GP overview 详细介绍
孕产史和生育史标记系统解说

孕产史和生育史标记系统解说随着辅助生殖技术的拓展和孕产监测的普及,许多新出现的情况混杂了原有的孕产标记系统,使得原本就颇具争议的标记出现了更多的变异。
中国现行的教科书甚至没有对这些命名进行过详细的阐释,因此有必要对当前普遍使用的孕产标记系统进行充分的解说。
孕产史用孕次和产次系统(GP系统)标记。
孕次(Gravidity,G)指的是母体经历妊娠的次数,只存在一种争议就是如何精确划定“妊娠”。
妊娠始于受精卵,但受精卵并非是妊娠的开始。
“妊娠”是用来评估母体的状态而非妊娠物的状态,因此“妊娠”指母体怀有妊娠物,也就是妊娠物与母体结合,更精确地说是滋养细胞侵入子宫内膜,即以“着床”为分界事件,临床可检测指标就是血HCG升高>5U/L或尿HCG阳性。
何谓“妊娠物”?从细胞学的角度说就是因为妊娠是滋养细胞侵入子宫内膜,因此凡是含有侵入子宫内膜的滋养细胞的,均可以定义为妊娠物,不管这种妊娠物是正常妊娠,还是葡萄胎。
绒癌作为妊娠的并发症,并不算作G,因为其绒毛膜细胞起源于前次妊娠的滋养细胞。
分泌HCG的肿瘤也不算做G,因为缺乏受精过程。
但值得一提的是,临床记录到的G小于实际发生的G,因为相当一部分生化妊娠被当做月经推迟等情况而忽略了。
换言之,生化妊娠作为血清/尿HCG阳性而无超声学发现的流产,因早孕试纸的广泛使用和辅助生殖的推广应用,被越来越多地发现,因此也算G。
产次(Parity,P)指的是母体经历娩出“基本存活胎儿”过程的次数。
P的争议普遍存在,其一与不同医疗水平下定义“基本存活胎儿”存在巨大差异有关,其二与一些人将分娩过程的次数和分娩物的个数相混淆有关。
譬如在美国,当前可认为>20W或体重>500g的个体即算作“基本存活胎儿”,因为在美国的医疗环境下,这样的胎儿多数能够存活,而20W或500g 以下的胎儿几无存活;又如在英国,>24W胎儿被认为是“基本存活胎儿”;在中国,我们仍沿用>28W为基本存活胎儿。
GP卡规范快速入门
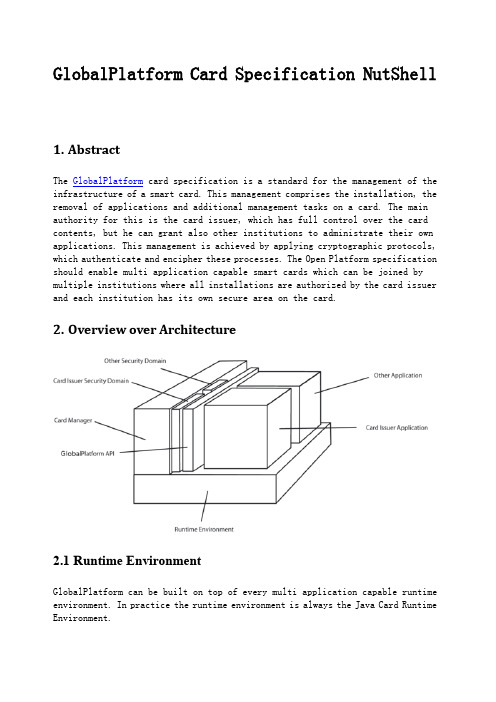
GlobalPlatform Card Specification NutShell1.AbstractThe GlobalPlatform card specification is a standard for the management of the infrastructure of a smart card. This management comprises the installation, the removal of applications and additional management tasks on a card. The main authority for this is the card issuer, which has full control over the card contents, but he can grant also other institutions to administrate their own applications. This management is achieved by applying cryptographic protocols, which authenticate and encipher these processes. The Open Platform specification should enable multi application capable smart cards which can be joined by multiple institutions where all installations are authorized by the card issuer and each institution has its own secure area on the card.2.Overview over Architecture2.1 Runtime EnvironmentGlobalPlatform can be built on top of every multi application capable runtime environment. In practice the runtime environment is always the Java Card Runtime Environment.2.2 Security DomainA Security Domain is a protected area on a smart card. To this Security Domain are assigned applications, which can use cryptographic services it offers. By default only the Security Domain of the card issuer exists on a card. If another institution wants to have its own Security Domain, e.g. for having its own secure application environment or managing its own applications, such a domain can be created with the help of the card issuer. Institutions managing their own applications are also referred to as Application Providers.2.3 Card ManagerThe card manager is the central component of a GlobalPlatform card. Every service is executed by it and it offers interfaces to use its services internal through the GlobalPlatform API and external through APDU commands. In addition the Card Manager includes the Security Domain of the card issuer, due to the fact that it can also own applications on the card.2.4 GlobalPlatform APIThe GlobalPlatform API gives applications on the card access to certain management functions of the Card Manager and the possibility to authenticate the communication partner and using a secure channel with it within the current active Security Domain.3.Concepts and FunctionalityFor a use case diagram illustrating the common usages see the following figure:3.1 Mutual Authentication and Negotiated Security LevelTo access the management functions of a card it is necessary to authenticate the host and the card against each other. Only in an early life cycle state of teh card, this is not necessary. If the Security Domain of the card issuer is not the default selected application or another Security Domain should be the context of the communication session it must be chosen by executing a SELECT command, which must be given the AID of the Security Domain. An AID is a hexadecimal identifier for application concerning card content. The most common default AID of the Security Domain of the card issuer is A0 00 00 00 03 00 00 00.Each Security Domain owns at least a set of three 3DES keys, the Secure Channel Keys, which must also be known to the host system. These three keys are the Encryption Key, which is used to generate an encryption session key for encrypting the transmitted messages, the Message Authentication Key, to generate a MAC session key for ensuring the integrity of transmitted messages and the Key Encryption Key to encrypt newly transferred keys. The first command sent to the card is the INITIALIZE UPDATE command. The INITIALIZE UPDATE command transmits a random number and states which key set version should be used during thefollowing session and at which key index the three successive keys are found. The values 0 for the key set version and 0 for the key index are used to denote the first available keys. The random number is encrypted with the Encryption Key in 3DES ECB mode and the resulting card cryptogram is sent back with an own random number to challenge the host. If the card cryptogram is verified successfully the host encrypts the random number of the card also in 3DES in ECB mode and sends the host cryptogram back in an EXTERNAL AUTHENTICATE command. The card verifies also this host cryptogram. With the EXTERNAL AUTHENTICATE command the host proposes a security level during the communication of this session. This security level can be plain text, where no integrity or confidentiality is given, the integrity of each message can be protected by appending a MAC using the MAC session key or in addition to the integrity also the confidentiality of the messages can be assured by using the encryption session key.3.2 Loading, Installation and Removal of contentsThe most noticeable task is the management of the card content. These are the loading, the installation and the removal of card contents. These tasks are performed in the context of a Security Domain.3.2.1 Loading and InstallationThe complete loading and installation happens in four steps:3.2.1.1 INSTALL [for load]The INSTALL [for load] command prepares the card to a following LOAD command. With this command the AID of the Load File Data Block is transmitted and the AID of the Security Domain, in which the Load File Data Block will be installed. A Load File Data Block is a data block, which contains one or more applicationsor libraries. In the case of the Java Card Runtime Environment this is equivalent to a package which can be saved in a format like the CAP format or the more common IJC format. Also parameters concerning the resource allocation on the card are indicated. These are the necessary space for storing the Load File Data Block referred to as Non Volatile Code Space Limit, the needed space of persistent memory to store the resulting data of the application, referred to as Non Volatile Data Space Limit and the amount of volatile memory space, which is needed during execution of the application, referred to as Volatile Data Space Limit. The most cards are only interested in the Non Volatile Code Space Limit. Optional a Load File DAP can be given. A Load File DAP is a hash to verify to correct transmission of a Load File. To accomplish this, the whole Load File is hashed by SHA-1. A Load File can contain in addition to a Load File Data Block prefixed Load File Data Block DAPs. The point DAP Verification and Mandated DAP Verification should clarify this. If all given arguments are checked, which is the case, if no content on the card has the same AID like this Load File Data Block, the associated Security Domain does exist and the requested resource allocations can be satisfied.3.2.1.2 LOADThe LOAD command transfers the Load File in one or multiple messages depending on the Load File size to the card. If a Load File DAP was contained in the INSTALL [for load] command, the validity of this hash is verified. From the contained Load File Data Block a so called Executable Load File is created with the same AID as the Load File Data Block. An entry of the Executable Load file is created in the registry of the Card Manager and its associated Security Domain. The registry contains information of all installed contents, its privileges and its associated Security Domains.3.2.1.3 INSTALL [for install]This command installs an application from an Executable Load File. Therefor the AID of the Load File Data Block, which is the Executable Load File, the AID of the one to be installed content in the Executable Load File and the intended AID of application instance is declared. The one to be installed content equals in the context of the Java Card an applet class. The AID of the application instance corresponds to the AID of the applet class instance which is running the whole card life and which is used to select the application. In addition the resource concerning parameters like in INSTALL [for load] for the application are given. Most cards are only interested in the amount of the Non Volatile Data Space Limit. Another mandatory argument is the application privileges. Some notable privileges here are the Security Domain privilege, which states that the installed application is a Security Domain and the privilege, that the application is the default selected application, which means that it is selected implicitly byconnecting to a card. Other privileges are mentioned in the following paragraphs. To the installed application a maximum of 32 bytes of install parameters can be passed. In the Java Card terminology the install method of the applet is called with these parameters. If the Executable Load File is existent on the card, the application is contained in the Executable Load File, the application instance AID is not used by another content on the card and the resource requirements can be satisfied, the Card Manager creates an application from the Executable Load File, an entry for the application instance in the registry and associates its Security Domain.3.2.1.4 INSTALL [for make selectable]The INSTALL [for make selectable] command makes the application available to be selected. The AID of the application instance and the applet privileges are required. If the AID exists the application instance is marked as SELECTABLE in its life cycle status. A life cycle state of an application defines the selectable state of an application. E.g. after the INSTALL [for install] command the application is in the state INSTALLED. A complete overview of the life cycle states is given in the paragraph Life Cycle Management. The last to steps can be combined in a INSTALL [for install and make selectable] command.3.2.2 Removal3.2.2.1 DELETEA DELETE command deletes content on a card by its AID. Before this is done it is checked if the AID exists in the registry and if this content is not referenced by another installed content on the card. E.g. installed applications depend on their Executable Load File. If the content can be deleted its entry is removed from the registry and all persistent is marked as available.3.3 Delegated ManagementBy default only the Security Domain of the card issuer is allowed to load, install and remove contents on a card. To enable also other Application Providers with their Security Domain on the card to manage their contents the privilege of Delegated Management was introduced. This privilege must be given to the Security Domain by installation time. In order that the card issuer keeps the control of the card each content change must be authorized by him. Content which is loaded and installed on a card must be signed by a digital signature of the card issuer. The loading of content is granted by the verification of a Load DAP, also referredto as Load Token, during the INSTALL [for load] phase. The installation of content is granted by the verification of a Install DAP, also termed Install Token, in the INSTALL [for install and make selectable] command. Separate INSTALL [for install] and INSTALL [for make selectable] commands are not possible. These DAPs are calculated with RSA PKCS#1 over the parameters given in the INSTALL [for install and make selectable] command. To verify the signature the Security Domain of the card issuer must has access to a public RSA key, referred to as Token Key. In the case of a DELETE command no DAP is necessary. The execution of the loading, installation and removal is confirmed by the return of the Receipt. A Receipt is the proof to the card issuer that the owner of the Security Domain with Delegated Management privilege has carried out the operation. The Receipt is a MAC with a variation of 3DES in CBC mode. To calculate this Receipt the Security Domain of the card issuer must know a 3DES key for the Receipt generation. This key is termed Receipt Key. There is one Receipt type according to each loading and installation process. Every Receipt signs some card unique data together with a confirmation counter. The card unique data is some data which makes this card distinguishable from other cards. The confirmation counter assures that no former Receipt can be used to forge the confirmation. The Load Receipt signs in addition the Executable Load File AID created by the LOAD command and the associated Security Domain AID. The Install Receipt signs also the Executable Load File AID and the application instance AID. The computation of the Delete Receipt includes the AID of the deleted content.3.4 DAP Verification and Mandated DAP VerificationDAP Verification permits another institution as the card issuer to verify the integrity of a Load File Data Block. This can be useful if a Security Domain has not the ability to load content to the card or if a controlling entity may require that all content is certified. At installation time the Security Domain must obtain the DAP Verification privilege and after its installation a DAP Verification Key, a 3DES key or public RSA key, must be deposited in it to verify the integrity of the loaded content. To check the integrity a Load File Data Block DAP must be created by calculating a digital signature with RSA PKCS#1 or a MAC with a variation of 3DES in CBC mode over the Load File Data Block. The result of this operation is also called DAP Block. This DAP Block is prefixing the Load File Data Block and transferred as Load File with the LOAD command. The DAP Block is verified by the Security Domain with its key. If the DAP Block is valid the loading is granted. The difference between DAP Verification and Mandated DAP verification is that the Card Manager only contacts the Security Domain with the first privilege if the Security Domain is the associated Security Domain of the content to be loaded while a Security Domain with the second privilege must always verify the content which is loaded to the card.3.5 Key ManagementTo support the management function a variety of keys are necessary. Apart from the mandatory Encryption Key, Message Authentication Key and Key Encryption Key the Security Domain of the card issuer can have a Token Key and a Receipt Key, referred to as Delegated Management Keys, to support Delegated Management. A Security Domain or another institution can have a DAP Verification Key.3.5.1 PUT KEYThe PUT KEY command is used to populate the Security Domain with keys or replace existing keys. The pure Open Platform specification does not provide a way to delete keys. Beneath the possibility to put or replace Secure Channel and Delegated Management Keys, single keys can also be managed. The PUT KEY command must be passed one or multiple keys, the key set version in which the key(s) should be added or replaced and the key index within this key set version where the first key should be stored. For Delegated Management Keys there may be restriction on the key set version number. On some card it is possible to view key information or delete keys. If the card does not offer a way of deleting keys and view key information the tracking of available keys is the responsibility of the owner of the Security Domain.3.5.2 Viewing Key InformationIf a card supports the retrieval of key information the GET DATA command is used to obtain key information templates of the selected Security Domain. Key information templates contain the key set version number the key belongs to, the key index of the key and the key type.3.6 DELETE [key]Another optional enhancement is the deletion of keys in a Security Domain. Necessary parameters are the key set version number and the key index. It is possible to delete a whole key set version by giving the key set version number and a key set index of zero. The same is possible for keys with the same key index by giving a key set version number of zero.3.7 Life Cycle ManagementTo reply to security violations each application, Executable Load File and the Card Manager have a life cycle state.For the card issuer Security Domain those values can be OP READY, INITIALIZED, SECURED, LOCKED and TERMINATED. The difference between OP READY and INITIALIZED is only administrative and both mean, that the card is ready for receiving command, but is not ready for card holder. The state INITIALIZED can mean that already a key set version is installed. The state SECURED means that the card is ready for the card holder. A key set version is installed and all communication must take place in a secure channel. The last three states are irreversible. The state LOCKED may mean that a security violation has occurred and no application except the Card Manager can be selected and no key and content change is allowed to happen. The state TERMINATED means the end of the life of the card and the card shall only respond to a GET DATA command. Usually only the Security Domain of the card issuer can lock or terminate the card. Other Security Domains must have the Card Manager Lock privilege and Card Terminate privilege respectively.An Executable Load File can only be in the state LOADED.An application has three possible life cycle states. These are INSTALLED, SELECTABLE and LOCKED. If an application should not be selectable the application can be LOCKED. An application can only be unlocked by its Security Domain.A Security Domain can be in state INSTALLED, SELECTABLE, PERSONALIZED and LOCKED. The state PERSONALIZED means that the Security Domain is equipped with some personal content like keys. A Security Domain can be associated with content in this state. For a Security Domain the state LOCKED means, that only the Security Domain of the card issuer can unlock it.3.7.1 GET STATUSWith this command the life cycle status of the Card Manager, Executable Load Files and applications can be obtained. Additional the application privileges are returned.3.7.2 SET STATUSThe command SET STATUS is used to set the life cycle state of an installed content. The AID of the card content to set the life cycle state must be given. Some lifecycle states can only be set with a method of the Open Platform API by an application on the card.3.8 Card DataThere is a variety of card data objects. The Open Platform specification proposes only that the CPLC data should be retrievable. CPLC is an abbreviation for Card Production Life Cycle. This data object contains information about the production process of the card like the operating system or the ICC manufacturer. The Card issuer BIN data contains usually the serial number of the card. Apart from that the user defined Card issuer data can be used e.g. for deriving the keys. Some other possible values can be the available resources like EEPROM space.3.8.1 GET DATAThe GET DATA command is used to retrieve the above data. Each card data object has a tag name which is used to access it.3.8.2 PUT DATAPossible writable data can be stored with the PUT DATA command. The same tag names for the card data objects like in GET DATA are used.。
01_Overview(概述)

JohnnyHuang © Extech Corp. 2011
Page 3
概述
JohnnyHuang © Extech Corp. 2011
Page 4
特色 全新的互交设计环境加快创பைடு நூலகம்速度
Solid Edge ST 是目前市场上最完善的基于特征的 2D/3D CAD系统。此系统将直接建模的速度与灵活性 与尺寸驱动设计的准确性结合在一起,提供最快、最 灵活的设计体验和全新的建模方式。 在同步建模技术的支持下,软件允许直接针对模型进 行设计工作,更快、更流畅地创建设计和进行编辑, 而且无需扩大当前的设计团队就能以比竞争对手更快 的速度进行创新。
JohnnyHuang © Extech Corp. 2011
Page 8
设计界面
JohnnyHuang © Extech Corp. 2011
Page 9
特色 全新的互交设计环境加快创新速度
JohnnyHuang © Extech Corp. 2011
Page 10
文件转换
JohnnyHuang © Extech Corp. 2011
Page 11
文件转换
JohnnyHuang © Extech Corp. 2011
Page 12
Exercises
JohnnyHuang © Extech Corp. 2011
Page 13
JohnnyHuang © Extech Corp. 2011
Page 7
特色 用2D的简单性驾驭3D的强大功能
由于软件允许在同一环境中使用统一的二维和三维建 模命令进行设计,因此它提供了一个二维和三维混合 设计的平台。在二维中使用的那些熟悉的命令也出现 在三维环境中。用户可以利用对二维设计系统中各项 常见技术的深刻理解,进行直接的设计和编辑。
GPRS原理概述

Doc Nr GPRS OVERVIEW
Composed by Ren Mingming
Approved by Zhang He
21/81
ACTION
• GPRS系统体系结构 • 手机和接入侧基本知识
• 网元基本功能
• 接口协议栈流程介绍 • GPRS移动性管理
• GPRS会话管理
• GPRS网络的发展
4/81
ACTION
什么是GPRS?
• 通用分组无线业务(General Packet Radio Service) 的英文缩写 • GPRS是在GSM技术的基础上提供的一种端到端分组 交换业务 • GPRS最大限度重用已有的GSM网络基础设施 • GPRS提供高效的无线资源利用率 • GPRS提供高达171.2Kbps的无线接入速率 • 与已有的GSM电路交换系统有很多交互 • GPRS系统基于标准的开放接口
C/I值与信道编码
• The GPRS have four channel coding schemes – CS1 9.05 kbps – CS2 13.4 kbps – CS3 15.6 kbps – CS4 21.4 kbps
•Rate
•CS4 •CS3 •CS2 •CS1
•C/I
Doc Nr GPRS OVERVIEW
Approved by Zhang He
23/81
ACTION
Gb数据传输平面
Application IP/X25 IP/X25
Application IP/X25
relay
SNDCP LLC RLC MAC Physical Layer RLC MAC Physical Layer
SNDCP
overview用法 -回复

overview用法-回复Overview是一个常用的词汇,在不同领域中都有各自的用法。
在本文中,我们将以"overview用法"为主题展开讨论,并一步一步回答与之相关的问题。
首先,我们来解释一下overview的含义。
Overview是英语中的一个名词,意为“概述”、“概览”或“总览”。
在不同情境中,它可以表示对某一主题、项目、计划或情况的概括性描述或总结。
在学术研究、商业报告、项目规划等场景中,overview通常是为了提供一个整体的把握,让读者或听众能够快速了解核心要点。
接下来,让我们一步一步回答与overview用法相关的问题。
1. 什么时候使用overview?- 当你需要对某个主题进行总体描述或概览时,你可以使用overview。
这可以帮助读者或听众快速获取信息,以便更全面地理解或评估相关内容。
2. 如何撰写一个好的overview?- 首先,明确你要描述的主题。
你需要深入了解这个主题,并将其核心要点整理出来。
要避免在overview中过于详细或涉及次要内容,因为这可能会导致信息混乱。
- 其次,使用简洁、明确的语言对主题进行总结。
尽量使用简单易懂的词汇和短句,避免使用过多的行话或专业术语,以确保广大受众都能理解。
- 最后,在概述中强调主要亮点和关键信息,可以通过使用粗体、强调句子或其他标记方法来突出重点。
3. 在哪些场景下常见到overview的使用?- 在学术研究中,研究论文通常会在摘要部分提供一个overview,即对研究目的、方法、结果和结论的简要总结。
- 在商业报告或市场分析中,overview可以提供公司业绩、市场趋势、竞争对手等方面的综合概述。
- 在项目规划或产品开发中,overview可能包含项目的目标、时间表、预算以及关键的里程碑事件等。
4. 如何在演讲或演示中有效使用overview?- 在演讲或演示中,overview可以用于开场白或导言部分,帮助听众快速掌握主题的要点和结构。
SAP PP OverView

20
L
SAP PP overview
BOM分类
单一 BOM 变体 BOM 多重 BOM
单一的 BOM 代表 单一材料
相似的材料表现 藉着在一个之上的 变体 BOM
BOM 表现可能是多 样的材料 举例来说不同的材料 而且不同数量
SAP PP overview
BOM有效性
有效期 有效范围
物料
SAP AG
SAP PP overview
内容
PP overview 组织要素 主数据
生产计划
生产车间控制
SAP PP overview
MRP总览
MRP
非独立需求 销售 订单 计划独立需求
预留
计划 订单 转换
生产订单
采购请求 采购 订单 仓库
交货计划
SAP PP overview
生产计划
成品
销售订单 / PIR 计划订单
工厂 1 工厂 1 有效性的起始日期 有效性的起始日期
物料 BOM 物料 BOM
物料
工厂 2 工厂 2
SAP AG
2
有效性的终止日期 有效性的终止日期
SAP PP overview
BOM报表
BOM 展开
单阶逐层展开 多层展开 BOM 汇总
物料反查
单阶反查 多阶反查
A
B
C
SAP PP overview
SAP PP overview
PP物料主数据
字段示例:
生产调度员
生产计划参数文件 物料 工作计划 交货容差数据
SAP PP overview
BOM
物料清单(BOM)
物料清单是由构成一个产品或部件的子件组成的完整的结构化清 单。、数量、计量单位和损耗等数据。 物料单是部件完整、正式的结构化清单,组成 物料清单的用途 一个产品或装配。该清单包括每个部件的项目 MRP 计算相关需求 计算产品成本( 号 、 数量和计量单位。 BOM 物 料 成 本) 生产的物料供应
HomePlug_GreenPHY_Overview[1]
![HomePlug_GreenPHY_Overview[1]](https://img.taocdn.com/s3/m/6ad550edaeaad1f346933f0c.png)
The HomePlug® Green PHY (GP) Specification is anew powerline technology designed to the specific requirements of Smart Grid applications, while interoperating with HomePlug AV products and the IEEE 1901 standard. It was developed in cooperation with major utilities with the goal of dramatically reducing power consumption and cost.The Green PHY Specification will be published and available for download from HomePlug’s website in June, 2010.HomePlug Green PHY SpecificationHomePlug GP targets smart grid applications such as HVAC/thermostats, smart meters, home appliances and plug-in electric hybrid vehicles. HomePlug GP has been developed in cooperation with major utility companies including Consumers Energy, Duke Energy, Pacific Gas & Electric, and Southern California Edison to help optimize the specification for real-world deployments.“The Smart Grid continues to be a major focus for HomePlug with the GP specification at the center ofour efforts,” said Rob Ranck, president of the HomePlug Powerline Alliance. “Our new GP spec meets the specific performance and interoperability requirements solicited from utilities and appliance manufacturers.”“HomePlug GP is a trimmed down, lower data rate, lower power version of HomePlug AV, making it easier for multiple silicon suppliers to produce Green PHY chips with relative ease and speed. Backwards interoperability allows use of current HomePlug AV chips to deploy prototypes and early implementations now.”HomePlug GP has ample bandwidth to support critical functionality such as IP networking, but with power consumption an am estimated 75% lower than HomePlug AV, with similar cost savings projected. Certified chips and products are expected to ship in the first half of 2011. HomePlug GP was developed to be a certification profile of the IEEE 1901 PLC standard. This means that products based on HomePlug GP will be fully interoperablewith HomePlug AV and IEEE 1901 products and will be included in HomePlug’s well-established Compliance and Interoperability Certification Logo program.Working with the IndustryThe HomePlug Powerline Alliance is committed to working with the industry in support of Smart Grid interoperability initiatives. Atheros Communications, Inc. has been awarded a $4.5 million grant by the U.S. Department of Energy for HomePlug GP development. Atheros is the only semiconductor company to receive such a grant under the $3.4 billion Smart Grid Investment Grant program for modernization of the U.S. power grid. The HomePlug Powerline Alliance has also worked with the ZigBee Alliance to develop the ZigBee/HomePlug Smart Energy Profile, a commonapplication layer enabling interoperability between applications which may run in ZigBee wireless and HomePlug powerline devices. The ZigBee/HomePlug Smart Energy Profile has also been named in theNational Institute for Standards and Technology Smart Grid interoperability standards roadmap.HomePlug devices account for over 80 percent of the world’s broadband powerline communications market, and over 45 million devices have shipped to date.About the Smart GridDevelopment of a smart grid involves overlaying a unified two-way communications capability on the existing power delivery infrastructure to provide the right information to the right entity – whether appliances in homes, transmission and distribution equipment or utilities – at the right time to take actions beneficial to the entire system. The smart grid should optimize power supply and delivery, minimize losses, be “self-healing” and enable next-generation energy efficiency and demand response applications.The Smart Grid infrastructure requires an open standard for two-way communications between many different transmission and distribution devices, appliances and other end-use devices, along with an advanced metering infrastructure (AMI), the two-way communications between a utility and its customers, and smart interconnections to distributed energy resources.The emerging Smart Grid will facilitate charging stationsfor plug-in hybrid electric vehicles (PHEVs) that can be plugged into electrical outlets – ultimately at homes and public places – for recharging.The Smart Grid will enable dynamic energy management that, along with smart energy-efficient end-use devices, advanced building control systems, and smart distributed energy resources will yield energy savings and peak demand reductions greater than what could otherwise be realized. A Smart Grid would potentially link all of these elements together and provide constant communications between a utility and its customers to optimize energy efficiency and mitigate emissions.The Alliance operates the powerline networking industry’s largest Compliance and Interoperability Certification Program to ensure true multi-vendor co-existence and interoperability. It has certified more than 190 products and will begin certifying IEEE 1901 products in 2010.Smart thermostats that communicate over home electrical wiring give users more control over their energy usage.Key Features of HomePlug Green PHY HomePlug Green PHY will be interoperable with HomePlug AV, IEEE 1901 (expected to become a certification profile of IEEE 1901) and the HomePlug AV2 Specification for next generation broadband (now under development).HomePlug Green PHY Enables Smart Homes While the smart grid comprises a variety of new technologies that would allow more efficient usage of energy on a local and national scale, it will ultimately enable Home Area Networks(HANs) inside homes and give homeowners more control over their individual energy usage and electricity rates. A HAN inside the home means home appliances can communicate with the power meter to determine themost economical times to run.The smart home’s HAN communicates through the smart meter to the smart grid WAN.In addition to Green PHY-enabled smart meters, consumers can expect the development of in-home displays to allow them to program their big Green PHY-enabled appliances. In addition to many different “smart” appliances in the home, companies are developing Programmable Communicating Thermostats (PCTs) that put monitoring and control of the HVAC system in the consumer’s hands. Also, charging stations for homes and public places are in development; these will also have powerline communications capability to inform the customer of the current rate or allow the home owner to program when the electric vehicle should be charged.Green PHY Features • Operate with 75% less power consumption(than current HomePlug AV implementations) • Reduce total Bill of Materials by 75% (from current HomePlug AV implementations) • Provide Internet (IP) networking (802.2, IPv6) support• Provide 256 Kbps minimum effectivenetworking throughput.• Provide 10 Mbps peak PHY rateKey Technical Working Group Contributors Arkados, Atheros Communications, Cisco, Corporate Systems, Duke Energy, GE Energy, Gigle Networks, Marvell, NEC Electronics, PG&E, Renesas, SPiDCOM, ST Microelectronics, and Watteco.About the HomePlug Powerline AllianceFounded in 2000, the HomePlug Powerline Alliance, Inc. is an industry-led initiative with 70 member companies that creates specifications and certification logo programs for using the powerlines for reliable home networking and Smart Grid applications. The Alliance accelerates worldwide adoption for HomePlug technology by collaboratingwith international standards organizations such as the IEEE and through market development and user education programs. Sponsor members include Atheros Communications (ATHR); Cisco (CSCO); Comcast (CMCSK); Duke Energy (DUK), GE Energy, an affiliate of General Electric Co. (NYSE: GE); Gigle Networks; Motorola, Inc. (MOT); Renesas Electronics Corporation (TSE: 6723); SPiDCOM Technologies, and ST Microelectronics (STM). Contributor members include Arkados (OTCBB: AKDS) and Corporate Systems Engineering. For more information, visit .HomePlug Powerline Alliance, Inc. 5200 SW Macadam Avenue, Suite 470 Portland, Oregon 97239 USATel: +1.503.766.2516 Fax: +1.503.863.3881。
overview用法 -回复

overview用法-回复Overview的基本用法是用来提供对某个主题或事物的概述、概况或总览。
一个好的overview应该包含对主要要点的简要介绍,以便读者可以快速了解文章的主题和内容。
接下来,我将按照要求的字数写一篇1500-2000字的文章,以一个假设的主题为例,逐步回答。
主题:介绍全球变暖问题的概述第一步:引入全球变暖问题(约200-250字)全球变暖是当今世界面临的最严重的环境问题之一。
随着工业化和人类活动的不断增加,温室气体排放,森林砍伐,以及大规模的城市化等问题导致了地球的气候变化。
本文将会对全球变暖的原因、影响以及应对措施进行概述。
第二步:解释全球变暖的原因(约400-500字)全球变暖的主要原因是温室气体的排放增加,特别是二氧化碳的排放。
燃烧化石燃料、森林砍伐和工业排放等活动产生的二氧化碳都会留在大气中引发温室效应,使得地球表面的温度上升。
此外,甲烷和氧化亚氮等温室气体也对全球变暖起到了推波助澜的作用。
人类社会的发展和经济活动的增长是导致温室气体排放增加的主要因素。
第三步:探讨全球变暖的影响(约600-700字)全球变暖对地球生态系统和人类社会产生了广泛而深远的影响。
首先,气候变化导致了极端天气事件的增加,如干旱、洪水和风暴。
这些天气事件不仅威胁到人们的生命和财产,还破坏了农田和生态系统的平衡,对粮食安全和生态多样性产生了负面影响。
其次,全球变暖导致冰川融化和海平面上升,给沿海地区和岛屿民众的生活造成了严重威胁。
还有,海洋酸化也是全球变暖的后果,对海洋生态系统的健康造成了不可逆转的损害。
此外,全球变暖还可能加剧现有的社会问题,例如饮水短缺、粮食危机和扩大贫富差距等。
第四步:提出应对全球变暖的措施(约250-300字)为了减缓和适应全球变暖带来的影响,国际社会采取了一系列的应对措施。
首先,减少温室气体的排放是最关键的一步。
各国应减少对化石燃料的依赖,推动清洁能源的发展,以及加强对能源效率的管理。
gp查看建表语句

gp查看建表语句摘要:1.了解GP查看建表语句的背景和意义2.分析GP查看建表语句的语法结构3.详细解释GP查看建表语句的各个部分4.演示如何在GP中使用查看建表语句5.总结GP查看建表语句的优点和局限性正文:作为一种关系型数据库管理系统,GP(GreenPlum)提供了丰富的查询语言,以满足数据处理和分析的需求。
在GP中,查看建表语句是一项重要的操作,它可以帮助我们了解表的结构、字段信息等。
本文将详细介绍GP查看建表语句的语法结构、使用方法以及优缺点。
1.了解GP查看建表语句的背景和意义在实际的数据库应用中,我们经常会遇到需要查看表结构的情况。
例如,在进行数据迁移、优化查询语句或编写触发器等操作时,了解目标表的结构变得尤为重要。
GP查看建表语句就是为了解决这个问题,它能够清晰地展示表的结构,方便用户进行相关操作。
2.分析GP查看建表语句的语法结构GP查看建表语句的语法结构如下:```SELECT * FROM information_schema.tables WHERE table_schema ="your_database_name" AND table_name = "your_table_name";```其中,`your_database_name`为要查询的数据库名称,`your_table_name`为要查询的表名称。
3.详细解释GP查看建表语句的各个部分- `SELECT *`:表示选择所有列。
如果需要查询特定列,可以将`*`替换为列名。
- `FROM information_schema.tables`:表示从`information_schema`数据库中查询表格信息。
- `WHERE table_schema = "your_database_name"`:表示只在指定数据库中查找表格。
- `AND table_name = "your_table_name"`:表示在指定数据库中查找特定表。
项目概况翻译

"项目概况" 的英文翻译是"Project Overview"。
"项目概况" 是对一个项目的基本信息和总体情况进行概述和总结的内容。
在项目管理中,项目概况通常是项目启动阶段的一个重要文档,用于向相关利益相关者(如项目发起人、项目团队成员、相关部门等)介绍项目的主要内容和目标。
项目概况包括以下主要内容:
项目背景:介绍项目的起因和背景,说明为什么要开展该项目。
项目目标:明确项目的预期成果和目标,描述项目的最终目标和期望达到的效果。
项目范围:描述项目的边界和范围,说明项目要包含的工作内容和要实现的功能。
项目进度:提供项目的计划时间表,包括项目开始和结束日期,以及里程碑或关键里程碑。
项目资源:列出项目所需的资源,包括人力资源、财务资源、技术资源等。
项目风险:识别项目可能面临的风险和挑战,以及应对措施。
项目关键干系人:罗列项目中的主要干系人和他们的利益,以及与他们的沟通计划。
GPPW使用基本操作

GPPW使用基本操作GPPW是Google Play出版商工具箱中的一款基本操作工具,它可以帮助开发者更好地管理和优化他们的应用程序。
以下是使用GPPW进行基本操作的一些步骤和指南。
1.安装和设置GPPW- 打开GPPW并使用您的Google Play开发者帐户进行登录。
2.创建新应用程序-在GPPW中选择“创建应用程序”选项。
-输入应用程序的名称和ID,并选择应用程序的默认语言和国家/地区。
-配置应用程序的其他设置,例如内容评级和应用程序类型。
3.上载应用程序包-在GPPW中选择“应用程序包”选项。
-点击“创建第一个应用程序包”按钮。
-选择要上传的应用程序包文件并等待上传完成。
-根据需要上传适配不同设备的多个应用程序包。
4.应用程序资源管理-在GPPW中选择“商店上的应用程序”选项。
-点击“存储列表”选项,您可以查看您已经上传的应用程序包。
-点击“商店声明”选项,您可以管理应用程序的元数据,例如应用程序标题、描述和截图。
5.发布应用程序-在GPPW中选择“发布管理”选项。
-点击“商店制作”选项,您可以设置应用程序的各种商店功能,例如价格、销售区域和应用内购买。
-点击“内容评级”选项,您可以指定应用程序的适用年龄范围和敏感内容。
-点击“发行状态”选项,您可以管理应用程序的发布渠道和版本控制。
6.销售和收益管理-在GPPW中选择“销售与定价”选项。
-点击“应用定价”选项,您可以设置应用程序的价格和货币。
-点击“内容订阅管理”选项,您可以创建和管理应用程序的订阅产品。
-点击“分析与收入”选项,您可以查看应用程序的安装和收入数据。
7.优化和改进应用程序-在GPPW中选择“质量和跟踪”选项。
- 点击“Android Vitals”选项,您可以查看应用程序的性能和稳定性数据。
-点击“应用内测量”选项,您可以管理应用程序的用户反馈和崩溃报告。
- 点击“最新评论(Alpha)”选项,您可以查看用户对应用程序的评论和评级。
西门子1LE0低压交流异步电动机说明书

SIMOTICS 1LE0 低压交流异步电动机SIMOTICS 1LE0 Low-voltage MotorsD81.5 2020.03/SIMOTICS_GP_1LE0目录Contents2总体介绍Overview (3)机械特性Mechanical design (7)电气特性Electrical design (14)变频应用Converter fed application (18)订货号和型号Order No. and Motor Type (20)选型技术数据表Technical data table (22)选件Options (44)外形尺寸Dimension drawings (48)认证Certificates (57)铸铁壳电机总体介绍 Overview3SIMOTICS 1LE0 系列电动机是通用型全封闭自扇冷却式三相异步电动机,其防护等级为 IP55,1LE0 系列电动机设计生产符合 ISO 、IEC 、GB 等相关标准的要求。
1LE0 系列电动机适用于连续工作制(S1)、恒转速或一定速度范围内的变频调速应用。
西门子 1LE0 系列电动机技术特性■ 机座材料:灰铸铁或铝合金;■ 标准颜色:石头灰(RAL 7030);■ 额定功率:0.55kW~315kW (50Hz)■0.75kW 及以上的 2、4、6 极电动机达到 GB18613-2012 标准能效等级 2或3 级,且 能满足 IEC 60034-30 标准中的 IE2或IE3 效率等级(50Hz );■ 优化的紧凑型结构;■标准安装结构类型(符合 IEC 60034-7 标准规定):IM B3、IM B5、IM B35 等;■ 所有的电动机设计防护等级为 IP55(IEC 60034-5);■FS 1) 280 ~ 355 标配再润滑装置,FS 1) 100 ~ 250 的作为选项;■ 对于 FS 100 ~ 355 范围电动机,可选择增强悬臂力设计;■电动机可选 PTC 或 PT100 热敏电阻或 KTY84-130 进行绕组保护;Features of Siemens 1LE0 series■ Frame material: grey cast iron or aluminum alloy.■ Standard color: stone grey (RAL 7030)■ Rated power output: 0.55kW~315kW at 50Hz.■Available in 2, 4, 6 pole motor (0.75kW and up) with efficiency grade 3 or 2. according to GB18613-2012 and efficiency class IE2 or IE3 (50Hz) according to IEC 60034-30.■ Optimized compact style construction.■Standard mounting construction according to IEC 60034-7: IM B3, IM B5, IM B35 and etc.■ All motors are designed to IP55 degree of protection (IEC 60034-5) .■Re-greasing devices for FS 1) 280 ~ 355 as standard, and for FS100 ~ 250 as option.■Reinforced bearings for increased cantilever forces for FS100 ~ 355 as option.■Winding protections with PTC, PT100 and KTY84-130 as option.1) FS ,机座的英文(Frame Size )缩写。
总论 introduction overview

总论 introduction overview
"总论"(Introduction/Overview)通常是一篇文章、报告、演讲或其他文本的开头部分,用于提供背景信息、引出主题、概述主要内容,并引导读者进入正文。
它的目的是为读者提供一个整体的框架和背景,帮助他们理解后续的详细内容。
总论应该简洁明了,能够吸引读者的兴趣,并为后续内容做好铺垫。
它通常包括以下几个部分:
1. 背景信息:介绍与主题相关的背景情况,包括相关领域的现状、发展趋势等,以使读者对主题有一个基本的了解。
2. 主题介绍:明确阐述文章或报告的主题,以及为什么这个主题重要或值得关注。
3. 目的和范围:说明写作的目的,以及文章或报告涵盖的范围和重点。
4. 方法概述:如果适用,简要介绍研究或分析的方法,使读者了解你是如何进行研究的。
5. 主要内容概述:概括文章或报告的主要内容和结构,让读者对后续的详细内容有一个预期。
6. 结论预览:在概述主要内容的基础上,提前透露一些文章或报告的结论或重要发现,以激发读者的兴趣。
7. 引导语:最后,用一句话或一段话来引导读者进入正文,例如"接下来,我们将详细探讨......"。
需要注意的是,总论的长度应根据具体情况而定,一般不宜过长,以保持读者的注意力和兴趣。
同时,总论应该具有吸引力,使读者愿意继续阅读下去。
Logistic_Overview

CLIENT
Reference Copy
PLANT 1
PLANT 2
PLANT 3
R
SAP AG
-17-
G-LUXON
Work Center
R
Basic •Description •Location •Hierarchy Scheduling • Formula • Queue times Costing • Cost center • Activity types
Sales Document Type Item Category Schedule Line Category
SAP AG
-14-
G-LUXON
PP Master Data
R
Work Center
10
Routing
Platz 1
20
30
Material Master
Bill of Material
R
Organizational units
Company
Controlling areas Sales organizations Company codes Purchasing organizations
Valuation areas
Plants
R
Storage locations/Batches/Special stocks
SAP R/3 - Modules
R
Logistics
SD
Sales & . MM Distrib Material . Manag
FI
Financial Accounting
Accounting
CO
Controlling
MMOG-LE Overview 培训教材

• 对于符合标准项目,应该包括证明 符合标准的客观证据和如何保持。
• 对于不适用的标准,应该包括定义 为不适用的原因以及所有用户相关 信息。
• 在初始评估过程中,评估员应该 在备注栏中对每个不适用标准记 录“不适用”原因。
• 必须包括用户的书面批准以便收 到不适用标准的分数信用。
• 第一个柱形图显示出,在评分总结 工作表中的评估日期之时,有多少 个标准是符合的。
• 柱形按分值(F3, F2, and F1)显示出 符合的和不符合标准的项目数量, 以及那些不适用或和“无目标日期” 的项目数量
• 后面的柱形显示的是,根据差距分 析中的目标日期,每个月月底相应 的状态。
Cindy Cheng QAD China
3)
Is the process documented in a procedure and/or work instruction that can be easily understood by all personnel,
including existing, new and backup employees (MMOG/LE 2.2.1)?流程有程序文件,作业指导书文档可以方便的让所有现
的长期、中期和短期需求进行比较。必须有一个流程以确保任何可能影响他们运作的风险 发生时,能快速的和客户沟通
领导层的信息
Bill Hurles Executive Director, GPSC
当今的汽车工业要求交货周期越来越短,物 料交付表现越来越可靠。要求供应链所有层 级的信息流动和产品流动更快,更灵活和更 有效比以往任何时候都明显。对已经使用 MMOG/LE自评工具的公司的追踪记录表明溢 价发运运费降低了,废品降低了,库存维持 成本降低及用户满意度提高了。
gp4502w英文操作手册

gp4502w英文操作手册The gp4502w is a versatile and powerful device that can be used for a wide range of applications. Whether you need to perform complex calculations, manage your schedule, or access a wealth of information, this device has the capabilities to meet your needs. In this user manual, we will provide a comprehensive overview of the gp4502w's features and functions, guiding you through the process of setting up and using this remarkable piece of technology.Getting StartedThe first step in using the gp4502w is to ensure that you have all the necessary components. This includes the device itself, a power adapter, and any necessary cables or accessories. Once you have gathered these items, you can begin the setup process.To power on the gp4502w, simply connect the power adapter to the device and plug it into a power outlet. The device will automatically turn on and display the initial setup screen. Follow the on-screen instructions to complete the setup process, which may include connecting to a wireless network, setting the date and time, andcustomizing the device's settings to your preferences.Key Features and FunctionsOne of the standout features of the gp4502w is its powerful processing capabilities. With a state-of-the-art processor and ample memory, this device can handle a wide range of tasks with ease. Whether you need to perform complex calculations, run resource-intensive applications, or multitask between multiple programs, the gp4502w is up to the challenge.In addition to its raw processing power, the gp4502w also boasts a stunning display that delivers crisp, vibrant visuals. The large, high-resolution screen makes it easy to view content, navigate menus, and interact with the device's various functions. Whether you're browsing the web, watching videos, or working on a project, the gp4502w's display will provide an immersive and enjoyable user experience.Another key feature of the gp4502w is its extensive connectivity options. The device is equipped with a range of ports and interfaces, including USB, HDMI, and Ethernet, allowing you to connect a variety of peripheral devices and accessories. This makes the gp4502w a versatile tool that can be integrated into a wide range of setups, from home entertainment systems to professional workstations.The gp4502w also comes with a robust suite of pre-installedsoftware and applications, covering a wide range of use cases. From productivity tools like word processors and spreadsheets to multimedia applications for entertainment and creative pursuits, the device offers a comprehensive ecosystem of software to meet your needs. Additionally, the gp4502w is compatible with a wide range of third-party applications, giving you access to an even broader range of functionality.One of the standout features of the gp4502w is its advanced security capabilities. The device is equipped with a range of security measures, including biometric authentication, data encryption, and secure boot processes, to protect your data and safeguard your privacy. This makes the gp4502w an ideal choice for users who need to handle sensitive information or work in high-security environments.Using the gp4502wTo begin using the gp4502w, simply power on the device and navigate through the intuitive user interface. The device's touchscreen display makes it easy to interact with the various menus and applications, allowing you to quickly access the features and functions you need.One of the key advantages of the gp4502w is its versatility. The device can be used for a wide range of tasks, from basic productivitywork to more advanced applications. Whether you need to write documents, create spreadsheets, or manage your schedule, thegp4502w has the tools and capabilities to get the job done.In addition to its productivity features, the gp4502w also excels in the realm of multimedia. The device's powerful hardware and high-quality display make it an excellent choice for watching videos, listening to music, or even engaging in light gaming. The device's built-in speakers and audio processing capabilities ensure that you'll enjoy a rich, immersive audio experience.For users who need to access a wide range of information or stay connected to the digital world, the gp4502w's internet connectivity and web browsing capabilities are a valuable asset. The device's fast and reliable internet connection, combined with its user-friendly web browser, make it easy to surf the web, check email, and stay up-to-date on the latest news and information.Maintenance and TroubleshootingTo ensure that your gp4502w continues to perform at its best, it's important to maintain the device properly. This includes keeping the device clean and free of dust, updating the software and firmware as necessary, and ensuring that the battery is properly charged and maintained.In the event that you encounter any issues or problems with your gp4502w, the device's comprehensive troubleshooting and support resources can help you quickly identify and resolve the problem. The user manual includes detailed instructions for common troubleshooting procedures, and the device's built-in diagnostic tools can provide valuable information to help you pinpoint the source of the issue.If you require additional assistance, the gp4502w's customer support team is available to help. Whether you need guidance on using a specific feature, help with troubleshooting, or information on product updates and enhancements, the support team is dedicated to ensuring that you get the most out of your gp4502w.ConclusionThe gp4502w is a powerful and versatile device that can be a valuable asset in a wide range of applications. With its advanced features, robust security capabilities, and comprehensive software ecosystem, the gp4502w is an ideal choice for users who demand high-performance and reliable technology. Whether you're a professional, a student, or simply someone who values the convenience and functionality of a capable device, the gp4502w is sure to exceed your expectations.。
gp全流程控制计划

gp全流程控制计划英文回答:GP Full-Process Control Plan.A GP full-process control plan is a document that describes the processes, activities, and resources needed to achieve the desired quality of a product or service. It includes the following elements:Objectives: The specific quality objectives that the control plan is intended to achieve.Scope: The processes, activities, and resources that are covered by the control plan.Responsibilities: The individuals or teams responsible for each process, activity, or resource.Procedures: The detailed instructions for how eachprocess, activity, or resource should be carried out.Inspection and testing: The methods used to inspect and test the product or service to ensure that it meets the desired quality objectives.Corrective actions: The steps to be taken if the product or service does not meet the desired quality objectives.A GP full-process control plan is an essential tool for ensuring the quality of a product or service. It provides a clear and concise roadmap for all of the processes, activities, and resources that are needed to achieve the desired quality objectives.中文回答:GP 全流程控制计划。
供应商质量阀评审检查清单
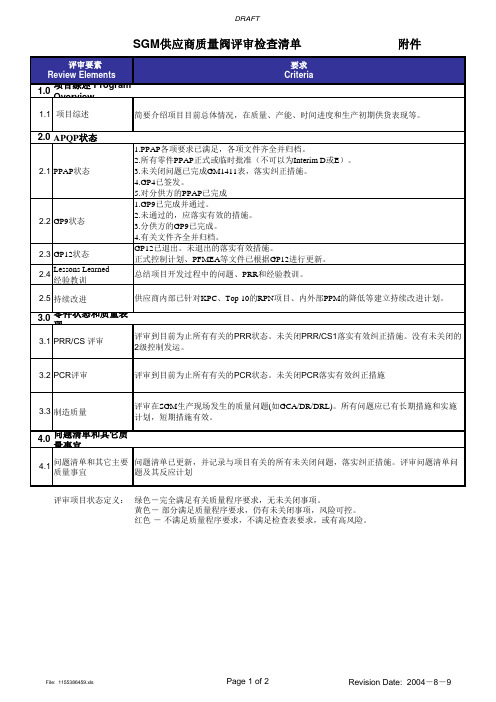
3.2 PCR评审
评审到目前为止所有有关的PCR状态。未关闭PCR落实有效纠正措施
3.3 制造质量
评审在SGM生产现场发生的质量问题(如GCA/DR/DRL)。所有问题应已有长期措施和实施 计划,短期措施有效。
4.0
问题清单和其它质 量事宜
4.1
问题清单和其它主要 质量事宜
问题清单已更新,并记录与项目有关的所有未关闭问题,落实纠正措施。评审问题清单问 题及其反应计划
2.3 GP12状态
2.4
Lessons Learned 经验教训
1.PPAP各项要求已满足,各项文件齐全并归档。 2.所有零件PPAP正式或临时批准(不可以为Interim D或E)。 3.未关闭问题已完成GM1411表,落实纠正措施。 4.GP4已签发。 5.对分供方的PPAP已完成 1.GP9已完成并通过。 2.未通过的,应落实有效的措施。 3.分供方的GP9已完成。 4.有关文件齐全并归档。 GP12已退出。未退出的落实有效措施。 正式控制计划、PFMEA等文件已根据GP12进行更新。
总结项目开发过程中的问题、PRR和经验教训。
2.5 持续改进
供应商内部已针对KPC、Top 10的RPN项目、内外部PPM的降低等建立持续改进计划。
3.0
零件状态和质量表 现
3.1 PRR/CS 评审
评审到目前为止所有有关的PRR状态。未关闭PRR/CS1落实有效纠正措施。没有未关闭的 2级控制发运。
评审项目状态定义: 绿色-完全满足有关质量程序要求,无未关闭事项。 黄色- 部分满足质量程序要求,仍有未关闭事项,风险可控。 红色 - 不满足质量程序要求,不满足检查表要求,或有高风险。
File: 1155386459.xls
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
SQL Server
IBM DB2
Informatica DataStage ……
SUN HP IBM ORACLE DB2
MySQL
Postgres
EMC Hitachi Cisco
• • • • • •
MicroStrategy Business Objects Cognos Hyperion SAS 线性代数、R语言
数据文件
支持各种 数据源
支持各种 ETL工具
支持众多硬件平台 支持ODBC/JDBC等多 种接口
支持SQL直接并行访问 外部数据文件 支持外部编程直接使用 SQL并行访问数据库
Greenplum - 新的方案
现在的解决方案 Greenplum
• “黑盒子” • “大铁箱” • 大磁盘
•开放平台(服务器、存储设备、网络) •通过软件提升处理能力
– 每个节点只处理其中一部分数据
Loading
• 最优化的I/O处理
– 所有的节点同时进行并行处理 – 节点之间完全无共享,无I/O冲突
• 增加节点实现线性扩展
– 增加节点可线性增加存储、查询和加载性能
7/5/2013
15
Greenplum 基本架构
MPP (Massively Parallel Processing) Shared-Nothing Architecture
64
45 46 77 48
50
56 63 44 53 55
Oct 20 2005 10
Oct 20 2005 82 Oct 20 2005 55
Order Date
数据分布方法
• Hash Distribution – CREATE TABLE … DISTRIBUTED BY (column [,…]) – Keys of the same value always sent to the segments same segments
Curt Monash, Monash Research Best clustering Solution
Fast 50
FY08 Asia South Achievement Award
“Greenplum leverages MapReduce technology to radically juice data scale, performance and analytics.”
Client
Segment Host
Master Host Master Host
千 兆 以 太 网 交 换 机
储数据字典
• Segment主机负责
Segment Host
– 业务数据的存储和存取 – 用户查询SQL的执行
Segment Host
数据均匀分布
- 并行处理的关键
策略: 数据尽可能的均匀分布到每个节点
Greenplum数据引擎内部架构 Greenplum
Interconnect—
• Master主机负责:
– 建立与客户端的连接和管理
– SQL的解析并形成执行计划
Segment Host
– 执行计划向Segment的分发 – 收集Segment的执行结果 – Master不存储业务数据,只存
LAN
过去Google™ 曾经用来实现信息搜索功能的技术, 现在被Greenplum用于数据仓库
13
Share-Nothing无共享的完全并行架构
MPP
完全共享 例如: SMP服务器
网络 共享磁盘 例如: Oracle RAC
无共享 例如: Greenplum
Master
网络
B DB DB DB
Oracle
Architecture Performance
Cost
• Shared-everything architecture, purposebuilt for OLTP, not BIDW • Query Coordinator cannot fully leverage parallelism
新一代数据管理和数据分析 解决方案
1
Agenda
• • • • •
Greenplum 介绍 案例分享 Greenplum 核心竞争优势 The Greenplum Enterprise Data Cloud™ 总结
关于Greenplum公司
• Greenplum是一家数据库软件公司,在数据处理和 BI/DW领域,提供容量 最大、速度最快、性价比最好的数据库引擎产品和服务。 • Greenplum总部位于圣马蒂奥,加利福尼亚州,美国,成立于2003年6月。 • Greenplum 中国于2008年12月正式成立.
Dana Gardner, ZDNet
强大并成长中的合作伙伴网络
Hardware Vendors
BI Tools
Solutions
Consultants And Resellers
Greenplum 核心竞争优势
11
典型的数据分析体系架构
Oracle
抽取、转换、加载 (ETL)
报表与分析、科学计算
Master Severs
Query planning & dispatch
SQL MapReduce
...
...
Network Interconnect
Segment Severs
Query processing & data storage
...
...
External Sources
Loading, streaming, etc.
Proprietary Expensive
Greenplum vs. Teradata
•Greenplum uses Open Source, PostgreSQL -Teradata uses Proprietary Software Language •Greenplum utilizes commodity hardware/machines like SUN, HP, IBM, DELL (SUN X4520, HP DL185, IBM X3650). Hardware reusable when hardware upgrades. -Teradata uses their own proprietary hardware. If customer needs to upgrade the hardware to bigger box to store more data, they have to throw away their old box. Old Teradata machines cannot be used for other applications. • Low Cost -Teradata is very expensive. In the range of Millions USD. • Very Scalable (Just need more commodity machines to scale) -Adding a new TD hardware is much more expensive • Less Power Consumption - TD uses more power consumption • Leverage on high performance local disks. Remove I/O bottleneck. Access Speed based on SUN X 4500 server is 2GB per second. - Uses External Storage. Uses Transverse Fiber Channel to access Data. Data access over high Fiber Channel is 400MB per second, which is 5 times lower than 2GB per second.
• Get answers faster than ever before
• Ensures consistent performance analysis as your data grows
7/5/2013 Confidential
8
奖项及分析师评论
Industry Awards
Global 250
Greenplum – 最强大的分析引擎
The World‘s Most Powerful Analytical Database
高扩展性
• No fear of data growth or starting small • Linear and costeffective scaling on commodity hardware 高性能 集成分析平台 • Single platform for warehousing, marts, ELT, text mining, statistical computing, • Enable parallel analysis on any data, at all levels with SQL, MapReduce, R, etc.
SAN/FC
磁盘 SAN/共享磁盘
磁盘
磁盘
磁盘
磁盘
注:蓝灰色表示共享资源
MPP/无共享架构的优势
• 最易于扩展的架构
– BI和数据分析的最佳选择
• 自动化的并行处理机制
Interconnect
– 内部处理自动化并行,无需人工分区或优化 – 加载与访问方式与一般数据库相同
• 数据分布在所有的并行节点上
官方网站:
2013-7-5
超级数据引擎的到来
