ccna4_chapter4
CCNA4 思科第四学期 v4.0 EWAN Chapter 8最新答案

请参见图示。
根据图中所示的输出可得出哪三点信息?(选择三项。
)出现了一个载波检测信号。
Keepalive 数据包接收成功。
此串行链路上采用了默认封装。
此接口上传输的数据包的大小不能超出 1 KB。
此链路的可靠性非常低。
LCP 协商阶段已完成。
窗体底端2窗体顶端广播流量过多一般表明哪一层出了问题?物理层数据链路层网络层传输层窗体底端3窗体顶端建议采用哪种故障排除方法来处理疑似由网络电缆故障引起的复杂问题?自下而上自上而下分治法从中切入窗体底端4窗体顶端逻辑网络图中一般含有哪两项信息?(选择两项。
)电缆类型连接器类型接口标识符虚电路的DLCI操作系统版本窗体底端5窗体顶端技术人员应要求排除现有交换网络的故障,但找不到VLAN 配置的文档。
技术人员可使用什么工具来发现和映射VLAN 和端口分配情况?电缆分析仪网络分析器协议分析器知识库窗体底端6窗体顶端下列IP 地址与通配符掩码的组合中,哪个组合可精确指定子网192.168.3.32 /28 最后8 个地址?192.168.3.32 0.0.0.7192.168.3.32 0.0.0.15192.168.3.40 0.0.0.7192.168.3.40 0.0.0.15窗体底端7窗体顶端下列关于逻辑网络模型的说法中哪两项正确?(选择两项。
)TCP/IP 将OSI 模型的最低层划分为两个相互独立的层。
TCP/IP 模型的顶层综合了OSI 模型的上面三层的功能。
使用TCP/IP 模型进行故障排除所需的技术与使用OSI 模型时不同。
网络接入层负责在TCP/IP 网络中的设备之间交换数据包。
Internet 层负责在处于不同主机上的应用(例如FTP、HTTP 和SMTP)之间提供通信。
TCP/IP 网络接入层对应于OSI 物理层和数据链路层。
窗体底端8窗体顶端收集症状以排查网络故障时,哪个步骤可能会牵涉到外部管理员?缩小范围收集可疑设备的症状分析现有症状确定所有权窗体底端9窗体顶端用户投诉访问网络资源时等待时间太长。
CCNA 4 - Chapter 7

CCNA 4 - Chapter 7Posted by beotron at 9:21 PM1. Why is it important to record baseline measurements of a prototype network?• Test results show security weaknesses after the baseline tests are run.• The baseline is the point at which the network is operating at its fullest potential.• Baseline measurements define a point at which network traffic has exceeded the designed capabilities of the network.• Te st results are compared to the baseline to see how the test conditions increase processor use or decrease available bandwidth.2. Refer to the exhibit. During prototype testing, verification of VLAN connectivity is being performed. Based on the information shown, what command produced the output?• show spanning-tree• show interfaces trunk*• show cdp neighbors• show interfaces• show ip interface brief3. How do designers decide which network functions need to be included in the prototype test?• They se lect the functions that align with the business goals.• They select the functions that occur at the network core.• They select the functions that do not exist in the existing network.• They select the functions from a list of generic network operations.4. Refer to the exhibit. A network administrator has been given the task of creating a design for a temporary classroom building that is to be set up outside an overcrowded school. In testing the prototype, it is found that the student PC cannot ping the teacher PC. All the switch interfaces are active and connected properly, as is interface Fa0/0 of the router. Given that only the commands shown have been added to the router configuration, what is the source of the problem?• The IP settings on the studen t PC are incorrect.• The default gateway on the teacher PC is misconfigured.• The router Fa0/0 interface has not been configured as a VLAN trunk.• The Fa0/0 physical interface has not been configured with an IP address and subnet mask.• The administrat or forgot to configure a routing protocol to allow the ping packets to reach the teacher PC subnet.5. Refer to the exhibit. What two measures can be taken to address the areas of weakness circled in the network design? (Choose two.)• Provide redundant co nnections to all end users.• Add another core switch to increase redundancy.• Add a switch in the server block connecting the server farm to each core switch.• Add an additional switch to the DMZ and direct links from the new switch to the core switches.• Provide a redundant firewall router connecting to a second ISP, the core switches, and the DMZ.6. Refer to the exhibit. After all the interfaces have stabilized, what is the spanning-tree state of all the enabled interfaces of SW11?• discarding• For warding• learning• listening7. A network engineer has decided to pilot test a portion of a new network design rather than rely on a prototype for proof-of-concept. What are two advantages of pilot testing a design concept? (Choose two.) • The test netwo rk experiences real-world network traffic.• Users within the enterprise are not affected by the test.• Network response can be tested in unplanned and unpredictable situations.• Unlikely failure conditions can be conveniently tested.• Network response can be tested in a highly controlled simulated environment.8. Refer to the exhibit. During prototype testing of the Cisco network shown, connectivity must be verified. Assuming all connections are working and CDP is enabled on all devices and interfaces, on which device was the command issued?• R1*• S1• R3• S2• R5• S39. Switch port Fa0/24 was previously configured as a trunk, but now it is to be used to connect a host to the network. How should the network administrator reconfigure switch port Fa0/24?• Use the switchport mode access command from interface configuration mode.• Enter the switchport nonegotiate command from interface configuration mode.• Administratively shut down and re-enable the interface to return it to the default.• Enter the n o switchport mode trunk command in interface configuration mode.• Use the switchport access vlanvlan number command from interface configuration mode to remove the port from the trunk and add it to a specific VLAN.10. Refer to the exhibit. A network technician is performing an initial installation of a new switch in the east wing. The technician removes the switch from the box, makes the connections to the network, and adds the configuration shown. The technician notifies the network administrator that the switch has been installed. When the network administrator at the home office attempts to telnet to the switch from host 192.168.0.1, the connection fails. What action should the network technician take?• Add an enable password to the switch.• Add a def ault gateway to the switch configuration.• Configure the switch with an IP access list to permit the host connection.• Enable the physical interfaces of the switch with the no shutdown command.11. Refer to the exhibit. The redundant paths are of equal bandwidth and EIGRP is the routing protocol in use. Which statement describes the data flow from Server to PC2?• EIGRP load balances across the R3 to R1 and R3 to R2 links.• EIGRP load balances across the R1 to Switch3 and R2 to Switch3 paths.• EIGRP lo ad balances across the Switch1 to Switch3 and Switch1 to Switch2 paths.• EIGRP does not load balance in this topology.12. In the router command encapsulation dot1q 10, what does the number 10 represent?• the metric used for a particular route• the numb er of the VLAN associated with the encapsulated subinterface• the priority number given to the device for the election process• the number that must match the Fast Ethernet subinterface number• the number used to program the router for unequal cost path load balancing13. Which protocol allows a switch port to transition directly to the forwarding state after a failure is detected?• STP*• BGP• RSTP• HSRP14. A network designer needs to determine if a proposed IP addressing scheme allows efficient route summarization and provides the appropriate amount of scalability to a design. What is useful for validating a proposed hierarchical IP addressing scheme?• NBAR• a pilot network• a route summary• a network simulator*• a physical topology map15. Refer to the exhibit. A network designer creates a test plan that includes the specification shown. In which section of the test plan would this specification be found?• Test Description• Test Procedures• Design and Topology Diagram• Actual Results and Co nclusions• Anticipated Results and Success Criteria16. While preparing a network test plan document, a network designer records all initial and modified device configurations. Which section of the document typically contains this information?• Appendix• Test Procedures• Test Description• Actual Results and Conclusions• Anticipated Results and Success Criteria17. Refer to the exhibit. The users on the 192.168.10.192 network are not allowed Internet access. The network design calls for an extended ACL to be developed and tested. Where should the ACL be placed for the least effect on other network traffic?• inbound on Fa0/0 of R3• outbound on Fa0/0 of R3• inbound on Fa0/1 of R3• outbound on Fa0/1 of R3• inbound on Fa0/1 of R2• outbound on S0/0 of R218. Refer to the exhibit. Why are interfaces Fa0/11, Fa0/23, and Fa0/24 not shown in this switch output? • Interfaces Fa0/11, Fa0/23, and Fa0/24 are trunks.*• Interfaces Fa0/11, Fa0/23, and Fa0/24 are shutdown.• Interfaces Fa0/11, Fa0/23, and Fa0/24 a re blocking.• Interfaces Fa0/11, Fa0/23, and Fa0/24 failed diagnostics.19. What OSI model Layer 2 security measure can a network engineer implement when prototyping network security?• a firewall at the network edge• port security at the access design l ayer• port security at the distribution design layer• IP access control lists at the access design layer20. Refer to the exhibit. During prototyping, Layer 2 functionality is being tested. Based on the output shown, which two pieces of information can be determined? (Choose two.)• Switch1 is the root bridge.• Interface Fa0/2 on Switch1 has no role in the operation of spanning tree.• Interface Fa0/2 on Switch1 is the alternate port used to reach the root bridge.• Based on the entries in the “Role” col umn, it can be concluded that RSTP has been implemented.• Interface Fa0/1 on Switch1 is the forwarding port selected for the entire spanning-tree topology.21. What Rapid Spanning Tree Protocol (RSTP) state is given to the forwarding port elected for every switched Ethernet LAN segment?• root• backup• alternate• Designated。
CCNA第二学期路由协议和概念chapter3答案

下列哪两项正确描述了管理距离与度量的概念?(选择两项。
)管理距离是指特定路由的可信度。
路由器会首先添加具有较大管理距离的路由。
网络管理员无法更改管理距离的值。
具有到目的地的最小度量的路由即为最佳路径。
度量总是根据跳数确定。
度量会根据所采用的第 3 层协议(如 IP 或 IPX)而发生变化。
Option 1 and Option 4 are correct.请参见图示。
下列关于 R1 如何确定与 R2 之间最佳路径的陈述中,哪一项正确?R1 会将使用网络 A 的 RIP 路由加入路由表,因为 RIP 的管理距离比 EIGRP 大。
R1 会将使用网络 A 的 RIP 路由加入路由表,因为 RIP 的路径开销比 EIGRP 低。
R1 会将使用网络 B 的 EIGRP 路由加入路由表,因为 EIGRP 的管理距离比 RIP 小。
R1 会将使用网络 B 的 EIGRP 路由加入路由表,因为 EIGRP 的路径开销比 RIP 低。
R1 会将 EIGRP 路由和 RIP 路由加入路由表,并在它们之间实施负载均衡。
2 points for Option 3下列关于无类路由协议的陈述,哪两项是正确的?(选择两项。
)在路由更新中发送子网掩码信息将完整的路由表更新发送给所有邻居受 RIP 第 1 版支持允许在同一拓扑结构中同时使用 192.168.1.0/30 和192.168.1.16/28 子网减少组织中可用地址空间的大小Option 1 and Option 4 are correct.网络管理员可使用下列哪一条命令来确定路由器是否启用了负载均衡?show ip protocolsshow ip routeshow ip interface briefshow ip interface2 points for Option 2存在下列哪两个条件时,使用距离矢量路由协议会比较有效?(选择两项。
)网络需要特殊的分层式设计网络必须能快速收敛网络使用的是集中星型拓扑结构网络使用的是平面设计相距最远的路由器之间超过 15 跳Option 3 and Option 4 are correct.路由协议有何作用?用于构建和维护 ARP 表。
Notch4_mRNA在口咽鳞癌组织中表达变化及其敲降癌细胞株增殖迁移侵袭能力观察

Notch4 mRNA 在口咽鳞癌组织中表达变化及其敲降癌细胞株增殖迁移侵袭能力观察薛绪亭1,张宇良1,郑希望1,董振1,2,刘红亮1,张春明1,21 山西医科大学第一医院耳鼻咽喉头颈肿瘤山西省重点实验室,太原 030001;2 山西医科大学第一医院耳鼻咽喉头颈外科摘要:目的 观察Notch4 mRNA 在口咽鳞癌组织和细胞株中的表达变化及敲降Notch4 mRNA 表达的口咽鳞癌细胞株增殖、迁移和侵袭能力。
方法 收集12对口咽鳞癌组织与癌旁组织,采用RT -qPCR 法检测癌组织、癌旁组织中Notch4 mRNA 。
培养口咽鳞癌细胞株Detroit 562、WSU -HN -30及对照细胞株HaCaT 、2BS ,检测细胞株中Notch4 mRNA 。
将人口咽鳞癌细胞株Detroit 562和WSU -HN -30随机分为si -NC 组、si -Notch4-1组和si -Notch4-2组,分别转染si -NC 双链核苷酸、si -Notch4-1双链核苷酸、si -Notch4-2双链核苷酸,检测各组细胞株中Notch4 mRNA ,使用RTCA 法观察各组细胞株的增殖能力(CI 值),通过Transwell 实验观察各组细胞株的侵袭和迁移能力。
结果 与癌旁组织相比,口咽鳞癌组织中Notch4 mRNA 相对表达量高(P <0.01);在对照细胞株HaCaT 和2BS 中Notch4 mRNA 相对表达量差异无统计学意义;与对照细胞株HaCaT 相比,口咽鳞癌细胞株Detroit 562、WSU -HN -30中Notch4 mRNA 相对表达量高(P 均<0.001)。
在口咽鳞癌细胞株Detroit 562、WSU -HN -30中,与si -NC 组相比,si -Notch4-1和si -Notch4-2组的细胞株增殖、迁移和侵袭能力降低(P 均<0.01)。
结论 Notch4 mRNA 在口咽鳞癌组织和细胞株中均高表达,敲降Notch4 mRNA 表达的口咽鳞癌细胞株增殖、迁移和侵袭能力降低。
NK4基因重组慢病毒载体的构建及在肝癌细胞中的表达_李霏

NK4基因重组慢病毒载体的构建及在肝癌细胞中的表达李霏,李松林,尹元琴(中国医科大学附属第一医院肿瘤研究所,沈阳110001)摘要目的构建共表达人NK4基因和增强型绿色荧光蛋白(EGFP )基因的重组慢病毒载体,转染人高侵袭转移肝癌细胞LM3(HCCLM3),观察其转染效率及表达情况。
方法采用DNA 重组技术,将NK4基因克隆至带EGFP 的慢病毒表达载体pLenti6.3-内部核糖体进入位点序列(IRES )-EGFP 中,并用脂质体介导法将慢病毒包装系统和带NK4基因的质粒pLenti6.3-NK4-IRES -EGFP 共转染293T 细胞,包装慢病毒并测定滴度。
以不同感染复数(MOI )的重组慢病毒感染293T 细胞,筛选最适MOI ,以最适MOI 重组慢病毒感染HCCLM3细胞,观察转染效率。
Western blot 法测定细胞中NK4蛋白表达水平。
结果成功构建共表达NK4基因和EGFP 基因的慢病毒载体pLenti6.3-NK4-IRES -EGFP ,并对其包装、纯化及浓缩后测定病毒滴度为1.08×108TU/mL 。
重组慢病毒感染HCCLM3细胞筛选其最适MOI 为7。
转染后HCCLM3细胞中可见明显的NK4蛋白表达,而未转染细胞中无NK4蛋白的表达。
结论成功构建了NK4基因的重组慢病毒载体,有效地转染HCCLM3细胞后可高表达NK4蛋白。
关键词NK4;慢病毒载体;人高侵袭转移肝癌细胞LM3;基因转染中图分类号R73文献标志码A文章编号0258-4646(2011)12-1081-04doiCNKI:21-1227/R.20111226.1615.028网络出版地址/kcms/detail/21.1227.R.20111226.1615.028.htmlConstruction of NK4Recombinant Lentiviral Vector and Its Expression in HCCLM3Cells 肝细胞肝癌(hepatocellular carcinoma ,HCC )是世界上常见的恶性肿瘤之一,位居全球恶性肿瘤发病率的第5位[1]。
CCNA完整知识点.

chapter 1L1:物理层PDU:bits 比特流作用:传输比特流(01000100101010...)介质:同轴电缆: coaxial cable 传输距离 500米双绞线(TP):twisted-pair cable 传输距离 100米非屏蔽双绞线(UTP):室内屏蔽双绞线(STP):室外(环境干扰强)直通线:AA BB 链接异性端口:pc-hub pc-sw sw-router交叉线:AB 链接同性端口:pc-pc router-router pc-router sw-sw反线:1-8 8-1 用于本地连接的console 控制线网线的两种制作方式:568A:白绿绿白橙篮白蓝橙白棕棕568B:白橙橙白绿篮白蓝绿白棕棕 1236 网线使用DCE:数据终端设备,需要配置clock rate DTE:数据终结设备对应传输介质的支持传输距离:1)1000base-cx 使用的是铜缆。
最大传输距离25米2)100Base-Tx/Fx100Base-Tx以5类非屏蔽双绞线为传输介质(最大传输距离是100米)100Base-Fx以光纤为传输介质(2000米)。
3)1000base-SX(MMF多模):最长传输距离是550米4)1000base-LX:可以使用单模光纤也可以使用多模光纤使用多模光纤的最大传输距离为550m,使用单模光纤的最大传输距离为3千米5)1000base-zx(单模):最长传输距离是70KM以太网 Ethernent传输模式:单工:只能发或者收半双工:即可以收也可以发,但是同一时间只能收或者发列如对讲机全双工:同一时间既可以收也可以发列如手机Auto:中继器(Repeater):对信号放大,双绞线的传输距离只有100M,使用中继器可以延长传输距离。
hub :多口中继,一个数据帧从一个入口进,会发送到HUB的所有其他端口而不进行过滤。
L2:数据链路层PDU:frame 帧作用:成帧,差错控制设备:网桥(bridge):基于MAC地址转发,根据mac-port表,数据包只发到和MAC地址相对应的port端口交换机(switch):多口网桥,独享带宽L2层编制:MAC地址MAC地址构成:48bit,12位十六进制数可以通过ipconfig/all 查询电脑的mac地址L2表:MAC-port表(mac地址表)冲突域:不可避免的数据冲突范围,由中继、hub链接构成并扩大,见到L2层端口截止,每一个交换机端口形成一个冲突域HUB:所有端口都在一个冲突域,是增加了冲突域的范围交换机:没一个端口都是一个冲突域,是增加了冲突域的数量,减少了冲突域的范围HUB:是共享带宽 10M 所有端口共享10M交换机:独享带宽 10M 每个端口同时有10ML3:网络层 PDU:packet 包作用:逻辑编制:ip地址、路由(路径的选择)IP地址与mac地址的区别?Mac地址通信:同一个网络,mac通信跨网络通信:ip地址IP地址:版本v4;32bit;点分是进制法 192.168.0.1IP=网络位+主机位掩码:mask:连续的1+连续的0,来确定IP地址的网络位+主机位,1位对应网络位,0位对应主机位。
ccna第二学期练习答案
ERouting Chapter 1 - CCNA Exploration: 路由协议和概念(版本 4.0)1 口令可用于限制对Cisco IOS 所有或部分内容的访问。
请选择可以用口令保护的模式和接口。
(选择三项。
)VTY 接口控制台接口特权执行模式2 路由器从相连的以太网接口收到消息后,会更改哪项报头地址,再将消息从另一个接口发送出去?第 2 层源地址和目的地址3请参见图示。
网络管理员已经为路由器连接到直连网络的接口配置了如图所示的IP 地址。
从路由器ping 相连网络上的主机口之间相互ping 都会遭到失败。
此问题最可能的原因是什么?必须使用no shutdown命令启用接口。
4请参见图示。
主机 A ping 主机B。
当R4 收到对以太网接口的ping 时,哪两块报头信息包括在内?(选择两项。
)5 网络管理员刚把新配置输入Router1。
要将配置更改保存到NVRAM,应该执行哪一条命令?Router1# copy running-config startup-config6您需要配置图中所示的串行连接,必须在Sydney 路由器上发出以下哪条配置命令才能与Melbourne 站点建立连接?(选Sydney(config-if)#Sydney(config-if)# no shutdownSydney(config-if)# clock rate 560007请参见图示。
从路由器的运行配置输出可得出什么结论?显示的命令决定了路由器的当前运行情况。
8请参见图示。
在主机 2 连接到LAN 上的交换机后,主机2 无法与主机 1 通信。
导致此问题的原因是什么?主机 1 和主机2 位于不同的网络中。
9 输入以下命令的作用是什么?R1(config)# line vty 0 4R1(config-line)# password check123R1(config-line)# login设置通过Telnet 连接该路由器时使用的口令10 以下哪一项正确描述了路由器启动时的顺序?加载bootstrap、加载IOS、应用配置11 加载配置文件时的默认顺序是怎样的?NVRAM、TFTP、CONSOLE12请参见图示。
CCNA_ERouting_Chapter_4

1Which event will cause a triggered update?an update routing timer expiresa corrupt update message is receiveda route is installed in the routing tablethe network is converged2T hree routers running a distance-vector routing protocol lost all power, including the battery backups. When the routers relo happen?They will share all routes saved in NVRAM prior to the power loss with their directly connected neighbors.They will multicast hello packets to all other routers in the network to establish neighbor adjacencies.They will send updates that include only directly connected routes to their directly connected neighbors.They will broadcast their full routing table to all routers in the network.3What is a routing loop?a packet bouncing back and forth between two loopback interfaces on a routera condition where a return path from a destination is different from the outbound path forming a "loop"a condition where a packet is constantly transmitted within a series of routers without ever reaching its intended destinthe distribution of routes from one routing protocol into another4Refer to the exhibit. If all routers are using RIP, how many rounds of updates will occur before all routers know all networks1234565What actions will occur after RouterA loses connectivity to network 114.125.16.0? (Choose two.)RouterB will include network 123.92.76.0 and 136.125.85.0 in its update to RouterA.During the next update interval, RouterB will send a RIP update out both ports that includes the inaccessible network.During the next update interval, RouterC will send an update to RouterB stating that network 114.125.16.0 is accessibRouter C will learn of the loss of connectivity to network 114.125.16.0 from RouterB.RouterB will include network 123.92.76.0 and 136.125.85.0 in its update to RouterC.6What does the RIP holddown timer do?ensures an invalid route has a metric of 15prevents a router from sending any updates after it has introduced a routing loop into the networkensures every new route is valid before sending an updateinstructs routers to ignore updates, for a specified time or event, about possible inaccessible routes 7W hich of the following can exist in a distance vector network that has not converged? (Choose three.)routing loopsinconsistent traffic forwardingno traffic forwarding until system convergesinconsistent routing table entriesrouting table updates sent to wrong destinations8What is the purpose of the TTL field in the IP header?used to mark routes as unreachable in updates sent to other routersprevents regular update messages from reinstating a route that may have gone badprevents a router from advertising a network through the interface from which the update camelimits the time or hops that a packet can traverse through the network before it should be discardeddefines a maximum metric value for each distance vector routing protocol by setting a maximum hop count9W hich three routing protocols are distance vector routing protocols? (Choose three).RIPv1EIGRPOSPFIS-ISRIPv210The graphic shows a network that is configured to use RIP routing protocol. Router2 detects that the link to Router1 has go then advertises the network for this link with a hop count metric of 16. Which routing loop prevention mechanism is in effectsplit horizonerror conditionhold-down timerroute poisoningcount to infinity11Which statement is true regarding cisco’s RIP_JITTER variable?It prevents the synchronization of routing updates by buffering the updates as they leave the router interfaces.It prevents the synchronization of routing updates by subtracting a random length of time ranging from 0% to 15% of interval time from the next routing update interval.It prevents the synchronization of routing updates by causing the router to skip every other scheduled update time.It prevents the synchronization of routing updates by forcing the router to listen when its time for other updates on th sending its update.12W hich of the following methods does split horizon use to reduce incorrect routing information?Routing updates are split in half to reduce the update time.Information learned from one source is not distributed back to that source.New route information must be learned from multiple sources to be accepted.The time between updates is split in half to speed convergence.New route information is suppressed until the system has converged.13Which two statements are true regarding the function of the RIPv1 routing updates? (Choose two).updates are broadcast only when there are changes to the topologyupdates are broadcast at regular intervalsbroadcast are sent to 0.0.0.0broadcasts are sent to 255.255.255.255updates contain the entire network topologyonly changes are included in the updates14A network administrator is evaluating RIP versus EIGRP for a new network. The network will be sensitive to congestion a respond quickly to topology changes. What are two good reasons to choose EIGRP instead of RIP in this case? (ChooseEIGRP uses periodic updates.EIGRP only updates affected neighbors.EIGRP uses broadcast updates.EIGRP updates are partial.EIGRP uses the efficient Bellman-Ford algorithm.11Which statement is true regarding cisco’s RIP_JITTER variable?It prevents the synchronization of routing updates by buffering the updates as they leave the router interfaces.It prevents the synchronization of routing updates by subtracting a random length of time ranging from 0% to 15% of interval time from the next routing update interval.It prevents the synchronization of routing updates by causing the router to skip every other scheduled update time.It prevents the synchronization of routing updates by forcing the router to listen when its time for other updates on th sending its update.12W hich of the following methods does split horizon use to reduce incorrect routing information?Routing updates are split in half to reduce the update time.Information learned from one source is not distributed back to that source.New route information must be learned from multiple sources to be accepted.The time between updates is split in half to speed convergence.New route information is suppressed until the system has converged.13Which two statements are true regarding the function of the RIPv1 routing updates? (Choose two).updates are broadcast only when there are changes to the topologyupdates are broadcast at regular intervalsbroadcast are sent to 0.0.0.0broadcasts are sent to 255.255.255.255updates contain the entire network topologyonly changes are included in the updates14A network administrator is evaluating RIP versus EIGRP for a new network. The network will be sensitive to congestion a respond quickly to topology changes. What are two good reasons to choose EIGRP instead of RIP in this case? (ChooseEIGRP uses periodic updates.EIGRP only updates affected neighbors.EIGRP uses broadcast updates.EIGRP updates are partial.EIGRP uses the efficient Bellman-Ford algorithm.15Refer to the exhibit. What path will packets from the 192.168.1.0/24 network travel to reach the 10.0.0.0/8 network if RIP is routing protocol?The path will be router A -> router B -> router C -> router E.The path will be router A -> router D -> router E.Router A will load balance between the router A -> router D -> router E and router A -> router B -> router C -> router E Packets will alternate paths depending on the order they arrive at router A.\\Which of the following statements are correct about RIP?uses a broadcast to update all other routers in the network every 60 secondsuses a multicast address to update other routers every 90 secondswill send out an update if there is a failure of a linkupdates only contain information about routes that have changed since last updateRefer to the exhibit. The routers in this network are running RIP. Router A has not received an upda minutes. How will Router A respond?The Holddown timer will wait to remove the route from the table for 60 seconds.The Invalid timer will mark the route as unusable if an update has not been received in 180 seThe Update timer will request an update for routes that were learned from Router B.The Hello timer will expire after 10 seconds and the route will be flushed out of the routing tab What metric does the RIP routing protocol consider to be infinity?1516224255。
OperationsManagementStevenson8thEdition…

Operations Management Stevenson 8th Edition Solutions ManualIf searching for the ebook Operations management stevenson 8th edition solutions manual in pdf form, then you have come on to faithful site. We presented the full version of this book in doc, DjVu, txt, PDF, ePub forms. You can read Operations management stevenson 8th edition solutions manual online or download. Additionally, on our website you can read the instructions and diverse artistic books online, or load their. We wish draw on attention what our website not store the eBook itself, but we provide url to website whereat you can download either read online. If need to load Operations management stevenson 8th edition solutions manual pdf operations-management-stevenson-8th-edition-solutions-manual.pdf, then you have come on to loyal site. We own Operations management stevenson 8th edition solutions manual PDF, DjVu, ePub, doc, txt forms. We will be glad if you get back more.download operations management stevenson 8th - Title: Operations Management Stevenson 8th Edition Solutions Manual: Abstract: Operations Management Stevenson 8th Edition Solutions Manual management by williamoperations management stevenson - - Operations Management Stevenson Price comparison. 10th Edition 8th Edition 9th Edition Student Study Guide Format. CD DVDsolution edition stevenson 8th william j - STEVENSON 8TH EDITION SOLUTION Operations Management William J Sign up to download Solution manual for operations management william stevenson. Dateoperations management 11th edition | rent 9780073525259 - Rent Operations Management 11th edition Stevenson's careful and the Eleventh Edition continues to offer more support for 'doing Operationsoperations management 12th edition, stevenson - Operations Management - 12th edition and the Twelfth Edition continues to offer more support for 'doing Operations Stevenson's Operations Managementoperations management solution manual | - Operations Management Solutions Manual Select your edition below Stevenson. 749 total problems in solution Operations Management solutions manual is one operations management william j stevenson 8th - OPERATIONS MANAGEMENT WILLIAM J STEVENSON 8TH EDITION SOLUTION Solution Manual For Operations Management William Stevensonoperations management stevenson 8th edition - Operations Management Stevenson 12th Edition Test Bank. Download Operations Management (11th Edition) (pdf) Fspdf. Download Operations Management (11th Edition) (pdfoperations management 11th edition textbook solutions | - There are many implications due to the differences between service and manufacturing operations. Operations Management | 11th Edition. Solutions Manualoperations management stevenson 10th edition - Operations Management Stevenson 10th Edition Solutions Manual calculus book+ solution manual + test bank 8th edition Anton calculus by gilbert strangoperations management 8th edition: william j - Operations Management 8th Edition Available from these sellers. Customers Who Viewed This Item Also Viewed. Page 1 of 1 Start over Page 1 of 1 .operations management stevenson 10th edition - - OPERATIONS MANAGEMENT STEVENSON 10TH EDITION 10th Edition Solutions Manual. Operations Management 11th Stevenson. Operations Management. 8th editionoperations management stevenson 11th edition - Solution Manual Stevenson Solution Manual Unit Operations Solution Management; Stevenson; 8th Edition stevenson 11th edition solution manualoperations management by william j stevenson 8th - operations management 8th edition Operations Management 10e William J. Stevenson solutions manual Operations Management 10e Tricia Joy Allsolution manual for operation management - Tricia's Compilation for 'solution manual for operation management stevenson 10th edition by Stevenson Solution Manual Hogg Tanis 8th Editionsolution manual for operations management - Operations Management Stevenson Hojati 4th Canadian edition solutions manual. solutions manual Operations Management Stevenson Hojati 4th Canadian edition.operations management - stevenson - 8th.pdf - - William J. Stevenson 8th edition 1-27 Introduction to Operations Management Operations Interfaces 17-21 Project Management Example 1 Solution Criticalsolution manual for operations management - Operations Management Stevenson 12th Edition Solutions Manual But now, with the Operations Management Solution Manual, you will be able tooperations management, by stevenson, 9th edition - buy, or sell Operations Management, by Stevenson, 9th Edition Bookbyte / Rent Textbooks / Operations Management, by Stevenson, Bookbyte is a pretty good operations management 11/e stevenson solution - Operations Management 11/e Stevenson Solution Operations Management 11th edition by Stevenson Solutions manual. Solution manual for Accounting 8th Editionoperations management, 7th edition - fox ebook - Operations Management, 7th Edition PDF we all experience and manage processes and operations. Operations Management focuses Retailing Management, 8thoperations management by william j. stevenson | 9780073195834 - Operations Management (New Edition The Eleventh Edition of Stevenson s Operations Management features to offer more support for 'doing Operations' thansolution manual for operations management 12th - Solution manual for Operations Management 12th edition Solutions manual for Operations Management 12th edition Information Technology 8th edition by James operations management - text only (9th 07 - old edition) by - Operations Management by William J Stevenson: The Ninth Edition of Operations Management features the latest concepts 15 JIT and Lean Operations 15Sdownload ebooks tagged with operations management - Operations Management Stevenson 8th Edition Solutions Operations Management Stevenson 8th Edition Solutions Manual operations management 8th edition by williamtest bank for operations management 12th edition - Buy Test banks and Solution Manuals Download test bank and You want Solution manual? Pay Now. Test bank for Operations Management 12th edition by William J chapter 3 answers operations management william j - Production/Operations Management, 9th Edition Study Operations Management William J. Stevenson 8th edition Biddle contracted his operations. Filetype:operations management stevenson 12th edition - Buy Now Operations Management Stevenson 12th Edition Solutions with the Operations Management Solution Manual, Operations and Supply Chain Management (2) operations management 7th edition p 3555892 - - Operations Management 7th Edition P 3555892 - Download as PDF File (.pdf), Text file (.txt) or read online. Scribd is the world's largest social reading andstevenppt - William J. Stevenson 8th edition Measurement of productivity Production and delivery Quality assurance Amount of inventory Operations Management includes:operations management by william j stevenson - new, rare - Operations Management by William J Stevenson starting at $ approachable format support students in understanding the important operations 12th Edition. Newoperations management stevenson solutions 8th - Operations Management Stevenson Solutions 8th Edition Manual management by william j stevenson 8th edition solutions manual foroperations management - text only 8th edition, - Summary: Stevenson's Operations Management surveys the field of operations in both the services and manufacturing. As always, this new edition offers complete operations management william stevenson 10th - William J. Stevenson, Operations Management, Operations Management 10e William J. Stevenson solutions manual. Operations management william stevenson 10thoperations management, by stevenson, 8th edition, - Rent, buy, or sell Operations Management, by Stevenson, 8th Edition, Study Guide - ISBN 9780072869118 - Orders over $49 ship for free! - Bookbyteoperations management / edition 11 by william stevenson - The Eighth Edition of Operations Management offers and flexible operations management management and management science. Dr. Stevenson is the author operations management stevenson 9th edition - - operations management 9th edition solutions heizer, Operations Management Stevenson 9th Edition Solution Manual On Management.operations management with student dvd & power - Operations Management with Student DVD & Power Web by Stevenson, William J. [2006, 8th Edition.] Hardcover [Stevenson] on . *FREE* shipping on qualifyingsolutions manual to operations management 10e - Solutions manual to Operations Management 10e Grainger & William Stevenson Solution Manual State Physics 8Th Edition by Kittel, Charles Solutionsolution manual operations management 12th - Solution manual for Operations Management 12th edition Stevenson doing Operations than any other.Solution Solution manual for Accounting 8th EditionRelated PDFs:kwikstage user guide, kubota 1720 operator manual, hyundai i30 service repair manual download, owners manual for fleetwood mallard travel trailers, washington manual surgery 6th, 96 eclipse service manual, 2015 vw cc service manual, haas vf 1 maintenance manual, solution manual individual income taxes 2015, 4010 ditch witch owners manual, robbins and myers s series hoist manual, service manual fiat cinquecento, ccna 1 module 1 study guide, furuno marine radar service manual, mariner 4hp manual, hesi assessment exam study guide, autocad civil 3d 2015 the complete guide, elgin pelican service manual broom, mercury 125hp 2 stroke manual, child life exam study guide, vw polo 2015 workshop manuals, befco c15 cyclone mower manual, algebra an introduction hungerford solutions manual, introduction to semiconductor devices neamen solutions manual, kewanee model 130 manual, tl1000r service manual, pzq60 manual, 4jk repair manual, manual gearboxs, econometrics solutions manual, cub cadet ltz 1046 service manual, physical science study guide waves electromagnetic spectrum, manual of accounting 2015 pwc, 1981 wagoneer manual, john deere 336 baler repair manuals, toyota t100 collision repair manual, renault laguna mk2 workshop manual, programming manual for fanuc 18m, ifr 1200 service manual, haynes falcon service manual。
(最新)思科网络第一学期1-5章中文测试题及答案

ENetwork Chapter 2 - CCNA Exploration: 网络基础知识(版本 4.0) 1在封装过程中,数据链路层执行什么操作?不添加地址。
添加逻辑地址。
添加物理地址。
添加进程的端口号。
2TCP/IP 网络接入层有何作用?路径确定和数据包交换数据表、编码和控制可靠性、流量控制和错误检测详细规定构成物理链路的组件及其接入方法将数据段划分为数据包3数据链路层封装添加的报尾信息有何主要功能?支持差错校验确保数据按照顺序到达确保送达正确目的标识本地网络中的设备帮助中间设备进行处理和路径选择4请参见图。
下列哪组设备仅包含终端设备?A、C、DB、E、G、HC、D、G、H、I、JD、E、F、H、I、JE、F、H、I J5OSI 模型各层从最高层到最低层的正确顺序如何?物理层、网络层、应用层、数据链路层、表示层、会话层、传输层应用层、物理层、会话层、传输层网络层、数据链路层、表示层应用层、表示层、物理层、会话层、数据链路层、传输层、网络层应用层、表示层、会话层、传输层、网络层、数据链路层、物理层表示层、数据链路层、会话层、传输层、网络层、物理层、应用层6下列哪三项陈述是对局域网(LAN) 最准确的描述?(选择三项)LAN 通常位于一个地域内。
此类网络由由一个组织管理。
LAN 中的不同网段之间一般通过租用连接的方式连接。
此类网络的安全和访问控制由服务提供商控制。
LAN 为同一个组织内的用户提供网络服务和应用程序访问。
此类网络的每个终端通常都连接到电信服务提供商(TSP)。
7第4 层端口指定的主要作用是什么?标识本地介质中的设备标识源设备和目的设备之间的跳数向中间设备标识过该网络的最佳路径标识正在通信的源终端设备和目的终端设备标识终端设备内正在通信的进程或服务8以下哪种特征正确代表了网络中的终端设备?管理数据流发送数据流重新定时和重新传输数据信号确定数据传输路径9请参见图示。
哪个术语正确判断出了包含于绿色区域中的设备类型?源终端传输中间10OSI 模型哪两层的功能与TCP/IP 模型的网络接入层相同?(选择两项)网络层传输层物理层数据链路层会话层11请参见图示。
CISCOCCNA网络工程师题库

培训大讲堂官方YY 频道:3660mCCNA题库考试代号:640-802考试时间:英文110+30=140分钟通过分数:825题库版本:V104.4鸿鹄论坛招募CCNA、CCNP答疑讲师答疑地点:鸿鹄官方YY频道3660CCNA(640-802)题库V104.4CCNA(640-802)题库V104.4(情人节版)V104系列是官方的终结版本,以后不会再出V105 V106 V108等等========================================更新内容:V104.1修正V104中错误题目,确定经典争议题目答案;V104.2增加拖图题并可完美模拟考试,VCE题库增加中文注释;V104.3针对思科CCNA考试变题,更新考试新增题目93Q,更新V104.2实验题;V104.4增加全文中文注释,汇总V104.3九次更新,删除部分旧题目,为目前最新官方正版题库;2011.8.1 增加每日新题,修订部分错误。
增加5道新题,分别是519、520、521、522、523题修改176题、375题、443题、482题答案错误修改59题、88题、453题、107题、270题注释错误增加个别疑难拖图题注释,优化实验题=============================================QUESTION 1When you are logged into a switch, which prompt indicates that you are in privileged mode?(当您登录到交换机,哪种提示表明你在特权模式?)A. %B. @C. >D. $E. #Answer: ESection: Chapter 4: Introduction to Cisco IOSExplanation/Reference:特权模式就是#提示符QUESTION 2Which command shows system hardware and software version information?(哪些命令显示系统硬件和软件的版本信息?)A. show configurationB. show environmentC. show inventoryD. show platformE. show versionAnswer: ESection: Chapter 4: Introduction to Cisco IOSExplanation/Reference:查看系统的软件和硬件信息使用的命令是show versionQUESTION 3Cisco Catalyst switches CAT1 and CAT2 have a connection between them using ports FA0/13. An 802. 1Q trunk is configured between the two switches. On CAT1, VLAN 10 is chosen as native, but on CAT2 the native VLAN is not specified.What will happen in this scenario?(思科Catalyst 交换机CAT1 和CAT2 有它们之间的连接使用端口FA0/13。
nectin4结构

nectin4结构摘要:1.介绍nectin4 的背景和作用2.nectin4 的结构特征3.nectin4 与细胞黏附和信号传导的关系4.nectin4 在生物医学领域的应用正文:ectin4,又称PVRL4,是一种糖蛋白,属于nectin 家族成员之一。
这个家族的成员在细胞黏附和信号传导过程中起着至关重要的作用,特别是在上皮细胞和内皮细胞的发育、分化和生理功能调控中。
本文将对nectin4 的结构进行详细的介绍,并探讨其与细胞黏附和信号传导的关系以及在生物医学领域的应用。
首先,让我们了解一下nectin4 的结构特征。
nectin4 是一种跨膜蛋白,其结构由三个主要部分组成:一个细胞外区域、一个跨膜区域和一个胞内区域。
细胞外区域包含许多糖基化位点,这使得nectin4 能够与其他细胞表面的糖蛋白相互作用。
跨膜区域负责将nectin4 锚定在细胞膜上,而胞内区域则与细胞内的信号传导途径相互作用,从而参与细胞的生长、分化和其他生物学过程。
ectin4 主要通过与细胞表面的其他糖蛋白相互作用,如E-钙粘蛋白和nectin 家族的其他成员,来介导细胞黏附。
此外,nectin4 还能与细胞外的基质蛋白相互作用,从而为细胞提供支持和稳定性。
在信号传导方面,nectin4能够通过激活细胞内的多种信号分子,如Rho GTP 酶和FAK,来调控细胞的形态、迁移和分化。
近年来,越来越多的研究发现,nectin4 在生物医学领域具有广泛的应用前景。
例如,在肿瘤发生、发展和转移过程中,nectin4 的表达异常升高,这使得nectin4 成为了肿瘤诊断和治疗的潜在靶点。
此外,nectin4 在神经系统发育、免疫细胞相互作用和伤口愈合等过程中也发挥着重要作用,为相关疾病的治疗提供了新的思路。
总之,nectin4 作为一种关键的糖蛋白,通过其特殊的结构特征,在细胞黏附和信号传导过程中发挥着重要作用。
对nectin4 的研究不仅有助于我们深入了解细胞生物学的基本原理,还为肿瘤诊断和治疗等生物医学领域的应用提供了有力支持。
ccna第三学期1-7套练习题答案(最新)

ESwitching Chapter 1 - CCNA Exploration: LAN 交换和无线(版本4.0)1、分层网络设计模型中的哪一层称为互连网络的高速主干层,其中高可用性和冗余性是该层的关键?A.接入层B. 核心层C. 数据链路层D. 分布层E. 网络层F. 物理层2、分层网络设计模型中的哪一层提供了将设备接入网络的途径并控制允许那些设备通过网络进行通信?A. 应用层B. 接入层C. 分布层D. 网络层E. 核心层3、分层设计模型中的哪一层使用策略来控制网络流量的流动并通过在虚拟局域网 (VLAN) 之间执行路由功能来划定广播域的边界?A. 应用层B. 接入层C. 分布层D. 网络层E. 核心层4、从传统的公司网络架构迁移到完全融合网络后,很可能产生什么影响?A. 可将本地模拟电话服务完全外包给收费更低的提供商B. 以太网 VLAN 结构会简化C. 会形成共享的基础架构,因此只需管理一个网络。
D. QoS 问题会大大减轻5、语音数据流和视频数据流争夺带宽的问题会减轻。
应该在分层网络的哪一层或哪几层实现链路聚合?A. 仅核心层B. 分布层和核心层C. 接入层和分布层D. 接入层、分布层和核心层6、下列哪种说法正确描述了模块化交换机?A. 外形纤细B. 允许通过冗余背板进行交换机互连C. 物理特性固定D. 特性灵活多变7、下列哪项功能可在交换网络中通过合并多个交换机端口来支持更高的吞吐量?A. 收敛B. 冗余链路C. 链路聚合D. 网络直径8、在处于不同的 VLAN 中的设备间配置通信需要使用 OSI 模型中的哪个层?A. 第 1 层B. 第 3 层C. 第 4 层D. 第 5 层9、企业级交换机有哪两项特点?(选择两项。
)A. 端口密度低B. 转发速度高C. 延时水平高D. 支持链路聚合E.端口数量预先确定10、Cisco 三层式分层模型中的三层都支持哪两项功能?(选择两项。
)A. 以太网供电B. 在冗余中继链路之间进行负载均衡C. 冗余组件D. 服务质量E. 链路聚合11、网络管理员选择的交换机将在网络核心层工作。
2009年CCNA最新中文版题库第三学期第五单元到final3全部答案
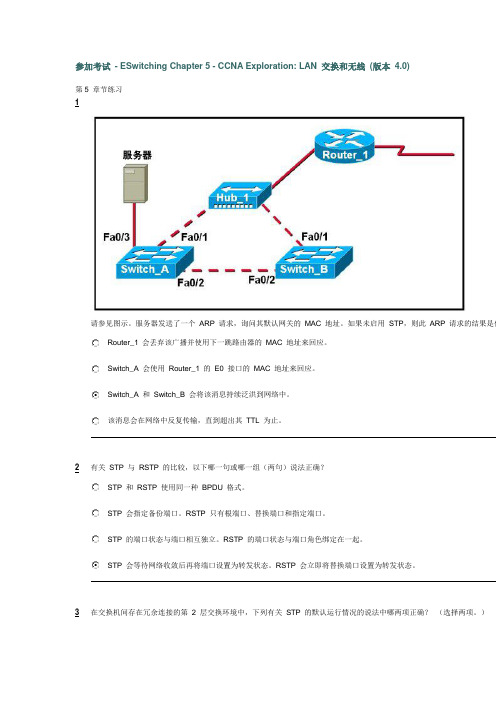
参加考试- ESwitching Chapter 5 - CCNA Exploration: LAN 交换和无线(版本 4.0)第5 章节练习1请参见图示。
服务器发送了一个ARP 请求,询问其默认网关的MAC 地址。
如果未启用STP,则此ARP 请求的结果是什Router_1 会丢弃该广播并使用下一跳路由器的MAC 地址来回应。
Switch_A 会使用Router_1 的E0 接口的MAC 地址来回应。
Switch_A 和Switch_B 会将该消息持续泛洪到网络中。
该消息会在网络中反复传输,直到超出其TTL 为止。
2有关STP 与RSTP 的比较,以下哪一句或哪一组(两句)说法正确?STP 和RSTP 使用同一种BPDU 格式。
STP 会指定备份端口。
RSTP 只有根端口、替换端口和指定端口。
STP 的端口状态与端口相互独立。
RSTP 的端口状态与端口角色绑定在一起。
STP 会等待网络收敛后再将端口设置为转发状态。
RSTP 会立即将替换端口设置为转发状态。
3在交换机间存在冗余连接的第2 层交换环境中,下列有关STP 的默认运行情况的说法中哪两项正确?(选择两项。
)根交换机是具有最高速端口的交换机。
当两个端口开销相等时,有关阻塞哪个端口的决策取决于端口优先级和身份标识。
所有中继端口均为指定端口,不会被阻塞。
根交换机上的所有端口均被设置为根端口。
每台非根交换机仅拥有一个根端口。
4在具有一个生成树实例的已收敛的网络中,将存在哪两项要素?(选择两项。
)每个网络有一个根桥所有非指定端口转发每个非根桥有一个根端口每个网段有多个指定端口每个网络有一个指定端口5每个交换以太网LAN 网段选举出的转发端口会被指派什么快速生成树协议(RSTP) 角色?备用备份指定根6当开发PVST+ 时,修改了网桥ID 是为了加入什么信息?网桥的优先级MAC 地址协议VLAN ID7端口处于哪种STP 状态下时会记录MAC 地址但不转发用户数据?阻塞学习禁用侦听转发8交换机通过哪两种方式使用BPDU 中的信息?(选择两项。
nectin4结构

Nectin4结构引言Nectin4是一种细胞间连接蛋白,属于Nectin家族的成员之一。
它在多种生物体中广泛表达,并在细胞黏附、细胞迁移和细胞信号传导中发挥重要作用。
本文将深入探讨Nectin4的结构特征、功能以及其在疾病中的潜在作用。
Nectin家族1. Nectin家族概述Nectin家族是一类单跨膜蛋白,包括Nectin1-4四个成员。
它们在细胞黏附和细胞间相互作用中发挥重要作用。
Nectin家族蛋白通过其细胞外结构域与邻近细胞的相应结构域发生相互作用,从而促进细胞间的黏附。
2. Nectin4的结构特征Nectin4是Nectin家族中的一个成员,其结构特征如下: - Nectin4是一种单跨膜蛋白,由细胞外结构域、跨膜域和细胞内结构域组成。
- 细胞外结构域包括三个Ig-like结构域,其中第一个和第二个Ig-like结构域通过一个长的可变区域相连。
- 跨膜域由一个疏水性氨基酸序列组成,起到连接细胞外和细胞内结构域的桥梁作用。
- 细胞内结构域包括一个短的保守区域和一个较长的胞质尾部区域。
Nectin4的功能Nectin4在多种生物学过程中发挥重要作用,主要包括: ### 1. 细胞黏附和细胞间相互作用 Nectin4通过其细胞外结构域与邻近细胞表面的相应结构域发生相互作用,从而促进细胞间的黏附。
这种细胞黏附有助于细胞的稳定连接以及细胞层的形成和维持。
2. 细胞迁移和细胞信号传导Nectin4参与调控细胞的迁移过程。
研究表明,Nectin4与其他细胞黏附蛋白和信号分子相互作用,调控细胞的黏附和迁移能力。
此外,Nectin4还参与细胞信号传导通路的调控,影响细胞的生长、分化和凋亡等过程。
3. 免疫应答调节Nectin4在免疫系统中也发挥重要作用。
研究发现,Nectin4参与调节免疫细胞的活化和功能。
它与其他免疫调节蛋白相互作用,影响免疫细胞的增殖和分化,调节免疫应答的强度和方向。
Nectin4与疾病的关联Nectin4在一些疾病中的异常表达与其功能紊乱有关,可能对疾病的发生和发展起到重要作用。
NLRC4蛋白自抑制机制的结构基础

NLRC4蛋白自抑制机制的结构基础作者:暂无来源:《科学中国人》 2014年第7期柴继杰教授清华大学生命科学学院1987获得大连轻工业学院化学工程系学士学位,在1997年获得中国协和医科大学药物分析学博士学位。
随后分别在中科院生物物理研究所和普林斯顿大学进行博士后的研究工作。
关注并研究在生物学及药学应用中的重要大分子结构与功能。
主要通过蛋白晶体衍射的方法及一些细胞生物学、生物化学等手段阐述这些生物大分子在结构和功能上的联系。
领导的实验室并不局限于已建立的研究框架,还在与北京生命科学研究所的其他研究小组合作,开展联合研究项目。
一个正进行的研究方向将关注于组蛋白的共价修饰调控基因转录的分子机制,主要集中于组蛋白甲基化及去甲基化酶催化机理的研究。
另外,一些调控蛋白如何特异性识别不同的组蛋白的共价修饰也属于其研究范围。
实验室另外的一个研究的领域是有关病原菌与宿主间的相互关系。
在植物与动物体中,都编码一类高度保守的蛋白质——NBS-LRR蛋白。
这类蛋白对动植物种的免疫反应都具有很重要的作用。
NLRC4蛋白自抑制机制的结构基础NOD样受体为近年来发现的一类位于细胞质内的模式识别受体,能够识别进入胞内的病原分子从而引起免疫应答,是机体天然免疫系统的重要组成部分。
NOD样受体的异常与很多疾病密切相关,包括如关节炎等各种自身免疫疾病、肥胖等各种代谢综合症、炎症性肠病以及肿瘤的发生。
对该家族蛋白作用机制的研究正成为基础免疫学领域的一个重要的热点领域。
研究组获得了小鼠NLRC4蛋白的晶体并通过X射线晶体衍射的方法解析了该蛋白分辨率为3.2的晶体结构。
结构显示单独的NLRC4蛋白以单体的形式处于自抑制状态。
该蛋白中的核苷酸结合结构域(nucleotide-bindingdomain,NBD)结合的是ADP,ADP介导的NBD同侧翼螺旋结构域(winged-helixdomain,WHD)之间的相互作用对维持NLRC4的自抑制状态十分关键。
nectin4结构

nectin4结构ectin4是一种细胞黏附蛋白,广泛存在于多种细胞类型中,起着重要的生物学作用。
近年来,科学家对nectin4的结构和研究越来越关注,旨在深入了解其在生物学及疾病中的作用机制。
一、nectin4结构简介ectin4蛋白由两个主要结构域组成:细胞外域(extracellular domain,ECD)和细胞质域(cytoplasmic domain,CD)。
ECD包含一个典型的免疫球蛋白(Ig)样结构,具有多个保守的受体结合结构域。
CD则与细胞内信号传导有关。
二、nectin4在生物学中的作用1.细胞黏附:nectin4作为细胞黏附分子,参与细胞与细胞之间的黏附过程,调控细胞排列和紧密连接。
2.免疫应答:nectin4在免疫细胞活化、免疫突触形成及免疫细胞间相互作用中发挥重要作用。
3.神经突触形成:nectin4在神经元之间发挥黏附作用,参与神经突触的形成和功能调控。
三、nectin4在疾病中的研究应用1.肿瘤:nectin4在某些肿瘤细胞中高表达,与肿瘤的发生、发展及侵袭转移密切相关。
研究nectin4在肿瘤中的作用,有助于发现新型治疗靶点和诊断标志物。
2.炎症性疾病:nectin4在炎症过程中的表达和作用,为炎症性疾病的治疗提供了新的研究方向。
3.神经系统疾病:nectin4在神经退行性疾病如阿尔茨海默病中的作用和机制,有助于寻找新的治疗策略。
四、nectin4结构与功能的关系ectin4的结构与其功能密切相关。
例如,ECD中的受体结合结构域负责与细胞表面分子结合,调控细胞黏附;而CD则通过与细胞内信号分子相互作用,进而影响细胞生物学效应。
五、未来研究方向与展望1.深入研究nectin4在不同疾病中的作用机制,挖掘新型治疗靶点。
2.探讨nectin4在神经发育和神经再生中的作用,为神经系统疾病的治疗提供新思路。
3.开发针对nectin4的生物制品,如抗体药物、小分子抑制剂等,用于疾病治疗。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Which two statements are true regarding network security? (Choose two.)Securing a network against internal threats is a lower priority because company em-ployees represent a low security risk.Both experienced hackers who are capable of writing their own exploit code and inexpe-rienced individuals who download exploits from the Internet pose a serious threat to network security.Assuming a company locates its web server outside the firewall and has adequate backups of the web server, no further security measures are needed to protect the web server because no harm can come from it being hacked.Established network operating systems like UNIX and network protocols like TCP/IP can be used with their default settings because they have no inherent security weak-nesses.Protecting network devices from physical damage caused by water or electricity is a ne-cessary part of the security policy.Scoring Rule For: correctness of responseOption 2 and Option 5 are correct.1 point for each correct option.0 points if more options are selected than required.Which two statements are true about network attacks? (Choose two.)Strong network passwords mitigate most DoS attacks.Worms require human interaction to spread, viruses do not.Reconnaissance attacks are always electronic in nature, such as ping sweeps or port scans.A brute-force attack searches to try every possible password from a combination of cha-racters.Devices in the DMZ should not be fully trusted by internal devices, and communication between the DMZ and internal devices should be authenticated to prevent attacks such as port redirection.Scoring Rule For: correctness of responseOption 4 and Option 5 are correct.1 point for each correct option.0 points if more options are selected than required.Users are unable to access a company server. The system logs show that the server is operating slowly because it is receiving a high level of fake requests for service. Which type of attack is occurring?reconnaissanceaccessDoSwormvirusTrojan horseScoring Rule For: correctness of response2 points for Option 30 points for any other optionAn IT director has begun a campaign to remind users to avoid opening e-mail messag-es from suspicious sources. Which type of attack is the IT director trying to protect users from?DoSDDoSvirusaccessreconnaissanceScoring Rule For: correctness of response2 points for Option 30 points for any other optionWhich two statements regarding preventing network attacks are true? (Choose two.) The default security settings for modern server and PC operating systems can be trusted to have secure default security settings.Intrusion prevention systems can log suspicious network activity, but there is no way to counter an attack in progress without user intervention.Physical security threat mitigation consists of controlling access to device console ports, labeling critical cable runs, installing UPS systems, and providing climate control. Phishing attacks are best prevented by firewall devices.Changing default usernames and passwords and disabling or uninstalling unnecessary services are aspects of device hardening.Scoring Rule For: correctness of responseOption 3 and Option 5 are correct.1 point for each correct option.0 points if more options are selected than required.Intrusion detection occurs at which stage of the Security Wheel?securingmonitoringtestingimprovementreconnaissanceScoring Rule For: correctness of response2 points for Option 20 points for any other optionWhich two objectives must a security policy accomplish? (Choose two.)provide a checklist for the installation of secure serversdescribe how the firewall must be configureddocument the resources to be protectedidentify the security objectives of the organizationidentify the specific tasks involved in hardening a routerScoring Rule For: correctness of responseOption 3 and Option 4 are correct.1 point for each correct option.0 points if more options are selected than required.What are three characteristics of a good security policy? (Choose three.)It defines acceptable and unacceptable use of network resources.It communicates consensus and defines roles.It is developed by end users.It is developed after all security devices have been fully tested.It defines how to handle security incidents.It should be encrypted as it contains backups of all important passwords and keys. Scoring Rule For: correctness of responseOption 1, Option 2, and Option 5 are correct.1 point for each correct option.0 points if more options are selected than required.Which two statements define the security risk when DNS services are enabled on the network? (Choose two.)By default, name queries are sent to the broadcast address 255.255.255.255.DNS name queries require the ip directed-broadcast command to be enabled on the Ethernet interfaces of all routers.Using the global configuration command ip name-server on one router enables the DNS services on all routers in the network.The basic DNS protocol does not provide authentication or integrity assurance.The router configuration does not provide an option to set up main and backup DNS servers.Scoring Rule For: correctness of responseOption 1 and Option 4 are correct.1 point for each correct option.0 points if more options are selected than required.What are two benefits of using Cisco AutoSecure? (Choose two.)It gives the administrator detailed control over which services are enabled or disabled. It offers the ability to instantly disable non-essential system processes and services.It automatically configures the router to work with SDM.It ensures the greatest compatibility with other devices in your network.It allows the administrator to configure security policies without having to understand all of the Cisco IOS software features.Scoring Rule For: correctness of responseOption 2 and Option 5 are correct.1 point for each correct option.0 points if more options are selected than required.Refer to the exhibit. A network administrator is trying to configure a router to use SDM, but it is not functioning correctly. What could be the problem?The privilege level of the user is not configured correctly.The authentication method is not configured correctly.The HTTP server is not configured correctly.The HTTP timeout policy is not configured correctly.Scoring Rule For: correctness of response2 points for Option 10 points for any other optionThe Cisco IOS image naming convention allows identification of different versions and capabilities of the IOS. What information can be gained from the filename c2600-d-mz.121-4? (Choose two.)The "mz" in the filename represents the special capabilities and features of the IOS. The file is uncompressed and requires 2.6 MB of RAM to run.The software is version 12.1, 4th revision.The file is downloadable and 121.4MB in size.The IOS is for the Cisco 2600 series hardware platform.Scoring Rule For: correctness of responseOption 3 and Option 5 are correct.1 point for each correct option.0 points if more options are selected than required.Refer to the exhibit. The network administrator is trying to back up the Cisco IOS router software and receives the output shown. What are two possible reasons for this output? (Choose two.)The Cisco IOS file has an invalid checksum.The TFTP client on the router is corrupt.The router cannot connect to the TFTP server.The TFTP server software has not been started.There is not enough room on the TFTP server for the software.Scoring Rule For: correctness of responseOption 3 and Option 4 are correct.1 point for each correct option.0 points if more options are selected than required.Which two conditions should the network administrator verify before attempting to up-grade a Cisco IOS image using a TFTP server? (Choose two.)Verify the name of the TFTP server using the show hosts command.Verify that the TFTP server is running using the tftpdnld command.Verify that the checksum for the image is valid using the show version command. Verify connectivity between the router and TFTP server using the ping command. Verify that there is enough flash memory for the new Cisco IOS image using the show flash command.Scoring Rule For: correctness of responseOption 4 and Option 5 are correct.1 point for each correct option.0 points if more options are selected than required.The password recovery process begins in which operating mode and using what type of connection? (Choose two.)ROM monitorboot ROMCisco IOSdirect connection through the console portnetwork connection through the Ethernet portnetwork connection through the serial portScoring Rule For: correctness of responseOption 1 and Option 4 are correct.1 point for each correct option.0 points if more options are selected than required.Which statement is true about Cisco Security Device Manager (SDM)? SDM can run only on Cisco 7000 series routers.SDM can be run from router memory or from a PC.SDM should be used for complex router configurations.SDM is supported by every version of the Cisco IOS software. Scoring Rule For: correctness of response2 points for Option 20 points for any other optionWhich step is required to recover a lost enable password for a router? Set the configuration register to bypass the startup configuration. Copy the running configuration to the startup configuration.Reload the IOS from a TFTP server from ROMMON.Reconfigure the router using setup mode.Scoring Rule For: correctness of response2 points for Option 10 points for any other optionWhat is the best defense for protecting a network from phishing exploits? Schedule antivirus scans.Schedule antispyware scans .Schedule training for all users.Schedule operating systems updates.Scoring Rule For: correctness of response2 points for Option 30 points for any other optionRefer to the exhibit. Security Device Manager (SDM) has been used to configure a re-quired level of security on the router. What would be accomplished when the SDM ap-plies the next step on the security problems that are identified on the router?SDM will automatically invoke the AutoSecure command.SDM will generate a report that will outline the proper configuration actions to alleviate the security issues.SDM will create a configuration file that can be copy and pasted into the router to recon-figure the services.SDM will reconfigu re the services that are marked in the exhibit as “fix it” to apply the suggested security changes.Scoring Rule For: correctness of response2 points for Option 40 points for any other optionRefer to the exhibit. What is the purpose of the "ip ospf message-digest-key 1 md5 cisco" statement in the configuration?to specify a key that is used to authenticate routing updatesto save bandwidth by compressing the trafficto enable SSH encryption of trafficto create an IPsec tunnelScoring Rule For: correctness of response2 points for Option 10 points for any other optionRefer to the exhibit. What is accomplished when both commands are configured on the router?The commands filter UDP and TCP traffic coming to the router.The commands disable any TCP or UDP request sent by the routing protocols.The commands disable the services such as echo, discard, and chargen on the router to prevent security vulnerabilities.The commands disable the BOOTP and TFTP server services to prevent security vulne-rabilities.Scoring Rule For: correctness of response2 points for Option 30 points for any other optionRefer to the exhibit. Security Device Manager (SDM) is installed on router R1. What is the result of opening a web browser on PC1 and entering the URL https://192.168.10.1? The password is sent in plain text.A Telnet session is established with R1.The SDM page of R1 appears with a dialog box that requests a username and pass-word.The R1 home page is displayed and allows the user to download Cisco IOS images and configuration files.Scoring Rule For: correctness of response2 points for Option 30 points for any other option。
