南京邮电大学通达学院毕业设计
《卖油翁毕设论文

南京邮电大学通达学院毕业设计(论文)题目:基于K均值的图像分类设计与实现专业自动化学生姓名施昊琛班级学号 ********指导教师朱松豪指导单位自动化学院日期:2012年3月14日至2012年6月17日摘要K均值算法在高光谱遥感影像的非监督分类中具有较强的实用性, 表现出了良好的优点。
首先采用了最大最小选心法确定初始类别中心, 然后使用了K均值算法实现遥感影像的分类。
在分类过程中采用了VC++2005作为开发平台, 极大地提高了遥感影像的分类速度, 同时还给出了实现K均值分类主要步骤的代码。
最后在深入分析不同迭代次数下得到的不同分类图的基础上, 研究了迭代次数值对最后分类结果的影响。
关键词:非监督分类; K均值算法; VC++2005ABSTRACTHuman Identification System Based on Biometrics is a totally brand-new technique different from traditional methods because it adopts the inherent organism's characteristics of human body. More and more people pay great attention to it as it is safer, more reliable and effective. It begins entering every realm of our society and meeting the challenge of new era.This paper first introduces the research background of the computer face recognition technology and the main method, and then propose a discriminant analysis based on Fourier transform and Face Recognition. Linear discriminant analysis (LDA) in the PCA combined with Fisher on the basis of the principle criteria used to extract feature vectors, the proposed removal of the feature vector retained the original image space in the major categories of information, and can the minimum mean square error reconstruction of the sense of the original image. The proposed method first uses Fourier transform to extract the face image is relatively stable low-frequency sub-band, blurring the facial expression and posture influence, and also reached a dimension reduction of the effect of the image vector, and then use the linear discriminant analysis and identification feature extraction components. The algorithm is compared with the traditional LDA methods, which greatly reduces the computational complexity, the extracted features further reflects the difference between the face and improve the recognition rate and noise performance, experimental results show that the proposed algorithm is accurate effective.Keywords:Pattern Recognition; Human Face Recognition; Fourier Transform;Linear Discriminant Analysis目录第一章绪论.............................................. - 1 -1.1 模式识别....................................................... - 1 -1.1.1 基本概念................................................. - 1 -1.1.2 模式识别系统............................................. - 1 -1.1.3 模式识别的主要方法....................................... - 2 -1.2 图像、图像处理与图像识别....................................... - 3 -1.3 人脸识别技术................................................... - 4 -1.3.1 生物特征识别技术......................................... - 4 -1.3.2 生物特征识别技术的应用和前景............................. - 5 -1.3.3 人脸识别的研究背景及意义................................. - 6 -1.3.4 人脸识别的发展历史....................................... - 8 -1.3.5 人脸识别的国内外发展现状................................. - 8 -1.3.6 人脸识别系统............................................. - 9 - 第二章傅里叶变换及其应用................................ - 11 -2.1 傅里叶变换的定义.............................................. - 11 -2.2 连续傅里叶变换................................................ - 11 -2.2.1 一维连续傅里叶变换...................................... - 11 -2.2.2 二维连续傅里叶变换...................................... - 12 -2.3 离散傅里叶变换................................................ - 13 -2.4 傅里叶变换在图像处理中的应用.................................. - 15 - 第三章基于傅里叶变换的线性鉴别分析 ...................... - 17 -3.1 线性鉴别分析(LDA)方法....................................... - 17 -3.1.1 基本思想................................................ - 17 -3.1.2 基本原理................................................ - 17 -3.2 基于LDA的人脸特征提取方法的优缺点............................ - 19 -3.3 基于傅里叶变换的LDA方法...................................... - 19 -3.4 本章小节...................................................... - 21 - 第四章实验结果......................................... - 22 -4.1 引言.......................................................... - 22 -4.2 人脸库介绍.................................................... - 22 -4.3 仿真实验...................................................... - 23 -4.3.1 图象预处理:............................................ - 23 -4.3.2 不同训练样本下的识别率.................................. - 24 -4.4 实验结果分析................................................... - 25 - 结束语 .................................................. - 26 - 致谢 .................................................. - 27 -参考文献................................................. - 28 - 附录A ................................................... - 30 -第一章绪论1.1 模式识别1.1.1 基本概念模式识别是人类的一项基本智能,在日常生活中,人们经常在进行“模式识别”。
毕设报告——精选推荐

南京邮电大学通达学院毕业设计(论文)题目: CMOS迟滞比较器专业:微电子学学生姓名:***班级学号: ********指导教师:**指导单位:电子科学与工程学院日期:年月日至年月日摘要在目前的应用市场上,数字通信系统和便携设备的需求量日益增加。
这些系统都离不开D/A和A/D转换器,而且还有高采样率和低功耗的性能要求。
作为转换器里面最主要的部件,比较器在应用市场上有十分重要的地位,尤其是高精度低功耗的高性能比较器。
集成电路新工艺的发展在一定程度上也提高了电路在精确度和功率消耗等方面的性能。
本篇论文所设计的比较器采用上华CSMC 0.5mμ工艺来实现比较器低功耗和高精确度的特性。
所设计的CMOS迟滞比较器电路通过设置内部正反馈网络,这个比较器在具有较高的分辨率的同时还有着很小的功率消耗。
由于芯片工作于存在噪音的环境,故要求比较器具有一定的抗噪音能力。
本设计通过为比较器设置外部有源分压反馈网络,使比较器具有了迟滞特性,具备了一定的抗干扰功能。
本篇论文中对这个比较器的性能、温度和工艺偏差等各种条件组合都进行了仿真,得出了若干关键参数,并对比较器内部的电流镜单元提出了改进设计。
使比较器具有了迟滞特性,具备了一定的抗干扰功能。
电路采用Candence工具进行了μ,迟滞上下门限为600mV,增益为71dB。
最仿真,仿真结果表明电路的静态功耗为530W后对比较器内部结构也作了一定的改进设计,完成了版图设计和后模拟,后模拟结果表明所有技术指标满足设计要求。
关键词:CMOS工艺;仿真;比较器;迟滞特性;后模拟ABSTRACTNow, in many application fields, the requirement for communication and portable equipments is rising. All those system require analog-to-digital converter (ADC) and digital-to-analog converter (DAC) with higher sampling rate, higher resolution, and lower power consumption. To realize this kind of ADC or DAC, a high-performance comparator is indispensable. The evolution of integrated circuit technology partially helps these requirements to be met by providing high speed devices and allowing complex functions in a given silicon area. In this paper, a very high precision comparator in 0.5mμstandard CMOS process was presented.This paper using Positive Feedback makes the CMOS Slow-moving Comparator having Slow-moving effect. The circuit has been tested by Candence. The simulation results indicateμ, achieves 71dB DC open gain, and Slow-moving voltage has that it consumes only 530Wmore than 600mV. At last, I improve and optimize the circuit design, finish the layout design and layout post-simulation, which indicate that all technology parameters meet design requirements. Key words:CMOS technology;simulation;Comparator;Slow-moving effect;Post-simulation目录第一章绪论 (1)1.1CMOS工艺概述 (1)1.2比较器应用概述 (2)1.3CMOS迟滞比较器概述 (3)1.4版图设计概述 (4)第二章比较器的工作特性 (6)2.1比较器模型 (6)2.2改进的比较器模型 (7)2.3运算放大器与比较器的区别 (7)第三章比较器的性能参数 (9)3.1比较器的主要性能参数 (9)3.2比较器设计中性能参数的折衷 (13)第四章 CMOS器件的工作特性...................错误!未定义书签。
新工科形势下独立学院毕业设计质量管理探索与实践——以南京邮电大学通达学院为例

图1
语
工科”概念的出现,是时代发展的产
业设计也应紧跟时代发展,适应新
于教育工作者来说,我们不仅要适应
要求,更要在新的工程浪潮下迎接挑
管理的过程中,应考虑新工程的要求
日常工作,并与独立学院的过程管理
合,使我们能够实现提高毕业设计
文提出的针对独立学院的毕业设计方
的具体情况,一方面希望提高毕业设
一方面,在“新工科”背景下,也有助
合能力,满足社会和市场发展的需要
【参考文献】
华.新工科建设的内涵与行动[J].高等工程2017(3):1-6.
廖志凌,邵学军,刘贤兴,等.高校本科毕业设计中存在的问题江苏大学学报:高教研究版,2004,26(2):82-85.
杜巧连,苗春雨,蒋洪奎,等.独立学院工科专业应用型人才培养模式探索[J].中国教育技术装备,2015(22).
工科专业毕业设计现状及对策分析[J].科技创新导报2015(10):218-218.
【参考文献】
梁漱溟.中国文化要义[M].上海:上海人民出版社
汤一介.我们要有文化上“反本开新”的自觉[N]. 2014-5-12(2).
张圣华.蔡元培教育名篇[M].北京:教育科学出版社
Science&Technology Vision科技。
基于51单片机_电子秤__开题报告
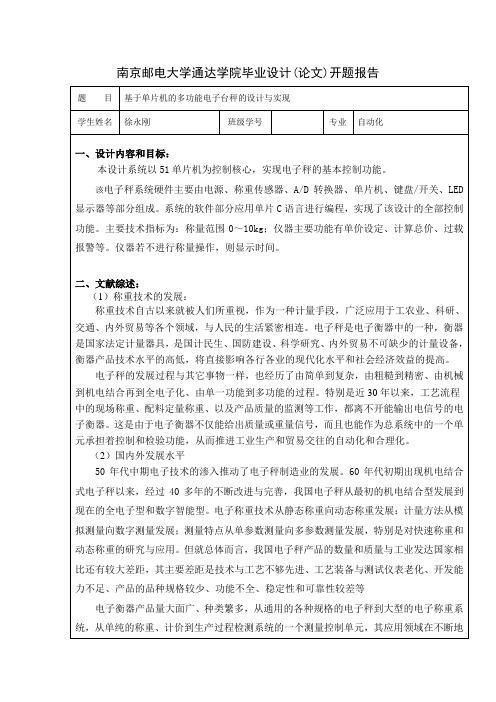
南京邮电大学通达学院毕业设计(论文)开题报告图1设计思路框图(1)数据采集:利用重力传感器获取重量数据,选用电阻应变式传感器。
(2)信号放大:将采集到的信号进行放大处理。
(3)模数转换:利用A/D转换器把输入的模拟信号转换成数字信号送到单片机。
(4)单片机控制:中央控制模块,接收外部数据,通过运算和处理,进行相应控制。
(5)人际交换:人机借口主要由键盘和LED显示管组成。
二,软件部分软件主要三个方面:一是初始化系统;二是按键检测;三是数据采集、数据处理并进行显示。
这三个方面的操作分别在主程序中来进行。
程序采用模块化的结构,这样程序结构清楚,易编程和易读性好,也便于调试和修改。
程序结构如图2所示。
图2 程序结构图系统程序固化在单片机内部的flash存储器中,分为主程序和若干子程序。
主程序的功能是系统初始化,管理和调用各个子程序。
本设计的程序流程图如图3所示。
图3 主程序流程图四、具体进度安排第七学期第12-13周:查阅相关文献资料,了解单片机设计的基本原理;第七学期第14-15周:进行功能需求分析,提出大致方案,并完成开题报告;第七学期第16-20周:进展情况检查,给出进展报告;第八学期第1周:设计信号采集部分,包括传感器的选型;第八学期第2周:设计系统的模数转换部分;第八学期第3周:完成LED的设计;第八学期第4周:提交与课程设计相关的专业外文资料译文;第八学期第5-6周:设计工作进展中期报告,明确存在的问题及解决措施;第八学期第7-12周:按设计方案进行调试仿真,完成整体设计;第八学期第13-15周:撰写毕业论文,交指导老师批阅;第八学期第16-17周:验收设计成果,按程序要求进行答辩。
五、主要参考文献[1] 赵广平,孙雯萍,孙建军. 电子称重技术现状及发展趋势[J]. 仪表技术传感器,2007,。
南京邮电大学通达学院毕业设计(论文)开题报告
主要参考文献:
[1]Arnaud Doucet, N.J. Gordon, and V. Krishnamurthy. Particle filters for state estimation of jump markov linear systems. IEEE Transactions on Signal Processing, 49(3):613–624, Mar. 2001.
3.帧间差分法方法研究
鉴于背景差分法和帧间差分法的优缺点,我们将这两种方法结合起来,使它们优势互补,从而克服相互的弱点,提高运动检测的效果。但是在实际的场景中,即便是室内环境,也存在光线等各种变化造成的干扰,或者人为造成的开灯等光线的强烈变化。所以在背景差分法的实现中,它的固定背景不能一成不变。如果不进行重新初始化,错误的检测结果将随时间不断累计,造成恶性循环,从而造成监控失效。因此,我们在提出检测算法的同时,要建立背景更新模型。保证背景图像能随着光线的变化而变化,确保检测的准确性。
[2]R.T. Collins, A.J. Lipton, and T. Kanade. Introduction to the special section on video surveillance. IEEE Transactions on Pattern Analysis and Machine Intelligence, 22(8):745–746, Aug. 2000.
7.实际方案
(1)图像预处理
本课题采用原始图像时彩色图像,并且伴有随即干扰和脉冲噪声。在本系统中不能用差分法直接对彩色图像进行处理,需将其转化为灰度图像。
(2)滤波降噪
数字图像的噪声主要来源于图像的获取(数字化过程)和传输过程。图像传感器的工作情况受到各种因素的影响,如图像获取中的环境条件和传感器元件自身的质量。
毕业设计(论文)基于visual_c++学生档案管理系统的设计

南京邮电大学通达学院毕业设计(论文)题目:基于Visual C++学生档案管理系统的设计专业:通信工程学生姓名:班级学号:指导教师:指导单位:通信与信息工程学院日期:2010年11 月22 日至2011年 6 月17 日摘要学生档案管理系统是典型的信息管理系统(MIS),其开发主要包括后台数据库的建立和维护以及前端应用程序的开发两个方面。
对于前者要求建立起数据一致性和完整性强、数据安全性好的库。
而对于后者则要求应用程序功能完备,易使用等特点。
这样就可以做到信息的规范管理、科学统计和快速查询,使学校的学生管理工作系统化、规范化、自动化,从而达到提高学校管理效率的目的。
本论文设计了一个学生信息管理系统,使用Microsoft Visual Studio开发组件中最为强大的编程工具Visual C++,其具有面向对象程序设计的功能,核心是Microsoft基础类库,即通常所说的MFC(Microsoft Foundation Class Library),采用消息映射机制进行程序设计。
这样可以由计算机来代替人工执行一系列诸如学生信息的录入与修改、院系信息的查看、课程设置信息的查询、学生成绩的管理、系统用户的查询和修改等操作。
关键词:学生档案管理;信息化;数据库;编程工具;基础类库ABSTRACTThe student records management system is the typical information management system (MIS), its development mainly includes the establishment of backstage database and the maintenance as well as front ends the application procedure development two aspects. Establishes the data uniformity and the integrity regarding former request is strong, the data security good storehouse. But requests the application procedure function regarding latter completely, is easy to use and so on the characteristic. Then we can achieve information standard management, scientific statistics and look up rapidly, make the school student management work systematization and standardization, automation, so as to achieve the purpose of improving the management efficiency.This paper designs a students' information management system, it uses Microsoft Visual Studio development component of the strongest programming tools Visual C+ +. It has the function of object oriented programming, the core is Microsoft base Class Library, what say normally namely MFC (Microsoft Foundation scale-up), adopt more emphases are programming news mapping mechanism. That the computer can be instead of artificially carries out a series of such as the students’ information inputting and modification, information of faculty and department review, the curriculum information query, student performance management, system user queries and modify etc operation.Key words:Student records management; Information; Database; Programming tools Base Class Library目录第一章可行性分析 (1)1.1可行性研究的前提 (1)1.2技术可行性和经济可行性 (1)第二章系统分析 (3)2.1需求分析 (3)2.2流程分析 (3)2.3系统功能设计 (3)2.3.1用户登录认证 (4)2.3.2数据库操作 (4)2.3.3 数据库逻辑结构设计 (4)第三章数据库理论 (5)3.1数据库知识 (5)3.2V ISUAL C++概述 (5)3.3使用A CCESS2003实现关系型数据库 (5)3.3.1实现数据库之间的联系 (5)3.3.2 使用VC连接Access数据库 (6)3.3.3 实现数据库之间的联系 (7)第四章系统具体实现与分析 (8)4.1系统登录 (8)4.2学生基本信息操作 (9)4.3照片管理 (9)4.11系统开发技术难点 (21)结束语 (23)致谢 (24)参考文献 (25)附录A (27)第一章可行性分析1.1可行性研究的前提要求和目标:●有关学籍等信息的输入,包括学生基本信息、所在班等。
毕设开题报告-及开题报告分析

开题报告如何写注意点1.一、对指导教师下达的课题任务的学习与理解这部分主要是阐述做本课题的重要意义2.二、阅读文献资料进行调研的综述这部分就是对课题相关的研究的综述落脚于本课题解决了那些关键问题3.三、根据任务书的任务及文件调研结果,初步拟定执行实施的方案(含具体进度计划)这部分重点写具体实现的技术路线方案的具体实施方法和步骤了,具体进度计划只是附在后面的东西不是重点南京邮电大学通达学院毕业设计(论文)开题报告题目基于python的网络爬虫系统的设计与实现学生姓名徐亚洲班级学号12003426 专业软件工程一、对指导教师下达的课题任务的学习与理解随着网络的快速发展和广泛应用,大数据时代的到来,网络就像一个巨大的数据宝库,如何快速获取其中的数据资源成为亟待完成的新需求。
然而网络上的信息资源大多是无组织并且动态变化的,光靠管理员手工去管理,很难将这些庞大,繁杂的数据进行有效的保存和利用,这就促使了网络爬虫技术的兴起。
网络爬虫源自Spider(或Crawler、robots)等的意译。
网络爬虫的定义有广义和狭义之分,狭义的定义为:利用标准的http协议,根据超链接和Web文档检索的方法遍历万维网信息空间的软件程序。
广义的定义为:所有能利用http协议检索Web文档的软件都称之为网络爬虫。
网络爬虫又被称为做网络蜘蛛、网络机器人,主要用于网络资源的收集工作。
是一种按照一定的规则,自动地抓取万维网信息的程序或者脚本。
另外一些不常使用的名字还有蚂蚁、自动索引、模拟程序或者蠕虫。
网络爬虫已经发展了很多年,并且搜索引擎也是爬虫的一种应用,通过搜索引擎能够更快速的获得有用的数据和信息。
但是,一些通用性的搜索引擎也存在着一定的局限性,通用搜索引擎返回的结果可能包含了大量用户不关心的网页内容,而且通用搜索引擎有限的服务器资源与无限的网络资源之间存在的矛盾进一步加深,还有,就是通用搜索引擎不能支持给据语义的信息提出的查询和搜索。
移动系统衰落信道

课题类型
设 计 内 容 与 技 术 要 求 、 成 果 形 式
移动通信系统的无线信道非常复杂, 由于传输空间的影响, 存在多径效应, 由于电波通过各个路径的距离不同,因而各路径来的反射波到达时间不同,相 位不同, 这样的多径信号在接收端叠加后的接收信号的幅度就会发生剧烈变化, 产生衰落。本课题就是采用仿真手段来研究这种移动信道。 本课题要求: 1、了解 CDMA 系统无线信道的概念。 2、学习用数学手段描述无线信道,并用 MATLAB 进行仿真,已达到对瑞利 衰落信道有较深入了解的目的。 该课题是理论研究,在研究其原理的基础上,需要用 MATLAB 进行仿真。
参 考 资 料
[1] 张贤达 保铮,通信信号处理,国防工业出版社,2000 [2] Rappaport,无线通信原理与应用,电子工业出版社,2006 [3] 樊昌信.通信原理[M].北京:国防工业出版社,2001. [4] M. Pätzold, U. Killat, F. Laue, and Y. Li, “On the statistical properties of deterministic simulation models for mobile fading channels,” IEEE Trans. Veh. Technol., vol. 47, no. 1, pp. 254-269, Feb. 1998. [5] M. Pätzold, A. Szczepanski and N. Youssef, “Methods for modeling of specified and measured multipath power-delay profiles,” IEEE Trans. Veh. Technology., vol. 51, no. 5, pp. 978-988, Sept. 2002.
南京邮电大学通达学院毕业设计(论文)开题报告范例

题 目
高校实验室管理系统设计与开发
学生姓名
班级学号
专业
提纲(开题报告2000字以上):
1.对指导教师下达的课题任务的学习与理解
2.阅读文献资料进行调研的综述
3.根据任务书的任务及文献调研结果,初步拟定的执行(实施)方案(含具体进度计划)
一、对指导教师下达的课题任务的学习与理解
①实验室建制管理:由管理员针对实验室建制机构进行管理,包括实验室建制(建制实验室与非建制实验室管理),实验室房间分配,实验室制度管理,实验室信息展示。
②实验室队伍建设:实验室管理系统与校人事处集成,抽取基本人事信息,通过筛选,确定实验室工作人员,主要针对实验室编制,实验室人员信息补录,实验室成果管理,实验室大型设备岗管理,培训管理等建设,为系统流程做铺垫。
基于以上各种业务的综合,组建针对高校实验室管理的系统,一方面便于学生与教师加强对于实验室情况的了解,另一方面便于管理者对于实验室相关业务的管理以及实验室情况的了解,简化管理的流程,实现管理的信息化。
三、根据任务书的任务及文献调研结果,初步拟定的执行(实施)方案(含具体进度计划)
第七学期第13-15周:学生进行调研,在教师指导下,写出开题报告;
确定了这样的一个目标,首先要了解目前高校针对实验室管理的管理办法,并且有目的性的对各个实验室进行实地调研,根据各个院系实习特点,具有针对性的设计系统的开发。
现阶段高校的管理办法(东南大学):学校设备处对实验室进行总体的管理,总得包括①实验室建制的管理(设备处对建制机构进行维护,各个院系针对实验室进行基本维护)。②实验室建设项目管理。③实验教学管理。④开放实验室管理。⑤相关实验室应用管理。其中多数模块还是人工管理,需要耗费大量的人力,也加大相关工作人员的工作量。所以目前急需要这样的一个网络管理系统,帮助办公管理流程的规范化,同时也减轻工作人员的工作量。
频率选择性衰落信道模型研究与仿真 开题报告
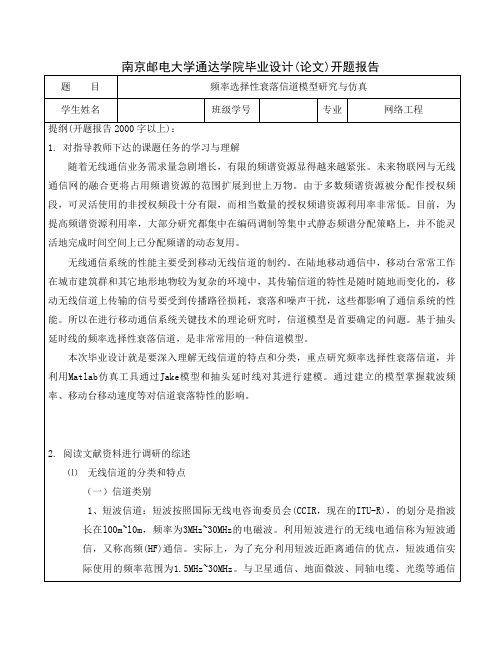
南京邮电大学通达学院毕业设计(论文)开题报告题目频率选择性衰落信道模型研究与仿真学生姓名班级学号专业网络工程提纲(开题报告2000字以上):1.对指导教师下达的课题任务的学习与理解随着无线通信业务需求量急剧增长,有限的频谱资源显得越来越紧张。
未来物联网与无线通信网的融合更将占用频谱资源的范围扩展到世上万物。
由于多数频谱资源被分配作授权频段,可灵活使用的非授权频段十分有限,而相当数量的授权频谱资源利用率非常低。
目前,为提高频谱资源利用率,大部分研究都集中在编码调制等集中式静态频谱分配策略上,并不能灵活地完成时间空间上已分配频谱的动态复用。
无线通信系统的性能主要受到移动无线信道的制约。
在陆地移动通信中,移动台常常工作在城市建筑群和其它地形地物较为复杂的环境中,其传输信道的特性是随时随地而变化的,移动无线信道上传输的信号要受到传播路径损耗,衰落和噪声干扰,这些都影响了通信系统的性能。
所以在进行移动通信系统关键技术的理论研究时,信道模型是首要确定的问题。
基于抽头延时线的频率选择性衰落信道,是非常常用的一种信道模型。
本次毕业设计就是要深入理解无线信道的特点和分类,重点研究频率选择性衰落信道,并利用Matlab仿真工具通过Jake模型和抽头延时线对其进行建模。
通过建立的模型掌握载波频率、移动台移动速度等对信道衰落特性的影响。
2.阅读文献资料进行调研的综述⑴无线信道的分类和特点(一)信道类别1、短波信道:短波按照国际无线电咨询委员会(CCIR,现在的ITU-R),的划分是指波长在l00m~l0m,频率为3MHz~30MHz的电磁波。
利用短波进行的无线电通信称为短波通信,又称高频(HF)通信。
实际上,为了充分利用短波近距离通信的优点,短波通信实际使用的频率范围为1.5MHz~30MHz。
与卫星通信、地面微波、同轴电缆、光缆等通信手段相比,短波通信也有着许多显著的优点:1)短波通信不需要建立中继站即可实现远距离通信,因而建设和维护费用低,建设周期短;2)设备简单,可以根据使用要求固定设置,进行定点固定通信。
南京邮电大学毕业设计(论文)开题报告

南京邮电大学毕业设计(论文)开题报告南京邮电大学毕业设计开题报告一、选题背景及意义随着信息技术的迅猛发展和互联网的普及,全球范围内的互联网应用不断增加,并对社会、经济以及个人生活产生了深远的影响。
这种影响带来了大量的数据和信息,如何利用这些数据和信息来获取有价值的洞察力成为了当前亟待解决的一个重要课题。
在此背景下,本文选取了“基于大数据分析的XX应用系统设计与实现”作为毕业设计的选题,通过对大数据的分析和挖掘,将有助于提高企业决策和发展的能力,并对社会经济发展产生积极的推动作用。
二、研究目的和内容本次毕业设计旨在设计和实现一个基于大数据分析的XX应用系统,通过对大量的数据和信息进行采集、清洗、整理和分析,从中发现问题、发现规律、提供决策依据,以帮助企业提高运营效率、优化资源配置、提高竞争力等。
具体研究内容包括以下几个方面:1. 数据采集与清洗:通过各种数据源(如数据库、网络爬虫等)获取数据,对数据进行清洗和预处理,确保数据的准确性和完整性。
2. 数据存储与管理:设计和实现数据的存储和管理系统,保证数据的安全和可靠性,并提供高效的数据检索和查询功能。
3. 数据分析与挖掘:利用各种数据分析和挖掘算法,对大数据进行分析、建模和挖掘,提取有价值的信息和规律。
4. 可视化与展示:设计和实现数据的可视化和展示功能,将分析结果以可视化的形式展示给用户,便于用户理解和运用。
三、研究方法和技术路线在本次毕业设计中,将采用以下研究方法和技术路线进行研究和实现:1. 数据采集与清洗:通过编写网络爬虫程序获取网络数据,并通过使用数据库技术实现数据的存储和清洗。
2. 数据存储与管理:采用关系型数据库技术(如MySQL、Oracle等)进行数据存储和管理,并借助NoSQL数据库(如MongoDB)进行非结构化数据的存储。
3. 数据分析与挖掘:应用数据挖掘算法(如聚类、关联规则挖掘等),利用Python等编程语言进行数据分析和建模。
南京邮电大学通达学院毕业设计教室

南京邮电大学通达学院毕业设计教室空调采购安装工程招标文件招标编号:TDHQ2016001招标人(章)南京邮电大学通达学院发放时间2016年1月6日第一章前附表第二章投标人须知1.项目名称:南京邮电大学通达学院毕业设计教室空调采购安装工程2.项目编号:TDHQ20160013.工程地点:南京邮电大学通达学院(扬州市邗江区润扬南路33号)4.招标方式:公开招标5.招标文件领取地点:南京邮电大学通达学院扬州校区行政楼9楼0914室,现场踏勘时间统一为2016年1月8日上午9:00,过期不候。
联系人:李小伟,联系电话:05,。
6.承包范围:采购安装空调一批,要求见本招标书第三章项目概况。
7.项目要求:投标单位负责运输、安装,直至验收合格,交付学院使用,承包方在运输、安装期间任何责任事故与甲方无关。
8.投标文件递送地点:南京邮电大学通达学院行政楼9楼0914室;9.投标文件接收截止时间:2016年1月12日上午11:30。
10.投标人应承担其编制投标文件与递交投标文件所涉及的一切费用。
不管投标结果如何,招标人对上述费用不负任何责任,且标书不予退还。
11.本套标书售价:200元;投标保证金1500元(中标后自动转为履约保证金)。
12.评标办法:综合评分法。
13.供货时间:合同签订起10天内安装到位。
14.质保期:6年(从甲方验收合格之日算起)15.付款方式:本合同无预付款,安装结束交付甲方验收合格后,付至合同总额的95%,壹年后无质量问题无息结清。
甲方付款前乙方需提供合法、有效、等额的票据,否则,甲方有权拒付相应款项。
16.投标人资质要求:①有能力提供本项目中所采购产品及服务、具有良好的财务状况和商业信誉、具有独立承担民事责任的法人资格。
②具有工商行政管理部门核发的有效企业法人营业执照、具有良好的信誉和售后服务记录的供货商。
③本次招标不接受联合体投标。
④2013年1月1日以来,投标人合同总价在30万元以上的类似项目业绩(以合同签订日期为准)须提供合同复印件(原件备查)。
通达学院08002136 程阳 毕设开题报告

南京邮电大学通达学院毕业设计(论文)开题报告台提供的SDK开发一款可以运行于Android移动软件平台开发RSS阅读器手机应用软件,从而达到掌握Java手机应用程序开发技术的目的。
JAVA简介:Java平台由Java虚拟机(Java Virtual Machine)和Java 应用编程接口(Application Programming Interface、简称API)构成。
Java 应用编程接口为Java 应用提供了一个独立于操作系统的标准接口,可分为基本部分和扩展部分。
在硬件或操作系统平台上安装一个Java平台之后,Java应用程序就可运行。
现在Java平台已经嵌入了几乎所有的操作系统。
这样Java程序可以只编译一次,就可以在各种系统中运行。
Java应用编程接口已经从1.1x版发展到1.2版。
目前常用的Java平台基于Java1.5,最近版本为Java1.7。
Java分为三个体系JavaSE(Java2 Platform Standard Edition,java平台标准版),JavaEE(Java 2 Platform,Enterprise Edition,java平台企业版),JavaME(Java 2 Platform Micro Edition,java平台微型版)。
Java SE(Java Platform,Standard Edition)。
Java SE 以前称为 J2SE。
它允许开发和部署在桌面、服务器、嵌入式环境和实时环境中使用的 Java 应用程序。
Java SE 包含了支持 Java Web 服务开发的类,并为 Java Platform,Enterprise Edition (Java EE)提供基础。
Java EE(Java Platform,Enterprise Edition)。
这个版本以前称为 J2EE。
企业版本帮助开发和部署可移植、健壮、可伸缩且安全的服务器端 Java 应用程序。
潘国青-翻译原文

南京邮电大学通达学院毕业设计(论文)外文资料翻译学院通达学院专业学生姓名班级学号外文出处Thomas Karagiannis, Andre Broido,Michalis Faloutsos, and Kimberly C.Claffy October 2004附件:1.外文资料翻译译文;2.外文原文附件2:外文原文Transport Layer Identification of P2P TrafficABSTRACTSince the emergence of peer-to-peer (P2P) networking in the late '90s, P2P applications have multiplied, evolved and established themselves as the leading `growth app' of Internet traffic workload. In contrast to first-generation P2P networks which used well-defined port numbers, current P2P applications have the ability to disguise their existence through the use of arbitrary ports. As a result, reliable estimates of P2P traffic require examination of packet payload, a methodological landmine from legal, privacy, technical, logistic, and fiscal perspectives. Indeed, access to user payload is often rendered impossible by one of these factors, inhibiting trustworthy estimation of P2P traffic growth and dynamics. In this paper, we develop a systematic methodology to identify P2P flows at the transport layer, i.e., based on connection patterns of P2P networks, and without relying on packet payload. We believe our approach is the first method for characterizing P2P traffic using only knowledge of network dynamics rather than any user payload. To evaluate our methodology, we also develop a payload technique for P2P traffic identification, by reverse engineering and analyzing the nine most popular P2P protocols, and demonstrate its efficacy with the discovery of P2P protocols in our traces that were previously unknown to us. Finally, our results indicate that P2P traffic continues to grow unabatedly, contrary to reports in the popular media.1. INTRODUCTIONOver the last few years, peer-to-peer (P2P) file-sharing has relentlessly grown to represent a formidable component of Internet traffic. P2P volume is sufficiently dominant on some links to intent increased local peering among Internet Service Providers [25], to observable yet unquantified effect on the global Internet topology and routing system not to mention competitive market dynamics. Despite this dramatic growth, reliable profiling of P2P traffic remains elusive. We no longer enjoy the fleeting benefit of first-generation P2P traffic, which was relatively easily classified due to its use of well-defined port numbers. Current P2P networks tend to intentionally disguise their generated traffic to circumvent both filtering firewalls as well as legal issues most emphatically articulated by the Recording Industry Association of America (RIAA). Not only do most P2P networks now operate on top of nonstandard, custom-designed proprietary protocols, but also current P2P clients can easily operate on any port number, even HTTP's port 80.These circumstances portend a frustrating conclusion: robust identification of P2P traffic is only possible by examining user payload. Yet packet payload capture and analysis poses a set of often insurmountable methodological landmines: legal, privacy, technical, logistic, and financial obstacles abound, and overcoming them leaves the task of reverse engineering a growing number of poorly documented P2P protocols. Further obfuscating workload characterization attempts is the increasing tendency of P2P protocols to support payload encryption. Indeed, the frequency with which P2P protocols are introduced and/or upgraded renders packet payload analysis not only impractical but also glaringly inefficient.In this paper we develop a systematic methodology to identify P2P flows at the transport layer, i.e., based on flow connection patterns of P2P traffic, and without relying on packet payload. The significance of our algorithm lies in its ability to identify P2P protocols without depending ontheir underlying format, which offers a distinct advantage over payload analysis: we can identify previously unknown P2P protocols. In fact during our analysis we detected traffic of three distinct P2P protocols previously unknown to us. To validate our methodology we also developed a payload-based technique for P2P traffic identification, by reverse engineering and analyzing the nine most popular P2P protocols.Specifically, the highlights of our paper include:·We develop a systematic profiling by identifying methodology for P2P traffic flow patterns and character-istics of P2P behavior, without examination of user payload.·Our methodology effectively identifies 99% of P2P flows and more than 95% of P2P bytes (compared to payload analysis), while limiting false positives to under 10%.·Our methodology is capable of identifying P2P flows missed by payload analysis. Using our methodology we identify approximately 10% additional P2P flows over payload analysis. ·Using data collected at an OC48 (2.5Gbps) link of a Tied Internet Service Provider (ISP), we provide realistic estimates and trends of P2P traffic in the wide-area Internet over the last few years. We find that in contrast to claims of a sharp decline, P2P traffic has been constantly growing.Our methodology can be expanded to support profiling of various types of traffic. Since mapping applications by port numbers is no longer substantially valid, a generalized version of our algorithm can support traffic characterization tasks beyond P2P workload. Indeed, to minimize false positives in P2P traffic identification, we assess, and then filter by, connection features of numerous protocols and applications (such as mail or DNS).The rest of this paper is structured as follows: Section 2 describes our backbone traces, which span from May 2003 to April 2004. Section 3 discusses previous work in P2P traffic estimation and analysis. Sections 4 and 5 describe in detail our payload and non payload methodologies for P2P traffic identification. Section 6 presents an evaluation of our algorithm by comparing the volume of P2P identified by our methods. In section 7 we challenge media claims that the pervasive litigation undertaken by the RIAA is causing an overall decline in P2P file-sharing activity. Section 8 concludes our paper.2.DATA DESCRIPTIONPart of the analyzed traces in this paper are included in CAIDA's Backbone Data Kit (BDK) [1], consisting of packet traces captured at an OC-48 link of a Tier 1 US ISP connecting POPS from San Jose, California to Seattle, Washington.Table 1 lists general workload dimensions of our datasets: counts of distinct source and destination IP addresses and the numbers of flows, packets, and bytes observed. We processed traces with CAIDA's Coral Reef suite [20].We analyze traces taken on May 5, 2003 (D09), January 22, 2004 (D10) February 25, 2004 (D11) and April 21, 2004 (D13). We captured the traces with Dag 4 monitors [14] and packet capture software from the University of Waikato and Endace [12] that supports observation ofone or both directions of the link.For our older traces (D01-D10), our monitors captured 44 bytes of each packet, which includes IP and TCP/UDP headers and an initial 4 bytes of payload for some packets.However,approximately 60%-80% of the packets in these traces are encapsulated with an extra 4-byte MPLS label which leaves no space for payload bytes.Fortunately we were able to capture the February and April 2004 traces (D11 and D13) with 16 bytes of TCP/UDP payload which allows us to evaluate our nonpayload methodology. To protect privacy, our monitoring system anonymized the IP addresses in these traces using the Cryptography-based Prefix-preserving Anonymization algorithm (Crypto-PAn) [33].3.PREVIOUS WORKMost P2P traffic research has thus far emphasized detailed characterization of a small subset of P2P protocols and/or networks [19] [15],often motivated by the dominance of that protocol in a particular provider's infrastructure or during a specific time period. Typical data sources range from academic network connections [27], [21] to Tier 2 ISPs [22].Other P2P measurement studies have focused on topological characteristics of P2P networks based on flow level analysis [29], or investigating properties such as bottleneck bandwidths [27], the possibility of caching [22], or the availability and retrieval of content [3] [13].Recently, Sen et al. developed a signature-based payload methodology [28] to identify P2P traffic. The authors focus on TCP signatures that characterize file downloads in five P2P protocols based on the examination of user payload. The methodology in [28] is similar to our payload analysis and it is further discussed in section 4.A number of Sprint studies [8] report on P2P traffic as observed in a major Tier 1 provider backbone. However, their volume estimates taxonomize applications based on fixed port numbers from CoralReef's database [23],which captures a small and decreasing fraction of p2p traffic.Our approach differs from previous work in three ways:• We analyze tra ffic sources of exceptionally high diversity, from major Tier 1 ISPs at the Internet core.• We study all popular P2P app lications available: Neither of our methodologies (payload and non payload) are limited to a subset of P2P networks. On the contrary we study those P2P applications that currently contribute the vast majority of P2P traffic.• We combine and cross-validate identification methods that use fixed ports, payload, and transport layer dynamics.4.PAYLOAD ANALYSIS OF P2P TRAFFIC AND LIMITATIONSOur payload analysis of P2P traffic is based on identifying characteristic bit strings in packet payload that potentially represent control traffic of P2P protocols. We monitor the nine most popular P2P protocols: eDonkey[10] (also includes the Overnet and eMule [11] networks), Fasttrack which is supported by the Kazaa client, BitTorrent [4], OpenNap and WinMx [32], Gnutella, M P2P [24],Soulseek [30], Ares [2] and Direct Connect [7].Each of these P2P networks operate on top of nonstandard, usually custom-designed proprietary protocols. Hence, payload identification of P2P traffic requires separate analysis ofthe various P2P protocols to identify the specific packet format used in each case. This section describes limitations that inhibit accurate identification of P2P traffic at the link level. In addition, we present our methodology to identify P2P flows.4.1 LimitationsWe had to carefully consider several issues throughout our study. While some of these restrictions are data related, others originate from the nature of P2P protocols. Specifically, these limitations are the following:Captured payload size: CAIDA monitors capture the first 16 bytes of user payloads of each packet (see section 2) for our February and April traces. While our payload heuristics would be capable of effectively identifying all P2P packets if the whole payload were available, this 16-byte payload restriction limits the number of heuristics that can reliably pinpoint P2P flows. Furthermore, our older traces (May 2003, January 2004) only contain 4 bytes of payload for a limited number of packets, since our monitors were used to capture 44 bytes for each packet (e.g., TCP options will push payload bytes out of the captured segment. Limitations for our older traces are described in detail in section 7).HTTP requests: Several P2P protocols use HTTP requests and responses to transfer files, and it can be impossible to distinguish such P2P traffic from typical web traffic given only 16 bytes of payload, e.g., "HTTP/1.1 206 Partial Content" could represent either HTTP or P2P. Encryption: An increasing number of P2P protocols rely on encryption and SSL to transmit packets and files. Payload string matching misses all P2P encrypted packets.Other P2P protocols: The widespread use of file-sharing and P2P applications yields a broad variety of P2P protocols. Thus our analysis of the top nine P2P protocols cannot guarantee identification of all P2P flows, especially given the diversity of the OC48 backbone link. However, our experience with P2P applications and traffic analysis convinces us that these nine protocols represent the vast majority of current P2P traffic.Unidirectional traces: Some of our traces reflect only one direction of the monitored link. In these cases we cannot identify flows that carry the TCP acknowledgment stream of a P2P download, since there is no payload. Even if we monitored both directions of the link, asymmetric routing renders it unlikely to find both streams (data and acknowledgment) of a TCP flow on the same link.We can overcome these limitations with our non payload methodology described in section 5.4.2 MethodologyOur analysis is based on identifying specific bit strings in the application-level user data. Since documentation for P2P protocols is generally poor, we empirically derived a set of distinctive bit strings for each case by monitoring both TCP and UDP traffic using tcpdump[31] after installing various P2P clients.We classify packets into flows, defined by the 5-tuple source IP, destination IP, protocol, source port and destination port. We use the commonly accepted 64-second flow time-out [6],i.e., if no packet arrives in a specific flow for 64 seconds, the flow expires. To address the limitations described in the previous section, we apply three different methods to estimate P2P traffic, listed by increasing levels of aggressiveness as to which flows it classifies as P2P:Ml: If a source or destination port number of a flow matches one of the well-known port numbers (Table 2) the flow is flagged as P2P.M2: We compare the payload (if any) of each packet in a flow against our table of strings. In case of a match between the 16-byte payload of a packet and one of our bit strings, we flag the flow as P2P with the corresponding protocol, e.g., Fasttrack, eDonkey, etc. If none of the packets match, we classify the flow as non-P2P.M3: If a flow is flagged as P2P, both source and destination IP addresses of this flow are hashed into a table. All flows that contain an IP address in this table are flagged as "possible P2P" even if there is no payload match. To avoid recursive misclassification of non-P2P flows as P2P, we perform this type of IP tracking only for host IPs that M2 identified as P2P.In all P2P networks, P2P clients maintain a large number of connections open even if there are no active file transfers. There is thus increased probability that a host identified as P2P from M2 will participate in other P2P flows. These flows will be flagged as "possible P2P" in M3. On the other hand, a P2P user may be browsing the web or sending email while connected to a P2P network. Thus, to minimize false positives we exclude from M3 all flows whose source or destination port implies web, mail, FTP, SSL, DNS (i.e., ports 80, 8000, 8080, 25, 110, 21, 22, 443, 53) for TCP and online gaming and DNS (e.g., 27015-27050, 53) for UDP.In general, we believe that M3 will provide an estimate closer to the real intensity of P2P traffic, especially with limited 4-byte payload traces, while M2 provides a loose lower bound on P2P volume. M3 takes advantage of our ability to identify IPs participating in P2P flows as determined by M2, facilitating identification of flows for which payload analysis fails. M3 is used only in section 7,where we examine the evolution of the volume of P2P traffic. In that section, we use M3 to overcome the problem of the limited 4-byte payload in our older traces. For all other analysis, payload P2P estimates are strictly based on payload string matching, namely M2.Recently, Sen et al. developed a similar signature-based payload methodology [28]. Theauthors concentrate on TCP signatures that characterize file downloads in five P2P protocols and identify P2P traffic based on the examination of all user payload bytes. [28] describes a subset of the signatures included in our methodology, since we also use UDP-based as well as protocol signaling signatures for a larger number of P2P protocols/networks (e.g., the WinMx/OpenNap network is not analyzed in [28],although it corresponds to a significant portion of P2P traffic[17] ). On the other hand, [28] presents the advantage of examining all user payload bytes. While examining all bytes of the payload should increase the amount of identified P2P traffic, we expect only a minimum difference in the number of identified P2P flows between [28] and the methodology described in this section.First, characteristic signatures or bit strings of P2P packets appear at the beginning of user payload; thus, 16 bytes of payload should be sufficient to capture the majority of P2P flows. Second, we expect that missed flows due to the payload limitation will be identified by our M3 method and/or by TCP and UDP control traffic originating from the specific IPs.5.NONPAYLOAD IDENTIFICATION OF P2P TRAFFICWe now describe our nonpayload methodology for P2P traffic profiling (PTP). Our method only examines the packet header to detect P2P flows, and does not in any way examine user payload. To our knowledge, this is a first attempt to identity P2P flows on arbitrary ports without any inspection of user payload.Our heuristics are based on observing connection patterns of source and destination IPs. While some of these patterns are not unique to P2P hosts, examining the flow history of IPs can help eliminate false positives and reveal distinctive features.We employ two main heuristics that examine the behavior of two different types of pairs of flow keys. The first examines source-destination IP pairs that use both TCP and UDP to transfer data (TCP/UDP heuristic, section 5.1). The second is based on how P2P peers connect to each other by studying connection characteristics of{IP, port} pairs (section 5.2). A high level description of our algorithm is as follows:•Data processing: We build the flow table as we observe packets cross the link, based on 5-tuples, similar to the payload method. At the same time we collect information on various characteristics of {IP, port} pairs, including the sets of distinct IPs and ports that an{IP, port} pair is connected to, packet sizes used and transferred flow sizes.•Identification of potential P2P pairs: We flag potential flows as P2P based on TCP/UDP usage and the {IP,port} connection characteristics.•False positives: We eliminate false positives by comparing flagged P2P flows against our set of heuristics that identify mail servers, DNS flows, malware, etc.5.1 TCP/UDP IP pairsOur first heuristic identifies source-destination IP pairs that use both TCP and UDP transportprotocols. Six out of nine analyzed P2P protocols use both TCP and UDP as layer-4 transport protocols. These protocols include eDonkey, Fasttrack, WinMx, Gnutella, MP2P and Direct Con- nect. Generally, control traffic, queries and query-replies use UDP, and actual data transfers use TCP. To identify P2P hosts we can thus look for pairs of source-destination hosts that use both transport protocols (TCP and UDP).While concurrent usage of both TCP and UDP is definitely typical for the aforementioned P2P protocols, it is also used for other application layer protocols such as DNS or streaming media. To determine non-P2P applications in our traces that use both transport protocols, we examined all source-destination host pairs for which both TCP and UDP flows exist. We found that besides P2P protocols, only a few applications use both TCP and UDP transport protocols: DNS, NETBIOS, IRC, gaming and streaming, which collectively typically use a small set of port numbers such as 135, 137, 139, 445, 53, 3531, etc. Table 3 lists all such applications found, together with their well-known ports. Port 445 is related to the Microsoft NETBIOS service. Port 3531 is used by an application called p2pnetworking.exe which is automatically installed by Kazaa. Although p2pnetworking. exe is related to P2P traffic, we choose to exclude it from our analysis since it is not under user control and specific only to the Kazaa client. Excluding flows using ports presented in Table 3, 98.5% of the remaining IP source-destination pairs that use both TCP and UDP in our traces are P2P, based on the payload analysis with M2 described in Section 4. In summary, if a source-destination IP pair concurrently uses both TCP and UDP as transport protocols, we consider flows between this pair P2P so long as the source or destination ports are not in the set in Table 3.5.2 {IP, port} pairsOur second heuristic is based on monitoring connection patterns of{ IP, port} pairs.Since the lawsuit against Napster, the prevalence of centralized P2P networks has decreased dramatically, and distributed or hybrid P2P networks have emerged. To connect to these distributed networks, each P2P client maintains a starting host cache. Depending on the network, the host cache may contain the IP addresses of other peers, servers or supernodes/superpeers. This pool of hosts facilitates the initial connection of the new peer to the existing P2P network. As soon as a connection exists to one of the IPs in the host cache (we will henceforth refer to these IPs as superpeers), the new host A informs that superpeer of its IP address and port number at which it will accept connections from peers. Host A also provides other information specific to each P2P protocol but not relevant here. While in first-generation P2P networks the listening port was well-defined and specific to each network, simplifying P2P traffic classification,newer versions of all P2P clients allow the user to configure a random port number (some clients even advise users to change the port number to disguise their traffic. The superpeer must propagate this information, mainly the{ IP,port} pair of the new host A, to the rest of the network. This { IP, port} pair is essentially the new host's ID, which other peers need to use to connect to it. In summary, when a P2P host initiates either a TCP or a UDP connection to peer A, the destination port will also be the advertised listening port of host A, and the source port will be an ephemeral random port chosen by the client.Normally, peers maintain at most one TCP connection to each other peer, but there may also be a UDP flow to the same peer, as described previously. Keeping in mind that multiple connections between peers is rare in our data sets, we consider what happens when twenty peers all connect to peer A. Each peer will select a temporary source port and connect to the advertised listening port of peer A. The advertised{ IP, port} pair of host A would thus be affiliated with 20distinct IPs and 20 distinct ports 5. In other words, for the advertised destination {IP, port} pair of host A, the number of distinct IPs connected to it will be equal to the number of distinct ports used to connect to it. Figure 1 illustrates the procedure whereby a new host connects to the P2P network and advertises its {IP, port} pair.Figure 1On the other hand, consider what happens in the case of web and HTTP. As in the P2P case, each host connects to a pre-specified {IP, port} pair, e.g., the IP address of a web server W and port 80. However, a host connecting to the web server will initiate usually more than one concurrent connection in order to download objects in parallel. In summary, web traffic will have a higher ratio than P2P traffic of the number of distinct ports versus number of distinct IPs connected to the {IP, port} pair {W, 80}.5.3 MethodologyOur non payload methodology builds on insights from previous sections 5.1 and 5.2. Specifically, for a time interval t we build the flow table for the link, based on the five-tuple key and 64-second flow timeout as with the payload methodology described in section 4. We then examine our two primary heuristics:•We look for source-destination IP pairs that concurrently use both TCP and UDP during t. If such IP pairs exist and they do not use any ports from table 3, we consider them P2P.•We examine all source { srcIP, srcport} and destination { dstIP, dstport} pairs during t (use of pairs will hence-forth imply both source and destination{ IP, port} pairs). We seek pairs for which the number of distinct connected IPs is equal to the number of distinct connected ports. All pairs for which this equality holds are considered P2P .In contrast, if the difference between connected IPs and ports for a certain pair is large (e.g., larger than 10), we regard this pair as non P2P.Whether a flow is considered P2P depends on the classification of its{ IP, port} pairs. If one of the pairs in the 5-tuple flow key has been classified as P2P, this flow is deemed P2P. Similarly, if one of the pairs is classified as non P2P, so is the flow. Additionally, if one of the IPs in a flow has been found to match the TCP/UDP heuristic, the flow is also considered as P2P.5.4 False positivesWe now describe heuristics developed to decrease the risk of false positives. Considering the diversity of backbone links that feature a vast number of IPs and flows, we expect the previous methodology to yield false positives, i.e., classifying non P2P pairs as P2P. False positives are most common in pairs with few connections, and also more frequent for specific applications/protocols whose connection behavior matches the P2P profile of our heuristics (e.g., one connection per {IP,port} pair), e.g., e-mail (SMTP, POP), DNS and gaming.To decrease the rate of false positives we review the connection and flow history of all pairs where the probability of a misclassification is high, e.g., the source or destination port is equal to25 and implies SMTP. Past flow history for these pairs enables accurate classification by investigating properties of specific IPs. In the following subsections, we describe heuristics that augment our basic methodology to limit the magnitude of false positives.。
南京邮电大学毕业设计(论文)开题报告
本课题在熟悉通信关于数字信号最佳接收系统理论分析的基础上,采用LabVIEW进行仿真研究影响各数字信号接收系统性能的因素、熟悉其的相关构建模块以及如何设计其最佳数字接收系统。
三.研究基础与条件
[1].硬件试验设备包括:
笔记本一台
[2]. 软件包括:
LabVIEW;
四. 根据任务书的任务及文献调研结果,初步拟定的执行(实施)方案(含具体进度计划)
在最佳接收机的实际应用中大都采用匹配滤波器来实现相关器的功能。所谓匹配滤波器是指输出信噪比最大的最佳线性滤波器。若T为码元周期,则匹配滤波器在t= T时刻的输出值恰好等于相关器的输出值,也即匹配滤波器可作为相关器。理论分析和实践都表明,如果滤波器的输出端能够获得最大信噪比,则能够最佳地判断信号的出现,从而提高系统的检测性能。因而二进制信号最佳接收机中的相关器完全可由匹配滤波器实现,其中比较器在T时刻进行采样。上面对二进制信号最佳接收机的理论推导,完全适用于多进制信号。
南京邮电大学毕业设计(论文)开题报告
题目
运用LabVIEW设计最佳数字接收系统
姓名
班级学号
专业
网络工程
一. 对指导教师下达的课题任务的学习与理解
通信系统中信道特性不理想及信道噪声的存在,直接影响接收系统的性能,而一个通信系统的质量优劣在很大程度上取决于接收系统的性能。研究从噪声中如何最好地提取有用信号,且在某个准则下构成最佳接收机,使接收性能达到最佳,这就是最佳接收理论。“数字”信号的“最佳接收”是由数字信号本身具有的特点决定的。即数字信号(以2进制为例)无论对信号如何变形,只要最终能恢复出正确的“1”和“0”就达到了通信的目的。所以只要不会引起误码,对信号进行一系列的处理是可行的。实际上,研究最佳接收机的意义在于为人们提出一个理论上的模型,我们在实际中设计的接收机的努力方向就是“最佳接收”。任何事情都没有绝对的“最佳”,因为衡量的标准不同。按这个标准得到的“最佳”,用另一个标准来看,则很可能不是最佳,因此我们这里所讲的“最佳”,是针对通信中公认的标准来衡量的,这些标准我们称之为准则。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
南京邮电大学通达学院毕业设计(论文)撰写规范
一、毕业设计(论文)内容的要求
毕业设计(论文)应包含以下几部分内容:设计题目、摘要和关键词、目录、正文、结束语、致谢、参考文献、附录等。
. 毕业设计(论文)题目
毕业设计(论文)题目应简短、明确,通过题目把毕业设计(论文)的内容、专业特点概括出来。
题目字数要适当,一般不宜超过个字。
如果有些细节必须放进题目,为避免冗长,可以将题目与副标题分列,把细节放在副标题里。
. 摘要和关键词(中文在前,英文在后)
摘要应反映毕业设计(论文)的精华,概括地阐述课题研究的基本观点、主要研究内容、研究方法、取得的成果和结论。
摘要字数要适当,中文摘要一般以字为宜。
关键词是直接选自题目和内容中具有实质意义、作为标引和检索文献主要概念的名词或词组。
关键词的个数一般取个左右。
. 目录
目录是毕业设计(论文)的篇章名目,要按顺序写清楚毕业设计(论文)构成部分的名称和正文中的小标题,并在每一个标题后面注明页码。
. 正文
正文为毕业设计(论文)的核心部分,包括理论分析、数据资料、实验方法、结果、本人的论点和结论等内容,还要附有各种有关的图表、照片、公式等。
要求理论正确、逻辑清楚、层次分明、文字流畅、数据真实可靠,公式推导和计算结果无误,图表绘制要少而精。
. 结束语
结束语是对主体的最终结论,应准确、完整、精炼。
阐述作者创造性工作在本研究领域的地位和作用,对存在的问题和不足应给予客观的说明,也可提出进一步的设想。
. 致谢
致谢通常以简短的文字对在课题研究与设计撰写过程中给予帮助的单位、指导教师、答疑教师和其他人员表示自己的谢意。
. 参考文献
参考文献是毕业设计(论文)中引用文献出处的目录表,在论文中引用参考文献时,引出处右上角用方括号标注阿拉伯数字编排的序号(必须与参考文献一致)。
参考文献应列出主要参考书和文献资料的作者姓名、书名、出版社或期刊名称、以及出版时间或期刊的卷数、期数、页码等。
. 附录
附录是作为学位论文主体的补充,包括下列内容:
()正文中过于冗长的公式推导;
()为读者阅读方便所需要的辅助性的数学工作或带有重复性的图表;
()由于过分冗长而不宜在正文中出现的计算机程序清单;
()对于一般读者并非必要阅读,但对本专业同行有参考价值的资料;
()附录编于正文后,与正文连续编页码,每一附录均另页起;
()附录依次用大写正体,,……编序号,黑体,三号。
如:附录;
()附录中的图、表、式、参考文献等与正文分开,用阿拉伯数字另行编序号,注意在数码前冠以附录的序码。
如:图;表;式();文献[]。
二、理工科各类毕业设计(论文)具体要求
理工科类毕业设计(论文)可以分为下述几种类型:理论研究、工程设计、产品开发、实验研究类等。
根据我校情况,分别对几种类型的毕业设计(论文)提出以下具体要求:
. 理论研究类
理论研究类课题内容包括问题的提出、研究的前提或假设条件、基本理论的阐述、数学模型的建立或理论论证、推理、计算、理论成果的应用、验证及分析。
正文字数应在字以上,但对具有独特见解的毕业设计(论文)不限字数。
. 工程设计类
工程设计类课题内容包括设计方案论证、结构设计、电路的设计与参数计算、软件开发(软件环境及使用方法、设计模型、软件功能与结构、程序编制、软件测试、软件应用)、设备与元器件的选择与使用、现场测试等。
正文字数应在字以上,但对具有创新性的设计不限字数。
软件开发类应写出字左右的软件使用说明书作为附录。
. 产品开发类
产品开发类课题内容包括市场调研、方案论证、电路设计、工艺流程、参数设计、造型设计、标准化设计制图、实验与参数测试、软件开发(软件环境及使用方法、设计模型、软件功能与结构、程序编制、软件测试、软件应用)等。
正文字数应在字以上,但对具有创新性的产品开发不限字数。
软件开发类应写出字左右的软件使用说明书作为附录。
.实验研究类
实验研究类课题内容包括实验方案论证、电路的设计与参数计算、设备与元器件的选择与使用、实验测试与结果分析等。
正文字数应在字以上,但对具有创新性的实验研究不限字数。
三、毕业设计(论文)的书写与装订
毕业设计(论文)用纸打印,页边距分别为:上2cm、下2cm、左3cm、右3cm。
页眉1.5cm,页脚1.75cm,装订线(0cm)位置靠左。
.相关表格填写
封面由学院统一印制,用钢笔或签字笔填写。
任务书、开题报告、过程检查记录表、中期检查表、指导教师评价表、评阅教师评阅评语表、成绩表、优秀毕业设计(论文)申请表、毕业设计(论文)重做申请表等用小四号宋体填写,打印后,请相关人员签字。
.行距设置
毕业设计(论文)内容及各种标题(包括摘要、目录、致谢、参考文献、附录等)的行距设置统一选用倍行距。
.字体设置
()“摘要”(“”选用“ ”)、“目录”、“结束语”、“致谢”、“参考文献”等字样均选用“三号黑体”。
