker
