CCNA第二学期第三章考试答案..
CCNA02-final3

1Which of the following are required when adding a network to the OSPF routing process conf iguration? (Choose three.)network addressloopback addressautonomous system numbersubnet maskwildcard maskarea ID2Using default settings, what is the next step in the router boot sequence after t he IOS loads from flash?Perf orm the POST routine.Search for a backup IOS in ROM.Load the bootstrap program f rom ROM.Load the running-config file from RAM.Locate and load the startup-config file from NVRAM.3Refer to the exhibit. What is the most efficient summarization of the routes attached to router R1?198.18.0.0/16198.18.48.0/21198.18.32.0/22198.18.48.0/23198.18.49.0/23198.18.52.0/224Refer to the exhibit. When troubleshooting a network, it is important to interpret the output of various router commands. On the basis of the exhibit, which three statem (Choose three.)The missing information f or Blank 1 is the command show ip route .The missing information f or Blank 1 is the command debug ip route .The missing information f or Blank 2 is the number 100.The missing information f or Blank 2 is the number 120.The missing information f or Blank 3 is the letter R.The missing information f or Blank 3 is the letter C.5Refer to the exhibit. Packets destined to which two networks will require the router to perform a recursive lookup? (Choose t wo.)10.0.0.0/864.100.0.0/16128.107.0.0/16172.16.40.0/24192.168.1.0/24192.168.2.0/246When presented with multiple valid routes to a destination, what criteria does a router use to determine which routes to add to the routing table?The router selects the routes with the best metric. All routes that hav e the same best metric are added to the routing table.The router f irst selects routes with the lowest administrative distance. The resulting routes are then prioritized by metric and the routes with the best metric arouting table.The router selects the routes with the lowest administrativ e distance. All routes with the same lowest administrative distanc e are added to the routing table.The router installs all routes in the routing table but uses the route with the best metric most when load balancing.7Refer to the exhibit. All routers in the network are running RIPv2 and EIGRP with default routing protocol settings and have interfaces configured with the bandwidths t exhibit. Which protocol will be used and how will traffic between the Router1 LAN and Router5 LAN be routed through the network?RIPv2 will load balance across both paths between Router1 and Router5.EIGRP will load balance across both paths between Router1 and Router5.RIPv2 traffic will use the path Router1, Router2, Router5 because it has the least hops.EIGRP traffic will use the path Router1, Router3, Router4, Router5 because it has the best metric.8Of the listed routing protocols, which two will propogate LSPs to all neighbors? (Choose two.)IS-ISEIGRPOSPFRIPv1RIPv29Refer to the exhibit. Routers 1 and 2 are directly connected over a serial link. Pings are f ailing between the two routers. W hat change by the administrator will correctSet the encapsulation on both routers to PPP.Decrease the bandwidth on Serial 0/1/0 on router 2 to 1544.Change the cable that connects the routers to a crossover cable.Change the IP address on Serial 0/1/0 on router 2 to 192.168.0.1/30.10Refer to the exhibit. Which three statements are true of the routing table for Router1? (Choose three.)The route to network 172.16.0.0 has an AD of 156160.Network 192.168.0.16 can best be reached using FastEthernet0/0.The AD of EIGRP routes has been manually changed to a value other than the default value.Router1 is running both the EIGRP and OSPF routing process.Network 172.17.0.0 can only be reached using a default route.No default route has been conf igured.11Which statement correctly describes a feasible successor in EIGRP?It is a primary route that is stored in the routing table.It is a backup route that is stored in the routing table.It is a primary route that is stored in the topology table.It is a backup route that is stored in the topology table.12Refer to the exhibit. A ping from R1 to 10.1.1.2 is successful, but a ping from R1 to 192.168.2.0 fails. What is the cause of this problem?There is no gateway of last resort at R1.The serial interf ace between the two routers is down.A default route is not configured on R1.The static route for 192.168.2.0 is incorrectly conf igured.13Refer to the exhibit. A network administrator has run the show interface command. The output of this command is displayed. What is the first step that is required toSwitch the cable with a known working cable.Issue the no shutdown command on the interface.Configure the interf ace as a loopback interface.Set the encapsulation for the interface.14Which two locations can be the source of the Cisco IOS that is used by a router during the bootup process? (Choose two.)flash memoryRAMNVRAMTFTP serverconfiguration register15All routers in a network are configured in a single OSPF area with the same priority value. No loopback interface has been set on any of the routers. Which secondrouters use to determine the router ID?The highest MAC address among the active interfaces of the network will be used.There will be no router ID until a loopback interf ace is configured.The highest IP address among the activ e FastEthernet interfaces that are running OSPF will be used.The highest IP address among the activ e interfaces will be used.16Refer to the exhibit. A network administrator has conf igured OSPF using the following command:network 192.168.1.32 0.0.0.31 area 0Which router interf ace will participate in OSPF?FastEthernet0/0FastEthernet0/1Serial0/0/0Serial0/0/117Refer to the exhibit. All routers are properly configured with default configurations and are running the OSPF routing protocol. The network is f ully converged. A host on th with a host on the 192.168.2.0/24 network.Which path will be used to transmit the data?The data will be transmitted v ia R3-R2.The data will be transmitted v ia R3-R1-R2.The traffic will be load-balanced between two paths — one via R3-R2, and the other via R3-R1-R2.The data will be transmitted v ia R3-R2, and the other path via R3-R1-R2 will be retained as the backup path.18Which two situations require the use of a link-state protocol? (Choose two.)Fast convergence of the network is critical.The network is very large.The network administrator has limited knowledge to configure and troubleshoot routing protocols.The network is a flat network.The capacity of the router is low.19Refer to the exhibit. What is the meaning of the highlighted value 120?It is the metric that is calculated by the routing protocol.It is the v alue that is used by the DUAL algorithm to determine the bandwidth for the link.It is the administrative distance of the routing protocol.It is the hold-down time, measured in seconds, before the next update.20In a lab test environment, a router has learned about network 172.16.1.0 through four different dynamic routing processes. Which route will be used to reach this nD 172.16.1.0/24 [90/2195456] via 192.168.200.1, 00:00:09, Serial0/0/0O 172.16.1.0/24 [110/1012] via 192.168.200.1, 00:00:22, Serial0/0/0R 172.16.1.0/24 [120/1] via 192.168.200.1, 00:00:17, Serial0/0/0I 172.16.1.0/24 [100/1192] via 192.168.200.1, 00:00:09, Serial0/0/021Which statement is true about the RIPv1 protocol?It is a link-state routing protocol.It excludes subnet information from the routing updates.It uses the DUAL algorithm to insert backup routes into the topology table.It uses classless routing as the default method on the router.22Refer to the exhibit. The 10.4.0.0 network f ails. What mechanism prevents R2 f rom receiving false update information regarding the 10.4.0.0 network?split horizonhold-down timersroute poisoningtriggered updates23Which statement is true about the metrics used by routing protocols?A metric is a value used by a particular routing protocol to compare paths to remote networks.A common metric is used by all routing protocols.The metric with the highest value is installed in the routing table.The router may use only one parameter at a time to calculate the metric.24Refer to the exhibit. Both routers are using the RIPv2 routing protocol and static routes are undef ined. R1 can ping 192.168.2.1 and 10.1.1.2, but is unable to ping 192.16 What is the reason for the ping f ailure?The serial interf ace between two routers is down.R2 is not forwarding the routing updates.The 192.168.4.0 network is not included in the RIP configuration of R2.RIPv1 needs to be configured.25Which statement correctly describes a feature of RIP?RIP is a link-state routing protocol.RIP uses only one metric—hop count— for path selection.Adv ertised routes with hop counts greater than 10 are unreachable.Messages are broadcast every 10 seconds.26Refer to the exhibit. When the show cdp neighbors command is issued f rom router C, which devices will be displayed in the output?B, DA, B, DD, SWH-2SWH-1, A, BSWH-1, SWH-2A, B, D, SWH-1, SWH-227Refer to the exhibit. Although R2 is conf igured correctly, host A is unable to access the Internet. What are two static routes that can be c onfigured on R1, either of which w (Choose two.)ip route 0.0.0.0 0.0.0.0 Fa0/0ip route 0.0.0.0 0.0.0.0 Fa0/1ip route 0.0.0.0 0.0.0.0 10.1.1.1ip route 0.0.0.0 0.0.0.0 10.1.1.2ip route 209.165.202.0 255.255.255.0 10.1.1.128Which component is typically used to connect the WIC interface of a router to a CSU/DSU?V.35 cableRJ-45 adaptercrossover cablestraight-through cable29Refer to the exhibit. Which combination of IP address and subnet mask can be used on the serial interf ace of Router2 in order to put the interf ace in the same networ interface of Router1?IP 172.16.0.18, subnet mask 255.255.255.0IP 172.16.32.15, subnet mask 255.255.255.240IP 172.16.0.18, subnet mask 255.255.255.252IP 172.16.32.18, subnet mask 255.255.255.25230Refer to the exhibit. Which host has a combination of IP address and subnet mask on the same network as Fa0/0 of Router1?host Ahost Bhost Chost D31Refer to the exhibit. OSPF is used f or the routing protocol and all interf aces are configured with the correct IP addresses and subnet masks. During testing, it is foun unable to form an adjacency with R2. What is the cause of this problem?Both routers have been configured with incorrect router IDs.Both routers have been configured in different OSPF areas.Both routers have been configured with an incorrect network type.Both routers have been configured with different hello and dead intervals.32You hav e been asked to explain converged networks to a trainee. How would you accurately describe a converged network?A network is converged when all routers have f ormed an adjacency.A network is converged immediately after a topology change has occurred.A network is converged when all routers flush the unreachable networks from their routing tables.A network is converged after all routers share the same information, calculate best paths, and update their routing tables.33 A network administrator is in charge of two separate networks that share a single building. What dev ice will be required to connect the two networks and add a comthe Internet that can be shared?hubrouteraccess pointEthernet switch34Which port should a terminal emulator be connected to in order to access a router without network connectivity?T1serialconsoleFastEthernet35Refer to the exhibit. What needs to be done to allow these two routers to connect successf ully?Add a clock rate to S0/0/0 on R1.Add an interface description to S0/0/1 on R2.Change the serial interface on R2 to S0/0/0 so that it matches R1.Change the IP address of S0/0/1 on R2 so that it is in the same subnet as R1.36Refer to the exhibit. Based on the partial output in the exhibit, why can users establish a console connection to this router without entering a password?The login command was not entered on the console line.The enable password should be an enable secret password.No username and password combination has been configured.Console connections cannot be conf igured to require users to provide passwords.37Refer to the exhibit. When a static IP address is being configured on the host, what address should be used for the default gateway?10.1.1.110.1.1.2172.16.1.1192.168.1.138Refer to the exhibit. The entire 192.168.1.0 network has been allocated to address hosts in the diagram. Utilizing VLSM with contiguous address blocks, which set of pref ixes could be used to create an addressing solution with a minimum waste of IP addresses?39What is a function of a router?It extends the Layer 2 broadcast domain.It eliminates collisions among PCs on the same local network.It provides connectivity among PCs on the same physical segment.It forwards packets to different IP networks based on Layer 3 inf ormation.40Refer to the exhibit. Which solution provides the most efficient use of router resources for forwarding traffic between BR and HQ?RIPRIPv2EIGRPstatic routes41Refer to the exhibit. A network administrator configures a static route on router R1 to reach the 192.168.1.0/24 network. Which IP address should be used as the next ip route command?192.168.1.1192.168.2.1192.135.250.1192.135.250.242Refer to the exhibit. The network is conf igured with RIPv2. However, network administrators notice that communication cannot be successfully completed f rom one L network administrator issues the show ip route command on the HQ router. Based on the output, what should be done to correct the problem?Disable the load balancing feature of RIPv2.Issue the no auto-summary command for RIPv2.Replace RIPv2 with EIGRP which supports VLSM.Make sure that the network statements include the correct subnet mask.43Which protocol is used by EIGRP to deliver and receive update packets?FTPRTPTCPTFTPUDP44Refer to the exhibit. What OSPF network statements are required for the router B to adv ertise the three networks that are attached?router ospf 1network 10.0.0.0 0.0.0.255 area 0router ospf 1network 10.1.1.0 0.3.255.255 area 0network 10.10.1.0 0.255.255.255 area 0network 10.20.1.0 0.255.255.255 area 0router ospf 1network 10.1.1.0 0.0.0.3 area 0network 10.10.1.0 0.0.255.255 area 0network 10.20.1.0 0.0.255.255 area 0router ospf 1network 10.1.1.0 0.0.0.3 area 0network 10.10.1.0 0.0.0.255 area 0network 10.20.1.0 0.0.0.255 area 045Which two v alues are used by default to calculate a metric in EIGRP? (Choose two.) loaddelayreliabilityhop countbandwidth46Refer to the exhibit. Which statement is true concerning the routing configuration?Using dy namic routing instead of static routing would hav e required f ewer configuration steps.The 10.1.1.0/24 and 10.1.2.0/24 routes have adjacent boundaries and should be summarized.Packets routed to the R2 Fast Ethernet interface require two routing table lookups.The static route will not work correctly.47Refer to the exhibit. On the basis of the show running-config output, which option correctly ref lects the routes that will be listed in the R2 routing table?48Refer to the exhibit. Which command should be issued to configure the address of the router interface that is attached to this computer?Router(config-if)# ip address 192.168.2.1 255.255.255.0Router(config-if)# ip address 192.168.2.2 255.255.255.0Router(config-if)# ip address 192.168.0.1 255.255.255.0Router(config-if)# ip address 192.168.0.2 255.255.255.049Refer to the exhibit. Which route will be removed from the routing table if manual EIGRP summarization is disabled on the Serial0/0/0 interface of Router3?0.0.0.0/0172.16.0.0/16172.16.1.0/24172.16.3.0/3050Refer to the exhibit. All interfaces are addressed and f unctioning correctly. The network administrator runs the tracert command on host A. Which two f acts could be output of this command? (Choose two.)The gateway for Host A is missing or improperly conf igured.The gateway for Host B is missing or improperly conf igured.The entry for 192.168.1.0/24 is missing f rom the routing table of R1.The entry for 192.168.1.0/24 is missing f rom the routing table of R2.The entry for 192.168.2.0/24 is missing f rom the routing table of R1.The entry for 192.168.2.0/24 is missing f rom the routing table of R2.。
CCNA考试自测题第3卷及答案

CCNA考试自测题第3卷及答案下面的问题将帮助你评价你在本章中学习到的内容。
仔细阅读所有的选项,因为正确答案可能多于1个。
选择每个问题中所有的正确答案。
1) The service provided by IPX is (IPX提供的服务是):A. Guaranteed deliveryB. DatagramC. Connection-orientedD. Sequenced2) The Transport Control field in the IPX header holds what information? (IPX报头中的传输控制字段保留何种信息)?A. The age of the packet.B. Protocol typeC. Router hop countD. Level of service required.3) What is the length of an IPX network number (IPX网络编号的长度是多少)?A. 16 bitsB. VariableC. 48 bitsD. 32 bits4) In the IPX address 0102.0000.8045.1700, what is the node address ( 在I P X地址0 1 0 2 . 0 0 0 . 8 0 4 5 . 1 7 0 0中,节点地址是多少)?A. 1700B. 0102.0000.8045C. 0102.0000D. 0000.8045.1700A. It is the address of a NetWare print serverB. It is an internal network addressC. The included socket number is 0001D. Nothing6) The Checksum field in the IPX header is normally set to (IPX报头中的校验和字段通常设置为):A. A checksum of the entire IPX packetB. A checksum of the IPX header fields onlyC. 0xFFFFD. 07) If an IPX node is configured to use the Ethernet_802.2 encapsulation, which other machines can it communicate with directly (without going through a router) on the same network (如果一个I P X节点配置为使用E t h e r n e t _ 8 0 2 . 3封装,它可以和相同网络上其他哪一个设备直接通信(不经过路由器) )?A. Machines running any encapsulationB. Machines running either Ethernet_802.2 or Ethernet_802.3C. Machines running Ethernet_IID. Machines running Ethernet_802.28) To run multiple encapsulations on a single physical interface, a router has to (为在一个物理接口上运行多个封装,路由器必须):A. Use a different network number for each encapsulationB. Use subinterfaces, not secondary networksC. Enable NLSP routingD. Use an access list9) Which protocol does a workstation use to locate a server providing a particular type of service (工作站使用哪一个协议来找到提供特定类型服务的服务器)?B. NCPC. SAPD. EIGRP10) Periodic SAP updates are sent by (定期S A P更新由谁发出):A. Routers and serversB. NetWare servers onlyC. Workstations and routersD. Workstations only11) The RIP protocol is used by (RIP协议由谁使用)?A. Routers onlyB. Servers onlyC. Workstations, servers, and routersD. Print servers12) Which command which must be given first to enable IPX (在启用I P X时,必须首先给出哪一个命令)?A. CISCO(CONFIG)#ENABLE IPX ROUTINGB. cisco>ipx routingC. cisco(config-if)#ipx routing onD. cisco(config)#ipx routing13) Which of the following allow you to use multiple IPX networks on a single physical interface (下面哪一个允许你在单个物理接口上使用多个I P X网络)?A. Secondary networksB. Dynamic frame typesC. Subinterfaces14) Which IOS command allows you to view the router’s internal SAP database (哪一个I O S 命令允许你查看路由器的内部S A P数据库)?A. SHOW SERV E R SB. show ipx serversC. serversD. ipx servers15) Which of the following kinds of information do you need to collect before you can configure IPX using IOS (你需要在用I O S配置I P X之前搜集下面各种信息中的哪一个)?A. The number of NetWare servers on the networkB. The encapsulations in useC. IPX network numbersD. The IPX address of another router16) What does this command do:CISCO(CONFIG-IF)#IPX NETWORK 3 (这个命令的作用是什么:C I S C O ( C O N F I G -IF)#IPX NETWORK3):A. Nothing. It is incomplete.B. Sets up a static route to Network 3C. Configures IPX Network 3 on this interface with the default frame typeD. Nothing. The router is in the wrong configuration mode.17) What does this IOS command do?IPX ROUTE 4 5.0000.8004.4563 FLOAT I N G - S TATIC (这个I O S命令的作用是什么I P X ROUTE 45.0000.8004.4563 FLOAT I N G - S TAT I C )?A. Configures 4 static routesB. Configures static SAP entries for servers of type 4D. Says that to get to network 5, you must go via network 418) In the command IPX ROUTE 4 5.0000.8004.4563 FLOAT I N G - S TATIC, what does the F L O AT I N G - S TATIC keyword on the end mean? ( 在命令IPX ROUTE 45.0000.8004.4563F L O AT I N G.S TAT I C中,最后的F L O AT I N G.S TA T I C意味着什么)?A. Set all static routes to floatingB. Allow this route to be overridden by a route received dynamicallyC. Apply this route to all network numbers from 1 to 4D. Lock this route so that it cannot be changed19) The IPX MAXIMUM-PATHS command does what (IPX MAXIMUM.PAT H S命令的作用是什么)?A. Allows IOS to share traffic to a given network over multiple pathsB. Allows a slow link to be used as a backup for a faster oneC. Sets the maximum number of router hops a packet can travelD. Sets the maximum number of interfaces IPX can be configured on20) Which command is used to show a concise list of the configured IPX interfaces (哪一个命令用于显示配置的I P X接口上的简明列表)?A. SHOW CONFIGB. show ipx interfaceC. show ipx interface briefD. show interface21) If two devices are plugged into the same physical network, but are using diff e r e n t encapsulations, what it required before they can communicate (如果在相同的物理网络中加入了两个设备,但是使用不同的封装,在它们通信之前需要完成什么)?A. A cross-over cableB. A repeaterC. A router configured for the appropriate encapsulations22) When does a workstation normally send a GNS request (工作站一般在什么时候发出G N S请求)?A. When trying to communicate with another workstationB. When trying to locate the nearest routerC. When it needs to send a SAP updateD. When trying to locate a server at initialization23) How many router hops does a GNS request travel (一个G N S请求经过多少个路由器跳)?A. 16B. NoneC. 4D. Unlimited24) In a SAP update packet, what does the Server Address field contain (在S A P更新数据包中,服务器地址字段中包含什么)?A. The network the server is onB. The server’s node numberC. The socket number the server is listening onD. All of the above.25) Which of the following protocols is used by servers to advertise their services to the clients (下面协议中的哪一个由服务器使用,以向客户通告它们的服务)?A. Routing Information protocol (RIP)B. Sequenced Packet Exchange (SPX)C. Network Core Protocol (NCP)D. Service Advertising Protocol (SAP)26) On an Ethernet LAN how many IPX encapsulation types are supported (在一个E t h e r n e t局域网上,可以支持多少个I P X封装)?B. 3C. 2D. 127) The frame check sequence checks with which fields in an Ethernet_802.3 frame (帧校验序列校验E t h e r n e t - 8 0 2 . 3帧中的哪一个字段)?A. The Source Address and Destination AddresB. The packet dataC. Everything from the Destination Address onD. Source Service Access Point (SSAP)28) Which of the following fields is not common to both Ethernet_802.3 and Ethernet_802.2 frames (下面字段中的哪一个不是E t h e r e n e t 8 0 2 . 3和E t h e r n e t 8 0 2 . 3帧所共有的)?A. Source AddressB. LengthC. DSAPD. Data29) In SAP packets, the numbers in the Service Type field are assigned by (在一个S A P数据包中,服务类型字段中的数字由谁给定)?A. The system administratorB. The end userC. NovellD. Server30) SAP requests, responses, or broadcasts can be recognized by which value of source or destination socket number (SAP 请求,响应或广播可以通过源或目的套接字数字中的哪一个值来识别)?A. 0x0452C. 0x03D. 0x045331) In RIP Packets, the Hops Away and Time Ticks fields are valid both for request and response packets (在R I P数据包中,“跳距离”和“时间嘀嗒数”字段对于请求和响应数据包都是合法的)。
CCNA认证基础课程-课后作业.习题答案

CCNA认证基础-习题分析讲义第一部分第一章1. Convert the binary number 10111010 into its hexadecimal equivalent. Select thecorrect answer from the list below. (3)1) 852) 903) BA4) A15) B36) 1C2. Convert the Hexadecimal number A2 into its Base 10 equivalent. Select thecorrect answer from the list below. (4)1) 1562) 1583) 1604) 1625) 1646) 1663. Which binary number is a representation of the decimal number 248? (3)1) 111010002) 111101003) 111110004) 111110104. Which of the following will test the internal loopback of a node? (3)1) ping 10.10.10.12) ping 192.168.1.13) ping 127.0.0.14) ping 223.223.223.2235) ping 255.255.255.2555. What can be verified by successfully pinging the reserved loopback address ona host? (2)1) Connectivity exists between two hosts on the LAN.2) The TCP/IP stack of the local host is configured correctly.3) A connection exists between a host and the default gateway.4) The route a packet takes from the local host to a remote host is valid.6. Which of the following commands could be used on a Windows-basedcomputer to view the current IP configuration of the system? (Choose two.) (3,4)1) configip2) ifconfig3) ipconfig4) winipcfg5) Winipconfig7.Refer to the exhibit. What must be configured on Host B to allow it to communicate withthe Host C? (Choose three.) (2,4,6)1)the MAC address of RTA router interface connected to Switch 12) a unique host IP address3)the IP address of Switch 14)the default gateway address5)the MAC address of Host C6)the subnet mask for the LAN8. What are important characteristics to consider when purchasing a networkinterface card? (Choose two.) (2,3)1) security used on the network2) media used on the network3) system bus used on the computer4) software installed on the network5) diagnostic tools installed on the network第二章1. Select the necessary information that is required to compute the estimated timeit would take to transfer data from one location to another. (Choose two.) (1,5)1) file size2) data format3) network in use4) type of medium5) bandwidth of the link2. Using the data transfer calculation T=S/BW, how long would it take a 4MB file tobe sent over a 1.5Mbps connection? (2)1) 52.2 seconds2) 21.3 seconds3) 6.4 seconds4) 2 seconds5) 0.075 seconds6) 0.0375 seconds3. What are features of the TCP/IP Transport layer? (Choose two.) (3,5)1) path determination2) handles representation, encoding and dialog control3) uses TCP and UDP protocols4) packet switching5) reliability, flow control and error correction4. Which of the following is the Layer 4 PDU? (4)1) bit2) frame3) packet4) Segment5. What is important to remember about the data link layer of the OSI model whenconsidering Peer to Peer communication? (Choose three.) (3,4,5)1) It links data to the transport layer.2) It encapsulates frames into packets.3) It provides a service to the network layer.4) It encapsulates the network layer information into a frame.5) Its header contains a physical address which is required to complete the datalink functions.6) It encodes the data link frame into a pattern of 1s and 0s (bits) for transmissionon the medium.6. Which statement describes a star topology? (2)1) Each host in the network is connected to a backbone cable that is terminated atboth ends.2) Each host is connected to a hub or switch, either of which acts as a central pointfor all network connections.3) Each host is directly connected to two other hosts to form a long chain of hosts.4) Each host has a connection to all other hosts in the network.7. Which statements describe the logical token-passing topology? (Choose two.)(2)1) Network usage is on a first come, first serve basis.2) Computers are allowed to transmit data only when they possess a token.3) Data from a host is received by all other hosts. Electronic tokens are passedsequentially to each other.4) Token passing networks have problems with high collision rates.8. Which technologies are considered to be LAN technologies? (Choose two.) (2,5)1) DSL2) Token Ring3) Frame Relay4) ISDN5) Ethernet9.Refer to the exhibit. Host A wants to send a message to host B. Place the following stepsin the correct order so that the message can be sent. (4)A - add network layer addressesB - transmit bitsC - create application dataD - add data link layer addresses1) B, A, D, C2) D, A, C, B3) A, D, A, B4) C, A, D, B5) C, D, A, B6) C, B, A, D10.After an uns u ccessful ping to the local router, the technician decides to investigate therouter. The technician observes that the lights and fan on the router are not operational.In which layer of the OSI model is the problem most likely occurring? (4)1) transport2) network3) data link4) physical11. Refer t o the exhibit. What is the order of the TCP/IP Protocol Data Units as datais moved as indicated through the OSI model? (3)1) data, segments, frames, packets, bits2) data, packets, segments, frames, bits3) data, segments, packets, frames, bits4) data, packets, frames, segments, bits第三章1. Which combinations of charges will be repelled by electric force? (Choose two.)(4,6)1) neutral and neutral2) neutral and positive3) neutral and negative4) positive and positive5) positive and negative6) negative and negative2. Which of the following are considered the best media for use in data networkcommunications? (Choose three.) (2,3,6)1) glass2) fibers3) copper4) gold5) plastic6) silicon7) Silver3. Which of the following wireless standards increased transmission capabilitiesto 11 Mbps? (2)1) 802.11a2) 802.11b3) 802.11c4) 802.11d4. What is attenuation? (3)1) opposition to the flow of current2) measurement of electrical signals relative to time3) degradation of a signal as it travels along the medium4) amount or volume of traffic that is flowing on the medium5. Which cable specifications are indicated by 10BASE-T? (3)1) 10 Mbps transmission speed, baseband signal, 500 meter cable length, coaxialcable2) 10 Mbps transmission speed, broadband signal, 100 meter cable length, coaxialcable3) 10 Mbps transmission speed, baseband signal, 100 meter cable length,twisted-pair cable4) 10 Gbps transmission speed, broadband signal, 500 meter cable length,twisted-pair cable6. For which Ethernet installations would fiber optic rather than Cat5 UTP be abetter media choice? (Choose two.) (2,4)1) a 3 meter connection between two 10BASE-T hubs2) an environment with many potential sources of EMI and RFI3) a peer to peer connection between two NICs with RJ45 connectors4) an installation between two buildings that are located 500 meters apart5) a single building installation where installation costs are the major concern7. Refer to the exhibit. Which type of UTP cable should be used to connect Host Ato Switch1? (4)1) rollover2) console3) crossover4) straight-through8. Refer to the exhibit. Which type of Category 5 cable is used to make an Ethernetconnection between Host A and Host B? (3)1) coax cable2) rollover cable3) crossover cable4) straight-through cable第四章1. During cable testing, which of the following are used to calculate theinformation carrying capacity of a data cable? (Choose two.) (2,5)1) bit speed2) attenuation3) wire map4) saturation limit5) analog bandwidth2. What type of wiring problem is depicted in this sample of a cable tester? (3)1) a fault2) a short3) an open4) a split a good map3. In a new network installation, the network administrator has decided to use amedium that is not affected by electrical noise. Which cable type will best meet this standard? (5)1) coaxial2) screened twisted pair3) shielded twisted pair4) unshielded twisted pair5) fiber optic4. How does network cable length affect attenuation? (3)1) Category 5 cable that is run in metal conduit has the highest attenuation in theshortest distance.2) Shorter cable lengths have greater signal attenuation.3) Longer cable lengths have greater signal attenuation.4) The length of the cable has no effect on signal attenuation.第五章1. The highest capacity Ethernet technologies should be implemented in whichareas of a network? (Choose three.) (3,4,5)1) between workstation and backbone switch2) between individual workstations3) between backbone switches4) between enterprise server and switch5) on aggregate access links2. What device must be used between an AUI port of a networking device and themedia to which it is being connected? (3)1) a transducer2) a transmitter3) a transceiver4) a transponder5) a port replicator3. An ISDN Basic Rate Interface (BRI) is composed of how many signalingchannels? (1)1) 12) 23) 34) 44. Which layer of the OSI model covers physical media? (1)1) Layer 12) Layer 23) Layer 34) Layer 45) Layer 56) Layer 65. What type of network cable is used between a terminal and a console port? (3)1) cross-over2) straight-through3) rollover4) patch cable6. What is the recommended maximum number of workstations configured on apeer-to-peer network? (3)1) 252) 153) 104) 55) 27. Which of the following increases the potential for a collision to occur? (4)1) the use of an active hub instead of an intelligent hub2) the use of an intelligent hub instead of an active hub3) a reduction in the number of devices attached to the hub4) an increase in the number of devices attached to the hub8. What is the maximum length of a media segment used for 100BASE-TX? (1)1) 100 meters2) 185 meters3) 400 meters4) 500 meters9. Which cable diagram displays the end to end pinout for a crossover cable usedwith Cisco devices? (3)1) Cable A2) Cable B3) Cable C4) Cable D第六章1. What does the "10" in 10Base2 indicate about this version of Ethernet? (2)1) The version uses Base10 numbering within the frames.2) The version operates at a transmission rate of 10 Mbps.3) Frames can travel 10 meters unrepeated.4) The maximum frame length is 10 octets.2. How is a MAC address represented? (4)1) four groups of eight binary digits separated by a decimal point2) four Base10 digits separated by a decimal point3) six hexadecimal digits4) twelve hexadecimal digits5) twenty-four Base10 digits3. Which of the following statements are correct about CSMA/CD? (Choose three.)(1,3,6)1) It is a media access method used in LANs.2) It is a media access method used in FDDI WANs.3) When a device needs to transmit, it checks to see if the media is available.4) A device sends data without checking media availability because all deviceshave equal access.5) Multiple devices can successfully transmit simultaneously.6) Only one device can successfully transmit at a time.4. Which devices shown in the graphic must have a MAC address? (5)1) only PC2) only router3) PC and router4) PC, hub, and router5) PC, printer, and router第七章1. Which of the following items are common to all 100BASE technologies?(Choose three.) (1,4,5)1) frame format2) media3) connectors4) timing5) multi-part encoding2. Which of the following does 1000BASE-T use to accomplish gigabit speeds onCat 5e cable? (4)1) the use of four conductors in full-duplex mode2) the use of two multiplexed pairs of wires, simultaneously3) the use of three pairs of wires for data and the fourth for stabilization andforward error correction4) the use of all four pairs of wires in full-duplex mode, simultaneously3. For which of the following is Ethernet considered the standard? (Choose three.)(1,4,5)1) inter-building connection2) mid-length voice3) video conferencing4) vertical wiring5) horizontal wiring6) diagonal wiring4. To make sure timing limitations are not violated when implementing a 10 MbpsEthernet network involving hubs or repeaters, a technician should adhere to which rule? (4)1) the 4-5-3 rule2) the 6-4-2 rule3) the 3-4-5 rule4) the 5-4-3 rule5. What is the maximum distance that 10BASE-T will transmit data before signalattenuation affects the data delivery? (1)1) 100 meters2) 185 meters3) 300 meters4) 500 meters6. When using Category 5 UTP cable, which RJ-45 pin pairs are used to exchangedata between hosts on an Ethernet network? (2)1) 1 and 2; 4 and 52) 1 and 2; 3 and 63) 3 and 6; 7 and 84) 4 and 5; 7 and 8第八章1. John has been hired as the network administrator of a local company and hasdecided to add more hubs to the company's existing network. Which of the following has been caused by John's inexperience? (1)1) collision domain extended2) an increased number of collision domains3) increased network performance4) increased bandwidth5) extended bandwidth2. "CompA" is trying to locate a new computer named "CompB" on the network.Which of the following does "CompA" broadcast to find the MAC address of "CompB"? (2)1) MAC request2) ARP request3) ping4) Telnet5) proxy ARP3. Which of the following is a term associated with replacing hubs with switchesto increase the number of collision domains? (3)1) encapsulation2) latency3) segmentation4) layered model5) broadcast domain6) Extended4. The accumulation of traffic from which of the following can cause a networkcondition called broadcast radiation? (Choose three.) (3,5,6)1) anonymous FTP servers2) telnet sessions3) video over IP applications4) NAS services5) ARP requests6) RIP updates5. Which of the following describes the use of Spanning Tree Protocol (STP)? (4)1) resolve routing loops2) eliminate Split Horizon errors3) limit collisions4) resolve switching loops6. Which term describes the delay in time that occurs when a frame leaves itssource device and reaches its destination? (4)1) collision2) backoff3) attenuation4) latency5) broadcast7. Based on the graphic above, which of the following occurs as each host systemcomes on line in the topology? (2)1) The switch sends its MAC address to each host.2) The switch adds MAC address to the bridge table as each host sends a frame.3) Each host exchanges MAC addresses with each other.4) The switch listens for data traffic to block since the switch lacks an IP address. 8. Which devices segment collision domains? (Choose two.) (2,3)1) transceiver2) router3) switch4) hub5) media9. Which protocol is used to eliminate switching loops? (3)1) Transmission Control Protocol2) Routing Information Protocol3) Spanning Tree Protocol4) Interior Gateway Routing Protocol5) Internetworking Protocol10. Refer to the exhibit. A network associate needs to establish an Ethernetconnection between Host A and Host B. However, the distance between the two hosts is further than the cabling standards allow. Which two devices that operate at the physical layer of the OSI can be used to allow Host A and Host B to communicate? (2,5)1) switch2) hub3) bridge4) router5) repeater第九章1. Which term describes an ARP response by a router on behalf of a requestinghost? (3)1) ARP2) RARP3) Proxy ARP4) Proxy RARP2. Which protocol functions at the internet layer of the TCP/IP protocol suite? (4)1) File Transfer Protocol (FTP)2) Trivial File Transfer Protocol (TFTP)3) Transmission Control Protocol (TCP)4) Internet Protocol (IP)5) User Datagram Protocol (UDP)6) Simple Mail Transport Protocol (SMTP)3. Which of these workstation installation and setup tasks are concerned withnetwork access layer functions? (Choose two.) (2,4)1) configuring the e-mail client2) installing NIC drivers3) configuring IP network settings4) connecting the network cable5) using FTP to download application software updates4. Which part of an IP address identifies a specific device on a network? (4)1) first two octets2) third and fourth octets3) network portion4) host portion5) only the fourth octet5. Which of the following are features of the Internet Protocol (IP)? (Choose two.)(1,3)1) It is the most widely implemented global addressing scheme.2) It allows two hosts to share a single address on a local area network.3) It is a hierarchical addressing scheme allowing addresses to be grouped.4) It is only locally significant, used primarily on local area networks.6. Which of the following are useable Class A IP addresses with a default subnetmask? (Choose three.) (2,3,5)1) 127.0.39.12) 111.9.28.303) 123.1.2.1324) 128.50.38.25) 105.1.34.16) 0.23.92.37. Which application layer protocols use UDP at the transport layer? (Choose two.)(2,4)1) FTP2) SNMP3) Telnet4) DHCP5) SMTP第十章1. Which OSI layer encapsulates data into packets? (3)1) session2) transport3) network4) data link2. Which OSI layer defines the functions of a router? (3)1) physical2) data link3) network4) transport5) session3. Which of the following are Cisco proprietary routing protocols? (Choose two.)(2,6)1) RIPv22) IGRP3) OSPF4) BGP5) RIPv16) EIGRP4. A company with a Class B license needs to have a minimum of 1,000 subnetswith each subnet capable of accommodating 50 hosts. Which mask below is the appropriate one? (4)1) 255.255.0.02) 255.255.240.03) 255.255.255.04) 255.255.255.1925) 255.255.255.2245. A small company has a class C network license and needs to create five usablesubnets, each subnet capable of accommodating at least 20 hosts. Which of the following is the appropriate subnet mask? (3)1) 255.255.255.02) 255.255.255.1923) 255.255.255.2244) 255.255.255.2406. When a network administrator applies the subnet mask 255.255.255.248 to aClass A address, for any given subnet, how many IP addresses are available to be assigned to devices? (6)1) 10222) 5103) 2544) 1265) 306) 67. Host A is assigned the IP address 10.18.97.55 /21. How many more networkdevices can be assigned to this subnetwork if Host A is the only one that has an IP address assigned so far? (4)1) 2542) 5093) 10214) 20455) 40946) 81908.Refe r to the exhibit. The network administrator wants to create a subnet for thepoint-to-point connection between the two routers. Which subnetwork mask would provide enough addresses for the point-to-point link with the least number of wasted addresses?1) 255.255.255.1922) 255.255.255.2243) 255.255.255.2404) 255.255.255.2485) 255.255.255.2529. What is the correct number of usable subnetworks and hosts for the IP networkaddress 192.168.35.0 subnetted with a /28 mask?1) 6 networks / 64 hosts2) 14 networks / 32 hosts3) 14 networks / 14 hosts4) 30 networks / 64 hosts10. Which subnet masks would be valid for a subnetted Class B address? (Choosetwo.) (5,6)1) 255.0.0.02) 255.254.0.03) 255.224.0.04) 255.255.0.05) 255.255.252.06) 255.255.255.19211. Refer to the exhibit. How will the Fohi router dynamically learn routes to the192.168.16.16/28, 192.168.16.32/28, and 192.168.16.48/28 subnetworks? (3)1) with a static route2) with a routed protocol3) with a routing protocol4) with a directly connected route12. How many broadcast domains are shown in the diagram? (1)1) three2) four3) five4) six5) seven6) eight13. How many collision domains are shown in the diagram? (5)1) three2) four3) five4) six5) seven6) eight14. A router interface has been assigned an IP address of 172.16.192.166 with amask of 255.255.255.248. To which subnet does the IP address belong?1) 172.16.0.02) 172.16.192.03) 172.16.192.1284) 172.16.192.1605) 172.16.192.1686) 172.16.192.17615. Refer to the exhibit. Host A is sending data to Host B. Once R2 determines thatdata from Host A must be forwarded to R1 to reach Host B, which layer of the OSI model will R2 use to address and build the frames destined for R1?1) physical2) data link3) network4) transport5) session6) presentation16. Which type of address is 192.168.170.112/28?1) host address2) subnetwork address3) broadcast address4) multicast address17. Which type of address is 223.168.17.167/29?1) host address2) multicast address3) broadcast address4) subnetwork address18. Which combination of network id and subnet mask correctly identifies all IPaddresses from 172.16.128.0 through 172.16.159.255?1) 172.16.128.0 255.255.255.2242) 172.16.128.0 255.255.0.03) 172.16.128.0 255.255.192.04) 172.16.128.0 255.255.224.05) 172.16.128.0 255.255.255.19219. Refer to the exhibit. The internetwork in the exhibit has been assigned the IPaddress 172.20.0.0. What would be the appropriate subnet mask to maximize the number of networks available for future growth?1) 255.255.224.02) 255.255.240.03) 255.255.248.04) 255.255.252.05) 255.255.254.06) 255.255.255.0第十一章1. If a network administrator needed to download files from a remote server, whichprotocols could the administrator use to remotely access those files? (Choose two.) (3,5)1) NFS2) ASCII3) TFTP4) IMAP5) FTP6) UDP2. What is established during a connection-oriented file transfer betweencomputers? (Choose two.) (2,5)1) a temporary connection to establish authentication of hosts2) a connection used for ASCII or binary mode data transfer3) a connection used to provide the tunnel through which file headers aretransported4) a command connection which allows the transfer of multiple commands directlyto the remote server system5) a control connection between the client and server3. Which of the following protocols are used for e-mail transfer between clientsand servers? (Choose three.) (3,4,5)1) TFTP2) SNMP3) POP34) SMTP5) IMAP46) postoffice4. Which type of institution does the domain suffix .org represent? (4)1) government2) education3) network4) non-profit5. Which of the following services is used to translate a web address into an IPaddress? (1)1) DNS2) WINS3) DHCP4) Telnet6. Which part of the URL http://www.awsb.ca/teacher gives the name of thedomain? (4)1) www2) http://3) /teacher4) awsb.ca7. Which protocols are TCP/IP application layer protocols? (Choose two.) (2,4)1) UDP2) FTP3) IP4) SMTP5) TCP8. What are three characteristics of the TCP protocol? (Choose three.) (3,4,6)1) has less overhead than UDP2) is used for IP error messages3) forces the retransmission undelivered packets4) creates a virtual session between end-user applications5) carries the IP address of destination host in the TCP header6) is responsible for breaking messages into segments and reassembling9. Two peer hosts are exchanging data using TFTP. During the current session, adatagram fails to arrive at the destination. Which statement is true regarding the retransmission of the datagram? (2)1) Datagram retransmission requires user authentication.2) Datagram retransmission is controlled by the application.3) Datagram retransmission relies on the acknowledgements at transport layer.4) Datagram retransmission occurs when the retransmission timer expires in thesource host.案例学习1. 子网计算练习:Answer2. 子网号及广播地址计算练习Answer3. 子网规划练习:已知:给定一个C类地址201.16.5.0/24。
CCNA第二学期练习答案chapter3

1Which two statements correctly describe the concepts of administrative distanc metric? (Choose two.)Administrative distance refers to the trustworthiness of a particular route.A router first installs routes with higher administrative distances.The value of the administarive distance can not be altered by the networkRoutes with the smallest metric to a destination indicate the best path.The metric is always determined based on hop count.The metric varies depending which Layer 3 protocol is being routed, such as2Refer to the exhibit. Which statement correctly describes how R1 will determinepath to R2?R1 will install a RIP route using network A in its routing table because theadministrative distance of RIP is higher than EIGRP.R1 will install a RIP route using network A in its routing table because the pafrom RIP is lower than EIGRP.R1 will install an EIGRP route using network B in its routing table because th administrative distance of EIGRP is lower than RIP.R1 will install an EIGRP route using network B in its routing table because th cost from EIGRP is lower than RIP.R1 will install an EIGRP route and a RIP route in its routing table and load b between them.3 Which two statements are true regarding classless routing protocols? (Choosesends subnet mask information in routing updatessends complete routing table update to all neighborsis supported by RIP version 1allows for use of both 192.168.1.0/30 and 192.168.1.16/28 subnets in the sareduces the amount of address space available in an organization4 Which command would the network administrator issue to determine if load balin effect on a router?s how ip protocolss how ip routes how ip interface briefs how ip interface5 Which two conditions would create a setting where the use of a distance-vectorprotocol would be efficient? (Choose two.)the network requires a special hierarchical designfast convergence of the network is crucialthe network is using a hub and spoke topologythe network is using a flat designthere are more than 15 hops between the most distant routers6 What is the purpose of a routing protocol?It is used to build and maintain ARP tables.It provides a method for segmenting and reassembling data packets.It allows an administrator to devise an addressing scheme for the network.It allows a router to share information about known networks with other route It provides a procedure for encoding and decoding data into bits for packet forwarding.7 Which of the following best describes the operation of distance vector routing pThey use hop count as their only metric.They only send out updates when a new network is added.They send their routing tables to directly connected neighbors.They flood the entire network with routing updates.8 What attribute is associated with link-state routing protocols?split horizonpoison reverselow processor overheadshortest-path first calculations9 Why is fast convergence desirable in networks that use dynamic routing protocRouters will not allow packets to be forwarded until the network has converg Hosts are unable to access their gateway until the network has converged.Routers may make incorrect forwarding decisions until the network has conv Routers will not allow configuration changes to be made until the network ha converged.10 Which of the following conditions must be met in order for a network to have conThe routers in the network are operating with dynamic routing protocols.The routers in the network are operating with compatible versions of IOS.The routers in the network are operating with the same routing tables.The routers in the network are operating with consistent routing knowledge.11 Which two statements are true regarding metrics? (Choose two.)RIP uses bandwidth as a metric.OSPF uses delay as a metric.EIGRP uses bandwidth as a metric.OSPF uses cost based on bandwidth as a metric.RIP uses delay as a metric.EIGRP uses hop count only as a metric.12 Which two statements are true regarding the advantages of the use of static routes? (Choosincreased securityreduced effort in configuring routesthe administrator maintains control over routingeasier to implement in a growing networkreduces the chance of routing errorsincreased router resource usage13 The following line of code is displayed in a routing table:R 209.165.201.0/24 [120/2] via 192.168.252.2, 00:00:16, S0/0/0What can be concluded from this output?A packet destined for host 192.168.252.2 will be forwarded out the interface connected t209.165.201.0/24.The value, 120, is used to determine the best path when a router has more than one rou protocol configured for the same destination network.This route was manually configured using the ip route command.192.168.252.2 is an interface on the router that produced this output.14 What will be the result of the following commands?ORL(config)# interface fastethernet 0/0ORL(config-if)# ip address 172.16.3.1 255.255.255.0ORL(config-if)# no shutdownThe 172.16.3.0 network will be routed by any dynamic routing protocol automatically.A routing table entry is made to the 172.16.3.0 network with a code of "C".A static route is required to route traffic to the 172.16.3.0 network.The commands will be saved to the startup-configuration automatically.15 An engineer creates a static route by entering the Router(config)# ip route 10.0.0.0 255.255192.168.1.2 command. What can be concluded about this route?The administrative distance of this route is 1.192.168.1.2 is the address of an interface on this router.This route will display as a directly connected network in the routing table.Packets with a destination IP address of 192.168.1.2 will be forwarded to the 10.0.0.0/24 first.16Refer to the exhibit. Router1 and Router2 are running EIGRP. All interfaces are operational a packets can be forwarded between all networks. What information will be found in the routing Router1?Router1 will have 6 directly connected networks.The administrative distance of the route to network 172.16.0.0 will be 90.The metric for routes to 172.16.0.0 will be 1.The interface that is used to forward packets to 172.16.0.0 will always be the S0/1 interfa 17 The following line of code is present in the routing table:O 10.16.1.0/27 [110/129] via 192.168.1.5, 00:00:05, Serial0/0/1What does the number 129 indicate in this output?The cost for this link has a value of 129.The clock rate on this serial interface is set to 129,000.The next-hop router is 129 hops away from this router.This route has been updated 129 times in this routing table.18 A growing medium-sized manufacturing company recently began to have routing instability iscompany uses static routes and has a mixture of over 30 Cisco and non-Cisco routers. The n administrator has decided to convert the network to dynamic routing. What characteristics of should be considered in this selection process?Distance vector routing protocols, such as RIP, converge more quickly than do link-state protocols.EIGRP can be used on all of the routers in the company.OSPF can be used between the routers.An exterior routing protocol, such as BGP, is recommended for growing companies.19Refer to the exhibit. If RIP is the routing protocol, what is the value metric from router A to network 192.168.5.0/24?345662472420 A router learns two paths with equal metrics to a destination network via the RIP routing protwill the router handle packets to the destination network?The router will install the first route it learned into the routing table.The router will install both routes in the routing table and load balance between the two.The router will put the first route in the routing table, and denote the second route as a ba route.The router will pick the path with the higher bandwidth and will place it in the routing tabl。
CCNA2第3章答案

CCNA2第3章答案1. 第3章简介本章讨论了局域网的部署和故障排除。
局域网是一个小范围内的计算机网络,通常被用于连接办公室或住宅中的设备。
本章重点介绍了局域网的构建和故障排除的一些基本概念和技术。
2. 局域网构建局域网的构建需要考虑以下几个关键因素:2.1 路由器和交换机•路由器是一个网络设备,用于将数据包在不同网络之间转发。
它可以连接不同的局域网,并在它们之间进行通信。
路由器通常具有多个接口,每个接口都可以连接到一个局域网。
•交换机是一个网络设备,用于在局域网内转发数据帧。
它可以将数据帧从一个端口转发到另一个端口,以便设备可以进行通信。
交换机根据MAC地址来转发数据帧,这使得局域网中的设备可以直接通信,而不需要经过路由器。
2.2 VLAN•VLAN(Virtual Local Area Network)是一种将局域网分割为多个虚拟网络的技术。
每个VLAN都有自己的逻辑分组,并且设备只能与同一VLAN中的设备进行通信。
VLAN可以提高网络的性能和安全性。
•VLAN可以通过交换机进行配置。
管理员可以将不同的端口分配给不同的VLAN,从而实现不同设备之间的逻辑隔离。
2.3 IP地址规划•IP地址是互联网上的设备进行通信的唯一标识符。
在构建局域网时,我们需要使用IP地址来唯一标识每个计算机或设备。
•IP地址可以手动配置,也可以通过DHCP服务器进行自动分配。
3. 局域网故障排除在网络运行过程中,可能会出现一些故障。
在这种情况下,我们需要进行故障排除来找出问题所在,并采取相应的措施进行修复。
以下是一些常见的局域网故障排除步骤:3.1 确定问题范围首先,我们需要确定问题的范围。
问题可能只影响特定的设备或特定的网络部分。
通过确定问题的范围,我们可以更方便地定位故障的根源。
3.2 确认基本连接检查设备之间的物理连接是否正确。
确保电缆连接可靠,并且没有松动或损坏。
3.3 使用ping工具测试连接使用ping工具测试设备之间的连通性。
CCNA第章考试答案

••试题反馈报告IntroductiontoNetworks(版本-ITN第3章考试以下是针对您未获得满分的试题给出的反馈。
某些交互式试题可能不显示您的答案。
分项分数:1两台计算机可以使用什么方法来确保数据包不会因为过多数据发送过快而被丢弃?正确响应您的响应封装访问方法流量控制响应超时为使两台计算机能够有效通信,必须具有让源和目标设置数据传输和接收时间的机制。
为了正确接收数据,流量控制可以确保数据不会发送的太快。
此试题参考以下领域的内容:IntroductiontoNetworks•规则2哪种类型的通信会向局域网上的所有设备发送消息?正确响应您的响应广播单播组播全播广播通信是一对所有的通信。
单播通信是一对一的通信。
组播是一对多的通信,其中消息会发送给一组特定主机。
全播不是一个描述消息传输的标准术语。
此试题参考以下领域的内容:IntroductiontoNetworks•规则3哪个过程用于将一个消息放入另一消息内以从源传输到目的地?正确响应您的响应流量控制封装访问控制解码封装是将一种消息格式放入另一种消息格式的过程。
例如,一个数据包在封装成帧时如何将其完整放入数据字段中。
此试题参考以下领域的内容:IntroductiontoNetworks•规则4Web客户端向Web服务器发送一个网页请求。
从客户端的角度来讲,用于准备传输请求的协议栈正确顺序是什么?正确响应您的响应HTTP、TCP、IP、以太网HTTP、IP、TCP、以太网以太网、TCP、IP、HTTP以太网、IP、TCP、HTTP用于控制Web服务器和客户端进行交互的方式。
用于管理Web服务器与客户端之间的每次会话。
负责通过最佳路径传输到目标。
4.以太网从IP获取数据包,并将其格式化以供传输。
此试题参考以下领域的内容:IntroductiontoNetworks•协议5下列有关网络协议的陈述哪项是正确的?正确响应您的响应只有在远程网络中的设备之间交换消息时才需要使用网络协议。
思科CCNA考试答案(全)

CCNA思科考试答案(全)第 1 章考试1一家拥有10 名员工的小型公司使用单个LAN 在计算机之间共享信息。
哪种类型连接适合此公司?由当地电话服务提供商提供的拨号连接能够使公司方便且安全地连接员工的虚拟专用网络通过当地服务提供商建立的私有专用线路通过当地服务提供商提供的宽带服务(如DSL)答案:4解析:对于这种小型办公室,比较适合通过被称为数字用户线路(DSL) 的常见宽带服务实现Internet 连接,这种服务由当地的电话服务提供商提供。
由于员工人数很少,带宽的问题并不突出。
如果公司较大,在远程站点有分支机构,则专用线路会更加适合。
如果公司员工需要通过Internet 与公司联系,则采用虚拟专用网。
2哪种网络情况需要使用WAN?员工工作站需要获取动态分配的IP 地址。
员工在出差时需要通过VPN 连接到公司电子邮件服务器。
分支机构的员工需要与同一园区网络上的另一座建筑物内的公司总部共享文件。
员工需要访问托管在其建筑物内DMZ 中的公司Web 服务器上的网页。
答案:2解析:当出差的员工需要通过WAN 连接到公司电子邮件服务器时,VPN 将通过WAN 连接在员工笔记本电脑与公司网络之间创建一个安全隧道。
通过DHCP 获取动态IP 地址是LAN 通信的功能。
在企业园区的不同建筑物之间共享文件可通过LAN 基础设施来实现。
DMZ 是企业LAN 基础设施内一个受保护的网络。
3以下哪项描述了WAN 的特征?WAN 和LAN 在同一地理范围内运行,但有串行链路。
WAN 网络归运营商所有。
所有串行链路均被视为WAN 连接。
WAN 可提供到园区主干网的终端用户网络连接。
答案:2解析:WAN 可用于将企业LAN 互连到远程分支机构站点LAN 和远程工作人员站点。
WAN 归运营商所有。
虽然WAN 连接一般通过串行接口实现,但并不是所有串行链路均连接至WAN。
LAN(而非WAN)可在组织中提供终端用户网络连接。
4电路交换WAN 技术的两个常见类型是什么?(请选择两项。
CCNA考试题

C C N A考试题(总9页) -CAL-FENGHAI.-(YICAI)-Company One1-CAL-本页仅作为文档封面,使用请直接删除第一部分:选择题1:提供可靠数据传输、流控的是OSI的第几层()A、表示层B、网络层C、传输层D、会话层E、链路层2:子网掩码产生在那一层()A、表示层B、网络层C、传输层D、会话层3:当路由器接收的IP报文的目的地址不是本路由器的接口IP地址,并且在路由表中未找到匹配的路由项,采取的策略是()A、丢掉该分组B、将该分组分片C、转发该分组D、以上答案均不对4:当一台主机从一个网络移到另一个网络时,以下说法正确的是()A、必须改变它的IP地址和MAC地址B、必须改变它的IP地址,但不需改动MAC地址C、必须改变它的MAC地址,但不需改动IP地址D、MAC地址、IP地址都不需改动5:ISO提出OSI的关键是()A、系统互联B、提高网络速度C、为计算机制定标准D、经济利益6:OSI参考模型按顺序有哪些层()A、应用层、传输层、网络层、物理层B、应用层、表示层、会话层、网络层、传输层、数据链路层、物理层C、应用层、表示层、会话层、传输层、网络层、数据链路层、物理层D、应用层、会话层、传输层、物理层7:LAN的拓扑形式一般以()为主。
A、总线型B、环型C、令牌环D、载波侦听与冲突检测CSMA/CD8:网段地址154.27.0.0的网络,若不做子网划分,能支持()台主机A、254B、1024C、65,534D、16,777,2069:路由器网络层的基本功能是()。
A、配置IP地址B、寻找路由和转发报文C、将MAC地址解释成IP地址10:选出基于TCP协议的应用程序()。
A、PINGB、TFTPC、TELNETD、OSPF11:某公司申请到一个C类IP地址,但要连接6个的子公司,最大的一个子公司有26台计算机,每个子公司在一个网段中,则子网掩码应设为()。
A、255.255.255.0B、255.255.255.128C、255.255.255.192D、255.255.255.22412:B类地址的缺省掩码是()。
ccna第二学期练习答案
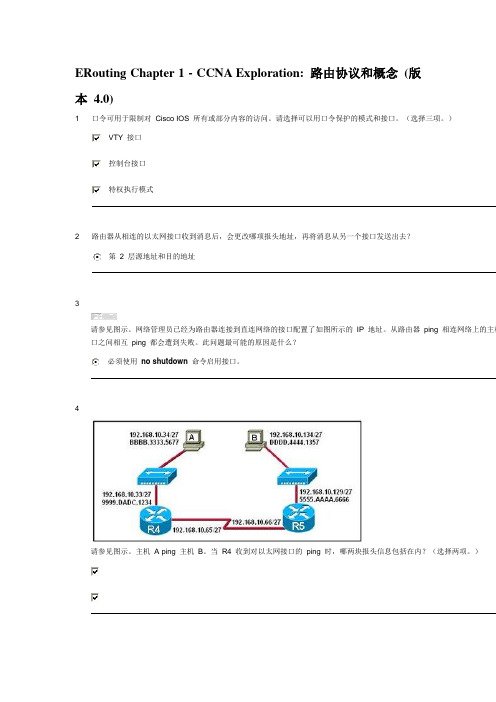
ERouting Chapter 1 - CCNA Exploration: 路由协议和概念(版本 4.0)1 口令可用于限制对Cisco IOS 所有或部分内容的访问。
请选择可以用口令保护的模式和接口。
(选择三项。
)VTY 接口控制台接口特权执行模式2 路由器从相连的以太网接口收到消息后,会更改哪项报头地址,再将消息从另一个接口发送出去?第 2 层源地址和目的地址3请参见图示。
网络管理员已经为路由器连接到直连网络的接口配置了如图所示的IP 地址。
从路由器ping 相连网络上的主机口之间相互ping 都会遭到失败。
此问题最可能的原因是什么?必须使用no shutdown命令启用接口。
4请参见图示。
主机 A ping 主机B。
当R4 收到对以太网接口的ping 时,哪两块报头信息包括在内?(选择两项。
)5 网络管理员刚把新配置输入Router1。
要将配置更改保存到NVRAM,应该执行哪一条命令?Router1# copy running-config startup-config6您需要配置图中所示的串行连接,必须在Sydney 路由器上发出以下哪条配置命令才能与Melbourne 站点建立连接?(选Sydney(config-if)#Sydney(config-if)# no shutdownSydney(config-if)# clock rate 560007请参见图示。
从路由器的运行配置输出可得出什么结论?显示的命令决定了路由器的当前运行情况。
8请参见图示。
在主机 2 连接到LAN 上的交换机后,主机2 无法与主机 1 通信。
导致此问题的原因是什么?主机 1 和主机2 位于不同的网络中。
9 输入以下命令的作用是什么?R1(config)# line vty 0 4R1(config-line)# password check123R1(config-line)# login设置通过Telnet 连接该路由器时使用的口令10 以下哪一项正确描述了路由器启动时的顺序?加载bootstrap、加载IOS、应用配置11 加载配置文件时的默认顺序是怎样的?NVRAM、TFTP、CONSOLE12请参见图示。
CCNA第3章考试答案

••试题反馈报告Introduction to Networks (版本6.00) - ITN 第3 章考试以下是针对您未获得满分的试题给出的反馈。
某些交互式试题可能不显示您的答案。
分项分数:1 两台计算机可以使用什么方法来确保数据包不会因为过多数据发送过快而被丢弃?正确响应您的响应封装访问方法流量控制响应超时为使两台计算机能够有效通信,必须具有让源和目标设置数据传输和接收时间的机制。
为了正确接收数据,流量控制可以确保数据不会发送的太快。
此试题参考以下领域的内容:Introduction to Networks• 3.1.1 规则2 哪种类型的通信会向局域网上的所有设备发送消息?正确响应您的响应广播单播组播全播广播通信是一对所有的通信。
单播通信是一对一的通信。
组播是一对多的通信,其中消息会发送给一组特定主机。
全播不是一个描述消息传输的标准术语。
此试题参考以下领域的内容:Introduction to Networks• 3.1.1 规则3 哪个过程用于将一个消息放入另一消息内以从源传输到目的地?正确响应您的响应流量控制封装访问控制解码封装是将一种消息格式放入另一种消息格式的过程。
例如,一个数据包在封装成帧时如何将其完整放入数据字段中。
此试题参考以下领域的内容:Introduction to Networks• 3.1.1 规则4 Web 客户端向Web 服务器发送一个网页请求。
从客户端的角度来讲,用于准备传输请求的协议栈正确顺序是什么?正确响应您的响应HTTP、TCP、IP、以太网HTTP、IP、TCP、以太网以太网、TCP、IP、HTTP以太网、IP、TCP、HTTP1.HTTP 用于控制Web 服务器和客户端进行交互的方式。
2.TCP 用于管理Web 服务器与客户端之间的每次会话。
3.IP 负责通过最佳路径传输到目标。
4.以太网从IP 获取数据包,并将其格式化以供传输。
此试题参考以下领域的内容:Introduction to Networks• 3.2.1 协议5 下列有关网络协议的陈述哪项是正确的?正确响应您的响应只有在远程网络中的设备之间交换消息时才需要使用网络协议。
ccna考试题及答案

ccna考试题及答案1. 以下哪项是网络层的功能?A. 路由选择B. 错误检测C. 流量控制D. 封装数据包答案:A2. 在OSI模型中,哪一层负责在网络中传输数据?A. 应用层B. 传输层C. 会话层D. 网络层答案:D3. 以下哪个协议是用于在IP网络中发现网络设备的?A. ARPB. RARPC. ICMPD. OSPF答案:A4. 在TCP/IP模型中,哪一层与OSI模型的传输层相对应?A. 应用层B. 互联网层C. 网络接口层D. 传输层答案:D5. 以下哪个地址是一个有效的IPv4地址?A. 192.168.1.256B. 192.168.1.1C. 10.0.0.0D. 172.16.300.1答案:B6. 在配置路由器时,以下哪个命令用于进入全局配置模式?A. enableB. configure terminalC. privileged execD. user exec答案:B7. 以下哪个命令用于在Cisco设备上显示当前配置?A. show running-configB. show startup-configC. show configD. show current-config答案:A8. 在Cisco设备上,以下哪个命令用于保存当前的配置到启动配置文件?A. copy running-config startup-configB. copy startup-config running-configC. save running-configD. save startup-config答案:A9. 以下哪个命令用于在Cisco设备上查看所有接口的状态?A. show interfacesB. show ip interface briefC. show interface statusD. show running-config interface答案:B10. 在Cisco设备上,以下哪个命令用于关闭接口?A. shutdownB. no shutdownC. disableD. no enable答案:A11. 以下哪个命令用于在Cisco设备上启用接口?A. shutdownB. no shutdownC. disableD. no enable答案:B12. 在配置静态路由时,以下哪个命令用于指定下一跳地址?B. ip static-routeC. route ipD. static-route ip答案:A13. 以下哪个命令用于在Cisco设备上清除ARP表?A. clear arp-cacheB. clear arpC. clear arp tableD. clear ip arp答案:D14. 在配置动态路由协议时,以下哪个命令用于在接口上启用RIP?A. ip rip enableB. ip rip receiveD. network rip答案:C15. 以下哪个命令用于在Cisco设备上查看RIP路由表?A. show ip ripB. show ip route ripC. show ripD. show ip protocols答案:B16. 在配置EIGRP时,以下哪个命令用于指定自动汇总?A. metric weightsB. auto-summaryC. network auto-summaryD. no auto-summary答案:B17. 以下哪个命令用于在Cisco设备上查看EIGRP邻居?A. show ip eigrp neighborsB. show eigrp neighborsC. show ip eigrpD. show eigrp interfaces答案:A18. 在配置OSPF时,以下哪个命令用于指定路由器ID?A. router-idB. router ospfC. networkD. area答案:A19. 以下哪个命令用于在Cisco设备上查看OSPF路由表?A. show ip ospfB. show ip ospf databaseC. show ospfD. show ip route ospf答案:D20. 在配置VLAN时,以下哪个命令用于创建一个新的VLAN?A. vlan databaseB. configure terminalC. vlan [vlan-id]D. new-vlan答案:C21. 以下哪个命令用于将接口分配给VLAN?A. switchport mode accessB. switchport mode trunkC. switchport access vlan [vlan-id]D. switchport trunk vlan [vlan-id]答案:C22. 在配置交换机时,以下哪个命令用于将接口设置为Trunk 模式?A. switchport mode accessB. switchport mode trunkC. switchport access vlan [vlan-id]D. switchport trunk vlan [vlan-id]答案:B23. 以下哪个命令用于在Cisco设备上查看VLAN配置?A. show vlanB. show vlan briefC. show vlan detailD. show vlan all答案:B24. 在配置VTP时,以下哪个命令用于将交换机设置为VTP服务器模式?A. vtp mode serverB. vtp mode clientC. vtp mode transparentD. vtp mode off答案:A25. 以下哪个命令用于在Cisco设备上查看VTP状态?A. show vtp statusB. show vtp statisticsC. show vtp passwordD. show vtp configuration答案:A26. 在配置STP时,以下哪个命令用于设置根桥?A. spanning-tree root primaryB. spanning-tree root secondaryC. spanning-tree root primary [priority]D. spanning-tree root secondary [priority]答案:C27. 以下哪个命令用于在Cisco设备上查看STP状态?A. show spanning-treeB. show spanning-tree detailC. show spanning-tree summaryD. show spanning-tree interface答案:A28. 在配置VLAN Trunking Protocol (VTP) 时,以下哪个命令用于设置VTP域名?A. vtp domain [domain-name]B. vtp password [password]C. vtp mode [mode]D. vtp version [version]答案:A29. 以下哪个命令用于在Cisco设备上查看当前的VTP版本?A. show vtp statusB. show vtp statisticsC. show vtp passwordD. show vtp configuration答案:A30. 在配置端口安全时,以下哪个命令用于限制接口上可以学习到的最大MAC地址数量?A. switchport port-security maximum [mac-count]B. port-security maximum [mac-count]C. switchport port-security violation restrictD. port-security violation shutdown答案:A这些题目和答案仅供学习和参考之用,实际的CCNA考试内容和形式可能会有所不同。
CCNA第二学期考试答案

以下是针对您未获得满分的试题给出的反馈。
某些交互式试题可能不显示您的答案。
分项分数:1与固定配置的交换机相比,模块化交换机具有哪两个优点?(请选择两项。
)正确响应您的响应每台交换机的成本更低可扩展性更高转发率更低需要的电源插座数目更少带宽聚合可以使用多个端口固定配置交换机价格较低,但是它具有指定数量的端口且不能添加端口。
它们提供的高速端口通常比较少。
为了在包含固定配置交换机的网络上扩展交换,需要购买更多的交换机。
这增加了需要使用的电源插座数量。
模块化交换机只需要购买额外的线卡便可以扩展。
带宽聚合也更容易,因为机箱的背板可以为交换机端口线卡提供所需的带宽。
此试题参考以下领域的内容:Routing and Switching Essentials• 1.1.2 交换网络2思科无边界架构接入层的基本功能是什么?正确响应您的响应聚合第 2 层广播域聚合第 3 层路由边界为用户提供访问权提供高可用性思科无边界架构接入层的功能是为用户提供网络访问。
第 2 层广播域聚合、第 3 层路由边界聚合和高可用性是分布层的功能。
也有说答案是聚合第 3 层路由边界此试题参考以下领域的内容:Routing and Switching Essentials• 1.1.1 融合网络3思科无边界架构分布层的基本功能是什么?正确响应您的响应充当主干聚合所有园区块聚合第 3 层路由边界为用户提供访问权思科无边界架构的分布层的一项基本功能是在不同的VLAN 之间路由。
充当主干和聚合园区块是核心层的功能。
为用户提供访问是接入层的功能。
此试题参考以下领域的内容:Routing and Switching Essentials• 1.1.1 融合网络4若将大端口密度、容错和低价作为重要指标,应使用哪个交换机外形因素?正确响应您的响应固定配置交换机模块化交换机可配备机架的1U 交换机可堆叠式交换机堆叠式交换机可以使用特殊电缆实现互联,从而在交换机之间提供高带宽的吞吐量,并像单个大型交换机一样运行。
CCNA第二学期官方章节考试题之《距离矢量路由协议》(附答案)46doc

数据包在路由器的两个环回接口之间来回传递
从目的地返回的路径与出发路径不同而形成
数据包在一系列路由器间不断传输却始终无法到达其真正的目的地的情况路由从一种路由协议到另一种路由协议的分布
2
用于在发送到其它路由器的更新中将路由标记为不可达
防止定期更新消息错误地恢复已经不可用的路由
防止从收到更新的接口通告同一网络
限制数据包在被丢弃之前在网络中传输的时间或跳数
通过设置最大跳数来为每一距离矢量路由协议定义最大度量值
4以
路由环路
不一致的流量转发
除非系统收敛,否则不会转发任何流量
路由表条目不一致
路由表更新被发送到错误的目的地
6运
立即将其加入路由表中
调整新路由的度量以显示增加的路由距离
将该路由从其传入接口以外的所有其它接口通告出去
发送
8下
它会在更新从路由器接口送出时缓冲更新,以此防止路由更新同步。
它会从下一次路由更新间隔中减去随机时间段(大小为指定间隔时间的
它会使路由器跳过每一个其它计划更新时间,以此防止路由更新同步。
它会强制路由器在发送自身更新之前侦听链路上的其它更新是何时发送的,以此防止路由更新同步10
13以15水
17R
19哪
抑制计时器将等候
如果在
更新计时器将请求有关从路由器Hello。
CCNA2思科第二学期v20ERoutingFinalExam3答案

1关于数据包通过路由器传输时的封装和解封的叙述,下列哪三项是正确的?(选择三项。
)路由器修改 TTL 字段,将其值减 1。
路由器将源 IP 更改为送出接口的 IP。
路由器保持相同的源IP和目的IP。
路由器将源物理地址更改为送出接口的物理地址。
路由器将目的IP更改为送出接口的IP。
路由器会从所有接口将数据包转发出去,包括路由器接收数据包时使用的那个接口。
Option1,Option3,andOption4arecorrect.2请参见图示。
当数据包发往哪两个网络时需要路由器执行递归查找?(选择两项。
)10.0.0.0/864.100.0.0/16128.107.0.0/16172.16.40.0/24192.168.1.0/24192.168.2.0/24Option 1 and Option 6 arecorrect.3对于为防止路由环路而通过毒性反转实现的水平分割方法,哪两项叙述正确?(选择两项。
)所有CiscoIOS都会默认启用此方法。
会将一个表示无穷大度量的值分配给路由以将其毒化。
将毒化路由更新发回该更新的发送接口。
指示路由器将可能会影响路由的更改保持一段特定的时间。
限制数据包在被丢弃之前能够在网络中传输的跳数。
Option2andOption3arecorrect.4网络管理员在所示网络图中的路由器B和C上启用了 RIP。
什么命令可防止向路由器 A发送RIP更新? A(config)#routerripA(config-router)#passive-interfaceS0/0B(config)#routerripB(config-router)#network192.168.25.48B(config-router)#network192.168.25.64A(config)#routerripA(config-router)#nonetwork192.168.25.32B(config)#routerripB(config-router)#passive-interfaceS0/0A(config)#norouterrip2pointsforOption45请参见图示。
CCNA 2 Final Exam Answers V3.1
1. What are two possible reasons a router would not load a valid IOS from flash? (Choose two.)The configuration register is set to 0×2142.The first boot system command executed in the startup configuration file is boot system rom.The configuration register is set to 0×2100.The boot field is set to the hexadecimal number 2.The startup configuration file is missing or corrupt.2. What are two recommended uses of login banners? (Choose two.)to display security warning messagesto welcome any user to the routerto warn people about misusing privileged EXEC modeto identify circuits and other devices connected to the routerto announce a scheduled system shutdown3.Router A and Router B have been correctly configured to use RIP as a dynamic routing protocol and all intefaces on Router A and Router B are reporting "interface is up, line protocol is up" status. RIP is then configured onRouter C using the following commands:RouterC(config)# router ripRouterC(config-router)# network 192.168.4.0RouterC(config-router)# network 172.16.0.0If no additional routing is configured on Router A, Router B, and Router C, what will be the result?Networks 192.168.12.0/24, 192.168.4.0/24, and 172.16.0.0/16 will be unreachable from Router A.Router A will have no knowledge of network 192.168.12.0/24, but will have routes to networks 192.168.4.0/24 and 172.16.0.0/16.All networks shown in the graphic will be reachable by Router A, Router B, and Router C.Networks 192.168.4.0/24 and 172.16.0.0/16 will be unreachable from Router A and Router B.4. What are the primary functions of a router? (Choose two.) determine the best path for packetsprevent collisions on the network LANregulate flow control between sender and receiverprovide domain name resolutionforward packets to the appropriate interface5. What are some reasons to change the configuration register setting? (Choose two.)to force the system to ignore the configuration file stored in NVRAM to monitor password changesto change the POST sequenceto force the router to boot the IOS from NVRAMto force the system into ROM monitor mode6. A network administrator issues the erase startup-config command on a configured router with the configuration register set to 0×2102 and observes the following output:Erasing the nvram filesystem will remove all files! Continue? [Confirm] [OK]Erase of nvram: completeIf the router unexpectedly loses power after this sequence, what will occur when power is restored?The router will enter ROM monitor mode upon completion of the power-on self test (POST).The router will load the last known valid configuration file.The router will enter Rx-boot mode.The router will prompt the user to enter setup mode or to continue without entering setup mode.7. Why are routed protocols important to networking? (Choose two.) Routed protocols detect collisions and fragments.Routers use routed protocols to calculate the best path to a destination. Routed protocols transport data across the network.The fields and formats used within a packet are defined by routed protocols.Routed protocols are used to configure the metrics used by routing protocols.8. The main router of XYZ company has enough flash and RAM to store multiple IOS images. An administrator wants to upload a second IOS image from a TFTP server to the flash of the router. Which method will accomplish this task?Paste the IOS filename to the command line of the router while in global configuration mode. Press enter. Then issue the copy tftp flash command.Use the setup utility to load the new image to flash.Copy the IOS image file from a TFTP server using the command copy filenameip address flash .Copy the IOS image file from a TFTP server using the command copy tftp flash. When prompted, provide the IP address or name of the TFTP server and the IOS image filename.9.A network administrator has a console connection to the Fremantle router. Pings to Melville are successful, but pings to Cottesloe and Nedlands fail. What could be a first step in troubleshooting the problem?Use an extended ping from Fremantle to each router in the network.Use the show interfaces command from a Telnet session on Melville to check the connection to Cottesloe.Use the traceroute command to discover exactly which link in the network is down.Use the show cdp neighbors detail command from Fremantle to gather information about all Cisco routers in the network.10.Refer to the exhibit. The new security policy for the company allows all IP traffic from the Engineering LAN to the Internet while only web traffic from the Marketing LAN is allowed to the Internet. Which ACL can be applied in the outbound direction of Serial 0/1 on the Marketing router to implement the new security policy?access-list 197 permit ip 192.0.2.0 0.0.0.255 anyaccess-list 197 permit ip 198.18.112.0 0.0.0.255 any eq wwwaccess-list 165 permit ip 192.0.2.0 0.0.0.255 anyaccess-list 165 permit tcp 198.18.112.0 0.0.0.255 any eq wwwaccess-list 165 permit ip any anyaccess-list 137 permit ip 192.0.2.0 0.0.0.255 anyaccess-list 137 permit tcp 198.18.112.0 0.0.0.255 any eq wwwaccess-list 89 permit 192.0.2.0 0.0.0.255 anyaccess-list 89 permit tcp 198.18.112.0 0.0.0.255 any eq www11.Hosts from the Limerick LAN are not allowed access to the Shannon LAN but should be able to access the Internet. Which set of commands will create a standard ACL that will apply to traffic on the Shannon router interface Fa0/0 implementing this security?access-list 42 deny 172.19.123.0 0.0.0.255 192.0.2.0 0.0.0.255 access-list 42 permit anyaccess-list 56 deny 172.19.123.0 0.0.0.255access-list 56 permit anyaccess-list 61 deny 172.19.123.0 0.0.0.0access-list 61 permit anyaccess-list 87 deny ip any 192.0.2.0 0.0.0.255access-list 87 permit ip any12. Which of the following commands will correctly configure an extended ACL? (Choose two).Router(config)# access-list 18 permit tcp host 192.168.73.3 eq 25Router(config)# access-list 102 permit tcp 10.43.0.0 0.0.255.255 any eq 80Router(config)# access-list 187 permit tcp host 192.168.42.34 172.29.0.0 0.0.255.255 eq 23Router(config)# access-list 99 permit host 10.217.32.3Router(config)# access-list 128 permit tcp host 192.168.100.31 eq 2313. What are the results of setting the boot field bits in the configuration register to "0000"? (Choose two.)The startup-config file will be ignored at bootup.The router will load the IOS from Flash.The router will enter ROM monitor mode upon reload.The router will enter boot ROM mode and have limited capabilities. The administrator can enter the b command to manually boot the IOS.14.Refer to the exhibit. Router D interface S0 on has gone down. What is the maximum time that will elapse before Router A learns that network 168.58.14.0 is down?5 seconds13 seconds17 seconds25 seconds30 seconds77 seconds15. During initial router bootup the following line appears: "NVRAM invalid, possibly due to write erase."What are two possible reasons for this result? (Choose two.)The startup-config file was not saved to RAM before reboot.The IOS has been erased.The router has not been configured.The startup-config file cannot be located.The router will not enter initial configuration dialog.16.The Suffolk router is directly connected to the networks shown in the graphic and has a default route that points to the Richmond router. All interfaces are active and properly addressed. However, when the workstation on network 172.29.5.0/24 sends a packet to destination address 172.29.198.5, it is discarded by the Suffolk router. What can be a reason for this result?The ip classless command is not enabled on the Richmond router.The route was ignored if the Richmond router did not include the 172.29.198.0/24 network in its routing updates.The Richmond router is in a different autonomous system than the Suffolk router.The ip subnet-zero command was not configured on the Suffolk router.The ip classless command is not enabled on the Suffolk router.17. access-list 199 deny tcp 178.15.0.0 0.0.255.255 any eq 23 access-list 199 permit ip any anyAssuming this ACL is correctly applied to a router interface, which statements describe traffic on the network? (Choose two.)All FTP traffic from network 178.15.0.0 will be permitted.All Telnet traffic destined for network 178.15.0.0 will be denied.Telnet and FTP will be permitted from all hosts on network 178.15.0.0 to any destination.Telnet will not be permitted from any hosts on network 178.15.0.0 to any destination.Telnet will not be permitted to any host on network 178.15.0.0 from any destination.18.What facts can be determined from the highlighted text shown in the exhibit? (Choose two.)A weak encryption was applied to all unencrypted passwords.The enable password is now more secure than the enable secret password.An MD5 hashing algorithm was used on all encrypted passwords.Any configured user EXEC mode or Telnet passwords will be encrypted in this configuration.The service password-encryption command was used to encrypt all passwords on the router including enable secret.19. What are three features of CDP? (Choose three.)provides information on directly connected devices that have CDP enabled tests Layer 2 connectivityenabled by default on each interfaceprovides a layer of securityused for debugging Layer 4 connectivity issues20. What information can be learned during the initial router bootup? (Choose two.)the configuration register valuethe number and types of interfaces installedthe router model and the amount of memory that is availablethe amount of memory required to load the IOS and configurationthe number of interfaces with connected cables21.What can be concluded from the output shown in the exhibit? (Choose three.)This is a standard IP access list.This is an extended IP access list.The keyword host is implied in the command line access-list 99 deny 10.213.177.76.The wildcard mask must be configured for this access list to function properly.Host 10.213.177.100 will be allowed access to the Serial0/1 interface.22. Which statements are true regarding setup mode? (Choose three.)Press Ctrl-z to terminate setup mode.Enter a question mark (?) for help at any point.Press Spacebar to accept the default settings.Use setup mode to enter complex protocol features.Press Enter to accept the default settings.Press Ctrl-c to abort configuration dialog.23.Refer to the graphic. Which series of commands will create static routes that will allow Router A and Router B to deliver packets destined for LAN A and LAN B, and direct all other traffic to the Internet?RouterA(config)# ip route 10.90.3.0 255.255.255.0 192.168.3.2RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1 RouterB(config)# ip route 0.0.0.0 0.0.0.0 s0/0RouterA(config)# ip route 10.90.3.0 255.255.255.0 192.168.3.2RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1 RouterB(config)# ip route 172.20.20.4 255.255.255.252 s0/0RouterA(config)# ip route 0.0.0.0 0.0.0.0 192.168.3.2RouterB(config)# ip route 192.168.2.0 255.255.255.0 192.168.3.1 RouterB(config)# ip route 0.0.0.0 0.0.0.0 s0/024.Which devices can be used to convert the data from a WAN router at the customer site into a form acceptable for use by the WAN service provider? (Choose three.)Ethernet switchDTEmodemhubDCE deviceCSU/DSU25.What will occur when the following ACL is applied inbound to both FastEthernet interfaces of Router A in the graphic?access-list 125 permit tcp 192.168.2.0 0.0.0.255 10.90.3.0 0.0.0.255 eq 23access-list 125 permit tcp 10.90.3.0 0.0.0.255 192.168.2.0 0.0.0.255 eq 23access-list 125 permit tcp 192.168.2.0 0.0.0.255 any eq wwwWorkstations A and B will be able to Telnet to each other. WorkstationA will be allowed to access Web servers on the Internet, while WorkstationB will be denied Internet Web access.Workstations A and B will be able to Telnet to each other. All other traffic will be denied.The ACL will have no effect because it should be applied in the outbound direction on the FastEthernet interfaces.The ACL will deny all traffic because of the implied deny ip any any statement at the end of the ACL.26. Based on this partial output of the show ip route command, which routing protocol is configured on the router?R 172.16.3.0/24 [120/3] via 172.16.2.2, 00:00:27, Serial0/0RIPEIGRPOSPFIGPBGP27.Which of the following are correct statements verified by the router output shown in the graphic? (Choose two.)Layer 3 connectivity exists between BigCity and the devices in the Device ID column.Layer 2 connectivity exists between BigCity and the devices in the Device ID column.All devices shown in the Device ID column use the TCP/IP protocol suite.All devices shown in the Device ID column can be pinged from BigCity.All devices listed in the Device ID column are directly connected to BigCity.28. A network administrator must configure a FastEthernet interface with an IP address. The configuration must also identify the remote site to which the interface is connected. Which set of commands will meet these requirements?StPetersburg(config)# banner San Jose T1StPetersburg(config)# interface fa0/0StPetersburg(config-if)# ip address 172.26.155.5 255.255.255.252StPetersburg(config)# interface fa0/0StPetersburg(config-if)# ip address 172.26.155.5 netmask255.255.255.252StPetersburg(config-if)# description San Jose T1StPetersburg(config)# interface fa0/0StPetersburg(config-if)# ip address 172.26.155.5 255.255.255.252 StPetersburg(config-if)# banner remote site San Jose T1StPetersburg(config)# interface fa0/0StPetersburg(config-if)# ip address 172.26.155.5 255.255.255.252 StPetersburg(config-if)# description San Jose T129. What are the features of a serial interface on a router? (Choose two.) enabled by defaultassigned a unique MAC addressmust be configured as a DCE in lab and production environmentsmust be configured with the default clock rate of 56000may be administratively enabled by using the no shutdown commandmust be configured with a valid IP address and subnet mask in order to forward packets30. Assuming the following ACL is correctly applied to a router interface, what can be concluded about this set of commands? (Choose two.) Router(config)# access-list 165 deny tcp 192.28.115.0 0.0.0.255 172.20.0.0 0.0.255.255 eq 23Router(config)# access-list 165 permit ip any anyThis is a standard IP access list that denies network 192.28.115.0 Telnet access to the 172.20.0.0 network.All Telnet traffic destined for 172.20.0.0 from any network will be denied access.Network 192.28.115.0 is denied Telnet access to the 172.20.0.0 network. Network 172.20.0.0 is denied Telnet access to the 192.28.115.0 network.All FTP and HTTP traffic destined for 172.20.0.0 will be permitted access.31. Which two steps describe how to create a functional physical connection between a router console and a terminal? (Choose two.)Use a crossover cable to connect the terminal serial port to the router console port.Use a rollover cable to connect the terminal NIC to the router console port.Use an RJ-45 to DB-9 adapter on the terminal serial port to connect to the cable going to the router console.Use a transceiver to connect a straight-through cable to the router console port.Use a straight-through cable to connect the router console port to the terminal NIC.Use a rollover cable to connect from a terminal serial port to the router console port.32. What critical information about the status of the router can be found in the outputs of both the show interfaces and show protocols commands? (Choose two.)the Layer 3 address of each configured interfacethe routing protocol configured to forward updates out of each interface the operational status of each interfacetraffic statistics for each interfacewhether the interface is configured as a DTE or DCE33.The following access list has been created to prevent traffic from the 192.0.2.63 host on the Sales LAN from accessing servers and hosts on the Payroll LAN.access-list 26 deny host 192.0.2.63access-list 26 permit anyRefer to the exhibit. Which group of commands will properly place the access list so that only the host on the Sales LAN is denied access to the 172.29.7.0 network but all other traffic is permitted?Payroll(config)# interface fa0/0Payroll(config-if)# ip access-group 26 outPayroll(config)# interface fa0/1Payroll(config-if)# ip access-group 26 outSales(config)# interface fa0/1Sales(config-if)# ip access-group 26 inSales(config)# interface fa0/0Sales(config-if)# ip access-group 26 out34.Refer to the exhibit. Assuming default metrics are used and the networkis fully converged, which path will RIP use to send a packet from Router A to Router F?A, D, E, FA, B, D, E, FA, C, D, E, G, FA, B, D, E, G, F35.Refer to the graphic. Communication is needed between the LAN connected to the fa0/0 interface of the Kansas router and the fa0/0 interface of the Maine router. All hosts on those LANs also need connectivity to the Internet. Which commands will allow this communication? (Choose three).Kansas(config)# ip route 192.168.6.0 255.255.255.0 172.18.64.2Kansas(config)# ip route 192.168.6.0 255.255.255.0 s0/1Kansas(config)# ip route 0.0.0.0 0.0.0.0 s0/1Maine(config)# ip route 192.168.6.0 255.255.255.0 172.18.64.1Maine(config)# ip route 0.0.0.0 0.0.0.0 s0/1Maine(config)# ip route 172.16.32.0 255.255.255.0 172.18.64.236. Why are interface descriptions used in router configurations? (Choose three).to enable support personnel to easily identify networks and customers that may be affected by a possible interface issueto provide comments on the interface without affecting the router functionalityto display access warning messages before users enter the interface configuration modeto eliminate the need to use IP addresses when using the ping and telnet commandsto identify the purpose and location of the interface37.A network administrator has enabled RIP on routersB andC in the network diagram. Which of the following commands will prevent RIP updates from being sent to Router A?A(config)# router ripA(config-router)# passive-interface S0/0B(config)# router ripB(config-router)# network 192.168.25.48B(config-router)# network 192.168.25.64A(config)# router ripA(config-router)# no network 192.168.25.32B(config)# router ripB(config-router)# passive-interface S0/0A(config)# no router rip38. What could a Cisco support technician learn from the IOS filename c2600-d-mz.121-3? (Choose three.)the format of the filethe RAM memory requirements of the filethe version number of the filethe size of the filethe device platform of the file39.While planning an IOS upgrade, the administrator issues the show version command. Based on the output in the graphic, what is the current IOS boot location?RAMNVRAMFlashROM40. A new technician must add boot system commands to one of the department routers. Which available commands will the router return as output when the command shown below is entered? (Choose two.)Router(config)# boot system ?RAMNVRAMIOSIP AddressTFTPFLASH41. From the running-config, the following configuration entries are displayed:Router(config)# line vty 0 2Router(config-line)# password g8k33prRouter(config-line)# loginWhat can be interpreted from the exhibited configuration? (Choose two.)Three Telnet lines are available for remote access.Two Telnet lines are available for remote access.Future configuration of the remaining Telnet lines will require the password to be set to g8k33pr.To login to the remote device, g8k33pr will be used as the Telnet and secret password.Remote access to this local router will require a Telnet password of g8k33pr.42. Which router component stores the information that is displayed by the show running-config command?flashNVRAMRAMROM43. What are two characteristics of the support for Telnet within Cisco IOS software? (Choose two.)Up to five separate Telnet lines are supported by default in standard edition IOS files.For security purposes, Telnet sessions are required to be established from the privileged mode.A router can host simultaneous Telnet sessions.Once established, a Telnet session can remain operational regardless of network status.Telnet tests wireless connectivity and does not require a physical connection between devices to gain remote access.44. Which router components and operations are correctly described? (Choose two.)RAM – stores the ARP cacheNVRAM – store the operating systemROM – stores the backup IOSPOST – verifies the validity of the running-configFlash – executes diagnostics at bootupDRAM – loads the bootstrap45.Given the output shown in the exhibit, in what order and location will the router search for the IOS if no boot system commands are found in the startup-config file?ROM, Flash, TFTP serverFlash, NVRAM, RAMROM, TFTP server, FlashRAM, Flash, NVRAMFlash, TFTP server, ROM46. What can a network administrator do to recover from a lost router password?perform a reload or resettelnet from another router and issue the show running-config command to view the passwordboot the router to ROM monitor mode and configure the router to ignore NVRAM when it initializesboot the router to bootROM mode and enter the b command to load the IOS manually47.Neither router in the exhibit has a host table or DNS available. The interfaces and passwords have been correctly configured. Which of the following commands will initiate a Telnet session? (Choose two.)Tottenham# telnet OxfordTottenham> telnet 198.18.139.1Oxford# connect 198.18.139.0Oxford> connect TottenhamOxford# telnet TottenhamOxford# 198.18.139.248. If a PC does not have network connectivity to a router, which router port can be used to establish communication?consoleEthernetserialVTY。
最新 CCNA第二学期章节测试 第三章 答案

参加考试- ERouting Chapter 3 - CCNA Exploration: 路由协议和概念(版本 4.0)1下列哪两项正确描述了管理距离与度量的概念?(选择两项。
)错误!未找管理距离是指特定路由的可信度。
到引用源。
错误!未找路由器会首先添加具有较大管理距离的路由。
到引用源。
错误!未找网络管理员无法更改管理距离的值。
到引用源。
错误!未找具有到目的地的最小度量的路由即为最佳路径。
到引用源。
错误!未找度量总是根据跳数确定。
到引用源。
错误!未找度量会根据所采用的第 3 层协议(如IP 或IPX)而发生变化。
到引用源。
2请参见图示。
下列关于R1 如何确定与R2 之间最佳路径的陈述中,哪一项正确?错误!未找R1 会将使用网络A 的RIP 路由加入路由表,因为RIP 的管理距离比EIGRP 大。
到引用源。
错误!未找R1 会将使用网络A 的RIP 路由加入路由表,因为RIP 的路径开销比EIGRP 低。
到引用源。
错误!未找R1 会将使用网络B 的EIGRP 路由加入路由表,因为EIGRP 的管理距离比RIP 小。
到引用源。
错误!未找R1 会将使用网络B 的EIGRP 路由加入路由表,因为EIGRP 的路径开销比RIP 低。
到引用源。
错误!未找R1 会将EIGRP 路由和RIP 路由加入路由表,并在它们之间实施负载均衡。
到引用源。
3下列关于无类路由协议的陈述,哪两项是正确的?(选择两项。
)错误!未找在路由更新中发送子网掩码信息到引用源。
错误!未找将完整的路由表更新发送给所有邻居到引用源。
错误!未找受RIP 第1 版支持到引用源。
错误!未找允许在同一拓扑结构中同时使用192.168.1.0/30 和192.168.1.16/28 子网到引用源。
错误!未找减少组织中可用地址空间的大小到引用源。
4网络管理员可使用下列哪一条命令来确定路由器是否启用了负载均衡?错误!未找show ip protocols到引用源。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
以下是针对您未获得满分的试题给出的反馈。
某些交互式试题可能不显示您的答案。
分项分数:1下列有关实施VLAN 的说法中,哪两项正确???(选择两项。
)正确响应您的响应冲突域的大小会减小。
网络中所需交换机的数量会减少。
VLAN 会对主机进行逻辑分组,而不管它们的物理位置如何。
由于增加了中继信息,网络负载会显著增加。
某一VLAN 中的设备不会收到其它VLAN 中的设备所发出的广播。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.1.1 VLAN 概述2下列哪三项陈述准确描述了VLAN 类型???(请选择三项。
)正确响应您的响应管理VLAN 是指经过配置可以访问交换机管理功能的任何VLAN。
数据VLAN 用于传输VLAN 管理数据和用户生成的流量。
未经配置的交换机初始启动后,所有端口都属于默认VLAN。
已分配本地VLAN 的802.1Q 中继端口同时支持标记流量和无标记流量。
语音VLAN 用于支持网络中的用户电话和电子邮件流量。
VLAN 1 总是用作管理VLAN。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.1.1 VLAN 概述3网络管理员正在确定VLAN 中继链路的最佳位置。
哪两种类型的点对点连接会使用VLAN 中继???(请选择两项。
)正确响应您的响应使用多个VLAN 的两台交换机之间交换机和客户端PC 之间交换机和带有802.1Q 网卡的服务器之间交换机和网络打印机之间共享同一VLAN 的两台交换机之间VLAN 中继链路用于允许所有VLAN 流量在设备之间传播,例如交换机和带有802.1Q-capable NIC 的服务器之间的链路。
交换机还可以使用中继链路连接到路由器、服务器和其他交换机。
此试题参考以下领域的内容:Routing and Switching Essentials3.1.2 多交换环境中的VLAN4 请参见图示。
某帧通过交换机在PC-A 与PC-B 之间传输。
下列有关此帧VLAN 标记的说法中,哪项是正确的???正确响应您的响应当此帧离开PC-A 时,会被添加VLAN 标记。
当交换机接收此帧时,此帧会被添加VLAN 标记。
当此帧从端口转出至PC-B 时,会被添加VLAN 标记。
无VLAN 标记添加至此帧。
VLAN 信息只有当它通过中继链路时才会添加到帧中。
因为这两台PC 是通过访问链路连接到交换机的,所以不会向帧中添加任何VLAN 信息。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.1.2 多交换环境中的VLAN5在交换机(VLAN 数据库中无此VLAN)的 Fa0/18 端口上发出switchport access vlan 20 命令有什么作用???正确响应您的响应此命令对该交换机无任何作用。
将自动创建VLAN 20。
将显示表明VLAN 20 不存在的错误,并且不创建VLAN 20。
将关闭端口Fa0/18。
如果尚无VLAN,switchport access vlan 命令会强制创建一个VLAN。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.2.1 VLAN 分配6交换机上的端口Fa0/11 已分配给VLAN 30。
如果在Fa0/11 接口上输入 no switchport access vlan 30 命令会发生什么情况???正确响应您的响应端口Fa0/11 将被关闭。
会显示错误消息。
端口Fa0/11 将返回到VLAN 1。
VLAN 30 会被删除。
当输入no switchport access vlan 命令时,该端口会被返回至默认的VLAN 1。
该端口作为VLAN 1 的成员保持活跃状态,而且VLAN 30 保持不变,即使没有与之相关联的其他端口仍是如此。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.2.1 VLAN 分配7哪条命令可用于仅从交换机上删除VLAN 20???正确响应您的响应delete vlan.datdelete flash:vlan.datno vlan 20no switchport access vlan 20no vlan vlan-id 命令用于从交换机删除特定VLAN。
d elete vlan.dat 和 delete flash:vlan.dat 命令可以在重新加载交换机后删除所有的VLAN。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.2.1 VLAN 分配8下列哪条命令可显示封装类型、语音VLAN ID 和Fa0/1 接口的访问模式VLAN???正确响应您的响应show vlan briefshow interfaces Fa0/1 switchportshow mac address-table interface Fa0/1show interfaces trunkshow interfaces switchport 命令将显示给定端口的以下信息:交换机端口管理模式运行模式管理中继的封装运行中继的封装中继协商访问模式VLAN中继本征模式VLAN管理本征VLAN 标记语音VLAN此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.2.1 VLAN 分配∙ 3.2.4 VLAN 和TRUNK 故障排除9网络管理员必须怎样做才能将快速以太网端口fa0/1 从VLAN 2 中删除并将其分配给VLAN 3???正确响应您的响应在全局配置模式下输入no vlan 2和vlan 3命令。
在接口配置模式下输入switchport access vlan 3命令。
在接口配置模式下输入switchport trunk native vlan 3命令。
在接口配置模式下输入no shutdown 使其恢复默认配置,然后为VLAN 3 配置该端口。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.2.1 VLAN 分配10添加了一台Cisco Catalyst 交换机,以支持将多个VLAN 用作企业网络的一部分。
网络技术人员发现,若要融合新的网络设计,必须清除交换机上的所有VLAN 信息。
技术人员应该如何完成此任务???正确响应您的响应删除运行配置,然后重新启动交换机。
删除启动配置,然后重新启动交换机。
删除已经分配给管理VLAN 的IP 地址,然后重新启动交换机。
删除启动配置和交换机闪存中的vlan.dat 文件,然后重新启动交换机。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.2.1 VLAN 分配11思科交换机当前允许标记为VLAN 10 和20 的流量经过中继端口Fa0/5。
在Fa0/5 上发出switchport trunk allowed vlan 30 命令有什么作用???正确响应您的响应允许在Fa0/5 上实施VLAN 1 至30。
允许在Fa0/5 上实施VLAN 10、20 和30。
允许在Fa0/5 上只实施VLAN 30。
允许在Fa0/5 上实施本征VLAN 30。
switchport trunk allowed vlan 30 命令允许标记为VLAN 30 的流量经过中继端口。
该中继端口上不允许任何该命令中未指定的VLAN。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.2.2 VLAN TRUNK12如果将允许使用中继链路的VLAN 范围设置为默认值,表示允许哪些VLAN???正确响应您的响应允许所有VLAN 使用中继链路。
只允许VLAN1 使用中继链路。
只允许本征VLAN 使用中继链路。
交换机将通过VTP 来协商允许使用中继链路的VLAN。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.2.2 VLAN TRUNK13为防止DTP 帧在思科交换机和非思科交换机之间传输,网络管理员应该实施下列哪条命令???正确响应您的响应S1(config-if)# switchport mode trunkS1(config-if)# switchport nonegotiateS1(config-if)# switchport mode dynamic desirableS1(config-if)# switchport mode accessS1(config-if)# switchport trunk allowed vlan none为防止思科交换机的接口生成DTP 帧,请使用S1(config-if)# switchport nonegotiate 命令。
DTP 是思科专有协议议,其他供应商不能使用。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.2.3 动态中继协议议14在哪两种情况下管理员应该在管理局域网的同时禁用DTP???(请选择两项。
)正确响应您的响应当思科交换机与非思科交换机连接时当邻居交换机使用动态自动DTP 模式时当邻居交换机使用动态期望DTP 模式时在不应中继的链路上在应动态尝试中继的链路上思科最佳实践建议议在不需要中继的链路上和在将思科交换机连接到非思科交换机时禁用DTP。
动态中继协商需要使用DTP。
此试题参考以下领域的内容:Routing and Switching Essentials∙ 3.2.3 动态中继协议议15请参见图示。
PC-A 与PC-B 都位于VLAN 60 中。
PC-A 无法与PC-B 通信。
问题出在哪里???正确响应您的响应本征VLAN 应该是VLAN 60。
本征VLAN 正在从链路中删除。
已使用 switchport nonegotiate 命令对中继进行了配置。
PC-A 所使用的VLAN 不在中继允许的VLAN 列表中。
因为PC-A 与PC-B 连接在不同的交换机上,所以它们之间的流量必须通过中继链路传输。
可以对中继进行配置,使其只允许指定VLAN 的流量通过链路。
如show interfaces trunk 输出所示,在本场景下,VLAN 60(与PC-A 和PC-B 相关联的VLAN)不允许通过链路。
此试题参考以下领域的内容:Routing and Switching Essentials3.2.4 VLAN 和TRUNK 故障排除16请参见图示。
