英文版风险评估模板27p
风险管理计划模板-英文版

TABLE OF CONTENTS1Introduction 1 1.1Document overview 1 1.2References 11.2.1Project References 11.2.2Standard and regulatory References 2 2Risk management during software development 2 2.1Organization and Responsibilities 2 2.2Qualification of personnel 2 2.3Objective of risk management activities 2 2.4Tasks, Planning 32.4.1Task n 32.4.2Risk analysis initialization 32.4.3Risk analysis update 4 2.5Criteria for Acceptability of Risk 4 2.6Verification and Risk traceability matrix 4 2.7Approvals 4 2.8Location of Risk Management File 4 3Risk management after software development 43.1Organization and Responsibilities 4 3.2Qualification of personnel 5 3.3Production and maintenance information 5 3.4Annual Audit 5 3.5Risk management of activities after software development 53.5.1Approvals 63.5.2Location of Risk Analysis Report out of design 6 4Ranking System for Risk Analysis 64.1Probability of Occurrence 6 4.2Consequences of Hazard 6 4.3Add your other criteria 6 4.4Determination of risk level 6 4.5Risk Index 7 4.6Criteria for acceptability 71Introduction1.1Document overviewThis document covers the risk management plan of XXX device, designed in XXX software development project.It contains:•the risk management organization and process during the software development project, •the risk management organization and process during maintenance, after final delivery of the software development project.Note: most of times, risk management organization is very different before and after design. You may split the risk management plan in two documents, the first one before end of design, the second one after the end of design.1.2References1.2.1Project References1.2.2Standard and regulatory ReferencesAdd the standard references to the table above. It may include ISO 14971, ISO 13485, IEC/TR 80002-1, IEC 62304, amongst others.2Risk management during software developmentThis chapter covers the risk management process and organization during the software development.2.1Organization and ResponsibilitiesDescribe the organization of the team responsible for risk management during design. You may add an organization chart or add a reference to your project management plan, where the organization of the project should be already described.2.2Qualification of personnelDescribe the qualification of personnel responsible for the risk management and risk analysis activities. Example:The personnel who participates to the risk analysis is composed of:•Experienced staff who was involved in the design process of similar products•The expert praticians who participate to the design process2.3Objective of risk management activitiesThe objective of risk management activities is to deliver a risk analysis report, which contains:•The device characteristics that could impact on safety (ISO 14971),•The software safety classification (IEC 62304),•The risk analysis table,•The risk traceability matrix with design requirements,•The overall assessment of residual risk.The risk analysis table and risk traceability matrix will be created and updated as necessary during software development, according to tasks described in §2.4.Data on the risk analysis table includes:•List the columns, according to your risk analysis table in your risk analysis report,•…Data on the risk analysis table includes:•List the columns, according to your risk traceability matrix in your risk analysis report, •…See my risk analysis report template for columns samples.Note: The Risk analysis should be performed by using the table B.1 in IEC/TR 80002-1.The risk analysis report will summarize whether identified and mitigated risks meet the acceptable values defined in this plan. It will also include a statement indicating whether all known hazards have been identified.The Risk Management File gathers this document and all documents quoted above.2.4Tasks, PlanningDescribe how the risk management activities are planned during the project.The planning of risk activities shall be coherent with the planning of the project found in §2.2 of the project management plan.Insert a table or list or diagram describing the planning.Important, list the deliverables and reviews of each phase of the project2.4.1Task nOptional, add a sub-section for each task with:•Inputs of the task•Content of the task•Outputs of the task•Task reviews (in, if necessary, and out)•Relationship with development planning.Note: The tasks may group sets of activities found in §4 to §7 of ISO14971.Examples of tasks below:2.4.2Risk analysis initializationDuring this phase, the following activities are performed: identification of intended use, identification of characteristics affecting the safety, assignation of safety class (see §2.5.1) identification of hazards, evaluation of hazards, and identification of foreseeable mitigation actions.•Inputs: publications, clinical data, any information prior to design phase•Two meetings with clinicians involved in the design process•Outputs: intended use, safety characteristics and hazards, creation of risk analysis•Relationship with development planning: Output data of this task is input data for specification•End of Task review: review of risk analysis in draft version.2.4.3Risk analysis updateDuring this phase, the following activities are performed: identification of mitigation actions, evaluation of hazards after mitigation and analysis of risk/patient outcome ratio.•Inputs: publications, clinical data, any information prior to design phase•Two meetings with clinicians involved in the design process and system architect•Outputs: Update of risk analysis•Relationship with development planning: this task is performed during specifications •End of Task review: review of risk analysis in first revision.2.5Criteria for Acceptability of RiskWarning: I recommend you to read carefully §3.4 of IEC 80002-1 to select adequate risk criteria.Risks will be evaluated in accordance with Risk Management Procedures for: •Probability of occurrence, read carefully §3.4 of IEC 80002-1•Consequence of hazard•Any other criteria of your choice, like probability of detection …Based on the level, for each hazard analyzed for XXXX , the Residual Risk will be considered Acceptable if the risk level value is less than <fix your number>.Based on the risk levels, the Overall Residual Risk for a device will be considered acceptable if the following conditions are satisfied:1.None of the identified hazards leads to an unacceptable risk (i.e., no risk level above<your number minus 1> is identified); and2.Another quantitative criterion of your choice3.Another one …Any risk levels above these values need to have actions taken to reduce the risk.2.6Verification and Risk traceability matrixVerification testing activities will be cross-referenced in the risk traceability matrix, as applicable.2.7ApprovalsThe Risk Management Plan must be reviewed and approved by XXXX prior to the start of the risk assessment process.The Risk Analysis Report will be reviewed and approved by XXXX to ensure completeness and conformance to this Risk Management Plan.2.8Location of Risk Management FileThe Risk Management File is located in XXX (for example a document management tool defined in the software development plan or project management plan). This file contains all the documents related to the management of risk for the device and is kept for the life of the product.3Risk management after software development3.1Organization and ResponsibilitiesDescribe the organization of the team responsible for risk management after software development. You may add an organization chart.3.2Qualification of personnelDescribe the qualification of personnel responsible for the risk management and risk analysis activities.3.3Production and maintenance informationThe Risk Management File is systematically reviewed and updated in the maintenance of the device, especially when:•The product is modified (iso-functional patch),•Analysis of data of post marketing surveillance triggers a reevaluation (internal defects, customer requests, maintenance, vigilance bulletins, of field information from any source),3.4Annual AuditReviews and updates to the Risk Management File will be done annuallyReviews and updates to any risk related document will be documented, approved, and included within the Risk Management File.3.5Risk management of activities after software developmentYour QMS should have been structured to mitigate risks after design (eg: a delivery procedure to mitigate the risk of delivering the wrong version to a customer). However, some specific risks may arise from a new software or system and may deserve a separate risk analysis report.A Risk Analysis Report out of design will be created and updated as necessary after software development. Risk linked to activities after software development will be evaluated in accordance with Risk Management Procedures, criteria for acceptability of Risk, Requirements for Review of Risk Management Activities.The activities are:•Sales & Marketing,•Production,•Storage,•Delivery,•Installation,•Maintenance,•Un-installation,•Disposal,•Add yours …3.5.1ApprovalsThe Risk Analysis Report out of design will be reviewed and approved by XXXX to ensure completeness and conformance to this Risk Management Plan.3.5.2Location of Risk Analysis Report out of designThe Risk Analysis Report out of design is located in XXX. (you may add it to the DHF or DMR)4Ranking System for Risk AnalysisThis section describes how the risk level is deduced from the characteristics of the risk: •List the criteria defined in §2.2.Describe in sub sections how you quantify your criteria4.2Consequences of Hazard4.3Add your other criteriaYour definition4.4Determination of risk levelA rule of your choice, like.Risk Level = criterion 1x criterion 2x criterion n4.5Risk Index4.6Criteria for acceptabilityAcceptable risk per risk level is:•If the risk level is 1 to xx - No recommended actions are required.•If the risk level is xx to yy - Some actions may be used, where possible, to lower the level.•If risk level is above yy the risk is unacceptable. Mitigation action must be implemented to lower the level.。
安全风险评估表.xls
驾驶员、押 运员drivers and supercargo
driver/ HSE
Comp. Linkag Remark Date日 e连接机 评论 期赔偿 构
金
2
火灾/fire
Risk
No 风险 序号
Risk Description
风险描述
Cause 原因
Consequence 后果
Original Risk 原始风险
condition, securing conditions
出车前检查车辆的安全性能, √ 发现问题及时处理Check the safety performance of vehicles before driving, timely deal with the problem found by it
/damage to others
transport
人身伤害、财产损失
√
、环境破坏、他人损
设备故障
失Personal injury/ Property
Failure of equipment loss/damage to
others/environmenta
l damage
经常检查物件的绑扎情况
√
Always check the binding
vehicle
provided
loss/damage to
others/environmenta
l damage
16 设备卸车
地面不平
人身伤害、环境破坏
√
Equipment/m uneven ground/floor Personal injury
aterial
/environmental
车间风险评估表
氩气泄漏
窒息
每日肥皂水检查
漏电 潜在爆炸隐患 粉尘
电击 人员受伤 尘肺
PPE的要求(专用眼镜、手套)
1,固定装置 2,在有资质的单位购买氩气瓶
PPE的要求(口罩)
氩弧焊存在火灾隐患
人员受伤
远离可燃物的要求
气压测试压手
操作不当压到手
安全教育
水压测试伤人
高压水管
放入测试箱
1
1
L 保持现有风险控制措施
领班,以确保所有的机械 师遵守安全注意事项
1
下料切割:调整锯带 长度
被锤子敲到手
手受伤
技术员手伤培训
领班,确保所有机械师遵
2
3 M 保持现有风险控制措施
循安全指令
2
下料切割:锯带锋利 的边缘
锯齿划手
手受伤
PPE的要求(手套)
2
3
M
增加PPE使裸露在外的锋利边缘 减少
领班,确保所有机械师遵 循安全指令
3
下料切割:工件安装 到锯台
工件太重,掉落下来
2. Risk Evaluation 风险评估
3. Risk Control 风险控制
1d
2a
2b 2c 2d 3a
3b
No. 序号
Work Activitity 工作 活动
Possible Accident/ Ill
Hazard 危险(包括职业危 害和环境因素)
Health & Persons-atRisk
PPE的要求(专用眼镜)
漏电保护器的要求
进行噪声调查/绘制。考虑工程手 领班,确保所有机械师遵
2
3
M 段减少过量的噪音。增加个人防 循安全指令
THE RISK ASSESSMENT MATRIX
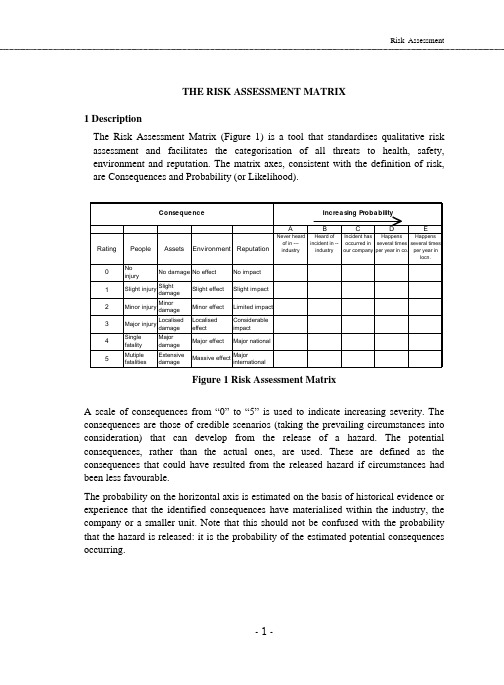
Risk AssessmentTHE RISK ASSESSMENT MATRIX1 DescriptionThe Risk Assessment Matrix (Figure 1) is a tool that standardises qualitative risk assessment and facilitates the categorisation of all threats to health, safety, environment and reputation. The matrix axes, consistent with the definition of risk, are Consequences and Probability (or Likelihood).Figure 1 Risk Assessment MatrixA scale of consequences from “0” to “5” is used to indicate increasing severity. The consequences are those of credible scenarios (taking the prevailing circumstances into consideration) that can develop from the release of a hazard. The potential consequences, rather than the actual ones, are used. These are defined as the consequences that could have resulted from the released hazard if circumstances had been less favourable.The probability on the horizontal axis is estimated on the basis of historical evidence or experience that the identified consequences have materialised within the industry, the company or a smaller unit. Note that this should not be confused with the probability that the hazard is released: it is the probability of the estimated potential consequences occurring.2 Classification of Potential ConsequencesThe consequences of the release of a hazard or effect are identified in each of thefour categories (harm to people, asset damage, environmental effect and potential impact on the reputation of the company) by selecting an appropriate row description on the vertical axis of the matrix. The definition of the categories isgiven in Appendix I.Risk is described, not only in terms of risk to health, safety and the environment,but also in terms of risk to reputation. Reputation is driven by perceptions and by societal issues. Risk in scientific terms may be reduced to the level reasonably practicable (ALARP), yet the overall risk to reputation may still remain high. Riskto reputation cannot be ignored and advice may be sought from Public Affairs experts.Consequences should be estimated on the basis of what might have resulted under slightly different circumstances. Examples are:Scenario ActualoutcomePotentialconsequenceA crane drops a load one meter besides a person. Damage to load. Fatal injury if a personhad been standingunder the load.Car rolls over on a desert road. Damage to car, no injury(seat belt was worn).Serious injury.Operator opens wrong valve: diesel fuel polluting river; quickly spotted by someone else. Minor pollution Major effect if the spillhad not been noticedso quickly.Exposure to H2S: quickly rescued and resuscitated 2 days observation inhospital: minor injury.Fatal or permanenttotal/partial disability.Exposure to benzene exceeding current occupational exposure limits None. Cancer(leukemia).Flare carries over some crude. Sooting flare. Oil in flare pit. Pit onfire. Heavy smoke.Soot on nearby housesand cars. Complaints.Media publicity.Damage claims.3 Assessment of ProbabilityThe horizontal axis represents the probability or the measure of likelihood of the occurrence of an undesired event following the release of a hazard. The scale of the horizontal axis is indicatively defined:“A - never heard of in the __ industry”,“B - heard of in the __ industry”,“C - has occurred in our company”,“D - happens several times per year in company”, and“E - happens several times per year in location”.This assessment is based on experience and is indicative of the likelihood of undesired consequences materialising. Note again that this should not be confused with the probability that the hazard is released: it is the probability of the estimated potential consequences occuring.In smaller Operating Units or new ventures where experience is limited, it is recommended that the probability is assessed on the basis of knowledge from similar operations in other Operating Units. In new ventures, the potential consequence scale only can be used and investigations carried out for all incidents with potential higher than 3. By doing so, every opportunity is used for learning from the potentially serious incidents, no matter how unlikely their occurence may be.4 Risk ClassificationUsing the Risk Assessment Matrix, risk is classified by three characters made up as follows: red event: A-E ∙the first character is a measure of the likelihood of an undesi∙the second character is the consequence severity that could occur withthat event: 1-5, and∙the third character shows to which consequence category the assessment pertains - People (P), Asset (A), Environmental (E) nature or Reputation(R).The intersection of the chosen column with the chosen row is the risk classification. For the same scenario, different classifications may apply to P, A, E, and R. Some examples of incident classification are given in Appendix II.5 The Application5.1 HSE Risk ManagementA suitable overlay for using the Risk Assessment Matrix as an element of theHSE management system to identify actions to reduce risk to ALARP is shown in Figure 2 below.Objective setting is at the heart of the HSE Management System and the Risk Assessment Matrix overlay format shown below is a useful tool that can help management in the interpretation of risk (expressed in the policy and strategic objectives of the company) and also help the line in understanding how this policy and these objectives are to be regarded (in terms of tolerable risk) in their day to day operations.strategic objectives)The definition of tolerable risk should be derived from the policy and strategic objectives of the company and can be indicated on the Risk Assessment Matrix by company management by shading-in the appropriate areas. The shading indicated in the matrix is recommended practice; deviations can be considered for small operating entities. The focus provided by using the Risk Assessment Matrix in this way enables company management to determine whether the risk levels inherent in the company's operations are tolerable and whether they fit with current corporate policies and objectives. For example, if an operation would result in scenarios which lie in an area on the Risk Assessment Matrix that the company would normally regard as “intolerable” in policy terms, then alternative ways of carrying out the operation should be investigated. If there are no alternative ways, then management must decide whether the operation should proceed or not. If it has to proceed then special treatment in regard to the level of control must be implemented before the operation takes place.The Risk Assessment Matrix overlay may also be used on a scenario by scenario basis to prioritise risk reduction efforts. It is adaptable to varying levels of information and depths of evaluation. It has a built-in presentation format that lends itself to review. Because it is qualitative and the scales relative, instead of absolute, exact knowledge is not required and thus riskunderstanding can be reached fairly easily. Examples of risk determination using the Risk Assessment Matrix are included in Appendix 2.A company should consider using the Risk Assessment Matrix as a part of itsimplementation of the HSE Management System and of HSE Cases (HSE Reports). The use of the Risk Assessment Matrix will: y and ALARP at all levels ∙enhance the appreciation of HSE risk tolerabilitin the company, company policy and standards and local company HSE ∙assist in making thepolicies relevant to day to day operations via the setting of clear risk basedobjectives that can be cascaded into the setting of individual tasks andtargets, and -based HSE ∙provide the basis for the implementation of the riskManagement System in accordance with PetroChina (Halfaya) Guidance. 5.2 In Incident InvestigationFor use in incident follow-up, the matrix can be used with an overlay as shown in Figure 3 to decide on depth of investigation, investigation team composition, reporting level, etcFigure 3 Incident Follow-up OverlaySuggestions for team composition, reporting and feedback to management are shown below. Company managements are encouraged to review and customise the table.Risk Rating Investigation teamcompositionReporting/discussionLow risk (unshaded area) local supervisor + HSEfocal pointreporting to departmentheadMedium Risk (lightly shaded area) asset holder + other linestaff as required + HSEadvisorreporting to OpcomanagementHigh Risk (heavily shaded area) Member of ManagementTeam + asset holder + HSEadvisor + independentperson e.g. from corporateorganisation + specialists asrequiredreporting to CEO andvoluntary reporting toService CompaniesThe Incident Follow-up Overlay is intended for use by location personnel after an incident occurrence to:∙assess the significance of an incident in terms of its ultimate potential for injury, damage, environmental and reputation effects,∙provide guidance in determining the depth or extent of an incident investigation and its follow-up, and∙increase the a wareness of Health, Safety and Environmental implications of any incident.Application of the tool is expected to:∙promote near -miss reporting, improve knowledge of potentially serious incidents,∙enhance the direction of safety efforts and make more ef ficient use of investigation time,∙improve management of risk reduction efforts, and focus on where the greatest benefits can be achieved,∙provide a broad incident occurrence indicator, and∙assist in media handling by the Public Affairs staff due to an improved insight into the potential severity of an incident.APPENDIX I CONSEQUENCE CATEGORYDEFINITIONHarm to PeopleNo. Description0 No injury or damage to health.1 Slight injury or health effects (including first aid case and medical treatment case) -Not affecting work performance or causing disability.2 Minor injury or health effects (Lost Time Injury) - Affecting work performance, suchas restriction to activities (Restricted Work Case) or a need to take a few days to fullyrecover (Lost Workday Case). Limited health effects which are reversible, e.g. skinirritation, food poisoning.3 Major injury or health effects (including Permanent Partial Disability) - Affecting workperformance in the longer term, such as a prolonged absence from work. Irreversiblehealth damage without loss of life, e.g. noise induced hearing loss, chronic backinjuries.4 Single fatality - From an accident or occupational illness (poisoning , cancer).5 Multiple fatalities - From an accident or occupational illness (poisoning, cancer).Asset DamageNo. Description (100% costs, USD)damage0 Zero1 Slight damage - No disruption to operation (costs less than 10,000)2 Minor damage - Brief disruption (costs less than 100,000)3 Local damage - Partial shutdown (can be restarted but costs up to 500,000)4 Major damage - Partial operation loss (2 weeks shutdown costs up to 10,000,000)5 Extensive damage - Substantial or total loss of operation (costs in excess of10,000,000)Environmental EffectNo. Description0 Zero effect - No environmental damage. No change in the environment. No financial consequences.1 Slight effect - Local environmental damage. Within the fence and within systems. Negligible financialconsequences.2 Minor effect - Contamination. Damage sufficiently large to attack the environment. Single exceedance ofstatutory or prescribed criterion. Single complaint. No permanent effect on the environment.3 Localised effect - Limited loss of discharges of known toxicity. Repeated exceedance of statutory orprescribed limit. Affecting neighbourhood.4 Major effect - Severe environmental damage. The company is required to take extensive measures torestore the contaminated environment to its original state. Extended exceedance of statutory or prescribed limits.5 Massive effect - Persistent severe environmental damage or severe nuisance extending over a large area. Interms of commercial or recreational use or nature conservancy, a major economic loss for the company.Constant, high exceedance of statutory or prescribed limits.Impact On ReputationNo. Description0 No impact - No public awareness1 Slight impact - Public awareness may exist, but there is no public concern.2 Limited impact - Some local public concern. Some local media and/or local political attention withpotentially adverse aspects for company operations.3 Considerable impact - Regional public concern. Extensive adverse attention in local media. Slight nationalmedia and / or local / regional political attention. Adverse stance of local government and/or action groups.4 National impact - National public concern. Extensive adverse attention in the national media. Regional /national policies with potentially restrictive measures and/or impact on grant of licences. Mobilisation of action groups.5 International impact - International public attention. Extensive adverse attention in international media.National / international policies with potentially severe impact on access to new areas, grants of licences and/or tax legislation.Risk Assessment APPENDIX II RISK ASSESSMENT MATRIXAPPLICATION EXAMPLESExamples In HSE Risk Management1. Risk Scenario: All the tanks in a terminal are within bunds. One of the tanks isreceiving gasoline from a tanker. The operation is started at night. The storage tankis overfilled and a large vapour cloud is formed by vaporising gasoline. Thevapour cloud is ignited by a passing vehicle. A major explosion and fire developwhich destroy 10 of the 15 tanks at the terminal, cause extensive damage, andresult in multiple fatalities. Such an accident has not occurred previously in theOperating Unit.Using the Risk Assessment Matrix (see the figure above), this scenario for people, assets and company reputation plots in the region categorised as Demonstrate ALARP by company management. This means that for this type of loss of containment event a cost benefit analysis should be undertaken to determine if there are additional cost effective measures that could be put in place to further reduce the risks to people, assets and company reputation. The risk to the environment should be managed for continuous improvement.2. A proposal for a new installation has two product movement scenarios: transportby truck or the installation of a pipeline.For the trucking scenario (indicated by a O on the matrix shown below), the following risk classifications were identified: C5(P), C2(A), D1(E), C1(R). The risk to people is categorised as “intolerable”. For this scenario to be undertaken special treatment in regard to protecting people must be implemented. Cost effective measures to reduce the risk to people should be undertaken.For the pipeline scenario (indicated by a on the matrix), the following risk classifications were identified: B2(P), B3(A), B3(E), B1(R). The risks to people,assets, environment and reputation are categorised as tolerable, and if the pipeline scenario is implemented, should be managed for continuous improvement in HSE performance.1. During a weekly off loading operation from a supply vessel, a roof section of acontainer became detached and fell into the sea striking the vessel on the port side.Containers containing chemicals are delivered once a month.The potential consequence to people from this incident is a single fatality. This corresponds to a severity rating code of 4. A similar incident with fatal consequences occurred 3 years ago. Several times per year local damage occurs as a result of loose items falling during off loading. The Incident Potentials determined are: ∙ C4(P) - fatality if a person was below falling roof. ∙ D3(A) - equipment damage causes partial shutdown. ∙ C1(E) - slight environmental effect.2. Bus carrying contract cleaning staff fails to stop at security check and hits thesecurity gate. There were no injuries. There have been previous occasions in company when sudden stops from hitting obstacles resulted in fractures or bruises.The following classifications are appropriate:∙ D3(P) - injuries from sudden stop.∙ D2(A) - damage to vehicle or obstacles3. Mechanical digger severed a live 415 Volt underground cable to a laboratory whileexcavating to lay water pipes. There were no injuries.∙ B4(P) - possible electrocution of driver (one person).∙ C2(A) - loss of ongoing experiment and equipment.4. Radioactive contamination found on work bench during routine monitoring.This incident would be classified:-∙ B4(P) - internal contamination can lead to cancer; cases are known in industry∙ E3(E) - repeated breach of statutory rules.5. While trying to jump start a car (12V) with a crane battery (24V) the car battery exploded,spraying acid on operator. Actual consequences : damage to clothing and car.∙ C3(P) - possible severe eye injury.∙ C2(A) - damage to car.6. Filing cabinet drawers are opened adjacent to a busy access route in an office. Thecabinet overbalances and falls over, nobody is hurt but people could have been passing. It has occurred once before in the Operating Unit that someone was seriously hurt by such an accident.∙ D3(P) - major injury to person passing.7. During “start-up” an exchanger joint fails releasing an estimated 5-tonne cloud ofpropane. The operator jumped away and sprained his ankle.∙ B5(P) - possible multiple fatalities if the gas cloud had been ignited.∙ B3(A) - damage in case of gas cloud explosion.8. During the loading of diesel from a tank, the ship's hose sprung a leak and the riverwas contaminated. The contamination was noted within minutes by an outsider who warned the loading master. The damage could have been much worse if it had not been spotted so quickly. Small leaks have occurred earlier in the company, but not a major one.∙ B3 (E) or D2 (E) - spills with minor effects have occurred, more serious local effect has not occurred previously in this company∙ D2 (R) - local population gets worried about frequent minor spills。
变更可行性和风险评估表(英语版)
e estimated amount (Dollars)
of cost / benefit analysis if possible
not run.
If no, an explanation of how the change can continue the requirements of the inspection.
If no, an explanation of how the change can continue the requirements of the production.
Attach evidence of cost / benefit analysis if possible
Feasible, change can pass to the acceptance stage.
Conclusion
Not Feasible, the analysis shows a high risk or benefits do not represent a tangible improvement so the change should not run.
Law and Regulations
EHS
HSF Requirement..such as RoHS, ELV, REACH, etc.?
Any risk in law & regulations related to cargo, import and export aspects… including one geographic region to others, countries of manufacturing and sales through-out the supply chain? Any additional aspects (e.g., occupational health, work safety, environmental pollution, chemical or gas discharge, energy consumption, etc.)? if yes, are the current control measures sufficient?
英文版房地产估价报告书模板范本

【最新资料,WORD文档,可编辑修改】REAL ESTATE APPRAISAL REPORTName of Project: Appraisal report on the evaluation of the value of Real Estate of Room0302,Unit11,Building1,No.196(Shangjie District),Changzhi Road, Taiyuan City Entrusting Party: ————————Appraising Institution: ————————CO., LTDAppraisers: ————————Appraisal Working Date:————————Appraisal Report No.: ————————————————CO., LTD(seal)Contents1.Letter to the entrusting party (3)2.Statement by the appraisers (4)3.Presumption and restrictive conditions (5)4.Appraisal result report (6)5.Appraisal technical report (11)6.Appendix (19)Letter to the Entrusting PartyDear Ms. Yang Fang ,We accepted your appointment to conduct the appraisal on your real estate that you have entrusted us. The appraised object is the real estate located at Room0302, Unit11,Building1,No.196(Shangjie District),Changzhi Road, Taiyuan City with the building area of 141.70 square meters.The appraisal date is July 08, 2010.Purpose of Appraisal: Supplying the reference basis of real estate market price for the entrusting party’s knowledgeAppraisal Result: The appraisers have assessed the value of the above-mentioned real estate on the basis of independence, impersonality, equity, legitimacy and cautiousness, adhering to on-spot inspection of the real estate as well as comprehensive collection of related market information and appraised object information, in the light of general analysis the elements which will influence the market value of the real estate, comply with state regulations on real estate appraisal, real estate appraisal rules and given appraisal purpose as well as by utilizing logical appraisal processes and methods. The appraisal result of the appraised object on July 08, 2010 is as follows (currency: RMB):Unit Price of the appraised object:RMB7623 Yuan/Square MeterTotal Price of the appraised object: RMB1,080,200.00 YuanCapitalization (the capital form of Chinese numerals): RMB one million nine eighty thousand and two hundred Yuan)For detailed appraisal results, process and related explanation, please refer to the ‘Appraisal Result Report’and ‘Appraisal Technical Report’.Taiyuan Wuyuetong Real Estate Appraisal Co., LtdJuly 13, 2010Taiyuan Wuyuetong Real Estate Appraisal CO., LTD(seal)Statement by the AppraisersWe hereby solemnly declare the following:1.All of the information which has been shown in this report is authentic and accurate.2.All of the analyses, comments and conclusions which have been shown in this report havebeen presented, given and drawn through our impartial analysis and professional knowledge.However, all of them have been restricted by the presumptions and restrictive conditions which have been explained in this report.3.We have not had the interest conflict with the appraised object, nor have common interestswith or prejudice against the entrusting party.4.According to Real Estate Appraisal Rules which is the State Standard of the People's Republicof China, we presented analyses, given comments, drawn conclusions and compose the report eventually.5.The on-site inspection of the appraised object has been done by our appraisers through whichthey are responsible for the objectivity, authenticity and impartiality of the inspection results.However, unless otherwise agreed, the scope of on-site inspection is restricted to appearance and use status of the appraised object. The appraisers do not shoulder the responsibility for investigating the structure and quality of the building as well as for examining other overlaid, unexposed and unreachable parts of the appraised object. The appraisers who take charge of on-site inspection are Duan Zhihong and Chai Hongbin.6.Not any important and professional assistance has been offered to the appraisal report.7.The appraisal is based on the relevant documents supplied by the entrusting party who shall beheld liable for the authenticity, completeness and consequences incurred. The appraisers shall be only held liable for the operation process and fairness of the appraisal method adopted.8.The registered real estate appraisers who take charge of the appraisal:Duan ZhihongRegisterDate of expiration:September 2010 (seal)Chai HongbinRegistered Public Real Estate Appraiser of P. R. China (Registration No.: 1420070031) Date of expiration:September 2010(seal)Presumption and Restrictive Conditions1.The entrusting party obtained the appraised object legally and the appraised object is in soundcondition at the appraisal time and is used legally, safely and normally at its optimal status.2.The real estate market at the appraisal time operates publicly, equally and voluntarily.3.Any operation mode and procedure relating to the appraised object shall comply with therelevant national and local laws and regulations.4.The owner, the location, the category of property, the building area and the function of theappraised object in this report shall be subject to what have been recorded in the House Proprietorship Certificate provided by the entrusting party.5.The appraisal result in this report is the market value of the real estate at the appraisal time of5th, July, 2010 and meets all the presumption and restrictive conditions. The real estate price shall be reappraised in case the conditions and purpose set in this report vary.6.The appraisal price in this report is objective and impartial market price, without consideringthe influence on the appraisal result by other rights such as mortgage and leasing right, risk of the future change of the real estate market, short-term disciplinary measures and relevant taxation, etc.7.The appraisal result shall remain effective within one year since the finalization of the report.If during the period, there is major change in national macroeconomic policy, the real estate market or the physical status of the appraised object which has major effects on the appraisal result, we shall be appointed again to perform the appraisal.8.The report shall only be used for the purpose of appraisal by the entrusting party, that is, tosupply referential basis for the entrusting party to determine the market value of the real estate. The report shall not be used for other economic activities.9.The report shall be used as a whole and we shall not be held liable for the relevant lossesresulted from the use of the part of the report.Appraisal Result ReportBing Wu Yue Tong Gu Zi [2010] No. 0706The Entrusting Party:Name: ————————Home Address: ————————The Entrusted Appraising Party:Company name:————————Co., LtdClass: ————————Legal representative: ————————Address: ————————Telephone: (————————————————CO., LTD(seal)Appraised ObjectThe appraised object: the appraised object is located at————————.The building have 7 floots and was built in 2004 . Building with steel reinforced concrete structure , the outside wall was tile fixing . The doors of Unites are intelligent security doors , the ground inside the building is waterstone , iron railings and wooden arms , inside wall is emulsion paint, The appraised object located at Room02 , Unit11 ,third floor of the building . It is a residence .Decoration status of the appraised object: High-grade decoration , the floor of the room is covered by import granite , the wall is painted by latex, and the flooring angular line is made of clad plate as well as the suspended ceiling is decorated by fluorescent lamp. Parlour is very artistic , the wall is black marble , integral ambry . The outer window of the room is decorated by top-grade insulating glass with aluminum alloy, stainless steel guard bar andmarble windowsill. What’s more, the door of the room consists of security door and wooden door , and the flooring angular line is made of ceramic tile, the suspended ceiling is decorated by fluorescent lamp as well. marble wash stand , sanitary fittings are complete ;there are water, electricity, central heating, gas, television, internet in the house .Status of Proprietorship: Fang Quan Zheng Bing Zi No.S0906546 “House Proprietary Certificate”which has been provided by the entrusting party shows: Owner: Sun Zhiyu Yang Fang ; Location: ————————d ; Category of Property: Private; Building No.: 1; Room No.0302; Structure: Steel reinforced concrete; Total Building Floors: 7; Floor No.of the Appraised Object: 3; Building Area:141.70 square meters; Use of Design: Residence .Purpose of Appraisal: Supplying the reference basis of real estate market price for the entrusting party’s knowledge.The appraisal date: July 08, 2010.Definition of Price: The appraisal adopts the market price standard of the real estate, that is, the appraisal is complying with the market price on July 08, 2010 which is the appraisal date. Appraisal Basis:1.“Administration Rule of Urban Real Estate of P. R. China”2.“Administration Rule of Land Use of P. R. China”3.National Standard “Regulations for Real Estate Appraisal” of P. R. China4.“Property Law of P. R. China”5.“House Proprietorship Certificate”6.The relevant documents supplied by the entrusting partyrmation of the on-site inspection of the appraised object by the appraisers8.Relevant documents concerning the real estate market mastered and collected by theappraising partyAppraisal Principles:1.Principle of legalityThe real estate appraisal shall be conducted on the basis of the legal proprietorship of the real estate, which contains the legal obtainment, legal use, legal transaction or disposition, etc.2.Principle of Maximal and Optimal UseThe appraisal of the real estate shall be based on the maximal and optimal use.The maximal and optimal use means enabling the appraised object to generate the maximal value legally allowed, technically possible, economically feasible and after reasonable argument.3.Principle of ReplacementThe appraisal result shall not deviate from the normal price of similar property under similar conditions obviously. Similar property refers to real estate in comparable search area and equal or similar to the appraised object concerning the function, scope, grade and building structure. Comparable search area means the regional range where the real estate may replace the appraised object or affect the price of the appraised object.4.Principle of Appraisal TimeThis principle emphasizes that the appraisal result is time dependent and time effective. As the real estate market is ever-changing, the same real estate always has different prices at different appraisal time. The appraisal result is the objective and reasonable price or value ofthe appraised object at the appraisal time.5.Principle of Objectiveness and FairnessThe appraisal is based on sufficient investigation, comprehension and analysis of the actual conditions of the appraised object, strictly obeys the relevant laws and decrees of the state, Shanxi Province and Taiyuan Municipality, considers the interests of correlative parties fully, follows scientific appraisal procedures, adopts reasonable and suitable appraisal methods and through careful and accurate calculation.6.Principle of PrudenceWe shall not overestimate benefits and costs, and shall not choose cases with higher deal price; we shall not underestimate cost rate and choose lower relative parameters either. Prudence is necessary before making professional judgment under uncertain situations.Anyway, in the process of the appraisal, we shall obey the relevant national and local laws and decrees, adheres to such principles as objectiveness, fairness, science and legitimacy so as to ensure rational appraisal procedure, scientific appraisal method, accurate appraisal result and the secret of the appraisal.Appraisal Method:According to the appraisal purpose, the development degree of Taiyuan Real Estate market and the appraisal maneuverability, on the basis of analyze the relevant data and investigate appraised object on-site. In view of the real estate of the same kind has a high frequency of leasing, as a result of this, the appraisers calculate the price of the appraised object by market comparison method. Consequently, according to the characteristics of the appraised object and the actual situation, as well as comply with the doctrine of real estate appraisal method, the method has been adopted to determine the market value of the appraised object.The method is to anticipate the normal net profit of the appraised object in the future and choose suitable capitalization rate to discount such profit to the appraisal time for accumulation, in order to estimate the objective and reasonable price or value of the appraised object .Appraisal ResultThe appraisers have assessed the value of the above-mentioned real estate on the basis of independence, impersonality, equity, legitimacy and cautiousness, adhering to on-spot inspection of the real estate as well as comprehensive collection of related market information and appraisal object information, in the light of general analysis the elements which will influence the market value of the real estate, comply with state regulations on real estate appraisal, real estate appraisal rules and given appraisal purpose as well as by utilizing logical appraisal processes and methods. The appraisal result of the appraised object on July 08, 2010 is as follows (currency: RMB):Unit Price of the appraised object:RMB7623 Yuan/Square MeterTotal Price of the appraised object: RMB1,080,200.00 YuanCapitalization (the capital form of Chinese numerals): RMB one million nine eighty thousand and two hundred Yuan)Appraisers:Duan ZhihongRegisterDate of expiration:September 2010 (seal)Chai HongbinRegistered Public Real Estate Appraiser of P. R. China (Registration No.: 1420070031) Date of expiration:September 2010(seal)Appraisal Working Date:From July 08, 2010 to July 13, 2010Validity Term of the Appraisal ReportThe appraisal result shall be valid within one year from the finalization of the report. Application Range of the Appraisal ReportThe report supp lies the basis for the reference price for the entrusting party’s knowledge of the market price of the real estate. It is ineffective for other economic activities.Taiyuan Wuyuetong Real Estate Appraisal CO., LTD(seal)Appraisal Technical ReportClause 1 General Situation of the Appraised Real Estate1.Individual Elements Analysis(1)Status of ProprietorshipFang Quan Zheng Bing Zi No.S0906546 “House Proprietary Certificate” which has been provided by the entrusting party shows: Owner: Sun Zhiyu Yang Fang ; Location: ————————; Category of Property: Private; Building No.: 1; Room No.0302;Structure: Steel reinforced concrete; Total Building Floors: 7; Floor No. of the Appraised Object: 3; Building Area:141.70 square meters; Use of Design: Residence(2)Substance Entity Condition(3)The appraised object: the appraised object is located at ————————.Thebuilding have 7 floots and was built in 2004 . Building with steel reinforced concrete structure , the outside wall was tile fixing . The doors of Unites are intelligent security doors , the ground inside the building is waterstone , iron railings and wooden arms , inside wall is emulsion paint, The appraised object located at Room02 , Unit11 ,third floor of the building . It is a residence .Decoration status of the appraised object: High-grade decoration , the floor of the room is covered by import granite , the wall is painted by latex, and the flooring angular line is made of clad plate as well as the suspended ceiling is decorated by fluorescent lamp. Parlour is very artistic , the wall is black marble , integral ambry . The outer window of the room is decorated by top-grade insulating glass with aluminum alloy, stainless steel guard bar and marble windowsill. What’s more, the door of the room consists of security door and wooden door , and the flooring angular line is made of ceramic tile, the suspended ceiling is decorated by fluorescent lamp as well. marble wash stand , sanitary fittings are complete ; there are water, electricity, central heating, gas, television, internet in the house .2.Regional Effects Analysis(1)District General ConditionXiaodian District is located at the southeast part of Taiyuan, and is the north of the Jinzhong Basin . Qingxu Town is at its sourth , Nanneihuan District and Yingze District are at north , Yuci City is at east , Fen River is at west .The transportation of this district is well developed.The concentrated communication network radiates in all directions to let the residents enjoy convenient transportation.The economic strength of Xiaodian District is abundant. It owns many existing businessenterprises, including commerce, diet, service and transportation, etc. Since it was established, the District Committee and Government vigorously implement the strategy of prosperity in virtue of business development by investing .(2)Location and Transportation ConditionMany bus routes have been distributed at surroundings, for instance, bus 39, 824, 838, 840, 849, 864, and 877. The location of the appraised object is in Level I-B commercial land range which enjoys geographical advantage and convenient transportation.(3)Surroundings and Peripheral FacilitiesSituated at the area where is equipped with a complete set of supporting facilities and advanced business service facilities, hospital, bank, school, hotel, supermarket and bus station, etc can all be found easily. Numbers of commercial mansions, such as, Huachen Mansion , Shanmei International Mansion , Changfeng Shopping Mall , Orient Home , Wholesale Market of Tee , Sangyou Electrical Equipment , Suning Electrical Equipment , Qiannian Chamber , Qinxian Hotel , Tianshuihua Hotel , Jinshengyuan Hotel and Furong Town Restaurant . In addition, many financial institutions, including China Citic Bank, China Merchants Bank, China Ever bright Bank, Huaxia Bank and Industrial and Commercial Bank are also scattered around here. The educational facilities and medical treatment facilities in this area are all in readiness, the former incorporates Yujie Kindergarten, Lele Art Kindergarten, Affiliated School of Taiyuan Normal College , Taiyuan No.38 Middle School , Taiyuan No.38 Middle School and Wenhua Middle School, the latter consists of Shanxi Meitan Central Hospital and Kangming Ophthalmologic Hospital and Changcheng Dental Specialist . The area endures sheer pedestrian volume, and enjoys business prosperity as well as graceful environment. (4)Infrastructural Facilities ConditionThe area has connected to the seven mains outside the red line, which is as follows:①Connect to water supplying line: The water is supplied by Taiyuan Running-WaterCompany which is highly reliable.②Connect to sewer pipe: The area possesses underground drainage network to separaterain from sewage.③Connect to electrical line: The electricity is supplied by Taiyuan Power SupplyBureau which is highly reliable.④Connect to communication cable: The communication cable has been spread out inthe area which is highly reliable.⑤Connect to gas line: The gas pipe network has been connected into this area which ishighly reliable.⑥Connect to flue gas duct: The area enjoys central heating supply which is highlyreliable.⑦Access to roads: The appraised object adjacent to Fuxi Street in the south.3.Market Background AnalysisTaiyuan municipality is the capital of Shanxi province which serves as the political, cultural, educational, scientific and technological, communication and information centers in Shanxi province. It is one of the twenty-two megalopolis in China. Taiyuan is situated at the combing site of the eastern, central and western economic belts which connects the west with the east, the north with the south of China and plays a two-way supporting role under the strategy of opening the country to the outside world and in economicdevelopment layout. According to the general requirement of ‘Moving southward, marching into the east’,‘Northward enlargement, eastward expansion’,‘prompt quality’and ‘reinvent image’as well as the construction guidance ‘Rebuild old city, construct new town, exploit ancient city ’and take action simultaneously. Taiyuan erected the image of ‘Brand-new Taiyuan’, all-sided speeded up the steps towards the construction of the city and enhanced the radiometric force, influence power and leading power as a city of provincial capital gradually. In recent years, remarkable results were achieved in term of transportation, communication, municipal administration and ecological environment. Due to a quintuple-level transportation network consisting of air routes, railways and highways have been completed, Taiyuan takes on a new look with each passing day. A good socioeconomic foundation can be laid for the further development of the Real Estate Market in Taiyuan with the continuous improvement in supporting facilities and infrastructure.In recent years, Taiyuan office building real estate market has experienced a process from emergence to instant development. At present, Taiyuan office building real estate market has presented the trend of stable development marked by increased volume of transaction and slowly increased price. We hold the opinion that Taiyuan office building real estate market will keep the trend of stable development continuously for quite a long time. In other words, the market prospect for the appraised object is optimistic.4.The Analysis of Maximal and Optimal UseReal estate estimate should be based on the best use of the appraised object, the analysis of maximal and optimal use really embody the objectivity of estimate, whether measuring, judging the appraised object is at best use or not should be judged from the following aspects:①Law permitting, not limited by the condition of current use, but based on law, thedirection of the plan development, and estimated by the possible best use.②In technology, that is, estimate according to the technical requirement in houseconstruction engineering.③In economy, estimated price should use the result of getting the best profits fromlimited put-in at all kinds of methods④Land and building, that is, judge its best condition or not based on the combination ofreal estate internal composing factors.⑤Coordination between real estate and environmental surroundings, that is, if realestate and environmental surroundings are coordinated or balanced.⑥Sustainability, that is, the appraisers should study not only the past and the currentprice, but also the current real estate market situation, the development trend and the effects of varied political and economic situation as well as policy shift in order to predict the future price trend and the change tendency of profit.According to these aspects mentioned above, the current use of the appraised real estate is at the best status.Clause II Analysis and Calculation of the Appraisal Price1.Choice of the Appraisal MethodAccording to the appraisal purpose, the development degree of Taiyuan Real Estate market and the appraisal maneuverability, on the basis of analyze the relevant data and investigate appraised object on-site. In view of the real estate of the same kind has a highfrequency of leasing, as a result of this, the appraisers calculate the price of the appraised object by market comparison method. Consequently, according to the characteristics of the appraised object and the actual situation, as well as comply with the doctrine of real estate appraisal method, the method has been adopted to determine the market value of the appraised object.The method is to anticipate the normal net profit of the appraised object in the future and choose suitable capitalization rate to discount such profit to the appraisal time for accumulation, in order to estimate the objective and reasonable price or value of the appraised object.2.Process of the Appraisal Price CalculationFormula for the market comparison method:1.Calculation Formula :Market Price of the Appraised Object=Price of Comparative Object×Transaction Rectification×Rectification of Trade Date×Rectification of Regional Factor×Rectification of Individual Factor2.Choose the Trade Case :A : Wenhuayuan Housing District , which is located at Changfeng Street , Buildingwith Steel reinforced concrete structure , 7 floors and was built in 1998 . the house is in the third floor , 110 square meter , common decoration , water , electricity , gas , television , the transaction price in June 2010 is RMB7,000.00 Yuan .B : Xinyuan Housing District , which is located at North Street of Wucheng , 6 floorsand was built in 2000 . Building with reinforced concrete brick structure , the house is in the second floor , 101 square meter , high-grade decoration , water , electricity , gas , television , the transaction price in May 2010 is RMB6,500.00 Yuan .C : Shangjie Housing District , which is located at Changzhi Road , 7 floors and wasbuilt in 2004 . Building with Steel reinforced concrete structure , the house is in the fifth floor , 112 square meter , common decoration , water , electricity , gas , television , the transaction price in June 2010 is RMB7,100.00 Yuan .the appraised object is :(7517+7881+7471)/3=7623 Yuan square meter5.Total Price of the appraised object=7623×141.70=1080179.1YuanThe result for the whole : 1,080,200.00 Yuan , Unit Price is 7623 Yuan square meter Clause III Determination of the Appraisal ResultAccording to the purpose of appraisal, the appraisers have assessed the value of theappraised object which is located at No. C, F/20, Unit A, Building 1 (WANGFUCommerce Building), No. 9, Fuxi Street, Taiyuan, on the basis of independence,impersonality, equity, legitimacy and cautiousness, adhering to on-spot inspection ofthe real estate as well as comprehensive collection of related market information andappraisal object information, in the light of general analysis the elements which willinfluence the market value of the real estate, comply with state regulations on realestate appraisal, real estate appraisal rules and given appraisal purpose as well as byutilizing logical appraisal processes and methods. The appraisal result of the appraisedobject on July 08, 2010 is as follows (currency: RMB):Unit Price of the appraised object:RMB7623 Yuan/Square MeterTotal Price of the appraised object: RMB1,080,200.00 YuanCapitalization (the capital form of Chinese numerals): RMB one million nine eightythousand and two hundred Yuan)————————CO., LTD(seal)Clause IV Relevant Notes1. The report is based on documents supplied by the entrusting party, who shall be heldliable for the authenticity, integrality and consequences resulted from the documentssupplied. The appraisers shall be only held liable for the operation procedure, and thefairness of the method adopted in this report.2. Without the consent in writing by the appraising institution and appraisers, the reportshall not be used by other Unit or individual than the entrusting party, report user andreport audit organ. All or part of the report shall not be released in the public media.3. Should the errors in the contents and figures owing to the typing or other reason befound, please inform us to make the amendment. Otherwise, the part with such errorsshall be null and void.4. The formal report other than duplicated or photocopied one shall be legally valid.————————Co., LtdJuly 13, 2010Appendix1. Photocopy of Identity Card of the Entrusting PartyPhotocopy of the House Proprietorship Certificate2. Photograph of the Appraised Object3. Photocopy of Business License and the Qualification Certificate of the Appraising。
供应商风险评估表范例
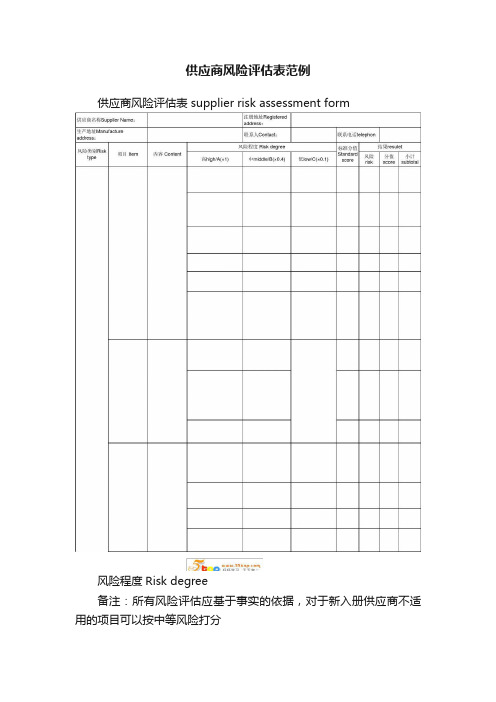
供应商风险评估表范例供应商风险评估表 supplier risk assessment form风险程度Risk degree备注:所有风险评估应基于事实的依据,对于新入册供应商不适用的项目可以按中等风险打分note: All risk evaluation is based on the actual , for new supplier, some item which could not be evalued shall evaluate as middle risk.◇必要时,可对供应商每两年执行1次现场考察或书面审查if necessary, should do on-site visit or writted review every two years.中风险middle risk低风险low risk ◇每批次物料需严格进行检验Each batch of material shall be inspected strictly.◇所有采购材料实时跟踪状态Real-time tracking of all purchasing materials ◇每半年年至少对供应商进行1次实地考察或书面调查one time on-site visit or written review every half a year at least.◇对每批次物料进行检验Each batch of material shall be inspected.◇每年跟踪一至二批材料的供料状态Track of one or two batch of m aterial yearly ◇每年对供应商进行1次实地考察或书面审查one time on-site visit or written review every year ◇对每批次物料进行检验,若供应商的历史交货质量状况良好,可降低抽样检验频率Each batch of material should be inspected, if the supplier's historical delivery quality is in good condition, could reduce the s ampling frequency ◇不跟踪材料的供应状态the supply status of the material is not tracked 评估结论:评估分值在15分以下为低风险,15-30分范围内为中等风险,30分以上为高风险(代理商得分5分以下为低风险,5-8分为中风险,8分以上为高风险)evaluation result: low risk when the evaluated score not more than 15, middle risk when the evaluated score between 15-30, high risk when the evaluated score more than 30(agents scoring 5 point or less is low risk, 5-8 is middle risk, 8 or more is high risk)高风险High risk管理措施Management method 备注:代理商仅考虑商务风险、物流风险和交货风险,不考虑其质量风险。
SGM风险评估表Action plan
RISK CATEGORY GUIDELINES风险范围指南THESE GUIDELINES ARE TO HELP INDICATE THE RELATIVE RISK OF A SUPPLY SITUATION. IF THE SITUATION DOES NOT CLEARLY FIT INTO AN EXAMPLE, USE COMMON SENSE.这些指南用于帮助识别和供应商状况有关的风险。
如果情况无法明显与例子相吻合,则使用常识进行判断。
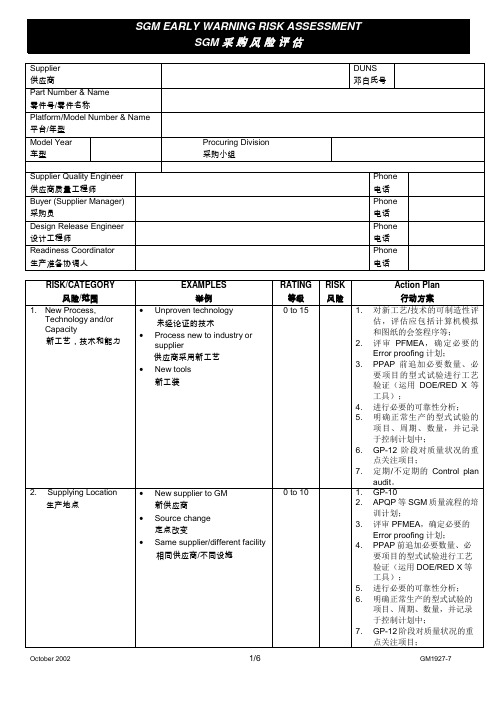
1. 新工艺,技术,能力0= 无8= 全新工艺 (如冲压模具成型原理发生变化,浇铸的流道、浇口发生变化)1= 新工装、模具,但工艺参数基本无变化10= 产品提速非常快,基本无加速过程,SSF后第二个月产量 > 2000台套3= 新工装、模具,但工艺参数需重新设定、调整10=对该公司为新技术15=对该行业为新技术2. 新生产地点0= 现有供应商,现有生产地点3= 重要零部件供应商,管理层重组1= 现有供应商,新生产地点,人员基本无变化5= 为当地的新建企业2= 现有供应商,新生产地点,人员变化 > 50% 8= 全新供应商,生产同类零件,但质量要求较低3=全新供应商,但生产同类零件,同等质量要求10= 全新供应商,未曾生产过同类零件10= 在该行业中为新企业3. GM SQ 支持0= 国内供应商5= 国外供应商,当地SQ支持初步形成3= 国外供应商,当地SQ 支持已建立10= 国外供应商,没有当地SQ 支持4. 新厂房结构0= 现有设施12= 新建厂房5= 现有厂房的扩建15= 新建厂房落后于时间进度10= 于进度前新建厂房5. 新设计0= 延用件设计3= 供应商负责设计&制造1= GM 或SGM负责设计5= 第三方负责设计6. 设计进度/ 稳定性 (包括SGM设计) 0= 设计符合进度5= 曾在FE功能匹配或Prototype送样后多次发生设计更改5= 设计改变或落后于进度超过1周10= 设计或更改使得项目严重落后于进度,PPAP无法按时完成15= OTS和部分认证试验无法在PPAP节点前完成7. 质量历史0= 几乎不发生问题5= 高PPM /PPH/ PRR或PRR未及时响应(PPM >=100或 PRR > 3件/年或DOWNTIME>=5MIN/年,对于PT:PPH>5)1= 小问题,快速响应,PRR <= 1件/年,无DOWNTIME历史10= 有PPAP曾被拒绝的历史3= 无数据 - 新供应商10= 有GP-9未满足质量要求的历史3= 小问题,但长期未解决,PRR <= 3件/年或DOWNTIME< 5MIN/年15= 重要问题频繁发生 (CS1/CS2 或PRR >= 5件/年,最近一年发生重大质量事故)8. 新工装/设备0= 使用原有工装3= 新工装,但制造时间 <= SGM给定时间85%1= 原有工装发生小更改,更改工时 <= 5天5= 新工装,但制造时间等于 SGM给定时间2= 新工装,但制造时间 <= SGM给定时间50% 5= 新工装调试时间 >= 50%制造时间8= 新工装制造时间+调试时间 >= SGM给定时间120%9. 项目进度0= 没有进度问题3= 释放或定点晚于计划 (包括SGM责任)3= PPAP延迟但仍在MRD 之前5= 释放或定点晚于计划时间超过1个月10= PPAP正式批准于可销售车生产开始之后10. 对顾客的影响0= 没有外观、安全或功能性要求3= 有对顾客产生影响的功能性要求1= 有外观要求5= 有安全要求11. 复杂的管理结构0= 管理稳定的公司5= 合资企业 (超过二方)2= 新合资企业 (二方) 5= 高速膨胀,销售额二年内增长大于50%2= 海外供应商,有超过二年的进口经验8= 第一年供货的国外供应商(包括通过贸易商供货)3= 高速膨胀,销售额二年内增长大于30%12. 项目管理0= 以往成功的生产启动5= 没有横向协调小组或该小组没有效用3= 新供应商或项目管理队伍没有得到足够授权(仅起信息沟通作用)5= 以往生产启动存在问题13. 产能0= 产能满足SGM要求5= 产能不足,必须增加新工装/设备,但进度刚好满足SGM要求(初始评估根据供应商提供的产能信息,包括各设备的生产节拍,生产该产品的计划安排生2= 产能不足,但可以通过提前做库存以满足SGM计划8= 产能不足,必须增加新工装/设备,但进度不能满足SGM要求产时间等。
Risk Assessment(英文版)(ppt 31页)

What Health & Safety Management Is
“Effective health and safety management is not ‘common sense’ but is based on a common understanding of risks and how to control them brought about through
(c) 2009 HSE Training - Sustainable Gh Ltd.
Hazard Identification
• Check manufacturers’ instructions or data sheets for chemicals and equipment (they can be very helpful in spelling out the hazards and putting them in their true perspective).
(c) 2009 HSE Training - Sustainable Gh Ltd.
Persons at Risk
• Some workers have particular requirements (e.g. new and young workers, new or expectant mothers and people with disabilities may be at particular risk).
• Injured while:
– Handling – Lifting
• Trapped by something • Drowning/Asphyxiation • Slips, Trips & Falls • Falls from heights • Exposure to:
项目风险评估报告(中英文对照)模板

项目风险评估报告(中英文对照)模板项目风险评估报告Risk Assessment Report for Project中文部分一、项目概述名称:XXX项目起止日期:XXXX年XX月XX日-XXXX年XX月XX日二、项目背景和目标项目背景:XXX项目旨在实施XXX系统,以提高组织内部运营效率,并改善客户体验。
项目目标:1. 实施XXX系统,确保在规定时间内上线,并符合预期的功能要求;2. 提高内部业务流程的自动化程度,降低人力投入成本;3. 提高客户满意度和忠诚度。
三、风险识别根据项目需求和项目经验,我们识别了以下风险因素:风险1:技术风险描述:由于XXX系统具有复杂的技术架构和集成要求,存在技术开发难度较高的风险。
解决方案:组建高水平的技术团队,进行充分的技术调研和准备工作,确保项目顺利进行。
风险2:人力资源风险描述:项目所需的专业人才在市场上供应相对紧张,有可能导致项目无法按时完成。
解决方案:及早确定项目所需的人力资源,并在人员招聘上提前准备,并制定合理的人力资源管理计划。
风险3:外部环境风险描述:外部环境因素,如政策法规变化、市场竞争加剧等,可能会对项目的进行产生不利影响。
解决方案:密切关注外部环境的变化,并及时调整项目策略以适应变化的环境。
四、风险影响评估根据风险发生的概率和影响程度,我们对各个风险进行评估。
风险1:技术风险概率:中影响程度:高评估结果:风险等级为高风险2:人力资源风险概率:高影响程度:中评估结果:风险等级为中风险3:外部环境风险概率:低影响程度:低评估结果:风险等级为低五、应对策略根据评估结果,我们制定以下应对策略:风险1:技术风险应对策略:加强技术准备工作,组建高水平的技术团队,并与供应商保持密切合作。
风险2:人力资源风险应对策略:提前制定人力资源管理计划,加强人员招聘和培训工作,确保项目所需人员及时到位。
风险3:外部环境风险应对策略:建立有效的信息收集机制,加强与政府和业内相关机构的合作,及时调整项目策略。
中英文 风险评估程序 模板

1.目的Purpose本程序为提高作业人员的风险管控能力,评估潜在的风险对完成既定任务可能产生的负面影响,从而控制并减小这些风险对人员、环境、船舶造成的损害。
This procedure aims to improve personnel’s ability of risk control and assess the adverse impact of possible and potential risks on planned tasks, so as to control and reduce the damage arising from these risks to personnel, the environment and vessels.2.适用范围Application本程序适用于公司纳入体系的所有部门、船舶和人员。
This procedure applies to all departments, vessels and personnel within the Company.3.定义Definitions3.1风险:是对不期望事件和不想要后果或损失发生可能性的一种测量。
Risk means the likelihood of occurrence of unexpected and unwanted consequence or loss.风险因素(风险值):事故发生的可能性和造成伤害的严重程度的组合。
Risk factor (risk value) means the combination of likelihood of incident occurrence and the severity of harm.3.2可能性,可以分为4种程度:The likelihood of risk occurrence is classified into 4 levels●可能性极低(1)行业内未发生过Highly unlikely, never occurred within the industry;●可能性小(2) 很长时间后才可能发生或行业内曾发生过Unlikely (may occur over long time), once occurred within the industry;●有可能 (3) 公司内曾发生过Likely, once occurred within the Company;●可能性很大(4) 在短时间内就可能发生或公司内多次发生Very likely (likely to occur in a short time), occurred repeatedly within the Company 危害的大小(严重程度),可分为四类:There are 4 levels of severity of harm:●没有危害(1)Not harmful(1)●轻度危害(2)Slightly harmful(2)●危害(3)Harmful(3)●严重危害(4)Very harmful(4)4.风险评估的原则Principles of risk identification4.1.公司船队采用共同的风险评估标准,根据风险的来源和船舶上的各类操作,识别行业公认的潜在风险和不期望的操作,制定控制风险的方法。
风险管理计划模板-英文版

2Risk management during software development 22.1Organization and Responsibilities22.2Qualification of personnel22.3Objective of risk management activities22.4Tasks, Planning32.4.1 Taskn 32.4.2 Risk analysis initialization 32.4.3 Risk analysis update 42.5Criteria for Acceptability of Risk42.6Verification and Risk traceability matrix42.7Approvals42.8Location of Risk Management File4Risk management after software development43.1Organization and Responsibilities43.2Qualification of personnel53.3Production and maintenance information53.4Annual Audit53.5Risk management of activities after software development53.5.1Approvals 63.5.2Location of Risk Analysis Report out of design 64 Ranking System for Risk Analysis 64.1Probability of Occurrence64.2Consequences of Hazard64.3Add your other criteria64.4Determination of risk level64.5Risk Index74.6Criteria for acceptability71 Introduction1.1Document overviewThis document covers the risk management plan of XXX device, designed in XXX software development projectIt contains:•the risk management organization and process during the software development project,•the risk management organization and process during maintenance, after final delivery of the software development project ・Note:most of times’ risk management organization is very different before and after design. You may split the risk management plan in two documents, the first one before end of design, tlie second one after the end of design・1.2References1.2.1Project ReferencesAdd the standard references to the table above. It may include ISO 14971, ISO 13485, IEC/TR 80002-1, IEC 62304, amongst others・2 Risk management during software developmentThis chapter covers the risk management process and organization during the software development.2.1Organization and ResponsibilitiesDescribe the organization of the team responsible for risk management during design. You may add an organization chart or add a reference to your project management plan, where the organization of the project should be already described.2.2Qualification of personnelDescribe the qualification of personnel responsible for tlie risk management and risk analysis activities. Example:The personnel who participates to the risk analysis is composed of:•Experienced staff who was involved in the design process of similar products•The expert praticians who participate to the design process2.3Objective of risk management activitiesThe objective of risk management activities is to deliver a risk analysis report, which contains:•The device characteristics that could impact on safety (ISO 14971),•The software safety classification (IEC 62304),•The risk analysis table,•The risk traceability matrix with design requirements,•The overall assessment of residual risk.The risk analysis table and risk traceability matrix will be created and updated as necessary during software development, according to tasks described in §2.4・Data on the risk analysis table includes:•List the columns, according to your risk analysis table in your risk analysis report, • • •Data on the risk analysis table includes:•List the columns, according to your risk traceability matrix in your risk analysis report, • • ■See my risk analysis report template for columns samples.Note: The Risk analysis should be performed by using the table B.l in IEC/TR 80002-1.The risk analysis report will summarize whether identified and mitigated risks meet the acceptable values defined in this plan. It will also include a statement indicating whether all known hazards have been identified・The Risk Management File gathers this document and all documents quoted above・2.4Tasks, PlanningDescribe how the risk management activities are planned during tlie project __________________________ The planning of risk activities shall be coherent with the planning of the project found in §2.2 of the project management plan.Insert a table or list or diagram describing the planning・Important, list the deliverables and reviews of each phase of the project2.4.1TasknOptional, add a sub-section for each task with:•Inputs of the task•Content of the task•Outputs of the task•Task reviews (in, if necessary, and out)•Relationship with development planning・Note: The tasks may group sets of activities found in §4 to §7 of ISO14971 ・Examples of tasks below:2.4.2Risk analysis initializationDuring this phase, the following activities are performed: identification of intended use, identification of characteristics affecting the safety, assignation of safety class (see §2.5.1) identification of hazards, evaluation of hazards, and identification of foreseeable mitigation actions.•Inputs: publications, clinical data, any information prior to design phase•Two meetings with clinicians involved in the design process•Outputs: intended use, safety characteristics and hazards, creation of risk analysis•Relationship with development planning: Output data of this task is input data for•End of Task review: review of risk analysis in draft version・2.4.3Risk analysis updateDuring this phase, the following activities are perfonned:identification of mitigation actions, evaluation of hazards after mitigation and analysis of risk/patient outcome ratio.•Inputs: publications, clinical data, any information prior to design phase•Two meetings with clinicians involved in the design process and system architect•Outputs: Update of risk analysis•Relationship with development planning: this task is performed during specifications•End of Task review: review of risk analysis in first revision.2.5Criteria for Acceptability of RiskWarning: I recommend you to read carefully §3.4 oflEC 80002-1 to select adequate risk criteria. Risks will be evaluated in accordance with Risk Management Procedures for:•Probability of occurrence, read carefully §3.4 oflEC 80002-1•Consequence of hazard•Any other criteria of your choice, like probability of detection …Based on the level, for each hazard analyzed for XXXX , the Residual Risk will be considered Acceptable if the risk level value is less than < fix your number >・Based on the risk levels, the Overall Residual Risk for a device will be considered acceptable if the following conditions are satisfied:1.None of the identified hazards leads to an unacceptable risk (i.e v no risk level above <yournumber minus 1> is identified); and2.Another quantitative criterion of your choice3.Another one ・・・Any risk levels above these values need to have actions taken to reduce the risk.2.6Verification and Risk traceability matrixVerification testing activities will be cross-referenced in the risk traceability matrix, as applicable ・2.7ApprovalsThe Risk Management Plan must be reviewed and approved by XXXX prior to the start of the risk assessment process・The Risk Analysis Report will be reviewed and approved by XXXX to ensure completeness and conformance to this Risk Management Plan.2.8Location of Risk Management FileThe Risk Management File is located in XXX (for example a document management tool defined in the software development plan or project management plan). This file contains all the documents related to the management of risk for the device and is kept for the life of the product3Risk management after software development3.1Organization and ResponsibilitiesDescribe the organization of the team responsible for risk management after software development. You may add an organization chart・Version: 01 Page 5/73.2Qualification of personnelDescribe the qualification of personnel responsible for the risk management and risk analysis activities.3.3Production and maintenance informationThe Risk Management File is systematically reviewed and updated in the maintenance of the device, especially when:•The product is modified (iso-functional patch),•Analysis of data of post marketing surveillance triggers a reevaluation (internal defects, customer requests, maintenance, vigilance bulletins, of field information from any source),3.4Annual AuditReviews and updates to the Risk Management File will be done annuallyReviews and updates to any risk related document will be documented, approved, and included within tlie Risk Management File.3.5Risk management of activities after software developmentYour QMS should have been structured to mitigate risks after design (eg: a delivery procedure to mitigate the risk of delivering the wrong version to a customer)・ However, some specific risks may arise from a new software or system and may deserve a separate risk analysis reportA Risk Analysis Report out of design will be created and updated as necessary after software development. Risk linked to activities after software development will be evaluated in accordance with Risk Management Procedures, criteria for acceptability of Risk, Requirements for Review of Risk Management Activities・The activities are:•Sales & Marketing,•Production,•Storage,•Delivery,•Installation,•Maintenance,•Un-installation,•Disposal,•Add yours …3.5.1ApprovalsThe Risk Analysis Report out of design will be reviewed and approved by XXXX to ensurecompleteness and conformance to this Risk Management Plan.3.5.2Location of Risk Analysis Report out of designThe Risk Analysis Report out of design is located in XXX. (you may add it to the DHF or DMR)4Ranking System for Risk AnalysisThis section describes how the risk level is deduced from the characteristics of the risk:• List the criteria defined in §2.2・Describe in sub sections how you quantify your criteria4.1 Probability of OccurrenceQuantitative probability is very difficult to assess for software・ For standalone software, a qualitative4.3Addyour other criteriaYour definition4.4Determination of risk levelA rule of your choice, like ・Risk Level = criterion 1x criterion 2x criterion n1 2 3 4 54.6Criteria for acceptabilityAcceptable risk per risk level is:•If the risk level is 1 to xx - No recommended actions are required・•If the risk level is xxtoyy ・ Some actions may be used, where possible, to lower the level.•If risk level is above yy the risk is unacceptable. Mitigation action must be implemented to lower the level.。
风险和危险危害因素评价RiskandHazardAssessment(

——评价和风险管理理论
1) 因果类型
(1)连锁型:认为任何一种可预防的事故
的发生都是一连串事件在一定顺序下所产生的 结果。
A1 A2 A3 A4 事故
© SGS SA 2012 ALL RIGHTS RESERVED
5
RA的理论基础
(2)多因致果型:多种各自独立的原因在同一 时间共同导致事故的发生。
HSE管理体系是建立在“所有事故都是可 以避免的”这一管理理念上的,即:如果我们能 够预先识别特定的一种危害因素,我们就能够通 过管理和发挥我们的技能来避免事故发生或是设 法使人、环境和财产免受损害,即能够对风险进 行控制。
© SGS SA 2012 ALL RIGHTS RESERVED
4
RA的理论基础
10
RA的理论基础
这五块骨牌依次是: M—人体本身(受社会环境和管理影响); P—按人的意志进行的动作,指人为失误; H—人的不安全行为和物的不安全状态引起的危险性; D—发生事故; A—受到伤害;
该理论的优点:正确分析了事故致因的事件链这 一概念。简单明了,形象直观。
© SGS SA 2012 ALL RIGHTS RESERVED
1、(定义)什么是RA? 2、(目的)为什么要做RA? 3、什么情况下需要做RA? 4、职责 5、怎么做RA? 6、RA的优缺点
© SGS SA 2012 ALL RIGHTS RESERVED
25
什么情况下需要做RA?
工作程序、流程或方法发生变化时,必须进行更新。 工作程序、流程或方法未发生变更时,必须每年进行一次复查。
© SGS SA 2012 ALL RIGHTS RESERVED
27
什么情况下需要做RA?
办事处定期风险研判安全材料范文

办事处定期风险研判安全材料范文英文版Office Regular Risk Assessment Safety Material Template As an integral part of our organization's security protocol, regular risk assessments are conducted at our office to ensure the safety and security of our personnel and assets. This document serves as a template for conducting these assessments and outlines the key considerations and procedures involved.1. IntroductionThe purpose of this template is to provide a structured approach for conducting regular risk assessments at our office. These assessments aim to identify potential threats, vulnerabilities, and hazards that may pose a risk to our operations and personnel. By identifying and evaluating these risks, we can develop appropriate mitigation measures to ensure the safety and security of our office.2. Scope of AssessmentThe scope of the assessment covers all aspects of office security, including but not limited to:Physical security: Access controls, surveillance cameras, alarm systems, and other physical security measures.Cybersecurity: Network security, data protection, and protection against cyber attacks.Personnel security: Employee training, awareness, and background checks.Operational security: Processes and procedures to ensure the secure handling of sensitive information and assets.3. MethodologyThe risk assessment will be conducted using a combination of qualitative and quantitative methods. This includes: Gathering information: Collecting relevant data and information from various sources, such as employee interviews, security audits, and intelligence reports.Identifying threats: Analyzing the collected information to identify potential threats and hazards.Assessing vulnerabilities: Evaluating the office's current security measures to identify any weaknesses or gaps.Determining risk levels: Assigning risk levels to each identified threat and vulnerability based on their severity and likelihood of occurrence.4. Mitigation MeasuresBased on the results of the risk assessment, appropriate mitigation measures will be developed and implemented. These measures may include:Improving physical security: Enhancing access controls, installing additional surveillance cameras, or upgrading alarm systems.Strengthening cybersecurity: Implementing stronger network security measures, improving data protection protocols, and conducting regular cyber security audits.Enhancing personnel security: Providing additional security training to employees, conducting background checks on new hires, and implementing secure personnel management practices.Improving operational security: Updating processes and procedures to ensure the secure handling of sensitive information and assets, and implementing additional security measures as needed.5. ConclusionRegular risk assessments are crucial for maintaining the safety and security of our office. By following this template and conducting thorough assessments, we can identify and mitigate potential risks, ensuring that our operations remain secure and protected.中文版办事处定期风险研判安全材料范文作为我们组织安全协议的重要组成部分,办事处定期进行风险评估,以确保我们的人员和资产的安全。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
【经典资料,WORD文档,可编辑修改】
【经典考试资料,答案附后,看后必过,WORD文档,可修改】
RISK ASSESSMENT REPORT TEMPLATE
Information Technology Risk Assessment For
Risk Assessment Annual Document Review History
T ABLE OF C ONTENTS
1INTRODUCTION (1)
2IT SYSTEM CHARACTERIZATION (2)
3RISK IDENTIFICATION (6)
4CONTROL ANALYSIS (8)
5RISK LIKELIHOOD DETERMINATION (12)
6IMPACT ANALYSIS (14)
7RISK DETERMINATION (16)
8RECOMMENDATIONS (18)
9RESULTS DOCUMENTATION (20)
L IST OF E XHIBITS
E XHIBIT 1:R ISK A SSESSMENT M ATRIX (20)
L IST OF F IGURES
F IGURE 1–IT S YSTEM B OUNDARY D IAGRAM (4)
F IGURE 2–I NFORMATION F LOW D IAGRAM (5)
L IST OF T ABLES
T ABLE A: R ISK C LASSIFICATIONS (1)
T ABLE B: IT S YSTEM I NVENTORY AND D EFINITION (2)
T ABLE C: T HREATS I DENTIFIED (4)
T ABLE D: V ULNERABILITIES,T HREATS, AND R ISKS (5)
T ABLE E:S ECURITY C ONTROLS (6)
T ABLE F:R ISKS-C ONTROLS-F ACTORS C ORRELATION (8)
T ABLE G:R ISK L IKELIHOOD D EFINITIONS (9)
T ABLE H:R ISK L IKELIHOOD R ATINGS (9)
T ABLE I:R ISK I MPACT R ATING D EFINITIONS (14)
T ABLE J:R ISK I MPACT A NALYSIS (14)
T ABLE K:O VERALL R ISK R ATING M ATRIX (16)
T ABLE L: O VERALL R ISK R ATINGS T ABLE (16)
T ABLE M: R ECOMMENDATIONS (18)
1 INTRODUCTION
Risk assessment participants:
Participant roles in the risk assessment in relation assigned agency responsibilities: Risk assessment techniques used:
2 IT SYSTEM CHARACTERIZATION
2 IT SYSTEM CHARACTERIZATION
Sensitivity Rating and Classification
H IGHM ODERATEL OW
IT System Classification
Must be “Sensitive” if overall sensitivity is “high”; consider as “Sensitive” if overall
sensitivity is “moderate”
S ENSITIVEN ON-S ENSITIVE
Description or diagram of the system and network architecture, including all components of the system and communications links connecting the components of the system, associated data communications and networks:
Figure 1 – IT System Boundary Diagram
Description or a diagram depicting the flow of information to and from the IT system, including inputs and outputs to the IT system and any other interfaces that exist to the system:
Figure 2 – Information Flow Diagram
3 RISK IDENTIFICATION
Identification of Vulnerabilities
Vulnerabilities were identified by:
Identification of Threats
Threats were identified by:
Identification of Risks
Risks were identified by:
The way vulnerabilities combine with credible threats to create risks is identified Table D.
4 CONTROL ANALYSIS
Table E correlates the risks identified in Table C with relevant IT security controls documented in Table D and with other mitigating or exacerbating factors.
Risk No.Risk Summary
Correlation of Relevant Controls & Other
Factors
1 2 3 4 5 6 7 8 9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
5 RISK LIKELIHOOD DETERMINATION
Table G defines the risk likelihood ratings.
Table G , evaluates the effectiveness of controls and the probability or motivation and capability of each threat to BFS and assigns a likelihood, as defined in Table F, to each risk documented in Table C. Risk No. Risk Summary
Risk Likelihood Evaluation
Risk Likelihood
Rating
1 2 3 4 5 6 7 8 9 10 11 12
Risk No.Risk Summary Risk Likelihood Evaluation
Risk Likelihood
Rating
13
14
15
16
17
18
19
Risk No.Risk Summary Risk Likelihood Evaluation
Risk Likelihood
Rating
20
21
22
23
24
25
6 IMPACT ANALYSIS
Table I documents the ratings used to evaluate the impact of risks.
Table J documents the results of the impact analysis, including the estimated impact for
Description of process used in determining impact ratings:
7 RISK DETERMINATION
Table K documents the criteria used in determining overall risk ratings.
Risk Scale: Low (1 to 10); Moderate (>10 to 50); High (>50 to 100) Table L assigns an overall risk rating, as defined in Table K, to each of the risks documented in Table D.
Description of process used in determining overall risk ratings:
8 RECOMMENDATIONS
Table M documents recommendations for the risks identified in Table D.
9 RESULTS DOCUMENTATION
Exhibit 1: Risk Assessment Matrix。
