icpp10
计算机领域EI和SCI收录期刊及影响因子

领域顶级国际会议,录取率 25%左右,2 年一次,中国大 陆每年论文数不超过 20 篇
模式识别,计算机 视觉,多媒体计算
15 DCC: Data Compression Conference
领域顶级国际会议,录取率很低,每年一次,目前完全 国内论文极少
数据压缩
16
ICML: International Conference on Machine Learning
网络通信领域
7
ACM MobiCom: International Conference on 无线网络领域顶级会议,录用率约为 10%,每年举行一
Mobile Computing and Networking
次。
无线网络领域
ACM SIGMETRICS: Conference on
8 Measurement and Modeling of Computer
Systems
偏重于建模和测量的重要国际会议,内容覆盖系统和网 络,录用率为 10%左右。
网络通信领域
MOBIHOC:
9
ACM International Symposium on Mobile Ad Hoc Networking and Comp
无线网络领域新兴的重要国际会议,内容侧重于 adhoc 网 络。
4:供博士生选择的相关刊物
序号 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17
刊物名称(以期刊名称的拼音为序) 总被引频次
电子学报(英文版、中文版)
中文版 1676
高技术通讯(英文版、中文版) 中文版 540
计算机辅助设计与图形学学报
945
计算机工程
儿童性早熟诊治进展分析

六、治疗4:
此药能有效抑制骨龄的增长。使
BA/CA下降,实现CA对BA的追赶。 从而成年身高增长。剂量5080ug/kg/ 次,每 4 周 1 次,对 BA>13 岁者一般不用。 停药后HPGA约一年恢复正常。
小结
女孩在8岁以前、男孩在9岁以前呈现性发育征象,即为性早
熟;性激素的分泌受下丘脑-垂体-性腺轴的调节。
三、病理生理6
( D)松果体分泌的黑素紧张素 对下丘脑 GnRH 释放有抑制作用, 推测青春发动与黑素紧张素有关。
三、病理生理7
青春发动除与内源性下丘脑发育的成熟
有关,尚有外周环境信号的干预,包括 营养、生长、应激、物理活动等。但其 可改变性成熟的进程,而非决定青春发 育所必需。
三、病理生理8
四、临床表现1:
A、CPP:女孩:乳房发育(<8y),
身高加速,继之阴毛发育,腋毛出现, 最终有初潮(<10岁)。 男孩:睾丸、阴囊增大、着色,阴茎 增大、腋毛、阴毛出现,身高增长加速, 喉结出现,继之遗精。 最终长骨骺闭合提前,生长早期停止, 成人期矮小。精神发育和体格发育间不 均衡。
性早熟分真性、假性、部分性。 特发性真性性早熟致骨骼成熟过快和骨彀提前愈合导致最终
矮小。
促性腺激素释放激素类似物(GnRHa)可以治疗此病,改
善身高。
思考题
哪种性早熟病人需要干预治疗?哪种可以 不治疗,暂时观察?
谢 谢
生长激素缺乏症
目的与要求ቤተ መጻሕፍቲ ባይዱ
掌握生长激素缺乏症的定义、病因分类,临
GHD的病理生理
大脑皮层 等
多巴胺、5-羟色胺、去甲肾上腺素
+ 下丘脑 垂 体
中枢性性早熟诊治

预测 成年身高 性征发育 进程迅速
骨龄/年龄>1, 骨龄/身高年龄>1 女<150 cm,男<160 cm 或<遗传靶身高-2SD 骨龄增长/年龄增长>1 每个发育期约1年,B2-初潮应>2年
中枢性性早熟治疗
• 慎用: 改善成年身高疗效差 • 始治BA 女≥11.5岁 男≥12.5岁 • 遗传靶身高(THt) < -2SD • 不宜治疗: • BA 女≥12.5岁 男≥13.5岁 • 女孩初潮、男孩遗精后1年 • 不应治疗: • 性成熟缓慢 BA<CA PAH>THt • 虽BA>CA 但HA>BA PAH佳
BV
GV
BV
GV
女孩BA和GV的关系
男孩BA 和GV的关系
BA加速(PBV)先于PHV 2年 PHV 后GV下降→骨骺融合→停止生长
BAV/GV平衡规律的启示 PBV-PHV的线性交叉点(男13,女11岁) 生长/成熟平衡点
交叉点后 BA进展慢,GnRHa治后更慢
BA ≥ 12岁(女),14岁(男):GV↓↓ GnRHa后GV↓↓是内在必然规律 骨龄抑制效果,GV维持
5 7 9 11 13 15 治疗开始时的骨龄(岁)
r= -0.54 P=0.00 7
第二年生长速度(cm/年)
6 5 4 3 2
r =-0.58 P=0.000
第二年生长速 度(c m/年)73456
7
8
9 10 11 12 13 第二年始年龄(岁)
图 GnRHa治疗中生长速度 与治疗开始骨龄相关图
GH是药理作用而非补充替代 要用药理量
GnRHa+蛋白同化类固醇
★ 司坦唑醇(ST),oxandrolone 对GnRHa作用下生长板: 增加高度,部分经上调IGF-1/IGF-R 介导促进软骨细胞增殖→促进生长 ★ 临床有进一步探讨必要、二线选择 Turner综合征E2低下 ST不引起BA↑ GnRHa→E2↓ ST BA↑??
计算机科学重要国际会议

1.2计算机科学与技术重要国际学术会议一、A类会议二、B类会议1.3自动化重要国际学术会议一、A类会议二、B类会议数据挖掘相关的权威期刊和会议-----------------------------------------------[Journals]1.ACM Transactions on Knowledge Discovery from Data (TKDD)2.IEEE Transactions on Knowledge and Data Engineering (TKDE)3.Data Mining and Knowledge Discovery4.Knowledge and Information Systems5.Data & Knowledge Engineering[Conferences]1.SIGMOD:ACM Conference on Management of Data (ACM)2.VLDB:International Conference on Very Large Data Bases (Morgan Kaufmann/ACM)3.ICDE:IEEE International Conference on Data Engineering (IEEE Computer Society)4.SIGKDD:ACM Knowledge Discovery and Data Mining (ACM)5.WWW:International World Wide Web Conferences (W3C)6.CIKM:ACM International Conference on Information and Knowledge Management (ACM)7.PKDD:European Conference on Principles and Practice of Knowledge Discovery in Databases (Springer-Verlag LNAI)JournalsACM TKDD /DMKD/content/1573-756X/?p=859c3e83455d41679ef1be783 e923d1d&pi=0IEEE TKDE /organizations/pubs/transactions/tkde.htm ACM TODS /tods/VLDB Journal /ACM Tois /pubs/tois/ConferencesSigKDD /ICDM /~icdm/SDM /meetings/sdm08/PKDD /VLDB /SigMod /sigmod/ICDE http://www.ipsi.fraunhofer.de/tcde/conf_e.htmlWWW /conferencesOnline Resources网址集合/Computers/Software/Databases/Data_Mining// A google co-op search engine for Data Mining/coop/cse?cx=006422944775554126616%3Aixcd3tdxkke Data Mining, University of Houston/boetticher/CSCI5931%20Data%20Mining.htmlData Mining Program, University of Central Florida / Data Mining Group, University of Dortmundhttp://www-ai.cs.uni-dortmund.de/index.htmlData Mining, MIT OCW/OcwWeb/Sloan-School-of-Management/15-062Data-MiningSpri ng2003/CourseHome/Data Mining Group, Tsinghua /dmg.html KDD oral presentations video Data Mining Events Feed /DataMiningEvents ToolsWeka /ml/weka/Rapid Miner(Yale) /content/view/3/76/lang,en/IlliMine /Alpha Miner http://www.eti.hku.hk/alphaminerPotter's Wheel A-B-C /abc/。
儿童性早熟课件

睾丸容积测量模具图
男性外生殖器发育分期
影响青春发育的因素
• 中枢神经系统的成熟 • 遗传、种族 • 合理的营养,达到适当体重和体脂含量 • 环境因素:如环境激素,杂志、电视的
视觉刺激(神经-内分泌-免疫网络) • 中枢神经系统疾病:难产、颅内肿瘤、
外伤、感染等
性早熟对孩子的影响
• 社会问题 • 心理问题 • 影响终身高
青春发育与成年终身高
• 出生时身高 50cm,1岁时身高75cm • 2岁后 生长速率 5~6cm/年 • 青春期前 占身高的80%左右 • 青春期 占身高的20%左右 • 男性终身高比女性高约12cm,其中50%
由于男孩青春期发育晚一些,50%由于 男孩青春期生长速率大一些
非GnRH依赖性(外周性)
男孩 同性性早熟(男性第二性征) • 先天性肾上腺皮质增生症(最常见) • 肾上腺皮质肿瘤 • 睾丸间质细胞瘤 • 异位分泌HCG的肿瘤 • 家族性高睾酮血症 • 外源性雄激素摄入等 异性性早熟(女性第二性征) • 产生雌激素的肾上腺皮质肿瘤、睾丸肿瘤、异位分泌
HCG的肿瘤 • 外源性雌激素摄入(避孕药)
枢性还是外周性)
诊断流程和辅助检查
(二)病因学诊断 • 头颅MRI(重点是鞍区),尤其是:①
所有CPP男孩;② 6岁以下发病的CPP女 孩;③性发育进程迅速或有其他中枢病 变表现 • 性腺或肾上腺影象学检查 • 如有明确外源性激素摄入者可酌情免除
治疗
• 部分性性早熟加强随访 • 外周性性早熟针对病因治疗 • 有器质性病变的CPP应针对病因治疗 • 中枢病变无手术指征者按ICPP治疗
ICPP治疗
• ICPP治疗目的 (1)抑制过早或过快的性发育 (2)防止或缓释患儿或家长因性早熟所 致的相关的社会或心理问题 (3)改善最终成年身高(FAH) 并非所有的ICPP均需要治疗。
性早熟

因为青春发育是一个动态的过程,故对 每个个体的以上指标需动态观察。对于 暂不需治疗者均需进行定期复查和评估, 调整治疗方案。
GnRHa治疗
GnRHa剂量:首剂80-100μg/kg,最大量 3.75mg;其后每4周注射1次,体重 ≥30kg者,曲普瑞林每4周肌注3-3.75mg。
已有初潮者首剂后2周宜强化1次。
GnRHa治疗监测和停药决定
治疗过程中每3-6个月测量身高以及性征发育 状况(阴毛进展不代表性腺受抑状况)
首剂3-6个月末复查GnRH激发试验,LH峰值在 青春前期水平提示剂量合适
其后对女孩需定期复查基础血清雌二醇(E2) 和子宫、卵巢B超;男孩需复查基础血清睾酮 浓度以判断性腺轴功能抑制状况。
6岁以下发病的女孩。 性成熟过程迅速或有其他中枢病变表现者。
病因学诊断-外周性性早熟
按照具体临床特征和内分泌激素初筛后 进行进一步的内分泌检查,并按需做性 腺、肾上腺或其他相关器官的影像学检 查。
如有明确的外源性性甾体激素摄入史者 可酌情免除复杂的检查。
诊断tips
随机的LH最有意义。LH>0.3U/L即可考虑 CPP;大多数青春期前女孩LH<0.1U/L
不完全性中枢性性早熟
最常见的类型为单纯性乳房早发育,表 现为只有乳房早发育而不呈现其他第二 性征,乳晕无着色,呈非进行性自限性 病程,乳房多在数月后自然消退
若发生于2岁内女孩,可能是由于下丘脑 -性腺轴处于生理性活跃状态,又称为 “小青春期”。
乳房早熟(thelarche)
8岁前单独出现乳房发育 其病源尚不十分清楚,可以是双侧,亦有
是单侧,与局部靶组织的敏感性有关 雌激素水平不高
中国计算机学会推荐国际学术会议和期刊目录-2019

中国计算机学会推荐国际学术会议和期刊目录(2019年)中国计算机学会中国计算机学会推荐国际学术期刊(计算机体系结构/并行与分布计算/存储系统)一、A类序号刊物简称刊物全称出版社网址1TOCS ACM Transactions on Computer Systems ACM http://dblp.uni-trier.de/db/journals/tocs/ 2TOS ACM Transactions on Storage ACM http://dblp.uni-trier.de/db/journals/tos/3TCAD IEEE Transactions on Computer-Aided Design ofIntegrated Circuits And System IEEE http://dblp.uni-trier.de/db/journals/tcad/4TC IEEE Transactions on Computers IEEE http://dblp.uni-trier.de/db/journals/tc/index.html 5TPDS IEEE Transactions on Parallel and Distributed Systems IEEE http://dblp.uni-trier.de/db/journals/tpds/二、B类序号刊物简称刊物全称出版社网址1TACO ACM Transactions on Architecture and Code Optimization ACM http://dblp.uni-trier.de/db/journals/taco/2TAAS ACM Transactions on Autonomous and Adaptive Systems ACM http://dblp.uni-trier.de/db/journals/taas/3TODAES ACM Transactions on Design Automation of Electronic Systems ACM http://dblp.uni-trier.de/db/journals/todaes/4TECS ACM Transactions on Embedded Computing Systems ACM http://dblp.uni-trier.de/db/journals/tecs/5TRETS ACM Transactions on Reconfigurable Technology and Systems ACM http://dblp.uni-trier.de/db/journals/trets/6TVLSI IEEE Transactions on Very Large Scale Integration(VLSI)Systems IEEE http://dblp.uni-trier.de/db/journals/tvlsi/7JPDC Journal of Parallel and Distributed Computing Elsevier http://dblp.uni-trier.de/db/journals/jpdc/8JSA Journal of Systems Architecture:Embedded Software Design Elsevier http://dblp.uni-trier.de/db/journals/jsa/9PARCO Parallel Computing Elsevier http://dblp.uni-trier.de/db/conf/parco/10Performance Evaluation:An International Journal Elsevier /performance-evaluation/三、C类序号刊物简称刊物全称出版社网址1JETC ACM Journal on Emerging Technologies inComputing SystemsACM http://dblp.uni-trier.de/db/journals/jetc/2Concurrency and Computation:Practice andExperienceWiley http://dblp.uni-trier.de/db/journals/concurrency/3DC Distributed Computing Springer http://dblp.uni-trier.de/db/journals/dc/4FGCS Future Generation Computer Systems Elsevier http://dblp.uni-trier.de/db/journals/fgcs/5TCC IEEE Transactions on Cloud Computing IEEE https://dblp.uni-trier.de/db/journals/tcc/6Integration Integration,the VLSI Journal Elsevier http://dblp.uni-trier.de/db/journals/integration/7JETTA Journal of Electronic Testing-Theory andApplicationsSpringer /journal/108368JGC Journal of Grid computing Springer https://dblp.uni-trier.de/db/journals/grid/9MICPRO Microprocessors and Microsystems:EmbeddedHardware DesignElsevier http://dblp.uni-trier.de/db/journals/mam/10RTS Real-Time Systems Springer http://dblp.uni-trier.de/db/journals/rts/ 11TJSC The Journal of Supercomputing Springer http://dblp.uni-trier.de/db/journals/tjs/中国计算机学会推荐国际学术会议计算机体系结构/并行与分布计算/存储系统一、A类序号会议简称会议全称出版社网址1PPoPP ACM SIGPLAN Symposium on Principles&Practice of Parallel ProgrammingACM http://dblp.uni-trier.de/db/conf/ppopp/2FAST Conference on File and Storage Technologies USENIX http://dblp.uni-trier.de/db/conf/fast/ 3DAC Design Automation Conference ACM https://dblp.uni-trier.de/db/conf/dac/ 4HPCA High Performance Computer Architecture IEEE http://dblp.uni-trier.de/db/conf/hpca/5MICRO IEEE/ACM International Symposium onMicroarchitectureIEEE/ACM https://dblp.uni-trier.de/db/conf/micro/6SC International Conference for High PerformanceComputing,Networking,Storage,and AnalysisIEEE http://dblp.uni-trier.de/db/conf/sc/7ASPLOSInternational Conference on Architectural Supportfor Programming Languages and Operating SystemsACM http://dblp.uni-trier.de/db/conf/asplos/8ISCA International Symposium on Computer Architecture ACM/IEEE http://dblp.uni-trier.de/db/conf/isca/9USENIX ATC USENIX Annul Technical Conference USENIX http://dblp.uni-trier.de/db/conf/usenix/index.html二、B类序号会议简称会议全称出版社网址1SoCC ACM Symposium on Cloud Computing ACM http://dblp.uni-trier.de/db/conf/cloud/ 2SPAA ACM Symposium on Parallelism in Algorithms and Architectures ACM http://dblp.uni-trier.de/db/conf/spaa/ 3PODC ACM Symposium on Principles of Distributed Computing ACM http://dblp.uni-trier.de/db/conf/podc/4FPGA ACM/SIGDA International Symposium on Field-ProgrammableGate ArraysACM http://dblp.uni-trier.de/db/conf/fpga/5CGO Code Generation and Optimization IEEE/ACM http://dblp.uni-trier.de/db/conf/cgo/ 6DATE Design,Automation&Test in Europe IEEE/ACM http://dblp.uni-trier.de/db/conf/date/ 7EuroSys European Conference on Computer Systems ACM http://dblp.uni-trier.de/db/conf/eurosys/ 8HOT CHIPS Hot Chips:A Symposium on High Performance Chips IEEE /9CLUSTER IEEE International Conference on Cluster Computing IEEE https://dblp.uni-trier.de/db/conf/cluster/ 10ICCD International Conference on Computer Design IEEE http://dblp.uni-trier.de/db/conf/iccd/ 11ICCAD International Conference on Computer-Aided Design IEEE/ACM http://dblp.uni-trier.de/db/conf/iccad/ 12ICDCS International Conference on Distributed Computing Systems IEEE http://dblp.uni-trier.de/db/conf/icdcs/13CODES+ISSS International Conference on Hardware/Software Co-design andSystem SynthesisACM/IEEE http://dblp.uni-trier.de/db/conf/codes/index.html14HiPEAC International Conference on High Performance and EmbeddedArchitectures and CompilersACM http://dblp.uni-trier.de/db/conf/hipeac/15SIGMETRICS International Conference on Measurement and Modeling ofComputer SystemsACM http://dblp.uni-trier.de/db/conf/sigmetrics/16PACT International Conference on Parallel Architectures andCompilation TechniquesIEEE/ACM http://dblp.uni-trier.de/db/conf/IEEEpact/17ICPP International Conference on Parallel Processing IEEE http://dblp.uni-trier.de/db/conf/icpp/ 18ICS International Conference on Supercomputing ACM http://dblp.uni-trier.de/db/conf/ics/ 19VEE International Conference on Virtual Execution Environments ACM http://dblp.uni-trier.de/db/conf/vee/ 20IPDPS International Parallel&Distributed Processing Symposium IEEE http://dblp.uni-trier.de/db/conf/ipps/21Performance International Symposium on Computer Performance Modeling,Measurements and EvaluationACM http://dblp.uni-trier.de/db/conf/performance/22HPDC International Symposium on High Performance DistributedComputingIEEE http://dblp.uni-trier.de/db/conf/hpdc/23ITC International Test Conference IEEE http://dblp.uni-trier.de/db/conf/itc/ 24LISA Large Installation System Administration Conference USENIX http://dblp.uni-trier.de/db/conf/lisa/ 25MSST Mass Storage Systems and Technologies IEEE http://dblp.uni-trier.de/db/conf/mss/26RTAS Real-Time and Embedded Technology and ApplicationsSymposiumIEEE http://dblp.uni-trier.de/db/conf/rtas/三、C类序号会议简称会议全称出版社网址1CF ACM International Conference on Computing Frontiers ACM http://dblp.uni-trier.de/db/conf/cf 2SYSTOR ACM International Systems and Storage Conference ACM http://dblp.uni-trier.de/db/conf/systor/index.html 3NOCS ACM/IEEE International Symposium on Networks-on-Chip ACM/IEEE http://dblp.uni-trier.de/db/conf/nocs 4ASAP Application-Specific Systems,Architectures,and Processors IEEE http://dblp.uni-trier.de/db/conf/asap 5ASP-DAC Asia and South Pacific Design Automation Conference ACM/IEEE http://dblp.uni-trier.de/db/conf/aspdac 6Euro-Par European Conference on Parallel and Distributed Computing Springer http://dblp.uni-trier.de/db/conf/europar/ 7ETS European Test Symposium IEEE http://dblp.uni-trier.de/db/conf/ets/ 8FPL Field Programmable Logic and Applications IEEE http://dblp.uni-trier.de/db/conf/fpl/ 9FCCM Field-Programmable Custom Computing Machines IEEE http://dblp.uni-trier.de/db/conf/fccm/10GLSVLSI Great Lakes Symposium on VLSI ACM/IEEE http://dblp.uni-trier.de/db/conf/glvlsi/11ATS IEEE Asian Test Symposium IEEE http://dblp.uni-trier.de/db/conf/ats/12HPCC IEEE International Conference on High PerformanceComputing and CommunicationsIEEE http://dblp.uni-trier.de/db/conf/hpcc/13HiPC IEEE International Conference on High PerformanceComputing,Data and AnalyticsIEEE/ACM http://dblp.uni-trier.de/db/conf/hipc/index.html14MASCOTS IEEE International Symposium on Modeling,Analysis,andSimulation of Computer and Telecommunication SystemsIEEE http://dblp.uni-trier.de/db/conf/mascots/15ISPA IEEE International Symposium on Parallel and DistributedProcessing with ApplicationsIEEE http://dblp.uni-trier.de/db/conf/ispa/16CCGRID IEEE/ACM International Symposium on Cluster,Cloud andGrid ComputingACM/IEEE http://dblp.uni-trier.de/db/conf/ccgrid/17NPC IFIP International Conference on Network and ParallelComputingSpringer http://dblp.uni-trier.de/db/conf/npc/18ICA3PP International Conference on Algorithms and Architectures forParallel ProcessingIEEE http://dblp.uni-trier.de/db/conf/ica3pp/19CASES International Conference on Compilers,Architectures,andSynthesis for Embedded SystemsACM http://dblp.uni-trier.de/db/conf/cases/index.html20FPT International Conference on Field-Programmable Technology IEEE http://dblp.uni-trier.de/db/conf/fpt/ 21ICPADS International Conference on Parallel and Distributed Systems IEEE http://dblp.uni-trier.de/db/conf/icpads/ 22ISCAS International Symposium on Circuits and Systems IEEE http://dblp.uni-trier.de/db/conf/iscas/23ISLPED International Symposium on Low Power Electronics andDesignACM/IEEE http://dblp.uni-trier.de/db/conf/islped/24ISPD International Symposium on Physical Design ACM http://dblp.uni-trier.de/db/conf/ispd/ 25HotI Symposium on High-Performance Interconnects IEEE http://dblp.uni-trier.de/db/conf/hoti/ 26VTS VLSI Test Symposium IEEE http://dblp.uni-trier.de/db/conf/vts/中国计算机学会推荐国际学术期刊(计算机网络)一、A类序号刊物简称刊物全称出版社网址1JSAC IEEE Journal of Selected Areas in Communications IEEE http://dblp.uni-trier.de/db/journals/jsac/ 2TMC IEEE Transactions on Mobile Computing IEEE http://dblp.uni-trier.de/db/journals/tmc/ 3TON IEEE/ACM Transactions on Networking IEEE,ACM http://dblp.uni-trier.de/db/journals/ton/二、B类序号刊物简称刊物全称出版社网址1TOIT ACM Transactions on Internet Technology ACM http://dblp.uni-trier.de/db/journals/toit/2TOMCCAP ACM Transactions on Multimedia Computing,Communications and ApplicationsACM http://dblp.uni-trier.de/db/journals/tomccap/3TOSN ACM Transactions on Sensor Networks ACM http://dblp.uni-trier.de/db/journals/tosn/ 4CN Computer Networks Elsevier http://dblp.uni-trier.de/db/journals/cn/ 5TCOM IEEE Transactions on Communications IEEE http://dblp.uni-trier.de/db/journals/tcom/ 6TWC IEEE Transactions on Wireless Communications IEEE http://dblp.uni-trier.de/db/journals/twc/三、C类序号刊物简称刊物全称出版社网址1Ad Hoc Networks Elsevier http://dblp.uni-trier.de/db/journals/adhoc/ 2CC Computer Communications Elsevier http://dblp.uni-trier.de/db/journals/comcom/3TNSM IEEE Transactions on Network and ServiceManagementIEEE http://dblp.uni-trier.de/db/journals/tnsm/4IET Communications IET http://dblp.uni-trier.de/db/journals/iet-com/ 5JNCA Journal of Network and Computer Applications Elsevier http://dblp.uni-trier.de/db/journals/jnca/ 6MONET Mobile Networks&Applications Springer http://dblp.uni-trier.de/db/journals/monet/ 7Networks Wiley http://dblp.uni-trier.de/db/journals/networks/ 8PPNA Peer-to-Peer Networking and Applications Springer http://dblp.uni-trier.de/db/journals/ppna/ 9WCMC Wireless Communications&Mobile Computing Wiley.http://dblp.uni-trier.de/db/journals/wicomm/ 10Wireless Networks Springer http://dblp.uni-trier.de/db/journals/winet/中国计算机学会推荐国际学术会议(计算机网络)一、A类序号会议简称会议全称出版社网址1SIGCOMM ACM International Conference on Applications,Technologies,Architectures,and Protocols forComputer CommunicationACM http://dblp.uni-trier.de/db/conf/sigcomm/index.html2MobiCom ACM International Conference on MobileComputing and NetworkingACM http://dblp.uni-trier.de/db/conf/mobicom/3INFOCOM IEEE International Conference on ComputerCommunicationsIEEE http://dblp.uni-trier.de/db/conf/infocom/4NSDI Symposium on Network System Design andImplementationUSENIX http://dblp.uni-trier.de/db/conf/nsdi/二、B类序号会议简称会议全称出版社网址1SenSys ACM Conference on Embedded Networked Sensor Systems ACM http://dblp.uni-trier.de/db/conf/sensys/ 2CoNEXT ACM International Conference on Emerging NetworkingACM http://dblp.uni-trier.de/db/conf/conext/Experiments and Technologies3SECON IEEE Communications Society Conference on Sensor and Ad HocIEEE http://dblp.uni-trier.de/db/conf/secon/Communications and Networks4IPSN International Conference on Information Processing in SensorIEEE/ACM http://dblp.uni-trier.de/db/conf/ipsn/Networks5MobiSys International Conference on Mobile Systems,Applications,andACM http://dblp.uni-trier.de/db/conf/mobisys/Services6ICNP International Conference on Network Protocols IEEE http://dblp.uni-trier.de/db/conf/icnp/ 7MobiHoc International Symposium on Mobile Ad Hoc Networking andACM/IEEE http://dblp.uni-trier.de/db/conf/mobihoc/Computing8NOSSDAV International Workshop on Network and Operating System SupportACM http://dblp.uni-trier.de/db/conf/nossdav/for Digital Audio and Video9IWQoS International Workshop on Quality of Service IEEE http://dblp.uni-trier.de/db/conf/iwqos/ 10IMC Internet Measurement Conference ACM/USENIX http://dblp.uni-trier.de/db/conf/imc/三、C类序号会议简称会议全称出版社网址1ANCS Architectures for Networking and Communications Systems ACM/IEEhttp://dblp.uni-trier.de/db/conf/ancs/E2APNOMS Asia-Pacific Network Operations and Management Symposium IFIP/IEEE http://dblp.uni-trier.de/db/conf/apnoms/ 3FORTE Formal Techniques for Networked and Distributed Systems Springer http://dblp.uni-trier.de/db/conf/forte/ 4LCN IEEE Conference on Local Computer Networks IEEE http://dblp.uni-trier.de/db/conf/lcn/ 5GLOBECOIEEE Global Communications Conference IEEE http://dblp.uni-trier.de/db/conf/globecom/ M6ICC IEEE International Conference on Communications IEEE http://dblp.uni-trier.de/db/conf/icc/ 7ICCCN IEEE International Conference on Computer Communications andIEEE http://dblp.uni-trier.de/db/conf/icccn/Networks8MASS IEEE International Conference on Mobile Ad-hoc and Sensor Systems IEEE http://dblp.uni-trier.de/db/conf/mass/index.html 9P2P IEEE International Conference on Peer-to-Peer Computing IEEE http://dblp.uni-trier.de/db/conf/p2p/ 10IPCCC IEEE International Performance Computing and CommunicationsIEEE http://dblp.uni-trier.de/db/conf/ipccc/Conference11WoWMoM IEEE International Symposium on a World of Wireless,Mobile andIEEE http://dblp.uni-trier.de/db/conf/wowmom/Multimedia Networks12ISCC IEEE Symposium on Computers and Communications IEEE http://dblp.uni-trier.de/db/conf/iscc/ 13WCNC IEEE Wireless Communications&Networking Conference IEEE http://dblp.uni-trier.de/db/conf/wcnc/ 14Networking IFIP International Conferences on Networking IFIP http://dblp.uni-trier.de/db/conf/networking/index.html15IM IFIP/IEEE International Symposium on Integrated NetworkIFIP/IEEE http://dblp.uni-trier.de/db/conf/im/index.htmlManagement16MSN International Conference on Mobile Ad-hoc and Sensor Networks IEEE https://dblp.uni-trier.de/db/conf/msn/ 17MSWiM International Conference on Modeling,Analysis and Simulation ofACM http://dblp.uni-trier.de/db/conf/mswim/Wireless and Mobile Systems18WASA International Conference on Wireless Algorithms,Systems,andSpringer http://dblp.uni-trier.de/db/conf/wasa/Applications19HotNets The Workshop on Hot Topics in Networks ACM http://dblp.uni-trier.de/db/conf/hotnets/中国计算机学会推荐国际学术期刊(网络与信息安全)一、A类序号刊物简称刊物全称出版社网址1TDSC IEEE Transactions on Dependable and Secure Computing IEEE http://dblp.uni-trier.de/db/journals/tdsc/ 2TIFS IEEE Transactions on Information Forensics and Security IEEE http://dblp.uni-trier.de/db/journals/tifs/ 3Journal of Cryptology Springer http://dblp.uni-trier.de/db/journals/joc/二、B类序号刊物简称刊物全称出版社网址1TISSEC ACM Transactions on Information and SystemSecurityACM http://dblp.uni-trier.de/db/journals/tissec/2Computers&Security Elsevier http://dblp.uni-trier.de/db/journals/compsec/ 3Designs,Codes and Cryptography Springer http://dblp.uni-trier.de/db/journals/dcc/ 4JCS Journal of Computer Security IOS Press http://dblp.uni-trier.de/db/journals/jcs/三、C类序号刊物简称刊物全称出版社网址1CLSR Computer Law and Security Review Elsevier /computer-law-and-security-review/2EURASIP Journal on Information Security Springer http://dblp.uni-trier.de/db/journals/ejisec/ 3IET Information Security IET http://dblp.uni-trier.de/db/journals/iet-ifs/ 4IMCS Information Management&Computer Security Emerald http://dblp.uni-trier.de/db/journals/imcs/ 5IJICS International Journal of Information and Computer Security Inderscience http://dblp.uni-trier.de/db/journals/ijics/ 6IJISP International Journal of Information Security and Privacy Idea Group Inc http://dblp.uni-trier.de/db/journals/ijisp/ 7JISA Journal of Information Security and Application Elsevier https://dblp.uni-trier.de/db/journals/istr/ 8SCN Security and Communication Networks Wiley http://dblp.uni-trier.de/db/journals/scn/中国计算机学会推荐国际学术会议(网络与信息安全)一、A类序号会议简称会议全称出版社网址1CCS ACM Conference on Computer andCommunications SecurityACM http://dblp.uni-trier.de/db/conf/ccs/2EUROCRYPT European Cryptology Conference Springer http://dblp.uni-trier.de/db/conf/eurocrypt/ 3S&P IEEE Symposium on Security and Privacy IEEE http://dblp.uni-trier.de/db/conf/sp/4CRYPTO International Cryptology Conference Springer http://dblp.uni-trier.de/db/conf/crypto/ 5USENIX Security Usenix Security Symposium USENIX Association http://dblp.uni-trier.de/db/conf/uss/二、B类序号会议简称会议全称出版社网址1ACSAC Annual Computer Security Applications Conference IEEE http://dblp.uni-trier.de/db/conf/acsac/2ASIACRYPT Annual International Conference on the Theory andApplication of Cryptology and Information SecuritySpringer http://dblp.uni-trier.de/db/conf/asiacrypt/3ESORICS European Symposium on Research in Computer Security Springer http://dblp.uni-trier.de/db/conf/esorics/ 4FSE Fast Software Encryption Springer http://dblp.uni-trier.de/db/conf/fse/ 5CSFW IEEE Computer Security Foundations Workshop IEEE http://dblp.uni-trier.de/db/conf/csfw/6SRDS IEEE International Symposium on Reliable DistributedSystemsIEEE http://dblp.uni-trier.de/db/conf/srds/7CHES International Conference on Cryptographic Hardware andEmbedded SystemsSpringer http://dblp.uni-trier.de/db/conf/ches/8DSN International Conference on Dependable Systems andNetworksIEEE/IFIP http://dblp.uni-trier.de/db/conf/dsn/9RAID International Symposium on Recent Advances in IntrusionDetectionSpringer http://dblp.uni-trier.de/db/conf/raid/10PKC International Workshop on Practice and Theory in PublicKey CryptographySpringer http://dblp.uni-trier.de/db/conf/pkc/11NDSS ISOC Network and Distributed System SecuritySymposiumISOC http://dblp.uni-trier.de/db/conf/ndss/12TCC Theory of Cryptography Conference Springer http://dblp.uni-trier.de/db/conf/tcc/三、C类序号会议简称会议全称出版社网址1WiSec ACM Conference on Security and Privacy in Wireless andMobile NetworksACM http://dblp.uni-trier.de/db/conf/wisec/2SACMAT ACM Symposium on Access Control Models andTechnologiesACM http://dblp.uni-trier.de/db/conf/sacmat/3DRM ACM Workshop on Digital Rights Management ACM http://dblp.uni-trier.de/db/conf/drm/4IH&MMSec ACM Workshop on Information Hiding and MultimediaSecurityACM http://dblp.uni-trier.de/db/conf/ih/5ACNS Applied Cryptography and Network Security Springer http://dblp.uni-trier.de/db/conf/acns/ 6AsiaCCS Asia Conference on Computer and Communications Security ACM http://dblp.uni-trier.de/db/conf/ccs/ 7ACISP Australasia Conference on Information Security and Privacy Springer http://dblp.uni-trier.de/db/conf/acisp/ 8CT-RSA Cryptographer's Track at RSA Conference Springer http://dblp.uni-trier.de/db/conf/ctrsa/9DIMVA Detection of Intrusions and Malware&VulnerabilityAssessmenthttp://dblp.uni-trier.de/db/conf/dimva/10DFRWS Digital Forensic Research Workshop Elsevier http://dblp.uni-trier.de/db/conf/dfrws/ 11FC Financial Cryptography and Data Security Springer http://dblp.uni-trier.de/db/conf/fc/12TrustCom IEEE International Conference on Trust,Security and Privacyin Computing and CommunicationsIEEE http://dblp.uni-trier.de/db/conf/trustcom/13SEC IFIP International Information Security Conference Springer http://dblp.uni-trier.de/db/conf/sec/ 14IFIP WG11.9IFIP WG11.9International Conference on Digital Forensics Springer*/Conferences/ 15ISC Information Security Conference Springer http://dblp.uni-trier.de/db/conf/isw/ 16ICDF2C International Conference on Digital Forensics&Cyber Crime Springer http://dblp.uni-trier.de/db/conf/icdf2c/17ICICS International Conference on Information and CommunicationsSecuritySpringer http://dblp.uni-trier.de/db/conf/icics/18SecureComm International Conference on Security and Privacy inCommunication NetworksACMhttp://dblp.uni-trier.de/db/conf/securecomm/19NSPW New Security Paradigms Workshop ACM http://dblp.uni-trier.de/db/conf/nspw/ 20PAM Passive and Active Measurement Conference Springer http://dblp.uni-trier.de/db/conf/pam/ 21PETS Privacy Enhancing Technologies Symposium Springer http://dblp.uni-trier.de/db/conf/pet/ 22SAC Selected Areas in Cryptography Springer http://dblp.uni-trier.de/db/conf/sacrypt/ 23SOUPS Symposium On Usable Privacy and Security USENIX http://dblp.uni-trier.de/db/conf/soups/ 24HotSec USENIX Workshop on Hot Topics in Security USENIX*/events/中国计算机学会推荐国际学术期刊(软件工程/系统软件/程序设计语言)一、A类序号刊物简称刊物全称出版社网址1TOPLAS ACM Transactions on Programming Languages&Systems ACM http://dblp.uni-trier.de/db/journals/toplas/2TOSEM ACM Transactions on Software Engineering and Methodology ACM http://dblp.uni-trier.de/db/journals/tosem/ 3TSE IEEE Transactions on Software Engineering IEEE http://dblp.uni-trier.de/db/journals/tse/二、B类序号刊物简称刊物全称出版社网址1ASE Automated Software Engineering Springer http://dblp.uni-trier.de/db/journals/ase/ 2ESE Empirical Software Engineering Springer http://dblp.uni-trier.de/db/journals/ese/ 3TSC IEEE Transactions on Service Computing IEEE http://dblp.uni-trier.de/db/journals/tsc/ 4IETS IET Software IET https://dblp.uni-trier.de/db/journals/iet-sen/ 5IST Information and Software Technology Elsevier http://dblp.uni-trier.de/db/journals/infsof/index.html 6JFP Journal of Functional Programming Cambridgehttp://dblp.uni-trier.de/db/journals/jfp/University Press7Journal of Software:Evolution and Process Wiley http://dblp.uni-trier.de/db/journals/smr/ 8JSS Journal of Systems and Software Elsevier http://dblp.uni-trier.de/db/journals/jss/ 9RE Requirements Engineering Springer http://dblp.uni-trier.de/db/journals/re/10SCP Science of Computer Programming Elsevier http://dblp.uni-trier.de/db/journals/scp/11SoSyM Software and System Modeling Springer http://dblp.uni-trier.de/db/journals/sosym/12STVR Software Testing,Verification and Reliability Wiley http://dblp.uni-trier.de/db/journals/stvr/index.html 13SPE Software:Practice and Experience Wiley http://dblp.uni-trier.de/db/journals/spe/三、C类序号刊物简称刊物全称出版社网址1CL Computer Languages,Systems and Structures Elsevier http://dblp.uni-trier.de/db/journals/cl/index.html 2IJSEKE International Journal on Software Engineering andWorld Scientific http://dblp.uni-trier.de/db/journals/ijseke/index.htmlKnowledge Engineering3STTT International Journal on Software Tools for TechnologySpringer http://dblp.uni-trier.de/db/journals/sttt/Transfer4JLAP Journal of Logic and Algebraic Programming Elsevier http://dblp.uni-trier.de/db/journals/jlp/jlap.html 5JWE Journal of Web Engineering Rinton Press http://dblp.uni-trier.de/db/journals/jwe/6SOCA Service Oriented Computing and Applications Springer http://dblp.uni-trier.de/db/journals/soca/7SQJ Software Quality Journal Springer http://dblp.uni-trier.de/db/journals/sqj/8TPLP Theory and Practice of Logic Programming Cambridge Universityhttp://dblp.uni-trier.de/db/journals/tplp/Press中国计算机学会推荐国际学术会议(软件工程/系统软件/程序设计语言)一、A类序号会议简称会议全称出版社网址1PLDI ACM SIGPLAN Conference on Programming Language Design&ImplementationACM http://dblp.uni-trier.de/db/conf/pldi/2POPL ACM SIGPLAN-SIGACT Symposium on Principles of ProgrammingLanguagesACM http://dblp.uni-trier.de/db/conf/popl/3FSE/ESEC ACM SIGSOFT Symposium on the Foundation of Software Engineering/European Software Engineering ConferenceACM http://dblp.uni-trier.de/db/conf/sigsoft/4SOSP ACM Symposium on Operating Systems Principles ACM http://dblp.uni-trier.de/db/conf/sosp/5OOPSLA Conference on Object-Oriented Programming Systems,Languages,andApplicationsACM http://dblp.uni-trier.de/db/conf/oopsla/6ASE International Conference on Automated Software Engineering IEEE/ACM http://dblp.uni-trier.de/db/conf/kbse/ 7ICSE International Conference on Software Engineering ACM/IEEE http://dblp.uni-trier.de/db/conf/icse/ 8ISSTA International Symposium on Software Testing and Analysis ACM http://dblp.uni-trier.de/db/conf/issta/ 9OSDI USENIX Symposium on Operating Systems Design and Implementations USENIX http://dblp.uni-trier.de/db/conf/osdi/二、B类序号会议简称会议全称出版社网址1ECOOP European Conference on Object-Oriented Programming AITO http://dblp.uni-trier.de/db/conf/ecoop/2ETAPS European Joint Conferences on Theory and Practice ofSoftwareSpringer http://dblp.uni-trier.de/db/conf/etaps/3ICPC IEEE International Conference on ProgramComprehensionIEEE http://dblp.uni-trier.de/db/conf/iwpc/4RE IEEE International Requirement Engineering Conference IEEE http://dblp.uni-trier.de/db/conf/re/5CAiSE International Conference on Advanced InformationSystems EngineeringSpringer http://dblp.uni-trier.de/db/conf/caise/6ICFP International Conference on Function Programming ACM http://dblp.uni-trier.de/db/conf/icfp/7LCTES International Conference on Languages,Compilers andTools for Embedded SystemsACM http://dblp.uni-trier.de/db/conf/lctrts/8MoDELS International Conference on Model Driven EngineeringLanguages and SystemsACM,IEEE http://dblp.uni-trier.de/db/conf/models/9CP International Conference on Principles and Practice ofConstraint ProgrammingSpringer http://dblp.uni-trier.de/db/conf/cp/10ICSOC International Conference on Service Oriented Computing Springer http://dblp.uni-trier.de/db/conf/icsoc/11SANER International Conference on Software Analysis,Evolution,and ReengineeringIEEE http://dblp.uni-trier.de/db/conf/wcre/12ICSME International Conference on Software Maintenance andEvolutionIEEE http://dblp.uni-trier.de/db/conf/icsm/13VMCAI International Conference on Verification,Model Checking,and Abstract InterpretationSpringer http://dblp.uni-trier.de/db/conf/vmcai/14ICWS International Conference on Web Services(ResearchTrack)IEEE http://dblp.uni-trier.de/db/conf/icws/15Middleware International Middleware Conference ACM/IFIP/USENIXhttp://dblp.uni-trier.de/db/conf/middleware/16SAS International Static Analysis Symposium Springer http://dblp.uni-trier.de/db/conf/sas/17ESEM International Symposium on Empirical SoftwareEngineering and MeasurementACM/IEEE http://dblp.uni-trier.de/db/conf/esem/18FM International Symposium on Formal Methods FME http://dblp.uni-trier.de/db/conf/fm/19ISSRE International Symposium on Software ReliabilityEngineeringIEEE http://dblp.uni-trier.de/db/conf/issre/20HotOS USENIX Workshop on Hot Topics in Operating Systems USENIX http://dblp.uni-trier.de/db/conf/hotos/。
IEEE会议排名

Rank 1:SIGCOMM: ACM Conf on Comm Architectures, Protocols & Apps INFOCOM: Annual Joint Conf IEEE Comp & Comm SocSPAA: Symp on Parallel Algms and ArchitecturePODC: ACM Symp on Principles of Distributed ComputingPPoPP: Principles and Practice of Parallel ProgrammingRTSS: Real Time Systems SympSOSP: ACM SIGOPS Symp on OS PrinciplesSOSDI: Usenix Symp on OS Design and ImplementationCCS: ACM Conf on Comp and Communications SecurityIEEE Symposium on Security and PrivacyMOBICOM: ACM Intl Conf on Mobile Computing and NetworkingUSENIX Conf on Internet Tech and SysICNP: Intl Conf on Network ProtocolsPACT: Intl Conf on Parallel Arch and Compil TechRTAS: IEEE Real-Time and Embedded Technology and Applications Symposium ICDCS: IEEE Intl Conf on Distributed Comp SystemsRank 2:CC: Compiler ConstructionIPDPS: Intl Parallel and Dist Processing SympIC3N: Intl Conf on Comp Comm and NetworksICPP: Intl Conf on Parallel ProcessingSRDS: Symp on Reliable Distributed SystemsMPPOI: Massively Par Proc Using Opt InterconnsASAP: Intl Conf on Apps for Specific Array ProcessorsEuro-Par: European Conf. on Parallel ComputingFast Software EncryptionUsenix Security SymposiumEuropean Symposium on Research in Computer SecurityWCW: Web Caching WorkshopLCN: IEEE Annual Conference on Local Computer NetworksIPCCC: IEEE Intl Phoenix Conf on Comp & CommunicationsCCC: Cluster Computing ConferenceICC: Intl Conf on CommWCNC: IEEE Wireless Communications and Networking ConferenceCSFW: IEEE Computer Security Foundations WorkshopRank 3:MPCS: Intl. Conf. on Massively Parallel Computing SystemsGLOBECOM: Global CommICCC: Intl Conf on Comp CommunicationNOMS: IEEE Network Operations and Management SympCONPAR: Intl Conf on Vector and Parallel ProcessingVAPP: Vector and Parallel ProcessingICPADS: Intl Conf. on Parallel and Distributed SystemsPublic Key CryptosystemsAnnual Workshop on Selected Areas in CryptographyAustralasia Conference on Information Security and PrivacyInt. Conf on Inofrm and Comm. SecurityFinancial CryptographyWorkshop on Information HidingSmart Card Research and Advanced Application ConferenceICON: Intl Conf on NetworksNCC: Nat Conf CommIN: IEEE Intell Network WorkshopSoftcomm: Conf on Software in Tcomms and Comp NetworksINET: Internet Society ConfWorkshop on Security and Privacy in E-commerceUn-ranked:PARCO: Parallel ComputingSE: Intl Conf on Systems Engineering (**)PDSECA: workshop on Parallel and Distributed Scientific and Engineering Computing with Applications CACS: Computer Audit, Control and Security ConferenceSREIS: Symposium on Requirements Engineering for Information SecuritySAFECOMP: International Conference on Computer Safety, Reliability and SecurityIREJVM: Workshop on Intermediate Representation Engineering for the Java Virtual MachineEC: ACM Conference on Electronic CommerceEWSPT: European Workshop on Software Process TechnologyHotOS: Workshop on Hot Topics in Operating SystemsHPTS: High Performance Transaction SystemsHybrid SystemsICEIS: International Conference on Enterprise Information SystemsIOPADS: I/O in Parallel and Distributed SystemsIRREGULAR: Workshop on Parallel Algorithms for Irregularly Structured ProblemsKiVS: Kommunikation in Verteilten SystemenLCR: Languages, Compilers, and Run-Time Systems for Scalable ComputersMCS: Multiple Classifier SystemsMSS: Symposium on Mass Storage SystemsNGITS: Next Generation Information Technologies and SystemsOOIS: Object Oriented Information SystemsSCM: System Configuration ManagementSecurity Protocols WorkshopSIGOPS European WorkshopSPDP: Symposium on Parallel and Distributed ProcessingTreDS: Trends in Distributed SystemsUSENIX Technical ConferenceVISUAL: Visual Information and Information SystemsFoDS: Foundations of Distributed Systems: Design and Verification of Protocols conferenceRV: Post-CA V Workshop on Runtime VerificationICAIS: International ICSC-NAISO Congress on Autonomous Intelligent SystemsITiCSE: Conference on Integrating Technology into Computer Science EducationCSCS: CyberSystems and Computer Science ConferenceAUIC: Australasian User Interface ConferenceITI: Meeting of Researchers in Computer Science, Information Systems Research & StatisticsEuropean Conference on Parallel ProcessingRODLICS: Wses International Conference on Robotics, Distance Learning & Intelligent Communication Systems International Conference On Multimedia, Internet & Video TechnologiesPaCT: Parallel Computing Technologies workshopPPAM: International Conference on Parallel Processing and Applied MathematicsInternational Conference On Information Networks, Systems And TechnologiesAmiRE: Conference on Autonomous Minirobots for Research and EdutainmentDSN: The International Conference on Dependable Systems and NetworksIHW: Information Hiding WorkshopGTVMT: International Workshop on Graph Transformation and Visual Modeling TechniquesIEEE通信领域的主要会议介绍:GLOBECOM (IEEE Global Communications Conference )ICASSP (IEEE International Conference on Acoustics, Speech, and Signal Processing)ICC (IEEE International Conference on Communications )INFOCOM (IEEE Conference on Computer Communications)MILCOM (IEEE Military Communications Conference )OFC (IEEE Optical Fiber Communication Conference and Exposition)PIMRC (IEEE International Symposium on Personal, Indoor and Mobile Radio Communications) SPAWC (IEEE Workshop on Signal Processing Advances in Wireless Communications)VTC (IEEE Vehicular Technology Conference)WCNC (IEEE Wireless Communications & Networking Conference)CSNDSP (IEEE Communication Systems, Networks & Digital Signal Processing)CTW (IEEE Communications Theory Workshop)ICACT (IEEE International Conference Advanced Communication T echnology)ICCCAS (IEEE International Conference of Communications, Circuits and Systems)INCC (IEEE International Networking and Communications Conference)ISCC (IEEE Symposium on Computers and Communications)ISSSTA (IEEE International Symposium on Spread Spectrum Techniques and Applications) ISWCS (IEEE International Symposium on Wireless Communication Systems)ISIT (IEEE International Symposium on Information Theory)CCNC (IEEE Consumer Communications & Networking Conference)1ACM SIGCOMM: ACM Conf on Communication Architectures, Protocols & AppsACM的旗舰会议之一,也是网络领域顶级学术会议,内容侧重于有线网络,每年举办一次,录用率约为10%左右。
计算机新技术(ACT)

李舟军教授:领导的团队承担了国家自然科学基金、国家863计划、国家密码发展基金、博士学科点专项科研基金、242课题、115、1025课题等国家和部委级科研项目。
在这些项目的资助下,在安全协议形式化分析、基于身份的密钥协商协议研究、P2P网络攻防技术、软件安全性分析与安全漏洞检测、数据挖掘与文本挖掘、社交网络与舆情分析等方面进行了深入的研究,取得了一系列具有国际先进水平的重要研究成果。
在包括IEEE Transactions on Knowledge and Data Engineering、Information Sciences 、Computer & Security、The Computer Journal、IEEE Communication Letters、Journal of Wireless Communications and Mobile Computing、Information Management & Processing、Journal of World Wide Web、Neurocomputing等重要SCI期刊和SIGCOMM 2009、ICNP 2009、P2P 2009、ICPP2010、FMSE 2008、ACL2010、SIGKDD2010、ACM Multimedia2011、Coling2012、SIGIR 2013、AAAI2013等重要国际会议发表学术论文180篇,150余篇论文被SCI和EI收录,并得到国际同行的关注和引用,其中获得第32届欧洲信息检索大会(ECIR 2010)的最佳论文奖(The Best Paper Award)。
此外,设计和实现了一个基于进程代数和逻辑程序的安全协议验证工具SPVT;在此基础上,设计并实现了一个自适应选择验证方法的高效协议验证工具SPVT-II,设计并实现了一个有效的时间敏感安全协议验证工具T-SPVT。
胰岛素样生长因子-1在儿童性早熟中的诊断价值

胰岛素样生长因子-1在儿童性早熟中的诊断价值林祥泉;杨晓红【摘要】目的:探讨胰岛素样生长因子-1(IGF-1)在儿童性早熟中的诊断价值。
方法收集特发性中枢性性早熟(ICPP)组101例、单纯性乳房早发育(SPT)组96例,同时收集青春发育前健康女童85例为对照组。
用化学发光法检测ICPP组、SPT组及对照组的IGF-1和LH峰值水平。
结果 ICPP组血清IGF-1水平[(361.26±108.55)ng/m1]明显高于SPT组[(232.62±81.14) ng/m1]和对照组[(221.44±88.91)ng/m1],差异有统计学意义(P<0.05);SPT 组IGF-1水平与对照组比较,差异无统计学意义(P>0.05); ICPP组IGF-1水平与LH峰值呈显著正相关(r2=0.6181,P<0.01);IGF-1>298.58ng/ml对诊断ICPP的灵敏度、特异度、阳性预测值分别为94.6%、96.0%、95.1%。
结论 IGF-1水平的测定可作为ICPP诊断的参考指标,对ICPP和SPT有鉴别诊断意义。
%Objective To discuss the diagnostic value of the insulin-like growth factor-1 (IGF-1) in children precocious pu-berty. Methods A total of 101 girls with idiopathic central precocious puberty (ICPP), 96 girls with simple premature thelarche (SPT) were collected as case groups, and 85 healthy girls in prepuberty were collected as the control group. The level of IGF-1 and the peak of luteinizing hormone (LH) in the serum of all the enrolled subjects were detected by using Chemiluminescence. Results The level of IGF-1 in ICPP groups were 361.26±108.55ng/ml, obviously higher than that in SPT groups (232.62±81.14ng/ml) and in controls groups(221.44±88.91ng/ml).The difference above was statistically significant(P<0.05), there was no signifi-cantly difference in the levels of IGF-1between SPT group and controls group (P>0.05); the levels of IGF-1 have a remarkable positive correlation with the peak of LH(r2=0.6181,P<0.01);the IGF-1>298.58ng/ml has the degree of sensitivity(94.6%), specific (96.0%) and positive predictive value (95.1%) for the diagnosis of ICPP. Conclusion The serum concentrate of IGF-1 has a value of reference index in the diagnosis of ICPP and a significance in distinguishing between ICPP and SPT.【期刊名称】《实验与检验医学》【年(卷),期】2015(000)004【总页数】3页(P427-429)【关键词】特发性中枢性性早熟;胰岛素样生长因子-1;促黄体生成素【作者】林祥泉;杨晓红【作者单位】福建省福州儿童医院/福建医科大学教学医院福建福州350005;福建省福州儿童医院/福建医科大学教学医院福建福州350005【正文语种】中文【中图分类】R585;R446.62近年来,儿童性早熟的发生率逐年增高,已成为常见的小儿内分泌系统疾病之一,女孩明显多于男孩,男女比例为1/23~1/3[1]。
中枢性(真性)性早熟诊治指南(学组2007)

中枢性(真性)性早熟诊治指南中华医学会儿科学分会内分泌遗传学代谢学组性早熟是儿科内分泌系统的常见发育异常,为了规范中枢性(真性)性早熟的诊断和治疗,中华医学会儿科学分会内分泌遗传代谢学组进行了专题讨论,制定以下指南供临床参考。
[定义]性早熟是指女童在8岁前,男童在9岁前呈现第二性征的发育异常性疾病。
中枢性性早熟(CPP)是缘于下丘脑提前增加了促性腺激素释放激素(GnRH)的分泌和释放量,提前激活性腺轴功能,导致性腺发育和分泌性激素,使内、外生殖器发育和第二性征呈现。
CPP 又称为GnRH依赖性性早熟,其过程呈进行性发展,直至生殖系统发育成熟。
[病因]1.中枢神经系统器质性病变;2.外周性性早熟转化而来。
3.特发性CPP(ICPP)无器质性病变。
女性患儿约80%~90%为ICPP;男性患儿则相反,80%以上是器质性的。
[诊断]应首先确定是否为GnRH依赖性性早熟,继之进行病因的鉴别诊断。
一、诊断依据1.第二性征提前出现:女童8岁前,男童9岁前。
2.血清促性腺激素水平升高达青春期水平。
(1)促性腺激素基础值:如果第二性征已达青春中期程度时,血清促黄体生成素(LH)基础值可作为初筛,如>5.0IU/L,即可确定其性腺轴已发动,不必再进行促性腺激素释放激素(GnRH)激发试验。
(2)GnRH激发试验:本试验对性腺轴功能已启动而促性腺激素基础值不升高者是重要的诊断手段,GnRH可使促性腺激素分泌释放增加,其激发峰值即可作为诊断依据。
GnRH激发试验方法:常规用GnRH (戈那瑞林)2.5 μg/kg或100 μg/m2静脉注射,于0 min、30 min、60 min时采血样,测血清LH和卵泡刺激素(FSH)浓度(GnRHa经典试验方法的120 min可省略),合成的GnRH类似物(GnRHa)的激发作用比天然者为强,峰值在60~120 min出现,但不推荐其在常规诊断中使用。
诊断CPP的LH激发峰值的切割(cut-point)值:取决于所用的促性腺激素检测方法,用放射免疫法测定时,LH峰值在女童应>12.0 IU/L、男童>25.0 IU/L、LH峰/FSH峰>0.6~1.0时可诊断CPP;用免疫化学发光法(ICMA)测定时,LH峰值>5.0 IU/L、LH峰/FSH峰>0.6(两性)可诊断CPP;如LH峰/FSH峰>0.3,但<0.6时,应结合临床密切随访,必要时重复试验,以免漏诊。
性早熟ppt课件
性
非特异性真性性早熟
早
同性性早熟
熟 的
假性性早熟(非GnRH依赖性、外周性) 异性性早熟
分
类
单纯性乳房早发育
不完全性性早熟(部分性性早熟) 单纯性阴毛早发育
单纯性早初潮
完整最新版课件
9
中枢性性早熟
特发性 下丘脑垂体病变
错构瘤、神经母细胞瘤 松果体病等,感染、外伤 头颅化疗、放疗等 先天畸形 脑积水、蛛网膜囊肿 中隔-视中隔发育不全 鞍上囊肿等 其他 原发性甲状腺功能减低症 肿瘤(分泌LH的腺瘤、 星形细胞瘤、胶质瘤等)
——中枢性性 早熟
完整最新版课件
13
完整最新版课件
女孩 ICPP 3岁
14
实验室检1查5
1.骨龄测定 2.B超检查 3.CT、MRI检查 4.血、尿激素检查
T、E2、T3、T4、FSH、LH LHRH刺激试验、尿17-酮类固醇测定
完整最新版课件
鉴别诊断 16
诊断过程主要是排除其他类型性早熟
英文关键词4
Puberty
(青春期)
precocious puberty
(性早熟)
Central precocious puberty( CPP)(中枢性性早熟)
完整最新版课件
定义 分类 临床表现 实验室检查 鉴别诊断 治疗
目录
5
完整最新版课件
定义 6
定义:女孩在8岁以前、男孩在9岁以前呈现性发育 征象,即为性早熟
完整最新版课件
外周性性早熟
肾上腺疾病 肾上腺皮质增生症、肾上腺瘤/癌等
性腺肿瘤 卵巢颗粒-泡膜细胞瘤 畸胎瘤、睾丸间质细胞瘤等
外源性 含雌激素药物、食物、化妆品等
其他 McCune-Albright综合征 肝胚细胞癌等
性早熟的诊治进展

性早熟的诊治进展性早熟(Precocious Puberty;Sexual Precocity)是常见的儿童发育异常,具有异质性,对患儿生理和心理上有双重不利影响。
调查数据表明在过去一个多世纪以来,初潮年龄发生了显著的变化,19世纪初期,初潮约在17岁左右,而到了20世纪则出现在13岁左右。
从19世纪70年代开始,欧洲和美国女童月经出现的年龄标准均有所降低[1]。
性早熟一般指男童在9岁前,女童在8岁前呈现第二性征[2]。
根据是否提前启动下丘脑-垂体-性腺轴(HPGA)及临床表现可分为中枢性性早熟(CPP)、外周性性早熟(PPP)及部分性性早熟[3]。
男女儿童中性早熟的发生率约为0.6%,女性多于男性,女性约占全部病例的3/4[4]。
近年来性早熟尤其是特发性性早熟发病率的较快增长可能与下列因素有关:(1)随着生活水平的提高,儿童普遍营养充足,生长发育呈提前和加速之趋势;(2)环境污染与环境内分泌干扰物的影响或误服性激素类药物等;(3)滥用含有激素成分或具有激素样效应的保健品、滋补品,如花粉、蜂王浆、鸡胚等;(4)遗传因素; (5)不良文化传媒等社会心理因素的影响:在很多音像制品和书刊等大众传媒中过多出现的性内容, 可使孩子性启蒙提前, 对性早熟有一定诱发作用。
1.病因与分类:1.1中枢性性早熟:中枢性性早熟(central precocious puberty, CPP)又称为真性性早熟,具有与正常青春发育类同的下丘脑-垂体-性腺轴(HPGA)发动、成熟的程序性过程,直至生殖系统成熟;即由下丘脑提前分泌和释放促性腺激素释放激素(GnRH),激活垂体分泌促性腺激素使性腺发育并分泌性激素,从而使内、外生殖器发育和第二性征呈现;同时有体型改变、身高生长加速、心理及行为的变化过程,可有神经系统症状和体征。
1.1.1 中枢神经系统器质性病变[5]:其中最常见的是颅内肿瘤。
(1)颅内肿瘤:如颅咽管瘤、星形细胞瘤、生殖细胞瘤、室管膜瘤、胶质瘤、神经纤维瘤1型、Sturge-Weber综合症、下丘脑错构瘤和各种松果体肿瘤,其中松果体区域的肿瘤是导致CPP的最常见颅内肿瘤。
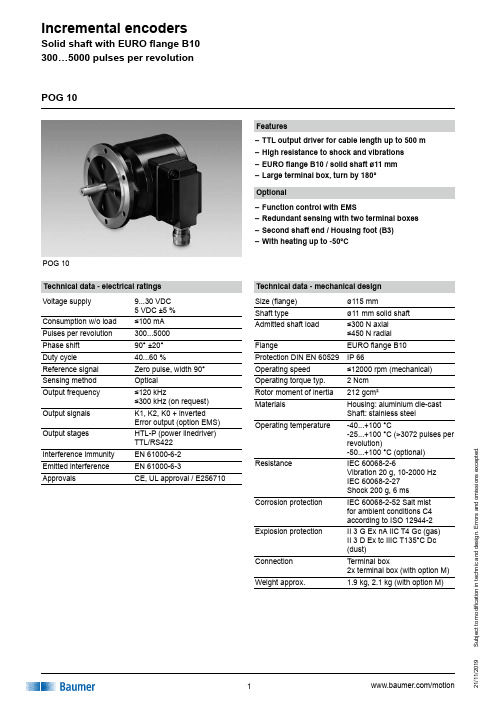
Baumer POG 10 增量编码器商品说明书
POG 10Features–TTL output driver for cable length up to 500 m –High resistance to shock and vibrations –EURO flange B10 / solid shaft ø11 mm –Large terminal box, turn by 180°Technical data - electrical ratings Voltage supply 9...30 VDC 5 VDC ±5 %Consumption w/o load ≤100 mA Pulses per revolution 300...5000Phase shift 90° ±20°Duty cycle 40...60 %Reference signal Zero pulse, width 90°Sensing method OpticalOutput frequency ≤120 kHz≤300 kHz (on request)Output signals K1, K2, K0 + inverted Error output (option EMS)Output stages HTL-P (power linedriver) TTL/RS422Interference immunity EN 61000-6-2Emitted interference EN 61000-6-3ApprovalsCE, UL approval / E256710POG 10Technical data - mechanical design Size (flange)ø115 mmShaft typeø11 mm solid shaft Admitted shaft load ≤300 N axial ≤450 N radial FlangeEURO flange B10Protection DIN EN 60529IP 66Operating speed ≤12000 rpm (mechanical)Operating torque typ. 2 Ncm Rotor moment of inertia 212 gcm²MaterialsHousing: aluminium die-cast Shaft: stainless steelOperating temperature-40...+100 °C-25...+100 °C (>3072 pulses per revolution)-50...+100 °C (optional)ResistanceIEC 60068-2-6Vibration 20 g, 10-2000 Hz IEC 60068-2-27 Shock 200 g, 6 ms Corrosion protection IEC 60068-2-52 Salt mist for ambient conditions C4 according to ISO 12944-2Explosion protectionII 3 G Ex nA IIC T4 Gc (gas) II 3 D Ex tc IIIC T135°C Dc (dust)Connection Terminal box2x terminal box (with option M)Weight approx.1.9 kg,2.1 kg (with option M)Optional–Function control with EMS–Redundant sensing with two terminal boxes –Second shaft end / Housing foot (B3) –With heating up to -50°CS u b j e c t t o m o d i fi c a t i o n i n t e c h n i c a n d d e s i g n . E r r o r s a n d o m i s s i o n s e x c e p t e d .S u b j e c t t o m o d i fi c a t i o n i n t e c h n i c a n d d e s i g n . E r r o r s a n d o m i s s i o n s e x c e p t e d .POG 10Part number POG10DNMounting type EURO flange B10B3Housing foot B3Voltage supply / signalsI 9...30 VDC / output stage HTL with inverted signals TTL 5 VDC / output stage TTL with inverted signals R 9...30 VDC / output stage TTL with inverted signalsPulse number - see tableOutput signals DN K1, K2, K0Redundant sensingWithout redundant sensingM With redundant sensing (not possible at version with housing foot B3)EMS - Enhanced Monitoring System Without EMS .2With EMSAccessoriesConnectors and cables HEK 8Sensor cable for encoders Mounting accessoriesK 35Spring washer coupling for solid shaft ø6...12 mm K 50Spring washer coupling for solid shaft ø11...16 mm K 60Spring washer coupling for solid shaft ø11...22 mm Diagnostic accessories 11075858Analyzer for encoders HENQ 1100Other pulse numbers on request.Incremental encoder Pulse number 30010002048409650010242500500051212003072Terminal assignmentPOG 10Output signals+UB Voltage supply (for the device); Ground (for the signals); Earth ground (housing)K1; A; A+ Output signal channel 1K1; A; A- Output signal channel 1 invertedK2; B; B+ Output signal channel 2 (offset by 90° tochannel 1)K2; B; B- Output signal channel 2 (offset by 90° tochannel 1) invertedK0; C; R; R+ Zero pulse (reference signal)K0; C; R; R- Zero pulse (reference signal) invertedErr; Err- Error output (option EMS)dnu Do not useTerminal significanceSubjecttomodificationintechnicanddesign.Errorsandomissionsexcepted.S u b j e c t t o m o d i fi c a t i o n i n t e c h n i c a n d d e s i g n . E r r o r s a n d o m i s s i o n s e x c e p t e d .DimensionsPOG 10 - Version with housing foot (B3)POG 10 (POG 10.2, POG 10 M, POG 10.2 M) - Version with Euro flange (B10)POG 10。
icp-20100例程

icp-20100例程
ICP (Iterative Closest Point) 算法是一种广泛用于点云配准的方法。
在2010年,David A. Fellner 和John A. Stetson 发表了一篇关于使用ICP 算法进行点云配准的教程,该教程详细描述了如何实现一个基于Python 的ICP 程序。
由于我不具备搜索特定代码的能力,所以无法提供您提到的"icp-20100例程"。
不过,如果您希望了解ICP 的基本原理和实现,我建议您参考这篇教程:David A. Fellner and John A. Stetson, "An Introduction to Iterative Closest Point Algorithms for 3D Shape Reconstruction", Tutorial Notes, Second International Symposium on 3D Data Processing, Visualization, and Transmission (3DPVT'10), pages 513-526, 2010.
此外,开源的点云库(PCL)也提供了ICP 的实现,并提供了详细的文档和示例代码。
如果您使用的是PCL,您可以查阅其官方文档以获取更多信息。
如果您能提供更多关于"icp-20100例程" 的详细信息,我可能能提供更有针对性的帮助。
光谱CT多参数定量评估胃腺癌病理分化程度及Lauren分型

光谱CT多参数定量评估胃腺癌病理分化程度及Lauren分型叶露1,李之珺1,高绪杰1,李绪斌1,刘海威2,叶兆祥1*1.天津医科大学肿瘤医院放射科,国家恶性肿瘤临床医学研究中心,天津市肿瘤防治重点实验室,天津市恶性肿瘤临床医学研究中心,天津300060;2.飞利浦(中国)投资有限公司,北京100600;*通信作者叶兆祥【基金项目】国家自然科学基金青年科学基金(82001909);天津市医学重点学科(专科)建设项目(TJYXZDXK-009A)【摘要】目的探讨光谱CT多参数定量评估胃腺癌组织学分化程度及Lauren分型的价值。
资料与方法回顾性分析天津医科大学肿瘤医院2019年10月—2021年12月经手术病理证实的134例胃腺癌患者的临床资料及光谱CT图像,测量病灶动脉期(AP)、静脉期(PP)40 keV低能级CT值、碘浓度、标准化碘浓度(nIC)及有效原子序数,比较不同分化程度及Lauren分型间各光谱参数的差异,将有统计学意义的指标绘制受试者工作特征曲线评价诊断效能并确定最佳阈值,再行二元Logistic回归分析得到诊断低分化胃癌和Lauren分型弥漫型胃癌的独立预测因子。
结果AP及PP低分化胃癌各光谱参数均显著高于中高分化组(P<0.001),其中nICPP鉴别低分化胃癌诊断价值最高,曲线下面积为0.786,诊断阈值为0.52,敏感度为62.5%,特异性度80.4%,nICPP为诊断低分化胃癌的独立预测因子(OR=0.005,95% CI 0.000~0.469,P=0.022)。
AP、PP弥漫型胃癌各光谱参数均高于混合型及肠型胃癌,PP各光谱参数差异均有统计学意义(P<0.05),其中nICPP鉴别弥漫型胃癌诊断价值最高,曲线下面积为0.704,诊断阈值为0.55,敏感度为69.8%,特异度为71.4%,nICPP为诊断弥漫型胃癌的独立预测因子(OR=0.041,95% CI 0.002~0.903,P=0.043)。
特发性中枢性性早熟儿童血清IGF-1与体格发育的关系

特发性中枢性性早熟儿童血清IGF-1与体格发育的关系摘要】目的:探讨胰岛素生长因子1(IGF1)与特发性中枢性性早熟儿童(ICPP)的体格发育的关系;方法:对106例ICPP女童,正常对照组女童70例测定身高、体重,记录性发育形态指标,采用TW3法计算骨龄;化学发光免疫法测定其血清IGFl;结果:ICPP患儿IGF1水平明显高于对照组(P<0.05),且在不同的发育期,其水平均有显著性差异(P<0.05);IGF1与骨龄(BA)、身高、体重、BMI均呈正相关(P均<0.001);结论:ICPP患儿体内IGF1明显高于对照组,且其在患儿骨骼成熟、生长加速的过程中起着促进作用;IGF1可作为肥胖儿童发生性早熟的监测指标之一。
【关键词】特发性中枢性性早熟胰岛素生长因子1 体格发育【中图分类号】R725 【文献标识码】A 【文章编号】1672-5085(2013)50-0072-02儿童的体格发育受多方面因素影响,其中促生长轴起着重要的作用,而胰岛素生长因子(IGF1)作为此轴的关键介导者,发挥促生长、促分化的作用,近年来,许多研究证明下丘脑-垂体-性腺(HPGA)轴与促生长轴存在相互作用,同样,在HPGA轴提前启动的特发性中枢性性早熟(ICPP)的儿童体内IGF1水平明显升高[1],而目前关于IGF1对于生长发育异常(尤其体格发育异常)的ICPP的关系的研究相对较少,本研究通过测定ICPP女童血清IGF1水平,探讨IGF1对ICPP女童体格发育的影响。
现报告如下。
1.资料与方法1.1 对象收集2012年9月至2013年9月期间,湖南省儿童医院儿童保健所就诊的106例6~10岁ICPP女童(均符合中枢性性早熟诊治指南[2] 的标准);其中tanner2期70例;3期27例,4期9例女童;平均年龄分别为7.6岁;8.6岁;9.3岁。
健康对照组70名,平均年龄分别7.8岁;两组均排除性腺、肾上腺及中枢神经系统肿瘤等疾病。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Achieving Fair or Differentiated Cache Sharing in Power-Constrained ChipMultiprocessorsXiaorui Wang,Kai Ma,and Yefu WangDepartment of Electrical Engineering and Computer ScienceUniversity of Tennessee,Knoxville,TN37996{xwang,kma3,ywang38}@AbstractLimiting the peak power consumption of chip multipro-cessors(CMPs)has recently received a lot of attention.In order to enable chip-level power capping,the peak power consumption of on-chip L2caches in a CMP often needs to be constrained by dynamically transitioning selected cache banks into low-power modes.However,dynamic cache re-sizing for power capping may cause undesired long cache access latencies,and even thread starving and thrashing, for the applications running on the CMP.In this paper,we propose a novel cache management strategy that can limit the peak power consumption of L2caches and provide fair-ness guarantees,such that the cache access latencies of the application threads co-scheduled on the CMP are im-pacted more uniformly.Our strategy is also extended to pro-vide differentiated cache latency guarantees that can help the OS to enforce the desired thread priorities at the archi-tectural level and achieve desired rates of thread progress for co-scheduled applications.Our solution features a two-tier control architecture rigorously designed based on ad-vanced feedback control theory for guaranteed control ac-curacy and system stability.Extensive experimental results demonstrate that our solution can achieve the desired cache power capping,fair or differentiated cache sharing,and power-performance tradeoffs for many applications.1IntroductionIn recent years,limiting the peak power consumption of chip multiprocessors(CMPs)has received a lot of attention [11,27,16,30].With the increased levels of core integration and transistor density,the gap between the peak and aver-age power consumption of a CMP widens and leads to un-necessarily more expensive cooling,packaging,and power supplies in the CMP design.To effectively reduce the costs while allowing higher computing densities with more cores and caches integrated on a single die,power capping can be enforced at different levels of a CMP for maximized perfor-mance under given power constraints.In addition,to en-able chip-level power capping,it is preferable that power can beflexibly shifted among the CPU cores and the shared on-chip L2caches within a CMP for performance optimiza-tion.Therefore,the peak power consumption of on-chip L2 caches in a CMP often needs to be constrained below a bud-get that is determined at runtime.An effective way of controlling the power of L2caches is to dynamically switch selected cache units(e.g.,ways, banks,or lines)between high-and low-power modes[7,17]. For example,recent work[3]has proposed power-efficient management schemes for the non-uniform cache architec-ture(NUCA)designed to reduce wire delays.However,as a tradeoff,putting cache units into low-power modes may cause undesired long cache access latencies for the applica-tions running on the CMP.As cache access latencies con-tribute significantly to the number of CPU stall cycles and thus are directly related to application performance such as IPC(instructions per cycle),how to select cache units for power capping is challenging.Simplistic solutions may al-locate too few cache units to some applications,resulting in undesired thread starving and thrashing.Therefore,it is im-portant to provide desired latency guarantees for the applica-tion threads running on the cores in a CMP,even when the active L2cache size is being dynamically changed to enforce a runtime power budget.There can be different ways to provide cache access latency guarantees in a power-constrained CMP.First,a straightforward way is to provide absolute latency guaran-tees for some applications based on their performance needs (e.g.,IPC requirements).However,since the active L2cache size can be significantly reduced at runtime to enforce a low power budget in scenarios such as thermal emergencies,the available active cache size can become too small to guaran-tee the absolute latencies for any applications.Therefore,it may not be feasible to provide absolute latency guarantees in power-constrained CMPs.The second and a more rea-sonable way is to provide fairness guarantees such that the cache access latencies of the applications are impacted more uniformly by cache resizing.As a result,execution time fair-ness,i.e.,how uniform the execution times of co-scheduled threads are changed,can be better achieved.While existing work addresses fairness in terms of cache miss rate[14],we choose to control the average access latencies because the la-tency of each single access can vary significantly in NUCA caches due to wire delays.As a result,miss rate may not accurately indicate the impact on application performance.Fair latency guarantees can also be extended to provide differentiated cache access latencies,since the applications co-scheduled on different cores in a CMP may have different performance needs or priorities.Differentiated latency guar-antees can allow higher priority applications to have shorterlatencies and so less performance degradation under the im-pacts of cache resizing.Differentiated cache sharing is im-portant because it can help the OS to enforce the desired thread priorities.The OS normally enforces thread priori-ties by assigning more time slices to higher priority threads, with the assumption that more time slices can lead to higher rates of progress among all the co-scheduled threads.How-ever,as cache implementation is traditionally thread-blind and priority-blind,a novel scheme is needed to help higher priority threads to achieve shorter cache latencies and so higher rates of progress at the architectural level.Differ-entiated latency guarantees can also be useful in accelerat-ing critical threads to reduce load imbalance.Existing work on thread criticality relies mainly on per-core dynamic volt-age and frequency scaling(DVFS)and task stealing[4,6]. However,some applications are not suitable for task stealing while some memory-intensive applications cannot be accel-erated by per-core DVFS alone.In addition,per-core DVFS is not supported by most existing CMPs and can be expen-sive for future CMPs[23].In this paper,we demonstrate that differentiated latency guarantees can provide another way to achieve desired rates of progress for application threads.As cache latencies may have small impacts on the performance of some applications,differentiated latency control should be combined with per-core DVFS and task stealing to accel-erate threads based on application characteristics.In this paper,we propose a novel L2cache manage-ment strategy that can enforce the desired power budget for on-chip L2caches in a power-constrained CMP by cache re-sizing.In order to achieve fair or differentiated cache sharing under the impacts of power capping,our strategy dynam-ically partitions the available active cache size among the threads on the cores for fair or differentiated cache access latencies.A key challenge in implementing fair or differ-entiated cache sharing in a power-constrained CMP is that the cache partition to achieve the desired degree of fairness or differentiation depends on two uncertain factors:work-loads that are unknown a priori and the total cache size that is dynamically varying.A main contribution of this paper is the introduction of a coordinated feedback control architec-ture for adapting cache partitioning and resizing such that the desired latency fairness or differentiation among threads on different cores can be achieved,while the cache power con-sumption can be controlled.Specifically,this paper makes the following major contributions:•We propose a novel L2cache management strategy that provides fair or differentiated cache sharing for threads running on a CMP whose power consumption must be constrained.While prior research in thisfield focuses primarily on reducing the power consumption of L2 caches,to our best knowledge,this paper presents the first study to limit the peak power consumption of L2 caches.•We design a two-tier coordinated feedback control ar-chitecture to simultaneously limit the peak cache power consumption and achieve the desired latency differen-tiation/fairness among different threads by dynamically conducting cache resizing and partitioning.•We use advanced feedback control theory as a theoreti-cal foundation to design and coordinate the two control loops for theoretically guaranteed control accuracy and system stability.The rest of this paper is organized as follows.Section2 introduces the proposed two-tier control architecture.Sec-tion3presents the modeling,design,and analysis of the latency fairness controller.Section4discusses the cache power controller.Section5provides the implementation de-tails of our control solution.Section6presents our experi-mental results.Section7reviews the related work.Finally, Section8summarizes the paper.2Two-tier Cache Control Architecture In this section,we provide a high-level description of our cache control system architecture,which features a two-tier controller design.As shown in Figure1,the primary control loop,i.e., the L2cache power control loop,limits the peak L2cache power consumption under the desired budget(e.g.,90%of the peak power consumption)by manipulating the total num-ber of active L2cache banks.Note that we use cache banks in NUCA caches as our actuation unit,but our controller can work withfiner actuation granularities,such as cache lines or blocks,with only minor changes and slightly more hard-ware overhead.The key components in the cache power con-trol loop include a power controller,a power monitor,and a cache resizing modulator.The control loop is invoked peri-odically.In each control period of the cache power control loop,the controller receives the total power consumption of the L2caches from the power monitor.Note that although the power consumption of L2caches cannot be directly mea-sured in today’s CMPs,it can already be precisely estimated with on-chip programmable event counters for control pur-pose[12].The cache power is the controlled variable of this loop.Based on the difference between the measured power value and the desired power budget,the controller then computes the number of cache banks in the chip that should stay active in the next control period,which is the manipulated variable.The controller then sends the number to the cache resizing modulator.The modulator changes the power modes of selected cache banks accordingly.There is only one cache power control loop in a CMP.The secondary control loop,i.e.,the latency fairness/d-ifferentiation control loop,achieves the desired latency fair-ness or differentiation for the threads on the cores by con-ducting cache partitioning at runtime on a smaller timescale. As shown in Figure1,in a CMP with N CPU cores,we have N−1latency fairness/differentiation control loops. There are two ways to implement the latency control loops. Thefirst way is that we select a reference thread on a core and then control the latencies of other threads relative to the latency of this reference thread.The second way is thatFigure1.Two-tier L2cache control architecture for power capping and fair/differentiated sharing.we can have a control loop to control the latency ratio be-tween the two active threads on every two adjacent cores. Since the controlled variable is the relative latencies among threads,the two implementations accomplish the same con-trol functions.We plot the second way in Figure1for eas-ier illustration.Specifically,to achieve fairness,we try to achieve approximately the same cache access latency for the active threads running on all the cores,despite the dynam-ically varying total cache size.Likewise,to achieve differ-entiation,we maintain the cache latency of a higher-priority thread shorter than that of a lower-priority thread.Note that previous fair cache sharing solutions[14,34]try to man-age the performance impacts of co-scheduling relative to the case when the applications are running alone on a CMP.As a result,they need to precisely know which applications are currently running on the CMP and then use corresponding off-line profiled performance measurements as references.A key advantage of our solution is that we do not assume such a prior knowledge and is thus more realistic.To han-dle multi-threaded applications,we can put cores running the same applications into groups and then conduct dynamic L2 cache partitioning among the groups.The key components in a latency fairness/differentia-tion control loop for two cores include a latency fairness/dif-ferentiation controller,two latency monitors for the threads on the two cores,and a shared cache partitioning modulator. The control loop is also invoked periodically and its period is selected such that multiple cache access requests can be received during a control period and the actuation overhead is small compared with the period.The following steps are invoked at the end of every control period:1)The latency monitors of the two cores measure the average absolute la-tencies of the two threads in the last control period and send the values to the controller through the feedback lane;2)The controller calculates the relative latency of the two threads, which is the controlled variable of the control loop.The dif-ference between the actual relative latency of the two threads and the desired value is the control error;3)The controller then relies on control theory to compute the ratio between the numbers of cache banks to be allocated to the two threads,which is the manipulated variable of the control loop.The absolute number of cache banks can be calculated based on the total number of active banks determined by the power control loop;4)The cache partitioning modulator then al-locates the desired number of cache banks to each thread. Note that we assume a cache bank is not shared by multiple threads in this prototype design,but this assumption can be easily relaxed in a real implementation by usingfiner actua-tion granularities with more hardware overhead.Clearly,the two control loops need to be coordinated based on advanced control theory,because every invocation of the cache power control loop may change the total number of active cache banks of the CMP,and thus affect the stability of the latency control loops.Therefore,in order to achieve stability for the two-tier control architecture,we adopt the method recently proposed in[31]to configure the period of the power control loop to be longer than the settling time of the latency fairness/differentiation control loops.This guar-antees that the latency loop can always enter its steady state within one control period of the power control loop,so that the two control loops are decoupled and can be designed in-dependently.As long as the two control loops are stable in-dividually,the coordinated control system is stable.Since the core of each control loop is its controller,we introduce the design and analysis of the two controllers in the next two sections,respectively.The details of cache re-sizing and partitioning in NUCA caches and the implemen-tation details of other components in the control loops are discussed in Section5.3Latency Fairness/Differentiation Controller In this section,we present the modeling,design and analysis of the cache latency controller.Given a CMP with N cores,as an example,we present the design process of the cache latency fairness/differentia-tion controller between Core i and Core j.The controller design between other pairs of cores is the same.Wefirst in-troduce the following notation.l i(k)is the absolute access latency of the thread running on Core i in the k th control pe-riod.l(k)is the relative latency ratio between the two threads on Core i and Core j.Specifically l(k)=l i(k)/l j(k).L is the reference latency ratio between the two threads on Core i and Core j for the desired fairness(if L=1).To achieve differentiation,the ratio L can be set(e.g.,by the OS)pro-portionally to the thread priorities or progress rates.It is important to note that L is not necessarily a constant and can be changed at runtime based on thread progress rates.For example,the thread criticality predictor in[4]can be used to predict how critical each of the co-scheduled threads is, such that proper reference ratios can be assigned to accel-erate critical threads at different times.The focus of this paper is on providing a control scheme that can achieve the desired differentiation specified by the OS.We plan to inves-tigate advanced algorithms for the OS to dynamically deter-mine the reference ratio based on the desired thread priorities and/or progress rates in our future work.e(k)is the differ-ence between the reference ratio and the actual latency ratio. Specifically e(k)=L−l(k).c i(k)is the number of active cache banks allocated to the thread on Core i in the k th con-trol period.c(k)is the ratio between the numbers of cache banks partitioned to the two threads on Core j and Core i, specifically c(k)=c j(k)/c i(k).In the k th control period,given the current access la-tency ratio l(k),the control goal is to dynamically choose cache partition ratio c(k)such that l(k+1)can converge to the set point L after afinite number of control periods.3.1System ModelingIn order to have an effective controller design,it is important to model the dynamics of the controlled system, namely the relationship between the controlled variable(i.e., l(k))and the manipulated variable(i.e.,c(k)).However,a well-established physical equation is unavailable to capture the relationship between the latency ratio of two threads and the ratio of cache banks partitioned to them,due to the com-plexity of cache systems in today’s computers.Therefore, we use a standard approach called system identification[8] to this problem.Based on control theory,we use the fol-lowing standard difference equation to model the controlled system:l(k)=n1j=1a j l(k−j)+n2j=1b j c(k−j)(1)where n1and n2are the orders of the system output(i.e., l(k))and system input(i.e.,c(k)),respectively.a j and b j are system parameters whose values need to be determined by system identification.The model can be generally explained from the systems perspective.The current latency ratio between two threads on two cores,l(k),is mainly determined by three factors:1) the ratio l(k−j)in the previous n1control periods,2)the cache partitioning actions c(k−j)happened in the previous n2control periods,and3)the cache latency properties of the workloads,which are captured by the system parameters a j and b j through system identification.The system parameters may change for two reasons:1)workloads may have phase changes at runtime,resulting in different latency properties and2)the system may run different workloads.The vari-ations of the system parameters must be theoretically ana-lyzed to guarantee system stability.For system identification,we need tofirst determine the right orders for the system,i.e.,the values of n1and n2in the difference equation(1).The order values are normally a compromise between model simplicity and modeling accu-racy.In this paper,we test different typical system orders. For each combination of n1and n2,we use white noise to generate a series of system inputs in a random fashion to stimulate the system and then measure the system output in each period.Based on the collected data,we use the Least Squares Method(LSM)to iteratively estimate the values of parameters a i and b i.Based on the method introduced in [22],we select four typical applications(mcf,gap,ammp, and crafty)in the SPEC CPU2000benchmark suite as our workloads.mcf represents a workload with a data set larger than the available cache size.gap has a large number of com-pulsory misses.ammp continuously benefits as the cache size is being increased.crafty has a small working set but needs to frequently request data from L2caches.We com-bine the four applications in10groups to conduct the system identification experiments.Based on our results,we choose to have the orders of n1=1and n2=1because this combi-nation has a reasonably small error while keeping the model orders low.Therefore,the nominal system model resulted from our system identification is:l(k)=a1l(k−1)+b1c(k−1)(2) where a1=0.595and b1=0.954are system parameters resulted from our experiments with the10groups of appli-cations.To verify the accuracy of the model,we change the seed of the white noise signal to generate a different se-quence of system inputs and then rerun the experiments to validate the results of system identification by comparing the actual system outputs and the estimated outputs based on the nominal model(2).Our results show that differences are sufficiently small.Note that the real model of the system may be different from the nominal model(2)at runtime due to workload dif-ferences or parameter variations.To quantitatively analyze the impact of workload variations on the controller perfor-mance,in an extended version of this paper[29],we model the variations caused by different workloads and prove that the system controlled by the controller designed based on the nominal model can remain stable as long as the variation of a1is within the range of[−0.69a1,1.18a1].3.2Controller Design and AnalysisThe goal of controller design is to achieve system stabil-ity,zero steady-state error,and short settling time.Follow-ing standard control theory[8],we design a Proportional-Integral(PI)controller to achieve the desired control per-formance.An important advantage of PI control is that it can provide robust control performance despite considerable modeling errors.In addition,PI control has a small compu-tational overhead and is thus suitable to be implemented inthe cache system.A more sophisticated PID(Proportional-Integral-Derivative)controller is not used because it is de-termined by the system model(2)that a derivative(D)term is not needed for the desired control performance.Having a derivative term unnecessarily might amplify the noise in the cache latency ratio.The designed PI controller in the Z-domain is:K p(z−K i)F(z)=5.1Simulation EnvironmentWe extend the SimpleScalar simulator with static-NUCA cache configuration[19]as our simulation environ-ment.In our simulations,we configure the CMPfloor plan to have4Alpha21264-like cores(65nm)with a frequency of5GHz.We calculate the leakage power using HotLeak-age[33]and calculate dynamic power using Wattch(built on CACTI)[5].In all our experiments,we use the SPEC CPU2000benchmark suite(V1.0)to test our two-tier cache control solution.The working temperature of the L2cache is set to80◦C to simulate a typical real CMP setting based on the study in[9].The L2cache is configured to be16MB (8-way set associative).The main memory latency is300 cycles.The L2cache replacement algorithm is LRU(Least Recently Used).The L1i-cache and d-cache are both32KB (2-way,64byte block size)with a3-cycle hit latency.The detailed simulation configuration parameters are provided in the extended version of this paper[29].5.2Implementation of Control LoopsWe now introduce the implementation details of each component in the two control loops.Cache Access Latency Monitor.We add two counters for each core:one counter counts the number of stall cycles induced by cache accesses while the other counts the total number of cache accesses.We use the average access la-tencies in one control period to calculate the relative latency between the threads on two cores.Cache Power Monitor.We use HotLeakage to calcu-late the leakage power consumption of the L2caches and Wattch to calculate the dynamic power.We then use the sum of the two parts as our cache power reading.Note that the power consumption of L2caches can be precisely estimated based on measurements feasible on physical chips[12].Controllers.As introduced in Sections3and4,both the latency controllers and cache power controller are PI con-trollers.Each controller is invoked once in one of its control period to receive the measured value of its controlled vari-able(i.e.,relative latency or cache power)from the moni-tor,and then conduct its control algorithm to compute the corresponding control output.As shown in the controller functions(4)and(7),each invocation of the controller only executes a couple of multiplications and additions.There-fore,the computational overhead of the controllers is small enough to be implemented in a real cache system.The con-trol period of the latency control loop is set to1M CPU cy-cles as a compromise between the system response speed and actuation overhead.A longer control period may fail to promptly react to some system dynamics while a shorter pe-riod may lead to increased actuation overhead.Based on our stability analysis,the control period of the cache power con-trol loop is set to10times that of the latency control loop, i.e.,10M cycles,in order to decouple the two controllers for global system stability.In a real system,there can be two ways to implement our controllers.First,as discussed in Section3,the compu-tational overhead of the two designed controllers is negligi-ble.As a result,the controllers can be implemented on chip (as in Intel ItaniumII)to allow cache managment on afine timescale.Second,our controllers can also be implemented in service processorfirmware(as in IBM POWER7)and so their power and computational overheads will not directly affect the main CMP.This implementation is moreflexible since thefirmware is programmable but the control periods cannot be too small due to the communication delay between the service processor and the main CMP.Cache Resizing and Partitioning Modulator.In or-der to implement cache resizing and partitioning for NUCA caches in a CMP with N cores,we add lg(N+1)flag bits for each cache bank,which have only negligible gate overhead to be implemented in real CMP chips.If a cache bank is al-located to Core i,we set theflag to the value i.A non-zero value indicates that the bank should be active.If the cache bank is not allocated to any core,we switch the cache bank to a low-power mode(i.e.,inactive).We use the Gated-Vdd technology[21]to implement the power mode switch of a cache bank.We assume that a cache bank is not shared by multiple threads in this prototype design,but afiner actua-tion granularity(e.g.,cache lines or blocks)is also available [13]and can be used in our control solution for even better control accuracy with a slightly higher hardware overhead.Since the NUCA caches have non-uniform cache access latency related to the wire length,we have a cache resizing policy to ensure that the active cache banks of each core are always the ones that are closest to the cache I/O port of the core.We adopt this policy for three reasons.First,in NUCA caches,a cache bank that is farther away from the core nor-mally has a longer access latency due to the longer wire.Sec-ond,a longer routing distance from the core may also lead to more routing hops,an increased probability of more con-tention,and thus reduced on-chip network routing capability. Third,if the dynamic data migration policy is enforced in the NUCA caches,cache banks that are far away from cores may get much less frequently accessed[2].Therefore,switching those cache banks to the low-power mode will lead to con-siderable power savings with only slight impacts on cache performance.After receiving the desired total active cache size from the power controller and the desired cache size ratios among threads on different cores from the latency controllers,the resizing and partitioning modulator calculates the number of active cache banks to be allocated to each thread.The modu-lator then uses the cache resizing policy to enforce the cache allocation.To implement the resizing policy,we maintain a table for each thread that records the cache banks allocated to the thread.In addition,in order to ensure that the active cache banks of a thread on a core are the ones that have the shortest distances to the core,the active cache area around the core needs to expand or shrink in both dimensions of the cache bank array.Therefore,we keep track of the cache row and column that are farthest from the core.Each core will expand or shrink in the farthest row and column alter-natively to enforce the desired cache bank allocation.Af-ter the modulator allocates the active banks to the thread on。
