08 - VLAN
划分vlan的四种方法

划分vlan的四种方法划分 VLAN 的四种方法VLAN(Virtual Local Area Network,虚拟局域网)是一种将物理上分散的设备通过逻辑上的方式组合在一起的网络技术。
它可以将一个物理上的网络划分为多个逻辑上的网络,从而提高网络安全性、灵活性和管理效率。
本文将介绍 VLAN 的四种划分方法。
第一种方法:基于端口基于端口的 VLAN 是最简单、最常见的 VLAN 划分方式。
它根据交换机端口来划分不同的 VLAN。
每个端口只能属于一个 VLAN,这样就可以实现不同 VLAN 之间互相隔离。
该方法的优点是易于实现和管理,缺点是不够灵活。
如果需要更改某个设备所属的 VLAN,则需要重新配置交换机端口。
第二种方法:基于 MAC 地址基于 MAC 地址的 VLAN 是根据设备的 MAC 地址来划分不同的VLAN。
每个设备都有唯一的 MAC 地址,因此可以通过 MAC 地址来确定设备所属的 VLAN。
该方法可以实现动态加入和移除设备,但也存在一些问题。
例如,如果某个设备更换了网卡,则需要重新配置其所属的 VLAN。
第三种方法:基于子网基于子网的 VLAN 是根据 IP 地址子网来划分不同的 VLAN。
每个子网可以对应一个 VLAN,这样就可以实现跨 VLAN 的通信。
该方法需要在交换机上配置IP 子网,因此需要一定的网络知识和技能。
同时,该方法也存在一些限制,例如无法实现跨子网的广播和多播。
第四种方法:基于协议基于协议的 VLAN 是根据网络协议来划分不同的 VLAN。
例如,可以将所有 VoIP 流量划分到一个 VLAN 中,将所有视频流量划分到另一个 VLAN 中。
该方法可以提高网络性能和管理效率,但也需要一定的网络知识和技能。
同时,该方法也存在一些限制,例如无法对混合流量进行精确控制。
总结以上是四种常见的 VLAN 划分方法。
每种方法都有其优缺点和适用场景。
在实际应用中,需要根据具体情况选择合适的方法,并结合其他网络技术进行综合应用。
二层交换机VLAN支持

二层交换机VLAN支持二层交换机VLAN支持2011-01-15 08:56VLAN,是英文Virtual Local Area Network的缩写,中文名为"虚拟局域网",VLAN是一种将局域网(LAN)设备从逻辑上划分(注意,不是从物理上划分)成一个个网段(或者说是更小的局域网LAN),从而实现虚拟工作组(单元)的数据交换技术。
VLAN这一新兴技术主要应用于交换机和路由器中,但目前主流应用还是在交换机之中。
不过不是所有交换机都具有此功能,只有三层以上交换机才具有此功能,这一点可以查看相应交换机的说明书即可得知。
VLAN的好处主要有三个:(1)端口的分隔。
即便在同一个交换机上,处于不同VLAN的端口也是不能通信的。
这样一个物理的交换机可以当作多个逻辑的交换机使用。
(2)网络的安全。
不同VLAN不能直接通信,杜绝了广播信息的不安全性。
(3)灵活的管理。
更改用户所属的网络不必换端口和连线,只更改软件配置就可以了。
VLAN技术的出现,使得管理员根据实际应用需求,把同一物理局域网内的不同用户逻辑地划分成不同的广播域,每一个VLAN都包含一组有着相同需求的计算机工作站,与物理上形成的LAN有着相同的属性。
由于它是从逻辑上划分,而不是从物理上划分,所以同一个VLAN内的各个工作站没有限制在同一个物理范围中,即这些工作站可以在不同物理LAN网段。
由VLAN的特点可知,一个VLAN内部的广播和单播流量都不会转发到其他VLAN中,从而有助于控制流量、减少设备投资、简化网络管理、提高网络的安全性。
VLAN除了能将网络划分为多个广播域,从而有效地控制广播风暴的发生,以及使网络的拓扑结构变得非常灵活的优点外,还可以用于控制网络中不同部门、不同站点之间的互相访问。
VLAN在交换机上的实现方法,可以大致划分为六类:1.基于端口的VLAN这是最常应用的一种VLAN划分方法,应用也最为广泛、最有效,目前绝大多数VLAN协议的交换机都提供这种VLAN配置方法。
不同的VLAN之间相互ping通

路由器的配置hedevic e isrunni ng!<Huaw ei><Huawe i>sysEnte r sys tem v iew,retur n use r vie w wit h Ctr l+Z.[Huaw ei]e0/0/0 ^Error: Unr ecogn izedcomma nd fo und a t '^' posi tion.[Hua wei]i nt e0/0/0.1[Hu awei-Ether net0/0/0.1]poD ec 24 2011 20:14:13-08:00 Huaw ei DS/4/DA TASYN C_CFG CHANG E:OID1.3.6.1.4.1.2011.5.25.191.3.1 conf igura tions have been chan ged.The c urren tcha nge n umber is 1, the chan ge lo op co unt i s 0,and t he ma ximum numb er of reco rds i s 409[Hua wei-E thern et0/0/0.1]vlan-t[H uawei-Ethe rnet0/0/0.1]vla n-typ e d [Huaw ei-Et herne t0/0/0.1]v lan-t ype d ot1q10[H uawei-Ethe rnet0/0/0.1]De c 24201120:14:23-08:00Huawe i DS/4/DAT ASYNC_CFGC HANGE:OID1.3.6.1.4.1.2011.5.25.191.3.1confi gurat ionshavebeenchang ed. T he cu rrent chan genu mberis 2, thechang e loo p cou nt is 0, a nd th e max imumnumbe r ofrecor ds is 4095. [H uawei-Ethe rnet0/0/0.1]ipadd 192.168.1.1 24[Huawe i-Eth ernet0/0/0.1]in t e0/0/0.2[Hua wei-E thern et0/0/0.2]Dec24 2011 20:15:03-08:00 Hu aweiDS/4/DATAS YNC_C FGCHA NGE:O ID1.3.6.1.4.1.2011.5.25.191.3.1 co nfigu ratio ns ha ve be en ch anged. The curr ent c hange numb er is 4, t he ch angeloopcount is 0, and themaxim um nu mberof re cords is 4095.[Hua wei-E thern et0/0/0.2]vlan-t[H uawei-Ethe rnet0/0/0.2]vla n-typ e d [Huaw ei-Et herne t0/0/0.2]v lan-t ype d ot1q20\^Erro r: Wr ong p arame ter f oundat '^' pos ition.[Hu awei-Ether net0/0/0.2]vlan-type dot1q 20[Huaw ei-Et herne t0/0/0.2]i p add192.Dec 24 2011 20:15:23-08:00 Hua wei D S/4/D ATASY NC_CF GCHAN GE:OI D1.3.6.1.4.1.2011.5.25.191.3.1 con figur ation s hav e bee n cha nged. Thecurre nt ch angenumbe r is5, th e cha nge l oop c ountis 0, andthe m aximu m num ber o f rec ordsis 4095. 168. ^Er ror:Unrec ogniz ed co mmand foun d at'^' p ositi on.[Huawe i-Eth ernet0/0/0.2]ip add192.168.2.1 24[Huaw ei-Et herne t0/0/0.2]q[Hua wei]Dec 24 2011 20:15:43-08:00 Hua wei D S/4/D ATASY NC_CF GCHAN GE:OI D1.3.6.1.4.1.2011.5.25.191.3.1 con figur ation s hav e bee n cha nged. Thecurre nt ch angenumbe r is6, th e cha nge l oop c ountis 0, andthe m aximu m num ber o f rec ordsis 4095. i nt e0/0/0[Huaw ei-Et herne t0/0/0]und os sh ut^Err or: U nreco gnize d com mandfound at '^' po sitio n.[H uawei-Ethe rnet0/0/0]undoshut交换机的配置<Huaw ei>sy sEnt er sy stemview, retu rn us er vi ew wi th Ct rl+Z.[Hua wei]v lan 10[Hu awei-vlan10]p [Huaw ei-vl an10]pDec 24 2011 19:58:52-08:00 H uaweiDS/4/DATA SYNC_CFGCH ANGE:OID 1.3.6.1.4.1.2011.5.25.191.3.1 c onfig urati ons h a ve b een c hange d. Th e cur rentchang e num ber i s 4,the c hange loop coun t is0, an d the maxi mum n umber of r ecord s is4095[Huaw ei-vl an10]int e0/0/10[Hu awei-Ether net0/0/10]portlin [Huaw ei-Et herne t0/0/10]po rt li nk-a[Hua wei-E thern et0/0/10]p ort l ink-t[Hu awei-Ether net0/0/10]portlink-typea[H uawei-Ethe rnet0/0/10]port link-type acce ss[Huawe i-Eth ernet0/0/10]intDec24 2011 20:01:02-08:00 Hu aweiDS/4/DATAS YNC_C FGCHA NGE:O ID1.3.6.1.4.1.2011.5.25.191.3.1 co nfigu ratio ns ha ve be en ch anged. The curr ent c hange numb er is 5, t he ch angeloopcount is 0, and themaxim um nu mberof re cords is 4095. e0/0/15[Huawe i-Eth ernet0/0/15]por t lin k-typ e acc ess[Huawe i-Eth ernet0/0/15]qui t[Hu awei]Dec24 2011 20:01:22-08:00 Hu aweiDS/4/DATAS YNC_C FGCHA NGE:O ID1.3.6.1.4.1.2011.5.25.191.3.1 co nfigu ratio ns ha ve be en ch anged. The curr ent c hange numb er is 6, t he ch angeloopcount is 0, and themaxim um nu mberof re cords is 4095.vlan10[H uawei-vlan10]po rt e0/0/10[Hua wei-v lan10]vlanDec24 2011 20:01:42-08:00 Hu aweiDS/4/DATAS YNC_C FGCHA NGE:O ID1.3.6.1.4.1.2011.5.25.191.3.1 co nfigu ratio ns ha ve be en ch anged. The curr ent c hange numb er is 7, t he ch angeloopcount is 0, and themaxim um nu mberof re cords is 4095. 20[Huawe i-vla n20]p ort e0/0/15[Hu awei-vlan20]De c 24201120:01:52-08:00Huawe i DS/4/DAT ASYNC_CFGC HANGE:OID1.3.6.1.4.1.2011.5.25.191.3.1confi gurat ionshavebeenchang ed. T he cu rrent chan genu mberis 9, thechang e loo p cou nt is 0, a nd th e max imumnumbe r ofrecor ds is 4095. [Hu awei-vlan20]dis vlanThetotal numb er of vlan s is: 3--------------------------------------------------------------------------------U: Up; D: Do wn; TG: Tagg ed; UT: Unta gged;MP:Vlan-mappi ng; ST: Vla n-sta cking;#:Proto colTr anspa rent-vlan;*: Man ageme nt-vl an;--------------------------------------------------------------------------------VID TypeP orts--------------------------------------------------------------------------------1 com mon UT:Et h0/0/1(D)E th0/0/2(D)Eth0/0/3(D) Eth0/0/4(D) E th0/0/5(D)Eth0/0/6(D) Eth0/0/7(D) Eth0/0/8(D) Eth0/0/9(D) Eth0/0/11(D) Eth0/0/12(D) Et h0/0/13(D) Eth0/0/14(D) Eth0/0/16(D) Et h0/0/17(D)E th0/0/18(D) Eth0/0/19(D) Et h0/0/20(D)E th0/0/21(D) Eth0/0/22(U) GE0/0/1(D) G E0/0/2(D)10 co mmon UT:E th0/0/10(U) 20 com mon UT:Et h0/0/15(U)VID Sta tus Prope rty M AC-LR N Sta tisti cs De scrip tion--------------------------------------------------------------------------------1 ena ble defau lt e nable dis able VL AN 0001 10 en able defa ult enabl e di sableV LAN 0010 20 e nable def ault enab le d isabl e VLAN0020[Huaw ei-vl an20]dis c ur[H uawei-vlan20]in t e0/0/22[Huaw ei-Et herne t0/0/22]po rt li n[H uawei-Ethe rnet0/0/22]port link-t[Huawe i-Eth ernet0/0/22]por t lin k-typ e t [Huaw ei-Et herne t0/0/22]po rt li nk-ty pe tr unk [Huaw ei-Et herne t0/0/22]D ec 24 2011 20:09:42-08:00 Huaw ei DS/4/DA TASYN C_CFG CHANG E:OID1.3.6.1.4.1.2011.5.25.191.3.1 conf igura tions have been chan ged.The c urren tcha nge n umber is 10, th e cha nge l oop c ountis 0, andthe m aximu m num ber o f rec ordsis 4095.p ort t[Hu awei-Ether net0/0/22]porttrunk ?allow-pass All owedvlanpvi d S pecif y cur rentport's PVI D VLA N cha racte risti cs[Huawe i-Eth ernet0/0/22]por t tru nk a[Hua wei-E thern et0/0/22]p ort t runkallow-pass ?vlan Virt ual L AN[Huawe i-Eth ernet0/0/22]por t tru nk al low-p ass v lan ?IN TEGER<1-4094> VLANIDall All[Hu awei-Ether net0/0/22]porttrunk allo w-pas s vla n all[Hua wei-E thern et0/0/22]Dec 24 2011 20:10:42-08:00 Hua wei D S/4/D ATASY NC_CF GCHAN GE:OI D1.3.6.1.4.1.2011.5.25.191.3.1 con figur ation s hav e bee n cha nged. Thecurre nt ch angenumbe r is11, t he ch angeloopcount is 0, and themaxim um nu mberof re cords is 4095.[Hua wei-E thern et0/0/22][Huaw ei-Et herne t0/0/22]in t e0/0/1[Huawe i-Eth ernet0/0/1]port link-t[Huawe i-Eth ernet0/0/1]port link-type t[Huawe i-Eth ernet0/0/1]port link-type trun k[H uawei-Ethe rnet0/0/1]portt[H uawei-Ethe rnet0/0/1]porttrunk a[Huawe i-Eth ernet0/0/1]port trun k all ow-pa ssD ec 24 2011 20:13:42-08:00 Huaw ei DS/4/DA TASYN C_CFG CHANG E:OID1.3.6.1.4.1.2011.5.25.191.3.1 conf igura tions have been chan ged.The c urren tcha nge n umber is 12, th e cha nge l oop c ountis 0, andthe m aximu m num ber o f rec ordsis 4095.v lan a ll[H uawei-Ethe rnet0/0/1]。
TP-LINK 8口VLAN交换机 TL-SF1008V 安装手册

工作说明 供电正常 端口工作在100Mbps模式 端口工作在10Mbps模式或链路未建立 链路建立 端口在收发数据 链路未建立
表1-1 指示灯工作状态描述
2 VLAN开关
面板中间有一个VLAN开关,当VLAN开关拨动到“ON”档位时,开机后将启动 MTU VLAN模式,此时端口1~7将不能相互通信,只能通过第8端口共享上联。当 VLAN开关拨动到“OFF”档位时,开机后TL-SF1008V可作为一款普通8口VLAN 交换机。
2222 安装工具准备
■■ 十字螺丝刀 ■■ 防静电手腕 ■■ 可选网线 ■■ 普通PC机
2222 产品安装
■■ 安装在桌面上
注意:交换机机壳周围预留5~10cm空隙,确保散热和空气流通,交换机表面避免摆放其他 重物。
该系列交换机可放置在平稳的桌面上。此种安装方式操作比较简单,具体安装步骤如下: 111 将交换机的底部朝上放置于足够大且稳定的桌面上; 222逐个揭去4个脚垫的胶面保护纸,分别黏贴在位于机壳底部四角的圆形凹槽中;如图2-1
说明: ■■ 对于10Base-T以太网,建议使用3类或以上UTP/STP线; ■■ 对于100Base-TX以太网,建议使用5类或以上UTP/STP线。
注意: ■■ 当交换机与工作站、服务器、路由器或其它以太网设备连接时,网线长度不能大于100米; ■■ 交换机以太网口Auto MDI/MDIX功能默认开启,采用5类双绞线连接以太网时,标准网线
1111 产品外观
■■ 前面板
TL-SF1008V的前面板如图1-1所示;
1 指示灯 2 VLAN开关 3 10/100/1000Mbps自适应RJ45端口
图图图图图 TL-SF1008V前面板示意图
1 指示灯含义 指示灯 Power 100Mbps
交换机的几种配置模式的介绍

交换机得几种配置模式介绍2016-08-03弱电行业网交换机得几种配置模式简介1、普通用户模式开机直接进入普通用户模式、在该模式下我们只能查询交换机得一些基础信息、如版本号(show version)等。
2、特权用户模式在普通用户模式下输入enable命令即可进入特权用户模式、在该模式下我们可以查瞧交换机得配置信息与调试信息等等。
3、全局配置模式在特权用户模式下输入c terminal命令即可进入全局配置模式、在该模式下主要完成全局参数得配置、具体配置以后介绍。
4、接口配置模式在全局配置模式下输入interface interface-list即可进入接口配置模式、在该模式下主要完成接口参数得配置、具体配置以后介绍。
5、vlan配置模式在全局配置模式下输入vlan vlan-number即可进入vlan配置模式、在该配置模式下可以完成vlan得一些相关配置。
6、恢复交换机得缺省配置在实验开始时、为了不让实验受交换机以前得配置影响、常常需要先恢复交换机得缺省配置。
在特权用户模式下顺序使用erase、restet 命令即可恢复交换机得缺省配置。
交换机说明说明1:在实验环境中、如果配置两个vlan:vlan1、vlan2、注意其中vlan1就是交换机默认得vlan、既不能创建也不能删除、所有端口都属于vlan1、所以应该首先创建vlan2、然后为各个vlan分配端口(switchport interface-list)。
说明2:① 在使用命令行进行配置得时候、在任何模式下均可以使用“?”来帮助我们完成配置。
② 使用“?”可以查询任何模式下可以使用得命令;或者某参数后面可以输入得参数;或者以某字母开始得命令。
例如在全局配置模式下输入“?”或“show ?”或“s?”、可以瞧瞧它们分别有什么帮助信息显示。
如果您不能确认当前模块所在得插槽得编号、可以通过命令行中得show 命令来查瞧插槽以及插槽上得端口信息;也可以在路由器特权EXEC模式下执行show version命令、在路由器版本信息中有每个模块所在插槽编号得信息。
第08章 Vlan dot1q tunnel配置

第8章Vlan dot1q tunnel配置本章主要讲述了交换机支持Vlan dot1q tunnel功能以及如何配置该功能。
章节主要内容:●Vlan dot1q tunnel(mapping)简介●应用实例●调试和监控8.1Vlan dot1q tunnel简介Vlan dot1q tunnel是基于802.1Q协议的扩展,在原有的802.1Q报文包头上又增加一层802.1Q标签(VLAN标签)实现,通过双层标签,使VLAN个数增加为4K×4K。
QinQ将用户私网VLAN Tag封装在公网VLAN Tag中,使报文带着两层VLAN Tag穿越运营商的骨干网络(公网)。
在公网中报文只根据外层VLAN Tag(即公网VLAN Tag)传播,用户的私网VLAN Tag被屏蔽,节约了公网VLAN ID,为用户提供一种较为简单的二层VPN隧道。
Vlan dot1q tunnel mapping也是基于802.1Q的扩展,与Vlan dot1q tunnel不同之处在于:Vlan dot1q tunnel mapping不是在报文原有802.1Q的基础上再封装一层802.1Q标签,而是将报文原有802.1Q标签替换成新的802.1Q表项,报文仍然只带有一层802.1Q表项。
8.1.1基本Vlan dot1q tunnel功能端口使能Vlan dot1q tunnel功能,当端口接收到报文,为报文增加一层VLAN Tag。
增加Tag的VLAN ID为端口缺省VLAN ID。
如果接收到的报文是Tag报文,该报文变成双层Tag报文;如果接口到的报文不带Tag,报文为单层Tag报文。
8.1.2灵活Vlan dot1q tunnel功能灵活Vlan dot1q tunnel功能是与端口VLAN相配合,对Vlan dot1q tunnel的一种灵活实现。
端口根据灵活Vlan dot1q tunnel(mapping)表项,根据报文Tag中的VLAN ID,为报文增加指定的外层VLAN Tag,Vlan dot1q tunnel mapping则是将报文Tag中的VLAN ID 替换为指定的VLAN ID 。
三层交换机08-添加或修改报文的VLAN Tag典型配置举例

H3C S5130-EI 添加或修改报文的VLAN Tag 配置举例目录1 简介···························································································································· 1-12 配置前提······················································································································ 2-23 QinQ配置举例··············································································································· 3-23.1 组网需求···················································································································3-23.2 配置思路···················································································································3-33.3 使用版本···················································································································3-33.4 配置注意事项·············································································································3-33.5 配置步骤···················································································································3-33.5.1 PE A的配置 ······································································································3-33.5.2 PE B的配置 ······································································································3-43.5.3 运营商网络设备的配置························································································3-43.6 验证配置···················································································································3-53.7 配置文件···················································································································3-54 1:2 VLAN映射配置举例··································································································· 4-64.1 组网需求···················································································································4-64.2 配置思路···················································································································4-74.3 使用版本···················································································································4-84.4 配置注意事项·············································································································4-84.5 配置步骤···················································································································4-84.5.1 PE A的配置 ······································································································4-84.5.2 PE B的配置 ······································································································4-94.5.3 公共网络设备的配置························································································· 4-114.6 验证配置················································································································· 4-114.7 配置文件················································································································· 4-115 使用QoS策略添加外层VLAN Tag并修改外层VLAN Tag的802.1p优先级配置举例······················5-135.1 组网需求················································································································· 5-135.2 配置思路················································································································· 5-155.3 使用版本················································································································· 5-155.4 配置注意事项··········································································································· 5-165.5 配置步骤················································································································· 5-165.5.1 Provider A的配置····························································································· 5-165.5.2 Provider B的配置····························································································· 5-195.5.3 运营商网络设备的配置······················································································ 5-215.6 验证配置················································································································· 5-215.7 配置文件················································································································· 5-226 1:1 和N:1 VLAN映射配置举例 ·························································································6-266.1 组网需求················································································································· 6-266.2 使用版本················································································································· 6-276.3 配置步骤················································································································· 6-276.3.1 Switch A的配置 ······························································································· 6-276.3.2 Switch B的配置 ······························································································· 6-286.3.3 Switch C的配置 ······························································································· 6-286.3.4 Switch D的配置 ······························································································· 6-306.4 验证配置················································································································· 6-306.5 配置文件················································································································· 6-317 2:2 VLAN映射配置举例··································································································7-347.1 组网需求················································································································· 7-347.2 使用版本················································································································· 7-357.3 配置注意事项··········································································································· 7-357.4 配置步骤················································································································· 7-357.4.1 Switch A的配置 ······························································································· 7-357.4.2 Switch B的配置 ······························································································· 7-367.4.3 Switch C的配置 ······························································································· 7-367.4.4 Switch D的配置 ······························································································· 7-377.5 验证配置················································································································· 7-377.6 配置文件················································································································· 7-378 使用QoS重标记功能修改报文内层VLAN Tag配置举例 ·························································8-398.1 组网需求················································································································· 8-398.2 配置思路················································································································· 8-398.3 使用版本················································································································· 8-408.4 配置步骤················································································································· 8-408.4.1 PE A的配置 ···································································································· 8-408.4.2 PE B的配置 ···································································································· 8-428.4.3 运营商网络设备的配置······················································································ 8-448.5 验证配置················································································································· 8-448.6 配置文件················································································································· 8-459 相关资料·····················································································································9-48。
简单网管交换机的 VLAN 功能设置及应用
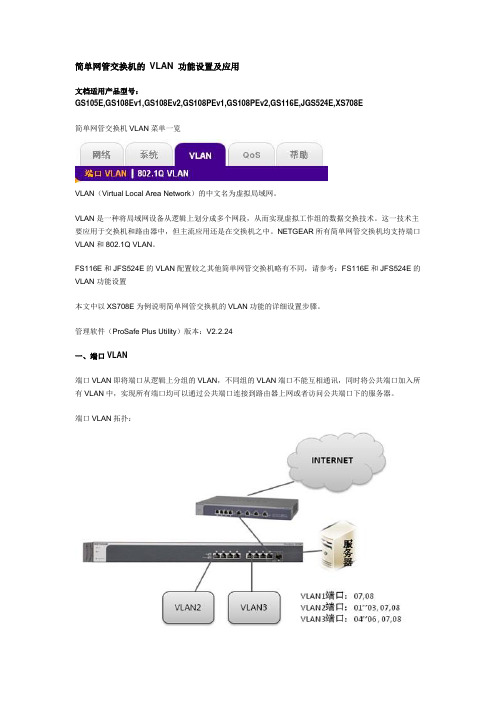
简单网管交换机的VLAN 功能设置及应用文档适用产品型号:GS105E,GS108Ev1,GS108Ev2,GS108PEv1,GS108PEv2,GS116E,JGS524E,XS708E简单网管交换机VLAN菜单一览VLAN(Virtual Local Area Network)的中文名为虚拟局域网。
VLAN是一种将局域网设备从逻辑上划分成多个网段,从而实现虚拟工作组的数据交换技术。
这一技术主要应用于交换机和路由器中,但主流应用还是在交换机之中。
NETGEAR所有简单网管交换机均支持端口VLAN和802.1Q VLAN。
FS116E和JFS524E的VLAN配置较之其他简单网管交换机略有不同,请参考:FS116E和JFS524E的VLAN功能设置本文中以XS708E为例说明简单网管交换机的VLAN功能的详细设置步骤。
管理软件(ProSafe Plus Utility)版本:V2.2.24一、端口VLAN端口VLAN即将端口从逻辑上分组的VLAN,不同组的VLAN端口不能互相通讯,同时将公共端口加入所有VLAN中,实现所有端口均可以通过公共端口连接到路由器上网或者访问公共端口下的服务器。
端口VLAN拓扑:XS708E的08号端口连接到出口路由器,07号端口连接公共服务器,01-03号端口划分到同一个VLAN2,04-06号端口划分到同一个VLAN3,实现VLAN2和VLAN3间的端口不能互访,所有端口均可以通过08号上网,并同时可访问07号端口的公共服务器。
以下两种方式任选其一进行配置即可:1. 基本设置进入VLAN>端口VLAN>基本设置,将基本端口VLAN设置为启用。
在基本端口VLAN组(1-8或全部)下,将01-03号端口的VLAN组改为2,将04-06号端口的VLAN组改为3,公共端口07和08修改为全部(注意:端口VLAN中的全部表示将端口加入所有VLAN)。
点击应用。
2. 高级设置进入VLAN>端口VLAN>高级设置,将高级端口VLAN设置为启用。
08-第8章 VPLS配置

目录第8章 VPLS配置 .................................................................................................................... 8-18.1 简介.................................................................................................................................... 8-18.1.1 VPLS概述 ............................................................................................................... 8-18.1.2 VPLS原理 ............................................................................................................... 8-28.1.3 VPLS实现 ............................................................................................................... 8-38.2 配置Kompella方式的VPLS .............................................................................................. 8-58.2.1 建立配置任务........................................................................................................... 8-58.2.2 使能BGP对等体交换VPLS信息的能力................................................................. 8-68.2.3 创建VSI并配置BGP信令 ...................................................................................... 8-78.2.4 检查配置结果........................................................................................................... 8-88.3 配置Martini方式的VPLS .................................................................................................. 8-98.3.1 建立配置任务........................................................................................................... 8-98.3.2 创建VSI并配置LDP信令..................................................................................... 8-108.3.3 将VSI与到CE的接口进行绑定............................................................................ 8-108.3.4 检查配置结果......................................................................................................... 8-118.4 配置VSI相关参数............................................................................................................ 8-118.4.1 建立配置任务......................................................................................................... 8-118.4.2 配置VSI的通用参数.............................................................................................. 8-128.4.3 配置MAC地址学习............................................................................................... 8-128.5 维护VPLS ........................................................................................................................ 8-138.5.1 调试VPLS ............................................................................................................. 8-138.5.2 使能/禁止VSI ........................................................................................................ 8-138.5.3 清除MAC地址表项............................................................................................... 8-148.6 配置举例........................................................................................................................... 8-148.6.1 配置Kompella方式VPLS示例............................................................................. 8-148.6.2 配置Martini方式VPLS示例 ................................................................................. 8-218.7 故障处理........................................................................................................................... 8-268.7.1 在VLAN接口上配置VPLS不成功........................................................................ 8-268.7.2 在以太网子接口上配置VPLS不成功 .................................................................... 8-278.7.3 配置VPLS后,发现PW状态为Down ................................................................. 8-288.7.4 配置VPLS后,两个PE间转发不通..................................................................... 8-288.7.5 配置Kompella方式的VPLS,VSI状态为Down .................................................. 8-29第8章 VPLS配置VPLS(Virtual Private LAN Service)是通过分组交换网络PSN(Packet Switched Network)连接多个以太网LAN网段,使它们像一个LAN那样工作。
关于VLAN和VXLAN的理解

版权声明:本文为博主原创文章,未经博主允许不得转载。
https:///octopusflying/art icle/details/77609199被公司调到新网路部门研究SDN,项目涉及到一些虚拟网络的概念。
初次接触VLAN和VXLAN技术,特整理资料学习下。
VLAN·概况VLAN (Virtual Local Area Network)意为虚拟局域网,是在交换机实现过程中涉及到的概念,由802.1Q标准所定义。
由于交换机是工作在链路层的网络设备,连接在同一台交换机的终端处于同一个三层网中,同时也处于同一个广播域。
当交换机接入较多的终端时,任意一台终端发送广播报文时(例如:ARP请求),报文都会传遍整个网络。
对于规模较大的组网场景,广播报文的泛滥对于网络通信将会造成较大的影响。
VLAN技术为这一问题提供了解决方案,VLAN将同一网络划分为多个逻辑上的虚拟子网,并规定当收到广播报文时,仅仅在其所在VLAN中进行广播从而防止广播报文泛滥。
VLAN技术在链路层的层次中实现了广播域的隔离。
·标准VLAN标准涉及到的RFC文献有2个:rfc3069、rfc5517。
rfc30 69阐述了利用VLAN技术来优化子网划分并节省IP地址数目的方案;rfc5517则给出了Cisco提出的私有VLAN的标准以满足网络安全方面的需求。
802.1Q标准所定义的以太网帧格式在基于传统以太网帧格式中添加了描述VLAN信息的字段,帧格式如下:802.1Q标准的以太网帧格式增加了802.1Q字段,该字段包含了T ype、PRI、CFI和VID 4个部分,各个部分的含义如下:·Type:长度为2 bytes,表示帧类型,802.1Q tag帧中Type字段取固定值0x8100,如果不支持802.1Q的设备收到802.1Q帧,则将其丢弃。
·PRI:priority字段,长度为3 bit,表示以太网帧的优先级,取值范围是0~7,数值越大,优先级越高。
烽火汇聚交换机常用配置

一.缺省用户名和密码admin12345二。
创建VLANconfig //进入配置模式后vlan 10,12,17,20,30-416,579,601—700,801,921,1000—1050,1201—1224,1301-1324,1401—1424,3999 //批量创建VLANinterface vlan 4000 //单独创建VLANip address 172。
31.20。
237/24 //给vlan添加IPip route—static 0.0。
0.0 0。
0。
0.0 172。
31。
20。
254 //config模式下缺省路由配置write file //保存当前所有配置三。
端口配置Interface gi 1/0/1 to gi 1/0/48 批量进入端口S7800—08(config-eth1)#no shutdown //启用端口S7800—08(config)#interface gigaethernet 6/0/1 //进入端口gigaethernet 6/0/1 S7800-08(config—ge6/0/1)#alias huangtan8220 //设置端口描述1)access 模式:port link—type access;port default vlan 10 // access 模式2)trunk 模式:port link—type trunk;port trunk allow—pass vlan 10,12 //trunk模式3)hybrid 模式:port link—type hybrid;port hybrid vlan 30—416,1000—1050 tagged;port hybrid vlan 3999untagged //hybird模式,内层标为tag,外层标untag(解标)建议端口使用hybrid模式,端口默认为hybrid模式。
1。
锐捷08-端口基本配置命令

目录
目录
第 1 章 端口基本配置命令 .......................................................................................................1-1
1.1 端口基本配置命令 .............................................................................................................. 1-1 1.1.1 broadcast-suppression ............................................................................................ 1-1 1.1.2 copy configuration ................................................................................................... 1-2 1.1.3 description ............................................................................................................... 1-4 1.1.4 display brief interface .........................................................................................
格林耐特S2008B基本配置
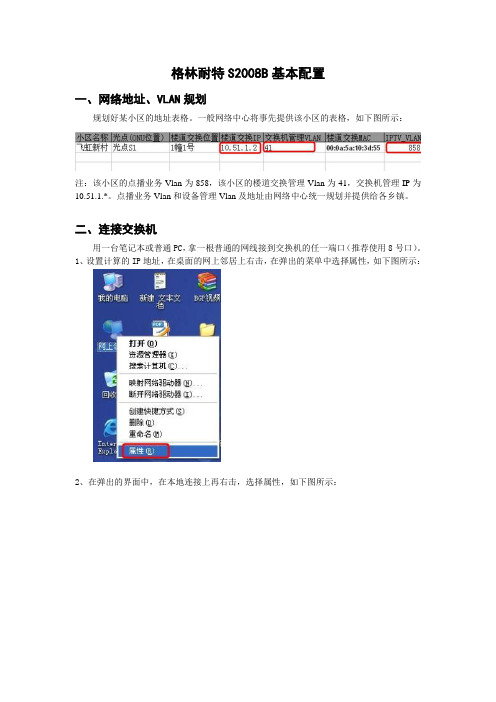
格林耐特S2008B基本配置一、网络地址、VLAN规划规划好某小区的地址表格。
一般网络中心将事先提供该小区的表格,如下图所示:注:该小区的点播业务Vlan为858,该小区的楼道交换管理Vlan为41,交换机管理IP为10.51.1.*。
点播业务Vlan和设备管理Vlan及地址由网络中心统一规划并提供给各乡镇。
二、连接交换机用一台笔记本或普通PC,拿一根普通的网线接到交换机的任一端口(推荐使用8号口)。
1、设置计算的IP地址,在桌面的网上邻居上右击,在弹出的菜单中选择属性,如下图所示:2、在弹出的界面中,在本地连接上再右击,选择属性,如下图所示:3、在中间的框框中找到,Internet协议(TCP/IP),选中后,点击下面的属性,如下图所示:4、选择使用下面的IP地址,在IP地址栏里输入:192.168.2.200(因为交换机出厂的默认地址是:192.168.2.1),为方便登录更改过后的IP地址,还要再设一个地址,点击下面的高级,如下图所示:5、点击添加,如下图所示:6、添加一个小区的交换机管理地址,如我们这个例子里的飞虹新村就是10.51.1.*的地址,我们设成10.51.1.200,填写完成后,点击“添加”,所有的窗口都点“确定”,完成计算IP 的设置。
三、配置交换机1、打开浏览器,在地址栏里输入:192.168.2.1,回车,如下图所示:2、在出现的登录界面中输入用户名和密码,默认是:admin,123456,输好后点击“OK”.3、对于一般基本的配置我们只用到“交换机管理”和“VLAN设置”这两项,点击可展开子菜单,如下图所示:4、在“交换机管理”展开的子菜单中,我们一般常用前面三个,如下图所示:5、点击“口令设置”,可以修改登录该交换机的用户名和密码,改好后点击“Update”。
6、点击“系统IP设置”,可以修改该交换机的IP地址,注意掩码和网关要设置正确。
7、点击“系统状态”可以查看交换机的MAC地址,软件版本,按要求把该交换机的MAC地址填入EXCEL表格。
简单网管交换机的 VLAN 功能设置及应用

简单网管交换机的VLAN 功能设置及应用文档适用产品型号:GS105E,GS108Ev1,GS108Ev2,GS108PEv1,GS108PEv2,GS116E,JGS524E,XS708E简单网管交换机VLAN菜单一览VLAN(Virtual Local Area Network)的中文名为虚拟局域网。
VLAN是一种将局域网设备从逻辑上划分成多个网段,从而实现虚拟工作组的数据交换技术。
这一技术主要应用于交换机和路由器中,但主流应用还是在交换机之中。
NETGEAR所有简单网管交换机均支持端口VLAN和802.1Q VLAN。
FS116E和JFS524E的VLAN配置较之其他简单网管交换机略有不同,请参考:FS116E和JFS524E的VLAN功能设置本文中以XS708E为例说明简单网管交换机的VLAN功能的详细设置步骤。
管理软件(ProSafe Plus Utility)版本:V2.2.24一、端口VLAN端口VLAN即将端口从逻辑上分组的VLAN,不同组的VLAN端口不能互相通讯,同时将公共端口加入所有VLAN中,实现所有端口均可以通过公共端口连接到路由器上网或者访问公共端口下的服务器。
端口VLAN拓扑:XS708E的08号端口连接到出口路由器,07号端口连接公共服务器,01-03号端口划分到同一个VLAN2,04-06号端口划分到同一个VLAN3,实现VLAN2和VLAN3间的端口不能互访,所有端口均可以通过08号上网,并同时可访问07号端口的公共服务器。
以下两种方式任选其一进行配置即可:1. 基本设置进入VLAN>端口VLAN>基本设置,将基本端口VLAN设置为启用。
在基本端口VLAN组(1-8或全部)下,将01-03号端口的VLAN组改为2,将04-06号端口的VLAN组改为3,公共端口07和08修改为全部(注意:端口VLAN中的全部表示将端口加入所有VLAN)。
点击应用。
2. 高级设置进入VLAN>端口VLAN>高级设置,将高级端口VLAN设置为启用。
VLAN技术及其应用

都是 在服 务器 端完成 的 。 改的结 果通 过T n发 给客 户端 , 修 u r k 客 户端 的V A L N数 据 库 也 会 发 生 相 应 的 变 化 , 就 是 说 , 户 端 内 也 客
的V AN 据库 总是 与服 务器 端 的V AN 据 库保 持 一致 ( L 数 L 数 同 步 ) 出于安 全 的考 虑 , 。 整个VT 域 还添 加 了 口令认 证 的功 能 . P 只有认 证通 过 ,客户端 交换 机 内的V A L N数据库 才 与服 务器端
用 来 在 不 同 的 交 换 机 之 间 进 行 连 接 。 保 证 在 跨 越 多 个 交 换 机 以
称 指 定 为 C M , 设 置 为 Cin模 式 , 体 命 令 如 下 : O 并 l t e 具 C M# l aa ae 入 VL N 置 模 式 O va d tb s进 n A 配
上 建 立 的 同 一 个 V AN 员 能 够 相 互 通 讯 。 L 成
C M(l )v o anC M设 置V P 理域 名称C M O v n#t d m i O a p T管 O C M(l )vpsre设 置交 换机 为服 务器模 式 O v n#t evr a
P Rlva aaae 入 V AN 置 模 式 A # l d tb s进 n L 配
11 T u k 术 . rn 技
V PD MA N 为管理 域 ,交换VT 更新 信 息的所 有 交换 T O I称 P 机必 须配 置为 相 同的管理 域 。 果所 有 的交 换机 都 以中继线 相 如
连 , 么 只 要 在 核 心 交 换 机 上 设 置 一 个 管 理 域 , 络 上 所 有 的 那 网 交 换 机 都 加 入 该 域 , 样 管 理 域 里 所 有 的 交 换 机 就 能 够 了 解 彼 这 此 的V A 列 表 。 对 本 需 求 。 先 在 核 心 交 换 机 C M上 设 置 管 L N 针 首 O
H3C配置命令08-qinq命令

【视图】 QinQ 视图
【参数】 vlan-id-list:表示的一组符合条件的 VLAN ID,表示方式为 vlan-id-list = { vlan-id | [ to { vlan-id } ] } & <1-10>,关键字 to 之后的 VID 号要大于或等于 to 之前的 VID 号, 命令中& <1-10>表示前面的参数最多可以重复输入 10 次。 all:表示所有的报文。 需要注意的是:由于 ACL 资源有限,目前不能够支持 vlan-id-list 为 1 to 4095 的配 置。
i
H3C S7500 系列以太网交换机 命令手册 QinQ
第 1 章 QinQ 命令
第1章 QinQ 命令
1.1 QinQ 命令
1.1.1 display port vlan-vpn
【命令】 display port vlan-vpn
【视图】 任意视图
【参数】 无
用来按顺序显示当前系统中 QinQ 的相关配置。
H3C S7500 系列以太网交换机 命令手册 QinQ
目录
目录
第 1 章 QinQ命令 ....................................................................................................................1-1 1.1 QinQ命令 ........................................................................................................................... 1-1 1.1.1 display port vlan-vpn ............................................................................................... 1-1 1.1.2 vlan-vpn enable ....................................................................................................... 1-1
vlan测试用例
VLAN测试用例版本历史目录1. 概述: (3)2. 参考文档 (3)3. 资源需求: (3)4. 关键字: (3)5. 测试用例列表 (4)6. 测试组网图 (6)7. 测试用例详细描述: (6)7.1 802.1Q帧格式 (6)7.2 创建VLAN (7)7.3 Access端口对标记处理 (9)7.4 Trunk端口对标记处理 (11)7.5 Hybrid端口对标记处理 (12)7.6 过滤功能 (13)7.7 Tag帧分类转发 (15)7.8 vlan端口类型测试 (16)7.9 vlan转发测试 (17)7.10 背景流环境测试 (18)7.11动态vlan的功能测试 (19)7.12功能兼容性测试 (26)7.13 设备兼容性测试 (29)7.14 性能测试 (30)1.概述:本文列出了针对在网管交换机上的VLAN功能测试点及对应测试用例,通过文中描述的测试用例完成对网管交换机上VLAN功能的测试,最终确保该功能在交换机上的实现规范、可靠。
2.参考文档《VLAN配置手册》3.资源需求:硬件需求:交换机 2台,Windows 2K/XP Client PC 2台软件需求:wireshark,anysend4.关键字:VLAN Virtual Local Area NetworkTrunkAccessHybrid5.测试用例列表6.测试组网图测试组网图:组网图1组网图说明:图中DUT为被测设备,其他为搭建环境的辅助设备,具体设备型号、类型根据实际情况决定。
初始化配置:说明:组网环境中除DUT外的其他设备尽量使用非DUT型号设备(便于测试过程中更充分地考验兼容性),所有设备只需默认配置,图中所有PC装抓包工具omnipeek。
7.测试用例详细描述:7.1 802.1Q帧格式7.2 创建VLAN7.3 Access端口对标记处理7.4 Trunk端口对标记处理7.5 Hybrid端口对标记处理7.6 过滤功能7.7 Tag帧分类转发7.8 vlan端口类型测试7.9 vlan转发测试7.10 背景流环境测试7.11动态vlan的功能测试7.12功能兼容性测试7.13 设备兼容性测试7.14 性能测试(注:可编辑下载,若有不当之处,请指正,谢谢!)。
中兴ZXR10配置说明

中兴ZXR10配置说明一、配置基础1、进入[BootManager]的密码为zte2、默认登陆用户:admin 密码(loginpass):zhongxing默认Enable密码(adminpass):zhongxing3、配置模式:序号模式命令提示符1 用户模式无zte>2 全局配置模式enable zte(cfg)#3 SNMP配置模式config snmp zte(cfg-snmp)#4 三层配置模式config router zte(cfg-router)#5 文件系统配置模式config tffs zte(cfg-tffs)#6 NAS配置模式config nas zte(cfg-nas)#7 集群管理配置模式config group zte(cfg-group)#4、VLAN划分:256个VLAN为一个段,红色字体的表示我们使用的VLAN段。
序号VLAN范围序号VLAN范围1 0-255 9 2048-23032 256-511 10 2304-25593 512-767 11 2560-28154 768-1023 12 2816-30715 1024-1279 13 3072-33276 1280-1535 14 3328-35837 1536-1791 15 3584-38398 1792-2047 16 3840-40945、采用Telnet用户远程认证后,交换机的管理用户和Radius服务器中设置的用户都可以登陆交换机。
二、配置规范举例:1、用户2#202接入Port 1,速率10M,全双工模式,用户vlan2500;2、上行端口为Port 25,速率100M,全双工模式,上行潜山路第二台MA5200的第18口(QSL-MA5200(2)-E18);3、管理vlan为981,管理ip为61.133.186.172/24;4、设置广播风暴抑制门限为24000-72000bytes;5、SNMP的只读团体名为share,目标主机为218.22.16.5和202.102.198.62;6、Telnet采用远程Radius认证方式,域名:domain_jrw Radius服务器218.22.16.2 认证端口UDP 1812;7、启用SSH功能。
博达交换机08-VLAN配置

基于端口的 VLAN,就是将端口归属到交换机支持的 VLAN 的一个子集中。 如果这个 VLAN 子集只有一个 VLAN,那么该端口就是访问模式(access) 端口;如果这个 VLAN 子集中有多个 VLAN,该端口为中继(trunk)端口, 其中有一个默认的 VLAN,它是该端口的 native VLAN,该 VLAN ID 就是 Port VLAN ID(PVID)。 z 支持端口 VLAN 的范围控制 vlan-allowed 参数用于控制端口所归属的 VLAN 范围;vlan-untagged 参 数用于控制端口发送不加上 VLAN 标签的报文到相应的 VLAN。
1.2 Dot1Q Tunnel概述
1.2对基于 802.1 Q 封装的隧道协议的一种形象化的称呼,定义在 IEEE 802.1ad 中。其核心思想是将用户私网 VLAN tag 封装到公网 VLAN tag 上,报文带 着两层 tag 穿越服务商的骨干网络,从而为用户提供一种较为简单的二层 VPN 隧道。 Dot1Q Tunnel 协议是一种简单而易于管理的协议,它不需要信令的支持,仅仅通过 静态配置即可实现,特别适用于小型的,以三层交换机为骨干的企业网或小规模城域 网。 BDCOM 的 Dot1Q Tunnel 特性正好满足了这部分用户的需求,它提供了一种廉价、 简洁的二层 VPN 解决方案,越来越多的小型用户倾向于使用该功能构建自己的 VPN 网络。在运营商网络的内部,P 设备也无需支持 Dot1Q Tunnel 功能,即传统的三层 交换机完全可以满足需求,极大地保护了运营商的投资。
1.2.2 Dot1Q Tunnel 实现方式
Dot1Q Tunnel 实现方式一种是基于端口的 Dot1Q Tunnel,一种是基于内层 CVLAN Tag 分类的 Dot1Q Tunnel。
VLAN、SVLAN、PVLAN、CVLAN的区别

VLAN、SVLAN、PVLAN、CVLAN的区别2009-08-05 08:27 A.M.VLAN、SVLAN、PVLAN、CVLAN的区别VLAN:一个VLAN就是一个广播域,用一个标签来表示.(802.1q 标准定义,在以太网ethernetII/802.3的SA后加面增加4字节用来给这个以太网帧打标签和优先级值)PVLAN:private vlan,VLAN的一种应用,是完全从实际应用角度而言的,用以实现一个VLAN内的用户之间有些能通信,有些不能通信,但这个VLAN里的所有用户都能通过同一个端口出去或者访问服务器这样一个实际需求包含primary VLAN,isolated VLAN和communicate VLAN,其中isloate VLAN和communicate VLAN绑定在primary VLAN上,isolated PVLAN内的用户之间互相隔离,但可以和primary vlan内的Promiscuous port通信, communicate PVLAN内的用户之间可以互相通信,也能与primary vlan内的Promiscuous port通信.SVLAN和CVLAN: Service provider VLAN和customer VLAN,由802.1ad定义, QinQ,在一个VLAN里再增一层标签,成为双标签的VLAN,外层的就是SVLAN,内层的就是CVLAN你提出的最后一个问题:"这三者SVLAN、PVLAN、CVLAN之间是否可以配合使用"当一个交换机启用double tagging mode也即802.1q tunneling的时候,用户数据包自身携带VID的就是CVLAN,进入交换机后,会被再打上一层标签SVLAN,成为一个双标签的数据,如果用户是ungtagged的数据包,交换机可以打上两层标签,内层打上端口的PVID成为CVLAN,外层打上SPVLAN.还可以是直接接把PVID作为SPVLAN,成为单标签数据.交换机处理时可以根据内层标签也可以根据外层标签,交换机不同可以有不同的实现方式.SVLAN和CVLAN是孪生兄弟,相对的概念,就是配合使用的,PVLAN是802.1q的应用方式,而VLAN和SLVAN能共存在,所以这三者完全可以配合使用。
- 1、下载文档前请自行甄别文档内容的完整性,平台不提供额外的编辑、内容补充、找答案等附加服务。
- 2、"仅部分预览"的文档,不可在线预览部分如存在完整性等问题,可反馈申请退款(可完整预览的文档不适用该条件!)。
- 3、如文档侵犯您的权益,请联系客服反馈,我们会尽快为您处理(人工客服工作时间:9:00-18:30)。
Proxim Product Training Class Tsunami 8100 Product family
VLANs
How is VLAN info carried in the frames?
DIX Ethernet v2 Encapsulation/802.3 Encapsulation
Max Frame size of 1518 Bytes
Destination Address Source Address Frame Type/ Length 6 Bytes 6 Bytes 2 Bytes 46 to 1500 Bytes 4 Bytes Data FCS
802.1p/Q extension
Added 4 bytes Total Max frame of 1522 Bytes
TPI 2 Bytes Priority 3 bits CFI 1 bit VLAN ID 12 bits
TCI (2 Bytes)
QB/MP-8100 VLANs
Only supported in Bridging Mode VLAN support
VLAN configuration locally on the unit Management VLAN Each interface is treated as an independent VLAN port Allow for untagged packet while in Trunk mode
EndPointA/Base
Transparent mode Trunk mode
Up to 256 entry into the Trunk table
EndPointB/Satellite
Transparent mode Access mode Trunk mode
Up to 16 entry into the Trunk table
QB/MP-8100 VLANs
There are different VLAN modes for EndPointA / Base and EndPointB / Satellite :
EndPointA / Base VLAN modes Transparent or Trunk EndPointB / Satellite VLAN modes Transparent, Trunk or Access
The following combinations are possible:
EndPointA / Base Transparent Trunk Trunk EndPointB / Satellite Transparent Access Trunk
Transparent VLAN Mode
Transparent VLAN mode
Applicable to both SU and BSU SU/BSU forwards both tagged an untagged frames received on the WORP interface or Ethernet Interface Management of the unit can be done through tagged or untagged frames, depending on how the unit is configured Used when the devices behind the BSU/SU are both VLAN aware and VLAN unaware
For frames incoming through either port: All Untagged frames will be passed untagged Frames tagged with any VLAN ID will be passed tagged as they came Management of the unit is possible through tagged or untagged frames. If a Management VLAN is configured, the unit will only accept management frames tagged with that specific VLAN ID.
Transparent BSU or SU
Access VLAN Mode
Access VLAN mode
Applicable to the SU only There will be 2 VLANs configured for an SU in Access mode:
“Access VLAN ID” (for the Network on the Ethernet side of the SU) “Management VLAN ID” (for the Management Interface of the SU)
All devices behind the SU “map” into one VLAN segment Used when the devices behind the SU are VLAN unaware
VLAN ID= 126
SU Configuration (done at the BSU): Mode=Access Access VLAN ID= 126 Mgmt VLAN ID= 1
Switch/Hub
Trunk VLAN Mode
Trunk VLAN mode
Applicable to both SU and BSU Up to 256 VLAN IDs can be configured for the BSU and up to 16 VLAN IDs can be configured for each SU Used when all devices behind the BSU/SU are VLAN aware Management of the unit can be done through tagged or untagged frames (same as in Transparent mode)
VLAN ID 4 VLAN ID 7
SU Configuration (done at the BSU): Mode= Trunk VLAN #1= 4 VLAN #2= 7 VLAN # 3, 4… 16= (leave empty) Mgmt VLAN= 1 1Q trunk port 4 4 7 7 1 Management Station in VLAN 1
VLAN Switch
Trunk VLAN mode example
SU 1 Trunk Mode
BSU in Trunk mode
SU 1 in Trunk mode SU 2 in Access mode
BSU Trunk Mode
SU 2 Access Mode
Company A Company B VLAN 4 VLAN 7
ISP VLAN 4 and 7
Company A VLAN 4
VLAN
VLAN>Ethernet>1 & 2
Return to agenda。
